Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2061 results about "Edge device" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
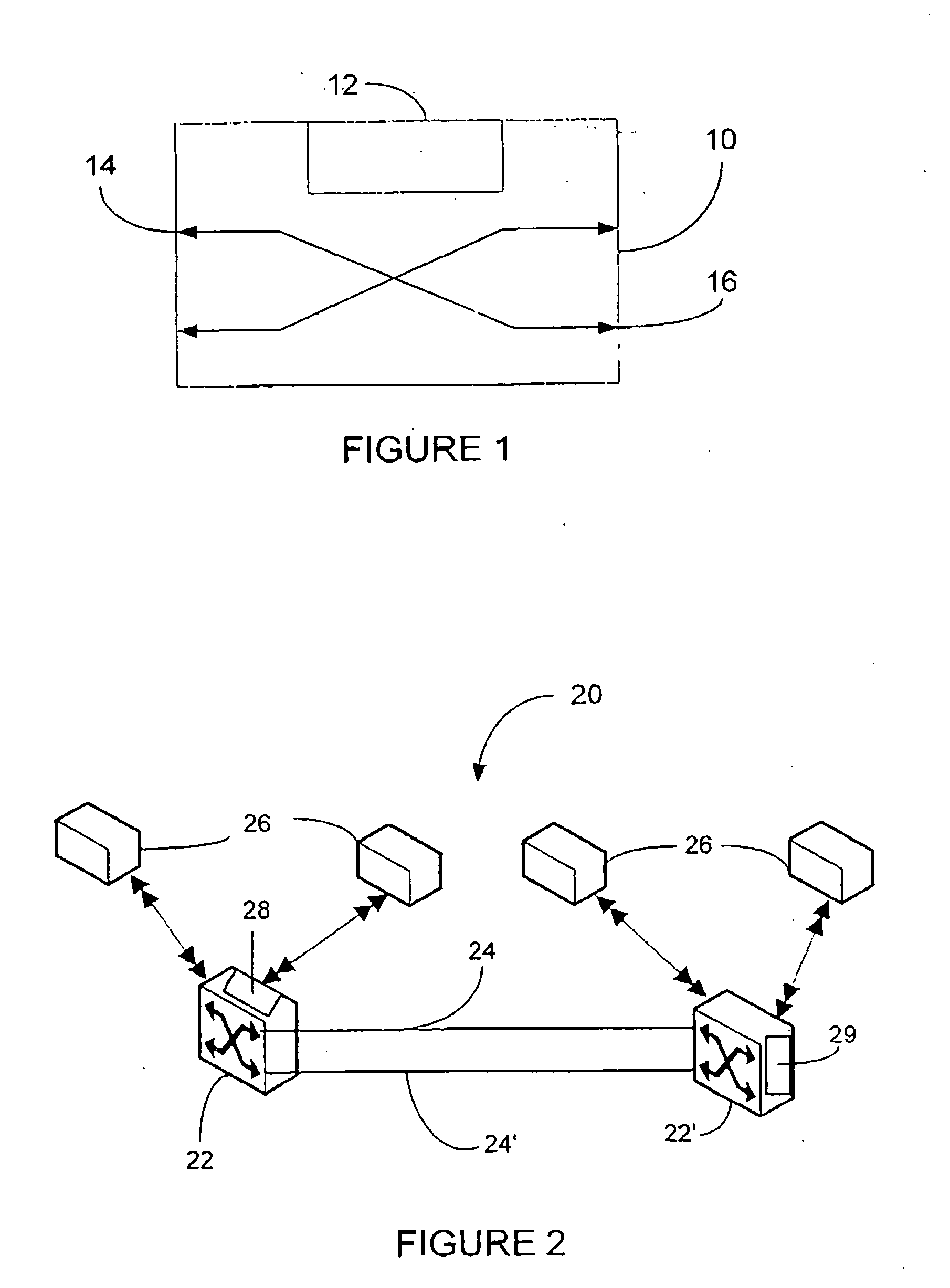
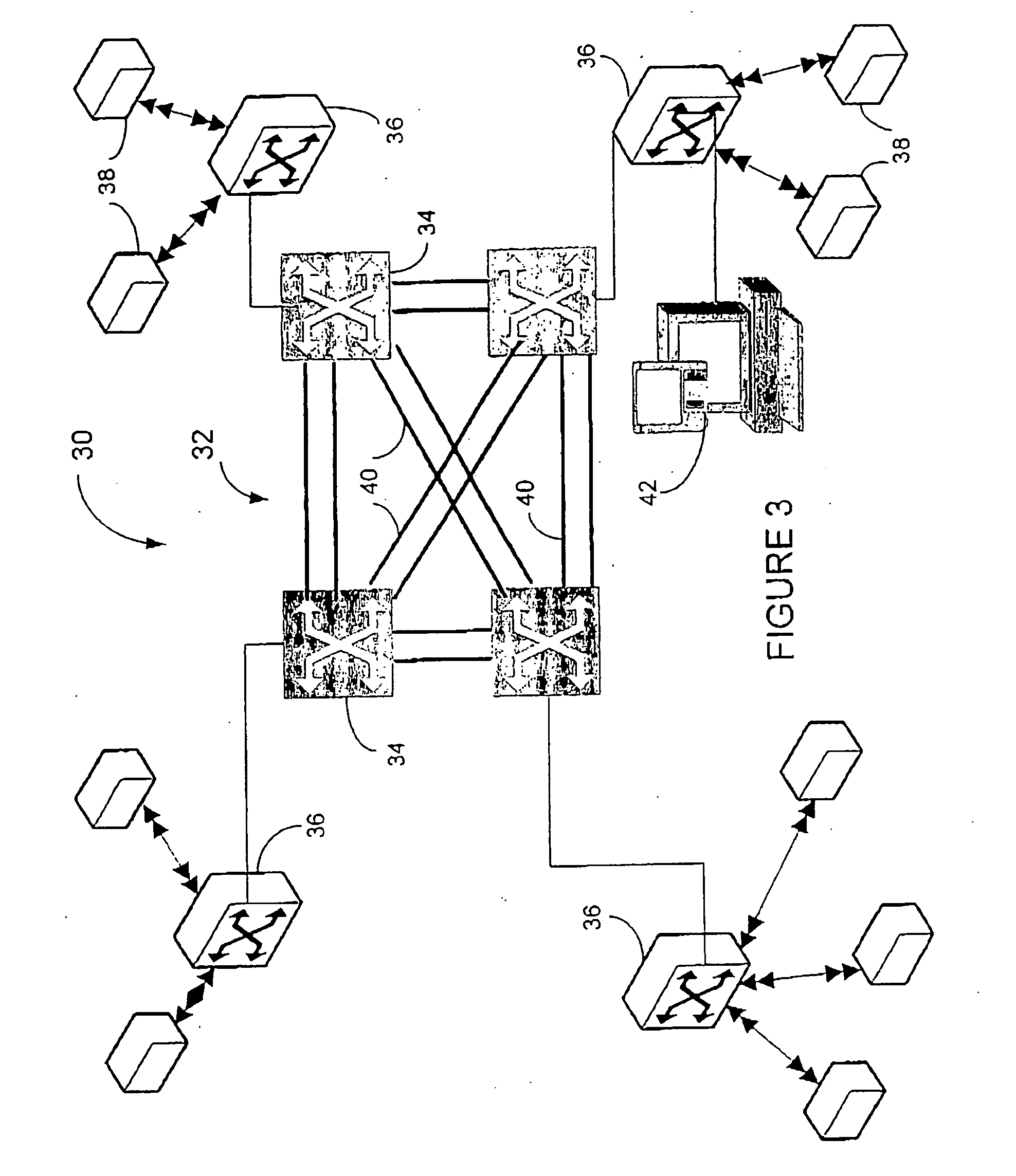
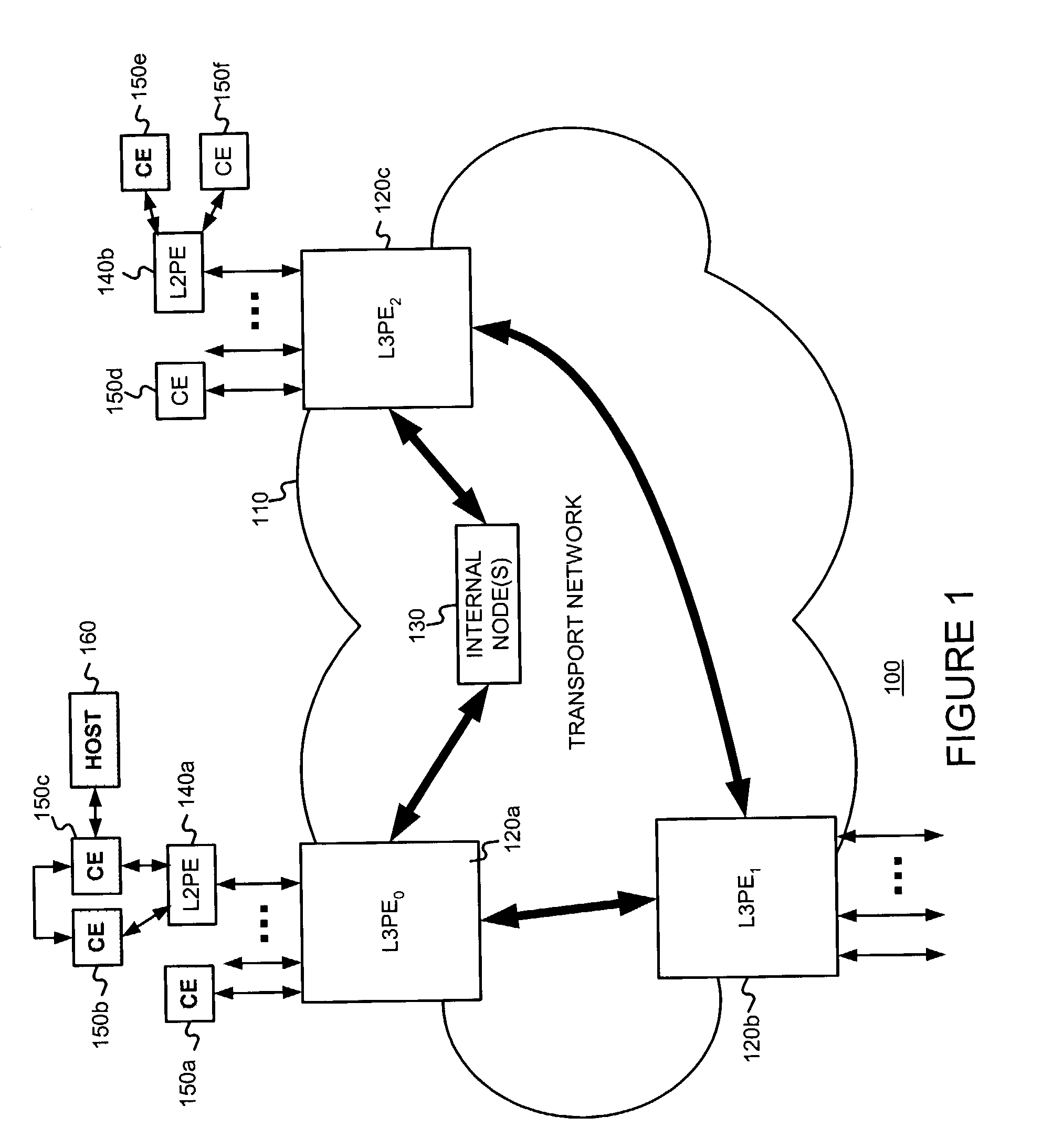
An edge device is a device which provides an entry point into enterprise or service provider core networks. Examples include routers, routing switches, integrated access devices (IADs), multiplexers, and a variety of metropolitan area network (MAN) and wide area network (WAN) access devices. Edge devices also provide connections into carrier and service provider networks. An edge device that connects a local area network to a high speed switch or backbone (such as an ATM switch) may be called an edge concentrator.
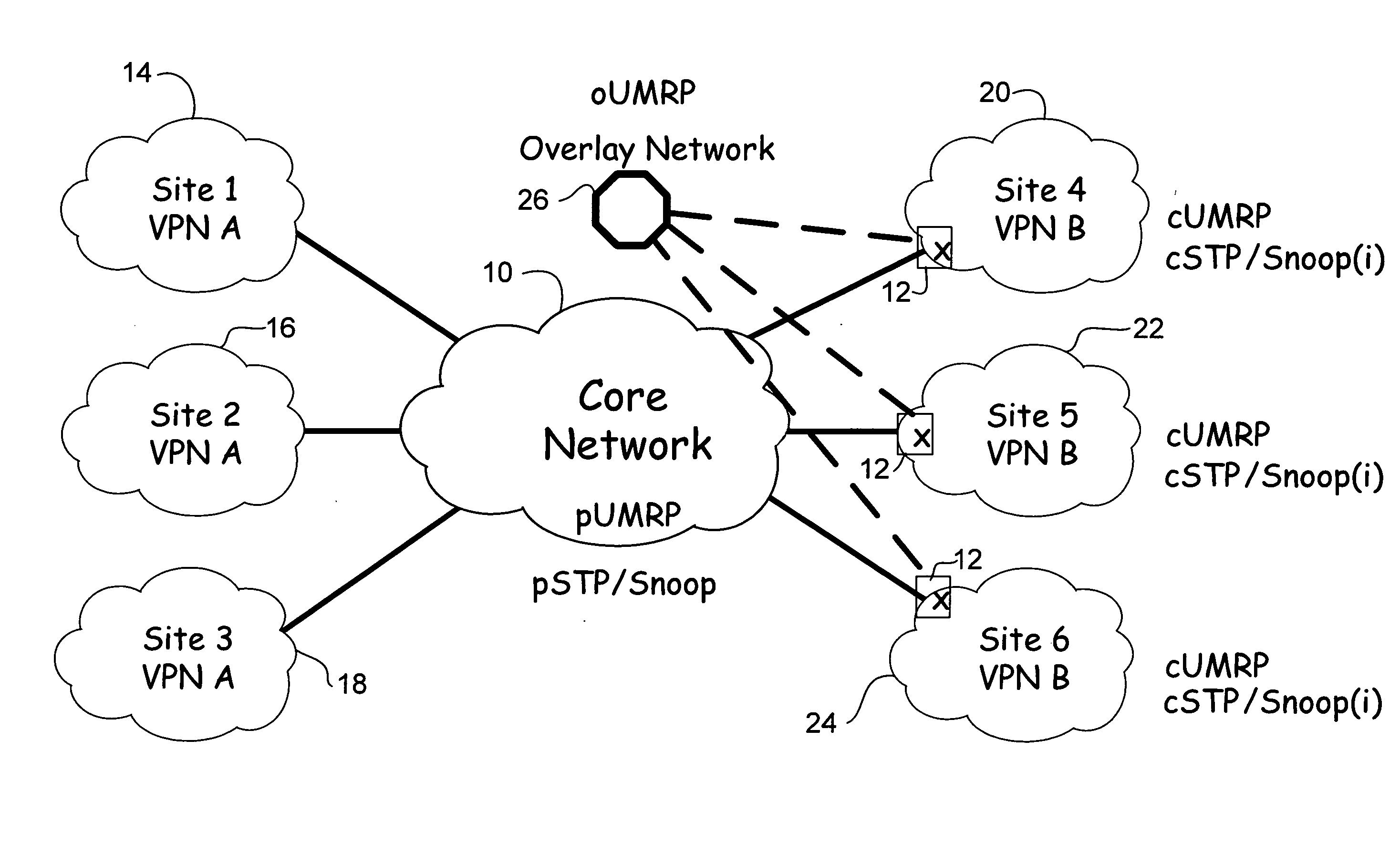
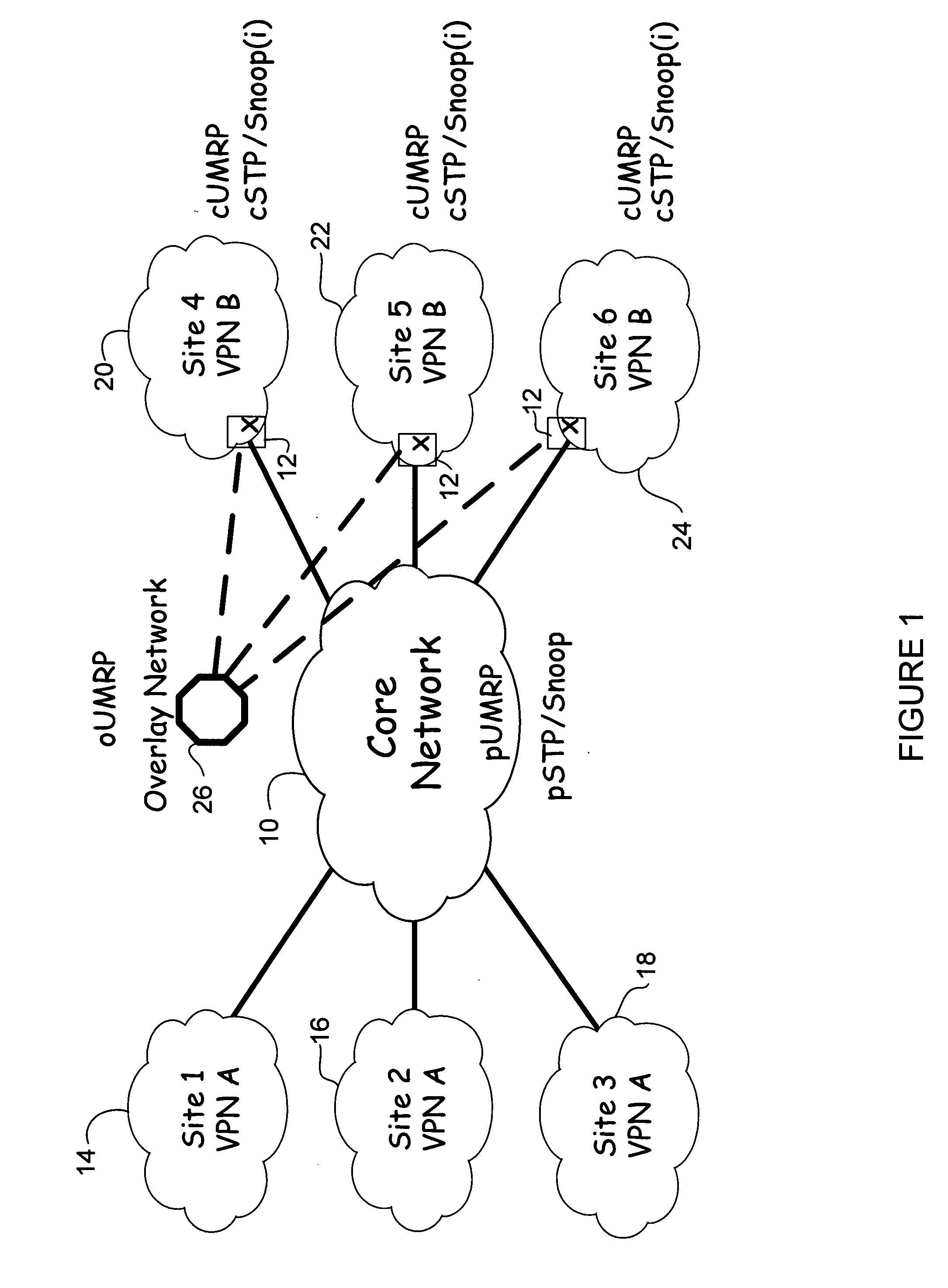
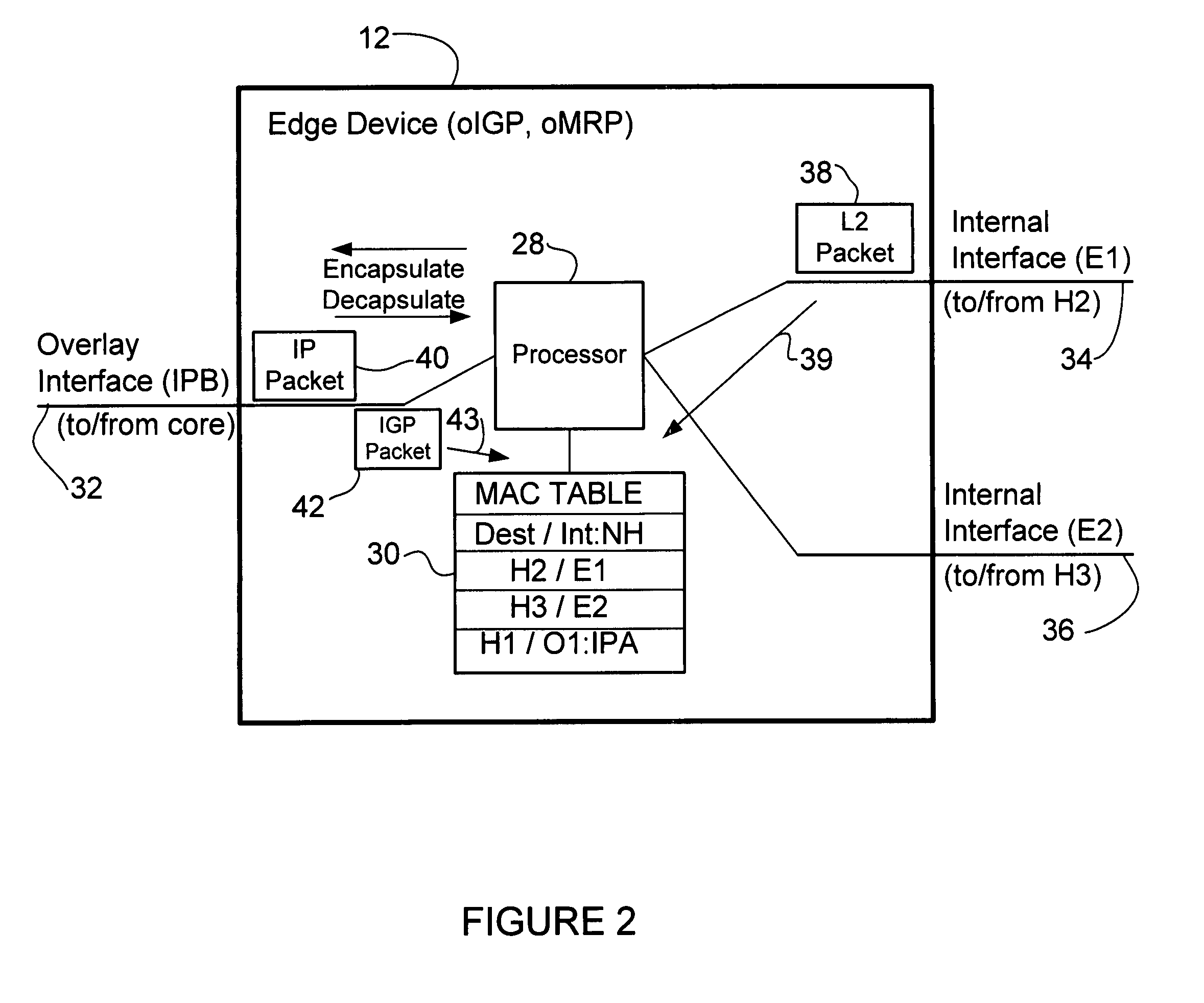
Overlay transport virtualization
ActiveUS20090037607A1Data switching by path configurationMultiple digital computer combinationsVirtualizationEdge device
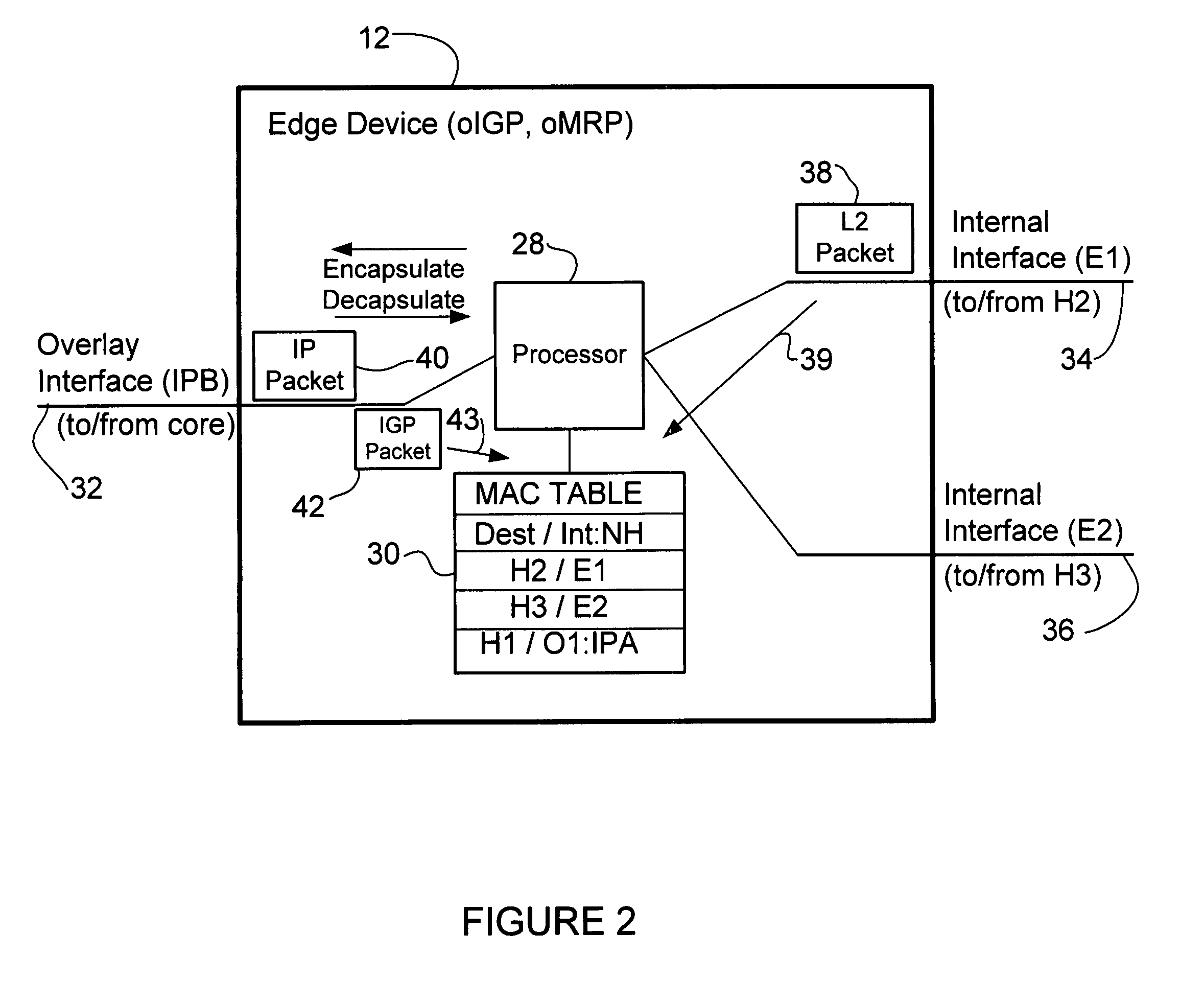
In one embodiment, an apparatus includes one or more internal interfaces in communication with one or more network devices in a first network site through a Layer 2 link, an overlay interface in communication through a Layer 3 link with a core network connected to one or more other network sites, and a table mapping addresses for network devices in the other network sites to addresses of edge devices in the same network site as the network device. The apparatus further includes a processor operable to encapsulate a packet received at one of the internal interfaces and destined for one of the network devices in the other network sites, with an IP header including a destination address of the edge device mapped to the destination network device, and forward the encapsulated packet to the core network.
