Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2276 results about "Level data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
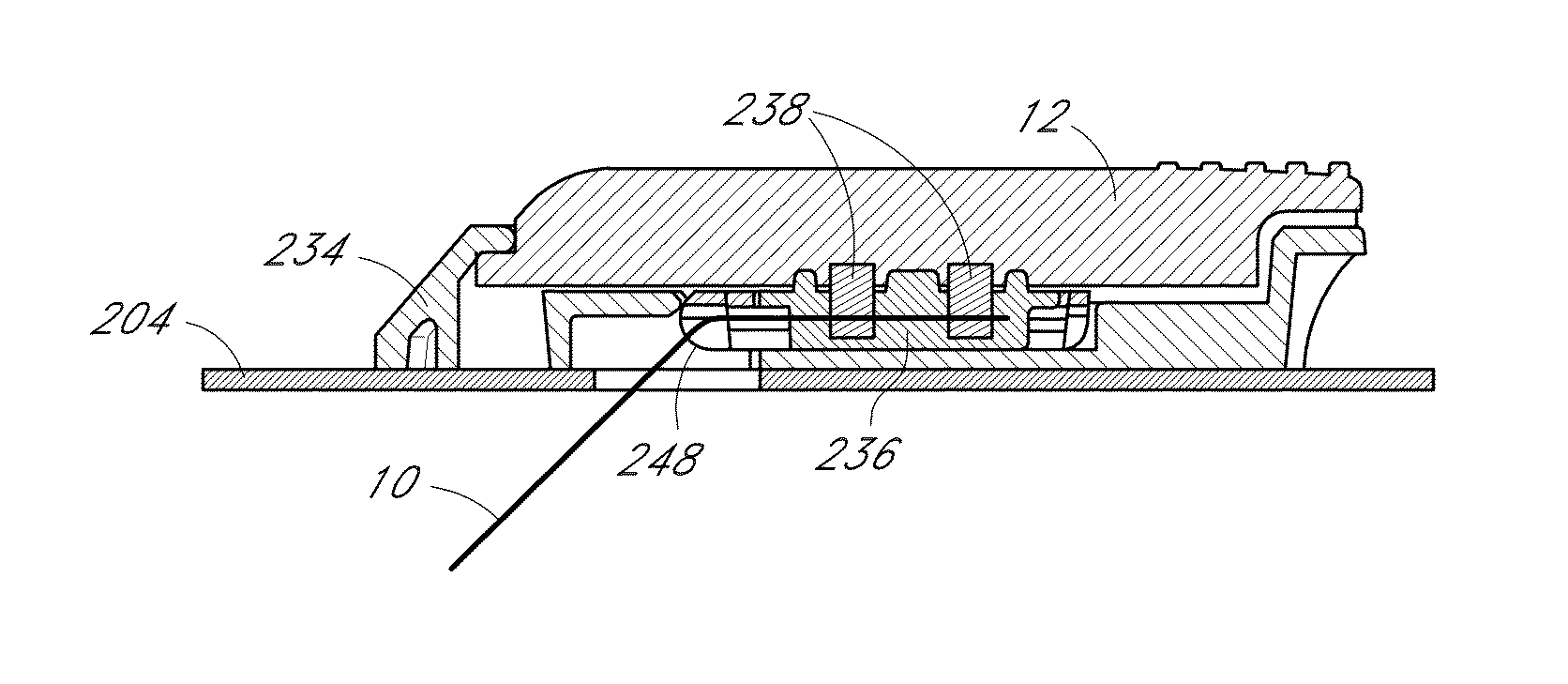
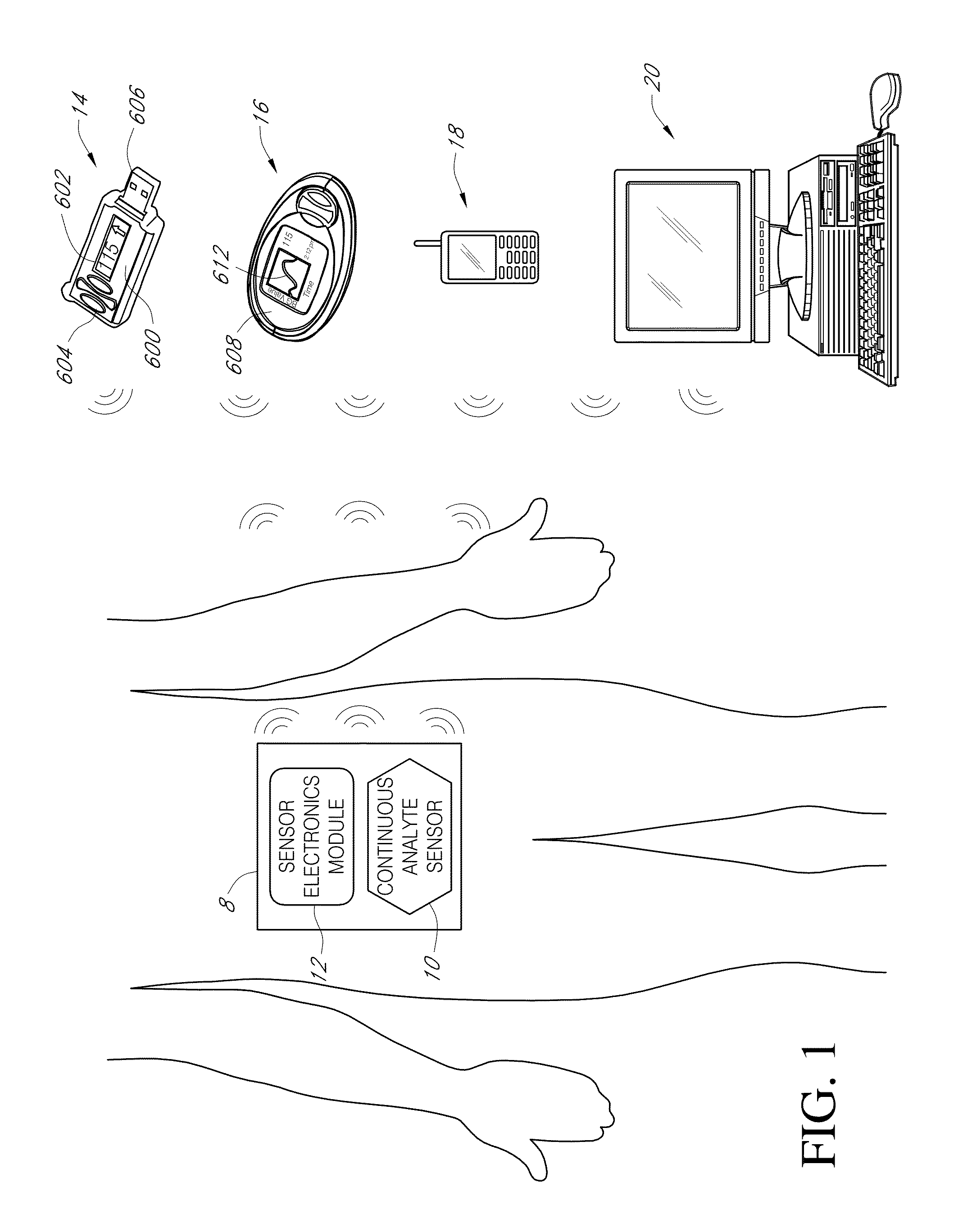
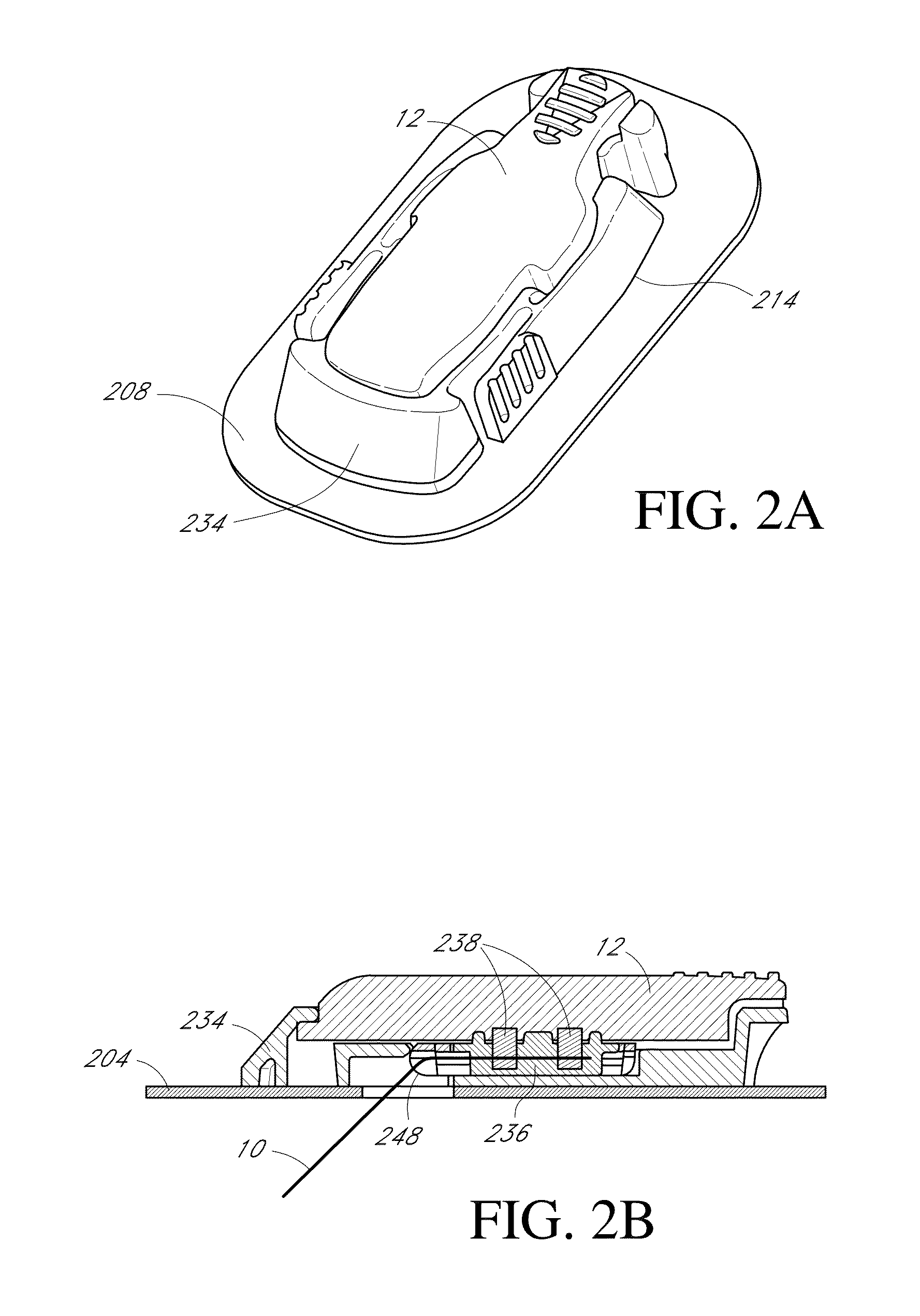
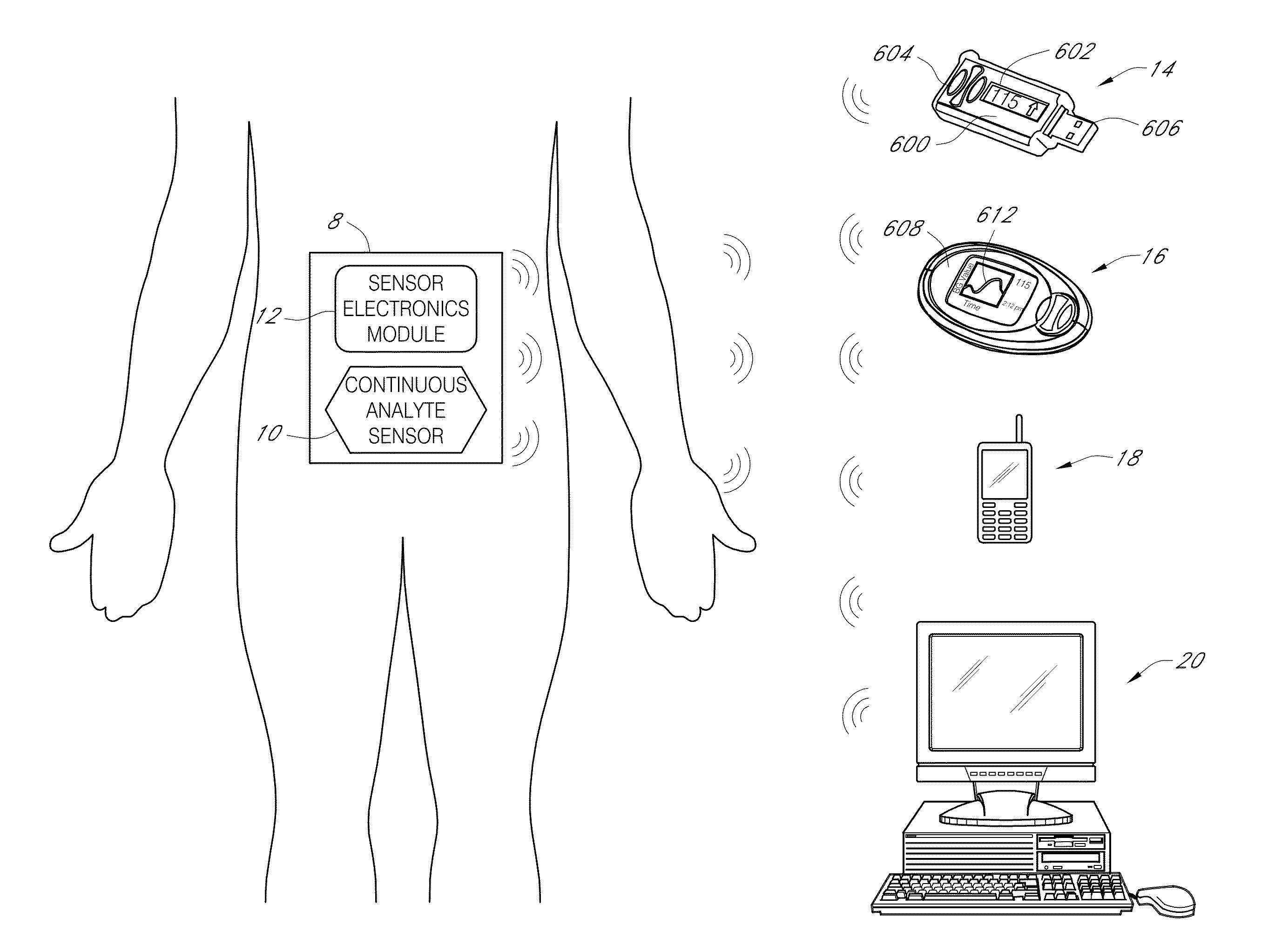
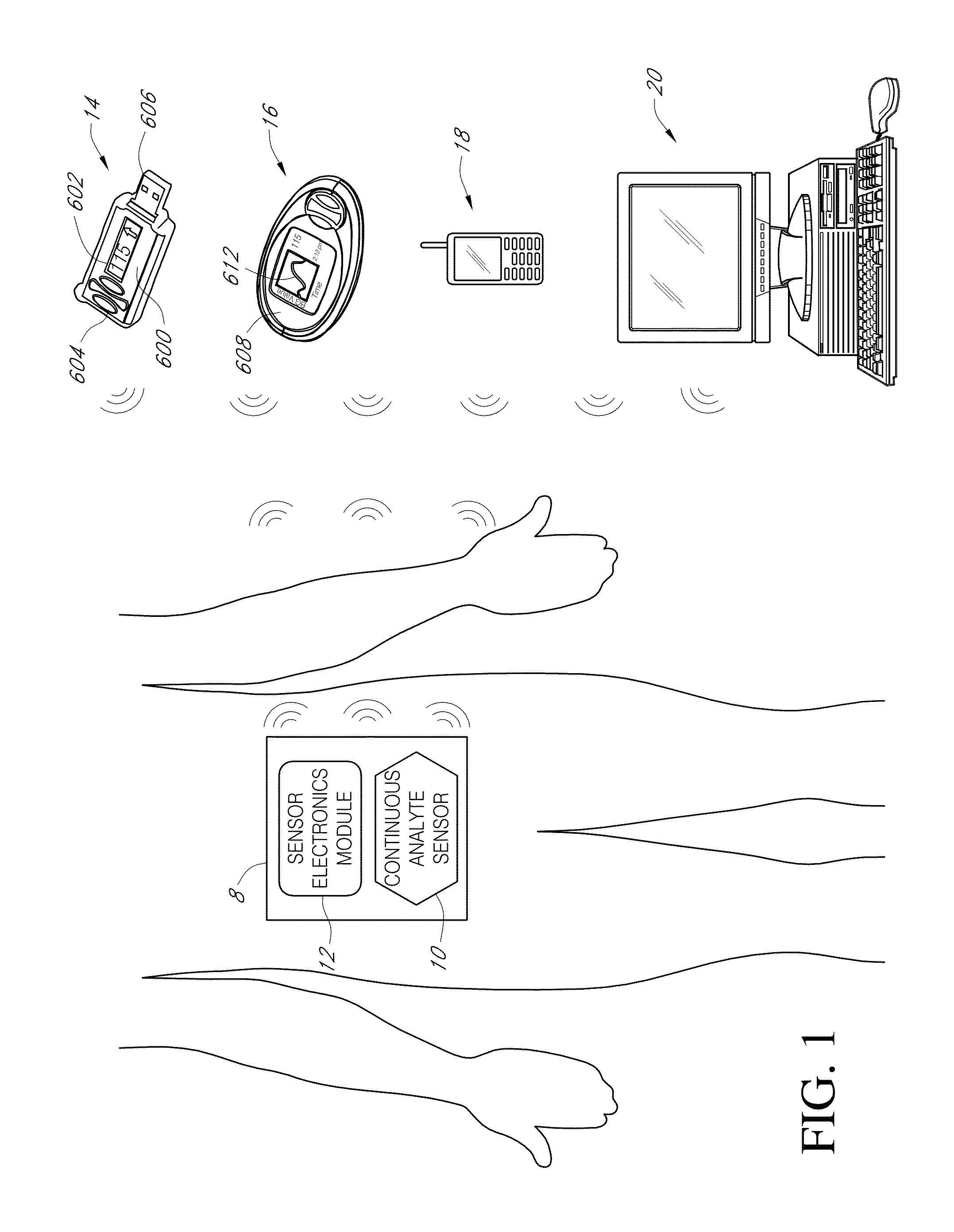
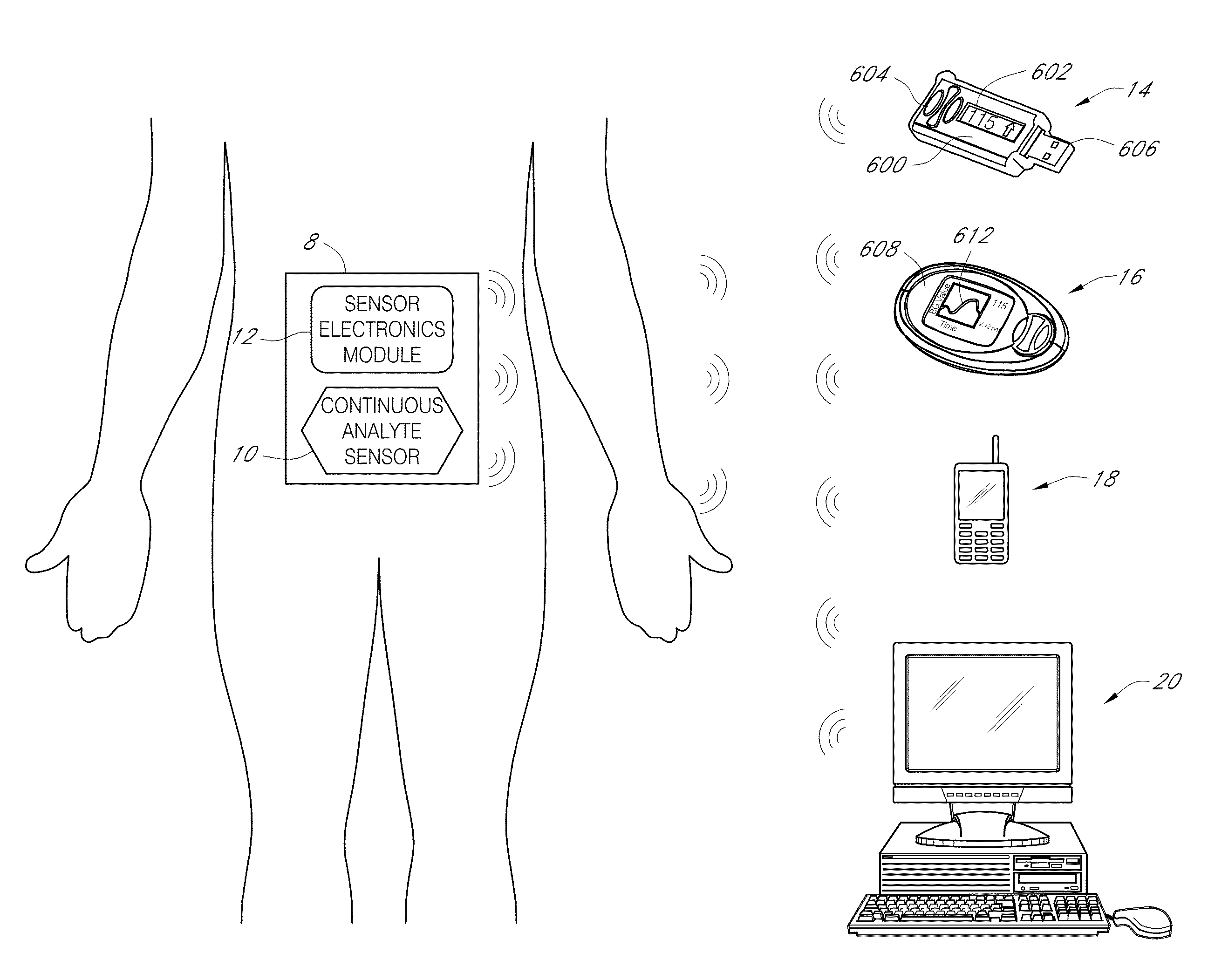
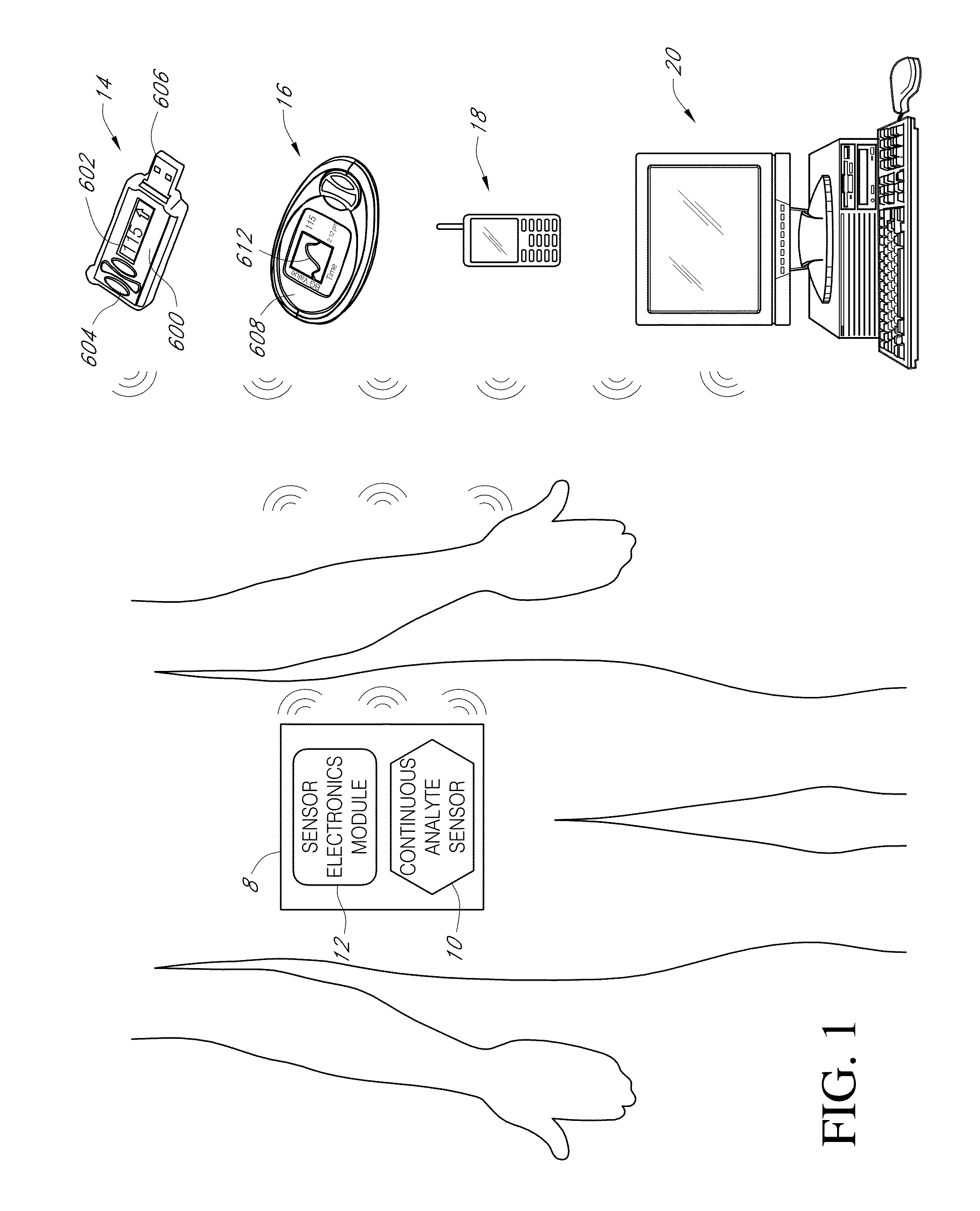
Systems and methods for detecting glucose level data patterns
Systems and methods for detecting and reporting patterns in analyte concentration data are provided. According to some implementations, an implantable device for continuous measurement of an analyte concentration is disclosed. The implantable device includes a sensor configured to generate a signal indicative of a concentration of an analyte in a host, a memory configured to store data corresponding at least one of the generated signal and user information, a processor configured to receive data from at least one of the memory and the sensor, wherein the processor is configured to generate pattern data based on the received information, and an output module configured to output the generated pattern data. The pattern data can be based on detecting frequency and severity of analyte data in clinically risky ranges.
Owner:DEXCOM
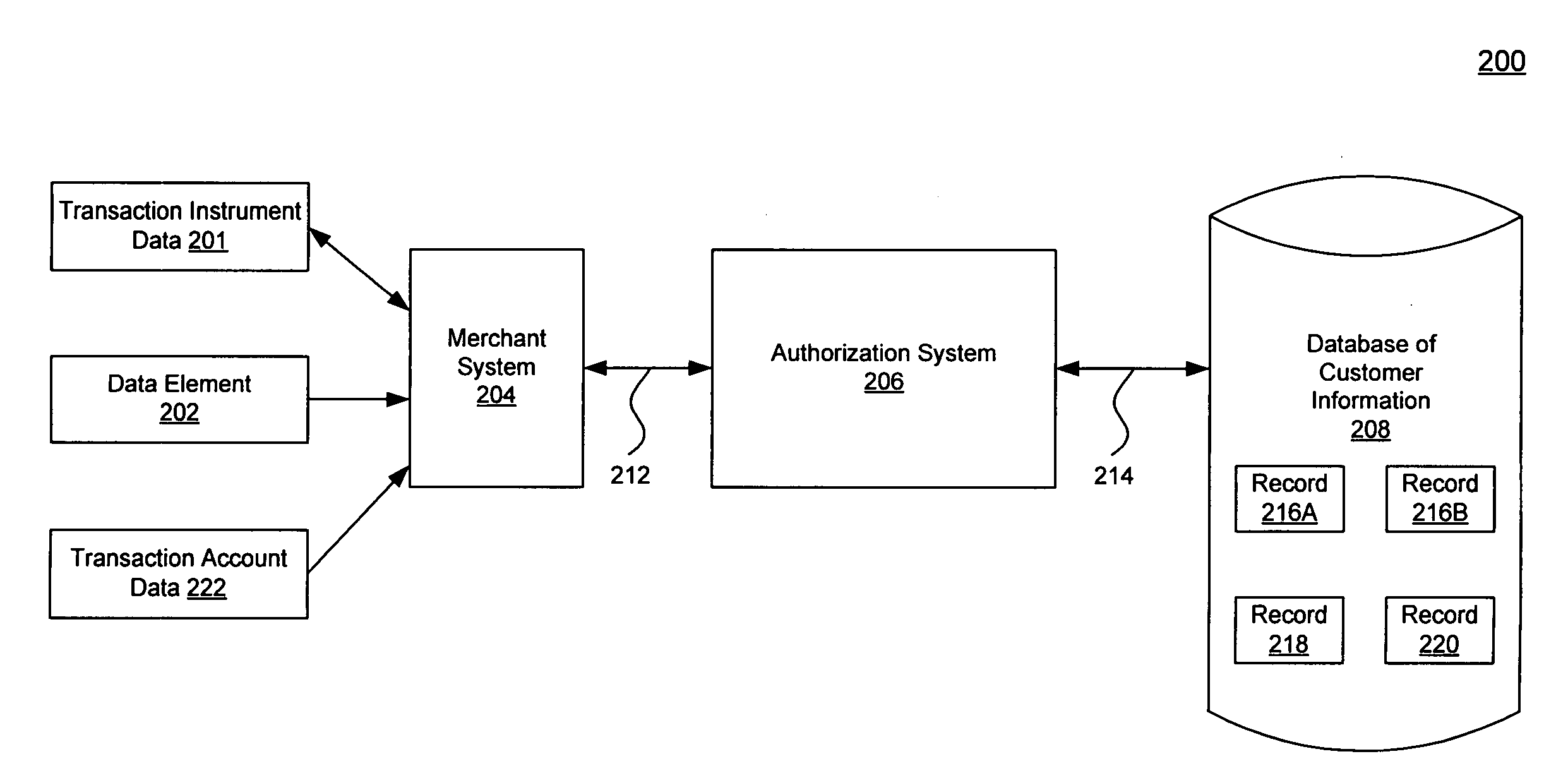
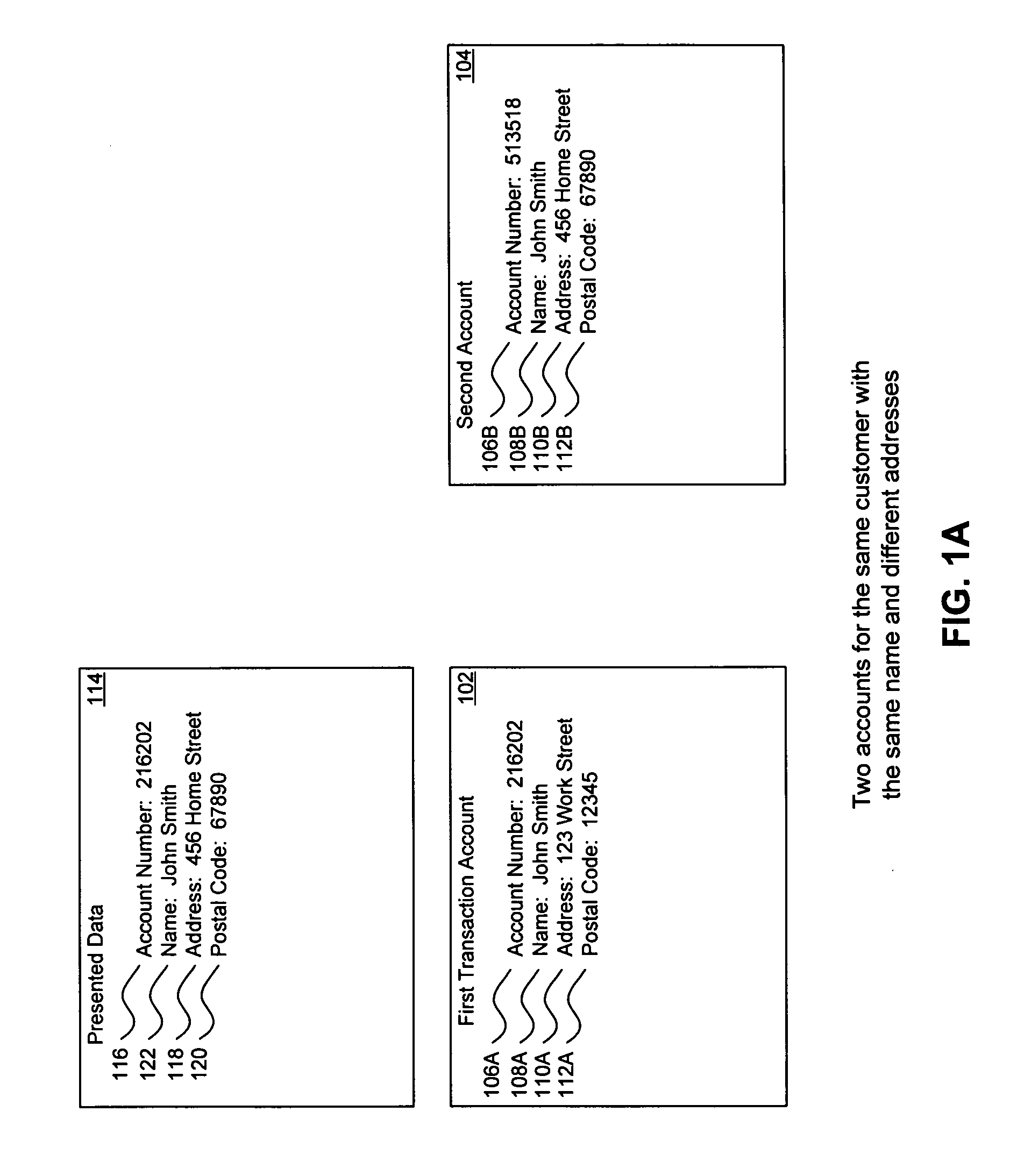
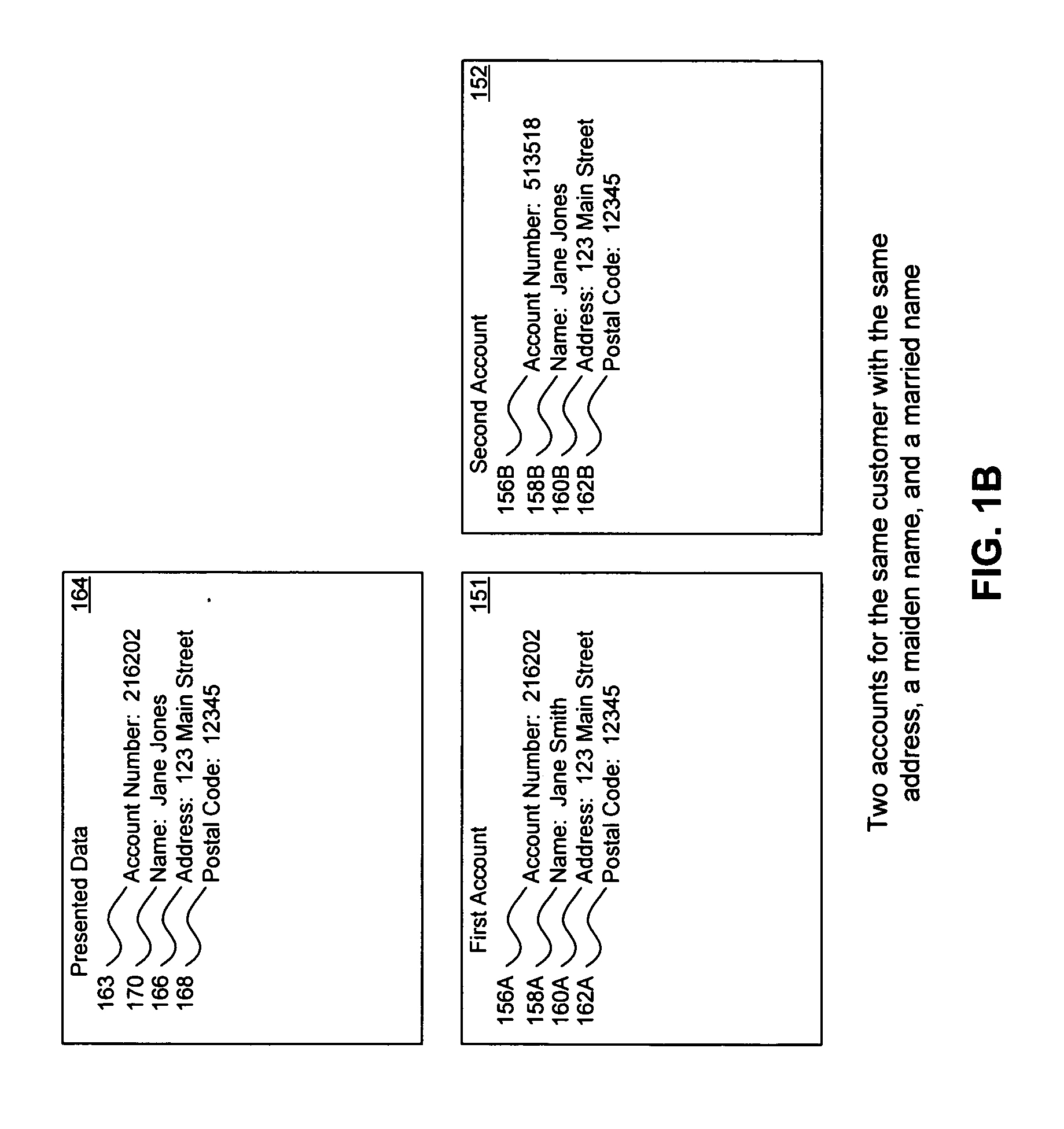
Method, system, and computer program product for customer-level data verification
ActiveUS20070284433A1Improve accuracyReduce error rateComplete banking machinesFinanceData validationSource Data Verification
A system, method, and computer program to reduce incorrectly declined transactions and improve risk calculation accuracy by reducing error probability during fraud detection. The tool first receives at least one data element as well as transaction account data and / or financial transaction instrument data. Then a customer is determined from a first record associated with the transaction account data and / or financial transaction instrument data. A record search is performed to identify at least one additional record associated with the customer. Finally, the data element is compared to the information contained in the additional record to create a comparison result that verifies a customer address. The comparison result may be used as an input to transaction risk calculations. The comparison result may also be provided to a merchant system and / or merchant for use in a decision-making process, for example, to verify customer identity.
