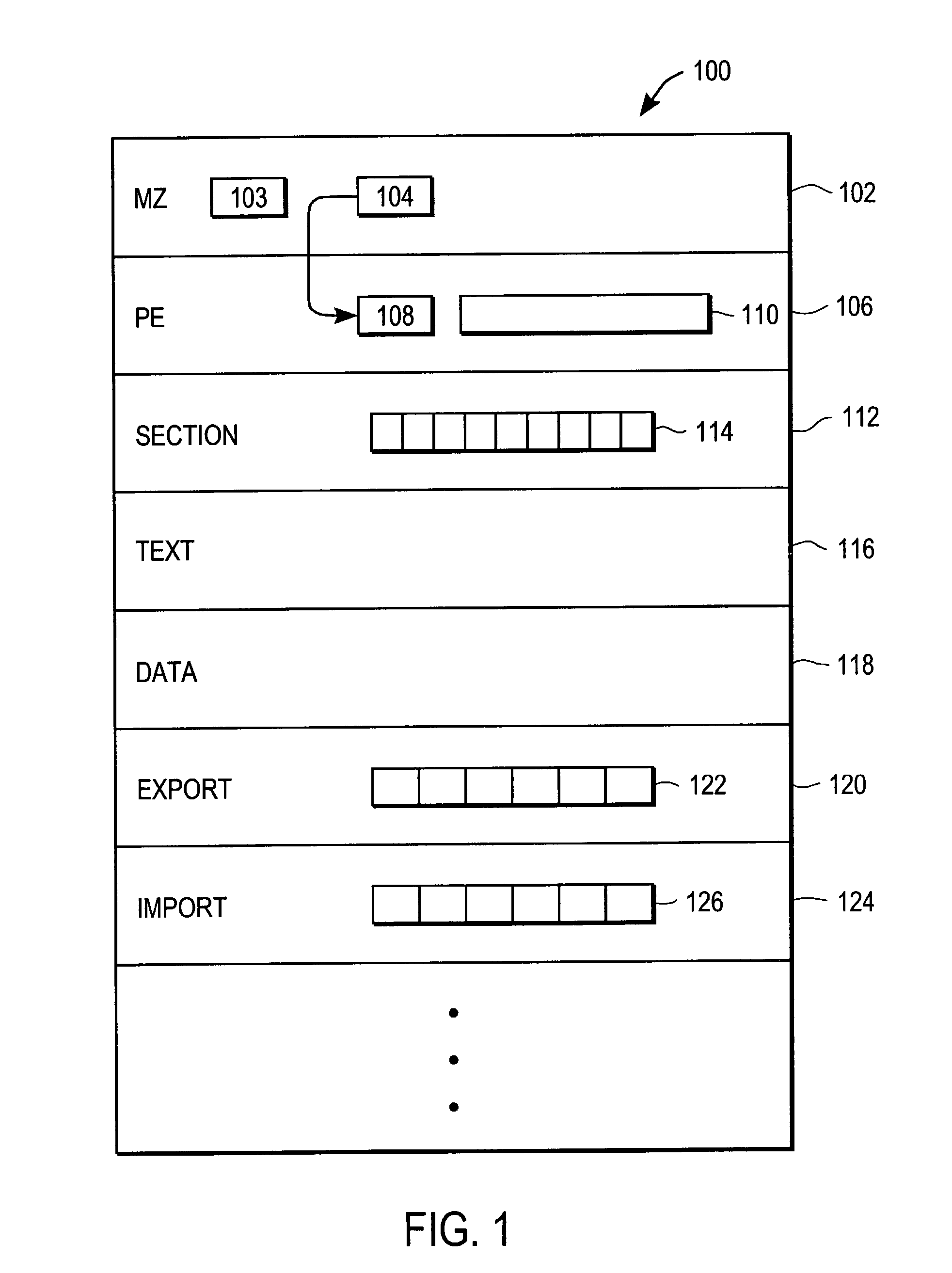
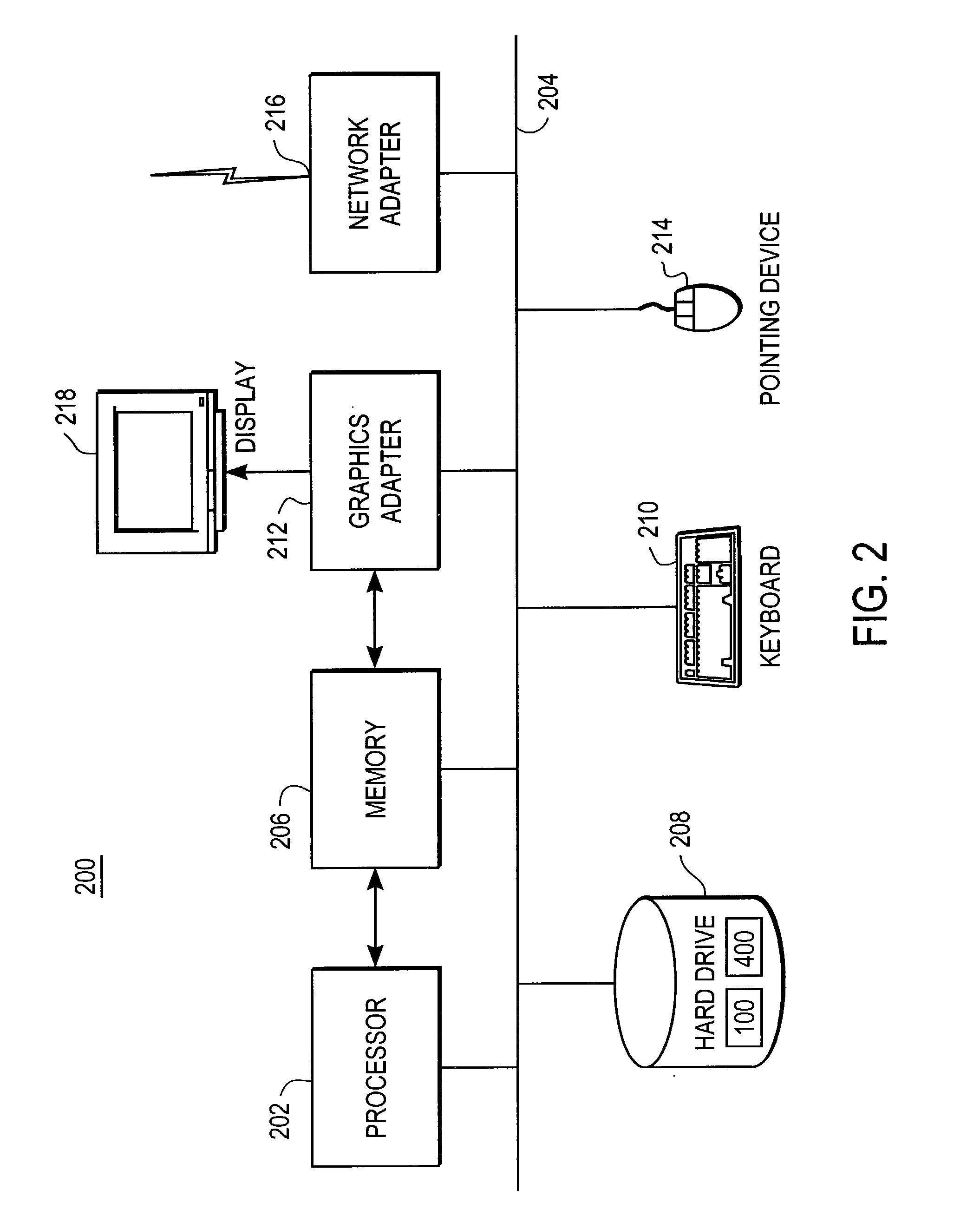
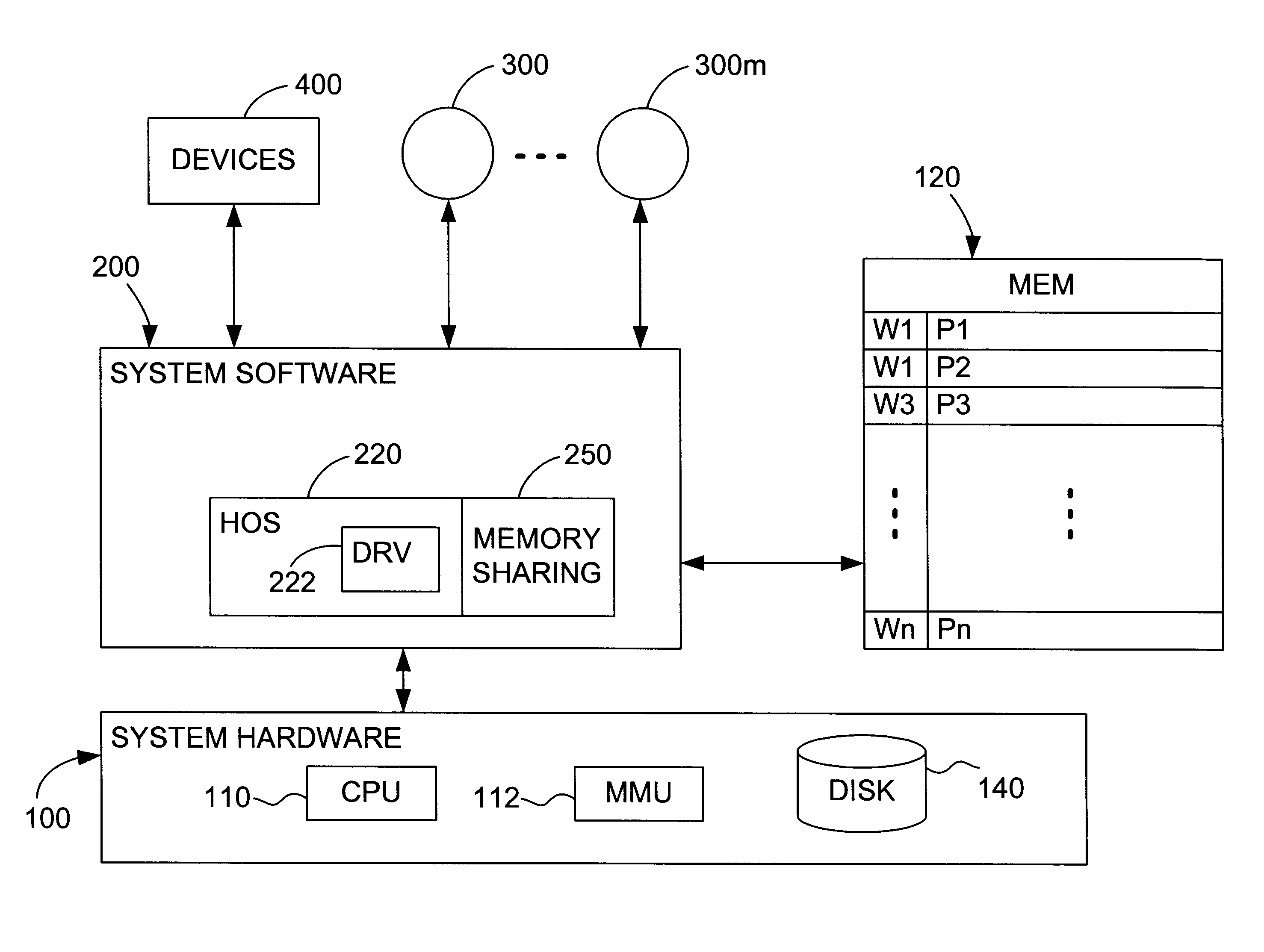
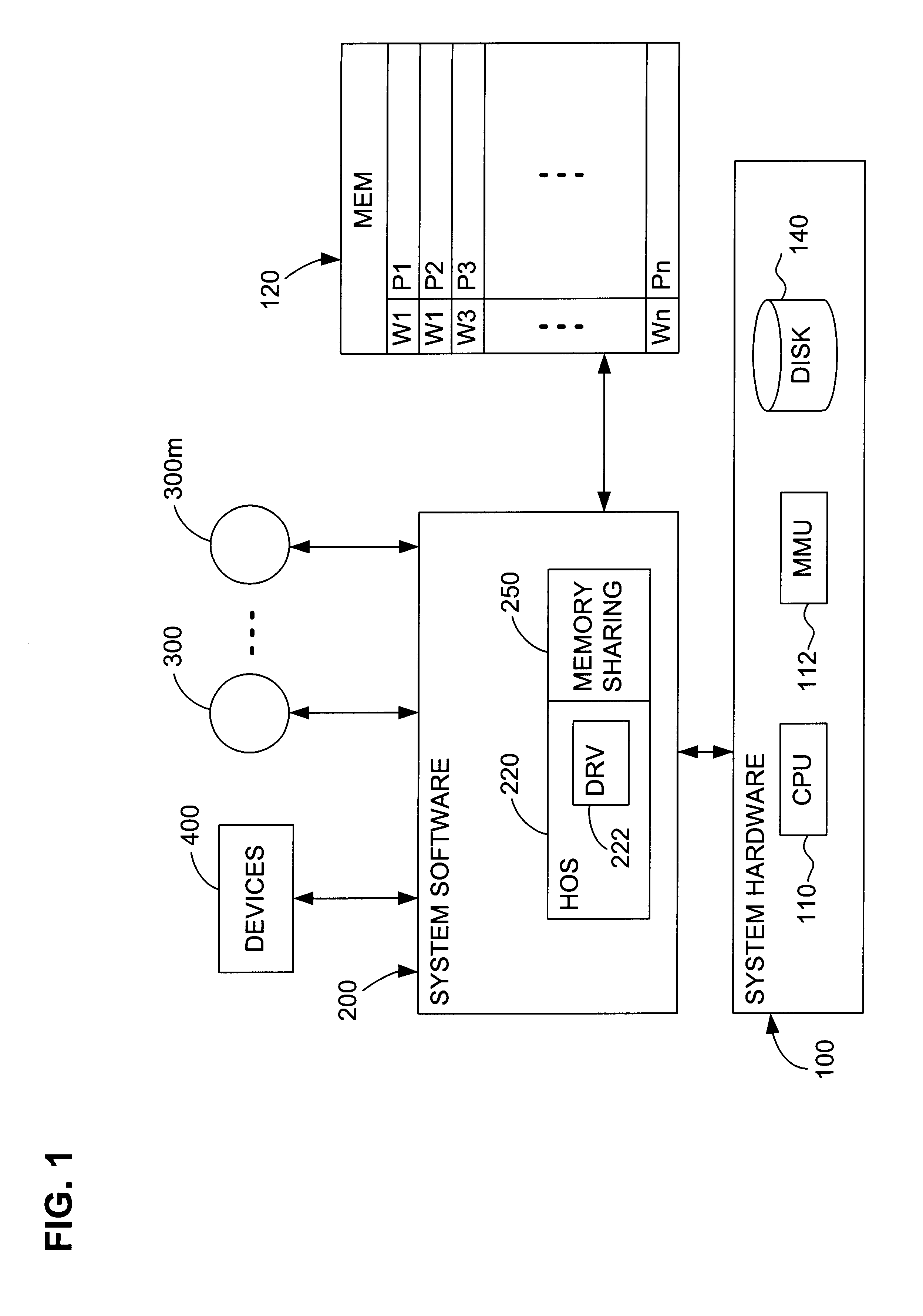
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1161 results about "Virtual memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, virtual memory (also virtual storage) is a memory management technique that provides an "idealized abstraction of the storage resources that are actually available on a given machine" which "creates the illusion to users of a very large (main) memory."
Malware Detector
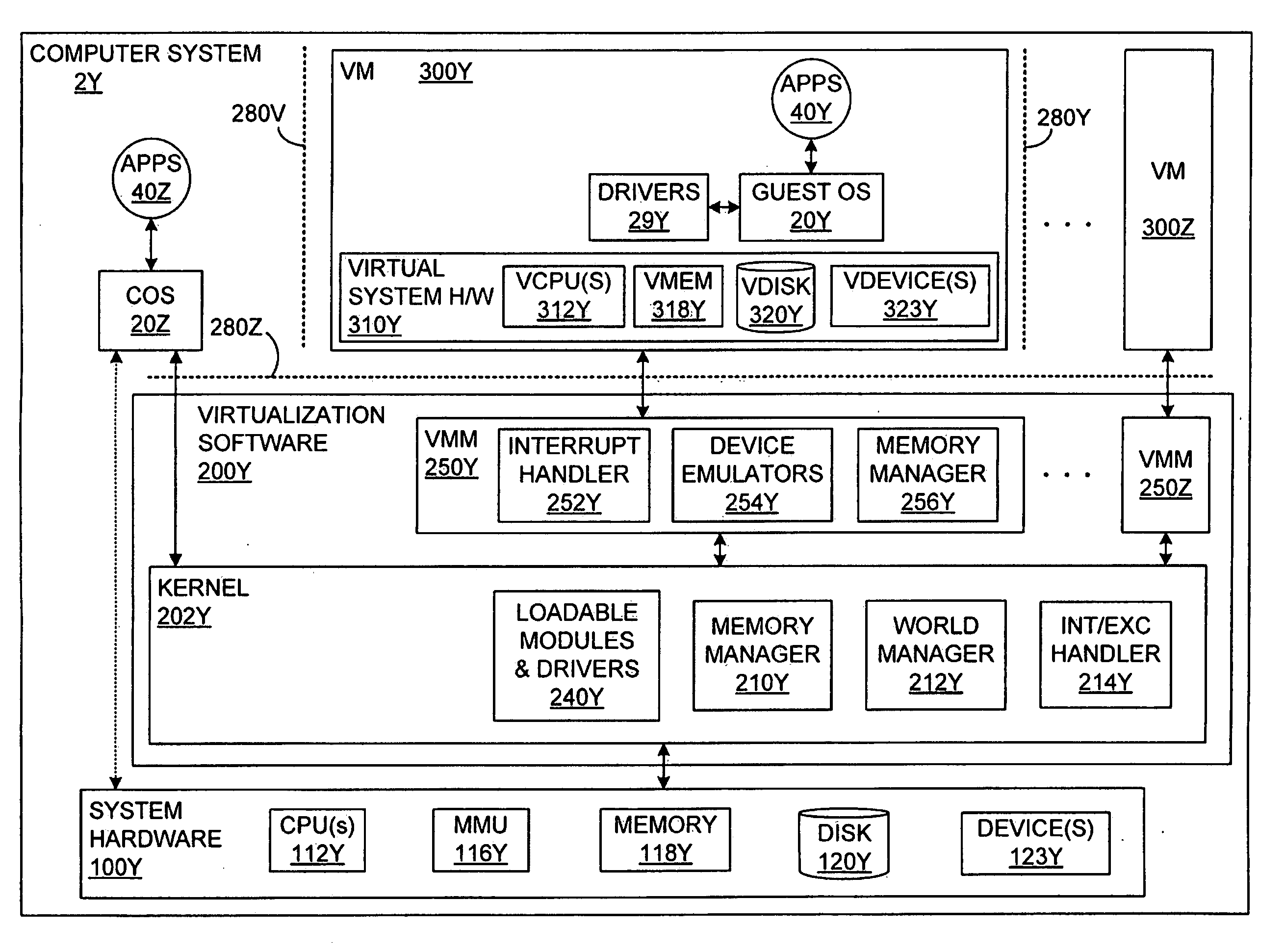
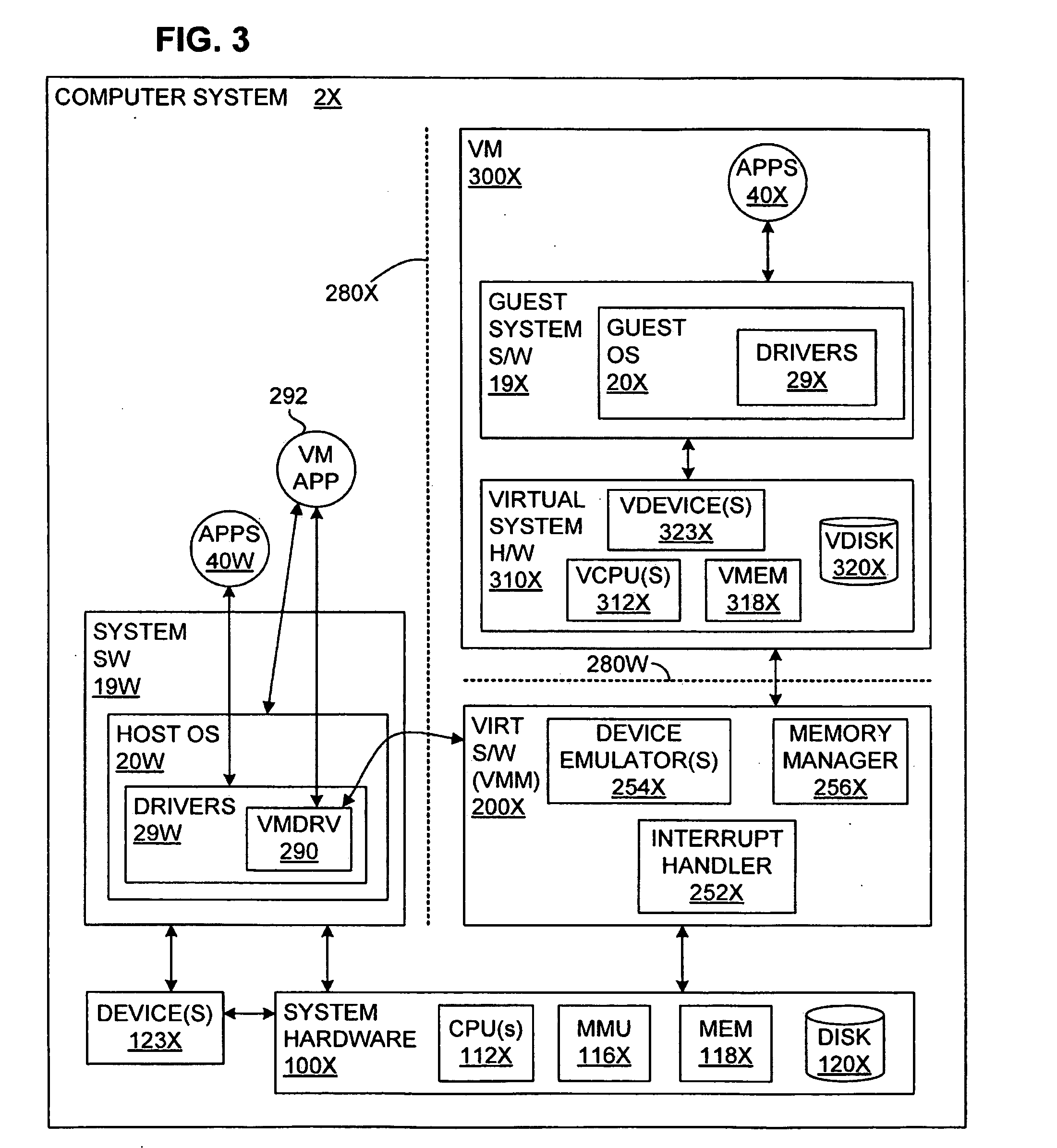
InactiveUS20080320594A1Memory loss protectionError detection/correctionVirtual memoryOperational system
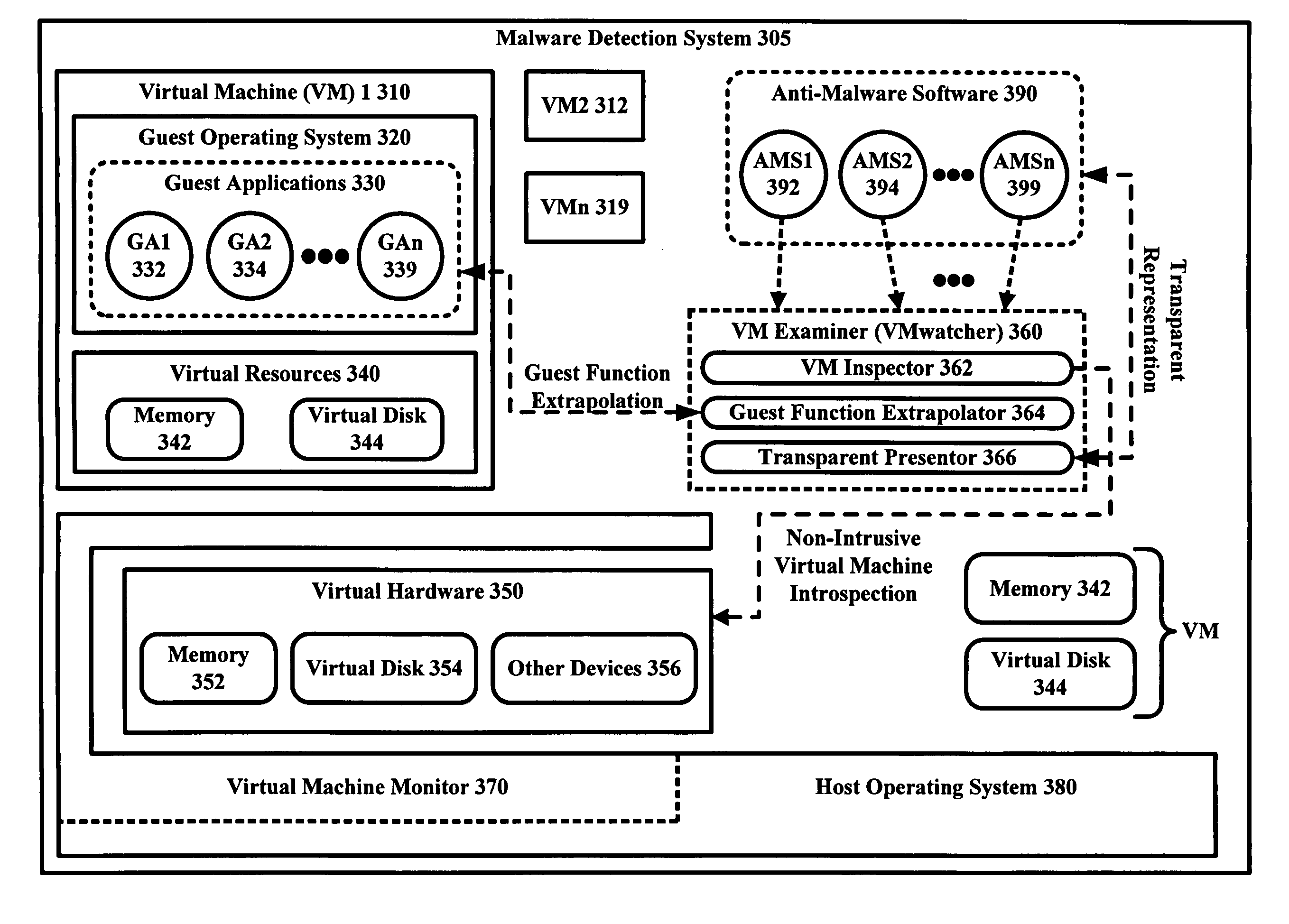
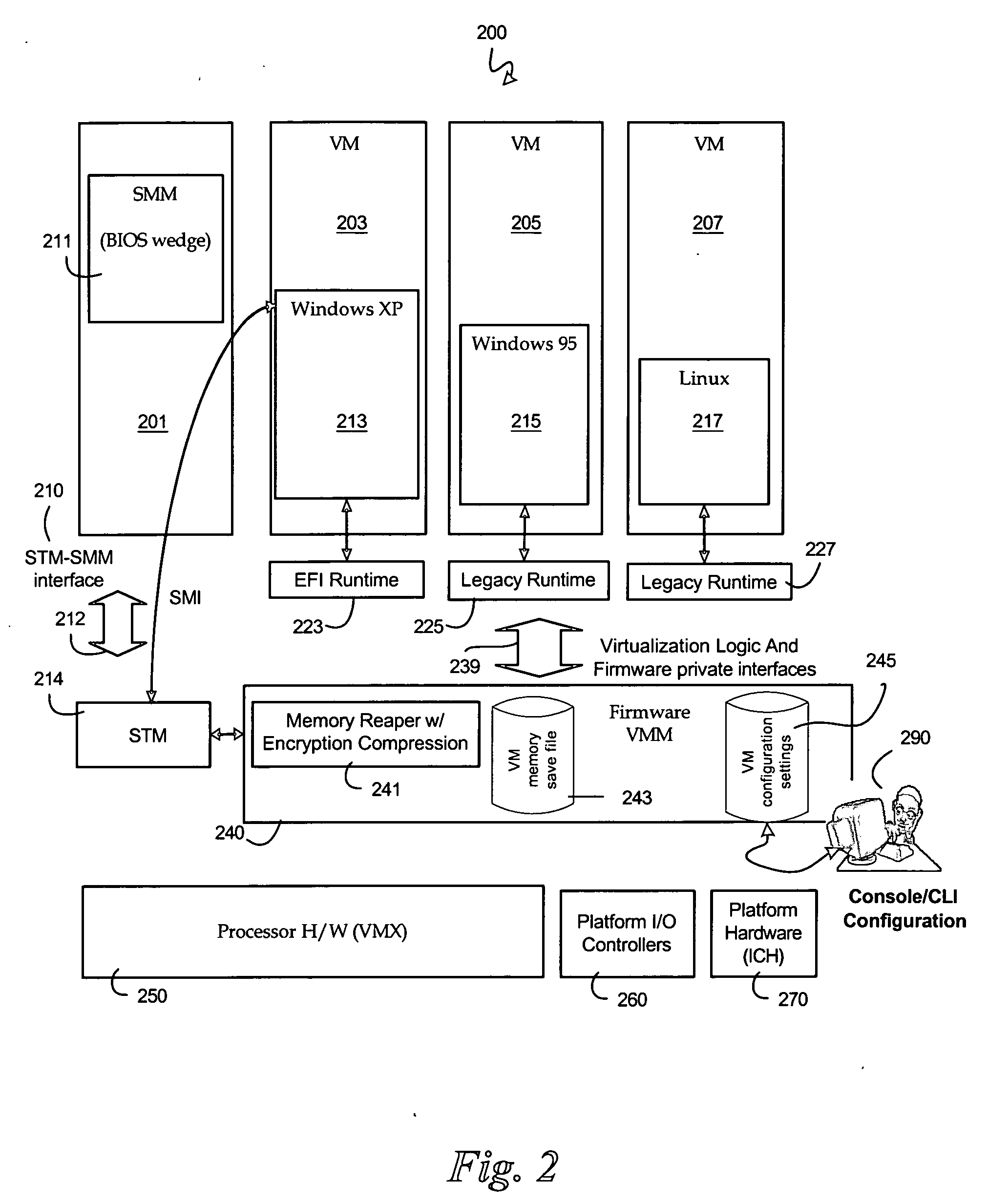
The malware detection system enables out-of-the box, tamper-resistant malware detection without losing the semantic view. This system comprises at least one guest operating system and at least one virtual machine, where the guest operating system runs on the virtual machine. Having virtual resources, the virtual machine resides on a host operating system. The virtual resources include virtual memory and at least one virtual disk. A virtual machine examiner is used to examine the virtual machine. With a virtual machine inspector, a guest function extrapolator, and a transparent presenter, the virtual machine examiner resides outside the virtual machine. The virtual machine inspector is configured to retrieve virtual machine internal system states and / or events. The guest function extrapolator is configured to interpret such states and / or events. The transparent presenter is configured to present the interpreted states and / or events to anti-malware software. The anti-malware software is configured to use the interpreted states and / or events to detect any system compromise.
