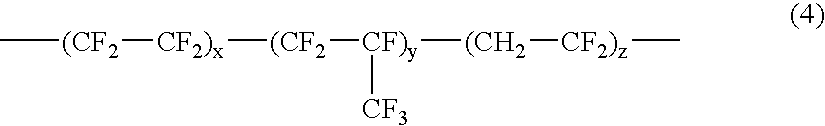Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
696results about How to "Optimize network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
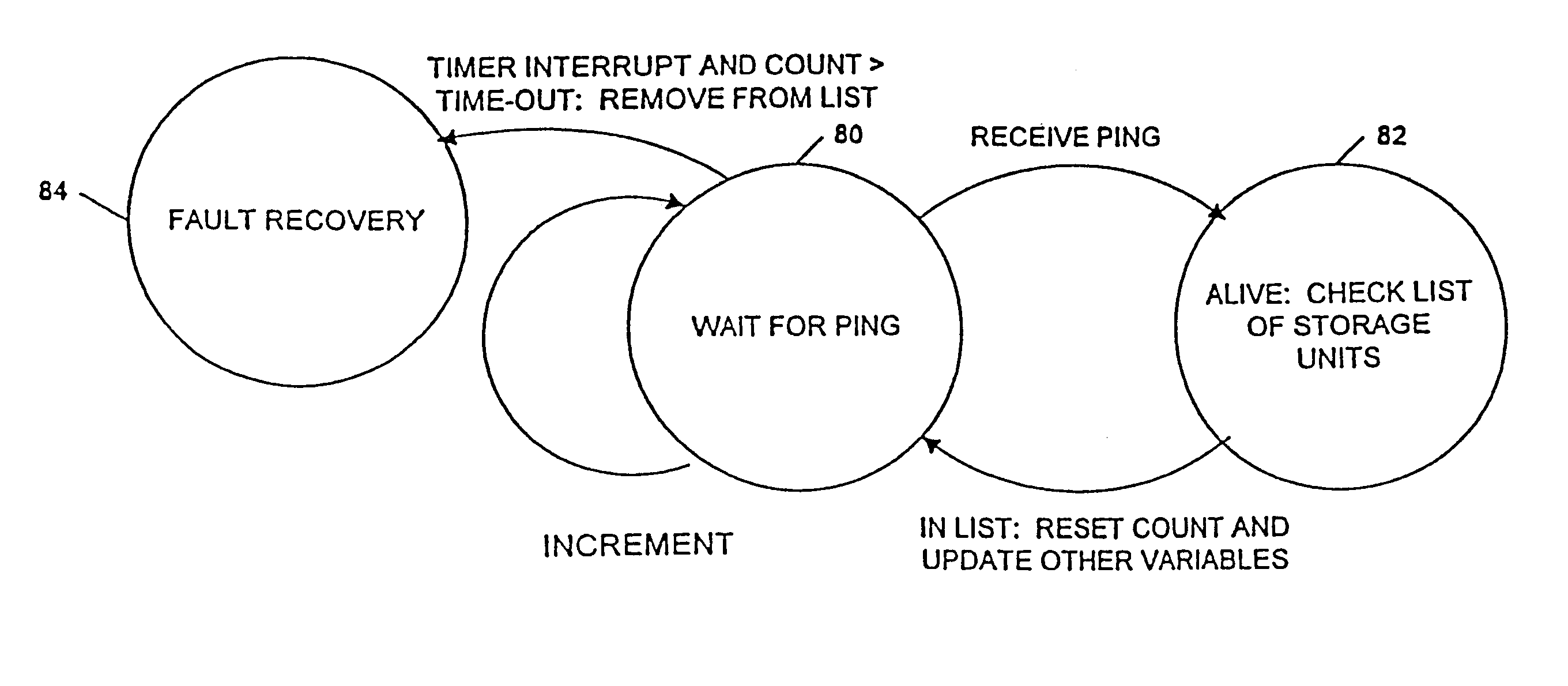
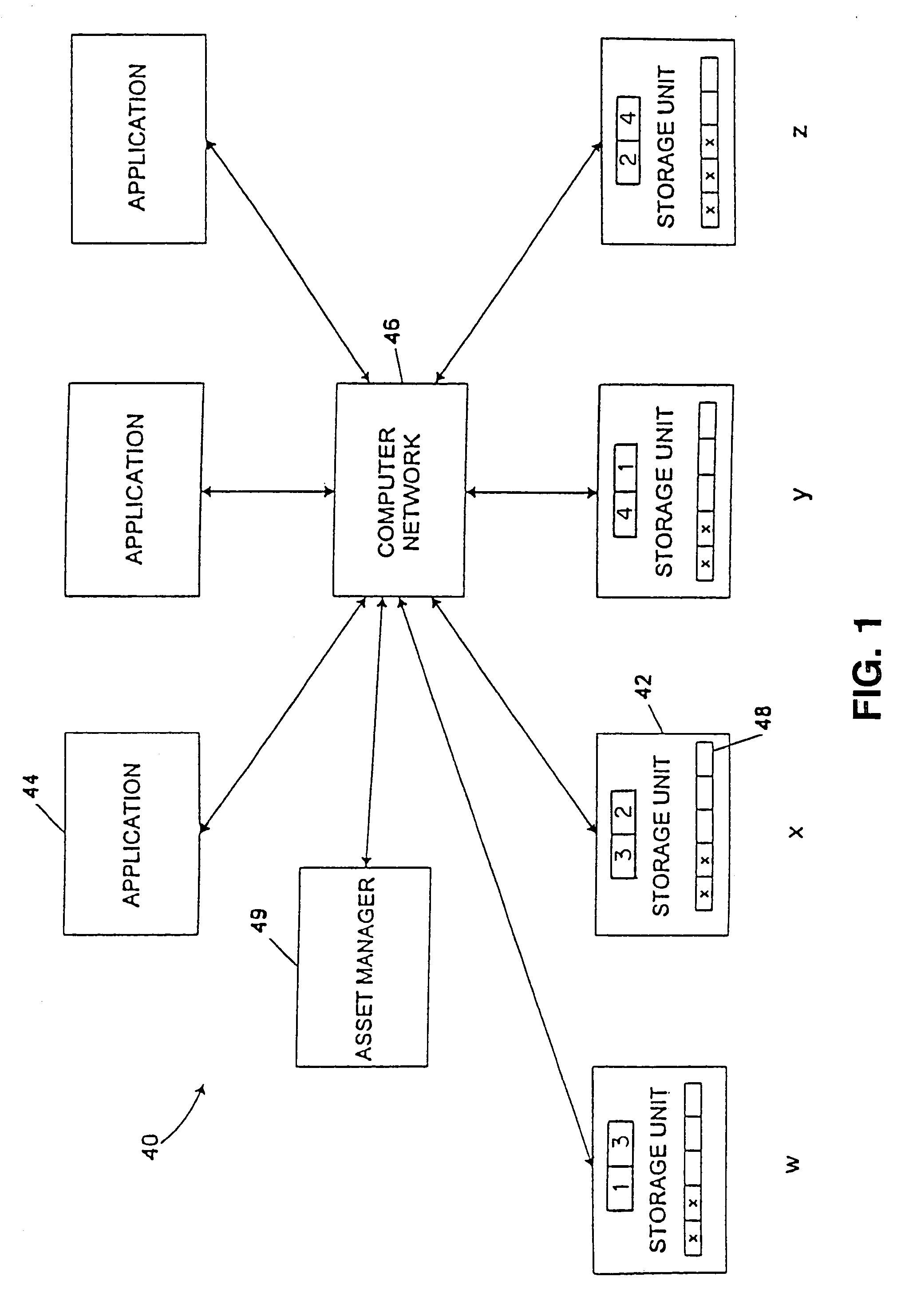
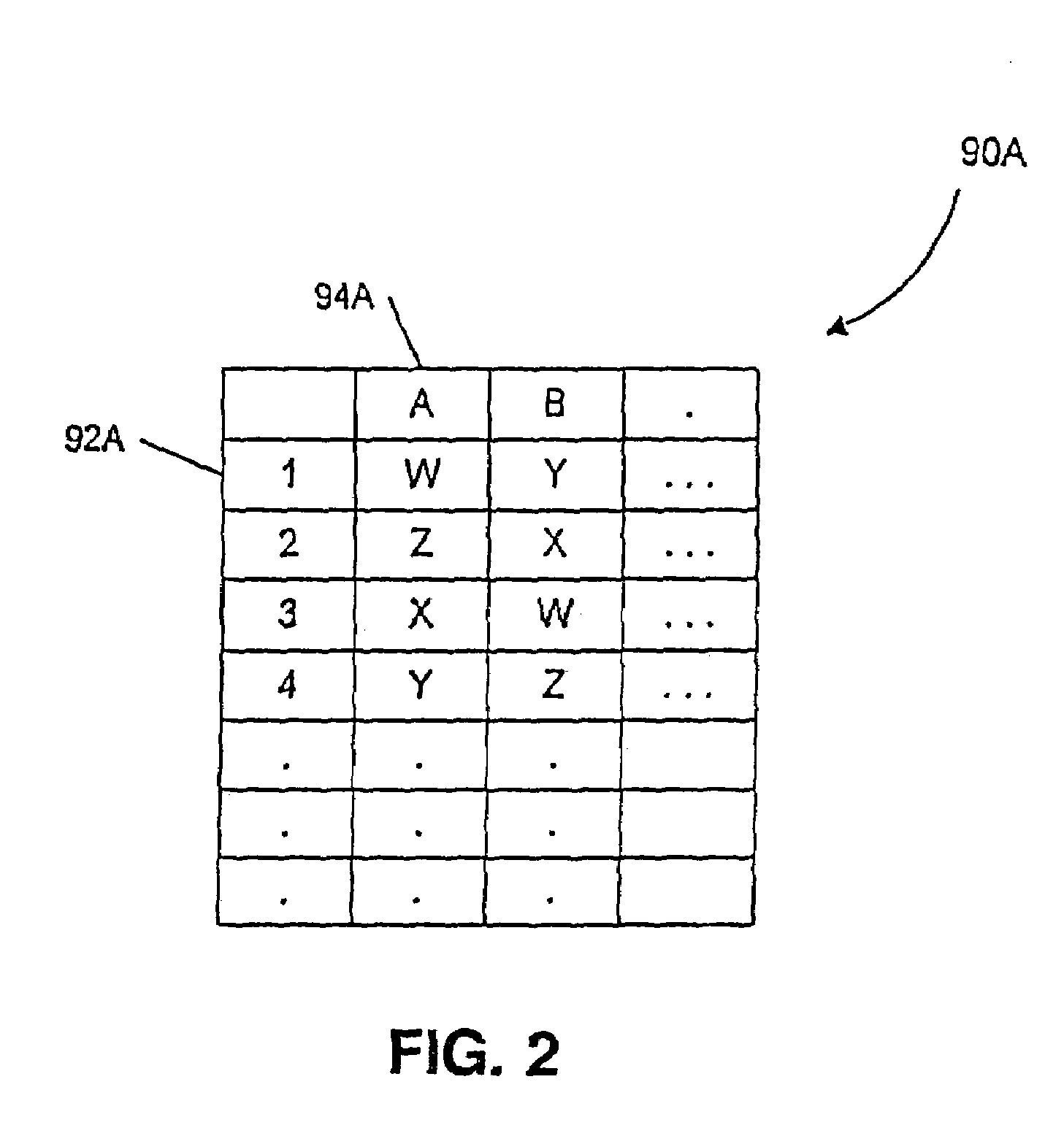
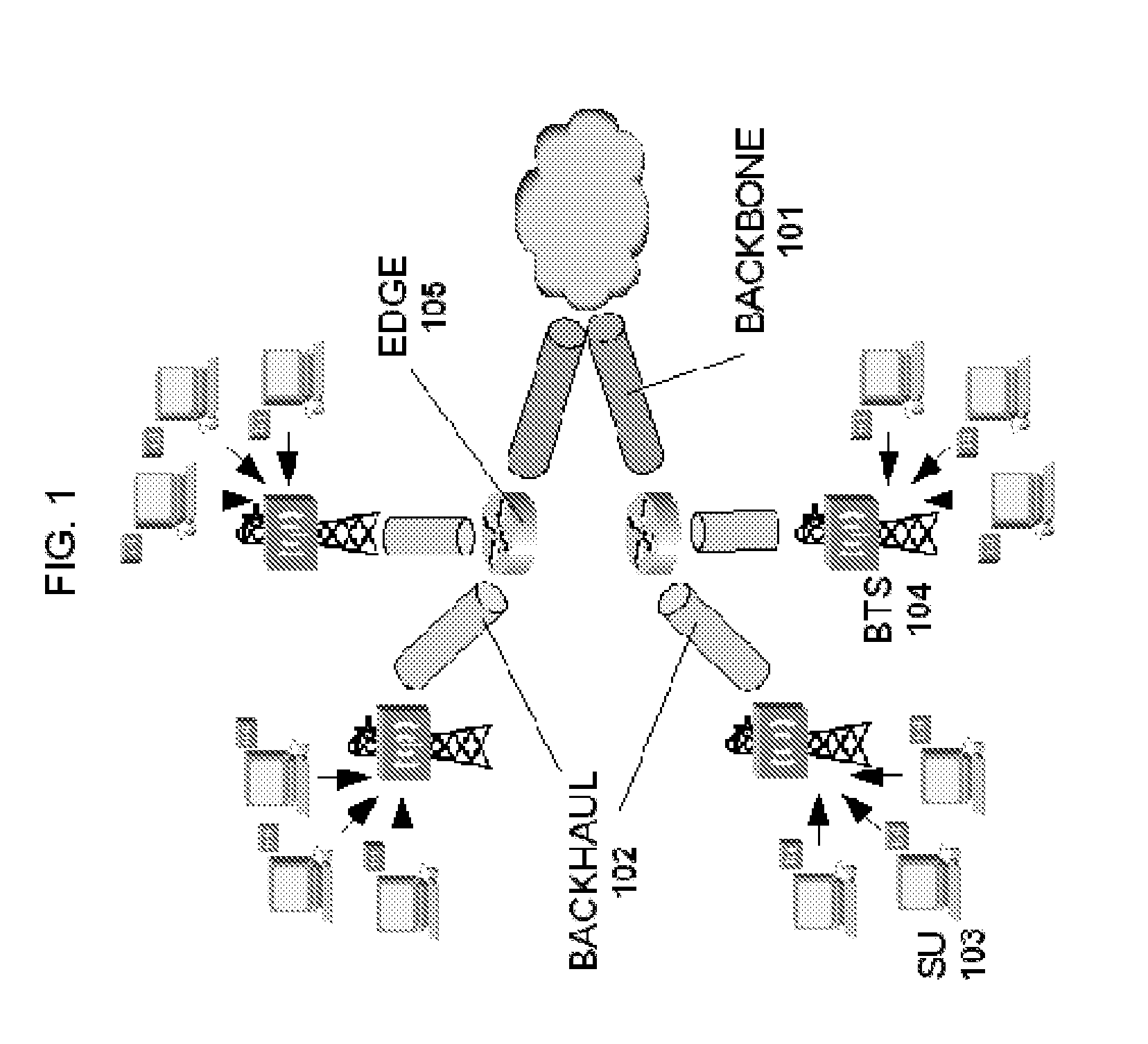
Computer system and process for transferring multiple high bandwidth streams of data between multiple storage units and multiple applications in a scalable and reliable manner
InactiveUS7111115B2Improve reliabilityImprove scalabilityInput/output to record carriersData processing applicationsHigh bandwidthData segment
Multiple applications request data from multiple storage units over a computer network. The data is divided into segments and each segment is distributed randomly on one of several storage units, independent of the storage units on which other segments of the media data are stored. At least one additional copy of each segment also is distributed randomly over the storage units, such that each segment is stored on at least two storage units. This random distribution of multiple copies of segments of data improves both scalability and reliability. When an application requests a selected segment of data, the request is processed by the storage unit with the shortest queue of requests. Random fluctuations in the load applied by multiple applications on multiple storage units are balanced nearly equally over all of the storage units. This combination of techniques results in a system which can transfer multiple, independent high-bandwidth streams of data in a scalable manner in both directions between multiple applications and multiple storage units.
Owner:AVID TECHNOLOGY
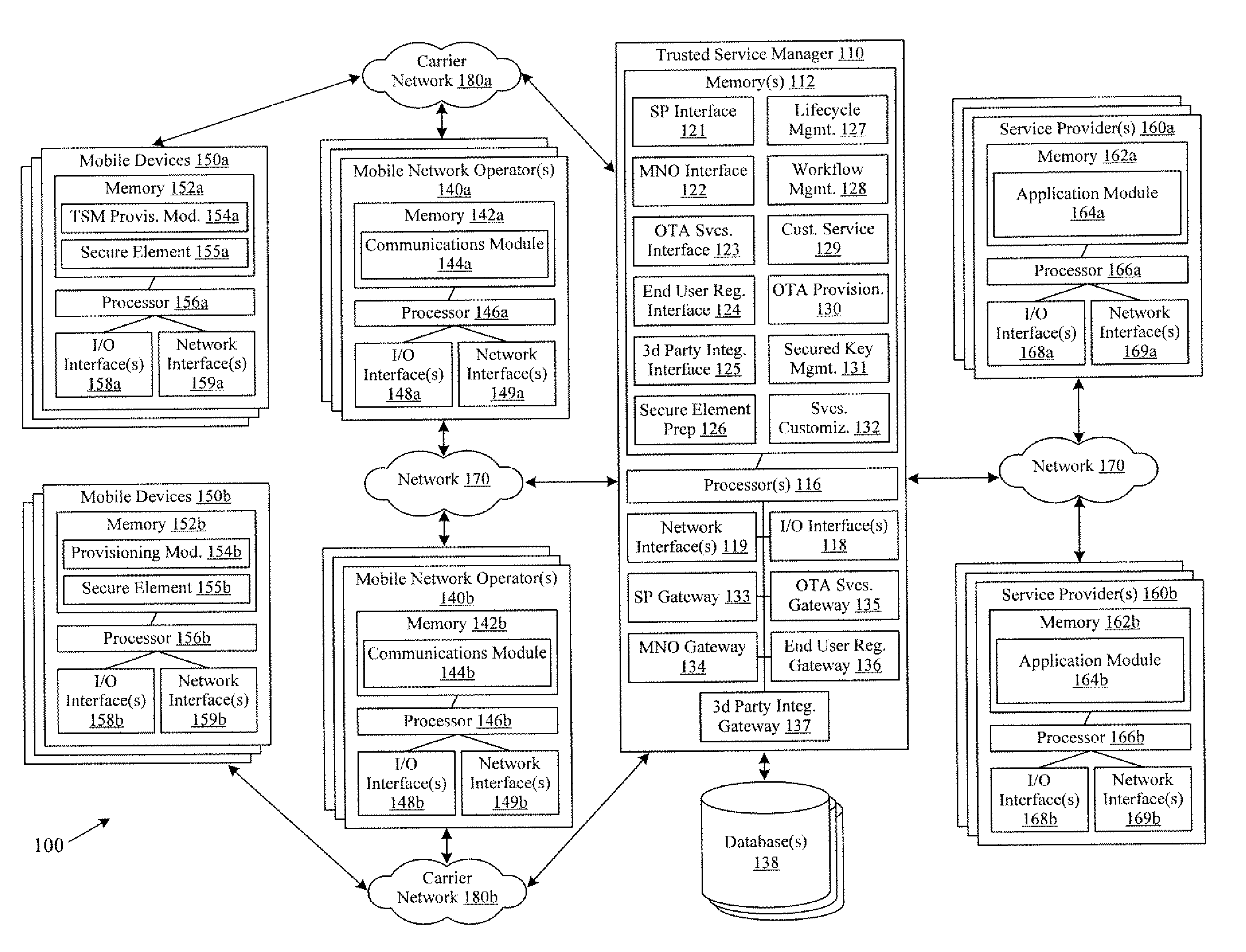
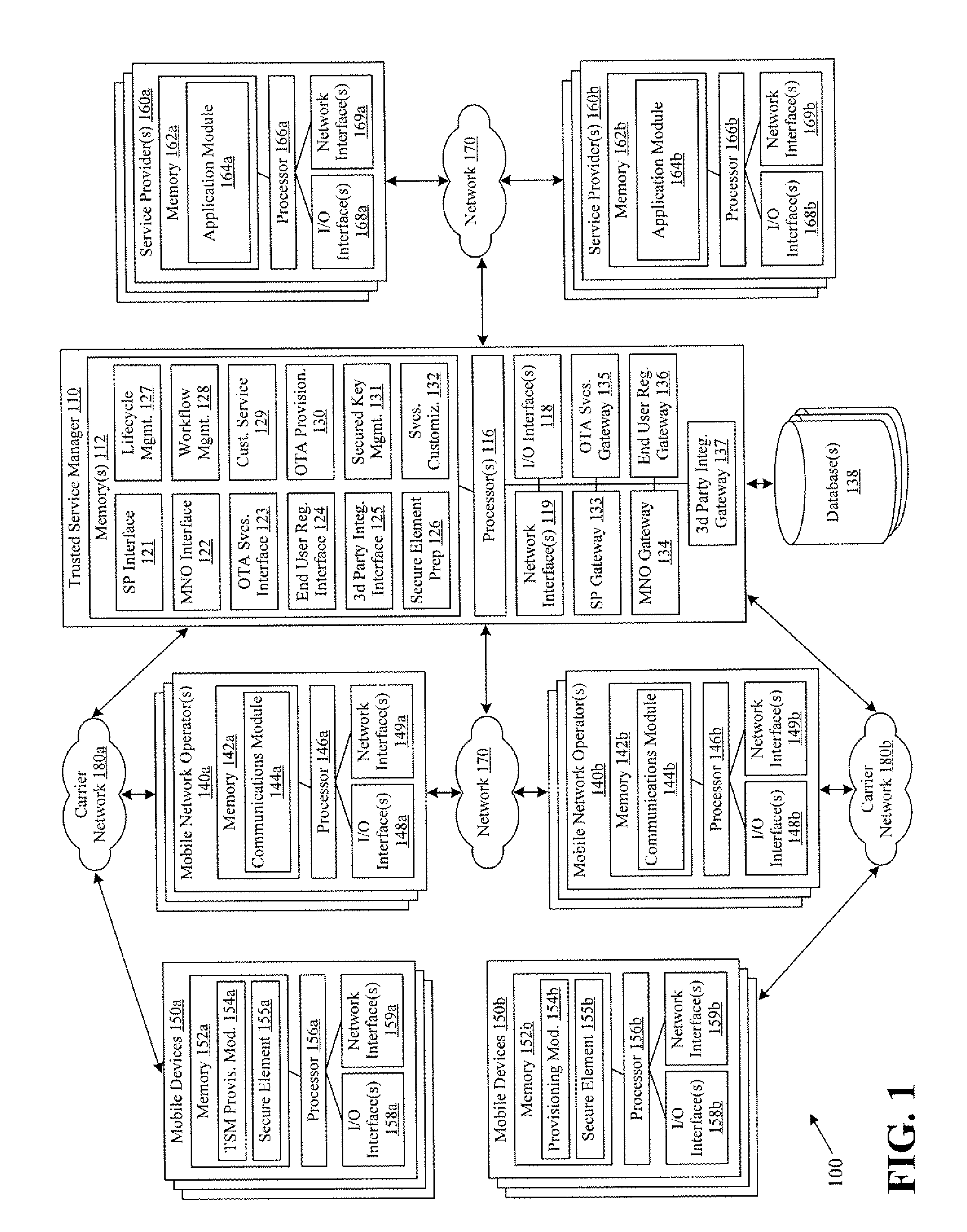
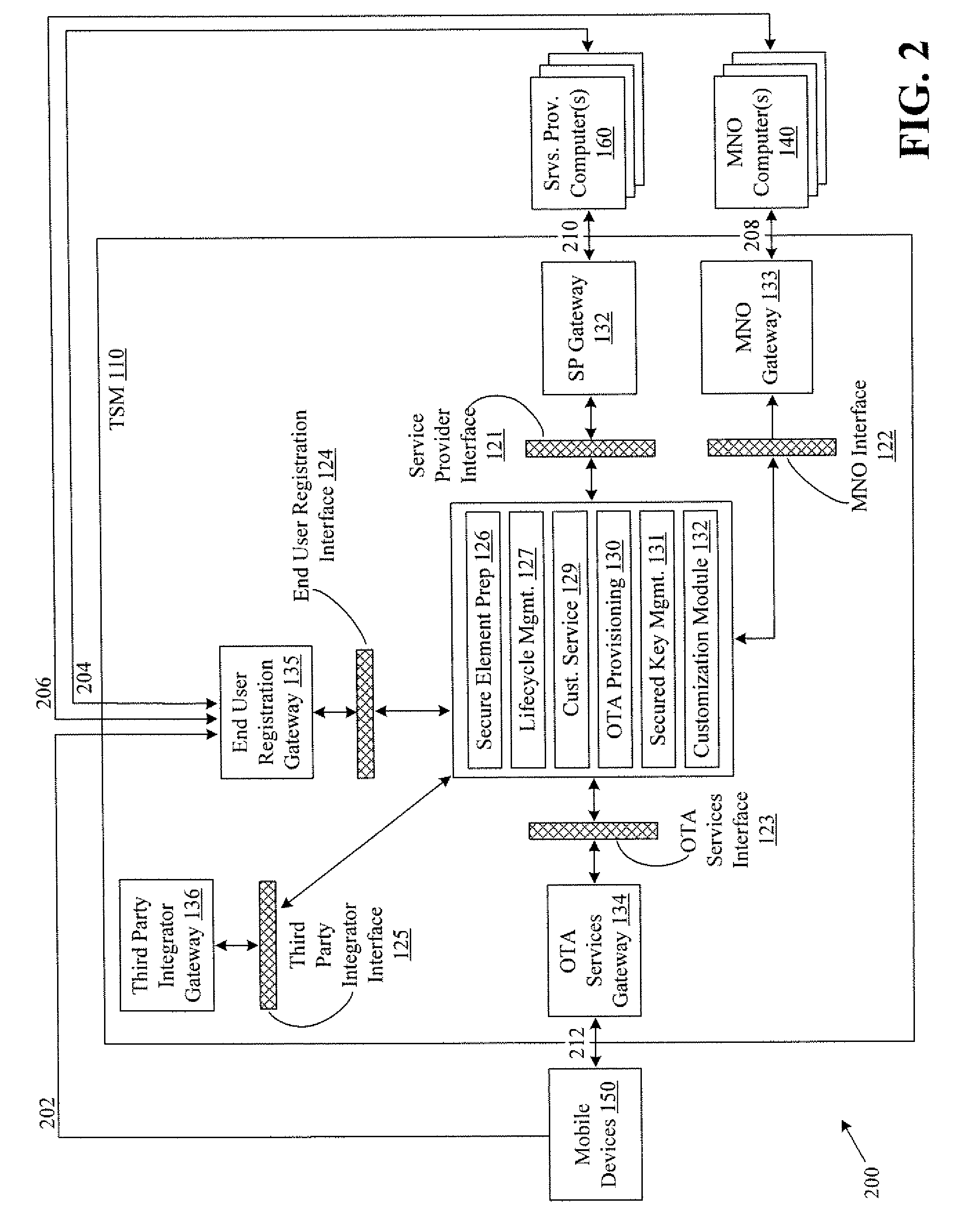
Systems and methods for providing trusted service management services
InactiveUS20100291904A1Easy maintenanceOptimize networkService provisioningSpecial service for subscribersService provisionMobile device
Embodiments of the invention provide systems and methods for providing trusted service management services. According to one embodiment, a system can include at least one service provider gateway operable to receive and transmit messages with multiple service providers; at least one mobile network operator gateway operable to receive and transmit messages with multiple mobile network operators; at least one provisioning gateway operable to transmit mobile device application data with multiple mobile devices and to receive messages from the plurality of mobile devices. The system can further include a processor operable to execute computer-executable instructions to: facilitate service provider communications by providing a common service provider interface for the service providers; facilitate mobile network operator communications by providing a common mobile network operator interface for the mobile network operators; facilitate provisioning multiple mobile device applications with the mobile devices; and facilitate communications with the mobile devices.
Owner:FIRST DATA
Storage server system including ranking of data source
InactiveUS6446141B1Improve performanceSimple equipmentInput/output to record carriersTransmissionCommunication interfaceOperational system
A storage server comprising: a processing unit, a bus system coupled with the processing unit, including a plurality of slots, slots in the plurality of slots including interfaces to respective data stores; a communication interface; and an operating system coupled with the processing unit the operating system including: logic controlling transfers among the plurality of slots over the bus system according to an internal format, logic for translating a storage transaction received over the communication interface into the internal format, and logic for configuring the plurality of slots according to a configuration data.
Owner:DELL PROD LP
Content delivery network system and method for building the same
InactiveUS20020116481A1Optimize networkSolve the real problemData switching by path configurationMultiple digital computer combinationsClient-sideContent delivery network
A content delivery network system is disclosed. The system comprises a communication network, a first network node for providing services for clients to access network, a second network node for managing hosts for network content providers and a third network node, wherein said third network node sets a default route and a VPN tunnel between the first and second network nodes, and provides a cache server at the bandwidth outlet of the first network node, said cache server stores a information content which has been requested and transmitted. When the client request an information content, the third network node searches the cache server. If the information content is found, the cache server provides said information content to the client directly. If the information content is not found, the cache server sends a request for catching the information content to the second network via the VPN tunnel, and transmits the information content to the client via the default route. The cache server records the data of the transmitted information content. The recorded data is provided to the second network node, so that the second network node can bill the network content provider accordingly.
