Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
196results about How to "Less memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Voice over internet protocol data overload detection and mitigation system and method
A system and method is disclosed for detecting and / or mitigating an attempted overload condition targeting a voice over data or Internet protocol system, and the like. A network connection receives a plurality of VOIP or IPTV requests, for example. A processor detects whether two or more of the requests are substantially duplicate. The processor discards further received requests that are determined to be substantially duplicate.
Owner:PROLEXIC TECHNOLOGIES
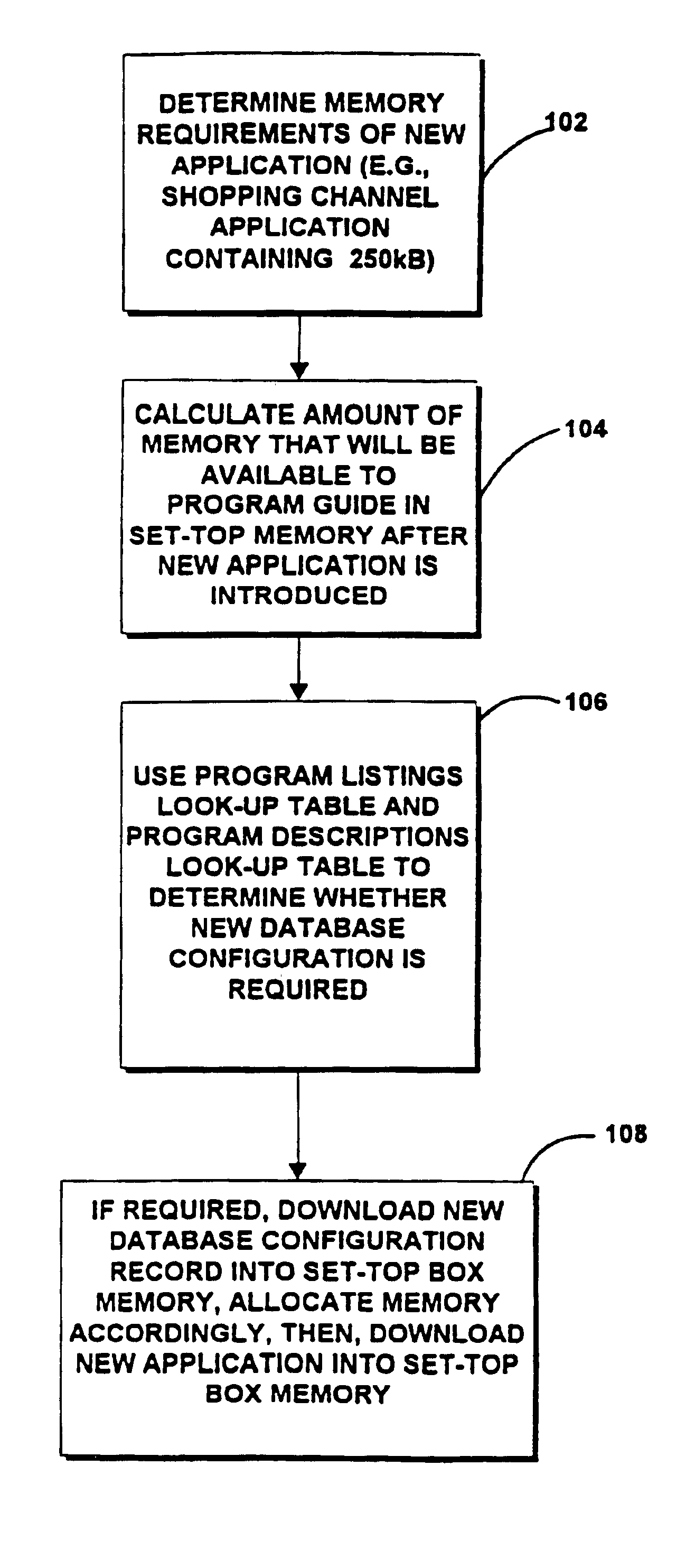
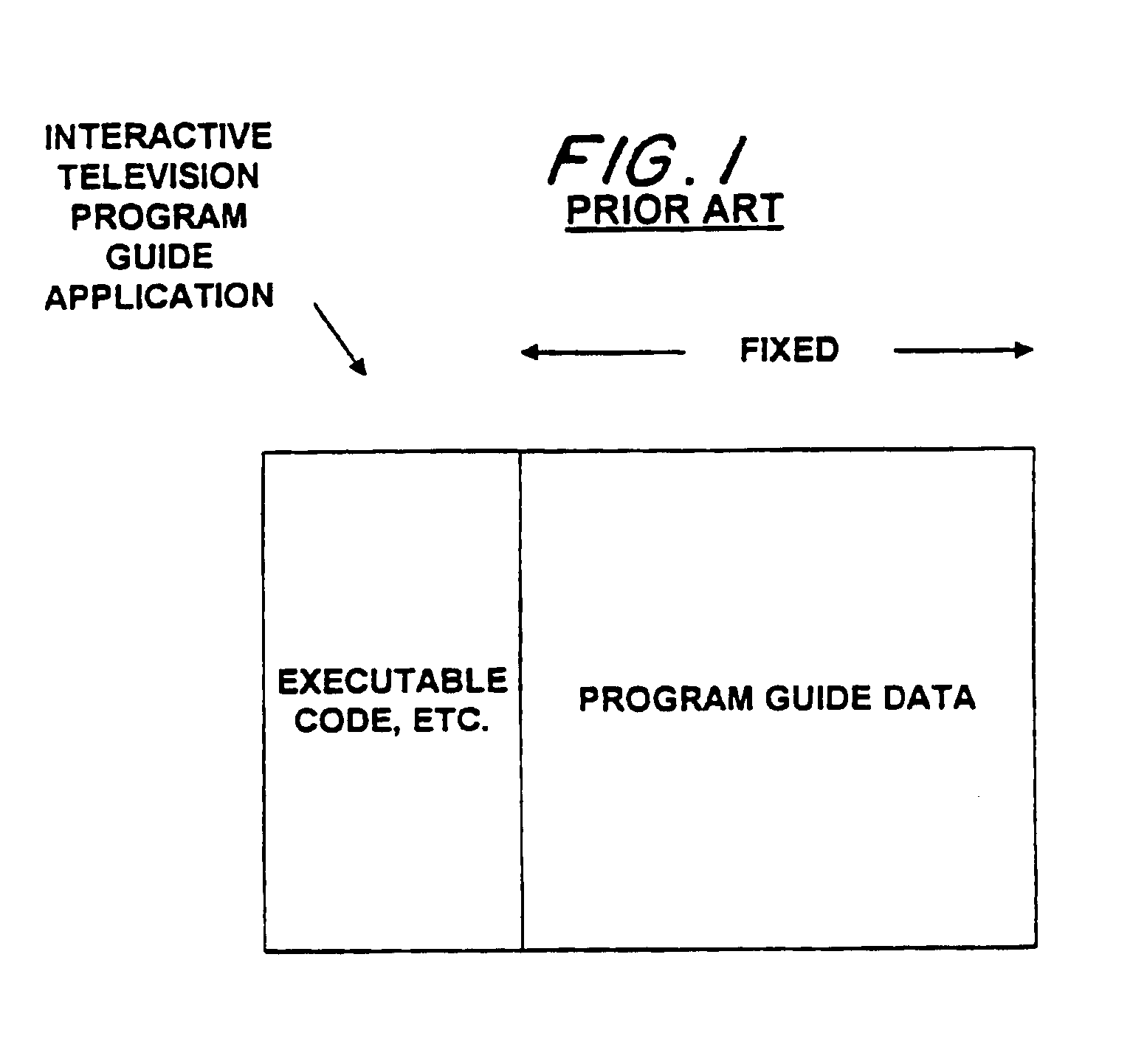
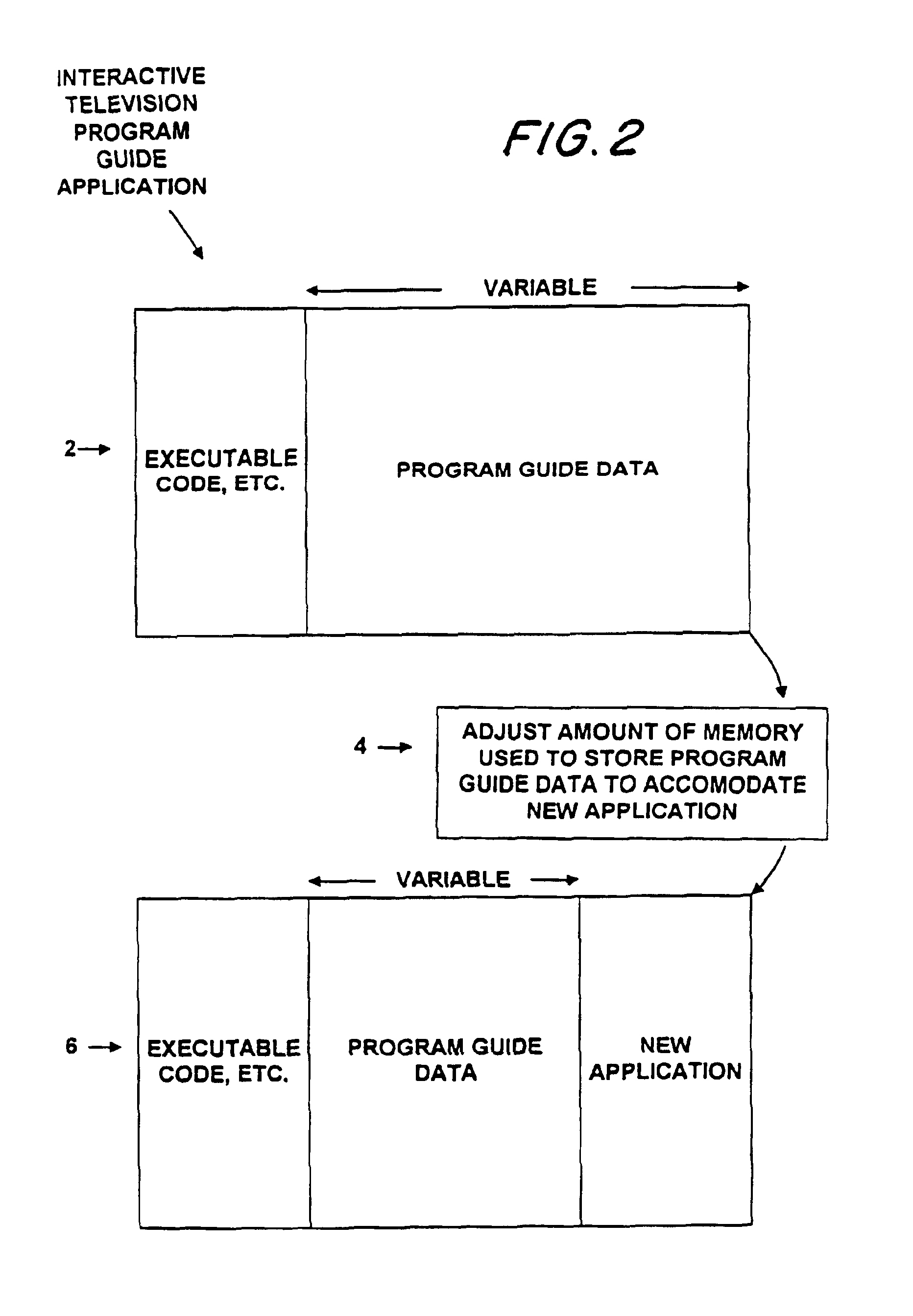
Interactive electronic television program guide with database configurability
InactiveUS6928653B1Less memoryTelevision system detailsAnalogue secracy/subscription systemsTelevision equipmentInteractive television
An interactive television program guide system is provided in which an interactive television program guide is implemented on user television equipment containing a memory. The system allocates the memory among different categories of program guide data used by the program guide. When new channels are added to the channel line-up, the program guide adjusts its memory allocation accordingly. When it is desired to install a new non-program-guide application on the user television equipment in addition to the program guide, memory can be reallocated to accommodate the new application.
Owner:PREVUE INT
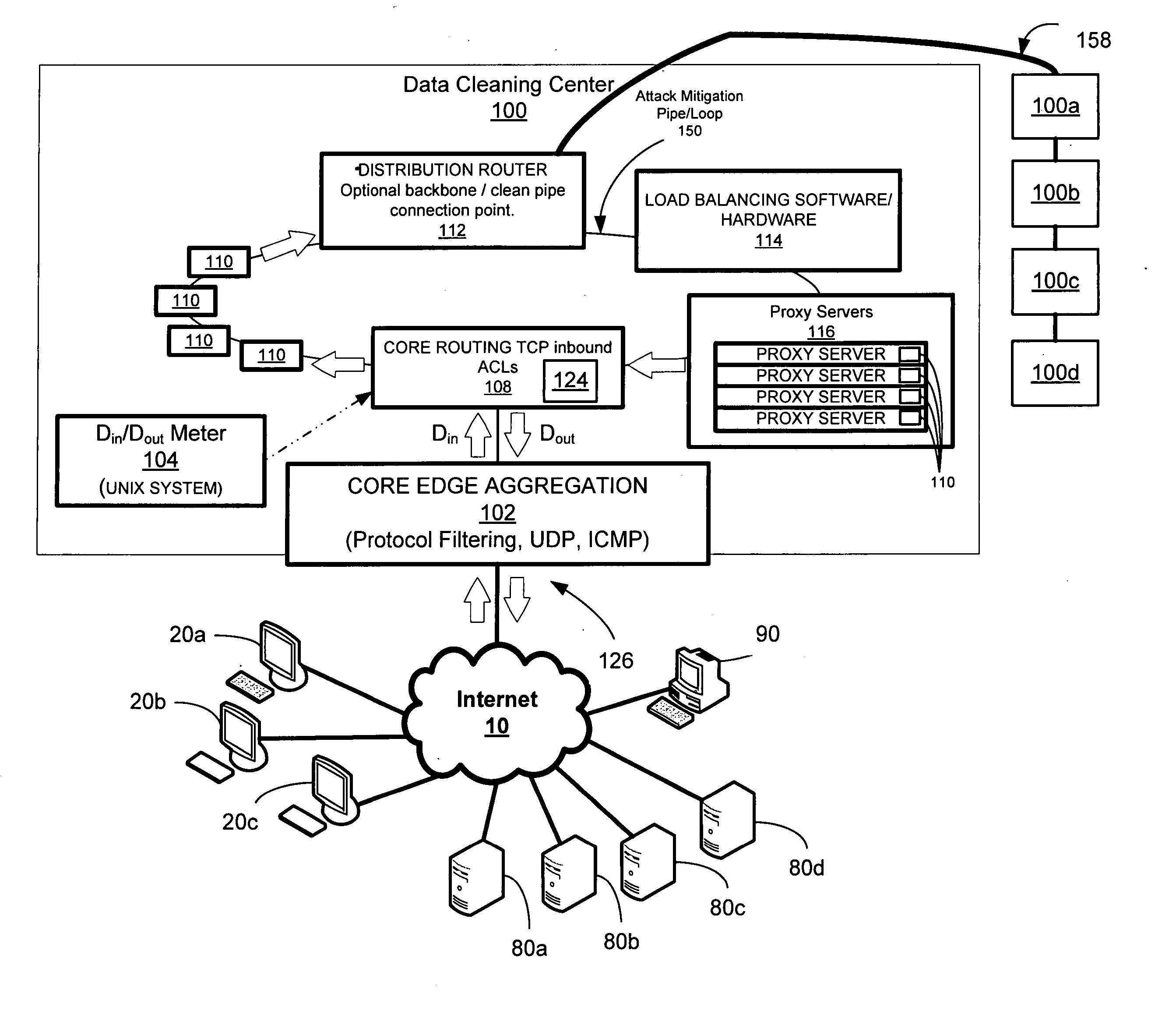
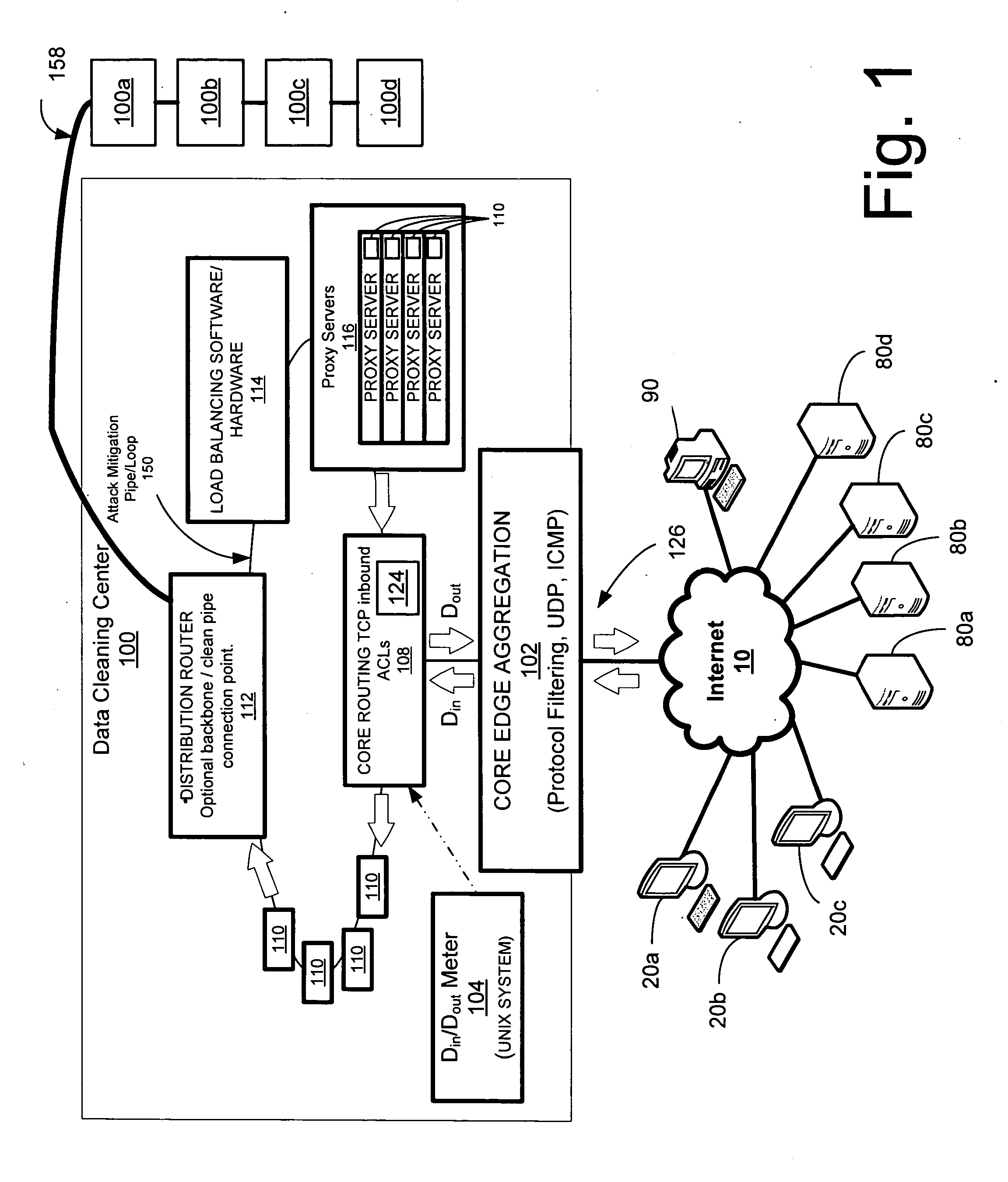
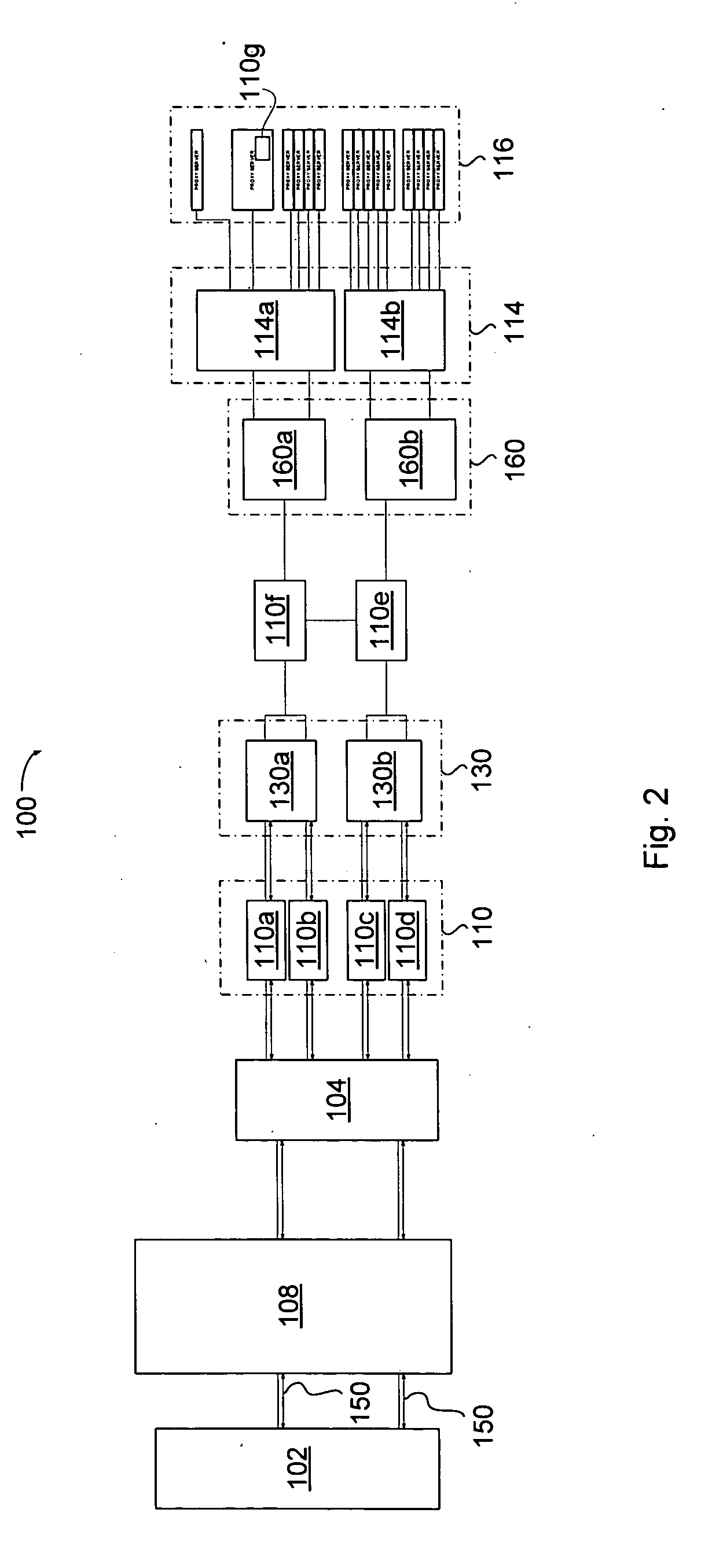
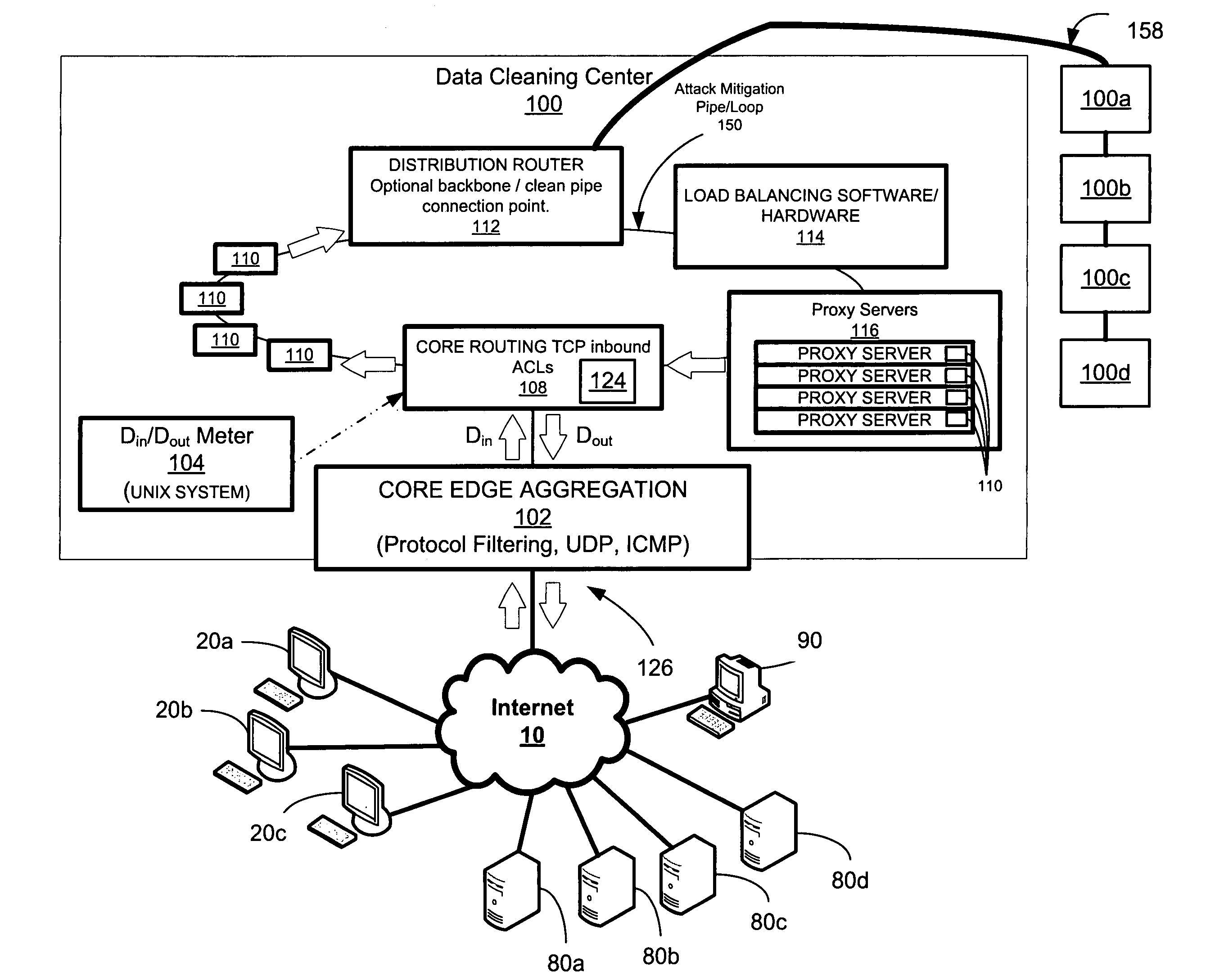
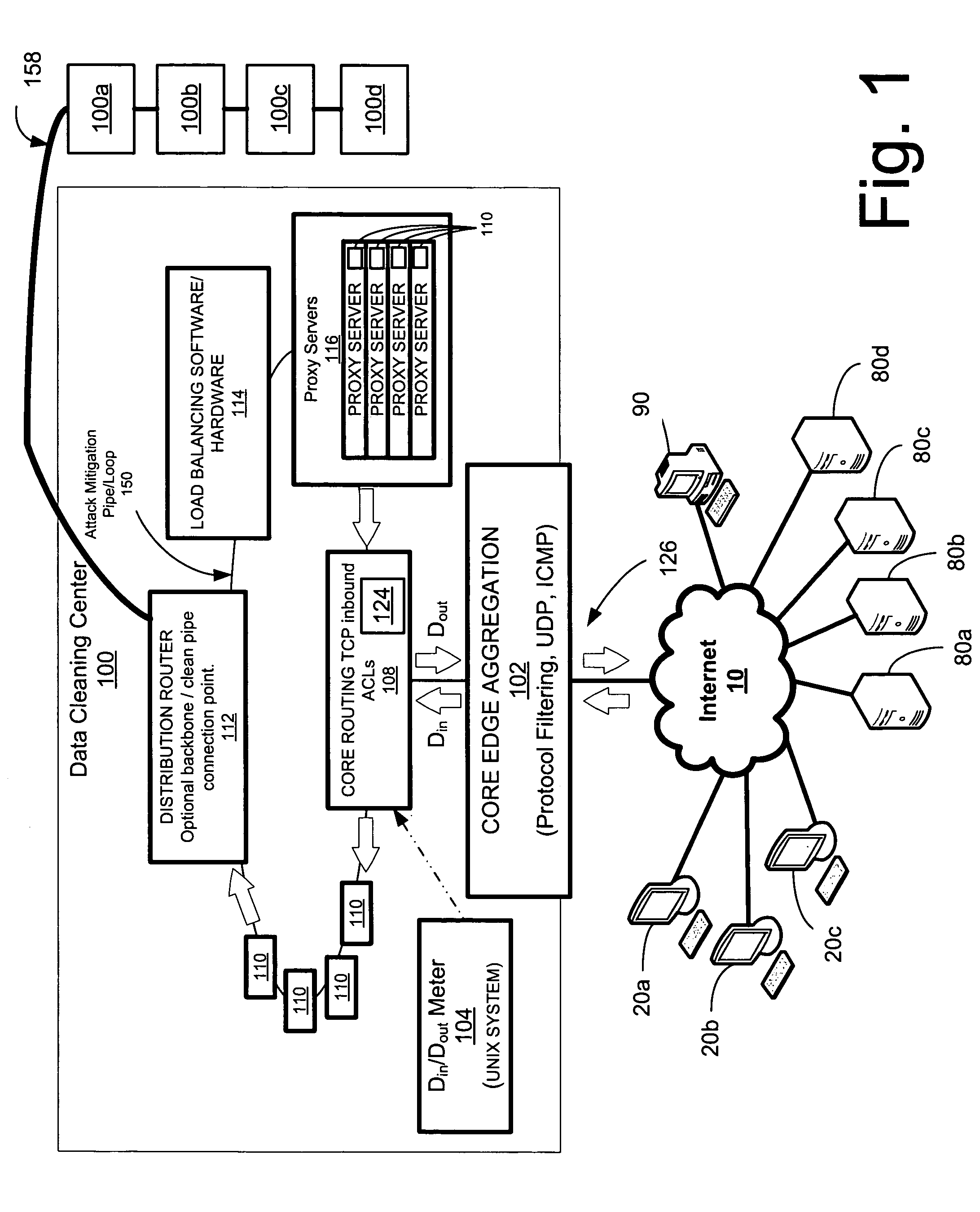
Network overload detection and mitigation system and method
A system and method is disclosed for detecting and / or mitigating an overload condition from one or more first computers, such as a distributed denial of service (DDoS) attack, viral attack, or the like, targeting one or more of a plurality of second computers located on a network. While one or more DDoS attacks are mitigated, a meter, detection apparatus, software, or method, detects the condition being mitigated in a data cleaning center, and provides an alert or notification regarding the mitigated attack.Another preferred embodiment relates, in general terms, to a system and method for detecting and / or mitigating an overload or attempted overload condition targeting a domain name server. A network connection is provided for receiving one or more DNS requests from one or more client computers located on a network. A preferred embodiment includes a processor for providing a response to the one or more DNS requests to the one or more client computers if more than a threshold number of duplicate DNS requests are received.Another preferred embodiment relates, in general terms, to a system and method for detecting and / or mitigating an attempted overload condition targeting a networked computer system that uses a redirection module to divert data until it is deemed to be clean.