Owner:GEORGE MASON INTPROP INC
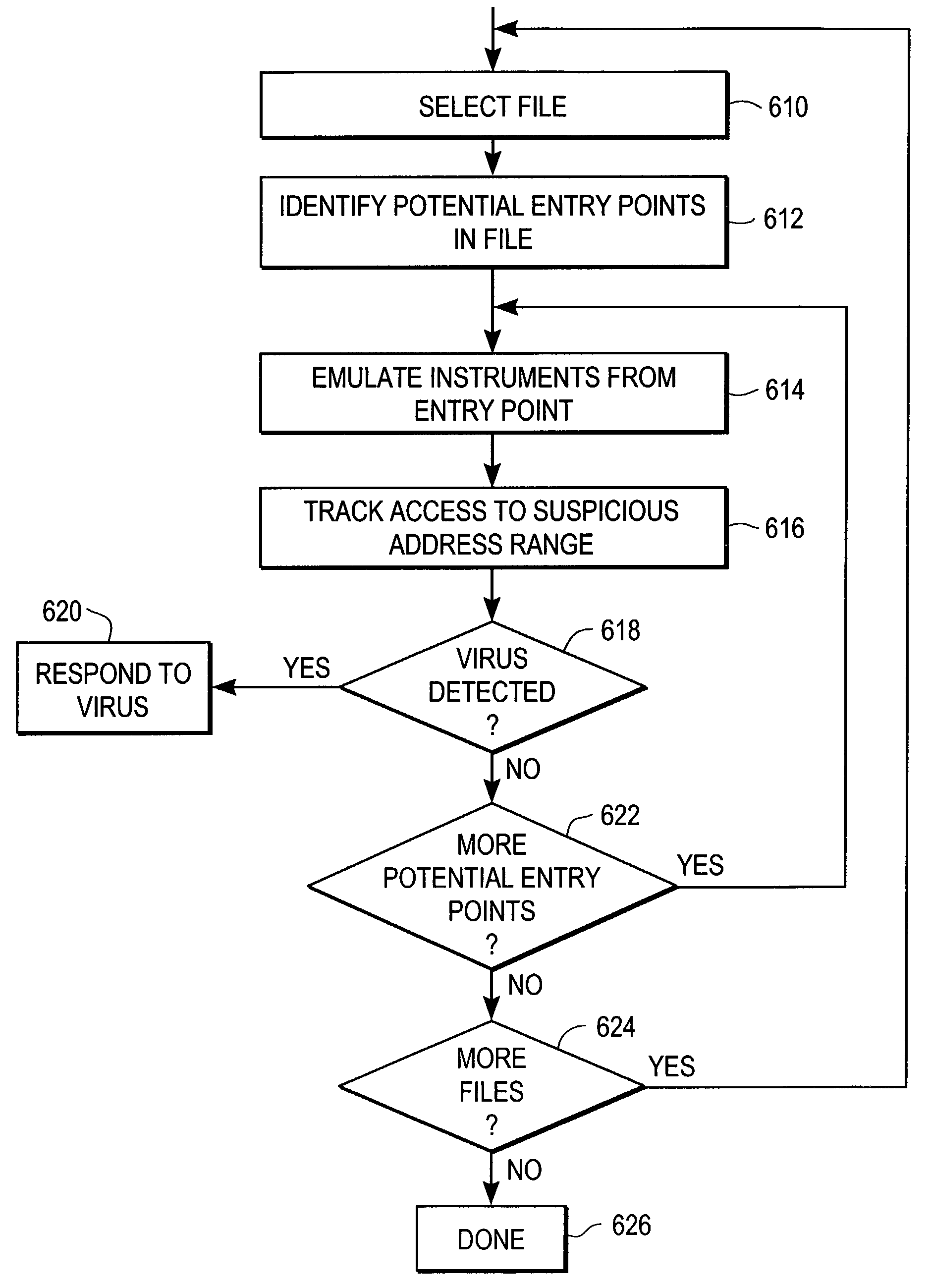
Heuristic detection of malicious computer code by page tracking
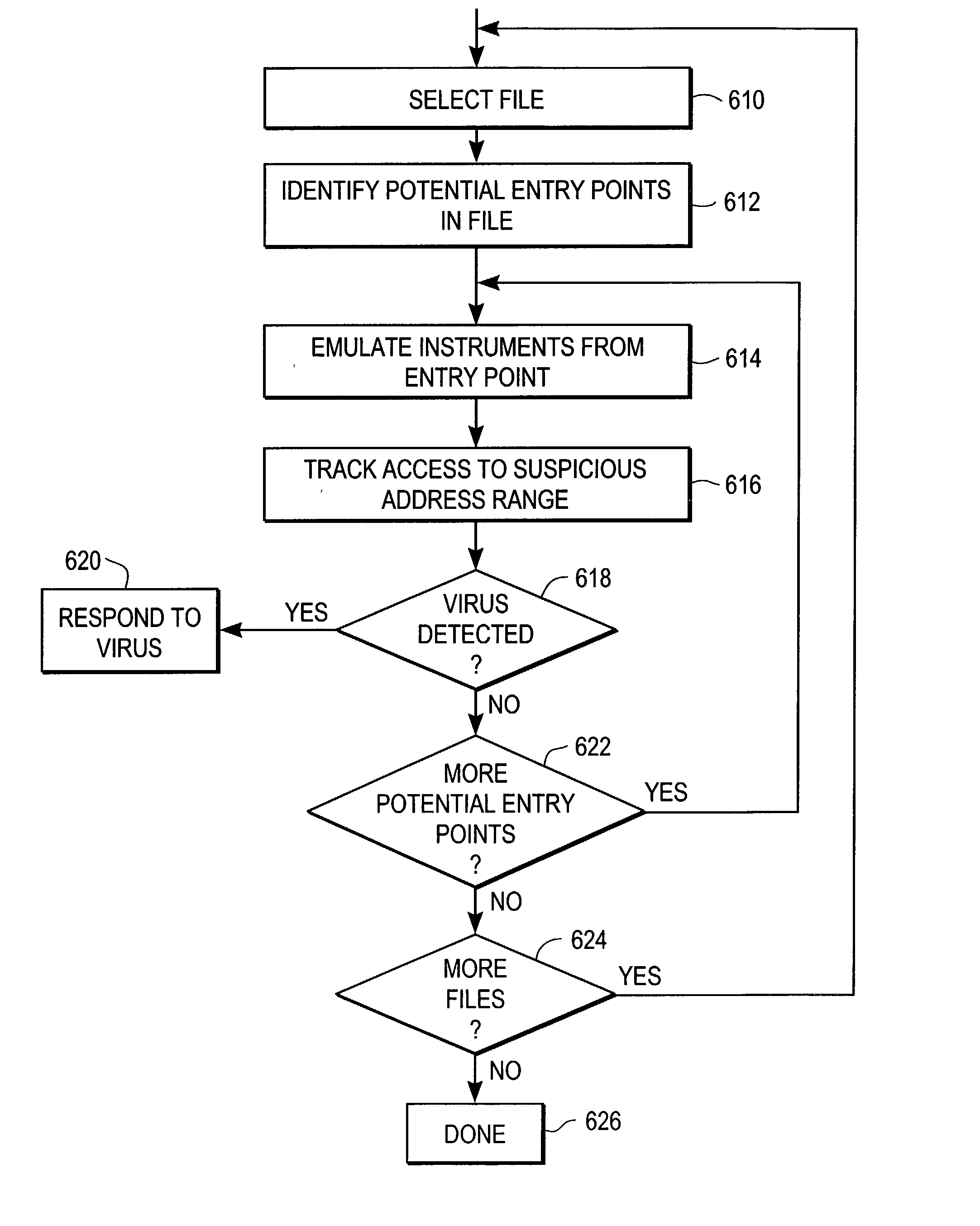
To detect a computer virus in a host file (100), an emulating module (414) emulates the host file (100) in a virtual machine (422) having a virtual memory (426). While emulating the host file (100), the system (400) tracks the host file's access of the virtual memory (426). Responsive to an access in a non-normal address range of the virtual memory (426) by the host file (100), a flag recording module (522) sets a flag. A virus reporting module (526) declares a potential virus based on whether the flag is set.
Owner:CA TECH INC
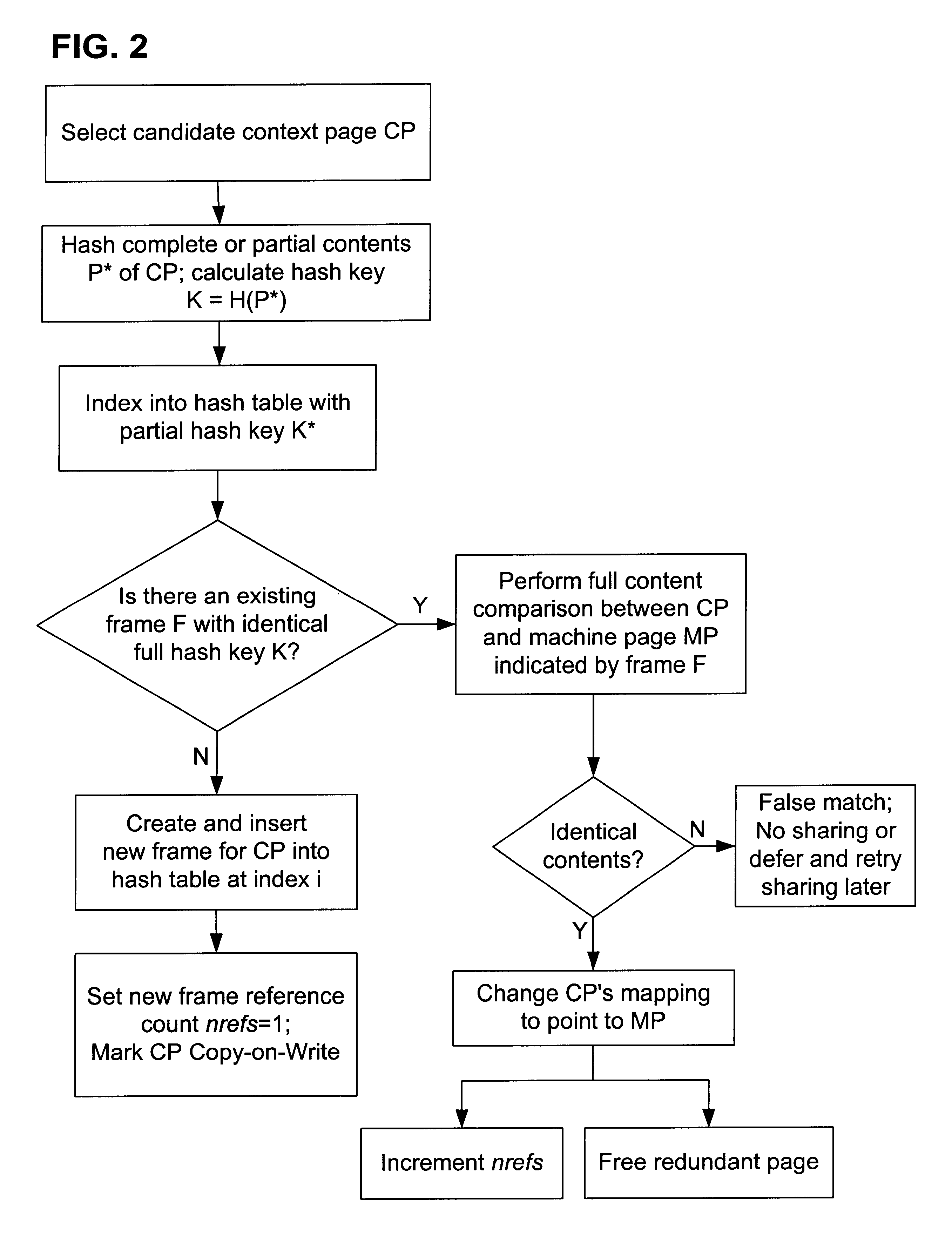
Content-based, transparent sharing of memory units
InactiveUS6789156B1Memory architecture accessing/allocationMemory adressing/allocation/relocationComputer hardwareMultiple context
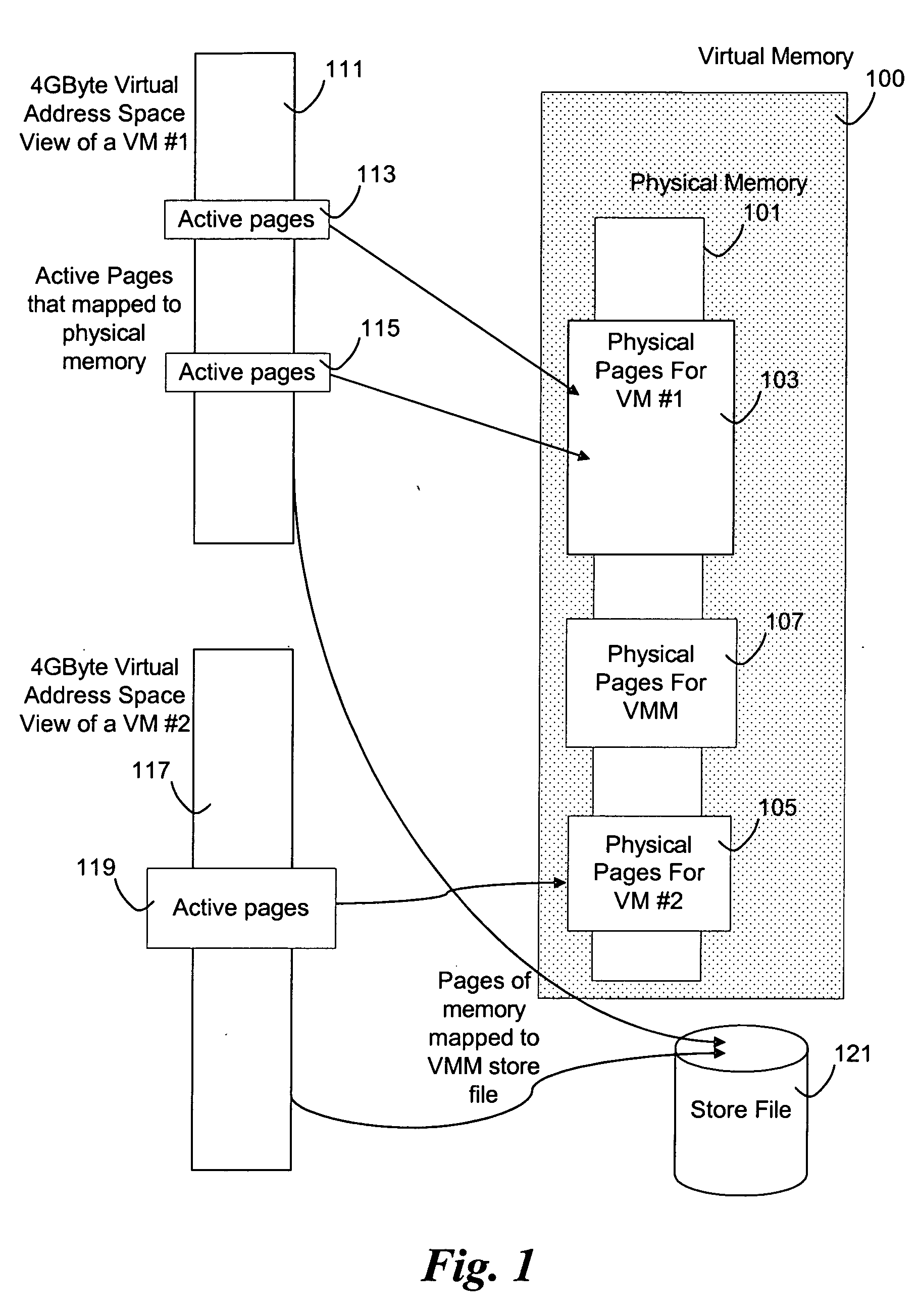
A computer system has one or more software context that share use of a memory that is divided into units such as pages. In the preferred embodiment of the invention, the context are, or include, virtual machines running on a common hardware platform. The context, as opposed to merely the addresses or page numbers, of virtual memory pages that accessible to one or more contexts are examined. If two or more context pages are identical, then their memory mappings are changed to point to a single, shared copy of the page in the hardware memory, thereby freeing the memory space taken up by the redundant copies. The shared copy is ten preferable marked copy-on-write. Sharing is preferably dynamic, whereby the presence of redundant copies of pages is preferably determined by hashing page contents and performing full content comparisons only when two or more pages hash to the same key.
Owner:VMWARE INC
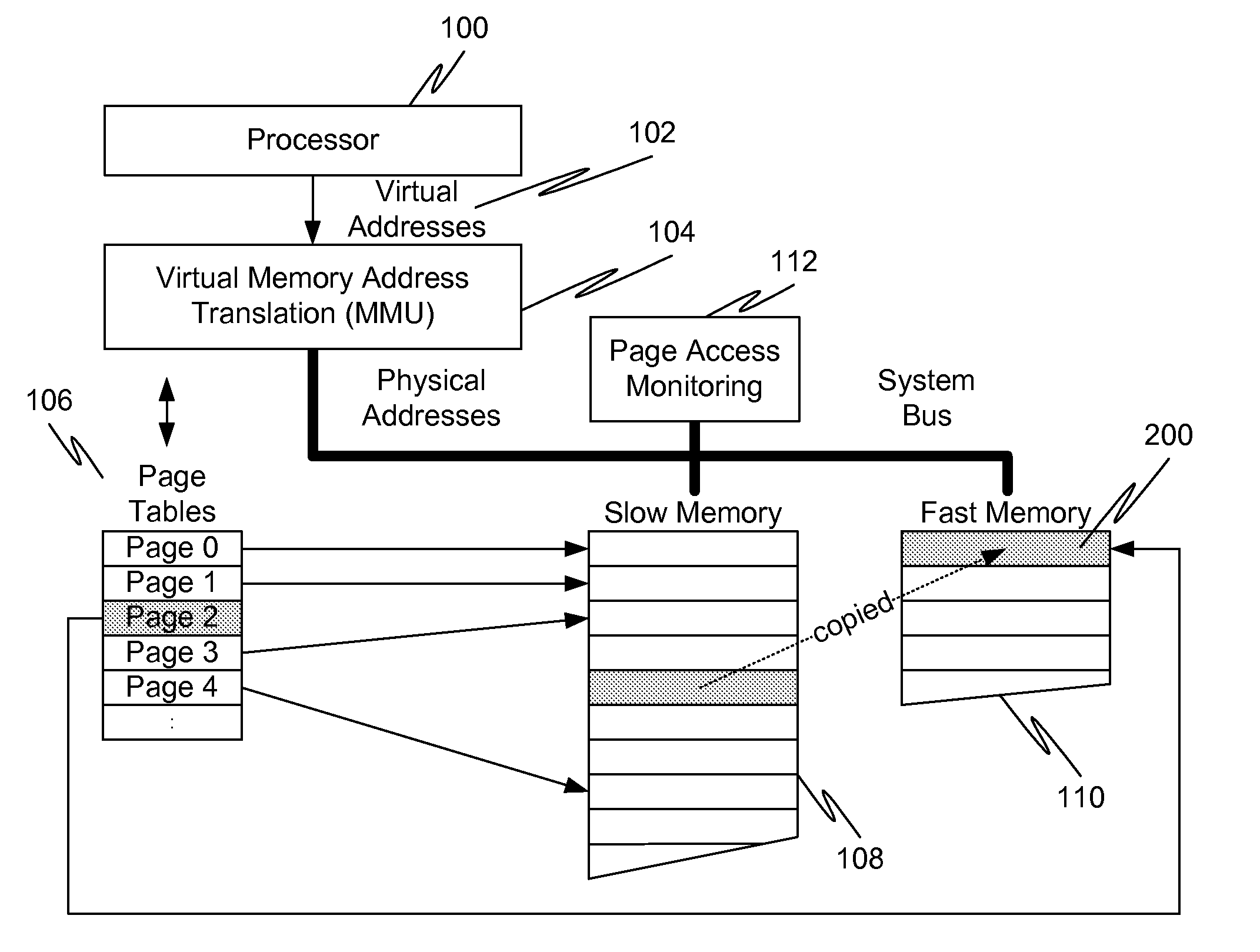
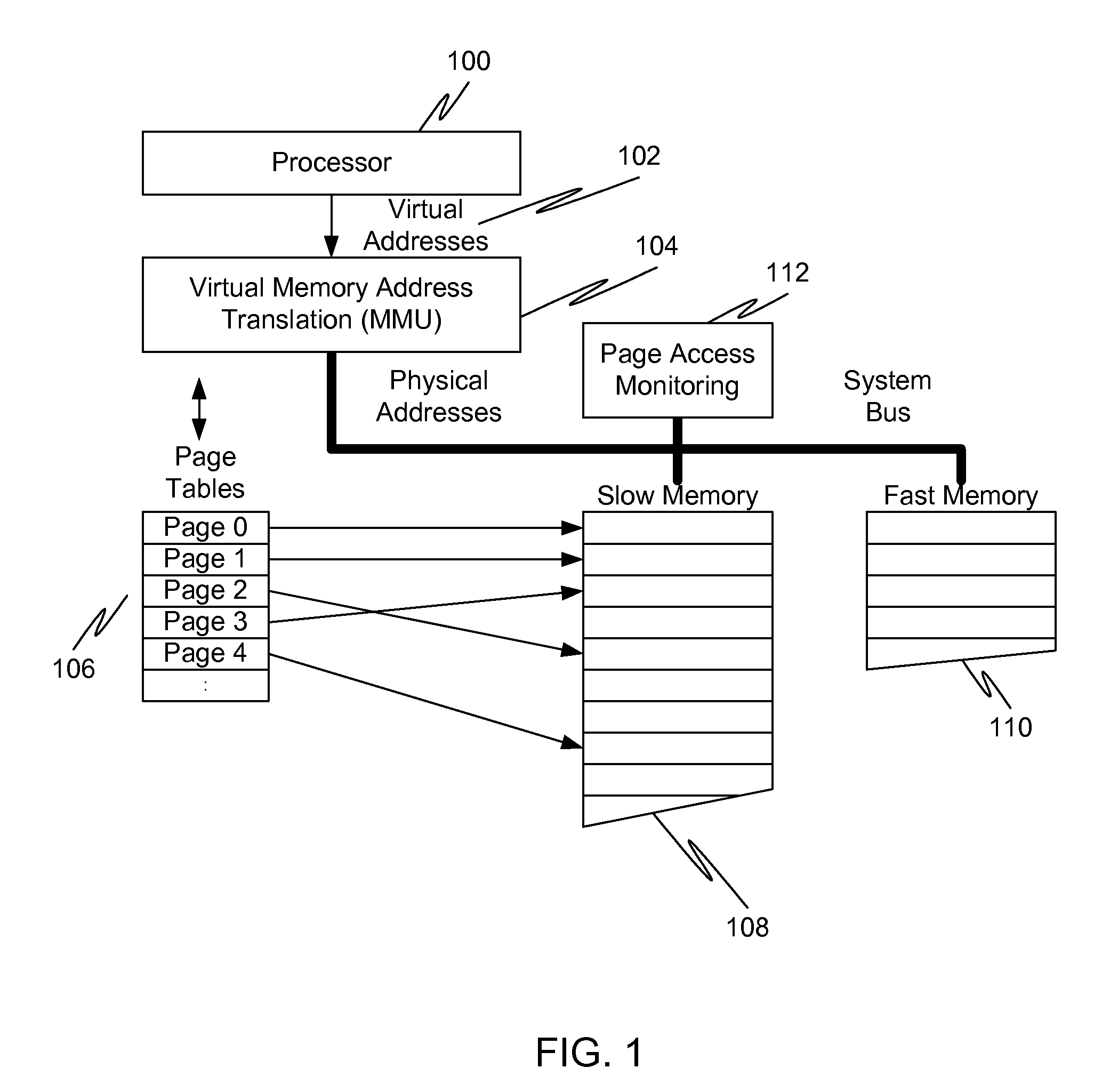
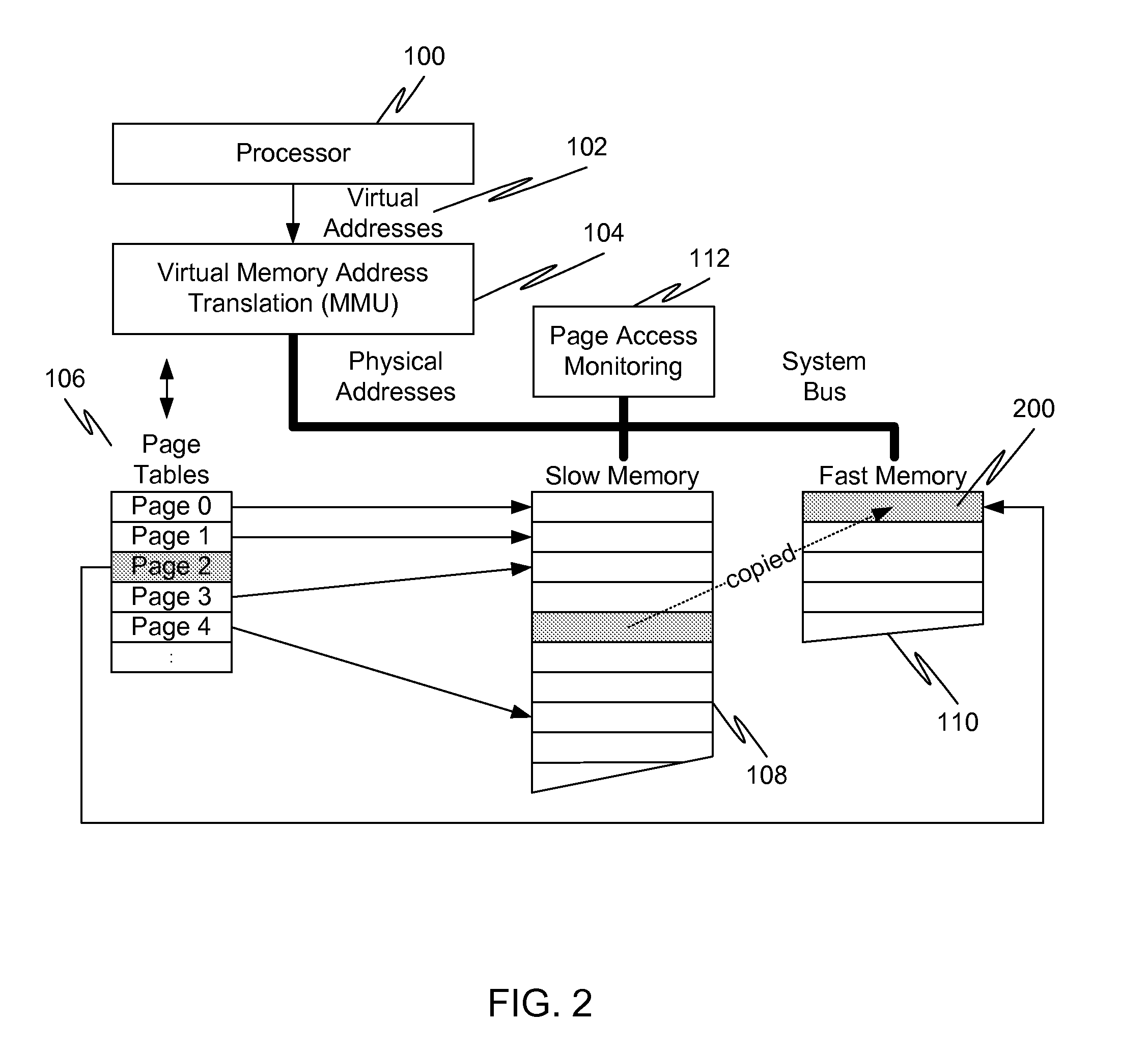
Caching using virtual memory
InactiveUS20120017039A1Memory architecture accessing/allocationMemory adressing/allocation/relocationVirtual memoryPage table
In a first embodiment of the present invention, a method for caching in a processor system having virtual memory is provided, the method comprising: monitoring slow memory in the processor system to determine frequently accessed pages; for a frequently accessed page in slow memory: copy the frequently accessed page from slow memory to a location in fast memory; and update virtual address page tables to reflect the location of the frequently accessed page in fast memory.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
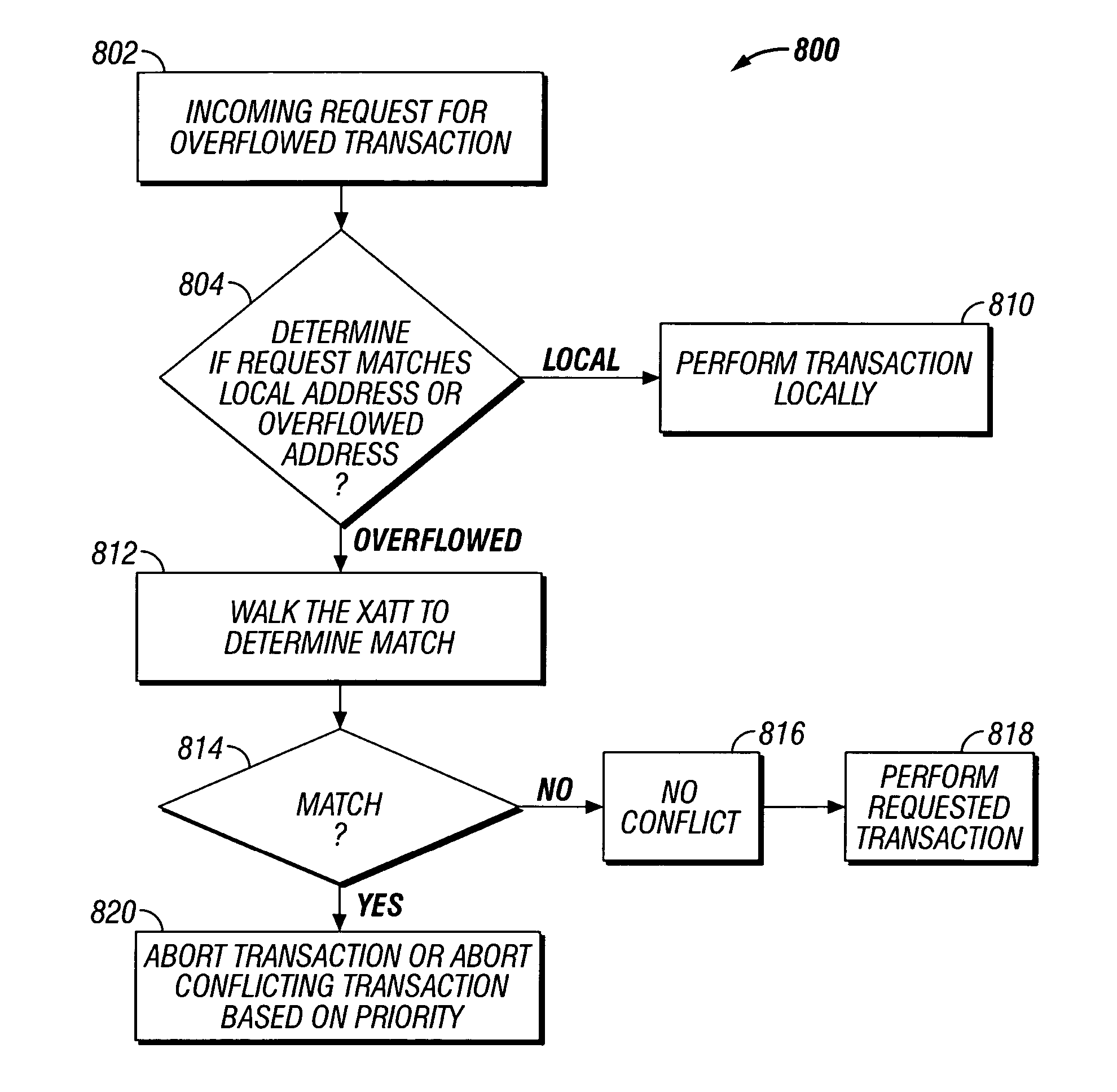
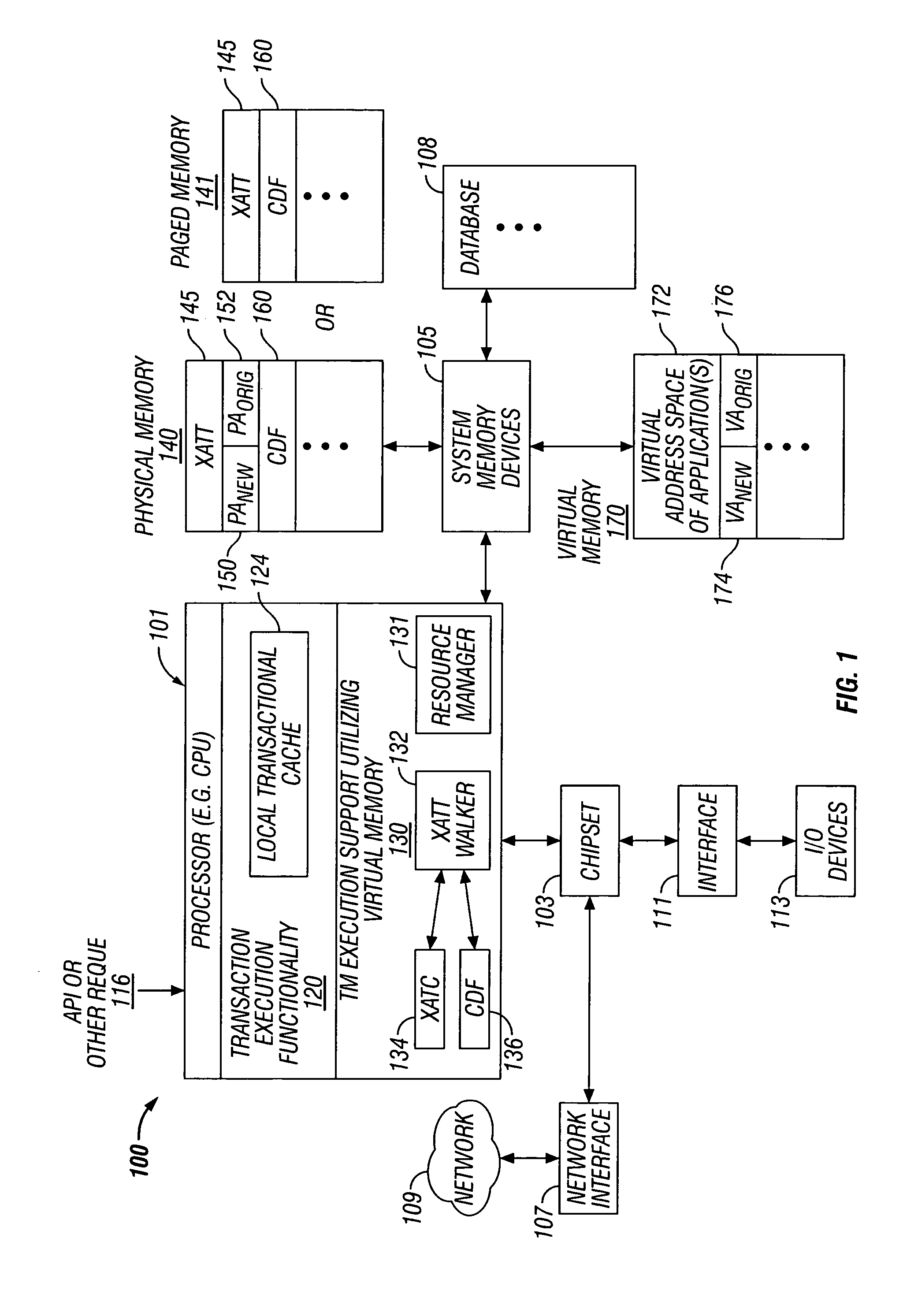
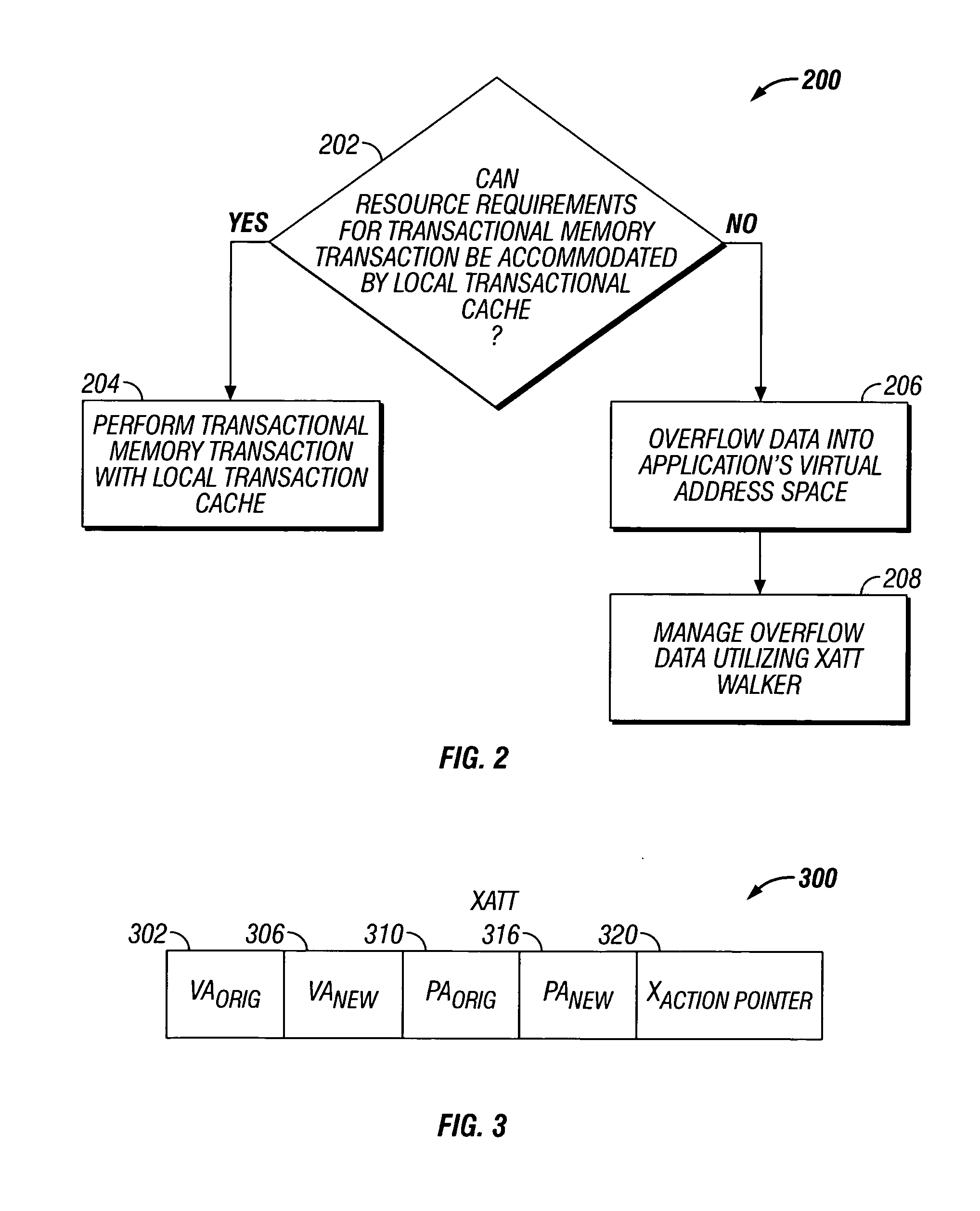
Transactional memory execution utilizing virtual memory
ActiveUS7685365B2Memory adressing/allocation/relocationTransaction processingVirtual memoryTransactional memory
Embodiments of the invention relate to transactional memory execution utilizing virtual memory. A processor includes a local transactional cache and a resource manager. The resource manager responsive to a transactional memory transaction request from a requesting thread determines whether the local transactional cache is capable of accommodating the transactional memory transaction request and, if so, the local transactional caches performs the transactional memory transaction. However, if the local transactional cache is not capable of accommodating the transactional memory transaction request, data for the transactional memory transaction request is overflowed into an application's virtual address space associated with the requesting thread.
