Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
583 results about "Data Corruption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data corruption refers to errors in computer data that occur during writing, reading, storage, transmission, or processing, which introduce unintended changes to the original data. Computer, transmission, and storage systems use a number of measures to provide end-to-end data integrity, or lack of errors.
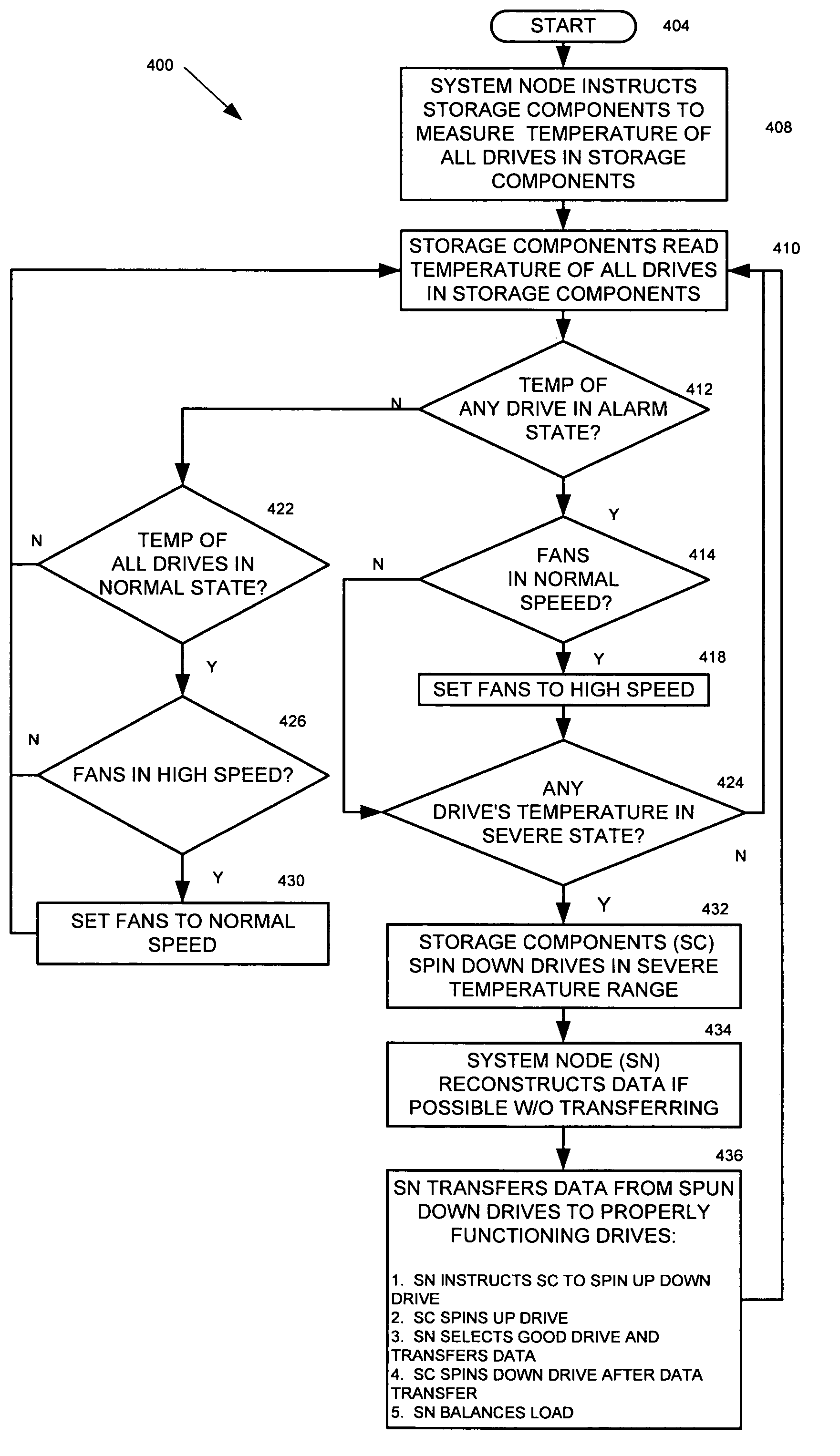
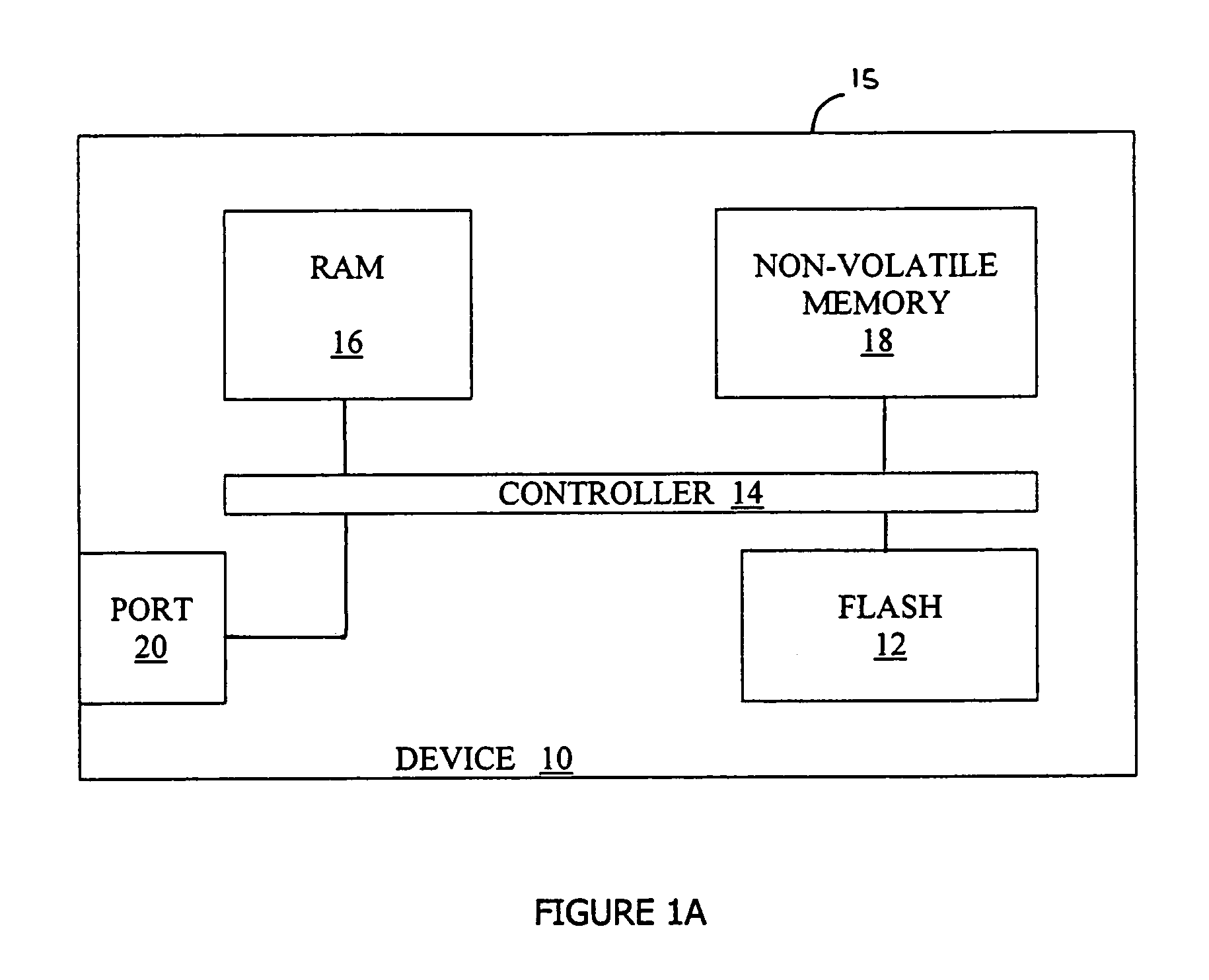
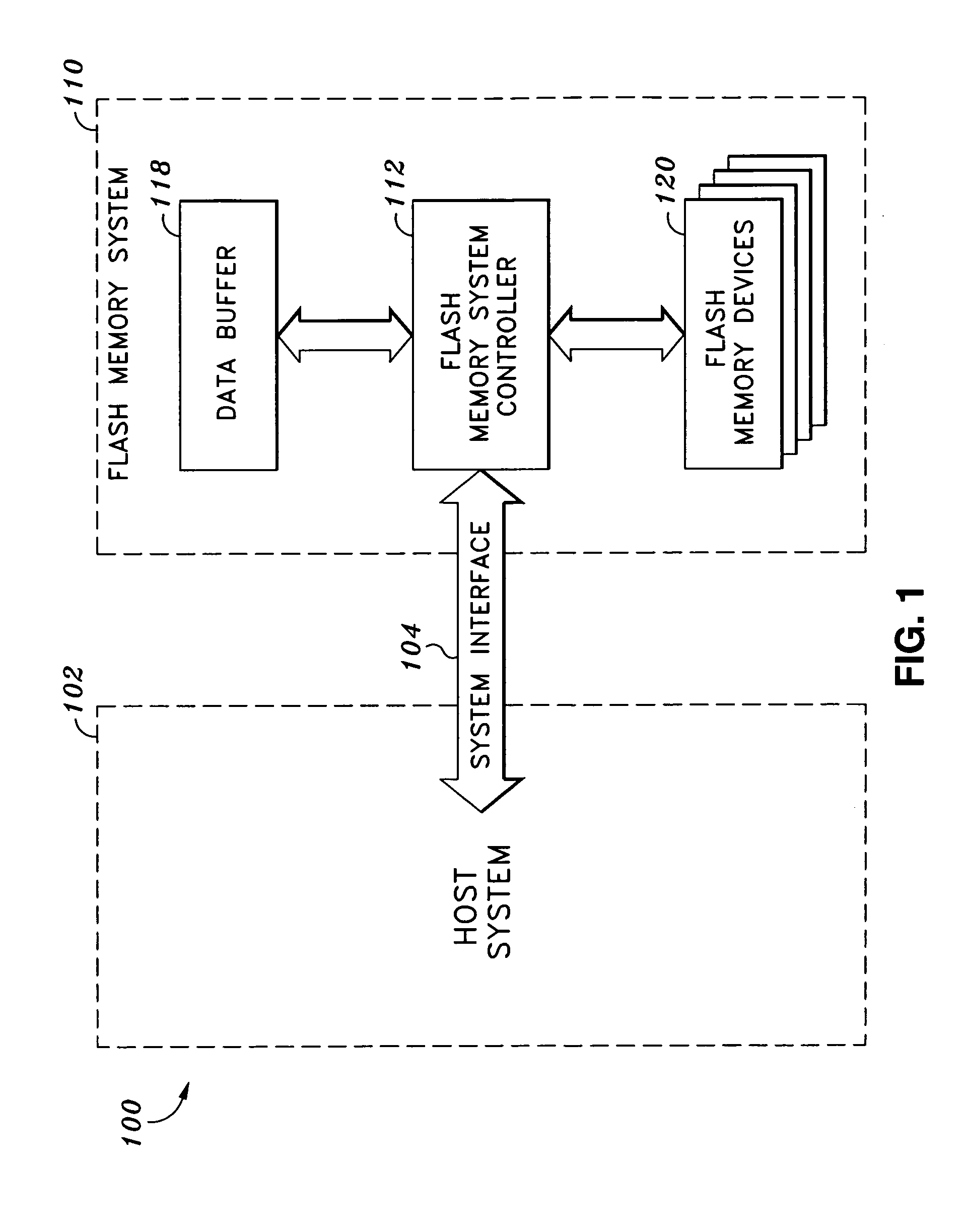
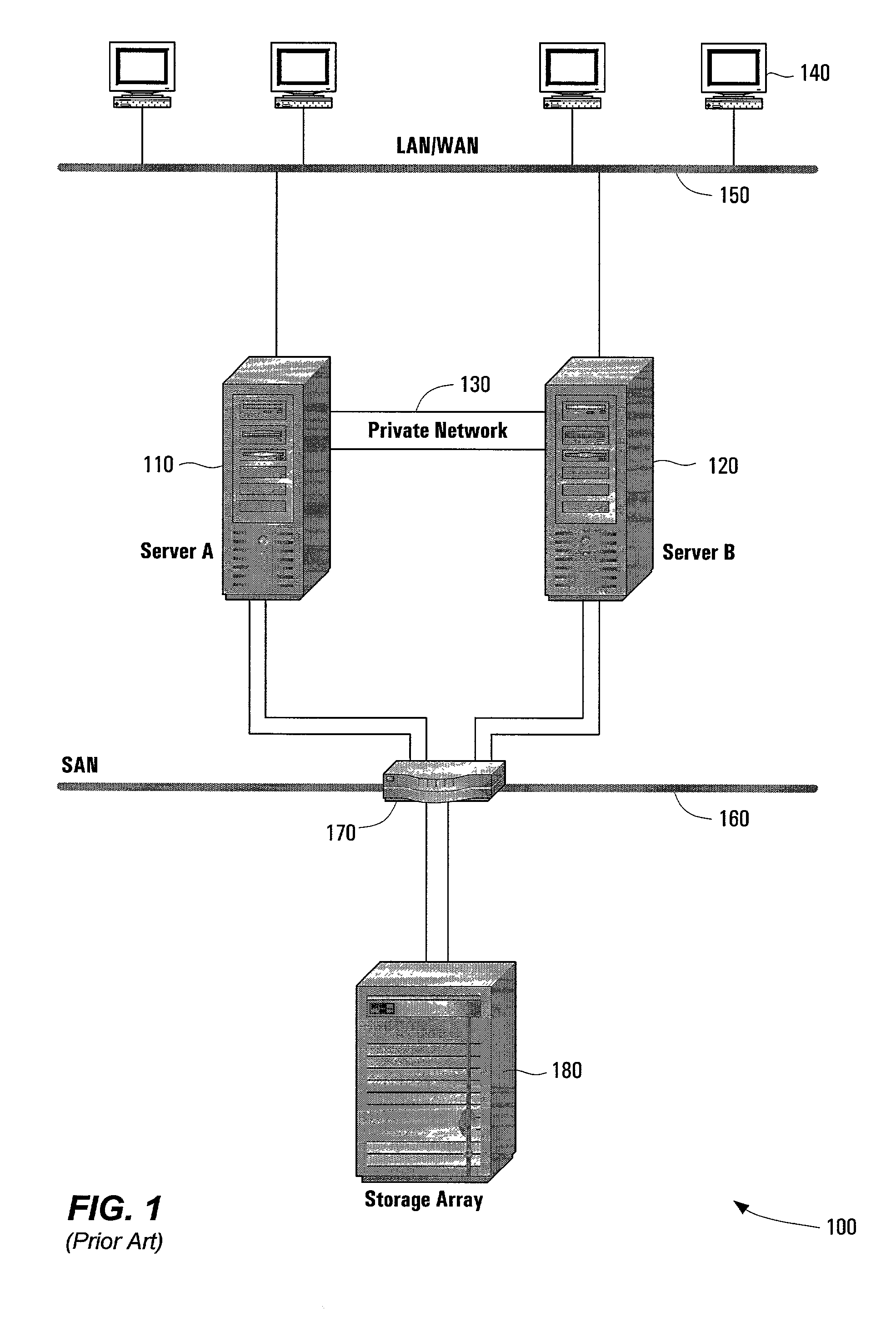
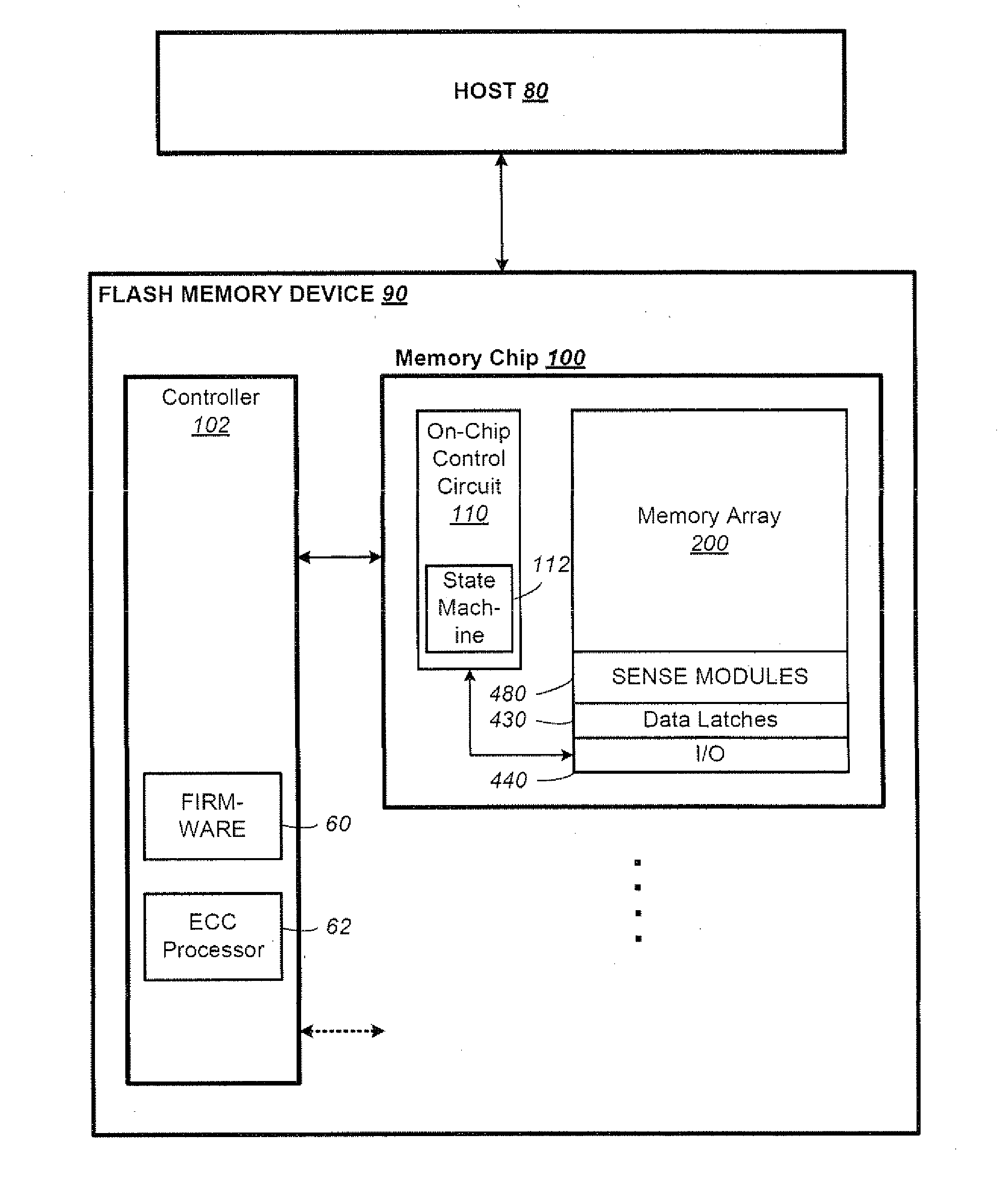
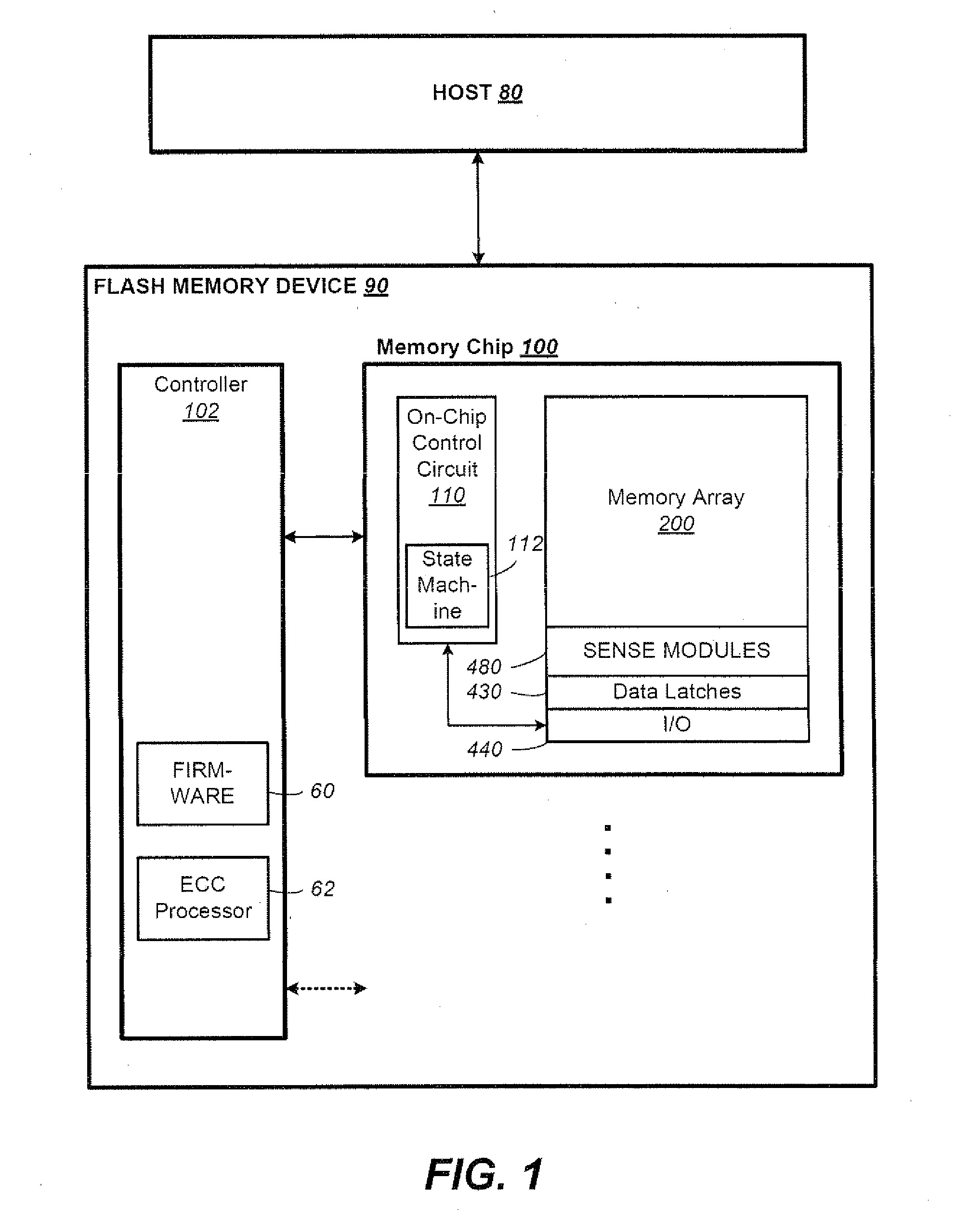
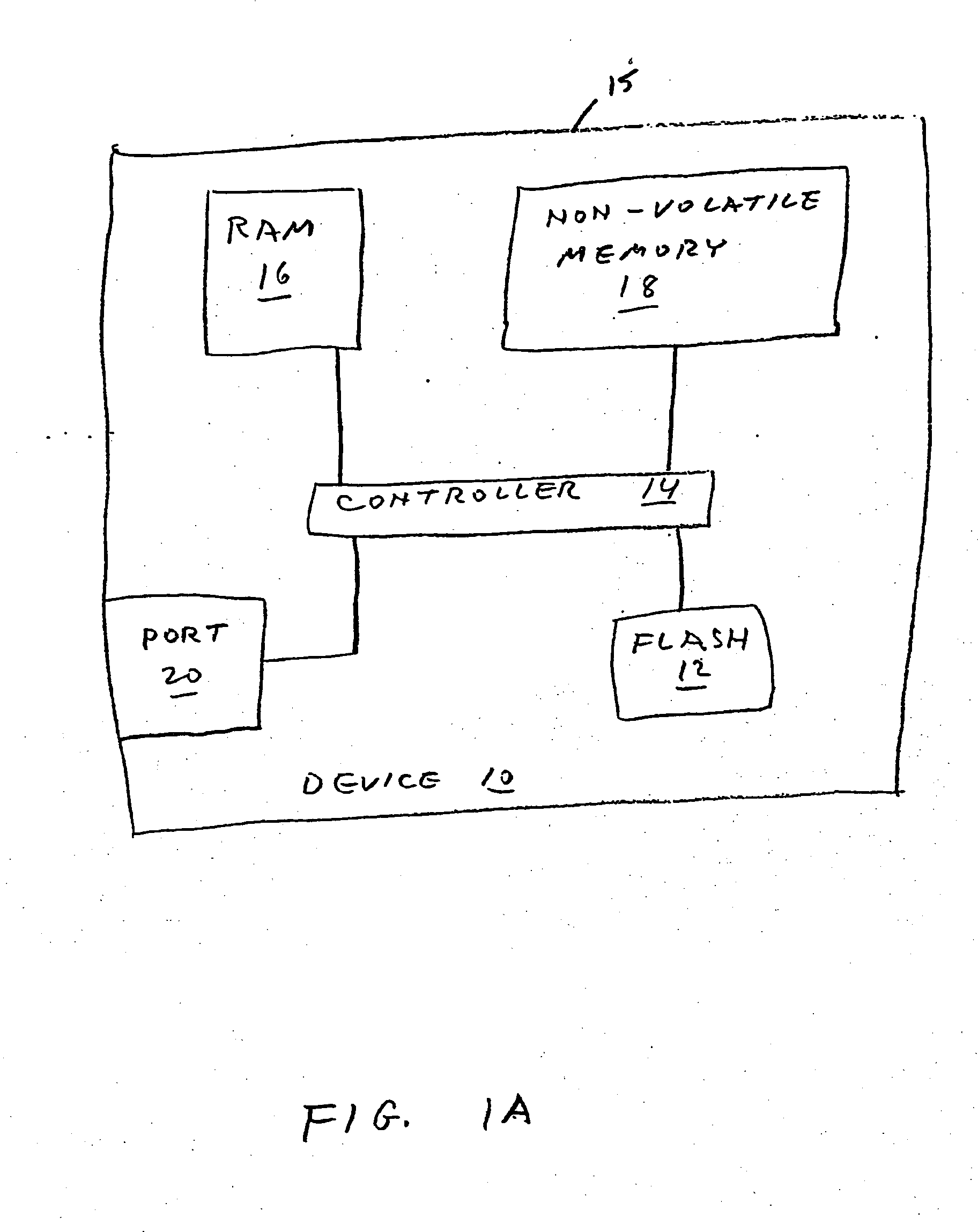
Preventing damage of storage devices and data loss in a data storage system
ActiveUS7146521B1Prolong lifeAvoid data lossThermometer detailsEnergy efficient ICTData CorruptionData loss
A data storage system and method capable of reducing the operating temperature of the data storage system, removing any overheating storage devices from operation, reconstructing data, and evacuating data from the overheating storage devices before the devices and the data are damaged or lost.
