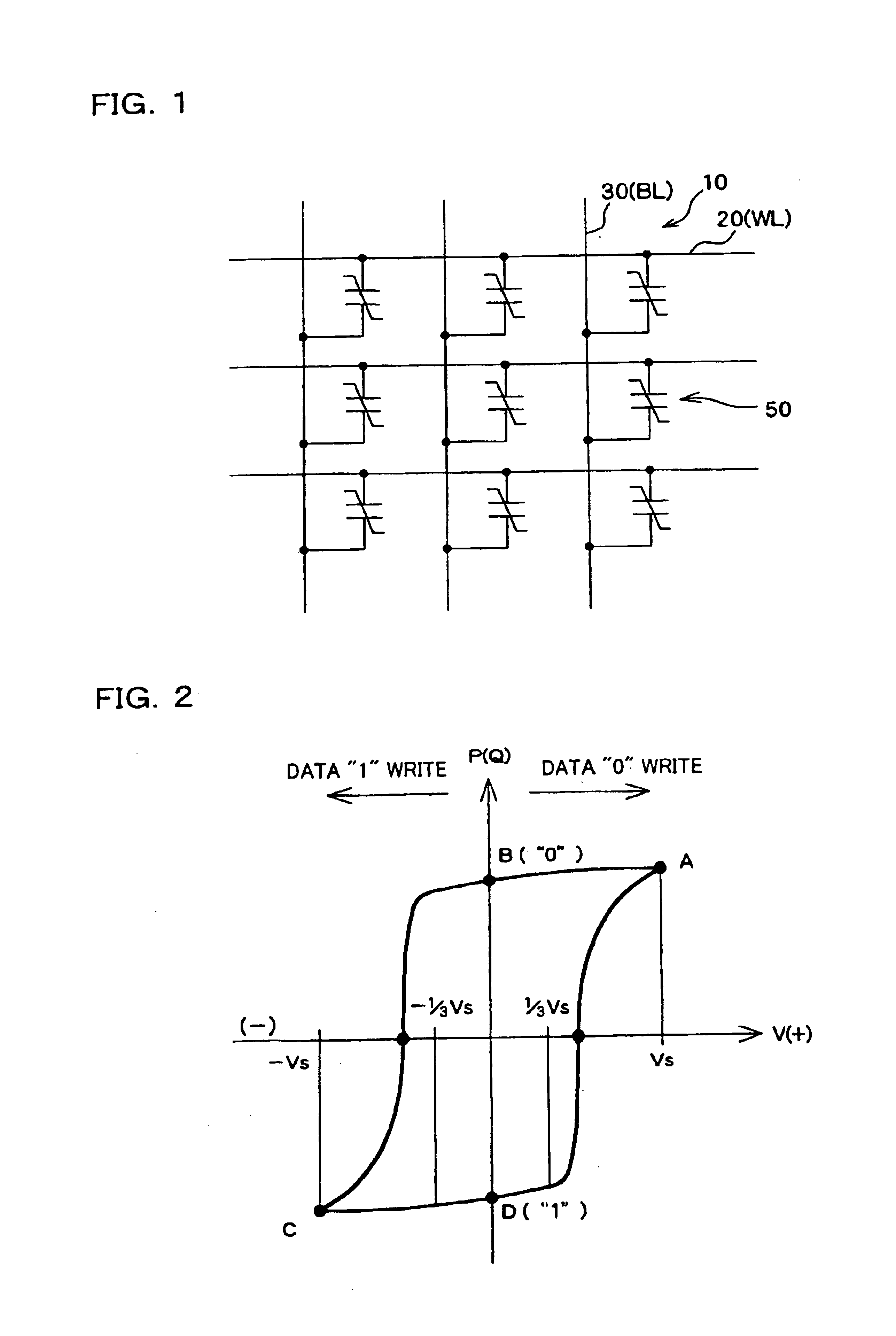
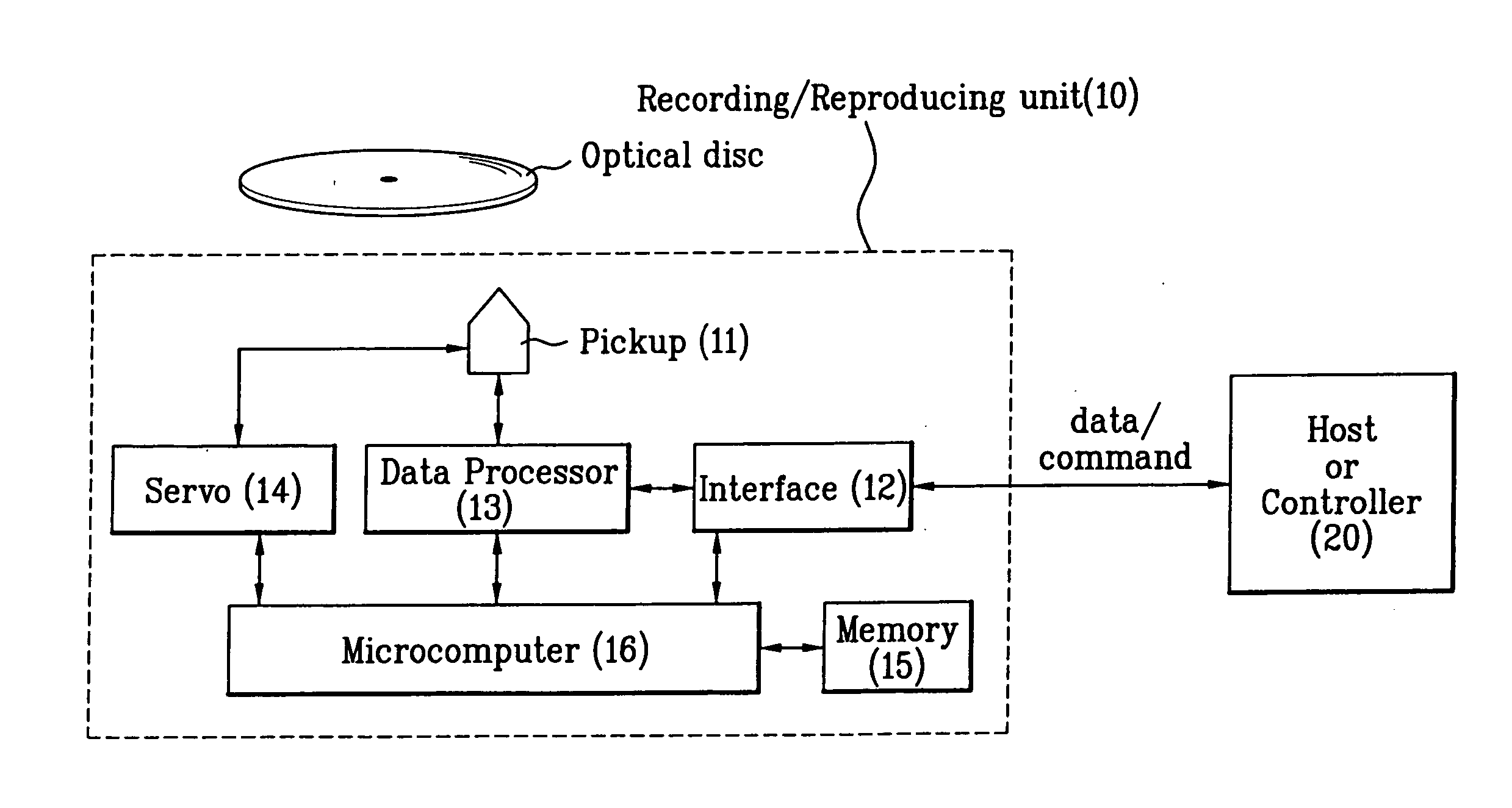
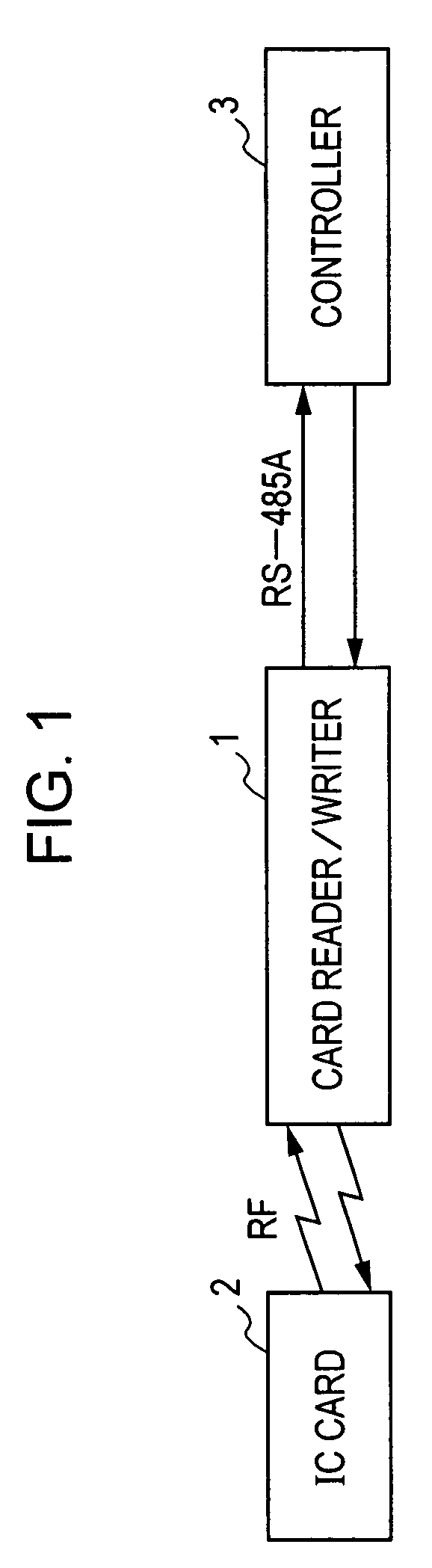
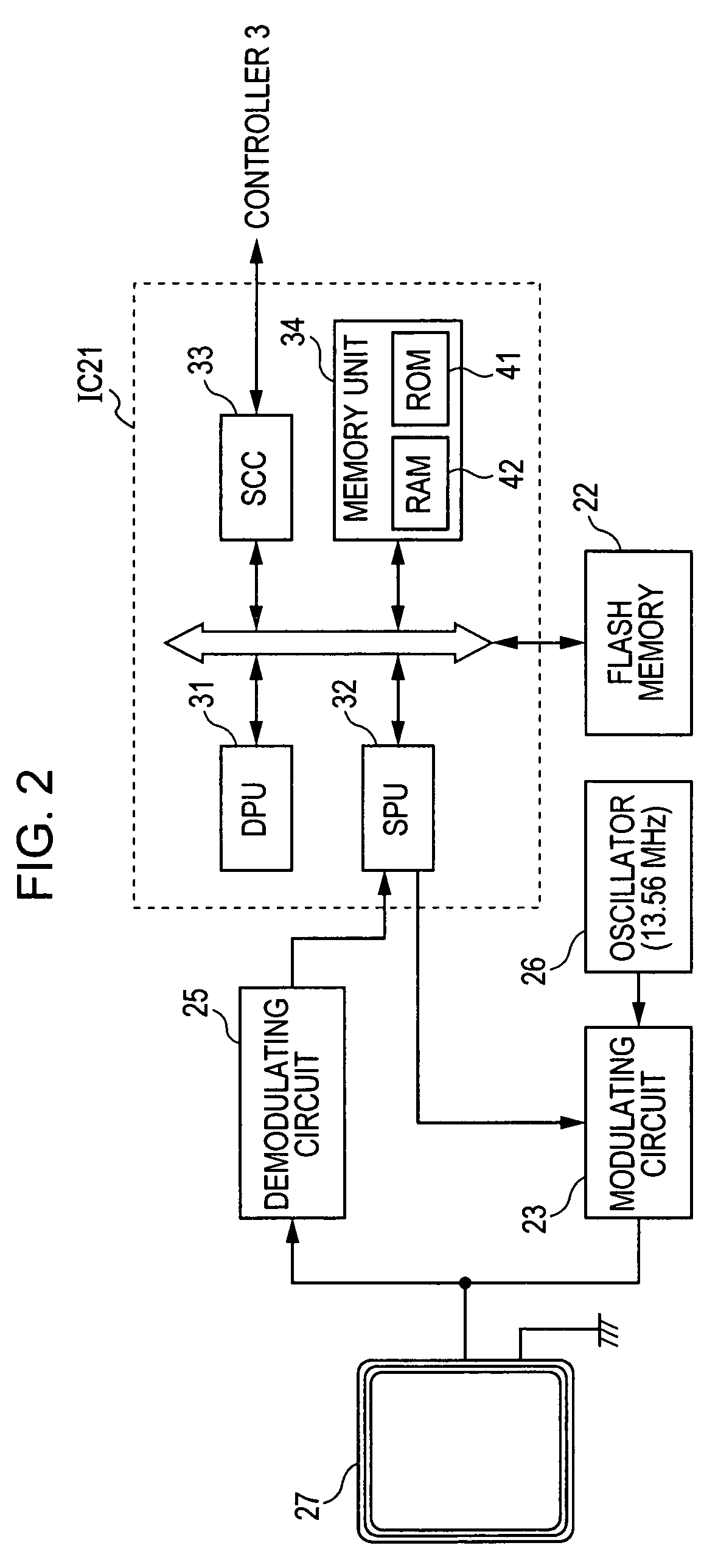
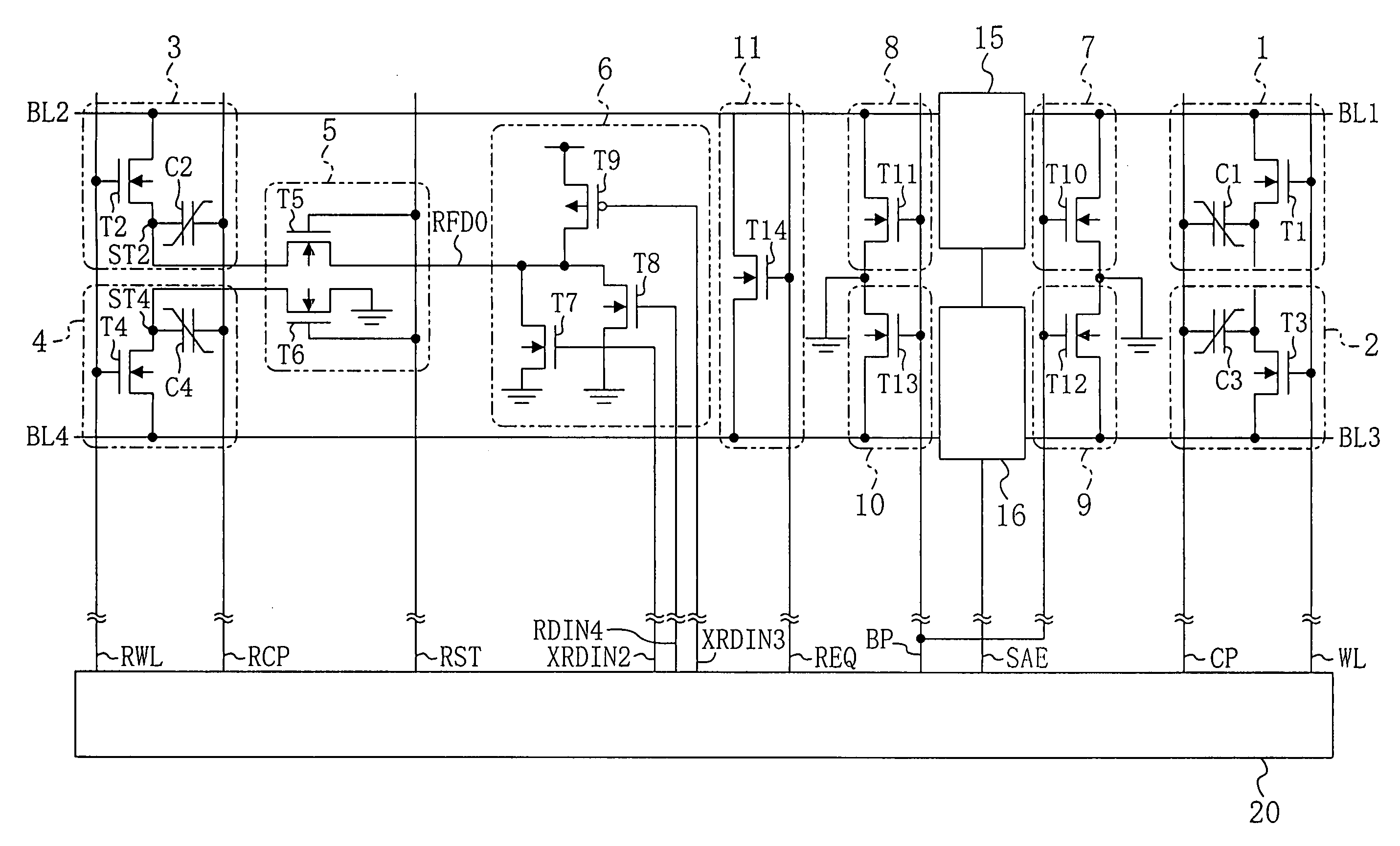
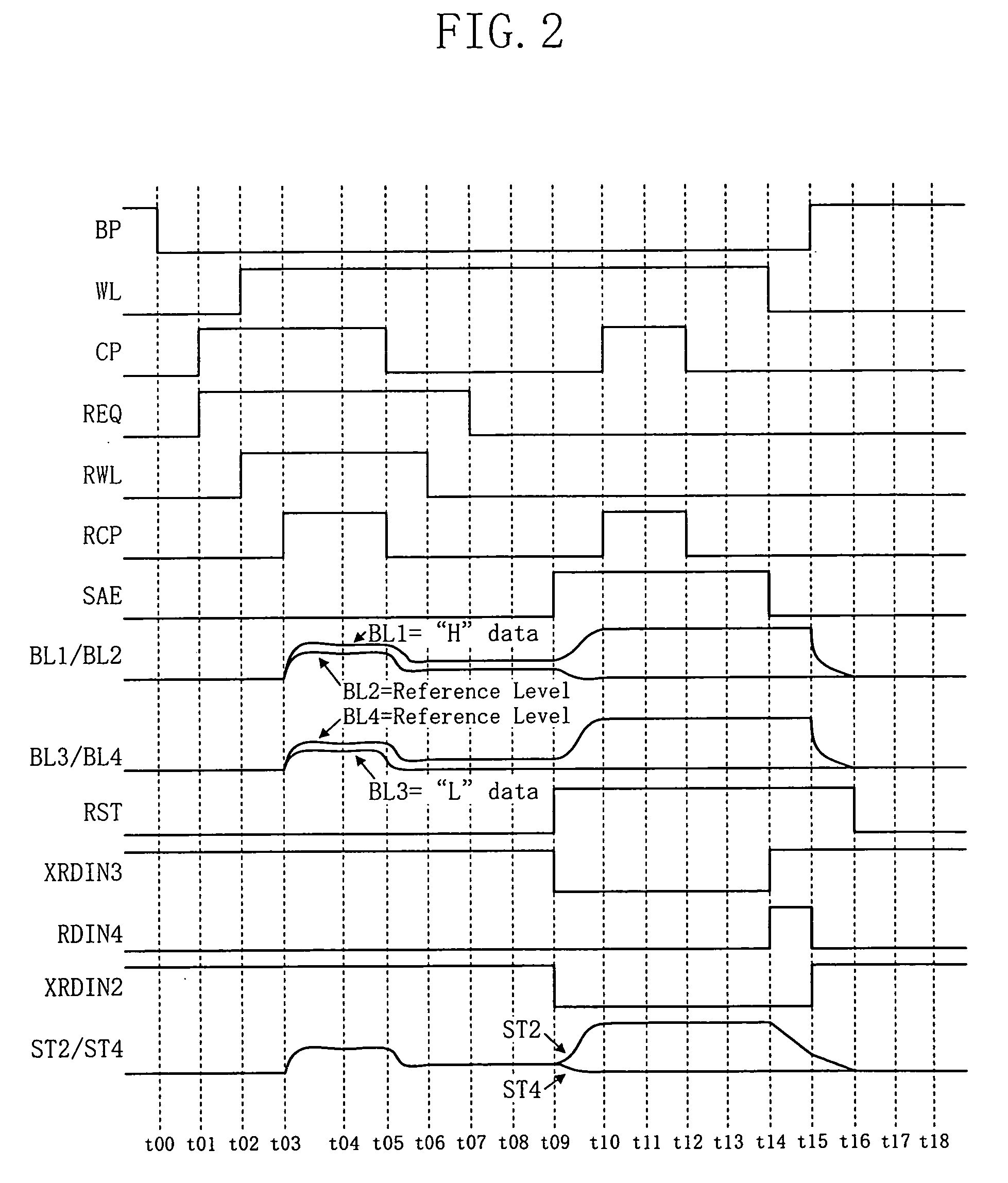
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
112results about How to "Avoid data corruption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
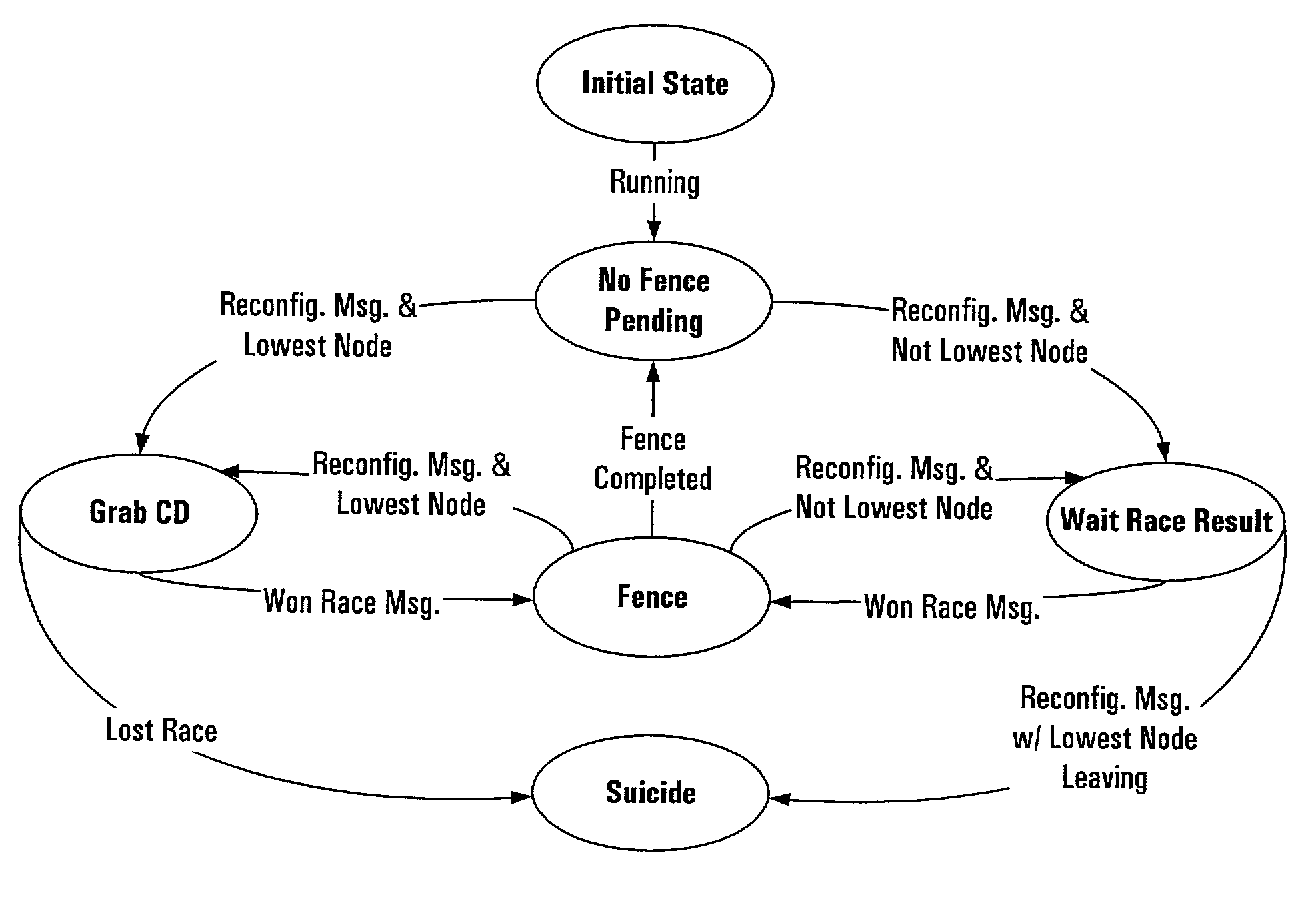
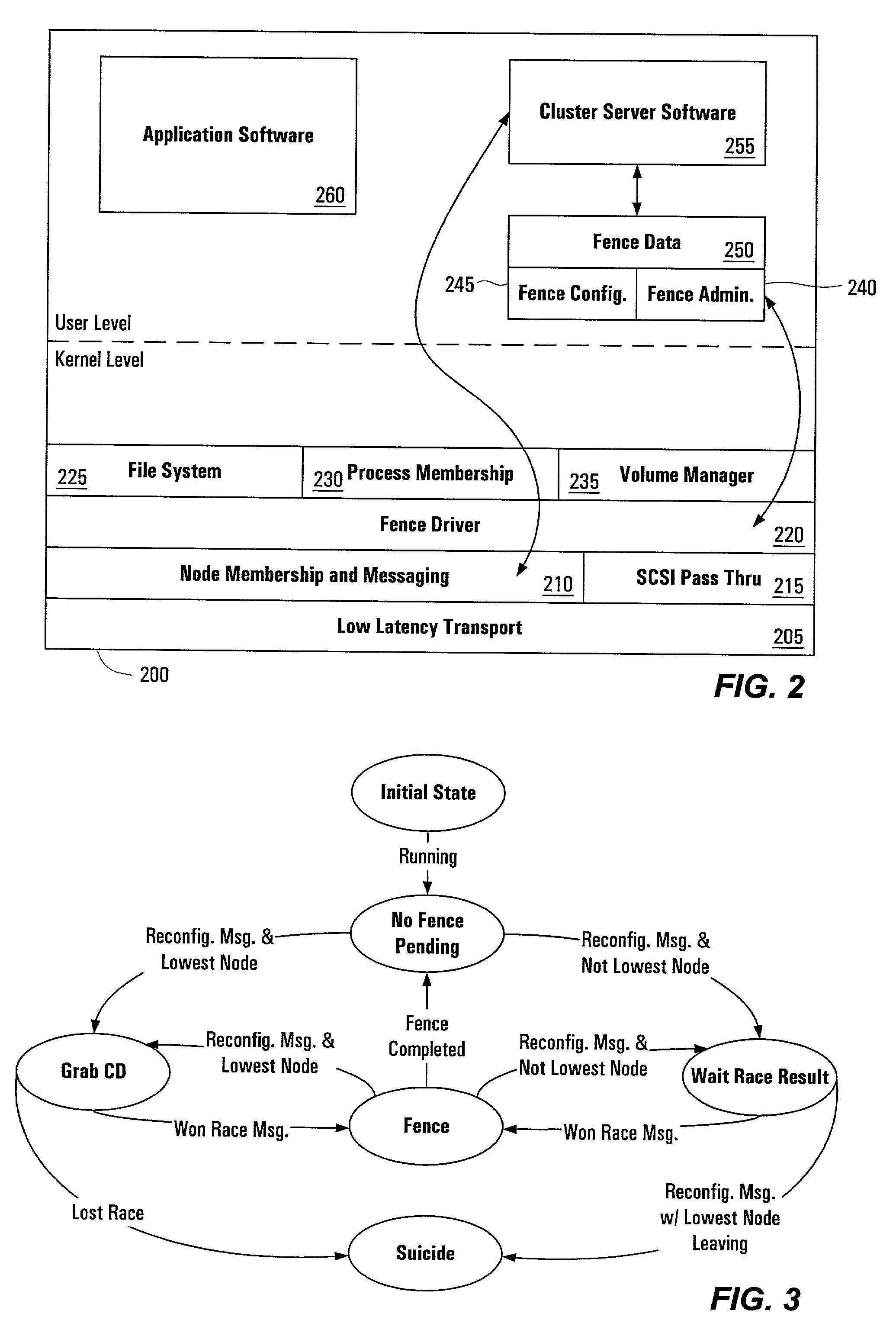
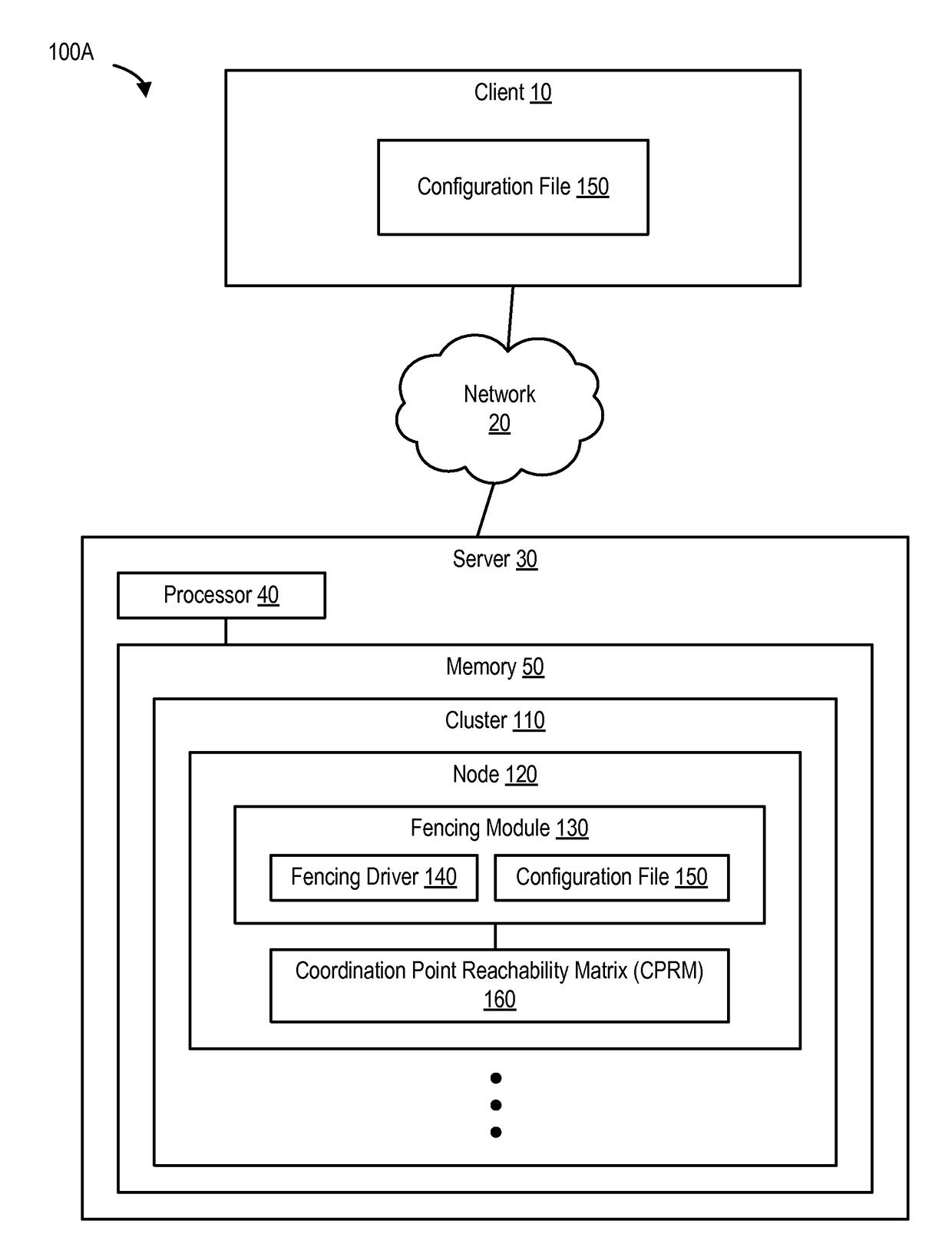
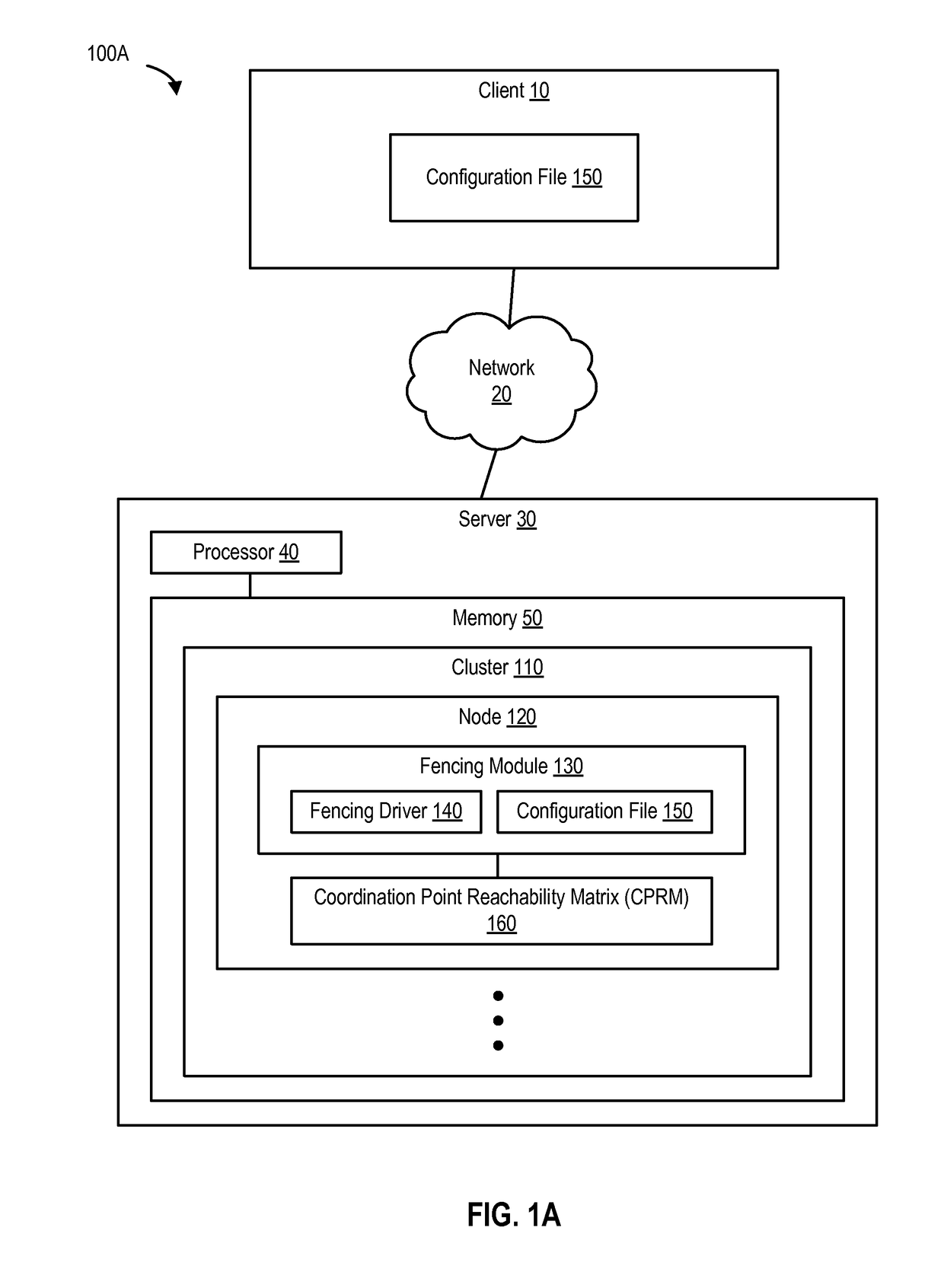
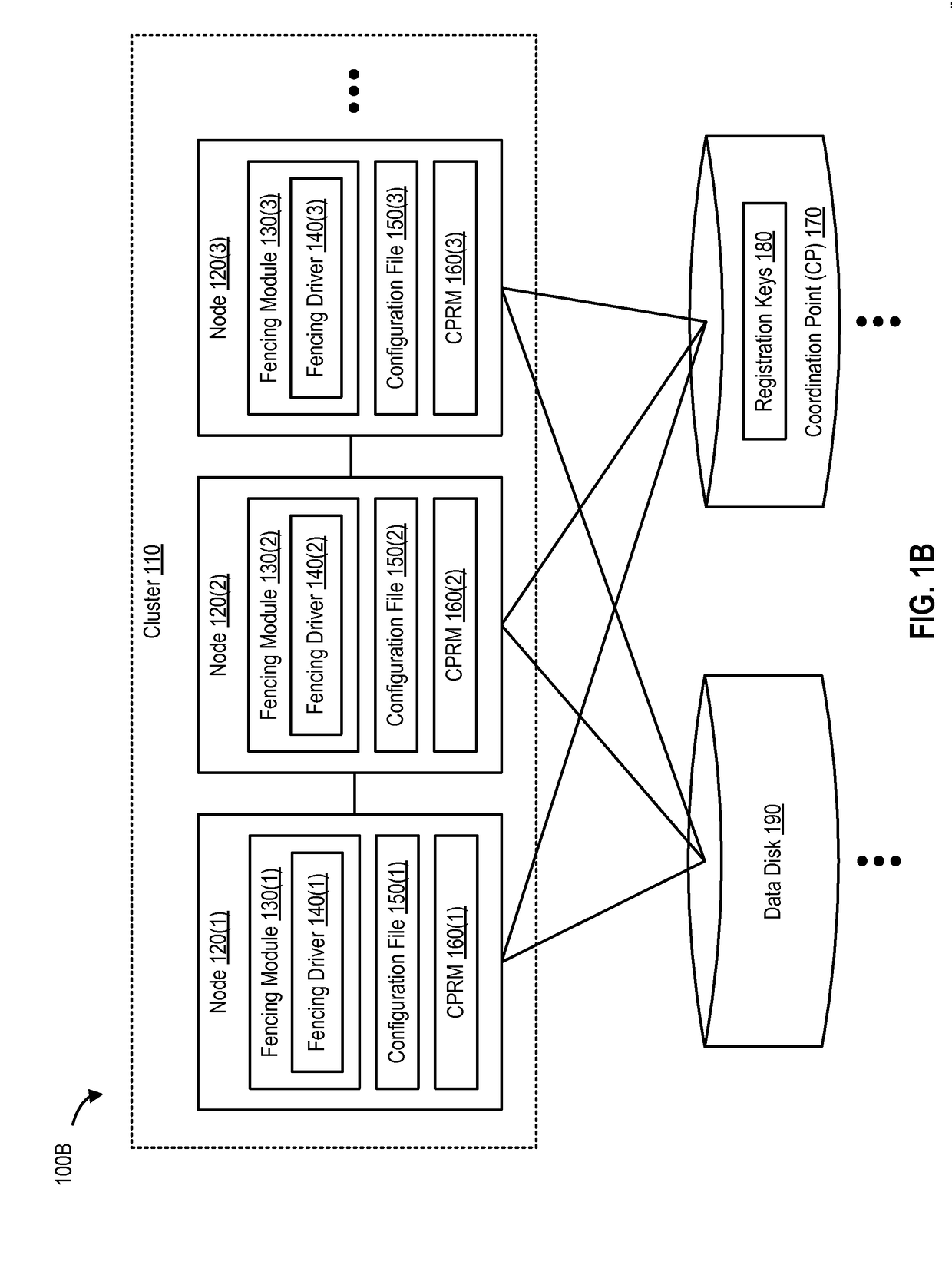
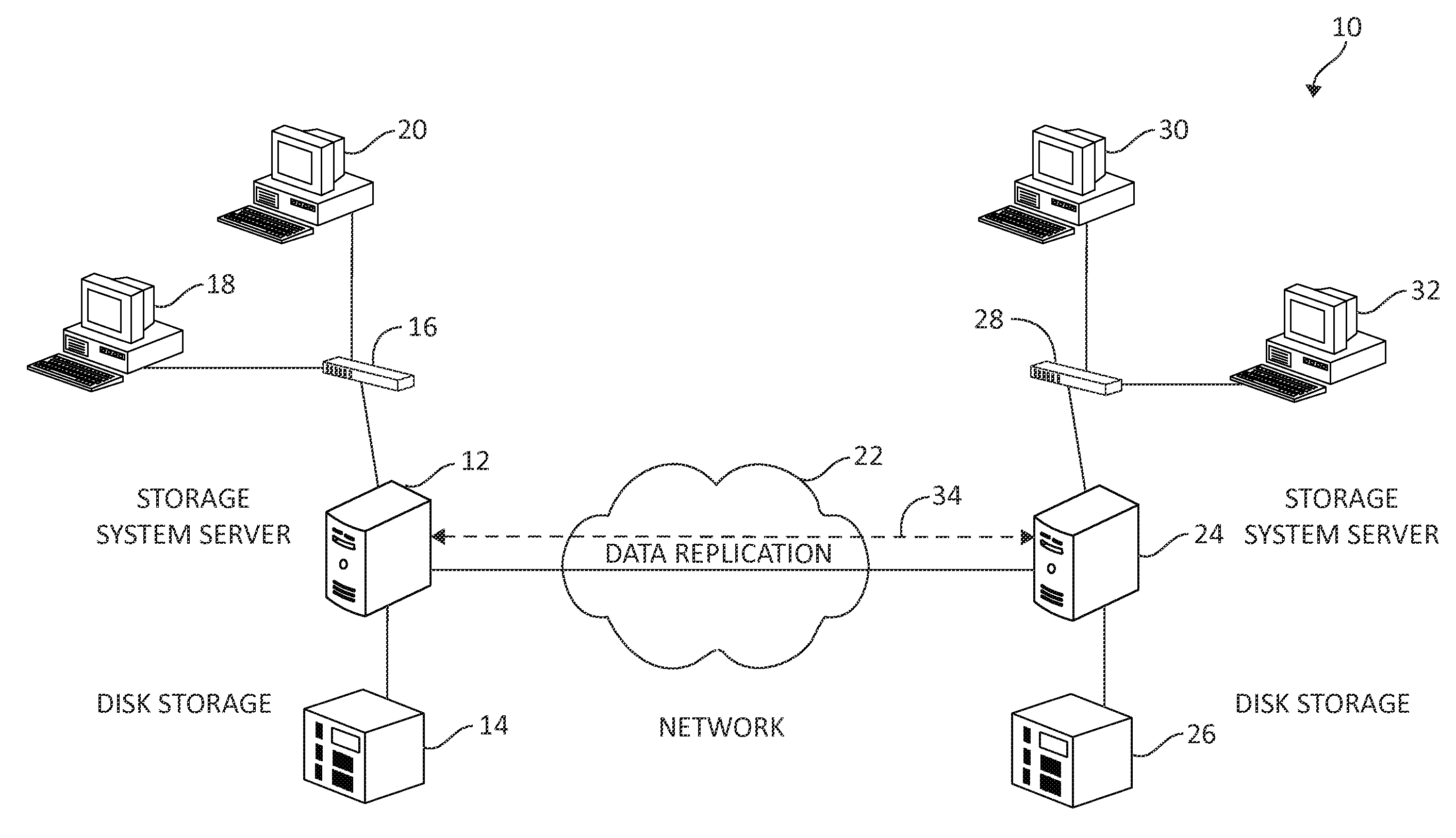
System and method for preventing data corruption in computer system clusters
InactiveUS7631066B1Reduce failover timeImprove the problemError detection/correctionDigital computer detailsCluster systemsComputerized system
Systems, methods, apparatus and software can make use of coordinator resources and SCSI-3 persistent reservation commands to determine which nodes of a cluster should be ejected from the cluster, thereby preventing them from corrupting data on a shared data resource. Fencing software operating on the cluster nodes monitors the cluster for a cluster partition (split-brain) event. When such an event occurs, software on at least two of the nodes attempts to unregister other nodes from a majority of coordinator resources. The node that succeeds in gaining control of the majority of coordinator resources survives. Nodes failing to gain control of a majority of coordinator resources remove themselves from the cluster. The winning node can also proceed to unregister ejected nodes from shared data resources. These operations can be performed in parallel to decrease failover time. The software can continue to execute on all nodes to prevent additional problems should a node erroneously attempt to reenter the cluster.
Owner:SYMANTEC OPERATING CORP
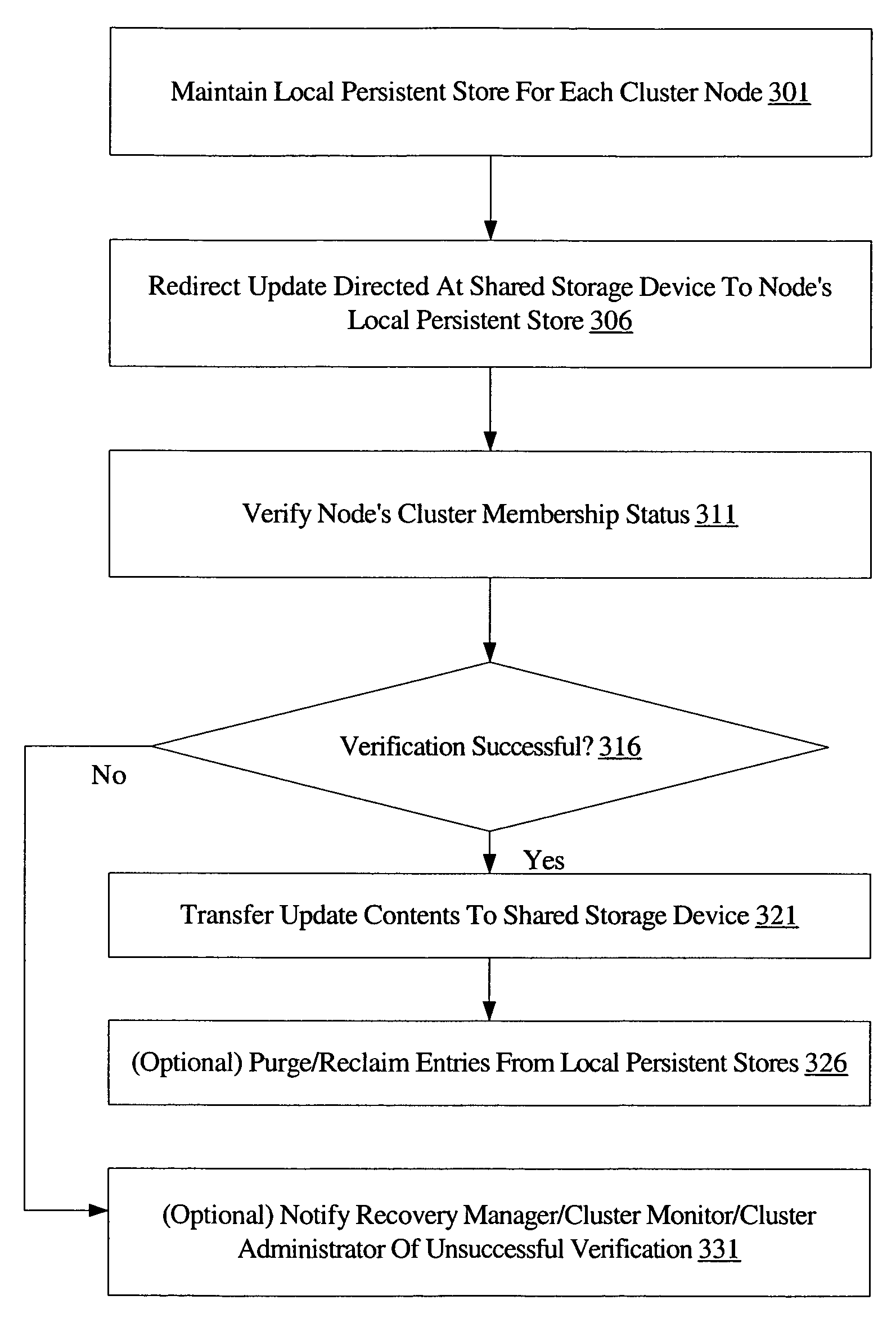
System and method to prevent data corruption due to split brain in shared data clusters
