Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
479 results about "ISCSI" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
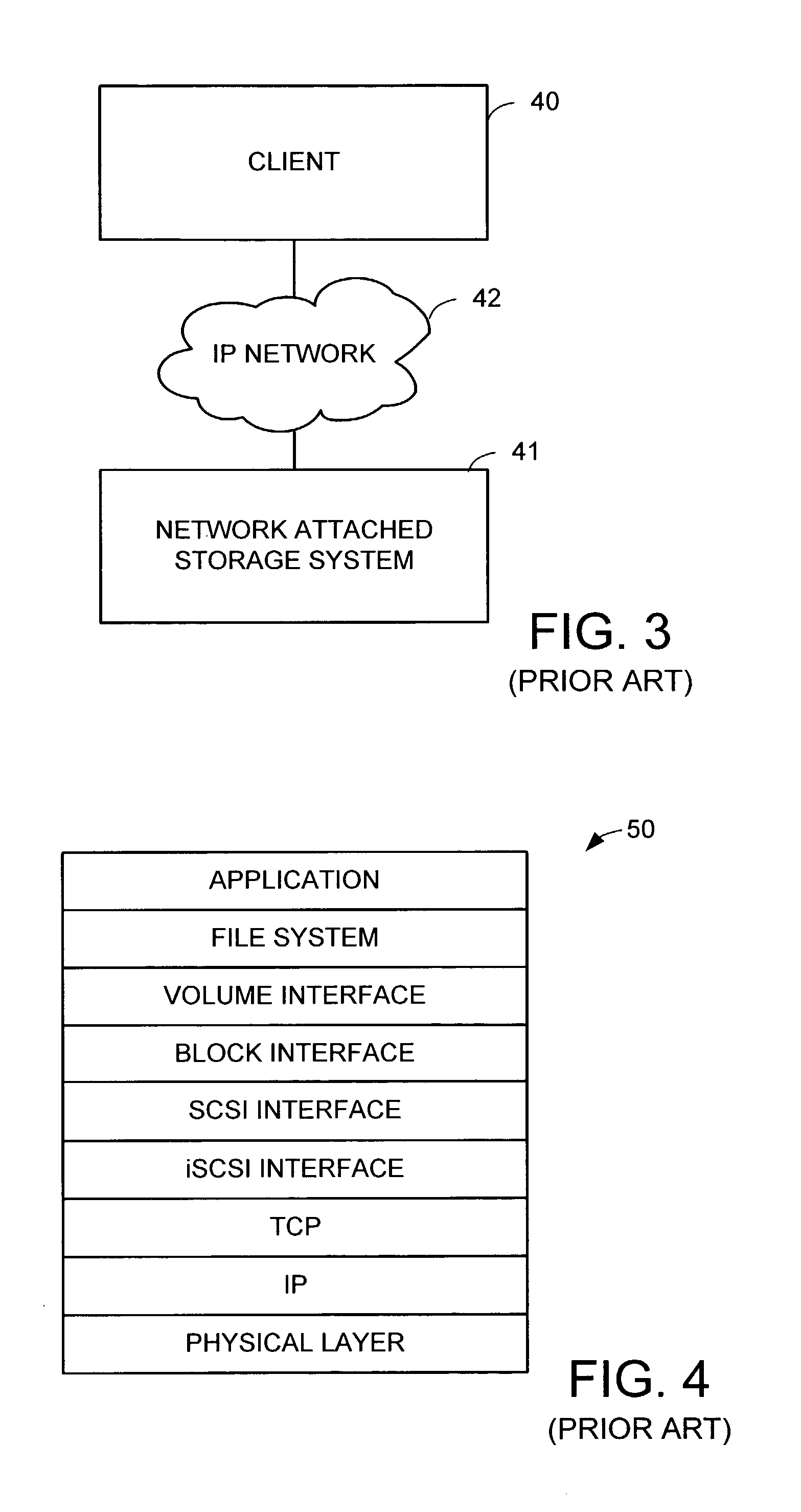
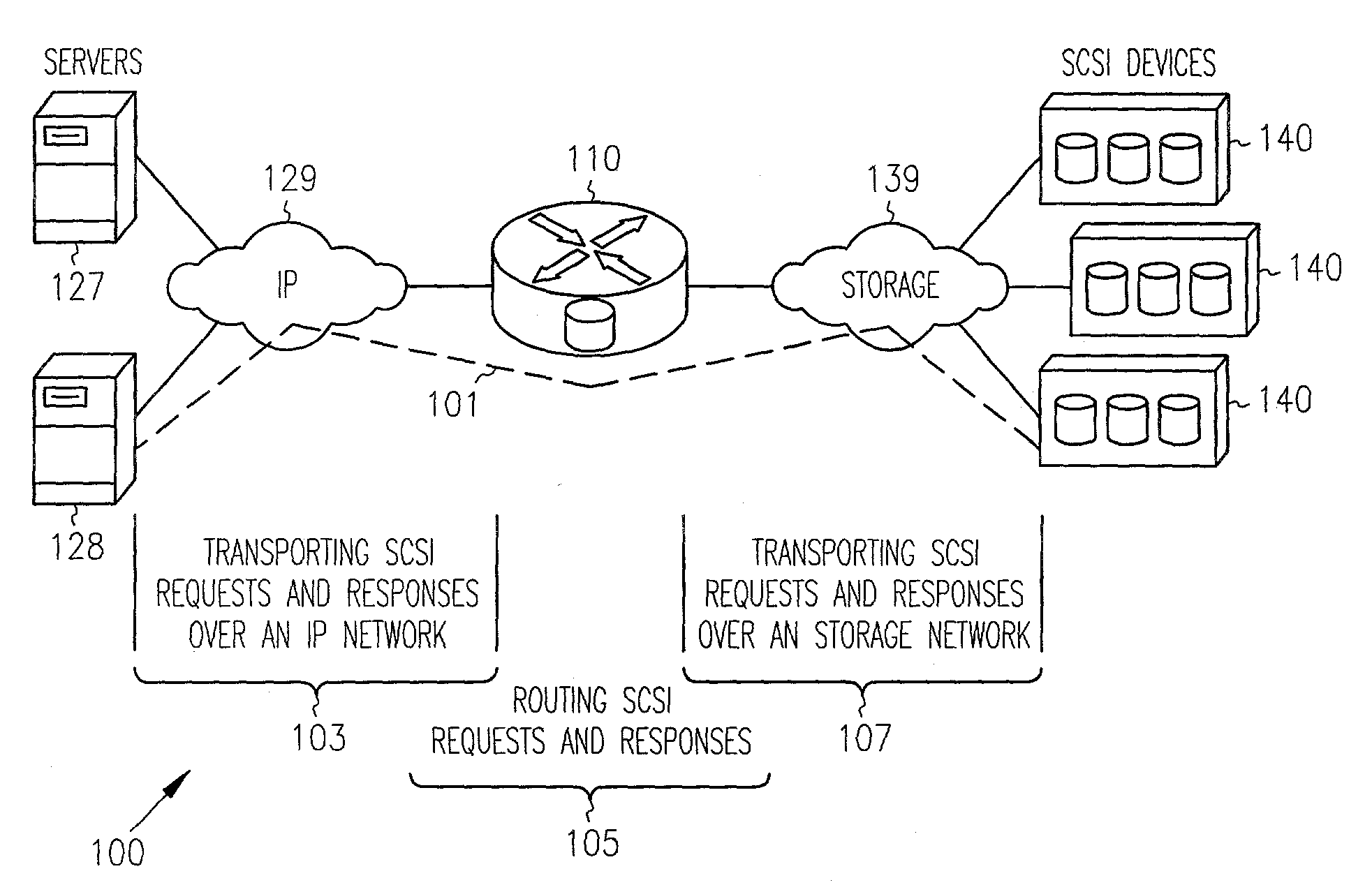
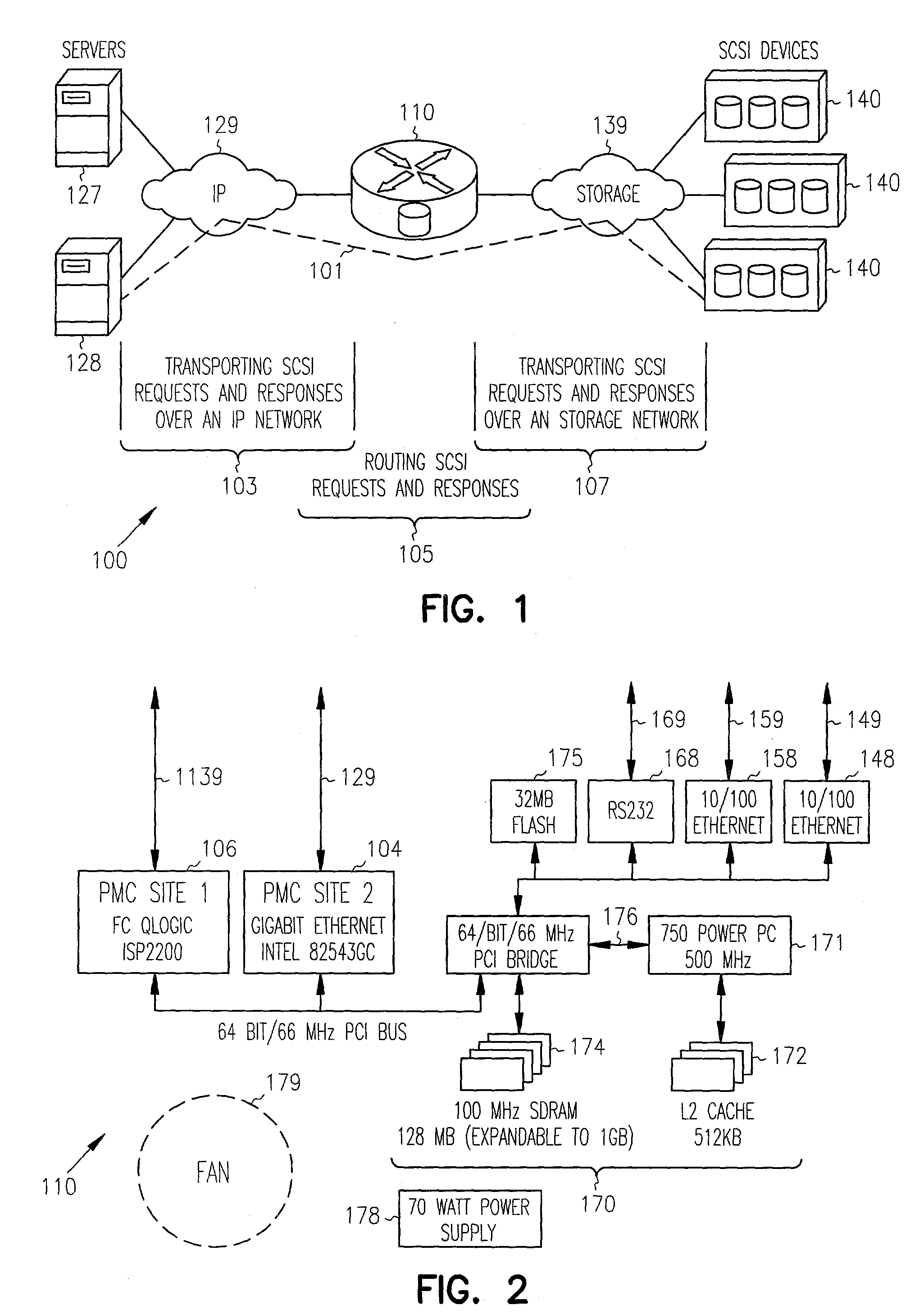
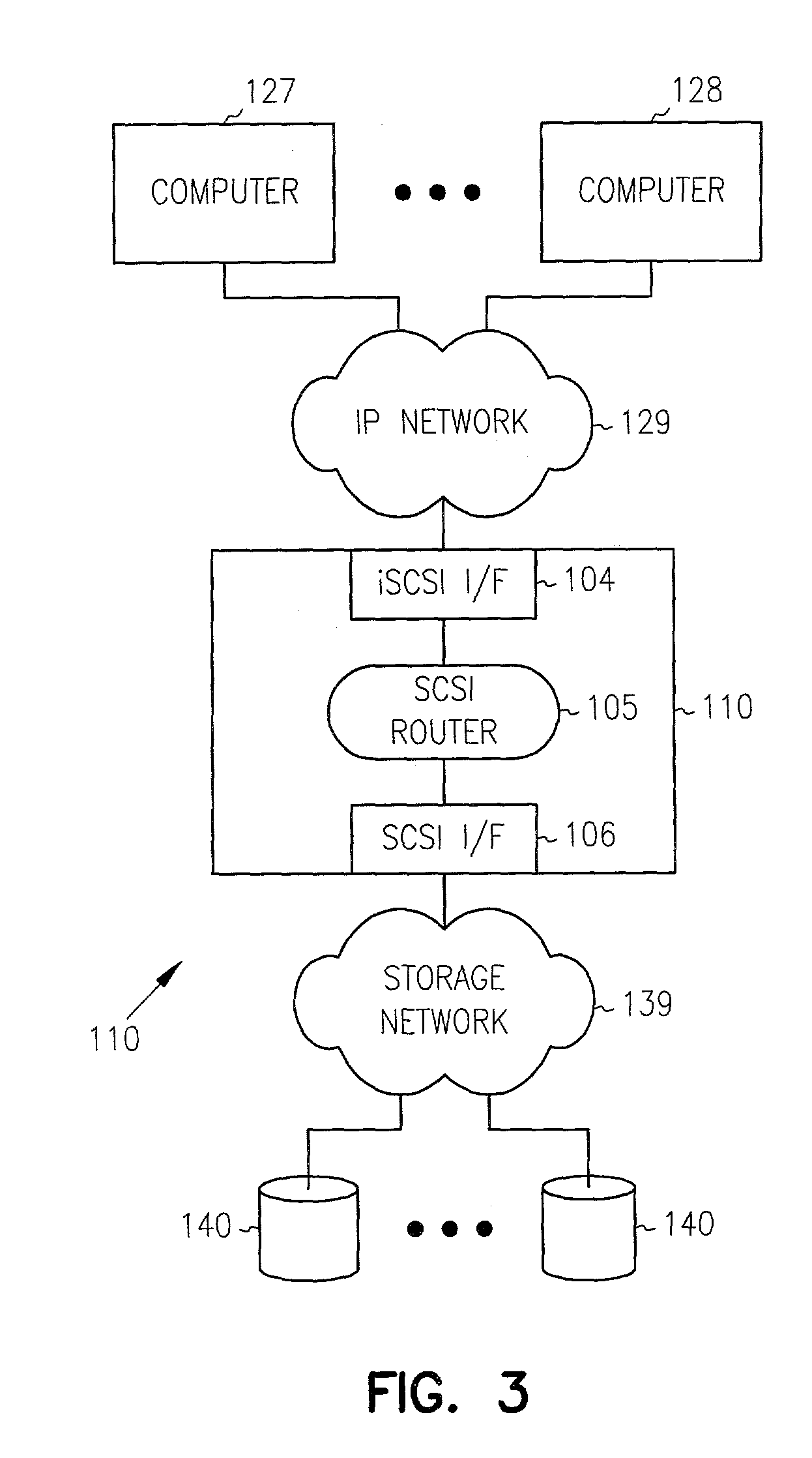
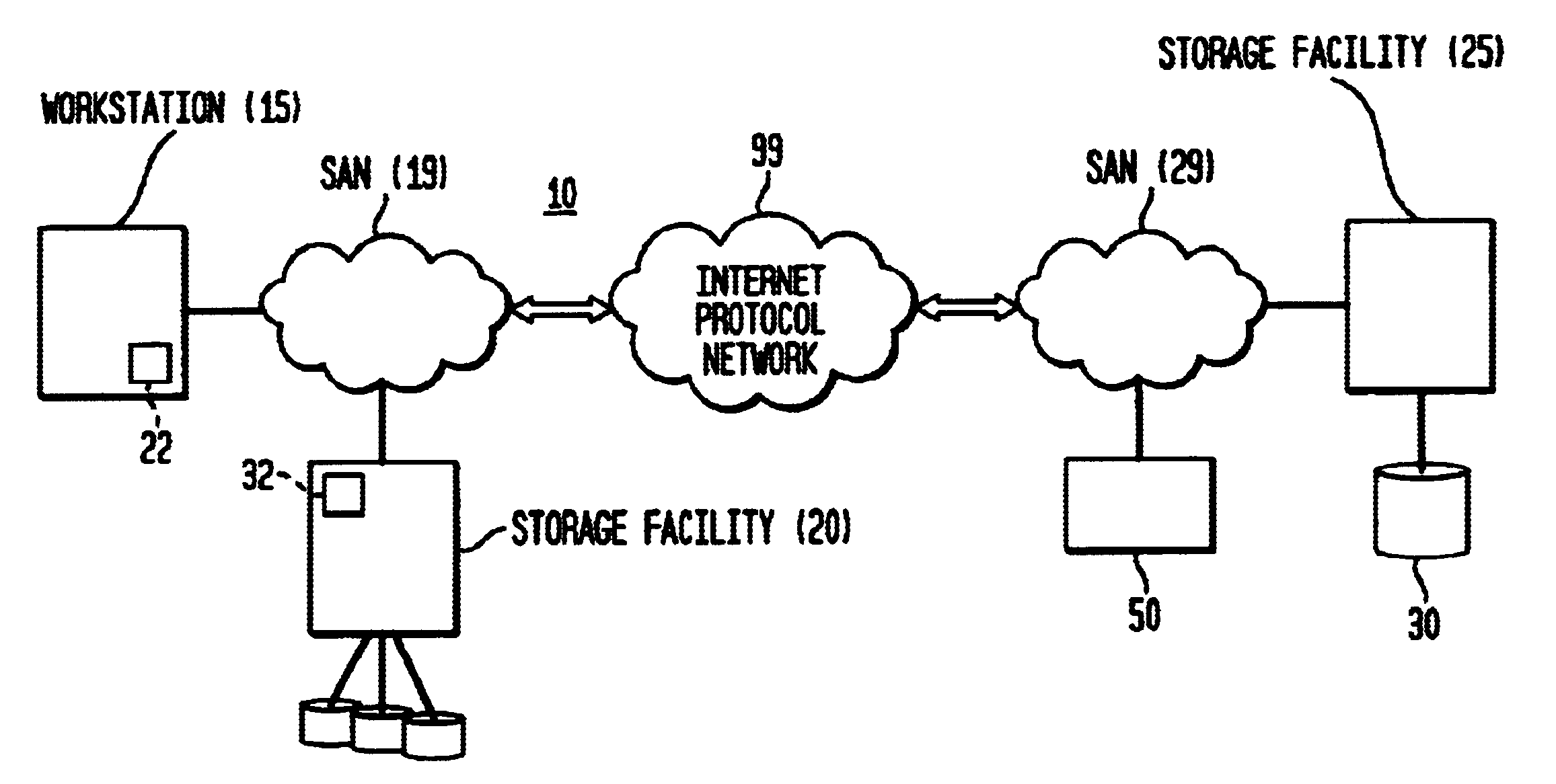
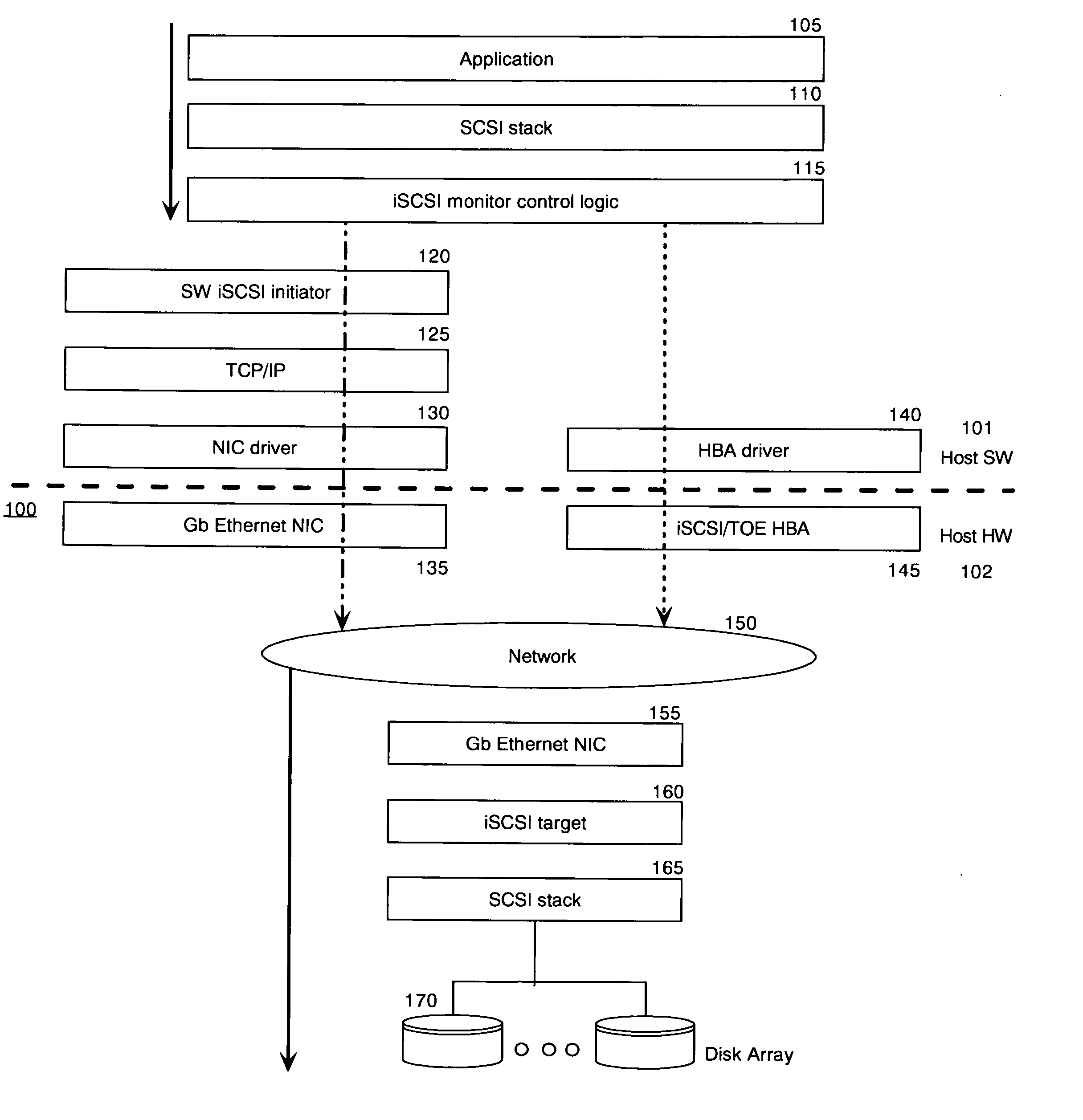
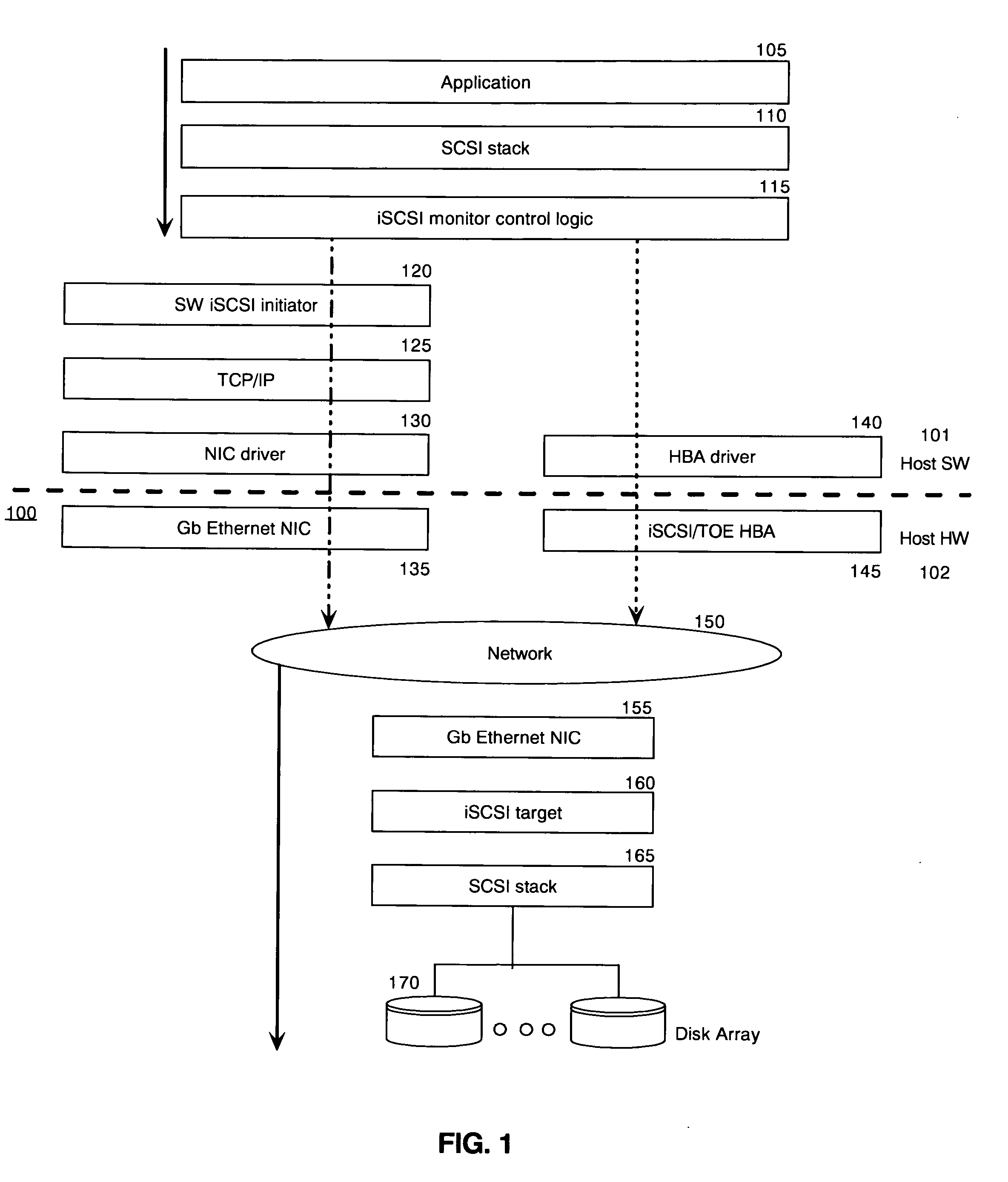
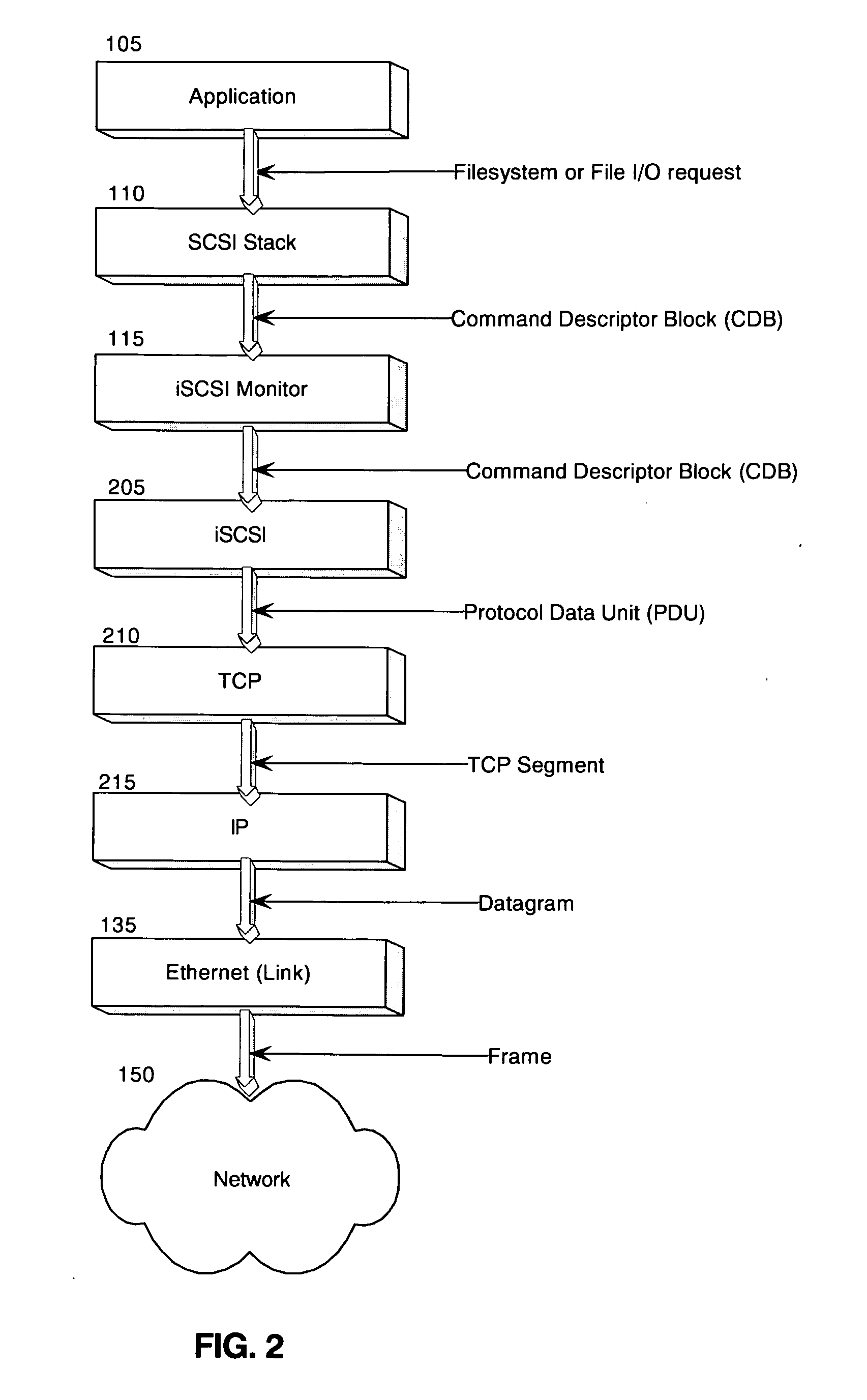
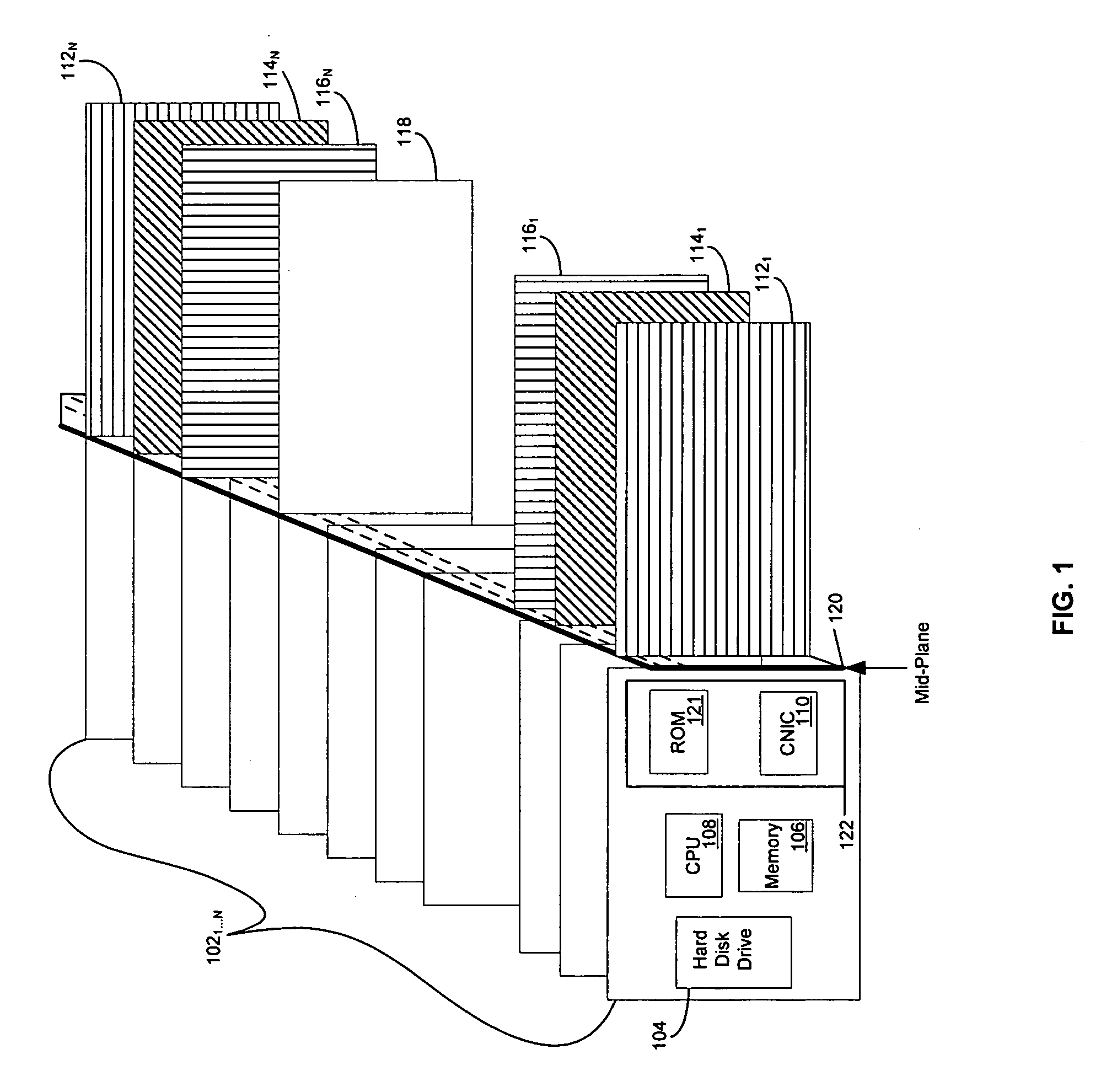
In computing, iSCSI (/ˈaɪskʌzi/ EYE-skuz-ee) is an acronym for Internet Small Computer Systems Interface, an Internet Protocol (IP)-based storage networking standard for linking data storage facilities. It provides block-level access to storage devices by carrying SCSI commands over a TCP/IP network. iSCSI is used to facilitate data transfers over intranets and to manage storage over long distances. It can be used to transmit data over local area networks (LANs), wide area networks (WANs), or the Internet and can enable location-independent data storage and retrieval.