Owner:AKAMAI TECH INC
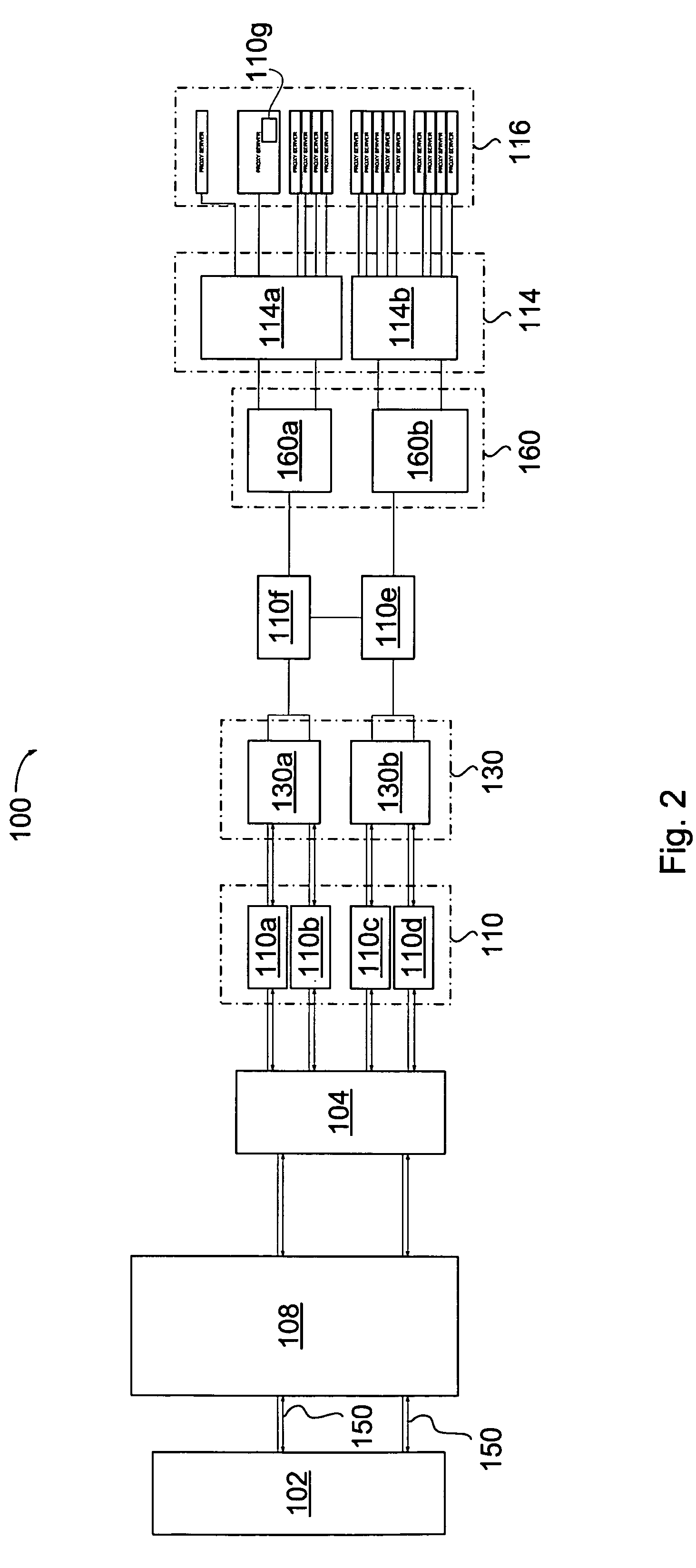
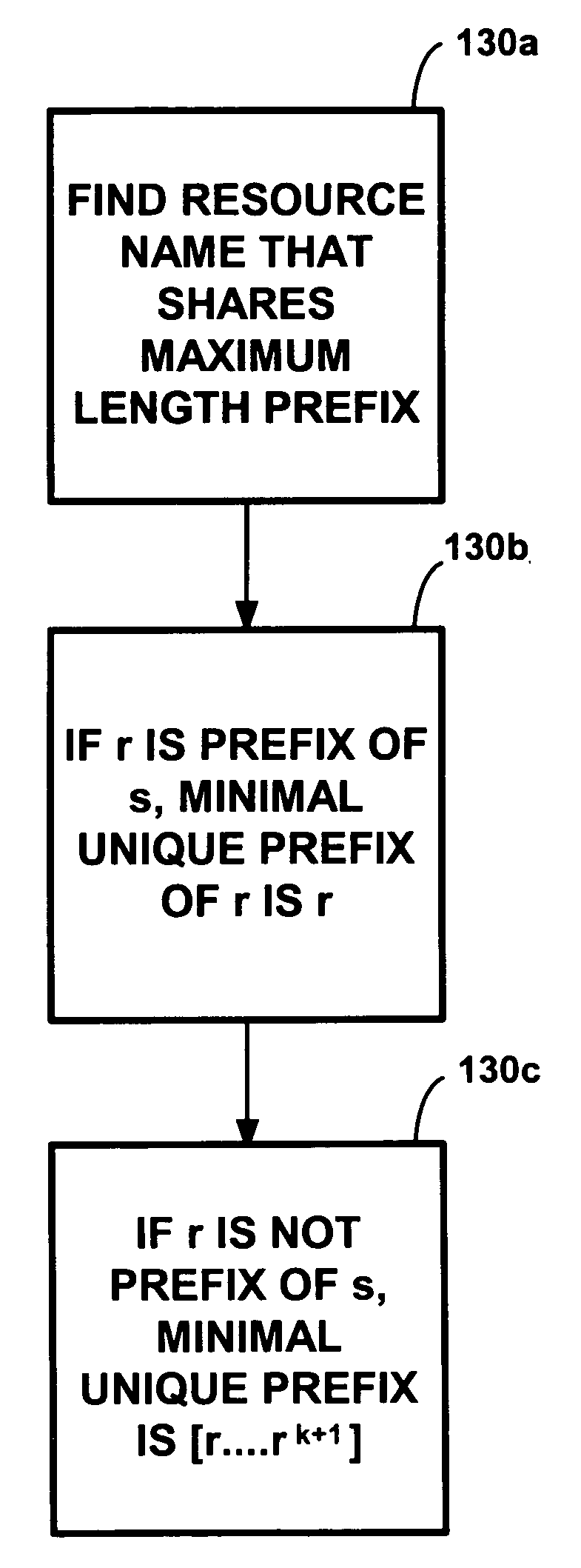
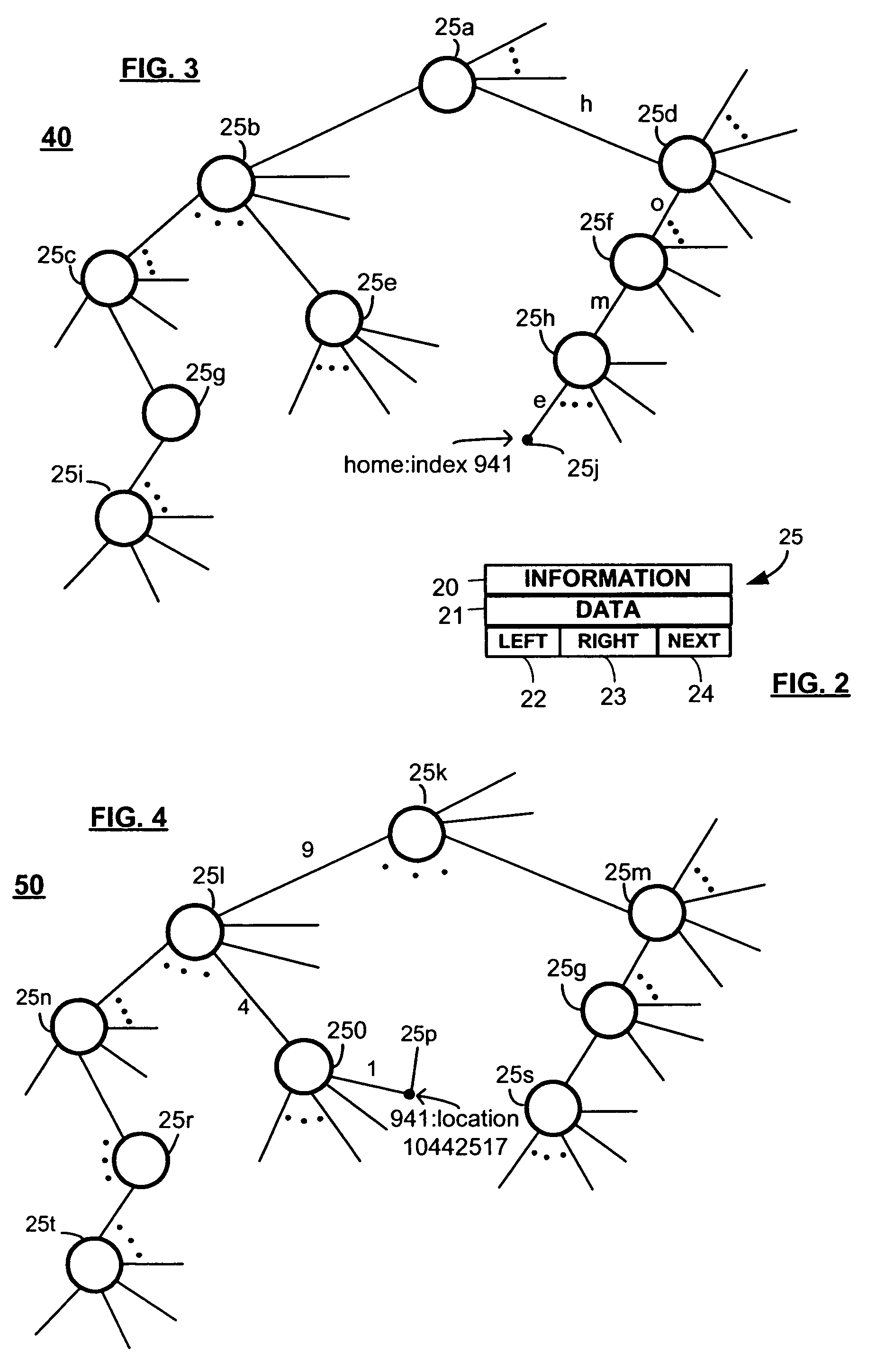
Method for locating digital information files
InactiveUS7013304B1Rapid positioningLess memoryMultiple digital computer combinationsSpecial data processing applicationsImproved methodUniform resource locator
Improved method, data structure and computer readable medium for searching for digital information files. Files referenced by URLs may be quickly located by finding a minimum unique prefix for the desired URL, breaking the prefix into substrings, and traversing a trie data structure to find indices to another trie data structure that will yield the physical location of the stored digital information file. A node data structure may be used to construct the trie data structures, and may be compressed to allow the tries to occupy less memory, thus allowing the tries to be maintained in memory and less access to storage devices. The result is faster retrieval times for digital information files.
Owner:XEROX CORP
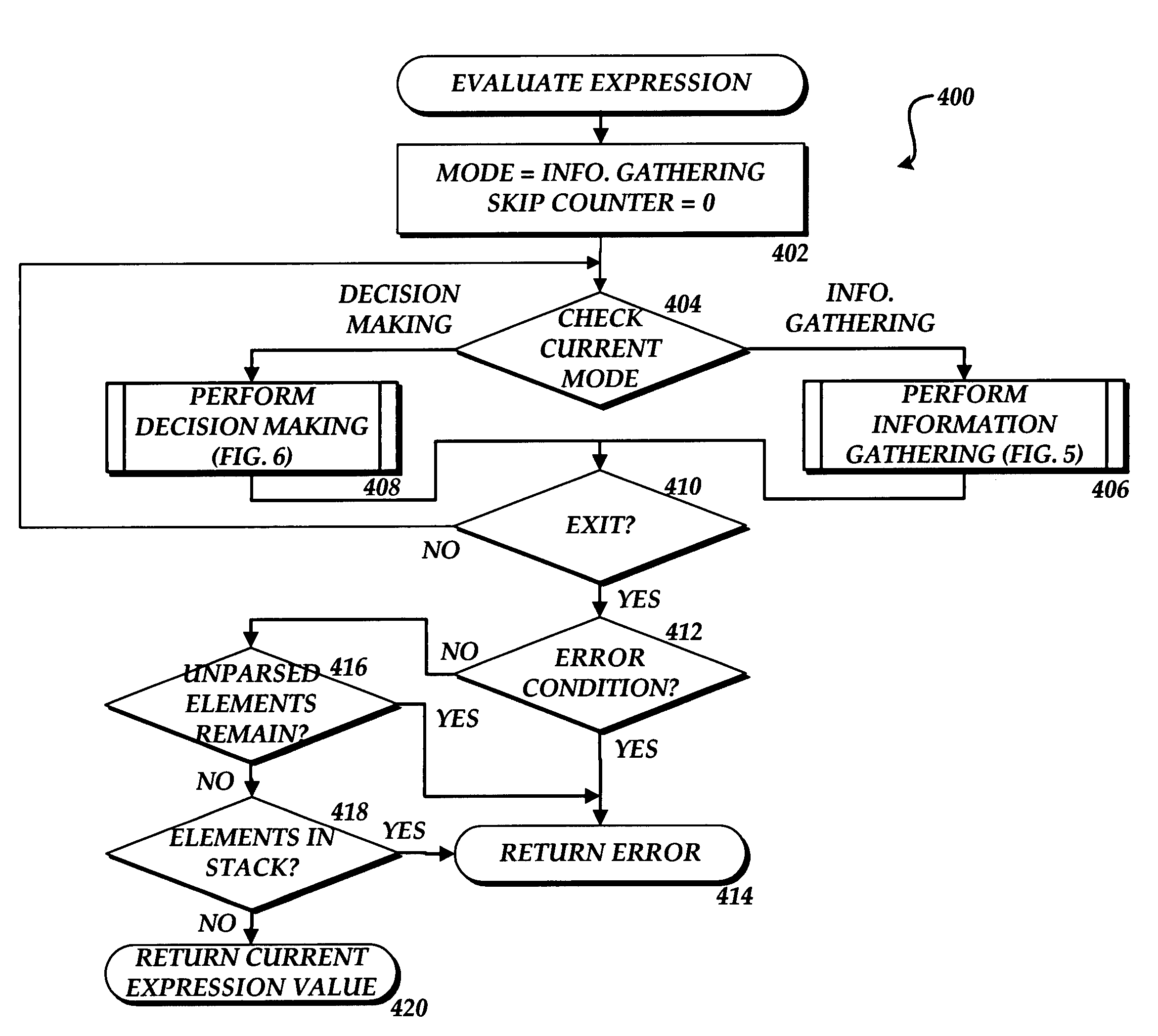
Method, system, and apparatus for efficient evaluation of boolean expressions
ActiveUS7406592B1Effective evaluationEvaluated more quicklySoftware engineeringDigital computer detailsOperandOperating system
Methods, systems, and computer-readable media are provided for efficiently evaluation Boolean expressions. According to the method, the Boolean expression is expressed using pre-fix notation. Each element in the pre-fix expression is then parsed. For each first operand for a Boolean operation, the value of the operand is determined. This may include evaluating a GUID. When an operator and a second operand are encountered, a decision is made as to whether the second operand should be evaluated. The determination as to whether the second operand should be evaluated is made based upon the value of the first operand and the type of operator. If the second operand need not be evaluated, no evaluation is performed thereby saving time and memory space. The evaluation of the Boolean expression continues in this manner until the entire expression has been evaluated. If the Boolean expression is evaluated as true, the program module associated with the Boolean expression may be loaded. Otherwise, the program module will not be loaded.
Owner:AMERICAN MEGATRENDS
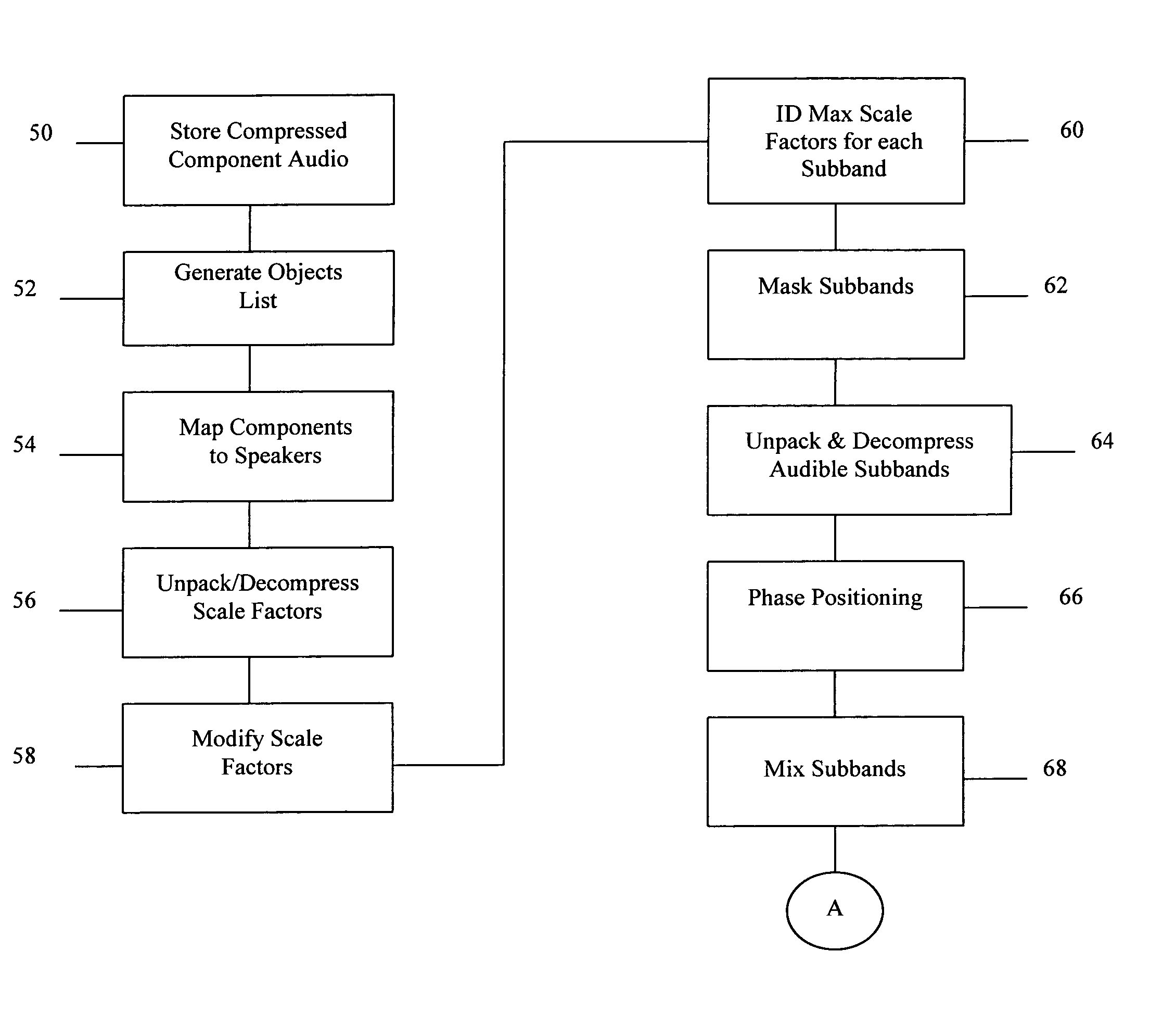
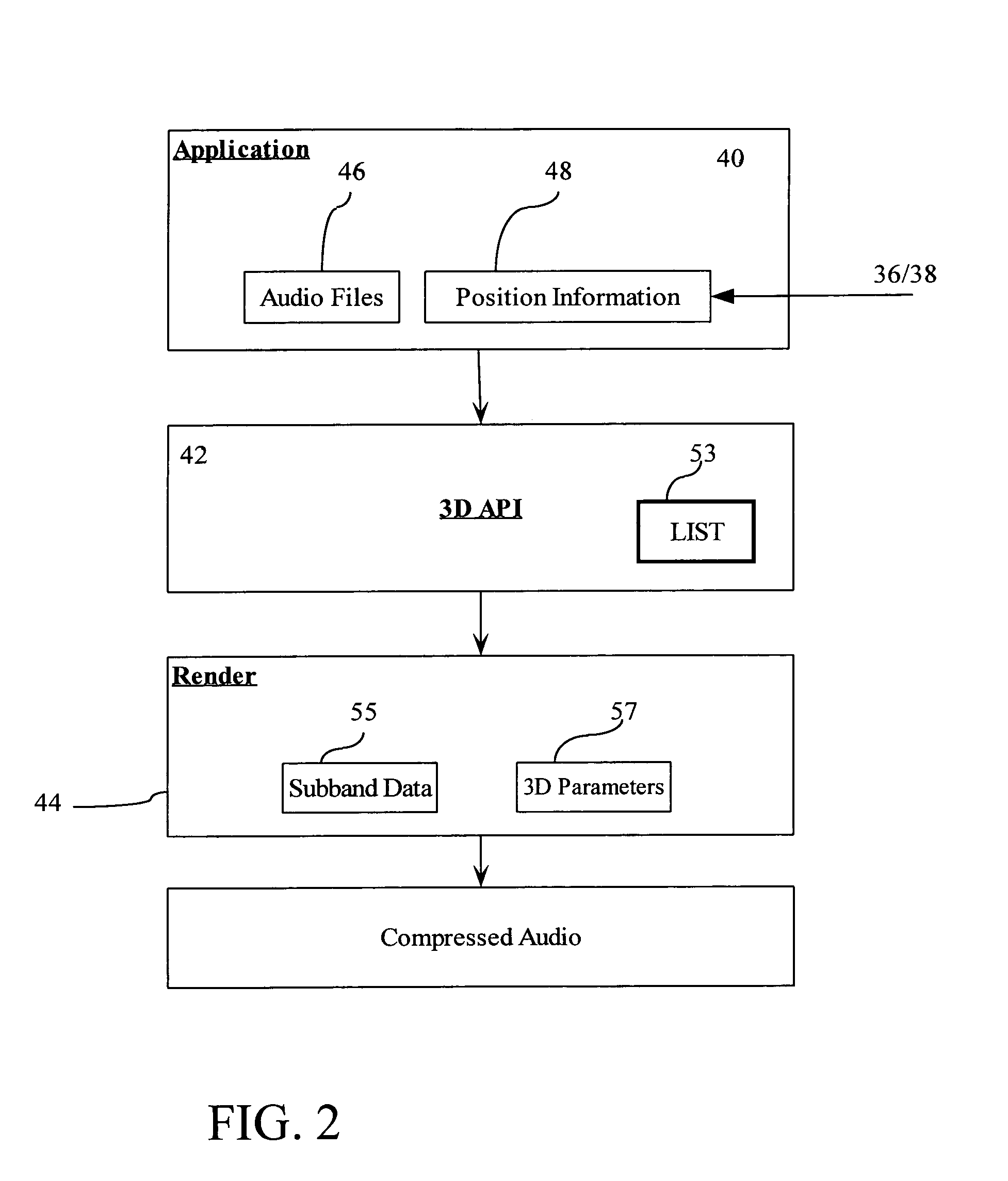
System and method for providing interactive audio in a multi-channel audio environment
InactiveUS6931370B1Low costImprove fidelityFluid pressure measurementPseudo-stereo systemsComputer hardwareVocal tract
DTS Interactive provides low cost fully interactive immersive digital surround sound environment suitable for 3D gaming and other high fidelity audio applications, which can be configured to maintain compatibility with the existing infrastructure of Digital Surround Sound decoders. The component audio is stored and mixed in a compressed and simplified format that reduces memory requirements and processor utilization and increases the number of components that can be mixed without degrading audio quality. Techniques are also provided for “looping” compressed audio, which is an important and standard feature in gaming applications that manipulate PCM audio. In addition, decoder sync is ensured by transmitting frames of “silence” whenever mixed audio is not present either due to processing latency or the gaming application.
Owner:DTS
Method and apparatus for health and disease management combining patient data monitoring with wireless internet connectivity
InactiveUS20050228245A1Maintain abilityLess memoryPhysical therapies and activitiesMechanical/radiation/invasive therapiesOperational systemPatient data
Embodiments of the invention provide a method and apparatus for a wireless health monitoring system for interactively monitoring a disease or health condition of a patient by connecting a mobile phone to or with a digital camera and / or a medical monitoring device. The health related data or visual information from the camera is transmitted to a server using standard internet protocols and may be integrated with various operating systems for handheld or wireless devices, especially those with enhanced capabilities for handing images and visual data.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV +1
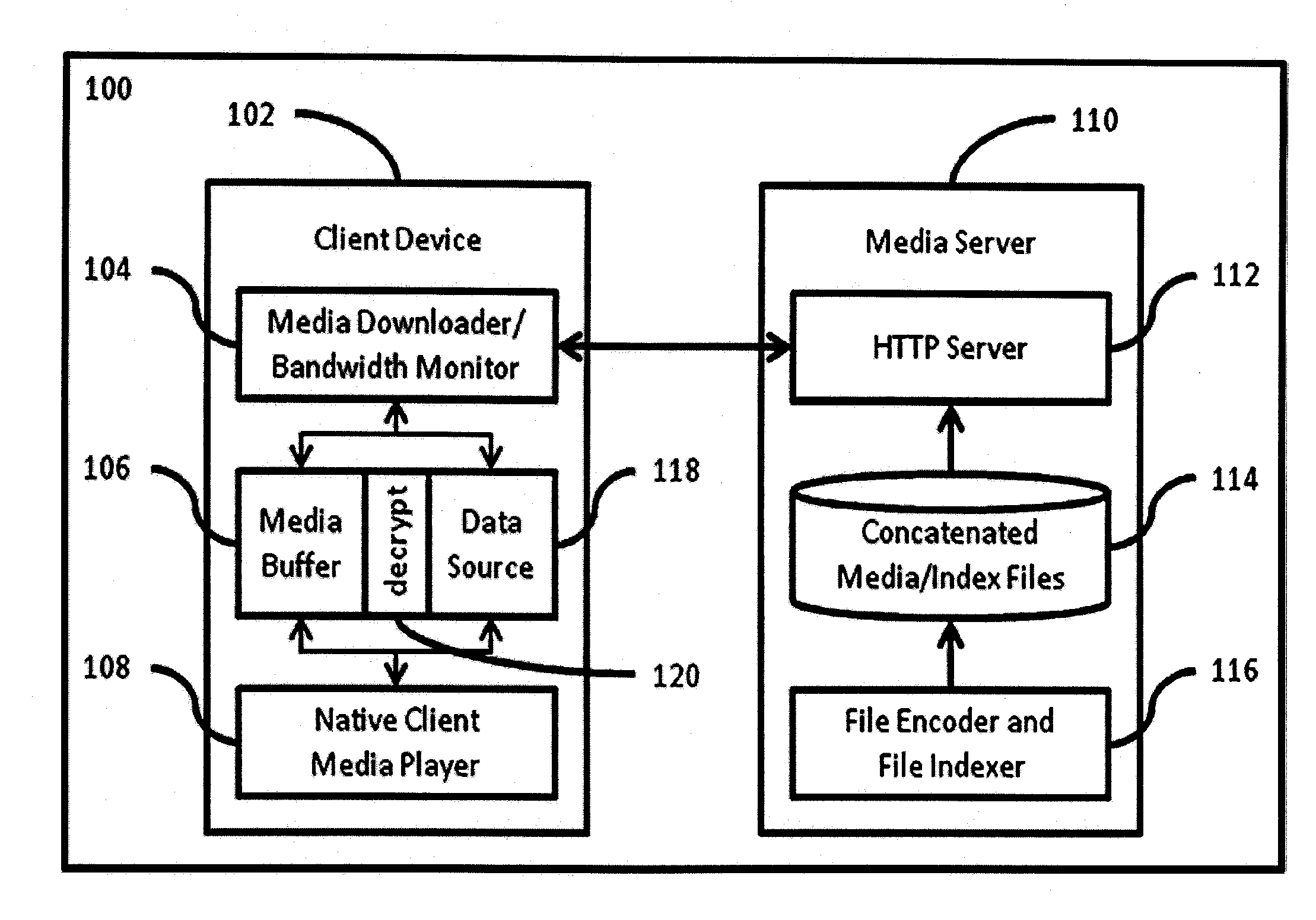
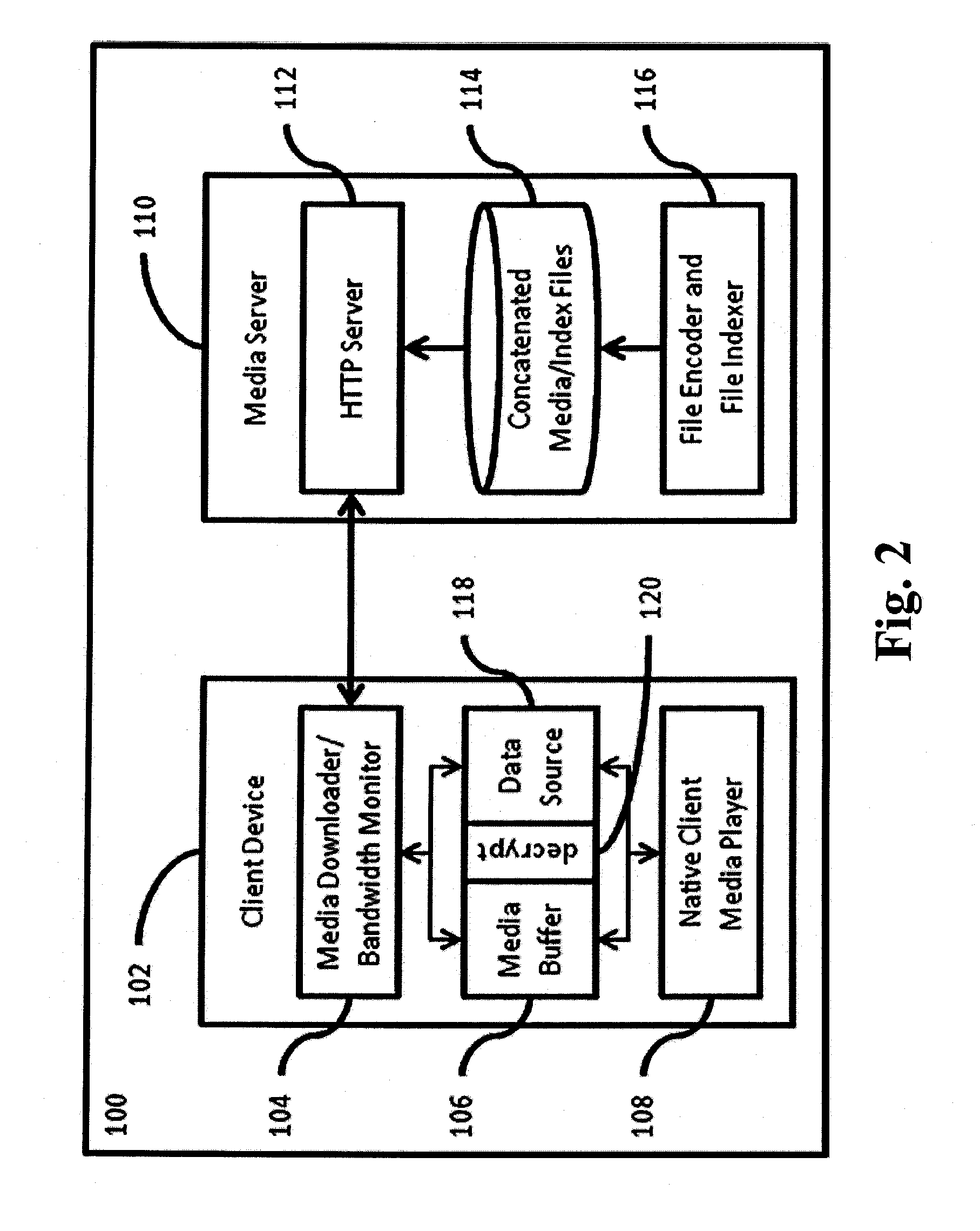
Method and system for efficient streaming video dynamic rate adaptation
ActiveUS20120005365A1Less memorySolve the excessive calculationMultiple digital computer combinationsTransmissionHigh bandwidthRate adaptation
A streaming media system employs dynamic rate adaptation. The method includes a file format compatible with legacy HTTP infrastructure to deliver media over a persistent connection. The method further includes the ability for legacy client media players to dynamically change the encoded delivery rate of the media over a persistent connection. The method provided works transparently with standard HTTP servers, requiring no modification and leverages standard media players embedded in mobile devices for seamless media delivery over wireless networks with high bandwidth fluctuations. A system is also specified for implementing a client and server in accordance with the method.
Owner:TELEFON AB LM ERICSSON (PUBL)
Representing a color gamut with a hierarchical distance field
InactiveUS6483518B1Reduce aliasing artifactReduce the amount requiredDrawing from basic elementsCathode-ray tube indicatorsGamutReconstruction method
The invention provides a method for representing a device color gamut as a detail directed hierarchical distance field. A distance field representing the device color gamut is enclosed with a bounding box. The enclosed distance field is partitioned into a plurality of cells. Each cell has a size corresponding to detail of the continuous distance field and a location with respect to the bounding box. A set of values of the enclosed distance field is sampled for each cell. A method for reconstructing the portion of the distance field enclosed by the cell is specified. The size, the location, the set of values, and the method for reconstructing is stored in a memory to enable reconstruction of the device color gamut by applying the reconstruction methods of the cells to the values.
