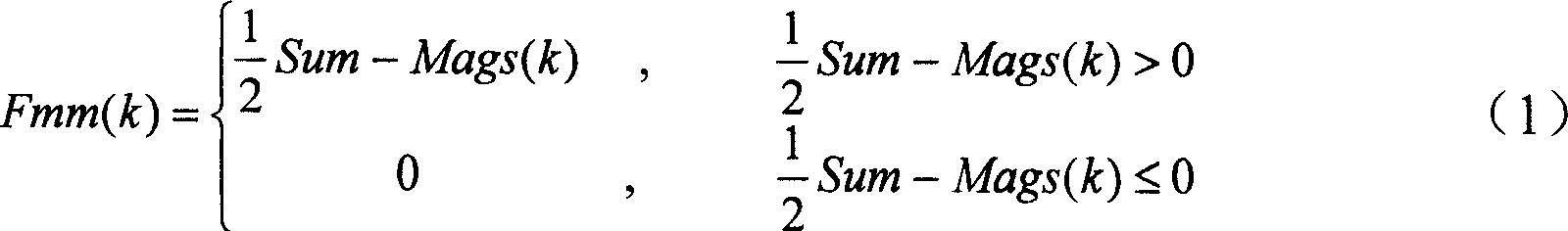Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
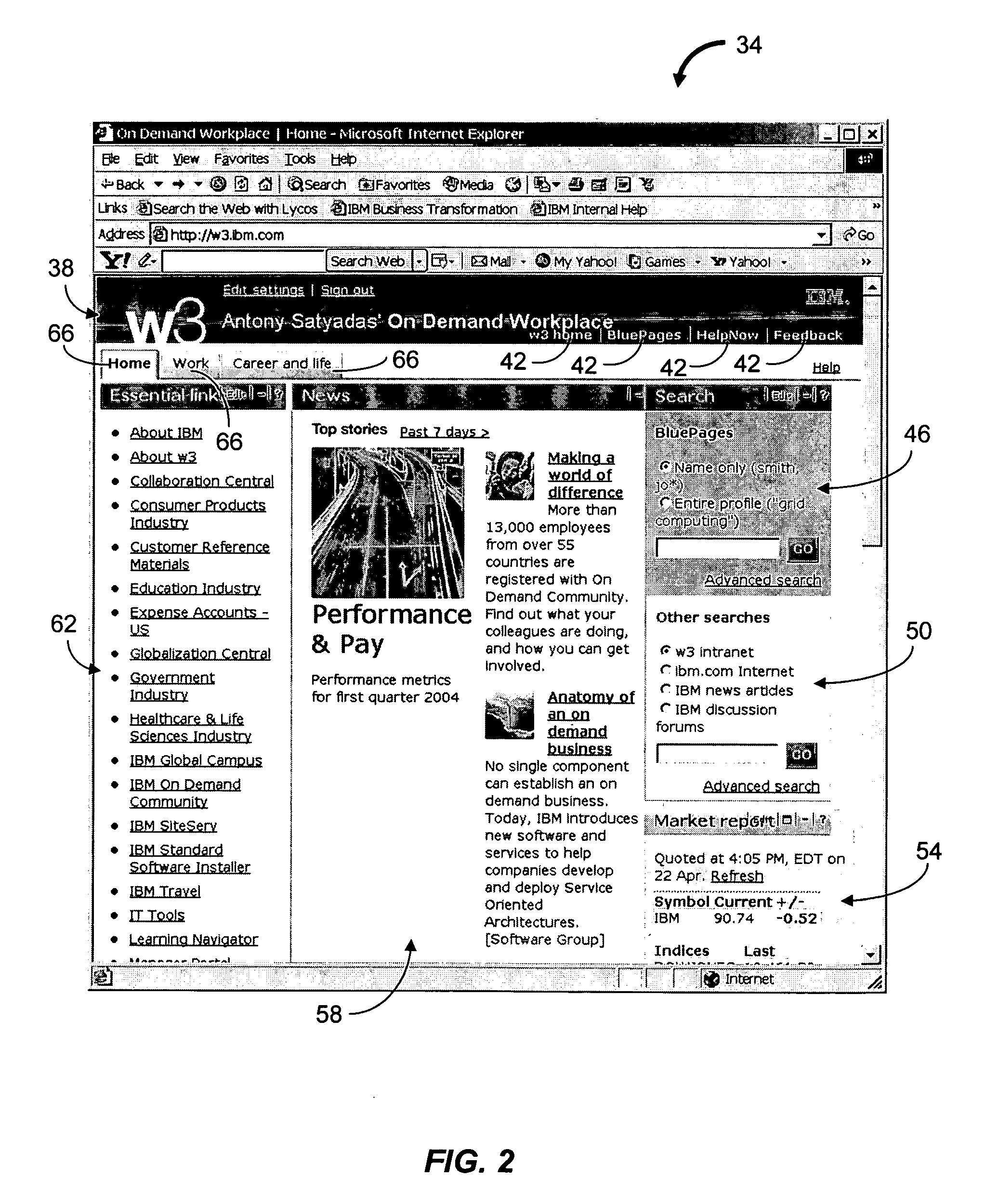
1523 results about "Selection algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a selection algorithm is an algorithm for finding the kth smallest number in a list or array; such a number is called the kth order statistic. This includes the cases of finding the minimum, maximum, and median elements. There are O(n)-time (worst-case linear time) selection algorithms, and sublinear performance is possible for structured data; in the extreme, O(1) for an array of sorted data. Selection is a subproblem of more complex problems like the nearest neighbor and shortest path problems. Many selection algorithms are derived by generalizing a sorting algorithm, and conversely some sorting algorithms can be derived as repeated application of selection.
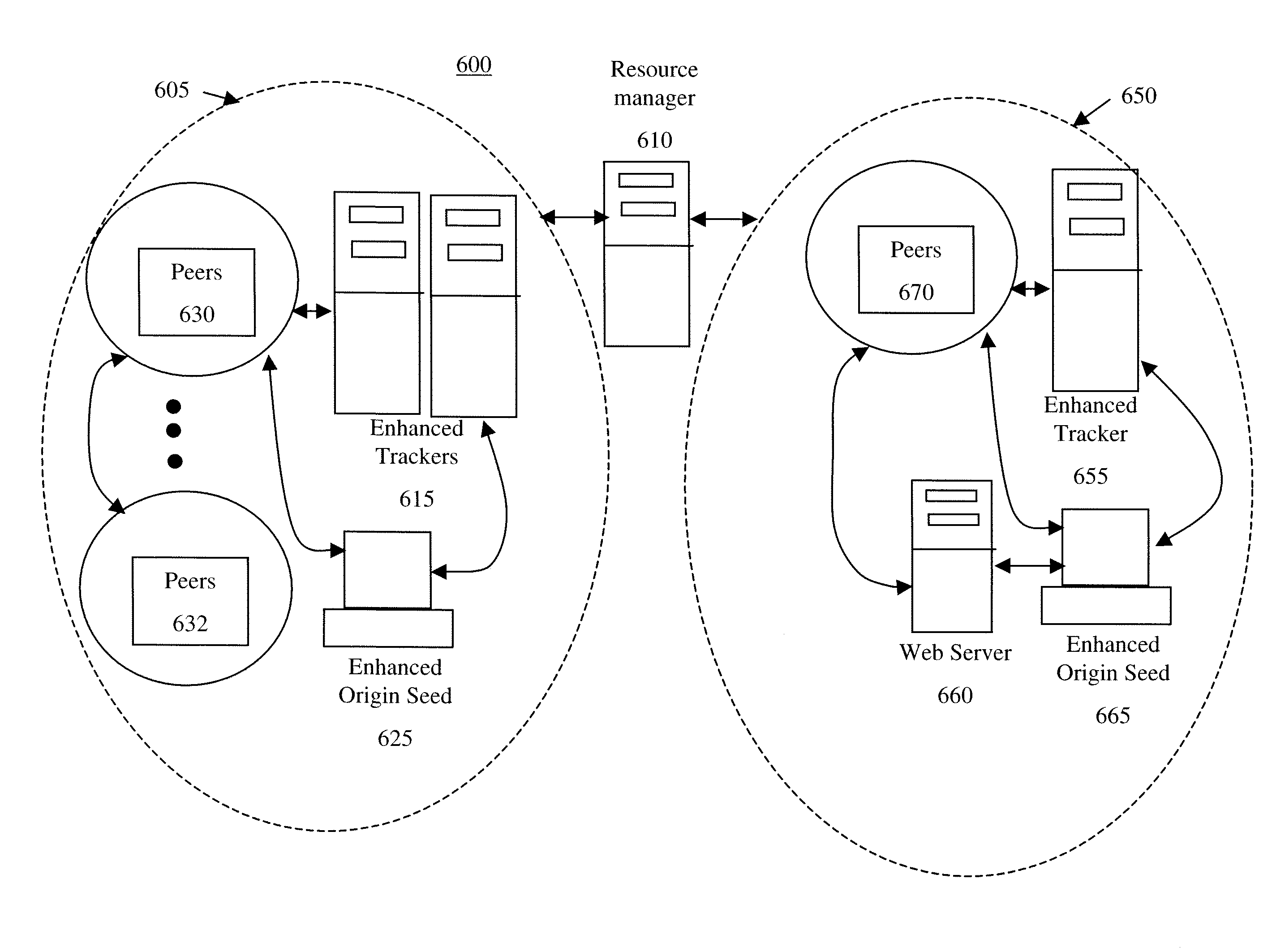
Accelerating peer-to-peer content distribution
ActiveUS20090182815A1Improving P2P performanceImprove service qualityMultiple digital computer combinationsElectric digital data processingContent distributionDistributed computing
The acceleration of peer-to-peer downloads of content files wherein a tracker performs a condition based peer selection that is dynamically adjustable. A further feature relates to the use of enhanced message scheme for communications. One embodiment is a system in a swarm having at least one origin seed capable of at least initially storing the content files with at least one tracker maintaining a list of peers wherein the tracker uses at least one dynamically adjusting peer selection algorithm to generate a condition based peer-list and provides the condition based peer-list to a requesting peer.
Owner:NBCUNIVERSAL
Virtualized shared protection capacity
The present disclosure relates a network, a network element, a system, and a method providing an efficient allocation of protection capacity for network connections and / or services. These may be for services within a given Virtual Private Network (VPN) or Virtual Machine (VM) instance flow. Network ingress / egress ports are designed to be VM instance aware while transit ports may or may not be depending on network element capability or configuration. A centralized policy management and a distributed control plane are used to discover and allocate resources to and among the VPNs or VM instances. Algorithms for efficient allocation and release of protection capacity may be coordinated between the centralized policy management and the distributed control plane. Additional coupling of attributes such as latency may provide more sophisticated path selection algorithms including efficient sharing of protection capacity.
Owner:CIENA
System and Method for Server-Based Antivirus Scan of Data Downloaded From a Network
ActiveUS20120110667A1Accurate and fast determinationFast and accurate selectionMemory loss protectionError detection/correctionWorkstationMalware
