Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1790 results about "Multi protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
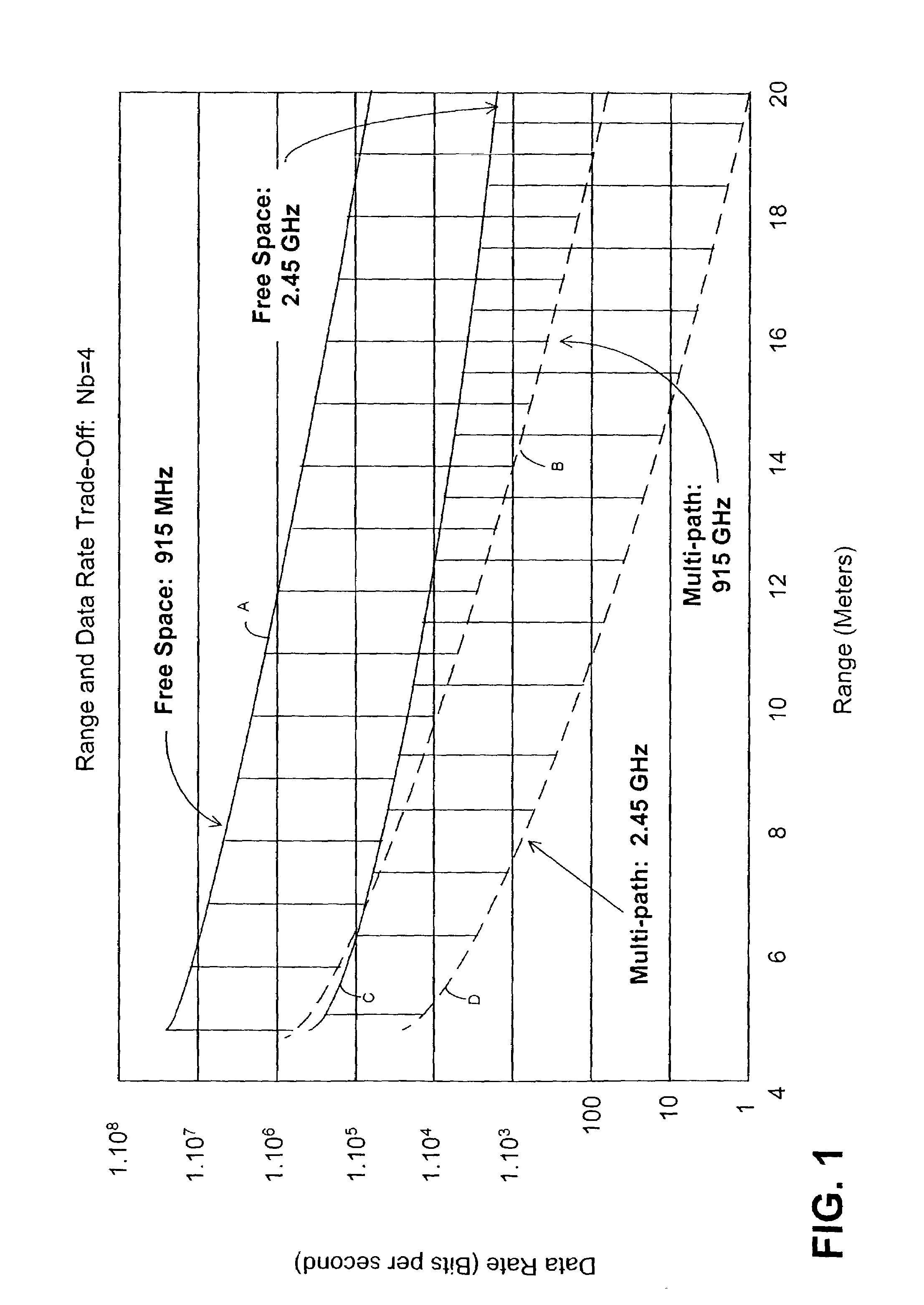
CCNA v6.0 Multi-Protocol Label Switching (MPLS) Explained with Examples. What is Multi-Protocol Label Switching (MPLS)? Multiprotocol Label Switching (MPLS) is a type of network data traffic technique which carries data from one network device to the next using short path labels instead of long and complex network router lookups in a routing table.
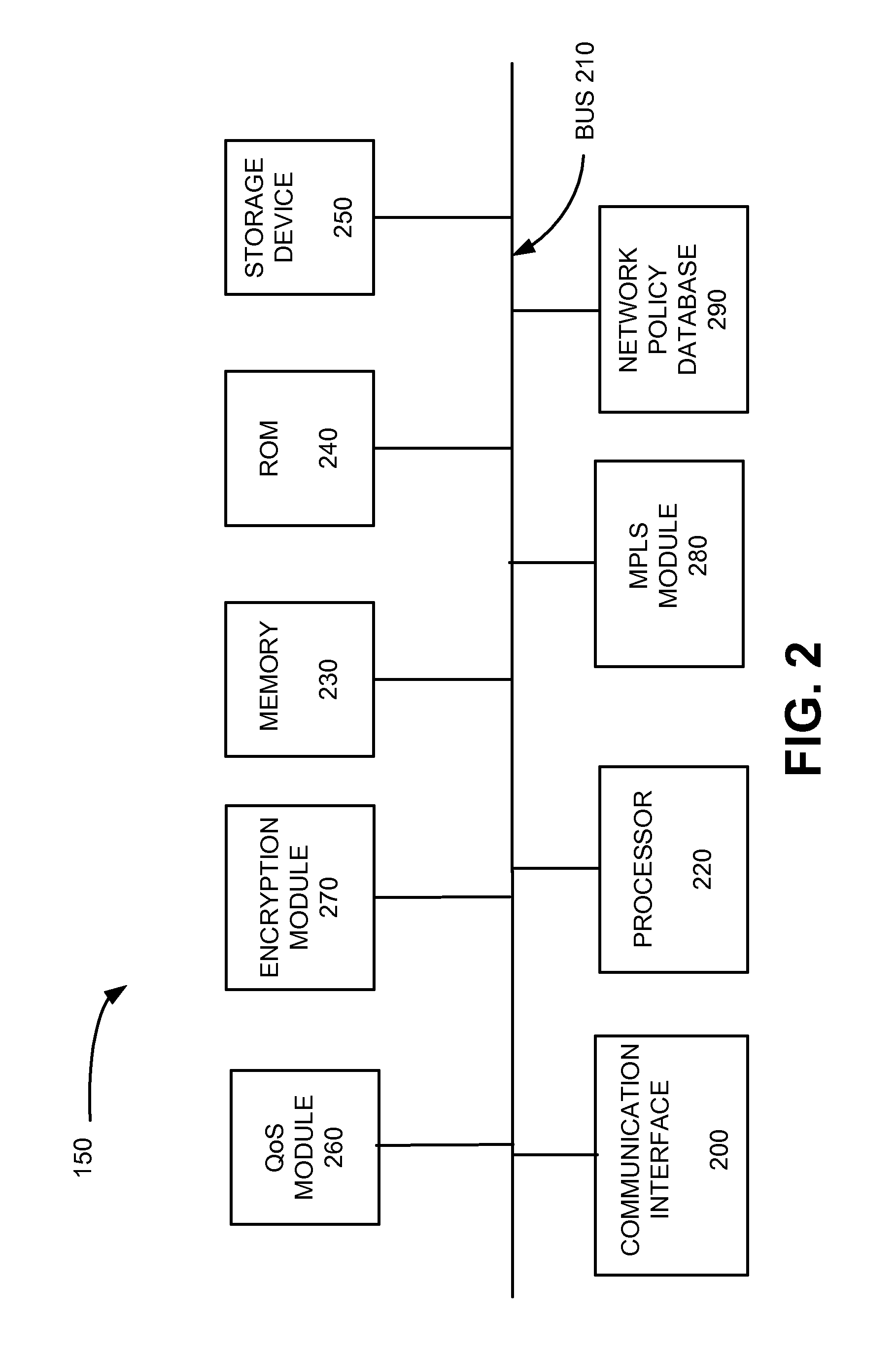
Software control plane for switches and routers
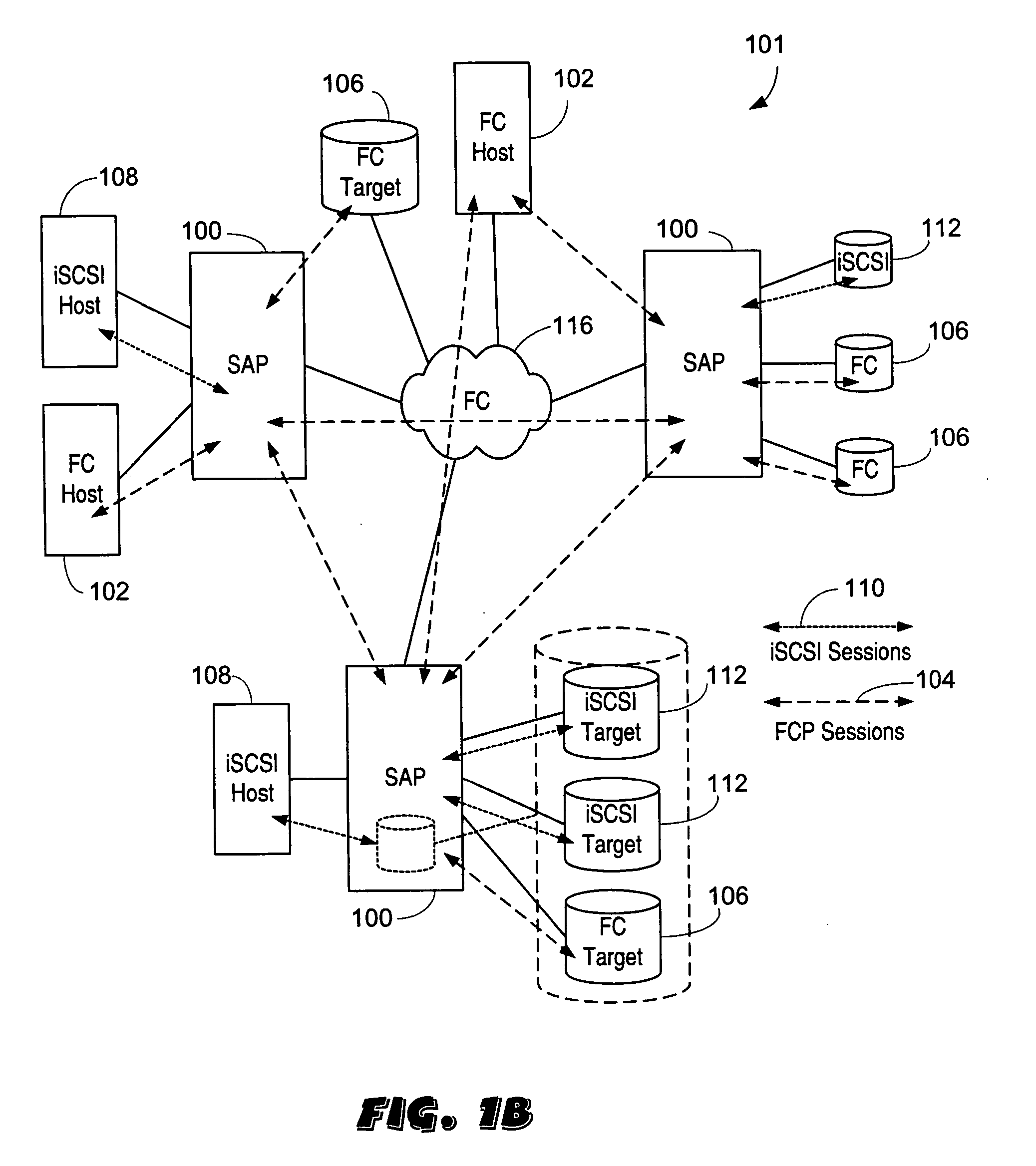
ActiveUS20080219268A1Bridging the gapImprove convenienceError preventionTransmission systemsQuality of serviceAbstraction layer
A Provider Network Controller (PNC) addresses the challenges in building services across Next Generation Network (NGN) architectures and creates an abstraction layer as a bridge, or glue, between the network transport and applications running over it. The PNC is a multi-layer, multi-vendor dynamic control plane that implements service activation and Layer 0-2 management tools for multiple transport technologies including Carrier Ethernet, Provider Backbone Transport (PBT), Multi-protocol Label Switching (MPLS), Transport MPLS (T-MPLS), optical and integrated networking platforms. Decoupling transport controls and services from the network equipment simplifies service creation and provides options for carriers to choose best-in-class equipment that leverages the PNC to enable rapid creation and management of transports and services. The PNC provides Service-Oriented Architecture (SOA) interfaces to abstract transport objects expressly designed to support both wholesale and retail services, and supports service offerings with varied bandwidth and Quality of Service (QoS) requirements, thus achieving enterprise Ethernet economics.
Owner:EXTREME NETWORKS INC
System and method for providing transformation of multi-protocol packets in a data stream
InactiveUS6944168B2Time-division multiplexData switching by path configurationStreaming dataData stream
A system and method for facilitating packet transformation of multi-protocol, multi-flow, streaming data. Packet portions subject to change are temporarily stored, and acted upon through processing of protocol-dependent instructions, resulting in a protocol-dependent modification of the temporarily stored packet information. Validity tags are associated with different segments of the temporarily-stored packet, where the state of each tag determines whether its corresponding packet segment will form part of the resulting modified packet. Only those packet segments identified as being part of the resulting modified packet are reassembled prior to dispatch of the packet.
Owner:RPX CORP
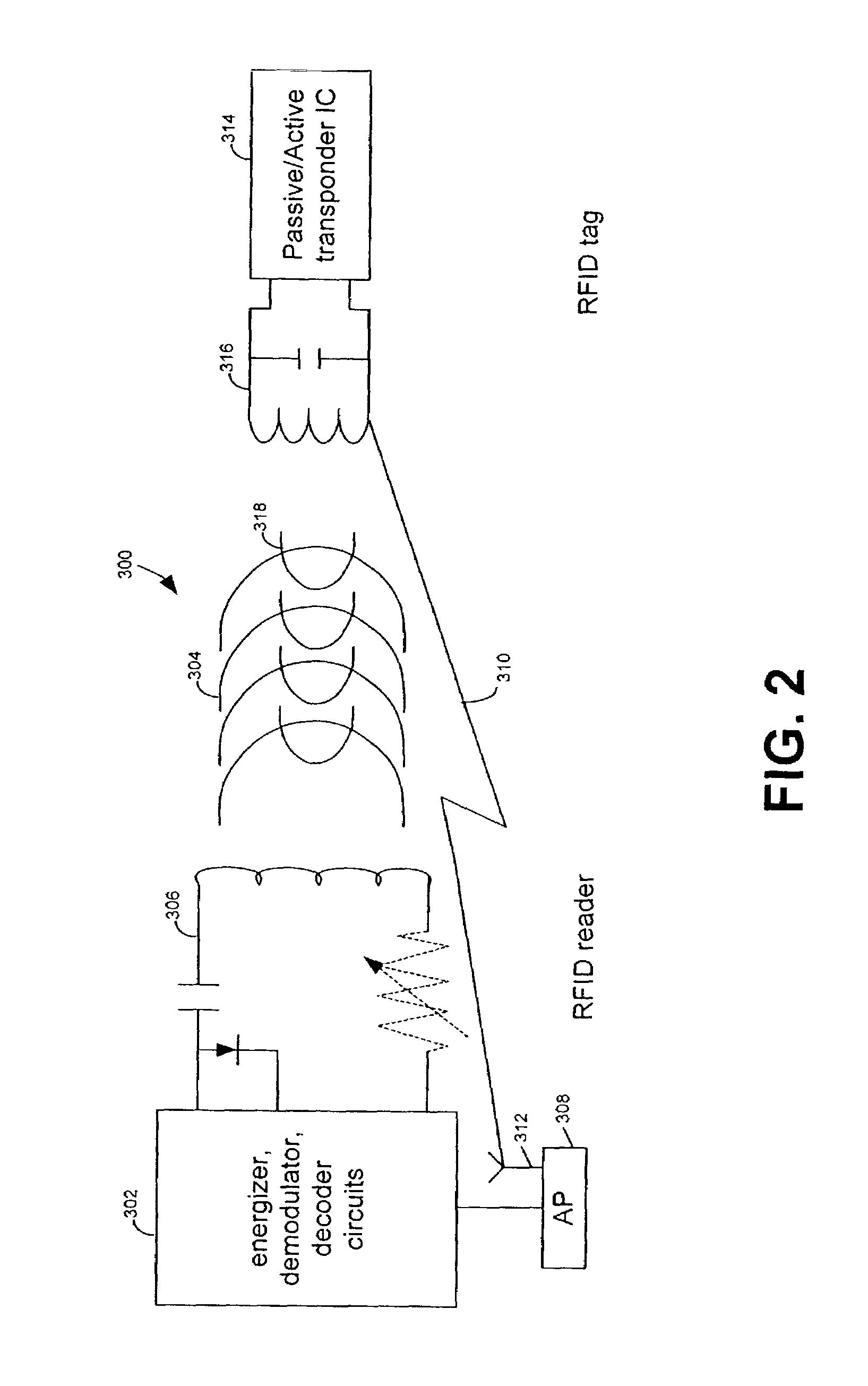
Diagnostic radio frequency identification sensors and applications thereof
ActiveUS20060290496A1Low costDevices with bluetooth interfacesBurglar alarm mechanical actuationPower sensorPoint of care
An integrated passive wireless chip diagnostic sensor system is described that can be interrogated remotely with a wireless device such as a modified cell phone incorporating multi-protocol RFID reader capabilities (such as the emerging Gen-2 standard) or Bluetooth, providing universal easy to use, low cost and immediate quantitative analyses, geolocation and sensor networking capabilities to users of the technology. The present invention can be integrated into various diagnostic platforms and is applicable for use with low power sensors such as thin films, MEMS, electrochemical, thermal, resistive, nano or microfluidic sensor technologies. Applications of the present invention include on-the-spot medical and self-diagnostics on smart skin patches, Point of Care (POC) analyses, food diagnostics, pathogen detection, disease-specific wireless biomarker detection, remote structural stresses detection and sensor networks for industrial or Homeland Security using low cost wireless devices such as modified cell phones.
Owner:ALTIVERA
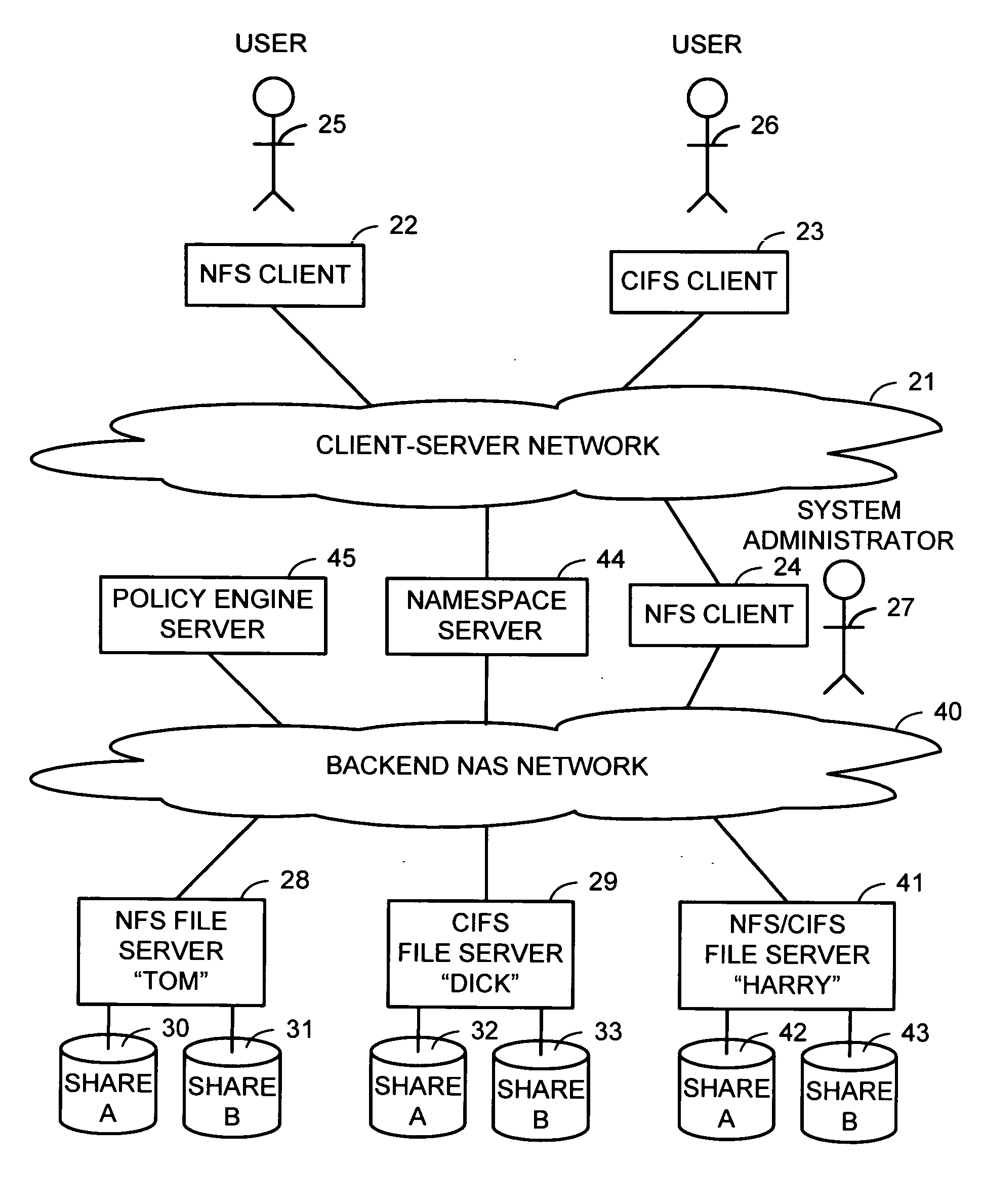
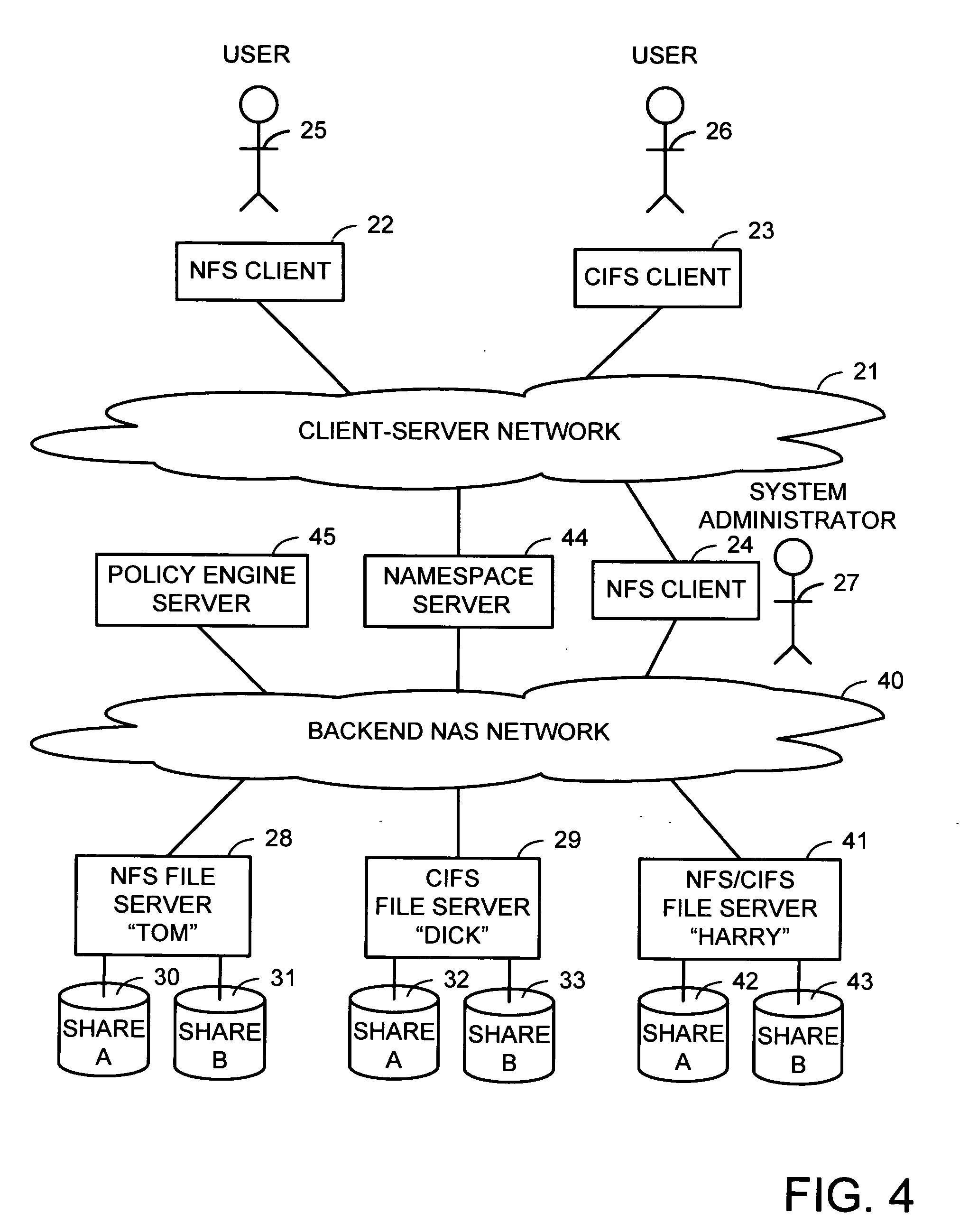
Intelligent network client for multi-protocol namespace redirection
InactiveUS20070088702A1Multiple digital computer combinationsTransmissionIntelligent NetworkEngineering
An intelligent network client has the capability of accessing a first network server in accordance with a first high-level file access protocol, and responding to a redirection reply from the first network server by accessing a second network server in accordance with a second high-level file access protocol. For example, the intelligent network client can be redirected from a CIFS / DFS server to a NFS server, and from an NFSv4 server to a CIFS server. Once redirected, the intelligent network client performs a directory mounting operation so that a subsequent client access to the same directory goes directly to the second network server. For example, the first network server is a namespace server for translating pathnames in a client-server network namespace into pathnames in a NAS network namespace, and the second network server is a file server in the NAS network namespace.