Owner:MITSUBISHI ELECTRIC RES LAB INC
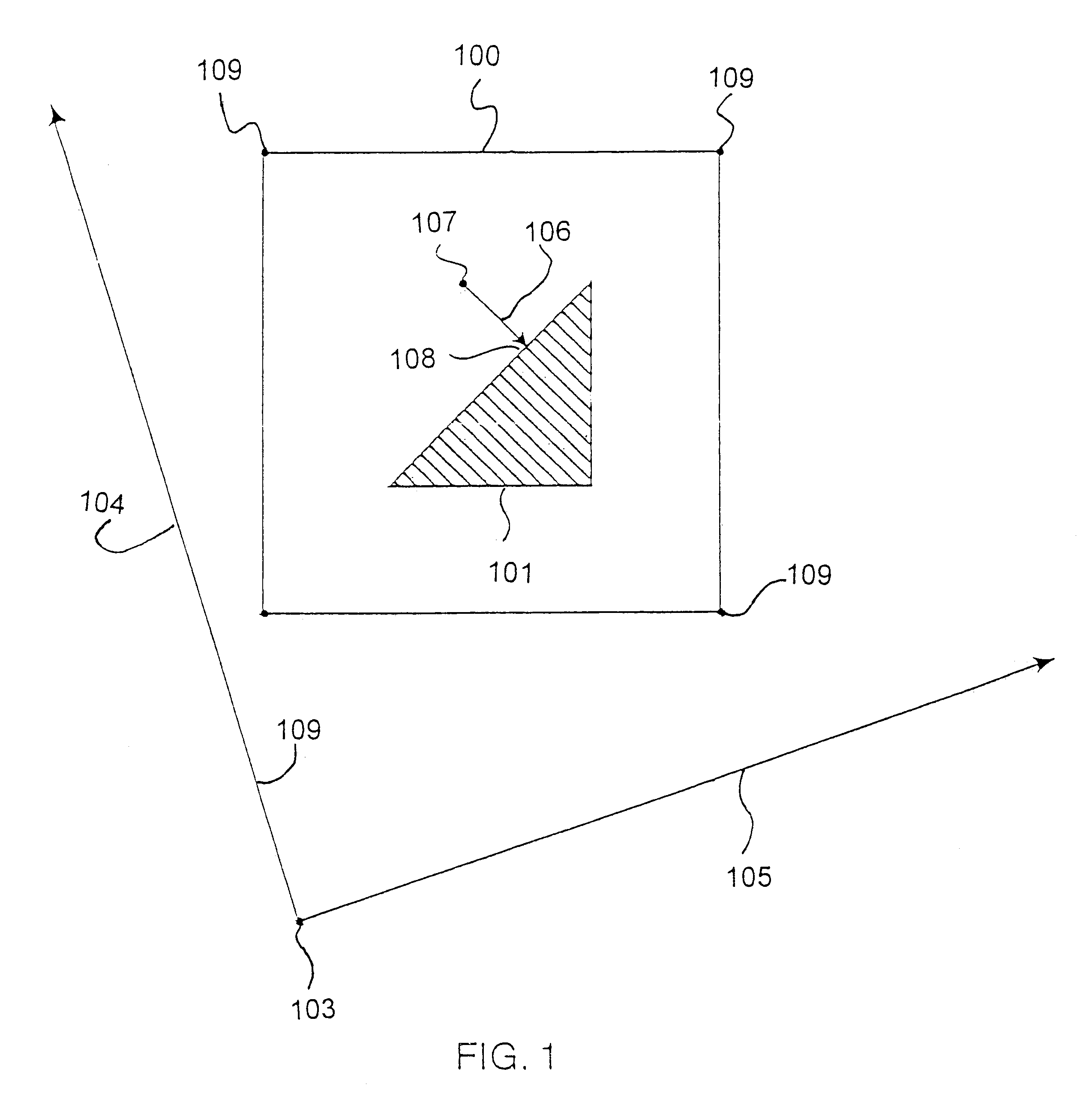
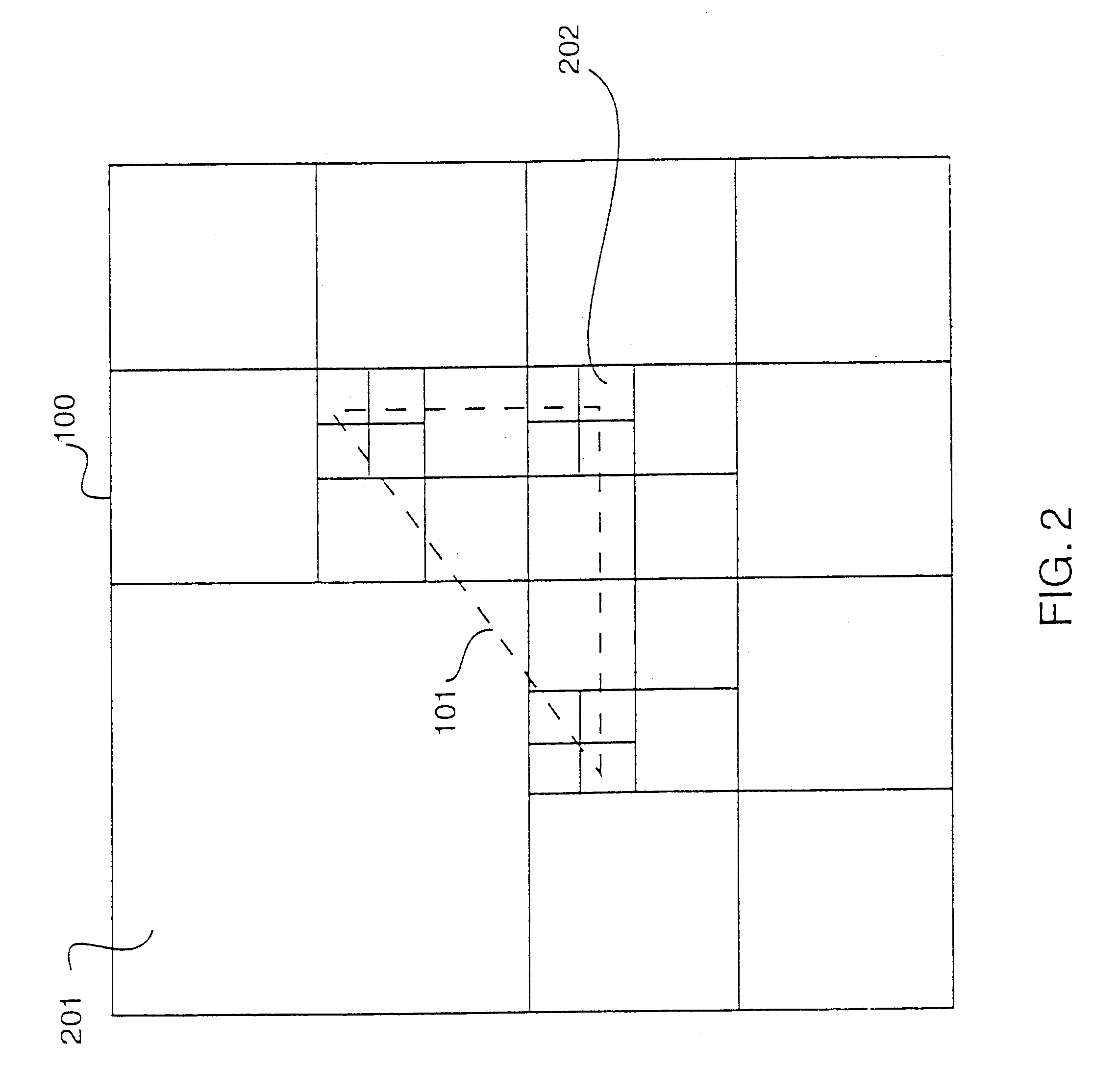
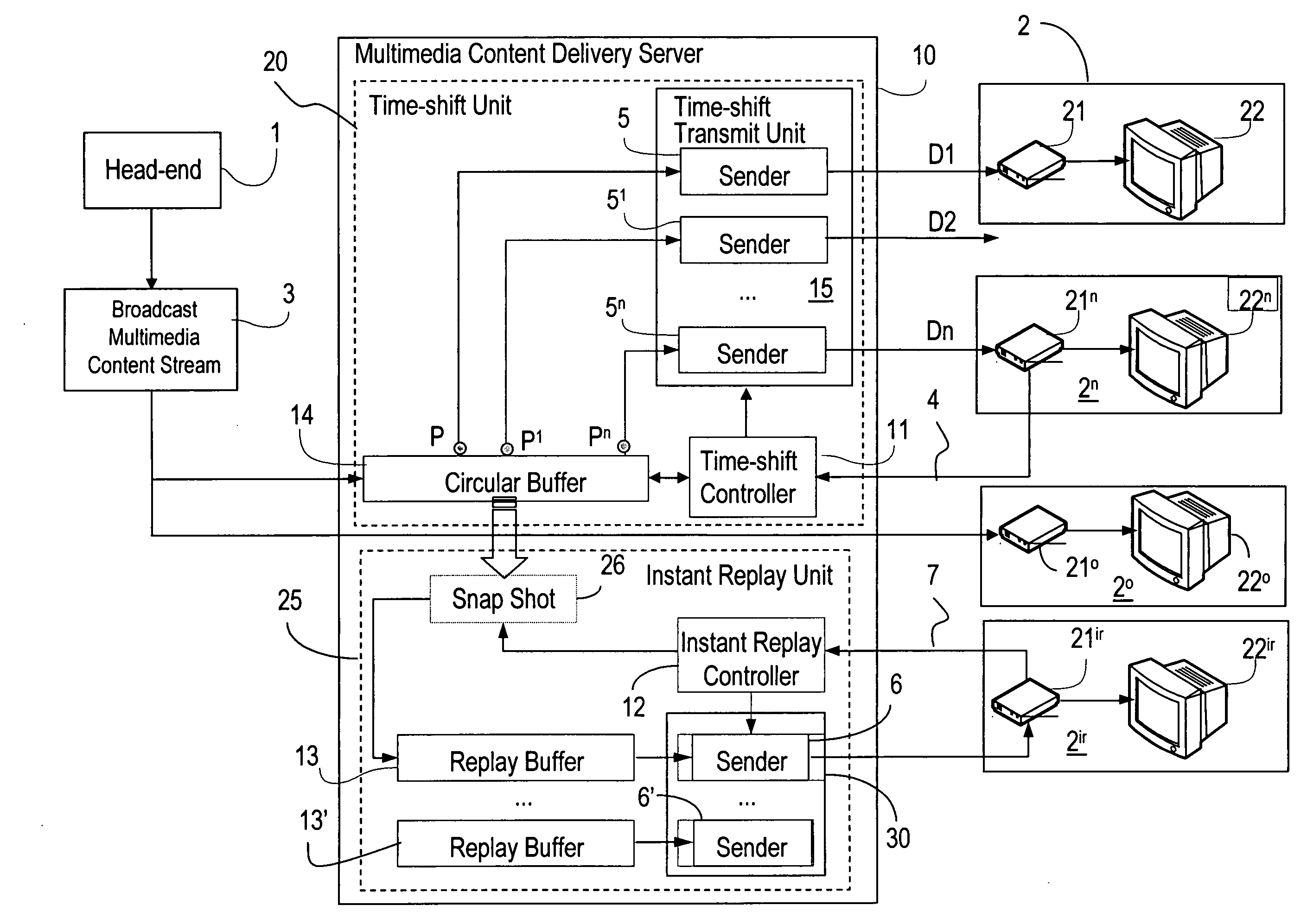
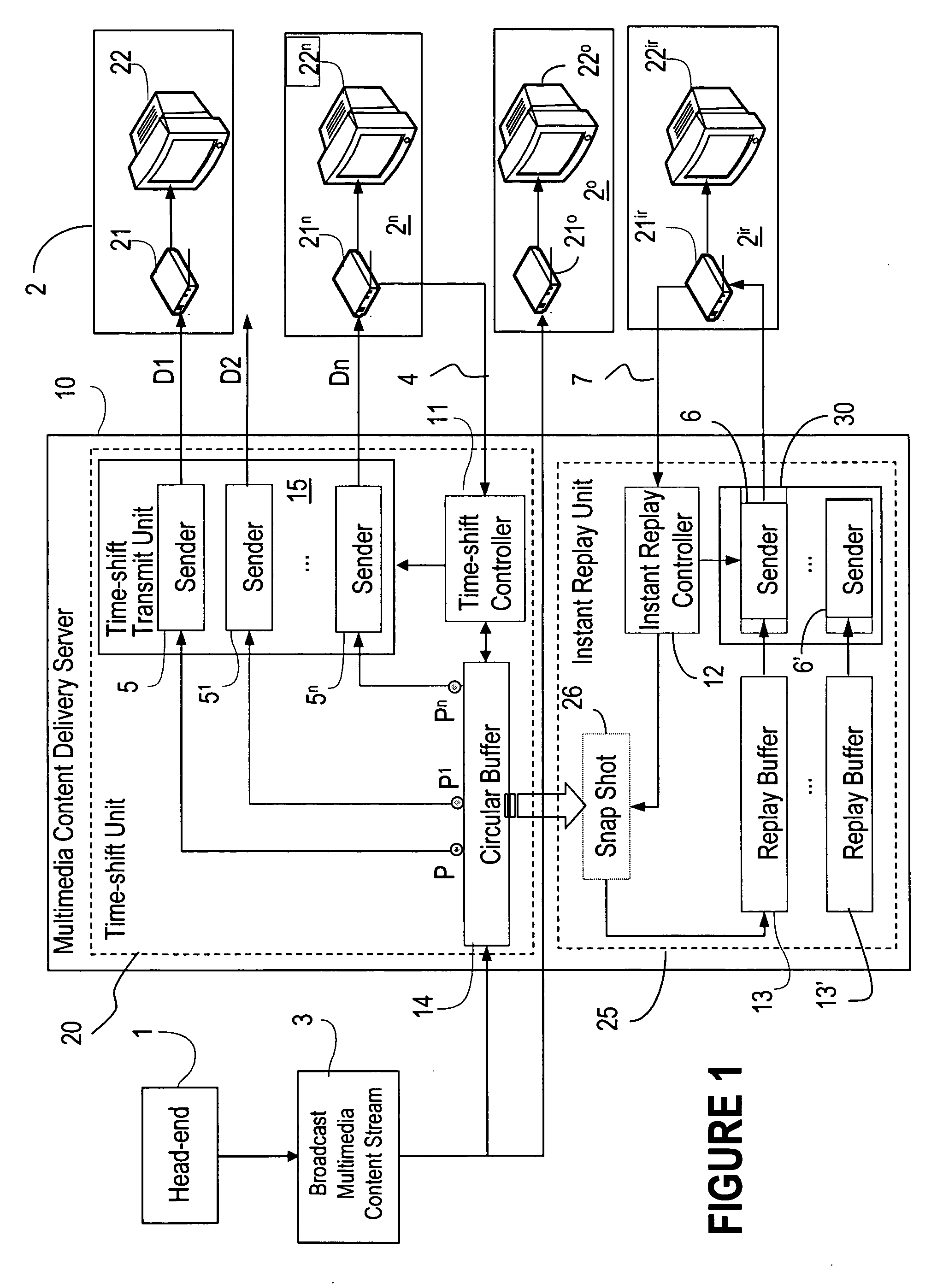
Network based instant replay and time shifted playback
InactiveUS20070130597A1Reduce complexityLess memoryTelevision system detailsBroadcast system return channelsVideo deliveryCircular buffer
A circular buffer in a video delivery server tracks a second copy of a live video stream to provide instant replay capability. When an end-user initiates the instant replay function, the circular buffer is copied to an instant-replay buffer, from which a replay of the video is sent to the end-user. During replay the end-user can use playback functions such as pause, slow-play, freeze frame, etc. Upon leaving the replay function the end user rejoins the live stream. The circular buffer also enables transmission of delayed copies of the live stream, time-shifted by predetermined intervals, which copies are multicasted to end-users. Upon request, an end-user may join a delayed version of interest. This allows the user to replay interesting content by jumping to a time-delayed version without missing the show and to catch up with real-time during e.g. commercial breaks.
Owner:ALCATEL LUCENT SAS
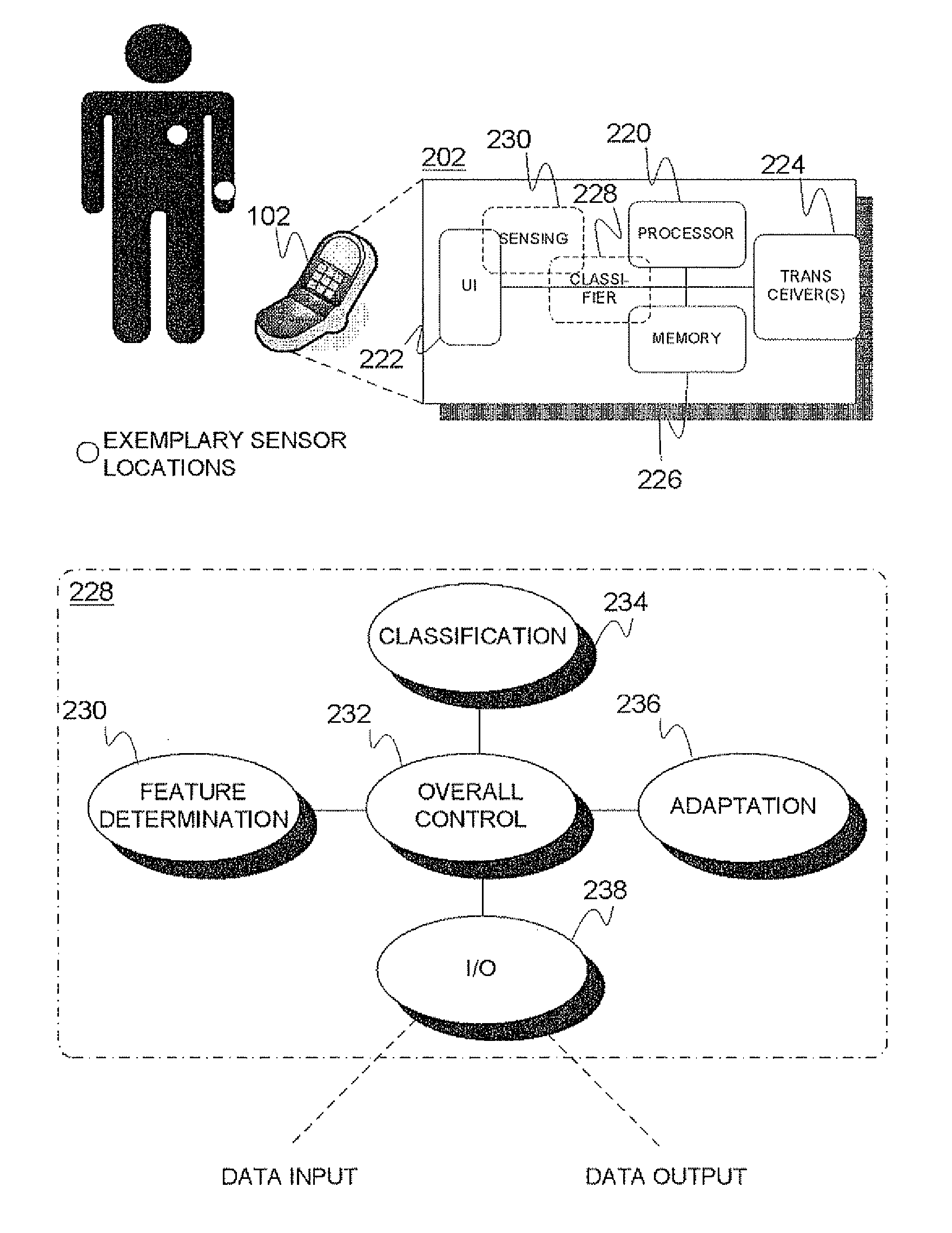
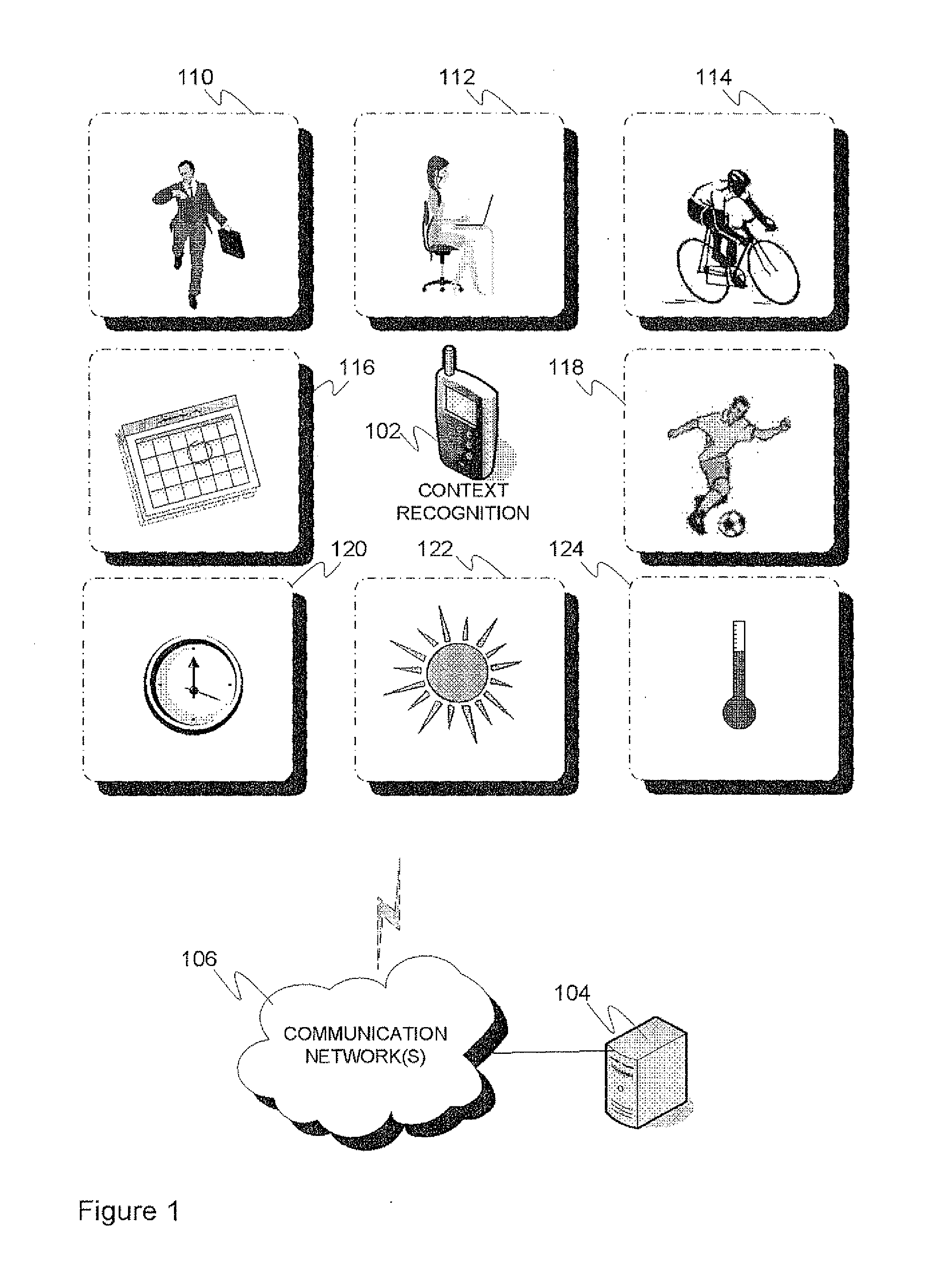
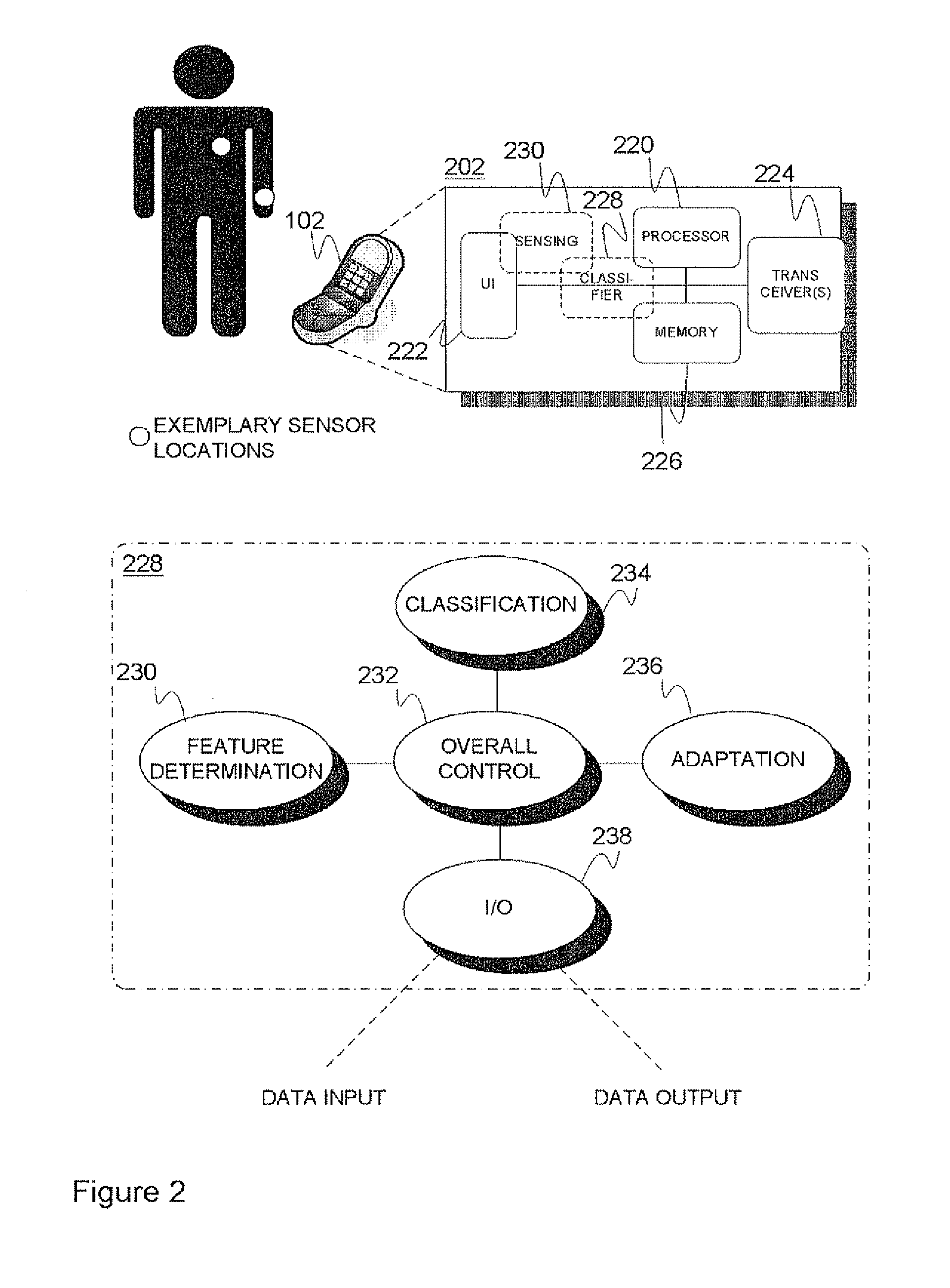
Context recognition in mobile devices
InactiveUS20120059780A1Reduce defectsLess memoryDevices with sensorDigital computer detailsContext recognitionMobile device
Mobile device (102) comprising a number of sensing entities (230) for obtaining data indicative of the context of the mobile device and / or user thereof, a feature determination logic (230) for determining a plurality of representative feature values utilizing the data, and a context recognition logic (228) including an adaptive linear classifier (234), configured to map, during a classification action, the plurality of feature values to a context class, wherein the classifier is further configured to adapt (236) the classification logic thereof on the basis of the feature values and feedback information by the user of the mobile device. A method to be performed by the mobile device is presented.
Owner:TEKNOLOGIAN TUTKIMUSKESKUS VTT
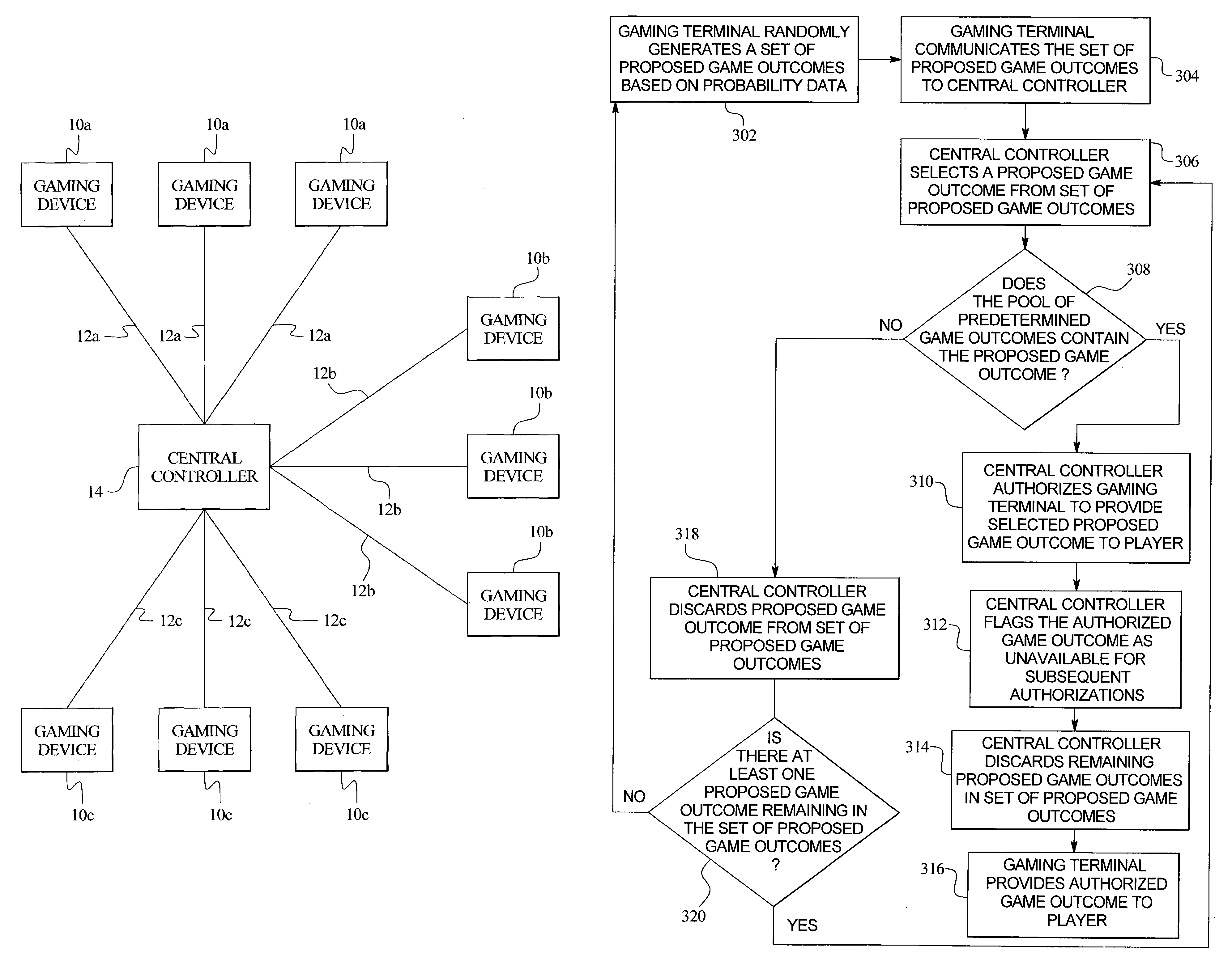
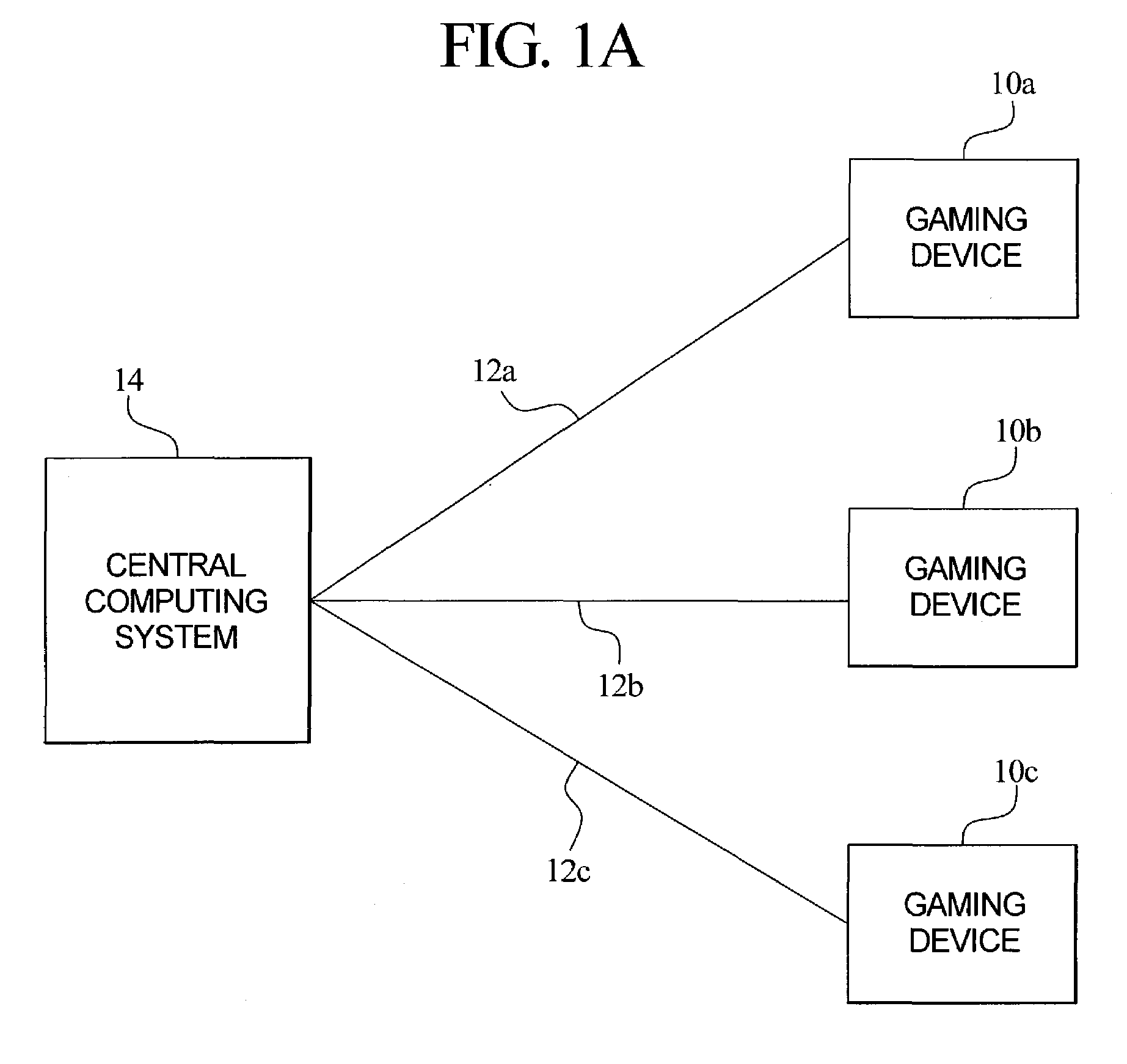
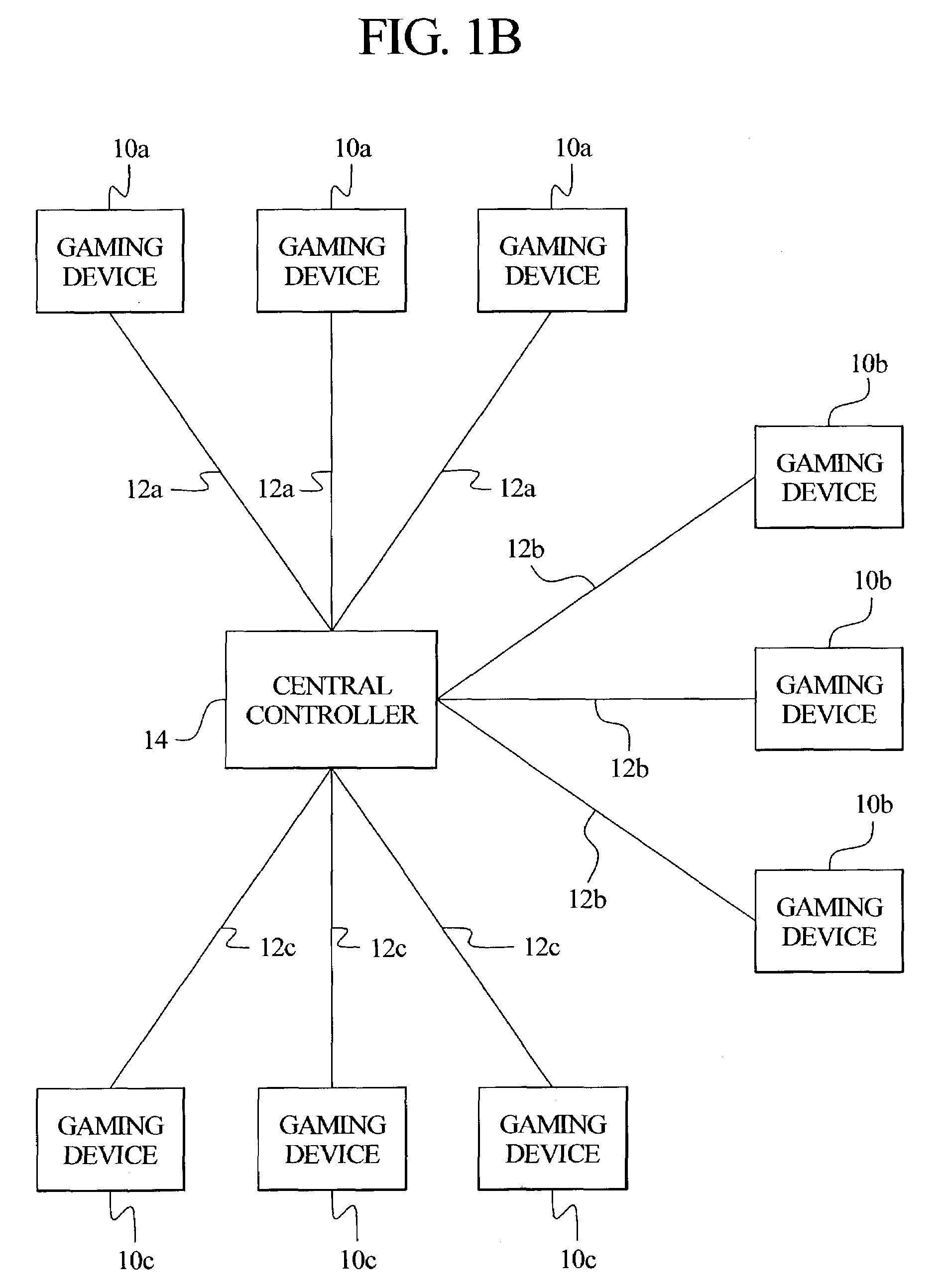
Central determination gaming system with a game outcome generated by a gaming terminal and approved by a central controller
ActiveUS7291069B2Less memoryReduce memory requirementsLottery apparatusApparatus for meter-controlled dispensingEngineeringComputer terminal
A central determination gaming system including a plurality of gaming terminals in communication with a central controller. In one embodiment, upon initiation of a game at one of the gaming terminals, the gaming terminal randomly generates a proposed game outcome. The proposed game outcome is communicated to the central controller. The central controller determines if a pool of predetermined game outcomes includes the proposed game outcome. If the pool includes the proposed game outcome, the central controller authorizes the proposed game outcome to be provided to the player, flags the authorized game outcome from further authorizations and communicates the authorized game outcome to the gaming terminal. The gaming terminal then provides the authorized game outcome to the player. If the pool does not include the proposed game outcome, the central controller discards the proposed game outcome and instructs the gaming terminal to generate another proposed game outcome for authorization.