Owner:VALTRUS INNOVATIONS LTD
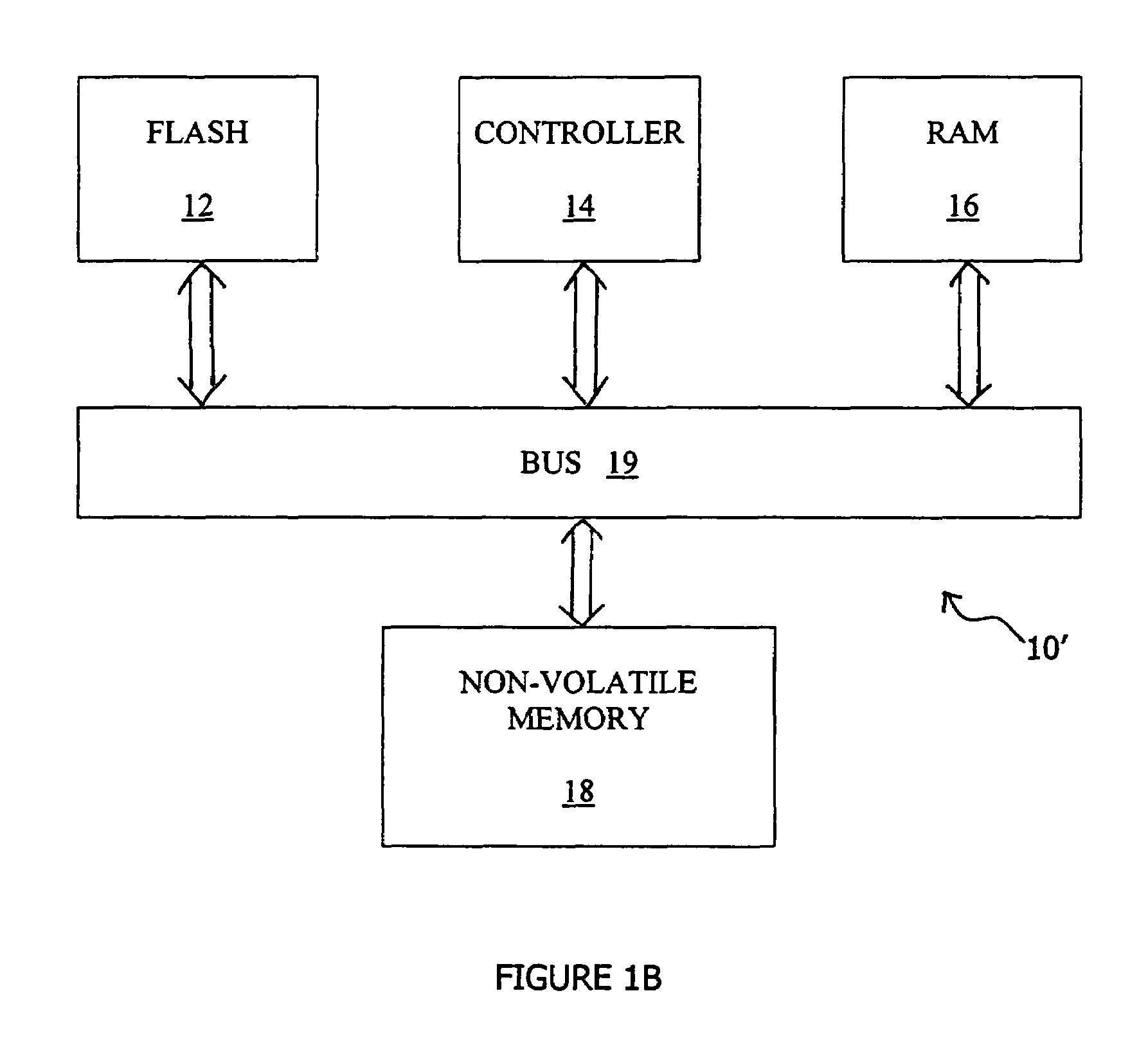
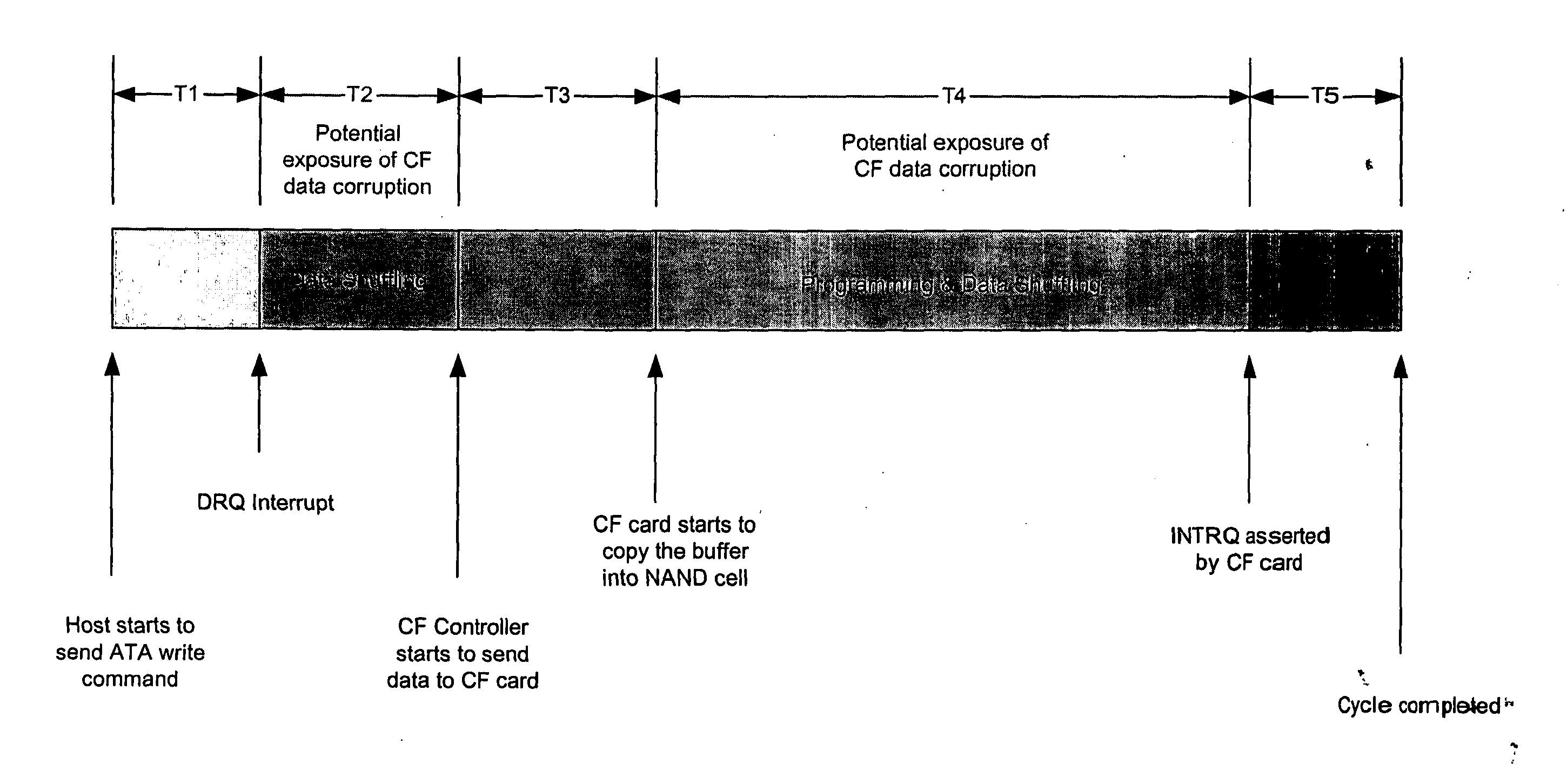
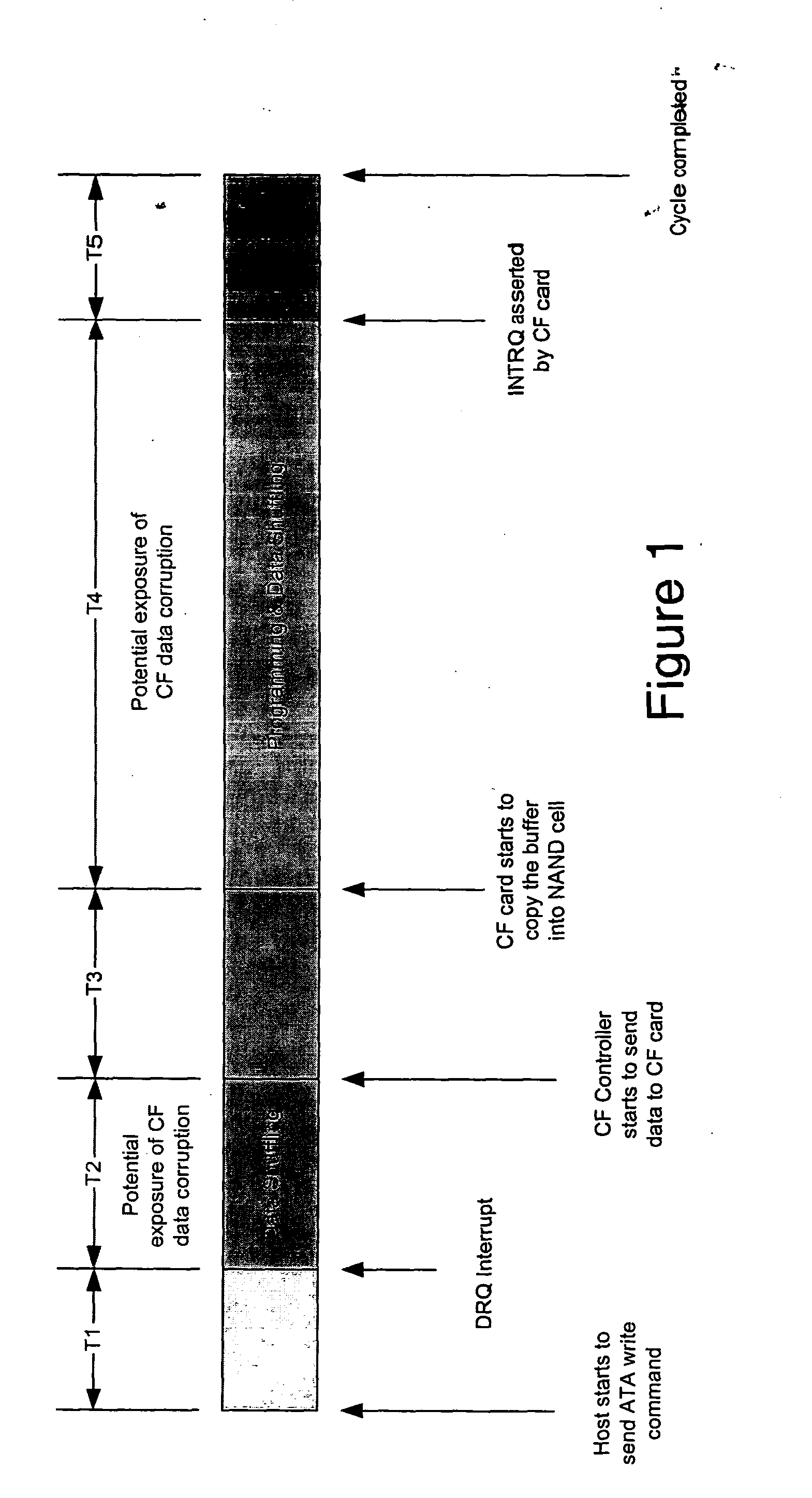
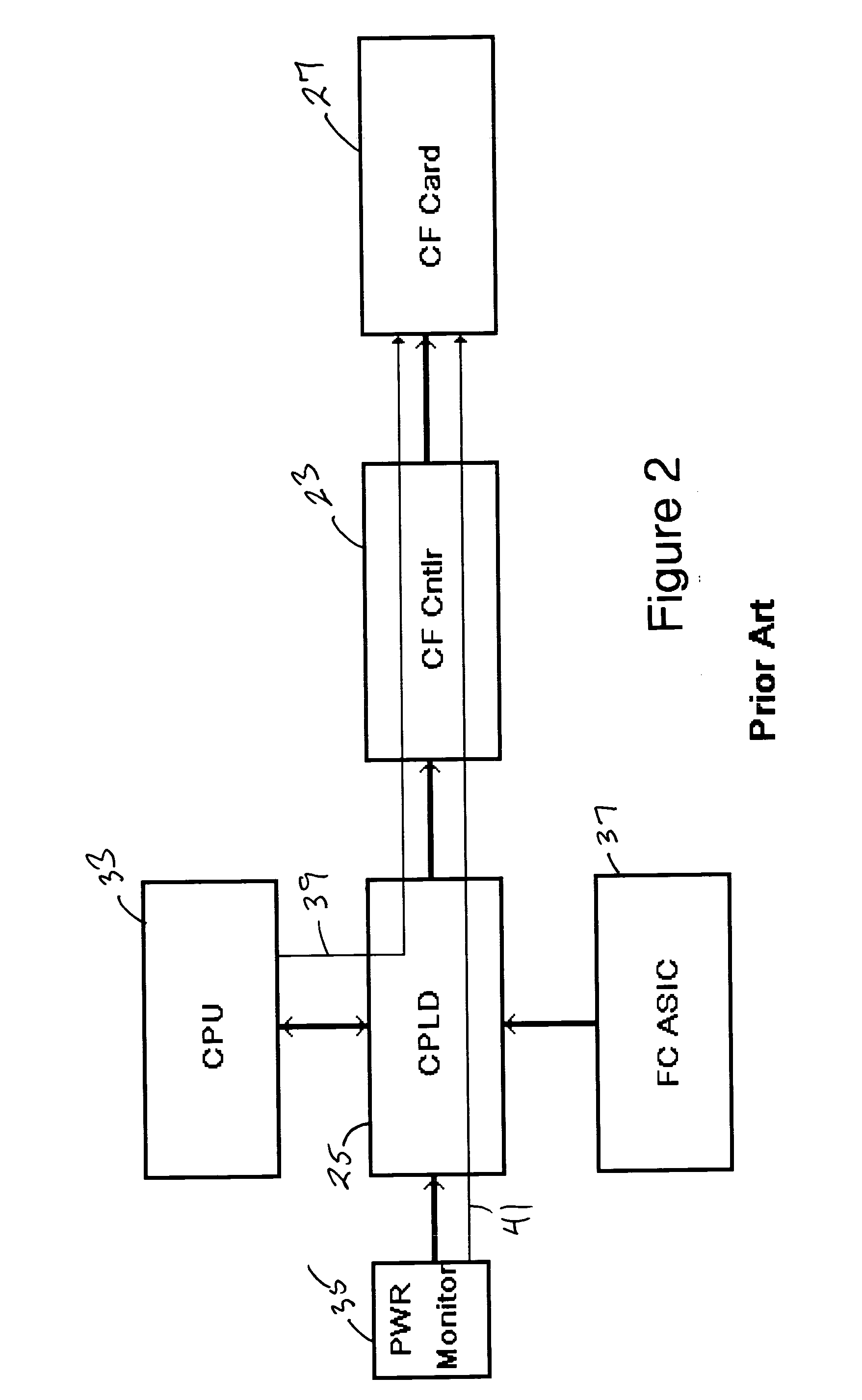
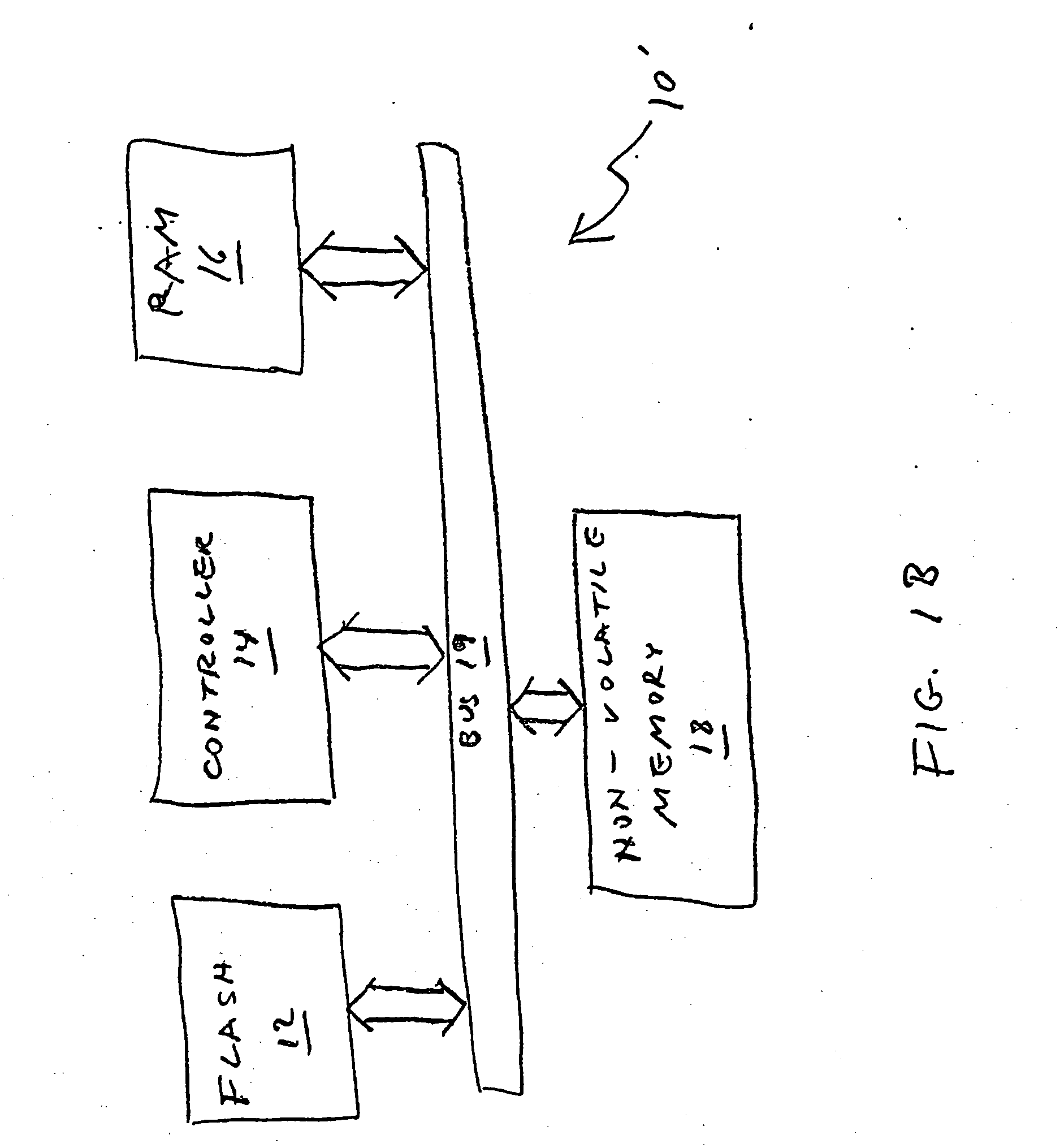
Flash memory management method that is resistant to data corruption by power loss
InactiveUS6988175B2Avoid dataMemory architecture accessing/allocationError detection/correctionElectricityRisk zone
A method for managing page-based data storage media such as flash media, a system that uses that method, and a computer-readable storage medium bearing code for implementing the method. New data are written to the storage medium in a manner that precludes corruption of old data if the writing of the new data is interrupted. Specifically, risk zones are defined, by identifying, for each page, the other pages whose data are put at risk of corruption if writing to the page is interrupted. A page, that otherwise would be the target of a write operation, is not written if any of the pages in its risk zone contain data that could be corrupted if the write operation is interrupted.
Owner:WESTERN DIGITAL ISRAEL LTD
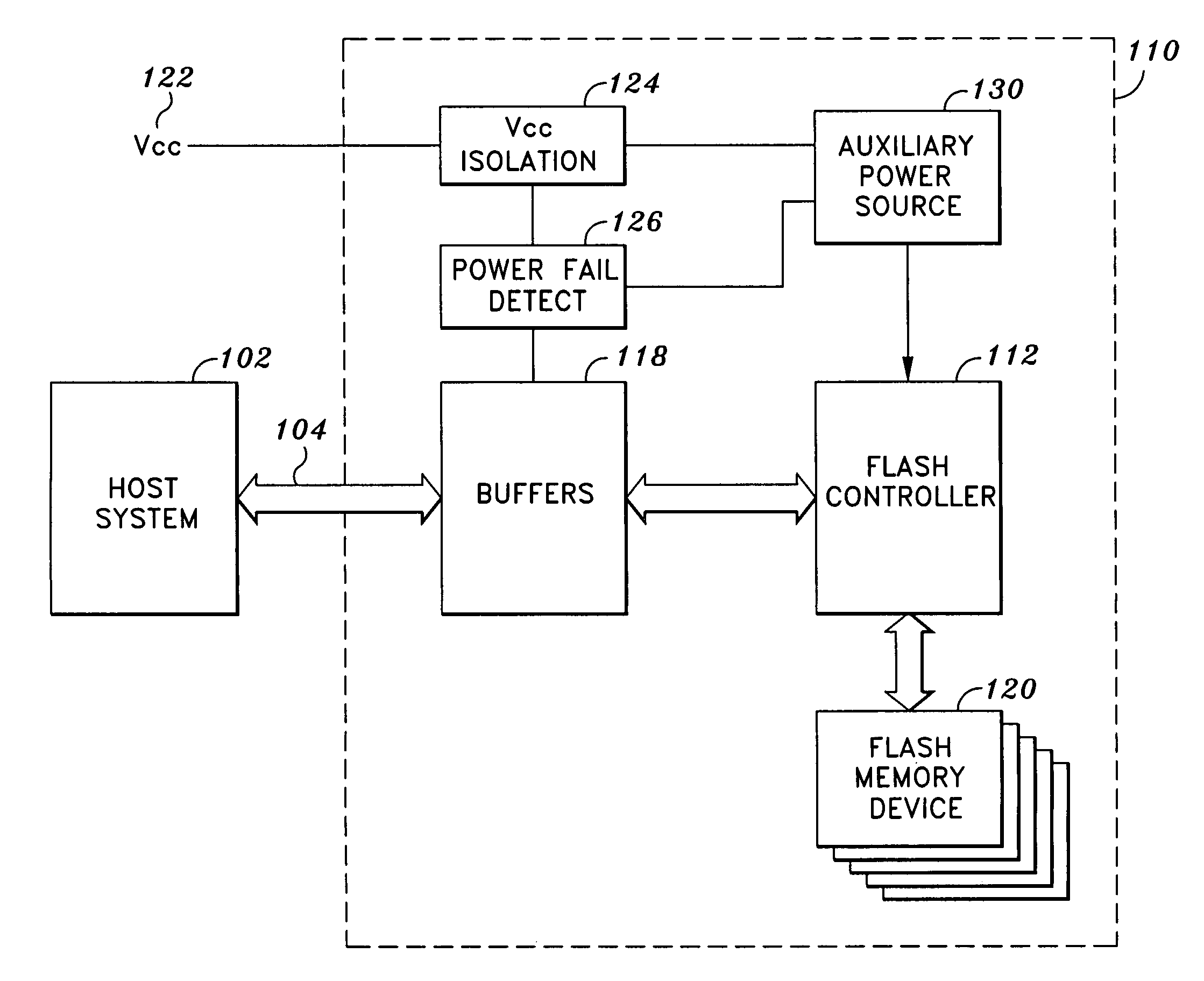
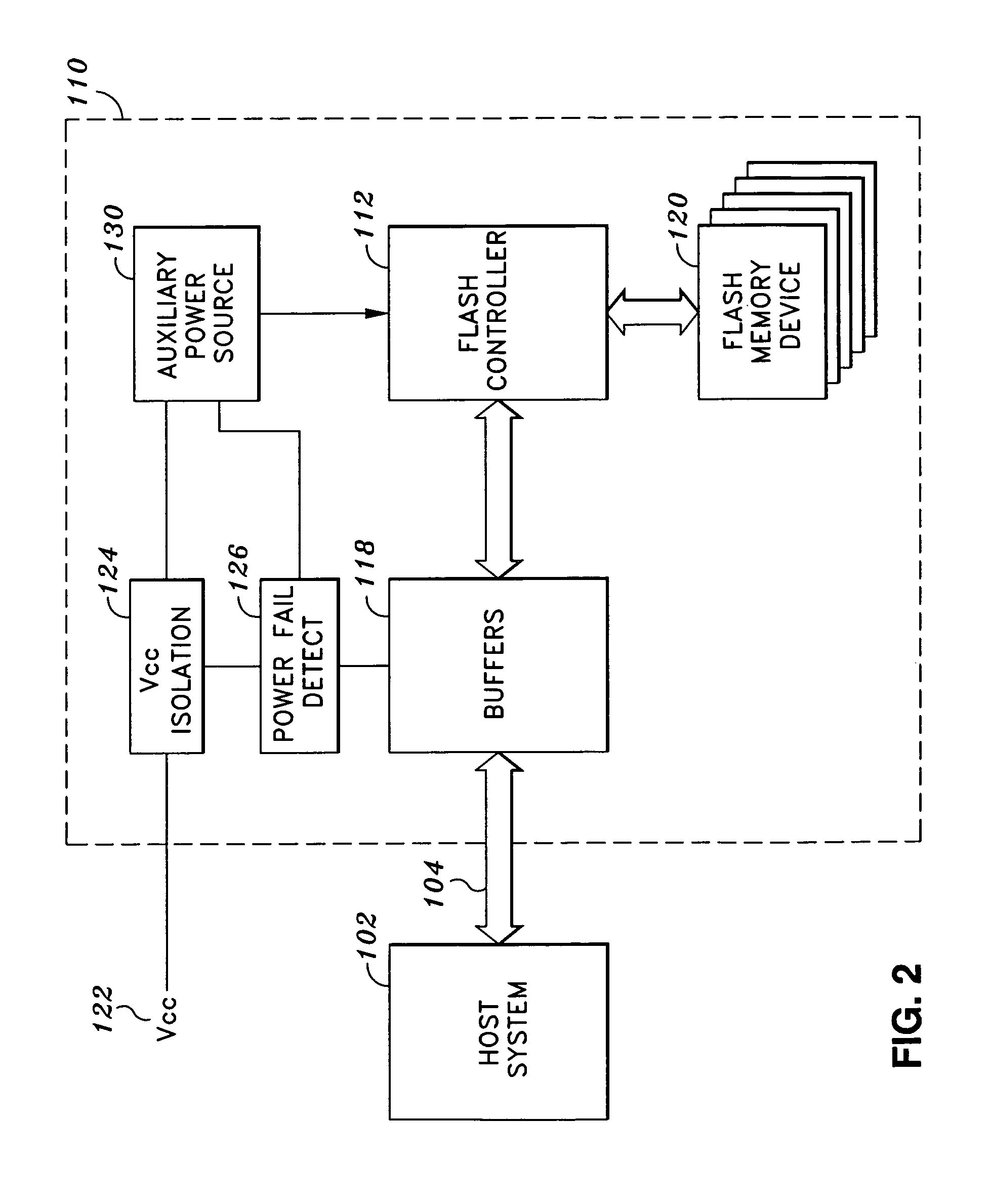
System and method for preventing data corruption in solid-state memory devices after a power failure
A data preservation system for flash memory systems with a host system, the flash memory system receiving a host system power supply and energizing an auxiliary energy store therewith and communicating with the host system via an interface bus, wherein, upon loss of the host system power supply, the flash memory system actively isolates the connection to the host system power supply and isolates the interface bus and employs the supplemental energy store to continue write operations to flash memory.
Owner:INNOVATIVE MEMORY SYST INC
Apparatus for reducing data corruption in a non-volatile memory
InactiveUS20050024968A1Loss and corruption can be preventedEliminate requirementsReliability increasing modificationsRead-only memoriesTime segmentData Corruption
The loss of data and / or the corruption of data that may occur in flash memory when a reset signal is received during a memory write cycle is prevented by delaying reset signals sent to the flash memory for a time period sufficient for a write cycle to be completed. The loss of data and / or the corruption of data that may occur in flash memory when the power supply is interrupted during a write cycle is prevented by providing a DC-to-DC converter with one or more large capacitors in parallel with its input as the power supply to the flash memory. If the system power supply fails or is interrupted, the discharge of the capacitor(s) delays the voltage decay at the input of the DC-to-DC converter such that the output of the DC-to-DC converter remains within tolerance for a time sufficient for the flash memory to complete a write cycle.