Owner:EMC CORP
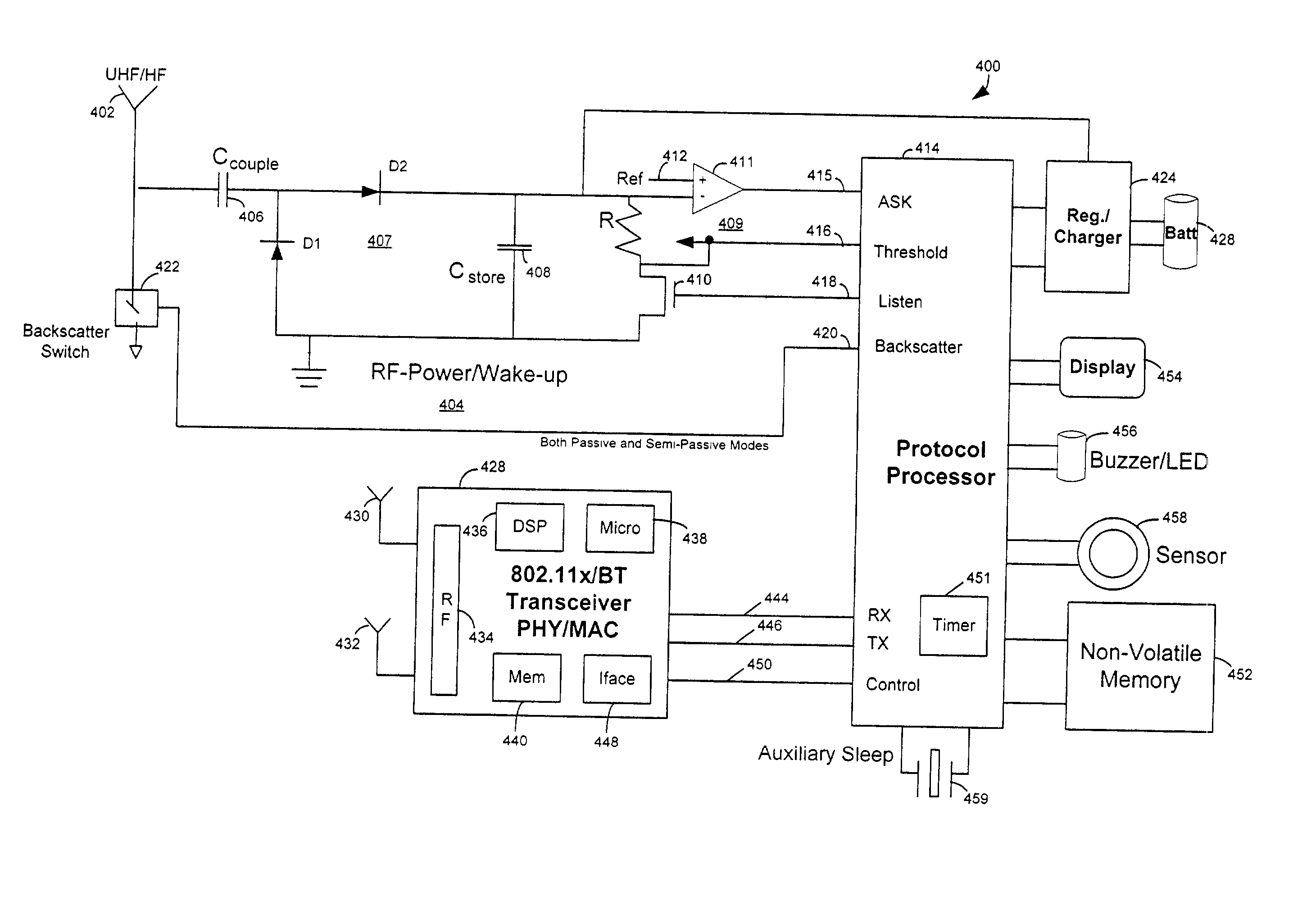
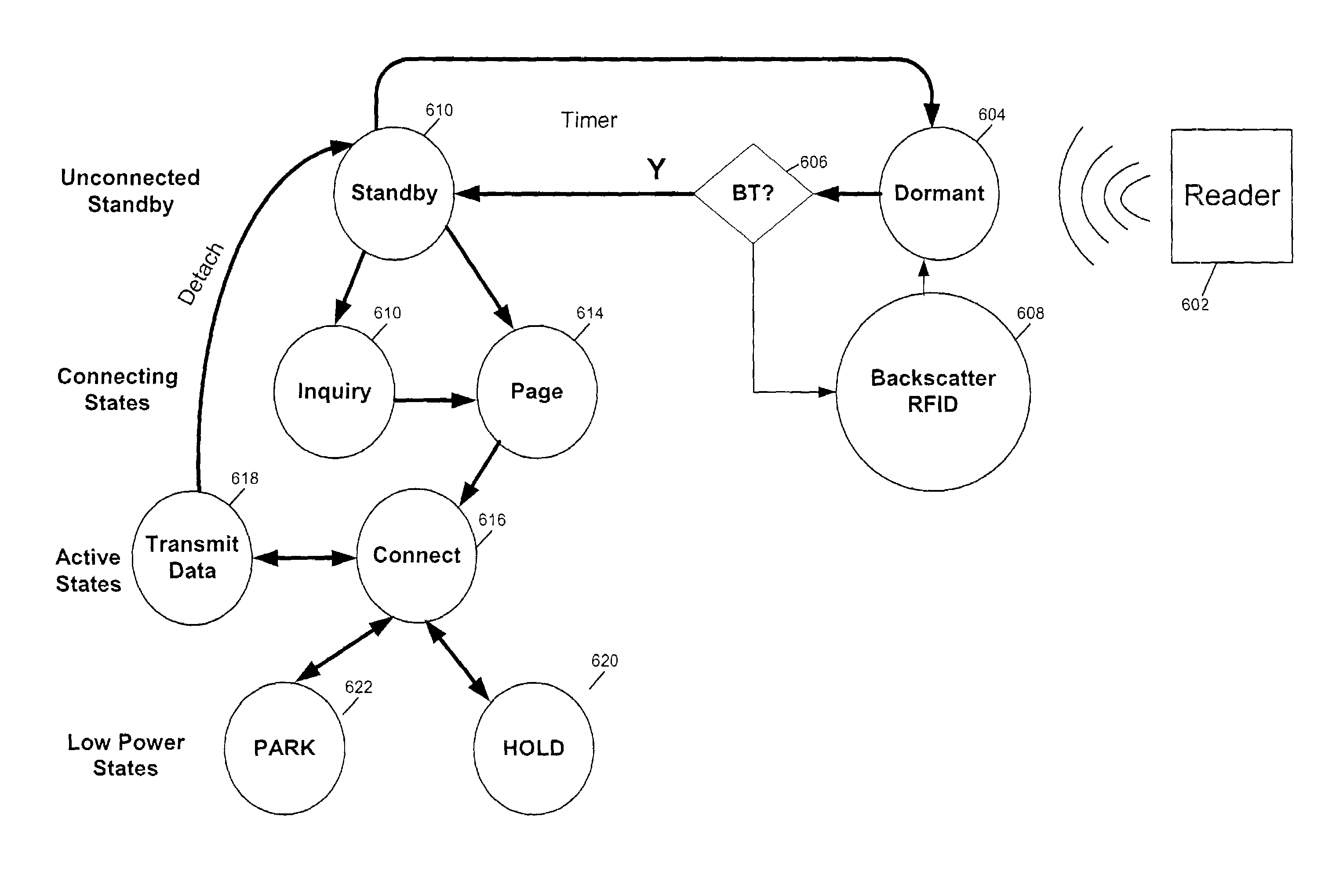
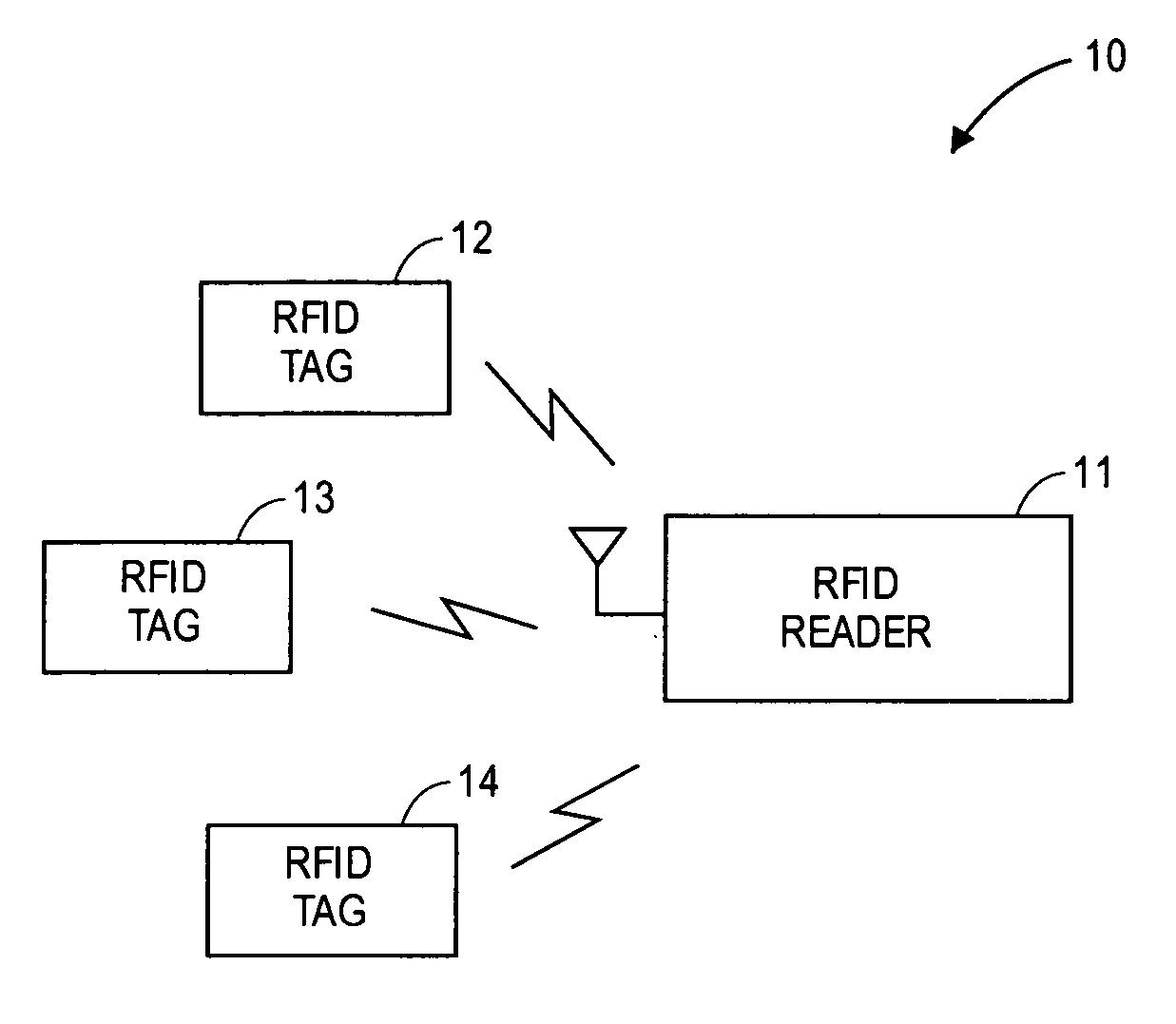
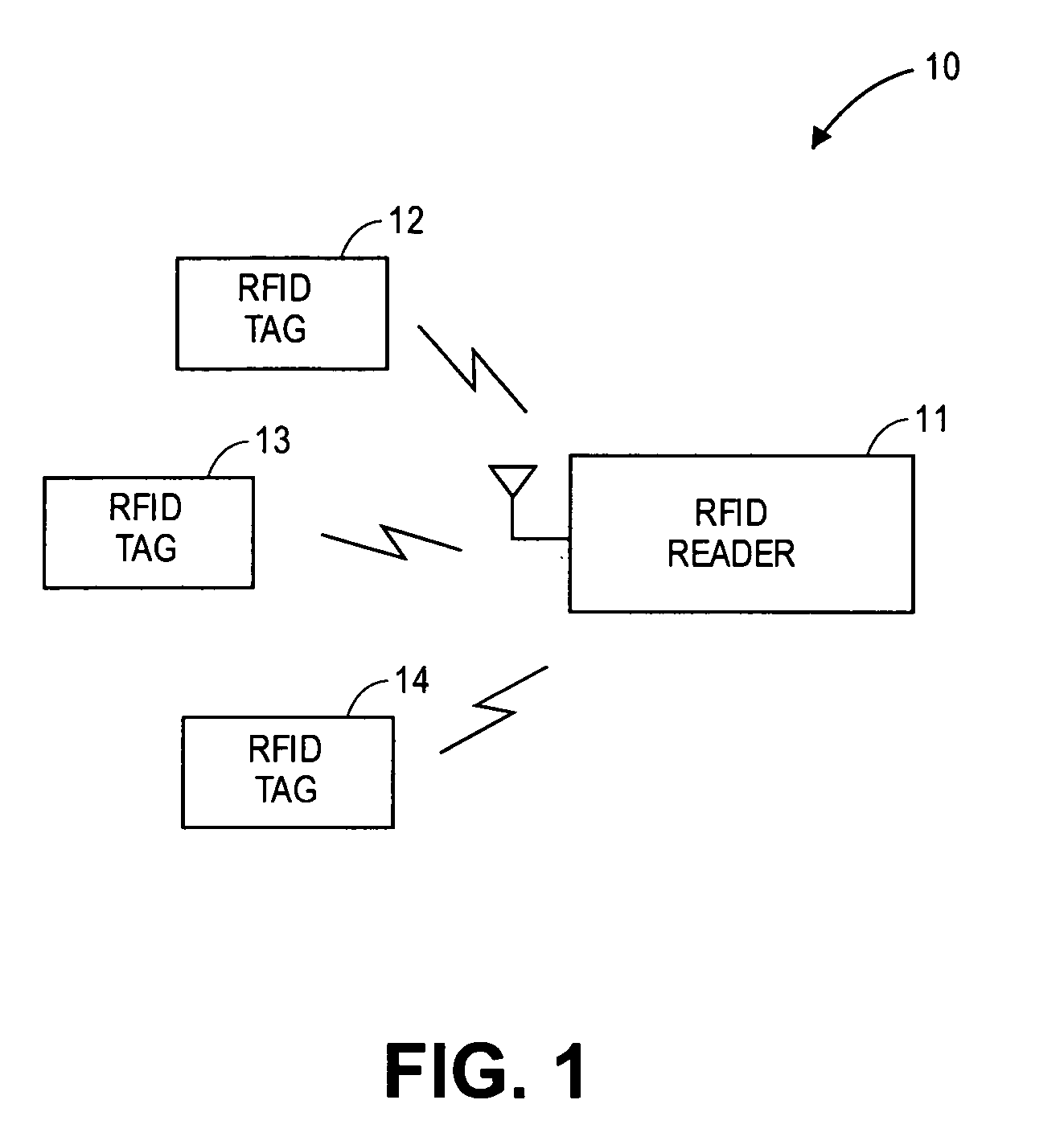
RFID device, system and method of operation including a hybrid backscatter-based RFID tag protocol compatible with RFID, bluetooth and/or IEEE 802.11x infrastructure
ActiveUS20030104848A1Near-field transmissionMemory record carrier reading problemsTransceiverAntenna impedance
An RFID system includes a hybrid backscatter-based RFID tag protocol-compatible with existing 802.11x / Bluetooth Standards as well as RFID standards. The tag is linked to a multi-protocol Interrogator via a generated RF Continuous Wave (CW) field. The tag includes an antenna coupled to an RFID and a Bluetooth / 802.11x transceiver section. A Protocol Processor services RFID and transceiver sections and is coupled to the antenna via a backscatter switch. The Interrogator can switch the tag to an RFID backscatter radiation mode where the processor switches the antenna impedance to reflect the CW signal. For transceiver operation the processor switches antenna impedance in synchronization with a frame organized bit stream. For reception, the RFID section utilizes demodulation techniques, typically Amplitude Shift Keying (ASK), and provides a wake up mode within a predetermined distance of the Interrogator. The transceiver may operate in a backscatter or regular mode as directed by an Access Point.
Owner:GOOGLE TECH HLDG LLC
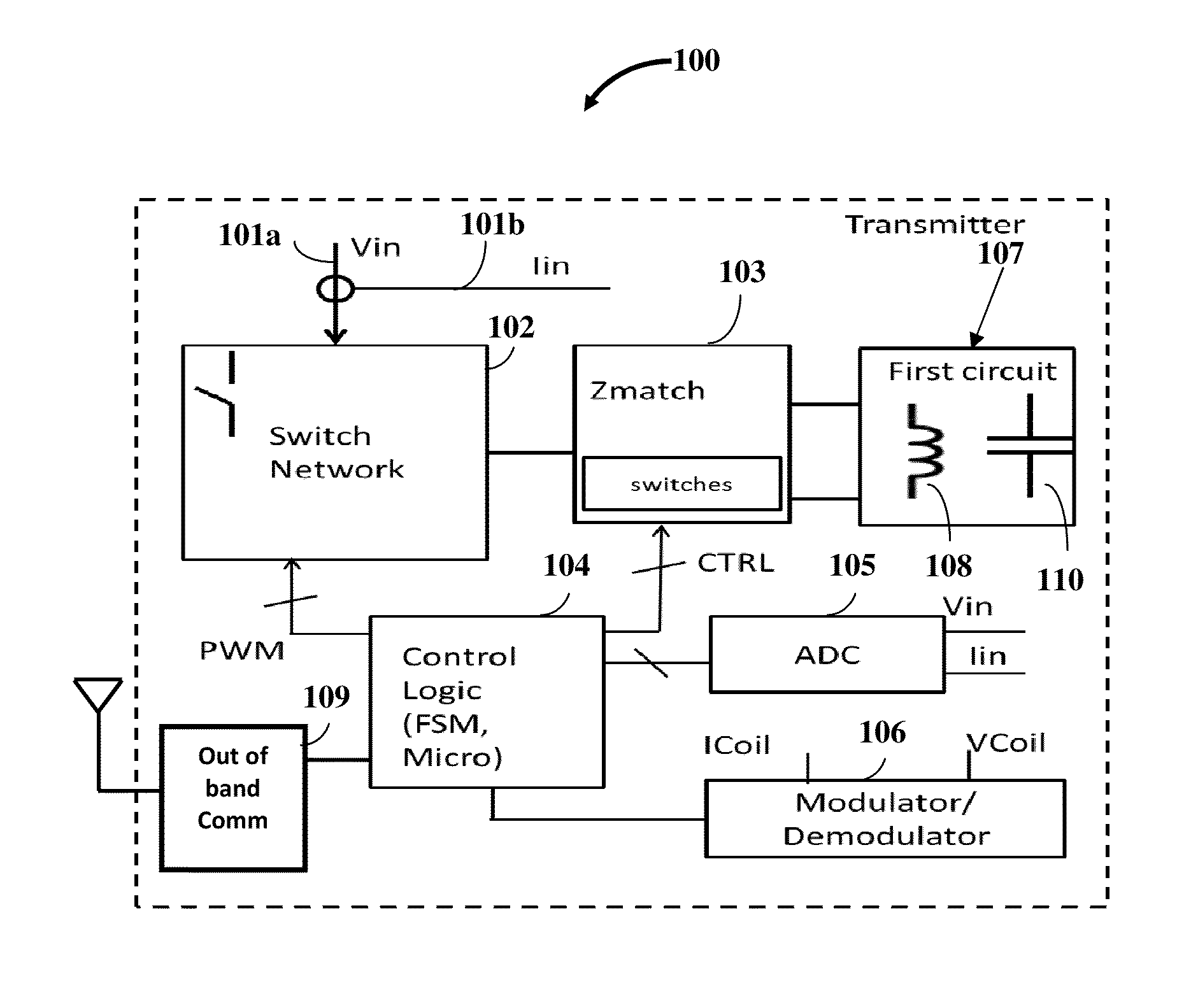
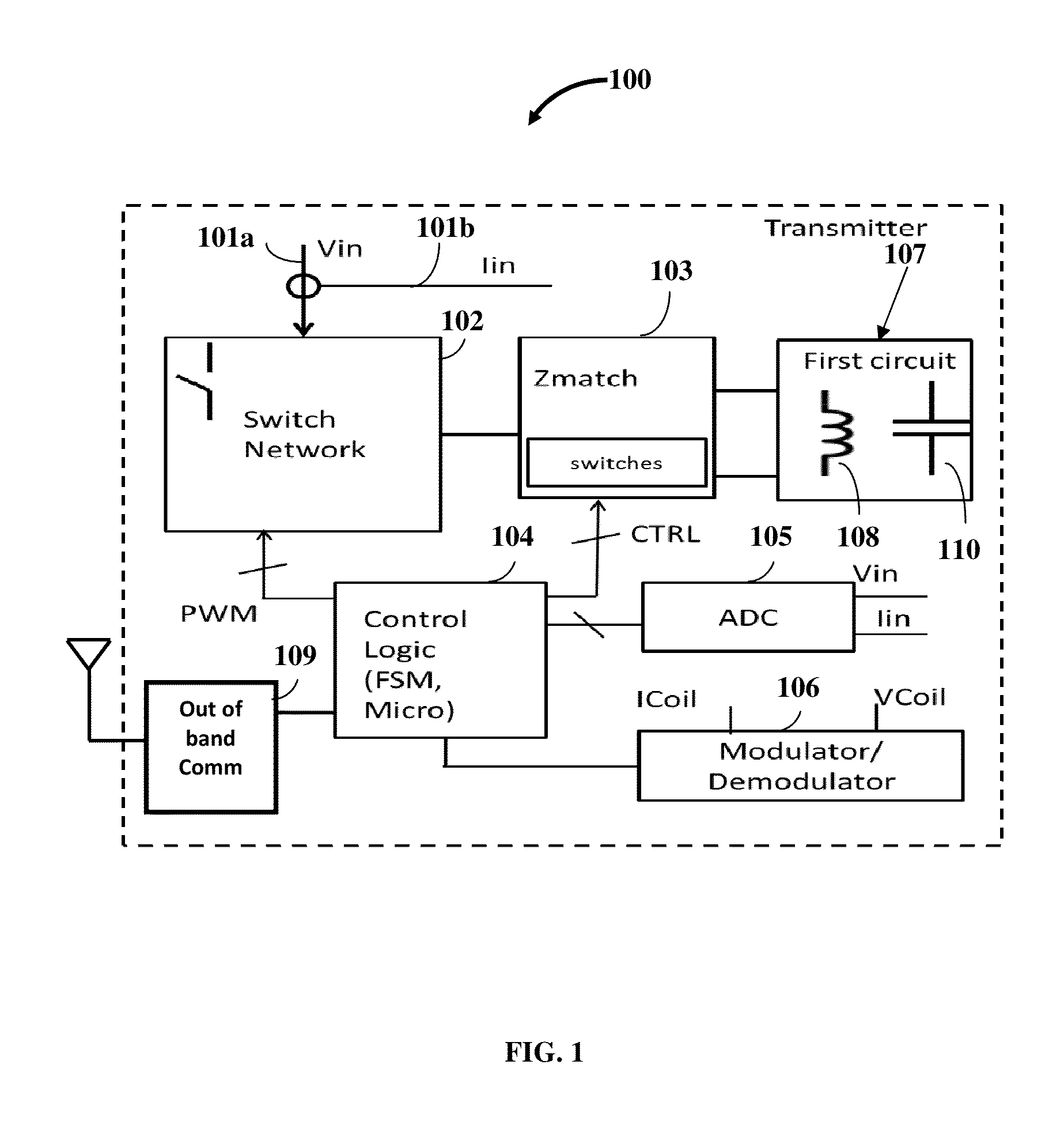
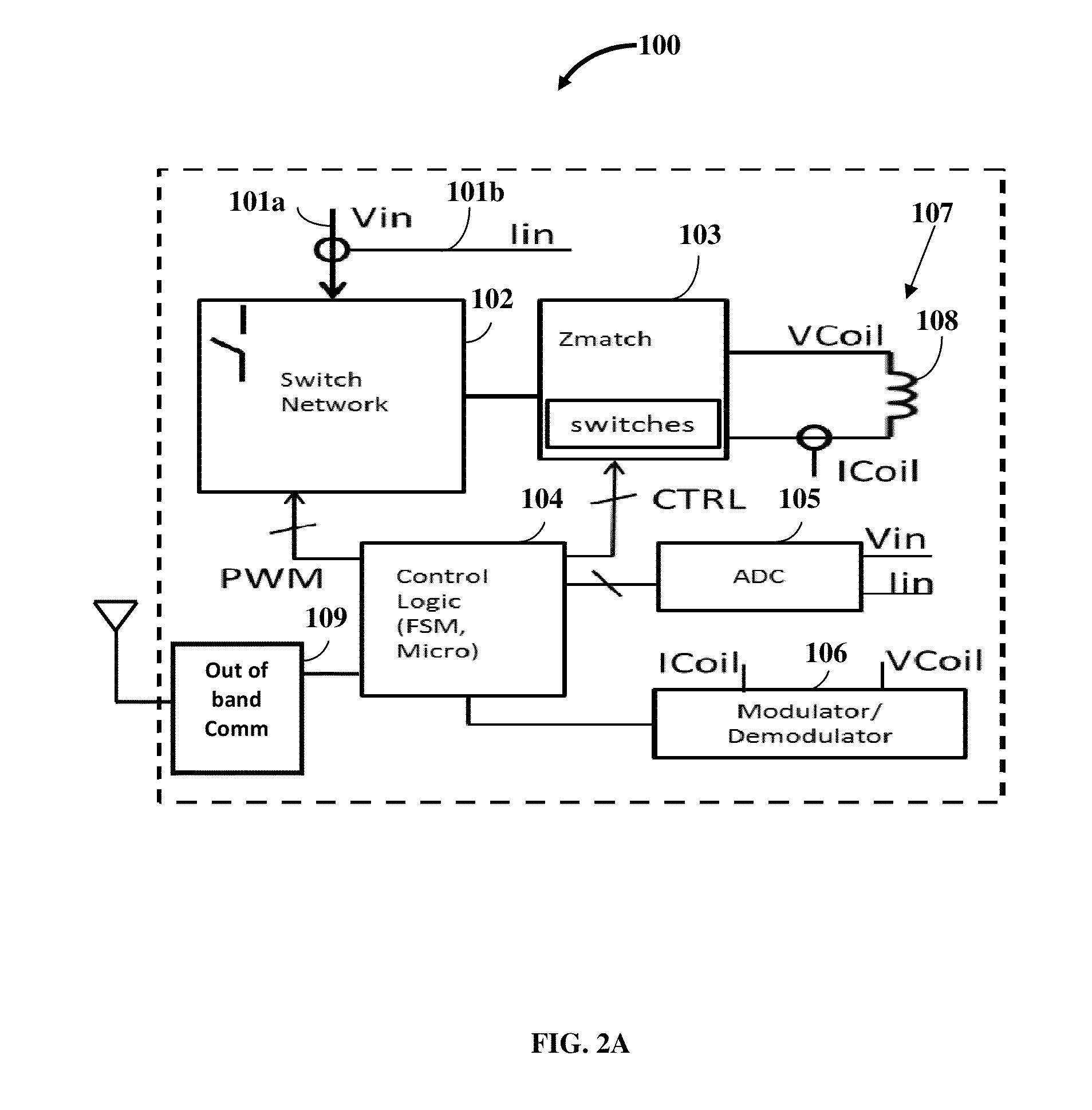
Multi-mode Multi-coupling Multi-protocol Ubiquitous Wireless Power Transmitter
InactiveUS20140139034A1Transmit power can be effectivelyGuaranteed normal transmissionBatteries circuit arrangementsElectromagnetic wave systemExchange networkTransmitted power
A multi-mode multi-coupling multi-protocol wireless power transmitter (WPT) and its embodiments transmit power to a wireless power receiver (WPR) in a power transfer mode (PTM) and a wireless power protocol (WPP) of the WPR. A first circuit of the WPT includes inductors or capacitors emanating power via a magnetic field or electric field PTM respectively. The WPT sequentially parses a test condition to identify a PTM, a power coupling linkage (PCL) between the WPT and the WPR, and a WPP of the WPR. The WPT identifies a match if the PTM of the first circuit and the WPP of the switch network, the variable matching circuit, a modulator / demodulator block or an out-of-band communication block, and a control logic circuit of the WPT match the PTM and the WPP of the WPR to transmit power to the WPR based on the match.