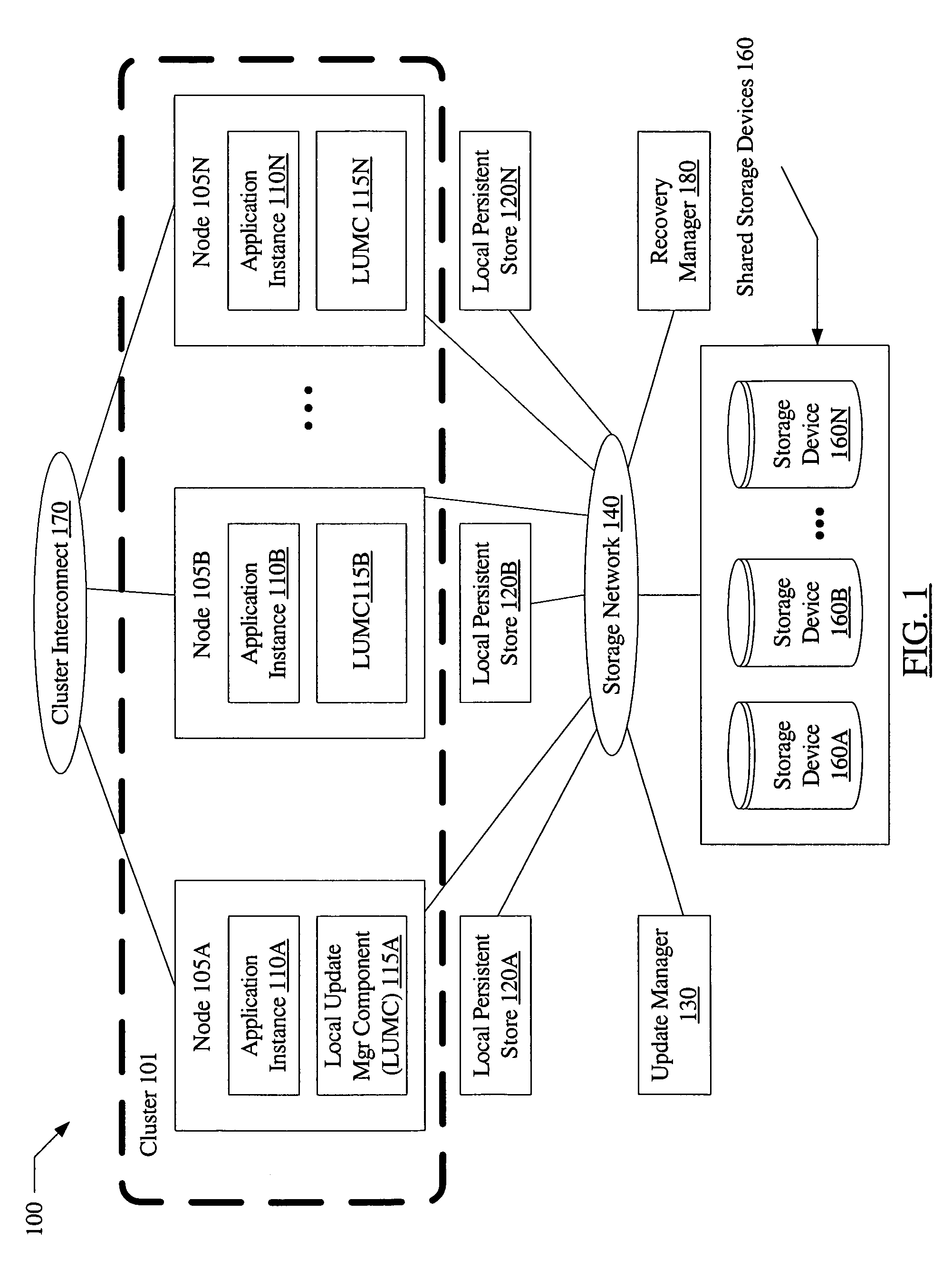
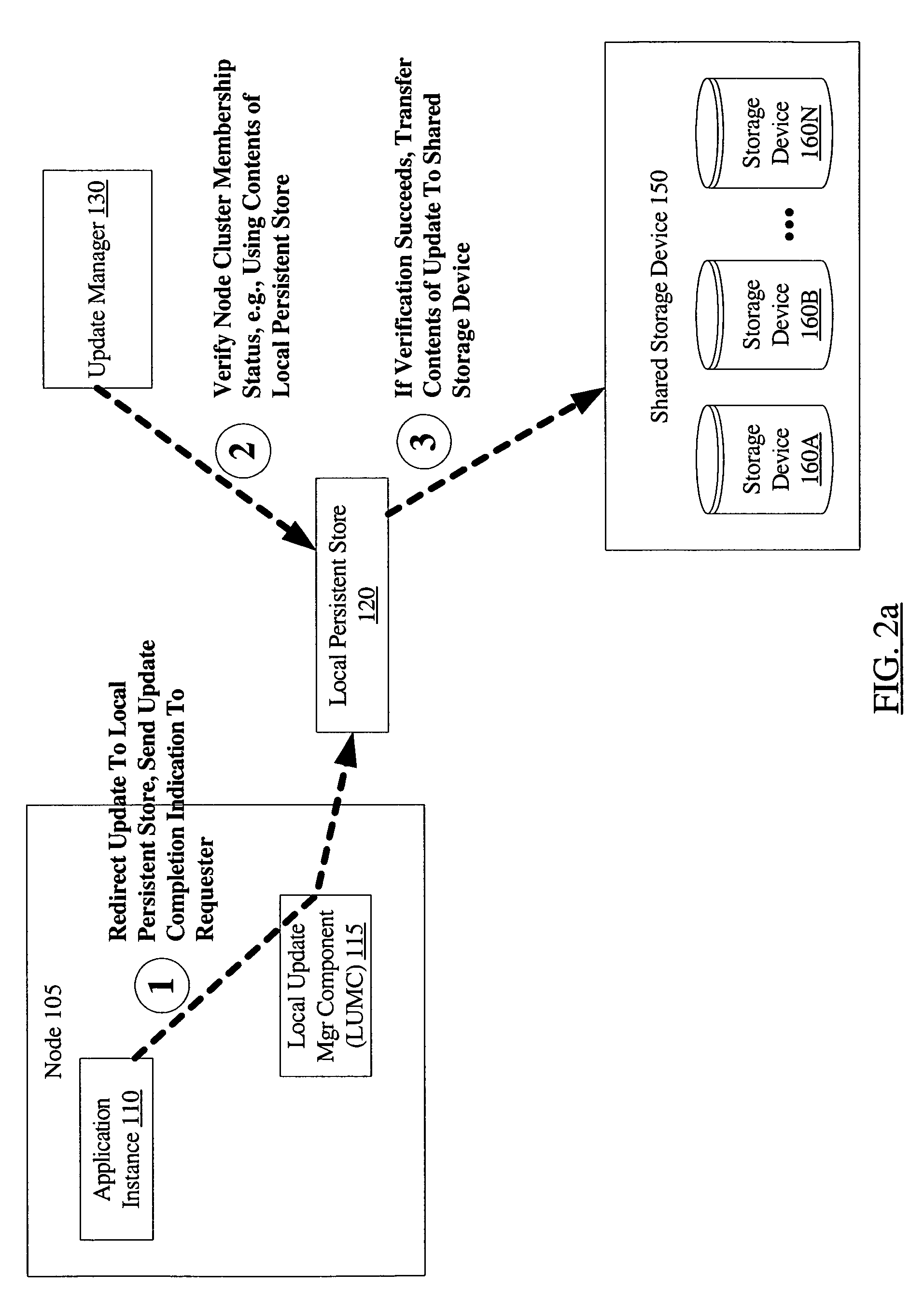
ActiveUS7739677B1Avoid data corruptionDigital data processing detailsError detection/correctionSplit-brainData Corruption
A system and to prevent data corruption due to split brain in shared data clusters includes two or more nodes of a cluster, a shared storage device, and an update manager. The update manager may be configured to maintain a local persistent store corresponding to each node of the cluster. On receiving an update request directed to the shared storage device from a first node, the update manager may be configured to redirect the update to the local persistent store corresponding to the first node. The update manager may be further configured to verify a cluster membership status of the first node, and to transfer the contents of the update from the local persistent store to the shared storage device if the cluster membership verification succeeds.
Owner:SYMANTEC OPERATING CORP
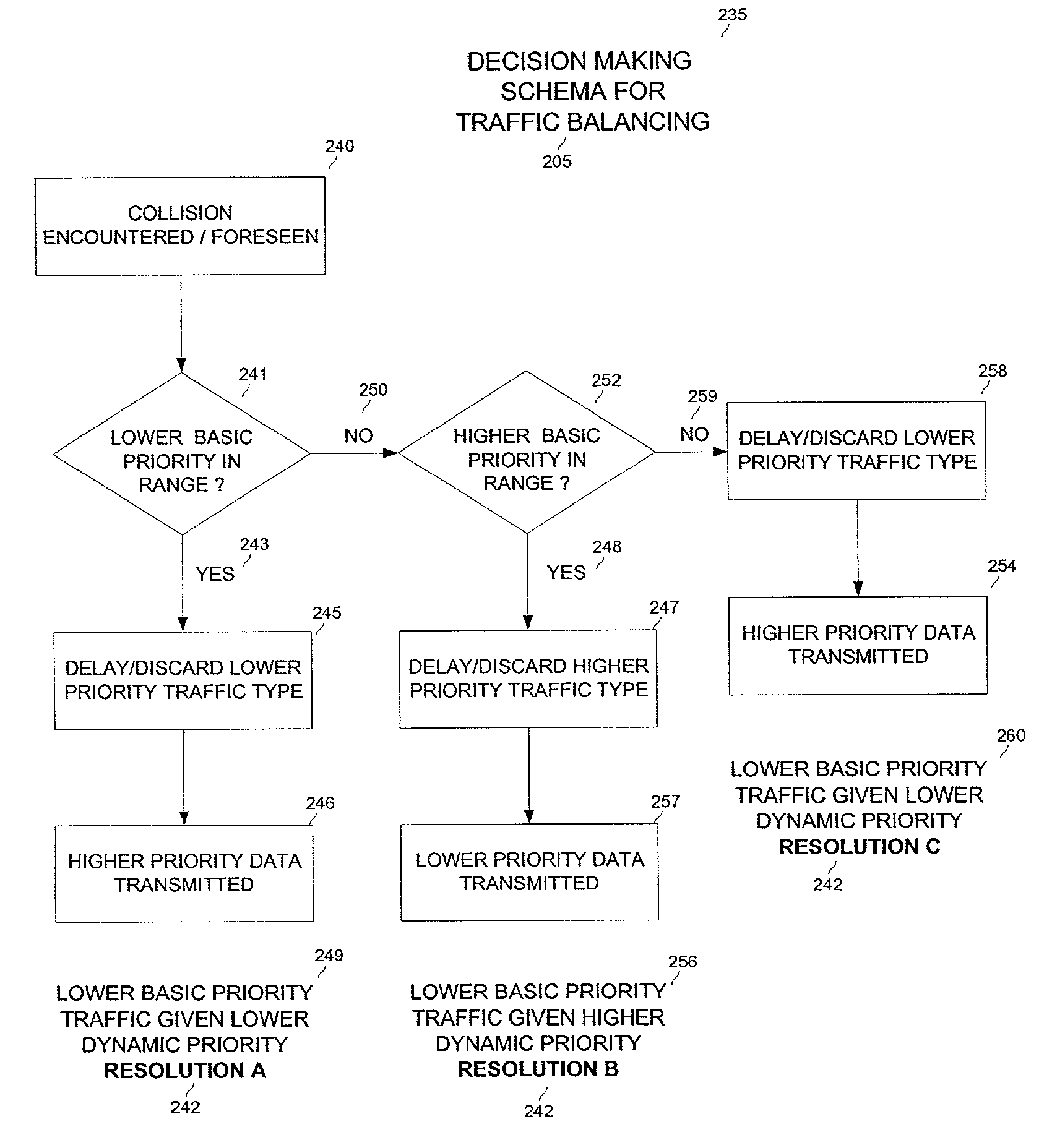
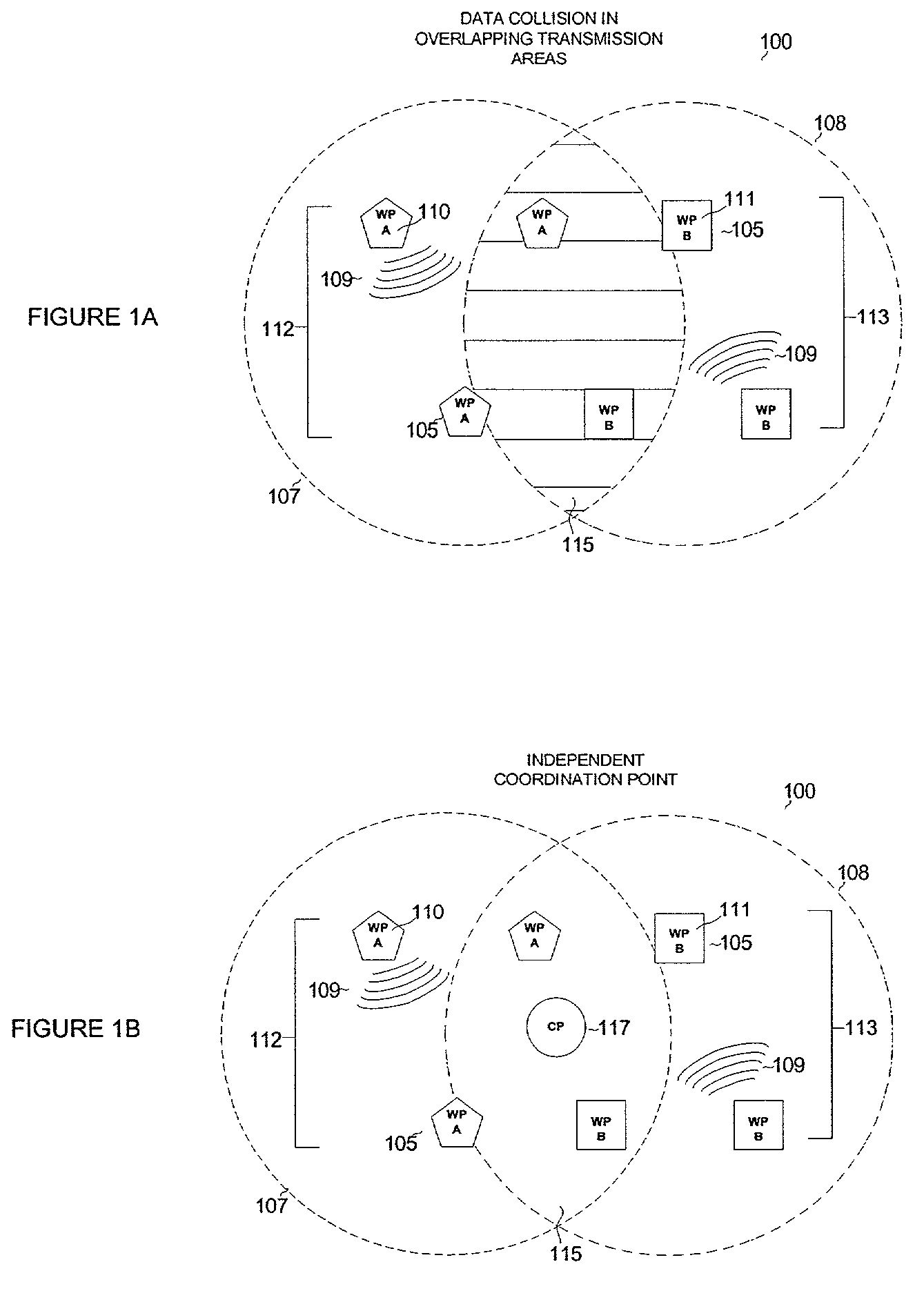
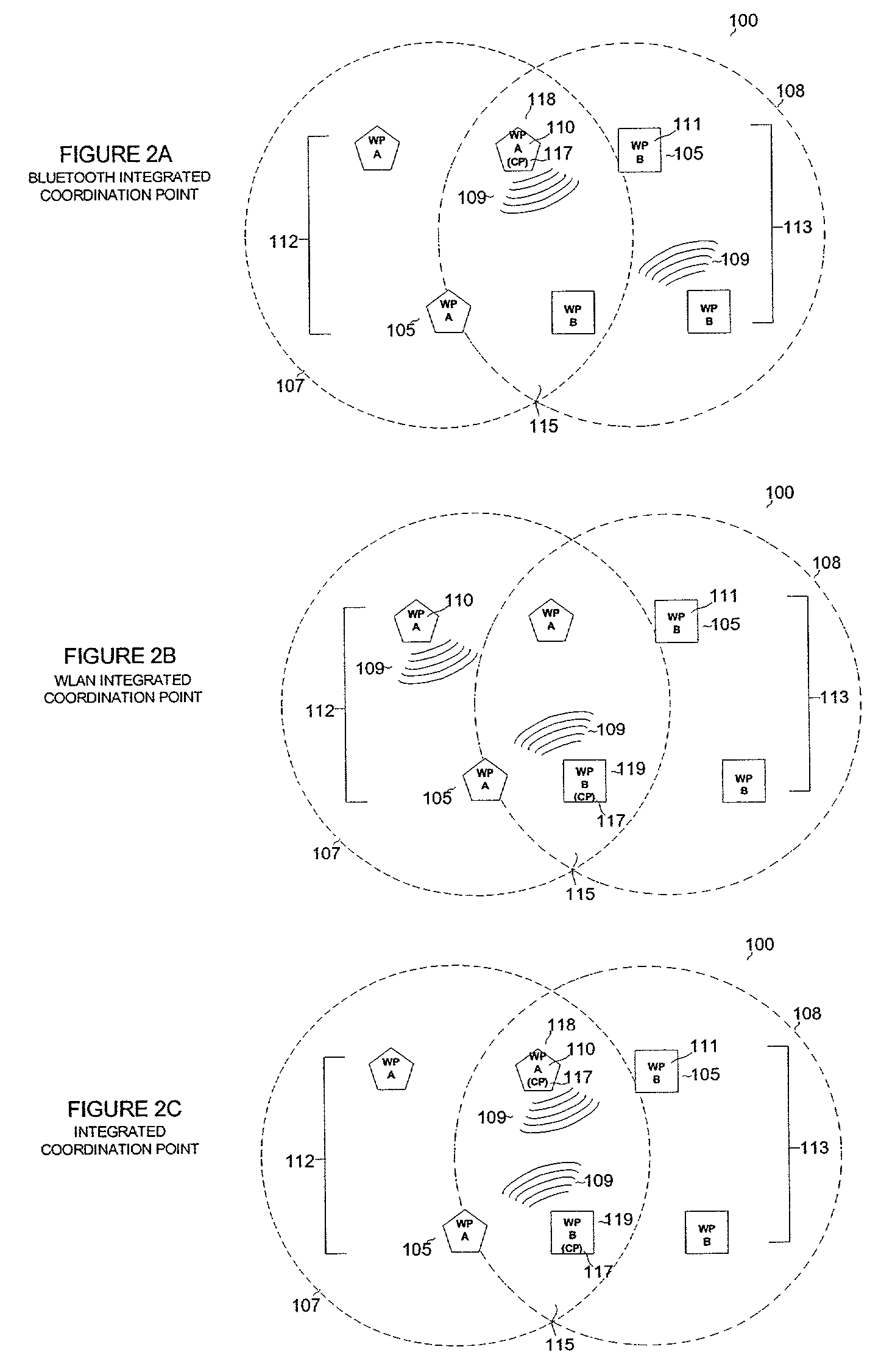
Coordination architecture for wireless communication devices using multiple protocols
ActiveUS7233602B2Reduce collisionImprove current qualityError prevention/detection by using return channelNetwork traffic/resource managementQuality of servicePointing device
A system and methods for coordinating transmissions in a wireless network wherein a plurality of frequency-overlapping protocols are used to exchange information between devices. In this system, a coordination point device integrates a monitoring functionality to identify impending data collisions between the frequency-overlapping protocols. The coordination point device further identifies quality of service parameters to determine if the protocols are operating within desirable ranges. Moderation one or more of the protocols is then performed to avoid data collisions arising from overlapping transmissions between the protocols while maintaining data throughput within acceptable ranges.