Owner:IGT
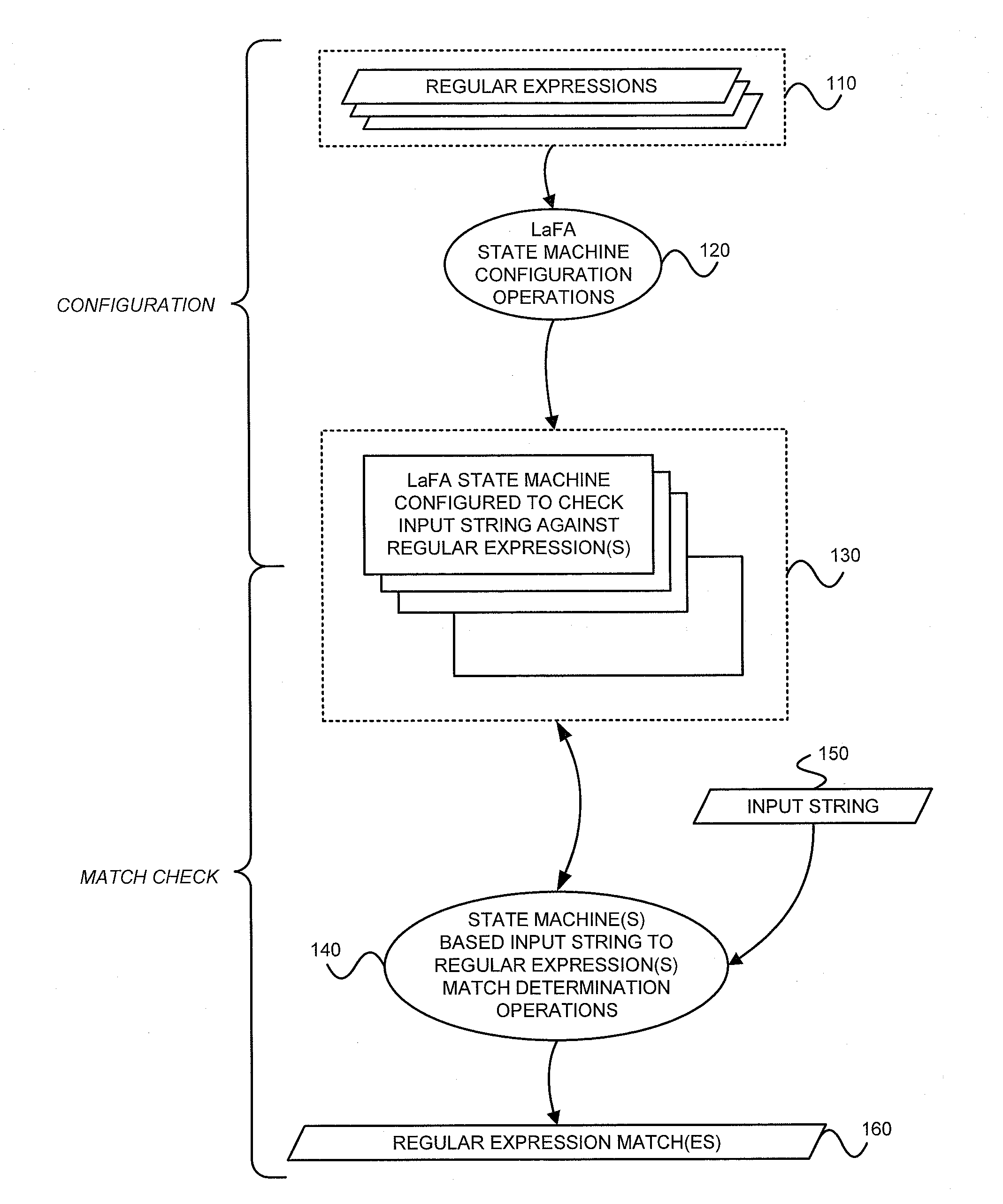
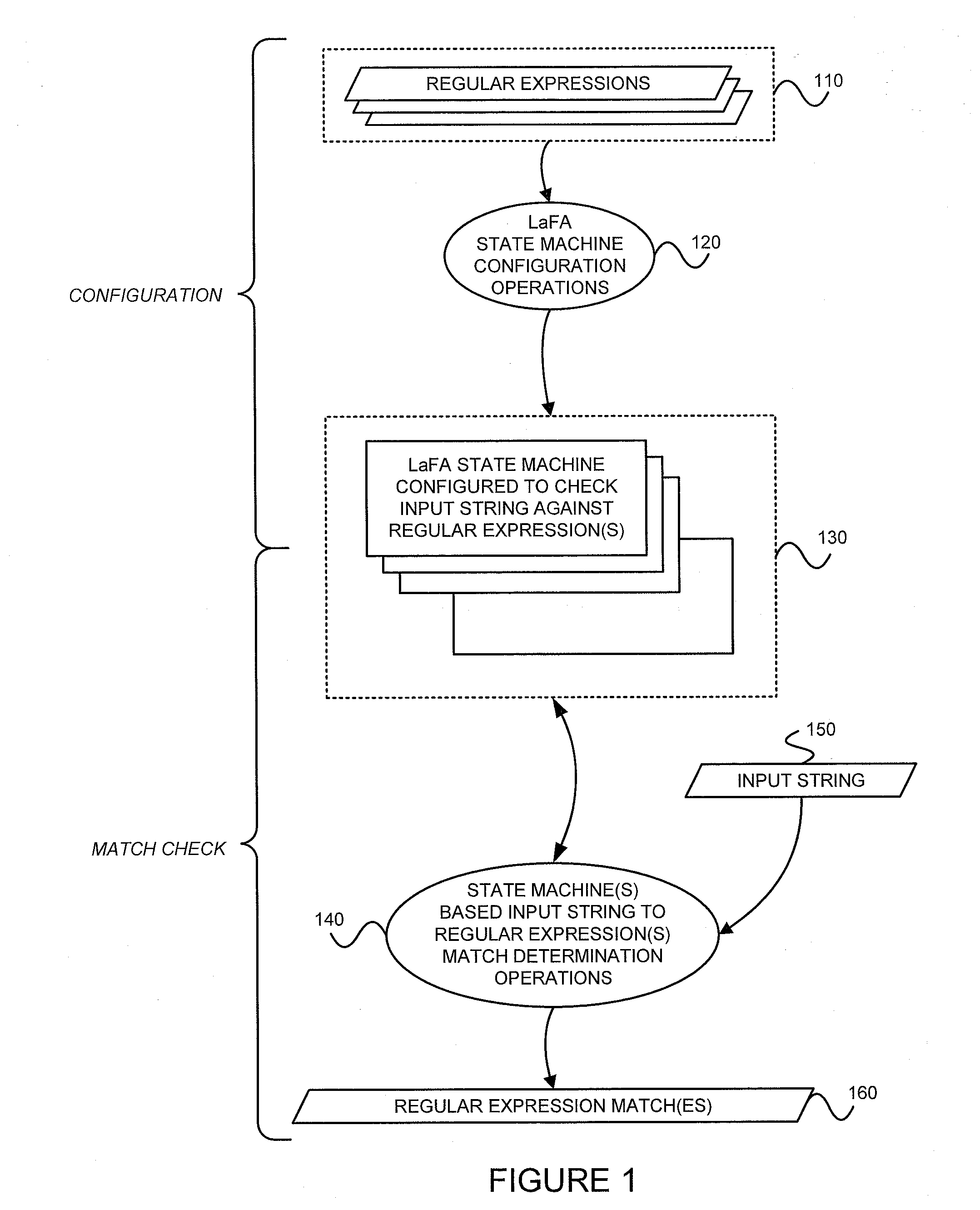
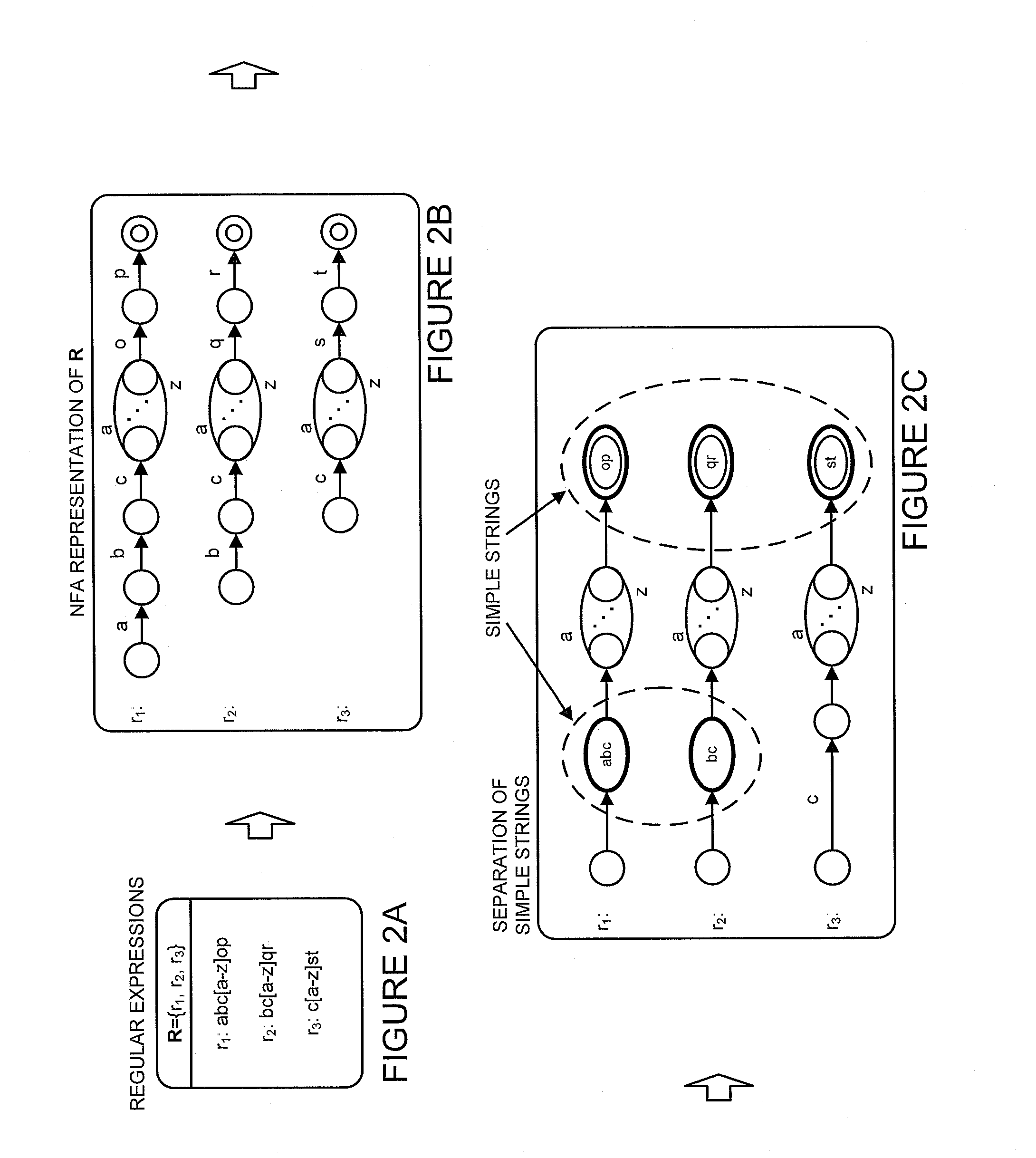
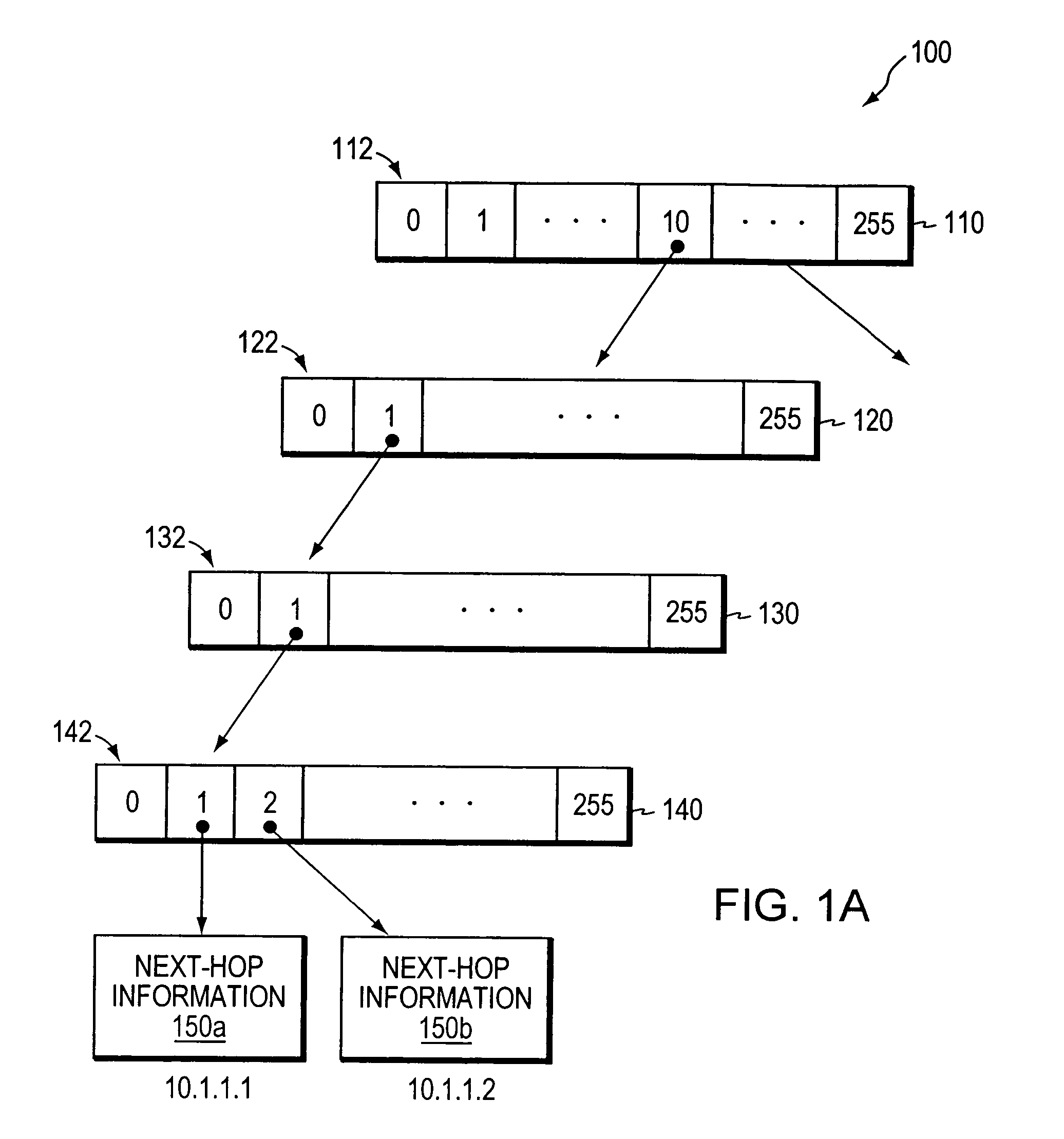
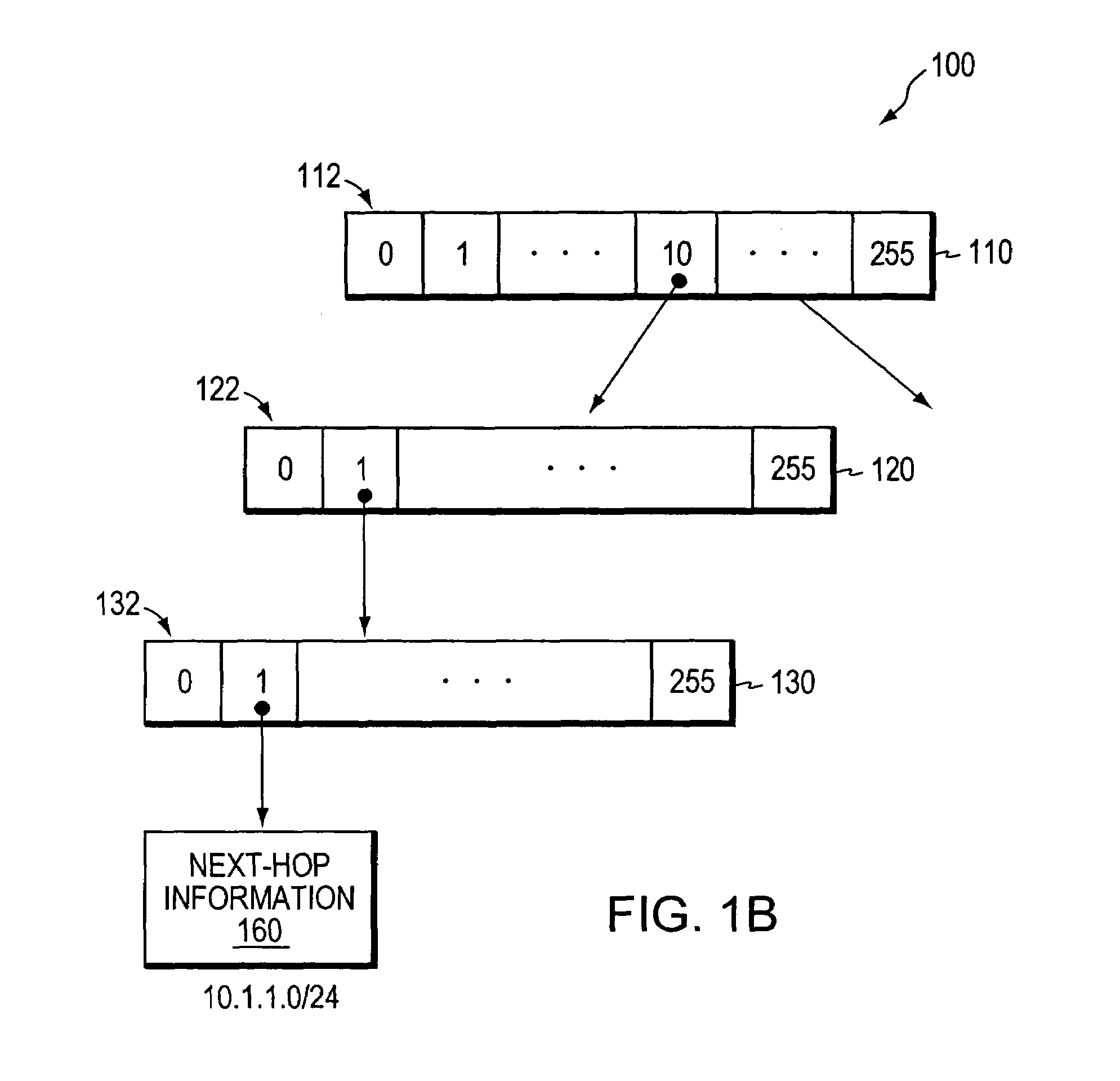
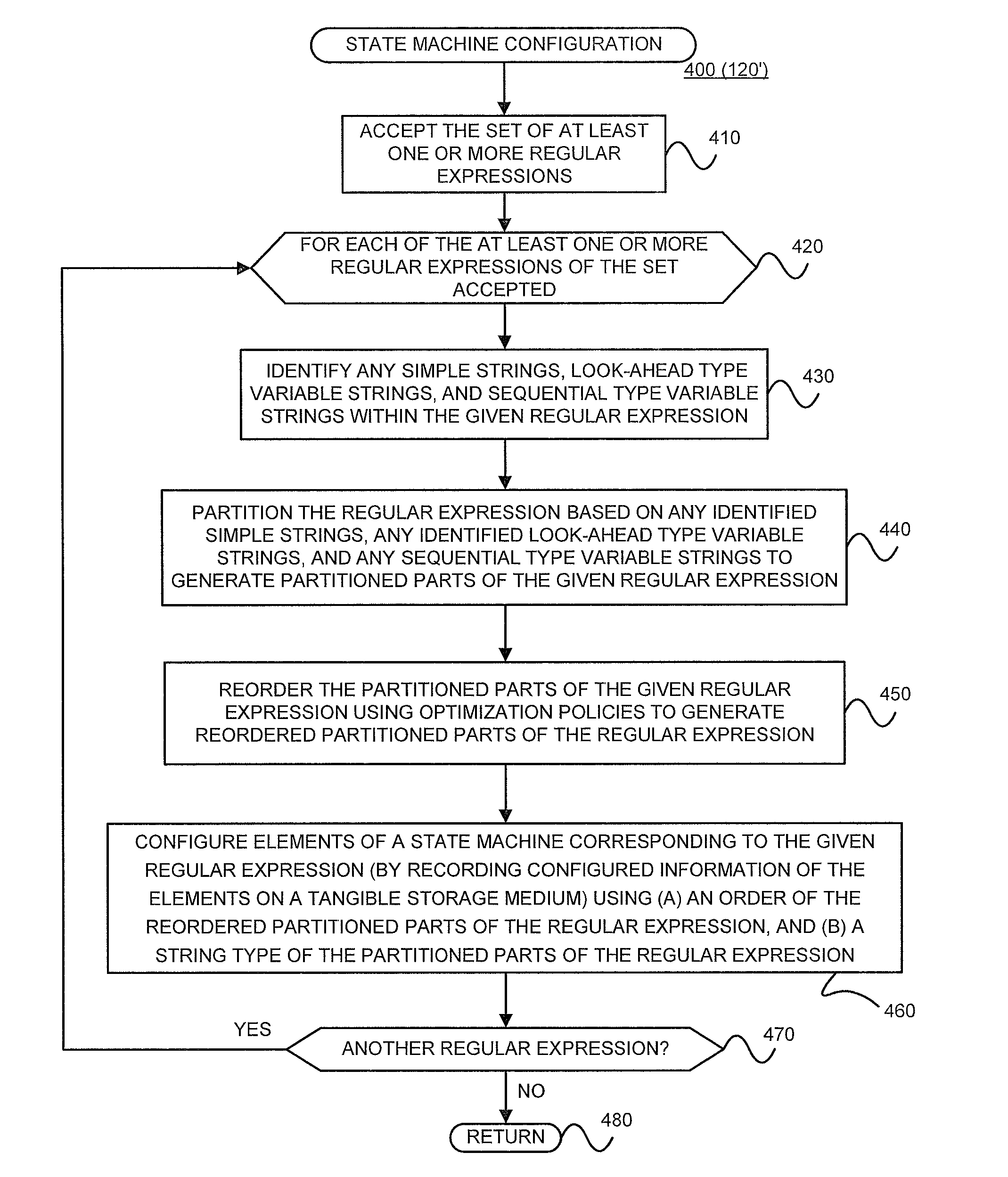
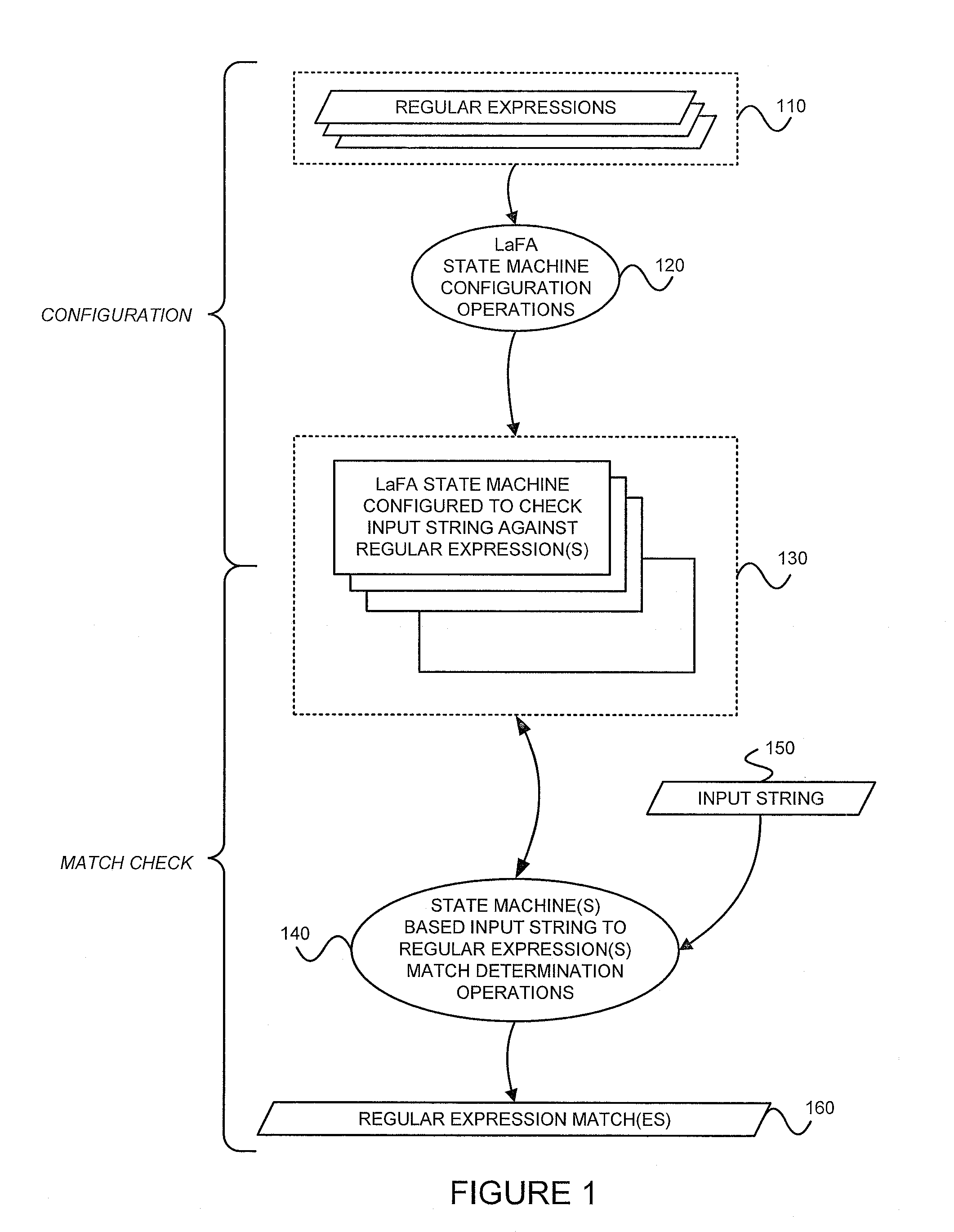
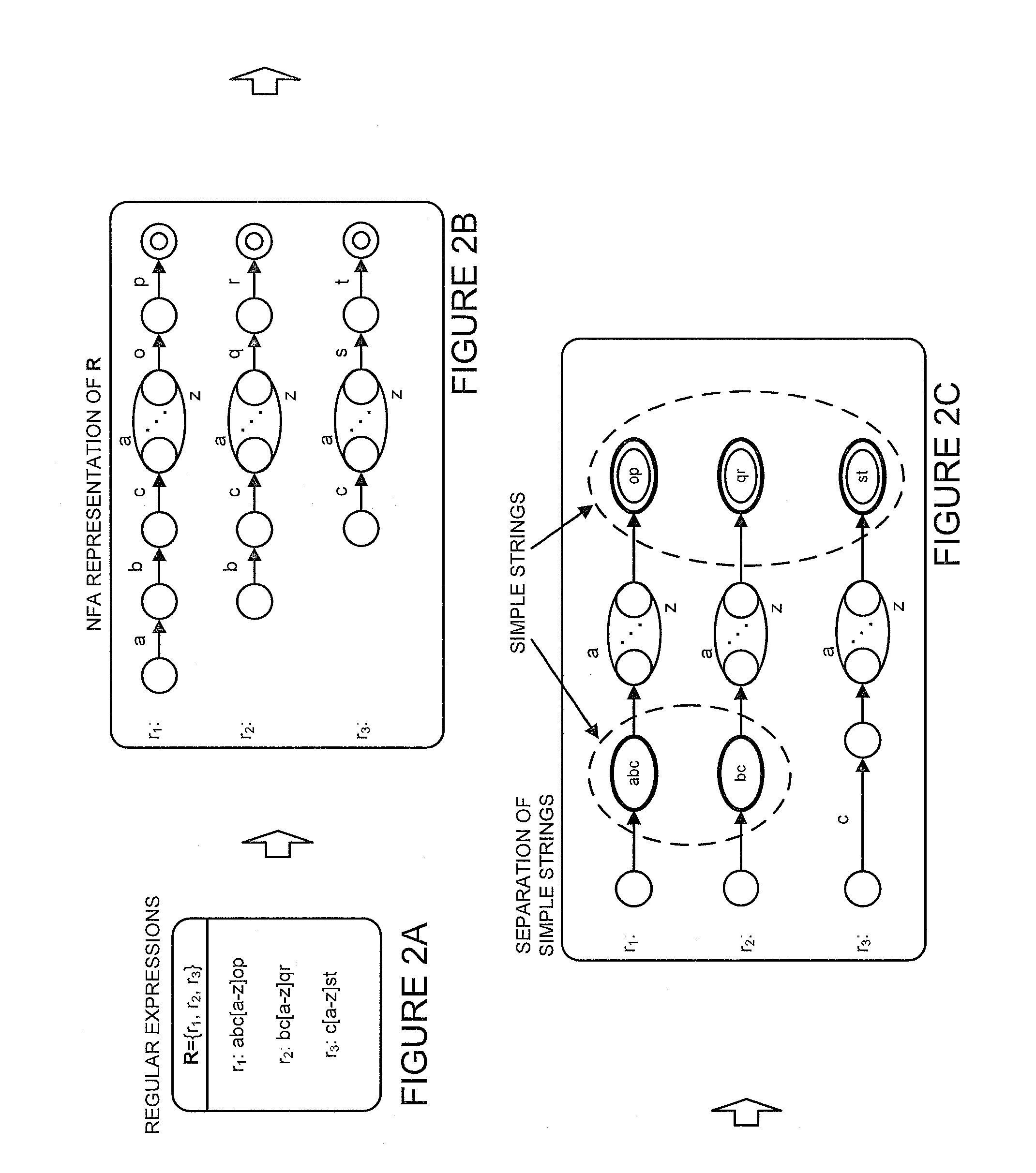
Determining whether an input string matches at least one regular expression using lookahead finite automata based regular expression detection
InactiveUS20110093496A1Small memory requirementLess memoryDigital data information retrievalMemory loss protectionRegular expressionAutomaton
Previously configured state machines may accept an input string, and for each of the regular expression(s), check for a match between the input string accepted and the given regular expression using the configured nodes of the state machine corresponding to the given regular expression. Checking for a match between the input string accepted and the given regular expression using configured nodes of a state machine corresponding to the given regular expression by using the configured nodes of the state machine may include (1) checking detection events from a simple string detector, (2) submitting queries to identified modules of a variable string detector, and (3) receiving detection events from the identified modules of the variable string detector.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
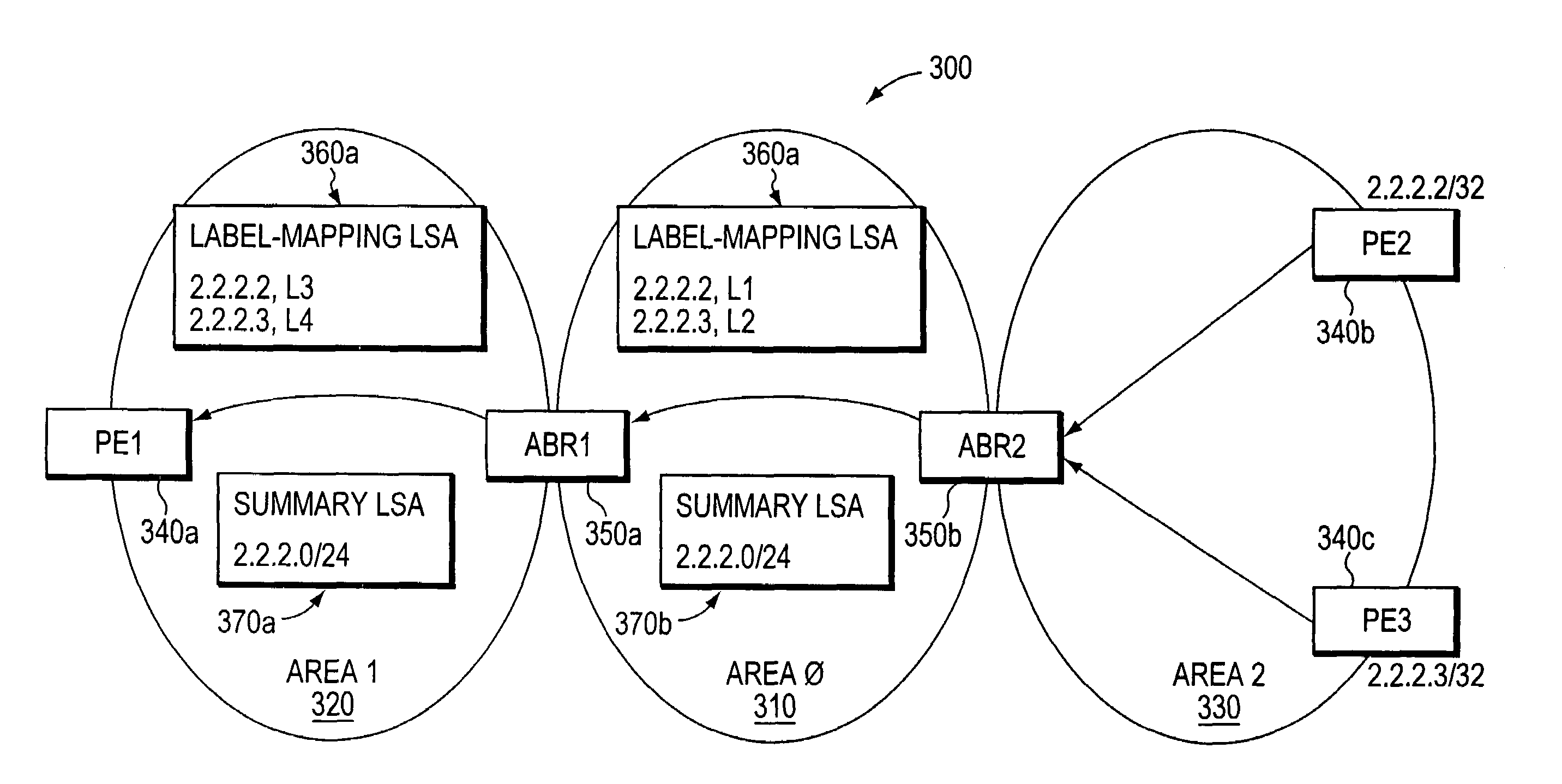
Hierarchical label distribution for inter-area summarization of edge-device addresses
ActiveUS7483387B2Less memoryFaster and efficient routing computationError preventionFrequency-division multiplex detailsDistributed computingEdge device
A system and method are provided for separately distributing edge-device labels and routing information across routing areas of a computer network. Because the edge-device labels are distributed separately from network routing information, the process of distributing the edge-device labels does not preclude conventional edge-device address summarizations. Illustratively, a novel “label mapping” LSA is employed for distributing the edge-device labels across routing areas. The label-mapping LSA may be embodied as an area-scope OSPF opaque LSA (type 10) or an IS-IS LSP containing TLVs of area scope. Advantageously, the present invention is generally applicable whenever label values are allocated to edge devices in a multi-area computer network and data is “tunneled” through the network from one edge device to another.