Owner:WIPQTUS
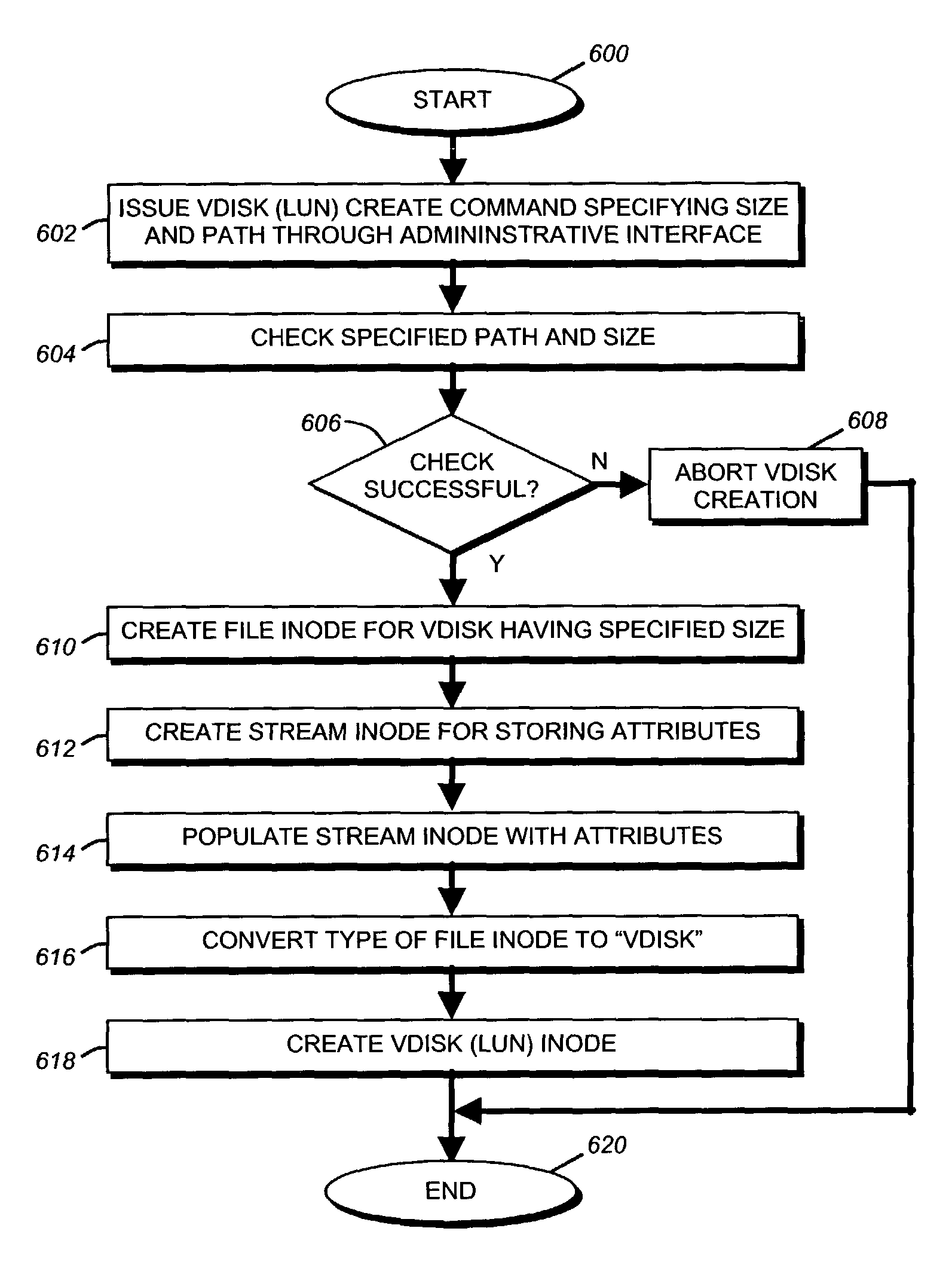
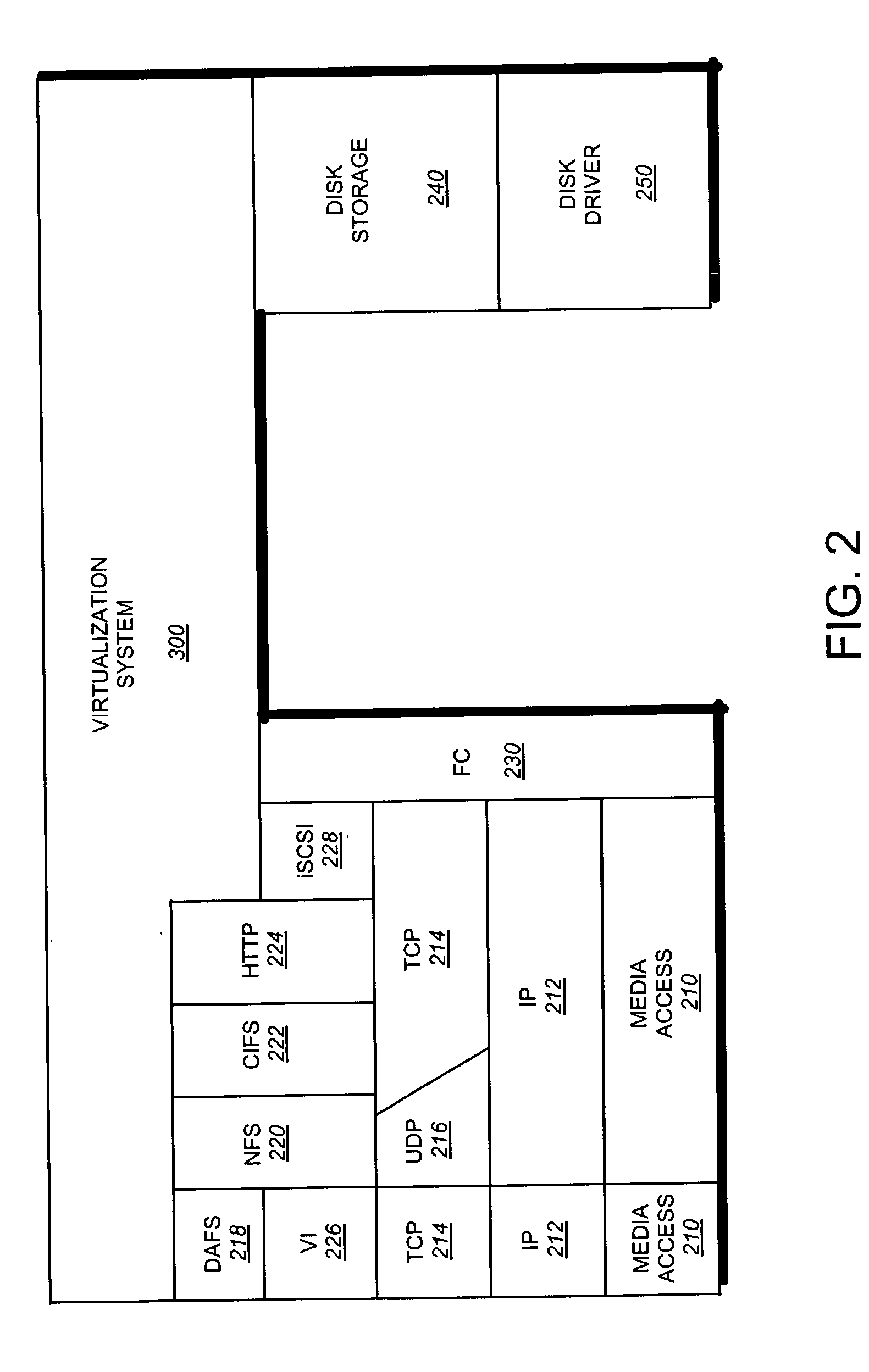
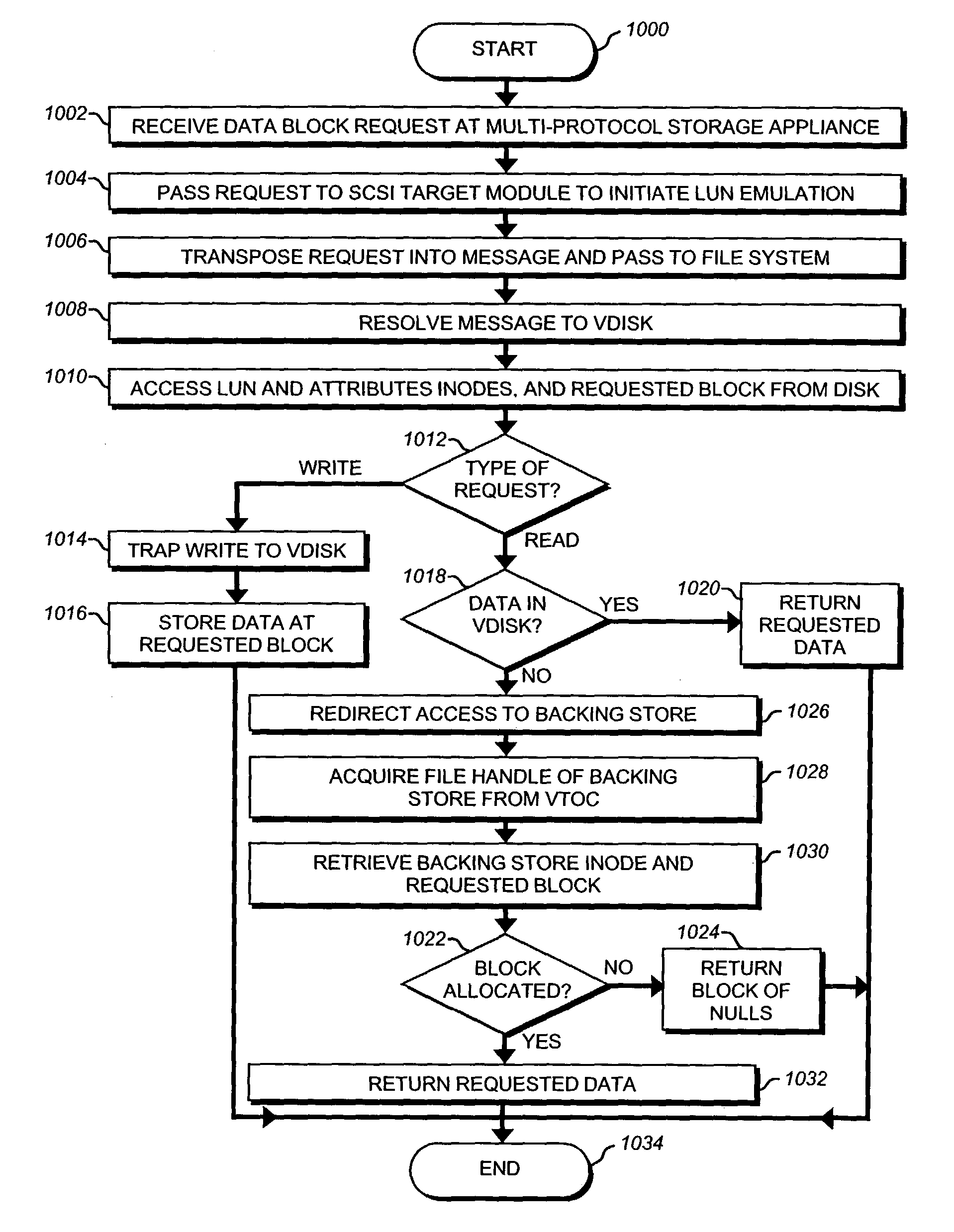
Storage virtualization by layering virtual disk objects on a file system
InactiveUS7107385B2Input/output to record carriersData processing applicationsOperational systemFile system
A storage virtualization selection technique “automates” a virtualization selection process to create virtual disk (vdisk) storage objects over a volume of a file system implemented by a storage operating system of a multi-protocol storage appliance. The file system provides a virtualization system that aggregates physical storage of a set of disks or portions (e.g., extents) of disks into a pool of blocks that can be dynamically allocated to form a vdisk. The file system also provides reliability guarantees for the vdisks in accordance with its underlying architecture. That is, the file system organizes its storage within volumes created among the managed disks. The vdisk is thereafter created as a storage object within a volume and, thus, inherits the underlying reliability configuration associated with that volume. The portions are aggregated and allocated as a vdisk with reliability guarantees in response to a request to create the vdisk from a user of the storage appliance and without further user involvement.
Owner:NETWORK APPLIANCE INC
RFID device, system and method of operation including a hybrid backscatter-based RFID tag protocol compatible with RFID, bluetooth and/or IEEE 802.11x infrastructure
ActiveUS7215976B2Near-field transmissionMemory record carrier reading problemsTransceiverAntenna impedance
Owner:GOOGLE TECHNOLOGY HOLDINGS LLC
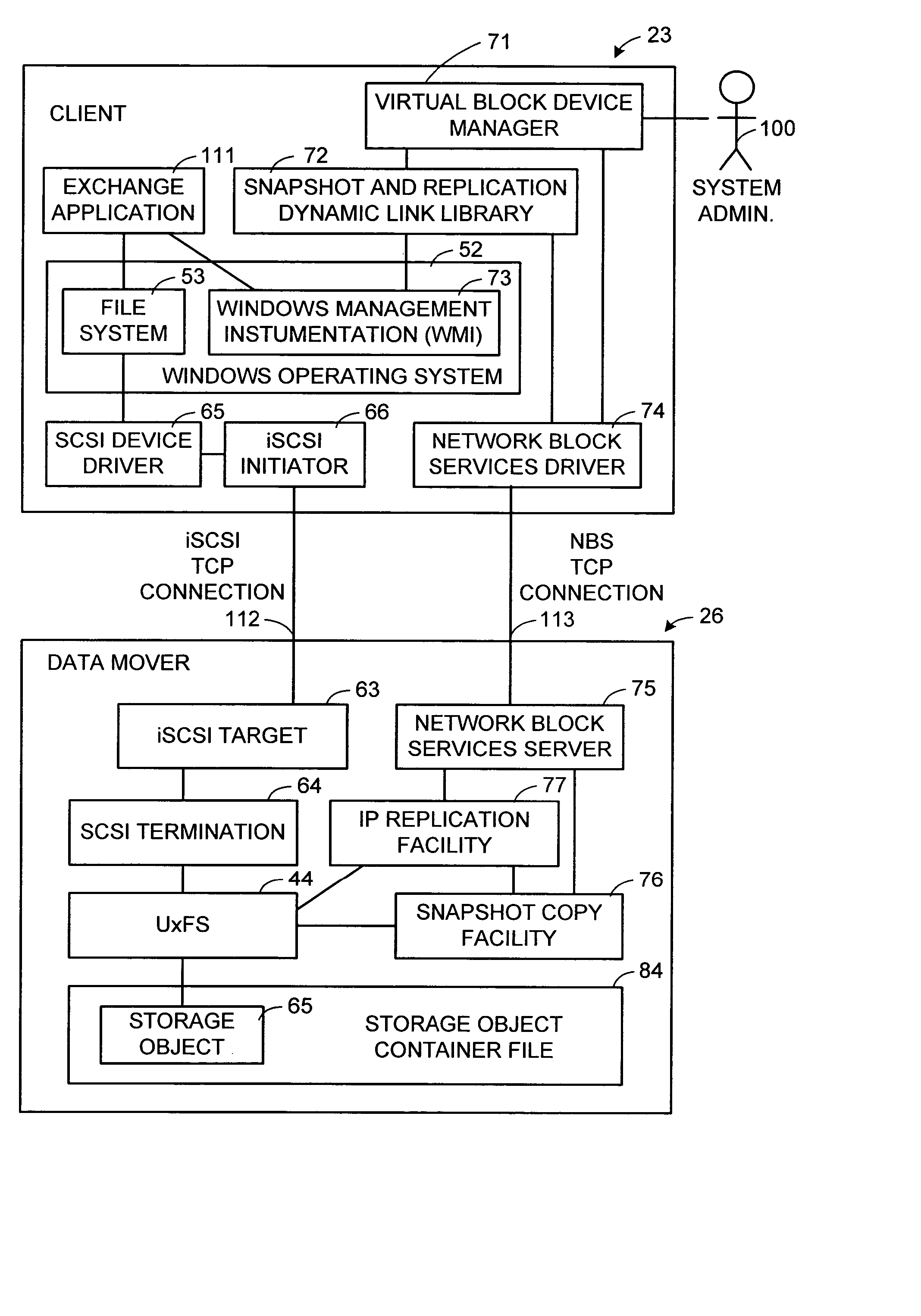
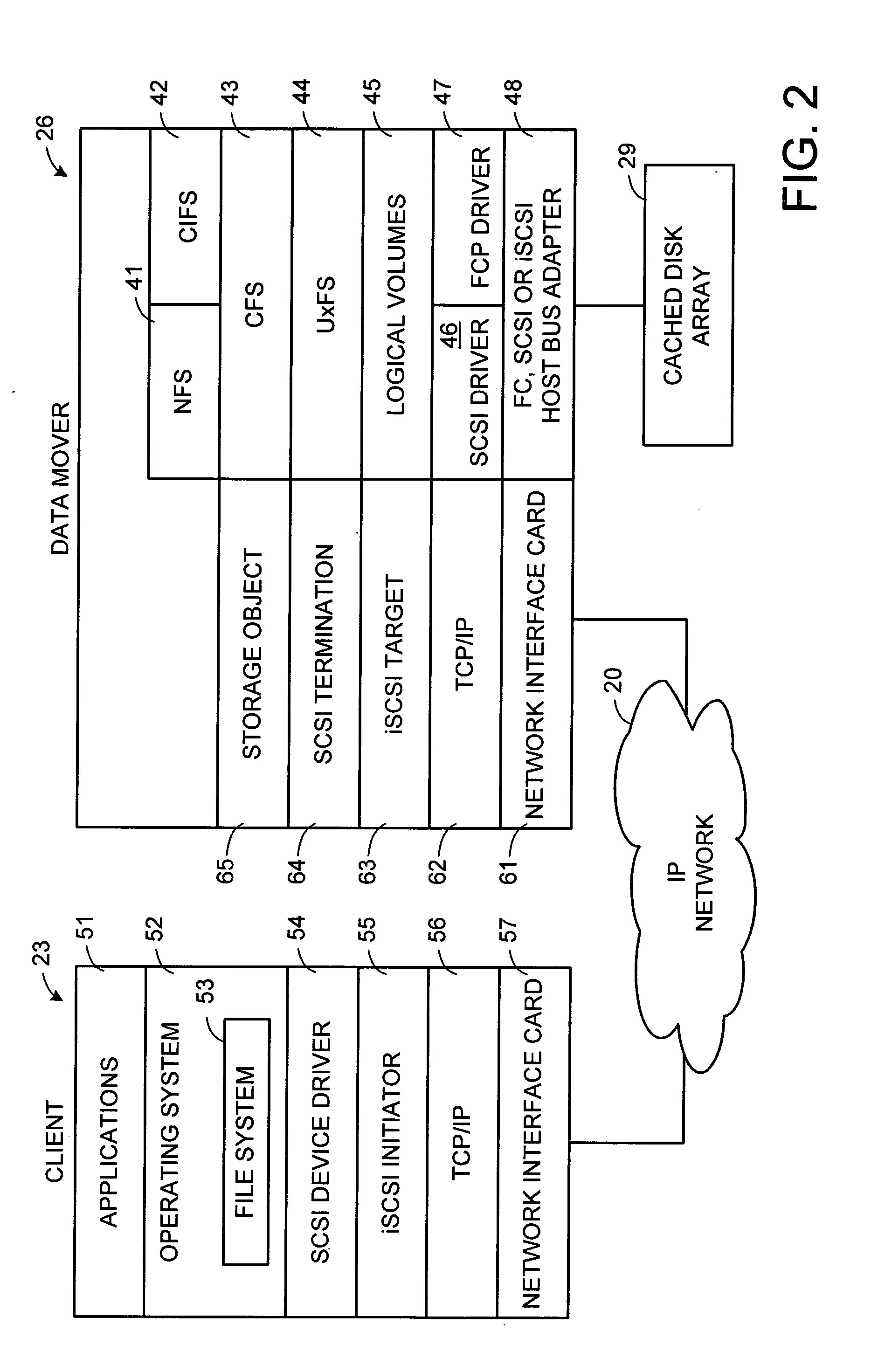
Multi-protocol sharable virtual storage objects
ActiveUS20050044162A1Digital data processing detailsMultiple digital computer combinationsUnixFile replication
A storage object such as a virtual disk drive or a raw logical volume is contained in a UNIX compatible file so that the file containing the storage object can be exported using the NFS or CIFS protocol and shared among UNIX and MS Windows clients or servers. The storage object can be replicated and backed up using conventional file replication and backup facilities without disruption of client access to the storage object. For client access to data of the storage object, a software driver accesses the file containing the storage object. For example, a software driver called a virtual SCSI termination is used to access a file containing a virtual SCSI disk drive. Standard storage services use the iSCSI protocol to access the virtual SCSI termination. An IP replication or snapshot copy facility may access the file containing the virtual SCSI disk drive using a higher-level protocol.
Owner:EMC IP HLDG CO LLC
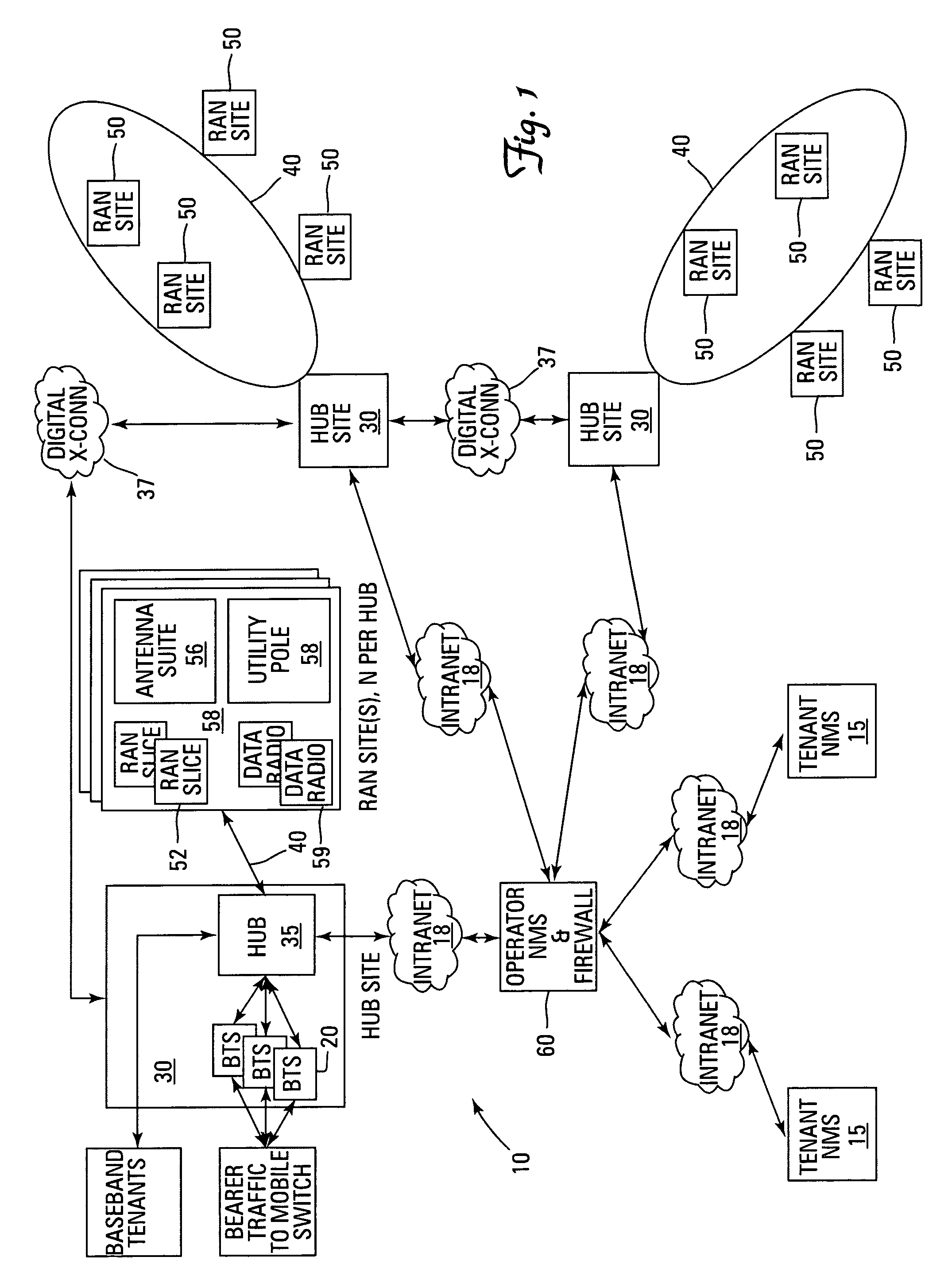
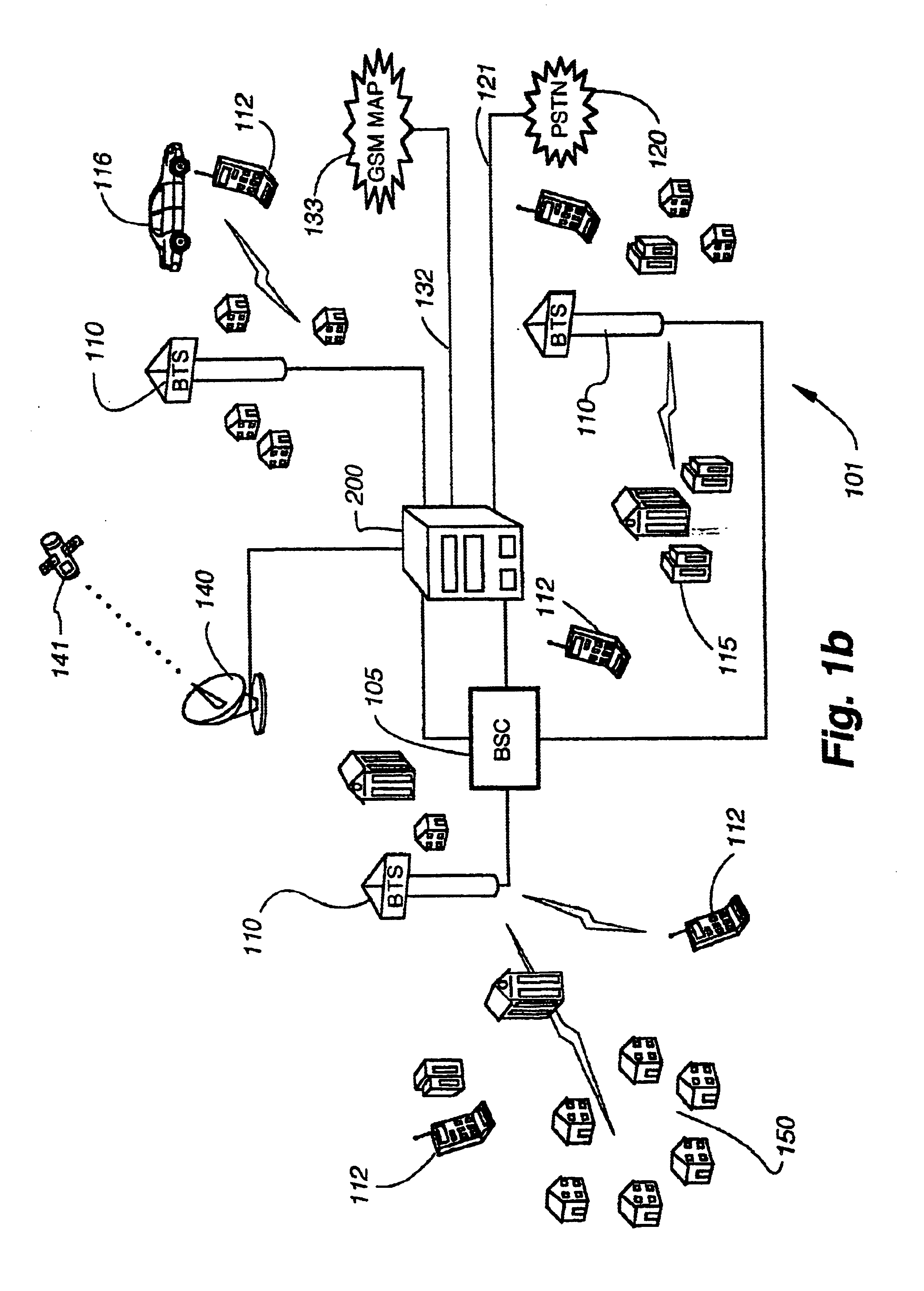
Multi-protocol distributed wireless system architecture
InactiveUS6963552B2Easy to shareRadio/inductive link selection arrangementsWireless commuication servicesAir interfaceDistribution system
An open access signal distribution system in which a variety of wireless voice, data and other services and applications are supported. The open access system makes use of a distributed Radio Frequency (RF) distribution network and associated network entities that enable the system operator to employ a wireless infrastructure network that may be easily shared among multiple wireless service providers in a given community. The open access system provides the ability for such operators and service providers to share the infrastructure regardless of the specific RF air interface or other signal formatting and / or managing messaging formats that such operators choose to deploy.
