Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
895 results about "Instruction code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
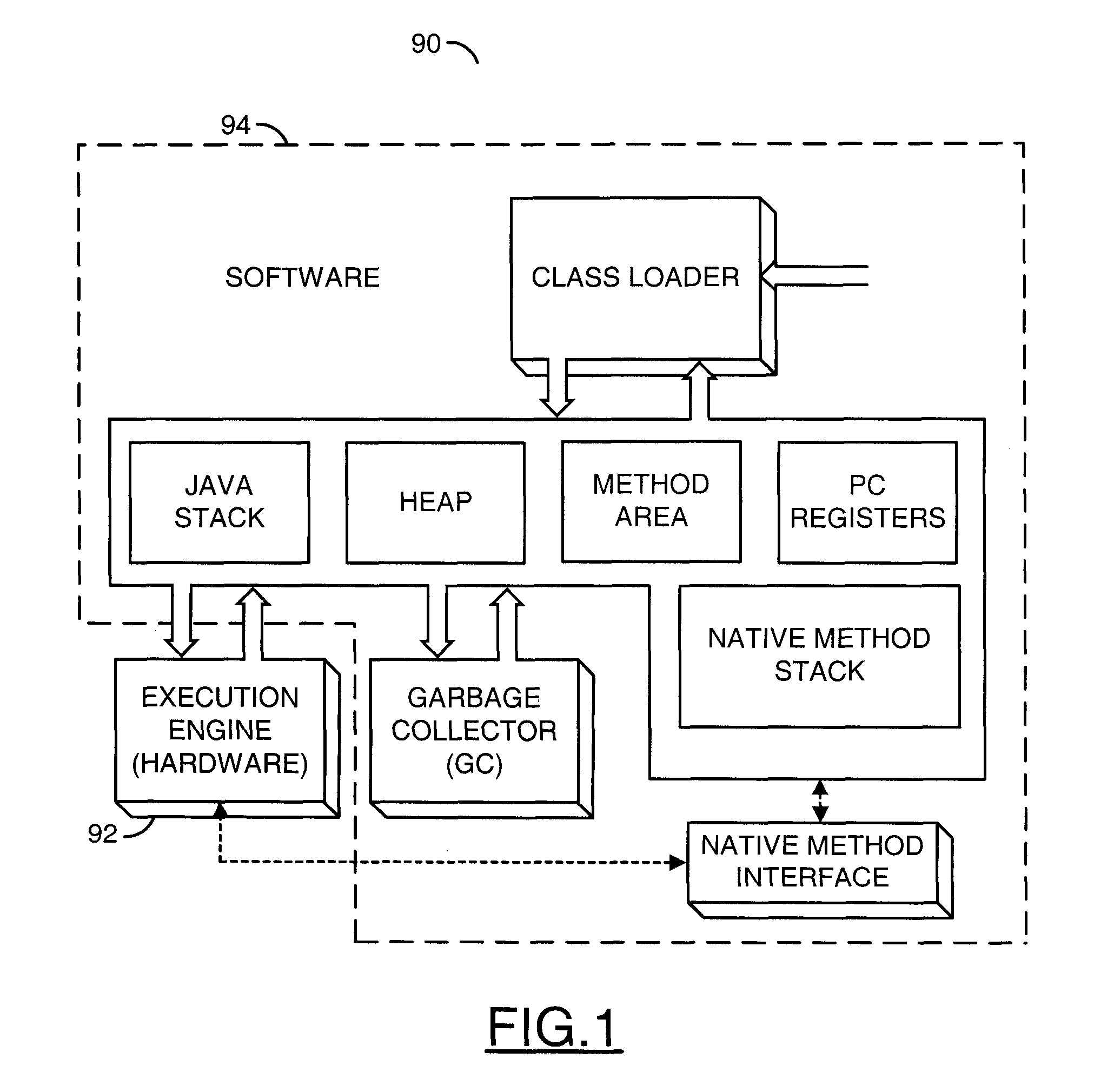
Biometric authentication of mobile financial transactions by trusted service managers
ActiveUS20090307139A1Digital data processing detailsUser identity/authority verificationUser inputFinancial transaction
A method for authenticating a financial transaction at a point of sale (POS) includes storing an application program in a first secure element of a mobile phone. The application is configured to generate instruction codes to effect the financial transaction upon verification of a user's identity. The user's credentials are stored in a second SE of the phone, which is operable to verify the user's identity from a biometric trait of the user input to the phone and to generate data authenticating the financial transaction in response to the verification of the user's identity. At the POS, the user invokes the application and then inputs a biometric trait to the phone. The second SE verifies the user's identity, and upon verification, generates data authenticating the transaction. The financial transaction data, including the instruction codes and the authenticating data, are then transmitted from the phone to the POS.
Owner:PAYPAL INC
Multi-function general purpose transceiver
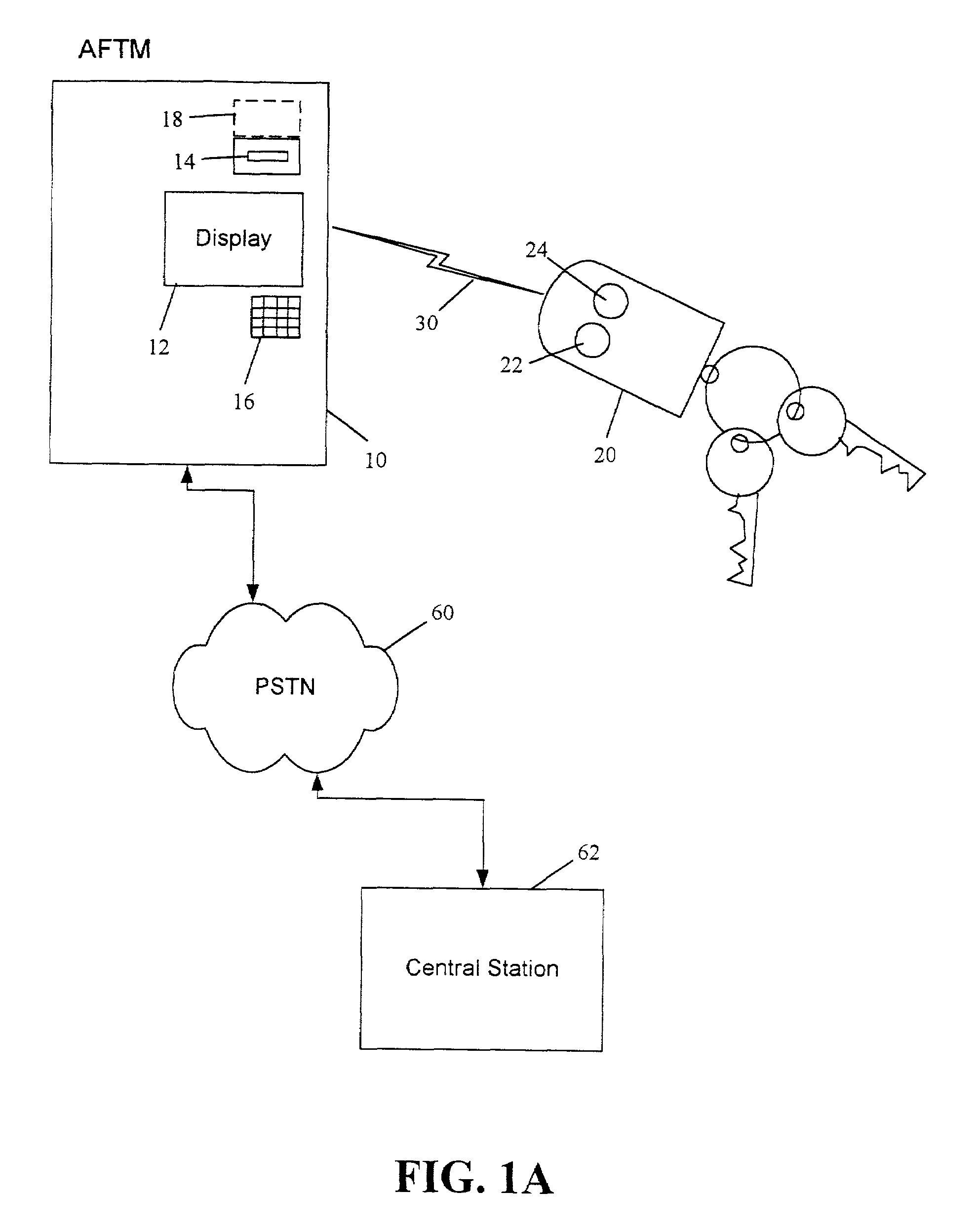
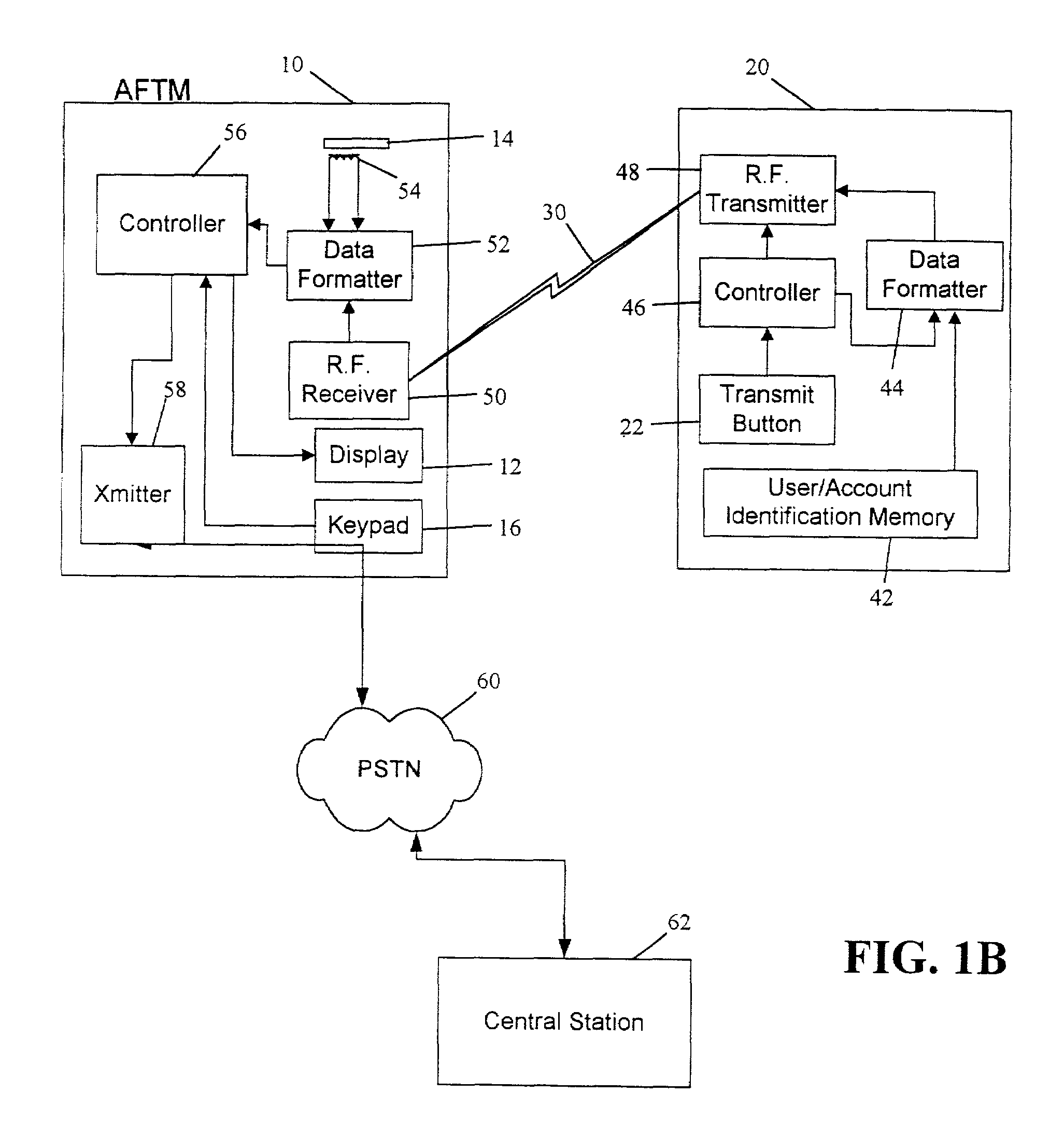
InactiveUS7397907B2Controlling coin-freed apparatusUnauthorised/fraudulent call preventionGeneral purposeTransceiver
The present invention is generally directed to a system and associated method for communicating information to a predetermined location. The system includes a transmitter disposed at a first location and configured to transmit a signal containing an instruction code that uniquely identifies an instruction to be carried out. The system further includes a transceiver disposed remotely from the transmitter and configured to receive the transmitted signal. The transceiver circuit includes a line interface circuit configured to interface with a telephone line that is part of the public switched telephone network (PSTN) and initiate a phone call over the telephone line. Finally, the system includes a central station remotely located from said transceiver but being in communication with said transceiver via the PSTN The central station further include a decoder configured to decode the instruction code. In accordance with a broader aspect, the invention is directed to a general purpose transceiver having a receiver for receiving an information signal and a transmitter configured to transmit an outgoing signal over a phone line to a central station A portion of the information signal includes an instruction code, which may be decoded by the central station and acted upon accordingly Consistent with the general purpose nature of the transceiver, the phone number of the central station may be transmitted to the transceiver as part of the information signal.