Owner:CISCO TECH INC
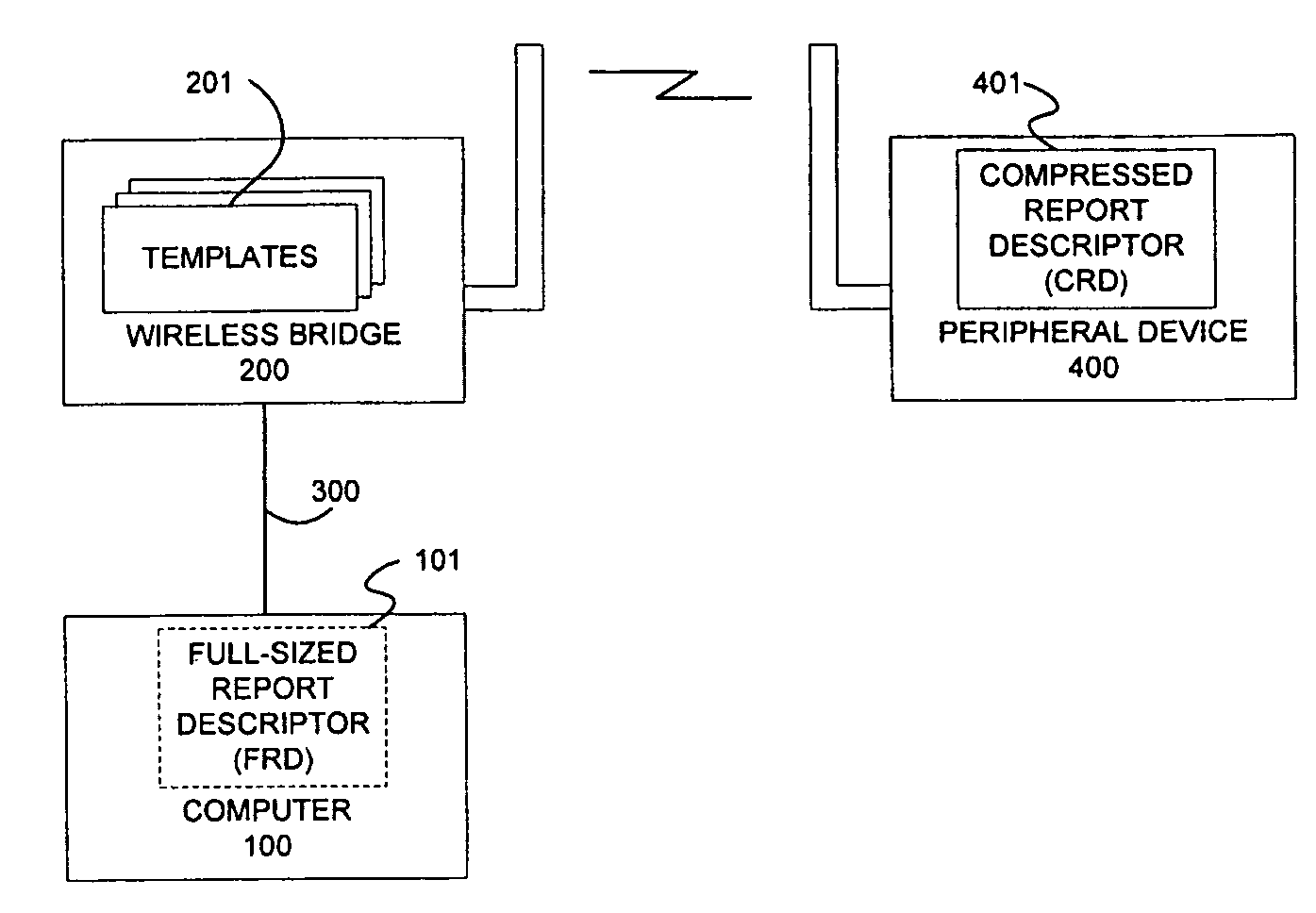
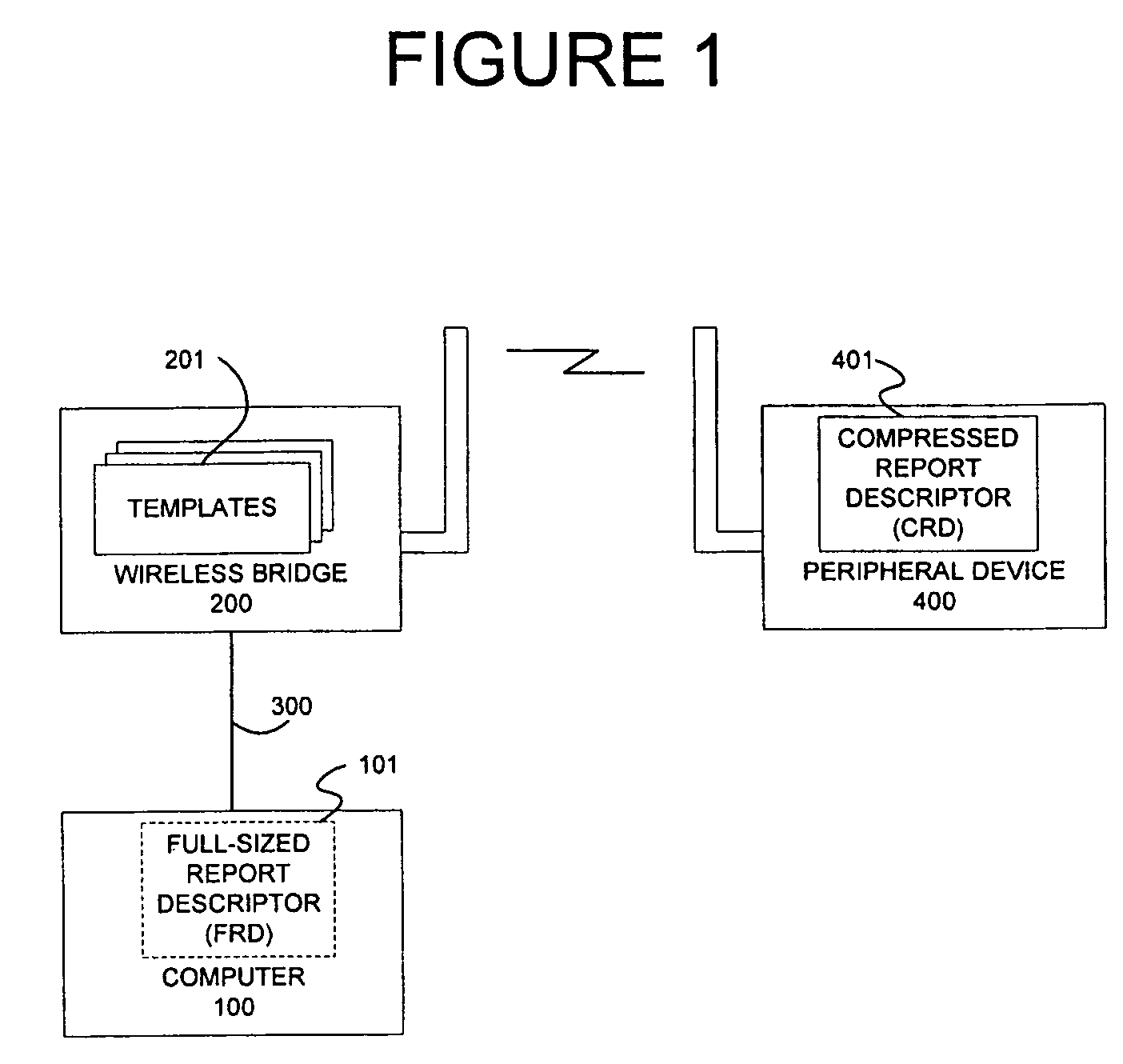
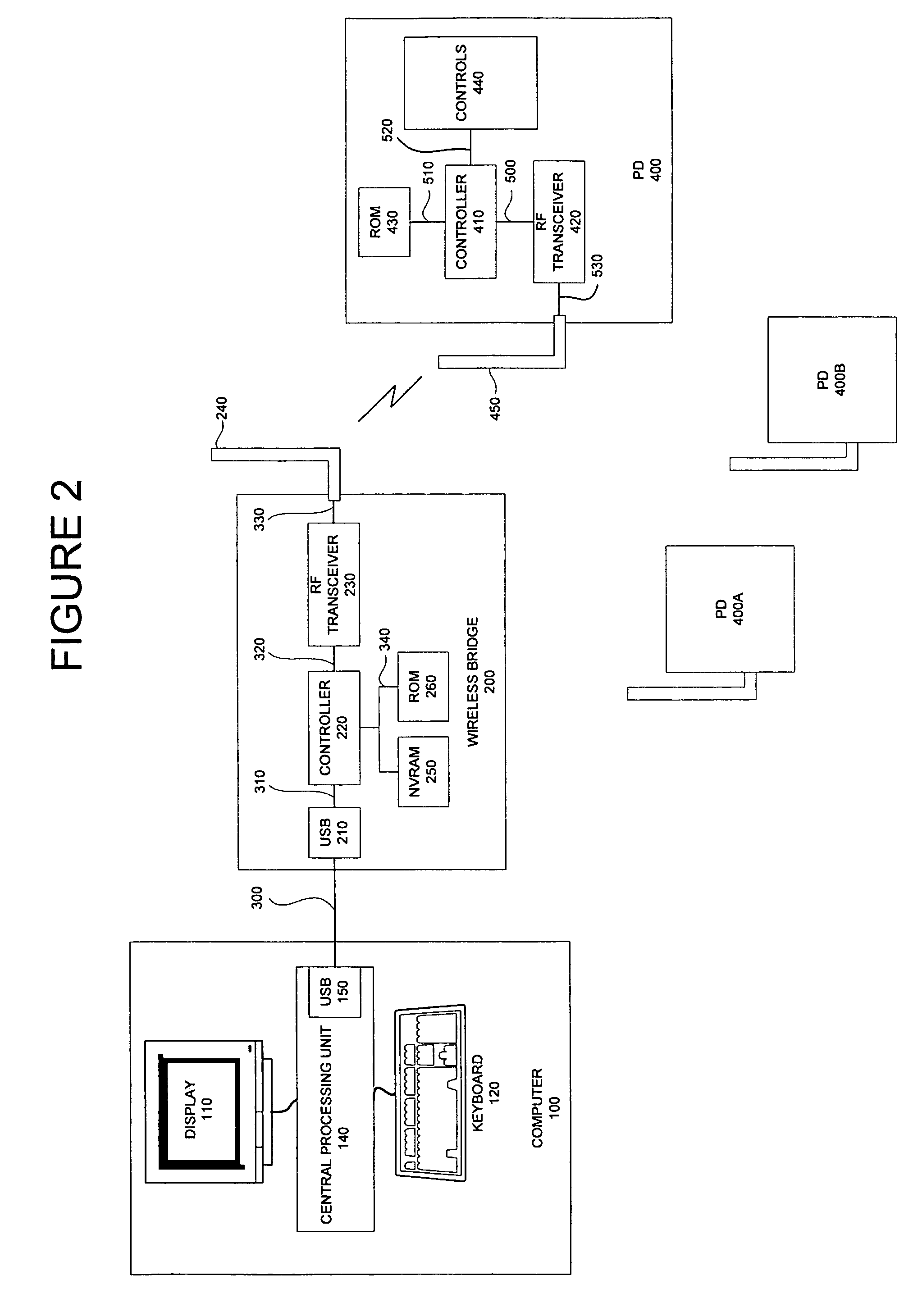
Compressed report descriptors for USB devices
ActiveUS7356635B2Less memory spaceLess timeEnergy efficient ICTEnergy efficient computingUSBComputer science
Owner:CYPRESS SEMICON CORP
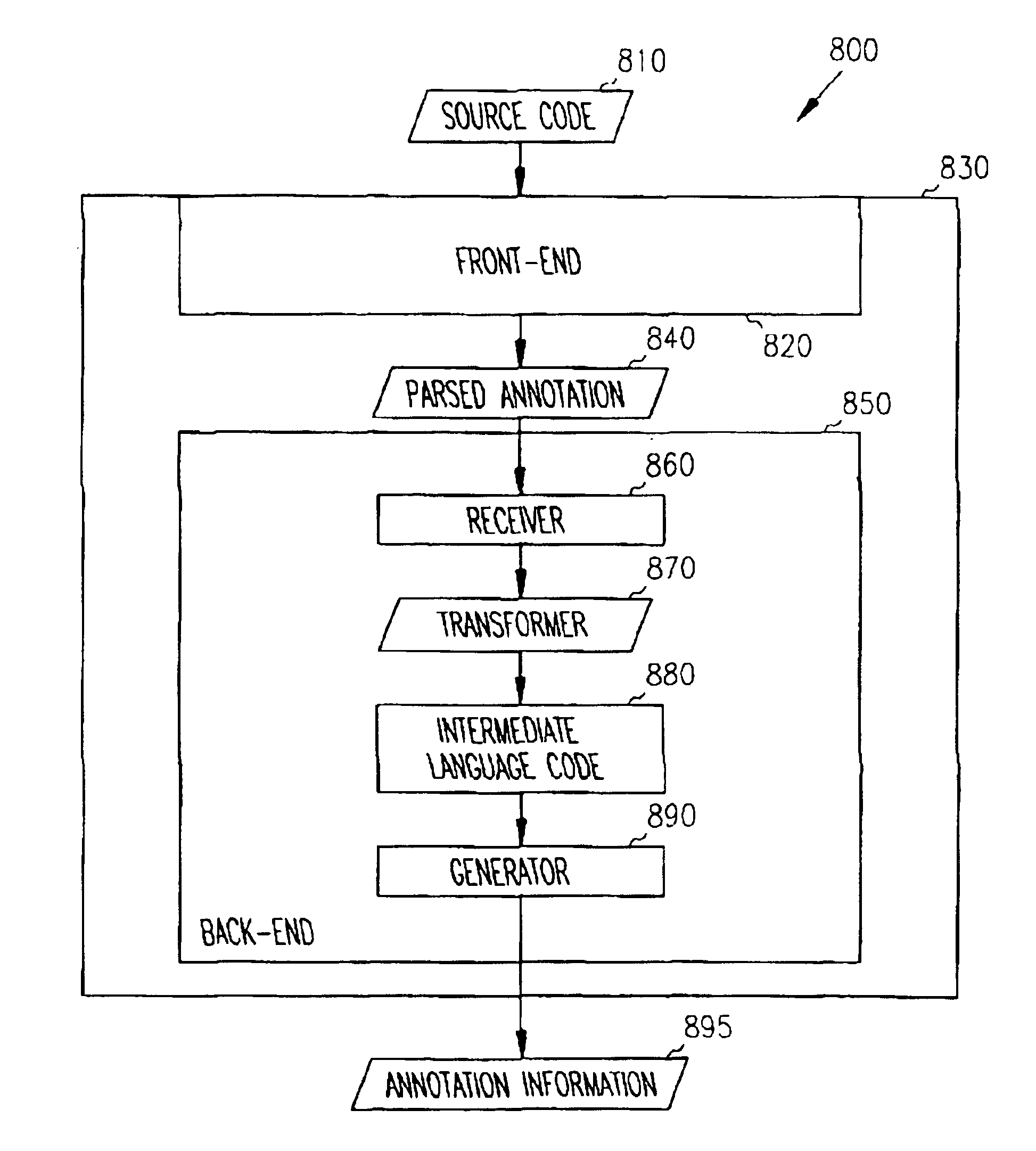
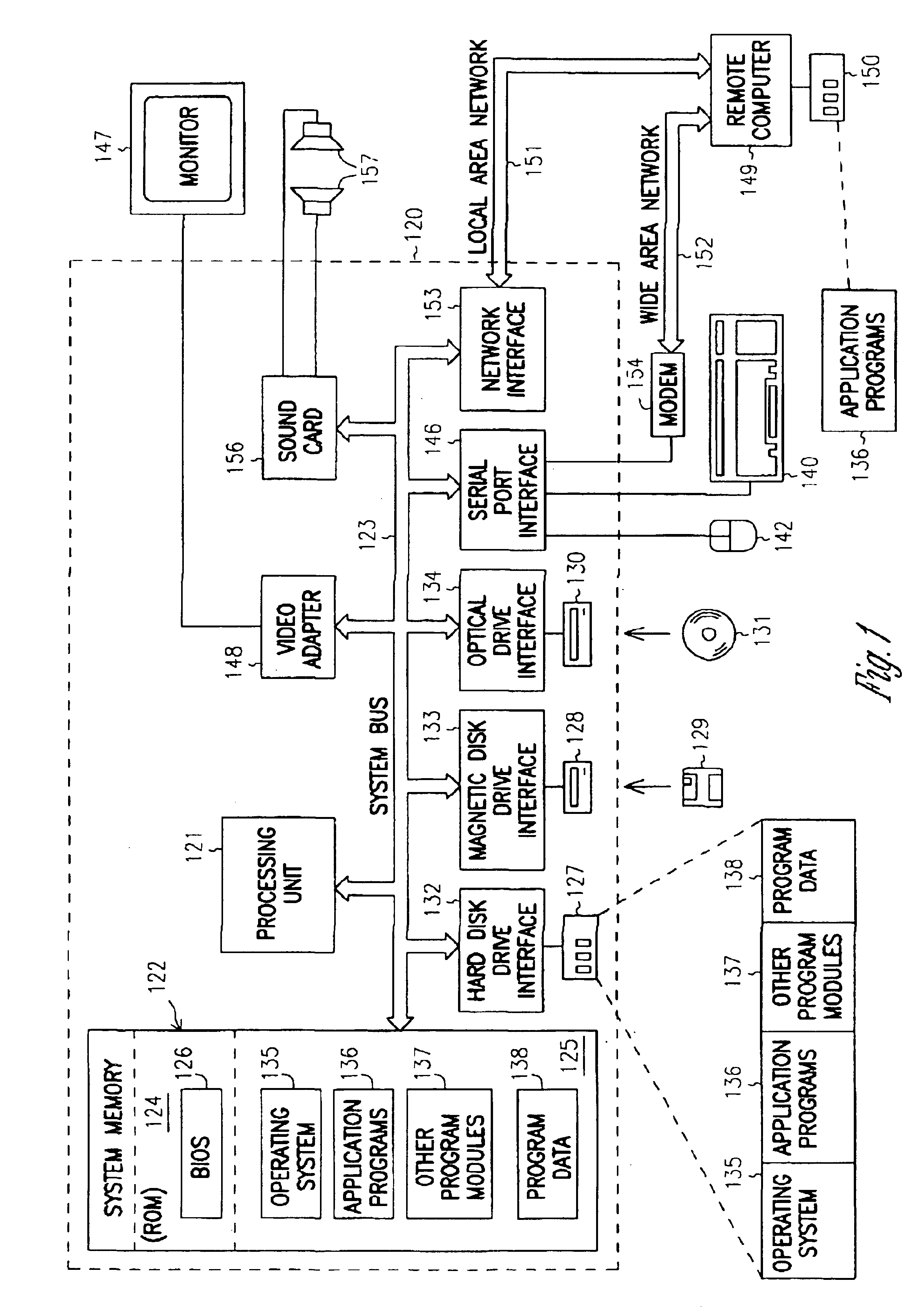
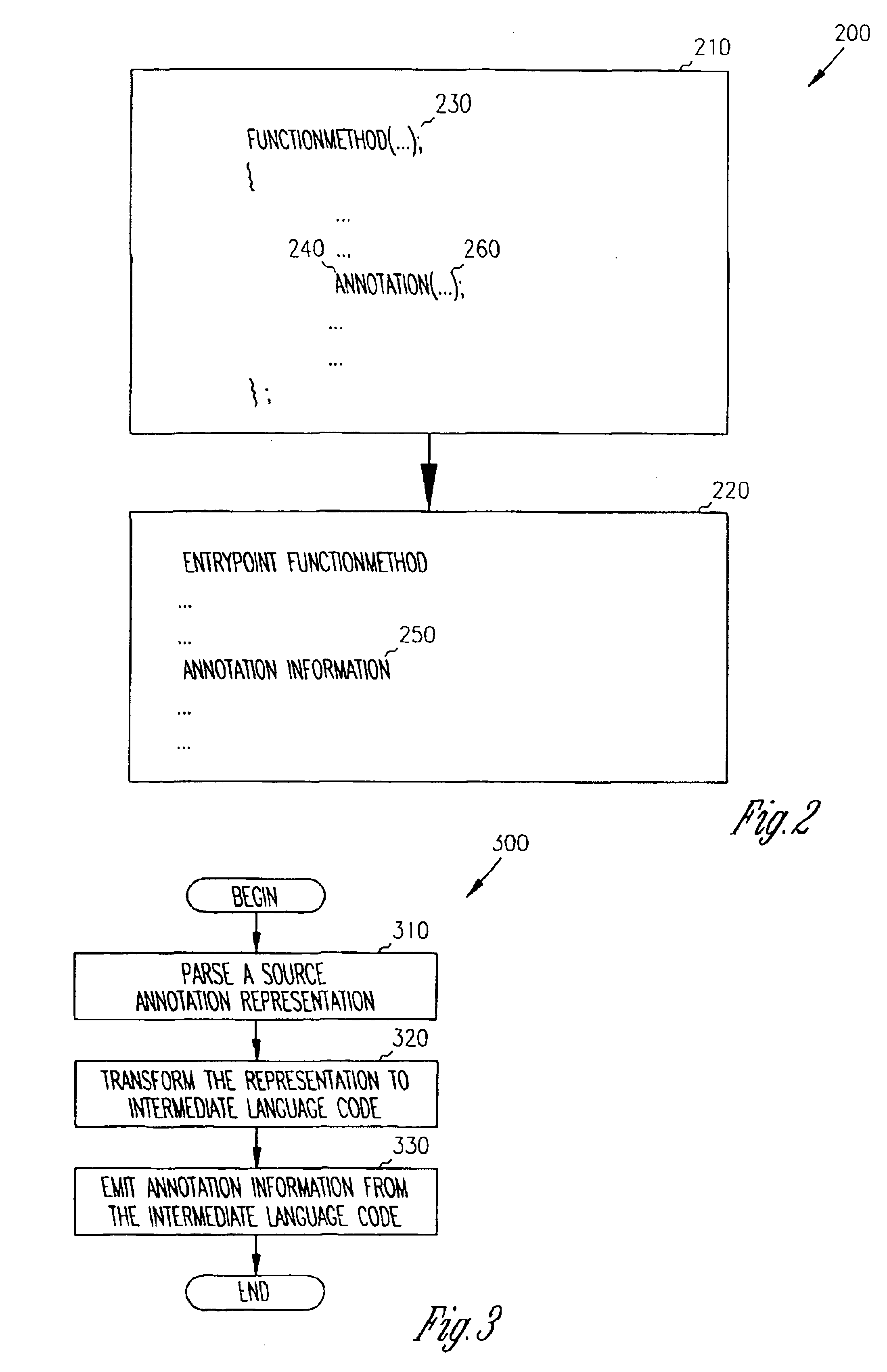
Debug annotations
InactiveUS6874140B1Less memoryEliminate needSoftware testing/debuggingSpecific program execution arrangementsCompilerAnnotation
An annotation source representation is supported by a compiler and / or linker to annotate program code, so that analysis tools, such as debuggers and profilers, have more information with which to analyze an executable program. The annotation source representation in the source code is compiled into annotation information so that the annotation remains in the executable code, but is not executed. The annotation information in the executable program is associated with the code that the annotation function is associated with. The present invention eliminates the need of parallel / companion input command files, eliminates the need of compiling a special version of the executable program for purposes of analysis, and eliminates the need of implementing debug statements in the source code.
Owner:MICROSOFT TECH LICENSING LLC
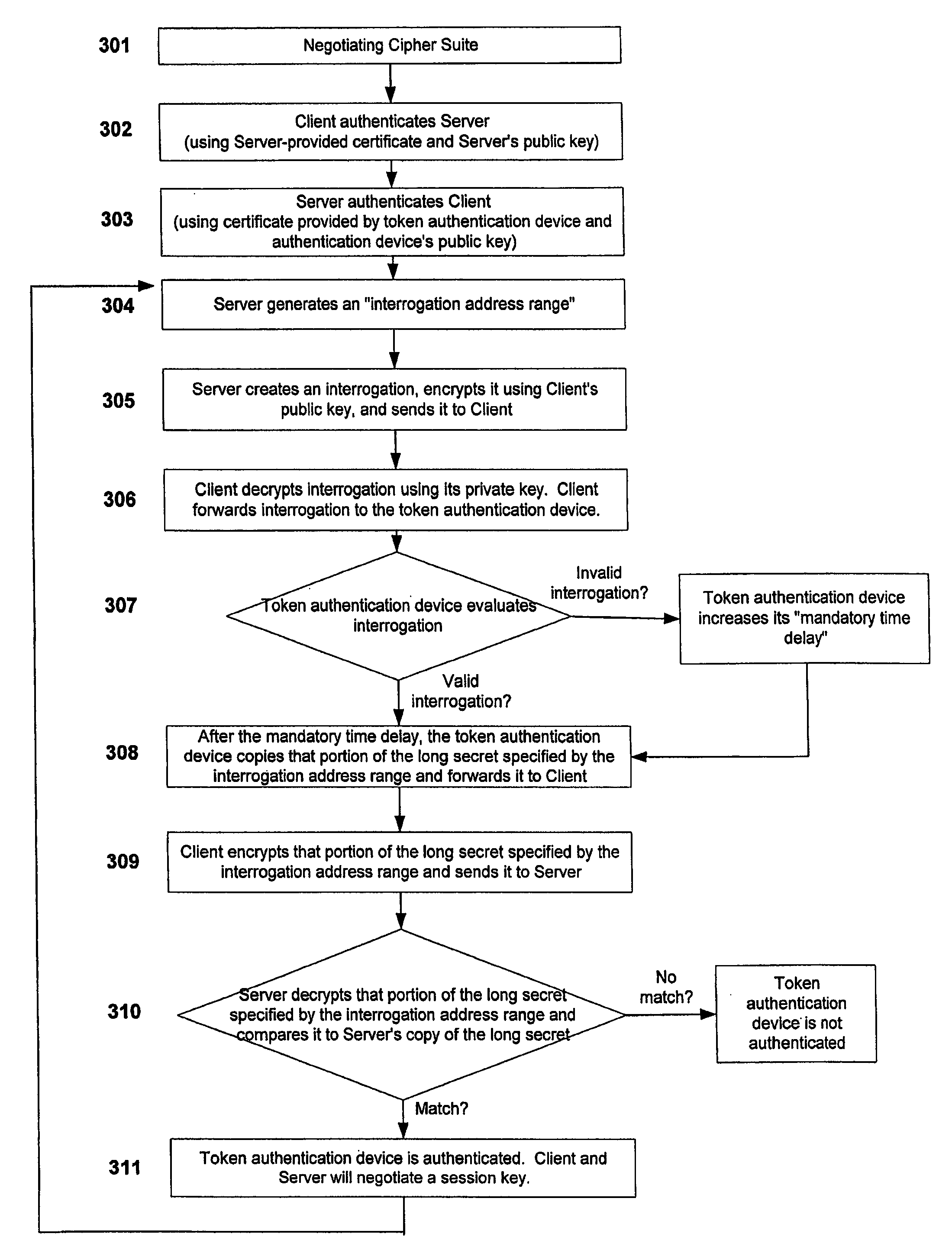
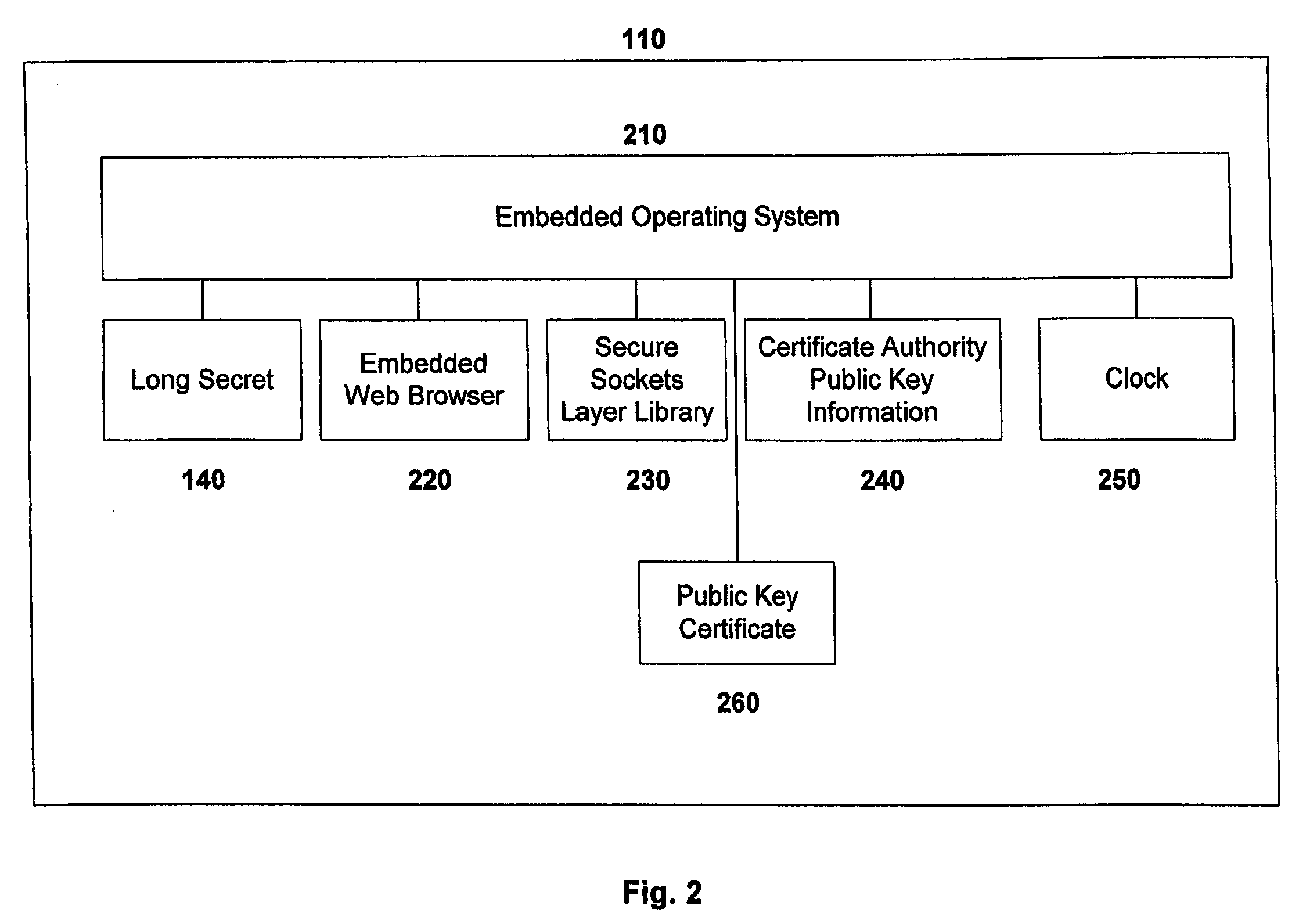
Apparatus, system, and method for authenticating users of digital communication devices
InactiveUS20080086771A1Short timeMinimizing chanceDigital data processing detailsUser identity/authority verificationDigital signatureComputer science
A computer authentication device comprising a memory containing a long secret or digital signature, portions of which are requested by a server computer or other device. The authentication device evaluates the nature and timing of authentication requests and selectively varies the time delay for responding to such authentication requests. Such selective variation in response times impedes the unauthorized or malicious copying of the authentication device's authentication credentials.