Owner:COMMSCOPE TECH LLC
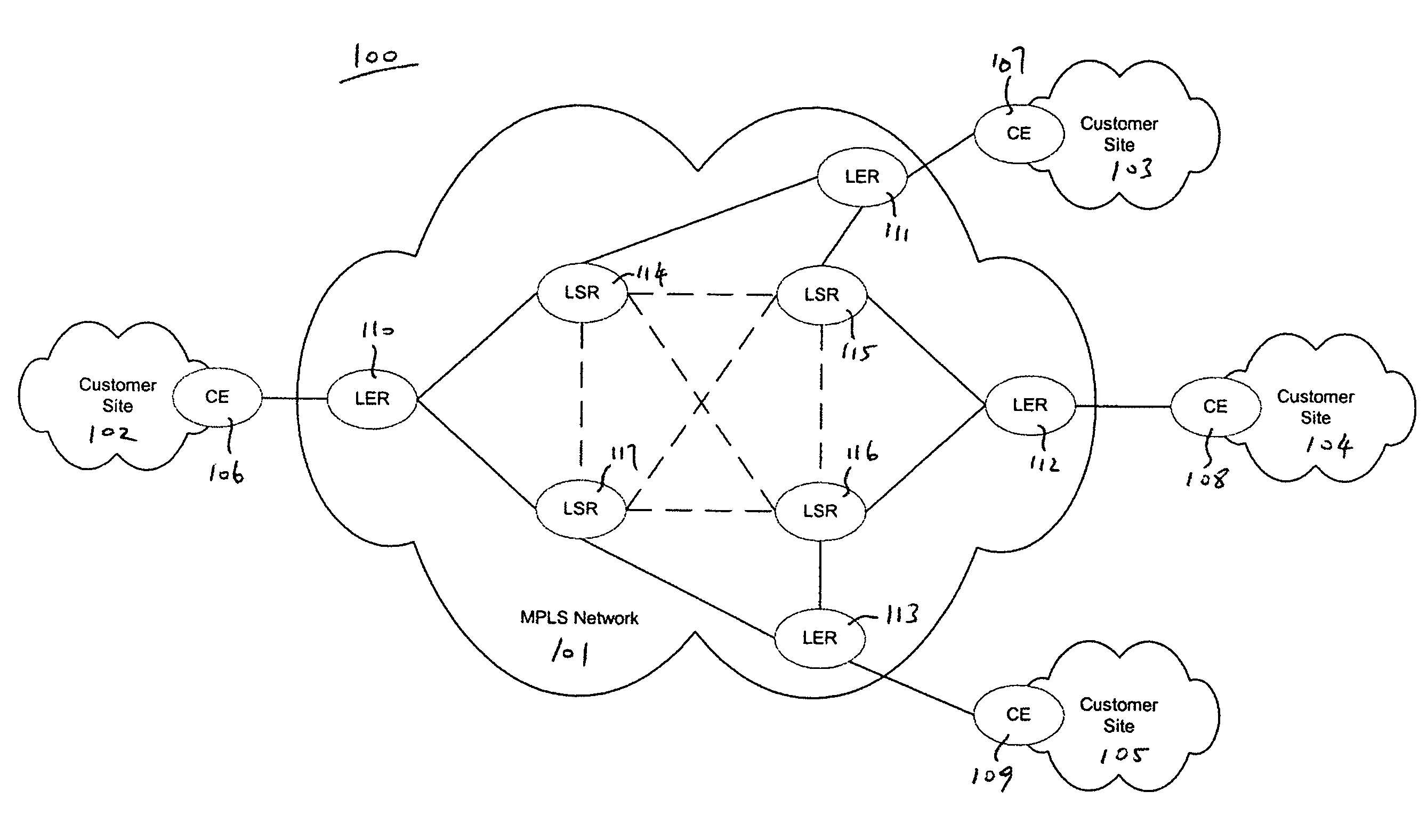
Policy based quality of service and encryption over MPLS networks
ActiveUS8279864B2Time-division multiplexData switching by path configurationQuality of serviceMulti protocol
A network device may store a plurality of LSP labels each associated with a network policy and desired quality of service, wherein each LSP label defines a path through a multi-protocol label switching (MPLS) network. Upon receiving a request to transmit data in accordance with a network policy and desired quality of service, the network device may transmit an appropriate LSP label for transmission through the MPLS network.
Owner:VERIZON PATENT & LICENSING INC
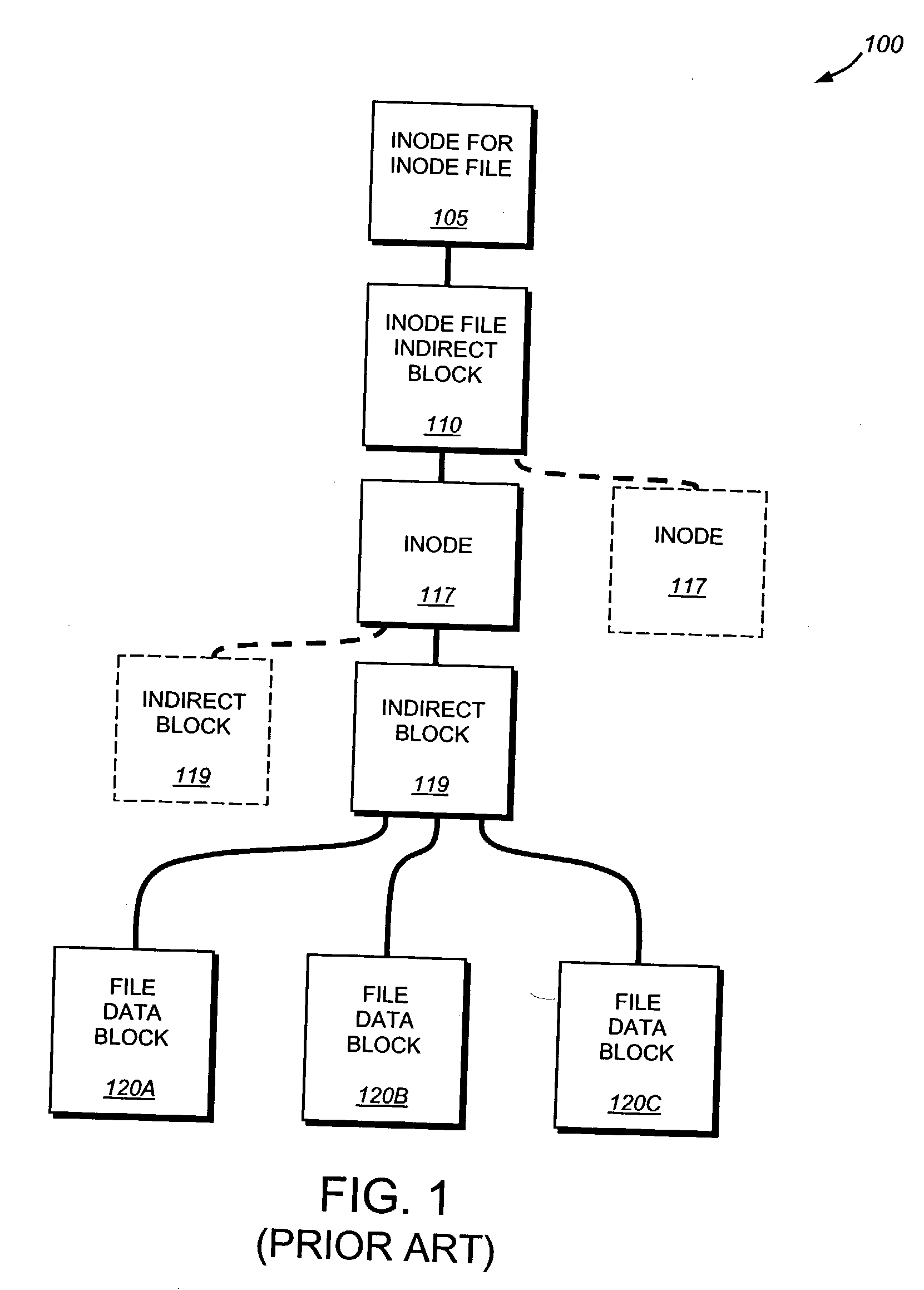
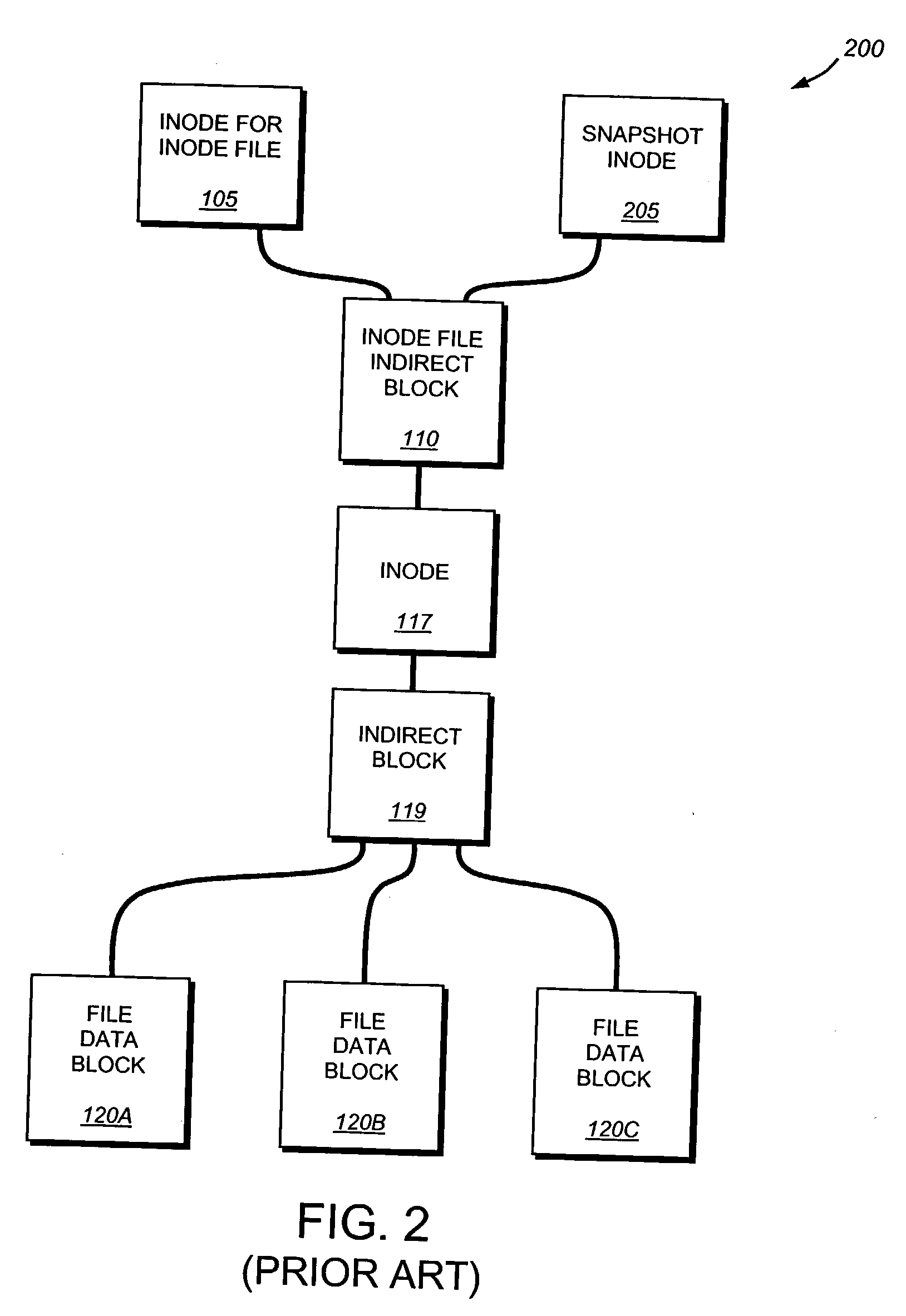
Writable read-only snapshots
ActiveUS20060179261A1Preserve integrityMemory loss protectionError detection/correctionFile systemMulti protocol
A technique enables creation and use of a writable, read-only snapshot of an active file system operating on a storage system, such as a multi-protocol storage appliance. The writable, read-only snapshot comprises a read-only “image” (file) residing in a snapshot and a writable virtual disk (vdisk) residing in the active file system. The writable vdisk is a “shadow” image of the snapshot file image and, as such, includes an attribute that specifies the snapshot file as a backing store.
Owner:NETWORK APPLIANCE INC
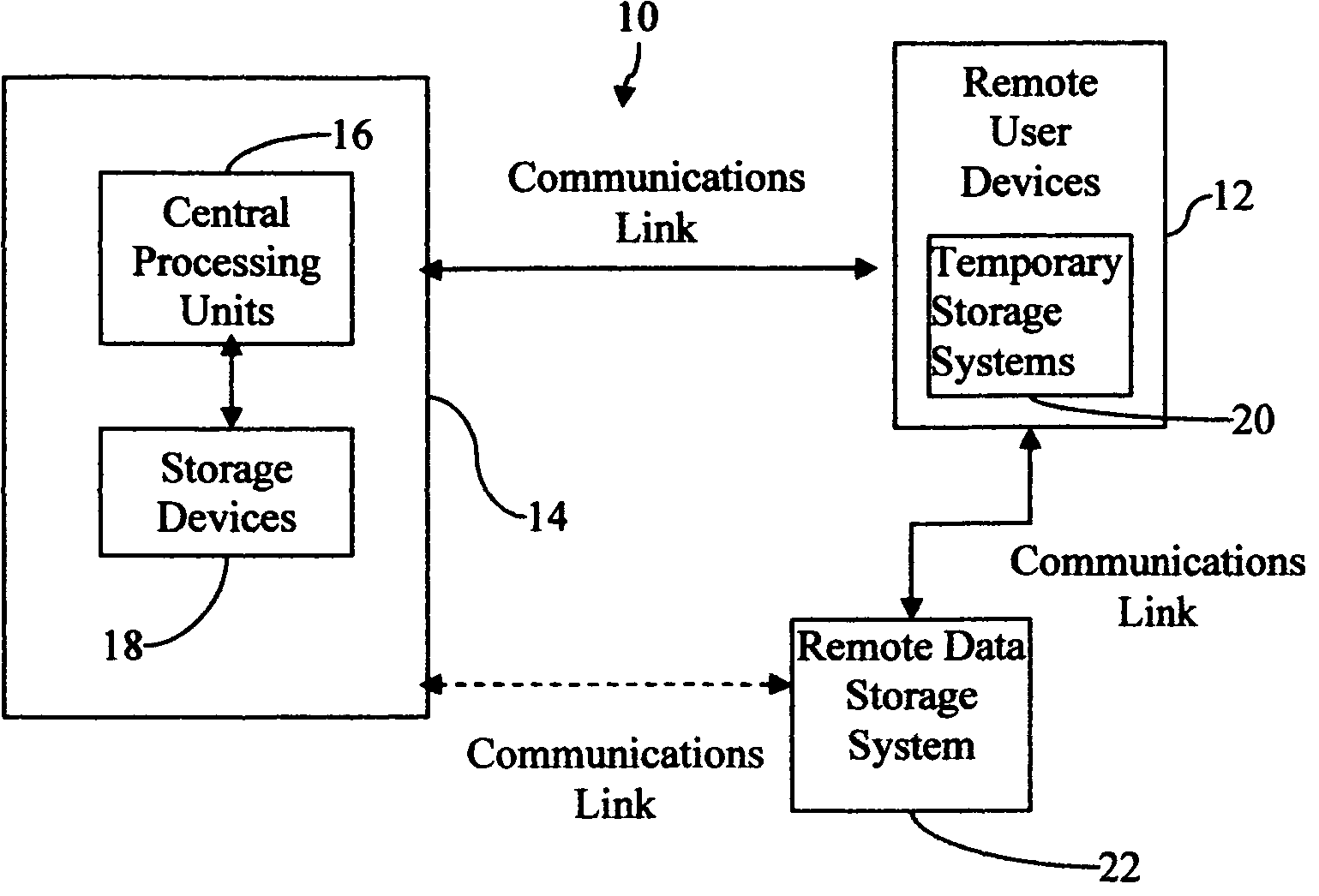
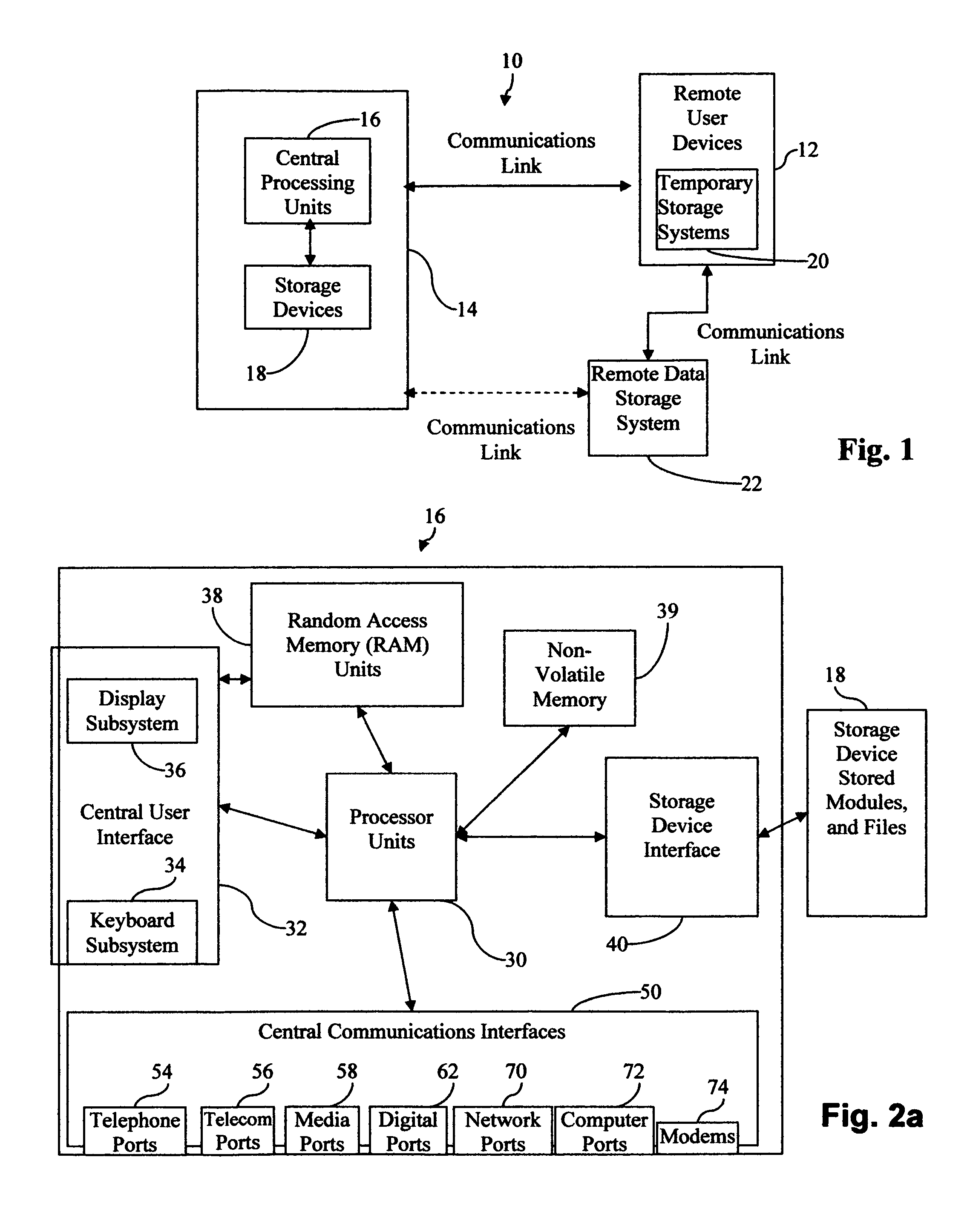
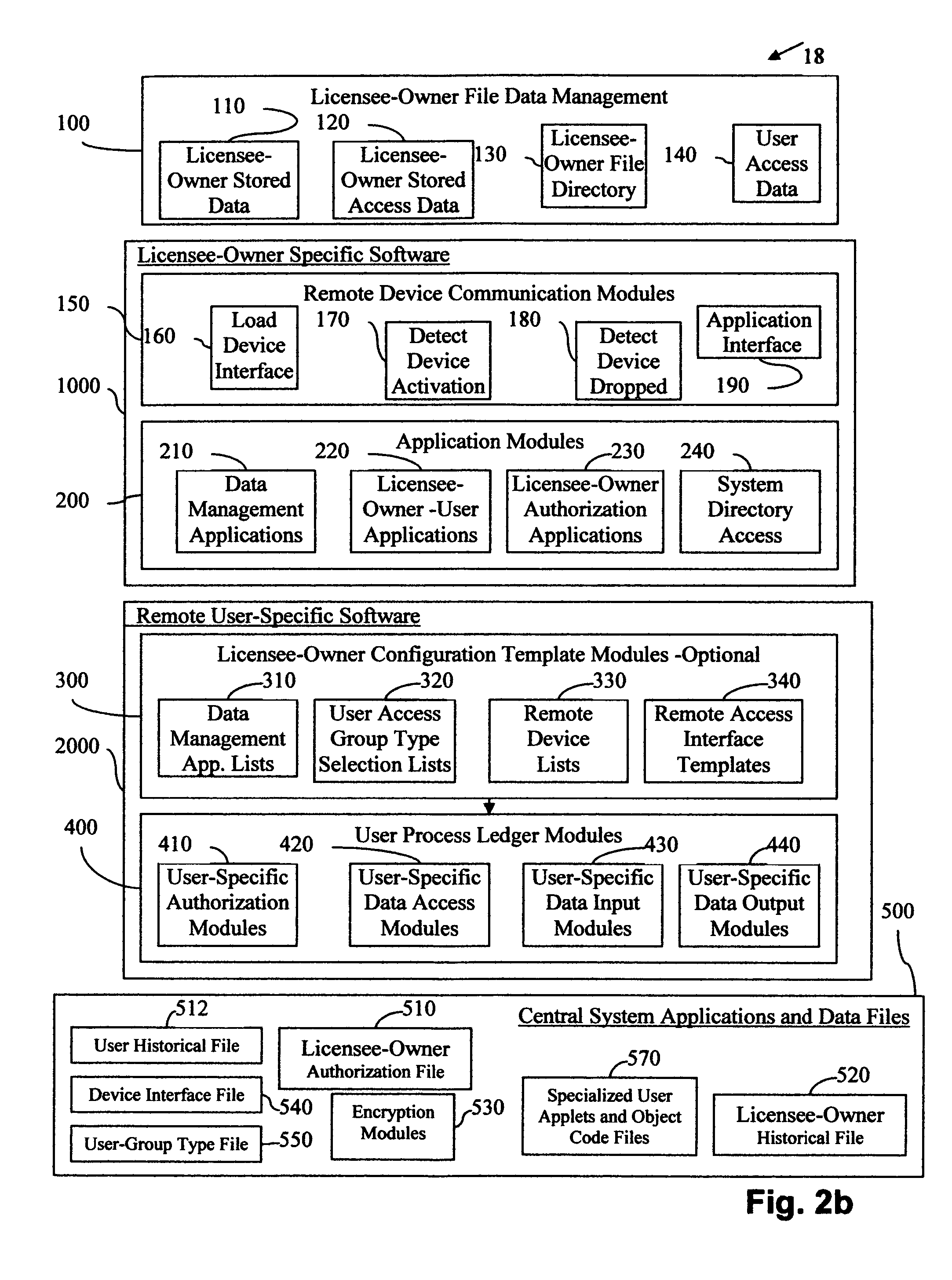
Central work-product management system for coordinated collaboration with remote users
InactiveUS7761591B2Easy accessFinanceMultiple digital computer combinationsService product managementMulti protocol
Client-specified methods, systems and computer program product with multi-protocol access for data input requests designed around a client's business application. It does this by interfacing IVR / telephony programming of multiple communication device protocols to separate data source input protocol programming, including remoting programming. Data input is by selected IVR / telephony responses designed around the needs of the individual client through selection process within a variety of configuration templates. The templates are designed to interface with the business applications through programming procedures for data entry specific to each application's protocol. The advantage, templates reduce user / client's interface with the business applications resulting in minimal time and knowledge of each applications data requirements, and limits each user's access to the system to specific data input. System response for data output is limited to the requested input for error reduction.