Owner:AVAGO TECH INT SALES PTE LTD
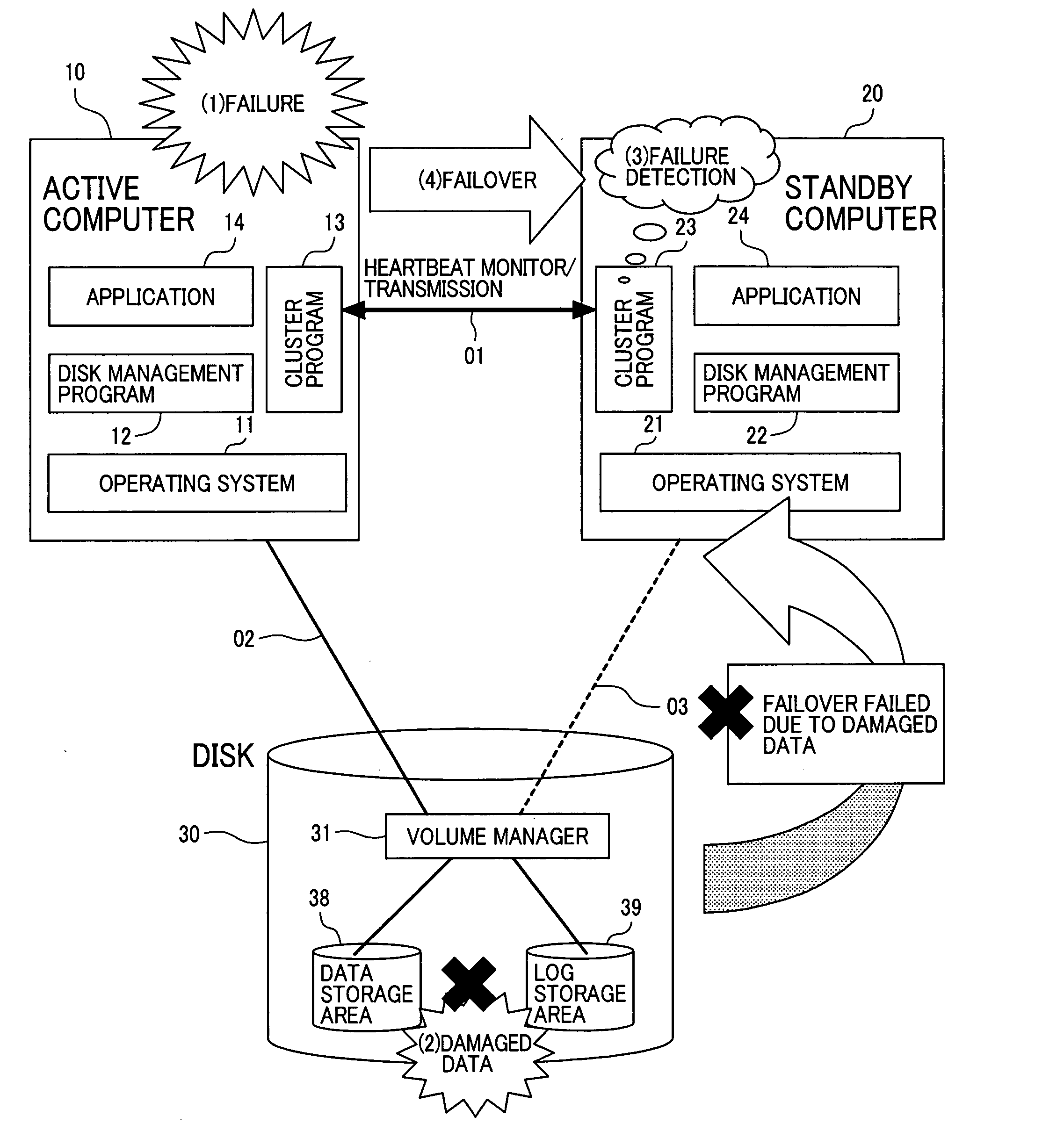
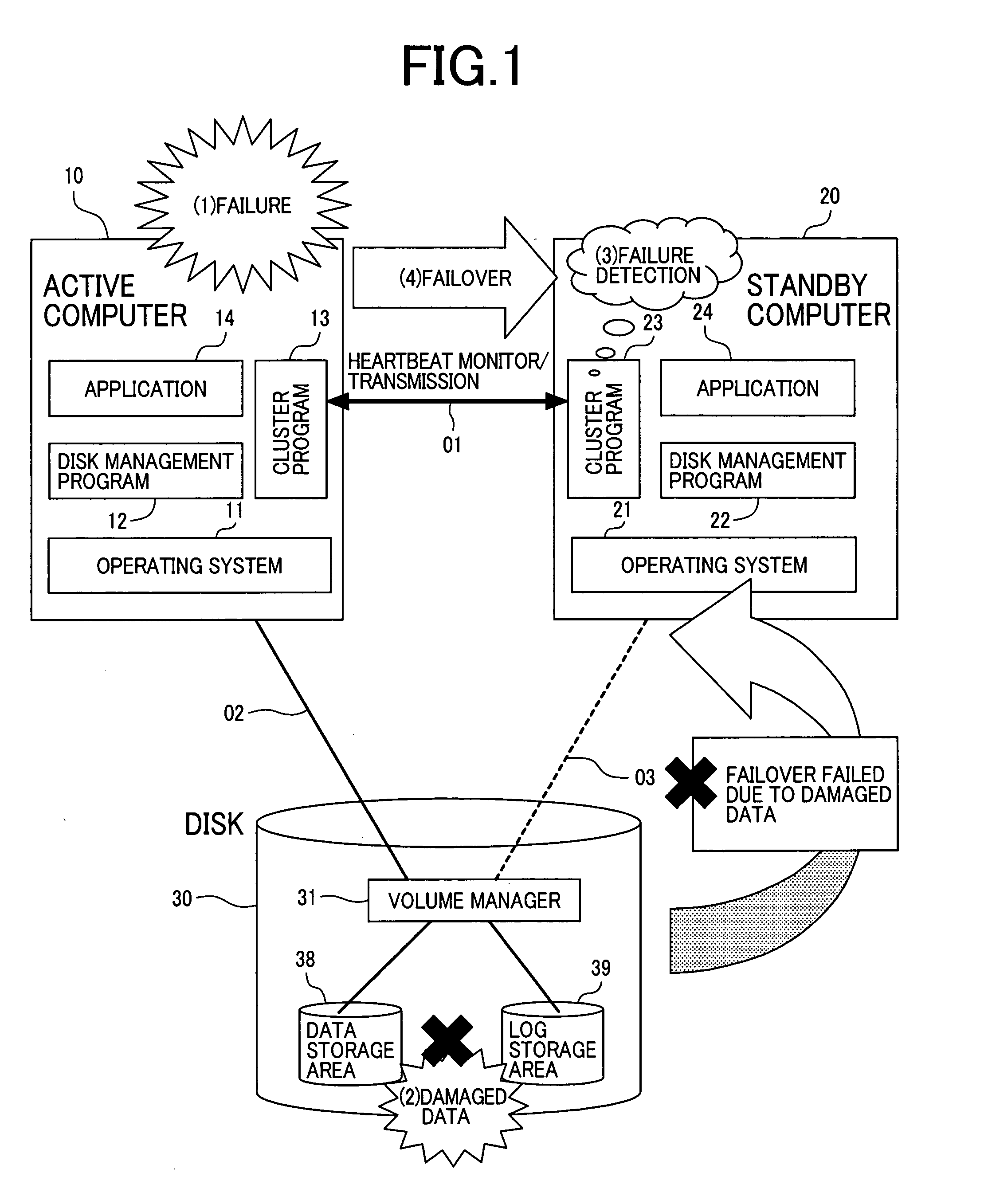
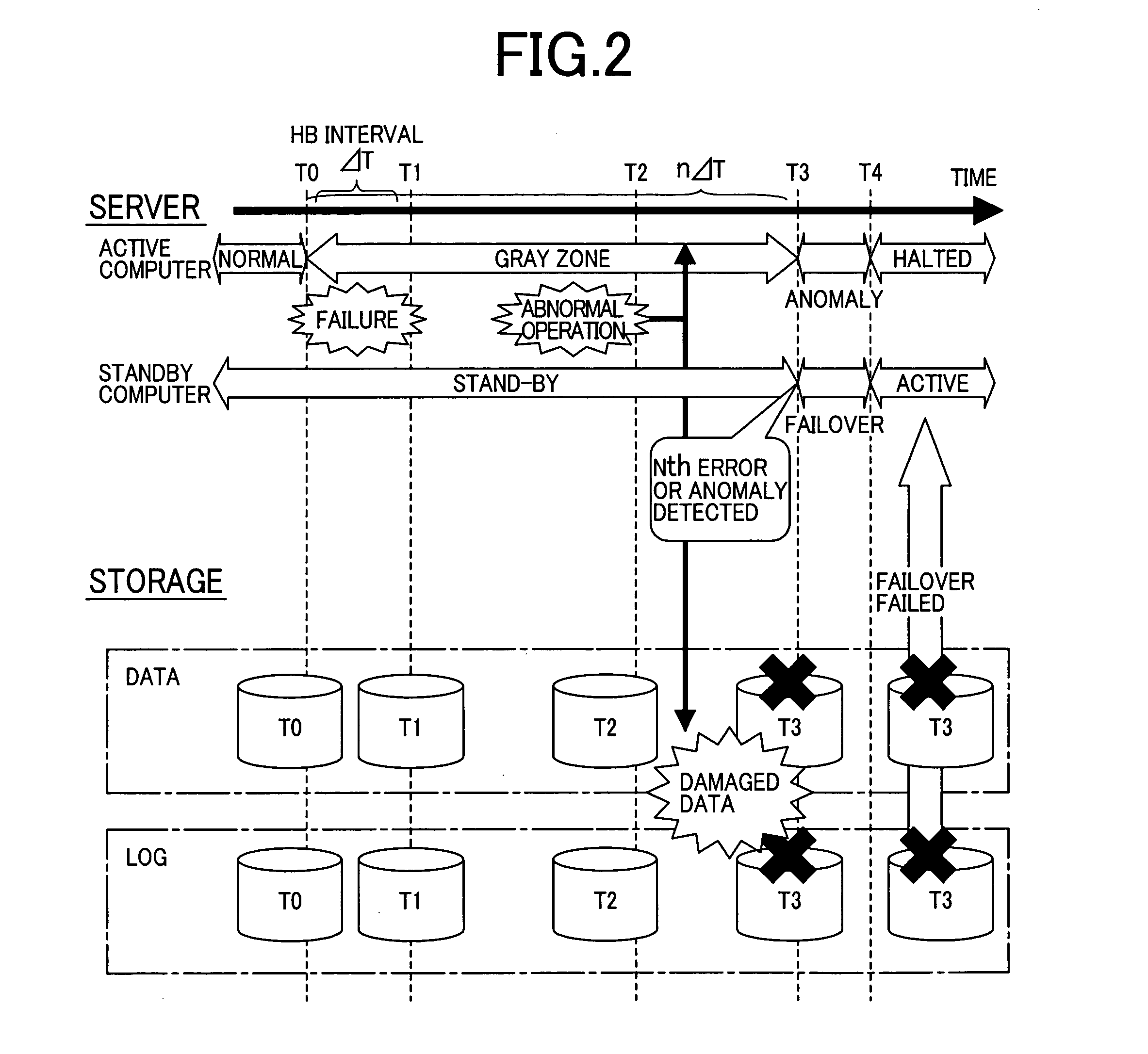
Failover method in a redundant computer system with storage devices
InactiveUS20050050392A1Avoid data corruptionPrevent corruptionMemory systemsRedundant hardware error correctionFailoverHigh availability
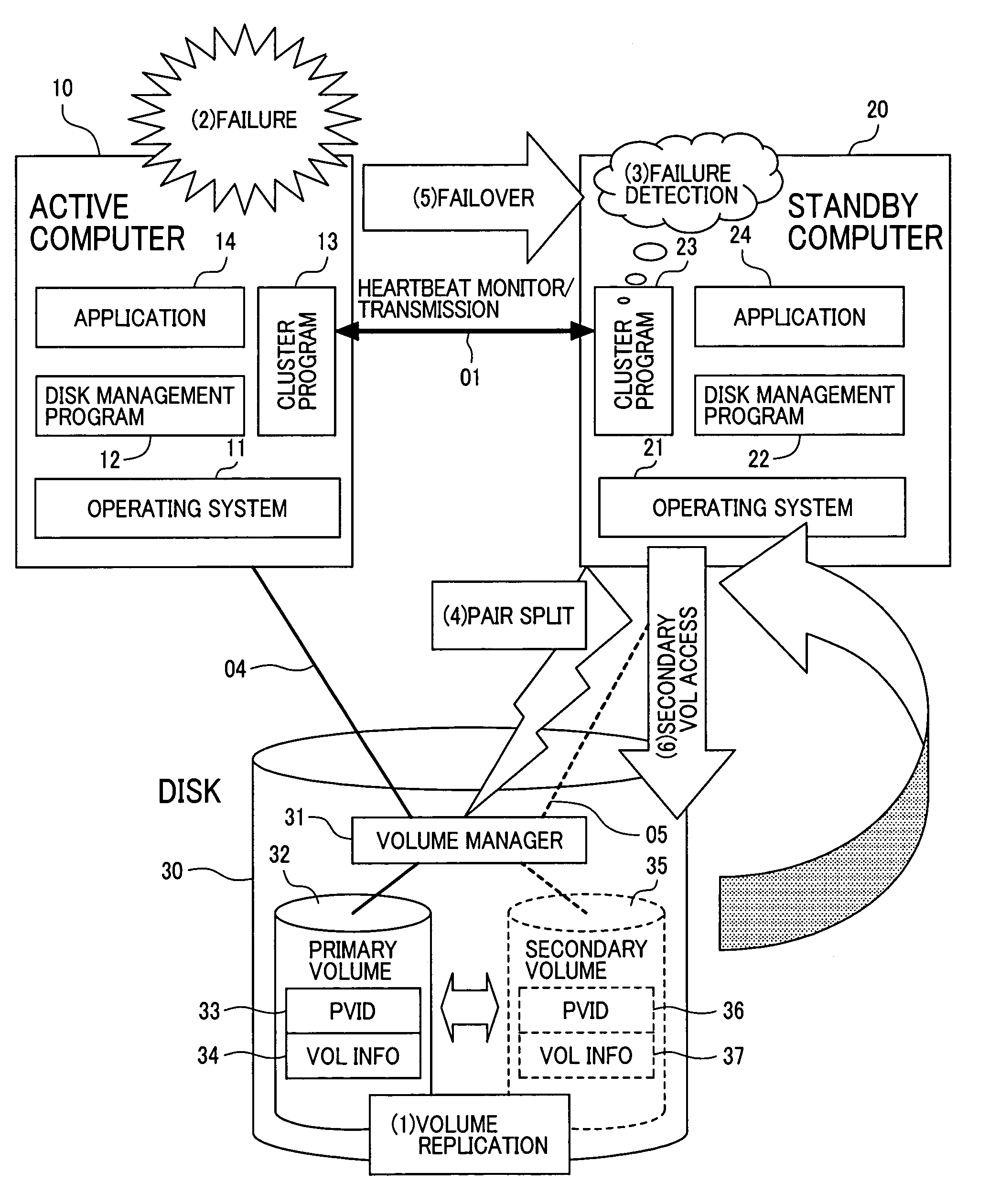
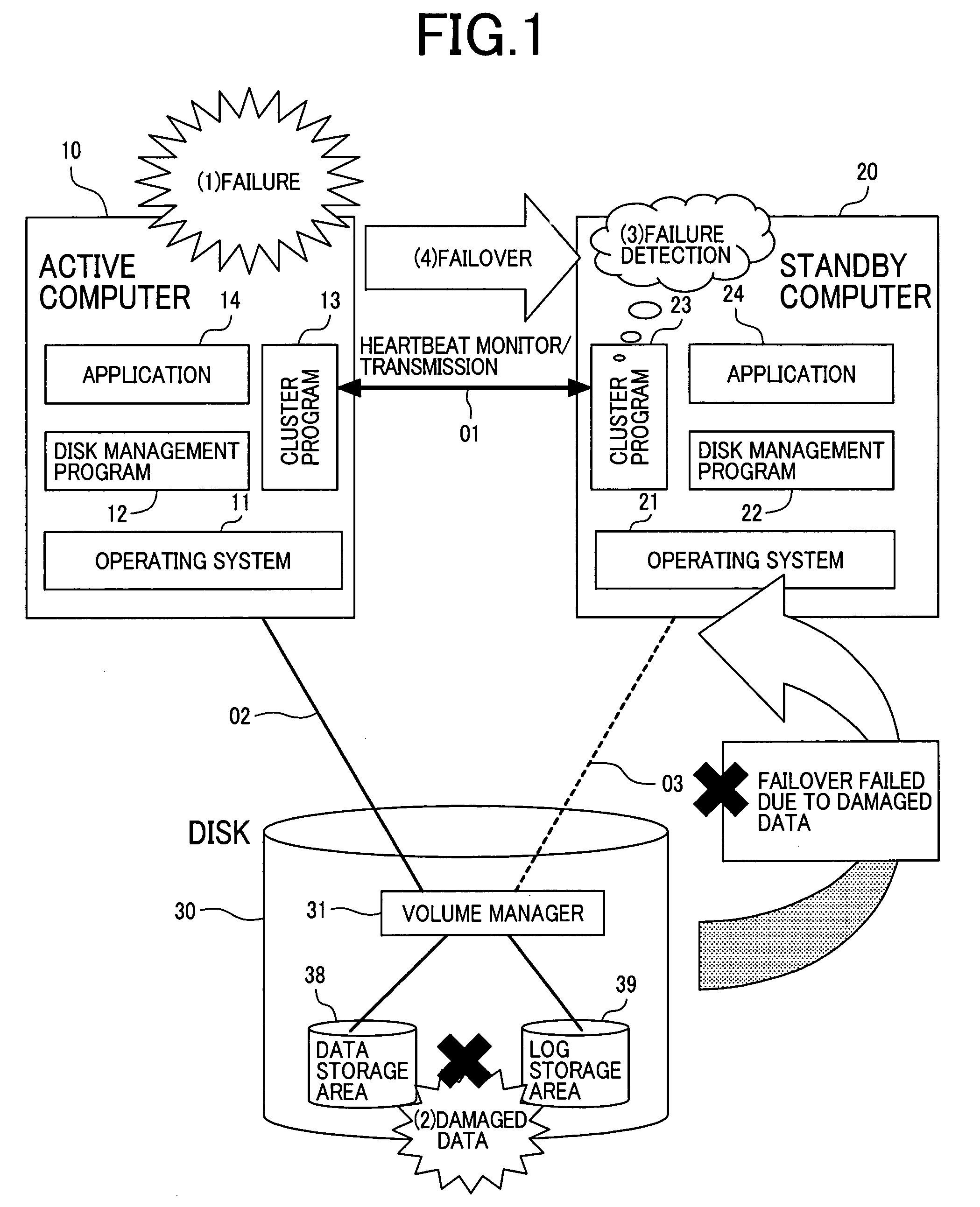
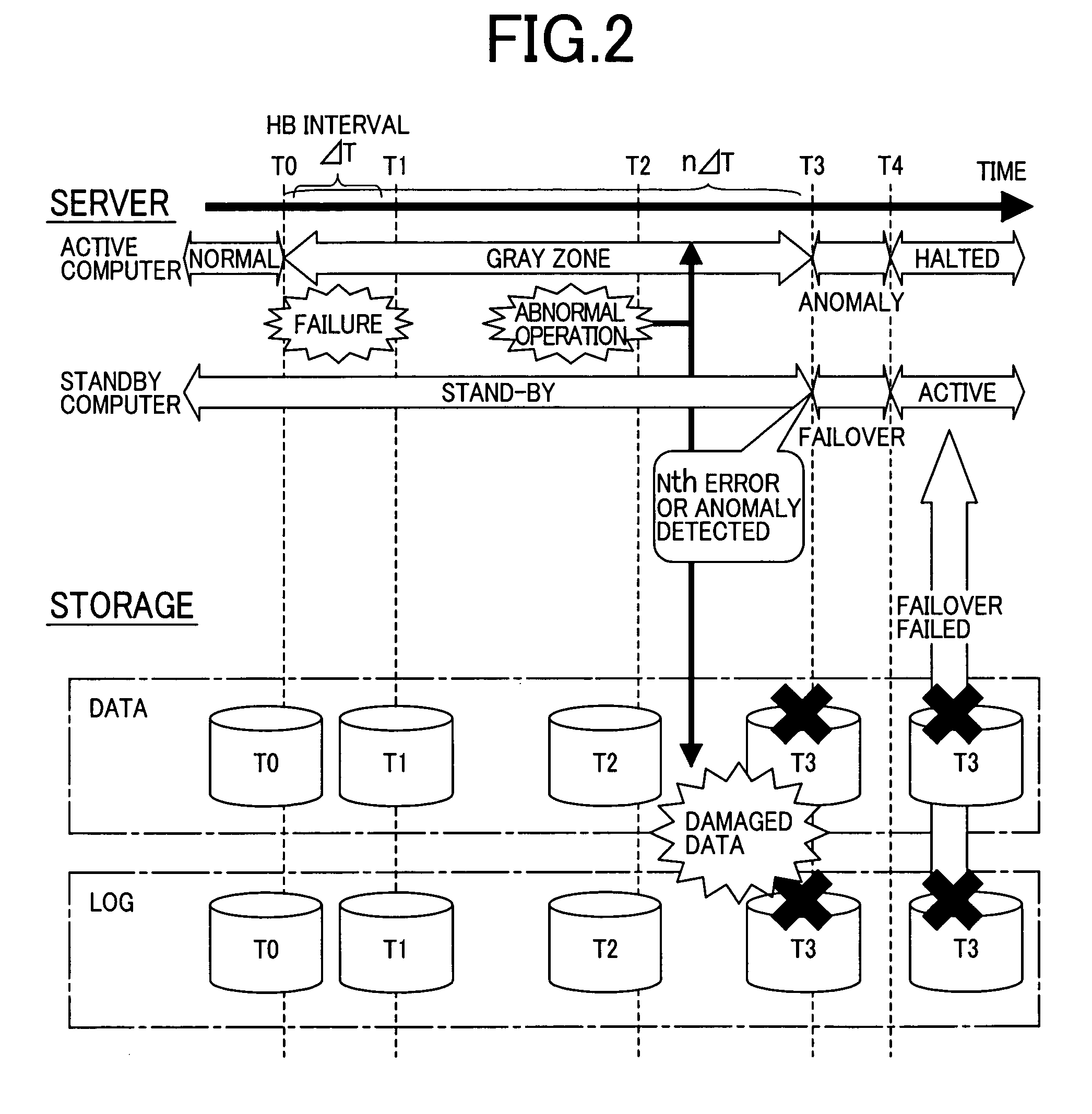
A high availability database system, subject to a failure causing data corruption in the active server system, may recover valid data prior to the corruption, and use the protected and recovered data to effect a failover. At the time T1 when a stand-by computer system detects the occurrence of a failure, a pair split is done to the data area to protect the data area time T0, just before the occurrence of the failure, and another pair split is done to the log area at the time, where the log area is corrupted or a time T3, where the failover is to take effect without corrupting data, to protect the log area containing data at a given time between time TO and time T3. By using the data and log areas thus protected, the stand-by computer system may take over valid data and log areas of the given time to perform a failover.