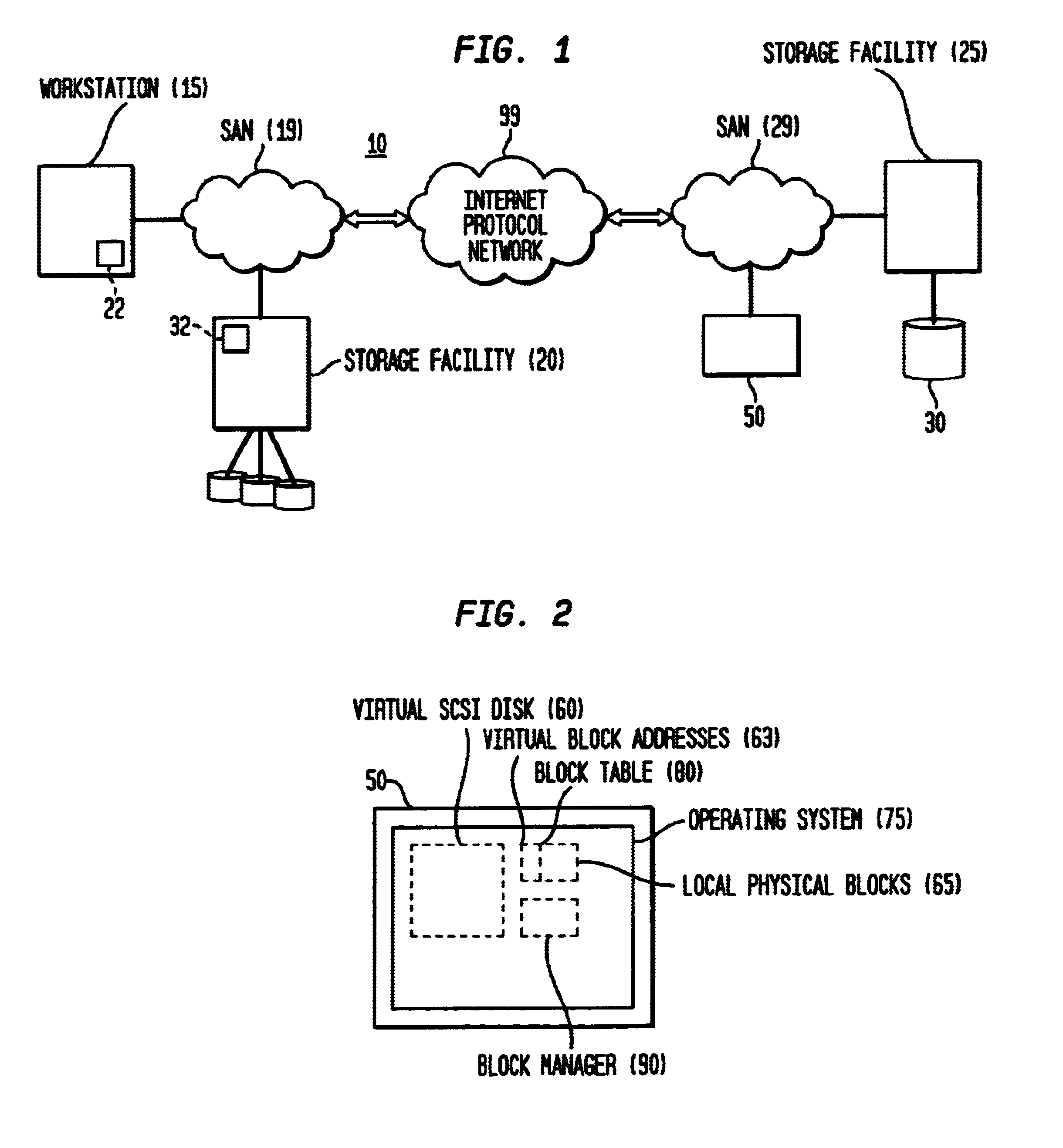
Multi-protocol sharable virtual storage objects
ActiveUS20050044162A1Digital data processing detailsMultiple digital computer combinationsUnixFile replication
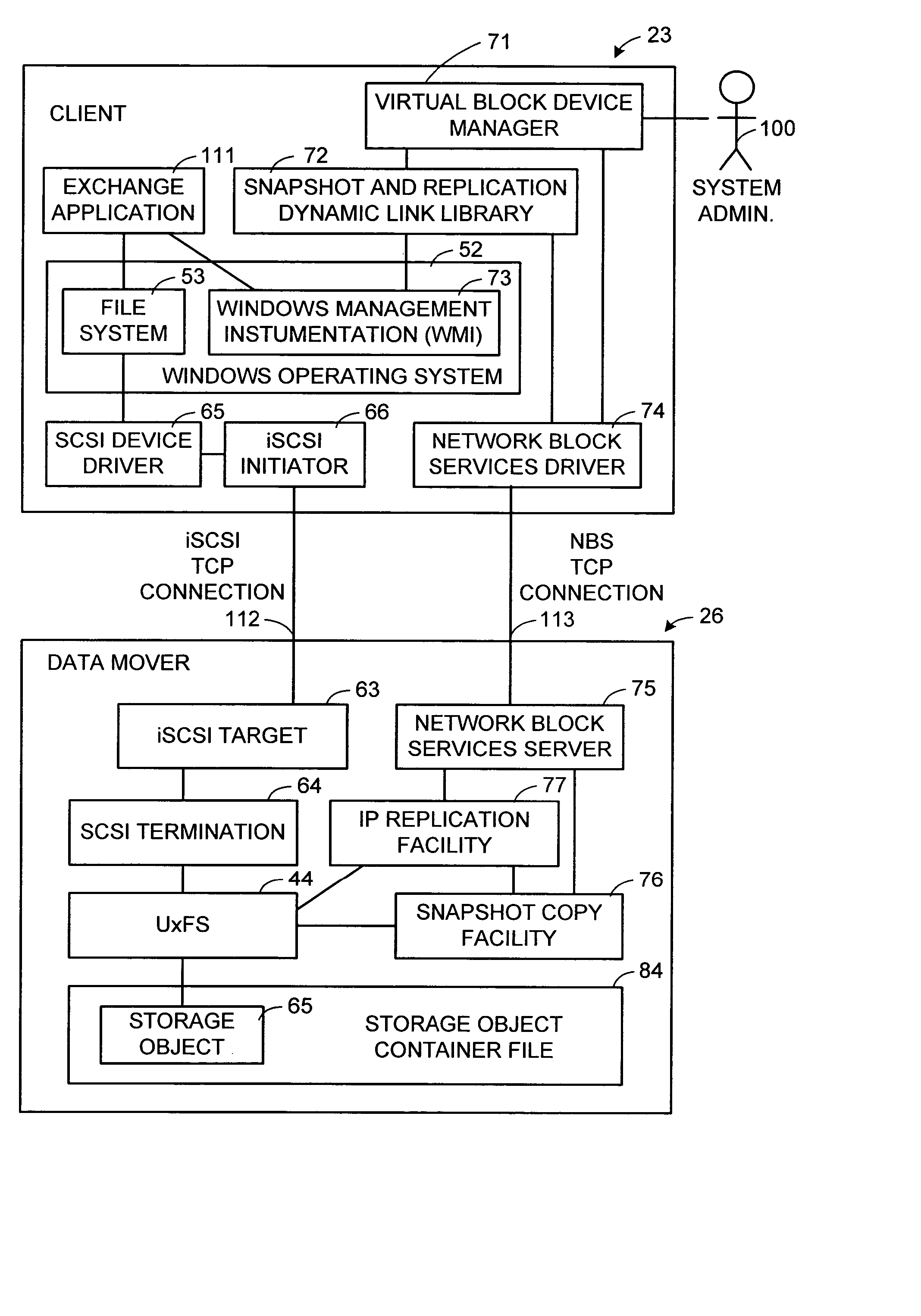
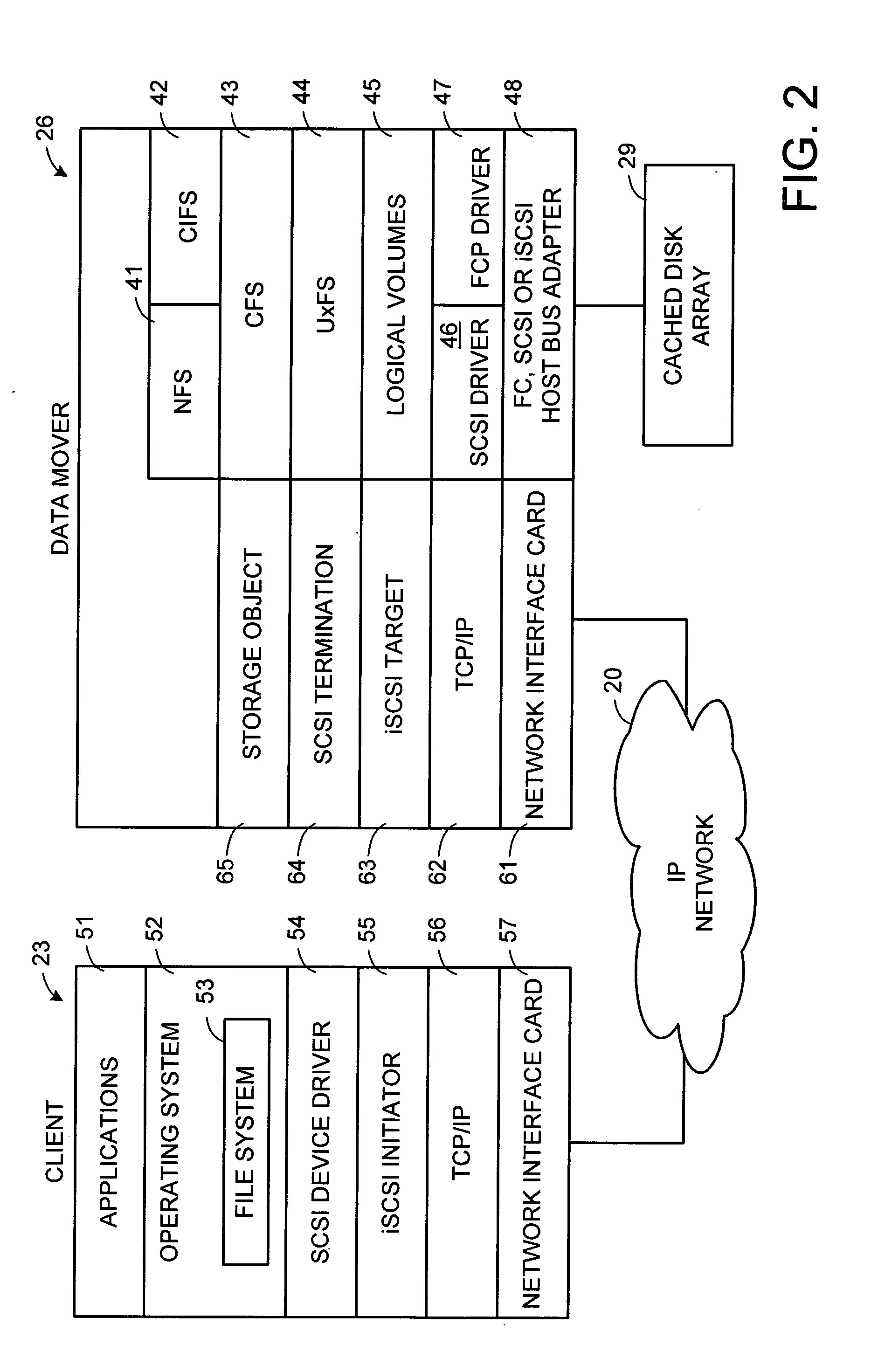
A storage object such as a virtual disk drive or a raw logical volume is contained in a UNIX compatible file so that the file containing the storage object can be exported using the NFS or CIFS protocol and shared among UNIX and MS Windows clients or servers. The storage object can be replicated and backed up using conventional file replication and backup facilities without disruption of client access to the storage object. For client access to data of the storage object, a software driver accesses the file containing the storage object. For example, a software driver called a virtual SCSI termination is used to access a file containing a virtual SCSI disk drive. Standard storage services use the iSCSI protocol to access the virtual SCSI termination. An IP replication or snapshot copy facility may access the file containing the virtual SCSI disk drive using a higher-level protocol.
Owner:EMC IP HLDG CO LLC
Thin provisioning of a file system and an iSCSI LUN through a common mechanism
ActiveUS7631155B1Digital data information retrievalData processing applicationsFile systemThin provisioning
A container file system is built on a sparse metavolume for enhanced decoupling of logical storage from physical storage and for providing common supplementary storage services for iSCSI block access and for NFS or CIFS file system access. The container file system contains a production file system or iSCSI LUN and may also contain snapshot copies of the production file system or iSCSI LUN. The container file system manages storage space among the production file system or iSCSI LUN and its snapshot copies, and also improves fault containment. The sparse metavolume provides thin provisioning of the container file system. A slice map indicates whether or not each slice of logical storage in the sparse metavolume is provisioned with an associated configured slice of data storage.
Owner:EMC IP HLDG CO LLC
System for Providing Multi-path Input/Output in a Clustered Data Storage Network
ActiveUS20060277383A1Avoid problemsImprove performanceDigital computer detailsTransmissionClustered dataStorage area network
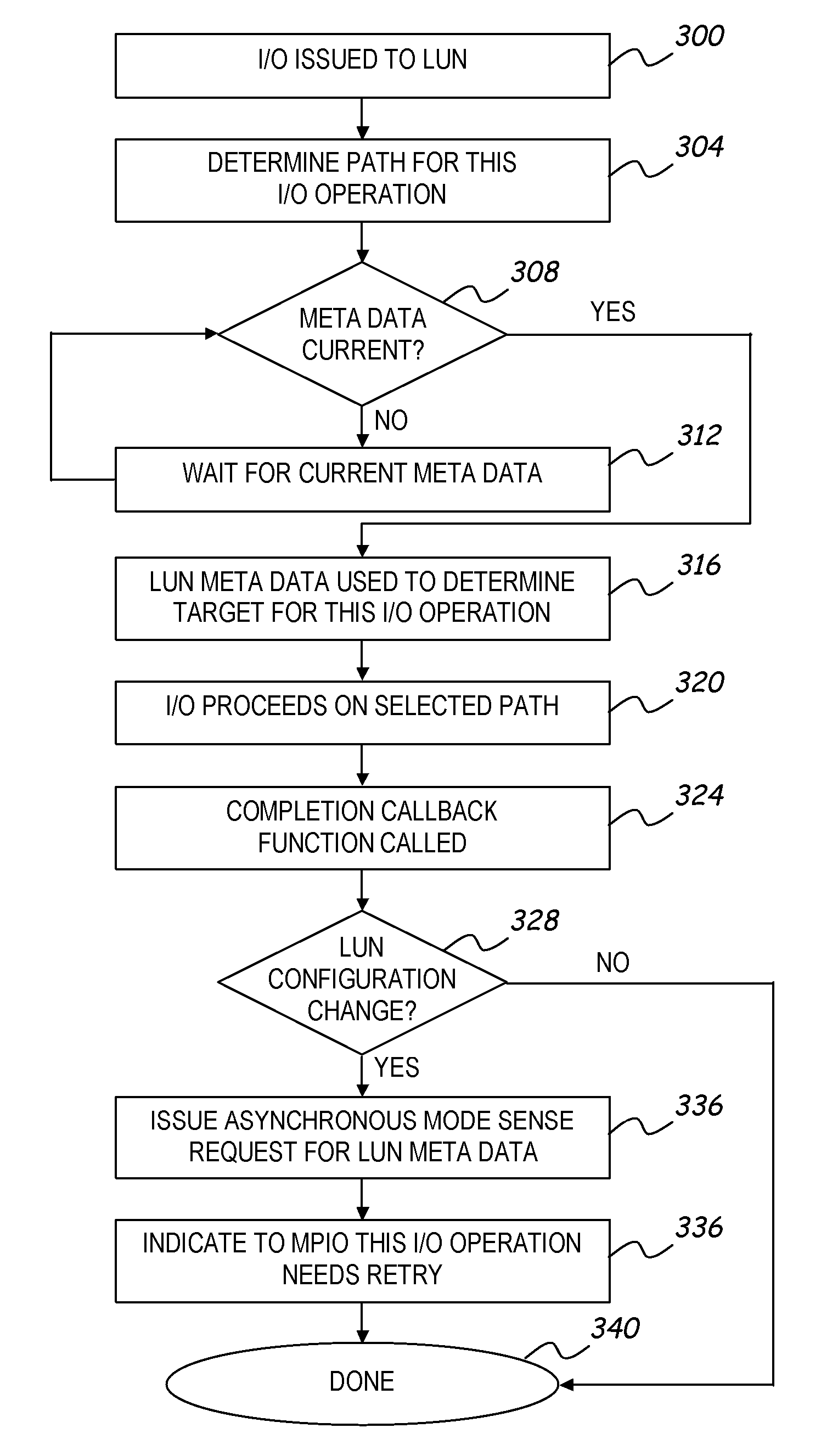
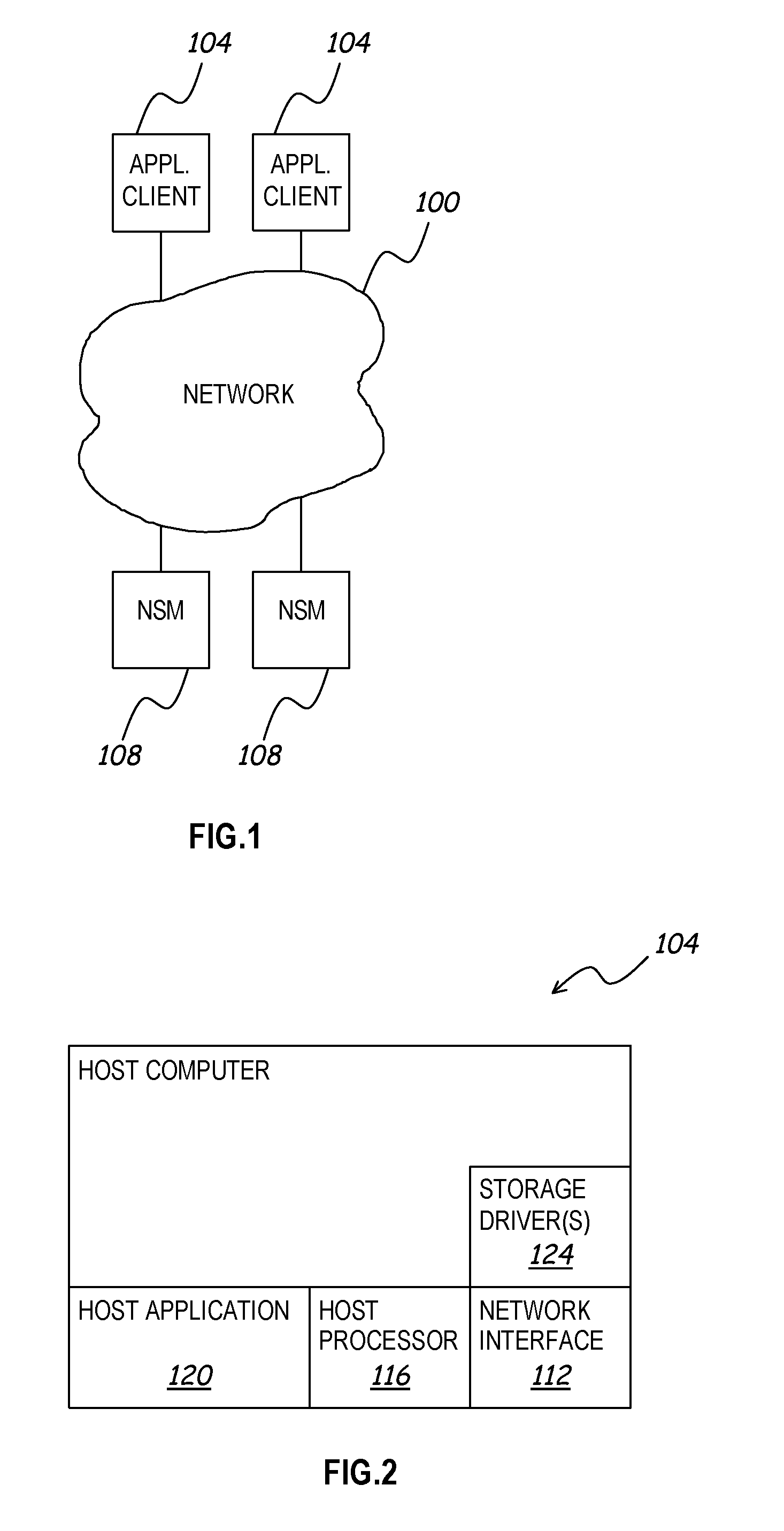
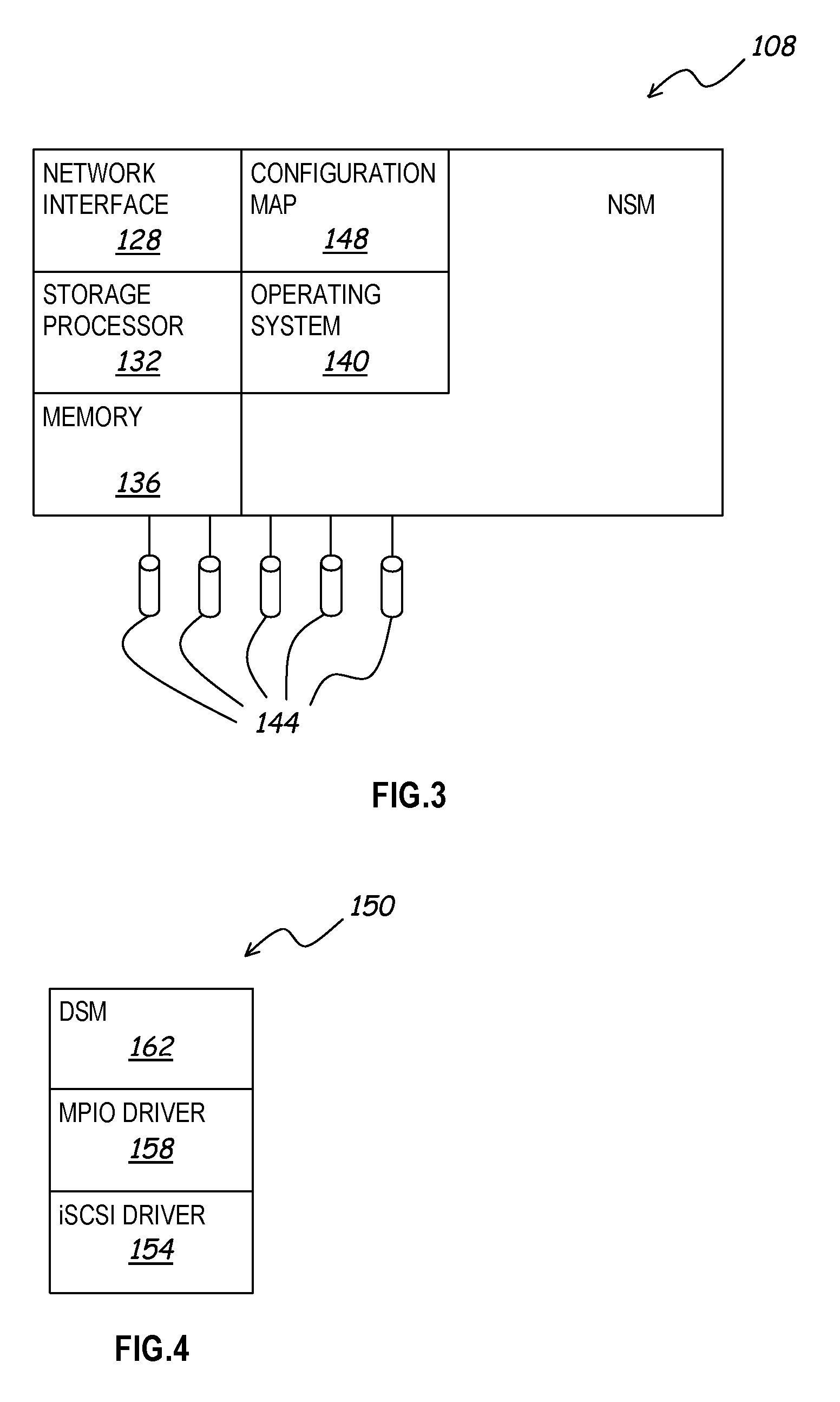
A distributed network storage system provides capability to send and receive storage information from multiple network storage servers in a storage area network using iSCSI commands. A storage server system comprising at least two data storage servers stores one or more logical volumes of data. A host computer receives a storage command from a host application, and determines one or more data storage servers has information to complete the storage command. The host computer generates one or more iSCSI network commands to carry out the storage command, and transmits the iSCSI network commands directly to each data storage server having necessary information. The storage servers receive iSCSI network commands, and return a response to the host. The host and storage servers verify the configuration of the storage network and are capable of correcting or updating the configuration as required.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
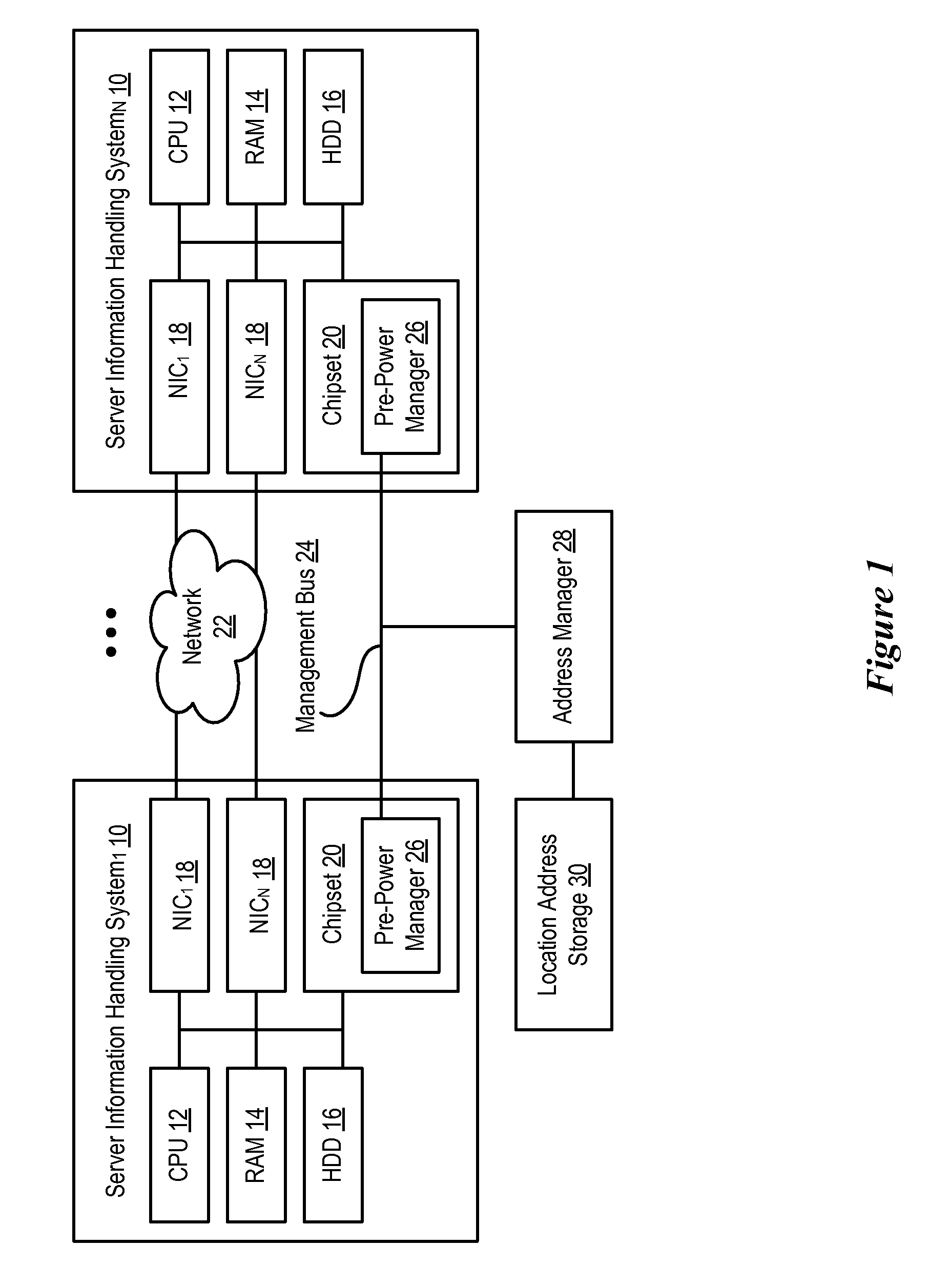
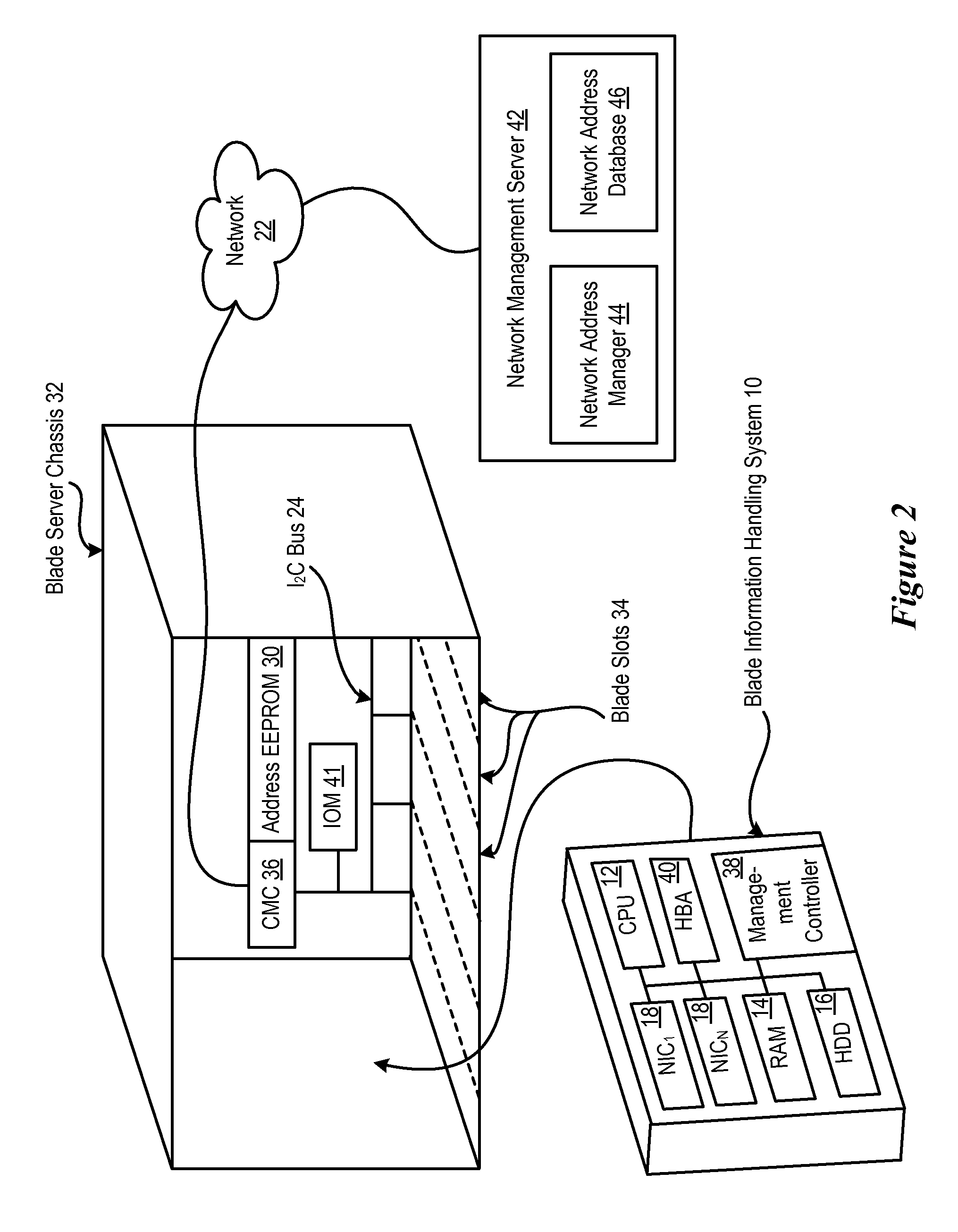
System And Method For Assigning Addresses To Information Handling Systems
ActiveUS20090077208A1Inadvertent duplication is preventedReduce disadvantagesError preventionFrequency-division multiplex detailsNetwork addressingNetwork communication
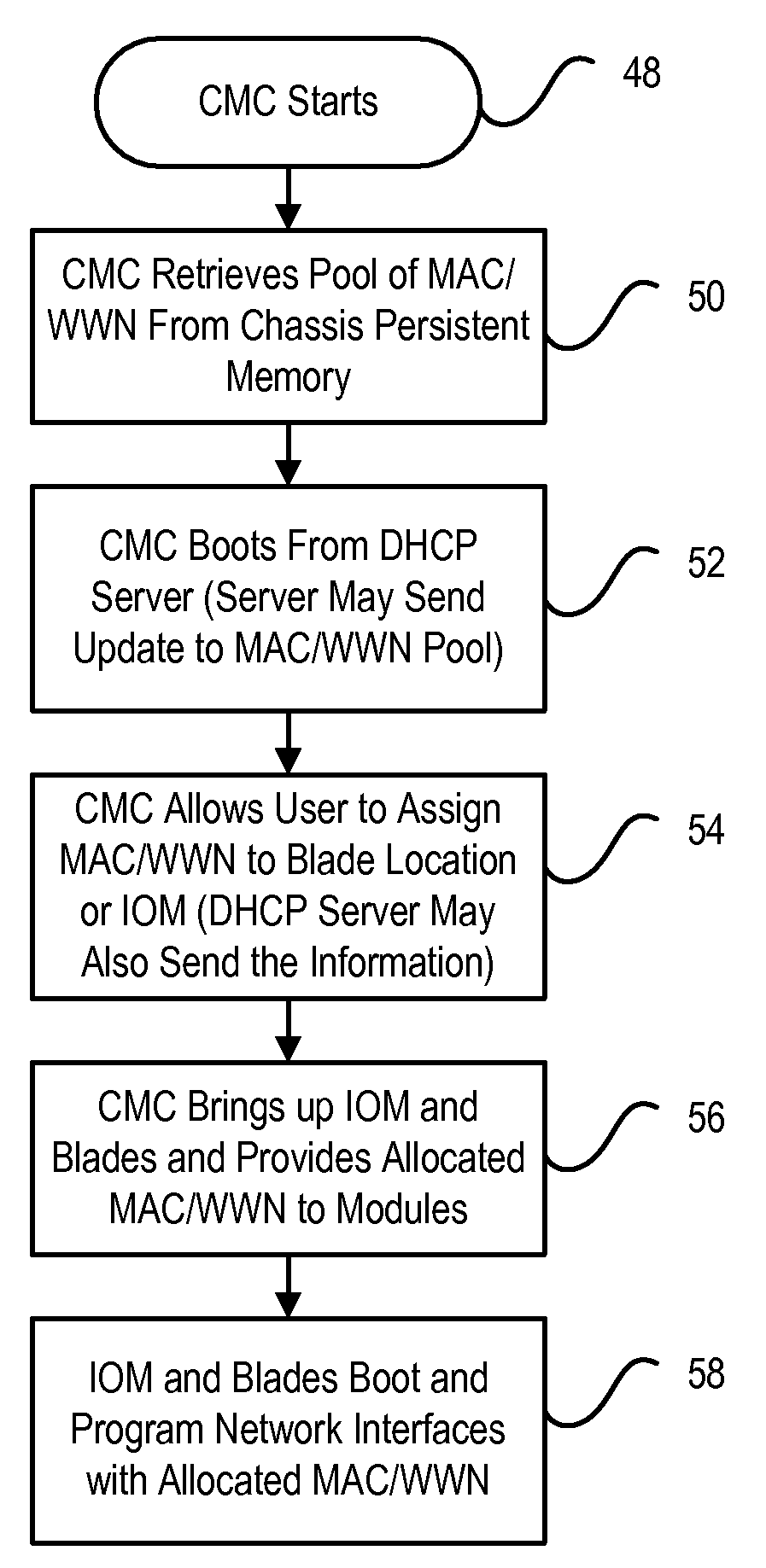
Information handling system network addresses are managed to support a consistent MAC address for iSCSI and fibre channel host bus adapter. For example, a management controller retrieves a MAC address from persistent memory, such as a network location, and assigns the MAC address to a non-persistent memory of a predetermined information handling system network component so that the MAC address remains consistent even if the network component is replaced. For example, an offload engine that supports network communications with iSCSI receives a MAC address from a network location and applies the MAC address for use by a host bus adapter. Alternatively, an offload engine supports Fibre Channel with World Wide Name or World Wide Identifier address assignments.