Owner:LIBERTY PEAK VENTURES LLC
Method and system for user profile match indication in a mobile environment
Methods and systems for determining a suitability for a mobile client to display information are disclosed. For example, a method for determining a suitability for a mobile client to receive a targeted content message includes generating user profile data by the mobile client, receiving a set of target profile data associated with the targeted content message, the set of target profile data being descriptive of the targeted content message, comparing the user profile data with the target set of profile data to produce a set of confidence-level data, a target set of profile data describing the content of a respective targeted-content message, and storing the targeted content message in the mobile client based upon the set of confidence-level data.
Owner:QUALCOMM INC
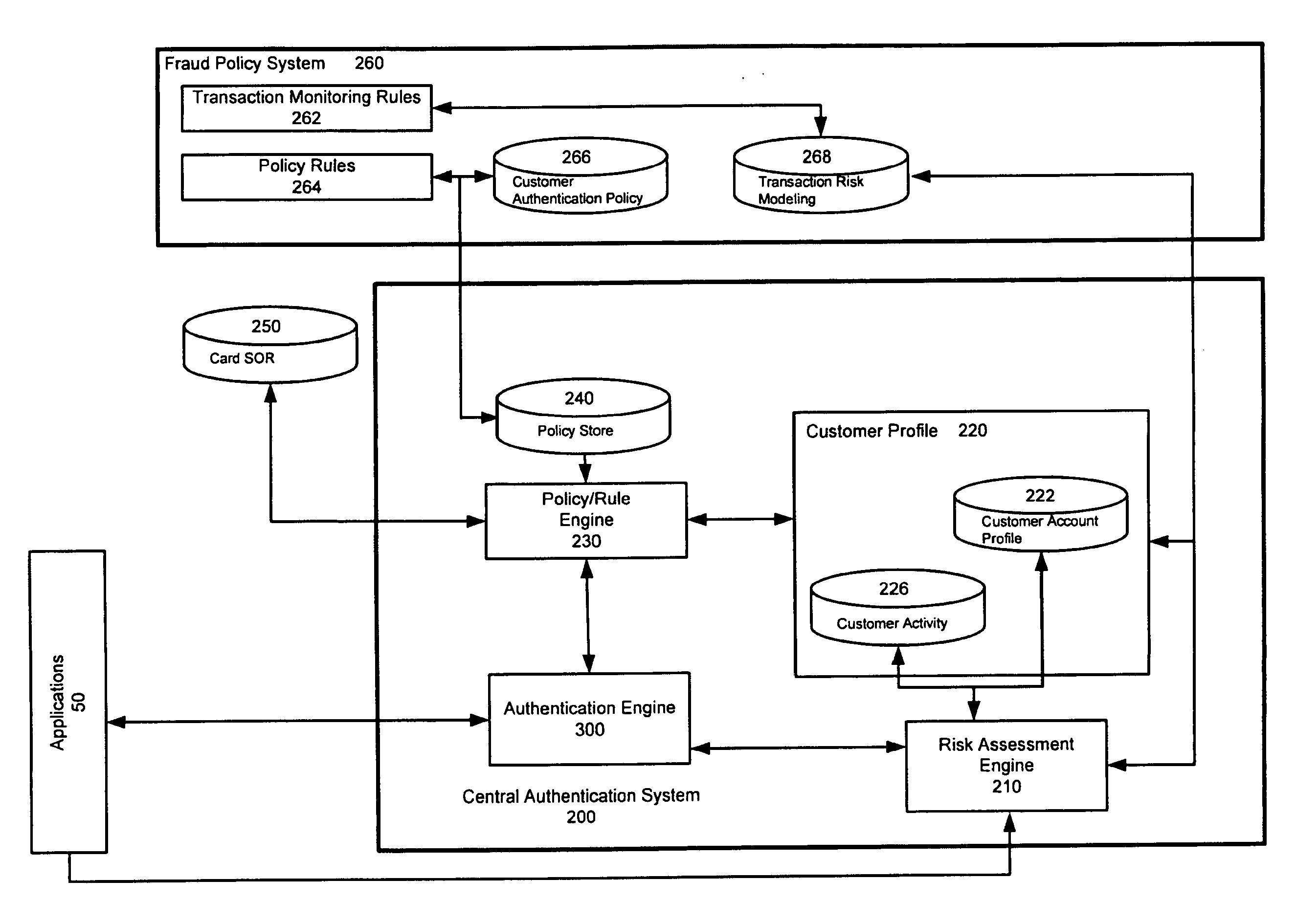
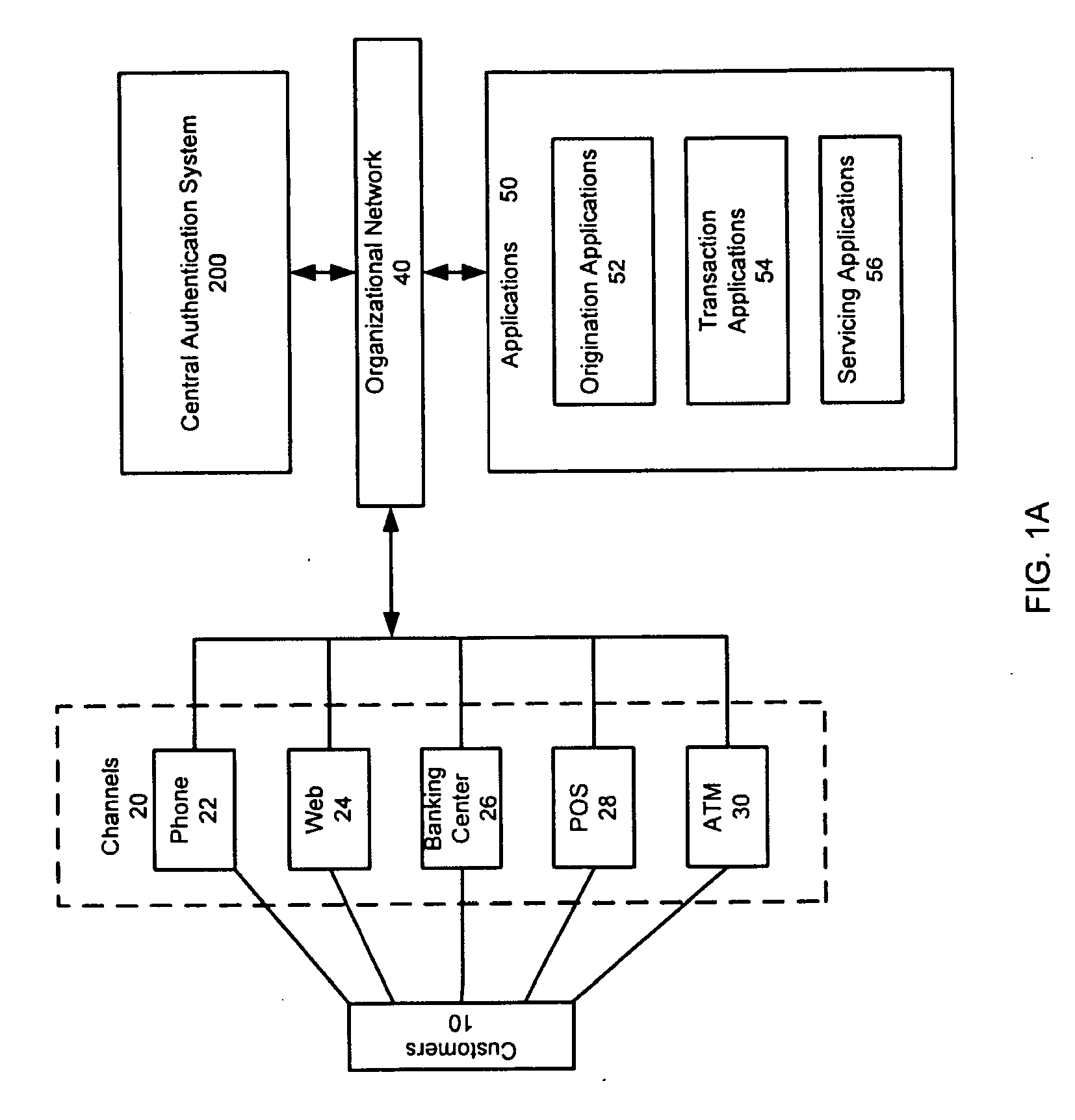
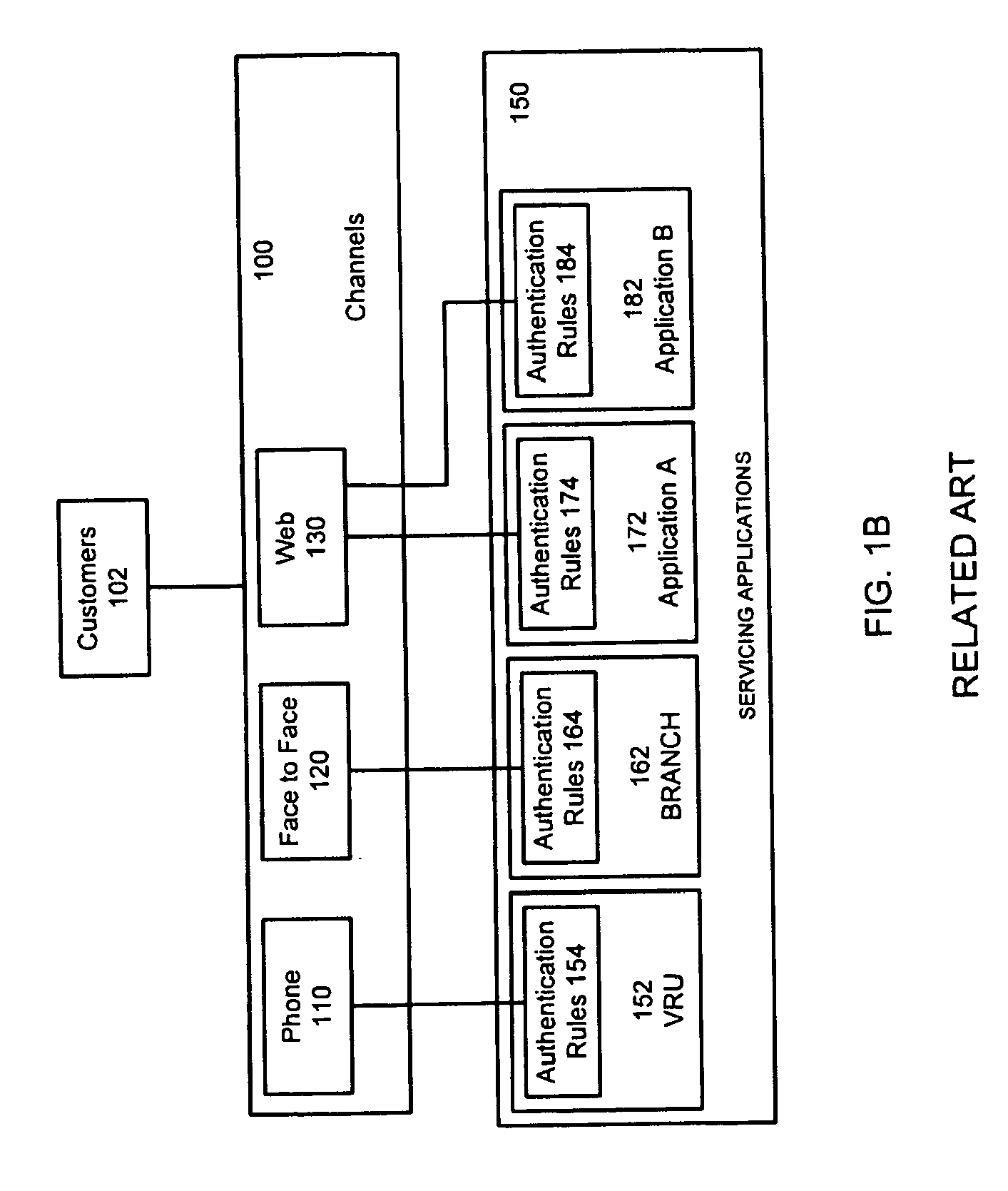
Authentication System and Method
ActiveUS20120297446A1Payment architectureDigital data authenticationInternet privacyCentralized management
Owner:JPMORGAN CHASE BANK NA
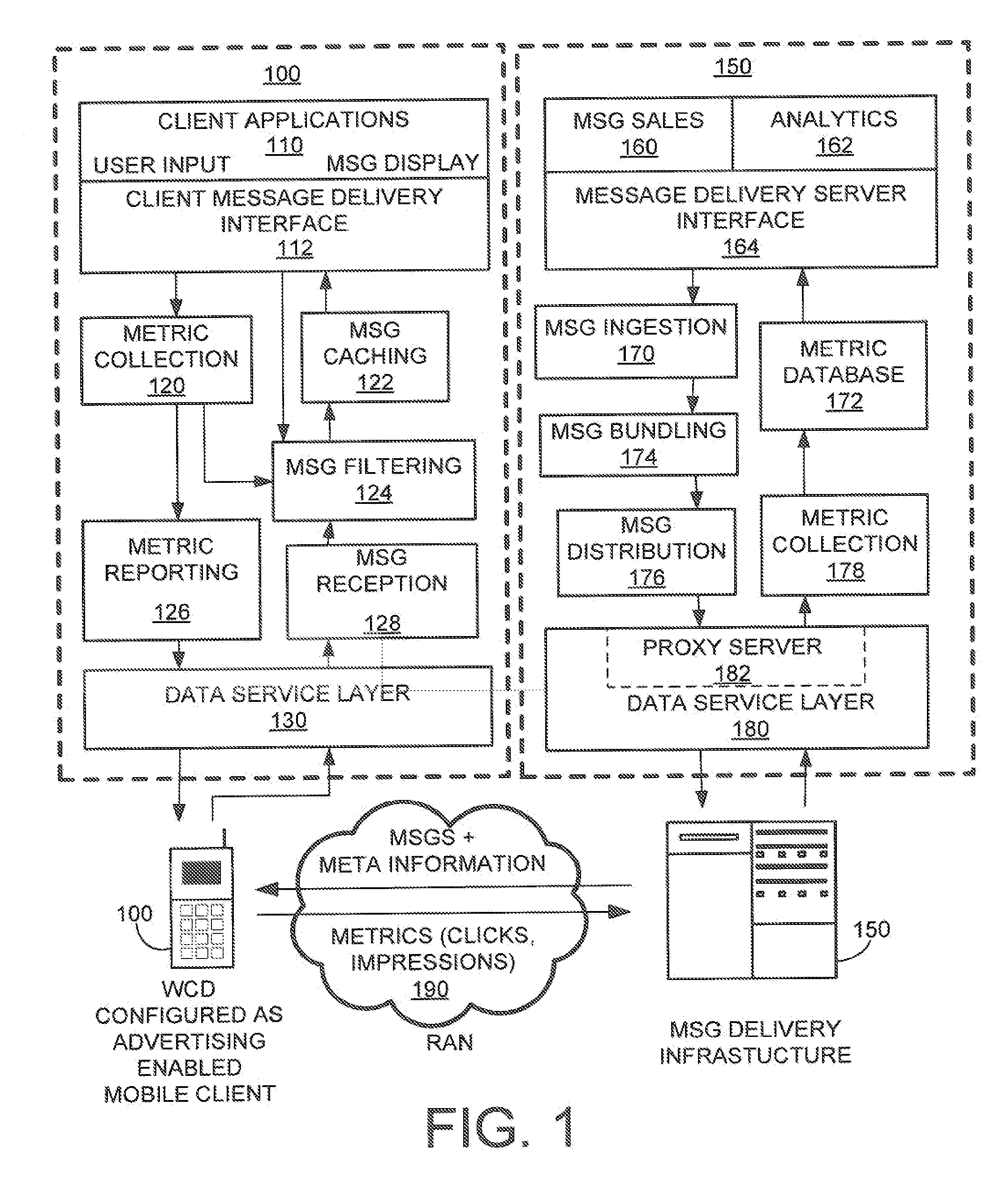
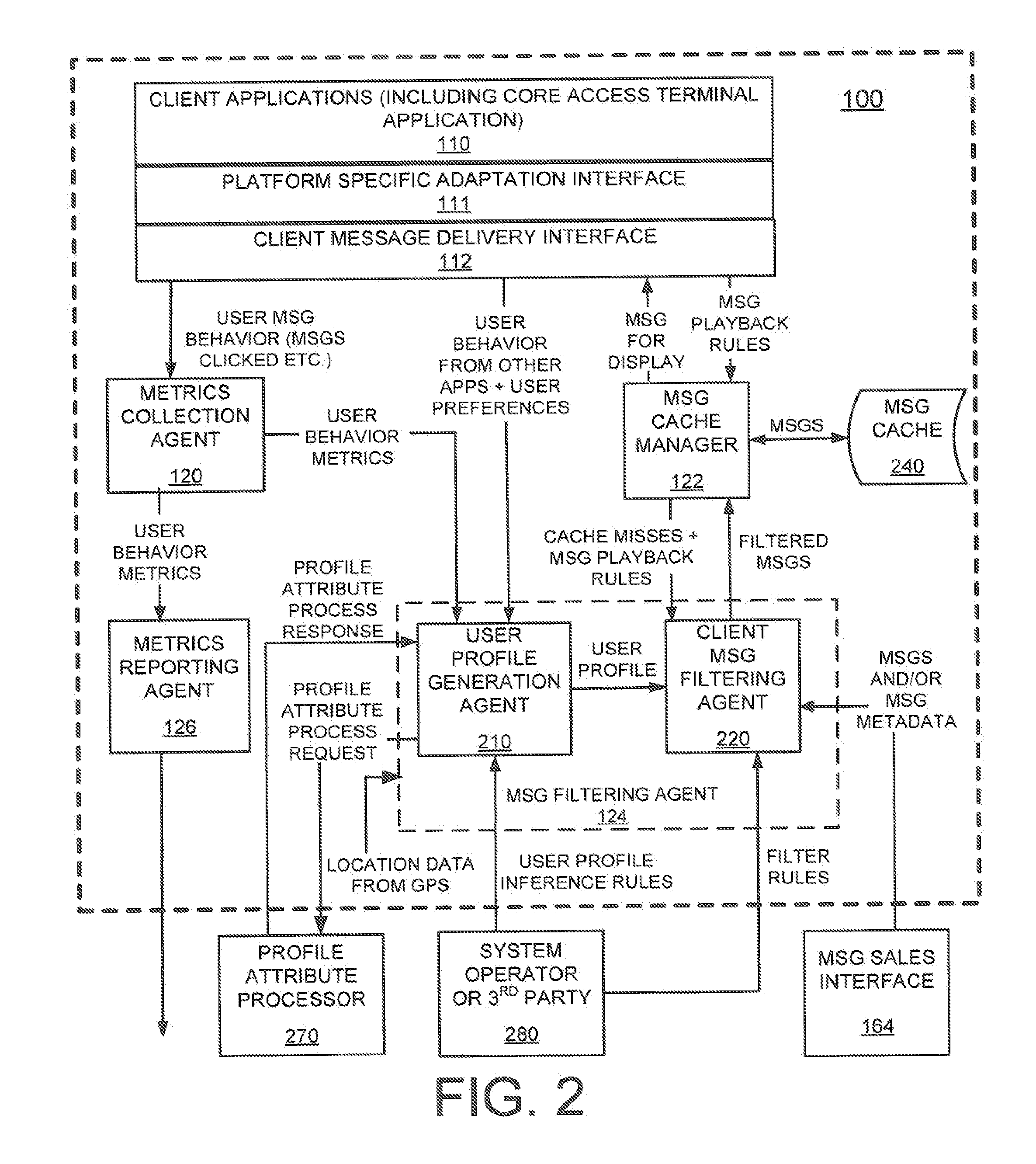
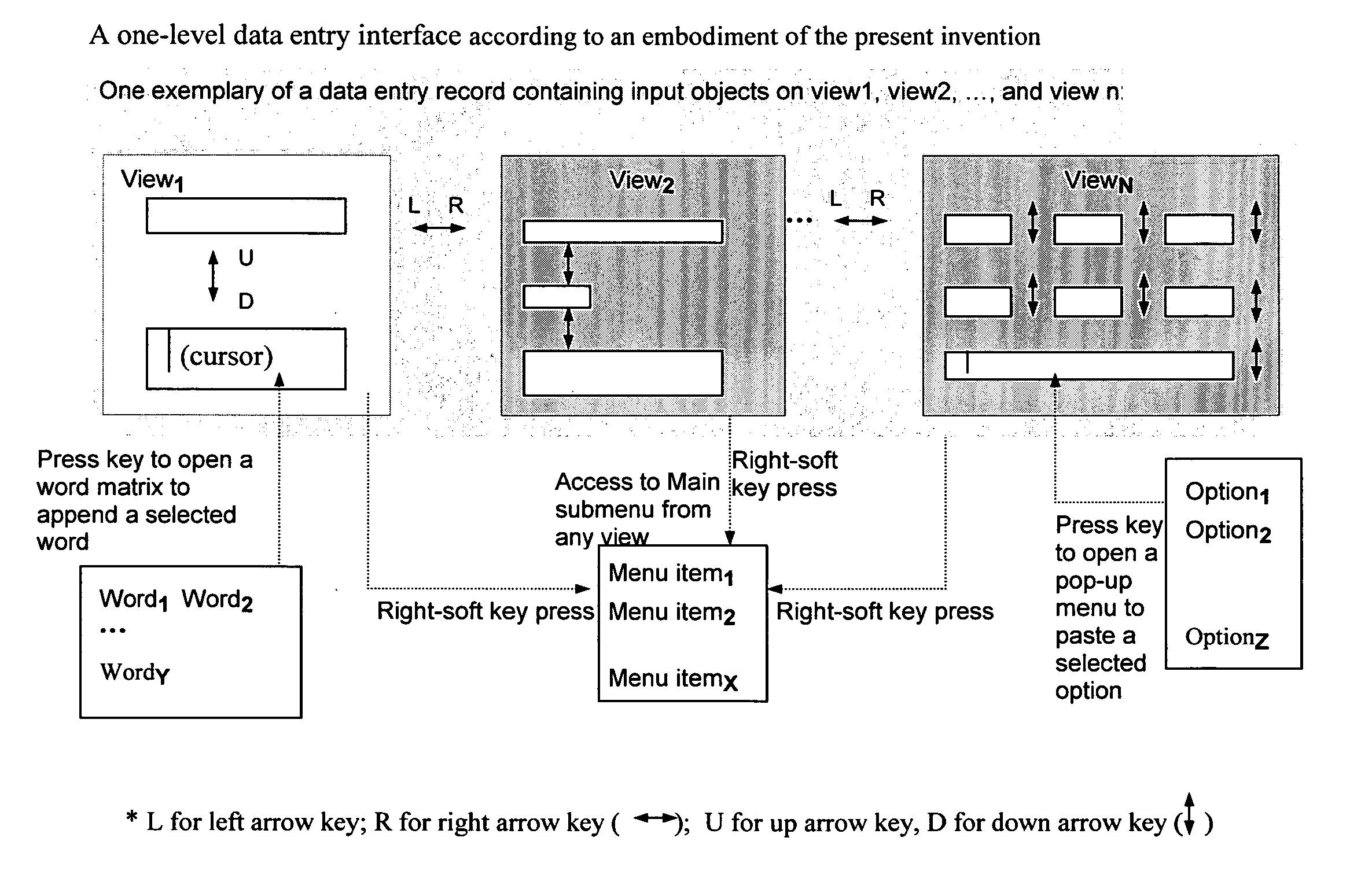
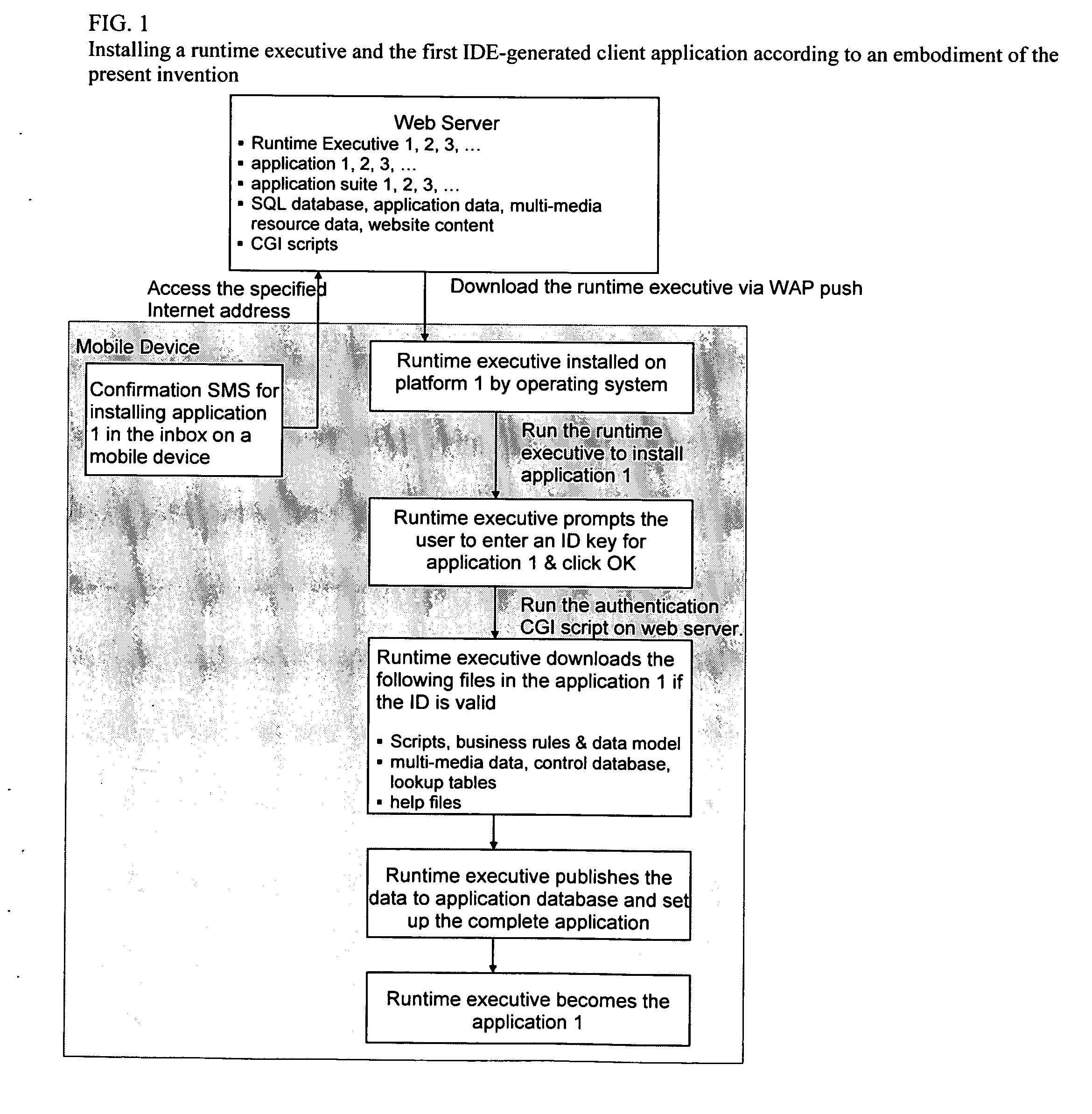
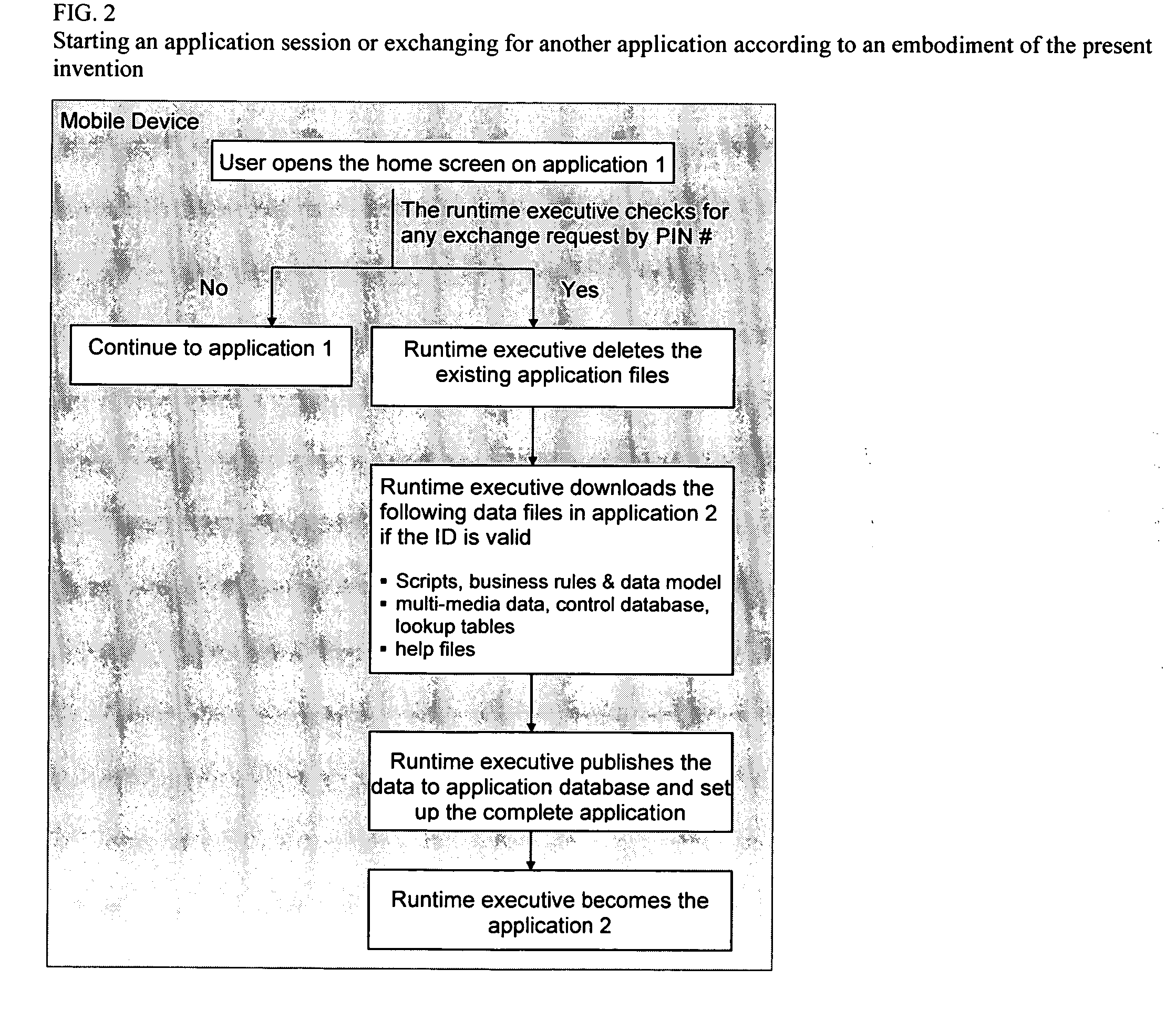
Method and system for designing, implementing, and managing client applications on mobile devices
InactiveUS20080046557A1Easy accessEasy to navigateSoftware engineeringMultiple digital computer combinationsTypingData file
A system that designs, implements, and manages client applications on mobile devices using runtime executives and an IDE. In one aspect, the runtime executive delivers consistent GUI and application behavior within and across mobile development platforms. In another aspect, the runtime executive can set up data files of an IDE-generated client application on mobile devices and then become that application itself while supporting a pay-per-download subscription service. The runtime executive delivers multimedia content in presentation format via a one-level browsing interface, enables data entries across tabbed views with minimal typing and drilidowns via a one-level data entry interface, and precisely processes scripts and commands, including calls to COM libraries. The IDE allows non-programmers to design the GUI and the scripts for mobile device applications and compile them into application data files for multiple development platforms, which are then loaded and executed by runtime executives.
Owner:CHENG JOSEPH C
Systems and methods for detecting glucose level data patterns
Systems and methods for detecting and reporting patterns in analyte concentration data are provided. According to some implementations, an implantable device for continuous measurement of an analyte concentration is disclosed. The implantable device includes a sensor configured to generate a signal indicative of a concentration of an analyte in a host, a memory configured to store data corresponding at least one of the generated signal and user information, a processor configured to receive data from at least one of the memory and the sensor, wherein the processor is configured to generate pattern data based on the received information, and an output module configured to output the generated pattern data. The pattern data can be based on detecting frequency and severity of analyte data in clinically risky ranges.