Owner:AVAGO TECH INT SALES PTE LTD
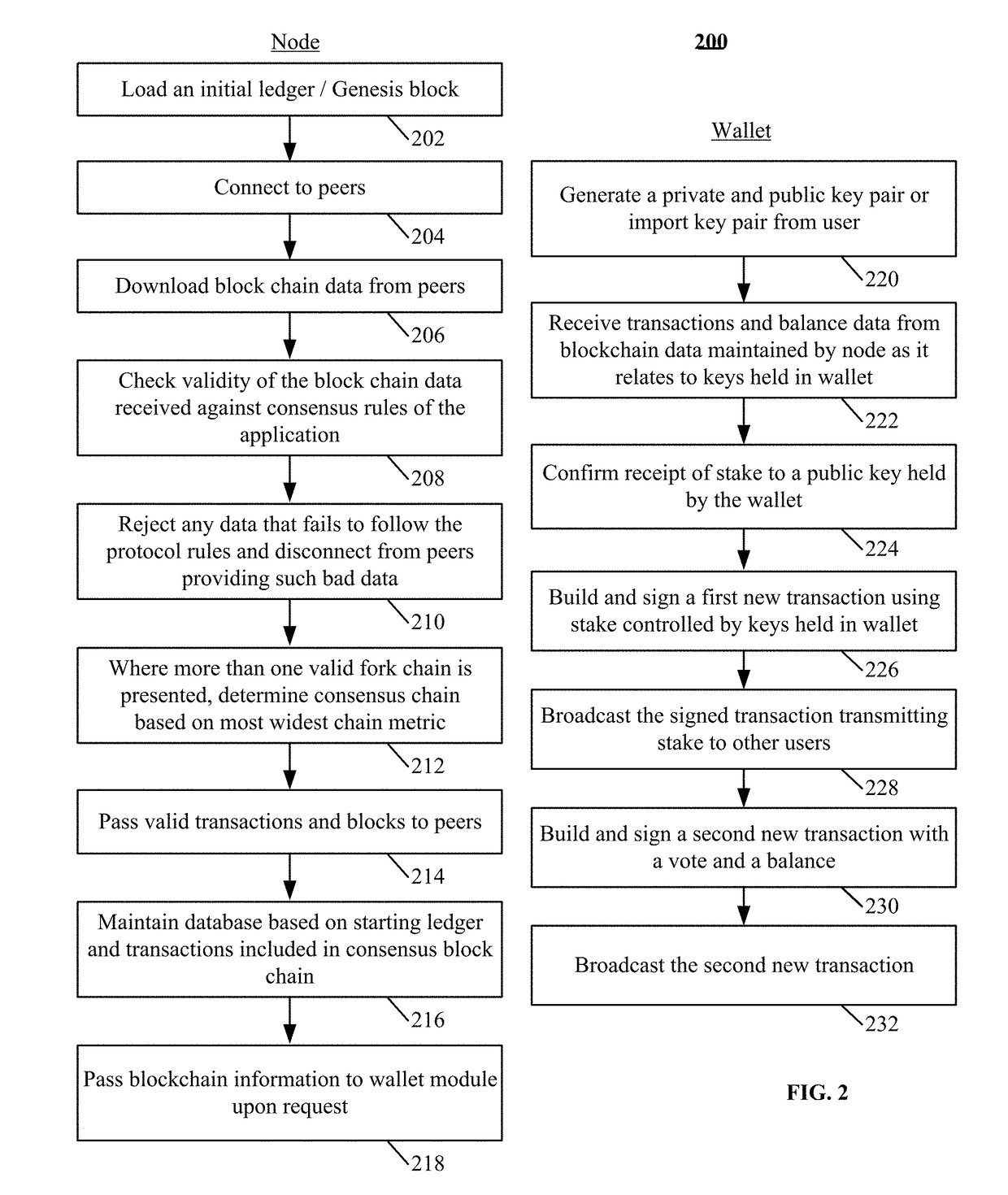
Consensus system for tracking peer-to-peer digital records
ActiveUS9875510B1Improve trustReduce overheadComplete banking machinesFinanceDigital recordingData Corruption
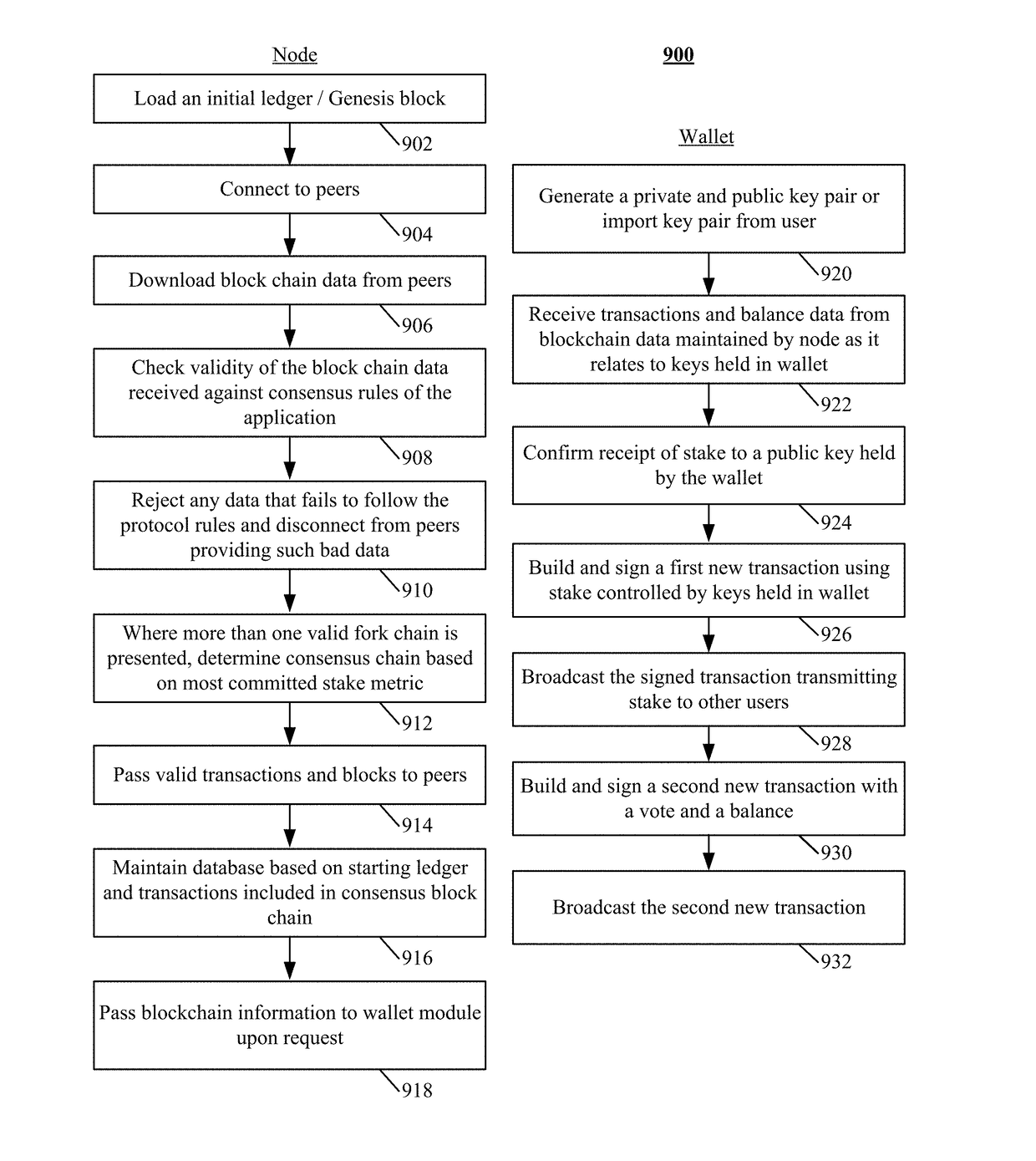
The disclosure describes a peer-to-peer consensus system and method for achieving consensus in tracking transferrable digital objects. The system achieves consensus on a shared ledger between a plurality of peers and prevents double spending in light of network latency, data corruption and intentional manipulation of the system. Consensus is achieved and double spending is prevented via the use of the most committed stake metric to choose a single consensus transaction record. A trustable record is also facilitated by allowing stakeholders to elect a set of trusted non-colluding parties to cooperatively add transactions to the consensus record. The voting mechanism is a real-time auditable stake weighted approval voting mechanism. This voting mechanism has far reaching applications such as vote directed capital and providing a trusted source for data input into a digital consensus system. The system further enables digital assets that track the value of conventional assets with low counterparty risk.
Owner:KASPER LANCE
Method and apparatus for efficient management of XML documents
InactiveUS6941510B1Rapid positioningConsistent interfaceDigital computer detailsNatural language data processingLocking mechanismData Corruption
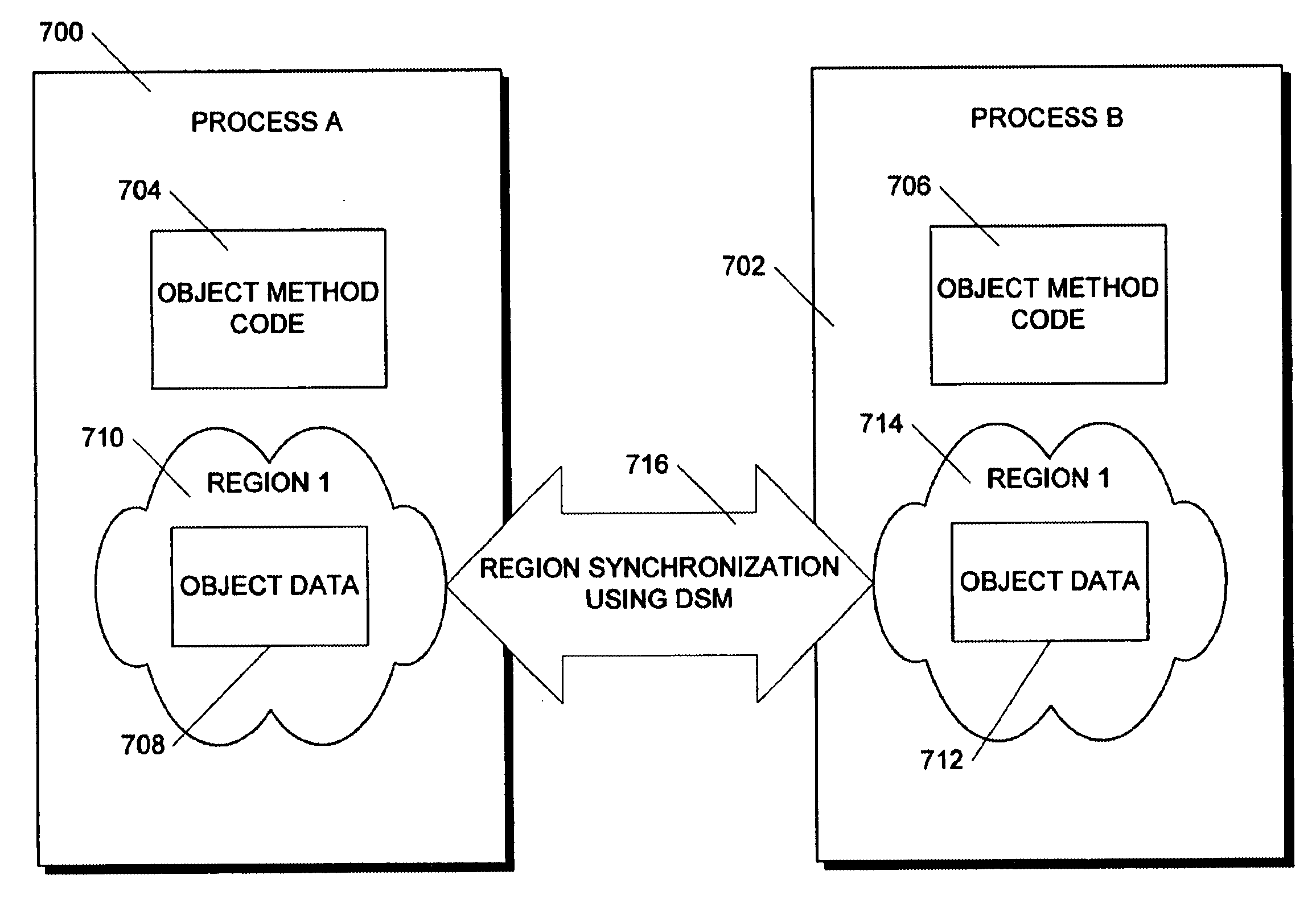
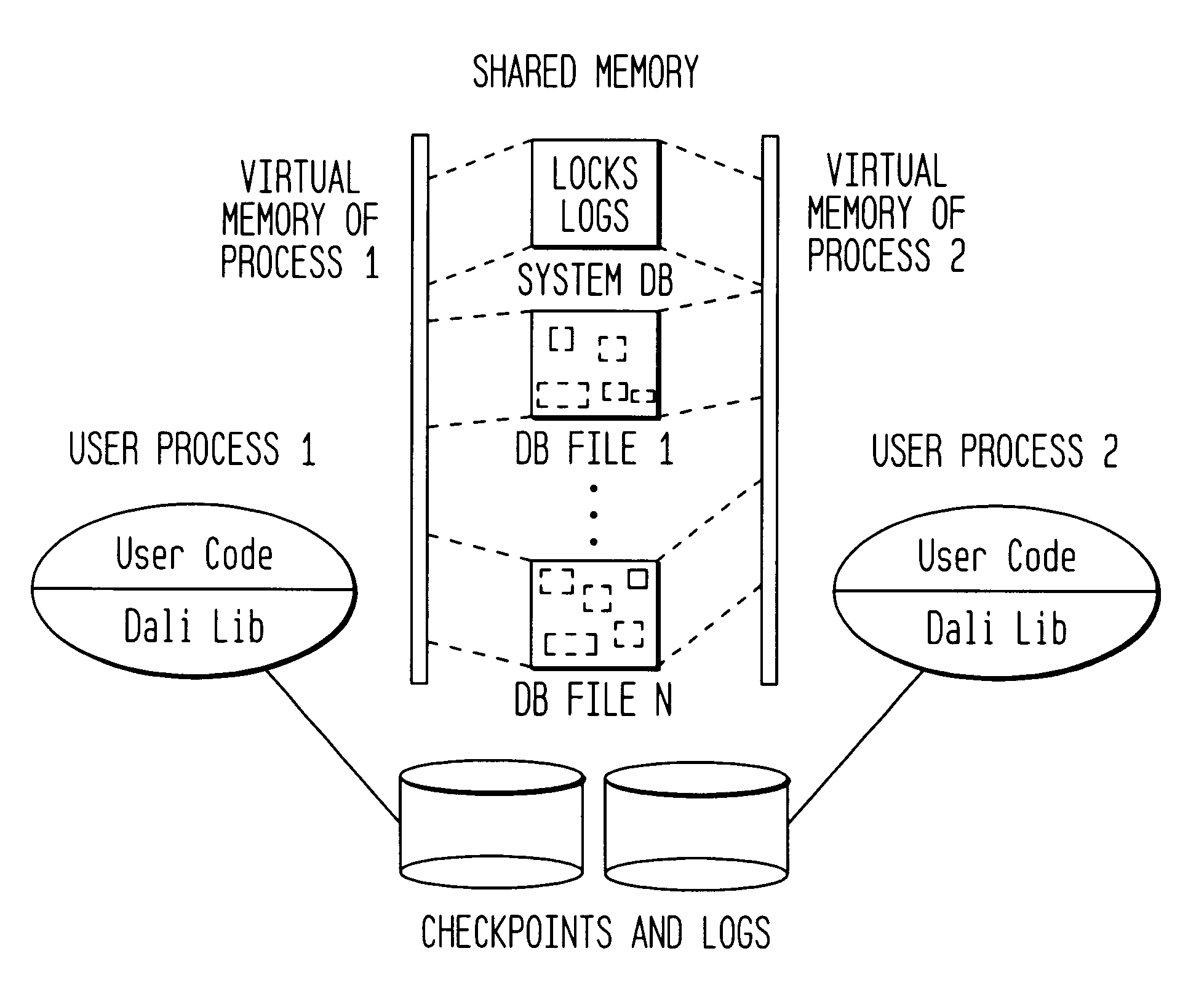
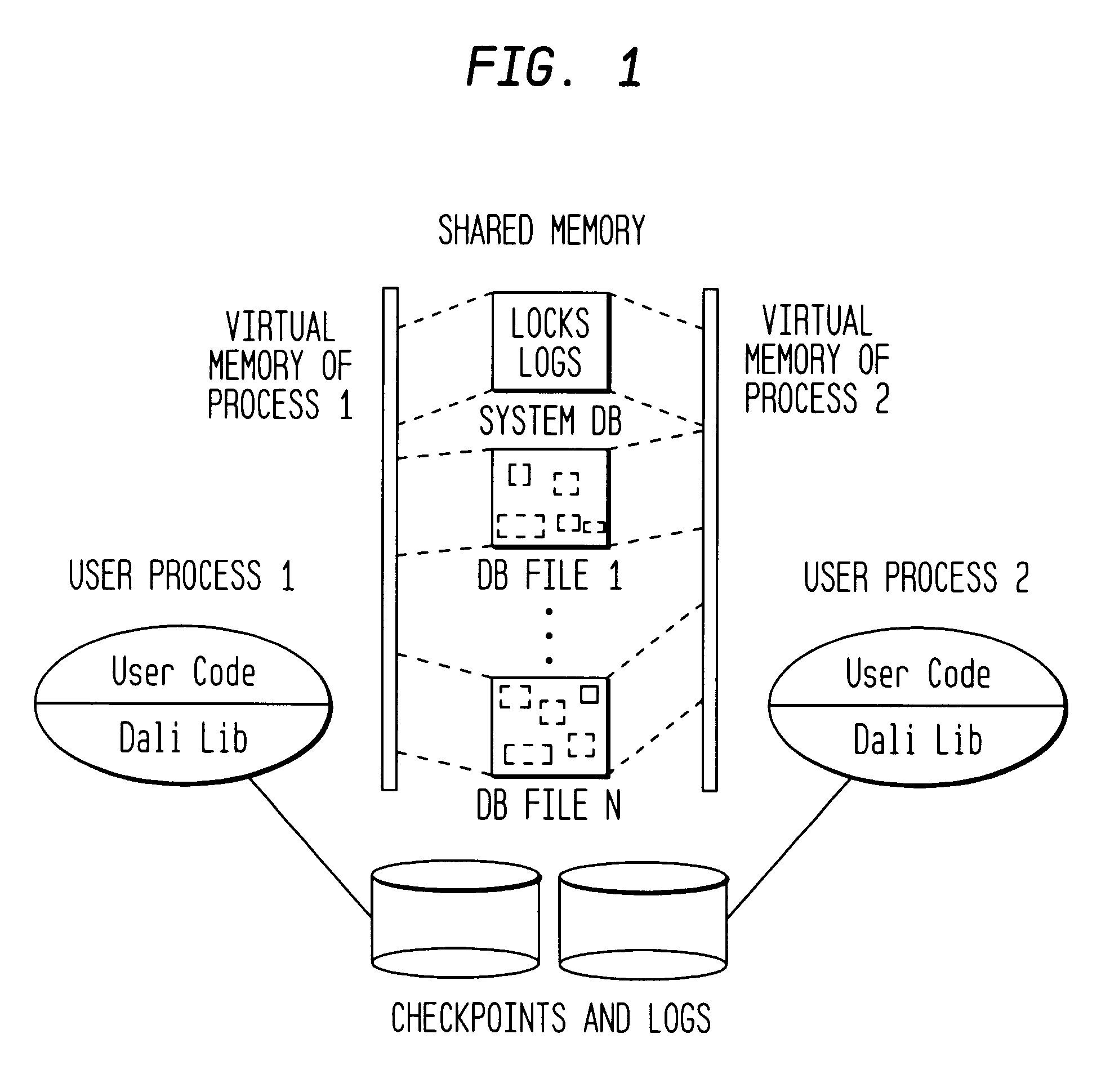
An in-memory storage manager represents XML-compliant documents as a collection of objects in memory. The storage manager allows real-time access to the objects by separate processes operating in different contexts. The data in the objects is stored in memory local to each process and the local memories are synchronized by means of a distributed memory system that stores the data in the same data region, but maps the data region to the address space of each process. Data corruption in the data region is prevented by a locking mechanism that prevents the processes from simultaneously modifying same data.
Owner:MICROSOFT TECH LICENSING LLC
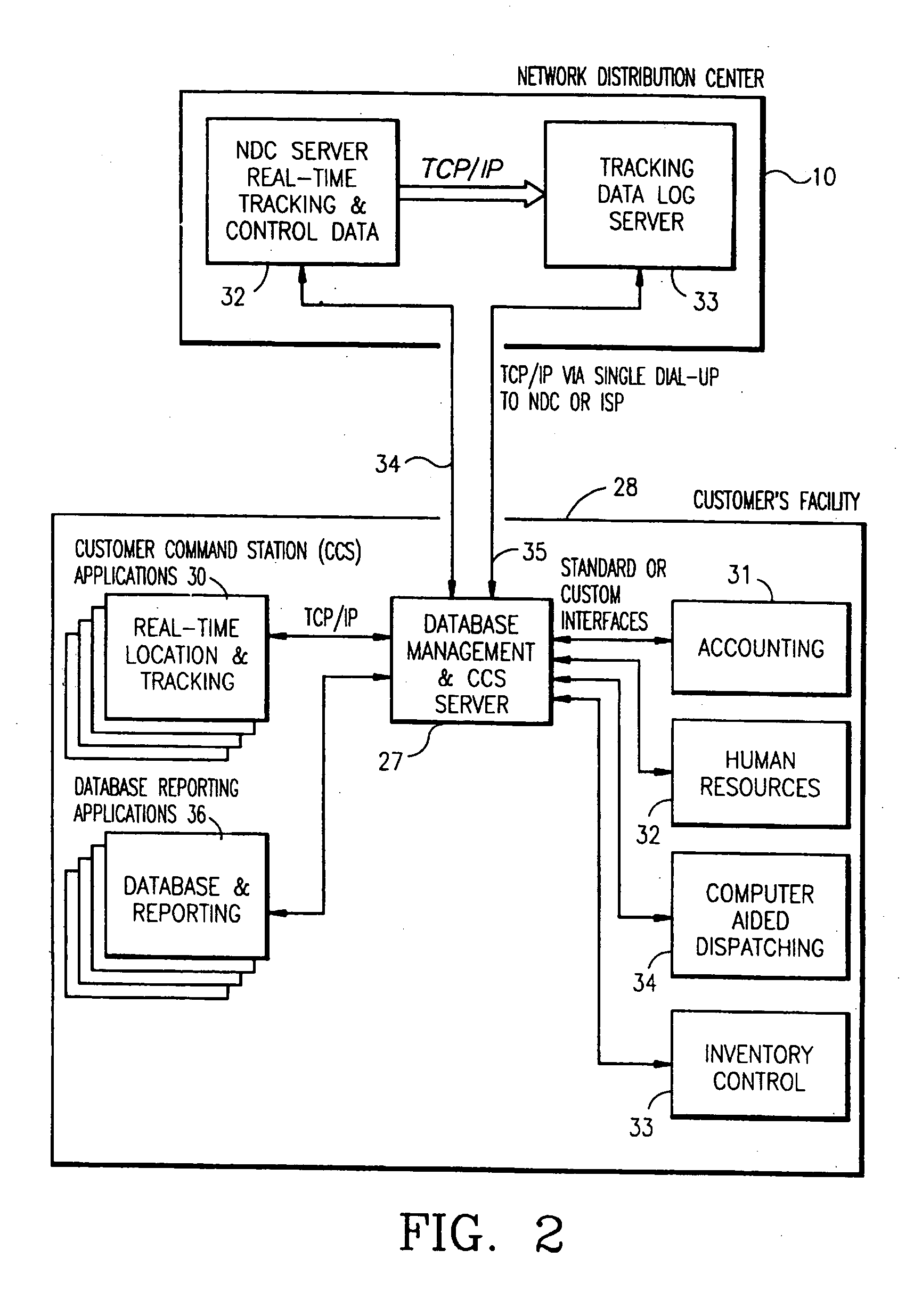
Vehicle tracking, communication and fleet management system
InactiveUS20060142913A1Management moreEfficient and reliableVehicle testingRegistering/indicating working of vehiclesFleet managementEngineering
A vehicle fleet management information system identifies location and direction of movement of each vehicle in a fleet in real-time, and automatically reports such information, as well as status of predetermined events in which the vehicle is engaged, directly to the fleet manager. Each fleet vehicle has an assigned time slot to transmit its reporting information over a communications network without interfering with transmissions from other vehicles in their own respective time slots. A timing control phase lock loop (PLL) provides precise time synchronization for timing corrections from a global positioning system (GPS) based time reference. A dual band full-duplex interface of the network has TDMA on one-half and broadcast on the other half. Microprocessor time processing units in components of the network perform precise clock synchronization. Space diversity performed on received vehicle transmitted messages avoids data corruption. Different vehicles have different periodic transmission intervals, by dynamically allocating the slots for various update rates. Auxiliary reporting slots enable prompt reporting of important data by the respective vehicle transmitters independent of the slower periodic transmission intervals.
Owner:TRIMBLE NAVIGATION LTD
Consensus system for manipulation resistant digital record keeping
ActiveUS20170323392A1Improve trustReduce overheadFinanceTransmissionData CorruptionDistributed computing
The disclosure describes a peer-to-peer consensus system and method for maintaining a manipulation resistant updateable shared ledger. The system achieves consensus on a shared ledger between a plurality of peers and prevents double spending in light of network latency, data corruption and intentional manipulation of the system. Consensus is achieved and double spending is prevented via the use of the widest chain metric to choose a single consensus transaction record. A trustable record is also facilitated by allowing stakeholders to elect a set of trusted non-colluding block signers to cooperatively add transactions to the consensus record. The voting mechanism is a real-time auditable stake weighted approval voting mechanism.
Owner:KASPER LANCE TIMOTHY +1
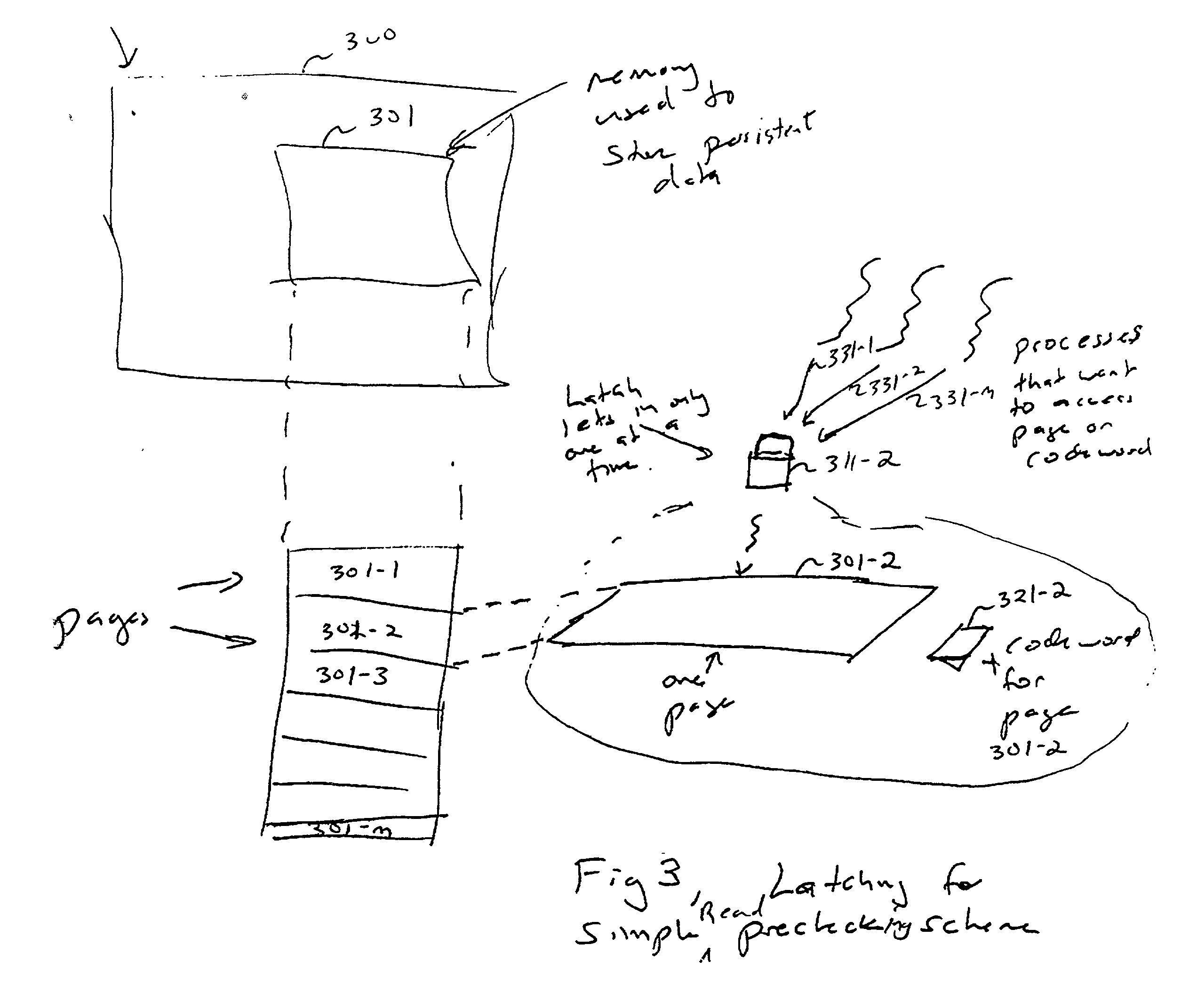
Method and apparatus for detecting and recovering from data corruption of a database via read prechecking and deferred maintenance of codewords
InactiveUS6374264B1Prevents transaction-carried corruptionLess expensiveData processing applicationsSpecial data processing applicationsDeferred maintenanceData Corruption
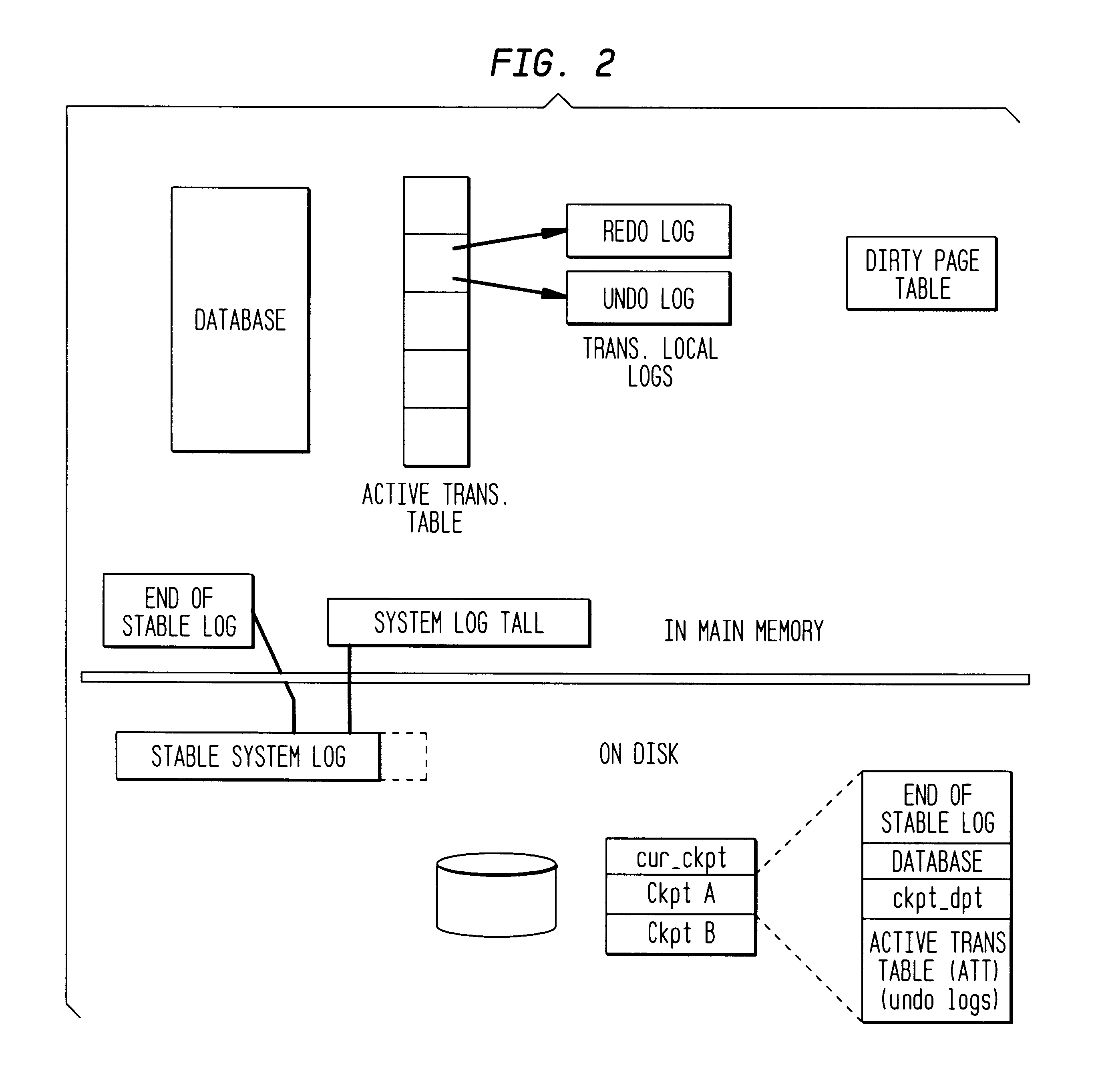
A method of detecting and recovering from data corruption of a database is characterized by the step of protecting data of the database with codewords, one codeword for each region of the database; and verifying that a codeword matches associated data before the data is read from the database to prevent transaction-carried corruption. A deferred maintenance scheme is recommended for the codewords protecting the database such that the method of detecting and recovering from data corruption of a database may comprise the steps of protecting data of the database with codewords, one codeword for each region of the database; and asynchronously maintaining the codewords to improve concurrency of the database. Moreover, the database may be audited by using the codewords and noting them in a table and protecting regions of the database with latches. Once codeword values are computed and checked against noted values in memory, a flush can cause codewords from outstanding log records to be applied to the stored codeword table.
