Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
13196 results about "PathPing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
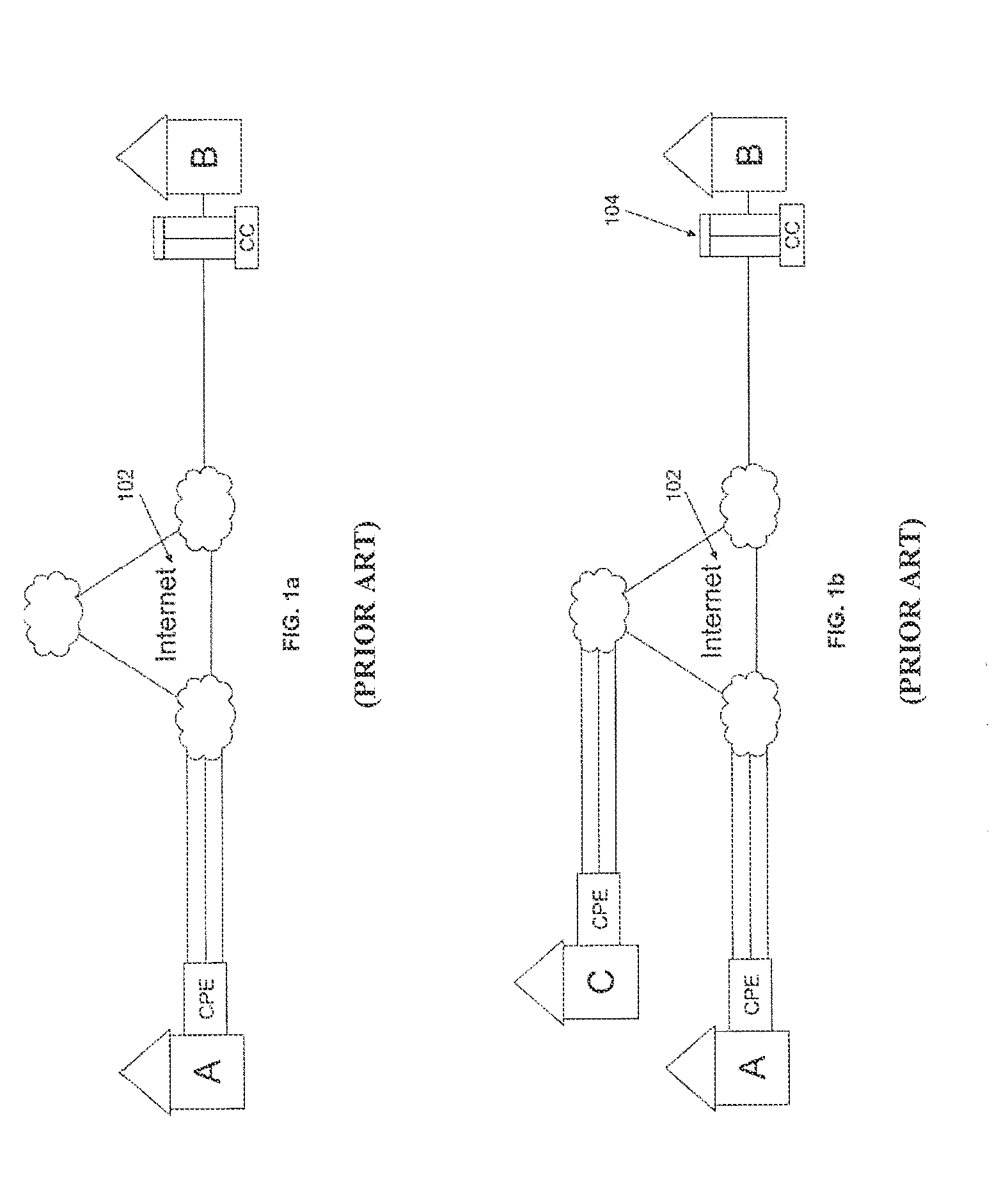
The PathPing command is a command-line network utility supplied in Windows 2000 and beyond that combines the functionality of ping with that of tracert. It is used to locate spots that have network latency and network loss.
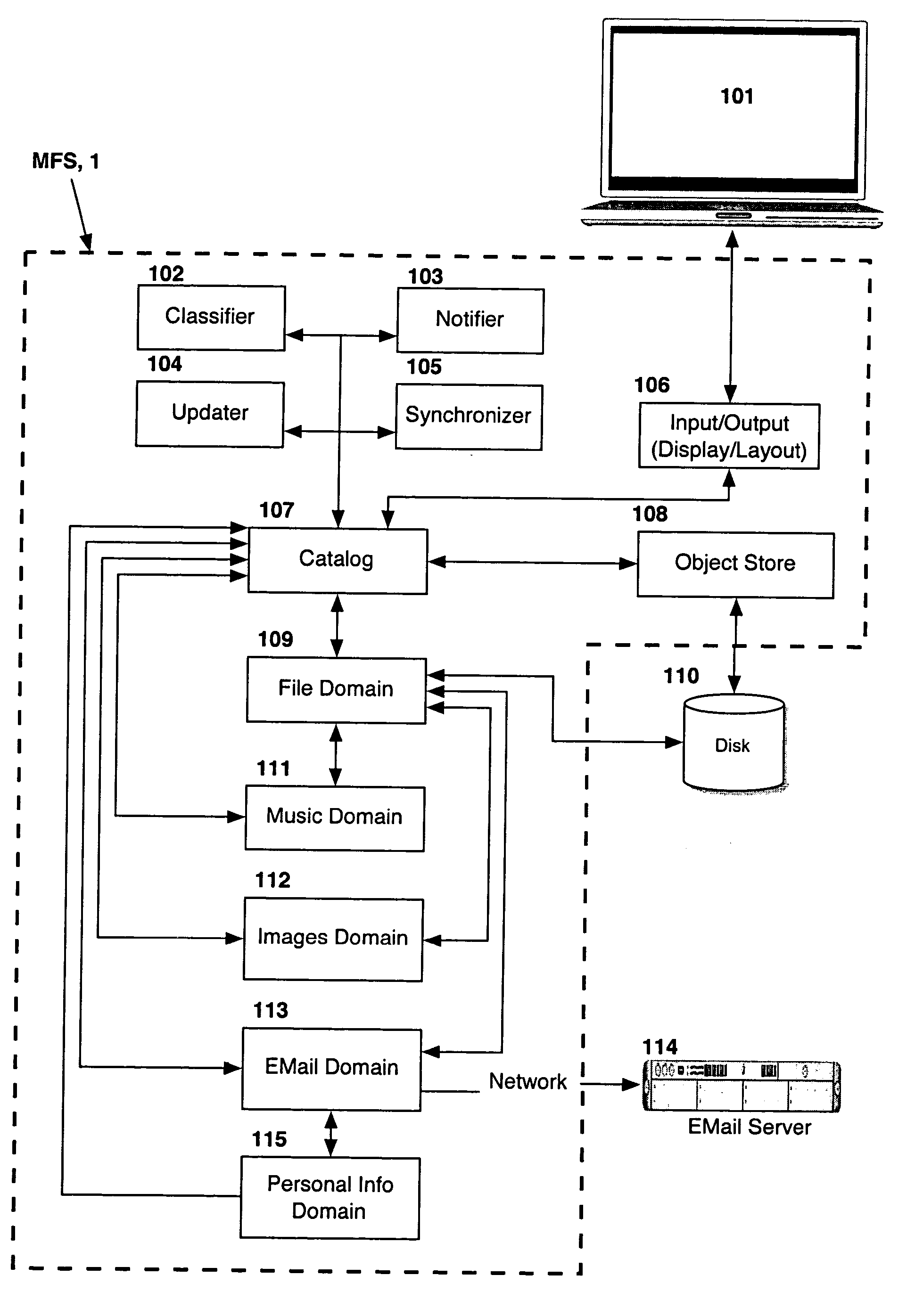
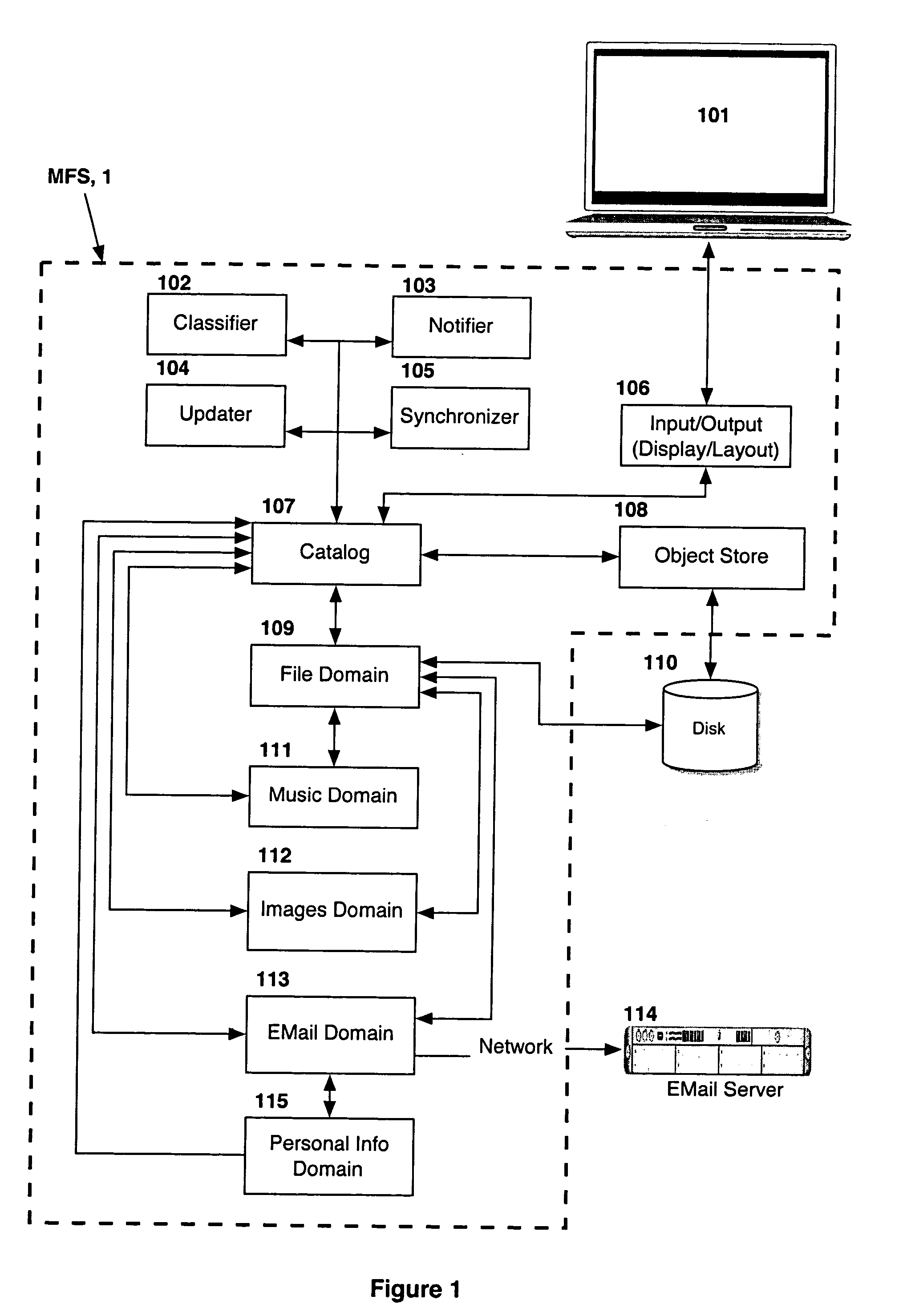
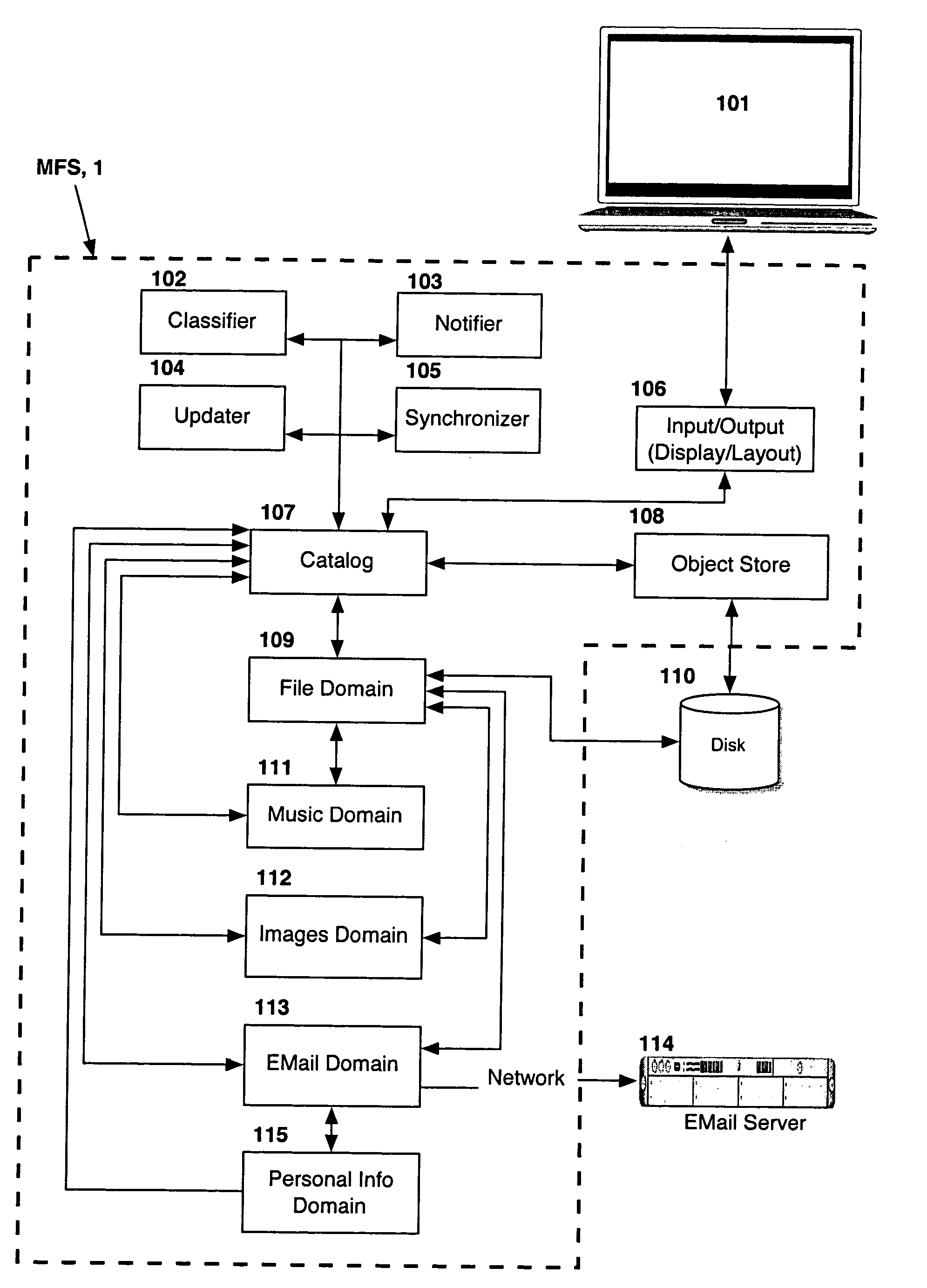
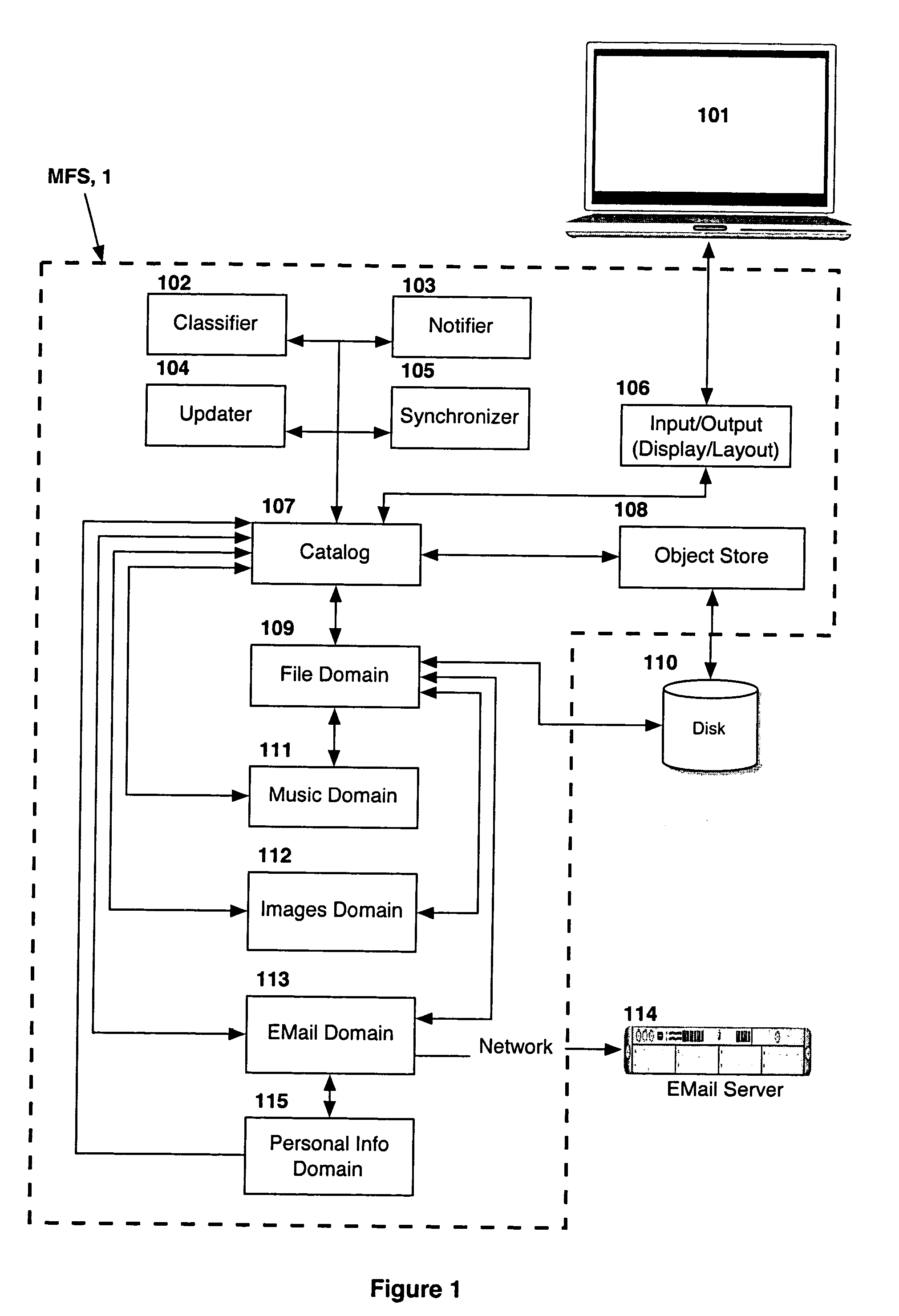
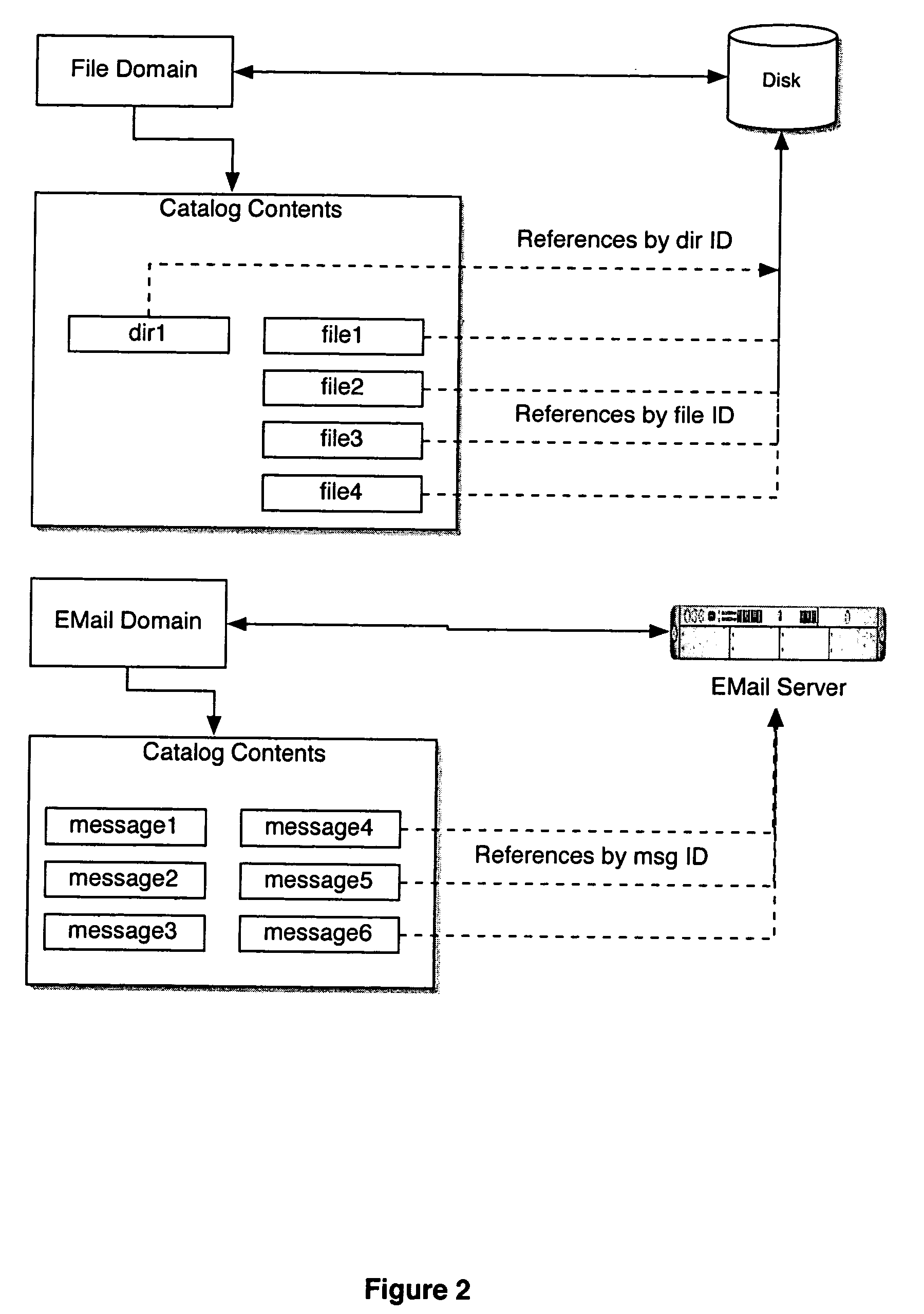
Computer system for automatic organization, indexing and viewing of information from multiple sources
ActiveUS20040177319A1Efficient storageMultimedia data indexingFile access structuresComputer data processingData processing
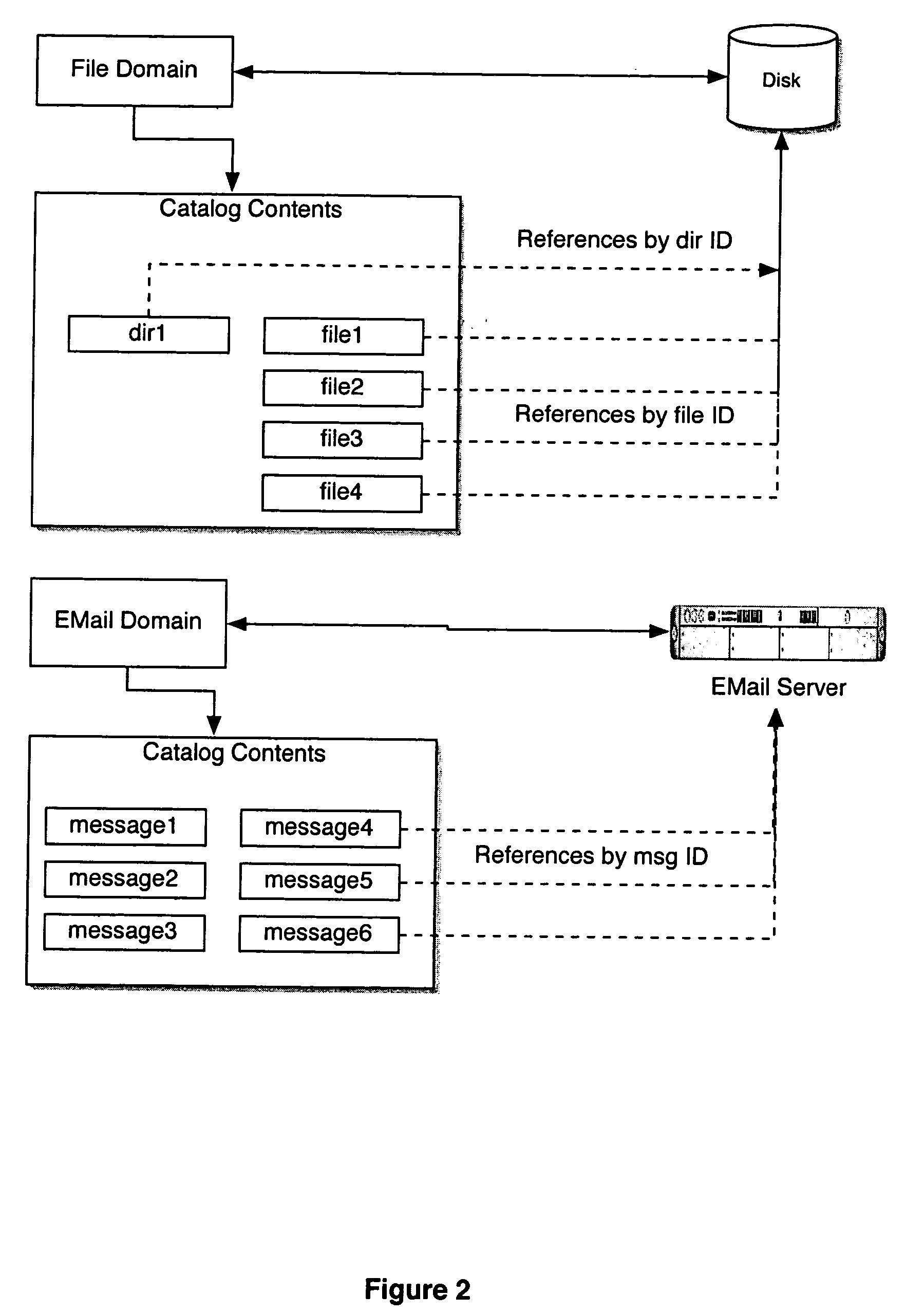
A computer data processing system including a central processing unit configured with a novel integrated computer control software system for the management of data objects including dynamic and automatic organization, linking, finding, cross-referencing, viewing and retrieval of multiple objects regardless of nature or source. The inventive system provides underlying component architecture having an object-oriented database structure and a metadata database structure which is unique in storing only one instance of each object while linking the object to multiple collections and domains by unique metadata links for the grouping into and retrieval from any of the collections. The system employs configurable, extensible attribute / properties of data objects in metadata format, and a truly user-friendly configurable interface that facilitates faster, more unified, comprehensive, useful and meaningful information management. Additional features include a sticky path object hierarchy viewing system, key phrase linking, viewing by reference, and drag-and-drop relationship link creation.