Owner:DEXCOM
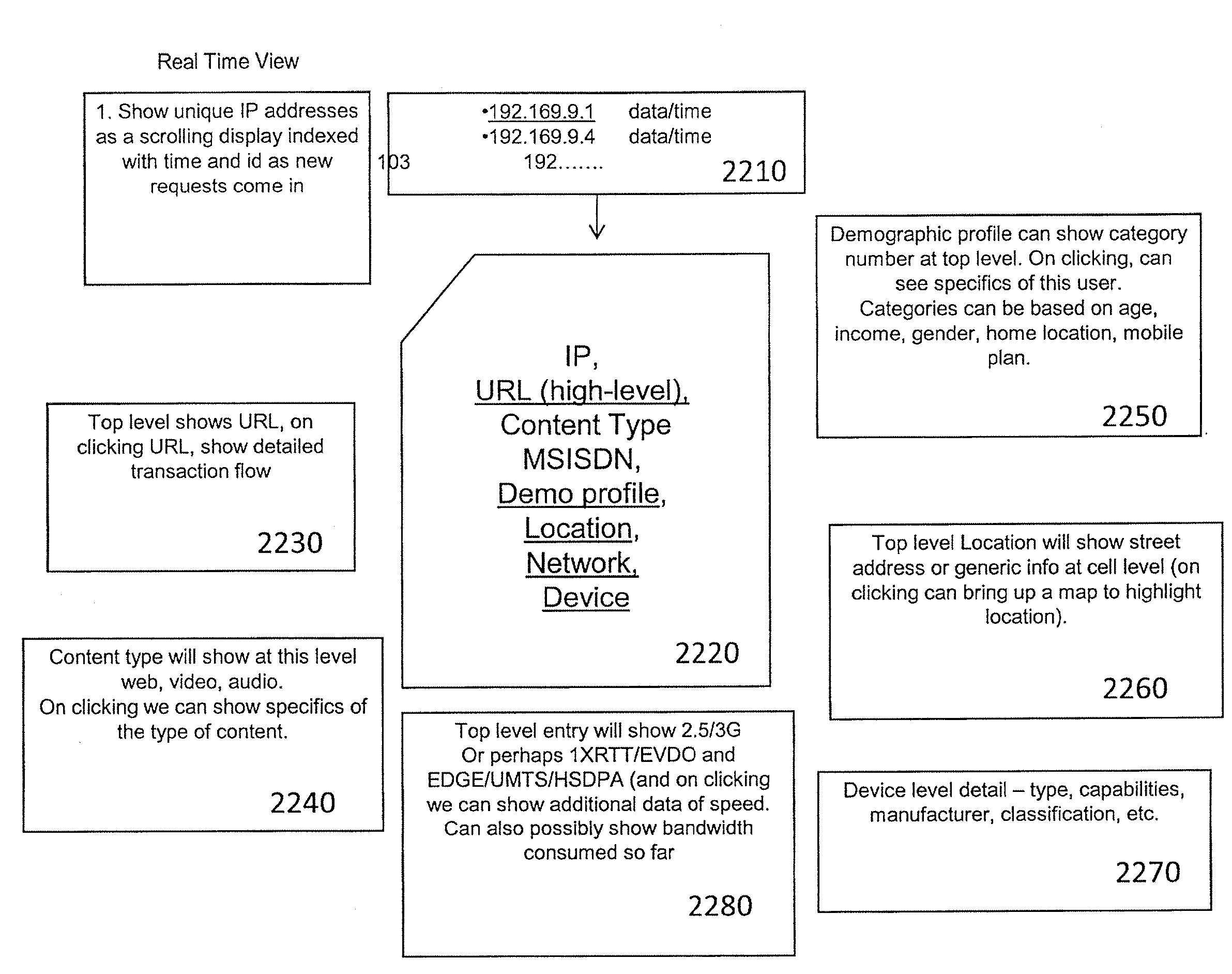
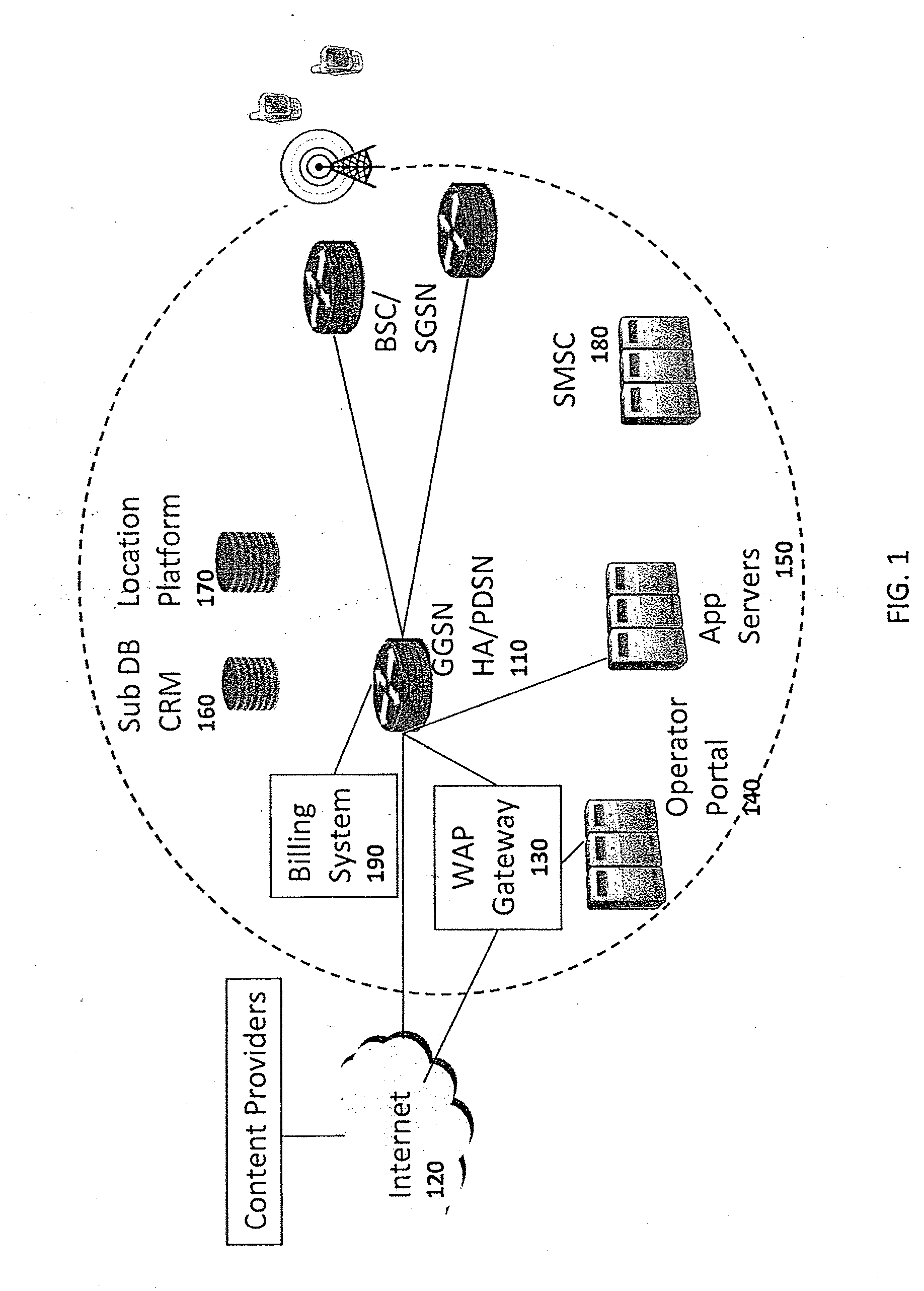
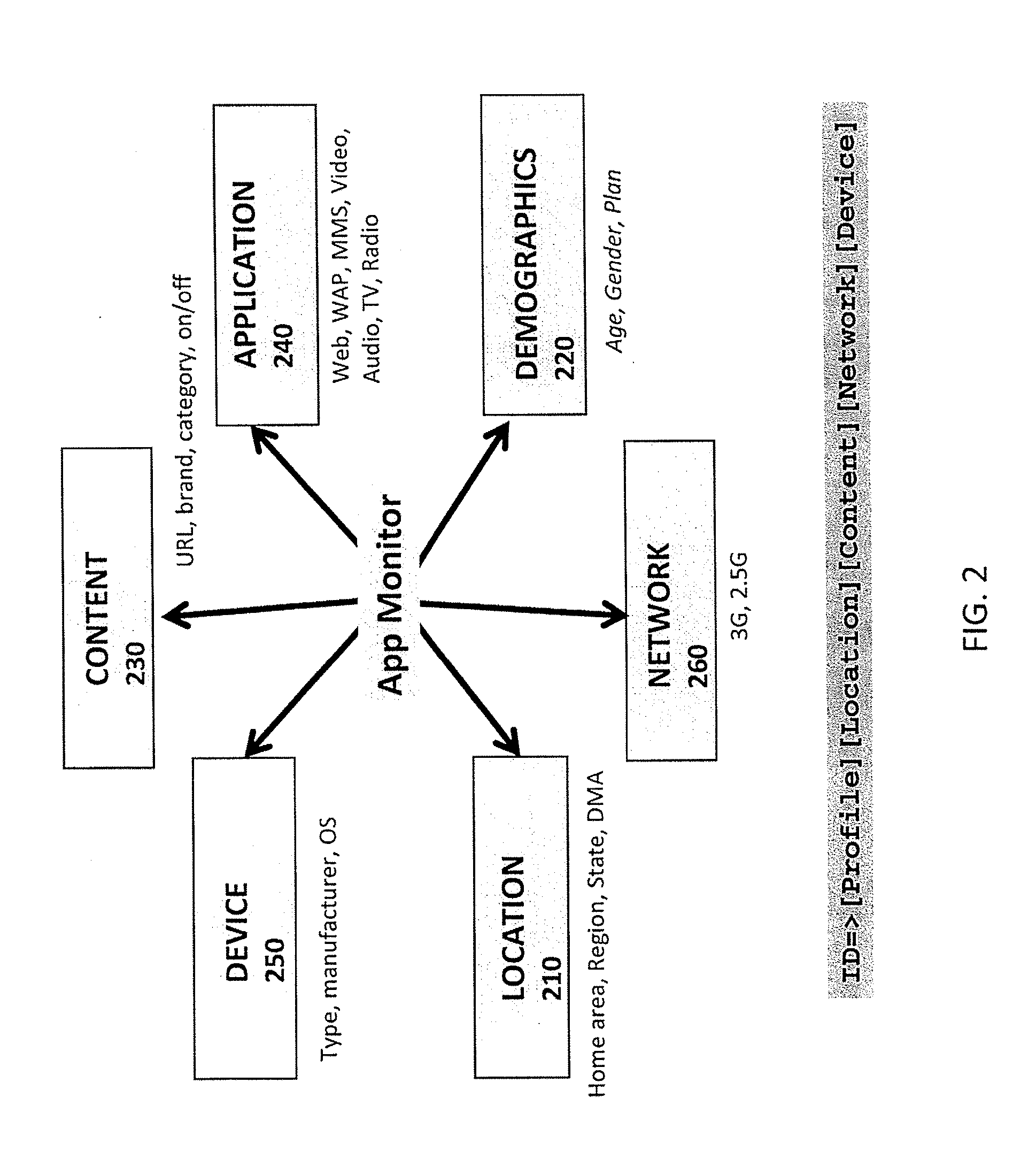
Method and apparatus for storing data on application-level activity and other user information to enable real-time multi-dimensional reporting about user of a mobile data network
A method and apparatus for storing data on application-level activity and other user information to enable real-time multi-dimensional reporting about a user of a mobile data network. A data manager receives information about application-level activity from a mobile data network and stores the information to provide dynamic real-time reporting on network usage. The data manager comprises a database, data processing module, and analytics module. The database stores the application-level data for a predetermined period of time. The data processing module monitors the data to determine if it corresponds to a set of defined reports. If the data is relevant, the processing module updates the defined reports. The analytics module accesses the database to retrieve information satisfying operator queries about network usage. If the operator chooses to convert the query into a defined report, the analytics module creates a newly defined report and populates it accordingly.
Owner:RIBBON COMM SECURITIES CORP
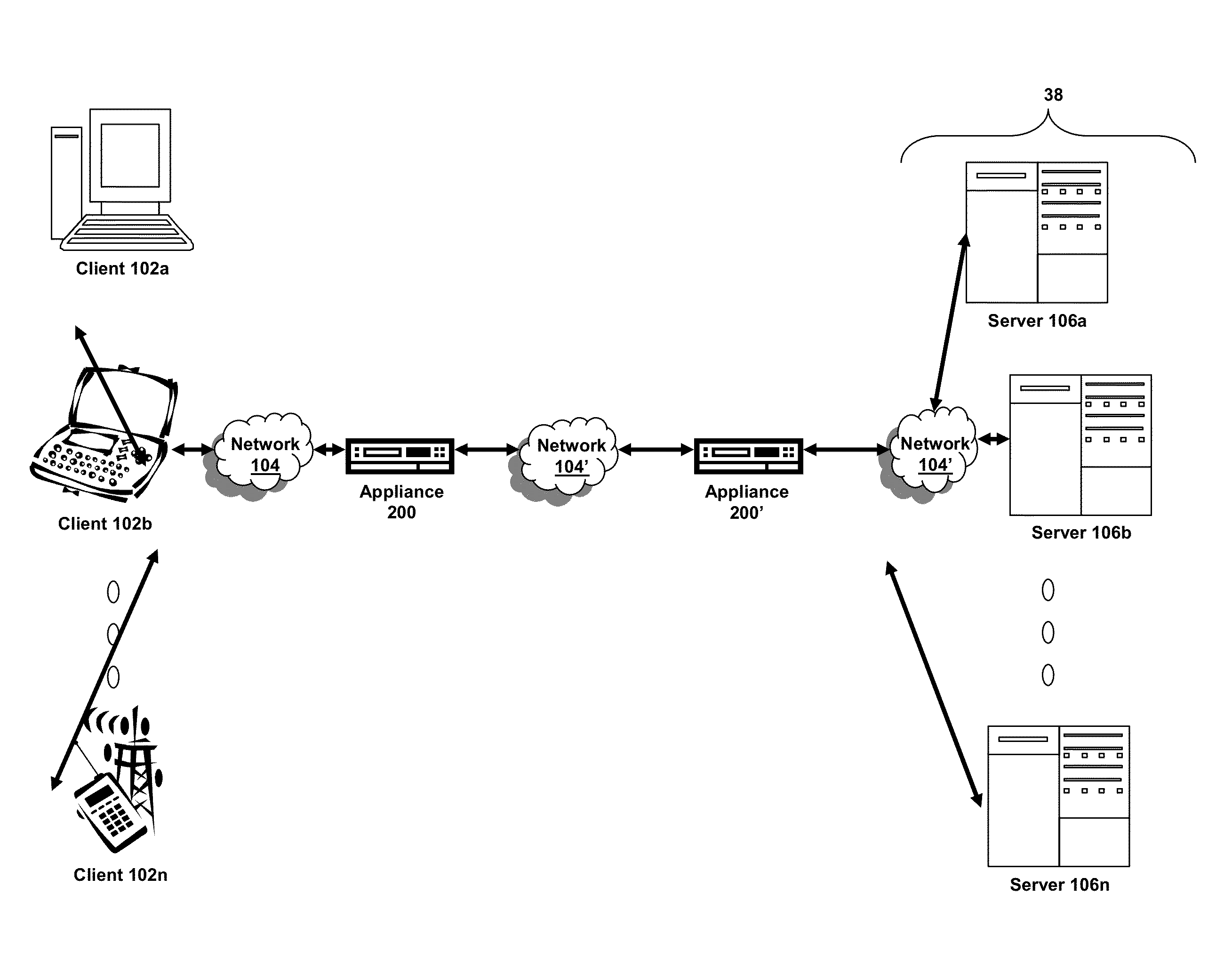
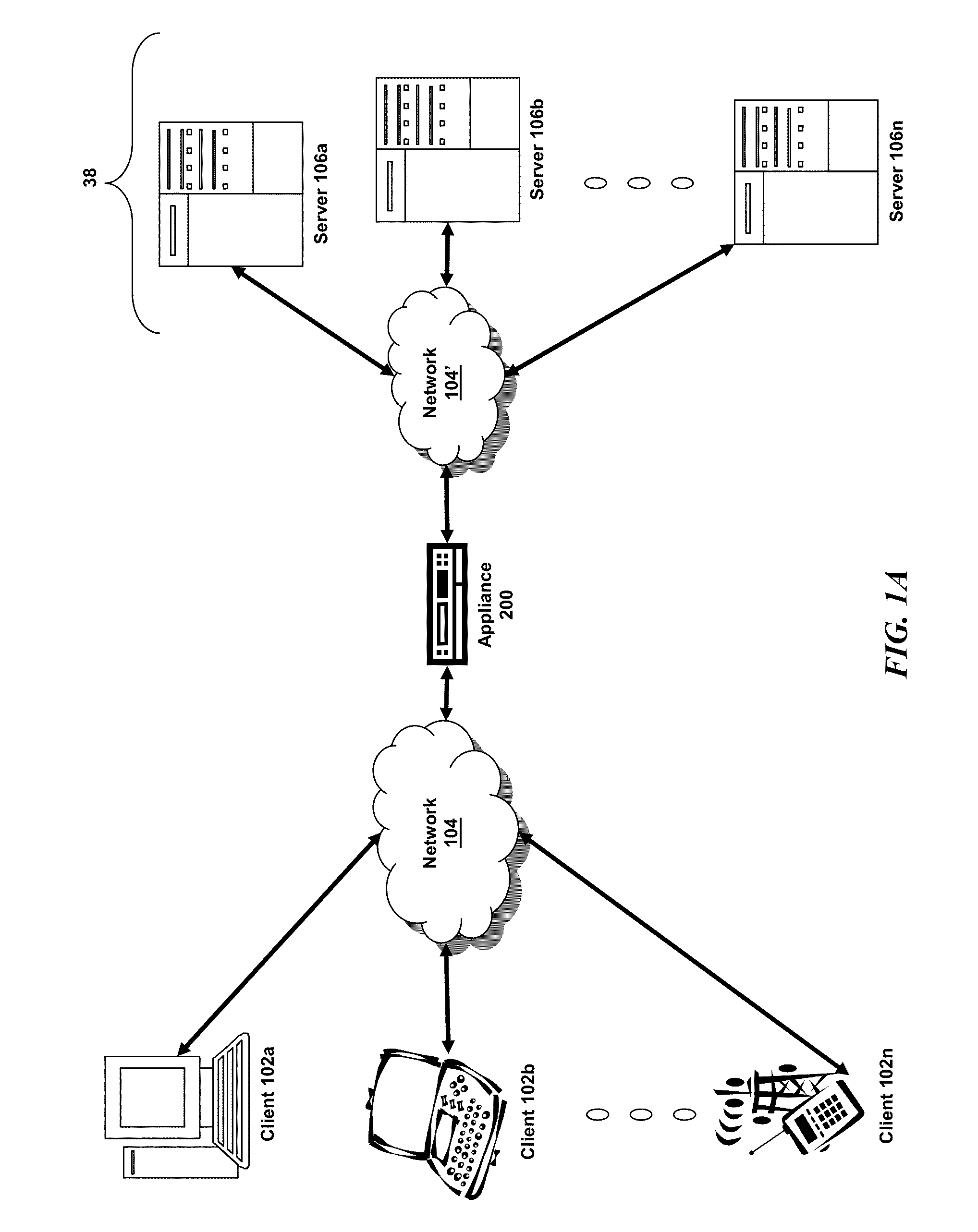
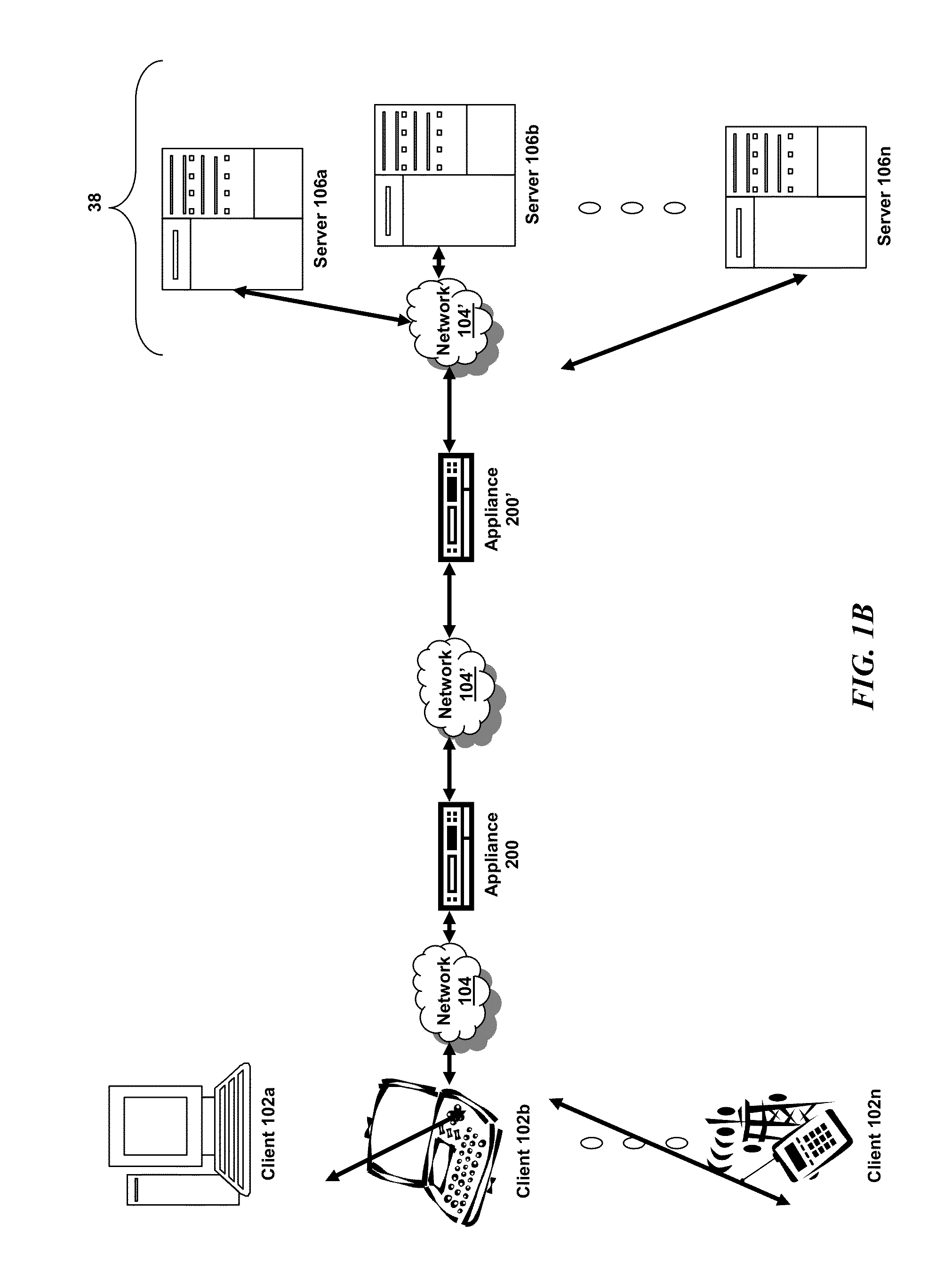
Systems and Methods for Tracking Application Layer Flow Via a Multi-Connection Intermediary Device
ActiveUS20130041934A1Energy efficient ICTMultiple digital computer combinationsGranularityTemplate based
The present disclosure is directed towards tracking application layer flow via a multi-connection intermediary. Transaction level or application layer information may be tracked via the intermediary, including one or more of: (i) the request method; (ii) response codes; (iii) URLs; (iv) HTTP cookies; (v) RTT of both ends of the transaction in a quad flow arrangement; (vi) server time to provide first byte of a communication; (vii) server time to provide the last byte of a communication; (viii) flow flags; or any other type and form of transaction level data may be captured, exported, and analyzed. The application layer flow or transaction level information may be provided in an IPFIX-compliant data record. This may be done to provide template-based data record definition, as well as providing data on an application or transaction level of granularity.
Owner:CITRIX SYST INC
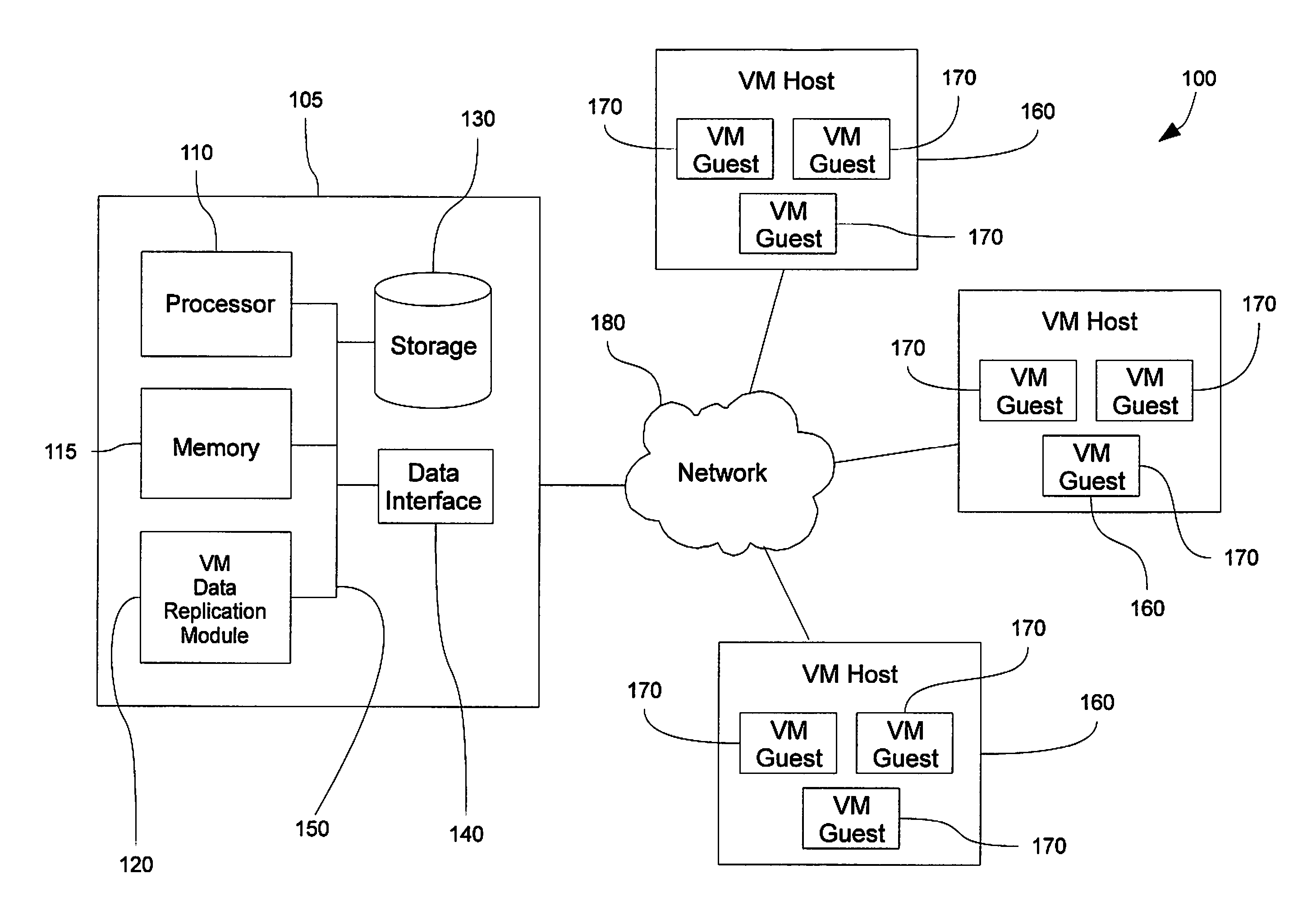
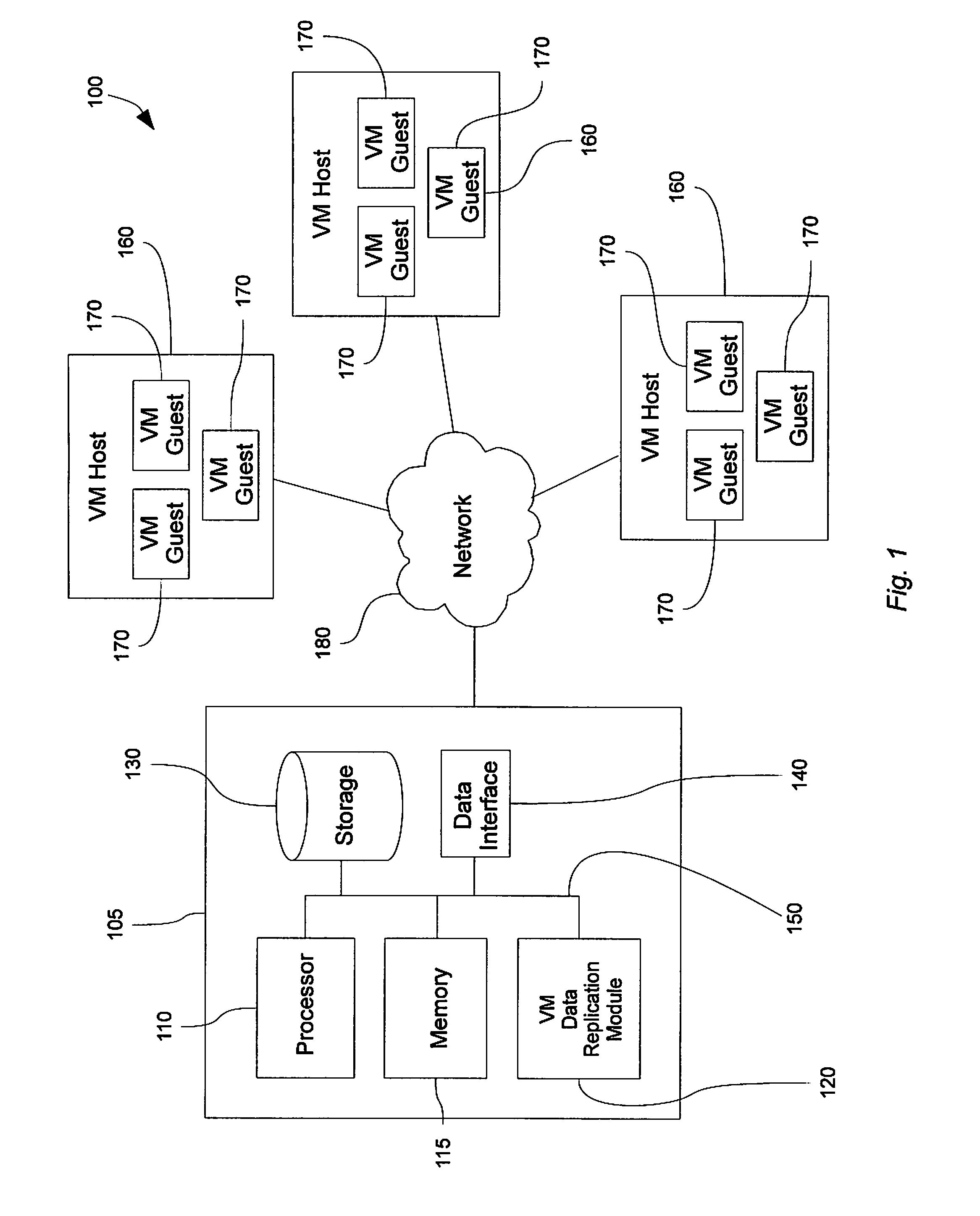
Virtual machine data replication
ActiveUS20100262586A1Efficiently restoring backup setShorten recovery timeError detection/correctionDigital data processing detailsHard disc driveData set
Disclosed is a method and system for selectively restoring file-level data from a disk image backup. In embodiments, a virtual machine backup may be performed by dividing a virtual machine virtual disk file into a plurality of discrete fixed-sized data blocks sharing a common index file that is stored on a backup medium, such as a hard drive, to form a backup set. Upon restoration of data from the backup set, individual blocks of the data set are compared to corresponding blocks of the target virtual machine file. Redundant data and unchanged blocks are skipped, and only those block which have changed are restored to the target file. In this manner network bandwidth and processor resources are conserved, and replication times decreased.