Owner:HITACHI LTD
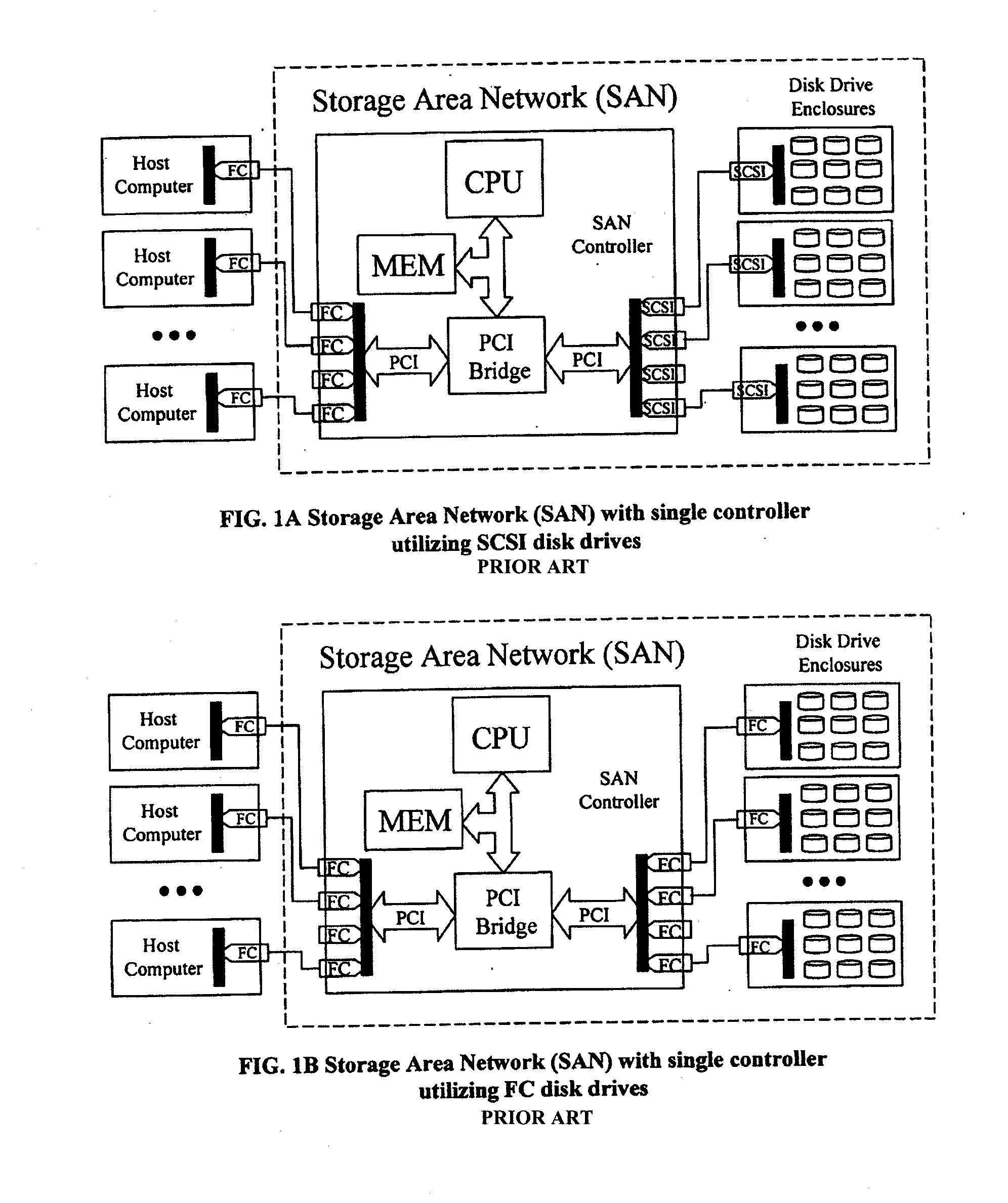
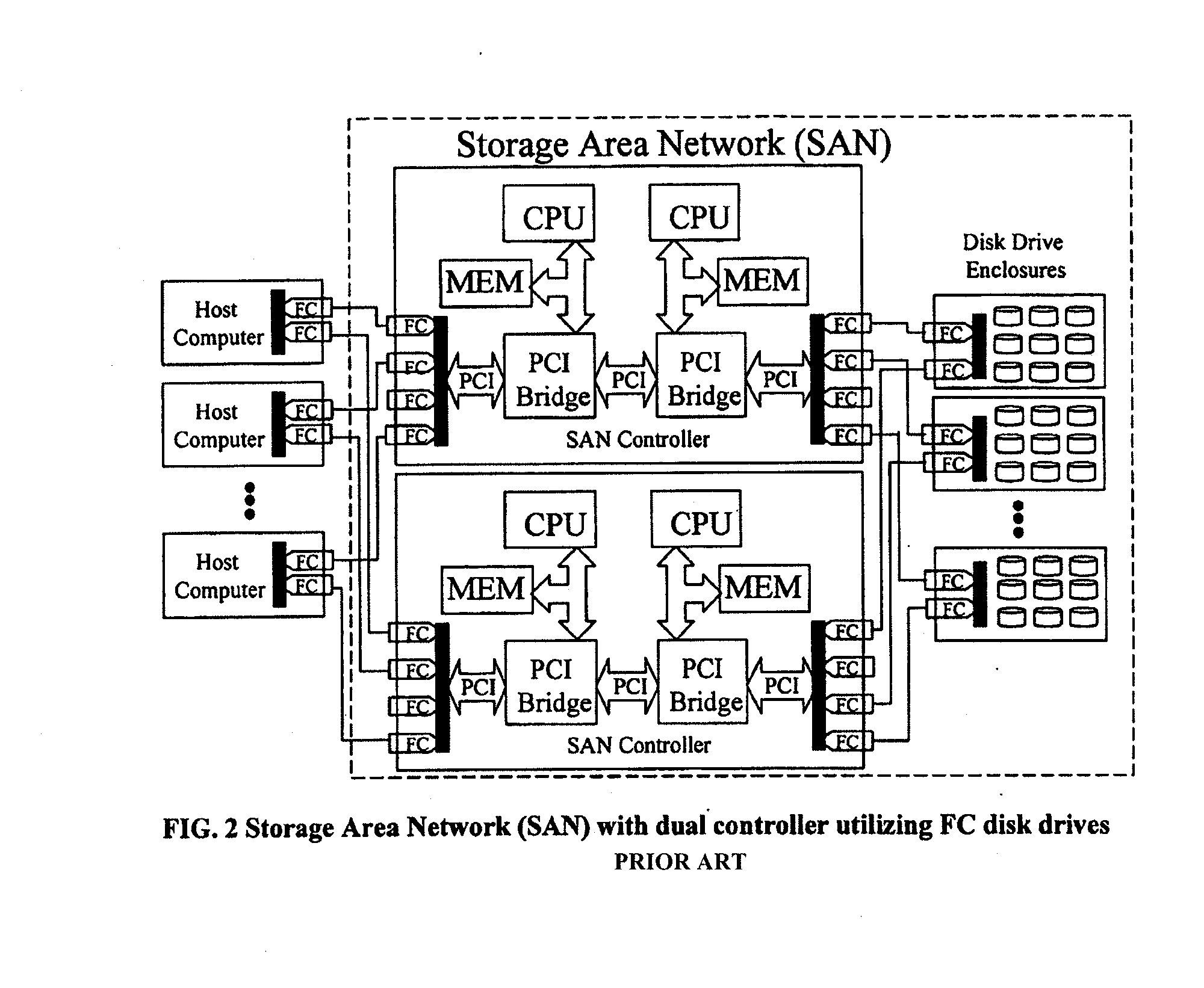
Scalable data storage architecture and methods of eliminating I/O traffic bottlenecks
ActiveUS8347010B1Increase storage capacityImprove system performanceMemory systemsInput/output processes for data processingExtensibilityFiber
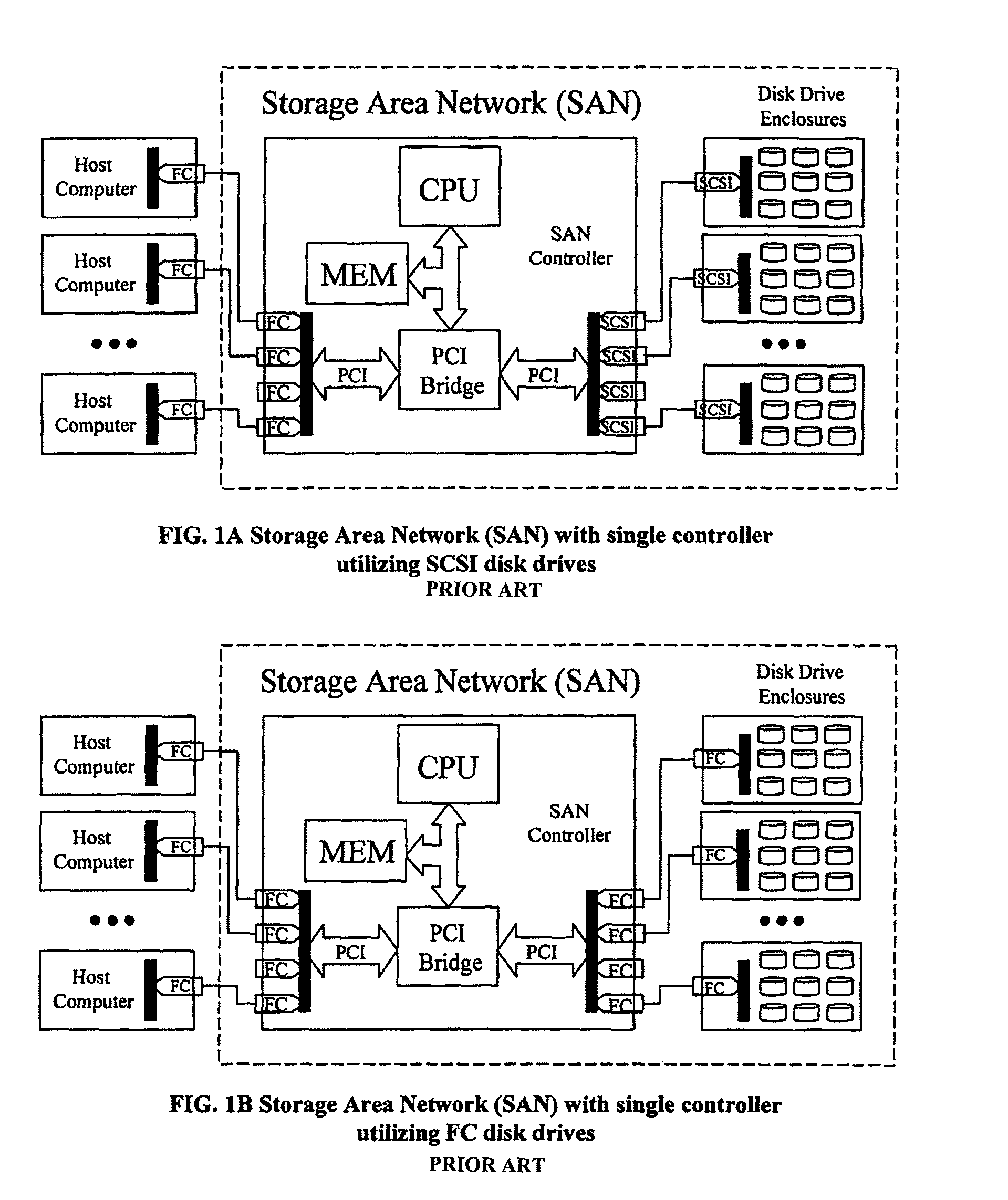
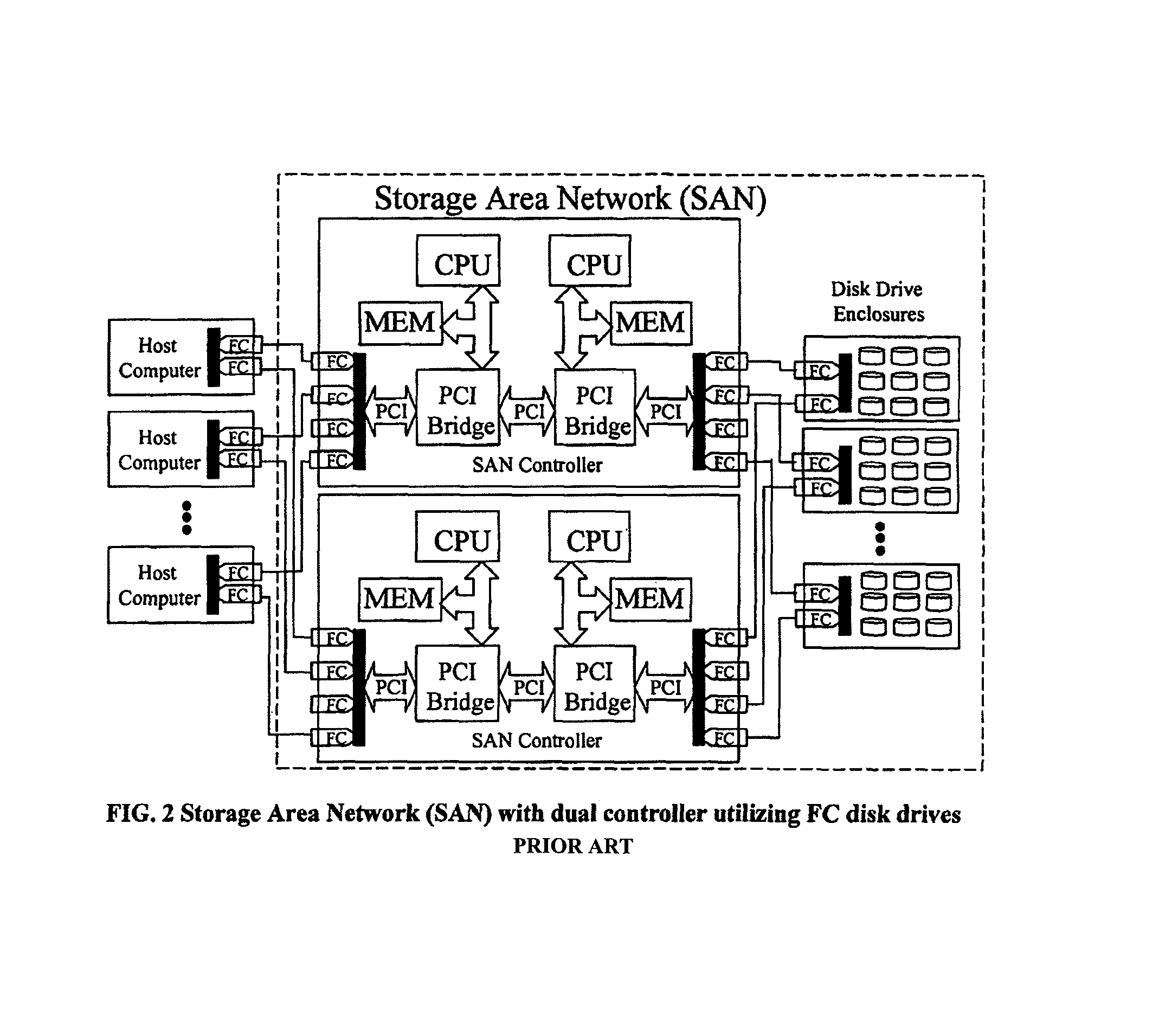
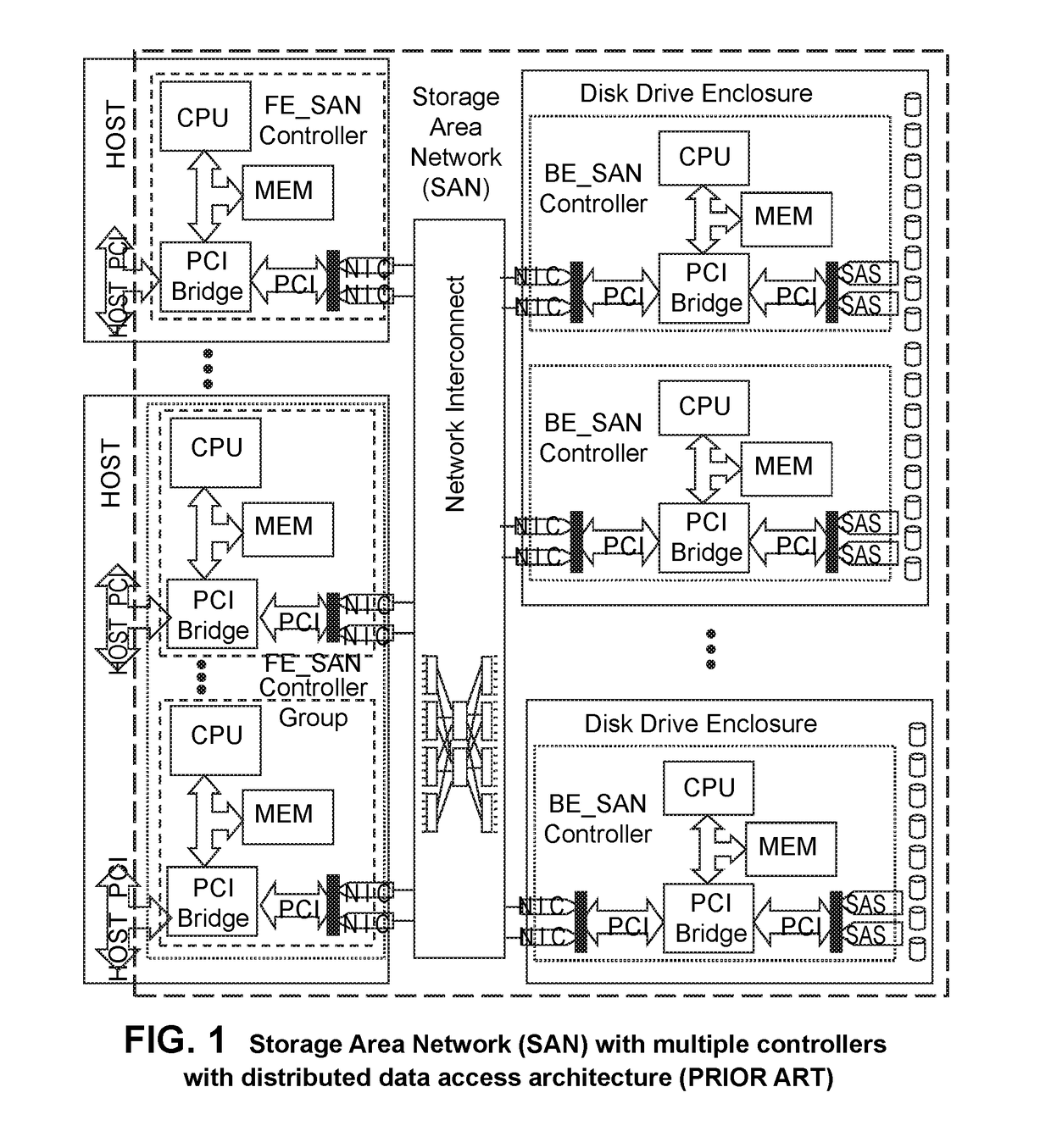
An apparatus and method implemented in hardware and embedded software that improves performance, scalability, reliability, and affordability of Storage Area Network (SAN) systems or subsystems. The apparatus contains host computers (application servers, file servers, computer cluster systems, or desktop workstations), SAN controllers connected via a bus or network interconnect, disk drive enclosures with controllers connected via network interconnect, and physical drive pool or cluster of other data storage devices that share I / O traffic, providing distributed high performance centrally managed storage solution. This approach eliminates I / O bottlenecks and improves scalability and performance over the existing SAN architectures. Although this architecture is network interconnect (transport) neutral, additional improvements and cost savings could be made by utilizing existing, of the shelf, low latency and high speed hardware such as Advanced Switching (AS) or Myrinet networks as a transport for data, Small Computer System Interface (SCSI) and other commands and messages. Using AS or Myrinet network as a replacement for Fiber Channel (FC) would significantly reduce the cost of such SAN systems and at the same time boost performance (higher data transfer rates and lower latencies). This invention is about defining hardware and software architectural solution that is specifically designed to eliminate I / O traffic bottlenecks, improve scalability, and reduce the overall cost of today's SAN systems or subsystems. This innovative solution, in addition to it's performance superiority compared to the existing solutions, should also provide 100% compatibility with the all existing Operating Systems (OS), File Systems (FS), and existing applications.
Owner:RADOVANOVIC BRANISLAV
Method of storing data in ferroelectric memory device
InactiveUS6940742B2Data in may deteriorateAvoid data corruptionDigital storageMemory systemsStorage cellParallel computing
Owner:SEIKO EPSON CORP
Failover method in a redundant computer system with storage devices
InactiveUS7117393B2Avoid data corruptionPrevent corruptionMemory systemsRedundant hardware error correctionFailoverHigh availability
A high availability database system, subject to a failure causing data corruption in the active server system, may recover valid data prior to the corruption, and use the protected and recovered data to effect a failover. At the time when a stand-by computer system detects occurrence of a failure, a pair split is done to the data area to protect the data area data of time T0, just before the occurrence of the failure, and another pair split is done to the log area at the time, where the log area is corrupted or a time T3, where the failover is to take effect without corrupting data, to protect the log area containing data at a given time between time T0 and time T3. By using the data and log areas thus protected, the stand-by computer system may take over valid data and log areas to perform a failover.
Owner:HITACHI LTD
Controlled take over of services by remaining nodes of clustered computing system
InactiveUS6789213B2Take over serviceSafely provide serviceError detection/correctionDigital computer detailsComputing systemsDistributed computing
Improved techniques for controlled take over of services for clustered computing systems are disclosed. The improved techniques can be implemented to allow one sub-cluster of the clustered computing system to safely take over services of one or more other sub-clusters in the clustered computing system. Accordingly, if the clustered computing system is fragmented into two or more disjointed sub-clusters, one sub-cluster can safely take over services of the one or more other sub-clusters after the one or more other sub-clusters have been shutdown. As a result, the clustered computing system can continue to safely provide services even when the clustered computing system has been fragmented into two or more disjointed sub-clusters due to an operational failure.
Owner:ORACLE INT CORP
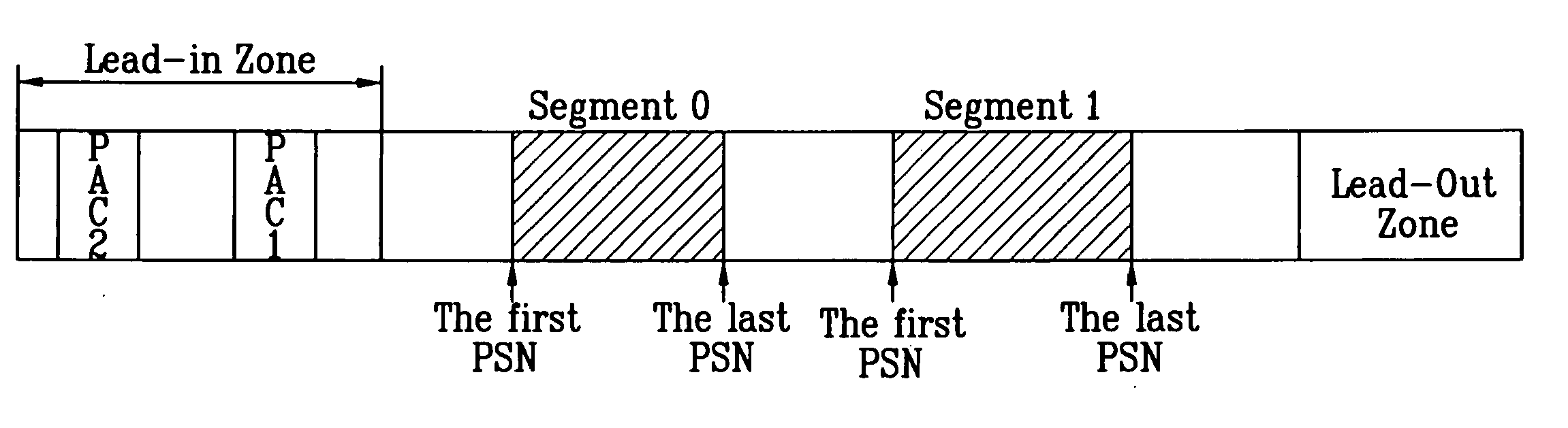
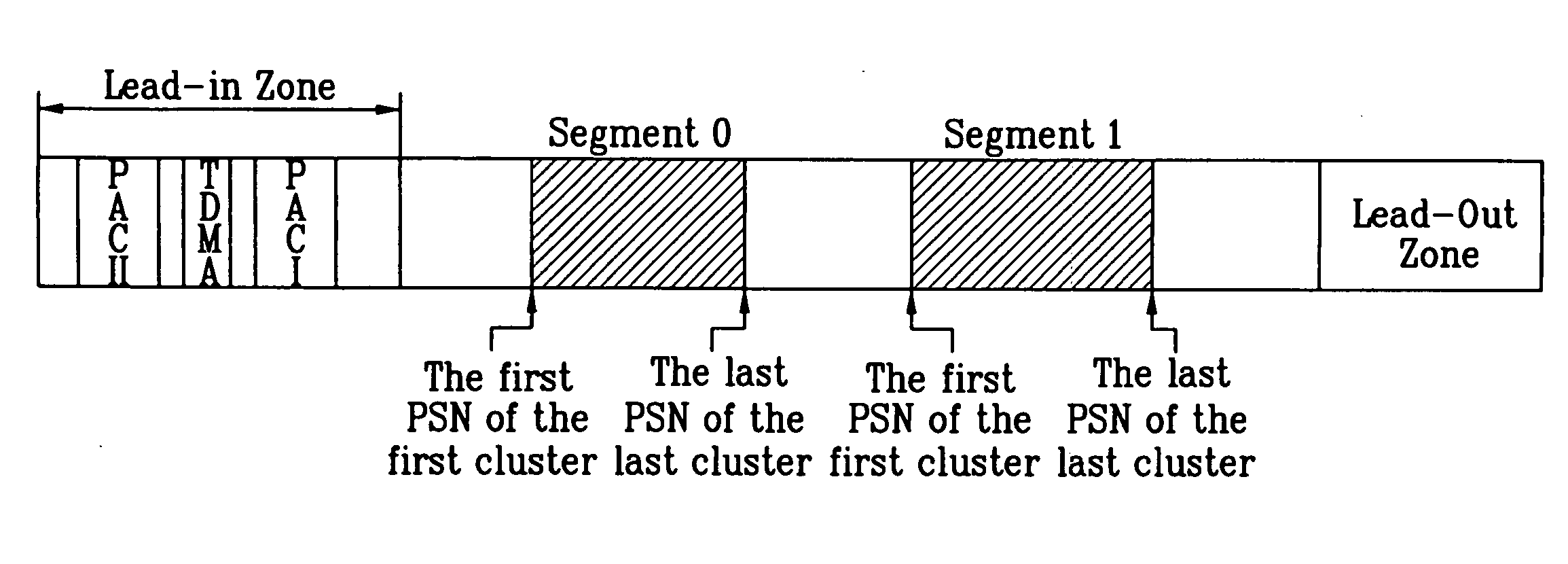
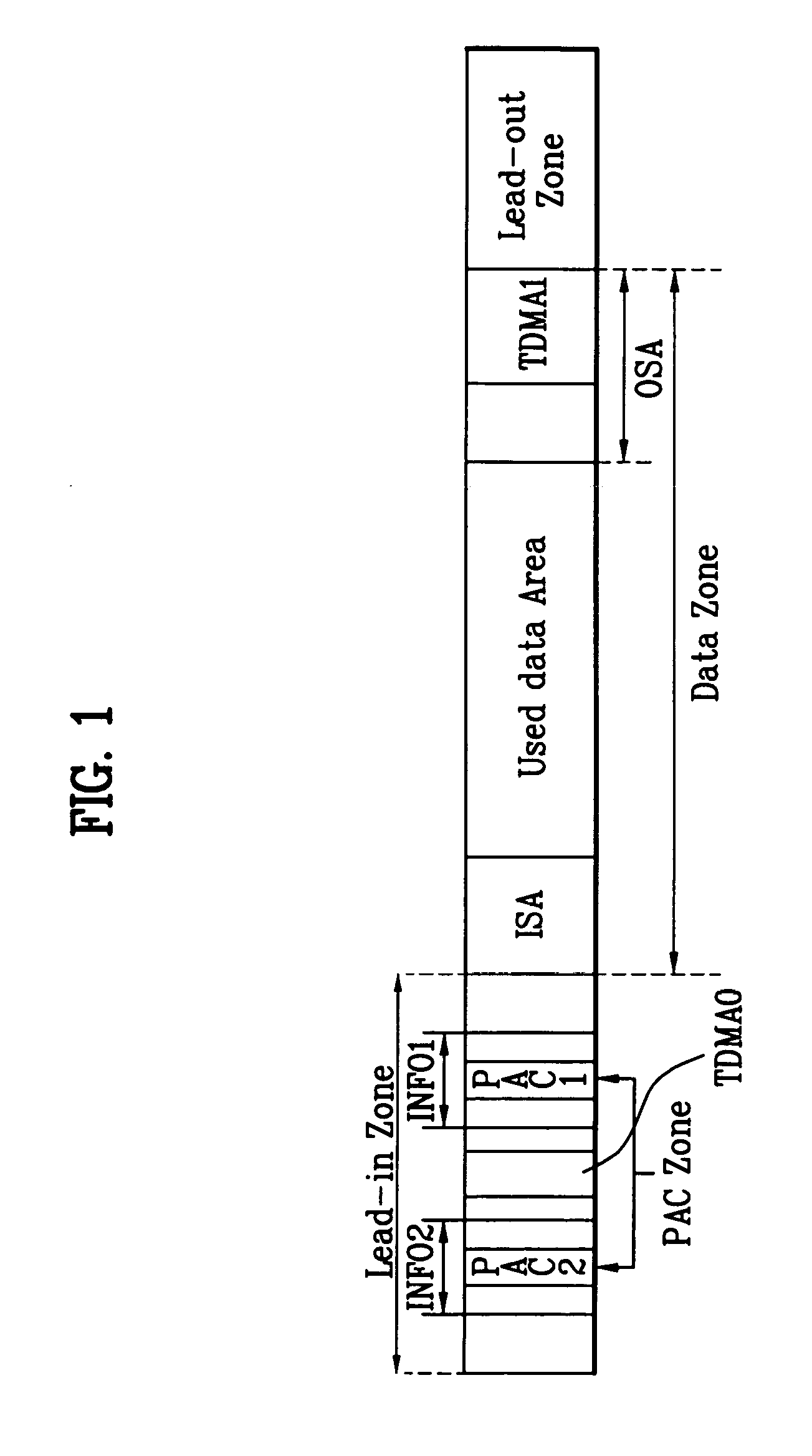
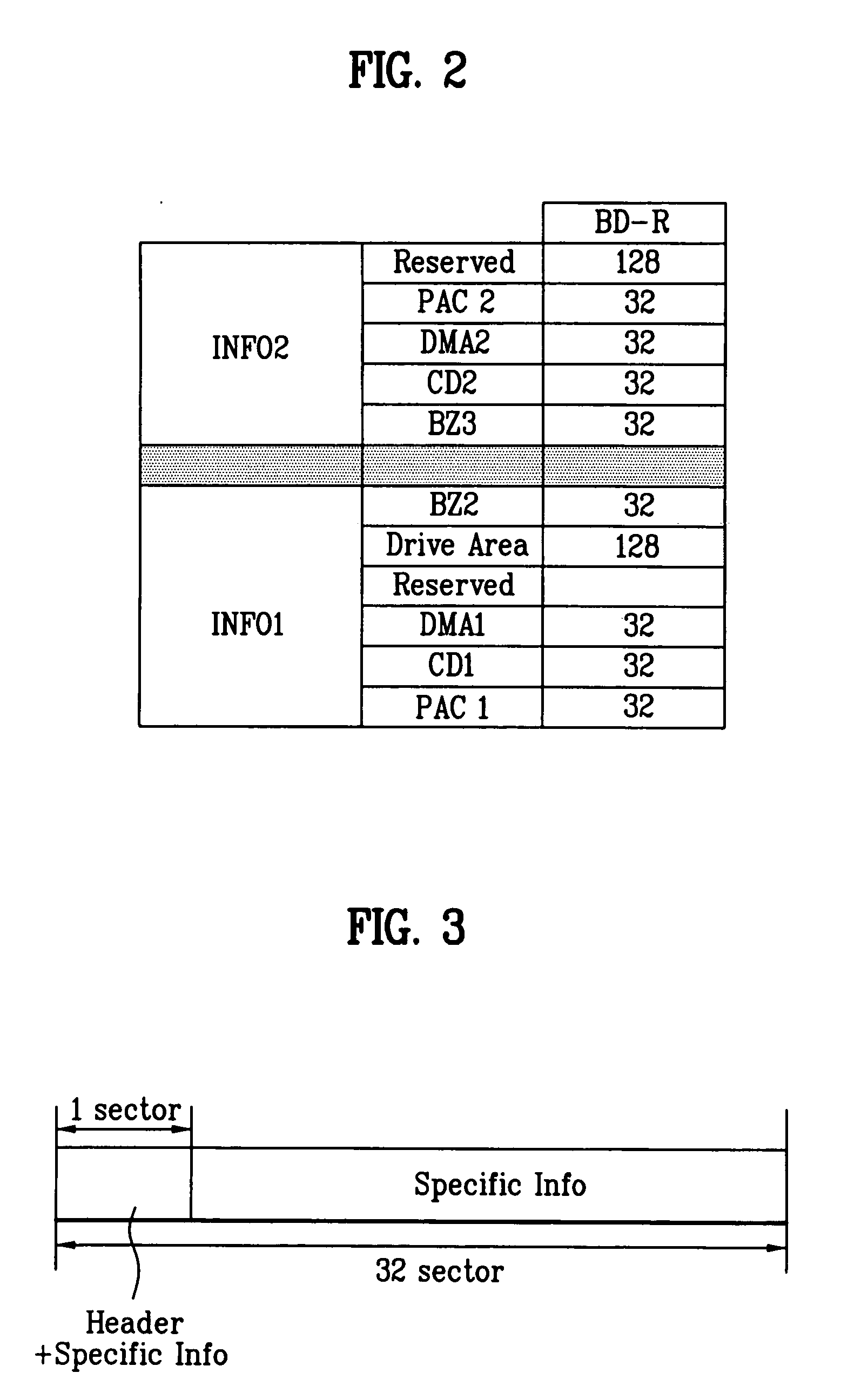
Recording medium with segment information thereon and apparatus and methods for forming, recording, and reproducing the recording medium
InactiveUS20050207318A1Avoid data corruptionImprove protectionInformation arrangementRecord information storageComputer hardwareHigh density
A recording medium, such as a high-density and / or optical recording medium including segment information recorded thereon, and apparatus and methods for recording to and reproducing from the recording medium, in order to improve data protection, data management and / or reproduction compatibility.
Owner:LG ELECTRONICS INC
Scalable Data Storage Architecture And Methods Of Eliminating I/O Traffic Bottlenecks
ActiveUS20130145064A1Storage subsystems more affordableIncrease storage capacityInput/output processes for data processingRAIDExtensibility
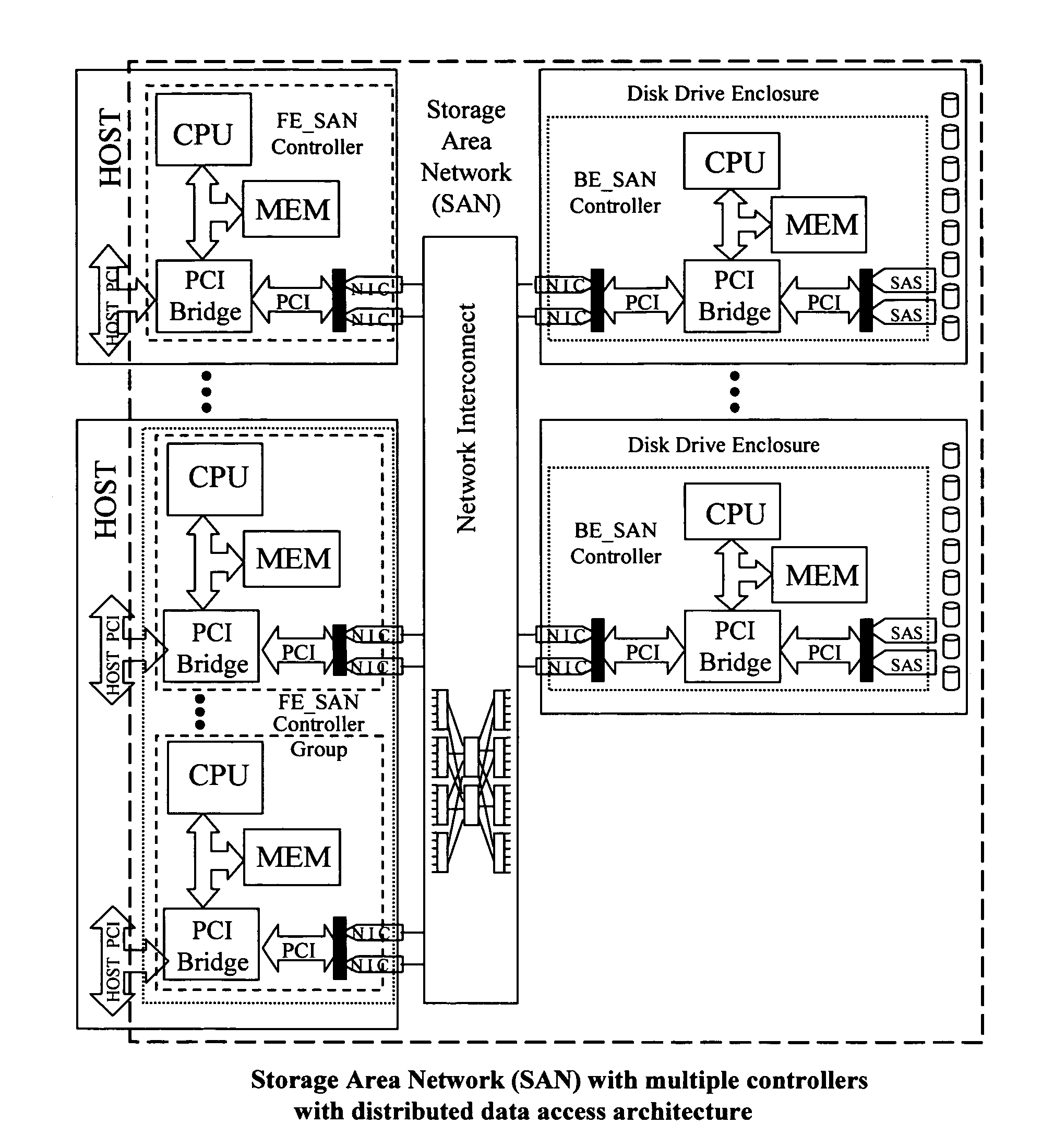
A Storage Area Network (SAN) system has host computers, front-end SAN controllers (FE_SAN) connected via a bus or network interconnect to back-end SAN controllers (BE_SAN), and physical disk drives connected via network interconnect to the BE_SANs to provide distributed high performance centrally managed storage. Described are hardware and software architectural solutions designed to eliminate I / O traffic bottlenecks, improve scalability, and reduce the overall cost of SAN systems. In an embodiment, the BE_SAN has firmware to recognize when, in order to support a multidisc volume, such as a RAID volume, it is configured to support, it requires access to a physical disk attached to a second BE_SAN; when such a reference is recognized it passes assess commands to the second BE_SAN. Further, the BE_SAN has firmware to make use of the physical disk attached to the second BE_SAN as a hot-spare for RAID operations.