Owner:EHIERARCHY LLC
Computer system for automatic organization, indexing and viewing of information from multiple sources
ActiveUS7275063B2Facilitate communicationMultimedia data indexingFile access structuresPathPingSoftware system
Owner:EHIERARCHY LLC
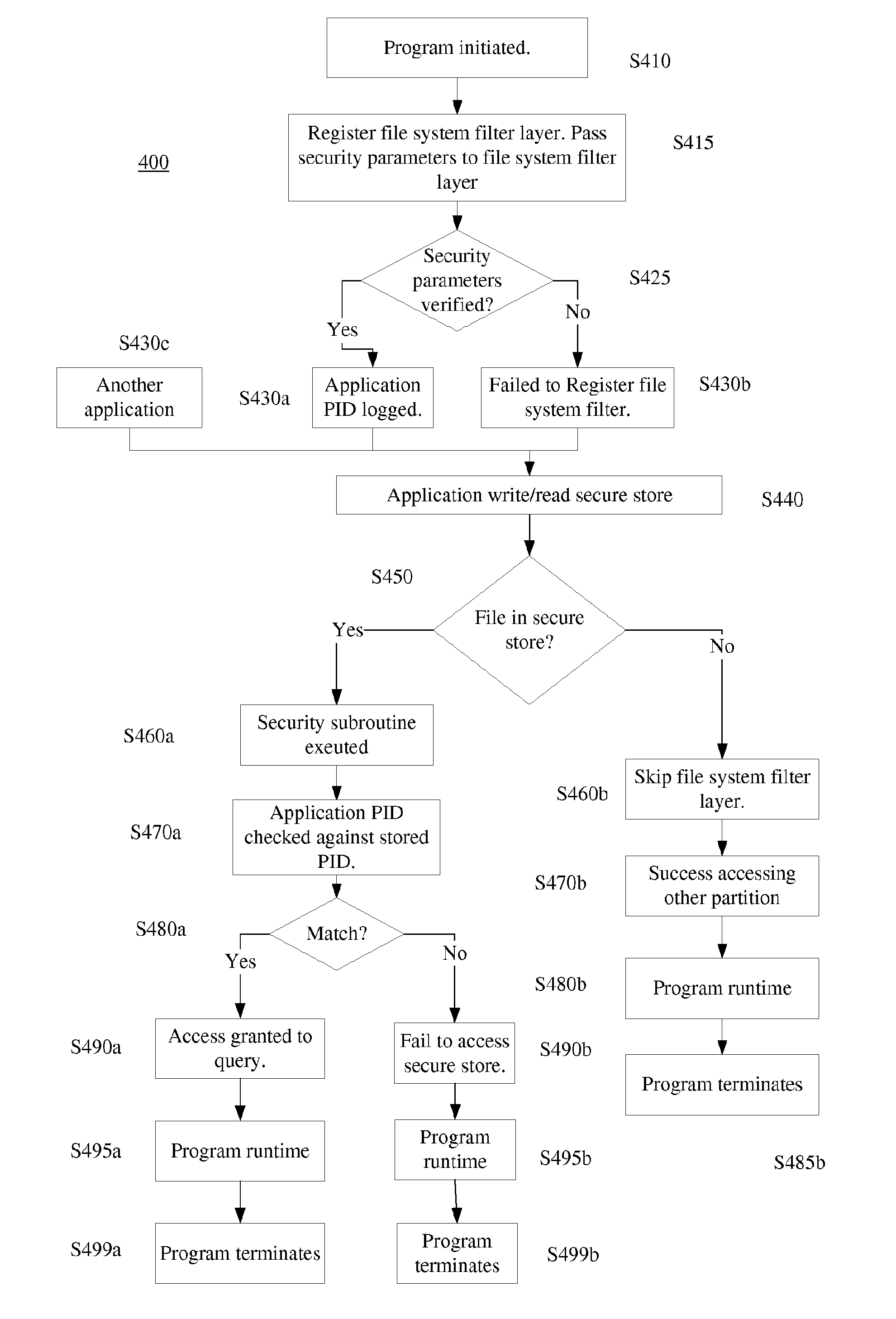
Design pattern for secure store
ActiveUS20150220753A1Improve securityDigital data processing detailsAnalogue secracy/subscription systemsPathPingFile system
A computer system, computer product, and method for accessing a secure store, which includes receiving a request to access a secure store, checking the file path of the request to make sure it exists in the secure store, verifying security parameters from the process at the file system filter layer, saving the PID of the process by the file system filter layer, comparing the saved PID to the process's PID, and allowing the process to access the path in the secure store specified in the request.
Owner:HONEYWELL INT INC
Detect and qualify relationships between people and find the best path through the resulting social network
InactiveUS20040122803A1Digital data information retrievalData processing applicationsAddress bookQualifying relationship
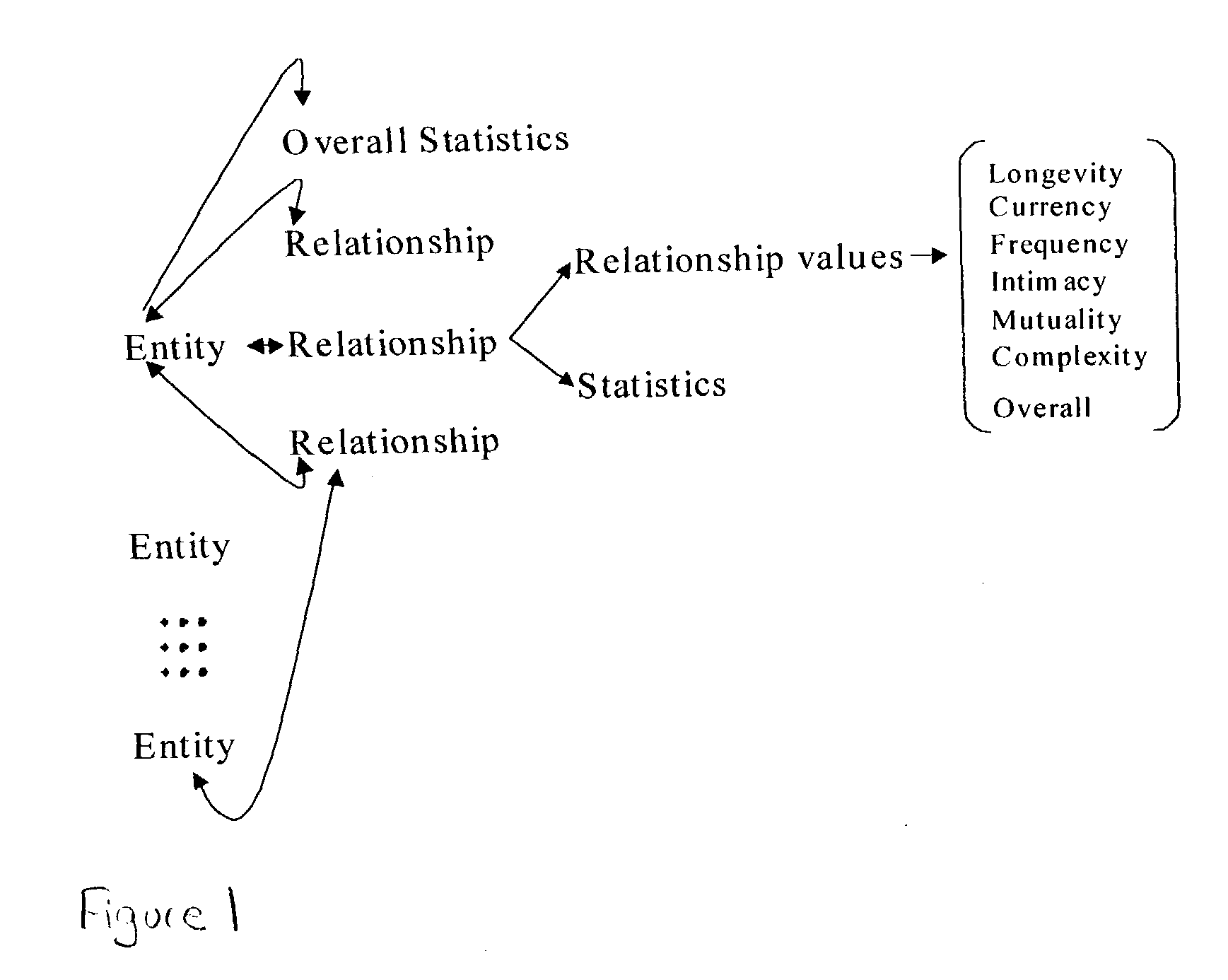
Disclosed is a method and structure that identifies relationships between users of a computerized network. The method extracts relationship information from databases in the network. The information includes address book information, calendar information, event information, to-do list information, journal information, and / or e-mail information. The invention evaluates the relationship information to produce relationship ratings of the users of the network. The invention determines the level of reciprocity of relations between different users; a longevity of relations between the different users; how current relations are between the different users; a frequency of relations between the different users; a level of exclusivity of relations between the different users; a level of complexity of relations between the different users; and / or a proximity of the different users.
Owner:IBM CORP
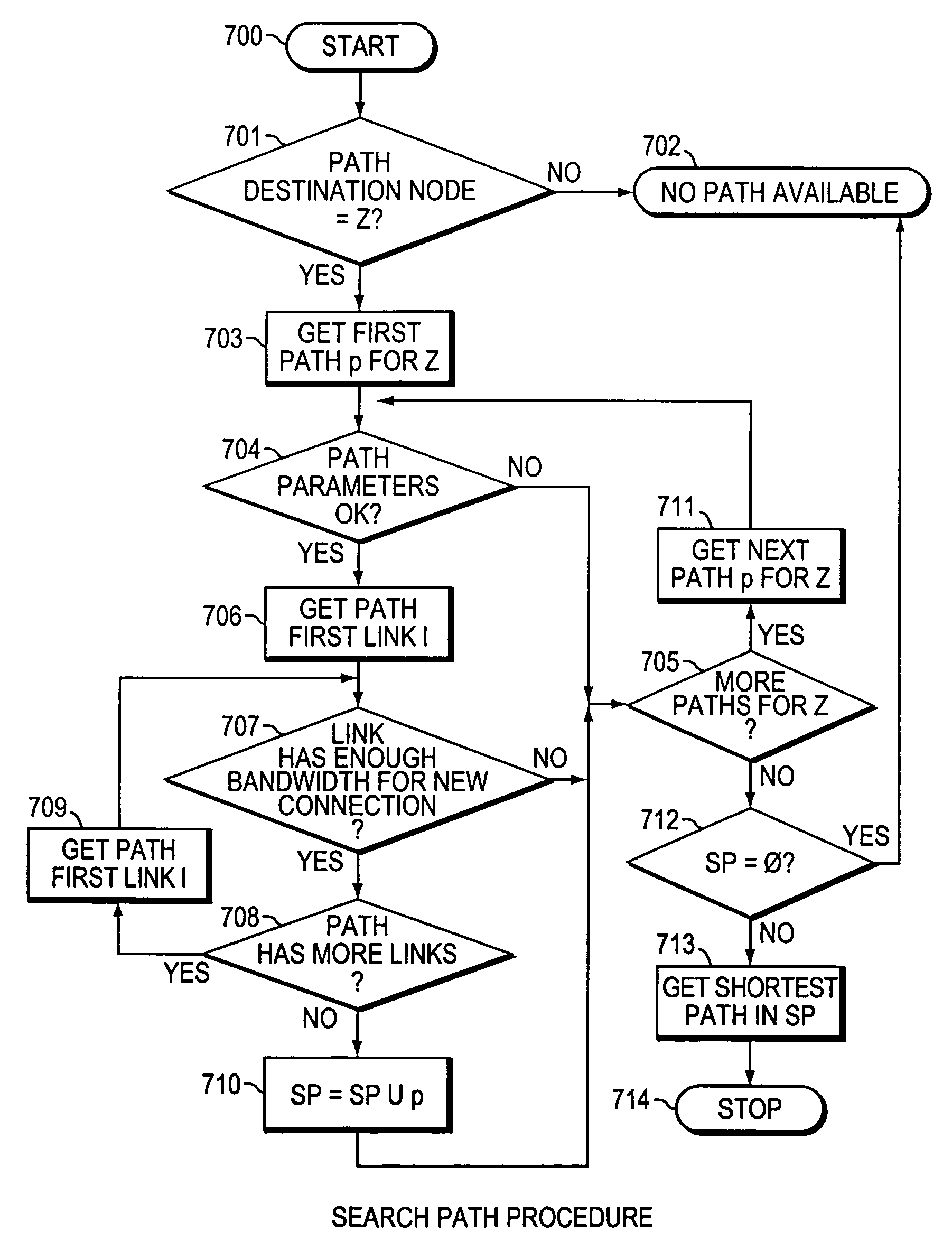
Method and system for minimizing the connection set up time in high speed packet switching networks
InactiveUS6934249B1Minimize delayMinimize in in to selectError preventionFrequency-division multiplex detailsTraffic capacityPacket switched
The present invention is directed to a high speed packet switching network and, in particular to a method and system for minimizing the time to establish a connection between an origin and a destination node. Due to high dynamicity of the traffic on transmission links, it is important to select a routing path according to a fully up-to-date information on all network resources. The simpler approach is to calculate a new path for each new connection request. This solution may be very time consuming because there are as many path selection operations as connection set up operations. On another hand, the calculation of paths based on an exhaustive exploration of the network topology, is a complex operation which may also take an inordinate amount of resources in large networks. Many of connections originated from a network node flow to the same destination network node. It is therefore possible to take a serious benefit in reusing the same already calculated paths for several connections towards the same node. The path calculated at the time the connection is requested is recorded in a Routing Database and updated each time a modification occurs in the network. Furthermore, alternate paths for supporting non-disruptive path switch on failure or preemption, and new paths towards potential destination nodes can be calculated and stored when the connection set up process is idle. These last operations are executed in background with a low processing priority and in absence of connection request.
Owner:CISCO TECH INC
Locking technique for control and synchronization
InactiveUS6973549B1Digital data information retrievalMultiprogramming arrangementsFast pathLocking mechanism
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
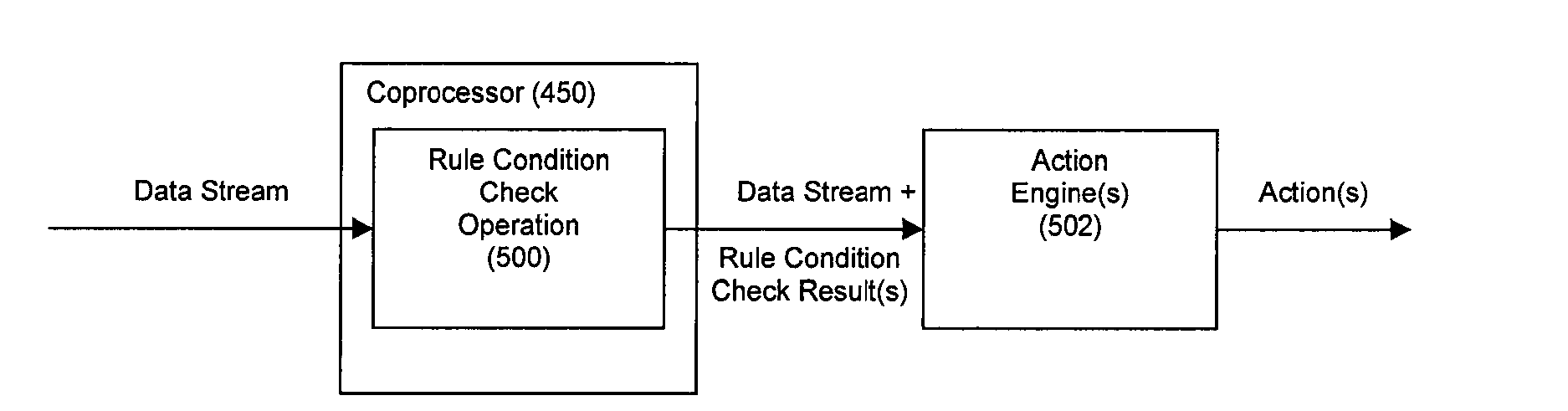
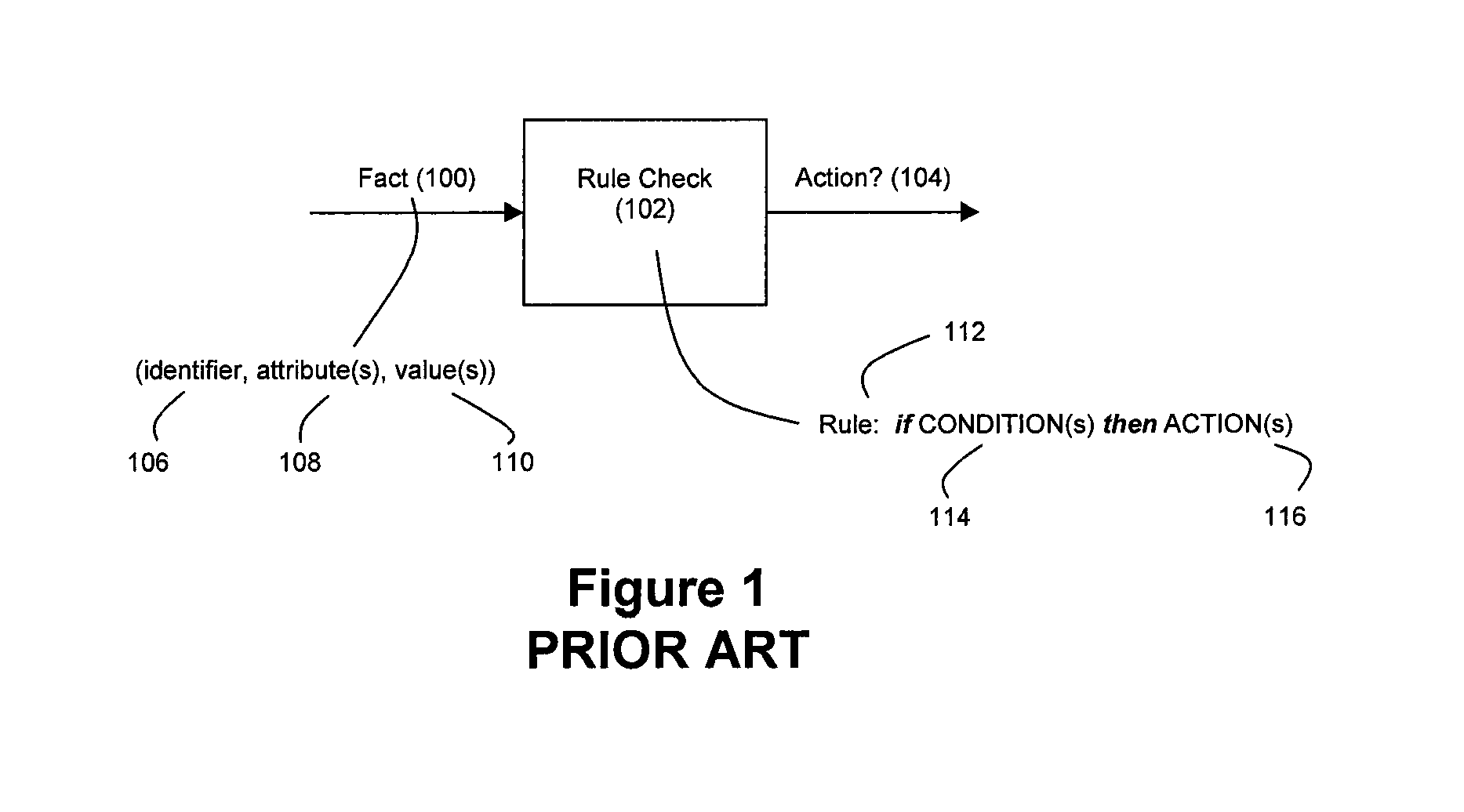
Method and System for Accelerated Stream Processing
ActiveUS20090287628A1Lower latencyImprove latencyDigital computer detailsCode conversionBusiness ruleEvent stream
Disclosed herein is a method and system for hardware-accelerating various data processing operations in a rule-based decision-making system such as a business rules engine, an event stream processor, and a complex event stream processor. Preferably, incoming data streams are checked against a plurality of rule conditions. Among the data processing operations that are hardware-accelerated include rule condition check operations, filtering operations, and path merging operations. The rule condition check operations generate rule condition check results for the processed data streams, wherein the rule condition check results are indicative of any rule conditions which have been satisfied by the data streams. The generation of such results with a low degree of latency provides enterprises with the ability to perform timely decision-making based on the data present in received data streams.