Owner:DELL PROD LP
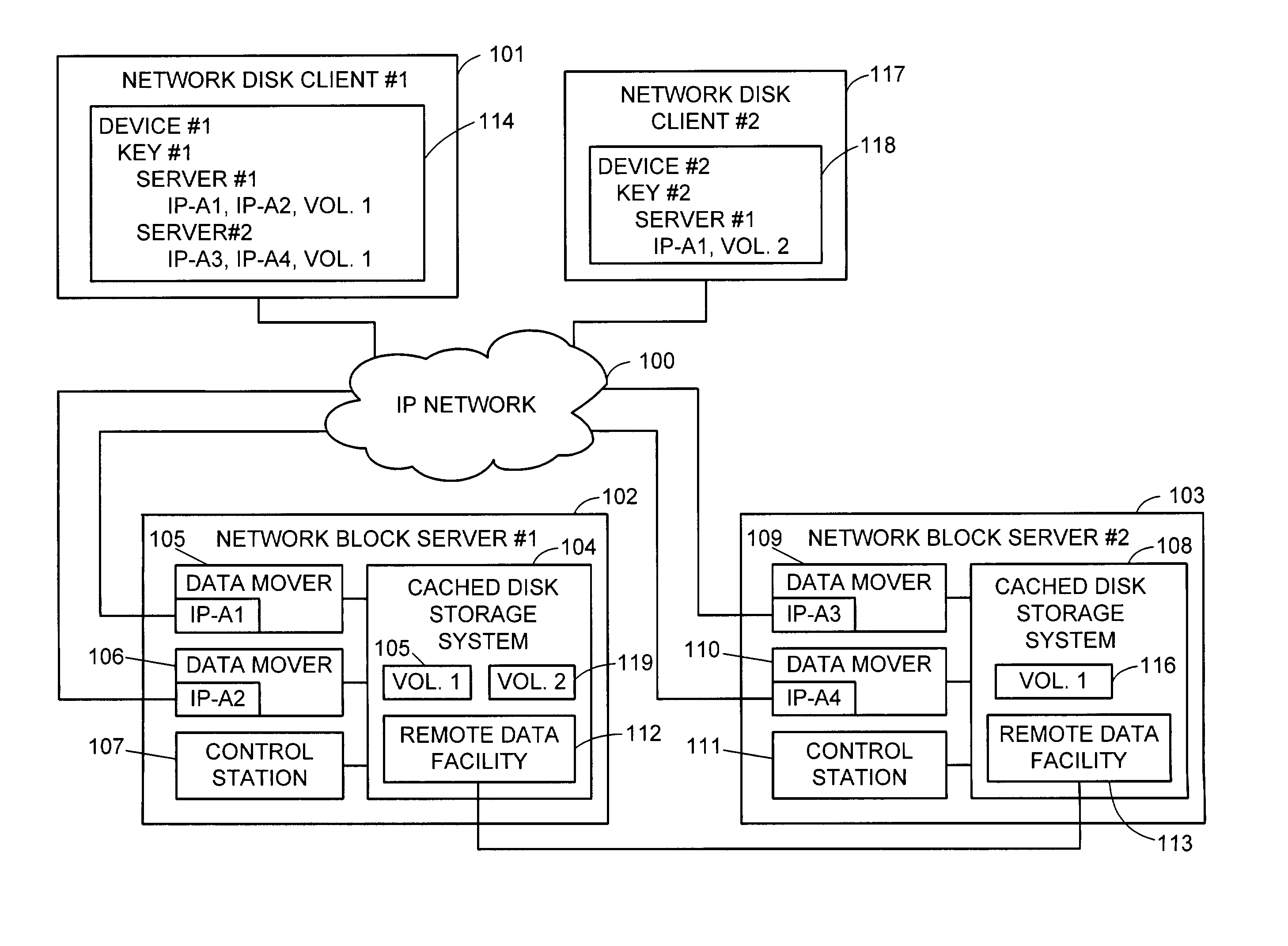
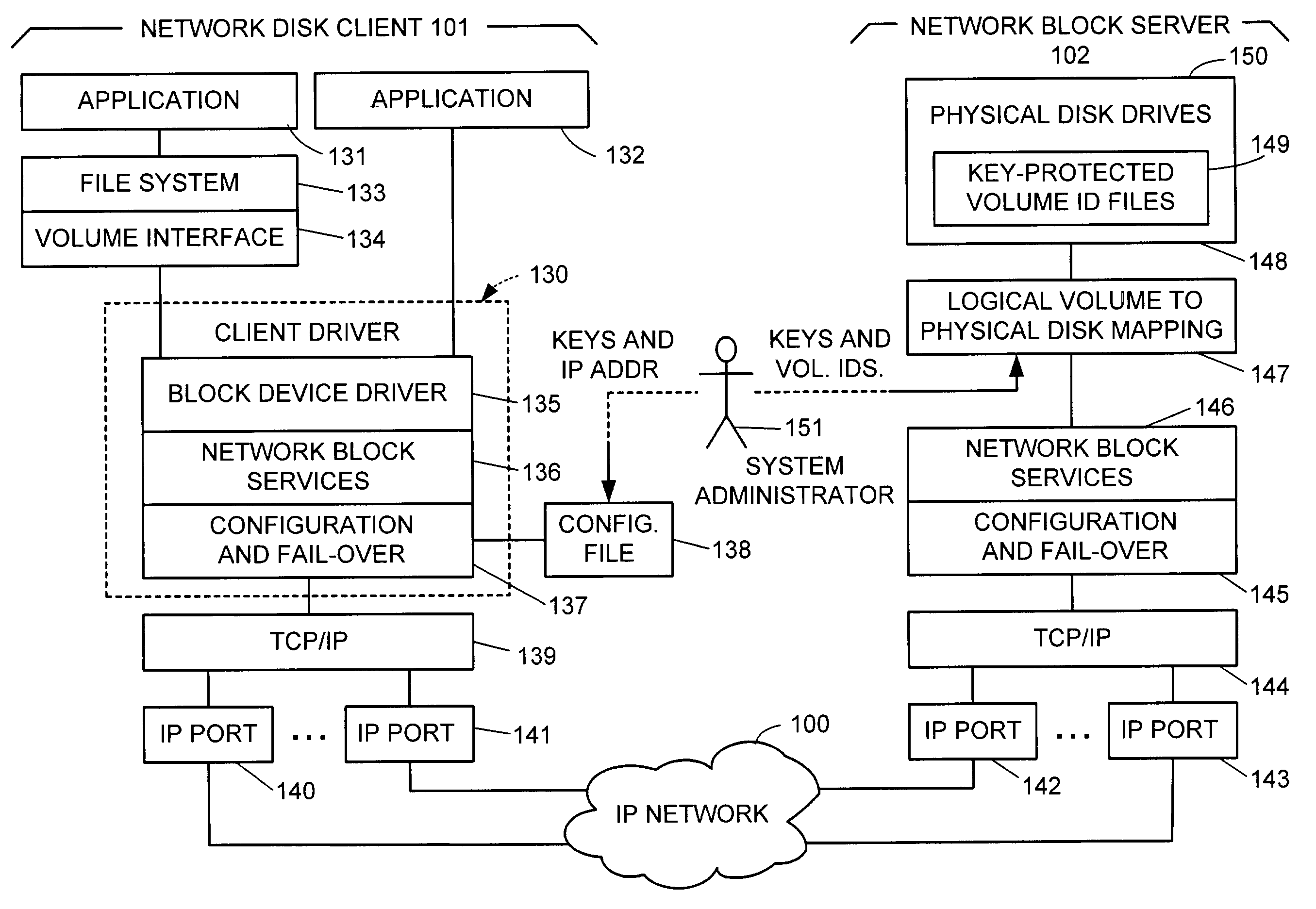
Network block services for client access of network-attached data storage in an IP network
ActiveUS20040059822A1Multiple digital computer combinationsTransmissionService protocolOperational system
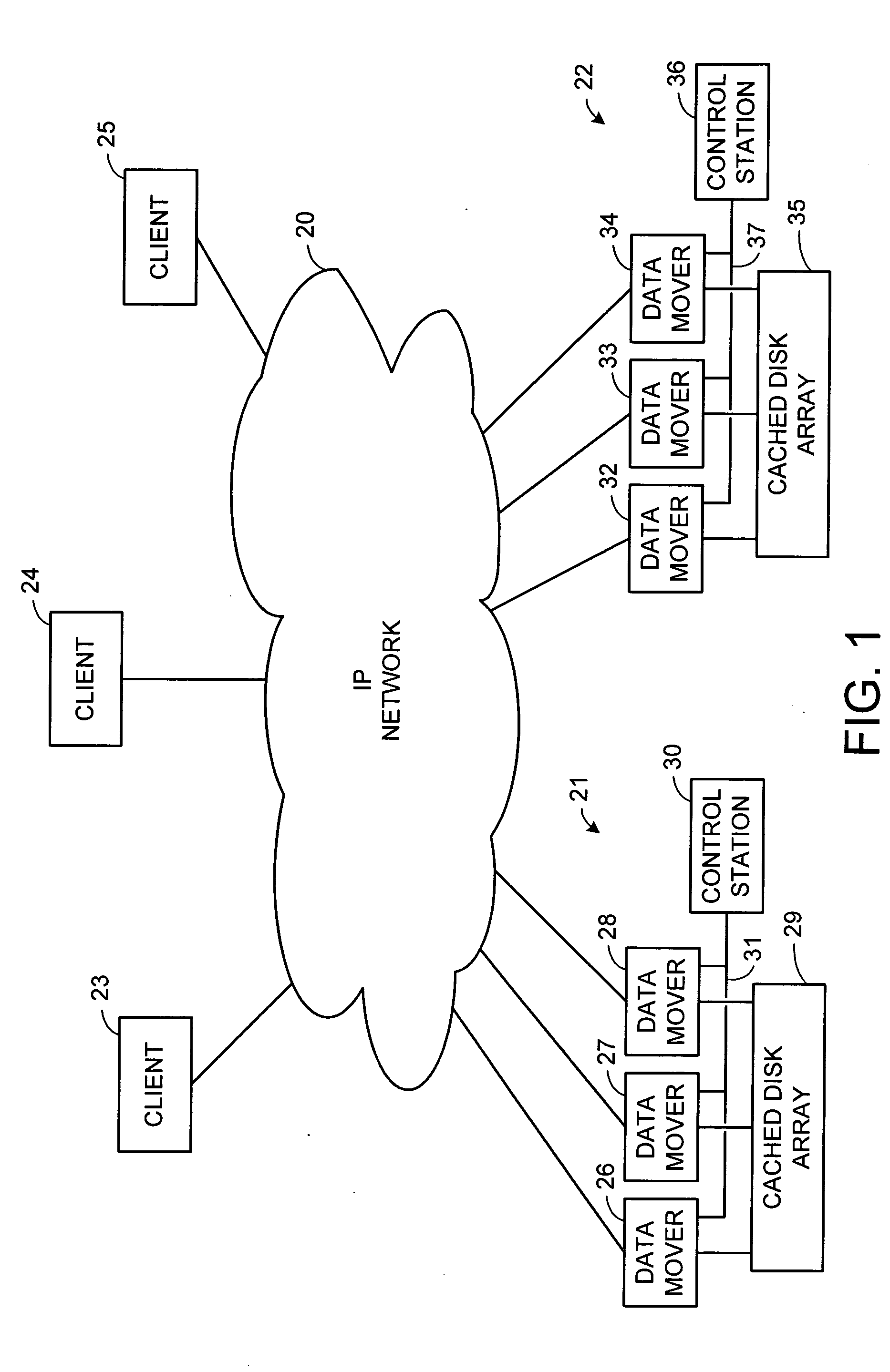
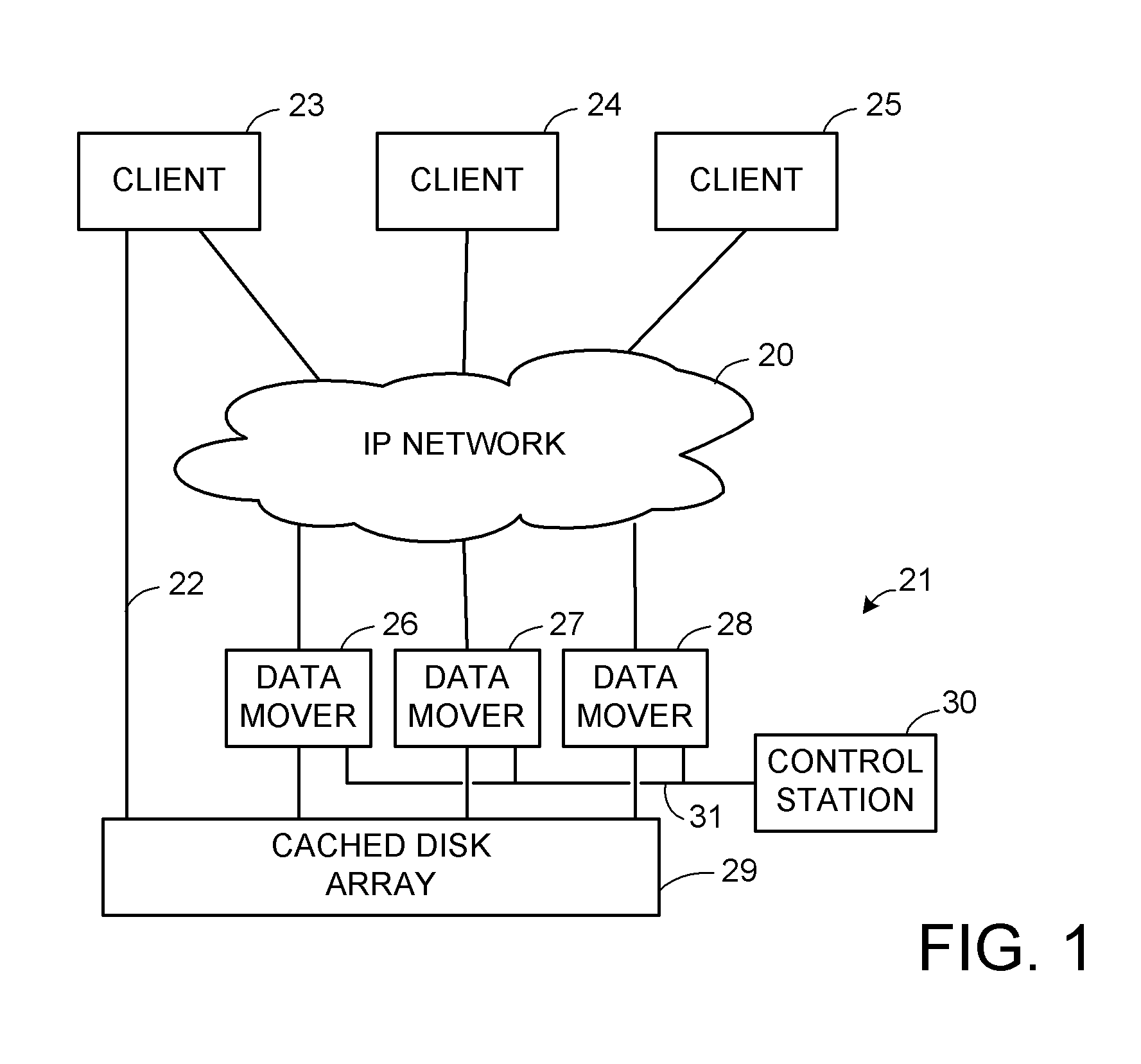
The SCSI and iSCSI layers over the TCP / IP layers of the protocol stack in an IP network client and in an IP network-attached storage server are replaced with a thin network block services layer. The network block services layer 71 implements a network block services protocol having a very reduced set of commands transmitted between the client and the storage server. The network block services protocol is used in a configuration process in which logical volumes of the network-attached storage are exported to the client and become local pseudo-disk instances. The client's operating system and application programs access the local pseudo-disk instances with what appears to be a standard device driver for a local disk device. The device driver maintains a TCP connection to each open device, and responds to connection failure by re-connecting with an alternative server IP port.
Owner:EMC IP HLDG CO LLC
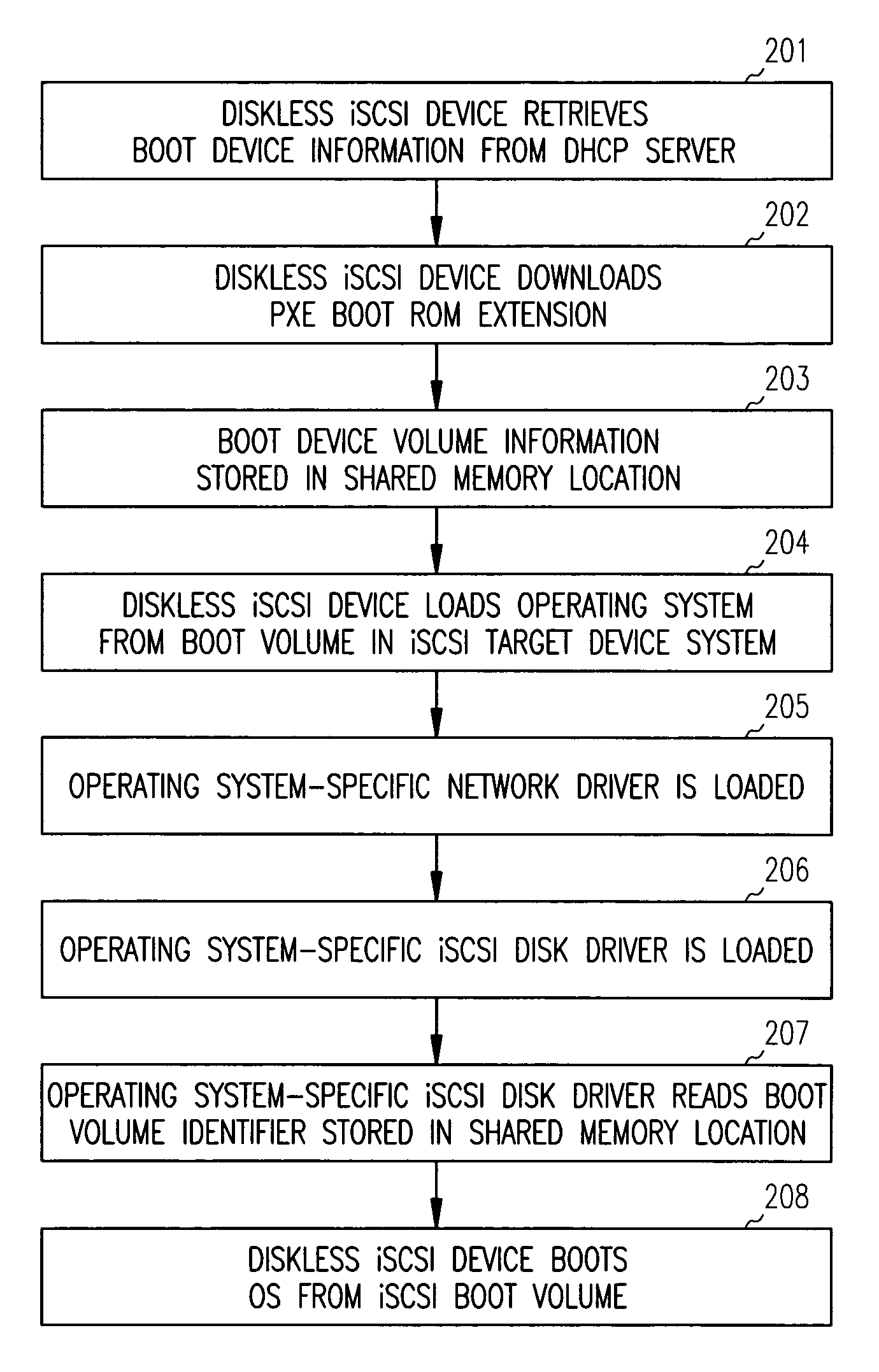
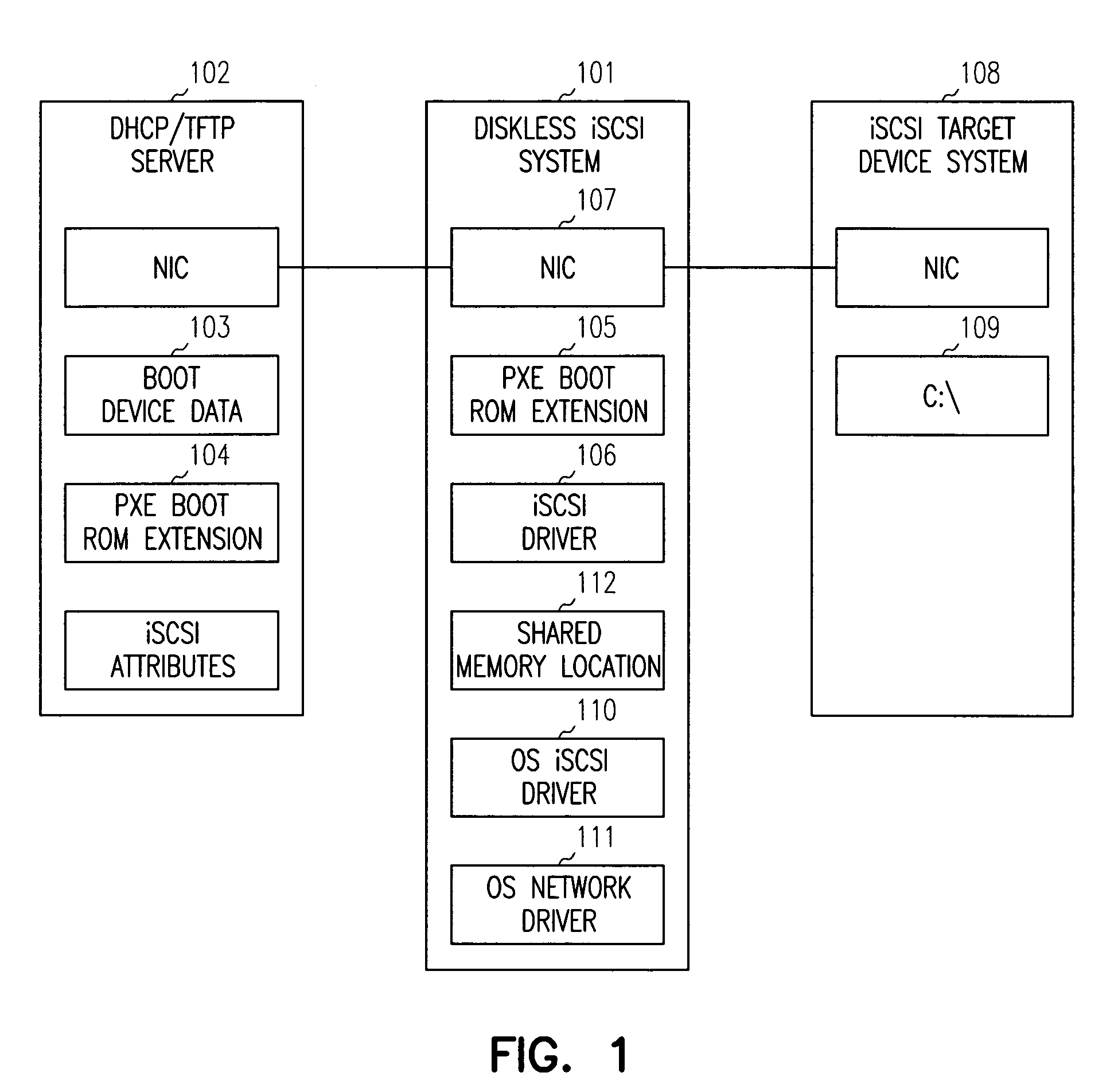
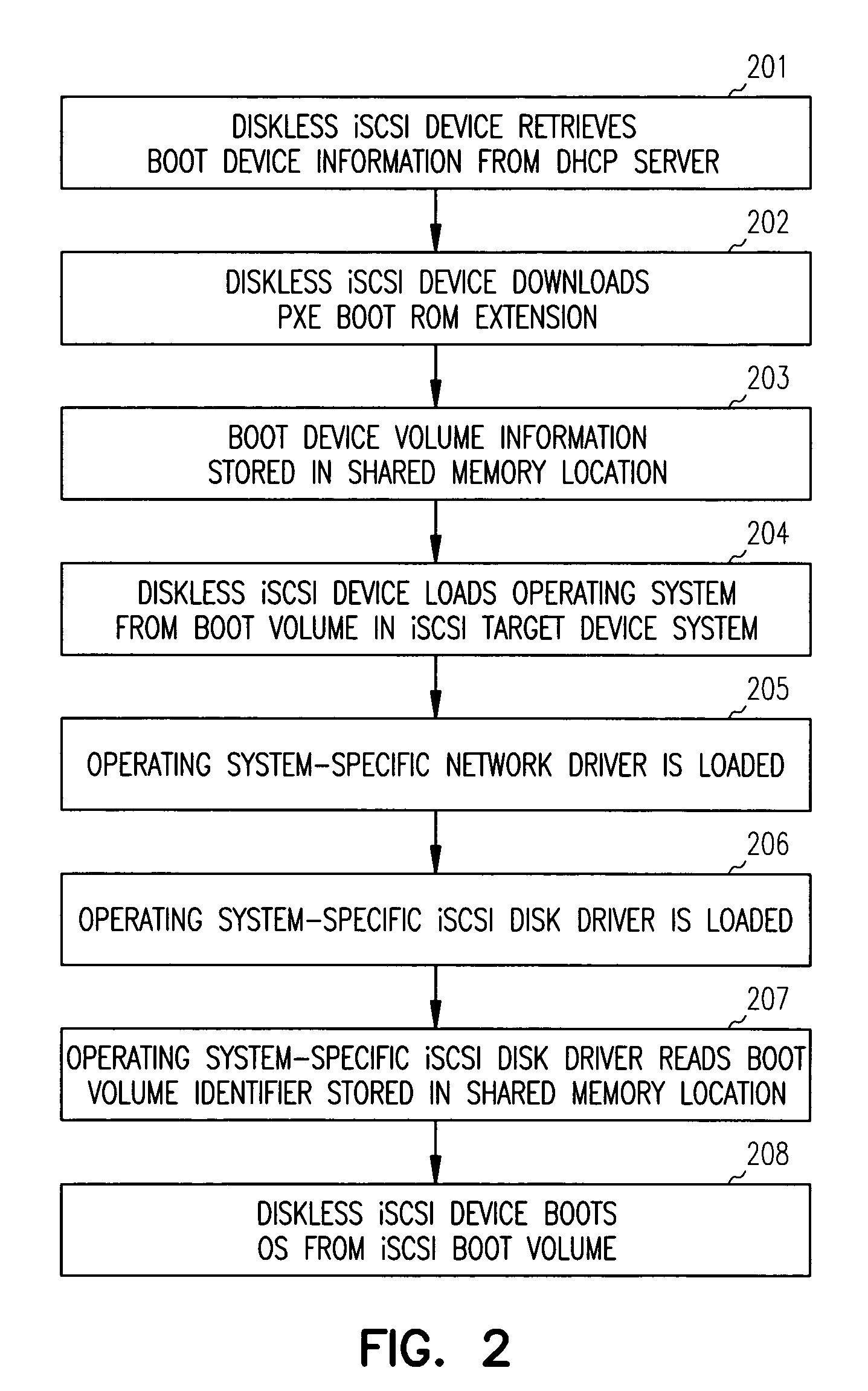
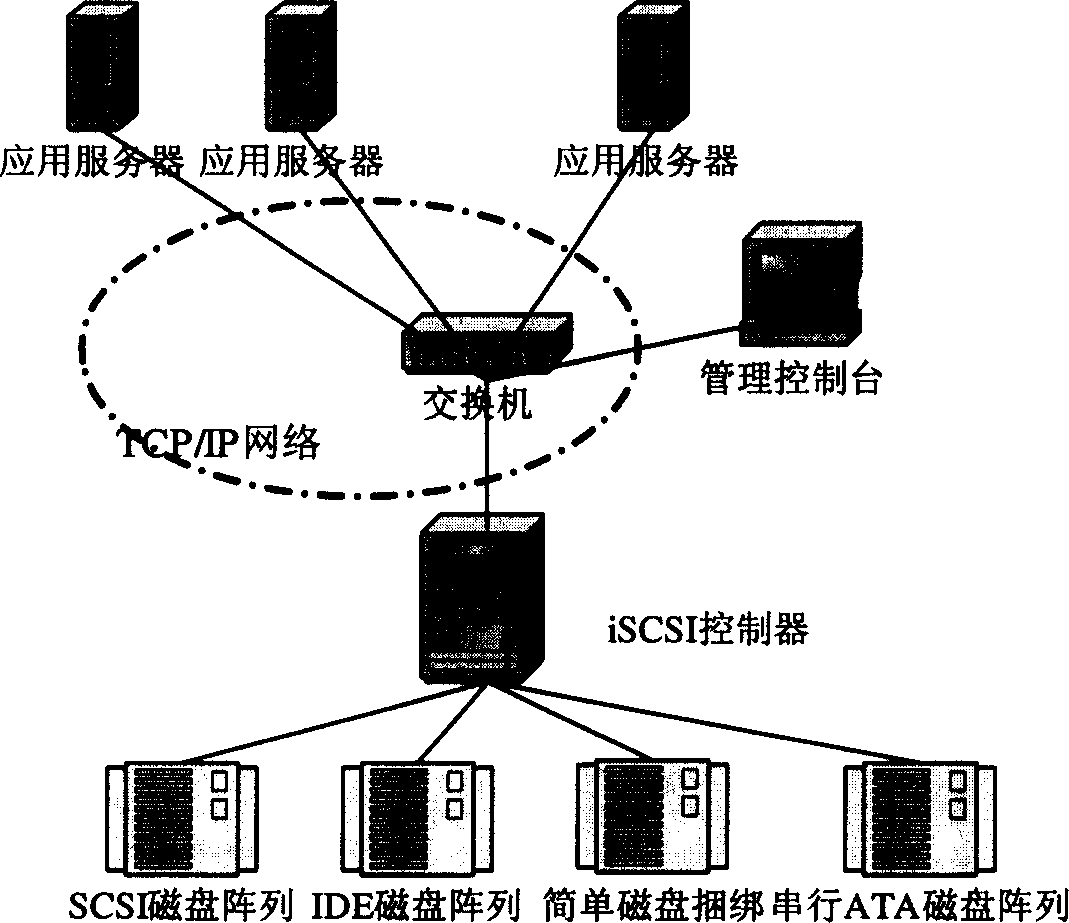
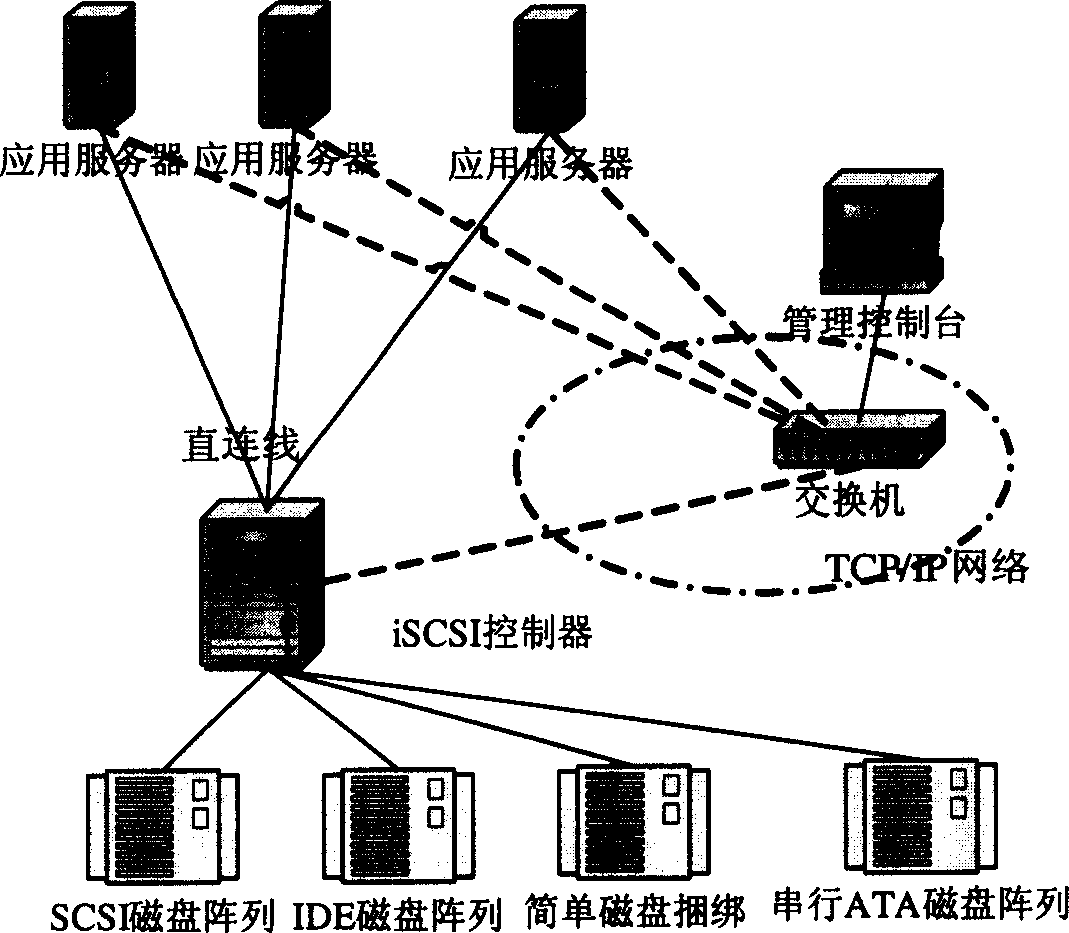
iSCSI system os boot configuration modification
A Pre-boot Execution Environment (PXE) boot extension is loaded upon system boot and is operable to store an iSCSI boot disk identifier identifying a remote disk drive to a shared memory location. As an operating system is loaded via iSCSI over a network connection to a remote disk, an operating system iSCSI driver is loaded. The operating system iSCSI driver reads the boot disk identifier stored in the shared memory location and uses the boot disk identifier to configure the operating system.
