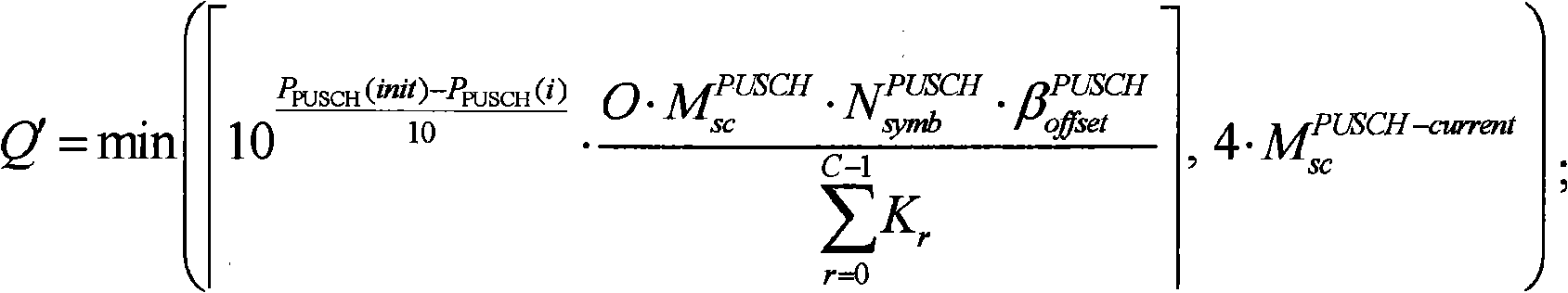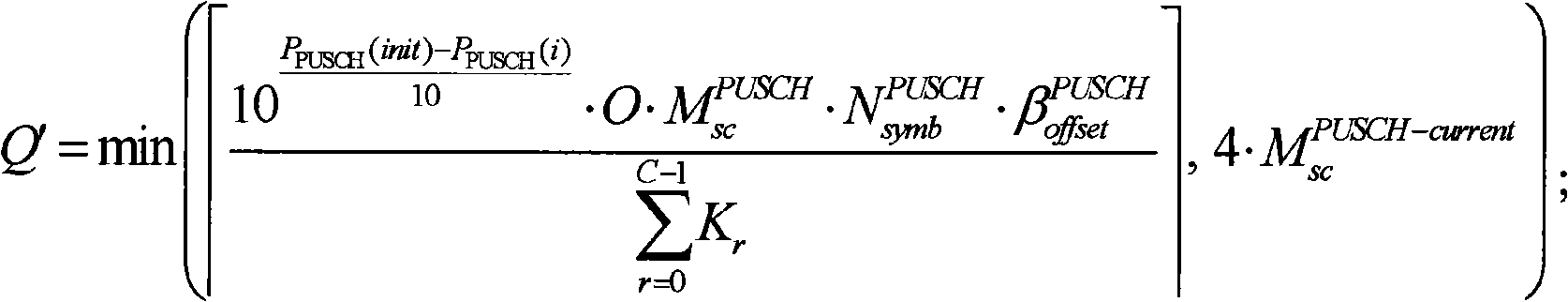Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1029 results about "Init" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
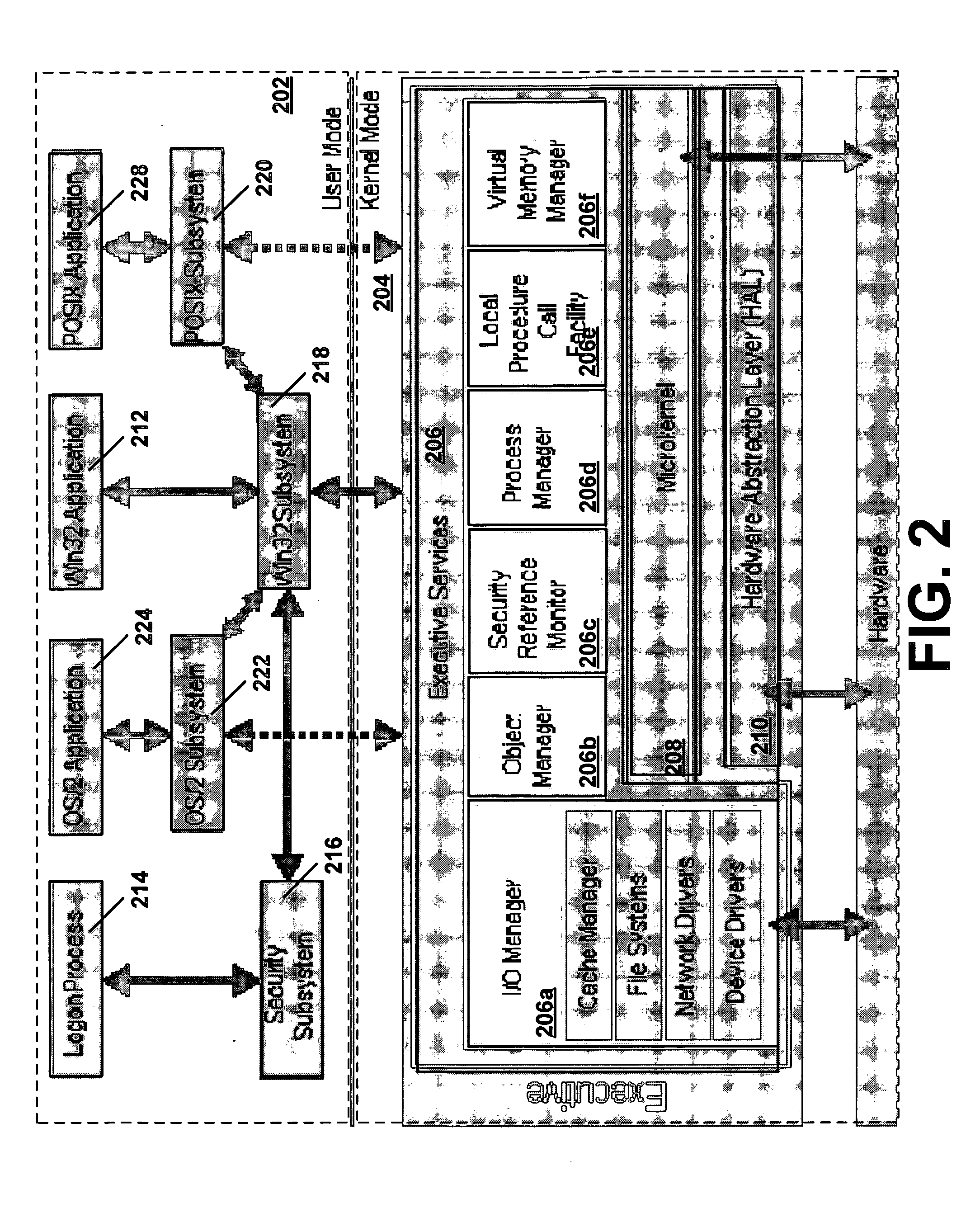
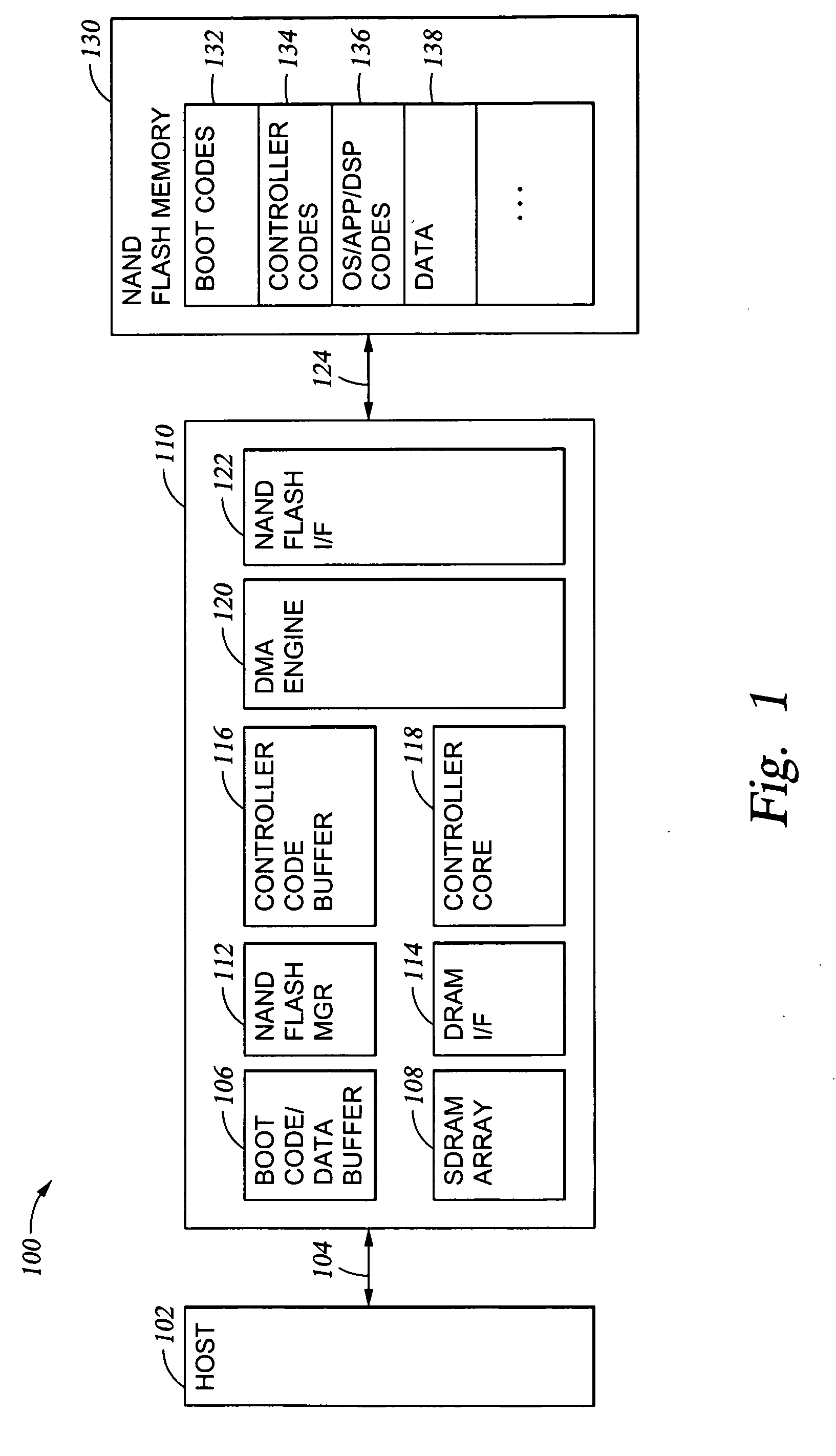
In Unix-based computer operating systems, init (short for initialization) is the first process started during booting of the computer system. Init is a daemon process that continues running until the system is shut down. It is the direct or indirect ancestor of all other processes and automatically adopts all orphaned processes. Init is started by the kernel during the booting process; a kernel panic will occur if the kernel is unable to start it. Init is typically assigned process identifier 1.
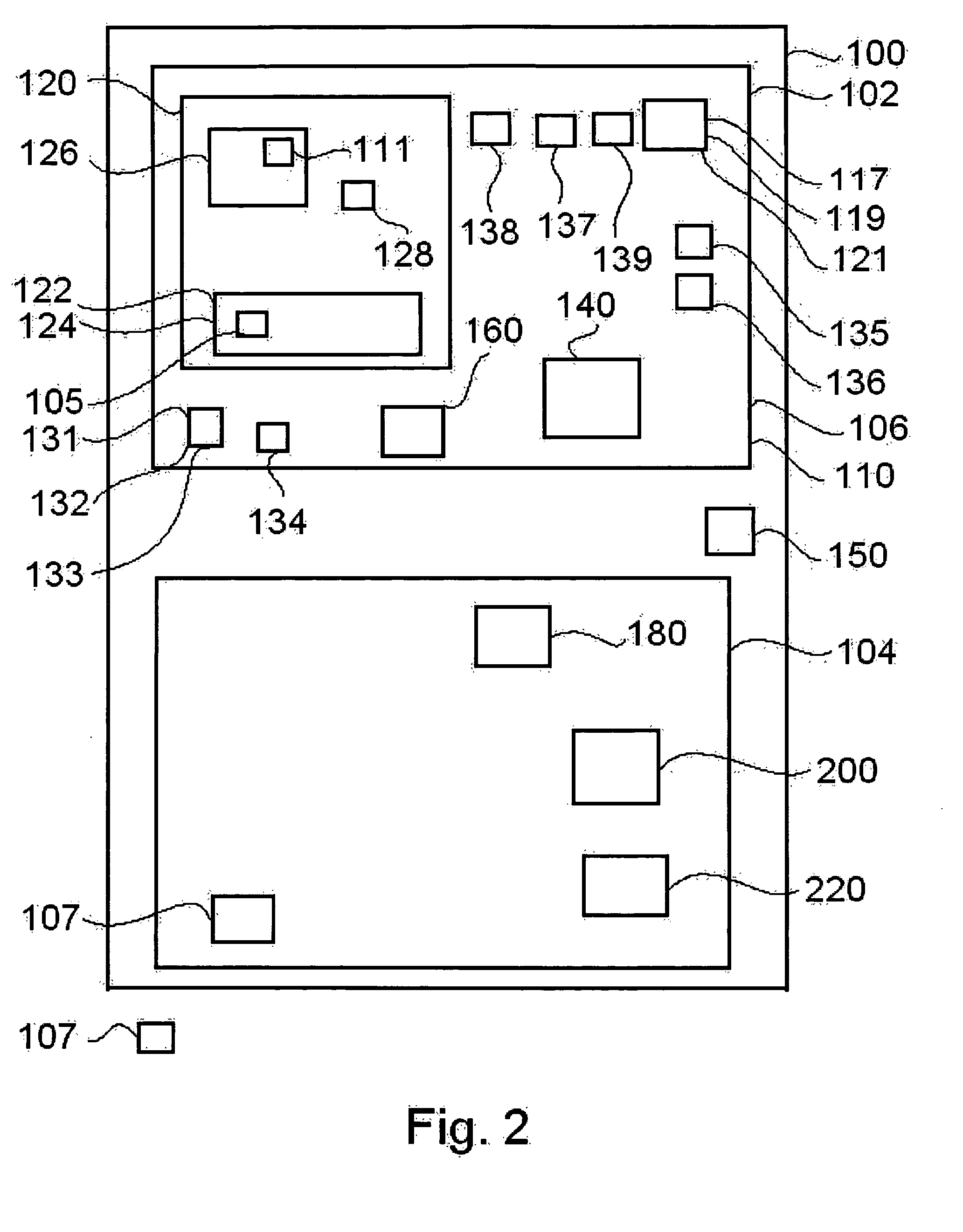
Wireless operation of a game device
ActiveUS20060046849A1Improve securitySuitable for processingApparatus for meter-controlled dispensingVideo gamesRemote controlInit
A gaming device which can be operated by wireless signals provided by a remote control unit or device after an initialization process. The initialization process insures that the initialized gaming device accepts signals solely from the initialized remote control unit and that other players are prevented from operating the gaming device using a different remote control unit. The wireless signals contain gaming commands for play of a primary wagering game as well as player identification and / or player tracking information.
Owner:IGT
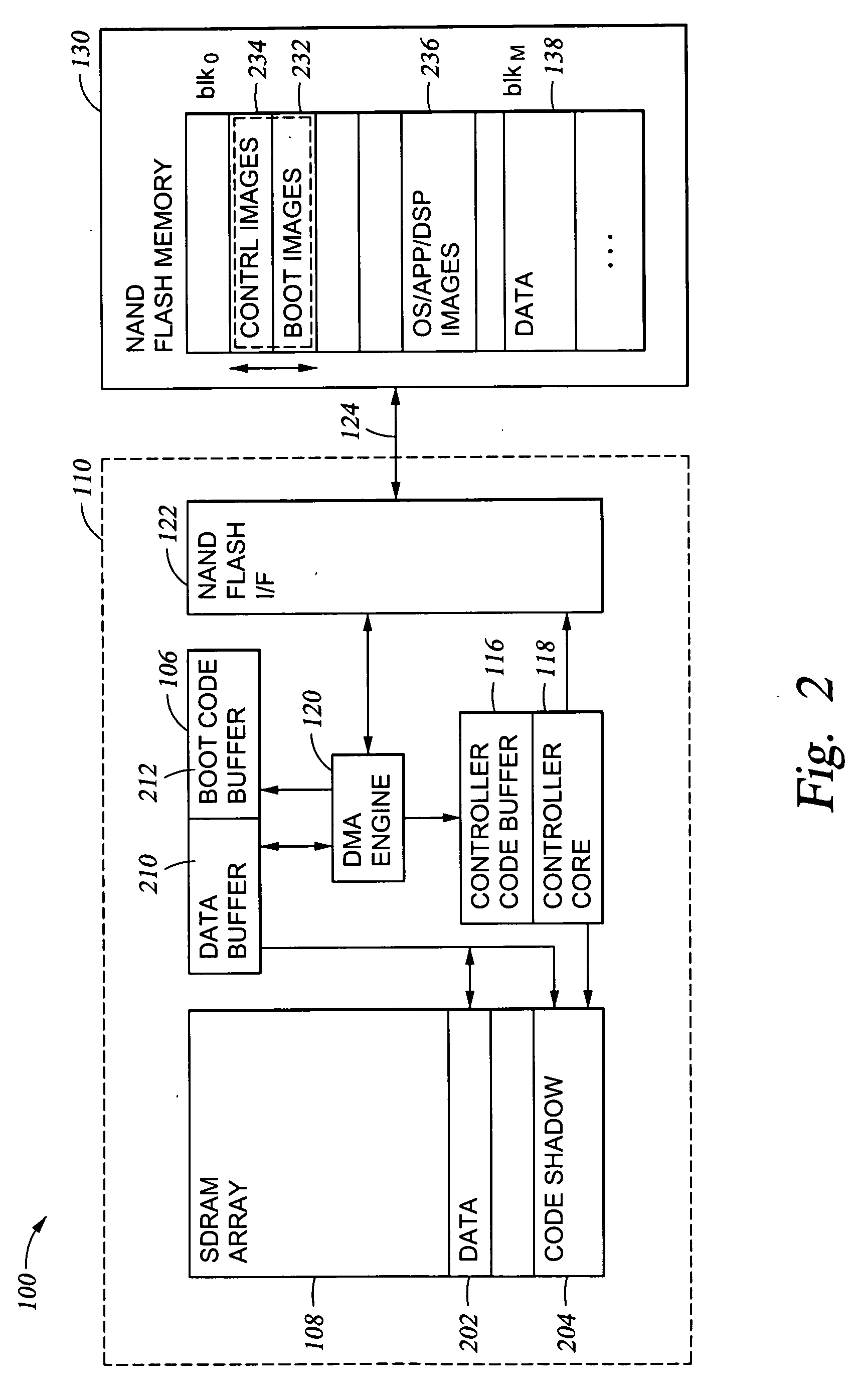
Operating system boot from network location
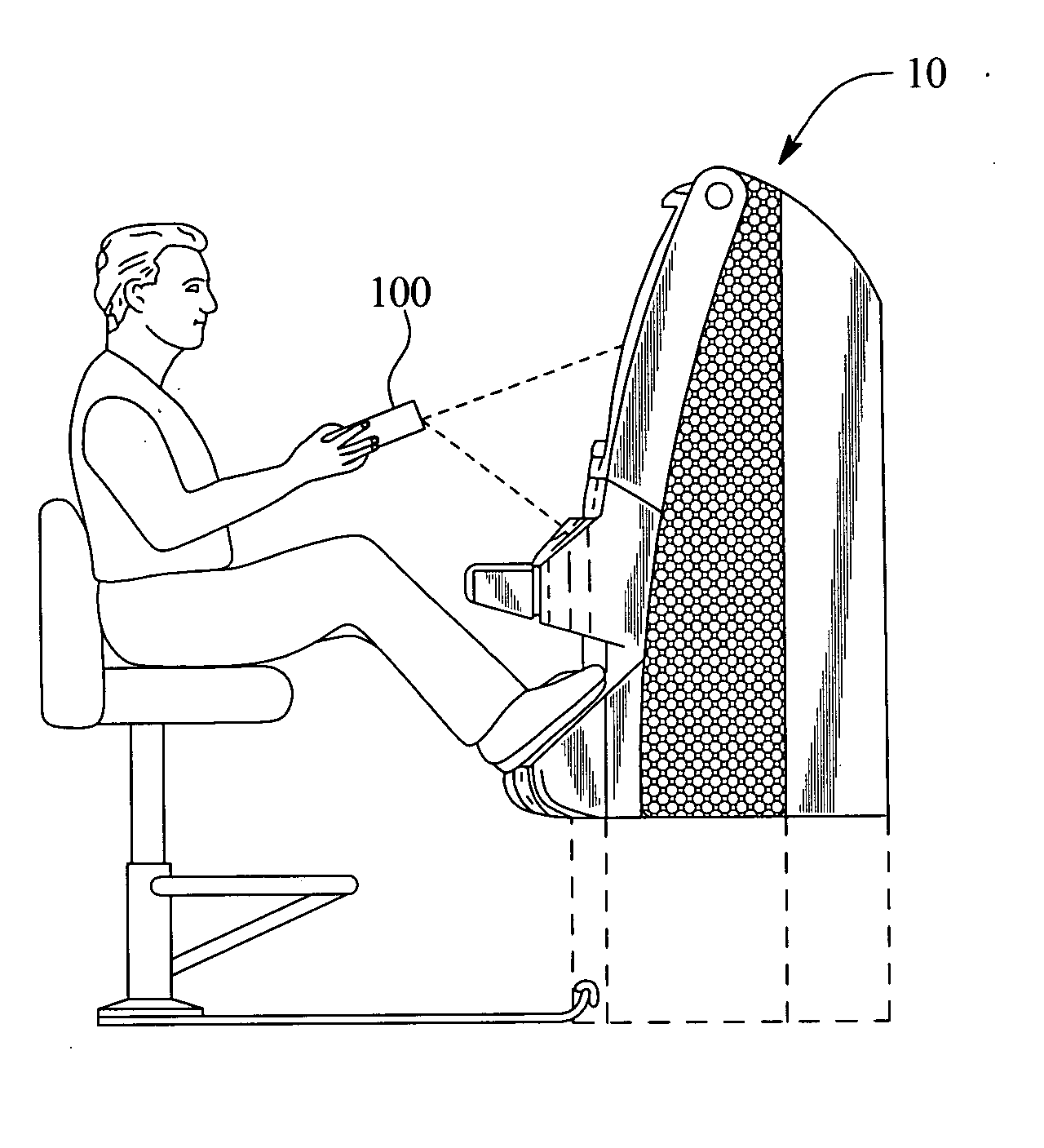
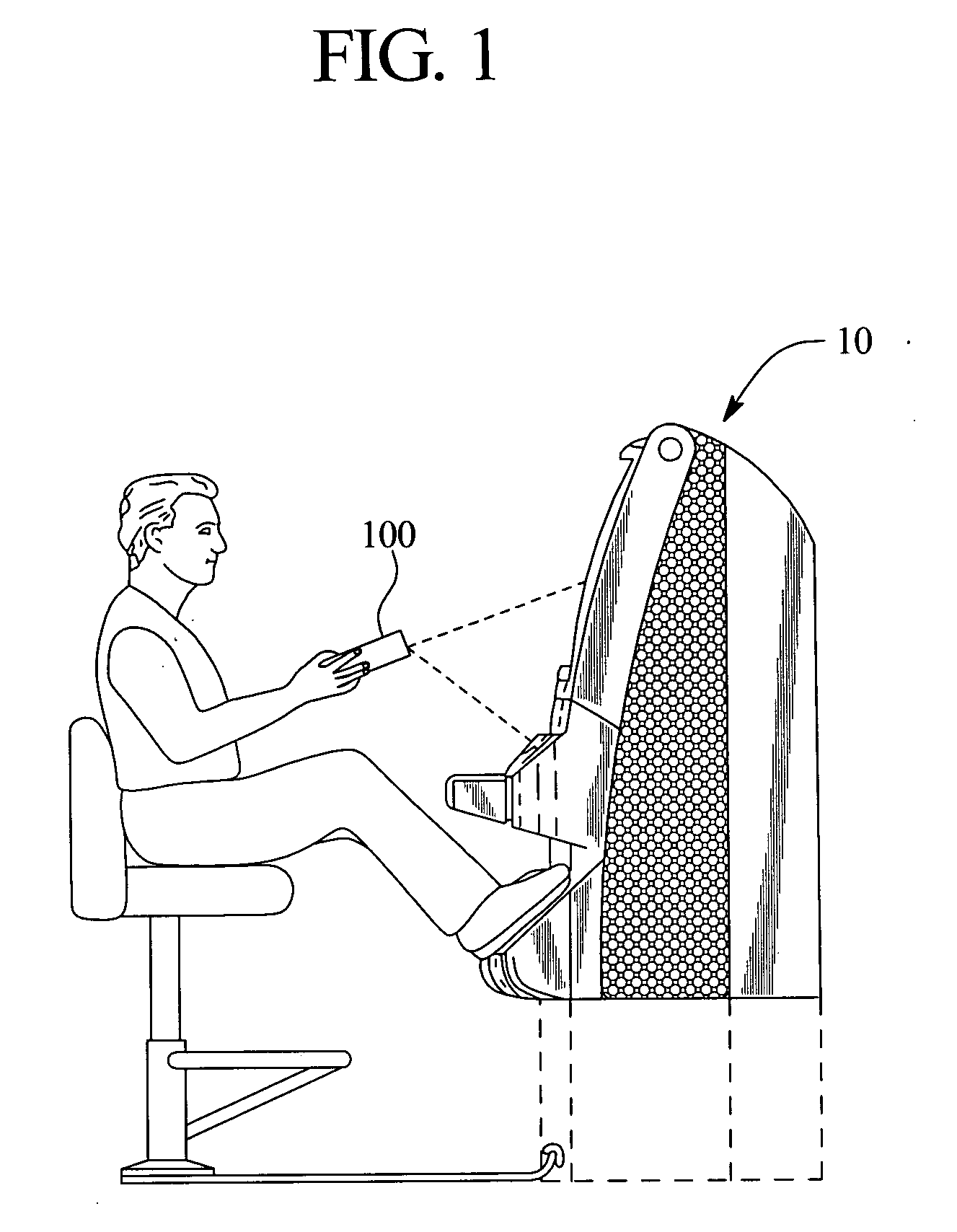
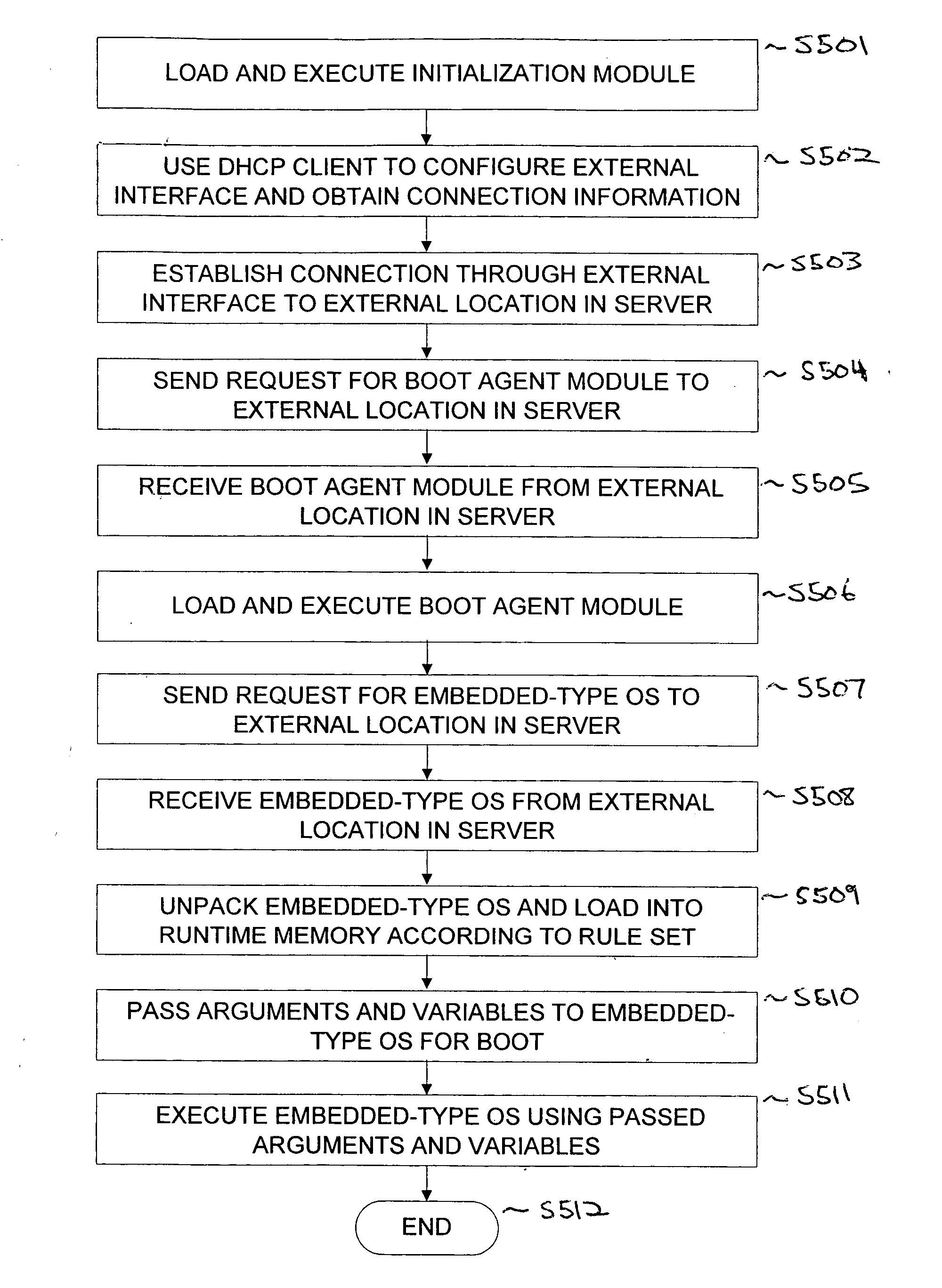
InactiveUS20060242395A1Easy to manageEasy to storeDigital computer detailsMemory systemsOperational systemInit
The present invention provides a system for booting an intelligent device with an embedded-type operating system obtained through an external interface disposed in the intelligent device, wherein the system includes an initialization module stored in a read-only memory provided in the intelligent device, the initialization module being executed in a processor disposed in the intelligent device and connecting to an external location through the external interface, and a server having a memory media which stores a boot agent module and an embedded-type operating system at the external location, the server sending the boot agent module to the intelligent device through the connection in response to a request from the initialization module, wherein the boot agent module is loaded into a runtime memory in the intelligent device and executed by the processor, the boot agent module then retrieving an embedded-type operating system image from the external location in the sever, whereupon the embedded-type operating system image is loaded into the runtime memory and executed by the processor.
Owner:WYSE TECH LLC
Consistency methods and systems
InactiveUS20070214194A1Maintain data consistencyError detection/correctionSpecial data processing applicationsTimestampDistributed data store