Owner:UNITRENDS
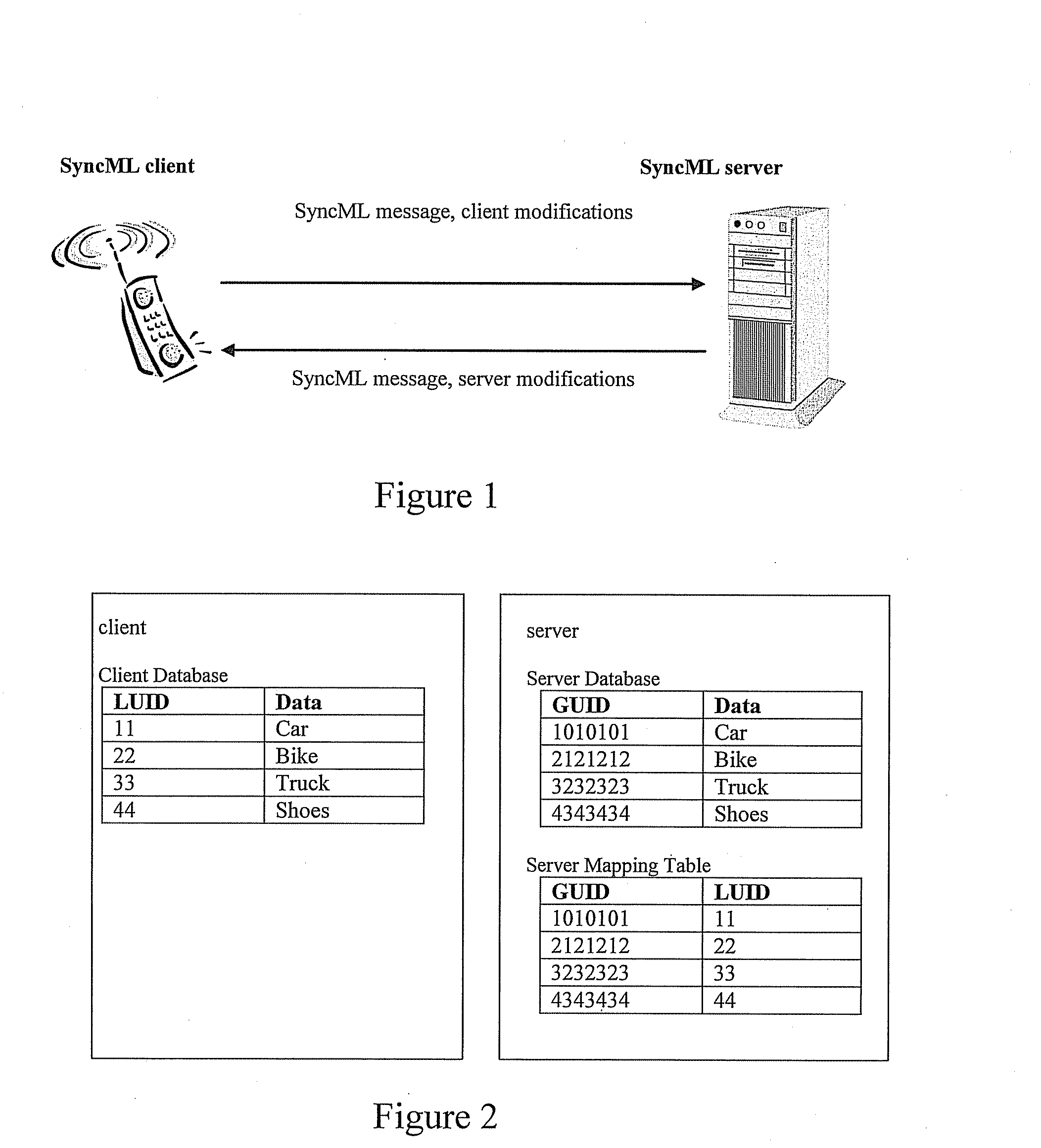
Method, system, client and server for implementing data sync
ActiveUS20080104277A1Improve data synchronization efficiencySave system resourcesMultiple digital computer combinationsTransmissionData synchronizationClient-side
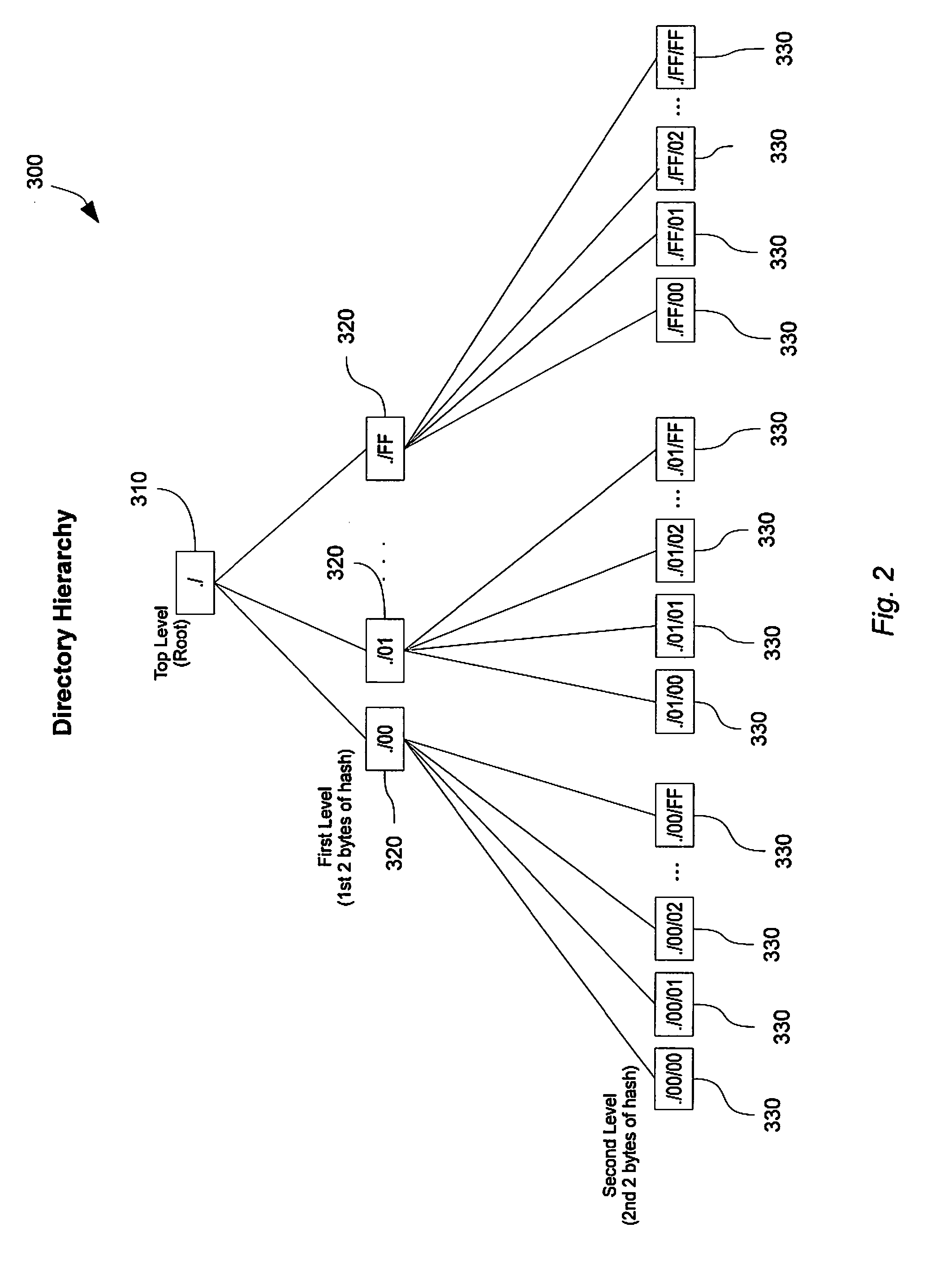
This invention discloses a method for synchronizing a plurality of devices, including: obtaining, by a first device, an extended address of an informational node of a plurality of informational nodes of a second device, the plurality of informational nodes arranged in a hierarchical tree structure; and utilizing the extended address to locate the informational node amongst the tree structure to enable synchronization of the informational node; wherein the extended address includes a hierarchical location of the informational node. This invention further discloses a system, client and server for data sync, and the folder-level data sync can be implemented by using the method of this invention.
Owner:HUAWEI TECH CO LTD
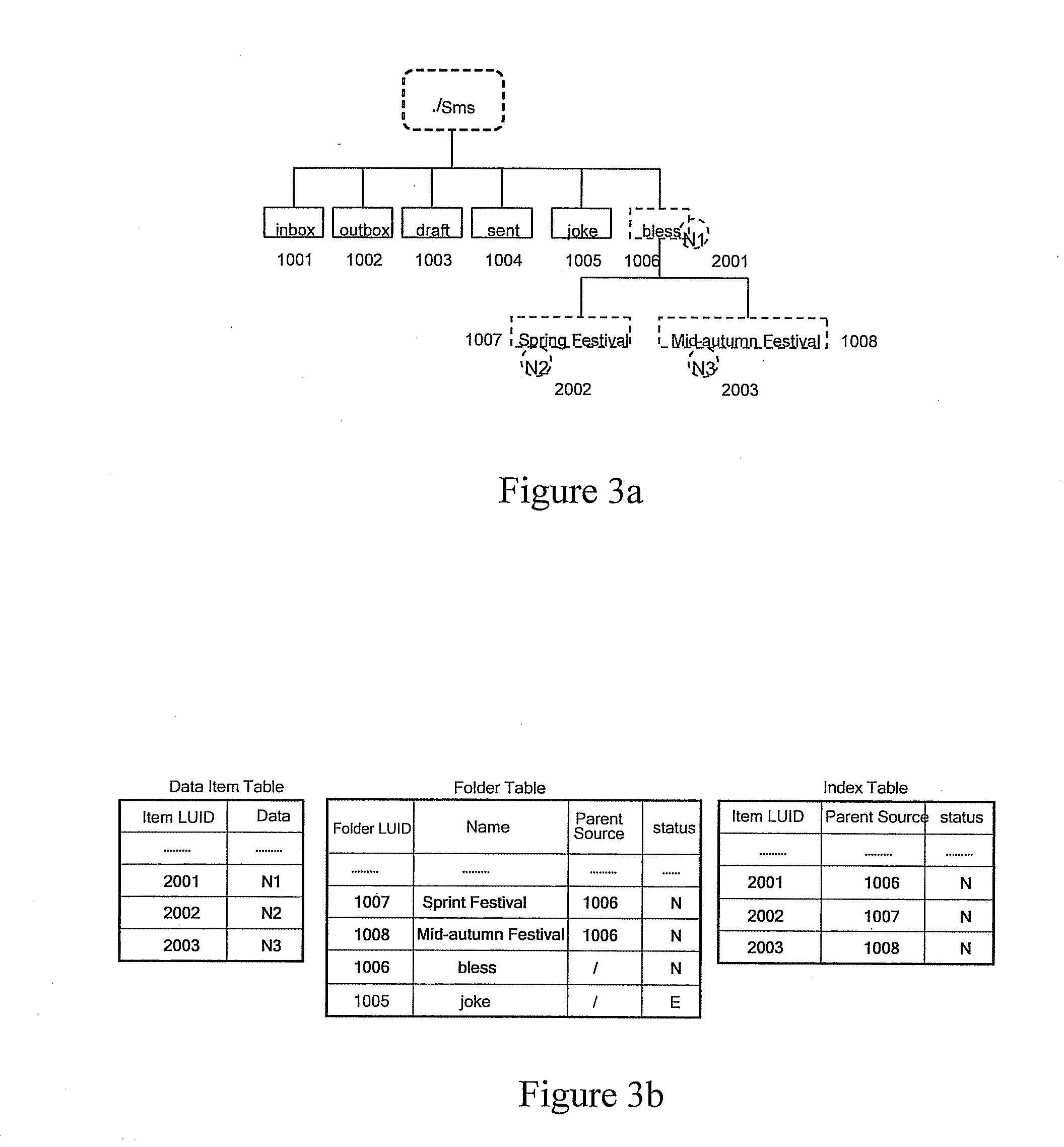
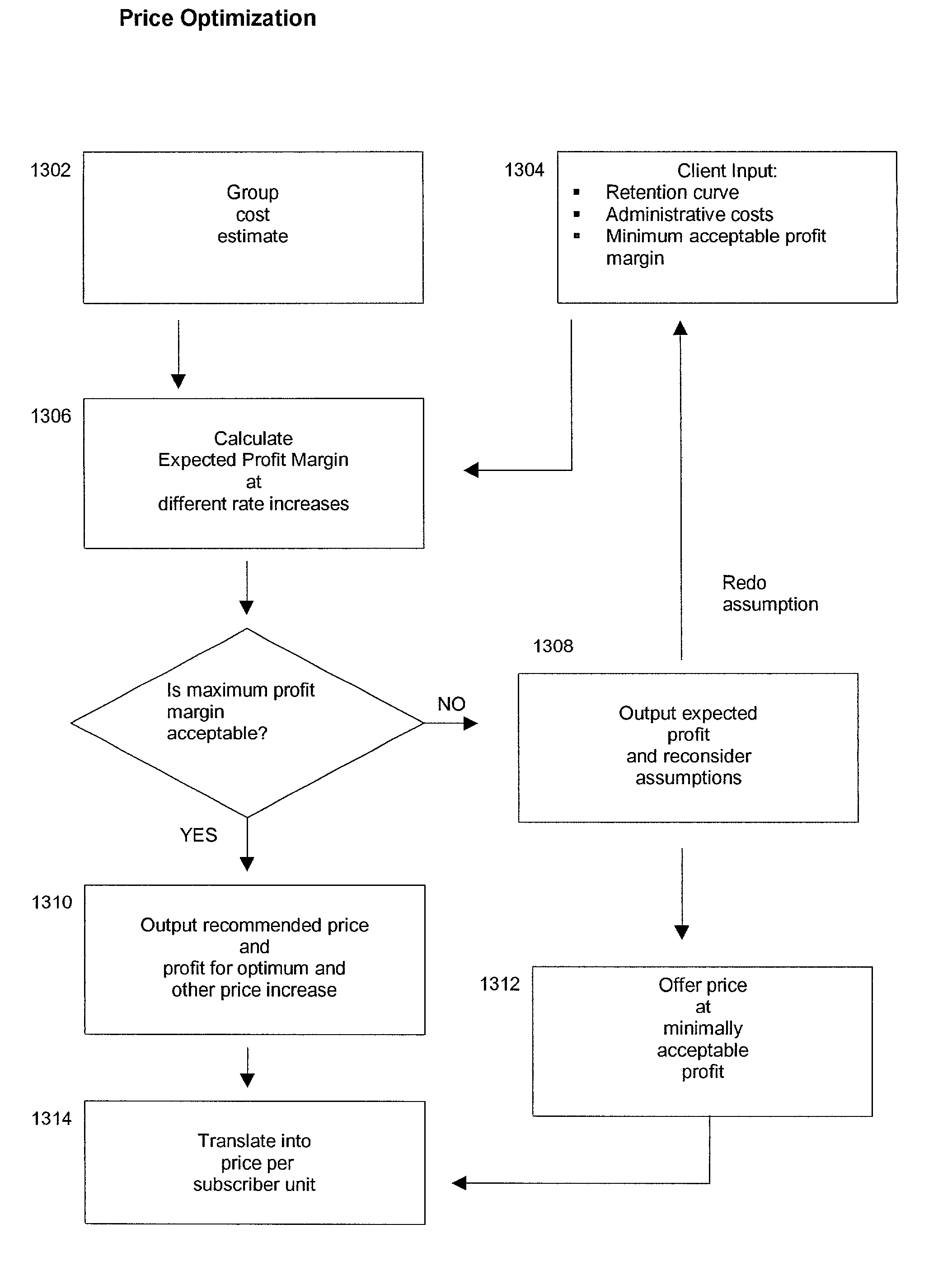
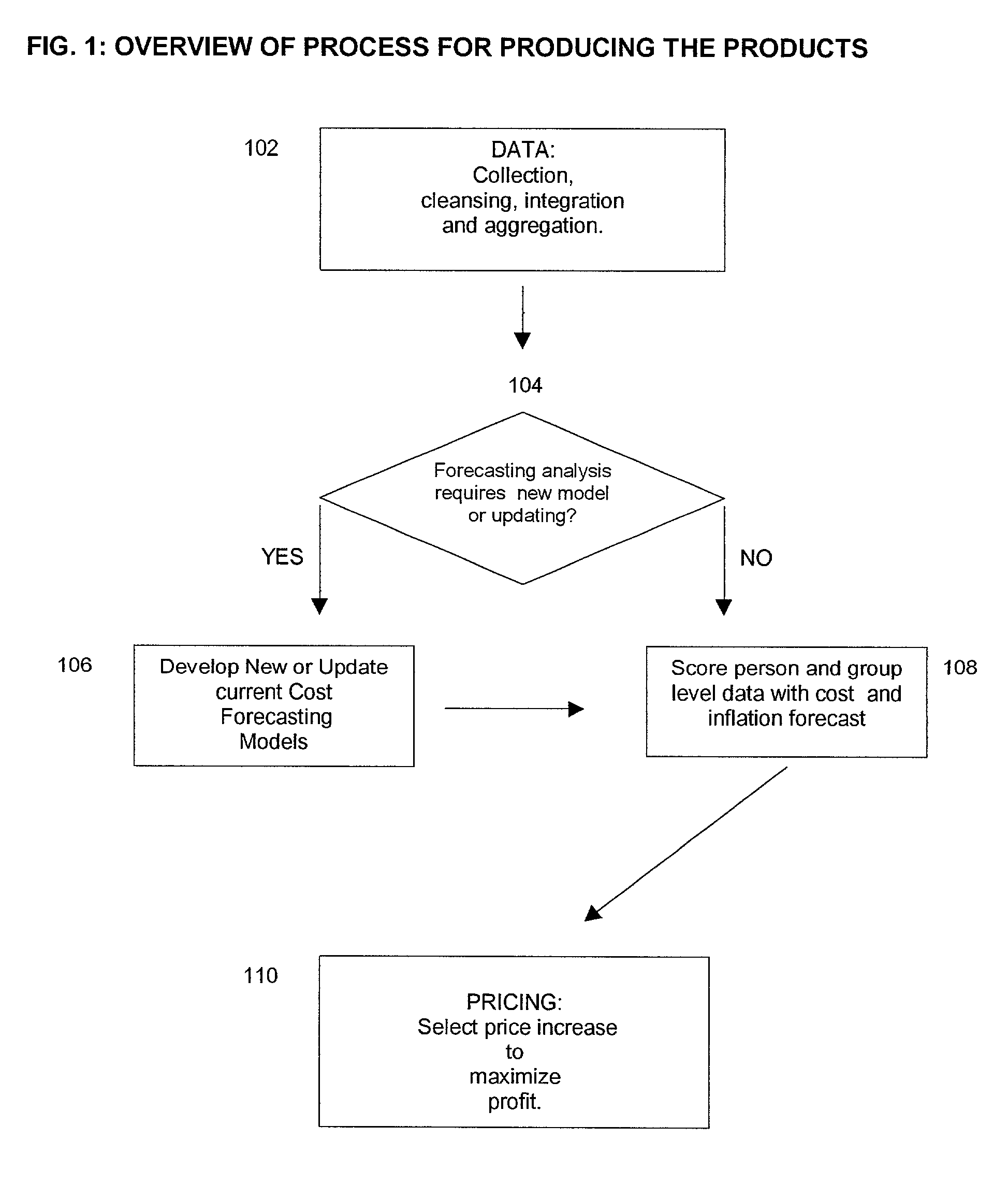
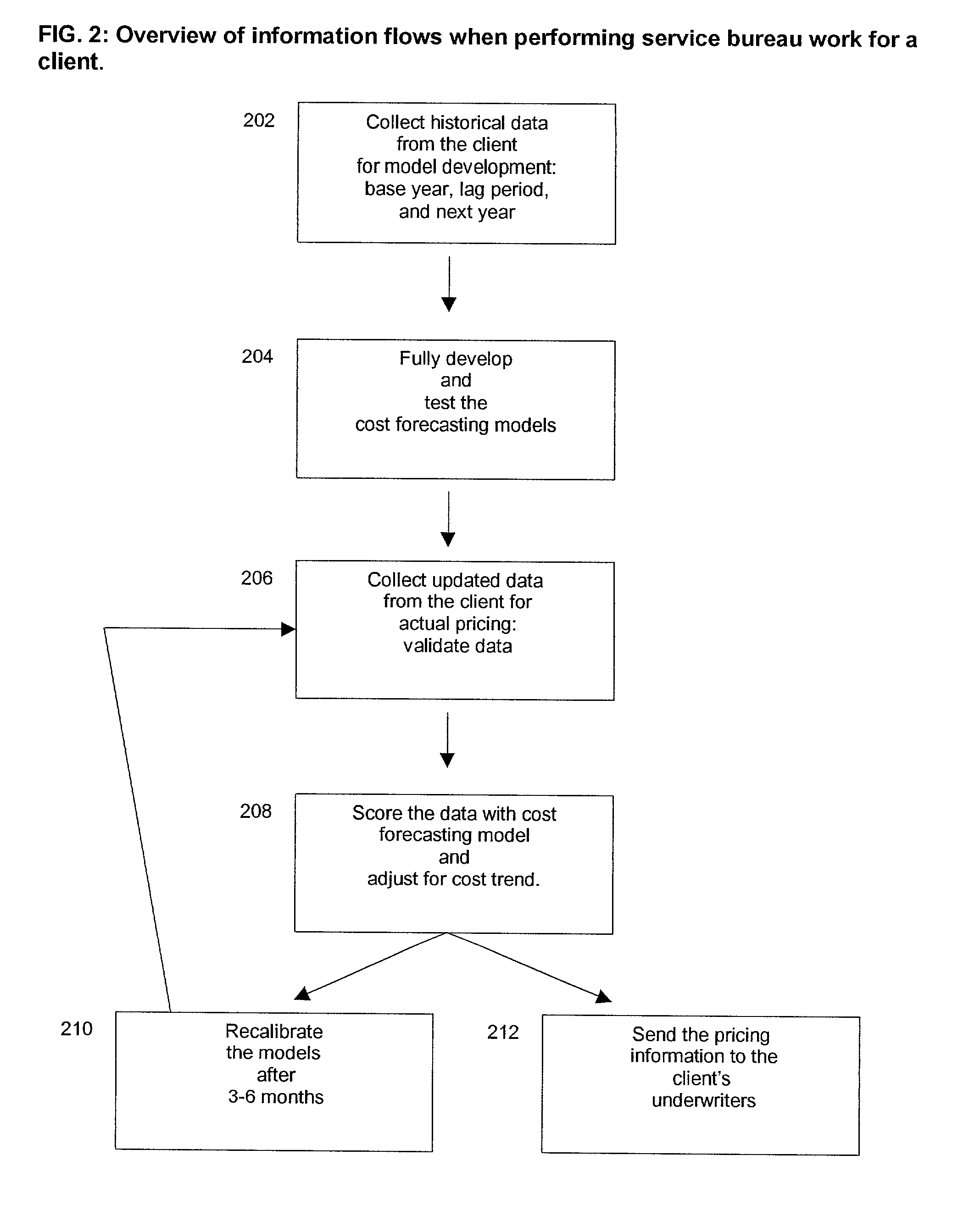
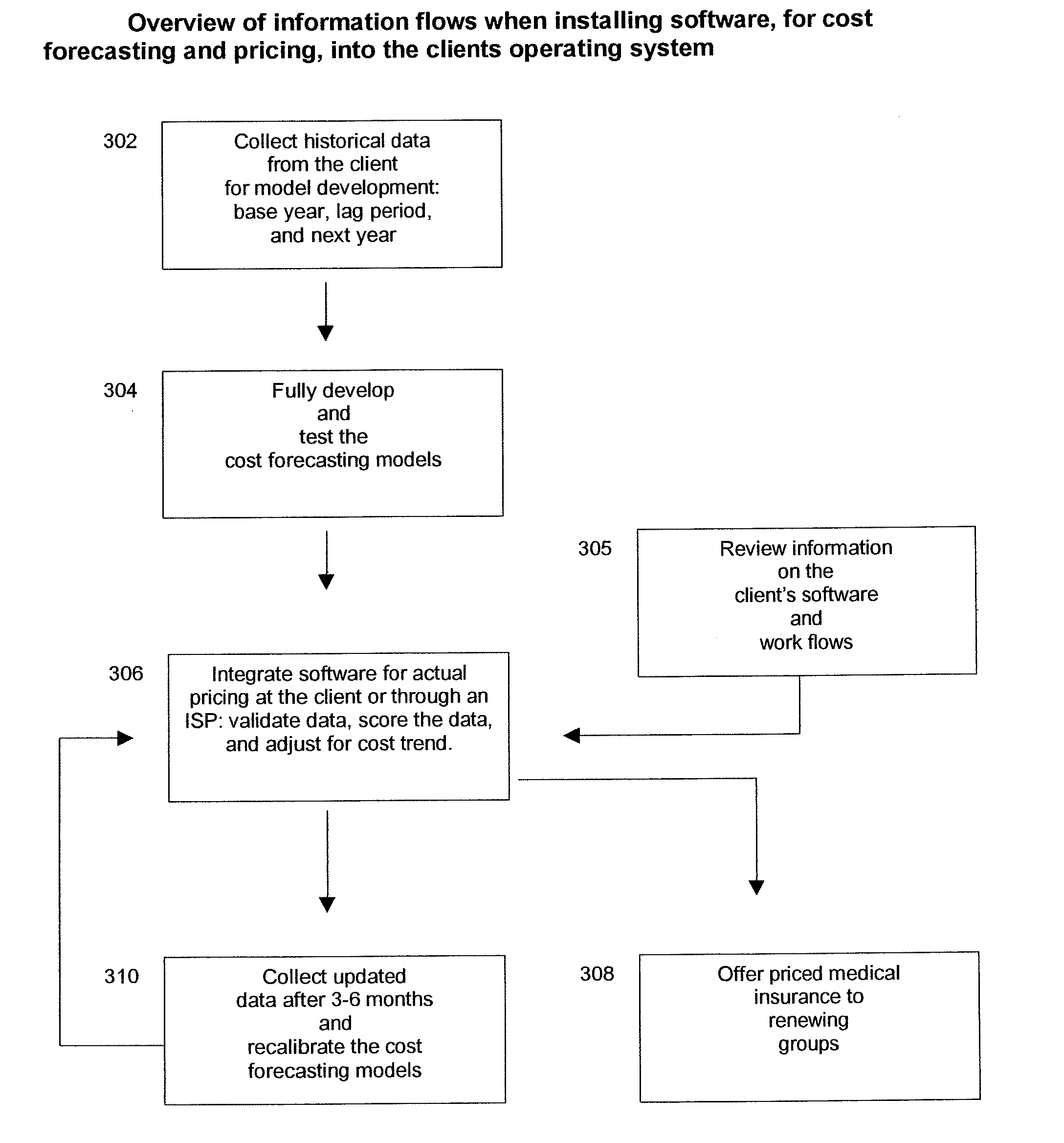
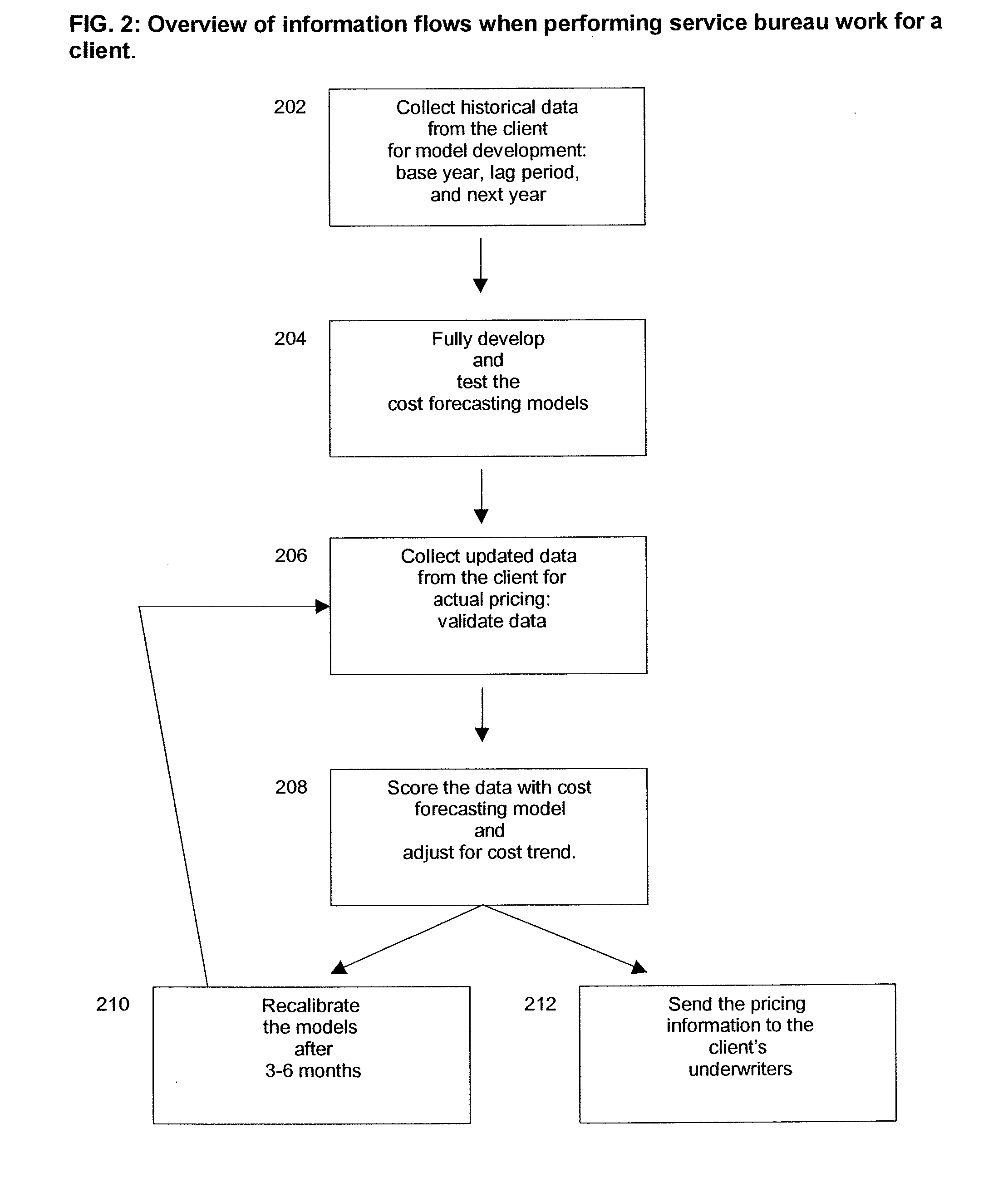
Insurance claim forecasting system
A computer-implemented process of developing a person-level cost model for forecasting future costs attributable to claims from members of a book of business, where person-level data are available for a substantial portion of the members of the book of business for an actual underwriting period, and the forecast of interest is for a policy period is disclosed. The process uses development universe data comprising person-level enrollment data, historical base period health care claims data and historical next period claim amount data for a statistically meaningful number of individuals. The process also provides at least one claim-based risk factor for each historical base period claim based on the claim code associated with the health care claim and provides at least one enrollment-based risk factor based on the enrollment data. The process also develops a cost forecasting model by capturing the predictive ability of the main effects and interactions of claim based risk factors and enrollment-based risk factors, with the development universe data through the application of an interaction capturing technique to the development universe data.
Owner:TRURISH L L C
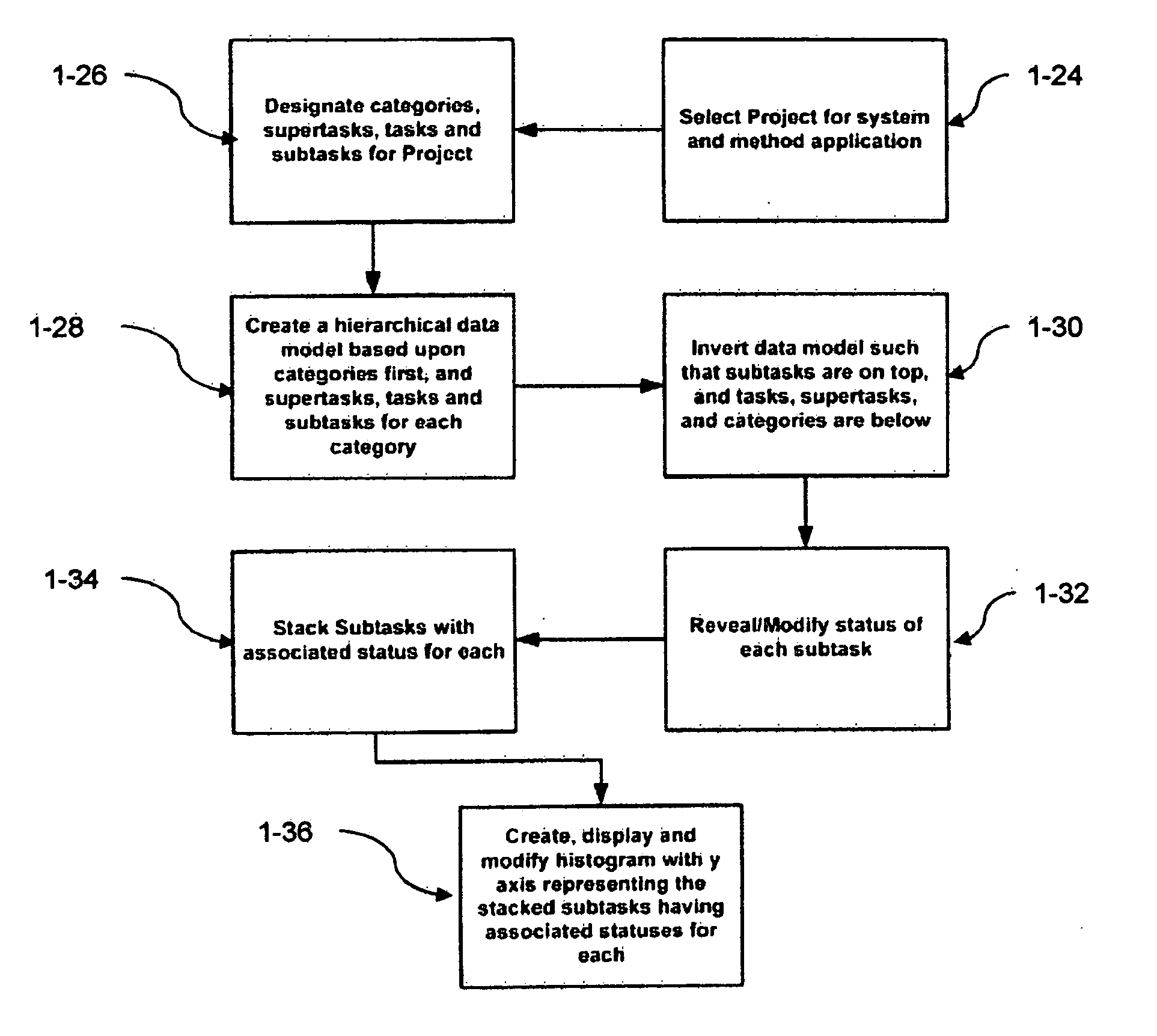
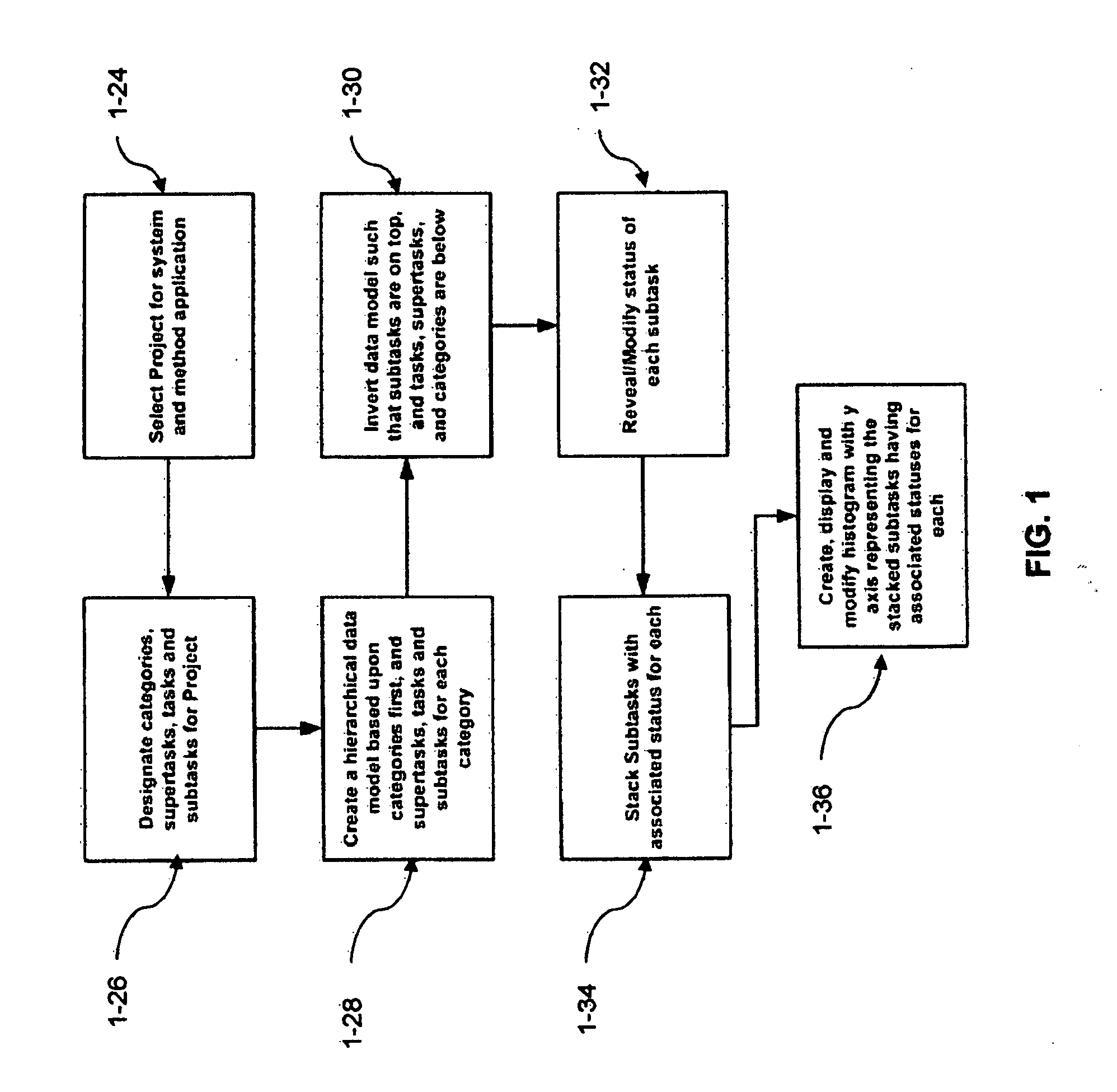
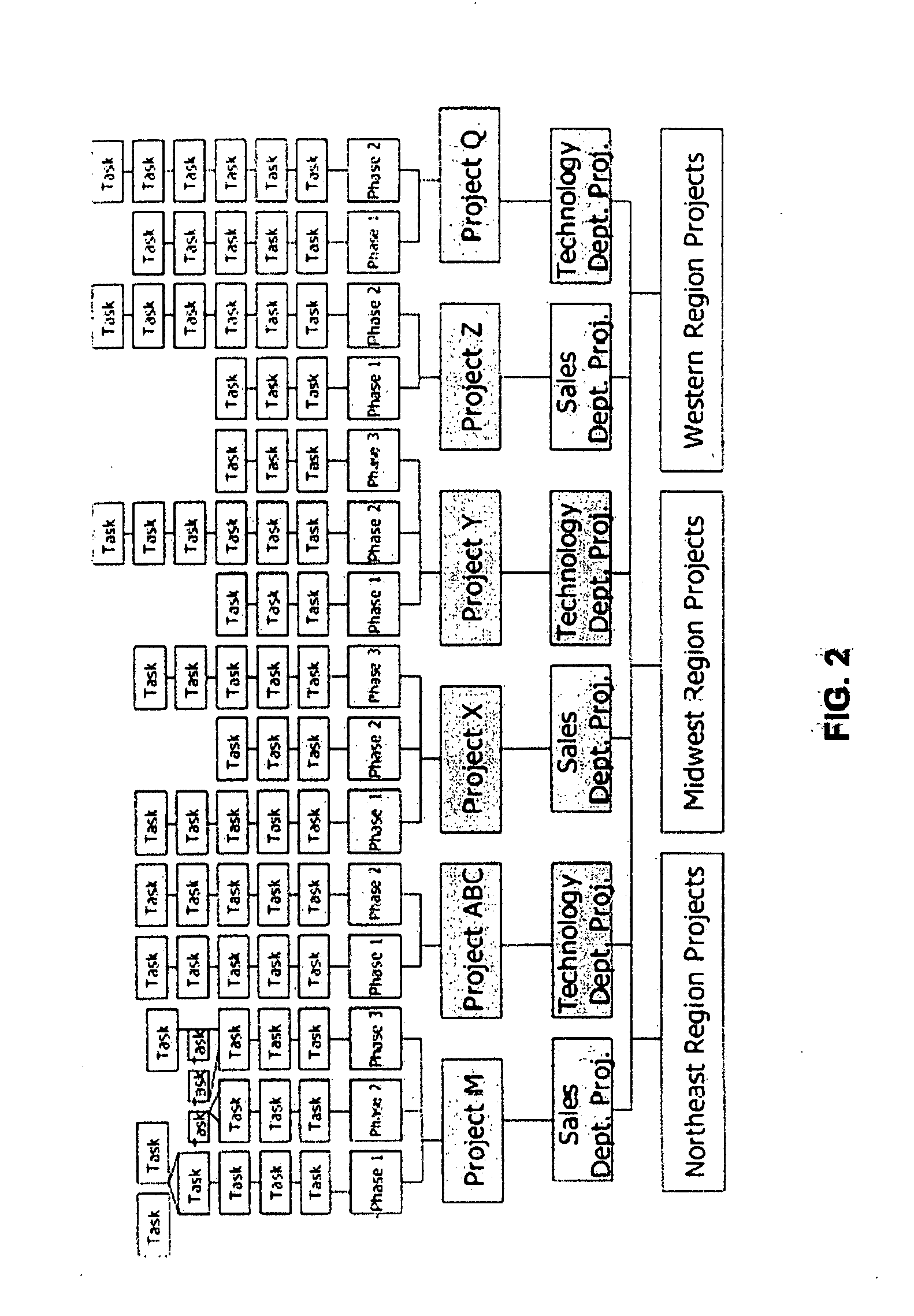
System and method for visually organizing, prioritizing and updating information
ActiveUS20080033777A1Available plotting areaConvenient drag/dropMultiprogramming arrangementsResourcesWorkflowLevel data
An improved method is provided herein of managing information that typically relates to a project, process, or workflow. The information is classified within various hierarchical levels of categories, subcategories and their lowest level data elements and is organized within an electronic graph in a corresponding hierarchical sequence. The graph comprises what is termed as “cell bodies” in the form of graphical objects. These graphical objects represent each of the categories, subcategories and data elements and are aligned against each other in various orthogonally stacked configurations where the cell bodies consist of one or more geometric shapes, symbols, characters and their respective features such as color, in a tight grouping, which together, represent several variables of a single data set record. Each cell body may be a cluster of one or more such graphical components.