Owner:SOUND VIEW INNOVATIONS
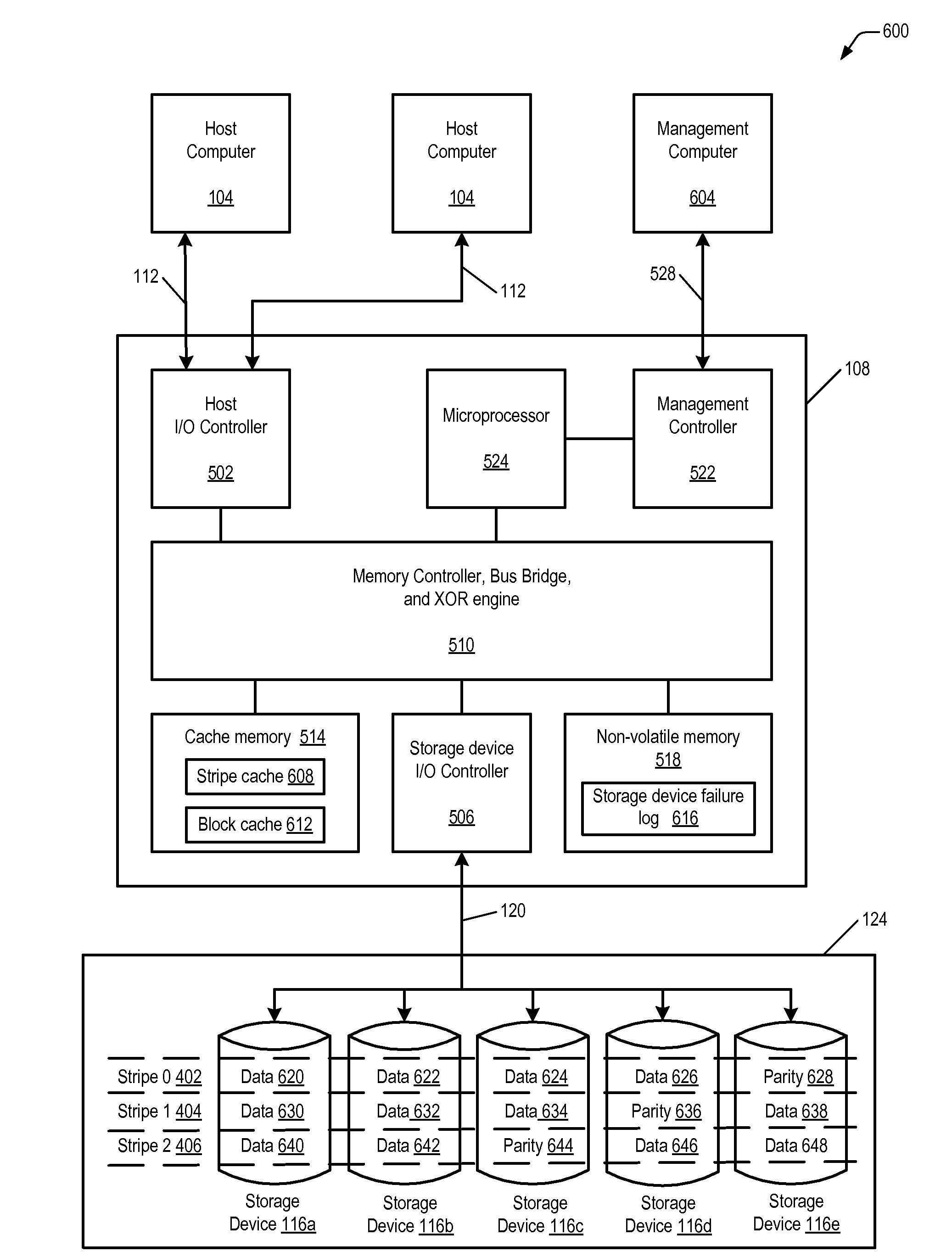
Detection and correction of block-level data corruption in fault-tolerant data-storage systems
ActiveUS20080115017A1Eliminate needEfficient detectionStatic storageRedundant data error correctionRAIDDisk controller
Various embodiments of the present invention provide fault-tolerant, redundancy-based data-storage systems that rely on disk-controller-implemented error detection and error correction, at the disk-block level, and RAID-controller-implemented data-redundancy methods, at the disk and disk-stripe level, in order to provide comprehensive, efficient, and system-wide error detection and error correction. Embodiments of the present invention use disk-level and stripe-level data redundancy to provide error detection and error correction for stored data objects, obviating the need for certain costly, intermediate levels of error detection and error correction commonly employed in currently available fault-tolerant, redundancy-based data-storage systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
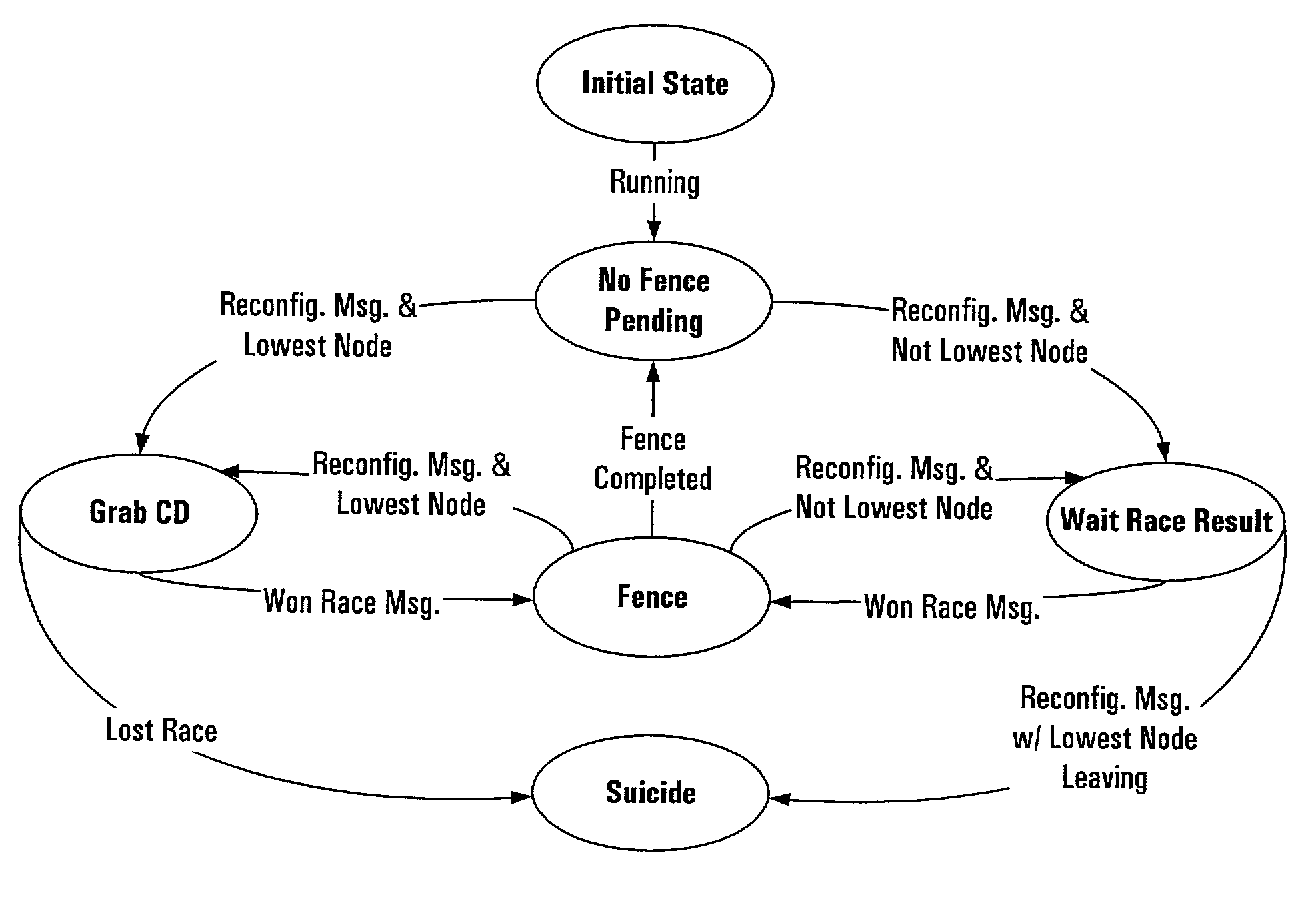
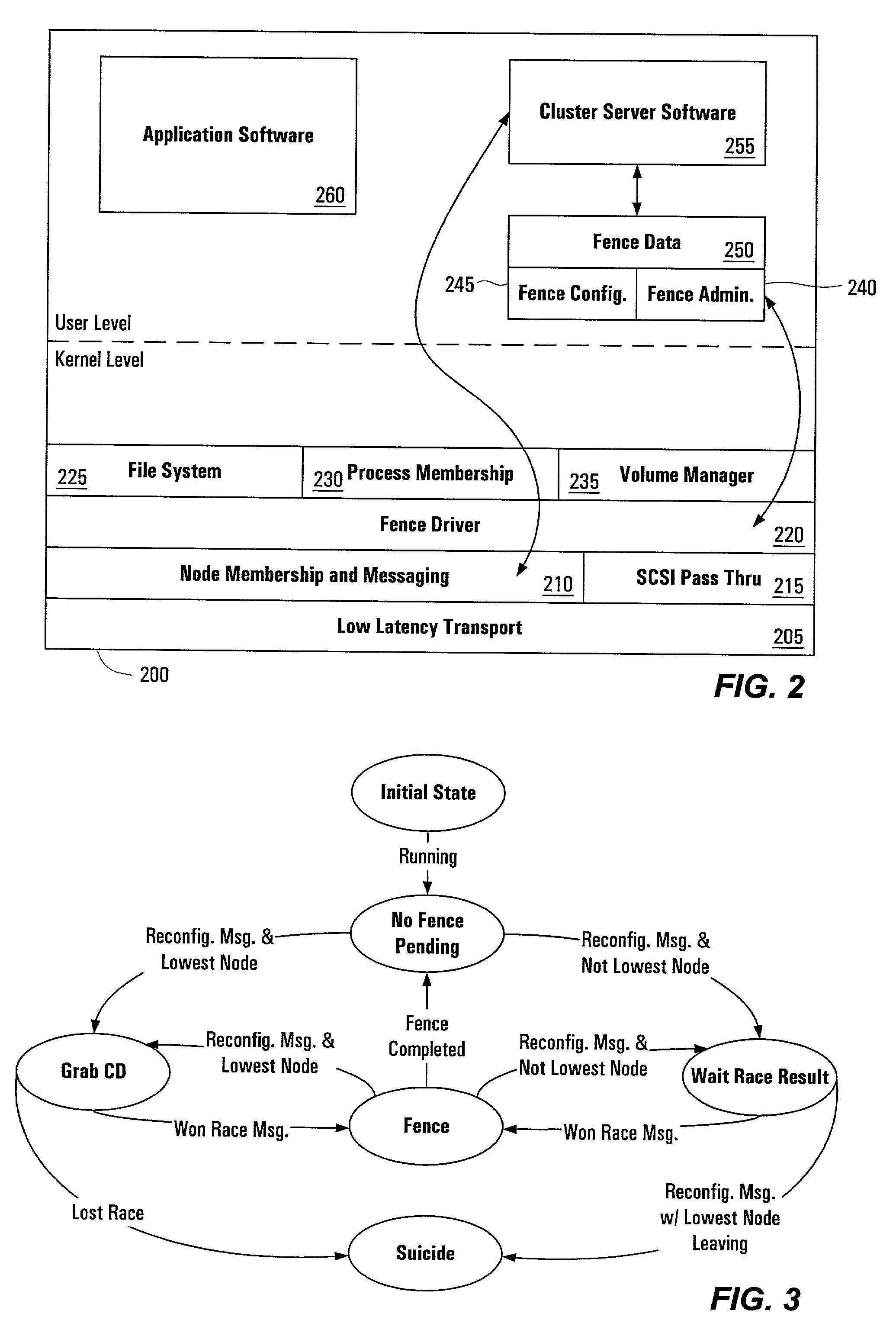
System and method for preventing data corruption in computer system clusters
InactiveUS7631066B1Reduce failover timeImprove the problemError detection/correctionDigital computer detailsCluster systemsComputerized system
Systems, methods, apparatus and software can make use of coordinator resources and SCSI-3 persistent reservation commands to determine which nodes of a cluster should be ejected from the cluster, thereby preventing them from corrupting data on a shared data resource. Fencing software operating on the cluster nodes monitors the cluster for a cluster partition (split-brain) event. When such an event occurs, software on at least two of the nodes attempts to unregister other nodes from a majority of coordinator resources. The node that succeeds in gaining control of the majority of coordinator resources survives. Nodes failing to gain control of a majority of coordinator resources remove themselves from the cluster. The winning node can also proceed to unregister ejected nodes from shared data resources. These operations can be performed in parallel to decrease failover time. The software can continue to execute on all nodes to prevent additional problems should a node erroneously attempt to reenter the cluster.
Owner:SYMANTEC OPERATING CORP
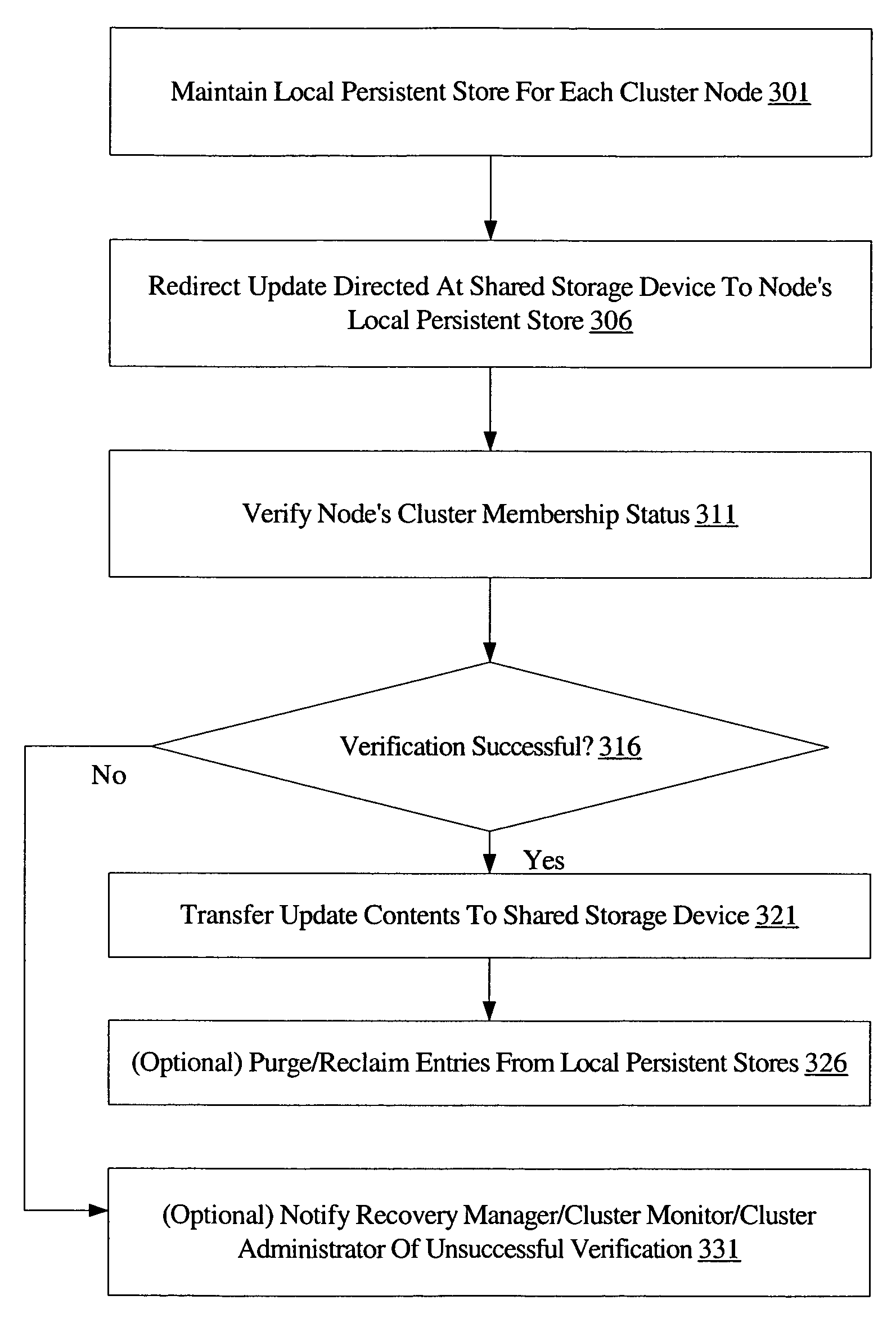
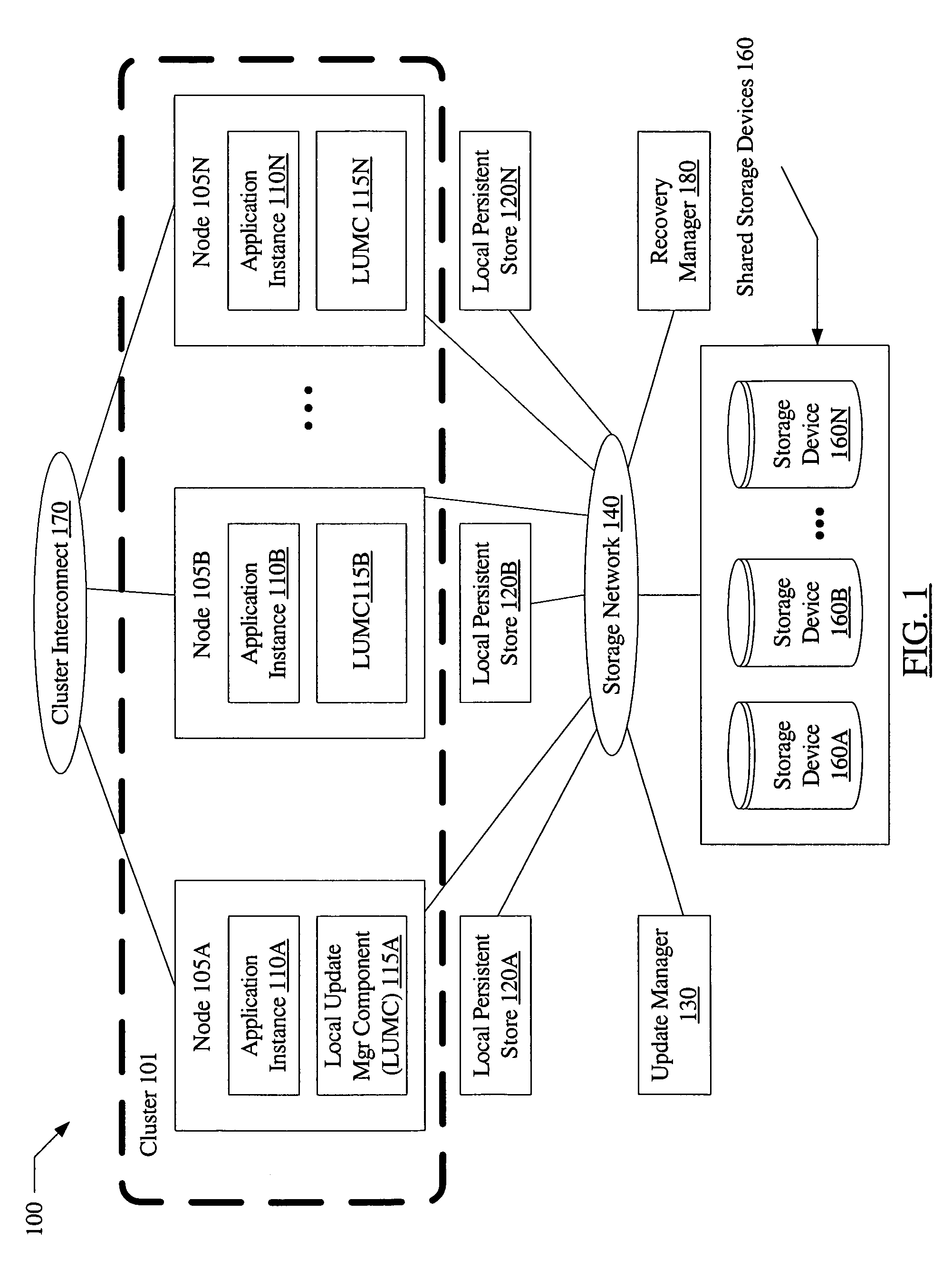
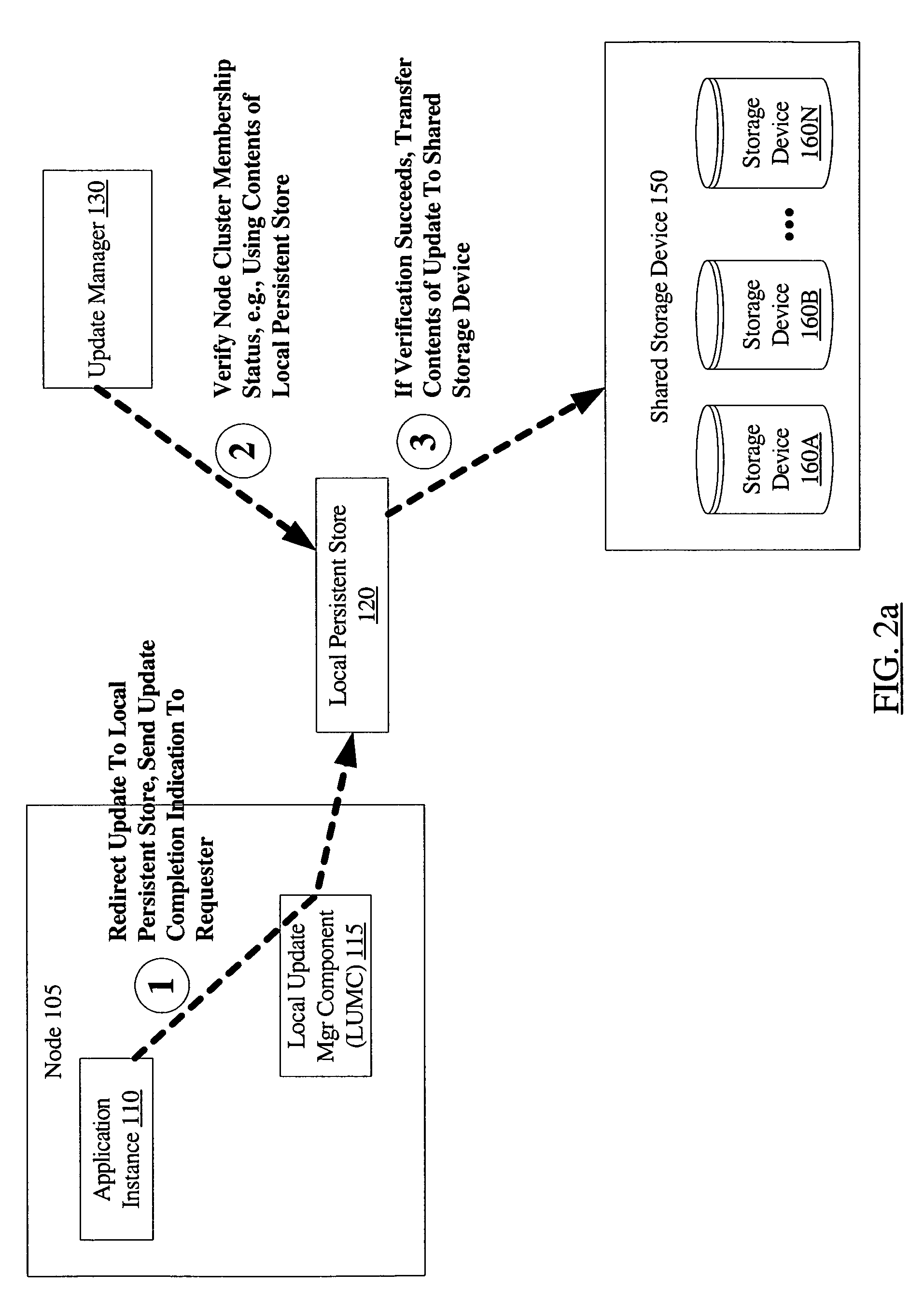
System and method to prevent data corruption due to split brain in shared data clusters
ActiveUS7739677B1Avoid data corruptionDigital data processing detailsError detection/correctionSplit-brainData Corruption
A system and to prevent data corruption due to split brain in shared data clusters includes two or more nodes of a cluster, a shared storage device, and an update manager. The update manager may be configured to maintain a local persistent store corresponding to each node of the cluster. On receiving an update request directed to the shared storage device from a first node, the update manager may be configured to redirect the update to the local persistent store corresponding to the first node. The update manager may be further configured to verify a cluster membership status of the first node, and to transfer the contents of the update from the local persistent store to the shared storage device if the cluster membership verification succeeds.
Owner:SYMANTEC OPERATING CORP
Apparatus and method for identifying disk drives with unreported data corruption
InactiveUS20090259882A1No great storage burdenSave cost and storage spaceRedundant operation error correctionMemory systemsRAIDData Corruption
A RAID controller uses a method to identify a storage device of a redundant array of storage devices that is returning corrupt data to the RAID controller. The method includes reading data from a location of each storage device in the redundant array a first time, and detecting that at least one storage device returned corrupt data. In response to detecting corrupt data, steps are performed for each storage device in the redundant array. The steps include reading data from the location of the storage device a second time without writing to the location in between the first and second reads, comparing the data read the first and second times, and identifying the storage device as a failing storage device if the compared data has a miscompare. Finally, the method includes updating the location of each storage device to a new location and repeating the steps for the new location.
Owner:DOT HILL SYST
Method and apparatus for detecting and recovering from data corruption of a database via read logging
InactiveUS6449623B1Data processing applicationsRedundant operation error correctionState modelTransaction model
A method of detecting and recovering from data corruption of a database is characterized by the step of logging information about reads of a database in memory to detect errors in data of the database, wherein said errors in data of said database arise from one of bad writes of data to the database, of erroneous input of data to the database by users and of logical errors in code of a transaction. The read logging method may be implemented in a plurality of database recovery models including a cache-recovery model, a prior state model a redo-transaction model and a delete transaction model. In the delete transaction model, it is assumed that logical information is not available to allow a redo of transactions after a possible error and the effects of transactions that read corrupted data are deleted from history and any data written by a transaction reading Ararat data is treated as corrupted.