Owner:LEE KIM MAN
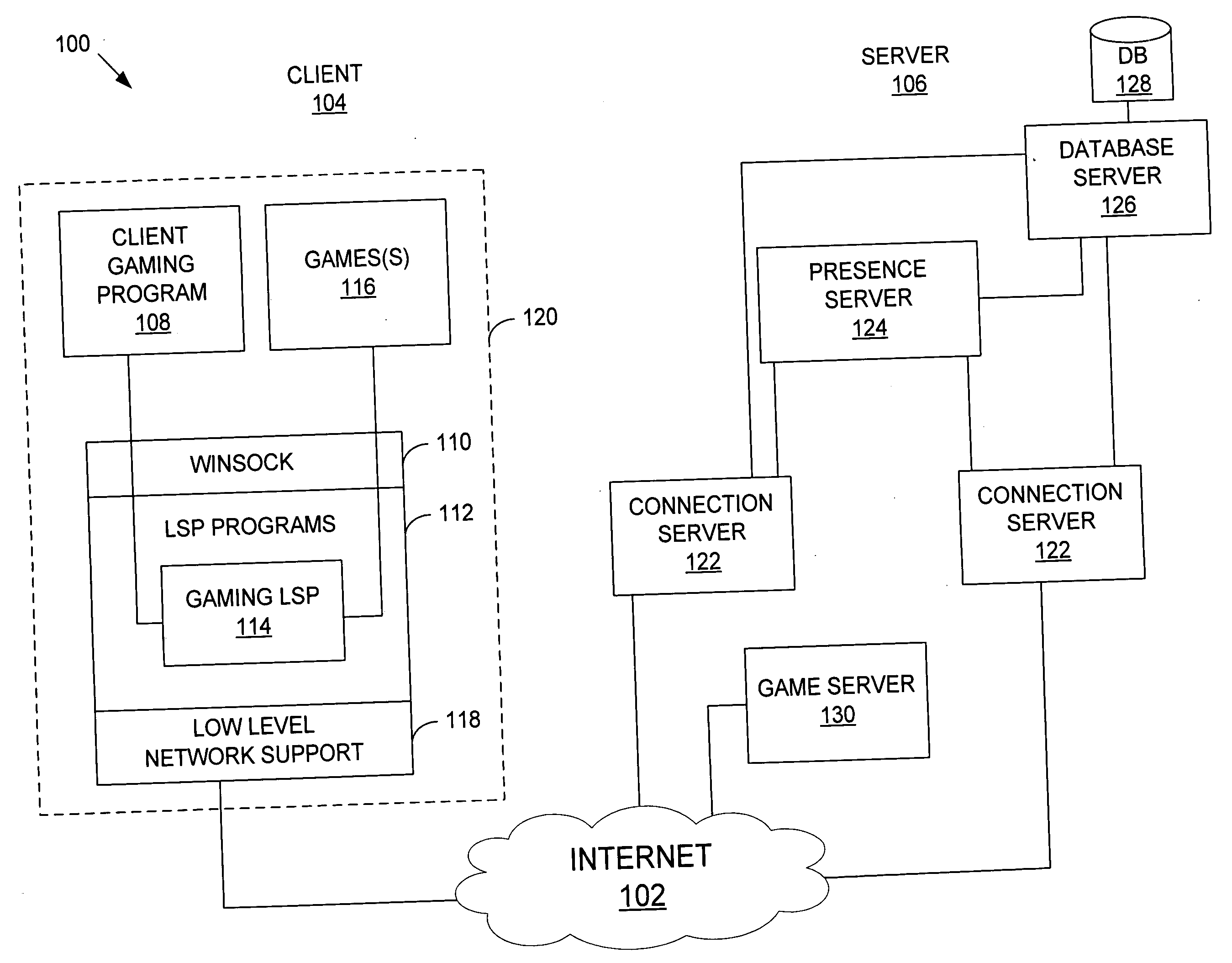
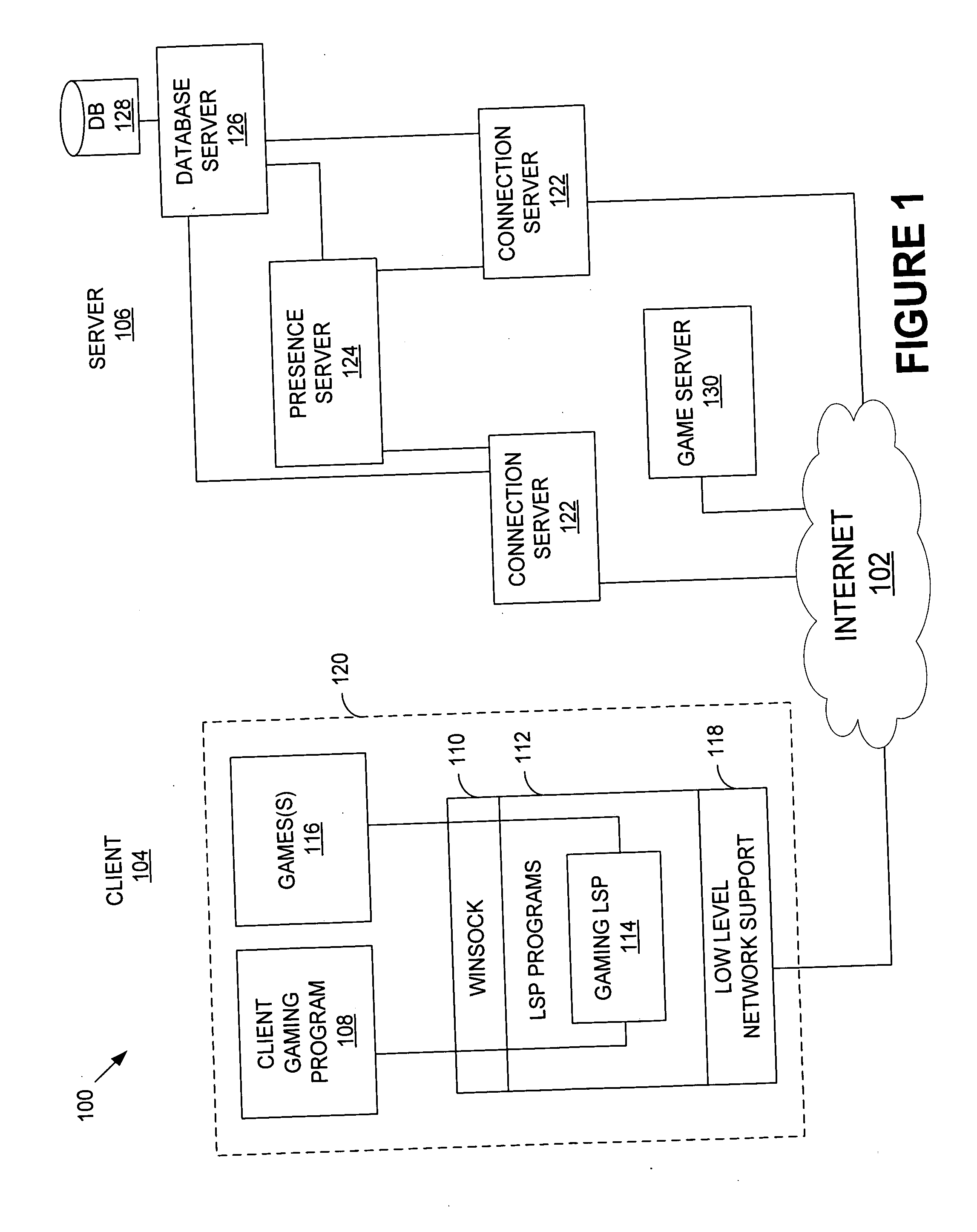
System and method for facilitating multiplayer online gaming
ActiveUS20050209002A1Easy to joinOptimize networkVideo gamesSpecial data processing applicationsReceiptGame client
A system and method for facilitating multiplayer online gaming is disclosed. The system 100 includes a client gaming program 108 and a gaming LSP 114, which are stored and operate on a client computer terminal 120. The client gaming program 108 detects when certain individuals identified by a user are playing online games and notifies the user of the individuals currently playing games online and the games that the individuals are playing. The client gaming program 108 allows the user to easily join the games in progress. The gaming program 108 and LSP 114 also monitor and detect games that are running on the terminal 120 and the connection status of the games. The gaming program 108 communicates data regarding the user, games and connection status over the computer network for receipt by selected individuals.
Owner:AG 18
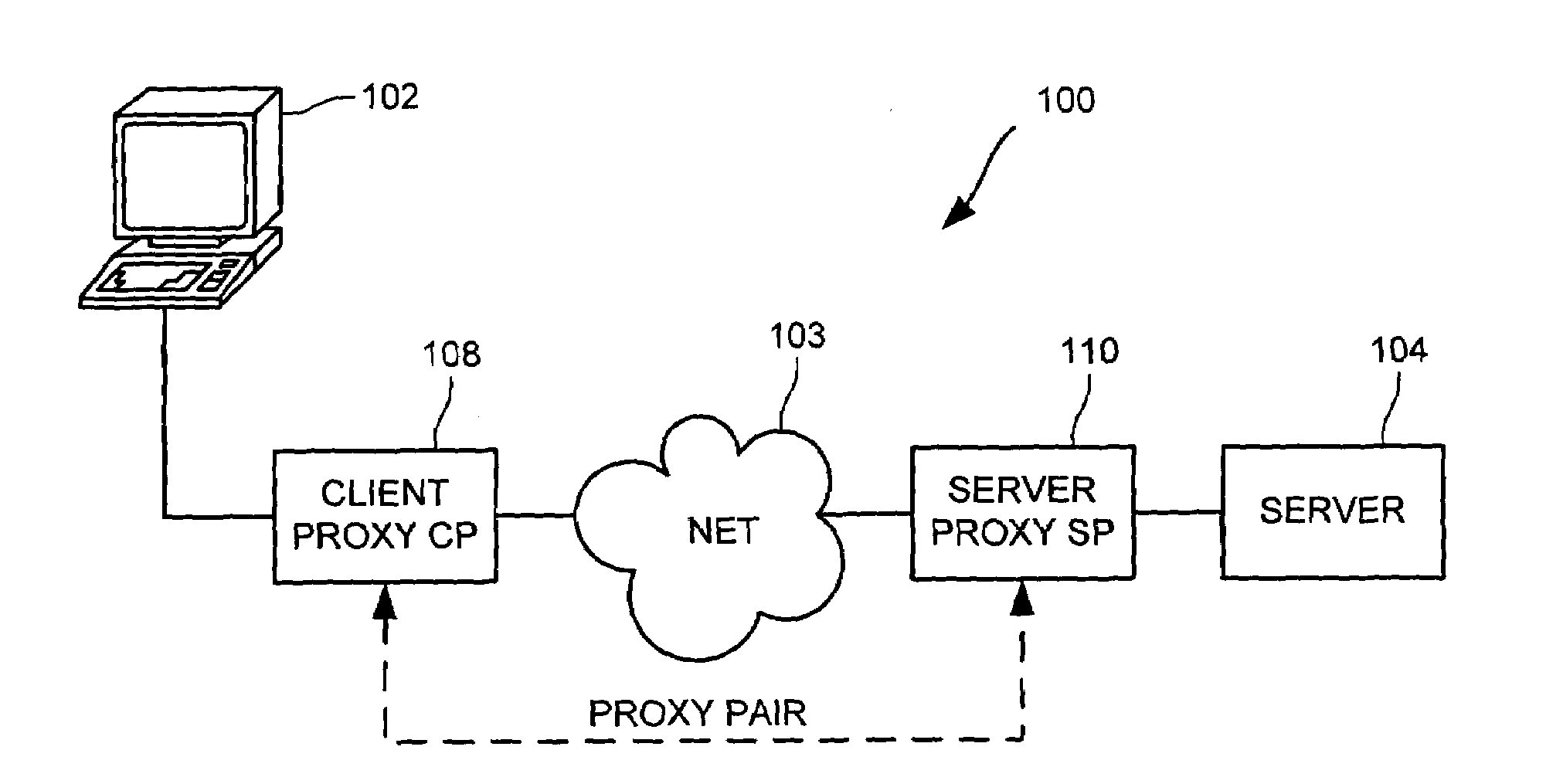
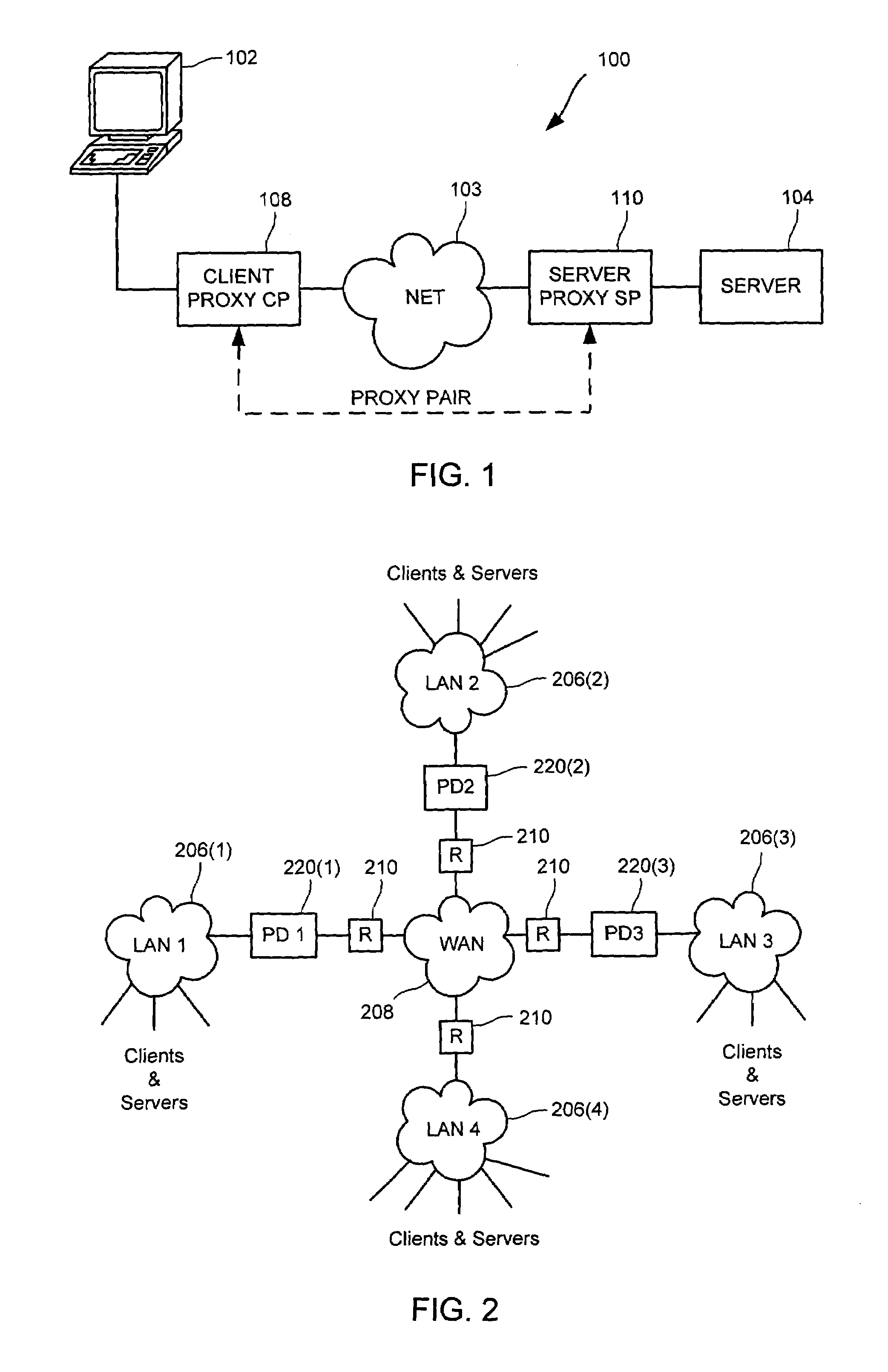
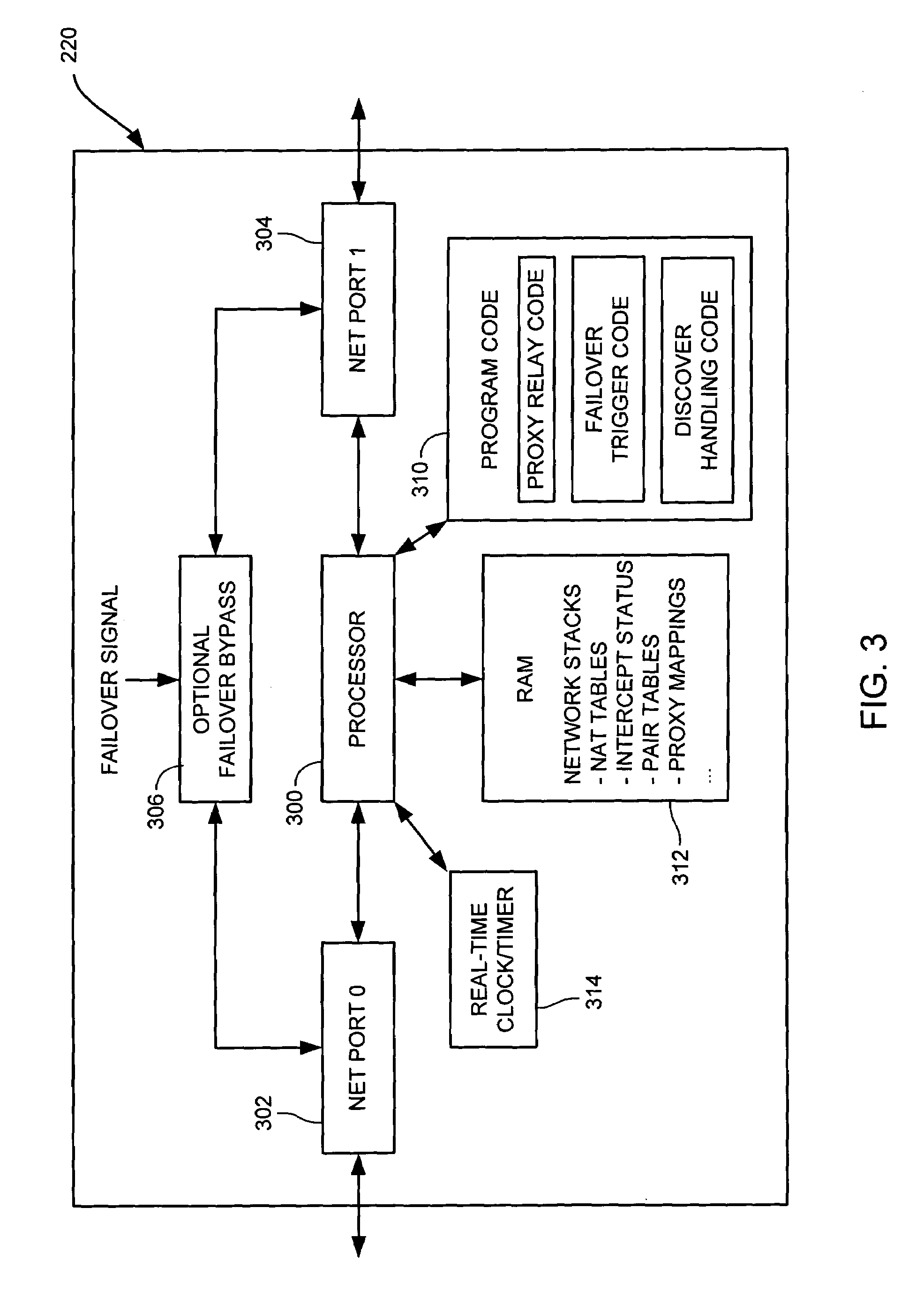
Cooperative proxy auto-discovery and connection interception
ActiveUS7318100B2Convenient online transactionsReduce bandwidth usageMultiple digital computer combinationsElectric digital data processingClient-sideServer-side
In a network supporting transactions between clients and servers and proxies that are interposable in a network path between at least one client and at least one server, wherein a pair of proxies can modify a packet stream between a client and a server such that packet data from the client to the server is transformed at a client-side proxy of the proxy pair and untransformed at a server-side proxy of proxy pair and such that packet data from the server to the client is transformed at the server-side proxy and untransformed at the client-side proxy, a method and apparatus for a discovering proxy to transparently discover its position in a proxy pair by using proxy signals to indicate to other proxies that could pair with the discovering proxy. A discovering proxy might determine that it is a client-side proxy by receipt of a packet from client without a proxy signal. A discovering proxy might determine that it is a server-side proxy by receipt of a packet from server without a return proxy signal. Once a proxy pair is discovered, that proxy pair might transform traffic from the server to the client or vice versa, transforming the traffic at one proxy of the proxy pair and untransforming the traffic at the other proxy of the pair.
Owner:RIVERBED TECH LLC
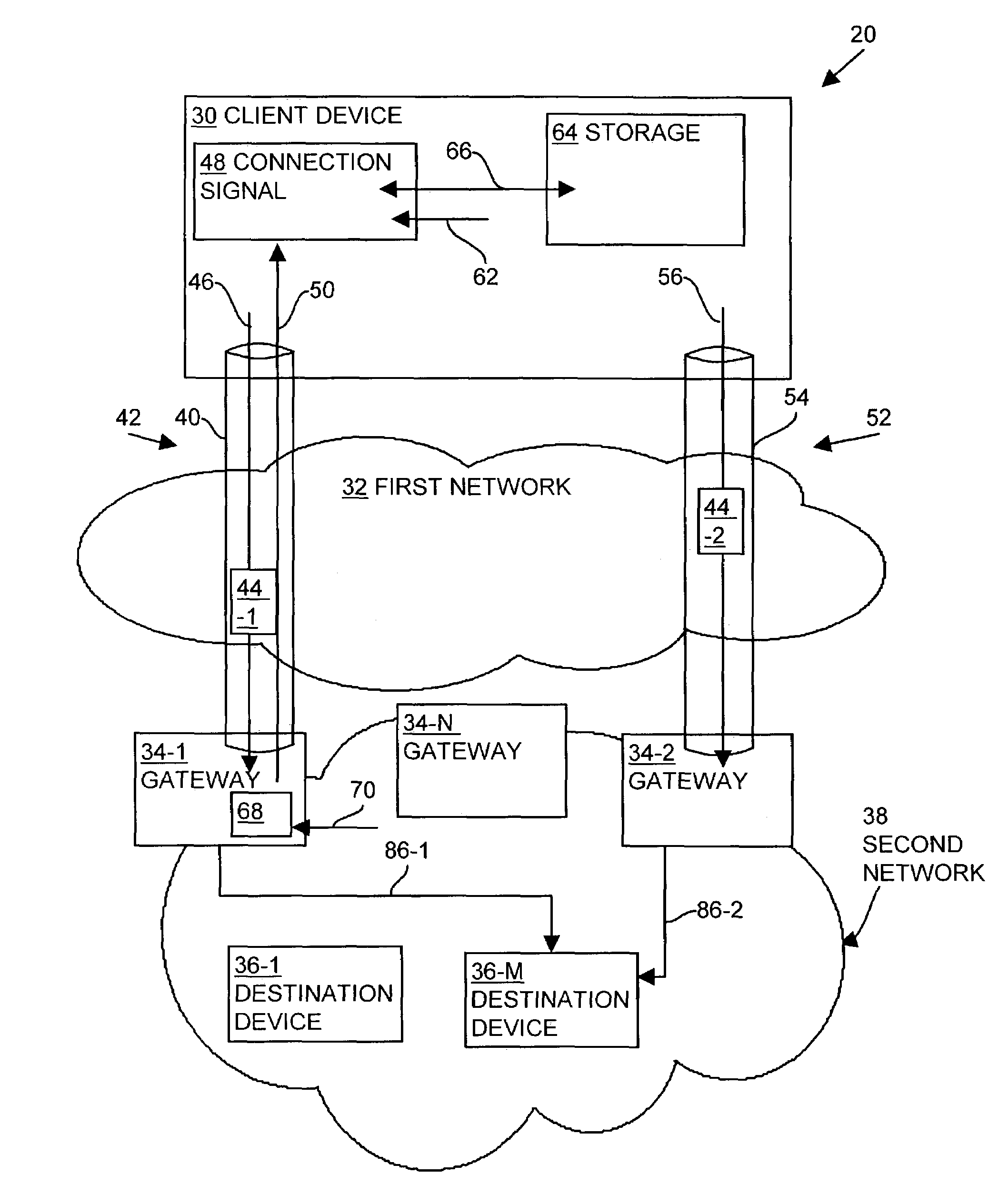
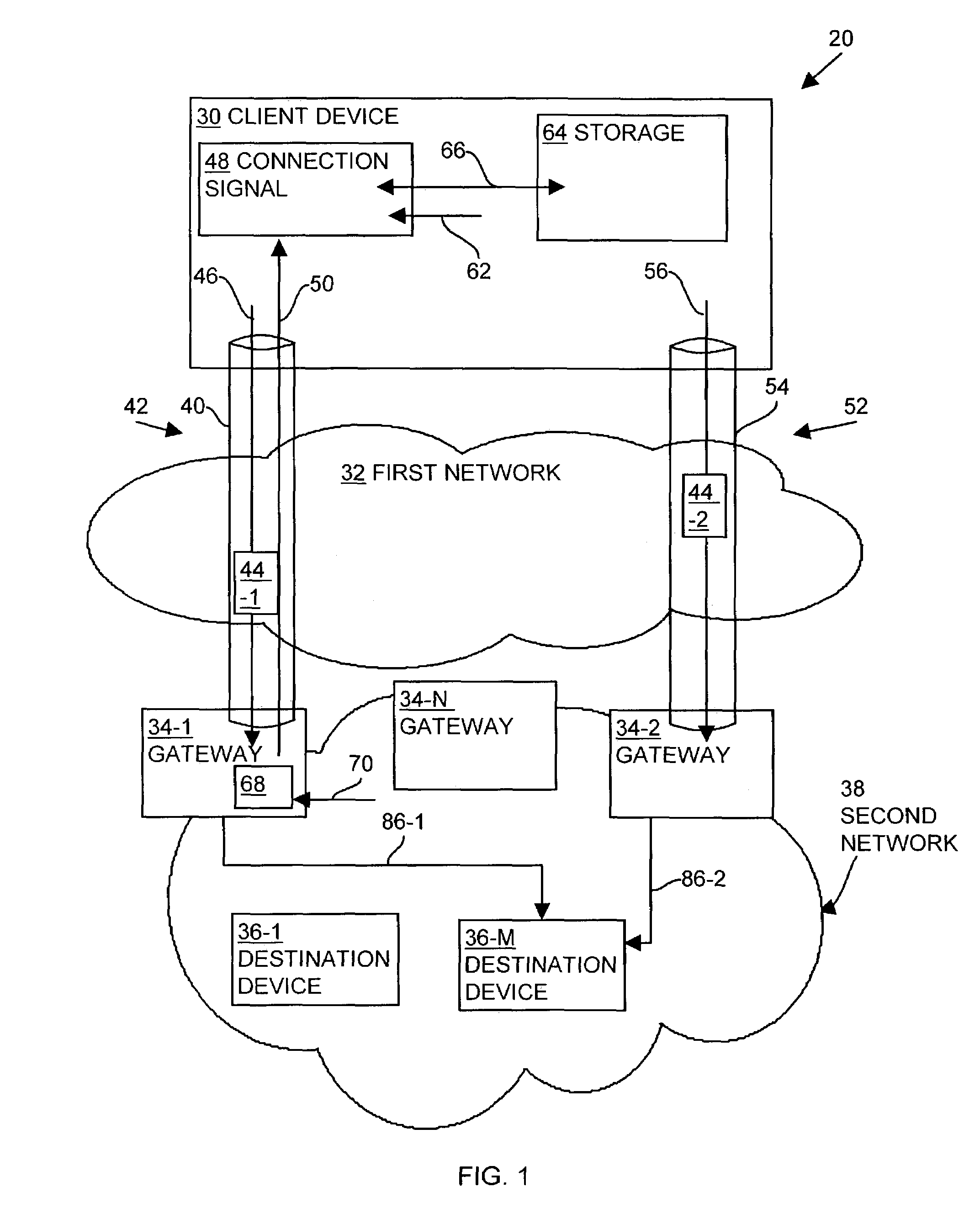
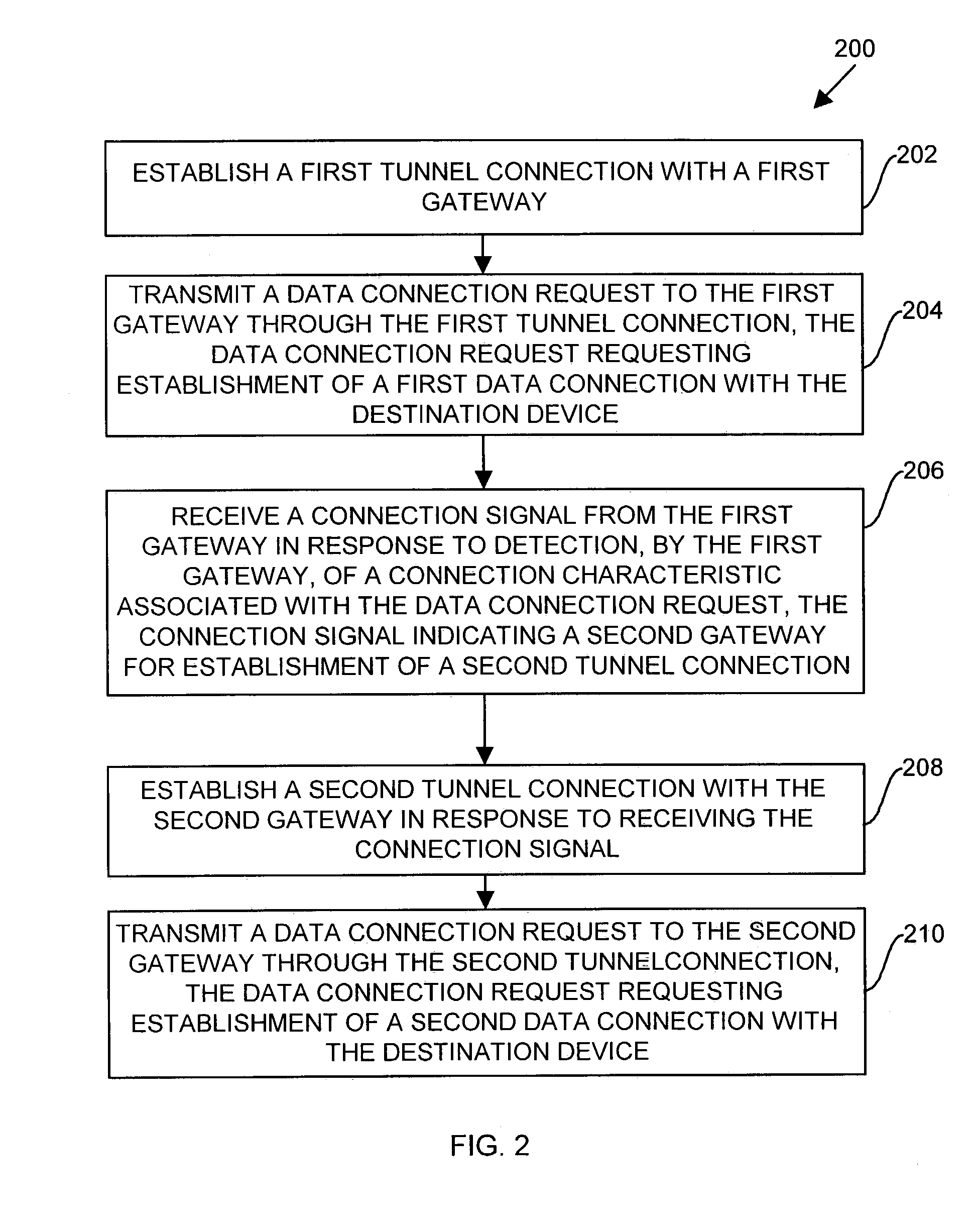
Methods and apparatus for establishing a computerized device tunnel connection
InactiveUS7673048B1Minimize bandwidth utilizationIncrease costError preventionTransmission systemsData connectionTelecommunications
A client device establishes a first tunnel connection or tunnel, through a public network, with a first gateway of a private network and establishes, through the tunnel connection, a data connection with a destination device within the private network. The first gateway monitors or analyzes the geographic locations of the gateways associated with the private network relative to geographic location of the destination device associated with the data connection. Based upon such the monitoring, the first gateway transmits information to the client device relating to establishment of a second tunnel connection or tunnel with a second gateway of the private network. The client device establishes the second tunnel connection with the second gateway and establishes a data connection with the destination device through the second gateway. By establishing the second tunnel connection with the second gateway, the client device utilizes the bandwidth of the public network to exchange data with the destination device, thereby decreasing data transmission costs to the private network and decreasing private network latency.