Owner:IP RESERVOIR
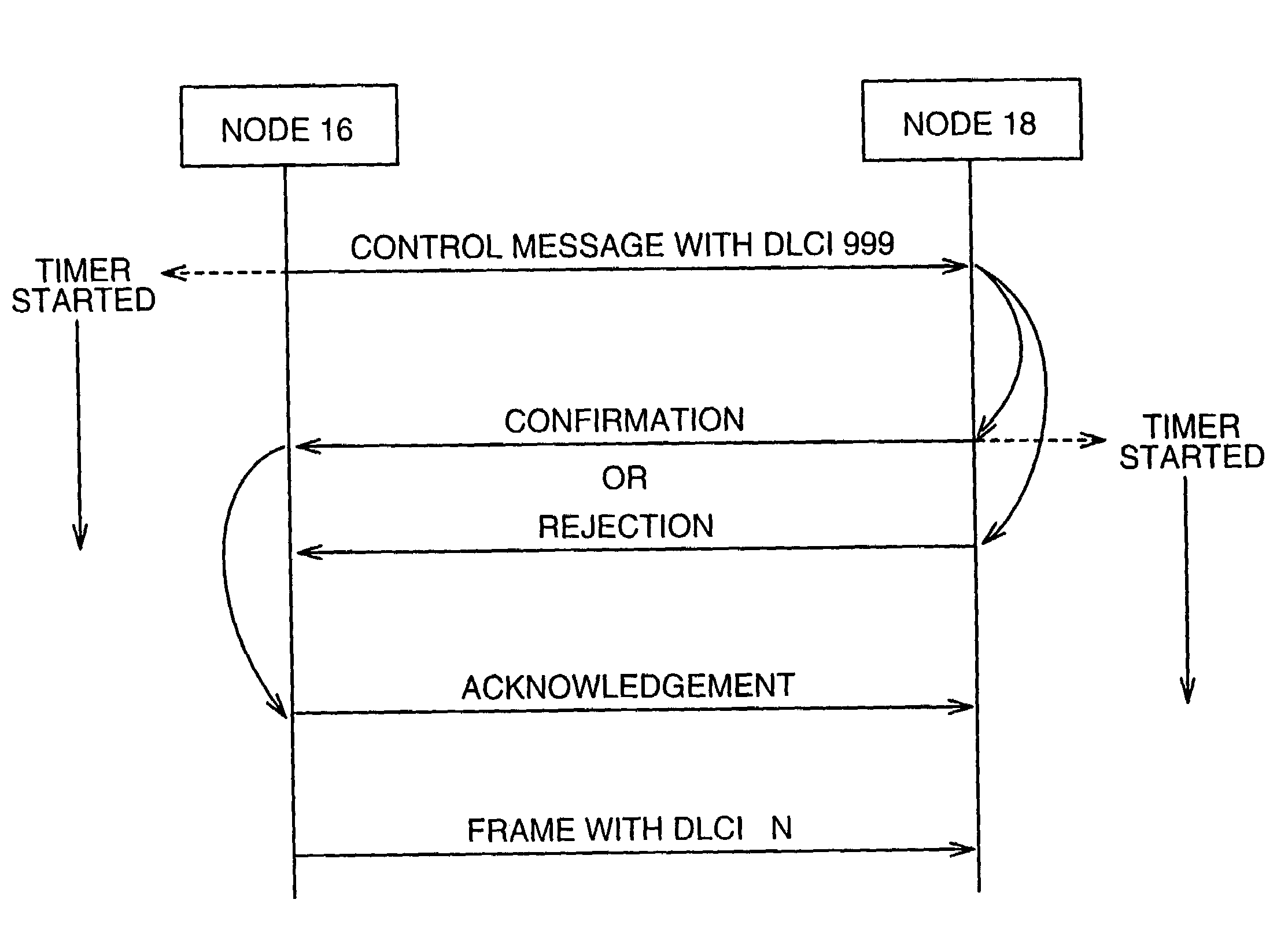
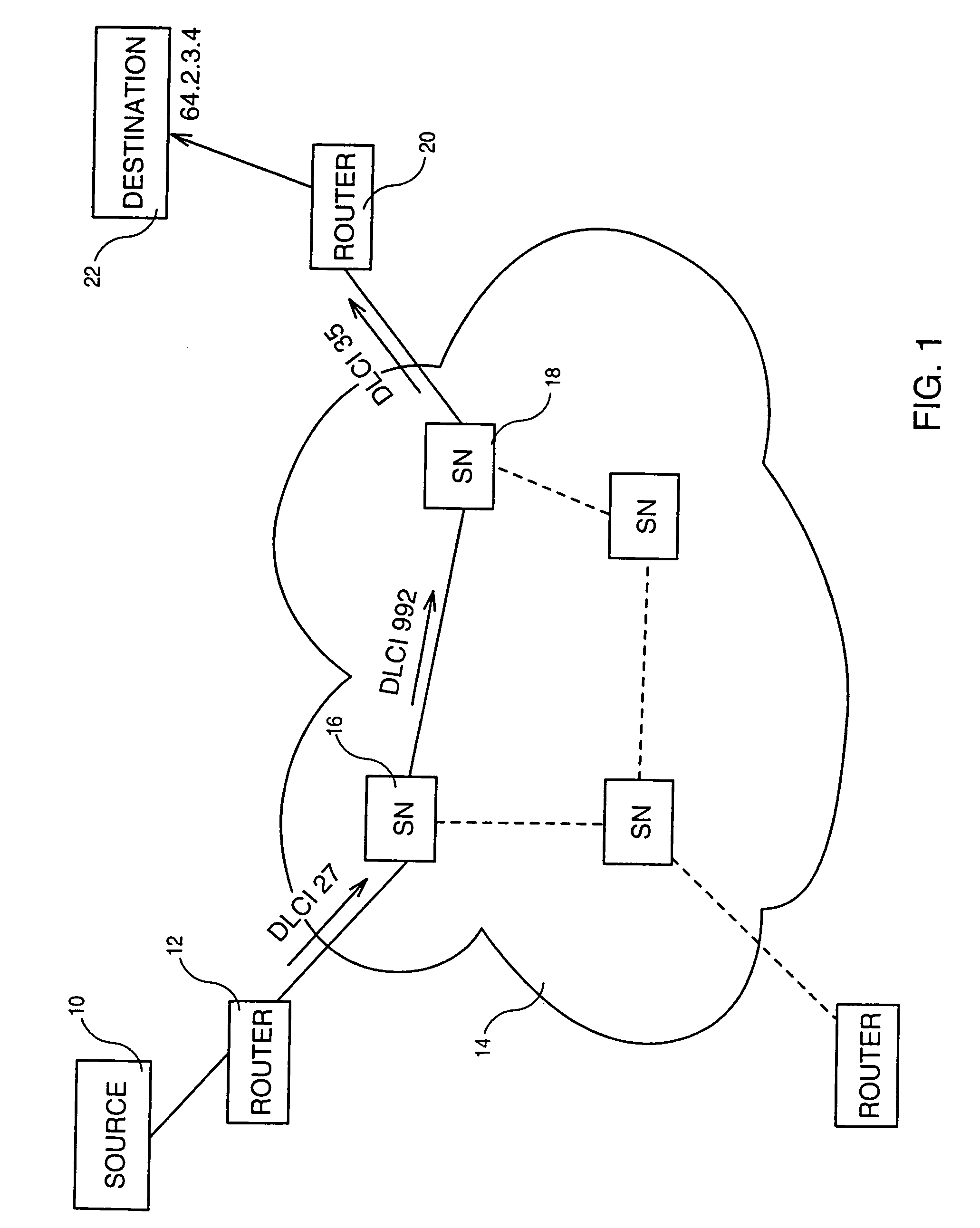
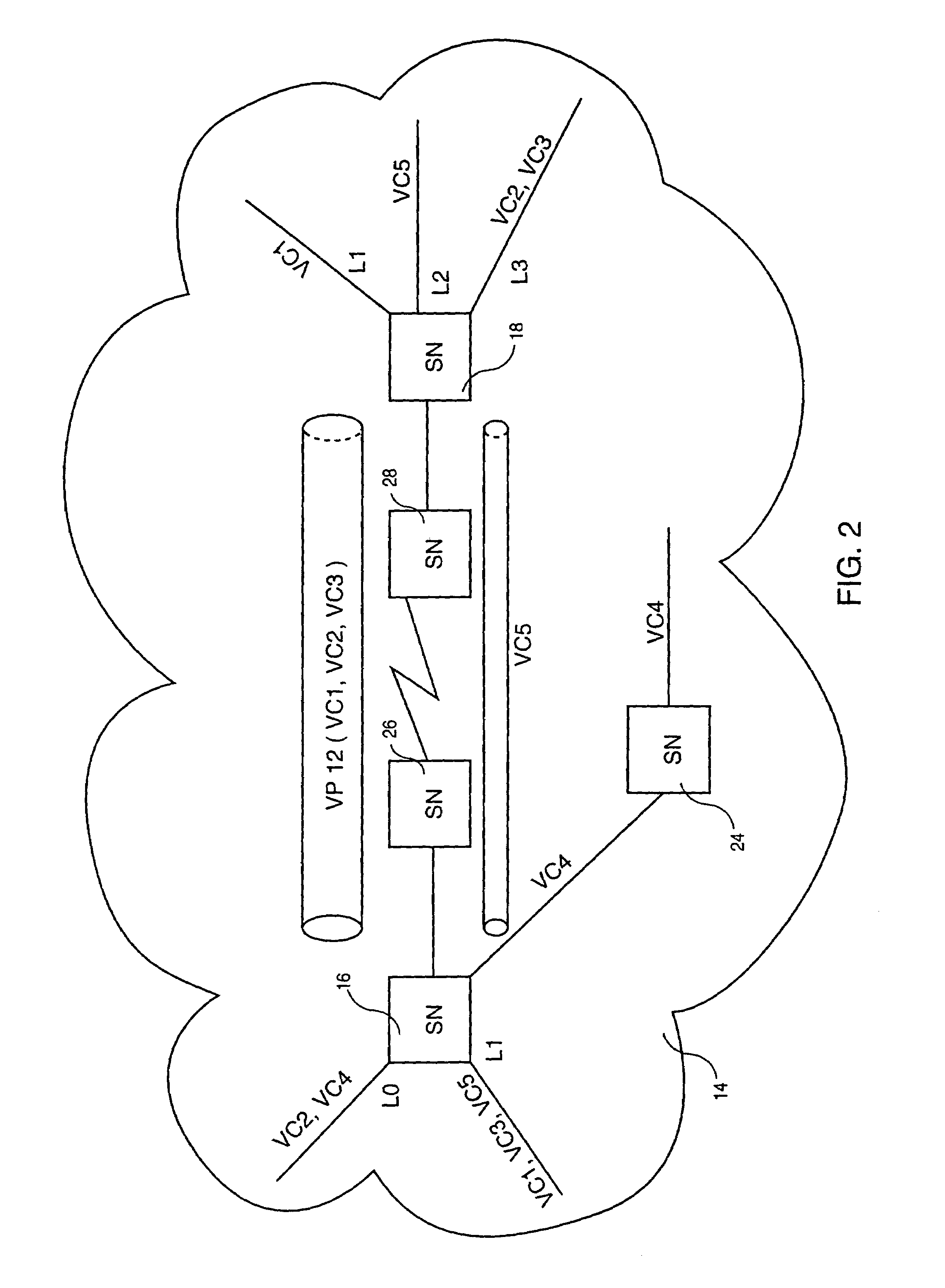
Method and system for establishing a virtual path capability in a frame relay network
A method and system for establishing a Virtual Path (VP12) capability in a Frame Relay network wherein frames are transmitted over a plurality of virtual circuits from a first switching node to a second switching node. A control message is transmitter from the first switching node to the second switching node with a Data Link Connection Identifier (DLCI) having a predetermined value indicating the purpose of the control message which is to define a virtual path aggregating at least two virtual circuits selected from multiple virtual circuits. The control message contains the identification of the virtual circuits aggregated in the defined virtual path.
Owner:IBM CORP
System and method for discovering information objects and information object repositories in computer networks
InactiveUS7162539B2Special service provision for substationDigital data information retrievalInformation repositoryInformation object
An address of an information object repository that should service a client request for an information object is returned in response to a request therefor. The address of the information object repository which is returned is selected according to specified performance metrics regardless of whether or not the information object repository maintains a local copy of the information object that is the client request. In some cases, the address of the information object repository is further selected according to an address of a client making the client request. Further, the address of the information object repository is selected from a number of addresses of information object repositories. The specified performance metrics may include one or more of an average delay from the information object repository to the client, average processing delays at the information object repository, reliability of a path from the information object repository to the client, available bandwidth in said path, and loads on the information object repository. In some cases, the information object repository may be instructed to obtain a copy of the information object after the address of the information object repository is returned in response to the request therefore.
Owner:ADARA NETWORKS
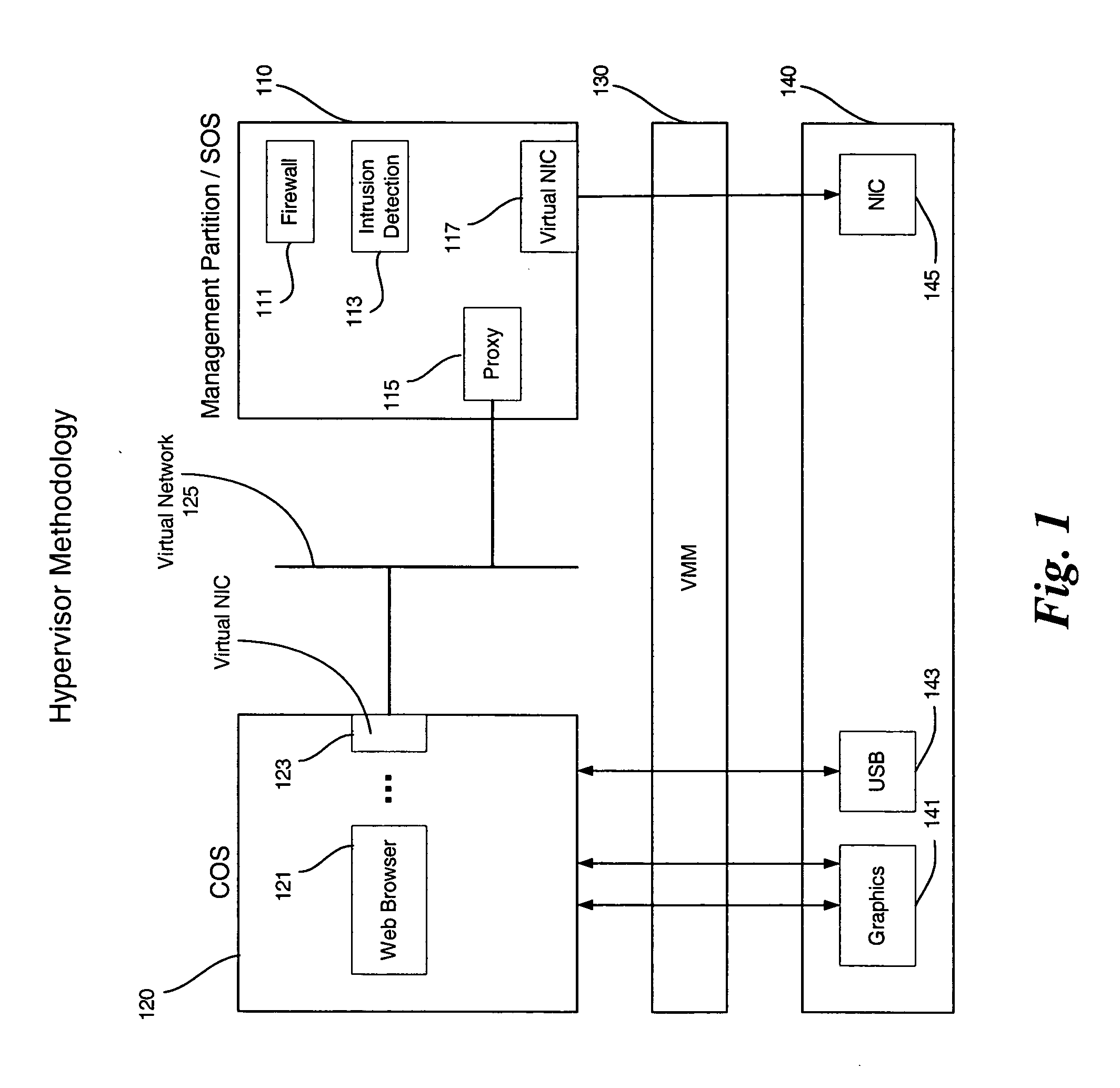
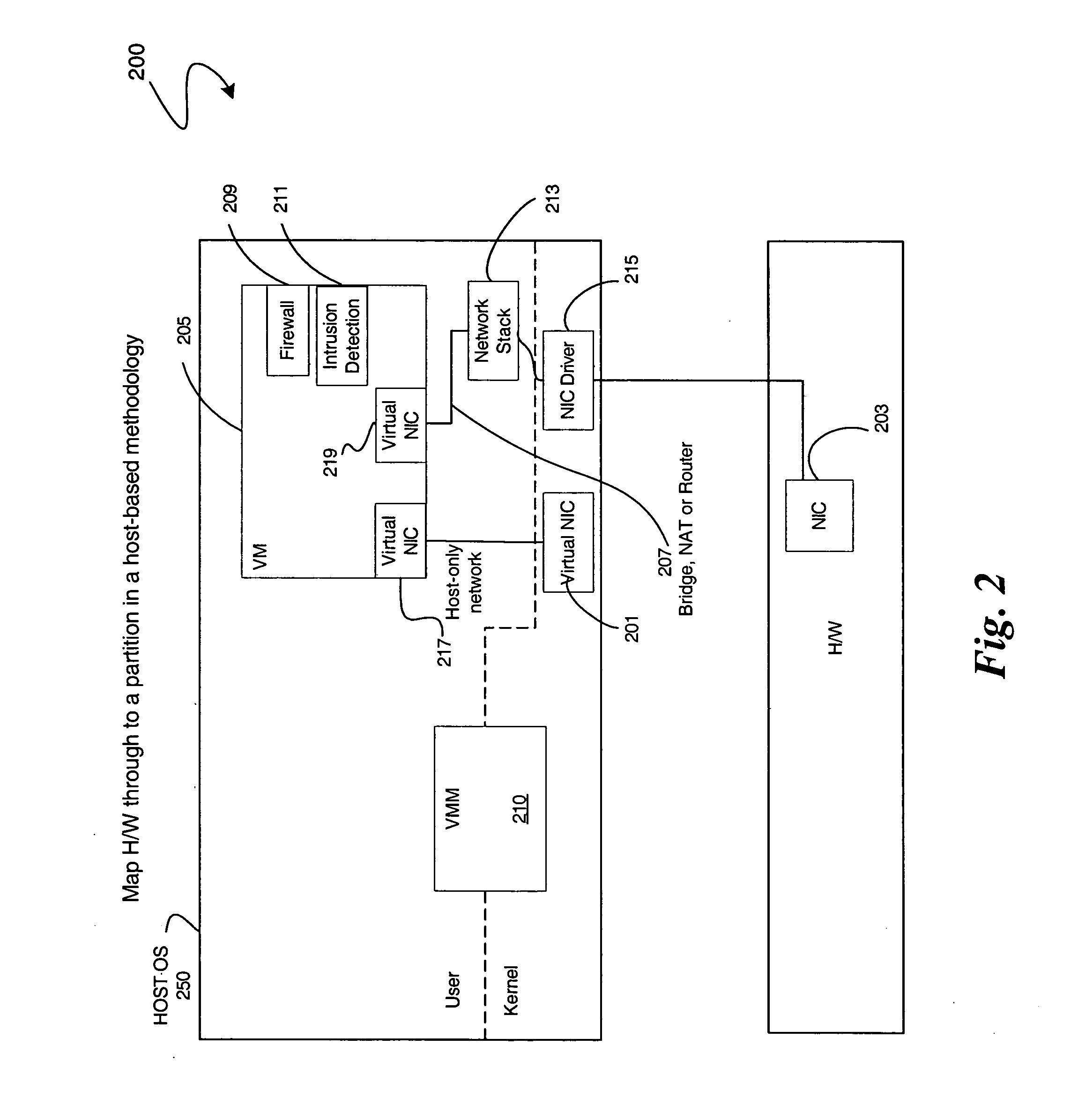
Enabling platform network stack control in a virtualization platform
InactiveUS20060070066A1TransmissionSoftware simulation/interpretation/emulationVirtualizationData pack
In some embodiments, the invention involves protecting network communications in a virtualized platform. An embodiment of the present invention is a system and method relating to protecting network communication flow using packet encoding / certification and the network stack. One embodiment uses a specialized engine or driver in the network stack to encode packets before being sent to physical network controller. The network controller may use a specialized driver to decode the packets, or have a hardware implementation of a decoder. If the decoded packet is certified, the packet is transmitted. Otherwise, the packet is dropped. An embodiment of the present invention utilizes virtualization architecture to implement the network communication paths. Other embodiments are described and claimed.
Owner:INTEL CORP
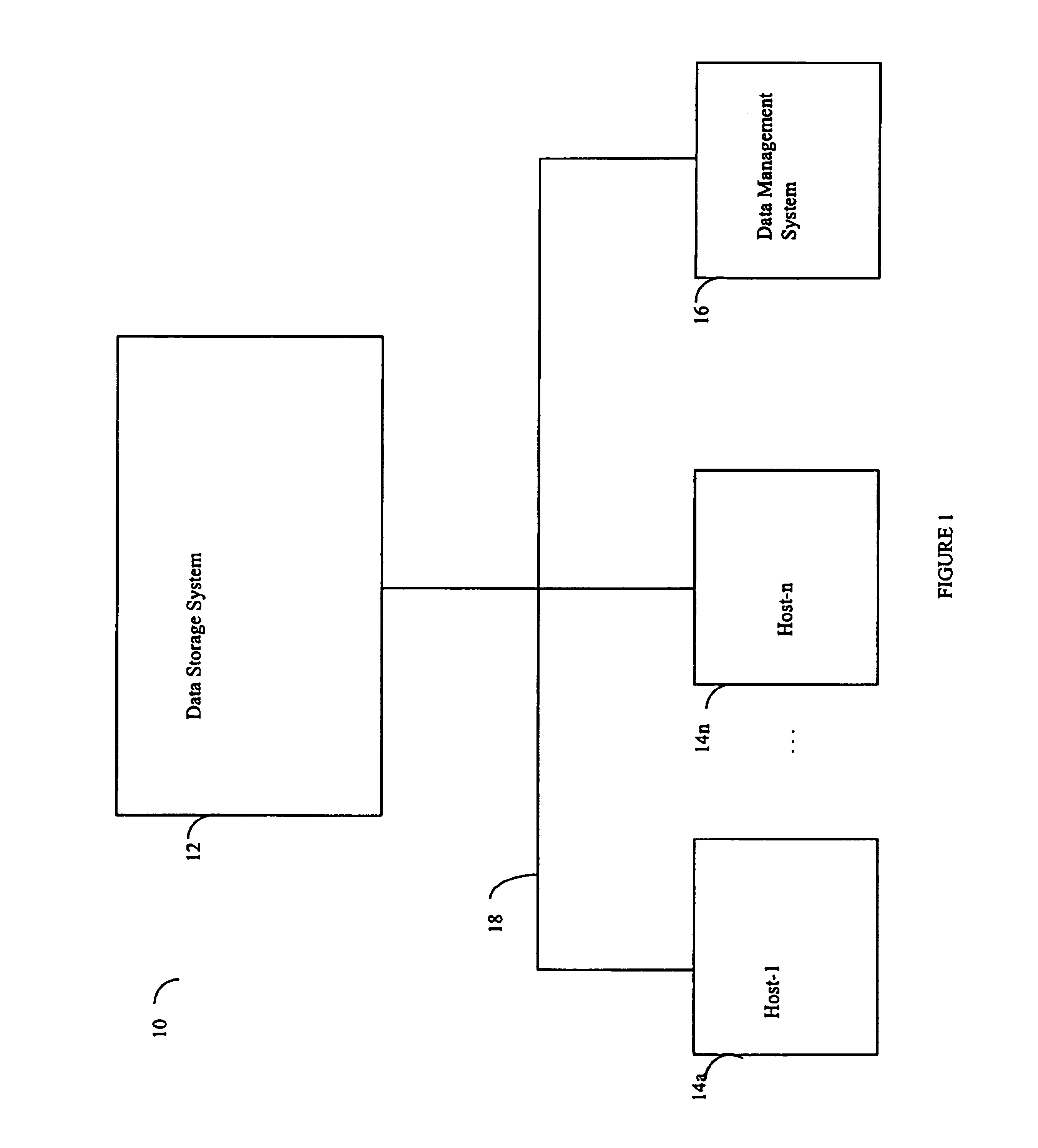
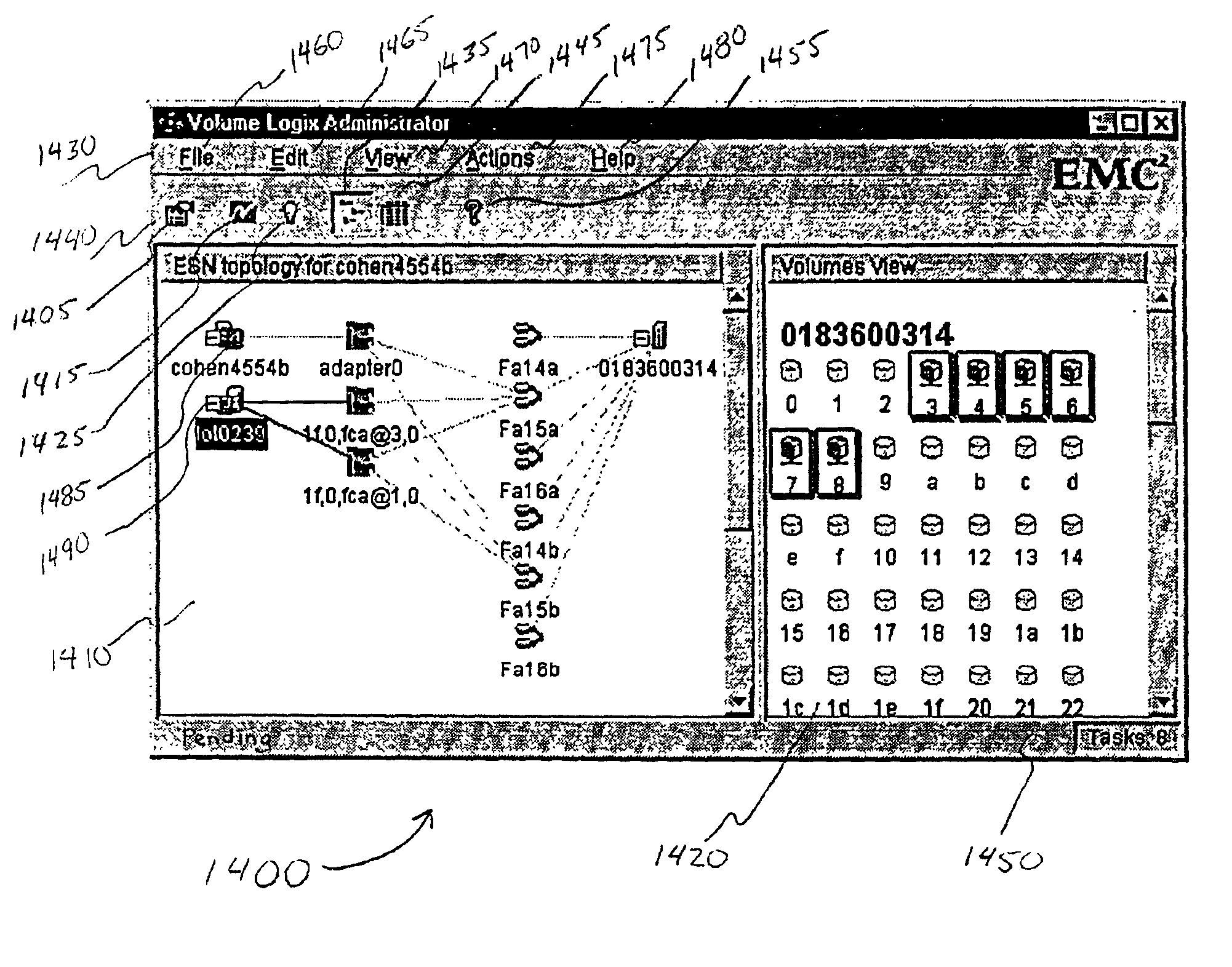
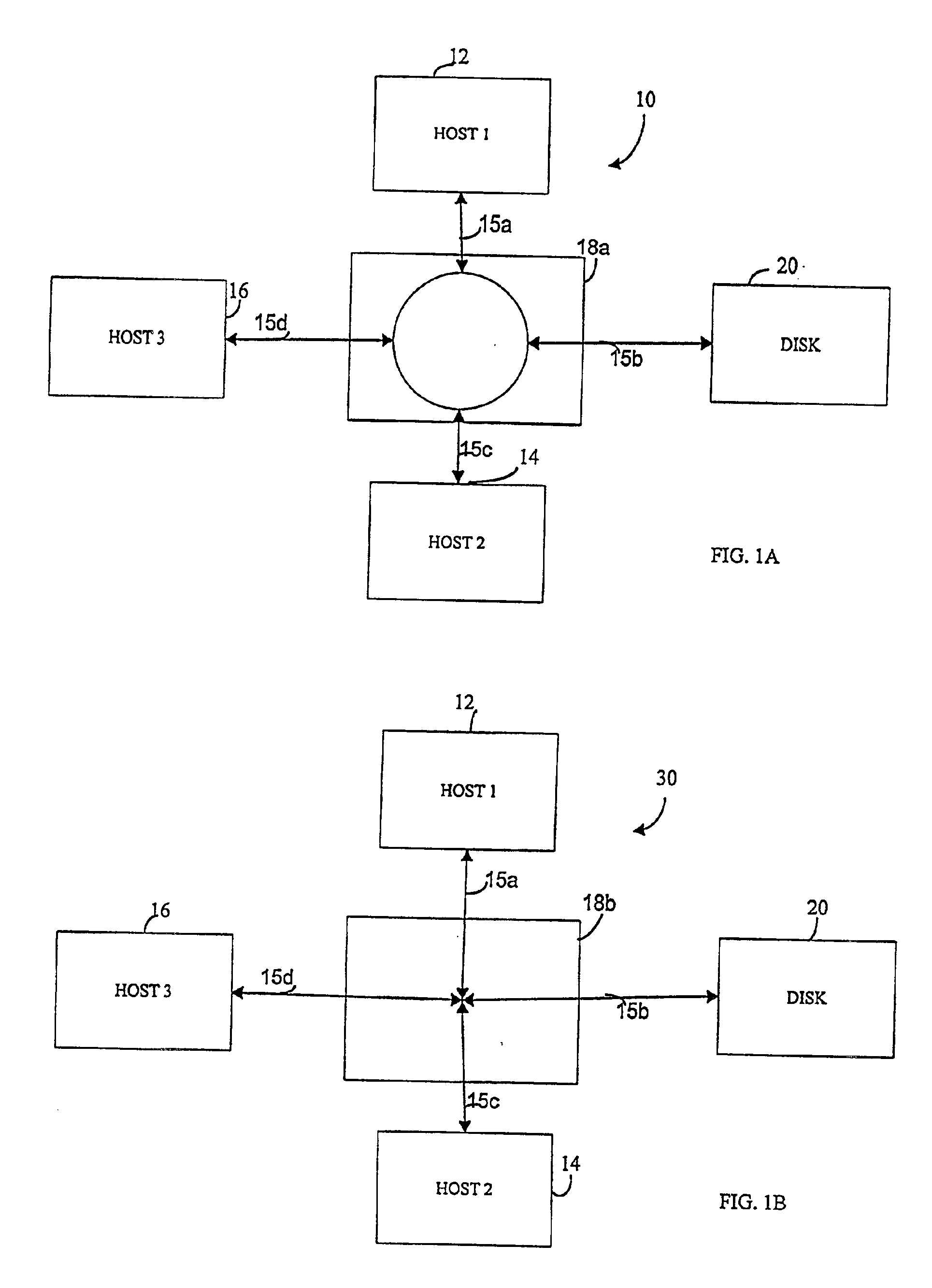
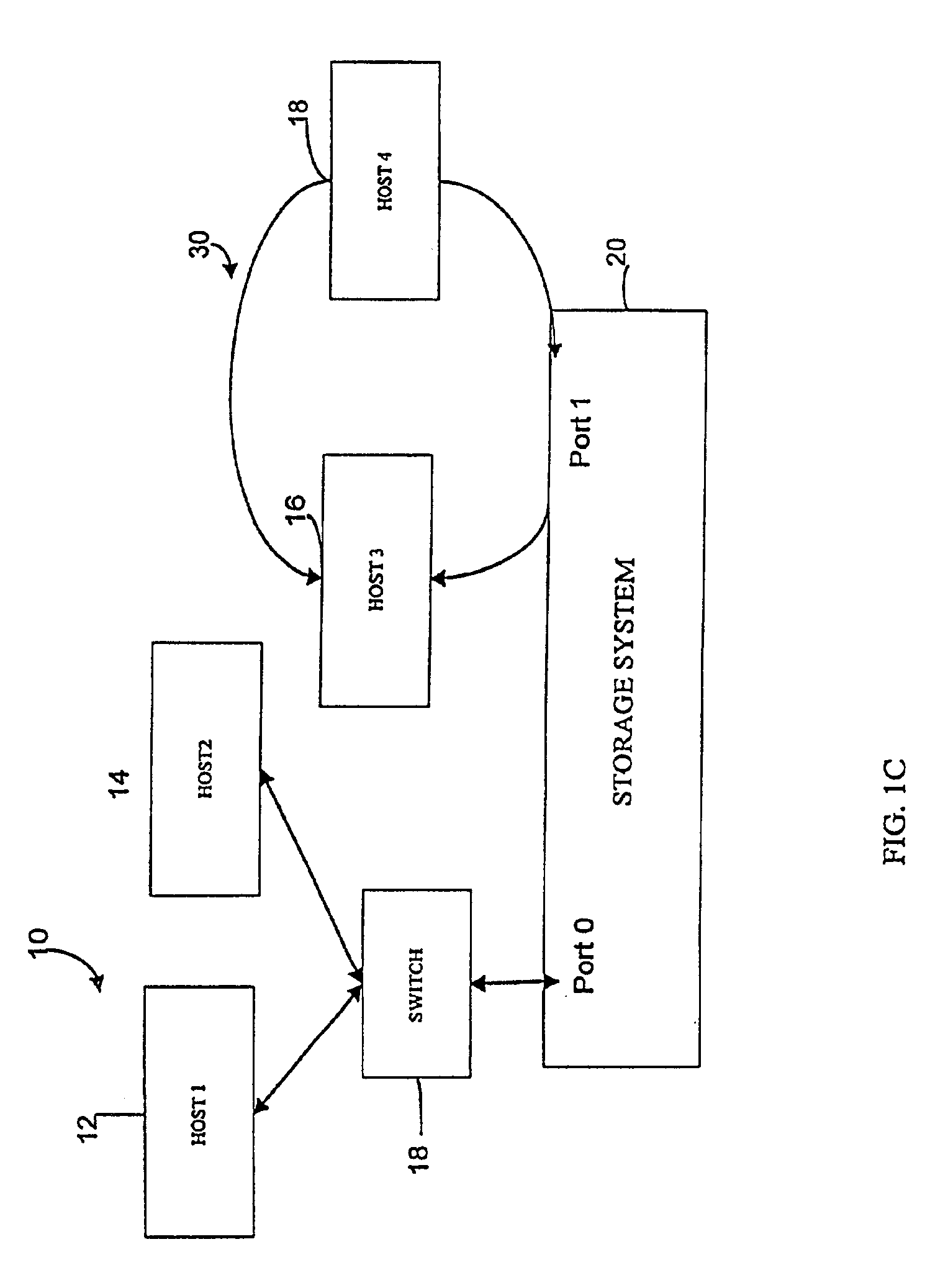
User interface for managing storage in a storage system coupled to a network
A method and apparatus for managing the availability and assignment of data in a storage system that is coupled to a network. A user interface is provided that executes on a host processor that is coupled to the storage system over the network. The user interface communicates with a configuration database in the storage system to identify host processors that are logged into the storage system over the network, to identify storage volumes on the storage system, to identify whether access to a particular storage volume on the storage system is permitted from a particular host processor, and to identify a network path by which host processors are logged into the storage system over the network. In one embodiment, a graphical user interface is provided that can be used to graphically represent host processors, host bus adapters, storage systems, and storage system adapters and storage volumes on the storage system. The graphical representation provided by the graphical user interface permits a user to graphically view a topology of the network at varying levels of detail, selectable by the user. The graphical user interface also permits a user to allow or deny access to storage systems or a particular storage volume on storage system from one or more of the host processors, host bus adapters, etc., by selecting and manipulating graphical representations thereof. In another embodiment, a command line user interface is provided with similar functionality.