Owner:LI KANG +1
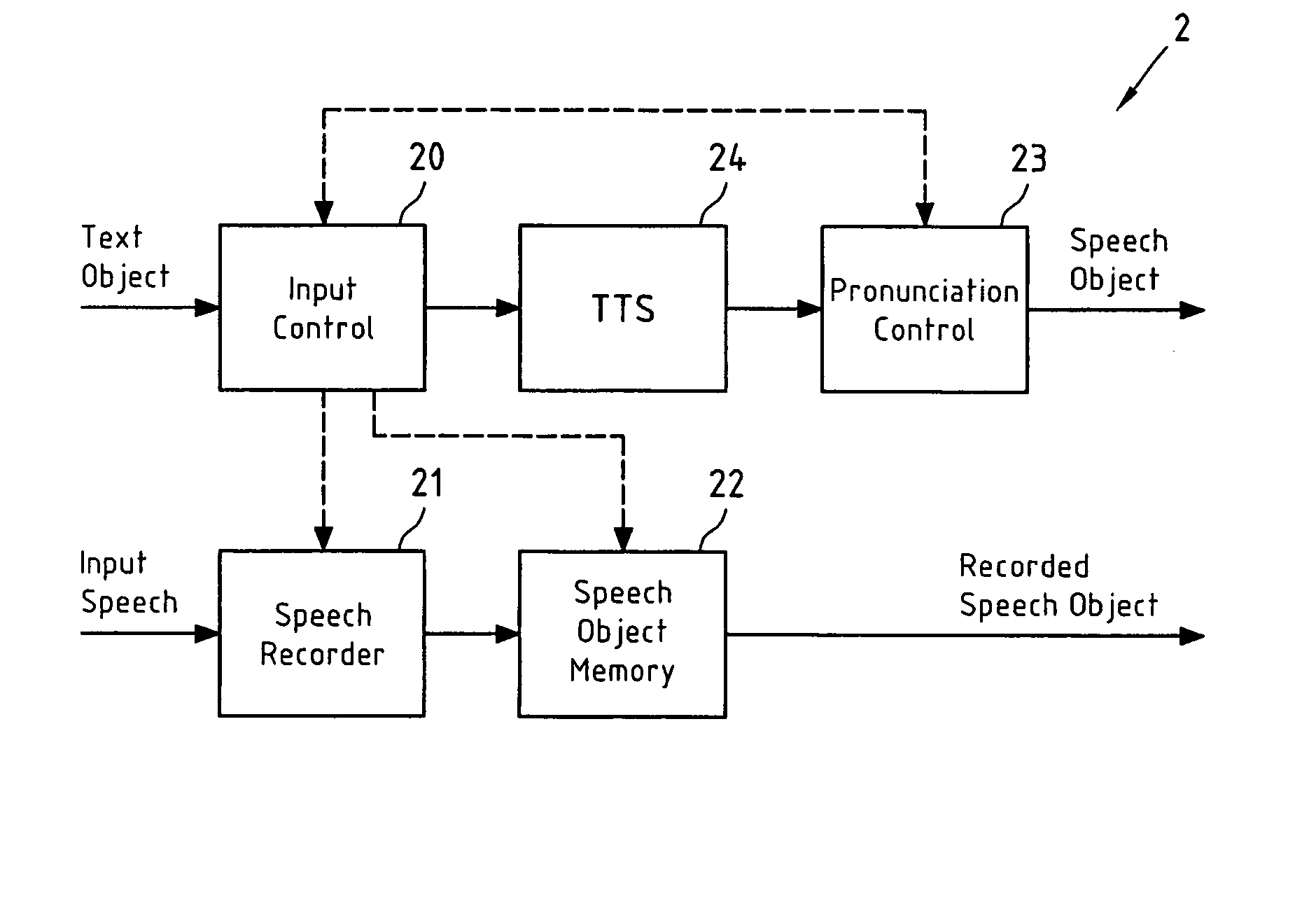
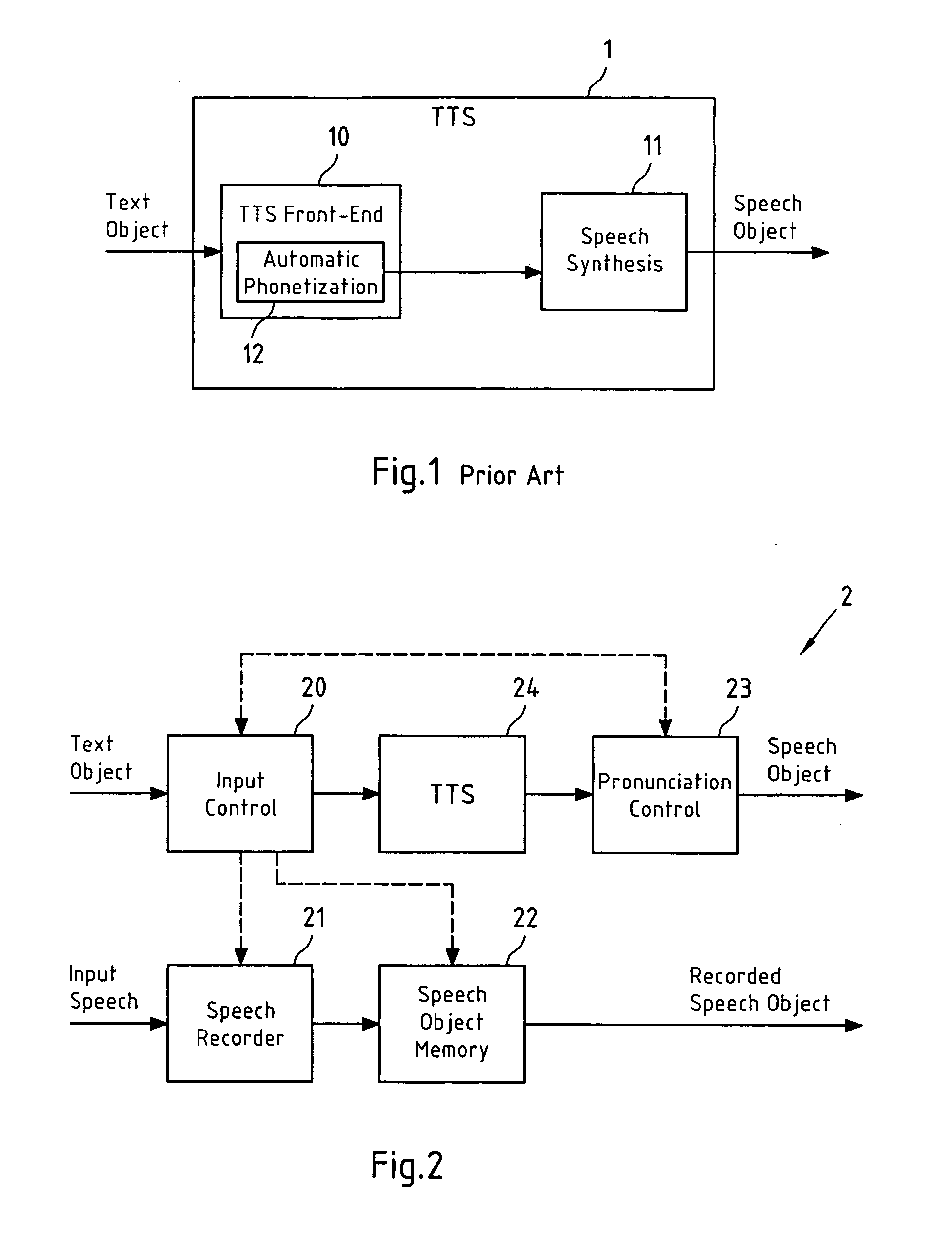
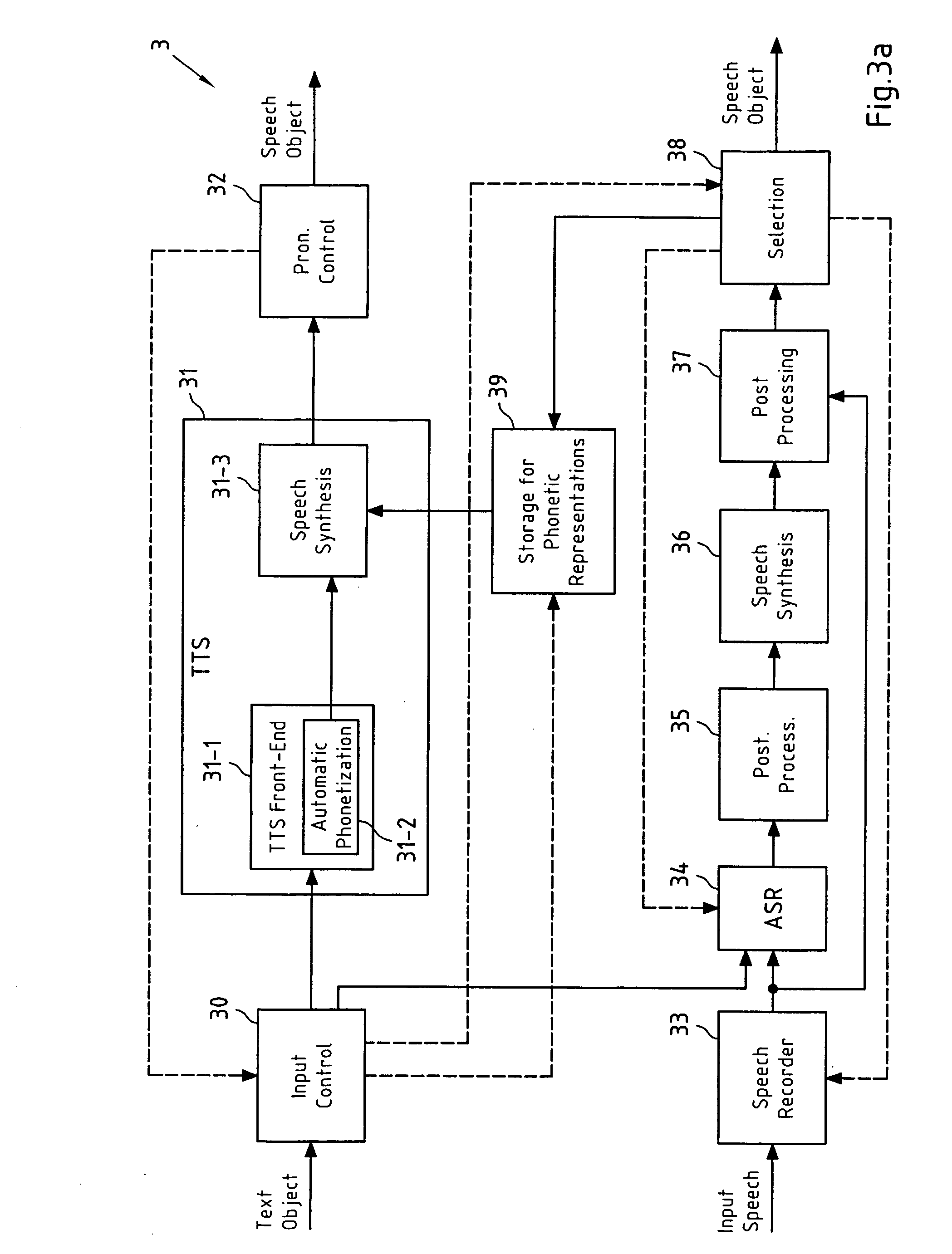
Correcting a pronunciation of a synthetically generated speech object
InactiveUS20070016421A1Less memoryAvoiding future mispronunciationSpeech recognitionSpeech synthesisSpeech soundSoftware
This invention relates to a method, a device and a software application product for correcting a pronunciation of a speech object. The speech object is synthetically generated from a text object in dependence on a segmented representation of the text object. It is determined if an initial pronunciation of the speech object, which initial pronunciation is associated with an initial segmented representation of the text object, is incorrect. Furthermore, in case it is determined that the initial pronunciation of the speech object is incorrect, a new segmented representation of the text object is determined, which new segmented representation of the text object is associated with a new pronunciation of the speech object.
Owner:NOKIA CORP
Method for controlling user access in sensor networks
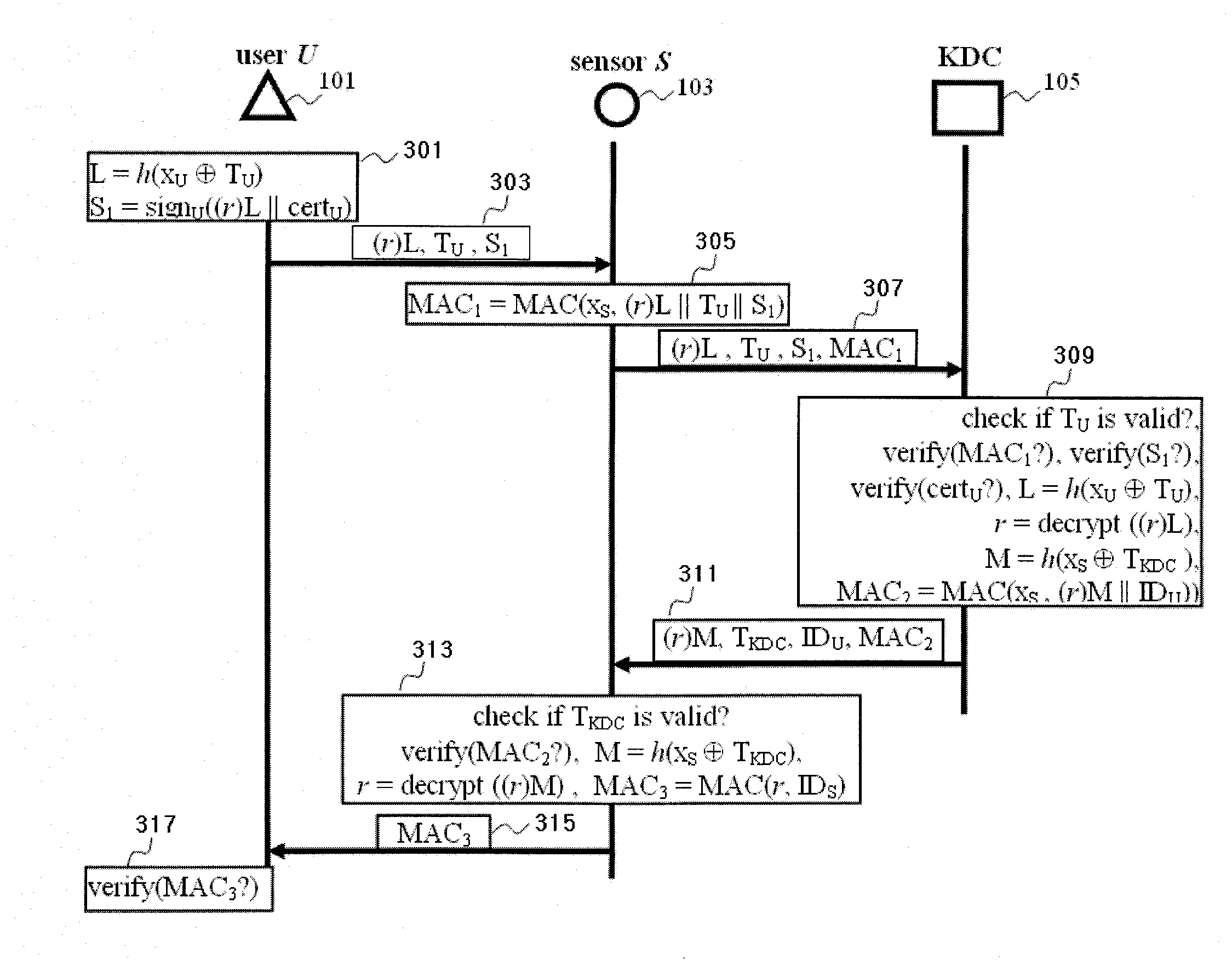
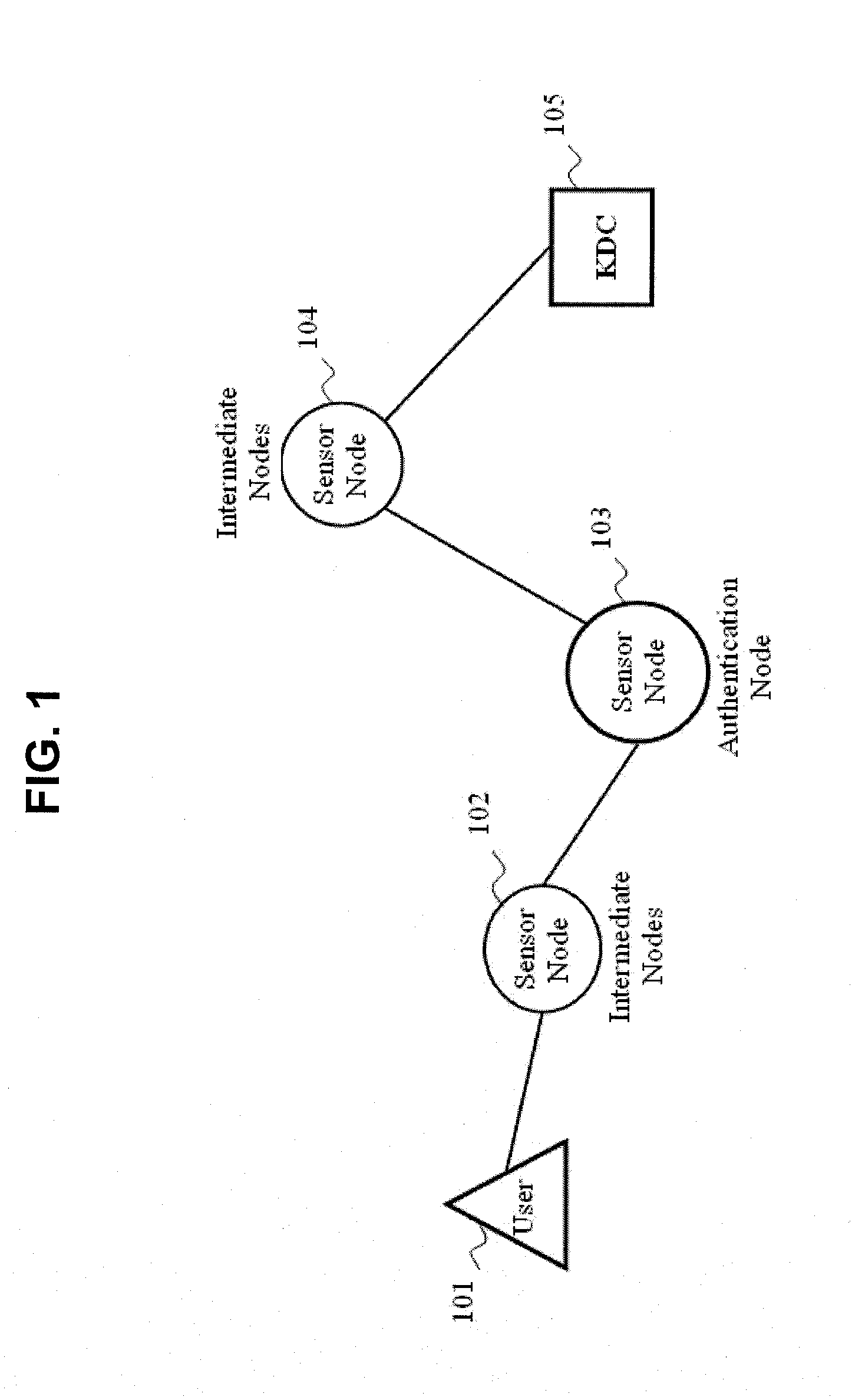
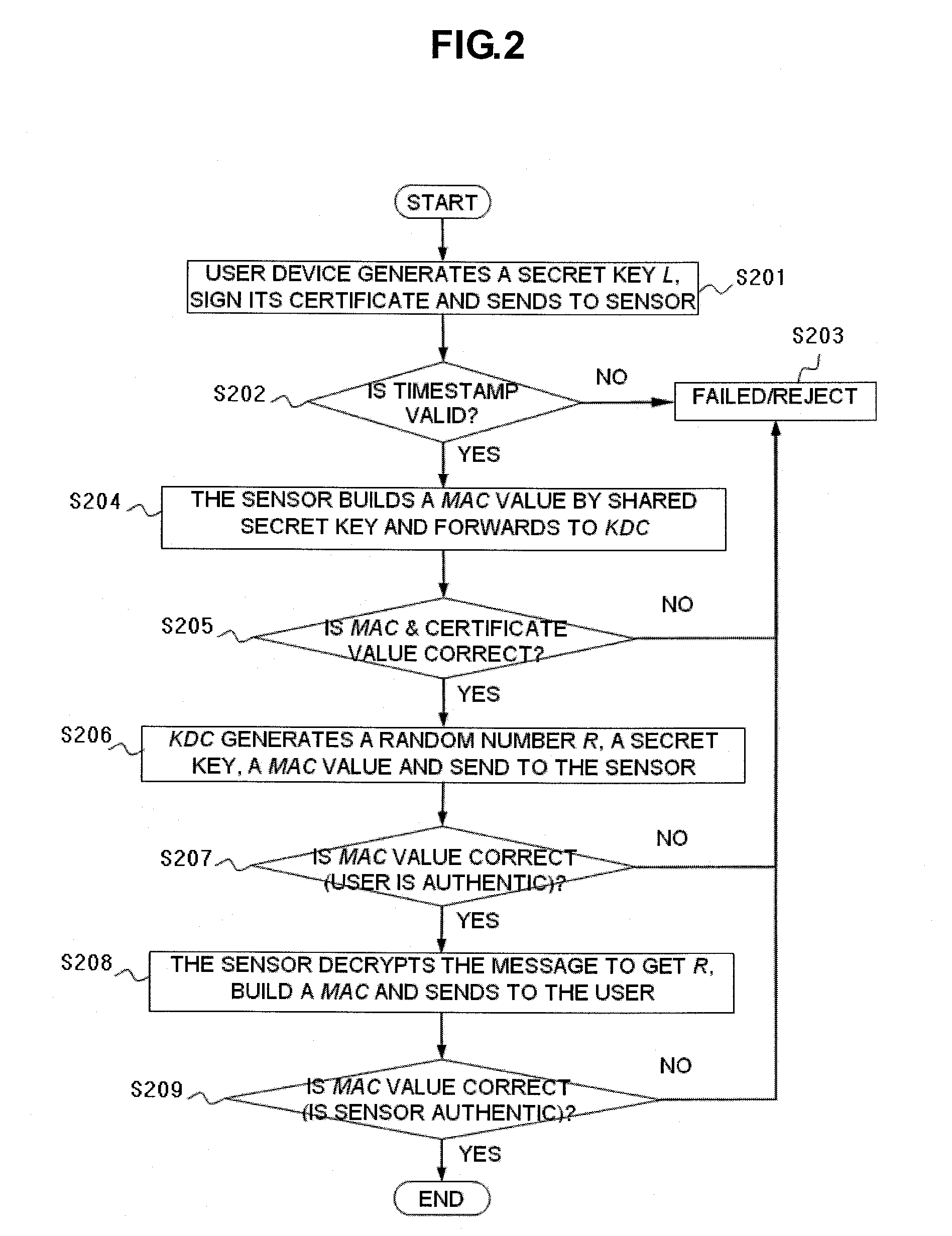
InactiveUS20110055553A1Easily deployLess memoryEnergy efficient ICTComputer security arrangementsKey distribution centerUser control
A method for implement an energy-efficient user access control to wireless sensor networks is disclosed. A user creates a secret key and sending it to a sensor. The sensor builds a first MAC value by the secret key and sends it to the Key Distribution Center which builds a second MAC value and sending it to the sensor. The sensor decrypts the second MAC value to get a random number, and builds a third MAC value by the random number. The third MAC value is used by the user to authenticate the sensor.
Owner:UNIV IND COOP GRP OF KYUNG HEE UNIV
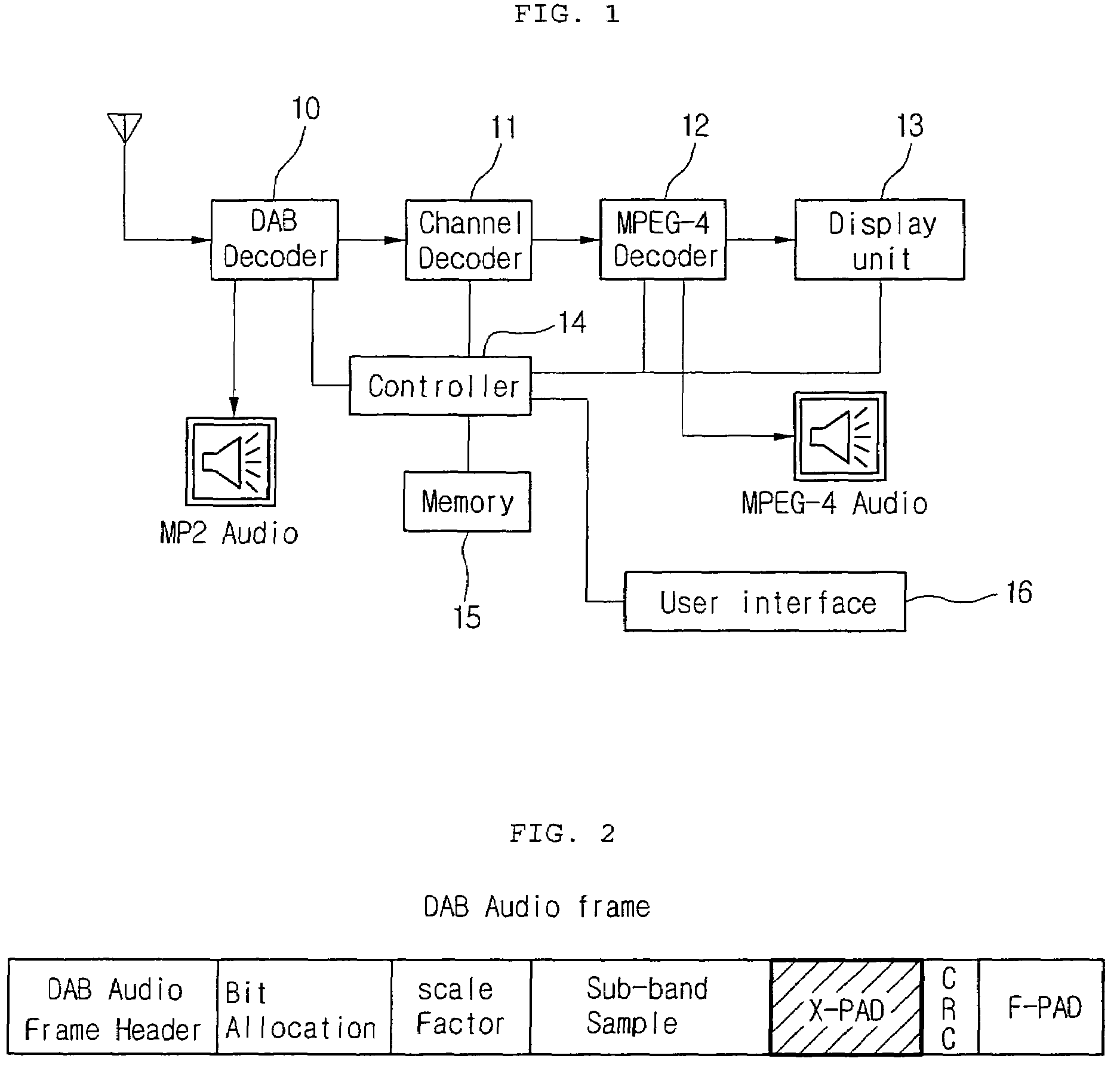
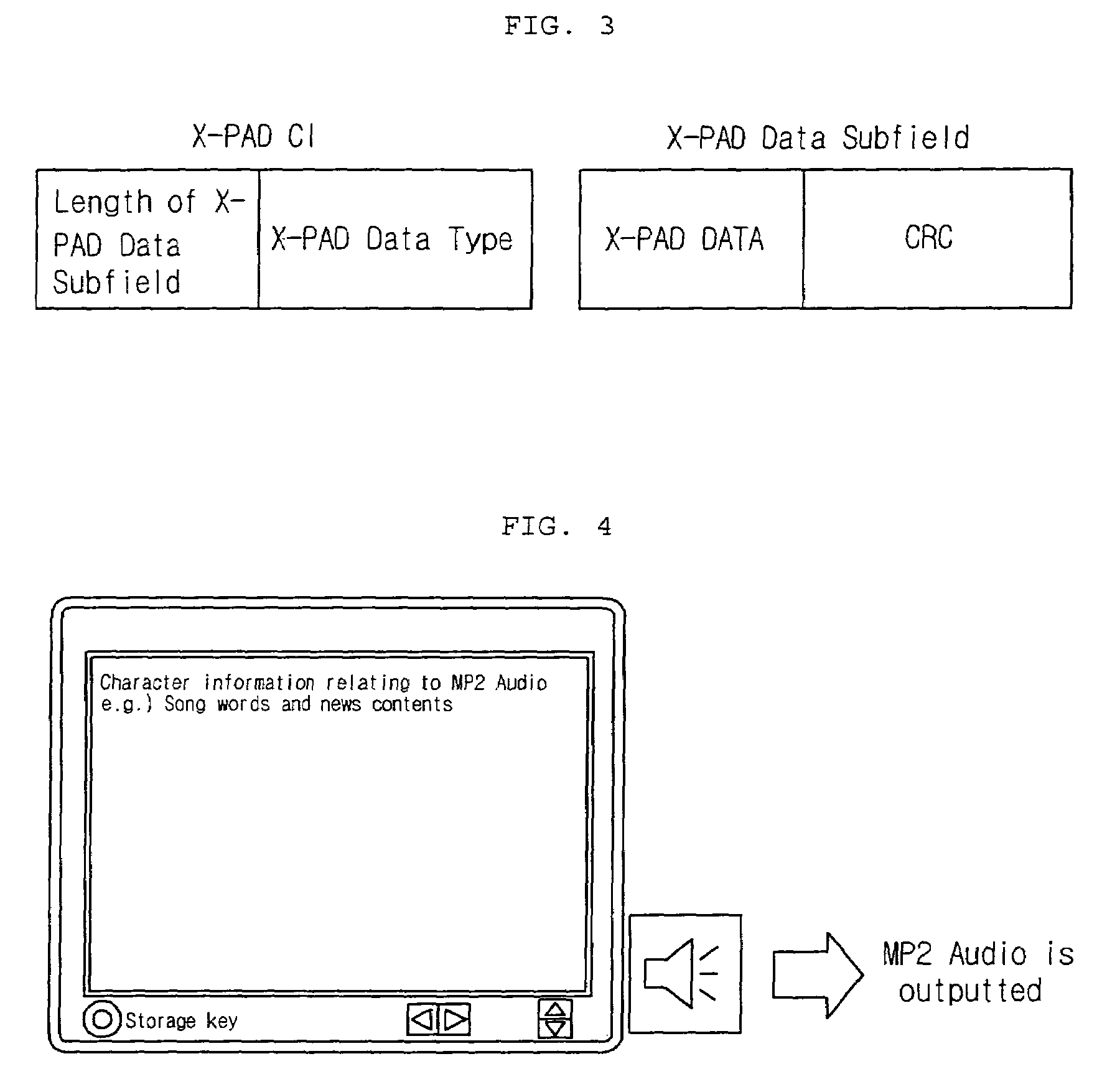
Digital multimedia broadcasting receiver, and method of using additional information thereof
ActiveUS7545440B2Easy to storeLess memoryTelevision system detailsPicture reproducers using cathode ray tubesComputer graphics (images)Digital multimedia broadcasting
A method of using additional information at a DMB (Digital Multimedia Broadcasting) receiver is provided. The method includes the steps of: extracting and displaying additional information from a DMB signal; selecting and storing a desired one of the displayed additional information; displaying a list of the stored additional information depending on a user's request command; and outputting additional information selected at the list of the additional information.