Owner:CISCO TECH INC
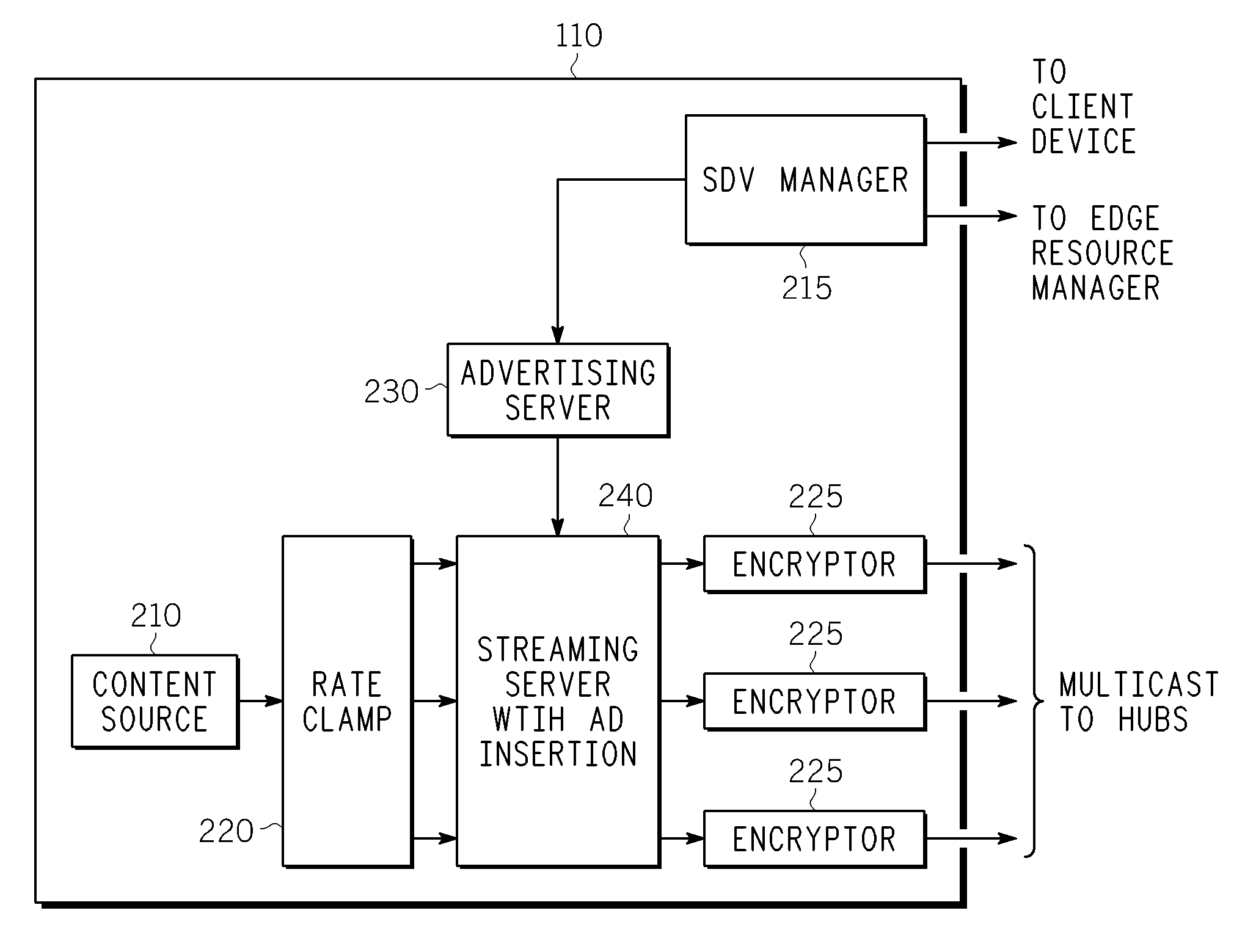
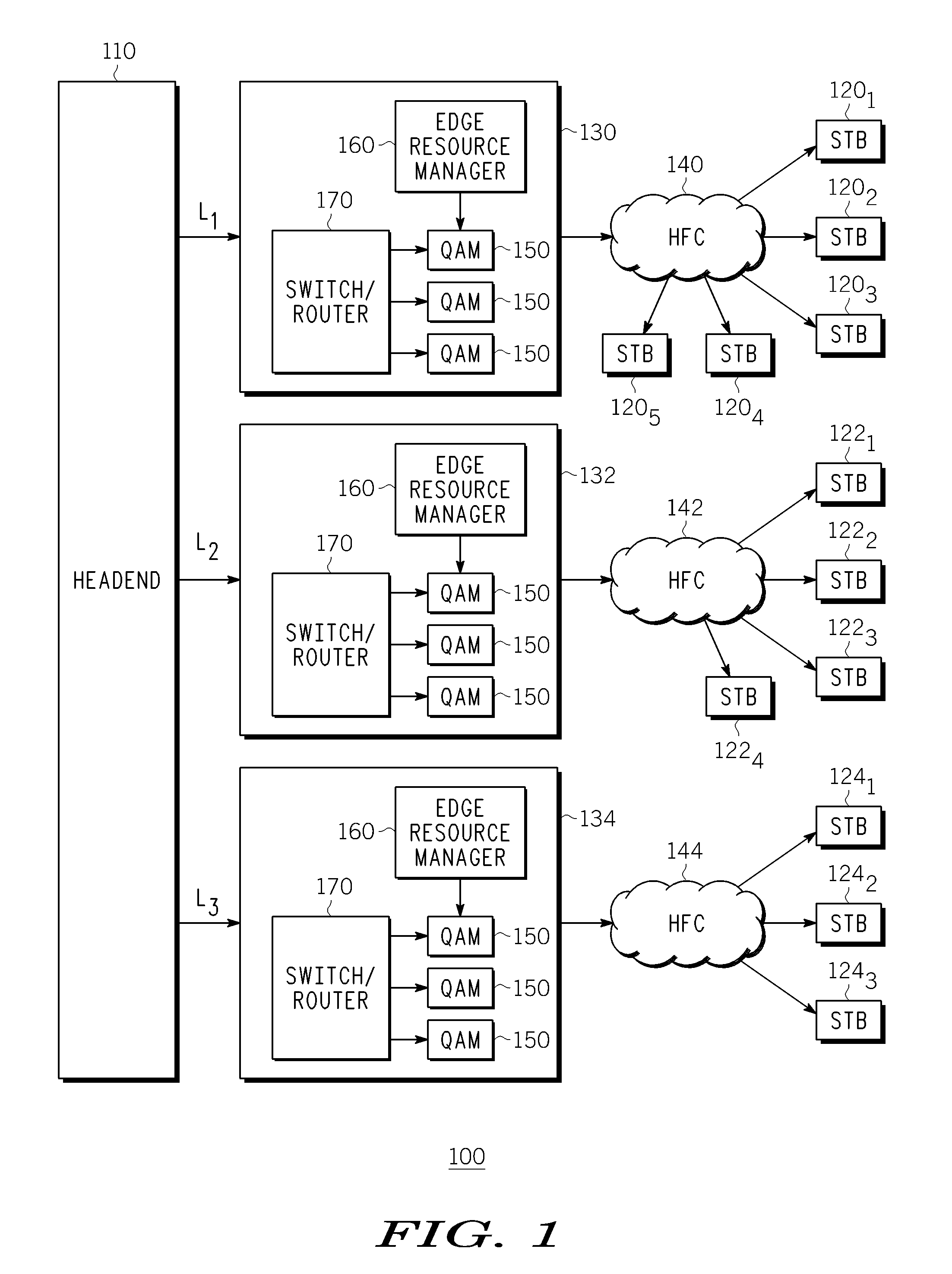
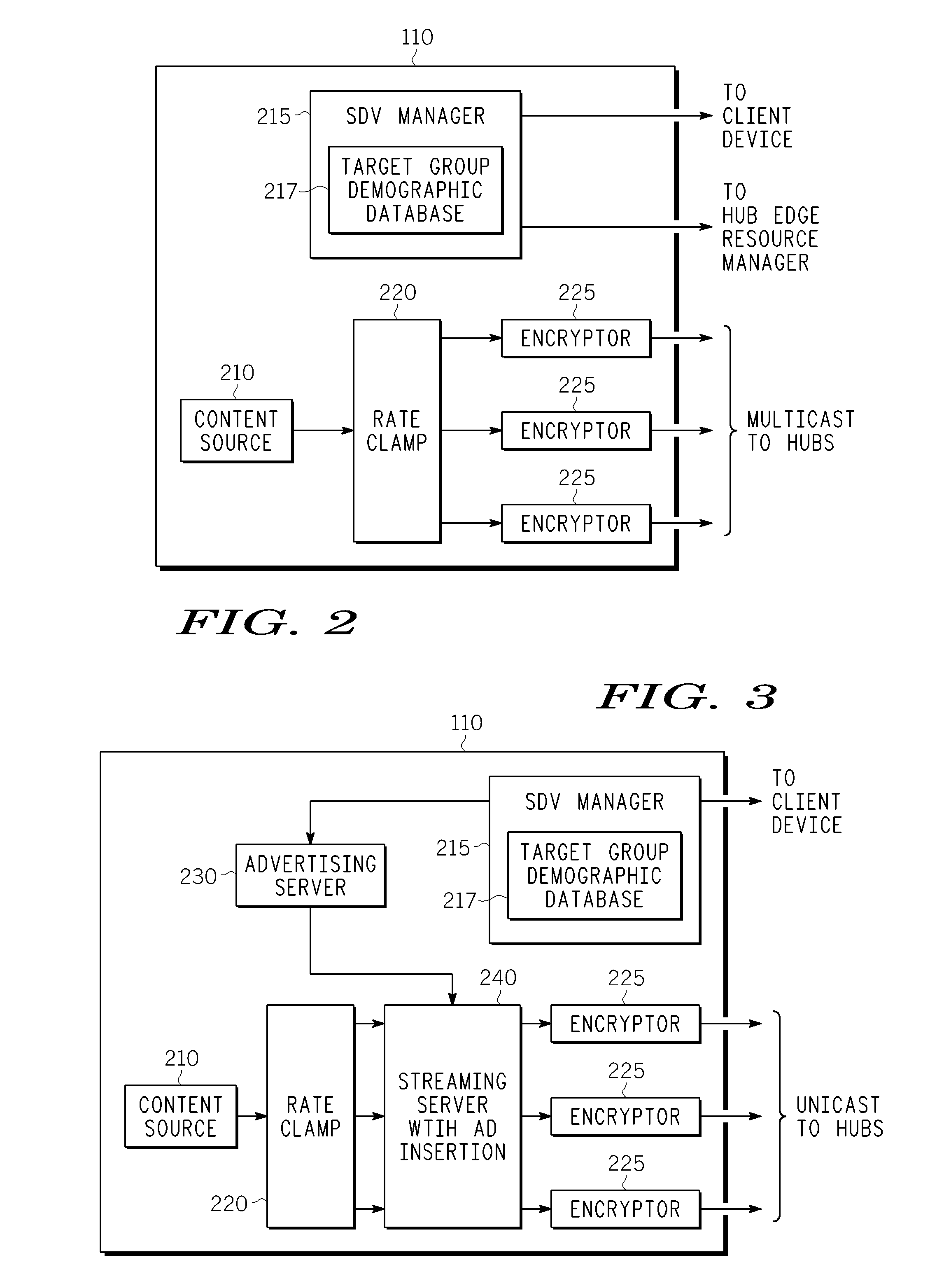
Method And Apparatus For Delivering SDV Programming With Targeted Advertising To Selected Groups Of Subscribers
InactiveUS20090150926A1Broadband local area networksTwo-way working systemsAccess networkDigital video
A switched digital video (SDV) system includes an SDV manager for coordinating a SDV session requested by a subscriber terminal and a storage medium on which resides content to be transmitted during the SDV session. The system also includes a plurality of edge devices for receiving a transport stream that includes content provided by the storage medium and transmitting the transport stream over an access network to the subscriber terminal on one of a plurality of SDV channels. The SDV manager is configured to cause different renditions of an SDV program to be provided by the edge devices to subscriber terminals associated with different target groups. The target groups each include a plurality of subscriber terminals that is less than a number of subscriber terminals serviced by a distinct edge device or devices.
Owner:GOOGLE TECH HLDG LLC
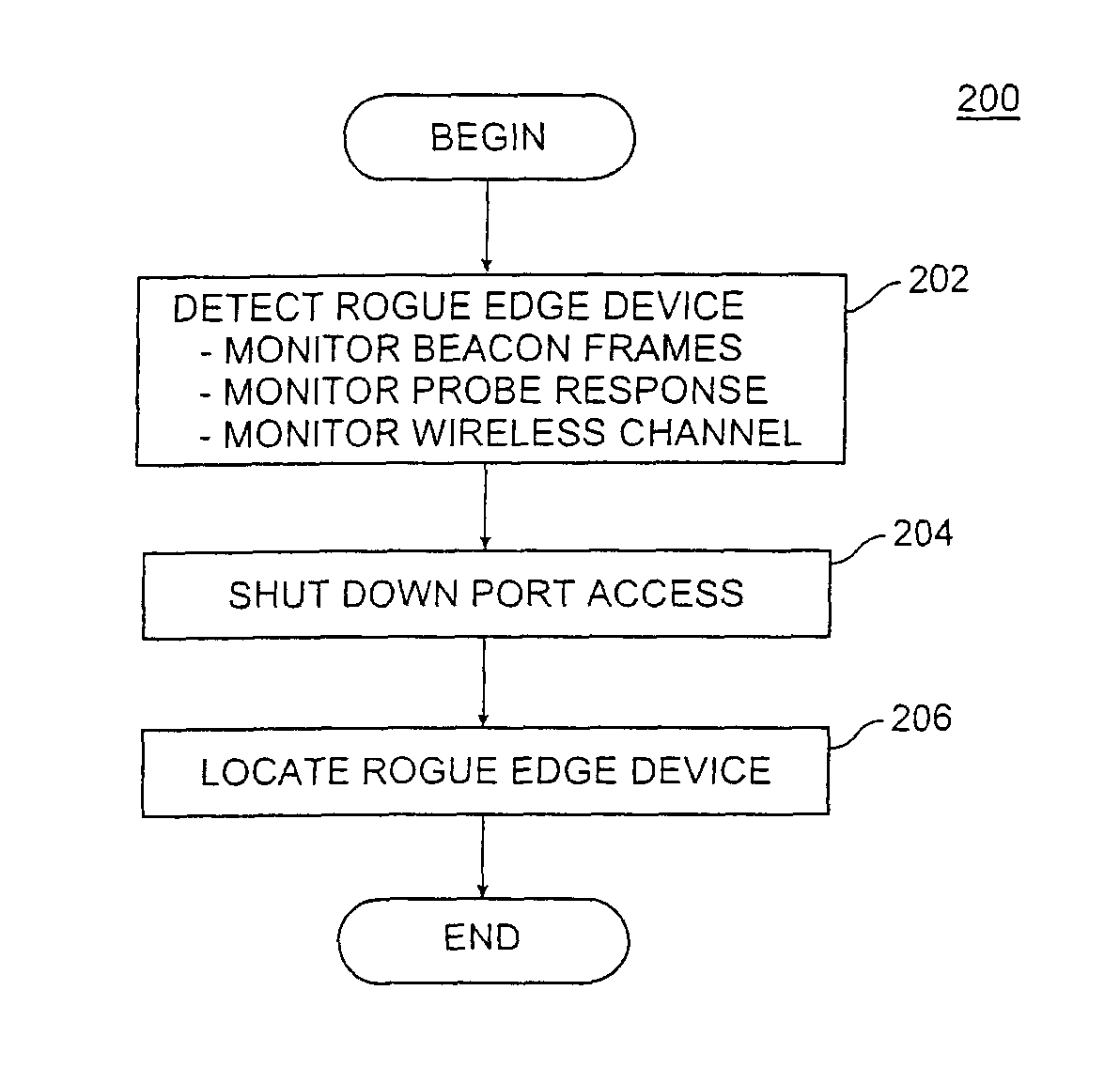
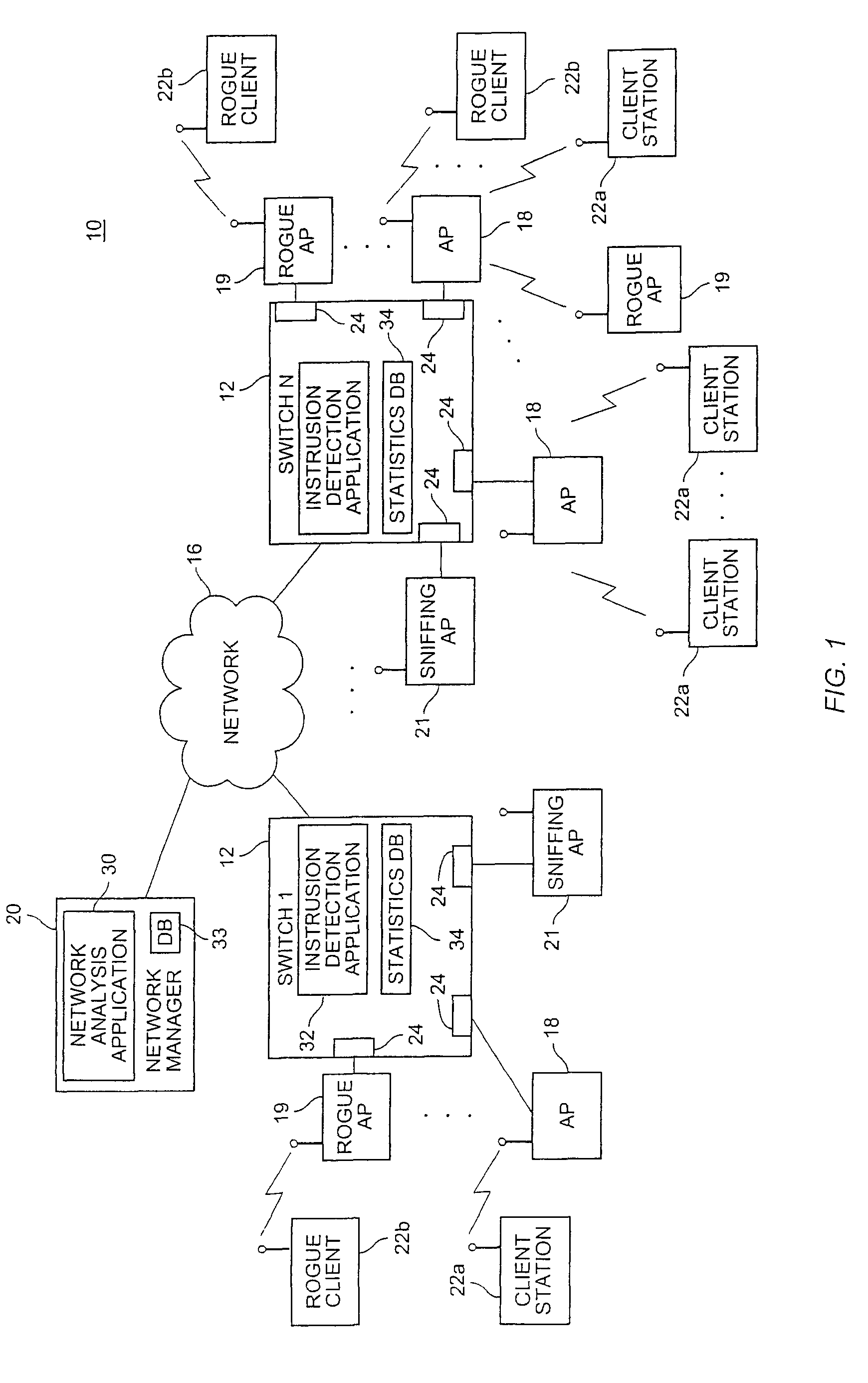
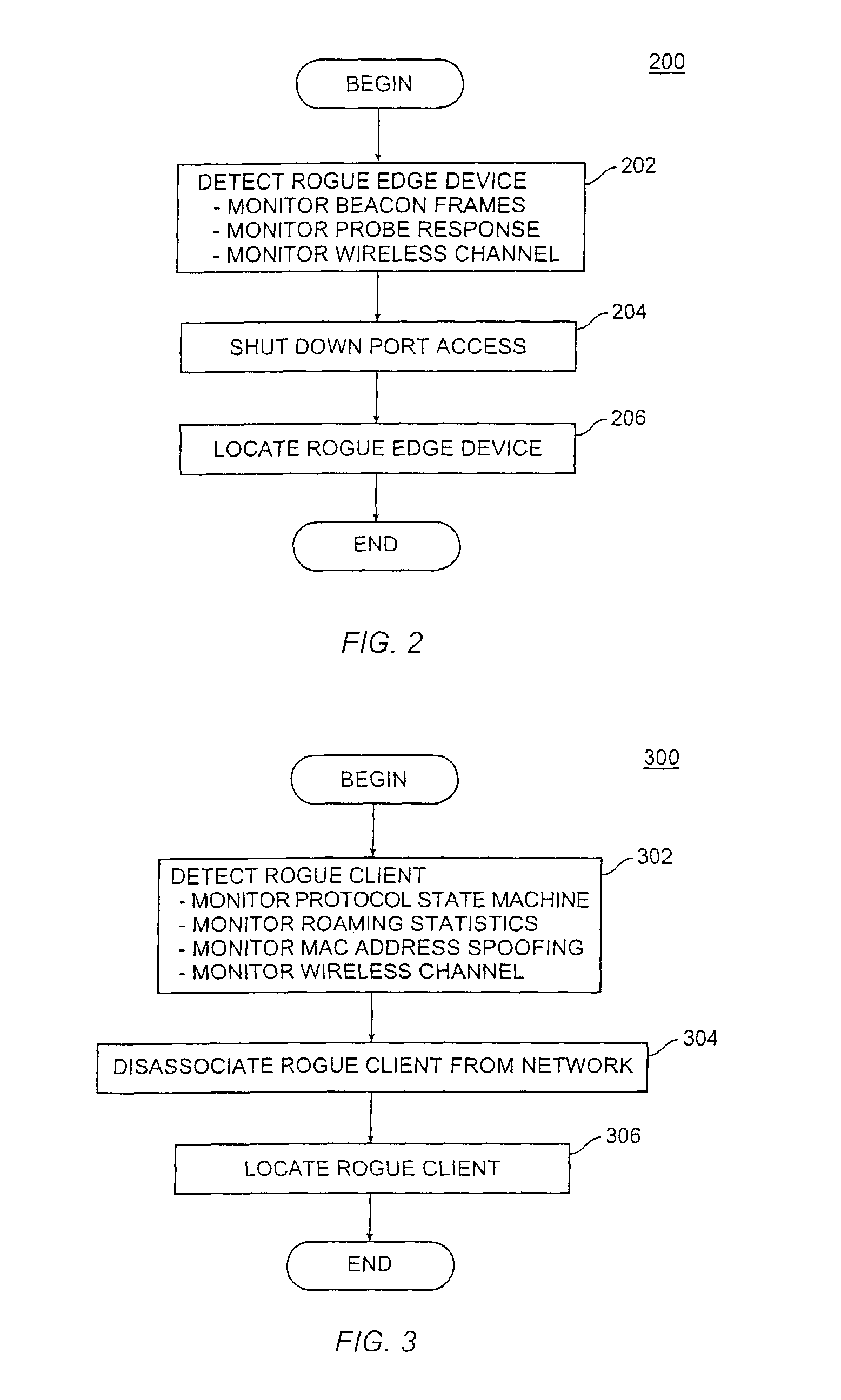
Method and system for detecting and preventing access intrusion in a network
ActiveUS8707432B1Memory loss protectionError detection/correctionNetwork connectionNetwork addressing
A wireless computer network includes components cooperating together to prevent access intrusions by detecting unauthorized devices connected to the network, disabling the network connections to the devices, and then physically locating the devices. The network can detect both unauthorized client stations and unauthorized edge devices such as wireless access points (APs). The network can detect intruders by monitoring information transferred over wireless channels, identifying protocol state machine violations, tracking roaming behavior of clients, and detecting network addresses being improperly used in multiple locations. Upon detecting an intruder, the network can automatically locate and shut off the physical / logical port to which the intruder is connected.