Owner:EMC IP HLDG CO LLC
Network Communication System With Improved Security
ActiveUS20120174218A1Effectively shut downEffectively shut down the targets internet connection capabilityMemory loss protectionError detection/correctionPathPingSoftware engineering
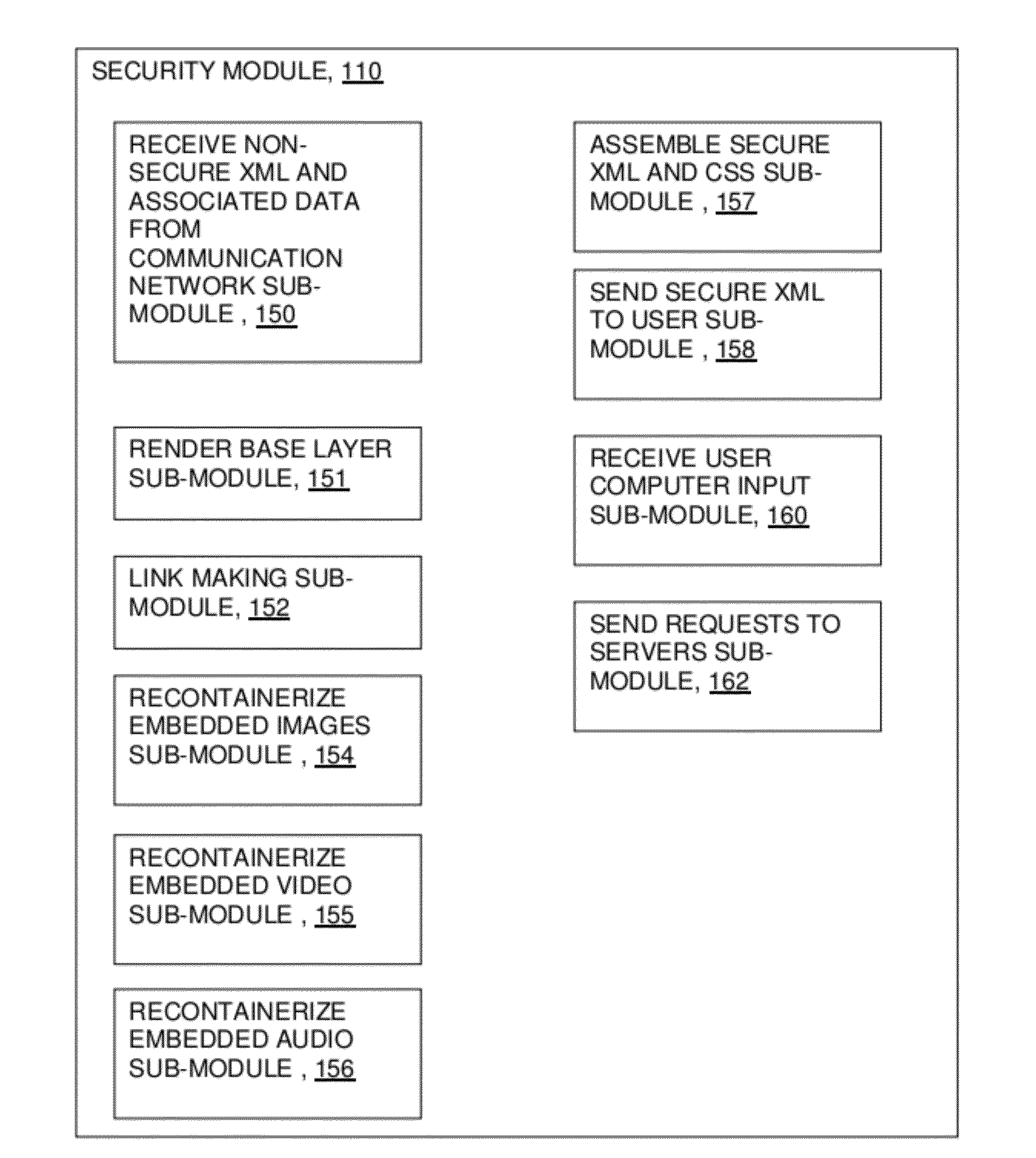
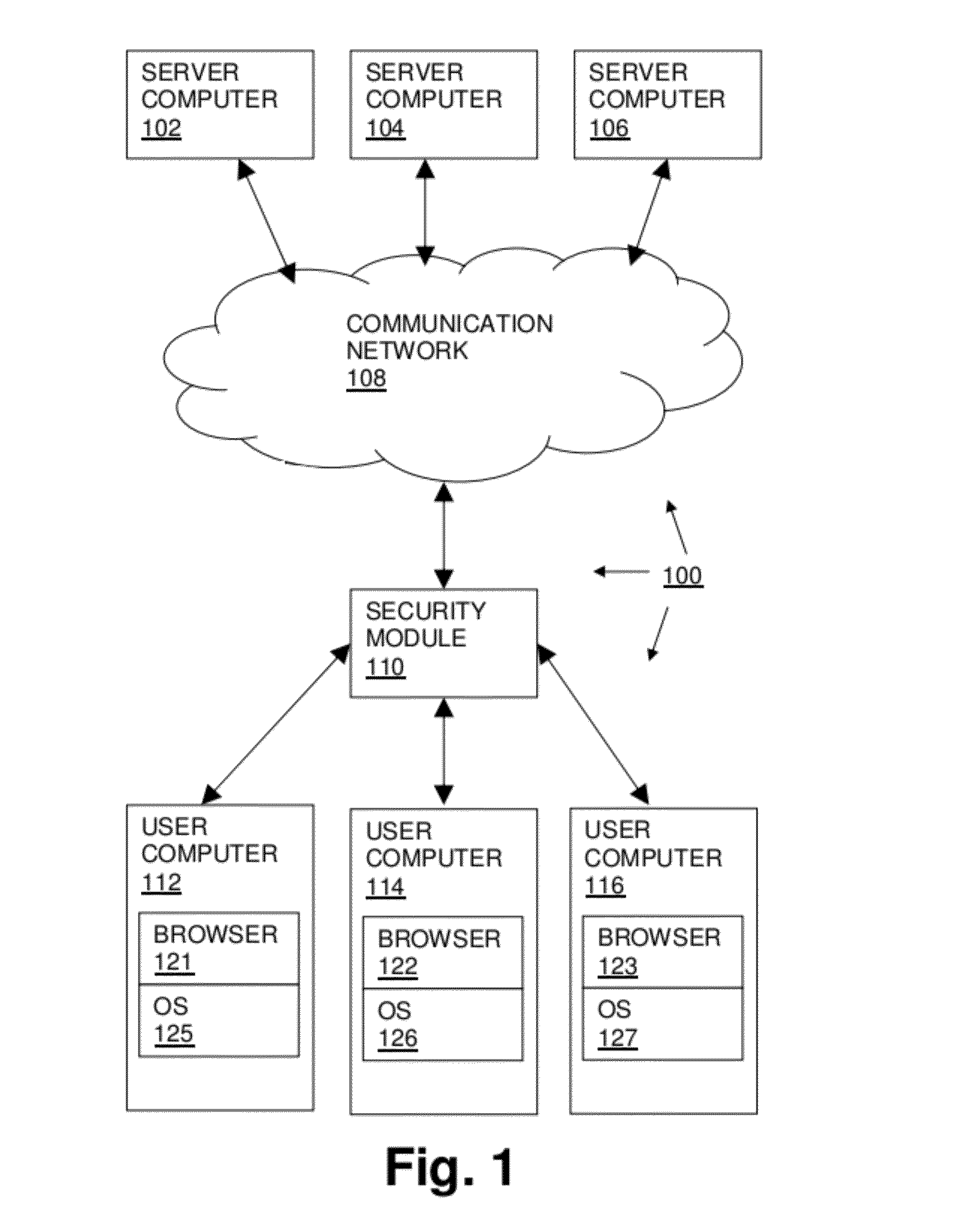
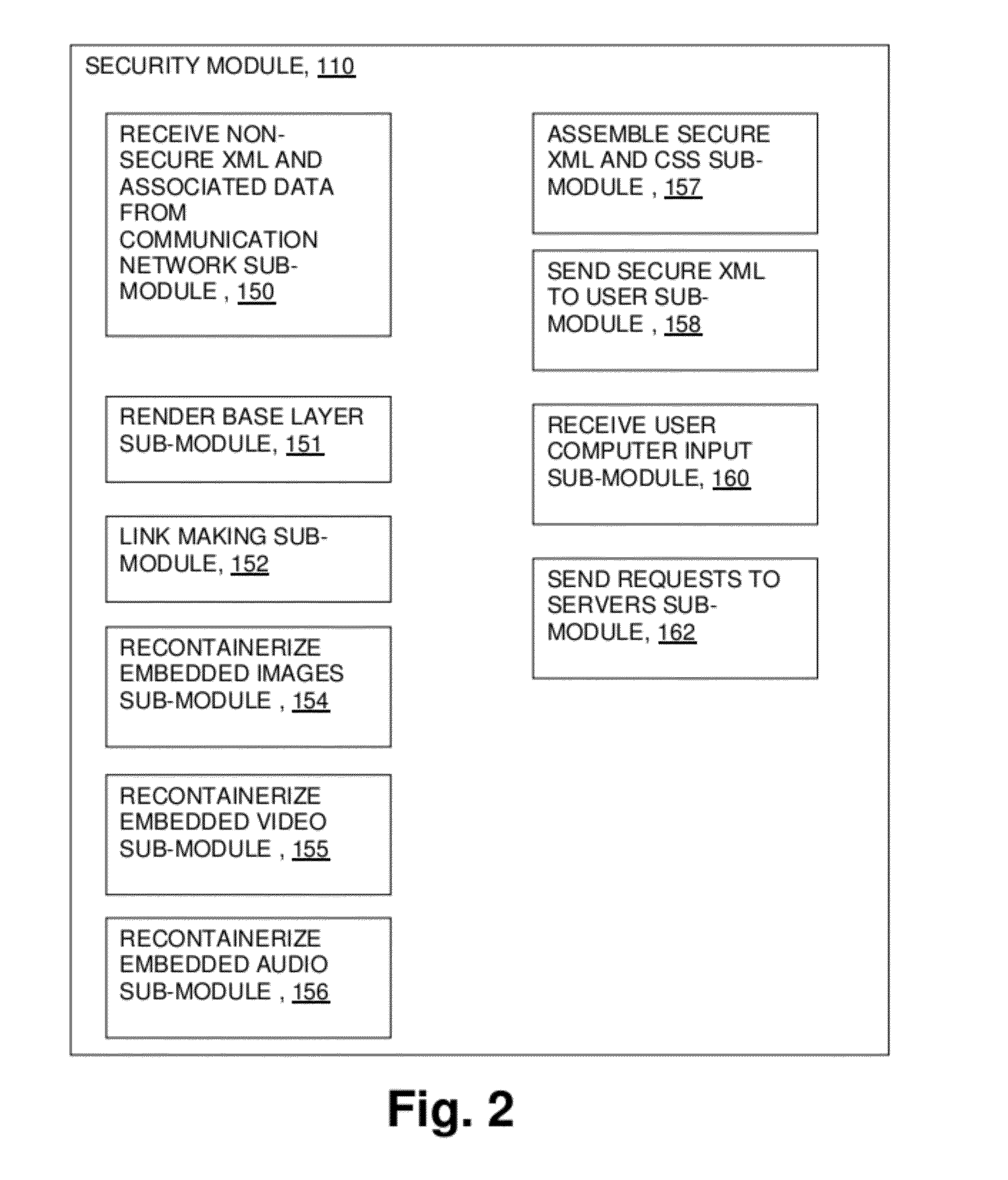
A computer network communication method and system wherein software rendering software is interposed in the data communication path between a browser running on a user computer and the internet data sources (for example, internet-accessible server computers) that the user browser wants to receive information from. The software rendering application gets data from internet data sources, but this data may contain malware. To provide enhanced security, the software rendering application renders this data to form a new browser readable code set (for example, an xml page with CSS layers), and this new and safe browser readable code set is sent along to the browser on the user computer for appropriate presentation to the user. As part of the rendering process, dedicated and distinct virtual machines may be used to render certain portion of the data, such as executable code. These virtual machines may be watched, and quickly destroyed if it is detected that they have encountered some type of malware.
Owner:TOUCHPOINT PROJECTION SOLUTIONS LLC
Method for authorizing in data transmission systems
InactiveUS6078908ALow costFacilitate communicationLock applicationsDigital data processing detailsPasswordPager
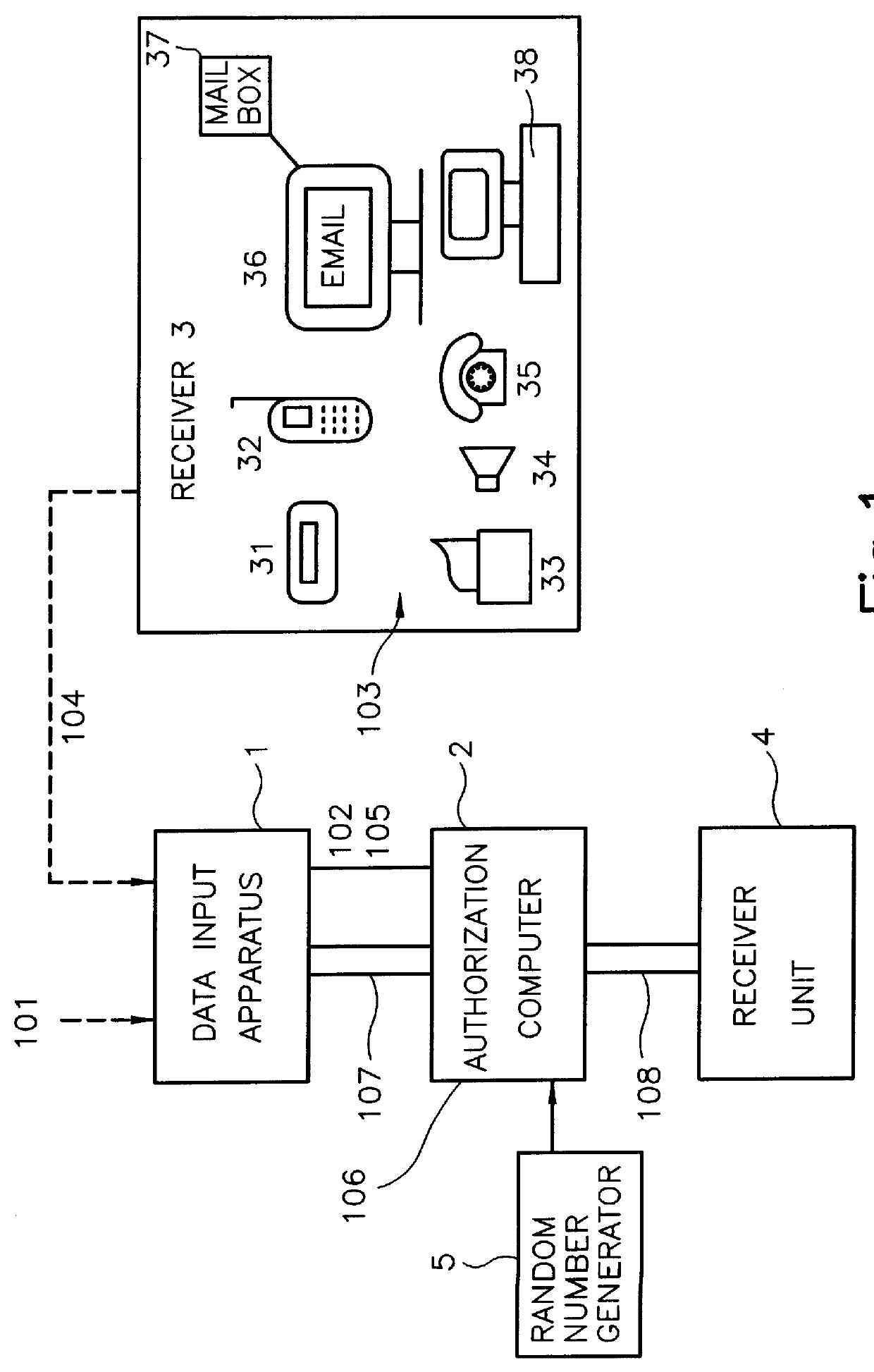
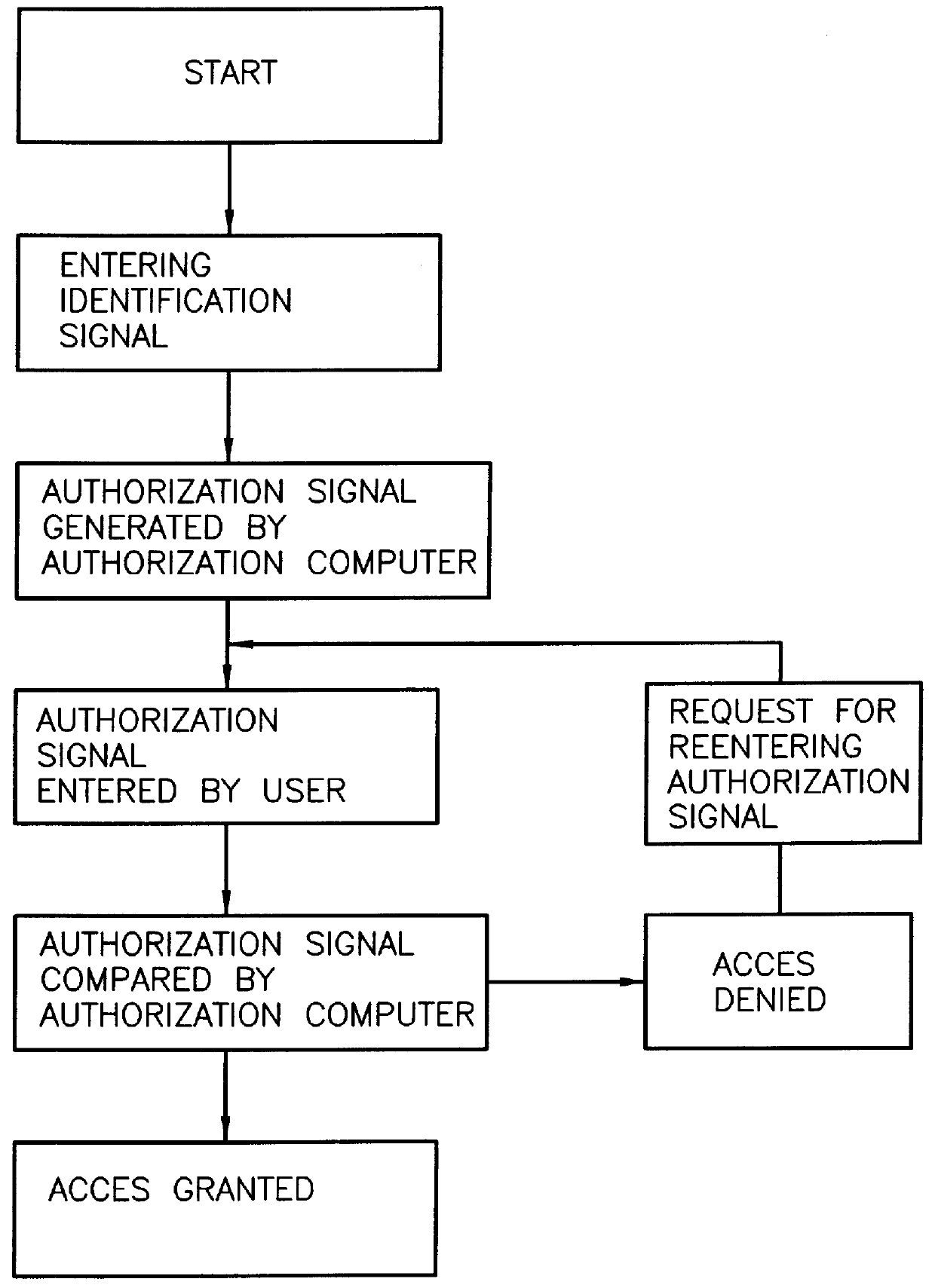
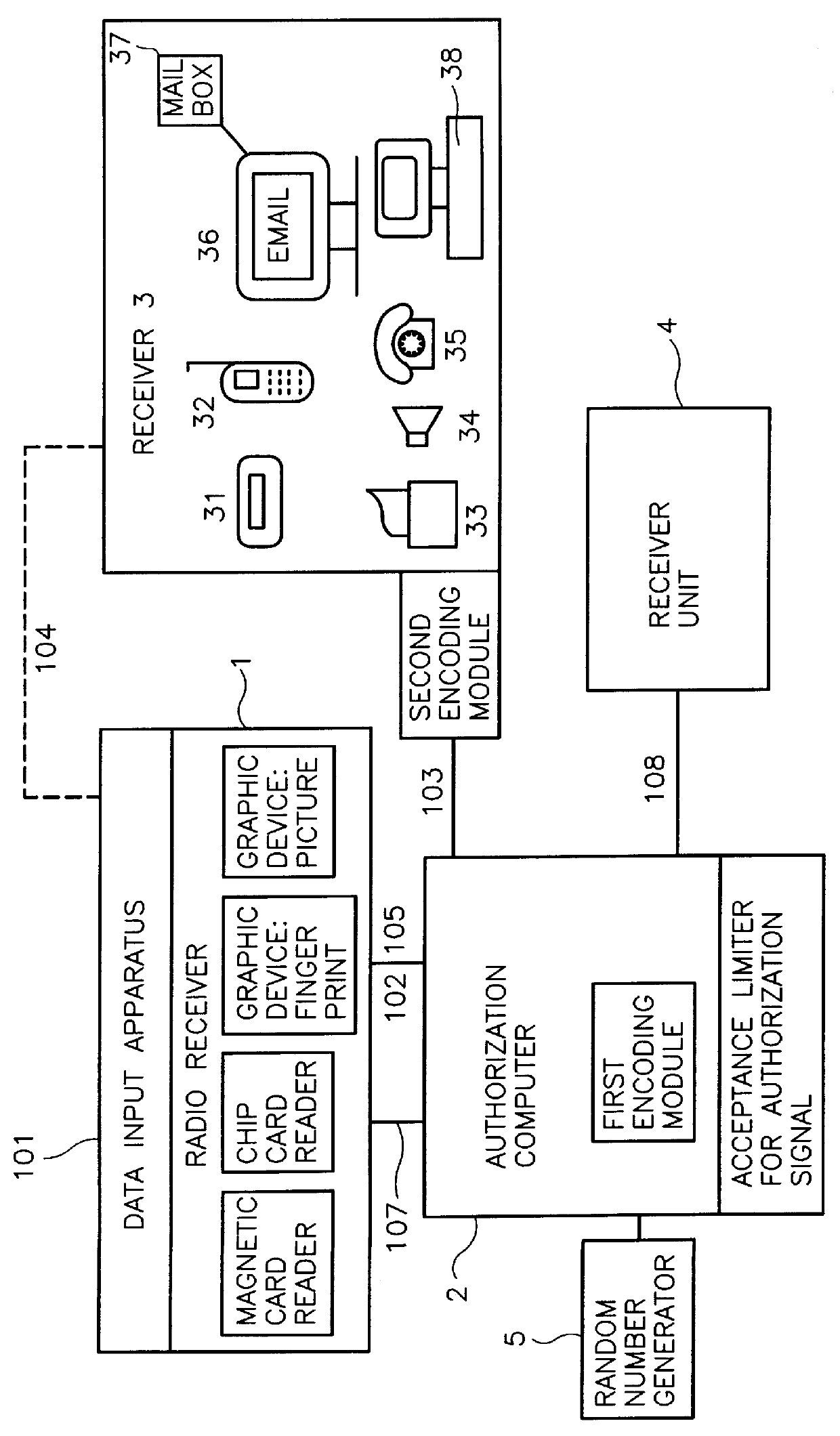
The invention relates to a method and to a device for the authorization in data transmission systems employing a transaction authorization number (TAN) or a comparable password. According to a first step, the user sends a qualifying identification of the data input apparatus together with a request for the generation or for the selection of a transaction authorization number TAN or of comparable password from a data file from the data input apparatus to an authorization computer. In a second step the authorization computer generates the transaction authorization number TAN or the comparable password or selects them form a data file. According to a third step, the authorization computer sends the transaction authorization number TAN or the comparable password over a second transmission path different from the first transmission path to a monitor, for example a pager. According to a fourth step, the user reads this transaction authorization number TAN or the comparable password from the receiver and enters the transaction authorization number TAN or the comparable password into the data input apparatus. According to a fifth step, this transaction authorization number TAN or the comparable password is transmitted to the authorization computer. According to a sixth step, the authorization computer verifies the validity of the transaction authorization number TAN or of the comparable password in order to establish or switch free, according to a seventh step, a connection between the data input apparatus and the receiver unit.
