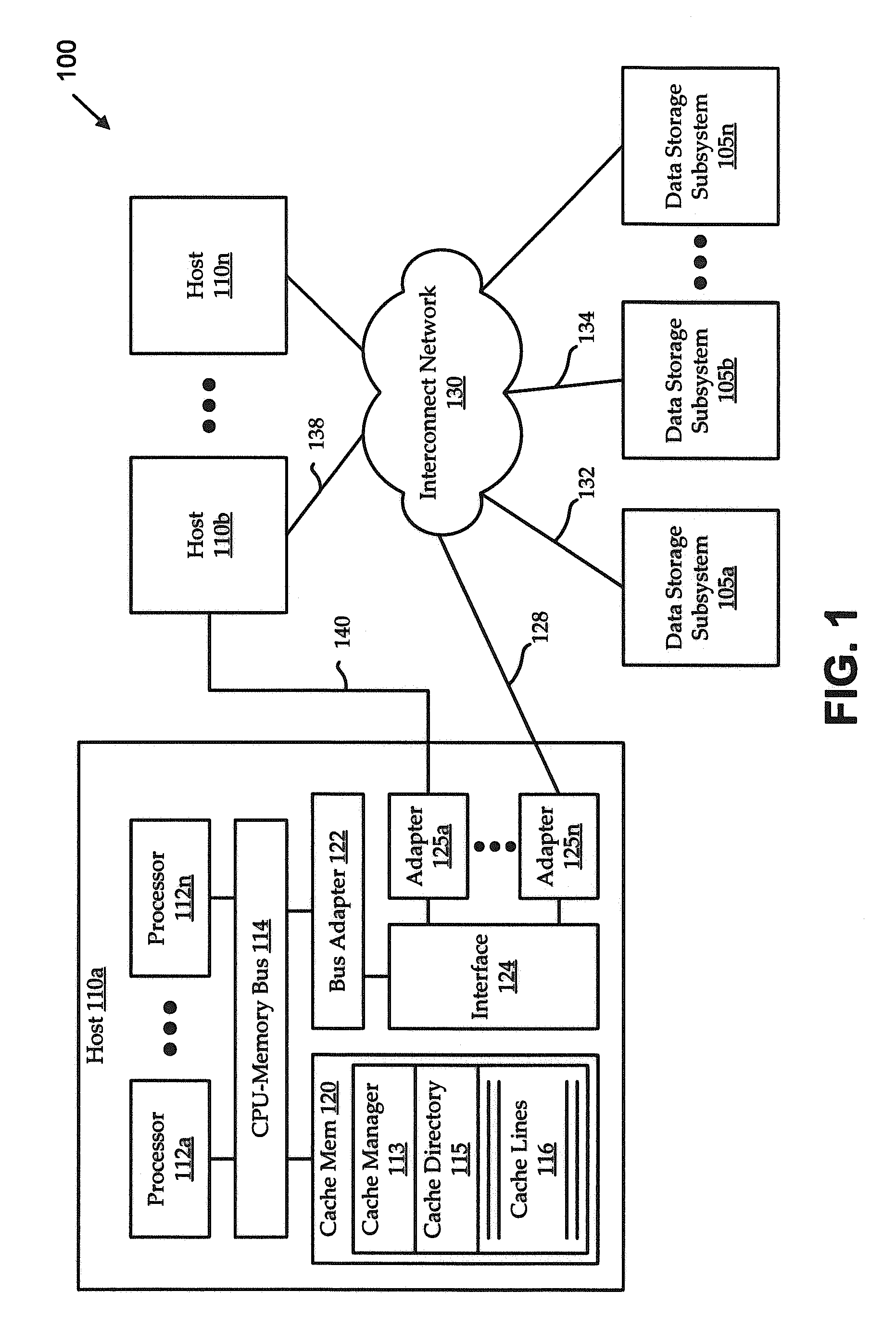
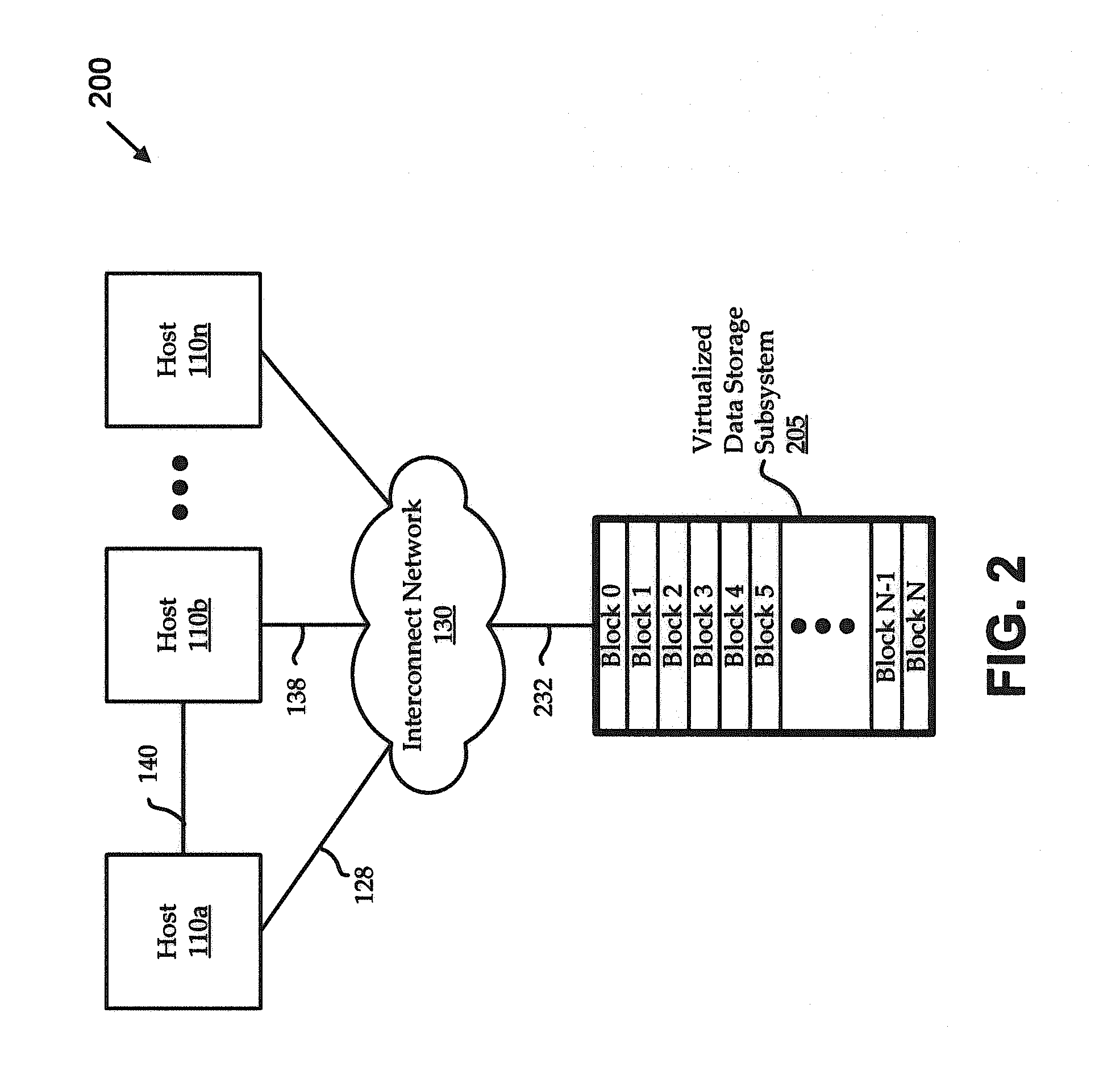
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
523 results about "Block level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
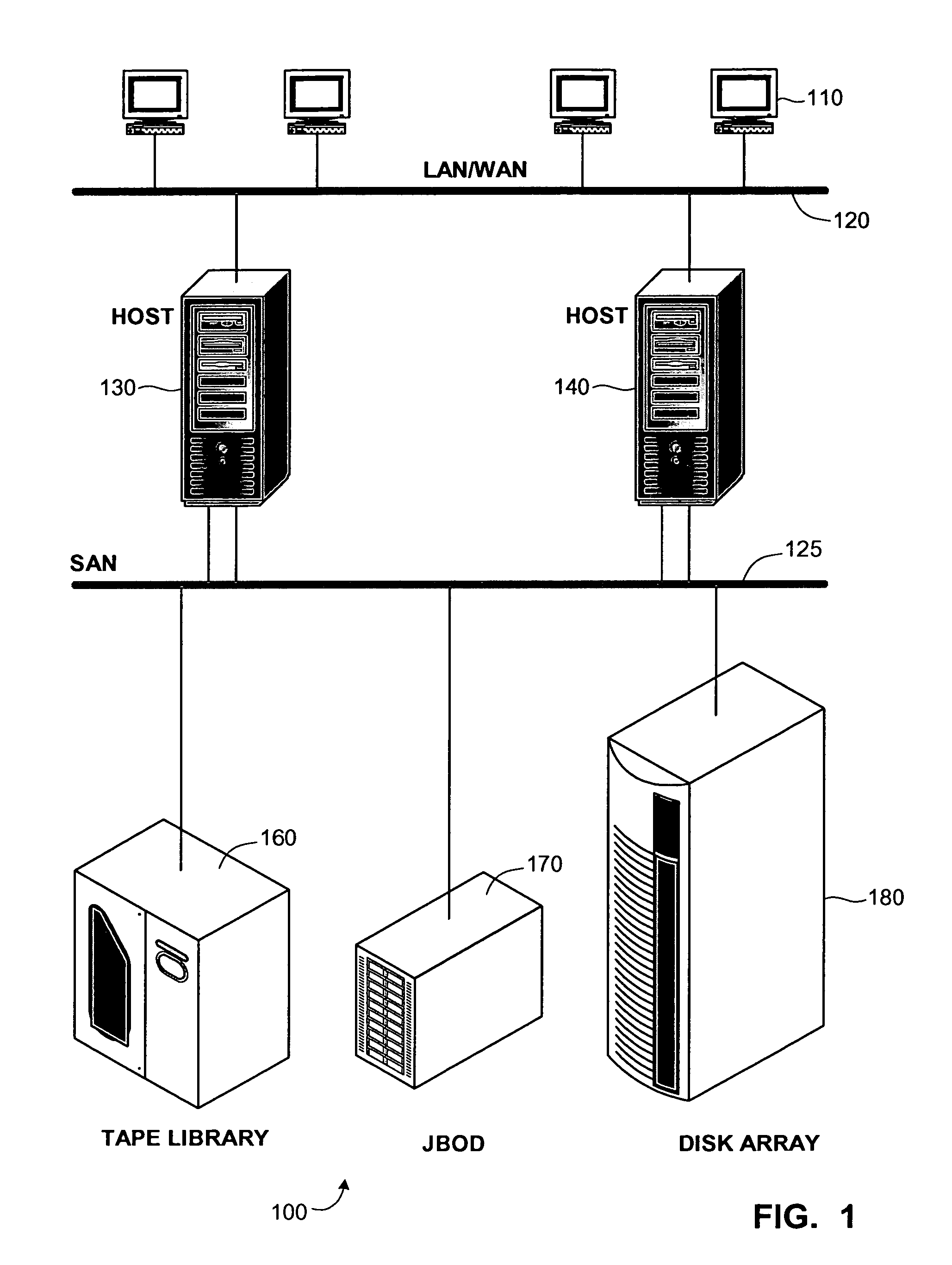
Definition of: block level. block level. Reading and writing a disk at the physical level. The disk controller in every computer and server reads and writes the disks at the block level. In storage area networks (SANs), where the disks are in cabinets external to the server, read/write access is also at the block level. Block Level vs. File Level.
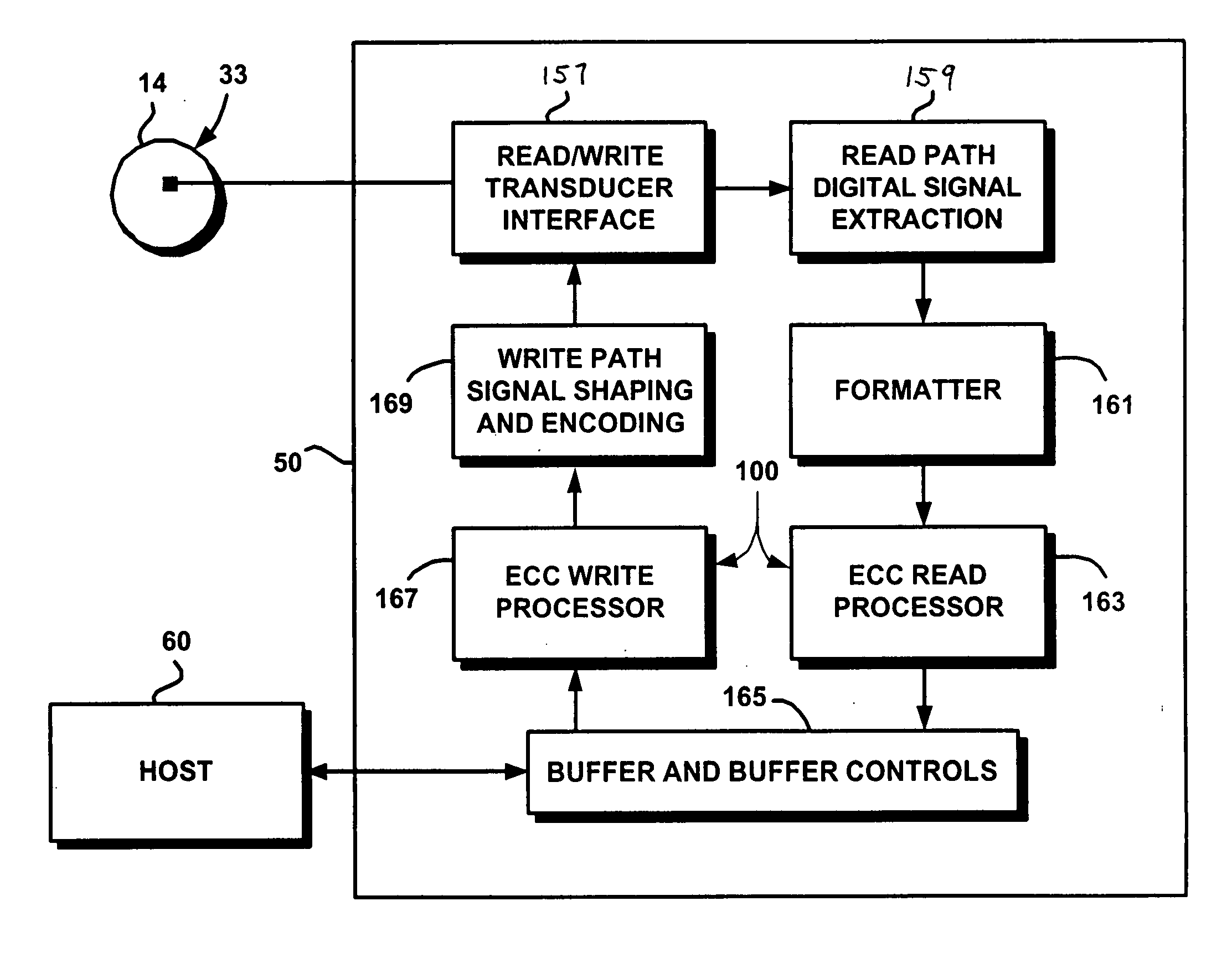
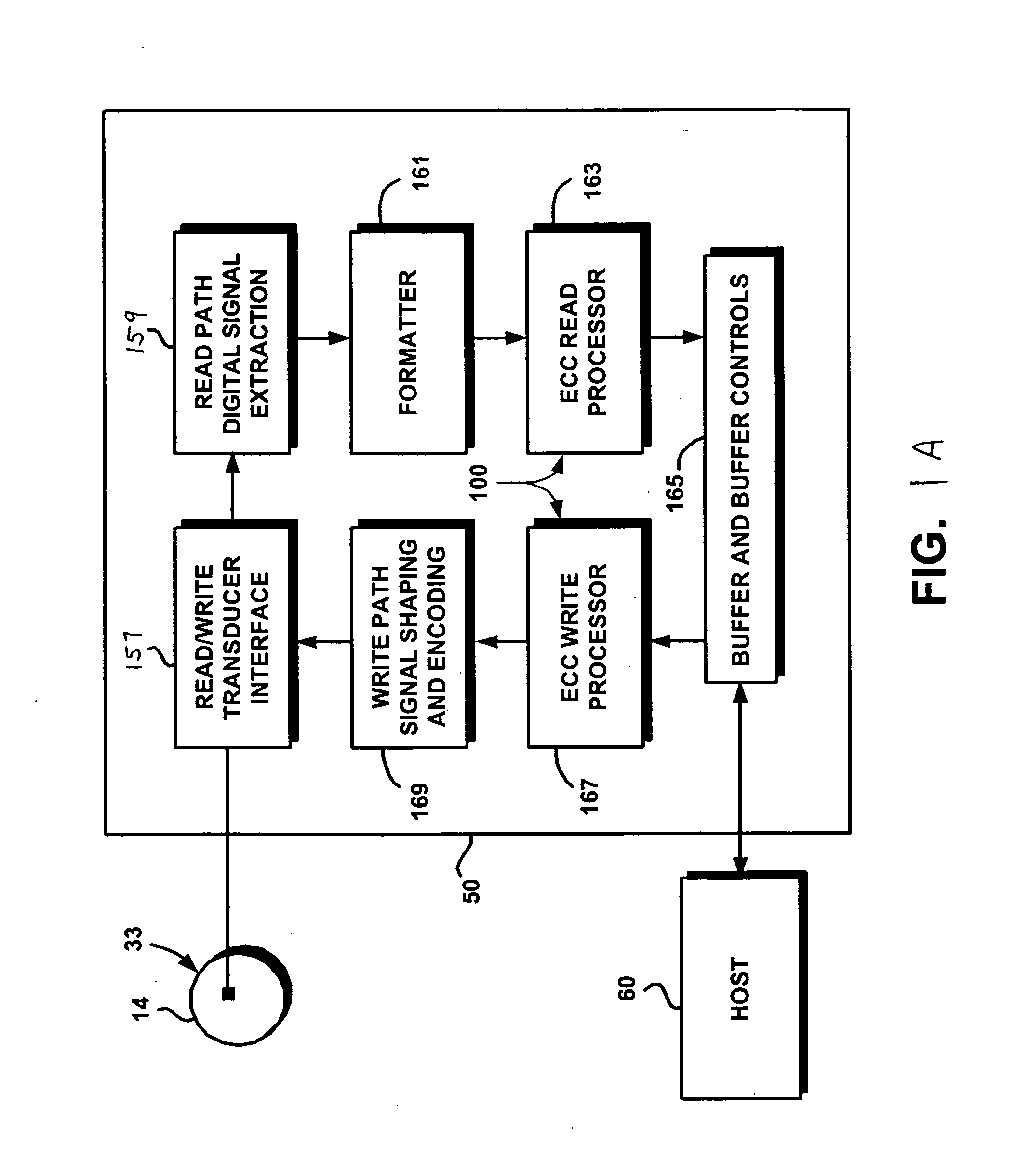
Techniques for detecting and correcting errors using multiple interleave erasure pointers
InactiveUS20050229069A1Correction capabilityTransmission systemsCode conversionBlock codeError location
Techniques for detecting and correcting burst errors in data bytes formed in a two-level block code structure. A second level decoder uses block level check bytes to detect columns in a two-level block code structure that contain error bytes. The second level decoder generates erasure pointers that identify columns in the two-level block structure effected by burst errors. A first level decoder then uses codeword check bytes to correct all of the bytes in the columns identified by the erasure pointers. The first level decoder is freed to use all of the codeword check bytes only for error byte value calculations. The first level decoder does not need to use any of the codeword check bytes for error location calculations, because the erasure pointers generated by the second level decoder provide all of the necessary error locations. This techniques doubles the error correction capability of the first level decoder.
Owner:HITACHI GLOBAL STORAGE TECH NETHERLANDS BV +1
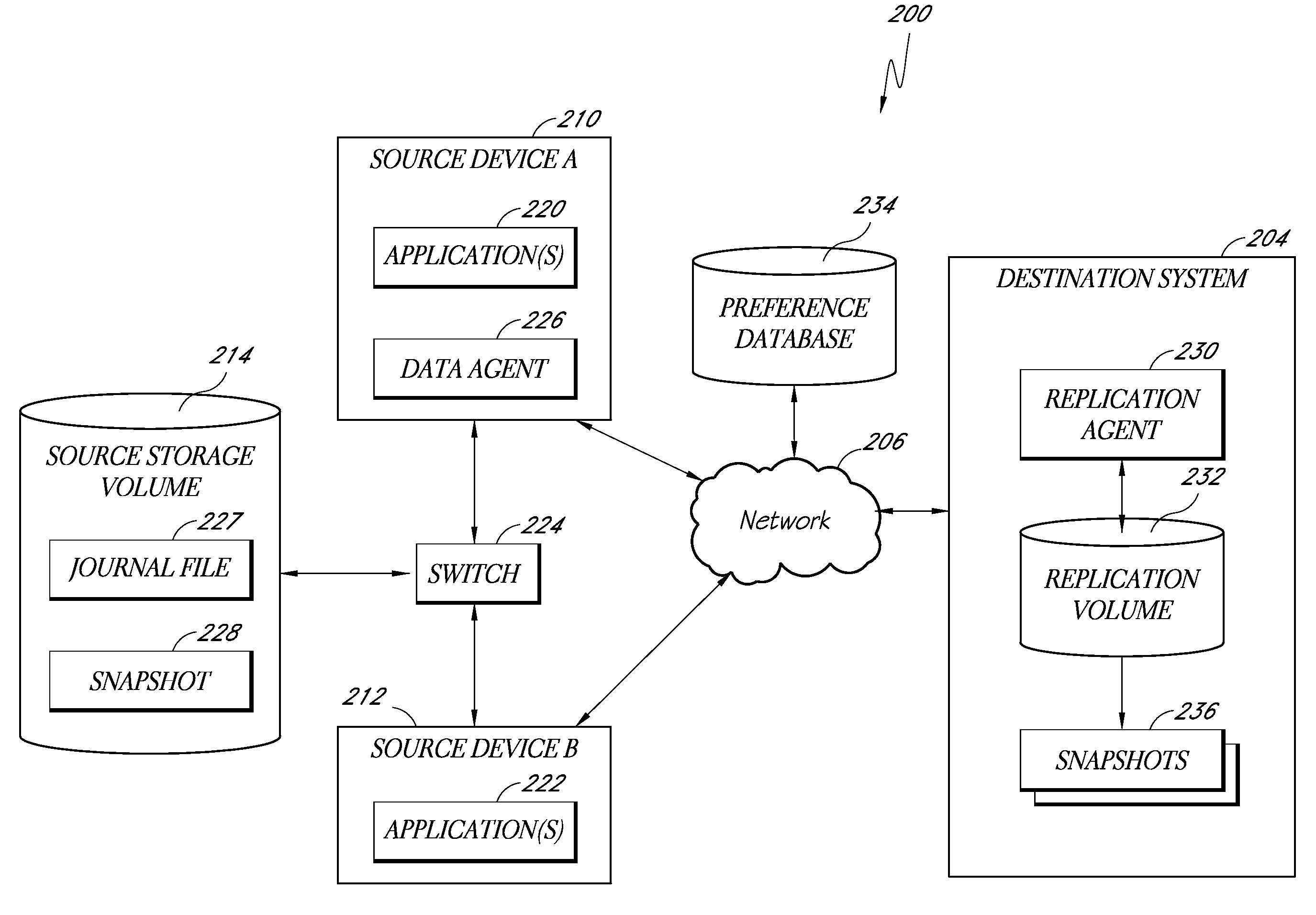
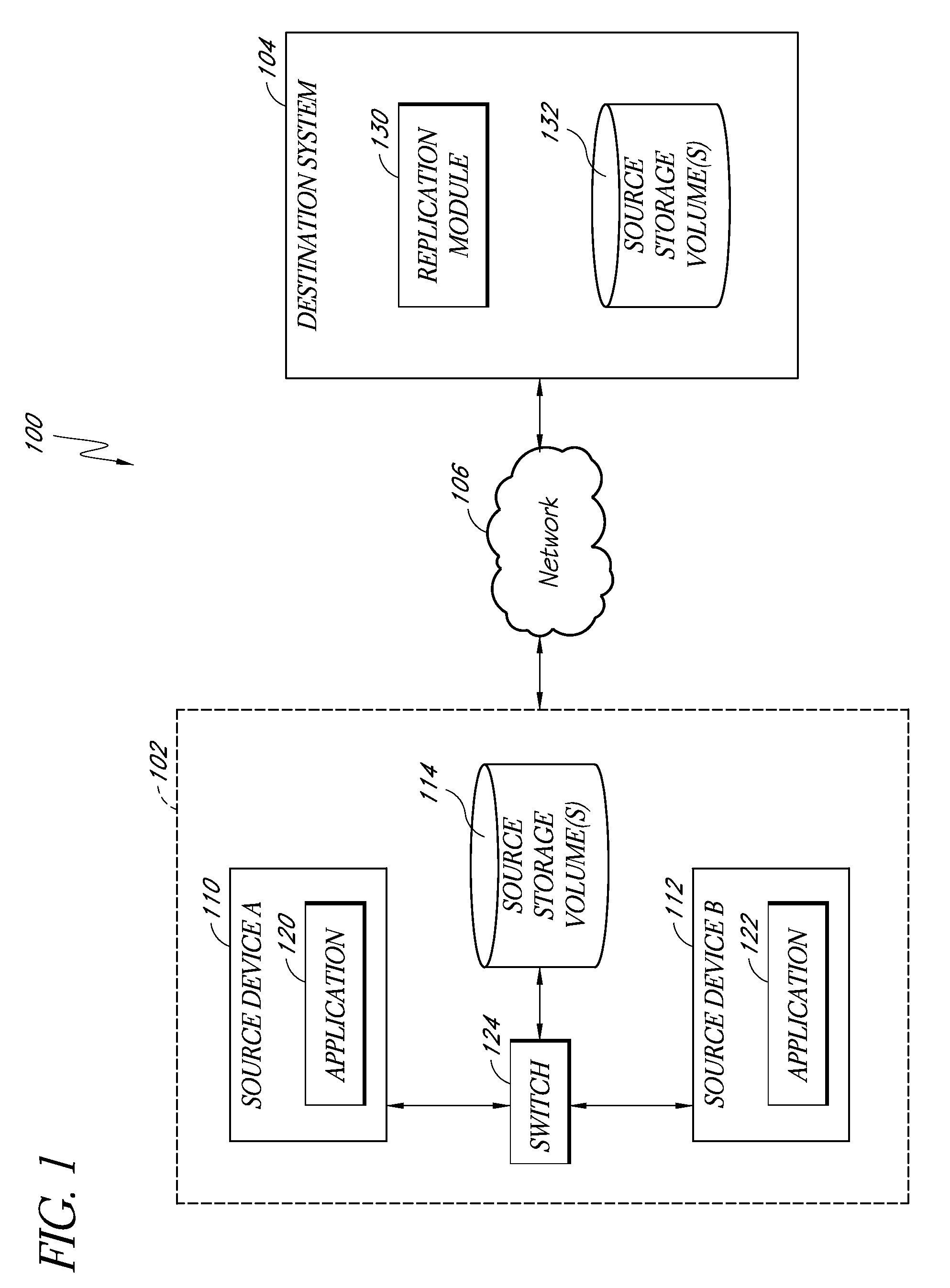
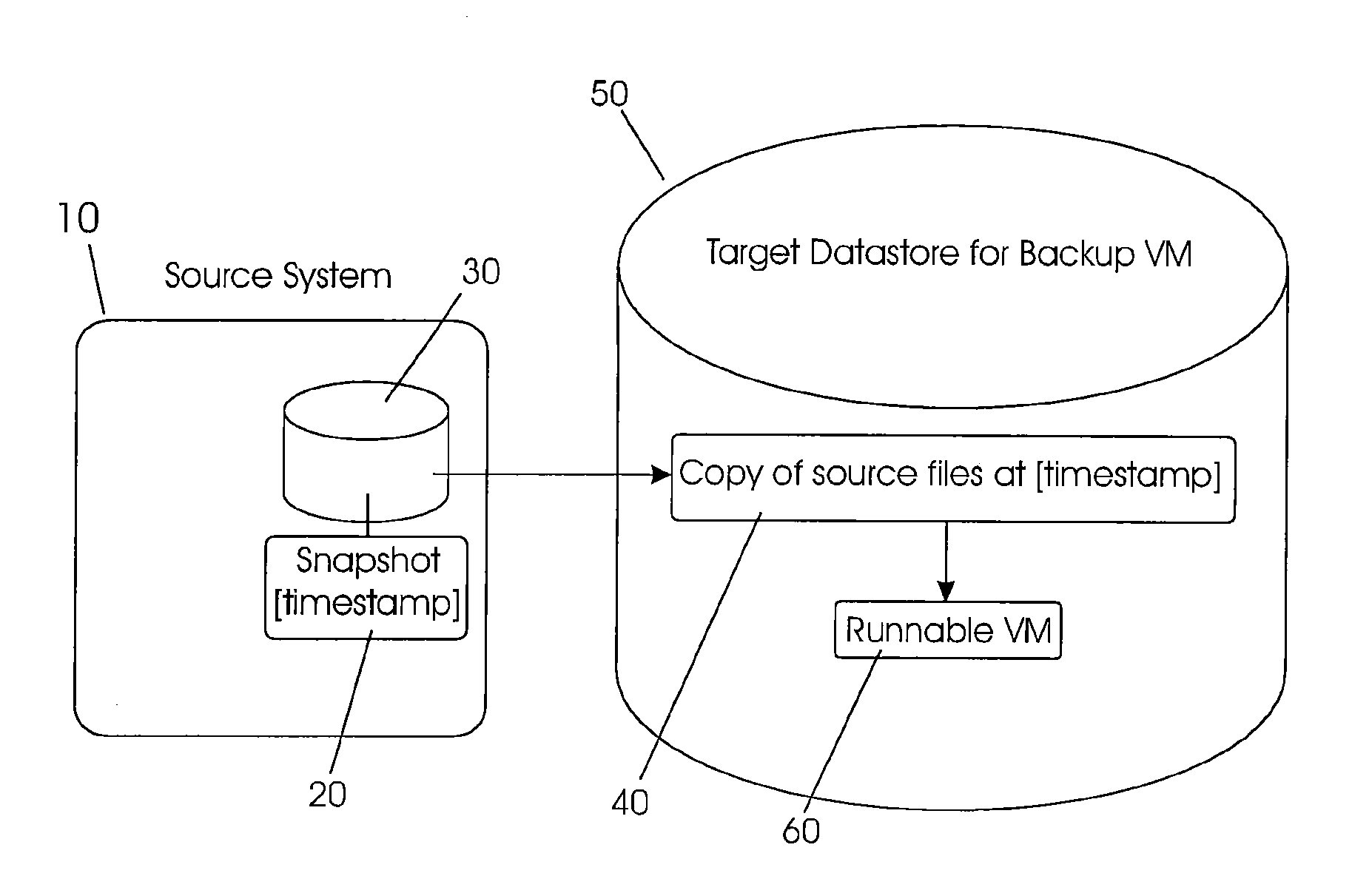
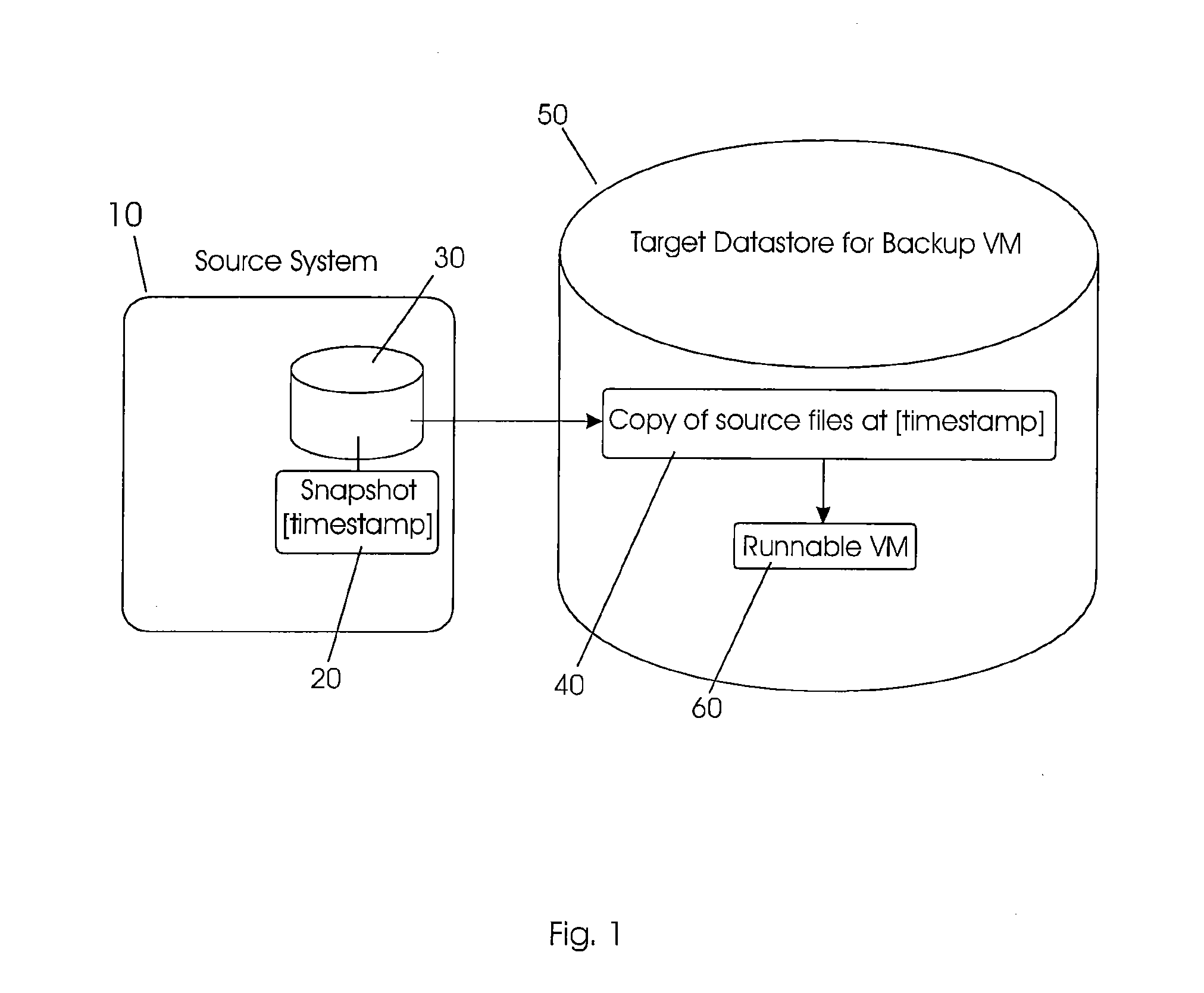
Systems and methods for performing discrete data replication
ActiveUS20100179941A1Reduce data volumeReduce consumptionDigital data information retrievalDigital data processing detailsBlock levelSource system
Systems and methods for performing intelligent replication of production data on a source storage device. In certain examples, a full backup of the production data is first performed and stored on a destination system. A journal module on the storage device (e.g., a shared storage device), or on at least one source system, tracks files on the storage device that change during a particular period of time. Following this period, a snapshot is taken of the production data. Upon mounting the snapshot, the replication system uses the journal information to identify modified files, conduct a block-level comparison of only the modified files with corresponding files on the destination system, and identify the particular data blocks that changed. The replication system then replicates only the changed blocks to the destination system. Certain systems further store information indicating a source system time of a known good state of the production data.