Owner:LG ELECTRONICS INC
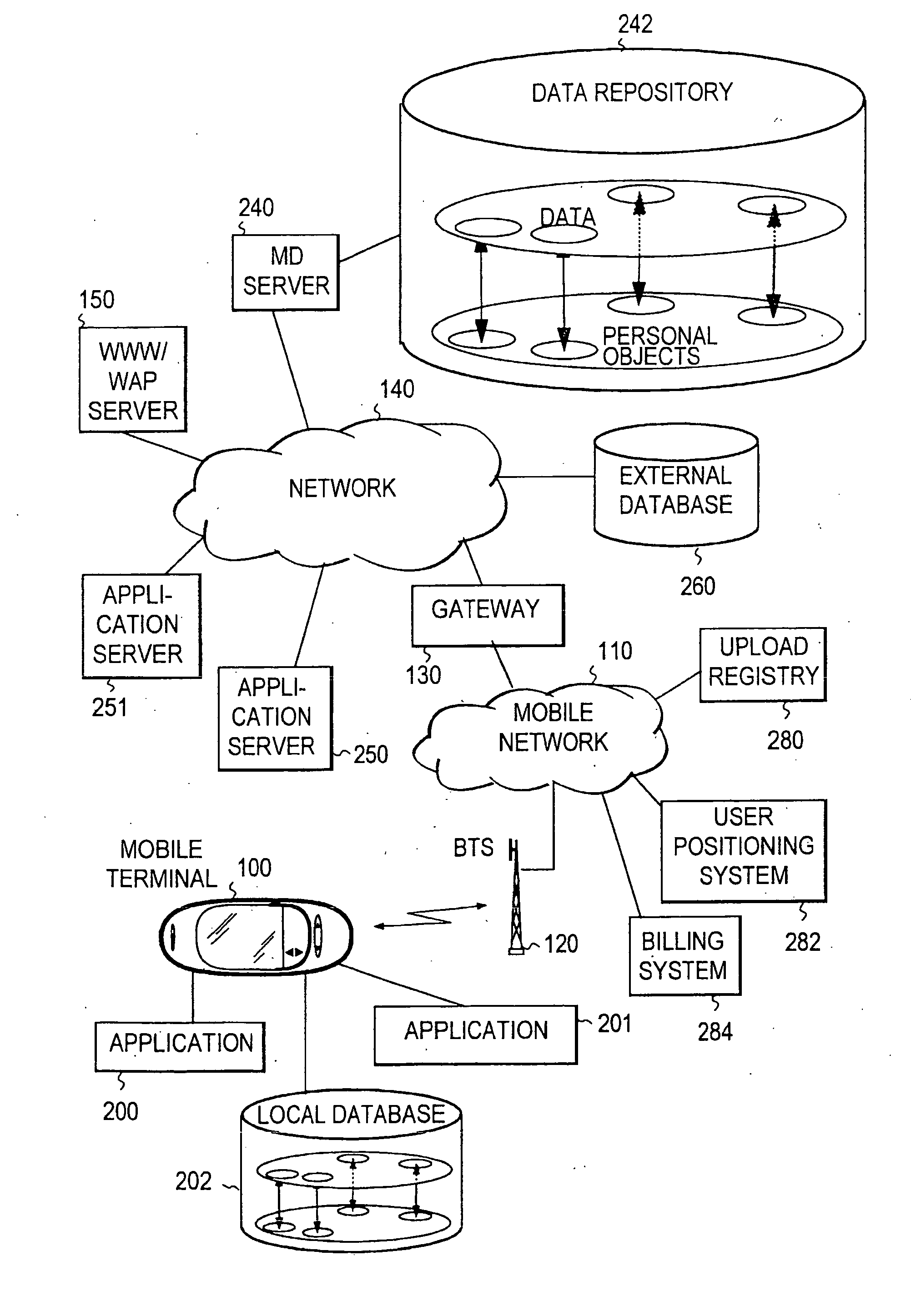
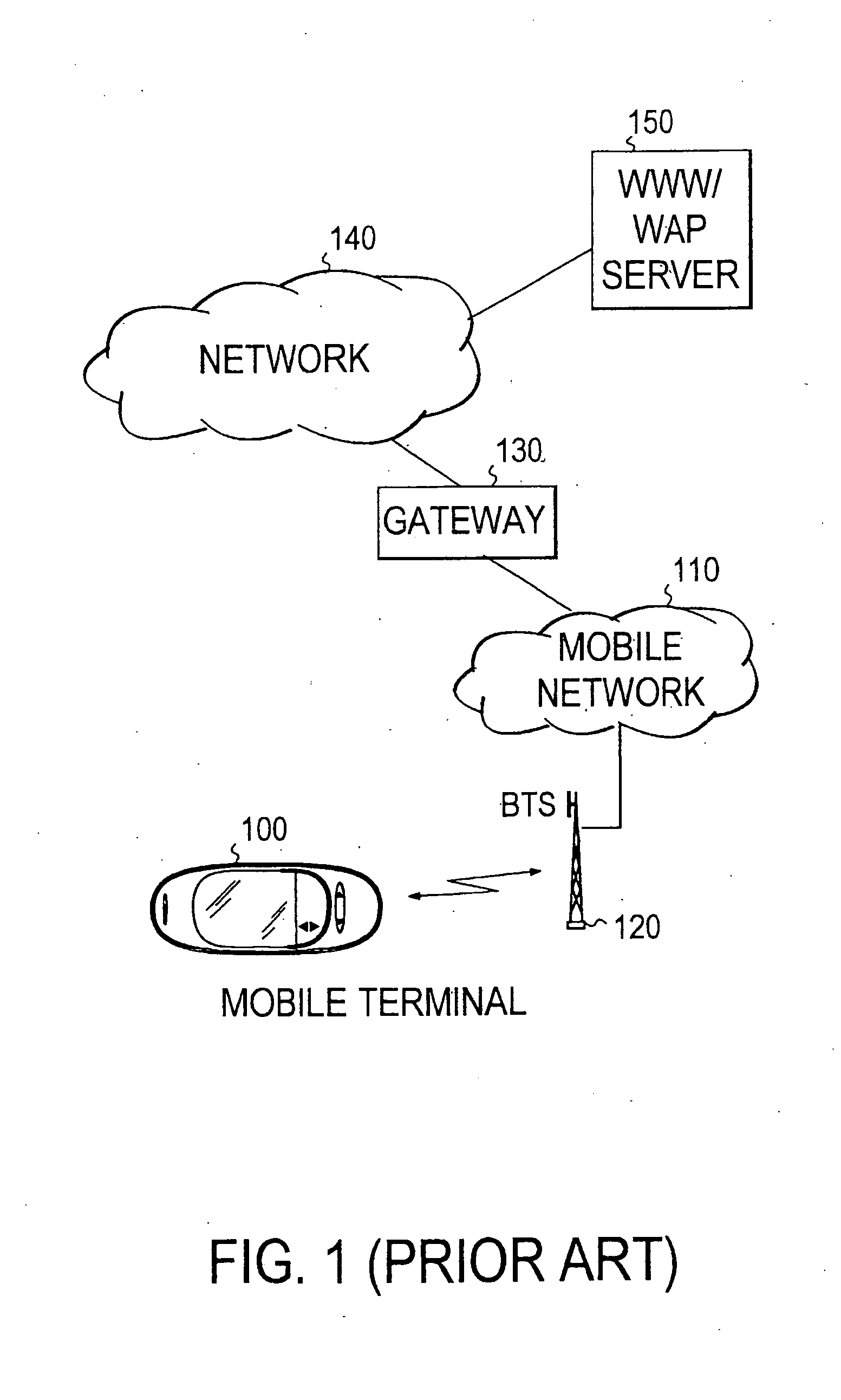
Providing personalized services for mobile users
InactiveUS20050289216A1Efficient use ofLess bandwidthDigital data information retrievalAccounting/billing servicesComputer networkPersonalization service
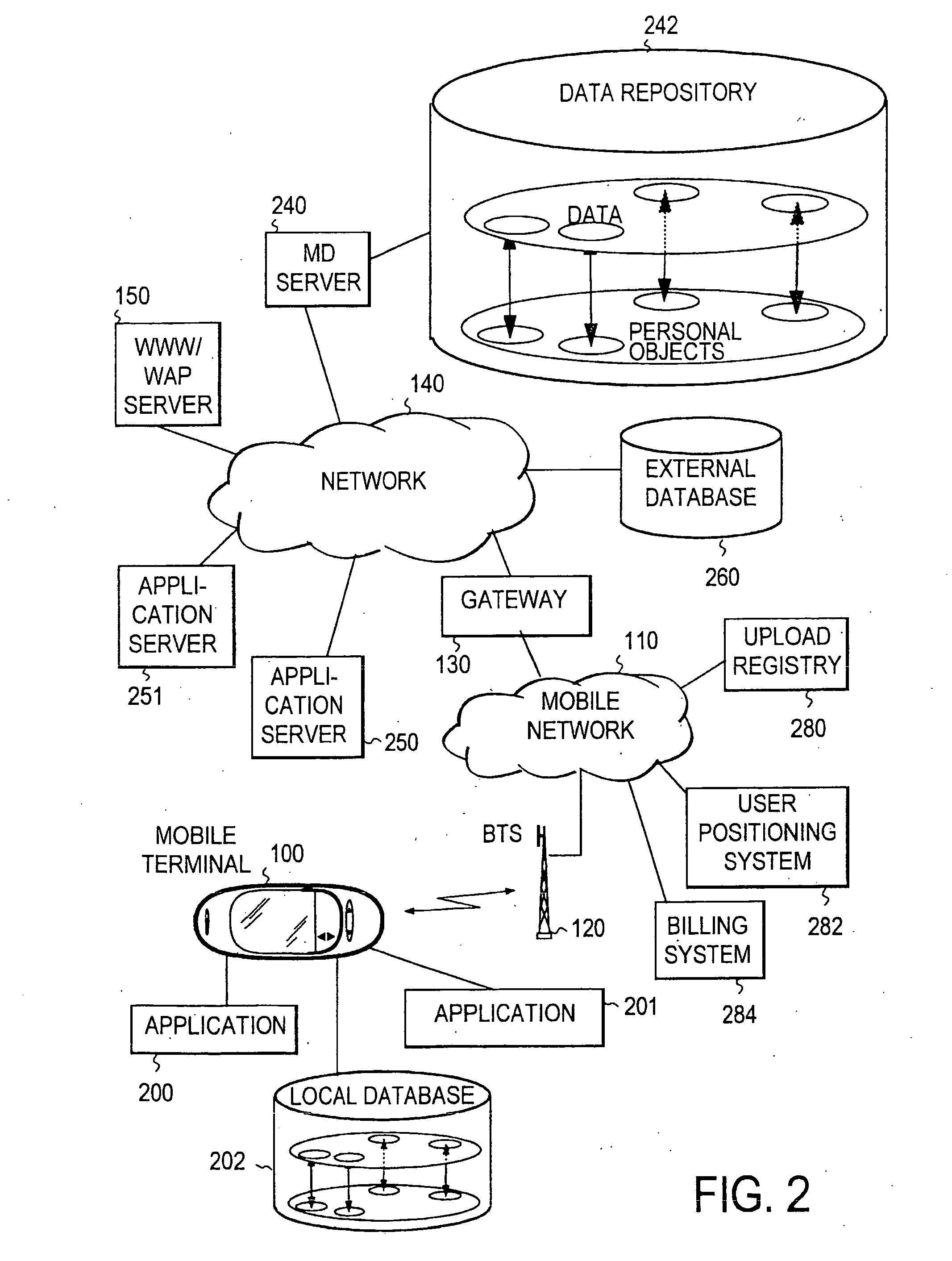
The invention relates to providing personalized services for mobile users. Personalized services can be provided to users, for example, by delivering them using mobile communications means or other delivery methods, such as printed magazines. Personal content is acquired by and stored on a mobile terminal. At least one remote repository is assigned for the use of each such terminal. Selected content can then be transferred from the mobile terminal to a remote data repository through a telecommunications system. Thereby, a transfer is preferably initiated when at least one predetermined criterion is fulfilled. The transferred personal content is subsequently stored in the remote data repository. Data is extracted from the personal content, and the personal content is associated with the extracted data. The latter step can be executed on the terminal and / or on the remote server.
Owner:NOKIA CORP
Map data processing method, system and mobile terminal based on mobile terminal
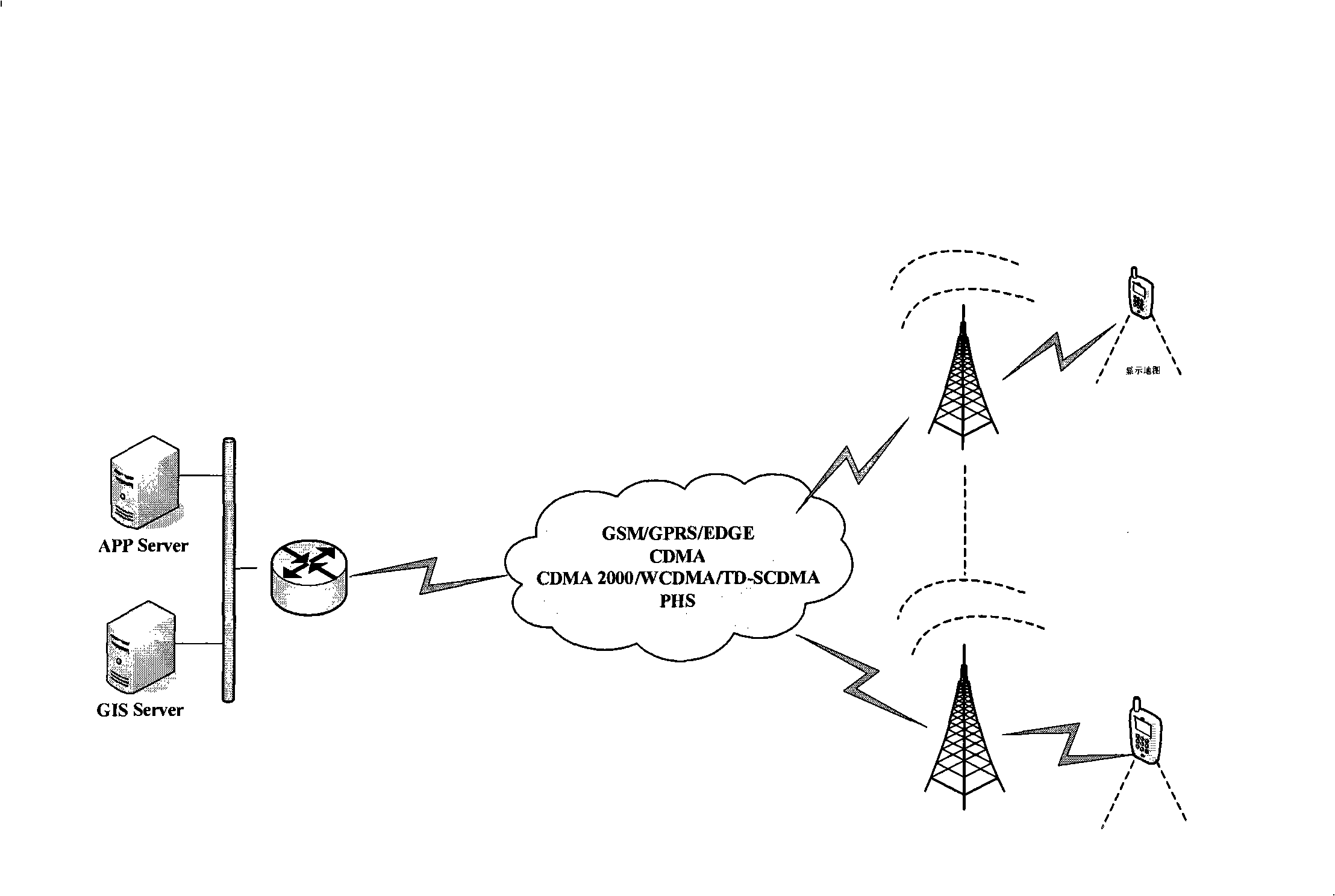
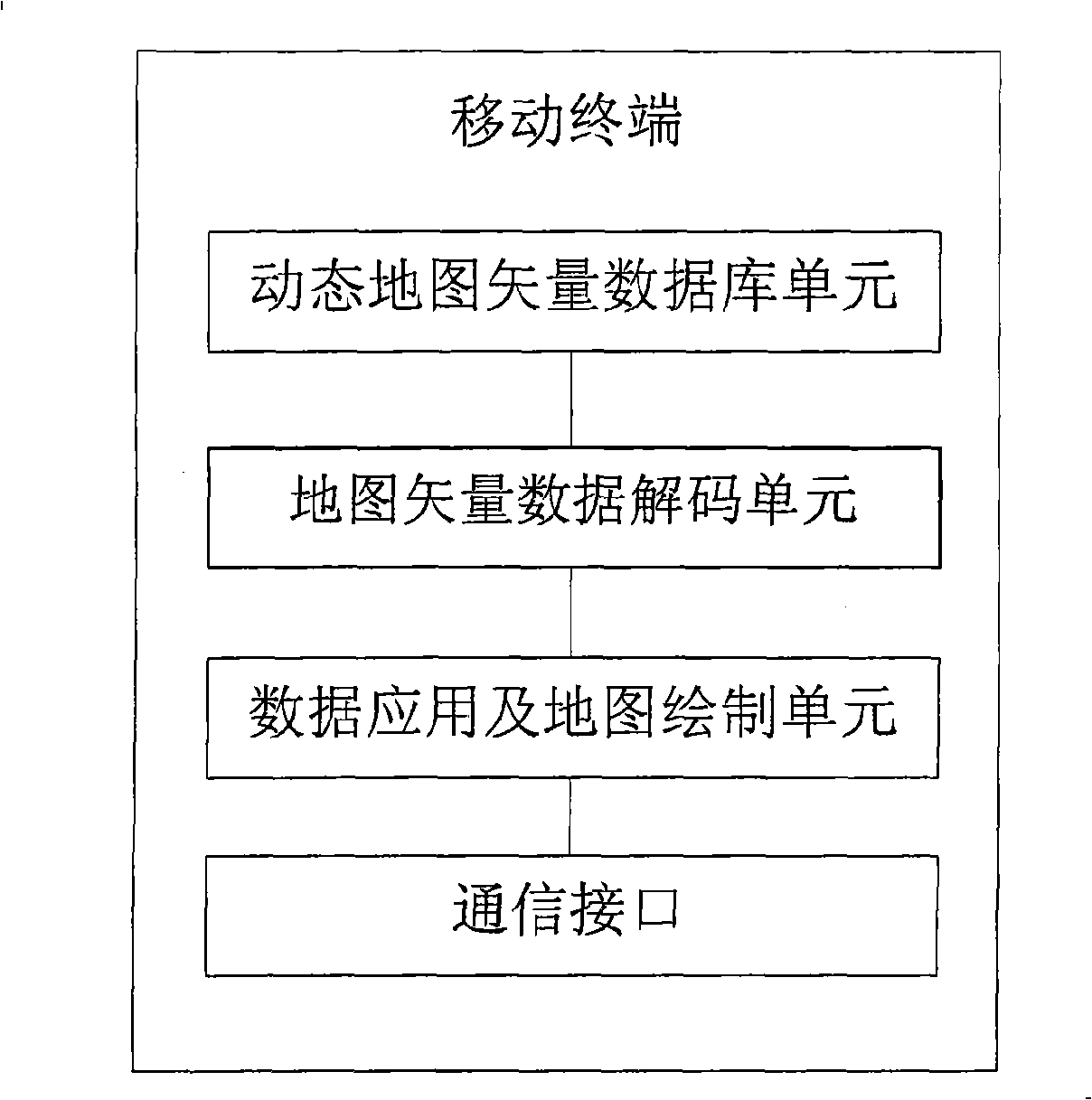
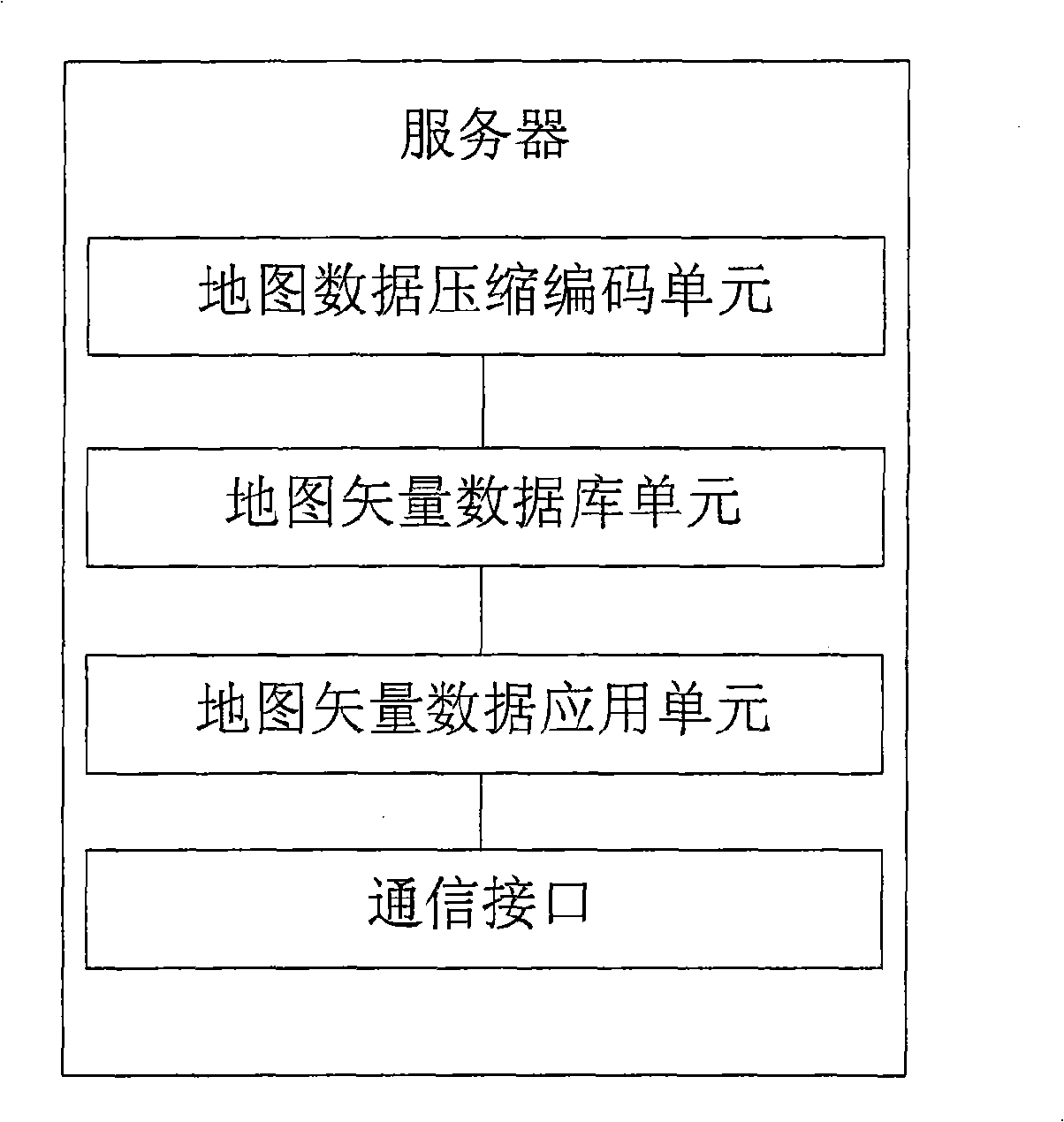
ActiveCN101290228ASmall amount of vector dataReduce data volumeInstruments for road network navigationSpecial data processing applicationsDisplay deviceComputer terminal
The invention provides a method for processing map data based on a mobile terminal, a system and the mobile terminal. The method comprises the following steps of: carrying out format conversion processing for the map data and generating map vector data; encoding the generated map vector data and generating the map vector data with a compressed format; constructing a dynamic vector database in the mobile terminal; downloading the map vector data with the compressed format into the dynamic vector database; reading the map vector data with the compressed format from the dynamic vector database and decoding the map vector data with the compressed format to obtain the map vector data; and mapping a map which is corresponding to the map vector data on a display of the mobile terminal according to the map vector data and mobile terminal display pixel data. The method, the system and the mobile terminal are used to solve the problem that map data storage is matched with display and real time map scanning, voice navigation, real time geographic information and interest point searching and the like on the mobile terminal are realized in deed.
Owner:ALIBABA (CHINA) CO LTD
System and method for efficiently handling multicast packets by ignoring VLAN context
InactiveUS6912589B1Unnecessary replicationPrevents unnecessary replicationSpecial service provision for substationMultiple digital computer combinationsClient-sideMulticast
A method and system for efficiently handling forwarding of multicast packets by ignoring VLAN (virtual local area network) context during lookup. In one embodiment, the present invention receives, at an intermediate device, multicast registration information for a client. The present embodiment then creates a forwarding database of the multicast registration information. In the present embodiment, when handling a multicast packet at an intermediate device, the present invention accesses the multicast registration information stored in the forwarding database. More particularly, in this embodiment, the present invention accesses the multicast registration information stored in the forwarding database without utilizing VLAN context of the client. As a result, the present invention allows the intermediate device to forward a single multicast packet which will later be supplied to registered member ports. The member ports apply the appropriate VLAN context. In so doing, the present invention prevents unnecessary replication of multicast packets and avoids superfluous expensive lookups in multicast registration tables.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
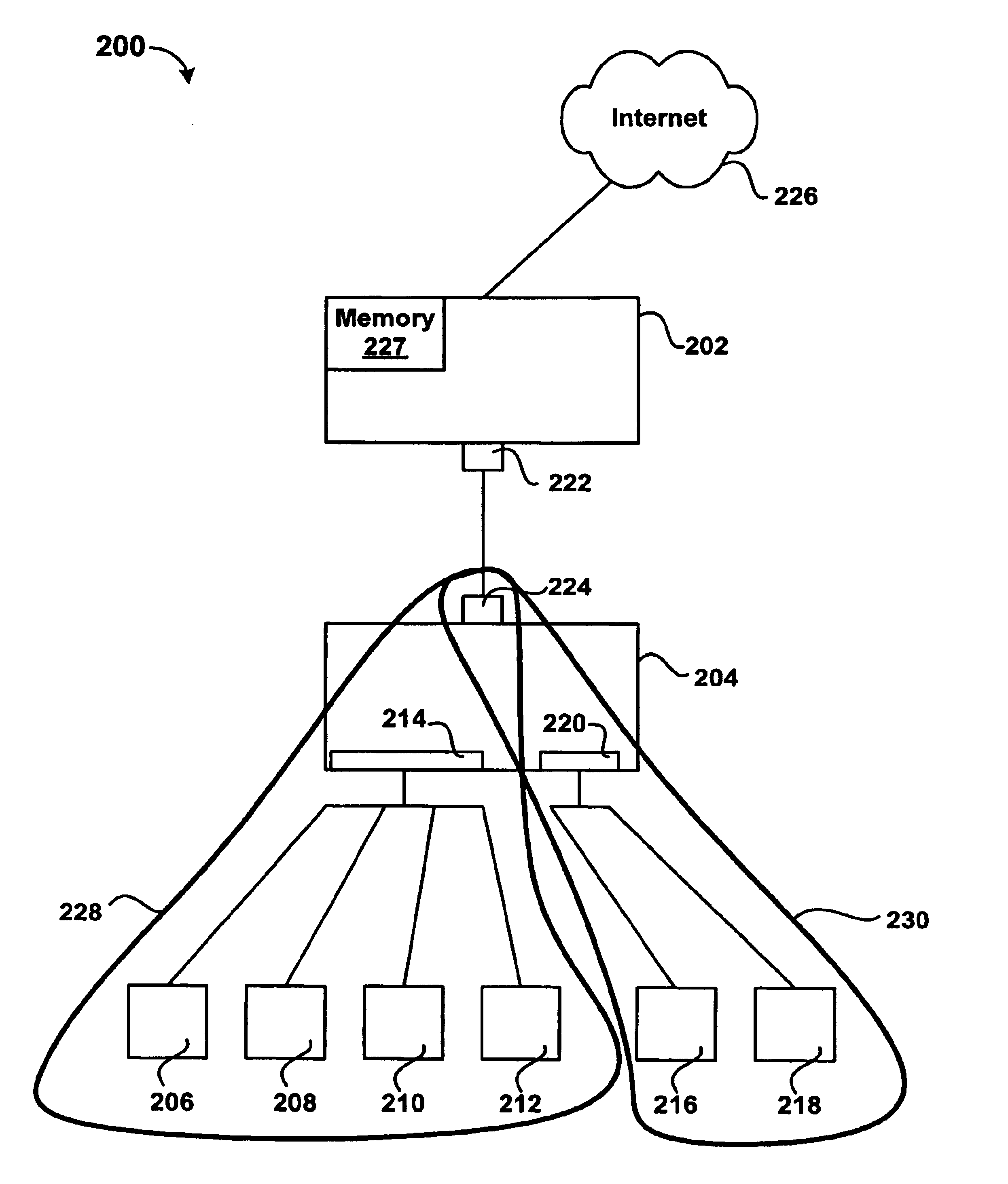
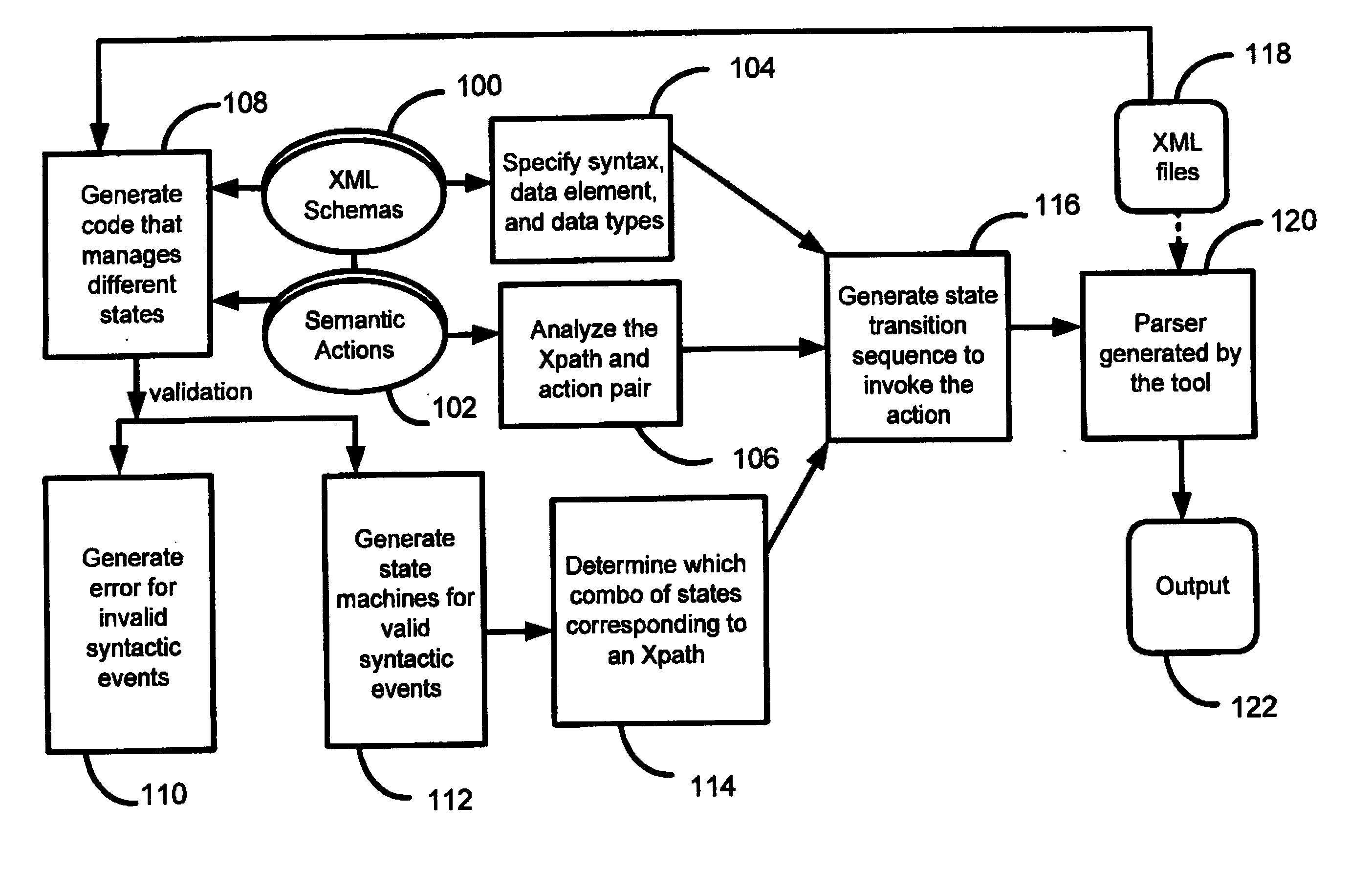
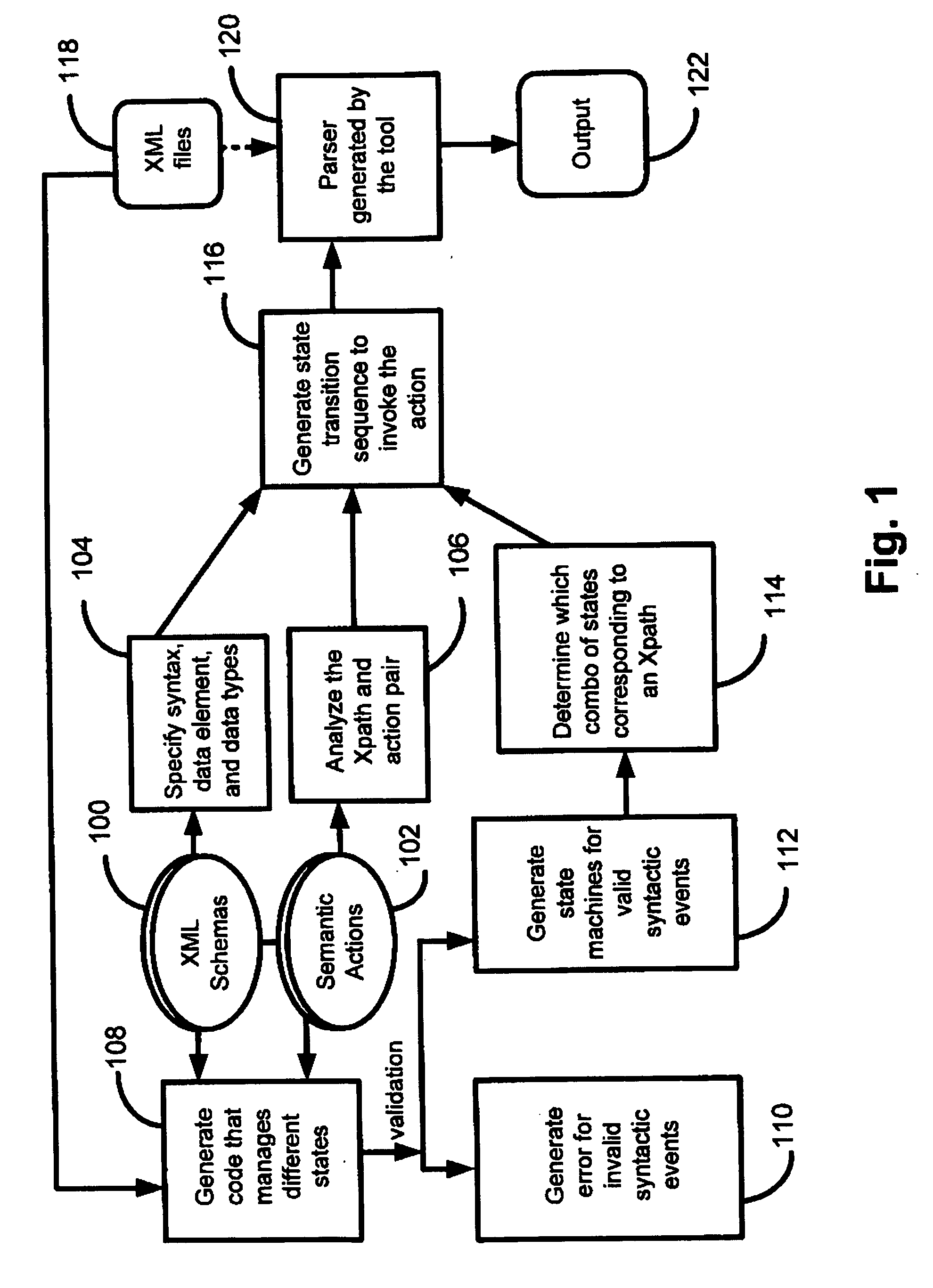
XML compiler that generates an application specific XML parser at runtime and consumes multiple schemas
InactiveUS20070113221A1Easy to processLittle codingProgram controlRequirement analysisXML schemaApplication specific
In accordance with the teachings of the present invention, a method is presented for generating an application-specific XML parser at runtime. Multiple XML schemas are received and used to generate a software generation tool. The software generation tool then produces an application-specific XML parser that can parse XML input files at runtime.