Owner:GRAHAM JEAN A
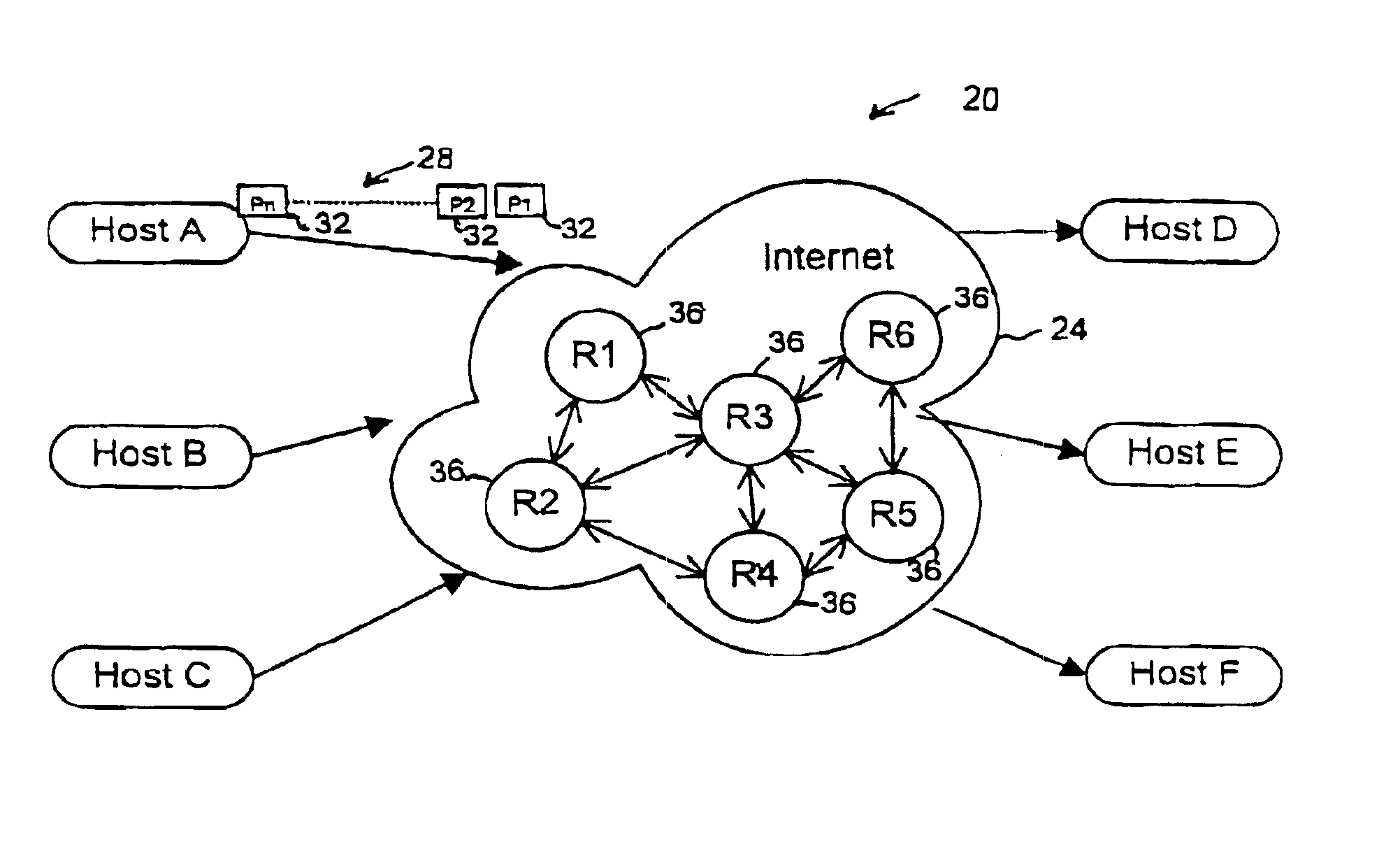
Transparent, look-up-free packet forwarding method for optimizing global network throughput based on real-time route status
ActiveUS20040032856A1Fast protection re-routingEfficient multicastingData switching by path configurationPrivate networkOSI model
A packet forwarding method for optimizing packet traffic flow across communications networks and simplifying network management. The invention provides look-up-free and packet-layer-protocol transparent forwarding of multi-protocol packet traffic among Layer-N (N=2 or upper in the ISO OSI model) nodes. The invention enables flexible and efficient packet multicast and anycast capabilities along with real-time dynamic load balancing and fast packet-level traffic protection rerouting. Applications include fast and efficient packet traffic forwarding across administrative domains of Internet, such as an ISP's backbone or an enterprise virtual private network, as well as passing packet traffic over a neutral Internet exchange facility between different administrative domains.
Owner:XENOGENIC DEV LLC
System and method for loop avoidance in multi-protocol label switching
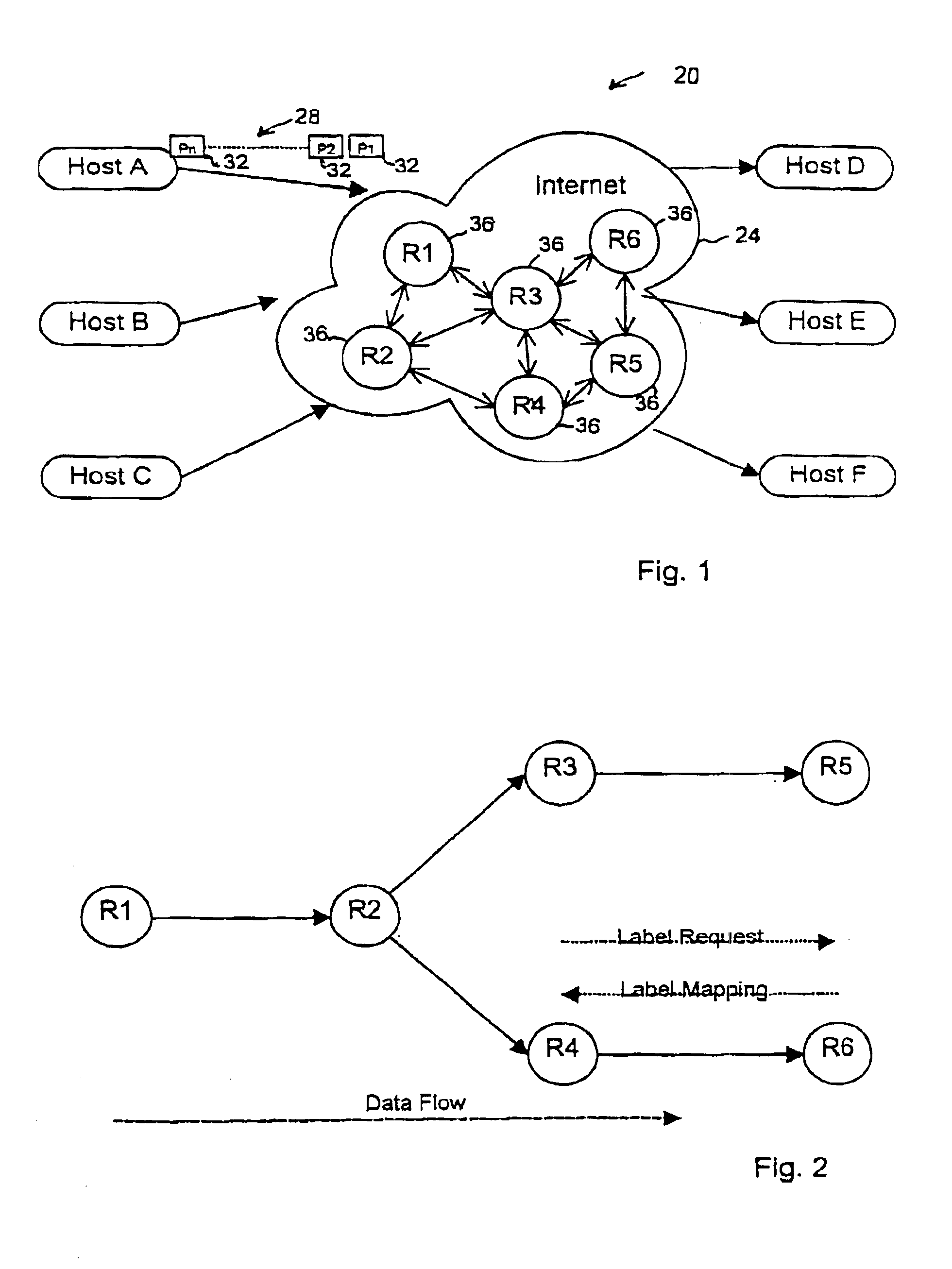
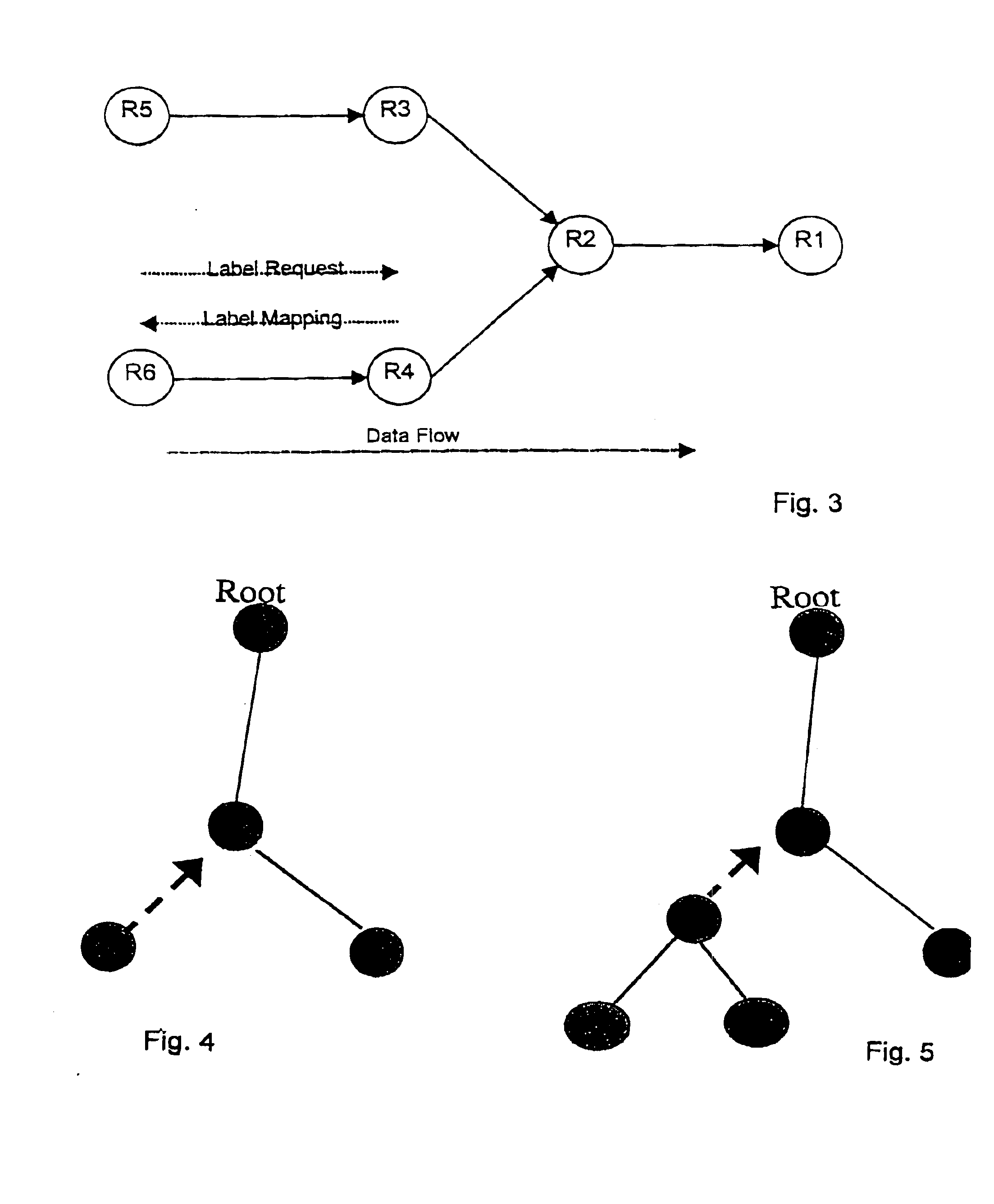
InactiveUS6879594B1Overcome disadvantagesSpecial service provision for substationData switching by path configurationMulti protocolLabel switching
A method for avoiding loops from forming when setting up label switched paths is provided. The method uses a Label Splicing Message is followed by an Acknowledgment message to determine if loops are formed in the process of joining a new node or subtree to a multicast MPLS tree. By verifying that the path towards the root of the MPLS tree is loop-free during the construction of the tree, this method complements the loop detection mechanism provided by the label switched protocol (LDP).
Owner:BIOSPHERICS
Multi-protocol wireless communication apparatus and method
InactiveUS6912230B1Easy to updateEasy accessTime-division multiplexSubstation equipmentMulti protocolUser interface
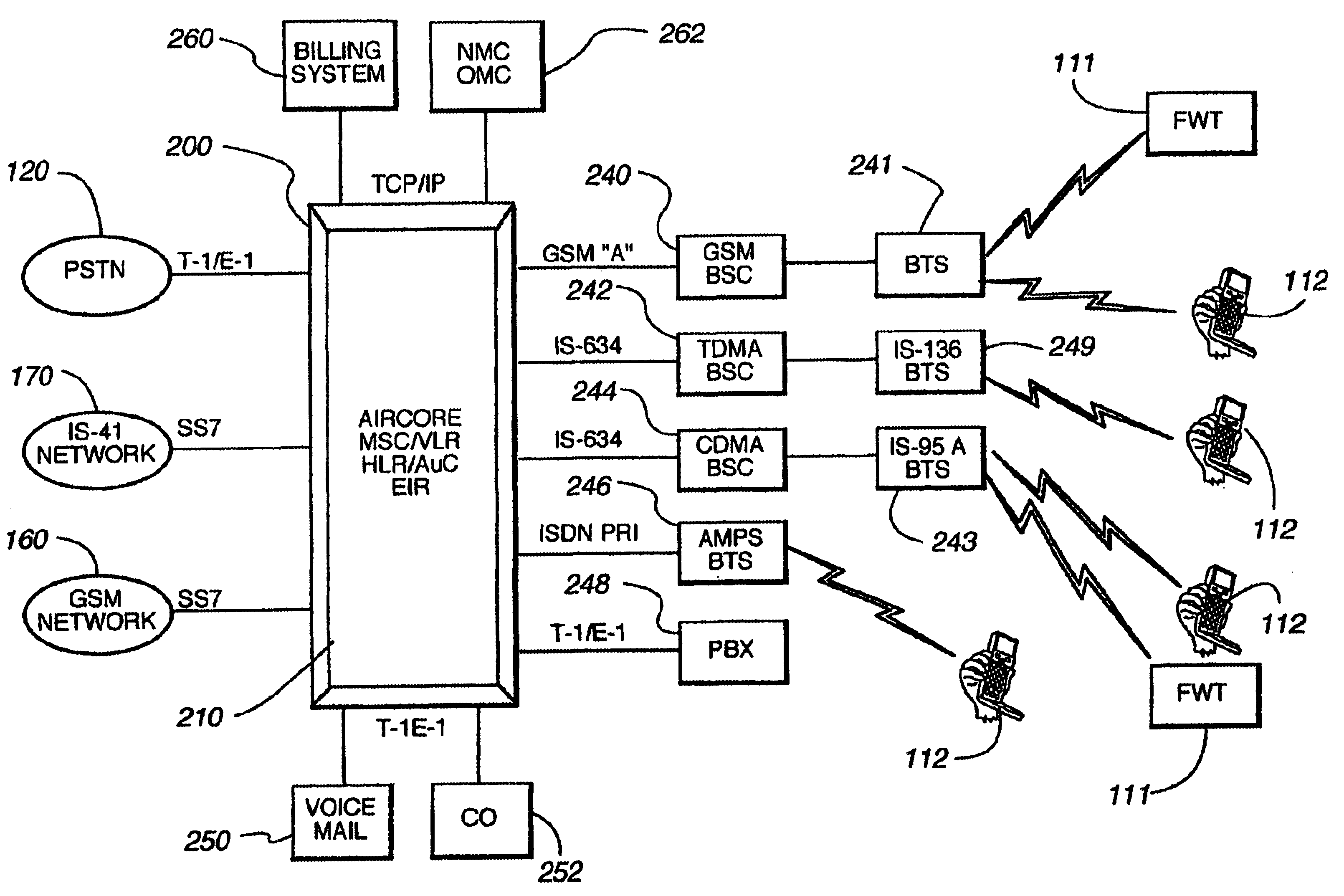
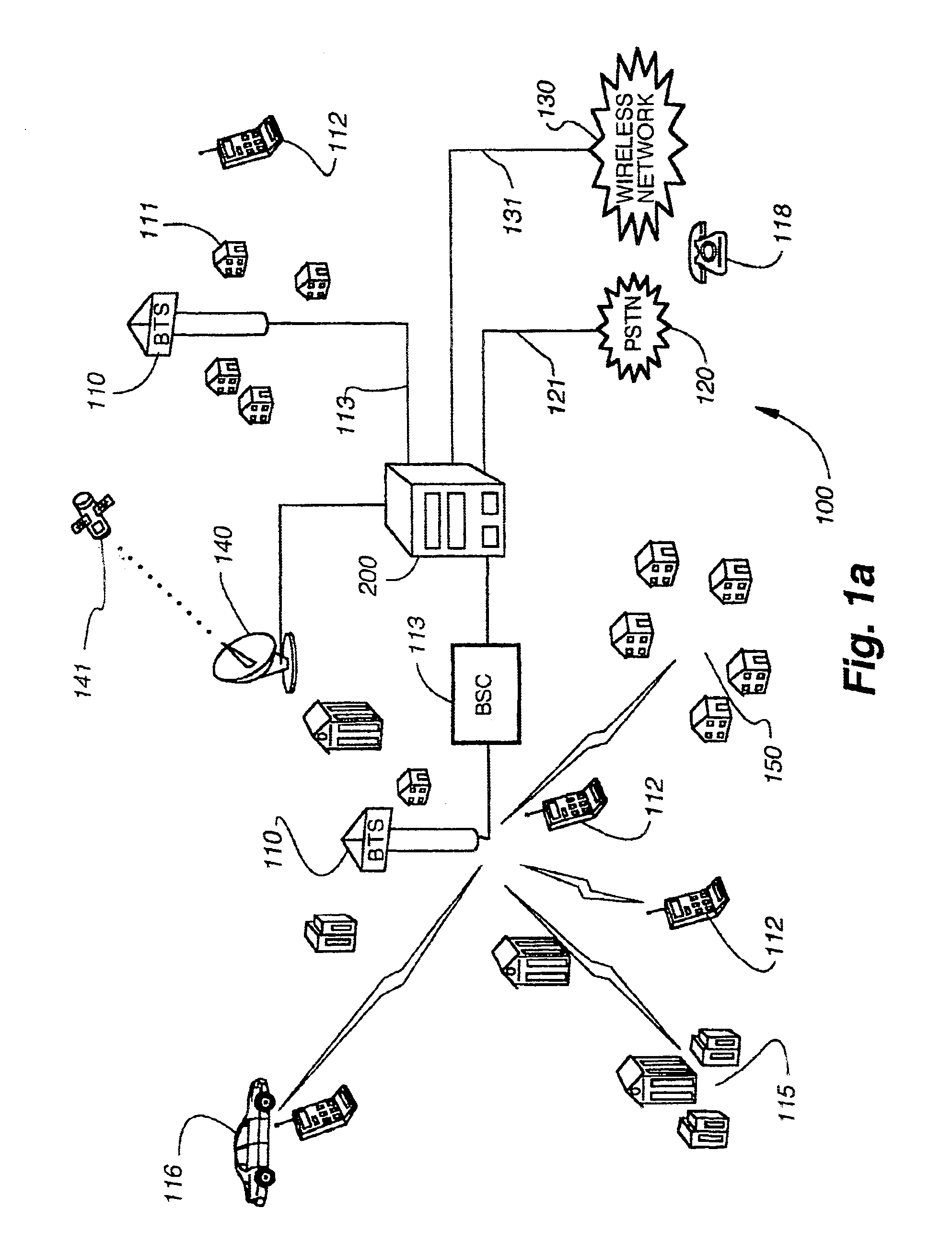
A scalable, multi-protocol mobile switching center in a wireless communications network provides communications control for digital and analog wireless communications devices including devices that operate according to GSM and IS-41 standards. The hardware and software architecture of the switching center is designed so that processing that is unique to a particular protocol is performed at the lowest possible level, and remaining processing can use generic procedures. The switching center incorporates a home location register and visitor location register that are used in conjunction with software applications to determine the protocol of mobile communications devices using the wireless communications network. The mobile switching center can be used to provide a large scale distributed wireless network or a small scale wireless network. The switching center can also be used as an adjunct to a private branch exchange to provide in-building wireless services and call control. Graphical user interfaces make the wireless communications network easy to maintain.
Owner:TECORE INC
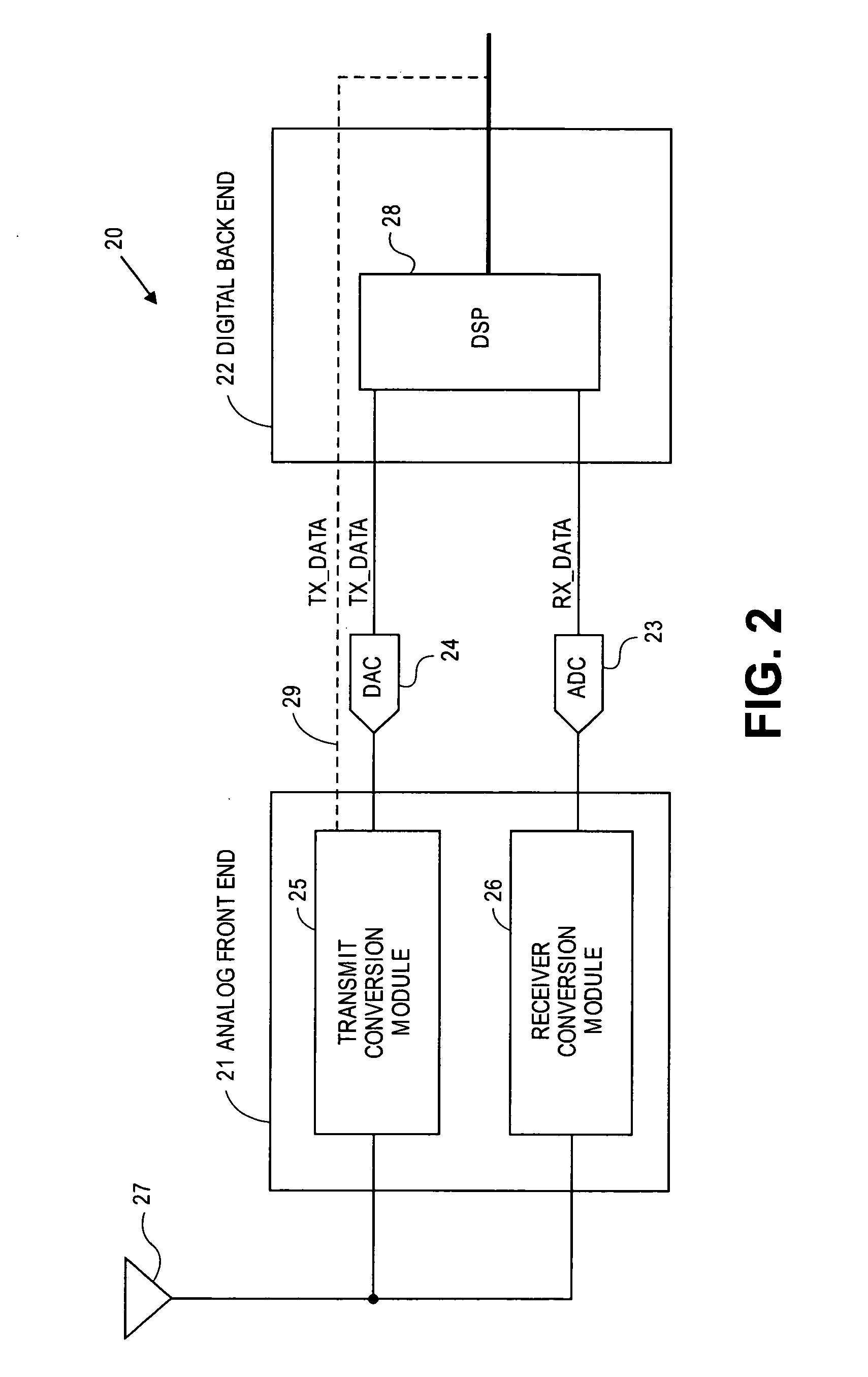
Multi-protocol radio frequency identification transponder transceiver
ActiveUS20060238301A1Memory record carrier reading problemsNear-field in RFIDTransceiverIn-phase and quadrature components
A transceiver for a RFID reader and a transceiver for a RFID transponder (tag) allow communication between the two devices. The RFID reader utilizes an analog front end and a digital backend. In the receiver portion of the transceiver, the front end of the RFID reader uses a pair of down-conversion mixers to demodulate a received signal into in-phase (I) and quadrature (Q) components and analog-to-digital converters (ADC) digitize the signal. A digital signal processor (DSP) in the back end processes the digital signal and uses a matched filter for data detection. The RFID tag receives an inductively coupled signal from the reader and the receiver portion of the tag uses a pulse / level detector that employs an analog comparator and a sample and hold circuit to detect the received signal. A digital decoder / controller is used to decode the incoming data and to establish a sampling clock for the pulse / level detector. An automatic gain control (AGC) circuit adjusts a receiver gain according to the received signal strength and controls tuning of magnetic coupling circuitry.