Owner:SHUKOOR SHABINA
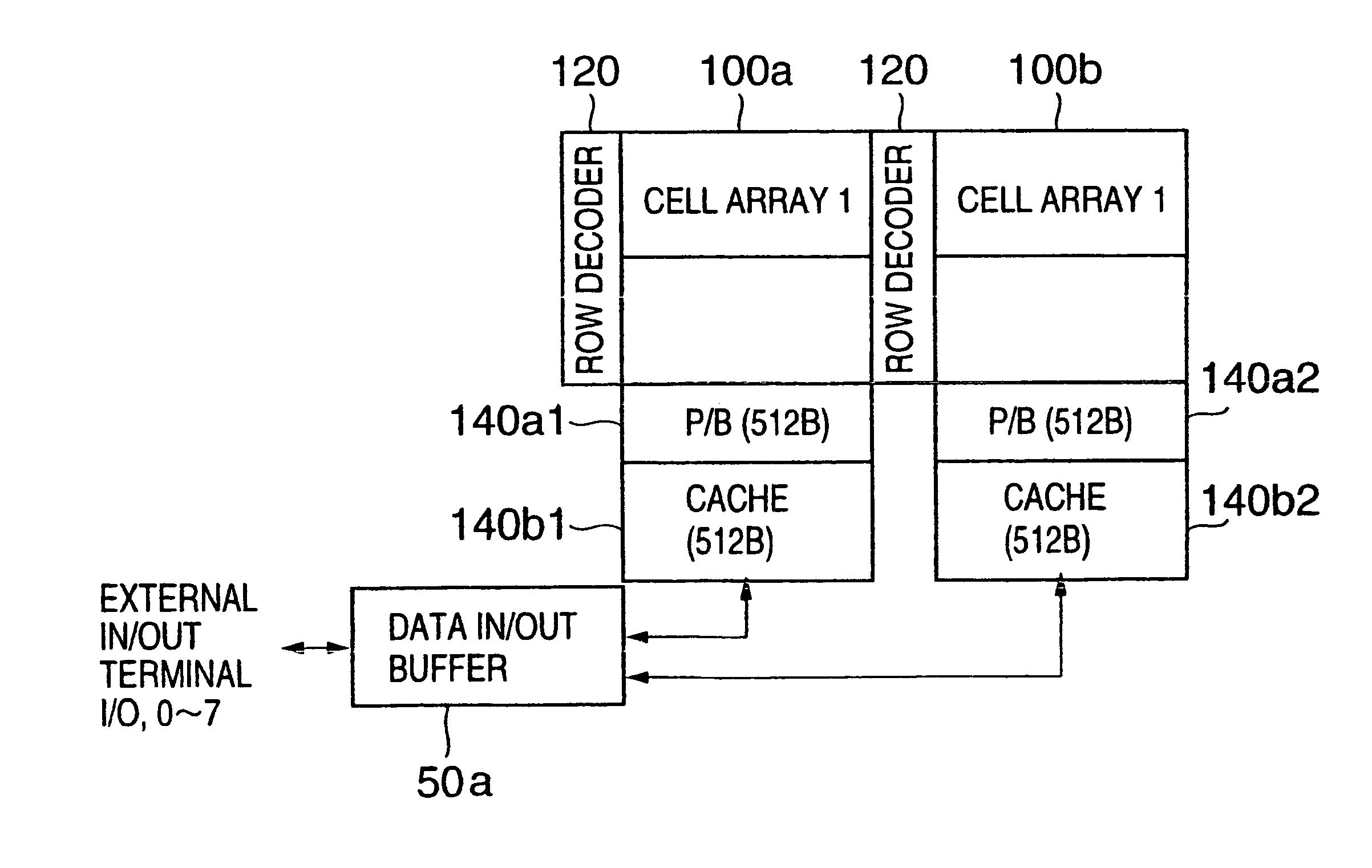
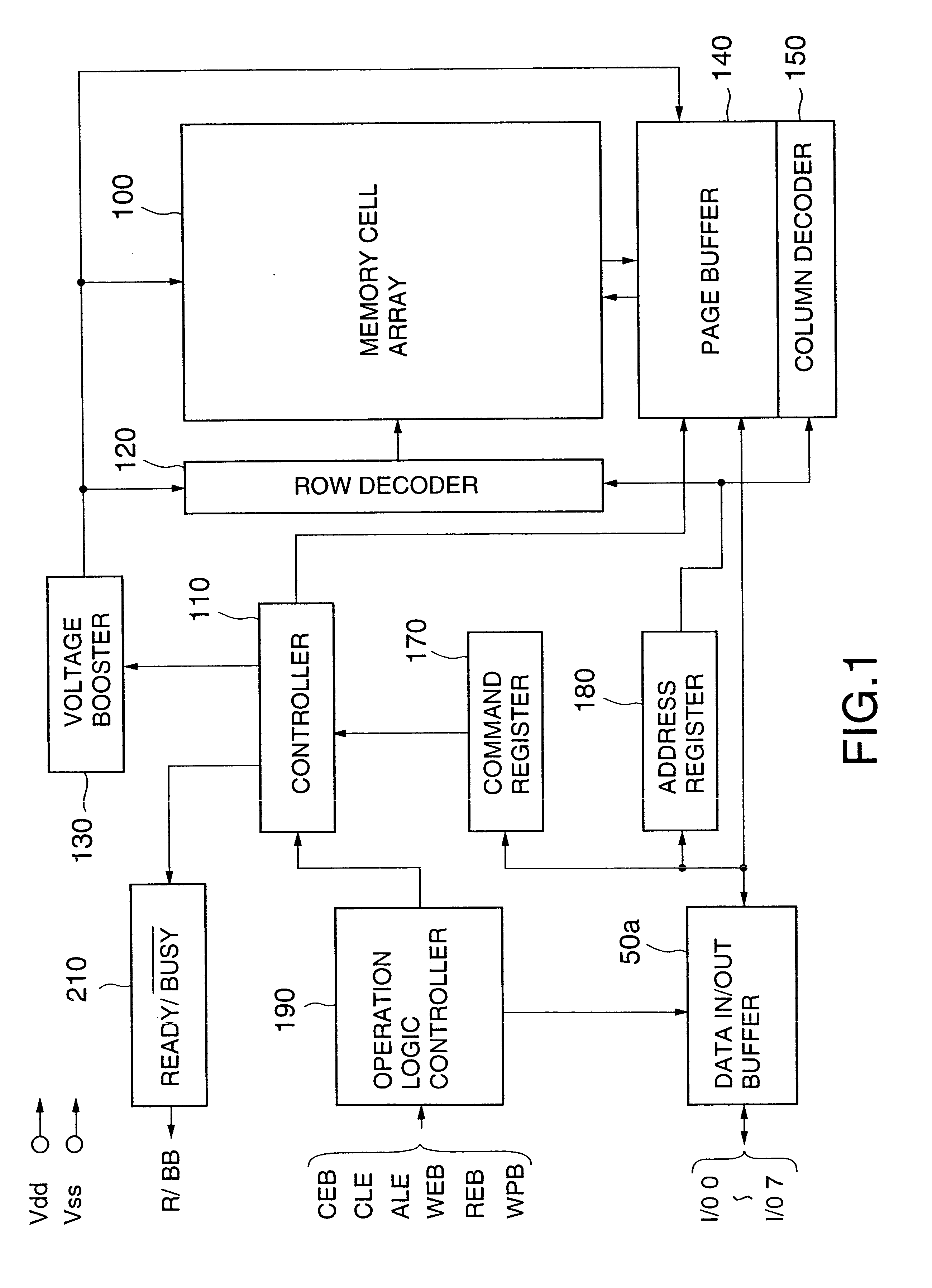
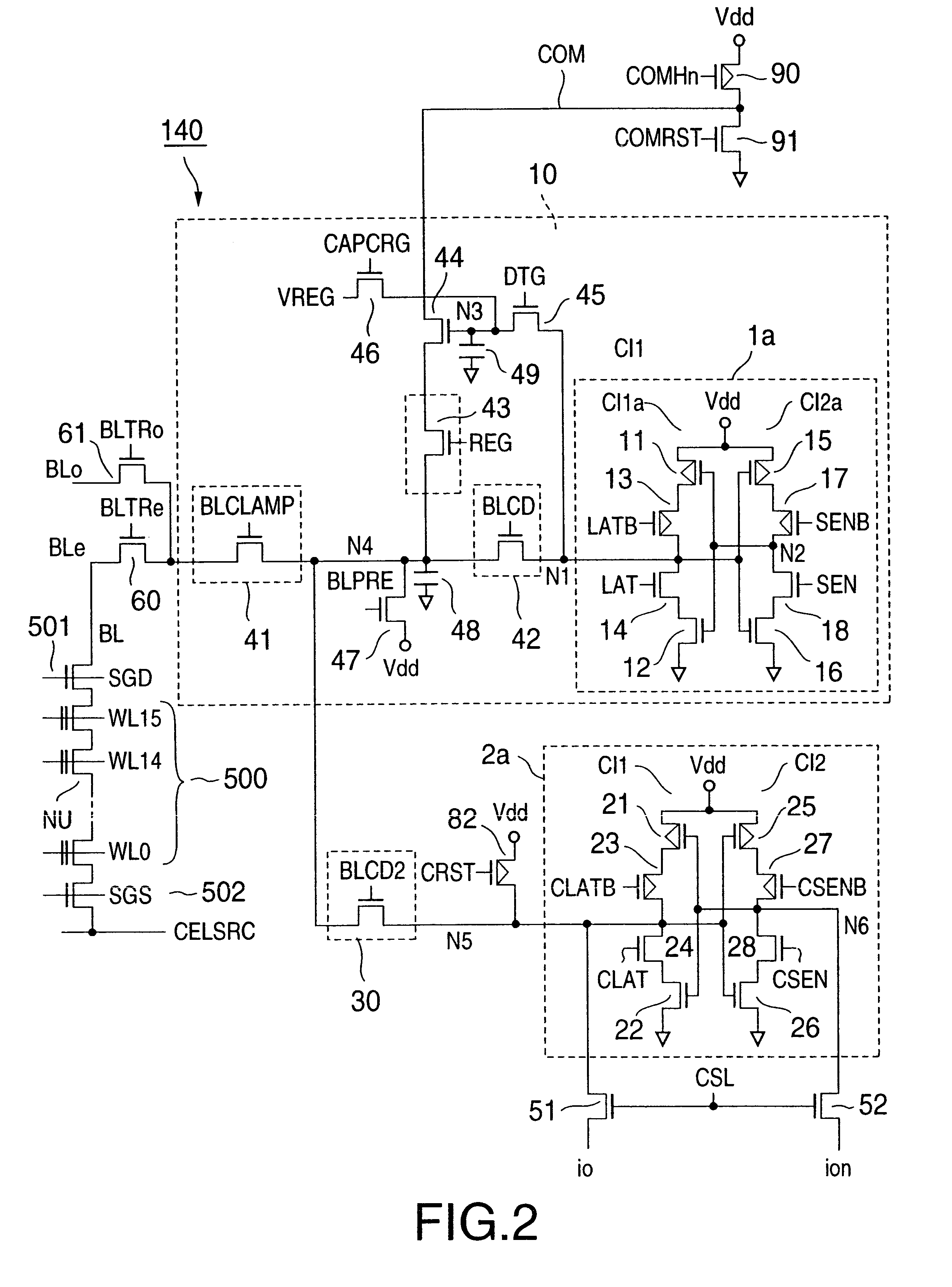
Non-volatile semiconductor memory
InactiveUS6937510B2Large storage capacityWider marginRead-only memoriesDigital storageSensing dataData retrieval
Owner:KIOXIA CORP
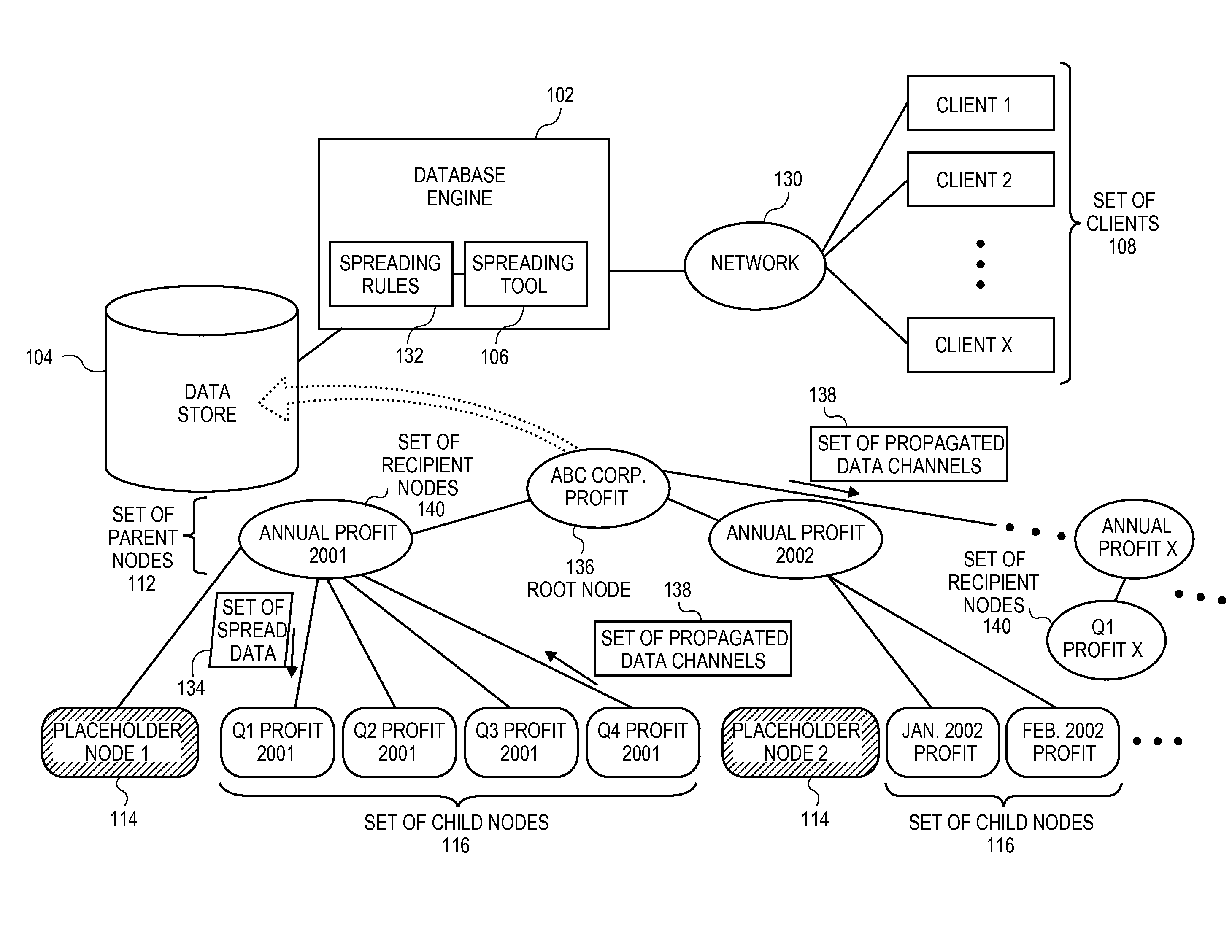
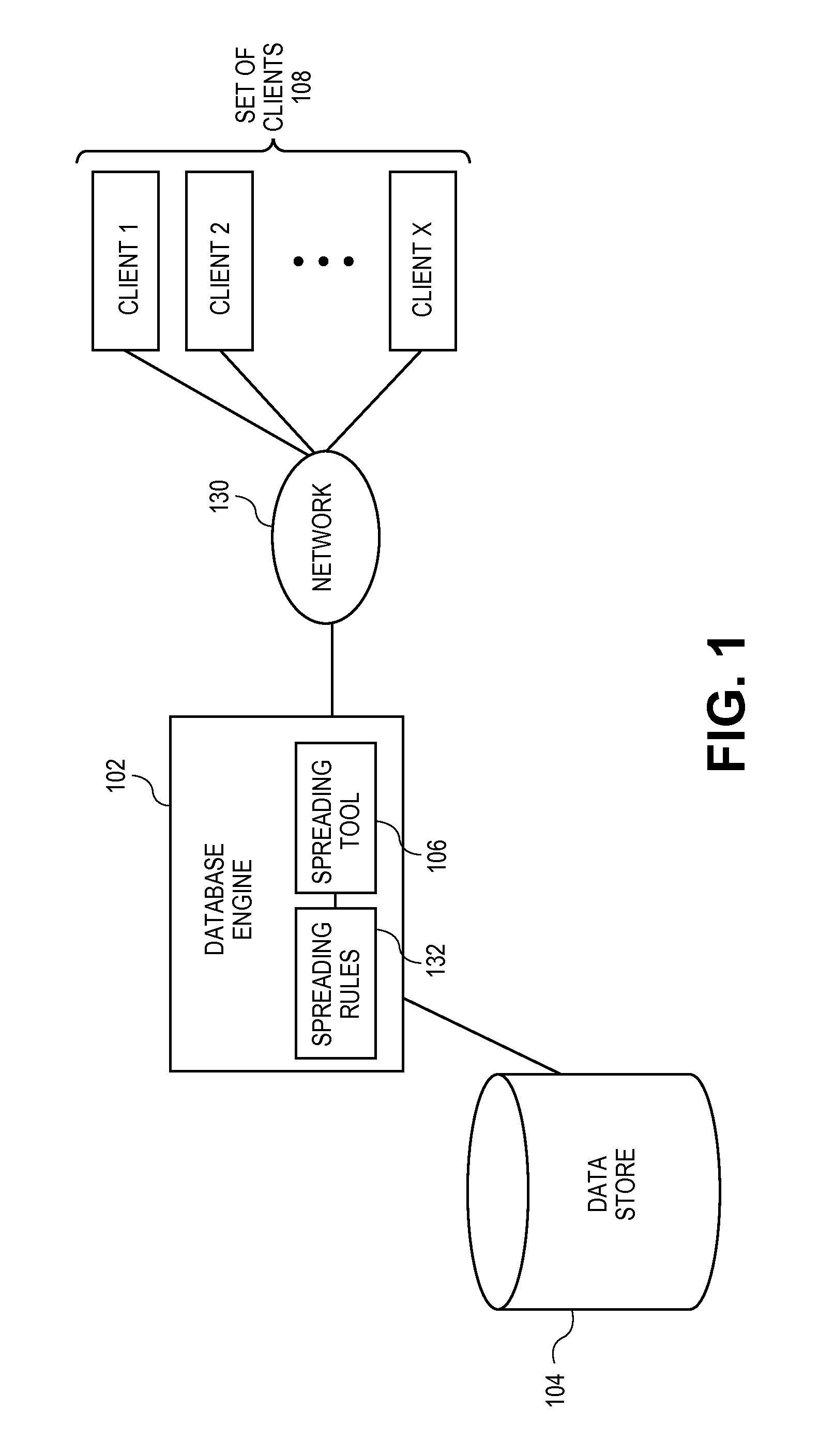
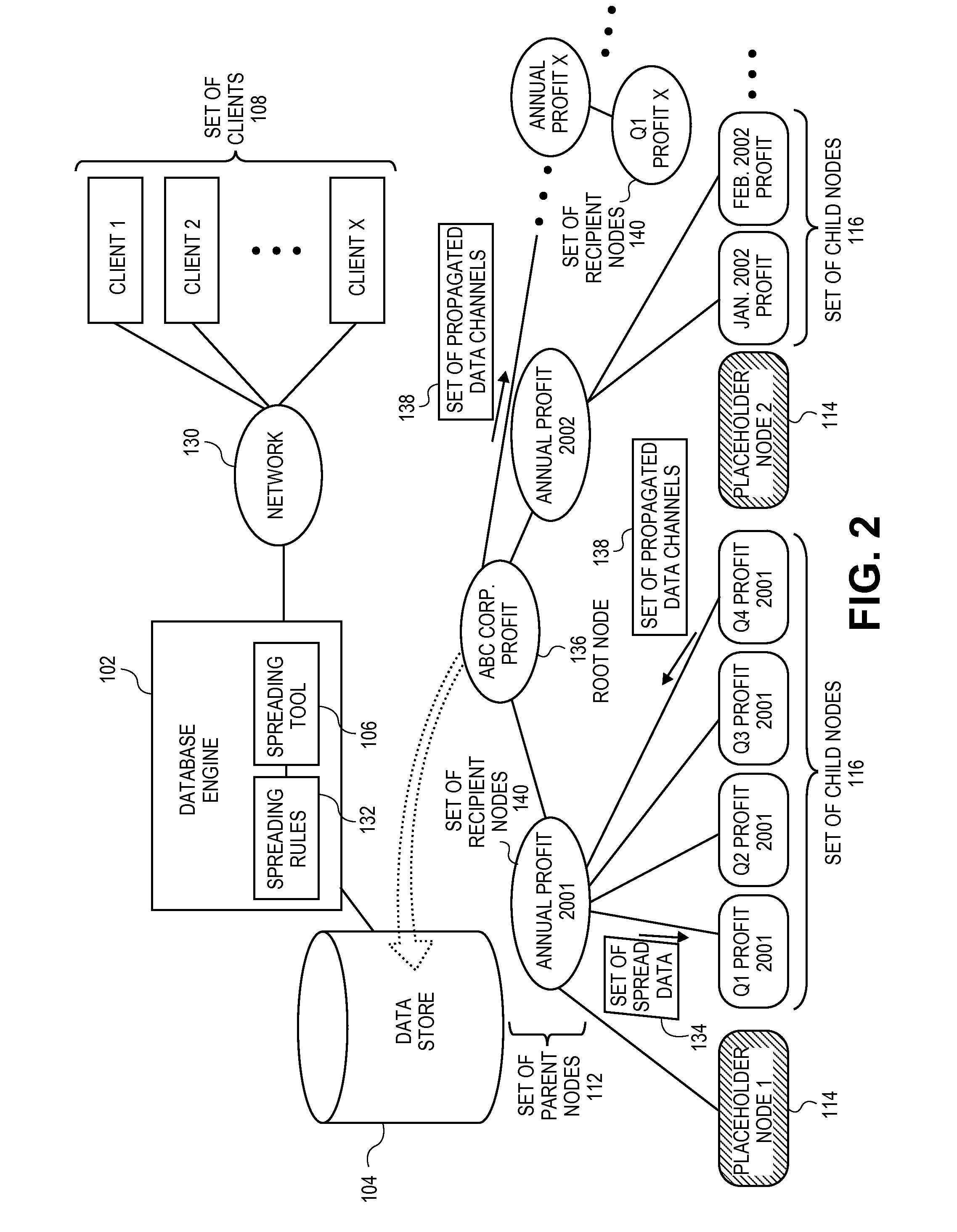
Systems and methods for automatic propagation of data changes in distribution operations in hierarchical database
ActiveUS20110161378A1Digital data information retrievalDigital data processing detailsOriginal dataData content
Embodiments relate to systems and methods for the automatic propagation of data changes in distribution operations in a hierarchical database. Higher-level data, such as yearly profit, may be desired to be spread from parent nodes to lower nodes in the store, such as quarters. Parent nodes can be associated with a set of programmatic placeholder nodes. A spreading tool can access or host sequence logic to ensure that data is spread in an order that takes dependencies, or other factors into account. In aspects, the spreading tool can be configured to generate a propagation trace to identify other nodes in the data store that may be connected to or depend on the data content of the recipient child node(s). A set of propagated data changes, such as updates to values, formatting, or other data, can be automatically transmitted to those other nodes upon completion of the original data spreading operations.
Owner:RED HAT
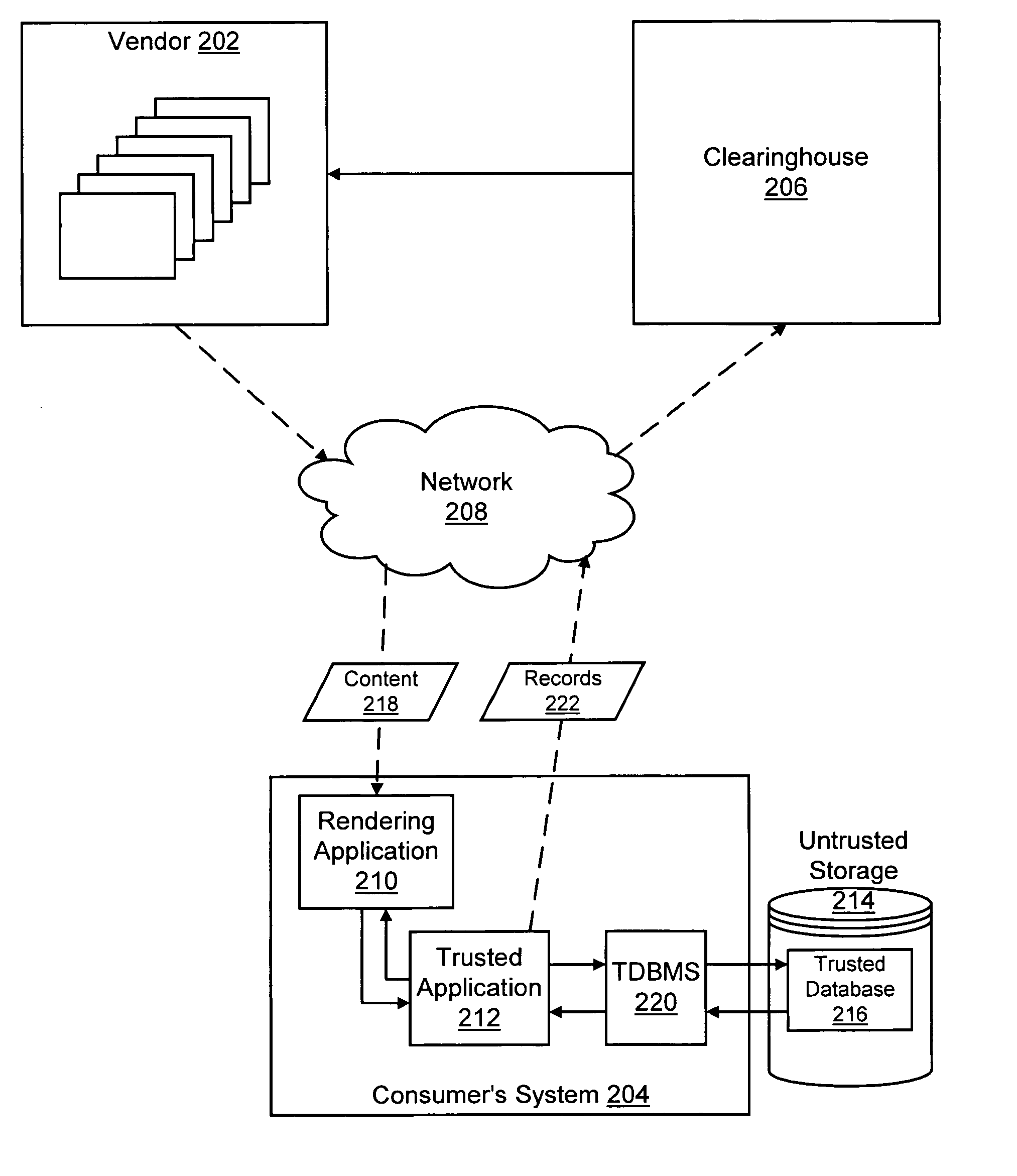
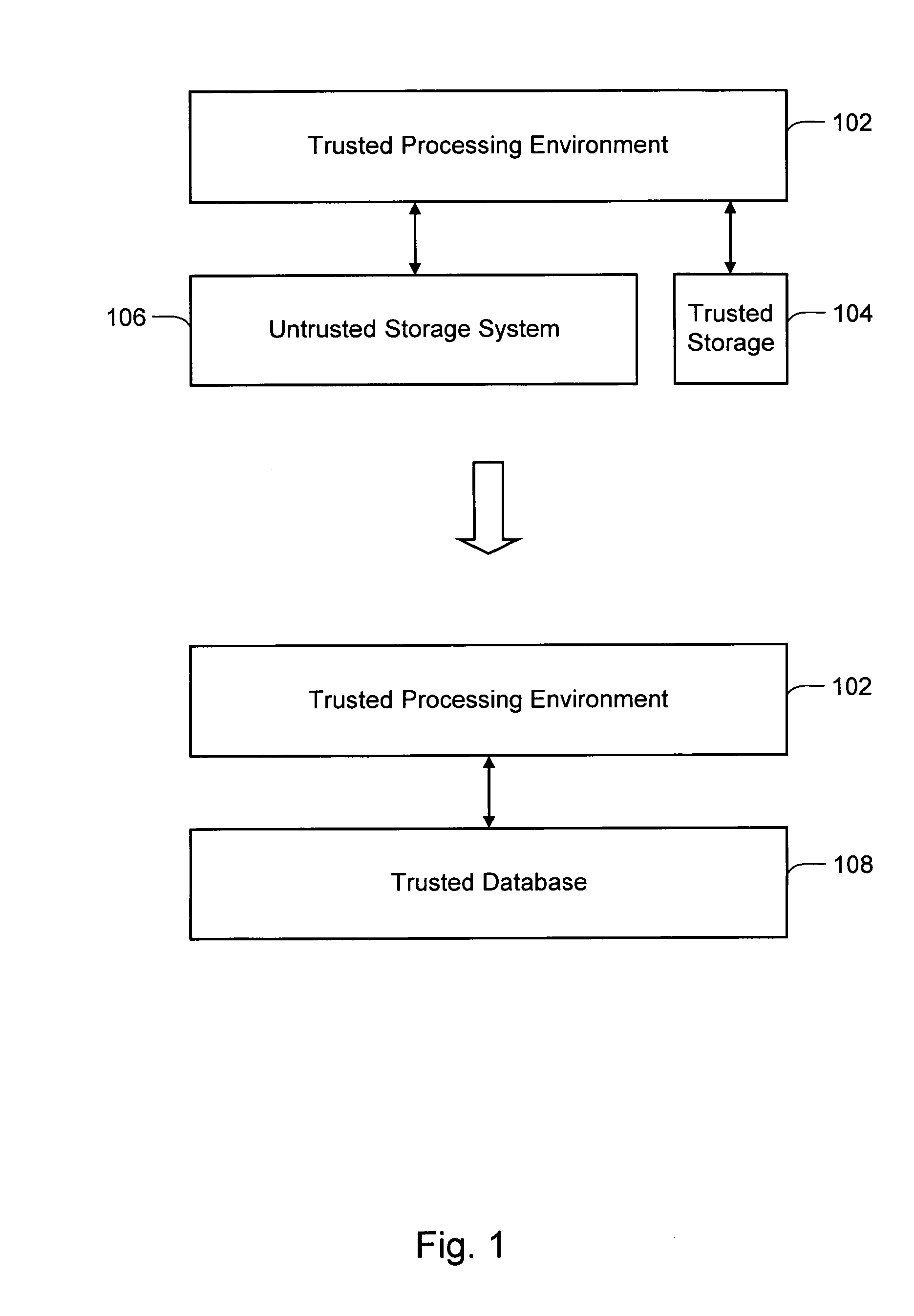
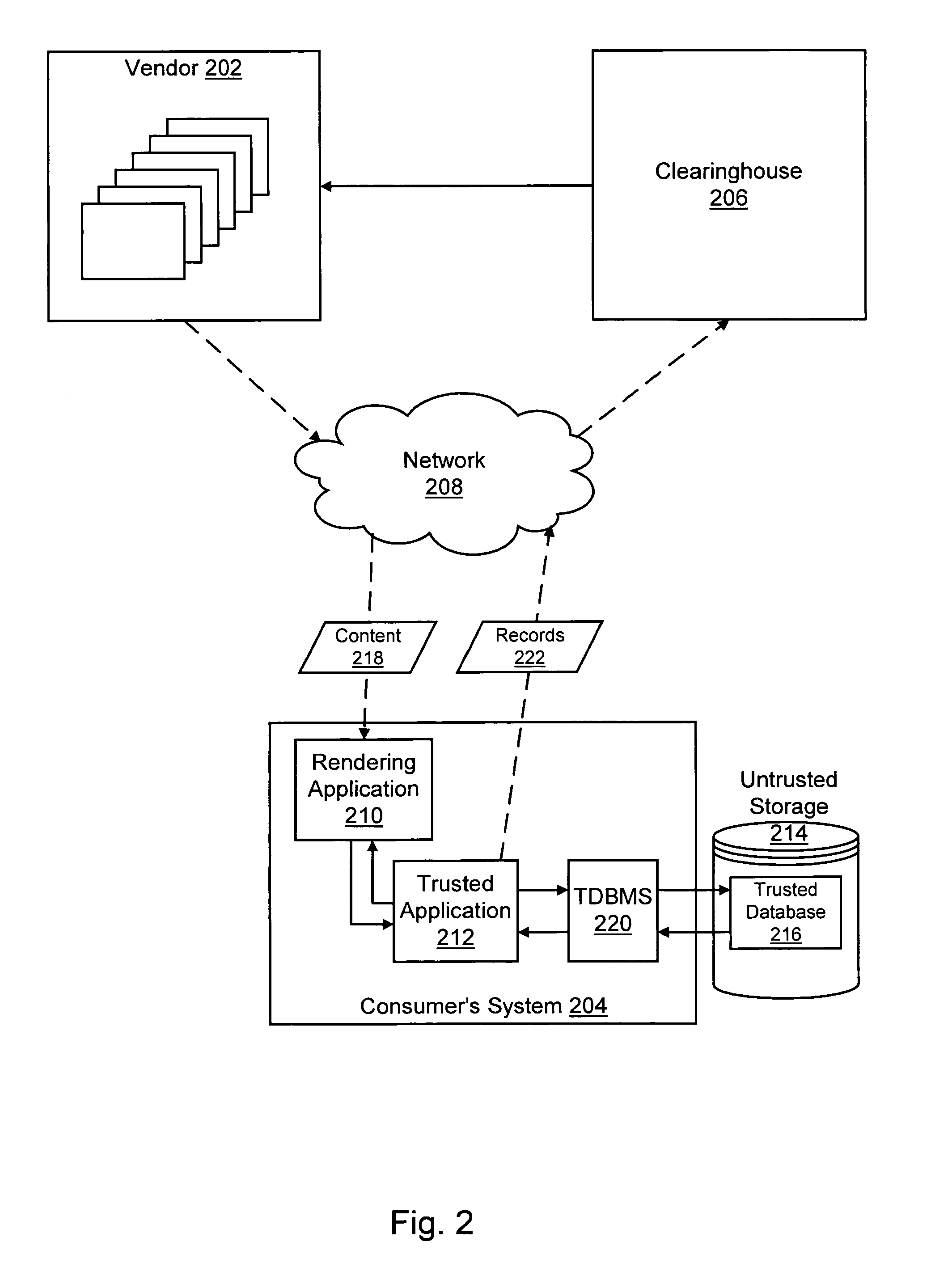
Trusted storage systems and methods
InactiveUS7152165B1Reduces predictabilityEasy to implementDigital data processing detailsUser identity/authority verificationData validationSource Data Verification
Systems and methods are disclosed for providing a trusted database system that leverages a small amount of trusted storage to secure a larger amount of untrusted storage. Data are encrypted and validated to prevent unauthorized modification or access. Encryption and hashing are integrated with a low-level data model in which data and meta-data are secured uniformly. Synergies between data validation and log-structured storage are exploited.