Owner:RADOVANOVIC BRANISLAV
Preventing data corruption due to pre-existing split brain
ActiveUS20170094003A1Avoid data corruptionSpecial service provision for substationError detection/correctionNODALSplit-brain
Various methods, systems, and processes to prevent data corruption caused by a pre-existing split brain condition in a cluster are presented. In response to determining that a node is no longer part of a sub-cluster, another node in the sub-cluster is designated as a racer node. The racer node accesses a matrix, and the matrix includes information to determine whether a majority of coordination points in a cluster are accessible by nodes in the sub-cluster. Based on the accessing, a determination is made that the information indicates that the majority of coordination points are accessible by the nodes. The information is then broadcasted.
Owner:VERITAS TECH
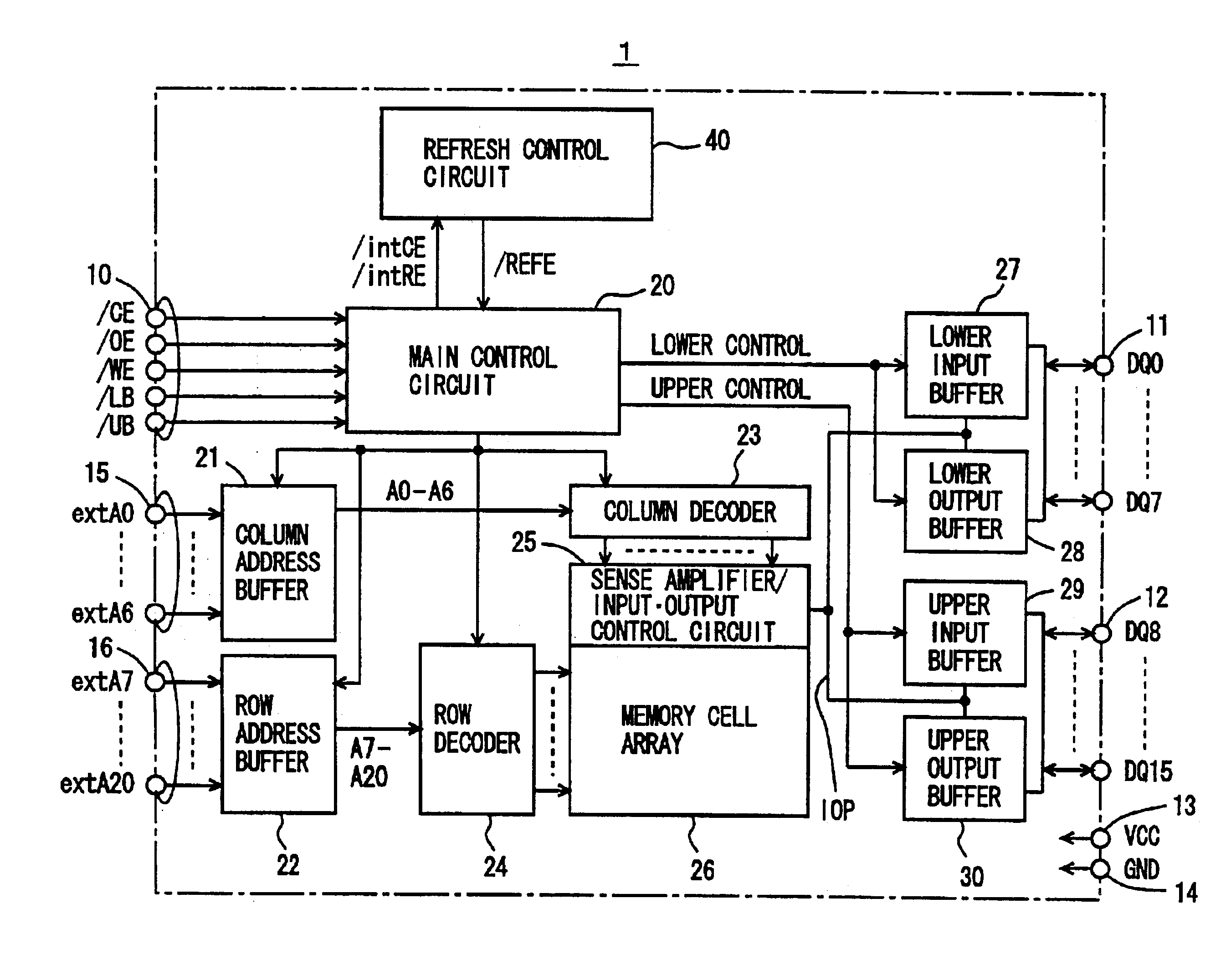
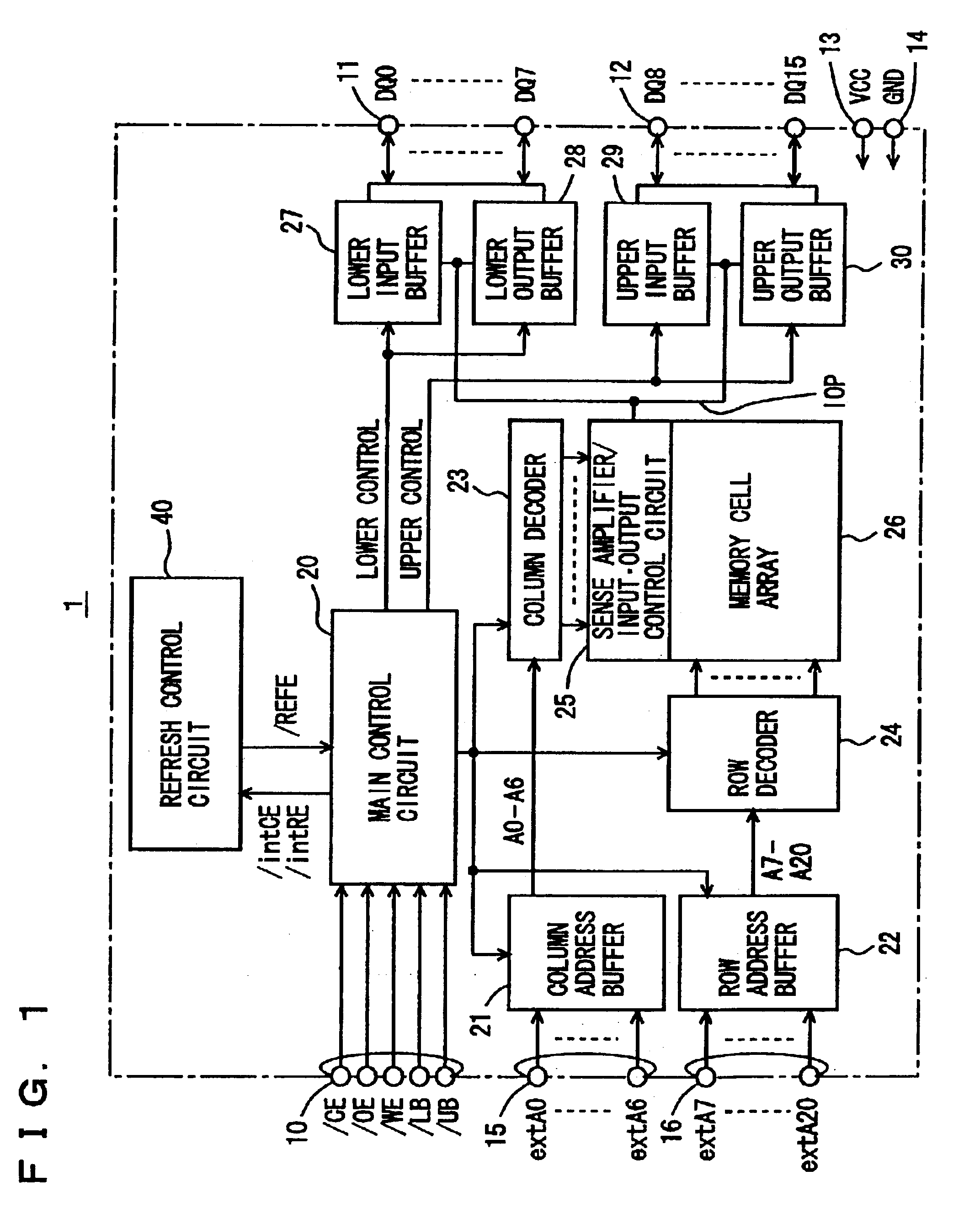
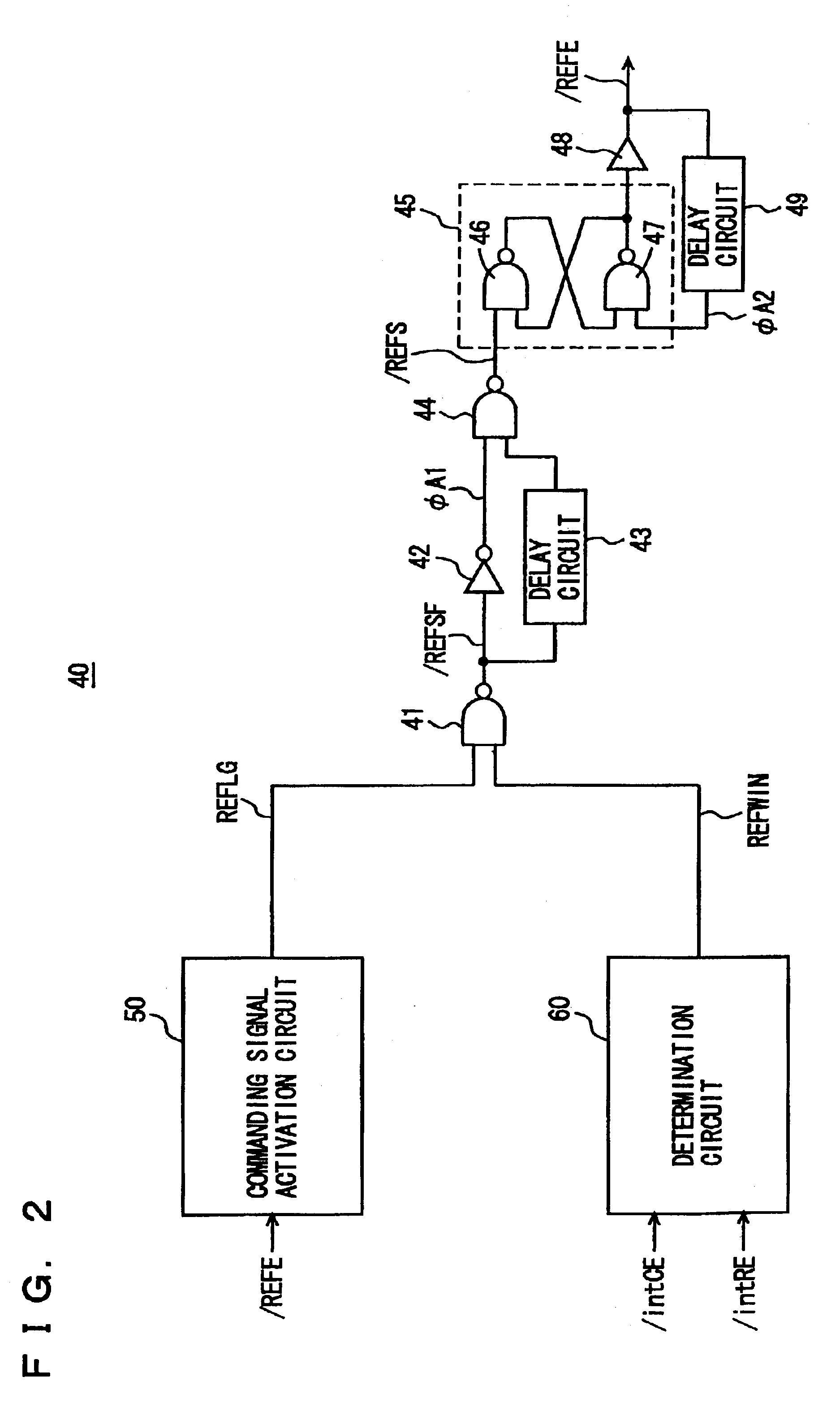
Fully-hidden refresh dynamic random access memory
InactiveUS6859415B2Avoid data corruptionDigital storageMemory systemsData accessBiological activation
A composite gate detects whether an internal array is in a selected state and an internal row activation signal is activated in accordance with a timing relationship between an output signal of the composite gate and an address transition detection signal. When the address transition detection signal is applied, the internal row activation signal is deactivated in accordance with generation timings of delayed restore period signal indicating whether the internal array is in a selected state and of the address transition detection signal to permit the next row access. With such a configuration, the next operation is allowed to start after an internal state is surely restored to an initial state. When the next address transition detection signal is applied during a period of a restoration operation, a column recovery operation, or a refreshing operation, data access is correctly performed without causing data destruction.
Owner:RENESAS ELECTRONICS CORP
Recording medium with segment information thereon and apparatus and methods for forming, recording, and reproducing the recording medium
InactiveUS20070211589A1Avoid data corruptionImprove protectionInformation arrangementFilamentary/web record carriersComputer hardwareHigh density
A recording medium, such as a high-density and / or optical recording medium including segment information recorded thereon, and apparatus and methods for recording to and reproducing from the recording medium, in order to improve data protection, data management and / or reproduction compatibility.
Owner:LG ELECTRONICS INC
Recording medium with segment information thereon and apparatus and methods for forming, recording, and reproducing the recording medium
ActiveUS20070211590A1Avoid data corruptionImprove protectionInformation arrangementFilamentary/web record carriersComputer hardwareHigh density
Owner:LG ELECTRONICS INC
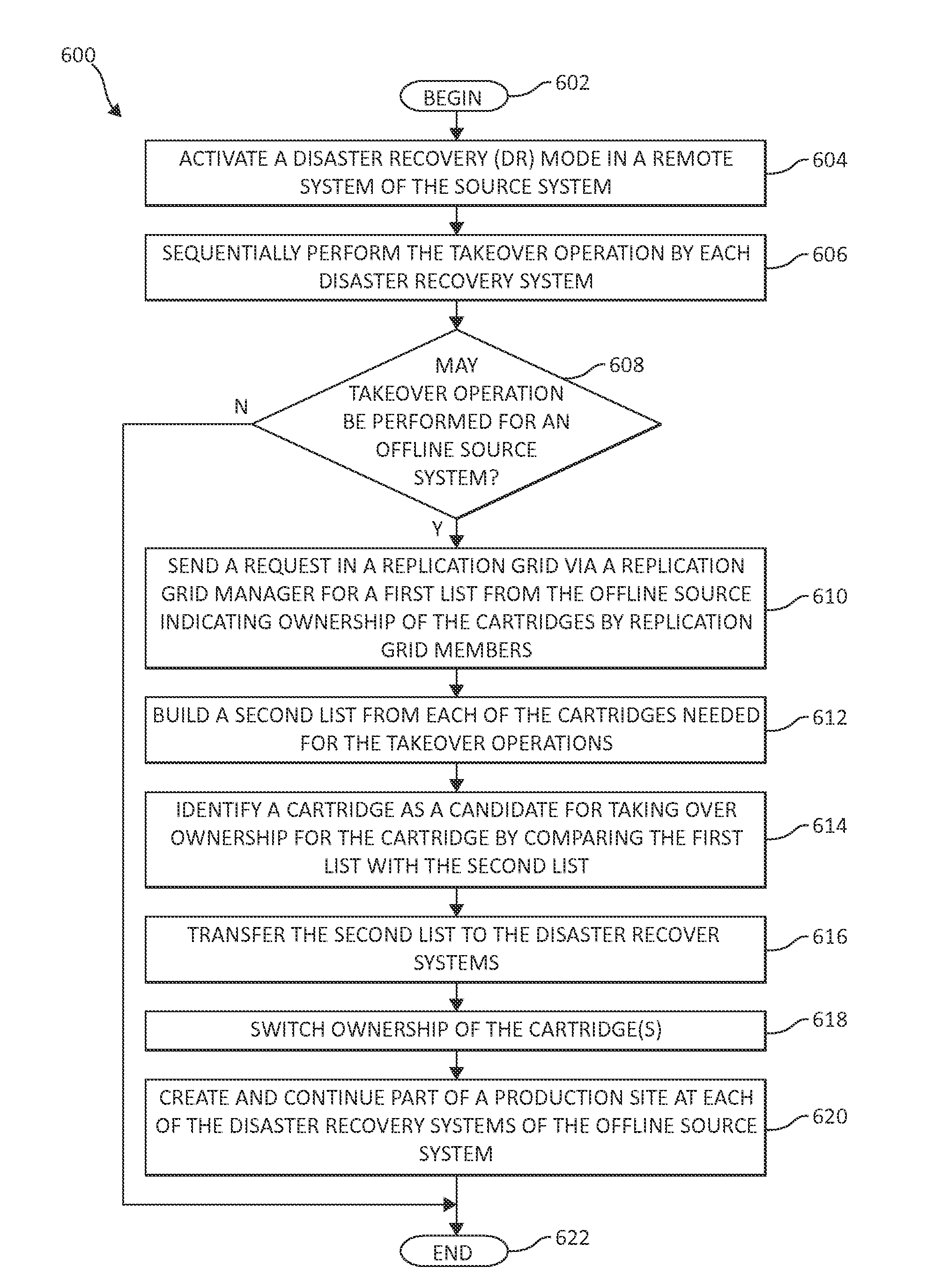
Coordinated disaster recovery production takeover operations
InactiveUS20120284559A1Reduce productivity and efficiencyCompromise integrityTransmissionRedundant hardware error correctionMagnetic tapeSource system
For coordinated disaster recovery, a reconciliation process is performed for resolving intersecting and non-intersecting data amongst disaster recovery systems for takeover operations. An ownership synchronization process is coordinated for replica cartridges via the reconciliation process at the disaster recovery systems. The disaster recovery systems continue as a replication target for source systems and as a backup target for local backup applications.
Owner:IBM CORP
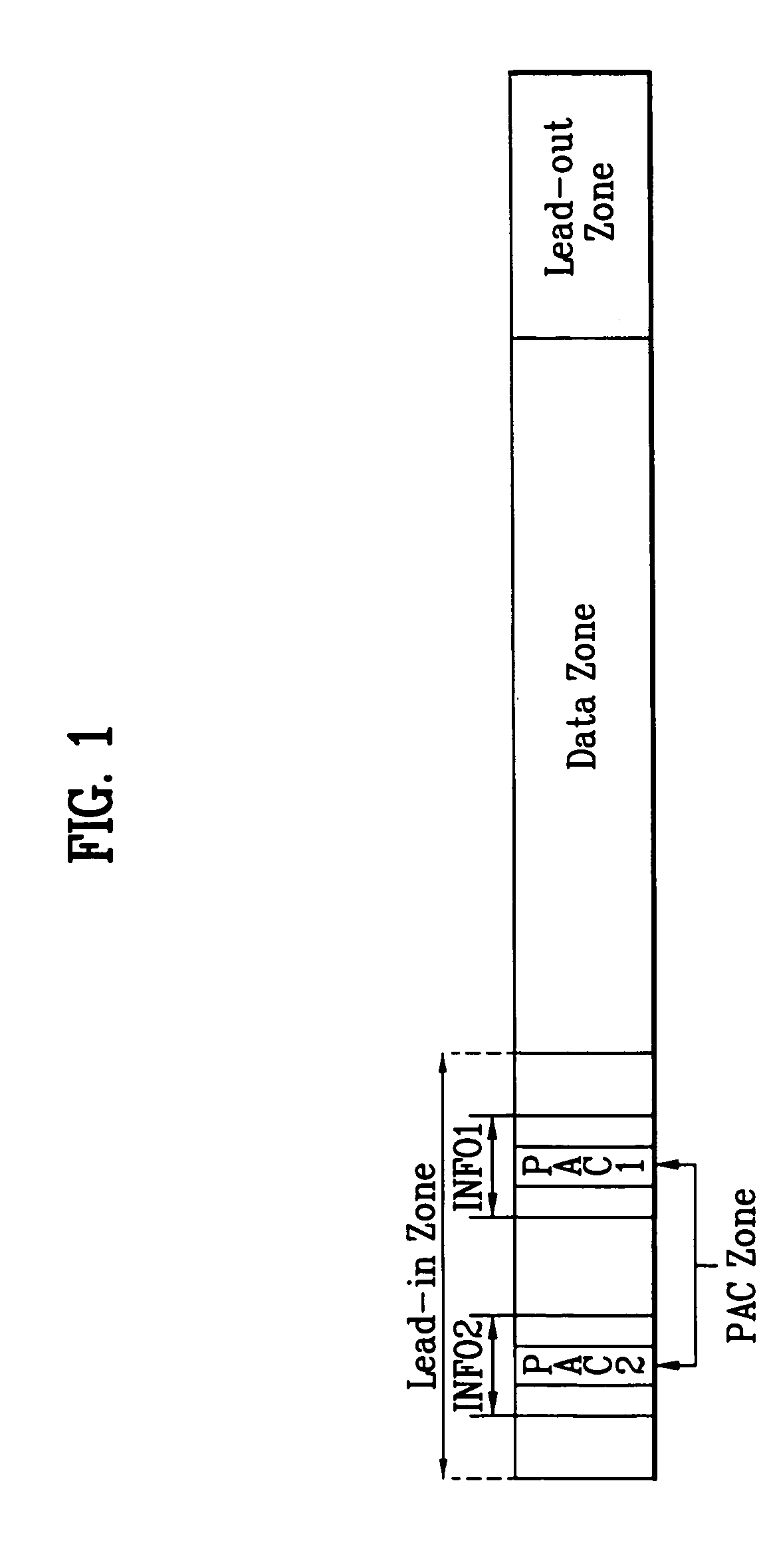
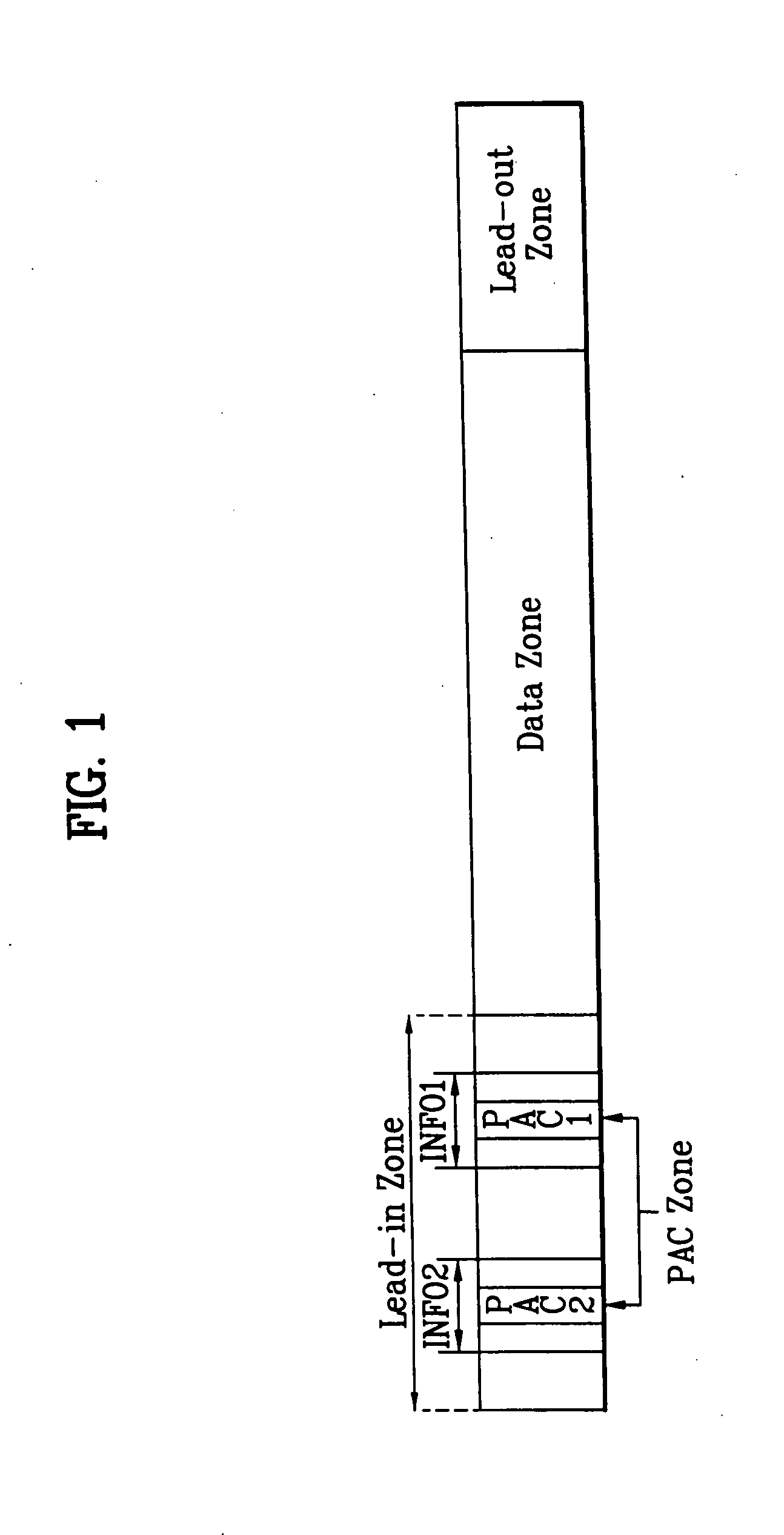
Recording medium with physical access control (PAC) cluster thereon and apparatus and methods for forming, recording, and reproducing the recording medium
InactiveUS20050207319A1Avoid data corruptionImprove protectionOptical discsRecord information storageComputer hardwareHigh density
A recording medium, such as a high-density and / or optical recording medium including at least one physical access control (PAC) cluster recorded thereon, and apparatus and methods for recording to and reproducing from the recording medium, in order to improve data protection, data management and / or reproduction compatibility.