Owner:NXP USA INC
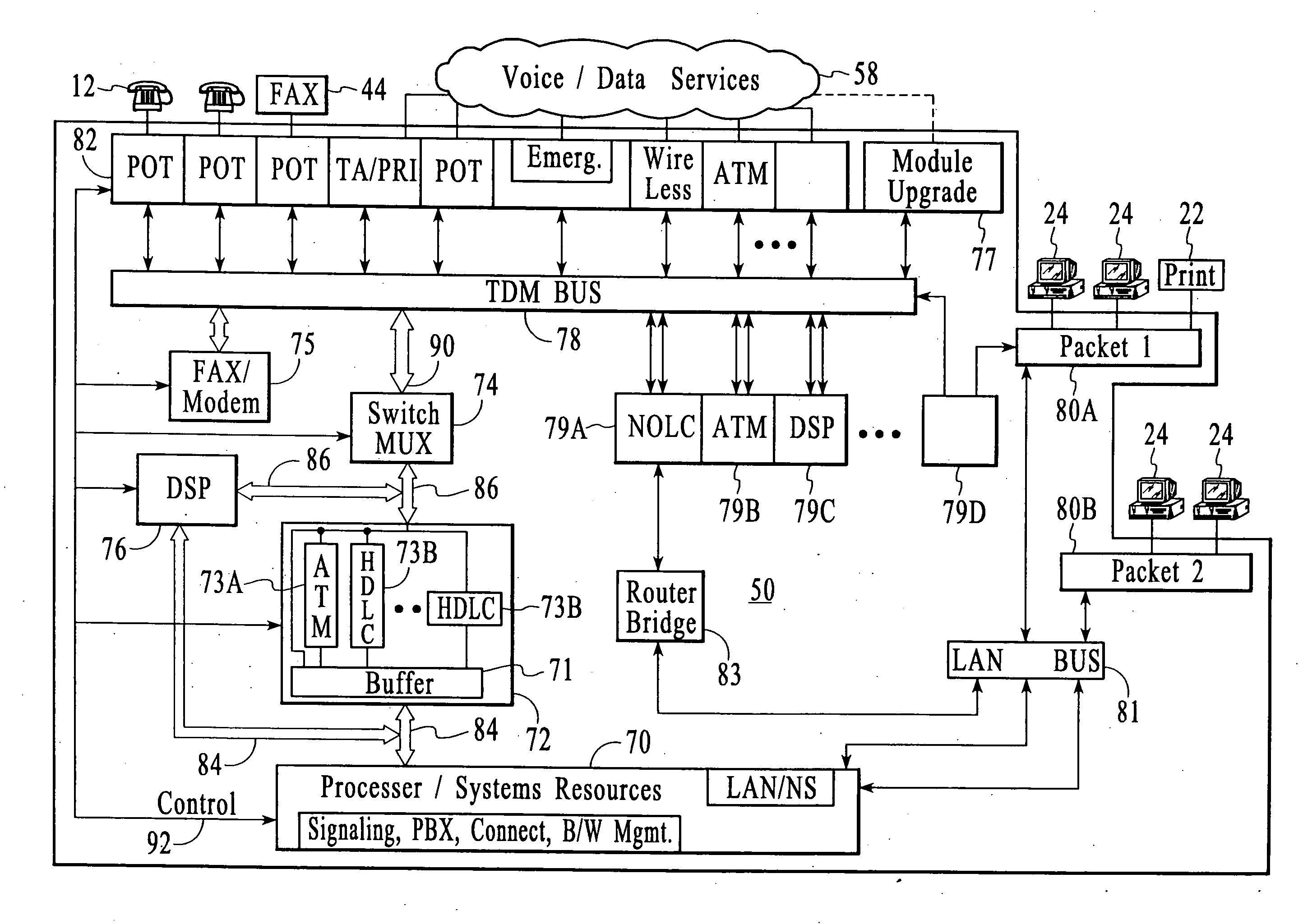
Systems and methods for multiple mode voice and data communications using intelligently bridged TDM and packet buses and methods for implementing language capabilities using the same
InactiveUS20070239429A1Effective supportPerformed conveniently and efficientlyNatural language translationAutomatic exchangesMulti protocolMultiple modes
Systems and methods by which voice / data communications may occur in multiple modes / protocols are disclosed. In particular, systems and methods are provided for multiple native mode / protocol voice and data transmissions and receptions with a computing system having a multi-bus structure, including, for example, a TDM bus and a packet bus, and multi-protocol framing engines. Such systems preferably include subsystem functions such as PBX, voice mail and other telephony functions, LAN hub and data router. In preferred embodiments, a TDM bus and a packet bus are intelligently bridged and managed, thereby enabling such multiple mode / protocol voice and data transmissions to be intelligently managed and controlled with a single, integrated system. A computer or other processor includes a local area network controller, which provides routing and hub(s) for one or more packet networks. The computer also is coupled to a buffer / framer, which serves to frame / deframe data to / from the computer from TDM bus. The buffer / framer includes a plurality of framer / deframer engines, supporting, for example, ATM and HDLC framing / deframing. The buffer / framer is coupled to the TDM bus by way of a switch / multiplexer, which includes the capability to intelligently map data traffic between the buffer / framer and the TDM bus to various slots of the TDM frames. Preferably, a DSP pool is coupled to buffer / framer in a manner to provide various signal processing and telecommunications support, such as dial tone generation, DTMF detection and the like. The TDM bus is coupled to a various line / station cards, serving to interface the TDM bus with telephone, facsimiles and other telecommunication devices, and also with a various digital and / or analog WAN network services. Language support for such systems is accomplished by way of a program / data structure so that additional language support may be readily implemented, for example, by a non-software programmer using grammar and voice prompt files, which are preferably located in a predetermined directory in the system.
Owner:RPX CORP
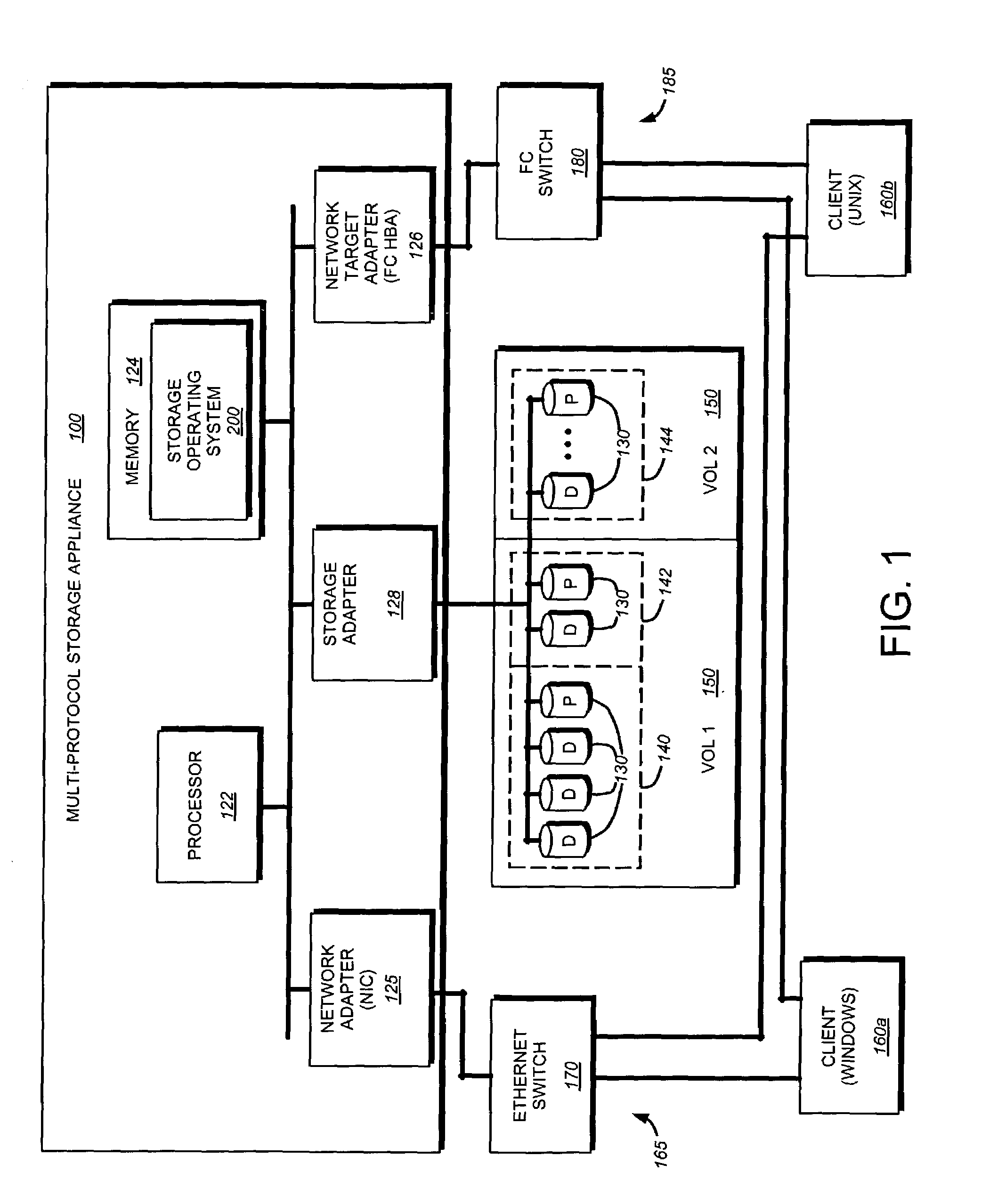
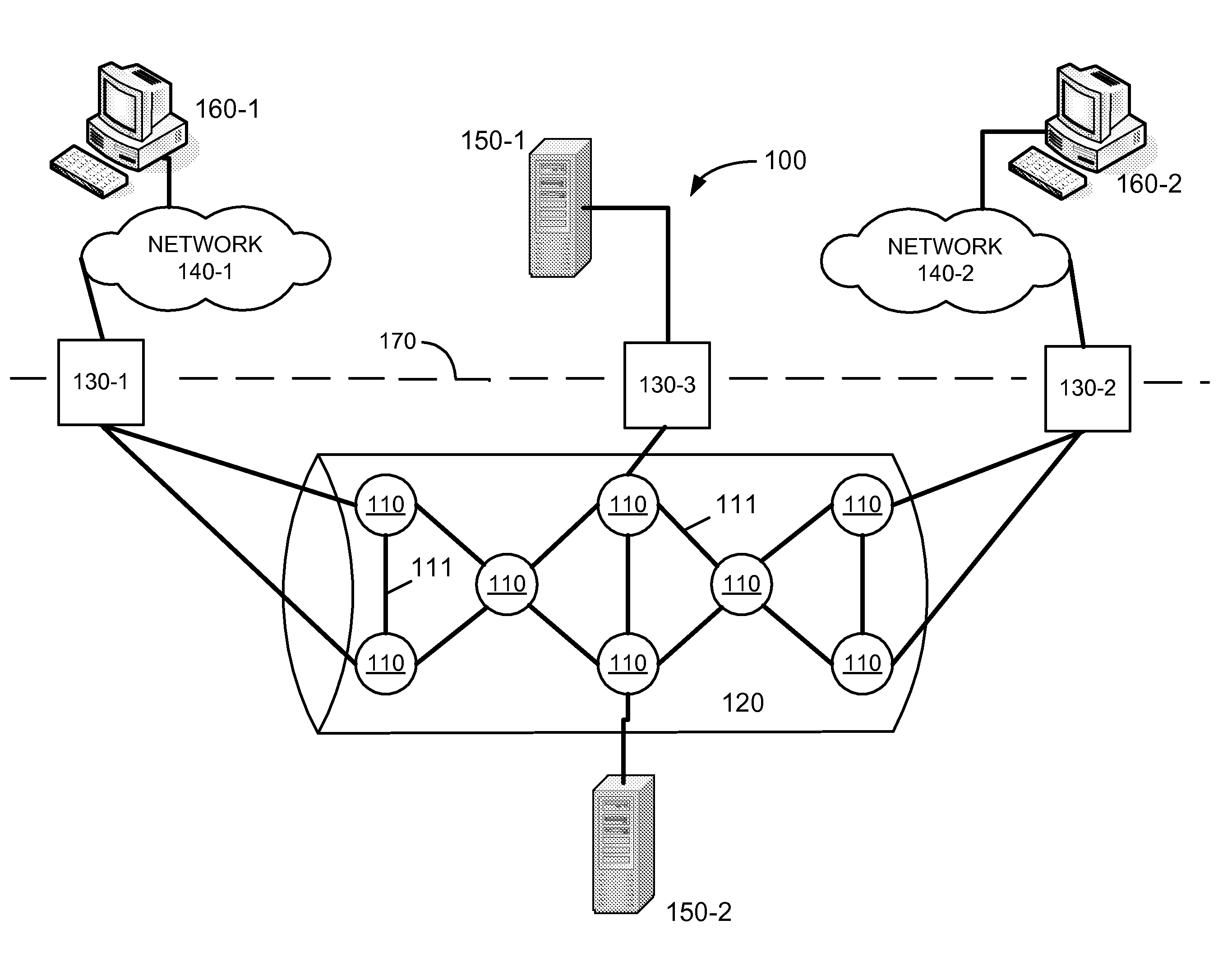
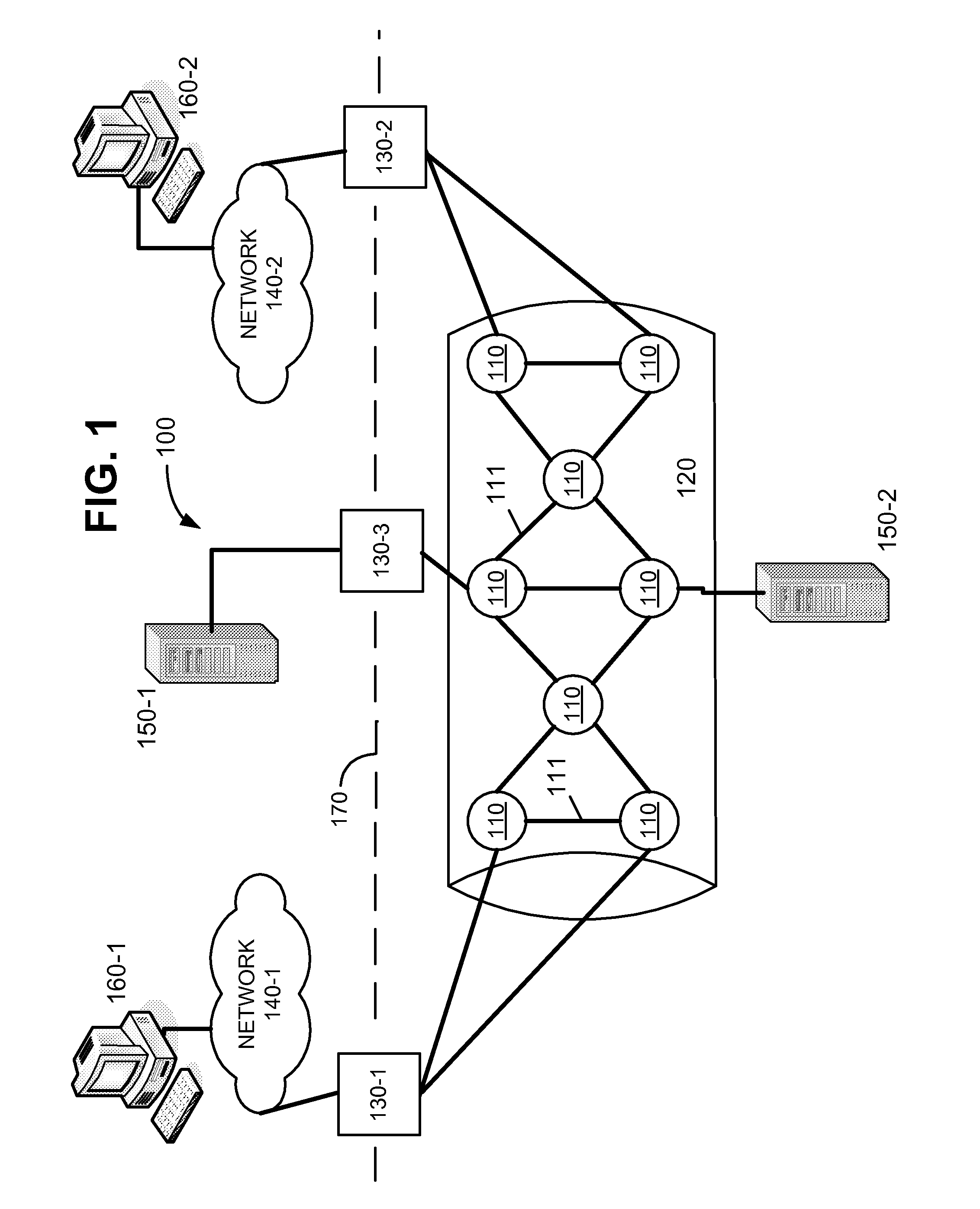
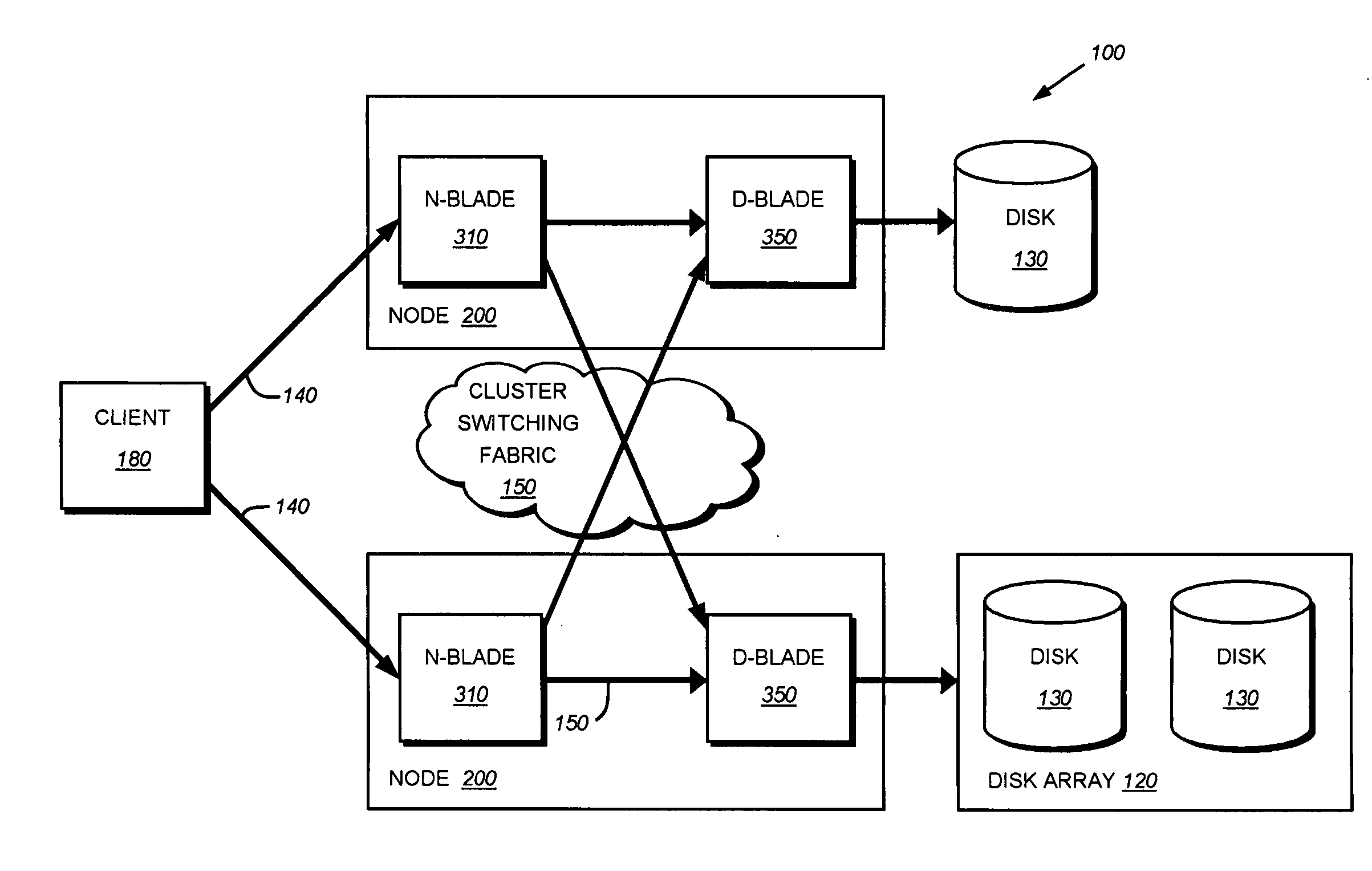
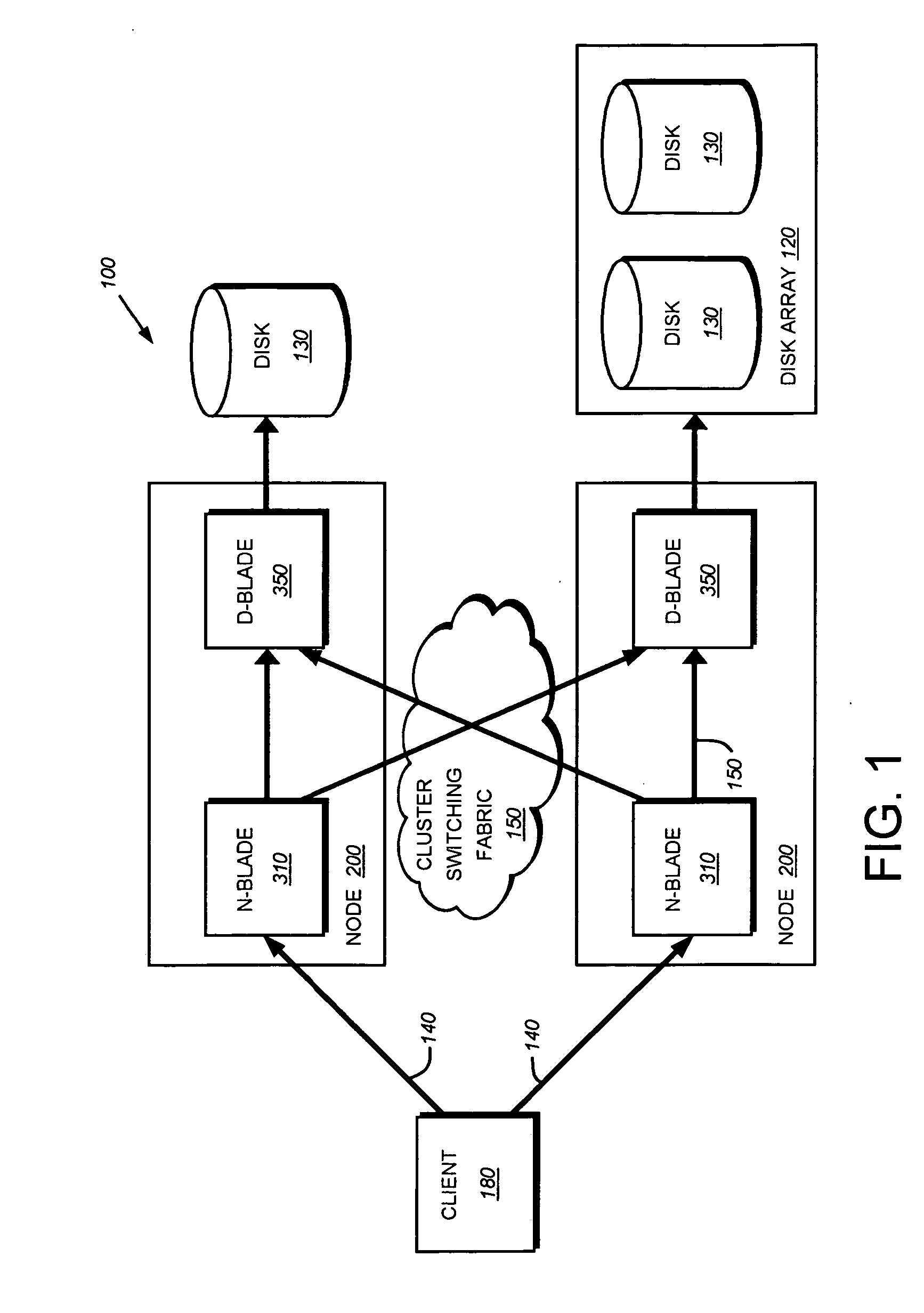
Storage system architecture for striping data container content across volumes of a cluster
ActiveUS20050192932A1Improve efficiencyOvercome disadvantagesDigital data processing detailsMultiple digital computer combinationsData accessMulti protocol
A storage system architecture comprises one or more volumes distributed across a plurality of nodes interconnected as a cluster. The volumes are organized as a striped volume set (SVS) and configured to store content of data containers served by the cluster in response to multi-protocol data access requests issued by clients. Each node of the cluster includes (i) a storage server adapted to service a volume of the SVS and (ii) a multi-protocol engine adapted to redirect the data access requests to any storage server of the cluster. Notably, the content of each data container is apportioned among the volumes of the SVS to thereby improve the efficiency of storage service provided by the cluster.
Owner:NETWORK APPLIANCE INC
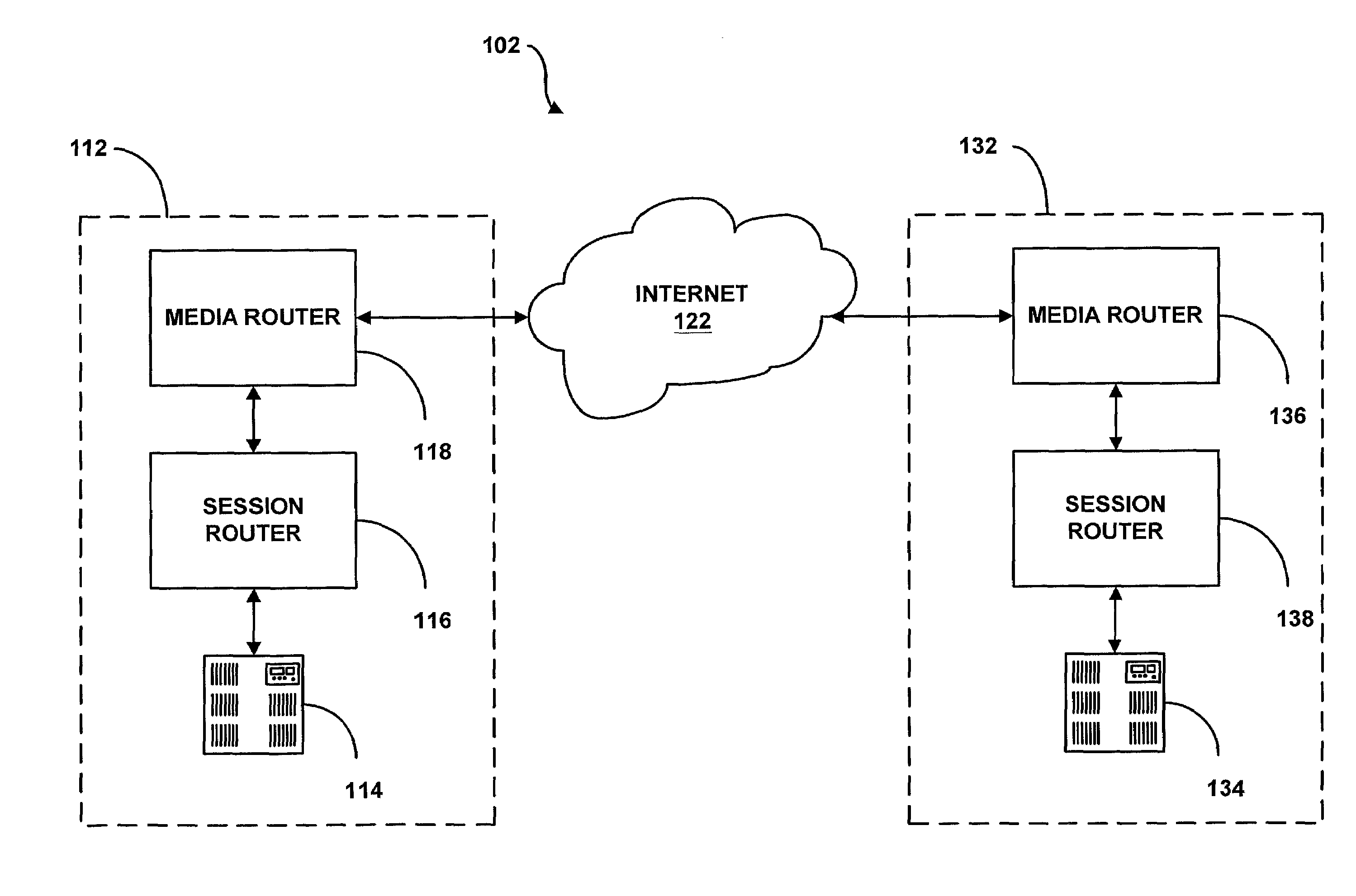
System and method for providing rapid rerouting of real-time multi-media flows
A system and method for providing rapid rerouting of real-time transport protocol (RTP) multi-media flows is disclosed. Generally, a first endpoint is connected to a second endpoint, wherein the first endpoint comprises a transceiver, software stored within the first endpoint defining functions to be performed by the first endpoint, and a processor configured by the software. The processor is configured to perform the steps of, performing flow processing on a data packet received at a first endpoint, from a second endpoint, removing a multi-protocol label switching (MPLS) tag from the data packet, translating a source address and destination address of the data packet, and determining a forwarding destination if more than one destination address of the data packet is provided.