Owner:INTERTRUST TECH CORP
Insurance claim forecasting system
A computer-implemented process of developing a person-level cost model for forecasting future costs attributable to claims from members of a book of business, where person-level data are available for a substantial portion of the members of the book of business for an actual underwriting period, and the forecast of interest is for a policy period is disclosed. The process uses development universe data comprising person-level enrollment data, historical base period health care claims data and historical next period claim amount data for a statistically meaningful number of individuals. The process also provides at least one claim-based risk factor for each historical base period claim based on the claim code associated with the health care claim and provides at least one enrollment-based risk factor based on the enrollment data. The process also develops a cost forecasting model by capturing the predictive ability of the main effects and interactions of claim based risk factors and enrollment-based risk factors, with the development universe data through the application of an interaction capturing technique to the development universe data.
Owner:BINNS GREGORY S +1
Systems and methods for detecting glucose level data patterns
Systems and methods for detecting and reporting patterns in analyte concentration data are provided. According to some implementations, an implantable device for continuous measurement of an analyte concentration is disclosed. The implantable device includes a sensor configured to generate a signal indicative of a concentration of an analyte in a host, a memory configured to store data corresponding at least one of the generated signal and user information, a processor configured to receive data from at least one of the memory and the sensor, wherein the processor is configured to generate pattern data based on the received information, and an output module configured to output the generated pattern data. The pattern data can be based on detecting frequency and severity of analyte data in clinically risky ranges.
Owner:DEXCOM
Detection and correction of block-level data corruption in fault-tolerant data-storage systems
ActiveUS20080115017A1Eliminate needEfficient detectionStatic storageRedundant data error correctionRAIDDisk controller
Various embodiments of the present invention provide fault-tolerant, redundancy-based data-storage systems that rely on disk-controller-implemented error detection and error correction, at the disk-block level, and RAID-controller-implemented data-redundancy methods, at the disk and disk-stripe level, in order to provide comprehensive, efficient, and system-wide error detection and error correction. Embodiments of the present invention use disk-level and stripe-level data redundancy to provide error detection and error correction for stored data objects, obviating the need for certain costly, intermediate levels of error detection and error correction commonly employed in currently available fault-tolerant, redundancy-based data-storage systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Scalable cloud storage architecture
InactiveUS20120179874A1Memory architecture accessing/allocationError detection/correctionTerm memoryCloud storage
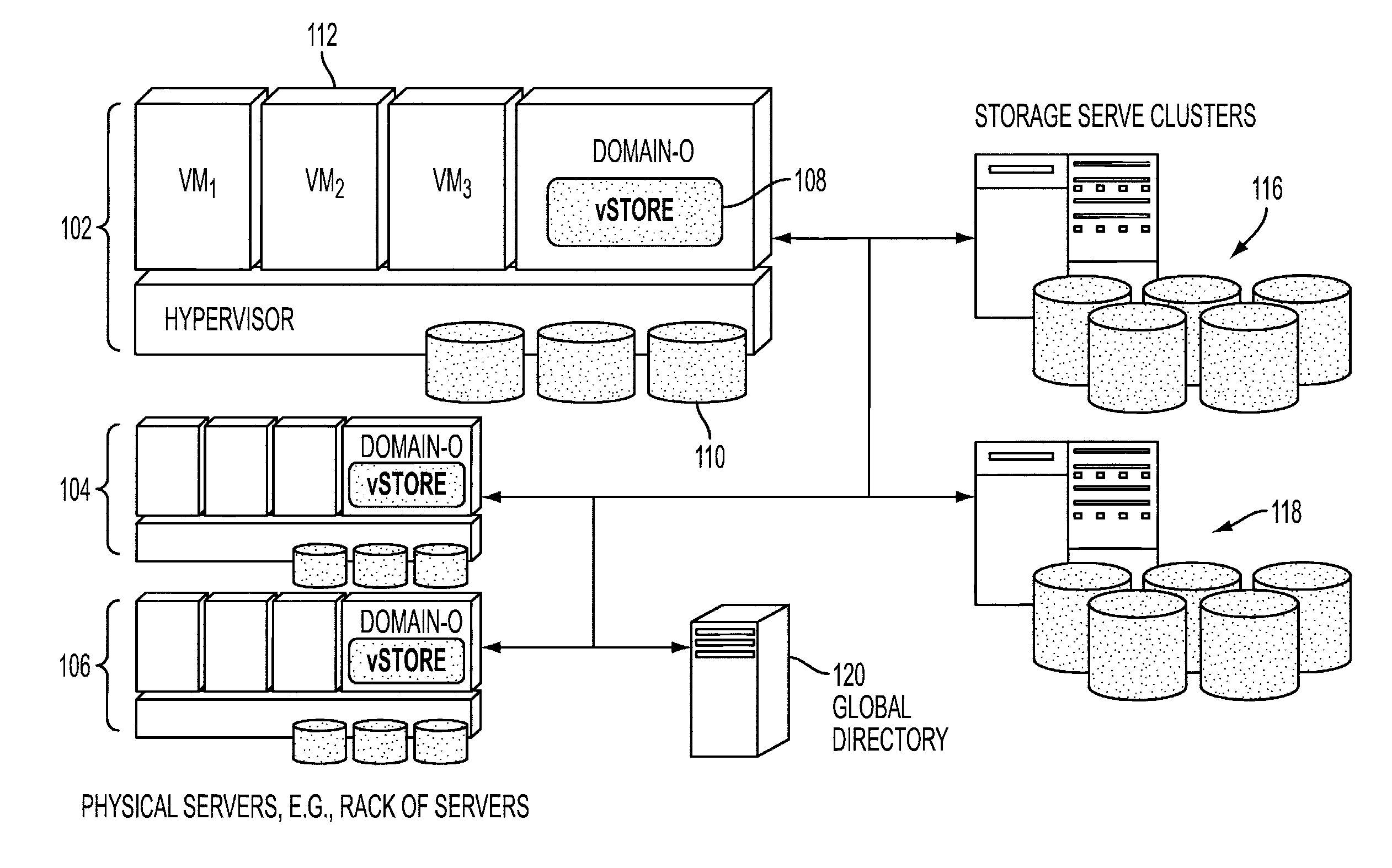
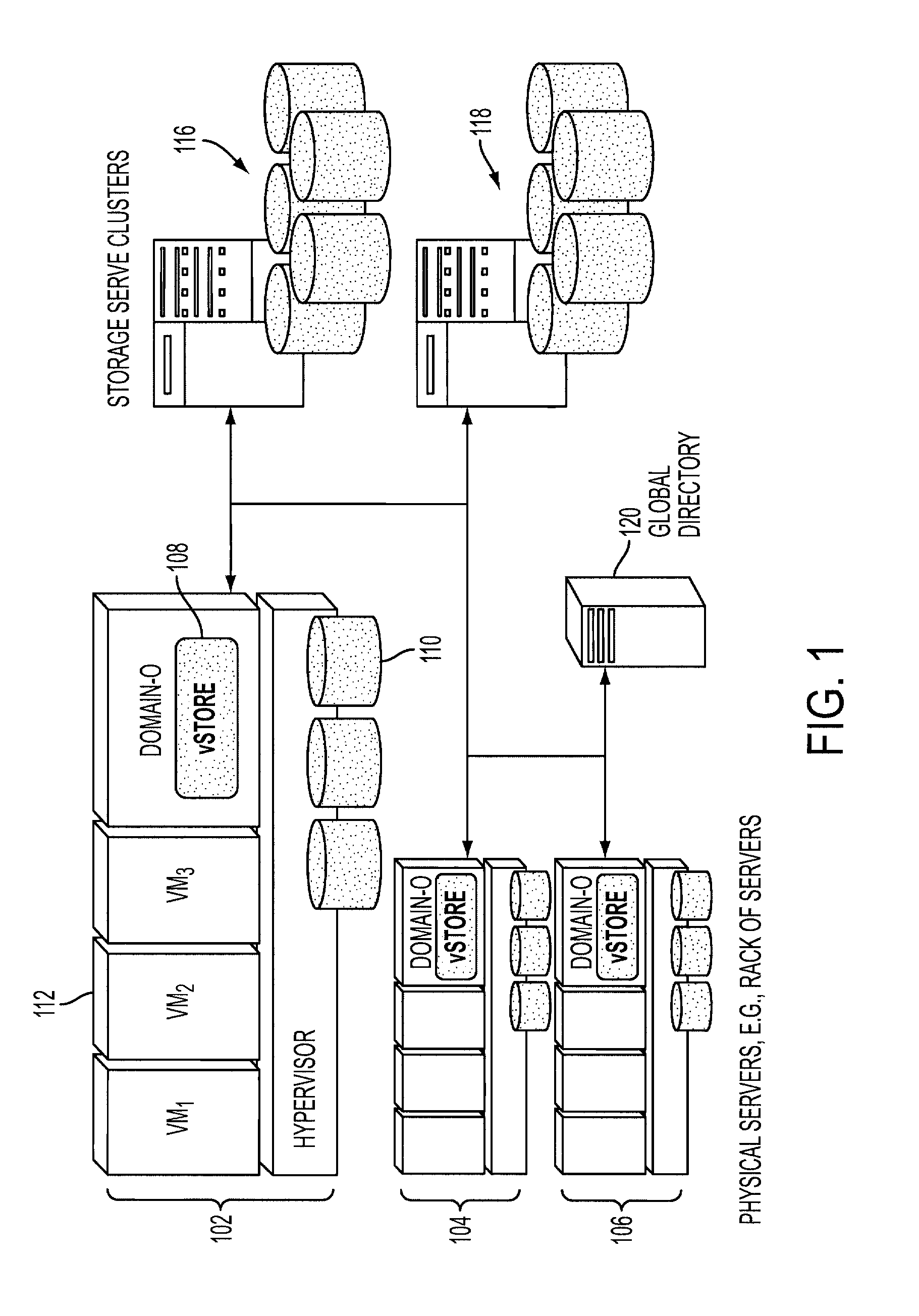
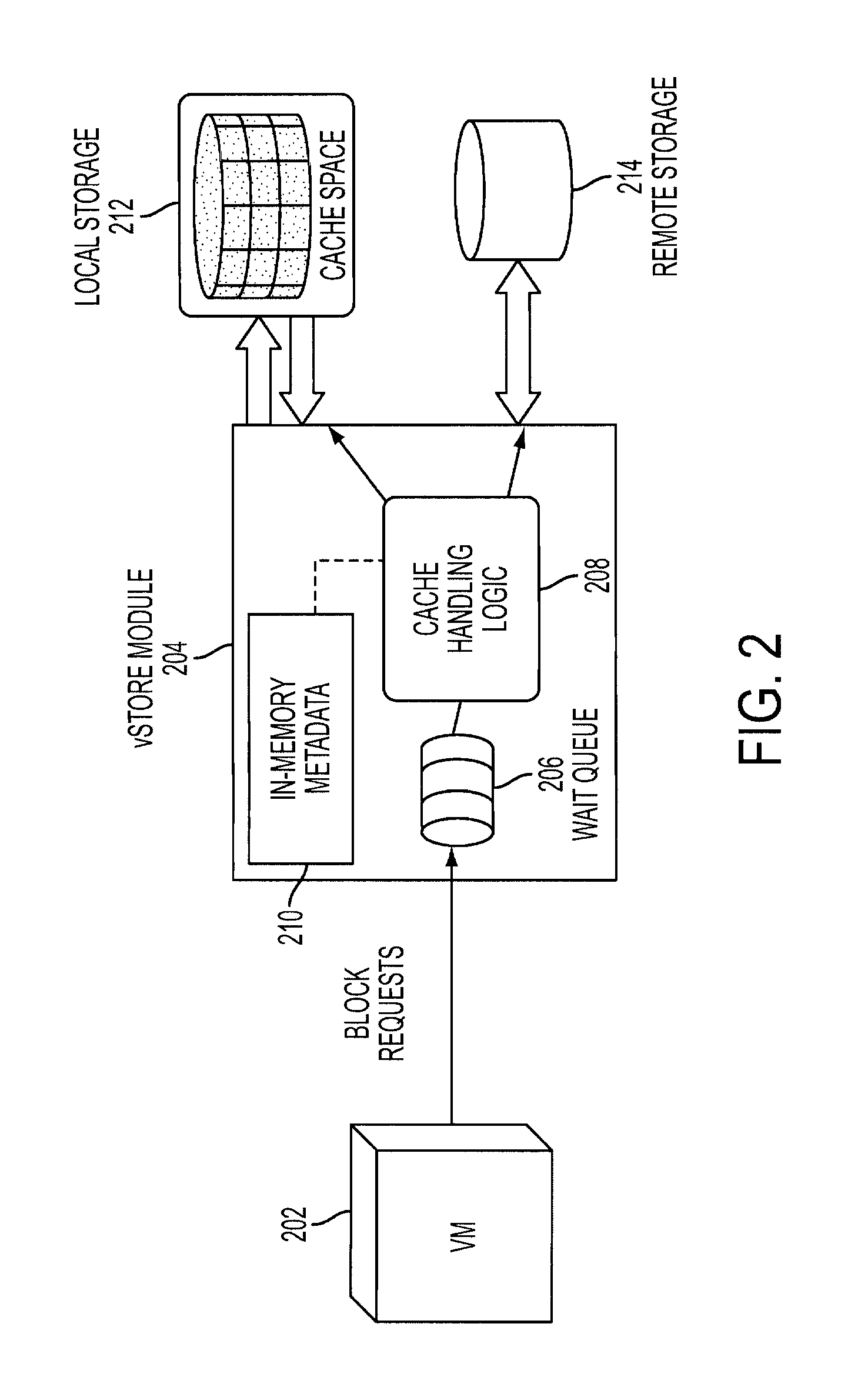
a virtual storage module operable to run in a virtual machine monitor may include a wait-queue operable to store incoming block-level data requests from one or more virtual machines. In-memory metadata may store information associated with data stored in local persistent storage that is local to a host computer hosting the virtual machines. The data stored in local persistent storage replicates a subset of data in one or more virtual disks provided to the virtual machines. The virtual disks are mapped to remote storage accessible via a network connecting the virtual machines and the remote storage. A cache handling logic may be operable to handle the block-level data requests by obtaining the information in the in-memory metadata and making I / O re-quests to the local persistent storage or the remote storage or combination of the local persistent storage and the remote storage to service the block-level data requests.
Owner:IBM CORP
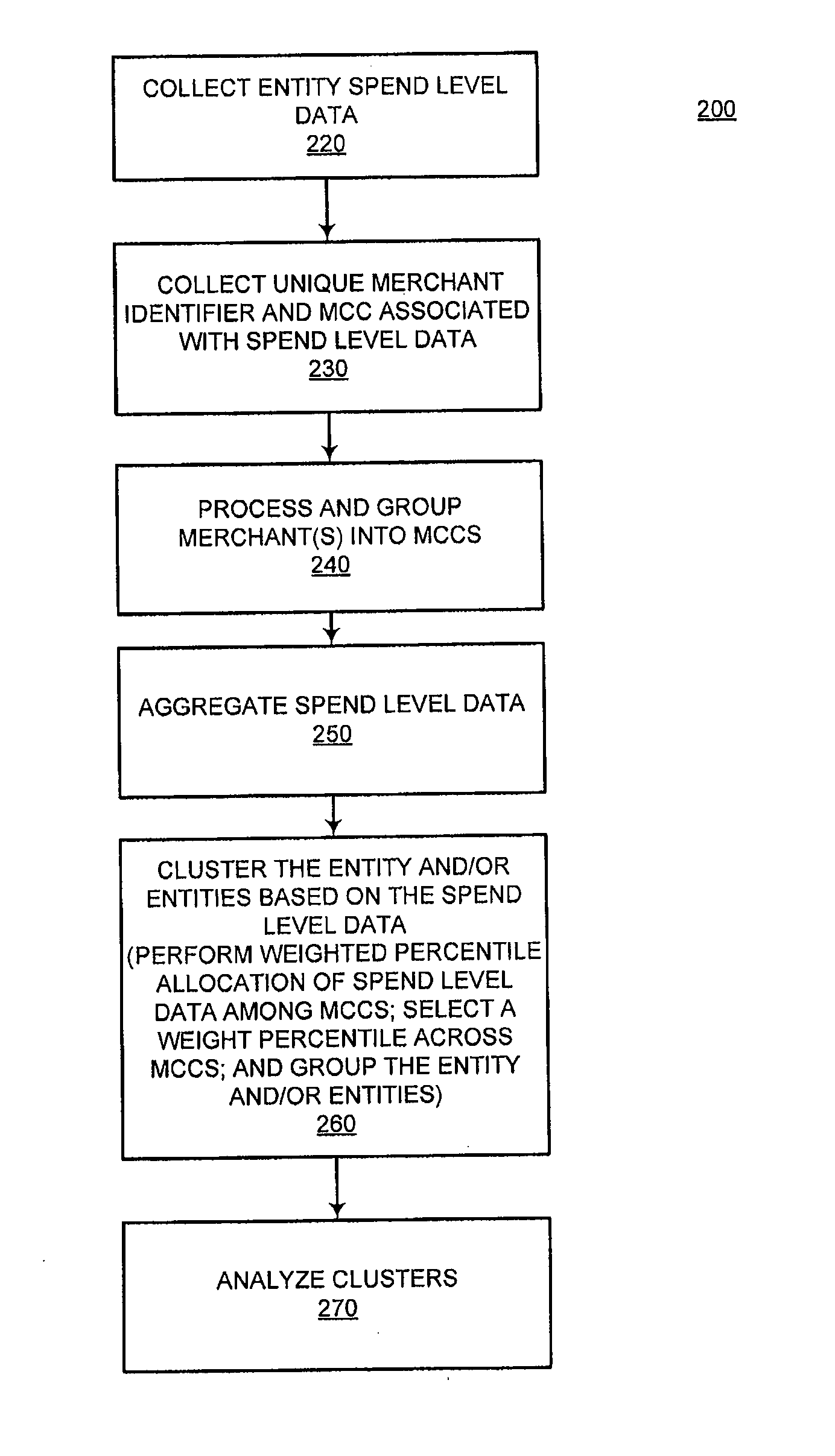
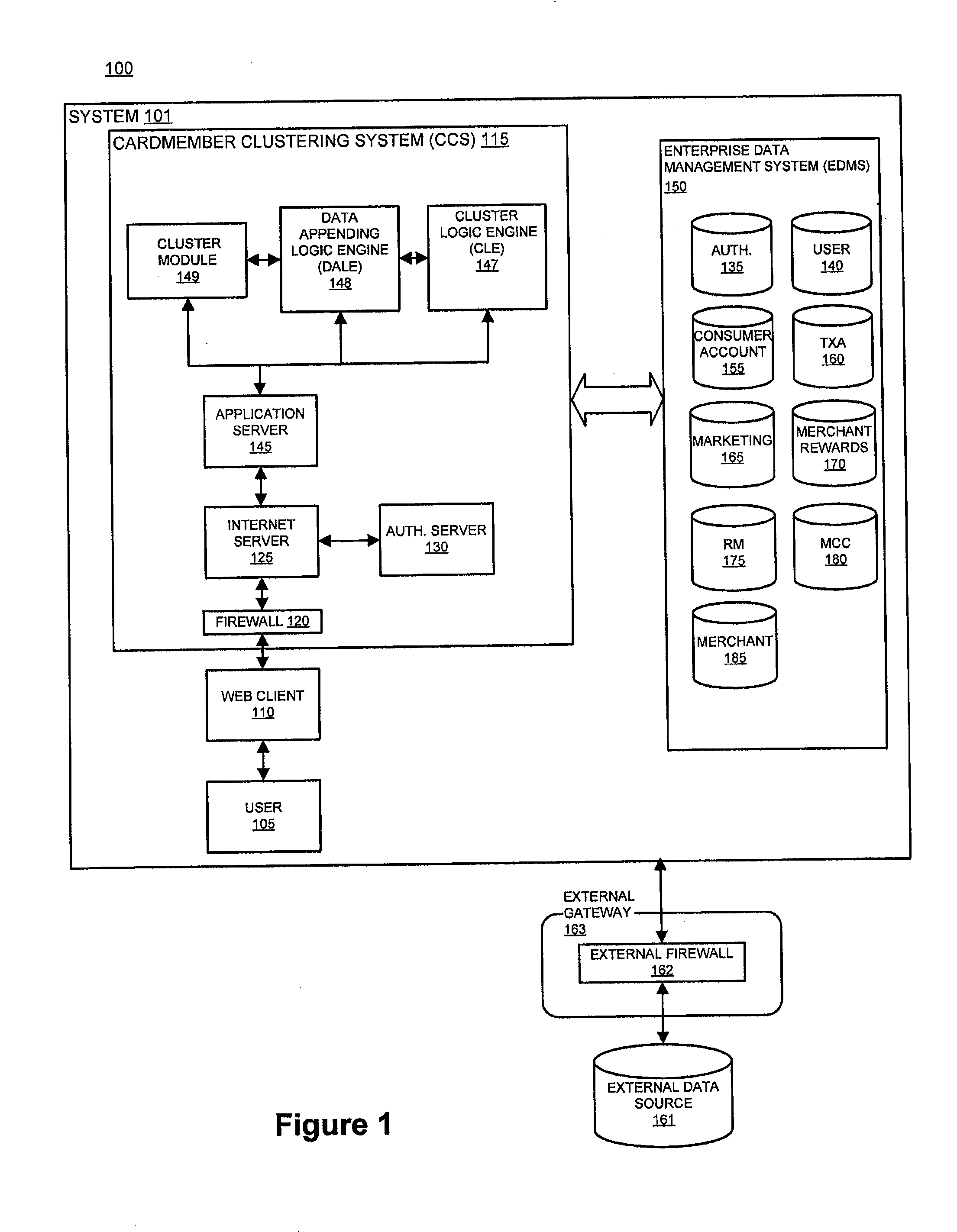
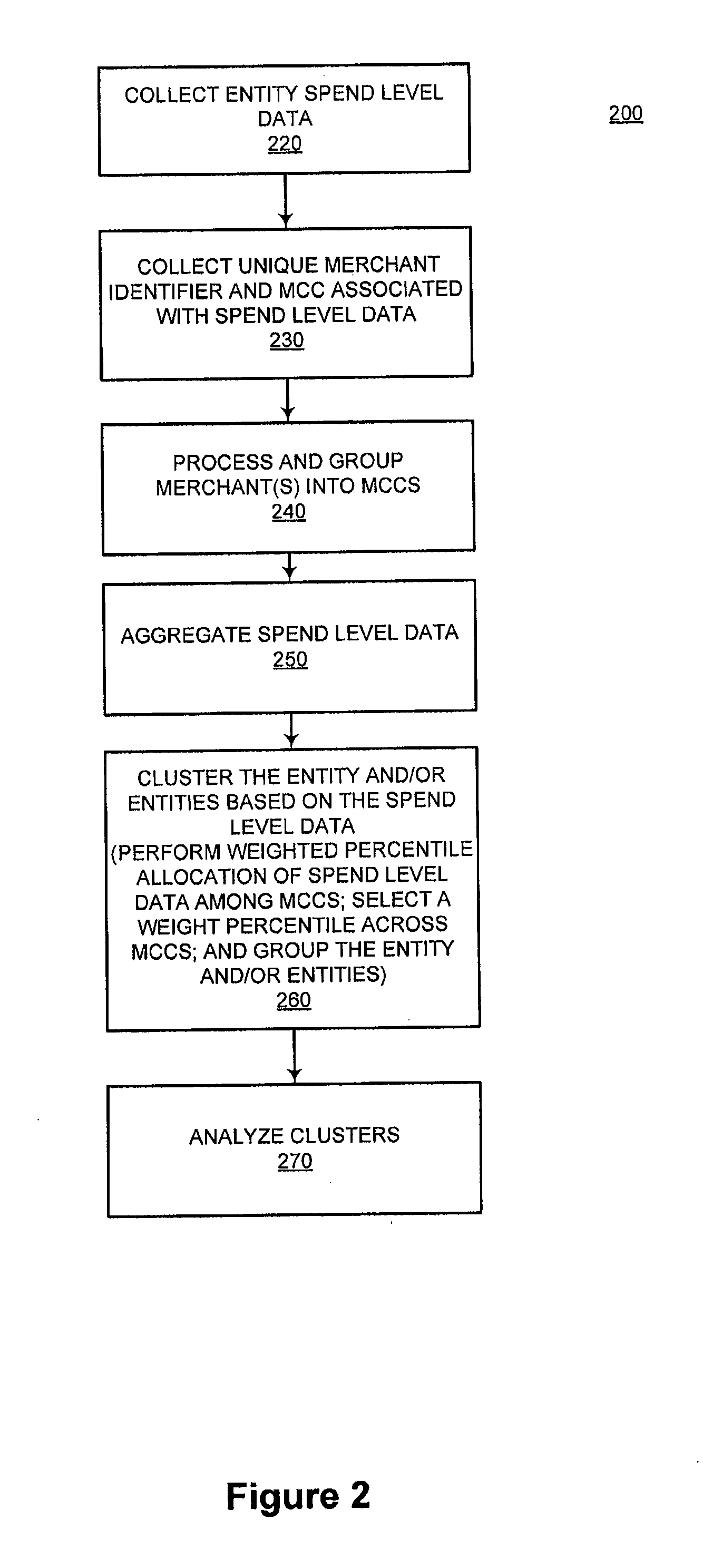
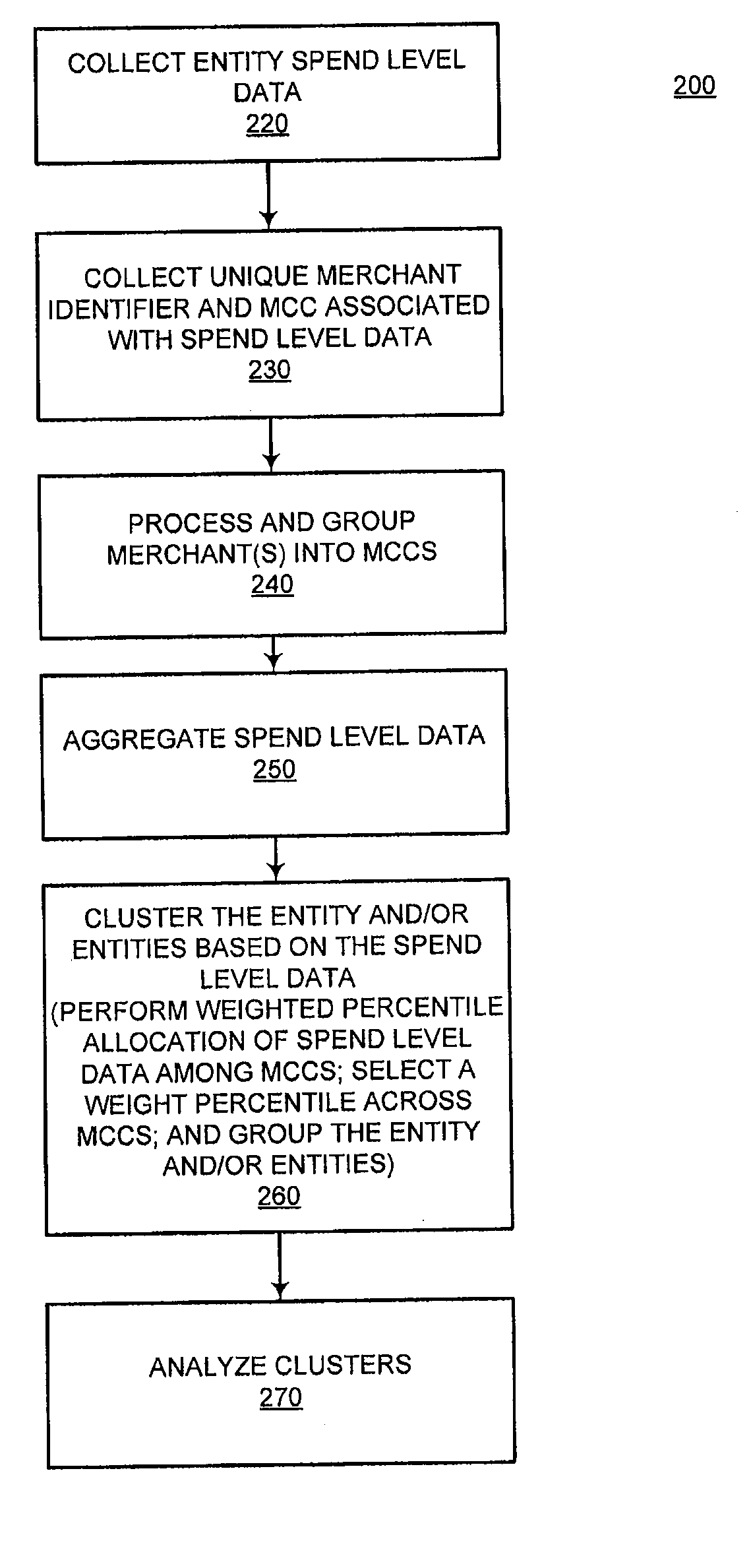
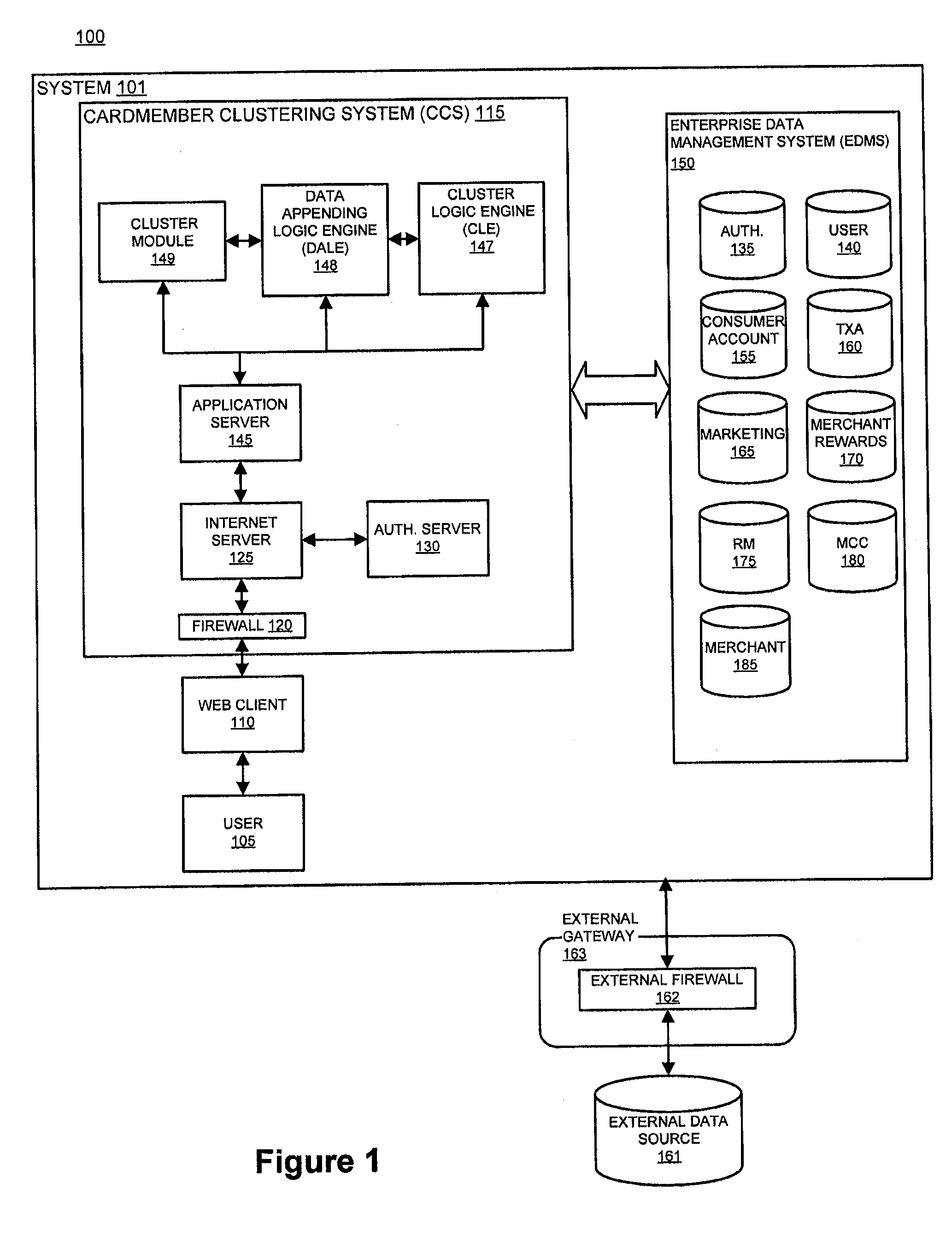
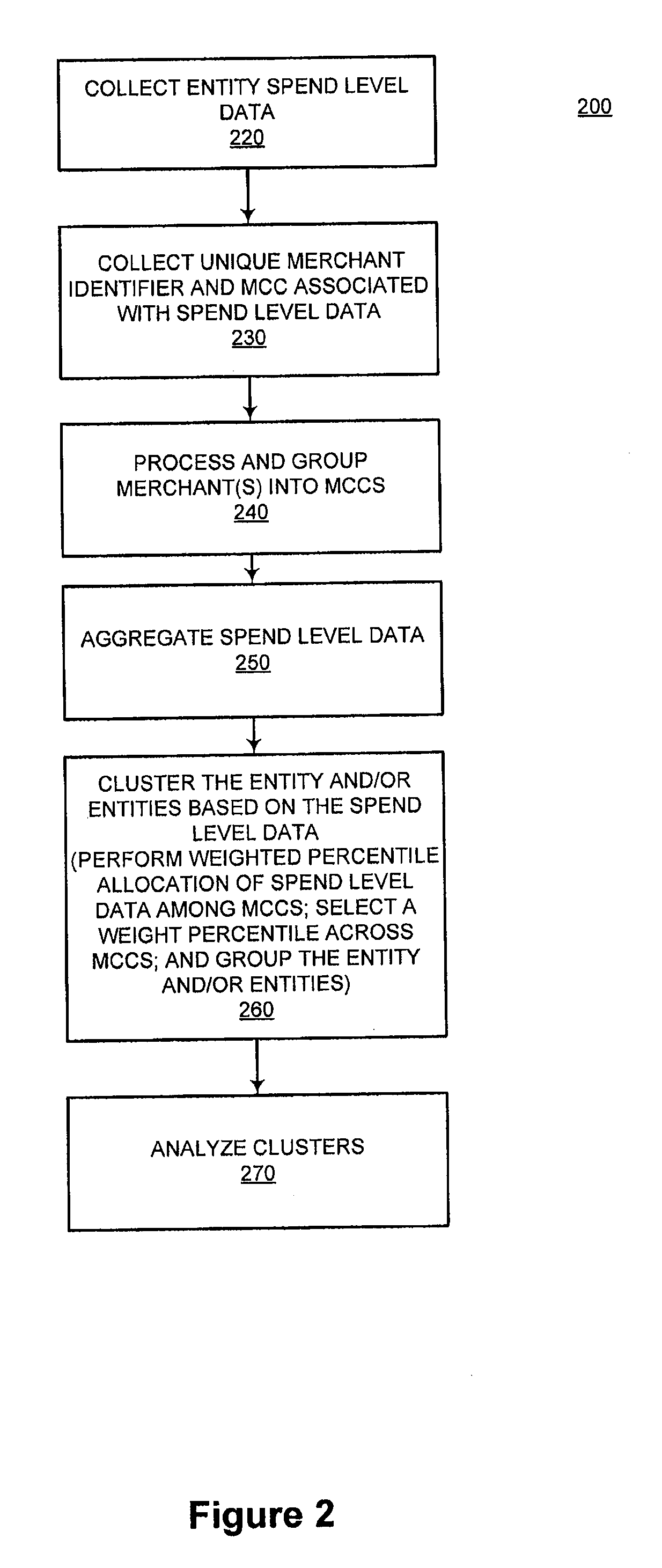
System and method for identifying attributes of a population using spend level data
InactiveUS20110178842A1Simple methodDigital data processing detailsRelational databasesData miningLevel data
The present invention improves upon existing systems and methods by providing a passive profile creation method. The data accessible to a financial processor, such as spend level data, is leveraged using sophisticated data clustering and / or data appending techniques. Associations are established among entities (e.g., consumers), among merchants, and between entities and merchants. In one embodiment, a system and method for passively collecting spend level data for a transaction of a first entity, aggregating the collected spend level data for a plurality of entities; and clustering the first entity with a subset of the plurality of entities, based on aggregated spend level data of the first entity is provided.