Owner:LG ELECTRONICS INC
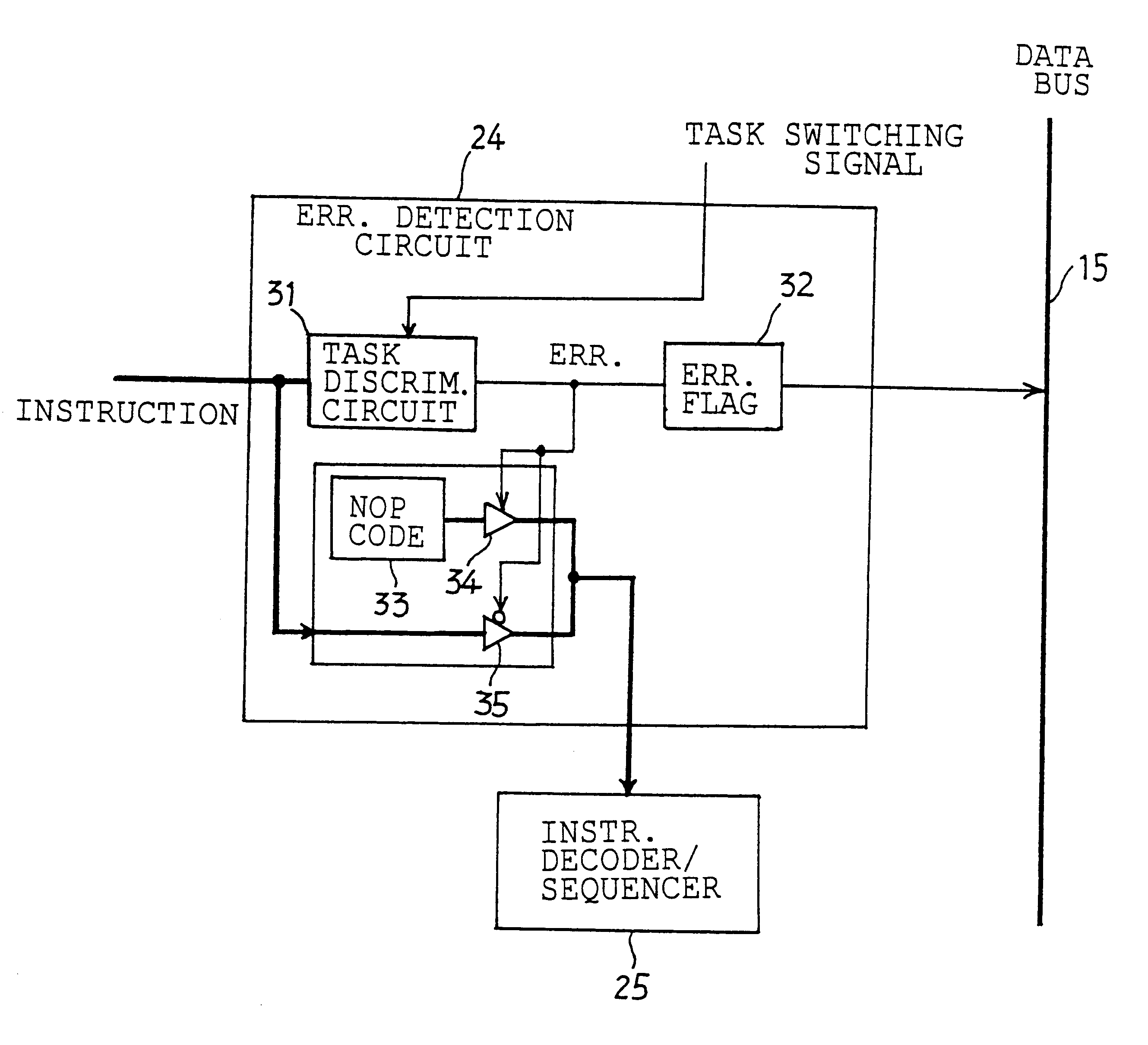
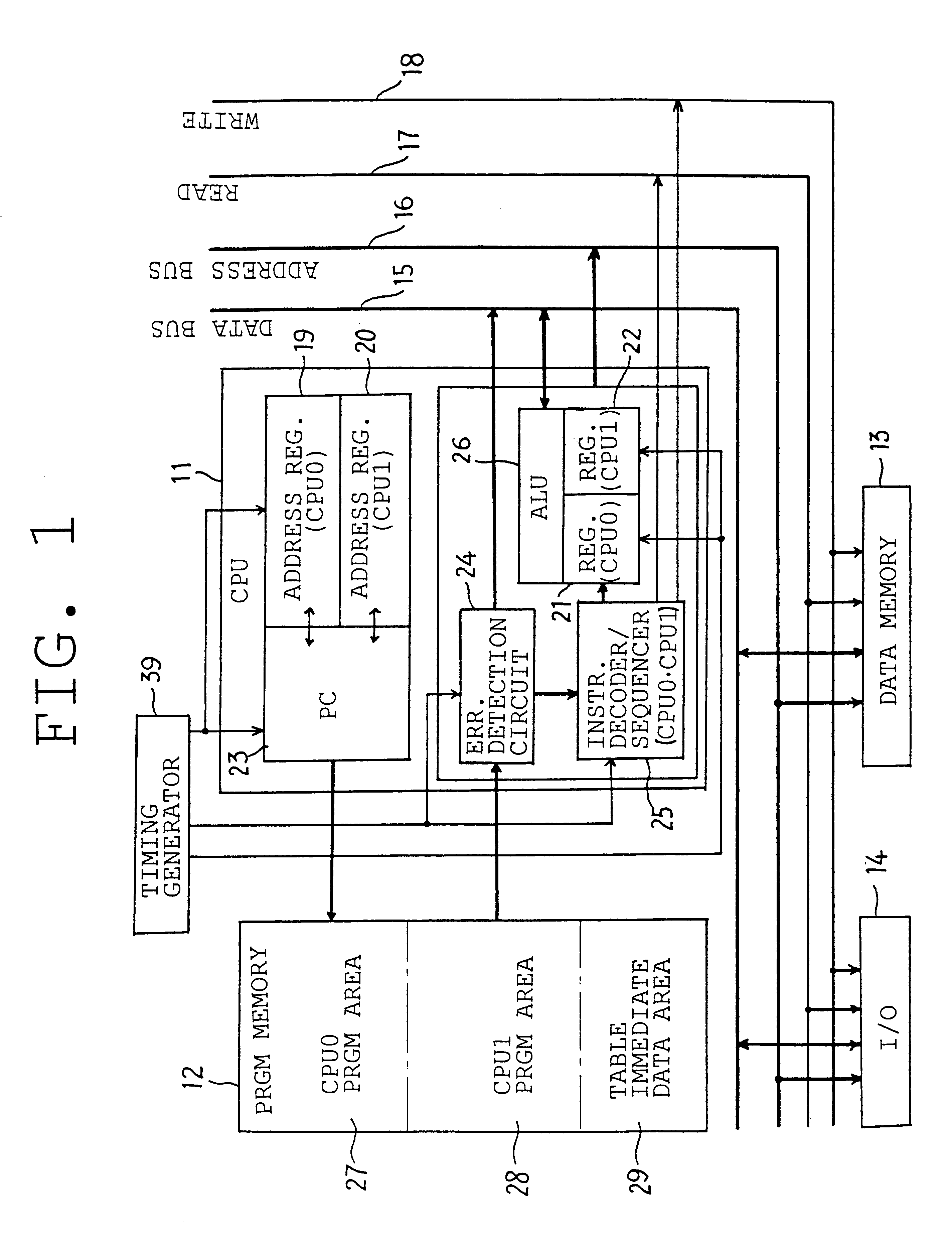
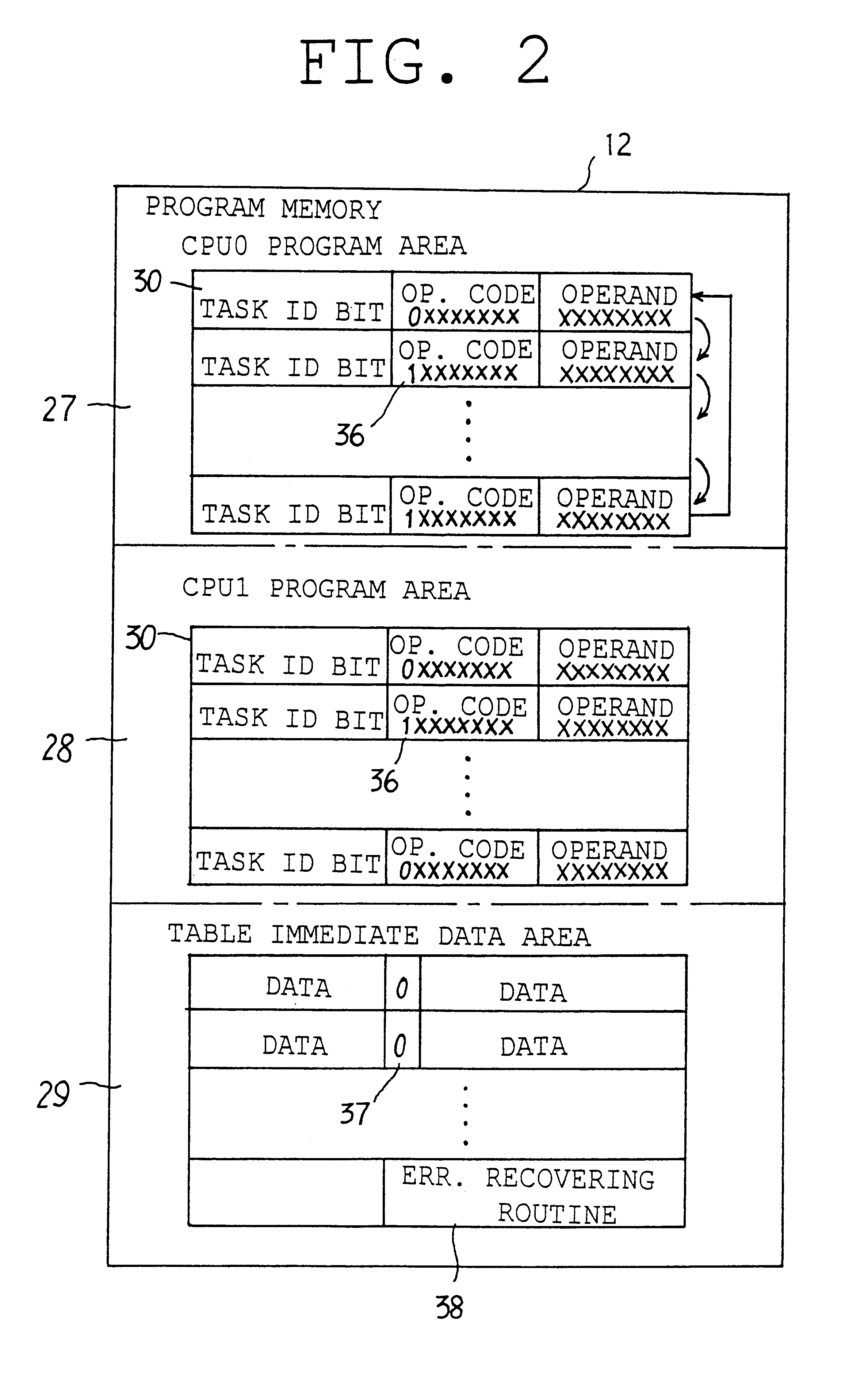
Multitask processing unit
InactiveUS6304957B1Rapid responseAvoid data corruptionProgram initiation/switchingDigital computer detailsMicrocomputerProcessor register
Owner:DENSO CORP
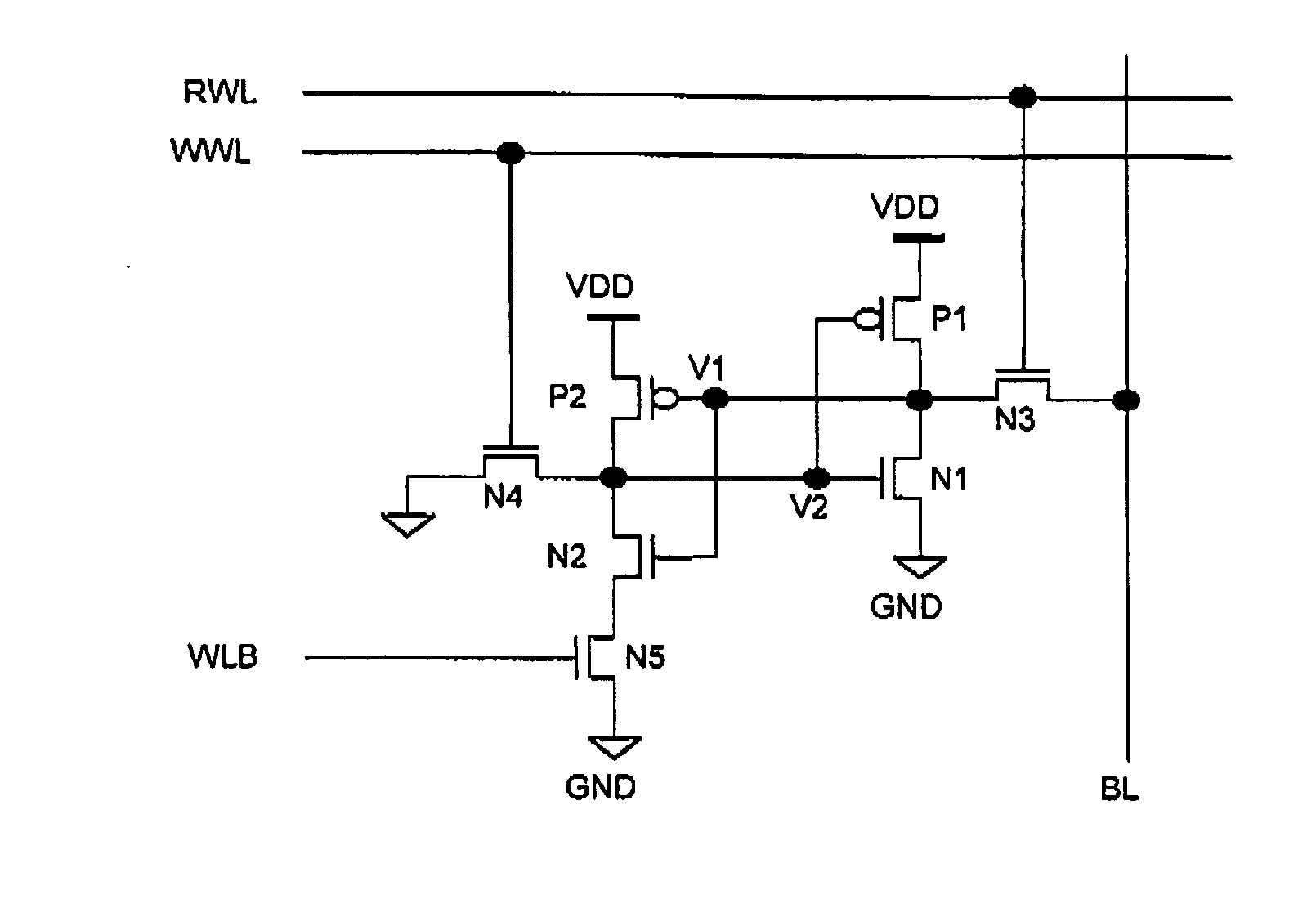
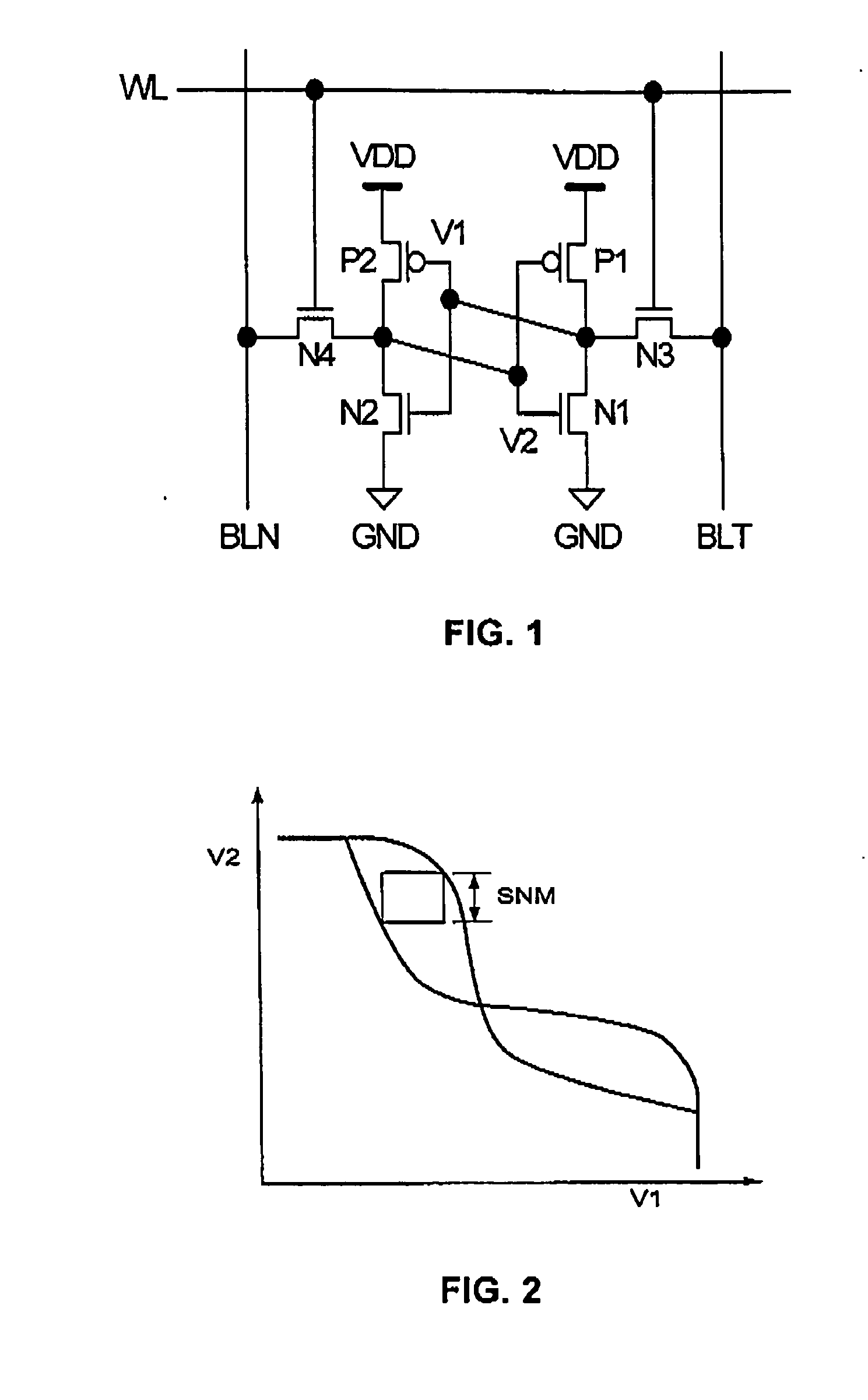
Semiconductor memory device
InactiveUS20070041239A1Reduced memory cell dimensionPrevent corruptionSolid-state devicesDigital storageAudio power amplifierSemiconductor storage devices
The SRAM cells of a semiconductor storage device each comprise first and second inverter circuits loop-connected with each other to form a hold circuit; two access transistors; and a hold control transistor connected in series with a drive transistor of the second inverter circuit. While the memory cell is not accessed, the hold control transistor causes the first and second inverter circuits to form the loop connected hold circuit for statically holding data. When the memory cell is accessed, the hold control transistor causes the first and second inverter circuits to be disconnected from the loop connection for dynamically holding data, thereby preventing data corruption that would otherwise possible occur due to a read operation. Moreover, a sense amplifier circuit that uses a single bit line to read data from a memory cell is disposed in a space appearing in the memory cell array, thereby effectively using the area.
Owner:NEC CORP
Scalable data access system and methods of eliminating controller bottlenecks
ActiveUS20170293428A1Improve executionImprove reliabilityMemory architecture accessing/allocationInput/output to record carriersWorkloadCentralized management
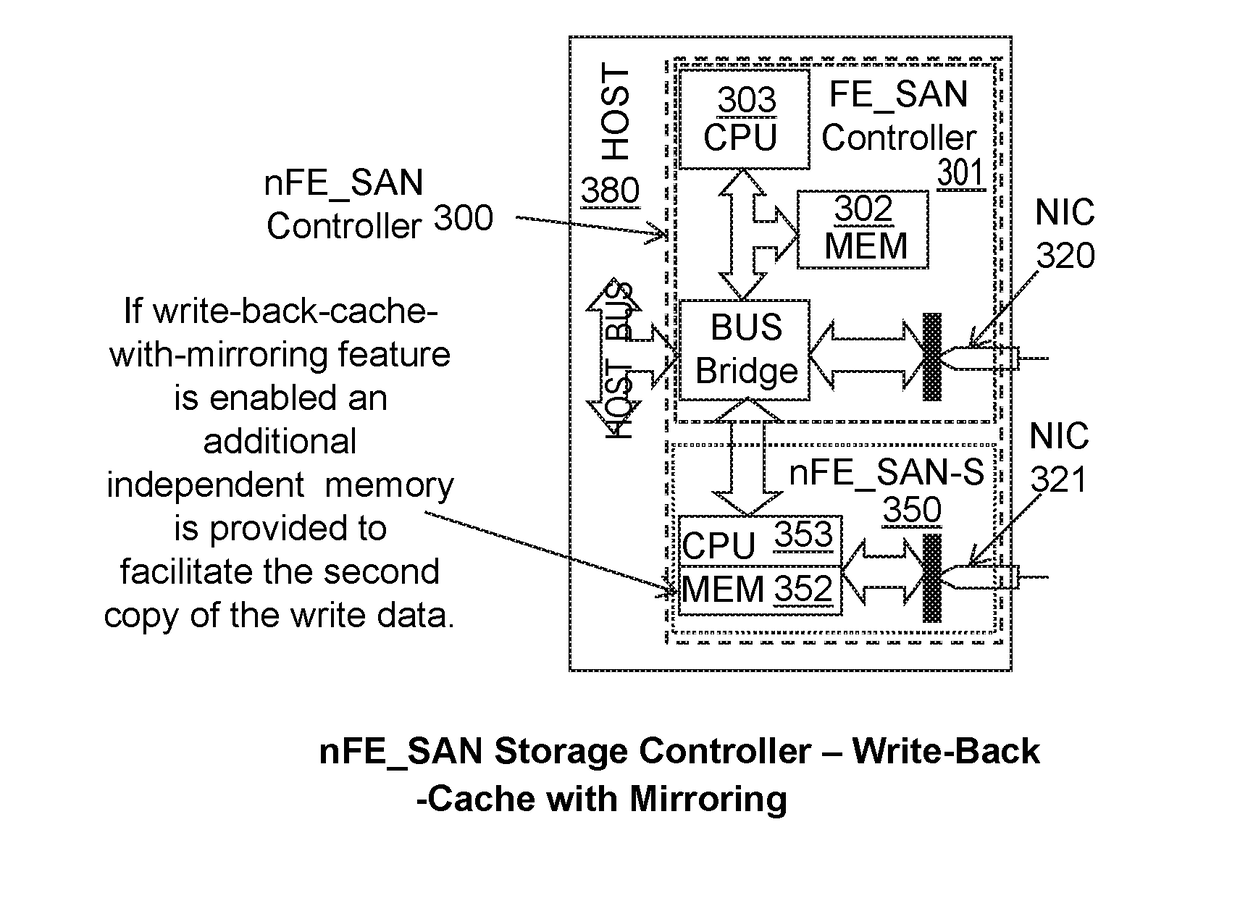
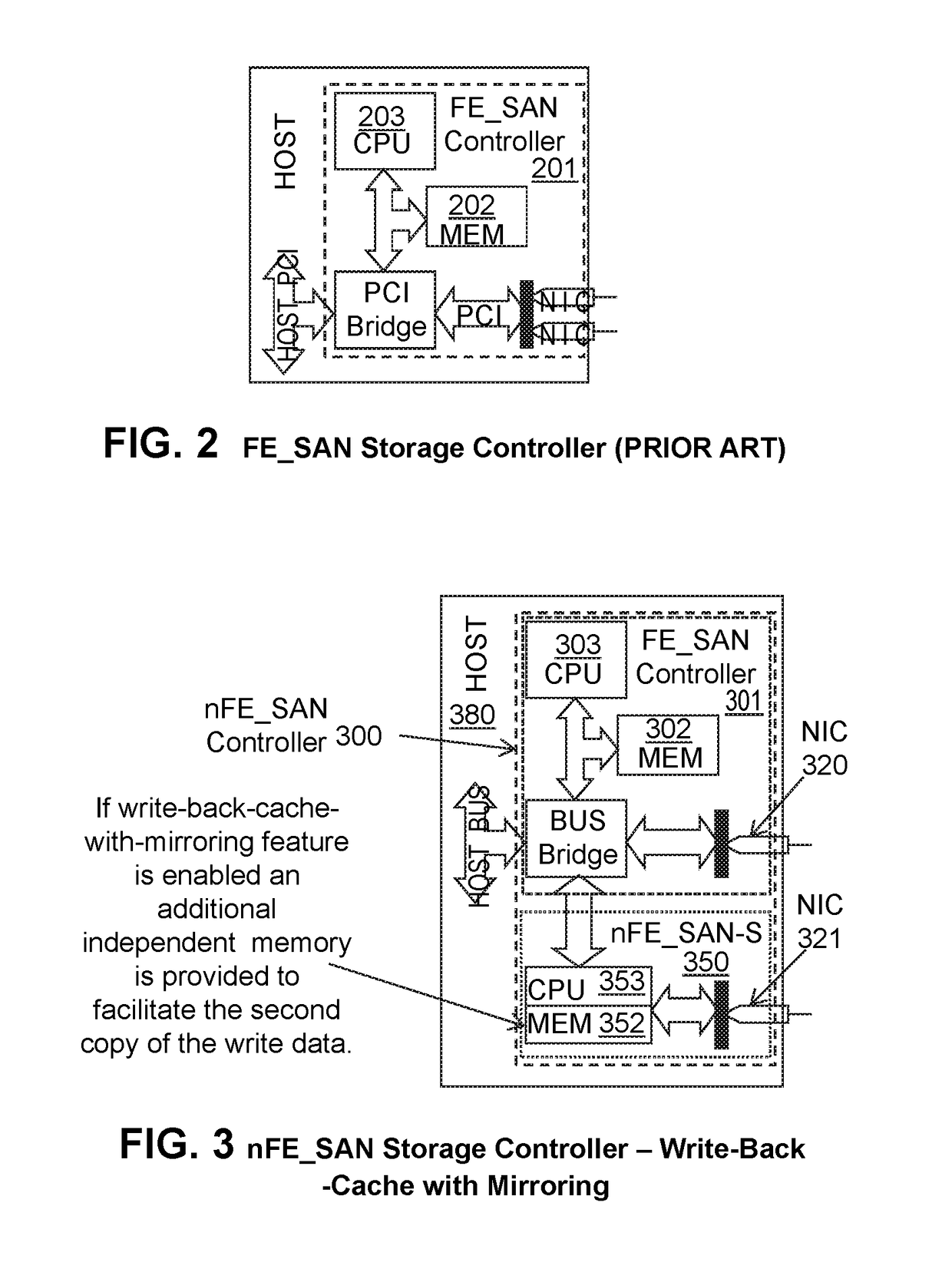
A data access system has host computers having front-end controllers nFE_SAN connected via a bus or network interconnect to back-end storage controllers nBE_SAN, and physical disk drives connected via network interconnect to the nBE_SANs to provide a distributed, high performance, policy based or dynamically reconfigurable, centrally managed, data storage acceleration system. The hardware and software architectural solutions eliminate BE_SAN controller bottlenecks and improve performance and scalability. In an embodiment, the nBE_SAN (BE_SAN) firmware recognize controller overload conditions, informs Distributed Resource Manager (DRM), and, based on the DRM provided optimal topology information, delegates part of its workload to additional controllers. The nFE_SAN firmware and additional hardware using functionally independent and redundant CPUs and memory that mitigate single points of failure and accelerates write performance. The nFE_SAN and FE_SAN controllers facilitate Converged I / O Interface by simultaneously supporting storage I / O and network traffic.
Owner:RADOVANOVIC BRANISLAV
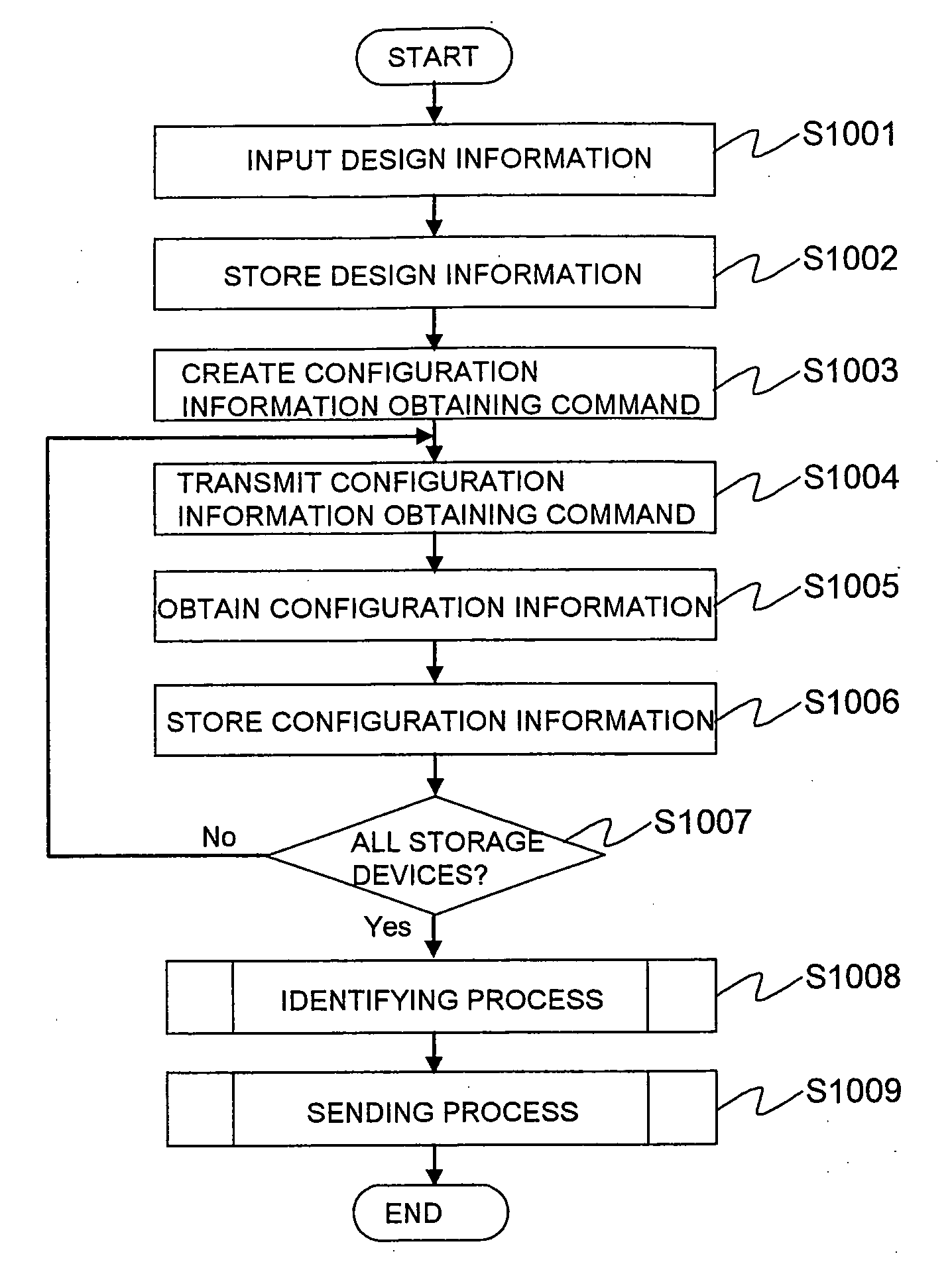
Computer system, management computer, storage device and volume allocation confirmation method
InactiveUS20070250678A1Avoiding unintended volume allocationAvoid data corruptionMemory systemsInput/output processes for data processingComputer architectureComputerized system
When configuring volume allocation on a storage device, it is confirmed that design information on the volume allocation is in compliance with an operational policy of a system and there is no mistake in design so as to configure the volume allocation on the storage device in the case where there is no problem. A computer system including: a host computer 2; a storage device 3 for providing a volume to the host computer 2 via a one network 5; and a management computer 1 connected to the storage device 3 via a network 6, wherein when a storage manager configures volume allocation of the storage device 3, the management computer 1 gathers configuration information on the volume allocation from the storage device 3 and makes a comparison between design information on the volume allocation to be configured on the storage device 3 inputted by the storage manager and the gathered configuration information on the volume allocation so as to identify changes.