Owner:CISCO TECH INC
System and method for storage virtualization
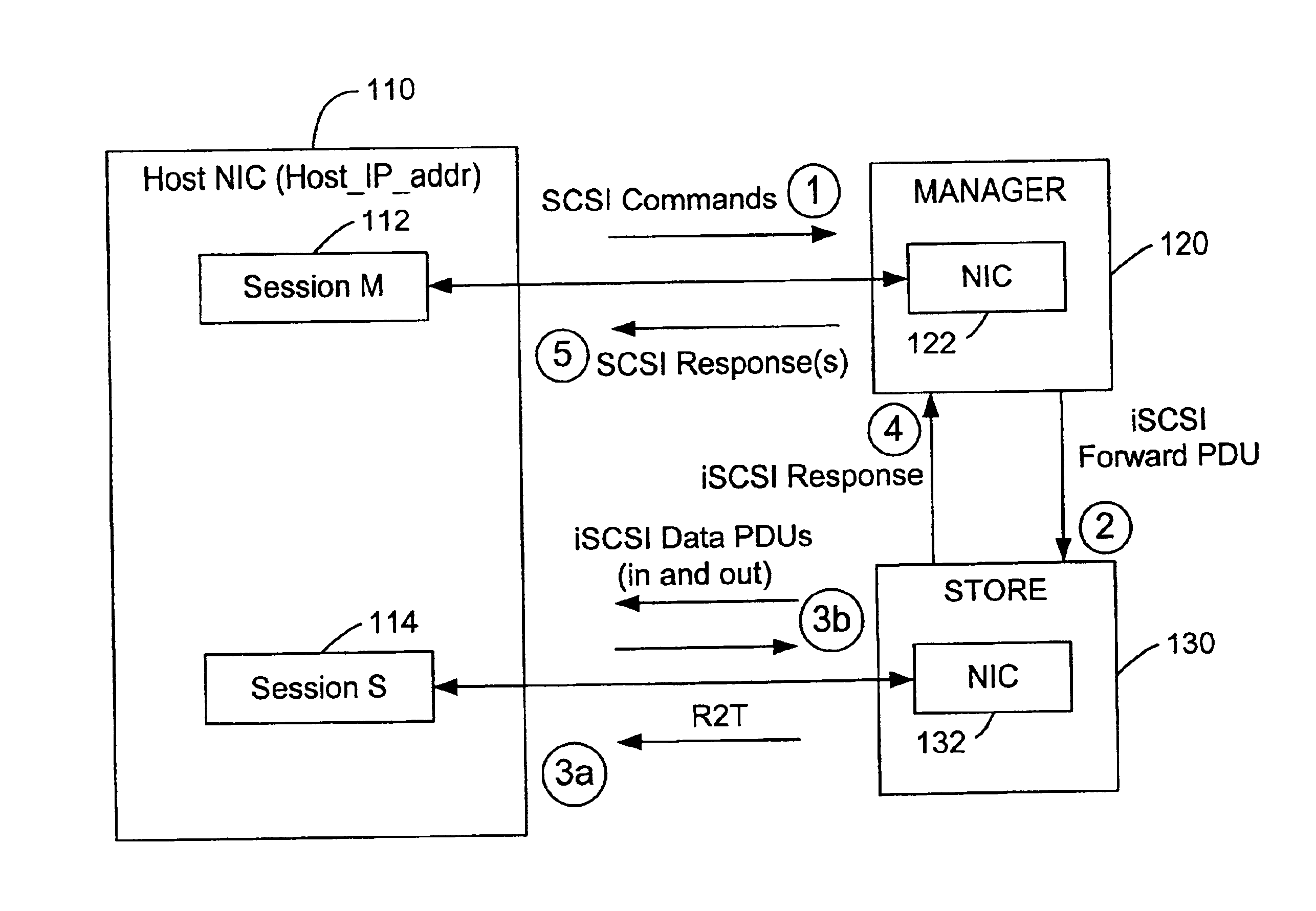
The present invention is generally directed to a system and method for virtualizing storage in a networked system. In accordance with one aspect of the invention, in a system having an initiator and at least one storage device, an inventive method determines, based upon a SCSI command received by a manager from the initiator, which of the data storage devices are implicated by the SCSI command. The method then forms an iSCSI command that is sent from the manager to each of the implicated storage devices, and receives at the manager an iSCSI response from each of implicated storage devices, after each of the storage devices has completed its implicated data transactions with the initiator. Finally, the method forms a SCSI response that is sent by the manager to the initiator. A corresponding system is also provided.
Owner:QUALCOMM INC
Adaptive cache engine for storage area network including systems and methods related thereto
InactiveUS20050243609A1Easy to processEnsures correctnessInput/output to record carriersMemory loss protectionFile systemStorage area network
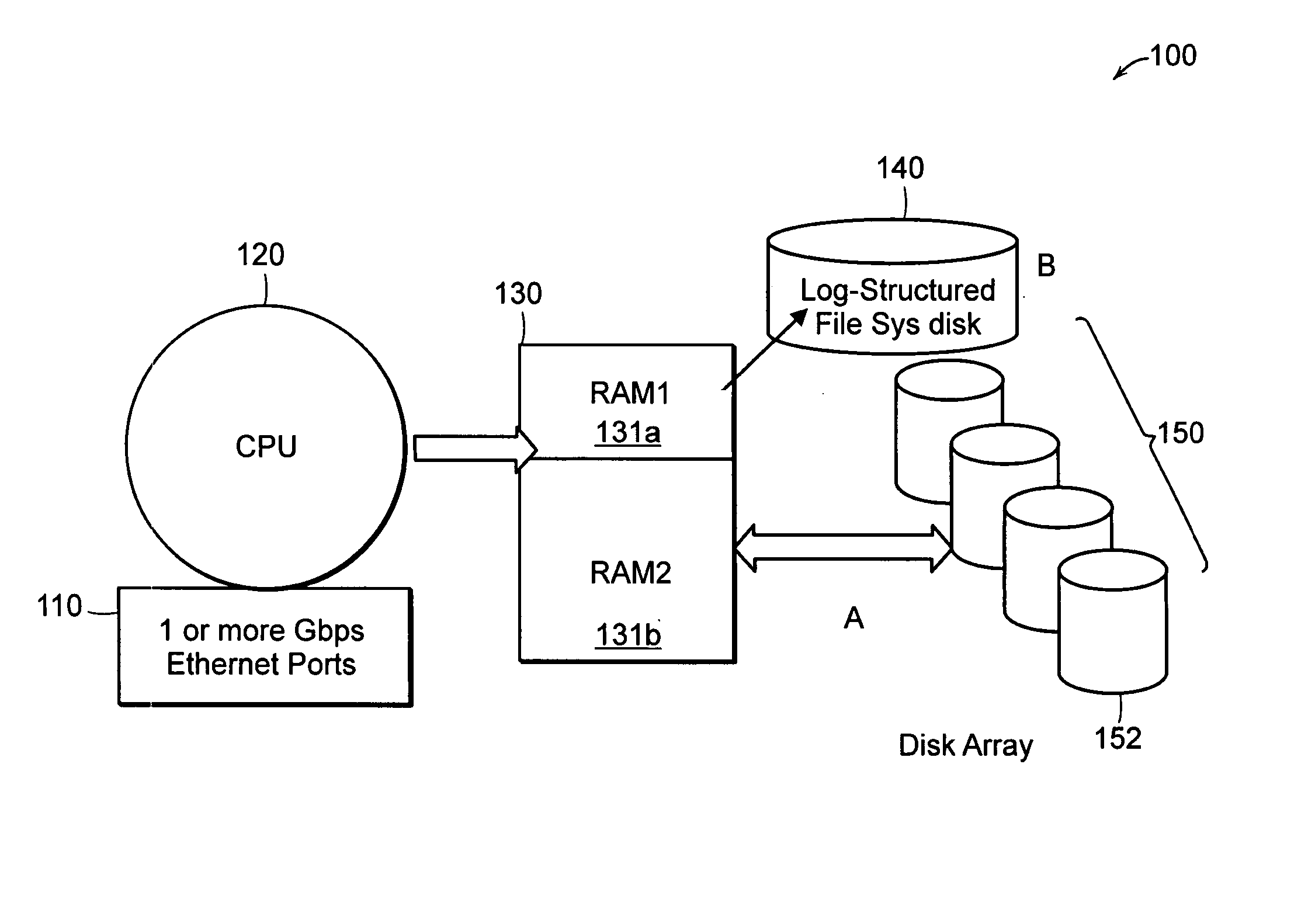
Featured is a data storage back-up system for replication, mirroring and / or backing-up data including one or more first and second data storage devices that embody iSCSI, FC or alike principals and that are operably coupled to each other preferably via a WAN. The first data storage device is configured and arranged so there are two writes of data, one write to a persistent storage device from which reads are done and another write to a SAPS device wherein the data is saved using log-structured file system (LSF) techniques. After saving data to the First storage device, the data logs in the SAPS device are communicated to the second data storage device whereat a de-staging process is conducted so as to de-stage the data logs and write the de-staged data to a persistent storage device in the second data storage device.
Owner:SLATER TECH FUND +1
Method and apparatus for accessing remote storage using SCSI and an IP network
InactiveUS6895461B1Network usageTime-division multiplexData switching by path configurationSCSITTEthernet
A storage router and method for creating a first session to a first information-handling system on a first network supporting IP packets, the network having a plurality of information-handling systems, creating a second session to the first information-handling system on a second network supporting IP packets, supporting iSCSI operations in the first session through an internet protocol (IP) port coupled to the first network, supporting management operations in the second session through an internet protocol (IP) port coupled to the second network, wherein the first and second sessions use a common IP layer, and preventing iSCSI operations from using the second network.
Owner:CISCO TECH INC
System for backing up cache memory in a double backup server structure
InactiveUS20080016301A1Speed up data transferImprove storage efficiencyMemory loss protectionRedundant hardware error correctionHigh bandwidthFibre Channel
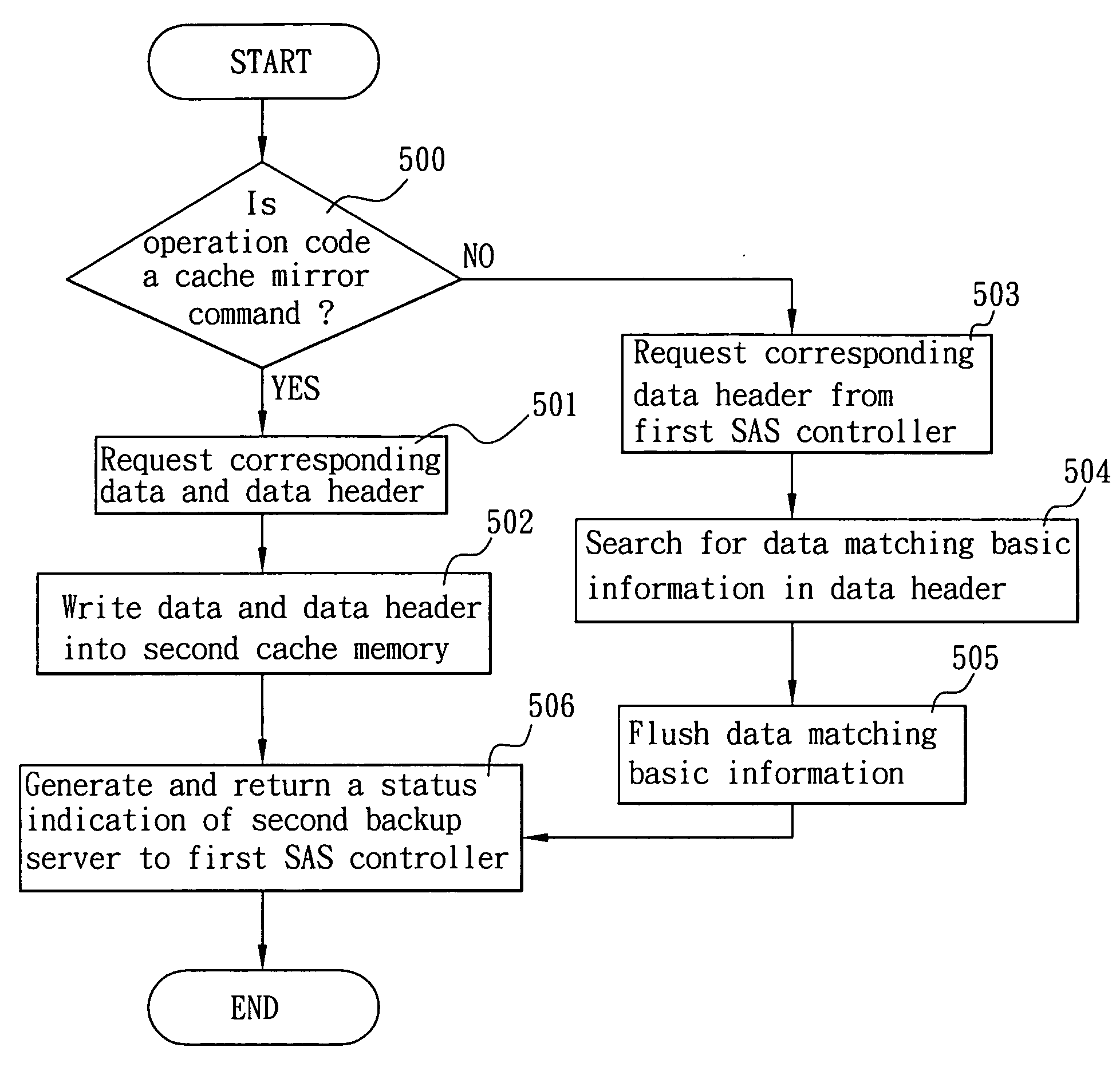
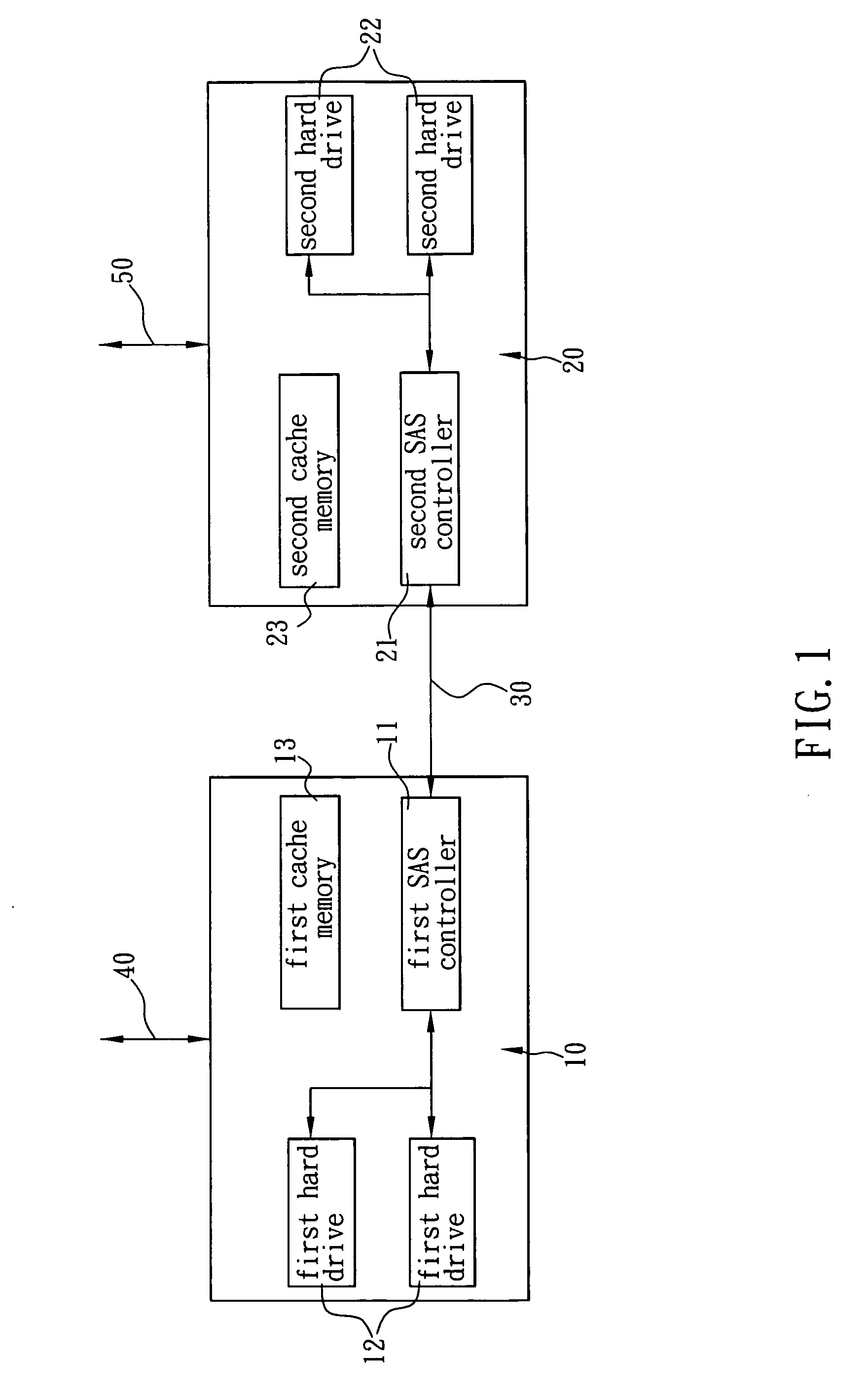
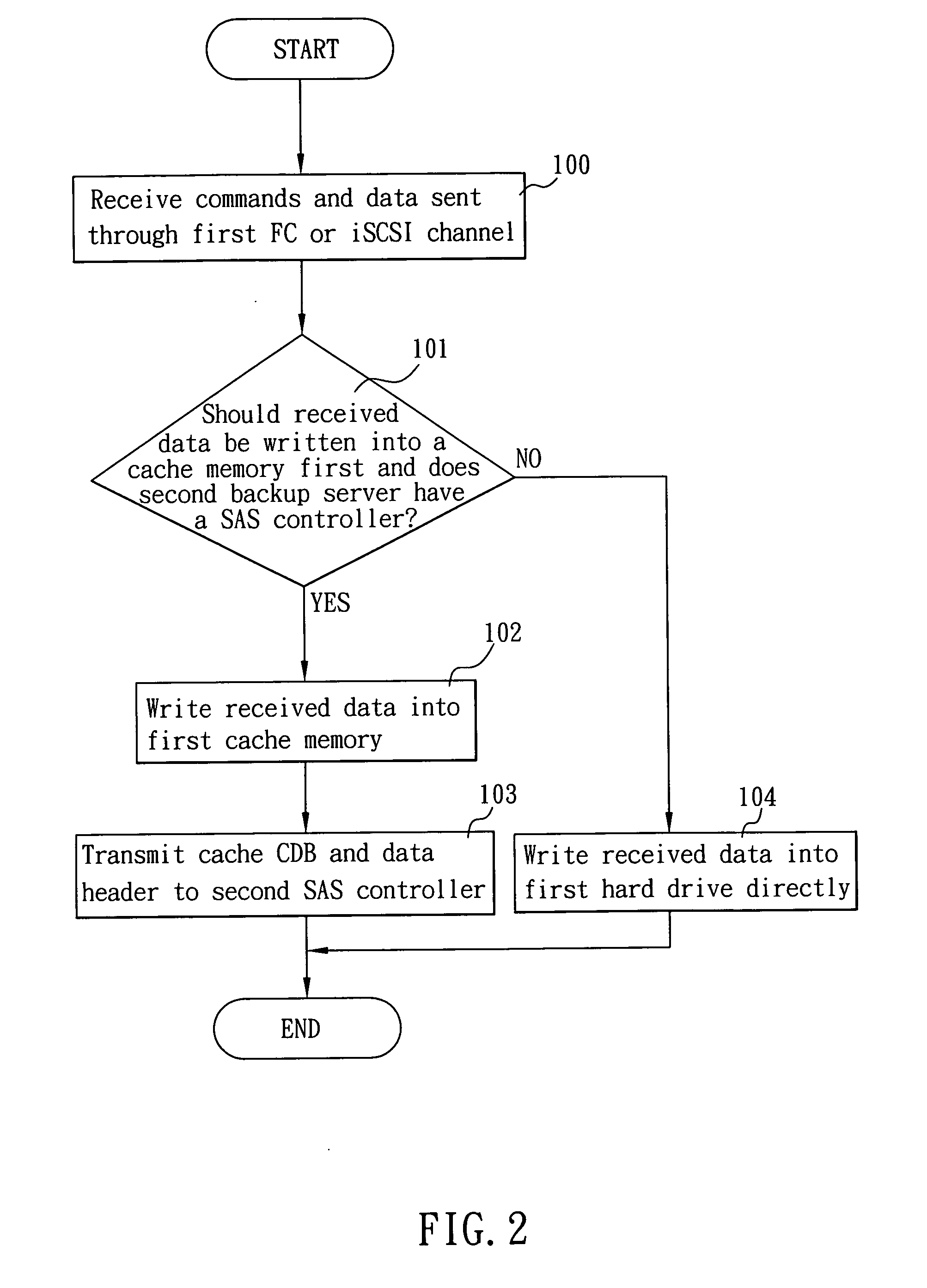
The present invention is to provide a system for backing up cache memory in a double backup server structure, which comprises a first backup server having a first SAS controller; a second backup server having a second SAS controller; and a SAS channel for connecting said first and second SAS controllers; wherein said first SAS controller and said second SAS controller each having a sending end initiator defining a cache mirror command. When said first backup server received a write command and write data through a Fiber Channel or iSCSI channel into a first cache memory, said first SAS controller also establishes a first Command Descriptor Block (CDB) with an operation code of a cache mirror command as well as a first data header for the cache data. Said first CDB and first data header are subsequently transmitted through said SAS channel to said second SAS controller and said second backup server writes said data into a second cache memory of its own. Accordingly, with the higher bandwidth facilitated by the SAS channel, considerable amount of cache data can be processes in high speed to improve the storage efficiency in a double backup server structure.
Owner:INVENTEC CORP
Gigabit Ethernet Adapter
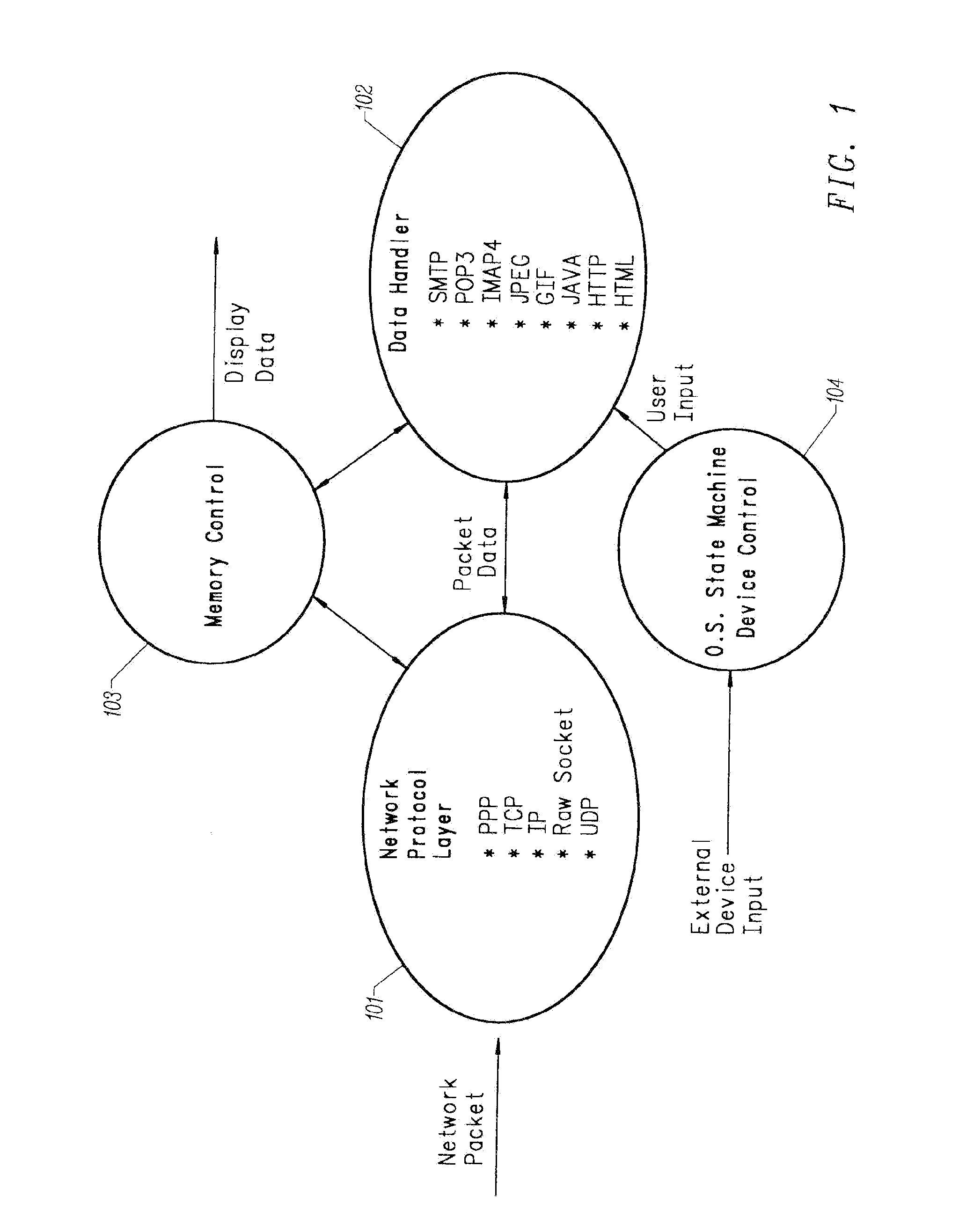
InactiveUS20070253430A1Fast communication speedCompact solutionWide area networksRaw socketSmall form factor
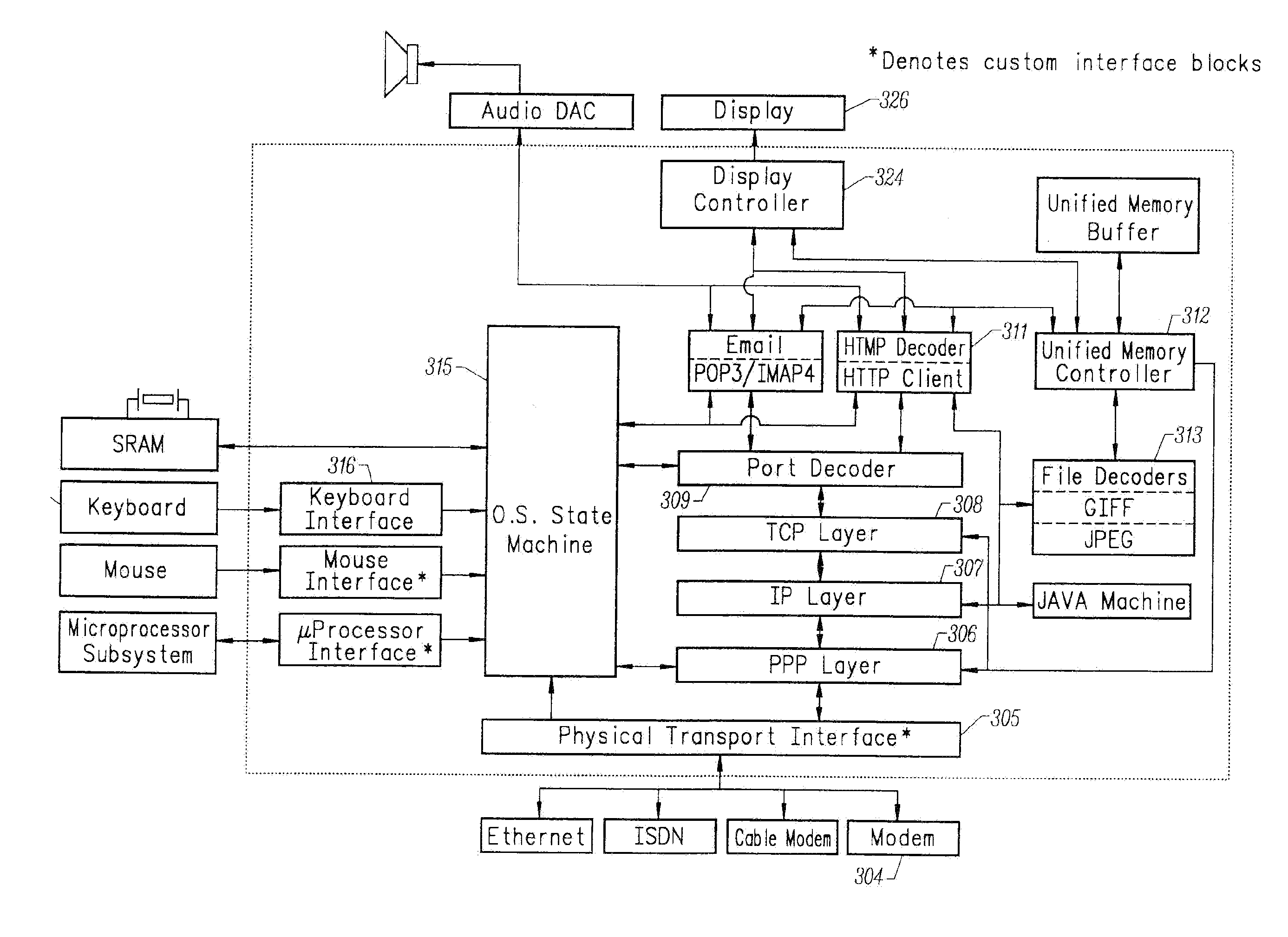
A gigabit Ethernet adapter provides a provides a low-cost, low-power, easily manufacturable, small form-factor network access module which has a low memory demand and provides a highly efficient protocol decode. The invention comprises a hardware-integrated system that both decodes multiple network protocols byte-streaming manner concurrently and processes packet data in one pass, thereby reducing system memory and form factor requirements, while also eliminating software CPU overhead. A preferred embodiment of the invention comprises a plurality of protocol state machines that decode network protocols such as TCP, IP, User Datagram Protocol (UDP), PPP, Raw Socket, RARP, ICMP, IGMP, iSCSI, RDMA, and FCIP concurrently as each byte is received. Each protocol handler parses, interprets, and strips header information immediately from the packet, requiring no intermediate memory. The invention provides an internet tuner core, peripherals, and external interfaces. A network stack processes, generates and receives network packets. An internal programmable processor controls the network stack and handles any other types of ICMP packets, IGMP packets, or packets corresponding to other protocols not supported directly by dedicated hardware. A virtual memory manager is implemented in optimized, hardwired logic. The virtual memory manager allows the use of a virtual number of network connections which is limited only by the amount of internal and external memory available.