Owner:COMMVAULT SYST INC
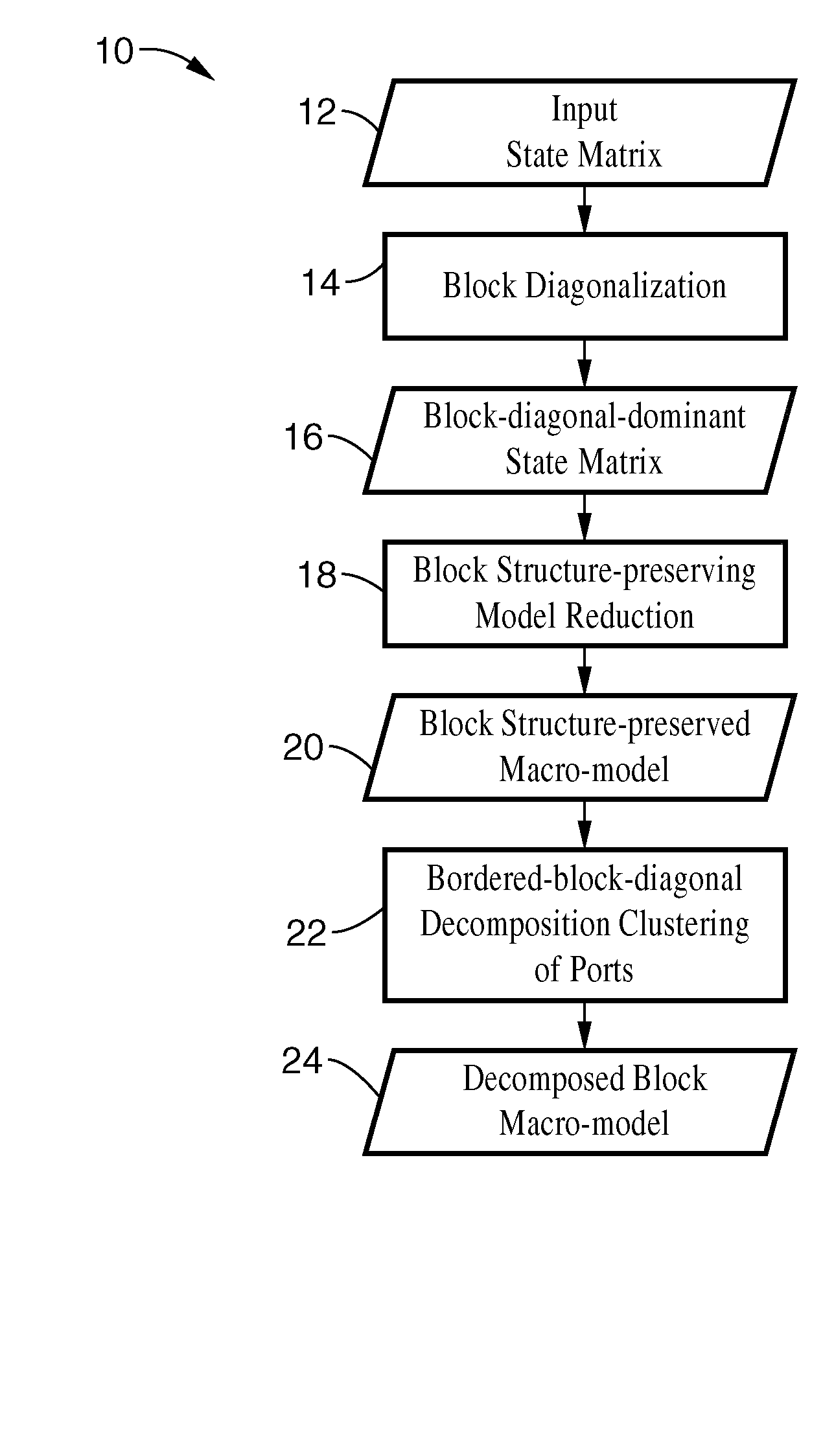
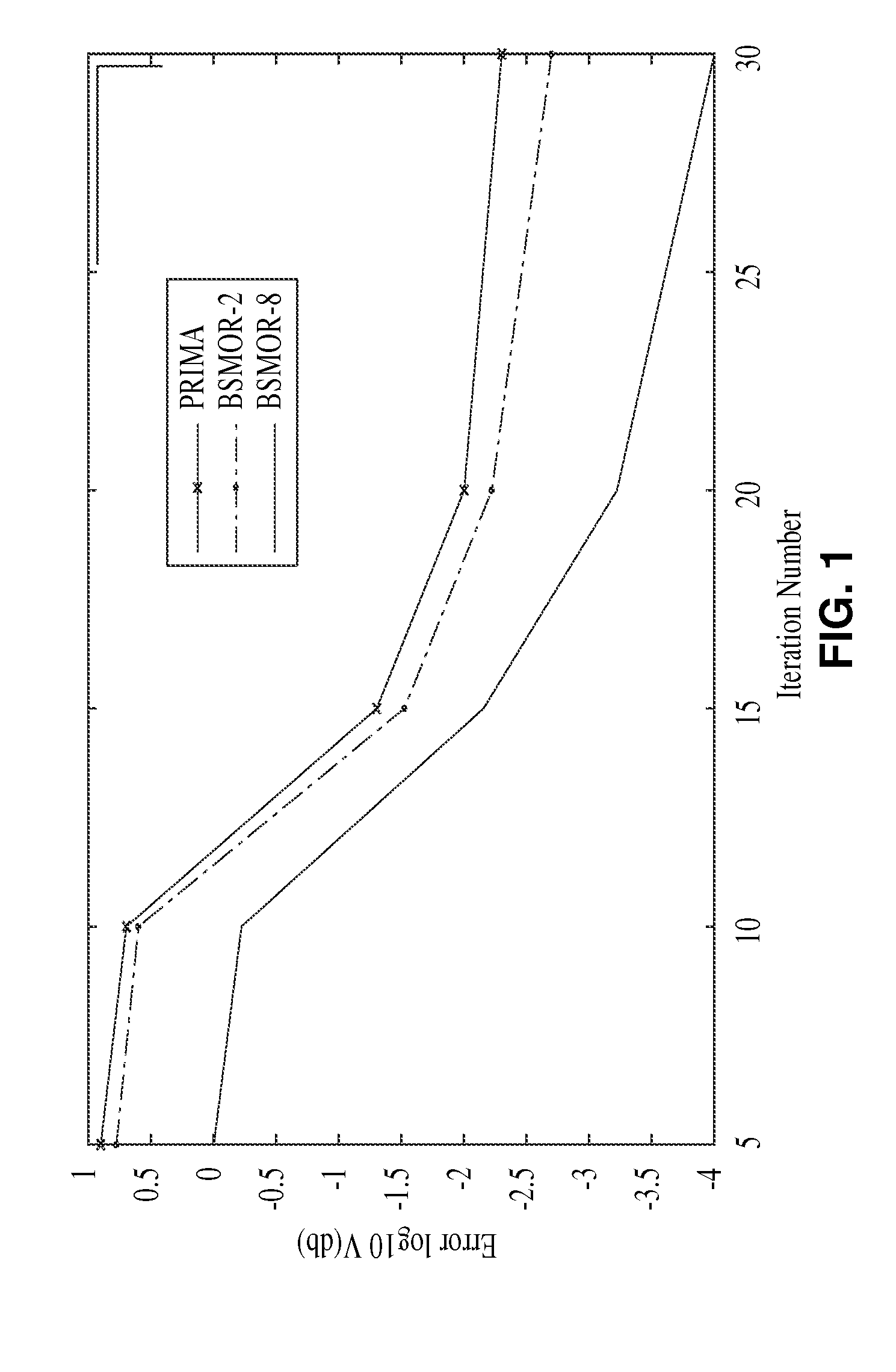
Structured and parameterized model order reduction
InactiveUS20080072182A1Reduce redundancyNon-uniformity is constantDetecting faulty computer hardwareComputation using non-denominational number representationStructured modelOrder reduction
Model-order reduction techniques are described for RLC circuits modeling the VLSI layouts. A structured model order reduction is developed to preserve the block-level sparsity, hierarchy and latency. In addition, a structured and parameterized model order reduction is developed to generate macromodels for design optimizations of VLSI layouts. The applications are thermal via allocation under the dynamic thermal integrity and via stapling to simultaneously optimize thermal and power integrity.
Owner:RGT UNIV OF CALIFORNIA
Logical access block processing protocol for transparent secure file storage
InactiveUS7334124B2Ensure integritySafe storageDigital data processing detailsUser identity/authority verificationComputer hardwareDigital signature
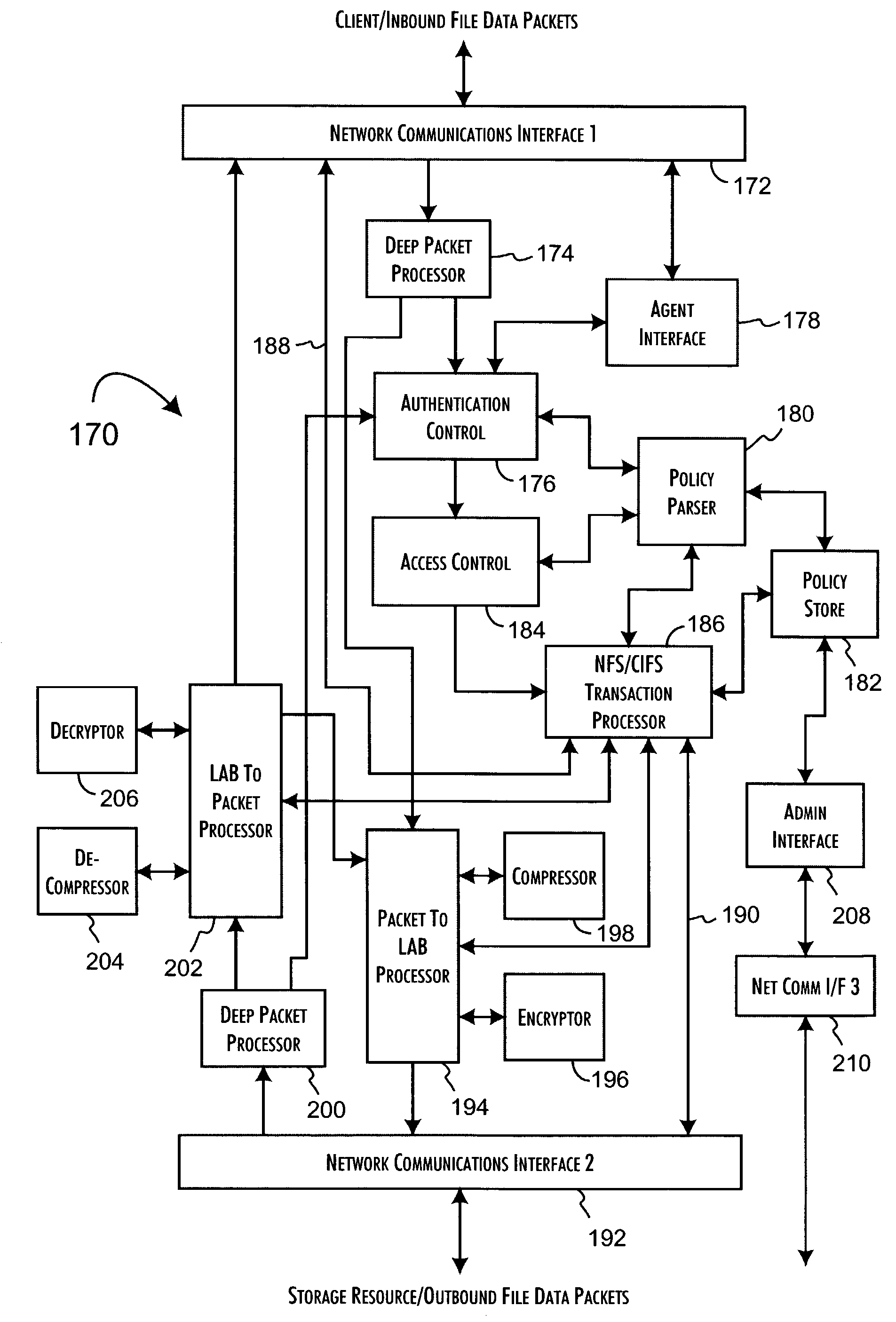
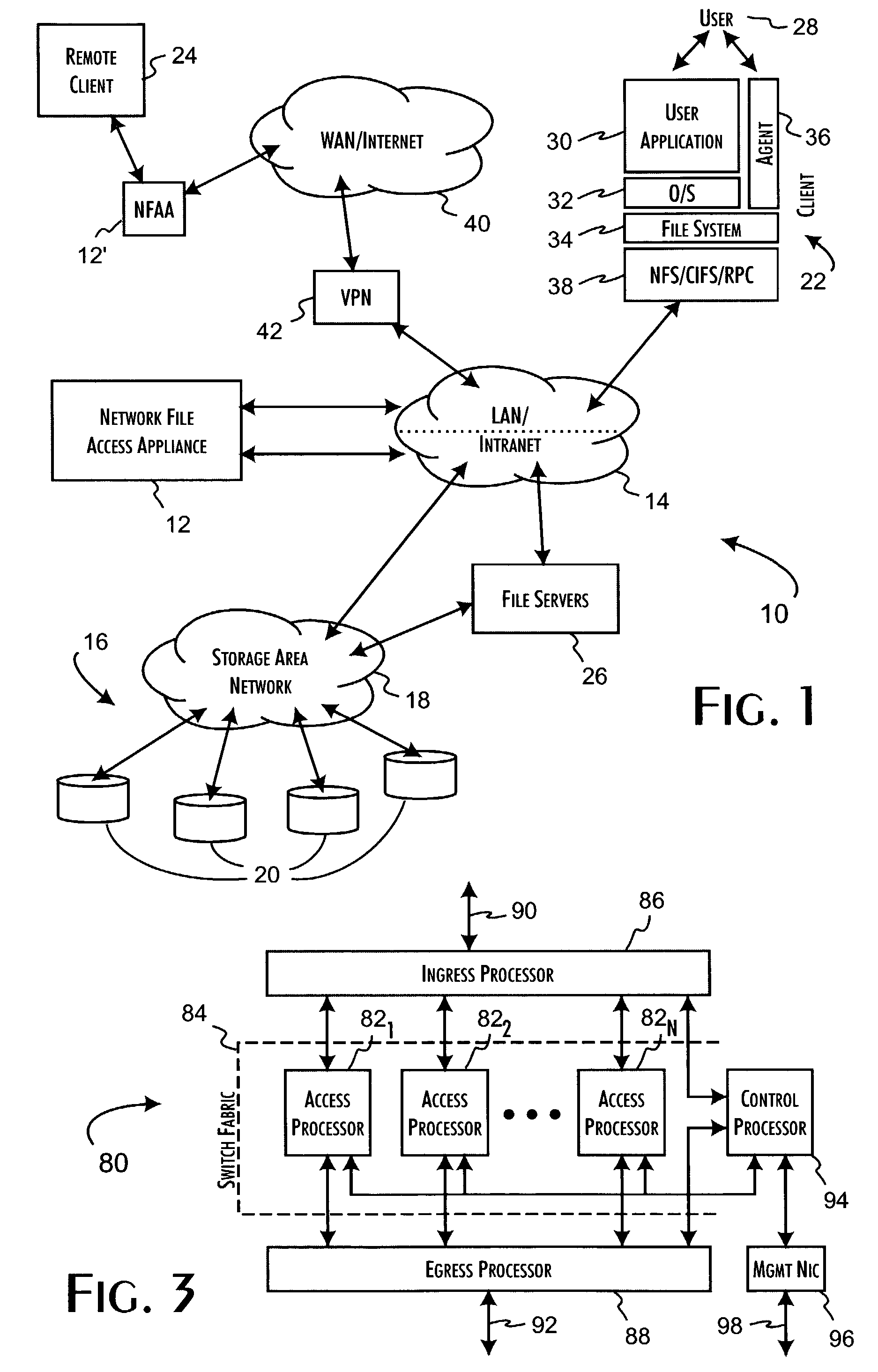
Network data files are secure through the operation of an infrastructure gateway-based network file access appliance. Network file data, corresponding to network pocket payload data, are further reduced to a sequence of data blocks that are secured through any combination of block encryption, compression, and digital signatures. File meta-data, including encryption, compression and block-level digital signatures are persistently stored with the file data, either in-band in the file as stored or out-of-band key as a separately stored file or file policy record. File meta-data is recovered with accesses of the file data to support bidirectional encryption and compression and to detect tampering with the file data by comparison against block-level digital signatures.
Owner:THALES ESECURITY INC
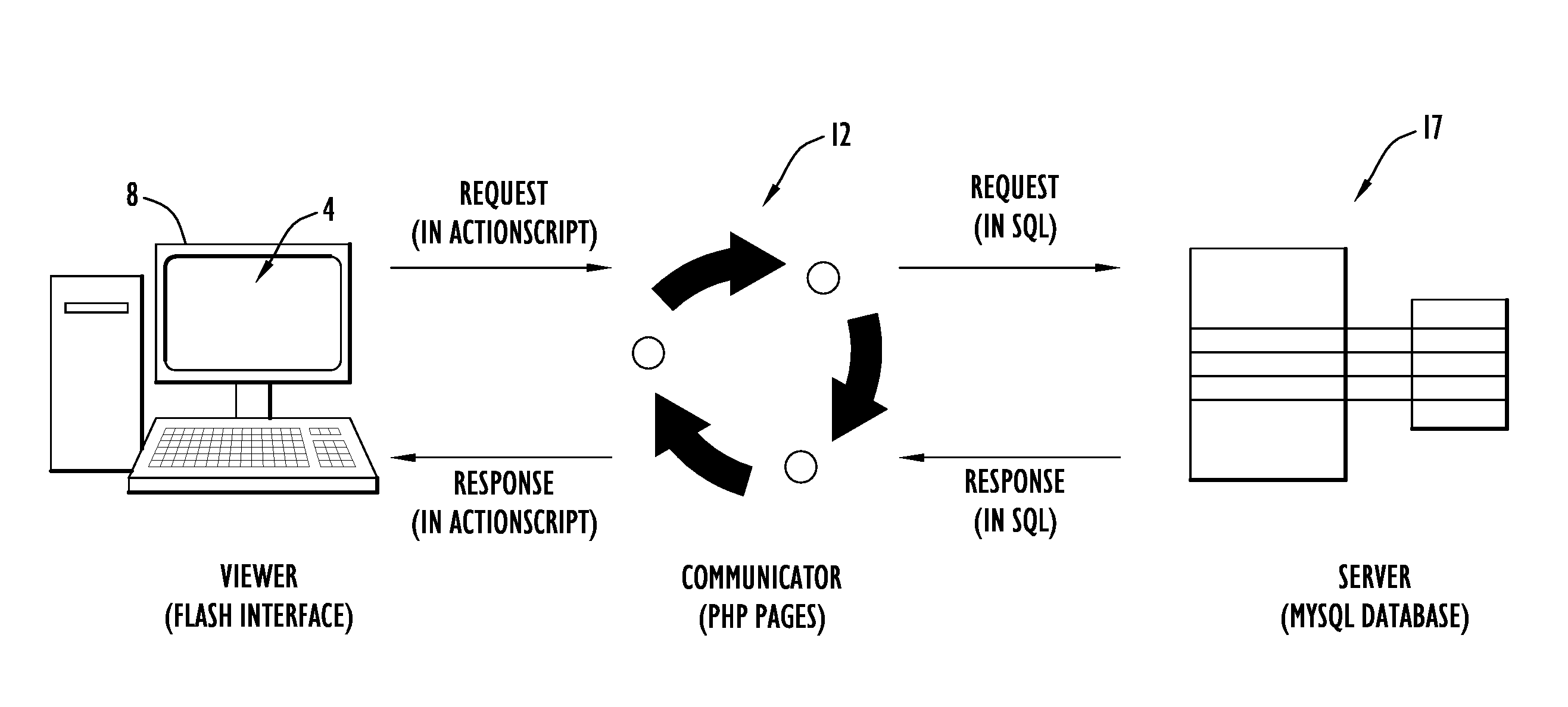
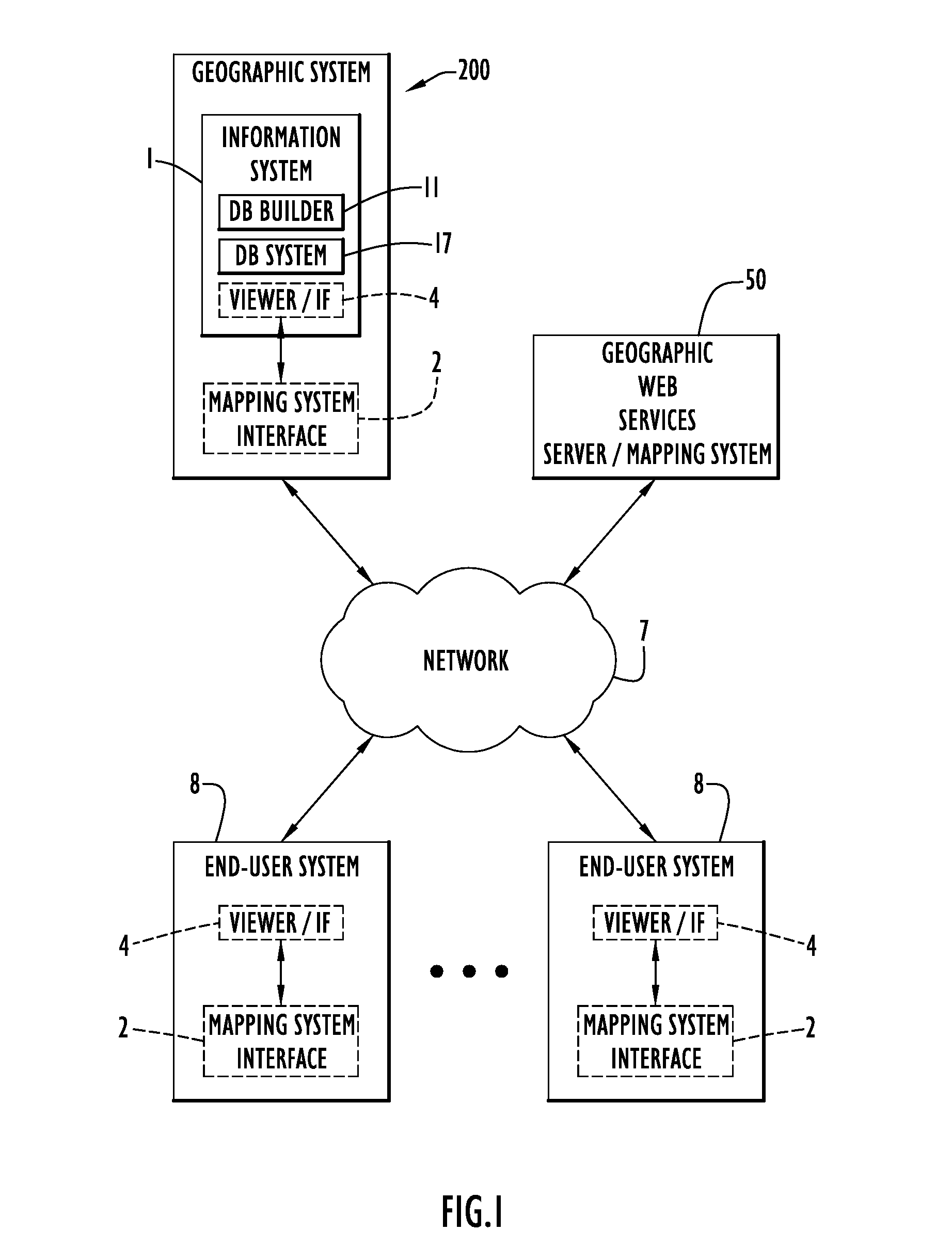
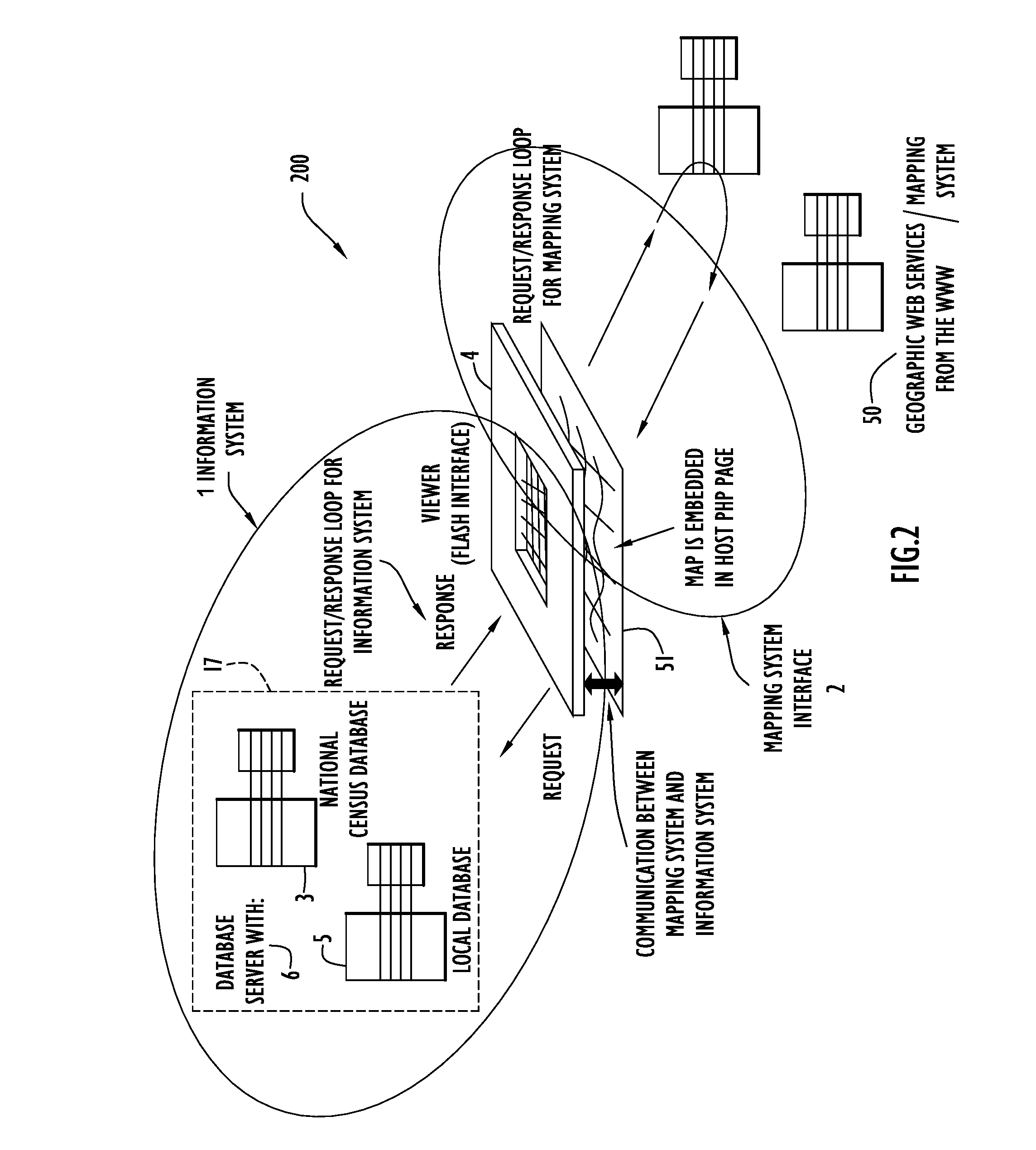
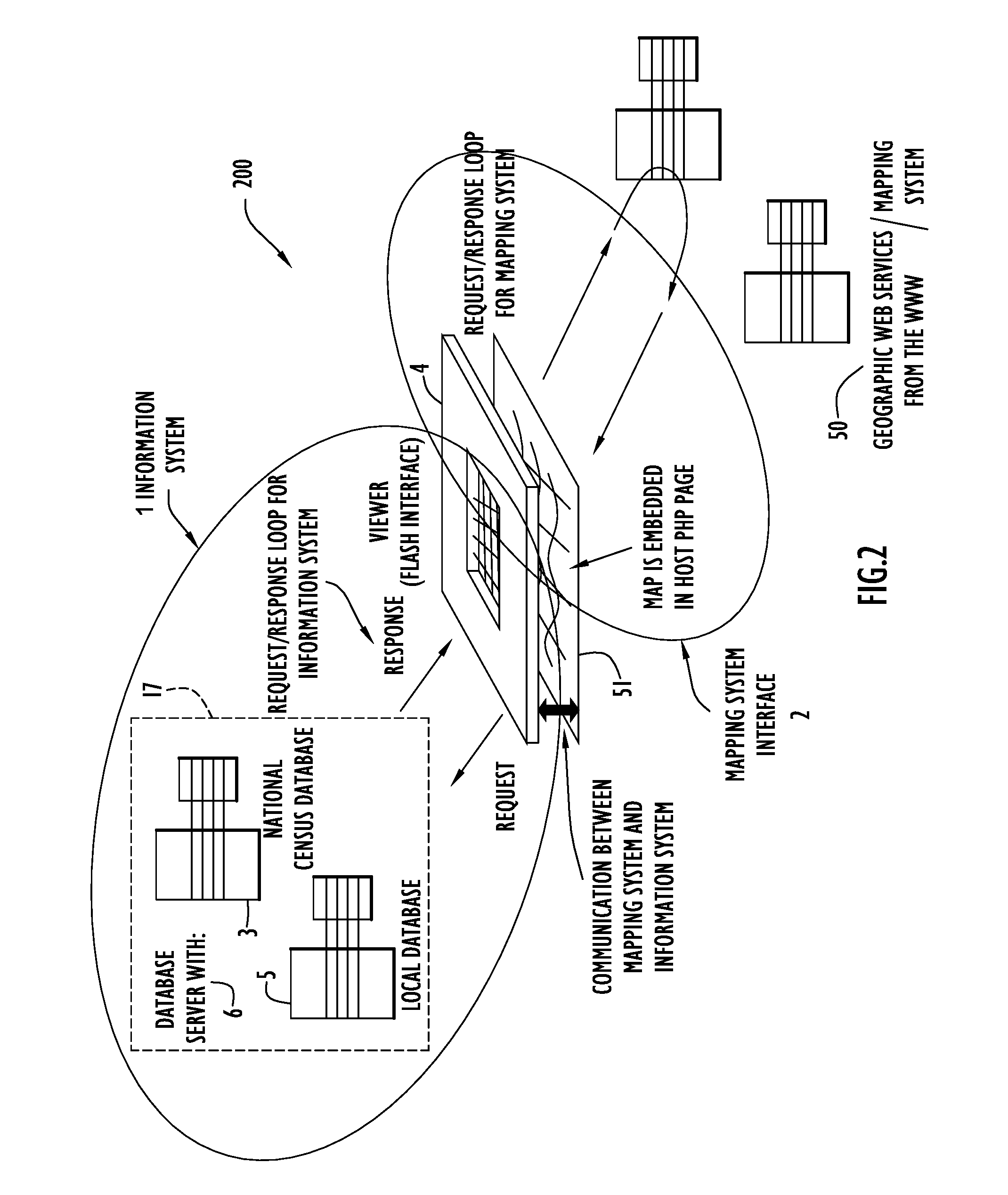
System and Method of Overlaying and Integrating Data with Geographic Mapping Applications
InactiveUS20080059889A1Comprehensive geographic breadthComprehensive detailDigital data processing detailsRadio transmissionRelational databaseTopic analysis
Owner:PARKER CHERYL +1
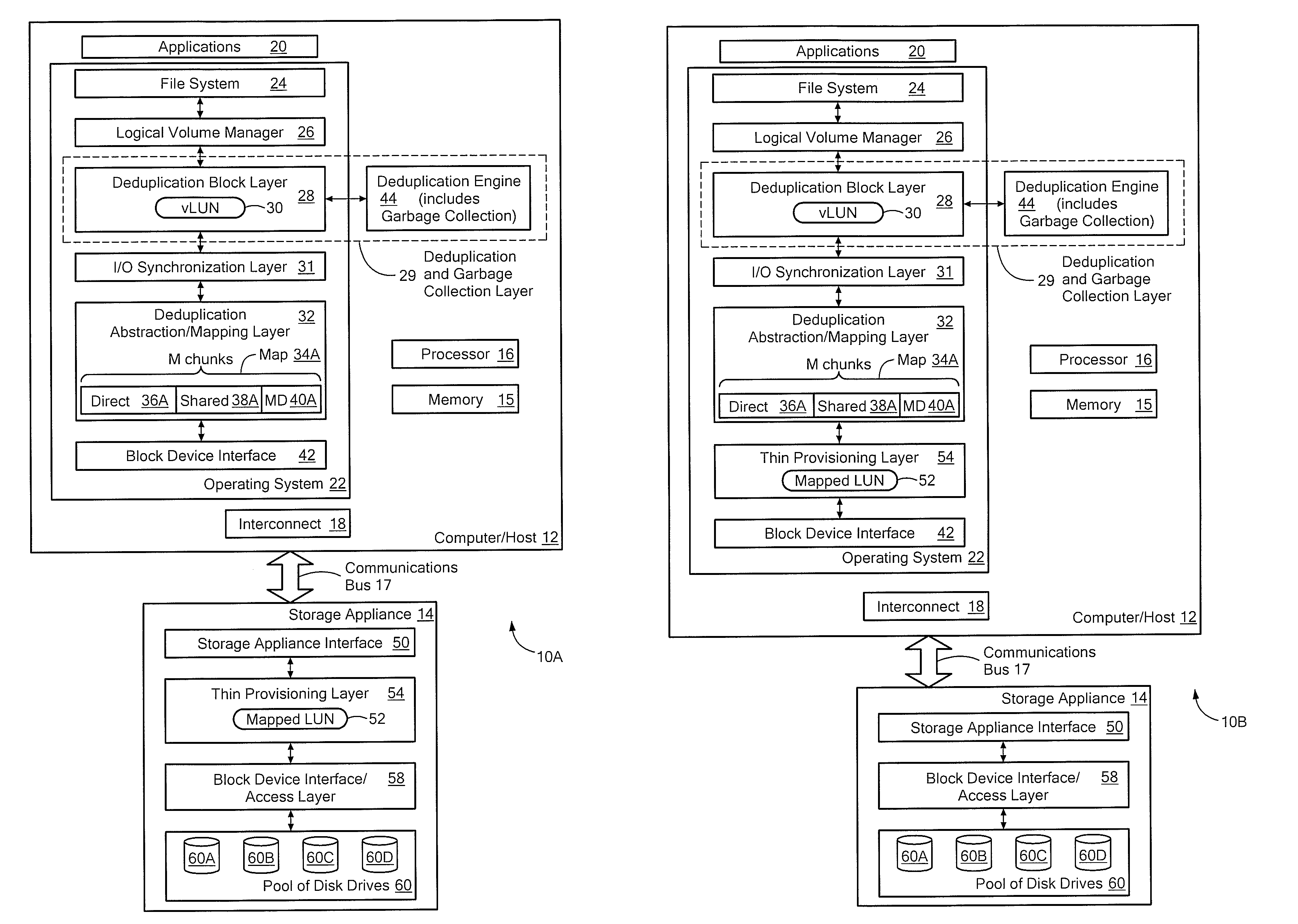
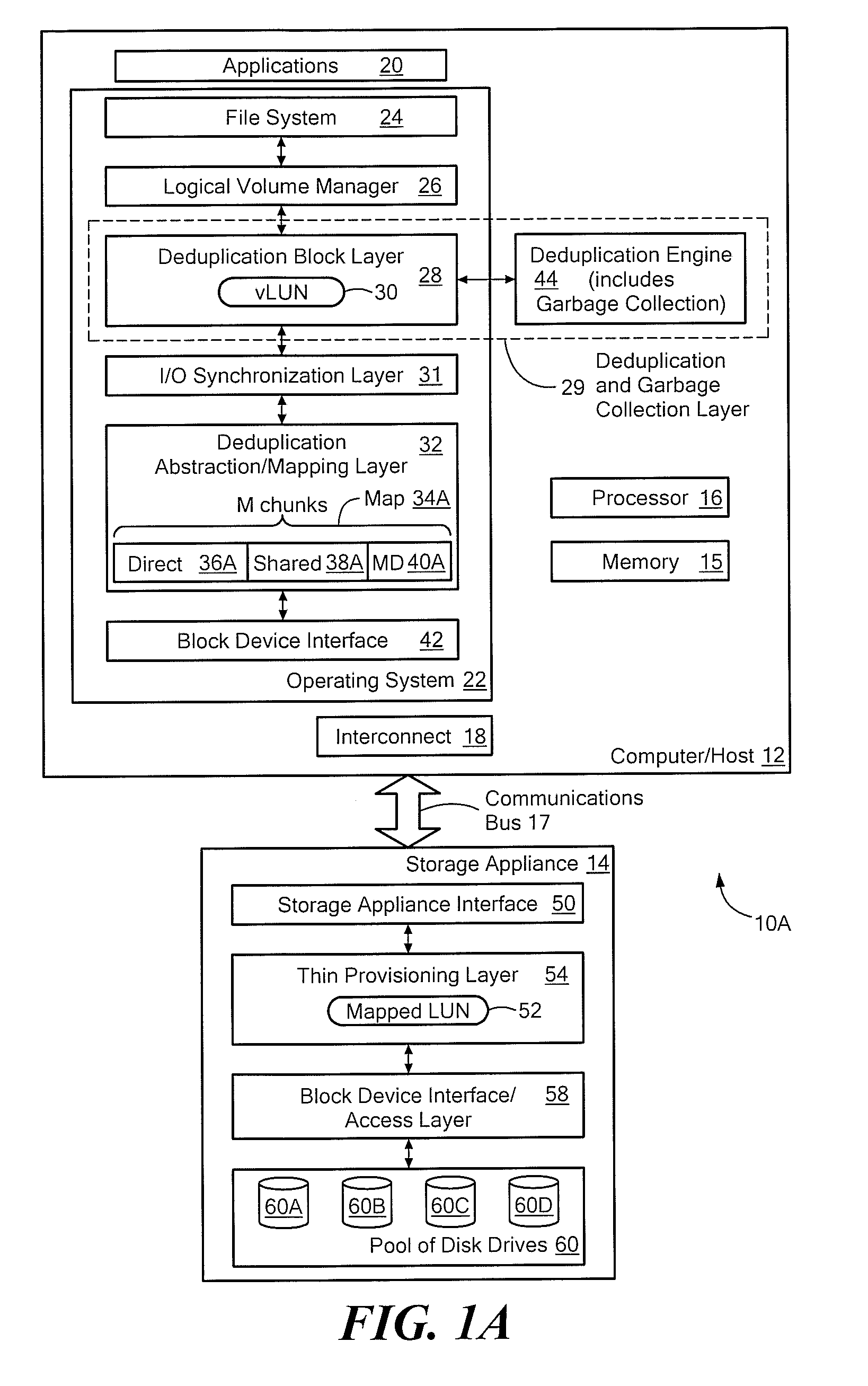
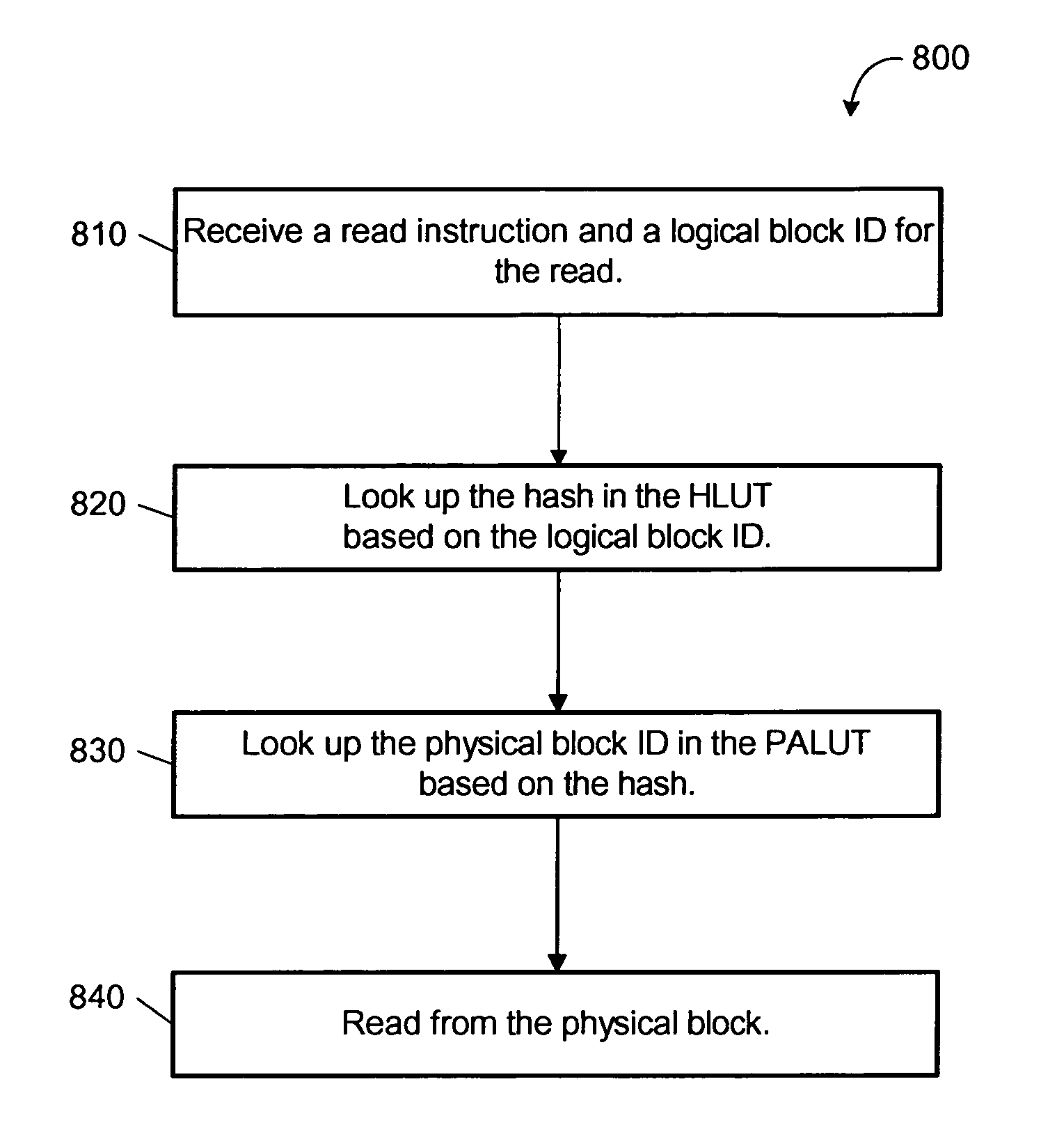
Efficient read/write algorithms and associated mapping for block-level data reduction processes
ActiveUS8140821B1Well formedFacilitates efficient read and write accessError detection/correctionDigital data processing detailsTheoretical computer scienceBlock level
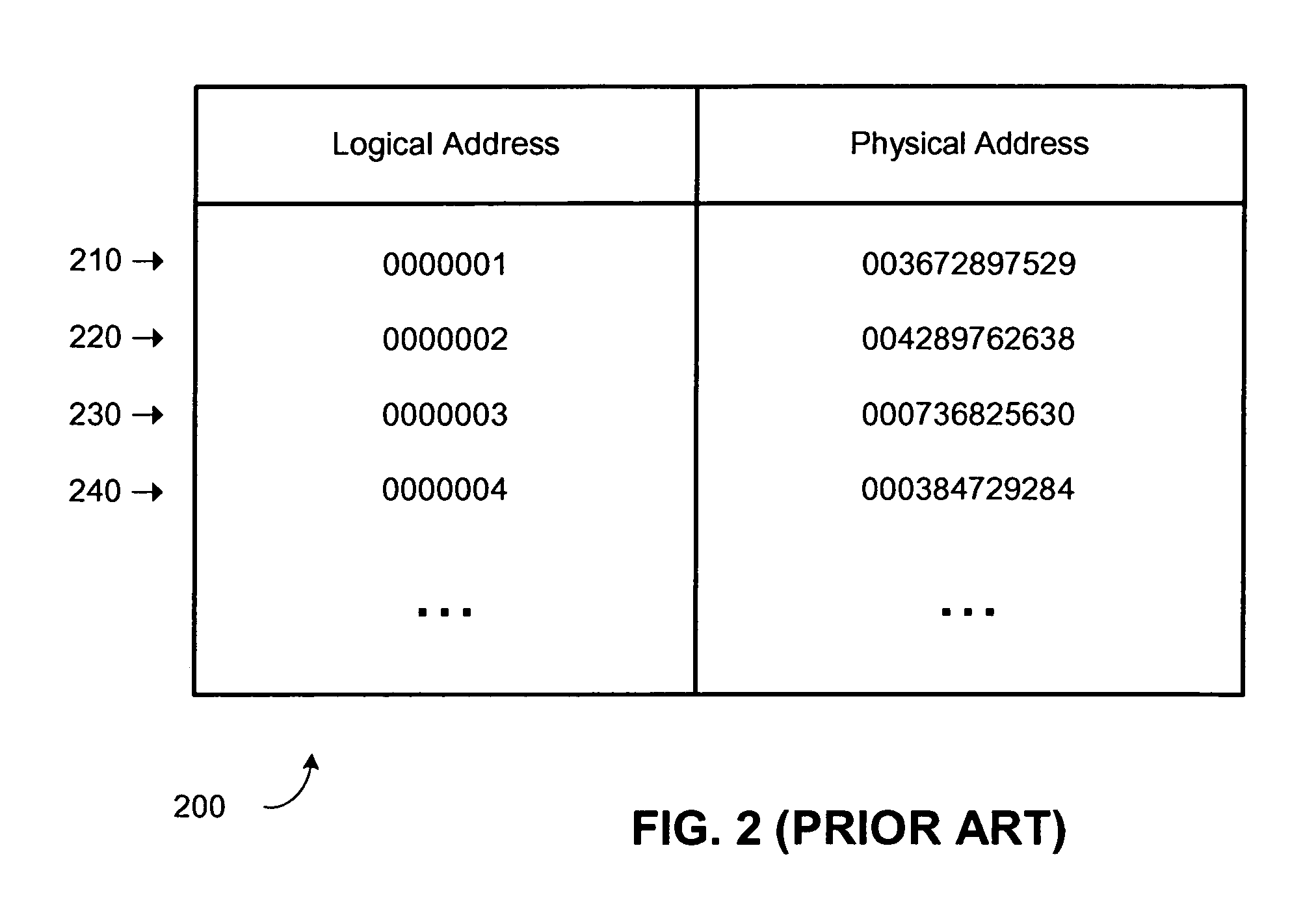
A system configured to optimize access to stored chunks of data is provided. The system comprises a vLUN layer, a mapped LUN layer, and a mapping layer disposed between the vLUN and the mapped LUN. The vLUN provides a plurality of logical chunk addresses (LCAs) and the mapped LUN provides a plurality of physical chunk addresses (PCAs), where each LCA or PCA stores a respective chunk of data. The mapping layer defines a layout of the mapped LUN that facilitates efficient read and write access to the mapped LUN.