Owner:HITACHI LTD
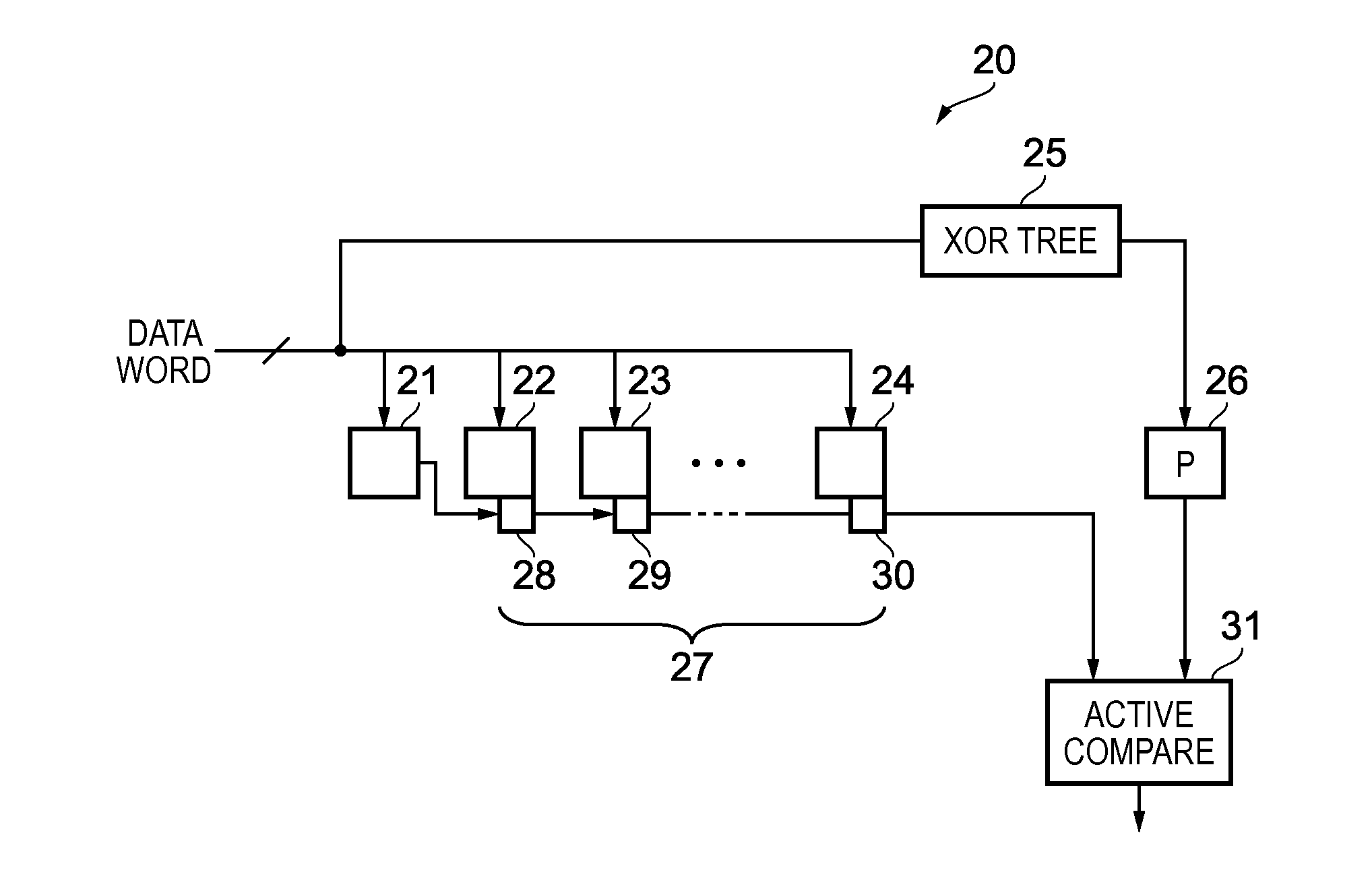
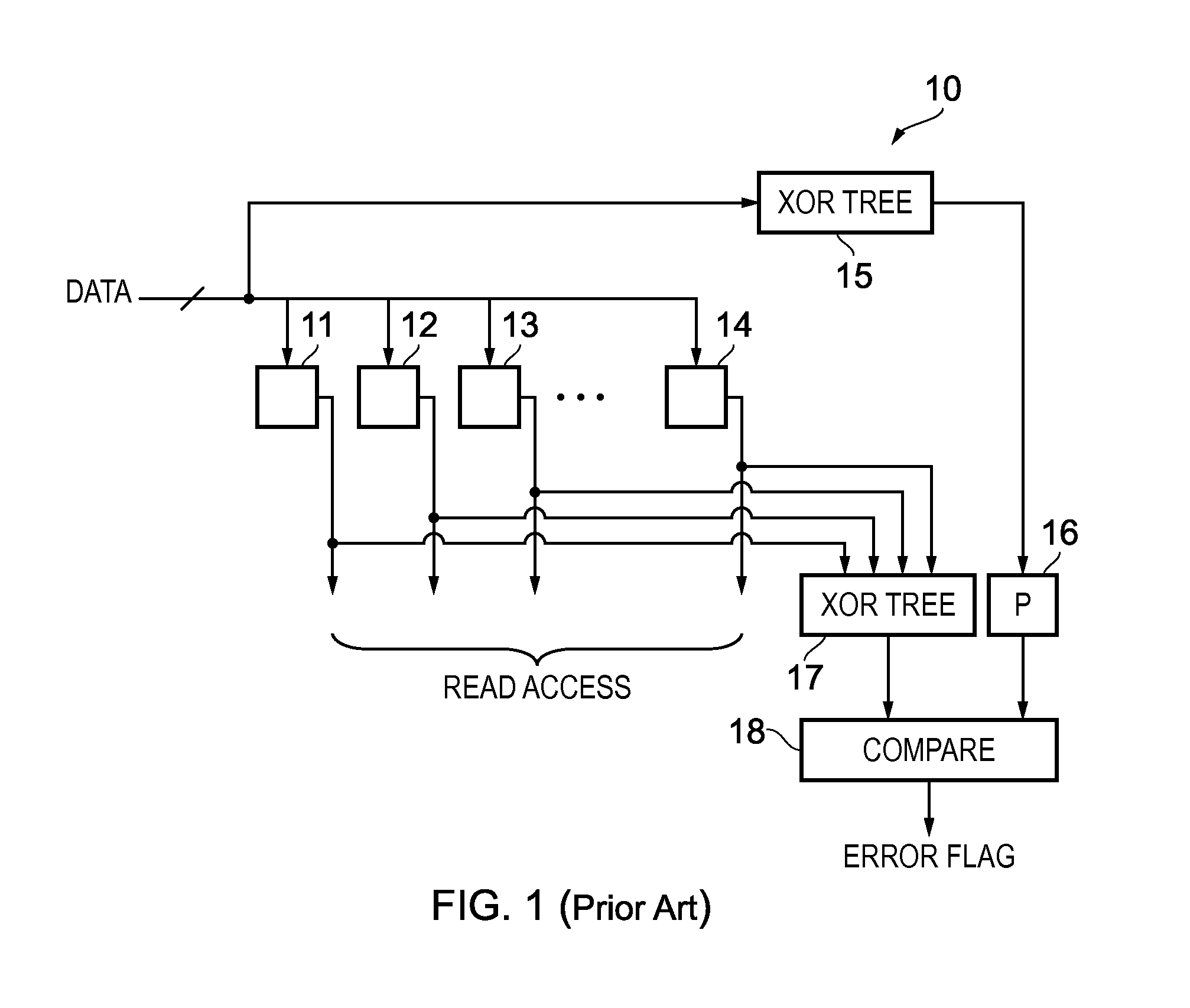
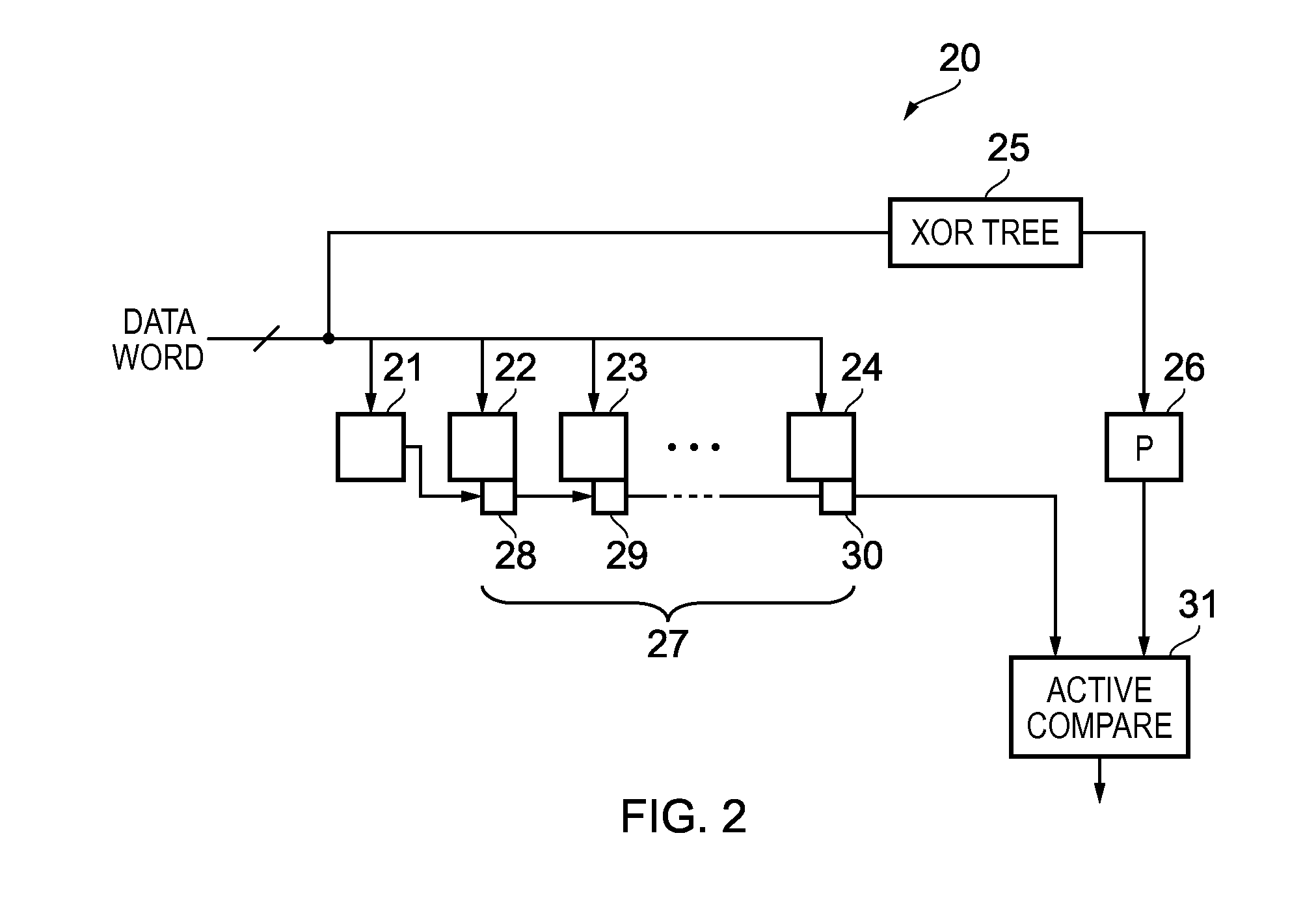
Error detection in stored data values
ActiveUS20150363268A1Reduces parity computation latencyAvoid accumulationCode conversionCoding detailsData storingData store
An apparatus has a plurality of storage units. A parity generator is configured to generate a parity value in dependence on the respective values stored in the plurality of storage units. The parity generator is configured such that determination of the parity value is independent of a read access to the data stored the plurality of storage units. A detector is configured to detect a change in value of the parity value.
Owner:ARM LTD
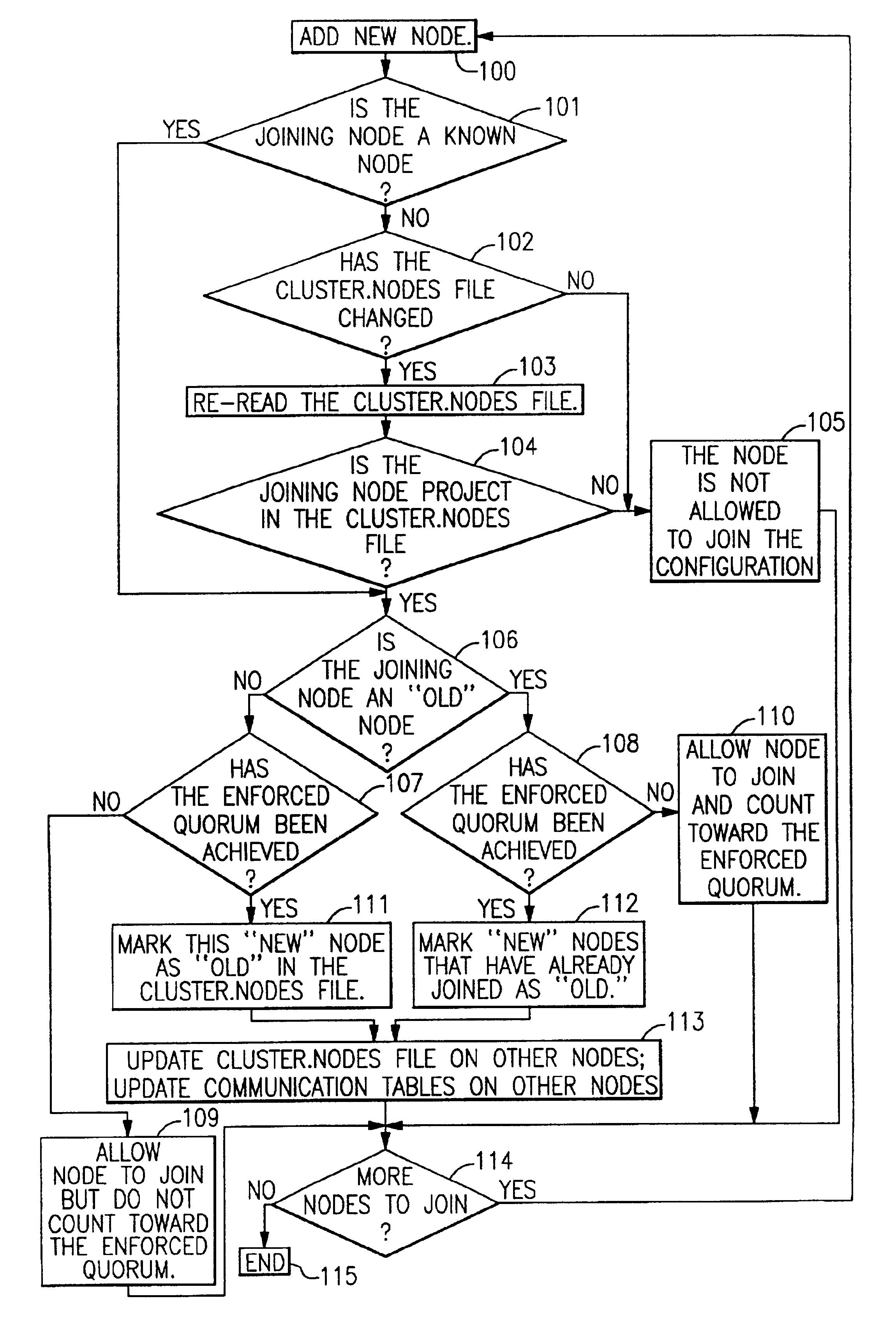
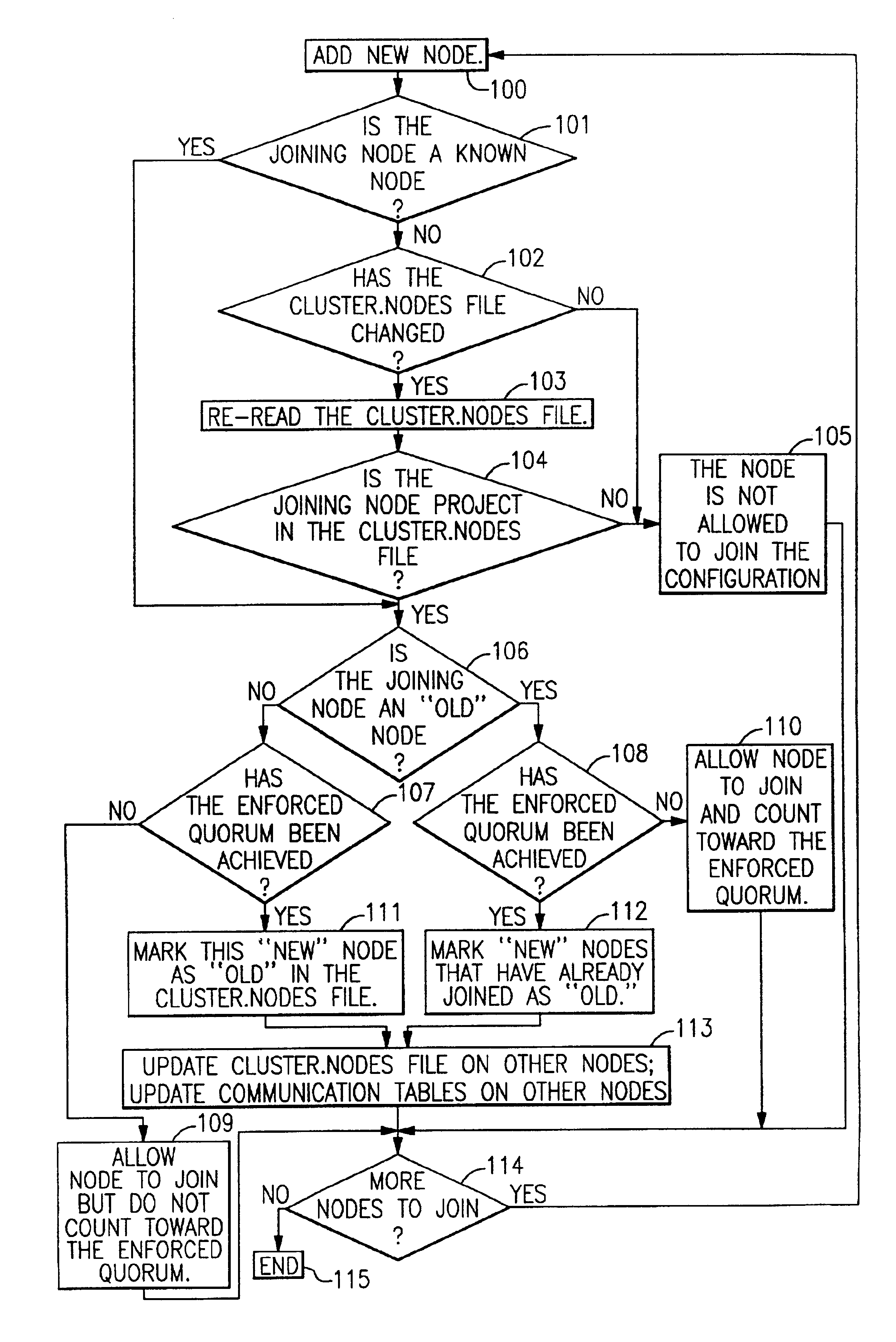
Dynamic quorum adjustment
InactiveUS6904448B2Improve efficiencyAvoid data corruptionData processing applicationsDigital data information retrievalData processing systemComputer network
In a multinode data processing system capable of partitioning operations a method is provided for adding nodes to a configuration of nodes in a manner which node quorums are employed but in which two quorum values (ideal and enforced) are employed and in which old nodes using a given file system are distinguished from new nodes. The method prevents even the transient use of inappropriate quorum values.
Owner:IBM CORP
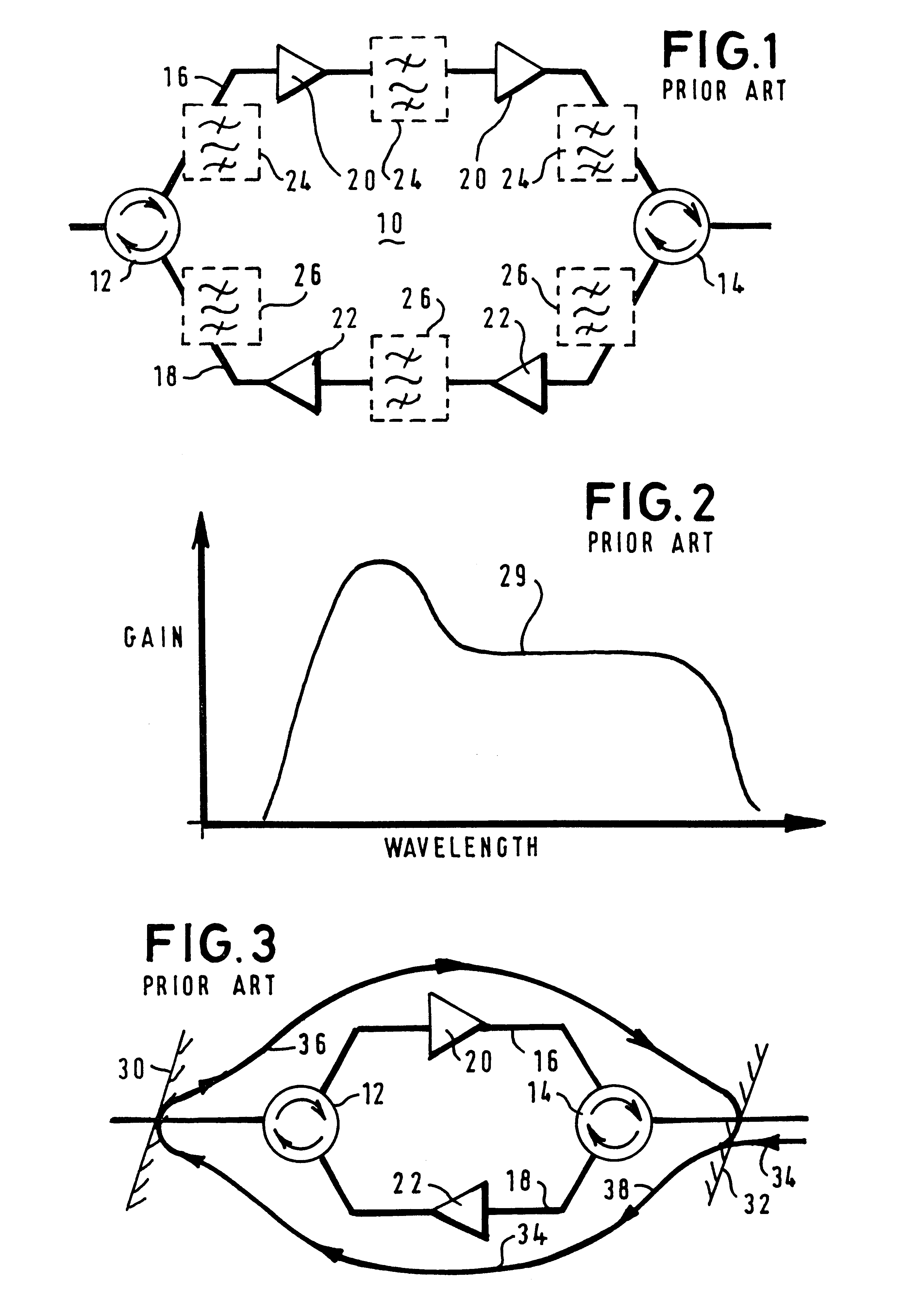
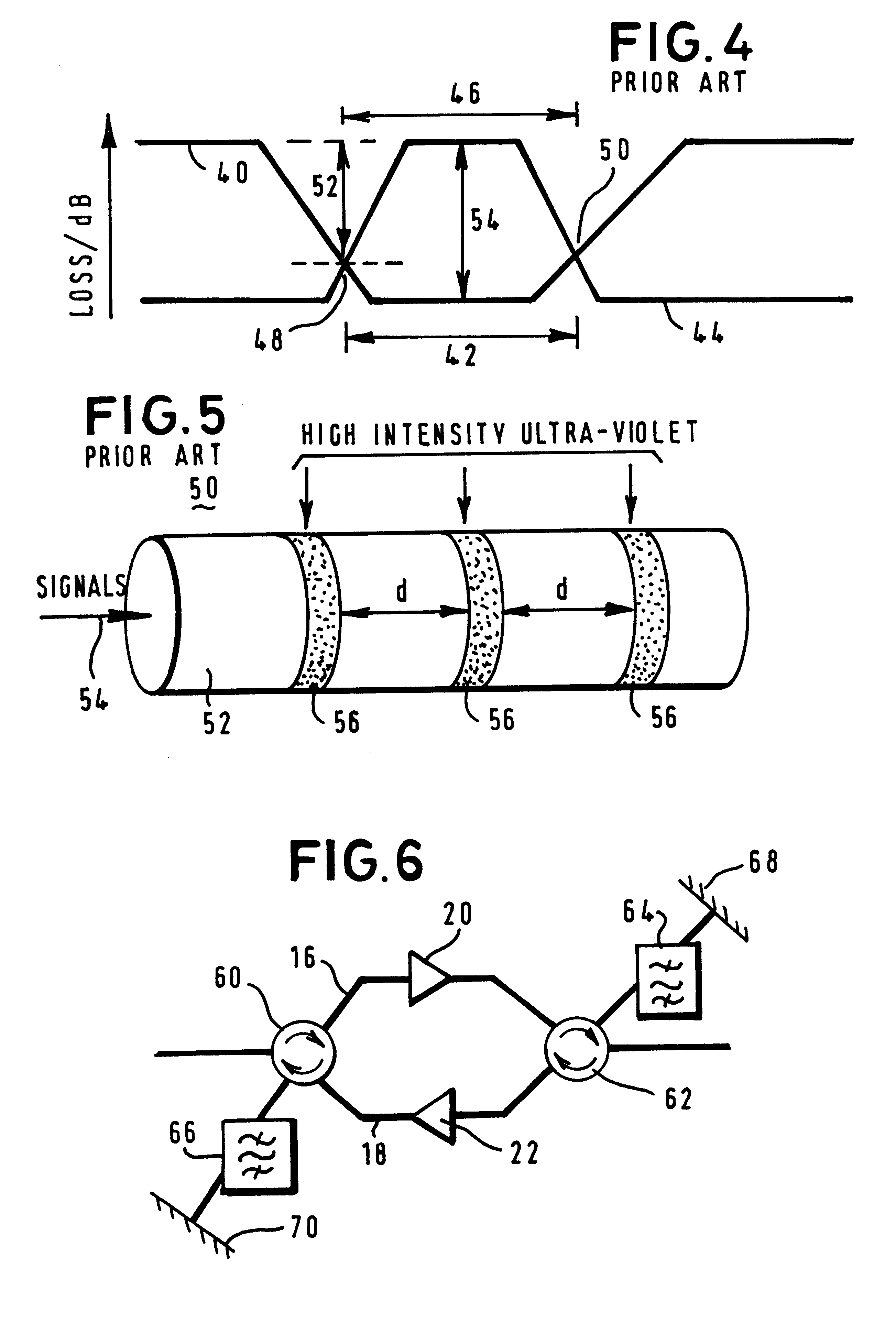
Circuit and channel assignment plan for optical transmissions
InactiveUS6751414B1High levelImprove signal integrityWavelength-division multiplex systemsElectromagnetic transmissionBroadbandEngineering
To support interleaving of optical channels and to provide sufficient isolation between such interleaved channels, a circulator (60-62) receives, on an optical fiber (16-18), a broadband signal containing a plurality of adjacent channels. The circulator selectively routes the broadband signal through a filter (64, 66) to isolate, on an individual basis, at least one desired channel. A filtered signal, corresponding to the at least one desired channel, is then output from the filter (64-66) and reflected back into the filter by a mirror (68-70) such that the at least one desired channel is subjected to a second filtering process that further improves isolation of the at least one desired channel. Following this second filtering process, the at least one desired channel is applied to the circulator (60-62) for re-inserting into the optical fiber (16-18), as illustrated in FIG. 6. To mitigate the effects of four-wave mixing in each bidirectional optical fiber, a channel assignment plan ensures that pairs of adjacent channels are assigned on a mutually exclusive basis to at least one of an up-link and a down-link direction.