Owner:LUCENT TECH INC
Detecting low-level data corruption
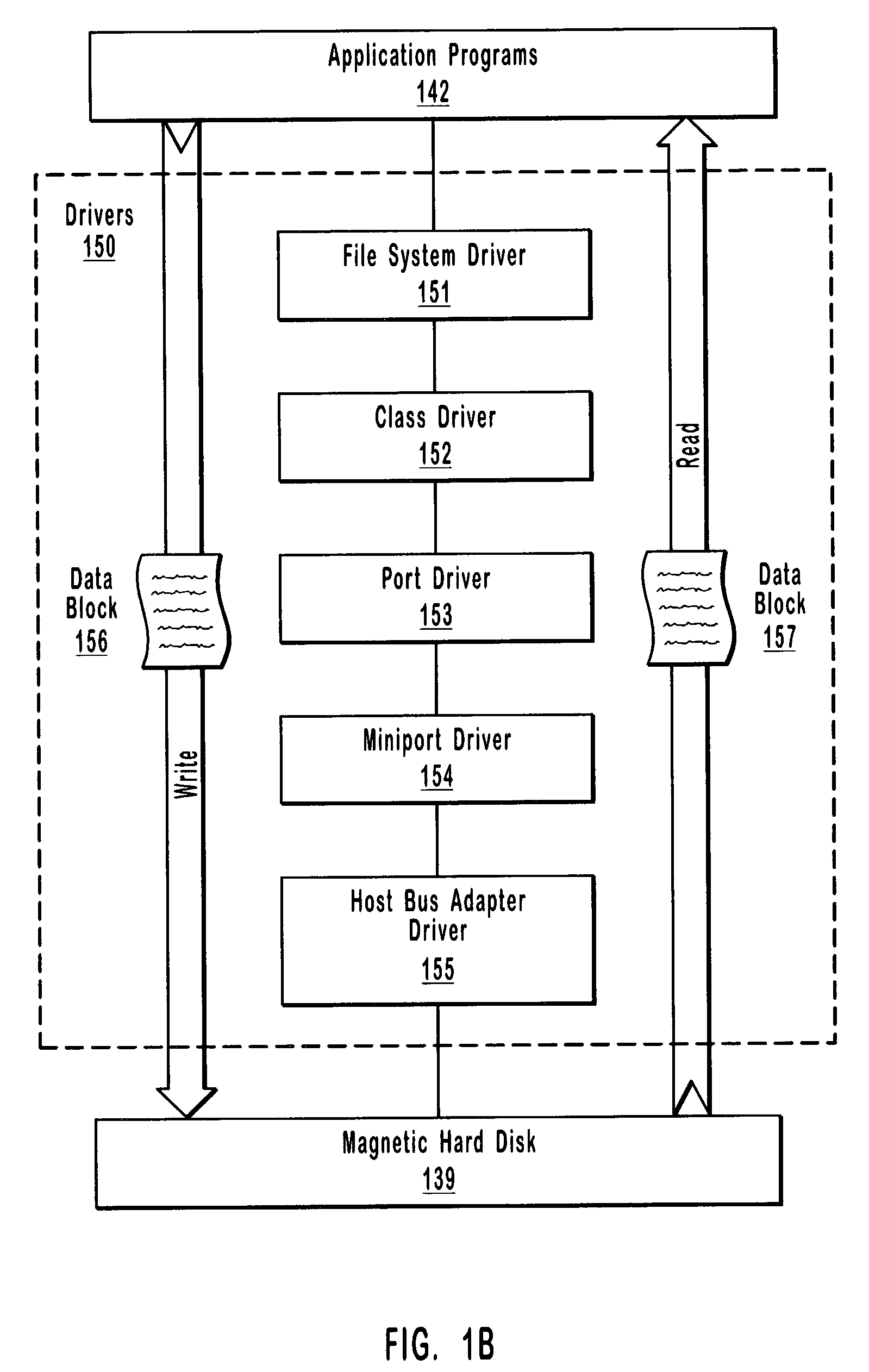
ActiveUS7020798B2Low levelError preventionRedundant data error correctionMass storageOperational system
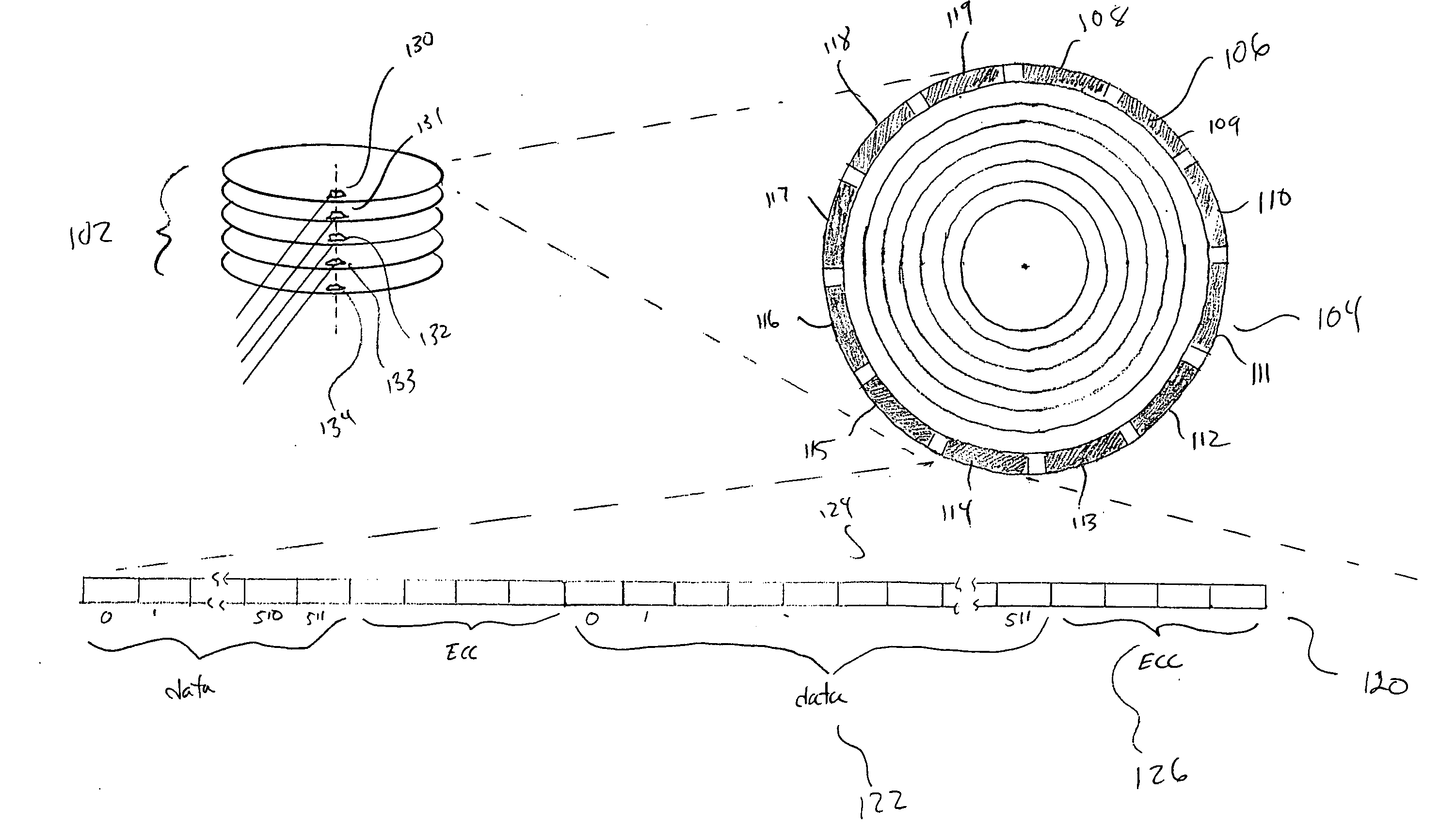
Checksum values are used to detect low-level data corruption. I / O operations, such as, for example, read operations and write operations, cause data blocks to pass through a number of low-level drivers when the data blocks are transferred between an operating system and mass storage location. A checksum filter driver intercepts a data block as the data block passes between low-level drivers as a result of the performance of an I / O operation. The checksum filter driver calculates a first checksum value for the data block. The checksum filter subsequently intercepts the data block as the data block passes between low-level drivers as a result of the performance of a subsequent I / O operation. The checksum filter driver calculates a second checksum value for the data block. The first checksum value and the second checksum value are compared. Data corruption is detected when a checksum mismatch occurs.
Owner:MICROSOFT TECH LICENSING LLC
On demand consistency checkpoints for temporal volumes within consistency interval marker based replication
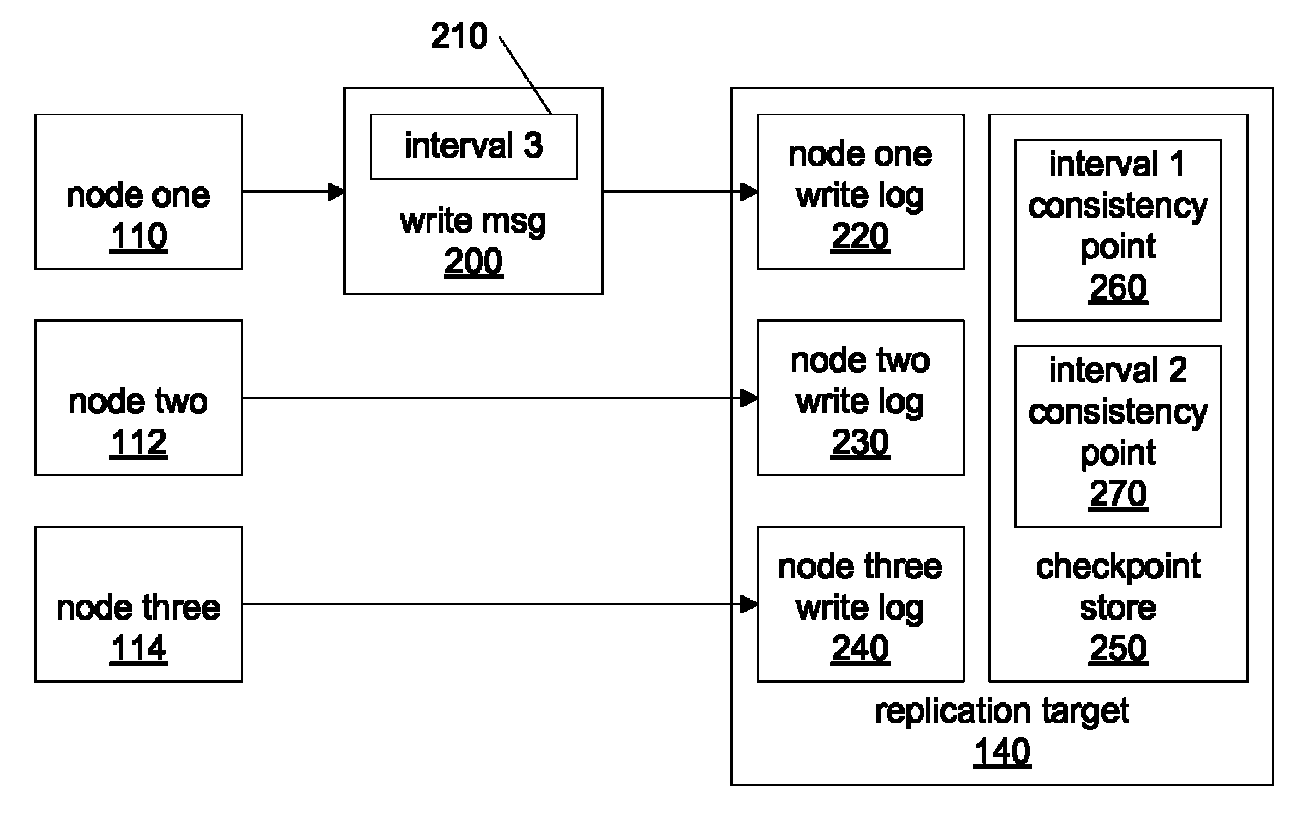
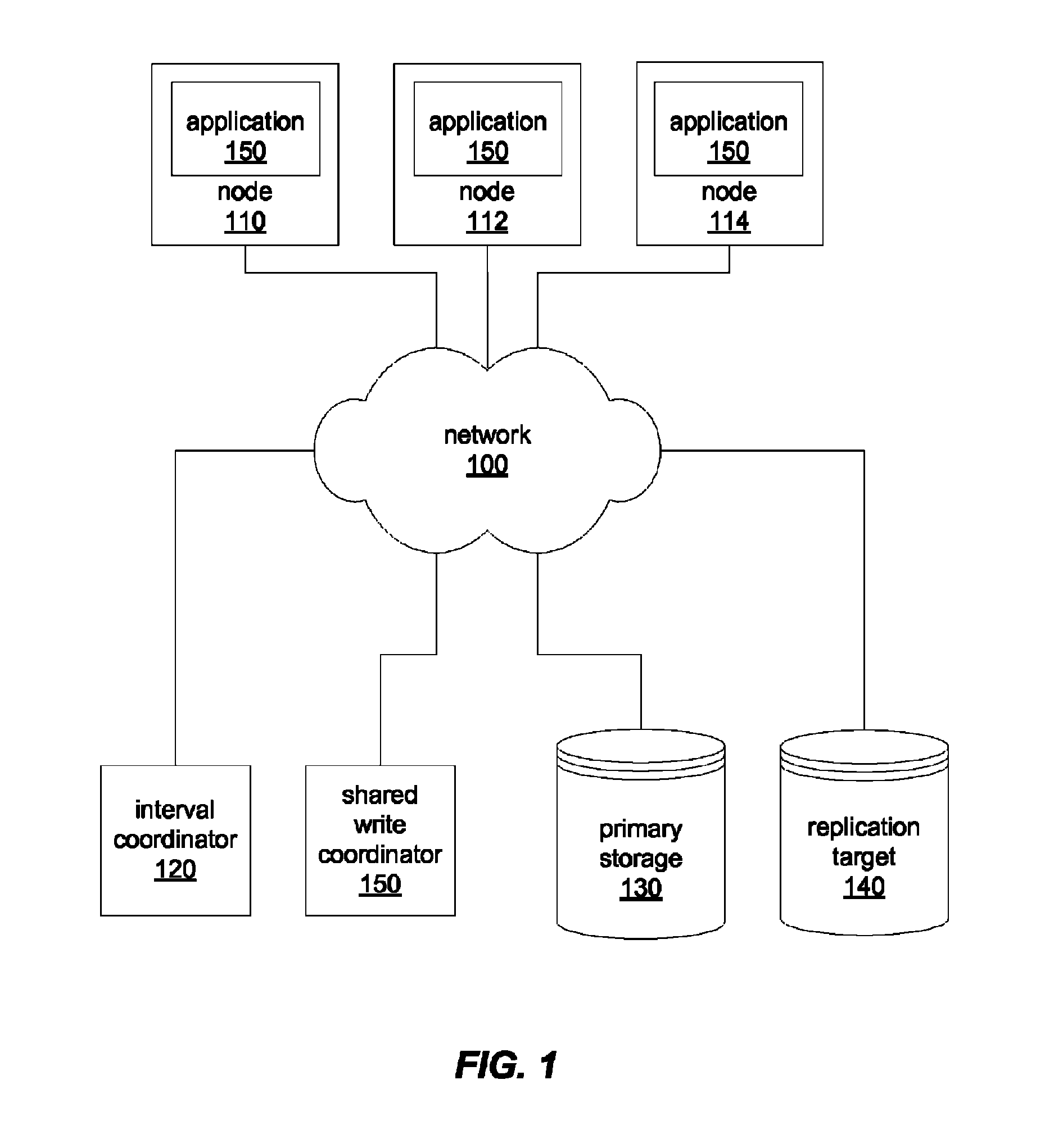
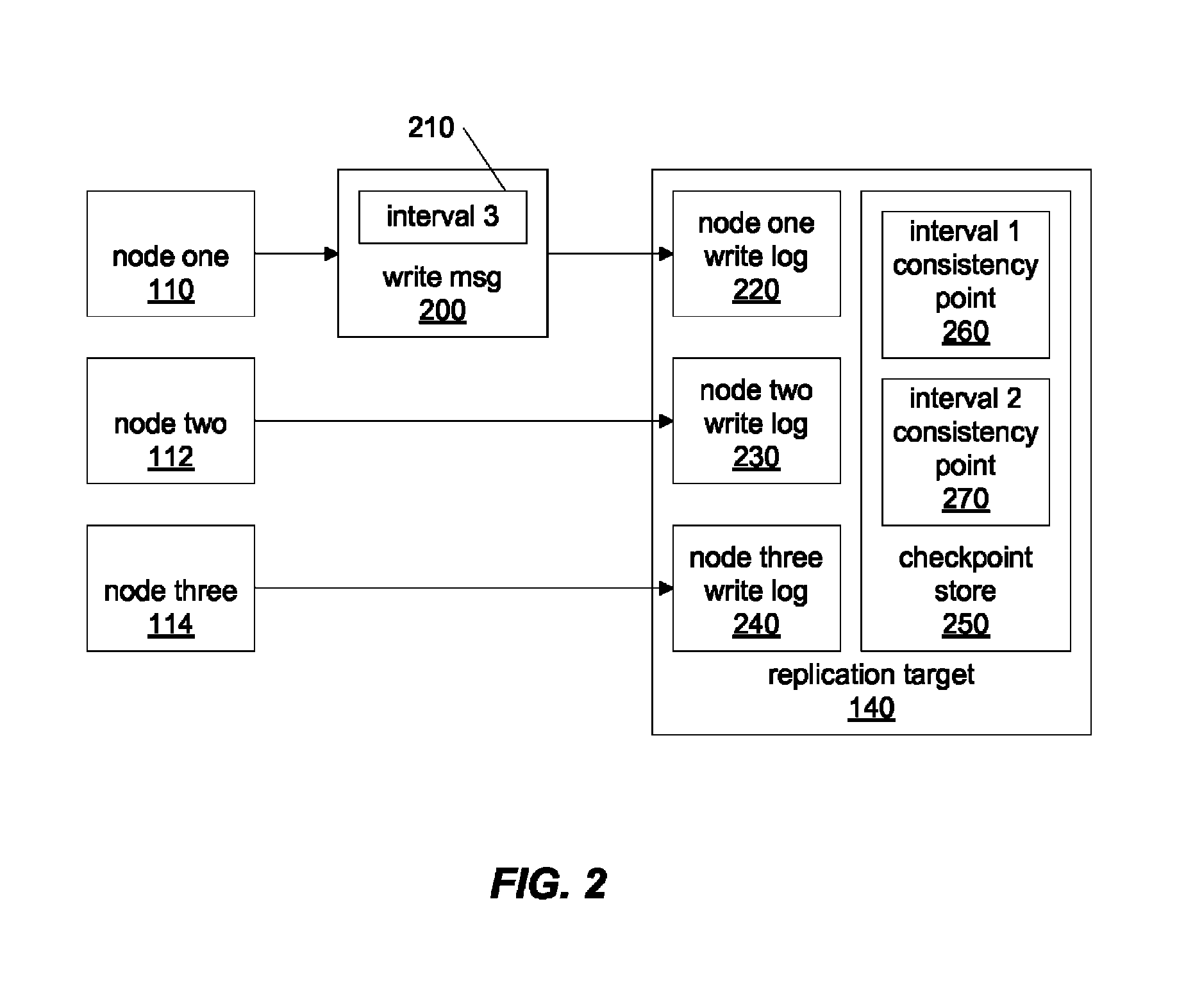
InactiveUS7885923B1Efficient and scalableConsistency can be compromisedMemory loss protectionDigital data processing detailsTimestampData Corruption
In distributed storage environments, nodes may send replicated writes for temporal volumes and may be configured to request on-demand consistency intervals in order to allow multiple nodes to transition between timestamps for temporal data in a uniform and coordinated manner. In response to a request from a node for a consistency interval transition, a consistency interval coordinator may end a current consistency interval and start another and may provide coordination to various nodes to enable the nodes to transition from one timestamp to another, and thus from one temporal version to another, while prevent data corruption or inconsistency between the temporal versions. Additionally, periodic consistency intervals may be utilized to provide consistent and coordinated transitions between temporal timestamps. In some embodiments, replicated writes including temporal timestamp information may be stored persistent spillover logs allowing offline updating and versioning of data to temporal volumes.
Owner:SYMANTEC OPERATING CORP
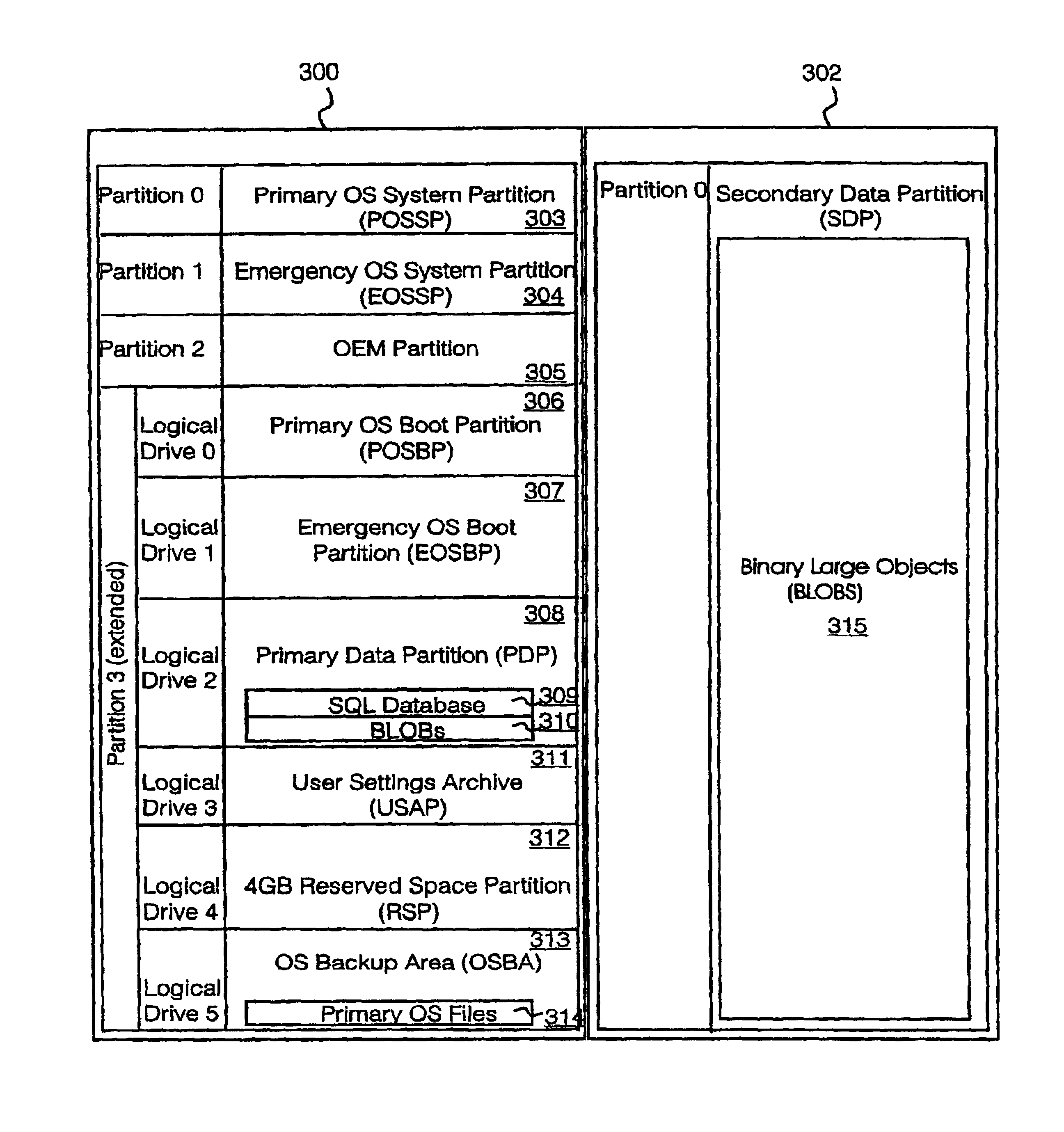
Memory including portion storing a copy of primary operating system and method of operating computer including the memory
InactiveUS6934881B2Redundant data error correctionRedundant operation error correctionOperational systemApplication software
A method of installing an operating system into a computer entity comprising at least one data storage device, a primary operating system and an emergency operating system, the method characterized by comprising the steps of: creating a copy of the primary operating system on an operating system back-up area of the data storage device of the computer entity; operating the computer entity using the emergency operating system; storing data of the computer entity on a user settings archive of the data storage device; replacing the primary operating system with the copy of the primary operating system; automatically checking for corrupted data on the user settings archive; restoring settings data of the computer entity from the user settings archive. In the event of a failure involving data corruption, application data may be deleted and recreated in a known good default state.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Incremental transparent file updating
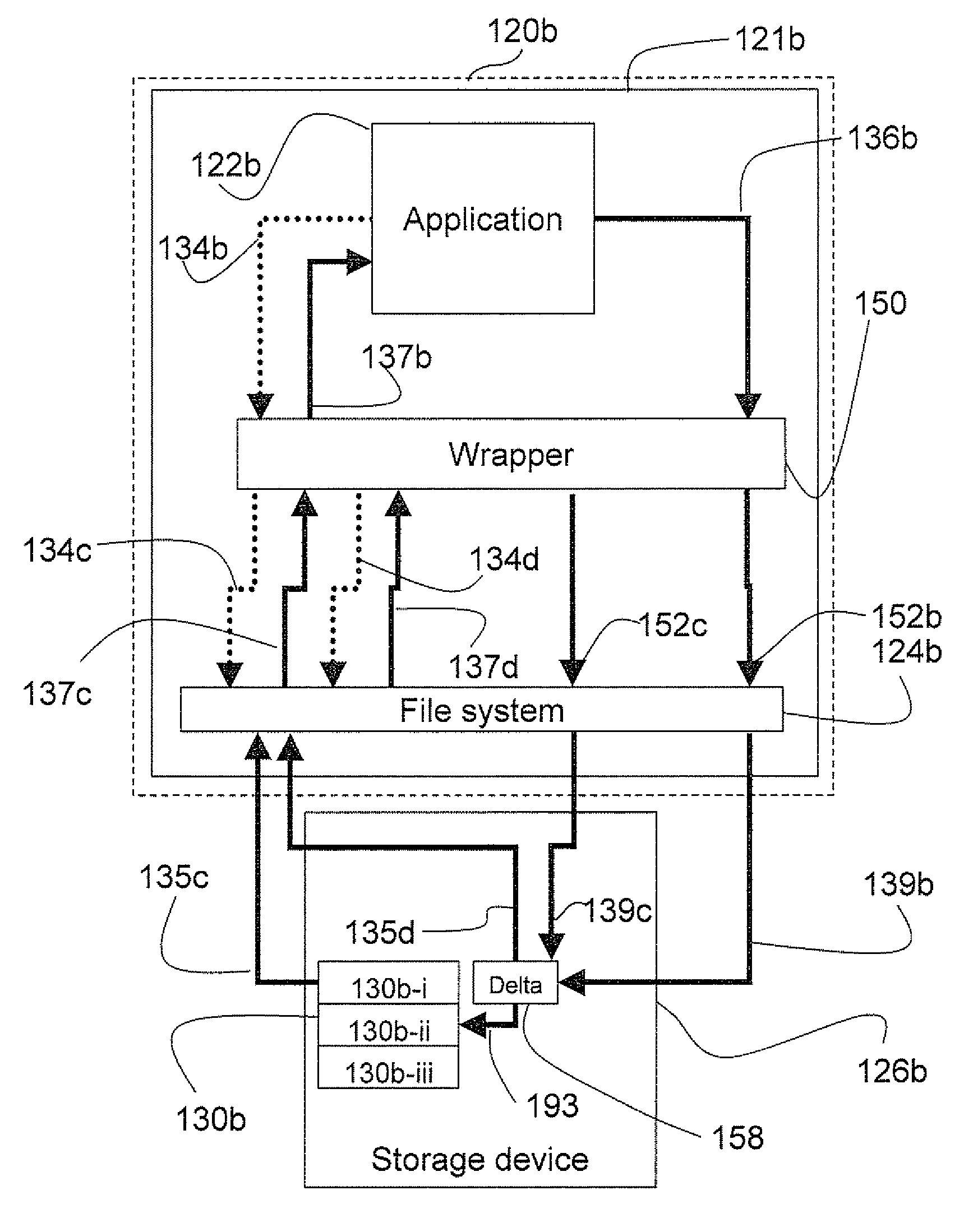
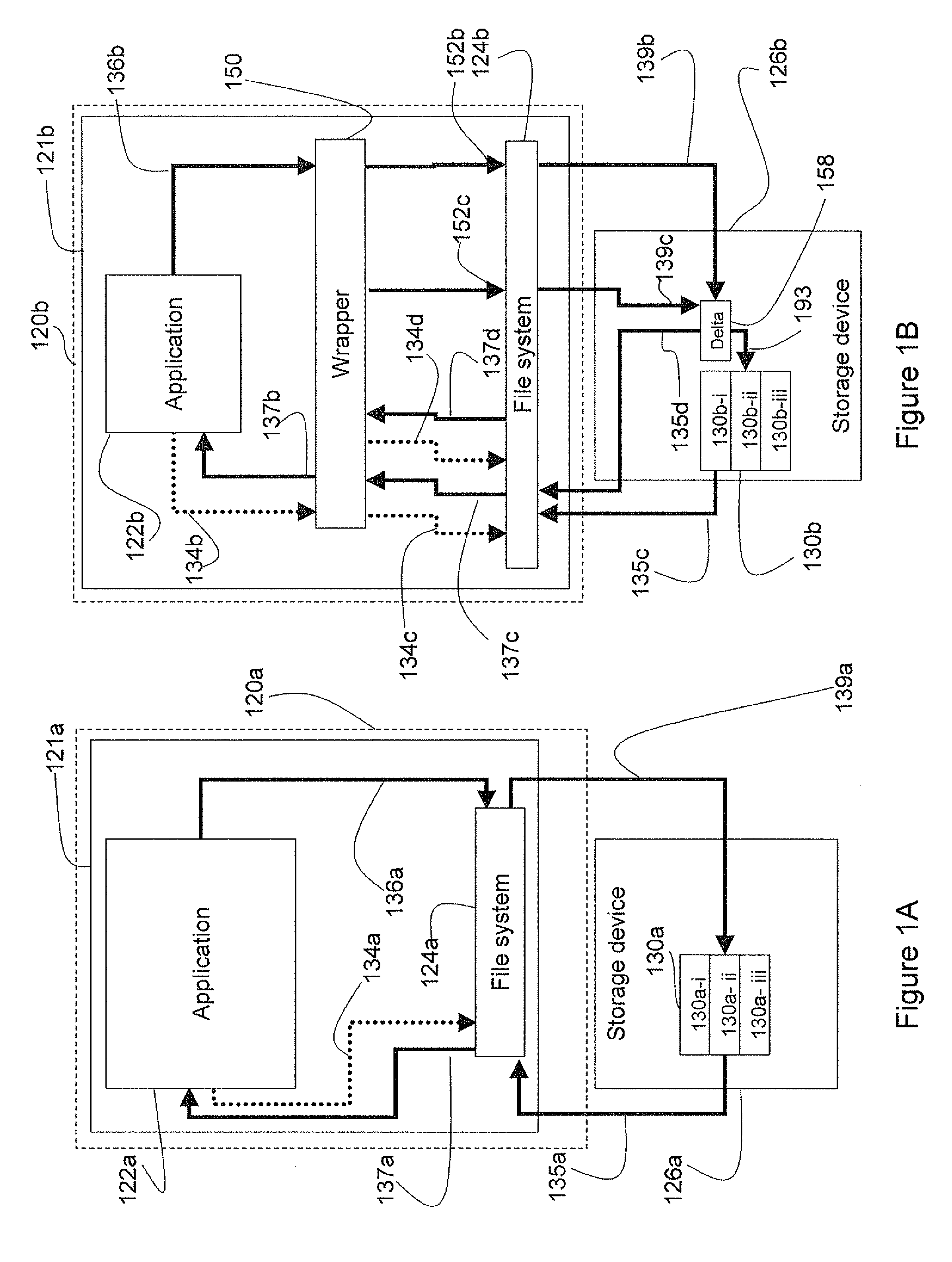
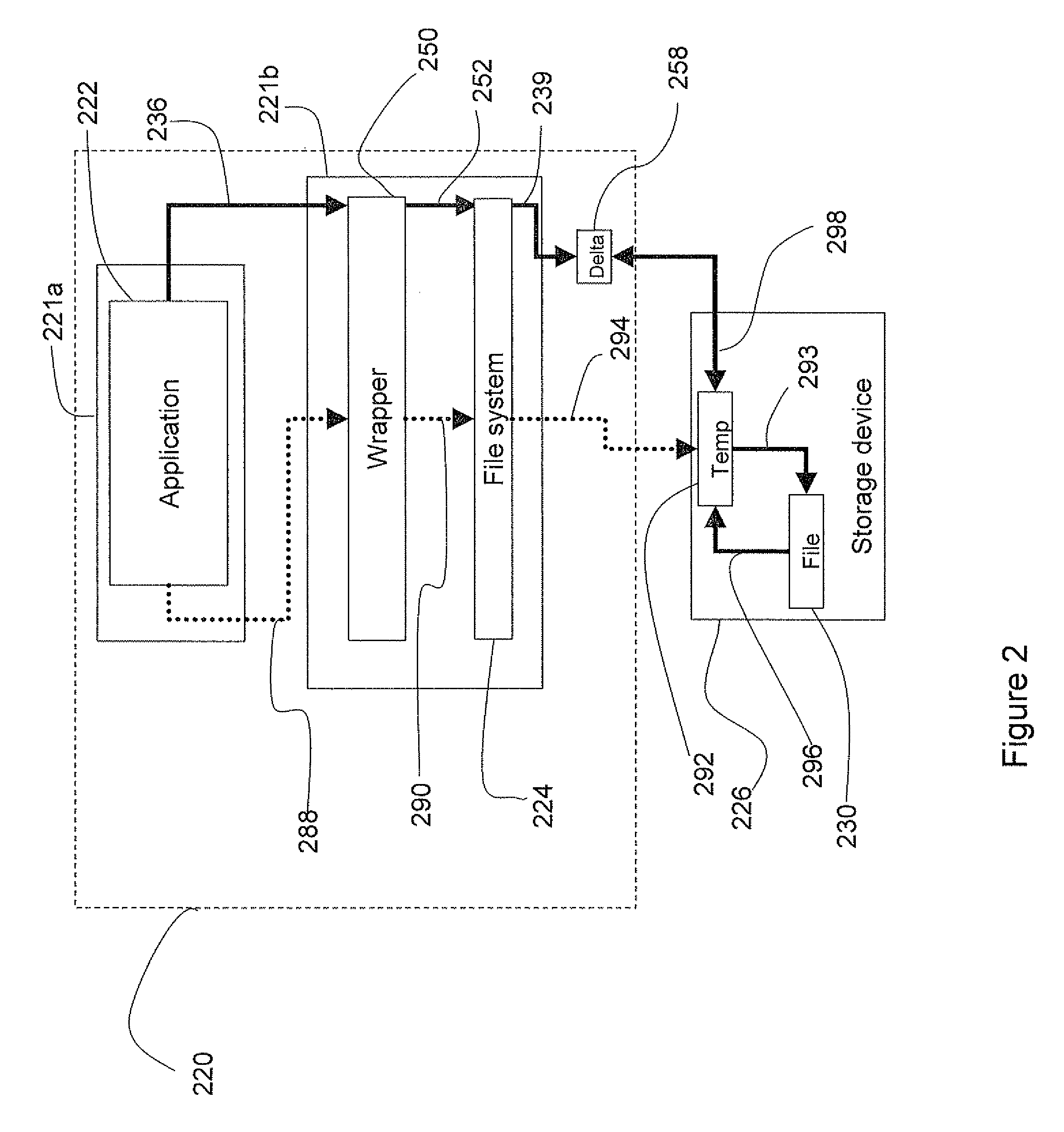
InactiveUS20080134163A1Protection from damageEfficient updateMemory loss protectionDigital data processing detailsData CorruptionApplication software
A system and method to protect a target file from data damage wherein a wrapper application transparently intercepts a write call operative to affect the target file and stores the pertinent data in a delta file. Occasionally the target file is backed up in a temporary file and then updated. The wrapper application also intercepts a read call operative to access the target file and merges the update information with data from the target file in a temporary file. The resulting merged data is returned as read results data.