Aspect of the invention are directed to antivirus scanning, by a proxy server, of data downloaded from the network onto a PC workstation. The antivirus scanning is optimized for each scan by selecting an algorithm for that scan based on a determined overall likelihood that the downloaded data contains malicious code. Determination of the overall likelihood is augmented by the strength, or confidence, of statistical data relating to malware screening of results of previous downloads having similar parameters to the instant download.
Owner:AO KASPERSKY LAB
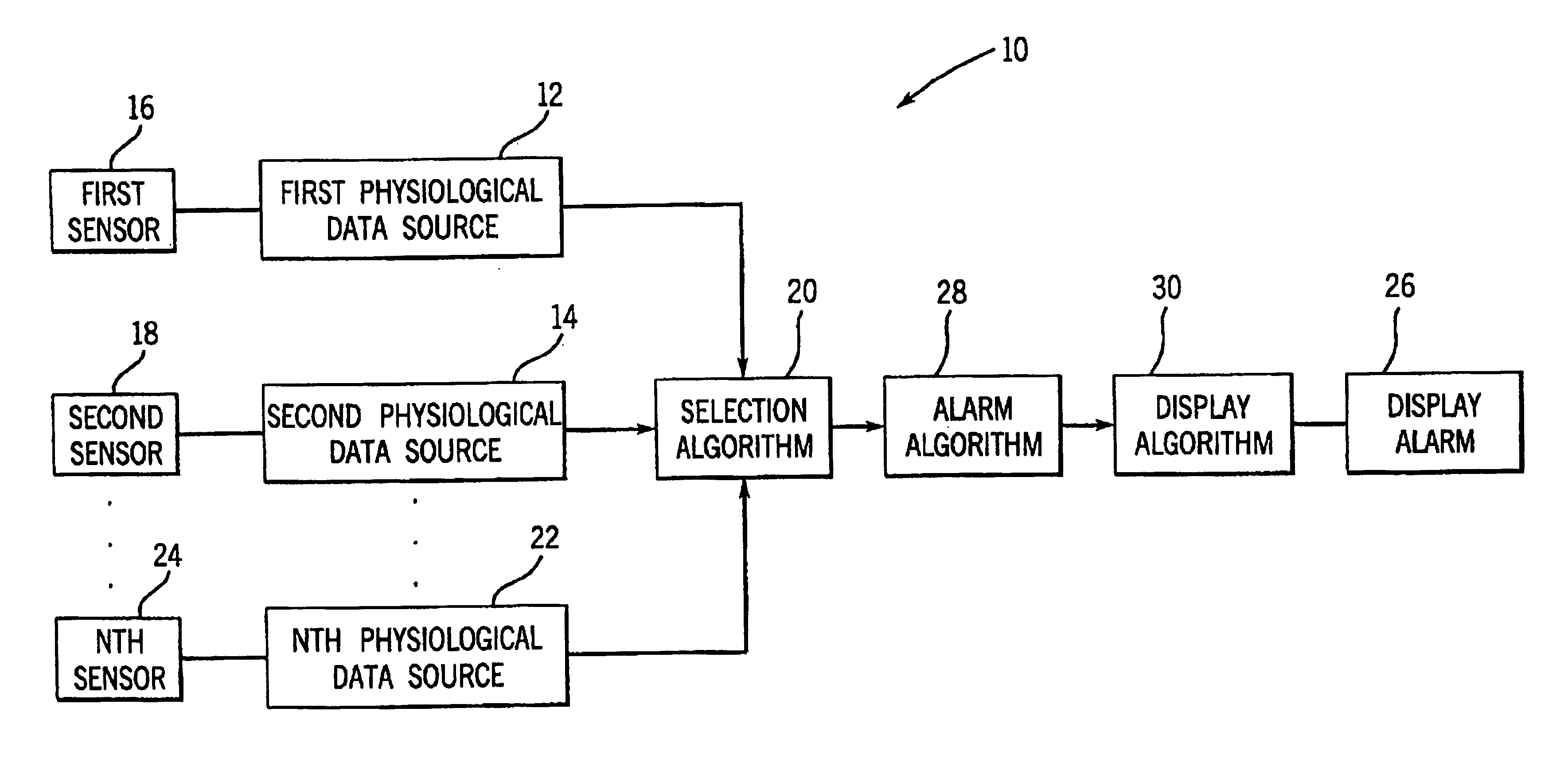
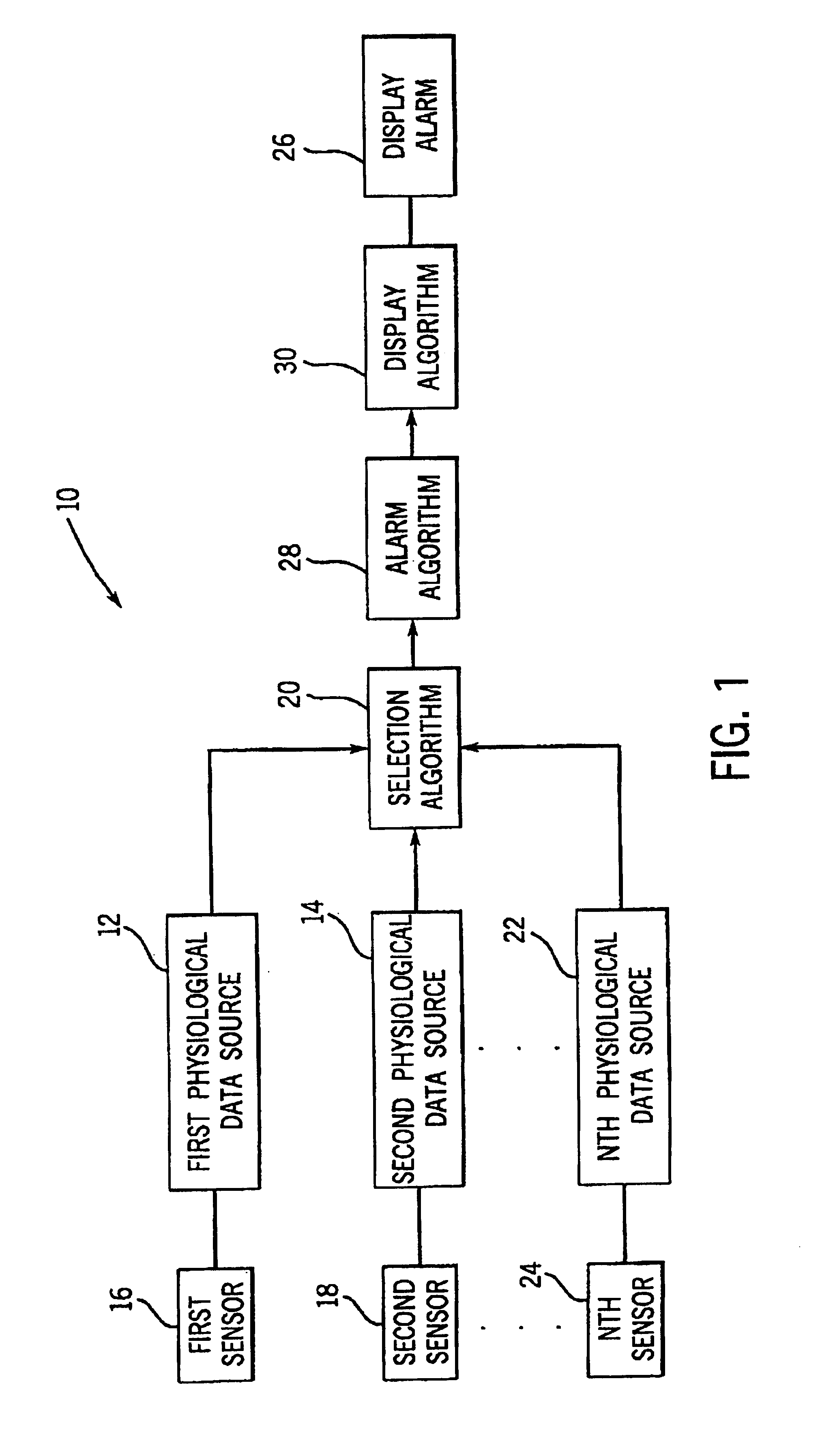
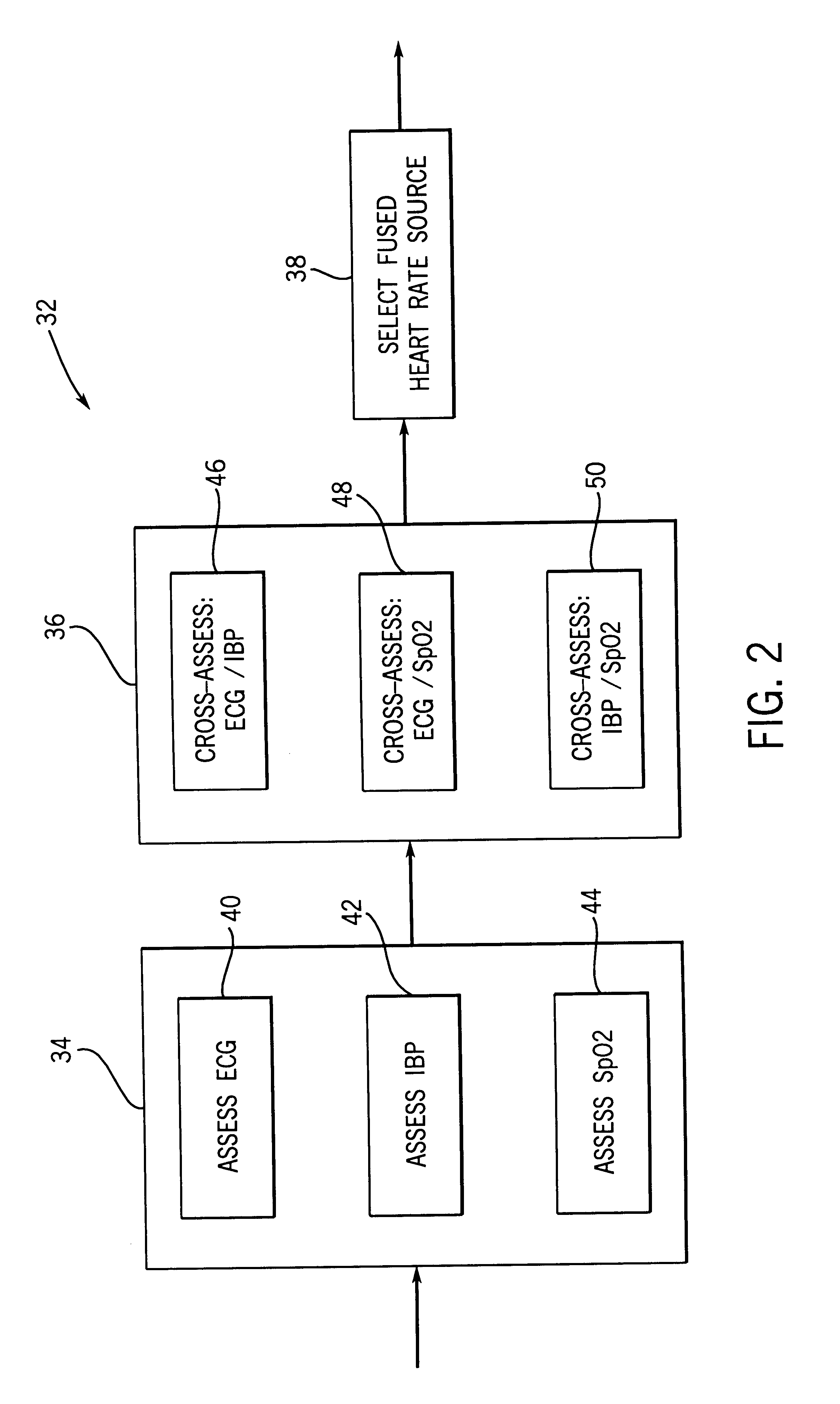
System and method for selecting physiological data from a plurality of physiological data sources
Owner:GE MEDICAL SYST INFORMATION TECH
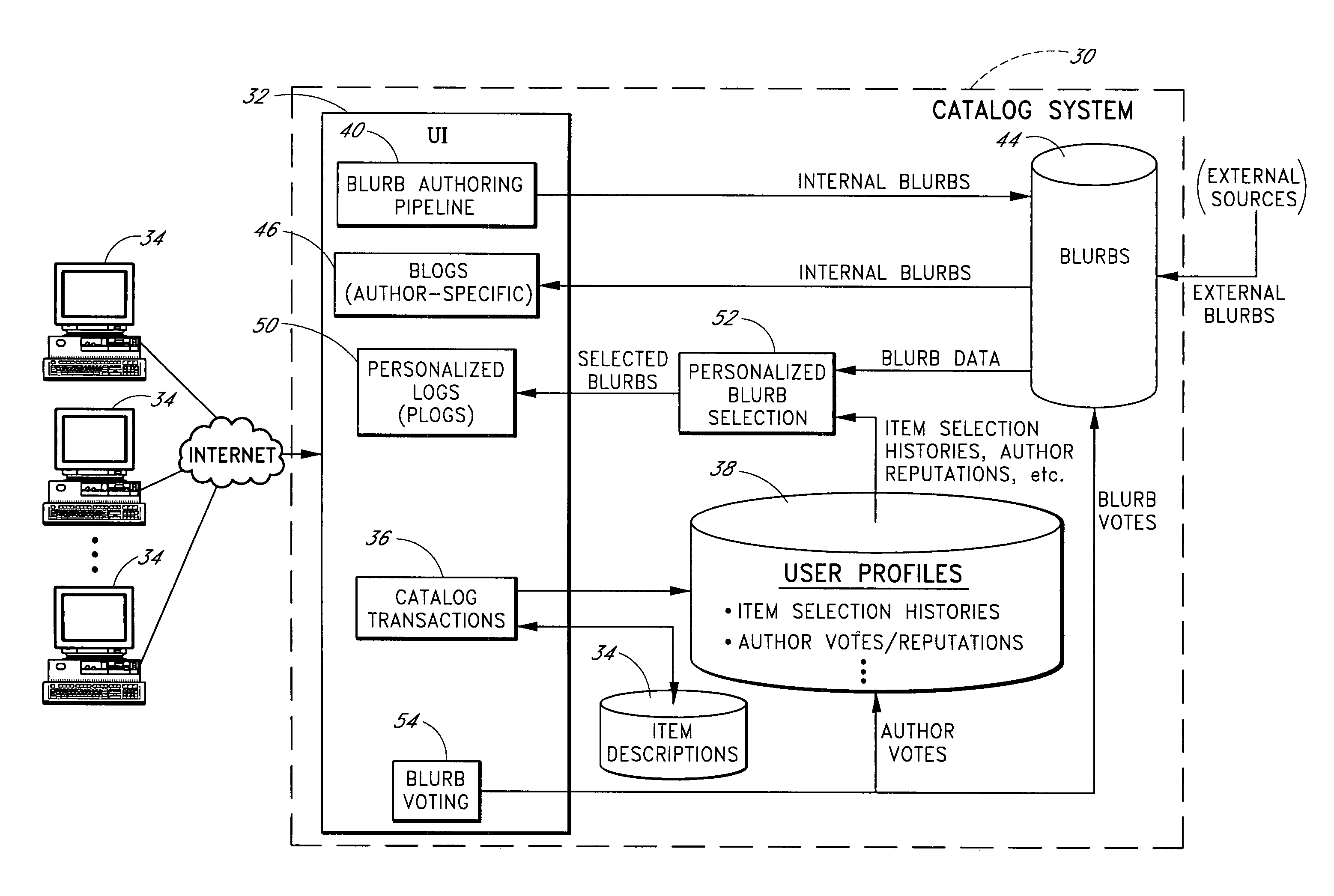
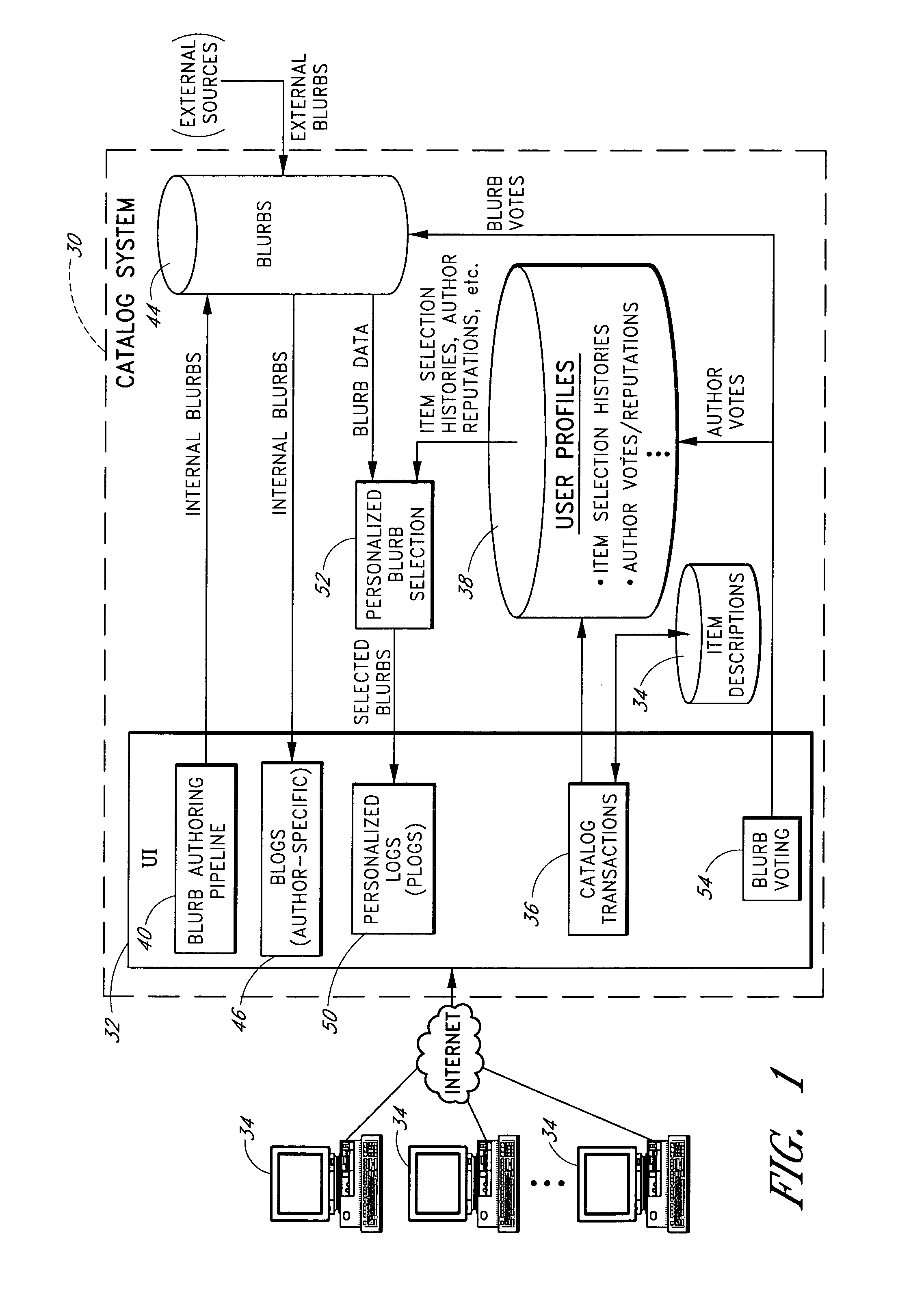
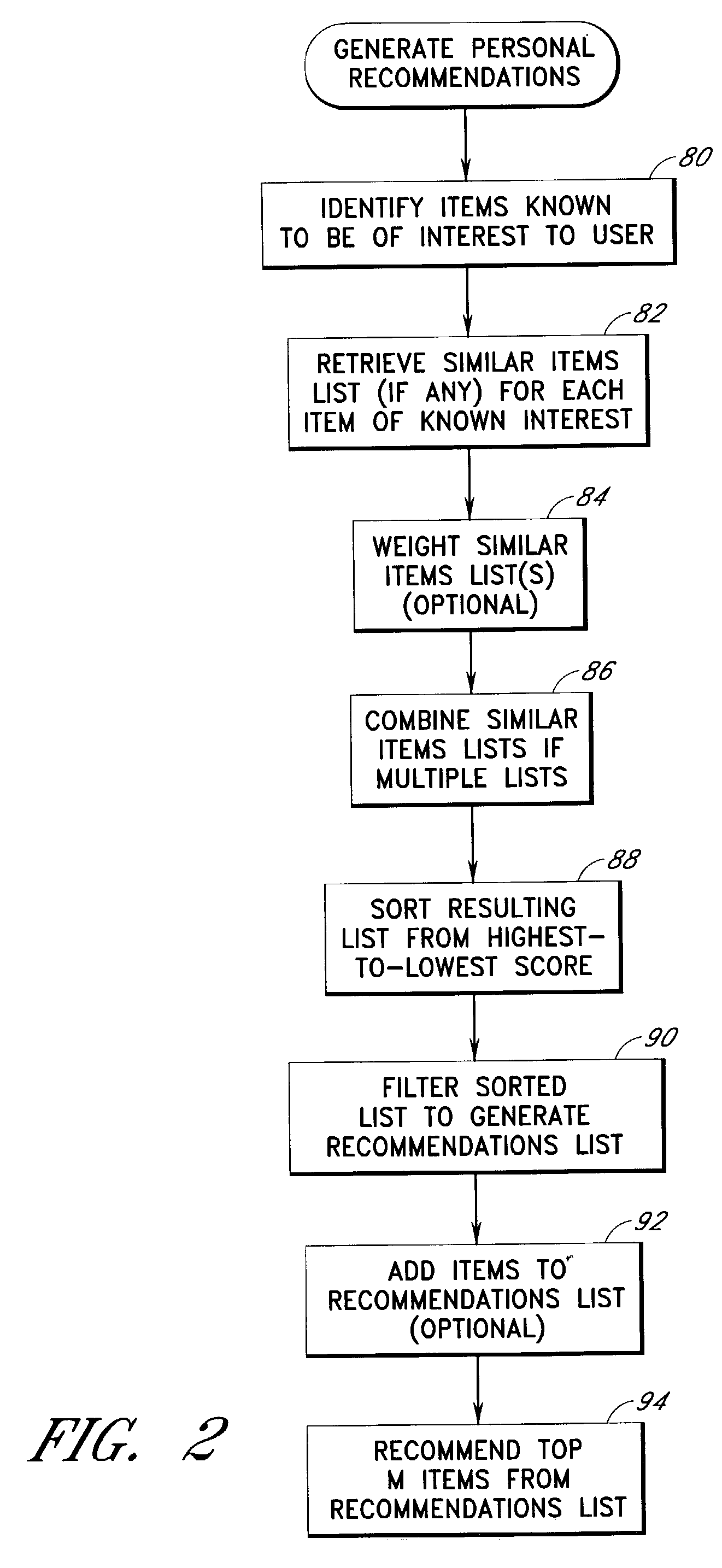
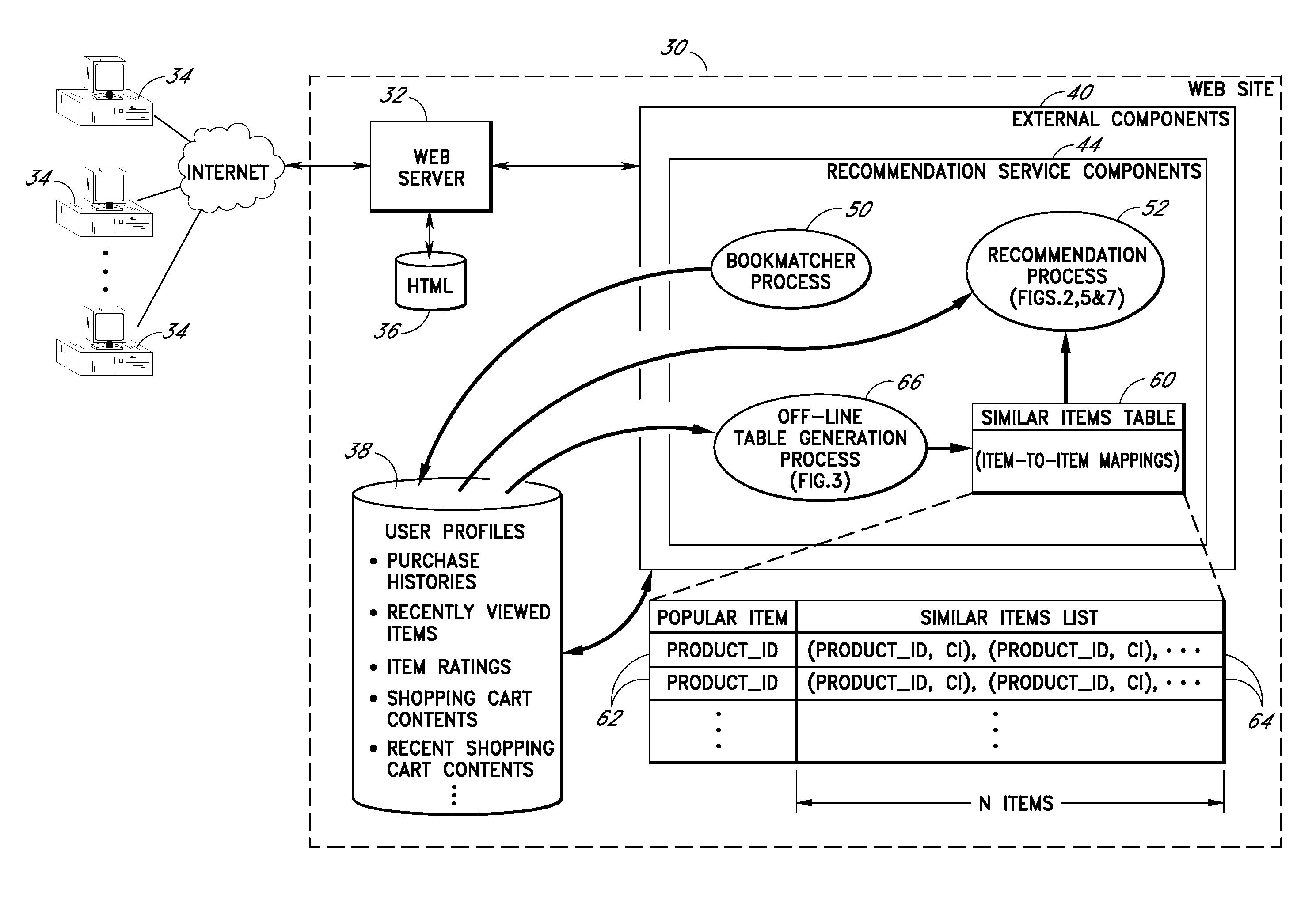
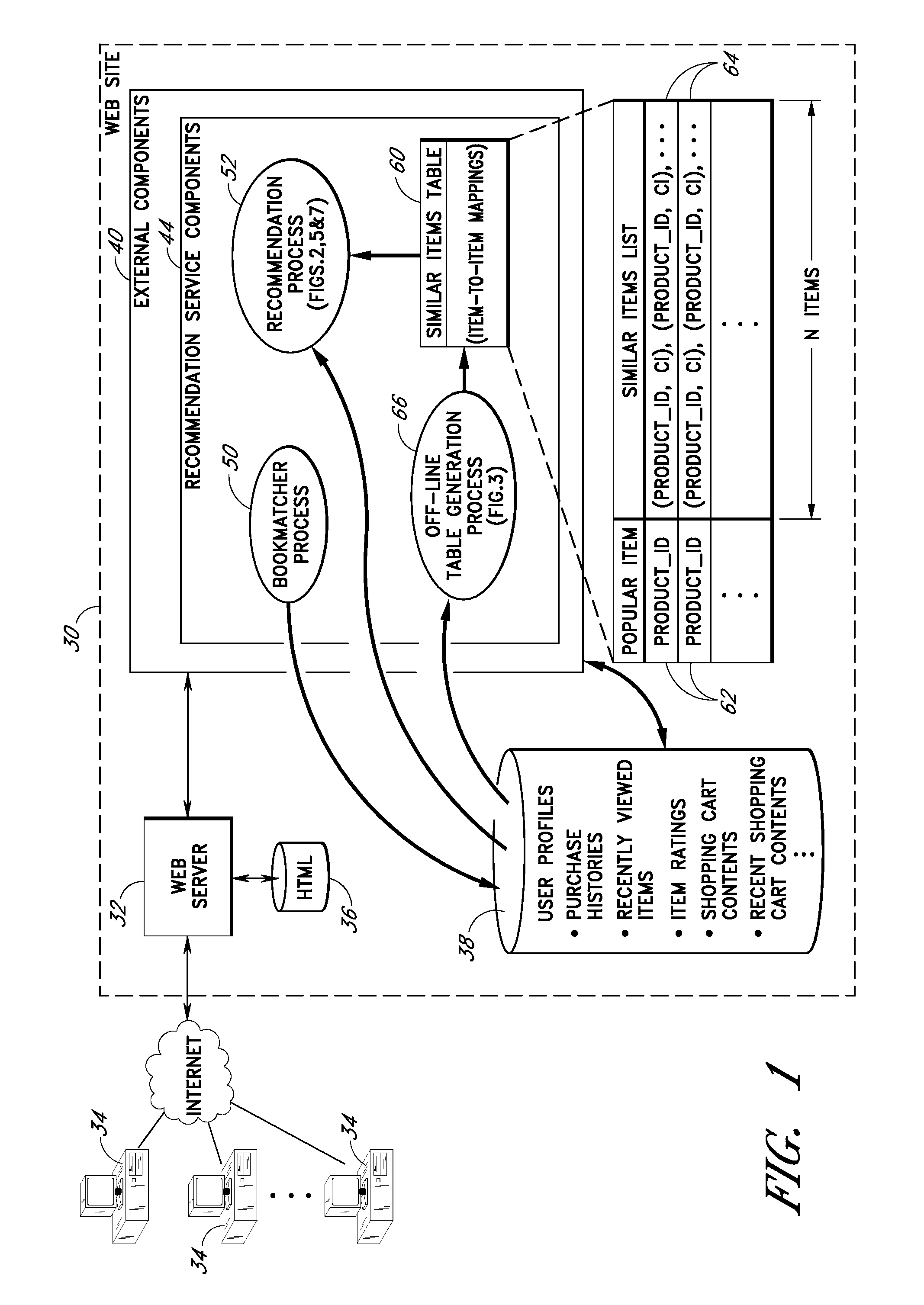
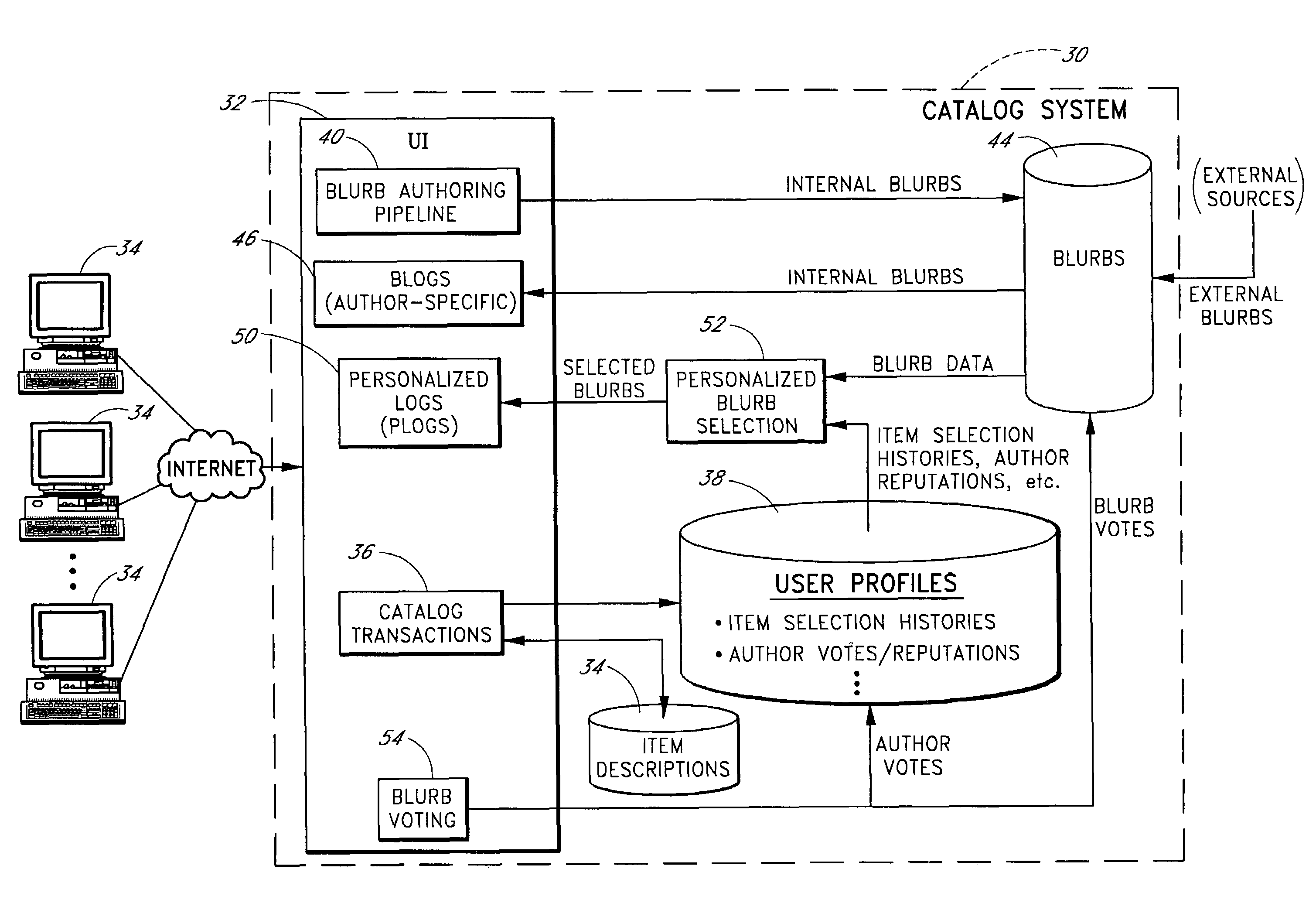
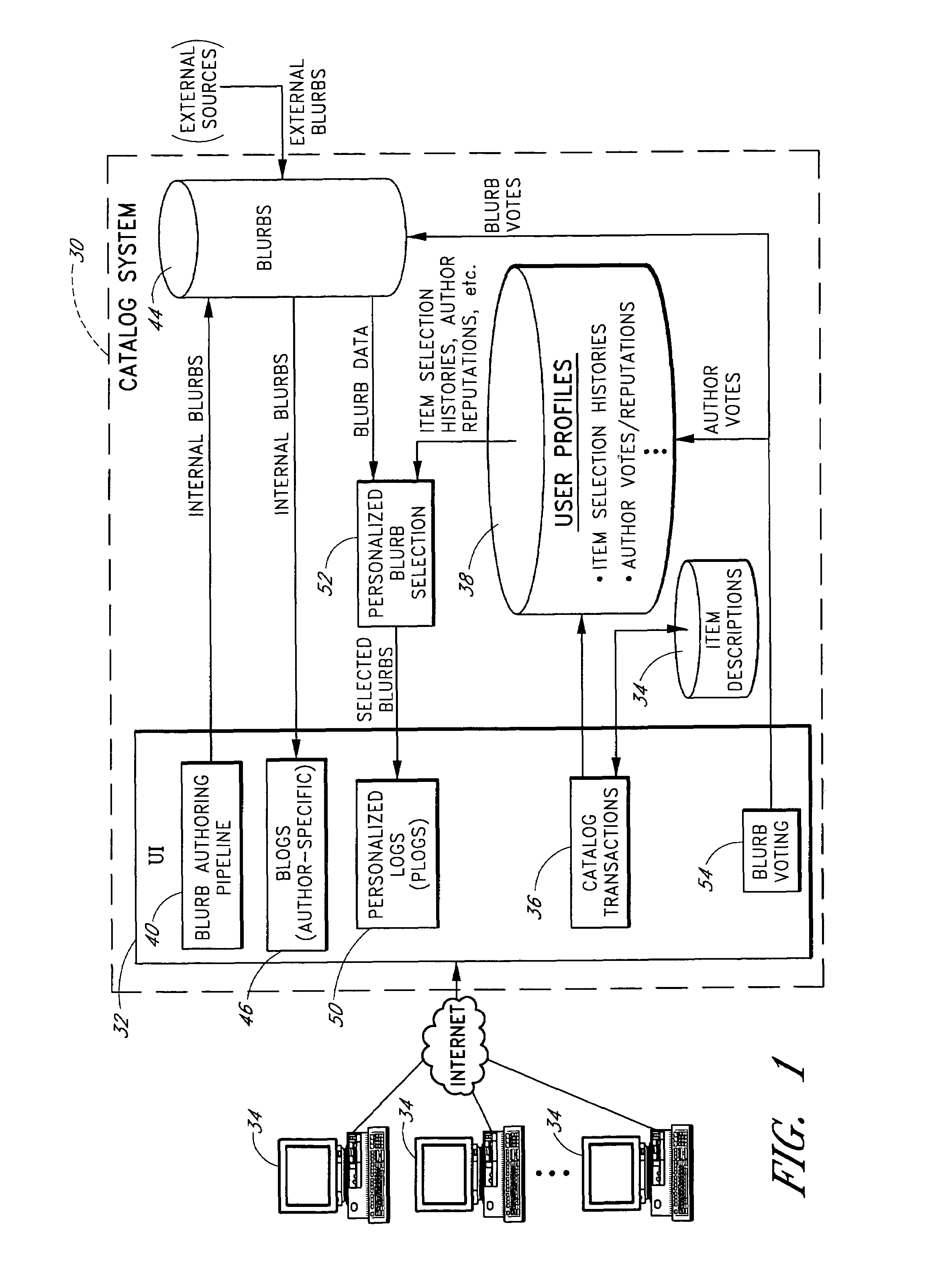
Personalized selection and display of user-supplied content to enhance browsing of electronic catalogs
An electronic catalog system provides an interface for users to author and post pieces of content, referred to as “blurbs,” for viewing by other users. The blurbs submitted by a particular author are made available for viewing in an author-specific blog (web log) format. Blurbs may also be obtained from external sources, such as from blogs hosted by various web sites. A personalized blurb selection component selects blurbs to present to users based on histories of catalog items selected by such users, and / or based on various other criteria. The blurbs selected for a particular user are presented within a personal log or “plog,” which may be updated daily and will typically contain entries from many different authors. User feedback provided on specific blurbs is taken into consideration by the personalized blurb selection algorithms.
Owner:AMAZON TECH INC
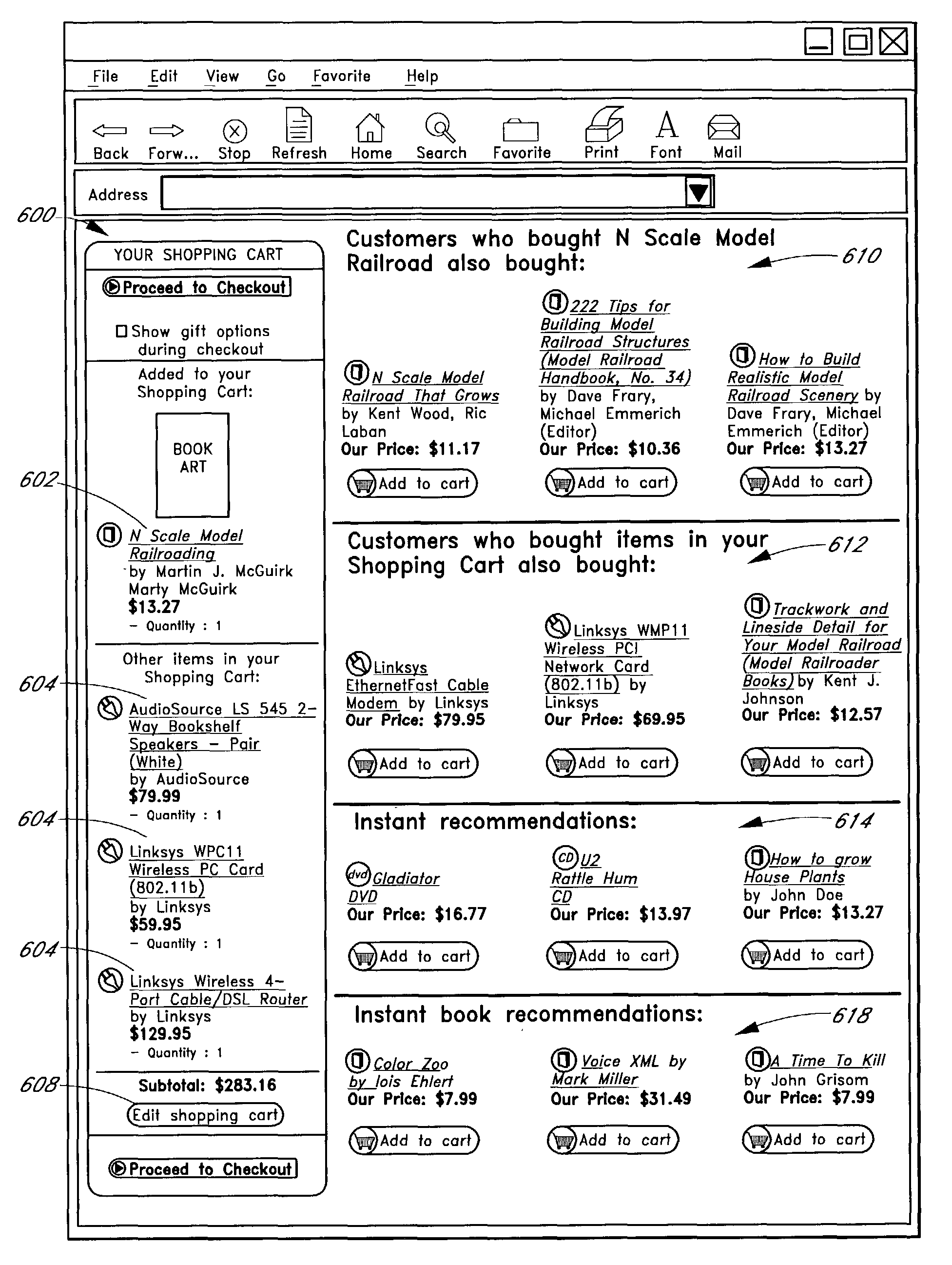
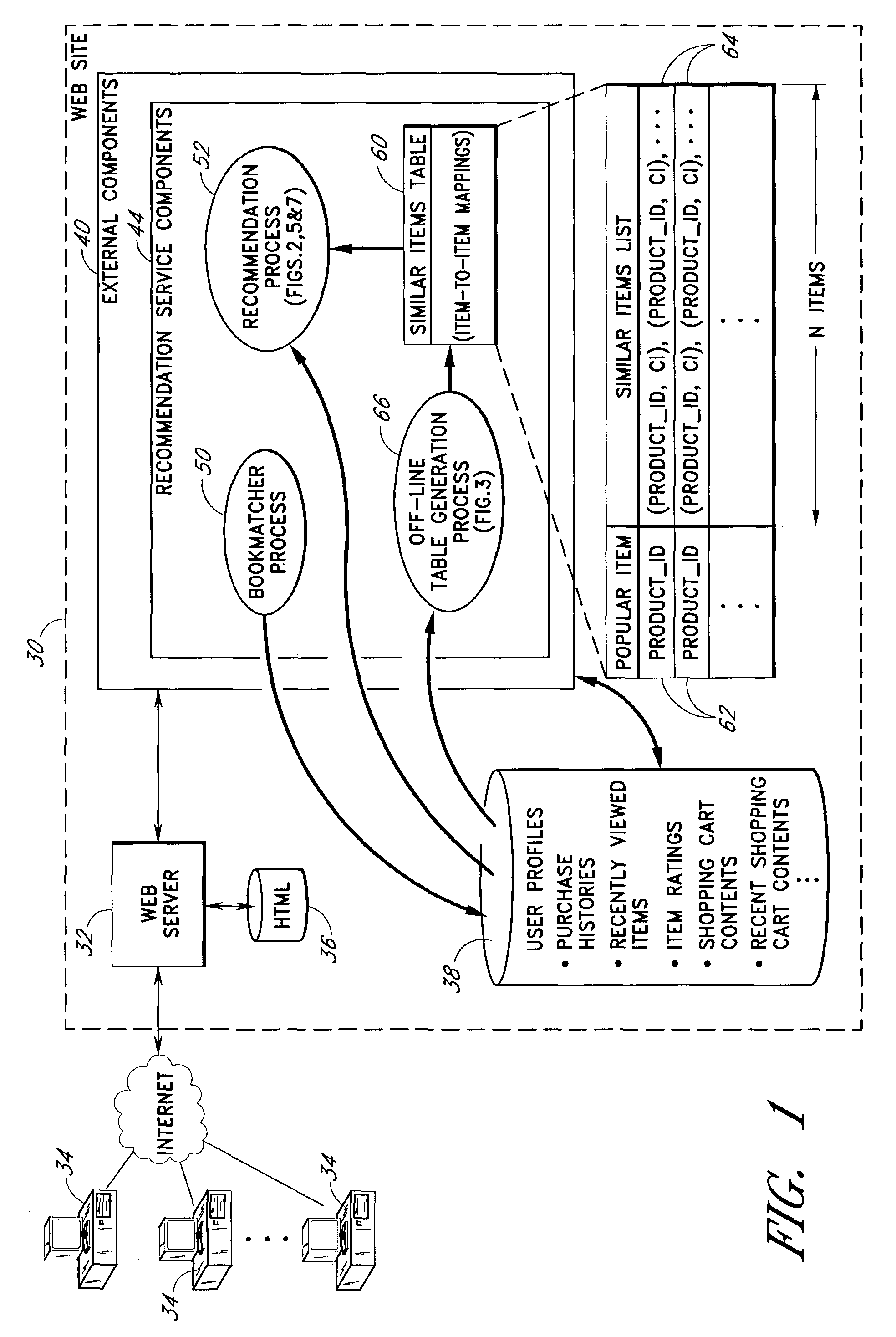
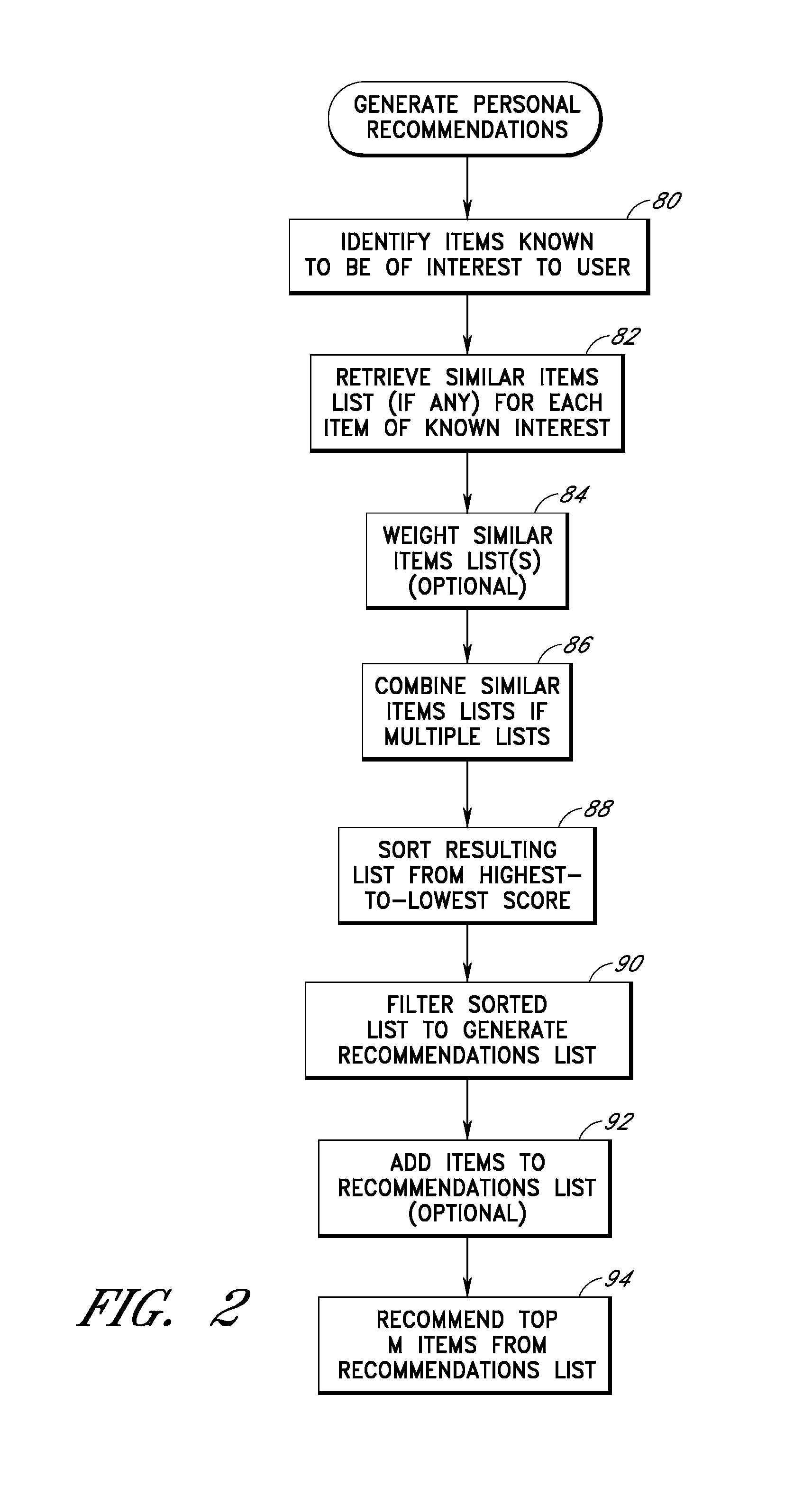
User interface and methods for recommending items to users
ActiveUS7720723B2Good user interfaceWithout sacrificing breadthAdvertisementsGeneration processScreen space
An improved user interface and method are provided for presenting recommendations to a user when the user adds an item to a shopping cart. In response to the shopping cart add event, a page generation process generates and returns a page that includes a recommendations portion and a condensed view of the shopping cart. The recommendations portion preferably includes multiple recommendation sections, each of which displays a different respective set of recommended items selected according to a different respective recommendation or selection algorithm (e.g., recommendations based on shopping cart contents, recommendations based on purchase history, etc.). The condensed shopping cart view preferably lacks controls for editing the shopping cart, and lacks certain types of product information, making more screen real estate available for the display of the recommendations content. A link to a full shopping cart page allows the user to edit the shopping cart and view expanded product descriptions.