Owner:CIENA
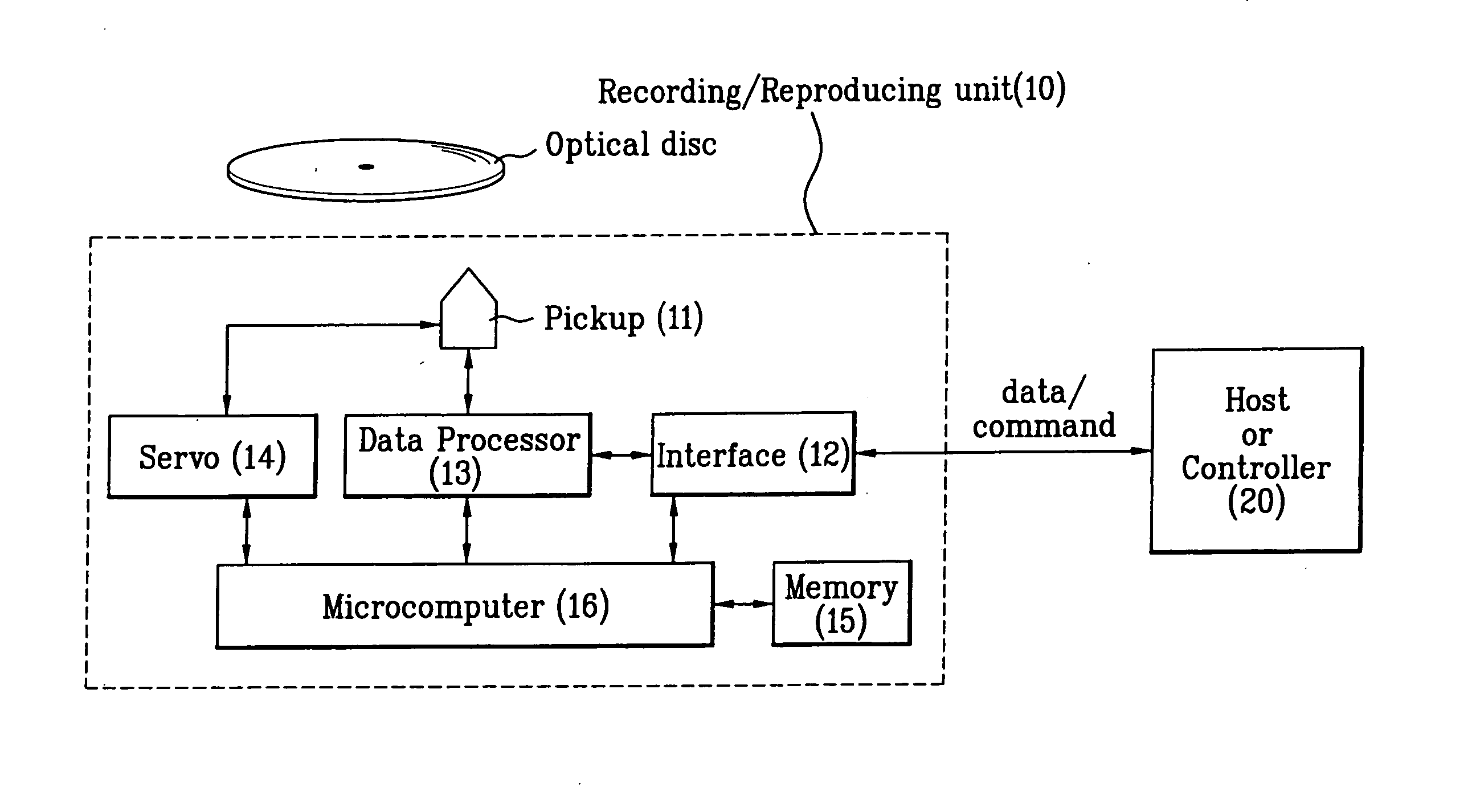
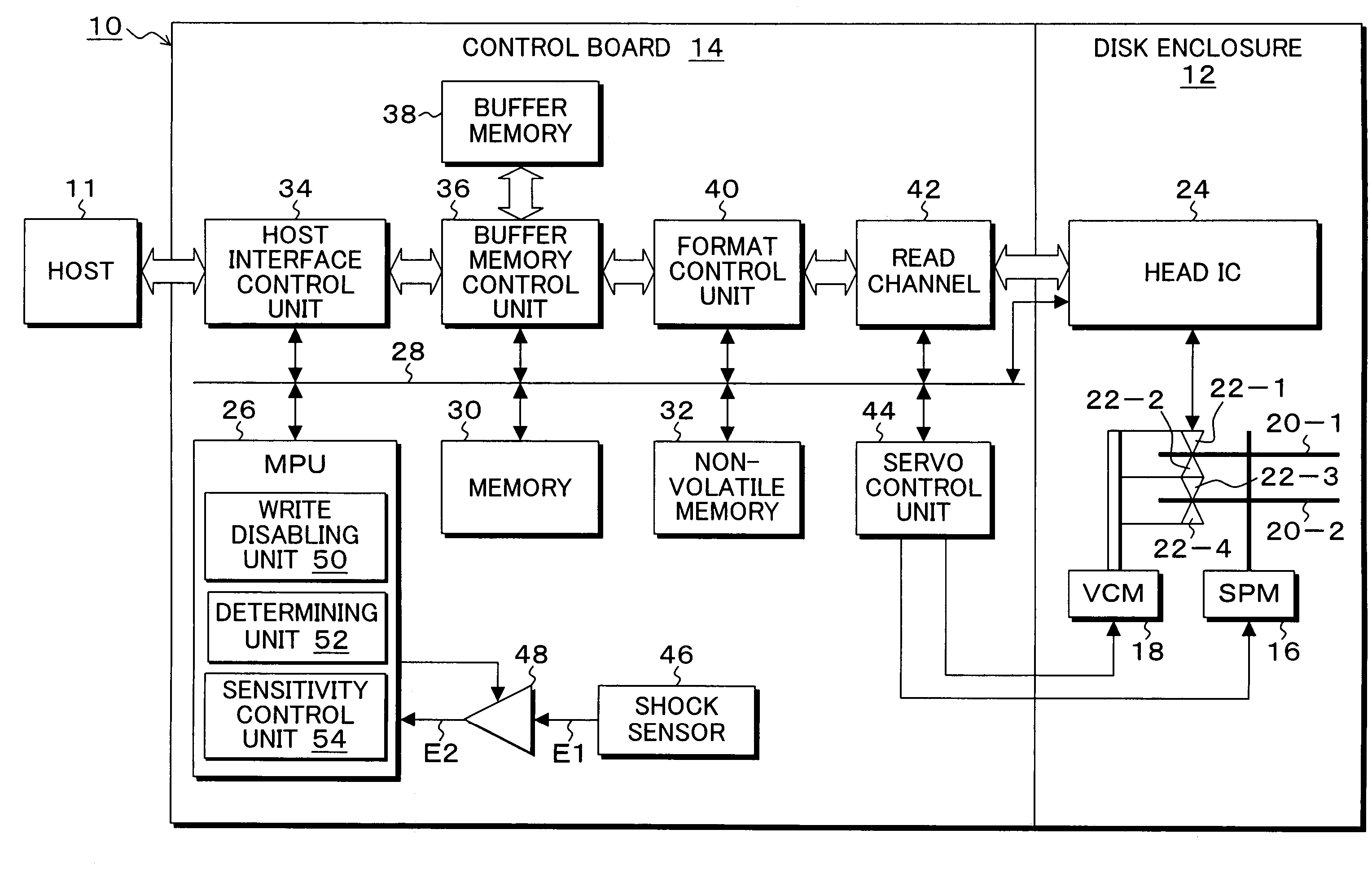
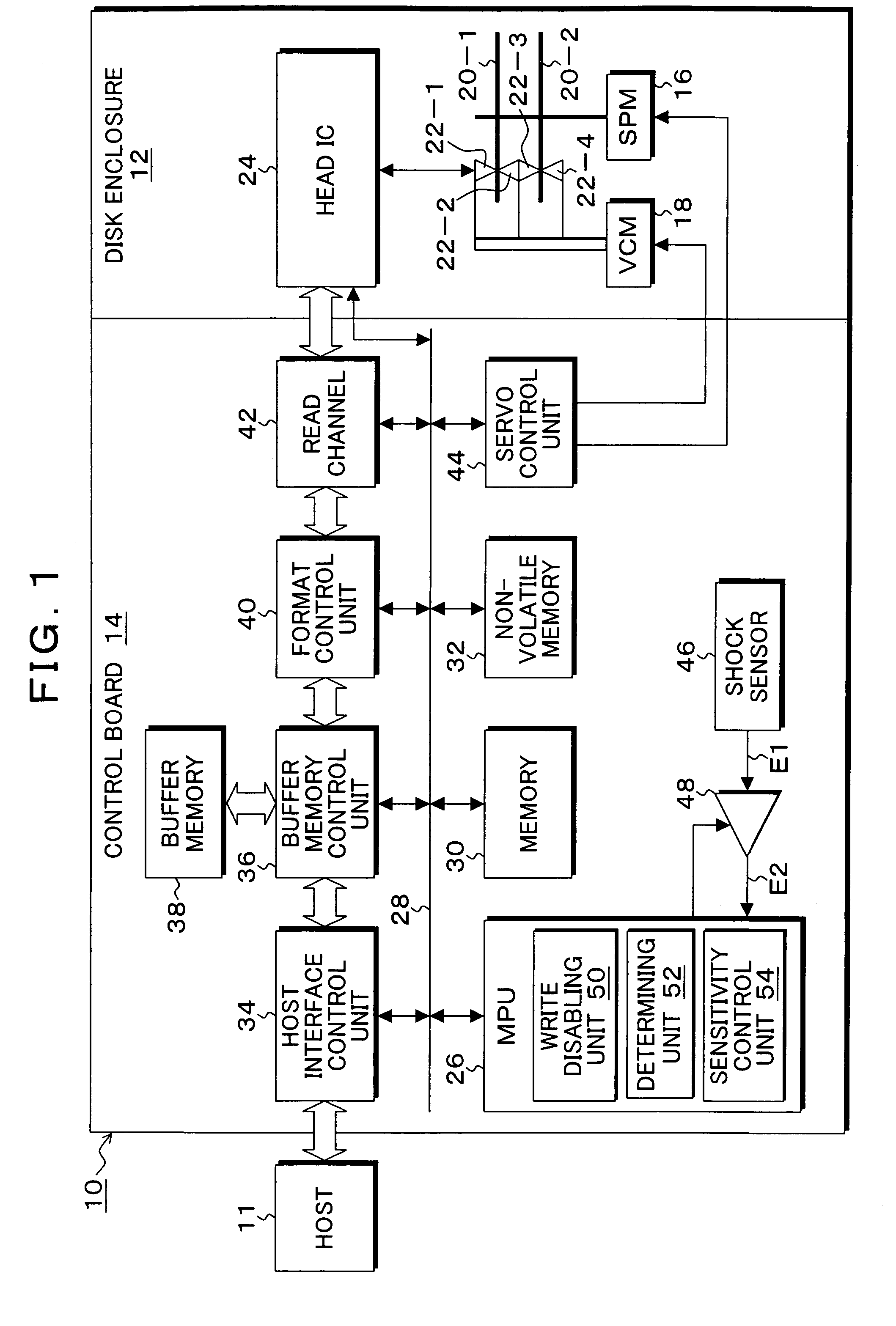
Storage apparatus, and control method and program
ActiveUS7382563B2Improve access capabilitiesAvoid misuseUndesired vibrations/sounds insulation/absorptionRecord information storageEngineeringControl unit
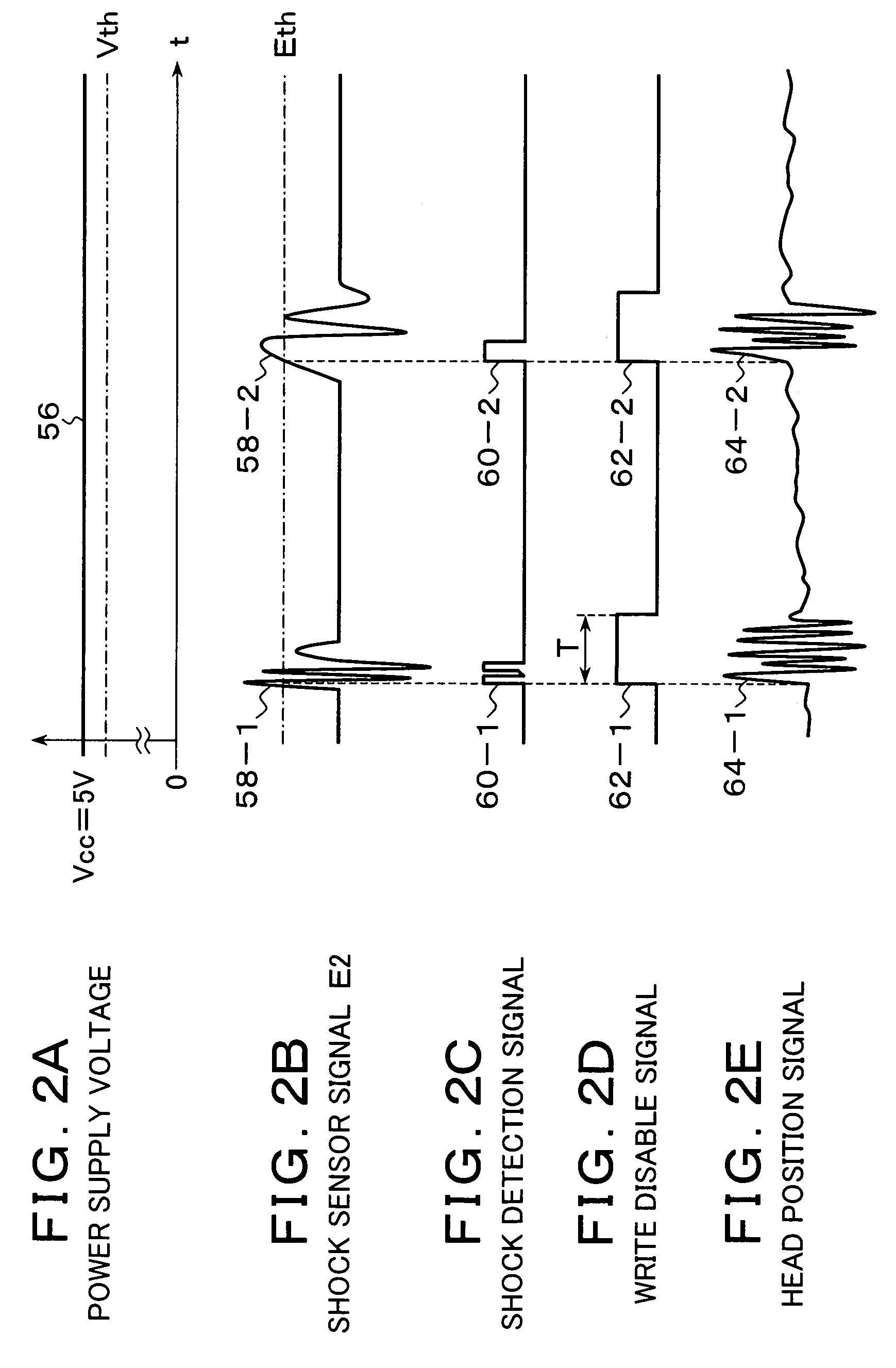
Upon obtaining a detection signal of a shock sensor that detects a shock applied to an apparatus for output, a write disabling unit disables writing by a head on a medium over a predetermined time corresponding to a shock convergence. A determining unit determines, during the write disable, whether an output of the shock sensor is a detection output of the shock sensor due to a shock or an erroneous detection output of the shock sensor due to power supply fluctuations. A sensitivity control unit increases a detection sensitivity of the shock sensor when the determining unit determines that the output is a detection output due to the shock, and decreases the detection sensitivity of the shock sensor and clears the write disable when the determining unit determines that the output is an erroneous detection output due to power supply fluctuations.
Owner:KK TOSHIBA
Semiconductor memory device, host device and semiconductor memory system
ActiveUS20100174951A1Avoid data corruptionEliminate the effect of errorMemory architecture accessing/allocationMemory adressing/allocation/relocationSemiconductorSemiconductor device
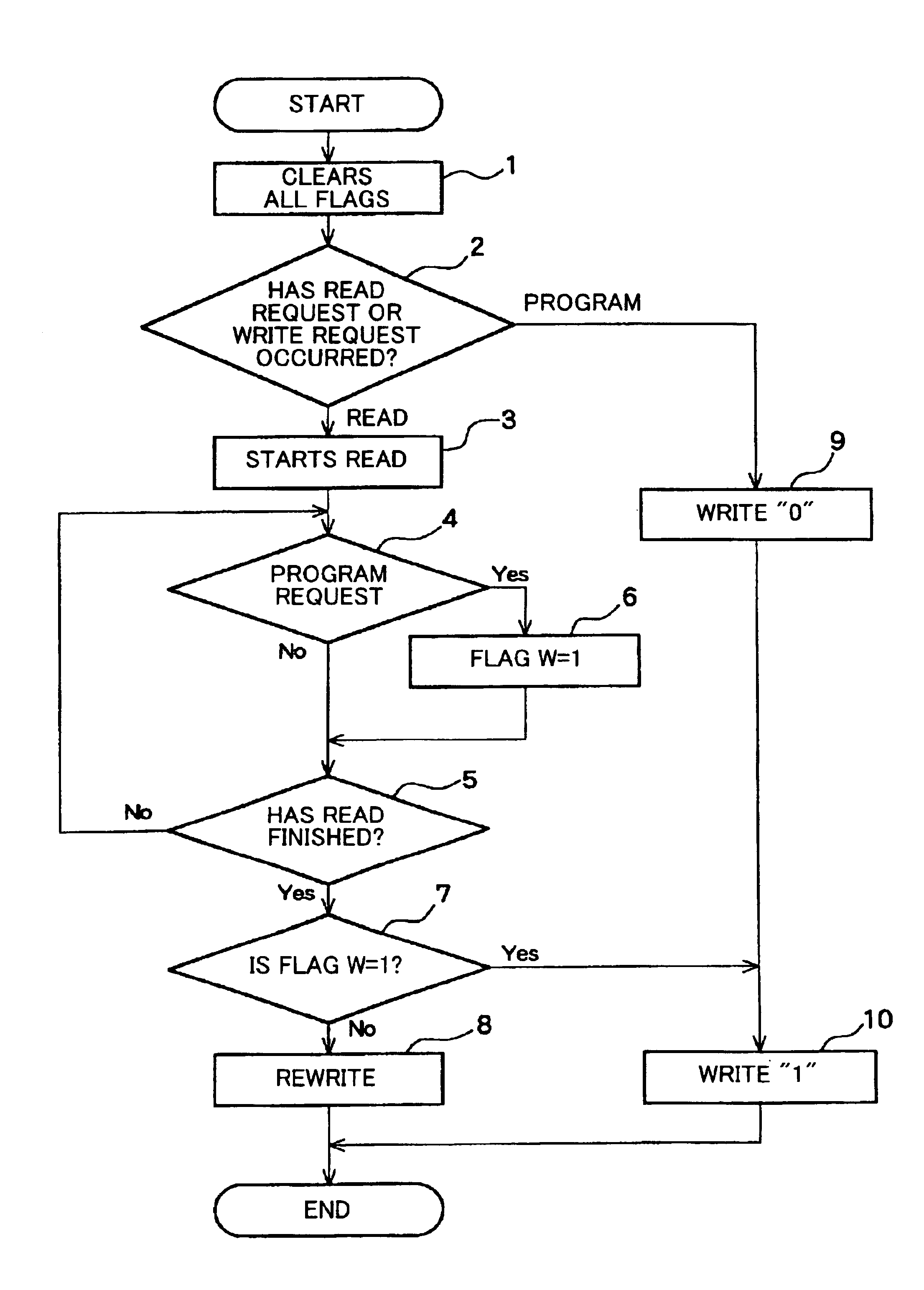
A host device 200A includes a data buffer 250. When data has been already written to a part of a physical block and data is additionally written to the physical block, it is determined whether or not the data written to the physical block is held in the data buffer. When the data is held, data is written to the block, and when an error exists, data in unit of physical blocks is rewritten. When the data is not held in the data buffer, a new physical block is required to be secured and then, data is written to the new block. Thereby, even when power is shut off or an error occurs during writing in the semiconductor memory device, destruction of data already written is prevented.
Owner:PANASONIC CORP
Coordinated disaster recovery production takeover operations
InactiveUS20120284556A1Efficiency and productivity be reduceReduce performanceDigital computer detailsTransmissionDisaster recoveryReliability engineering
For coordinated disaster reovery, a reconciliation process is performed for resolving intersecting and non-intersecting data amongst disaster recovery systems for takeover operations. An ownership synchronization process is coordinated for replica cartridges via the reconciliation process at the disaster recovery systems. The disaster recovery systems continue as a replication target for source systems and as a backup target for local backup applications.
Owner:IBM CORP
Information processing device and information processing method for data recovery after failure
InactiveUS7478270B2Avoid data corruptionPrevent corruptionMemory loss protectionRead-only memoriesInformation processingStart time
An information processing device and information processing method including a management table that includes three pages. A pair of first and second pages is alternately used as a valid page and an invalid page to secure the data. The valid page is copied to a third page. Even when the power is shut off in the process of updating the page, at the next start time, the status of the data writing operation when the power is shut off is determined based on the validity and stability of the pages. Therefore, the data is restored without any corruption of valid page by using a proper restoring method.
Owner:SONY CORP
Ferroelectric memory and method for reading data from the ferroelectric memory
InactiveUS20050259461A1Improve reliabilityHigh speed operationSolid-state devicesDigital storageFerroelectric capacitorElectrical and Electronics engineering
A ferroelectric memory of the present invention comprises: a plurality of normal cells, each of which includes a first ferroelectric capacitor for holding data and a first transistor connected to a first electrode of the first ferroelectric capacitor; a first bit line connected to the first transistor; a first bit line precharge circuit which is a switch circuit provided between the first bit line and a ground; and a word line connected to a gate of the first transistor. The word line is deactivated to disconnect the first ferroelectric capacitor from the first bit line before the first bit line precharge circuit is driven to discharge a potential of the first bit line.
Owner:PANASONIC CORP
Data storage method, storage array and host computer server
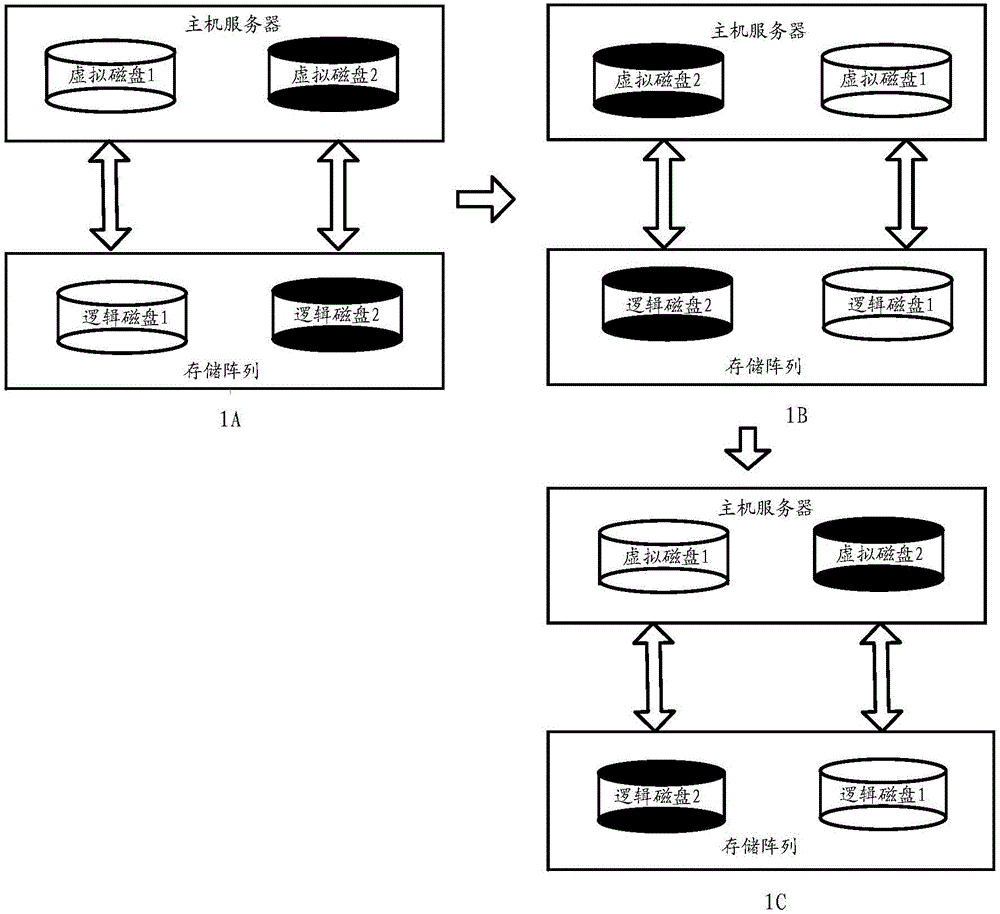
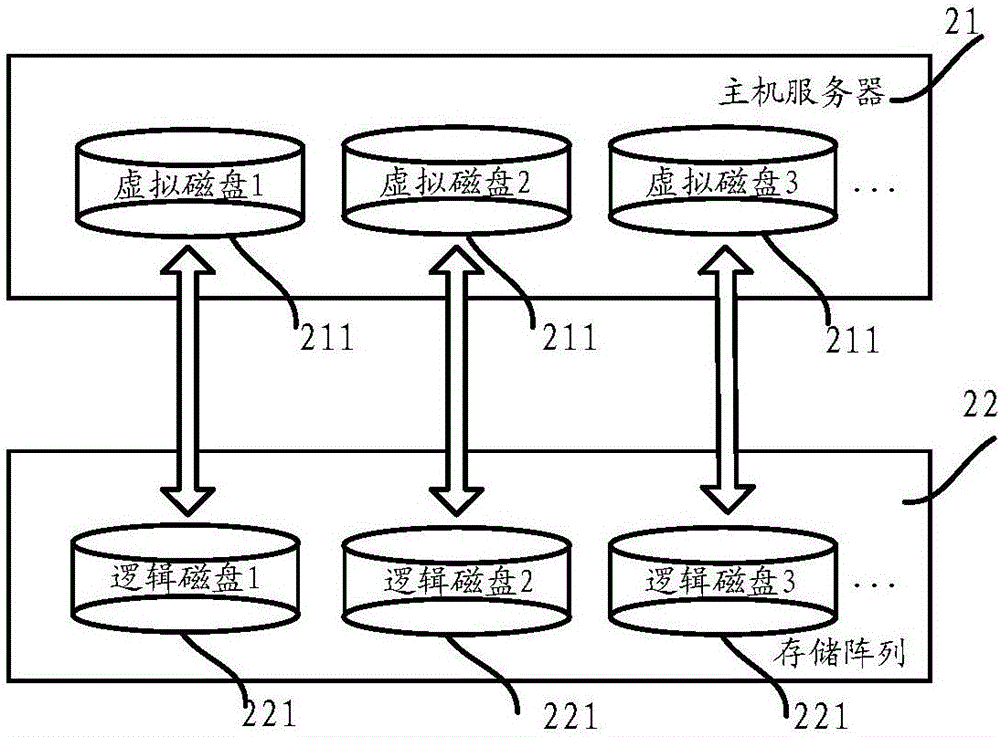
ActiveCN106557280AImprove reliabilityAvoid data corruptionInput/output to record carriersData CorruptionLogical disk
The embodiment of the invention provides a data storage method, a storage array and a host computer server, relates to the technical field of storage, and solves the problem of data corruption or service interruption caused by the fact that the change of a mapping relation between a logical disk in the storage array and a virtual disk in the host computer server cannot be updated in real time on the host computer server after the change of the mapping relation cannot be solved completely in the prior art. The method comprises the following steps: receiving an I / O request sent by the host computer server by the storage array, wherein the I / O request is carried with a first token; matching the first token with a plurality of current tokens by the storage array; if one current token same as the first token exists in the current tokens, processing the I / O request through the logical disk corresponding to the current token same as the first token by the storage array, and sending a message that the I / O request is successfully processed to the host computer server; and if the one current token same as the first token does not exist in the current tokens, sending a message that the I / O request is unsuccessfully processed to the host computer server by the storage array.
Owner:BEIJING HUAWEI DIGITAL TECH
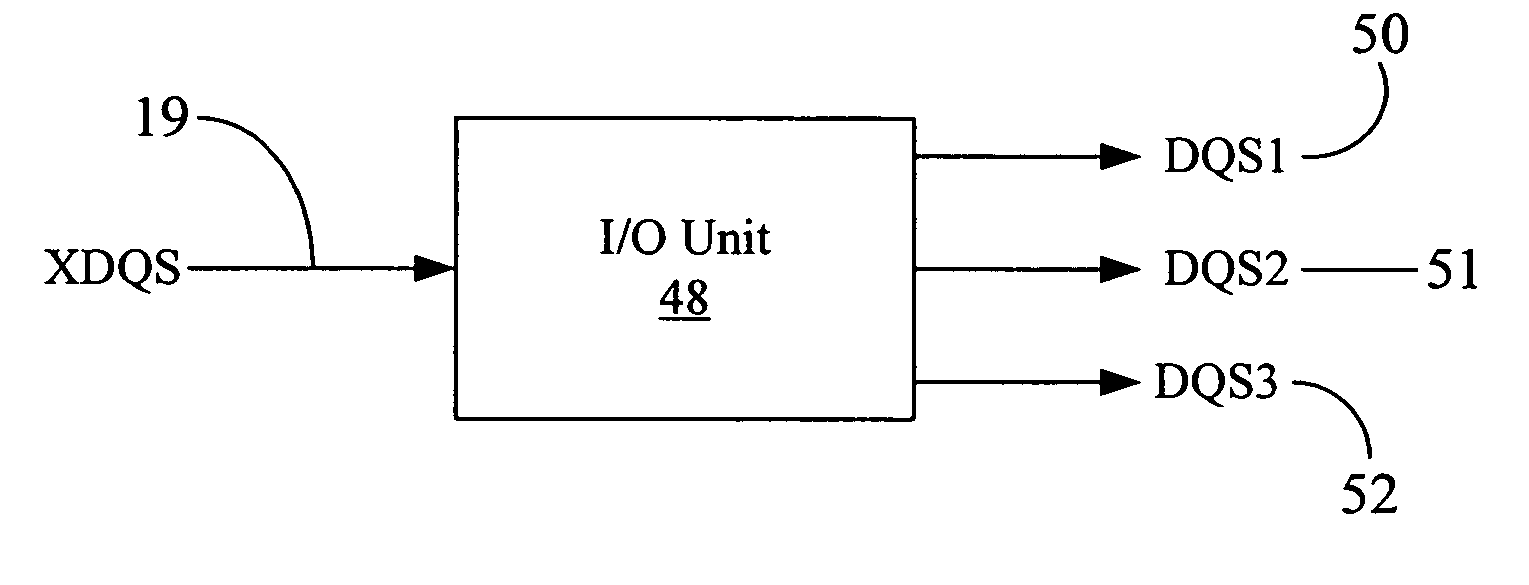
Solution to DQS postamble ringing problem in memory chips
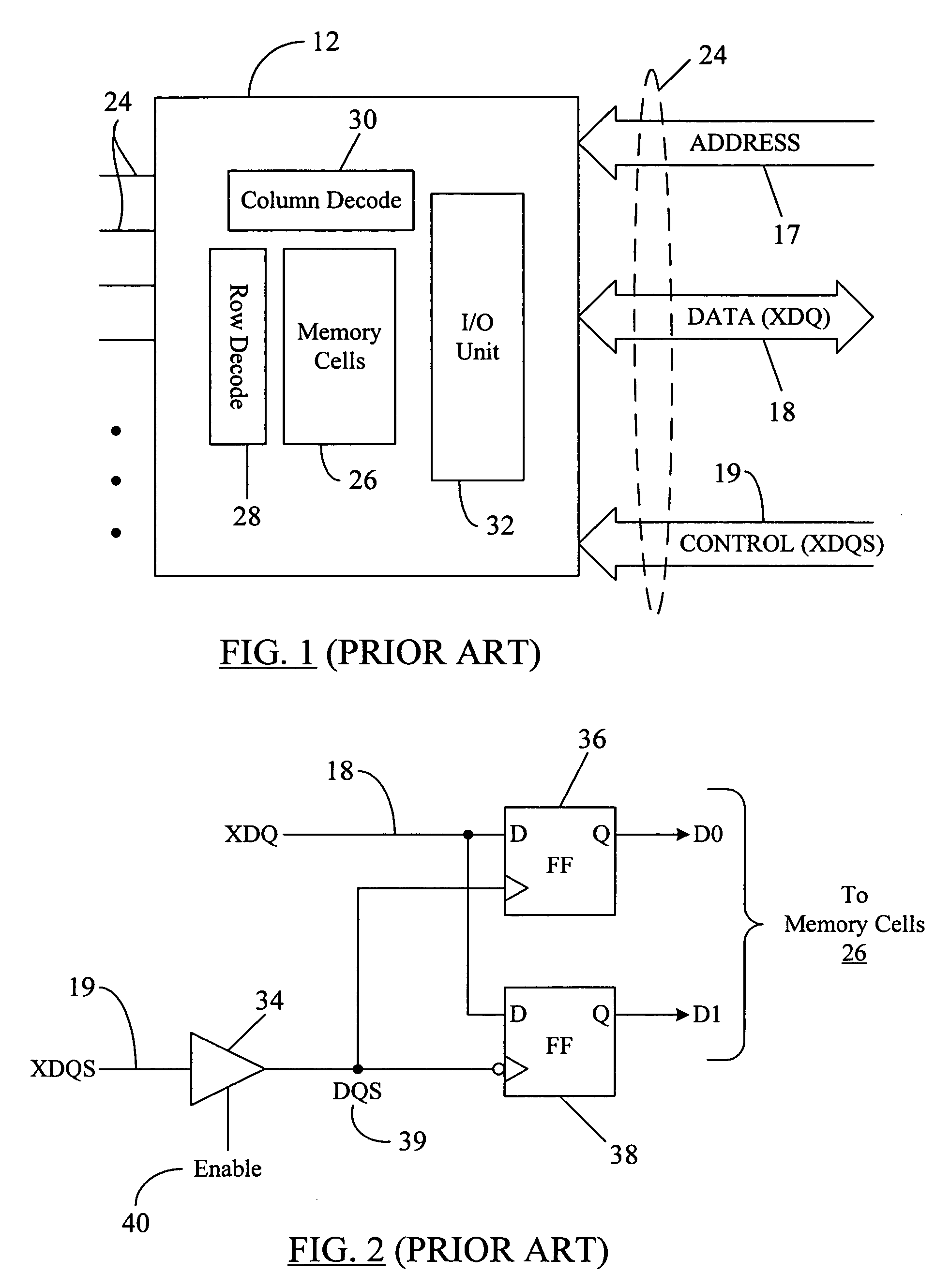
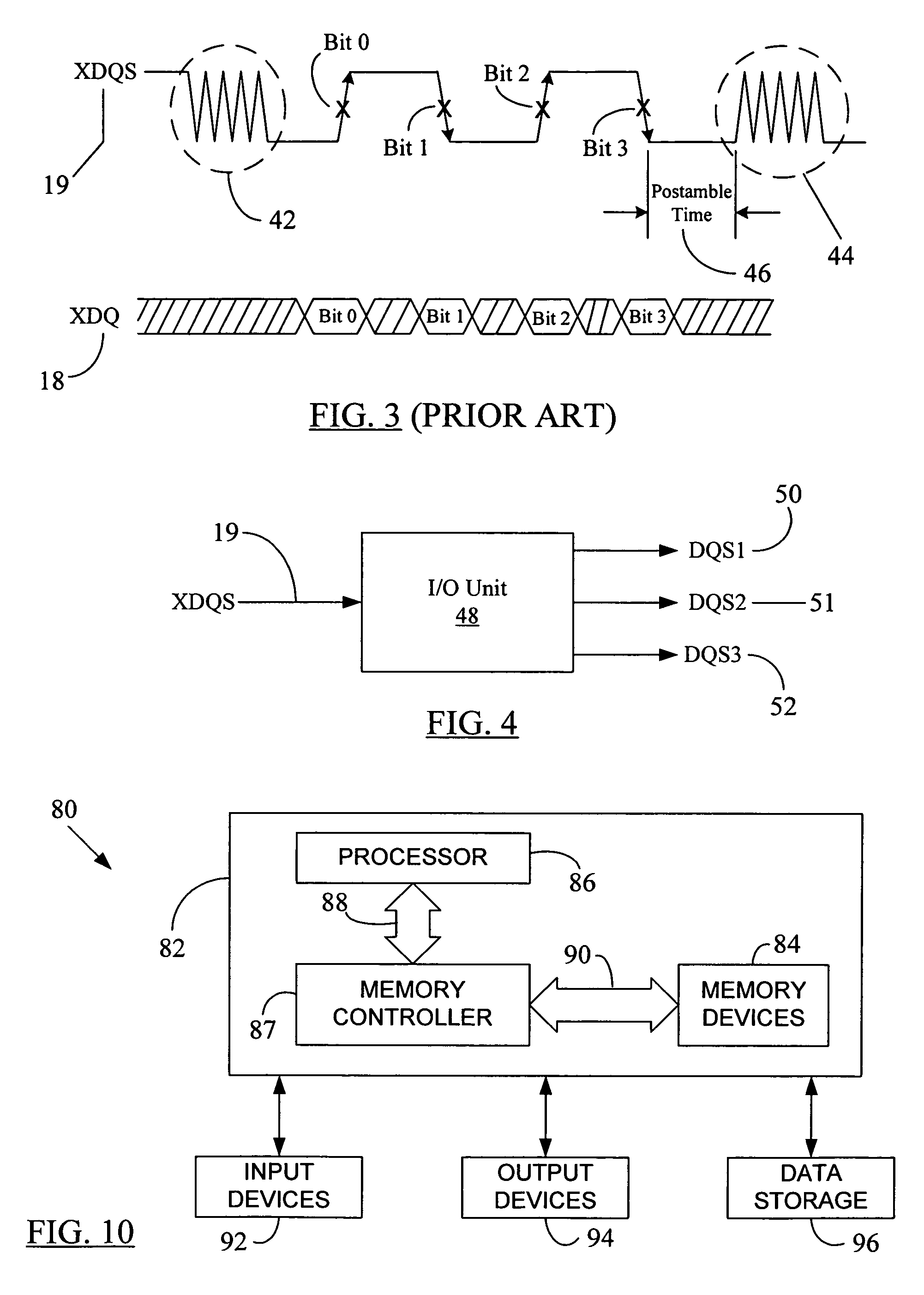
The disclosed system and method significantly reduce or eliminate DQS postamble ringing problem in modern high-speed memory chips, allowing the memory chips to be operated at significantly faster clock speeds. The external strobe signal (XDQS) may be used to generate at least two derivative strobe signals therefrom. Instead of the XDQS signal, the derivative strobe signals are then used, in a predetermined order, to clock in or strobe the data to be written into memory cells. The last generated derivative strobe signal may be used to finally transfer the data bits into memory cells. Once the last of the derivative strobe signals is activated, and so long as there are no more data writes pending in the command pipe for the next clock cycle, the rising or falling edge of the last derivative strobe signal can be detected to turn off further generation of the strobe signals prior to any onset of postamble ringing on the XDQS signal. Thus, false data may not get “clocked in” or written into the memory chip because of postamble ringing. This prevents data corruption and preserves the integrity of the data written into a memory chip.
Owner:ROUND ROCK RES LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com