Owner:WESTERN DIGITAL ISRAEL LTD
Method and apparatus for detecting and recovering from data corruption of database via read logging
InactiveUS20020091718A1Data processing applicationsRedundant operation error correctionState modelTransaction model
A method of detecting and recovering from data corruption of a database is characterized by the step of logging information about reads of a database in memory to detect errors in data of the database, wherein said errors in data of said database arise from one of bad writes of data to the database, of erroneous input of data to the database by users and of logical errors in code of a transaction. The read logging method may be implemented in a plurality of database recovery models including a cache-recovery model, a prior state model a redo-transaction model and a delete transaction model. In the delete transaction model, it is assumed that logical information is not available to allow a redo of transactions after a possible error and the effects of transactions that read corrupted data are deleted from history and any data written by a transaction reading Ararat data is treated as corrupted.
Owner:LUCENT TECH INC
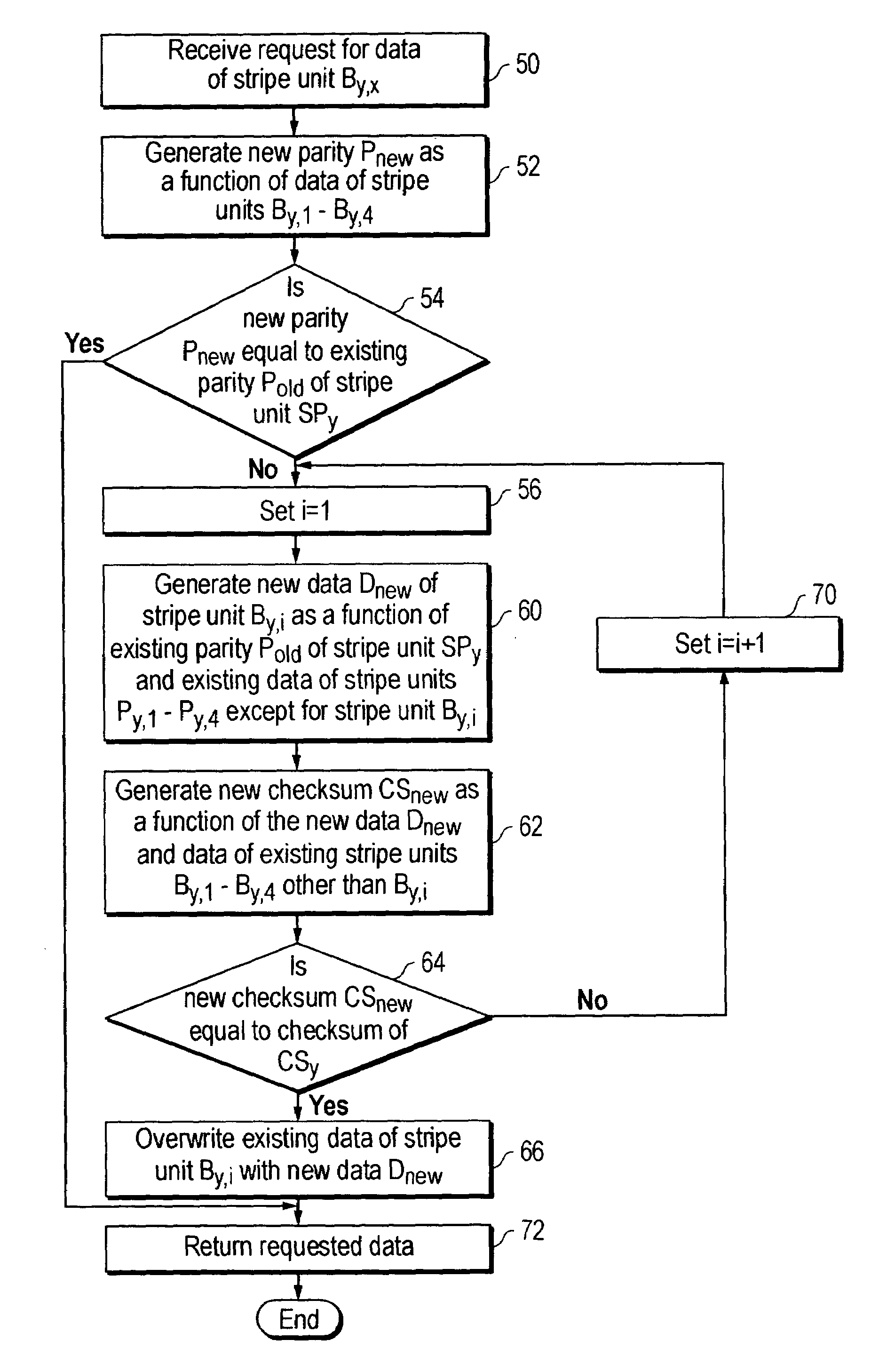
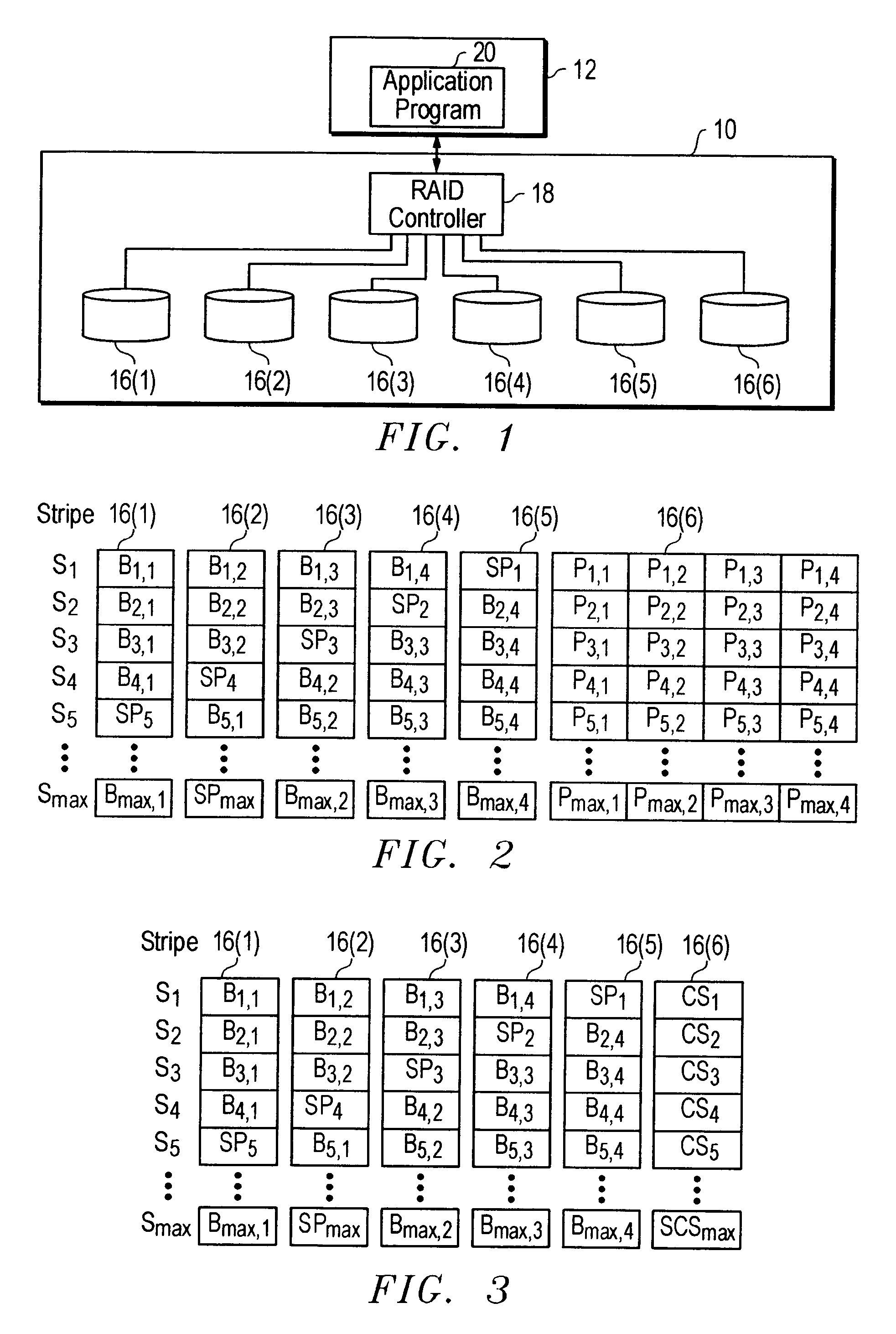
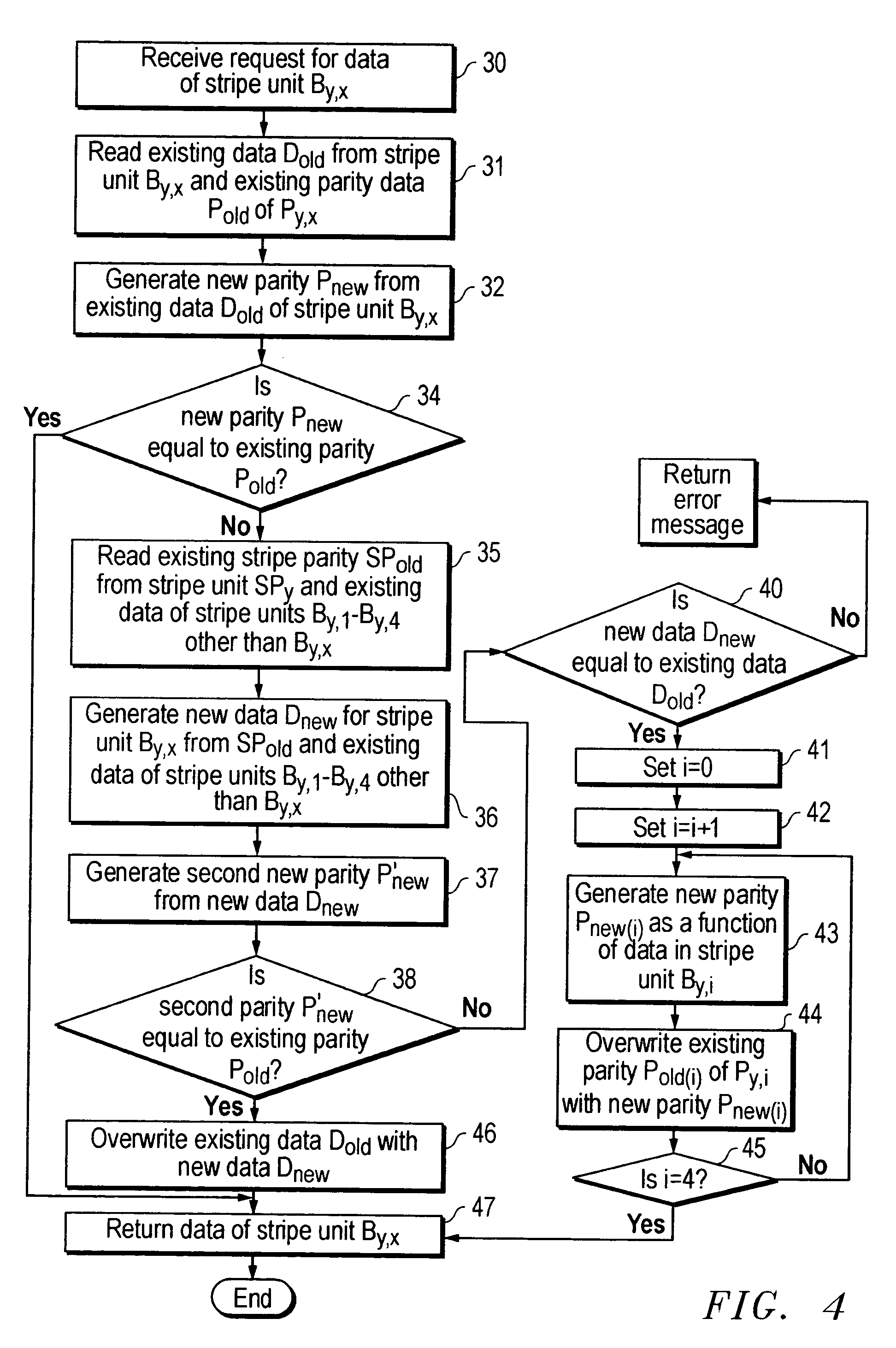
Automated recovery from data corruption of data volumes in parity RAID storage systems
The present invention relates to an apparatus or computer executable method of detecting corrupt data in a RAID data storage system before the corrupted data is provided to a computer system coupled to the RAID data storage system. In one embodiment of the invention, the process of detecting corrupt data begins when a request to read data is received from a computer system in data communication with the RAID data storage system. The requested data is stored in a stripe unit of the RAID data storage system. New parity data is generated as a function of the stripe unit data in response to receiving the request. This newly generated parity data is compared with existing parity data stored in the RAID data storage system. The existing and newly generated parity data are generated using the same algorithm. If the existing and newly generated parity data do not compare equally, the data of the stripe unit is considered corrupt and should not be returned to the computer system.
Owner:SYMANTEC OPERATING CORP
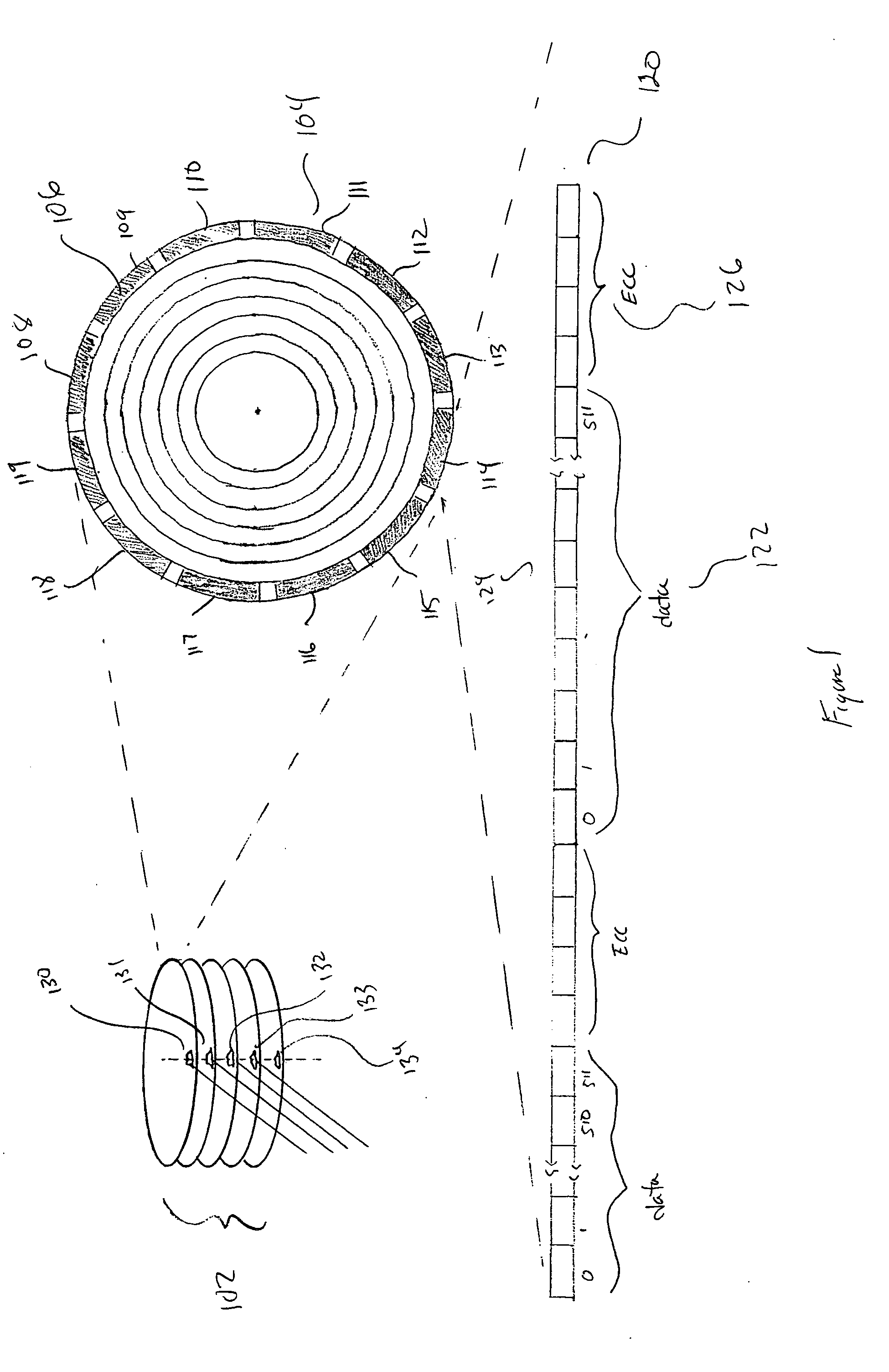
Data Recovery for Defective Word Lines During Programming of Non-Volatile Memory Arrays
The recovery of data during programming, such as in the case of a broken word-line, is considered. The arrangement described assumes that k pages may be corrupted when the system finishes programming a block. Then these corrupted pages can be recovered using an erasure code. In order to recover any k pages, the system will compute and temporarily store k parity pages in the controller. These k parity pages may be computed on-the-fly as the data pages are received from the host. Once programming of the block is finished, a post-write read may be done in order to validate that the data is stored reliably. If no problem is detected during EPWR, then the parity pages in the controller may be discarded. In case a problem is detected, and data in up to k pages is corrupt on some bad word-lines, then the missing data is recovered using the k parity pages that are stored in the controller and using the other non-corrupted pages that are read from the block of the memory array and decoded. Once the recovery is complete the block can be reprogrammed and the temporary parity pages in the controller may be discarded upon successfully reprogramming.
Owner:SANDISK TECH LLC
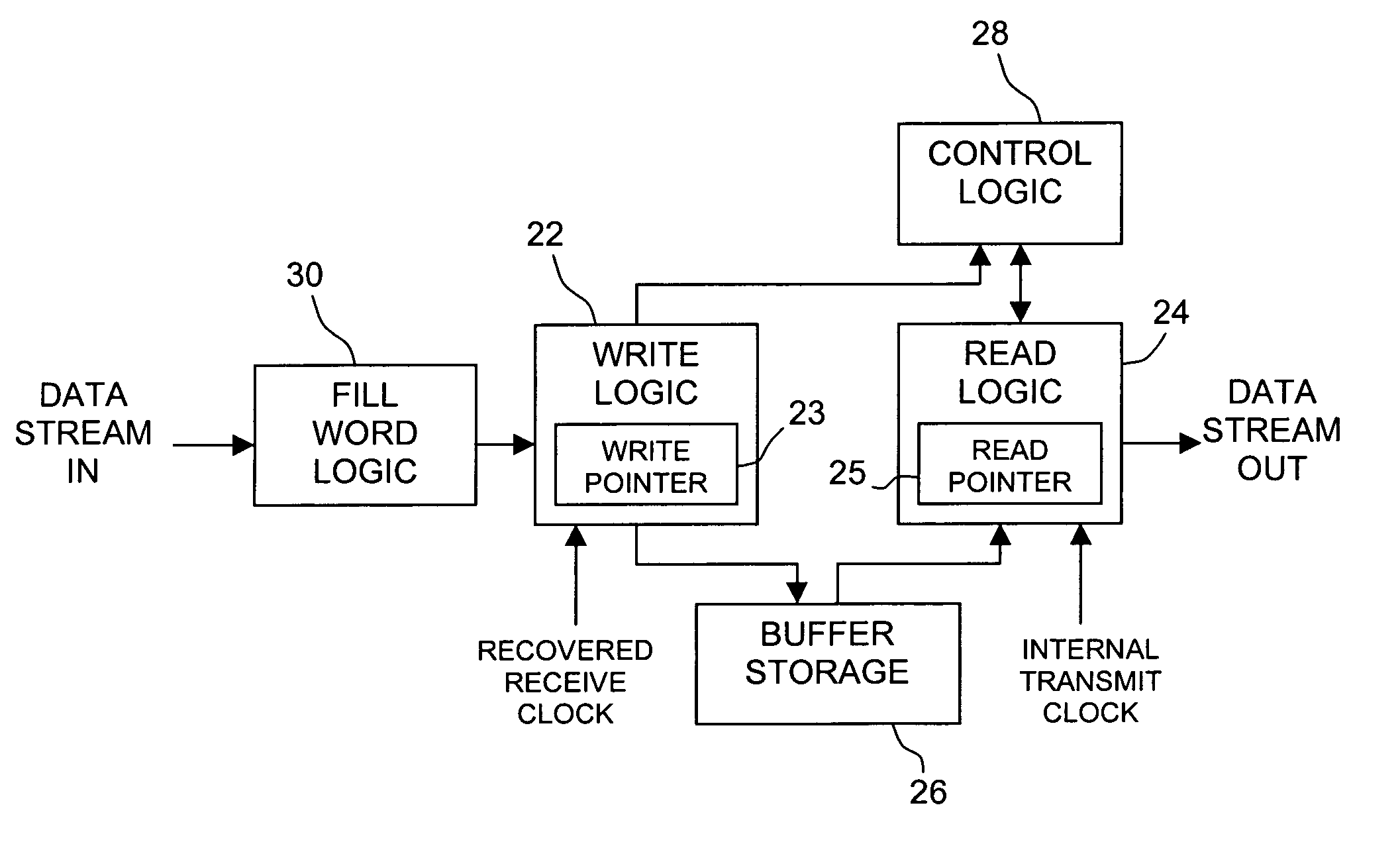
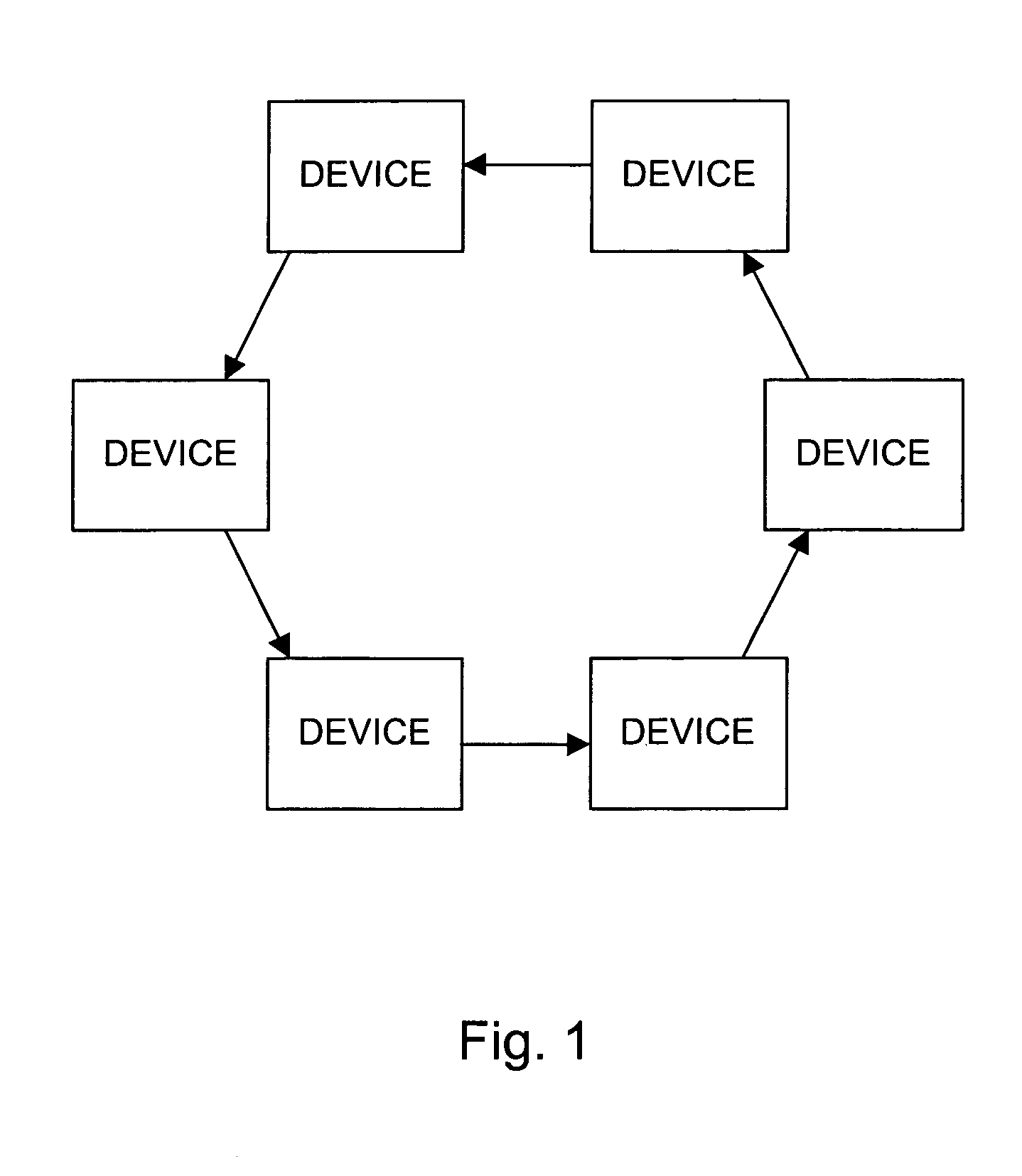
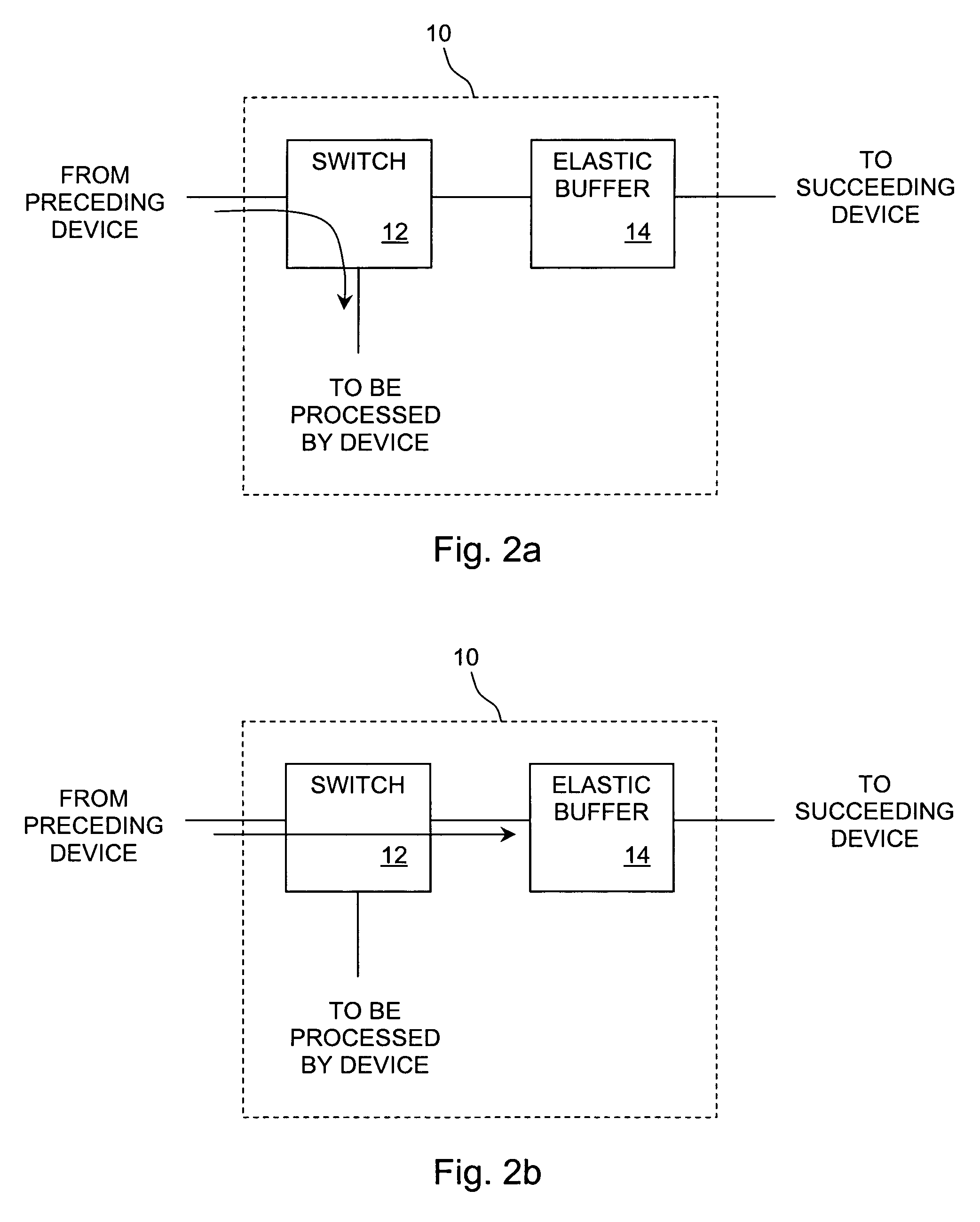
System and method for jitter compensation in data transfers
InactiveUS6977897B1Reduce in quantitySimplify comparison logicError preventionFrequency-division multiplex detailsCircular bufferData Corruption
A system and method for compensating for differences between a recovered receive clock and an internal transmit clock in an elastic buffer and thereby preventing corruption of data. In one embodiment, the system comprises a circularly accessed buffer coupled to read and write logic. The read and write logic read and write to locations within the circular buffer as indicated by respective read and write pointers. The system further comprises control logic which compares the pointers to determine whether the buffer is approaching an underflow or overflow condition and adds or deletes fill words between frames of data to compensate for the underflow or overflow condition. In one embodiment, the system includes fill word logic which is configured to add a fill word bit to each received word and to set or clear the fill word bit to indicate whether or not the corresponding word is a fill word.