Owner:EMC IP HLDG CO LLC
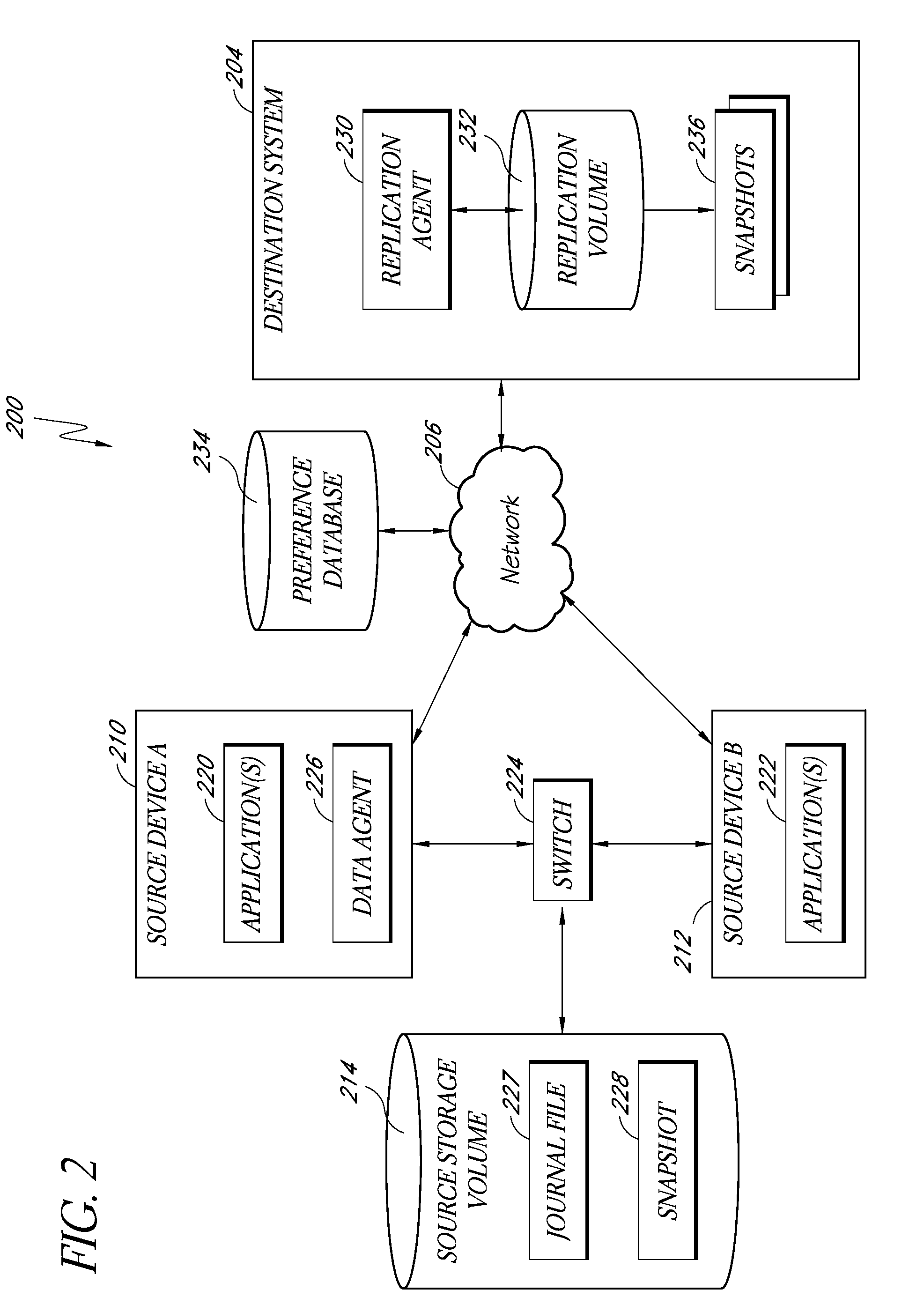
Tracking Block-Level Changes Using Snapshots
ActiveUS20100077165A1Memory loss protectionDigital data processing detailsBlock levelOperating system
Writes to blocks of a protected storage volume that occur between the beginning of a prior backup interval and the beginning of a current backup interval are tracked using a first snapshot that is maintained through the current backup interval. At the beginning of the current backup interval, a second snapshot is generated. Blocks that are indicated by a dirty block list of the first snapshot as having been changed are read from the snapshot volume for the second snapshot and copied to a backup storage volume. For the next backup interval, the second snapshot or alternatively, a newly generated third snapshot, is used to track writes to blocks of a protected storage volume that occur between the beginning of the current backup interval and the beginning of a next backup interval.
Owner:VMWARE INC
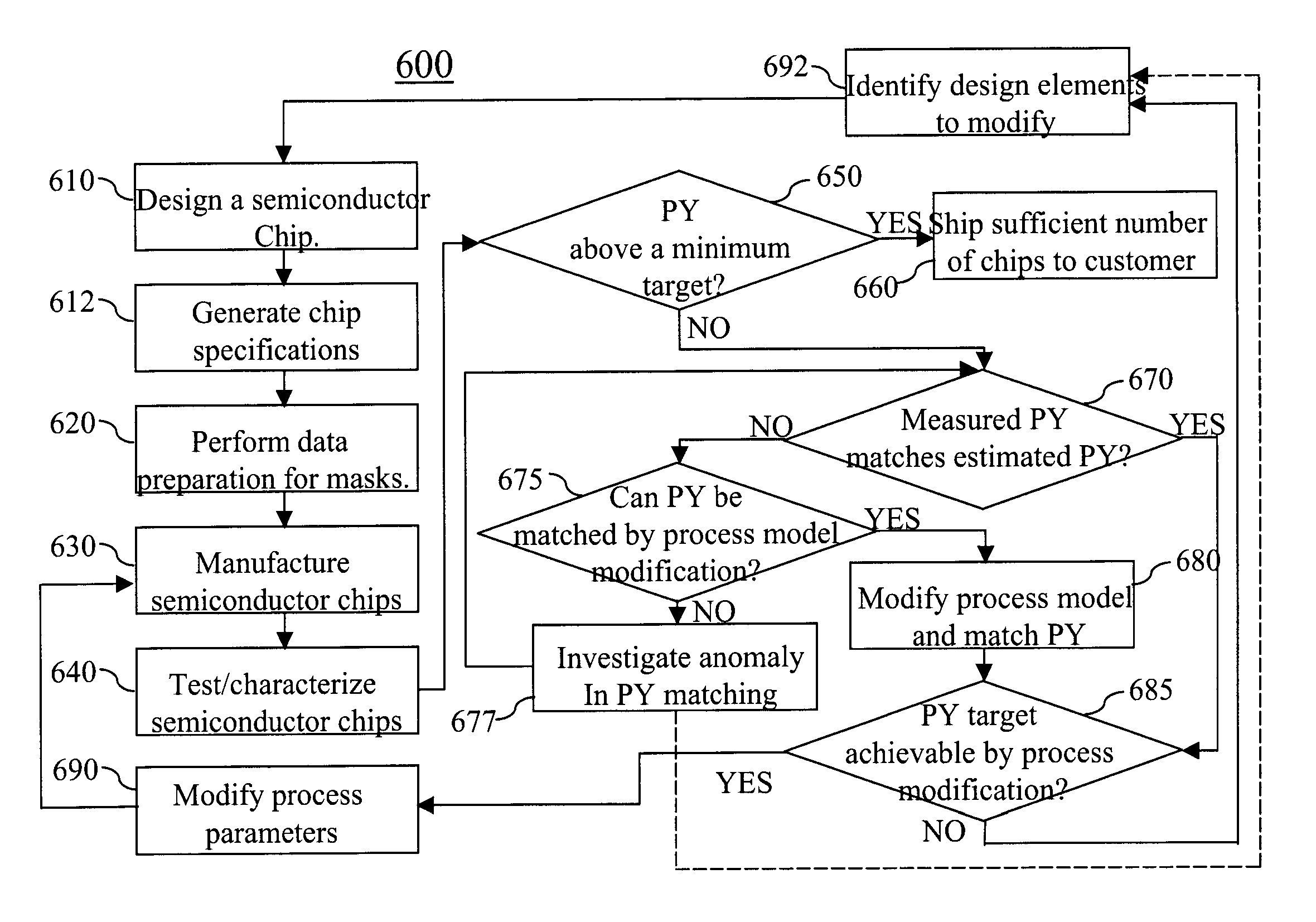
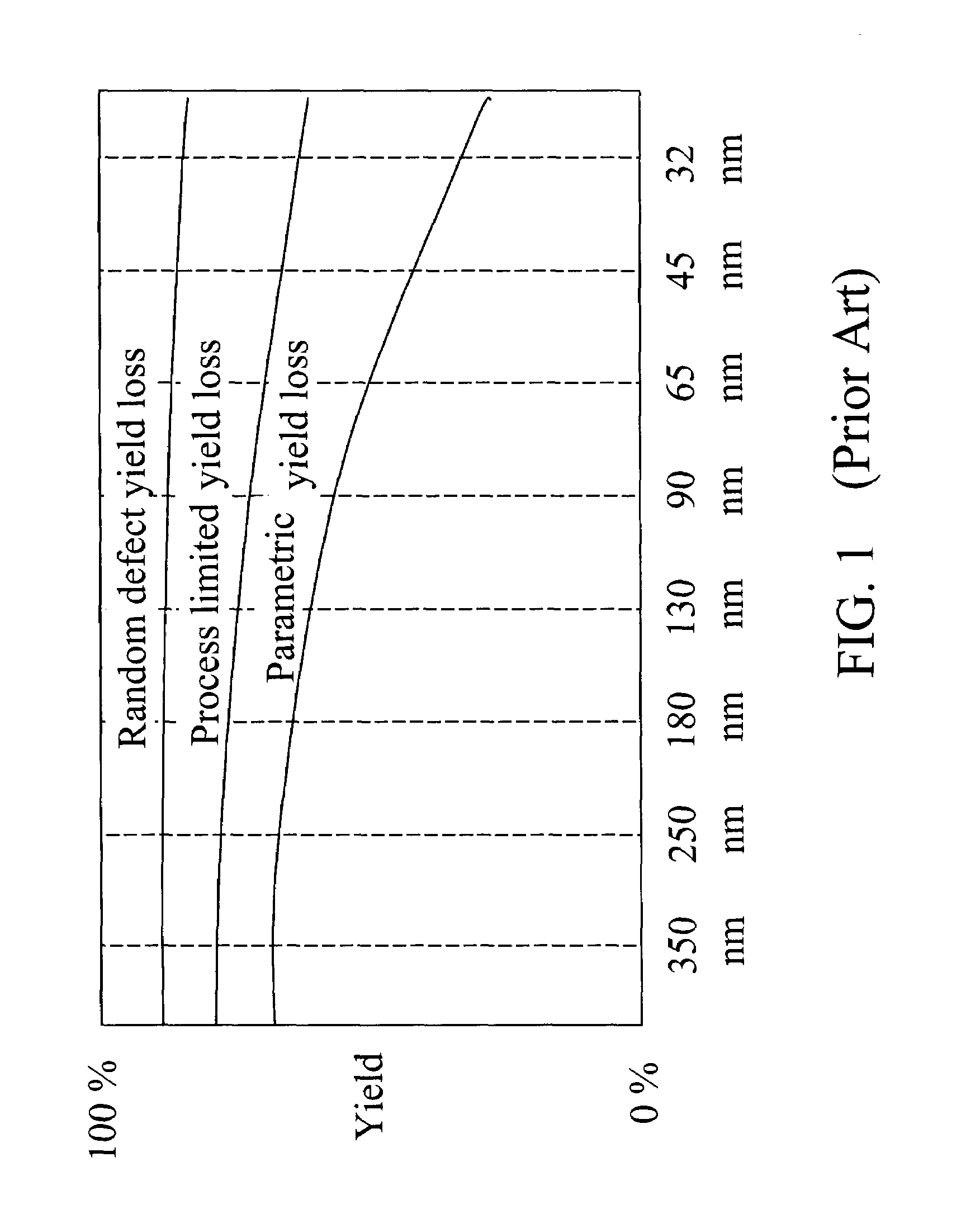
Methods and system for analysis and management of parametric yield
InactiveUS20090106714A1Improve accuracyCAD circuit designSoftware simulation/interpretation/emulationDesign phaseThermionic emission
Impact on parametric performance of physical design choices for transistors is scored for on-current and off-current of the transistors. The impact of the design parameters are incorporated into parameters that measure predicted shift in mean on-current and mean off-current and parameters that measure predicted increase in deviations in the distribution of on-current and the off-current. Statistics may be taken at a cell level, a block level, or a chip level to optimize a chip design in a design phase, or to predict changes in parametric yield during manufacturing or after a depressed parametric yield is observed. Further, parametric yield and current level may be predicted region by region and compared with observed thermal emission to pinpoint any anomaly region in a chip to facilitate detection and correction in any mistakes in chip design.
Owner:MENTOR GRAPHICS CORP
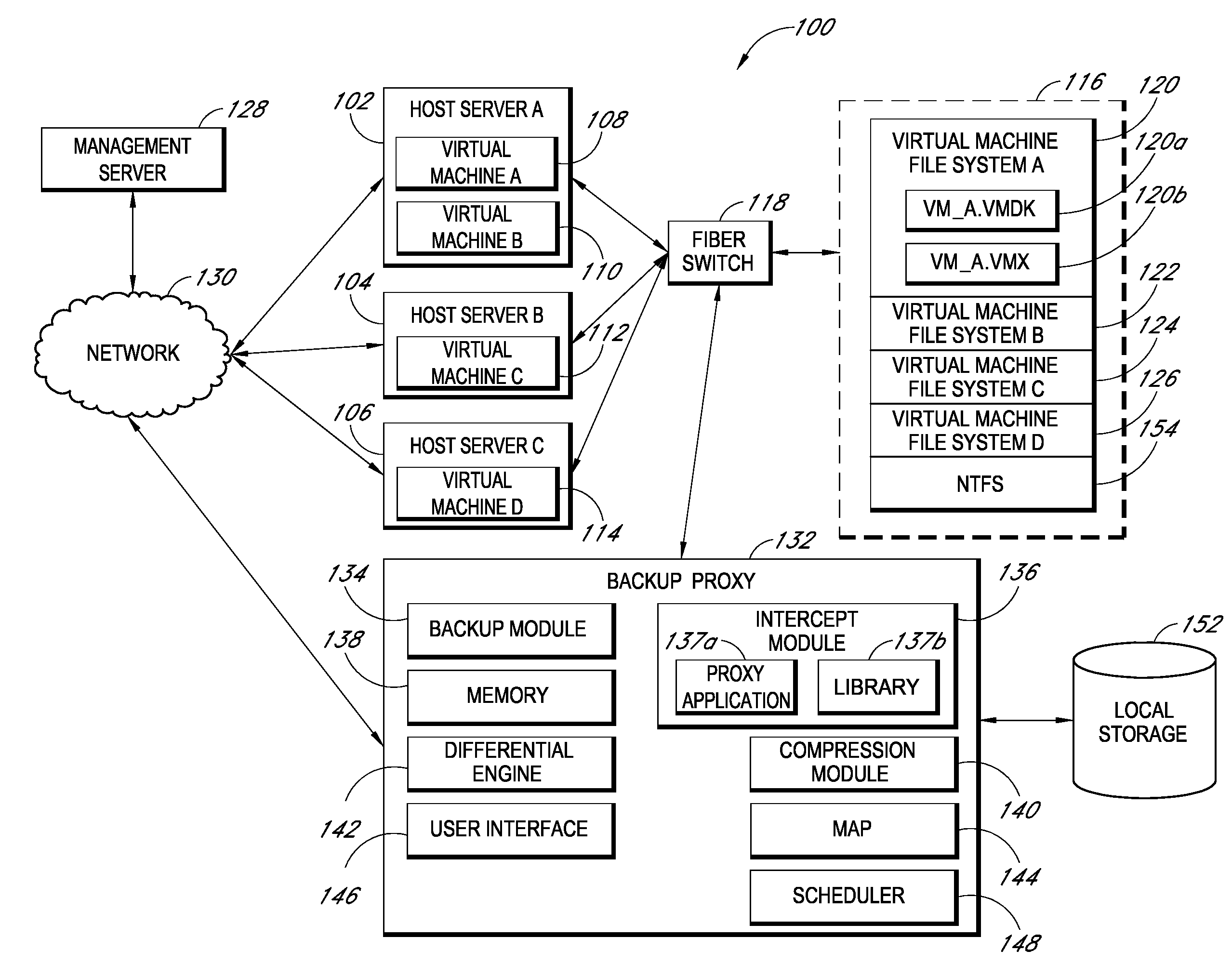
Backup systems and methods for a virtual computing environment
ActiveUS8060476B1Reduce the amount requiredReduce image sizeError detection/correctionDigital data processing detailsApplication programming interfaceApplication software
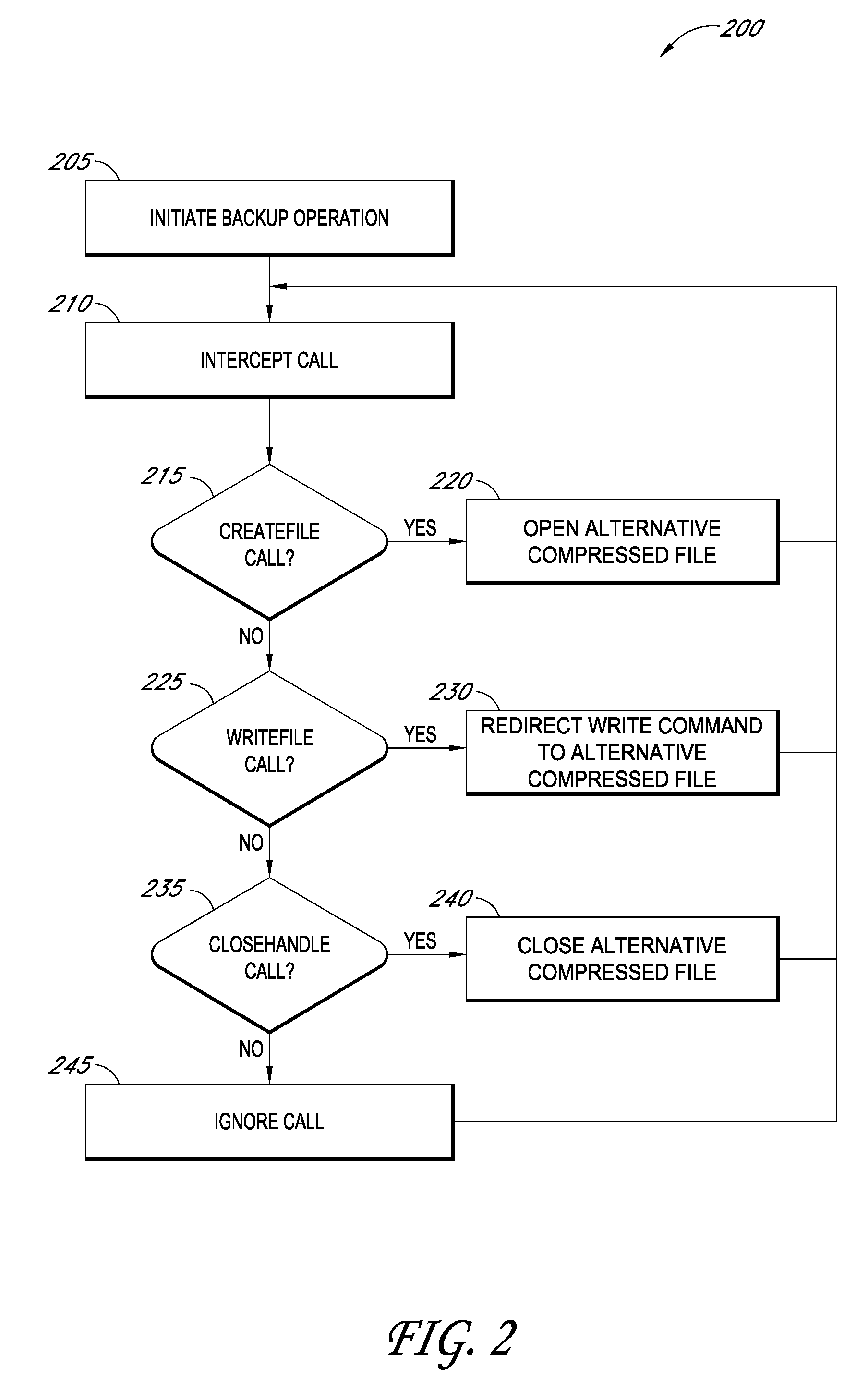
Improved backup and storage operations are disclosed for virtual computing environments using a backup proxy server to perform storage operations on one or more virtual machine disks. The proxy server can include a module that intercepts application programming interface (API) calls, for writing backup data to a first location, prior to the data arriving on the proxy disk. During the intercept process, the data can be compressed in memory pages of the proxy server and redirected to an alternative backup disk location. The proxy server can also include a differential engine that identifies changes to the virtual machine disk at the block level since the last full backup. The differential engine can advantageously leverage memory pages of the proxy server to compare differences between signatures of blocks of the last full backup with signatures of new blocks. Subsequently, only blocks with non-matching signatures are processed for backup.