Owner:EXTREME NETWORKS INC
Hierarchical label distribution for inter-area summarization of edge-device addresses
ActiveUS20060262735A1Less memoryFaster FIB lookupError preventionFrequency-division multiplex detailsDistributed computingEdge device
A system and method are provided for separately distributing edge-device labels and routing information across routing areas of a computer network. Because the edge-device labels are distributed separately from network routing information, the process of distributing the edge-device labels does not preclude conventional edge-device address summarizations. Illustratively, a novel “label mapping” LSA is employed for distributing the edge-device labels across routing areas. The label-mapping LSA may be embodied as an area-scope OSPF opaque LSA (type 10) or an IS-IS LSP containing TLVs of area scope. Advantageously, the present invention is generally applicable whenever label values are allocated to edge devices in a multi-area computer network and data is “tunneled” through the network from one edge device to another.
Owner:CISCO TECH INC
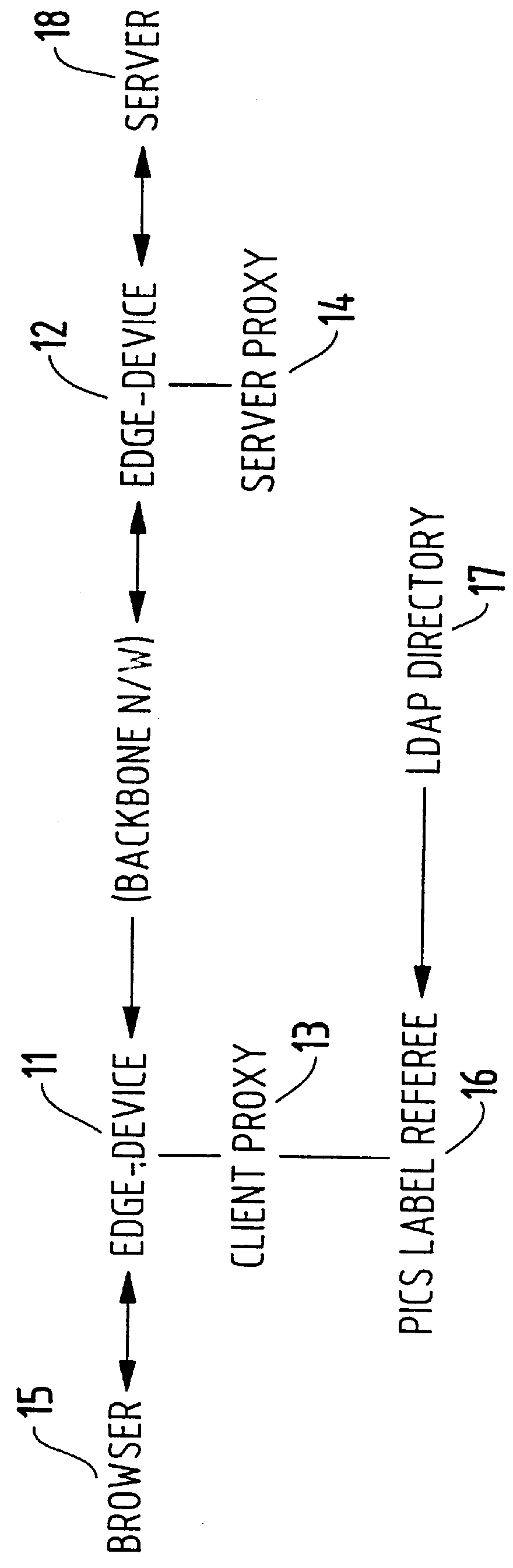
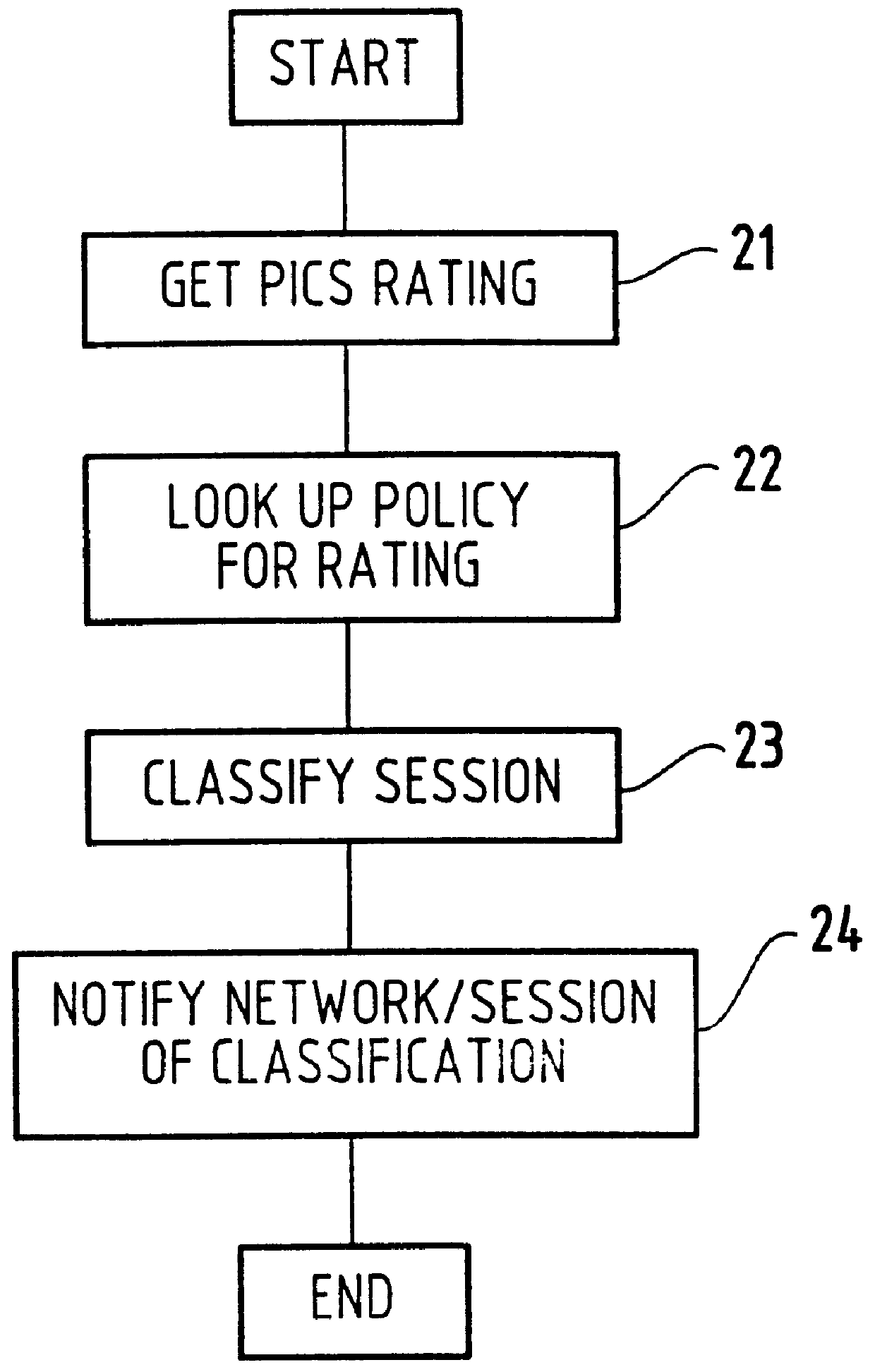
Method for supporting different service levels in a network using web page content information
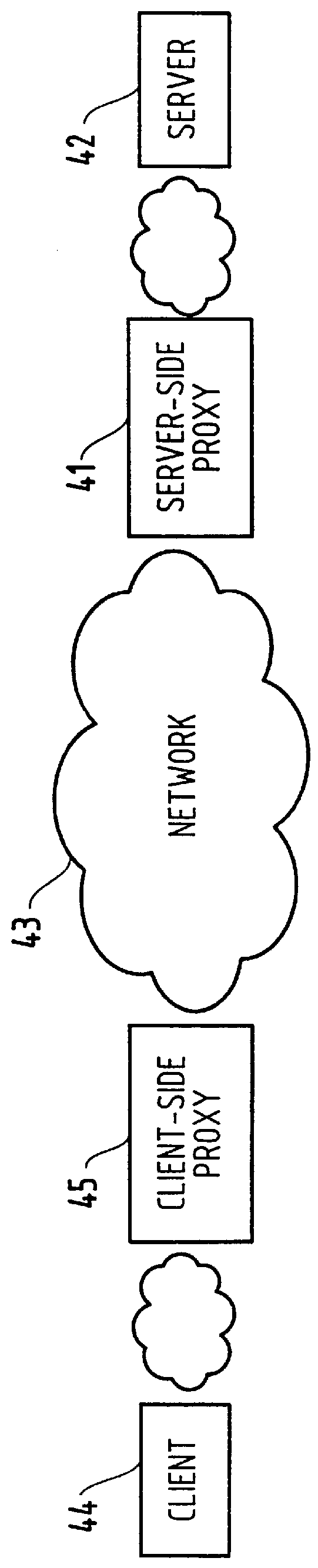
A method for classifying different pages accessed by a web-browser into different service-levels on a granularity finer than that of the connection. The method augments each edge device with two applications, a Client-Proxy and a Server-Proxy. The Client-Proxy obtains identifying information from the client's request, and the obtain PICS labelling information from a label referee. This information is used to obtain a service level from an LDAP based SLA directory, and this service level information is then imbedded along with a unique identifier for the network operator organization in the HTTP header request which is transferred to the Server-Proxy. The Server-Proxy then strips the header containing the PICS information from the request and forwards the request to the server. When the Server-Proxy gets a response, it uses the PICS information to mark the packets.
Owner:IBM CORP
Edge devices for providing a transparent LAN segment service and configuring such edge devices
ActiveUS7463639B1Avoid the needData processing applicationsDigital data processing detailsTransport networkEdge device
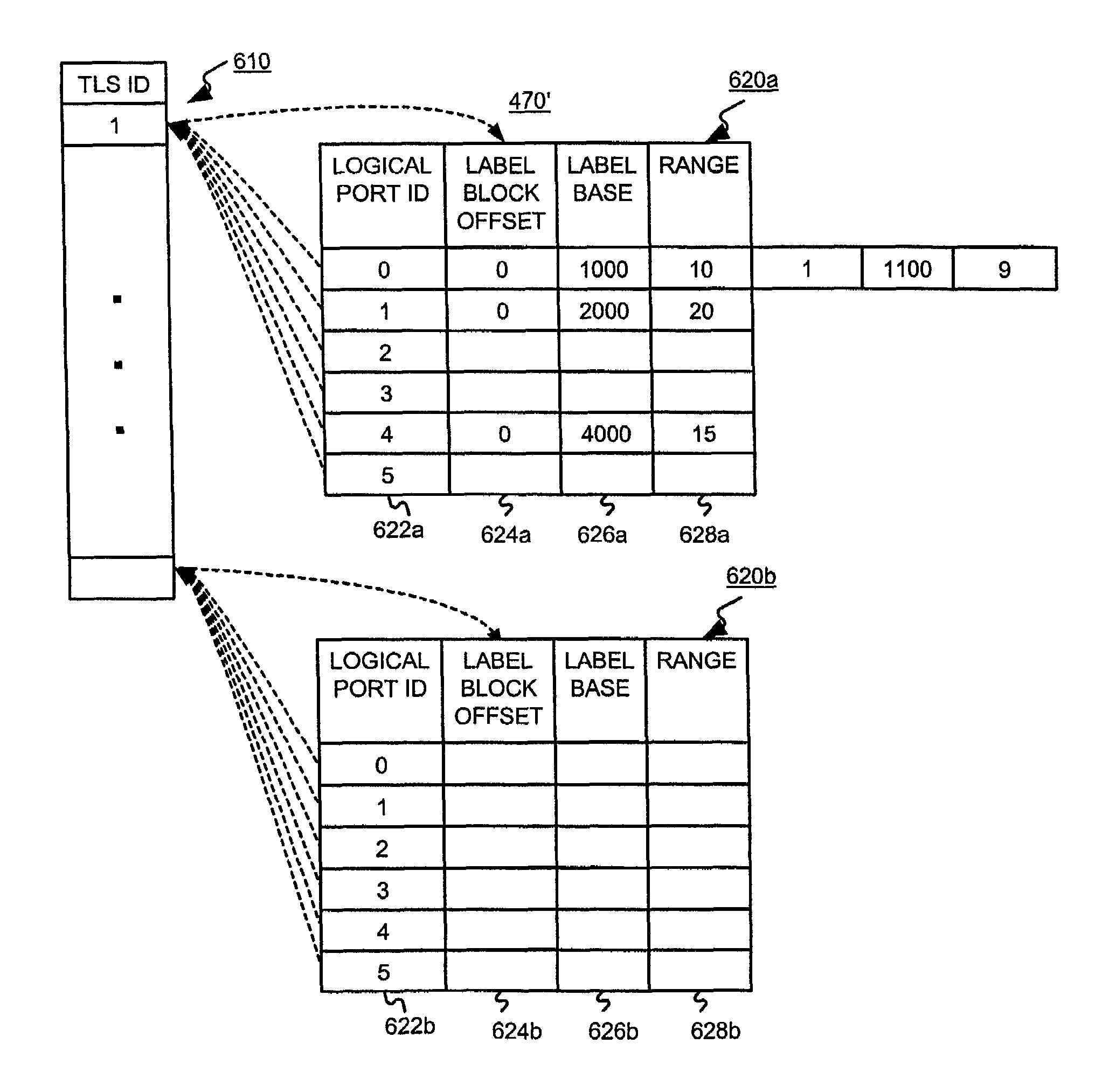
A transport LAN segment service is provided over a transport network. The transport network will include edge devices configured to support one or more transparent LAN segments. Configuration is simplified by advertising TLS-port-label information, layer 2 address learning, and multicasting when the needed configuration information has not yet been learned or discovered.
Owner:JUMIPER NETWORKS INC
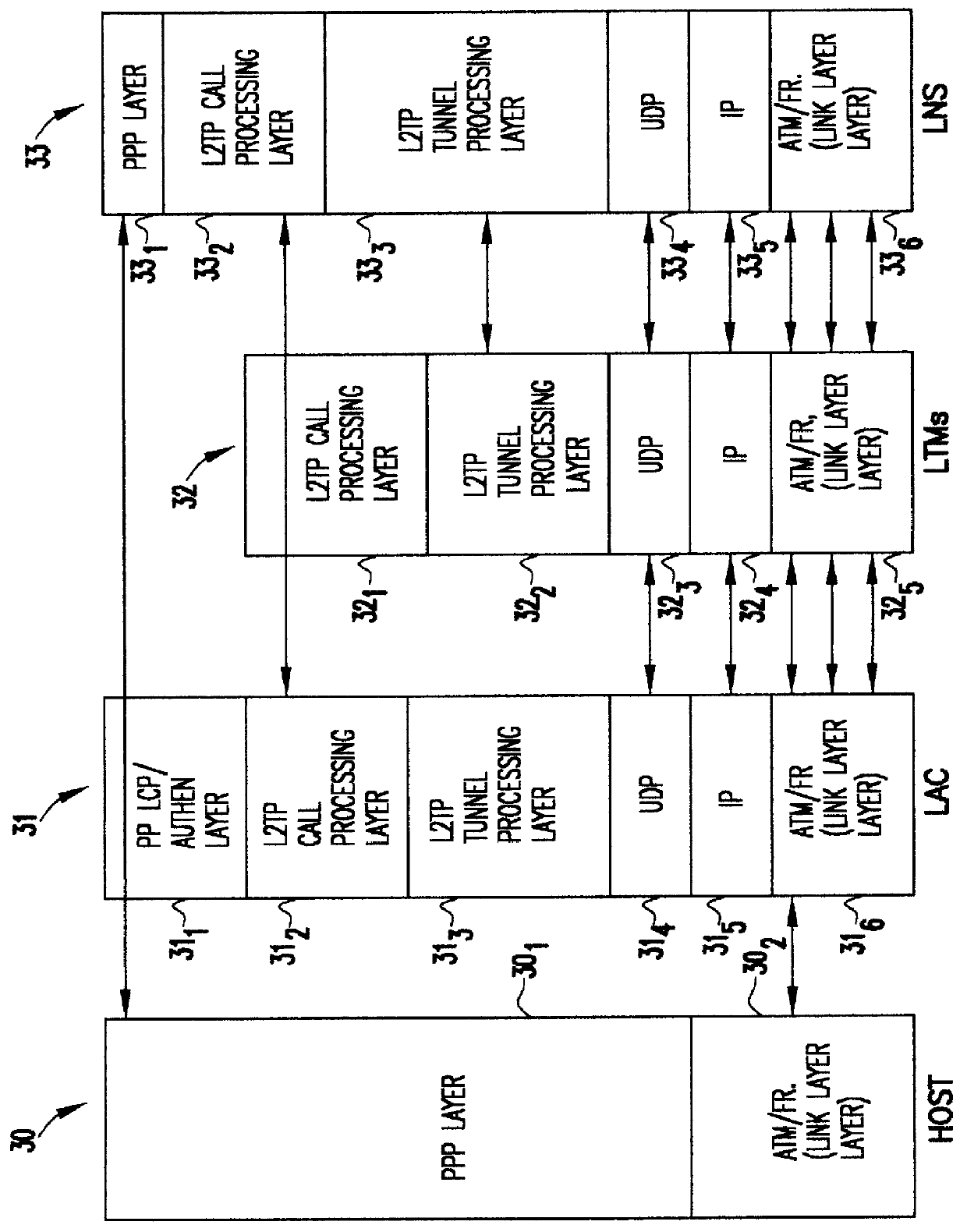
Layer two tunneling protocol (L2TP) merging and management
InactiveUS6094437AEasy to implementReduce complexityData switching detailsNetworks interconnectionDistributed computingEdge device
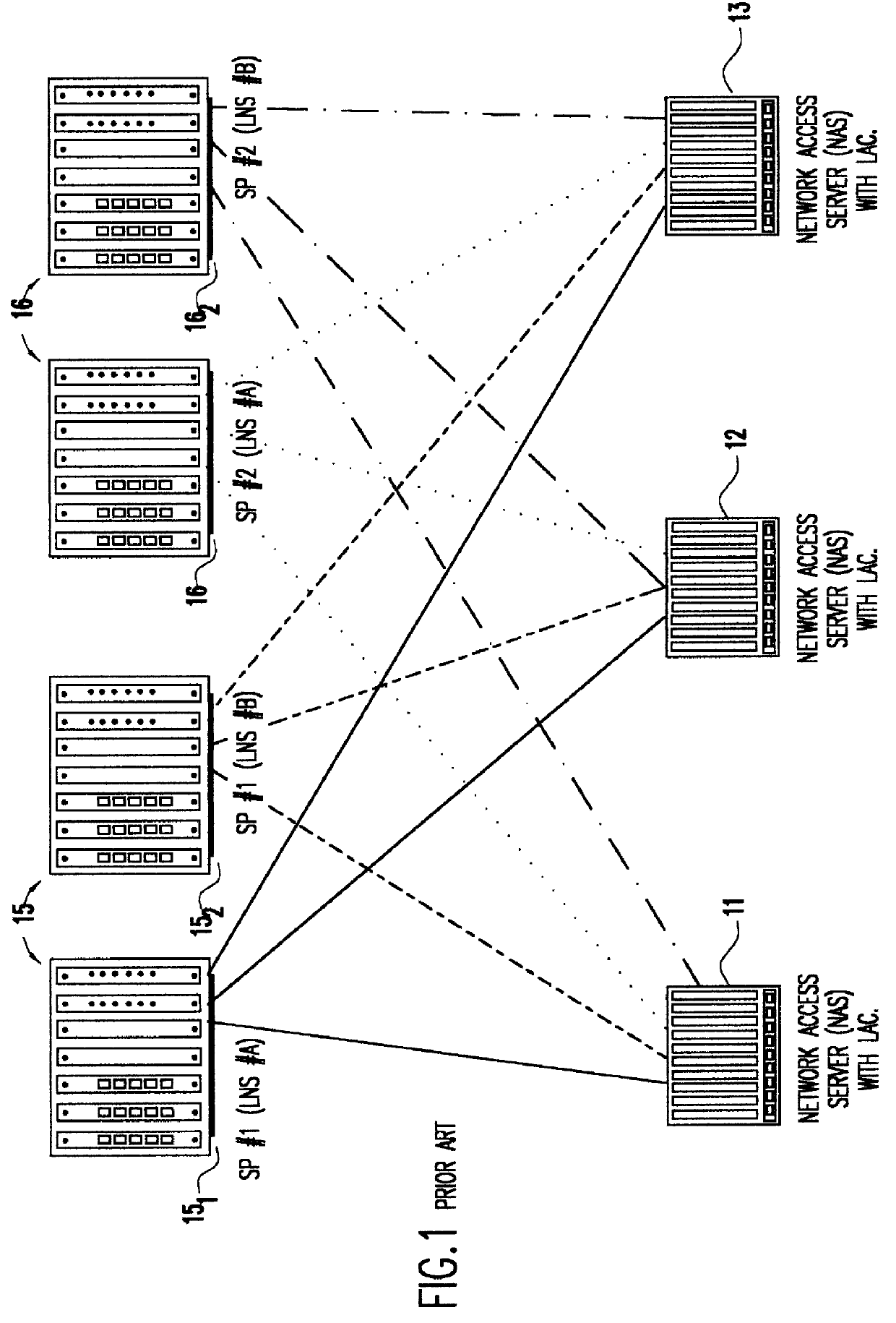
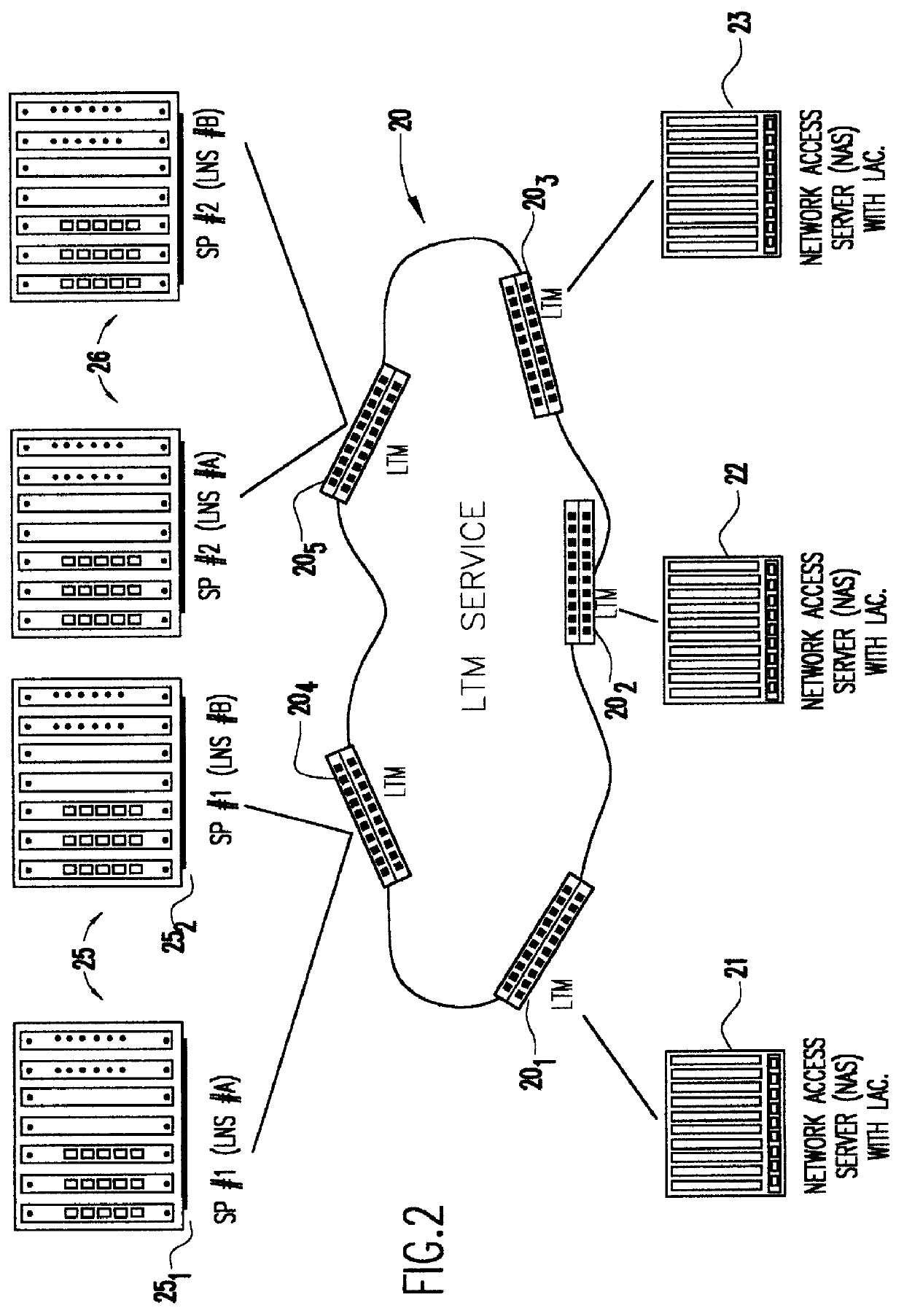
A system is provided for creating a tunneling service from the use of a traditional tunneling protocol, such as the layer two tunneling protocol (L2TP). In particular, the L2TP tunneling protocol, which is designed to go point-to-point between an L2TP Access Concentrator (LAC) and an L2TP Network Server (LNS), is abstracted so that L2TP becomes an access protocol to a tunneling service. A new L2TP tunnel merger and management (LTM) service is created which severs the tight configuration relationships between LAC and LNSs. Only a tight configuration between an LAC and its LTM edge device and between an LNS and its LTM edge device is required. An internal trunk protocol (INT protocol) carries needed information between LTM edge devices to establish ingress / egress L2TP access calls inside of separate L2TP access tunnels on opposite LTM edge devices. The addition of another LAC is accomplished by re-routing L2TP tunnels within the LTM service without reconfiguration of the LNSs, and the addition of another LNS is accomplished by re-routing L2TP tunnels within the LTM service without reconfiguration of the LACs. The LTM service determines the need for both additional trunk and access resources and establishes both new trunk / access tunnels to provide additional resources. The LTM service also determines excess resources on both trunk and access entities and releases trunk / access tunnels to provide the needed additional resources.