Owner:STATSIGNAL IPC
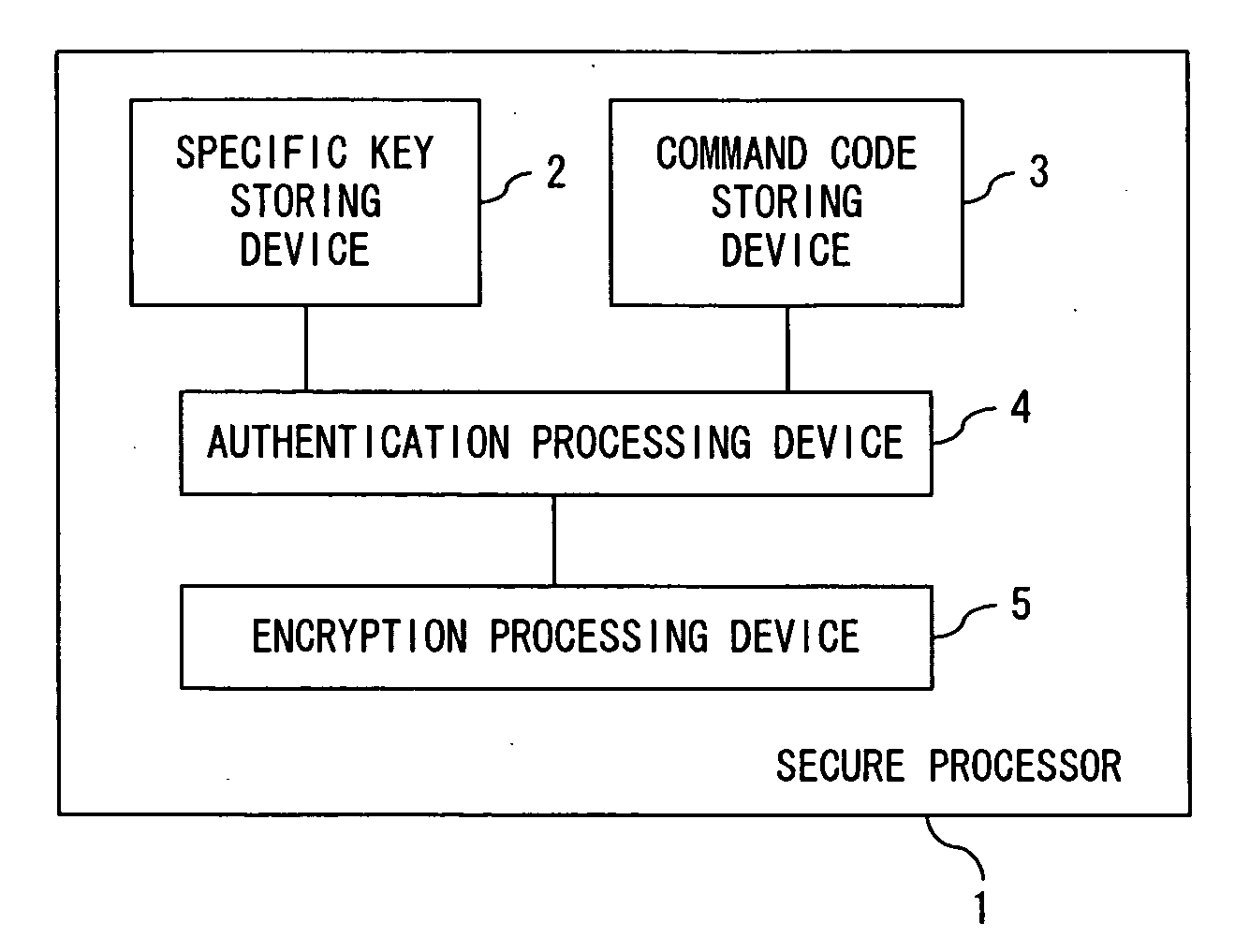
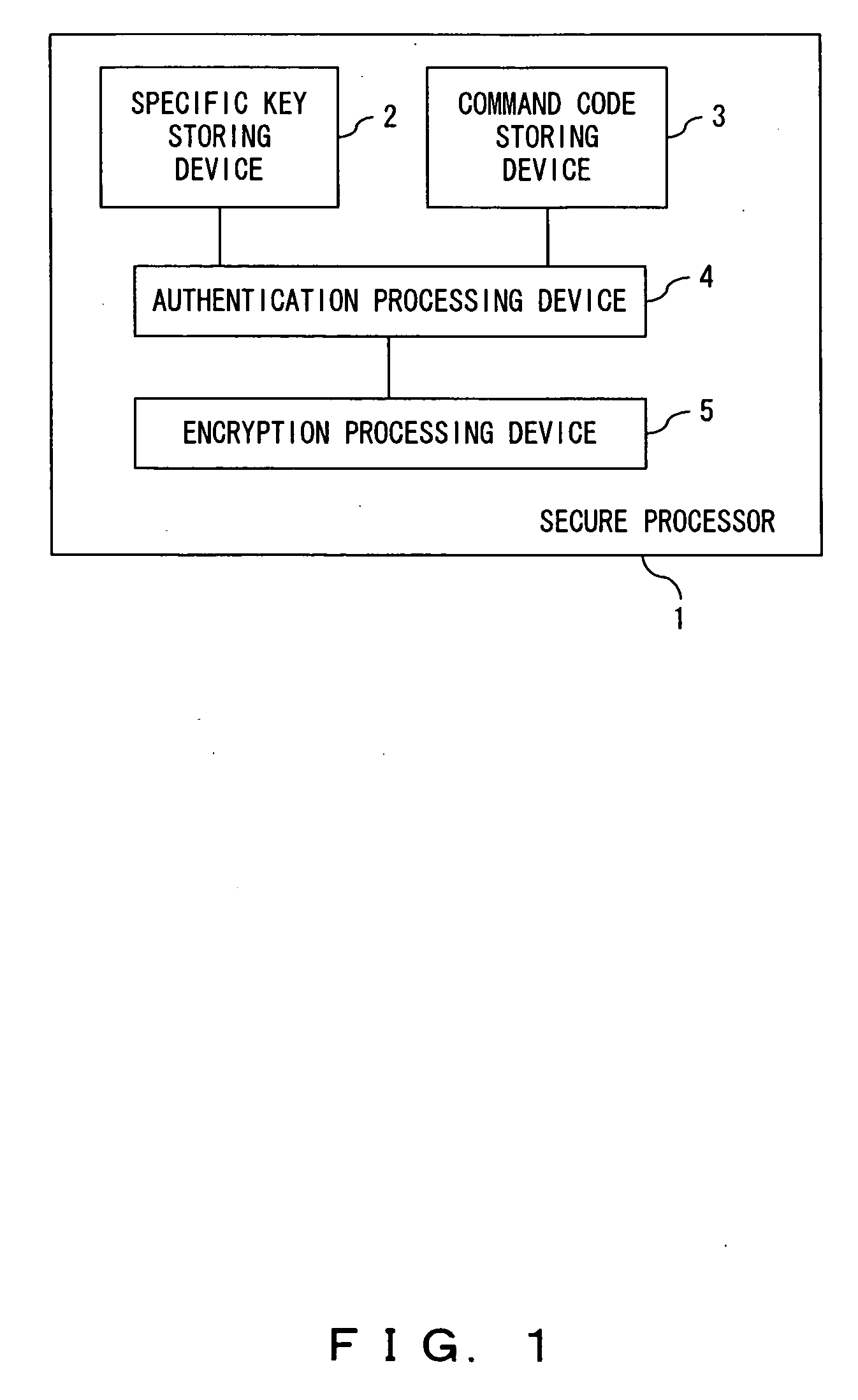
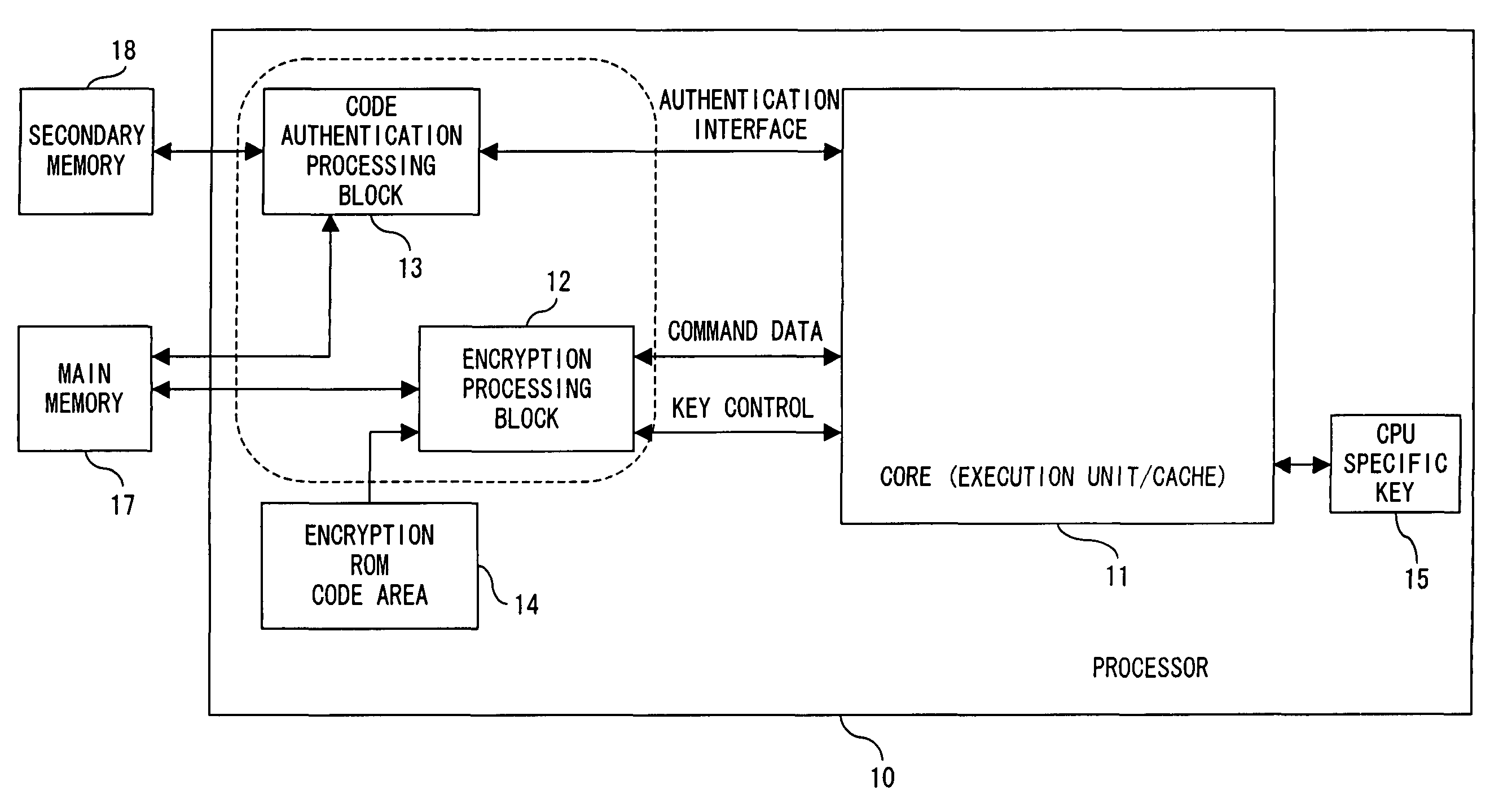
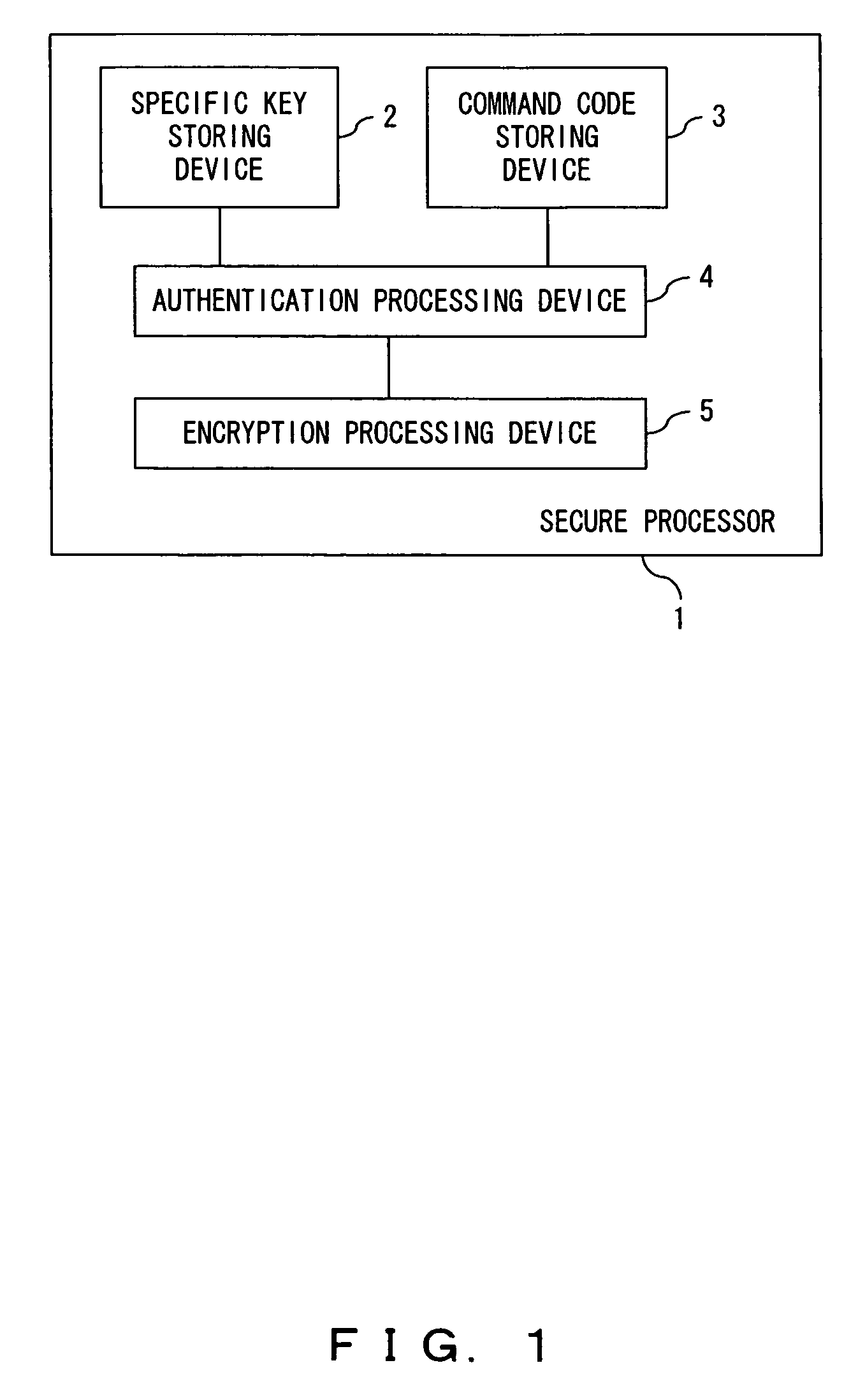
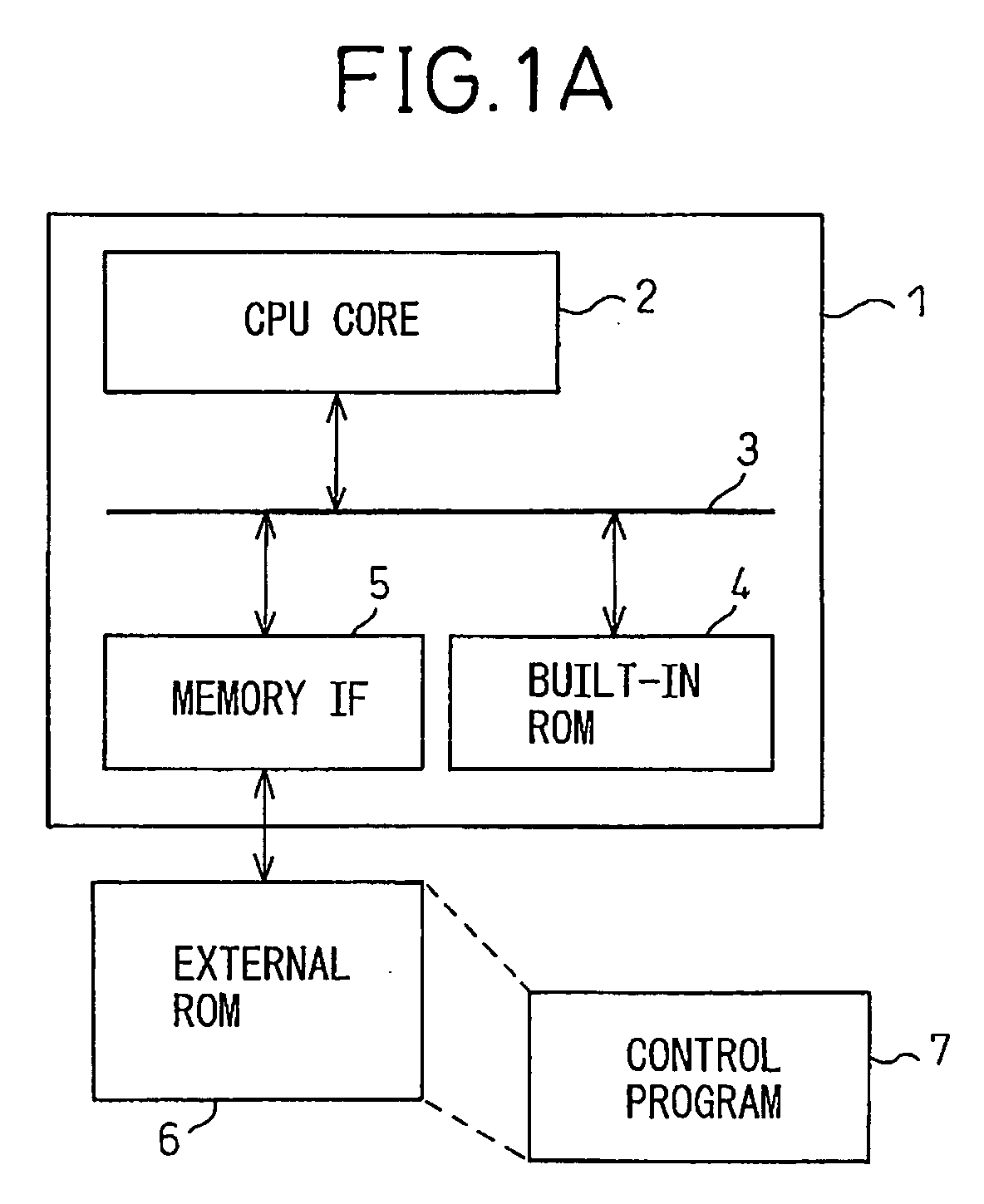
Secure processor and a program for a secure processor
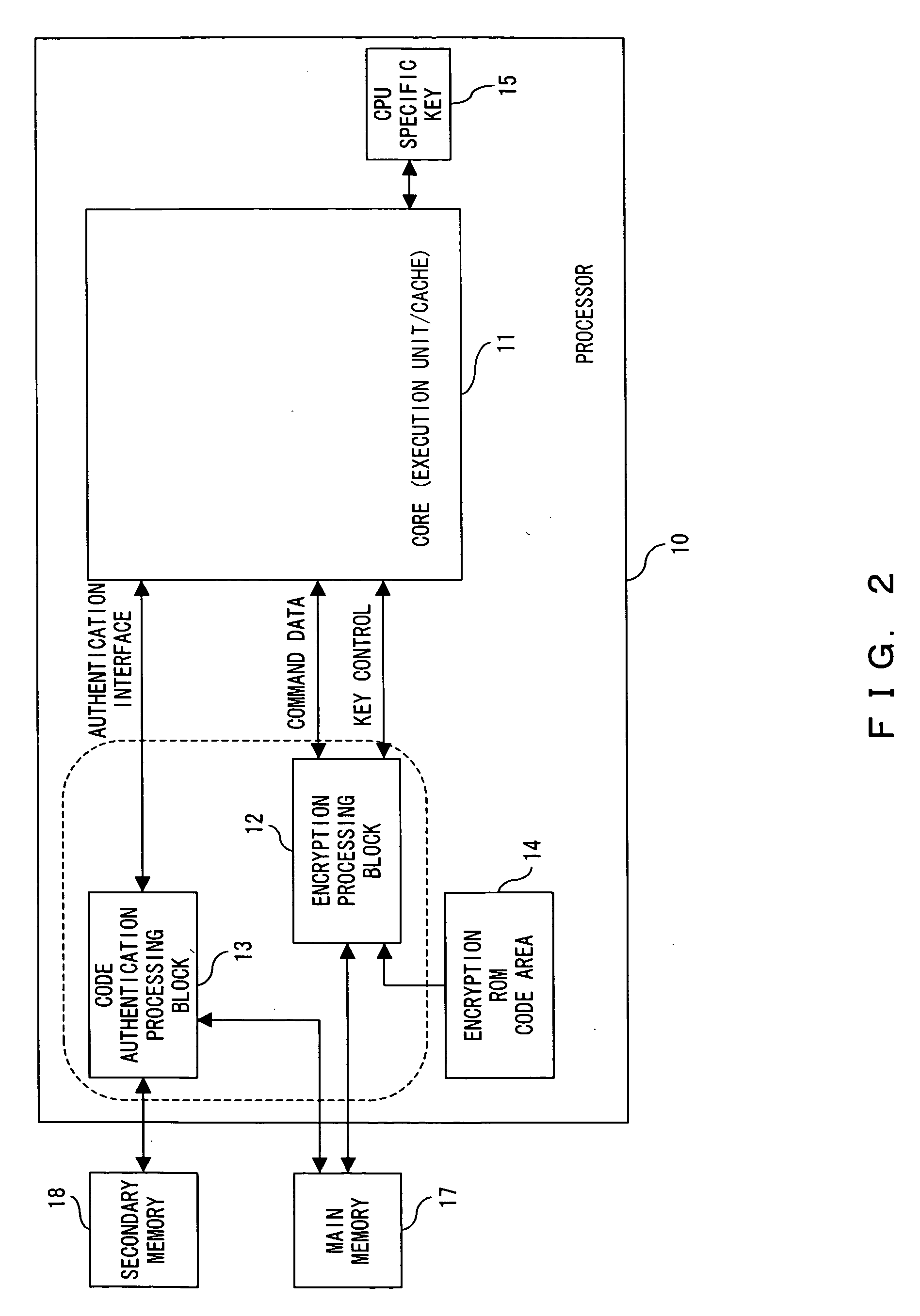
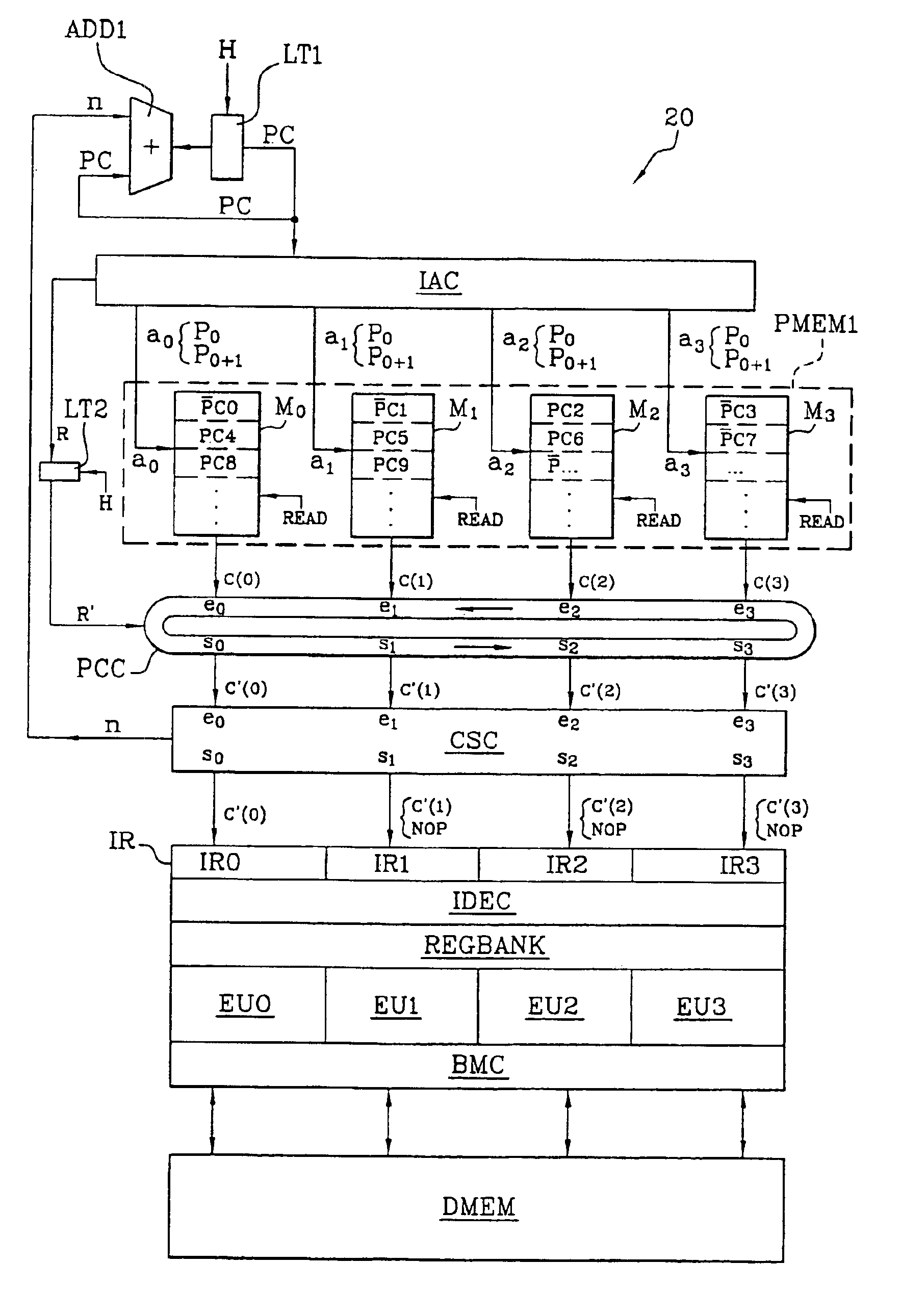
ActiveUS20060015748A1Increase rangeReliable applicationMemory architecture accessing/allocationUnauthorized memory use protectionEncryptionInstruction code
The instruction code including an instruction code stored in the area where the encrypted instruction code is stored in a non-rewritable format is authenticated using a specific key which is specific to the core where the instruction code is executed or an authenticated key by a specific key to perform an encryption processing for the input and output data between the core and the outside.
Owner:SOCIONEXT INC
Multi-function general purpose transceivers & devices
InactiveUS20090068947A1Controlling coin-freed apparatusRadio relay systemsGeneral purposeTransceiver
The present invention is generally directed to a system and associated method for communicating information. In some embodiments, the invention is directed to a general purpose transceiver having a receiver for receiving an information signal and a transmitter configured to transmit an outgoing signal to a central station. A portion of the information signal can include an instruction code, which may be decoded and acted upon accordingly. Other embodiments and features are also claimed and described.