Owner:NVIDIA CORP
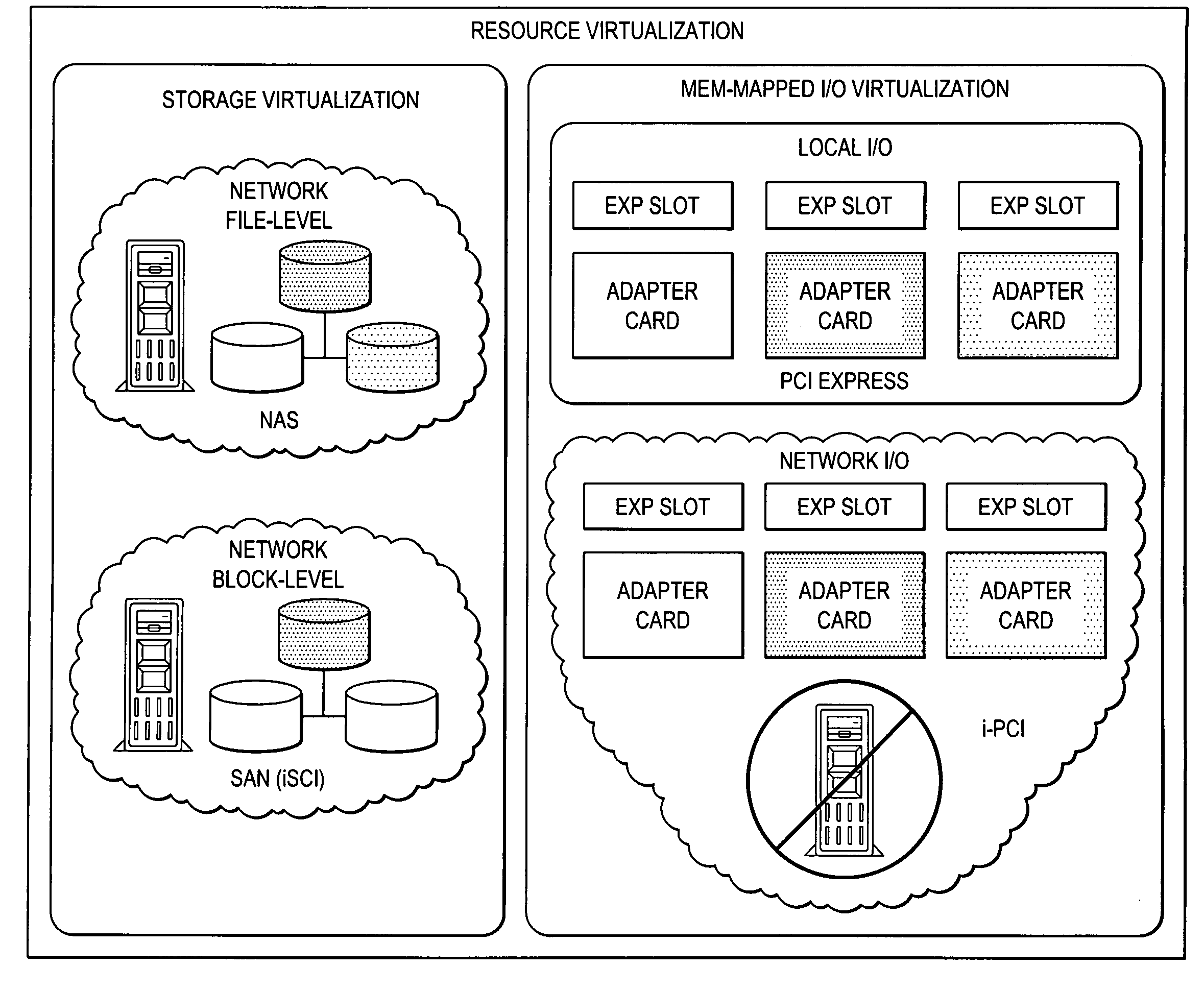
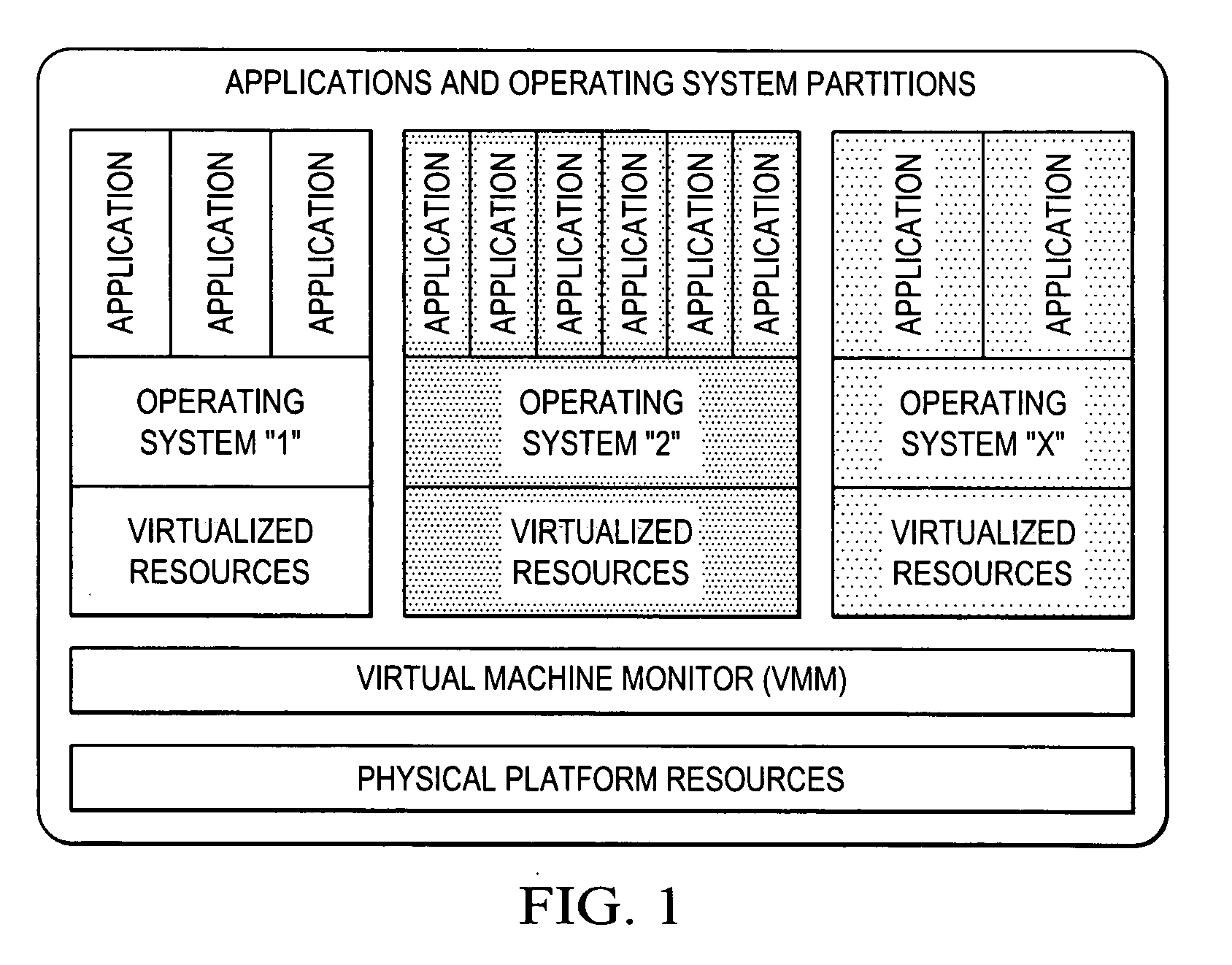
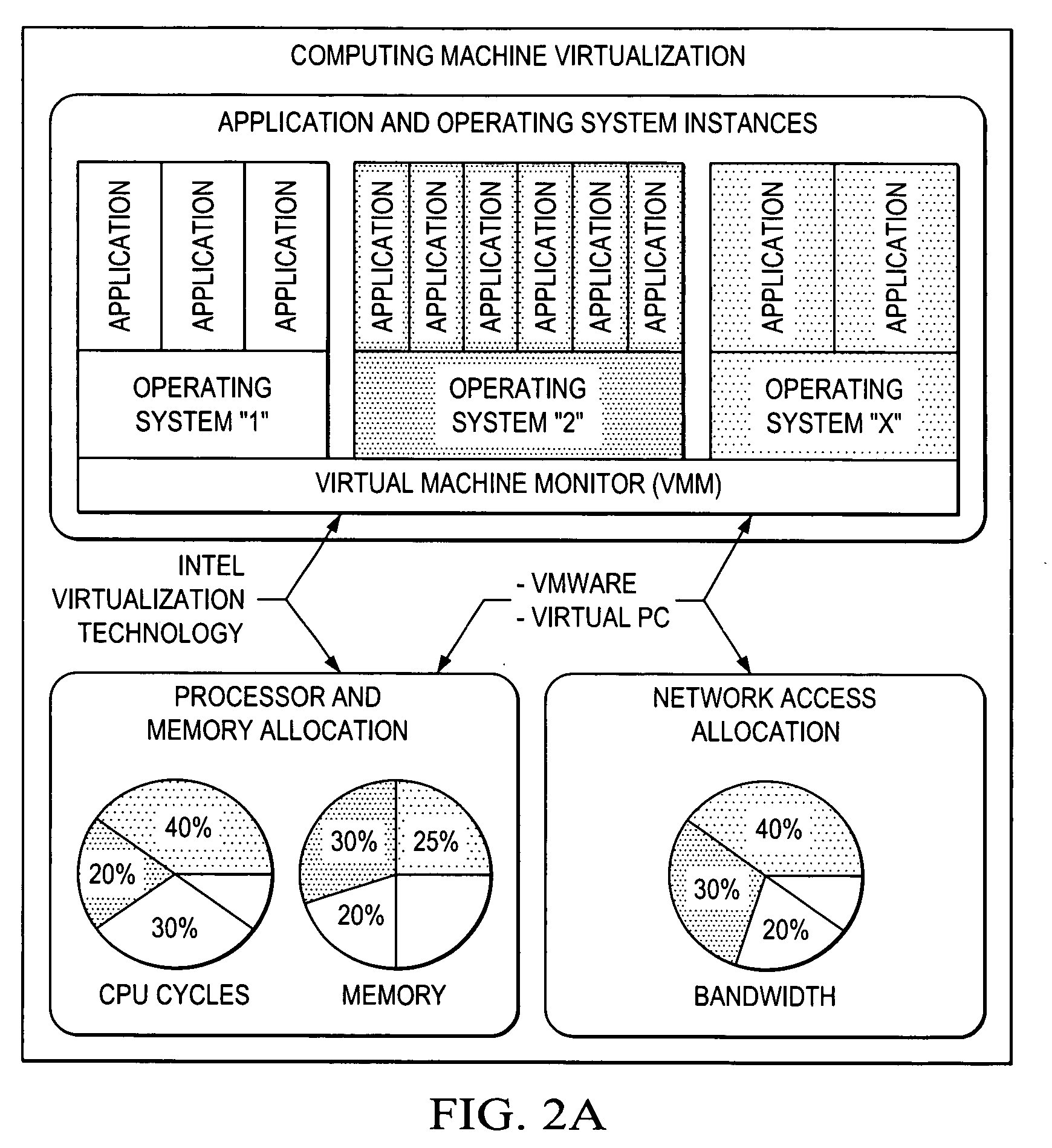
Virtualization of a host computer's native I/O system architecture via the internet and LANs
InactiveUS20090006710A1Unprecedented reachUnprecedented flexibilityTime-division multiplexMultiple digital computer combinationsVirtualizationTTEthernet
Owner:NUON
Virtualization of a host computer's native I/O system architecture via the internet and LANs
InactiveUS7734859B2Unprecedented reachUnprecedented flexibilityTime-division multiplexMultiple digital computer combinationsVirtualizationTTEthernet
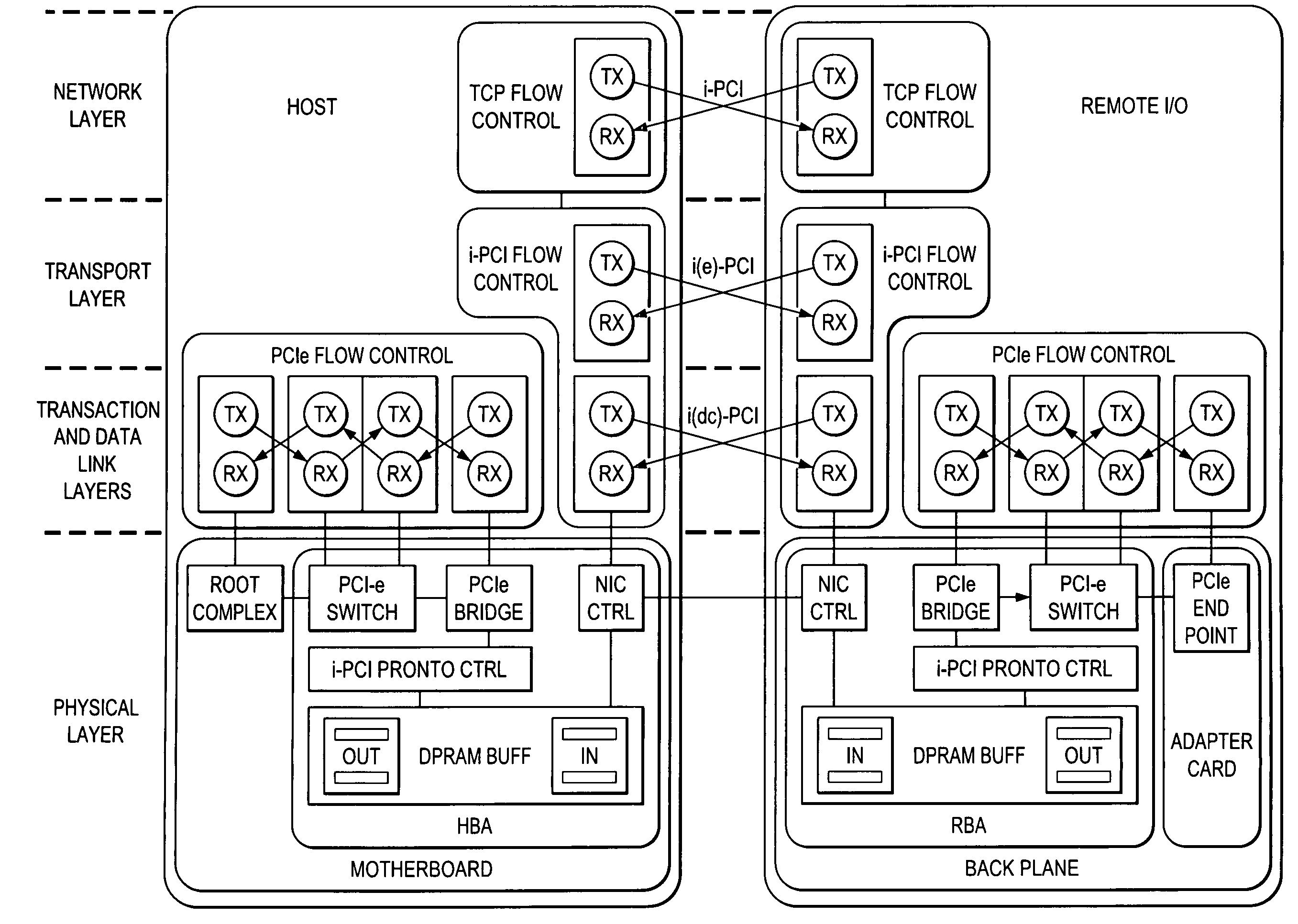
A hardware / software system and method that collectively enables virtualization of the host computer's native I / O system architecture via the Internet and LANs. The invention includes a solution to the problems of the relatively narrow focus of iSCSI, the direct connect limitation of PCI Express, and the inaccessibility of PCI Express for expansion in blade architectures.
Owner:NUON
iSCSI boot drive system and method for a scalable internet engine
InactiveUS20050138346A1Digital computer detailsProgram loading/initiatingOperational systemThe Internet
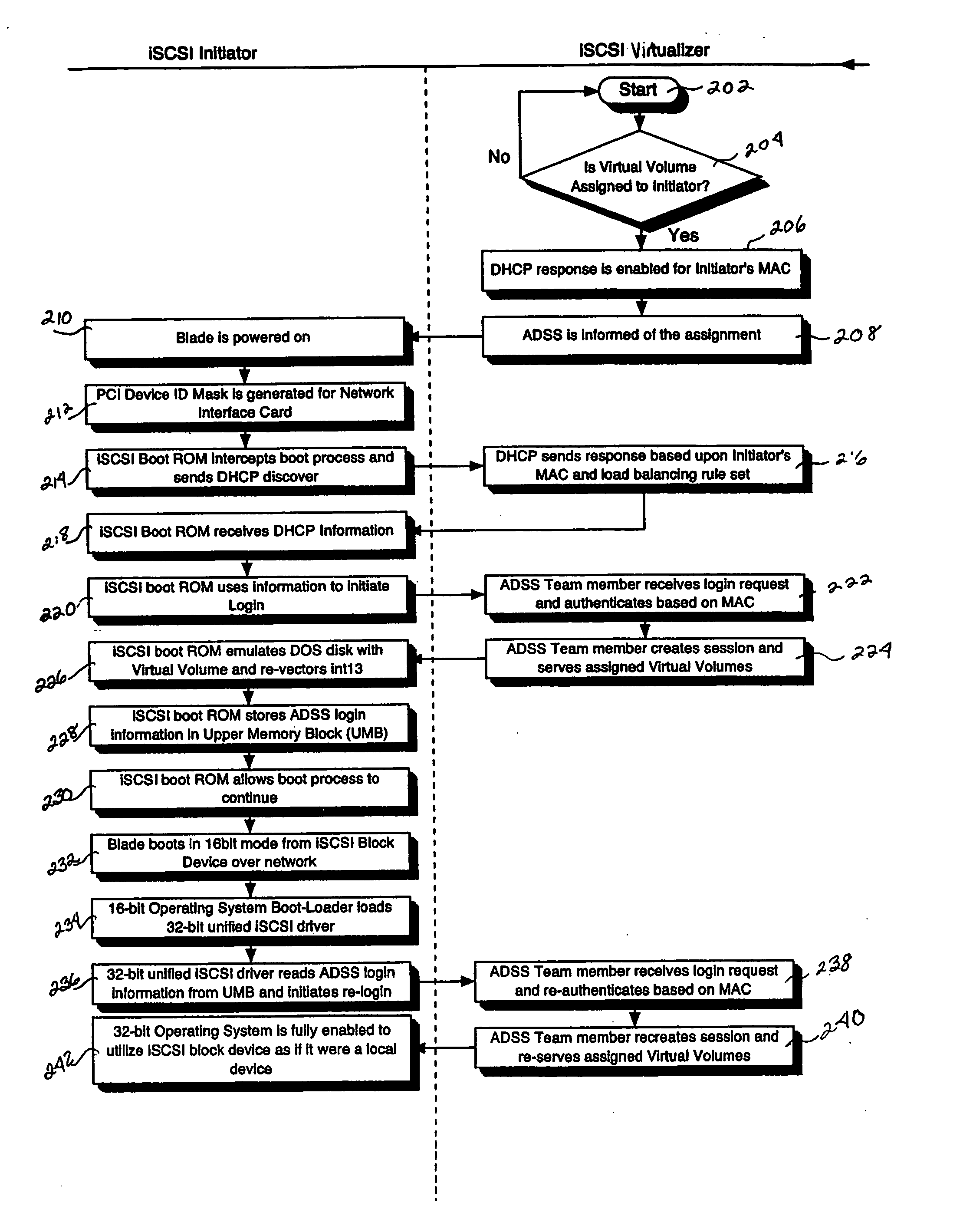
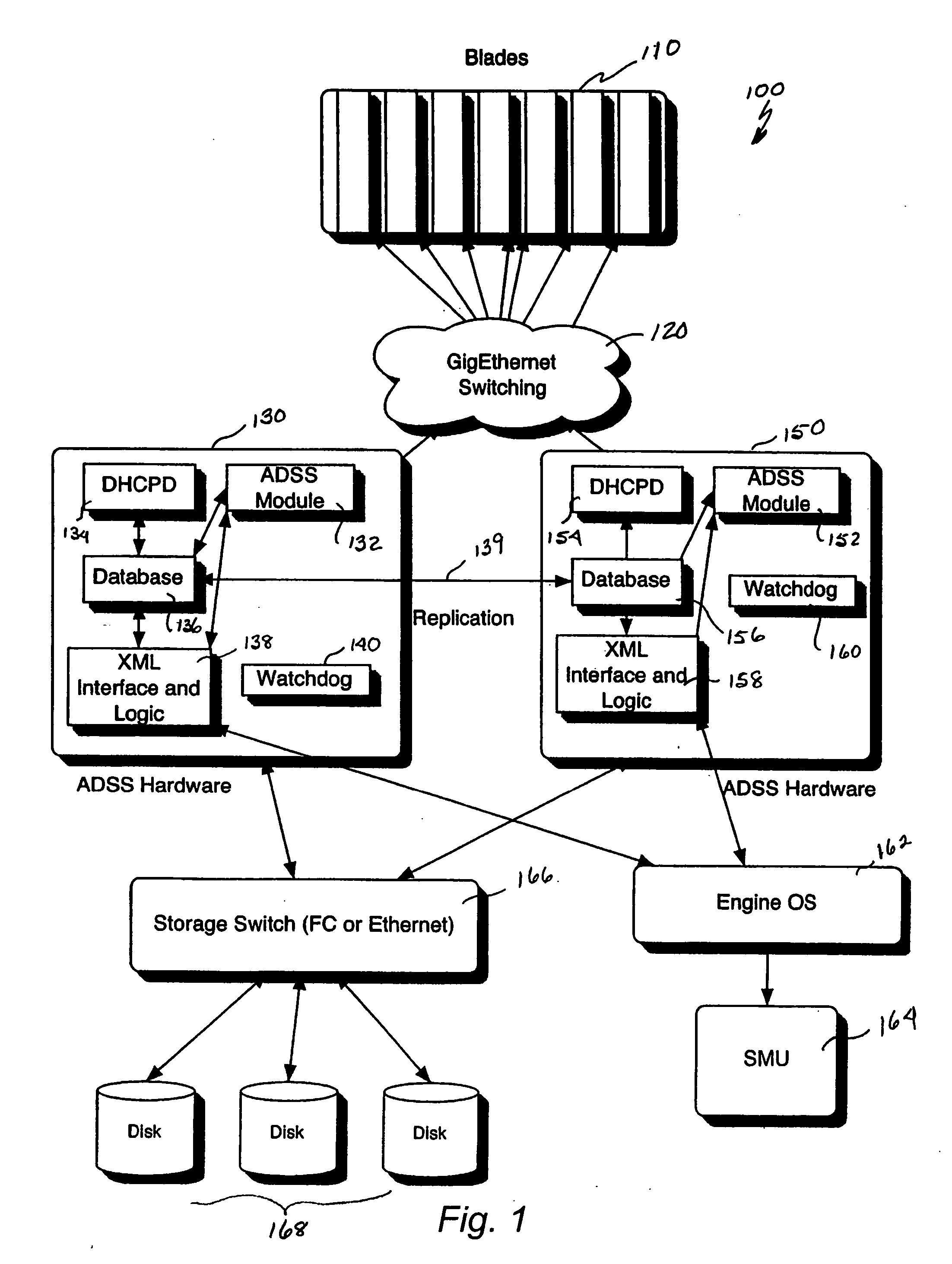
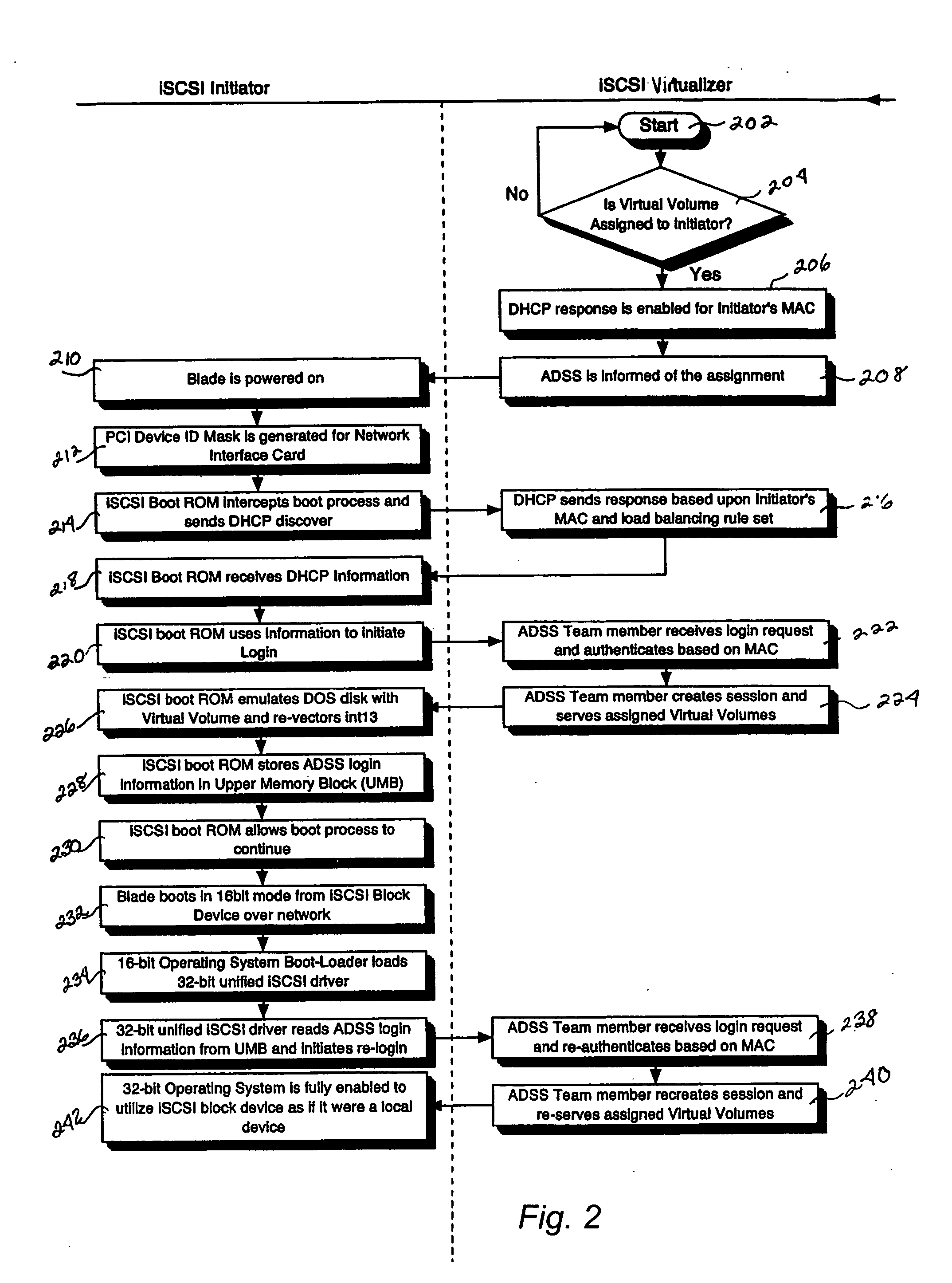
A system for remote booting of a server generally includes a client initiator, an iSCSI virtualizer, and an iSCSI initiator. The client initiator requests access to the server and the iSCSI virtualizer receives the access request. Then, the iSCSI initiator acts upon the request received by the iSCSI virtualizer to initiate login to the server through use of an iSCSI Boot ROM on the server and to emulate a disk operating system through use of the iSCSI Boot ROM, which enables the server to boot. The server boots in both an 8-bit and a subsequent 32-bit mode. The iSCSI Boot ROM appears as a local device upon the completion of the server boot. The iSCSI virtualizer authenticates the login at least twice. The iSCSI virtualizer includes a pair of replicated active directory service servers (ADSS).