Owner:QUEST SOFTWARE INC
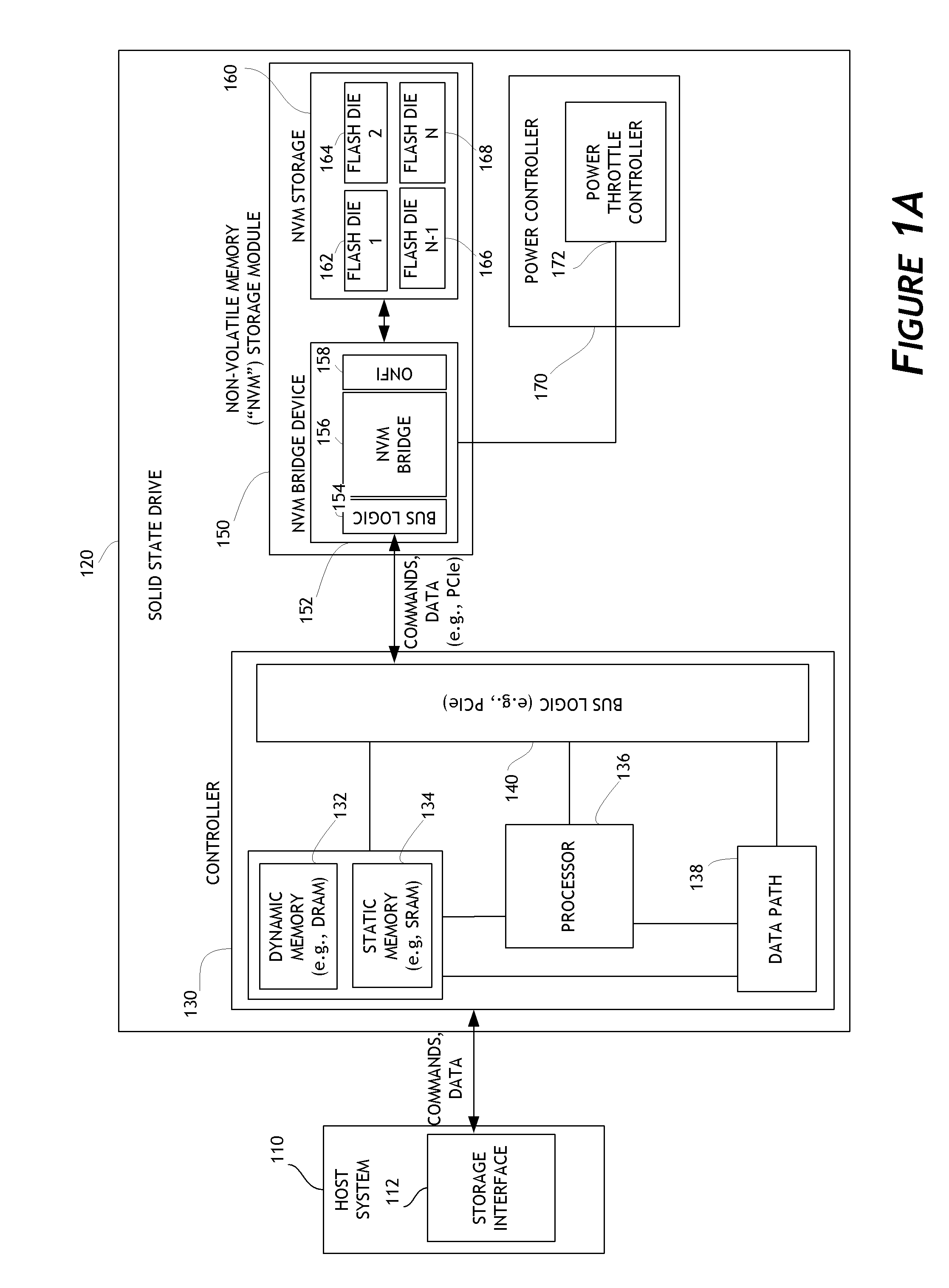
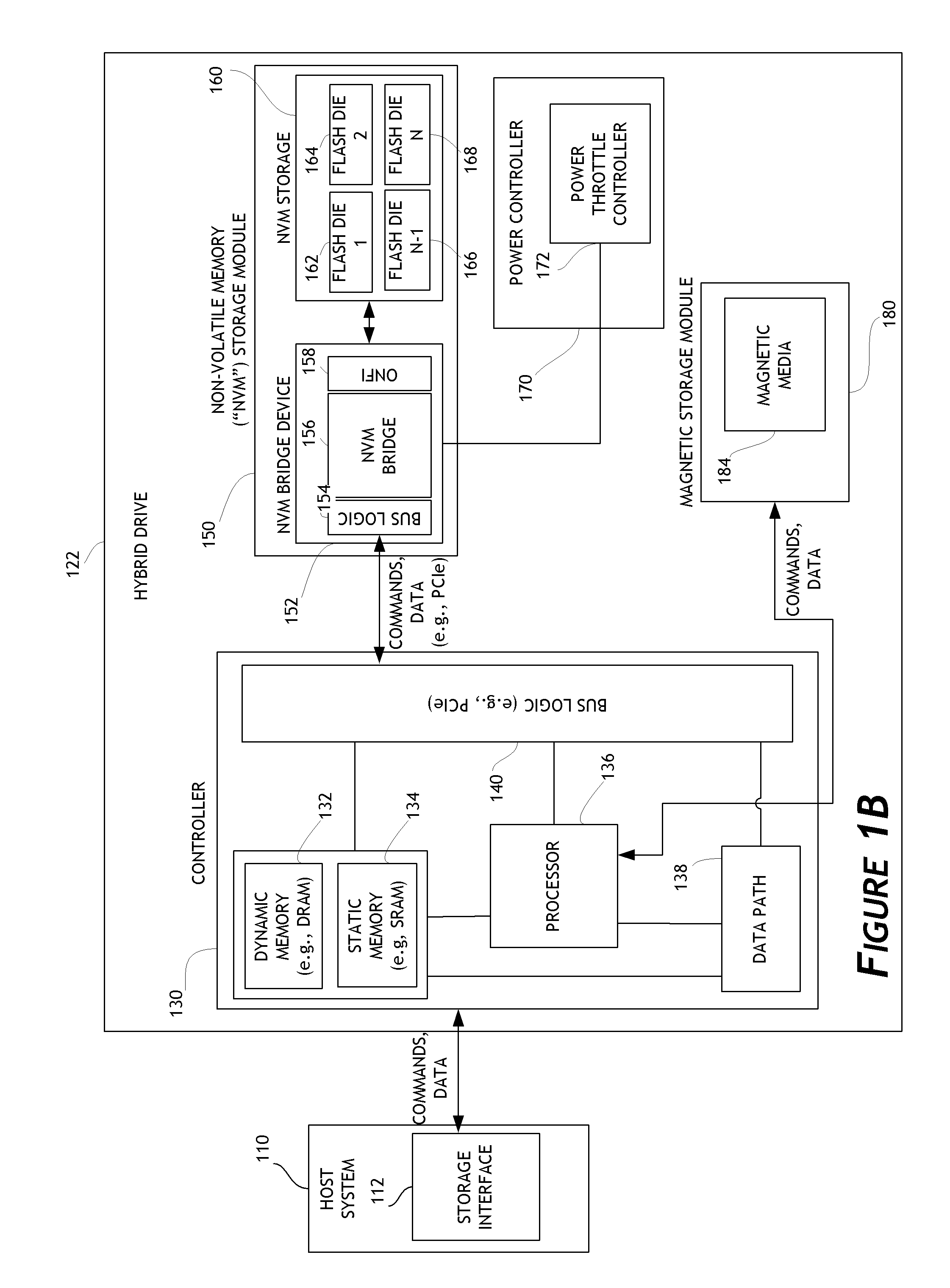
Systems and methods for an enhanced controller architecture in data storage systems
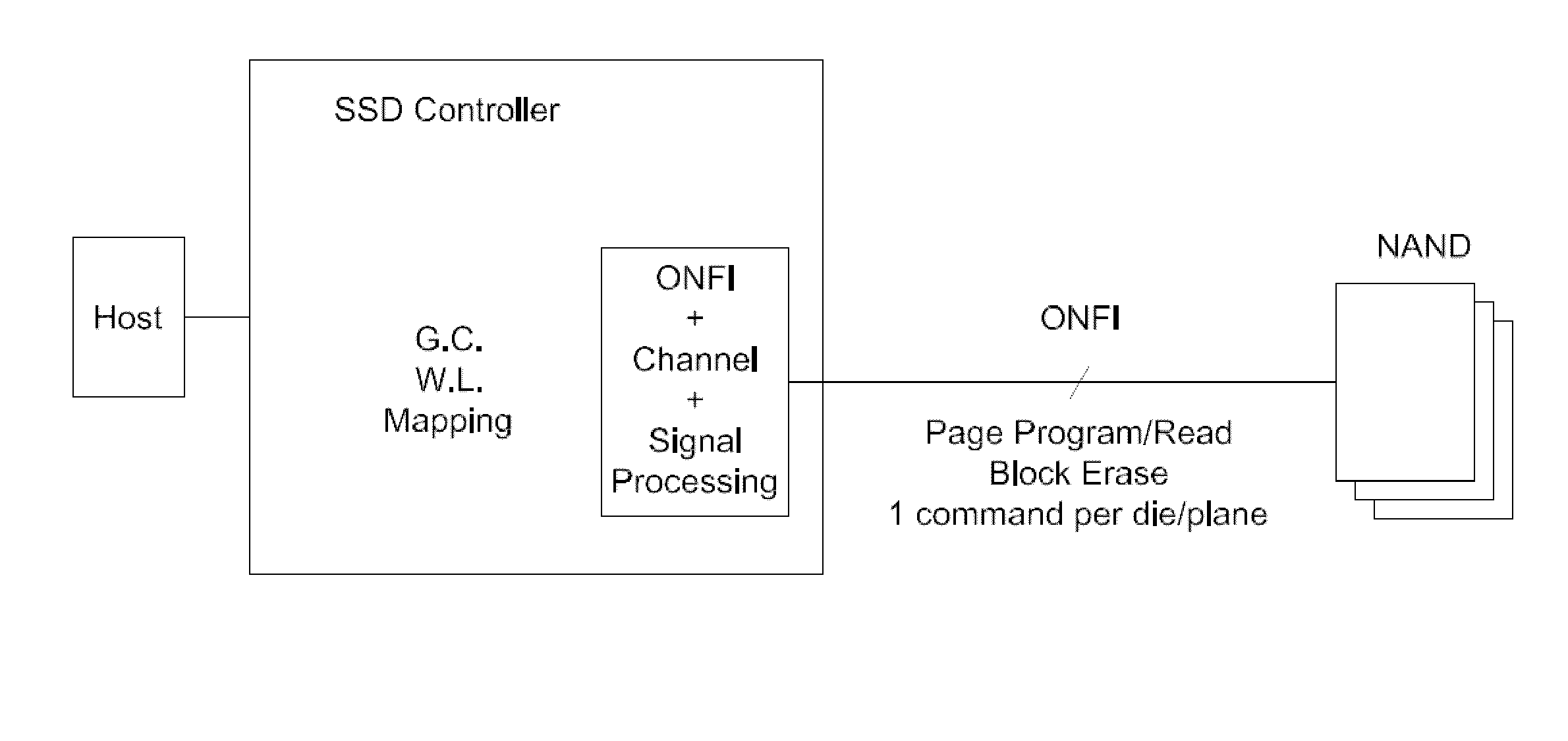
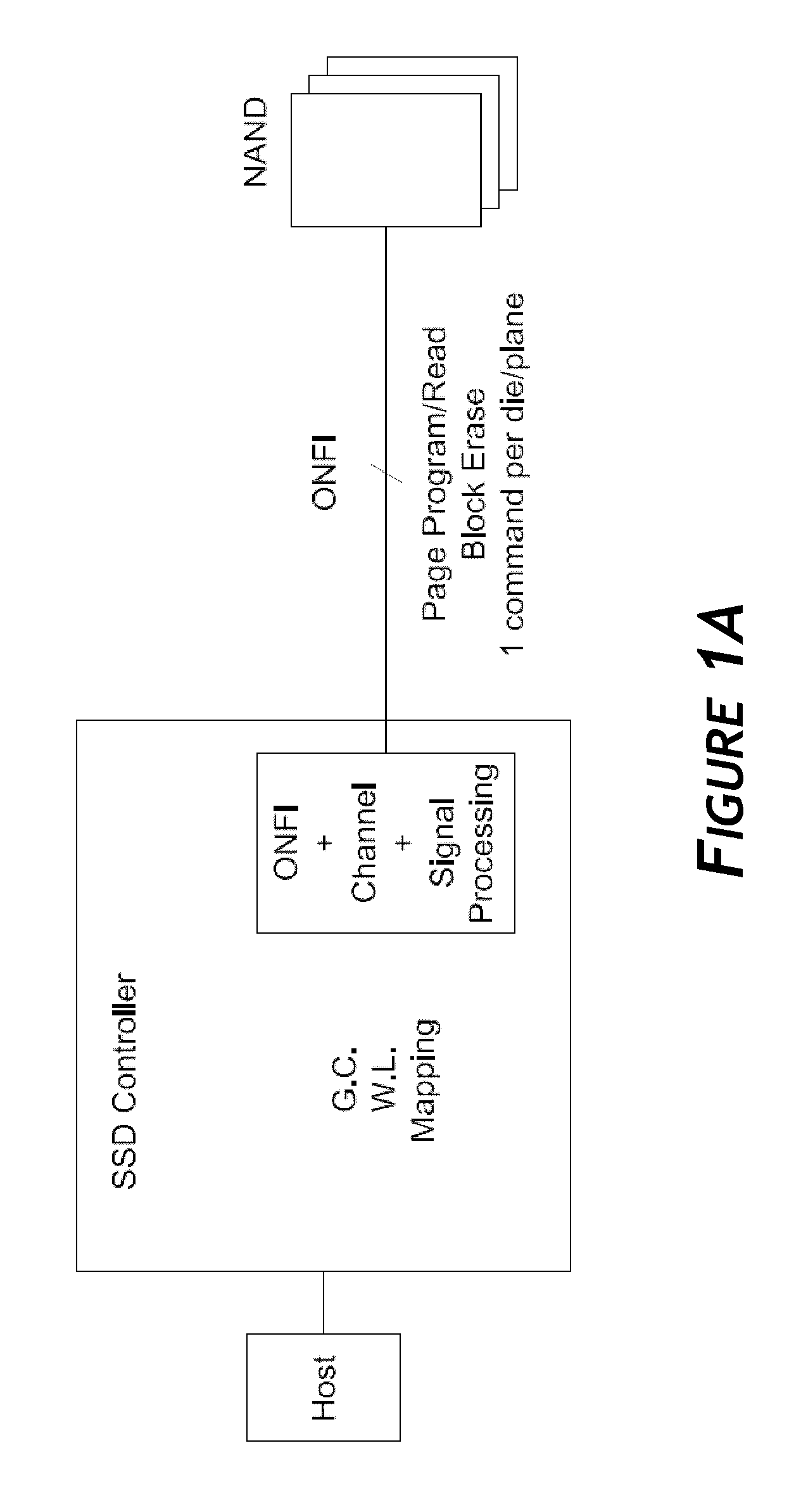
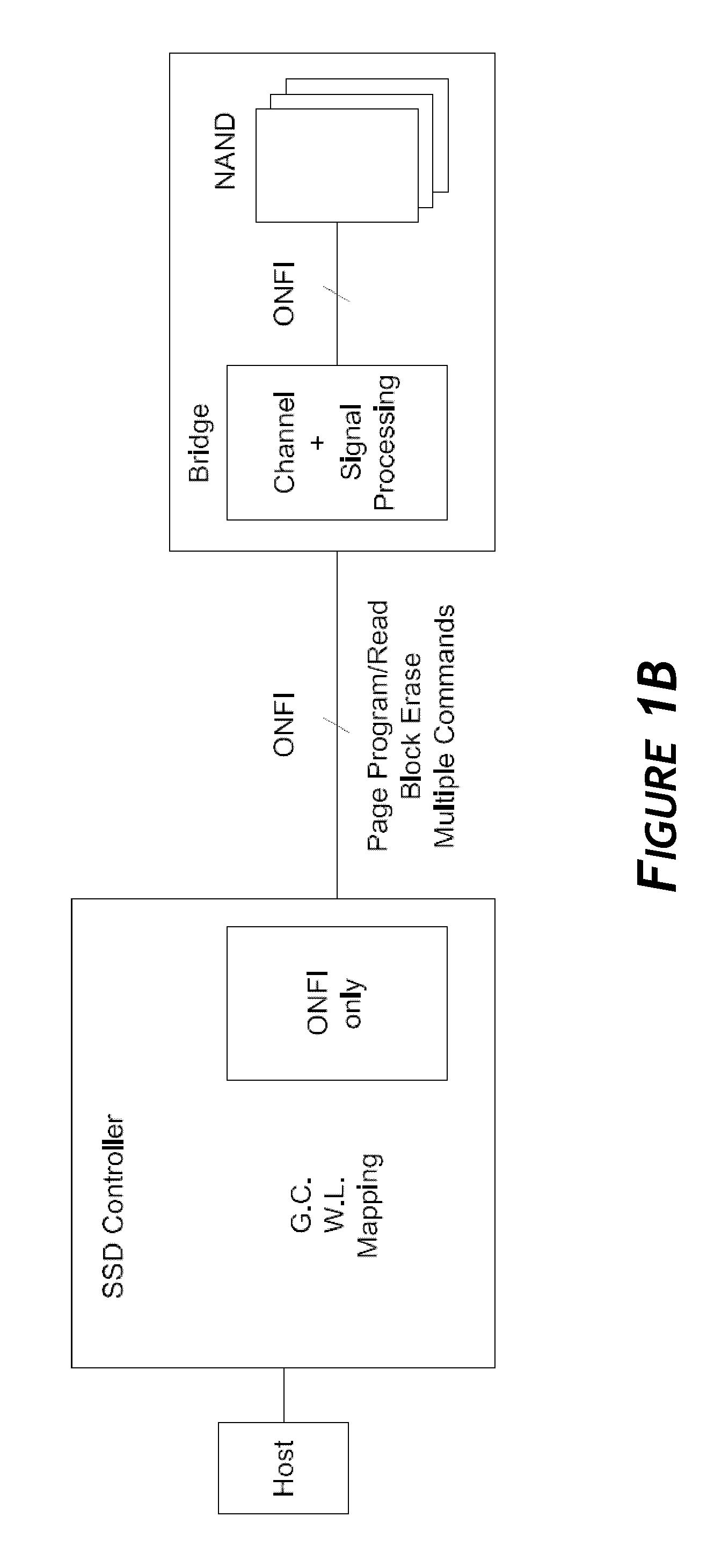
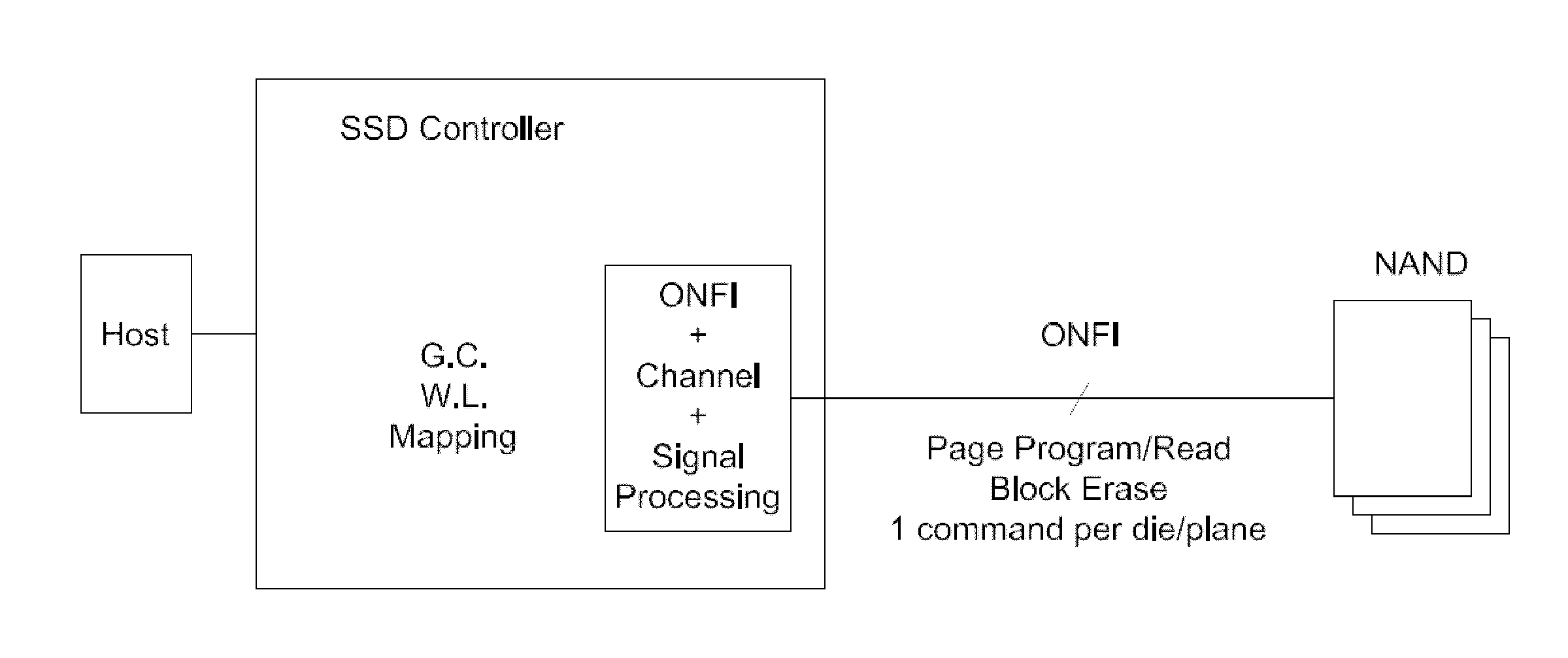
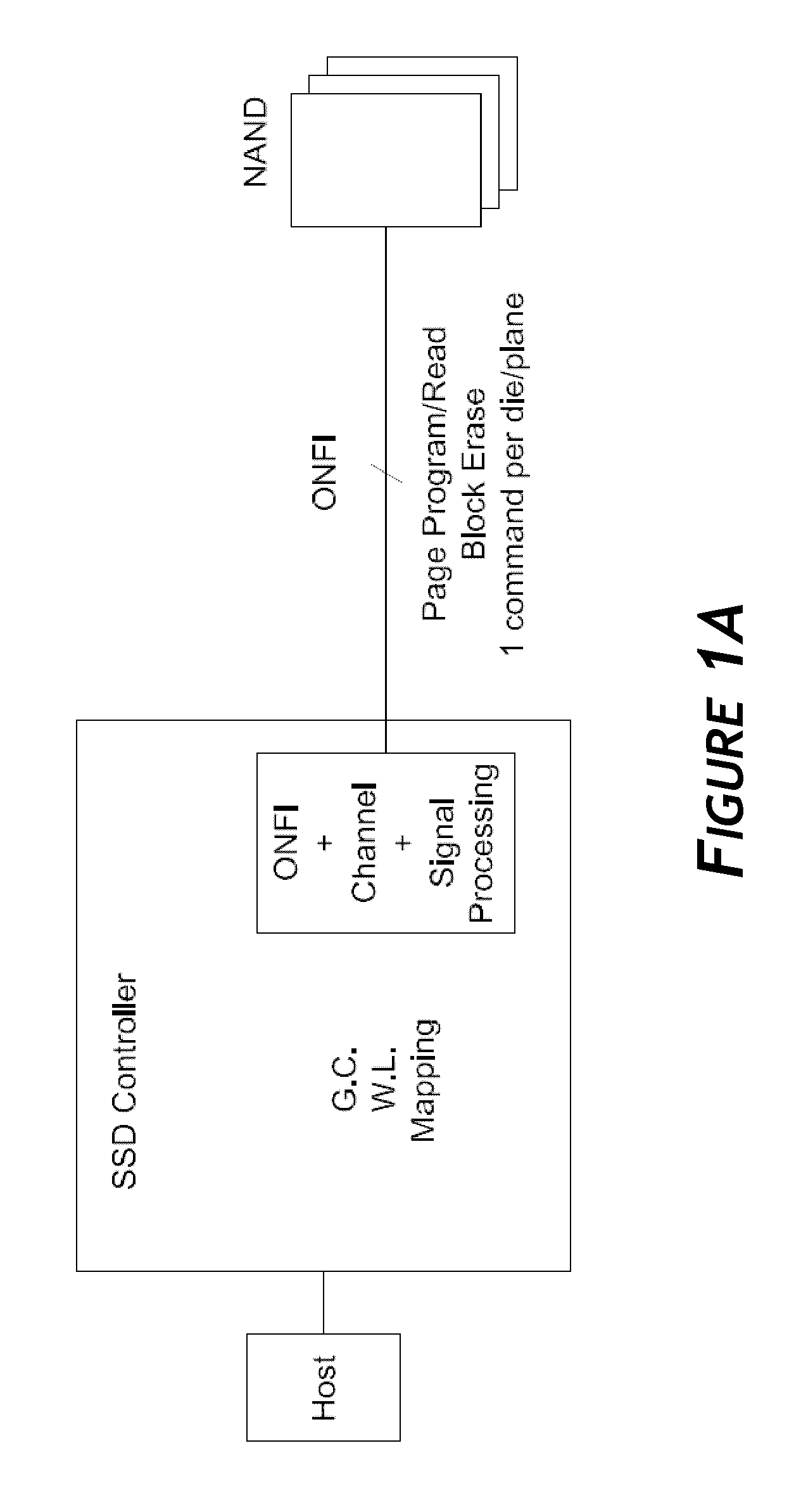
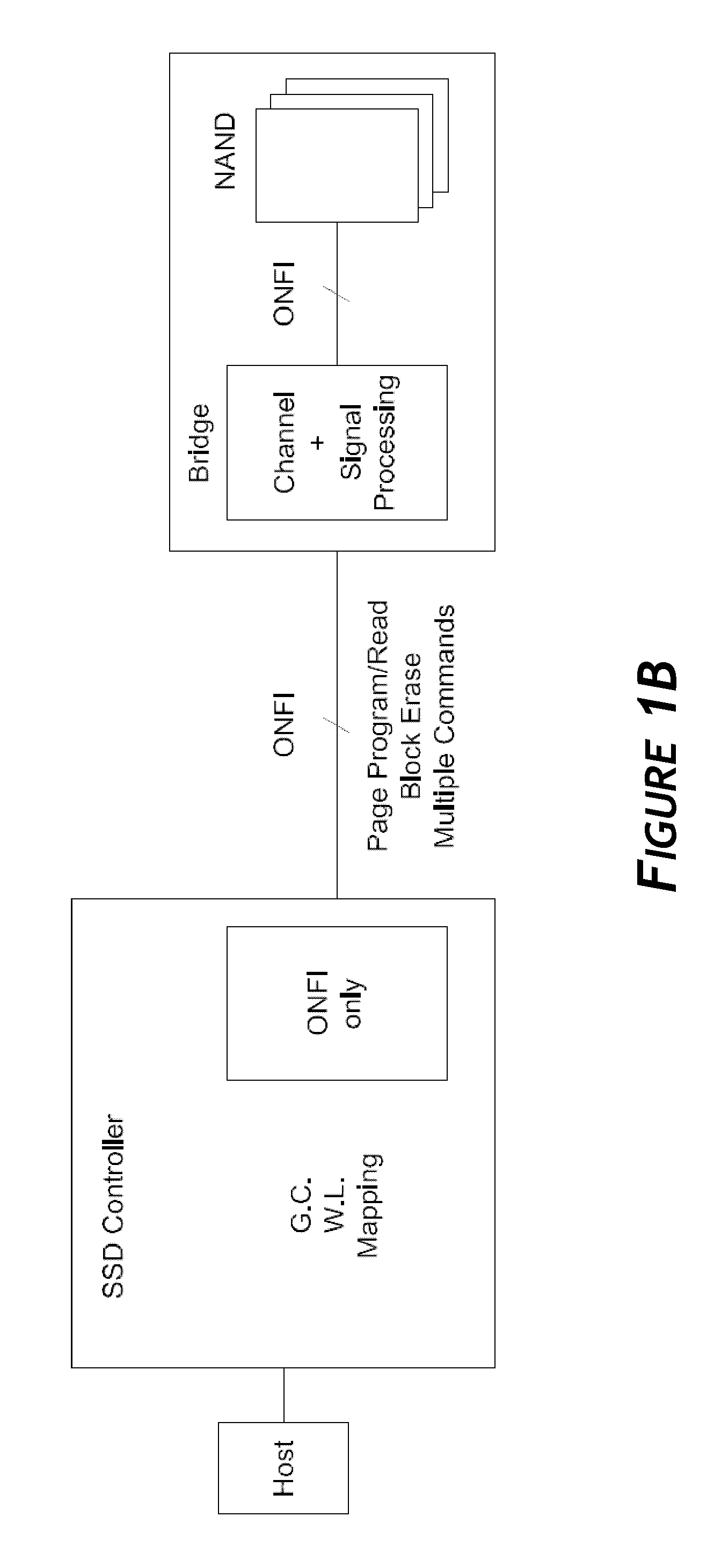
Disclosed herein is a controller architecture that pairs a controller with a NVM (non-volatile memory) storage system over a high-level, high speed interface such as PCIe. In one embodiment, the NVM storage system includes a bridge that communicates with the controller via the high-level interface, and controls the NVM via an interface (e.g., ONFI). The controller is provided a rich set of physical level of controls over individual elements of the NVM. In one embodiment, the controller is implemented in a higher powered processor that supports advanced functions such as mapping, garbage collection, wear leveling, etc. In one embodiment, the bridge is implemented in a lower powered processor and performs basic signal processing, channel management, basic error correction functions, etc. This labor division provides the controller physical control of the NVM over a fast, high-level interface, resulting in the controller managing the NVM at both the page and block level.
Owner:WESTERN DIGITAL TECH INC
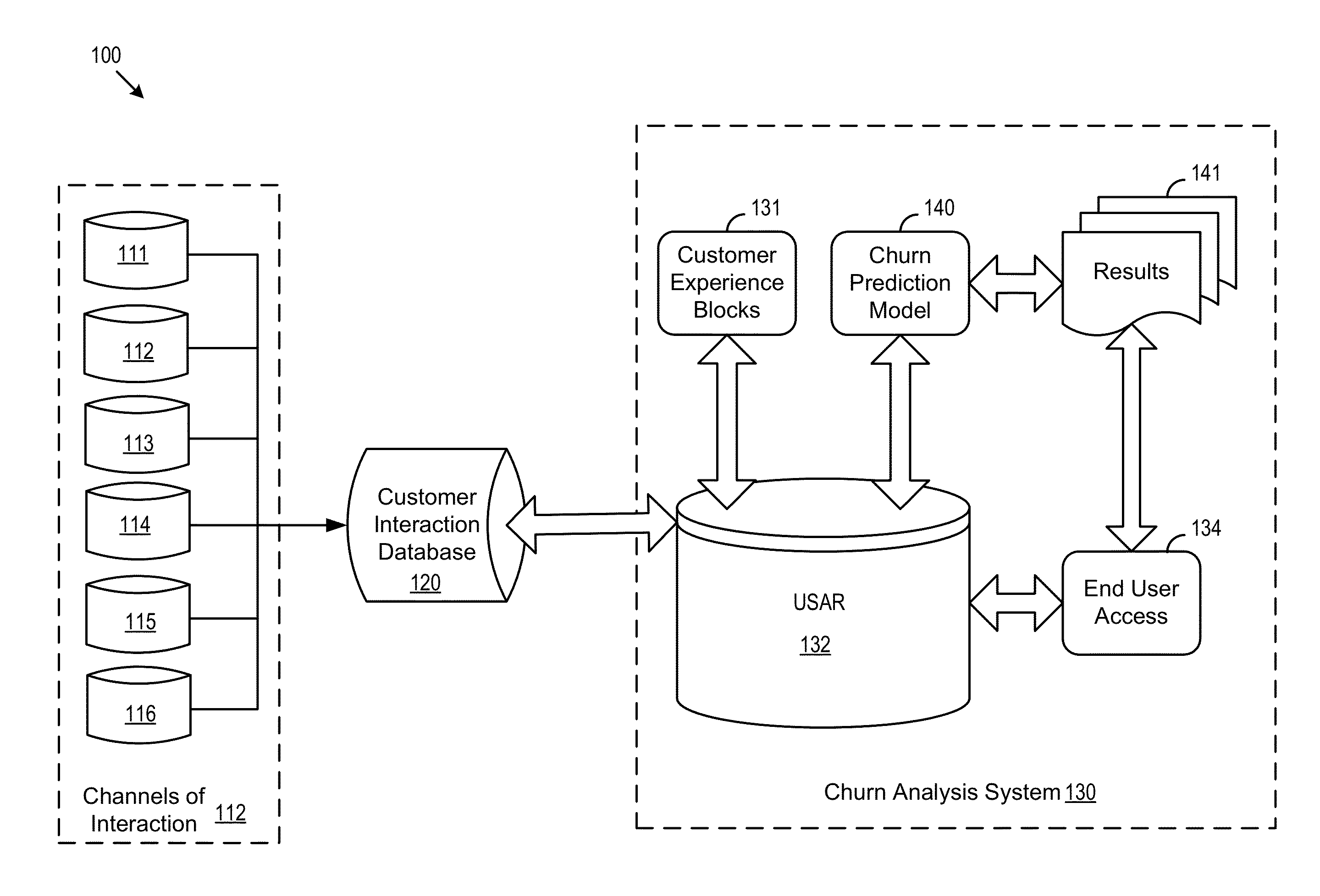
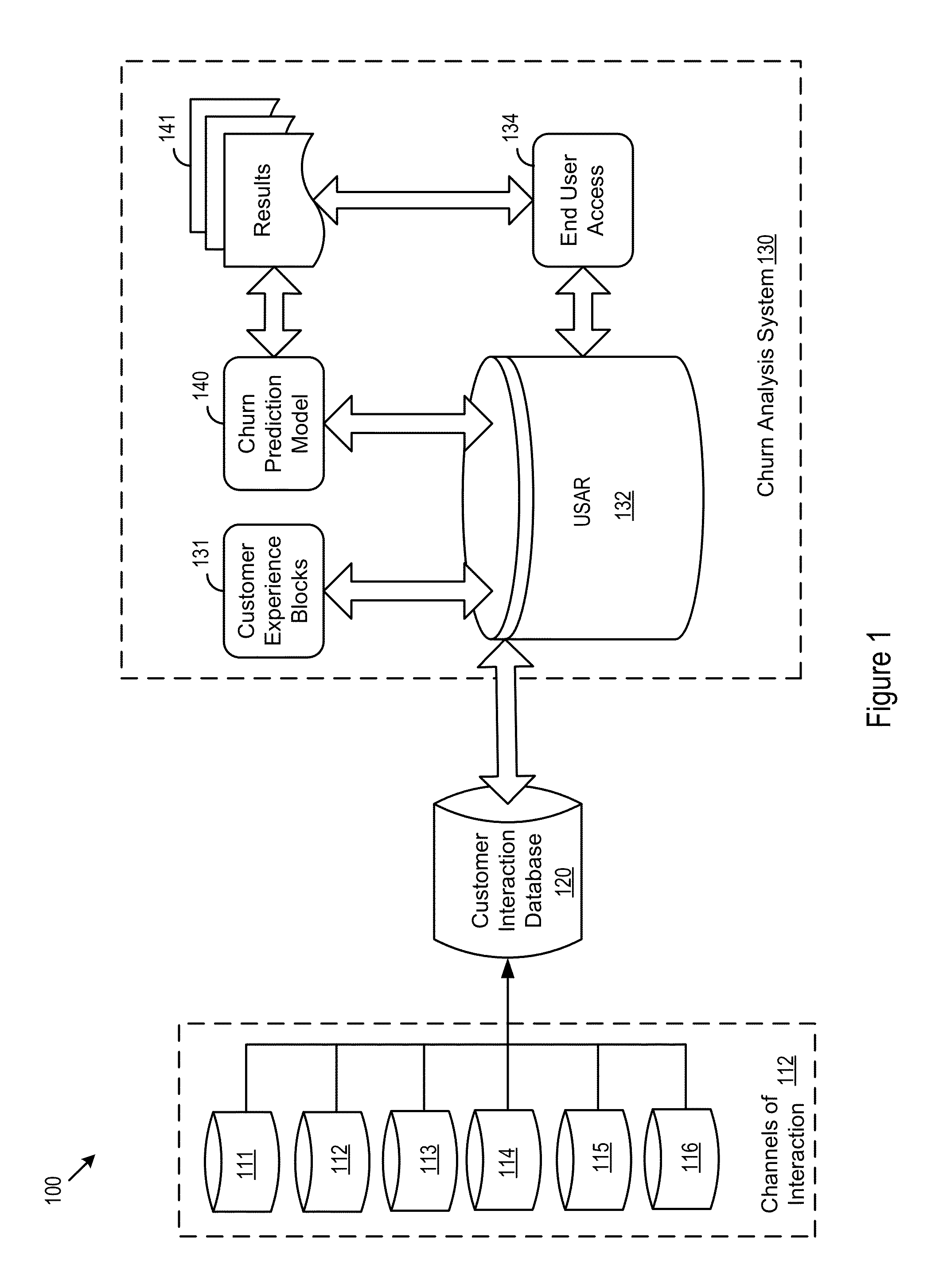
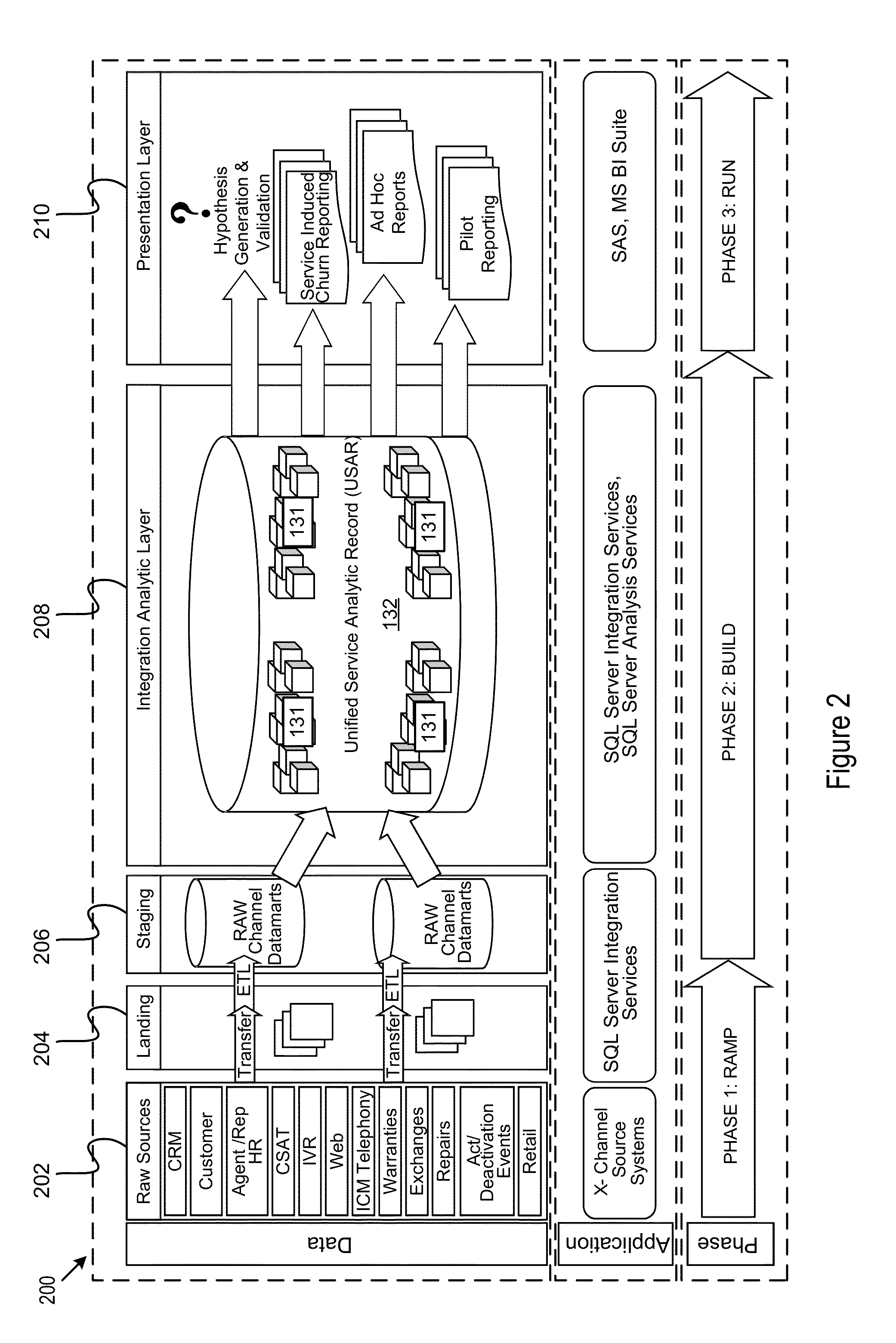
Churn analysis system
A churn analysis system helps a business analyze, predict, and reduce customer churn. The system analyzes customer experiences by using an insightful block level approach to correlate customer experience with customer churn. Through the block level approach, the system is able to more accurately predict and effectively reduce future customer churn. As a result, businesses are able to reduce customer acquisition costs and improve customer retention rates.