Owner:CISCO TECH INC
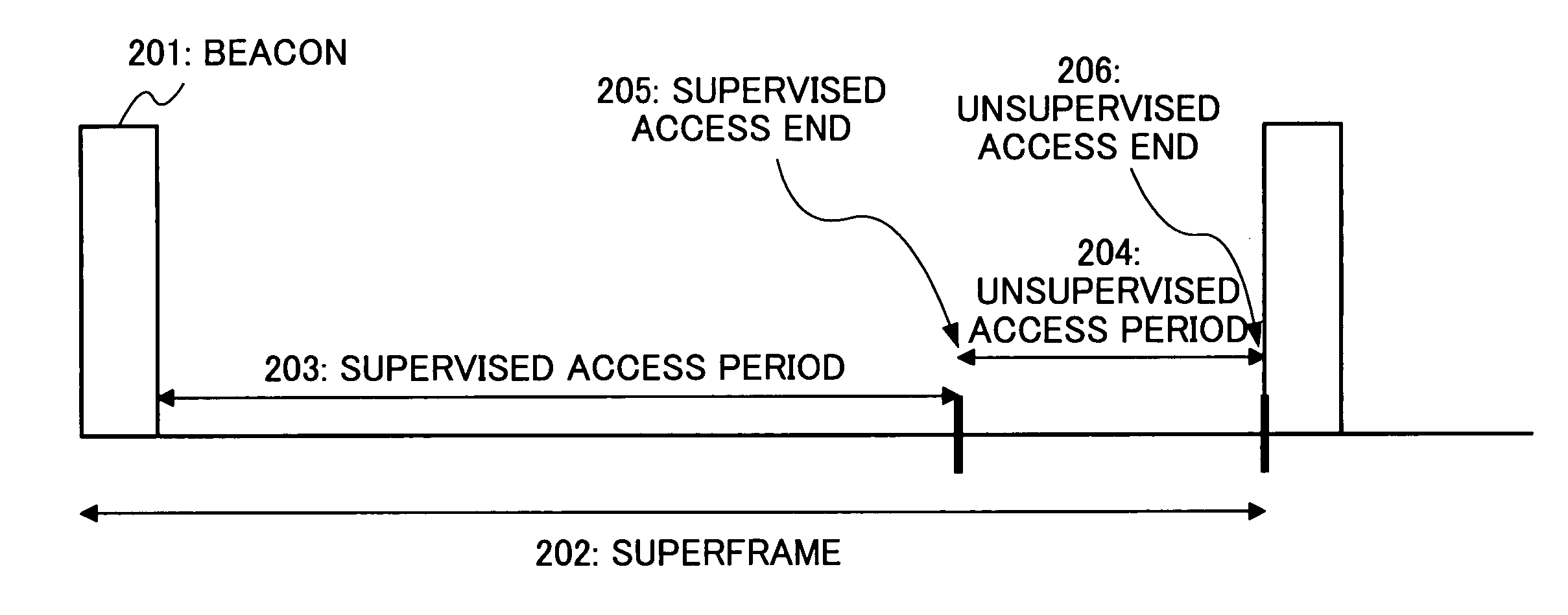
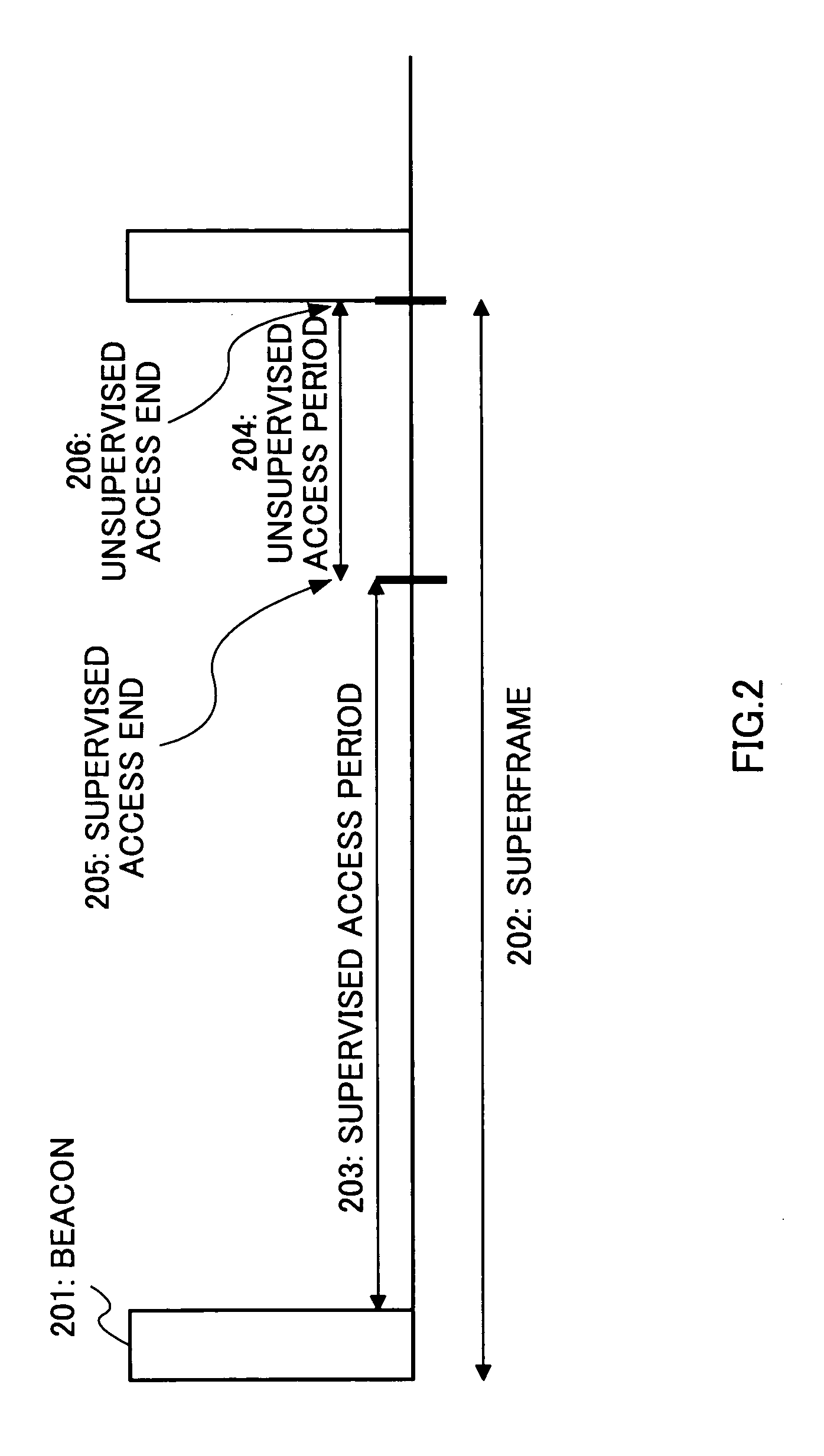
Method and system for controlling medium access in a wireless network
InactiveUS20060164969A1Simple designEasy to manufactureEnergy efficient ICTSpatial transmit diversityFrequency spectrumSpectral efficiency
A method and system are disclosed that can be applied to achieve high-throughput in a WLAN. Central to the present invention is the use of an SDMA compatible multi-beam antenna system by a WLAN access point. A system based on two types of antennas-dynamic beam forming and fixed beam antennas—is described. A mechanism and protocol are described that implement simultaneous transmissions with respect to an SDMA compatible access point and thereby improve spectral efficiency, and by extension achieve higher throughput. Based on the recognition that current WLAN MAC has major limitations in throughput, certain MAC extensions (that can be applied independently of SDMA) are described. Also disclosed are power-saving and power control techniques that improve battery performance and contribute to a reduction in station size, and a means of reducing channel interference. The present invention also deals with the problem of backward compatibility with conventional devices that implement the protocol that is a subset covered by the present invention.
Owner:SOVEREIGN PEAK VENTURES LLC
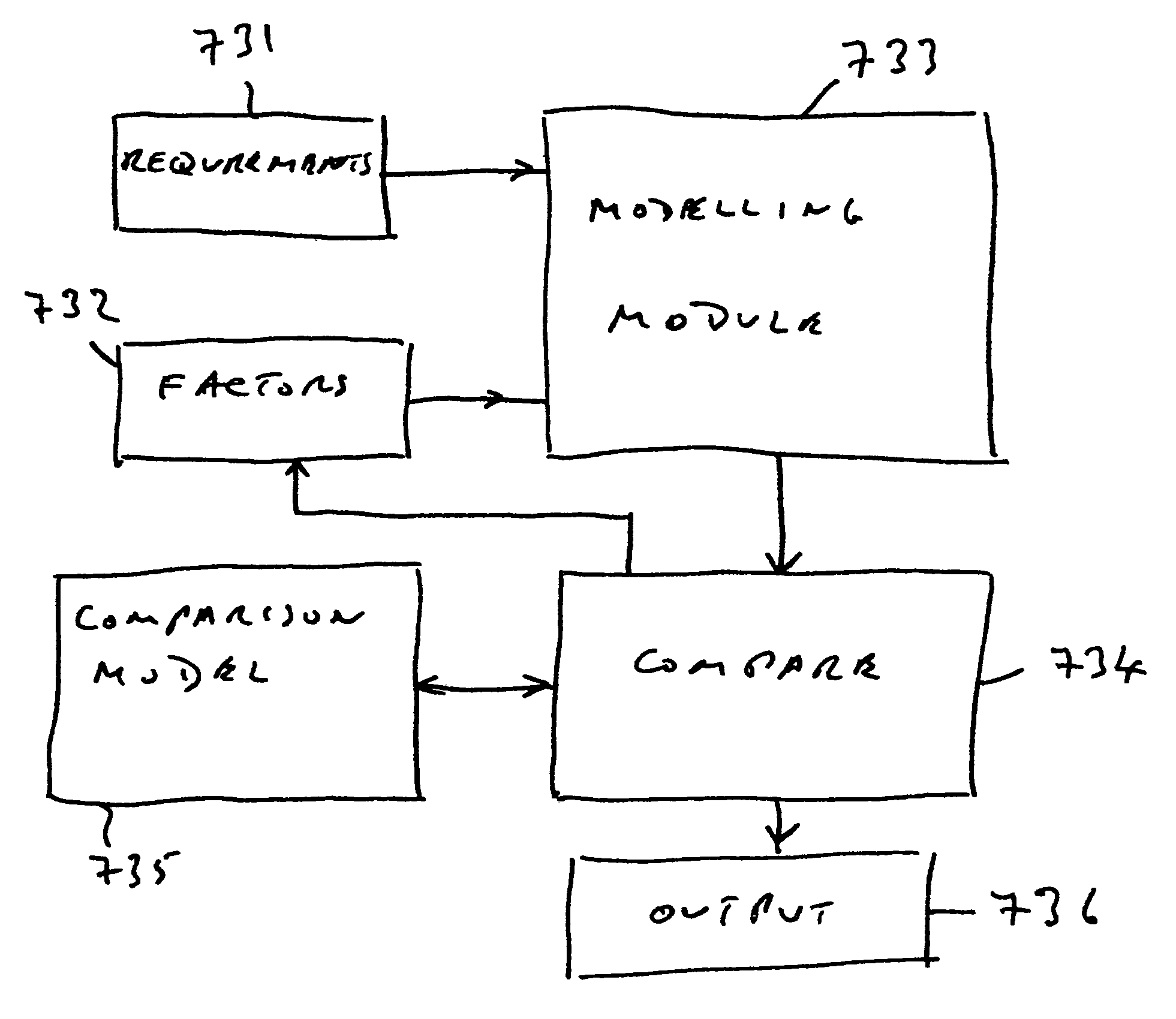
Network planning tool
InactiveUS7103003B2Easy to optimizeOptimize networkError preventionFrequency-division multiplex detailsComputer scienceReal-time computing
Owner:RPX CLEARINGHOUSE
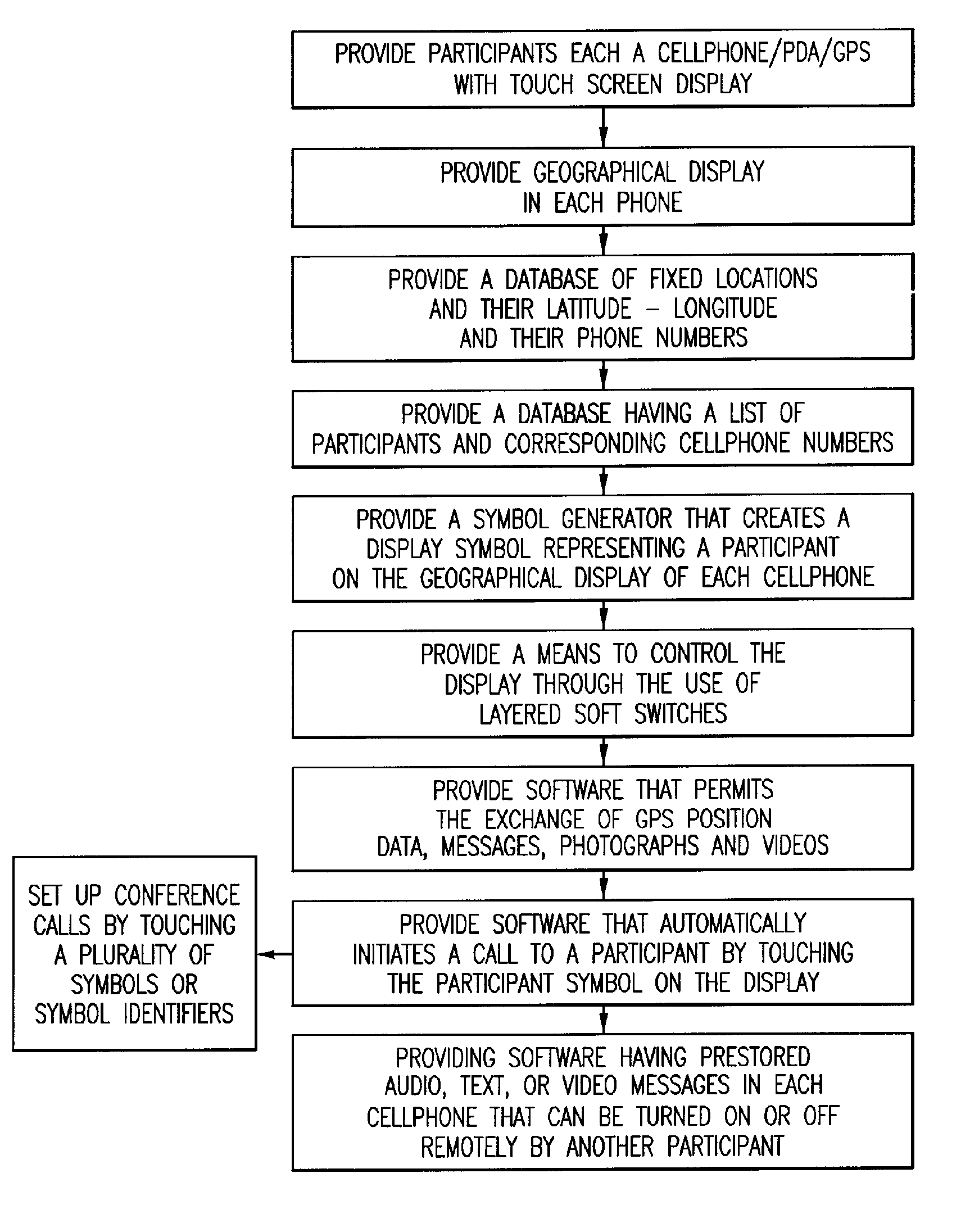
Method of providing a cellular phone/pda communication system
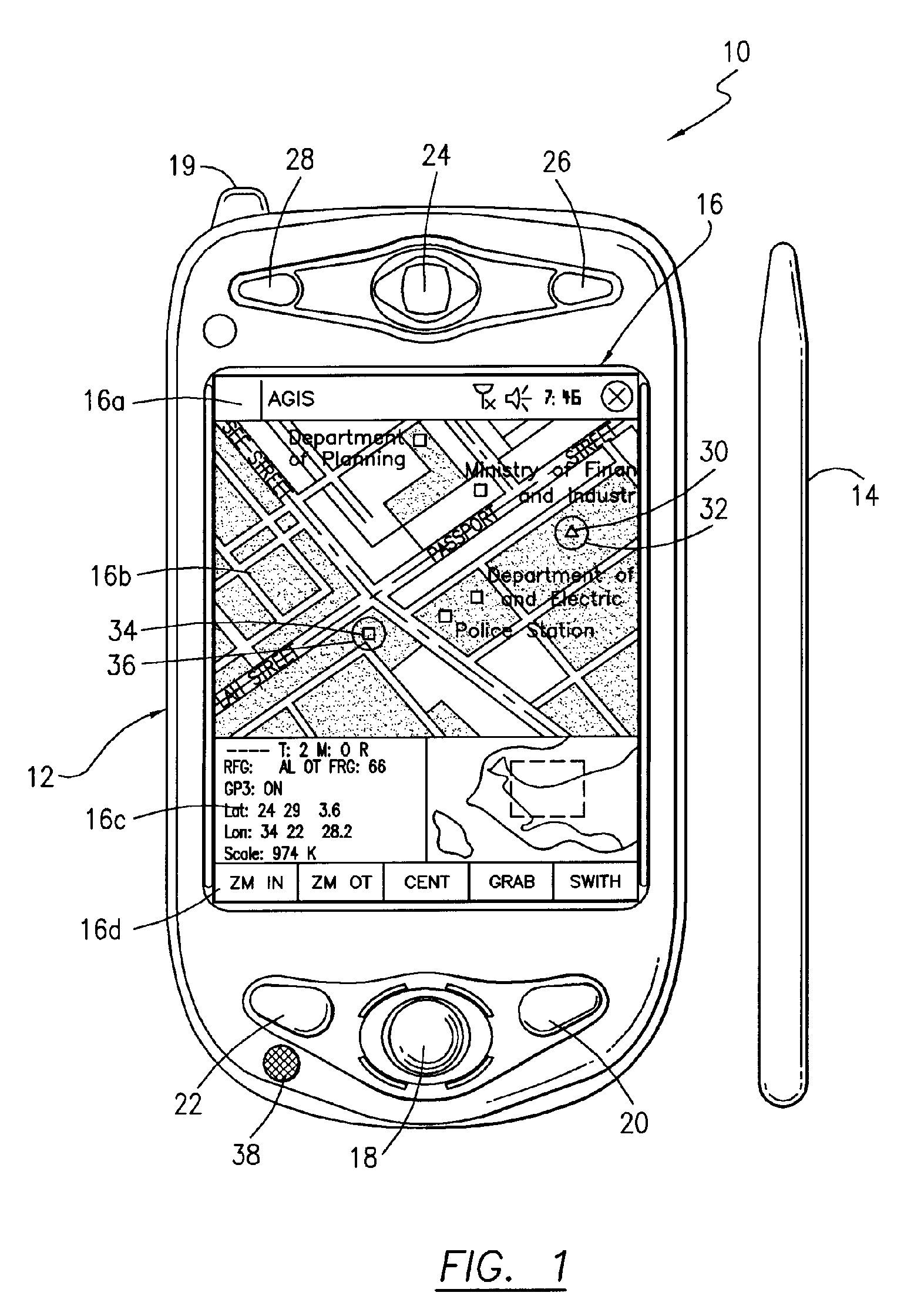
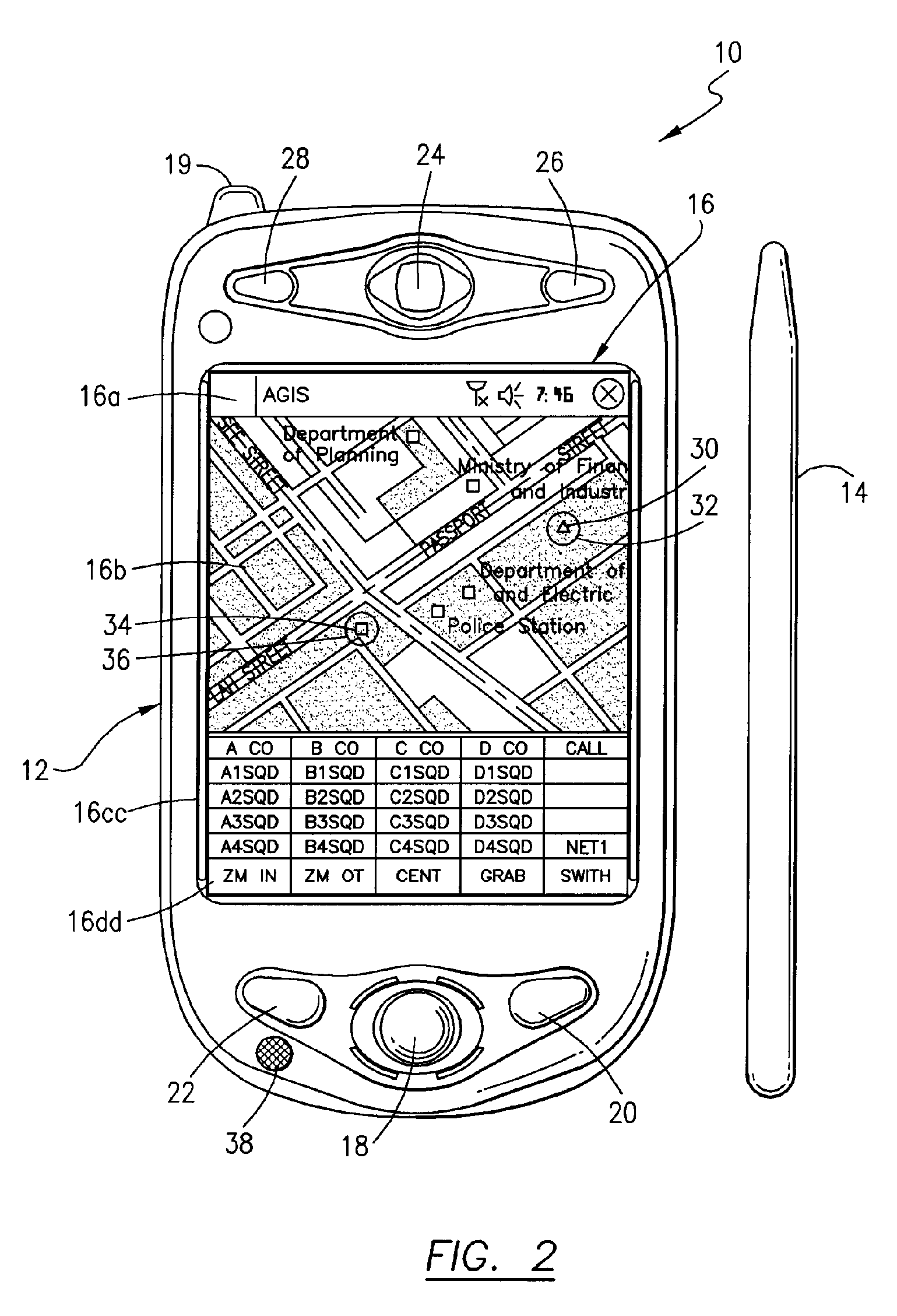
ActiveUS20060199612A1Transmission easilyDecreasing the operator actions necessaryDevices with GPS signal receiverDevices with wireless LAN interfaceVideo transmissionDisplay device
A cellular, PDA communication device and communication system for allowing a plurality of cellular phone users to monitor each others' locations and status, to initiate cellular phone calls by touching a symbol on the touch screen display with a stylus which can also include point to call conferencing calling. Each participant's cellular phone PDA device includes GPS navigation receiver with application software for point to call cellular phone initiation to participants and geographical entities including vehicles, persons or events, conference calls and video transfers. The method and system also includes automatic shifting from GPRS / EDGE / CDMA / 1XEVDO to SMS when any of the cellular phones in the communication network is in the voice mode and in use and for automatic shifting back to GPRS / EDGE / CDMA / 1XEVDO upon completion of the voice phone call. In addition, using the system, a full transfer of photographs, video clips and high speed data can be used between any cellular phones regardless of who the cellular phone vendors or cellular phone companies are and in either CDMA, GSM, WiFi or a combination of the two.