Owner:TDC THE
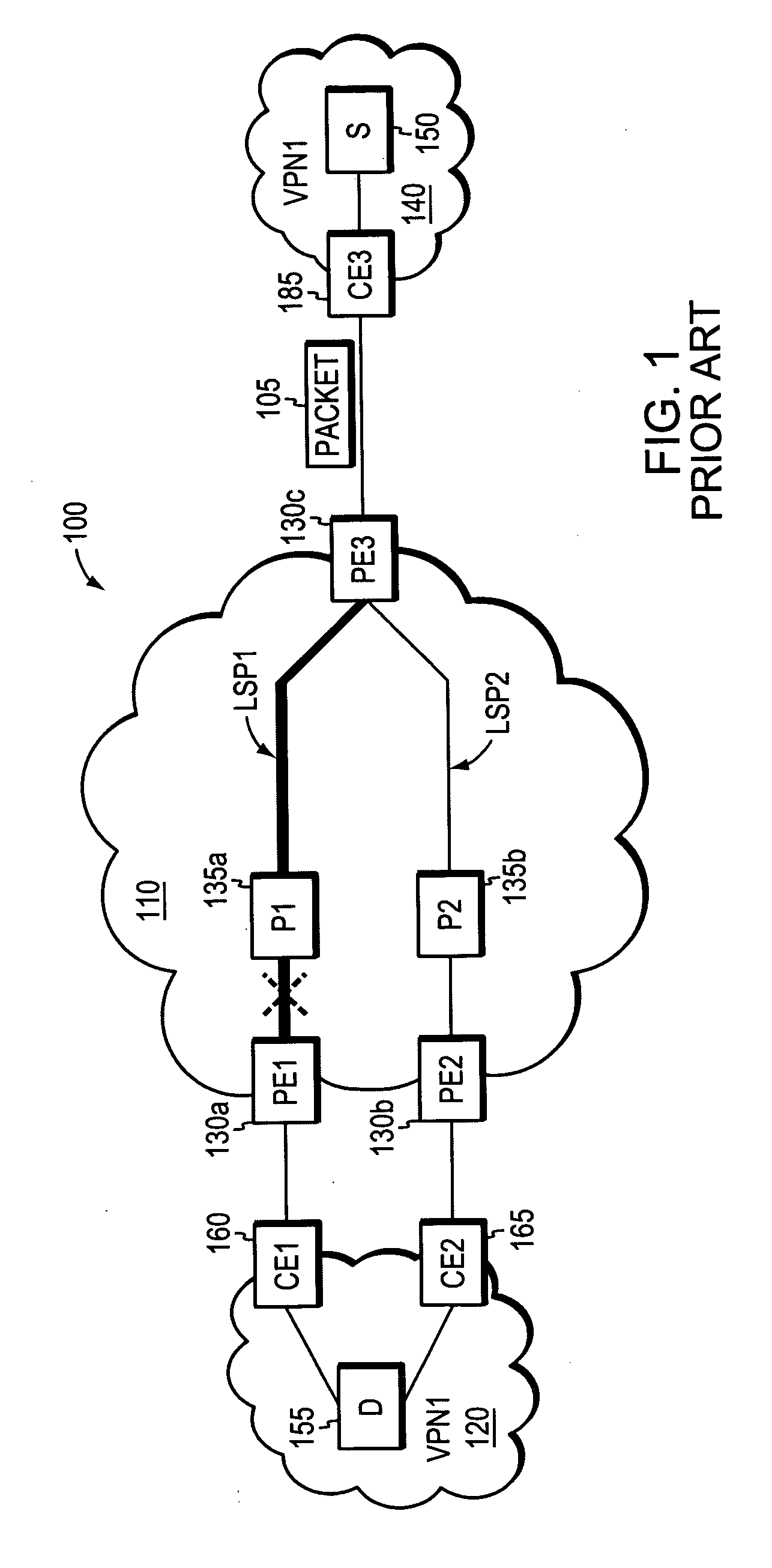
System and method for PE-node protection
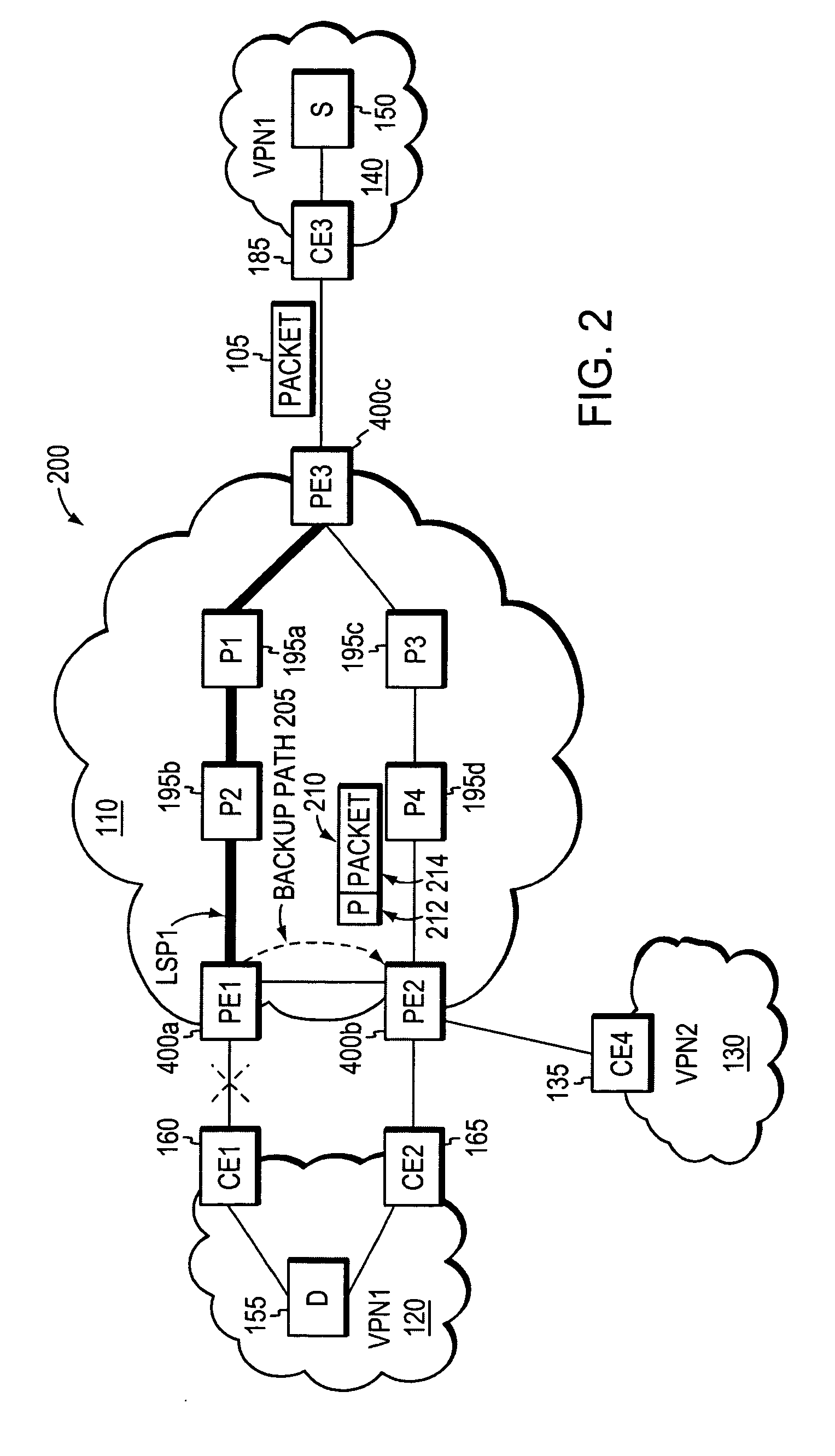
ActiveUS20070121486A1Fast reroute (FRR)Quickly and efficiently reroutingError preventionFrequency-division multiplex detailsNetwork ConvergenceNetwork packet
A novel fast reroute (FRR) technique is provided for quickly and efficiently rerouting selected types of network traffic in response to a node or link failure at the edge of a computer network. According to the technique, the network includes first and second edge devices that function as “FRR mates,” such that network traffic originally destined for one FRR mate may be quickly rerouted to the other without having to wait for conventional network convergence. When an edge device receives rerouted packets originally destined for its FRR mate, the device responds by forwarding only those rerouted packets matching the selected traffic types; rerouted packets that do not match the selected traffic types are dropped or otherwise discarded. The first and second edge devices may be statically configured as FRR mates, e.g., by a network administrator, or they may be configured to automatically detect their compatibility as FRR mates.
Owner:CISCO TECH INC
Fast reroute (FRR) protection at the edge of a RFC 2547 network
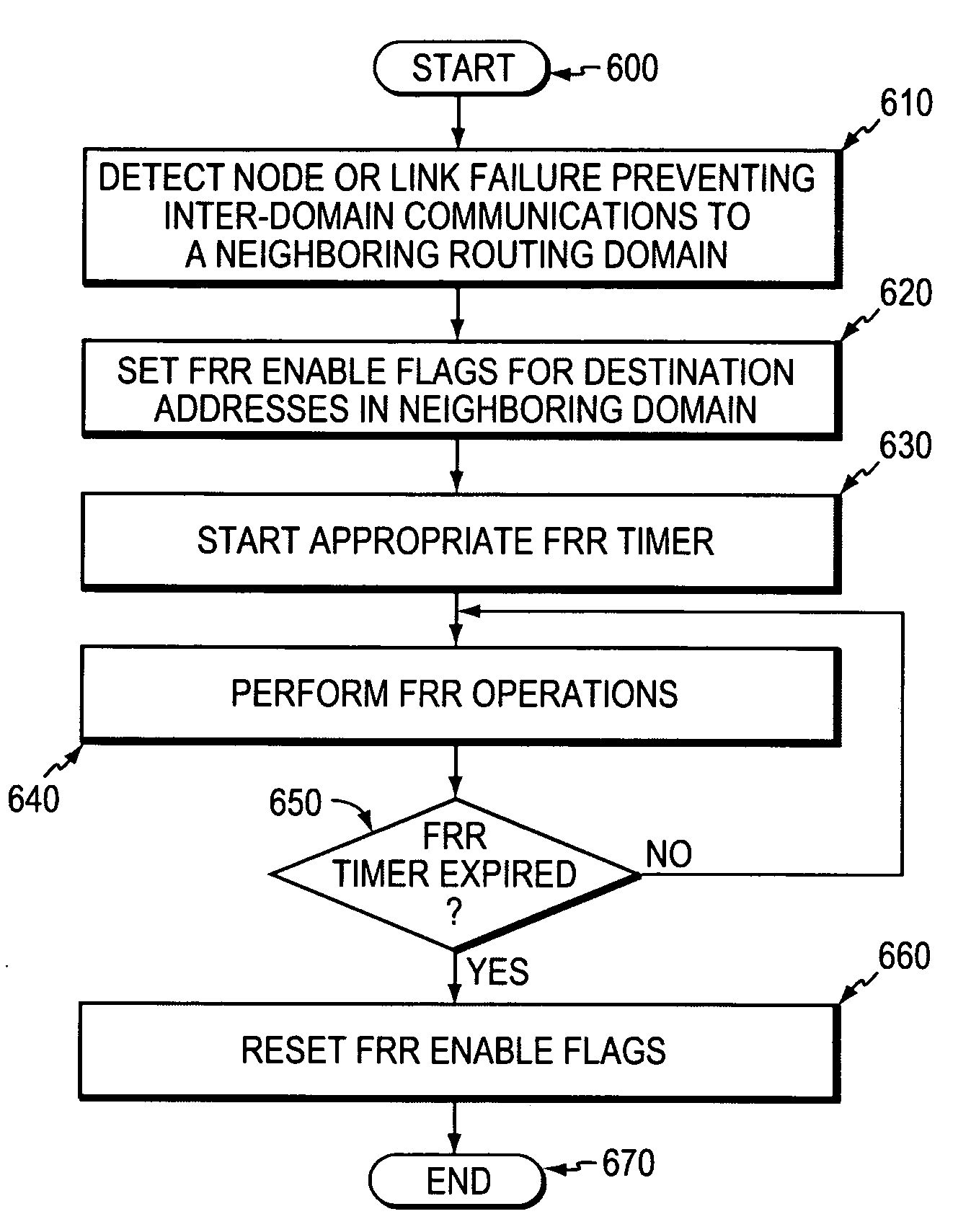
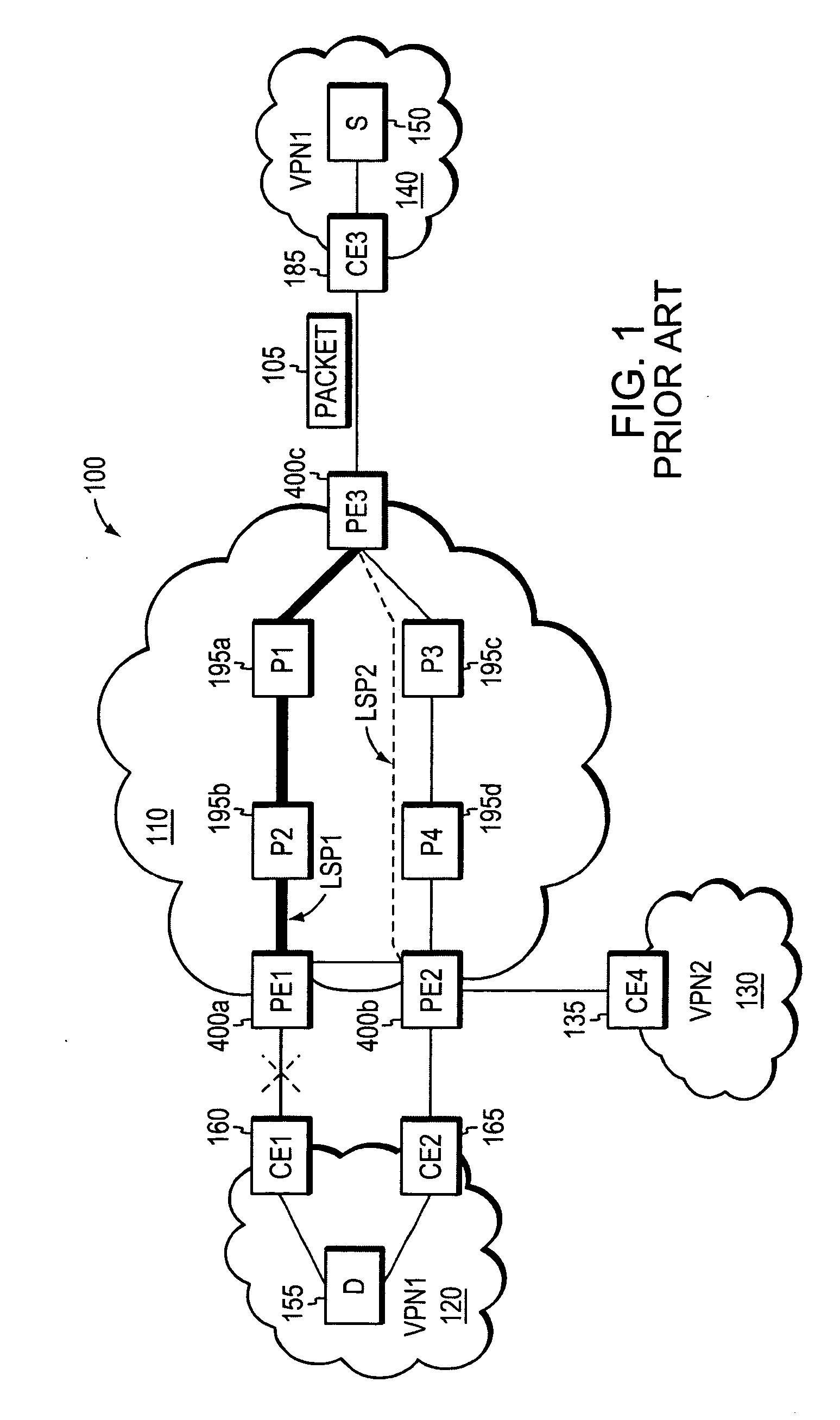
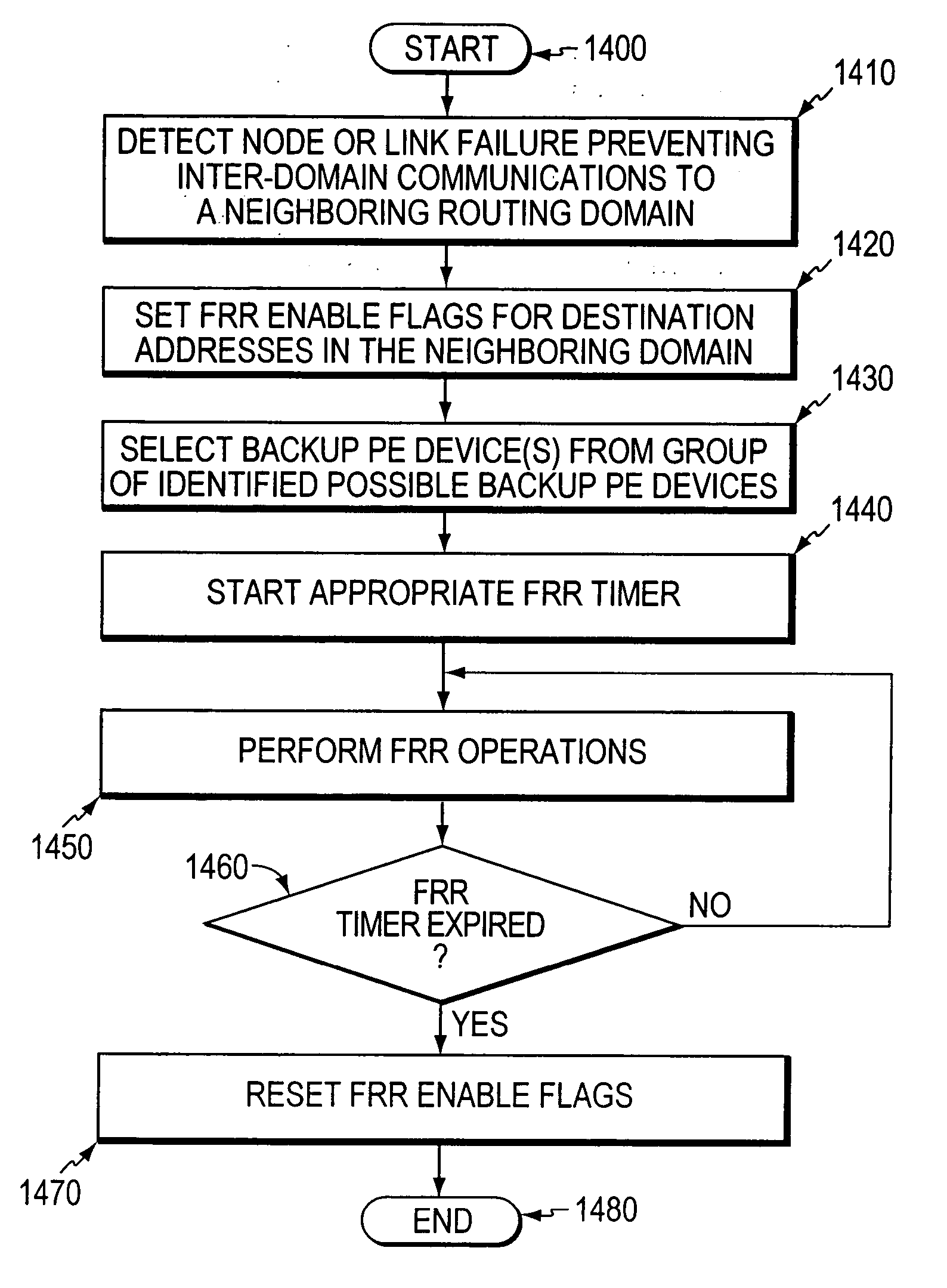
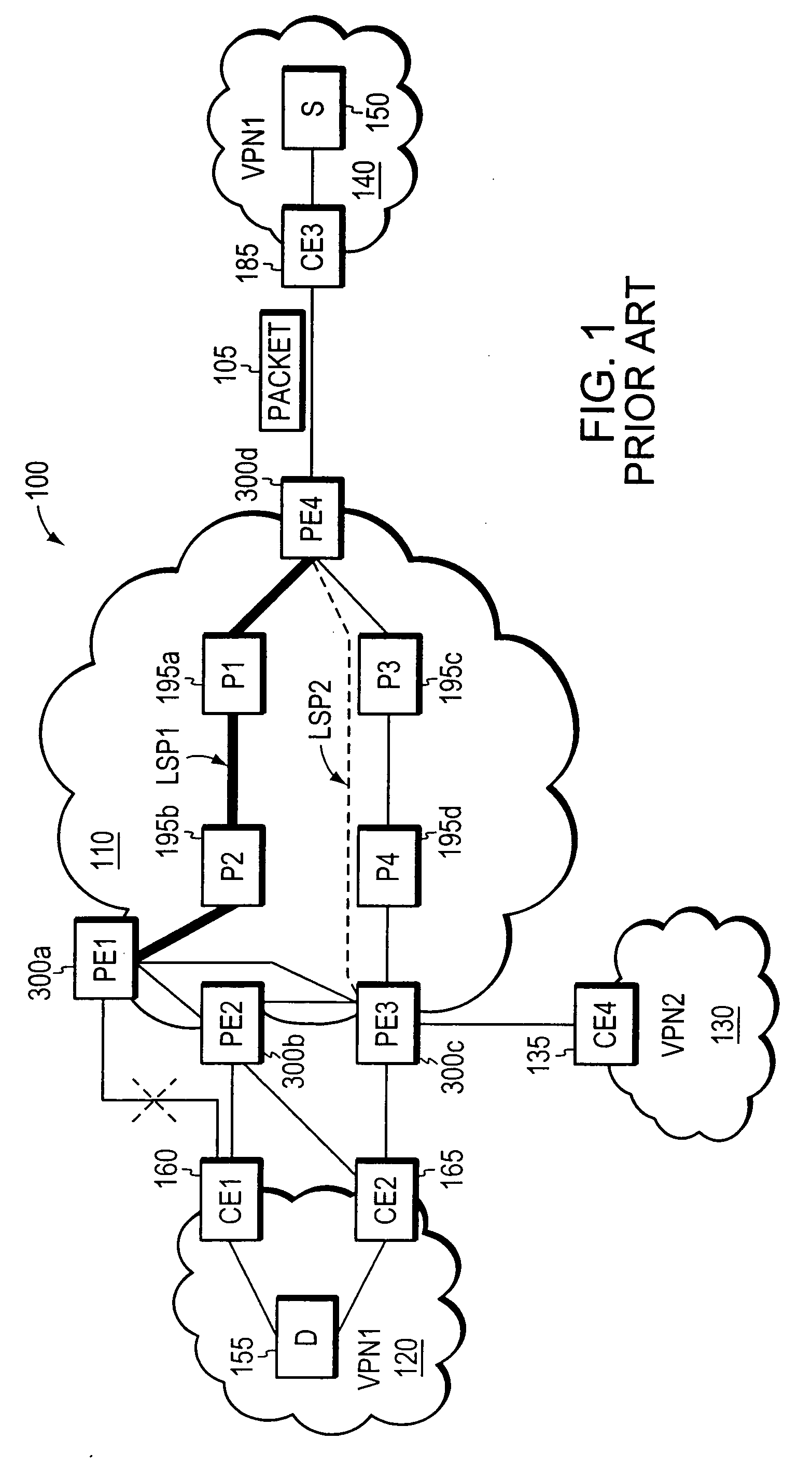
InactiveUS20060126496A1Quickly and efficiently forwardedFast reroute (FRR)Error preventionFrequency-division multiplex detailsRouting domainInter-domain
A fast reroute (FRR) technique that may be deployed at the edge of a network having first and second edge devices coupled to a neighboring routing domain. If the first edge device detects a node or link failure that prevents it from communicating with the neighboring domain, the first edge device reroutes at least some data packets addressed to the neighboring domain to the second edge device. The second edge device receives the rerouted packets and then forwards the packets to the neighboring domain. Notably, the second edge device is not permitted to reroute the received packets a second time, e.g., upon identifying another inter-domain node or link failure. As such, loops are avoided at the edge of the network and packets are rerouted to the neighboring routing domain faster and more efficiently than in prior implementations.