Embodiments of the present invention are directed to methods for maintaining data consistency of data blocks during migration or reconfiguration of a current configuration within a distributed data-storage system to a new configuration. In one embodiment of the present invention, the current configuration is first determined to be reconfigured. The new configuration is then initialized, and data blocks are copied from the current configuration to the new configuration. Then, the configuration states maintained by component data-storage systems that store data blocks of the current and new configurations are synchronized. Finally, the current configuration is deallocated. In a second embodiment of the present invention, a current configuration is determined to be reconfigured, and, while carrying out continuing READ and WRITE operations directed to data blocks of the current configuration in a data-consistent manner, the new configuration is initialized, data blocks are copied from the current configuration to the new configuration, and the timestamp and data states for the data blocks of the current and new configurations are synchronized.
Owner:HEWLETT PACKARD DEV CO LP
Method and system for document draft reminder based on inactivity
The present invention provides a flexible system and method for notifying a user when the user has an open document which is inactive over a predetermined period of inactivity defined by the user. The user may be able to set a desirable period of inactivity for each application at the time of the system initialization and change the desirable period of inactivity for an inactive document after the user receives notification.
Owner:IBM CORP
System and method for establishing and/or maintaining a data session across packet data networks
InactiveUS20050043026A1Assess restrictionData switching by path configurationCommunications systemService provision
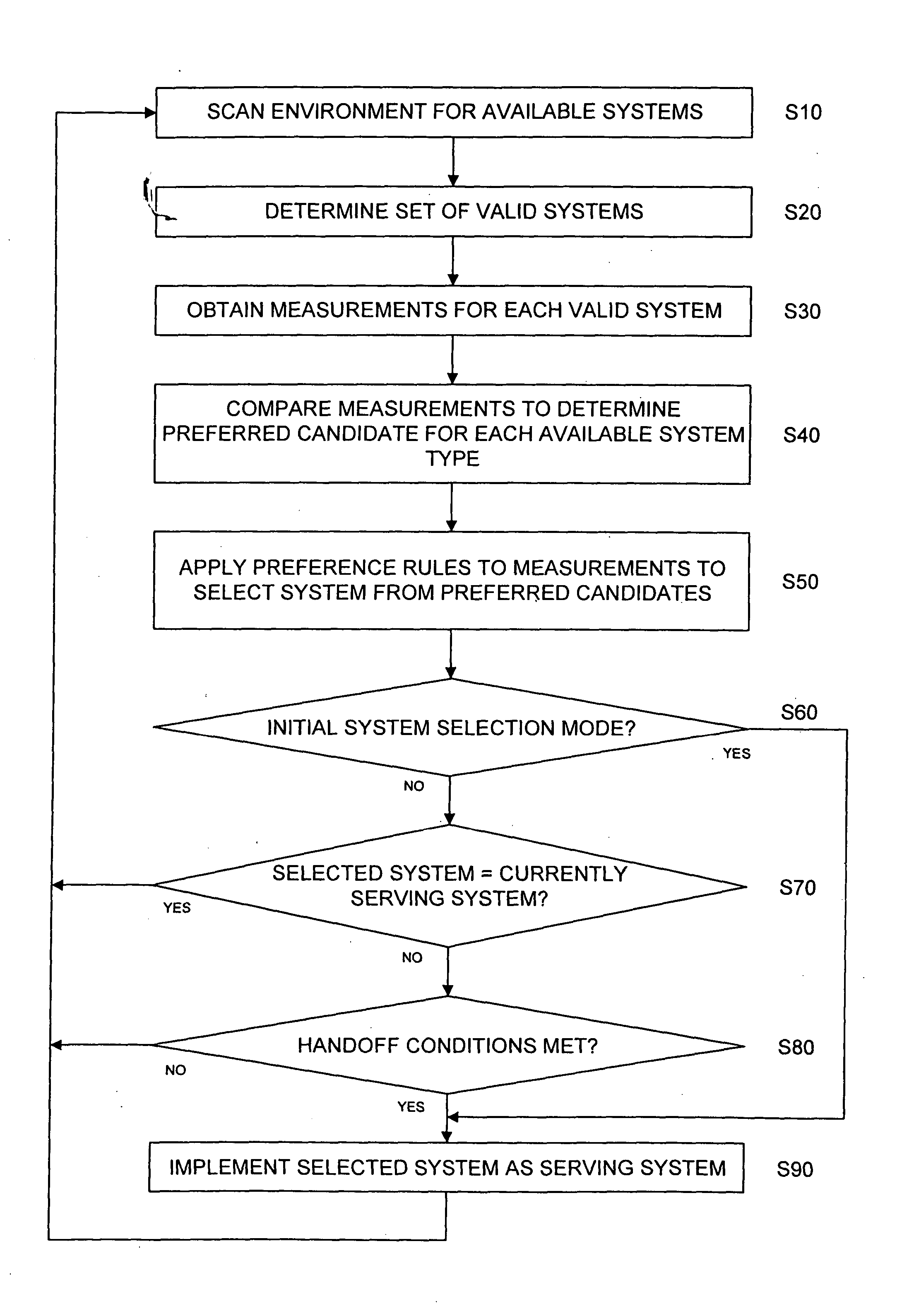
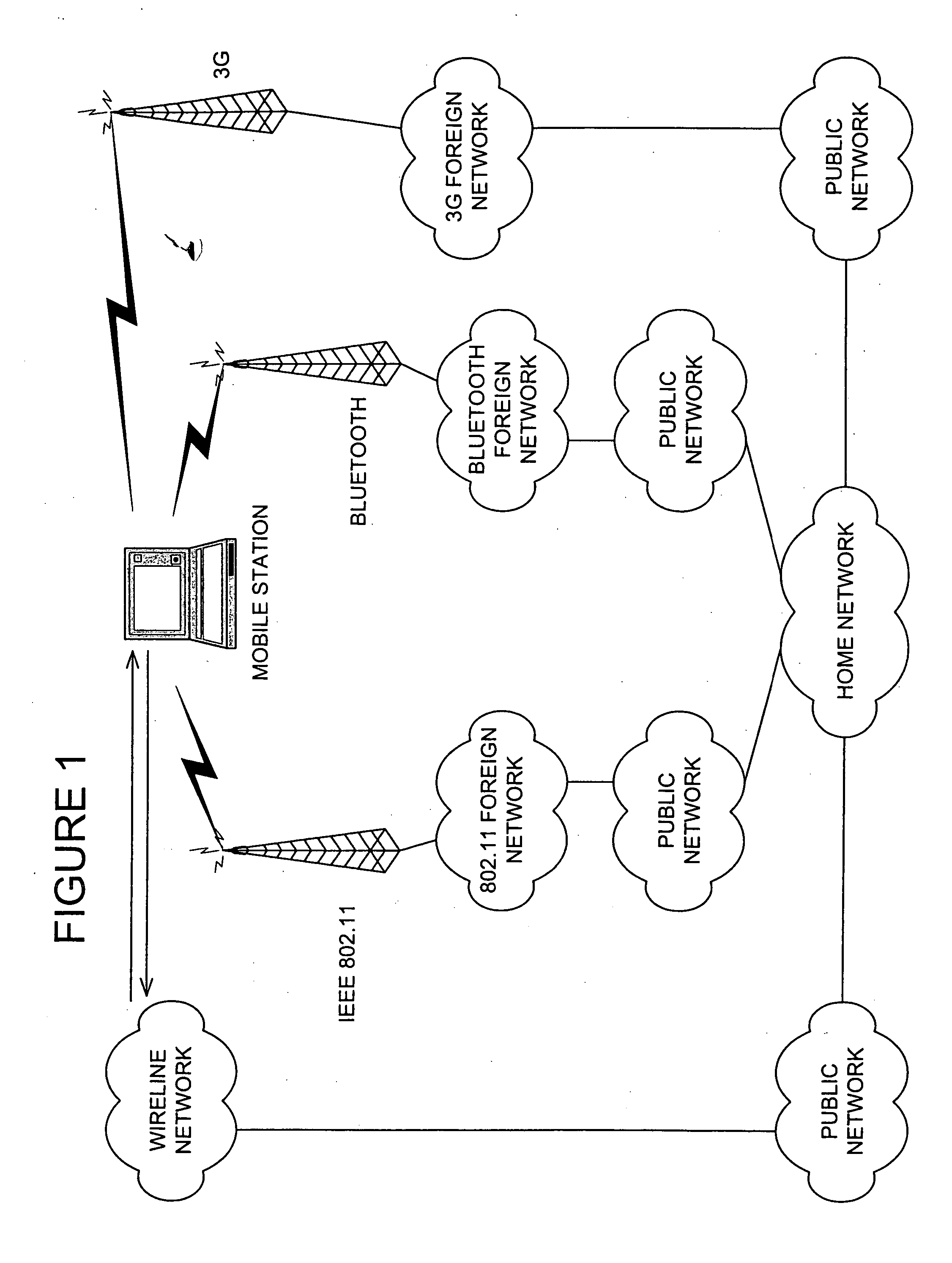
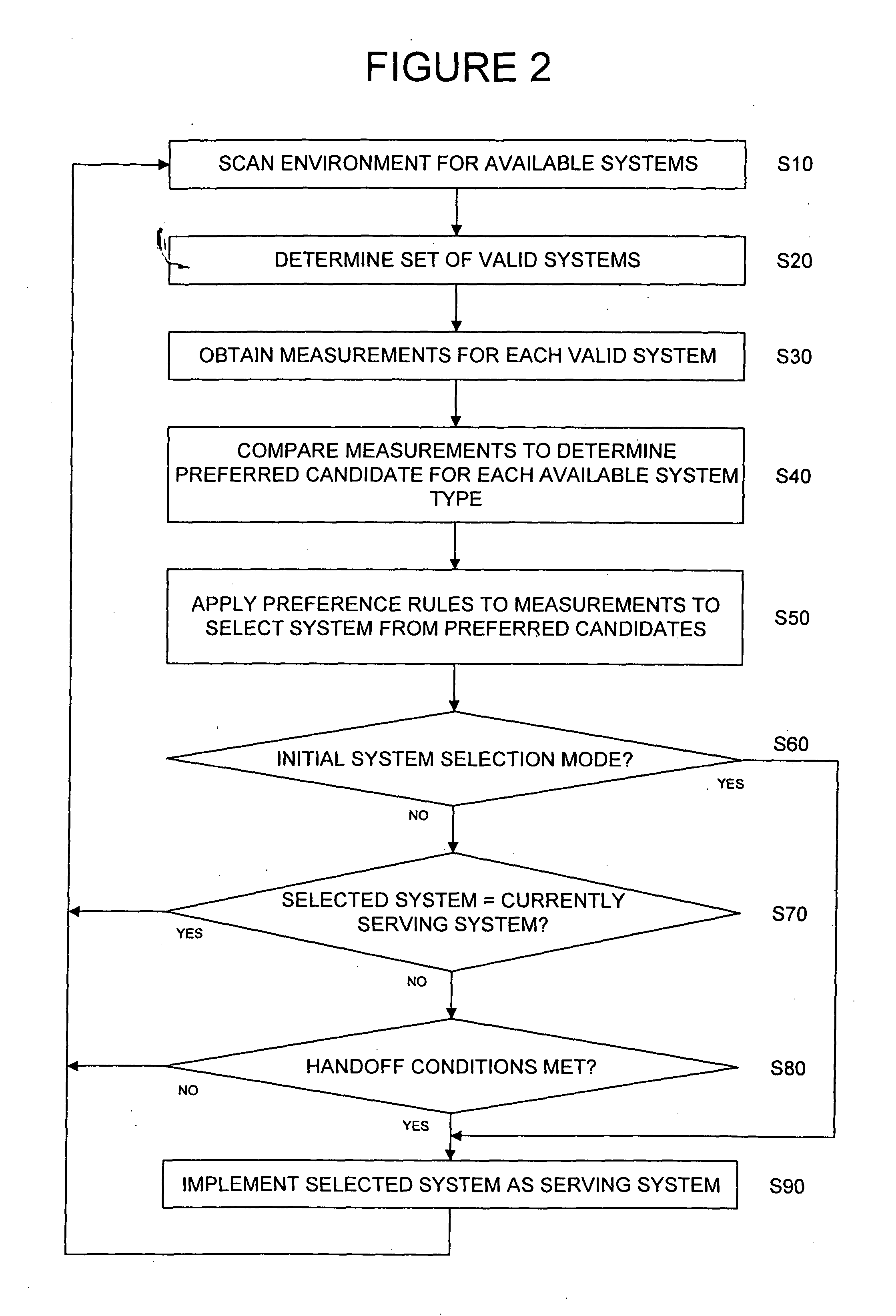
A communication system selection algorithm (SSA) implemented by a mobile station chooses between available systems to select a system to serve the mobile station. During initialization, the SSA causes the mobile station to scan the environment and compare available communication systems to determine the best system to provide service. After an initial system is chosen, the SSA causes the mobile station to continuously, or at discrete time intervals, scan the environment for available systems, thus allowing for a seamless switch to an available system whenever a handoff is desired. The SSA chooses the best available system based on conditions such as bit rate and cost of each available system and applying preference rules defined by a service provider and / or user of the mobile station.
Owner:LUCENT TECH INC
Device, method and system for authorizing transactions
A system, device, and method for authorizing transactions of a plurality of applications. The system comprises a plurality of application servers operable to authorize transactions of applications and a plurality of user devices. Each transaction authorization is dependent upon receipt, by the authorizing server, of a transmitted code verified by the server as being an appropriate transaction code for the selected application. Each user device is operable to verify the identity of a user by comparing real-time biometric input from the user with data derived from biometric input provided by the user during device initialization. Each user device is further operable to select an application from among a plurality of applications and to emit a non-repeating non-guessable transaction code appropriate for the selected application. Emission of the transaction code is dependent upon biometric verification, by the user device, of the user's identity.