Owner:CF DB EZ +1
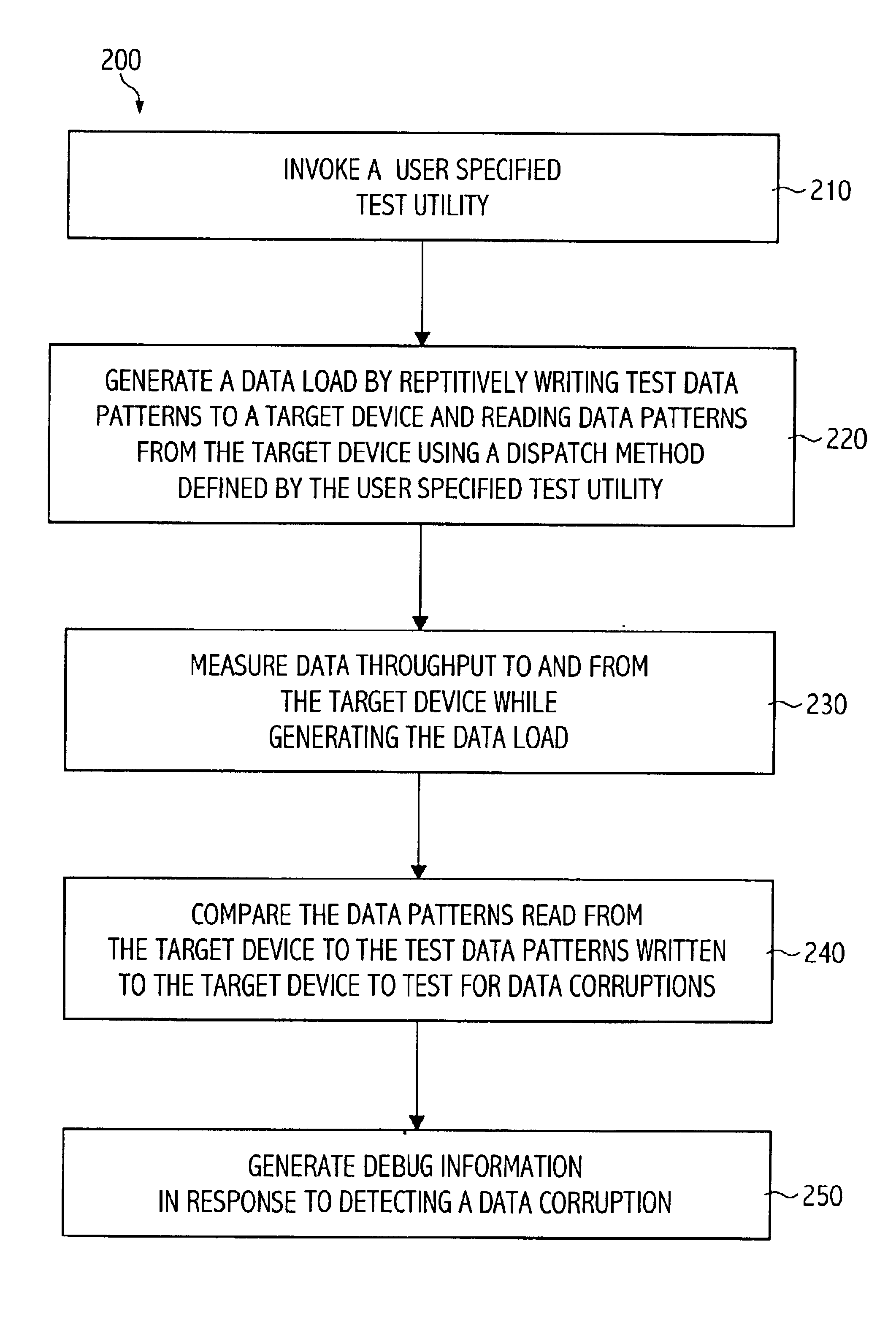
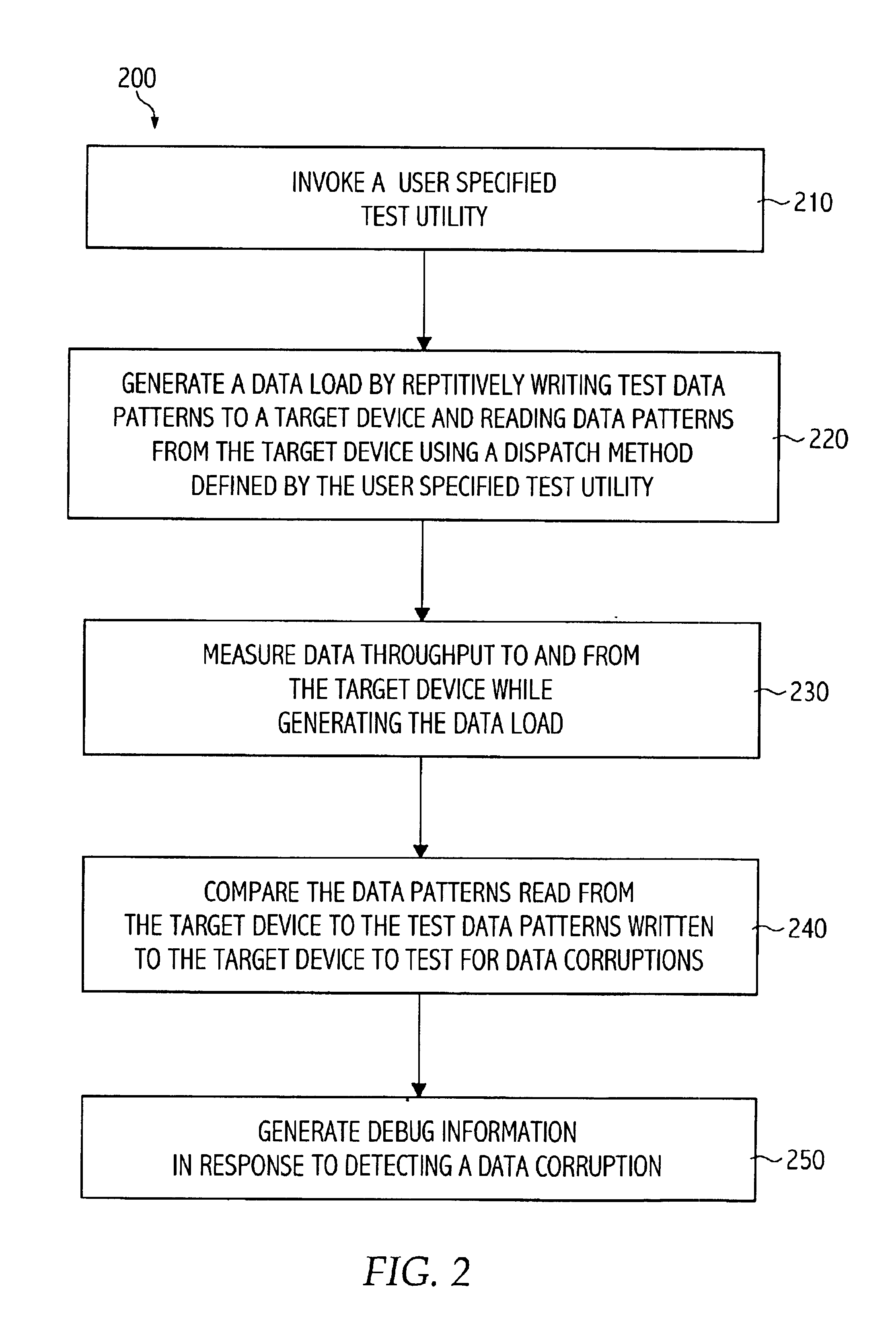
Scalable multithreaded system testing tool
InactiveUS6889159B2Input/output to record carriersResistance/reactance/impedenceData connectionSystem testing
Embodiments of the present invention generally provide a system and method for testing integrity of data transmitted to and from a target device through a data connection. In one embodiment, the method generally includes creating one or more test threads. The method further includes, for each test thread, generating a data load on the data connection by repetitively writing test data patterns to the target device and reading data patterns from the target device using a synchronous I / O dispatch method, measuring data throughput to and from the target device while generating the data load, comparing the data patterns read from the target device to the test data patterns to detect data corruptions. The method may further include generating debug information if a data corruption is detected by one of the test threads.
Owner:VIAVI SOLUTIONS INC
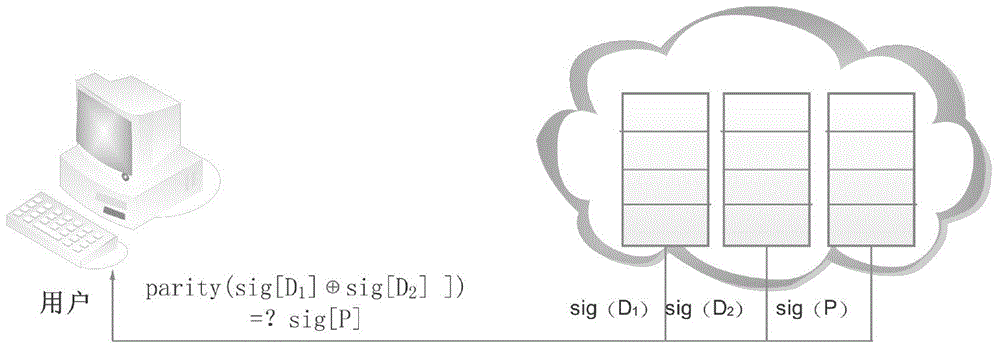
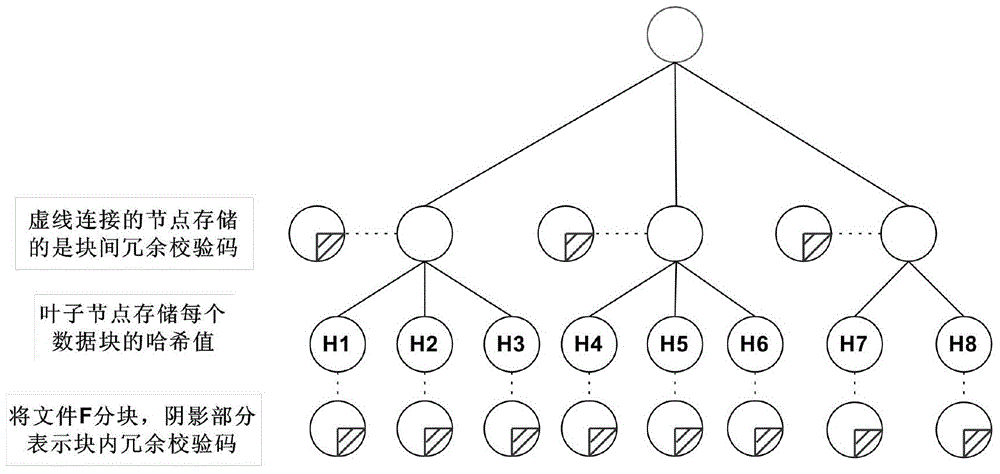
User-oriented cloud storage data integrity protection method
InactiveCN105320899ASave storage spaceAvoid Lost Security RisksDigital data protectionData integrityOriginal data
The invention discloses a user-oriented cloud storage data integrity protection method. The method includes the steps of 1, uploading, wherein a user side segments and numbers a file to generate intra-block redundancy check codes, the hash value of each file block is calculated and saved as a range-based 2-3 tree, the hash values are linked into one value and signed with private keys, and inter-block redundancy check codes are generated and encrypted with stream substitution secret keys; 2, verification, wherein a cloud management node sends a verification request to a corresponding cloud storage server, corresponding original data and algebraic signatures of the inter-block redundancy check codes corresponding to the original data are calculated and returned to the user side for data integrity verification, and the step 3 is executed if data destruction is found; 3, recovery, wherein the user side acquires all the file blocks on corresponding branch trees from a cloud side according to tree information and performs error recovery on the file blocks through erasure codes of the file blocks. According to the method, integrity verification and recovery are performed on the dynamic data stored in the cloud side from the user perspective.
Owner:PEKING UNIV
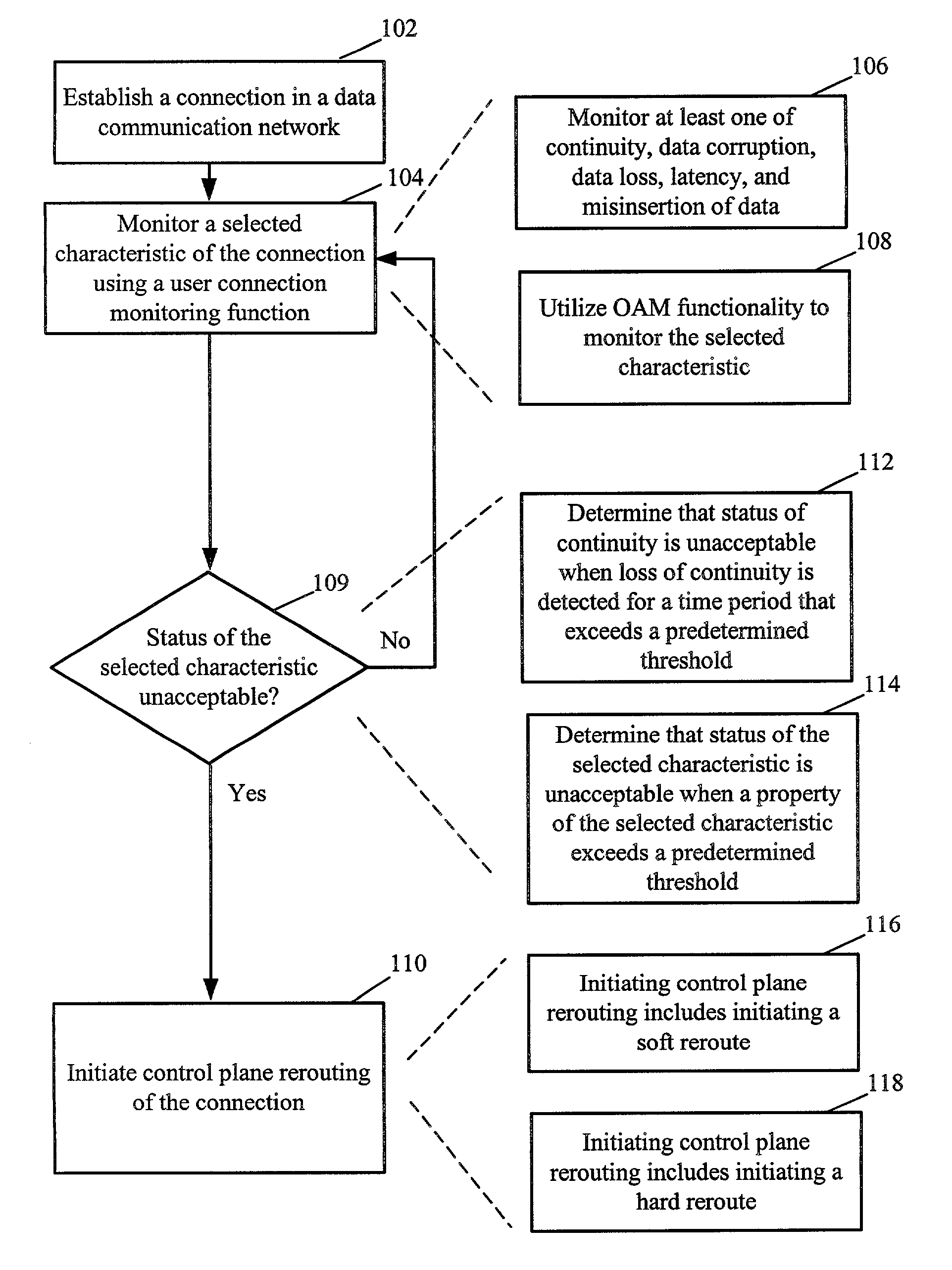
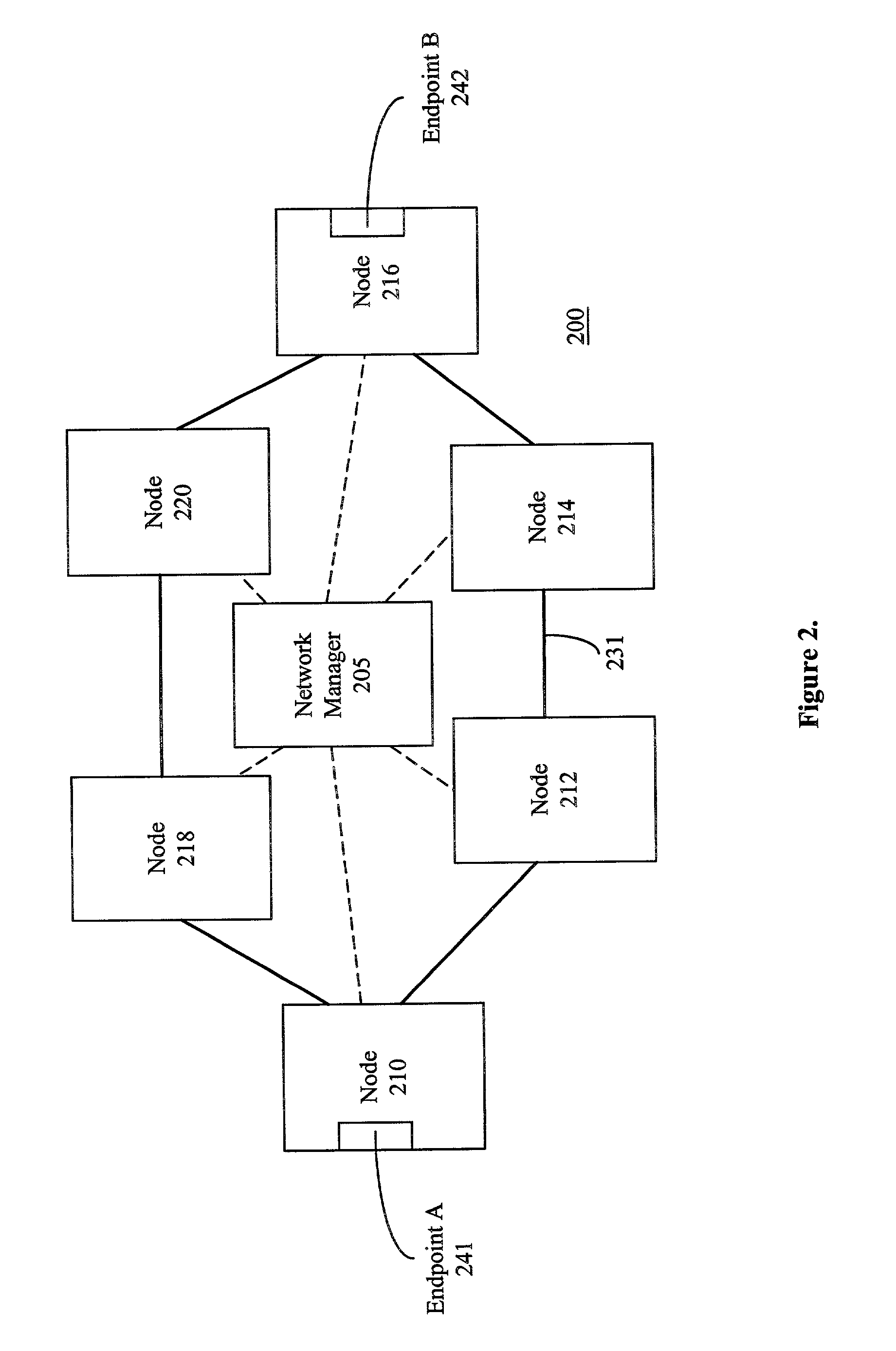
Method and apparatus for rerouting a connection in a data communication network based on a user connection monitoring function
A method and apparatus for rerouting connections in a data communication network based on detection of faults or other undesirable characteristics using a user connection monitoring function is presented. After a connection is established that is managed by a control plane, the status of characteristics of the connection is monitored using a user connection monitoring function. In one embodiment, the user connection monitoring function includes the use of operation and management (OAM) cells. When the status of one or more of the selected characteristics being monitored is determined to be unacceptable, control plane rerouting of the connection is initiated. Selected characteristics that may be monitored using the user connection monitoring function include, for example, continuity, data corruption, data loss, latency, and misinsertion of data. The reroute initiated in response to the unacceptable characteristic may be a hard reroute or a soft reroute.
Owner:ALCATEL LUCENT SAS
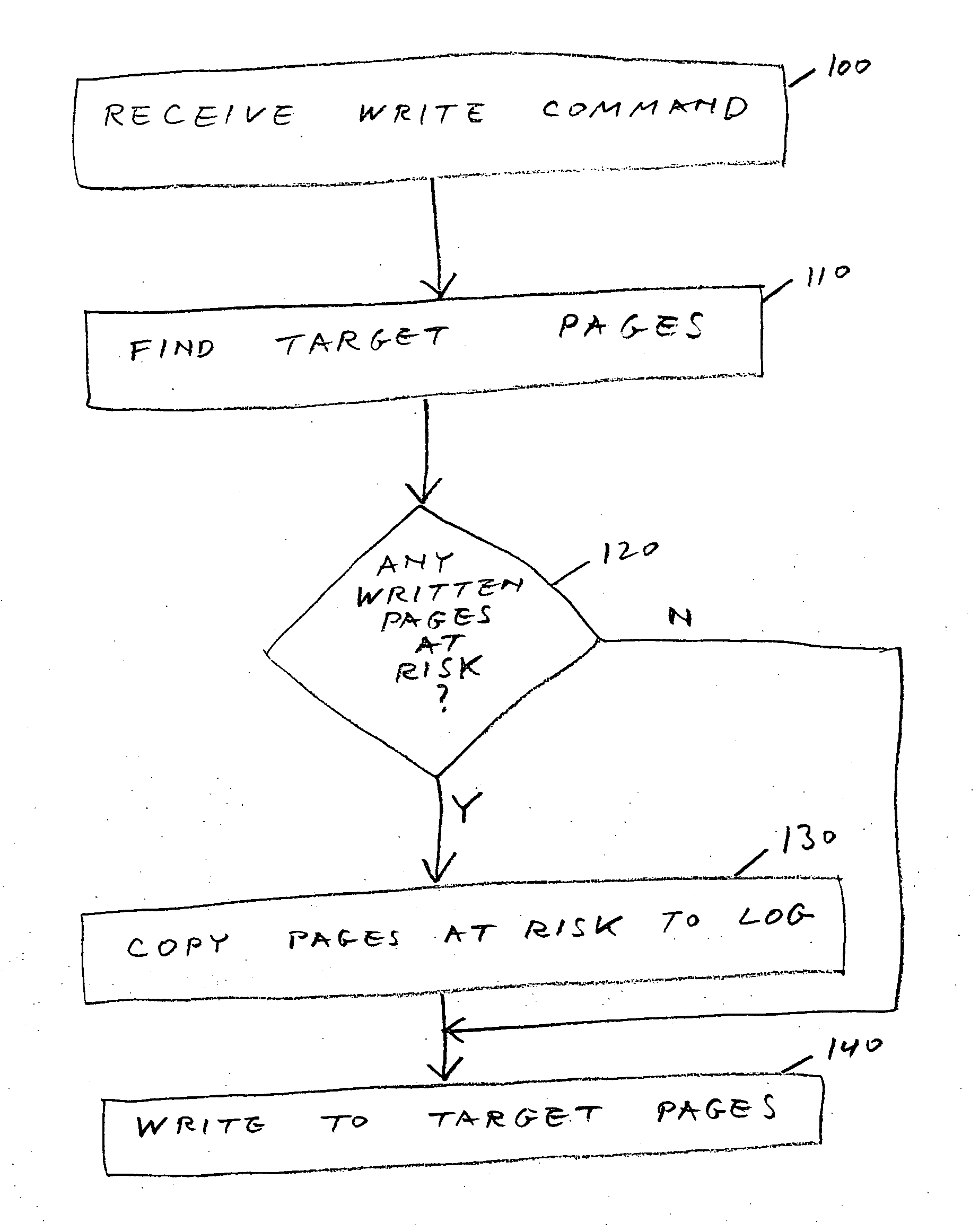
Flash memory management method that is resistant to data corruption by power loss
ActiveUS20060259718A1Use can be riskyMemory loss protectionError detection/correctionElectricityData Corruption
A method of managing page-based data storage media such as flash media, a system that uses the method, and a computer-readable storage medium bearing code for implementing the method. For each page, a corresponding risk zone, of other pages whose data are put at risk of corruption if writing to the page is interrupted, is identified. When a page is selected for writing new data, the written pages in its risk zone are copied to a log. As necessary, corrupt data are replaced with corresponding data from the log.