Owner:PRIMARY NETWORKS +1
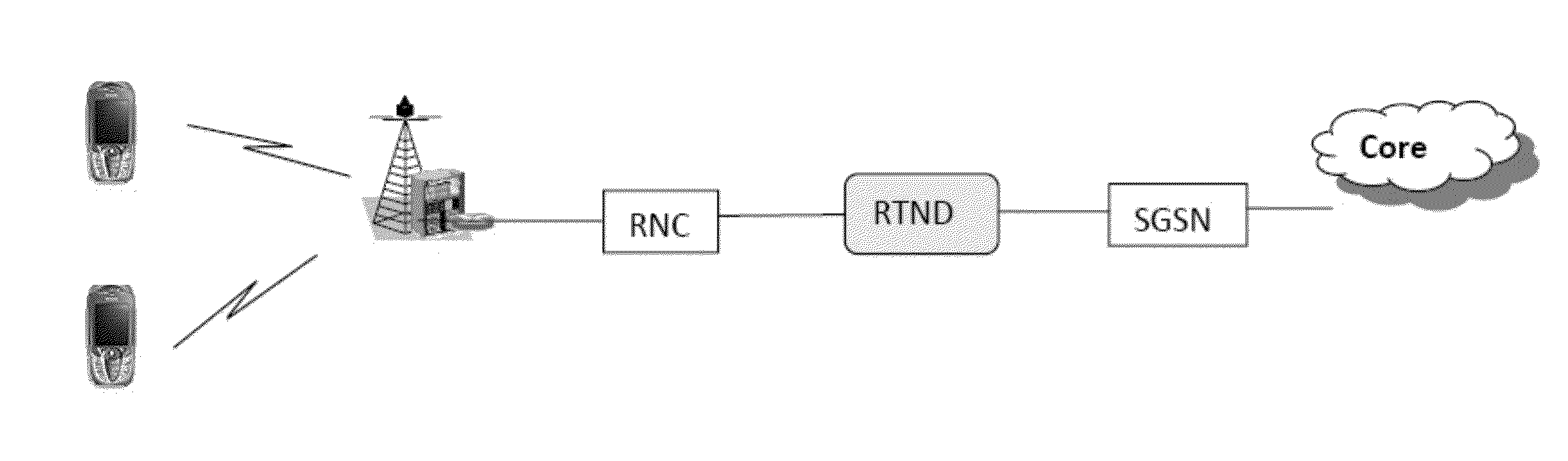
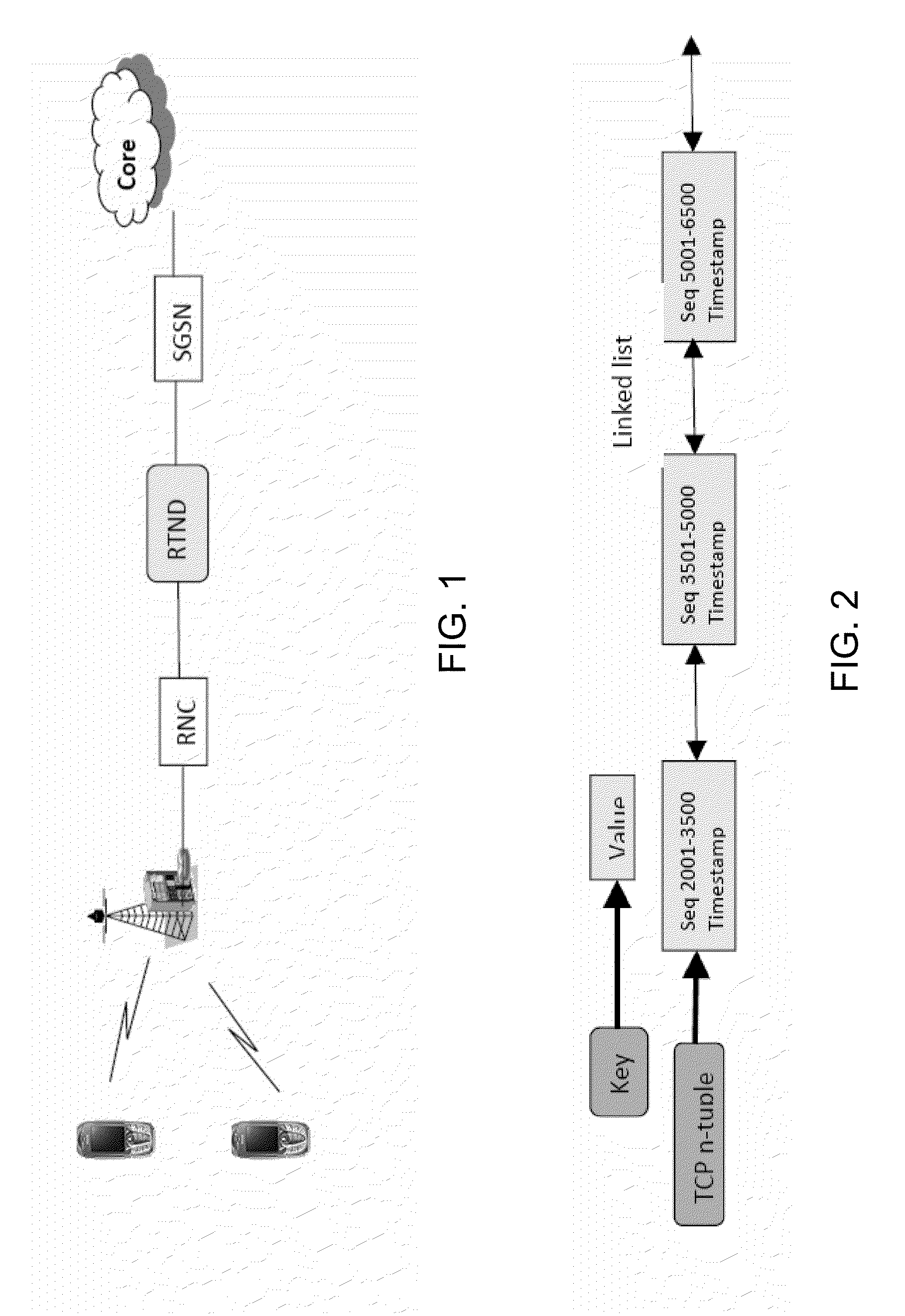
RAN Analytics, Control And Tuning Via Multi-Protocol, Multi-Domain, And Multi-RAT Analysis
ActiveUS20130021933A1Error preventionNetwork traffic/resource managementTransit networkAccess network
The present invention identifies methods and procedures for correlating control plane and user plane data, consolidating and abstracting the learned and correlated data in a form convenient for minimizing and exporting to other network devices, such as those in the Core Network and the Access Network, or the origin server, CDN devices or client device. These correlation methods may use Control Plane information from a plurality of interfaces in the RAN, and User plane information from other interfaces in the RAN or CN. IF the device is deployed as an inline proxy, this information may be exported using in-band communication, such as HTTP extension headers in HTTP Request or Response packets, or another protocol header, such as the IP or GTP-U header field. Alternatively, this information can be exported out-of-band using a separate protocol between the RAN Transit Network Device (RTND) and the receiving device.
Owner:RIBBON COMM SECURITIES CORP
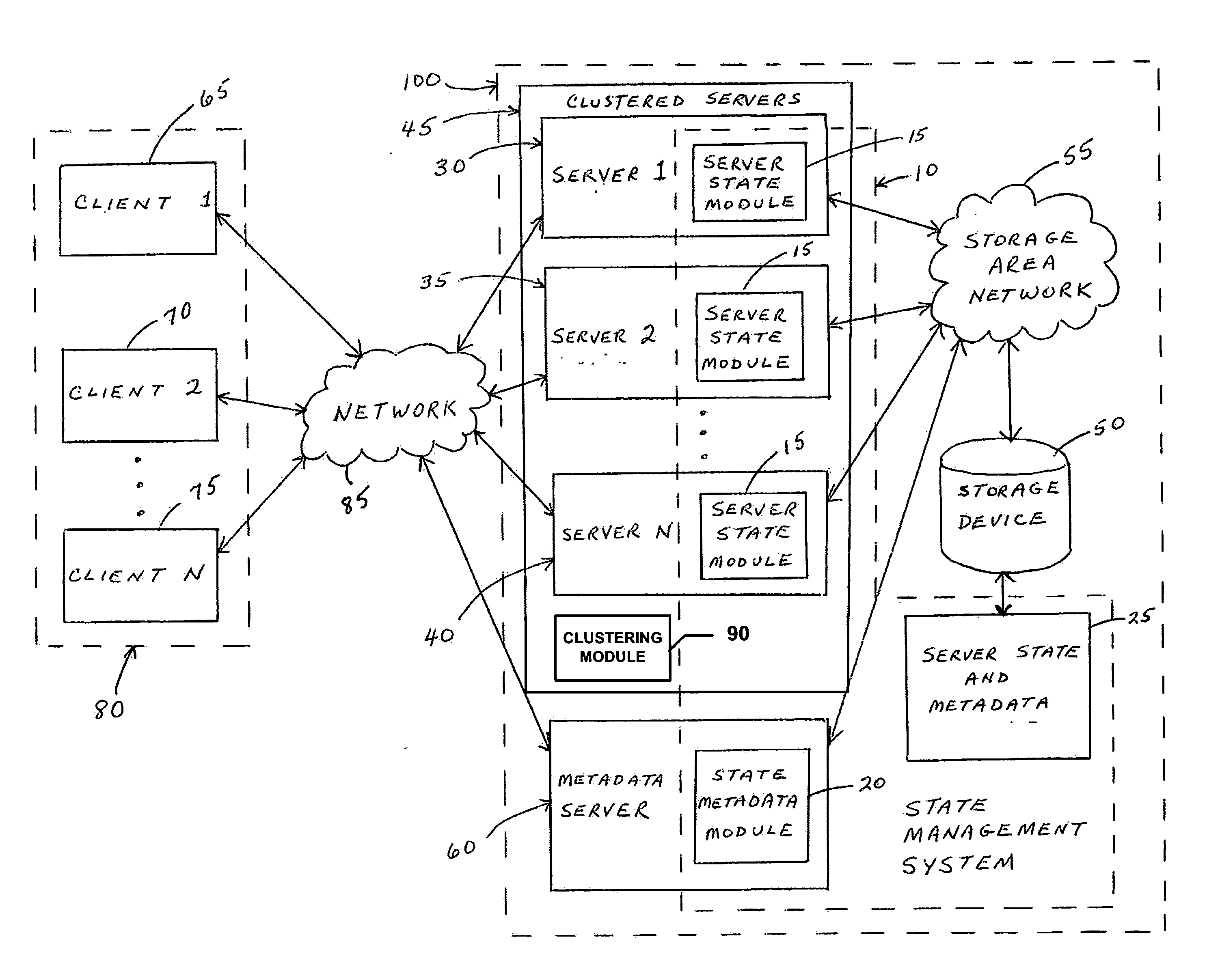
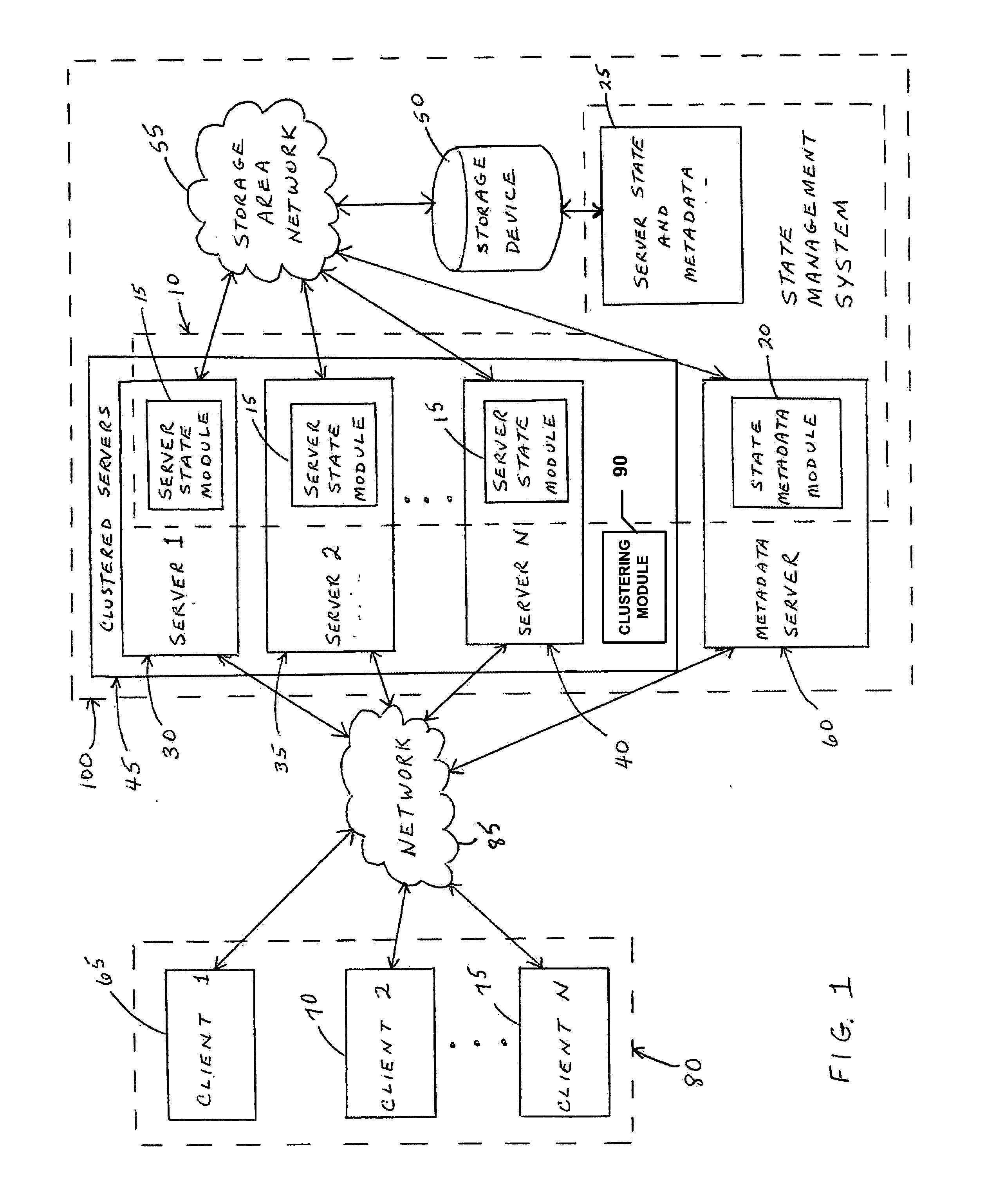
System and method for preserving state for a cluster of data servers in the presence of load-balancing, failover, and fail-back events
InactiveUS20060212453A1Avoid collisionMeet actual needsDigital data information retrievalError detection/correctionFailoverLoad Shedding
A state management system preserves a state for a cluster of file servers in a cluster file system in the presence of load balancing, failover, and fail-back events. The system provides a file and record locking solution for a clustered network attached storage system running on top of a cluster file system. The system employs a lock ownership scheme in which ownership identifiers are guaranteed to be unique across clustered servers and across various protocols the clustered servers may be exporting. The system supports multi-protocol clustered NAS gateways, NAS gateway server failover and fail-back, and load-balancing architectures. The system further eliminates a need for a lock migration protocol, resulting in improved efficiency and simplicity.
Owner:IBM CORP
Transparent, look-up-free packet forwarding method for optimizing global network throughput based on real-time route status
ActiveUS7254138B2Improve performanceFast and efficient packet-level traffic protection re-routingError preventionTransmission systemsPrivate networkOSI model
Owner:XENOGENIC DEV LLC
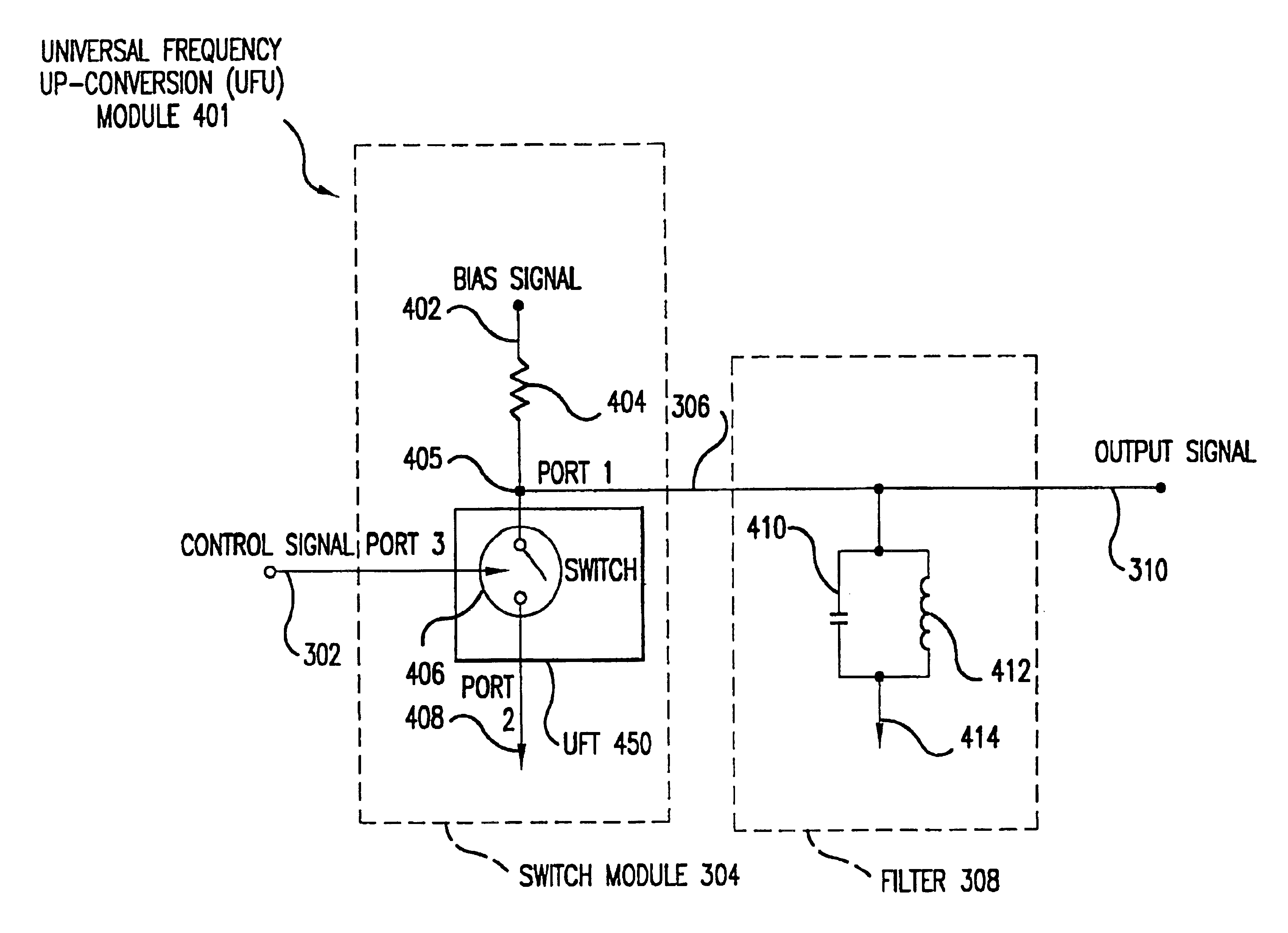
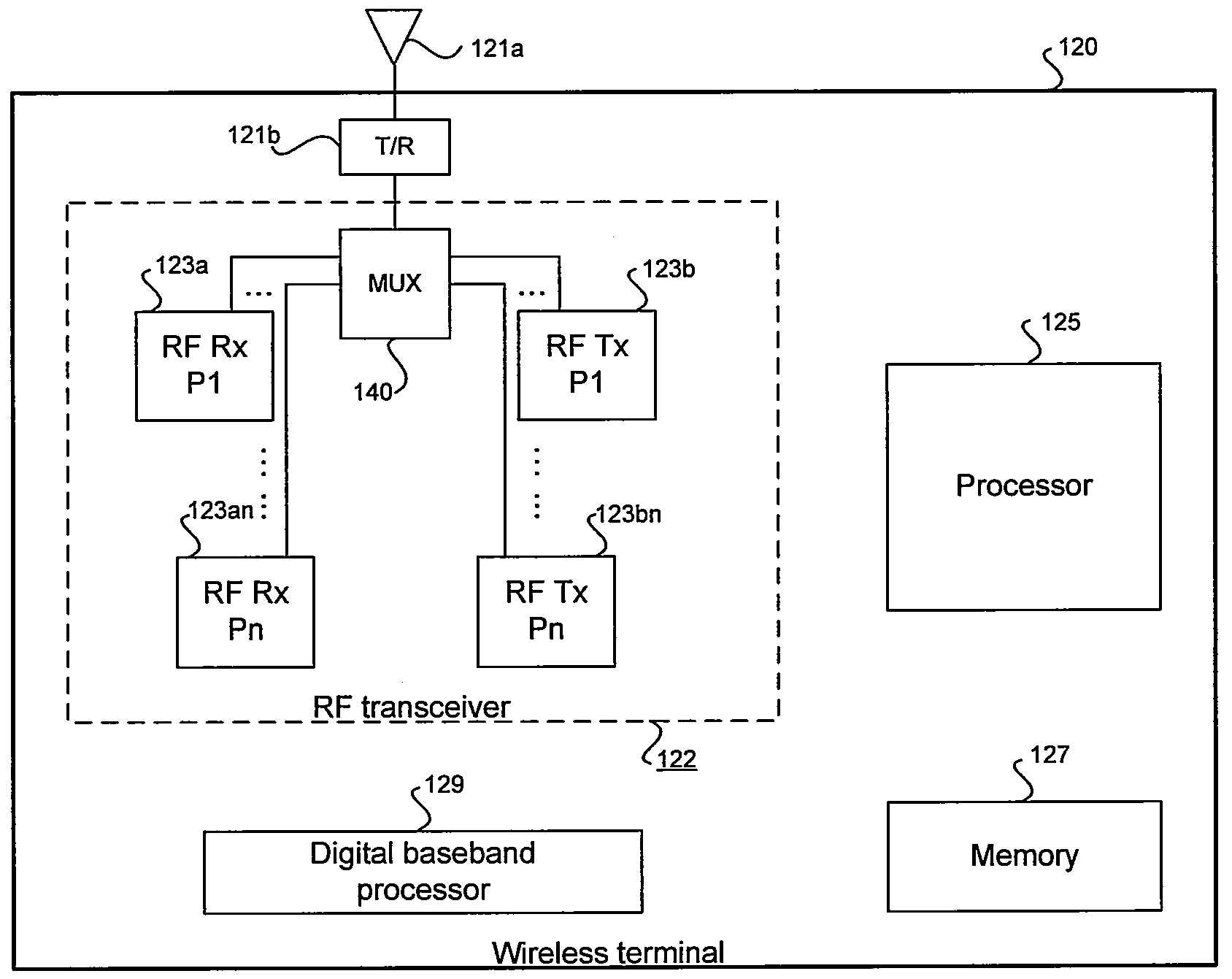
Universal platform module and methods and apparatuses relating thereto enabled by universal frequency translation technology
InactiveUS6873836B1Modulation transferenceTransmission noise suppressionTransceiverCommunications system
A communication system comprising a multi-protocol, multi-bearer sub-system is described herein. The sub-system is a universal platform module that can transmit and receive one or more information signals in one or more protocols using one or more bearer services. In one embodiment, the sub-system may form a portion of a transceiver that is composed of a transmitter and a receiver, and which is a gateway server between a personal area network (PAN) and the global wireless network.