Owner:SIPCO
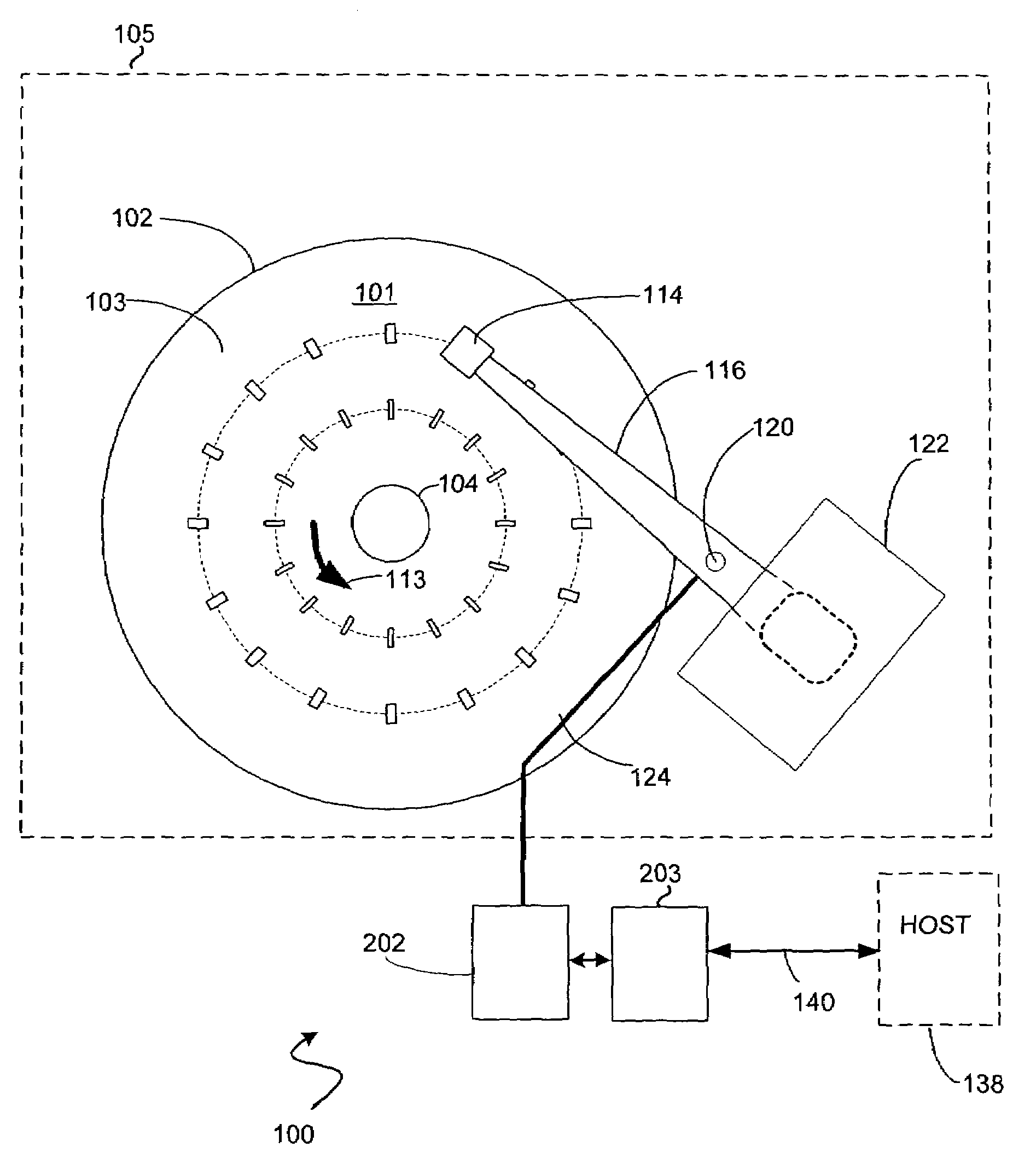
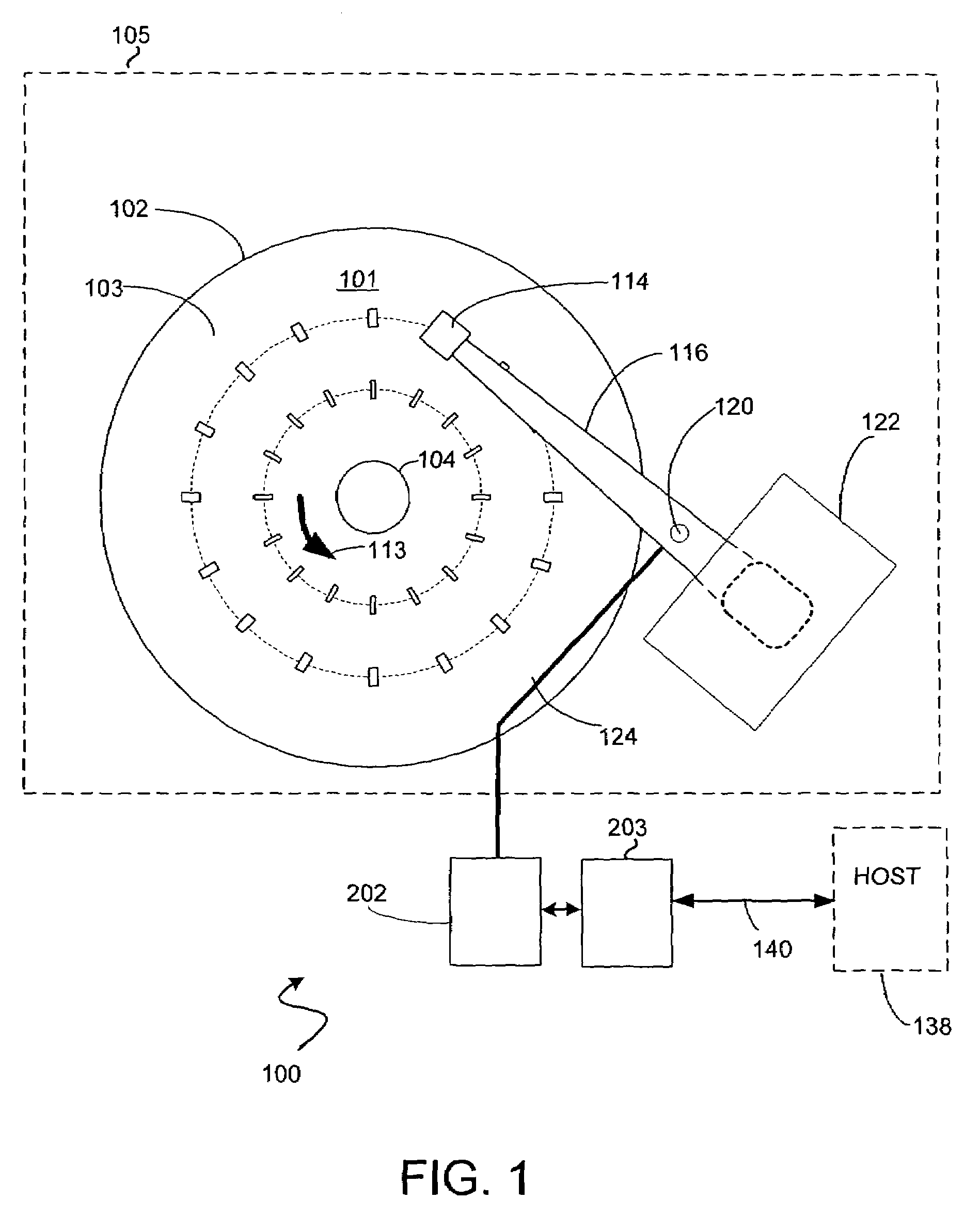
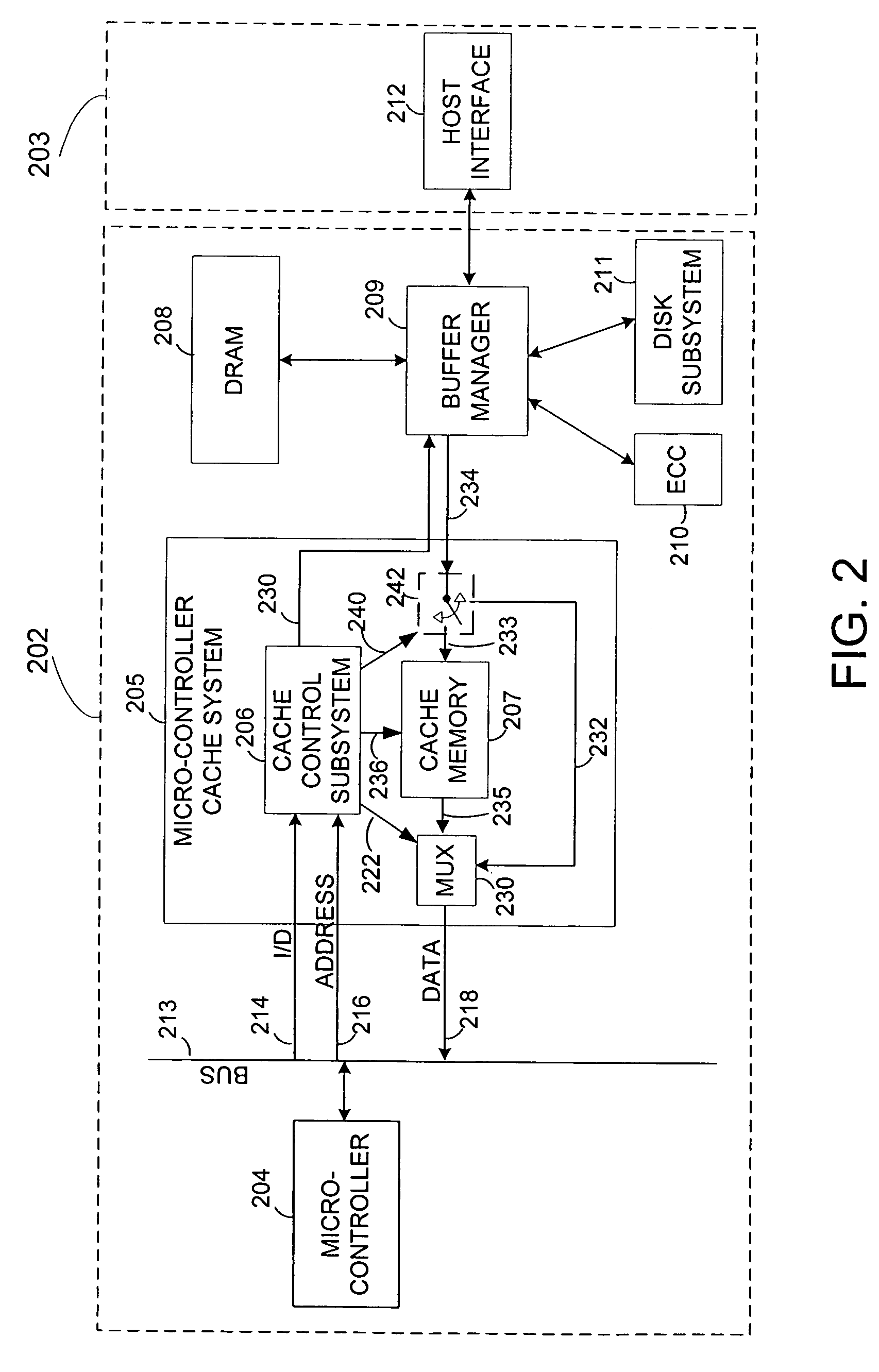
Fetch operations in a disk drive control system
InactiveUS7194576B1Easy to operateMemory architecture accessing/allocationMemory adressing/allocation/relocationControl systemParallel computing
A method and system for improving fetch operations between a micro-controller and a remote memory via a buffer manager in a disk drive control system comprising a micro-controller, a micro-controller cache system having a cache memory and a cache-control subsystem, and a buffer manager communicating with micro-controller cache system and remote memory. The invention includes receiving a data-request from micro-controller in cache control subsystem wherein the data-request comprises a request for at least one of instruction code and non-instruction data. The invention further includes providing the requested data to micro-controller if the requested data reside in cache memory, determining if the received data-request is for non-instruction data if requested data does not reside in cache memory, fetching the non-instruction data from remote memory by micro-controller cache system via buffer manager, and bypassing cache memory to preserve the contents of cache memory and provide the fetched non-instruction data to micro-controller.