Owner:CISCO TECH INC
Quality of service network and method
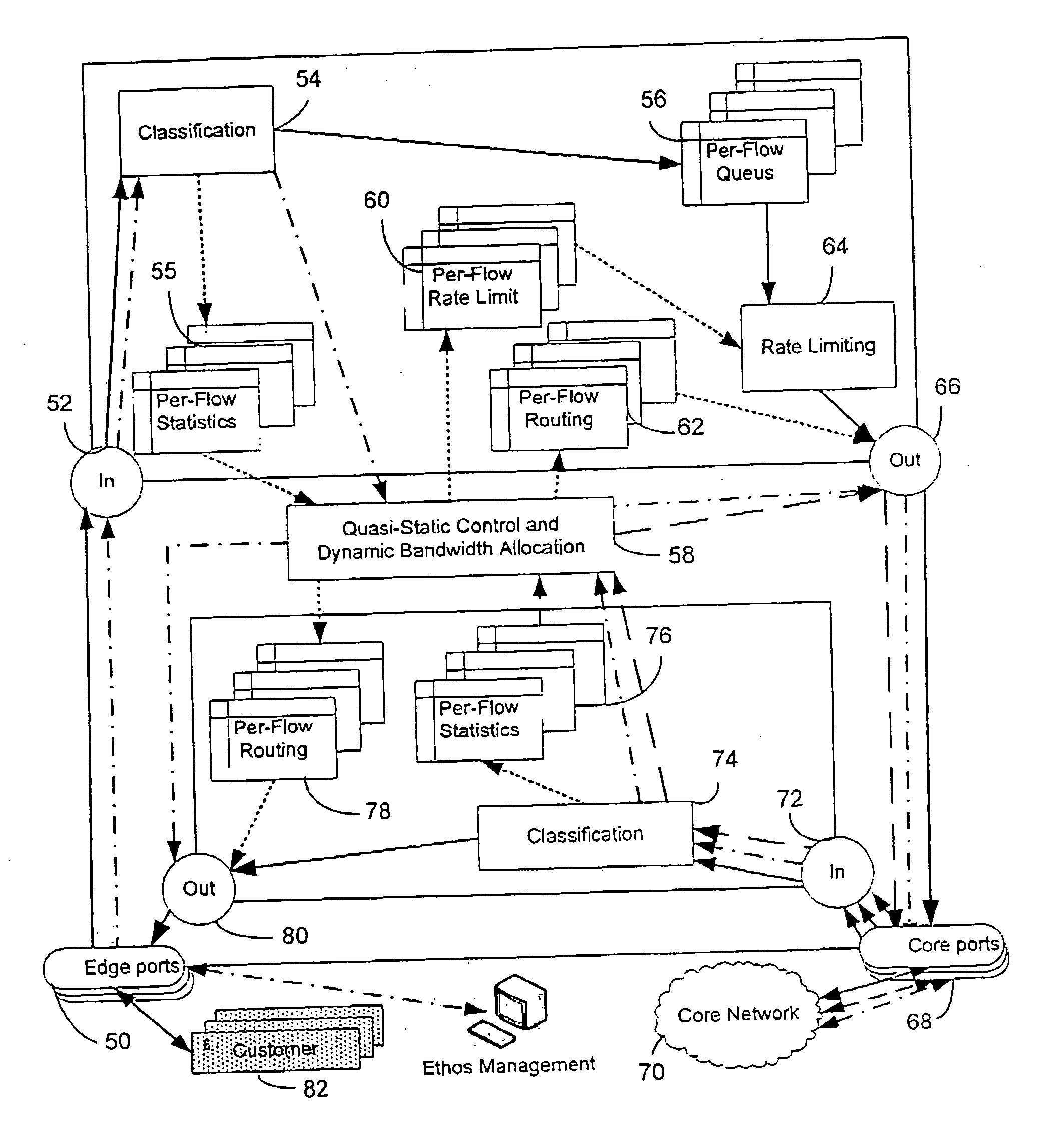
InactiveUS20060250959A1Improve network efficiencyError preventionFrequency-division multiplex detailsQuality of serviceAdmission controller
A configurable edge device for use in a network, the edge device being adapted and configured to be coupled to at least one other edge device in a network, and including an admission controller for controlling admission of data traffic onto a pre-defined flow over a physical link, and a router for routing the data traffic through the edge device onto the pre-defined flow in accordance with a pre-defined routing scheme, wherein operation of the admission controller and the router is controlled in accordance with data defining all physical and logical links in the network; a telecommunications carrier network for data traffic, the network including at least two such configurable edge devices, and a method for transmitting data traffic through such an edge device.
Owner:TEJAS NETWORKS
System and Method for Inter-Cell Interference Coordination
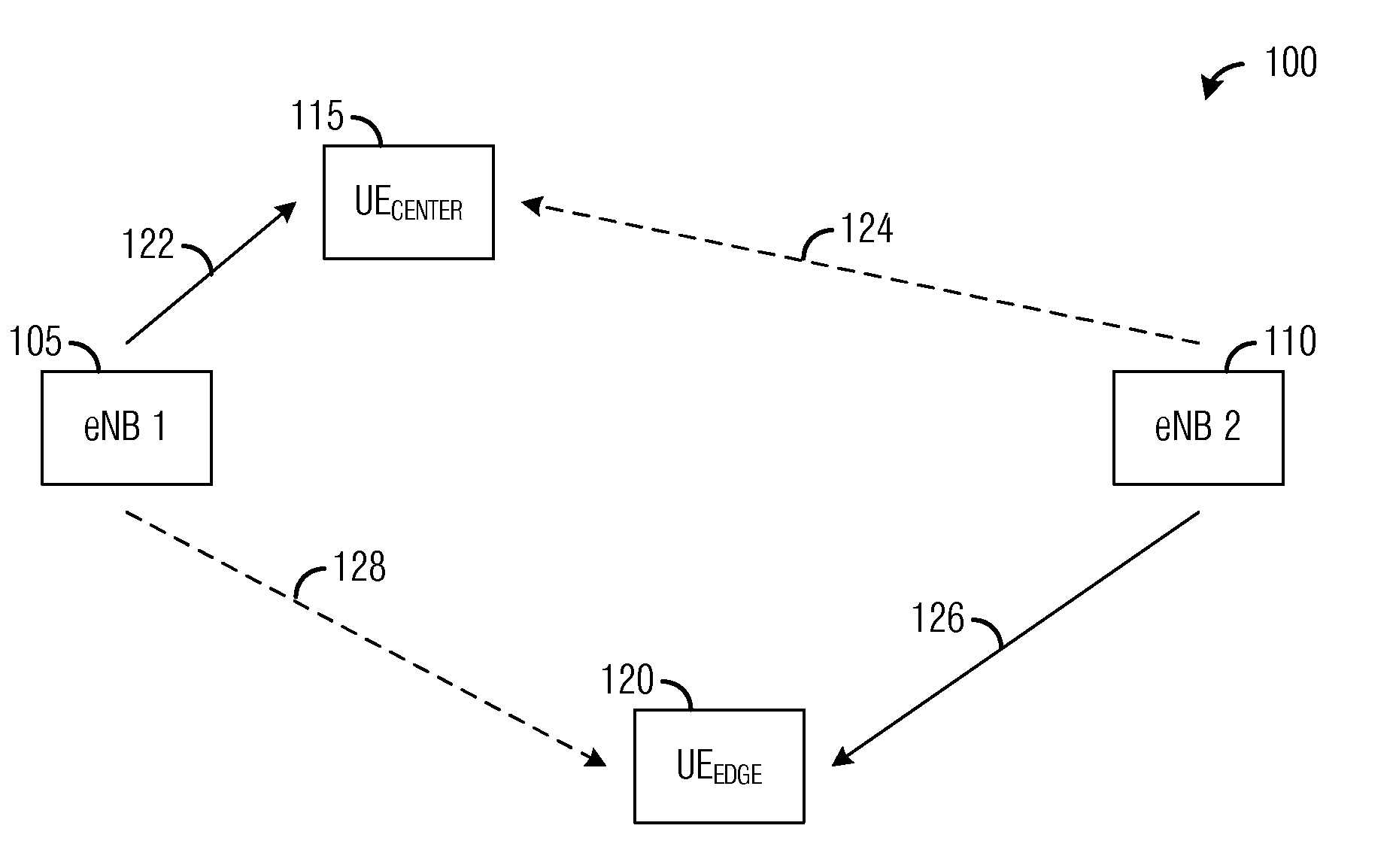
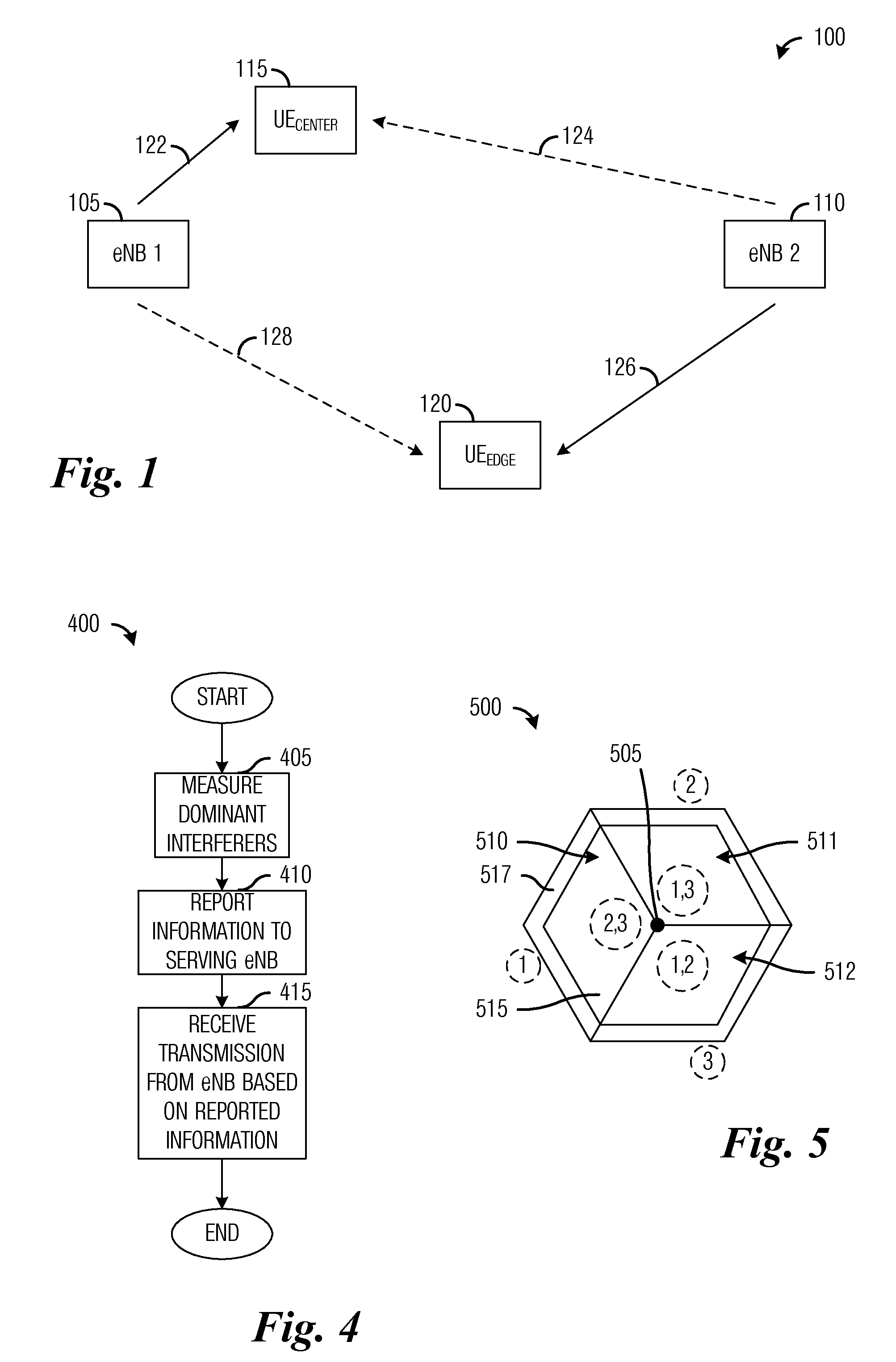
InactiveUS20110081865A1Eliminate the problemIncrease data ratePower managementAssess restrictionDistributed computingEdge device
A system and method for inter-cell interference coordination is provided. A method for controller operation includes receiving interferer information from a device served by the controller, scheduling a cell edge device based on the received interferer information, and reporting usage information of the subset of resources to neighboring controllers. The cell edge device operates in a periphery of a coverage area of the controller, and the cell edge device is scheduled to a subset of resources. The method also includes from each neighboring controller, receiving neighboring usage information of a neighboring subset of resources reserved for cell edge devices served by the neighboring controller. The method further includes scheduling a cell center device based on the received usage information from the neighboring controllers, and transmitting to scheduled devices over their respective scheduled resources. Cell center device is scheduled to resources not in the subset of resources.
Owner:FUTUREWEI TECH INC
Edge devices for providing a transparent LAN segment service and configuration such edge devices
InactiveUS20090080431A1Data processing applicationsTime-division multiplexTransport networkComputer science
Owner:JUMIPER NETWORKS INC
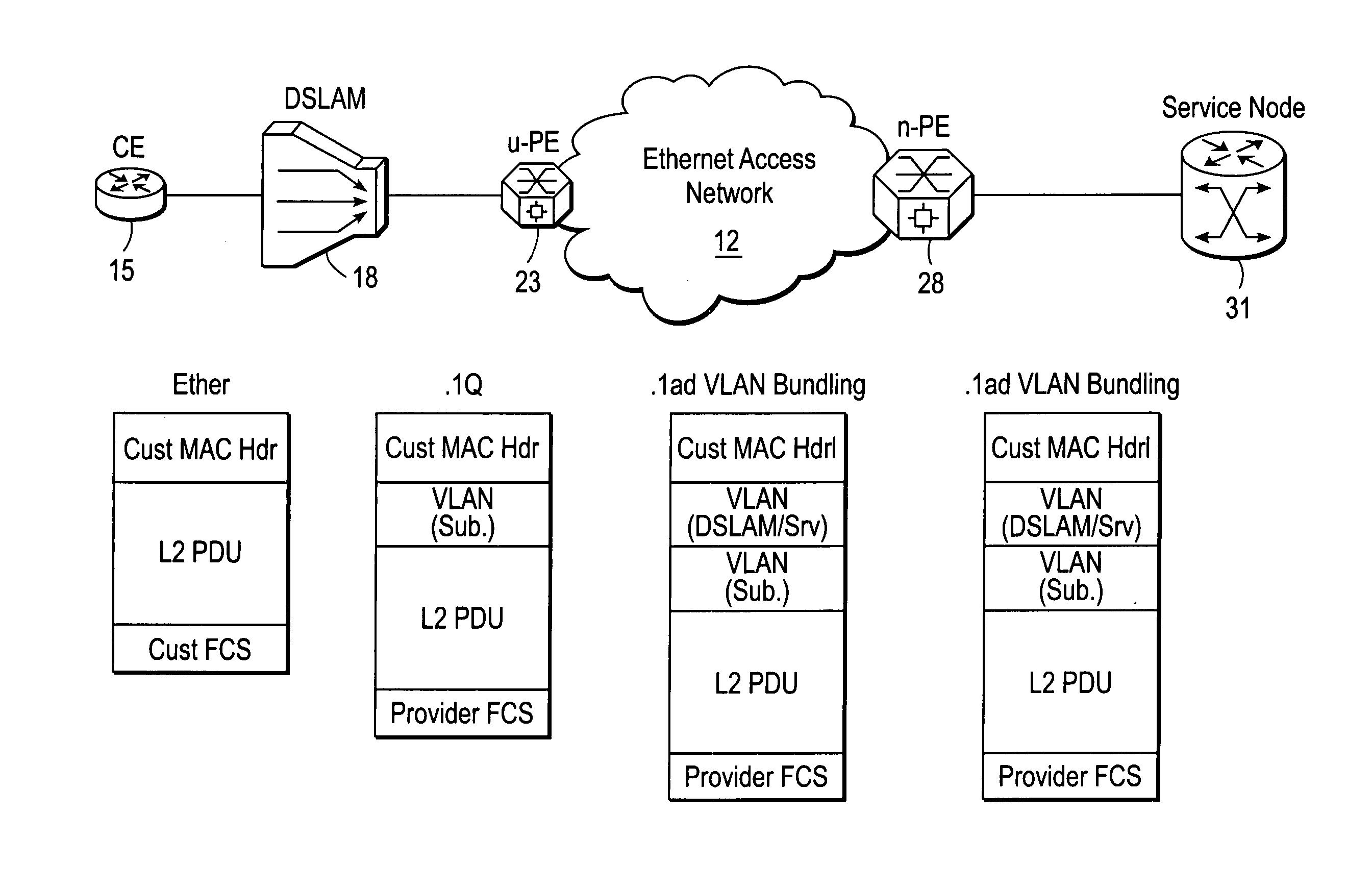
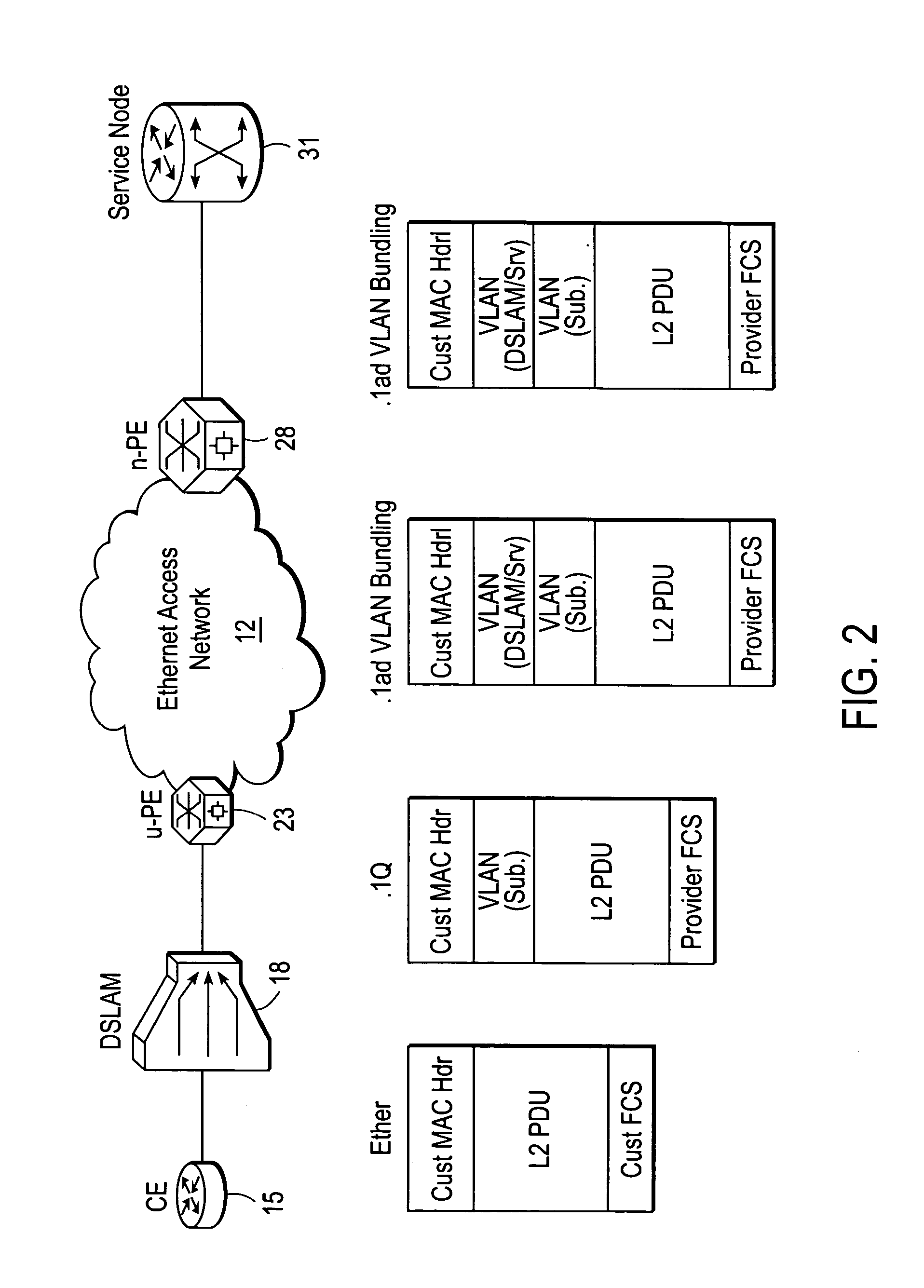
System and method for DSL subscriber identification over ethernet network
ActiveUS20060245439A1Data switching by path configurationNetwork connectionsDigital subscriber lineAccess network
A DSLAM aggregation topology VLAN bundling mechanism includes an edge device port that receives a packet from a Digital Subscriber Line Access Multiplexer (DSLAM) device, the packet including an inner Virtual Local Area Network (VLAN) tag that identifies a Digital Subscriber Line (DSL) subscriber. A processor of the edge device adds an outer VLAN tag to the packet, the outer VLAN tag identifying the DSLAM and a destination server coupled to an Ethernet access network. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72(b).
Owner:CISCO TECH INC
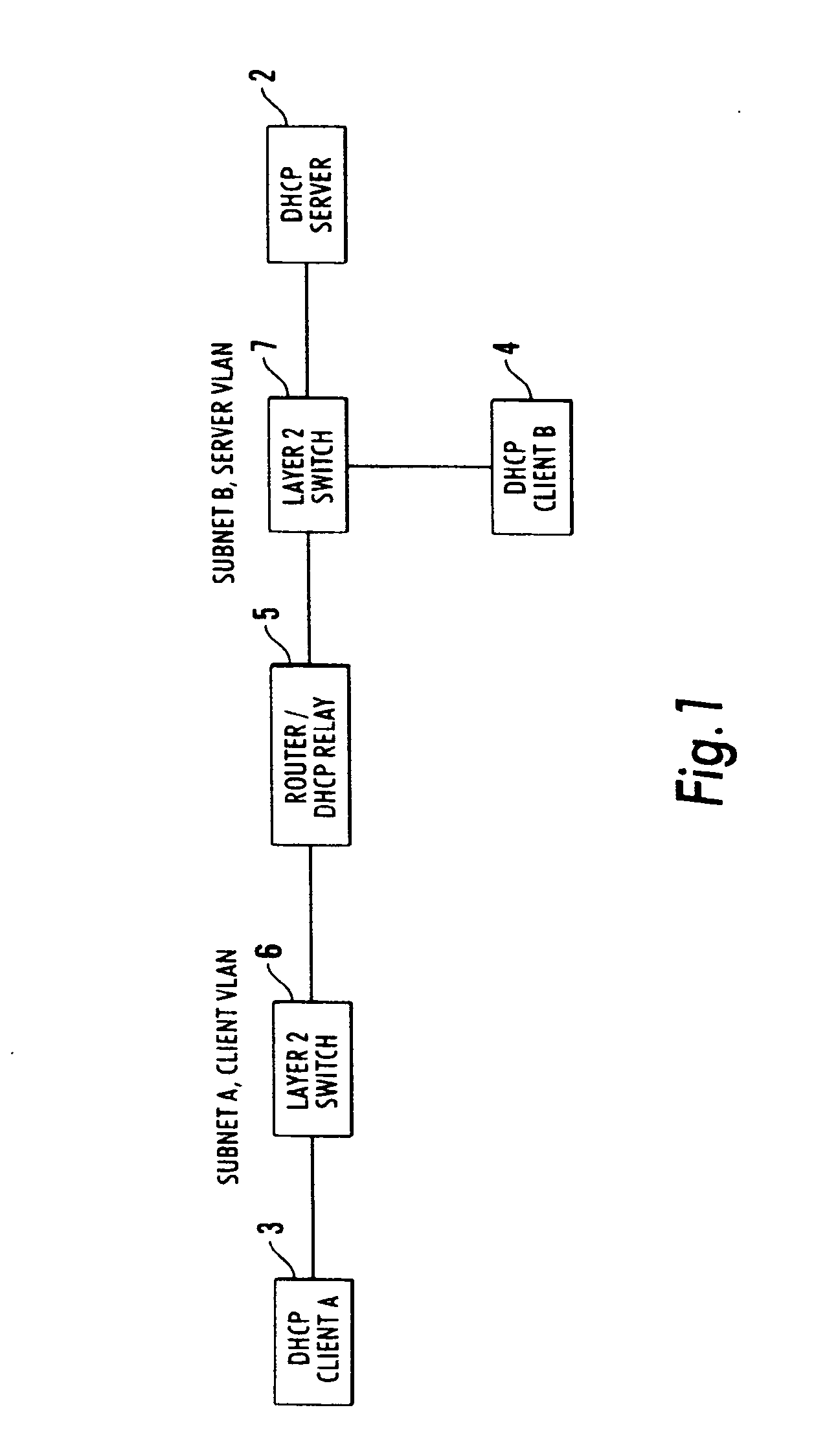
Network including snooping
ActiveUS20060248229A1Avoid accessMultiple digital computer combinationsNetworks interconnectionTraffic signalIp address
A computer network including: at least one switch connecting at least one edge device to the remainder of the network, said at least one switch including: snooping apparatus using DHCP to monitor the signal traffic through the switch to or from the each edge device to determine, without changing the traffic signals, for each edge device, the MAC address, the IP address, and the port of the switch to which it is connected, and a dynamic table within said switch of, for each edge device, the MAC address, the IP address, and the port which it is connected, the contents of the table being provided by said snooping apparatus
Owner:VALTRUS INNOVATIONS LTD +1
System for distributed intelligent remote sensing systems
ActiveUS20180054490A1Detection of traffic movementPosition fixationDistributed intelligenceSystem of systems
An Internet of things (IoT) system, including a distributed system of virtual machines, includes at least one IoT platform system control engine, that includes a platform system control engine secure system space and a IoT platform system control engine user defined space, at least one network node device that includes a network node device secure system space and an IoT network node device user defined space, and at least one edge device that includes an edge device secure system space and an edge device user defined space, where the secure system space of the control engine, the network node device, and the edge device are each configured to be secured to prevent unauthorized access, and the user defined spaces of the platform system control engine, the network node device and the edge device each define a respective virtual machine.