Owner:SCHMITZ KIM
System, apparatus and method for providing a virtual network edge and overlay with virtual control plane
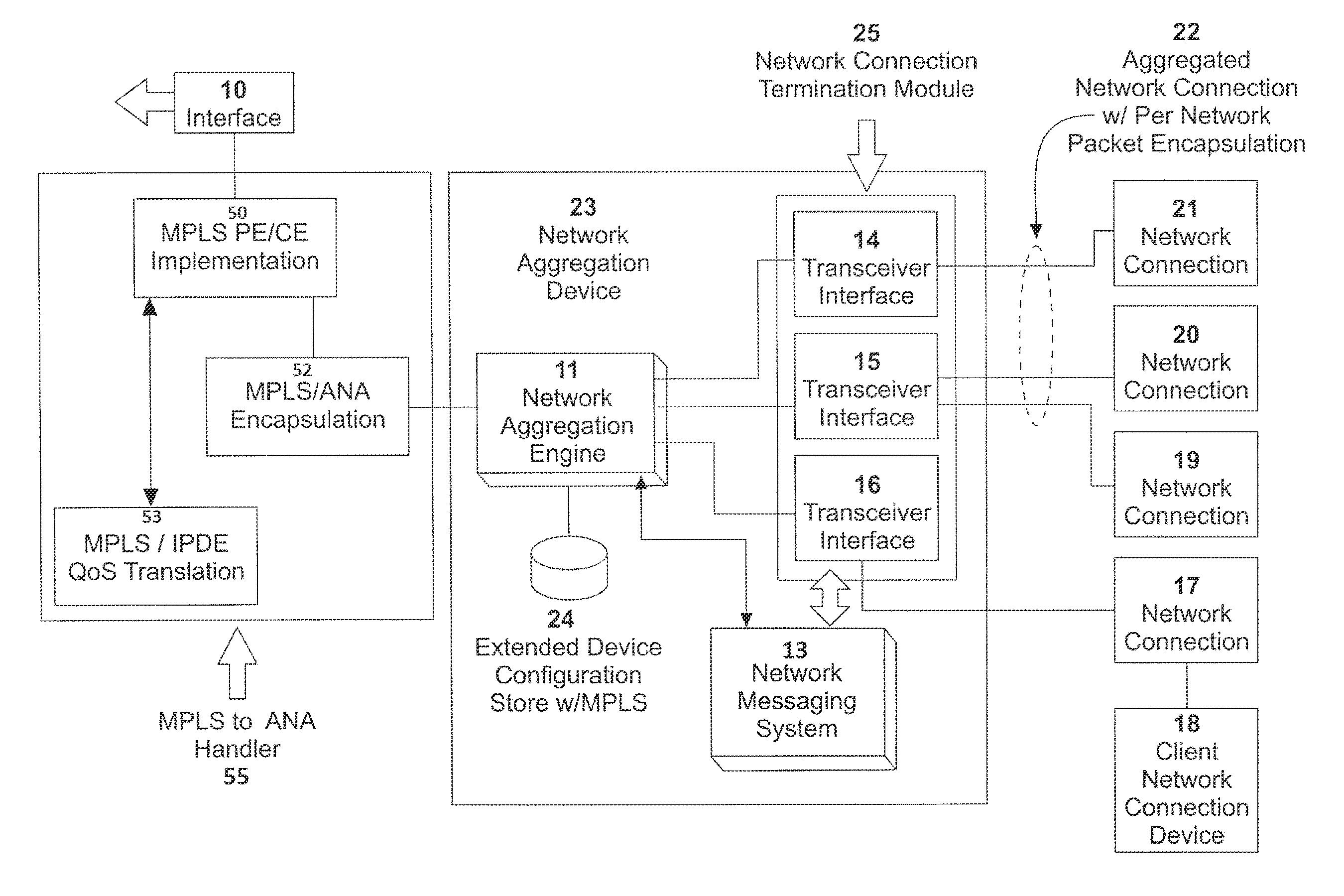
ActiveUS20160072669A1Improve communication performanceImprove throughputDigital computer detailsNetworks interconnectionTraffic capacityNetwork connection
A network system is provided between at least a first client site and a second client site. A client site network component is implemented at least at the first client site, the client site network component aggregating one or more diverse network connections so as to configure an aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the aggregated connection between the client site network component and the network server component. The network server component includes a virtual control plane interface configured to establish a unicast path between the network server component and each of a plurality of remote network server components.
Owner:ADAPTIV NETWORKS INC
Zeroclick
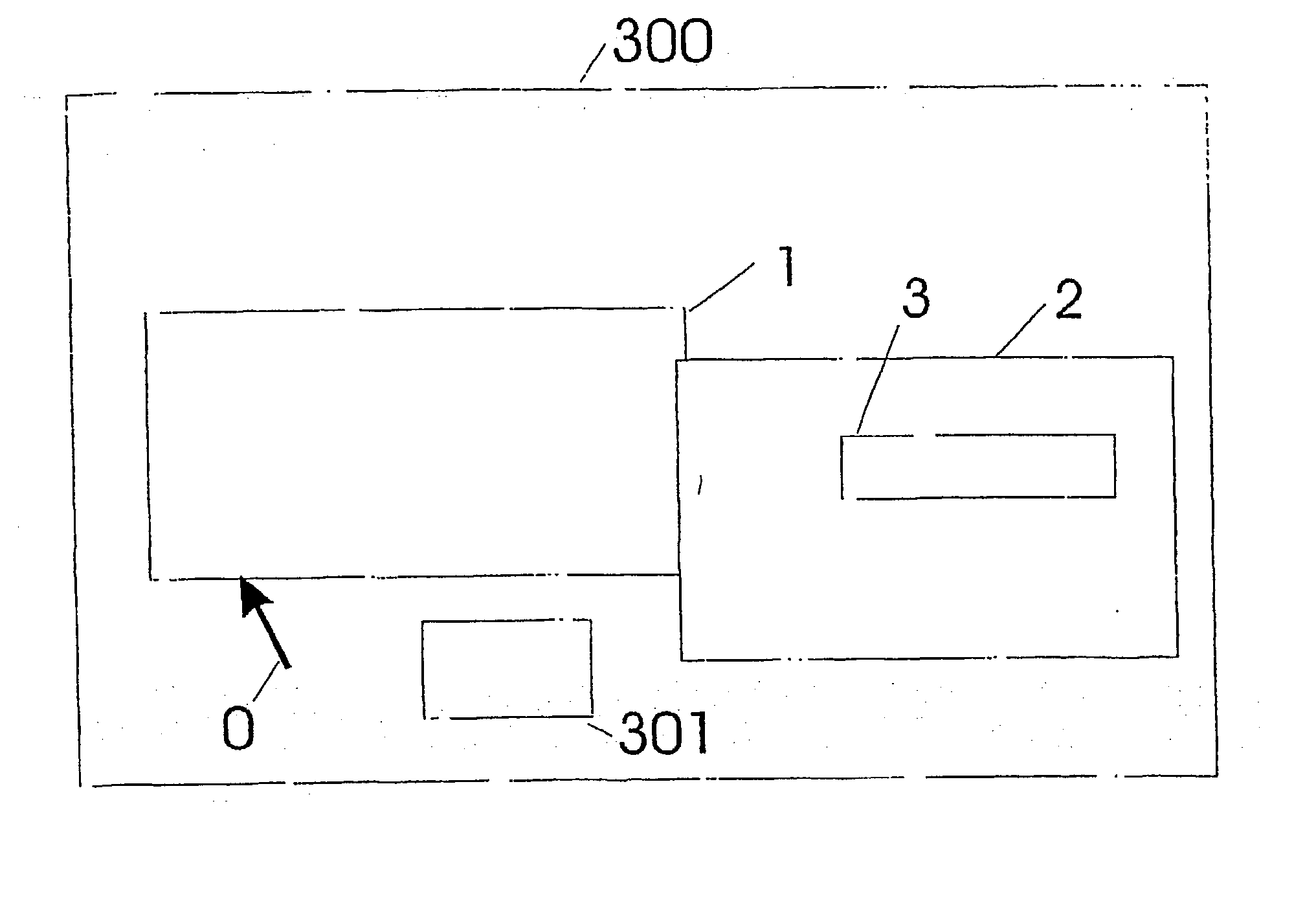
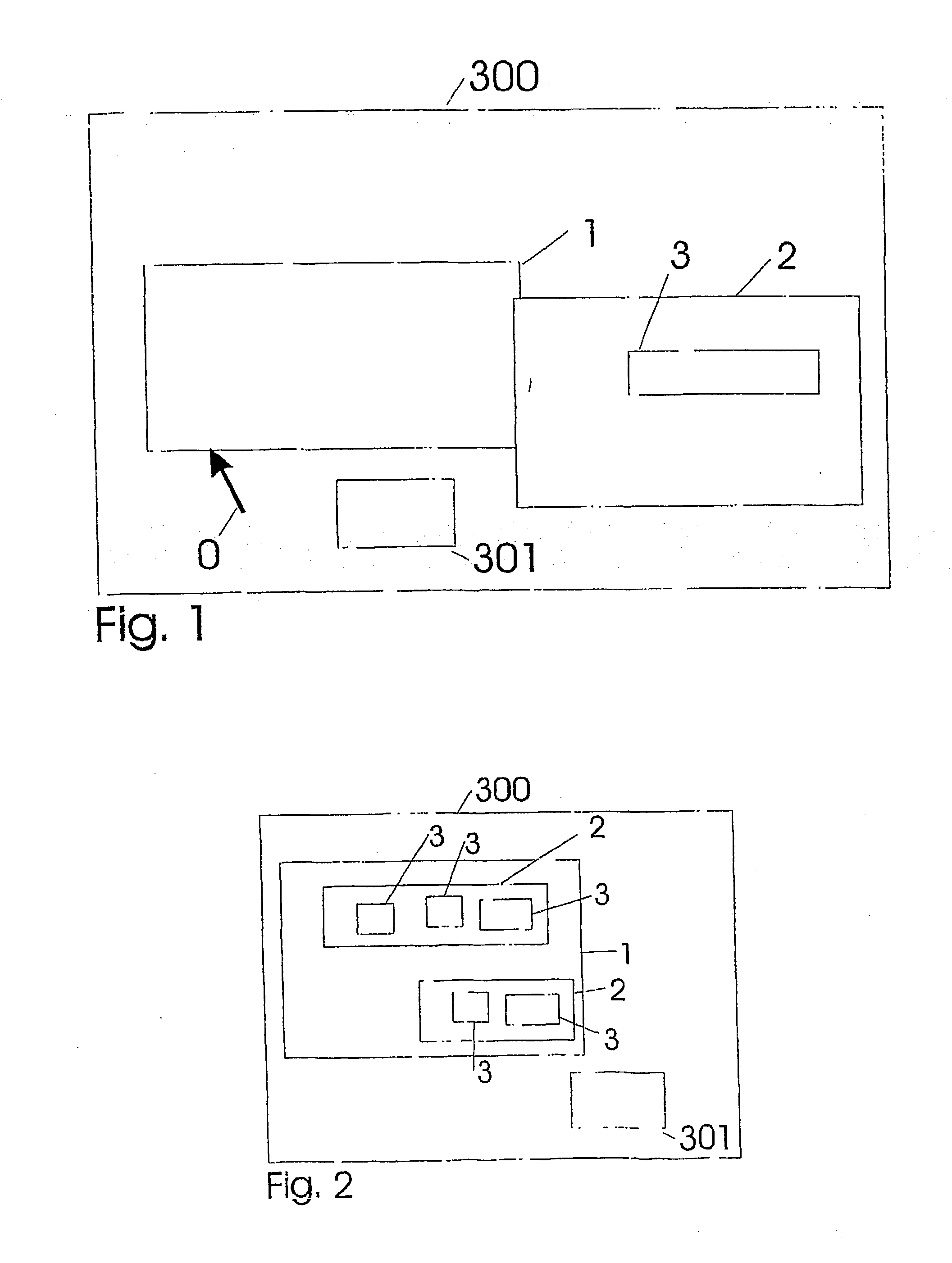
InactiveUS20030197744A1Cathode-ray tube indicatorsInput/output processes for data processingEmbedded systemPathPing
A GUI interface, a method of programming a GUI interface, and an apparatus which enables functions of controls in the GUI to be activated by a movement to a control and then another subsequent movement related to that control. It may be defined more precisely below. A GUI in which, when a pointer 0 old>0 < / highlight>is immediately adjacent or passerea 1, a procedure is initiated whereby subsequentdure is initiated whereby subsequent movement of t area 3 generates a "click" event which simulates < / highlight>generates a "click" event which simulae the predetermined path area 3 prior to completioight>and moving outside the predetermined path areinter has never started along the predetermined paath <bold>3 < / highlight>resets the control to as if the pointer has never started along the predetermined path area <bold>3. < / highlight>
Owner:ZEROCLICK LLC
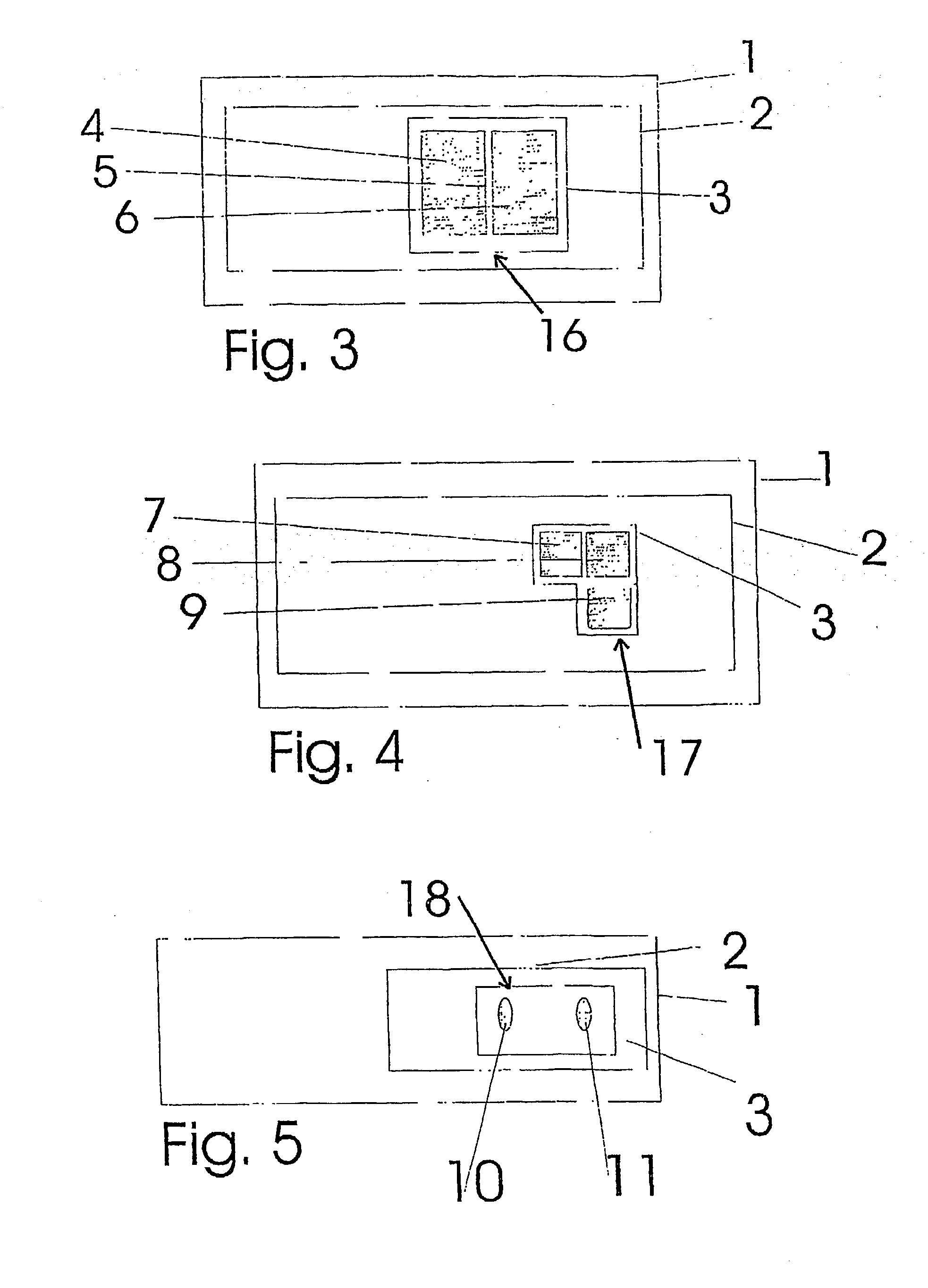
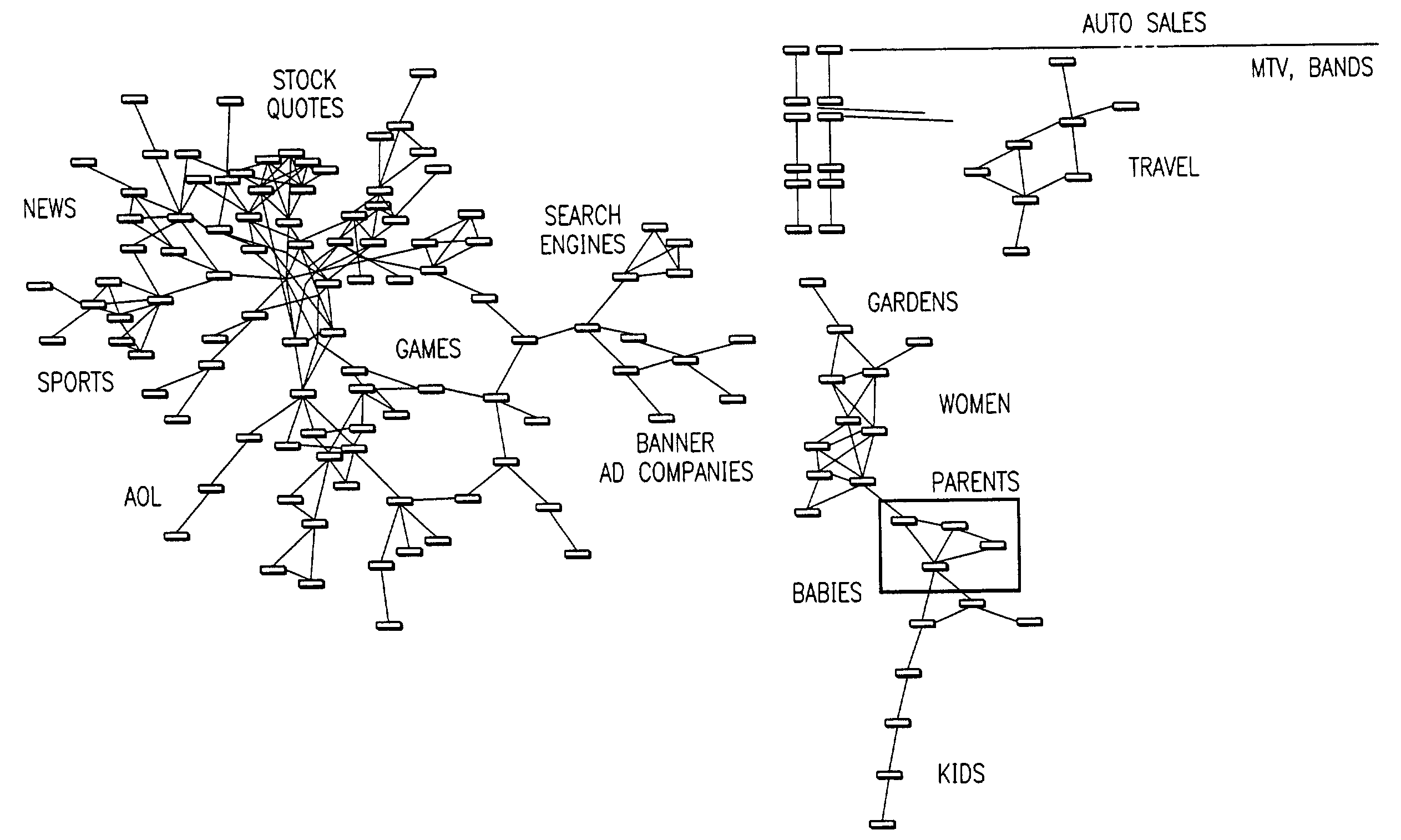
Visualization and analysis of user clickpaths
Methods and data processing system readable media have been created to graph user clickstream data over a network or at a network site to yield meaningful and visually esthetic information. In one set of embodiments, the method can comprise (i) performing a significance test on data from a network log and generating significance results. The method can also comprise (ii) determining which of network addresses and clicktrails between network addresses meet a traffic flow criterion. The data that meet a significance criterion, traffic criterion, or both can form (iii) graphable addresses and relationships. The method can further comprise (iv) generating statistics about the graphable addresses and relationships. The method can still further comprise (v) generating a graph based on the statistics about the graphable addresses and relationships, and (vi) changing any or all of the traffic flow, significance criterion, and statistics being computed, and regenerating the graph.
Owner:OPEN TEXT SA ULC
Method and apparatus for securing electronic data
ActiveUS7681034B1Facilitate access control managementGood synchronizationDigital data processing detailsUnauthorized memory use protectionPathPingEngineering
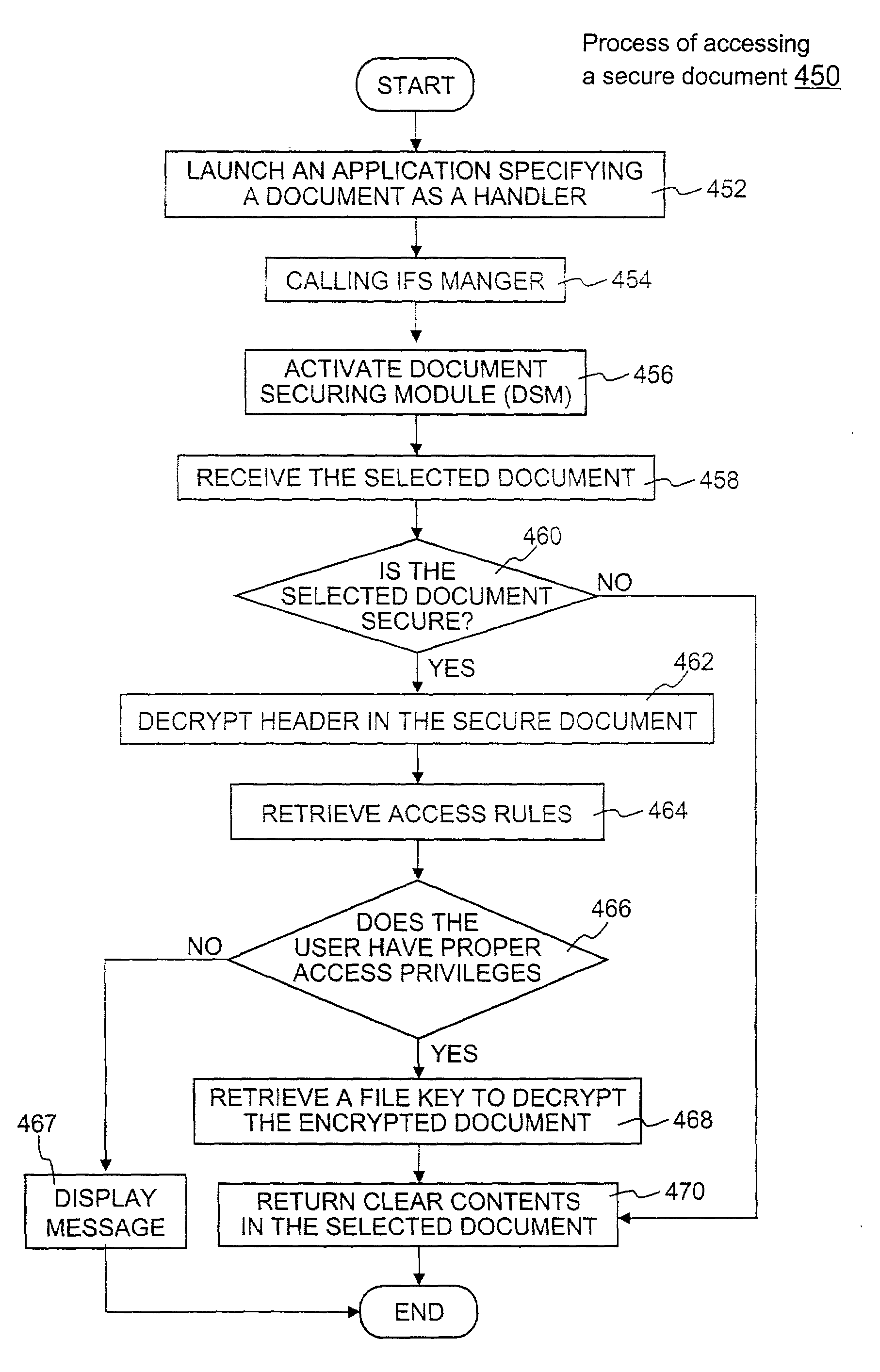
Techniques for securing electronic data and keeping the electronic data secured at all times are disclosed. According to one embodiment, a client module in a client machine is configured to provide access control to secured documents that may be located in a local store, another computer machine or somewhere over a data network. The client module includes a document-securing module configured to operate in a path through which a document being accessed is caused to pass so that the document can be examined or detected for the security nature. If the document is secured, the document-securing module obtains a user or group key to decrypt security information in the secured document for access rules therein. If a user accessing the document is determined to have the access privilege to the secured document, a file key is retrieved from the security information and a cipher module is activated to decrypt the encrypted data portion with the file key. Likewise, if a document is to be secured, the cipher module encrypts clear data from the document to create the encrypted data portion. The document-securing module integrates proper or desired security information with the encrypted data portion to produce the secured document.