Owner:AMAZON TECH INC
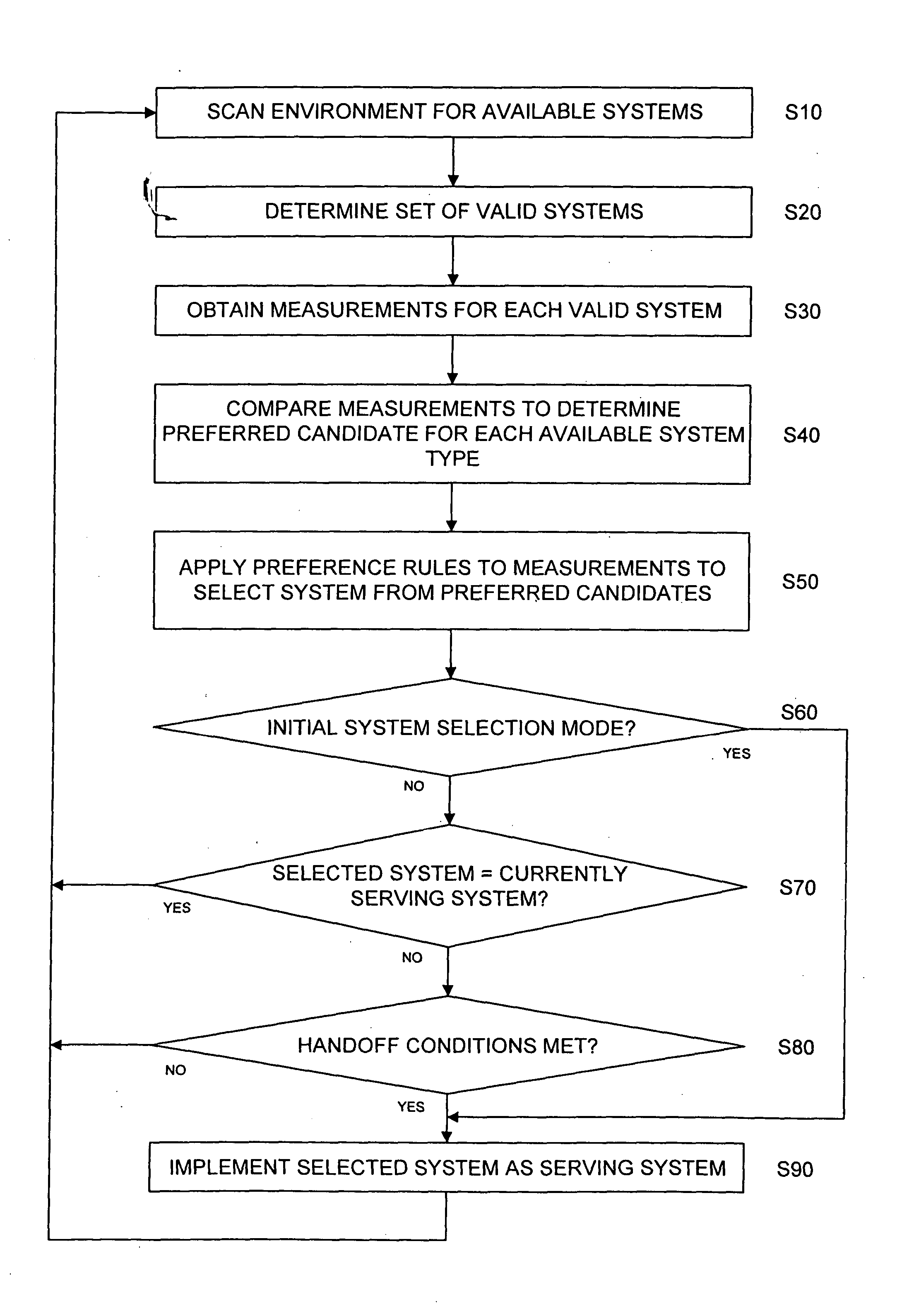
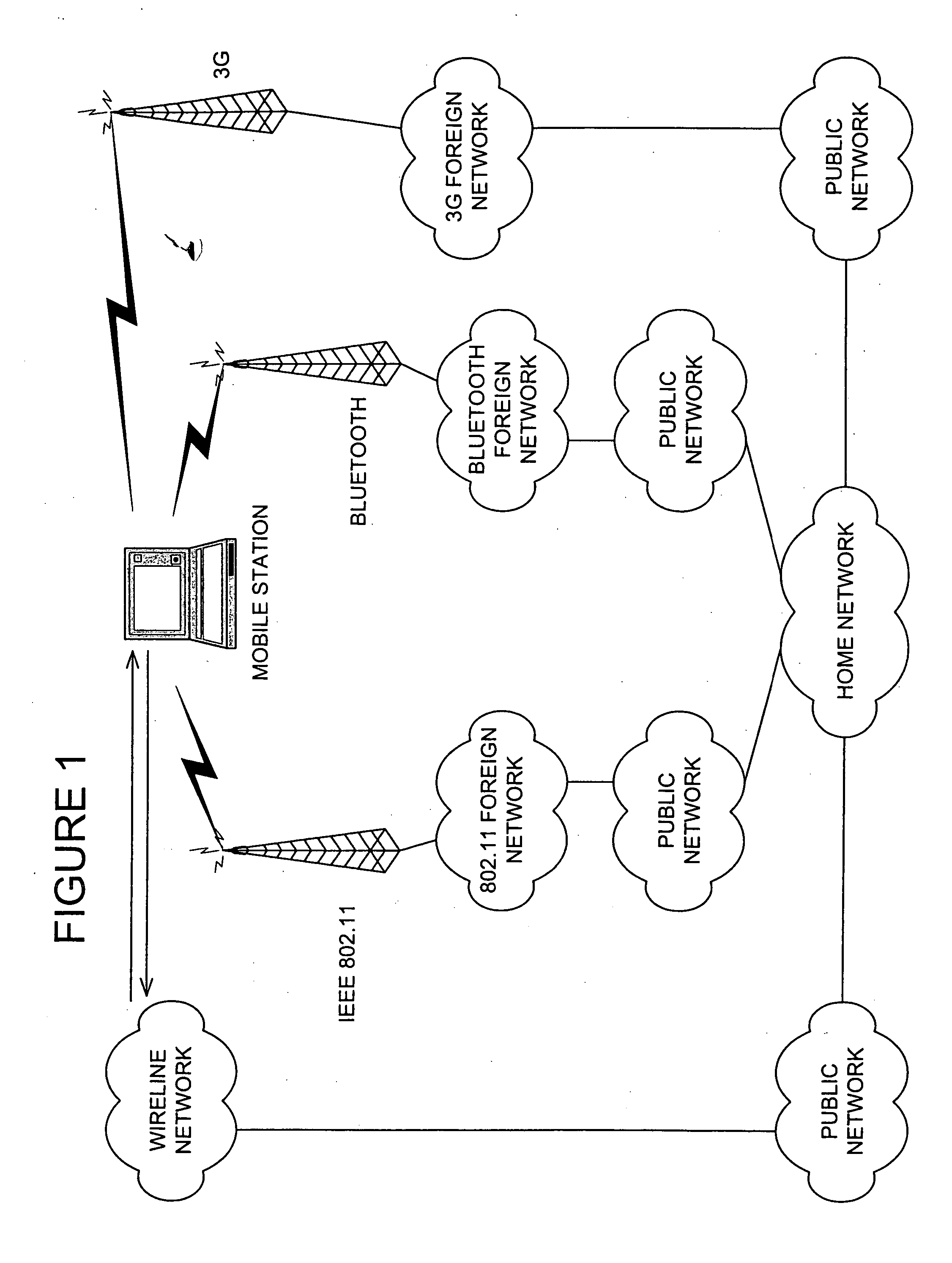
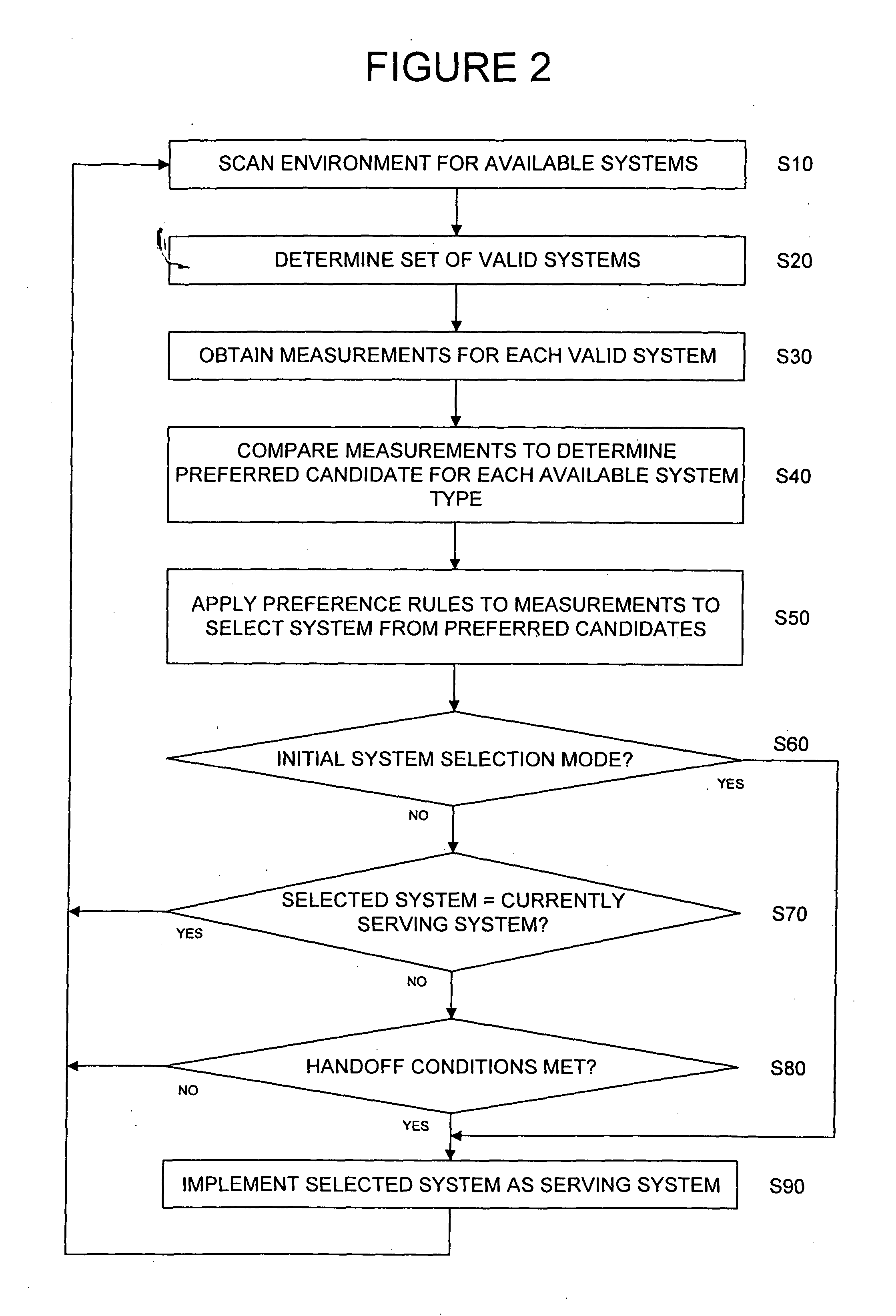
System and method for establishing and/or maintaining a data session across packet data networks
InactiveUS20050043026A1Assess restrictionData switching by path configurationCommunications systemService provision
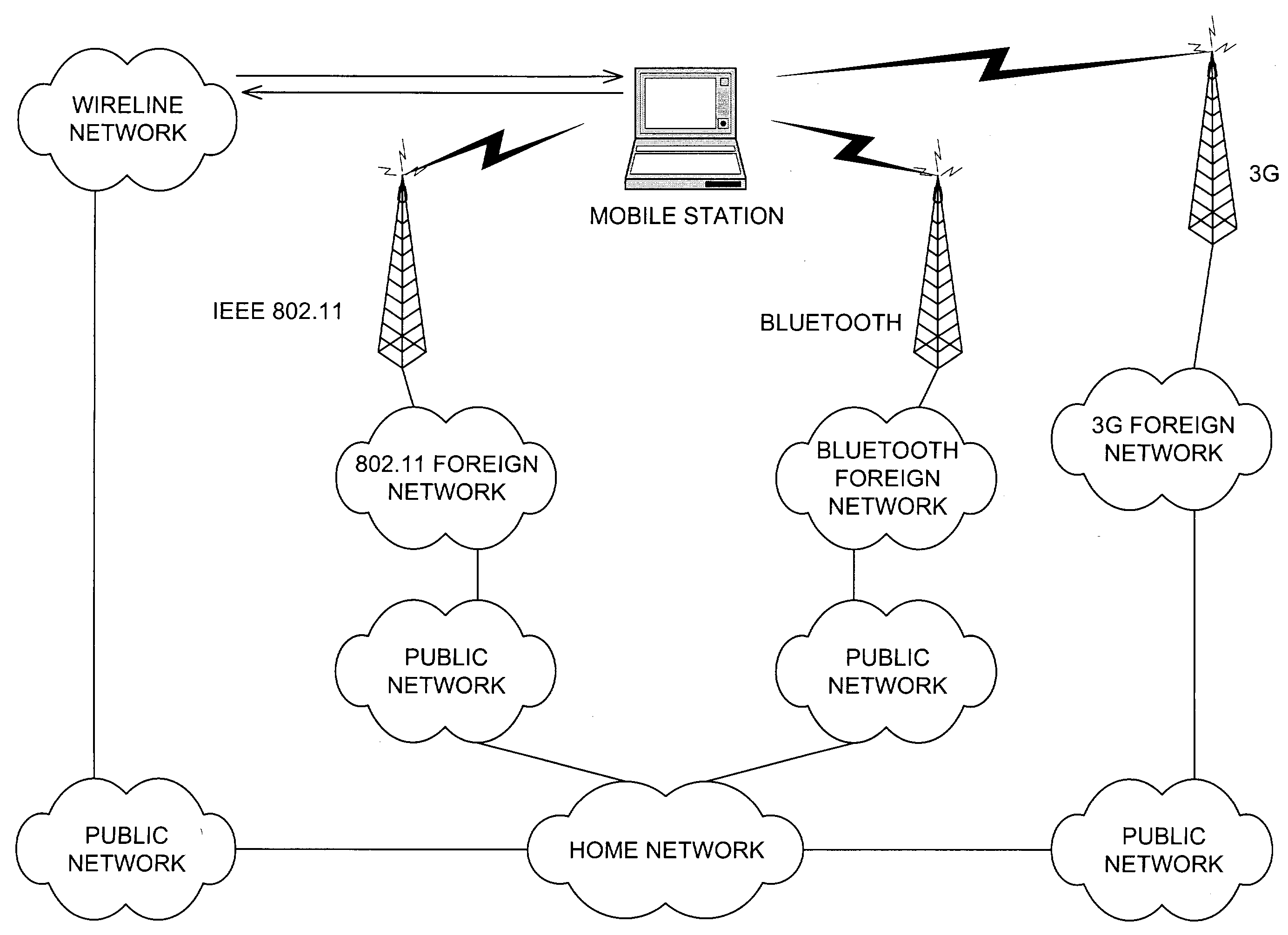
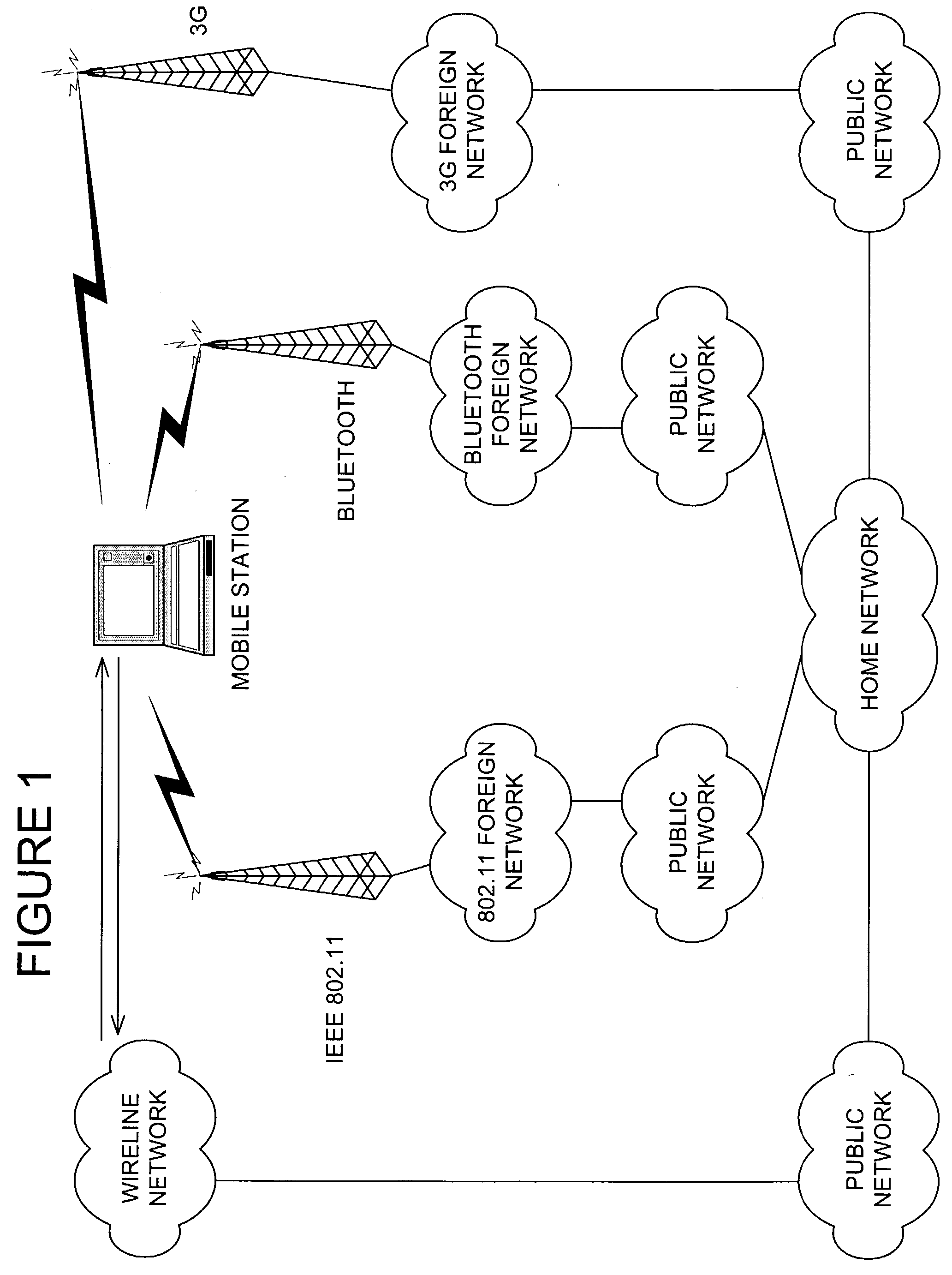
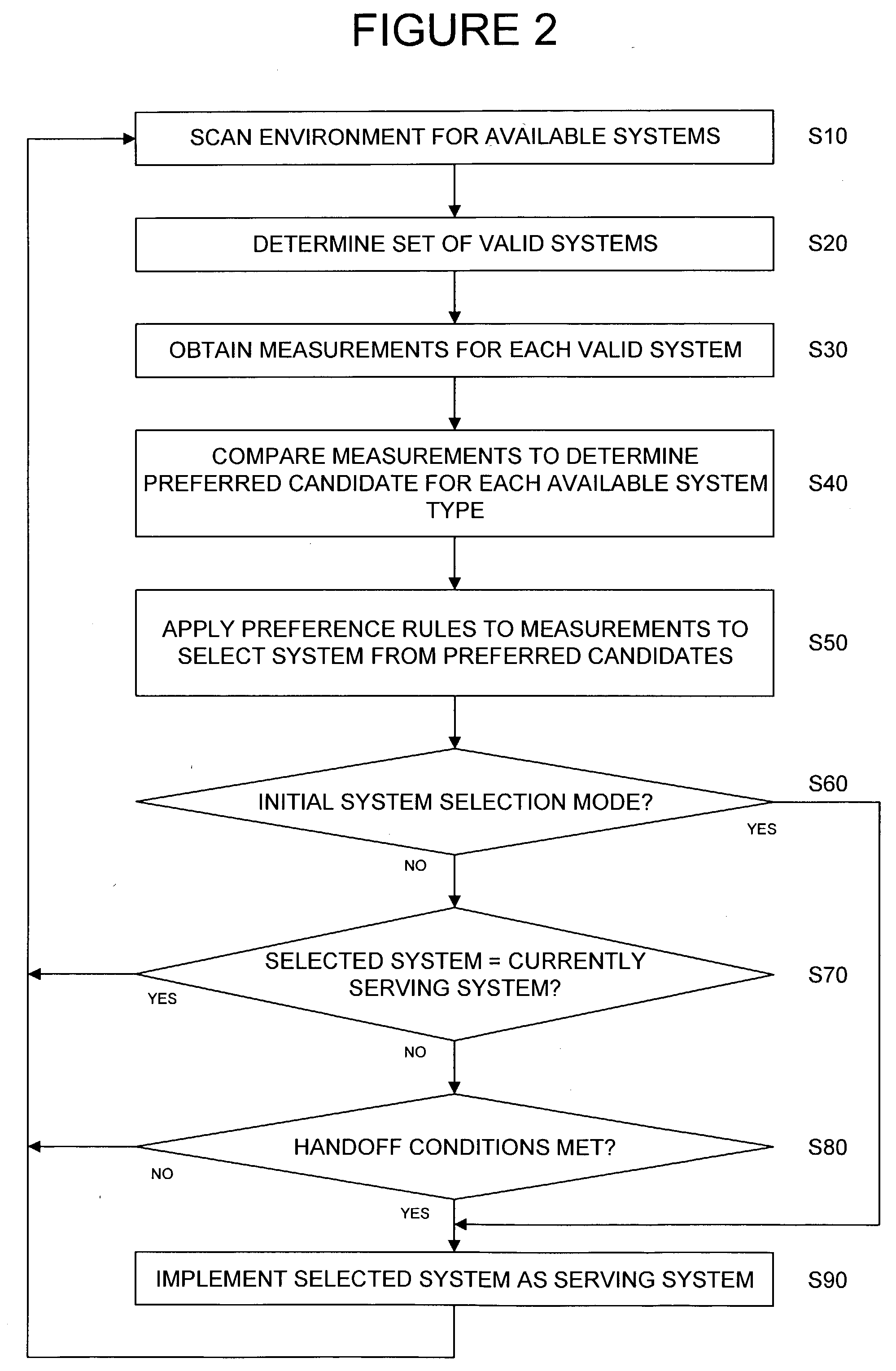
A communication system selection algorithm (SSA) implemented by a mobile station chooses between available systems to select a system to serve the mobile station. During initialization, the SSA causes the mobile station to scan the environment and compare available communication systems to determine the best system to provide service. After an initial system is chosen, the SSA causes the mobile station to continuously, or at discrete time intervals, scan the environment for available systems, thus allowing for a seamless switch to an available system whenever a handoff is desired. The SSA chooses the best available system based on conditions such as bit rate and cost of each available system and applying preference rules defined by a service provider and / or user of the mobile station.
Owner:LUCENT TECH INC
User interface and methods for recommending items to users
InactiveUS20100191582A1Without sacrificing breadthQuick buildMarketingGeneration processUser interface
An improved user interfaces and methods are provided for presenting item recommendations to a user when the user selects an item to add to a shopping cart. In response to the user's selection, a page generation process generates and returns a page that includes a plurality of recommendations sections, each of which displays item recommendations generated using a different respective recommendation or selection algorithm (e.g., recommendations based on shopping cart contents, recommendations based on purchase history, etc.). These recommendation algorithms may be selected based on collected information regarding the user. The page may also include a shopping cart section which displays contents of the shopping cart.