Owner:FYBR
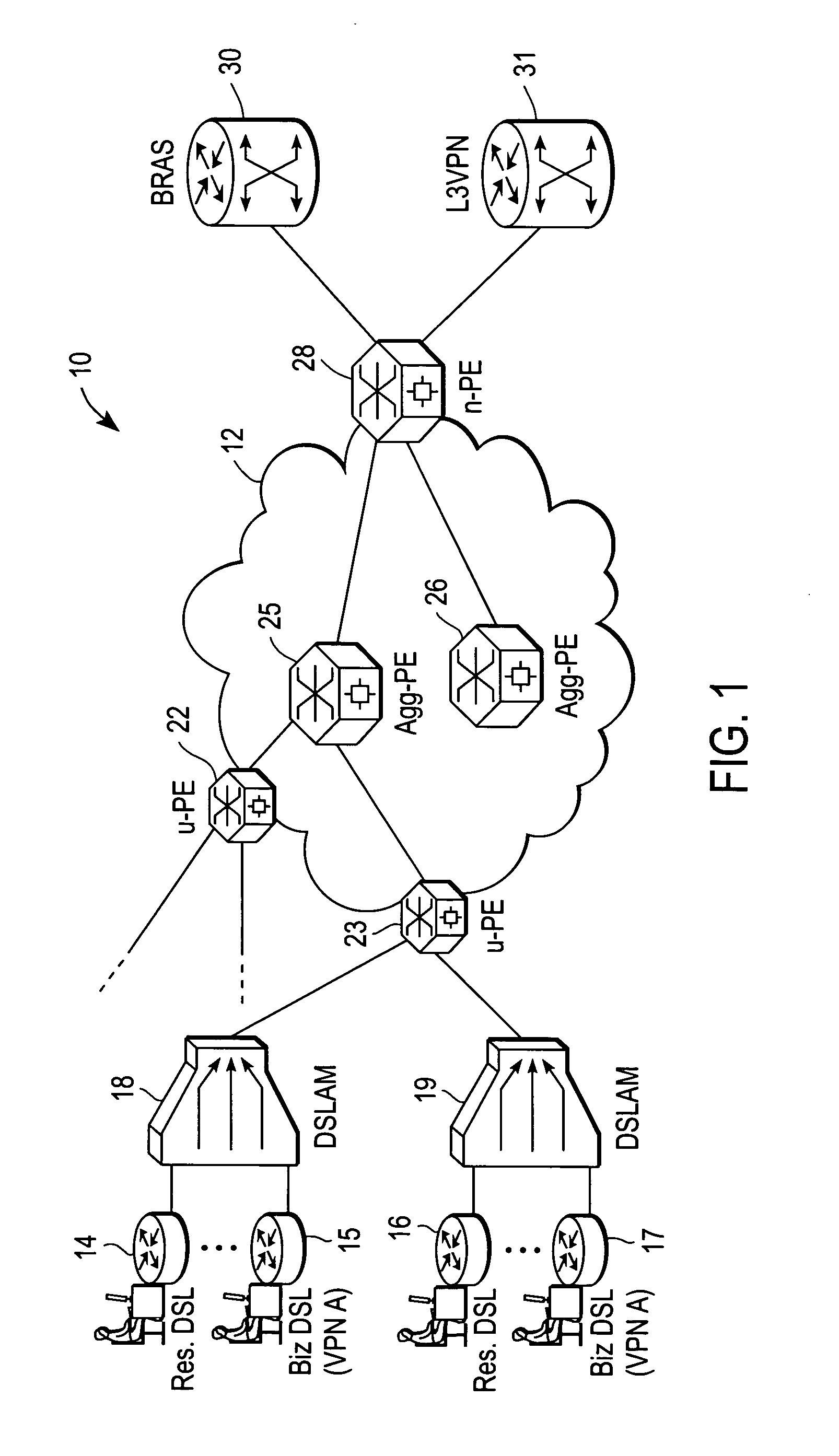
Redundant pseudowires between Ethernet access domains
A computer network includes first and second Ethernet access domain networks, each of Ethernet access domain networks including a user-facing provider edge (u-PE) device, and a stack group of network-facing provider edge (n-PE) devices coupled with the u-PE device, the n-PE devices running a bidding protocol to select one of the n-PE devices as a primary n-PE device for a single pseudowire connection path between the first and second Ethernet access domain networks. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72(b).
Owner:CISCO TECH INC
Simple peering in a transport network employing novel edge devices
Simple peering is provided in a novel network in which transport technology is independent of network access technology. An out-of-band network may be used to carry advertisements to an update facility. The update facility may use layer 3 destination address information and at least a part of context information (to identify customers uniquely) to determine a layer 3 address of an edge device of the transport network associated with an addressed customer device. Virtual private networks are supported, as context information is used to distinguish different customers with overlapping layer 3 addresses.
Owner:VERIZON PATENT & LICENSING INC
Edge-gateway multipath method and system
In one exemplary aspect, an edge-gateway multipath method includes the step of providing an edge device in a local network communicatively coupled with a cloud-computing service in a cloud-computing network. A set of wide area network (WAN) links connected to the edge device are automatically detected. The WAN links are automatically measured without the need for an external router. The edge device is communicatively coupled with a central configuration point in the cloud-computing network. The method further includes the step of downloading, from the central configuration point, an enterprise-specific configuration data into the edge device. The enterprise-specific configuration data includes the gateway information. The edge device is communicatively coupled with a gateway in the cloud-computing network. The communicatively coupling of the edge device with the gateway includes a multipath (MP) protocol.
Owner:NICIRA
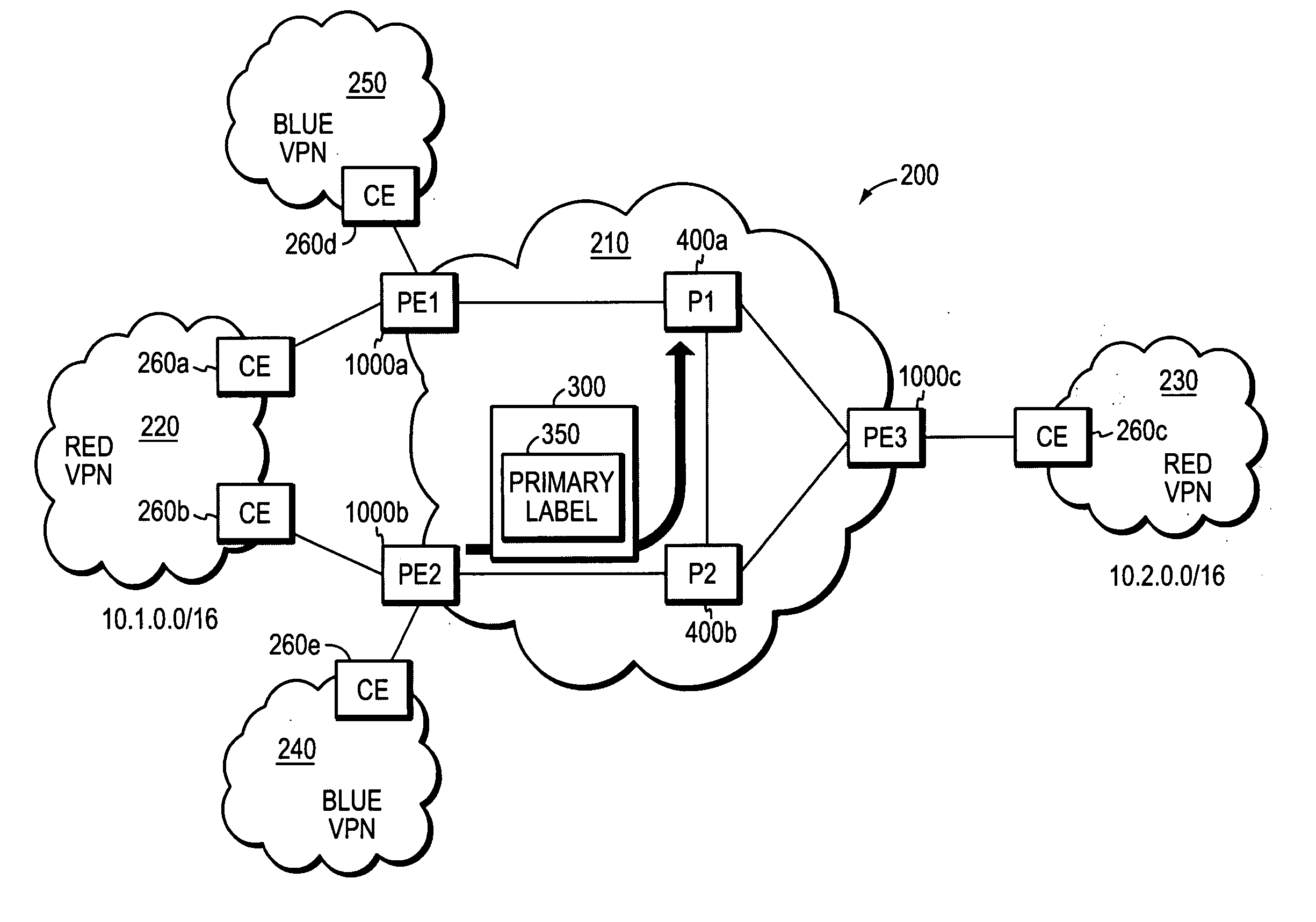
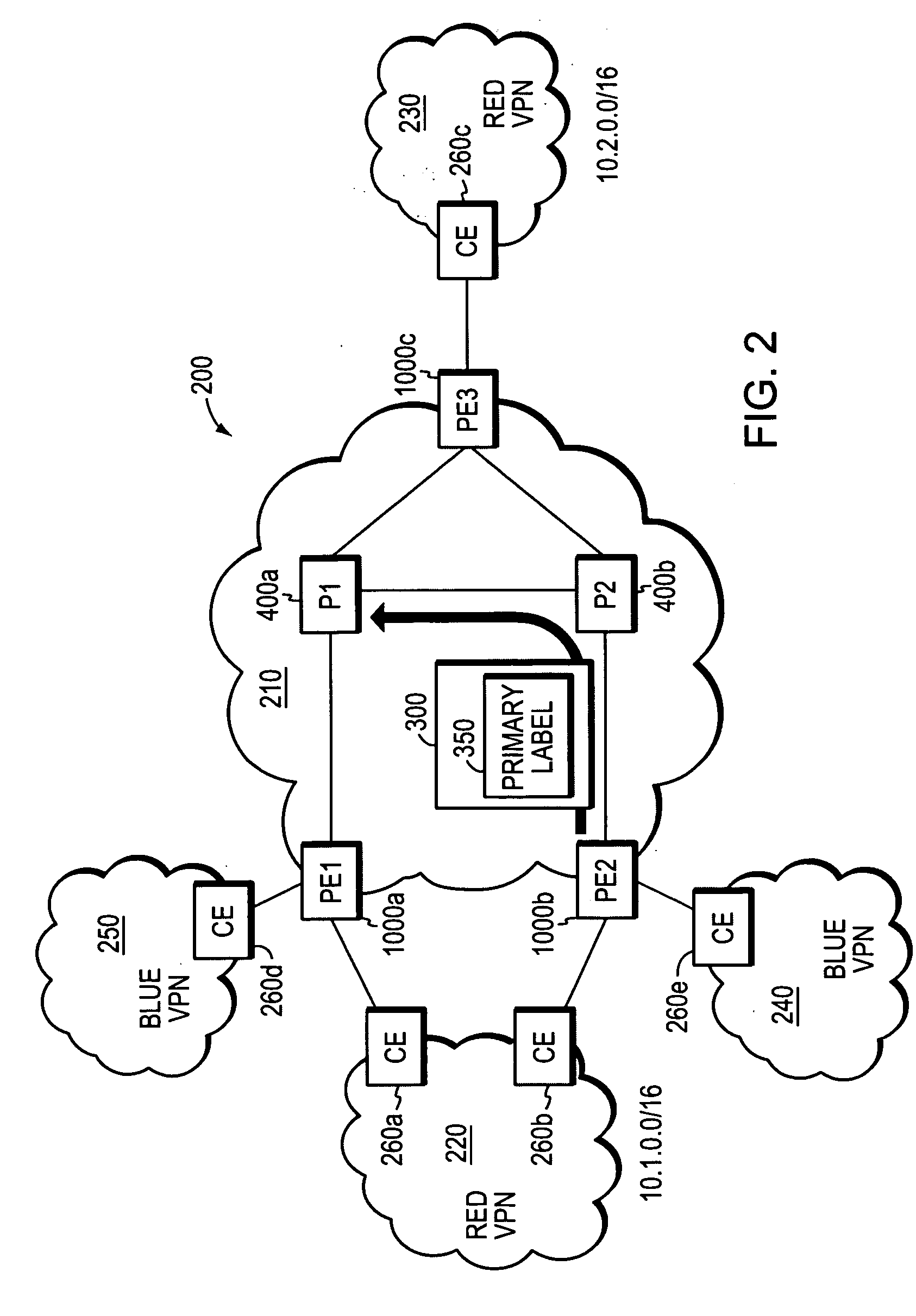
Loop prevention technique for MPLS using two labels
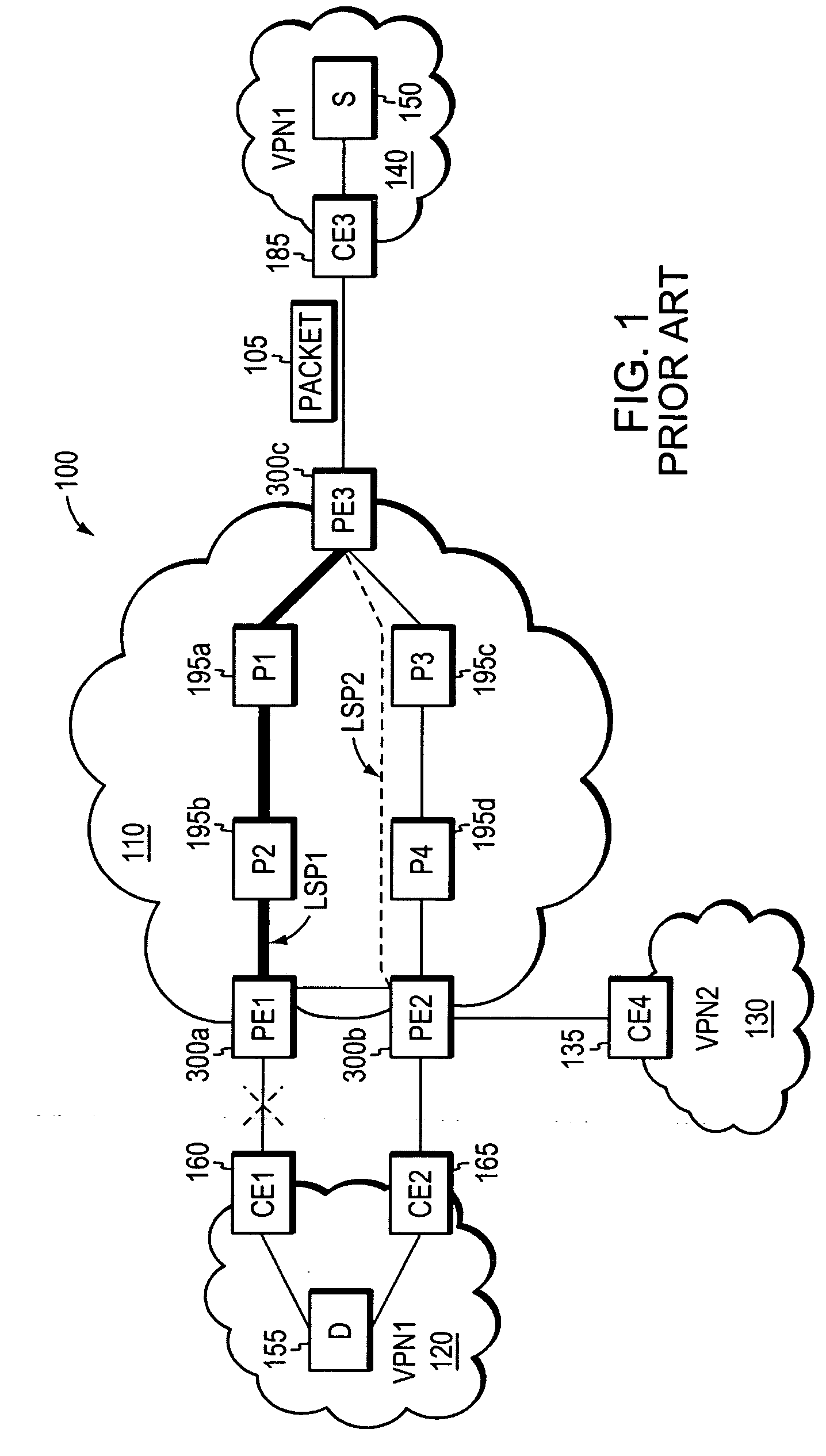
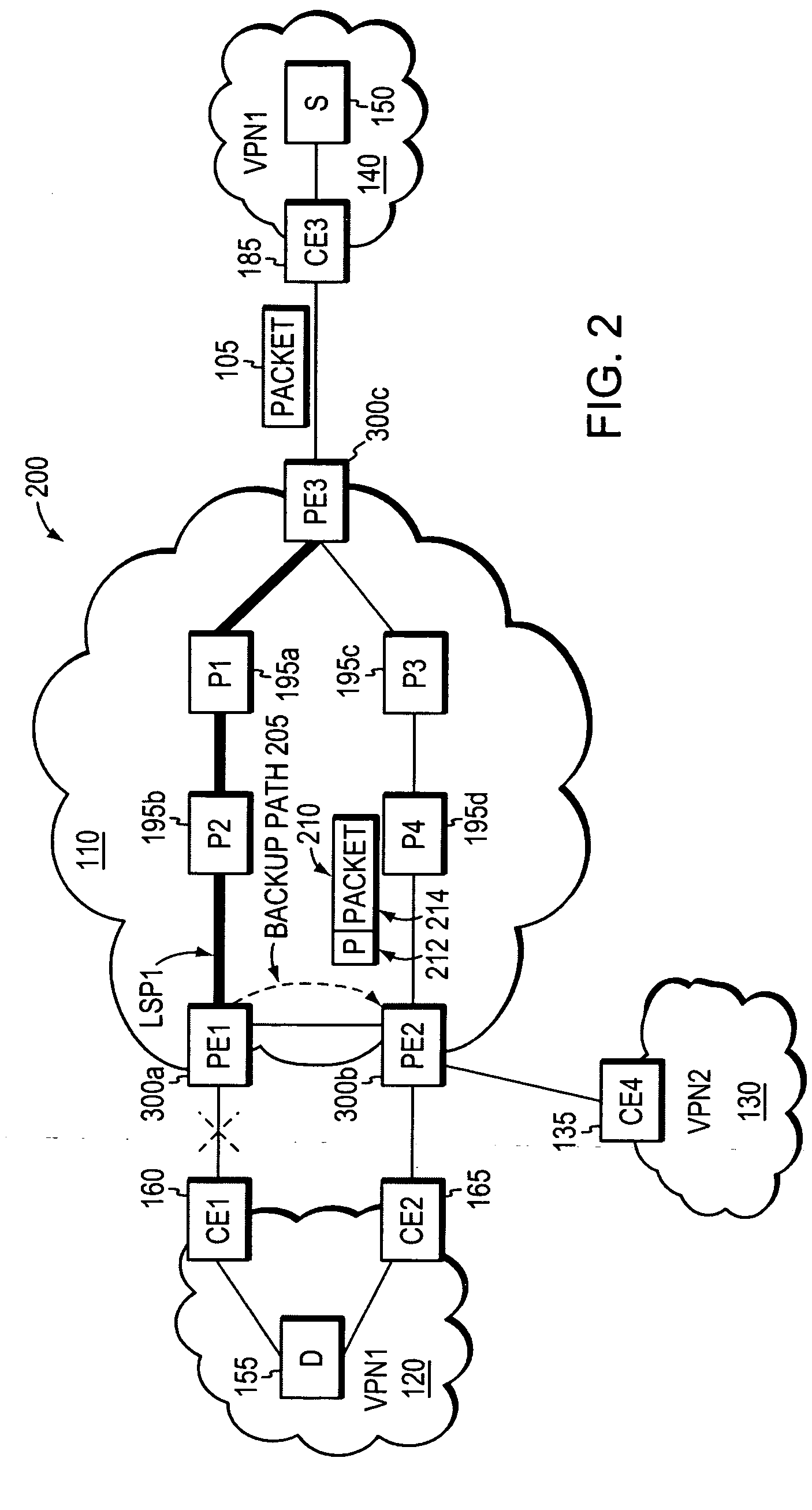
InactiveUS20060164975A1Fast and efficientProtect dataError preventionTransmission systemsInternet trafficRouting domain
A fast reroute (FRR) technique is implemented at the edge of a network. In accordance with the technique, if an edge device detects a node or link failure that prevents it from communicating with a neighboring routing domain, the edge device reroutes at least some data packets addressed to that domain to a backup edge device which, in turn, forwards the packets to the neighboring domain. The rerouted packets are designated as being “protected” (i.e., rerouted) data packets before they are forwarded to the backup edge device. To differentiate which data packets are protected and which are not, the backup edge device employs different sets of VPN label values for protected and non-protected network traffic. That is, the backup edge device may allocate two different VPN label values for at least some destination address prefixes that are reachable through the neighboring domain: a first VPN label value for FRR protected traffic and a second VPN label value for non-protected traffic. Upon receiving a data packet containing a protected VPN label value, the backup edge device is not permitted to reroute the packet a second time, e.g., in response to another inter-domain node or link failure, thereby preventing loops from developing at the edge of the network.
Owner:CISCO TECH INC
Algorithm for backup PE selection
InactiveUS20060209682A1Reduce settingsError preventionFrequency-division multiplex detailsRouting domainMetric selection
A fast reroute (FRR) technique is implemented at the edge of a computer network. If an edge device detects a node or link failure that prevents it from communicating with a neighboring routing domain, the edge device reroutes at least some data packets addressed to that domain to a backup edge device which, in turn, forwards the packets to the neighboring domain. The backup edge device is not permitted to reroute the packets a second time. According to the inventive technique, the edge device first identifies a group one or more possible backup edge devices and then selects at least one preferred backup edge device from the group. The edge device makes its selection based on the values of one or more metrics associated with the possible backup edge devices. The metrics are input to a novel selection algorithm that selects the preferred backup edge device(s) using a hierarchical selection process or a weighted-metric selection process, or some combination thereof.