Owner:INTEL CORP
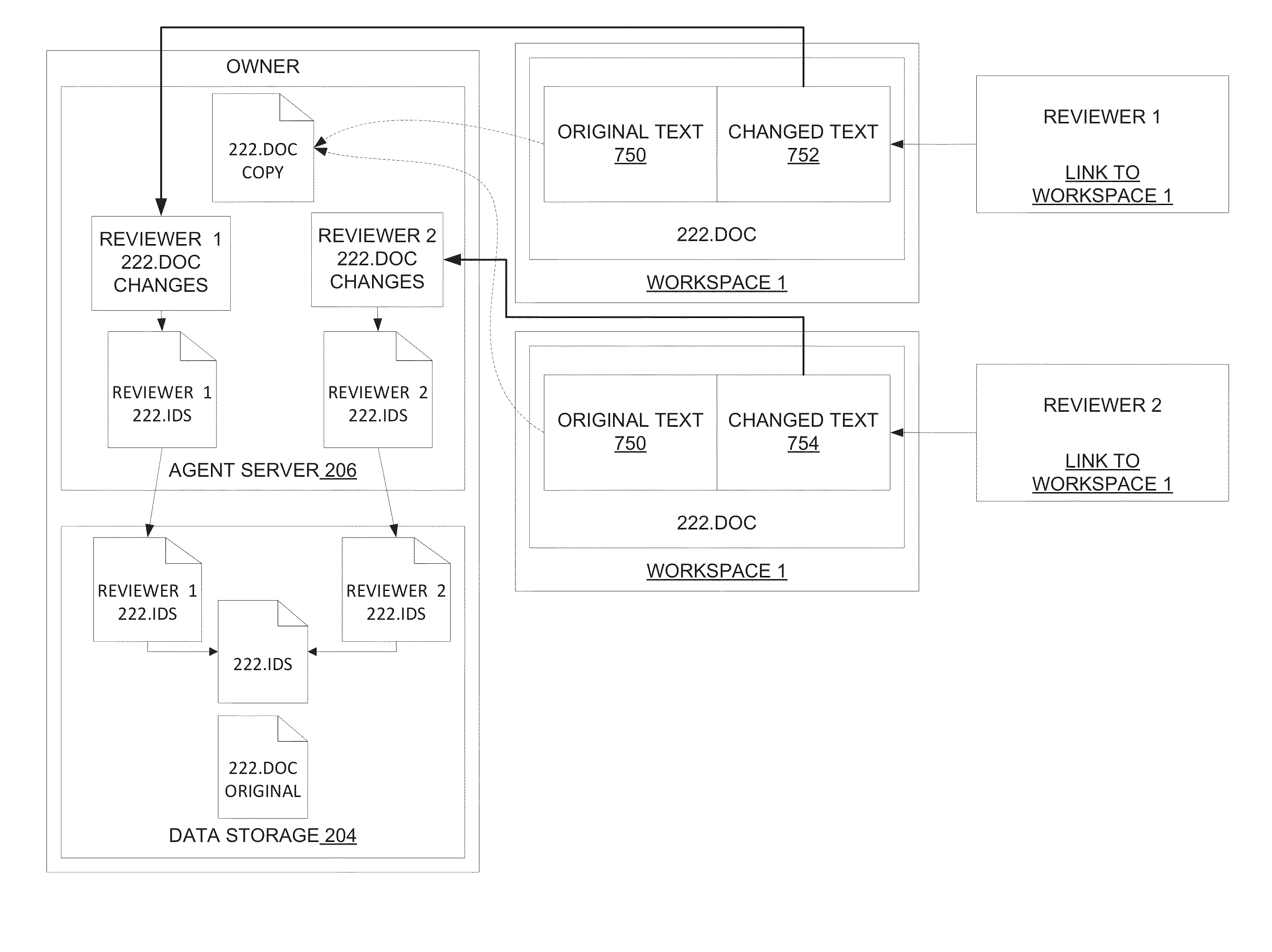
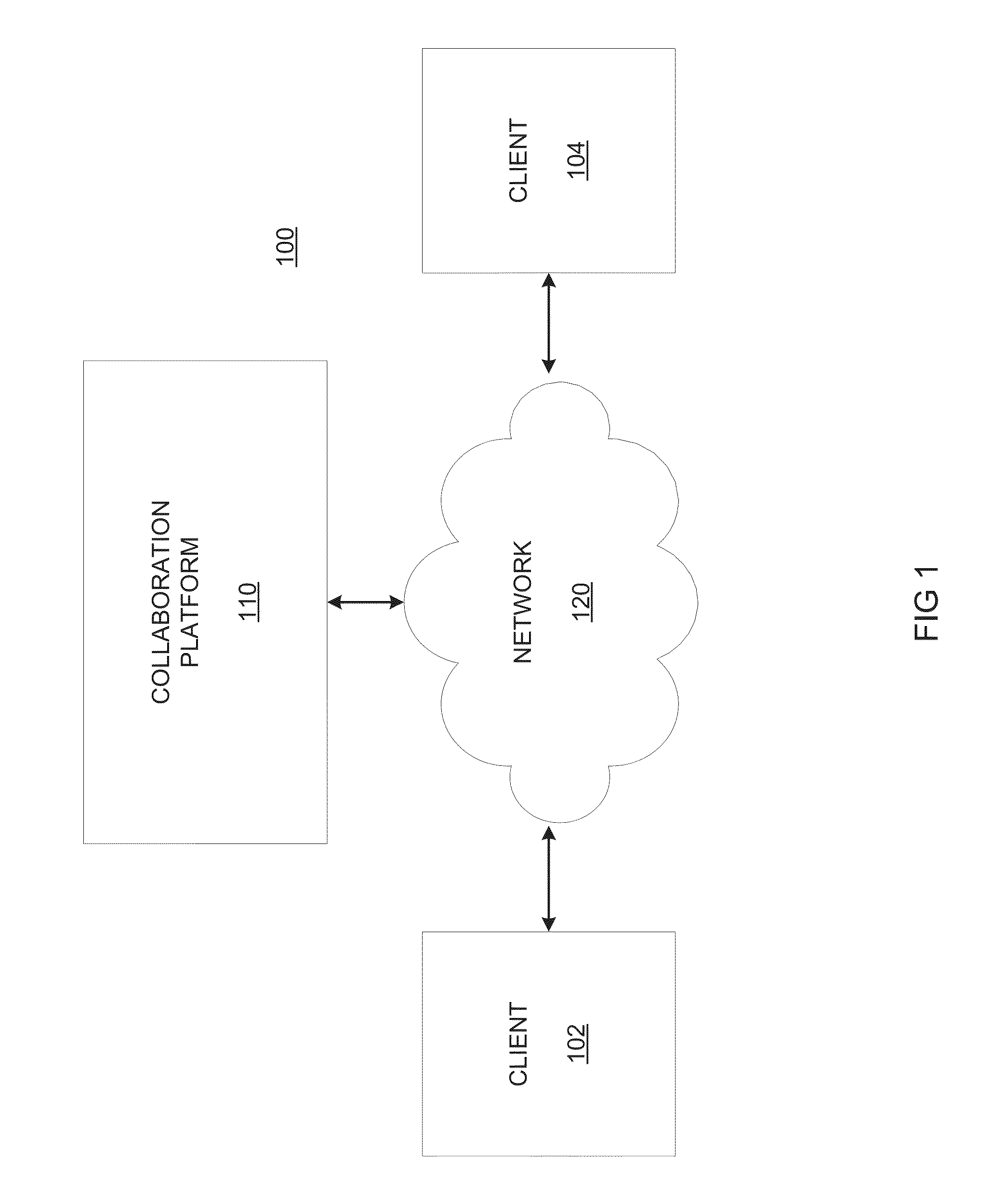
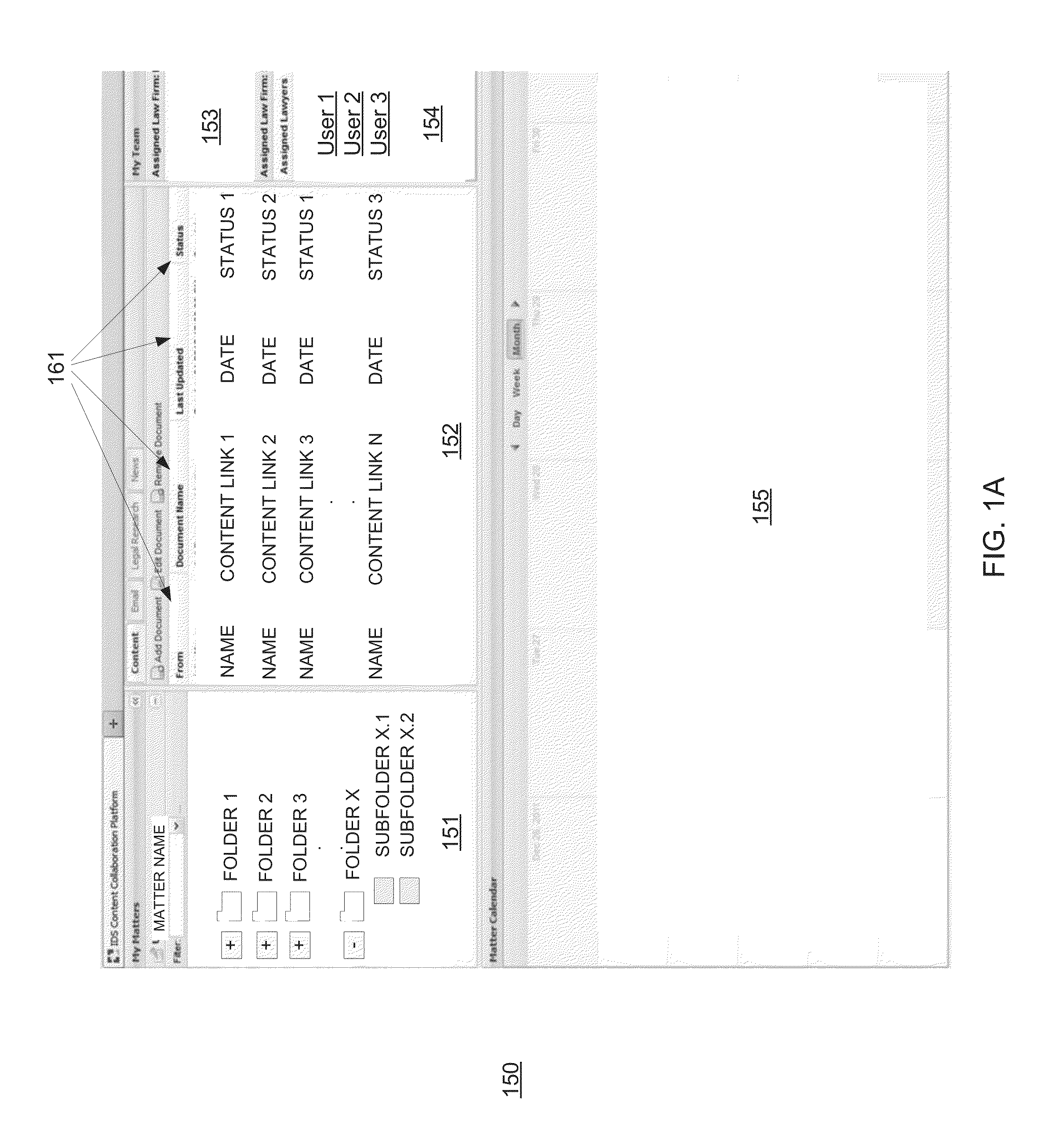
System and method for synchronizing bi-directional document management
ActiveUS20130246901A1Digital data information retrievalNatural language data processingVirtual memoryDocumentation procedure
Systems and methods consistent with various disclosed embodiments provide for collaborating information over a computer network. In one embodiment, a system is disclosed for collaborating information over a network. The system may include a storage device and one or more processors. The processor(s) may maintain documents in the storage device and publish content links to the documents in a workspace rendered by a collaboration platform. The processor(s) may provide content to the collaboration platform in response to a content link selection by a reviewer and receive the reviewer's changes, with the collaboration platform temporarily storing the document in a virtual memory for rendering to the reviewer and deleting it after the communication session ends. The processor(s) may synchronize the changes bi-directionally from the workspace with the original document through a collaboration document, such that the original document remains unaltered, and by re-publishing an updated content link to the workspace.
Owner:LITERA CORP
Heuristic detection of malicious computer code by page tracking
To detect a computer virus in a host file (100), an emulating module (414) emulates the host file (100) in a virtual machine (422) having a virtual memory (426). While emulating the host file (100), the system (400) tracks the host file's access of the virtual memory (426). Responsive to an access in a non-normal address range of the virtual memory (426) by the host file (100), a flag recording module (522) sets a flag. A virus reporting module (526) declares a potential virus based on whether the flag is set.
Owner:CA TECH INC
TLB miss fault handler and method for accessing multiple page tables
ActiveUS7111145B1Memory adressing/allocation/relocationComputer security arrangementsVirtual memoryError processing
A virtual memory system implementing the invention provides concurrent access to translations for virtual addresses from multiple address spaces. One embodiment of the invention is implemented in a virtual computer system, in which a virtual machine monitor supports a virtual machine. In this embodiment, the invention provides concurrent access to translations for virtual addresses from the respective address spaces of both the virtual machine monitor and the virtual machine. Multiple page tables contain the translations for the multiple address spaces. Information about an operating state of the computer system, as well as an address space identifier, are used to determine whether, and under what circumstances, an attempted memory access is permissible. If the attempted memory access is permissible, the address space identifier is also used to determine which of the multiple page tables contains the translation for the attempted memory access.
Owner:VMWARE INC
Providing VMM Access to Guest Virtual Memory
ActiveUS20090113110A1Memory architecture accessing/allocationError detection/correctionVirtual memoryVirtual storage
A virtual-machine-based system provides a mechanism for a virtual machine monitor (VMM) to process a hypercall received from an application running in the virtual machine (VM). A hypercall interface causes the virtual memory pages, needed by the VMM to process the hypercall, to be available to the VMM. In one embodiment, when virtual memory pages needed by the VMM to process the hypercall are not available to the VMM, the application is caused to access the needed pages, in response to which the required virtual memory becomes available to the VMM.