Owner:AMAZON TECH INC
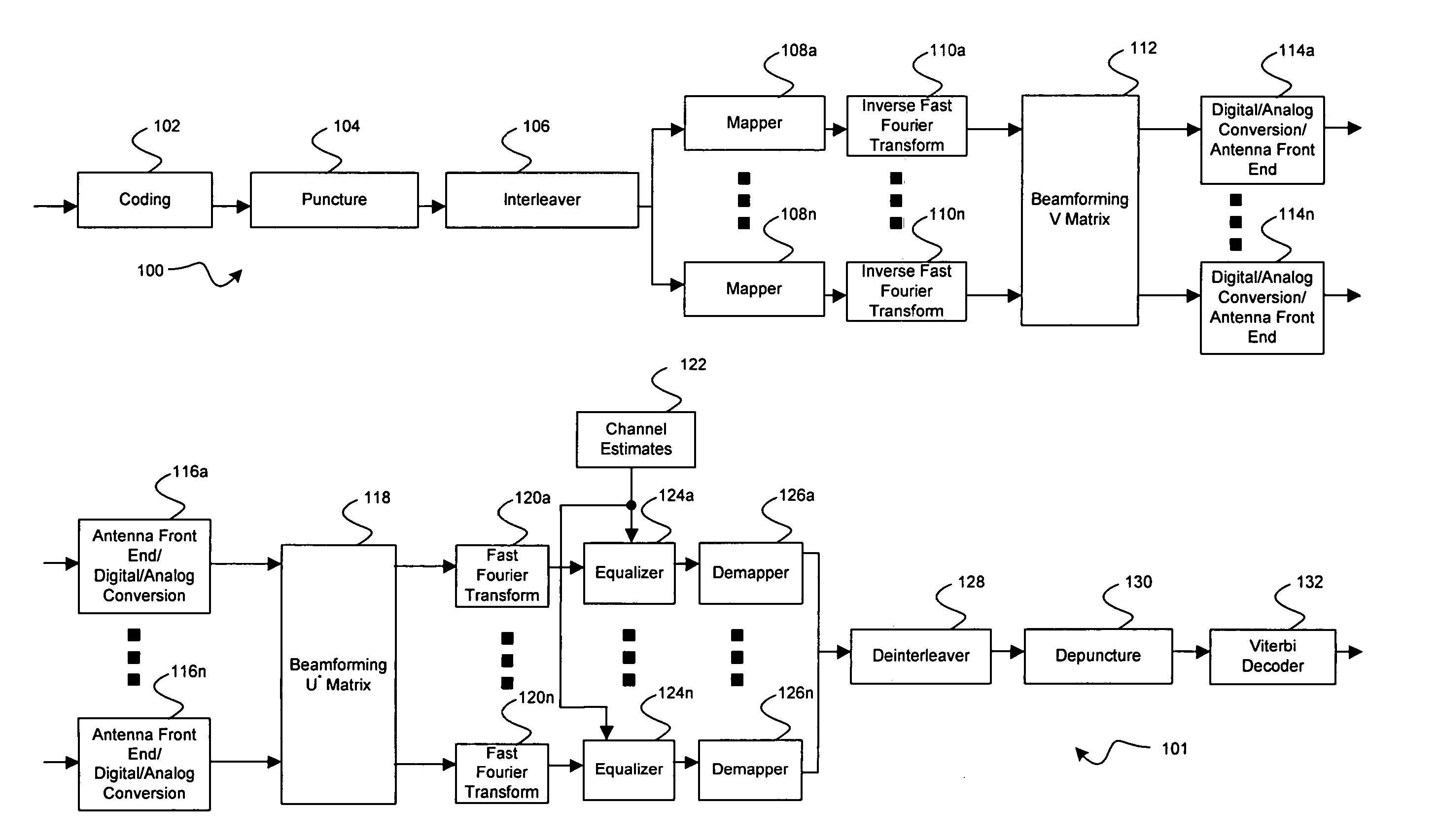
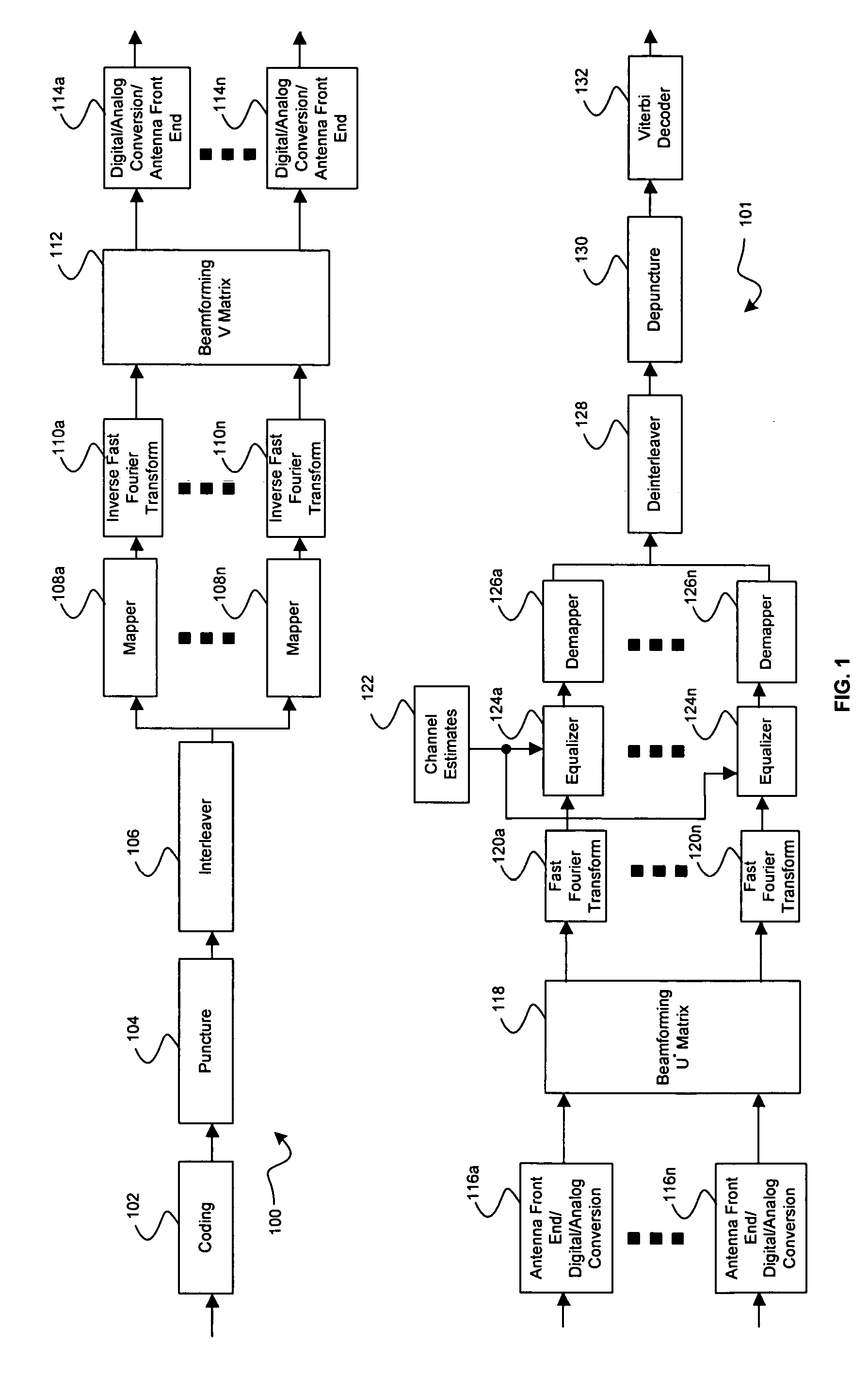
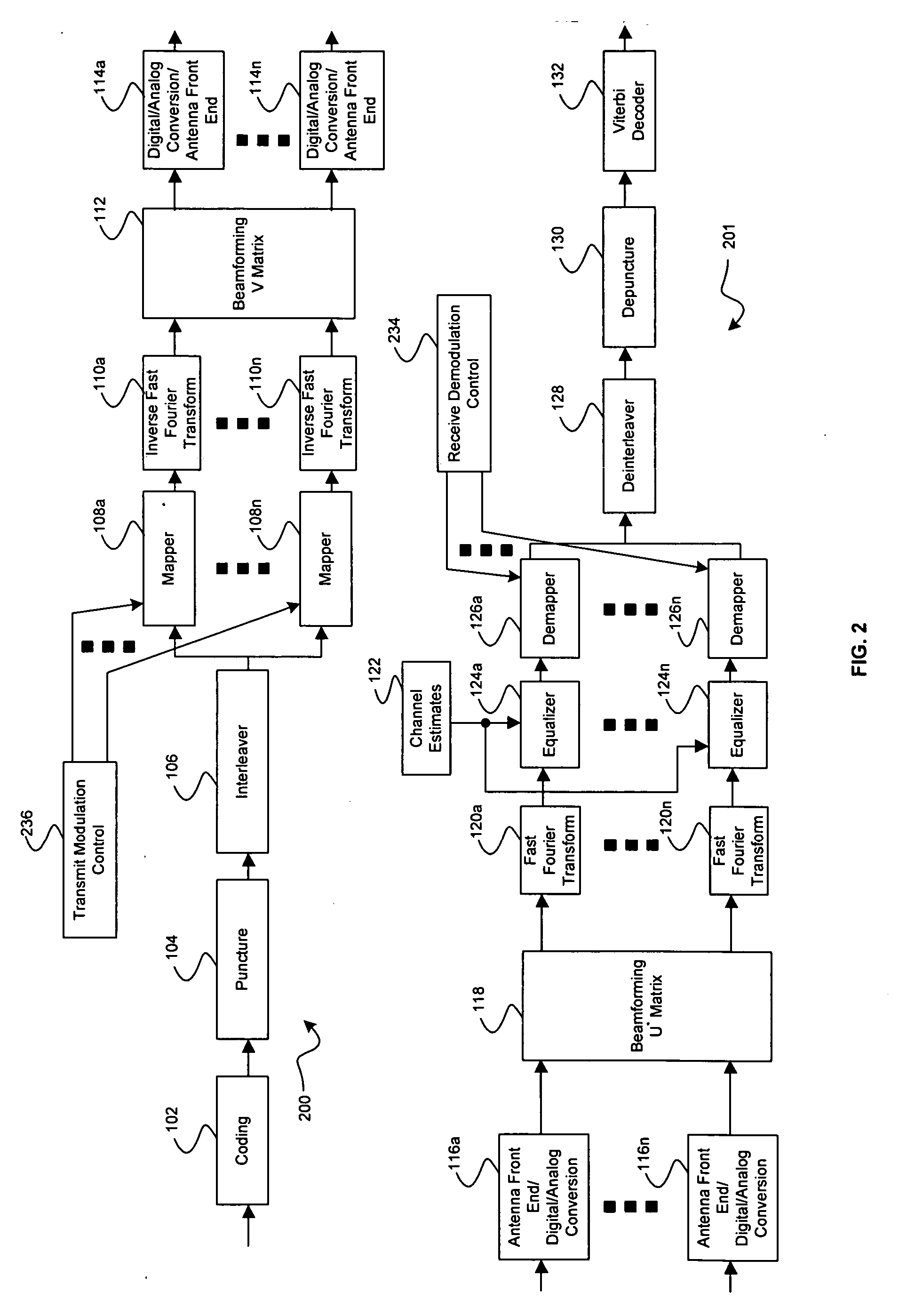
Method and system for rate selection algorithm to maximize throughput in closed loop multiple input multiple output (MIMO) wireless local area network (WLAN) system
ActiveUS20060159120A1Improve throughputNetwork traffic/resource managementNetwork topologiesSignal qualityClosed loop
Aspects of a method and system for rate selection algorithm to maximize throughput in closed loop multiple input multiple output (MIMO) wireless local area network (WLAN) system are provided and may comprise computing a maximum number of binary bits to be simultaneously transmitted via an RF channel based on signal quality. A modulation technique may be selected based on the computed maximum, communicating feedback information comprising the selected modulation technique. Subsequently transmitted data may be received via an RF channel which is modulated based on the feedback information. Another aspect of the method may comprise receiving feedback information comprising at least one of a selected modulation technique and coding rate via an RF channel, and transmitting subsequent data via said at least one of a plurality of RF channels which either modulated, or coded, based on the feedback information.
Owner:AVAGO TECH INT SALES PTE LTD
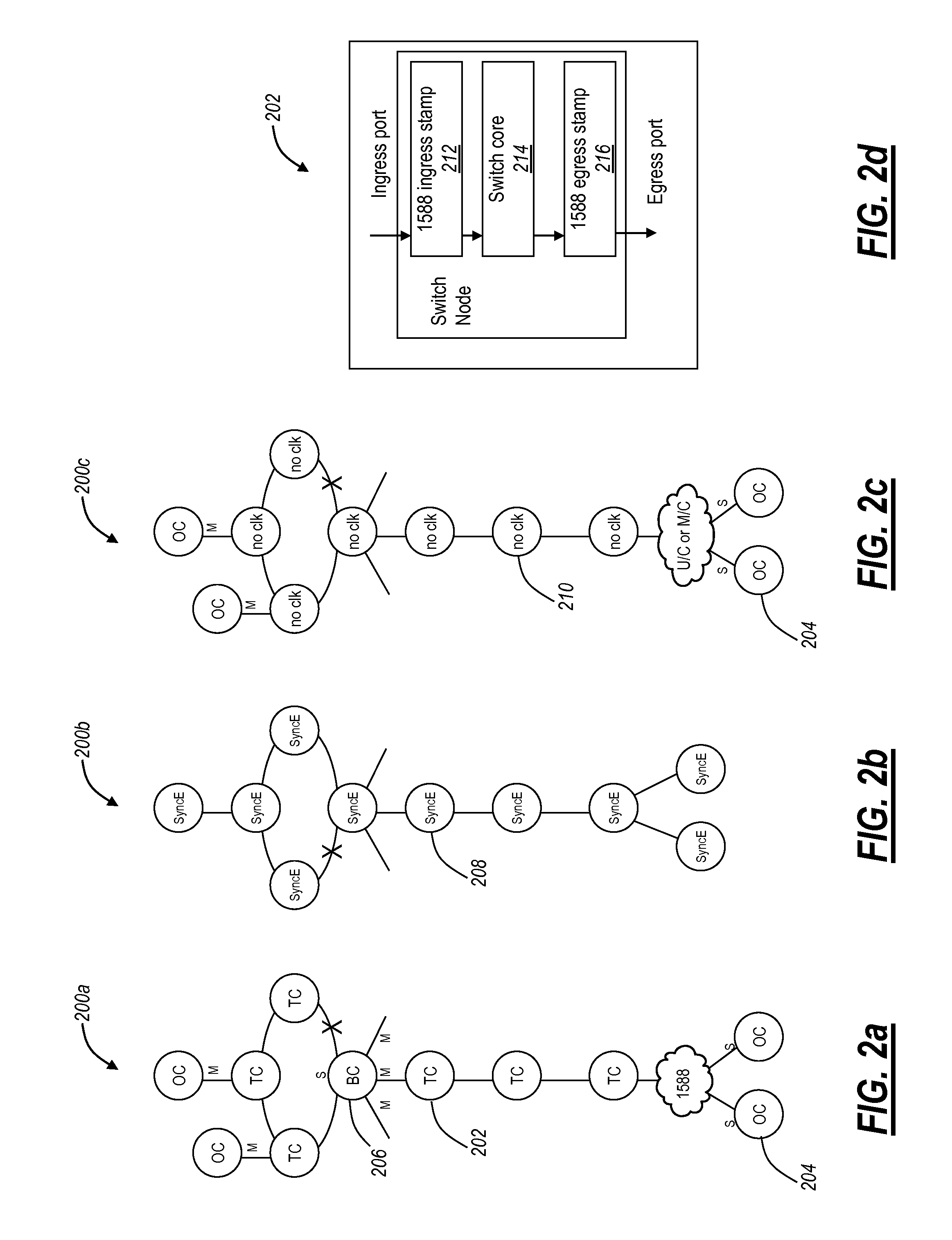
Ethernet network synchronization systems and methods
ActiveUS20110200051A1Reduce in quantityImprove stabilityTime-division multiplexData switching by path configurationSynchronization systemSynchronous Ethernet
The present disclosure relates to Ethernet synchronization systems and methods that combines Synchronous Ethernet (Sync-E) and Precision Time Protocol (PTP) IEEE 1588 algorithms. The present invention includes systems and methods for Ethernet networks and node configurations that include a set of rules on node placement, such as Boundary Clock (BC) nodes and Sync-E nodes, a clock selection algorithm, a holdover algorithm, and the like. Advantageously, the present invention provides an architecture that allows practical and real-world useful clock propagation through placement of BCs and Sync-E nodes for best performance. Practical experience and theoretical design are embodied in the present invention to define a very specific set of rules on how to build a network capable of providing accurate and reliable synchronization. The present invention includes clock selection that unifies Sync-E and 1588 algorithms.
Owner:CIENA
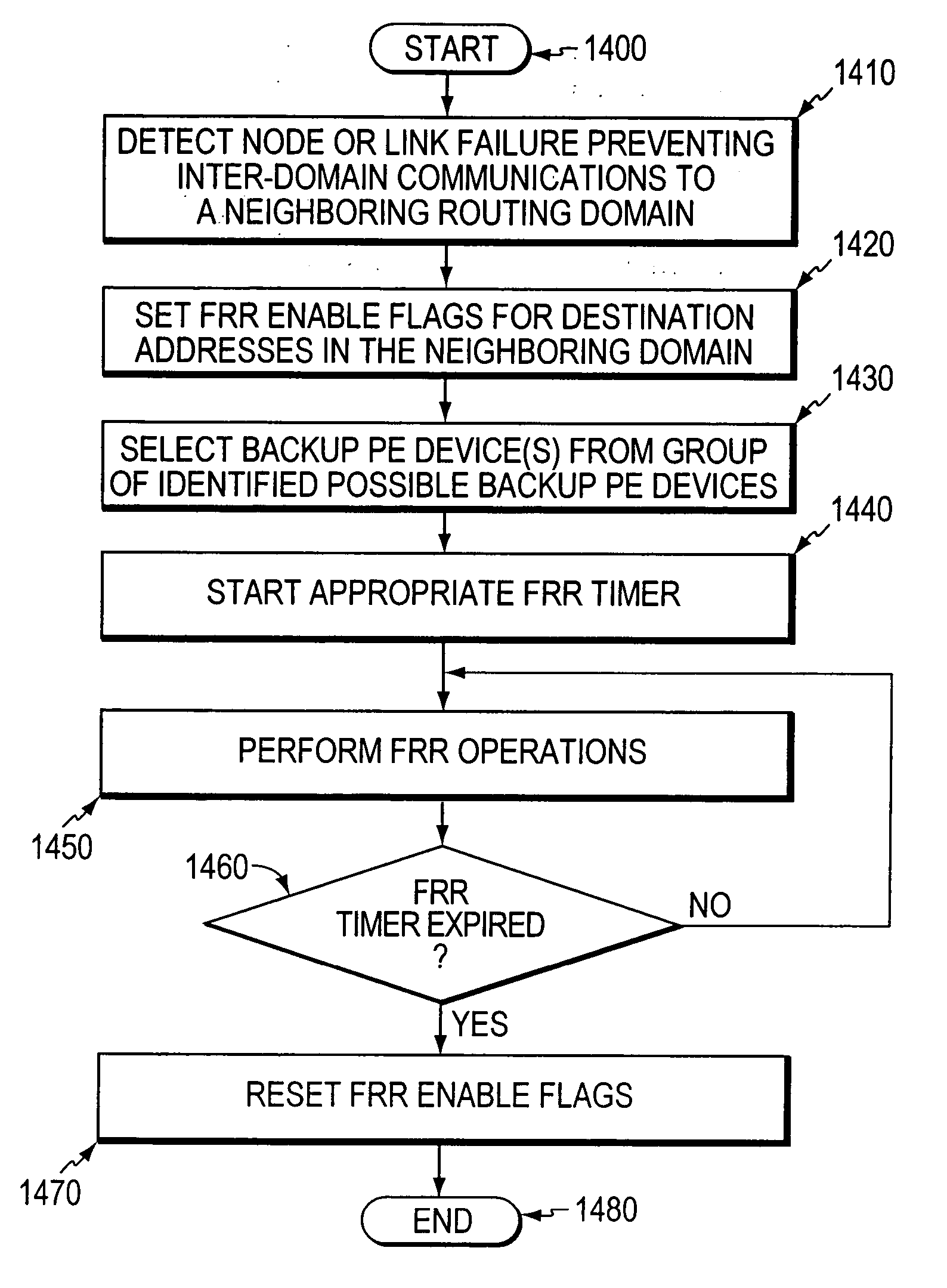
Algorithm for backup PE selection
InactiveUS20060209682A1Reduce settingsError preventionFrequency-division multiplex detailsRouting domainMetric selection
A fast reroute (FRR) technique is implemented at the edge of a computer network. If an edge device detects a node or link failure that prevents it from communicating with a neighboring routing domain, the edge device reroutes at least some data packets addressed to that domain to a backup edge device which, in turn, forwards the packets to the neighboring domain. The backup edge device is not permitted to reroute the packets a second time. According to the inventive technique, the edge device first identifies a group one or more possible backup edge devices and then selects at least one preferred backup edge device from the group. The edge device makes its selection based on the values of one or more metrics associated with the possible backup edge devices. The metrics are input to a novel selection algorithm that selects the preferred backup edge device(s) using a hierarchical selection process or a weighted-metric selection process, or some combination thereof.
Owner:CISCO TECH INC
Personalized selection and display of user-supplied content to enhance browsing of electronic catalogs
An electronic catalog system provides an interface for users to author and post pieces of content, referred to as “blurbs,” for viewing by other users. The blurbs submitted by a particular author are made available for viewing in an author-specific blog (web log) format. Blurbs may also be obtained from external sources, such as from blogs hosted by various web sites. A personalized blurb selection component selects blurbs to present to users based on histories of catalog items selected by such users, and / or based on various other criteria. The blurbs selected for a particular user are presented within a personal log or “plog,” which may be updated daily and will typically contain entries from many different authors. User feedback provided on specific blurbs is taken into consideration by the personalized blurb selection algorithms.
Owner:AMAZON TECH INC
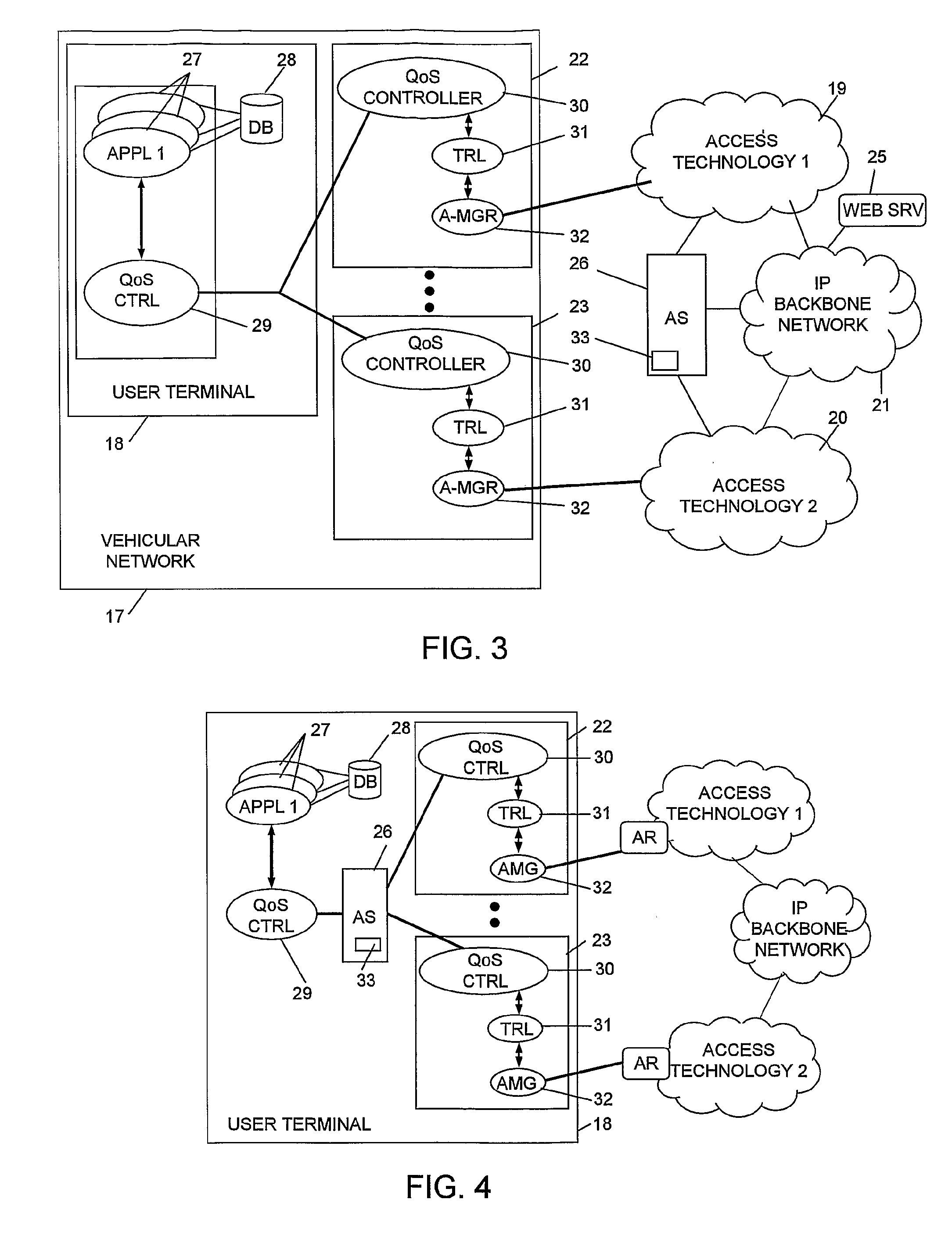
System and Method for Multi-Access
InactiveUS20070217349A1Network traffic/resource managementAssess restrictionAccess networkRadio access network
A system and a method allowing a user terminal (18) in a network to simultaneously access a plurality of radio based access networks (19, 20) of diverse access technologies. Characteristic features of the invention are access selection adapters (22, 23), each one associated with a respective radio based access network, and an access technology independent access selector (26). An access adapter has means (32) for receiving access technology dependant information from its respective access network and means (31) for translating the information into access technology independent status information. The access selector comprises an access selection algorithm (33) interacting with applications (27) resident in the user terminal and with each access adapter for selection of a radio access network based on an individual QoS profile associated with each respective application and on said access technology independent status information. The invention also relates to a method for service scheduling.