Owner:INTELLECTUAL VENTURES I LLC
Multipath routing process
ActiveUS20070094361A1Reduce load effectShorten the timeError detection/correctionDigital computer detailsPathPingIp address
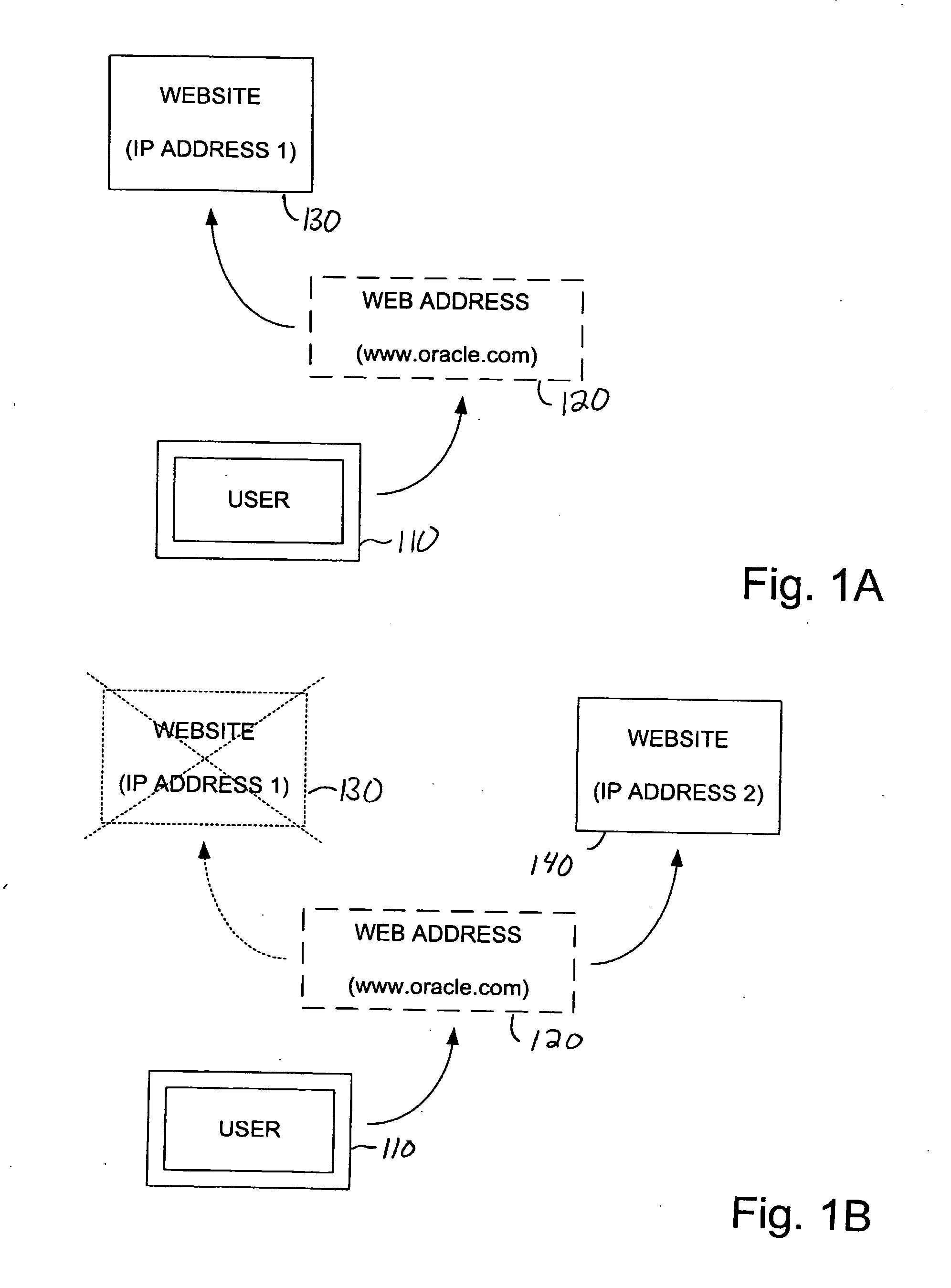
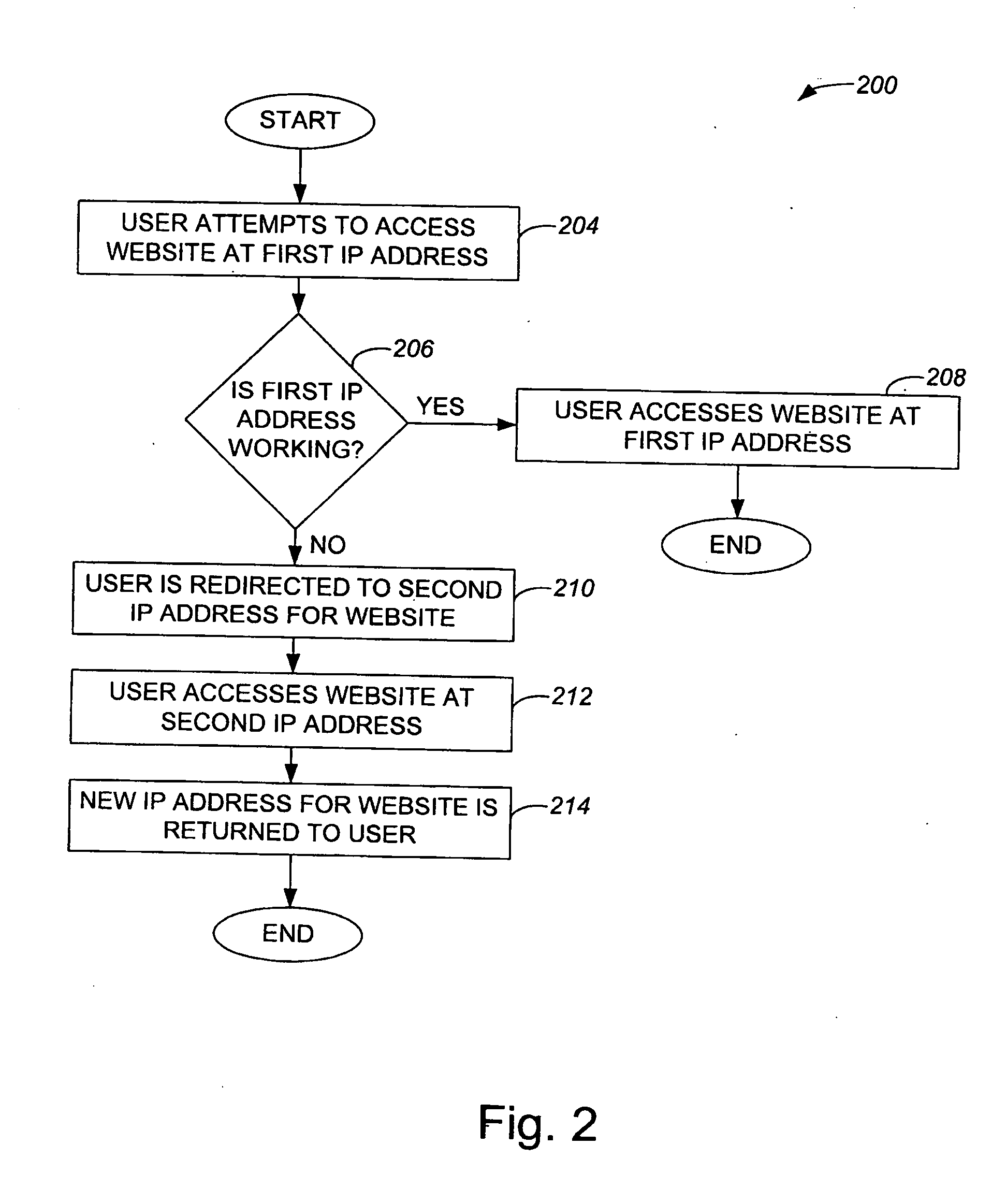
Methods and apparatus that enable more than one server to host a resource using a shared IP address such that a client may generally access the resource on any of the servers using the shared IP address are disclosed. According to one aspect of the present invention, a method for providing paths that allow a client to access a resource in a TCP / IP network includes obtaining an IP address, as well as associating the IP address to first and second servers. The first and second servers support the resource at the IP address, and a first path of the plurality of paths that allow the client to access the resource is between the client and the first server and a second path of the plurality of paths that allow the client to access the resource is between the client and the second server.
Owner:ORACLE INT CORP
Multi-tasking adapter for parallel network applications
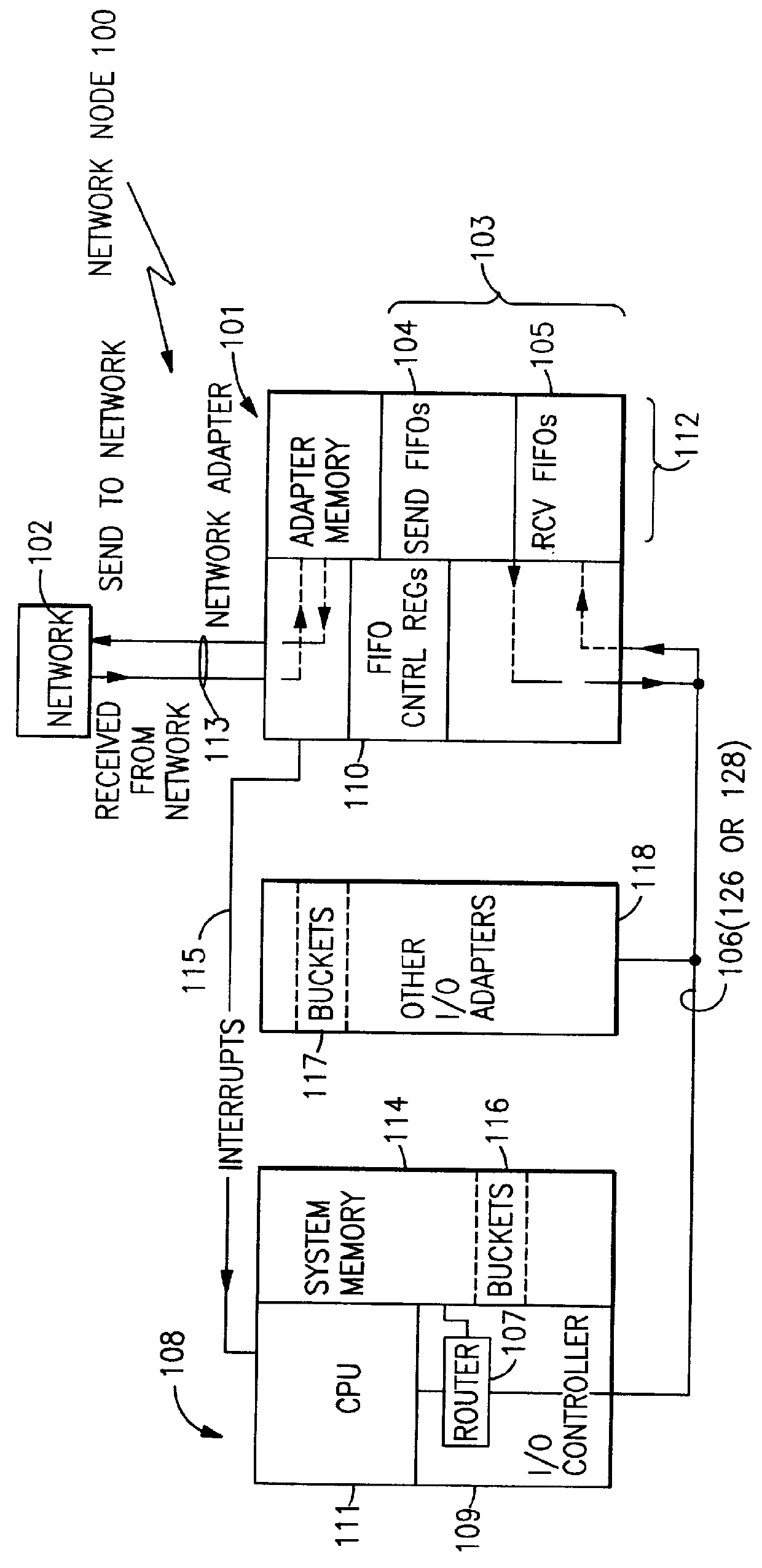
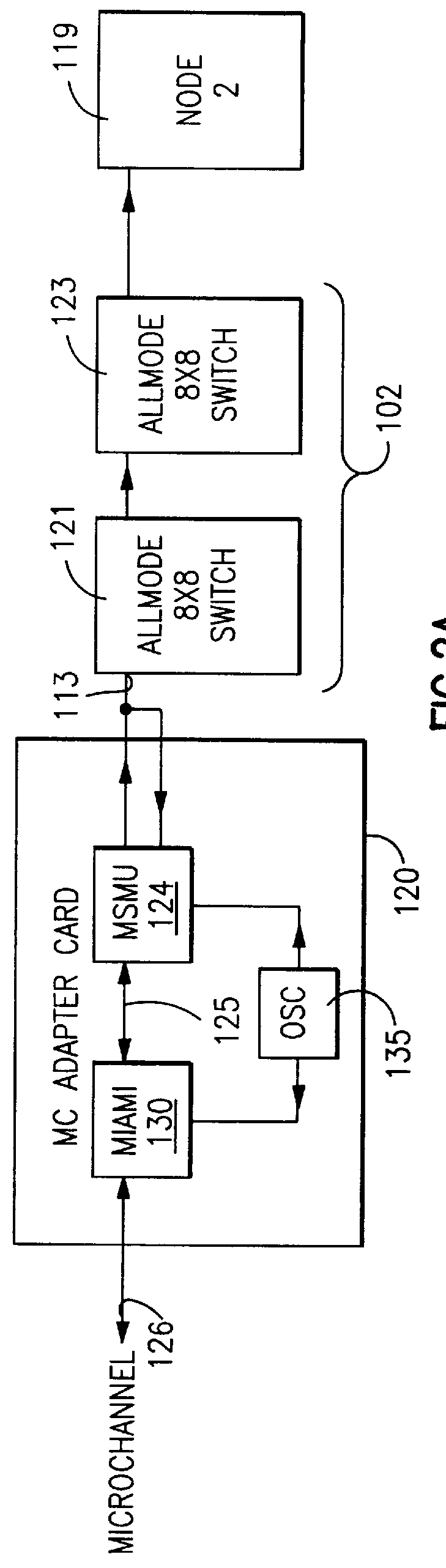
A communications apparatus is provided comprising a plurality of FIFO buffers, each with independent control and priority logic under software control for supporting different types of message traffic, both send and receive, such as comprise a multimedia server system. Processor software directs messages to specific, optimized FIFO buffers. Further, a system is provided including a plurality of nodes wherein a sending node specifies the communications path through the system, selecting specific FIFO buffers in each node for buffering its messages.
Owner:IBM CORP
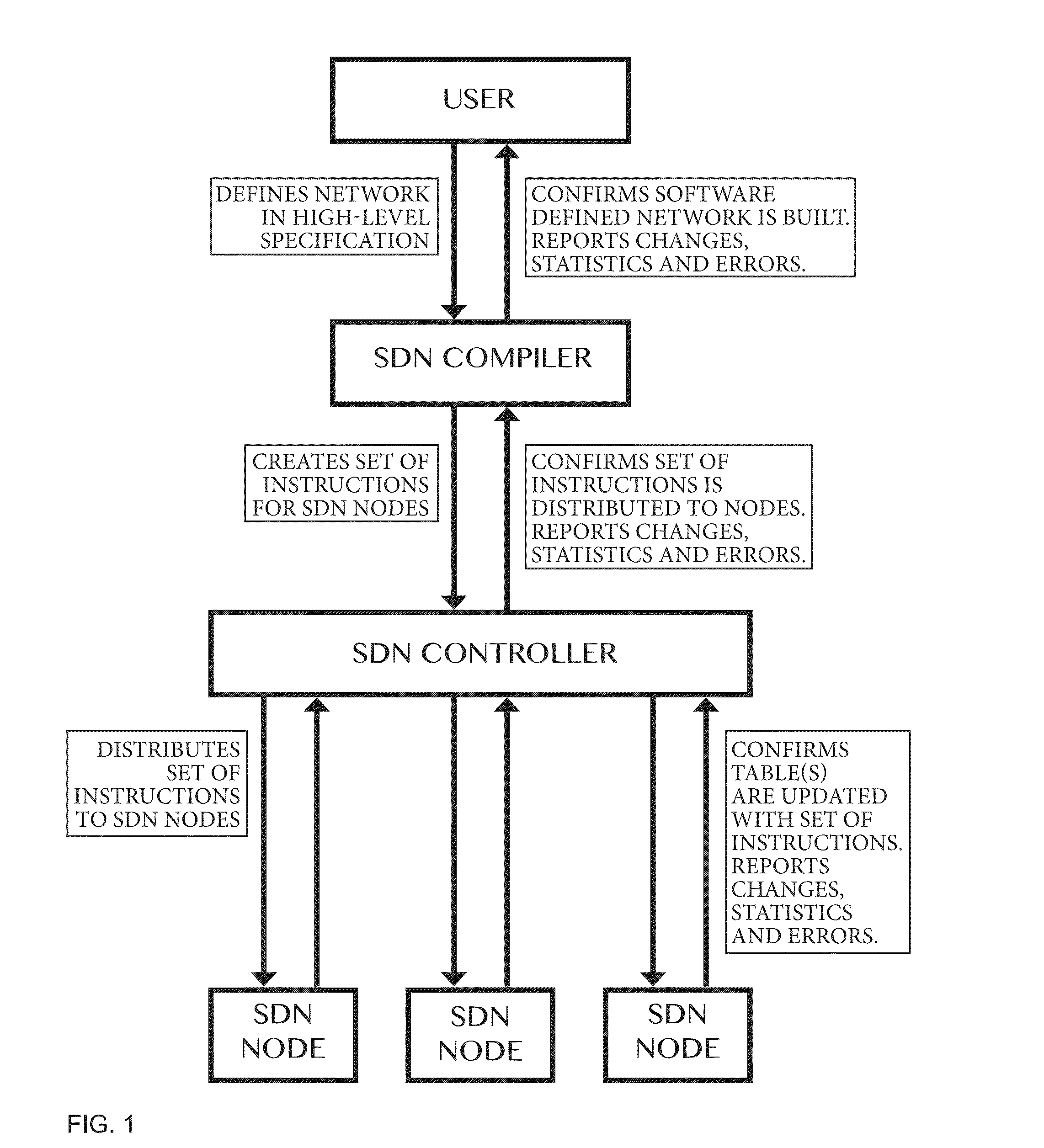
Compiler for and method for software defined networks
ActiveUS20160173338A1Small sizeSpeed up the calculation processDigital computer detailsData switching networksLogical networkSoftware define network
Method of and a compiler for controlling a network based on a logical network model. The network has physical nodes and virtual nodes. The physical nodes are interconnected by physical links in accordance with a physical network layout. The logical network model has logical nodes indicated with a logical node name which refers to at least one physical or at least one virtual node in the network. The method uses a physical forwarding point-of-attachment relation defining physical paths of the physical network in dependence on a physical forwarding policy, a first mapping relation defining how the virtual nodes and the physical nodes are mapped to one another, and a second mapping relation defining how the logical nodes are mapped to the physical nodes and the virtual nodes. The method also includes transforming paths in the physical network to paths between the physical nodes and the virtual nodes.