Owner:VMWARE INC
Method, apparatus and virtual machine for detecting malicious program
ActiveUS20140351935A1Detect presenceMemory loss protectionError detection/correctionVirtual memoryVirtual storage
Owner:BEIJING QIHOO TECH CO LTD
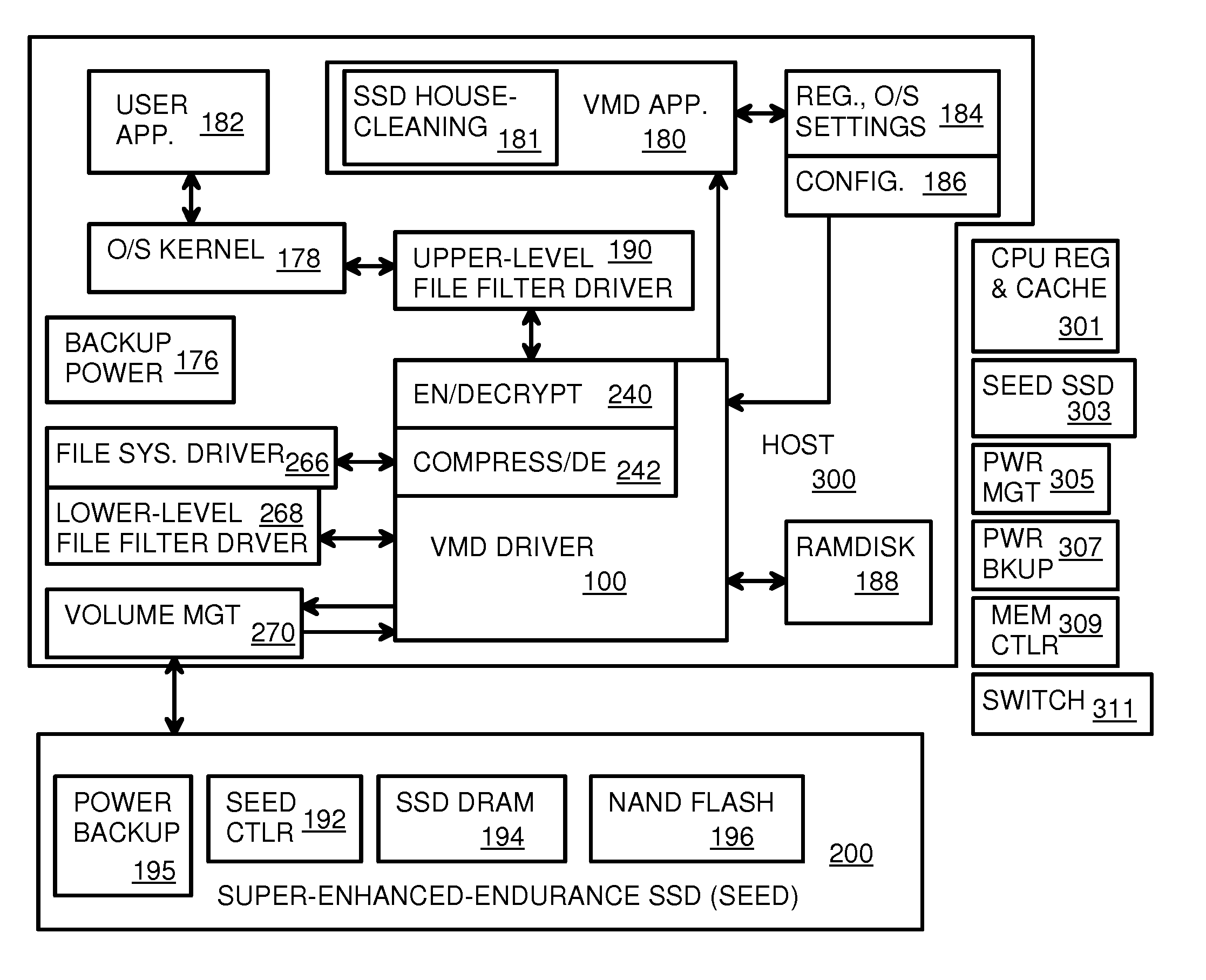
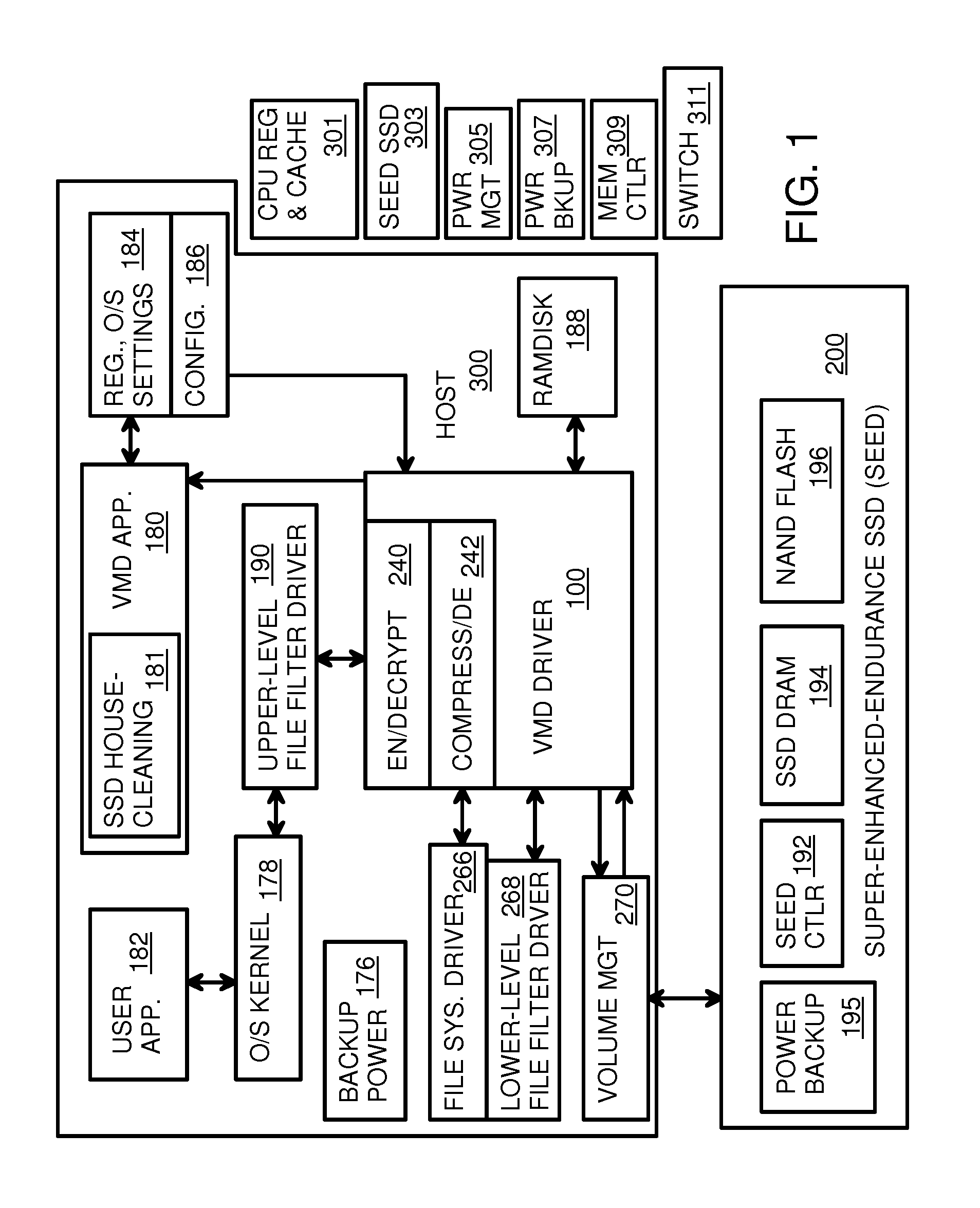
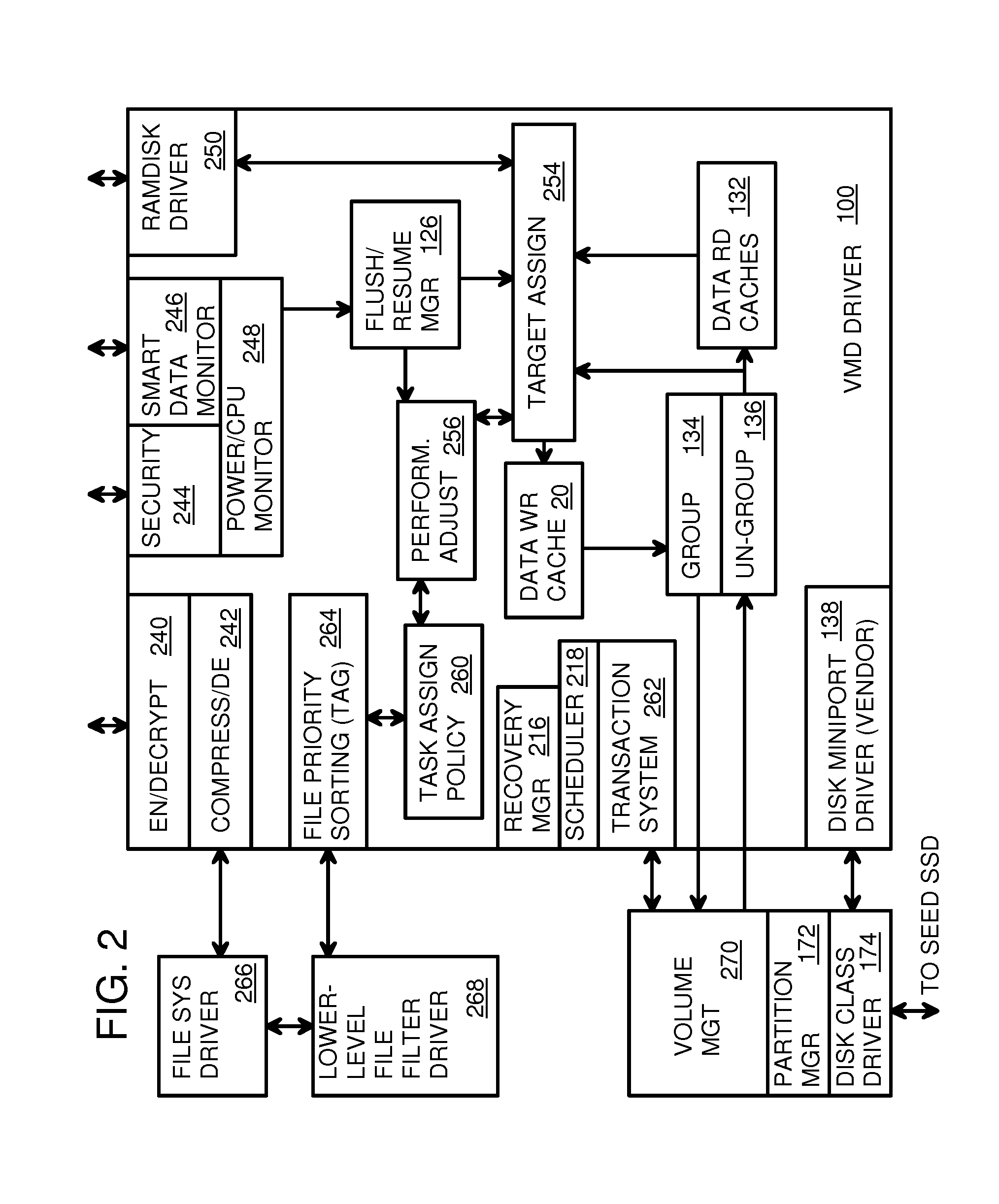
Virtual Memory Device (VMD) Application/Driver with Dual-Level Interception for Data-Type Splitting, Meta-Page Grouping, and Diversion of Temp Files to Ramdisks for Enhanced Flash Endurance
ActiveUS20130145085A1Memory architecture accessing/allocationMemory adressing/allocation/relocationFilename extensionData file
A Virtual-Memory Device (VMD) driver and application execute on a host to increase endurance of flash memory attached to a Super Enhanced Endurance Device (SEED) or Solid-State Drive (SSD). Host accesses to flash are intercepted by the VMD driver using upper and lower-level filter drivers and categorized as data types of paging files, temporary files, meta-data, and user data files, using address ranges and file extensions read from meta-data tables. Paging files and temporary files are optionally written to flash. Full-page and partial-page data are grouped into multi-page meta-pages by data type before storage by the SSD. ramdisks and caches for storing each data type in the host DRAM are managed and flushed to the SSD by the VMD driver. Write dates are stored for pages or blocks for management functions. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
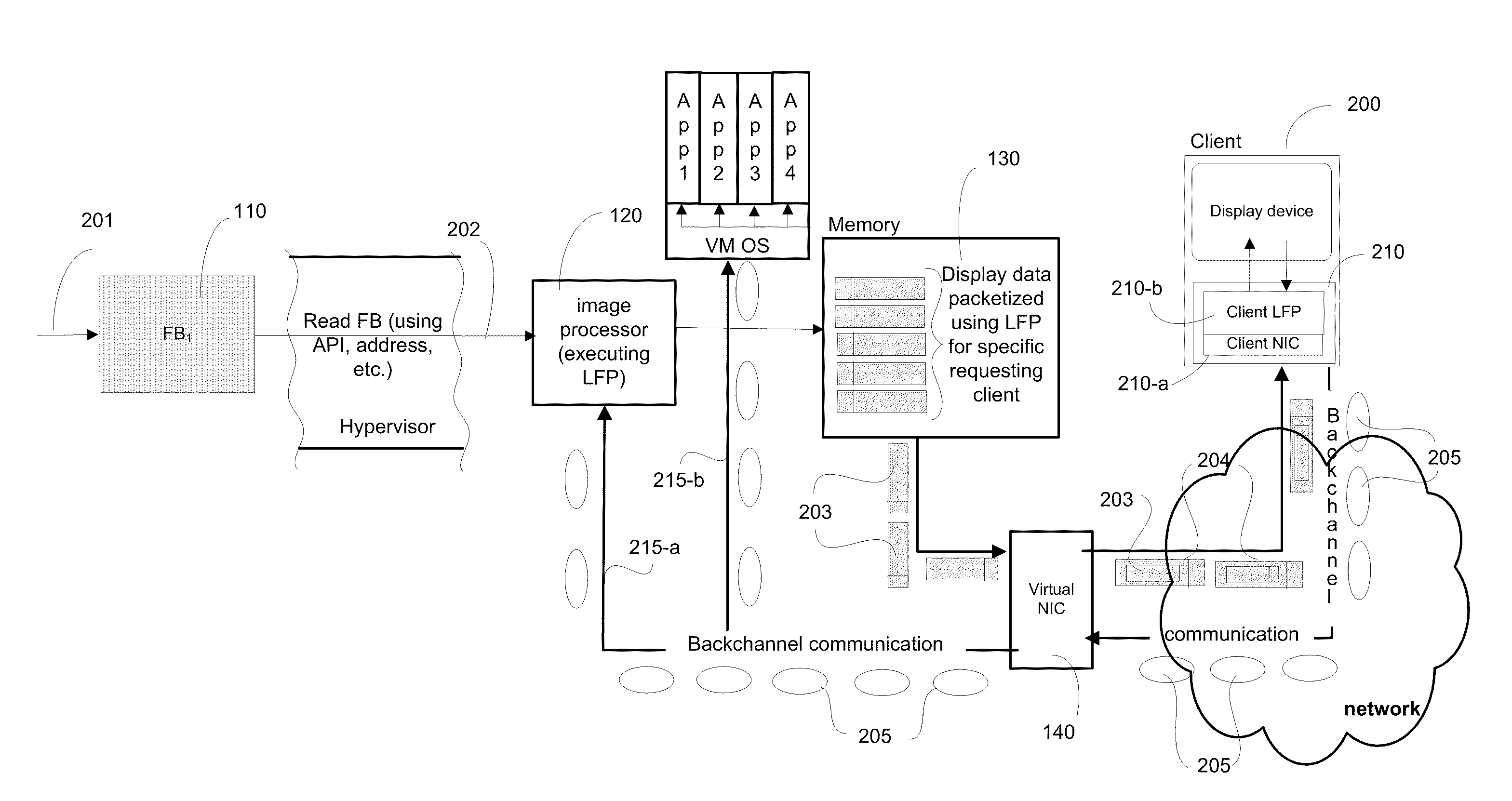
Systems and Algorithm For Interfacing With A Virtualized Computing Service Over A Network Using A Lightweight Client
ActiveUS20110126110A1High performance imageEasy to decompressInterprogram communicationMultiple digital computer combinationsVirtual memoryNetwork packet
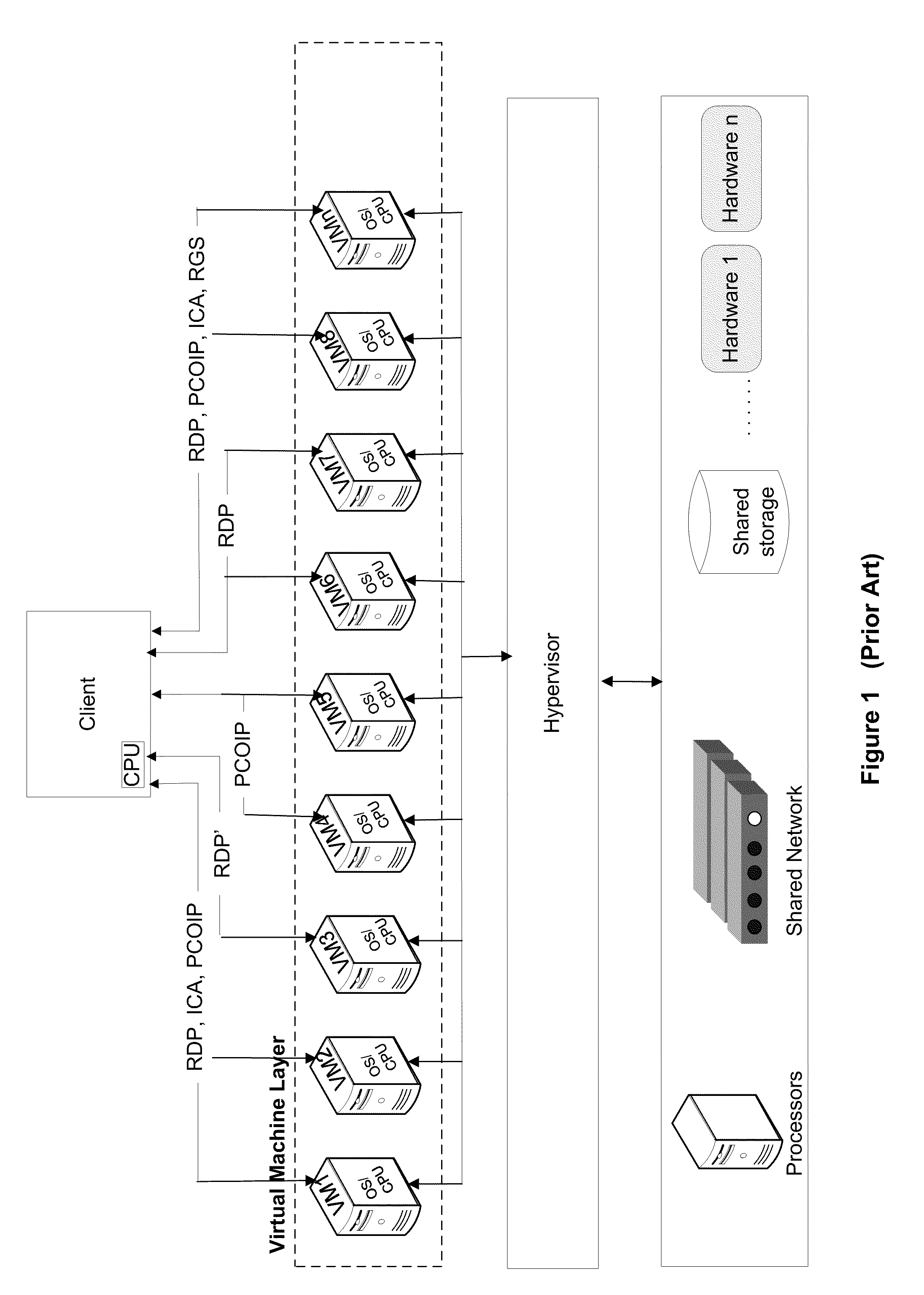
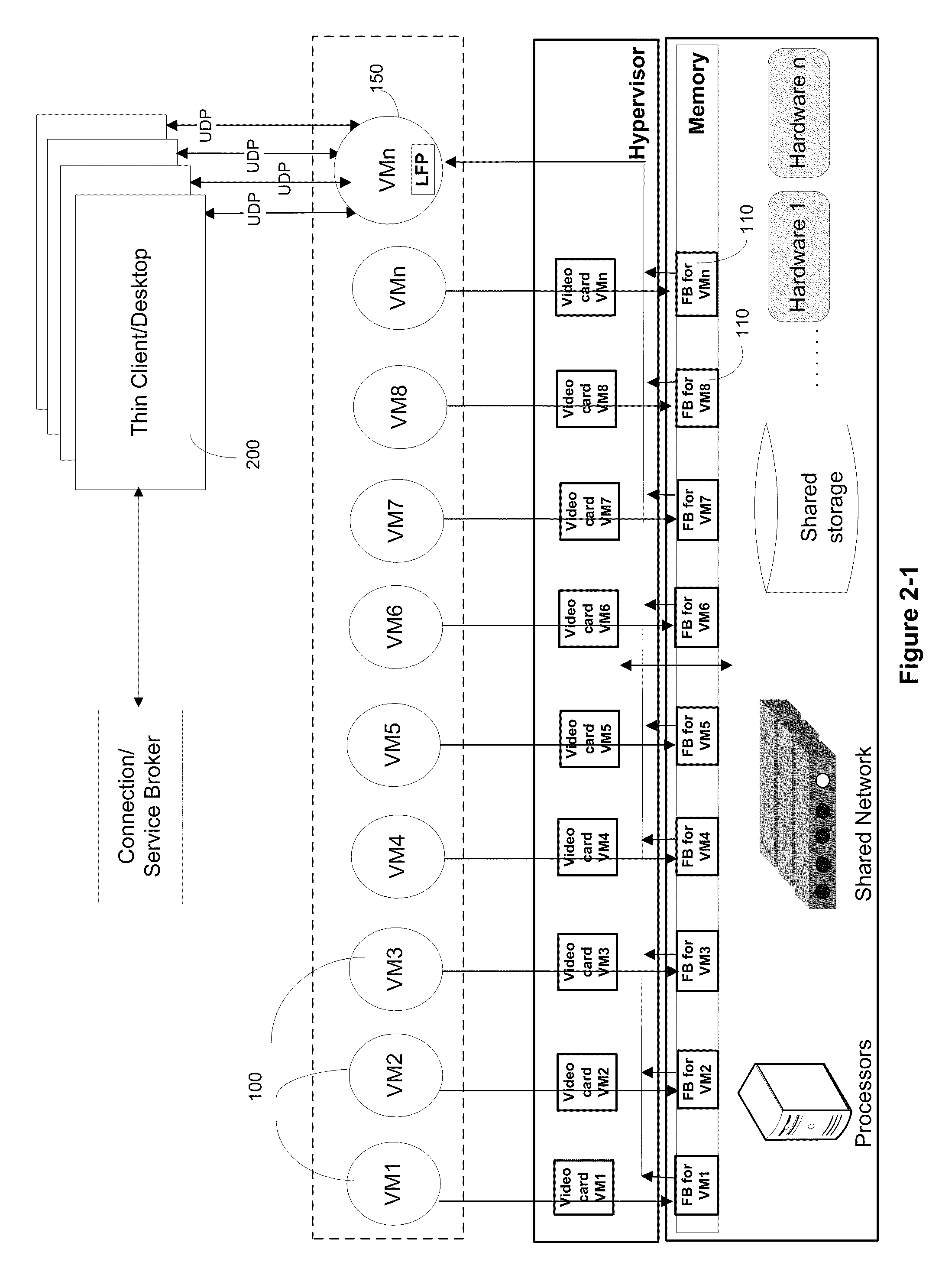
Systems and algorithm for controlling a virtualized computer service remotely through a client includes defining a virtual infrastructure in which a plurality of virtual machines are running on a hypervisor with at least one of the virtual machine executing an image processor algorithm. The image processor algorithm is configured to receive a connection request from the client for controlling the virtualized computer service (or simply, virtual service) available at a specific virtual machine. The request includes a plurality of connection parameters that describe the connection requirements of the client and is received at the virtual machine that is equipped with the image processor algorithm. The connection parameters are interrogated using the image processor algorithm to identify a specific virtual machine that provides the requested virtualized computer service. A framebuffer data for the identified virtual machine located in virtual memory is accessed and read directly through a hypervisor. The framebuffer data is processed into a plurality of image data packets using the image processor algorithm and transmitted to the client for presenting on a display device associated with the client. The image data packet grammar is tailored to the client and represents an image of the virtual machine display for the identified virtual machine.
Owner:CITRIX SYST INC
Method, system, and program for managing memory for data transmission through a network
InactiveUS20050080928A1Memory adressing/allocation/relocationMultiple digital computer combinationsVirtual memoryData transmission
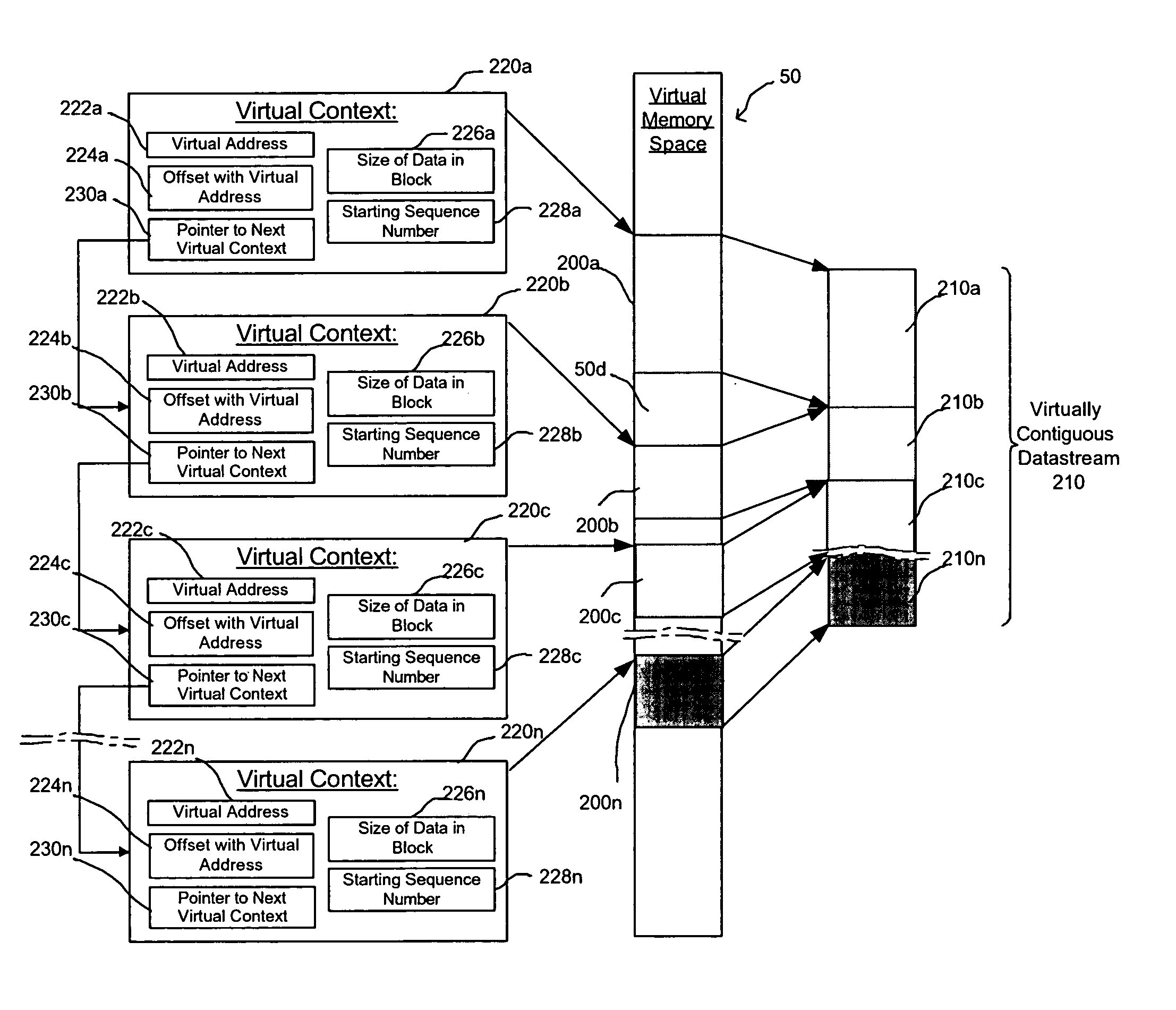
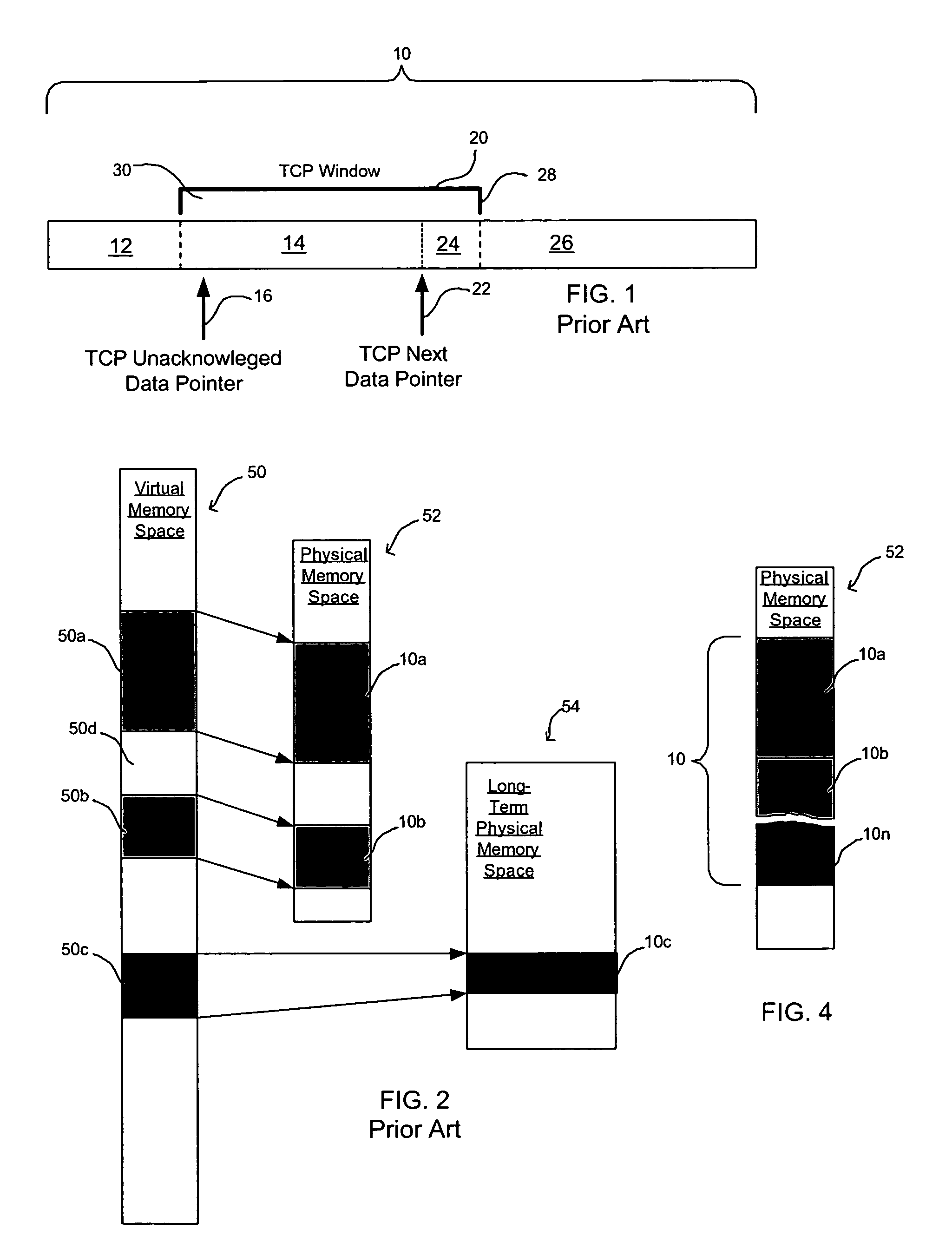
Provided are a method, system, and program for managing memory for data transmission through a network. Virtual memory addresses of the data to be sent are provided to a sending agent. The sending agent provides to a host the virtual addresses of requested data. In response, the requested data addressed by the virtual addresses or the physical memory locations of the requested data are provided to the sending agent for sending to a destination.