Owner:ACCENTURE GLOBAL SERVICES LTD
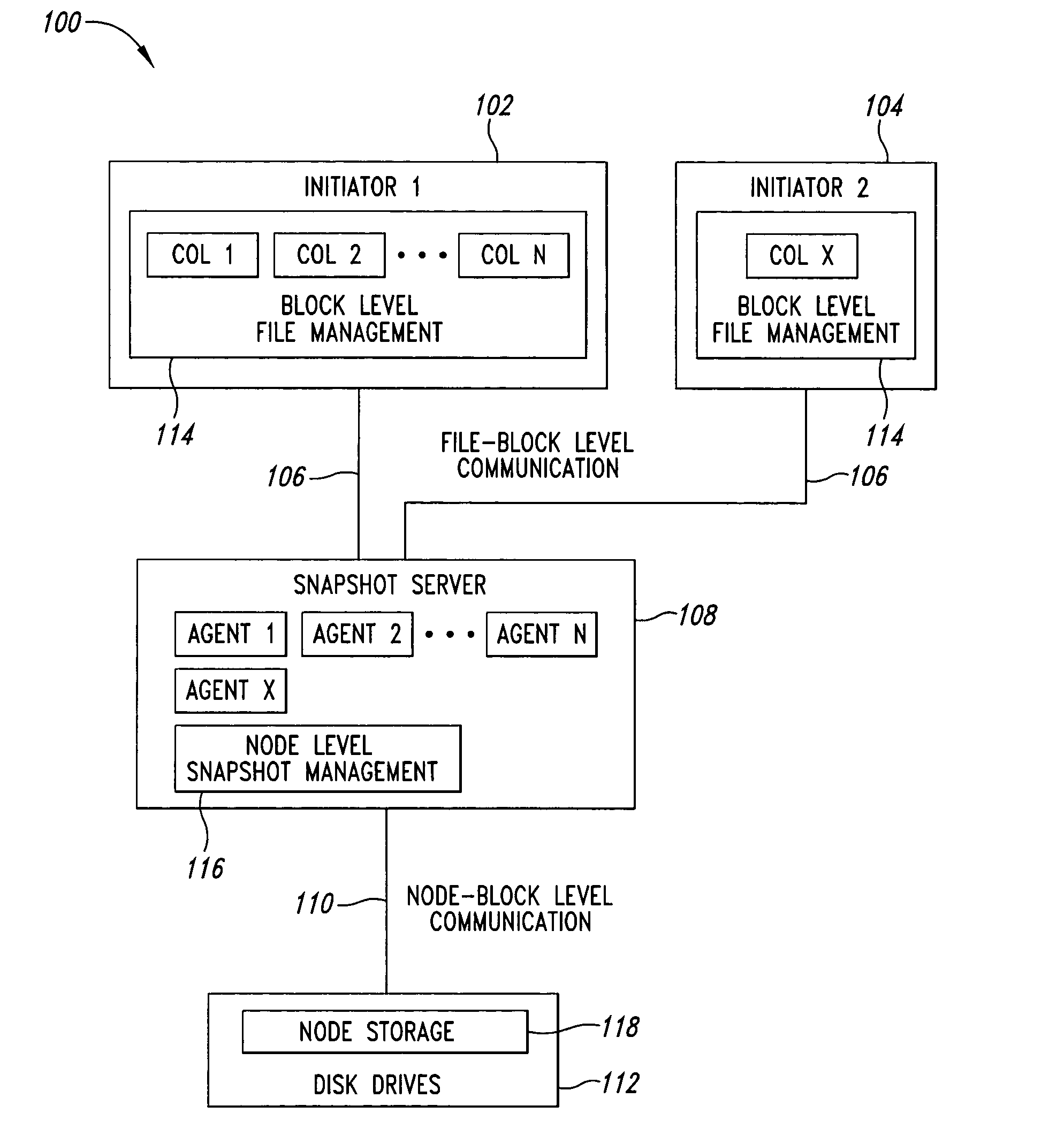
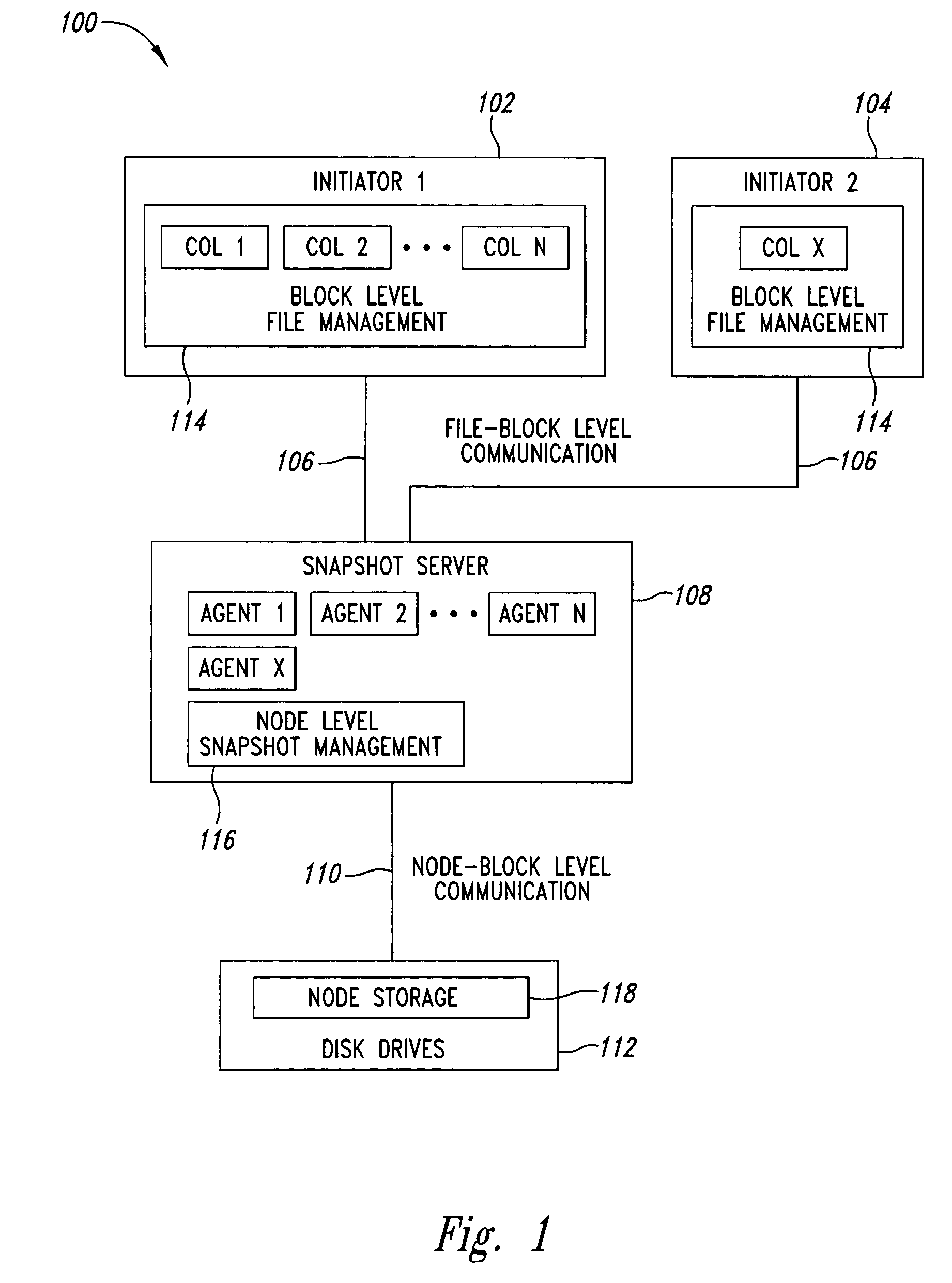
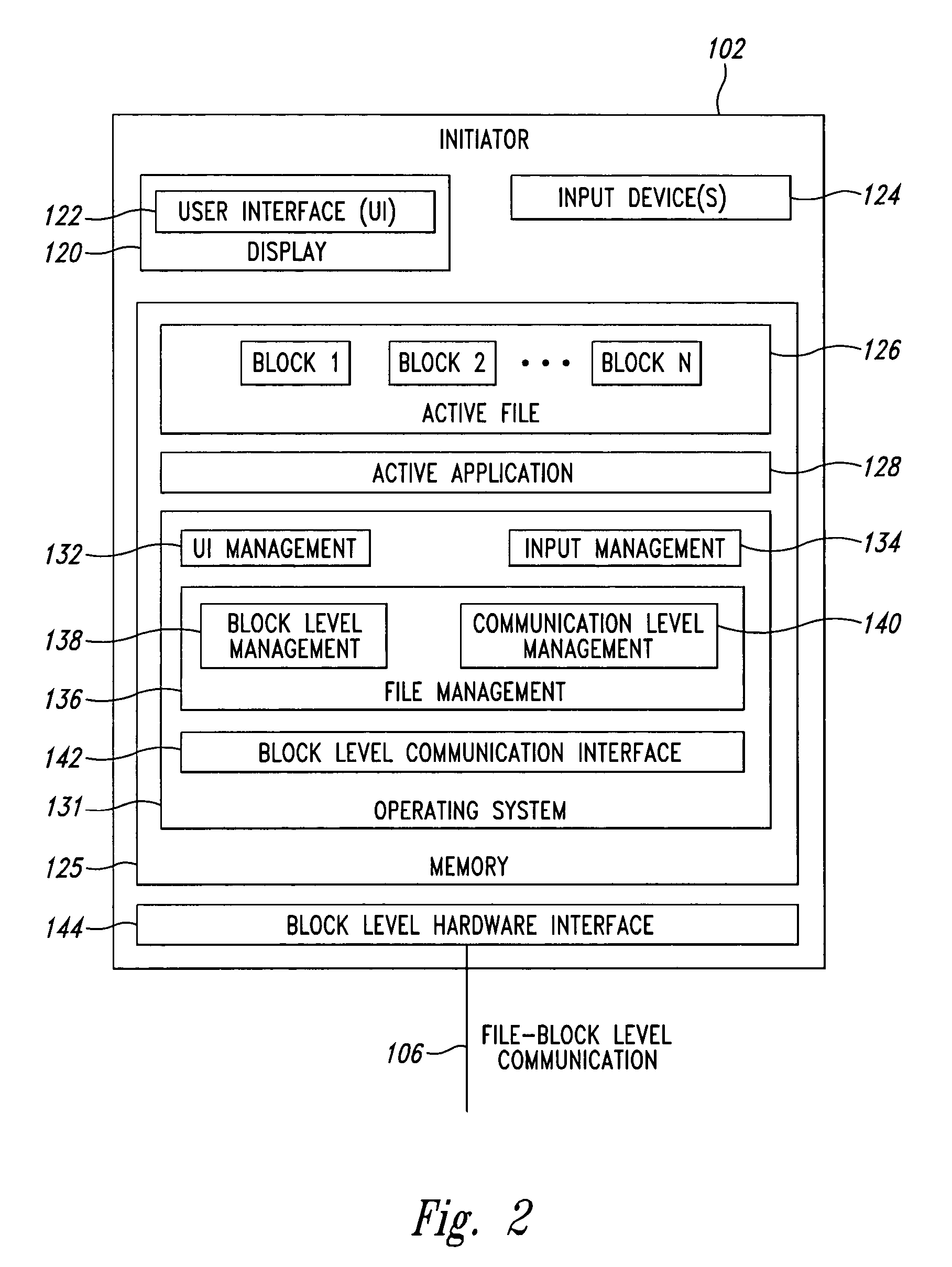
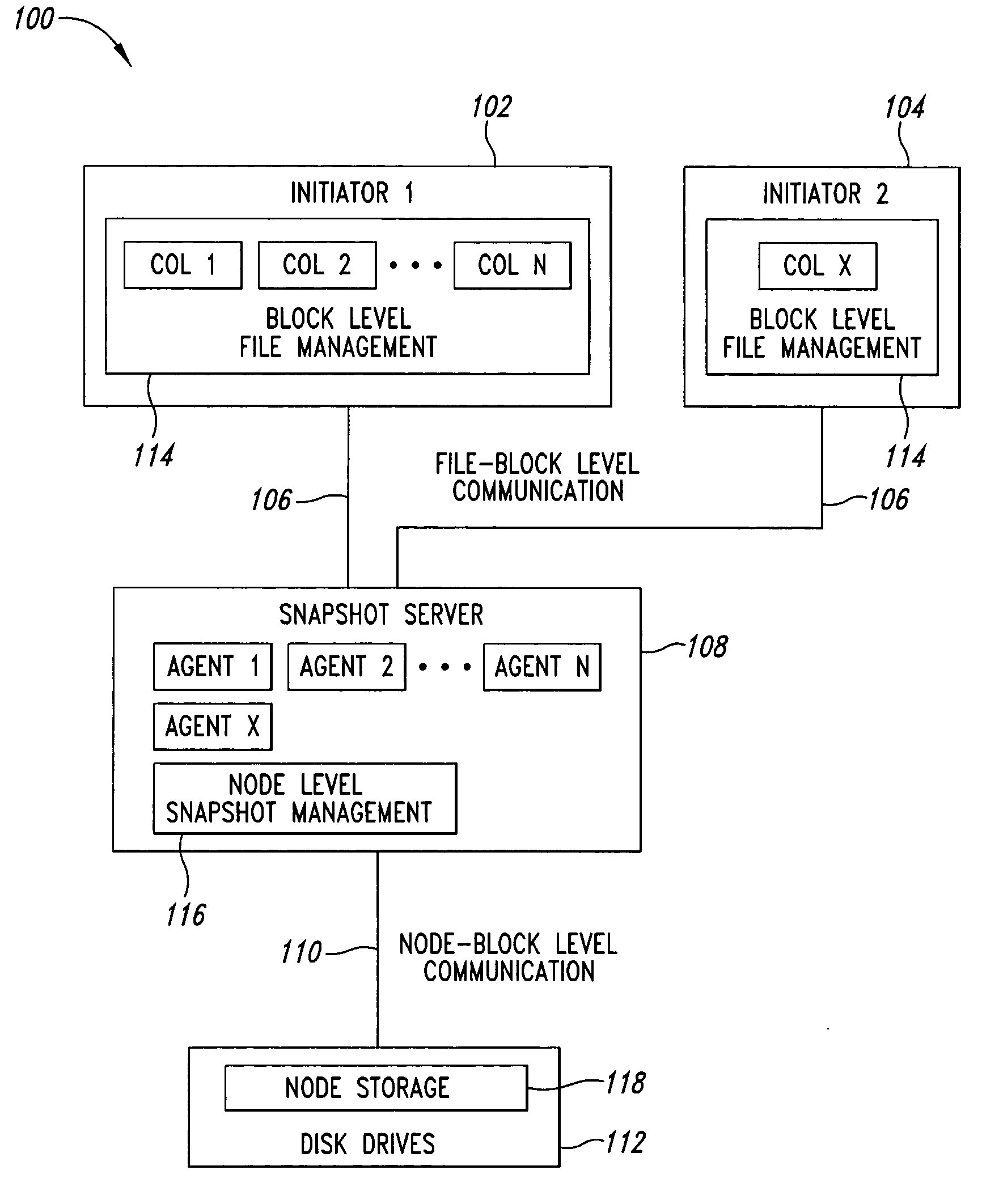
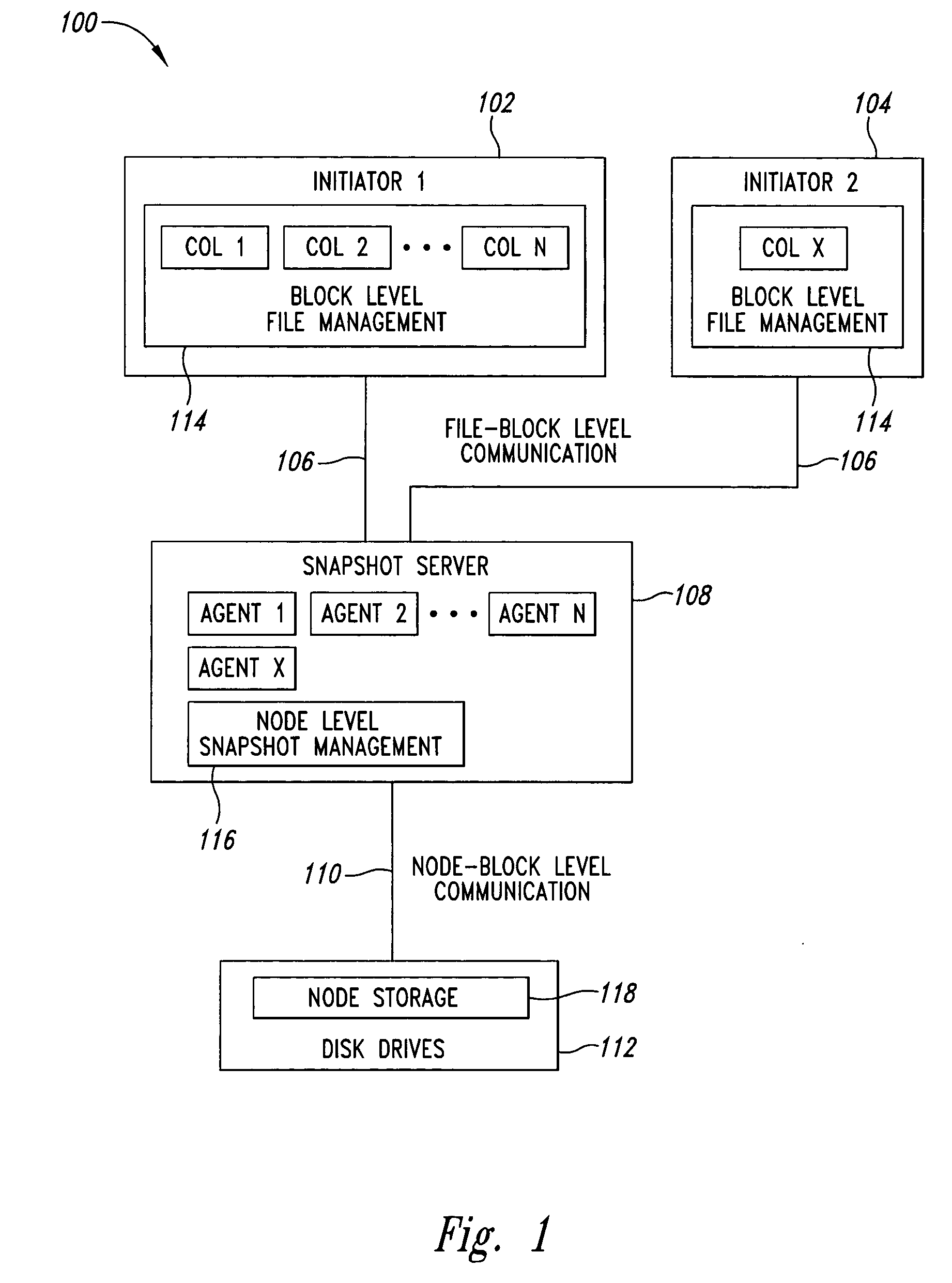
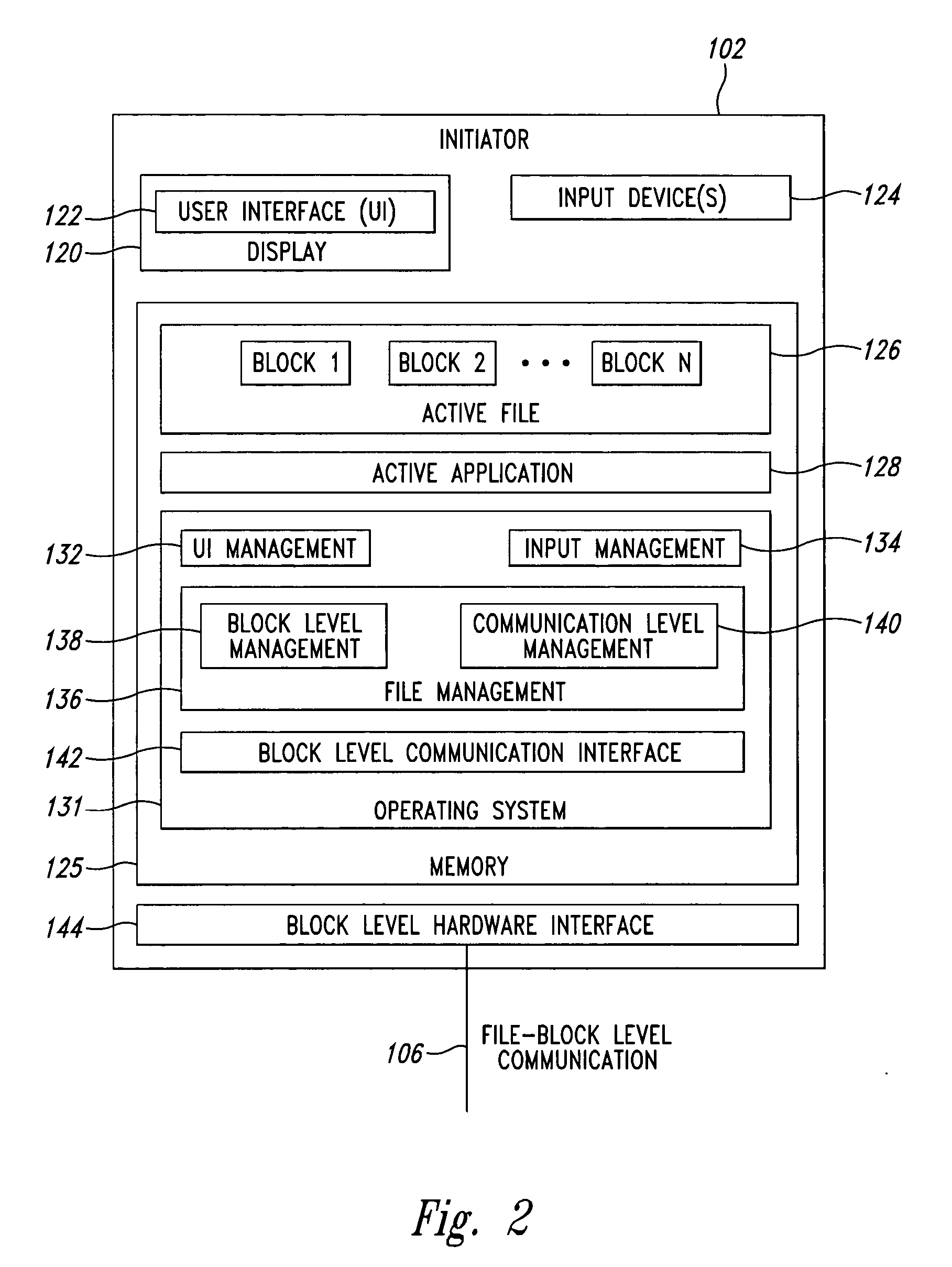
Block level data snapshot system and method
A block level data snapshot system uses agents to convert block level file commands from devices such as computer workstations intended for block level devices such as hard disks. The block level file commands are converted into instructions for a node based snapshot data system for taking snapshots at the block level. By converting the block level file commands into instructions suitable for the node based snapshot system, snapshots are able to be taken at the block level, which allows for disk storage savings and speed enhancements. One resultant feature is that the block level data snapshot system can be used as a block level storage device for one or more workstations thus allowing relatively simple integration of a snapshot system with existing workstations.
Owner:OVERLAND STORAGE INC
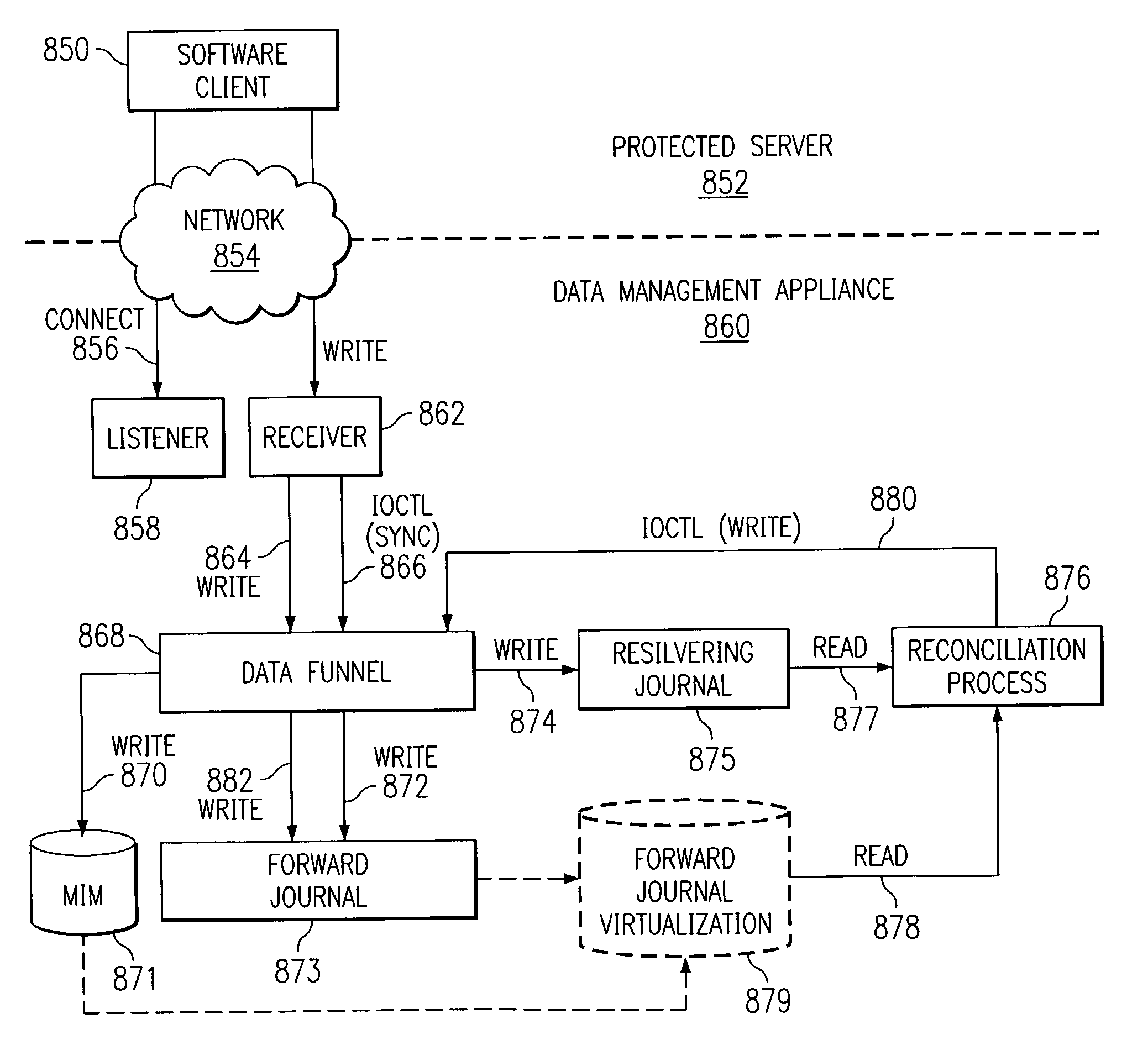
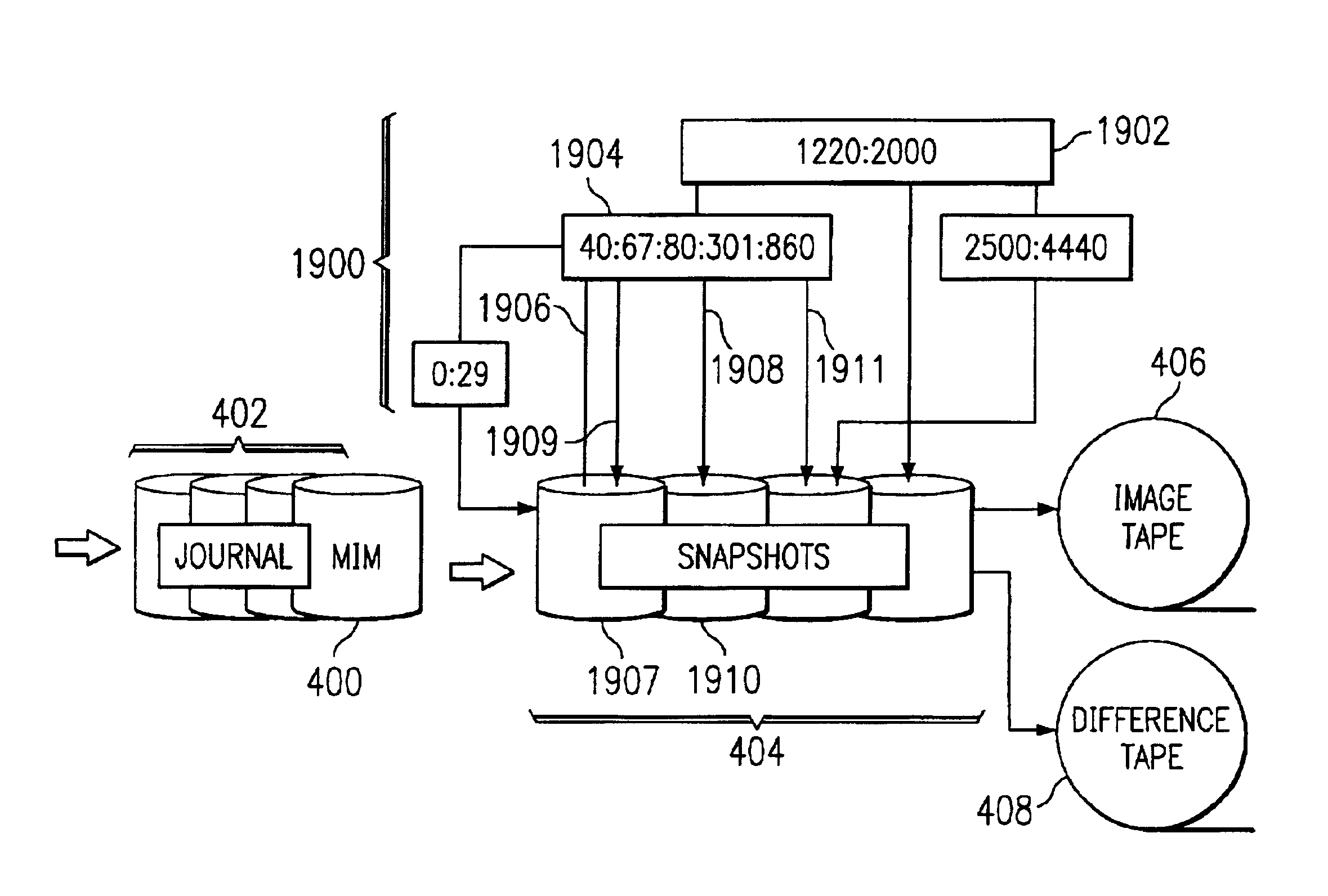
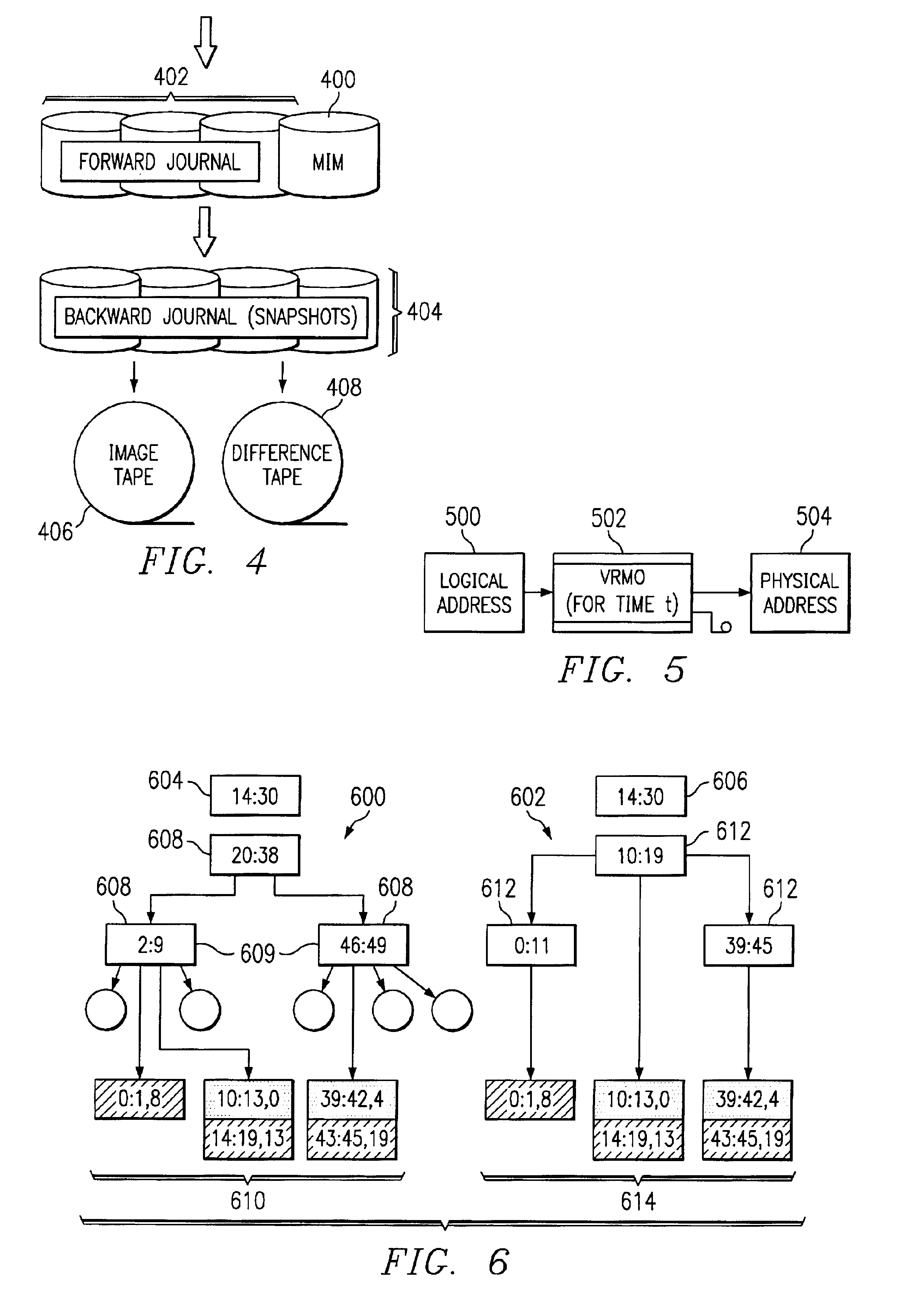
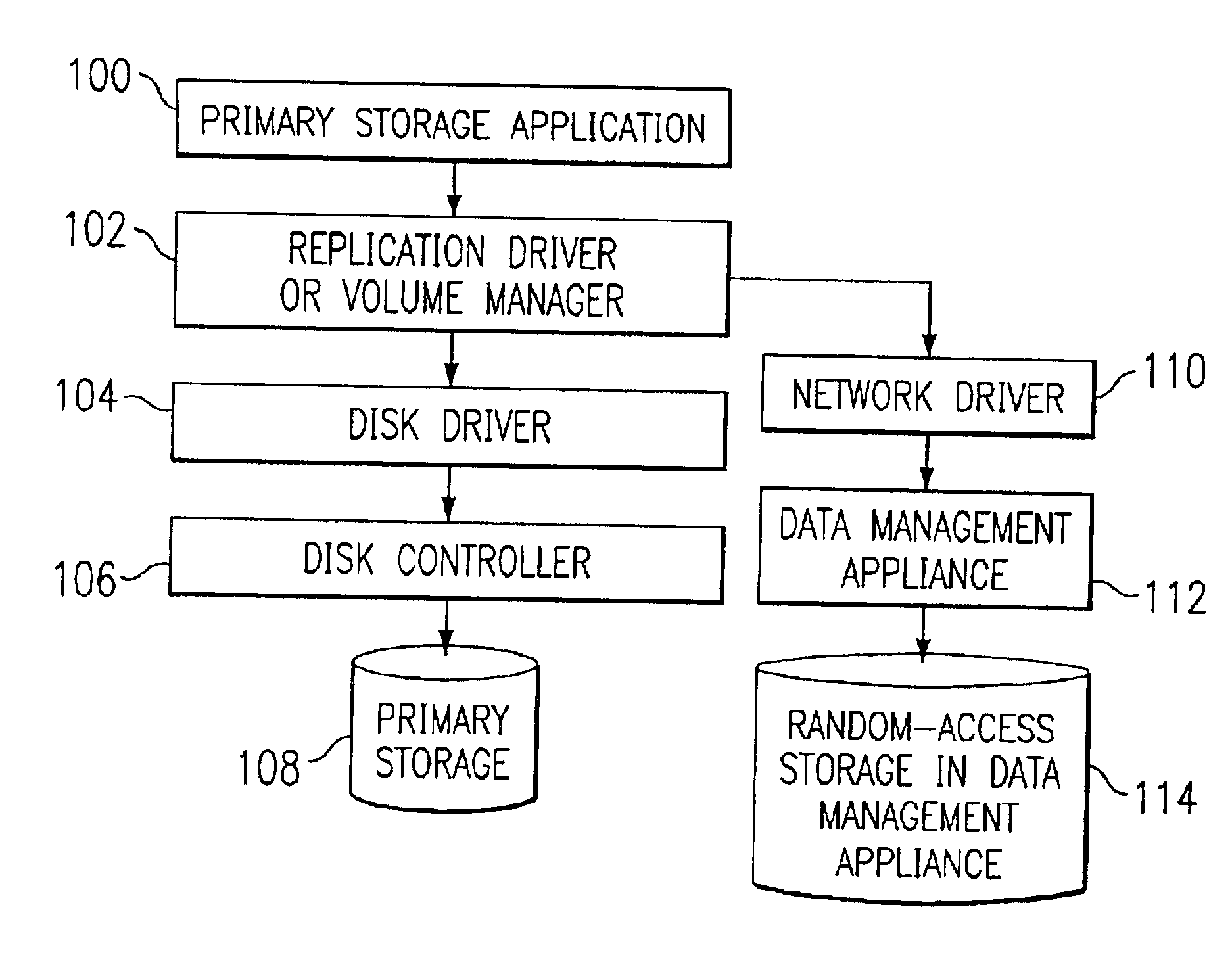
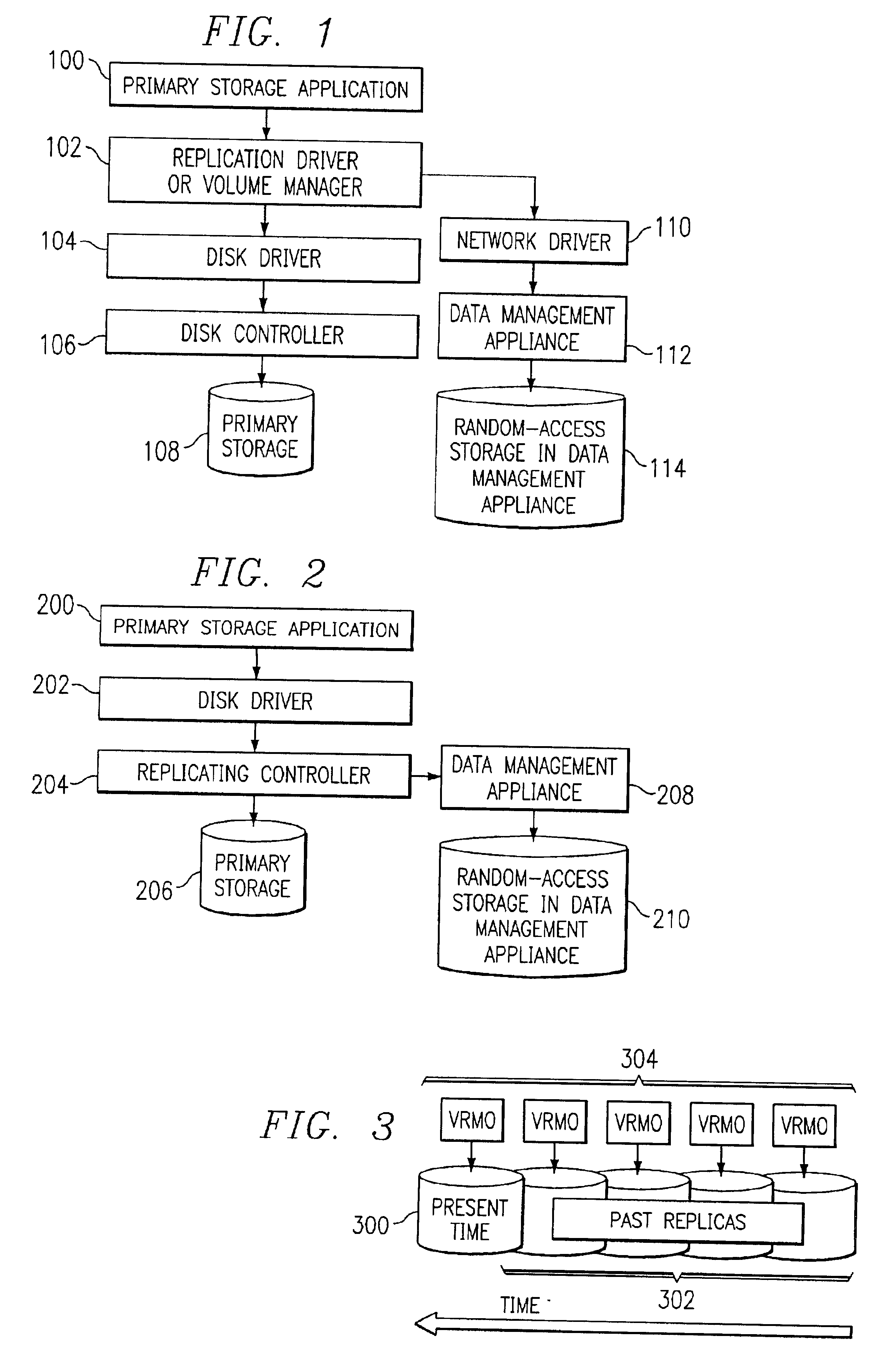
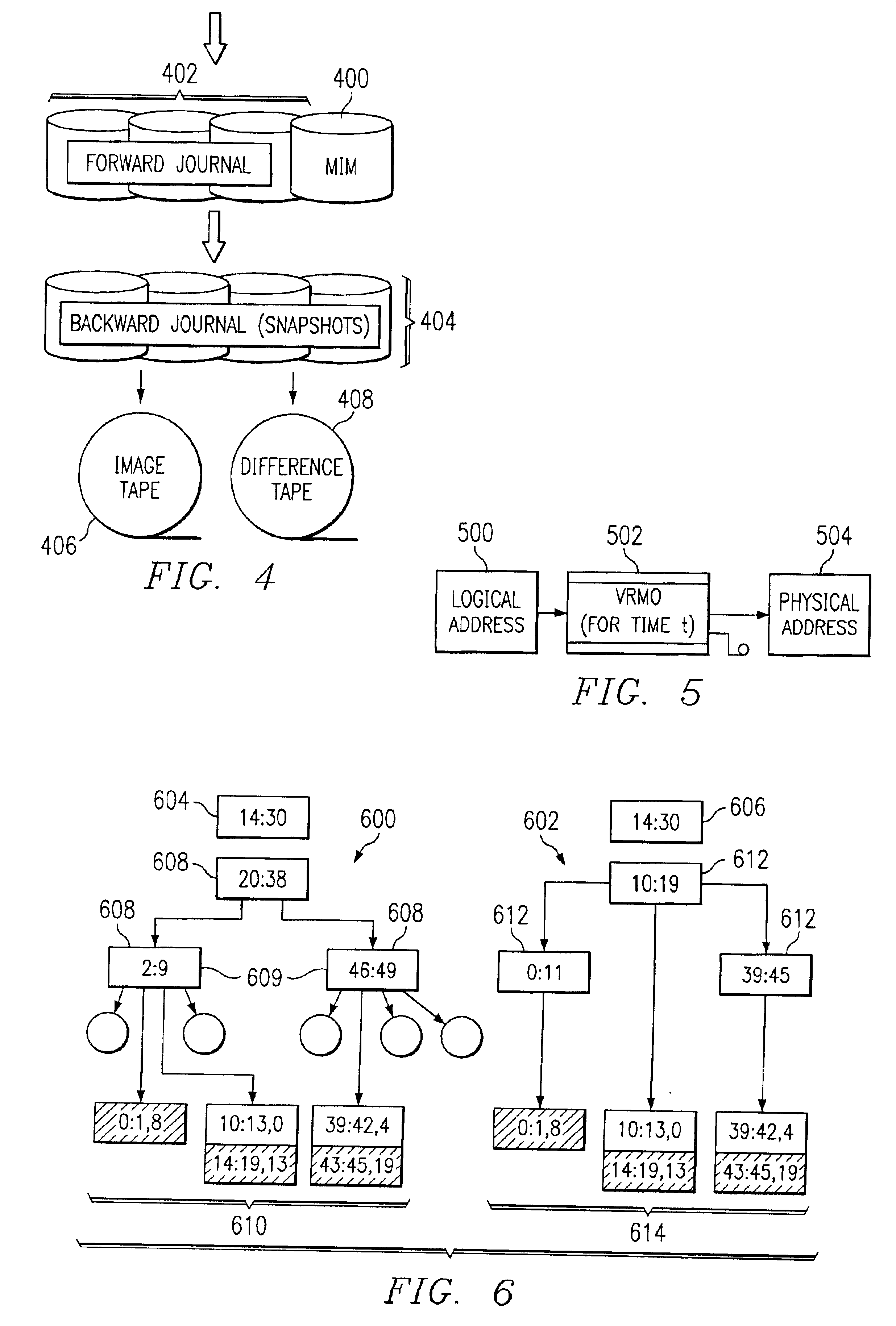
Storage backup system for backing up data written to a primary storage device to multiple virtual mirrors using a reconciliation process that reflects the changing state of the primary storage device over time
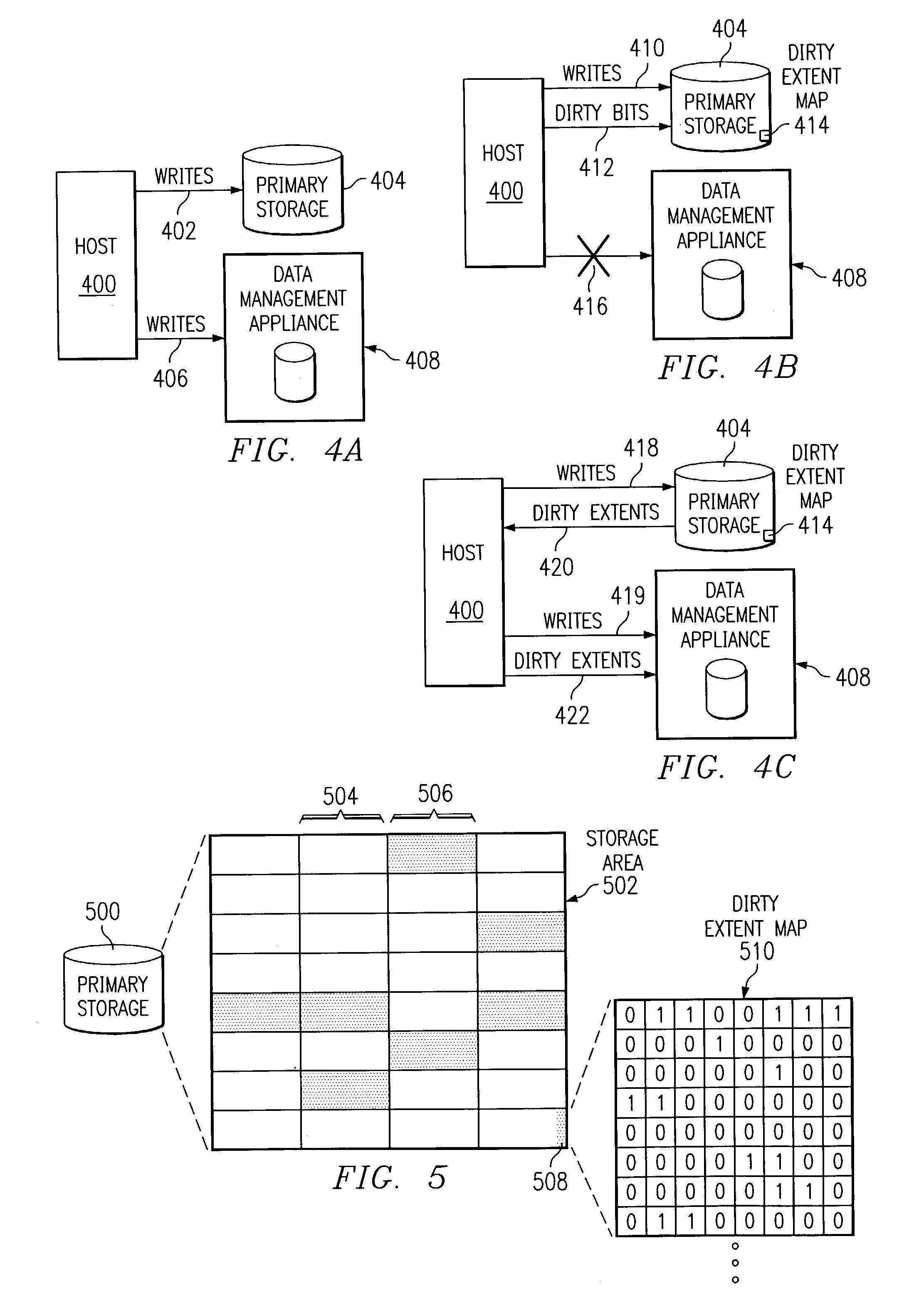
The present invention is directed toward the resumption of a journaling process in a data management appliance after a period of unavailability. The data management appliance is a random-access storage system that at the logical block level replicates the contents of a primary storage system over time. A small “dirty extent map” is established on the primary storage device. The dirty extent map keeps track of which portions of primary storage are written to while journaling is interrupted. When journaling is resumed, the contents of the dirty extents are compared to the latest replica of the primary storage to identify the differences. These differences are then journaled as if they were write commands. Meanwhile, new write commands are also journaled by the data management appliance. Once the differences of all of the dirty extents have been journaled, the data management appliance may resume normal journaling operation.
Owner:ORACLE INT CORP
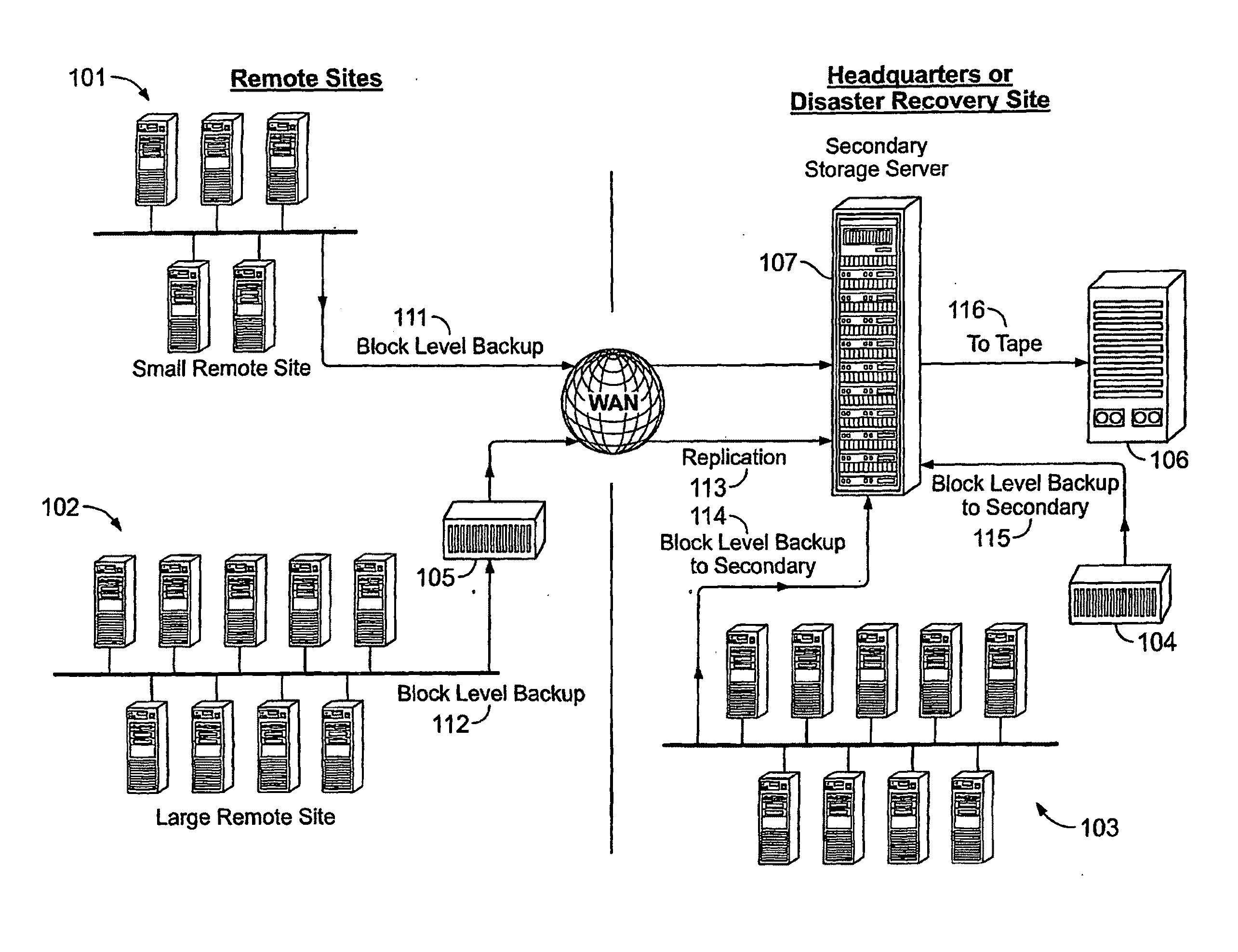
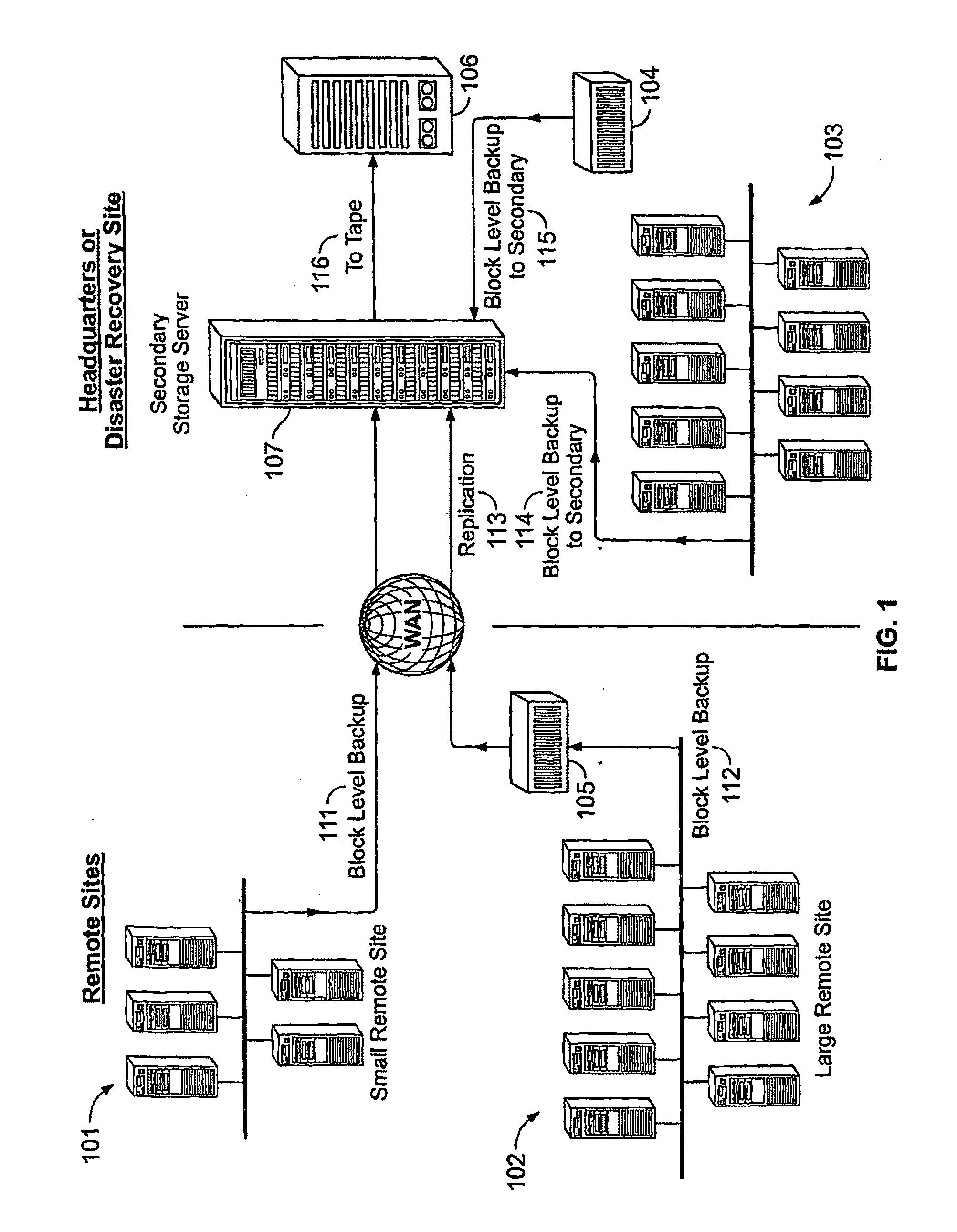
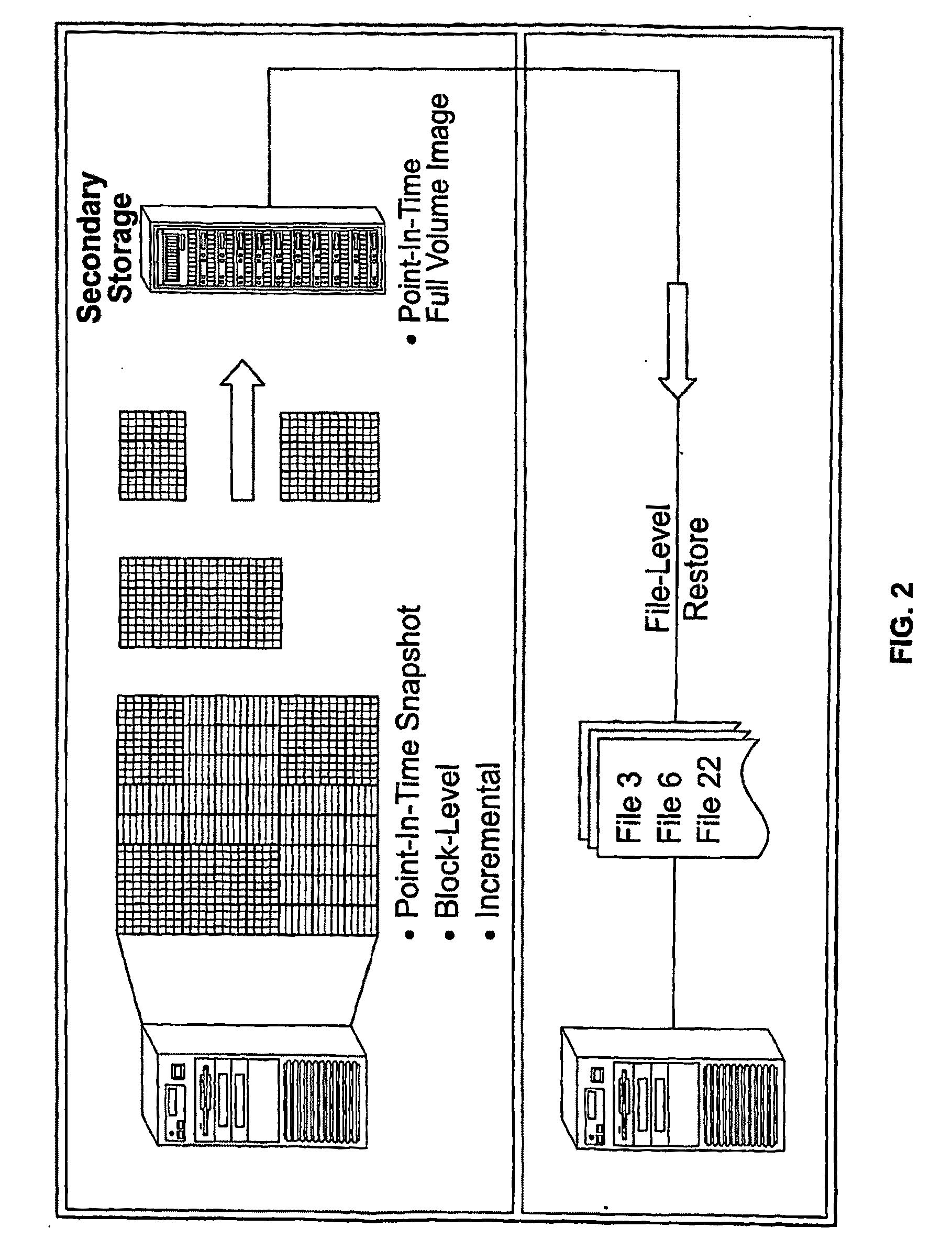
System And Method for High Performance Enterprise Data Protection
ActiveUS20100077160A1Improve performanceEliminate redundancyMemory loss protectionError detection/correctionOperational systemFile system