Owner:AGIS SOFTWARE DEVEMENT LLC +1
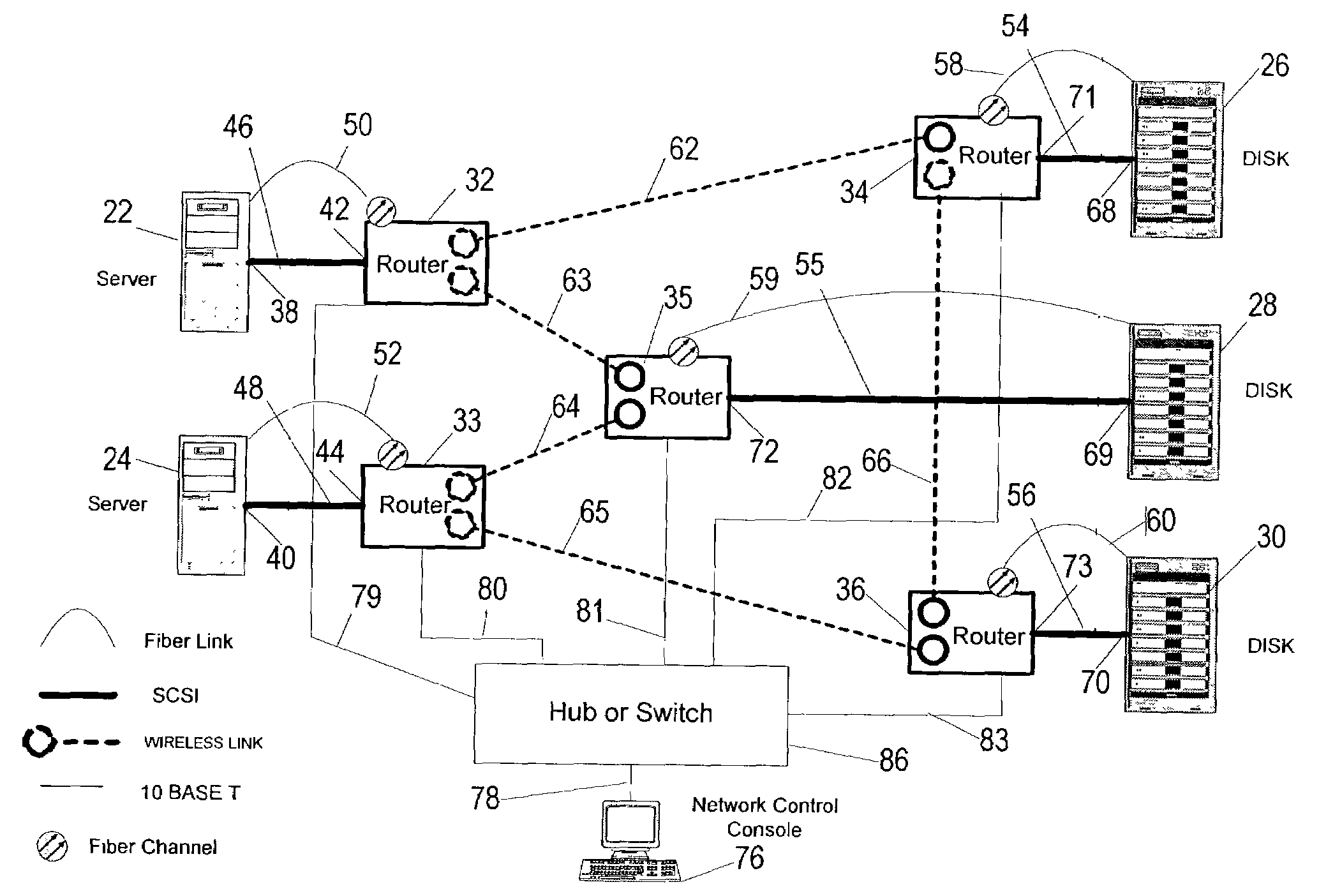
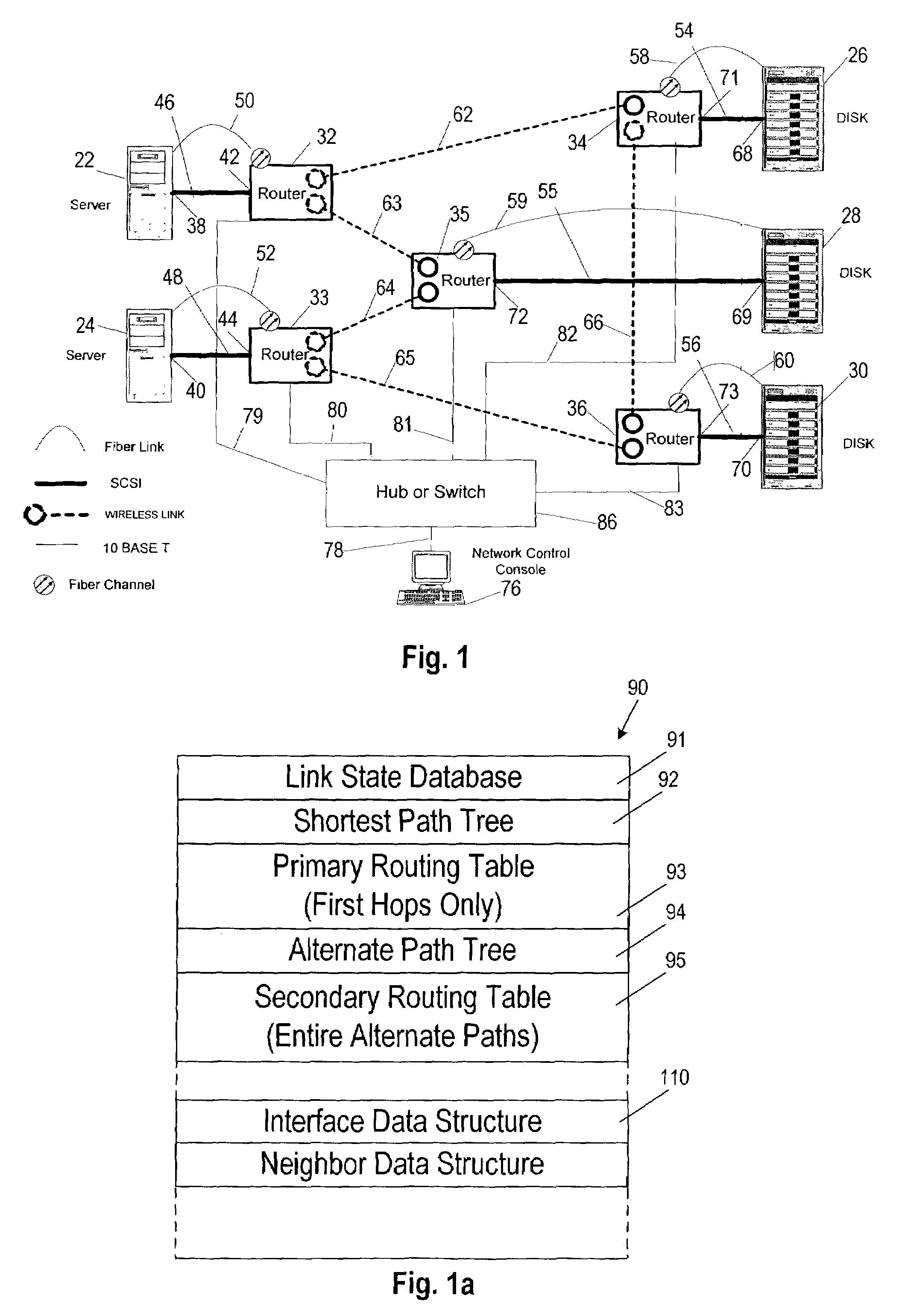
Agile digital communication network with rapid rerouting
ActiveUS7362709B1Low reliabilityImprove reliabilityError preventionFrequency-division multiplex detailsUser deviceBackup path
An agile digital communications network has a number of routers that serve as nodes in a mesh network communicating between a user device (e.g., computer, server, etc.) and a target device (e.g., disc storage cabinets, tape, jukebox, etc.). The routers operate on an open shortest path first protocol, each router having two or more interfaces or links to other routers. When a link connected to a router is down and is in the shortest path to another router identified in a communication packet, the packet is forwarded to the identified router on a precalculated alternate route that does not use the unavailable link. IP tunneling assures that routing loops do not occur and send the packet back to the router with the unavailable link because it would have been in the shortest path of an intermediate router. A tunneling technique is provided that maximizes the levels of encapsulation needed at two, regardless of the size or configuration of the network. An unavailable link is not broadcast immediately throughout the network, giving the link an opportunity to be restored before all of the routers are called on to recalculate the shortest paths and alternate paths. During a short interval following the discovery of an unavailable link, then, a router connected to that link is in a state identified as the Use Alternate Path state, and the link is repeatedly checked for availability. Each router calculates and stores the alternative paths to each other router after first calculating the shortest path to each other router. The alternate paths are pulled up and used when an unavailable link is detected. Dijkstra's algorithm is used to calculate the shortest paths. A new algorithm called the iterative dynamic Dijkstra's algorithm is used to calculate the alternative routes.
Owner:THE ARIZONA BOARD OF REGENTS ON BEHALF OF THE UNIV OF ARIZONA
Multi-mode audio recognition and auxiliary data encoding and decoding
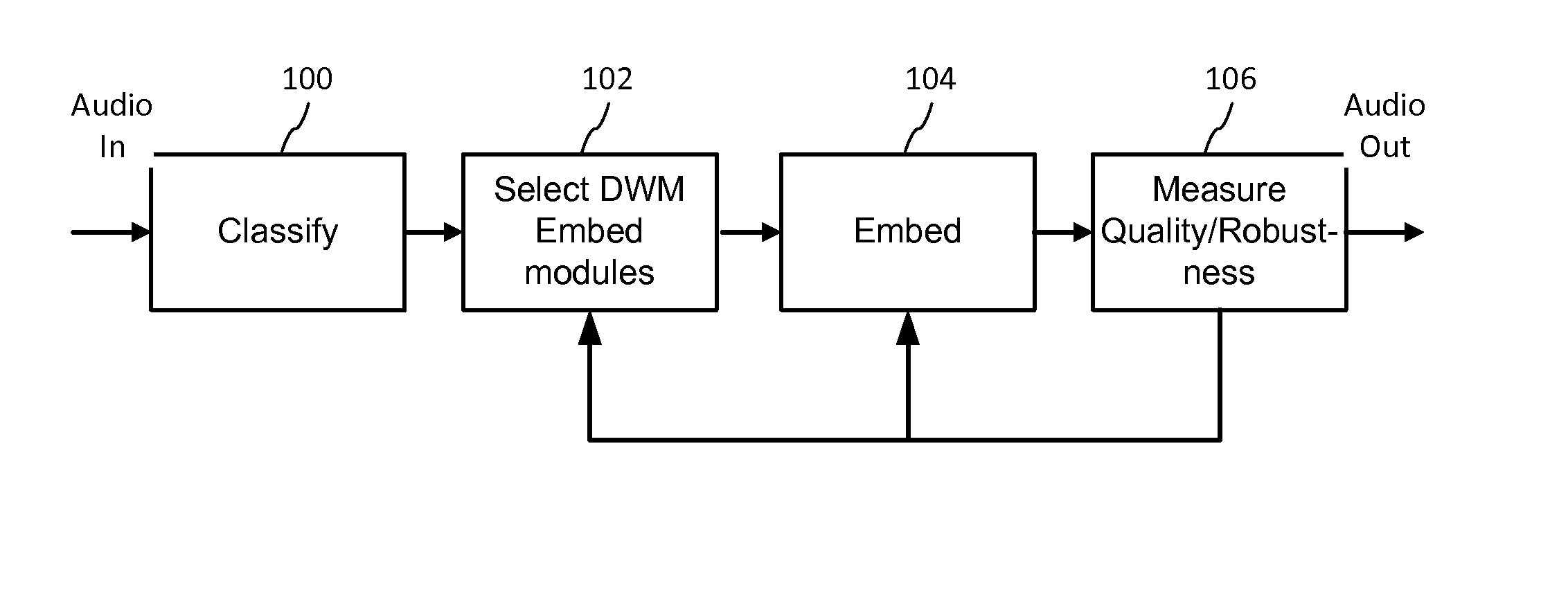
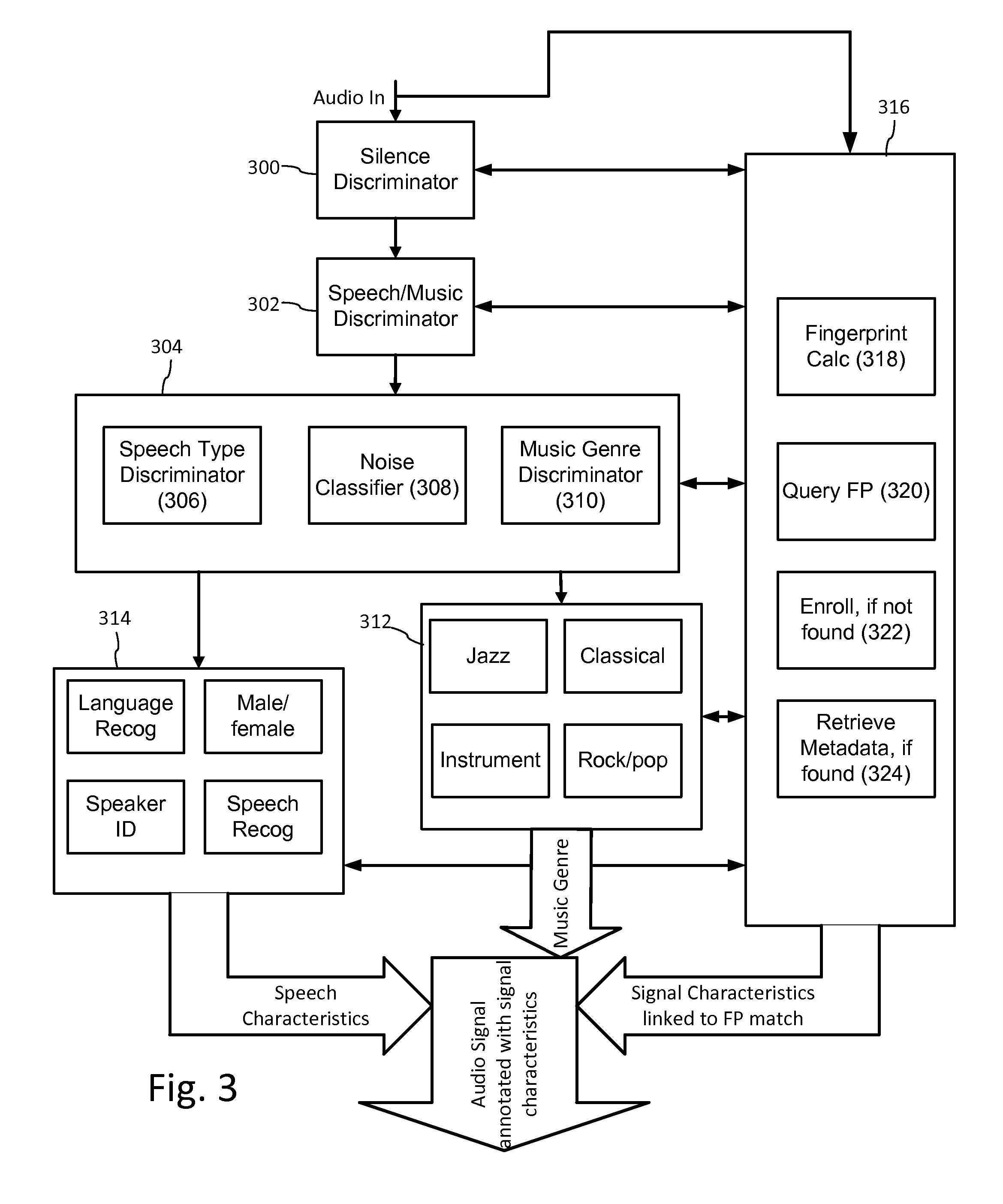
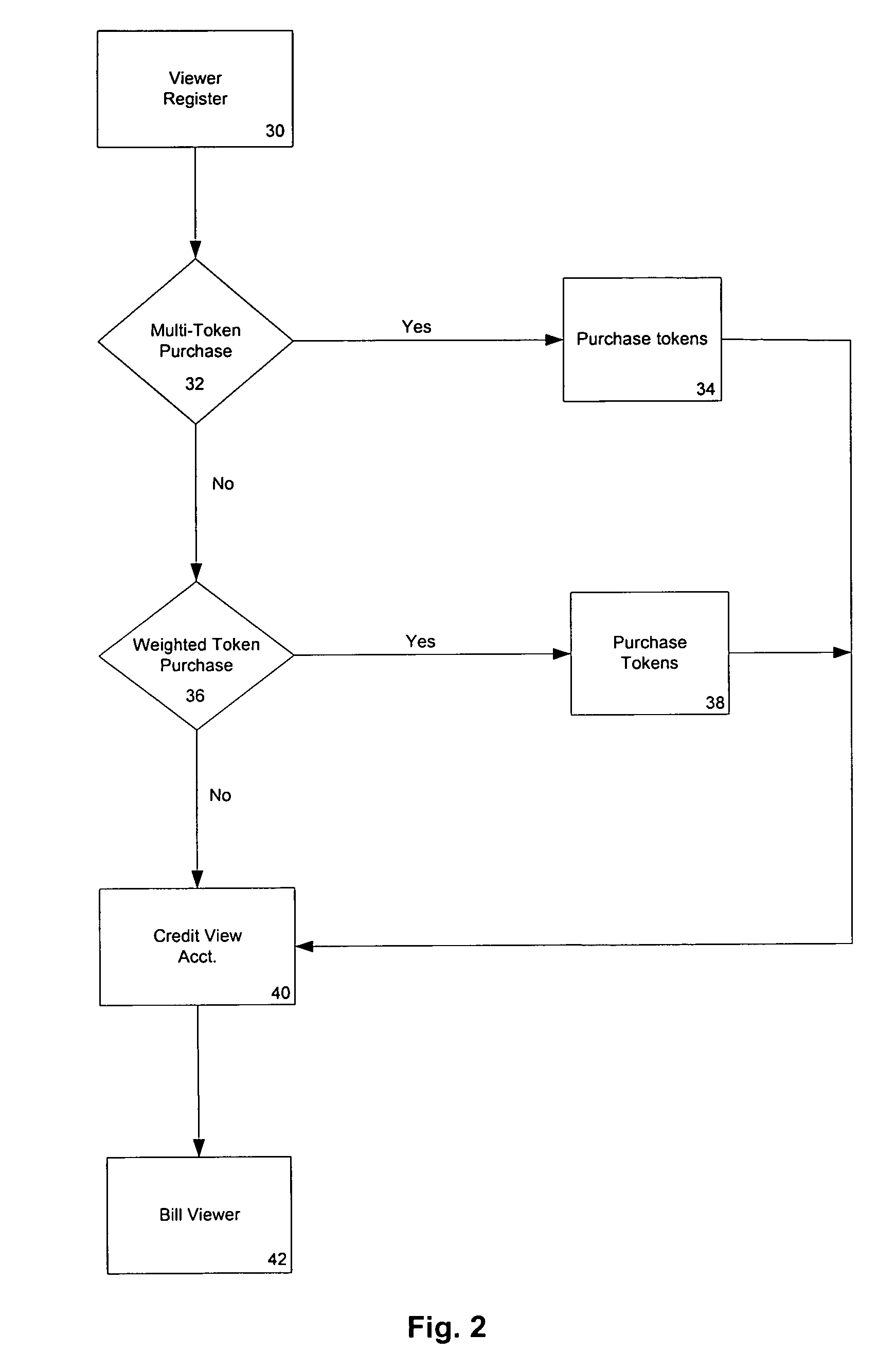
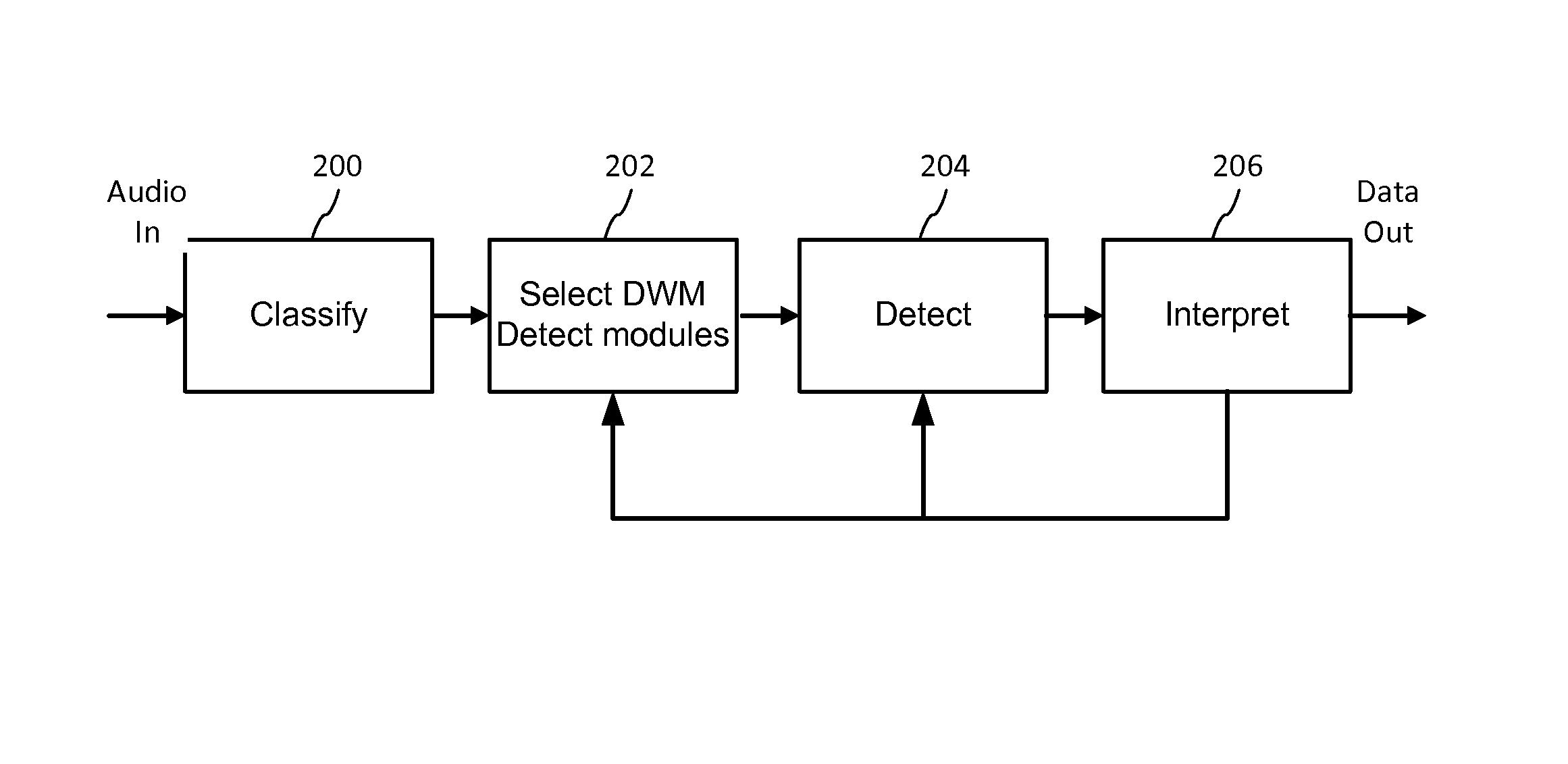
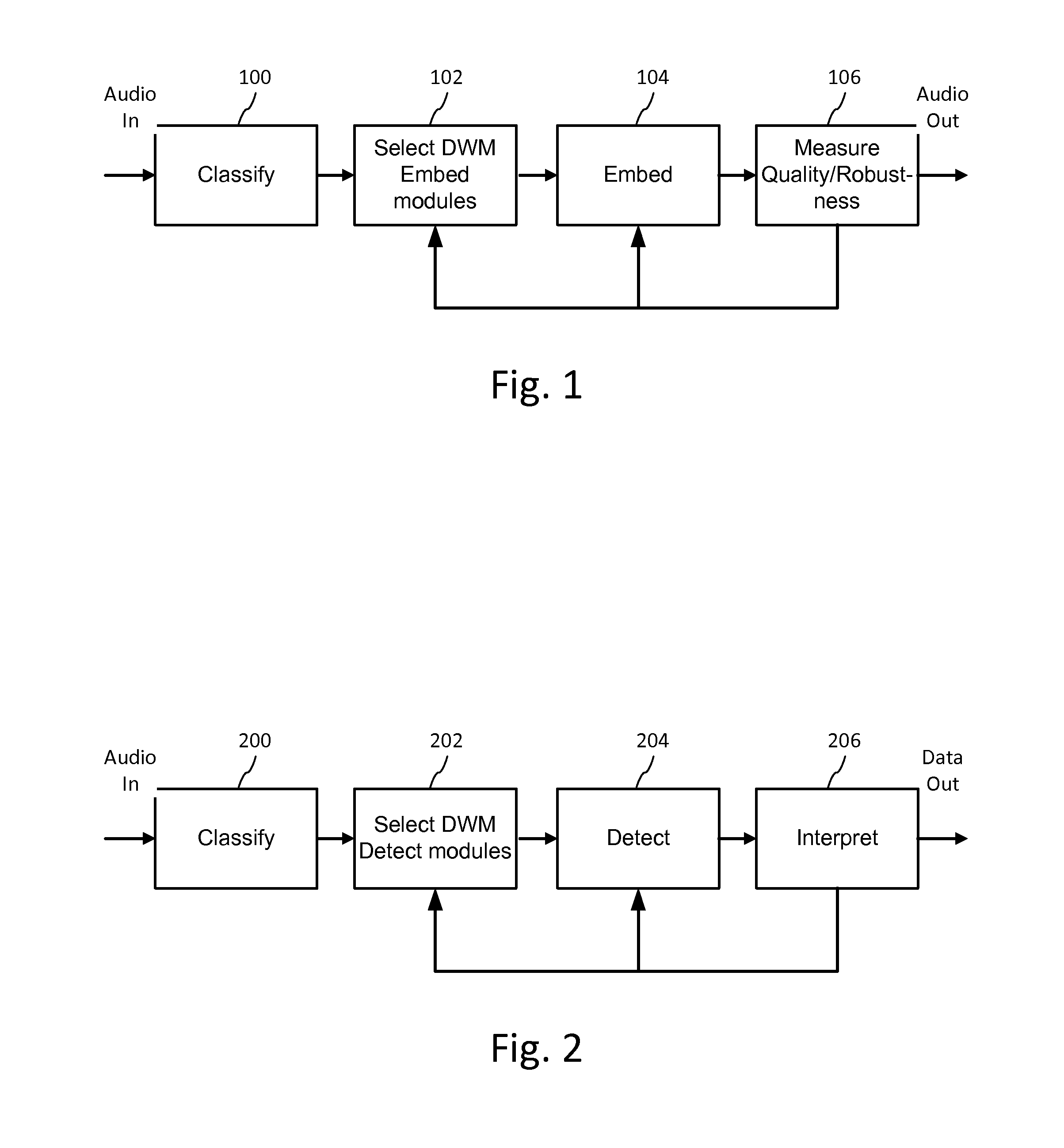
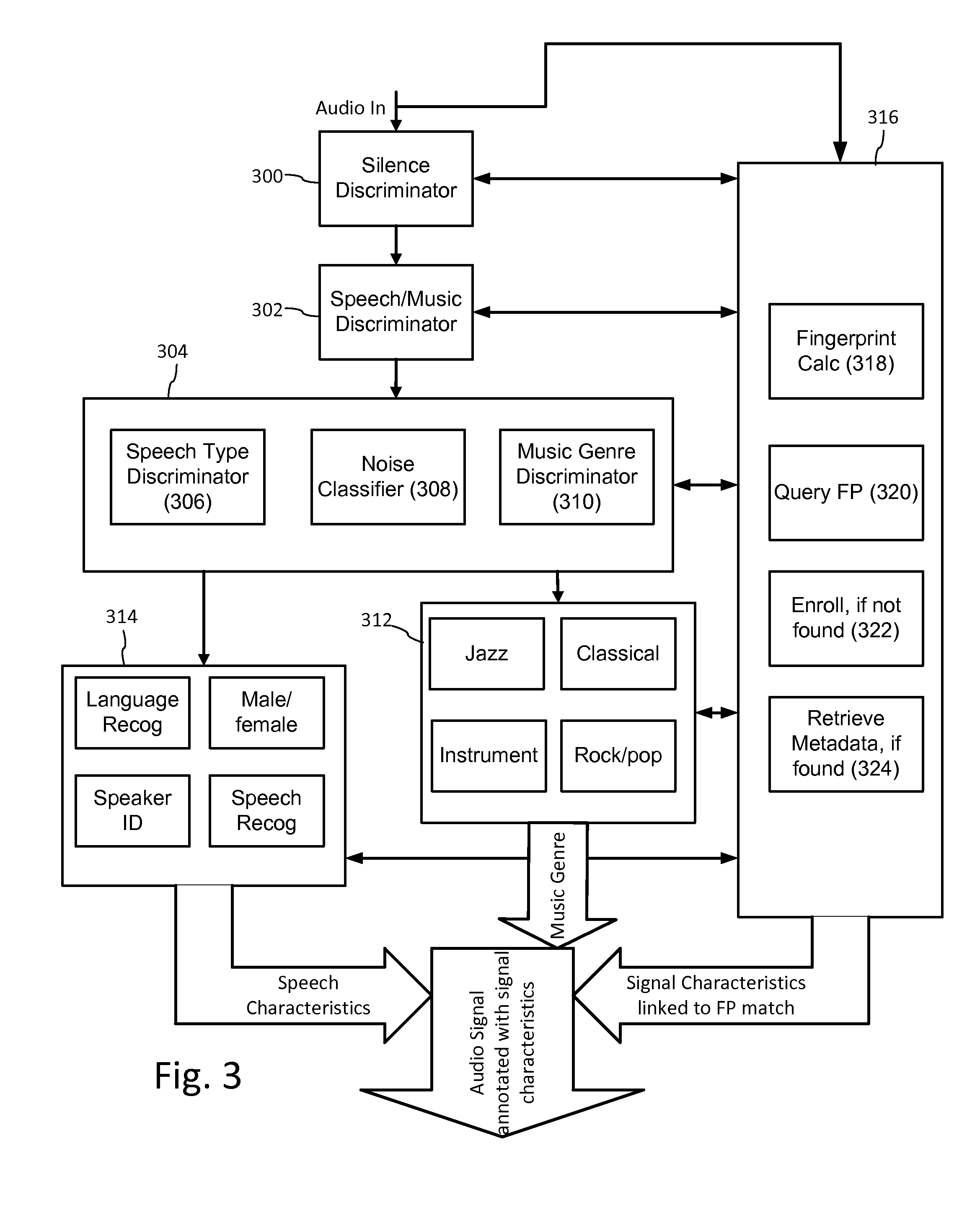
ActiveUS20140108020A1Improving communication over networkOptimize networkSpeech analysisData capacityFeature extraction
Audio signal processing enhances audio watermark embedding and detecting processes. Audio signal processes include audio classification and adapting watermark embedding and detecting based on classification. Advances in audio watermark design include adaptive watermark signal structure data protocols, perceptual models, and insertion methods. Perceptual and robustness evaluation is integrated into audio watermark embedding to optimize audio quality relative the original signal, and to optimize robustness or data capacity. These methods are applied to audio segments in audio embedder and detector configurations to support real time operation. Feature extraction and matching are also used to adapt audio watermark embedding and detecting.