Owner:INTEL CORP
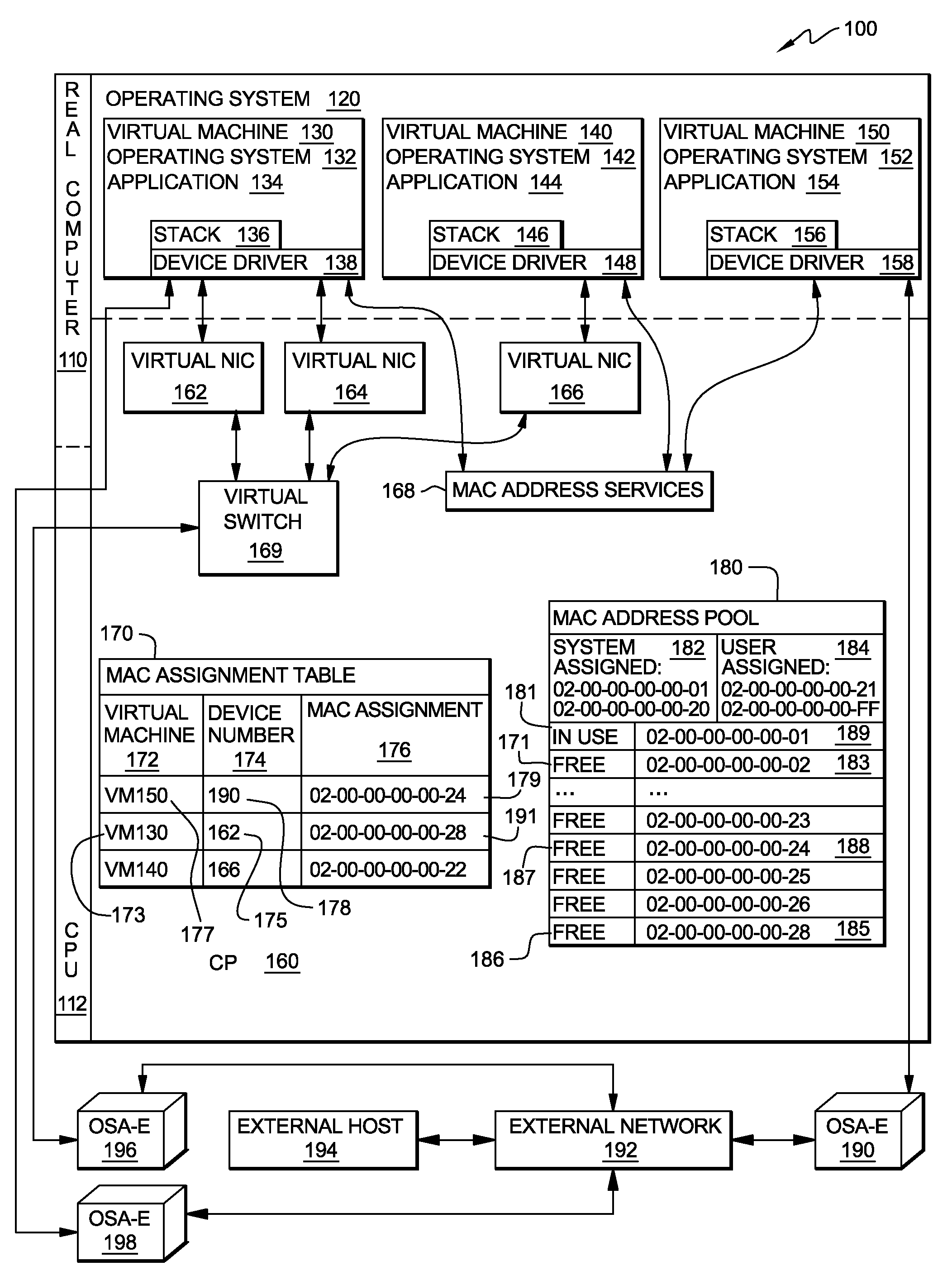
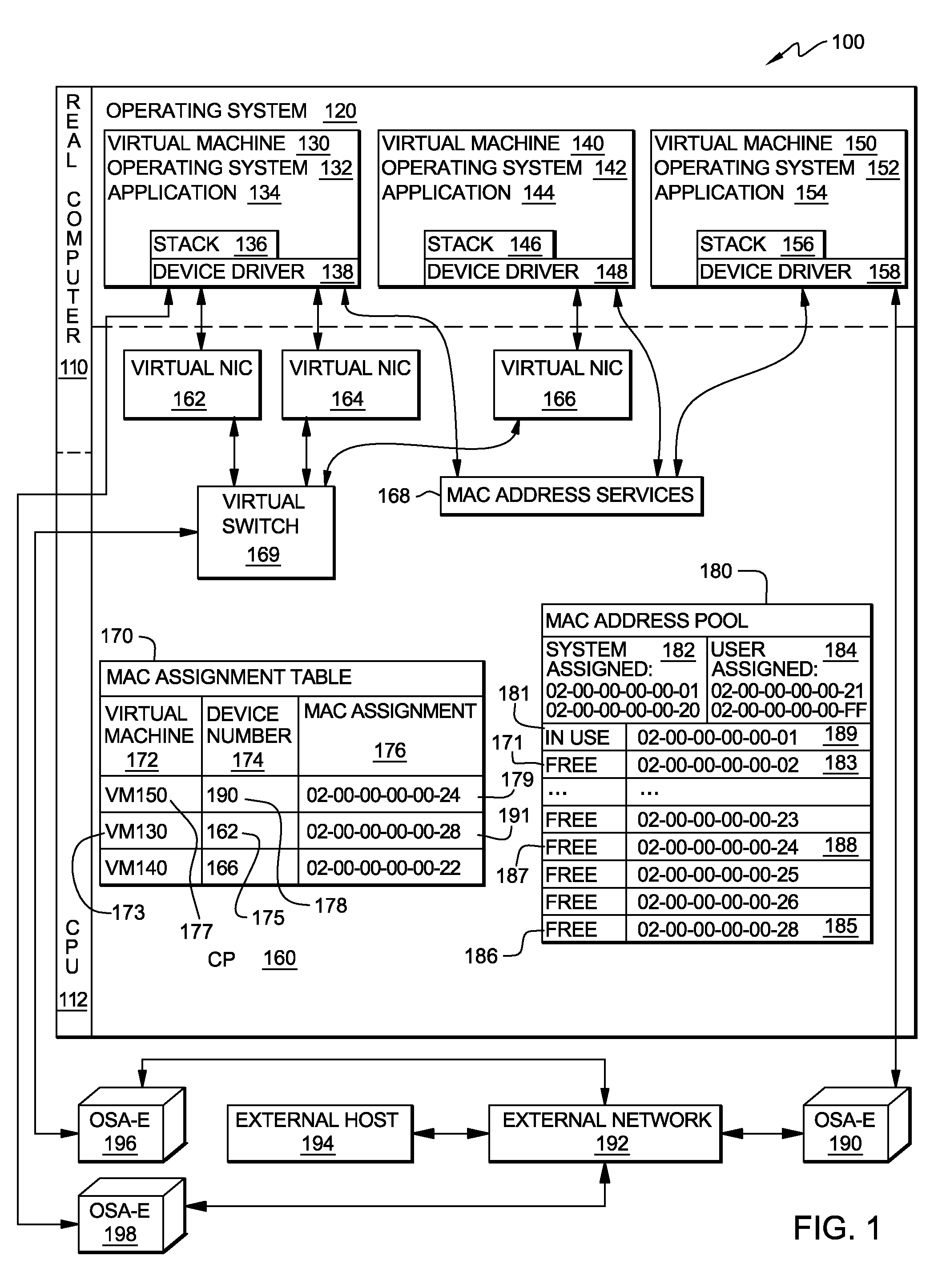
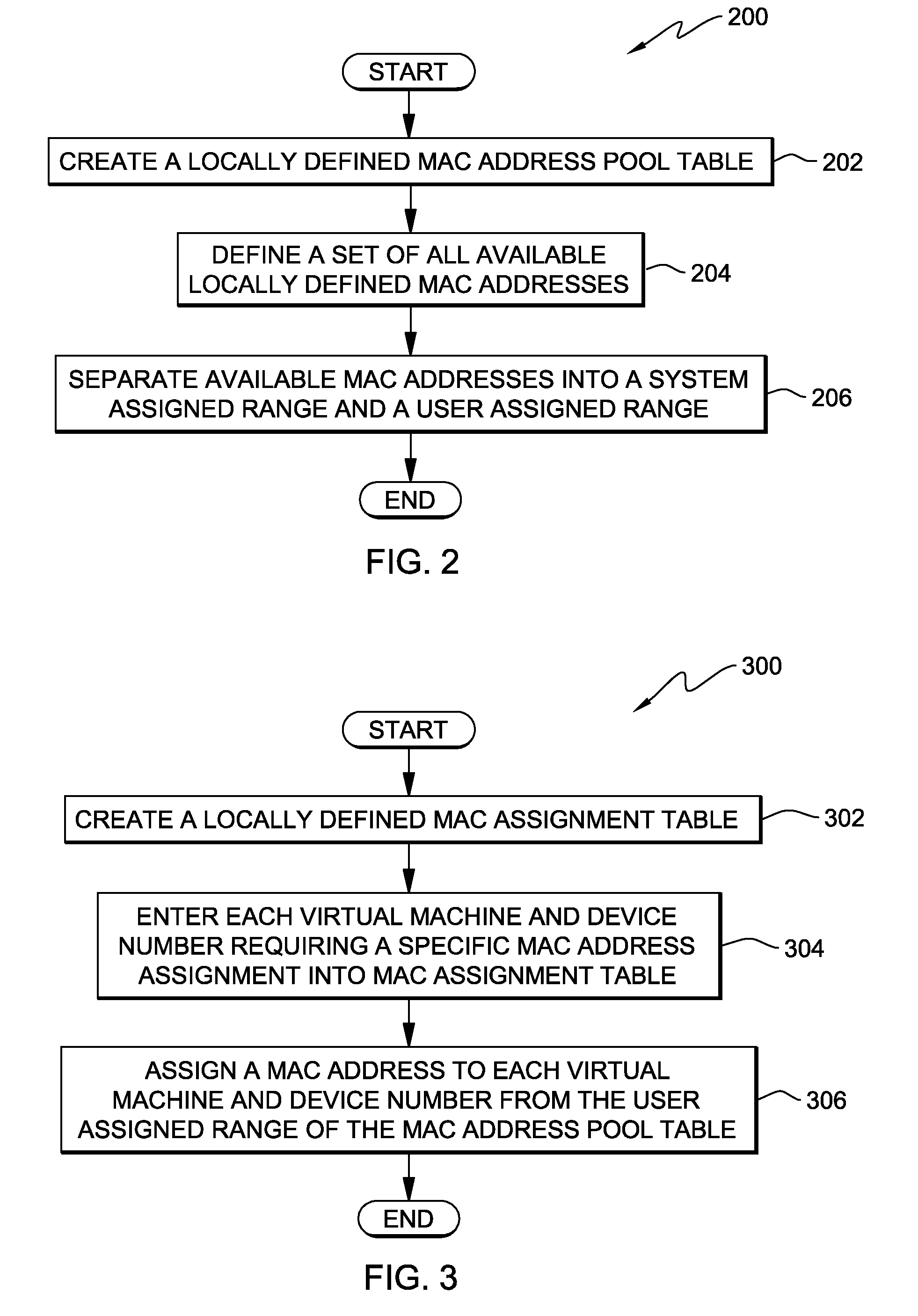
Method, system and program product for managing assignment of mac addresses in a virtual machine environment
InactiveUS20090327462A1Multiprogramming arrangementsMultiple digital computer combinationsVirtual memoryOperational system
A method, system and program product for managing assignment of virtual physical addresses. The method includes requesting, using a services function provided by a virtual machine operating system, a MAC address assignment for a real device and searching, in a MAC assignment table created and stored within a virtual memory space, to determine whether or not an explicit MAC address is assigned to the device. If an explicit MAC address is determined to be assigned to the device, retrieving the explicit MAC address upon verifying that the MAC address is not in use by another device and forwarding, using the services function, the explicit MAC address retrieved for assignment to the real device. If an explicit MAC address is not assigned to the device, retrieving an available MAC address from a MAC address pool table and forwarding the available MAC address retrieved for assignment to the real device.
Owner:IBM CORP
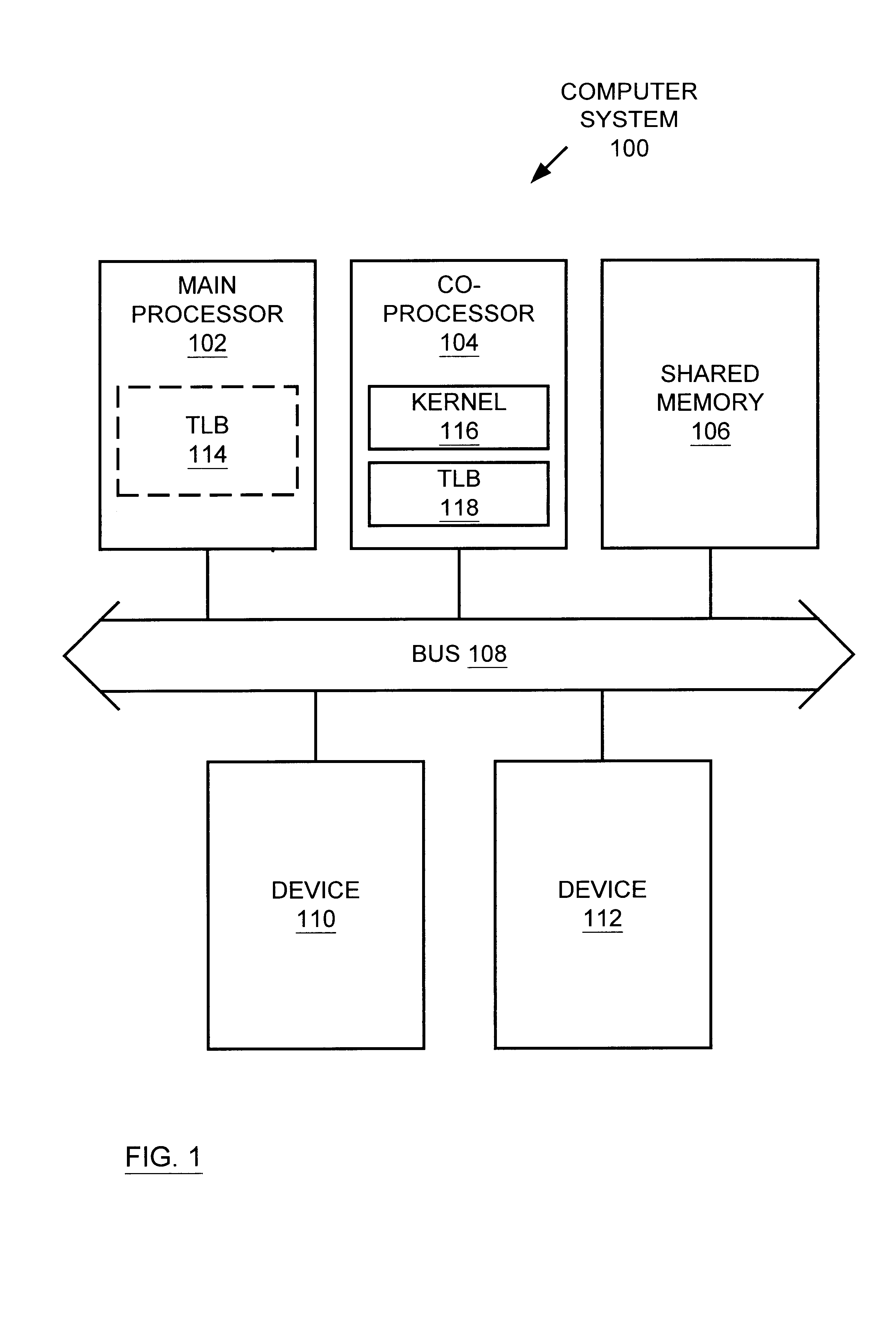
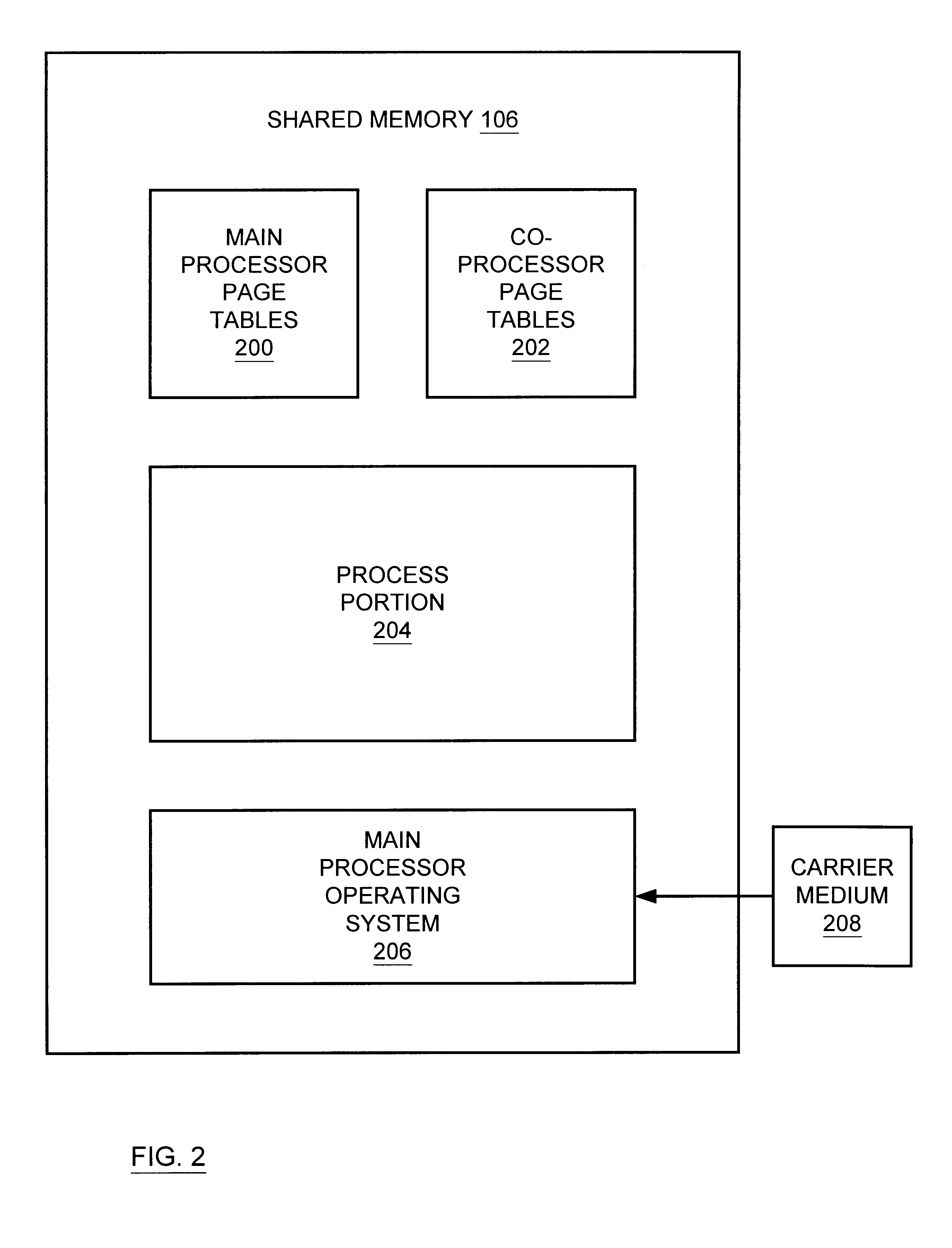
Multiprocessor system implementing virtual memory using a shared memory, and a page replacement method for maintaining paged memory coherence
InactiveUS6684305B1Memory architecture accessing/allocationMemory adressing/allocation/relocationVirtual memoryComputer architecture
A computer system including a first processor, a second processor in communication with the first processor, a memory coupled to the first and second processors (i.e., a shared memory) and including multiple memory locations, and a storage device coupled to the first processor. The first and second processors implement virtual memory using the memory. The first processor maintains a first set of page tables and a second set of page tables in the memory. The first processor uses the first set of page tables to access the memory locations within the memory. The second processor uses the second set of page tables, maintained by the first processor, to access the memory locations within the memory. A virtual memory page replacement method is described for use in the computer system, wherein the virtual memory page replacement method is designed to help maintain paged memory coherence within the multiprocessor computer system.
Owner:GLOBALFOUNDRIES US INC
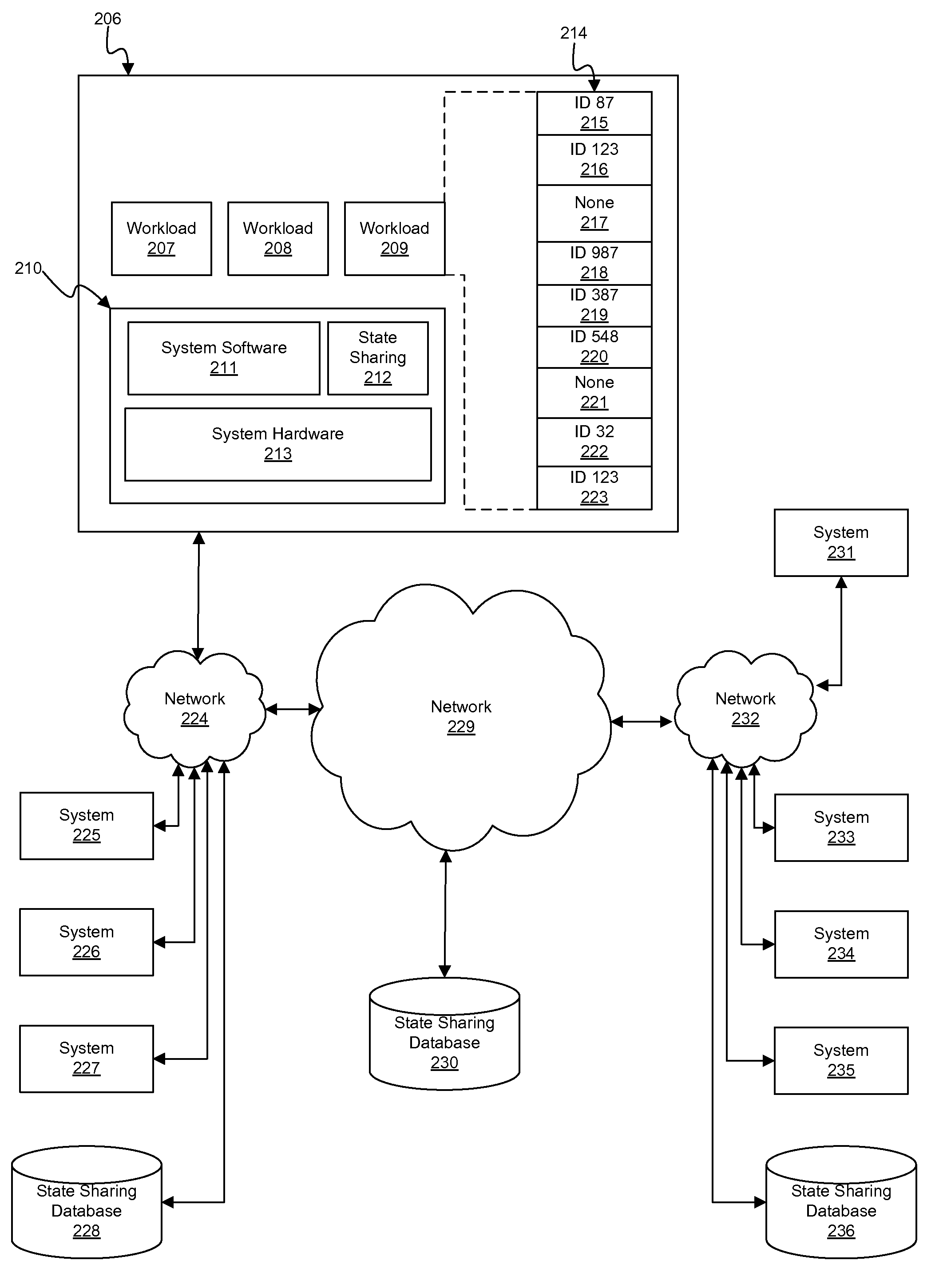
Using memory equivalency across compute clouds for accelerated virtual memory migration and memory de-duplication
InactiveUS20090204718A1Memory adressing/allocation/relocationComputer security arrangementsComputational scienceVirtual memory
A memory state equivalency analysis fabric which notionally overlays a given compute cloud. Equivalent sections of memory state are identified, and that equivalency information is conveyed throughout the fabric. Such a compute cloud-wide memory equivalency fabric is utilized as a powerful foundation for numerous memory state management and optimization activities, such as workload live migration and memory de-duplication across the entire cloud.
Owner:LAWTON KEVIN P +1
Dynamically creating or removing a physical-to-virtual address mapping in a memory of a peripheral device
ActiveUS7065630B1Easy to useMemory adressing/allocation/relocationInput/output processes for data processingVirtual memoryParallel computing
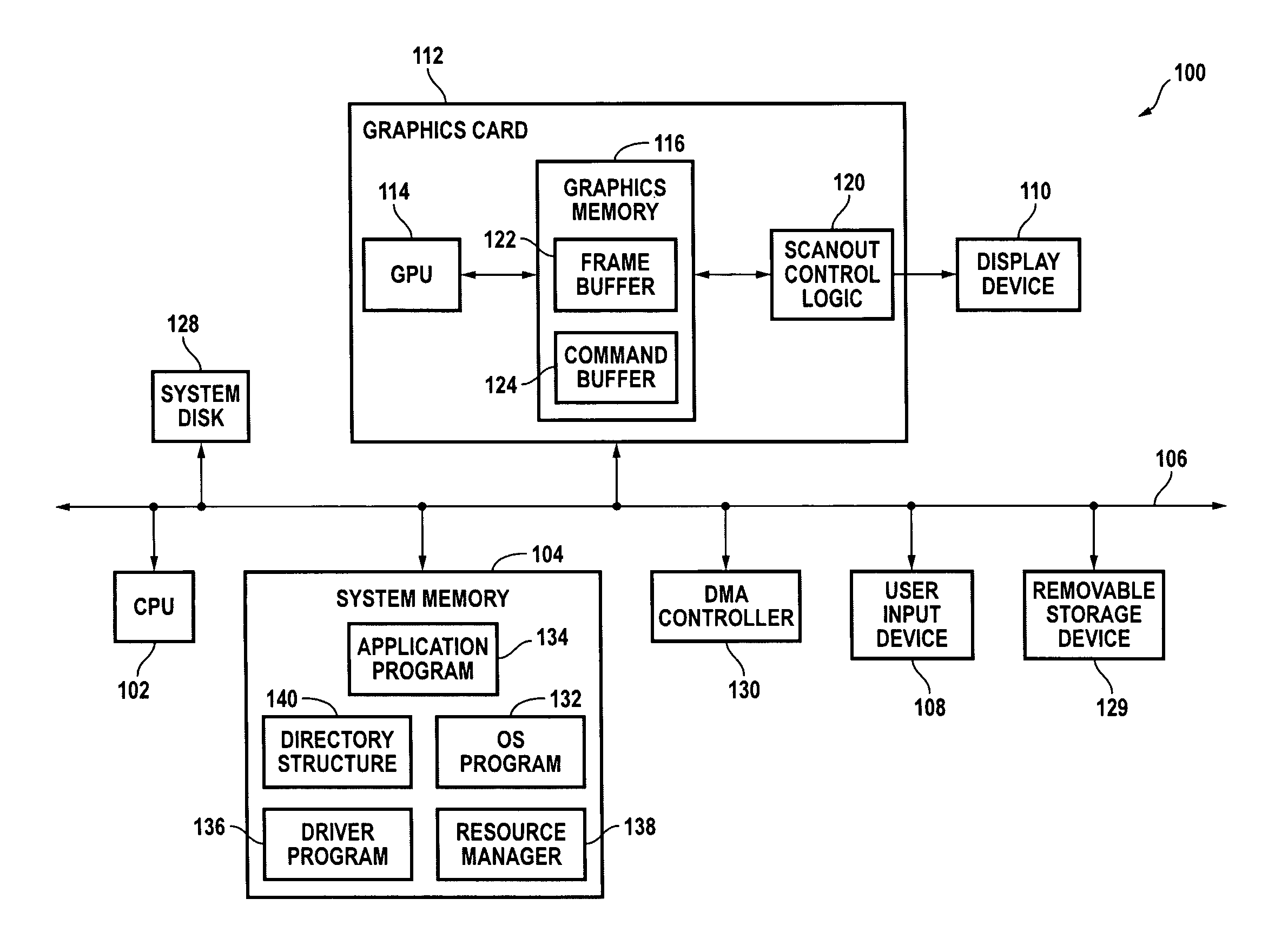
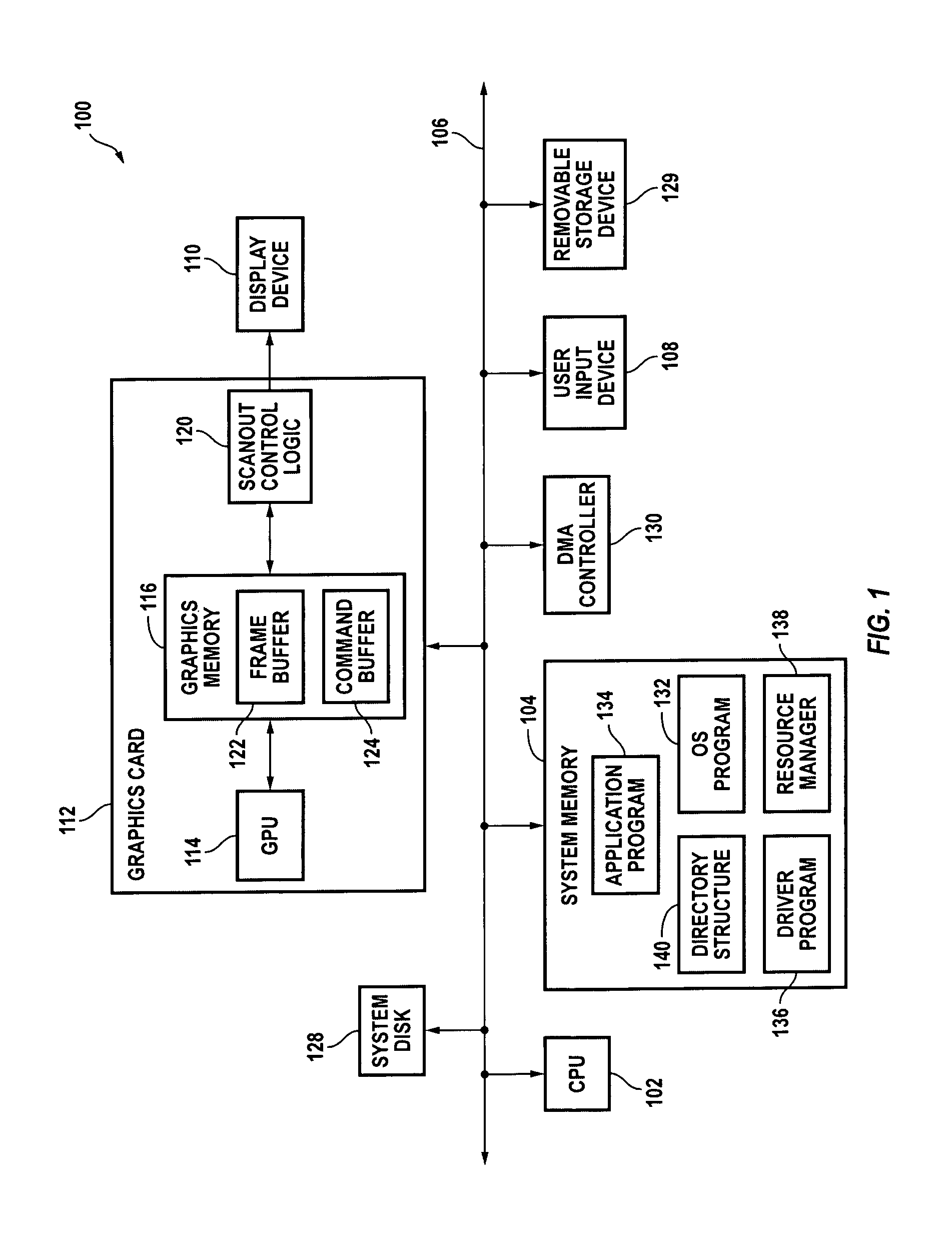
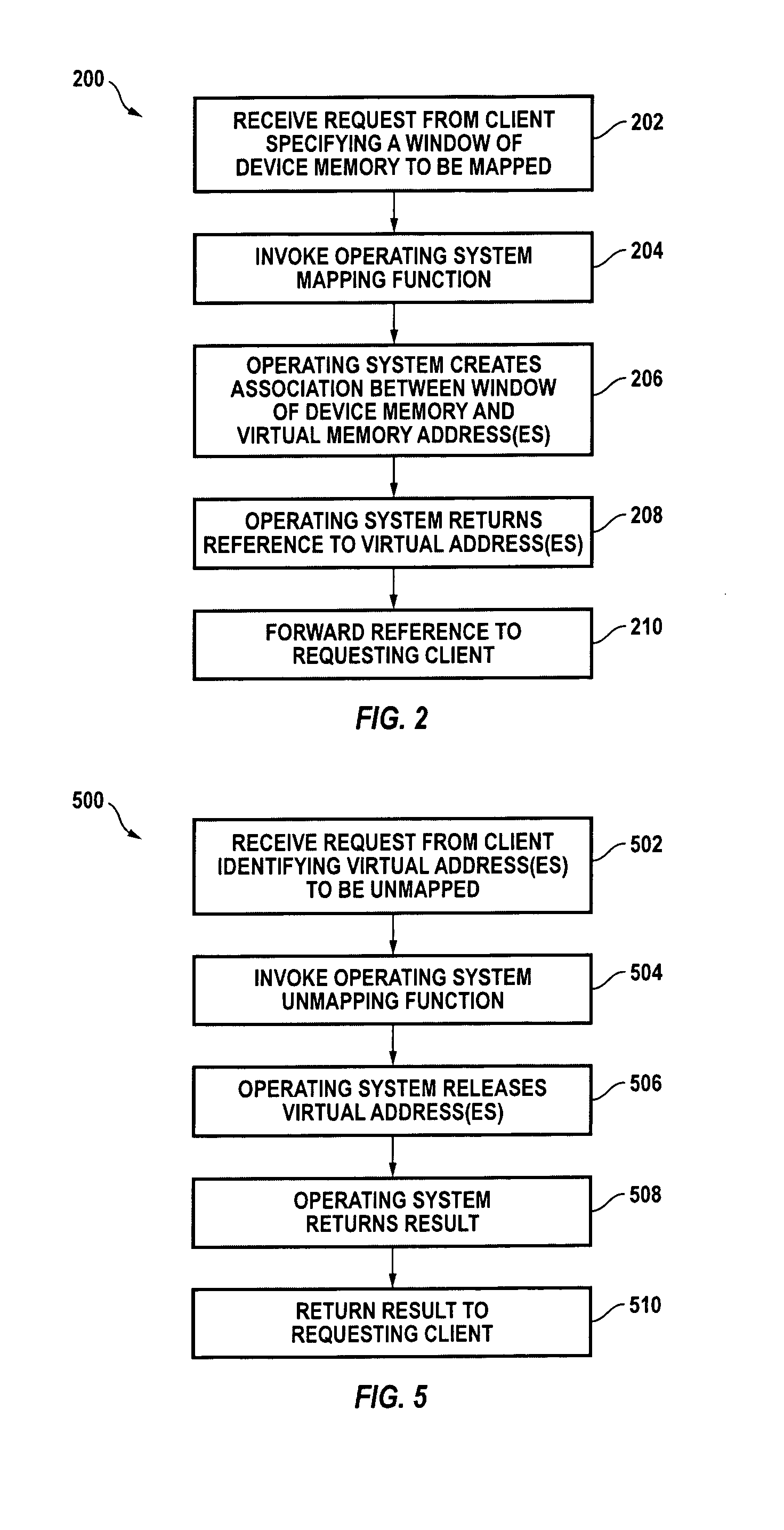
Systems and methods for providing on-demand memory management. In response to a mapping request from a device driver or other program, a first portion of the memory is mapped to one or more virtual addresses in a first region of a virtual memory space so that it can be directly accessed by the CPU. In response to an unmapping request the first portion of the memory is unmapped. Mapping and unmapping requests may be made at any time.