Owner:RPX CORP
Method for securing data storage in a storage area network
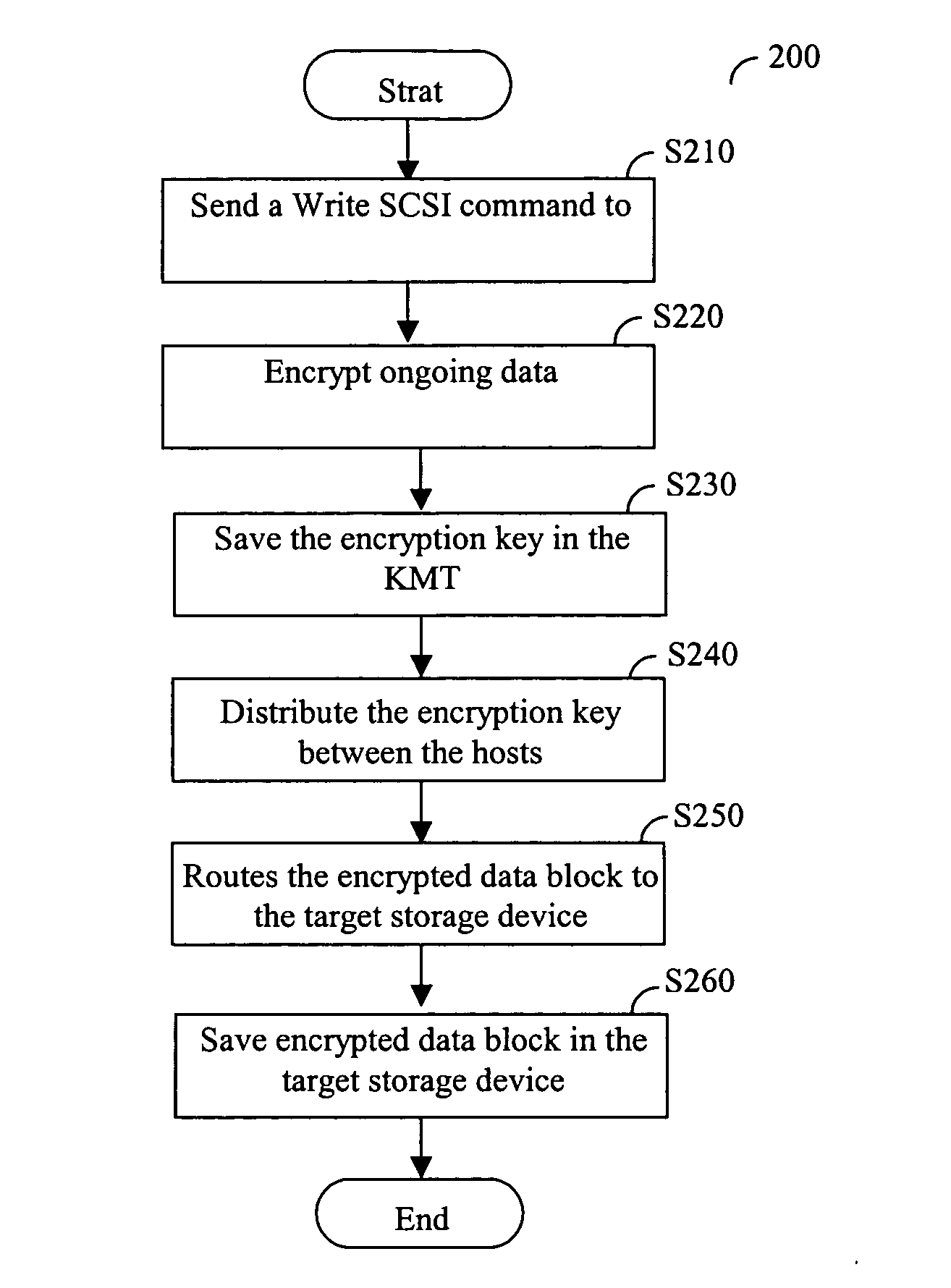
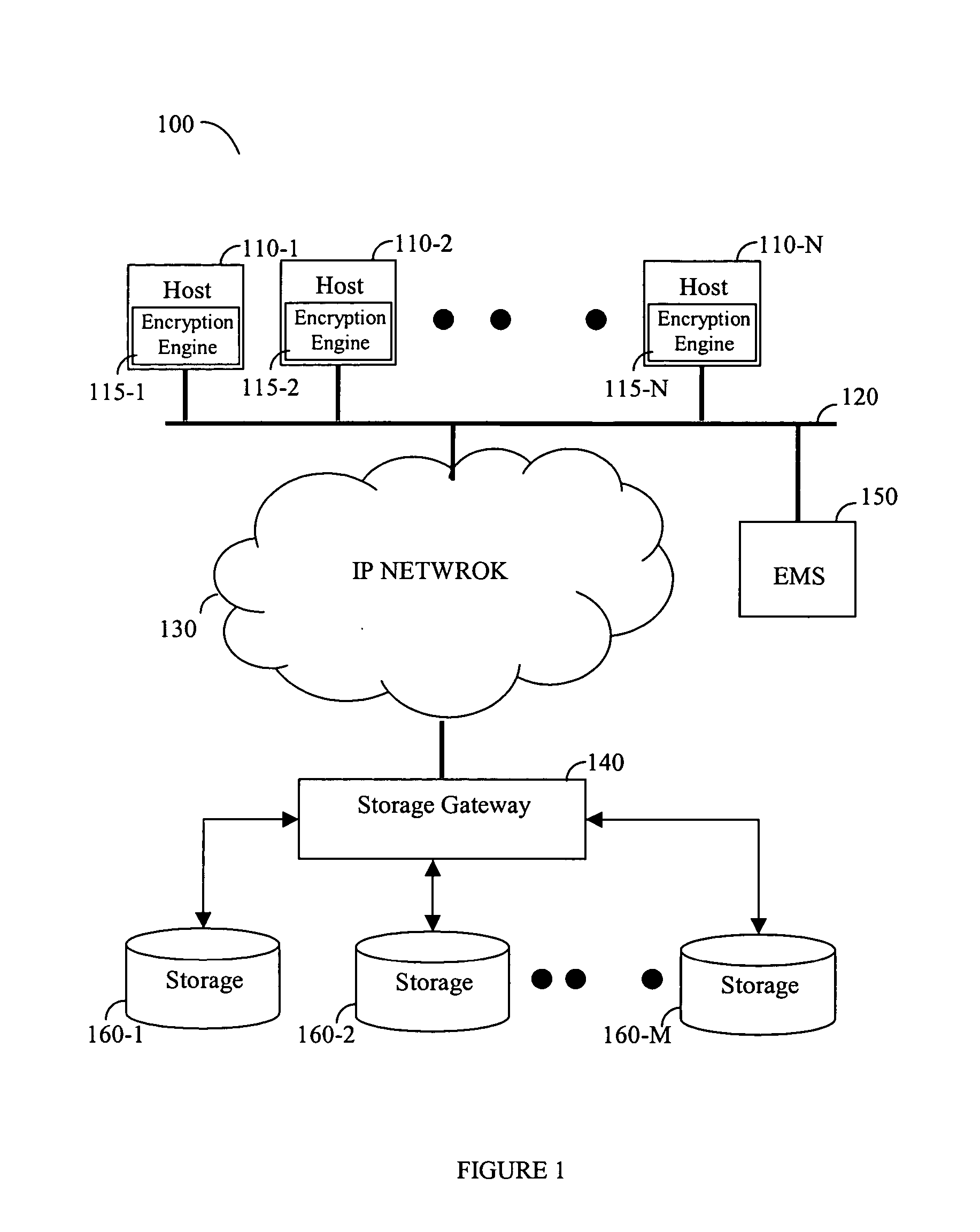
InactiveUS20050013441A1Key distribution for secure communicationComputer security arrangementsPrivate IPPrivate network
Disclosed is a device and method for securing stored data in an IP based storage area network (SAN), where the physical storage media is located in an unprotected site. The connection between the client and the unprotected site is established over a public or private IP network preferably by means of an iSCSI protocol. According to the present invention a data block to be saved in a remote site is encrypted at the initiator host using a private encryption key and an encrypt key. The private encryption key is saved in a key management table which is shared among other hosts that may access the encrypted data block.
Owner:SANRAD +1
Network block services for client access of network-attached data storage in an IP network
ActiveUS7475124B2Multiple digital computer combinationsTransmissionService protocolOperational system
The SCSI and iSCSI layers over the TCP / IP layers of the protocol stack in an IP network client and in an IP network-attached storage server are replaced with a thin network block services layer. The network block services layer 71 implements a network block services protocol having a very reduced set of commands transmitted between the client and the storage server. The network block services protocol is used in a configuration process in which logical volumes of the network-attached storage are exported to the client and become local pseudo-disk instances. The client's operating system and application programs access the local pseudo-disk instances with what appears to be a standard device driver for a local disk device. The device driver maintains a TCP connection to each open device, and responds to connection failure by re-connecting with an alternative server IP port.
Owner:EMC IP HLDG CO LLC
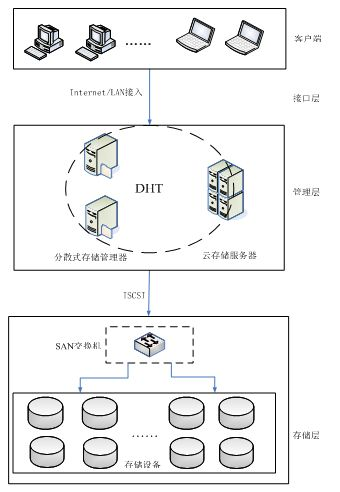
Distributed storage oriented cloud storage security architecture and data access method thereof
InactiveCN102088491AImprove usabilityImprove reliabilityTransmissionStorage area networkConfidentiality
The invention discloses a distributed storage oriented cloud storage security architecture and a data access method thereof. The distributed cloud storage oriented security architecture comprises a cloud storage server, a distributed storage manager, a wafer breaker and storage devices, wherein the distributed storage manager and the cloud storage server are respectively connected with a client-side; the distributed storage manager and the cloud storage server are connected by a fiber channel (FC) or a routing switch; the wafer breaker is imbedded in the distributed storage manager; the distributed storage manager is connected with the storage devices by the FC or Iscsi; and the storage devices are connected by a network attached storage (NAS) or a storage area network (SAN). The storage devices are located at different places and are redundant mutually, thus improving the fault-tolerant ability of the devices and the optimal storage use ratio; the wafer breaker is used for carrying out fragment on stored data, so that the data are fragmented into data fragments which can not be identified by other authentication systems, and the fragmented data have relative confidentiality and security in the process of network transmission and data storage; and the storage devices and the server are the devices with higher cost performance, thus reducing the cost.
Owner:XI'AN UNIVERSITY OF ARCHITECTURE AND TECHNOLOGY
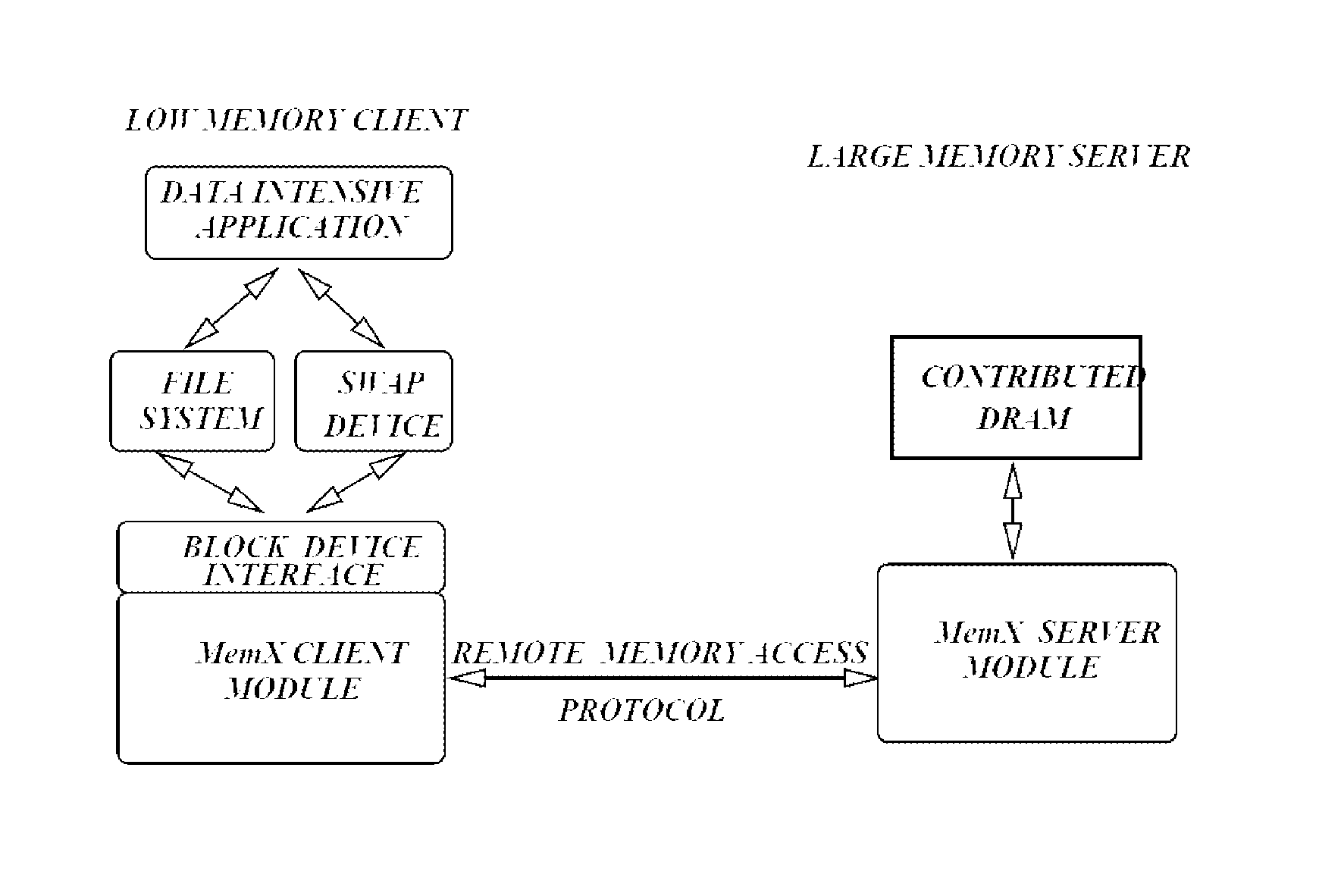
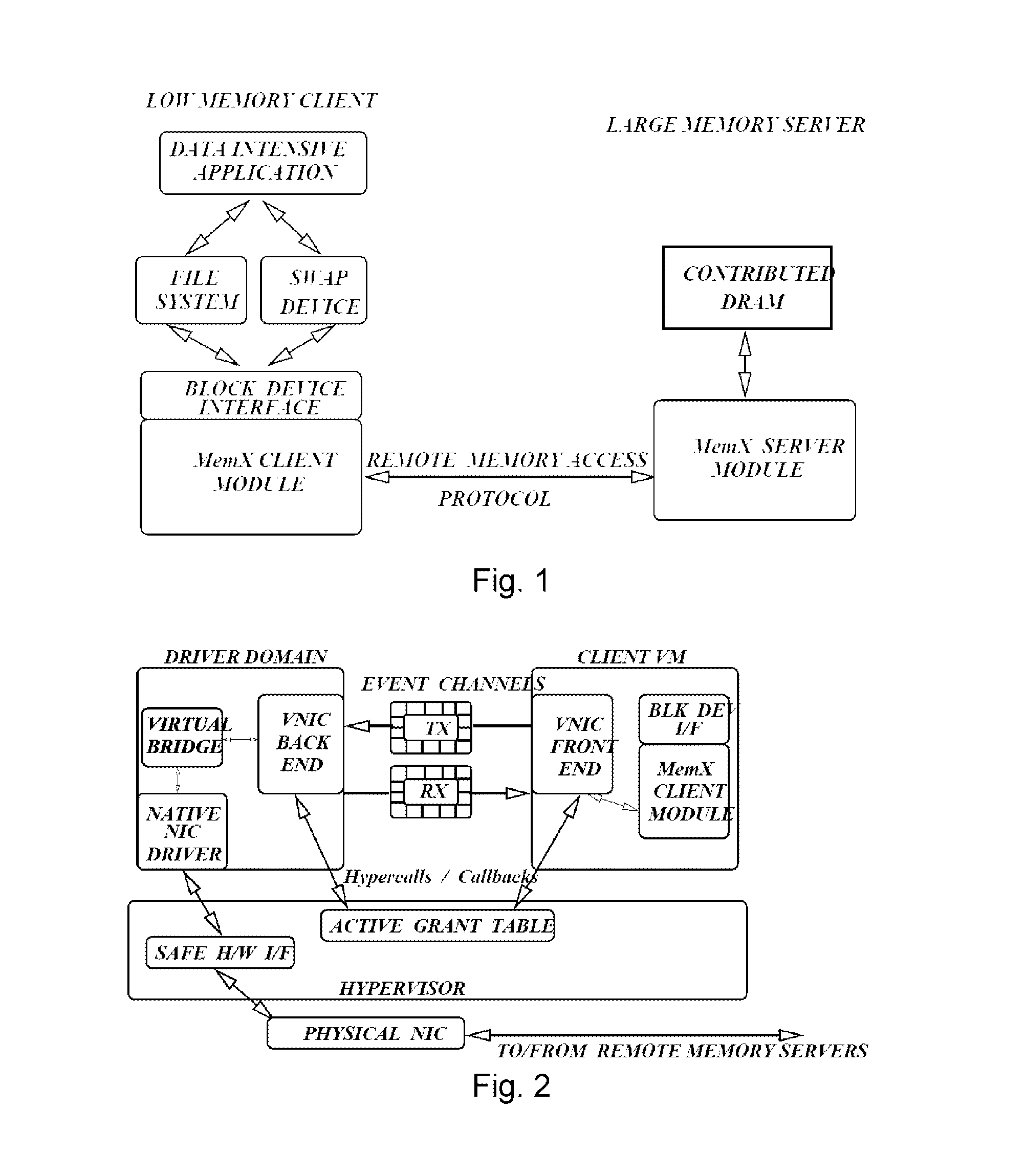
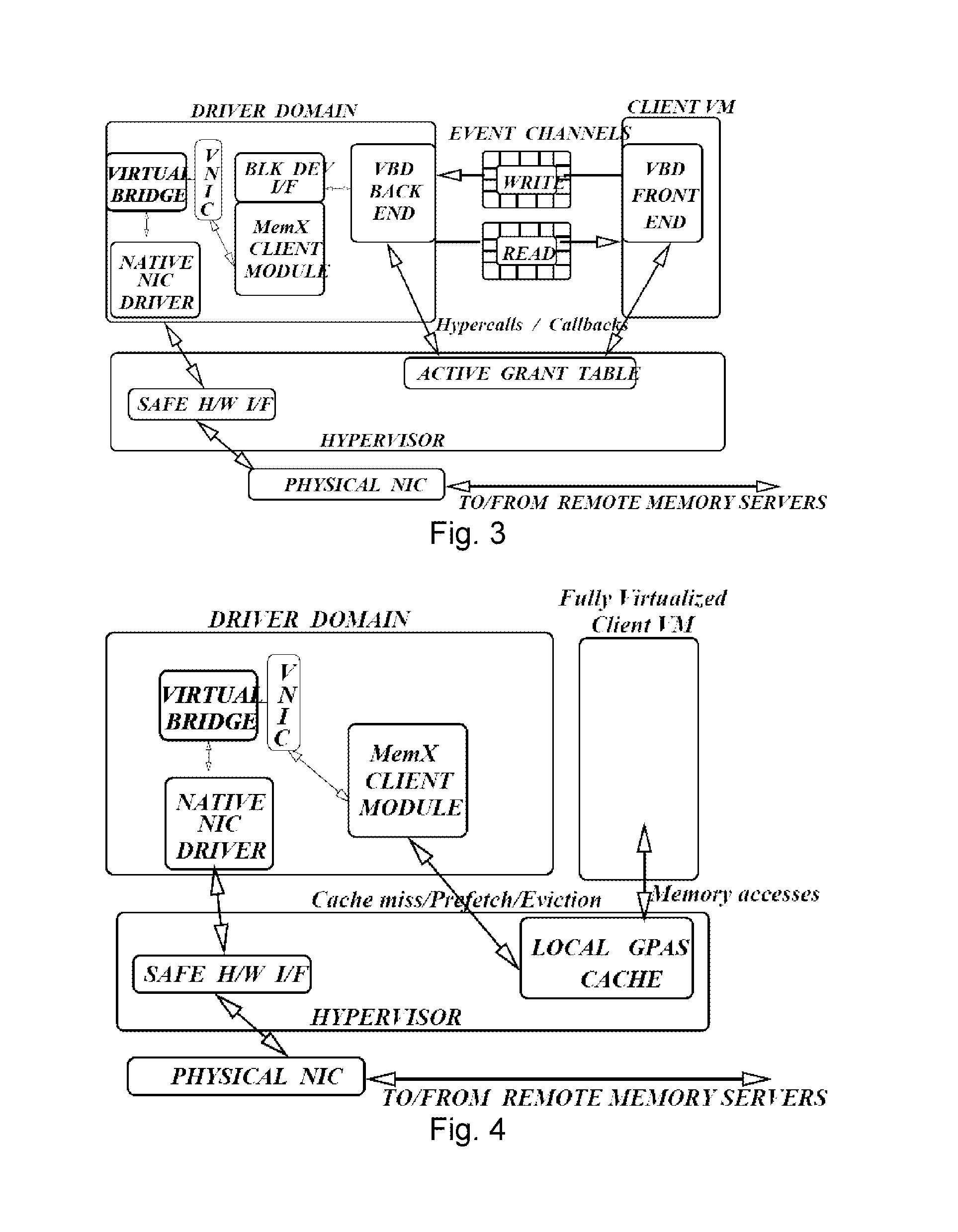
MemX: virtualization of cluster-wide memory
ActiveUS8935506B1Eliminate needReduced execution timeMemory systemsMicro-instruction address formationNODALData set
MemX provides a distributed system that virtualizes cluster-wide memory to support data-intensive and large memory workloads in virtual machines (VMs), and provides benefits in virtualized settings: (1) VM workloads that access large datasets can perform low-latency I / O over virtualized cluster-wide memory; (2) VMs can transparently execute very large memory applications that require more memory than physical DRAM present in the host machine; (3) reduces the effective memory usage of the cluster by de-duplicating pages that have identical content; (4) existing applications do not require any modifications to benefit from MemX such as the use of special APIs, libraries, recompilation, or relinking; and (5) supports live migration of large-footprint VMs by eliminating the need to migrate part of their memory footprint resident on other nodes. Detailed evaluations show that large dataset applications and multiple concurrent VMs achieve significant performance improvements using MemX compared against virtualized local and iSCSI disks.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
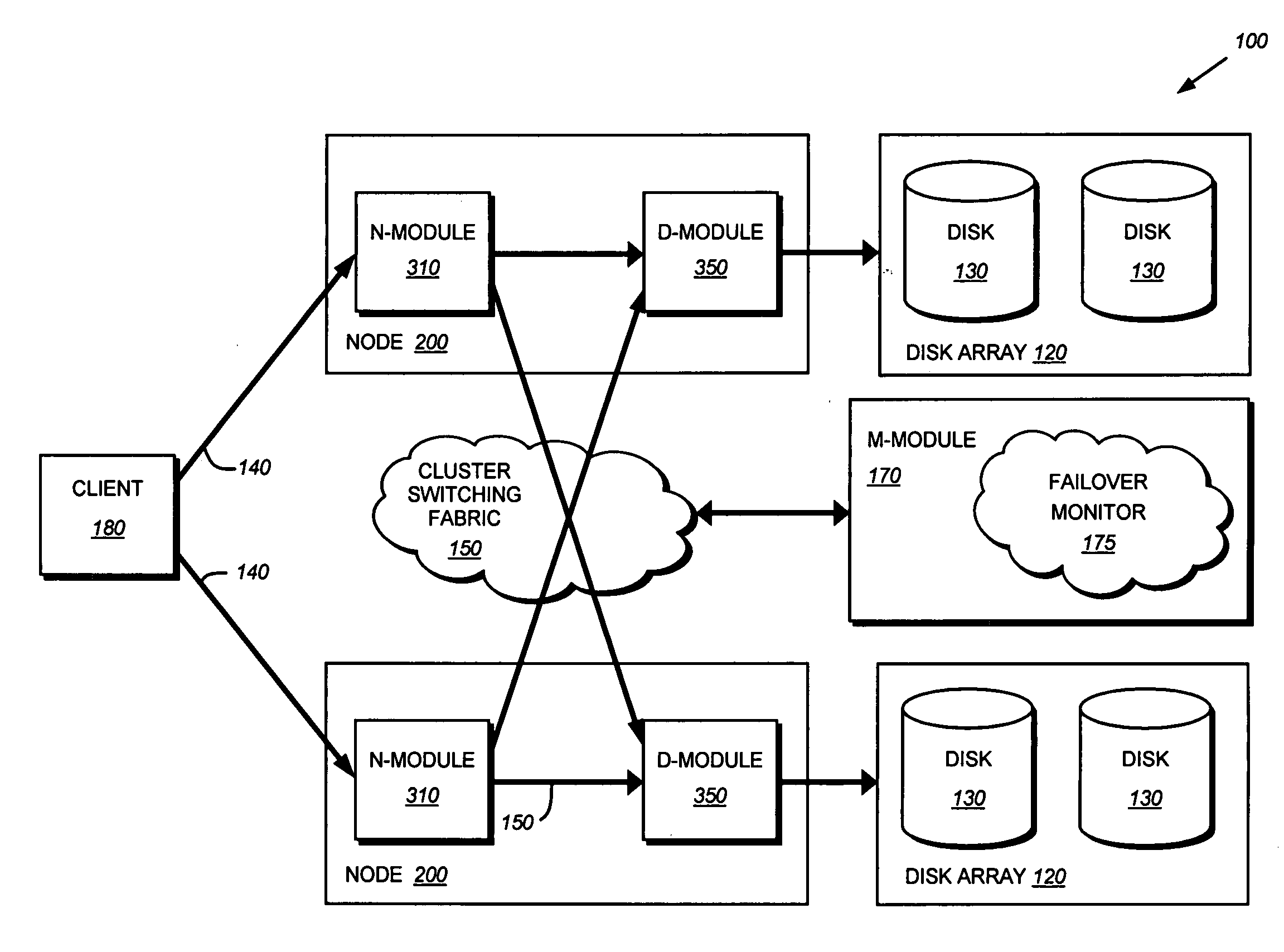
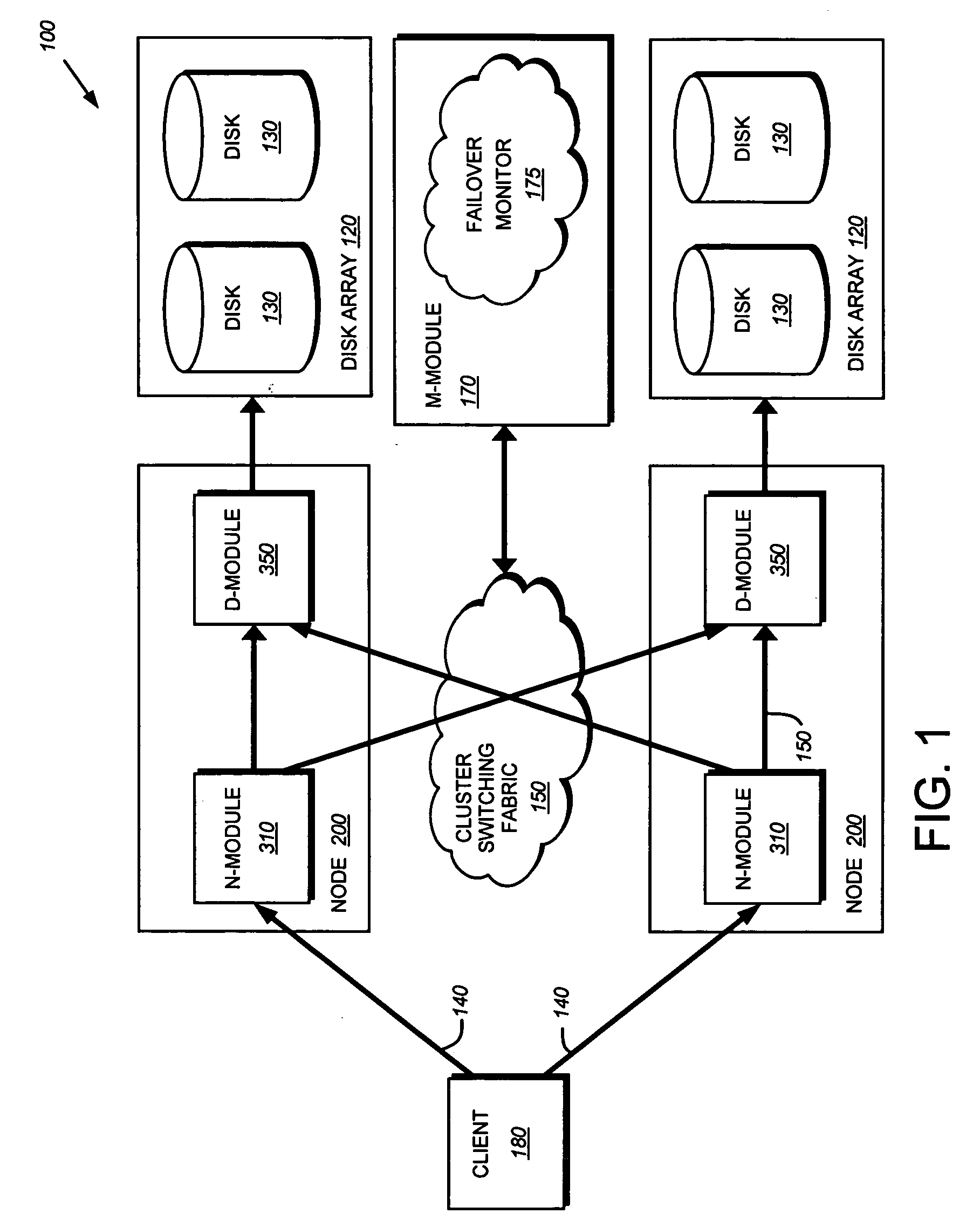
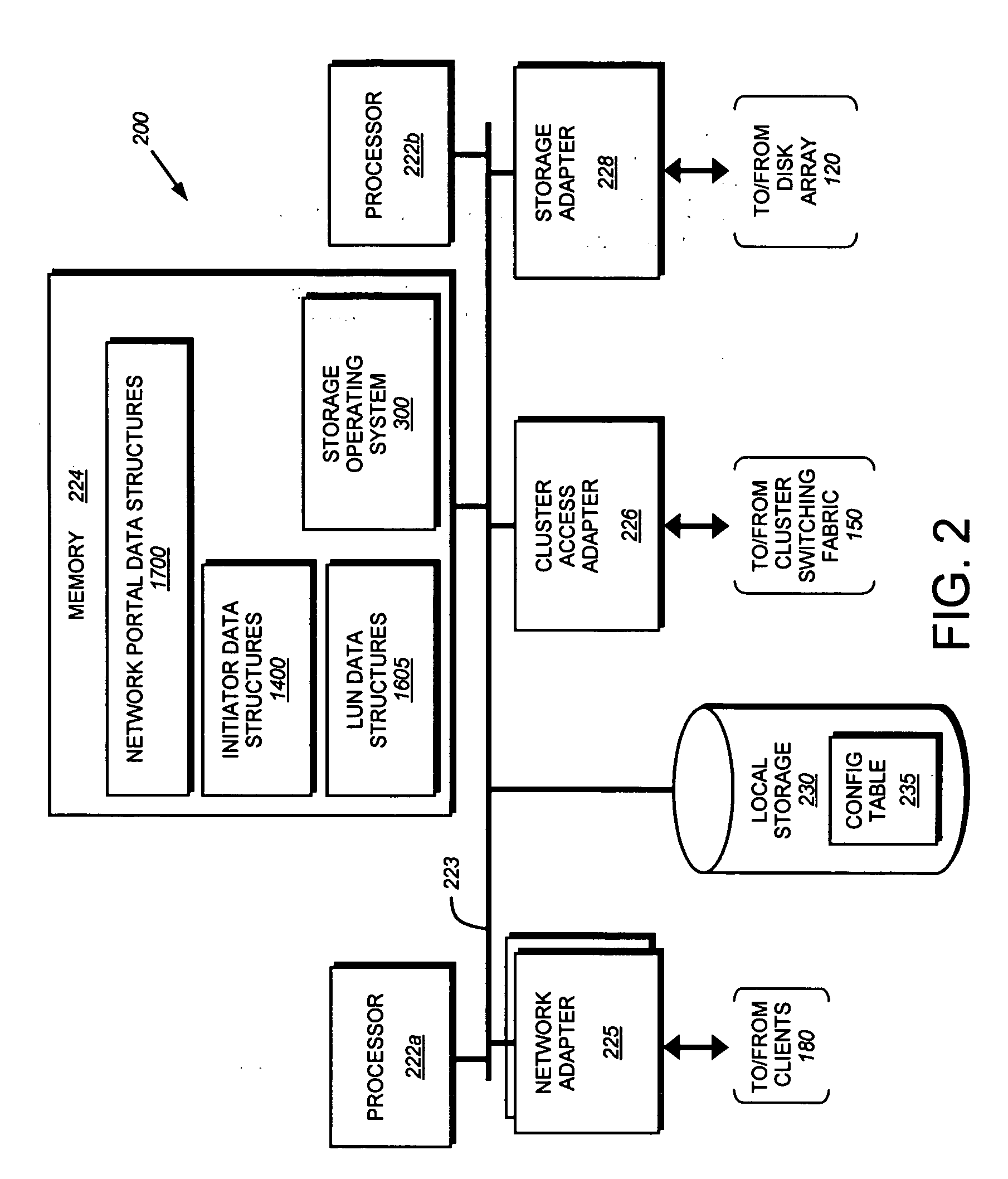
System and method for failover of iSCSI target portal groups in a cluster environment
ActiveUS20070168693A1Overcome disadvantagesRedundant hardware error correctionFailoverSystems management
A system and method for the failover of iSCSI target portal groups (TPGs) is provided. Each network portal within a storage system is associated with a network portal data structure identifying a destination storage system in the event of failover / takeover operation. A management module ensures that all network portals associated with a target portal group have the same destination as a failover storage system. During a failover operation, all network portals within a TPG failover to the same destination storage system.