Owner:DIGIMARC CORP
Path recovery on failure in load balancing switch protocols
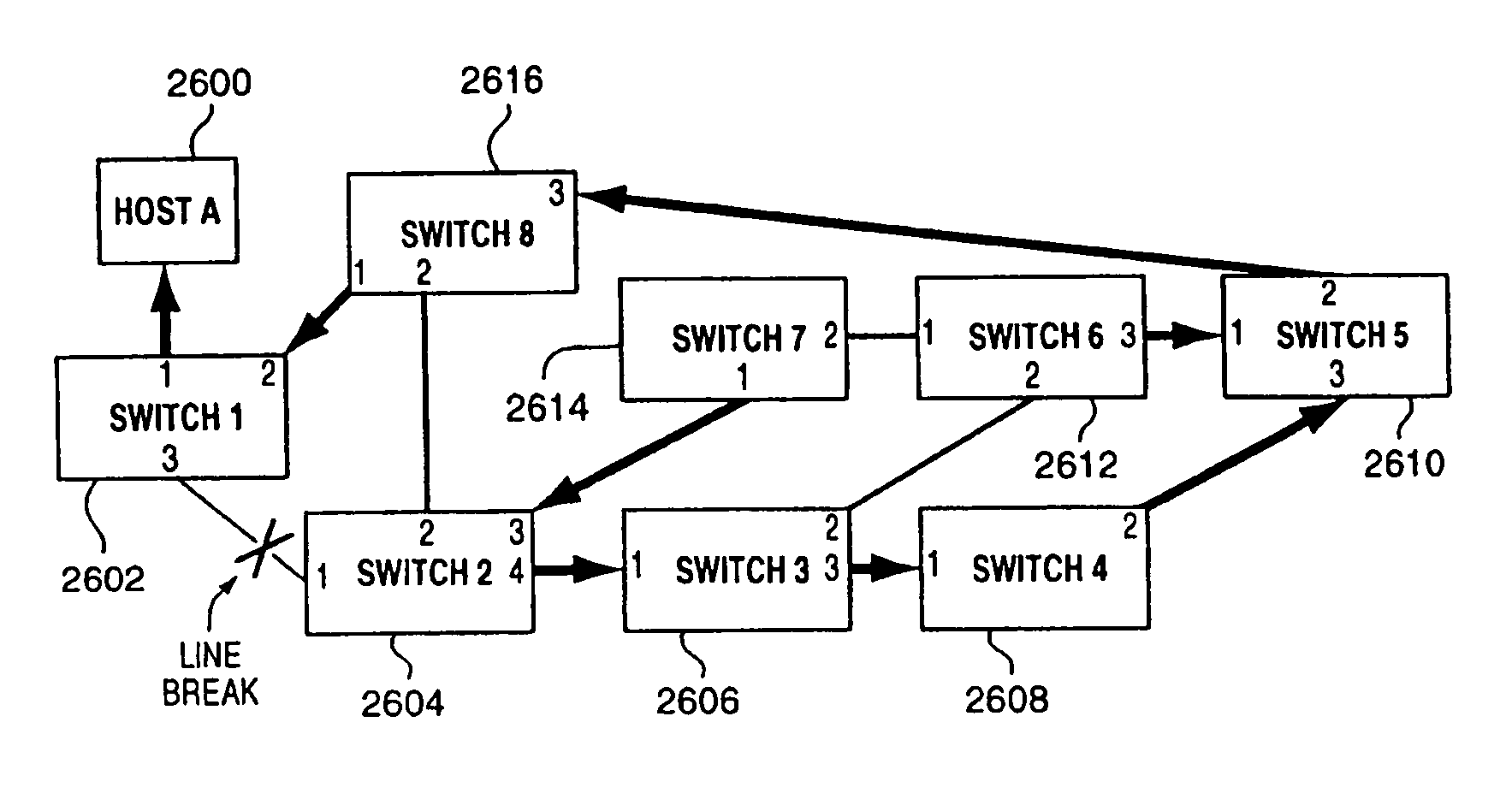
InactiveUS7430164B2Increase profitQuick identificationError preventionTransmission systemsBackup pathNetwork switch
A method for managing multiple active paths among a plurality of network switches to identify and select an alternate path in response to failure of a path from a switch to a device. Load balancing protocols of the present invention enable the simultaneous use of multiple paths between network devices through a mesh of compliant network switches. When a port of a network switch fails (or the link connected to a port fails), a switch in accordance with the present invention selects an alternate port which may be used for forwarding packets to devices normally reached through the failed port. Networks switches operable in accordance with the structures and protocols of the present invention exchange messages to identify potential alternate paths. A potential alternate path is used to send a query message to a neighboring network switch to determine if a path to the identified devices is available through the neighboring network switch. Such query messages are propagated through all intermediate network switches between the switch sensing the failed port up to the identified network device. Acknowledgment messages are returned to verify potential availability of an alternate path. Where an intermediate network switch determines that the complete path is not available through it to the identified device, or where a potentially better path exists, a regenerated query message so indicating is returned along the path that initiated the query message.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
System and method for influencing dynamic community shared elements of audio, video, and text programming via a polling system
InactiveUS6947966B1Affect outcomeIncrease engagementSpecial service provision for substationVoting apparatusPolling systemBroadcasting
A system and method for interactively affecting the course of a program or programming content. Viewer purchase electronic tokens which can be used to vote on the sequence of content in a broadcast whether it be audio, video or a combination thereof. Users are periodically polled by a server to vote on the direction that a broadcast is taking. The broadcast is then modified with real-time or stored content based upon the polling results from the viewers. Thus communities of voters have a chance to vote on the direction of content. The invention also allows sub-communities to be formed to pre-vote on a broadcast so that the sub-community can possible vote as a bloc on the direction and content of programming that is presented.
Owner:SERVICE
Multi-mode audio recognition and auxiliary data encoding and decoding
ActiveUS20140142958A1Improving communication over networkOptimize networkSpeech analysisData capacityFeature extraction
Audio signal processing enhances audio watermark embedding and detecting processes. Audio signal processes include audio classification and adapting watermark embedding and detecting based on classification. Advances in audio watermark design include adaptive watermark signal structure data protocols, perceptual models, and insertion methods. Perceptual and robustness evaluation is integrated into audio watermark embedding to optimize audio quality relative the original signal, and to optimize robustness or data capacity. These methods are applied to audio segments in audio embedder and detector configurations to support real time operation. Feature extraction and matching are also used to adapt audio watermark embedding and detecting.
Owner:DIGIMARC CORP
Automatic configuration of the network devices via connection to specific switch ports
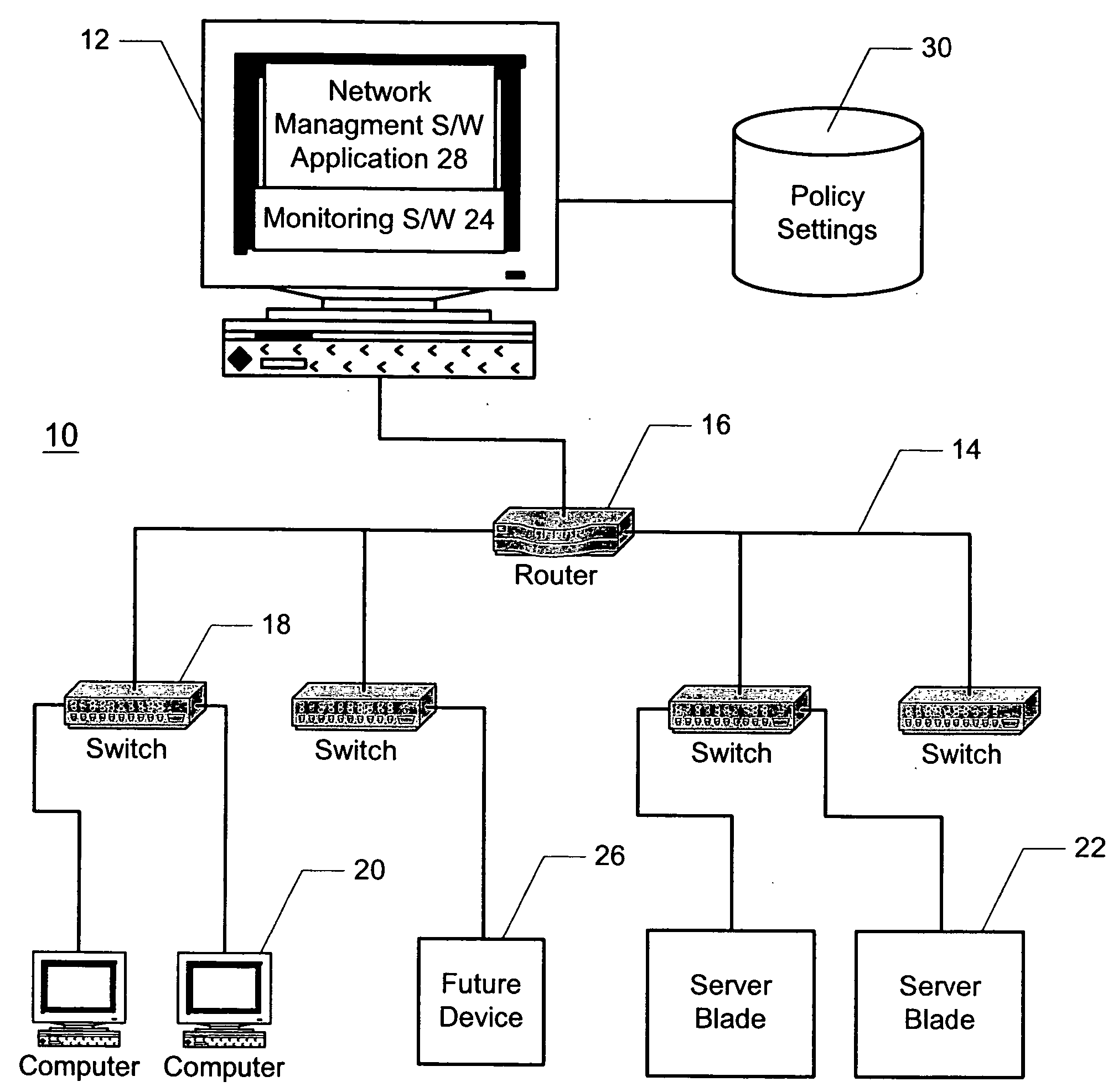
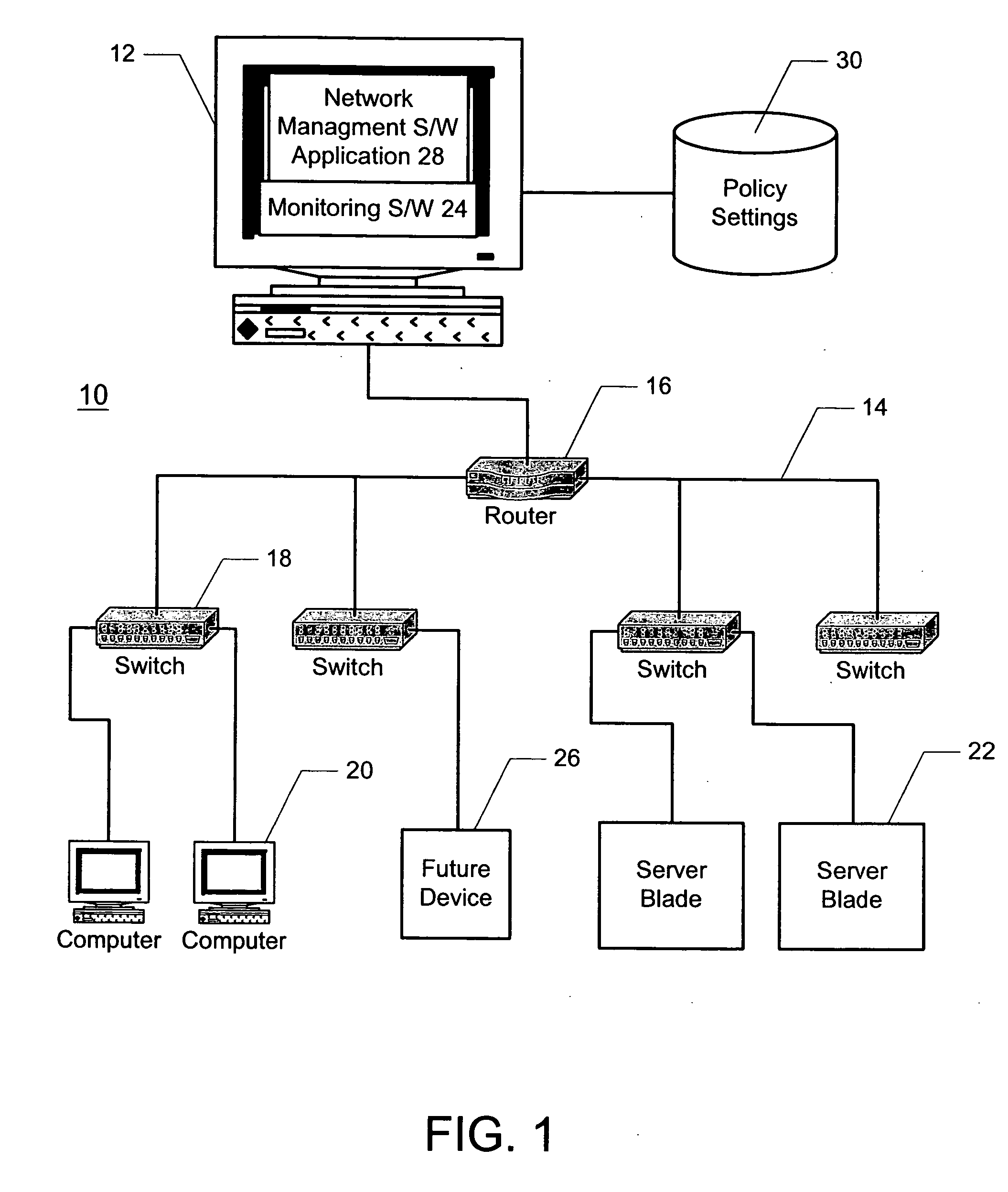
InactiveUS20050114474A1Optimize networkDigital computer detailsLocation information based serviceAuto-configurationNetwork management application
A method and system for automatically configuring devices in a network is disclosed. A network management software application is provided that enables a user to associate policy settings with physical locations in the network. During an operational mode of the network management application, the application automatically detects when a network device is plugged into the network, and determines a location of the device in the network. The device is then automatically configured based on the policy settings associated with the corresponding location.
Owner:IBM CORP
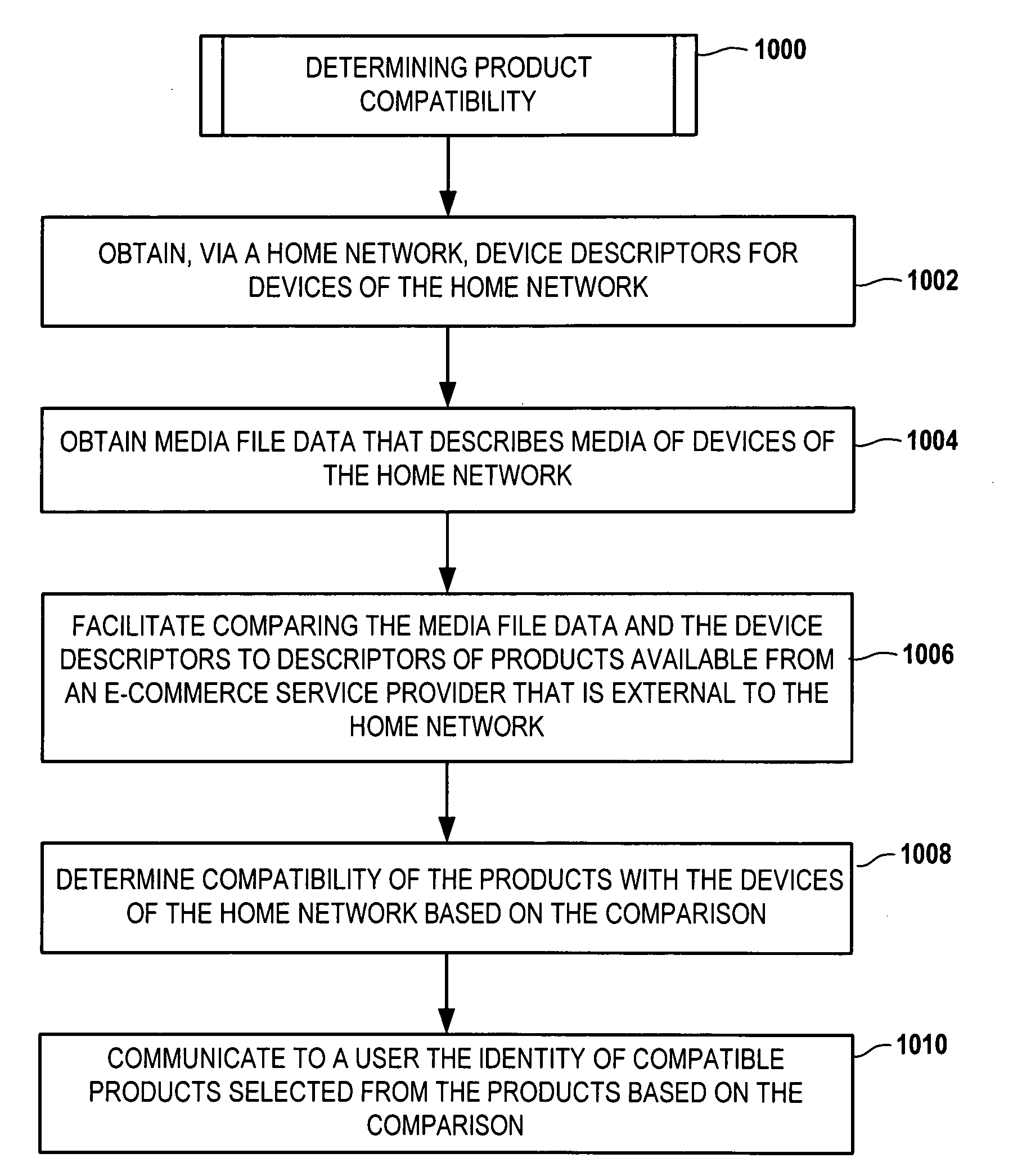
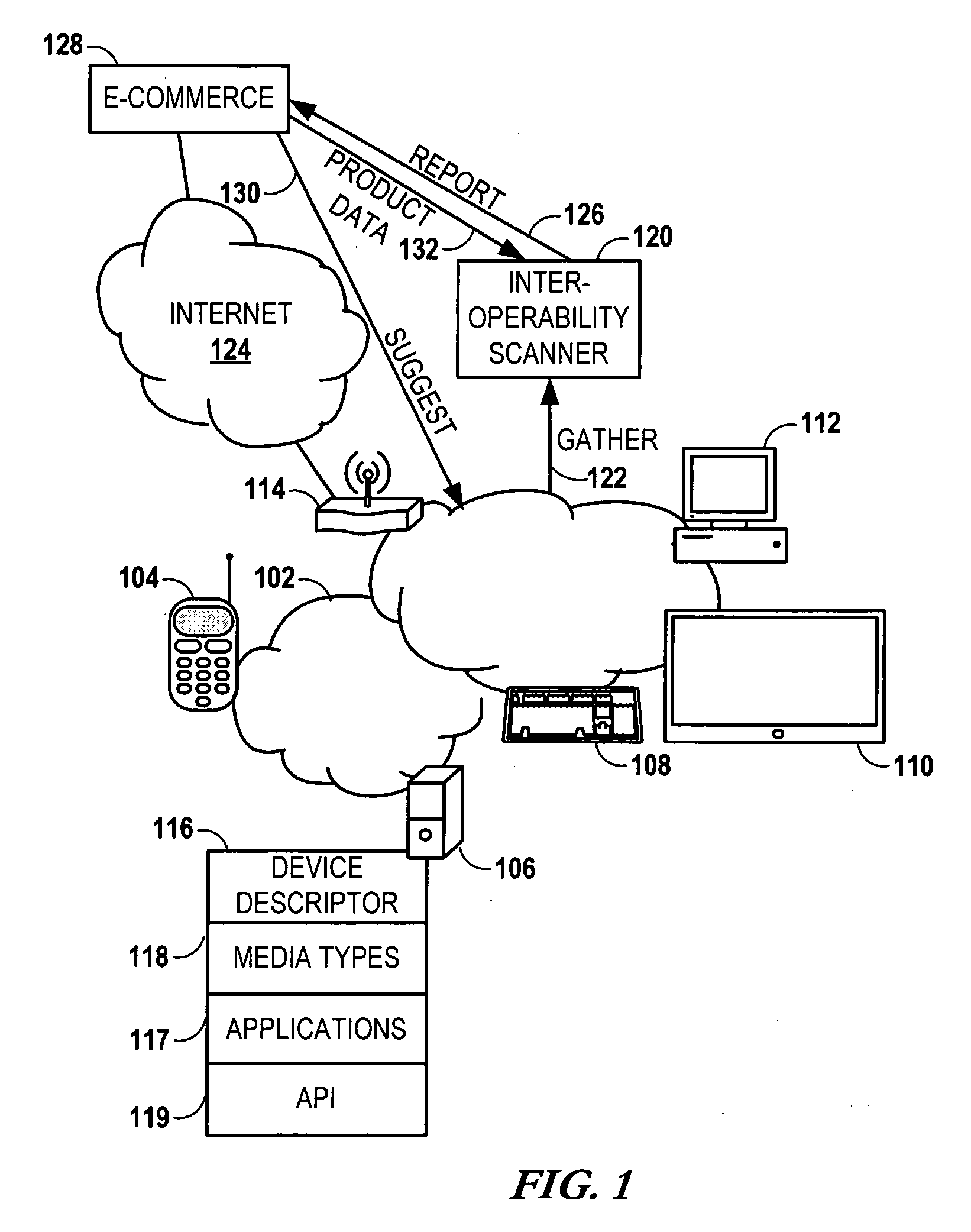
Use of network composition descriptors for determining product compatibility
ActiveUS20090259515A1Optimize networkMultiple digital computer combinationsMarketingComputer compatibilityProduct base
Using peer-to-peer device descriptors for determining product compatibility involves obtaining, via a home network, descriptors that describe a composition of the home network. The home network composition descriptors are compared to descriptors of products available from an e-commerce service provider that is external to the home network. The comparison determines compatibility of the products with the devices of the home network. Identity of compatible products selected from the products based on the comparison is communicated to a user.
Owner:RPX CORP
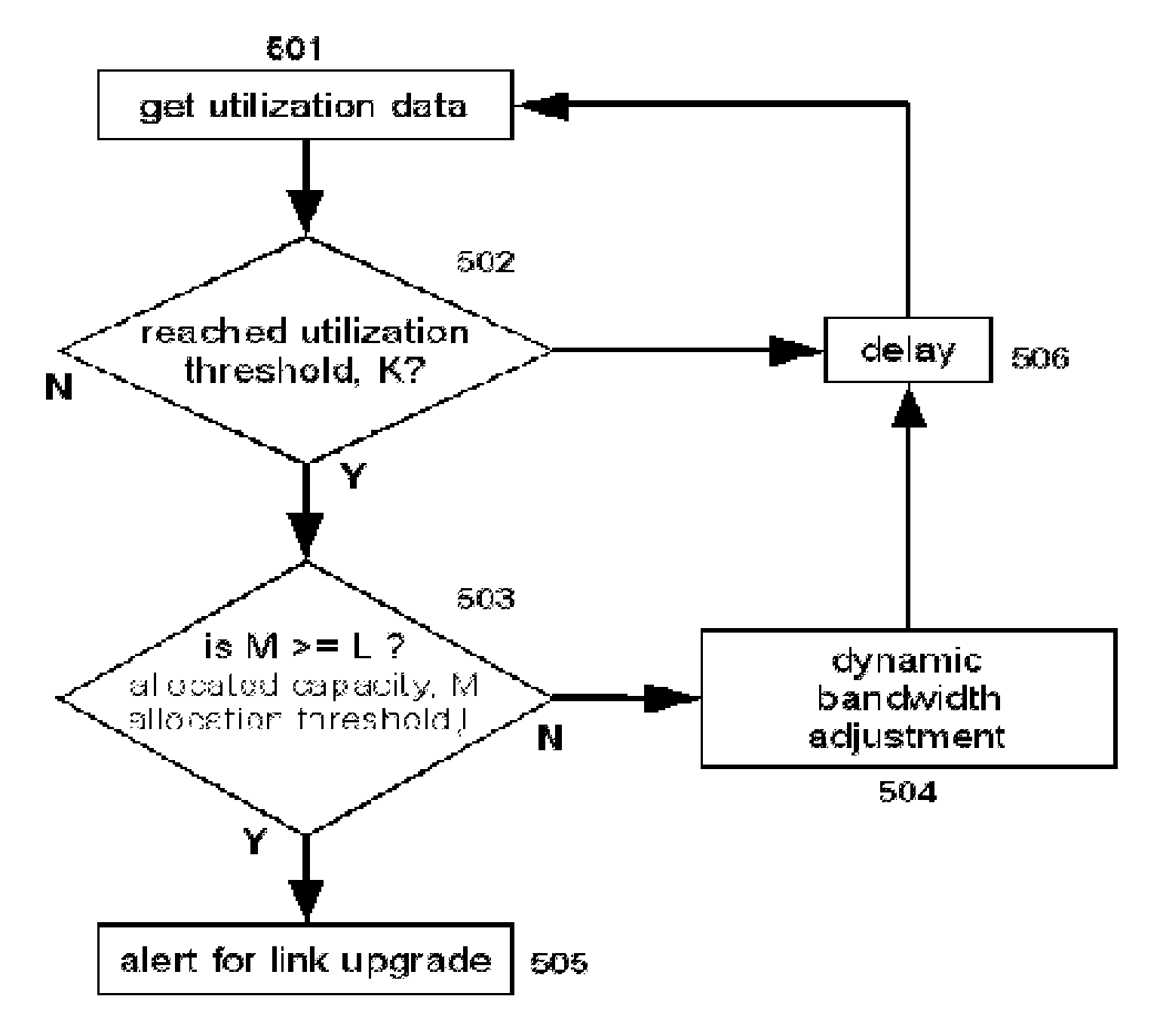
Methods and systems for providing quality of service in packet-based core transport networks
InactiveUS7599290B2Effective carryFair sharingEnergy efficient ICTError preventionService-level agreementTraffic capacity
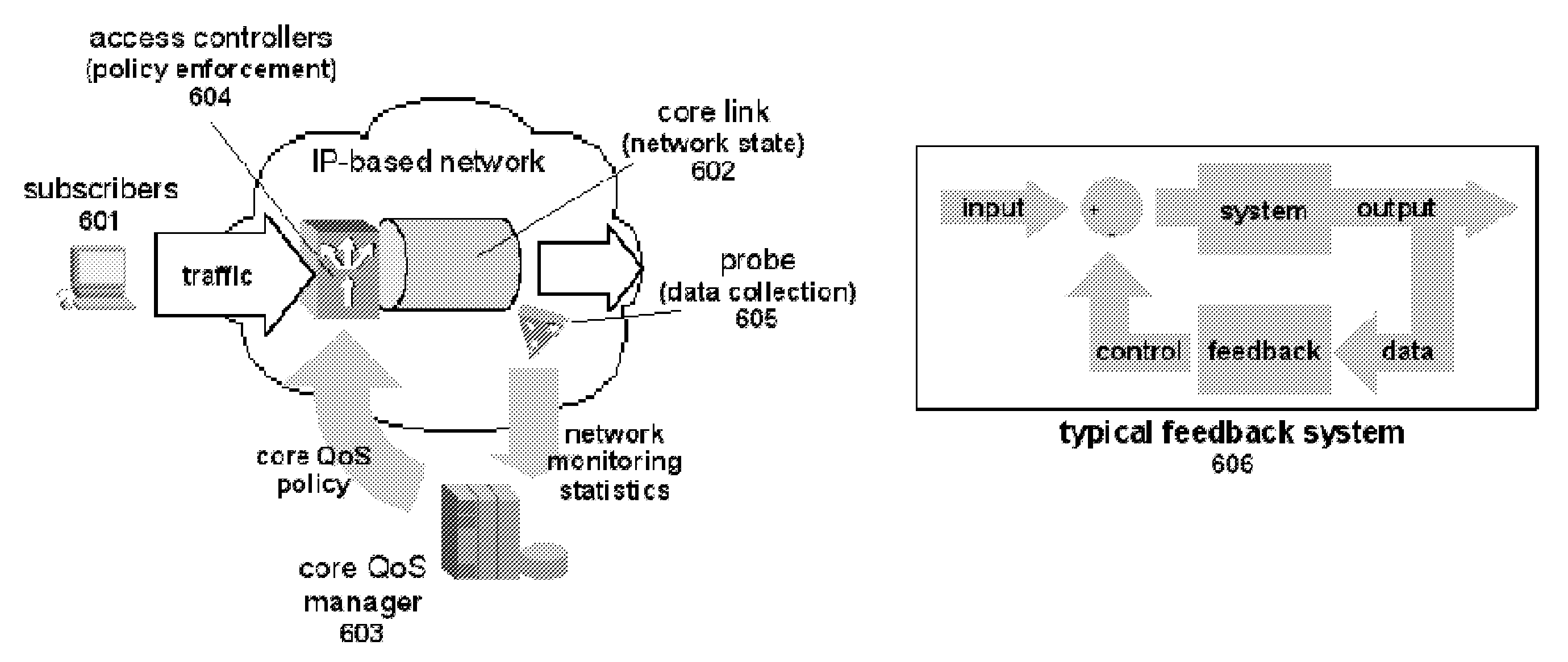
Methods and systems for providing necessary and sufficient quality-of-service (QoS), in a packet-based core transport network that utilizes dynamic setting of bandwidth management pipes or thresholds to obviate link congestion are disclosed. Congestion avoidance is a necessary and sufficient requirement in order to guarantee Quality of Service (QoS) in packet-based core networks.A typical network is composed of a plurality of backbone links connecting edge nodes where backhaul links are aggregated. The backhaul links connect the backbone links to the remote sites serving the subscribers. In order to enforce bandwidth management policies, Access Controllers, which perform traffic shaping, are situated on each remote site.In the event of a violation of certain link threshold settings, dynamic adjustment of the bandwidth management policies on affected Access Controllers is enforced. Various algorithms in determining the correlation between the link nearing congestion and the source or destination of traffic streams are also discussed. This invention implements a feedback control loop wherein probes at various points in the network checks for congestion states to guide bandwidth management threshold decisions in order to maintain the condition of non-congestion throughout the network. Capacity planning and congestion avoidance mechanisms work hand-in-hand to fulfill Service Level Agreements (SLA).