Owner:NVIDIA CORP
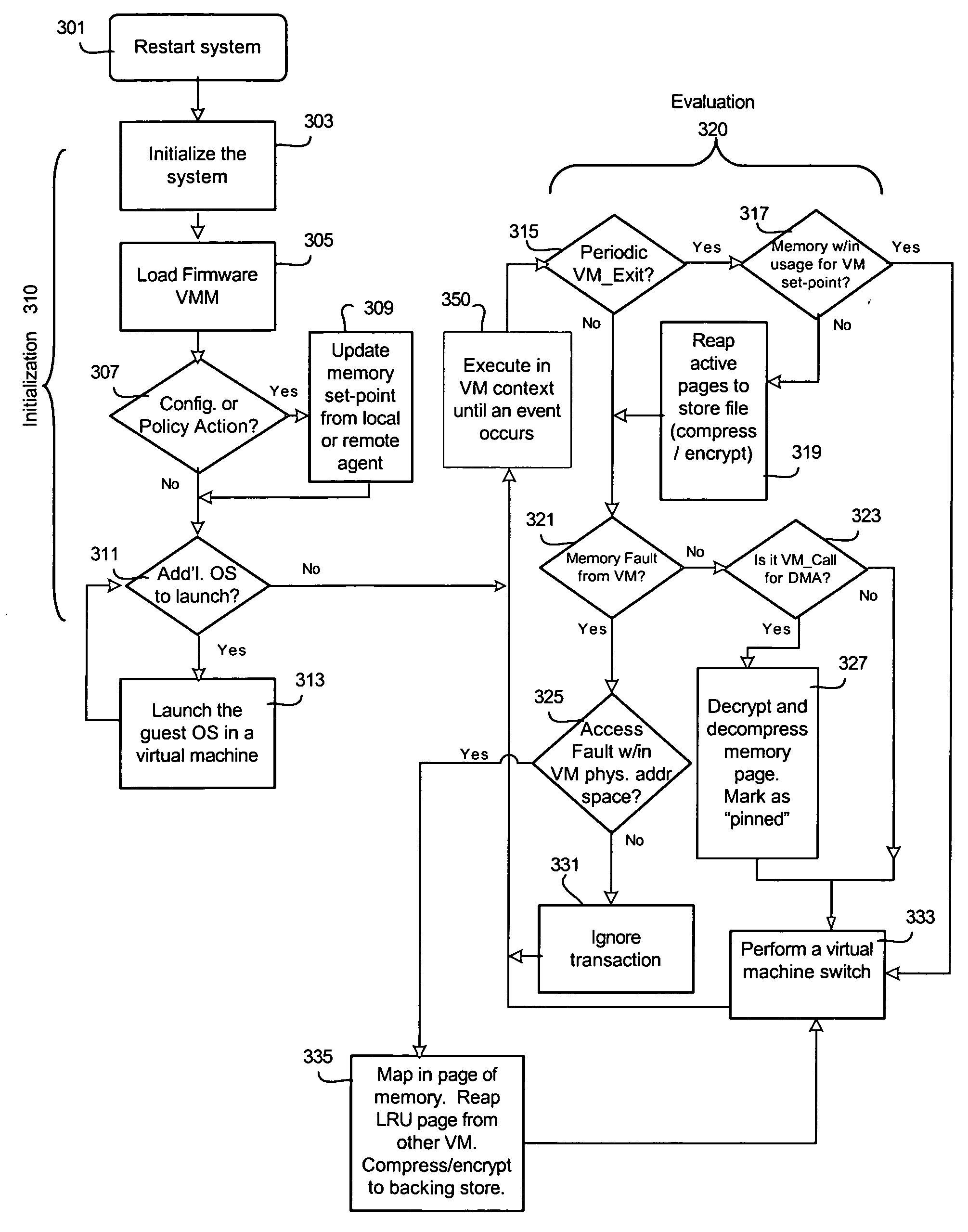
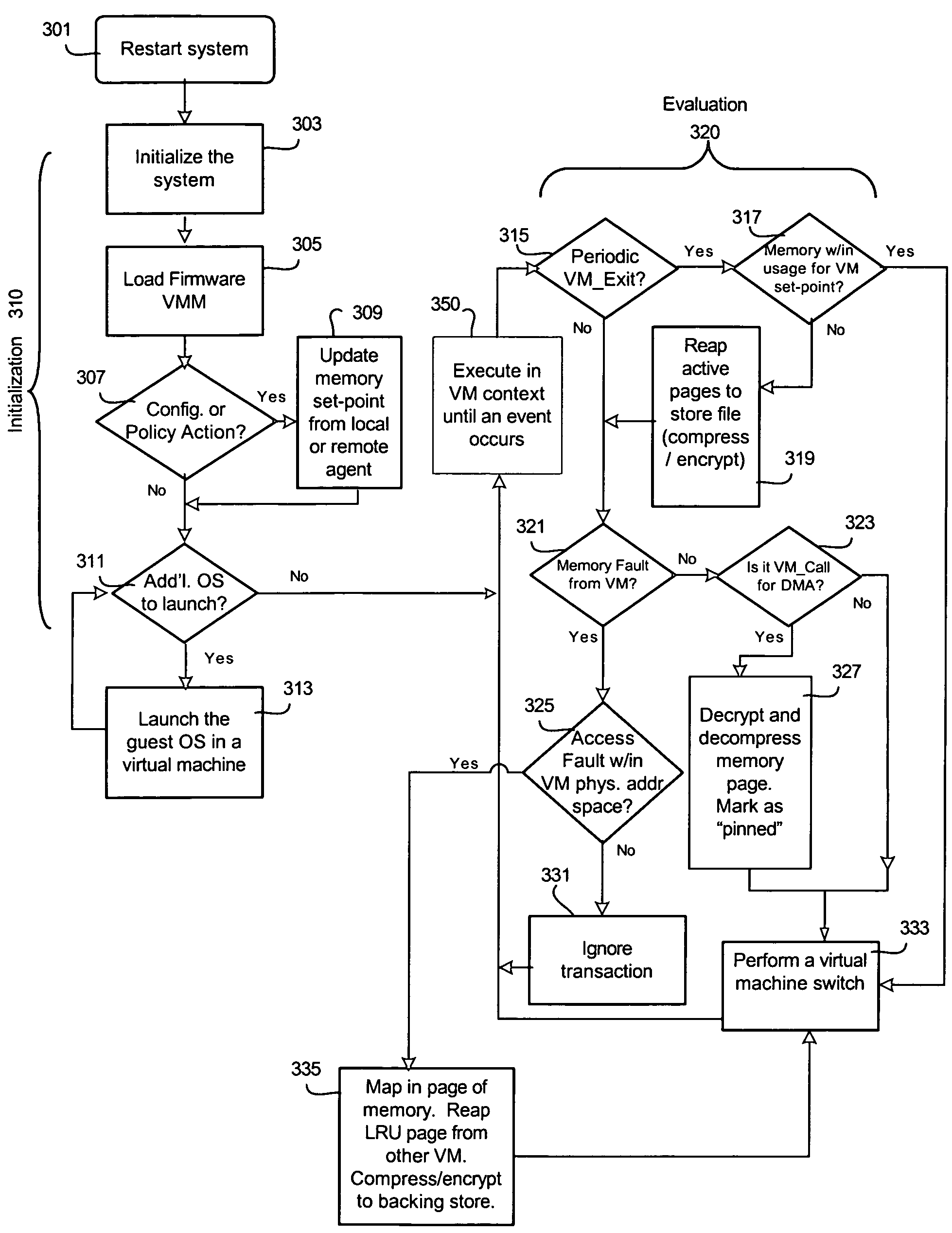
Method to manage memory in a platform with virtual machines
An embodiment of the present invention enables the virtualizing of virtual memory in a virtual machine environment within a virtual machine monitor (VMM). Memory required for direct memory access (DMA) for device drivers, for example, is pinned by the VMM and prevented from being swapped out. The VMM may dynamically allocated memory resources to various virtual machines running in the platform. Other embodiments may be described and claimed.
Owner:TAHOE RES LTD
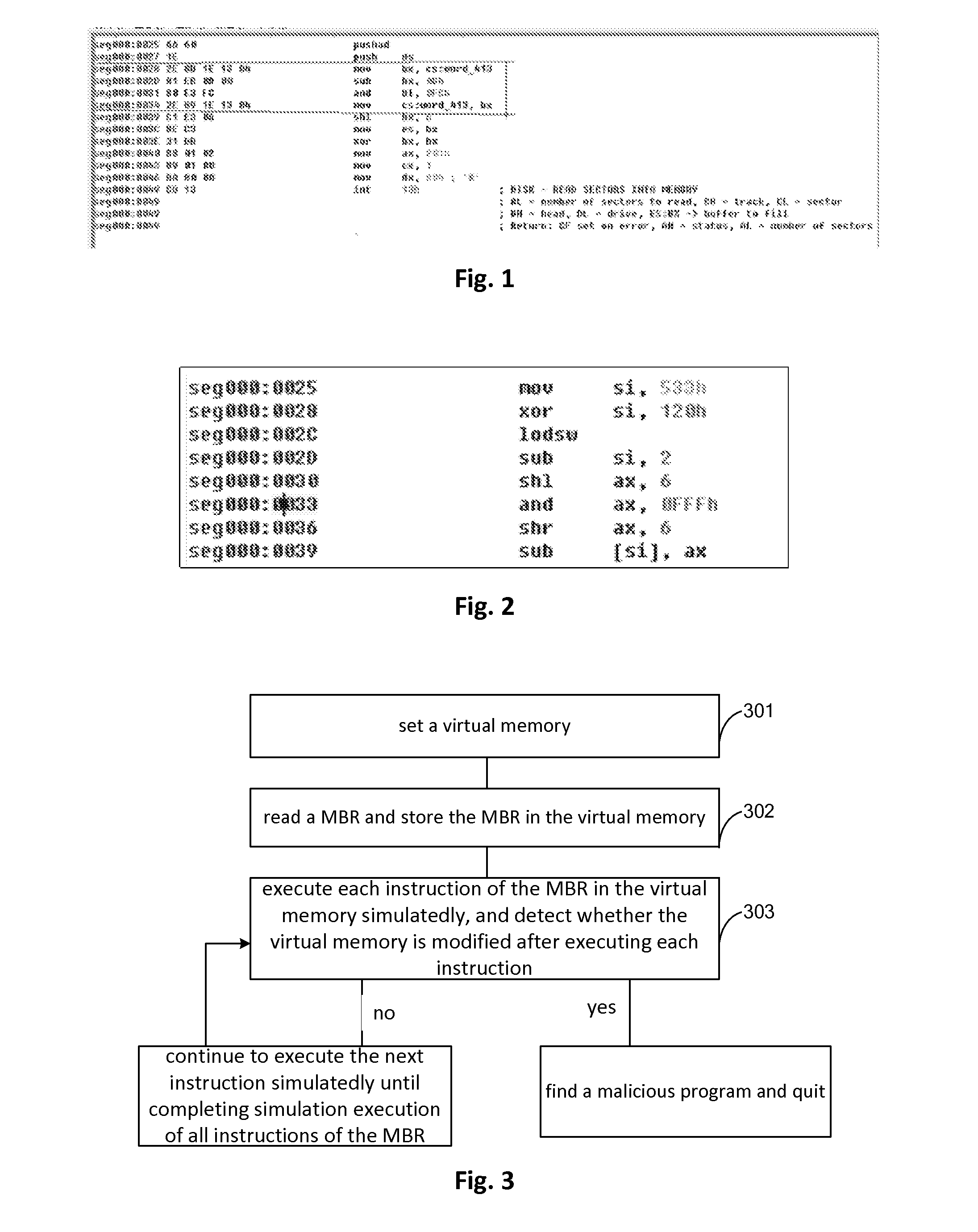
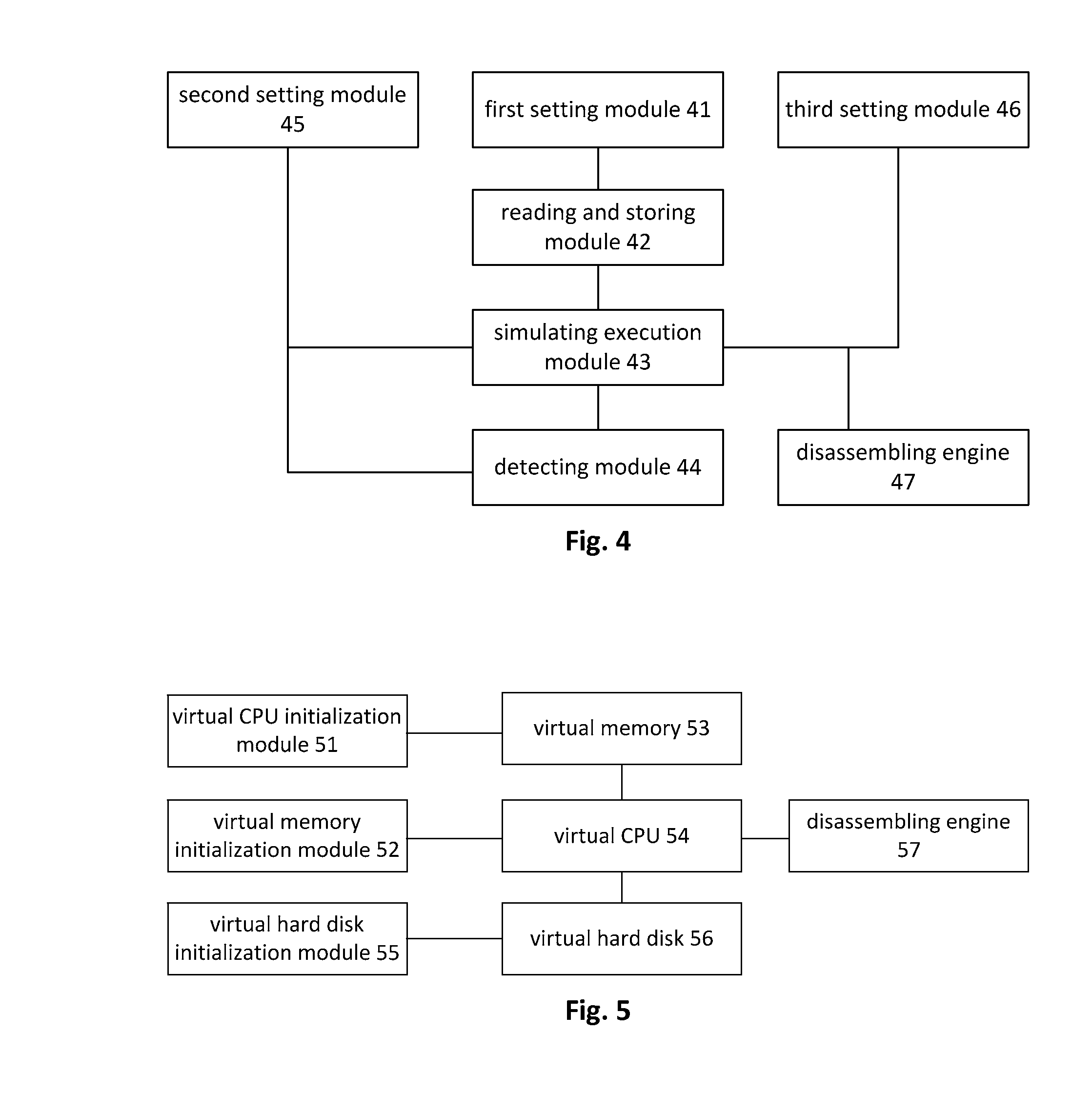
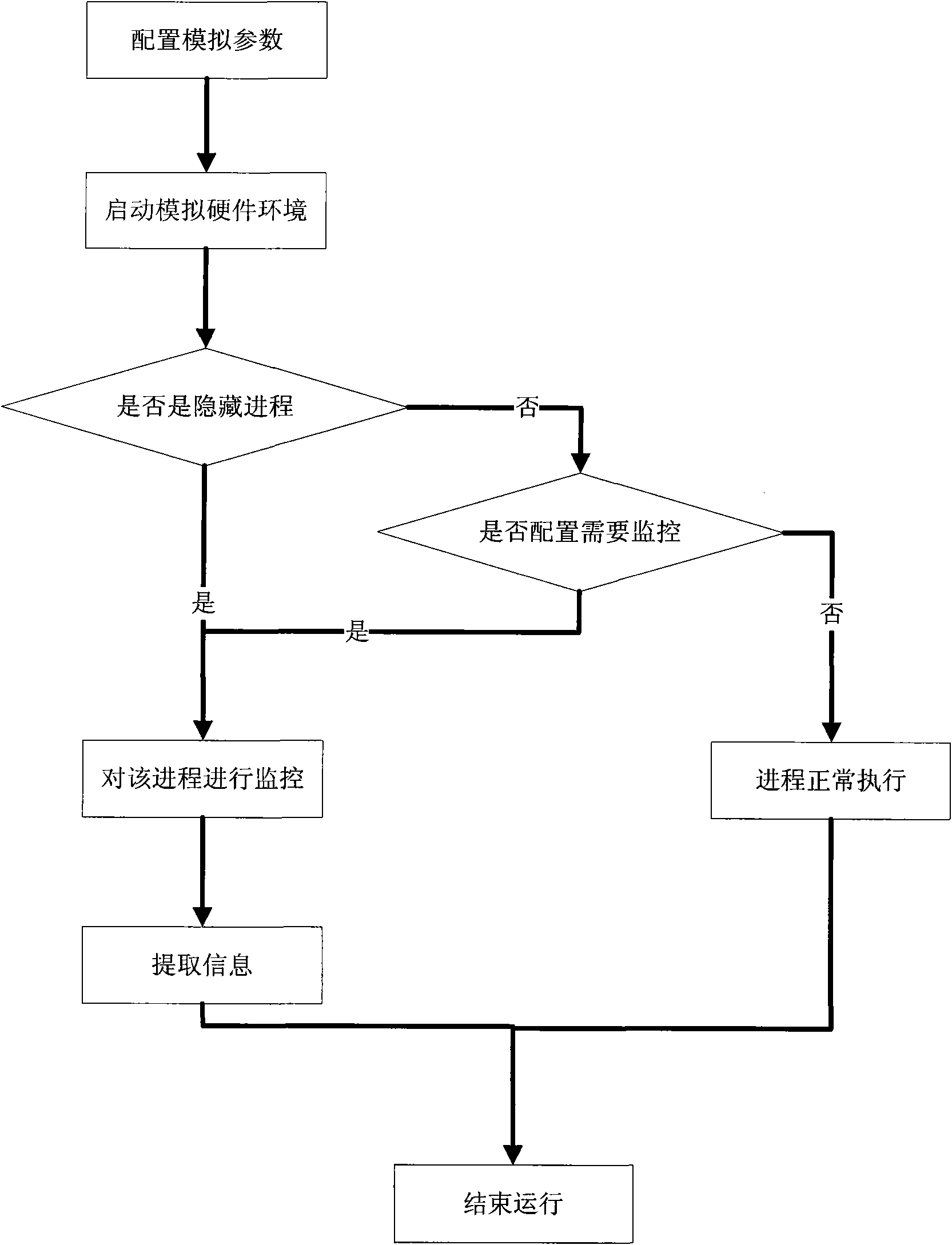
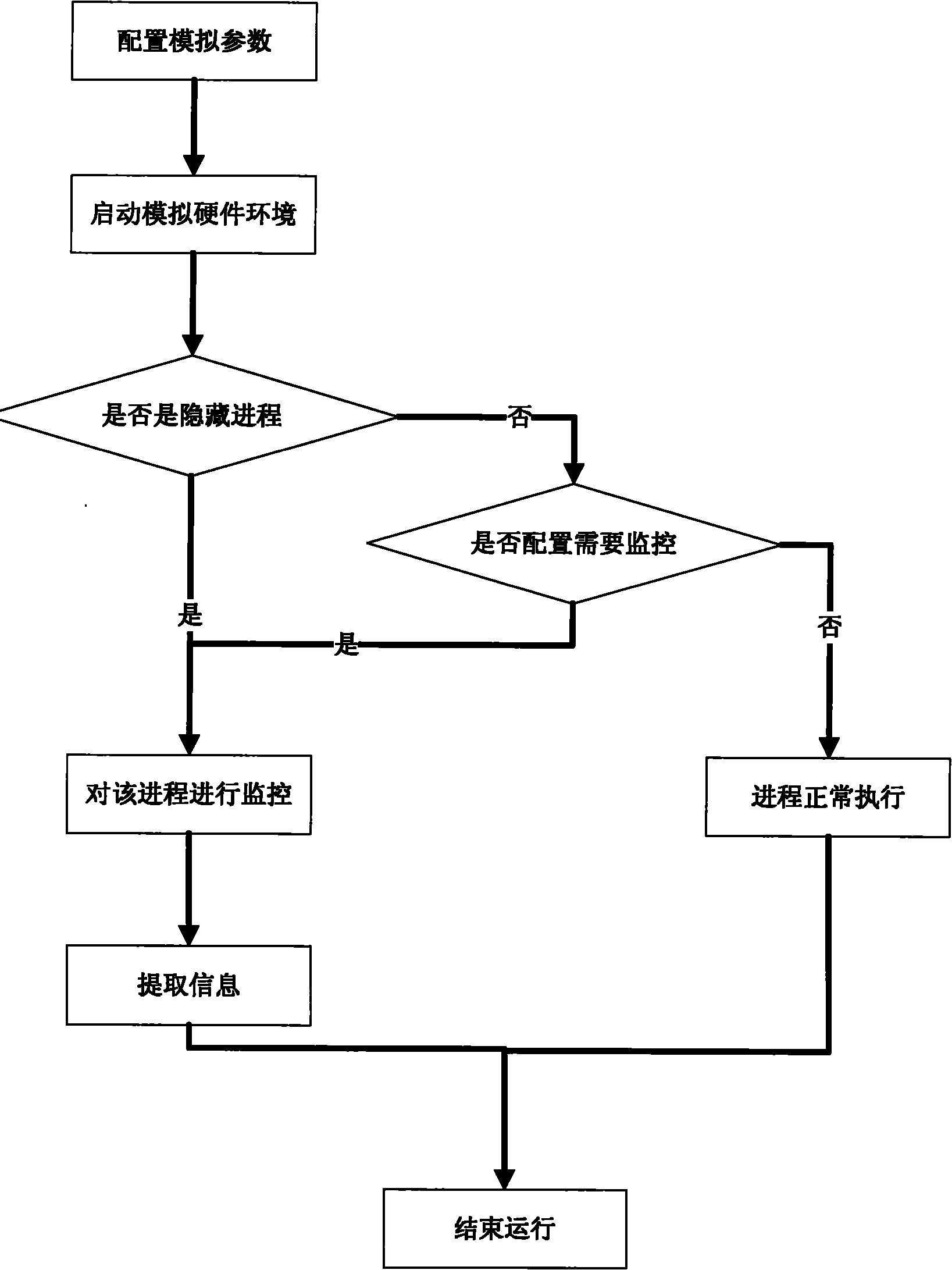
Method for processing hidden process based on hardware simulator
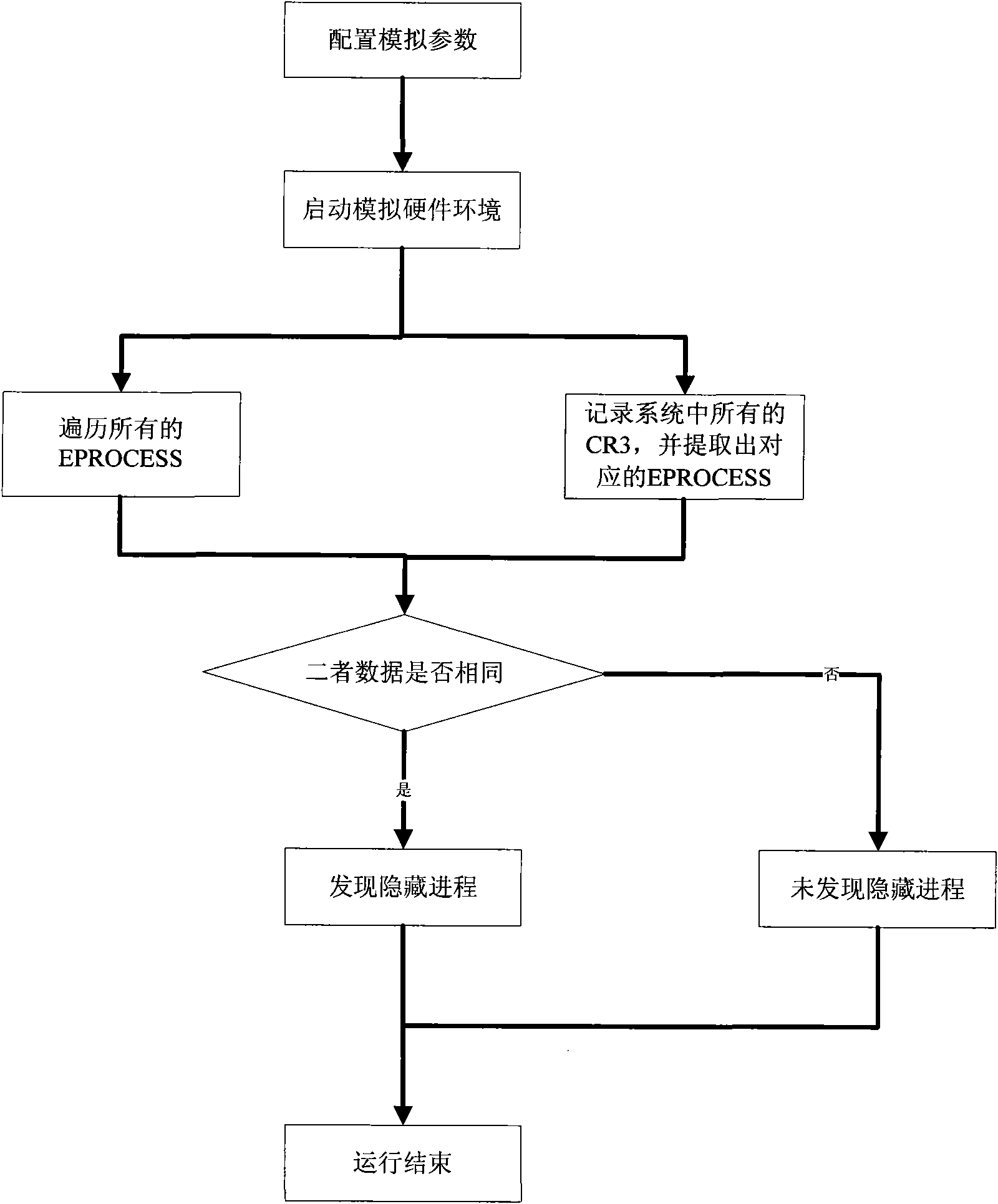
InactiveCN101770551ATransparent analysisEnsure transparencyPlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtual memoryData acquisition
The invention belongs to the technical field of network security and particularly relates to a method for processing a hidden process based on a hardware simulator. By establishing a running environment of malicious codes in hidden codes in a hardware simulating environment and operating and controlling instructions simulating a CPU and various accessing operations simulating a memory, marked by a CR3 value in a CR3 register, the hidden process is detected, the running process of the hidden process is monitored, and the running information of the malicious codes in the hidden process is recorded by a data acquisition module; and the invention also provides a mirror image which extracts the malicious codes directly from a virtual memory. All instructions of a virtual CPU and various hardware operations of a hardware simulating device are executed in simulation after translation and are not executed in a real machine by using code segments directly, and the running time of the instruction in the instruction running process can be accurately calculated, thus realizing fully transparent analysis of the malicious codes in the hidden process.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Method to manage memory in a platform with virtual machines
ActiveUS7421533B2Resource allocationComputer security arrangementsVirtual memoryDirect memory access
An embodiment of the present invention enables the virtualizing of virtual memory in a virtual machine environment within a virtual machine monitor (VMM). Memory required for direct memory access (DMA) for device drivers, for example, is pinned by the VMM and prevented from being swapped out. The VMM may dynamically allocated memory resources to various virtual machines running in the platform. Other embodiments may be described and claimed.
Owner:TAHOE RES LTD
System and method for maintaining translation look-aside buffer (TLB) consistency
InactiveUS6105113AMemory architecture accessing/allocationMemory adressing/allocation/relocationVirtual memoryMemory address
A system and method for maintaining consistency between translational look-aside buffers (TLB) and page tables. A TLB has a TLB table for storing a list of virtual memory address-to-physical memory address translations, or page table entries (PTES) and a hardware-based controller for invalidating a translation that is stored in the TLB table when a corresponding page table entry changes. The TLB table includes a virtual memory (VM) page tag and a page table entry address tag for indexing the list of translations The VM page tag can be searched for VM pages that are referenced by a process. If a referenced VM page is found, an associated physical address is retrieved for use by the processor. The TLB controller includes a snooping controller for snooping a cache-memory interconnect for activity that affects PTEs. The page table entry address tag can be searched by a search engine in the TLB controller for snooped page table entry addresses. The TLB controller includes an updating module for invalidating or updating translations associated with snooped page table entry addresses. Translations in TLBs are thus updated or invalidated through hardware when an operating system changes a PTE, without intervention by an operating system or other software.