Owner:WESTERN DIGITAL TECH INC
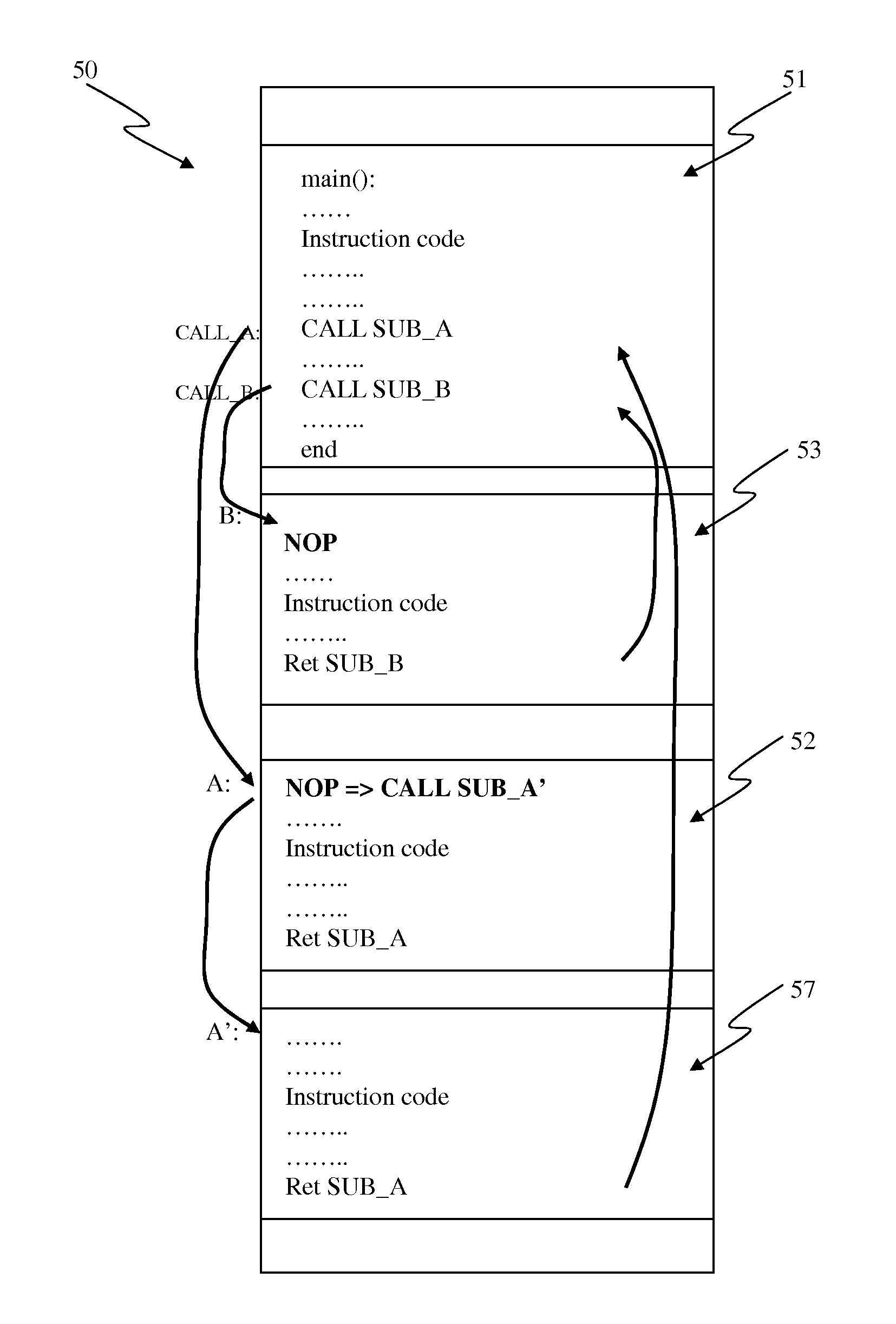
Method and System of Using One-Time Programmable Memory as Multi-Time Programmable in Code Memory of Processors
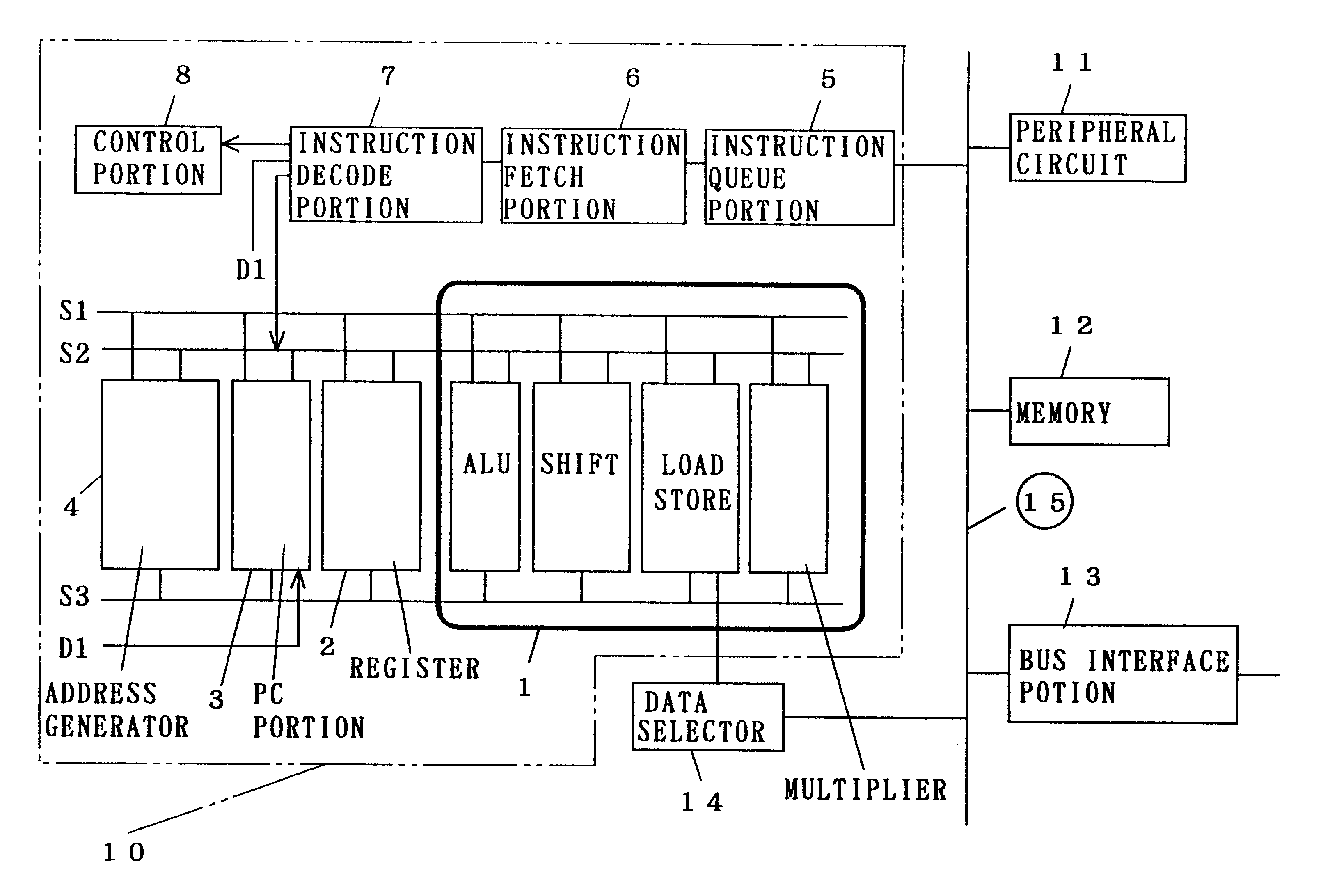
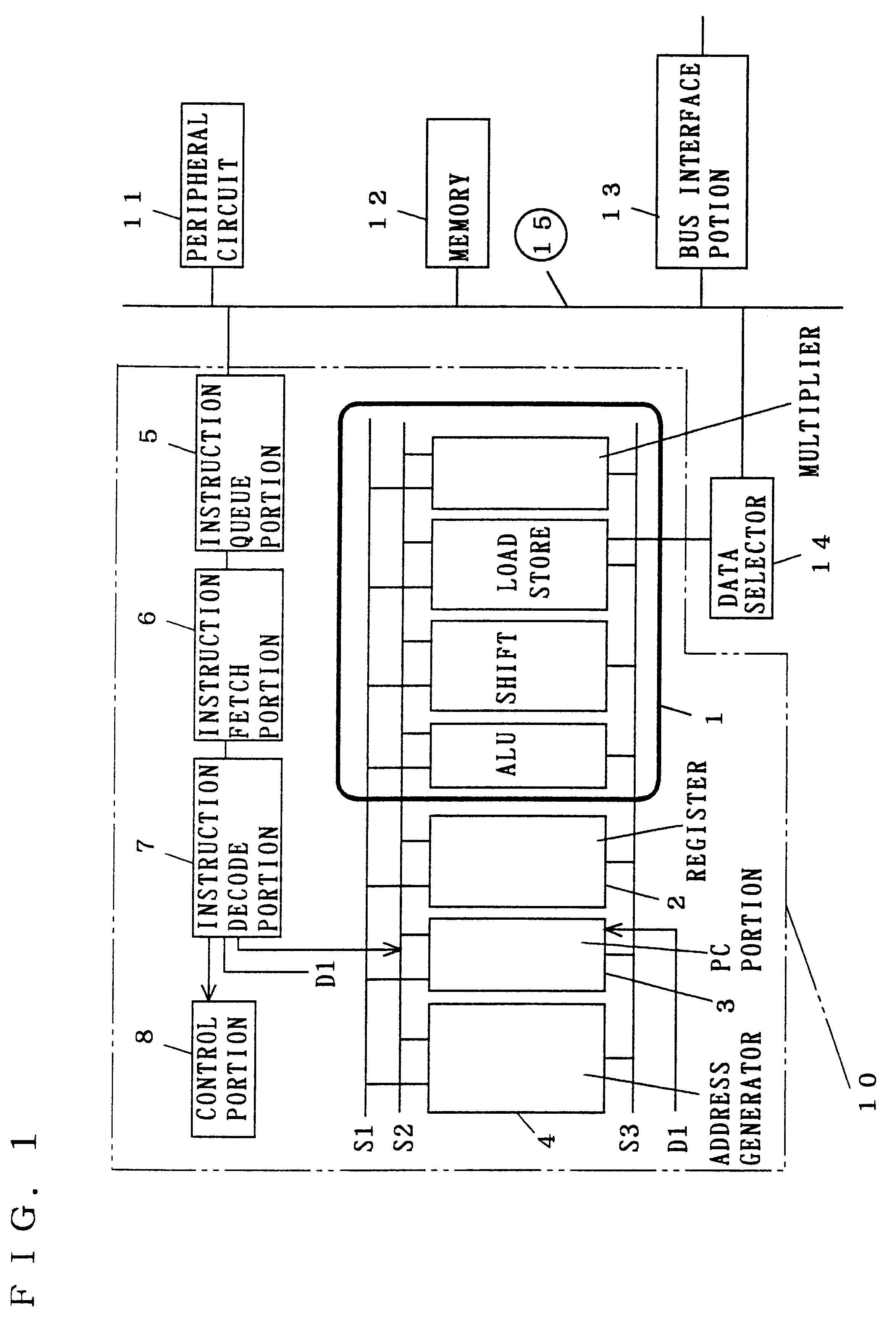
A method, device and system of using an One-Time-Programmable (OTP) memory as an Multiple-Time Programming (MTP) memory equivalent is disclosed. The use of OTP memory in this manner allows code to be updated one or more times and yet remain small in size and relatively easy to process (fabricate). The code can be program code for a processor, such as boot code, boot code kernel or other instruction code. According to one aspect, an OTP memory is able to functionally operate as if it were a MTP memory through intelligent use of NOPs, which are no operations. Subsequently, if a particular subroutine or function in the program code needs to be modified, an instruction (e.g., JUMP instruction) can be programmed into the NOP so that certain existing instructions can be bypassed and the execution of instructions of a new module can be performed.
Owner:ATTOPSEMI TECH CO LTD
Implementing instruction set architectures with non-contiguous register file specifiers
ActiveUS20080189519A1Register arrangementsInstruction analysisProcessing InstructionProcessor register
There are provided methods and computer program products for implementing instruction set architectures with non-contiguous register file specifiers. A method for processing instruction code includes processing a fixed-width instruction of a fixed-width instruction set using a non-contiguous register specifier of a non-contiguous register specification. The fixed-width instruction includes the non-contiguous register specifier.
Owner:INT BUSINESS MASCH CORP
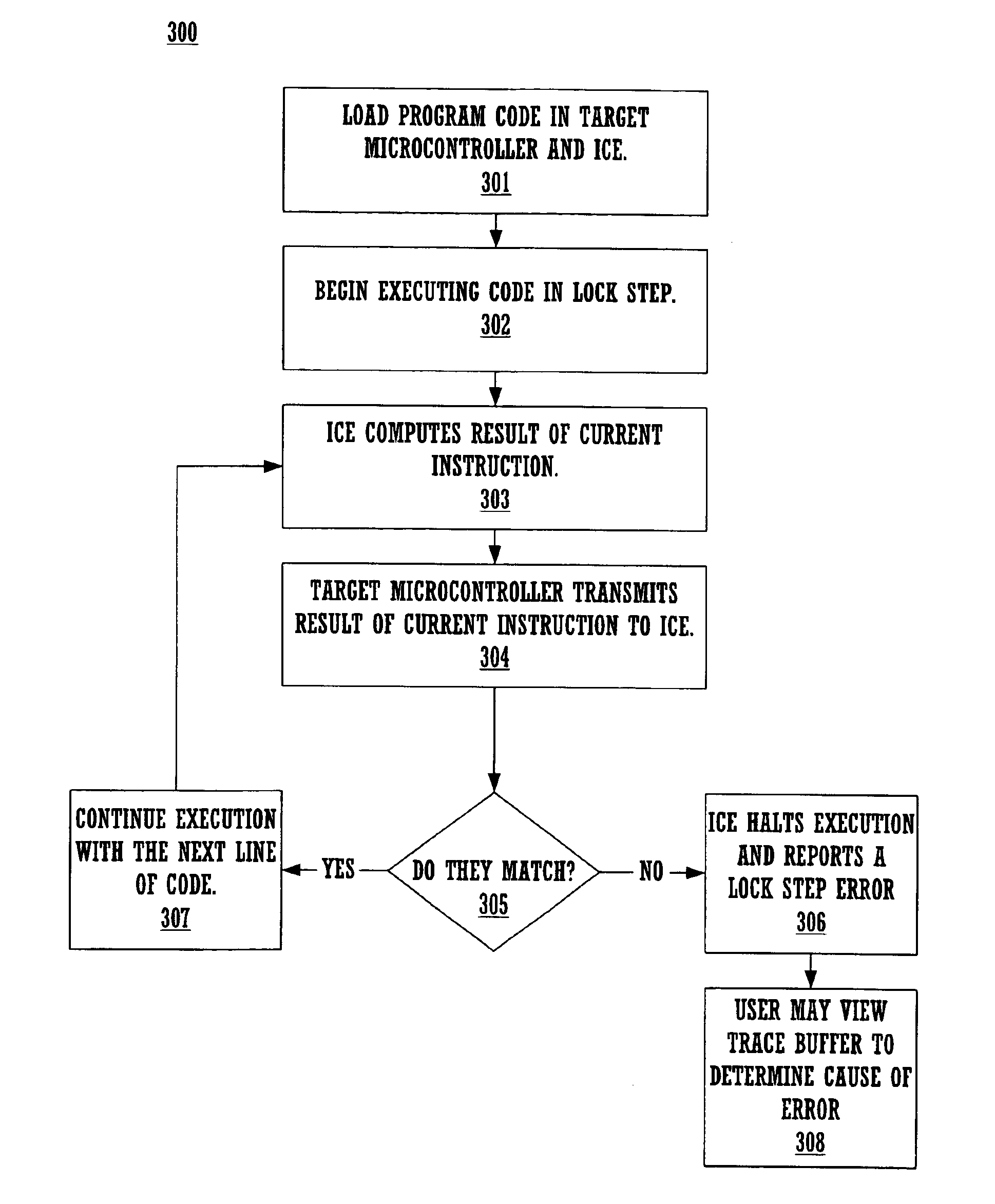
System and a method for checking lock step consistency between an in circuit emulation and a microcontroller while debugging process is in progress
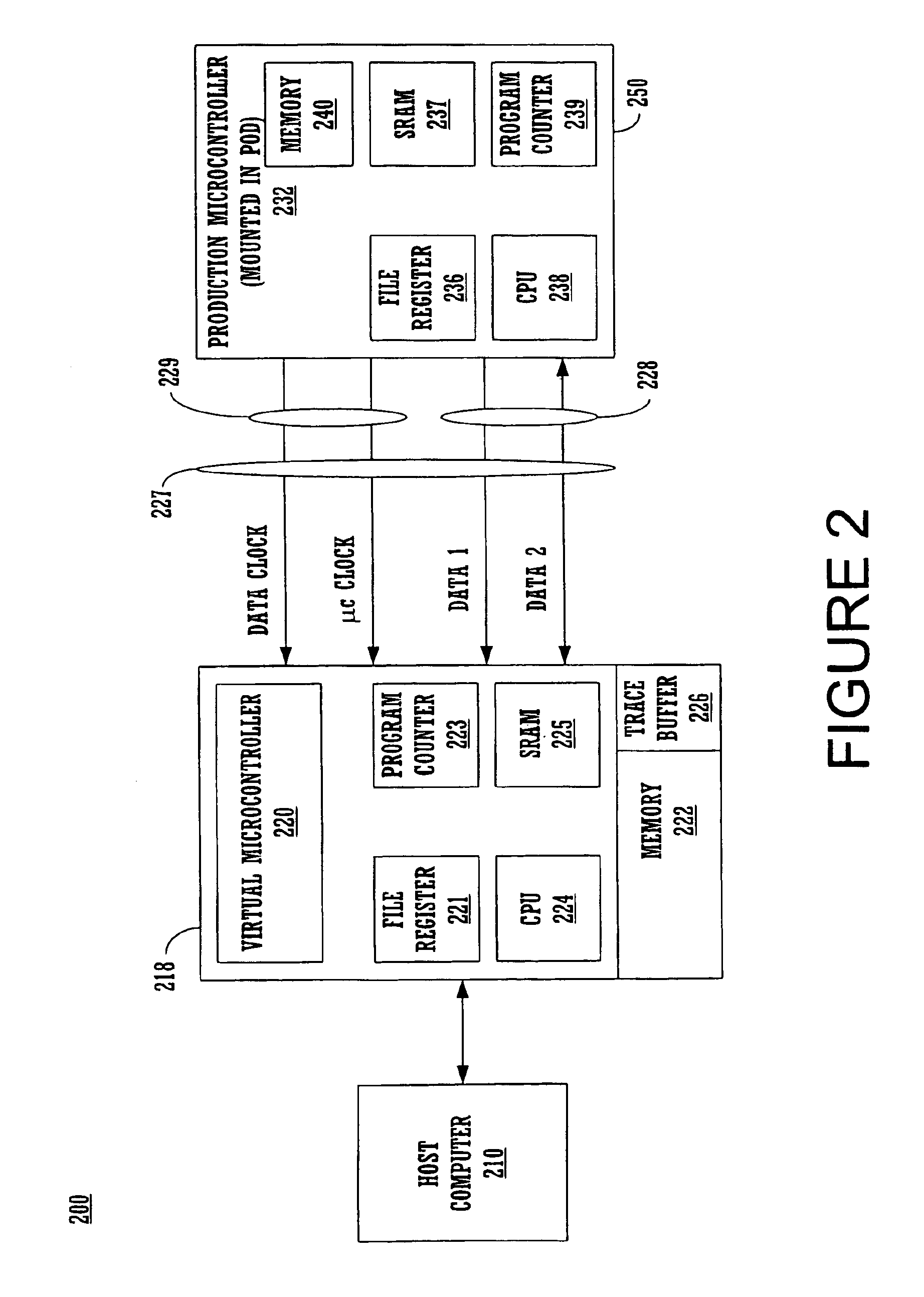
InactiveUS6922821B1Analogue computers for electric apparatusFunctional testingMicrocontrollerParallel computing
Checking the consistency of a lock step process while debugging a microcontroller code is in progress. A method provides a production microcontroller to execute an instruction code and provides the result of the instruction code to an ICE. The ICE, independent from the production microcontroller and simultaneously, executes the same instruction code and produces a result. The ICE compares the result of its computation and the result received from the production microcontroller. The ICE issues a “lock step error” when the result of the comparison is a mismatch. A trace buffer residing in the host device provides the location of the line of code causing the mismatch. After identifying the line of code causing the mismatch the user debugs the erroneous line of code. The debugging process resumes on the next line of code in the microcontroller code under test.