High performance, enterprise-level data protection system and method provides efficient block-level incremental snapshots of primary storage devices, and instant availability of such snapshots in immediately mountable form that can be directly used in place of the primary storage device. Related systems and applications are described, including an “Enterprise Image Destination” (EID) for backup images; a mirroring technique whereby a replacement physical primary facility may be created while working with a second storage unit as the primary source file system; and a technique for eliminating redundant data in backup images when multiple systems with partially common contents (e.g., operating system files, common databases, application executables, etc.) are being backed up. A number of examples showing “Fast Application Restore” (FAR) with the use of the invention are also provided.
Owner:CATALOGIC SOFTWARE
Systems and methods for detailed error reporting in data storage systems
ActiveUS8713357B1Efficient discoveryEasy to understandInput/output to record carriersFault responseData operationsData access
Embodiments of the invention are directed to providing detailed error reporting of data operations performed on a NVM storage device. In one embodiment, a controller interfaces with a NVM storage device including NVM storage coupled with a bridge. In one embodiment, the controller is provided physical, page-level access to the NVM via the bridge, and the bridge provides detailed error reporting of the data operations that the bridge performs on the NVM on behalf of the controller. For example, the bridge may provide page level reporting indicating which page(s) failed during a read operation. Detailed error reporting allows the controller to better understand the failures that occurred in a data access operation in the NVM. It also enables the controller to manage the flash media at the physical page / block level. In one embodiment, detailed error reporting also enables the return of discontinuous ranges of data with the error portions removed.
Owner:WESTERN DIGITAL TECH INC
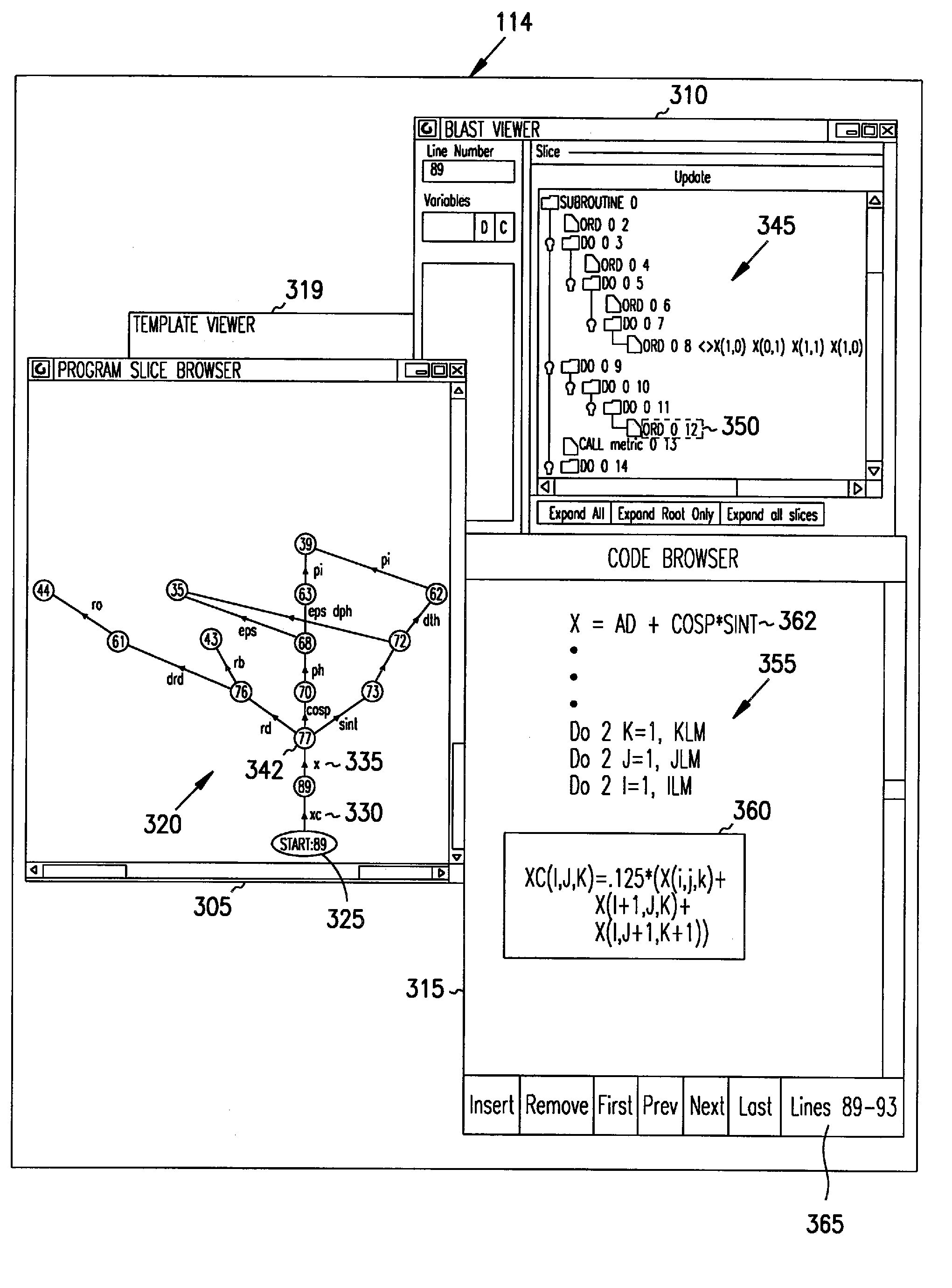
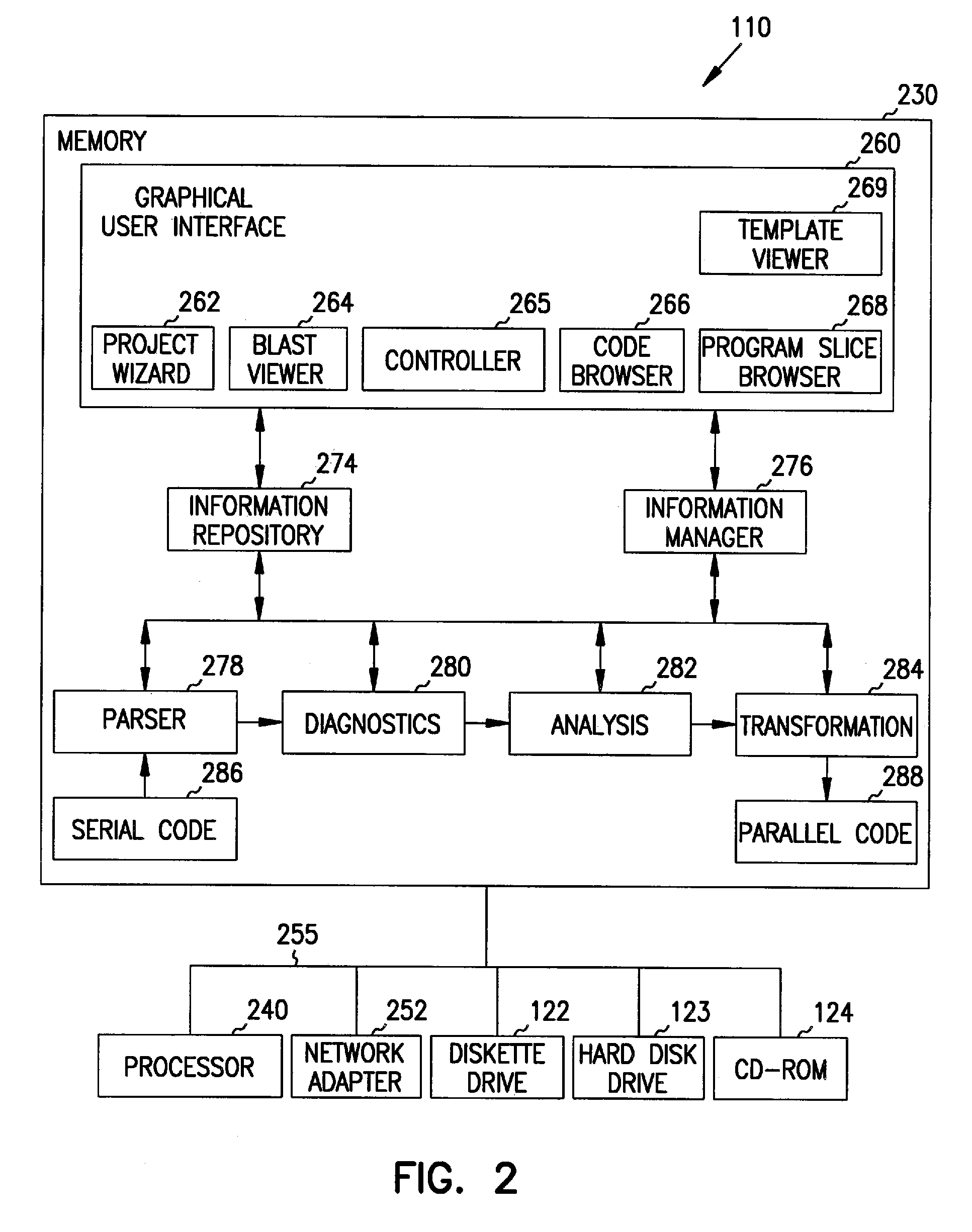
Integrated interactive software visualization environment
InactiveUS7174536B1Error detection/correctionSpecific program execution arrangementsBlock levelSubroutine
A method, system, apparatus, and program product for displaying a program slice diagram, which represents source code. The program slice diagram includes a directed graph that has multiple nodes and arcs connecting the nodes. Nodes can correspond to statements within a selected subroutine of the source code, variable references outside the subroutine, or calls made to other subroutines that are considered part of the program slice. Arcs represent data flow dependencies between the nodes. In another aspect, the invention encompasses a software environment for visualizing source code that includes a code browser, a block-level abstract syntax tree viewer, a program slice browser, and a template viewer. This software visualization environment is integrated, allows cross-referencing between its components, and is coupled with a performance visualization environment.