Owner:UNWIRED PLANET
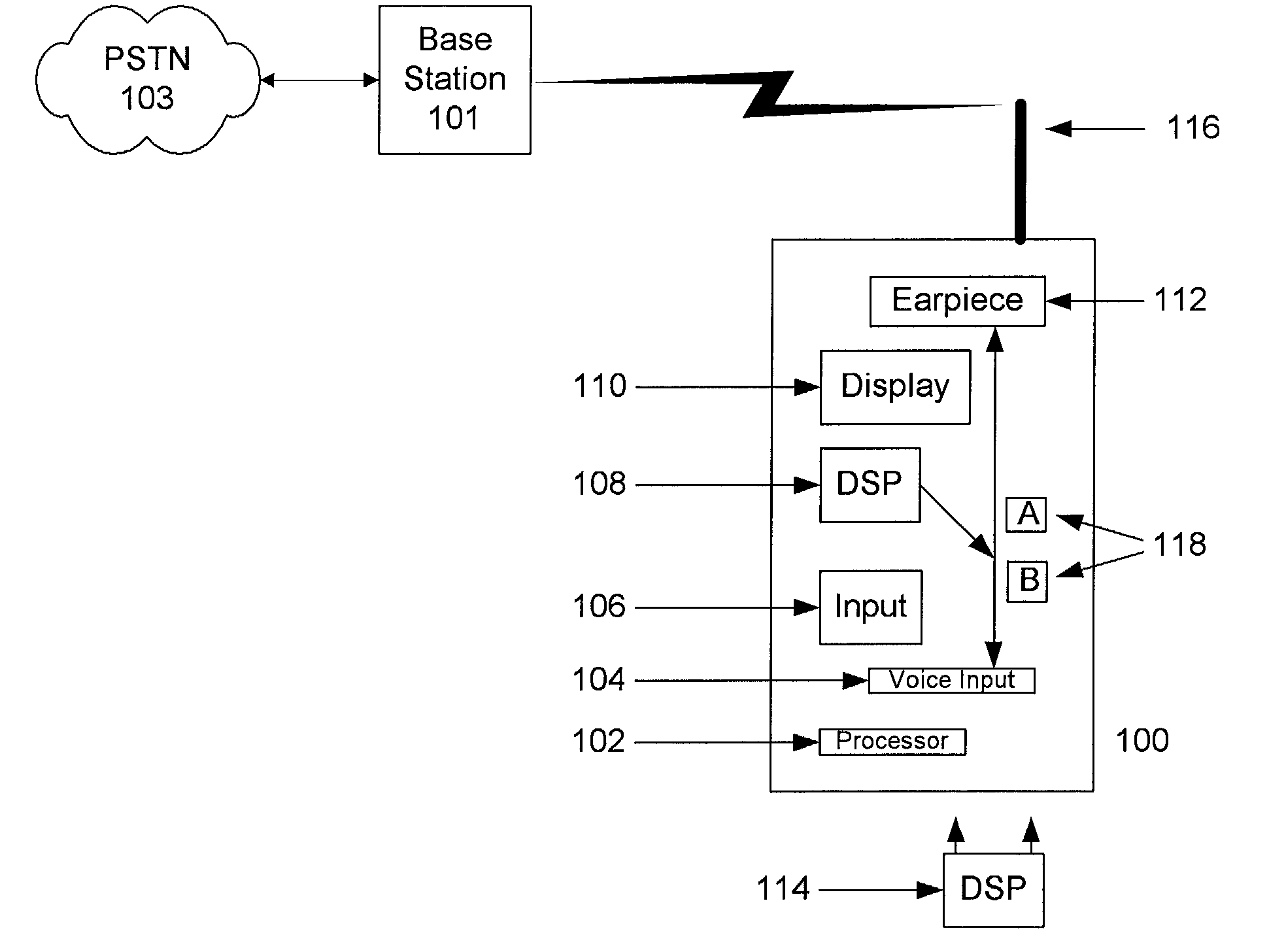
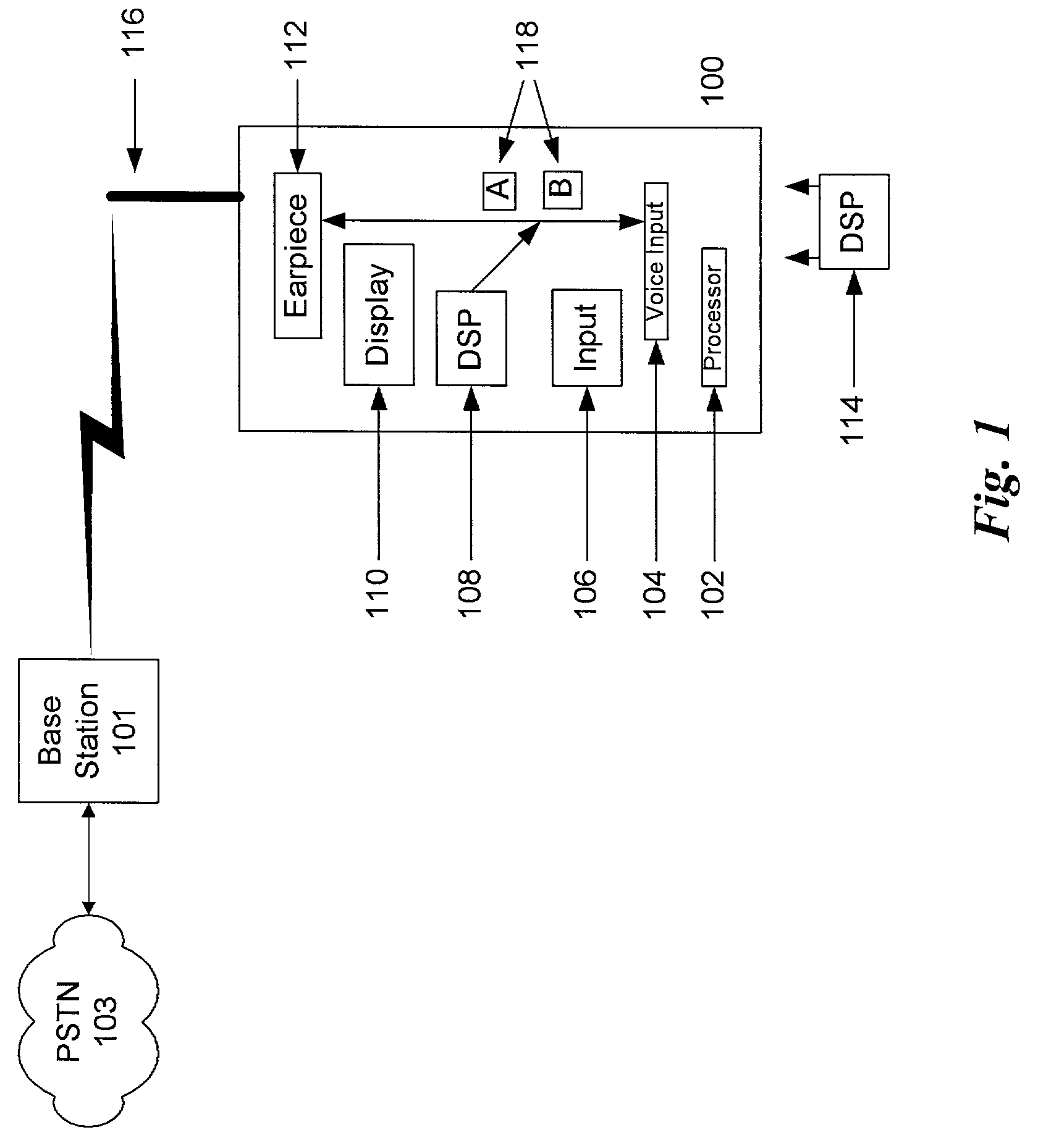
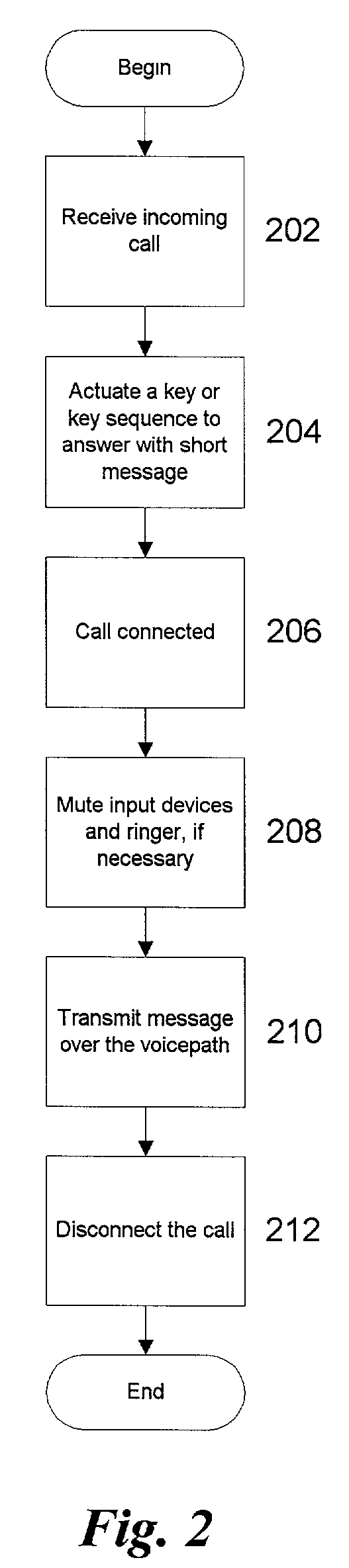
System and method for providing an automatic response to a telephone call
InactiveUS7010288B2Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersGraphicsThird party
Disclosed embodiments include a system and method for providing an automatic response to a telephone call. The automatic response module may be integral to a wireless phone or may be added afterwards, such as with a plug-in module, or may be provided by a third party provider, such as on a network. In one embodiment, the user of a wireless phone may select one or more automatic responses in the form of pre-recorded messages that will be played to a caller when an incoming telephone call is received. In another embodiment, the pre-recorded messages may be text or other graphical messages. In an alternative embodiment, a selection algorithm may be used that selects the appropriate automatic response based on pre-determined criteria, such as information in the user's calendar, contact list, etc. Many other alternatives and alternative embodiments are also disclosed.
Owner:AT&T WIRELESS SERVICES
System and method for establishing and/or maintaining a data session across packet data networks
ActiveUS20040142693A1Assess restrictionData switching by path configurationCommunications systemService provision
A communication system selection algorithm (SSA) implemented by a mobile station chooses between available systems to select a system to serve the mobile station. During initialization, the SSA causes the mobile station to scan the environment and compare available communication systems to determine the best system to provide service. After an initial system is chosen, the SSA causes the mobile station to continuously, or at discrete time intervals, scan the environment for available systems, thus allowing for a seamless switch to an available system whenever a handoff is desired. The SSA chooses the best available system based on measurements of each available system and applying preference rules defined by a service provider and / or user of the mobile station.
Owner:LUCENT TECH INC
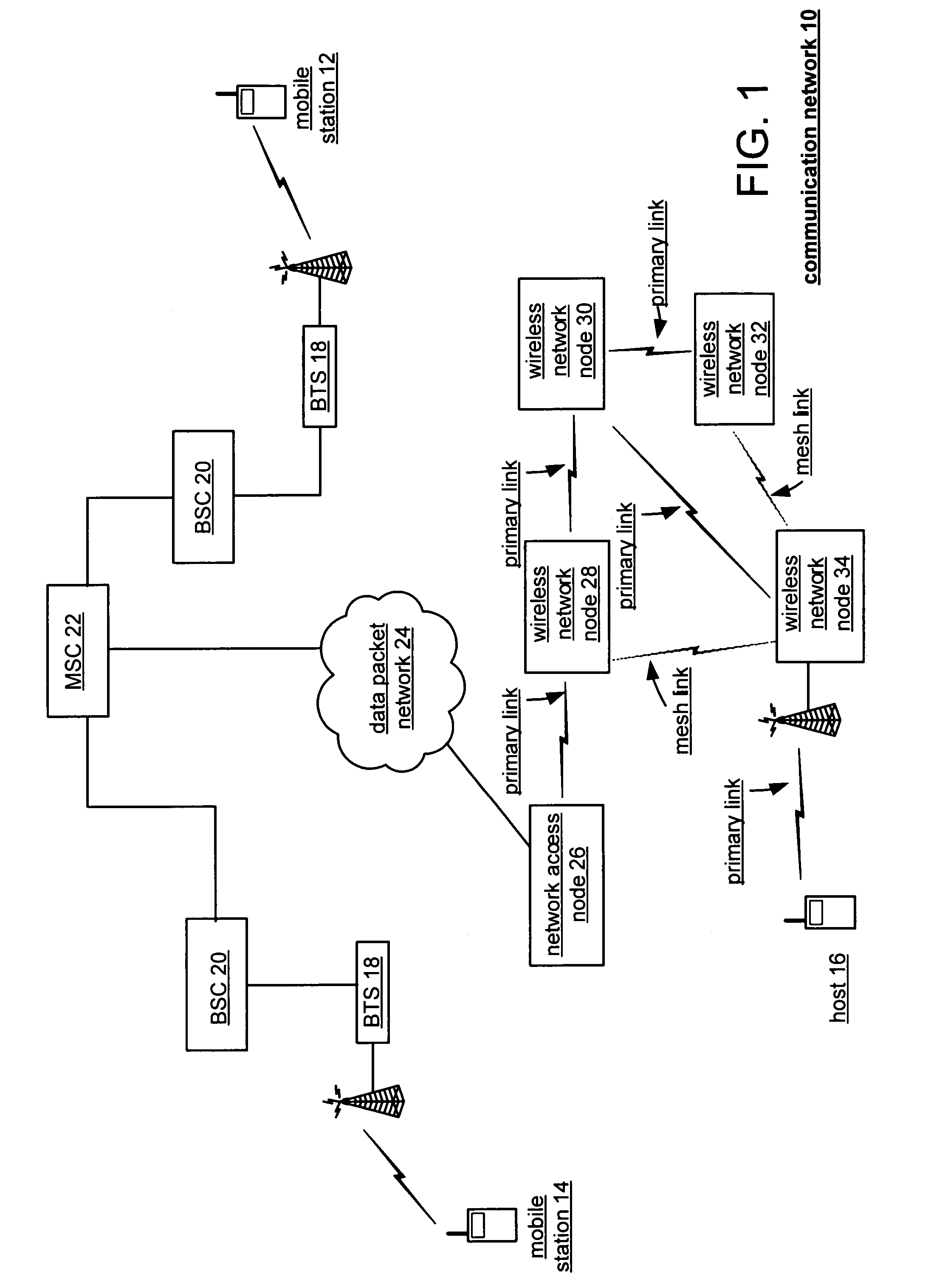
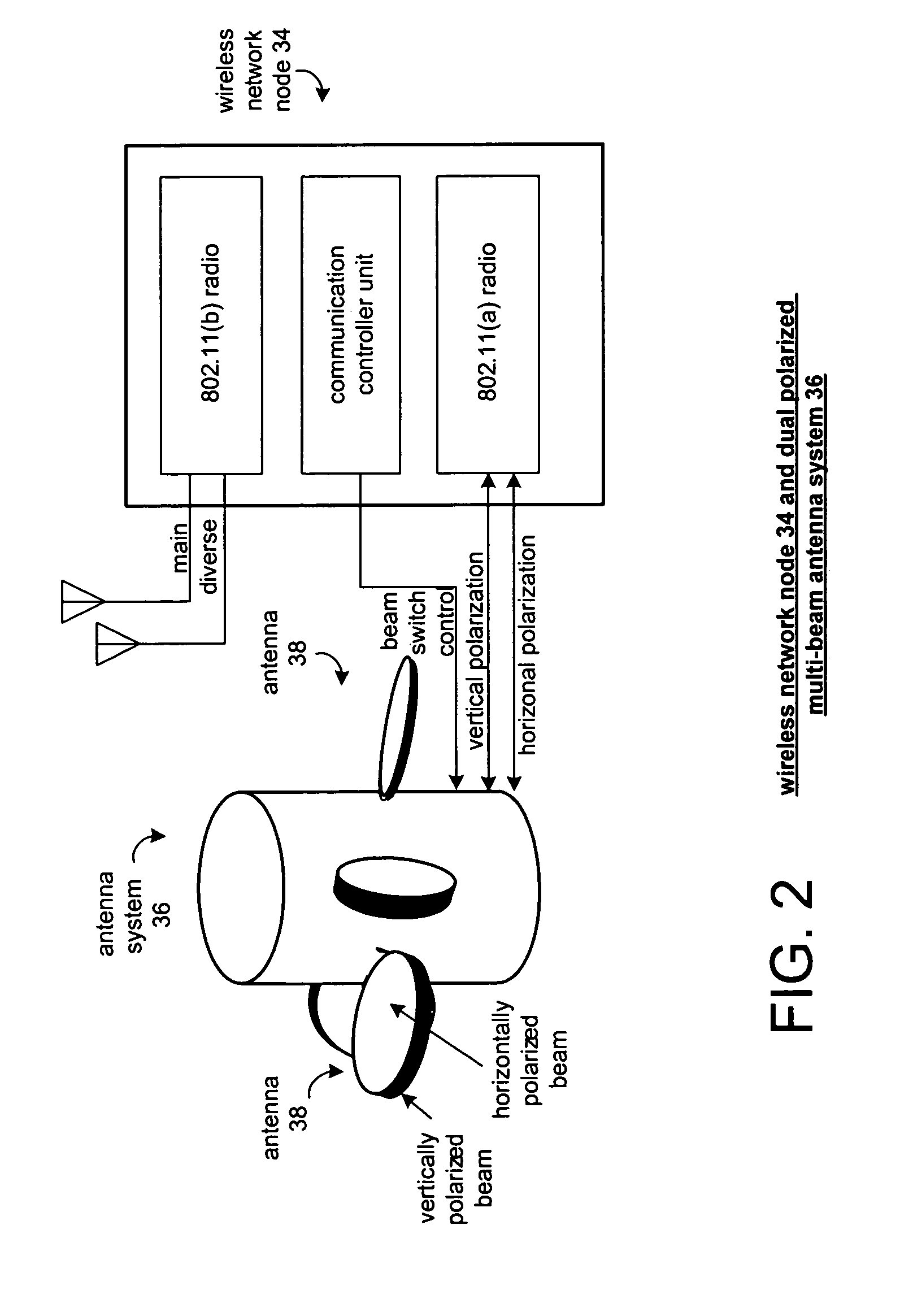
Self-selection of radio frequency channels to reduce co-channel and adjacent channel interference in a wireless distributed network
ActiveUS7174170B2Low costShorten the timeRadio/inductive link selection arrangementsWireless commuication servicesAdjacent-channel interferenceRadio frequency
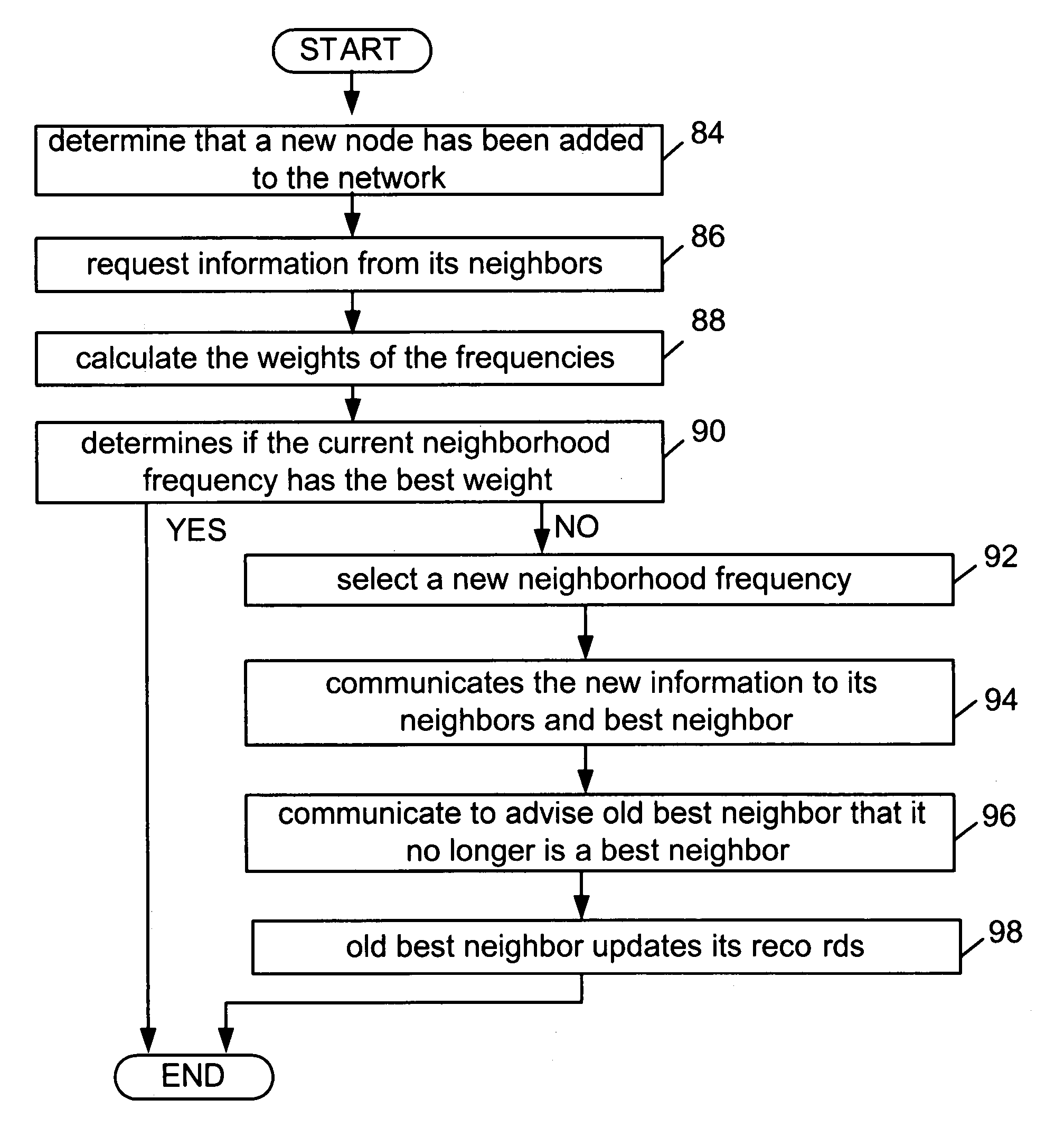
A wireless network node and a network provide for automatic self-deployment of the radio frequency channels without the need for preplanning. Each wireless network node adapts to the inclusion of a new node and to changing local conditions without requiring manual configuration at deployment or re-deployment. When a node is added to the network, it scans and finds its neighbors, and enters a frequency self-selection phase of its initialization process. The method for frequency self-selection involves transmitting and receiving a sequence of messages to / from neighbors and performing related processing within the controller unit of the node. Three sets of parameters are used in the frequency self-selection algorithm. The three parameter sets include a routing cost function, the frequencies in use by neighbors (and those that may be blocked), and the antenna beams used for the respective frequencies.
Owner:APPLE INC
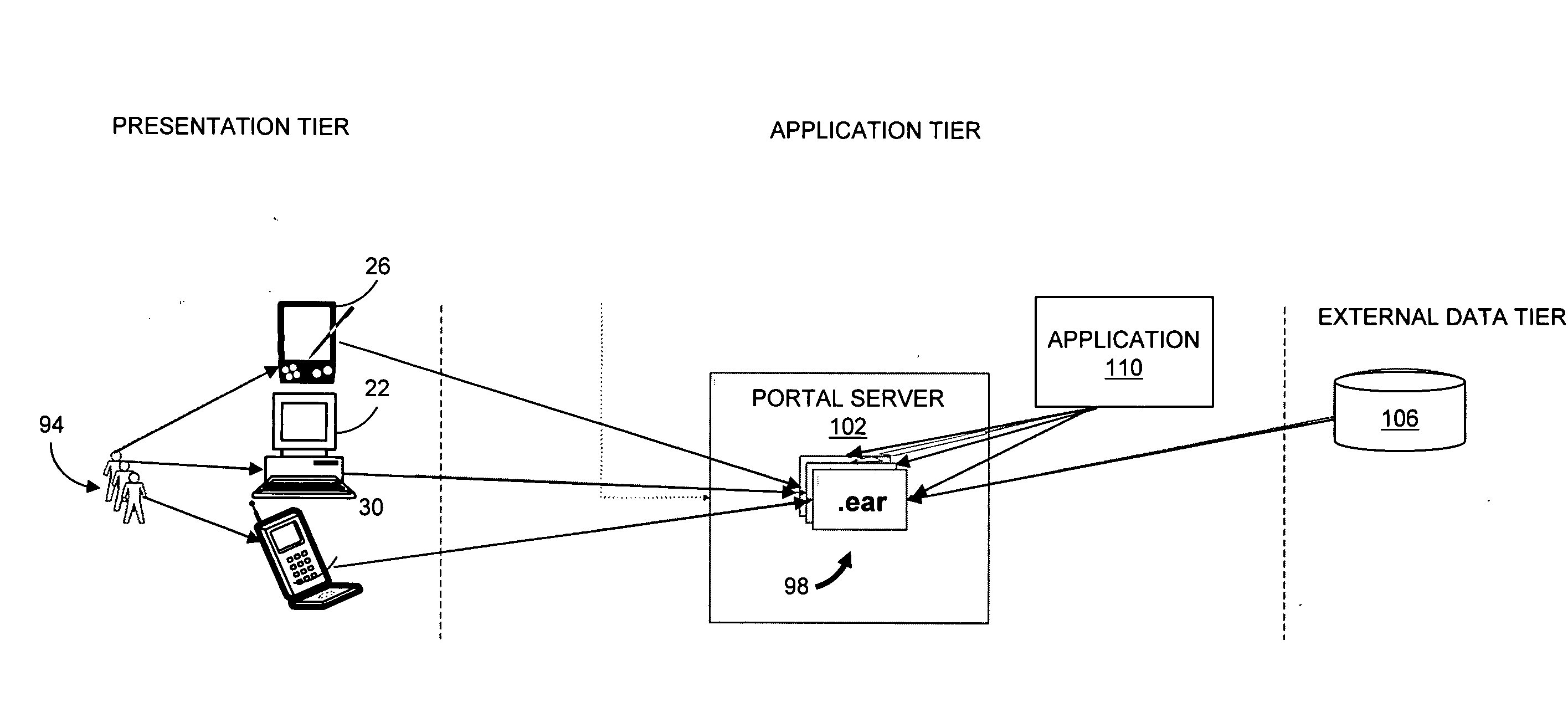
Web services based portlet catalog
Described is a method for determining a portlet for inclusion in a portal for an industry specific business role. The portlet provides access to a web based capability associated with the business role. Industry specific information associated with the business role is mapped to the desired web based capabilities to generate metadata. An internal portlet catalog and an external portlet catalog accessible over a network are searched to identify portlets matched to the metadata. The portlets in the portlet catalogs can be arranged according to categories to facilitate searching. One of the identified portlets is selected according to a selection algorithm. The selection algorithm can be based on a historical ranking of the identified portlets. If no portlets are identified from the search, a new portlet developed to provide the desired web based capability can be published in the external catalog to allow third party use.
Owner:IBM CORP
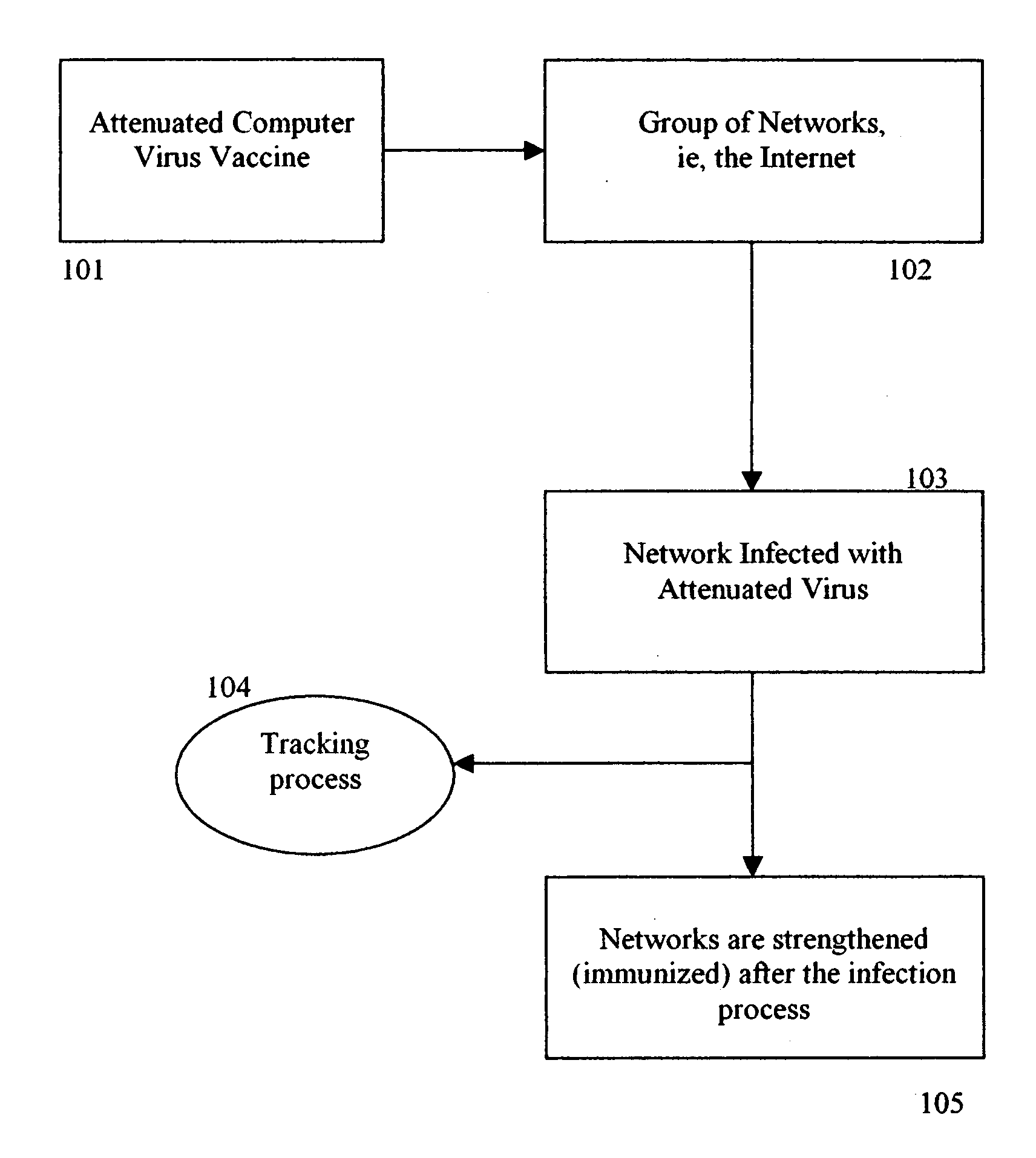
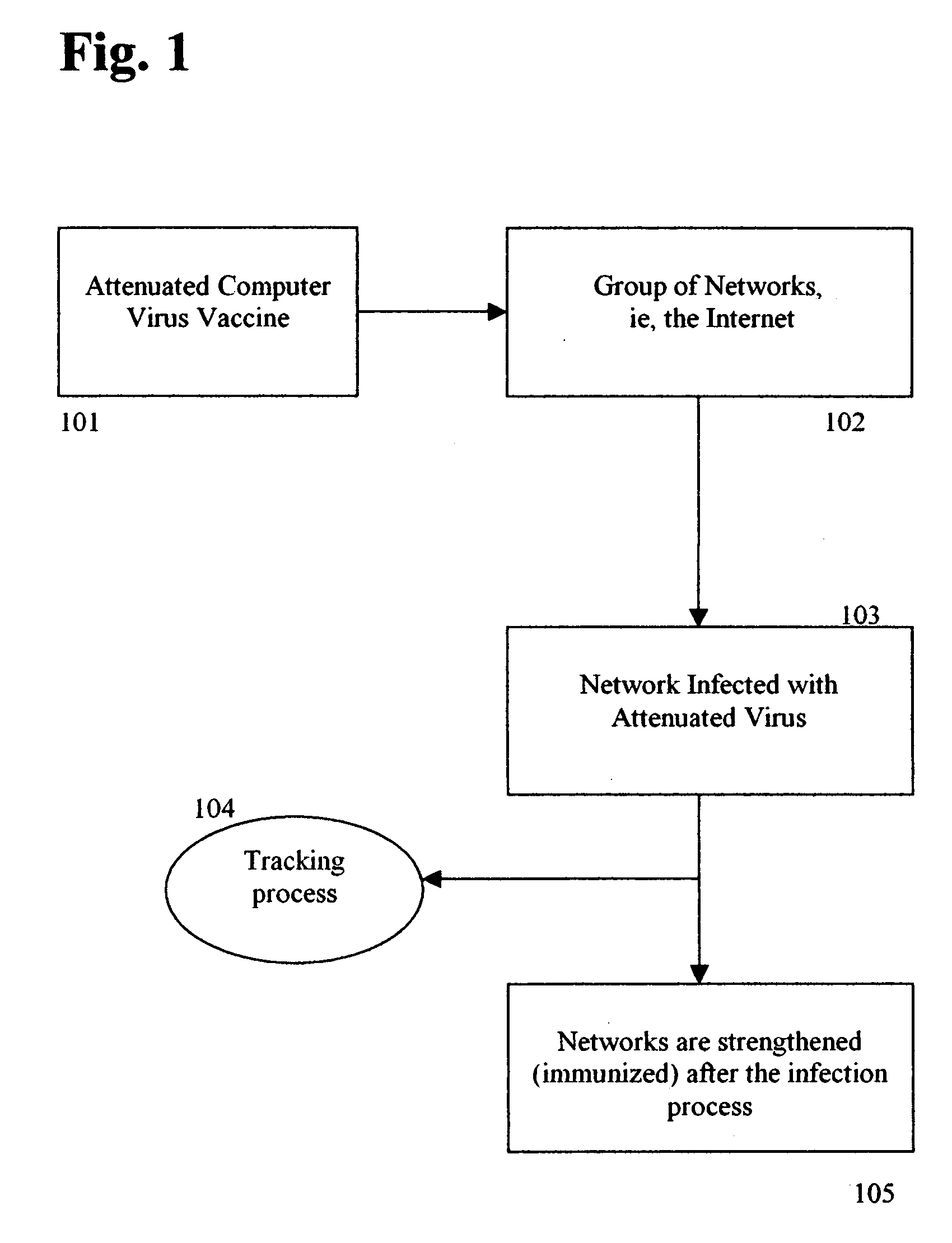
Attenuated computer virus vaccine
InactiveUS20050204150A1Increase in bandwidth consumptionReduce rateUser identity/authority verificationUnauthorized memory use protectionIp addressSelection algorithm
A method and apparatus optimizes the protection of computing networks. This protection utilizes attenuated (weakened) strains of live, replicating, malicious code such as viruses and worms, analogous to the development of live, attenuated, human vaccines in the medical field. In a preferred embodiment, this is achieved by (1) attenuating a malicious program, e.g. a virus or worm, or software vulnerability by limiting its virulence, i.e., limiting its damage and resource usage, (2) modifying the virus to confer immunity on the network that it infects, e.g., automatically patching a vulnerability, or marking the infected host as immune to further infection, (3) releasing the newly attenuated virus into the network, (4) tracking the attenuated virus and its success rate (e.g., rate and ratio of successfully patched to un-patched vulnerable hosts), and (5) limiting the spread of the virus vaccine, e.g., emergency termination, timeout to die, “white-list” of hosts not to touch, network IP address limitation, restricted IP ranges, variable address selection algorithm.