Owner:MONTEREY RES LLC
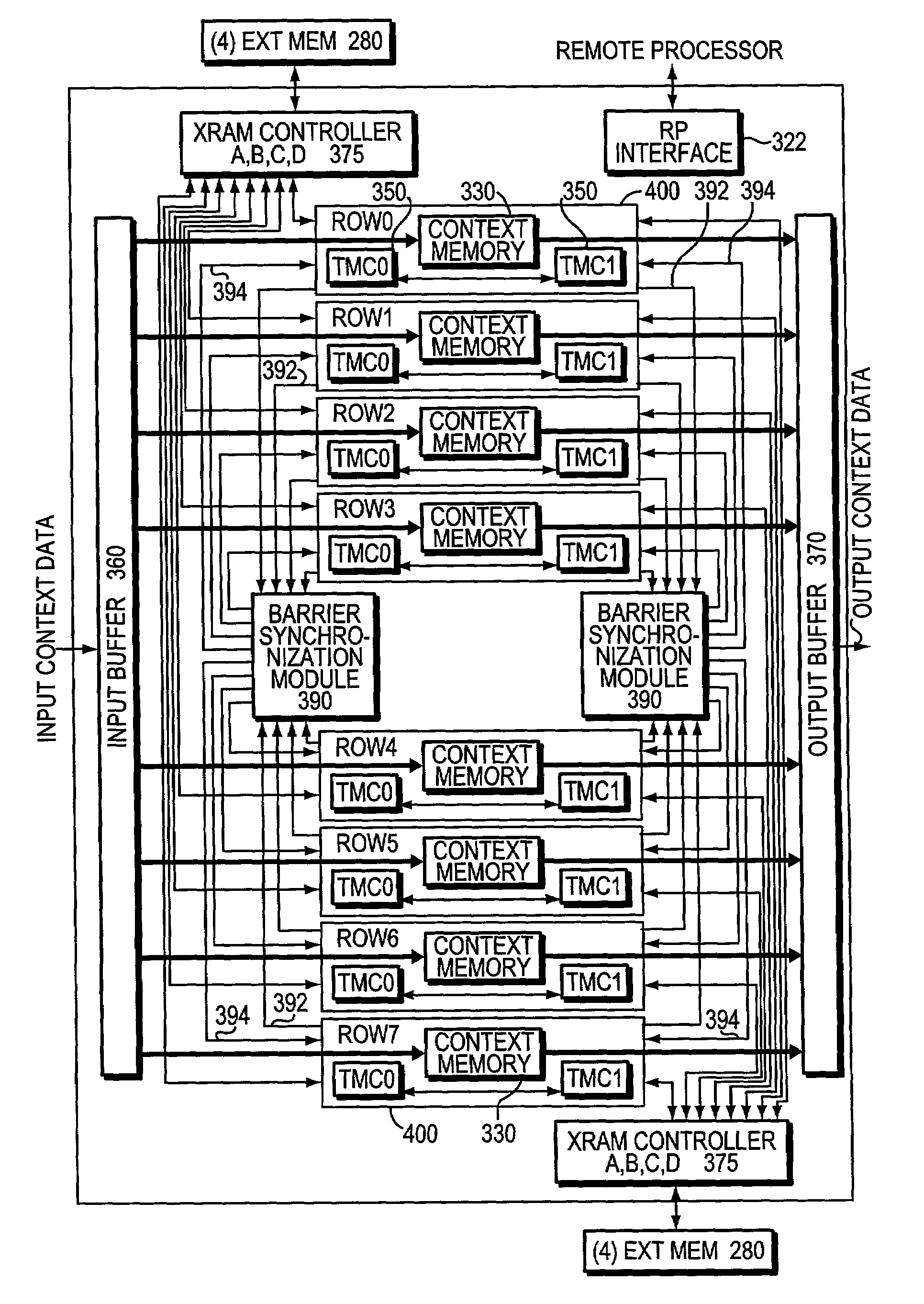
Barrier synchronization mechanism for processors of a systolic array
InactiveUS7100021B1Without consuming substantial memory resourceImprove latencyProgram synchronisationGeneral purpose stored program computerSystolic arrayCommon point
A mechanism synchronizes among processors of a processing engine in an intermediate network station. The processing engine is configured as a systolic array having a plurality of processors arrayed as rows and columns. The mechanism comprises a barrier synchronization mechanism that enables synchronization among processors of a column (i.e., different rows) of the systolic array. That is, the barrier synchronization function allows all participating processors within a column to reach a common point within their instruction code sequences before any of the processors proceed.
Owner:CISCO TECH INC
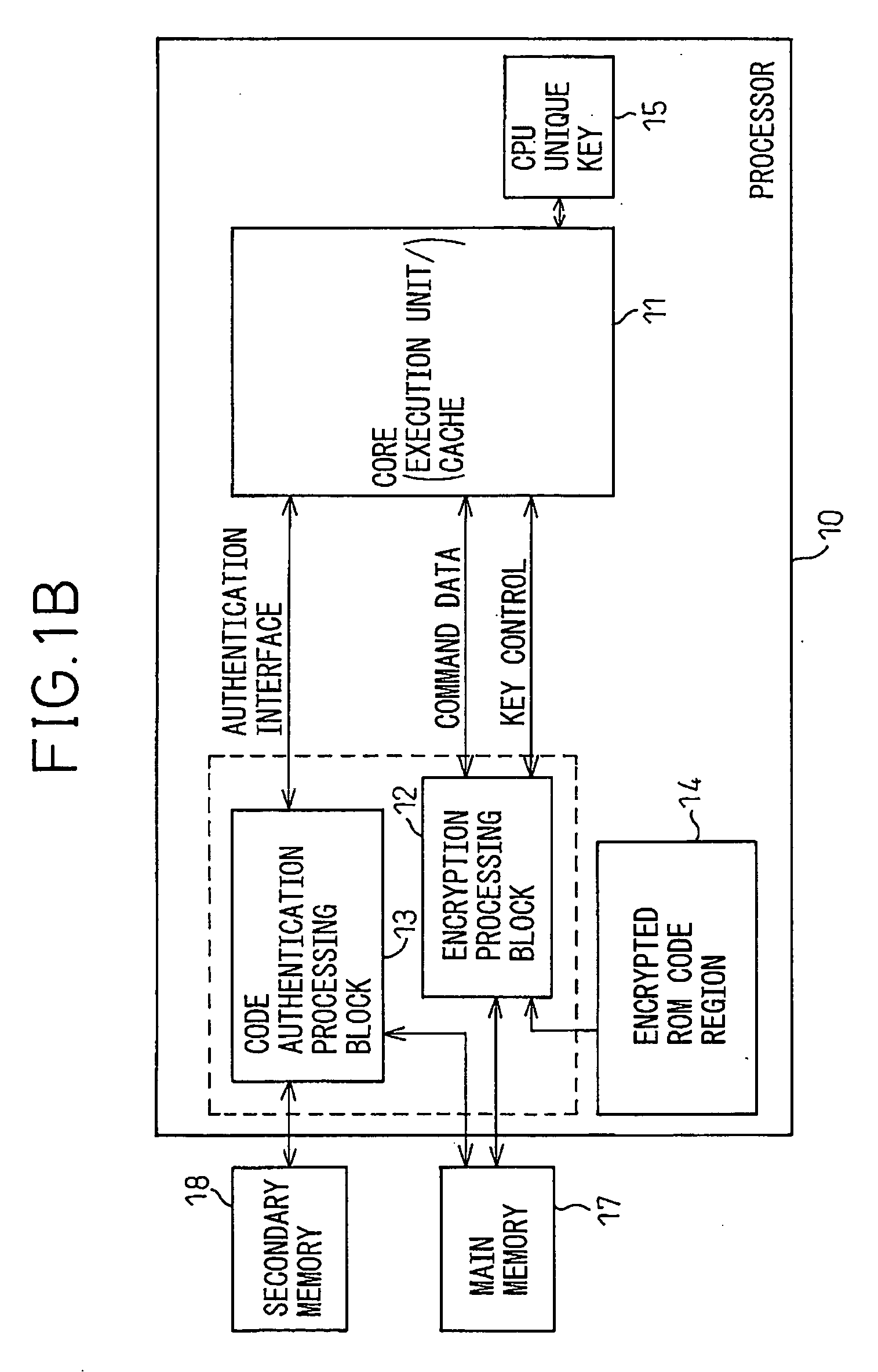
Secure processor and a program for a secure processor
ActiveUS7865733B2Increase rangeEasy to processMemory architecture accessing/allocationUser identity/authority verificationSecure cryptoprocessorInstruction code
The instruction code including an instruction code stored in the area where the encrypted instruction code is stored in a non-rewritable format is authenticated using a specific key which is specific to the core where the instruction code is executed or an authenticated key by a specific key to perform an encryption processing for the input and output data between the core and the outside.