Owner:LATITUDE BROADBAND
System and method for selecting secure card numbers
InactiveUS20090132417A1The process is convenient and fastEasy accessFinanceBuying/selling/leasing transactionsCredit cardFinancial transaction
Embodiments of the present disclosure provide a plug-in feature for a browser that allows for secure financial transactions on a communication network. The plug-in feature generates secure card numbers (e.g., single and multi-use credit card numbers) to pay for purchases. The plug-in feature auto-fills billing and shipping information. The plug-in feature allows a user to store receipts in an efficient and convenient manner to track online shopping activities. The plug-in feature may be implemented in a toolbar of a browser.
Owner:EBAY INC
Controlling many different devices from a smart controller
InactiveUS20140244001A1Reduce operating costsExpand the populationTransmission systemsTransmissionEmbedded systemControl equipment
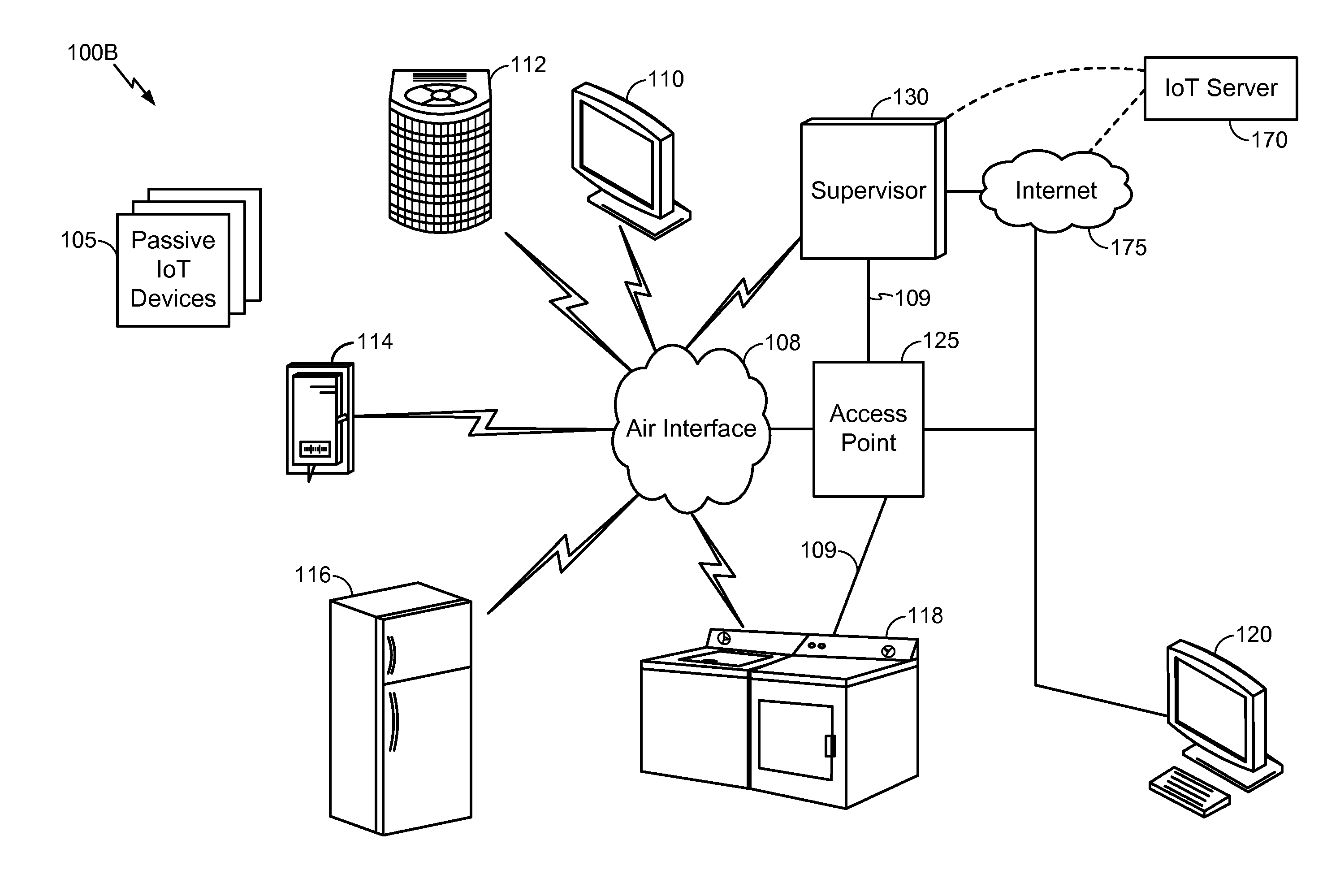
The disclosure is directed to controlling of Internet of Things (IoT) devices based on detecting a device and obtaining control information and associated rules for controlling the device. The control functions available to a smart controller can vary based on the condition of the various rules and / or the interaction of the various devices detected.
Owner:QUALCOMM INC
Methods And Systems For Providing Quality Of Service In Packet-Based Core Transport Networks
InactiveUS20080037552A1Effective carryFair sharingEnergy efficient ICTError preventionService-level agreementTraffic capacity
Methods and systems for providing necessary and sufficient quality-of-service (QoS), in a packet-based core transport network that utilizes dynamic setting of bandwidth management pipes or thresholds to obviate link congestion are disclosed. Congestion avoidance is a necessary and sufficient requirement in order to guarantee Quality of Service (QoS) in packet-based core networks.A typical network is composed of a plurality of backbone links connecting edge nodes where backhaul links are aggregated. The backhaul links connect the backbone links to the remote sites serving the subscribers. In order to enforce bandwidth management policies, Access Controllers, which perform traffic shaping, are situated on each remote site.In the event of a violation of certain link threshold settings, dynamic adjustment of the bandwidth management policies on affected Access Controllers is enforced. Various algorithms in determining the correlation between the link nearing congestion and the source or destination of traffic streams are also discussed. This invention implements a feedback control loop wherein probes at various points in the network checks for congestion states to guide bandwidth management threshold decisions in order to maintain the condition of non-congestion throughout the network. Capacity planning and congestion avoidance mechanisms work hand-in-hand to fulfill Service Level Agreements (SLA).
Owner:LATITUDE BROADBAND
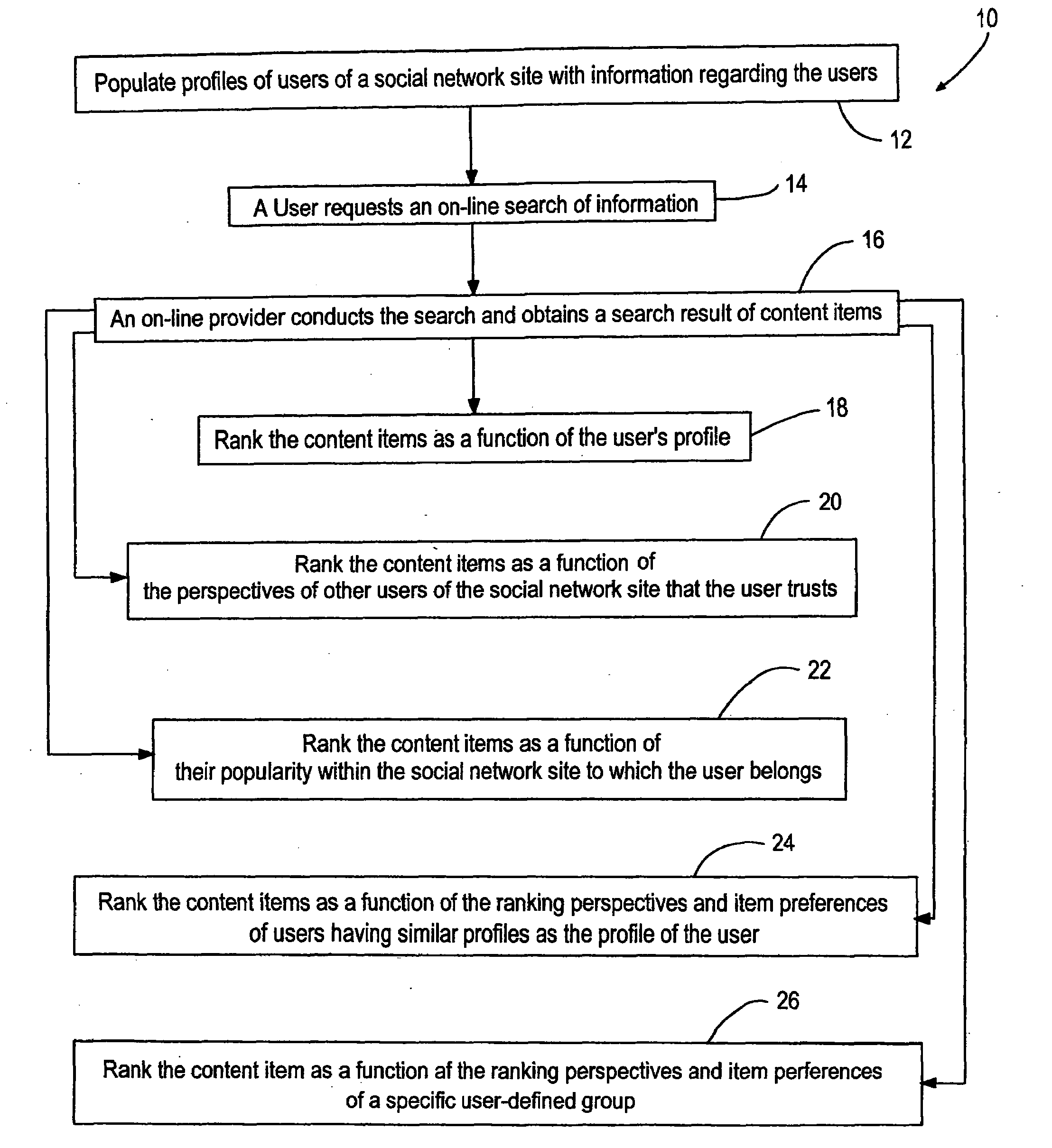
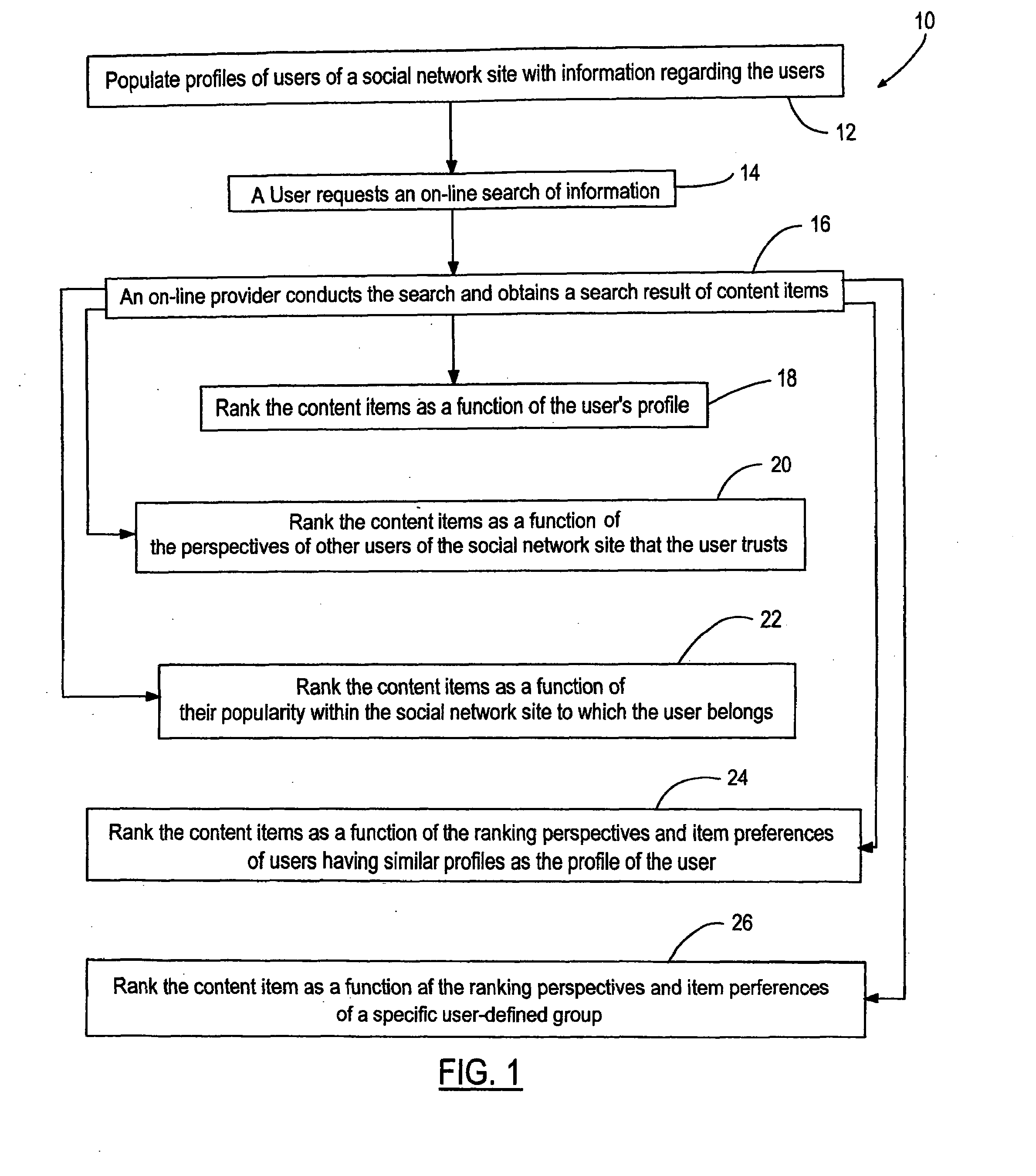
Ranking search results presented to on-line users as a function of perspectives of relationships trusted by the users
ActiveUS20070214121A1Optimize networkDigital data information retrievalData processing applicationsWeb siteSocial network
A method of ranking search results presented to a user of a social network site on the Internet. Each user of the social network site has a user profile with information regarding the user. The method includes obtaining content items satisfying a search of information on the Internet by a first user of the social network site. The content items are organized as a function of at least one of the user profiles for presentation of the content items in a list to the first user.
Owner:CUSTOMERFORCE COM
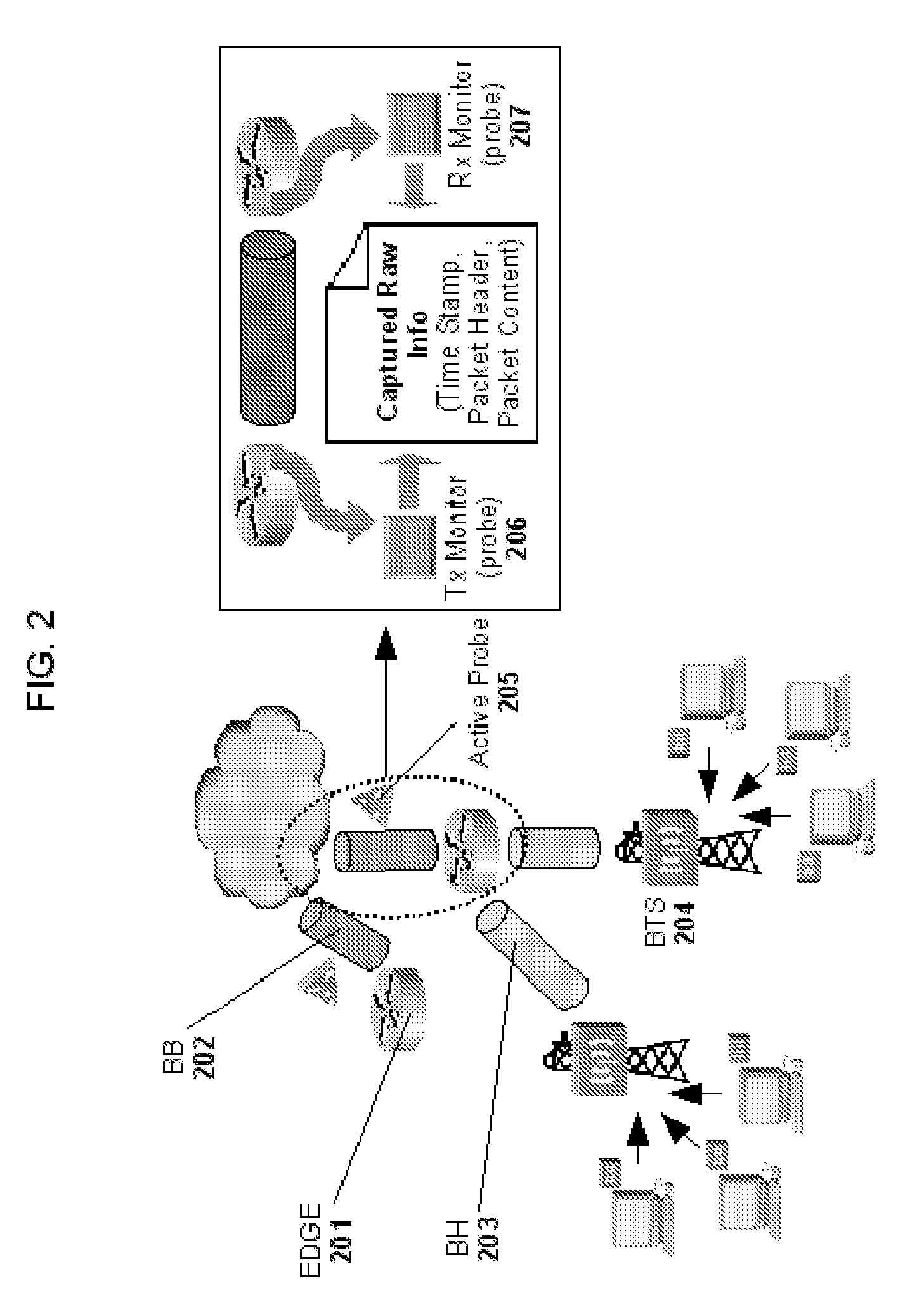
Method, device and system for monitoring network performance
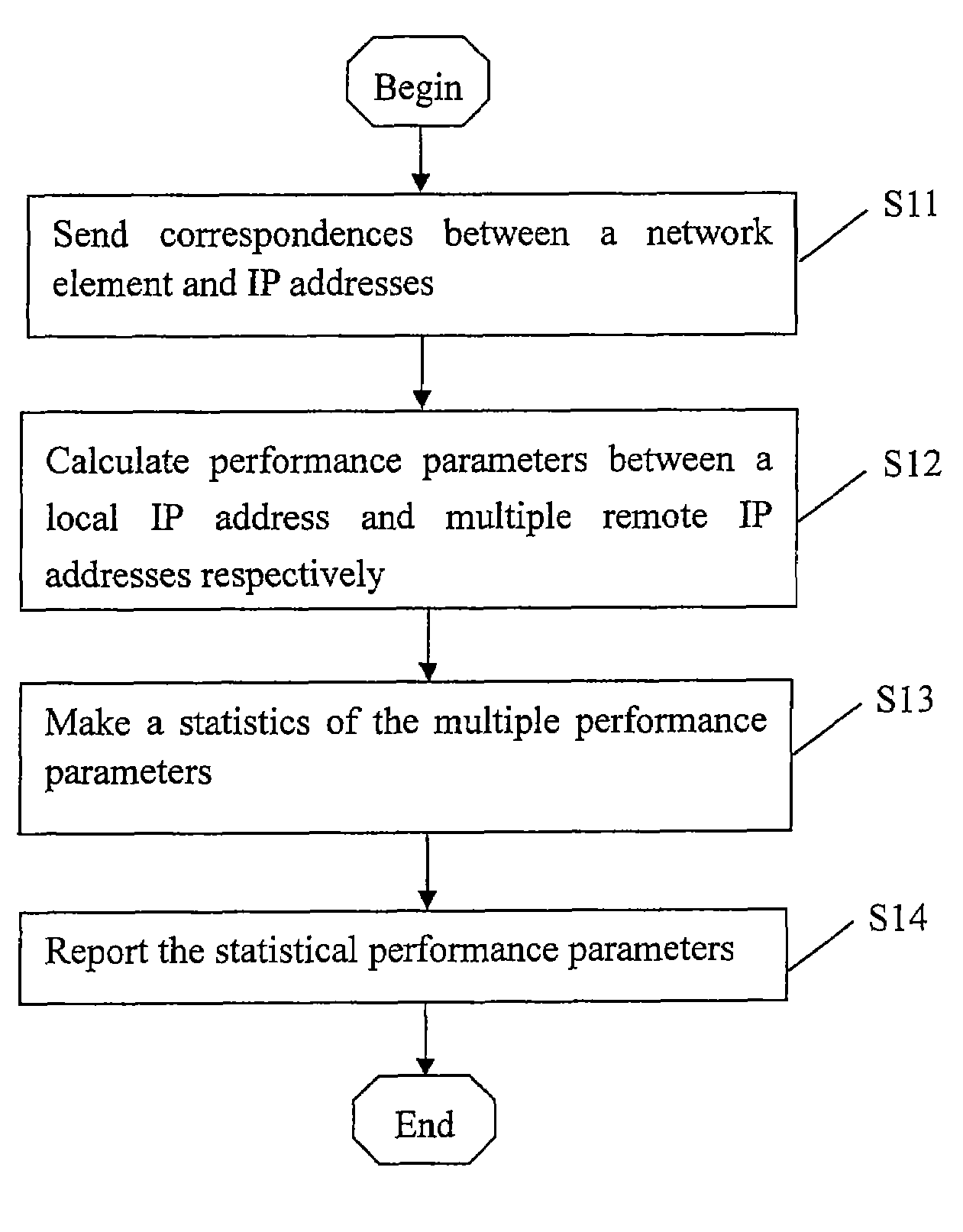
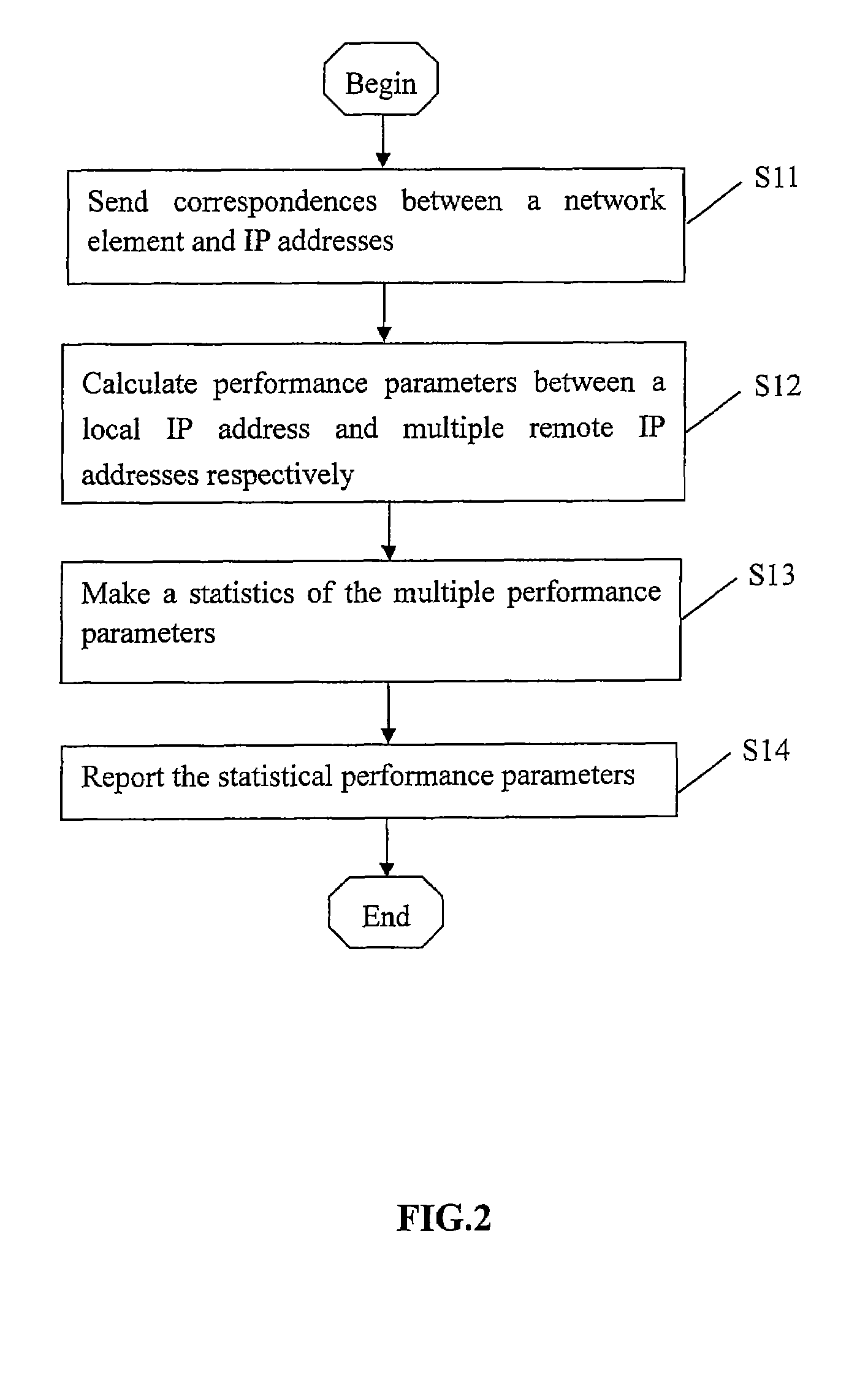
ActiveUS7653005B2Save bandwidthReduce network loadError preventionTransmission systemsIp addressNetworked system
A method for monitoring network performance includes: sending correspondences between a remote network element and a plurality of IP addresses thereof from a network management device to a local network element; according to the correspondences, calculating performance parameters between the local IP address and the plurality of remote IP addresses respectively, by the local network element; making a statistics of the calculated performance parameters by the local network element. A network element for monitoring network performance, connected with a network management device and a remote network element, includes: a receiving unit, a performance parameter processing unit, a performance parameter statistics unit, and the transmitting unit. A network system for monitoring network performance is further provided. According to embodiments of this invention, the efficient measurement of network performance including IP QoS between each two MGWs of an IP network, RTP stream bandwidths, and the like, is realized, thus the message bandwidth of performance test can be saved and processing load of the network management device can be reduced.