Owner:LIBERTY PEAK VENTURES LLC
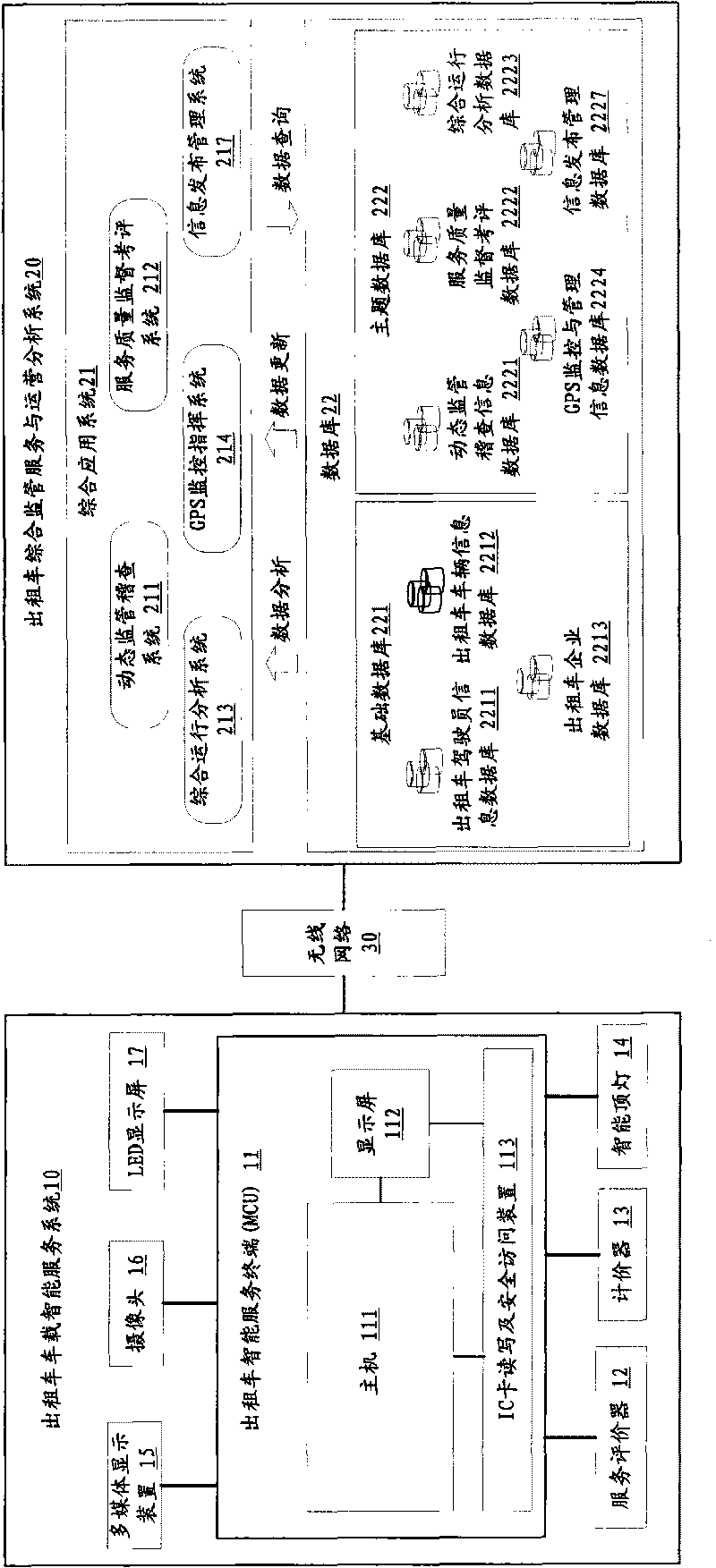
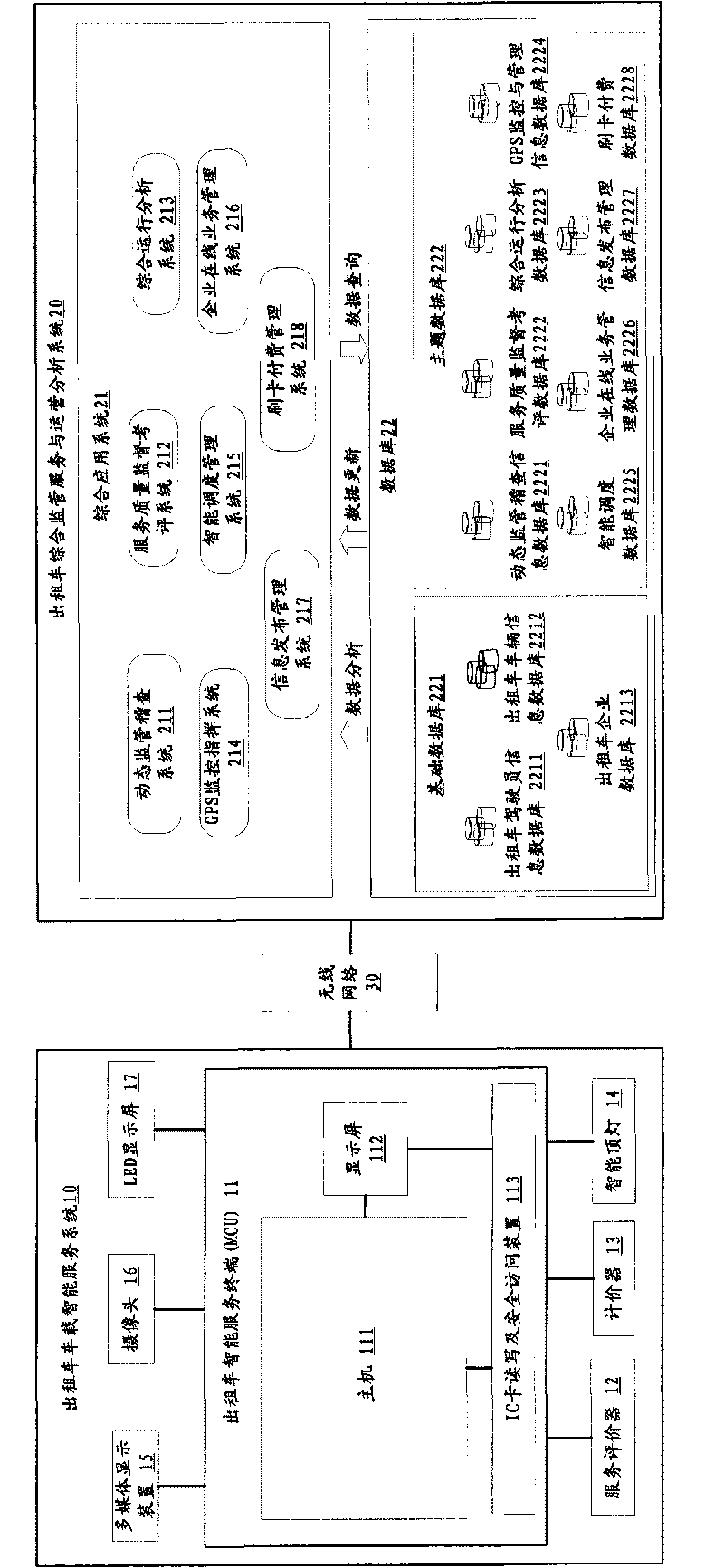
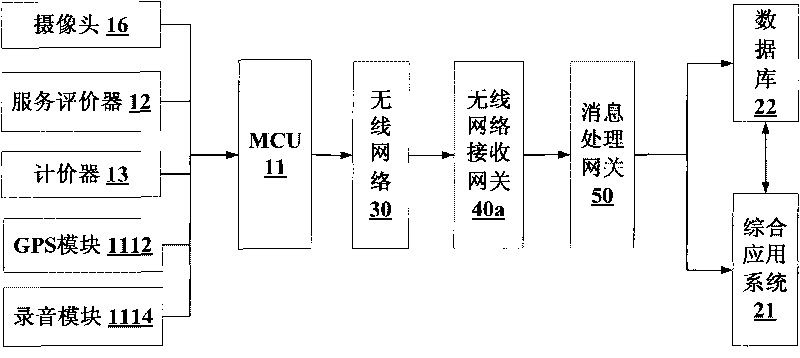
Taxi intelligent comprehensive supervision and service system
InactiveCN101739615AComprehensiveSolve the dilemma of unfounded complaintsResourcesDriver/operatorIn vehicle
The invention relates to a taxi intelligent comprehensive supervision and service system which comprises a taxi vehicle intelligent service system and a taxi comprehensive supervision service and operation analysis system. The taxi vehicle intelligent service system is connected with the taxi comprehensive supervision service and operation analysis system through a wireless network and sends on and off duty signing data of a driver, operation detail data, service evaluation data, passenger volume investigation and statistics data and alarm data to the taxi comprehensive supervision service and operation analysis system in real time; and the taxi comprehensive supervision service and operation analysis system receives and carries out mining analysis on the data and sends terminal control data, driver service quality star-level data, dynamic check data and public information data to the taxi vehicle intelligent service system, therefore, the invention can enhance the scientificity of industry management and decision and strengthen the supervision of a taxi industry, thereby enhancing the service level and the passenger satisfaction of the taxi industry.
Owner:交通部公路科学研究院
System and method for clustering a population using spend level data
The present invention improves upon existing systems and methods by providing a passive profile creation method. The data accessible to a financial processor, such as spend level data, is leveraged using sophisticated data clustering and / or data appending techniques. Associations are established among entities (e.g., consumers), among merchants, and between entities and merchants. In one embodiment, a system and method for passively collecting spend level data for a transaction of a first entity, aggregating the collected spend level data for a plurality of entities; and clustering the first entity with a subset of the plurality of entities, based on aggregated spend level data of the first entity is provided.
Owner:LIBERTY PEAK VENTURES LLC
Detecting low-level data corruption
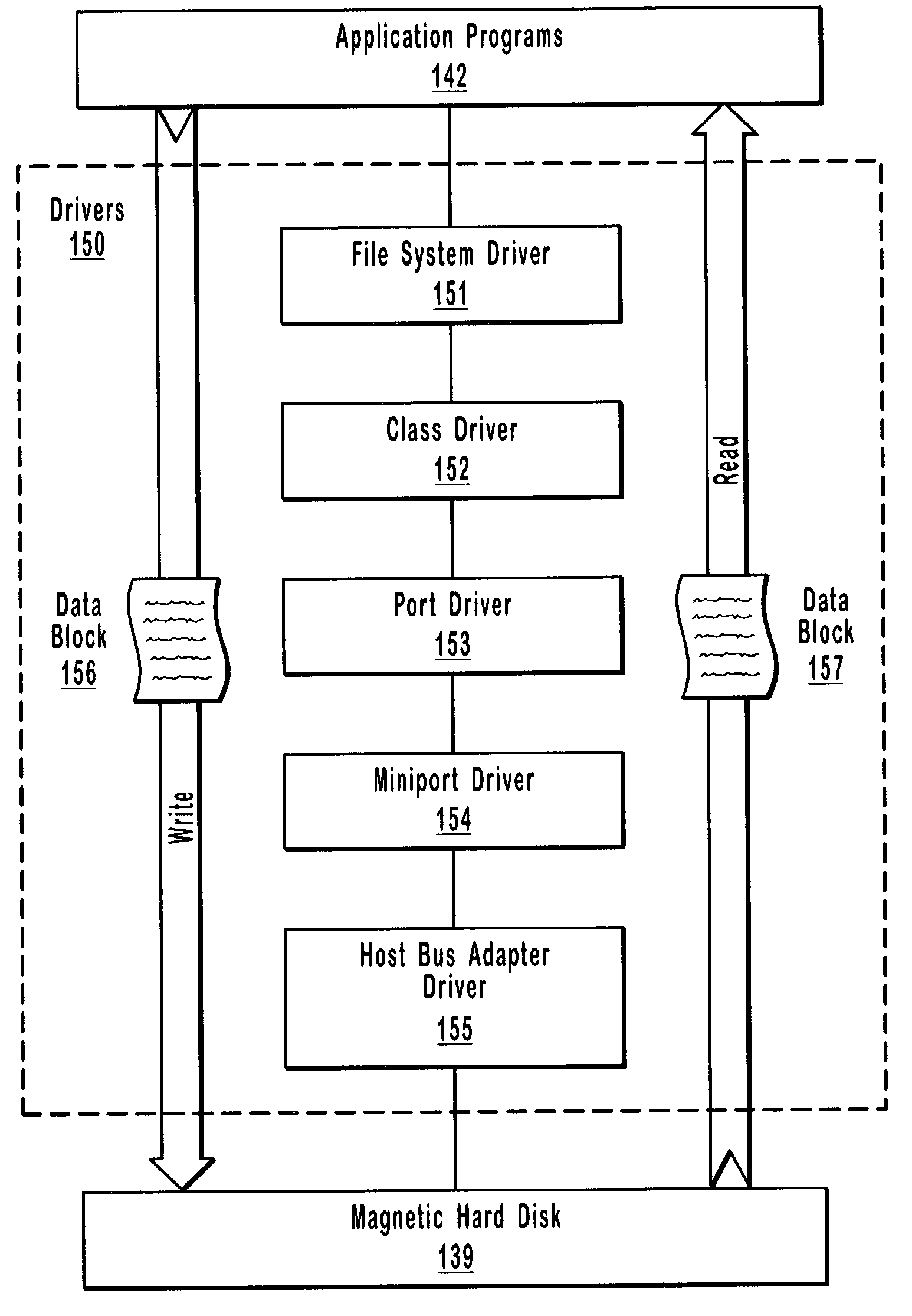
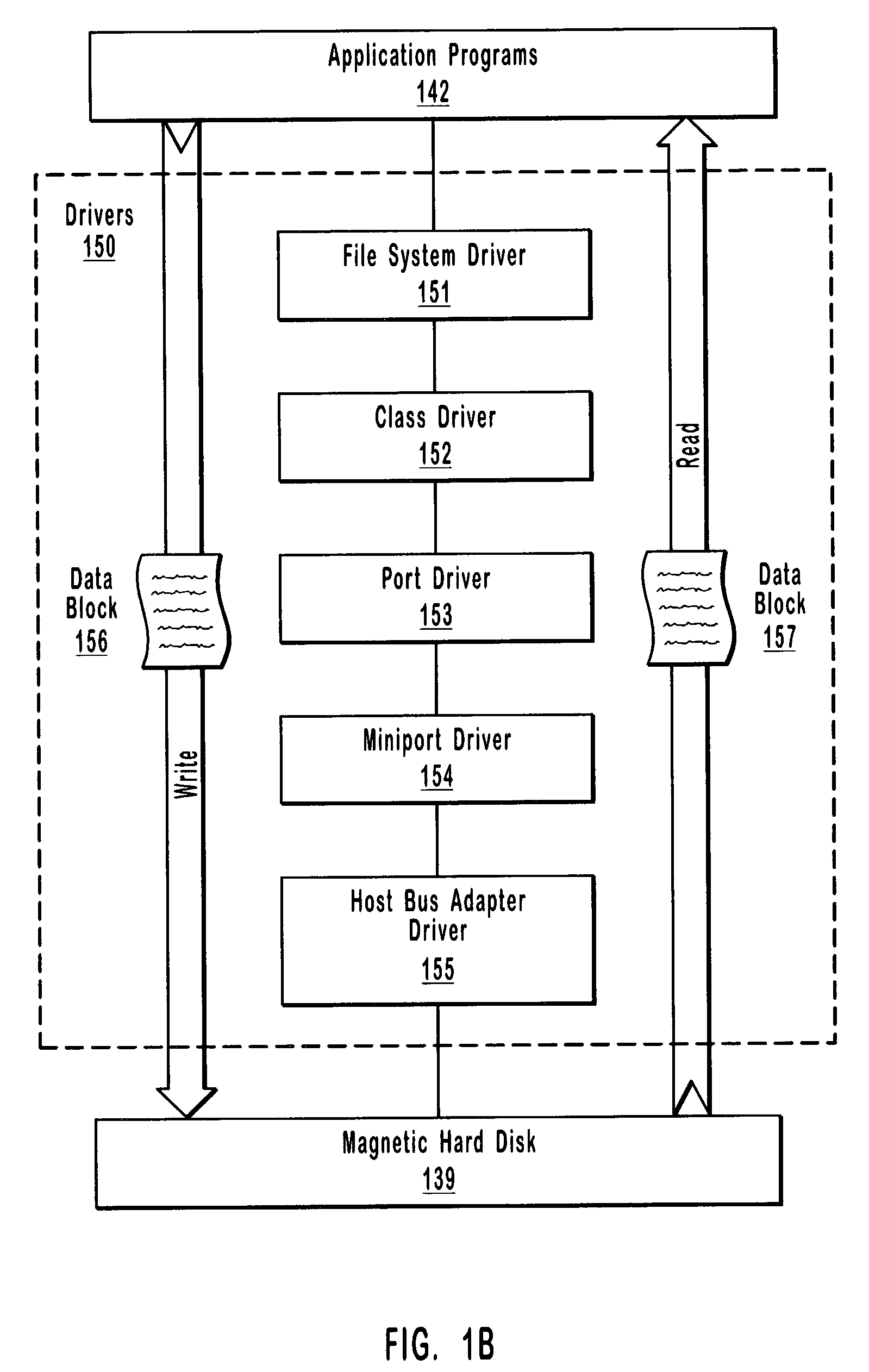
ActiveUS7020798B2Low levelError preventionRedundant data error correctionMass storageOperational system
Checksum values are used to detect low-level data corruption. I / O operations, such as, for example, read operations and write operations, cause data blocks to pass through a number of low-level drivers when the data blocks are transferred between an operating system and mass storage location. A checksum filter driver intercepts a data block as the data block passes between low-level drivers as a result of the performance of an I / O operation. The checksum filter driver calculates a first checksum value for the data block. The checksum filter subsequently intercepts the data block as the data block passes between low-level drivers as a result of the performance of a subsequent I / O operation. The checksum filter driver calculates a second checksum value for the data block. The first checksum value and the second checksum value are compared. Data corruption is detected when a checksum mismatch occurs.
Owner:MICROSOFT TECH LICENSING LLC
Managing the quality of service levels (QoS) of network traffic
Owner:BRITISH TELECOMM PLC
Method of city-level data sharing exchange platform technology
InactiveCN103139251AImprove acceleration performanceIncrease opennessData switching networksInformation resourceResource based
A method of a city-level data sharing exchanging platform technology is characterized by comprising a pre-positioned subsystem, a central exchange subsystem, a resource base and a shared information base. The method solves the technical problems that electronic governmental information resources can not be co-built or shared, and information can not reach a consensus, so that the invention provides the method of the city-level data sharing and exchanging technology.
Owner:DIGITAL CHINA INFORMATION SYST
Virtual machine file-level restoration
ActiveUS20100262585A1Error detection/correctionDigital data processing detailsHard disc driveVirtual file system
Disclosed is a method and system for selectively restoring file-level data from a disk image backup. In embodiments, a virtual machine backup may be performed by dividing a virtual machine virtual disk file into a plurality of discrete fixed-sized data blocks sharing a common index file that is stored on a backup medium, such as a hard drive, to form a backup set. The index file is referenced to determine which fixed-sized block contains volume information, such as a partition table, of the backed-up virtual machine file. The individual blocks are processed as a virtual filesystem which is presented to an access module, which traverses the filesystem and provide access to individual files in the image backup to a client process, the restore files may be delivered to the client in a container file, which may be compressed to increase transfer speed. The container file may include executable instructions for automatically restoring the files to a desired location.
Owner:UNITRENDS
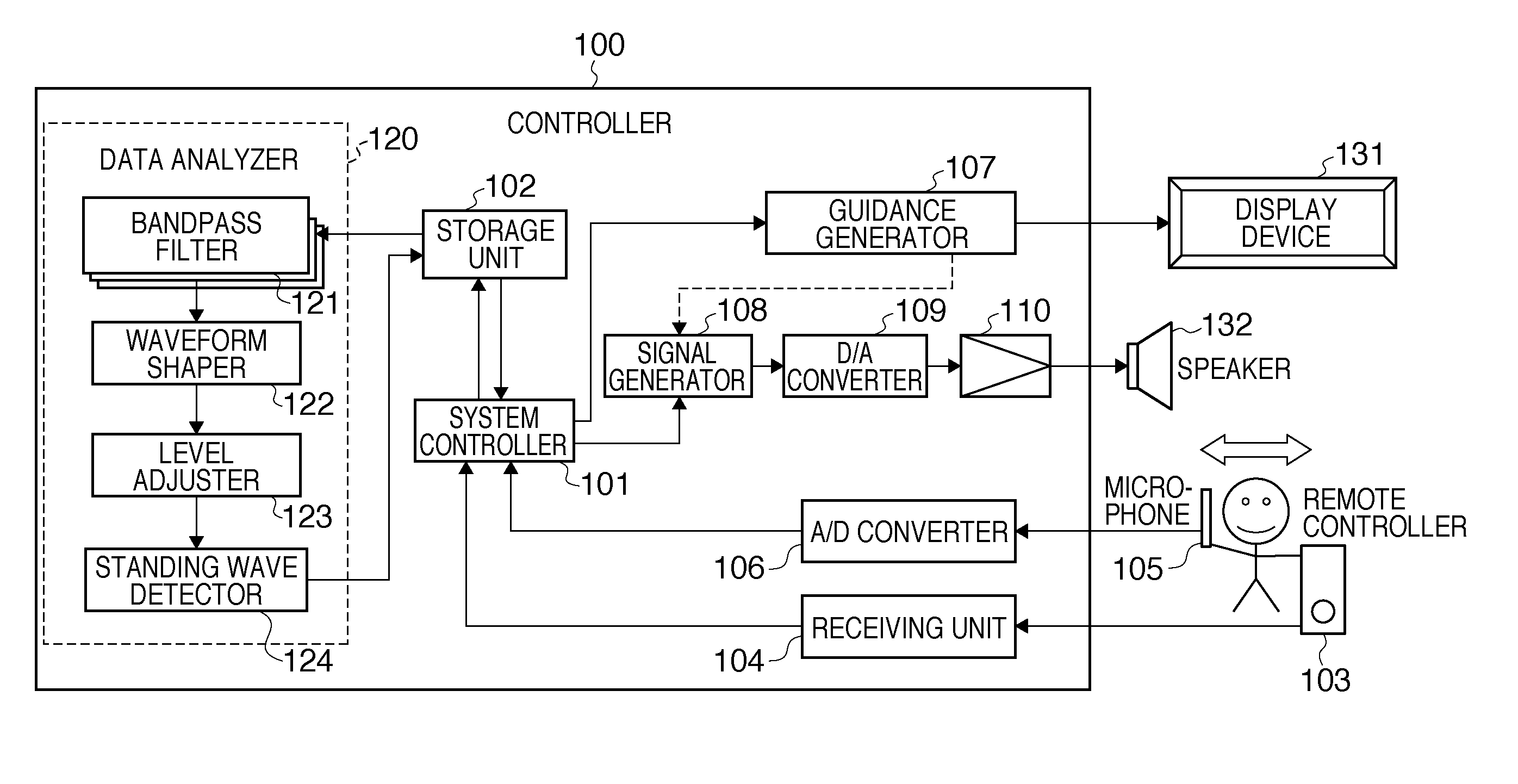
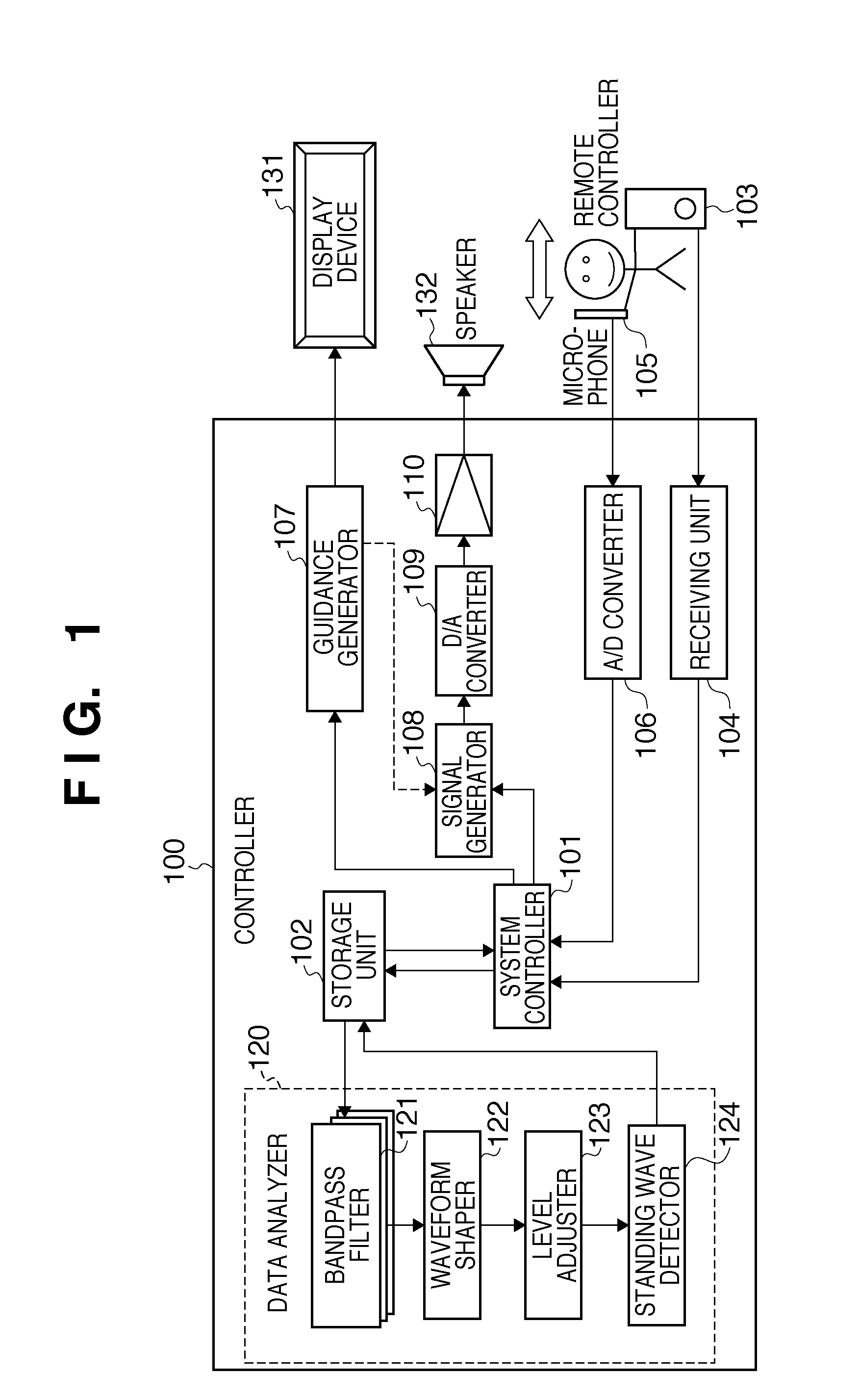
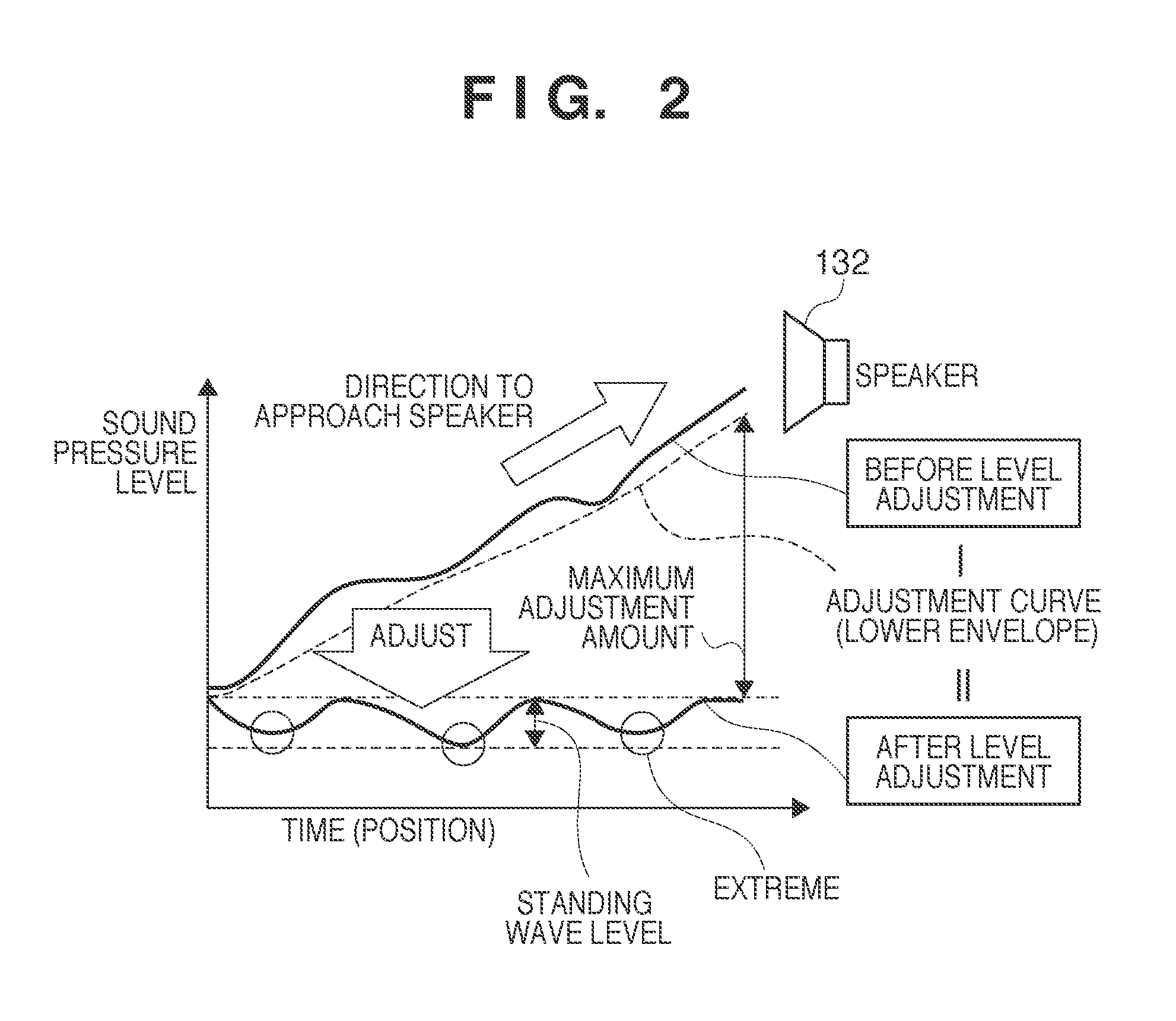
Standing wave detection apparatus and method of controlling the same
To efficiently detect a standing wave generated in a room, a standing-wave detection apparatus for detecting a standing wave in a predetermined space, comprises: a sound-receiving unit adapted to receive a sound generated from a sound source arranged in the predetermined space; a storage unit adapted to store time series sound pressure level data acquired by the sound-receiving unit during movement along a path in the predetermined space; an adjustment unit adapted to adjust the time series sound pressure level data stored in the storage unit, based on an adjustment curve determined using a lower envelope of the time series sound pressure level data stored in the storage unit; and a detection unit adapted to detect an existence position of a standing wave in the predetermined space based on the adjusted time series sound pressure level data.