Owner:CISCO TECH INC
Method for building MAC (Media Access Control) address table and provider edge device
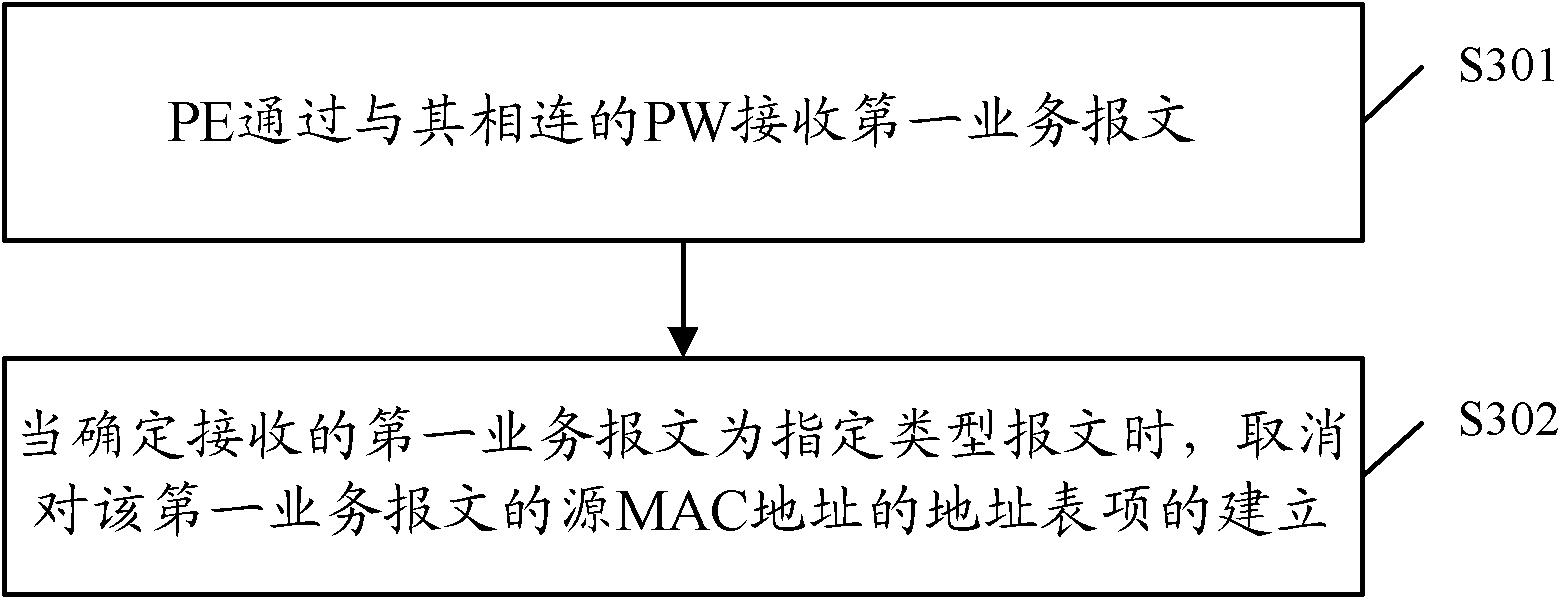
ActiveCN102164091AReduce in quantityReduce capacityData switching networksAddress Resolution ProtocolMedia access control
The invention discloses a method for building an MAC (Media Access Control) address table and a provider edge device. In the method, a PE (Provider Edge Device) receives a first service message by a PW (Pseudo Wire) connected with the PE; when the first received service message is confirmed to be a specific-type message, the building of the address table entry of the source MAC address of the first service message is cancelled, wherein the specific-type message is an unknown unicast message, a multicast message or the broadcasting message of a non-free ARP (Address Resolution Protocol) message. According to the scheme provided by the embodiment of the invention, the amount of the address table entries built by the PE is reduced so as to reduce the volume of the MAC address table.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Methods and apparatus for automated edge device configuration in a heterogeneous network
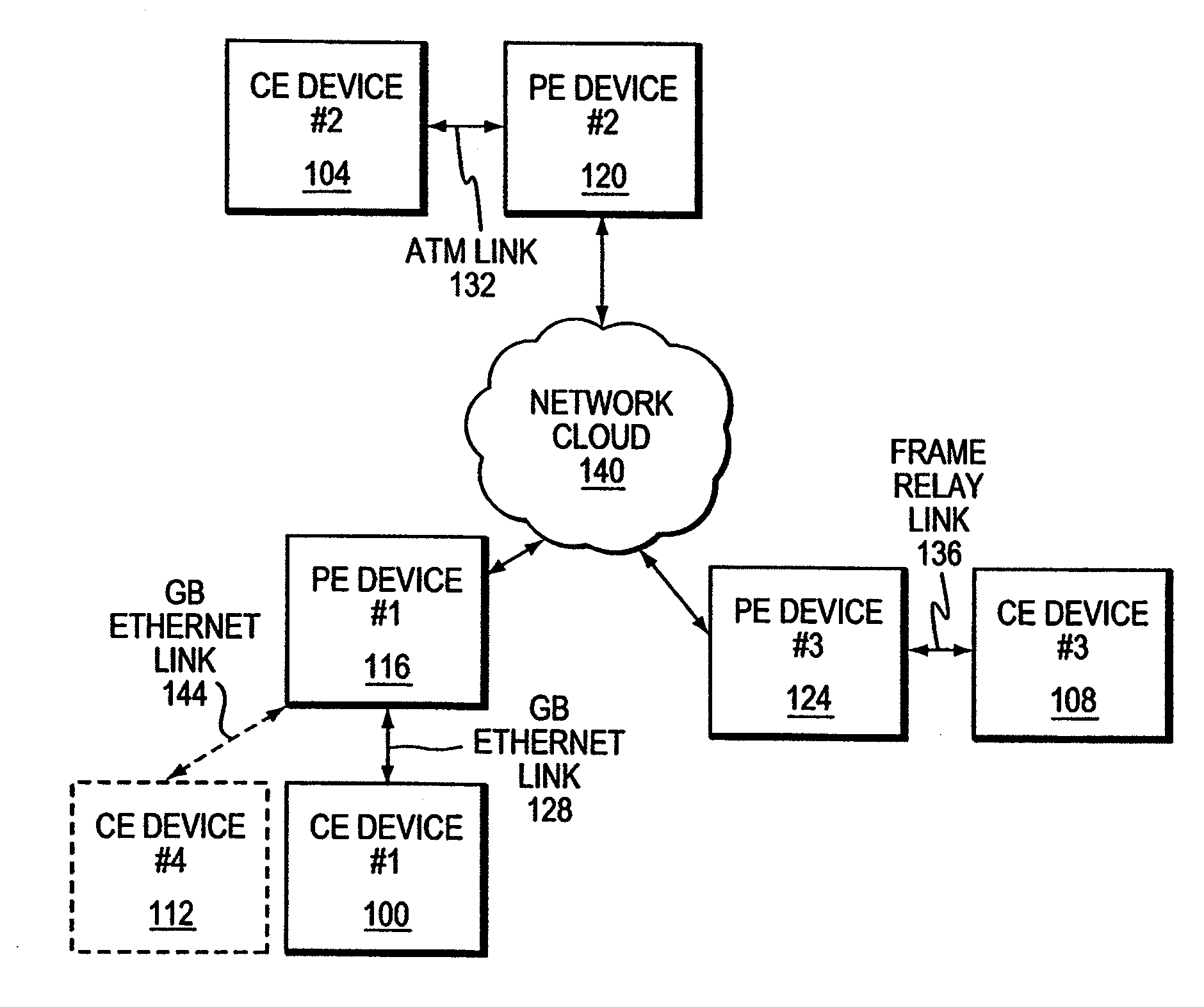
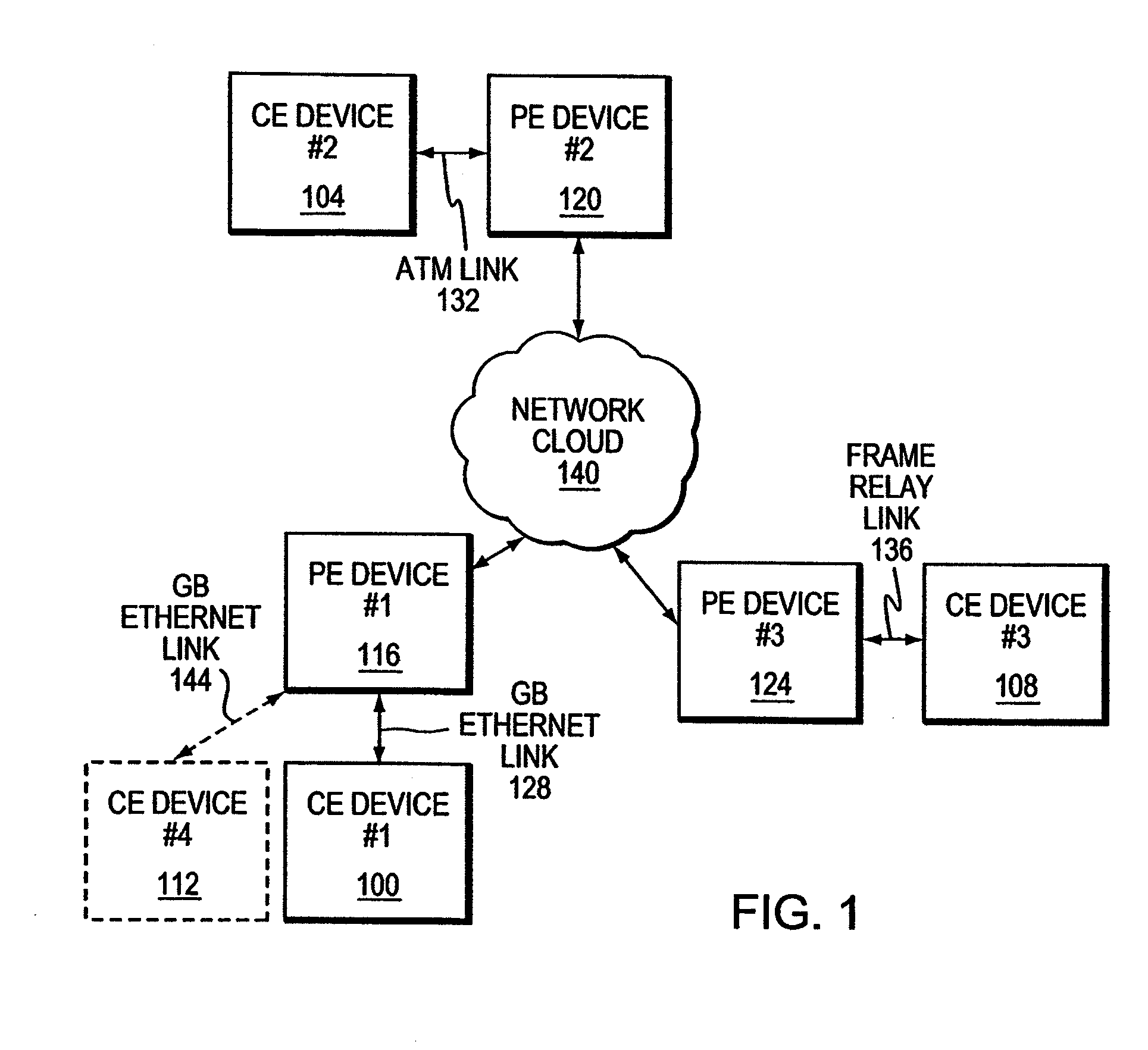
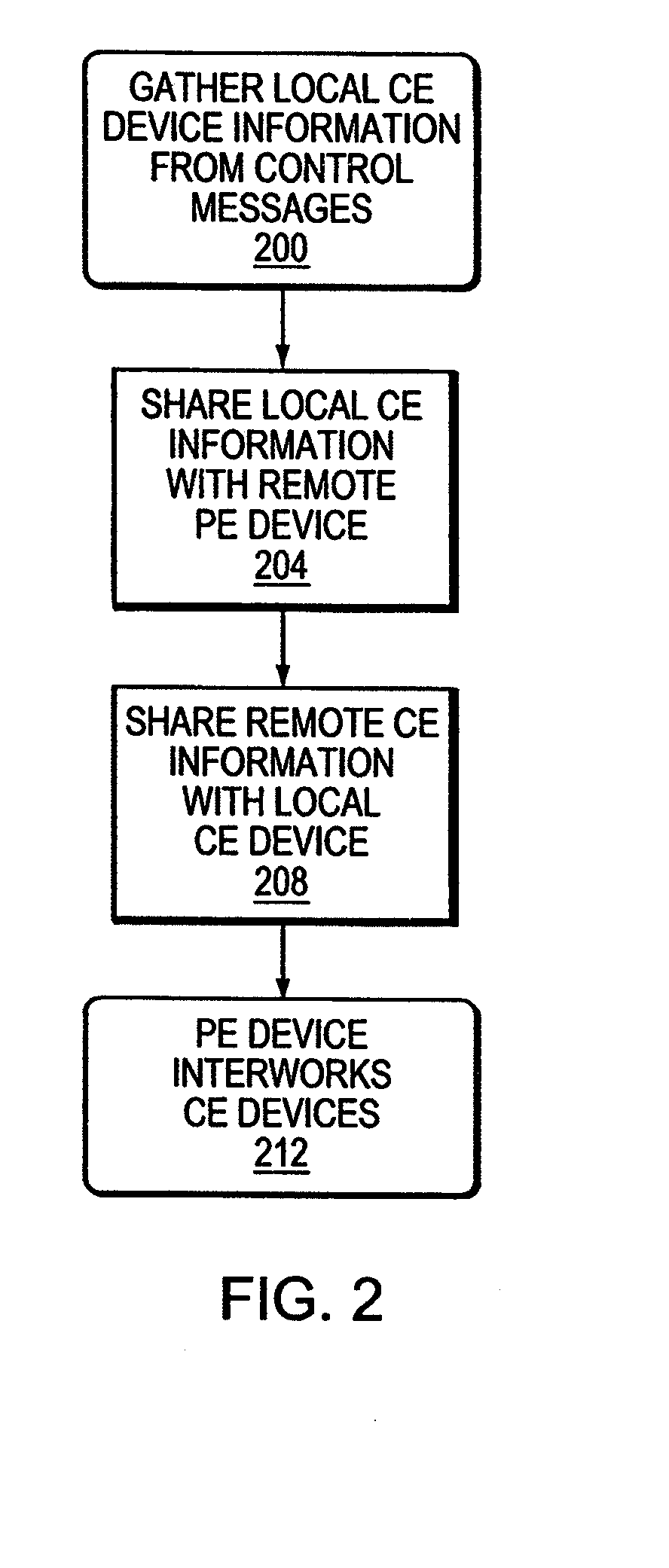
InactiveUS20080219276A1Facilitates automated configurationDigital computer detailsNetworks interconnectionComputer hardwareAuto-configuration
A PE device learns the address of a local CE device by monitoring the control messages, such as address resolution messages, originating from those local devices. In one embodiment, automated configuration of the PE devices participating in a Layer 2 VPN is facilitated by permitting a PE device to share the addresses for its locally-attached CE devices with the remote PE devices in the VPN. A PE device may share the addresses of the remote CE devices with the local CE devices by initiating its own control message or responding to an control message issued by one of its local CE devices. This latter mechanism in effect hides the distributed, heterogeneous nature of the network from a local CE device.
Owner:ENTERASYS NETWORKS
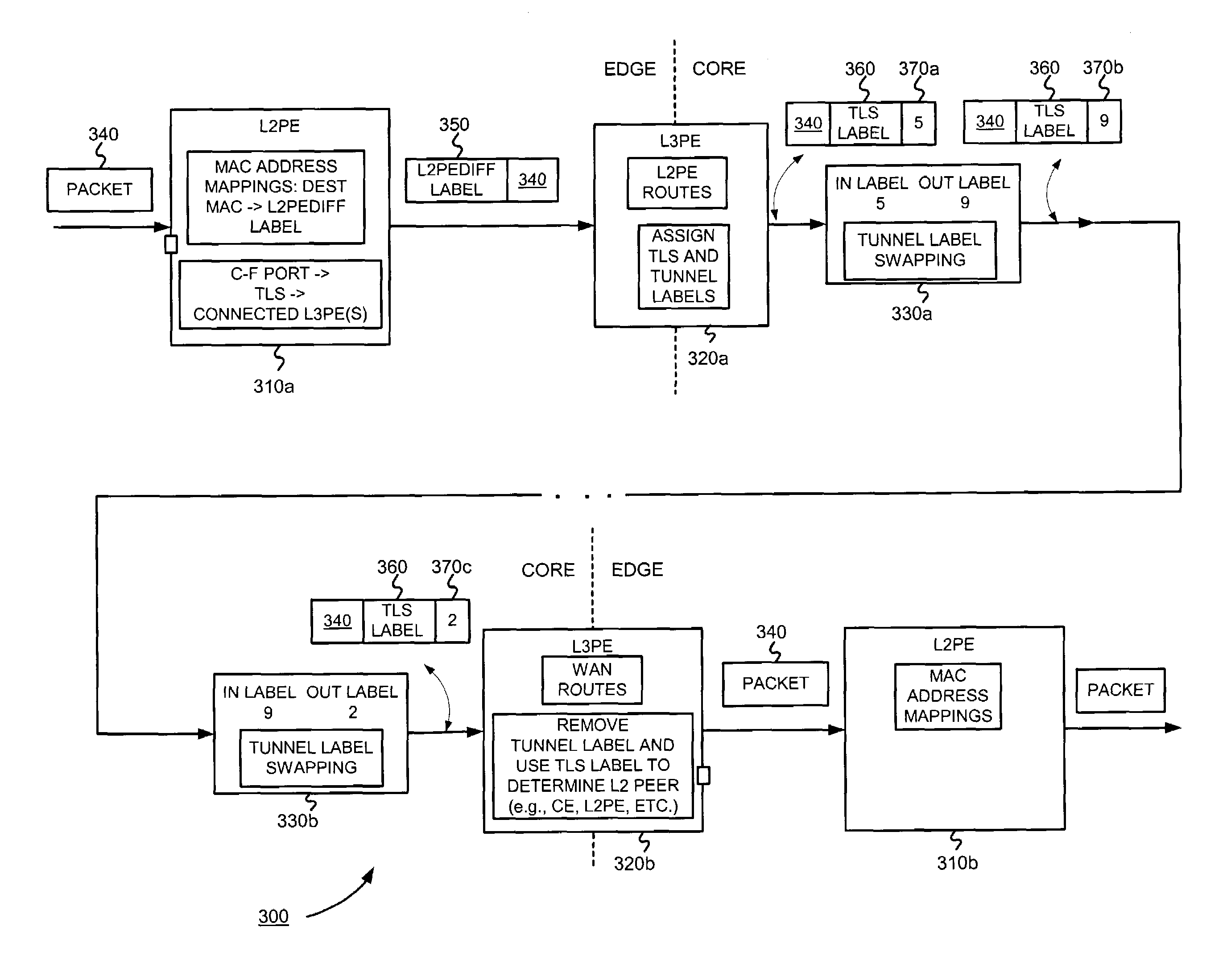
Decoupling functionality related to providing a transparent local area network segment service
ActiveUS7577143B1Simple configurationData switching by path configurationTransport networkNetwork segment
A transport LAN segment service is provided over a transport network. Responsibilities for configuring, provisioning and forwarding over a transport LAN segment are divided between layer 2 and 3 service provider edge devices, where the layer 3 edge device handles discovery and tunneling responsibilities, the layer 2 edge device handles learning and flooding responsibilities, and information can be exchanged between the layer 2 and 3 edge devices. Configuration is simplified by advertising TLS-label information, layer 2 address learning, and flooding when the needed configuration information has not yet been learned or discovered.
Owner:JUMIPER NETWORKS INC
Ethernet to ATM interworking with multiple quality of service levels
A method of supporting multiple quality of service (QoS) levels for data being transmitted between two networking devices, such as customer equipment (CE), that use Ethernet and Asynchronous Transfer Mode (ATM). The method supports multiple QoS services in a network where a first CE is connected to a first edge device (interworking unit) using the Ethernet protocol and a second CE is connected to a second edge device using the ATM protocol. The edge devices may be directly connected together or they may be connected through a network backbone using any generally accepted network protocol. The first CE may be connected to the first edge device using a single Ethernet port, multiple Ethernet ports, a single virtual local area network (VLAN), or multiple VLAN's. The second CE is connected to an edge device using a single virtual circuit connection (VCC), a single virtual path connection (VPC), or multiple VCC's. The method ensures QoS for data transmitted between the first and the second CE via the Ethernet protocol to the ATM protocol and vice versa.
Owner:NORTEL NETWORKS LTD
Edge-gateway multipath method and system
In one exemplary aspect, an edge-gateway multipath method includes the step of providing an edge device in a local network communicatively coupled with a cloud-computing service in a cloud-computing network. A set of wide area network (WAN) links connected to the edge device are automatically detected. The WAN links are automatically measured without the need for an external router. The edge device is communicatively coupled with a central configuration point in the cloud-computing network. The method further includes the step of downloading, from the central configuration point, an enterprise-specific configuration data into the edge device. The enterprise-specific configuration data includes the gateway information. The edge device is communicatively coupled with a gateway in the cloud-computing network. The communicatively coupling of the edge device with the gateway includes a multipath (MP) protocol.
Owner:NICIRA
Overlay transport virtualization
ActiveUS8166205B2Data switching by path configurationMultiple digital computer combinationsGPRS core networkVirtualization
In one embodiment, an apparatus includes one or more internal interfaces in communication with one or more network devices in a first network site through a Layer 2 link, an overlay interface in communication through a Layer 3 link with a core network connected to one or more other network sites, and a table mapping addresses for network devices in the other network sites to addresses of edge devices in the same network site as the network device. The apparatus further includes a processor operable to encapsulate a packet received at one of the internal interfaces and destined for one of the network devices in the other network sites, with an IP header including a destination address of the edge device mapped to the destination network device, and forward the encapsulated packet to the core network.