Owner:IOWA STATE UNIV RES FOUND
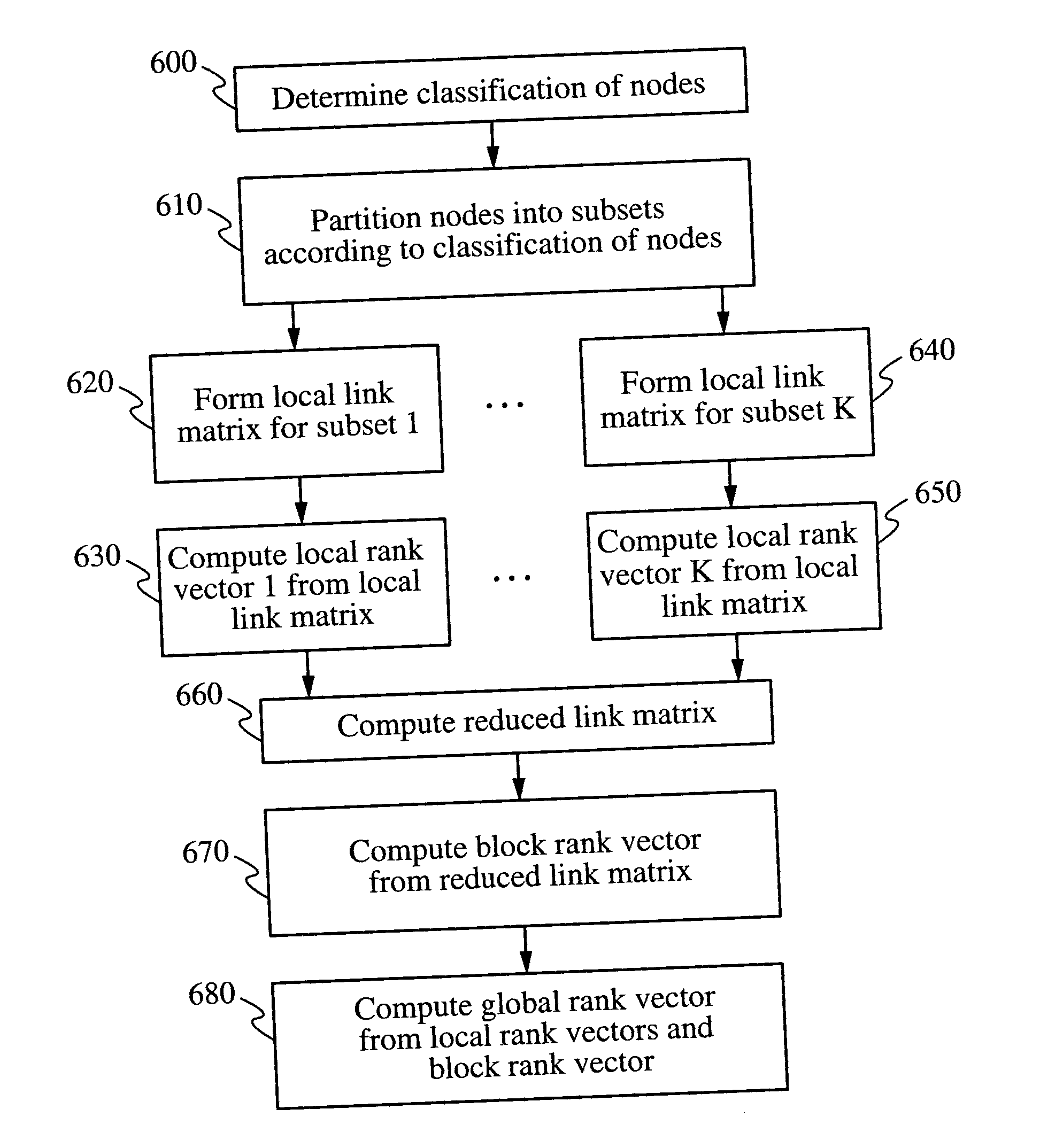
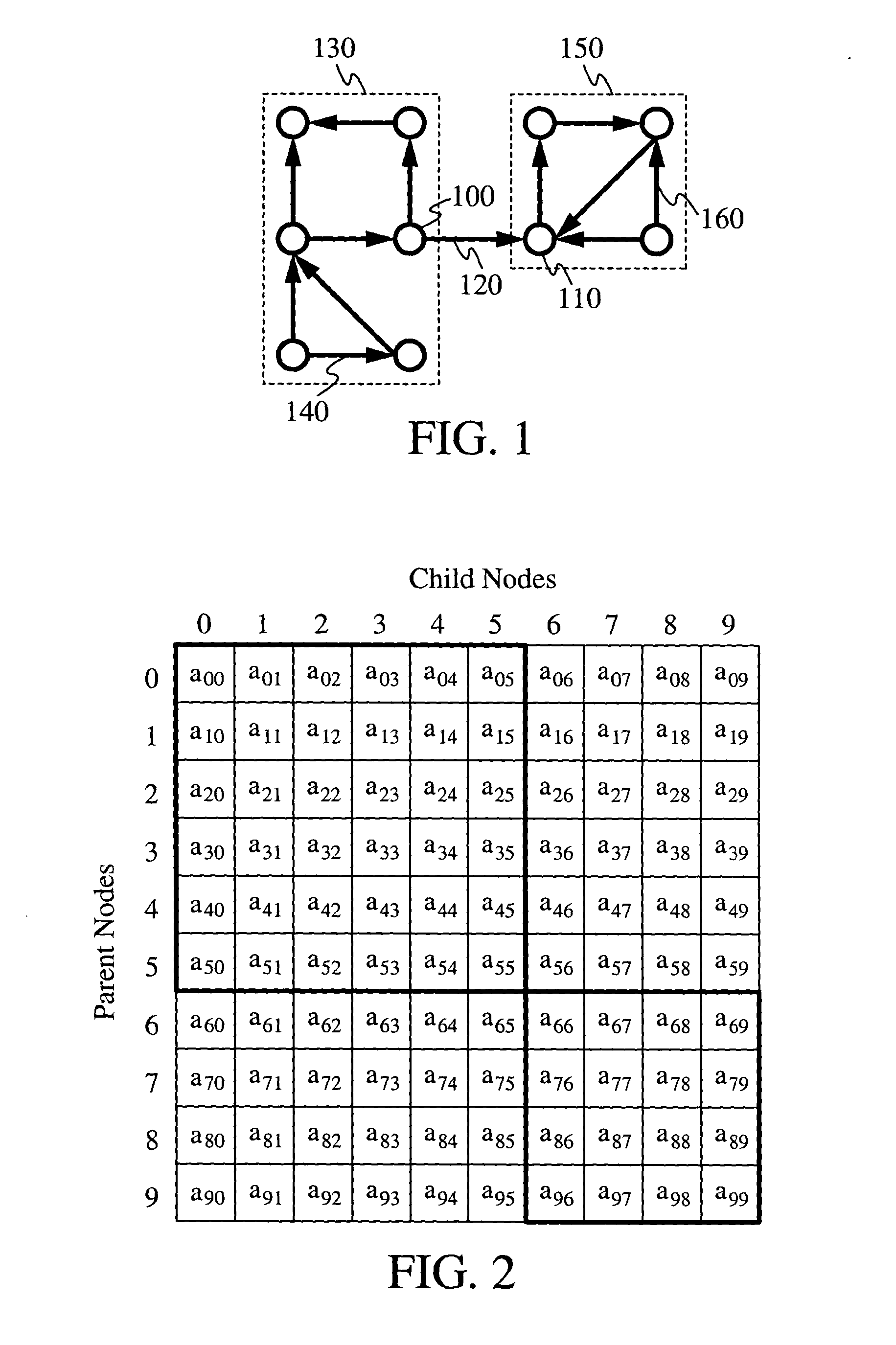
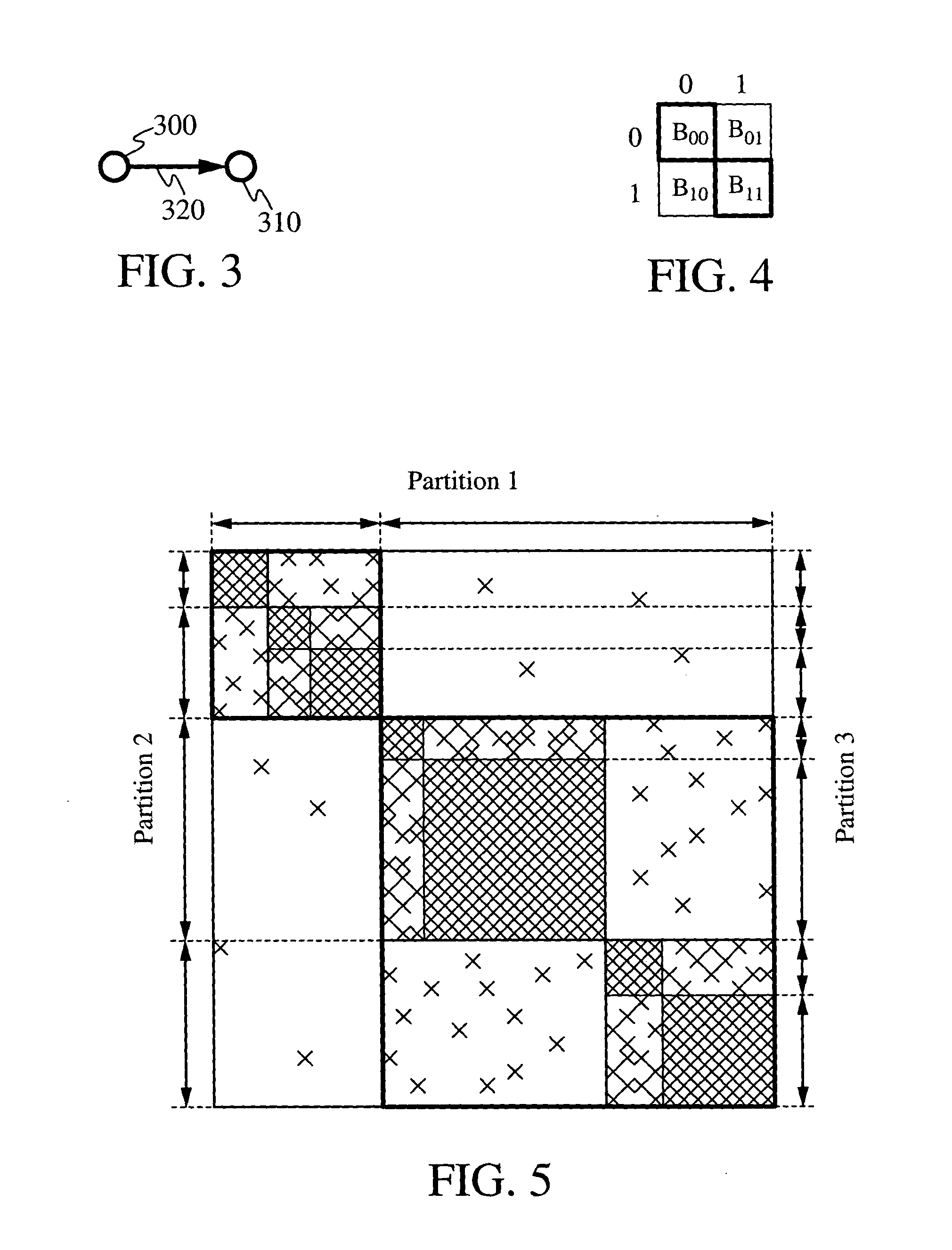
Methods for ranking nodes in large directed graphs
ActiveUS20050033742A1Increase speedSimple calculationData processing applicationsWeb data indexingDirected graphDistributed Computing Environment
Techniques for assigning ranks to nodes in a large linked database, such as world wide web or any other hypermedia database, partition the nodes so that the link matrix has a predominantly block-diagonal form. Within each block, a local rank is computed for nodes in the block, possibly by different computer in a distributed computing environment. A block rank is then estimated for each block as a whole, and may optionally include block-level weights to implement customized ranking. The local ranks and block ranks are then combined to form a global rank, which may be used to rank the nodes. Alternatively, a global rank vector for the database may be used as an initial vector in an iterative link-based ranking scheme to obtain more accurate global ranks for the nodes. The global rank vector may be divided to provide local rank vectors for use in subsequent applications of the method.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
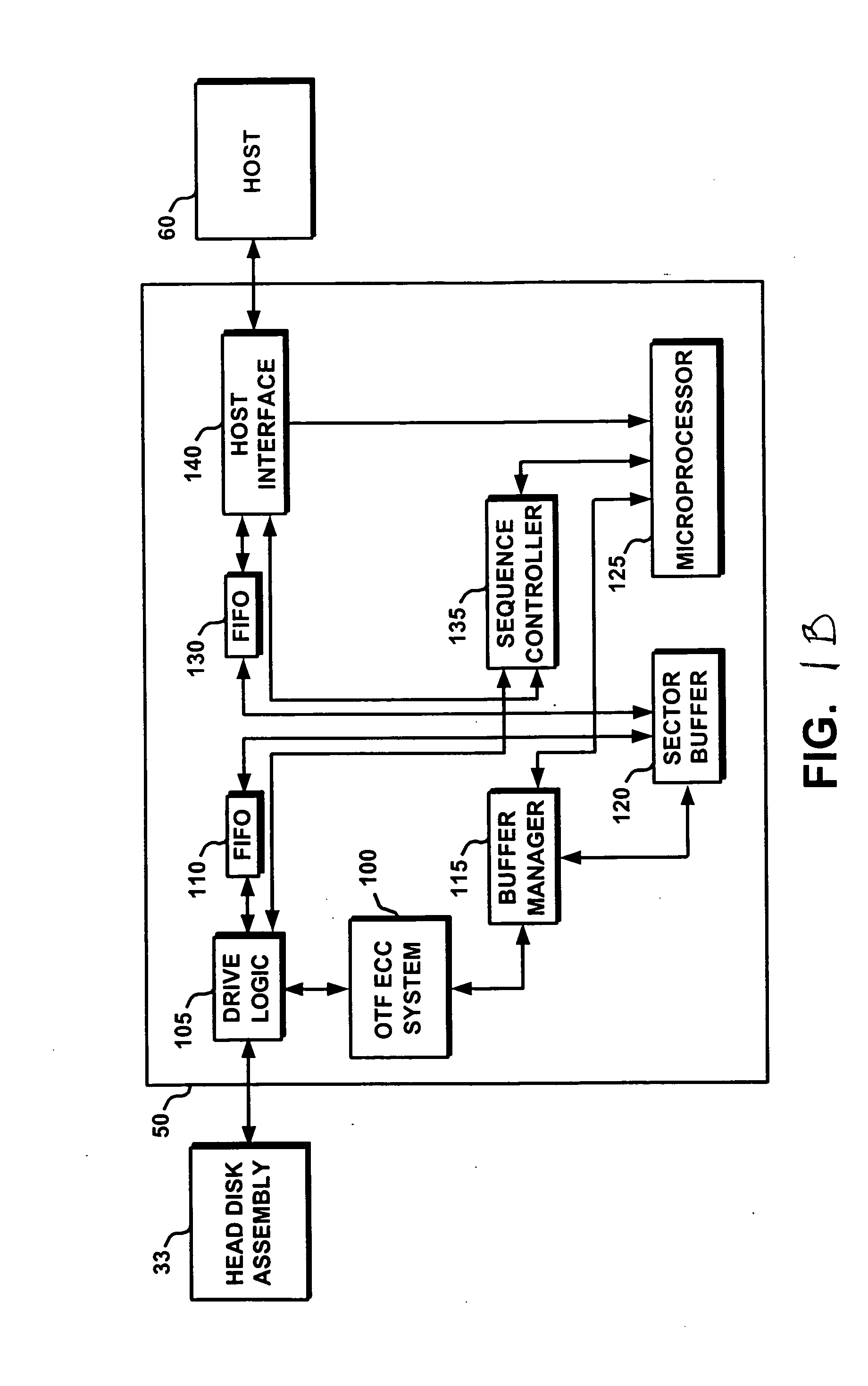
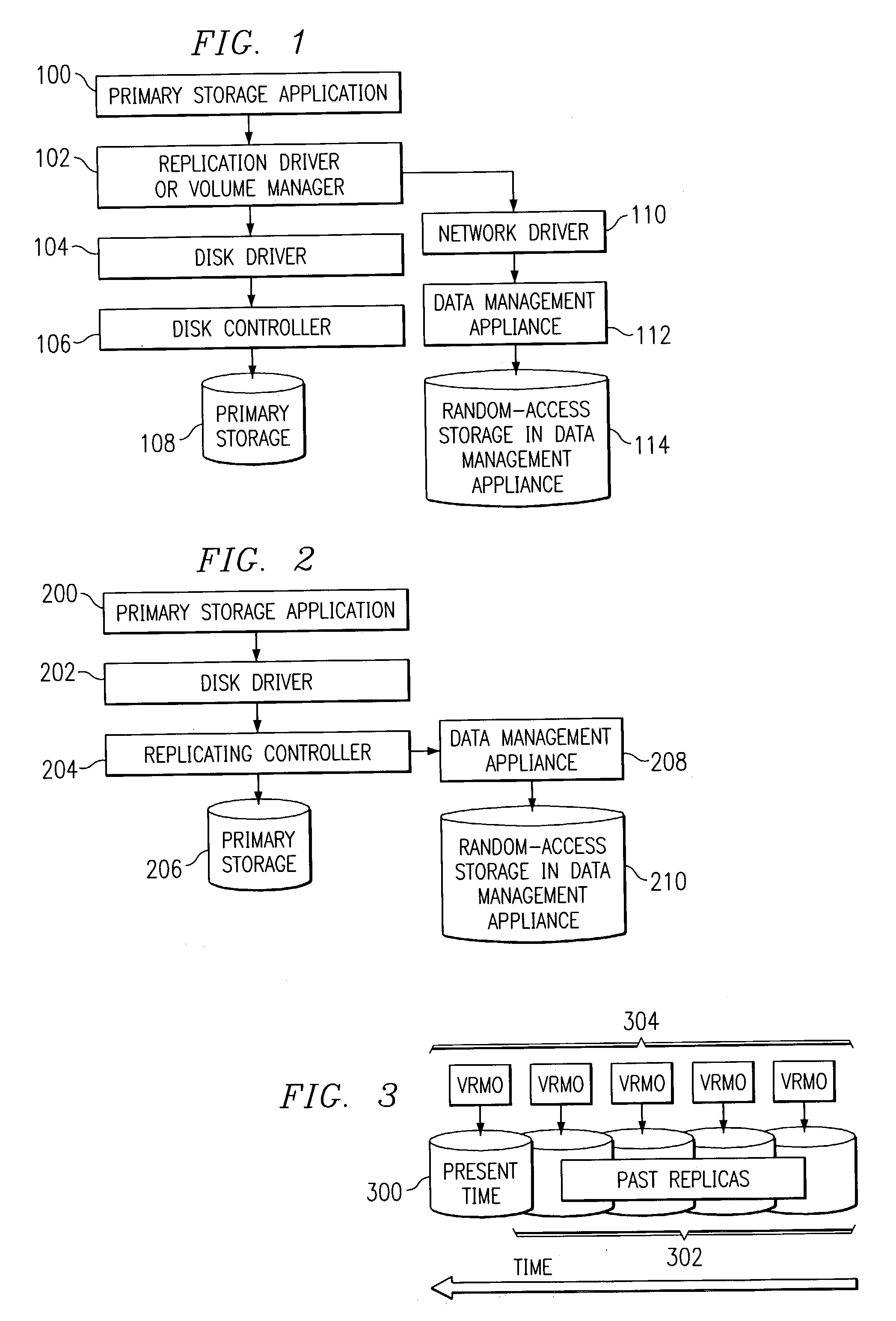
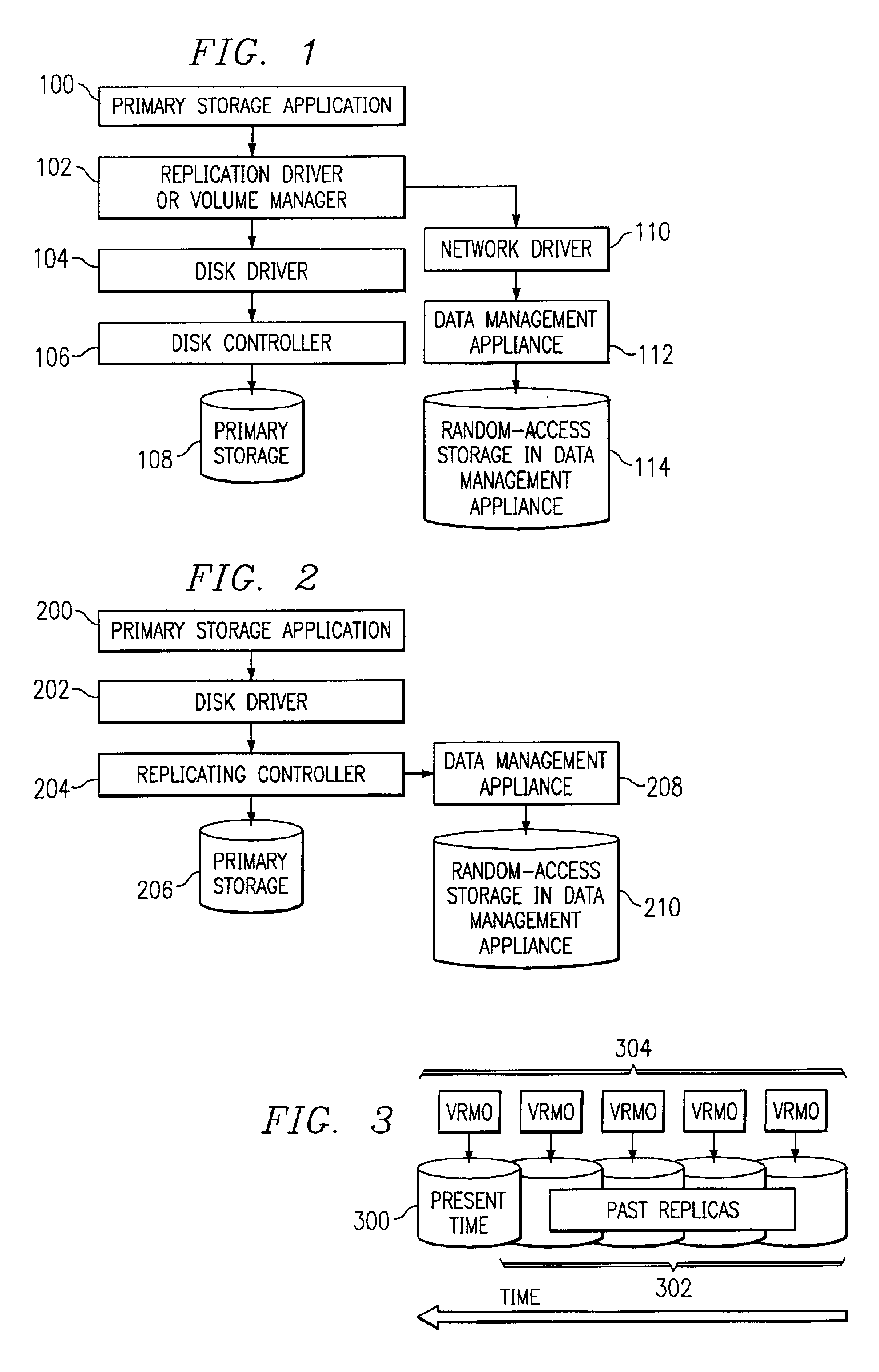
Data management appliance
ActiveUS6898688B2Quick and random-access recovery of dataError preventionError detection/correctionAssistive technologyData management
The present invention is directed toward a data management appliance and ancillary technologies for replicating data written to a primary storage system. The data management appliance is a random-access storage system that at the logical block level replicates the contents of a primary storage system over time.
Owner:ORACLE INT CORP
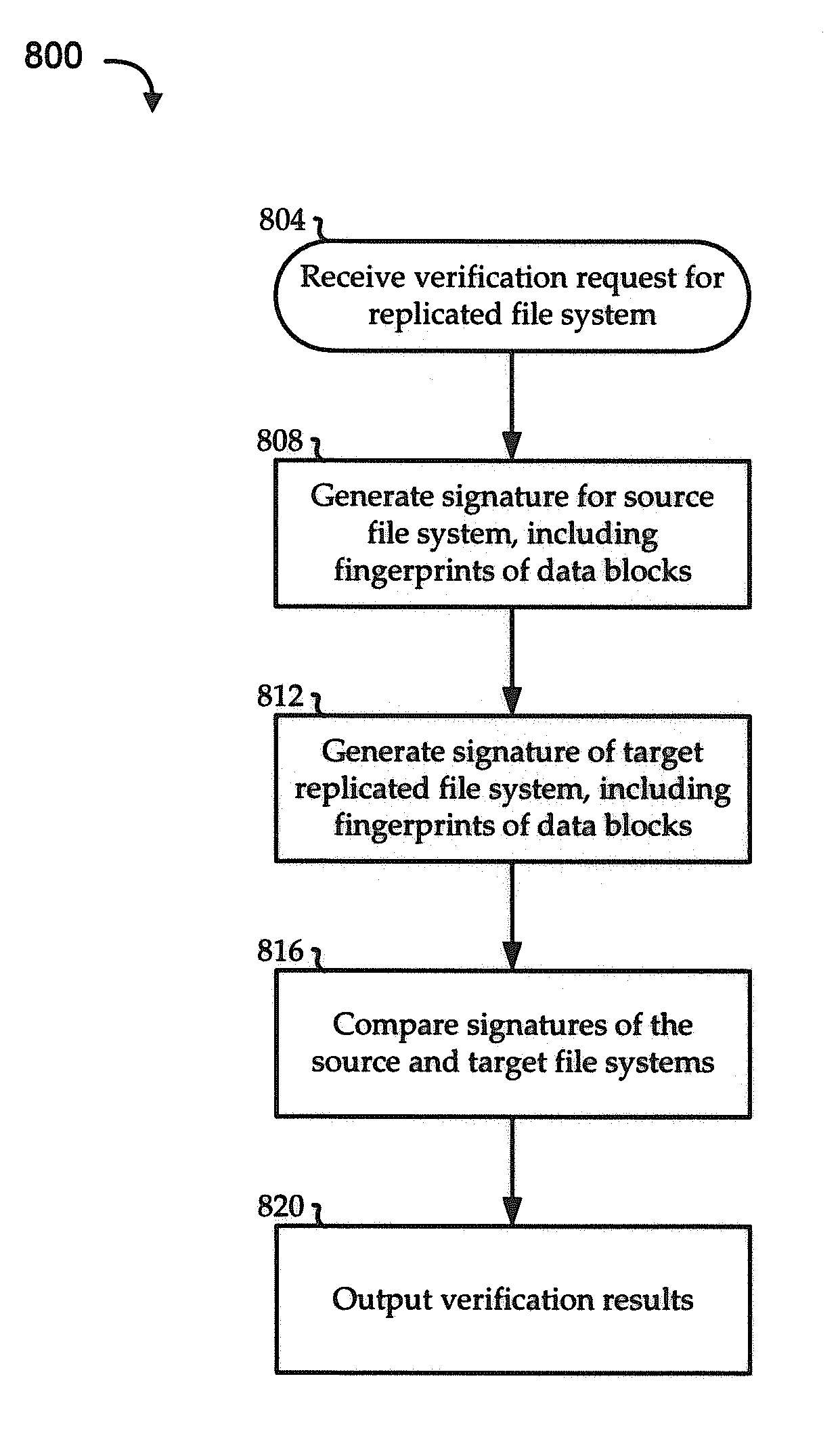
Offline verification of replicated file system
Embodiments of the invention include systems and methods for providing block-level verification of replicated file systems. Embodiments operate in context of data storage environments, which may typically have multiple file systems, snapshots of file systems, and replicas of file systems. In one illustrative scenario, a replica is created of a file system having multiple associated snapshots, and a user desires to verify the accuracy of the replica. A signature is created for each of the source active file system and the target replica file system, so that each signature includes records of both block-level signatures and block-level allocations. The signatures are compared to discover any differences. The differences may then be reconciled, where possible, to determine whether the differences indicate a corrupt or otherwise invalid replica.
Owner:ORACLE INT CORP
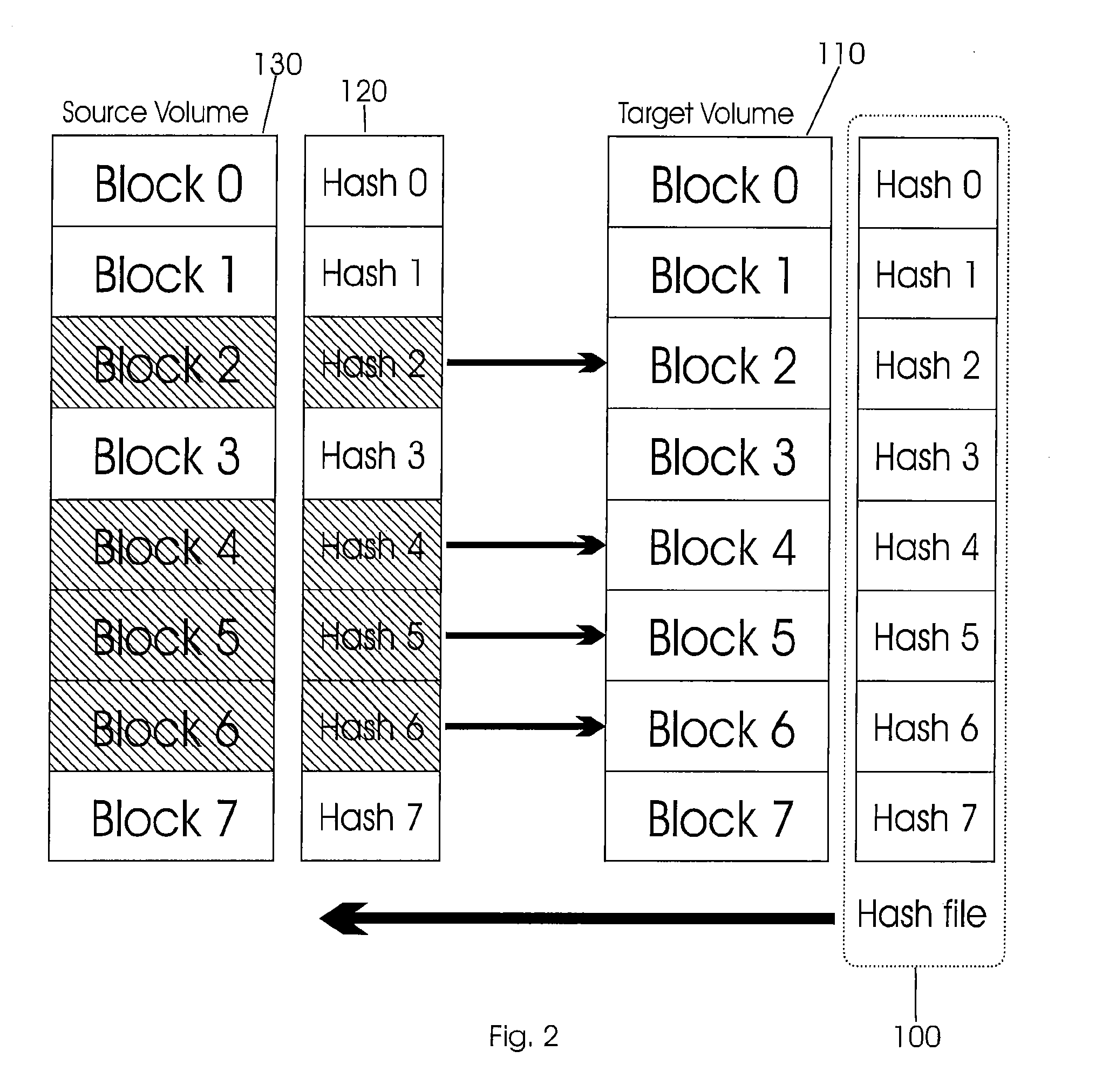
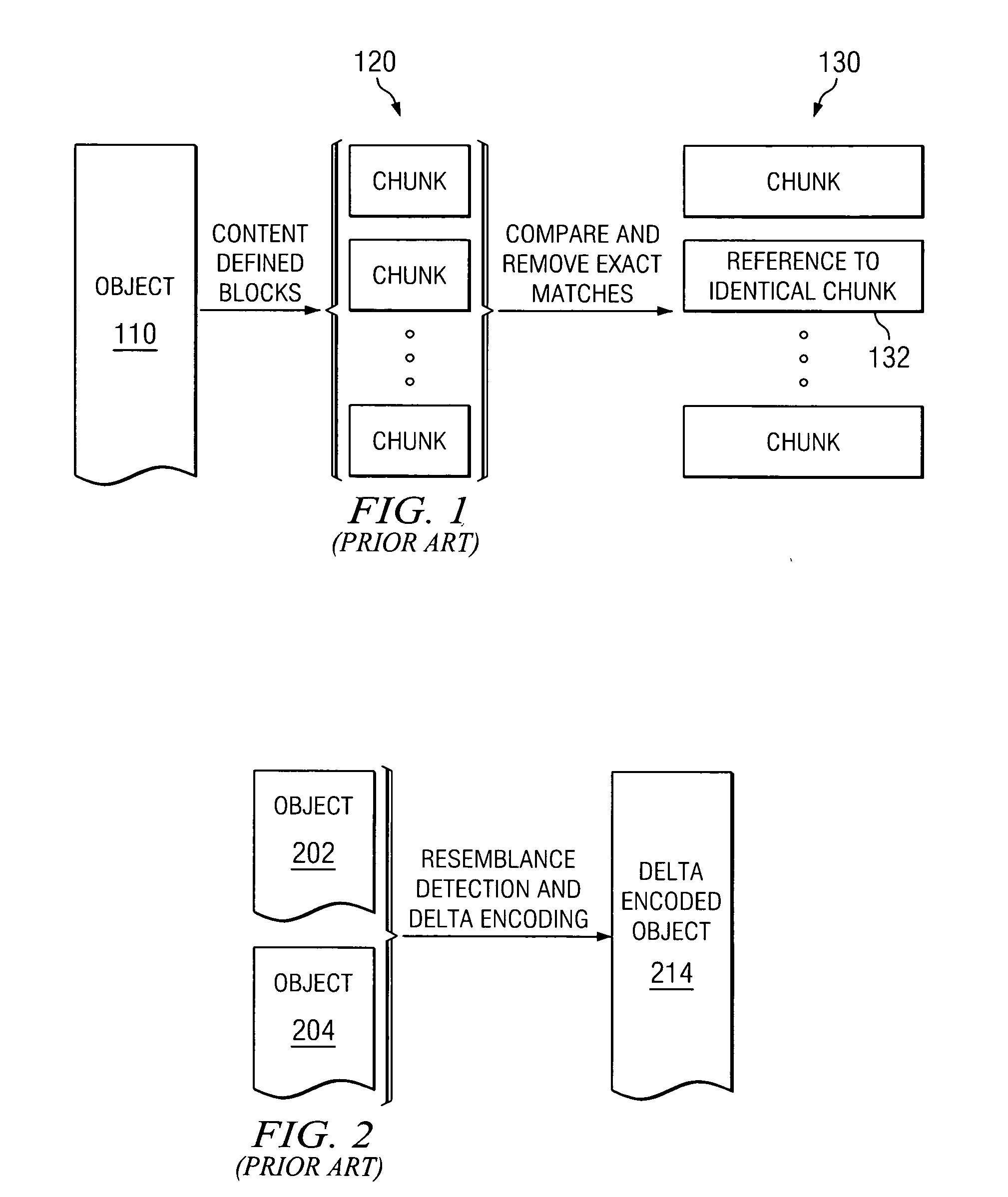
Method and apparatus for data redundancy elimination at the block level
InactiveUS20050131939A1Error detection/correctionDigital data processing detailsIncremental encodingComputer science
A redundancy elimination mechanism is provided, which applies aspects of duplicate block elimination and delta encoding at the block level. The redundancy elimination mechanism divides file objects into content-defined blocks or “chunks.” Identical chunks are suppressed. The redundancy elimination mechanism also performs resemblance detection on remaining chunks to identify chunks with sufficient redundancy to benefit from delta encoding of individual chunks. Any remaining chunks that do not benefit from delta encoding are compressed. Resemblance detection is optimized by merging groups of fingerprints into super fingerprints. This merging can be constructed to ensure that if two objects have a single super fingerprint in common, they are extremely likely to be substantially similar.