Owner:PEIKARI CYRUS
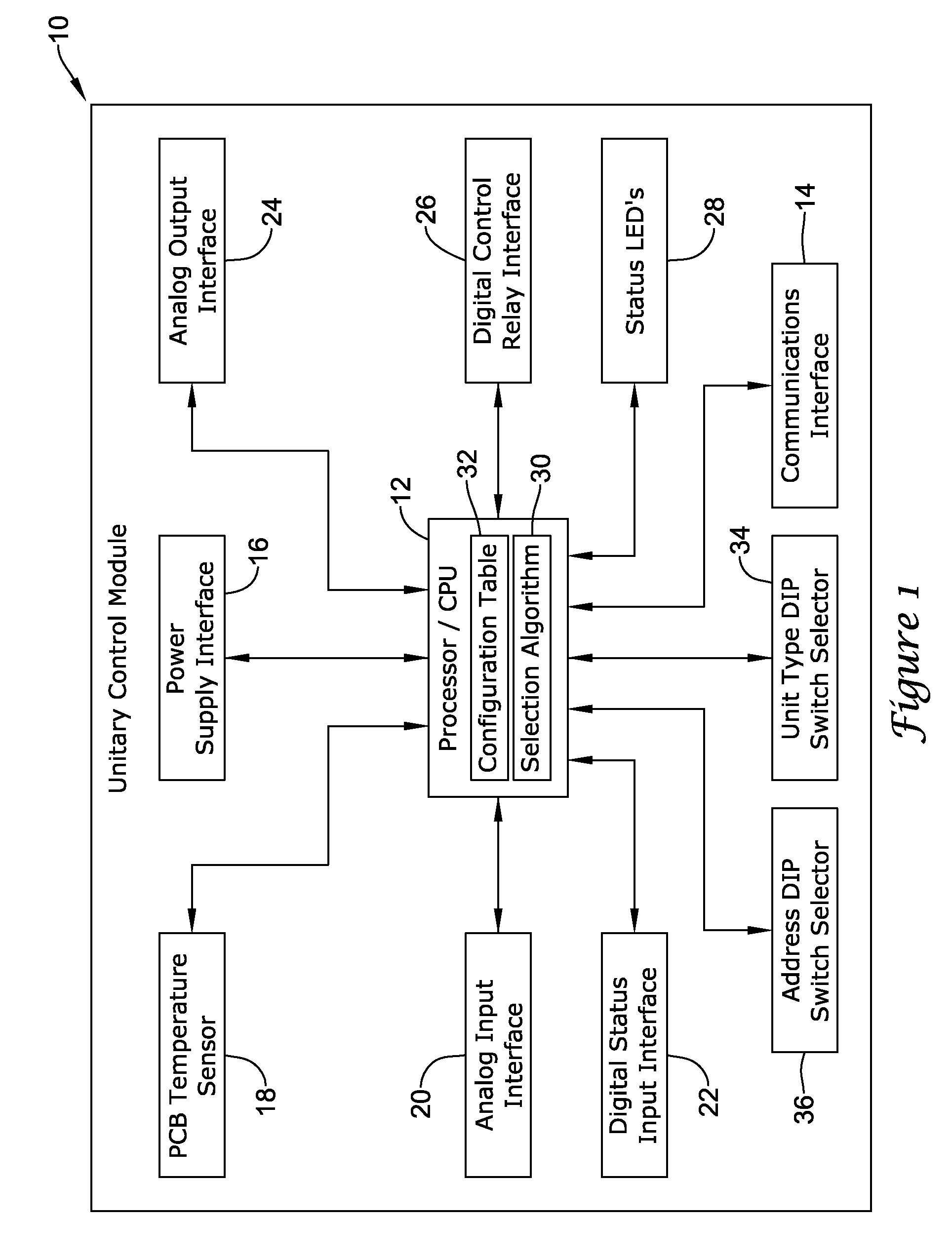
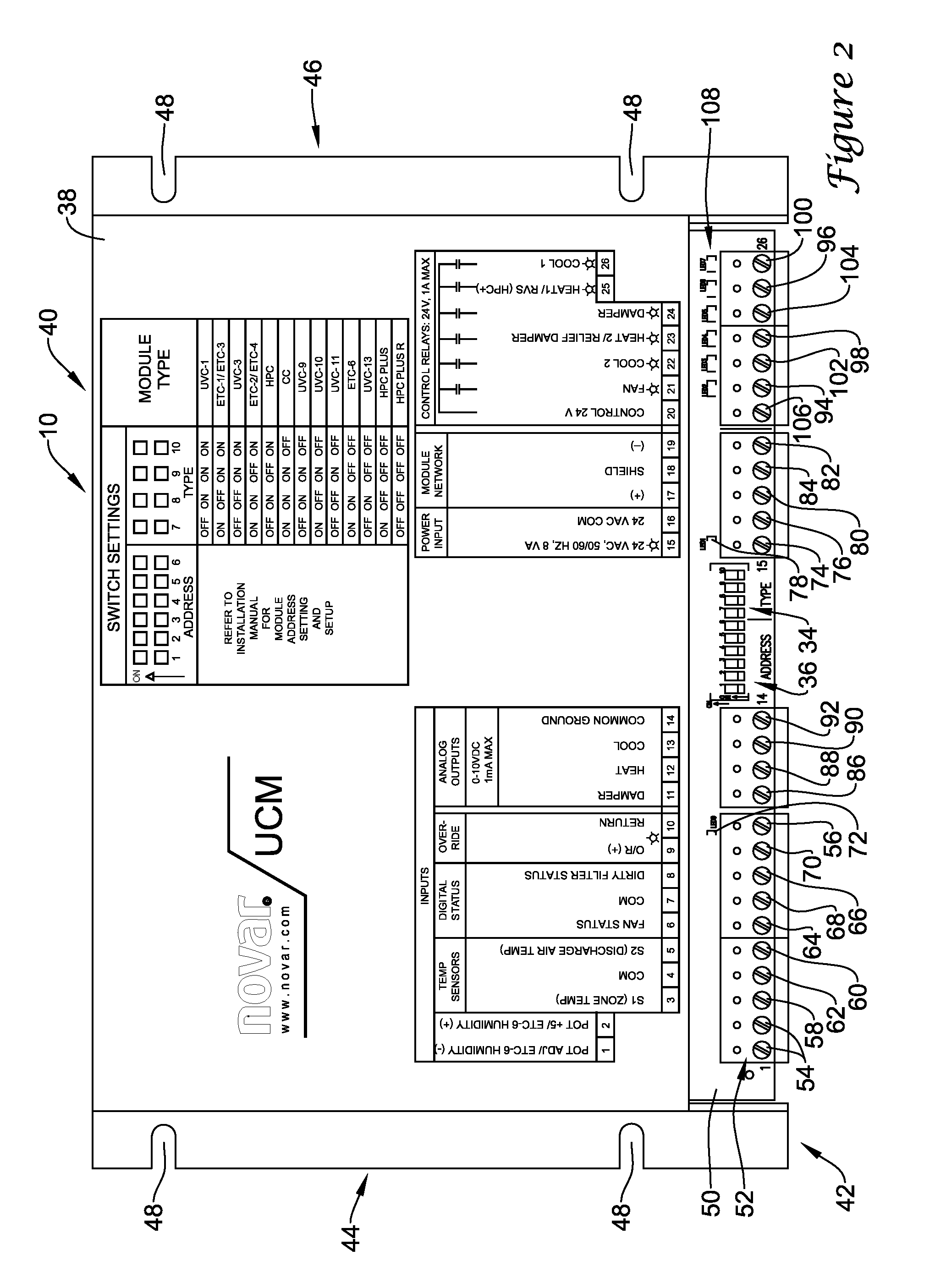
Unitary control module with adjustable input/output mapping
A unitary control module having adjustable input and output mapping functionality, including methods of configuring such devices for use in different applications, are disclosed. The unitary control module can include a unit type selector such as a DIP-switch that can be used by an installer to configure the control module to emulate a particular type of controller. The control module can be configured to run a selection algorithm for configuring the mapping of the input terminals and output terminals for the device based on the controller type selected. In use, the control module may run different control algorithms for controlling the system components based on the controller type selected.
Owner:HONEYWELL INT INC
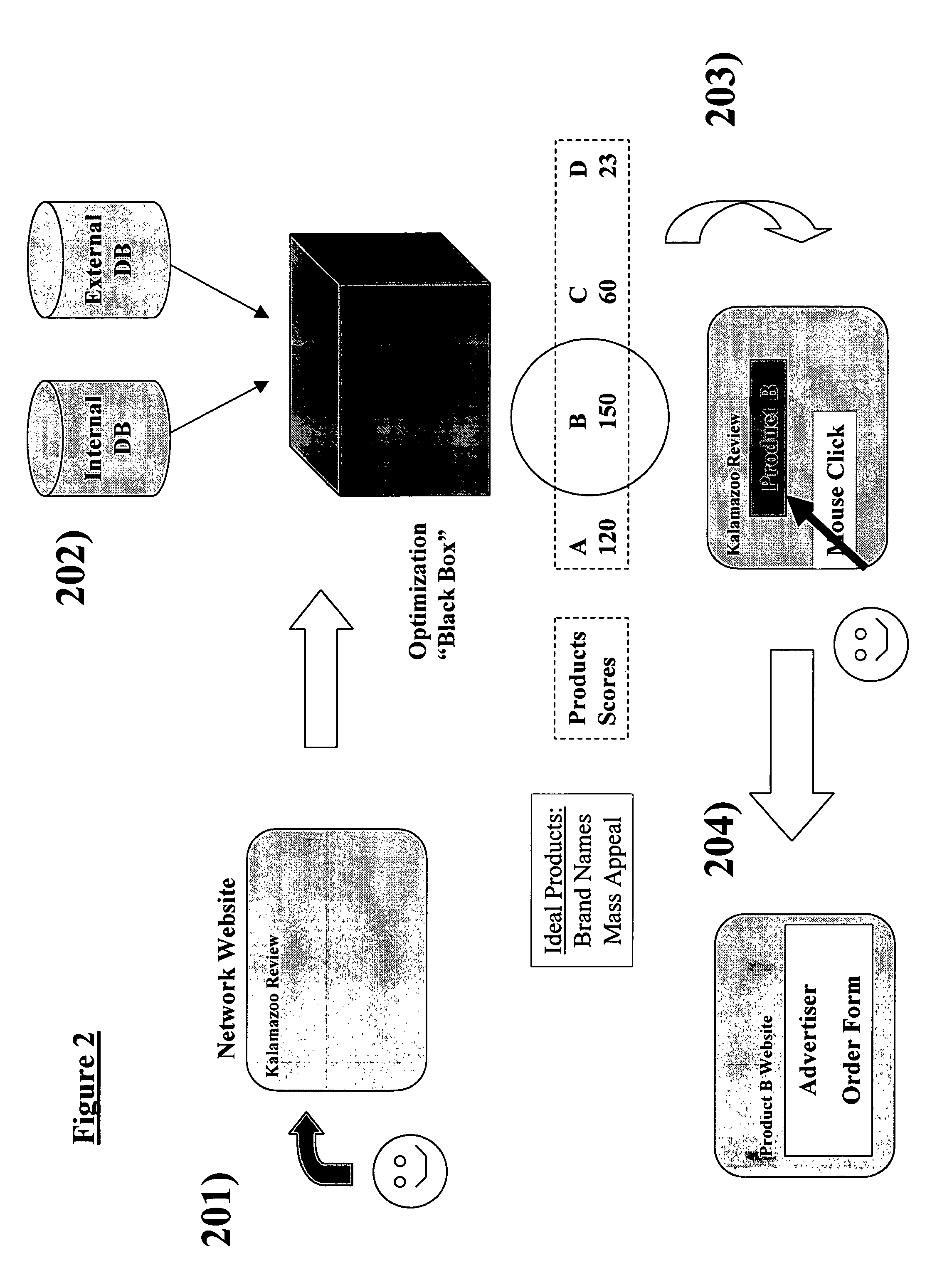
Optimal internet ad placement
This invention concerns optimal ad selection for Web pages by selecting and updating an attribute set, obtaining and updating an ad-attribute profile, and optimally choosing the next ad. The present invention associates a set of attributes with each customer. The attributes reflect the customers' interests and they incorporate the characteristics that impact ad selection. Similarly, the present invention associates with each ad an ad-attribute profile in order to calculate a customer's estimated ad selection probability and measure the uncertainty in that estimate. An ad selection algorithm optimally selects which ad to show based on the click probability estimates and the uncertainties regarding these estimates.
Owner:META PLATFORMS INC
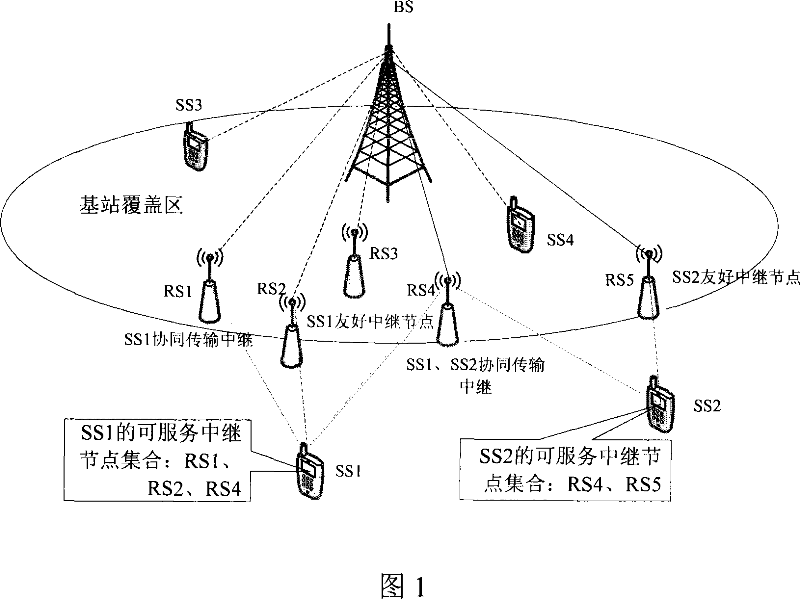
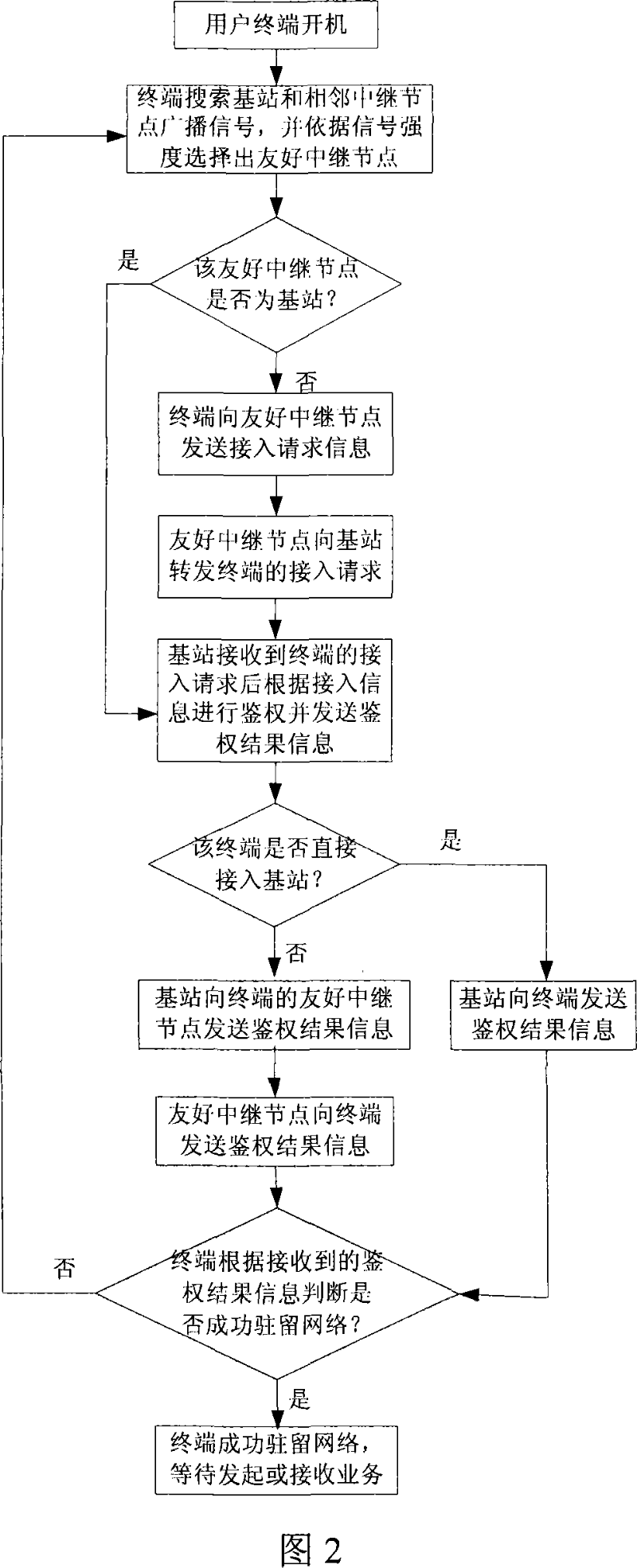
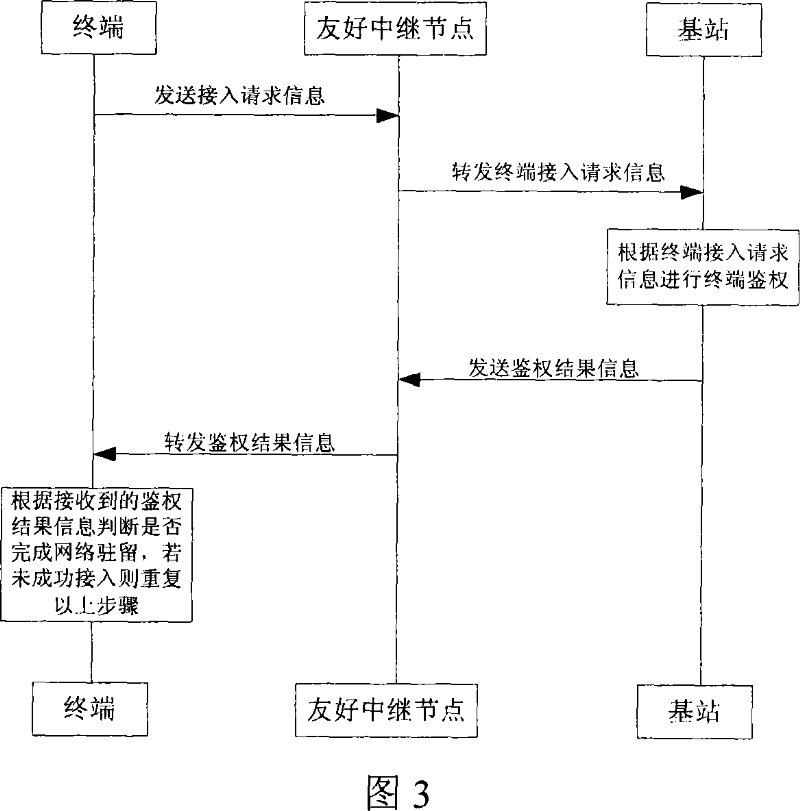
Method for selecting user stay and relay node of central control wireless relay network
ActiveCN101039526AExcellent resource schedulingExcellent power controlAssess restrictionUser identity/authority verificationMulti hop relayWireless mesh network
The present invention relates to a selection method of a user resident mechanism pf a wireless multi-hop relay network and synergy relay nodes centralizedly controlled by the base station. The present invention provides a user resident mechanism, uses thefriendly relay nodes relay and control the signaling transmission to complete; at the same time provides a relay node selection method of carrying out the centralized control and management to the entire relay node selection process by the base station, which is carried in synergies through potential relay nodes and the target terminal. The identification and selection of the relay node are divided into two steps: the first step is to identify the appropriate relay nodes, to constitute an alternative assembly; and the second step is to select a relay nodes subset to tansmit the carrying business from the alternative assembly according to the multi-optimization objective selection algorithm, and contemporarily completing the business carrying configuration of the relay nodes in the subset based on the business properties, as well as the hollow characteristics. The method not only focuses on a two-hop wireless relay network, but also can extend to the multi-hop wireless relay networks, or even extends to a wireless Mesh network and a wireless sensor network.
Owner:COMBA TELECOM SYST CHINA LTD
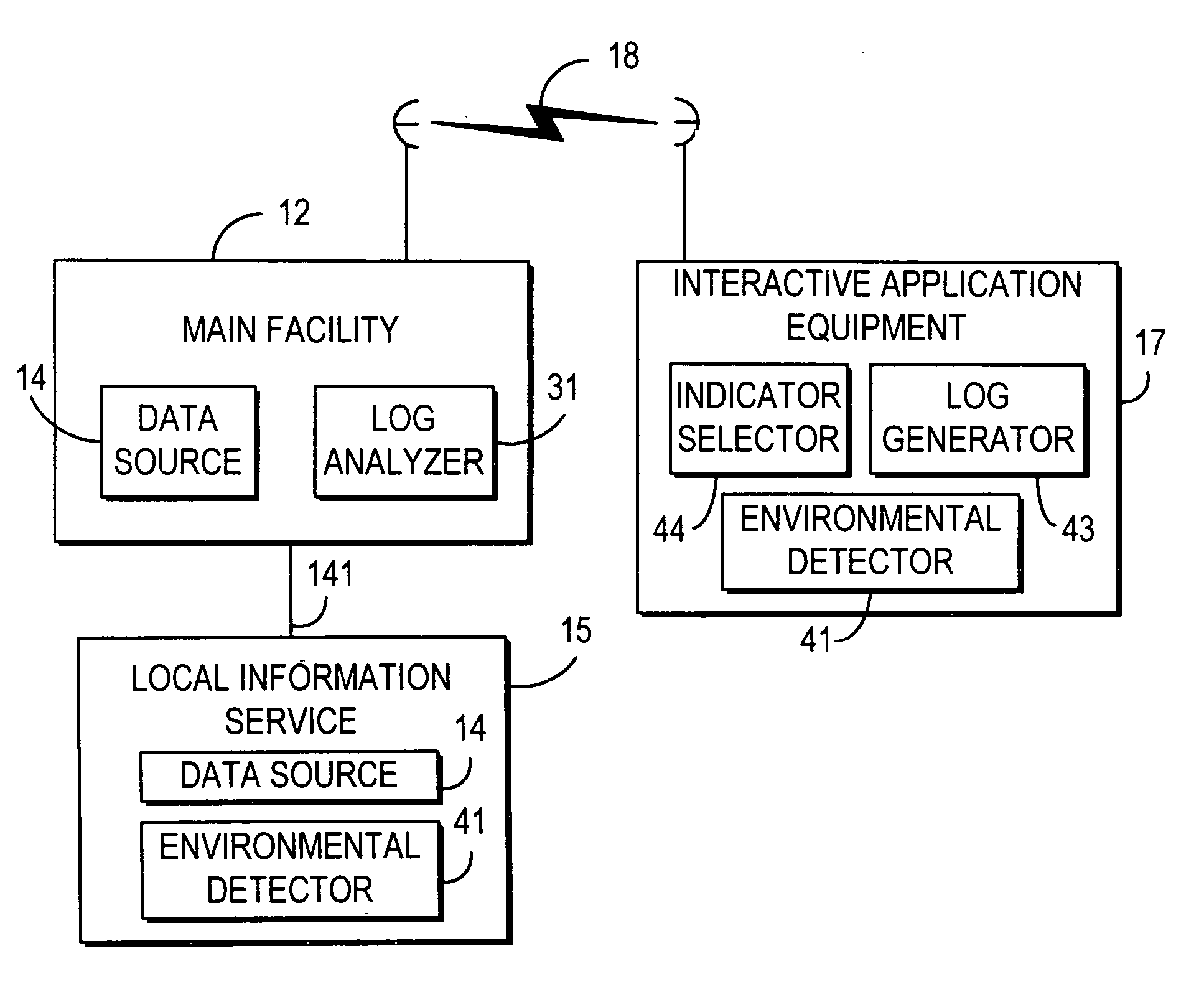
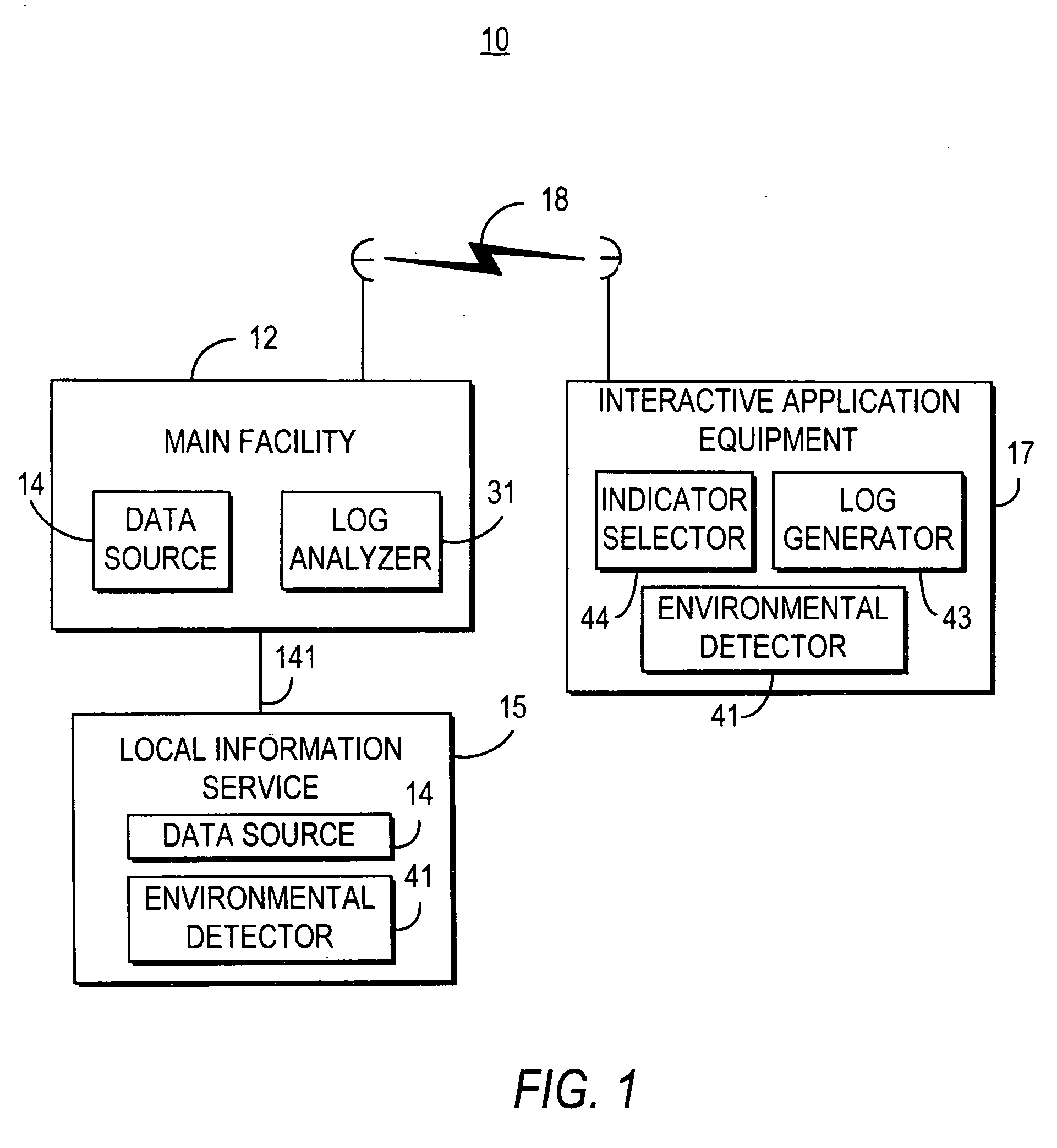
Promotional philosophy for a video-on-demand-related interactive display within an interactive television application
InactiveUS20050125823A1Facilitates desirable resultTelevision system detailsAnalogue secracy/subscription systemsInteractive televisionDisplay device
Systems and methods for providing an interactive display having indicators of video-on-demand programs are described. The systems and methods select indicators for inclusion in the interactive display according to a promotional selection algorithm.