Owner:RPX CORP +1
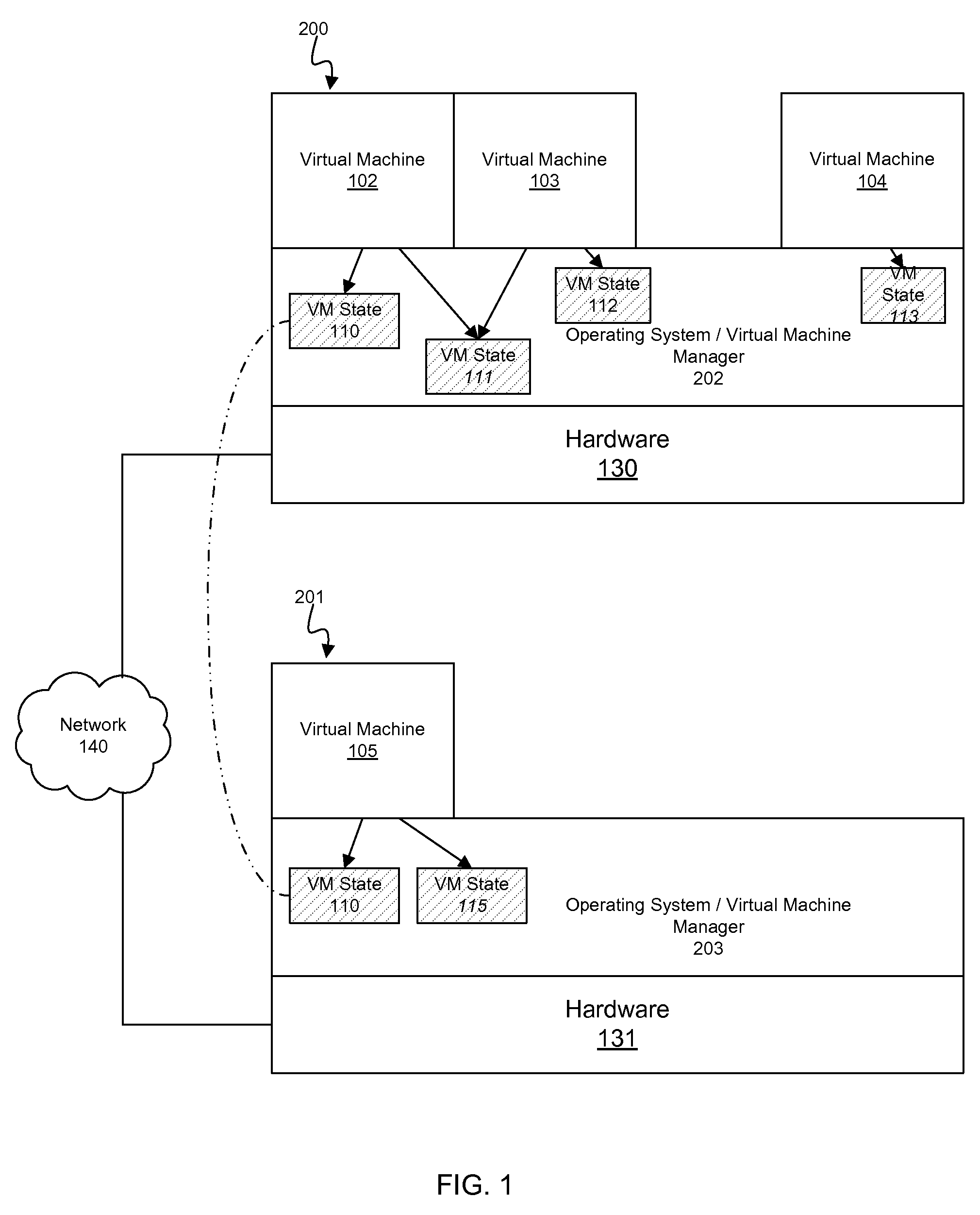
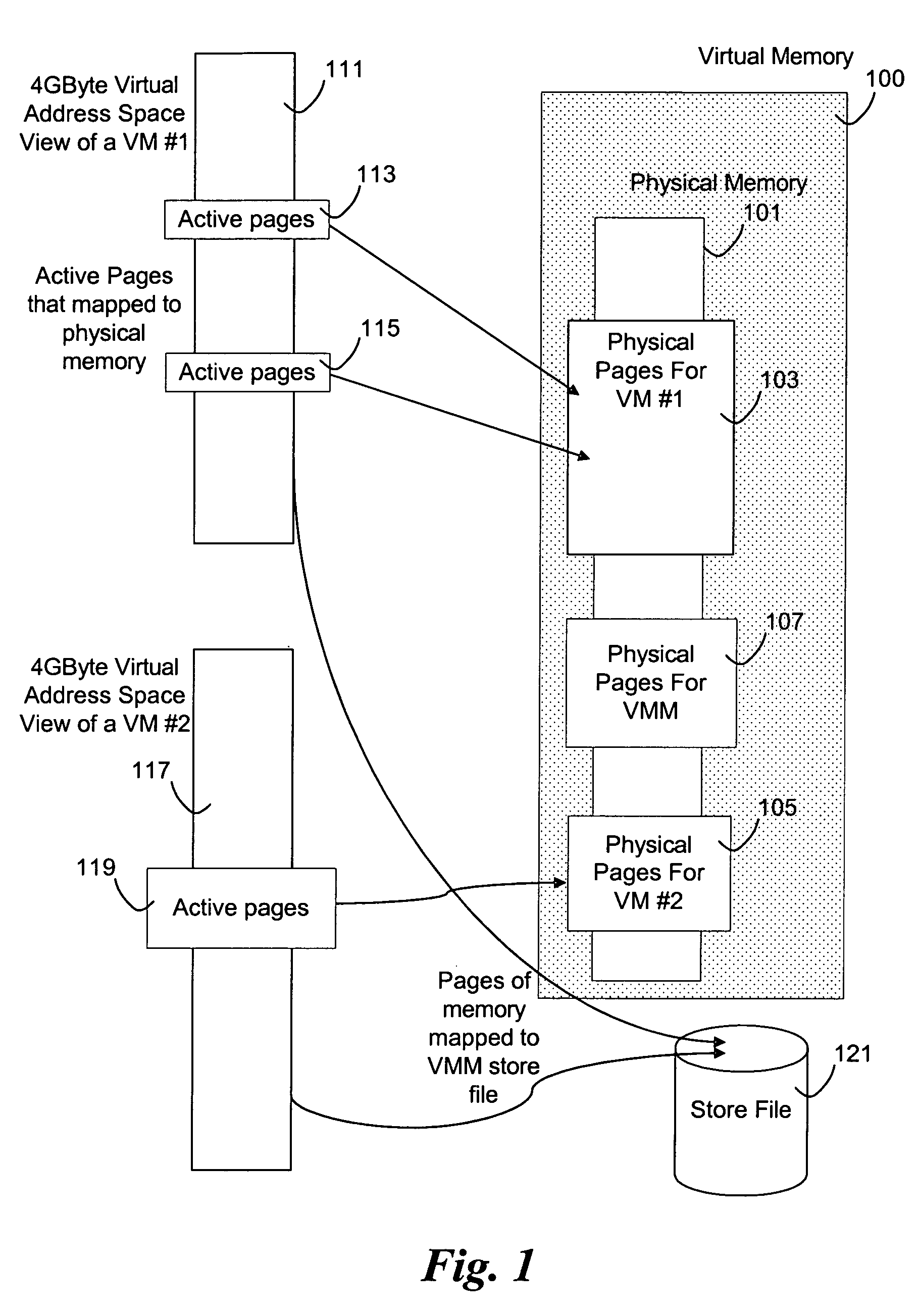
System, method and program to manage memory of a virtual machine
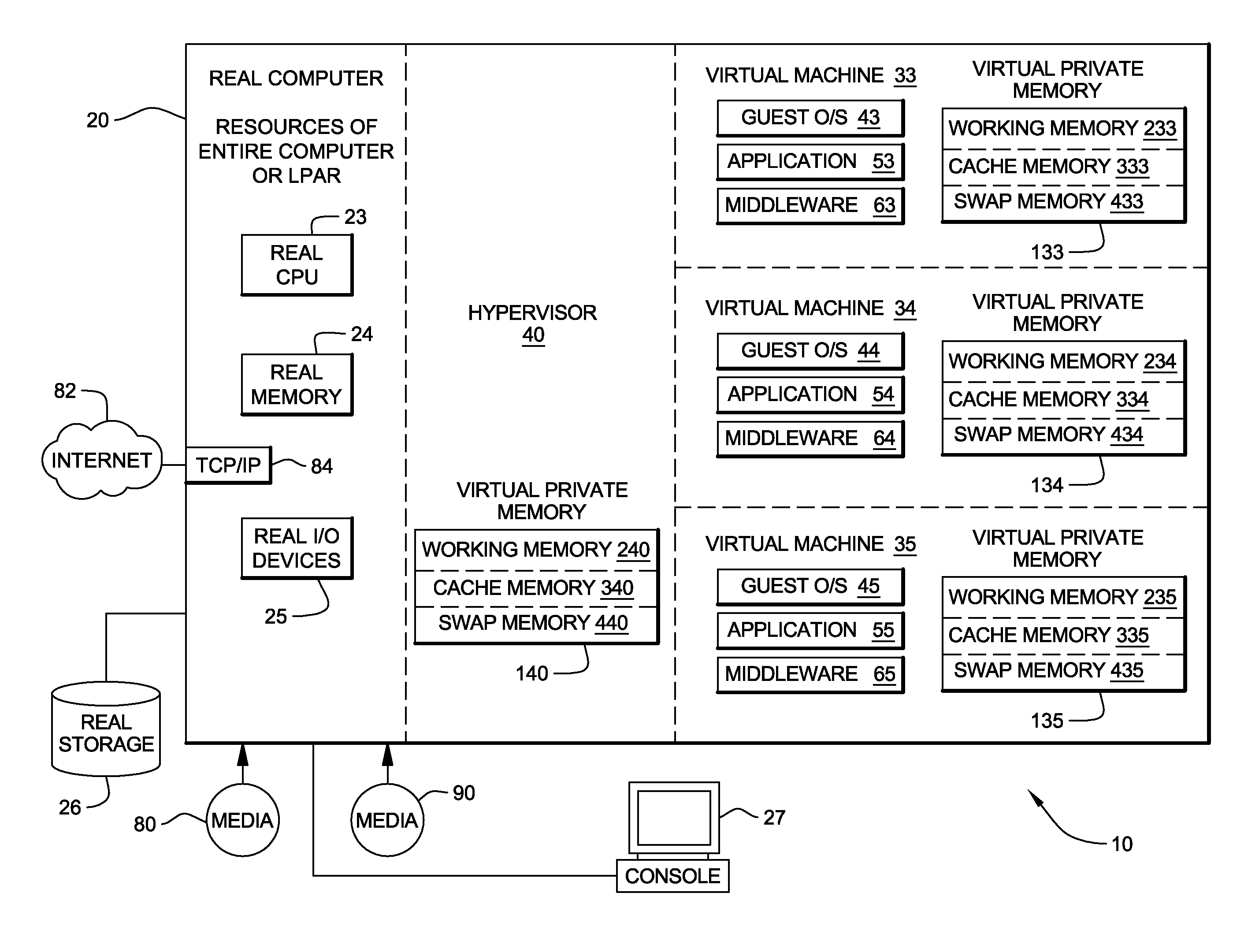
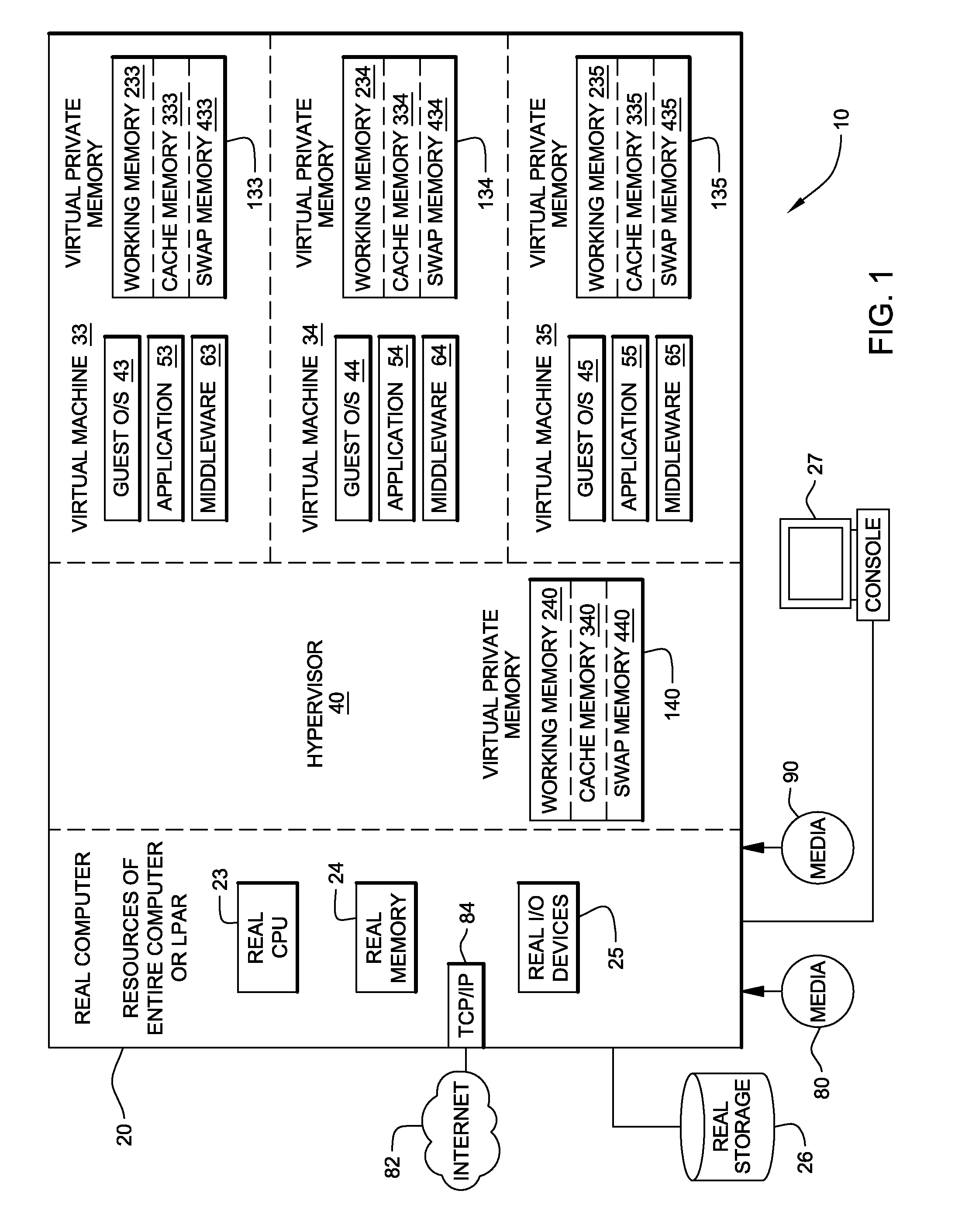
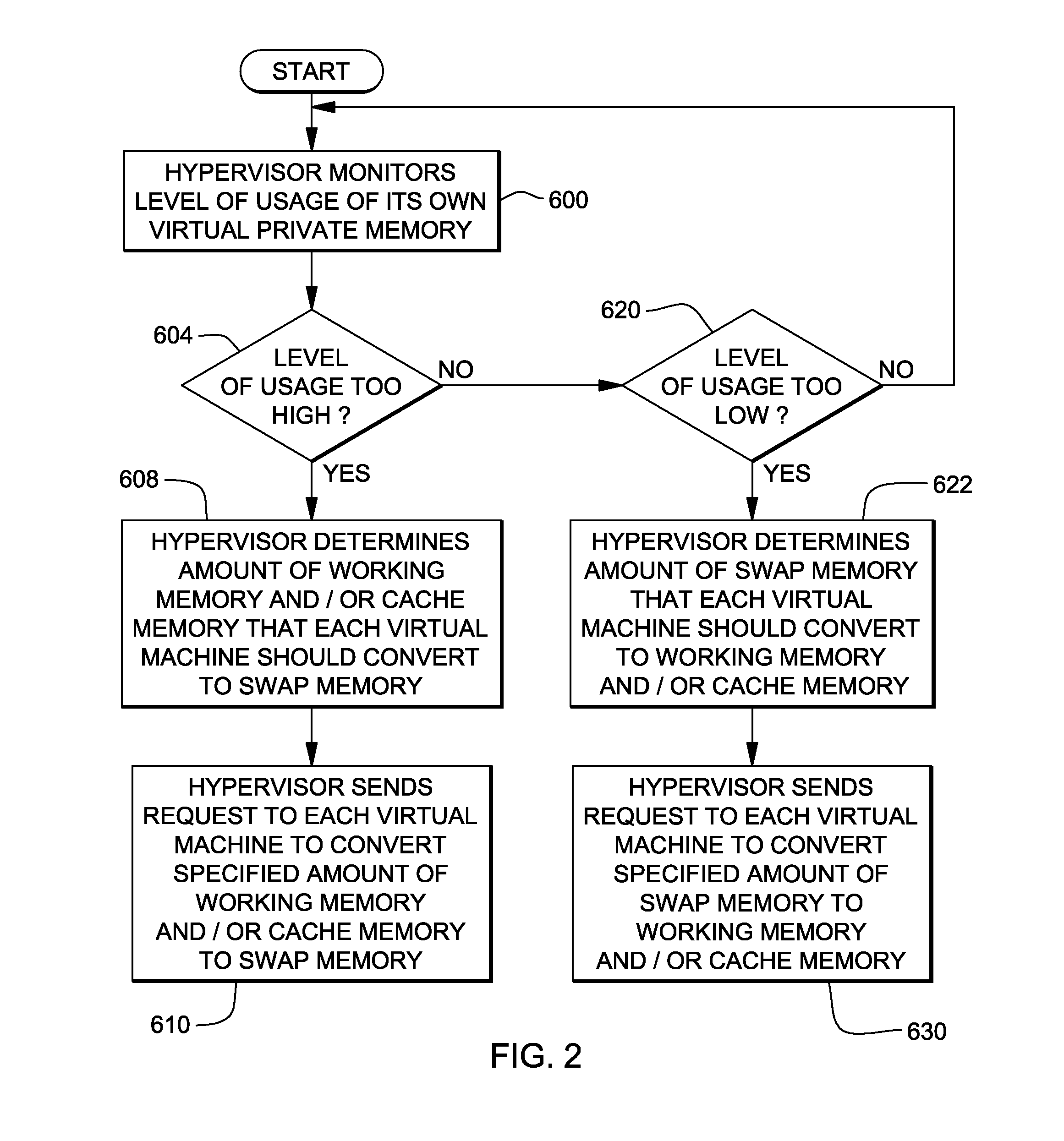
ActiveUS20090006801A1Less virtual memory allocationResource allocationMemory adressing/allocation/relocationVirtual memoryWork memory
Management of virtual memory allocated by a virtual machine control program to a plurality of virtual machines. Each of the virtual machines has an allocation of virtual private memory divided into working memory, cache memory and swap memory. The virtual machine control program determines that it needs additional virtual memory allocation, and in response, makes respective requests to the virtual machines to convert some of their respective working memory and / or cache memory to swap memory. At another time, the virtual machine control program determines that it needs less virtual memory allocation, and in response, makes respective requests to the virtual machines to convert some of their respective swap memory to working memory and / or cache memory.
Owner:IBM CORP
Mechanism to support flexible decoupled transactional memory
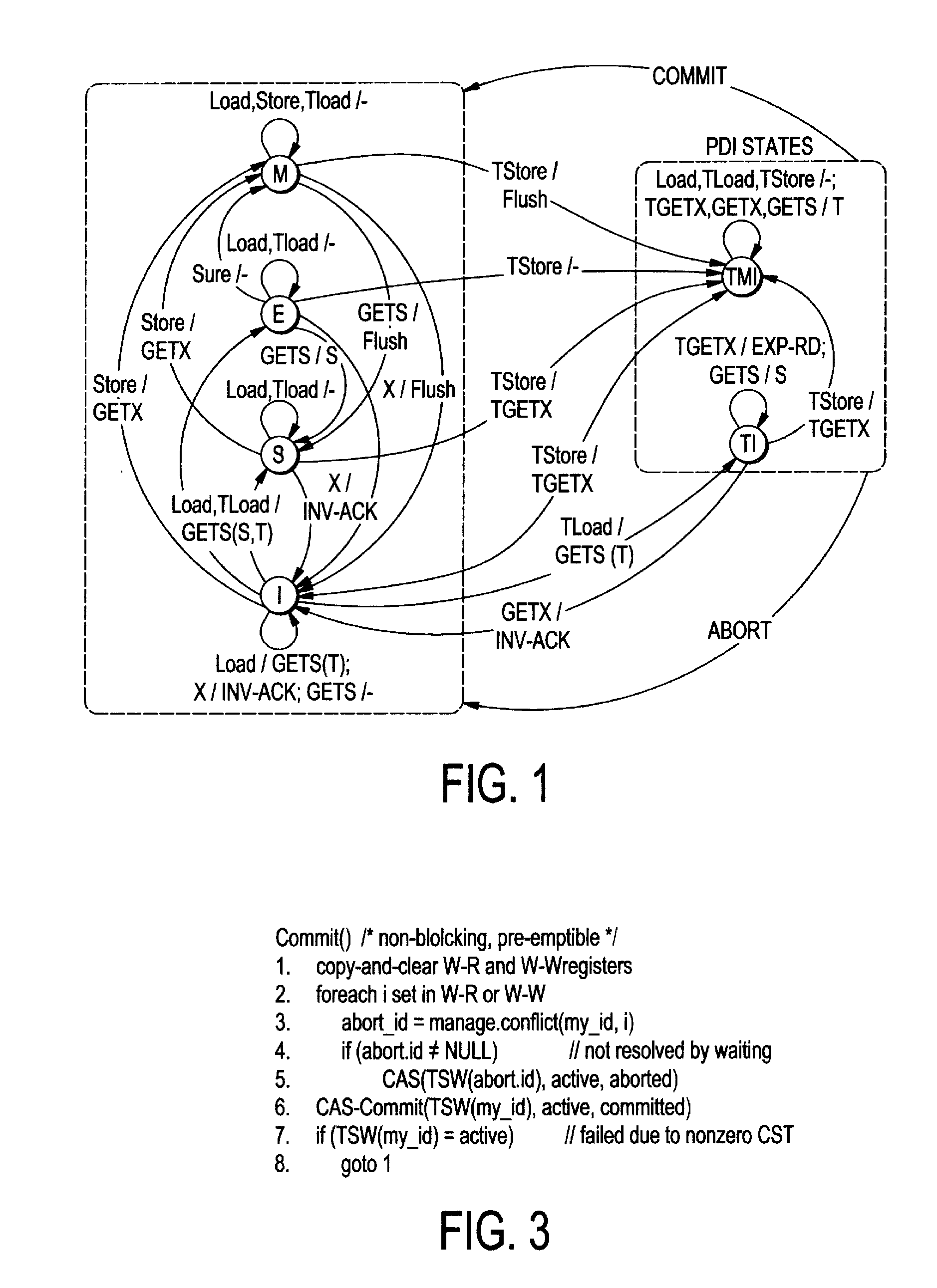
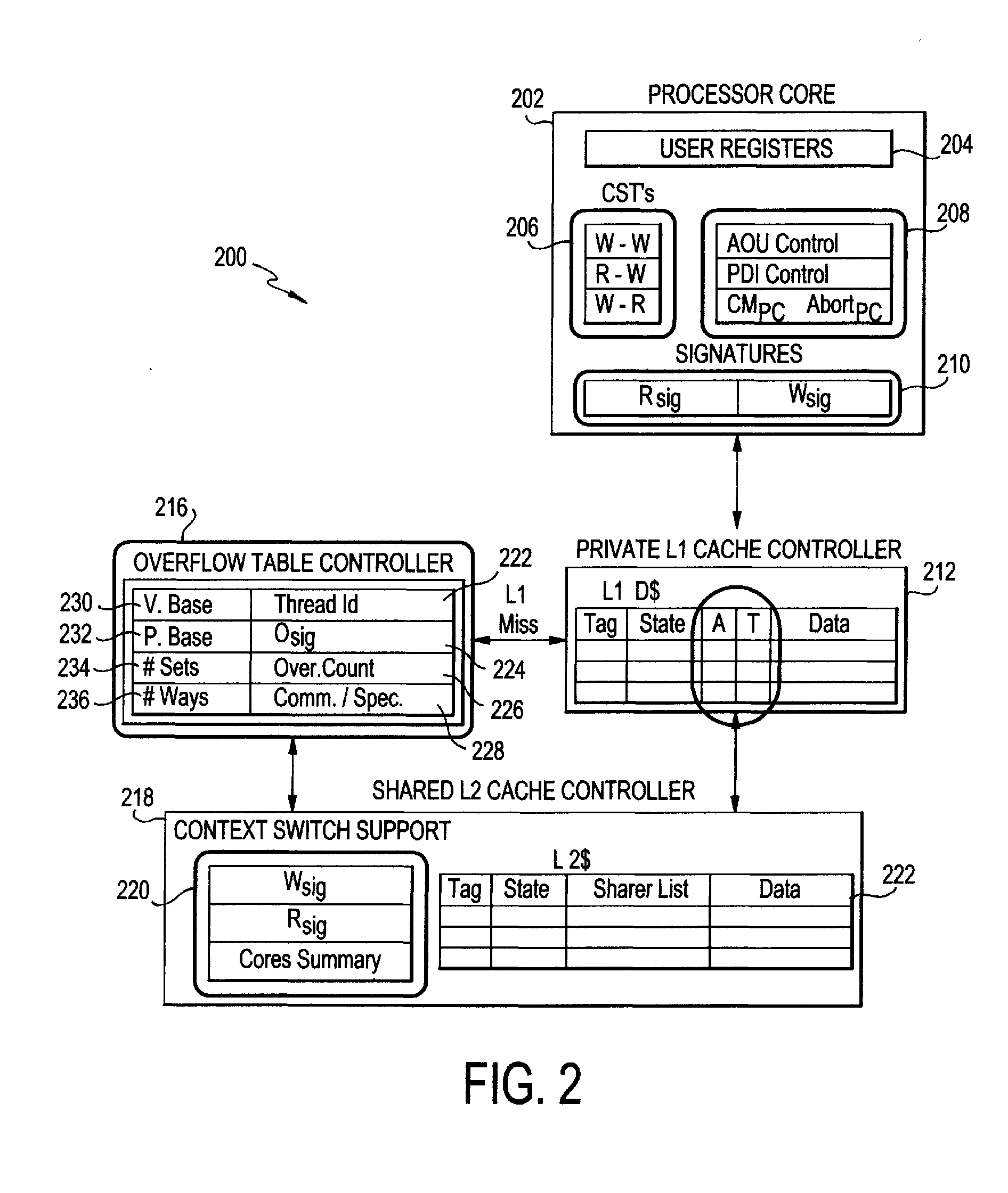
ActiveUS20120179877A1Maximize concurrencyEncourages forward progressMemory adressing/allocation/relocationProgram controlVirtual memoryVirtualization
The present invention employs three decoupled hardware mechanisms: read and write signatures, which summarize per-thread access sets; per-thread conflict summary tables, which identify the threads with which conflicts have occurred; and a lazy versioning mechanism, which maintains the speculative updates in the local cache and employs a thread-private buffer (in virtual memory) only in the rare event of an overflow. The conflict summary tables allow lazy conflict management to occur locally, with no global arbitration (they also support eager management). All three mechanisms are kept software-accessible, to enable virtualization and to support transactions of arbitrary length.
Owner:UNIV OF ROCHESTER OFFICE OF TECH TRANSFER
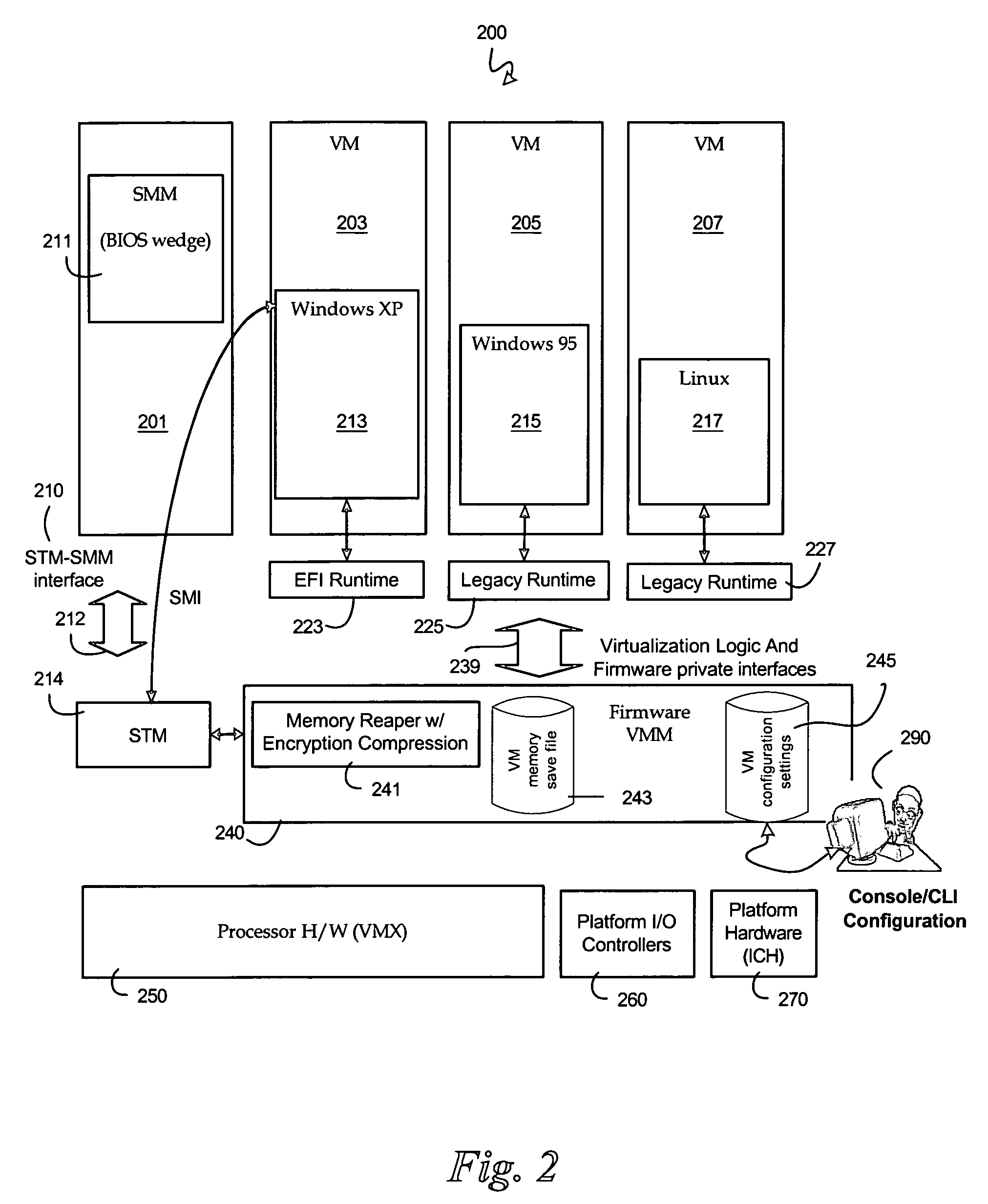
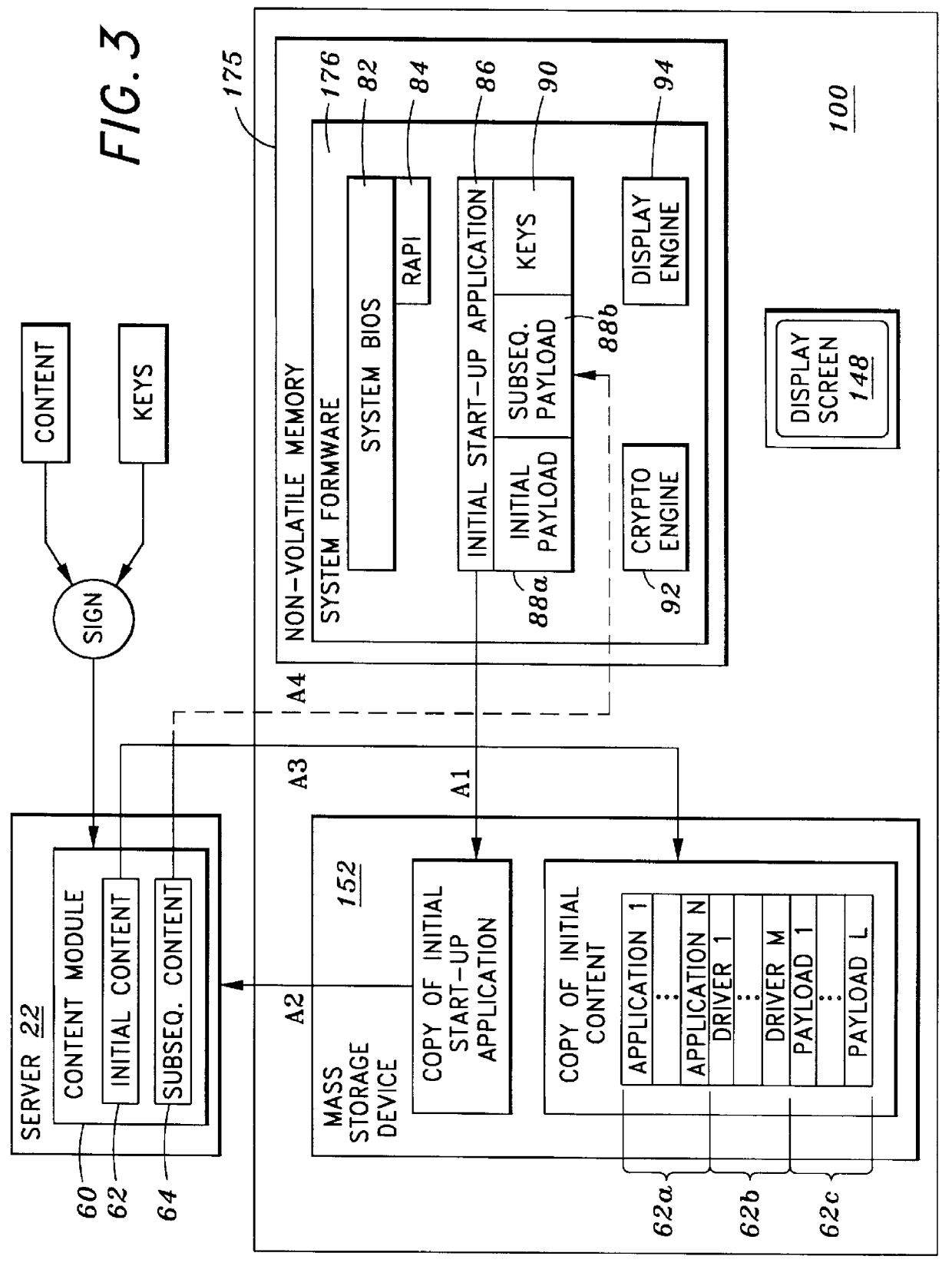
System and method for securely utilizing basic input and output system (BIOS) services
InactiveUS6148387AResource allocationDigital data processing detailsVirtual memorySoftware engineering
In accordance with one aspect of the current invention, the system comprises a memory for storing instruction sequences by which the processor-based system is processed, where the memory includes a physical memory and a virtual memory. The system also comprises a processor for executing the stored instruction sequences. The stored instruction sequences include process acts to cause the processor to: map a plurality of predetermined instruction sequences from the physical memory to the virtual memory, determine an offset to one of the plurality of predetermined instruction sequences in the virtual memory, receive an instruction to execute the one of the plurality of predetermined instruction sequences, transfer control to the one of the plurality of predetermined instruction sequences, and process the one of the plurality of predetermined instruction sequences from the virtual memory. In accordance with another aspect of the present invention, the system includes an access driver to generate a service request to utilize BIOS services such that the service request contains a service request signature created using a private key in a cryptographic key pair. The system also includes an interface to verify the service request signature using a public key in the cryptographic key pair to ensure integrity of the service request.