Owner:HOFI EYAL
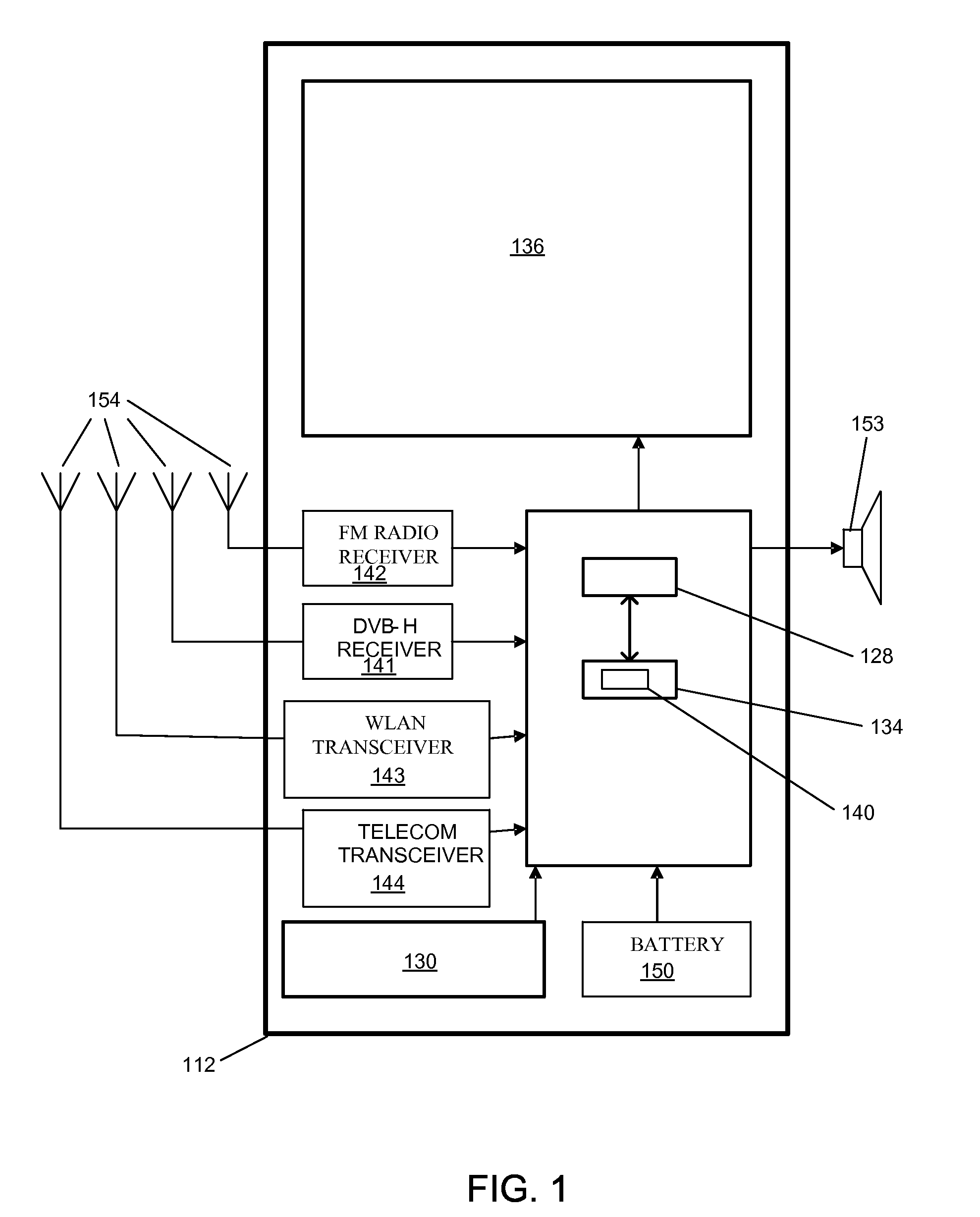
Language for performing high level actions using hardware registers
InactiveUS20050060525A1Easy to useDigital computer detailsProgram loading/initiatingComputer hardwareHuman language
A system and method that utilizes a common hardware register pseudo-language are disclosed. The present invention employs a common platform to specify hardware functionality and to execute hardware action(s). Hardware actions can be effectuated by performing a series of instructions, which comprise hardware register primitives and resources utilized by the primitives. The hardware register primitives are operations defined according to the common hardware register pseudo-language. The series of instructions can be loaded prior to boot or during initialization.
Owner:MICROSOFT TECH LICENSING LLC
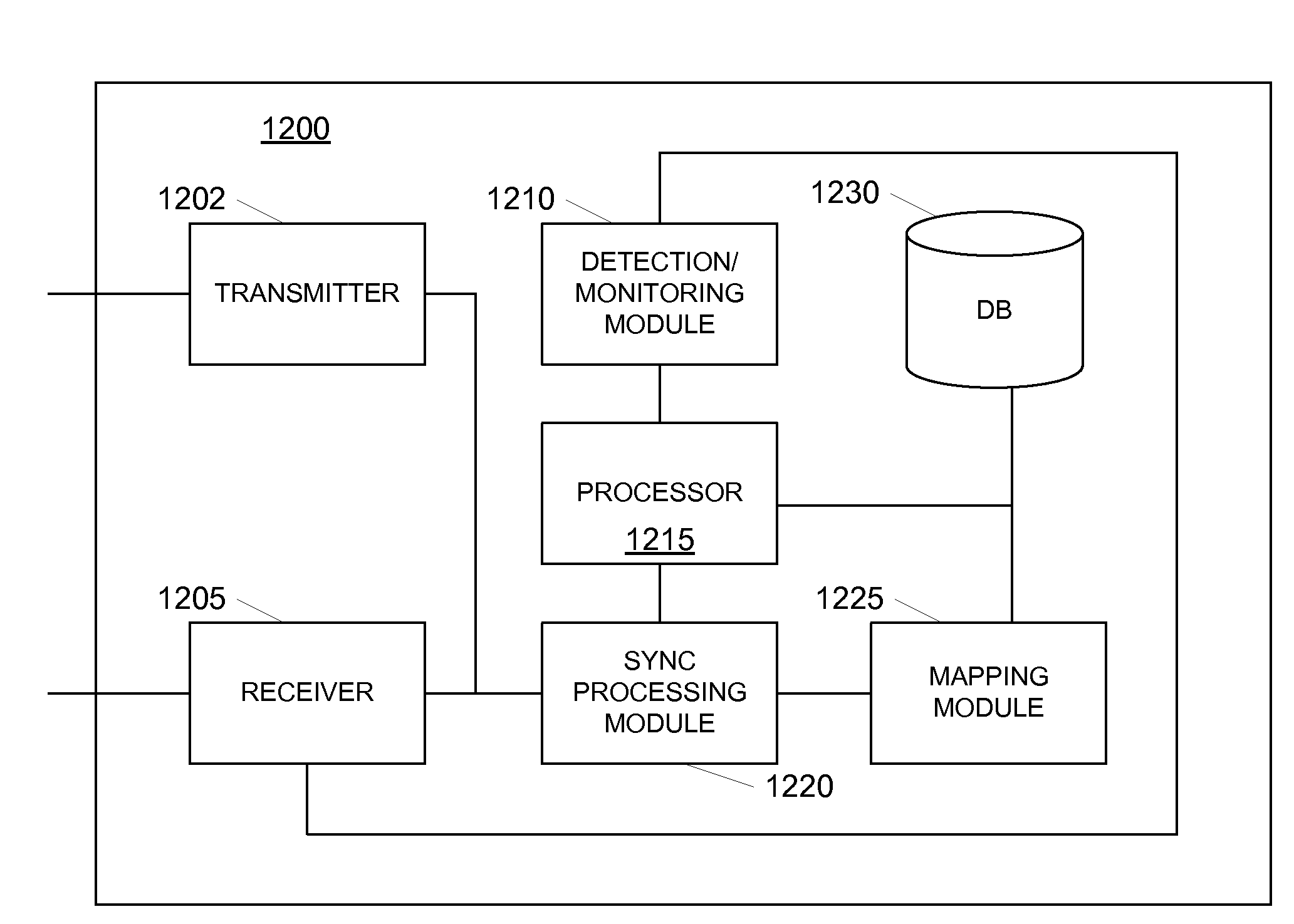
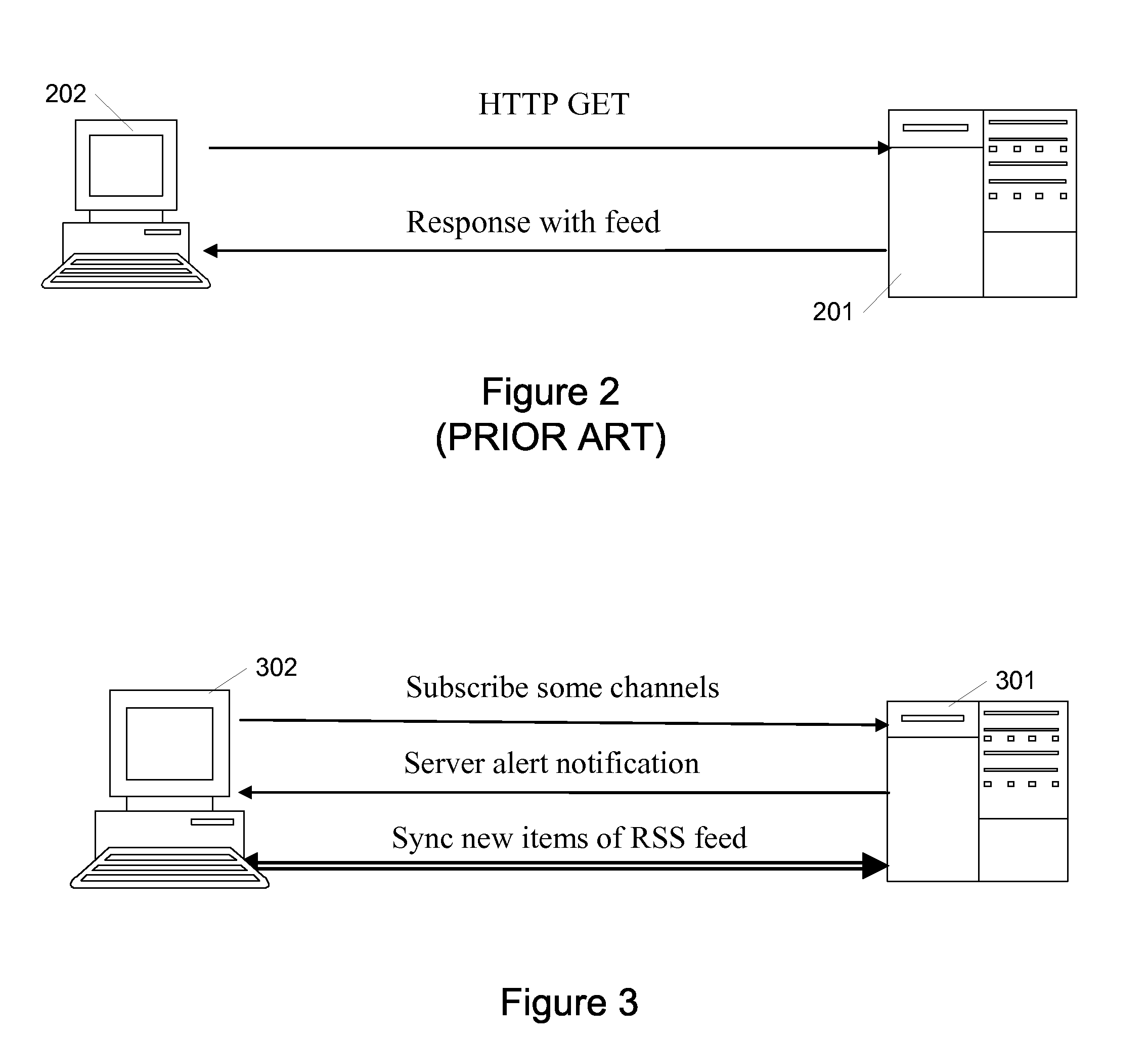
System and method for updating information feeds
InactiveUS20080155112A1Easy to retrieve dataImprove efficiencyMultiple digital computer combinationsData switching networksInitClient-side
Systems and methods for transmitting and updating information feeds from a server to a client are provided to increase bandwidth efficiency and improve the timeliness of information feed updates. Using OMA DS protocols, the updating of RSS feeds, for example, may be performed without having to transfer an entire RSS feed. That is, in some arrangements, only the new RSS items are synchronized with a client. A server may alert the client when a new RSS item has been added to an RSS feed. A synchronization session may then be initialized between the server and the client. A client may send a synchronization alert to the server identifying the feed or feeds for which synchronization is desired. The server may respond with one or more new items corresponding to the identified feeds. RSS item identification information may further be mapped between the client and the server.
Owner:NOKIA CORP
System and method for providing terrestrial digital broadcasting service using single frequency network
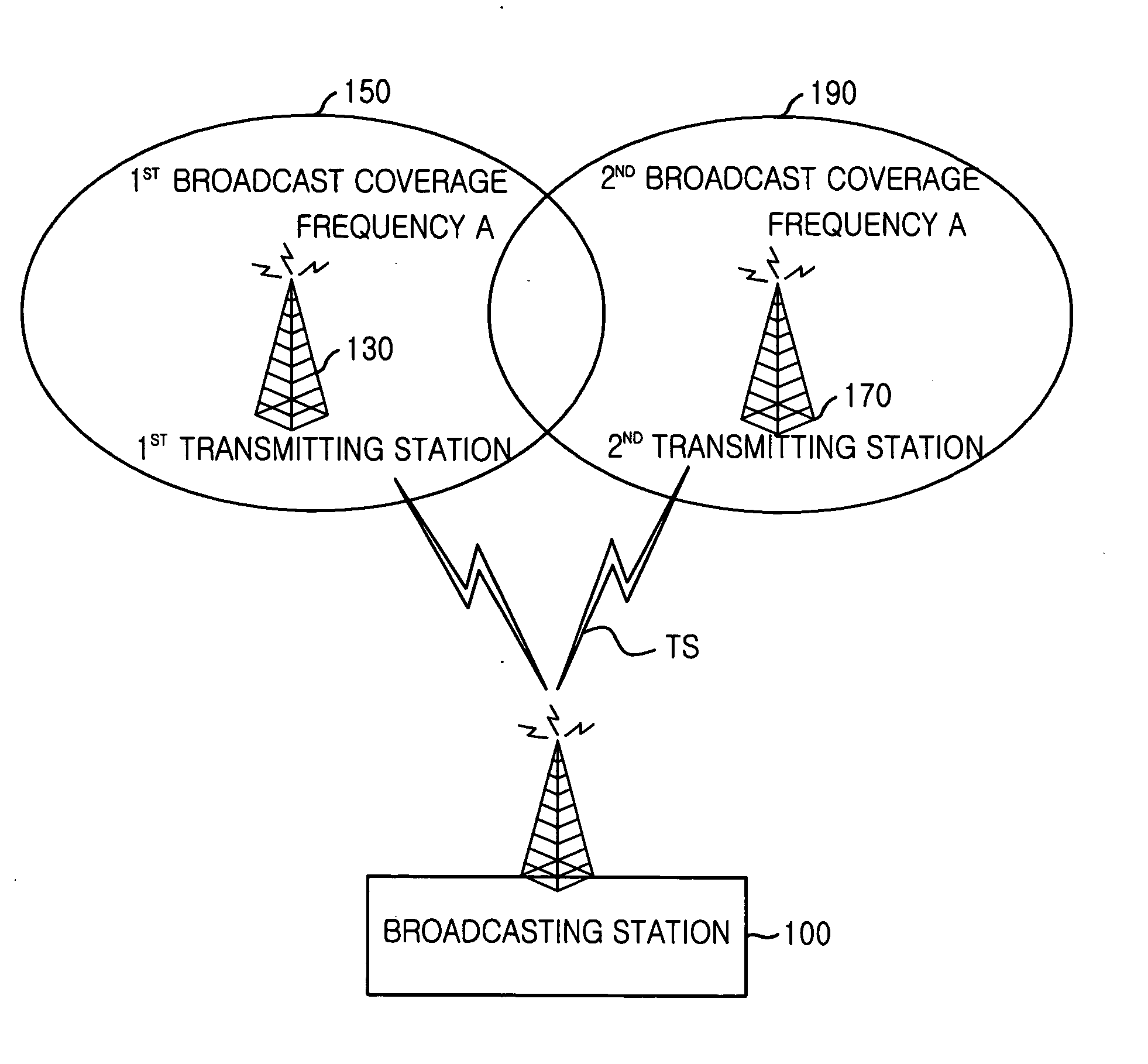
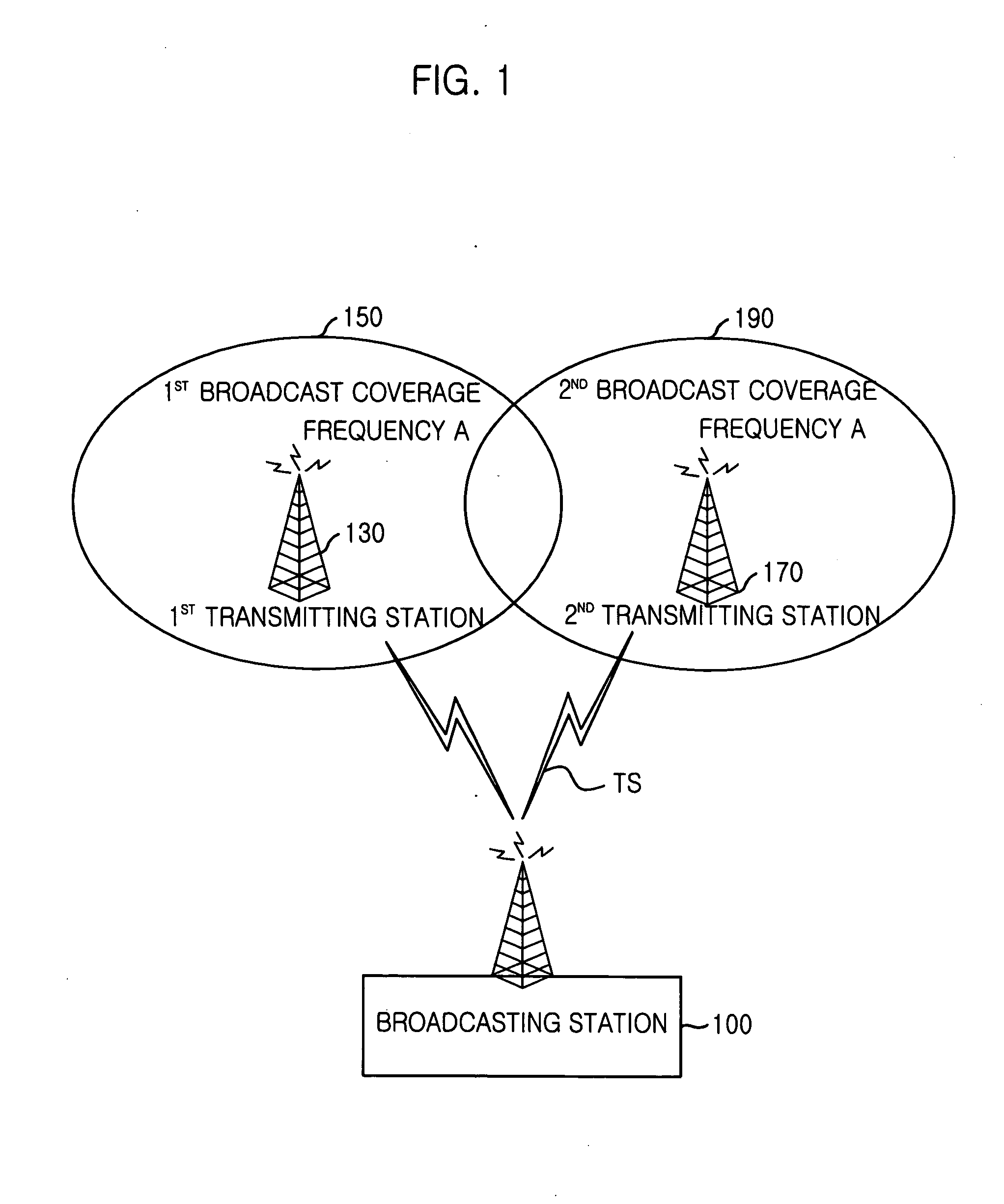
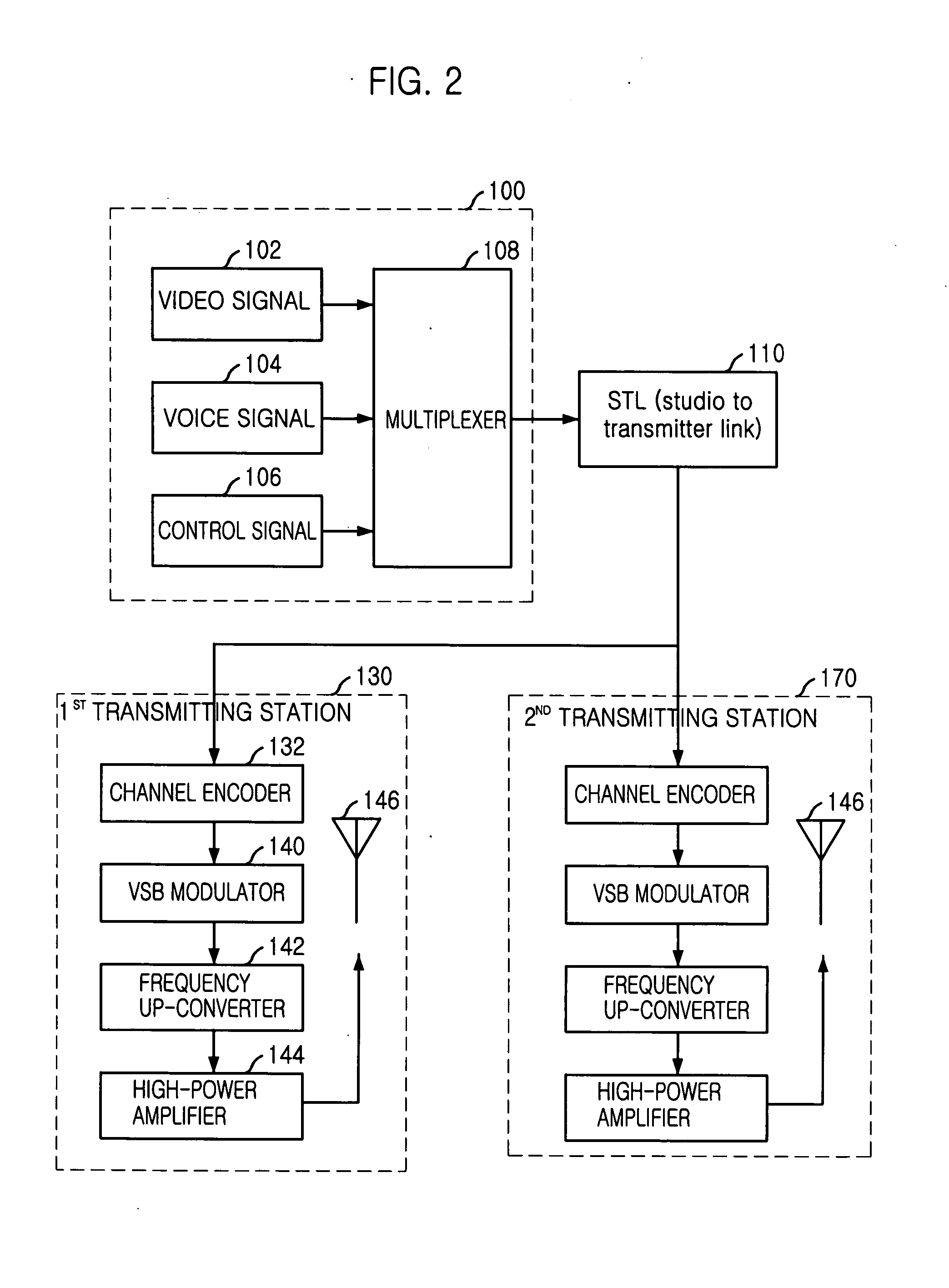
InactiveUS20060253890A9Television system detailsData representation error detection/correctionMultiplexingInit
Provided is a system and method for terrestrial digital broadcasting service using a single frequency network without additional equipment. The system and method synchronizes input signals into transmitting stations by inserting a transmission synchronization signal into a header of TS periodically, and solves the problematic ambiguity of the trellis encoder by including a trellis encoder switching unit separately and initializing a memory of the trellis encoder. The terrestrial digital broadcasting system includes: a broadcasting station for multiplexing video, voice and additional signals into transport stream (TS) and transmitting the TS to the transmitting stations and a transmitting stations for receiving the TS and broadcast the TS to receiving stations through a single frequency network
Owner:ELECTRONICS & TELECOMM RES INST
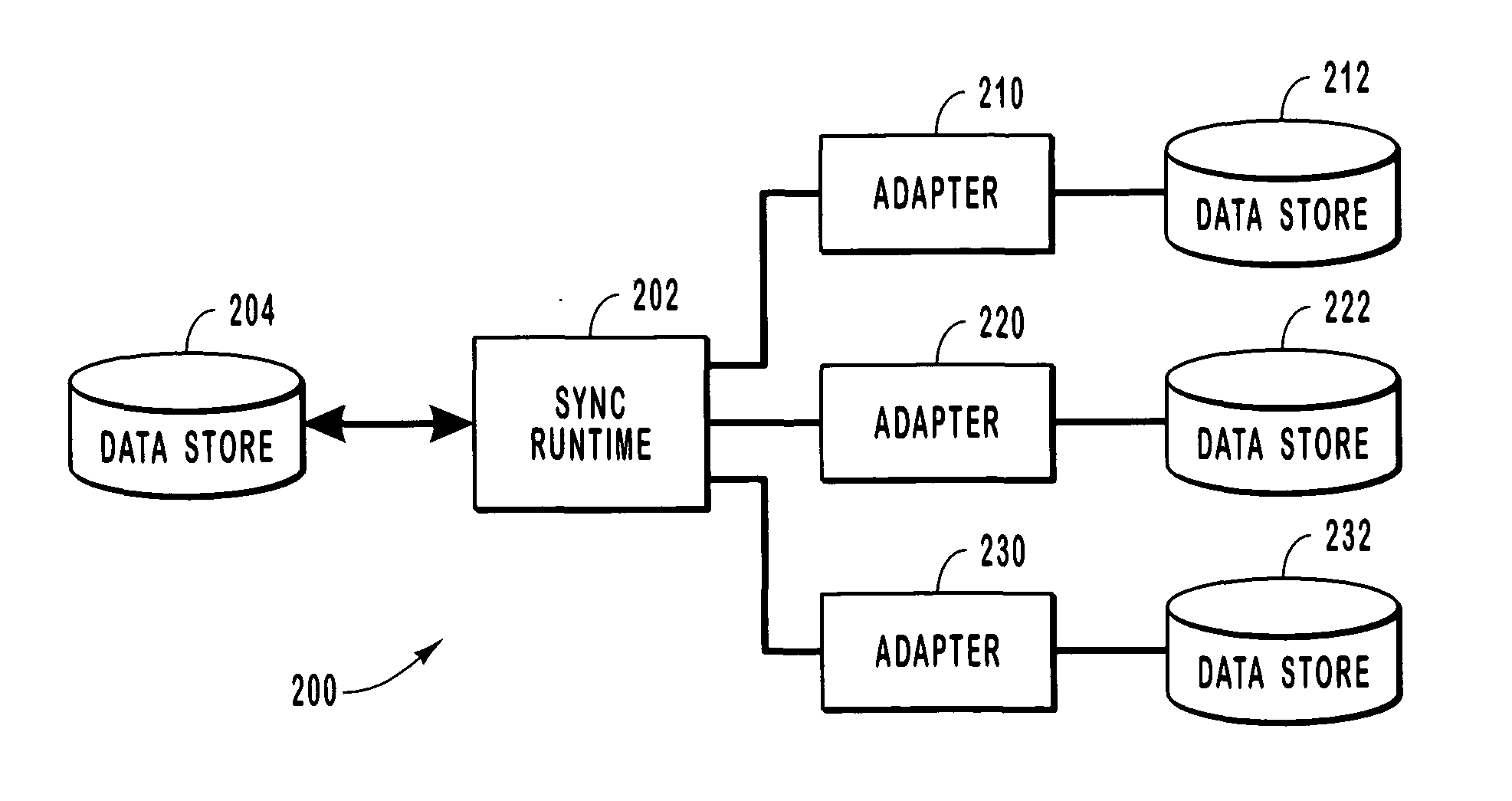
Systems and methods for synchronizing with multiple data stores
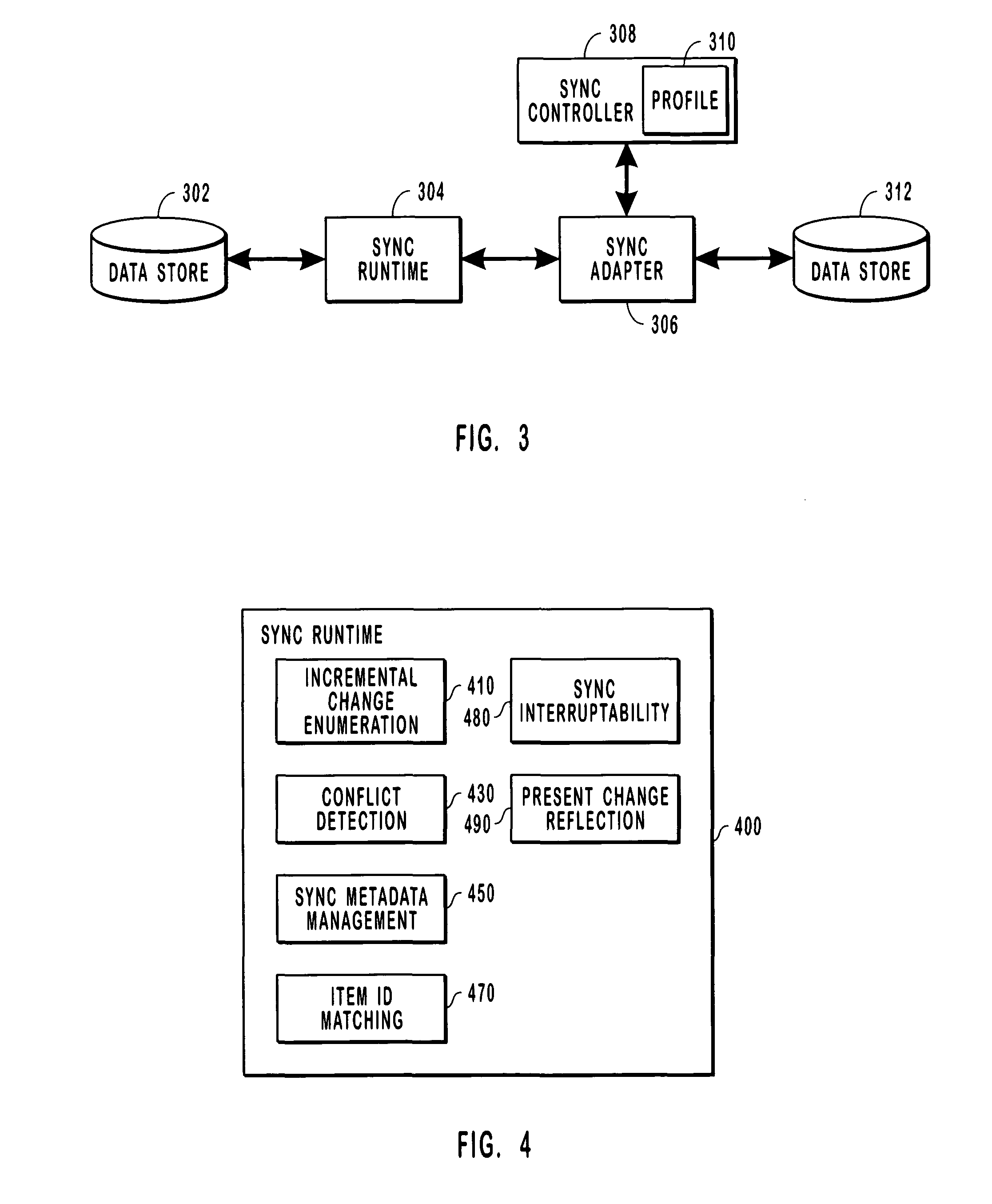
ActiveUS20050027755A1Overcome limitationsDigital data information retrievalData processing applicationsMetadata managementApplication programming interface