Owner:HUAWEI TECH CO LTD
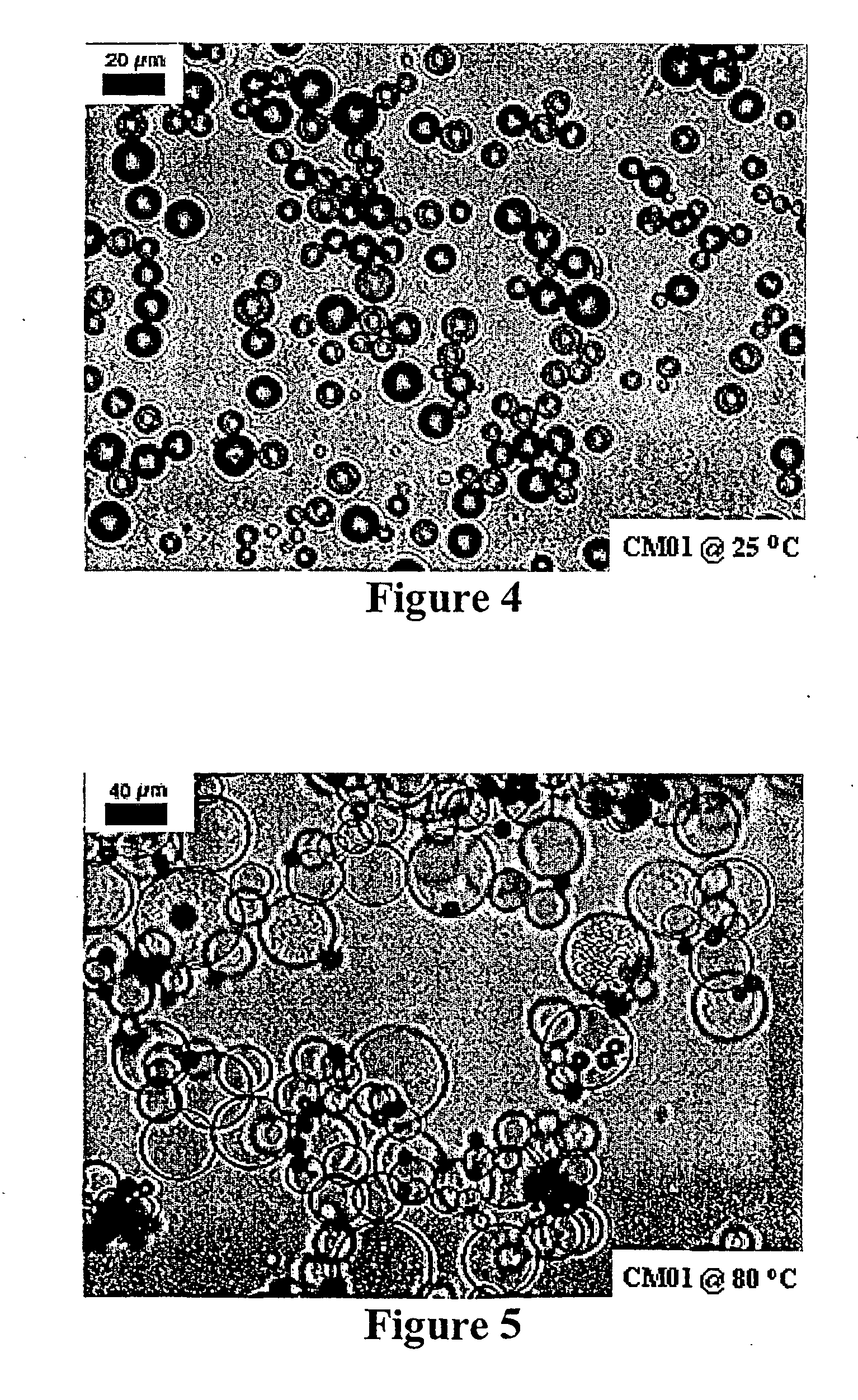
Expandable microspheres for foam insulation and methods
InactiveUS20050079352A1Use in some applicationHigh of encapsulationLiquid surface applicatorsGlass/slag layered productsPolymer scienceFoaming agent
Hollow thermoexpandable particles or microspheres are provided that contain hydrocarbon blowing agents and have a shell polymer that can be softened at the onset of the expansion temperature and solidified at a higher temperature (thermoset) in an expanded state. Preferably, the microspheres have a shell of thermally expandable and thermally crosslinkable polymer and a hollow interior that contains a hydrocarbon liquid that boils at a temperature below the heat activated crosslinking temperature of the polymer shell. The crosslinking of the shell polymer during or after expansion, which is heat activated at an elevated temperature, can solidify the shell polymer and, then, maintain the expanded volume of the microspheres. The thermoexpandable thermoset polymer particles are useful in insulation, packaging, for making foam materials such as polyurethane or polyisocyanurate rigid foams. The invented thermoset microspheres can substantially improve the close cell percentage and compressive strength of the foam materials and make the foam manufacturing less hazardous.
Owner:IP RIGHTS +1
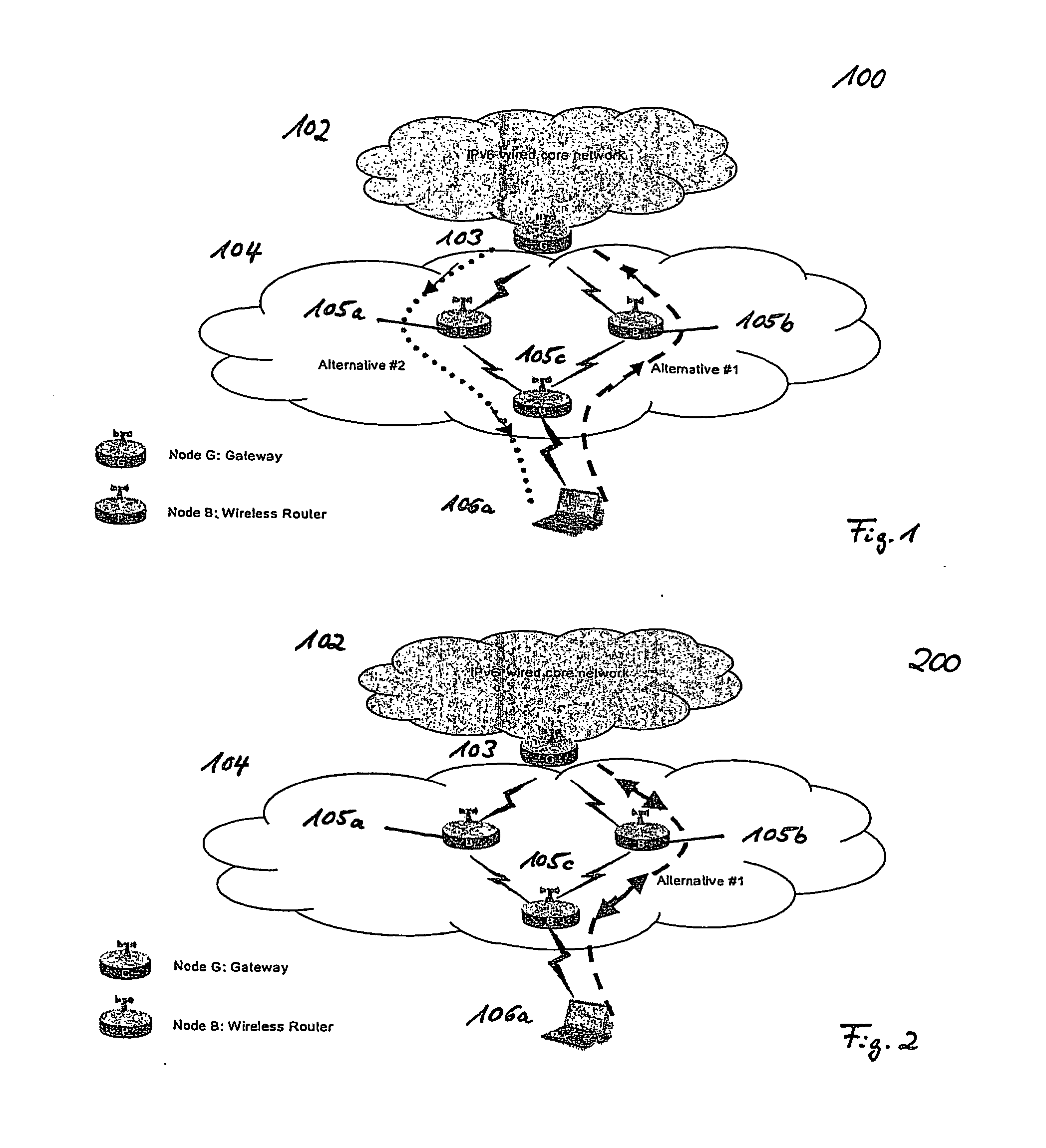
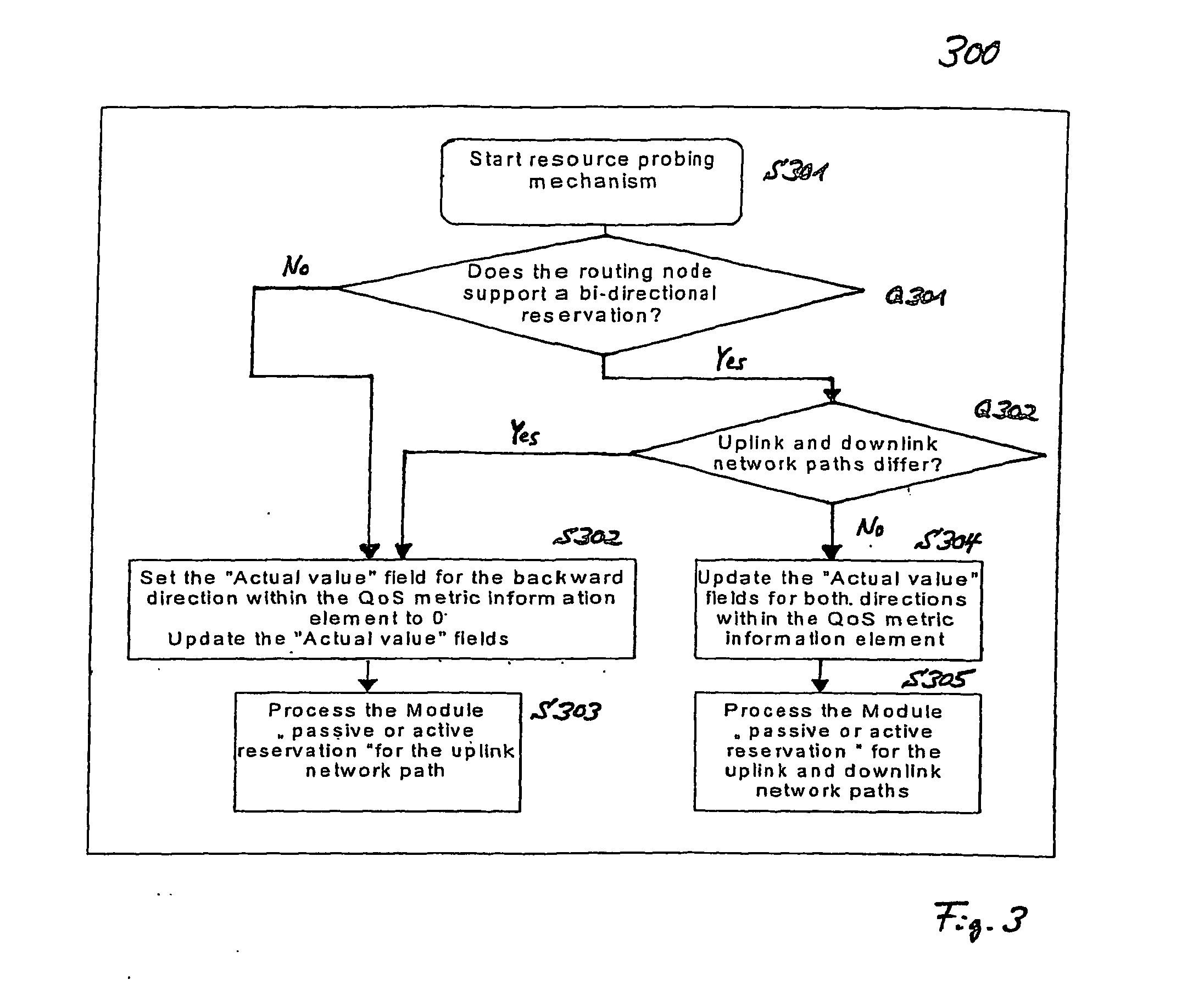
Bidirectional Qos Reservation Within an in-Band Signaling Mechanism
InactiveUS20070217406A1Optimize networkImprove network utilizationNetwork traffic/resource managementNetwork topologiesReal time servicesWireless ad hoc network
A mechanism for a bidirectional reservation procedure within an in-band signaling mechanism gives symmetric real-time services running on mobile devices, which are used to support different access technologies in dynamic, mobile, wireless IP networks where the quality of the node connectivity can sometimes be unpredictably time-varying, the possibility to mutually reserve, monitor and adapt resources and service parameters for upstream and downstream direction along a communication path. The mechanism optimizes reservation mechanisms, especially for adaptive real-time services in wireless and wireless ad-hoc networks, by making use of a dynamic bidirectional reservation in-band signaling approach.
Owner:NOKIA SIEMENS NETWORKS GMBH & CO KG +1
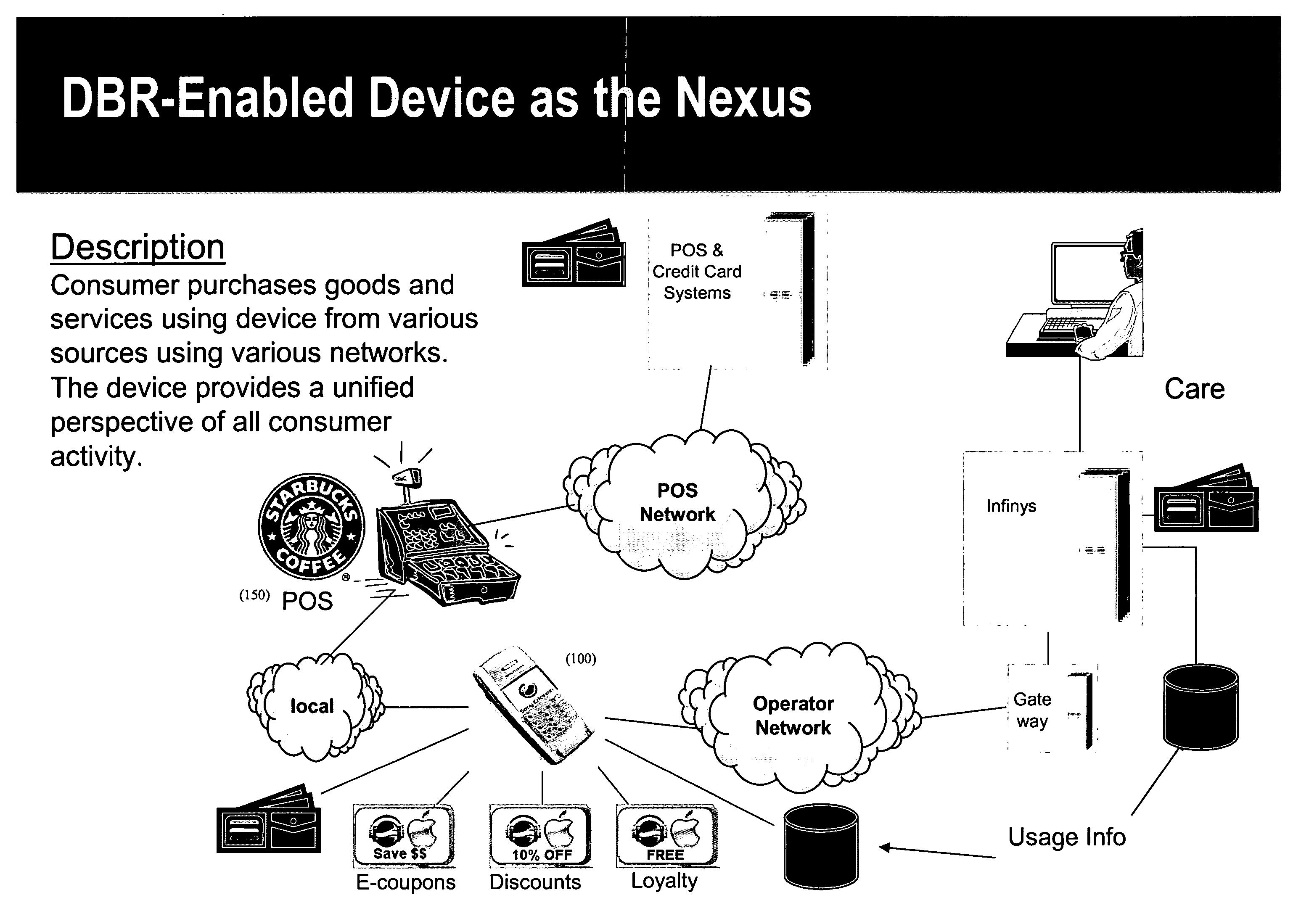
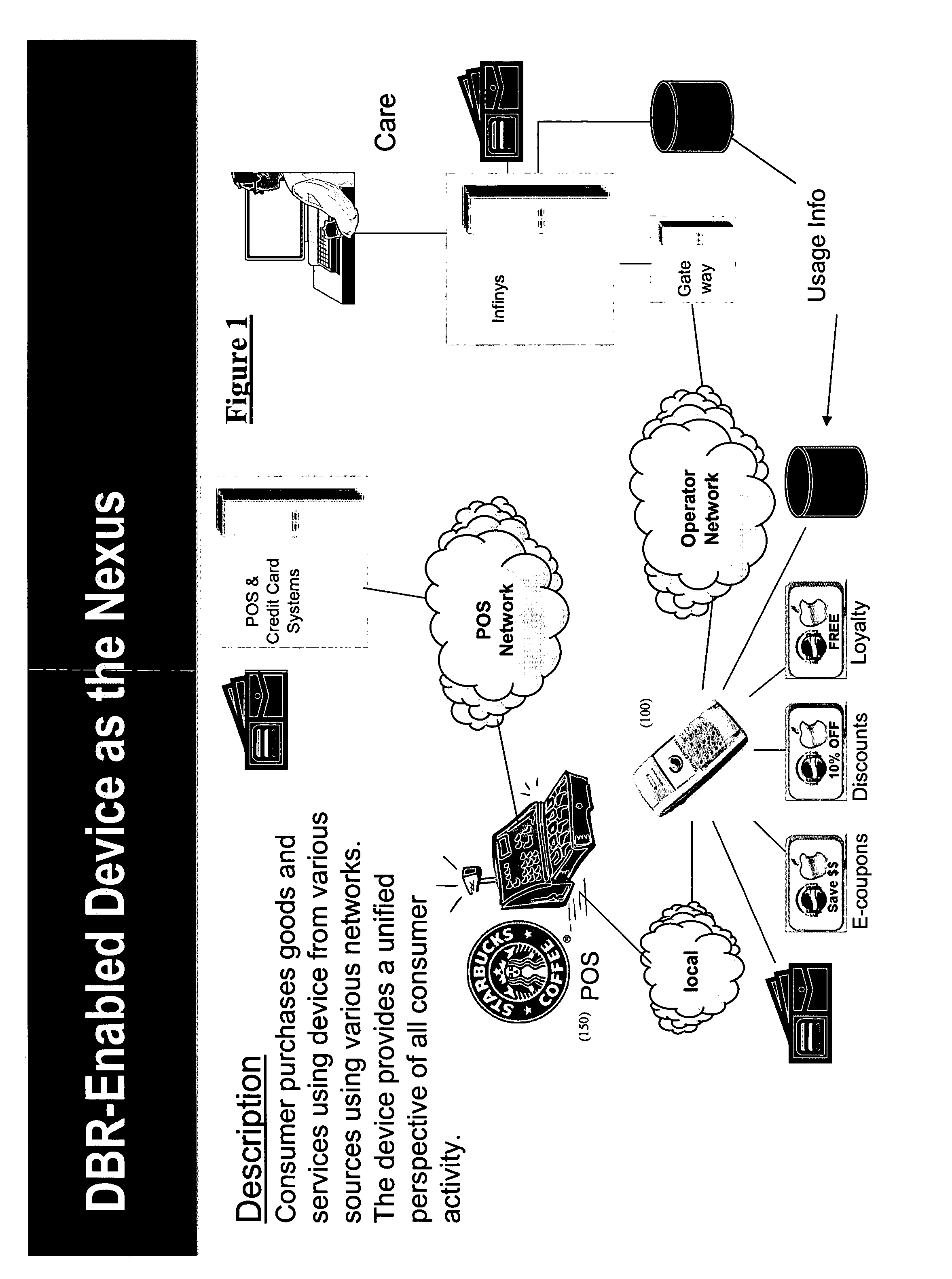
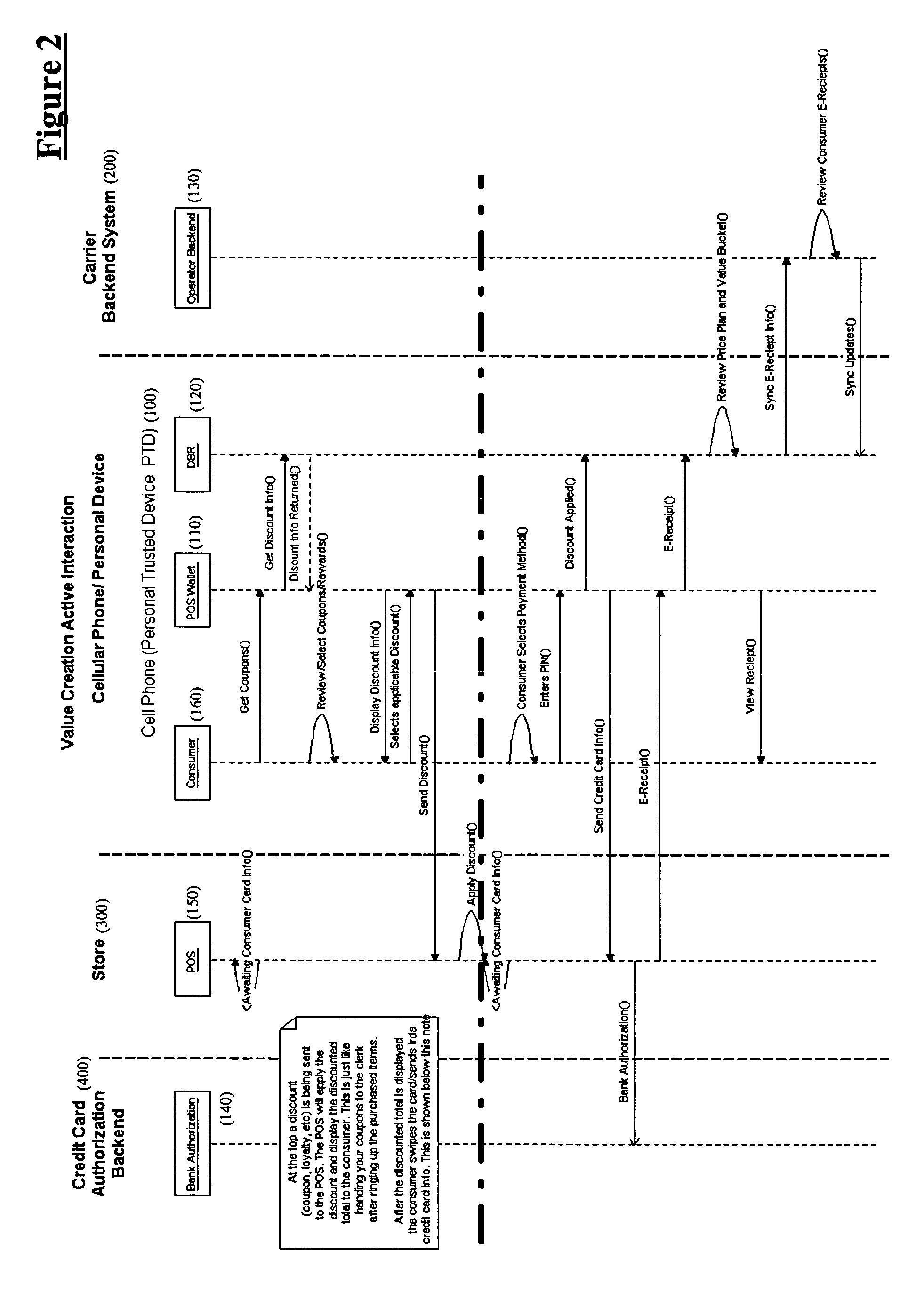
System and method for value creation
There is disclosed a system and method for creating value by facilitating third party participation in mobile commerce transactions, providing consumers with a unified perspective of commercial activity, and selectively implementing discounts. The system may include a computerized engine and a point of sale wallet, which may be embedded in a personal trusted device. The computerized engine may be programmed to selectively implement a discount associated with a particular transaction. The personal trusted device may comprise a wireless communications technology, which enables the device to communicate with a back-end system and / or other point of sale devices. The personal trusted device may serve as the nexus of consumer transactions by facilitating payment as well as receipt and storage of electronic receipts. The personal trusted device may also be configured to transmit electronic receipts via the communications technology.
Owner:NETCRACKER TECH SOLUTIONS
Fluoropolymer coating compositions with olefinic silanes for anti-reflective polymer films
InactiveUS20060147177A1Low compositionIncreased durabilityMaterial nanotechnologyOrganic chemistrySilanesRefractive index
An economic, optically transmissive, stain and ink repellent, durable low refractive index fluoropolymer composition for use in an antireflection film or coupled to an optical display. In one aspect of the invention, the composition is formed from the reaction product of a fluoropolymer, a C═C double bond group containing silane ester agent, and an optional multi-olefinic crosslinker. In another aspect of the invention, the composition further includes surface modified inorganic nanoparticles. In another aspect, the multi-olefinic crosslinker is an alkoxysilyl-containing multi-olefinic crosslinker.