Owner:UNITED VIDEO PROPERTIES
Declaration programming language extension for procedural programming languages
InactiveUS6145120AImprove performanceGuaranteed independence and securitySoftware engineeringKnowledge representationPerformance enhancementProcedural programming
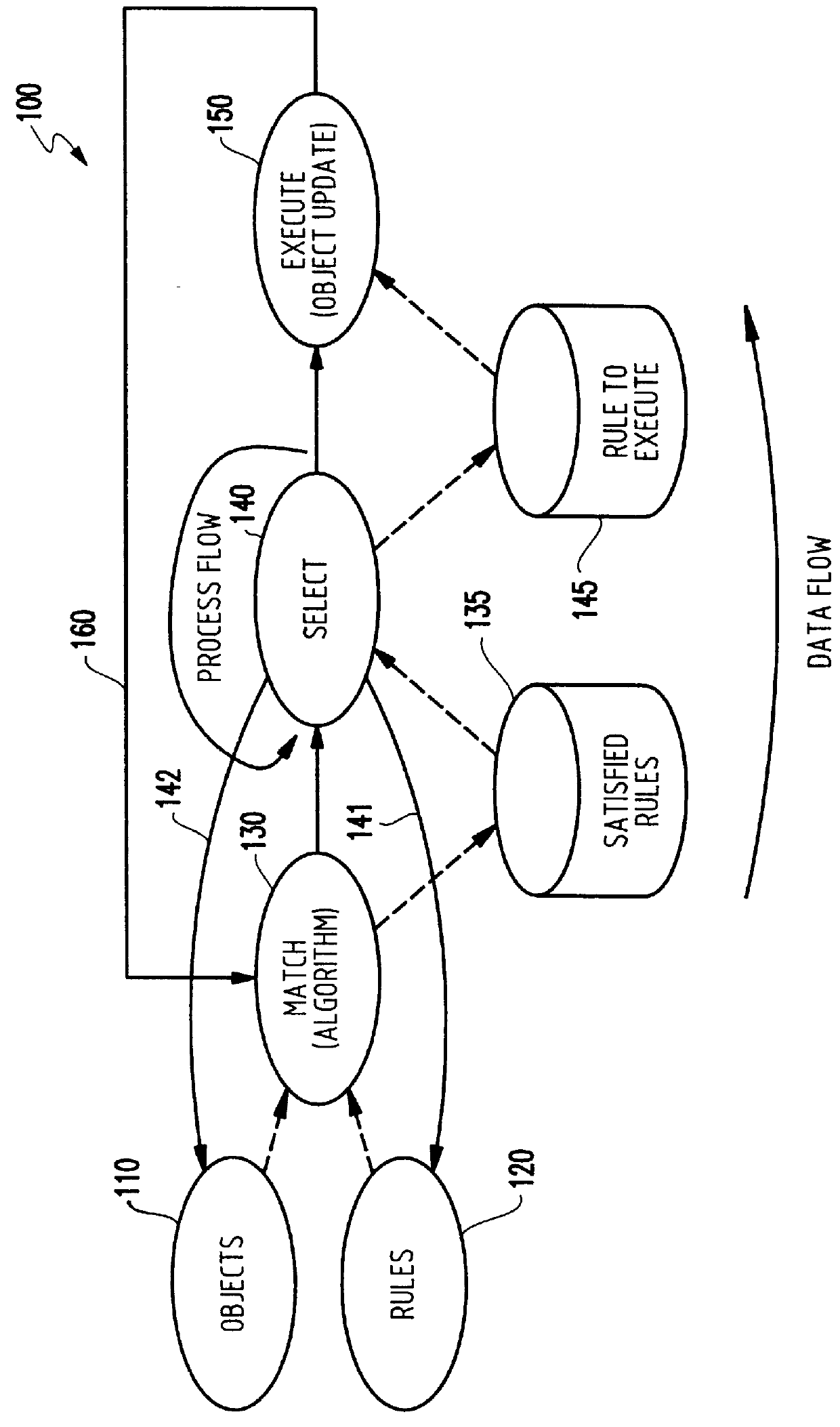
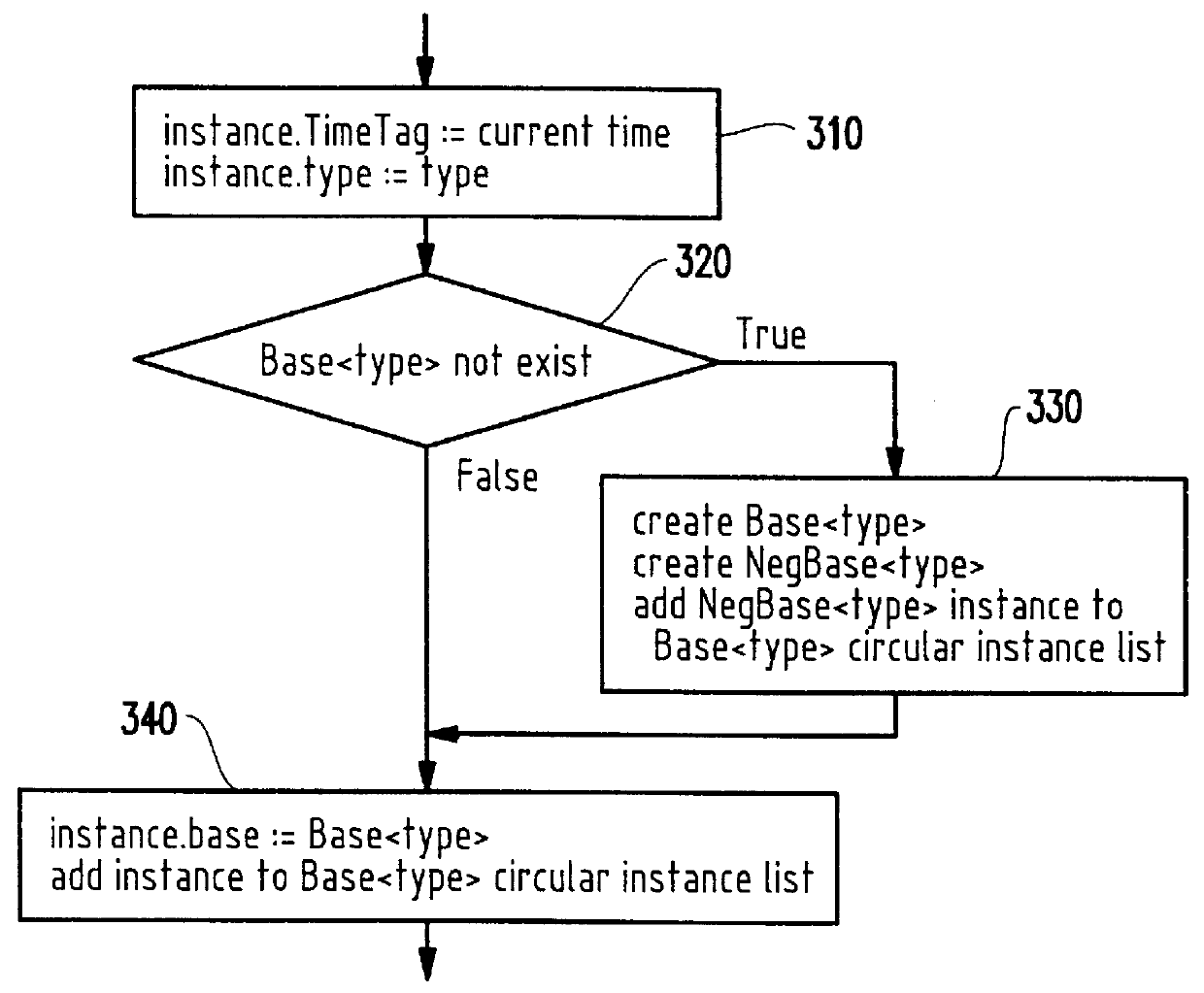
Complex declarative programming capabilities are provided through an underlying procedural programming code by functionally providing the selection algorithm of known declarative processing arrangements in explicit conditional constructs in procedural language embodying a rule or rule function statement. This approach simultaneously provides declarative processes easily and simply in a relatively few lines of procedural code while isolating the processing to the rules and objects, themselves, thereby providing reduction in hardware overhead requirements and performance enhancements which will be more fully discussed below. Further, by providing for updating of attributes and relationships of objects together with time tags associated with the update and removal of objects from list for evaluation, imprecise evaluation and heuristic reasoning may be readily developed while providing further performance enhancements to known Lazy Evaluation procedures.
Owner:LOCKHEED MARTIN CORP
Choosing pattern recognition algorithms and data features
InactiveUS20130073490A1Digital computer detailsElectric digital data processingFeature setChromosome encoding
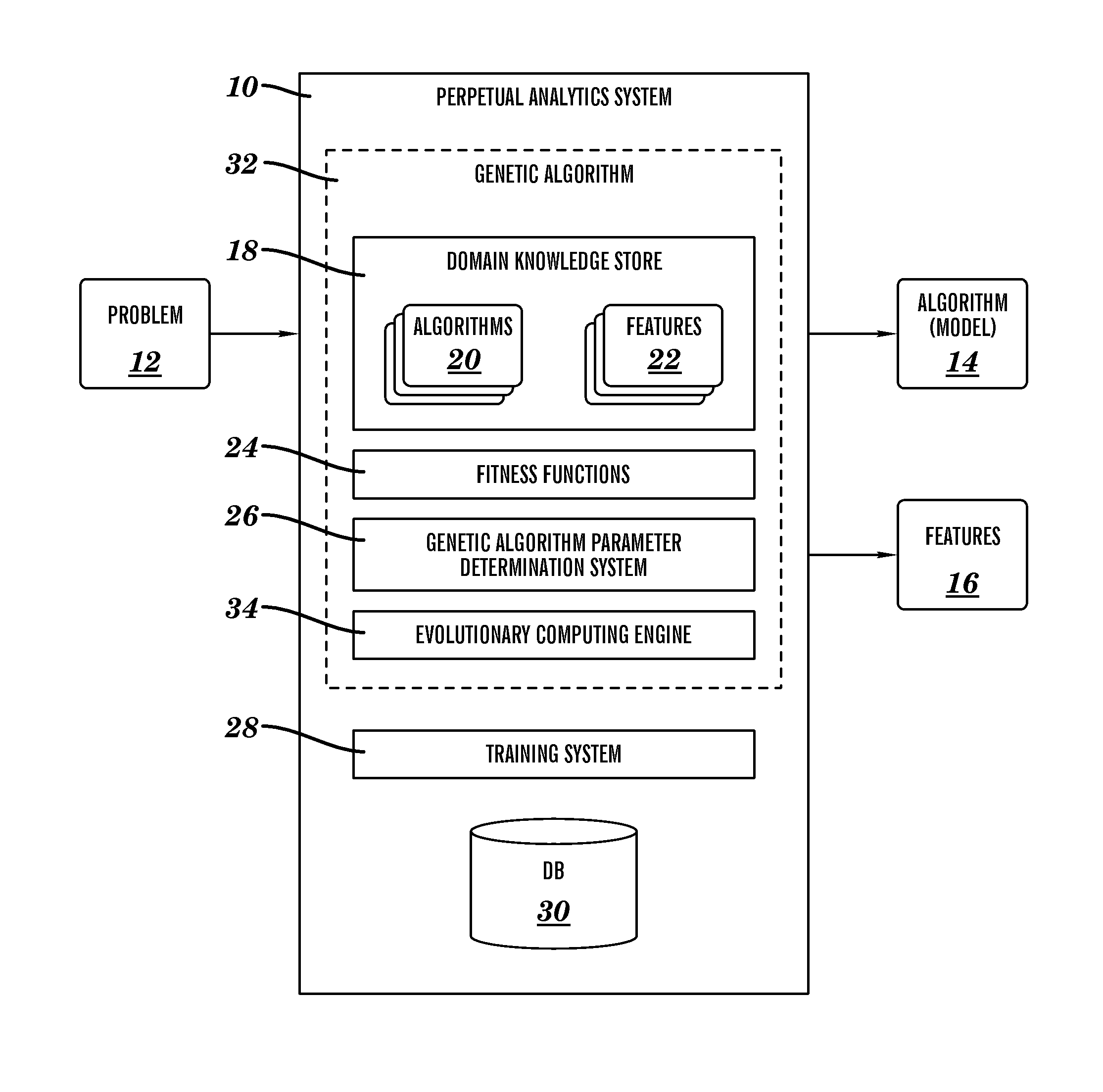
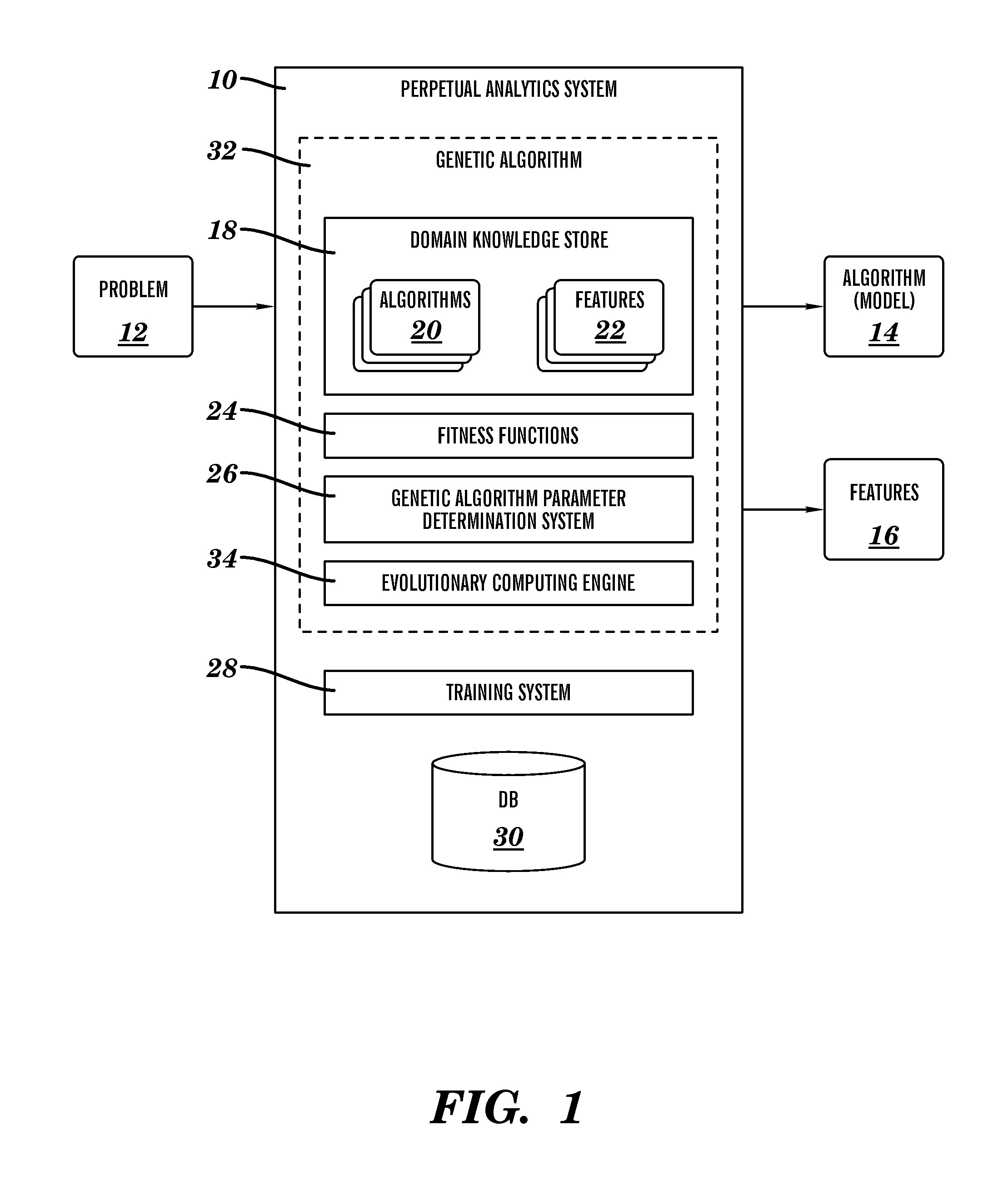
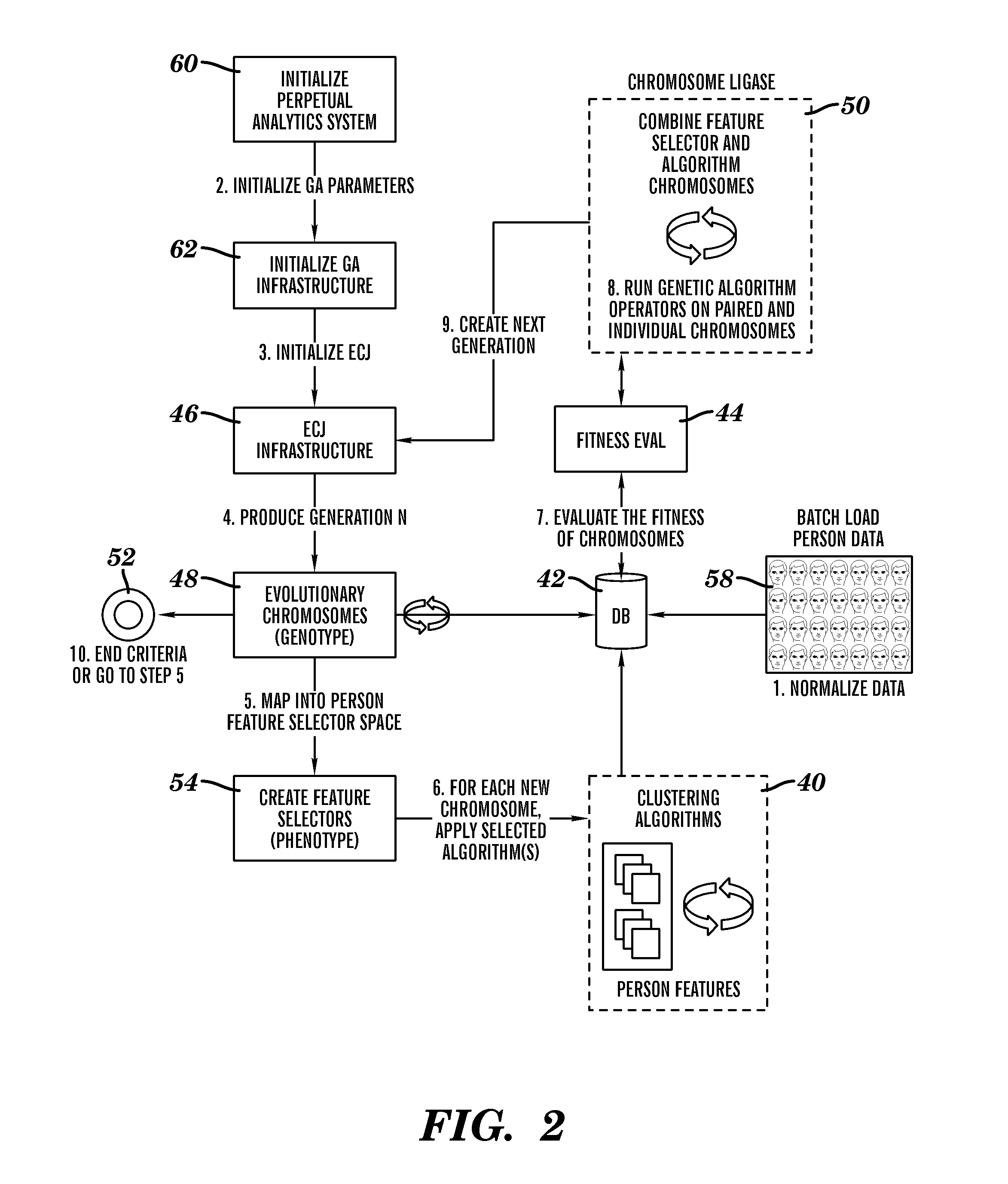
A system, method and program product for selecting an algorithm and feature set to solve a problem. A perpetual analytics system is disclosed that provides a genetic algorithm for jointly selecting an algorithm and feature set to solve a problem, comprising: an evolutionary computing engine for processing data encoded as chromosomes, wherein each chromosome encodes an algorithm and a feature set; a domain knowledge store that maintains a plurality of algorithms and a plurality of features; a system for applying a generation of chromosomes to a set of data to provide a set of results; and a fitness function for evaluating the set of results to rate a performance of each chromosome in the set of chromosomes; wherein the evolutionary computing engine is adapted to evolve a subset of the set of chromosomes into a new generation of chromosomes.
Owner:IBM CORP
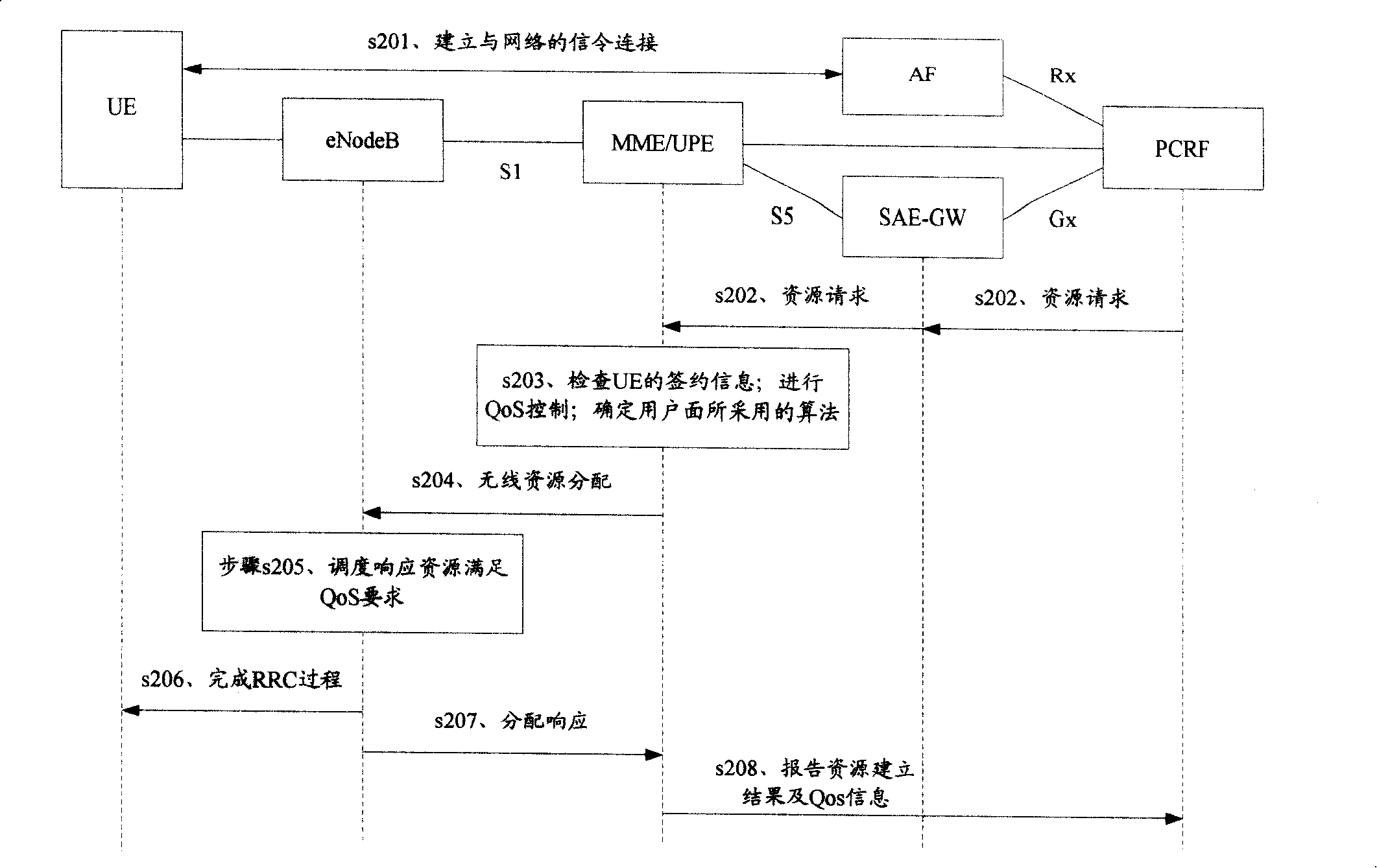
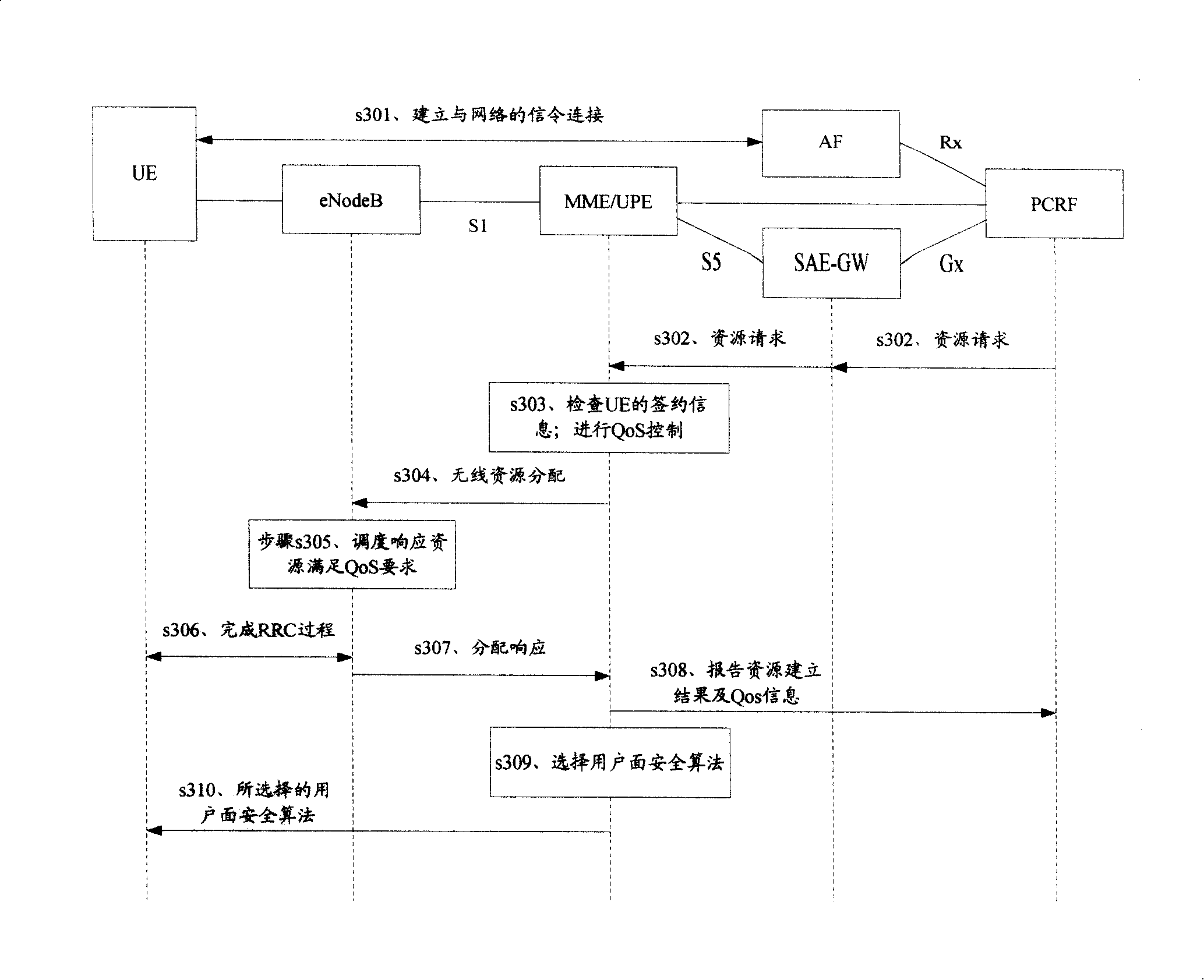
Method, system and device for selection algorithm of user plane
ActiveCN101242629AUser identity/authority verificationRadio/inductive link selection arrangementsSecurity levelSecurity information
The invention discloses a selection method for user plane security algorithm, including steps of: entity at the other end of the network receives request sent by user terminal; entity at the other end of network acquires and selects user plane algorithm according to security information of user terminal. The invention also provides a system and device for selecting user plane security algorithm. By the invention, network could select algorithm of different security level according to service or user's demand, namely that algorithm is negotiated based on different services or different users, so that encryption operation in network is more flexible, and protection on different levels is provided to users and services with different security demand.