Systems and methods for synchronizing data stores. A framework including a sync runtime enables consistent and manageable synchronization between a data store and multiple, diverse back end data stores. The sync runtime provides services such as change enumeration, conflict detection, metadata management, item ID matching, sync interruptability, and the like that are accessible to configurable adapters over an application programming interface. Each synchronizing data store can uses a sync controller to initialize an adapter that can access the services provided by the sync runtime. The sync controller can use a profile to configure each adapter. The profile can identify conflict resolution policies, synchronization filters, source and destination folders, sync direction, and the like.
Owner:MICROSOFT TECH LICENSING LLC
System, method, and computer program product for filtering messages
The present invention provides systems, methods, computer program products, and combinations and subcombinations thereof for filtering received messages. The invention includes a client system having filtering logic, a statistical classifier module, and a classifier database. The classifier module is automatically trained, without manual intervention, when the score generated by the classifier for a received message is inconsistent with a user-defined authoritative status indication. In addition, the classifier module is initialized using user-identified messages in a ratio representative of the ratio of non-spam to spam messages received by the user.
Owner:COMP ASSOC THINK INC
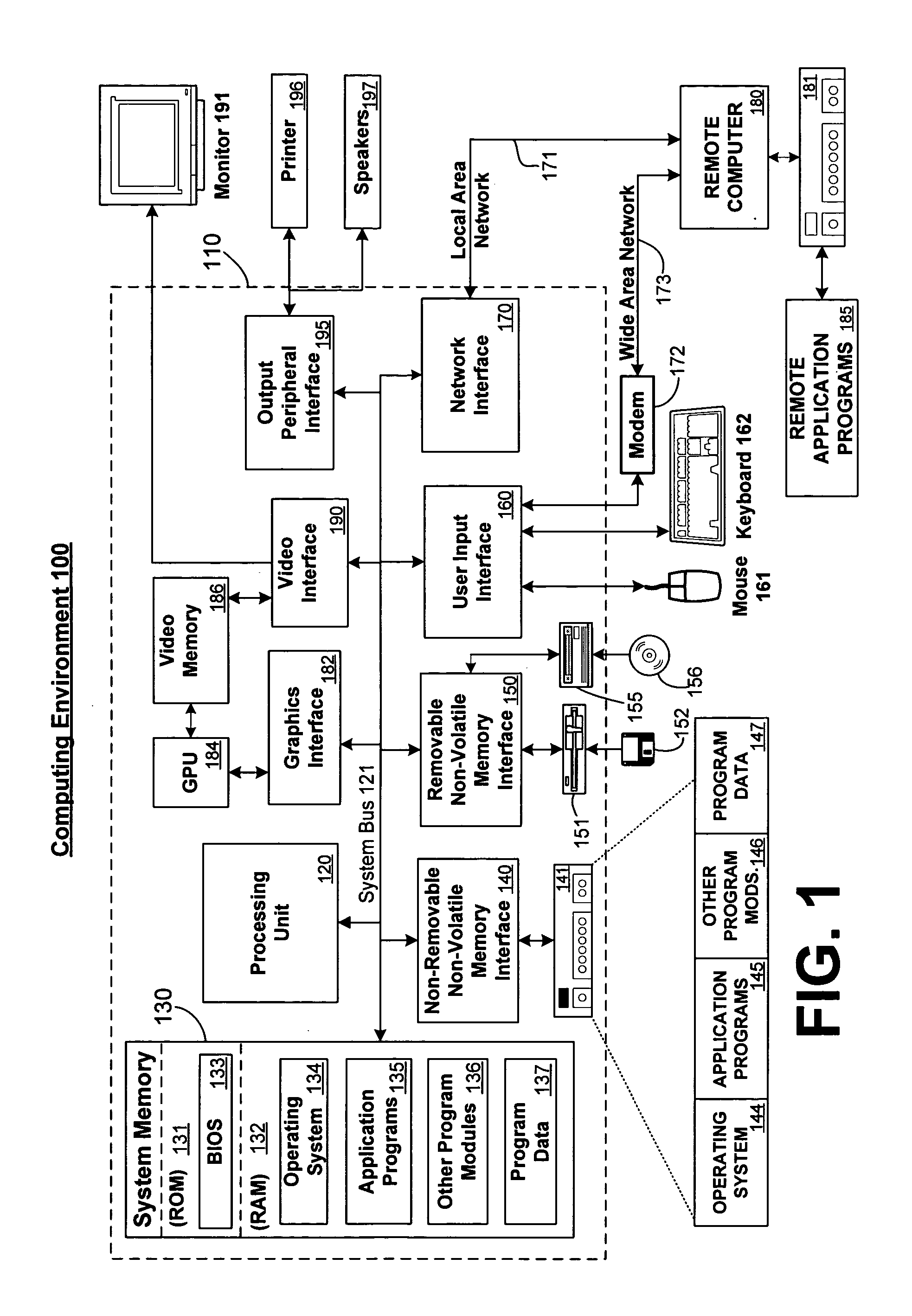
System and method for accelerated device initialization
InactiveUS20050038981A1Digital computer detailsProgram loading/initiatingOption ROMOperational system
A system and method for initialization of a computer system is described. Faster initialization of a computer system is possible by allowing certain device driver initialization tasks to overlap with other initialization and operating system tasks. option-ROMs resident on hardware device drivers define the initialization tasks to be performed prior to device driver initialization. Initial computer code for booting the computing device, such as a BIOS, is executed. As option-ROMs for hardware devices are scanned and executed, specific device initialization information is accessed from the devices and placed in pre-defined buffer areas. These accesses occur in parallel to other start up tasks. When device drivers are loaded, some of their initialization has already completed, thereby shortening the time necessary to boot the system.
Owner:INTEL CORP
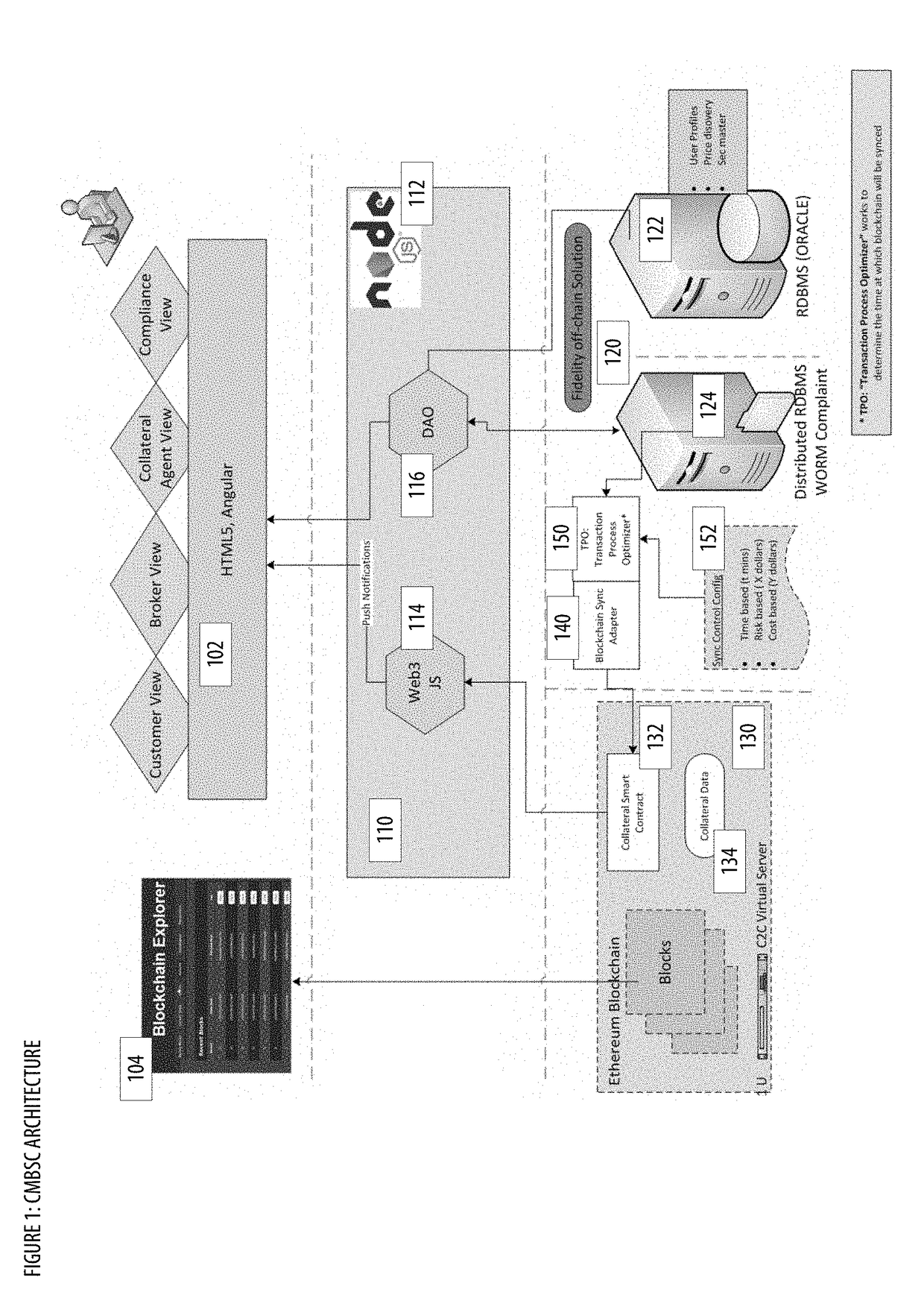
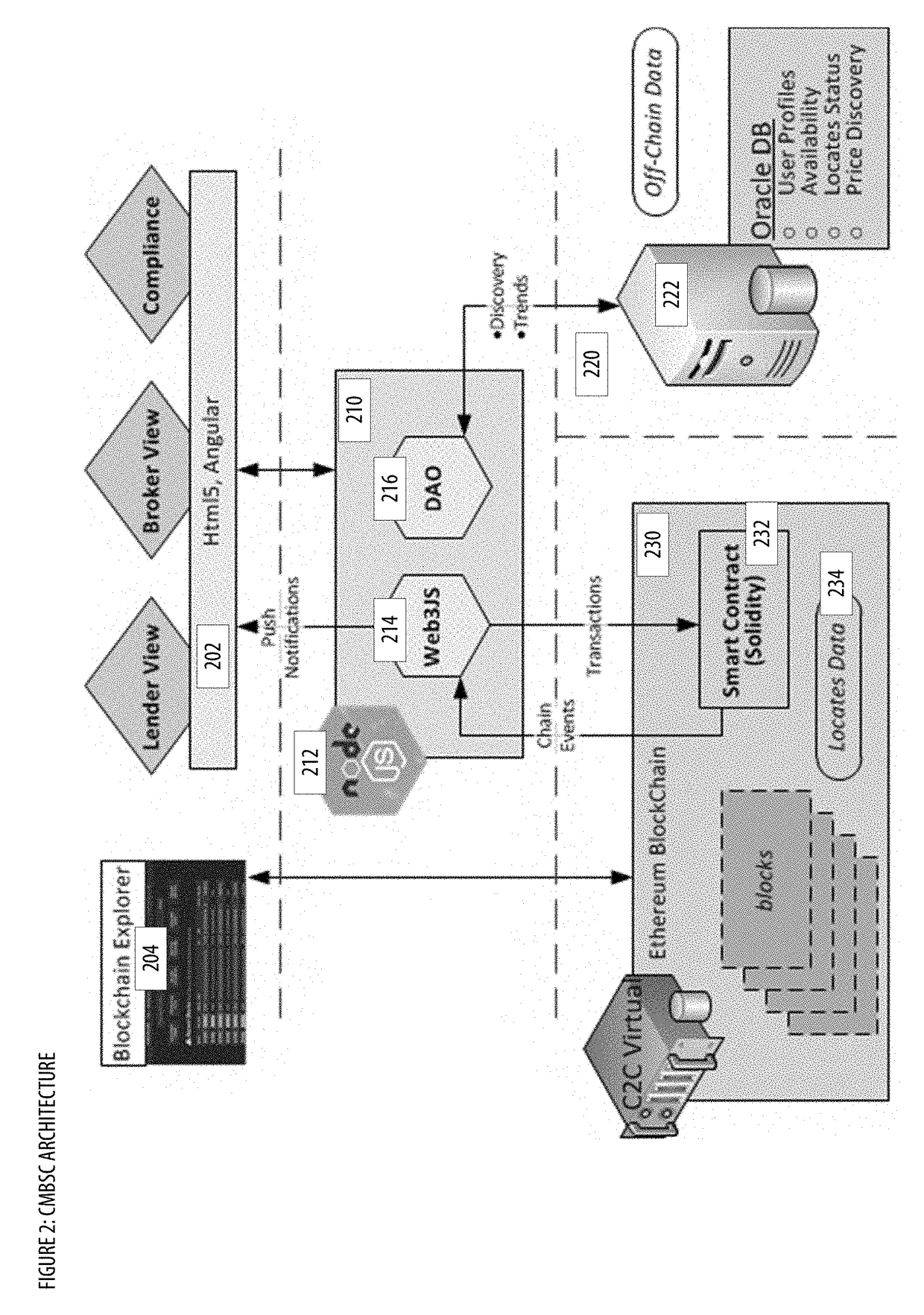
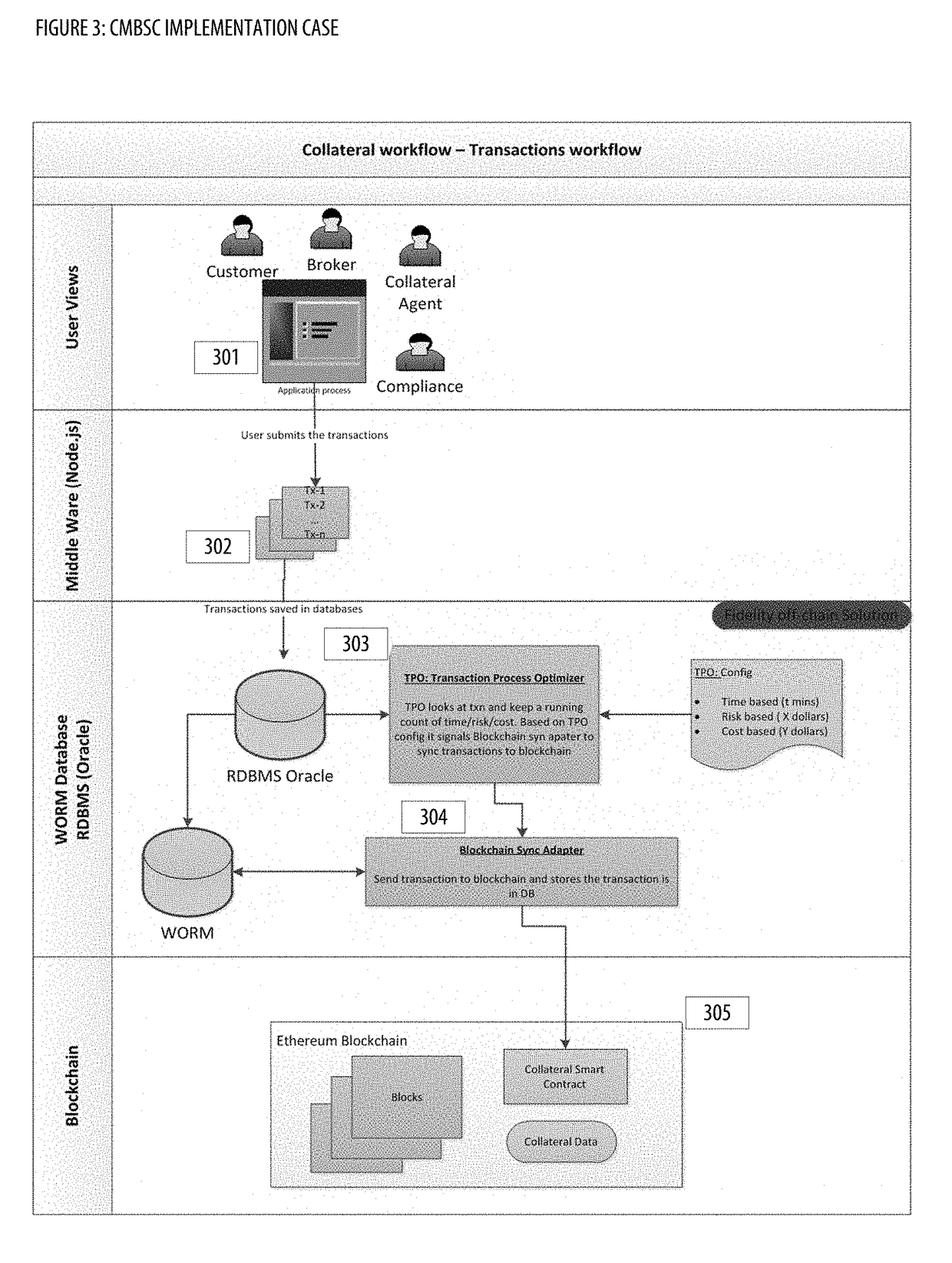
Collateral Management With Blockchain and Smart Contracts Apparatuses, Methods and Systems
PendingUS20190005469A1Borrowing and/or returning assets (e.g., stocks) may be facilitatedFacilitate actionFinanceEncryption apparatus with shift registers/memoriesCollateral managementInit
The Collateral Management with Blockchain and Smart Contracts Apparatuses, Methods and Systems (“CMBSC”) transforms borrow transaction request inputs via CMBSC components into borrow transaction init notification, borrow transaction sync notification outputs. A borrow transaction request associated with a borrow transaction is obtained. Transaction attributes associated with the borrow transaction are stored in a database. The transaction process optimizer component is notified regarding the borrow transaction. A blockchain sync notification associated with the borrow transaction is obtained from the transaction process optimizer component. The stored transaction attributes associated with the borrow transaction are filtered. A smart contract associated with the borrow transaction is generated. The generated smart contract is sent to a blockchain node of a blockchain network. A smart contract notification associated with the smart contract is received. A push notification regarding the smart contract notification is provided to a user interface component of a user's client.