Owner:PARKER VISION INC
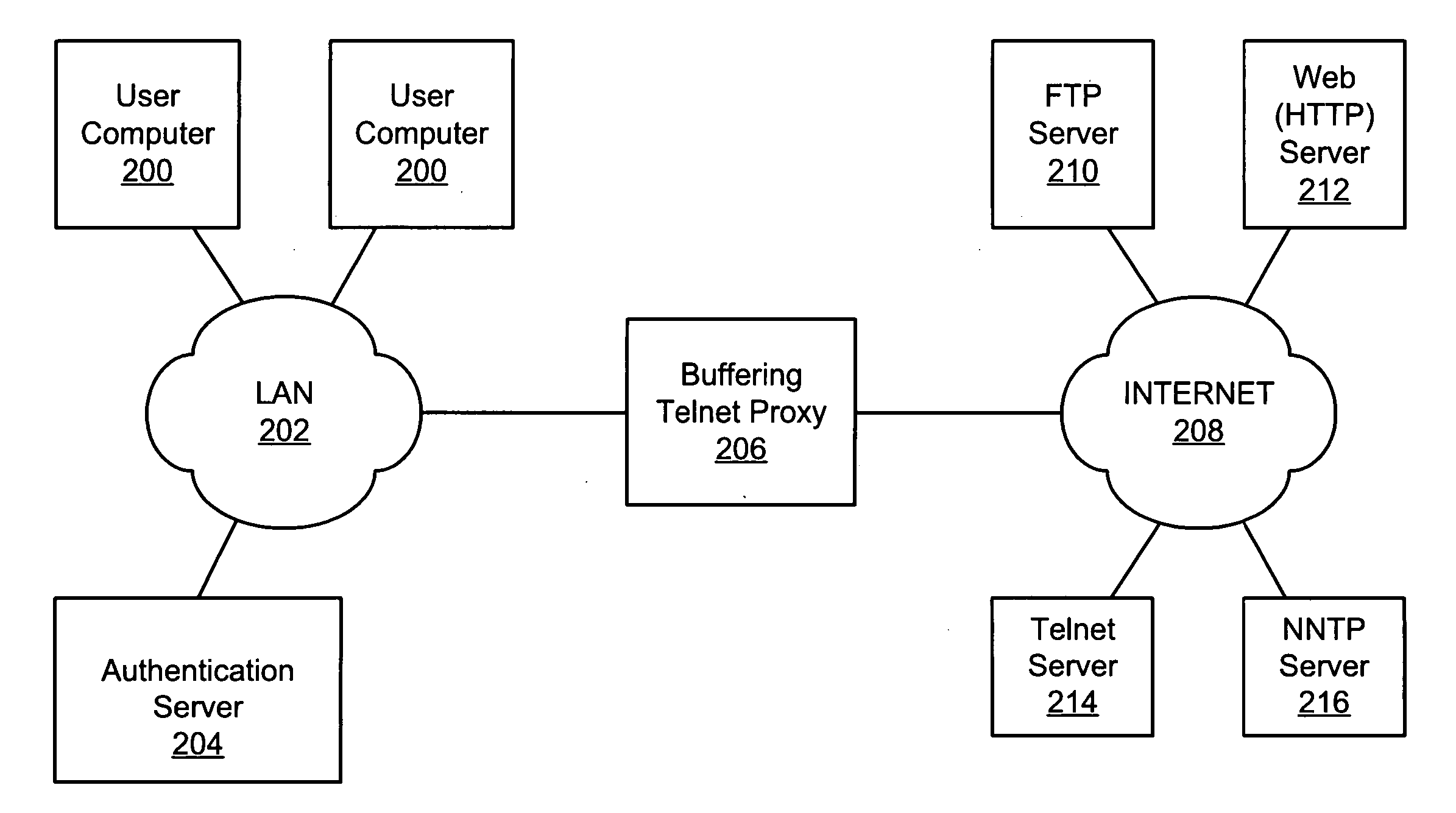
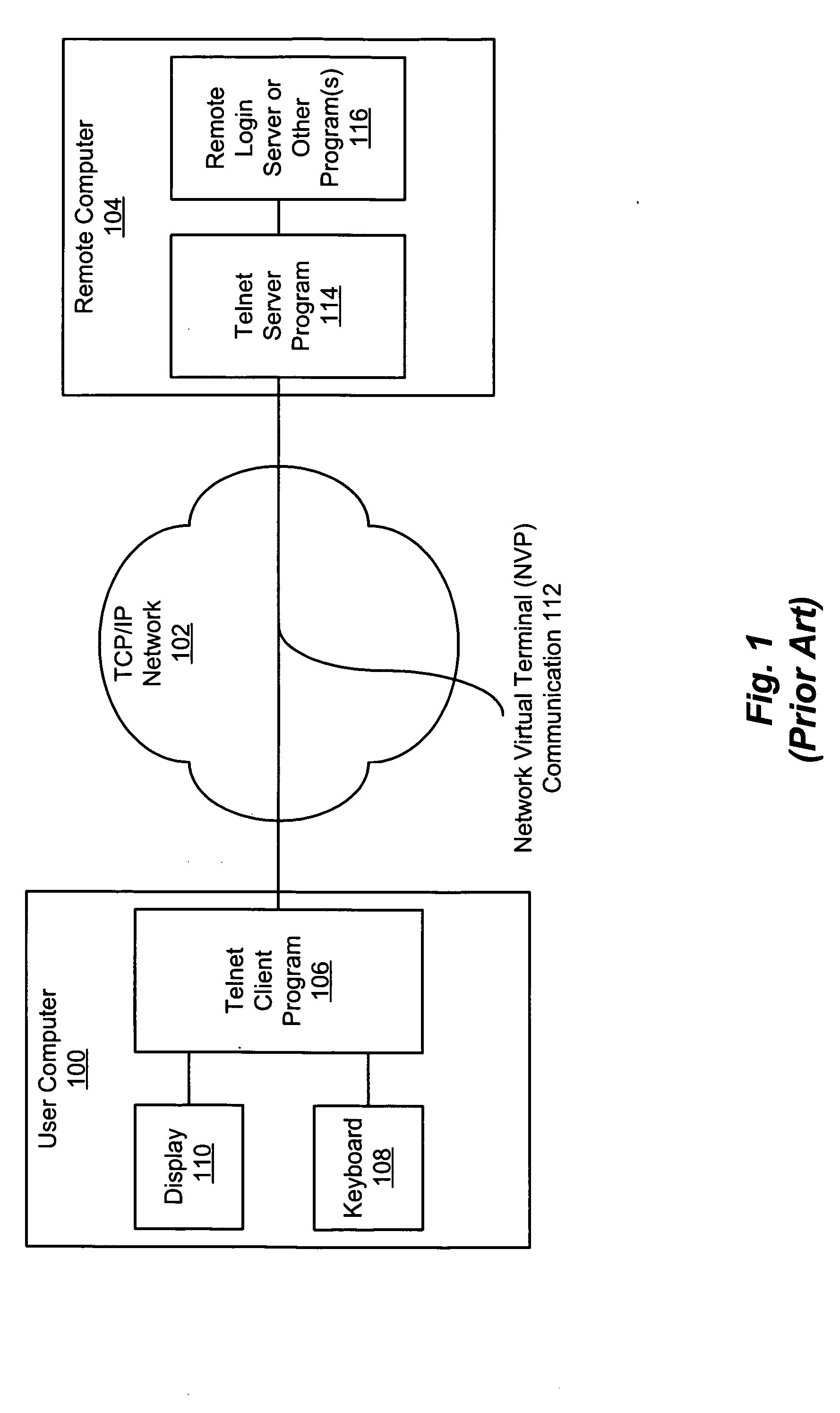
Buffering proxy for telnet access
A single- or multi-protocol buffering proxy accepts communication option negotiation commands from a client before establishing a connection between the client and a host. The proxy negotiates a limited set of options with the client before the connection is established and buffers (accepts and temporarily stores without responding to) other option negotiation commands from the client. The proxy accepts credentials from a user and establishes, or denies the connection based on the credentials. If the connection is established, the proxy buffers option negotiation commands sent by the host. After the proxy logs in to the host on behalf of the user or the user logs in directly, the proxy sends each party's buffered option negotiation commands to the other party, ceases buffering option negotiation commands and enters a “pass-through” mode, in which the proxy passes characters and commands between the parties until the session ends. The proxy uses the credentials to allow or deny subsequent connection requests, without re-prompting for credentials.
Owner:CA TECH INC
Apparatus and method for data virtualization in a storage processing device
ActiveUS20050033878A1Achieve scaleProvide flexibilityMultiplex system selection arrangementsInput/output to record carriersInternet trafficMulti protocol
A system including a storage processing device with an input / output module. The input / output module has port processors to receive and transmit network traffic. The input / output module also has a switch connecting the port processors. Each port processor categorizes the network traffic as fast path network traffic or control path network traffic. The switch routes fast path network traffic from an ingress port processor to a specified egress port processor. The storage processing device also includes a control module to process the control path network traffic received from the ingress port processor. The control module routes processed control path network traffic to the switch for routing to a defined egress port processor. The control module is connected to the input / output module. The input / output module and the control module are configured to interactively support data virtualization, data migration, data journaling, and snapshotting. The distributed control and fast path processors achieve scaling of storage network software. The storage processors provide line-speed processing of storage data using a rich set of storage-optimized hardware acceleration engines. The multi-protocol switching fabric provides a low-latency, protocol-neutral interconnect that integrally links all components with any-to-any non-blocking throughput.
Owner:AVAGO TECH INT SALES PTE LTD
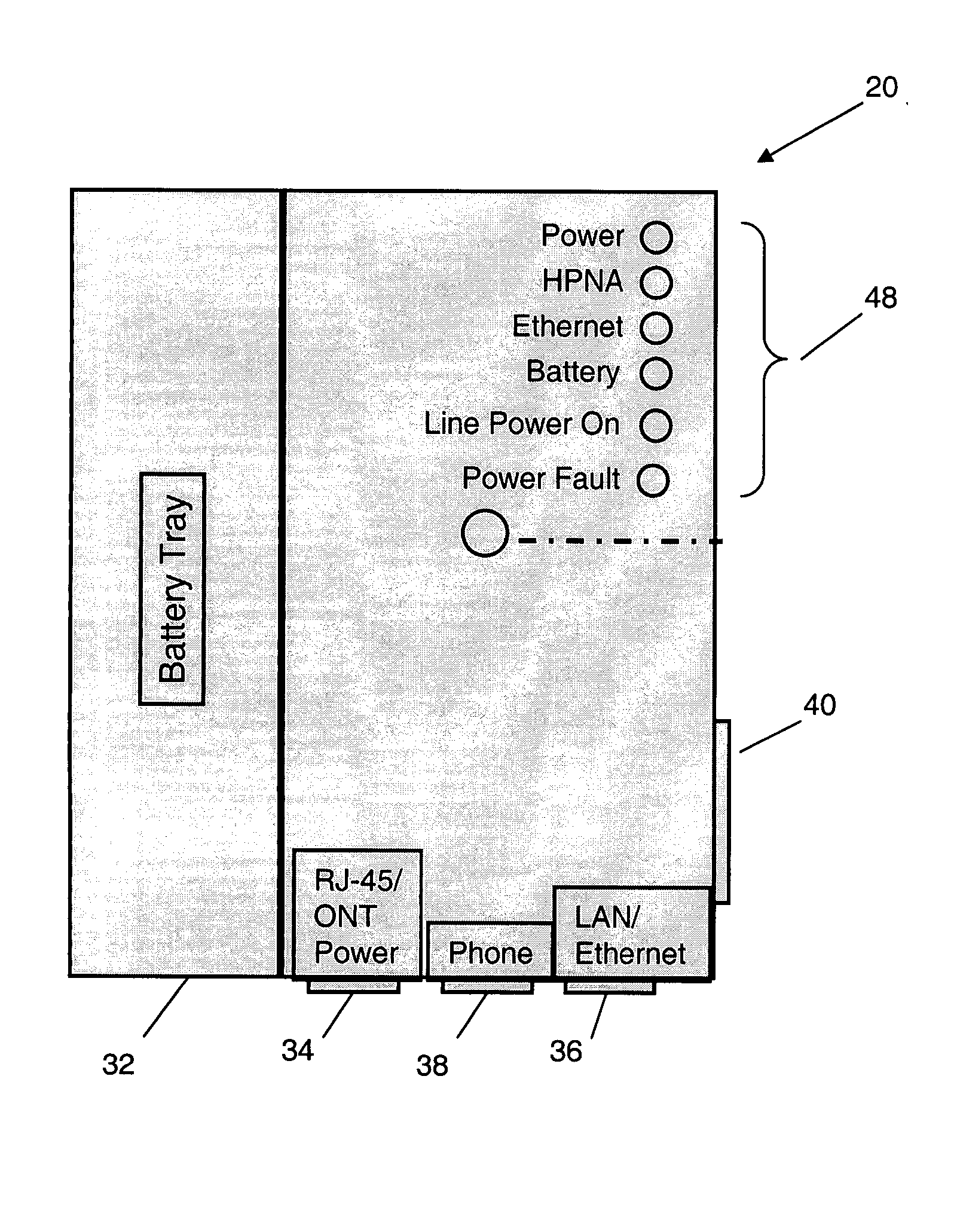
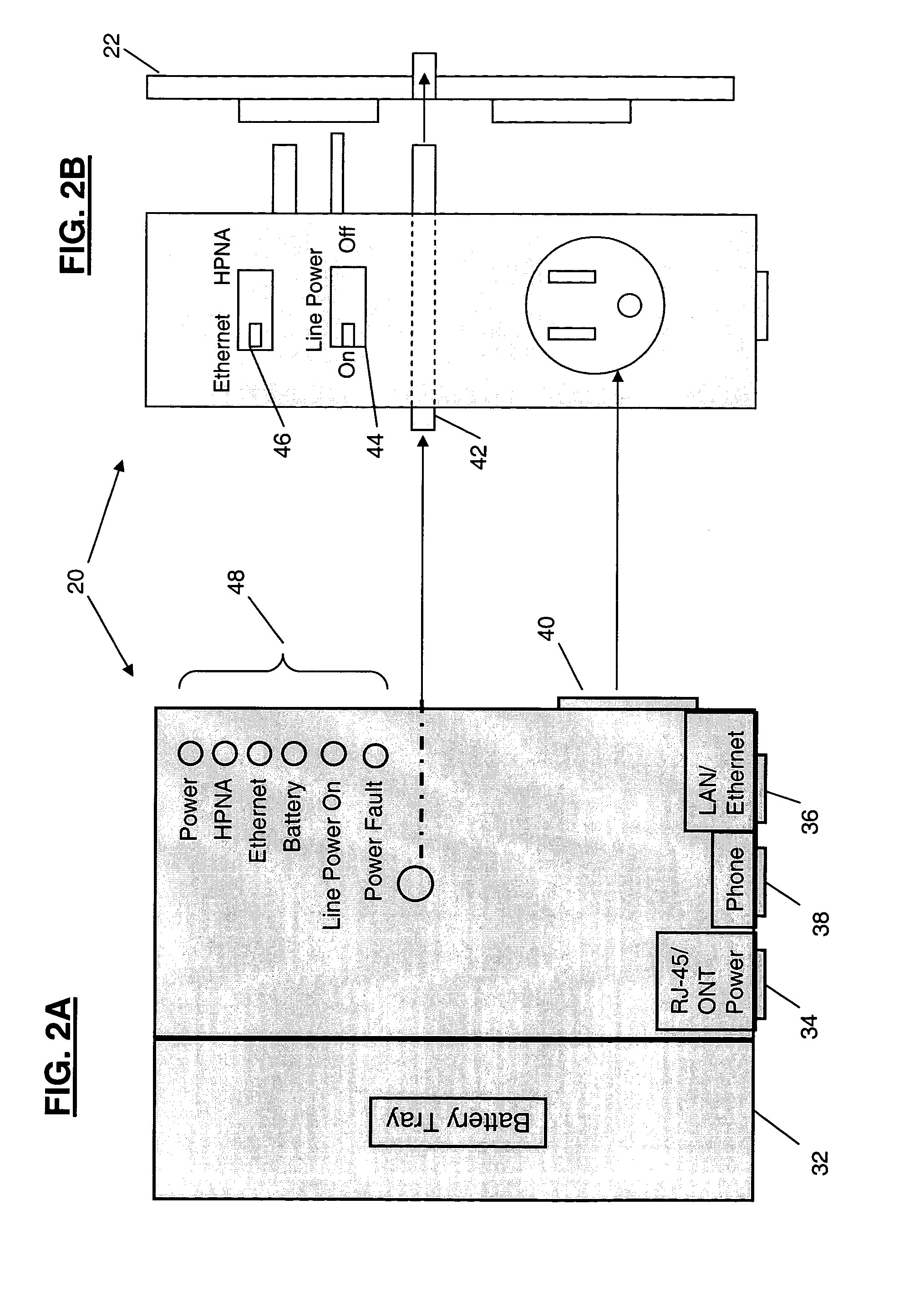
Power adapter and broadband line extender system and method
ActiveUS20040268160A1Volume/mass flow measurementTwo-part coupling devicesNetwork terminationData port
A power adapter, in a presently preferred embodiment, includes a power converter and multiple data ports, and is configured for ease of coupling the power converter into pre-existing premises power connectors. Thus, premises power can be supplied from the power converter and a first data port, via data cabling, to a network terminating device for an external network. Multi-protocol adapters, such as an HPNA (Home Phoneline Network Alliance protocol compliant) / Ethernet adapter, may also be included to provide extension of a protocol (such as Ethernet) over pre-existing premises wiring. A back-up battery is optionally provided, as well as appropriate switches and indicators. Specialized male-female connectors may also be used.
Owner:TELLABS VIENNA
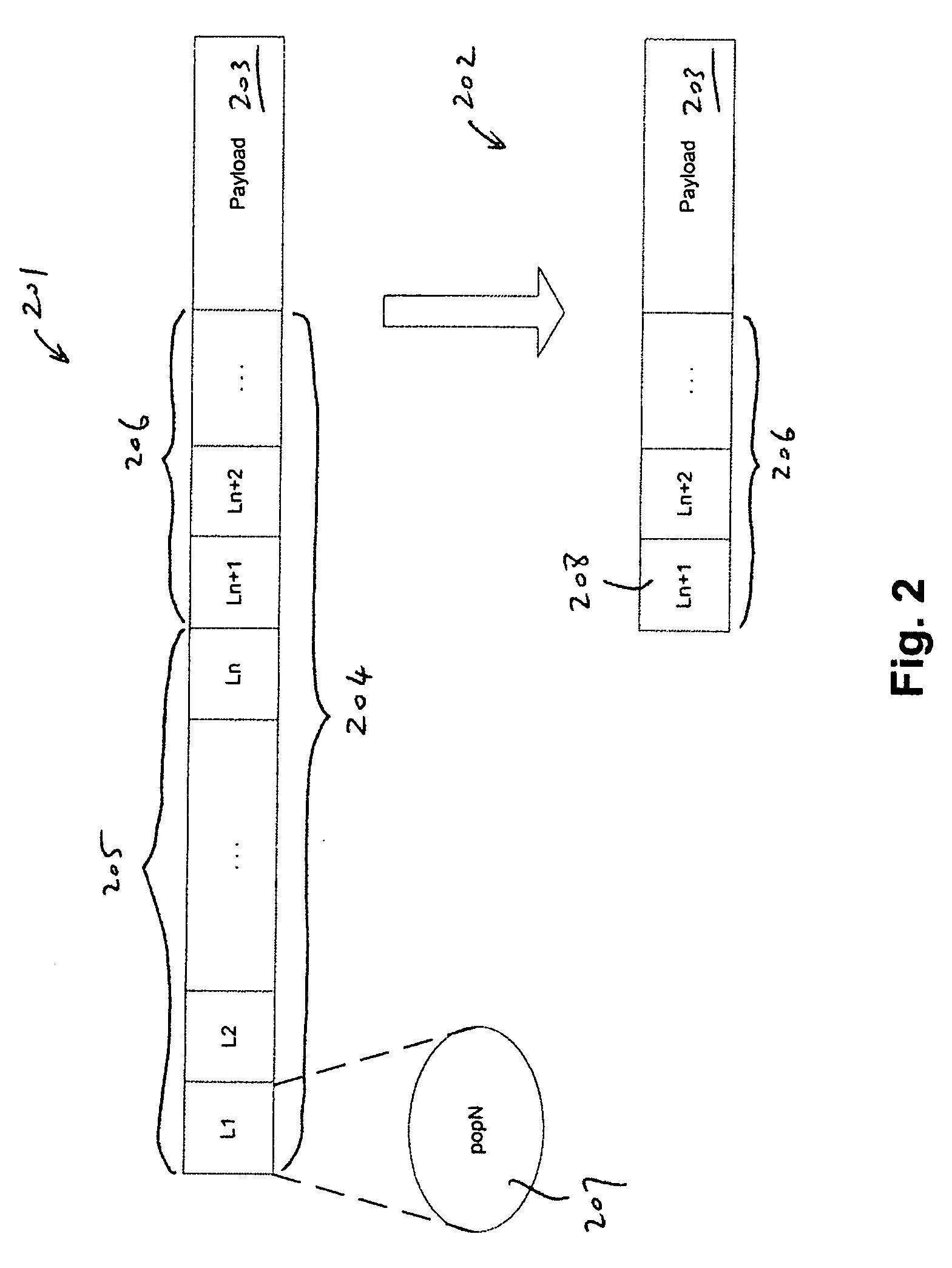
Source routed multicast LSP
Source routed multicast LSP is described herein. In one embodiment, when a first node receives a first packet having a label stack including a plurality of labels compatible with MPLS (multi-protocol label switching), in response to a first label on a top of the label stack, the first packet is duplicated into a second packet. In addition, at least two labels are popped from the top of the label stack of the second packet forming a third packet. Thereafter, the first and third packets are processed based on a label on the top of the label stack of the first and third packets respectively. Other methods and apparatuses are also described.
Owner:TELEFON AB LM ERICSSON (PUBL)
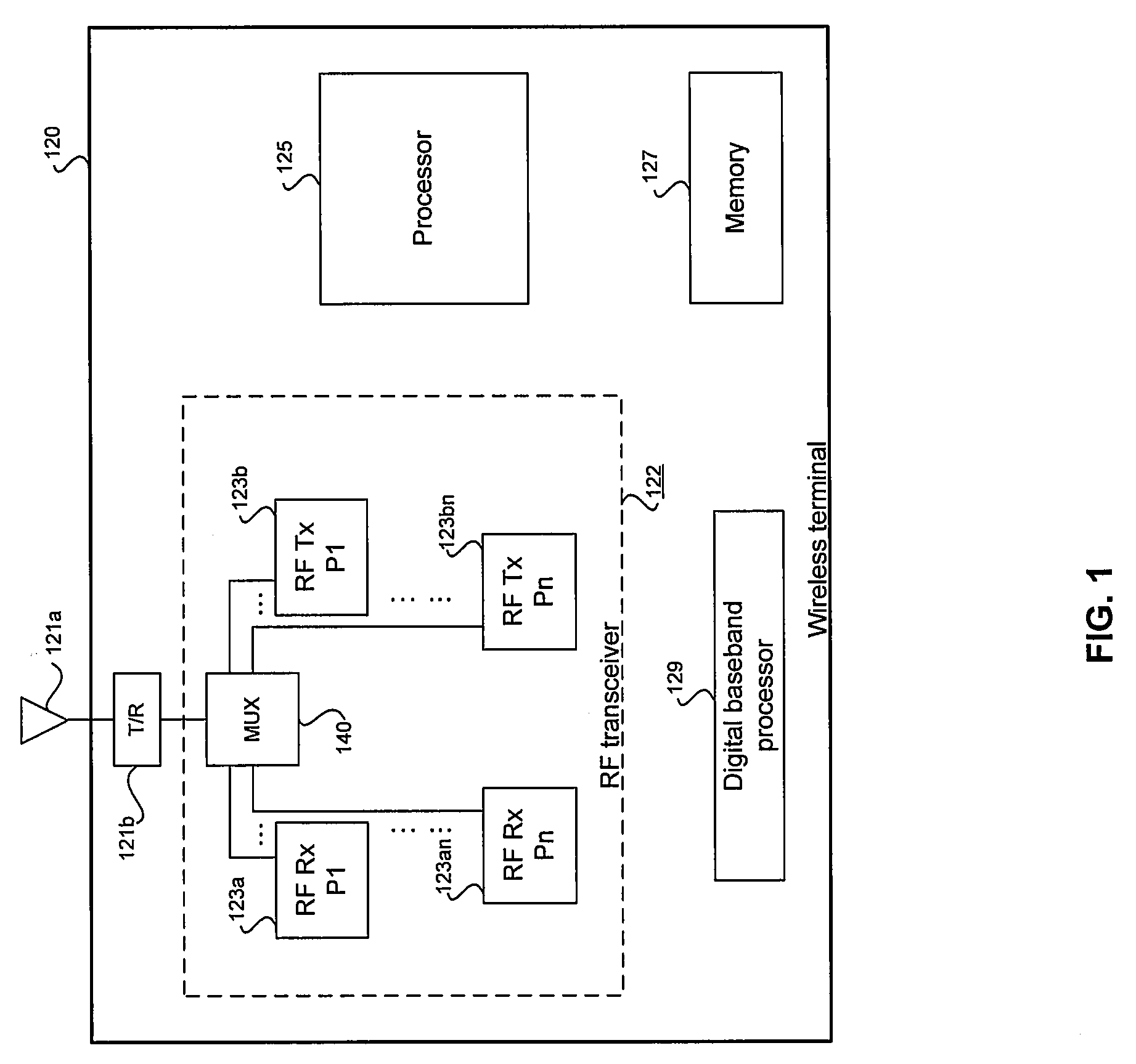
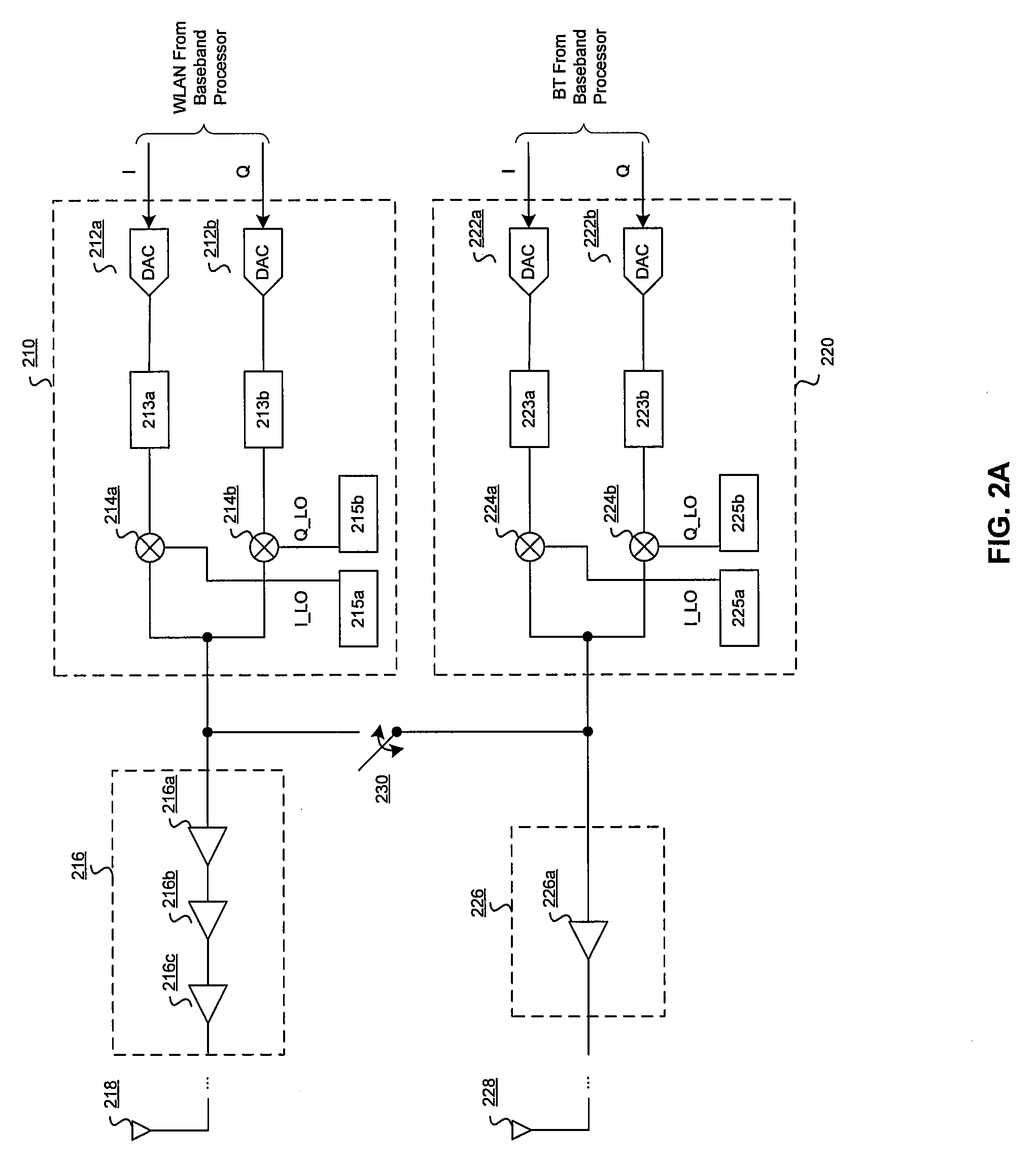
Method and System for Shared High-Power Transmit Path for a Multi-Protocol Transceiver
InactiveUS20080137566A1Network topologiesData switching by path configurationTransceiverAudio power amplifier
Aspects of a method and system for a shared high-power transmit path for a multi-protocol transceiver are disclosed. Aspects of one method may include sharing a first power amplifier with a WLAN signal and a Bluetooth signal. The first power amplifier may amplify the WLAN signal and / or the Bluetooth signal simultaneously, or individually. A second power amplifier may be used to amplify the Bluetooth signal, where the first power amplifier may have a higher gain than the second power amplifier. Power may be reduced to the second power amplifier in instances where the first power amplifier is used to amplify the Bluetooth signal. The Bluetooth signal may be communicated to the first power amplifier via a switching circuit, which may comprise one or more switching stages.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Collaborative coexistence of co-located mobile wimax, wireless lan, and/or bluetooth radios
Collaborative coexistence of co-located mobile WiMAX, wireless LAN, and / or Bluetooth radios. Within a communication device that includes multi-protocol communication capability, the various radio modules included within such a communication device operate cooperatively such that collisions are avoided between those various radios. When a first of the radio modules operates as governed by a relatively rigid frame structure, a second of the radio modules capitalizes upon that predetermined nature (of the relatively rigid frame structure) to support communication during times in which that first radio module has a lower level of activity (e.g., turned off completely, within a power savings mode, in a sleep mode, etc.). The radio module operation is performed within a time-orthogonal manner, such that multiple radio modules are not attempting to transmit or receive simultaneously. Moreover, CTS2SELF operation can be employed alone or in conjunction with power savings operation of co-located radios within a communication device.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com