Owner:WOLTING HLDG
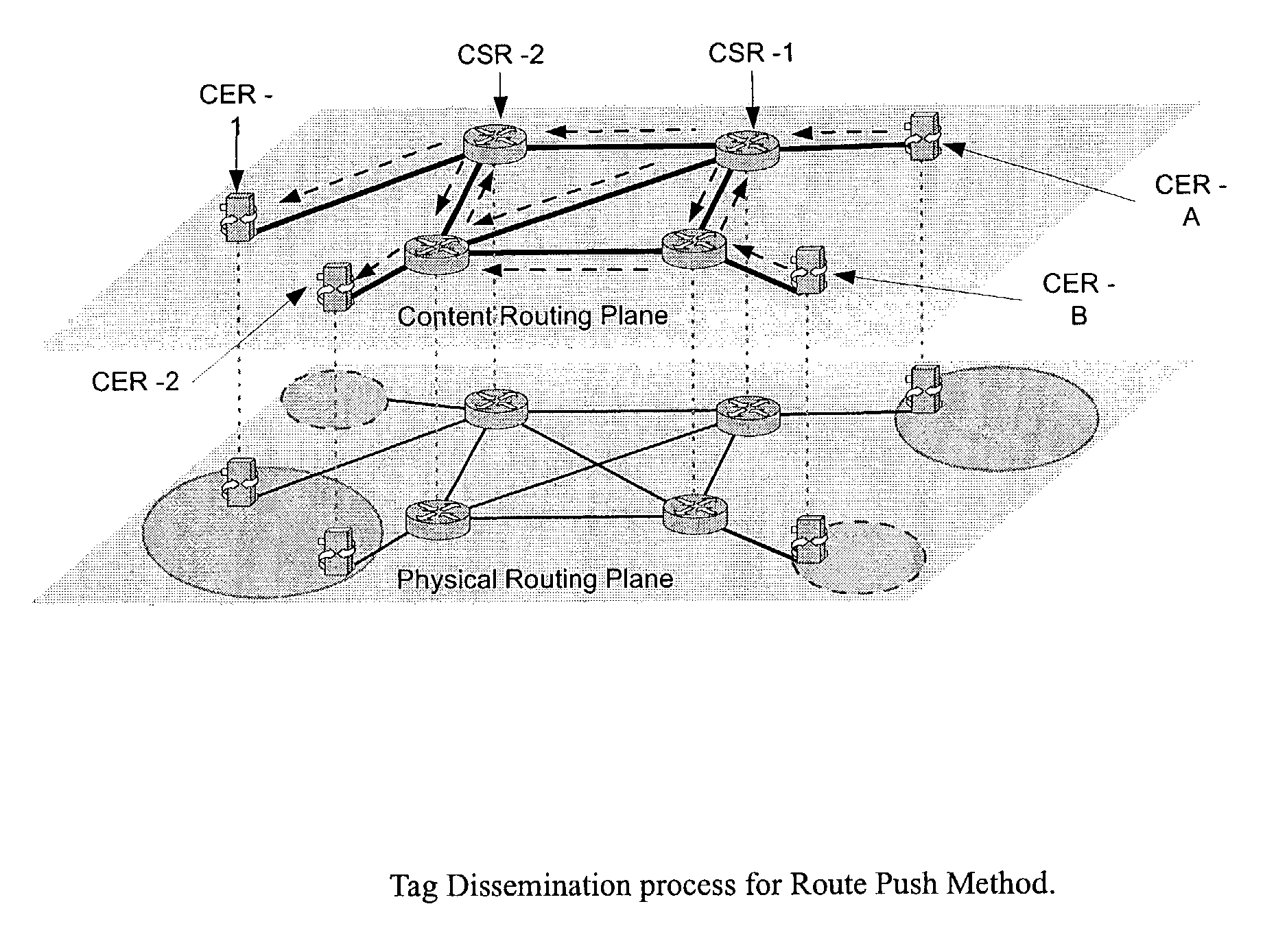
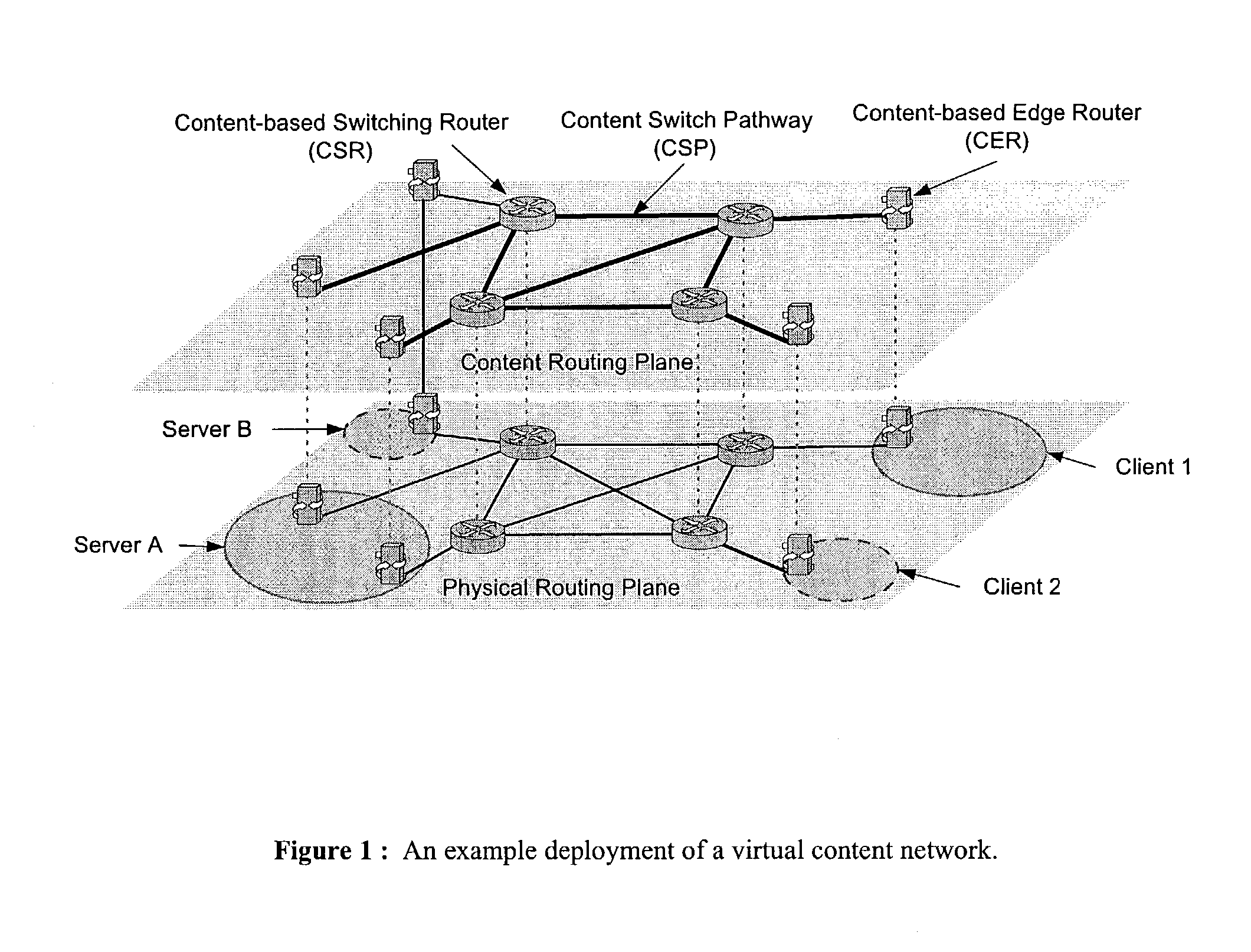
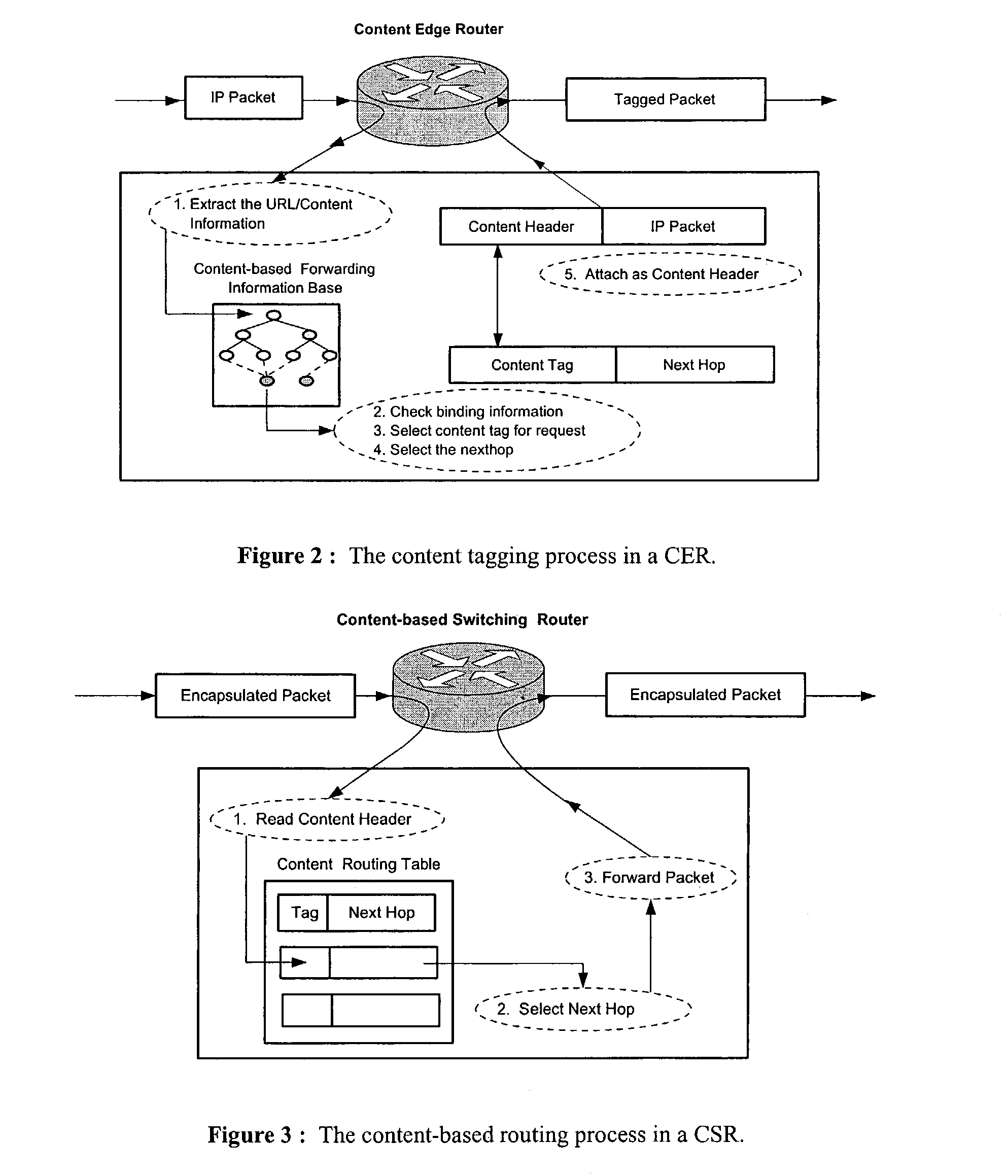
Wide-area content-based routing architecture
Owner:TELECOMM RES LAB
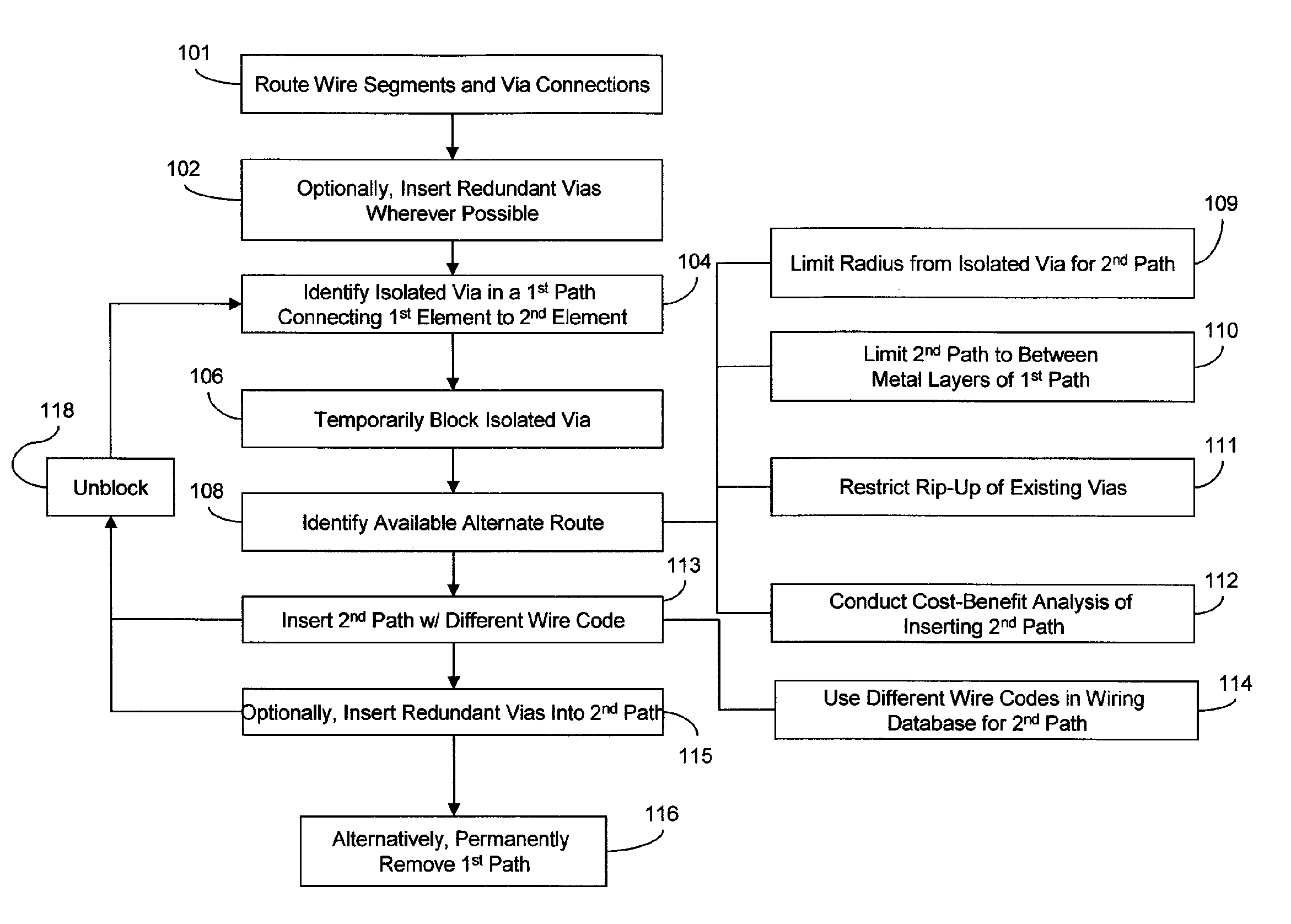
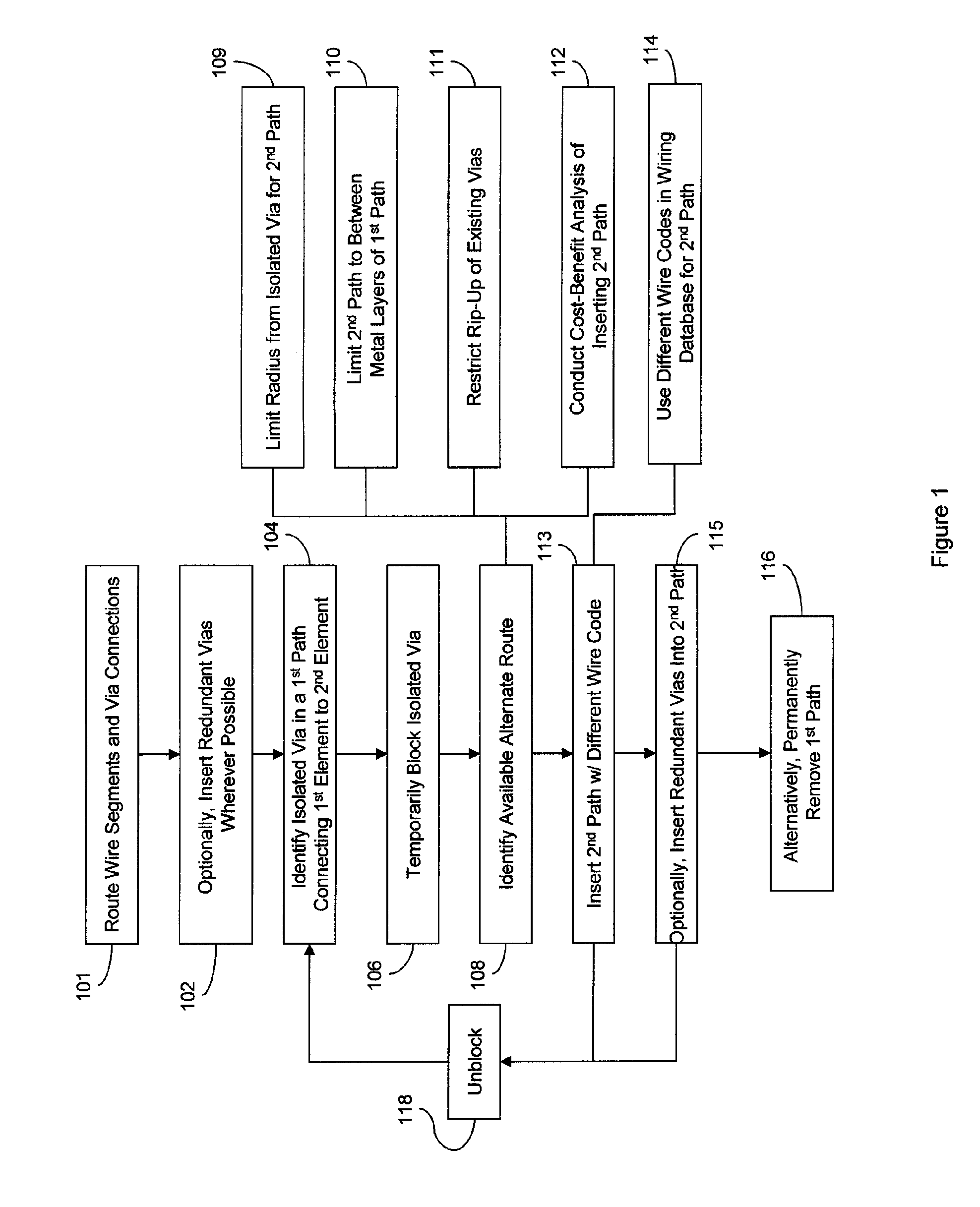
Use of redundant routes to increase the yield and reliability of a VLSI layout
ActiveUS7308669B2Increase redundancyReduce sensitivityCAD circuit designSoftware simulation/interpretation/emulationEngineeringVlsi layout
Disclosed is a method and system for inserting redundant paths into an integrated circuit. Particularly, the invention provides a method for identifying a single via in a first path connecting two elements, determining if an alternate route is available for connecting the two elements (other than a redundant via), and for inserting a second path into the available alternate route. The combination of the first and second paths provides greater redundancy than inserting a redundant via alone. More importantly, such redundant paths provide for redundancy when congestion prevents a redundant via from being inserted adjacent to the single via. An embodiment of the method further comprises removing the single via and any redundant wire segments, if all of the additional vias used to form the second path can be made redundant.
Owner:GLOBALFOUNDRIES US INC
System and method for providing masquerading using a multiprotocol label switching
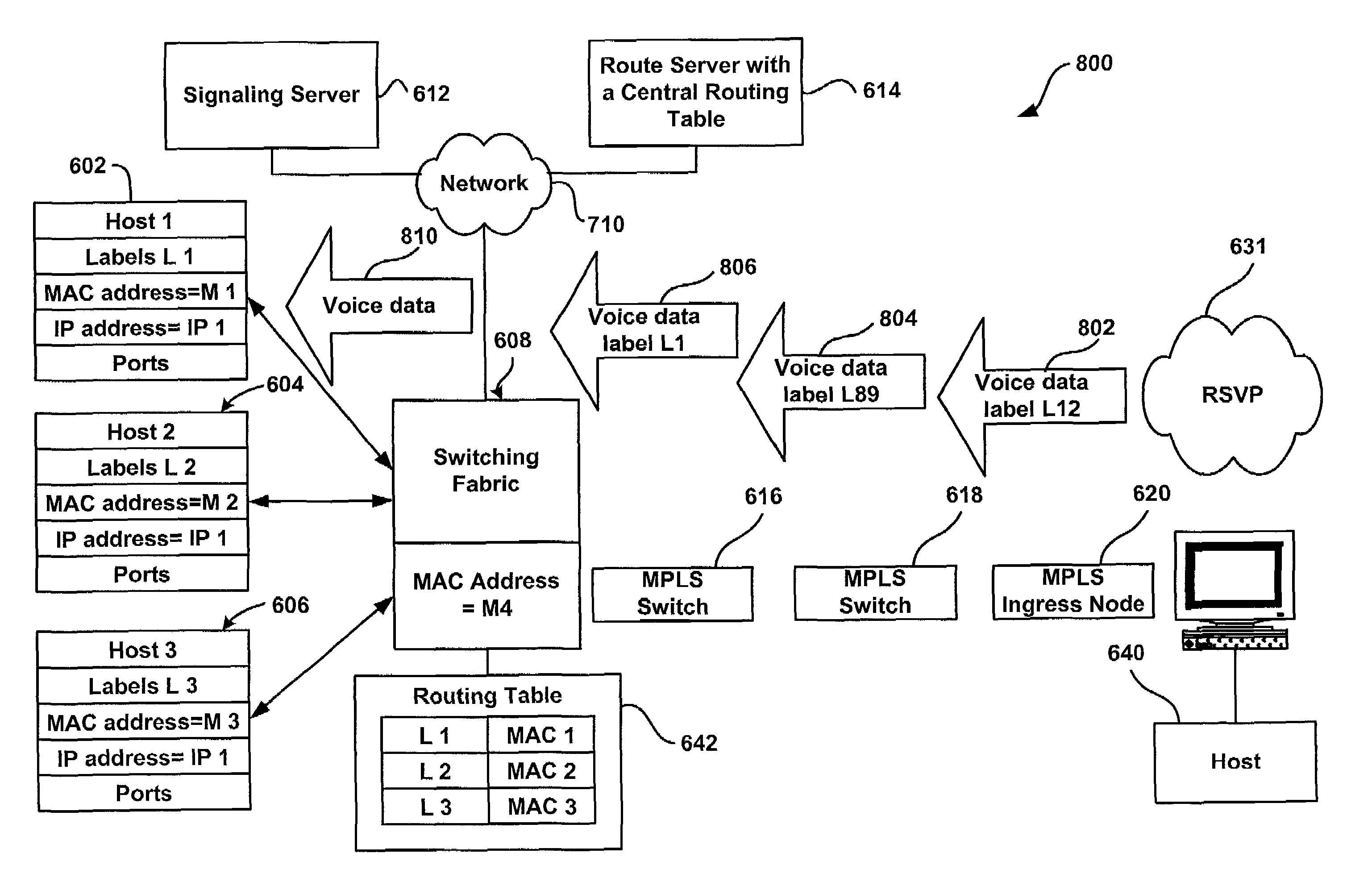
A system and method for transmitting information between a source host and a destination host. A source host generates a message and forwards the message via a label switched path to the destination host so that when a central routing module receives the message, the message includes a label. A central routing module establishes a local master mapping table including a plurality of physical addresses, and each of the plurality of physical addresses is associated with a unique identifier such as a label. When a switch egress module receives the message with the label, the switch egress module determines a physical address associated with the label, maps the physical address to the message, and forwards the message to the destination host associated with the label.
Owner:VALTRUS INNOVATIONS LTD
System and method for loop avoidance in multi-protocol label switching
InactiveUS6879594B1Overcome disadvantagesSpecial service provision for substationData switching by path configurationMulti protocolLabel switching
A method for avoiding loops from forming when setting up label switched paths is provided. The method uses a Label Splicing Message is followed by an Acknowledgment message to determine if loops are formed in the process of joining a new node or subtree to a multicast MPLS tree. By verifying that the path towards the root of the MPLS tree is loop-free during the construction of the tree, this method complements the loop detection mechanism provided by the label switched protocol (LDP).