Owner:FMR CORP
Creating secure process objects
InactiveUS20060259487A1Precise processingReduce in quantityDigital data processing detailsAnalogue secracy/subscription systemsVirtual memoryInit
A secure process may be created which does not allow code to be injected into it, does not allow modification of its memory or inspection of its memory. The resources protected in a secure process include all the internal state and threads running in the secure process. Once a secure process is created, the secure process is protected from access by non-secure processes. Process creation occurs atomically in kernel mode. Creating the infrastructure of a process in kernel mode enables security features to be applied that are difficult or impossible to apply in user mode. By moving setup actions previously occurring in user mode (such as creating the initial thread, allocating the stack, initialization of the parameter block, environment block and context record) into kernel mode, the need of the caller for full access rights to the created process is removed. Instead, enough state is passed from the caller to the kernel with the first system call so that the kernel is able to perform the actions previously performed using a number of calls back and forth between caller and kernel. When the kernel returns the handle to the set-up process, some of the access rights accompanying the handle are not returned. Specifically, those access rights that enable the caller to inject threads, read / write virtual memory, and interrogate or modify state of the threads of the process are not returned to the caller.
Owner:MICROSOFT TECH LICENSING LLC
System and method for on-the-fly migration of server from backup
ActiveUS7937612B1Digital data processing detailsSpecial data processing applicationsOperational systemInit
A system, method and computer program product for migrating a server include creating an image of a storage device of a first server; during execution of a boot loader on a second server, starting an initialization application that at least partially restores, to a storage device of the second server, operating system data from the image; analyzing a hardware configuration of the second server; modifying at least one driver of an operating system based on the analyzed hardware to enable the operating system of the second server to interface to the storage device of the second server; rebooting the second server using the at least partially restored operating system data; and restoring unaltered portions of remaining data from the image. The second server identification and / or authentication data stored on the image is updated before the rebooting. Identification data of the second server is at least partially replaced with corresponding data stored on the image. The image is unchanged until completion of the restoring step. The restoration step uses an incremental image of the storage device. A boot loader is started in case of failure of the first server.
Owner:MIDCAP FINANCIAL TRUST
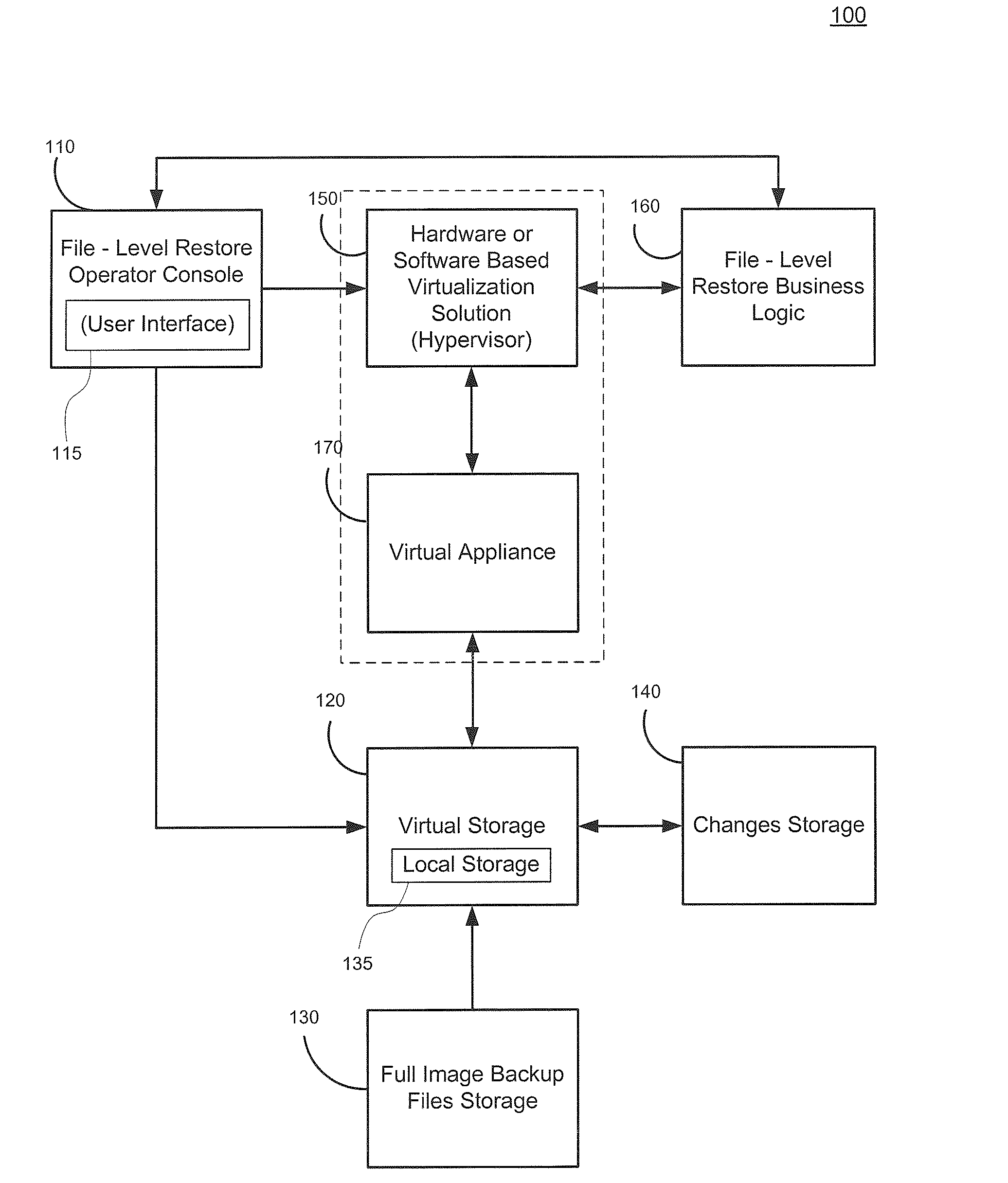
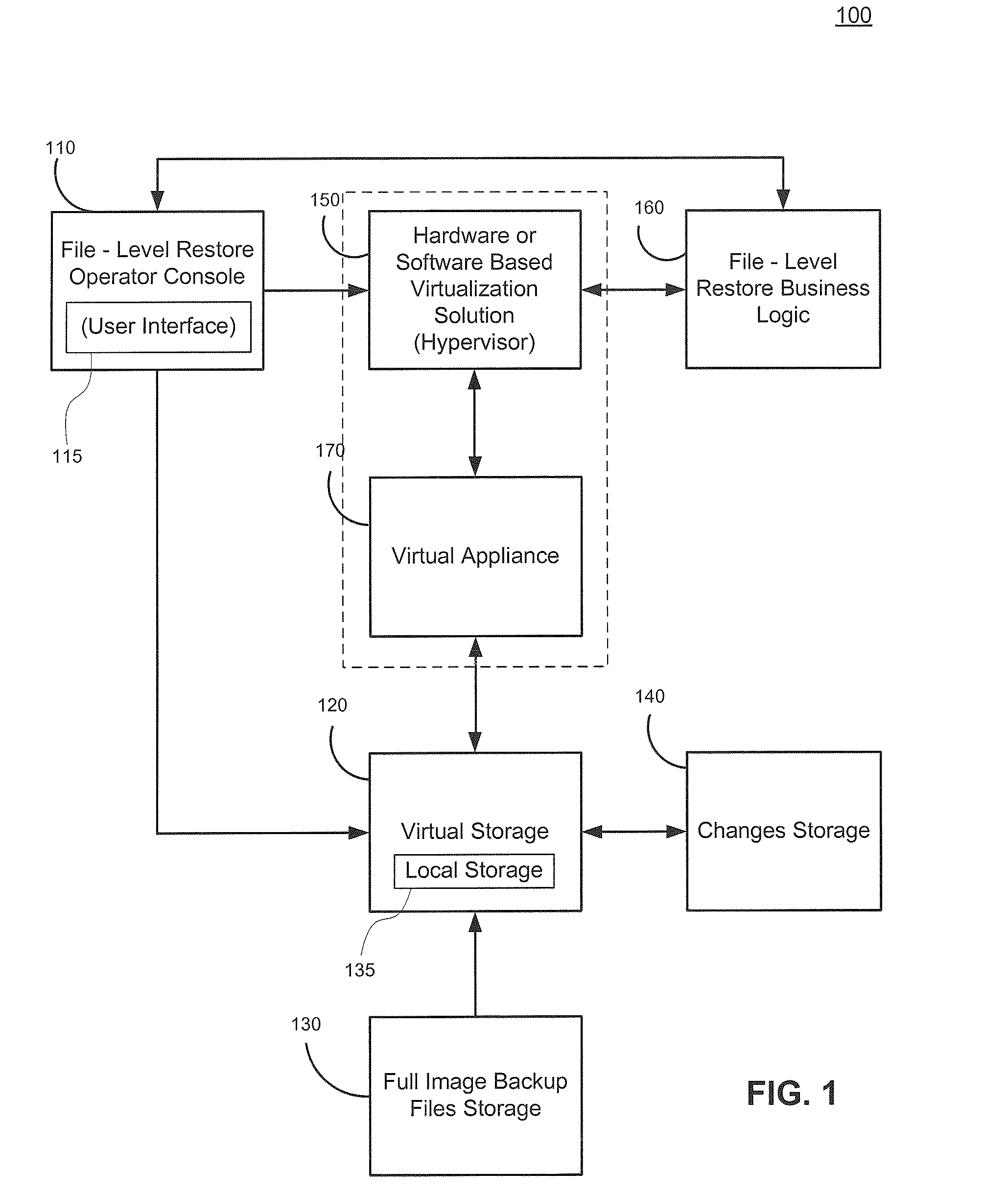
Cross-platform object level restoration from image level backups
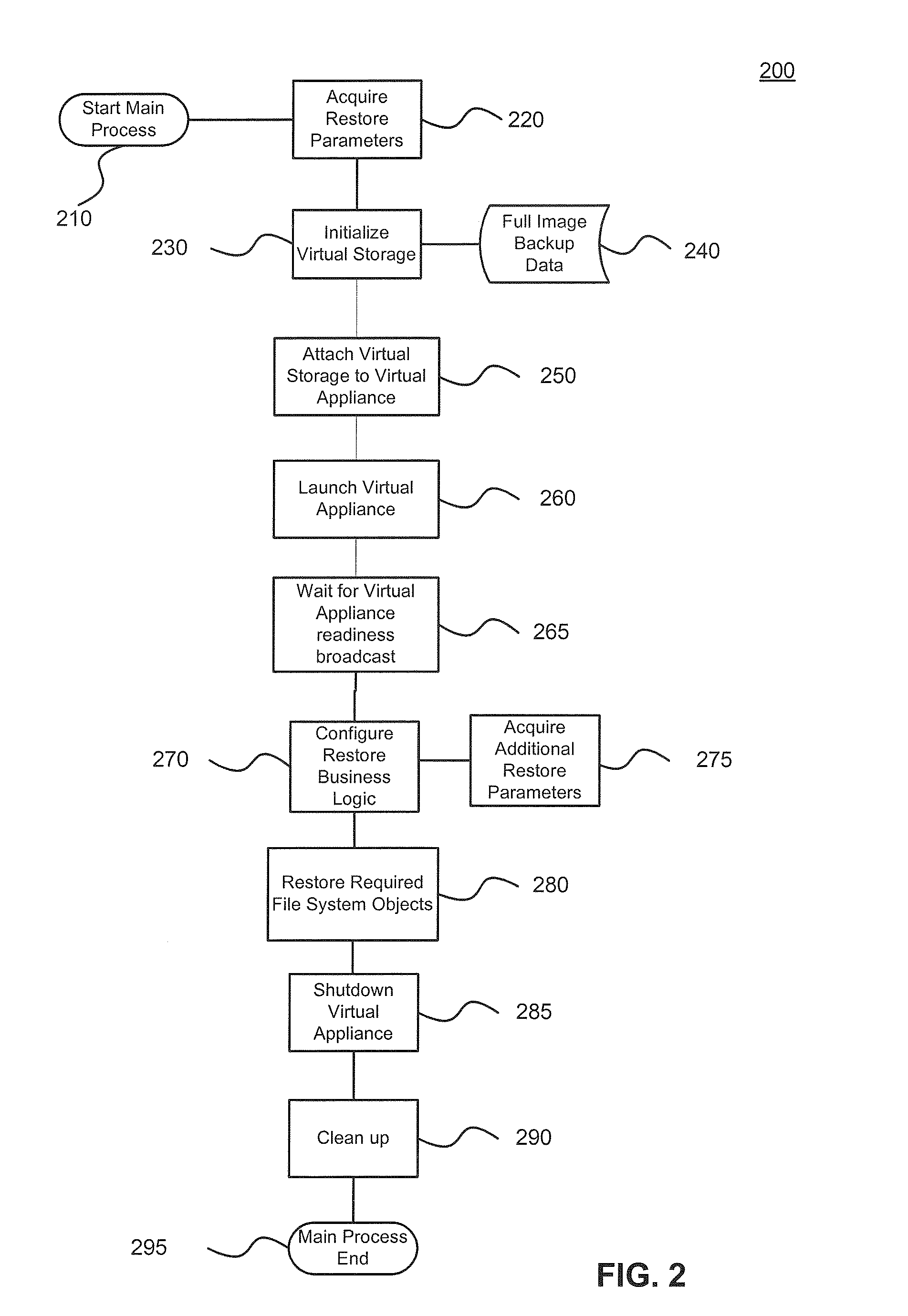
ActiveUS20110196842A1Avoid system instabilityReduce developmentDigital data processing detailsError detection/correctionOperational systemFile system
Systems and methods for restoring file system objects from image level backups of servers. The method receives a selection of an image level backup of a source, file system object(s) to be restored, and restoration parameters identifying a destination. The method initializes and attaches a virtual storage to a virtual appliance and an associated hypervisor. The method stores virtual storage data changes resulting from the file system object restoration in changes storage. The method preserves file system object information, wherein the file system object information corresponds to the source operating system (OS) and file system. The method preserves file system object information such as permissions and ownership through business logic that ensures that the file system object information for restored file system object(s) on the destination match file system object information from the source, even when the method operates on a host running a different OS than the source server.
Owner:VEEAM SOFTWARE GROUP GMBH
Location service-providing system and deferred location request service-providing method using previously computed location in location service-providing system
ActiveUS20070082681A1Analogue secracy/subscription systemsRadio/inductive link selection arrangementsInitAncillary data
A location service-providing system and a method for providing a deferred location request service by using previously computed position estimates. In the system and the method, if an H-SLP transmits an SUPL INIT message including location information to a target SUPL Enabled Terminal (SET) according to a location service request from an SUPL AGENT, the location information including at least one of a previous position estimate and previous assistant data, the target SET receives the SUPL INIT message, determines whether it is possible to provide the location service by reusing at least one of the location information in the SUPL INIT message and previously stored location information, when it is possible, determining position information by reusing at least one of the location information in the SUPL INIT message and the previously stored location information, and providing the SUPL AGENT with the position information..