Owner:KINGLITE HLDG INC
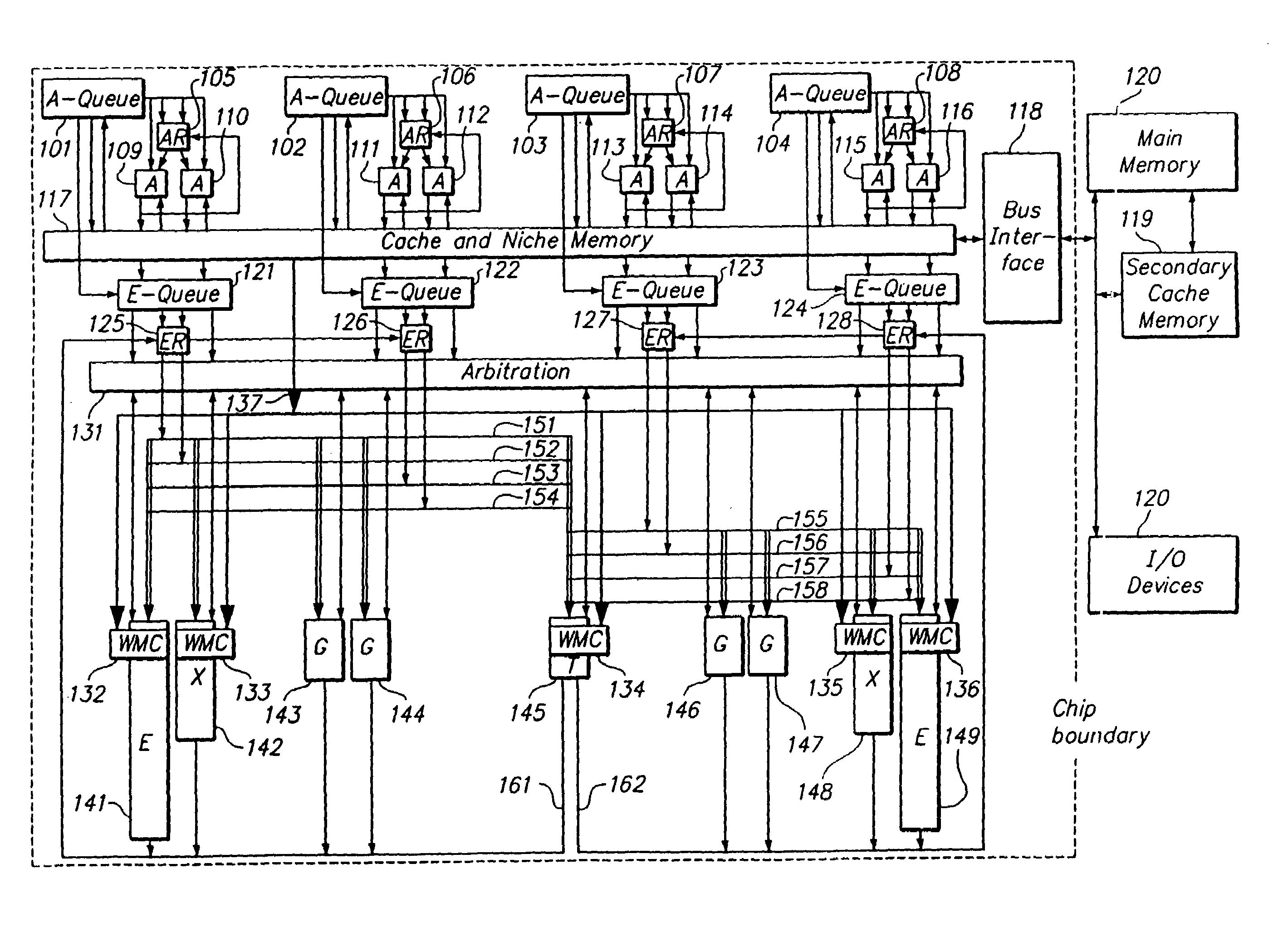
Programmable processor with group floating-point operations
InactiveUS7216217B2Reduce in quantityImprove performanceInstruction analysisMemory adressing/allocation/relocationComputer architectureEngineering
A programmable processor that comprises a general purpose processor architecture, capable of operation independent of another host processor, having a virtual memory addressing unit, an instruction path and a data path; an external interface; a cache operable to retain data communicated between the external interface and the data path; at least one register file configurable to receive and store data from the data path and to communicate the stored data to the data path; and a multi-precision execution unit coupled to the data path. The multi-precision execution unit is configurable to dynamically partition data received from the data path to account for an elemental width of the data and is capable of performing group floating-point operations on multiple operands in partitioned fields of operand registers and returning catenated results. In other embodiments the multi-precision execution unit is additionally configurable to execute group integer and / or group data handling operations.
Owner:MICROUNITY
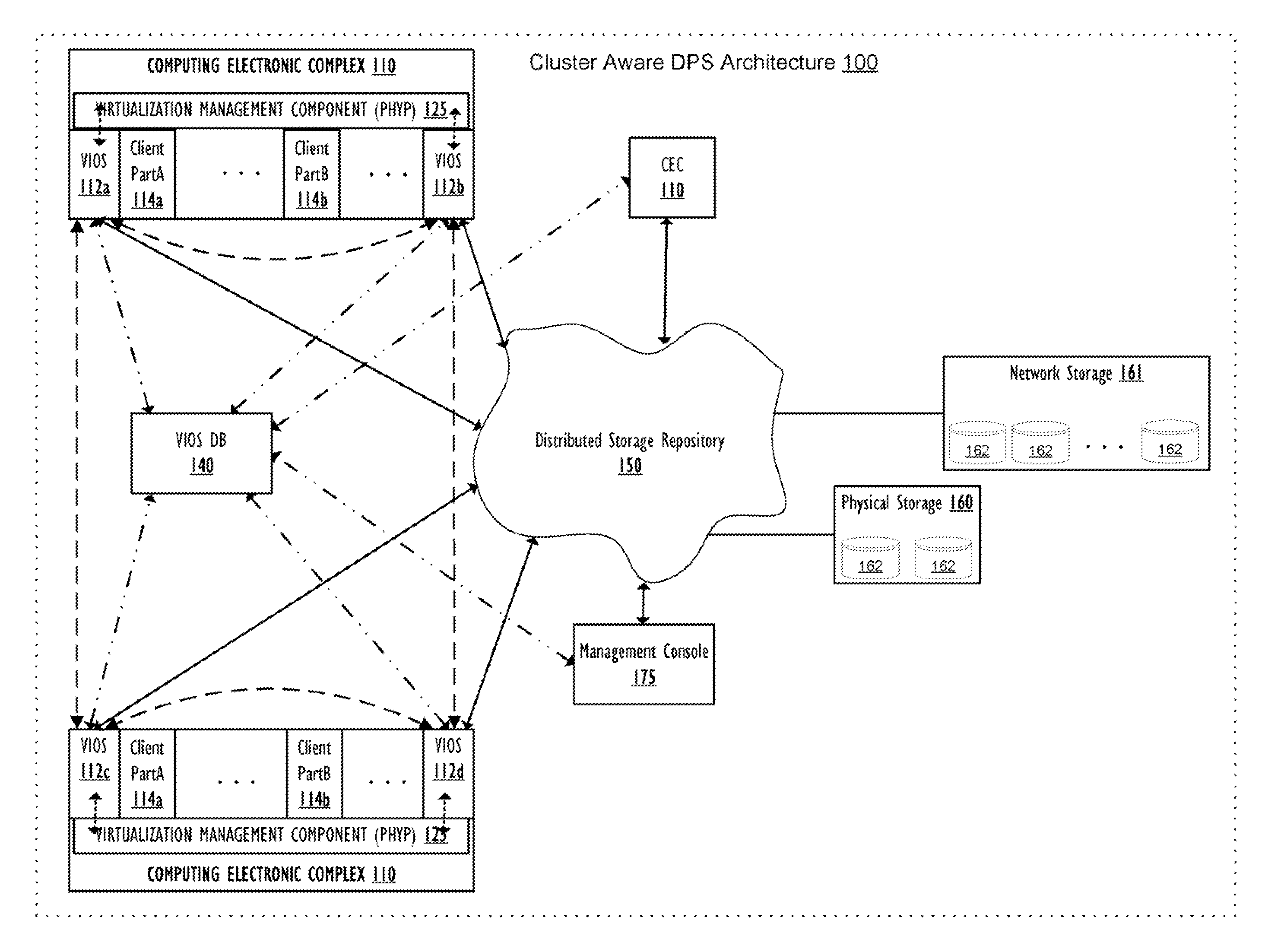
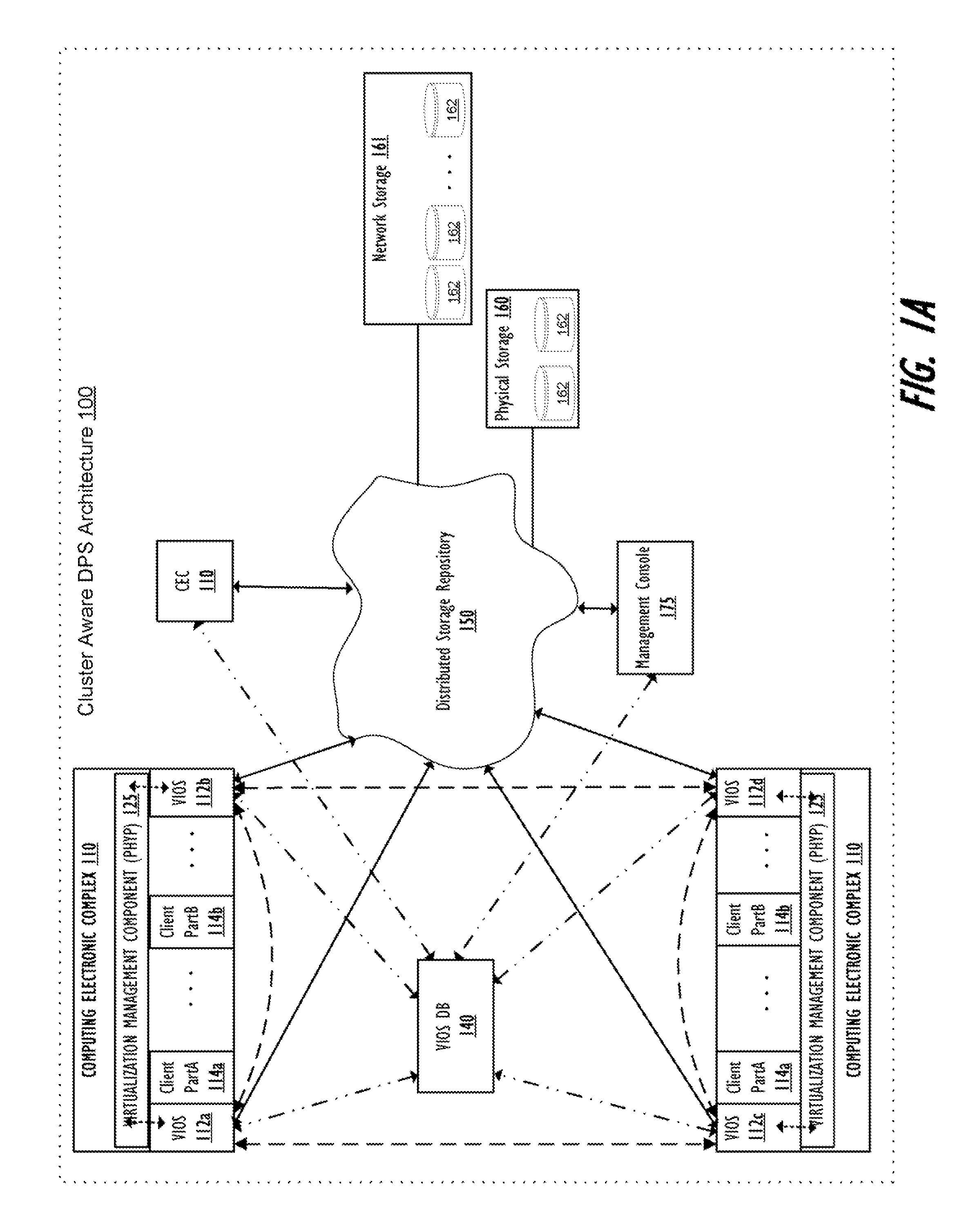
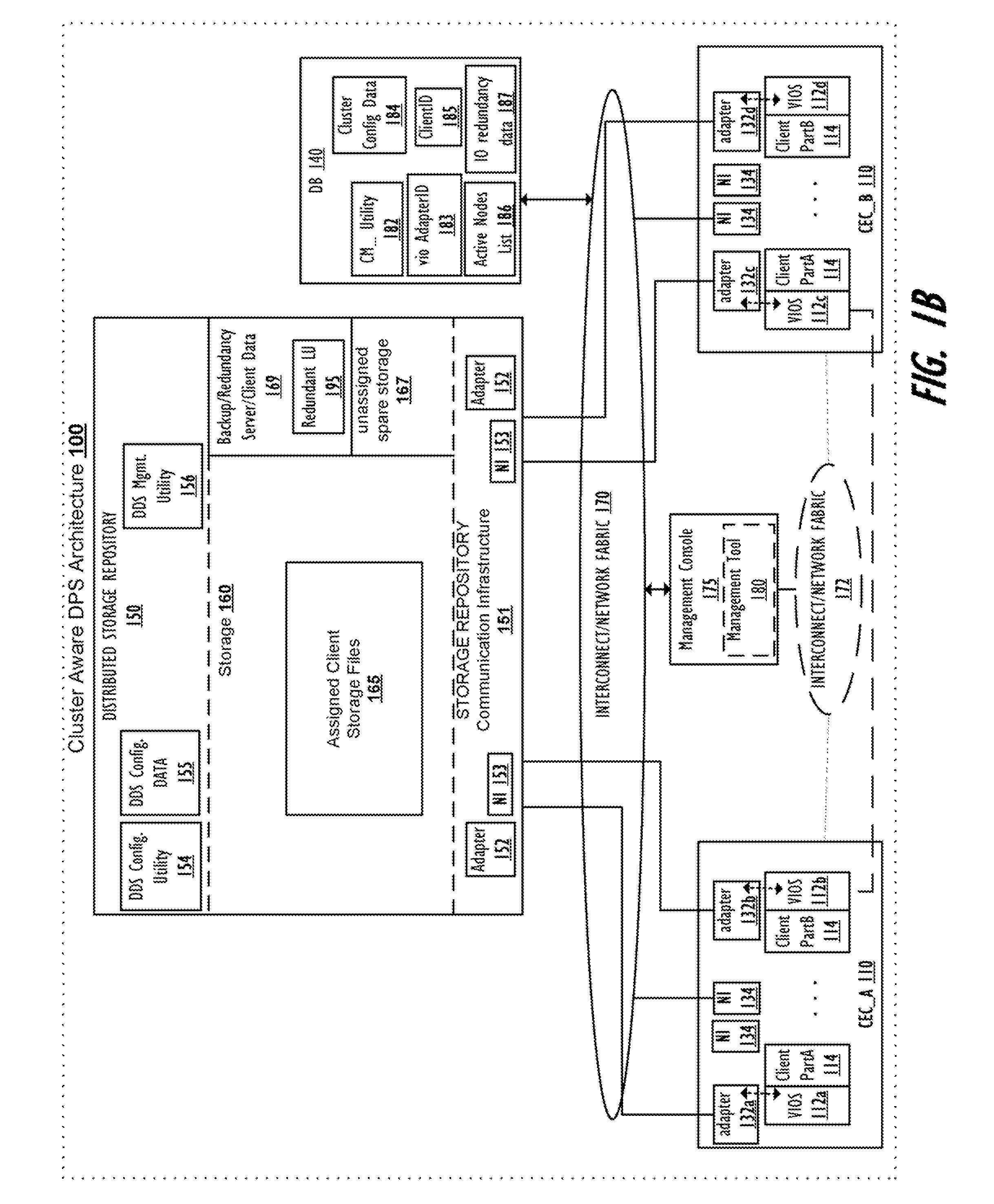
Supporting Virtual Input/Output (I/O) Server (VIOS) Active Memory Sharing in a Cluster Environment
InactiveUS20120110275A1Promote migrationMemory architecture accessing/allocationMemory adressing/allocation/relocationVirtual memoryActive memory
A method, system, and computer program product provide a shared virtual memory space via a cluster-aware virtual input / output (I / O) server (VIOS). The VIOS receives a paging file request from a first LPAR and thin-provisions a logical unit (LU) within the virtual memory space as a shared paging file of the same storage amount as the minimum required capacity. The VIOS also autonomously maintains a logical redundancy LU (redundant LU) as a real-time copy of the provisioned / allocated LU, where the redundant LU is a dynamic copy of the allocated LU that is autonomously updated responsive to any changes within the allocated LU. Responsive to a second VIOS attempting to read a LU currently utilized by a first VIOS, the read request is autonomously redirected to the logical redundancy LU. The redundant LU can be utilized to facilitate migration of a client LPAR to a different computing electronic complex (CEC).
Owner:IBM CORP
Creating secure process objects
InactiveUS20060259487A1Precise processingReduce in quantityDigital data processing detailsAnalogue secracy/subscription systemsVirtual memoryInit
A secure process may be created which does not allow code to be injected into it, does not allow modification of its memory or inspection of its memory. The resources protected in a secure process include all the internal state and threads running in the secure process. Once a secure process is created, the secure process is protected from access by non-secure processes. Process creation occurs atomically in kernel mode. Creating the infrastructure of a process in kernel mode enables security features to be applied that are difficult or impossible to apply in user mode. By moving setup actions previously occurring in user mode (such as creating the initial thread, allocating the stack, initialization of the parameter block, environment block and context record) into kernel mode, the need of the caller for full access rights to the created process is removed. Instead, enough state is passed from the caller to the kernel with the first system call so that the kernel is able to perform the actions previously performed using a number of calls back and forth between caller and kernel. When the kernel returns the handle to the set-up process, some of the access rights accompanying the handle are not returned. Specifically, those access rights that enable the caller to inject threads, read / write virtual memory, and interrogate or modify state of the threads of the process are not returned to the caller.
Owner:MICROSOFT TECH LICENSING LLC
Bypassing guest page table walk for shadow page table entries not present in guest page table
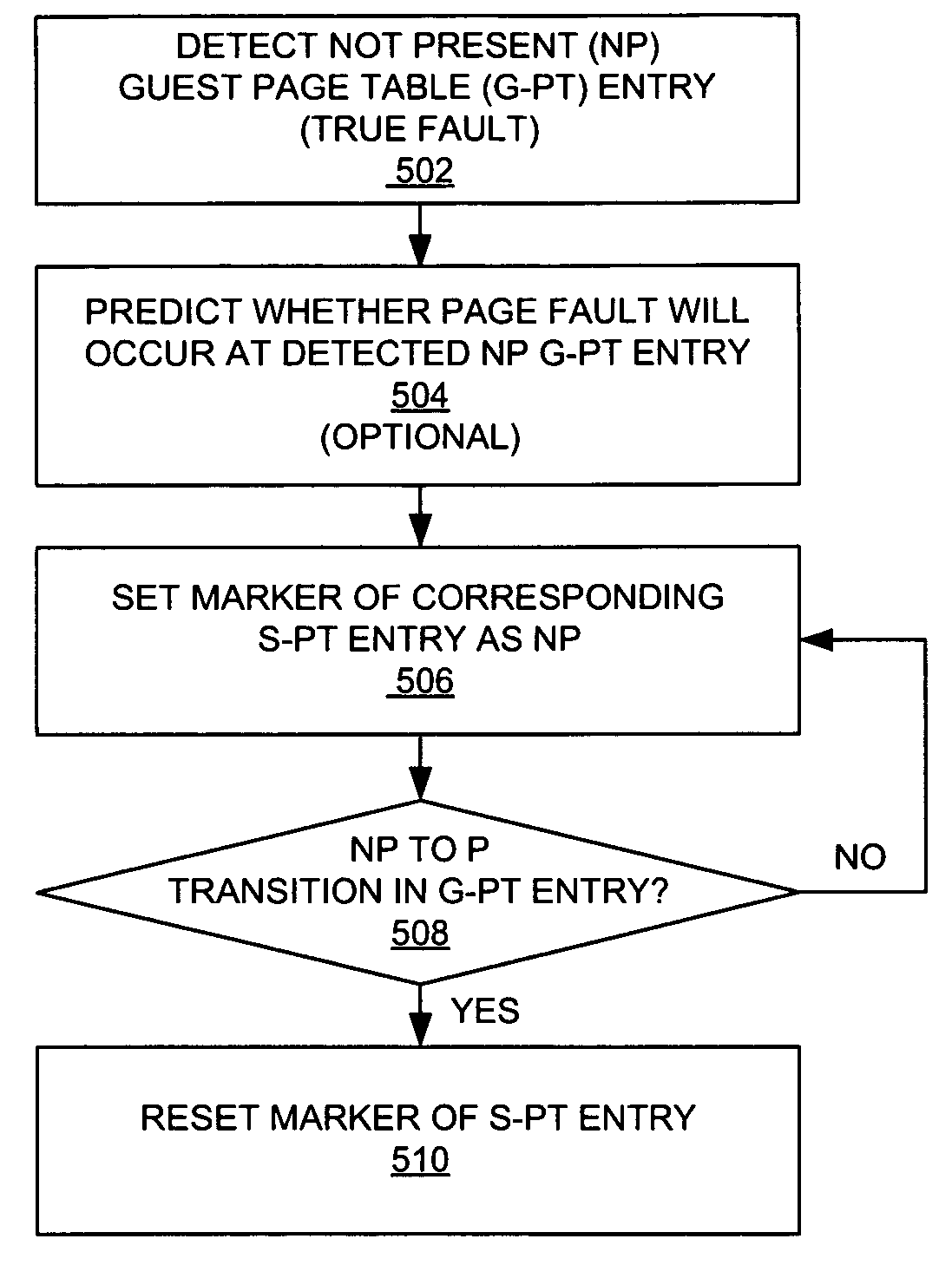
ActiveUS8015388B1Less of computational burdenReduce the burden onMemory architecture accessing/allocationMemory systemsVirtual memoryPage table
A method and system are provided that does not perform a page walk on the guest page tables if the shadow page table entry corresponding to the guest virtual address for accessing the virtual memory indicates that a corresponding mapping from the guest virtual address to a guest physical address is not present in the guest page tables. A marker or indicator is stored in the shadow page table entries to indicate that a mapping corresponding to the guest virtual address of the shadow page table entry is not present in the guest page table.
Owner:VMWARE INC
Method for monitoring access to virtual memory pages
InactiveUS20060036830A1Internal/peripheral component protectionMemory systemsVirtual memoryOperational system
Various embodiments of the present invention are directed to efficient methods for virtual-machine monitors to detect, at run time, initial attempts by guest operating systems and other higher-level software to access or execute particular instructions or values corresponding to the particular instructions, that, when accessed for execution, need to be emulated by a virtual-machine monitor, rather than directly accessed by guest operating systems. In certain embodiments of the present invention, the virtual-machine monitor assigns various guest-operating-system-code-containing memory pages to one of a small number of protection-key domains. By doing so, the virtual-machine monitor can arrange for any initial access to the memory pages assigned to the protection-key domains to generate a key-permission fault, after which the key-permission-fault handler of the virtual-machine monitor is invoked to arrange for subsequent, efficient access or emulation of access to the protected pages. In alternative embodiments, protection domains can be implemented by using page-level access rights or translation-lookaside-buffer entry fields.
Owner:HEWLETT PACKARD DEV CO LP
Method and apparatus for protecting translated code in a virtual machine
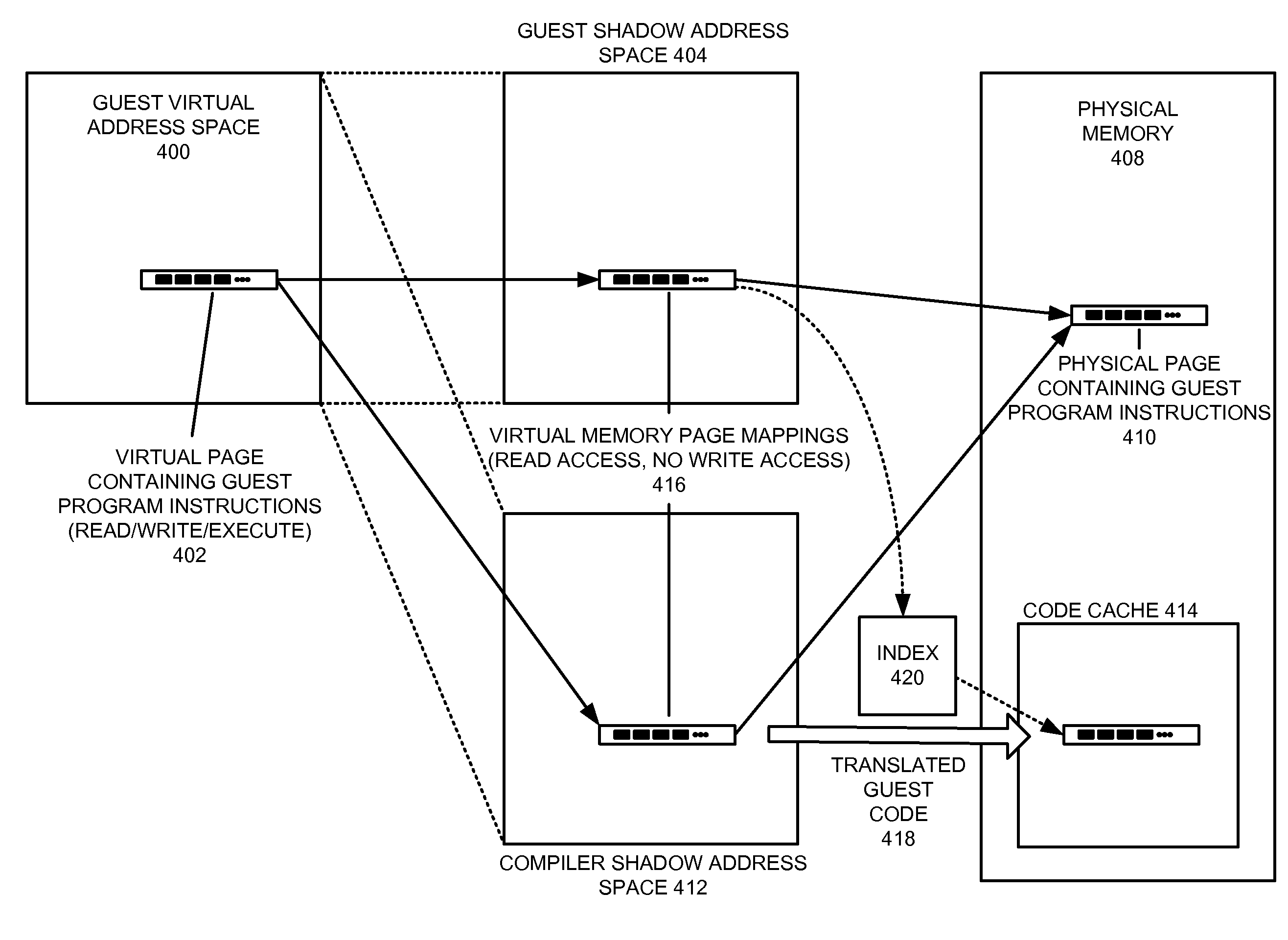
ActiveUS8799879B2Reduced overhead and checkSoftware simulation/interpretation/emulationMemory systemsDynamic compilationVirtual memory
One embodiment provides a system that protects translated guest program code in a virtual machine that supports self-modifying program code. While executing a guest program in the virtual machine, the system uses a guest shadow page table associated with the guest program and the virtual machine to map a virtual memory page for the guest program to a physical memory page on the host computing device. The system then uses a dynamic compiler to translate guest program code in the virtual memory page into translated guest program code (e.g., native program instructions for the computing device). During compilation, the dynamic compiler stores in a compiler shadow page table and the guest shadow page table information that tracks whether the guest program code in the virtual memory page has been translated. The compiler subsequently uses the information stored in the guest shadow page table to detect attempts to modify the contents of the virtual memory page. Upon detecting such an attempt, the system invalidates the translated guest program code associated with the virtual memory page.
Owner:SUN MICROSYSTEMS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com