Owner:CISCO TECH INC
System and method for fast start-up of live multicast streams transmitted over a packet network
InactiveUS20060083263A1Analogue secracy/subscription systemsFrequency-division multiplexData packVideo bitstream
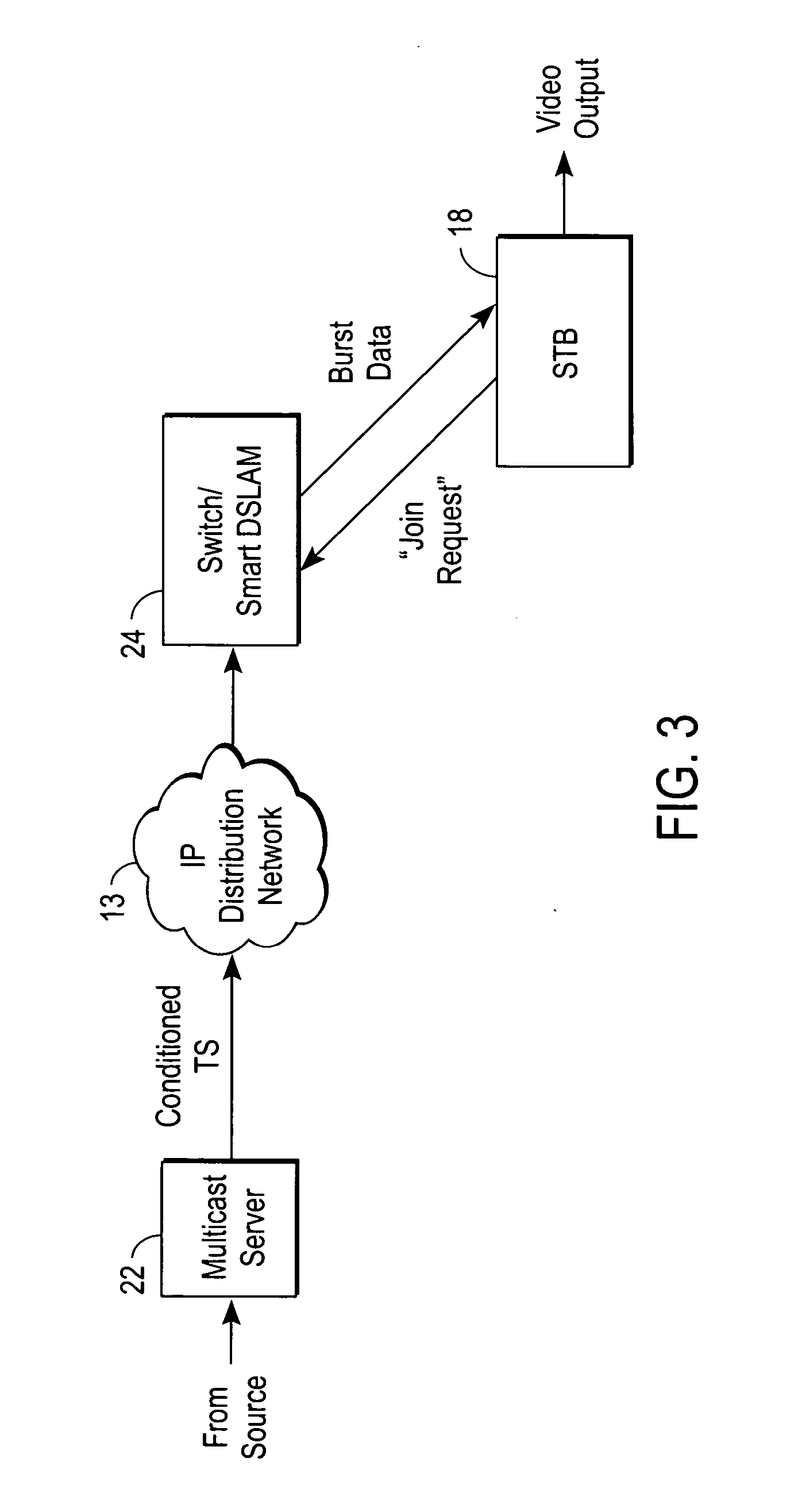
A system for multicast streaming of programs over a packet network includes a node having a processor that conditions a video bitstream such that packets containing an I-frame are located near program specific information (PSI) packets, the processor marking a random join point (RJP) in the video bitstream immediately preceding the I-frame and PSI packets, the node outputting the conditioned and marked video bitstream across the packet network. An edge device of the network includes a buffer that caches packets of the conditioned and marked video bitstream video starting at the RJP, and sends the cached packets to a client receiver. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
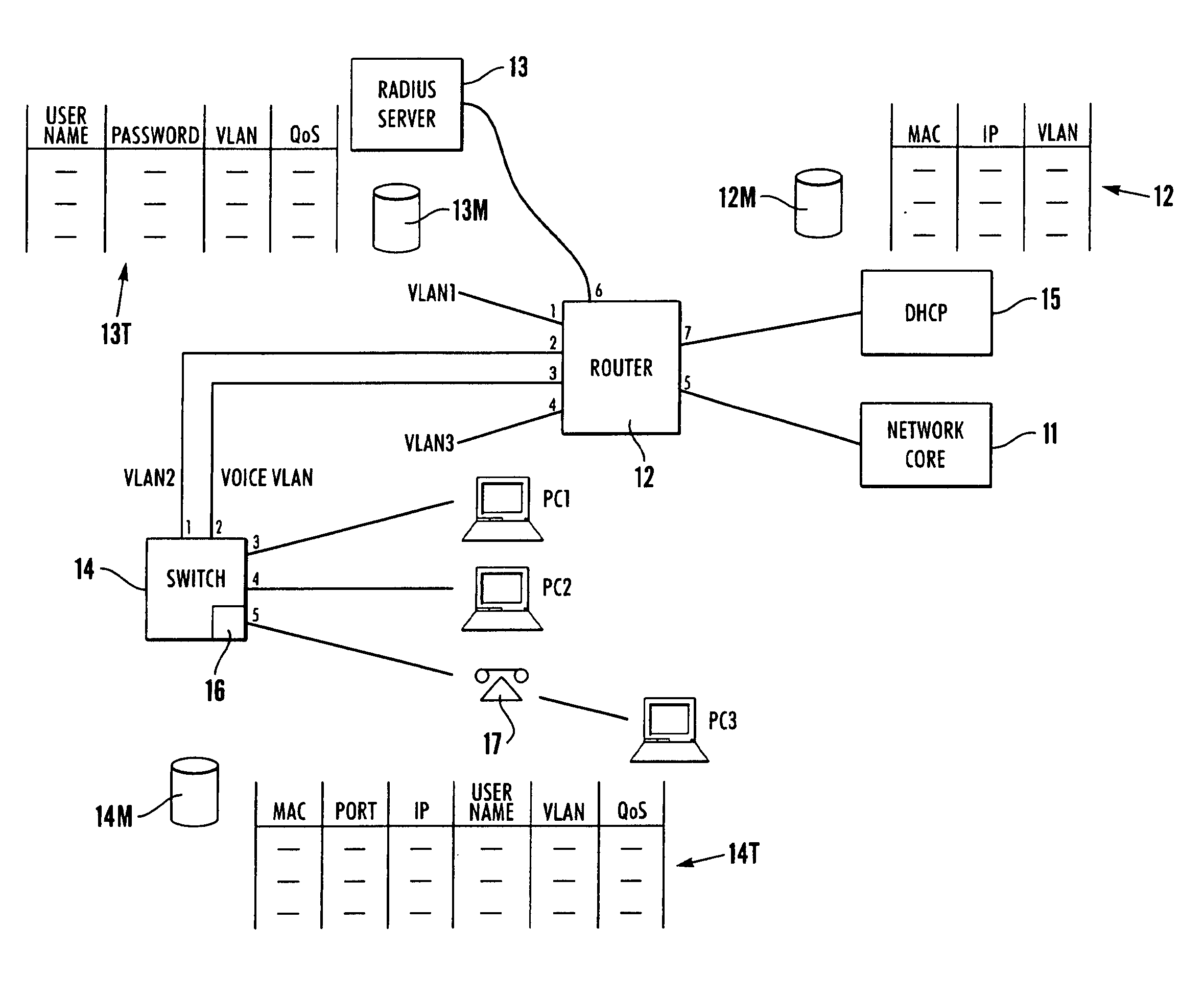
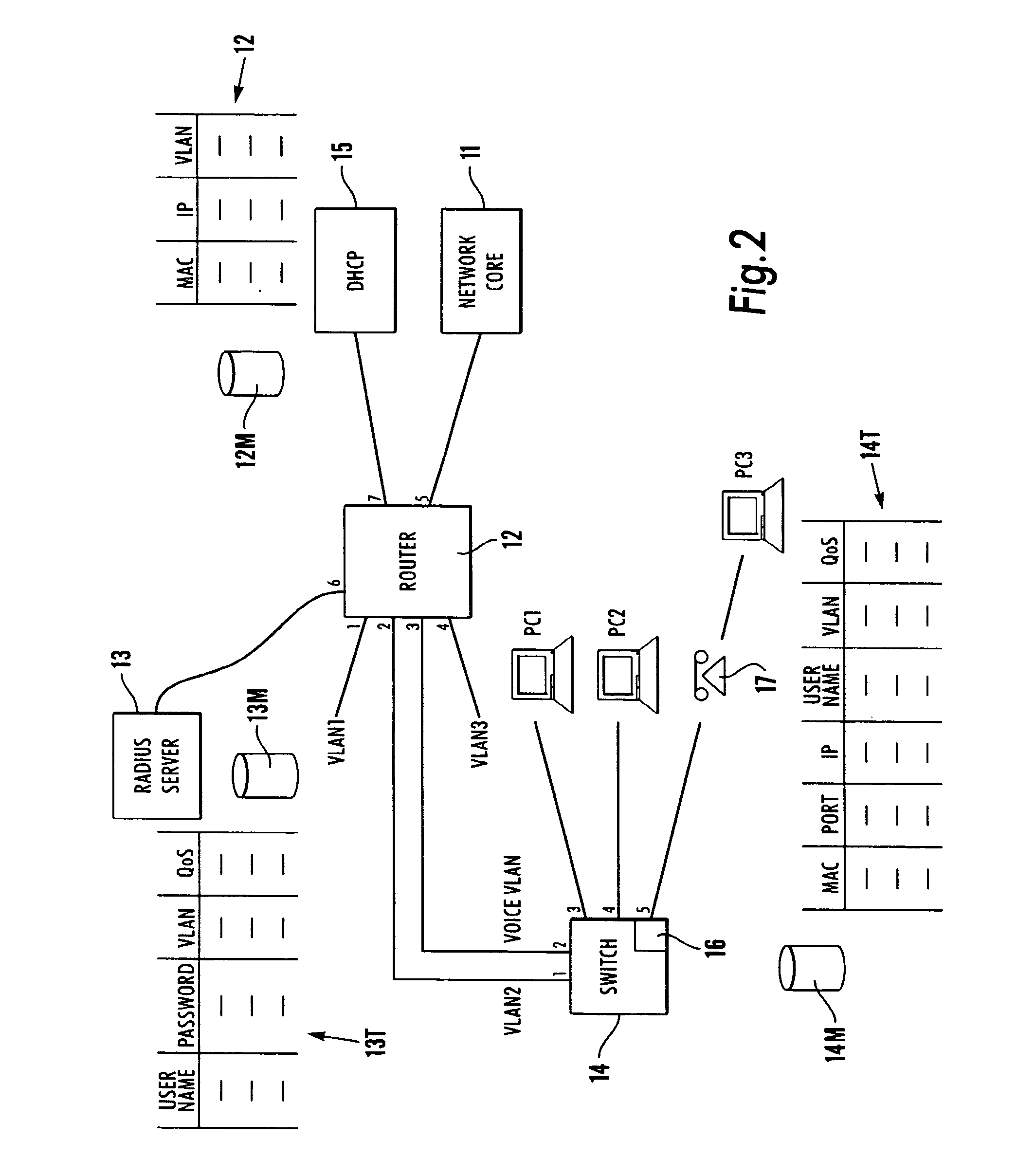
Deterministic user authentication service for communication network
InactiveUS6874090B2Digital data processing detailsUser identity/authority verificationPersonalizationInternet Authentication Service
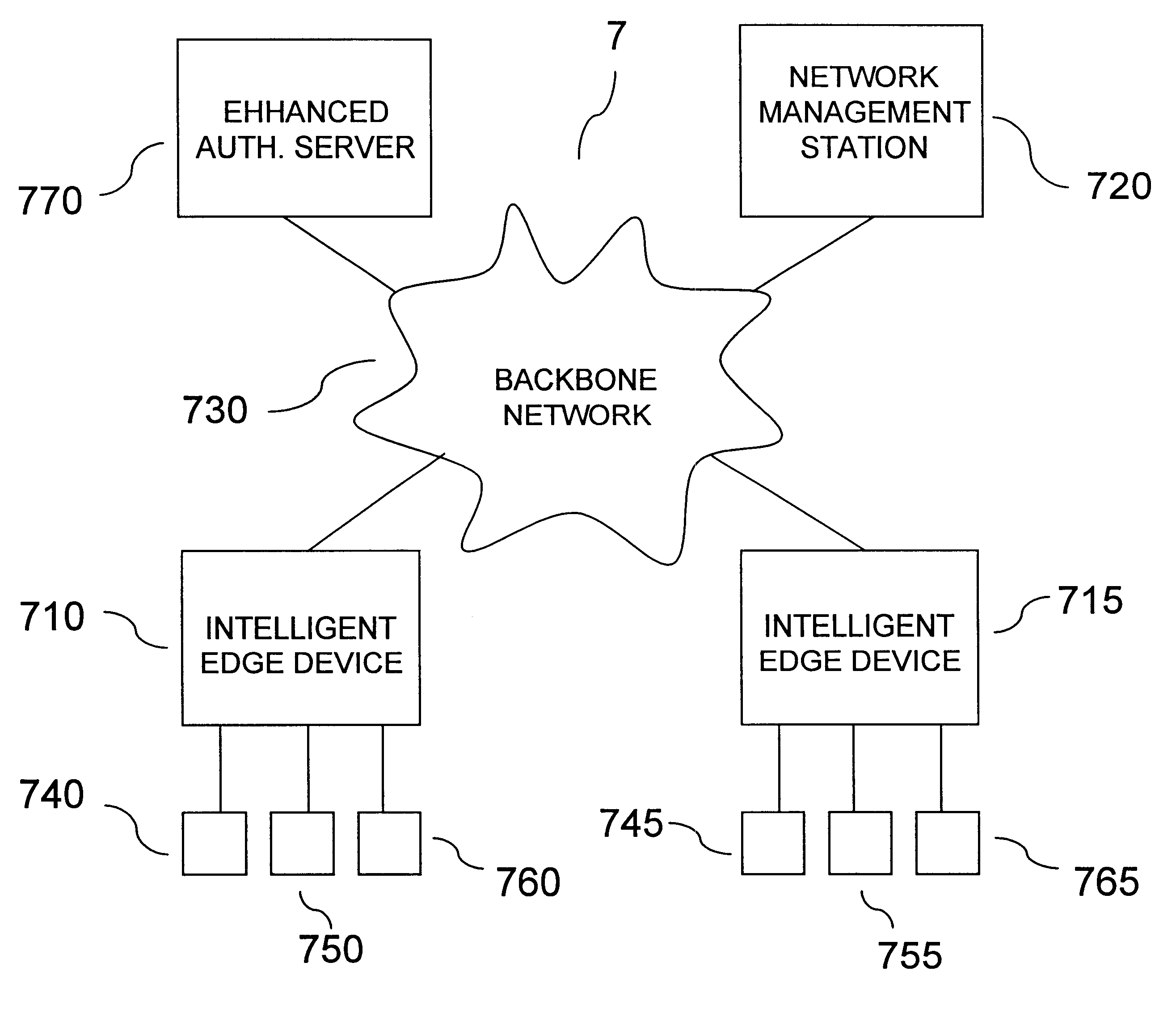
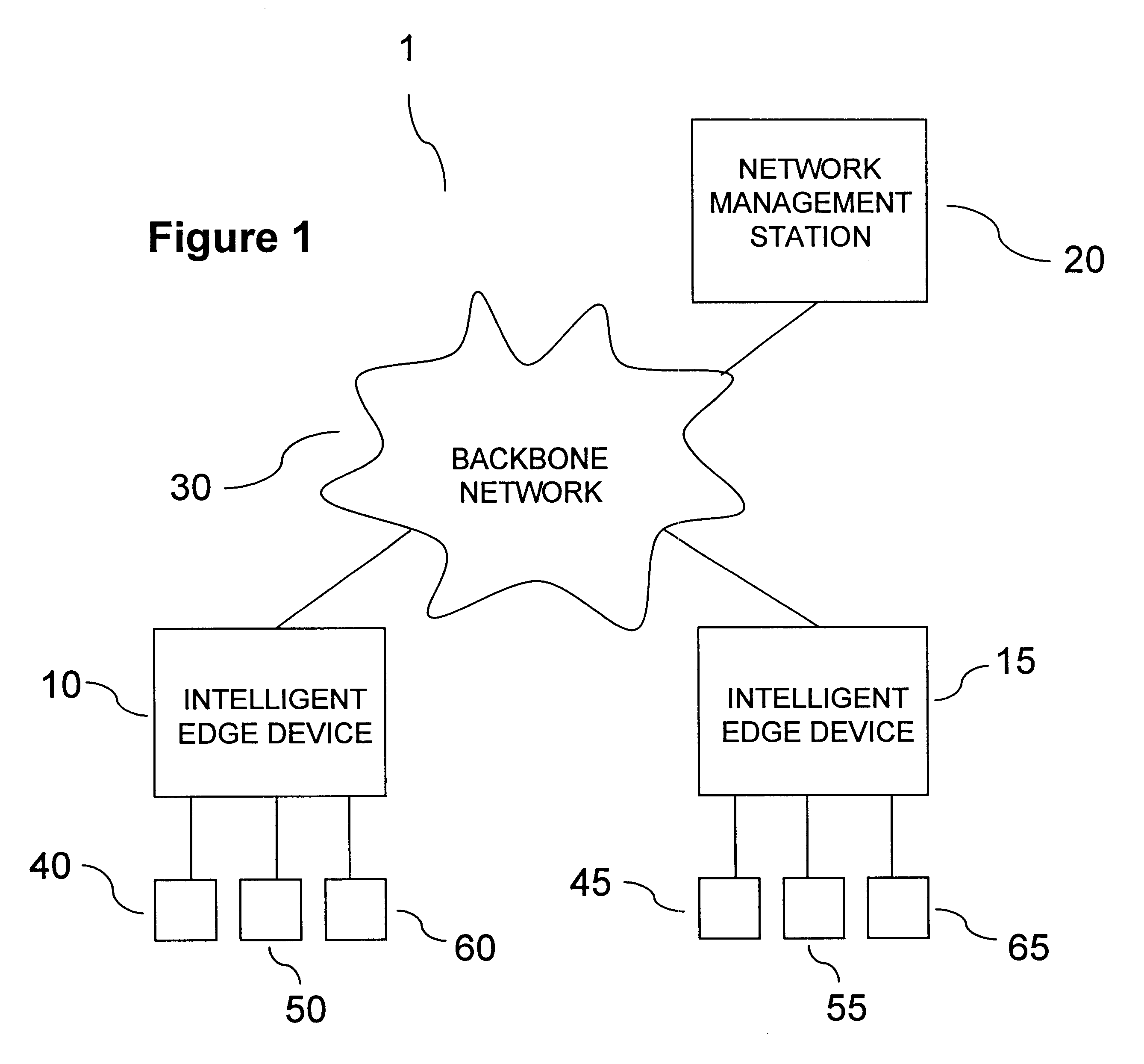
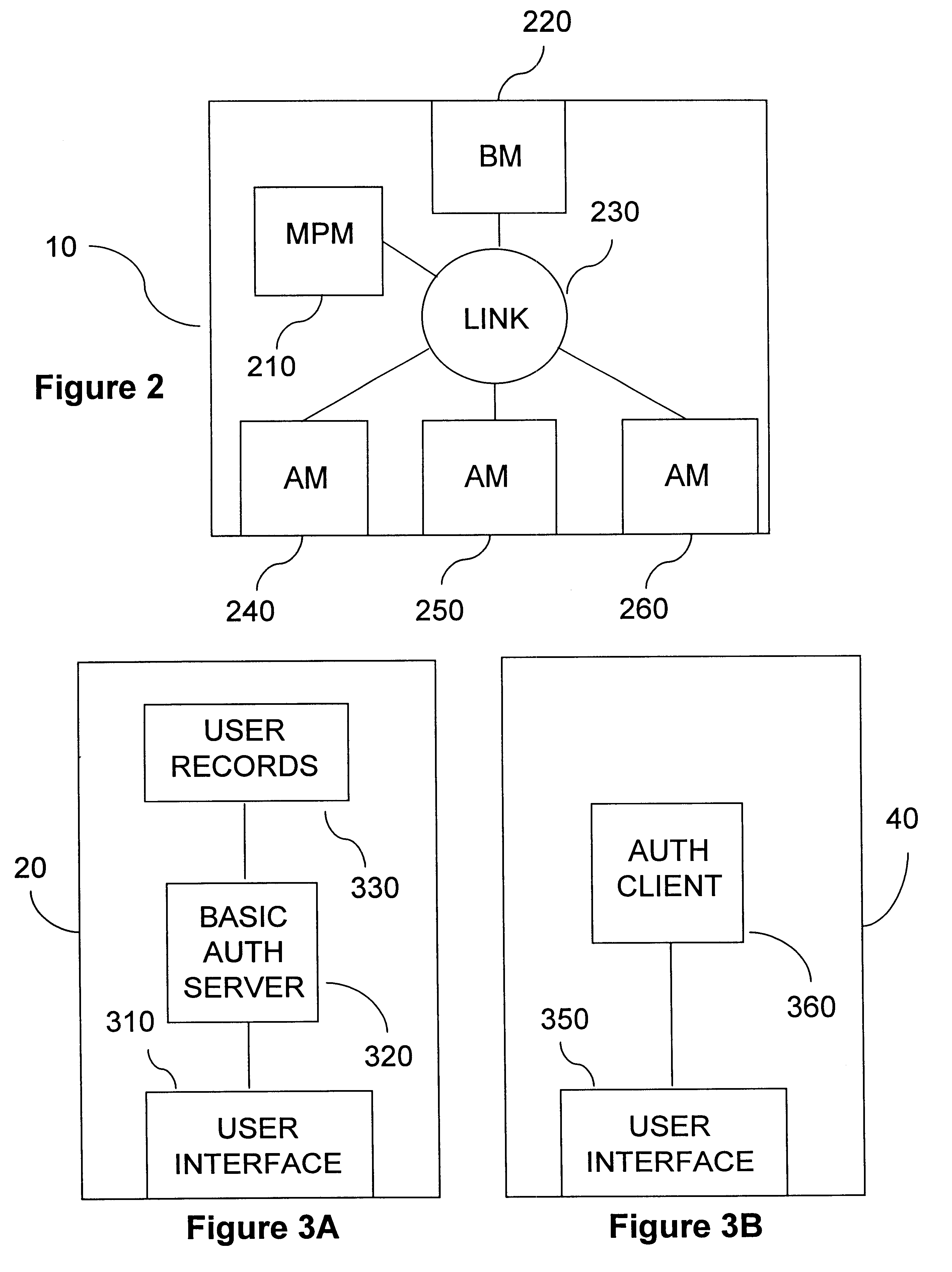
A user authentication service for a communication network authenticates local users before granting them access to personalized sets of network resources. Authentication agents on intelligent edge devices present users of associated end systems with log-in challenges. Information supplied by the users is forwarded to an authentication server for verification. If successfully verified, the authentication server returns to the agents authorized connectivity information and time restrictions for the particular authenticated users. The agents use the information to establish rules for filtering and forwarding network traffic originating from or destined for particular authenticated users during authorized time periods. An enhanced authentication server may be engaged if additional security is desired. The authorized connectivity information preferably includes identifiers of one or more virtual local area networks active in the network. Log-in attempts are recorded so that the identity and whereabouts of network users may be monitored from a network management station.
Owner:ALCATEL LUCENT SAS
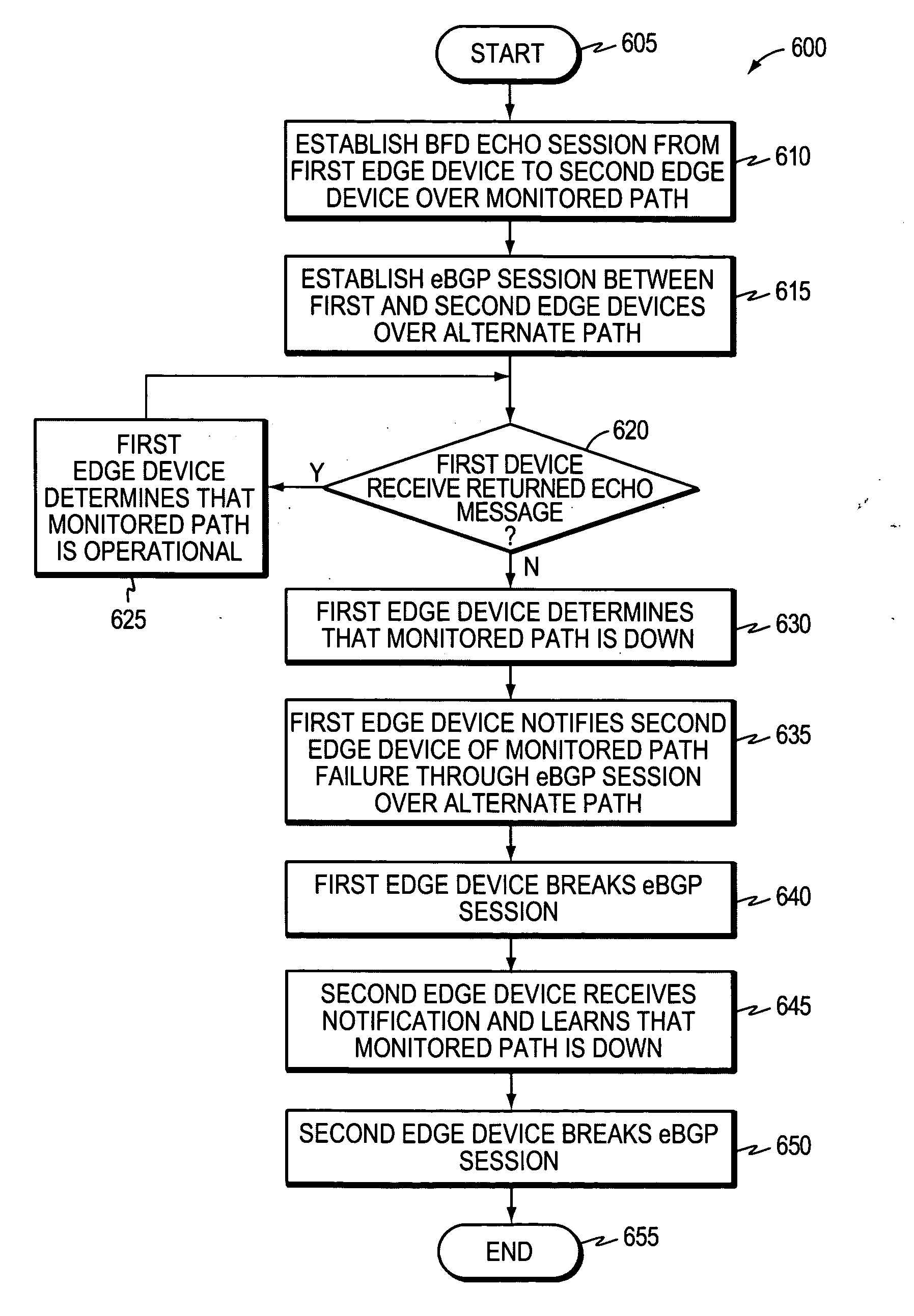
Technique for enabling bidirectional forwarding detection between edge devices in a computer network
ActiveUS20070180104A1Shorten the timeSave moneyMultiple digital computer combinationsTransmissionBorder Gateway ProtocolBidirectional Forwarding Detection
A technique enables bidirectional forwarding detection (BFD) between first and second edge devices in a computer network, wherein the second edge device is not configured for BFD. According to the novel technique, a BFD Echo session is established from the first edge device to the first edge device via the second edge device, i.e., along a monitored path (e.g., a single link). Also, an external border gateway protocol (eBGP) session is established between the first and second edge devices over an alternate path (e.g., an eBGP multi-hop session). The first edge device determines that the monitored path is down upon not receiving a returned BFD Echo message from the second edge device. In response, the first edge device notifies the second edge device that the monitored path is down through the eBGP session over the alternate path. Notably, upon notifying the second edge device that the monitored path is down, the first edge device breaks the eBGP session, and upon receiving the notification, the second edge device also breaks the eBGP session.
Owner:CISCO TECH INC
Intelligent Edge Computing Platform with Machine Learning Capability
An edge computing platform with machine learning capability is provided between a local network with a plurality of sensors and a remote network. A machine learning model is created and trained in the remote network using aggregated sensor data and deployed to the edge platform. Before being deployed, the model is edge-converted (“edge-ified”) to run optimally with the constrained resources of the edge device and with the same or better level of accuracy. The “edge-ified” model is adapted to operate on continuous streams of sensor data in real-time and produce inferences. The inferences can be used to determine actions to take in the local network without communication to the remote network. A closed-loop arrangement between the edge platform and remote network provides for periodically evaluating and iteratively updating the edge-based model.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com