Owner:SAMSUNG ELECTRONICS CO LTD
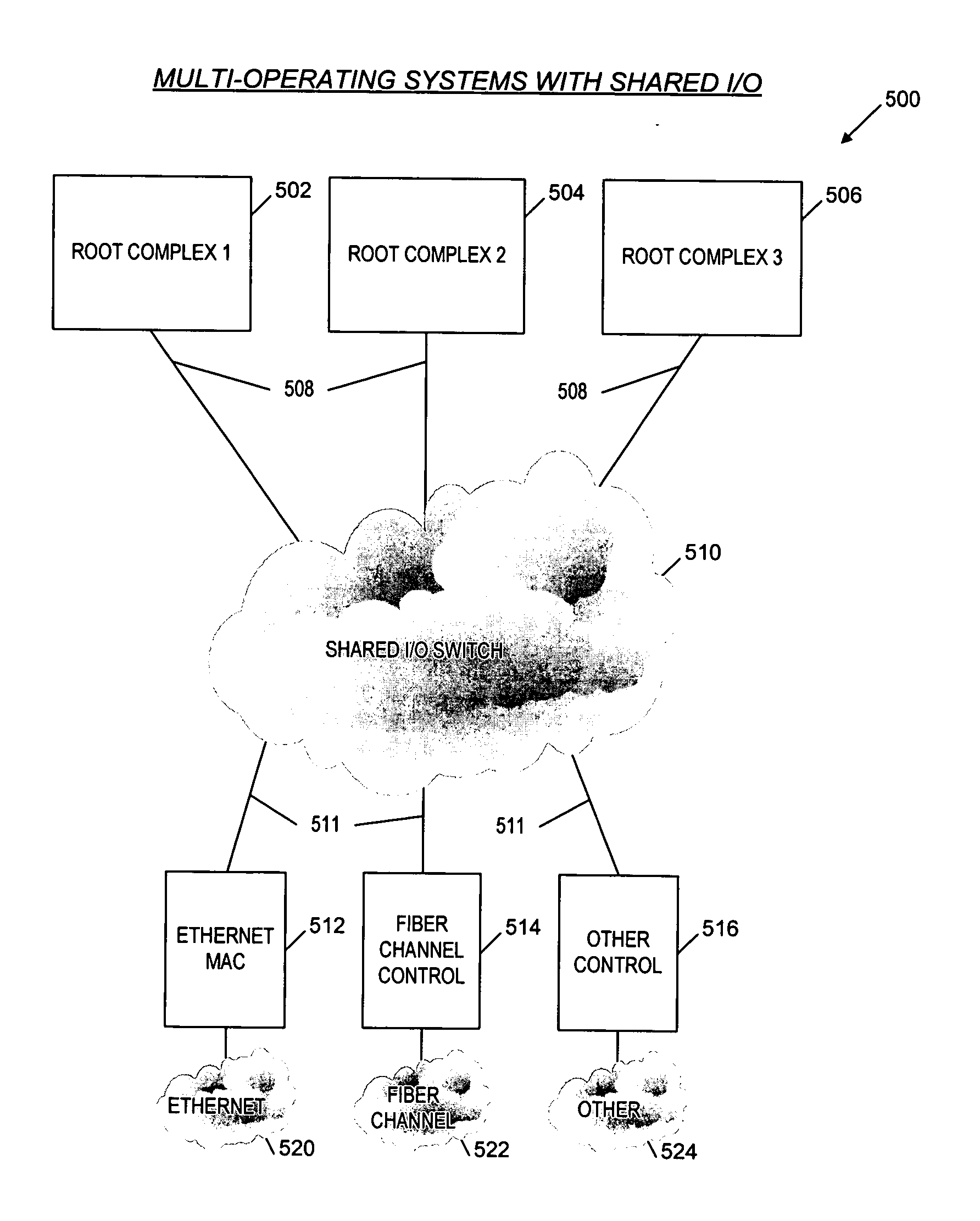
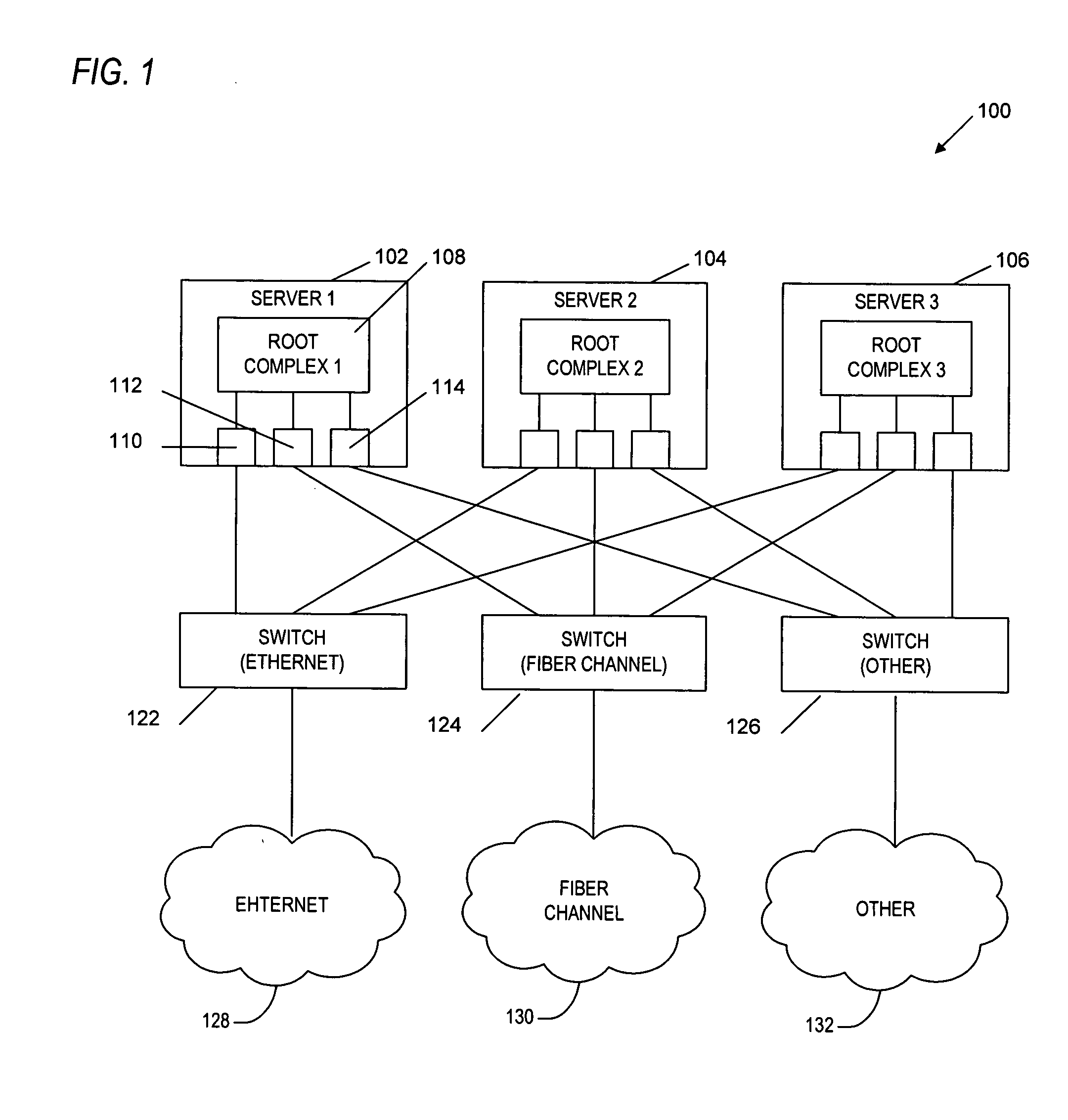
Switching apparatus and method for link initialization in a shared I/O environment
An apparatus and method are provided that enable I / O devices to be shared among multiple operating system domains. The apparatus has a first plurality of I / O ports, a second I / O port, and link training logic. The first plurality of I / O ports is coupled to a plurality of operating system domains through a load-store fabric. Each of the first plurality of I / O ports is configured to route transactions between the plurality of operating system domains and the switching apparatus. The second I / O port is coupled to a first shared input / output endpoint. The first shared input / output endpoint is configured to request / complete the transactions for each of the plurality of operating system domains. The link training logic is coupled to the second I / O port. The link training logic initializes a link between the second I / O port and the first shared input / output endpoint to support the transactions corresponding to the each of the plurality of operating system domains. The link is initialized in a manner that is transparent to the plurality of operating system domains.
Owner:AVAGO TECH INT SALES PTE LTD
Systems and methods for accelerated loading of operating systems and application programs
InactiveUS20070043939A1Input/output to record carriersDigital computer detailsOperational systemInit
Systems and methods for providing accelerated loading of operating system and application programs upon system boot or application launch. In one aspect, a method for providing accelerated loading of an operating system comprises the steps of: maintaining a list of boot data used for booting a computer system; preloading the boot data upon initialization of the computer system; and servicing requests for boot data from the computer system using the preloaded boot data. The boot data may comprise program code associated with an operating system of the computer system, an application program, and a combination thereof. In a preferred embodiment, the boot data is retrieved from a boot device and stored in a cache memory device. In another aspect, the method for accelerated loading of an operating system comprises updating the list of boot data during the boot process, wherein updating comprises adding to the list any boot data requested by the computer system not previously stored in the list and / or removing from the list any boot data previously stored in the list and not requested by the computer system. In yet another aspect, the boot data is stored in a compressed format on the boot device and the preloaded boot data is decompressed prior to transmitting the preloaded boot data to the requesting system. In another aspect, a method for providing accelerated launching of an application program comprises the steps of: maintaining a list of application data associated with an application program; preloading the application data upon launching the application program; and servicing requests for application data from a computer system using the preloaded application data.
Owner:REALTIME DATA
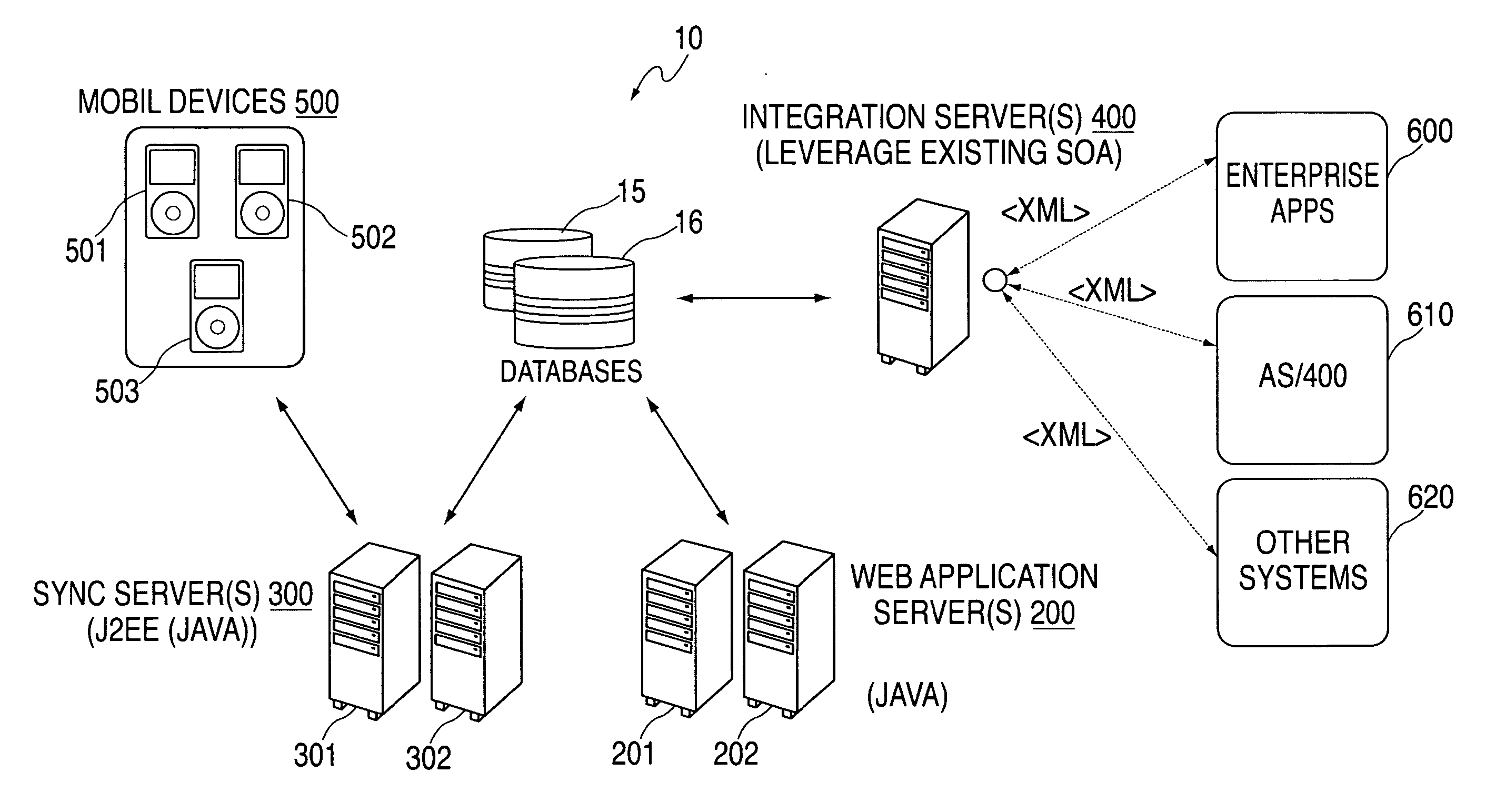
Method and apparatus for mobile data collection and management
InactiveUS20070260475A1Reduce costs and risksDigital data processing detailsMarketingData synchronizationTablet computer
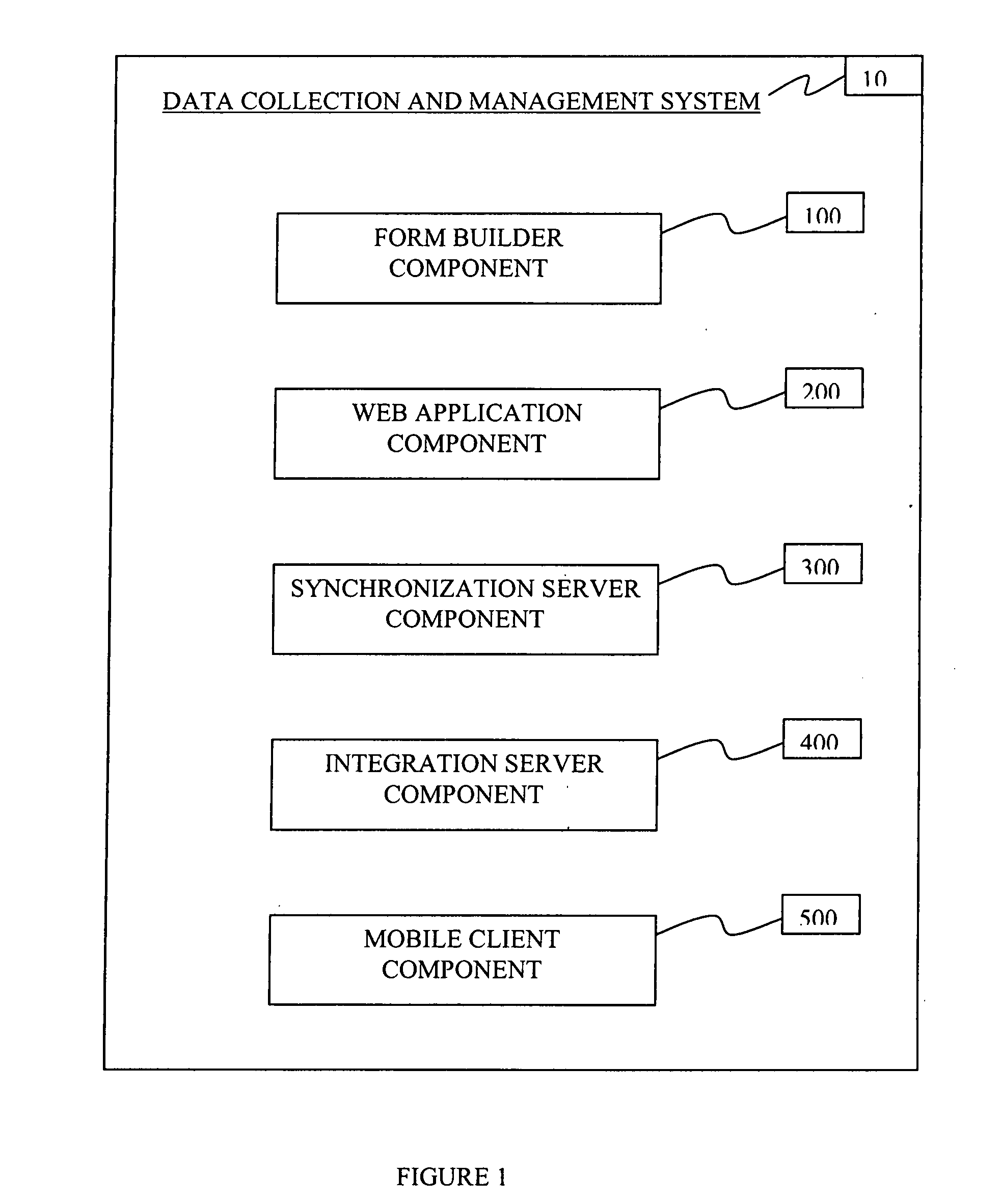
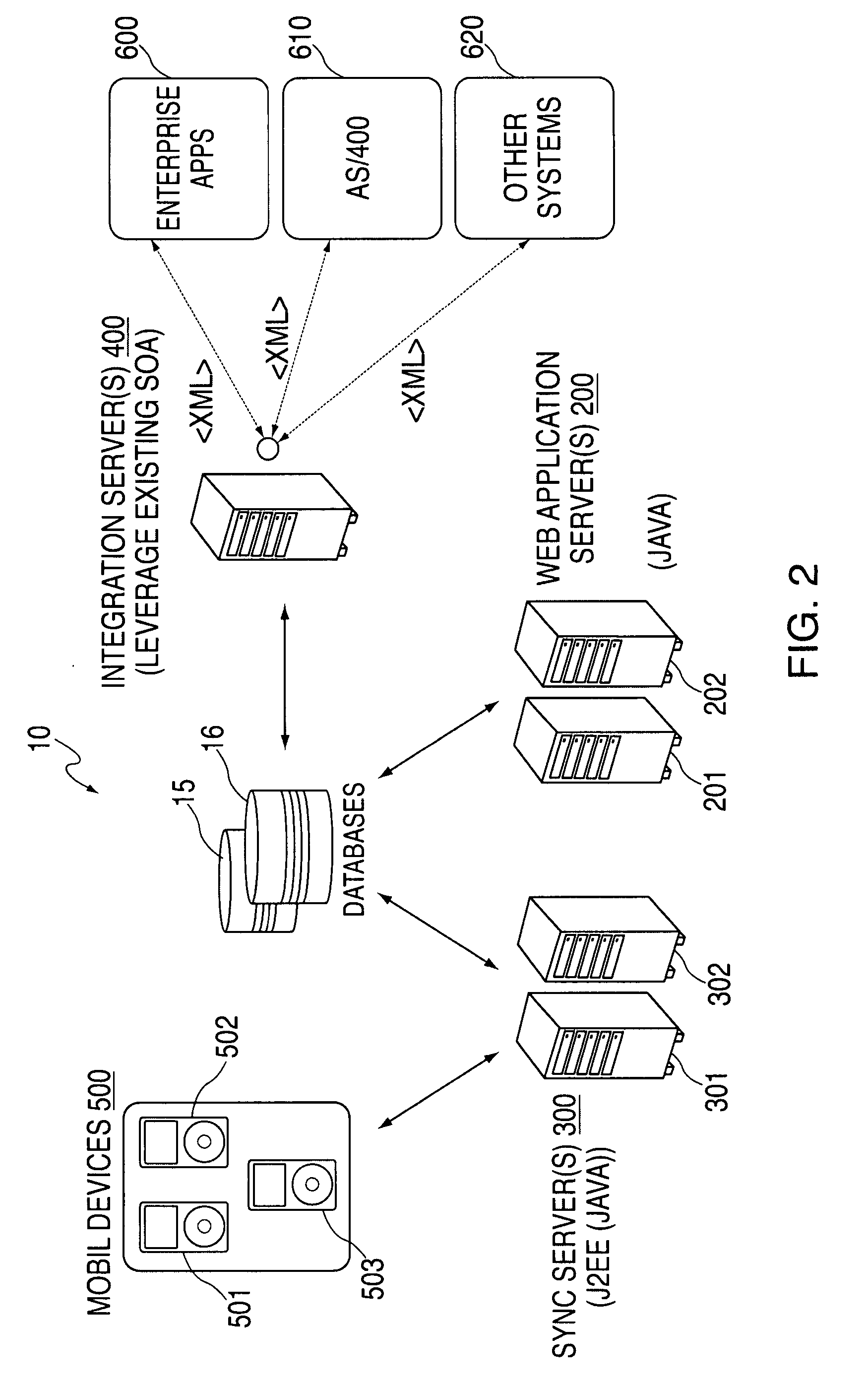
A method and apparatus for a middleware approach to initializing and updating required data entry fields, pushing such required data entry fields to mobile devices and applications, collecting entered data from such mobile devices, and the synchronizing and integrating of the data is presented. A “form builder” software component of the present invention allows for the creation of easy to read and use data entry forms by company management. A “web application” software component of the present invention allows for the forms to then be distributed via electronic and / or wireless means to mobile client devices, such as PDA's, Tablets, and Laptops, and to Desktop computers. The mobile client devices run applications to utilize the data entry forms and are that into which collected data can be entered. A “synchronization server” software component of the present invention then allows for two-way communication, storage and conflict resolution (versioning) of the collected data. An “integration server” software component of the present invention allows for external access to the collected and versioned data and modeling / mapping of such data. Thus seamless data entry, collection, updating, conflict resolution, versioning, storage, access and utilization is available.
Owner:VERIFONE INC
Method for transmitting ascending control information and method for calculating transmission parameter
ActiveCN101409894AGuaranteed performanceSystem performance guarantee caused by performance mismatchPower managementNetwork traffic/resource managementChannel dataInit
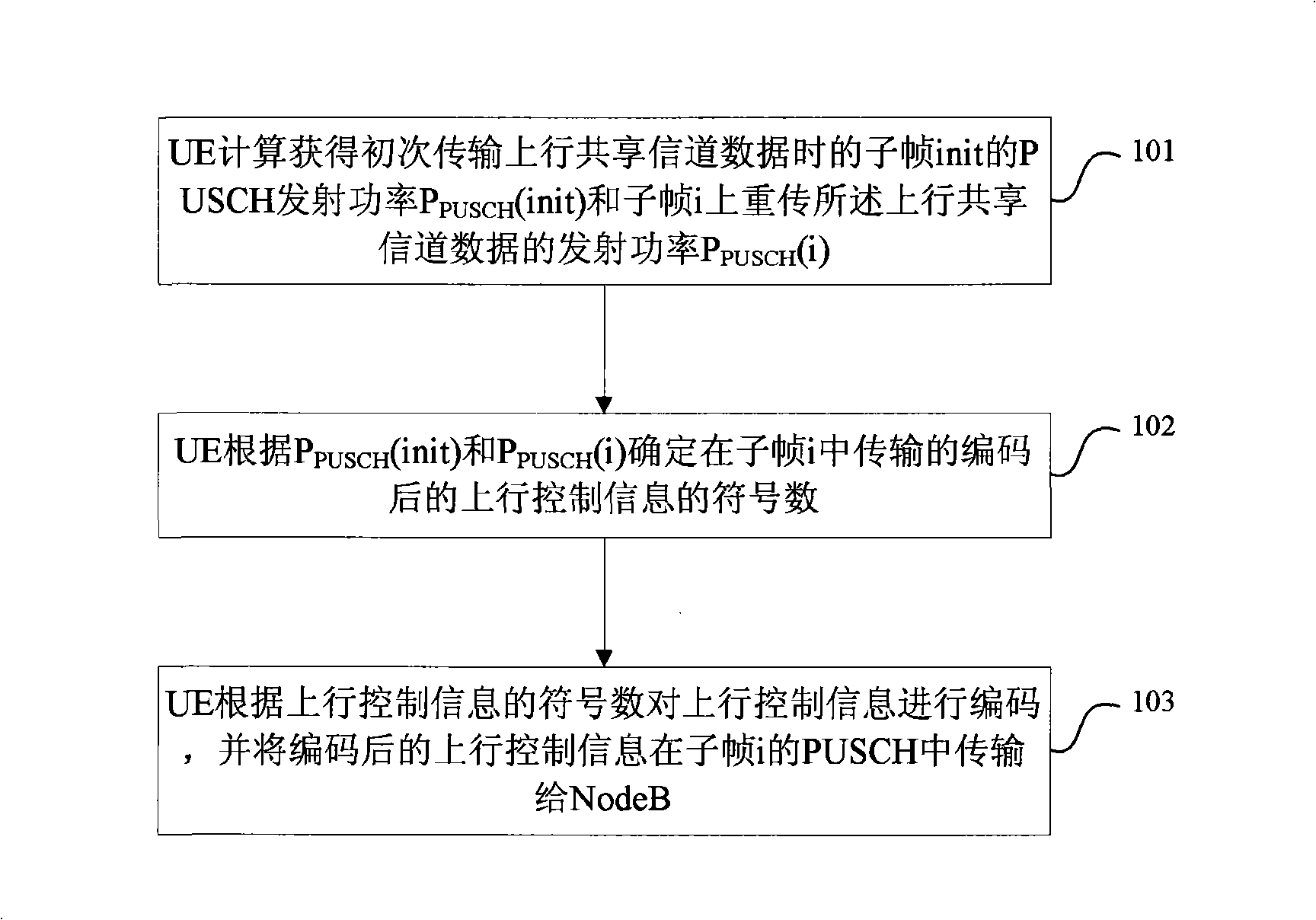
The invention provides a method for transferring uplink control information. The method comprises the steps as follows: when uplink shared channel data and the uplink control information are required to be transferred in an uplink shared channel PUSCH of a subframe i simultaneously, a user terminal obtains the transmission power P<PUSCH> (init) of primarily transferred uplink shared channel data and the transmission power P<PUSCH> (i) of the uplink shared channel data transferred in the subframe i; the user terminal confirms the symbol quantity of the uplink control information after being coded in the subframe i according to the comparison relation between P<PUSCH> (init) and P<PUSCH> (i) and the size and the bandwidth of a transmission block when the uplink shared channel data is transferred primarily; the user terminal codes the uplink control information according to the symbol quantity of the uplink control information after being coded and transfers the coded uplink control information to a base station in the PUSCH of the subframe i.