Owner:3M INNOVATIVE PROPERTIES CO
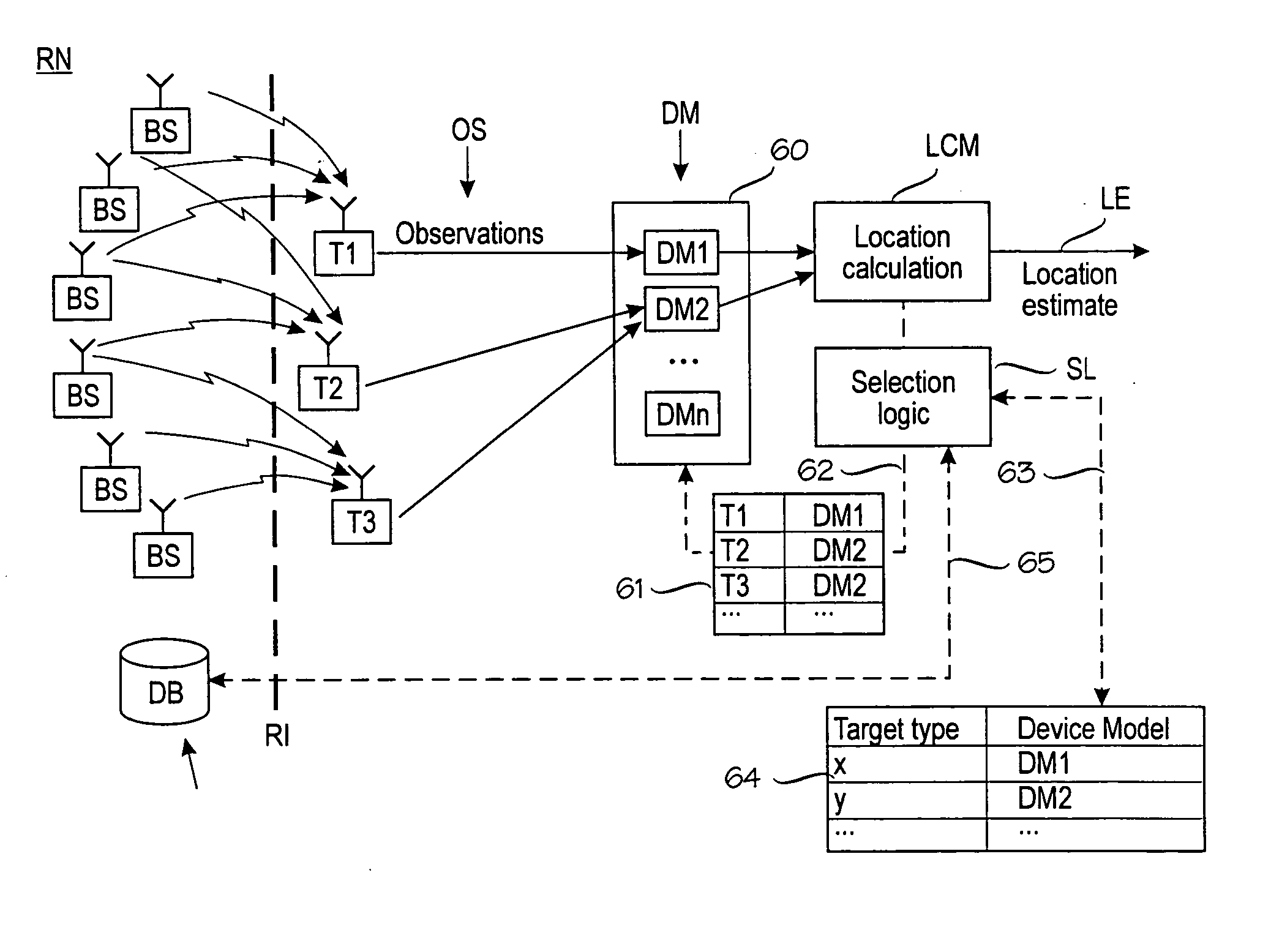
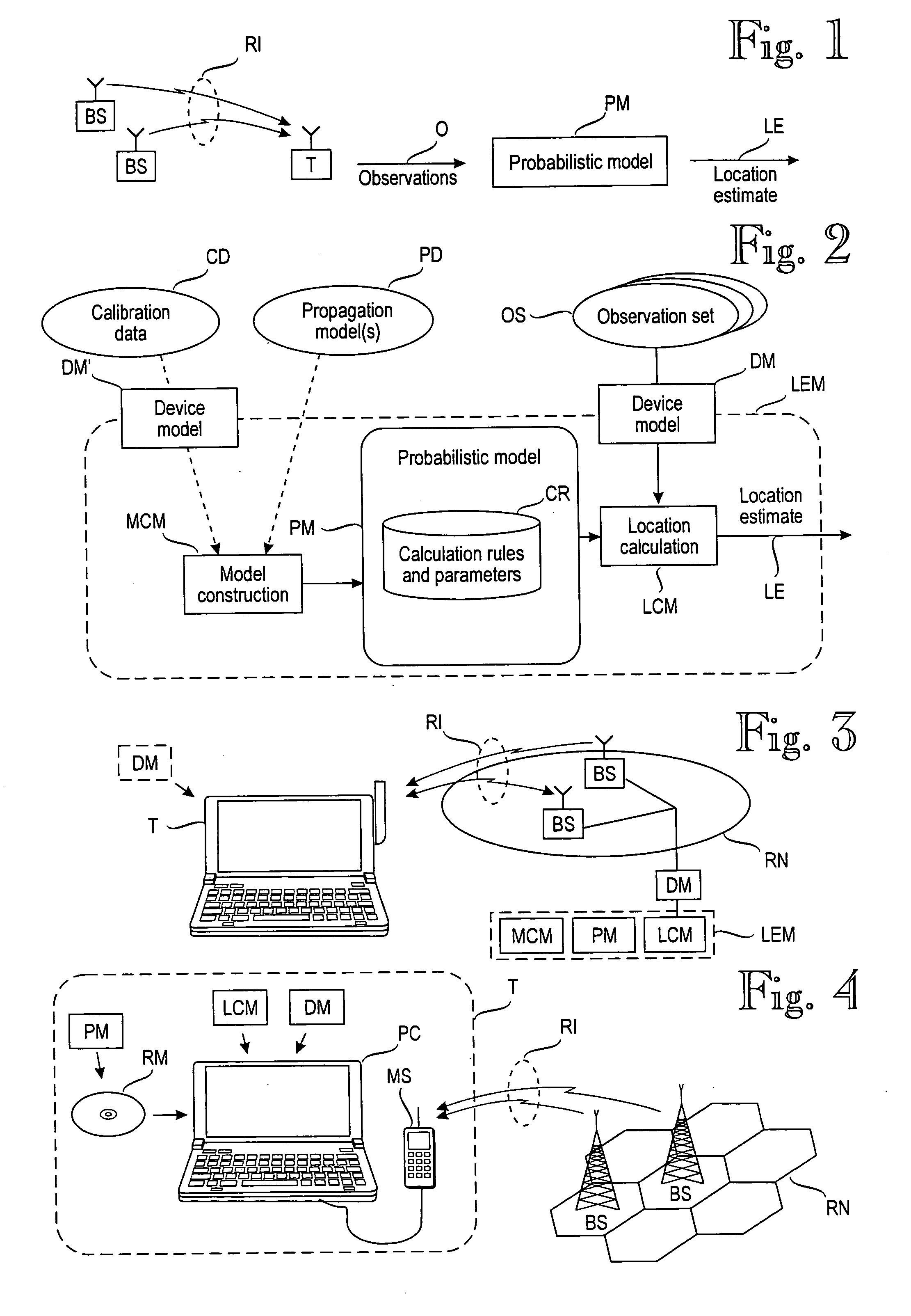
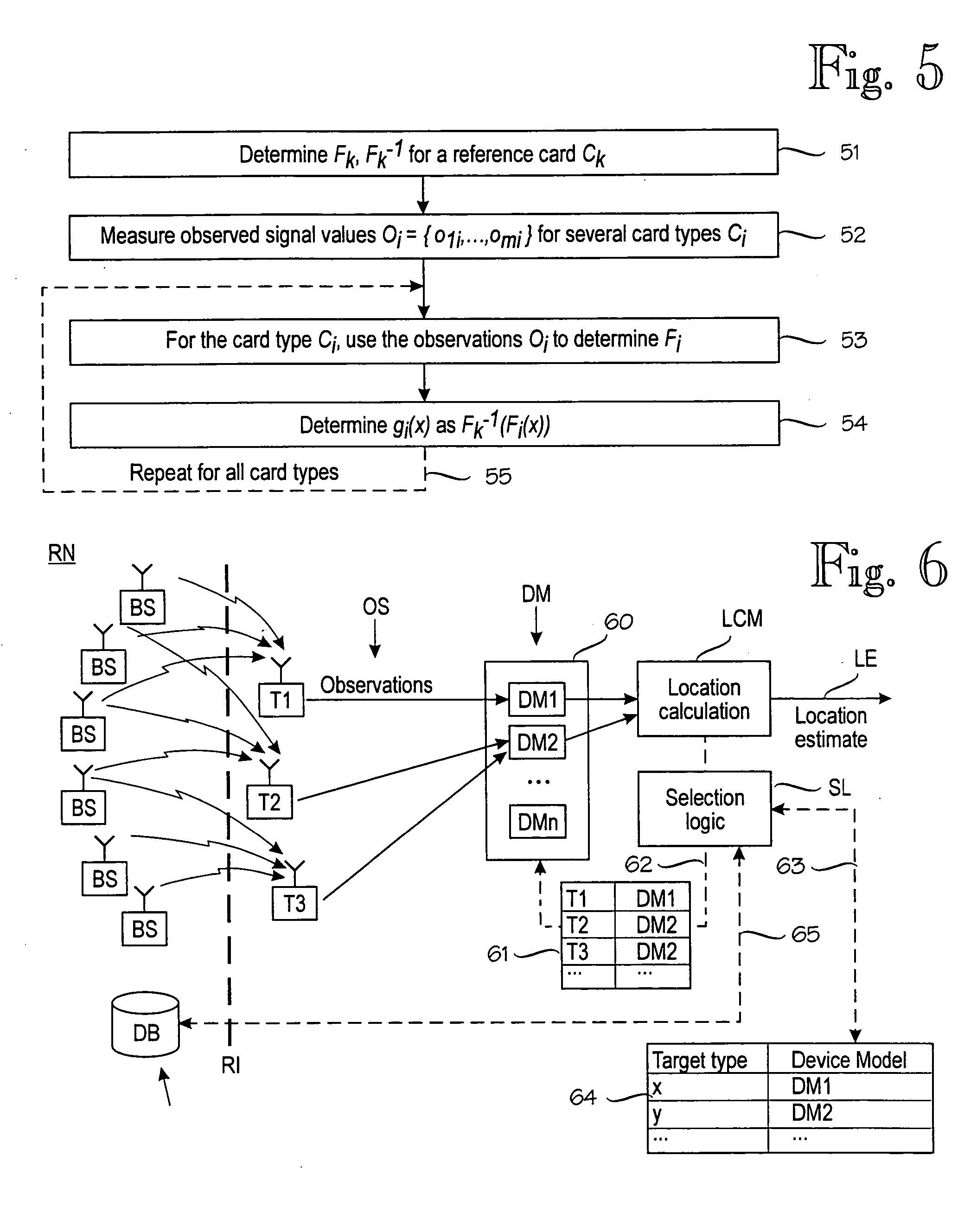
Applications of signal quality observations
ActiveUS20050181804A1Improve accuracyImprove reliabilityPosition fixationData switching by path configurationSignal qualityComputer science
A method and apparatus for using at least one signal quality parameter in an application. A target device makes observations of at least one signal quality parameter in a wireless communication environment. Because there are gross differences between different target devices' observations, there are one or more device models that compensate for the differences. A selection logic selects an optimal device model for each target device. The observations made by the target device are processed with the selected device model and applied to an application, such as a positioning application or network planning.
Owner:AIRISTA FLOW INC +1
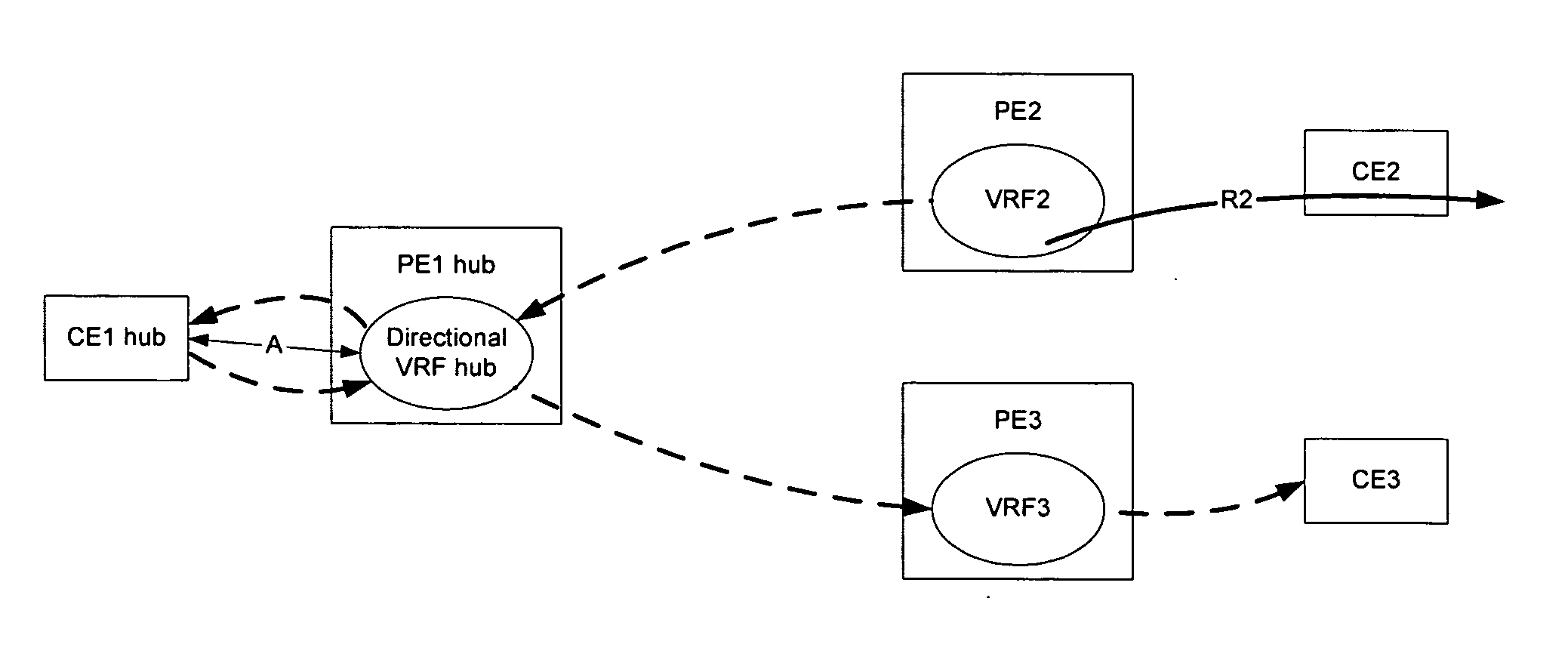
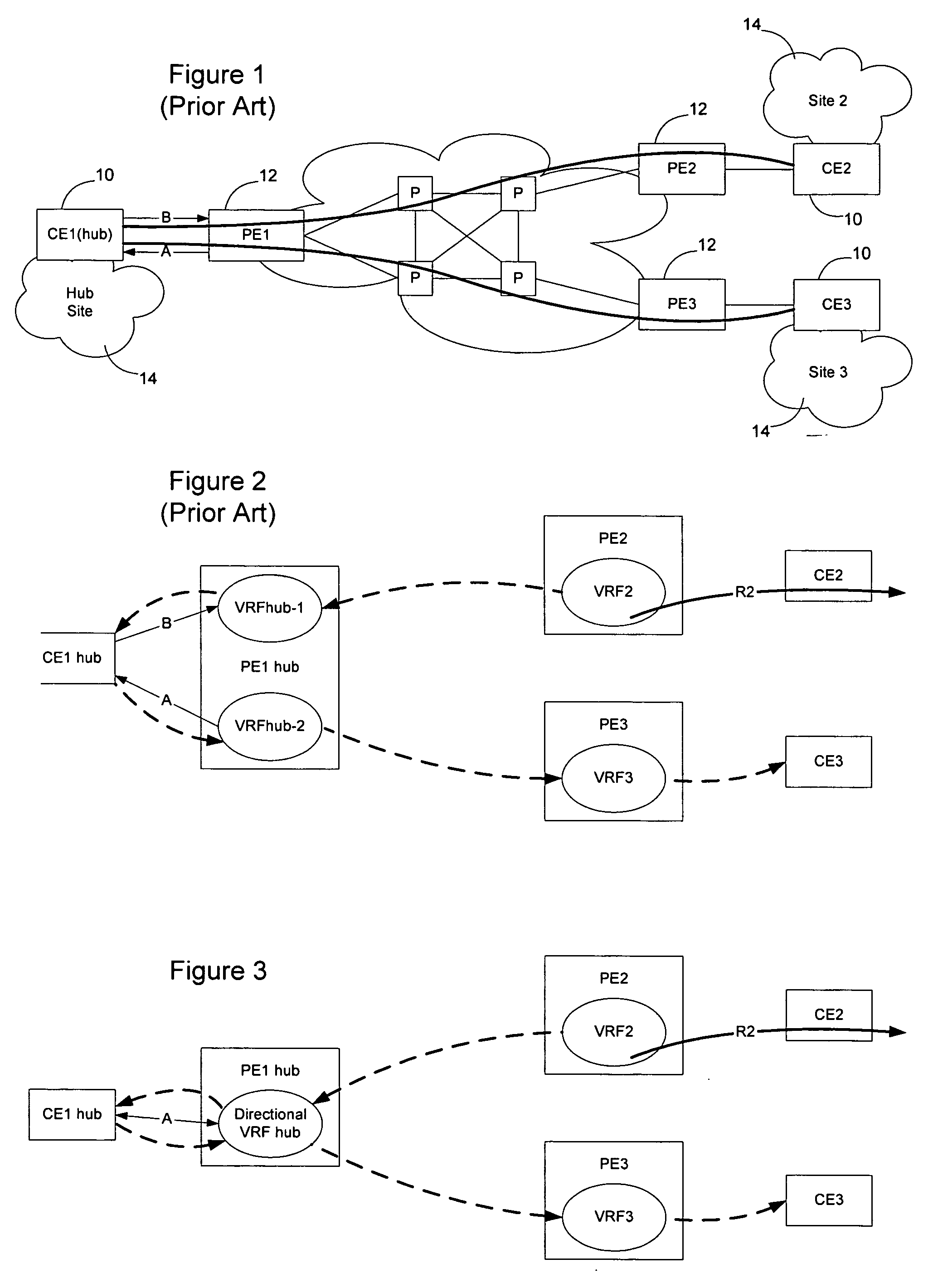
Method and apparatus for implementing hub-and-spoke topology virtual private networks
Deployment of a hub-and-spoke (HaSP) topology virtual private network (VPN) may be facilitated by implementing a bi-directional VRF on a hub PE and using the hub PE as a hub-reflector. Route distinguishers and route targets may be used to differentiate traffic originating on the spokes from traffic originating on the hub. Using a bi-directional VRF allows a HaSP VPN to be created using a single link between the hub CE and hub PE. Allowing the hub CE to control spoke route distribution, and differentiating the direction of the flow by route target and route designator, enables the hub to control traffic between the spokes. Configuring the hub PE as a route reflector allows communication between the spokes to take place without having the CE hub inspect every piece of traffic. Optionally, other services may be provided by the hub PE as well, such as NAT, firewall, and AAA services.
Owner:RPX CLEARINGHOUSE
Wireless local area network context control protocol
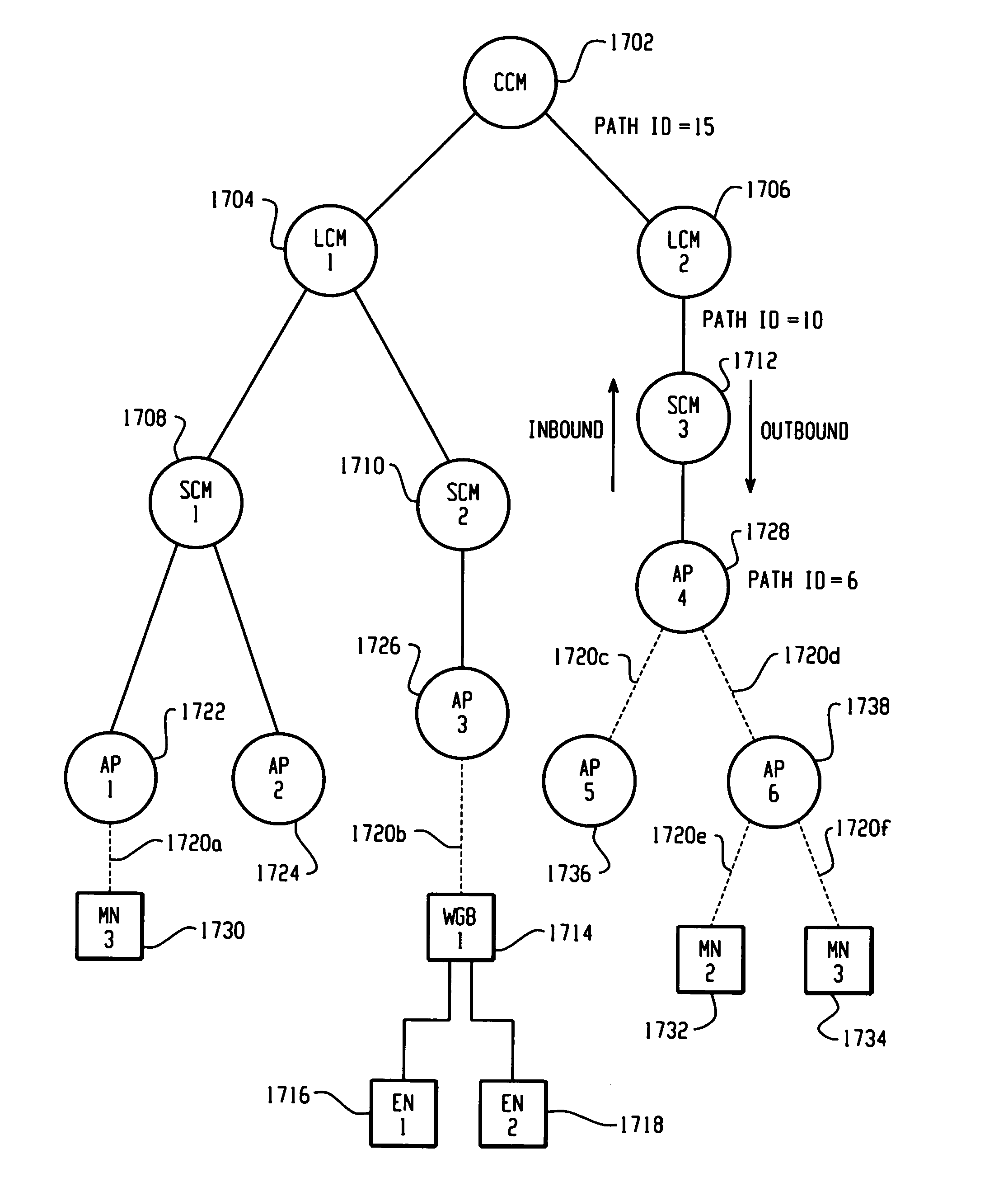
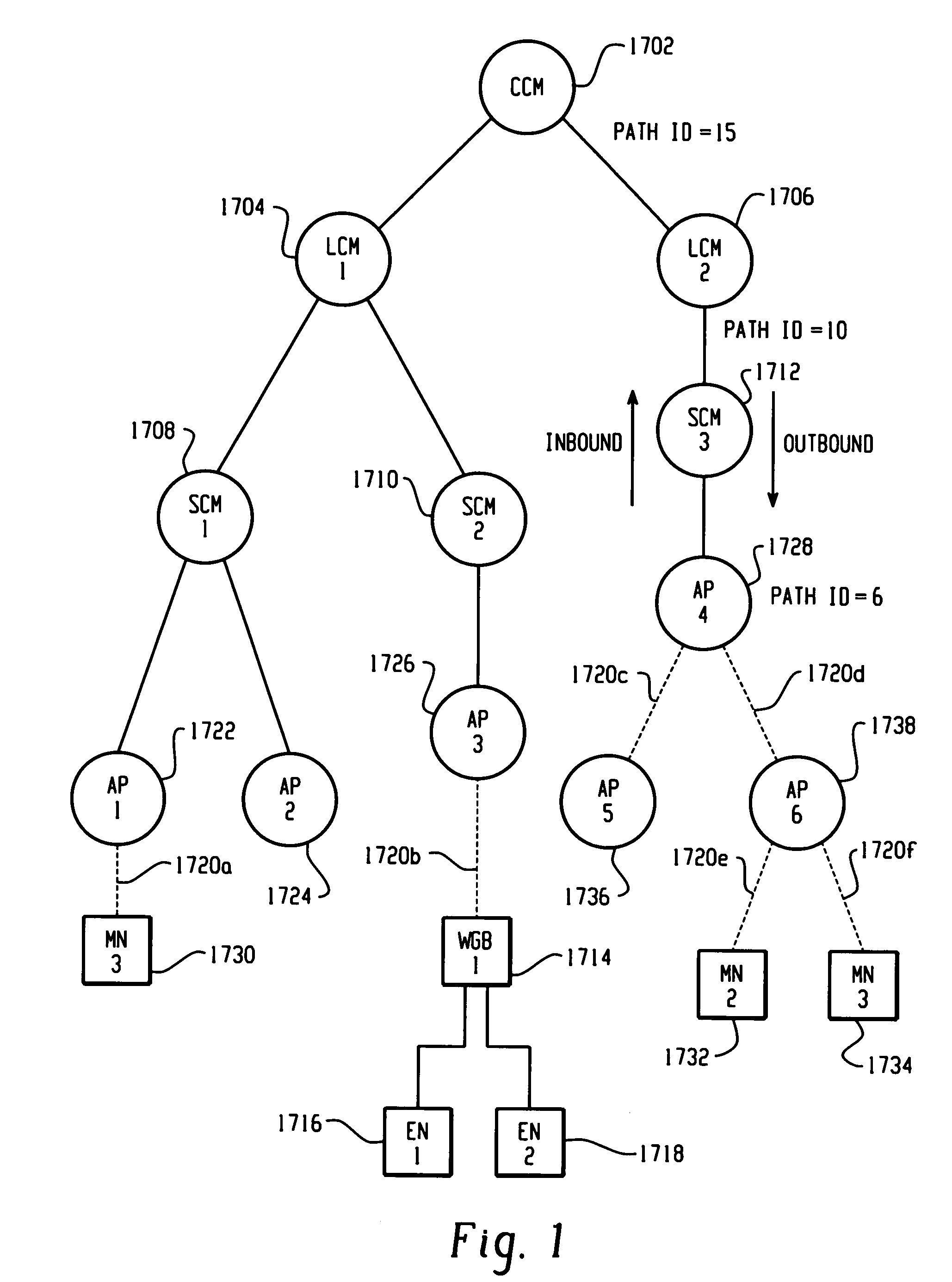
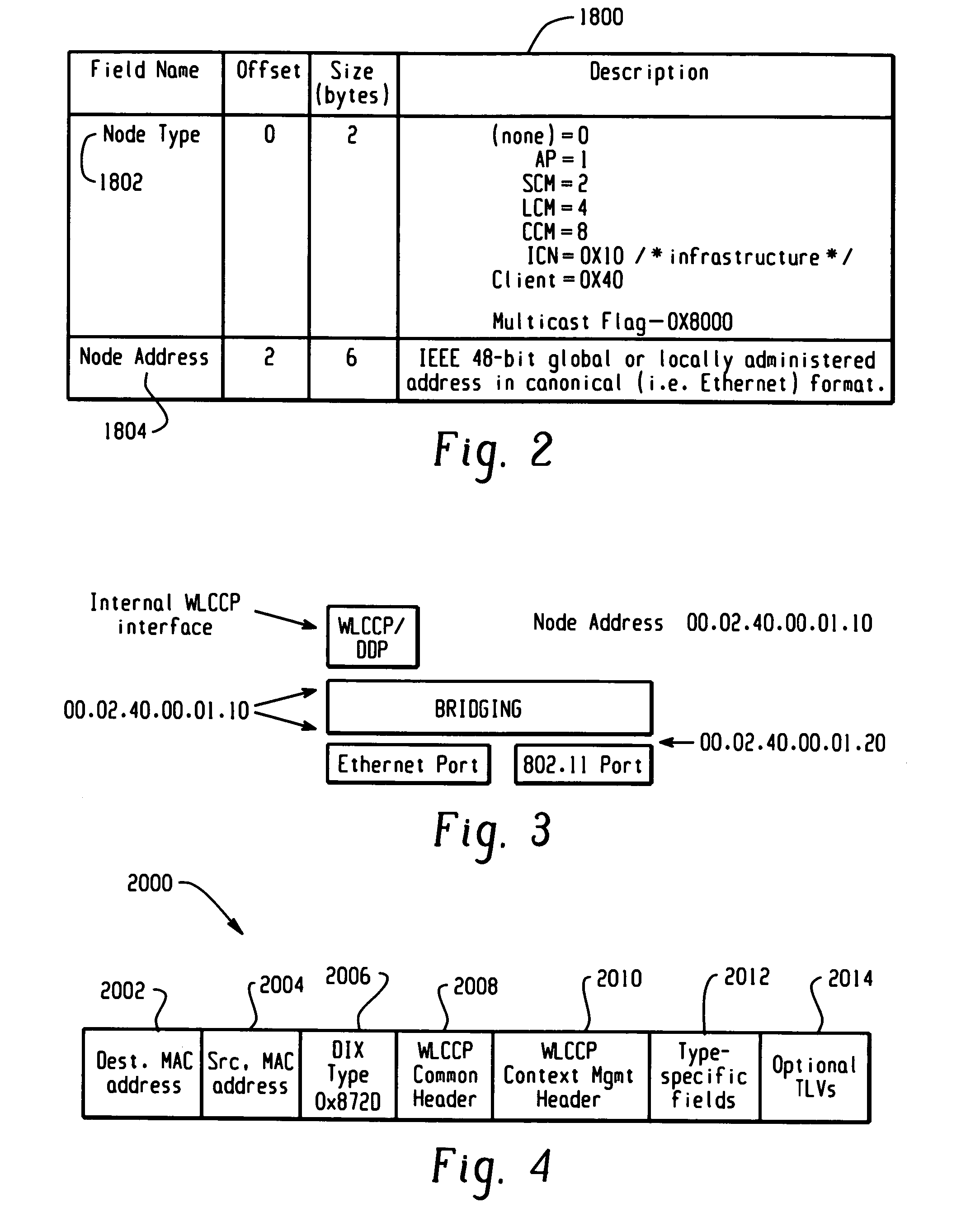
ActiveUS20050220054A1Easy to optimizeOperational securityNetwork topologiesDigital computer detailsPathPingMobile station
A Wireless LAN Context Control Protocol (WLCCP) is used to establish and manage a wireless network topology and securely manages the “operational context” for mobile stations in a campus network. The WLCCP registration protocol can automatically create and delete links in the network, securely distribute operational context, and reliably establish Layer 2 forwarding paths on wireless links. A single infrastructure node is established as the central control point for each subnet, and enables APs and MNs to select the parent node that provides the “least-cost path” to a backbone LAN. Context messages provide a general-purpose transport for context and management information. WLCCP “Trace” messages facilitate network diagnostic tools. Ethernet or UDP / IP encapsulation can be used for WLCCP messages. Ethernet encapsulation is employed for intra-subnet (e.g. AP-to-AP or AP-to-SCM) WLCCP messages. IP encapsulation is used for inter-subnet WLCCP messages and may also be used for intra-subnet WLCCP messages.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com