Owner:IBM CORP
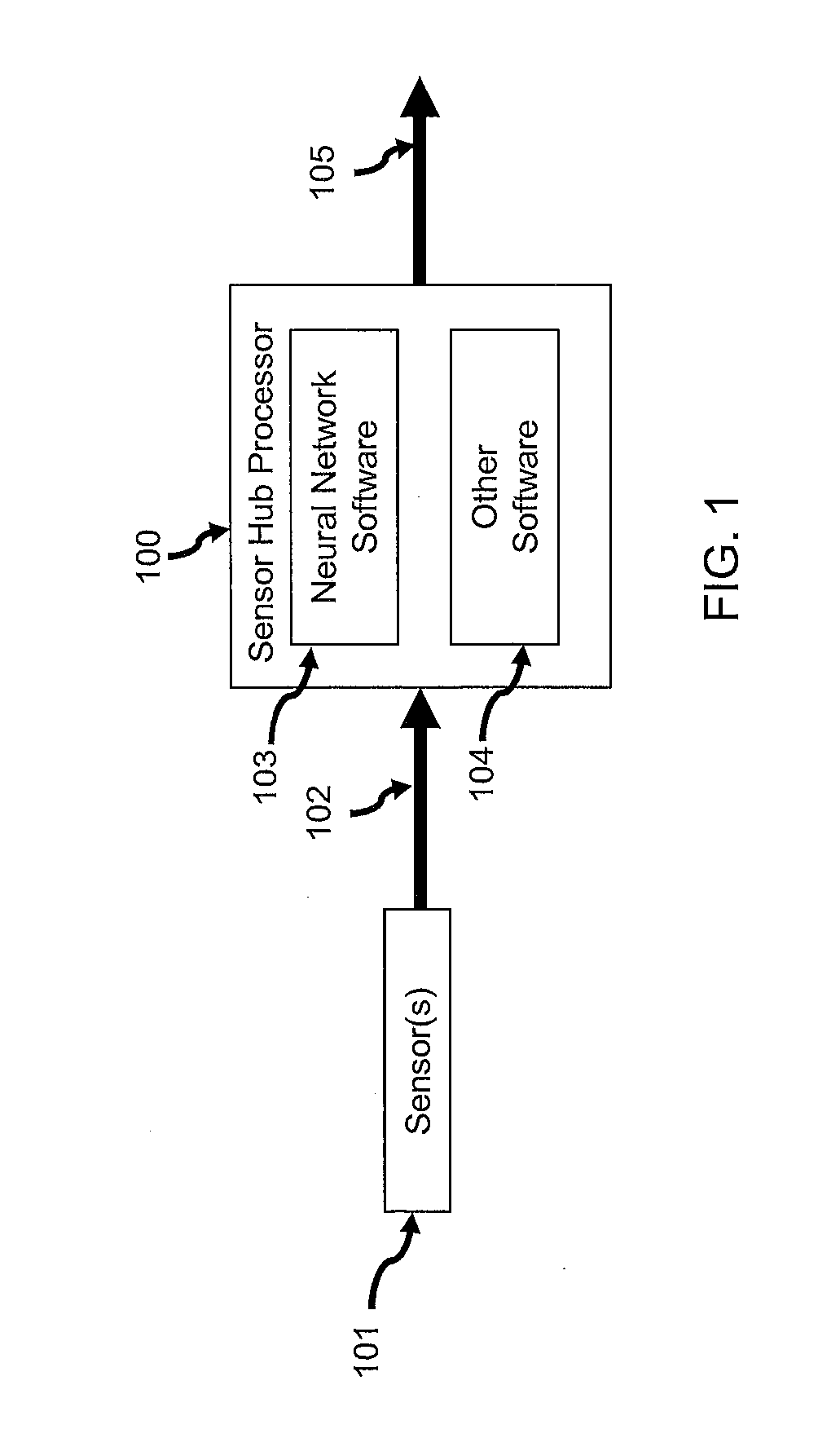
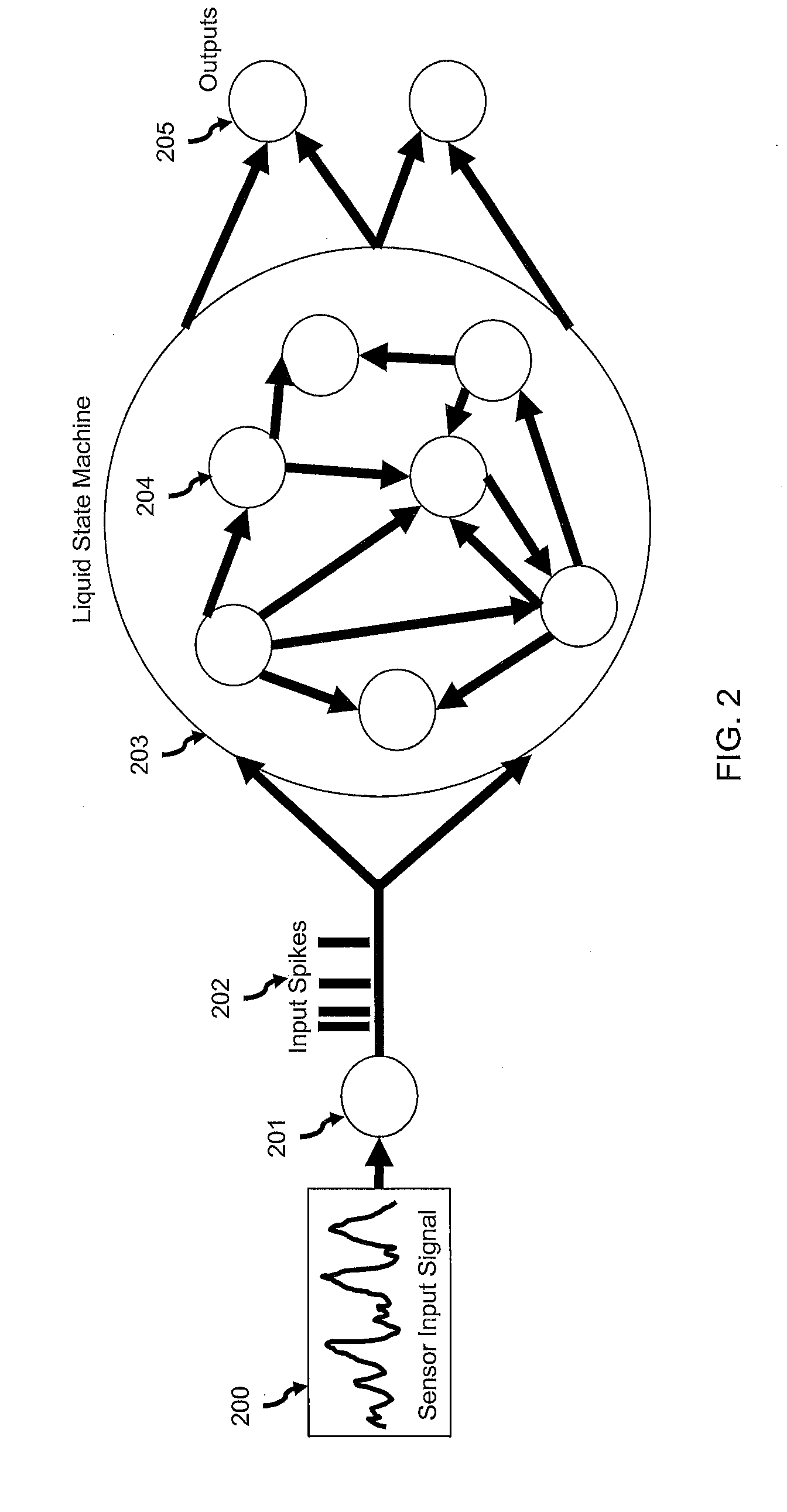
Neural sensor hub system
InactiveUS20160335534A1Less powerControl performanceNeural architecturesNeural learning methodsNerve networkSensory analysis
Systems and methods for a sensor hub system that accurately and efficiently performs sensory analysis across a broad range of users and sensors and is capable of recognizing a broad set of sensor-based events of interest using flexible and modifiable neural networks are disclosed. The disclosed solution consumes orders of magnitude less power than typical application processors. In one embodiment, a scalable sensor hub system for detecting sensory events of interest comprises a neural network and one or more sensors. The neural network comprises one or more dedicated low-power processors and memory storing one or more neural network programs for execution by the one or more processors. The output of the one or more sensors is converted into a spike signal, and the neural network takes the spike signal as input and determines whether a sensory event of interest has occurred.
Owner:THALCHEMY
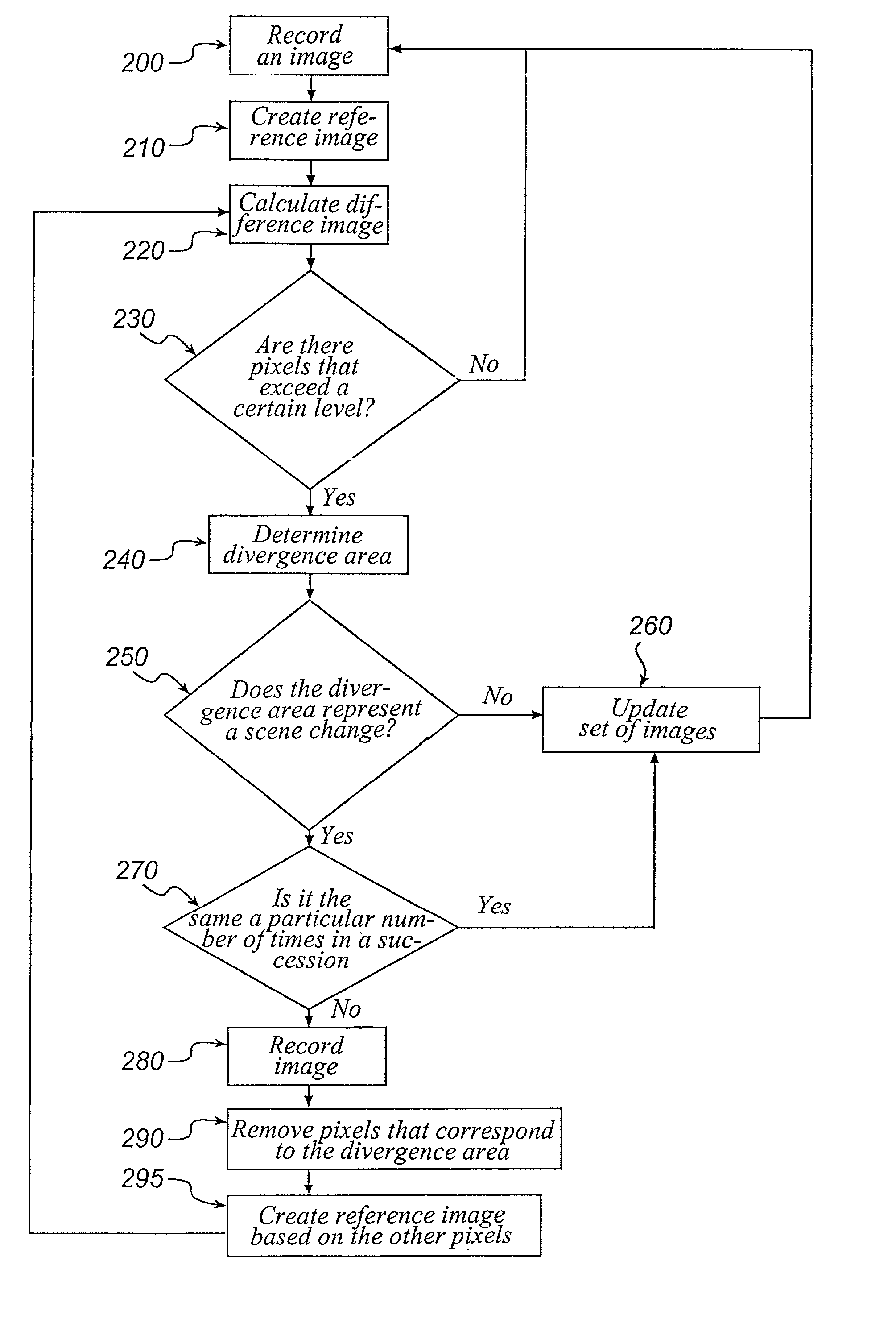
Multiple backgrounds
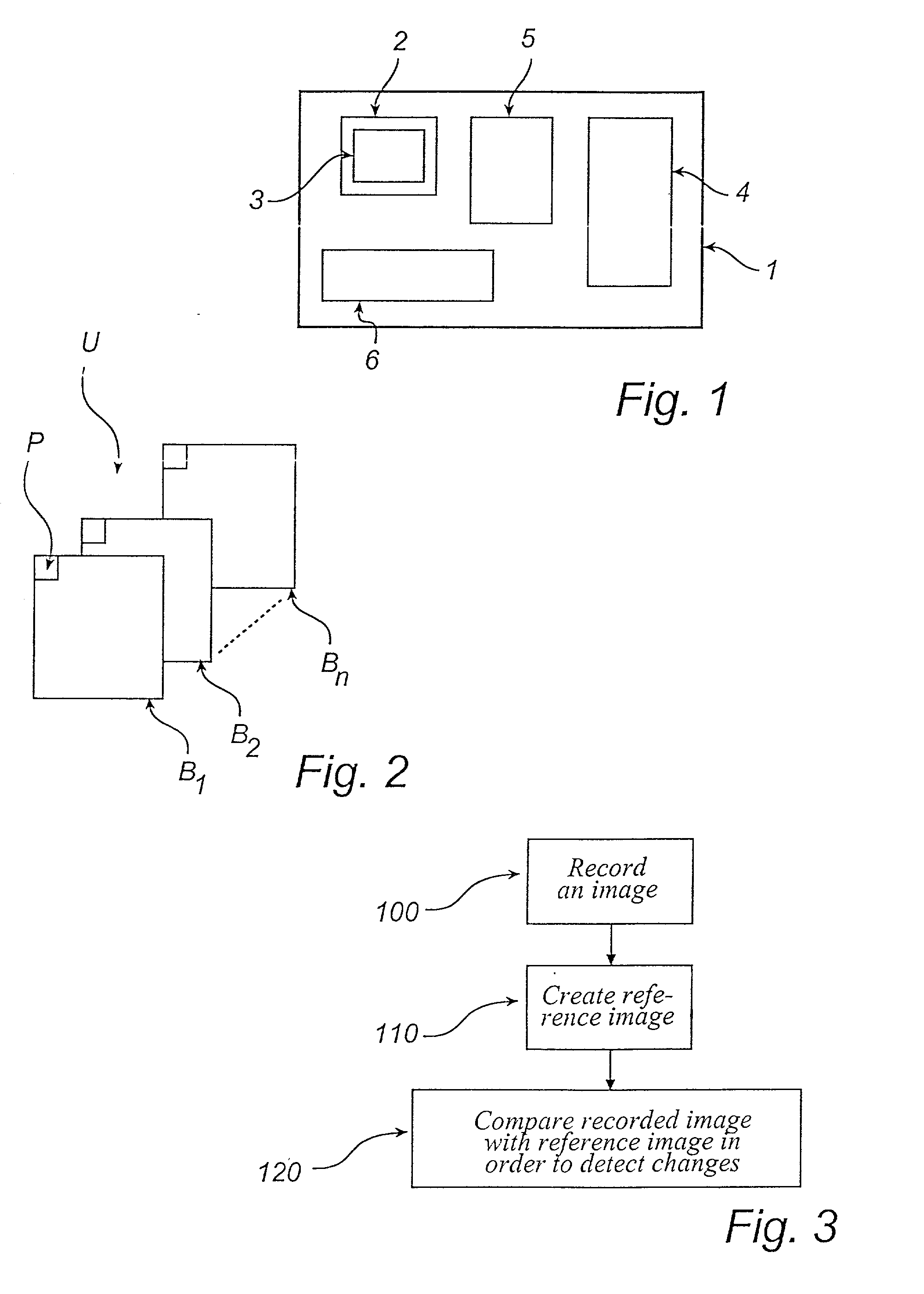
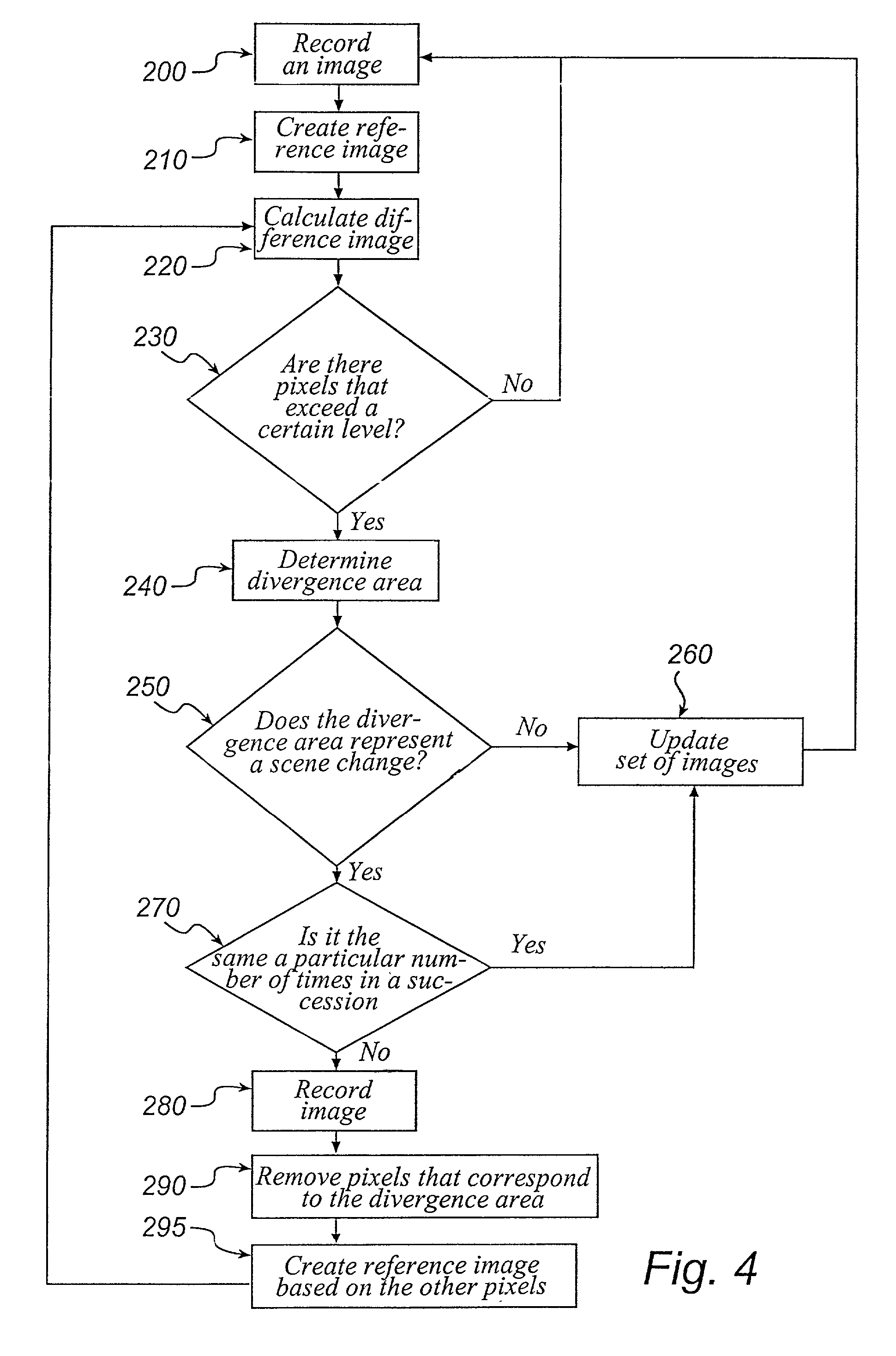
InactiveUS20020039135A1Enhance the imageThe process is simple and fastTelevision system detailsImage analysisReference image
A method for monitoring a monitored area comprising the steps of recording an image of the monitored area and of comparing the recorded image with a reference image in order to determine whether there is an alarm situation. The method further comprises the step of creating the reference image by combining at least two previously stored images from a set of images, so that the lighting conditions in the reference image are adjusted to the lighting conditions in the recorded image.
Owner:SECUMANAGEMENT
Systems and Methods for Accessing Secure and Certified Electronic Messages
ActiveUS20100005293A1Less memoryUser identity/authority verificationDigital data authenticationInternet privacyEmail management
The present disclosure provides systems and methods for accessing secure and certified electronic messages using a combination of biometric security, a separate and secure network and email infrastructure, email management processes, and the addition of text, audio and visual format options to sending emails messages.
Owner:PRIVACYDATASYST
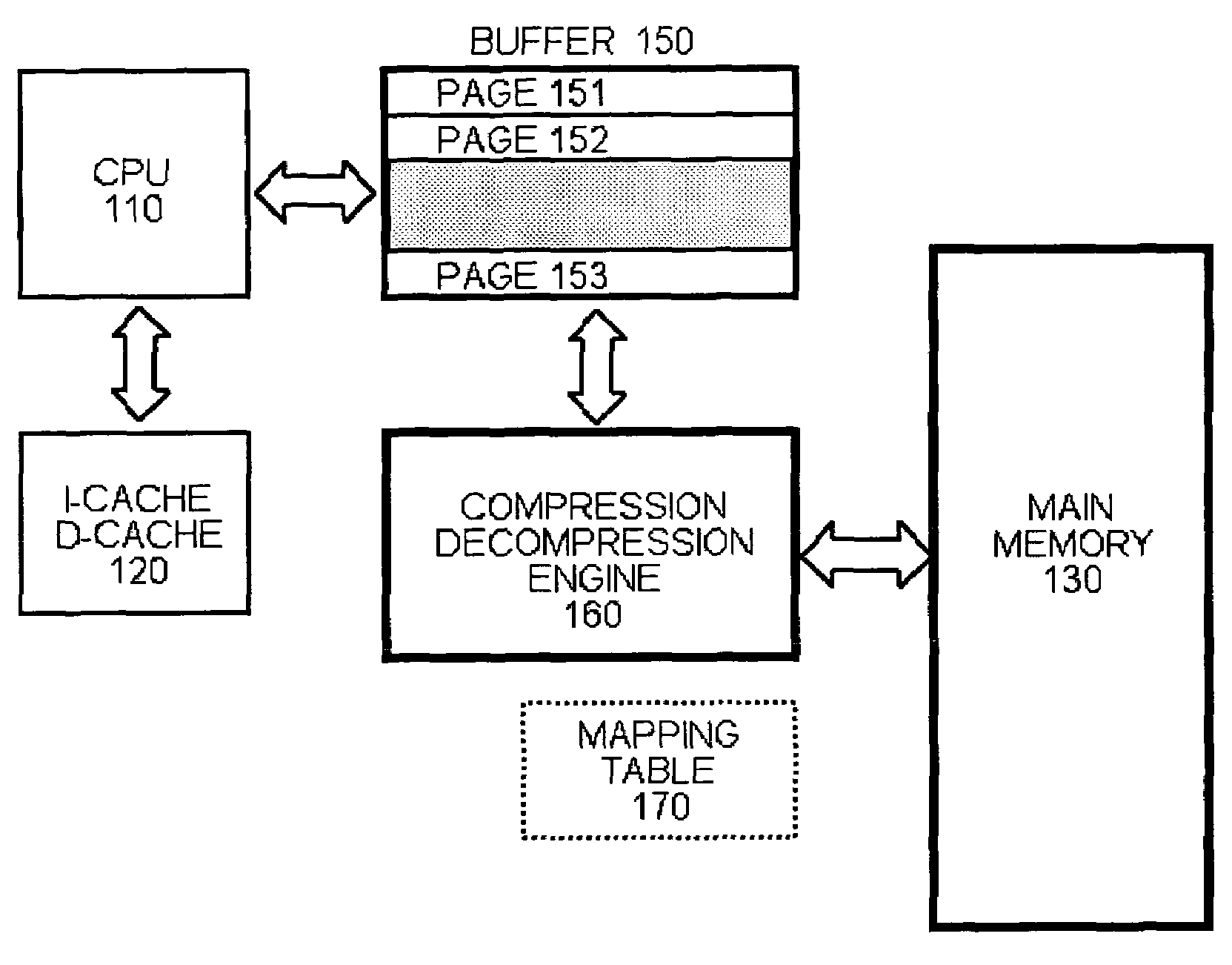
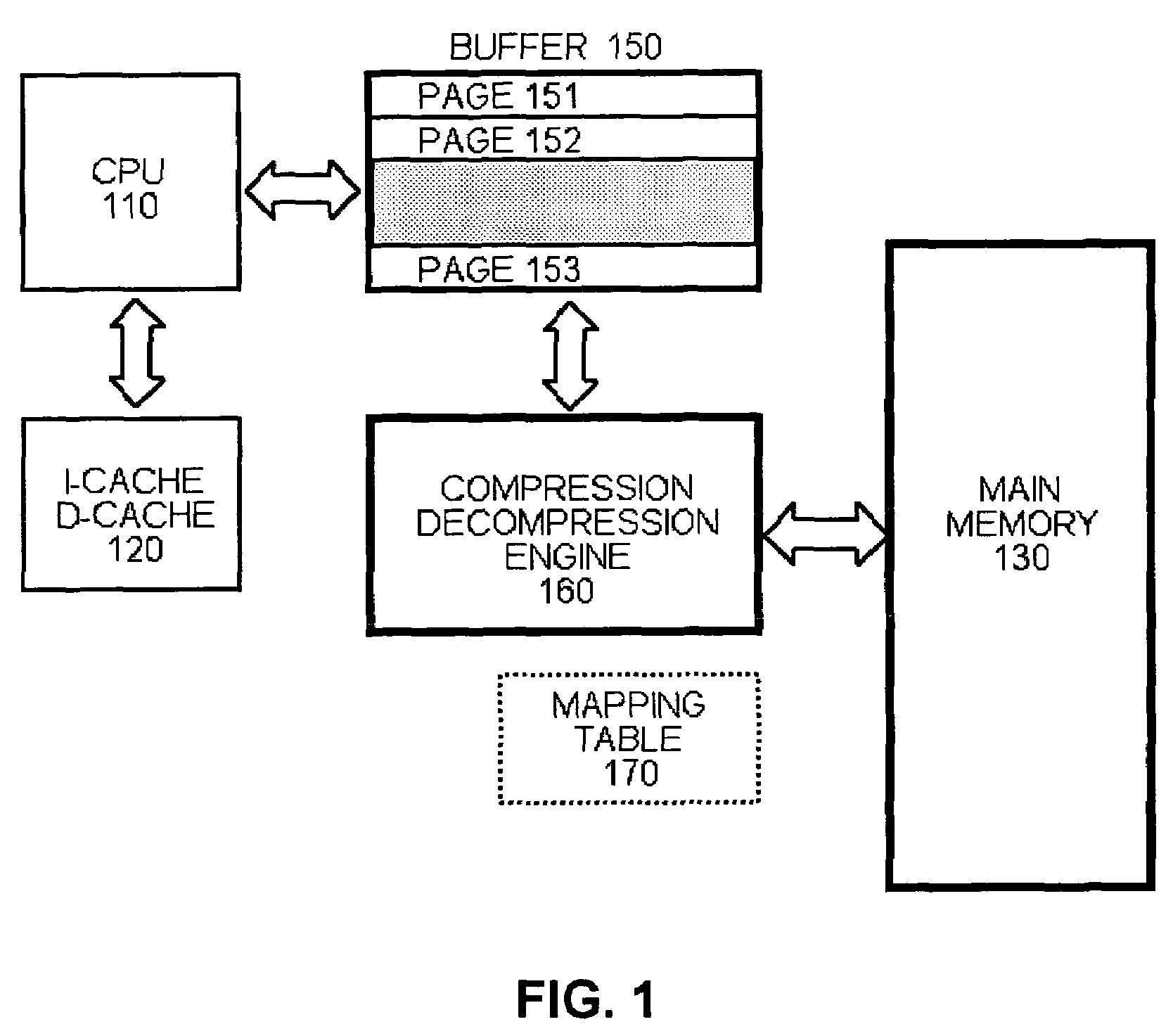
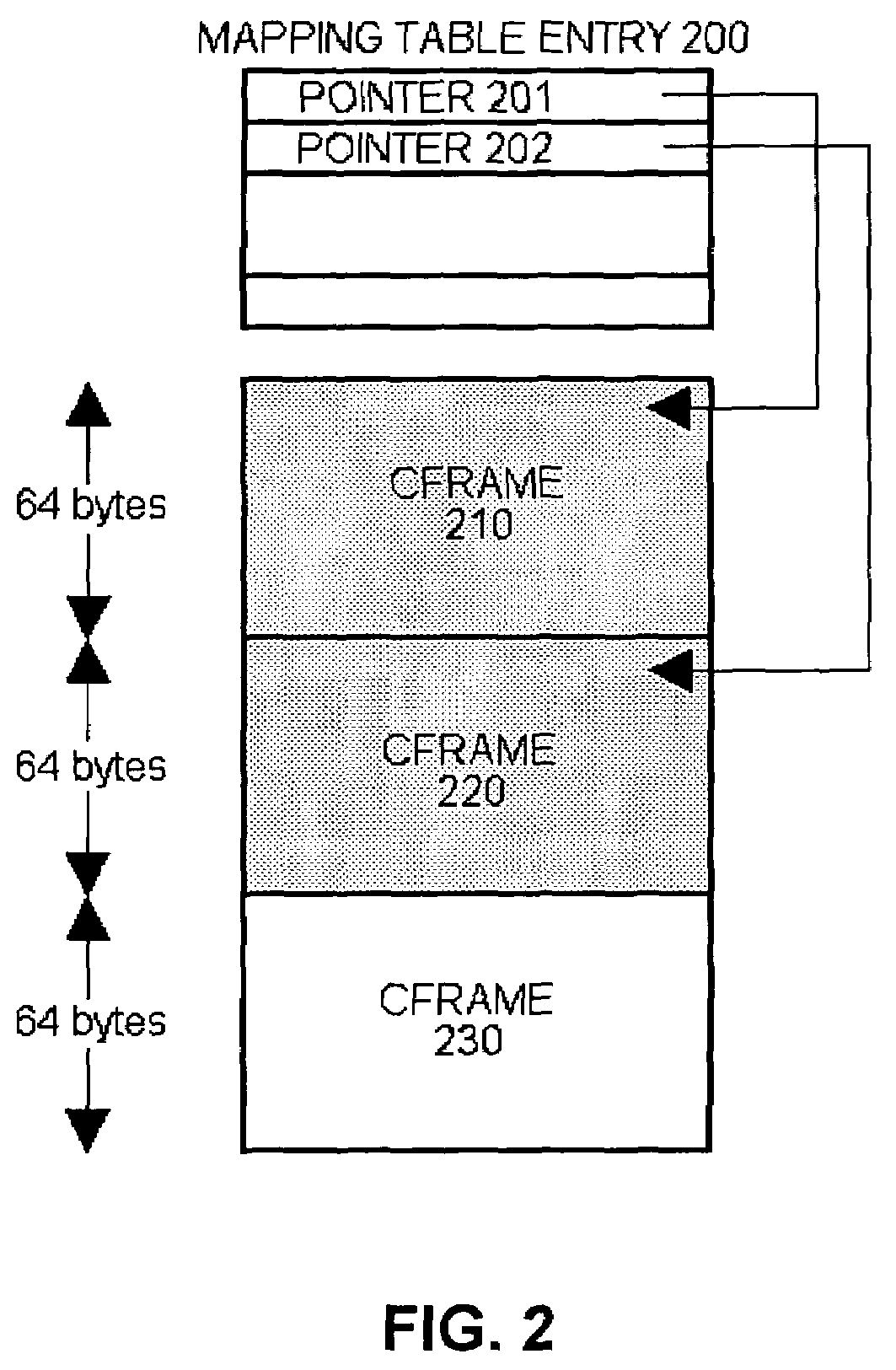
Compressed memory architecture for embedded systems
InactiveUS7302543B2Efficient compressionHigh levelMemory architecture accessing/allocationCode conversionProcessing InstructionComputer architecture
An embedded systems architecture is disclosed which can flexibly handle compression of both instruction code and data.
Owner:NEC CORP
Systems and Methods for Displaying Animations on a Mobile Device
The invention provides for systems, devices, and methods for displaying animations on devices with low-memory capacity or low-processing power, such as a mobile device. Animation sequences can by created using scene graphs of nodes. Nodes can be embedded nodes, collection nodes, or image nodes. Embedded nodes can be an embedded scene graph, a collection node can be a collection of nodes that reference collection of image sets, and an image node can be a reference to an image file and an affine transformation. Image sequences can be used using affine transformations. The affine transformation matrices can then be exported to an animation data file. Inclusion of affine transformation matrices with animation data files can reduce the memory required to store multiple image files and can reduce the computation power required to display animations. The systems, devices, and methods for displaying animations can allow for a high degree of creative freedom while reducing memory and processing requirements on a client device.
Owner:A THINKING APE TECH
Configuring state machines used to order and select matching operations for determining whether an input string matches any of at least one regular expression using lookahead finite automata based regular expression detection
InactiveUS8554698B2Small memory requirementLess memoryDigital data information retrievalDigital data processing detailsAutomatonRegular expression
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com