Owner:ZTE CORP
Method, computer program product, and system for non-blocking dynamic update of statically typed class-based object-oriented software
ActiveUS20110283256A1Efficient forwardingSoftware engineeringSpecific program execution arrangementsSoftware updateInit
Under the present invention, a method, computer program product, and system for non-blocking dynamic update of statically-typed class-based object-oriented software executing as byte-code on a virtual machine within an actively running computer system is provided. A set of objects instantiated from an existing module or multiple modules (identifiable collections of application resources and class definitions in the form of byte-code representations) is ready for execution on a virtual machine in an actively running computer system. New versions of one or more modules corresponding to those already loaded into the actively running virtual machine are dynamically loaded into the virtual machine for the purpose of updating the running software. The class definitions within the loaded modules are prepared for dynamic update by inserting byte-code that enables; transparent state transfer and shared object identity between objects of a former version and the new version of a class. On the event of a software update, the objects instantiated from a former version of an updated class become un-initialized surrogate objects with the potential to redirect to their future corresponding objects. Corresponding objects are created lazily on first access of the declaring class members. Besides lazy redirection of the behavior of objects and classes, non-blocking dynamic update is achieved by lazy migration of the state of former objects and classes while locking on a temporary field access lock. Thus, the algorithm for controlling field access and state migration is completely lock-free both before and after state migration; hence the performance degradation is minimal. Finally, any unreferenced objects are removed from memory.
Owner:ZEROTURNAROUND
Natural language access to application programming interfaces
ActiveUS9015730B1Promote resultsBroaden their knowledgeInterprogram communicationSpecific program execution arrangementsApplication programming interfaceInit
Users of online services may avoid having to gain knowledge of the intricacies of specific Application Programming Interface (API) syntaxes and elements by using natural language requests which are processed to extract components of the request. The components are then used to find one or more matches of known APIs, and then at least one structured API call is constructed by mapping the request's components to the structured API call's elements. The system can then invoke the online service on behalf of the client, and return the results to the client, or it can return the constructed structured API call to the client. The known API details can be initialized and updated by ingesting the description documents for the structured APIs, and then using natural language processing to extract components from the descriptions, which can then be utilized in the matching process to further enhance the results of the tool.
Owner:IBM CORP
Implementation of an integrity-protected secure storage
ActiveUS20060259790A1Reduce complexityLow costKey distribution for secure communicationAcutation objectsInitSafe handling
An internal but not integrated security token is provided for a device which includes a first integrated circuitry including a secure processor. The security token is provided by a second integrated circuitry separate from the first circuitry. The second integrated circuitry includes a secure non-volatile storage. The secure processor communicates information to the second circuitry in a secure manner for the secure information to be securely stored in the secure non-volatile storage, and the second integrated circuitry communicates information stored in its secure non-volatile storage to the secure processor in a secure manner. Communications is secured by means of cryptography. The first integrated circuitry and the second integrated circuitry are internal parts of the device. An initialization method for distributing a secure key to be shared between the circuitries and to be used in cryptography is also disclosed.
Owner:NOKIA TECHNOLOGLES OY
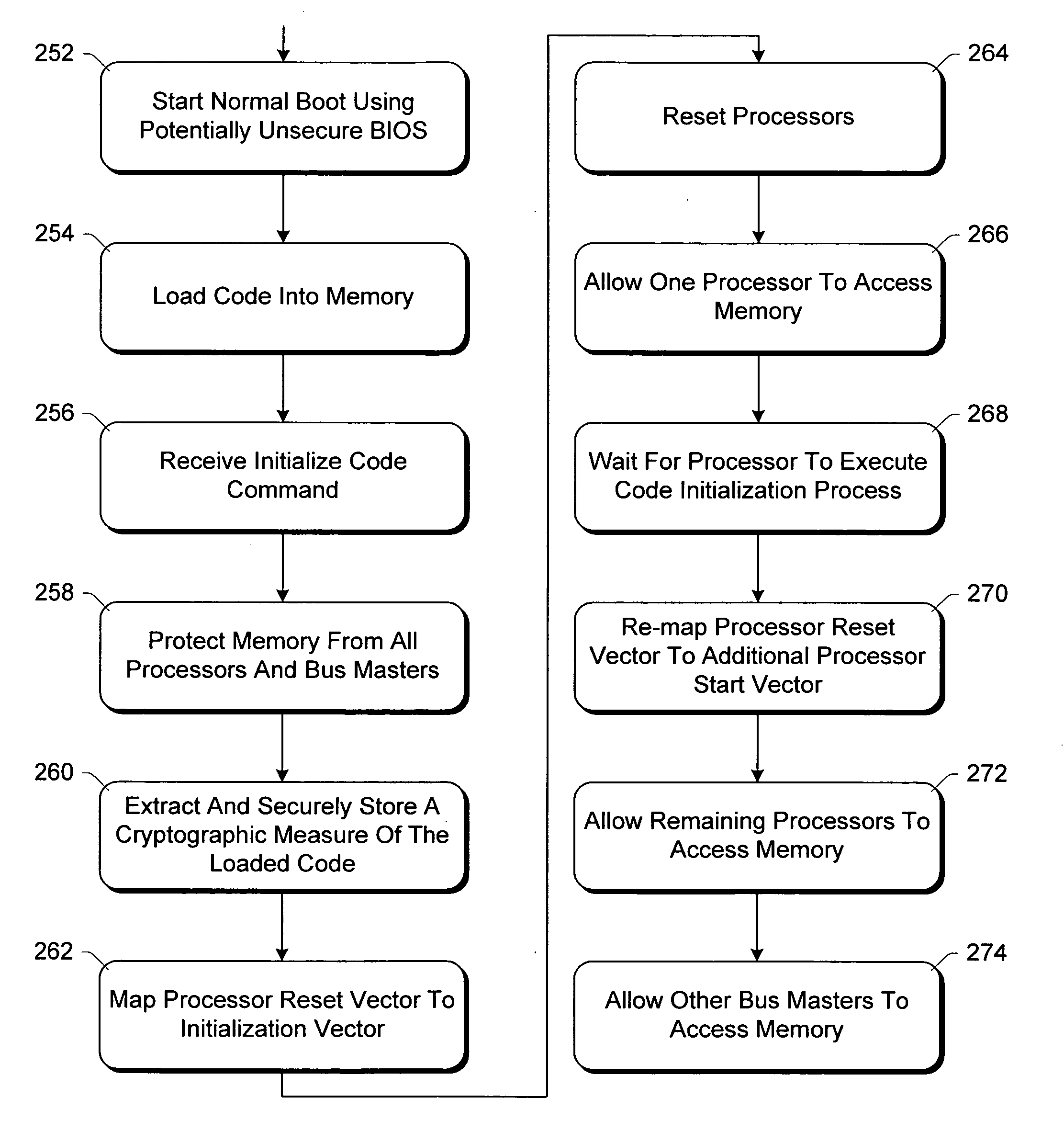
Method and system for allowing code to be securely initialized in a computer
InactiveUS20050235166A1User identity/authority verificationDigital computer detailsComputer hardwareInit
A memory controller prevents CPUs and other I / O bus masters from accessing memory during a code (for example, trusted core) initialization process. The memory controller resets CPUs in the computer and allows a CPU to begin accessing memory at a particular location (identified to the CPU by the memory controller). Once an initialization process has been executed by that CPU, the code is operational and any other CPUs are allowed to access memory (after being reset), as are any other bus masters (subject to any controls imposed by the initiated code).
Owner:MICROSOFT TECH LICENSING LLC
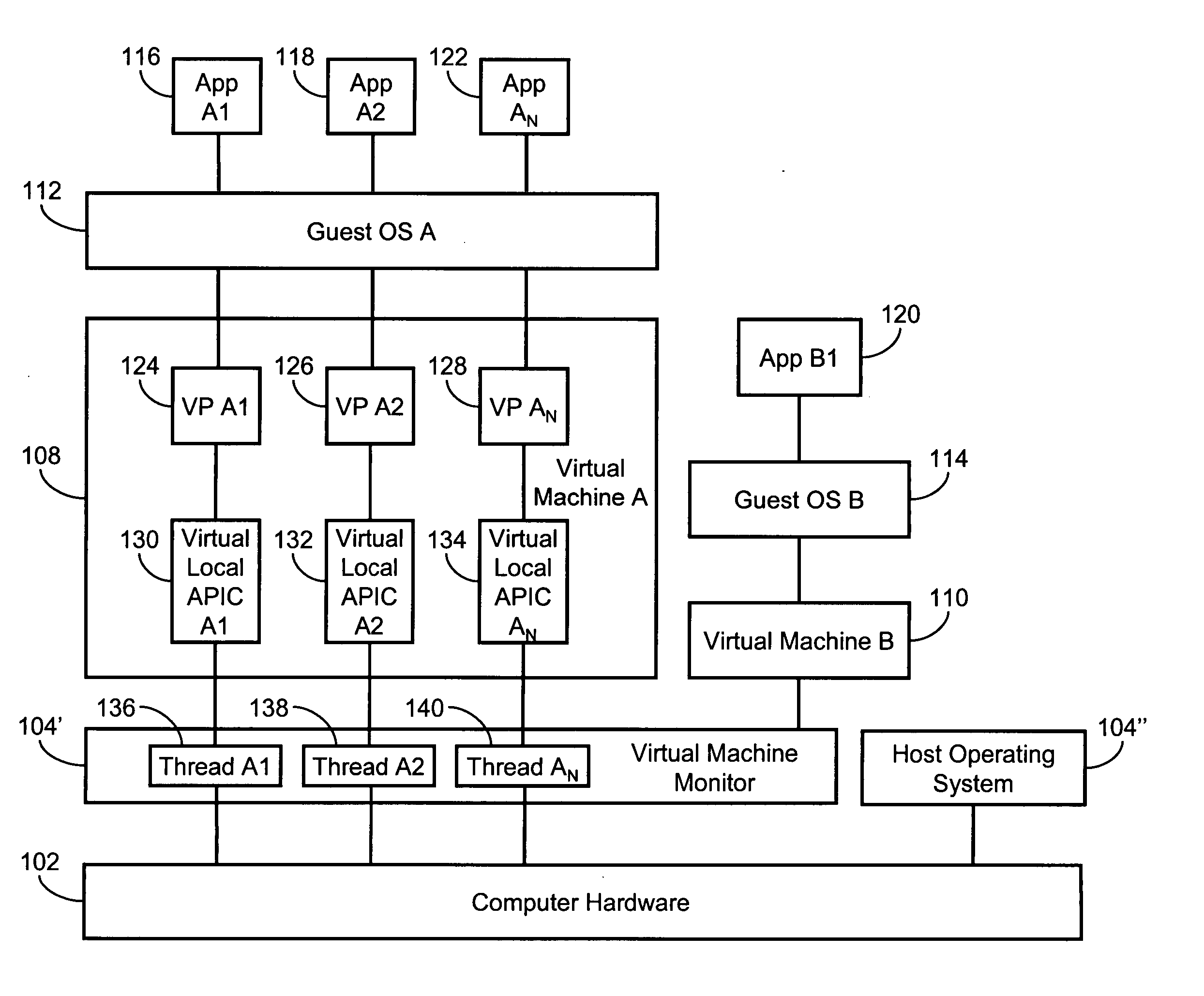
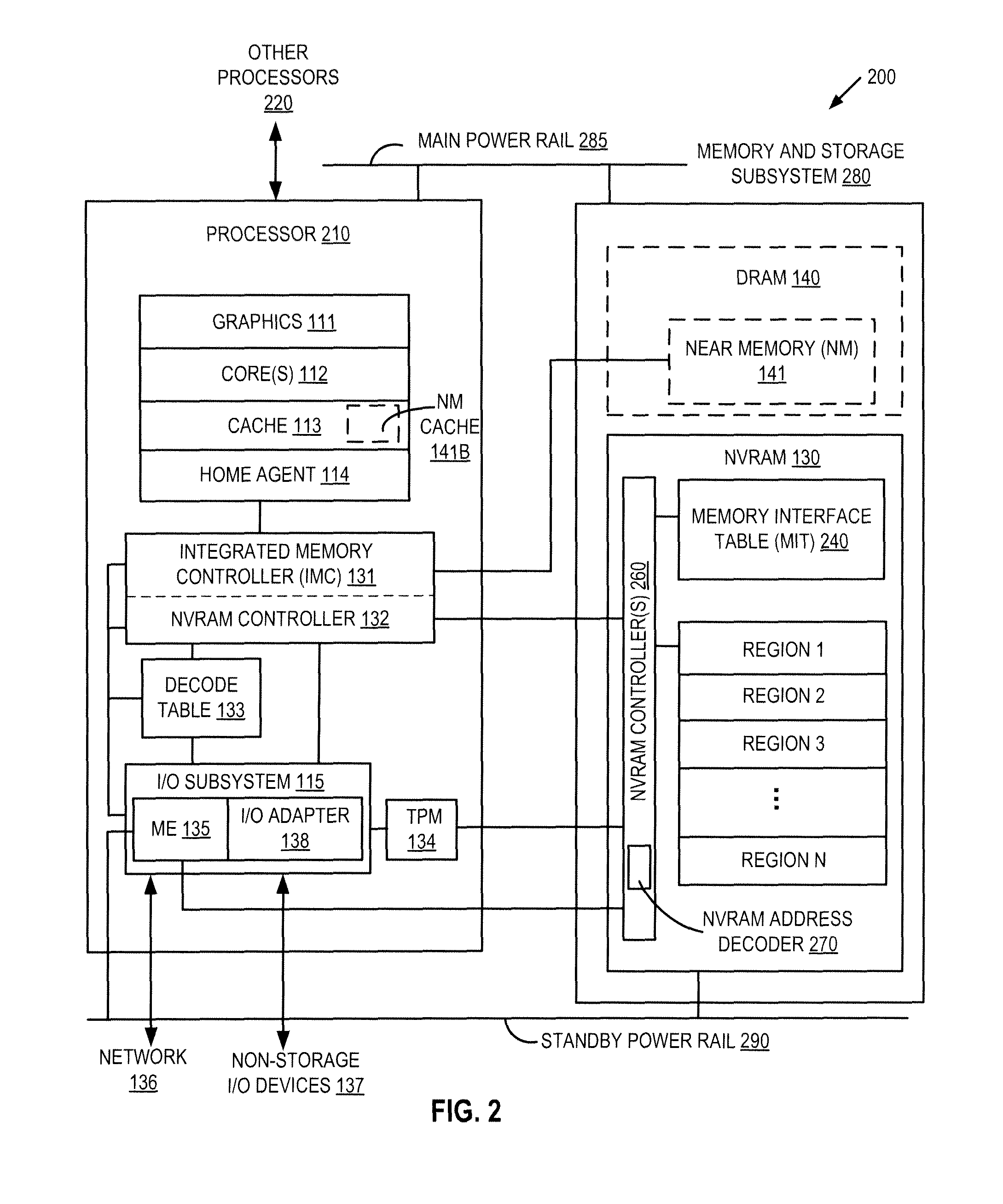
Systems and methods for initializing multiple virtual processors within a single virtual machine
ActiveUS20060005188A1Improve efficiencyProgram initiation/switchingSoftware simulation/interpretation/emulationMulti processorInit
The present invention is a system for and method of initializing multiple virtual processors in a virtual machine (VM) environment. The method of initializing multiple virtual processors includes the steps of the host creating a multiple processor VM and activating a “starter virtual processor,” the “starter virtual processor” issuing a startup command to a next virtual processor, the virtual machine monitor (VMM) giving the target virtual processor the highest priority for accessing the hardware resources, the VMM forcing the “starter virtual processor” to relinquish control of the hardware resources, the VMM handing control of the hardware resources to the target virtual processor, the target virtual processor executing and completing its startup routine, the VMM forcing the target virtual processor to relinquish control of the hardware resources, and the VMM handing control of the hardware resources back to the “starter virtual processor” for activating subsequent virtual processors.
Owner:MICROSOFT TECH LICENSING LLC
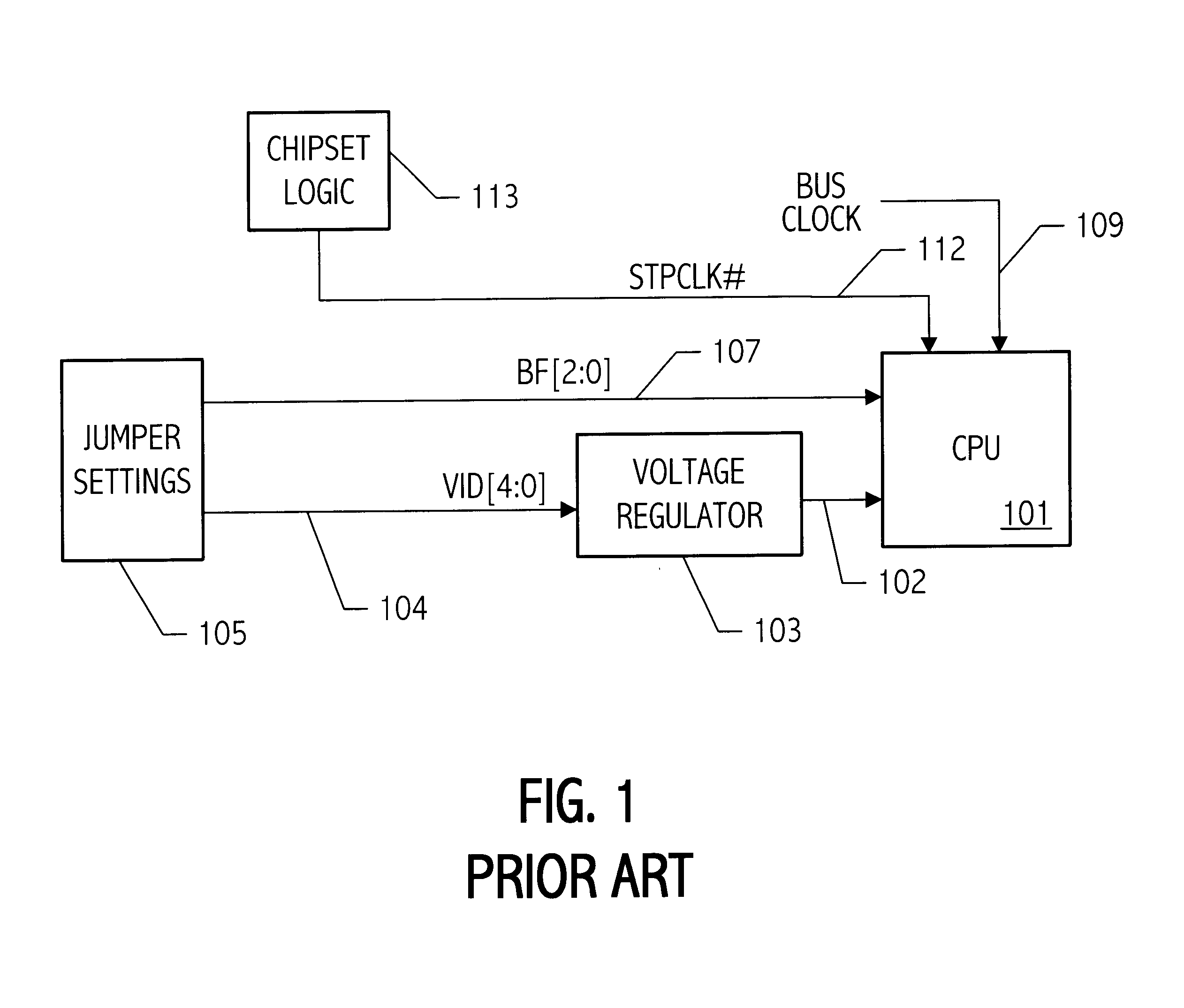
Method for initializing an electronic device using a dual-state power-on-reset circuit
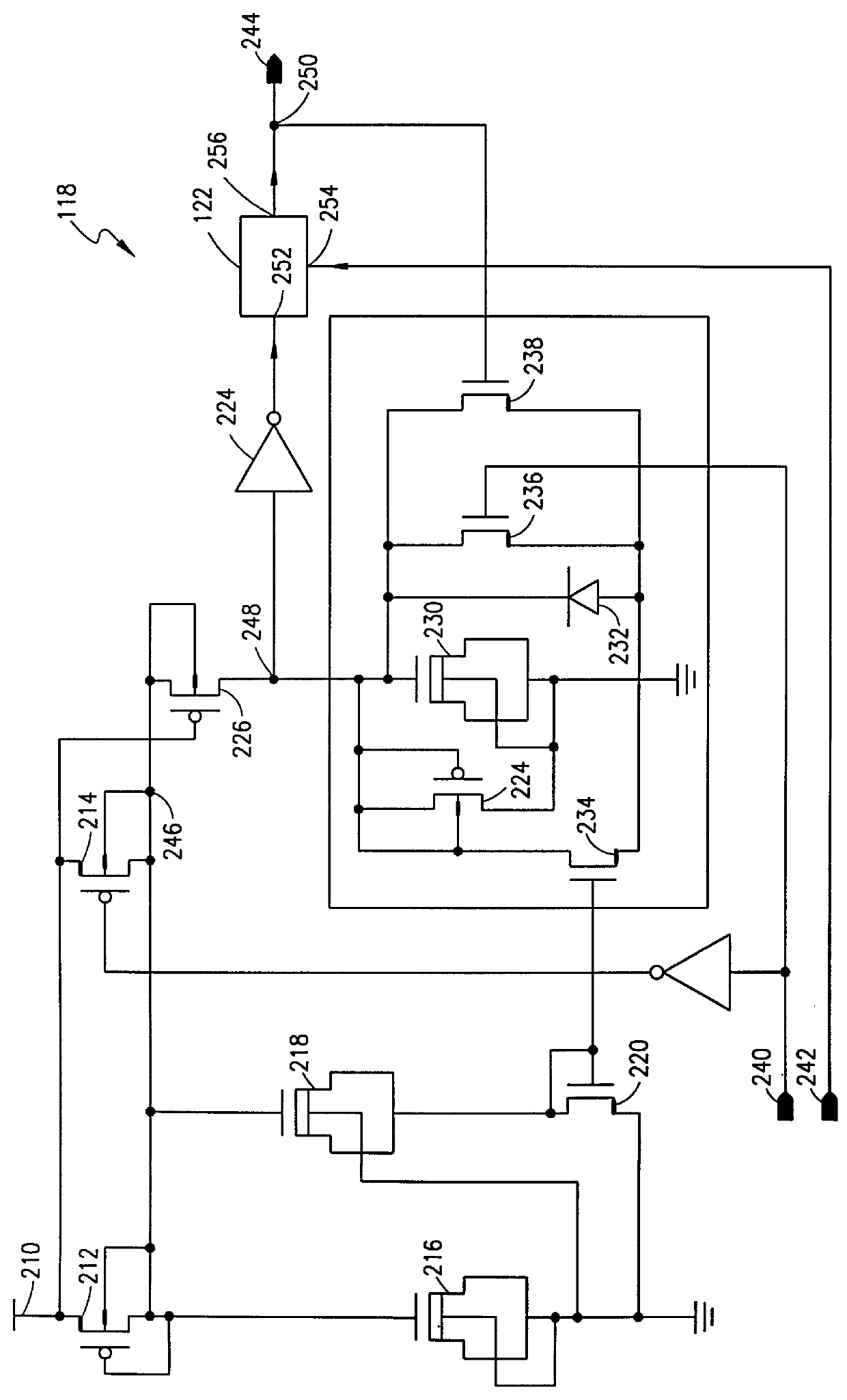
InactiveUS6141764AMinimum power consumptionPulse automatic controlVolume/mass flow measurementPower-on resetElectricity
An initializer that responds to change in a power supply potential level, for generating an initialize signal to initialize a circuit to a select state, the initializer includes a power-on reset circuit that switches between an active and a powered-down state, and is for generating the initialize signal. The initializer also includes a wake-up circuit that monitors the power supply potential level and switches the power-on reset circuit from the powered-down state to the active state when selected change in the power supply potential level occurs.