Owner:BIOSPHERICS
Network routing with path identifiers
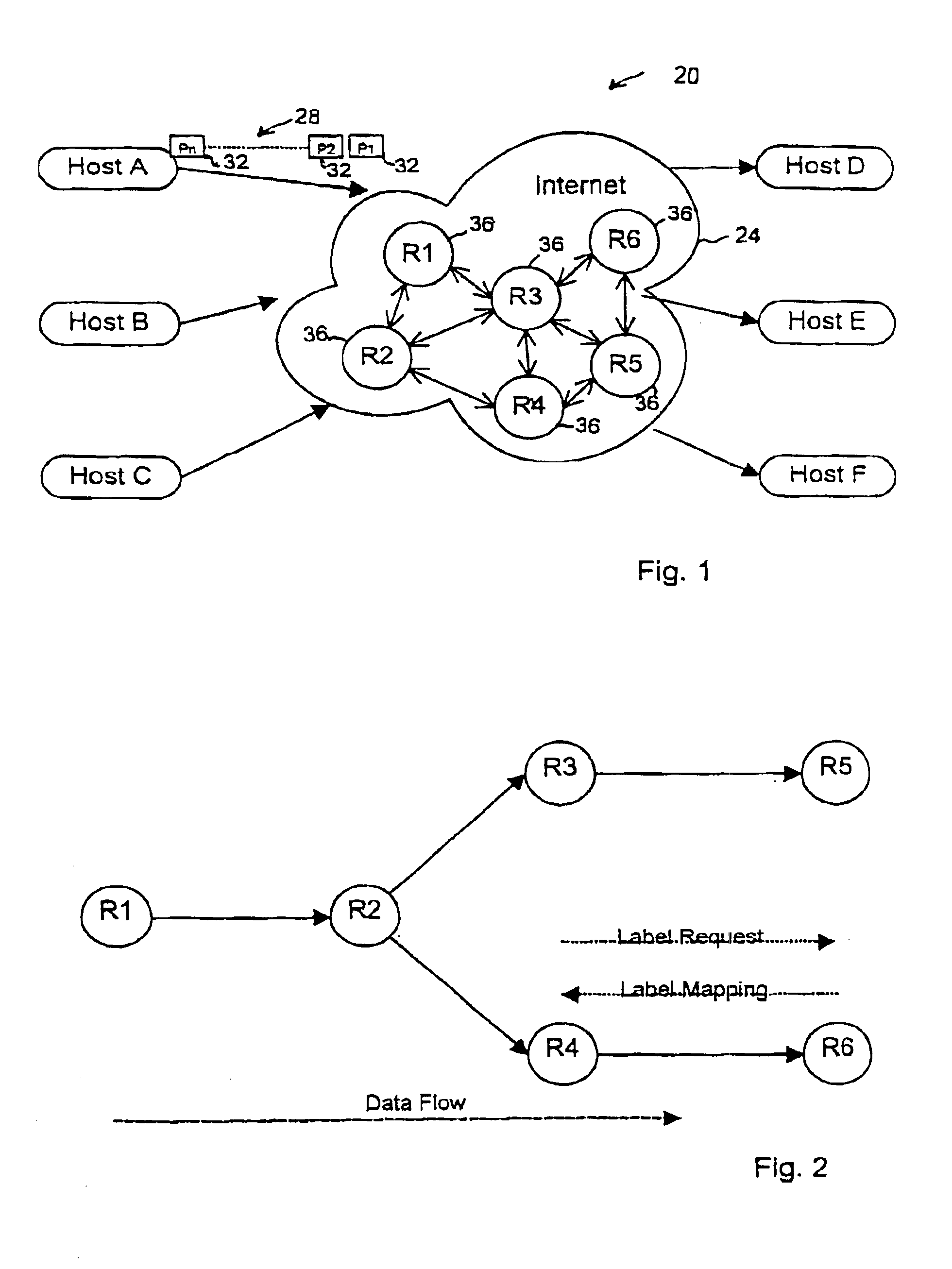
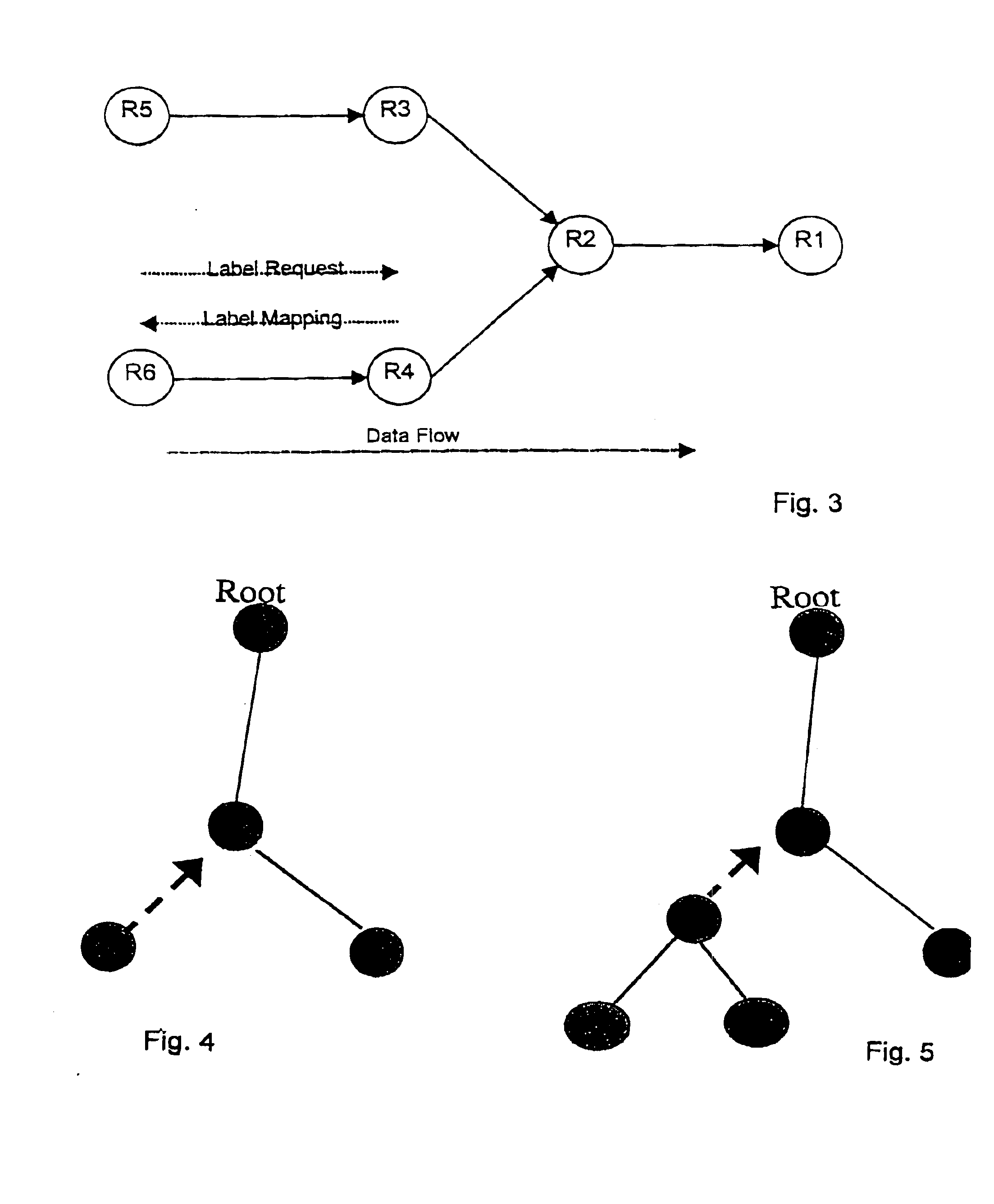
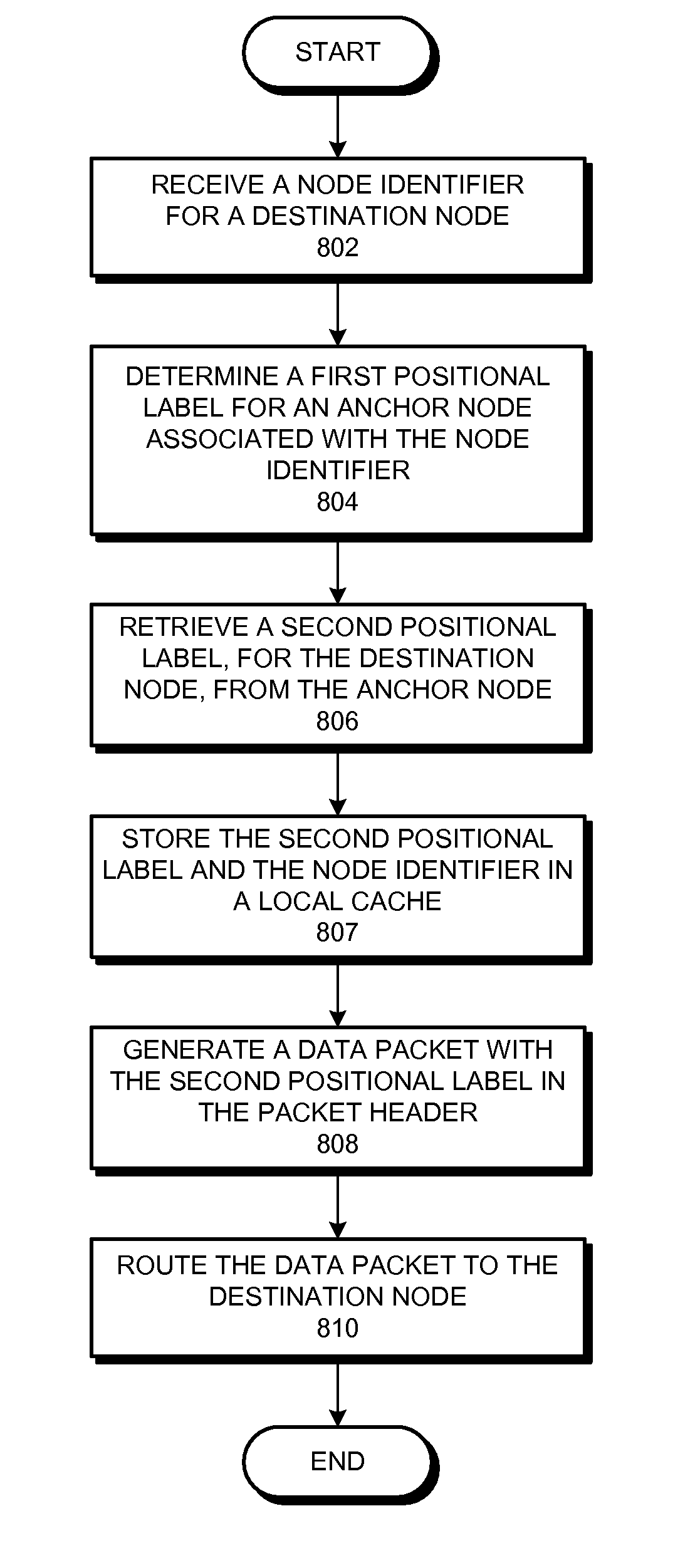
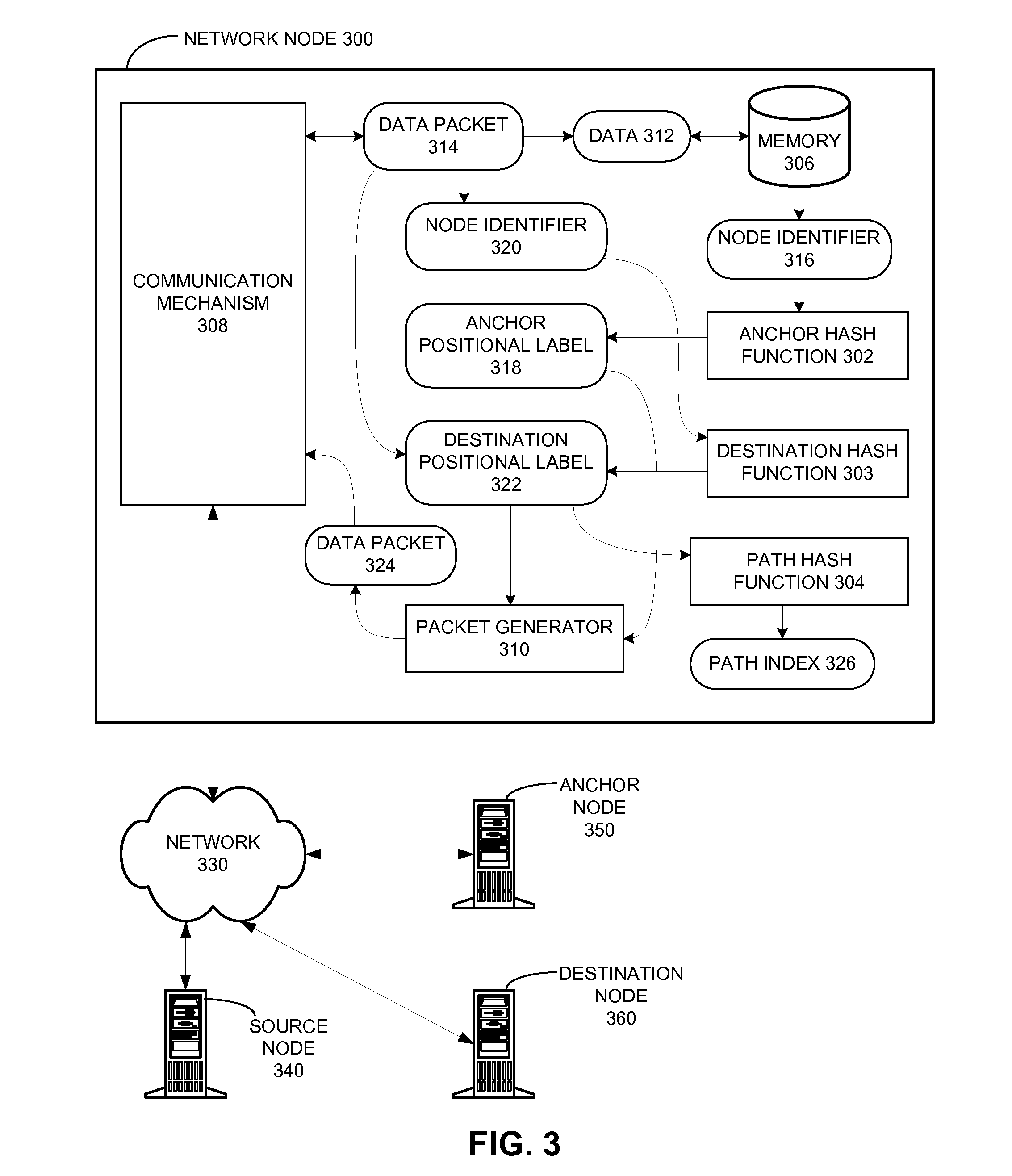
One embodiment of the present invention provides a system that communicates a data packet in a network to a target node. In doing so, the system receives a node identifier for the target node, and determines a first positional label, based in part on the node identifier, for reaching a first anchor node from a root node in the network. The first anchor node stores a second positional label for reaching the target node from the root node in the network, which comprises a number of nodes coupled to the root node in a tree topology. The system then retrieves the second positional label from the first anchor node, and communicates the data packet to the target node based in part on the second positional label.
Owner:CISCO TECH INC
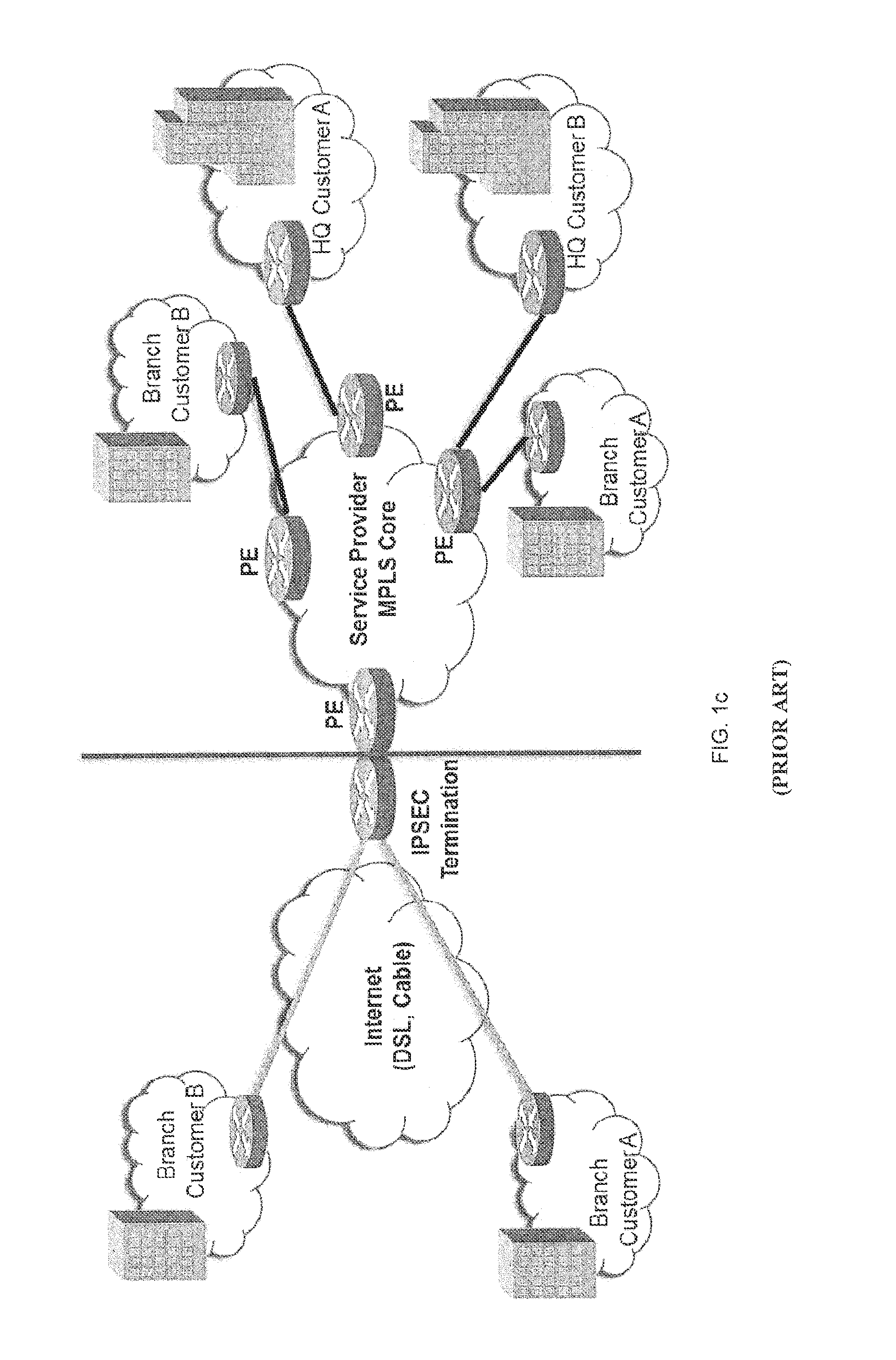
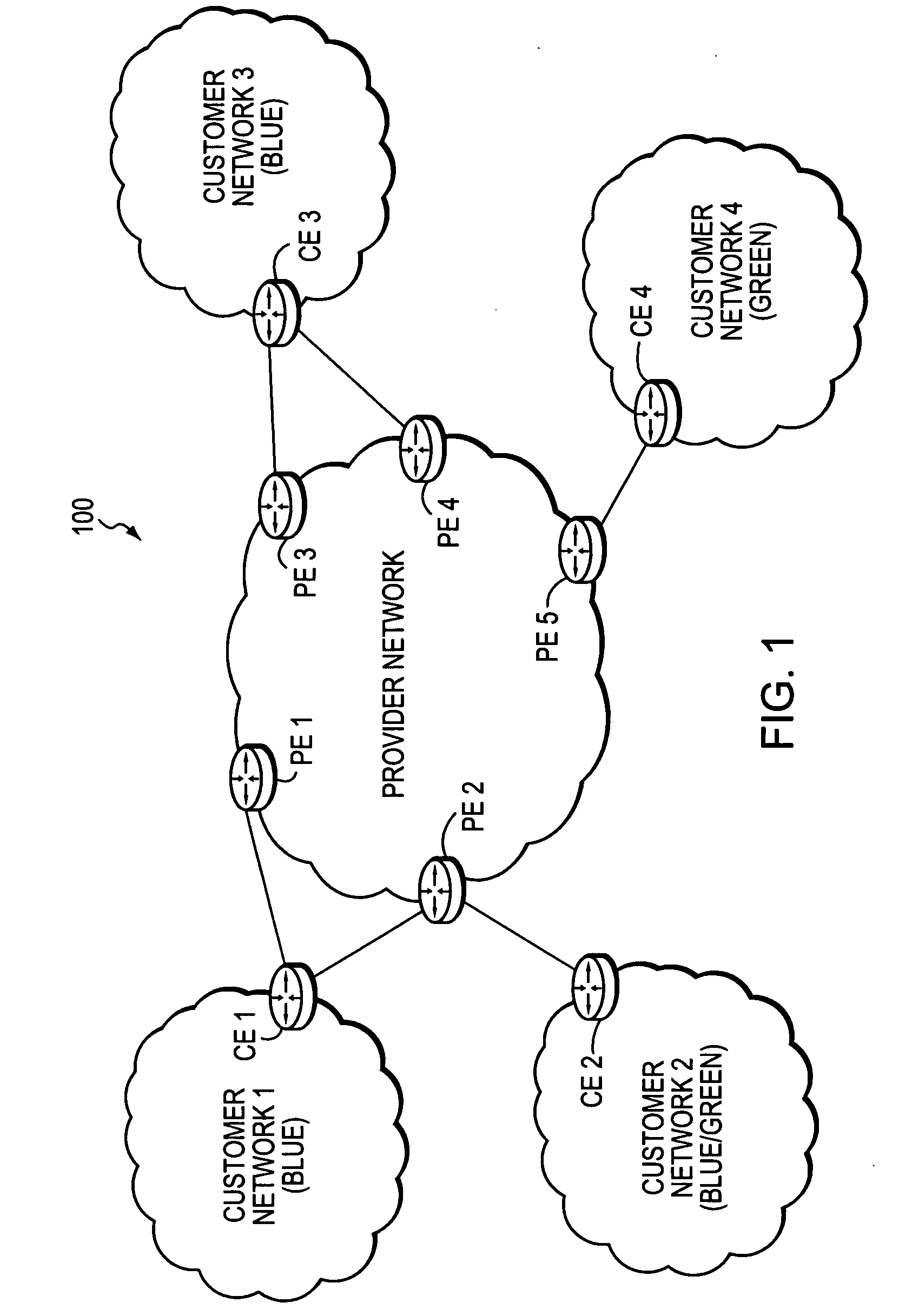
Technique for enabling traffic engineering on CE-CE paths across a provider network
ActiveUS20070133406A1Create efficientlyReduce needError preventionTransmission systemsPrivate networkDistributed computing
A technique enables Traffic Engineering (TE) on paths between customer edge devices (CEs) across a provider network (“CE-CE paths”) in a computer network. According to the novel technique, TE is configured on a link from a sending provider edge device (PE) to a first CE (“PE-CE link”), e.g., a CE of one or more virtual private networks (VPNs). The sending PE conveys TE information of the PE-CE link to one or more receiving PEs in the provider network. Upon receiving the TE information, each receiving PE expands a TE database (TED) for information regarding the provider network (i.e., a “core TED”) to include TE-configured PE-CE links, e.g., by updating one or more corresponding VPN TEDs (VTEDs) for each VPN maintained by the receiving PE. Once the receiving PEs have the TE information for configured PE-CE links from the provider network, one or more TE techniques may be applied to paths from a second CE of the receiving PE to the first CE (a CE-CE path) to thereby facilitate, e.g., establishment of TE-LSPs along CE-CE paths.
Owner:CISCO TECH INC
Method for ensuring referential integrity in multi-threaded replication engines
ActiveUS20050021567A1Digital data information retrievalDigital data processing detailsTransaction dataLoad capacity
During replication of transaction data from a source database to a target database via a change queue associated with the source database, one or more multiple paths are provided between the change queue and the target database. The one or more multiple paths cause at least some of the transaction data to become unserialized. At least some of the unserialized data is reserialized prior to or upon applying the originally unserialized transaction data to the target database. If the current transaction load is close or equal to the maximum transaction load capacity of a path between the change queue and the target database, another path is provided. If the maximum transaction threshold limit of an applier associated with the target database has been reached, open transactions may be prematurely committed.
Owner:INTEL CORP
Load balancing switch protocols
A switch to switch protocol for network load balancing which permits parallel redundant paths in a network to be utilized while reducing broadcast or problems inherent in prior switch configuration protocols. In particular, the present invention includes in the protocol a hello packet protocol which serves to exchange load balancing information among switches within a common load balance domain. Further, the hello packet protocol of the present invention enables detection and correction of improperly configured loops outside a load balance domain.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
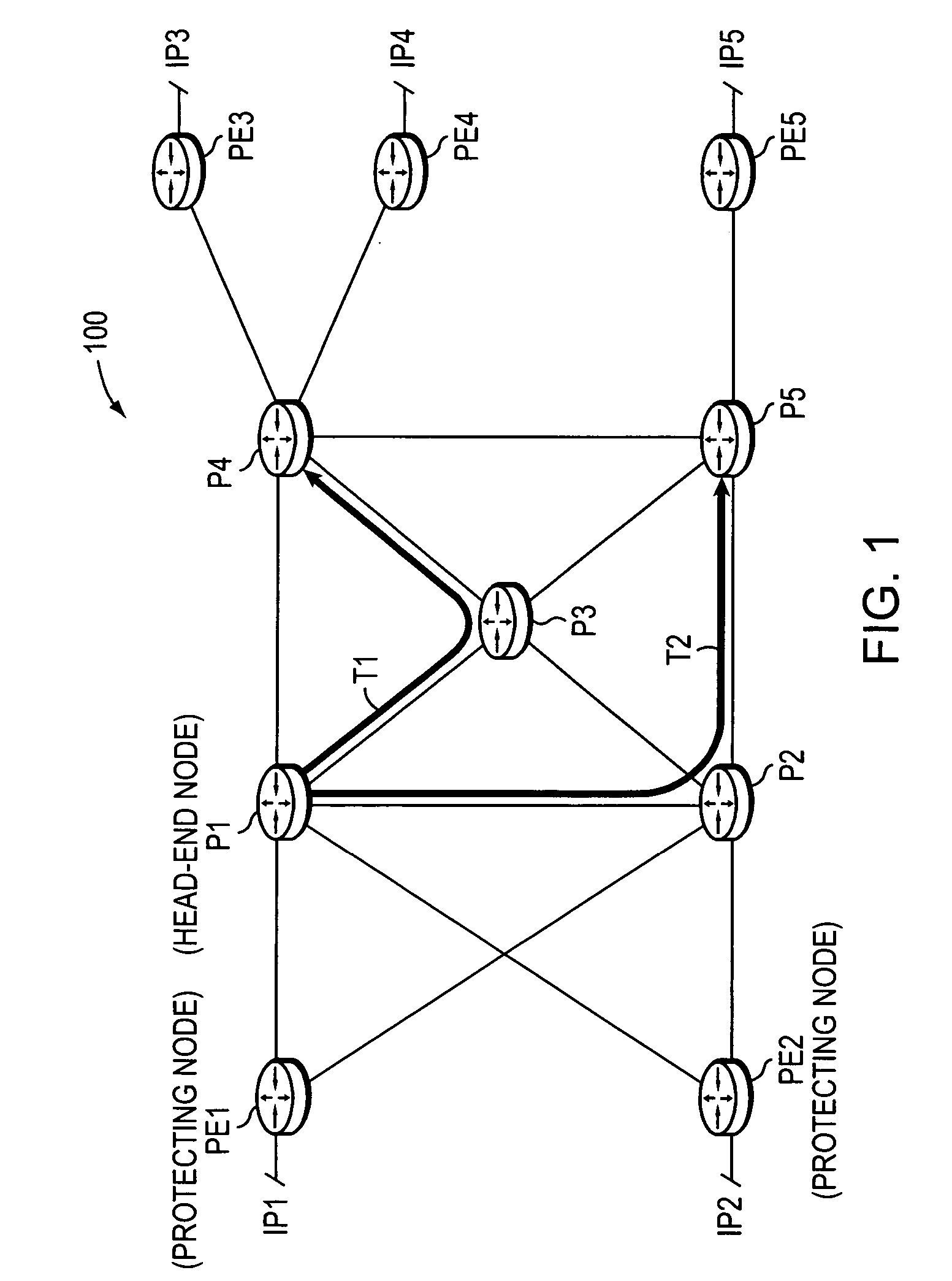
Dynamic protection against failure of a head-end node of one or more TE-LSPs
ActiveUS20070165515A1Preserving scalabilityReduce needError preventionTransmission systemsTraffic capacityLabel switching
A technique dynamically protects against failure of a head-end node of one or more primary Traffic Engineering Label Switched Paths (TE-LSPs) in a computer network. According to the novel technique, a neighboring upstream node (“protecting node”) of the head-end node learns of the primary TE-LSPs (and their respective state control blocks) extending from the head-end node to one or more address prefixes. The protecting node establishes a repair TE-LSP for each of the primary TE-LSPs to a corresponding downstream neighboring node of the head-end node (a “next-next-hop”). In response to detecting a failure of the head-end node, the protecting node locally reroutes traffic destined for the address prefixes to an appropriate repair TE-LSP. Due to the failure of the head-end node, the protecting node then refreshes the states of the primary TE-LSPs using replicated state control blocks accordingly, until the repair TE-LSPs are no longer needed.
Owner:CISCO TECH INC
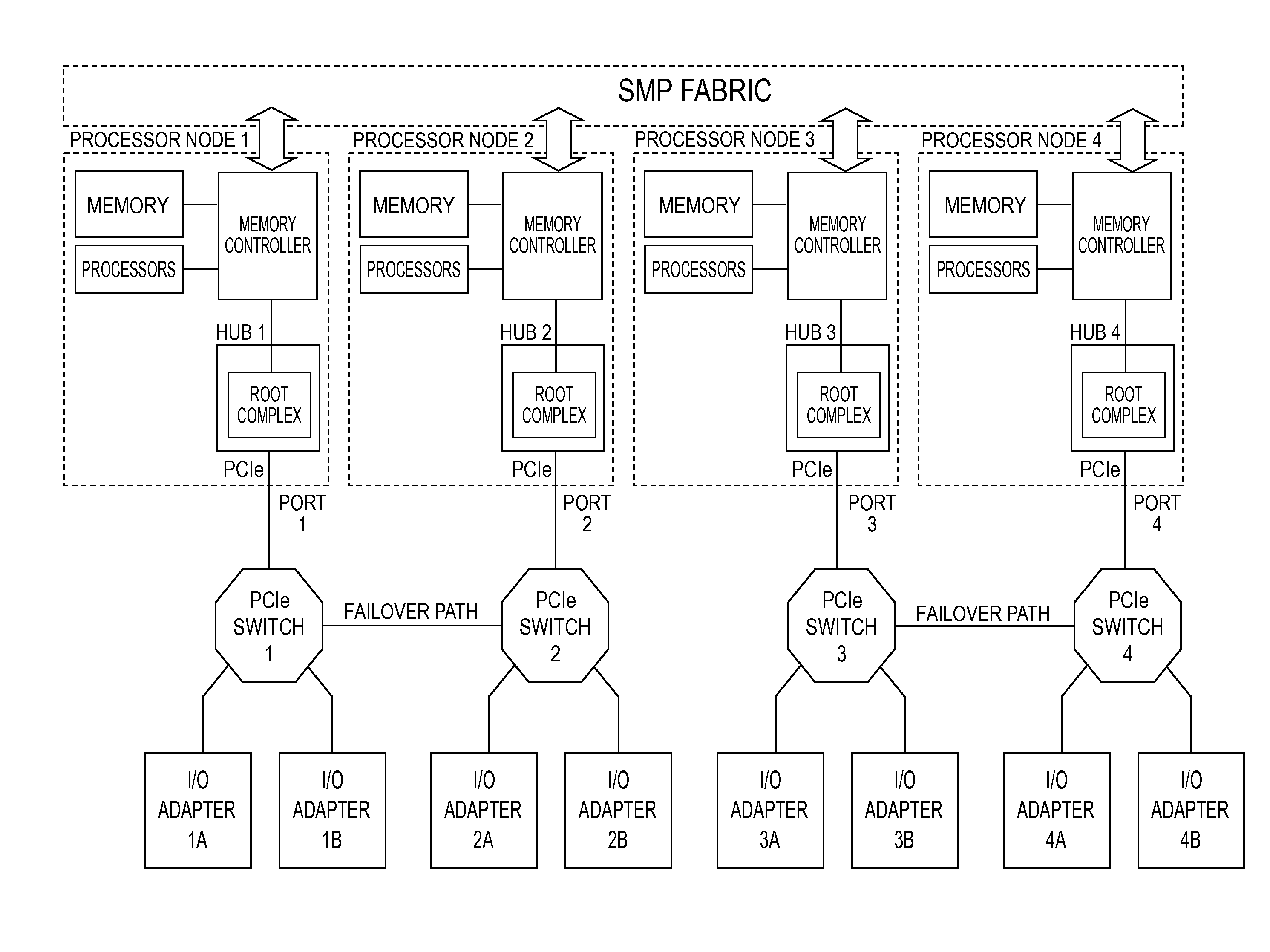
Switch failover control in a multiprocessor computer system
A system and a method for failover control comprising: maintaining a primary device table entry (DTE) in a first table activated for a first adapter in communication with a first processor node having a first root complex via a first switch assembly and maintaining a secondary DTE in standby for a second adapter in communication with a second processor node having a second root complex via a second switch assembly; maintaining a primary DTE in a second table activated for the second adapter and maintaining a secondary DTE in standby for the first adapter; and upon a failover, updating the secondary DTE in the first table as an active entry for the second adapter and forming a path to enable traffic to route from the second adapter through the second switch assembly over to the first switch assembly and up to the first root complex of the first processor node.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com