Owner:CANON KK
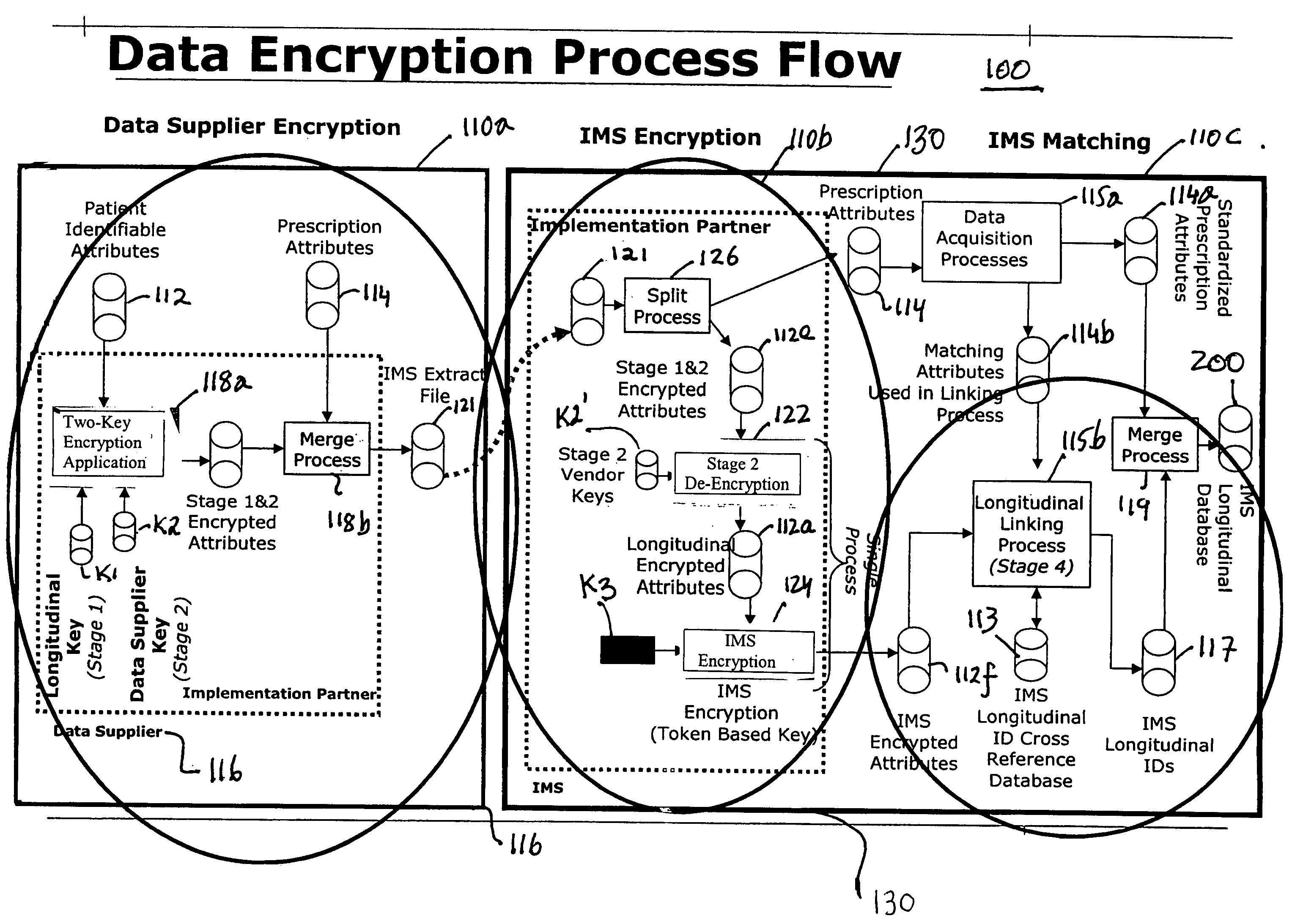
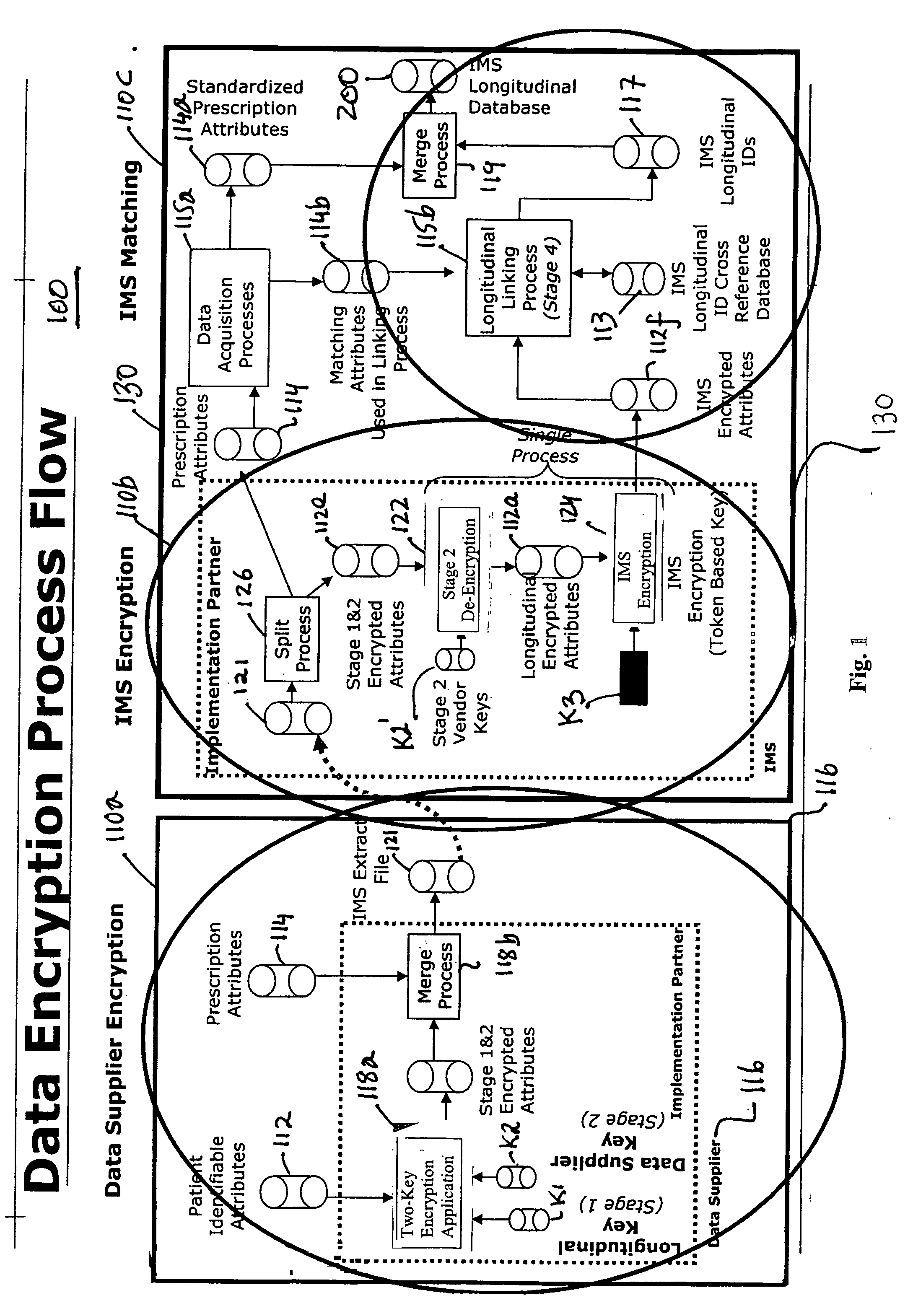
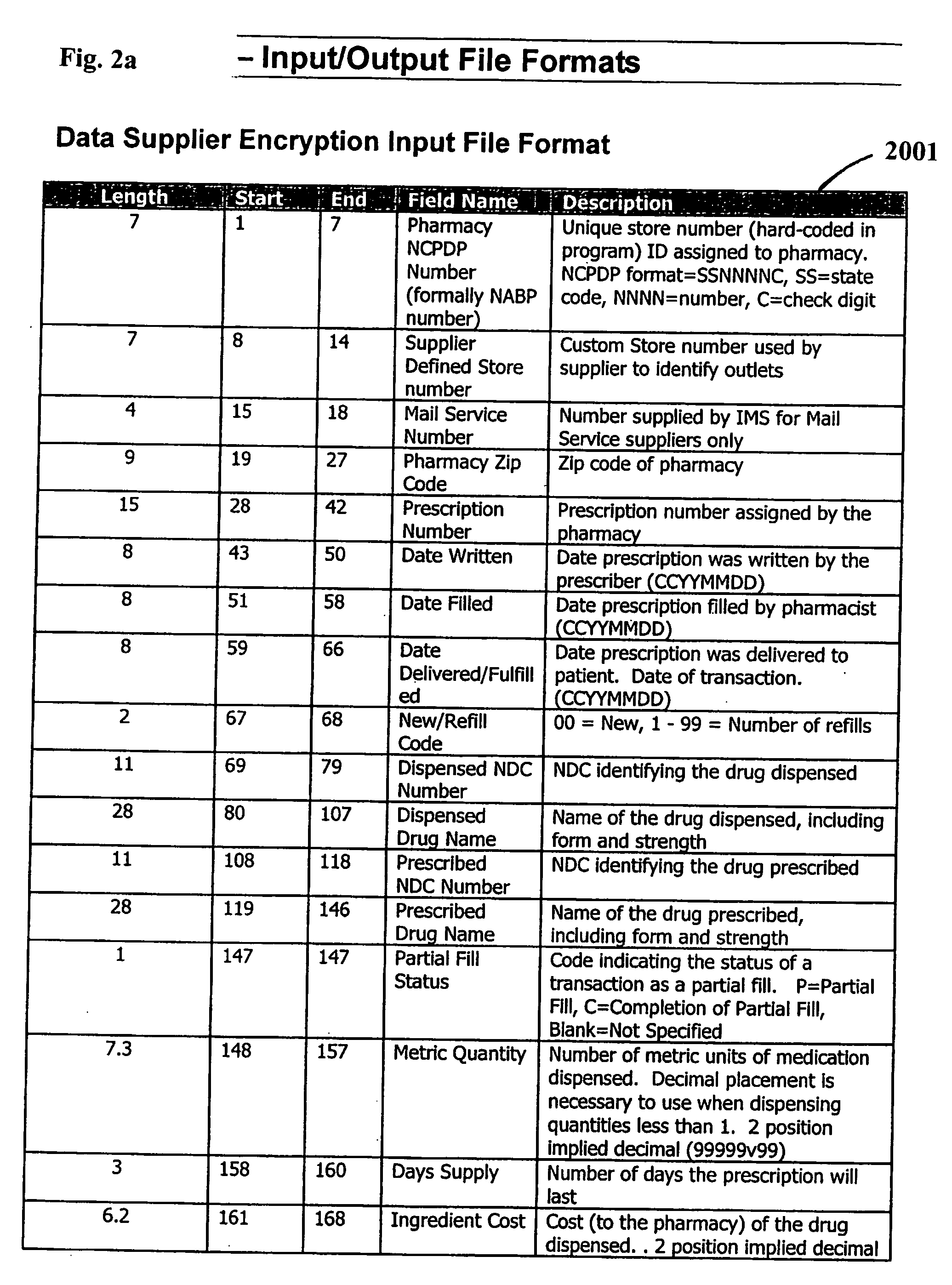
Data encryption applications for multi-source longitudinal patient-level data integration
InactiveUS20050256742A1Computer security arrangementsPatient personal data managementData providerPatient level data
Software applications are provided for integrating individual multi-sourced patient healthcare transaction data records in a longitudinal database. The data records are processed in a manner which preserves patient privacy by encrypting patient-identifying attributes in the data records and thereby rendering sensitive personal information inaccessible. The applications, which may be organized as modules using common frame work components, are designed to process the multi-sourced data records at data supplier sites and at a common database assembly facility. The applications provide the data supplier sites and the database facility with methods for acquiring attributes, standardizing formats, encryption key generation, and encrypting and decrypting attributes in the data records. The encryption application provides methods for double encryption of the data records at data supplier sites using a key specific to a data supplier and a key specific to the database facility.
Owner:IMS SOFTWARE SERVICES
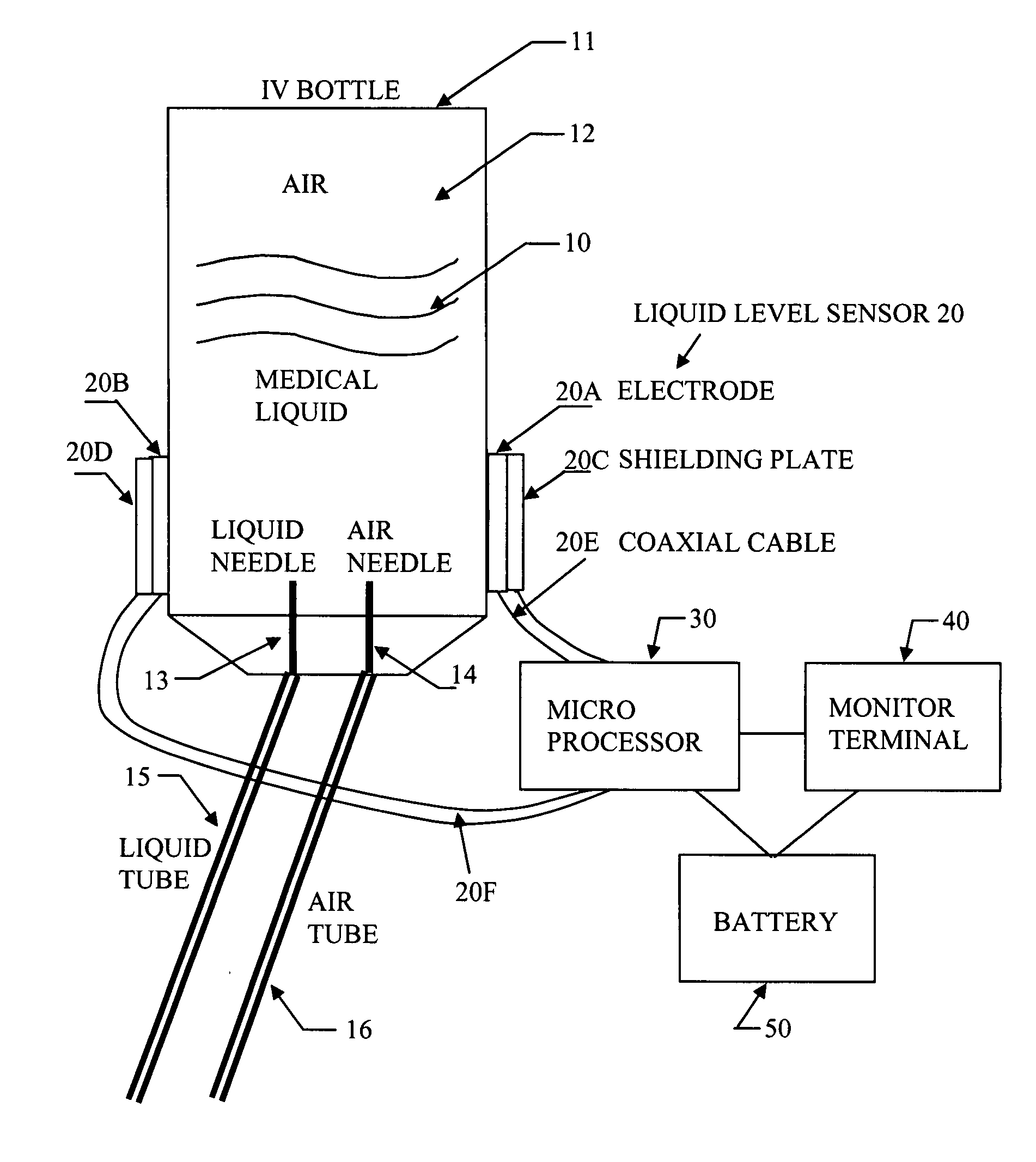
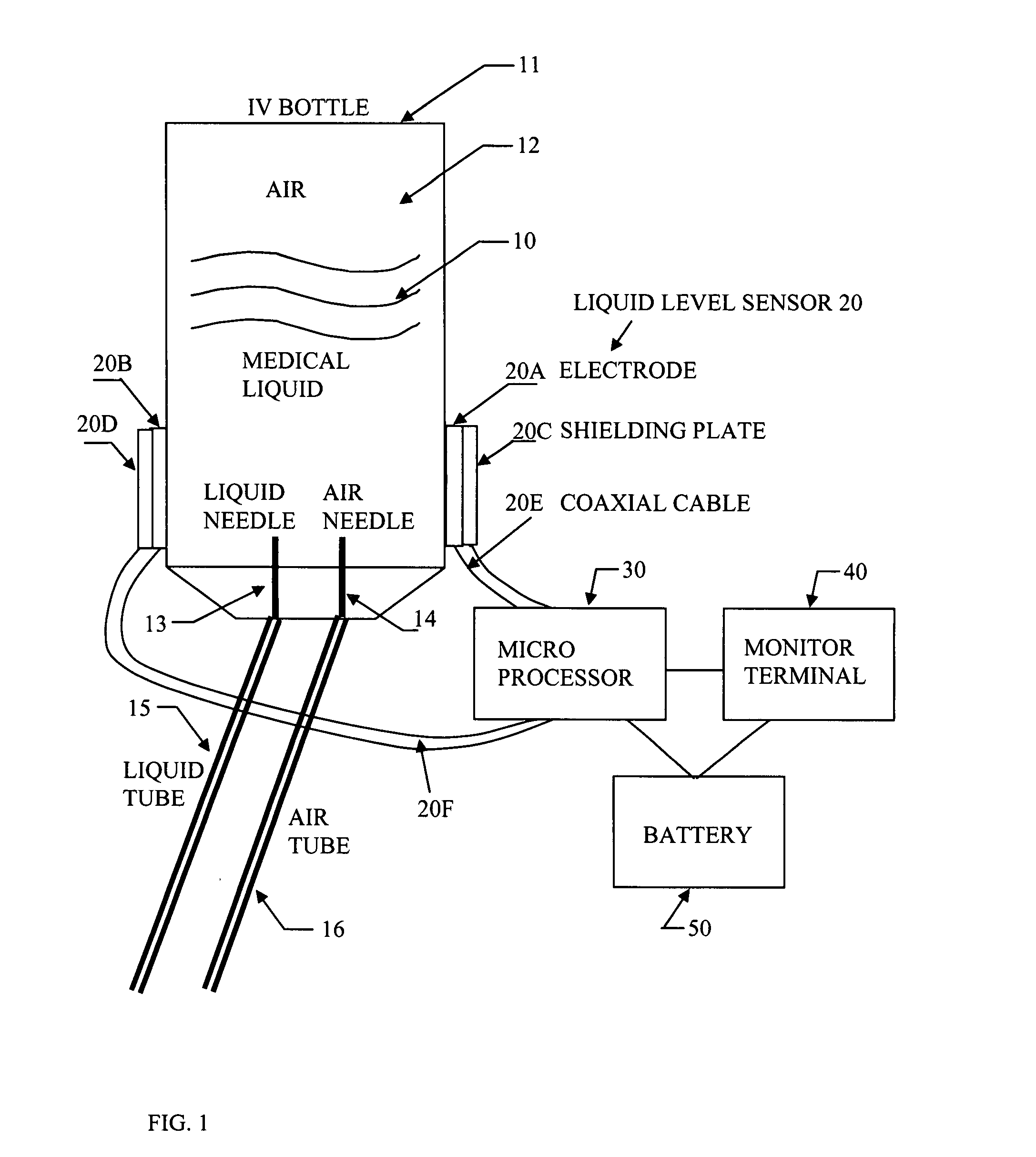
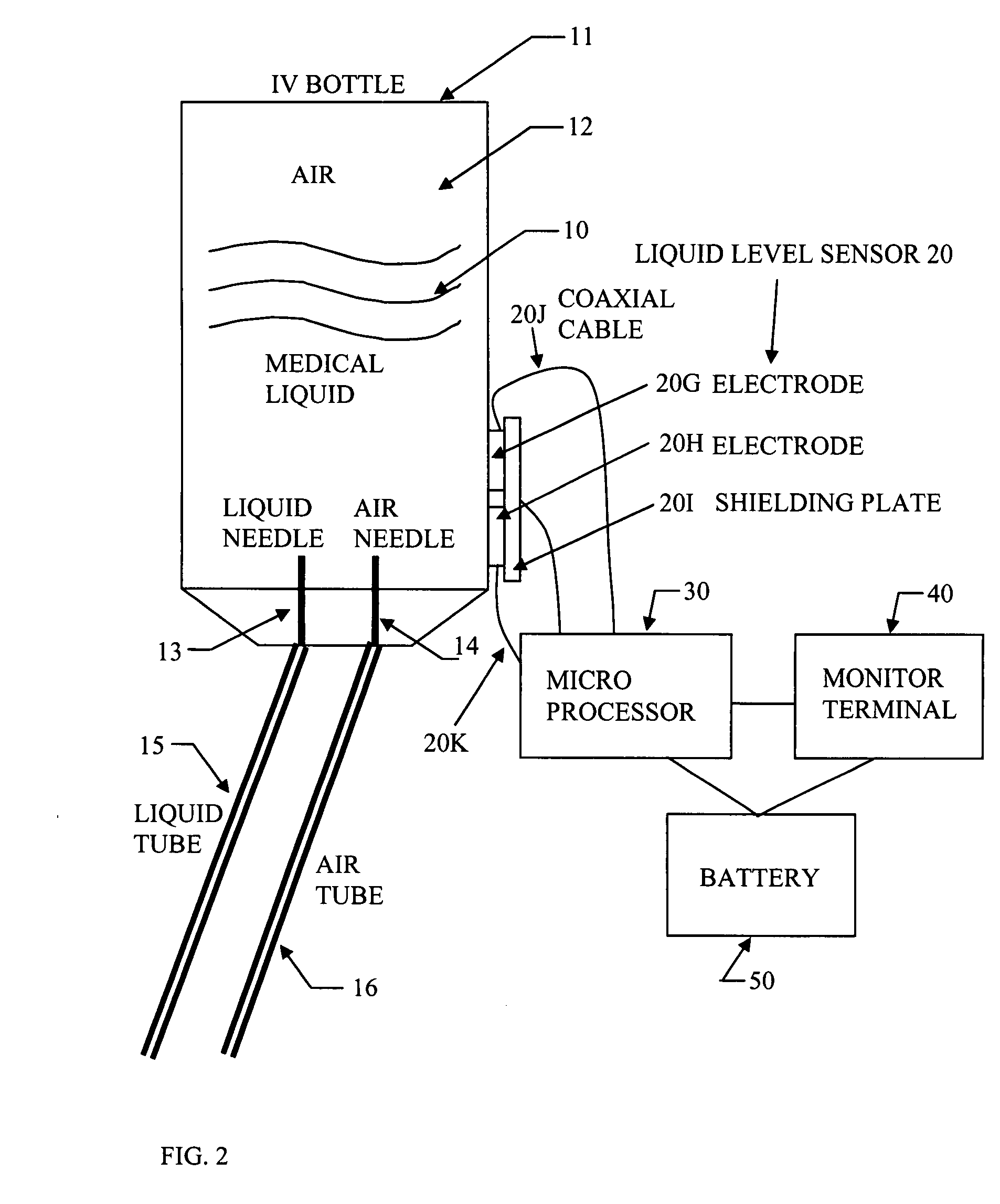
Portable IV infusion mornitoring system
InactiveUS20070293817A1Improve detection accuracyLow reliabilityMedical devicesFlow monitorsSignaling networkBottle
A portable infusion monitoring system displays the liquid level and flow rate data during infusion process, as well as gives an alarm for patents and nurses in hospital as the medical liquid in an IV bottle drops to a predetermined low level. This system comprises a set of liquid level sensor, a microprocessor, and a monitor terminal. The liquid level sensor generates an electric signal related to the liquid level inside the IV bottle. The microprocessor analyzes the electric parameters detected from the electric signal, and obtains the liquid level data. The liquid level data are sent to the monitor terminal for display, and an alarm is activated when the medical liquid inside the IV bottle drops to a predetermined low lever. Further functions of the monitor terminal includes an automatic switch to cut off the IV feeding process and send the alarm signal to a nurse station through signal network by wire or wirelessly. Several interference filtering methods are applied to increase signal / noise ratio, and therefore warrant the operation reliability.
Owner:FENG JUN +1
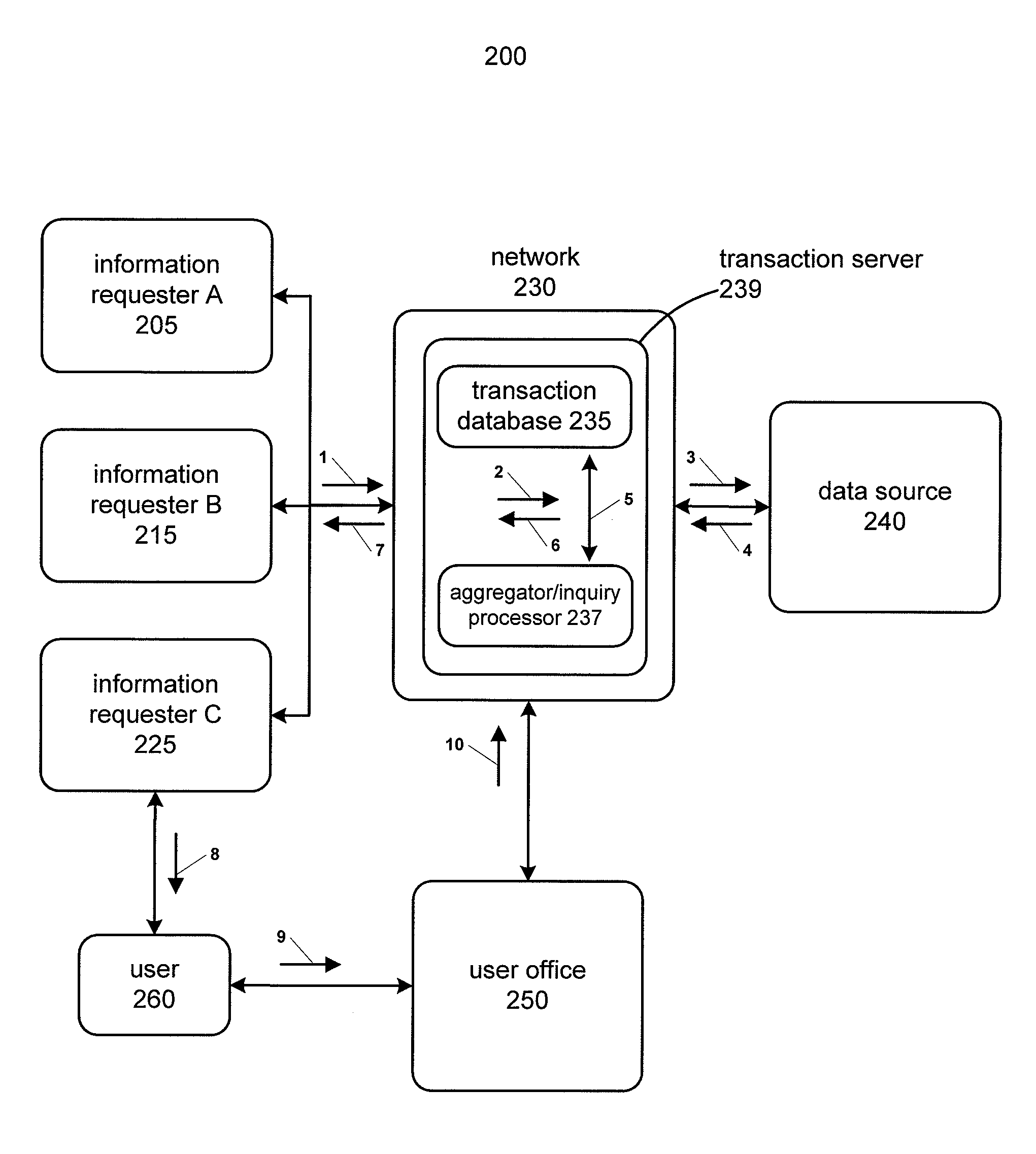
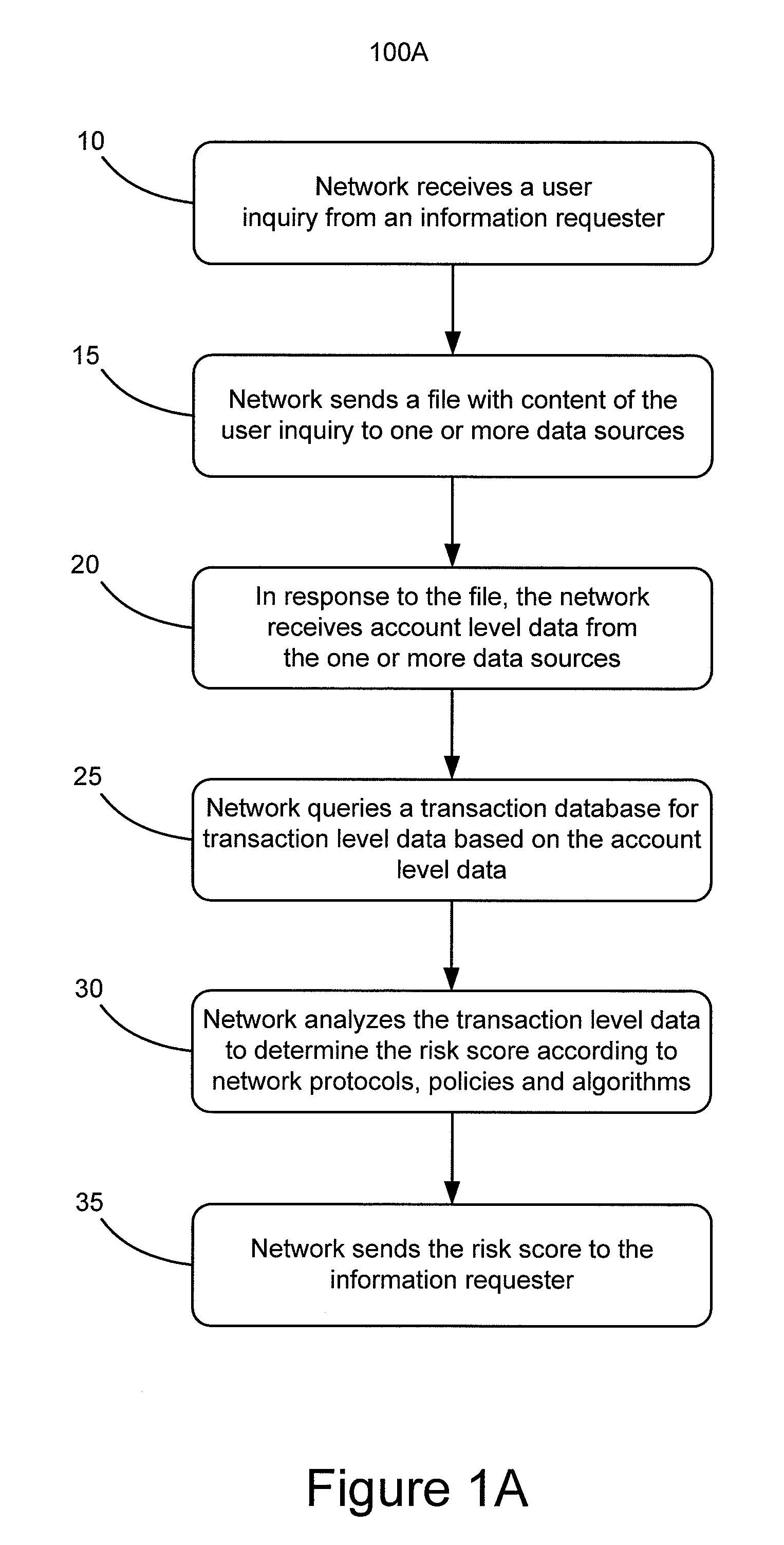
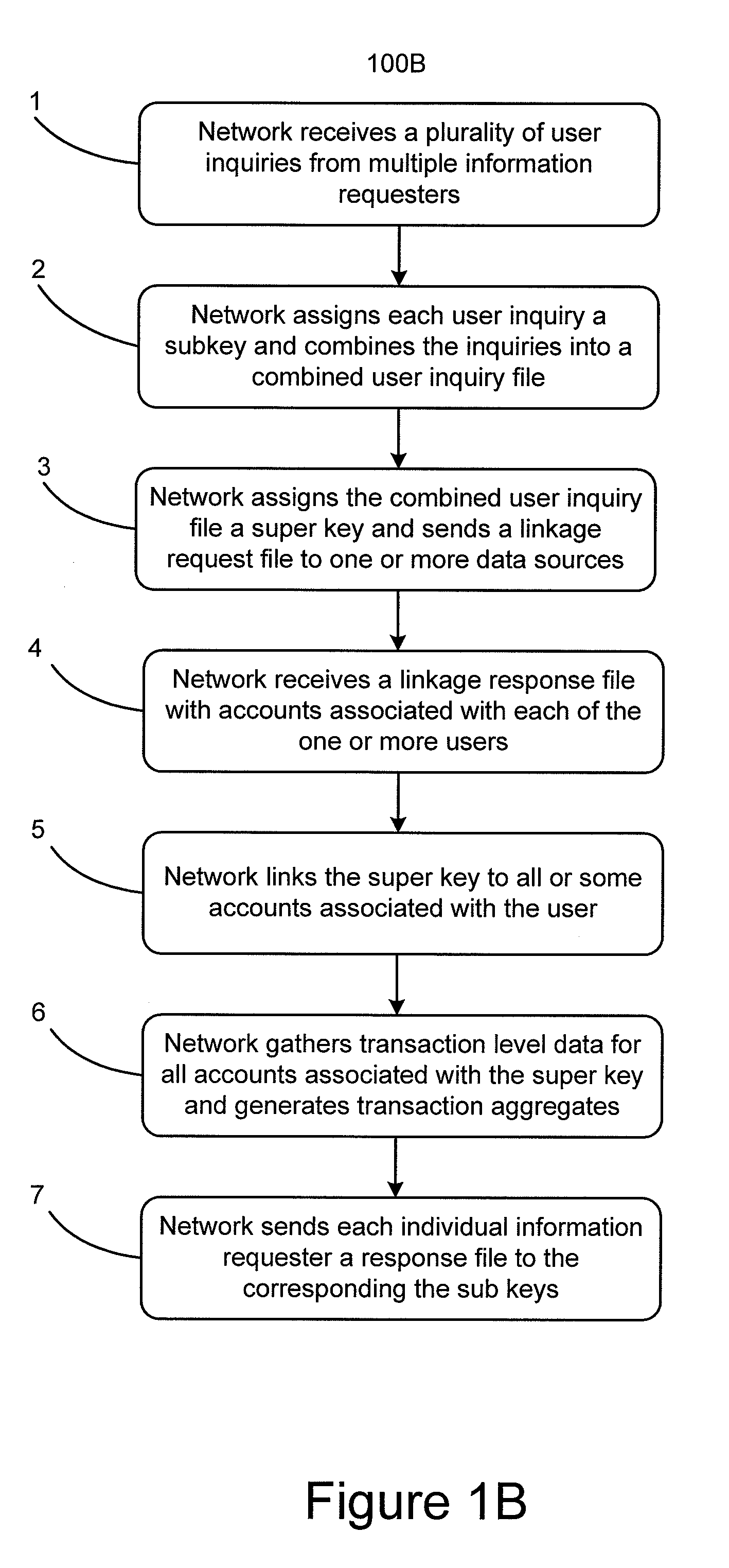
System and method using superkeys and subkeys
Systems and methods for providing aggregated transaction level data for a particular user to multiple information requesters are disclosed. Subkeys are assigned to user inquiries from multiple information requesters and a super key is assigned to those subkeys to link them to one or more user identifiers such as a username or Social Security number. Account level data is provided based on the super key and the user identifiers. Duplicate requests for aggregated transaction level data contained in the user inquiries can be deleted. User inquiry response files containing transaction level aggregate data can be sent to the information requesters based on the assigned subkeys.
Owner:VISA INT SERVICE ASSOC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com