Owner:MAXIM INTEGRATED PROD INC
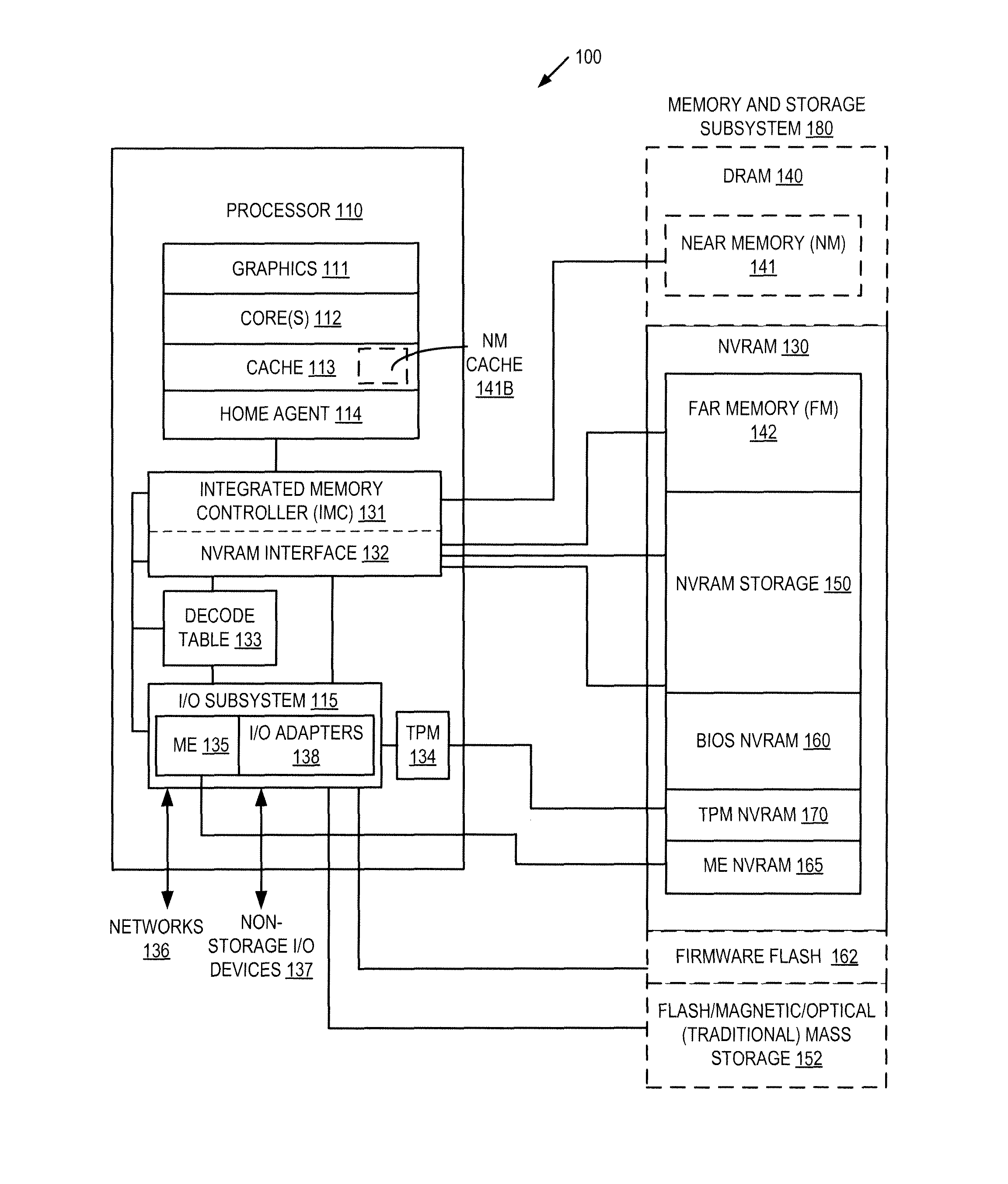
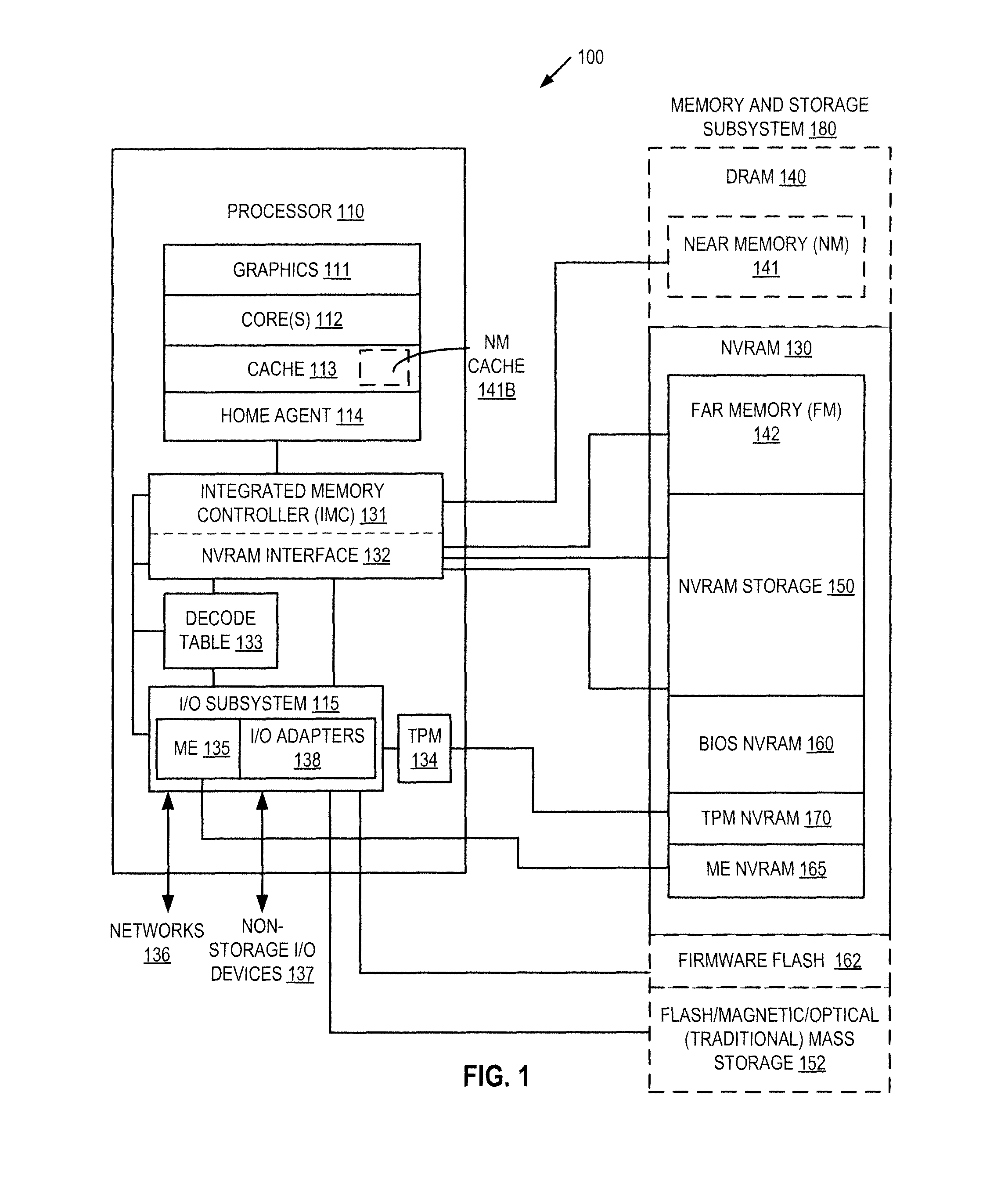
Autonomous initialization of non-volatile random access memory in a computer system
A non-volatile random access memory (NVRAM) is used in a computer system to store information that allows the NVRAM to autonomously initialize itself at power-on. The computer system includes a processor, an NVRAM controller coupled to the processor, and an NVRAM that comprises the NVRAM controller. The NVRAM is byte-rewritable and byte-erasable by the processor. The NVRAM stores a memory interface table containing information for the NVRAM controller to autonomously initialize the NVRAM upon power-on of the computer system without interacting with the processor and firmware outside of the NVRAM. The information is provided by the NVRAM controller to the processor to allow the processor to access the NVRAM.
Owner:INTEL CORP
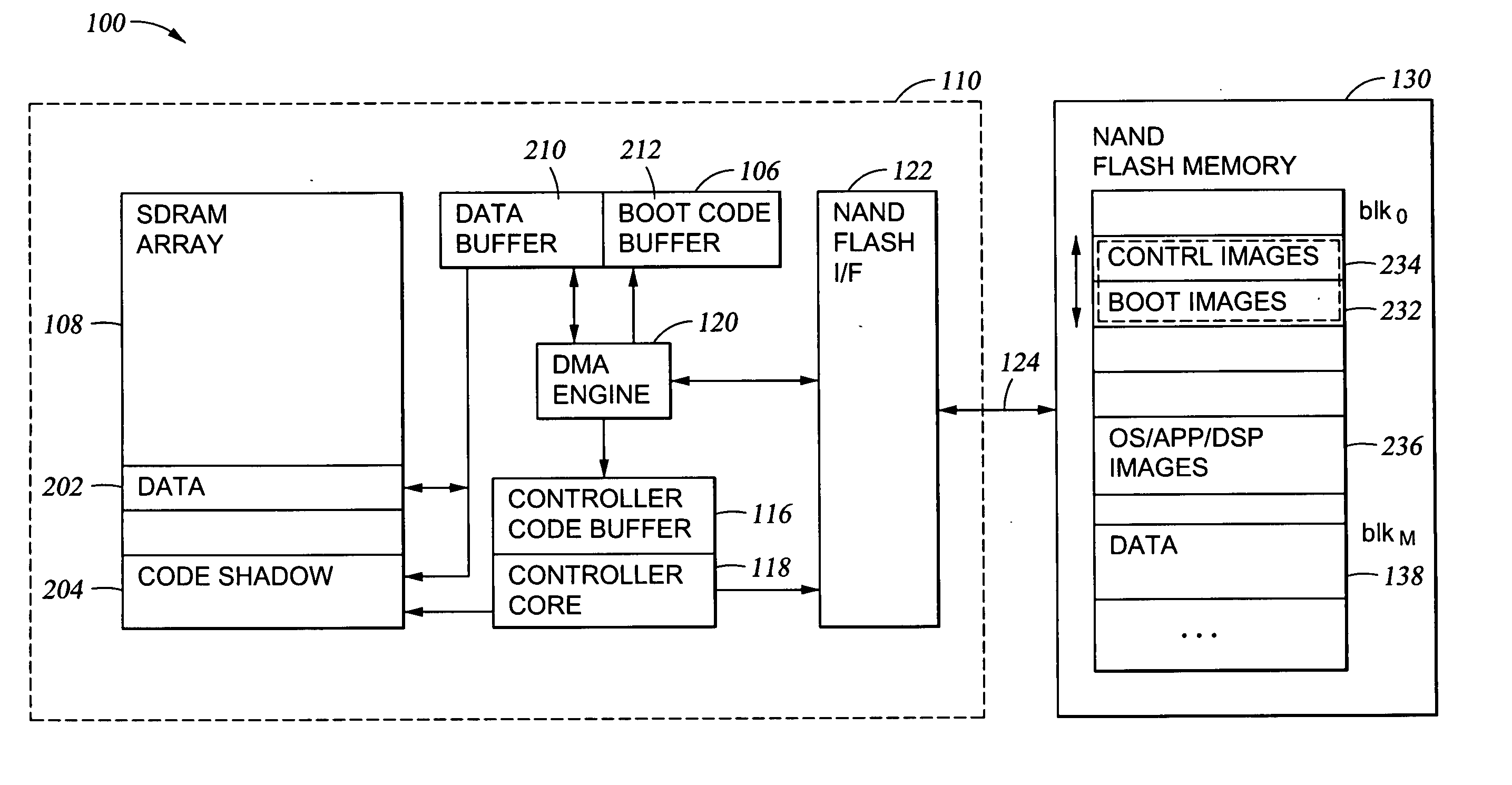
Method of system booting with a direct memory access in a new memory architecture
Embodiments of the invention provide a method and apparatus for initializing a computer system, wherein the computer system includes a processor, a volatile memory, and a non-volatile memory. In one embodiment, the method includes, when the computer system is initialized, automatically copying initialization code stored in the non-volatile memory to the volatile memory, wherein circuitry in the volatile memory automatically creates the copy, and executing, by the processor, the copy of the initialization code from the volatile memory.
Owner:POLARIS INNOVATIONS LTD
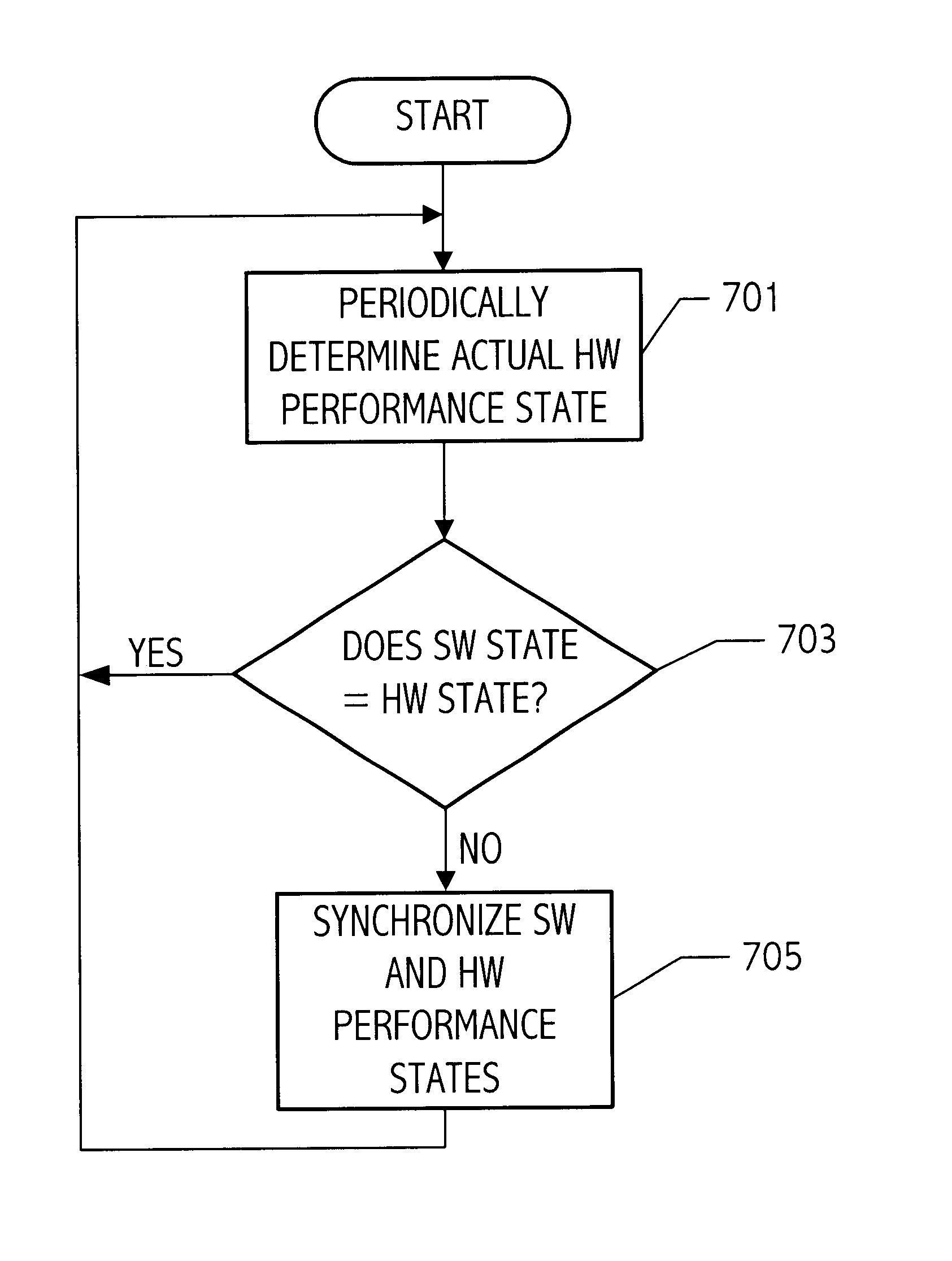
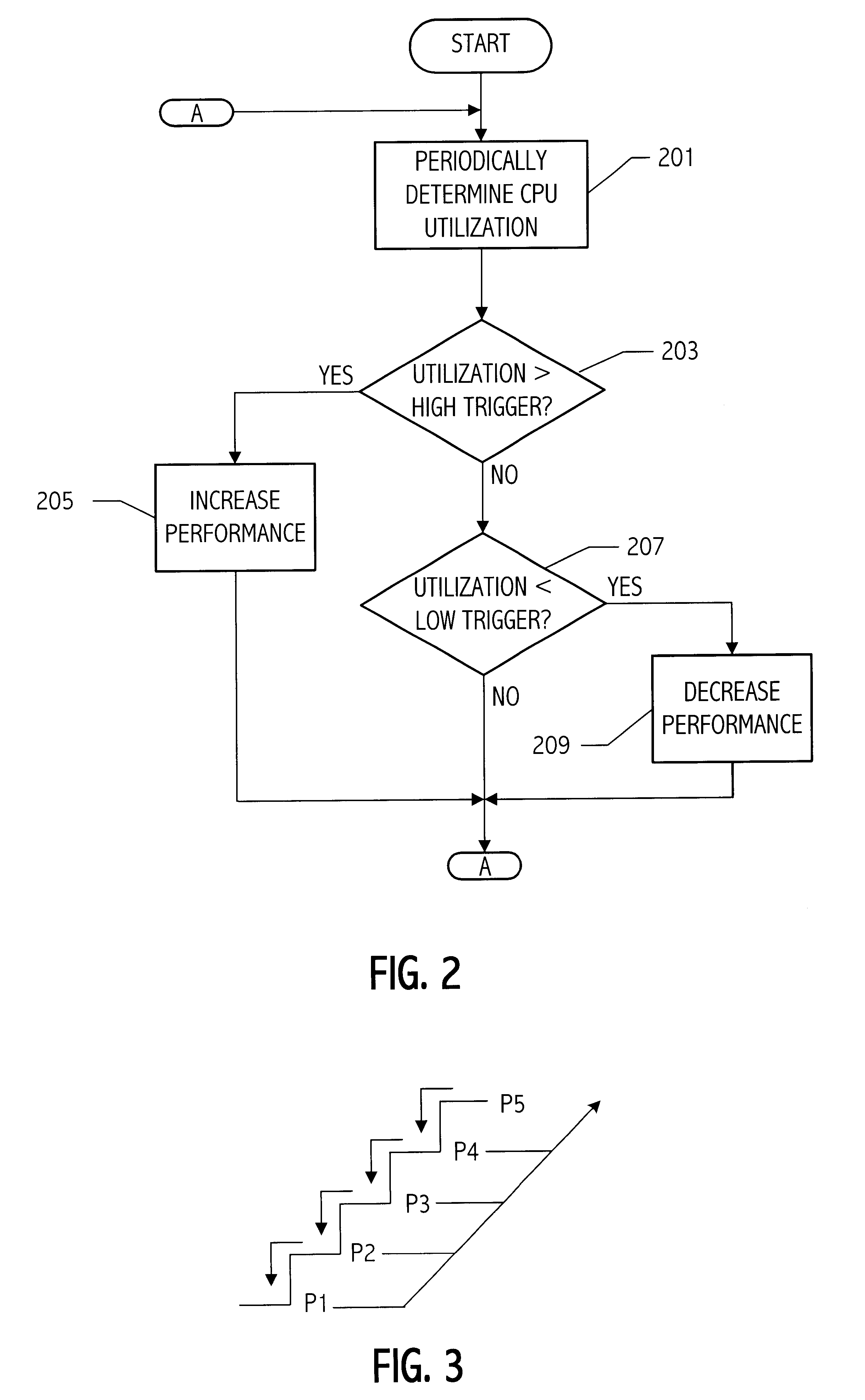
Power state resynchronization
InactiveUS6795927B1Volume/mass flow measurementPower supply for data processingComputer hardwareInit
A computer system has multiple performance states. The computer system periodically determines if the software power state maintained by power management software that represents the power state of the processor or other computer system component matches the actual power state of the processor or other computer system component. If not, the actual power state and the software power state are resynchronized, for example, by reinitializing the power management software or otherwise causing the software power state to match the hardware power state.
Owner:MEDIATEK INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com