Owner:NETWORK APPLIANCE INC
Asymmetric data storage system for high performance and grid computing
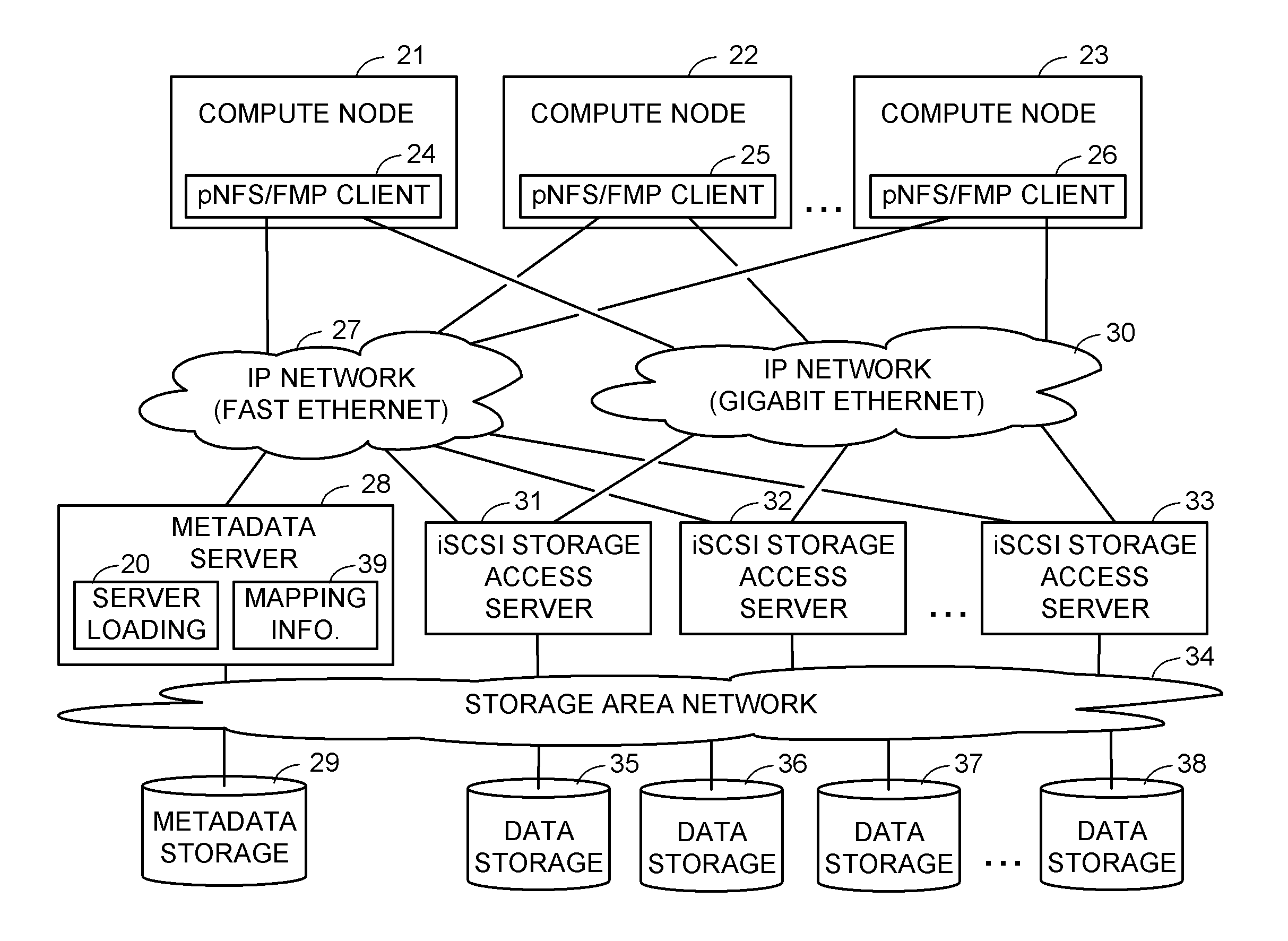
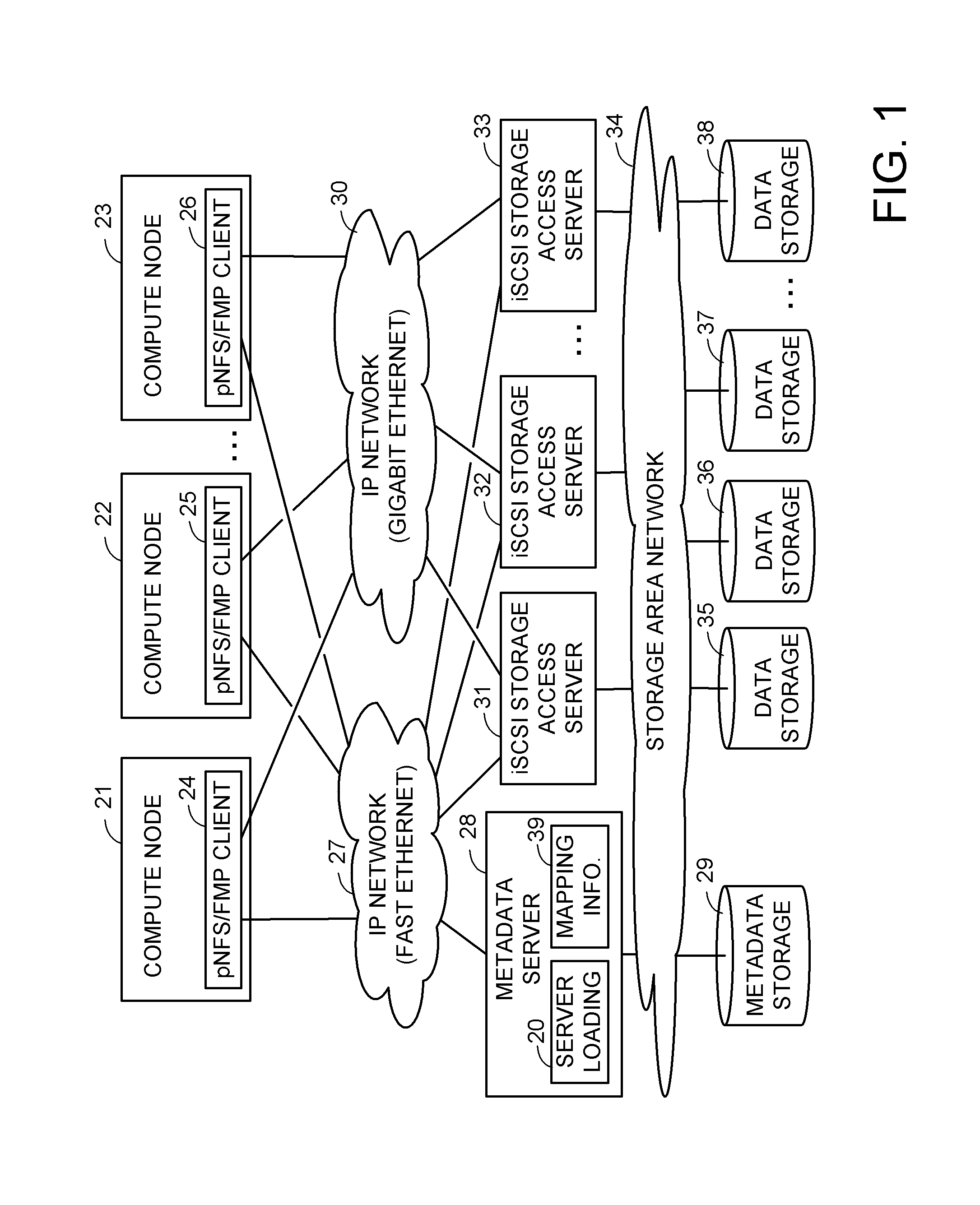
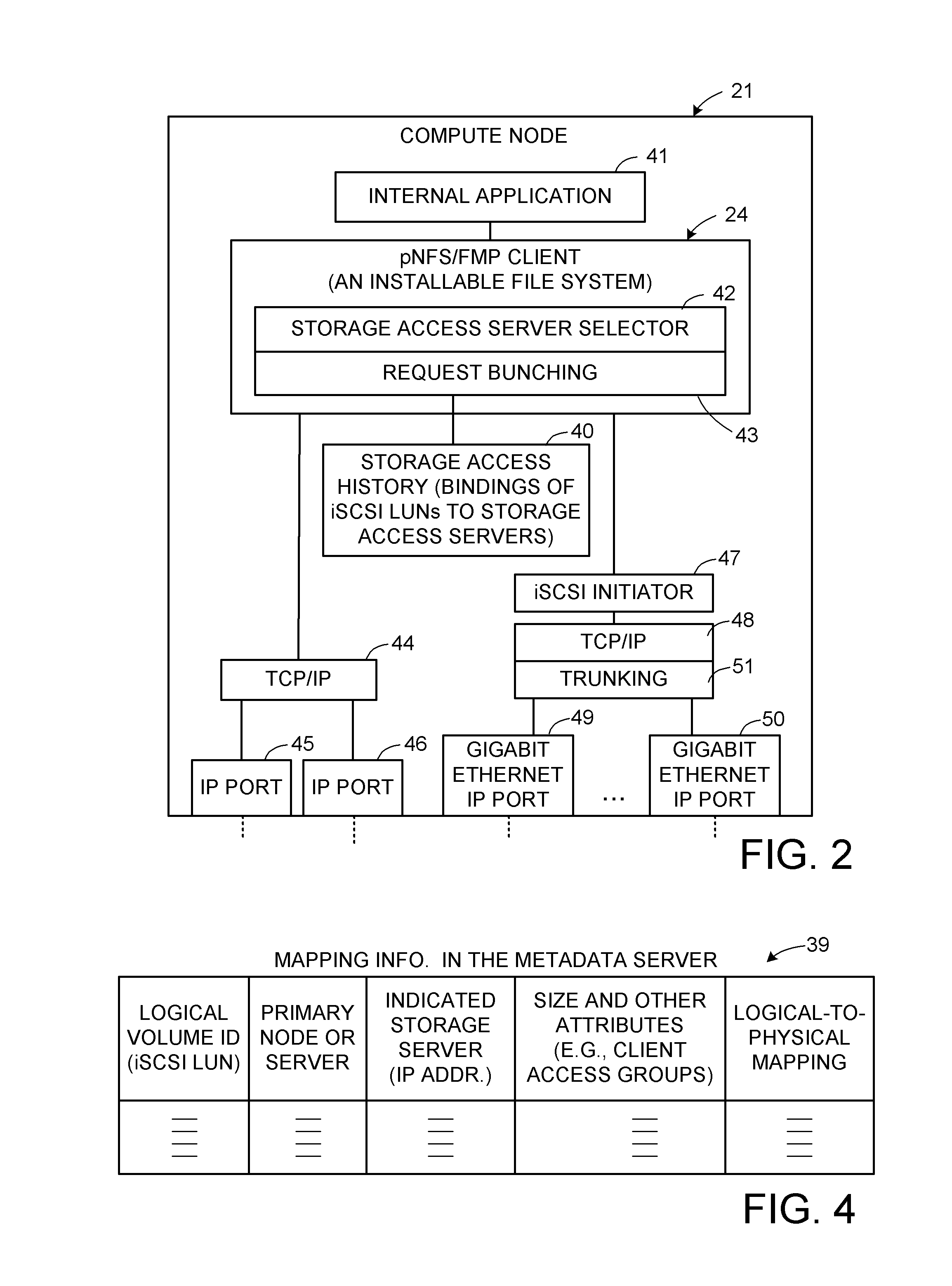
ActiveUS8589550B1Easy accessEnsure load balanceDigital computer detailsSpecial data processing applicationsData processing systemData treatment
A data processing system includes compute nodes, at least one metadata server, iSCSI storage access servers, and data storage devices. The metadata server services requests from the compute nodes for file mapping information identifying iSCSI LUNs and logical blocks of file data. The storage access servers service iSCSI I / O requests from the compute nodes, and report server loading to the metadata server. A Gigabit Ethernet IP network transfers read and write data between the compute nodes and the storage access servers. The storage access servers are linked to the data storage devices for parallel access to iSCSI LUNs of the file data in the data storage devices. The metadata server is programmed for server load balancing by indicating to the compute nodes respective ones of the storage access servers that should be used for access to the iSCSI LUNs.
Owner:EMC IP HLDG CO LLC
A method for implementing iSCSI memory system
A realization method for ISCSI storage system characterizes in realizing ISCSI protocol on ISCSI controller including a net card binding module realizing different load balances, a storage device management module providing fixed virtual device identifier and the heat plug function, an adaptive IQ load control program controlling parallel IQ load of low end storage device and a multi-path module for IQ requiring controlling different storage array channels. Storage device image module controlling the access limitation of a starter to the storage device, a block device support module realizing the transformation of SCSI order and soft device IQ and a software RAID module are added if necessary.
Owner:TSINGHUA UNIV
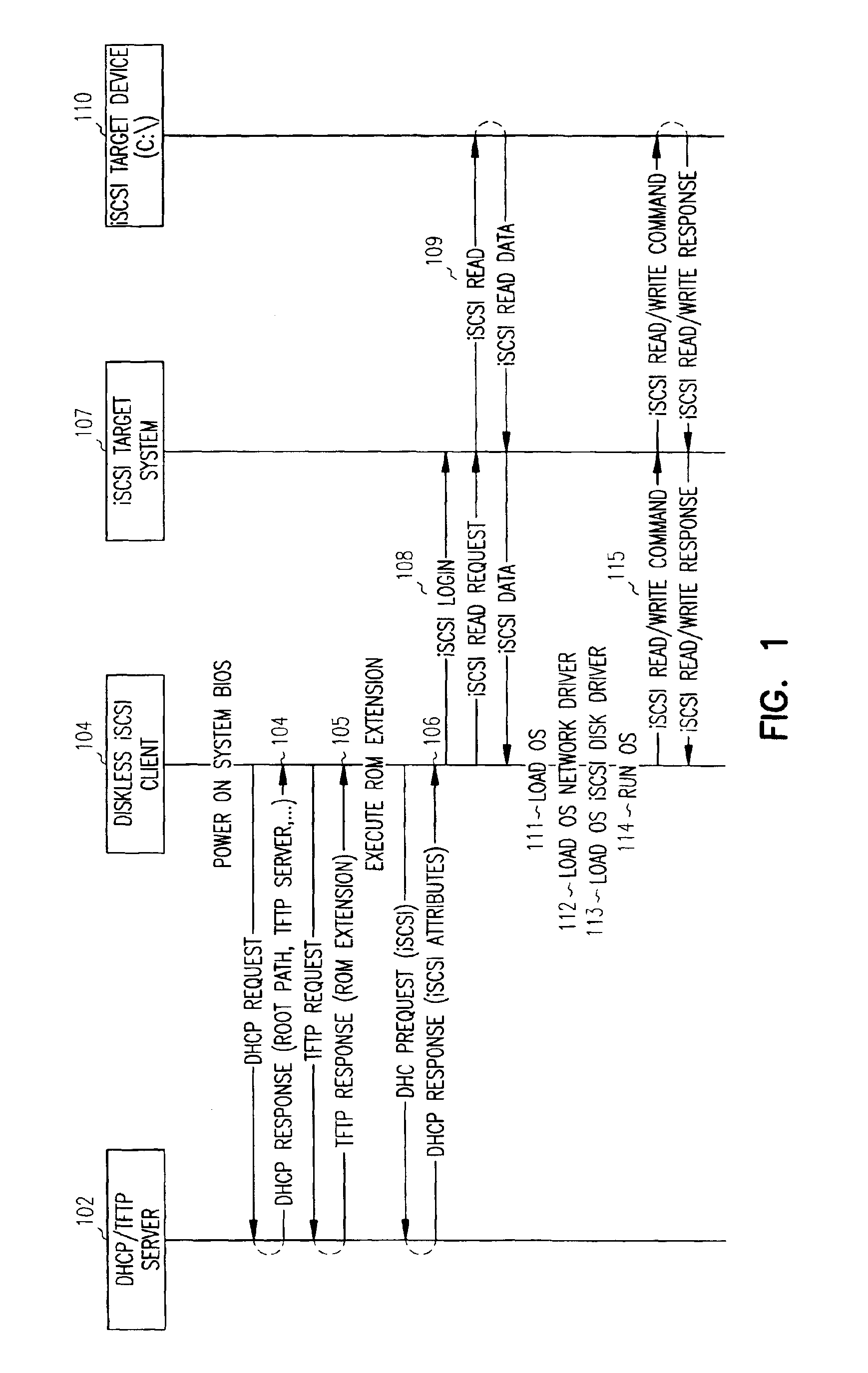
Modified operating system boot sequence for iSCSI device support
InactiveUS6857069B1Easy to operateAvailable for useMultiple digital computer combinationsProgram loading/initiatingSCSIOperational system
SCSI commands are transported over the TCP / IP connection to provide access to a bootable operating system stored on a second networked computerized system, and the networked computerized system is booted from the bootable operating system stored on the second networked computerized system via the SCSI commands transported over the TCP / IP connection. A network driver is loaded in the booting operating system before the booting operating system's disk driver is loaded.
Owner:CISCO TECH INC
Session-based target/LUN mapping for a storage area network and associated method
A storage router having an internet protocol (IP) port for coupling to a network supporting IP packets, a fibre channel port for coupling to a fibre channel network to a plurality of storage devices, and a SCSI router having an iSCSI interface that extracts SCSI command and data information from packets received through the IP port, wherein the SCSI router passes the extracted SCSI command and data information to the fiber channel port. Some embodiments further include a session to an information-handling system. The session supports a target-only mapping (wherein a source-specified target value is replaced by a mapped target value that is then passed by the SCSI router toward a first storage device and its LUNs), or target-and-LUN mapping (wherein source-specified target and LUN information is replaced by mapped target-and LUN information such as a loop-ID and LUN combination, a WWPN and LUN combination, or a WWNN).
Owner:CISCO TECH INC
Virtual disk image system with local cache disk for iSCSI communications
InactiveUS6925533B2Improve speed performanceImprove welfareInput/output to record carriersMemory adressing/allocation/relocationTransmission protocolSCSI
A system and method for caching data received over a network connection comprising: a target device for receiving requests for routing data packetized for transport according to an Internet SCSI (iSCSI) transport protocol, the target device including an iSCSI drive for processing received SCSI commands; an initiator device for generating SCSI commands for reading data and writing data from / to storage devices associated with the iSCSI drive; a local disk at the initiator device for storing a copy of data read from or written to the storage devices associated with the iSCSI drive; and, a mapping device for mapping addresses associated with data stored at storage devices associated with the iSCSI drive with local data storage units in the local disk device, wherein seamless local caching of data at the initiator from data at remote data storage devices associated with the iSCSI drive is provided.
Owner:IBM CORP
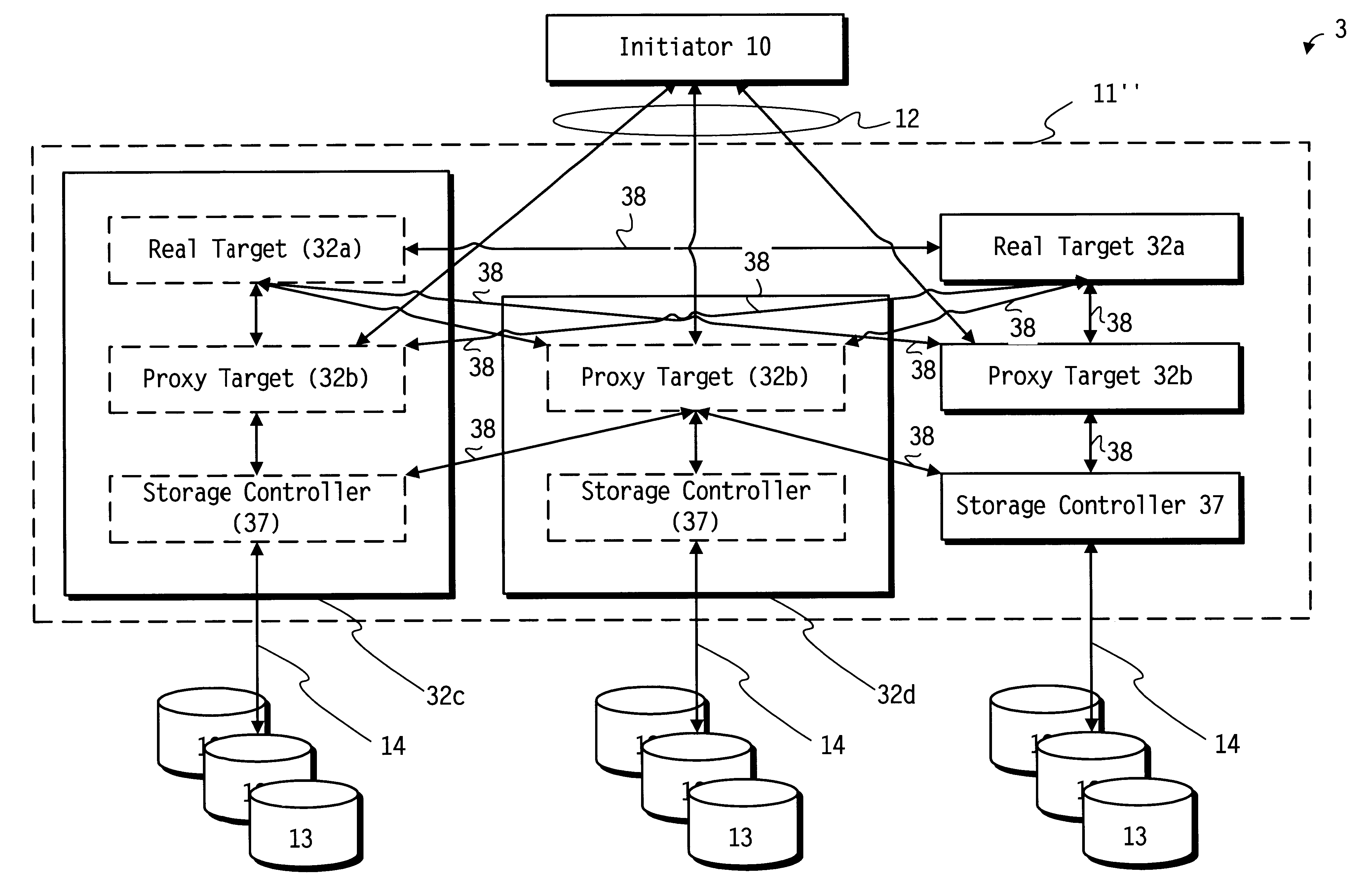
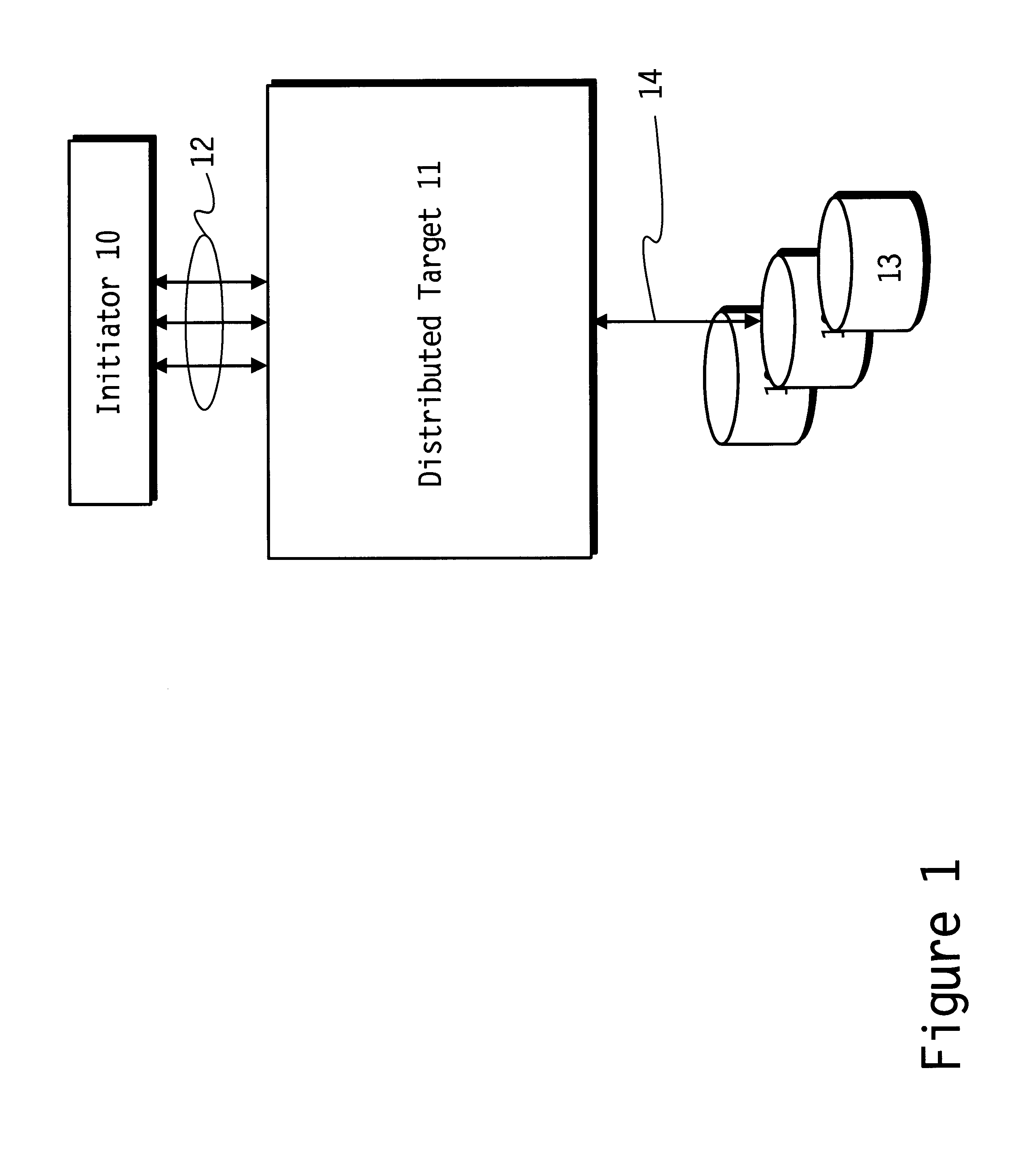
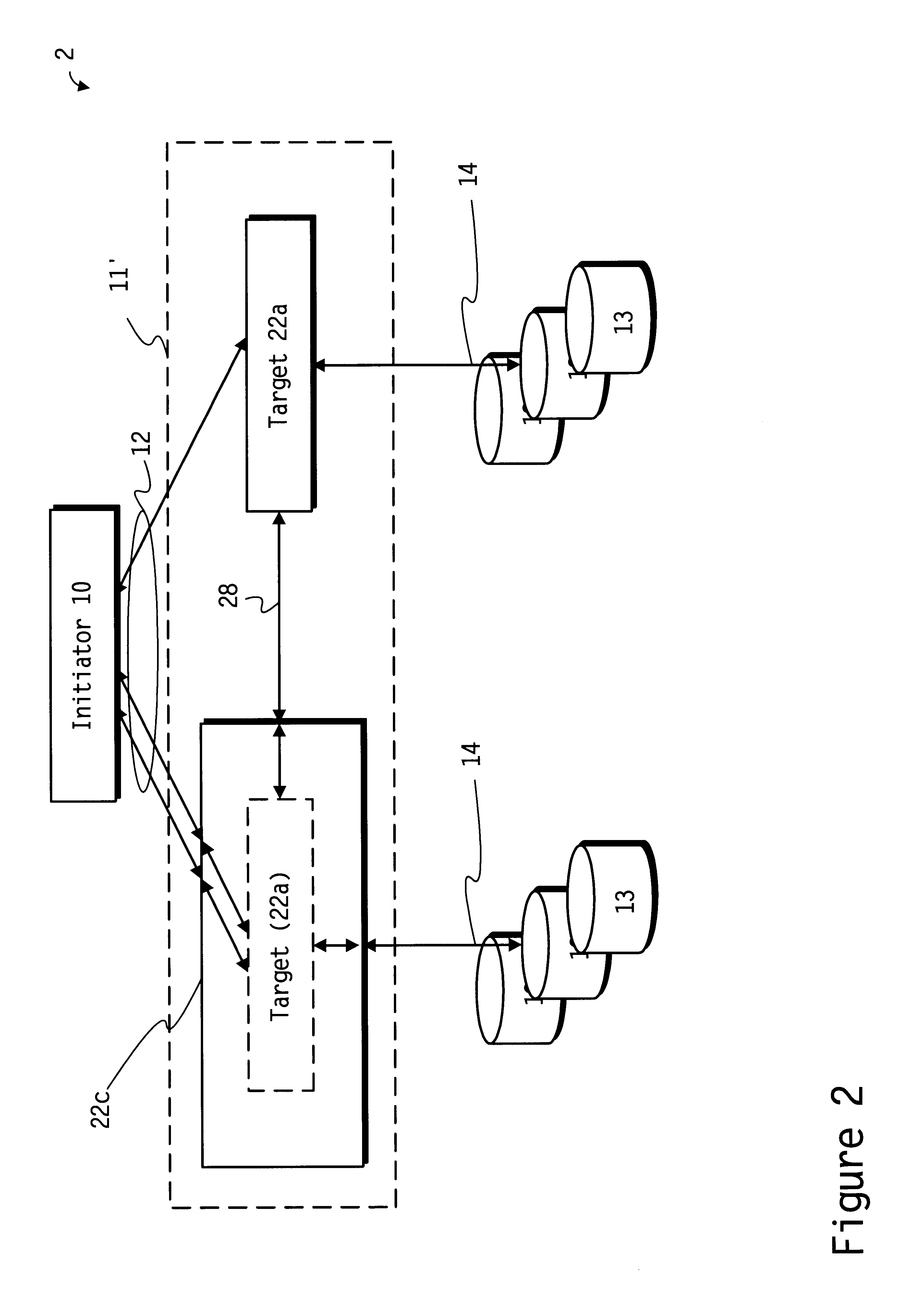
Distributed iSCSI and SCSI targets
Apparatus and methods for distributing iSCSI and SCSI targets. The initiator may assist in the distribution and order the SCSI commands. A subset of target storage processors may act as proxies. Target storage processors forward requests to a selected target storage processor which decides whether any and which of the other target storage processors is to process a forwarded request. The target storage processors may act as peers. A target storage processor communicates each received request to all of the other storage processors. Each of the target storage processors determines whether a request it received is to execute. A target storage processors may arrange themselves into layers to divide the SCSI and iSCSI protocol work. A distributed system associates each of multiple egress target storage processors with a respective ingress target storage processor and associates a set of blocks of storage with each of the egress target storage processors.