Owner:IBM CORP
System and method of overlaying and integrating data with geographic mapping applications
InactiveUS7925982B2Comprehensive geographic breadth and detailHigh resolutionDigital data processing detailsRadio transmissionSubject analysisRelational database
The present invention embodiments include a geographic overlay system including an information system, a mapping system interface to communicate with a mapping system and a database system including National Census geographic boundaries and data files. The geographic overlay system utilizes a client / server model that streams geographic data from a server system to dynamically render vector-based map layers inside a client browser. The geographic overlay system employs a Nationwide database of Census geographies that may be rendered as interactive point, line or polygon objects over a National base map provided by the mapping system. A database builder interface enables users to build the database and server pages. The present invention embodiments overlay translucent, interactive dynamically generated vector-based polygonal Census boundary map layers over geographical maps from the mapping system. The overlaying vector map layers perform thematic analysis, enable information retrieval, display mouse-over tool-tips and query a dynamic block-level National spatial-relational database.
Owner:PARKER CHERYL +1
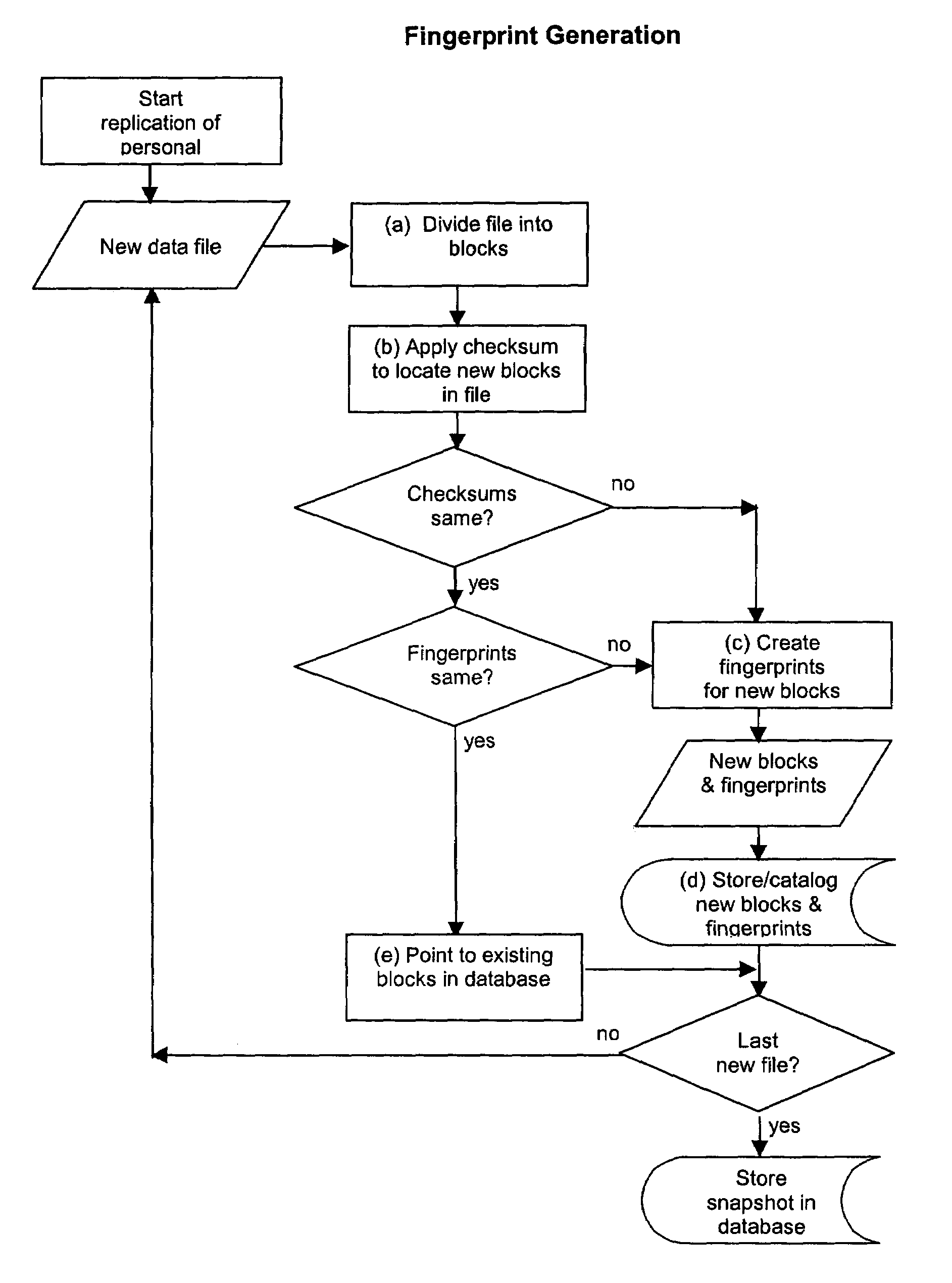
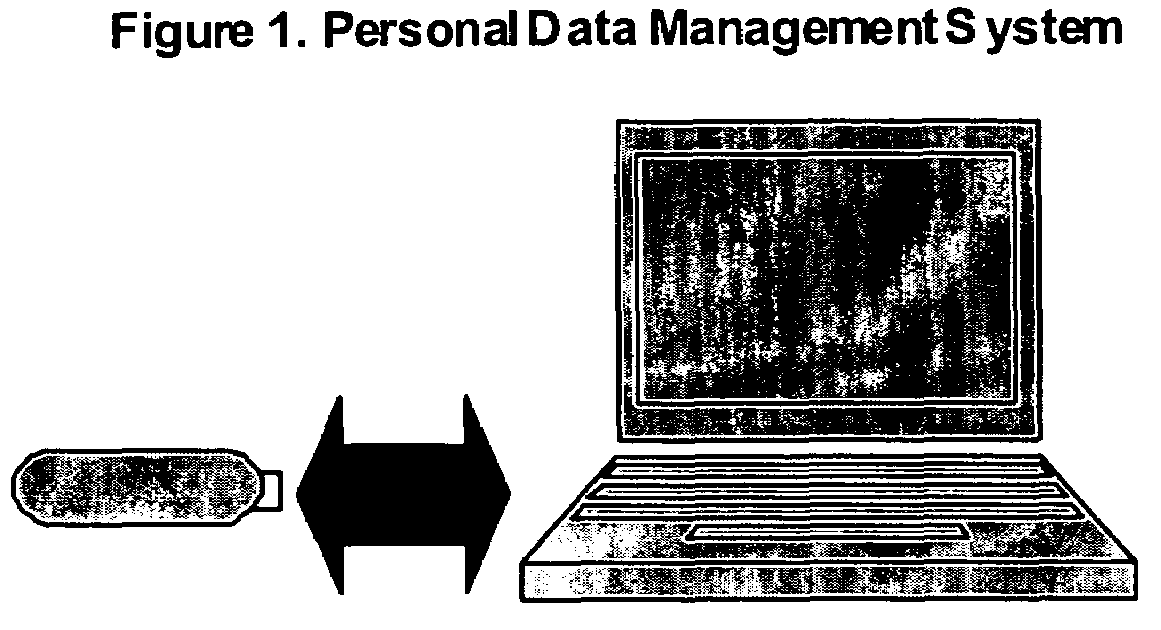
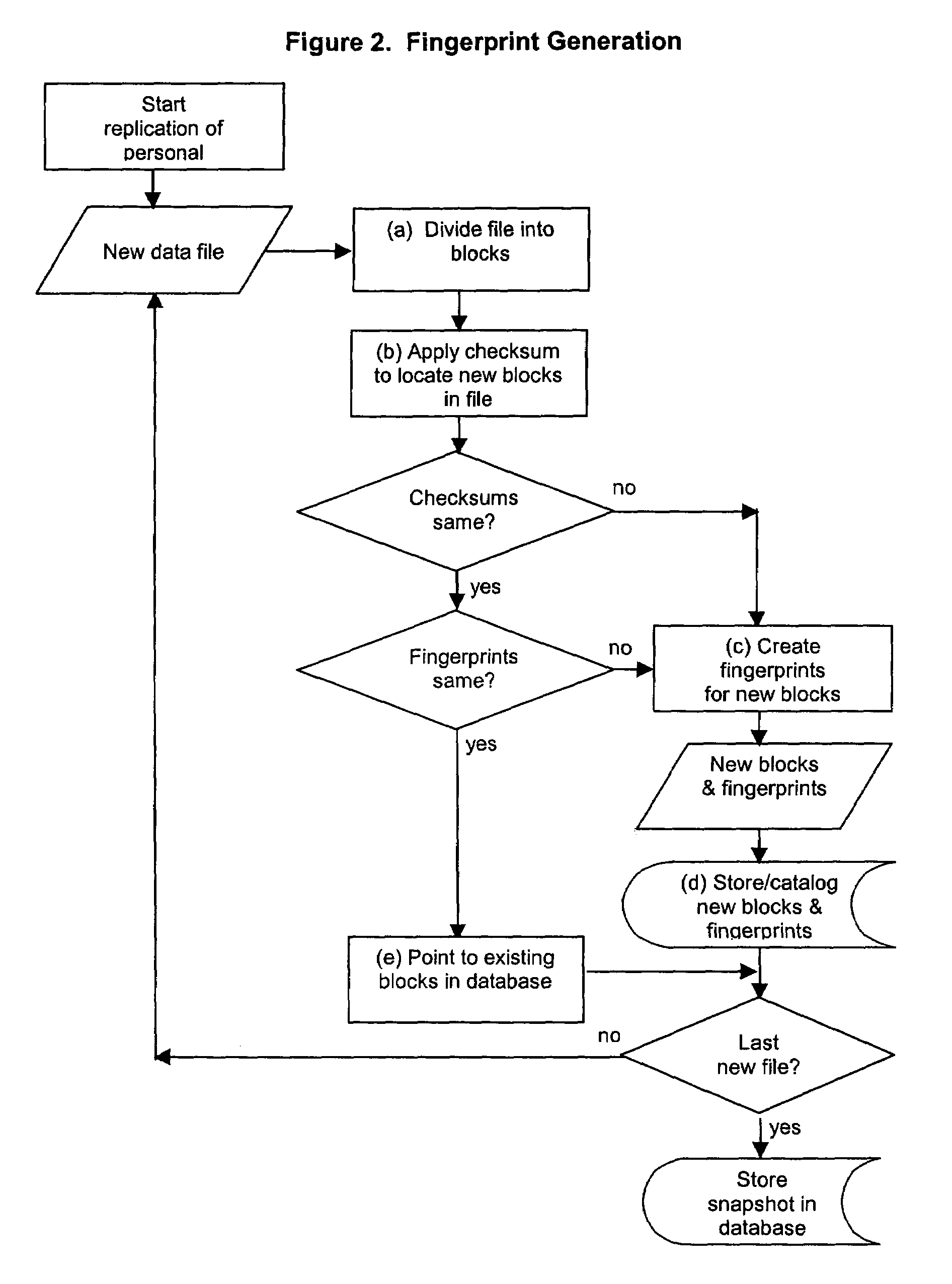
Method, system, and program for personal data management using content-based replication
ActiveUS7454443B2Efficient replicationData efficientData processing applicationsDigital data information retrievalOperational systemFile system
Data management systems and methods that can catalog, store, and protect data from hard disk failure on a mobile or stationary computer, using a computer program and a portable data storage device are provided. The program uses a combination message-digest and check-function based algorithm that can back up, manage, and protect data independent of specific computer operating system or file system. The program can check files for block-level content changes from previously stored data blocks and catalogs and stores only new data blocks. By storing only new data blocks and cataloging information within a comprehensive, backup archive composed of these blocks, the size of each backup is reduced.
Owner:WESTERN DIGITAL TECH INC
Data management appliance
InactiveUS6839819B2Quick and random-access recovery of dataRedundant operation error correctionMemory systemsAssistive technologyData management
The present invention is directed toward a data management appliance and ancillary technologies for replicating data written to a primary storage system. The data management appliance is a random-access storage system that at the logical block level replicates the contents of a primary storage system over time.
Owner:ORACLE INT CORP
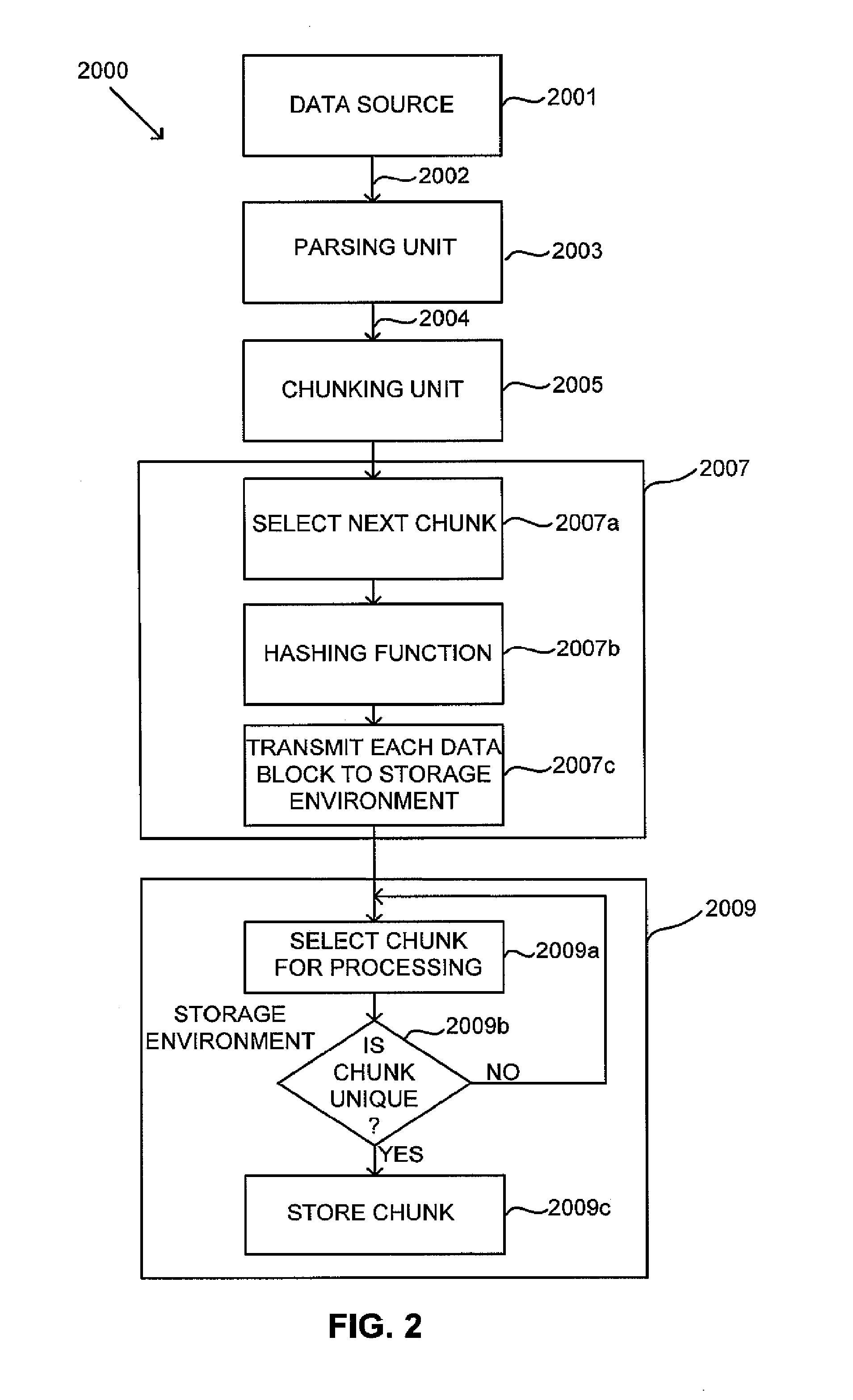
Method and apparatus for block level data de-duplication
ActiveUS8200923B1Memory loss protectionError detection/correctionComputer hardwareDistributed object
Techniques for performing de-duplication for data blocks in a computer storage environment. At least one chunking / hashing unit receives input data from a source and processes it to output data blocks and content addresses for them. In one aspect, the chunking / hashing unit outputs all blocks without checking to see whether any is a duplicate of a block previously stored on the storage environment. In another aspect, each data block is processed by one of a plurality of distributed object addressable storage (OAS) devices that each is selected to process data blocks having content addresses with a particular range. The OAS devices determine whether each received data block is a duplicate of another previously stored on the computer storage environment, and when it is not, stores the data block.
Owner:EMC IP HLDG CO LLC
Location independent scalable file and block storage
InactiveUS20120011176A1Fast and therefore expensiveSmall sizeDigital data information retrievalSpecial data processing applicationsFile systemBlock level
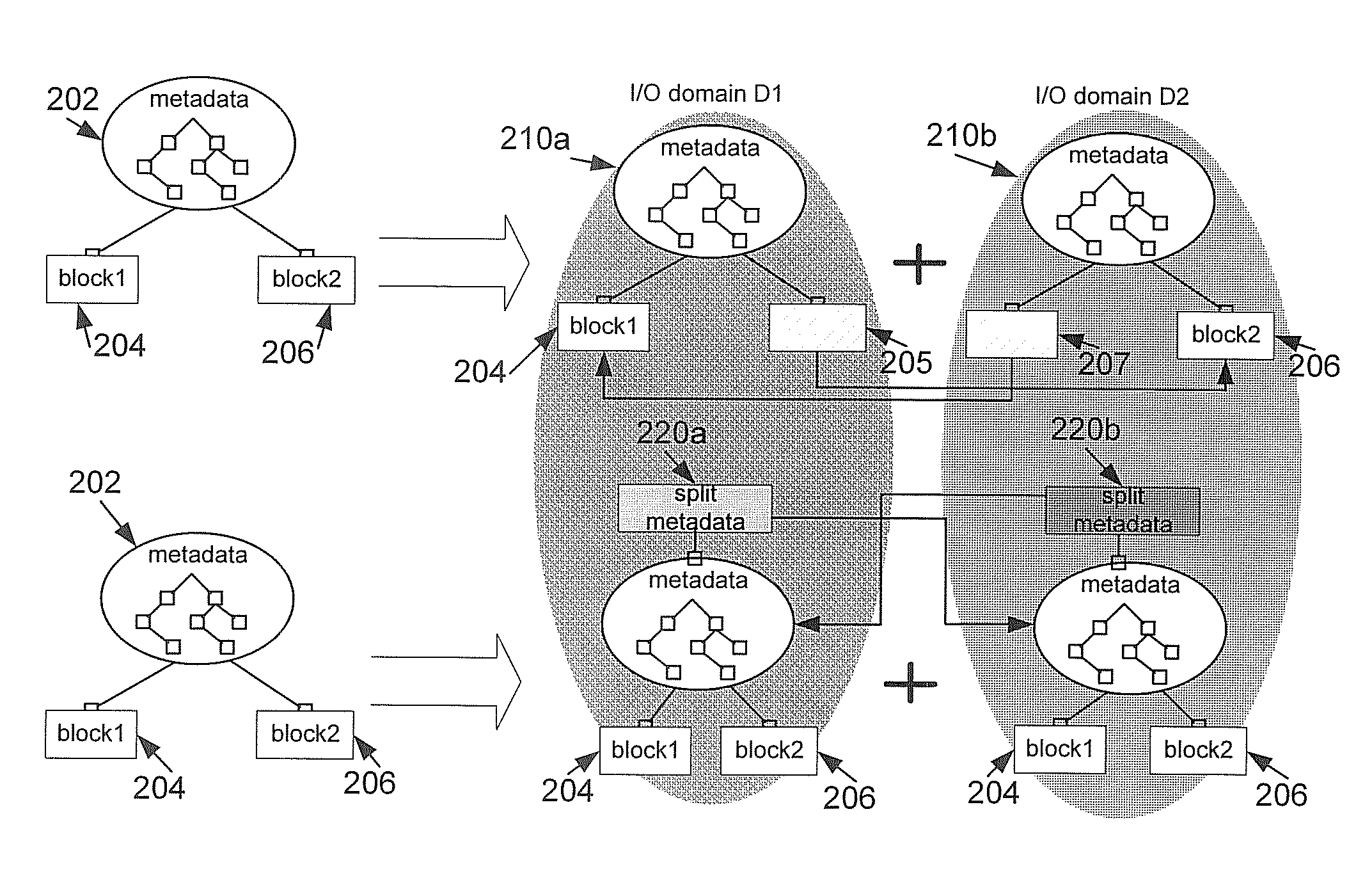
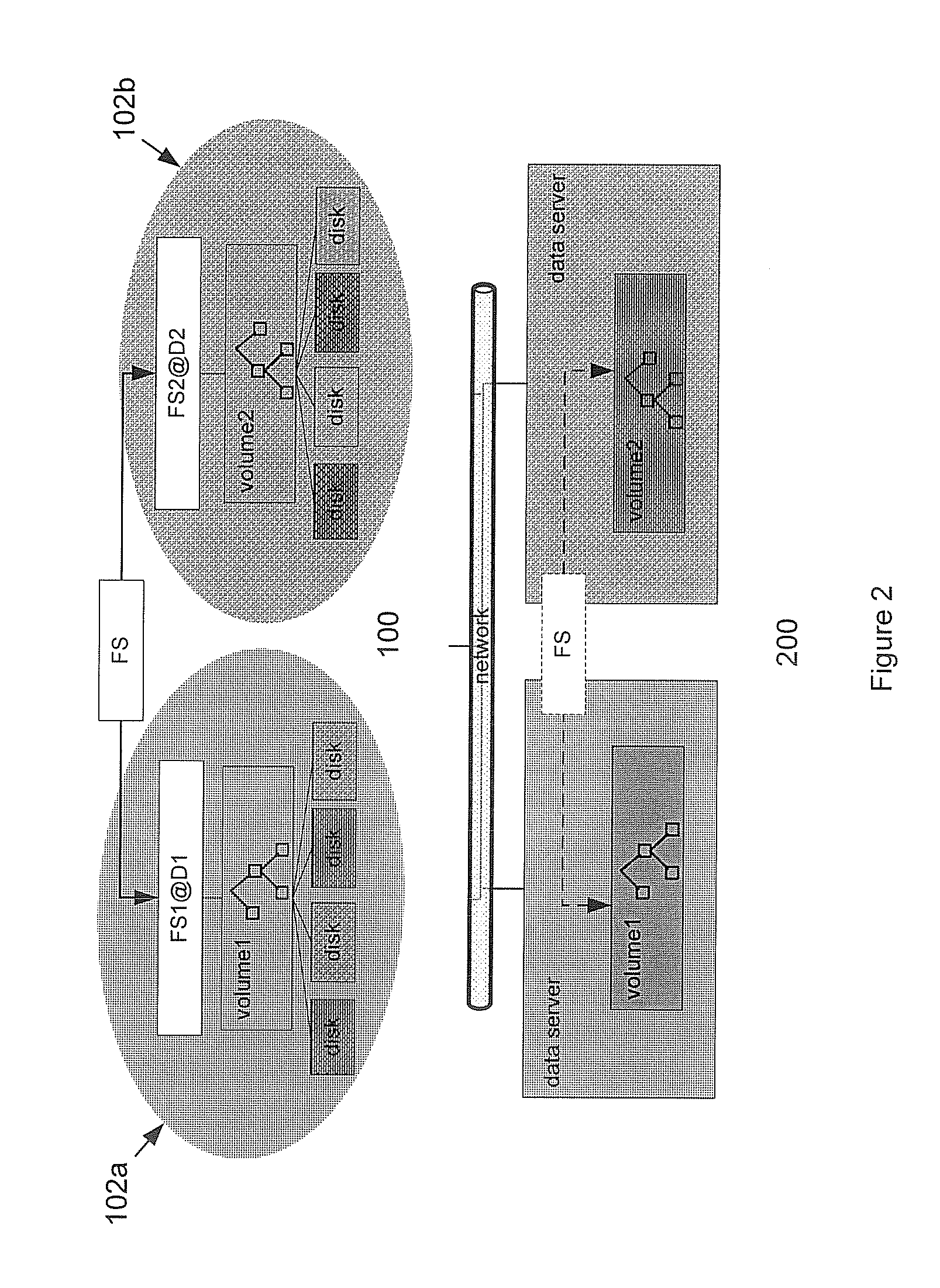
A method and system is disclosed for resolving a single server bottleneck. Logically associated data is typically collocated within a single filesystem or a single block device accessible via a single storage server. A single storage server can provide a limited I / O bandwidth, which creates a problem known as “single I / O node” bottleneck. The method and system provides techniques for spreading I / O workload over multiple I / O domains, both local and remote, while at the same time increasing operational mobility and data redundancy. Both file and block level I / O access are addressed.
Owner:NEXENTA SYSTEMS
Detection and correction of block-level data corruption in fault-tolerant data-storage systems
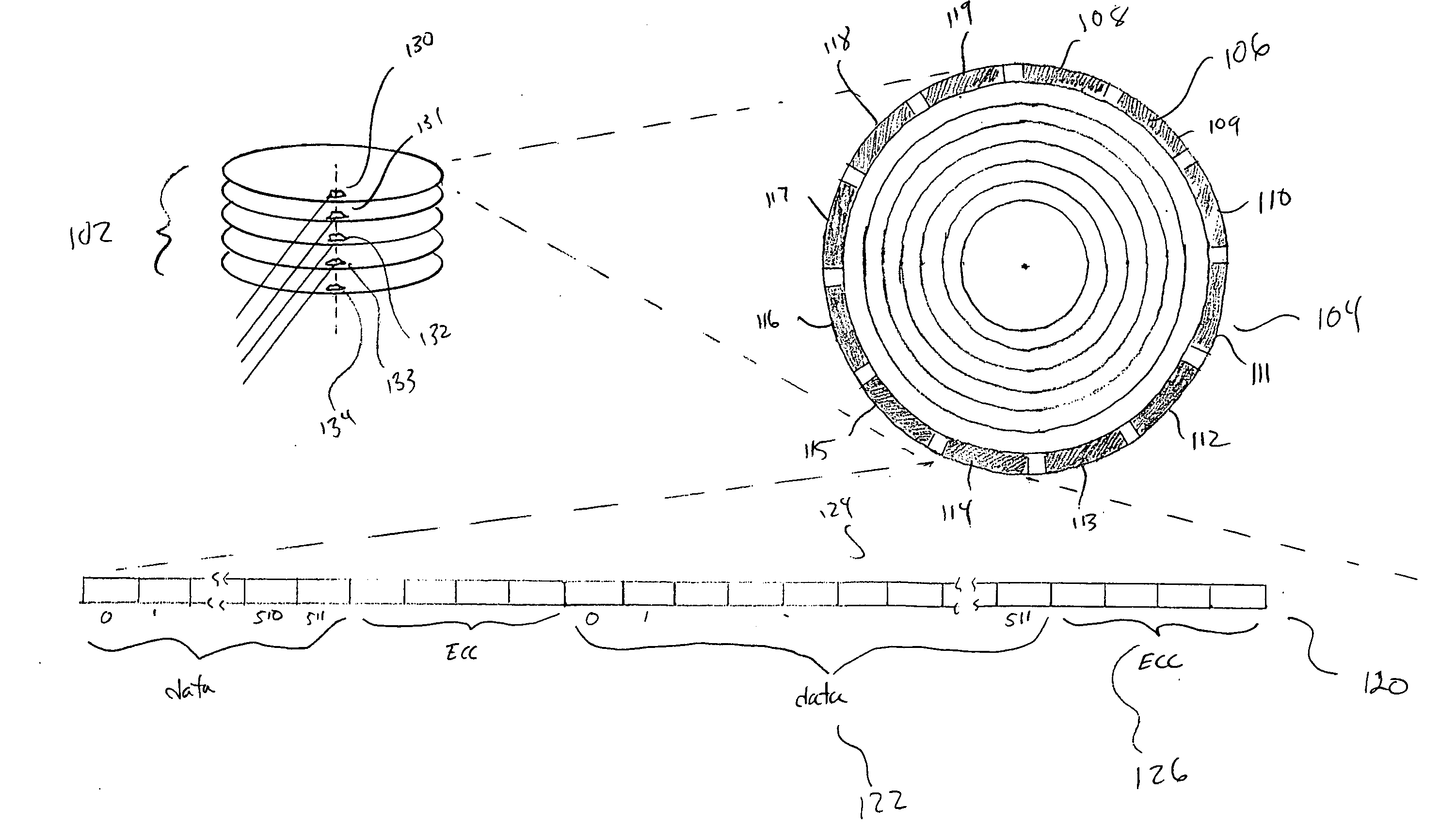
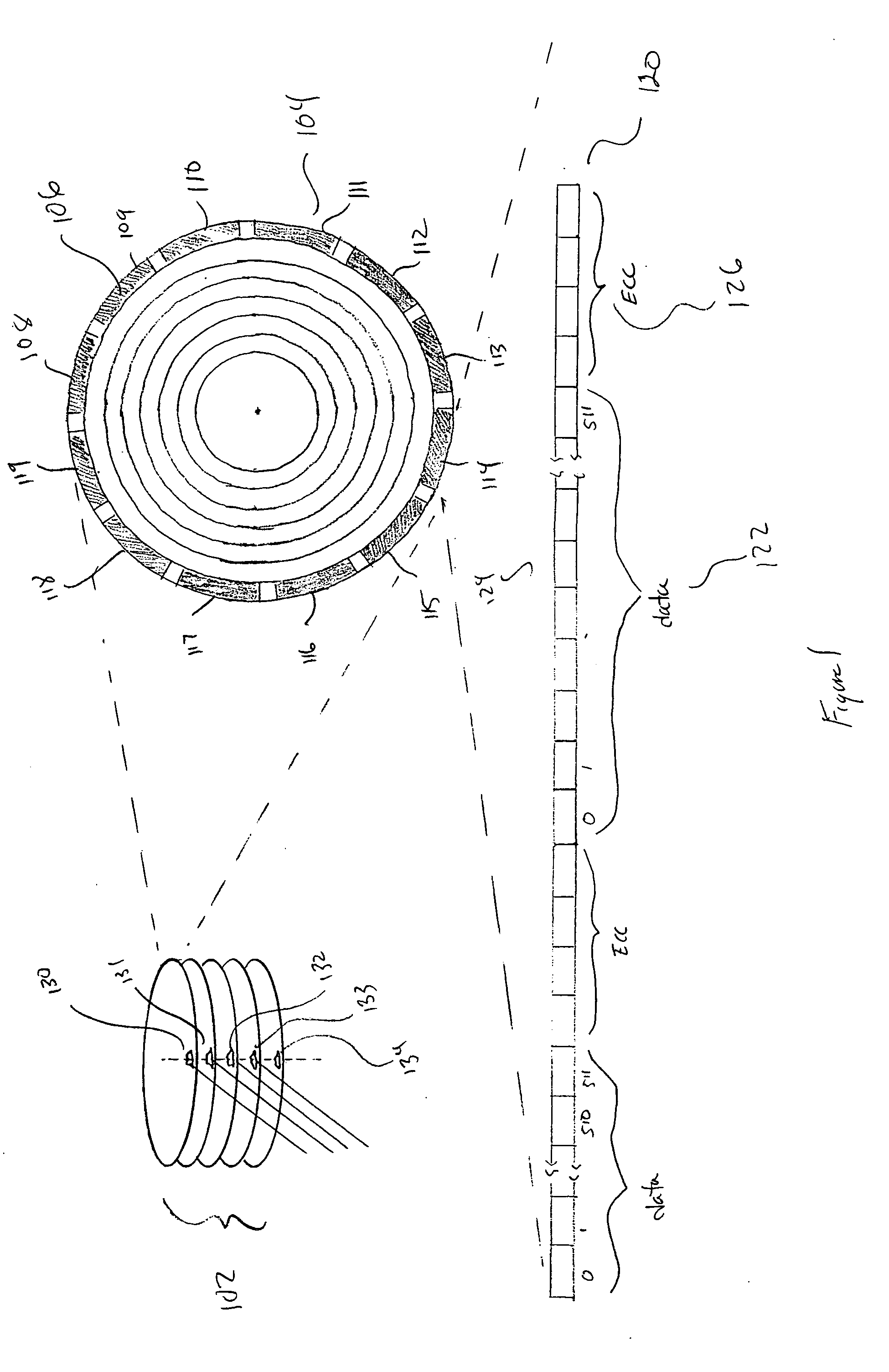
ActiveUS20080115017A1Eliminate needEfficient detectionStatic storageRedundant data error correctionRAIDDisk controller
Various embodiments of the present invention provide fault-tolerant, redundancy-based data-storage systems that rely on disk-controller-implemented error detection and error correction, at the disk-block level, and RAID-controller-implemented data-redundancy methods, at the disk and disk-stripe level, in order to provide comprehensive, efficient, and system-wide error detection and error correction. Embodiments of the present invention use disk-level and stripe-level data redundancy to provide error detection and error correction for stored data objects, obviating the need for certain costly, intermediate levels of error detection and error correction commonly employed in currently available fault-tolerant, redundancy-based data-storage systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Single column layout for content pages
ActiveUS7362311B2Eliminate needEasy to eliminateInput/output for user-computer interactionDigital data information retrievalUser needsBackground image
A system and method for small computing devices that present a single column of content such as a web page such that a user need only scroll vertically to see the content. A parser converts HTML to CSS as necessary, and a single column style sheet modifies content for a more-optimized viewing experience. To this end, tables and tables cells are rendered as blocks, with no padding / border / margins and any explicit widths and heights changed to automatic. Other table elements are rendered as block level elements, and horizontal margins are eliminated or re-enabled on some elements in a reduced manner. Spacer images are removed, as well as cell background images and small images. Content such as text is wrapped, and images are resized as necessary based on the screen display width. The result is a single content column that facilitates viewing and scrolling in only one direction.
Owner:MICROSOFT TECH LICENSING LLC
Block level data snapshot system and method
A block level data snapshot system uses agents to convert block level file commands from devices such as computer workstations intended for block level devices such as hard disks. The block level file commands are converted into instructions for a node based snapshot data system for taking snapshots at the block level. By converting the block level file commands into instructions suitable for the node based snapshot system, snapshots are able to be taken at the block level, which allows for disk storage savings and speed enhancements. One resultant feature is that the block level data snapshot system can be used as a block level storage device for one or more workstations thus allowing relatively simple integration of a snapshot system with existing workstations.
Owner:OVERLAND STORAGE INC
Block-level and hash-based single-instance storage
ActiveUS7454592B1Remove redundant informationDigital data information retrievalError detection/correctionFile systemLookup table
A method for reading data in a block-level single-instance storage system may involve receiving a first address of a data block, retrieving a signature corresponding to the first address, and reading data from a second address corresponding to the signature. A storage system may include a storage manager and first and second lookup tables. The storage manager may interface with an application (such as a database system or a file system) that uses a first set of identifiers for data blocks. The storage manager may use a second set of identifiers for the data blocks, and translates between the first and second identifiers using the lookup tables. The first lookup table indexes data block signatures according to the first set of identifiers. The second lookup table indexes the second set of identifiers according to the data block signatures. The second lookup table may be pruned to provide single instance storage.
Owner:VERITAS TECH
Systems and methods for an enhanced controller architecture in data storage systems
ActiveUS20130060981A1Memory adressing/allocation/relocationDigital computer detailsController architectureEngineering
Disclosed herein is a controller architecture that pairs a controller with a NVM (non-volatile memory) storage system over a high-level, high speed interface such as PCIe. In one embodiment, the NVM storage system includes a bridge that communicates with the controller via the high-level interface, and controls the NVM via an interface (e.g., ONFI). The controller is provided a rich set of physical level of controls over individual elements of the NVM. In one embodiment, the controller is implemented in a higher powered processor that supports advanced functions such as mapping, garbage collection, wear leveling, etc. In one embodiment, the bridge is implemented in a lower powered processor and performs basic signal processing, channel management, basic error correction functions, etc. This labor division provides the controller physical control of the NVM over a fast, high-level interface, resulting in the controller managing the NVM at both the page and block level.
Owner:WESTERN DIGITAL TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com