Owner:HUAWEI TECH CO LTD
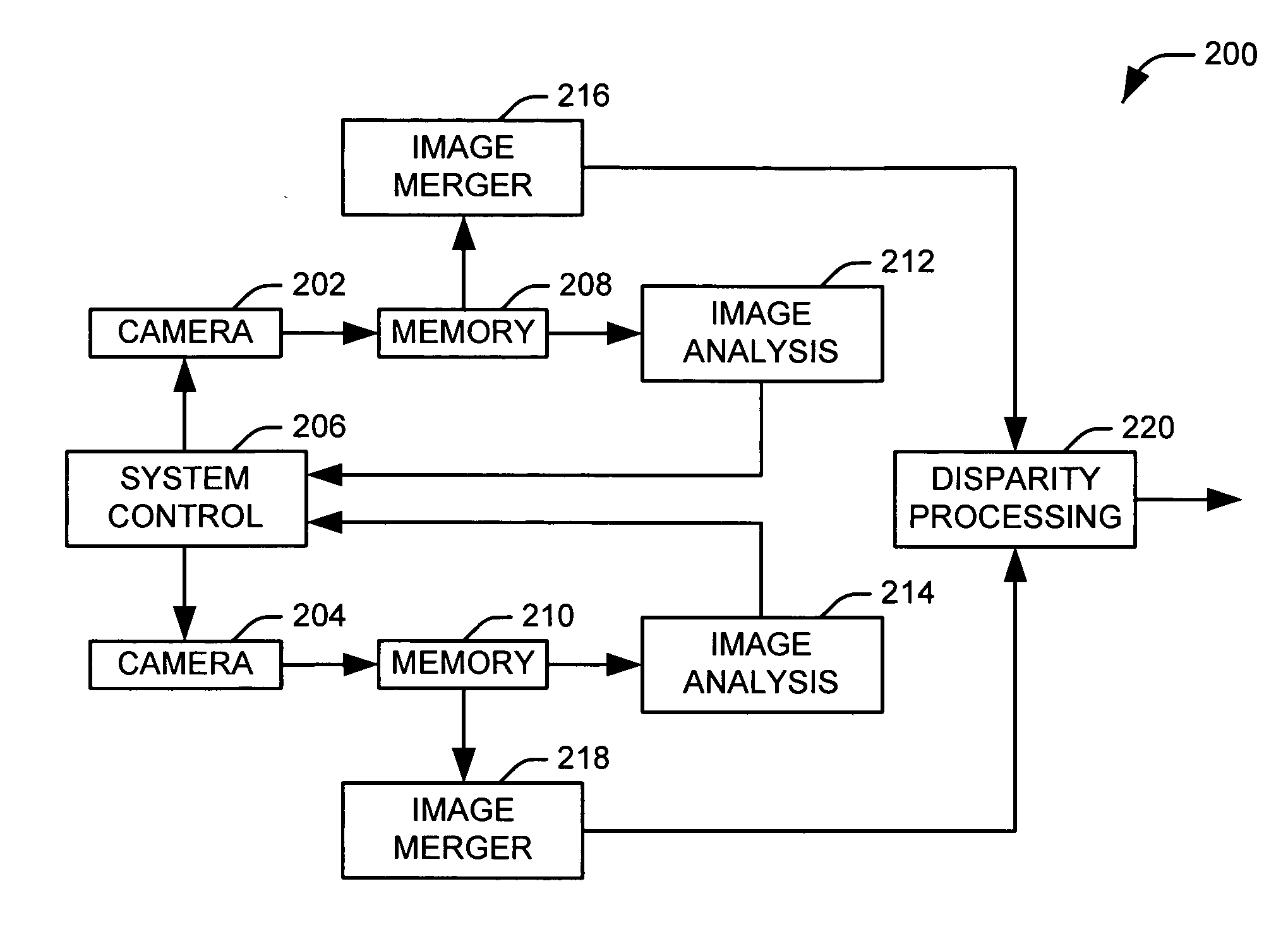
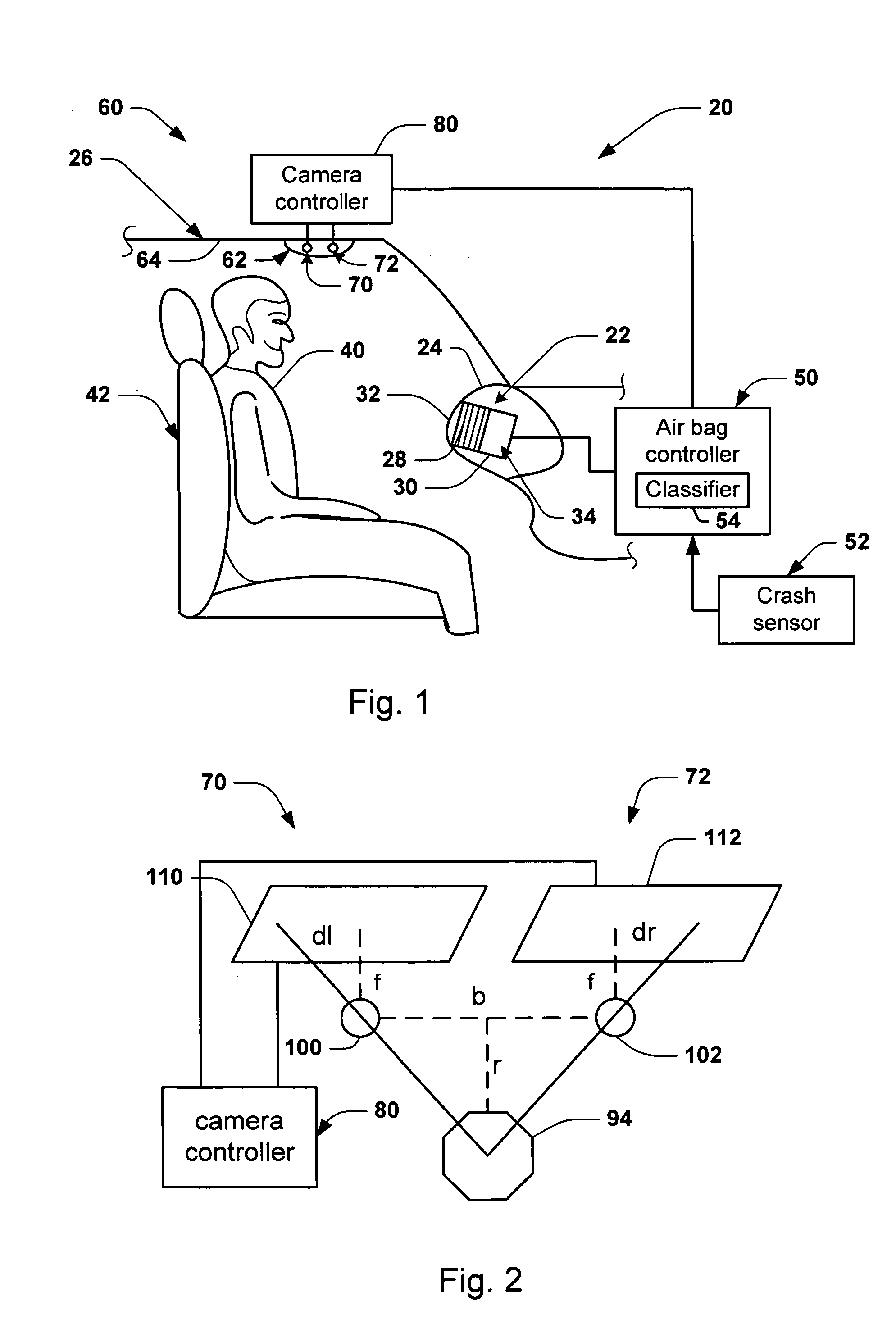
Method and apparatus for enhancing the dynamic range of stereo vision system
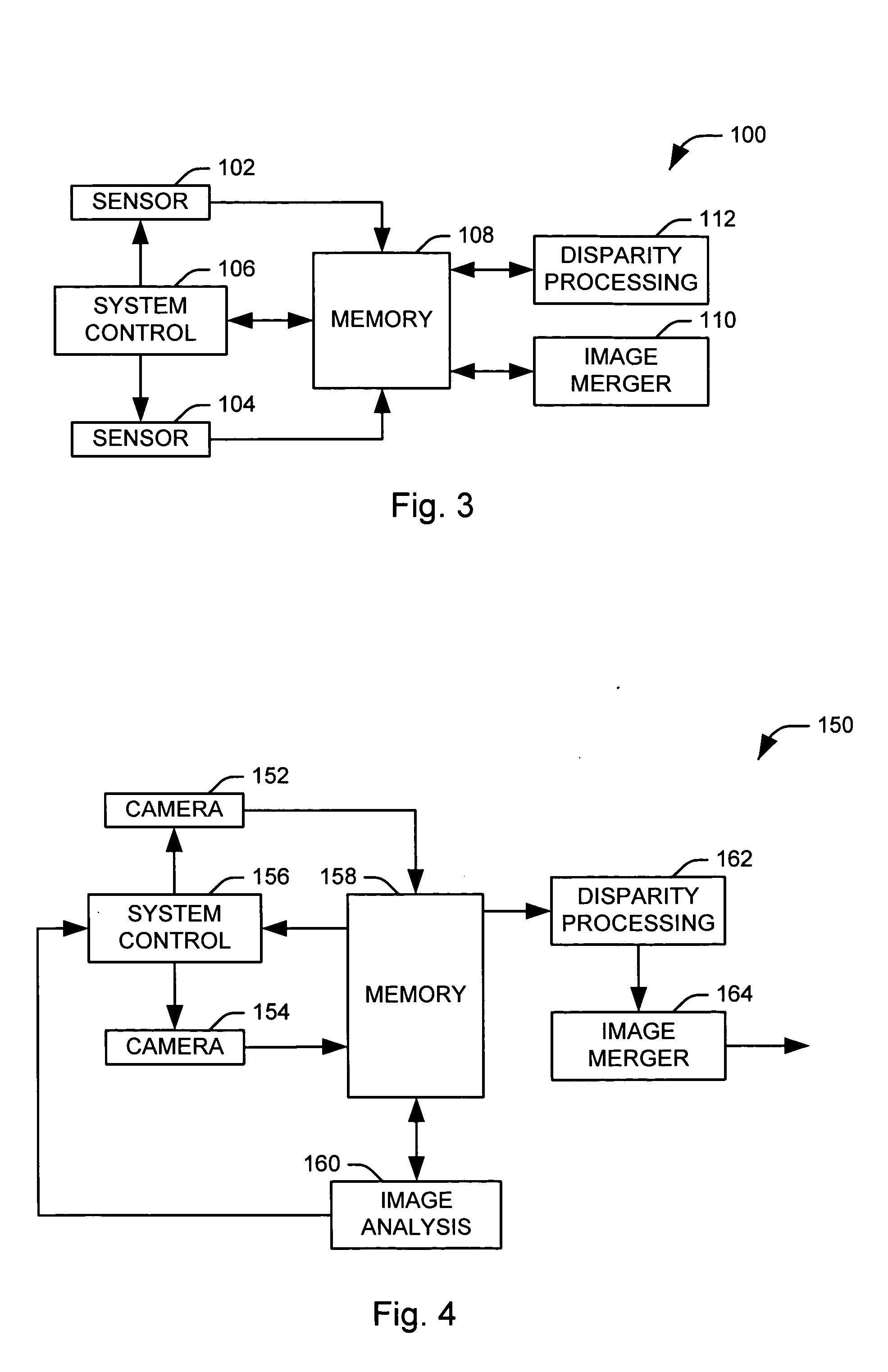
Systems and methods are provided for producing a stereo disparity map representing an imaged subject. A plurality of sensors (102 and 104) are operative to produce a plurality of images. Each image has an associated exposure according to an exposure level of an associated sensor. A system control (106) determines exposure levels for the plurality of sensors according to an exposure selection algorithm. A disparity processing component (112) is operative to generate a stereo disparity map from a plurality of images. An image merger (110) is operative to merge a plurality of images to produce a composite image having an increased dynamic range.
Owner:TRW AUTOMOTIVE US LLC
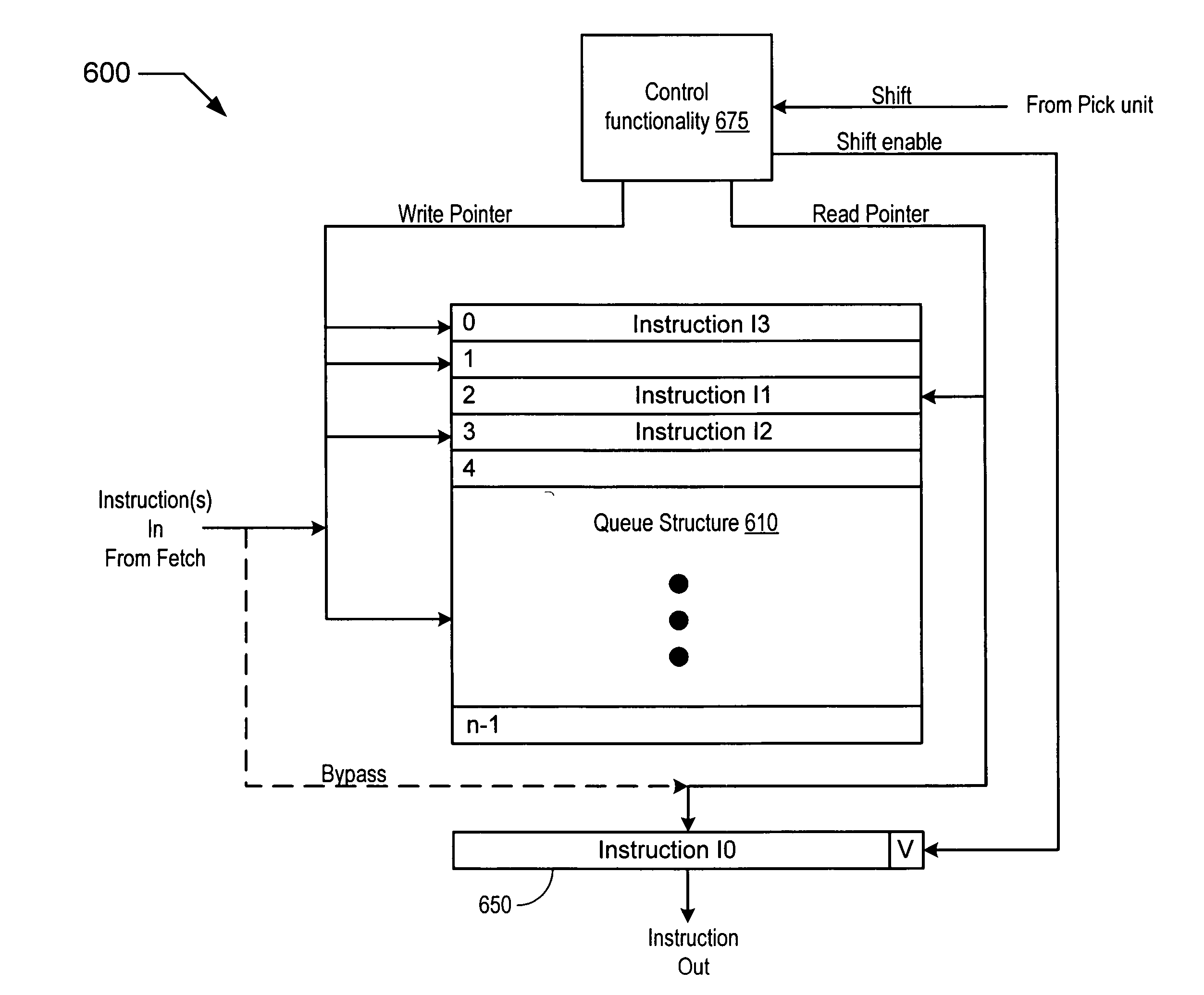
Mechanism for selecting instructions for execution in a multithreaded processor
In one embodiment, a multithreaded processor includes a plurality of buffers, each configured to store instructions corresponding to a respective thread. The multithreaded processor also includes a pick unit coupled to the plurality of buffers. The pick unit may pick from at least one of the buffers in a given cycle, a valid instruction based upon a thread selection algorithm. The pick unit may further cancel, in the given cycle, the picking of the valid instruction in response to receiving a cancel indication.
Owner:SUN MICROSYSTEMS INC
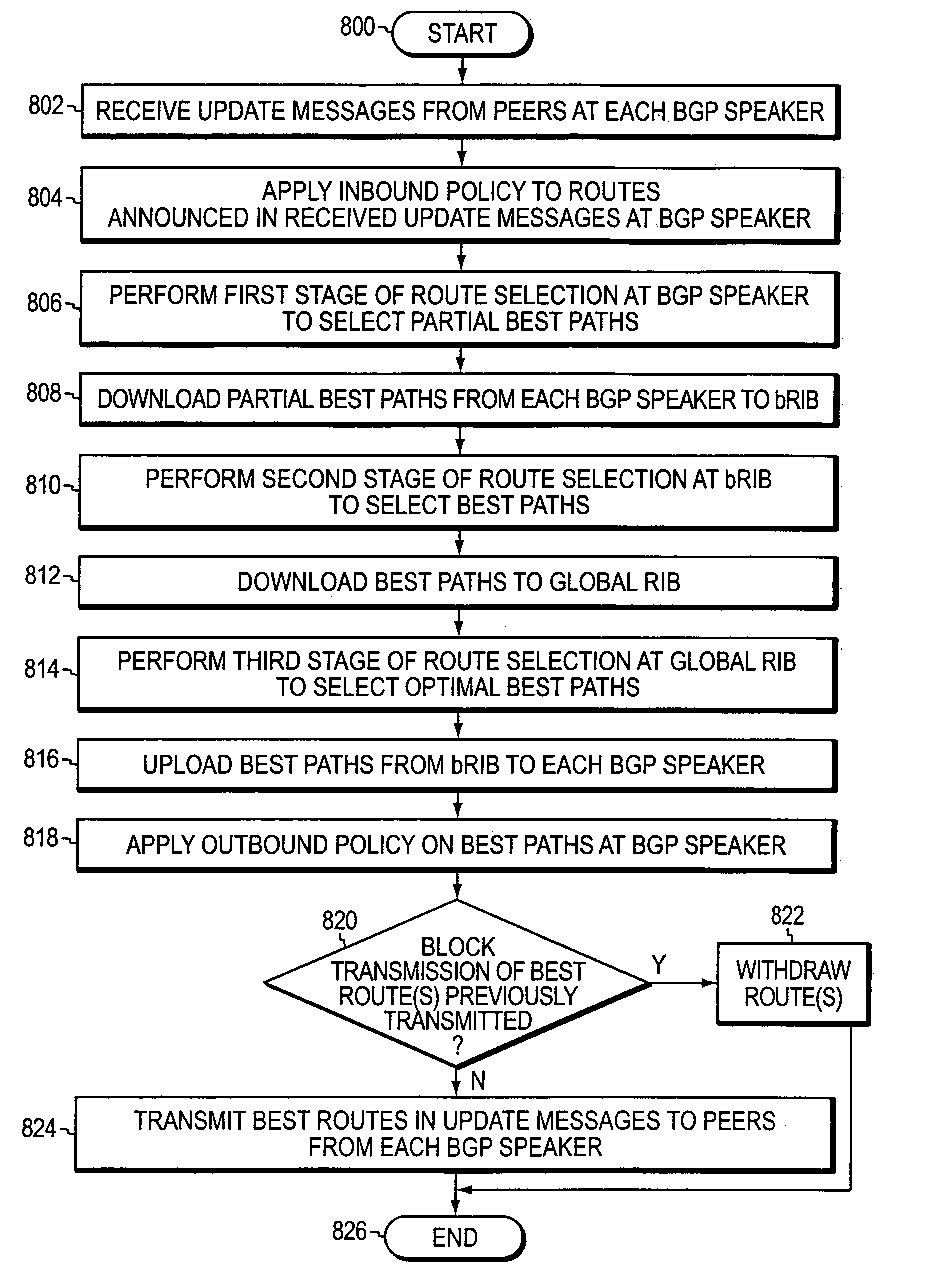
System and method for distributing route selection in an implementation of a routing protocol
ActiveUS7023808B2Reduce memory usageOvercome disadvantagesError preventionTransmission systemsPathPingData pack
Owner:CISCO TECH INC
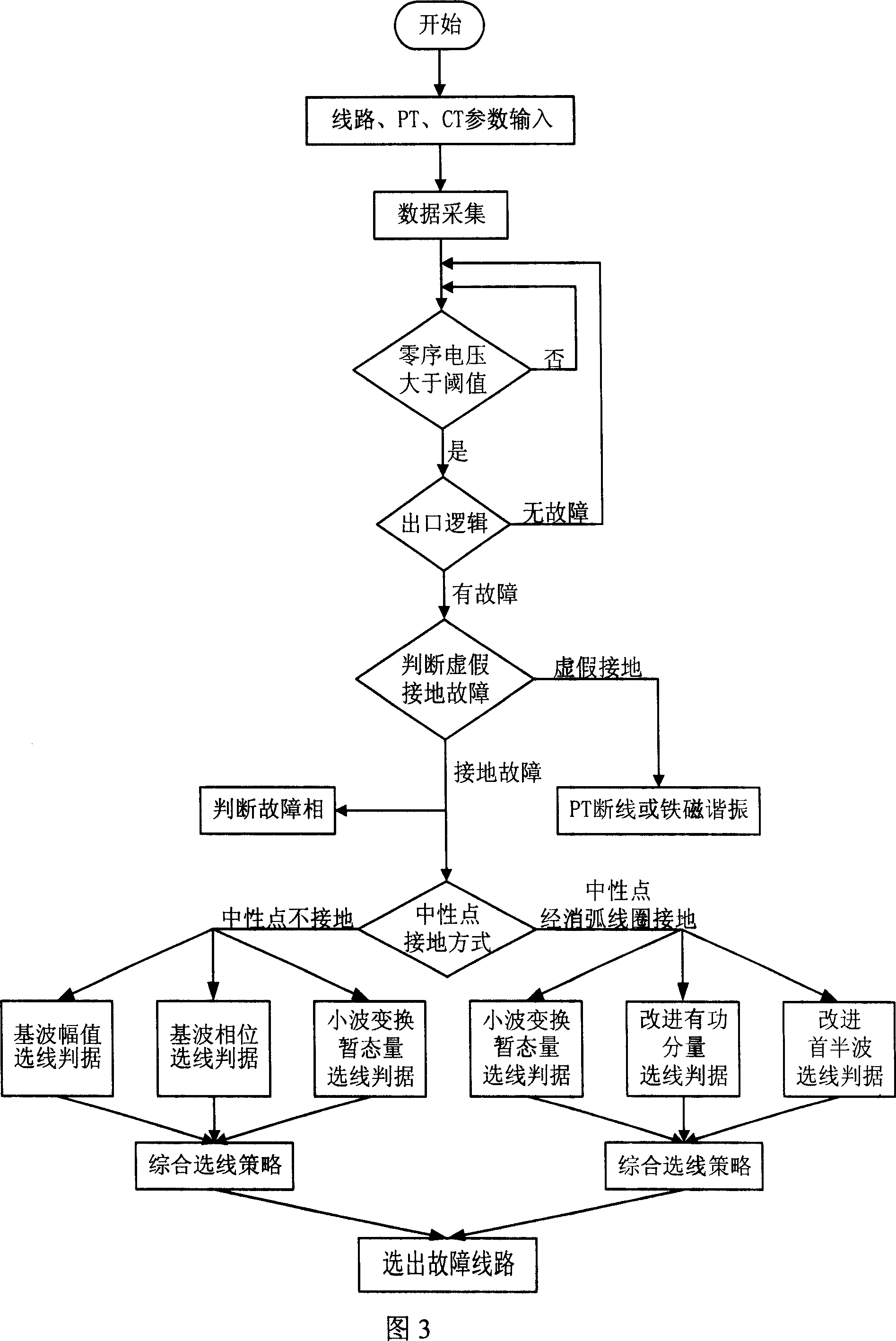
Small earthing current electric network single phase fault wire selecting method and apparatus
InactiveCN101022216AImprove reliabilityGuaranteed accuracyEmergency protective circuit arrangementsFault locationHuman–machine interfacePotential transformer
This invention discloses a method and a device for selecting single-phase fault of small earth current nets, which integratedly processes multiple kinds of fault signals based on the earth situation of the non-earth and arc-extinguishing coils, applies multiple kinds of line selention criteria to constitute quantification espressions showing that a line may be a fault one to get the final line selection result by integrated judgment, the selection device has good man-machine interface and is easily operated and installed, the hardware of the device is a PCI bus industrial control mainboard, and the selection algorithm is realized by virtual instrument technology to differentiate faults of single-phase earth, breakage of voltage mutual-inductors and ferromagnetic resonance and displayed by LCD.
Owner:YANSHAN UNIV
Method for realizing vehicle-mounted mobile self-organized network routing
InactiveCN101720059AReal-time adjustmentLower latencyNetwork topologiesWireless commuication servicesDelayed timeSelf-organizing network
The invention relates to a method for realizing vehicle-mounted mobile self-organized network routing, which is characterized by comprising the following steps that: (1) a static node is arranged at each intersection; (2) when forwarding a data packet, a source node can forward the data packet to the static node relatively close to a target static node at one end of a road section where the source node is positioned; (3) when forwarding the data packet, the static node firstly judges whether the static node closer to the target static node is in a neighbouring list or not, if so, the static node directly forwards the data packet to the corresponding static node, otherwise, the static node selects a neighbouring road section according to a road section selection algorithm, and then appoints another static node on the selected road section as the static node of a road section receiving terminal, wherein the neighbouring road section is not the road section which just receives the data packet; and the road section direction of the neighbouring road section is close to the target static node; and (4) when receiving the same data packet transmitted from the same source node from different road sections, a routing static node selects an optimal route which is high in the success rate for receiving the data packet and relatively short in delay time, and forbids the receiving routes which are not optimal at the same time.
Owner:ZHEJIANG UNIV CITY COLLEGE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com