Owner:SOCIONEXT INC
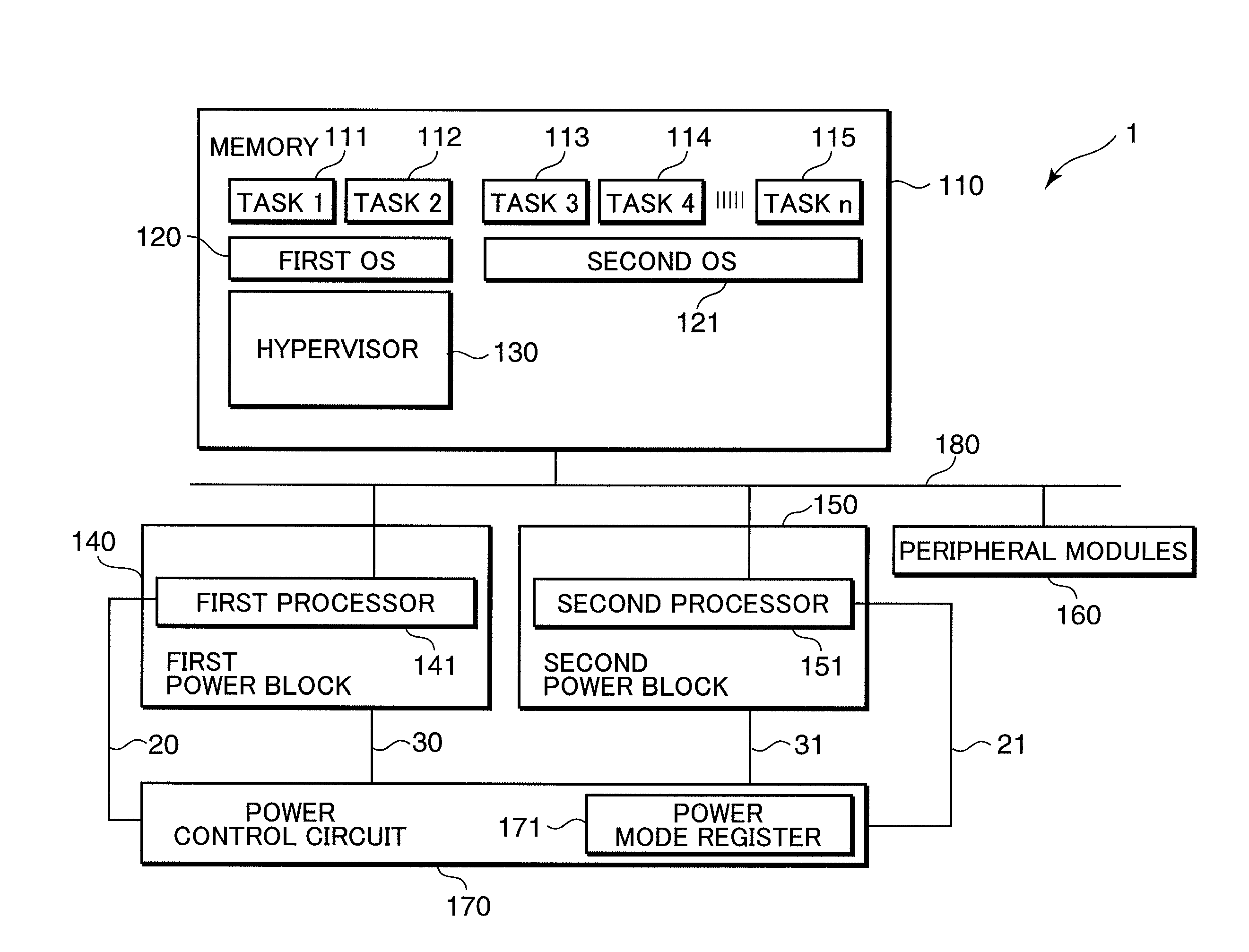
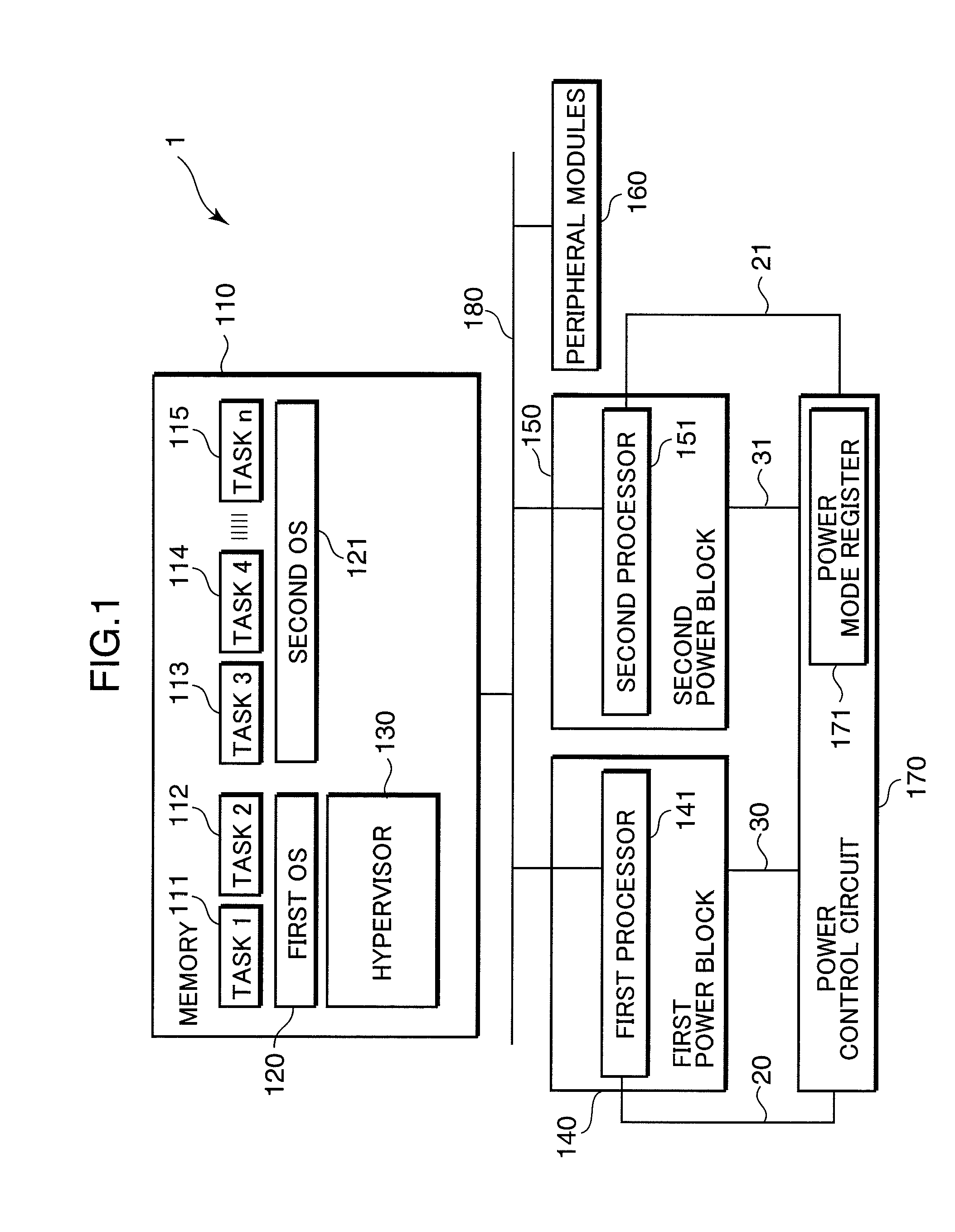
Multiprocessor control apparatus, multiprocessor control method, and multiprocessor control circuit
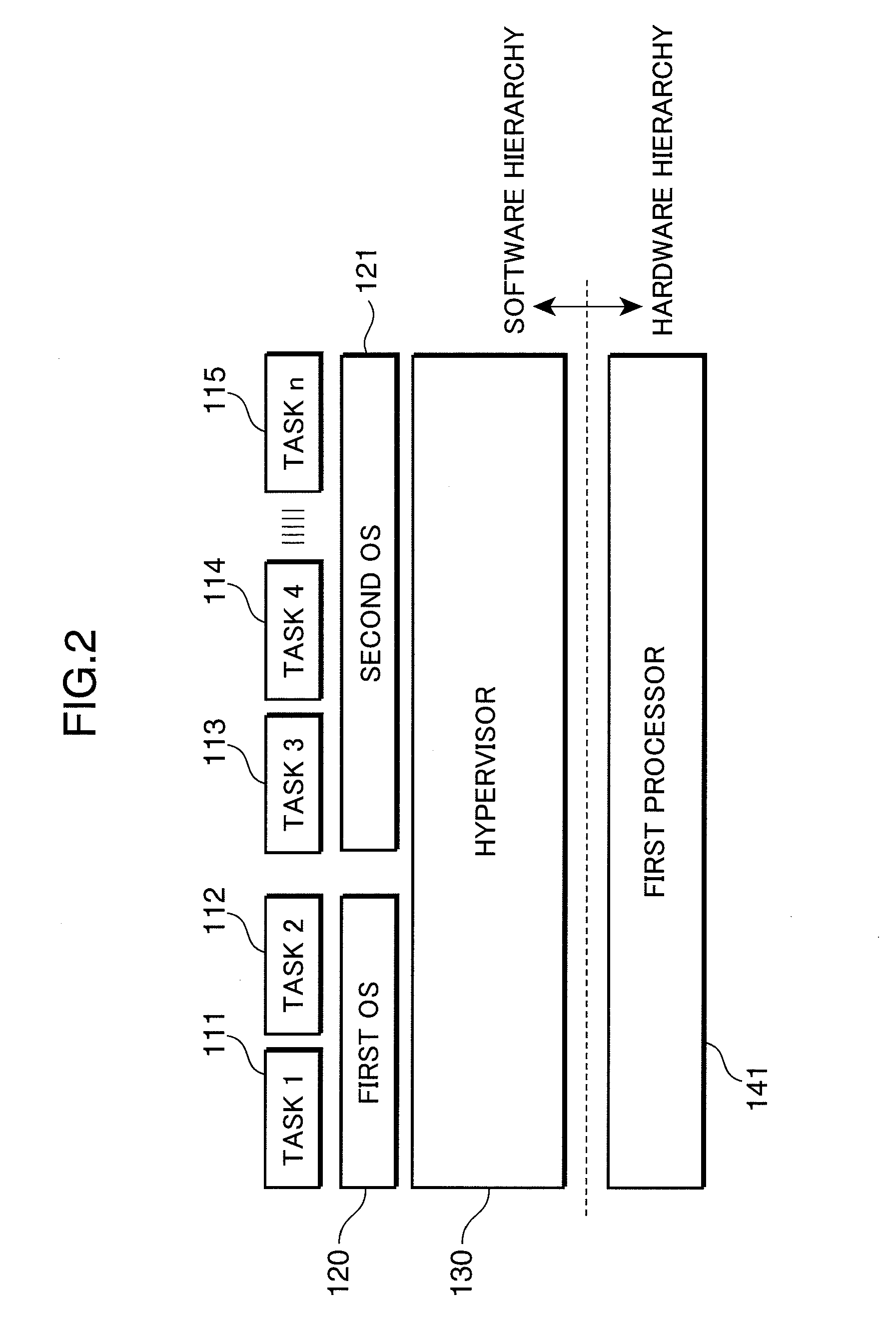
ActiveUS20100185833A1Reduce power consumptionReduce the number of timesMemory architecture accessing/allocationSusbset functionality useMulti processorParallel computing
An object of the invention is to reduce the electric power consumption resulting from temporarily activating a processor requiring a large electric power consumption, out of a plurality of processors. A multiprocessor system (1) includes: a first processor (141) which executes a first instruction code; a second processor (151) which executes a second instruction code, a hypervisor (130) which converts the second instruction code into an instruction code executable by the first processor (141); and a power control circuit (170) which controls the operation of at least one of the first processor (141) and the second processor (151). When the operation of the second processor (151) is suppressed by the power control circuit (170), the hypervisor (130) converts the second instruction code into the instruction code executable by the first processor (141), and the first processor (141) executes the converted instruction code.