Owner:WESTERN DIGITAL ISRAEL LTD
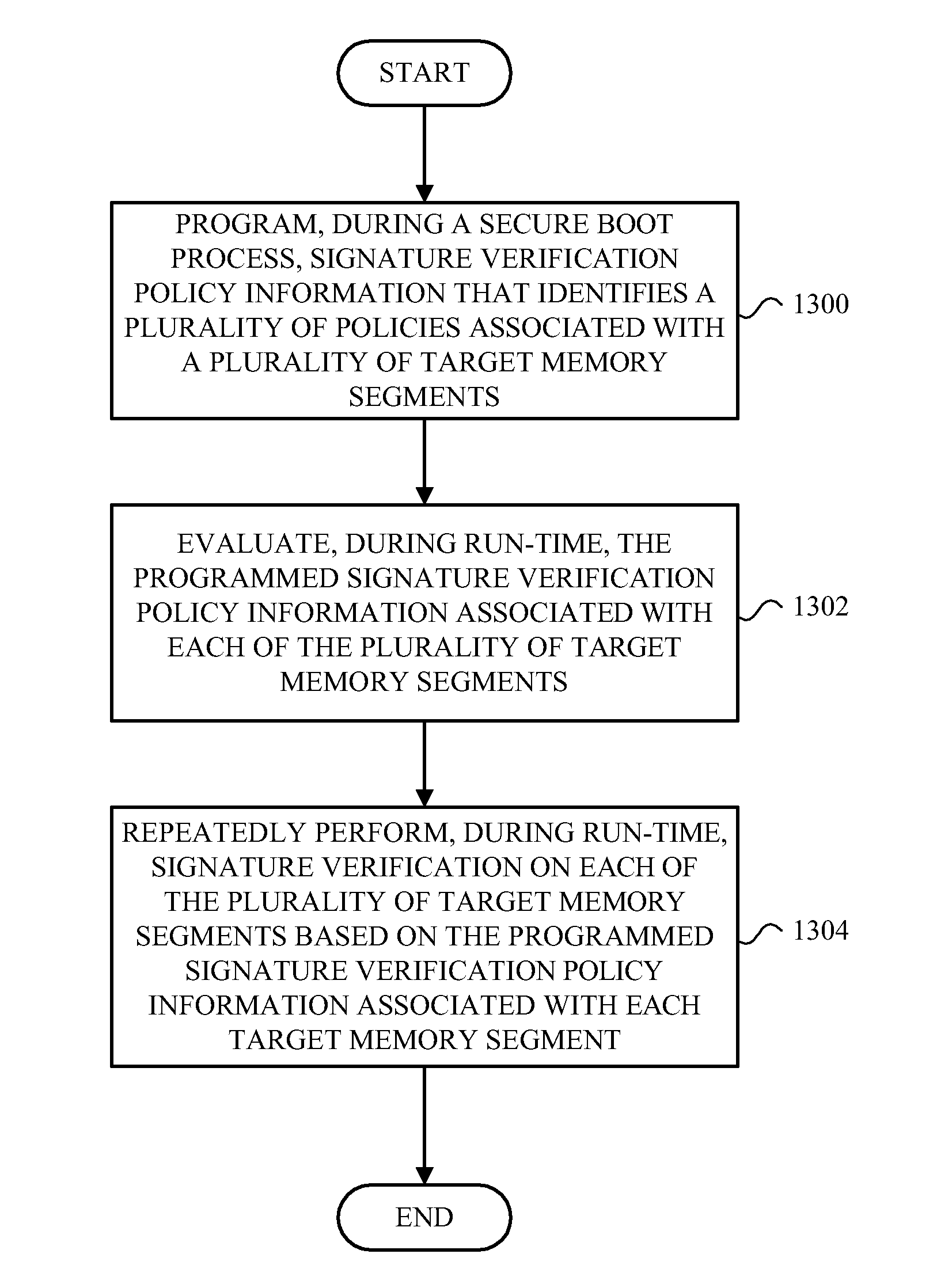
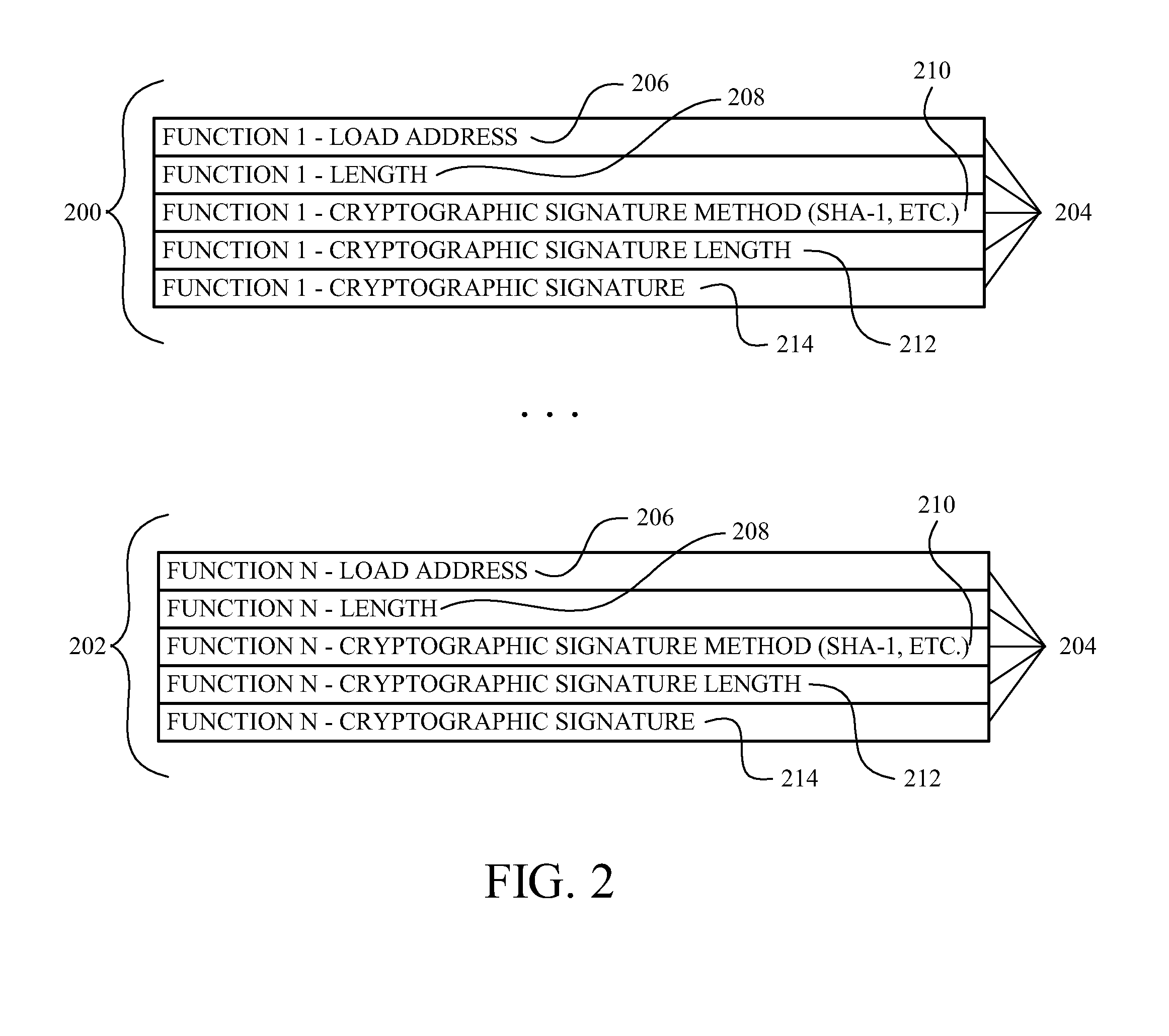
Method, Apparatus, and Device for Protecting Against Programming Attacks and/or Data Corruption
The method and accompanying apparatus and device protects against programming attacks and / or data corruption by computer viruses, malicious code, or other types of corruption. In one example, signature verification policy information that identifies a plurality of policies associated with a plurality of target memory segments is programmed during a secure boot process. The programmed signature verification policy information associated with each of the plurality of target memory segments is then evaluated during run-time. Signature verification is then repeatedly performed, during run-time, on each of the plurality of target memory segments based on the programmed signature verification policy information associated with each target memory segment.
Owner:ADVANCED MICRO DEVICES INC
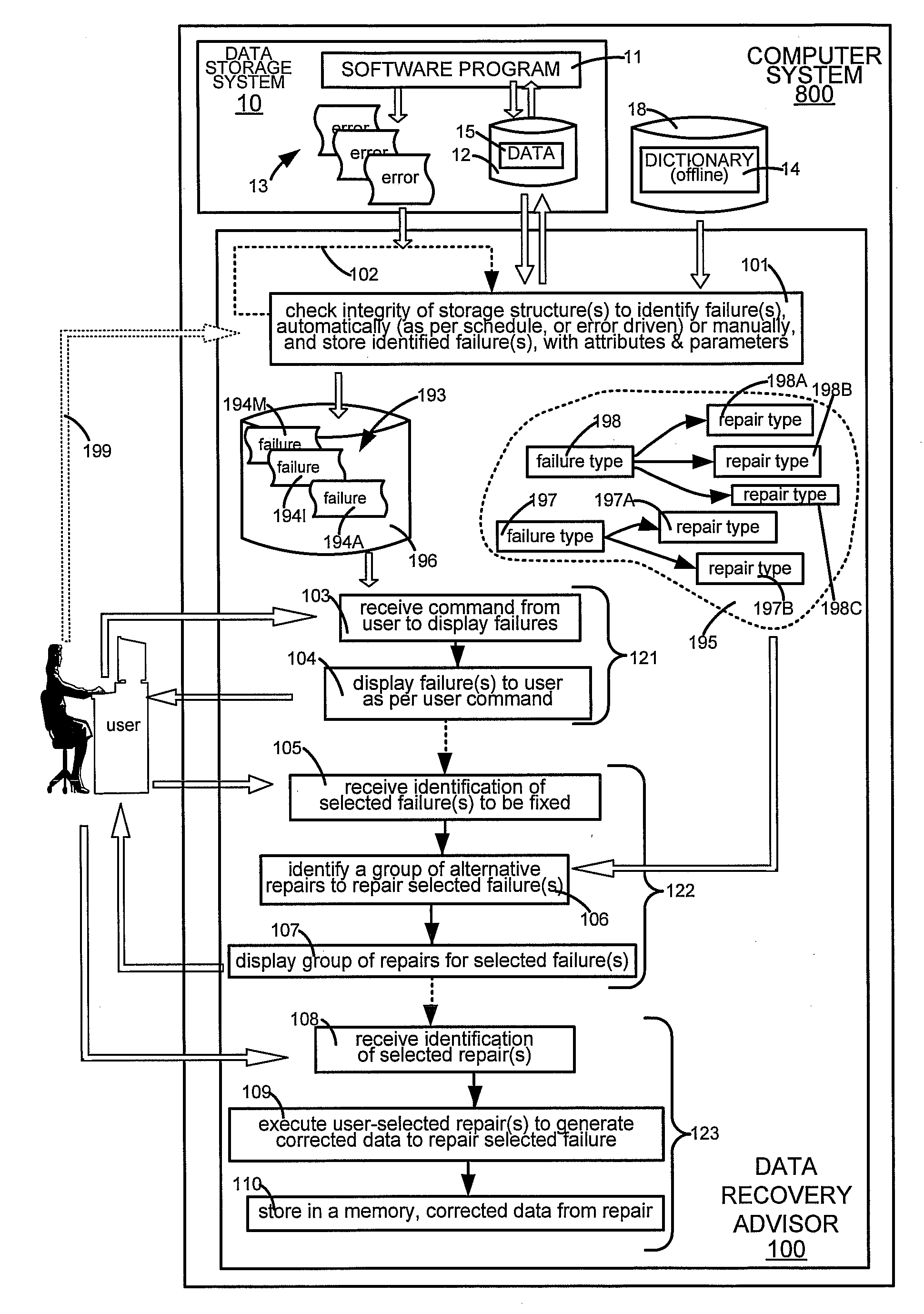
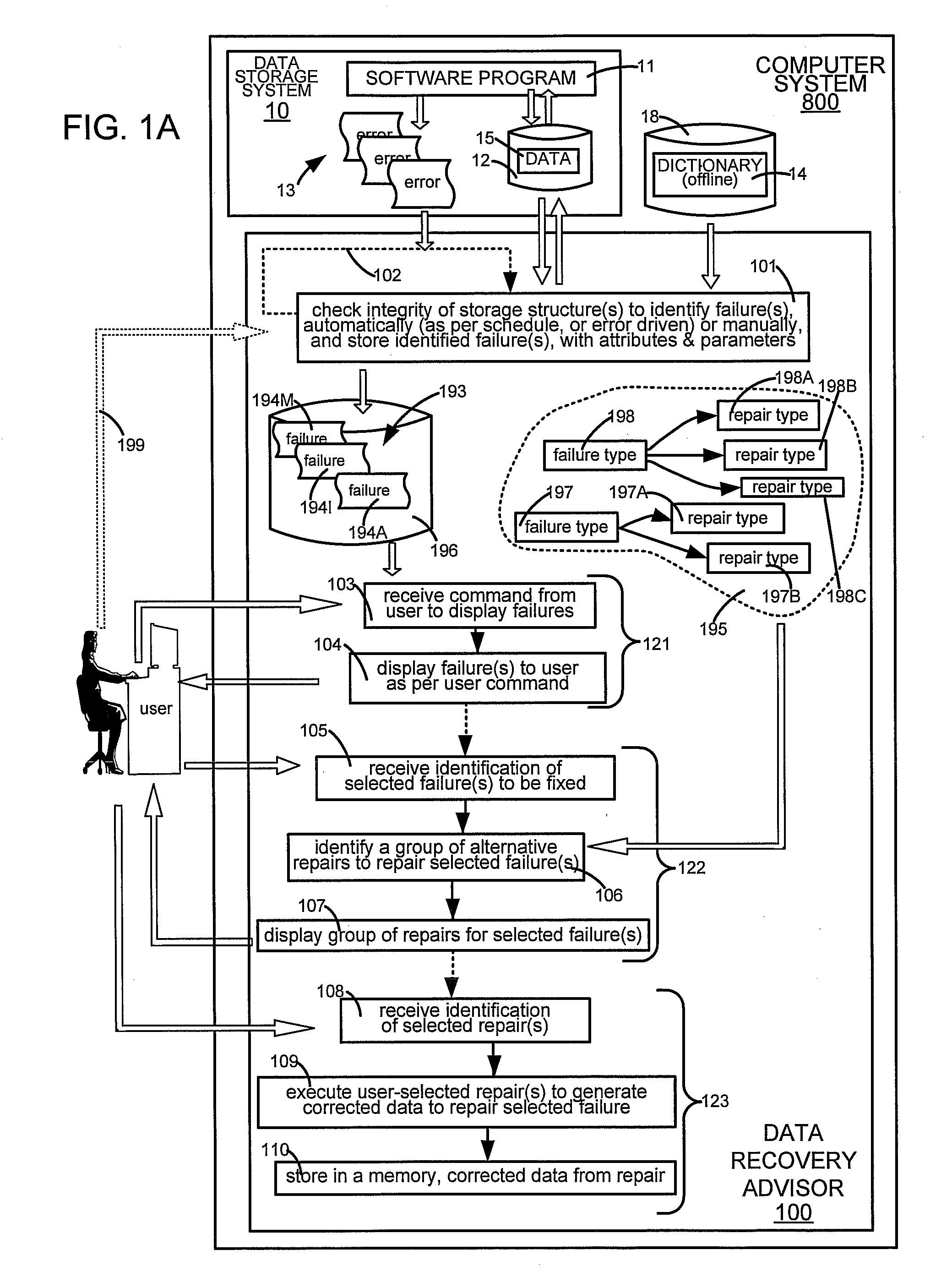
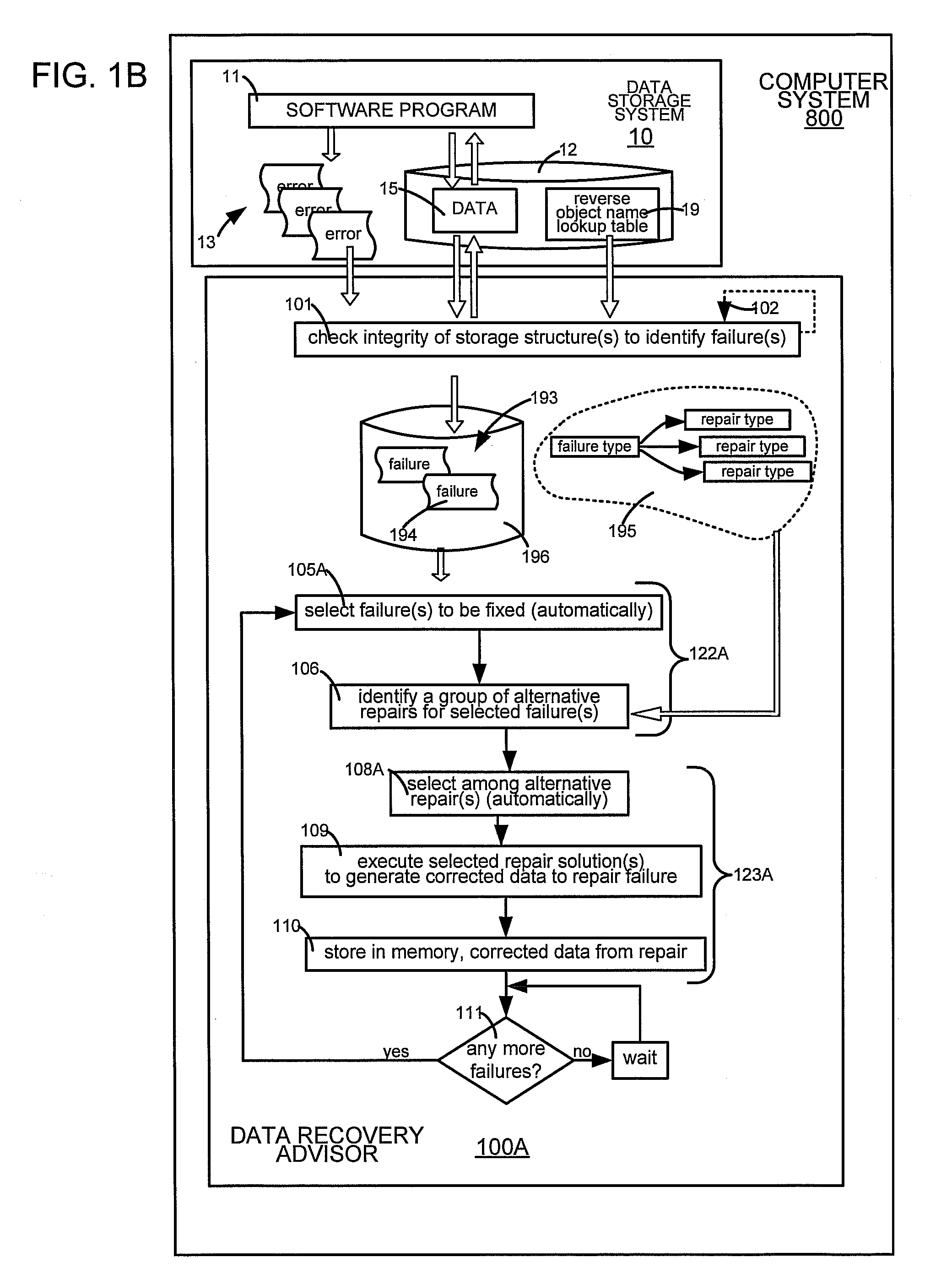
Data Corruption Diagnostic Engine
ActiveUS20090106603A1Digital data processing detailsNon-redundant fault processingTime scheduleDiagnostic program
A computer is programmed to execute a diagnostic procedure either on a pre-set schedule or asynchronously in response to an event, such as an error message, or a user command. When executed, the diagnostic procedure automatically checks for integrity of one or more portions of data in the computer, to identify any failure(s). In some embodiments, the failure(s) may be displayed to a human, after revalidation to exclude any failure that no longer exists.
Owner:ORACLE INT CORP
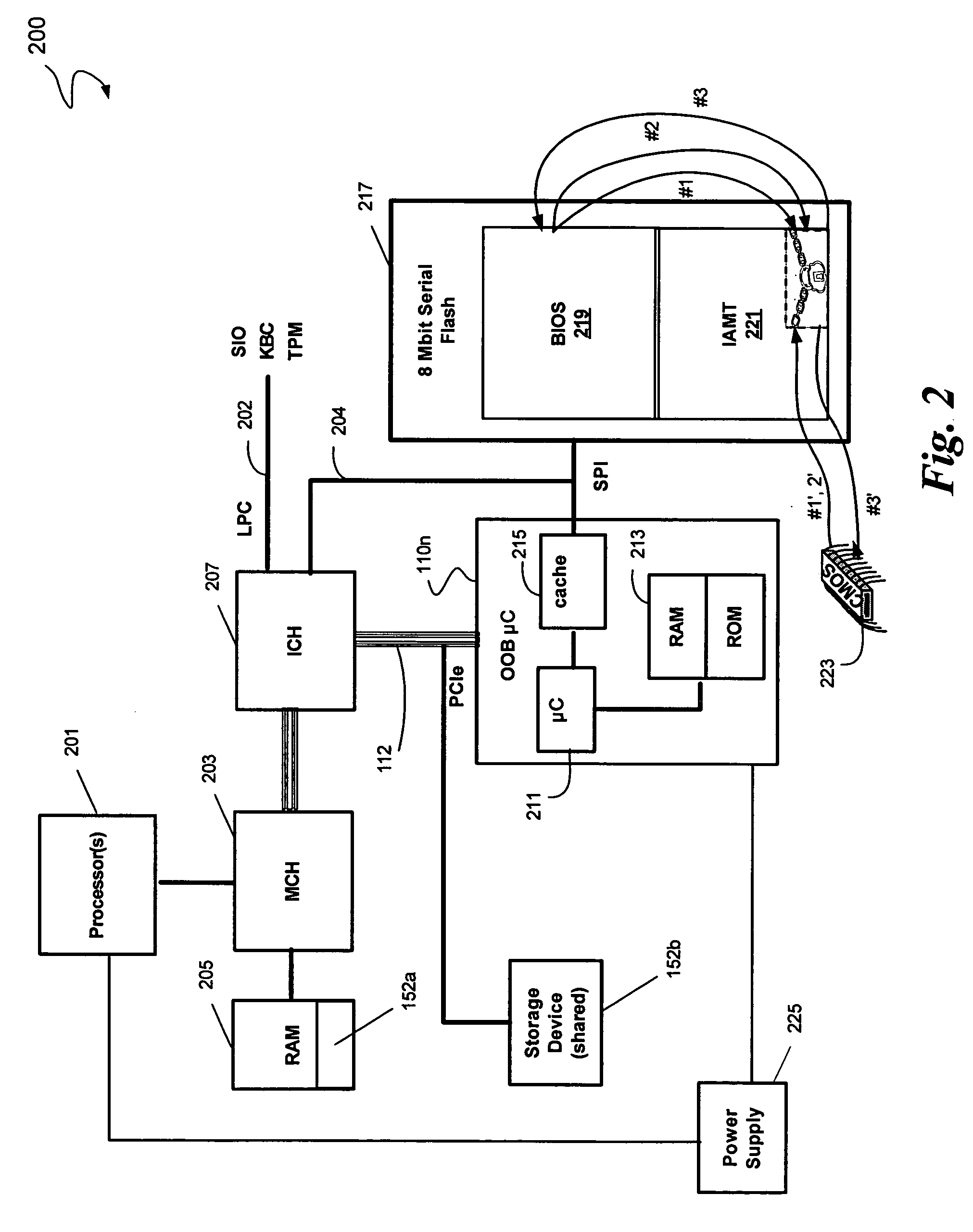
Method to provide autonomic boot recovery
In some embodiments, the invention involves a system and method relating to autonomic boot recovery. In at least one embodiment, the present invention utilizes an out-of-band (OOB) microcontroller to safeguard boot information to be used in the event of a boot failure. The OOB microcontroller enables the preservation of “Last Known Good” boot configurations as well as providing an agent to provide self-healing to a platform which might have run into some type of corruption of critical data. In some embodiments a variety of intelligent filter mechanisms are enabled to allow a user to target the preservation of only certain types of configuration data. Other embodiments are described and claimed.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Mobile imaging platform calibration
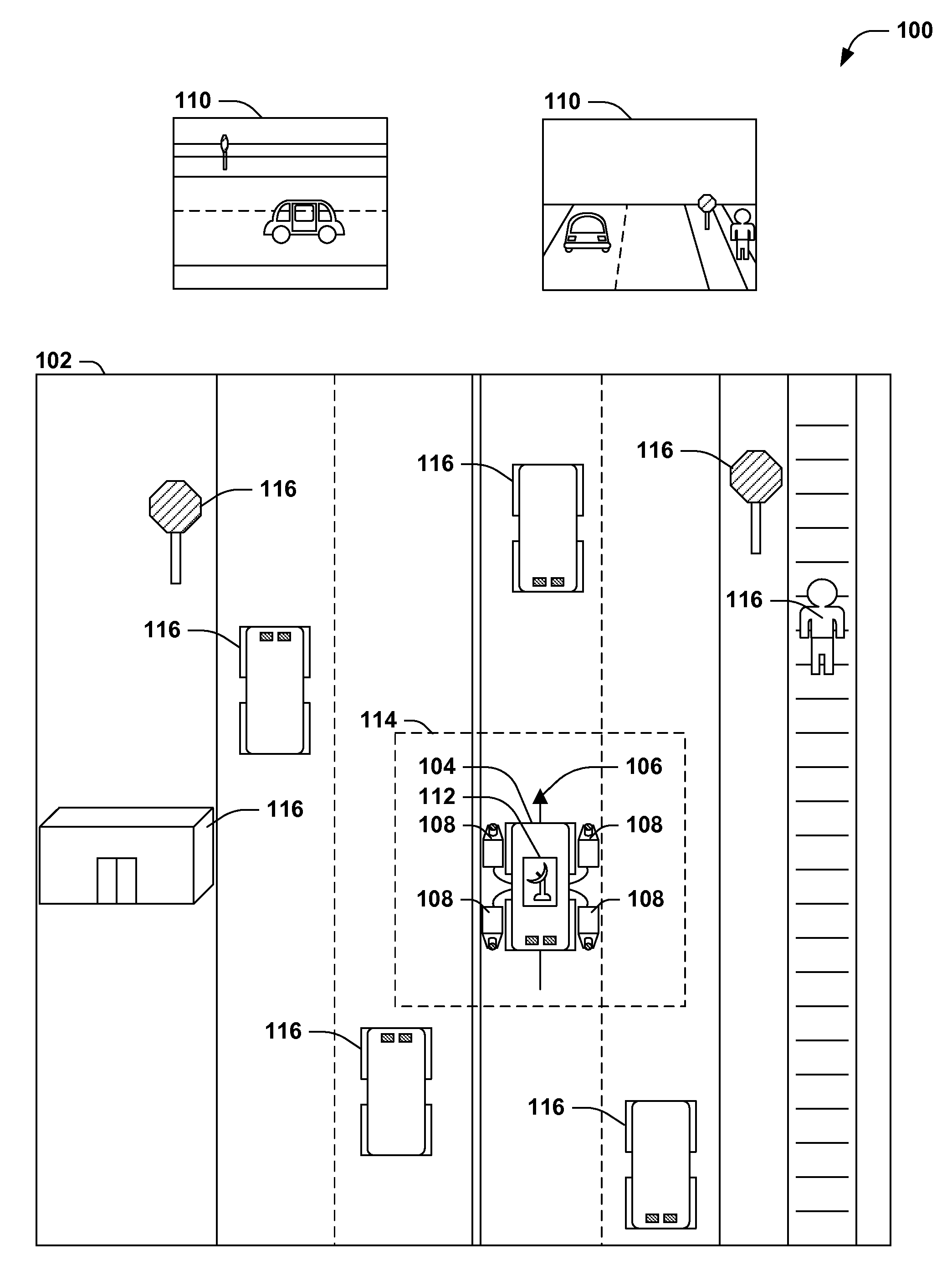
ActiveUS20140368651A1Faster and accurate techniqueLow efficiencyImage analysisOptical rangefindersLaser scanningComputer vision
Mobile platforms are used to capture an area using a variety of sensors (e.g., cameras and laser scanners) while traveling through the area, in order to create a representation (e.g., a navigable set of panoramic images, or a three-dimensional reconstruction). However, such sensors are often precisely calibrated in a controlled setting, and miscalibration during travel (e.g., due to a physical jolt) may result in a corruption of data and / or a recalibration that leaves the platform out of service for an extended duration. Presented herein are techniques for verifying sensor calibration during travel. Such techniques involve the identification of a sensor path for each sensor over time (e.g., a laser scanner path, a camera path, and a location sensor path) and a comparison of the paths, optionally after registration with a static coordinate system, to verify that the continued calibration of the sensors during the mobile operation of the platform.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com