Owner:OPEN INVENTION NEWTORK LLC
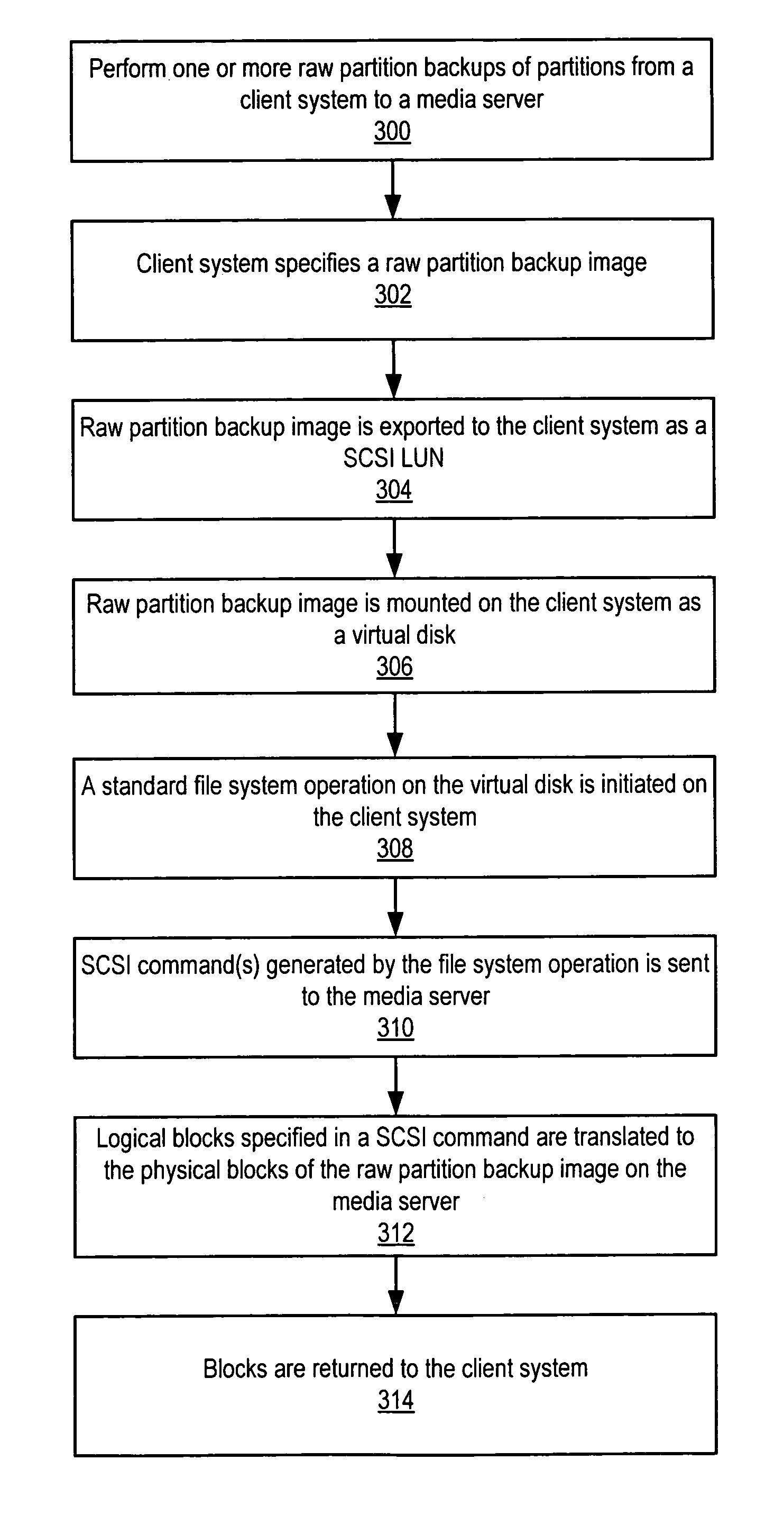
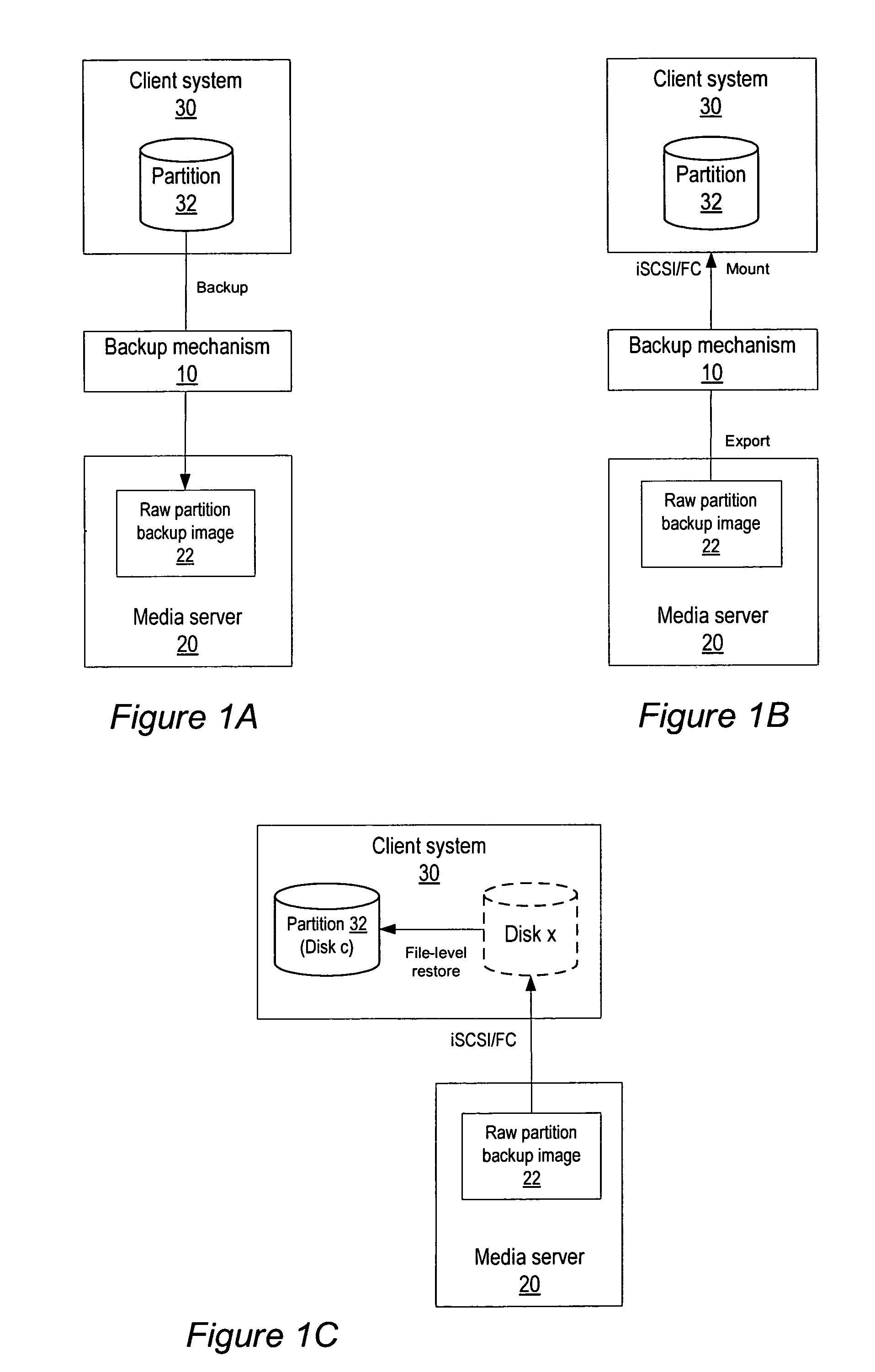
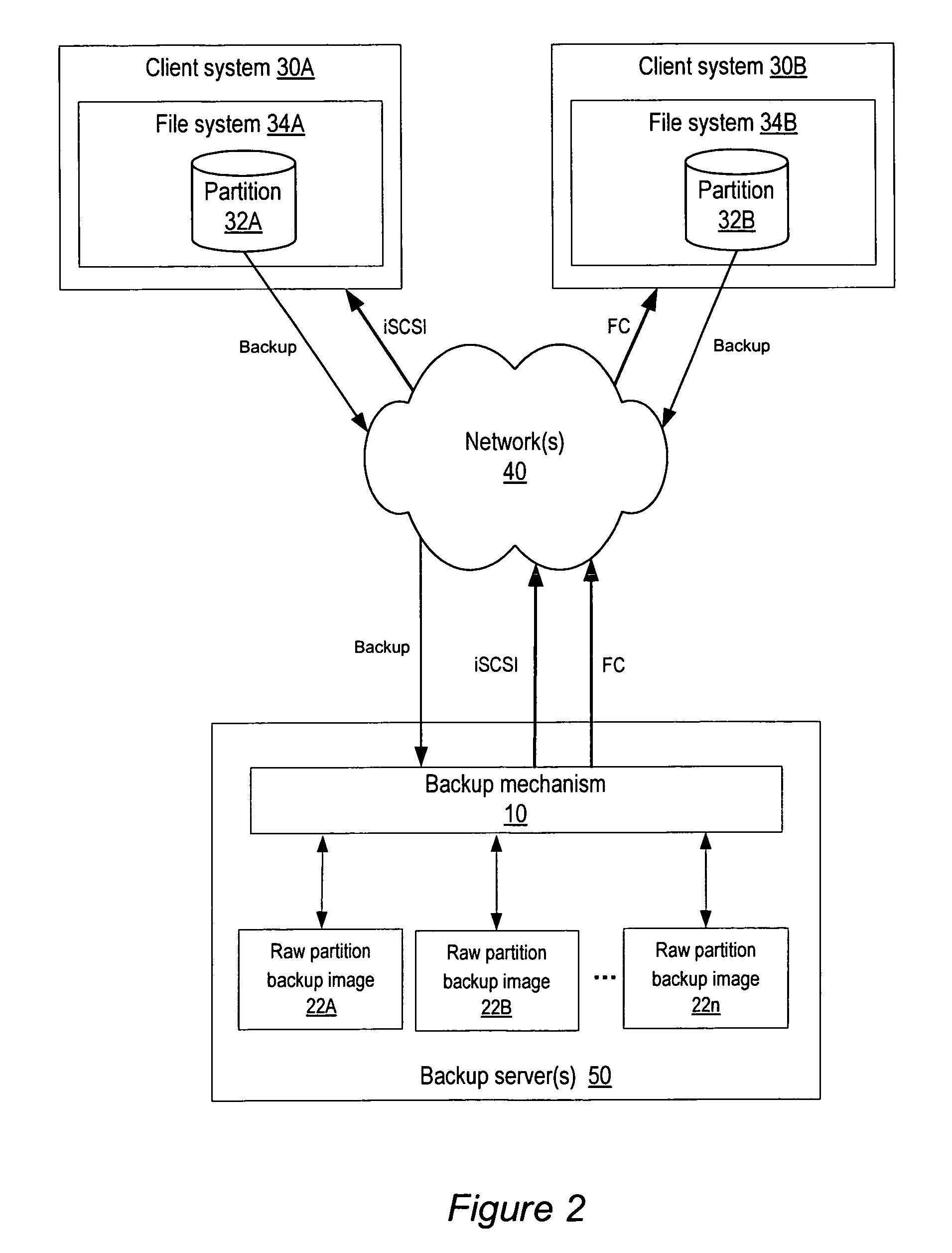
Method and apparatus for file-level restore from raw partition backups
ActiveUS7937545B1Quick backupError detection/correctionMultiple digital computer combinationsFile systemTechnical standard
Method and apparatus for file-level restore from raw partition backups. A backup mechanism may be provided that is configured to perform raw partition backups to a media server and to support file-level restores from the raw partition backups through, for example, Fibre Channel (FC) or iSCSI Logical Unit (LUN) export of the raw partition backup images to client systems. Once a LUN is exported and mounted on the client system, direct file manipulation using standard file system commands may be performed. Embodiments achieve both fast backup and individual file retrieval without the necessity of understanding native file system formats and without requiring a file system mapping of the source (client) partition. Thus, embodiments may be used in heterogeneous environments.
Owner:SYMANTEC OPERATING CORP
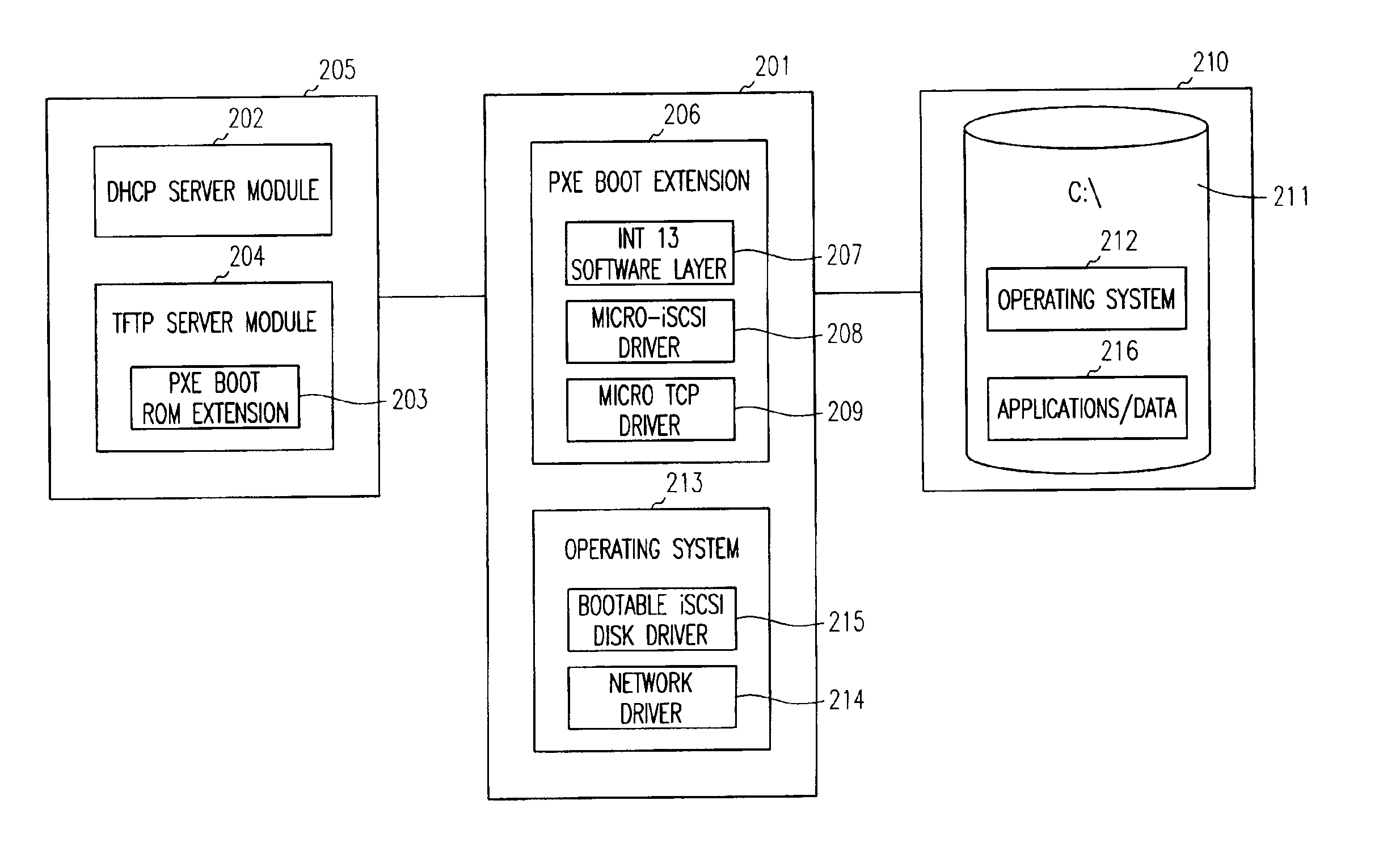
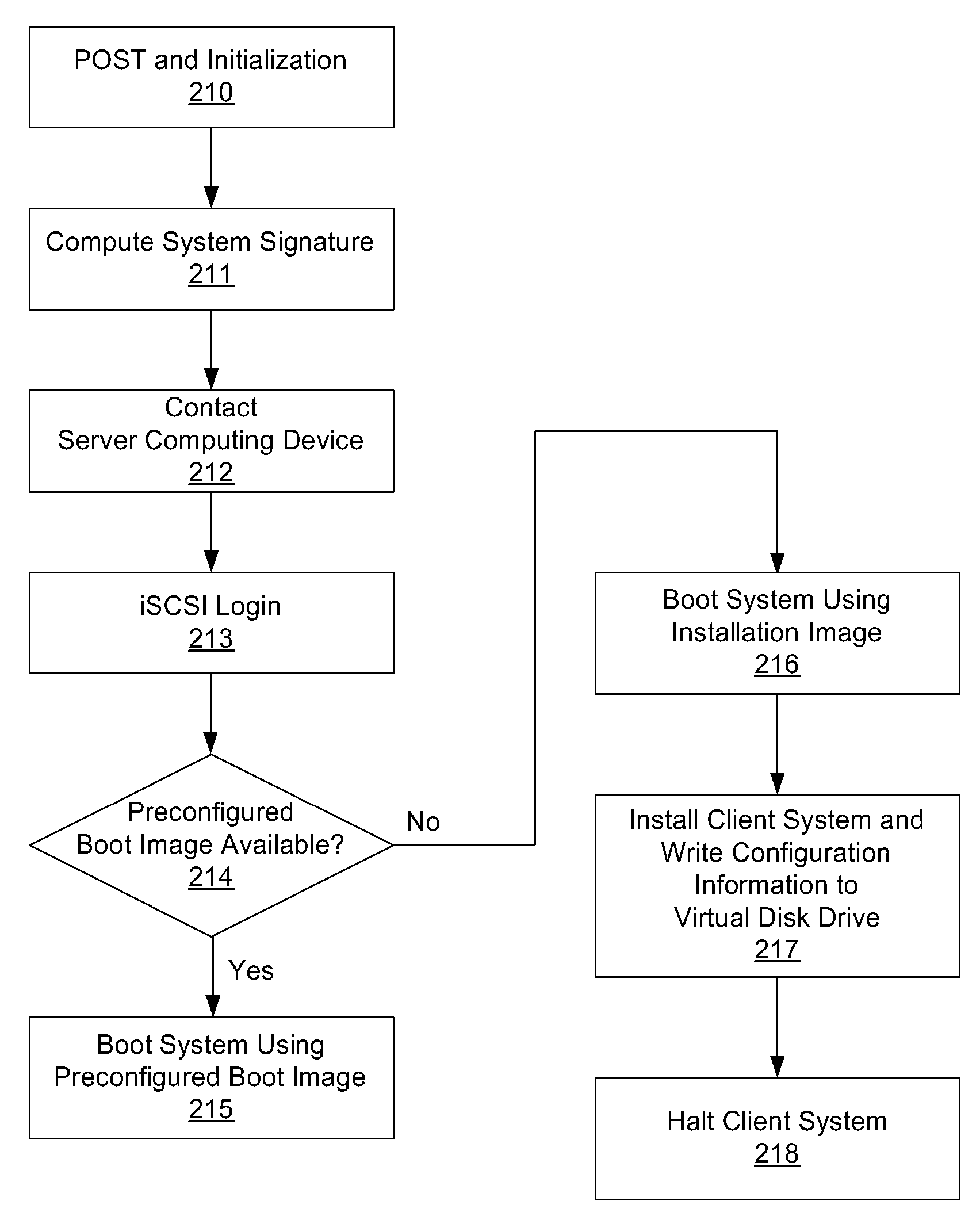
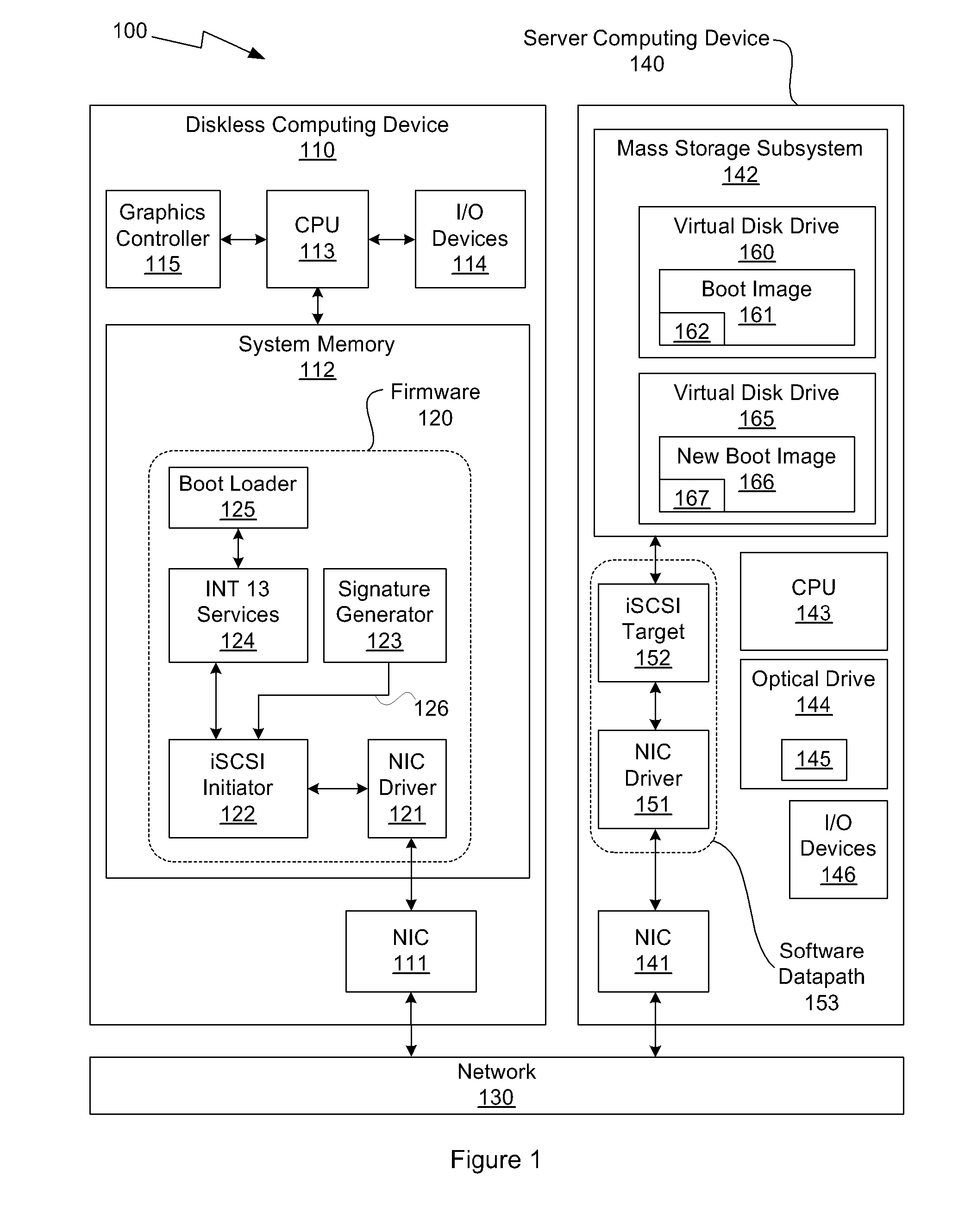
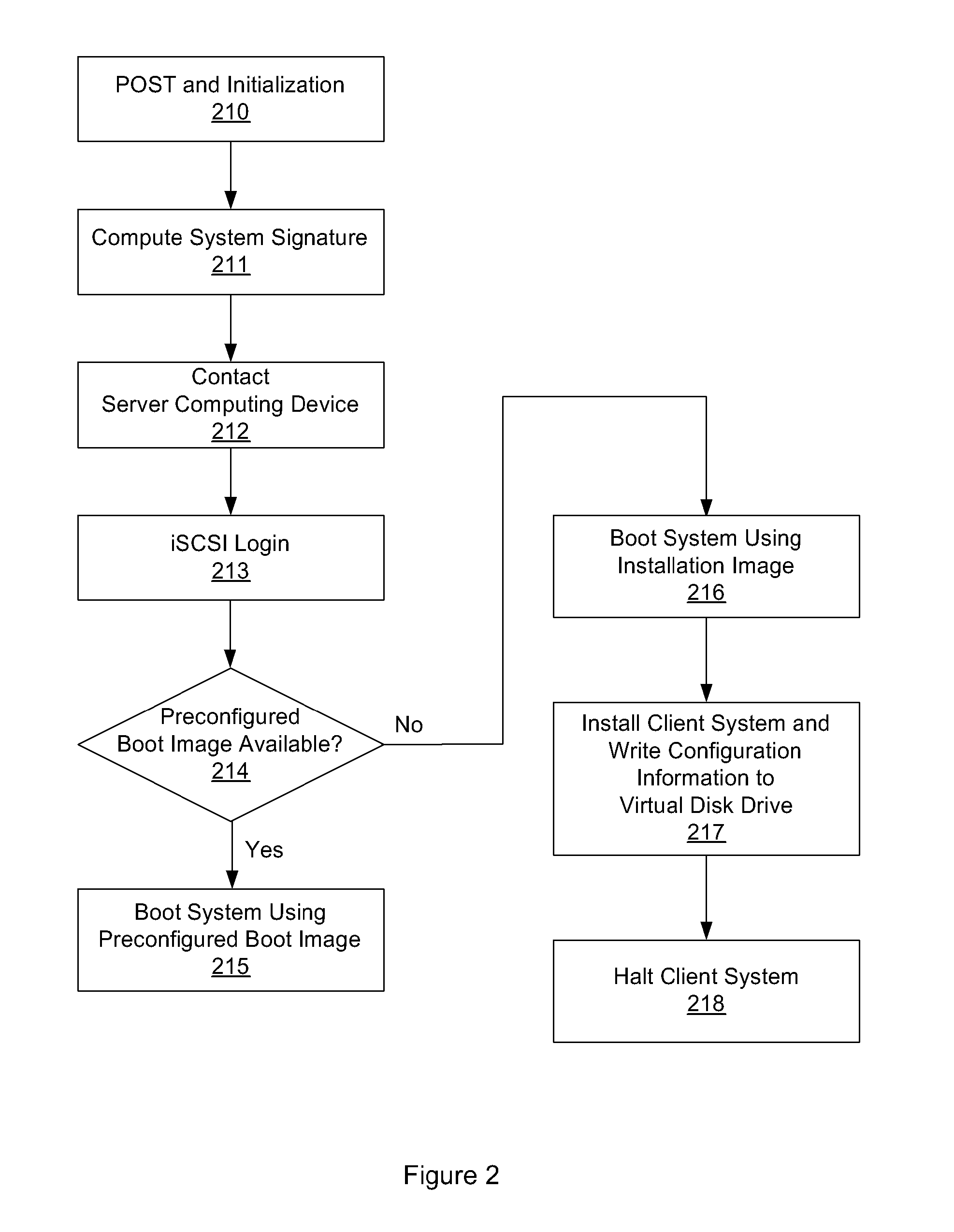
System and method for operating system installation on a diskless computing platform
One embodiment of the present invention sets forth a technique for automatically provisioning a diskless computing device and an associated server system. A diskless computing device client incorporates an iSCSI initiator that is used to access resources provided by an iSCSI target that is resident on a server computing device. The iSCSI initiator is implemented in the client firmware, providing INT13 disk services entry points, thereby enabling the client to transparently access virtual storage devices at boot time. The client device conducts an apparently local installation using the virtual storage devices provided by the server computing device. A short signature value is associated with the boot image, uniquely associating the boot image with the specific client hardware configuration. When the client device boots normally, the signature value of the client device is presented to the server computing device to automatically reference the appropriate boot image.
Owner:NVIDIA CORP
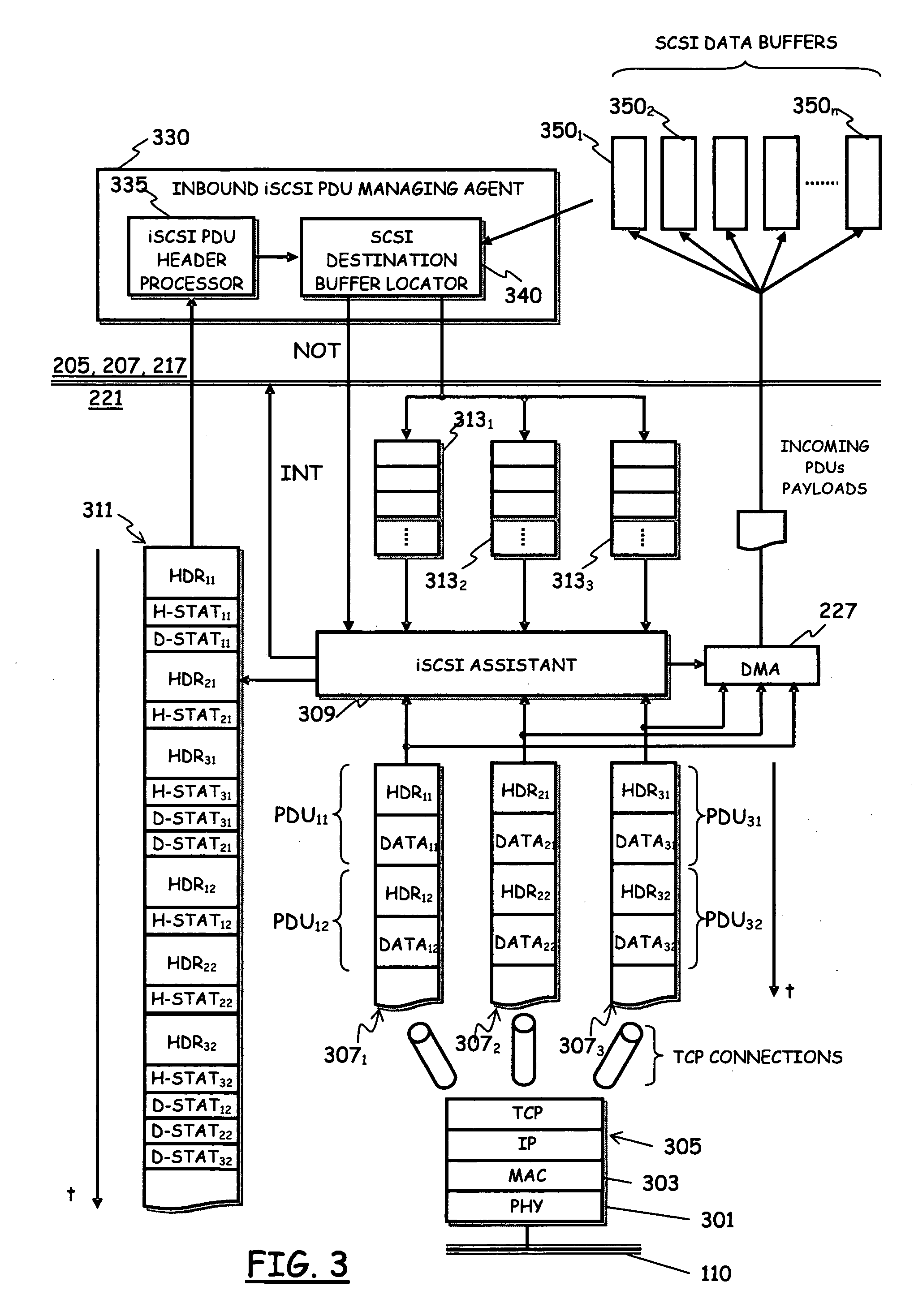
Method of offloading iSCSI TCP/IP processing from a host processing unit, and related iSCSI TCP/IP offload engine
InactiveUS20060056435A1Reduce the burden onData switching by path configurationData streamIp processing
A method of offloading, from a host data processing unit (205), iSCSI TCP / IP processing of data streams coming through at least one TCP / IP connection (3071,3072,3073), and a related iSCSI TCP / IP Offload Engine (TOE). The method including: providing a Protocol Data Unit (PDU) header queue (311) adapted to store headers (HDR11, . . . , HDR32) of iSCSI PDUs received through the at least one TCP / IP connection; monitoring the at least one TCP / IP connection for an incoming iSCSI PDU to be processed; when at least a iSCSI PDU header is received through the at least one TCP / IP connection, extracting the iSCSI PDU header from the received PDU, and placing the extracted iSCSI PDU header into the PDU header queue; looking at the PDU header queue for ascertaining the presence of iSCSI PDUs to be processed, and processing the incoming iSCSI PDU based on information in the extracted iSCSU PDU header retrieved from the PDU header queue.
Owner:IBM CORP
Method for selectable software-hardware internet SCSI
Embodiments of the present invention address the deficiencies of the art in respect to application performance and provide a novel and non-obvious data processing method, system and computer program product for selecting between separate hardware implemented and software implemented iSCSI paths to process an input / output request in a data communication environment. In one embodiment, a method for selecting between separate hardware implemented and software implemented iSCSI paths to process an input / output request can include transmitting a stream of requests to access at least one logical block address in at least one storage device in an IP storage system is provided. The utilization of a first processor in a host configured to transmit the stream of requests, where the host provides a first iSCSI implementation can be monitored along with the utilization of a second processor in an adapter coupled to the storage device, where the adapter provides a second iSCSI implementation. In addition, a request in the stream of requests can be routed to the first iSCSI implementation in the host and the second iSCSI implementation in the adapter based upon a value of the utilization of the first processor in the host and a value of the utilization of the second processor in the adapter. The first iSCSI implementation can be a software iSCSI and the second iSCSI implementation can be a hardware iSCSI.
Owner:LENOVO ENTERPRISE SOLUTIONS SINGAPORE
Method and system for iSCSl boot
Certain aspects of a method for iSCSI boot may include loading boot BIOS code from a host bus adapter or a network interface controller (NIC) by an iSCSI client device. A connection may be established to an iSCSI target by the iSCSI client device after loading the boot BIOS code. The boot BIOS code may be chained to at least one interrupt handler over iSCSI protocol. An operating system may be remotely booted from the iSCSI target by the iSCSI client device based on chaining the interrupt handler. An Internet protocol (IP) address and / or location of the iSCSI target may be received. At least one iSCSI connection may be initiated to the iSCSI target based on chaining at least one interrupt handler. The iSCSI target may be booted in real mode if at least one master boot record is located in the memory.
Owner:AVAGO TECH INT SALES PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com