Owner:GK BRIDGE 1
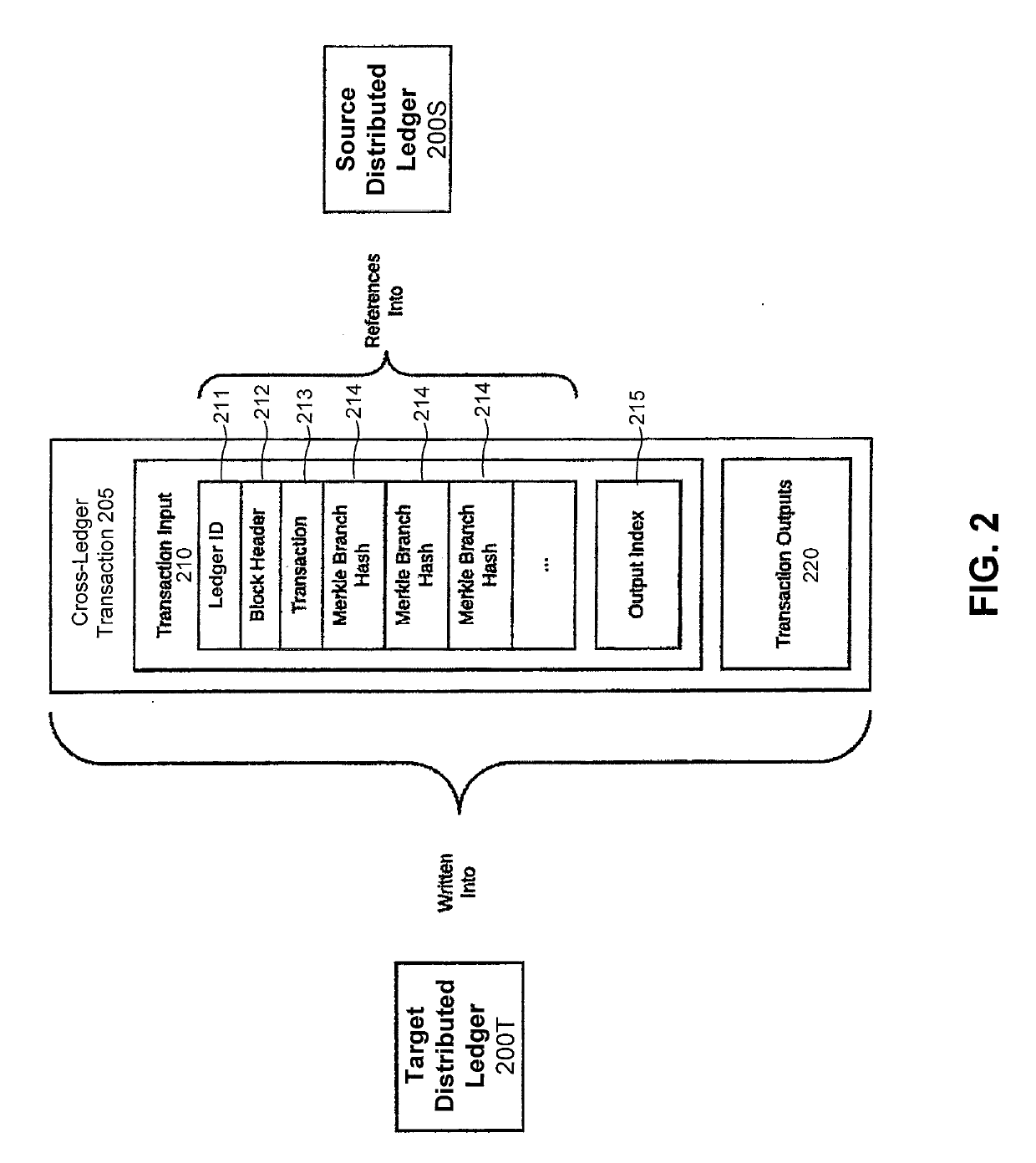
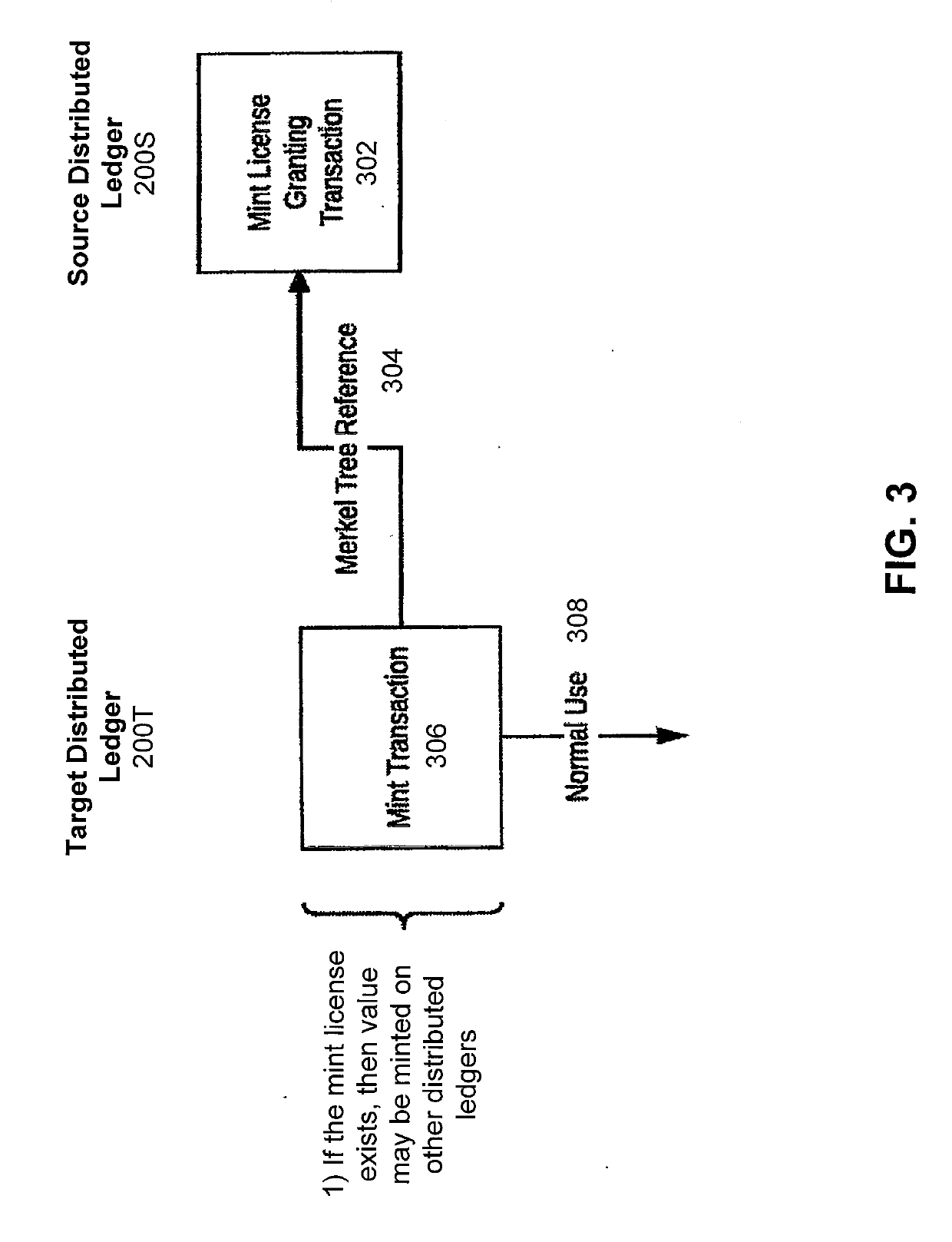
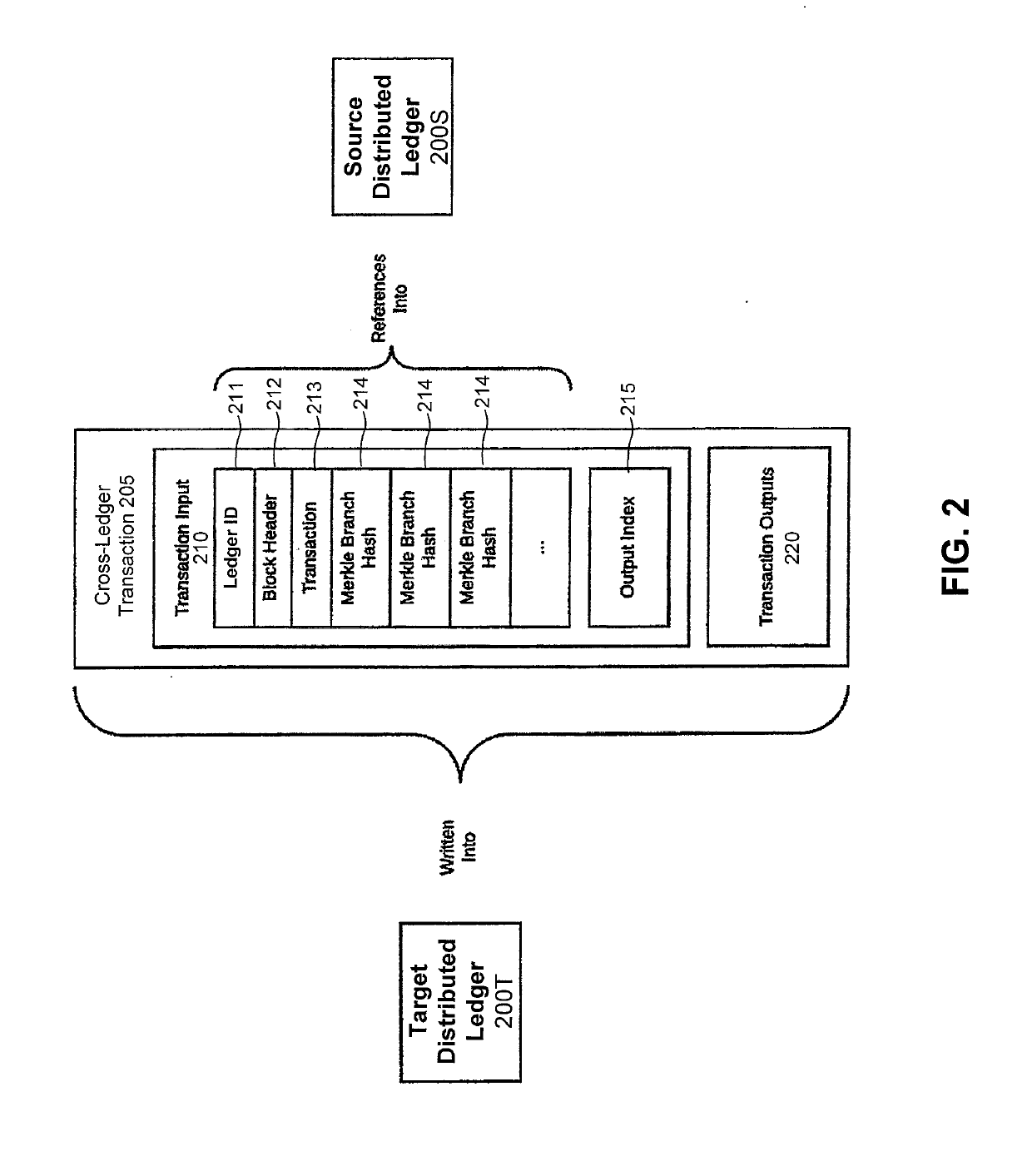
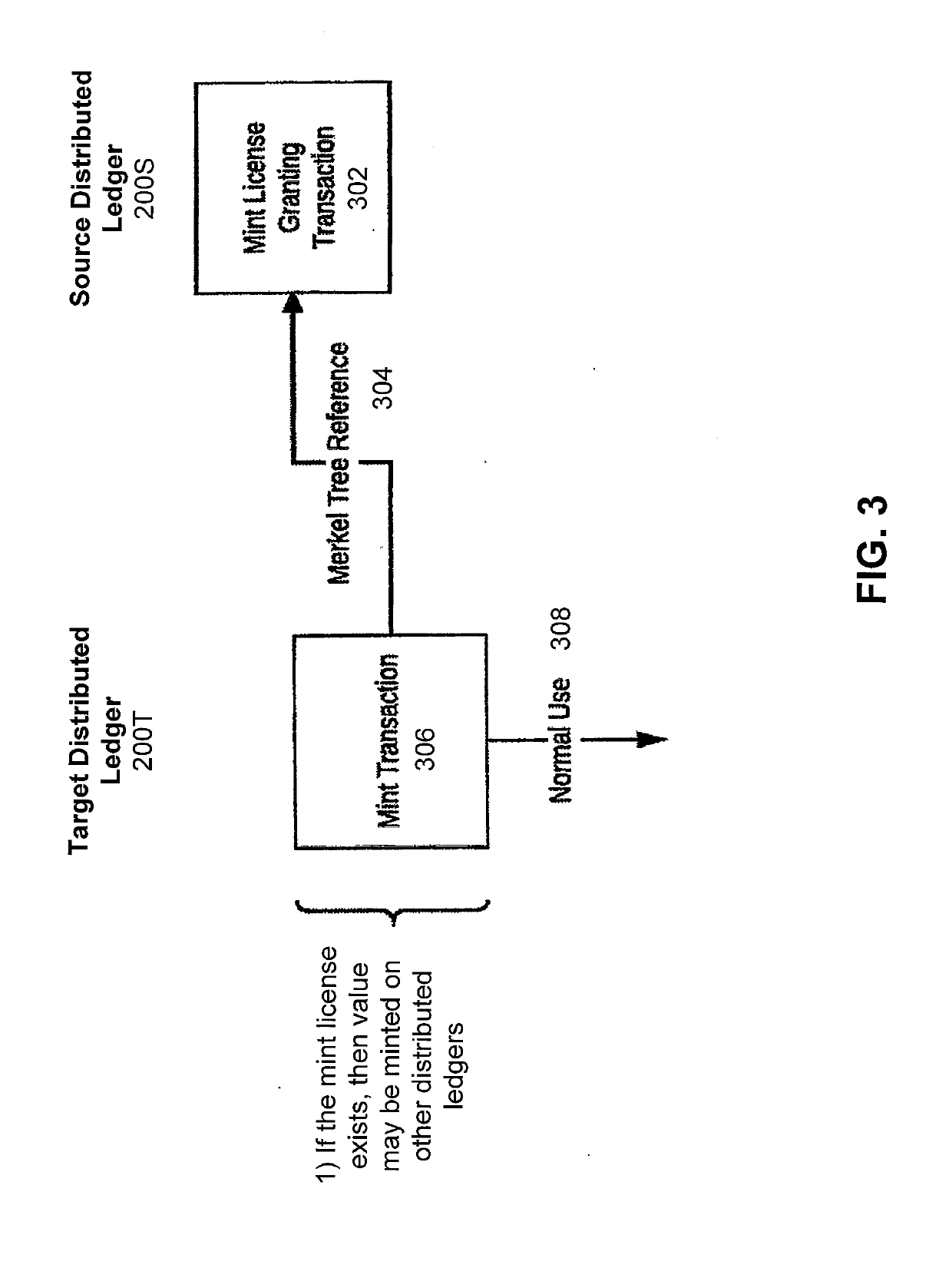
Systems of multiple distributed ledgers using cross-ledger transfers for highly-scalable transaction throughput
PendingUS20190188697A1Block valueCryptography processingTelephonic communicationTarget distributionDistributed computing
The presently-disclosed solution provides cross-ledger transfers between distributed ledgers to achieve highly-scalable transaction throughput. Disclosed are methods and instruction code for writing a cross-ledger transfer in a way that effectively transfers value from a source distributed ledger to a target distributed ledger while preventing double spending of the value. This results in the transformation of the ledgers in that the total value in the source ledger is decreased by the transferred value while the total value in the target ledger is increased by the same amount. Also disclosed are system architectures that utilize cross-ledger transfers between multiple distributed ledgers to achieve highly-scalable transaction throughput. Also disclosed are computer apparatus configured to implement cross-ledger transfers between distributed ledgers. Other embodiments and features are also disclosed.
Owner:TBCASOFT INC
Signal processor executing variable size instructions using parallel memory banks that do not include any no-operation type codes, and corresponding method
InactiveUS6944748B2Memory adressing/allocation/relocationGeneral purpose stored program computerMemory bankParallel computing
A digital signal processor is designed to execute variable-sized instructions that may include up to N elementary instruction codes. The processor comprises a memory program comprising I individually addressable, parallel-connected memory banks in which the codes of a program are recorded in an interlaced fashion, and a circuit for reading the program memory arranged to read a code in each of the I memory banks during a cycle for reading an instruction. A cycle for reading an instruction in the program memory includes reading a sequence of codes that includes the instruction code or codes to be read and can also include codes, belonging to a following instruction, that are filtered before the instruction is applied to execution units. The program memory of the digital signal processor does not include any no-operation type codes.
Owner:STMICROELECTRONICS SRL
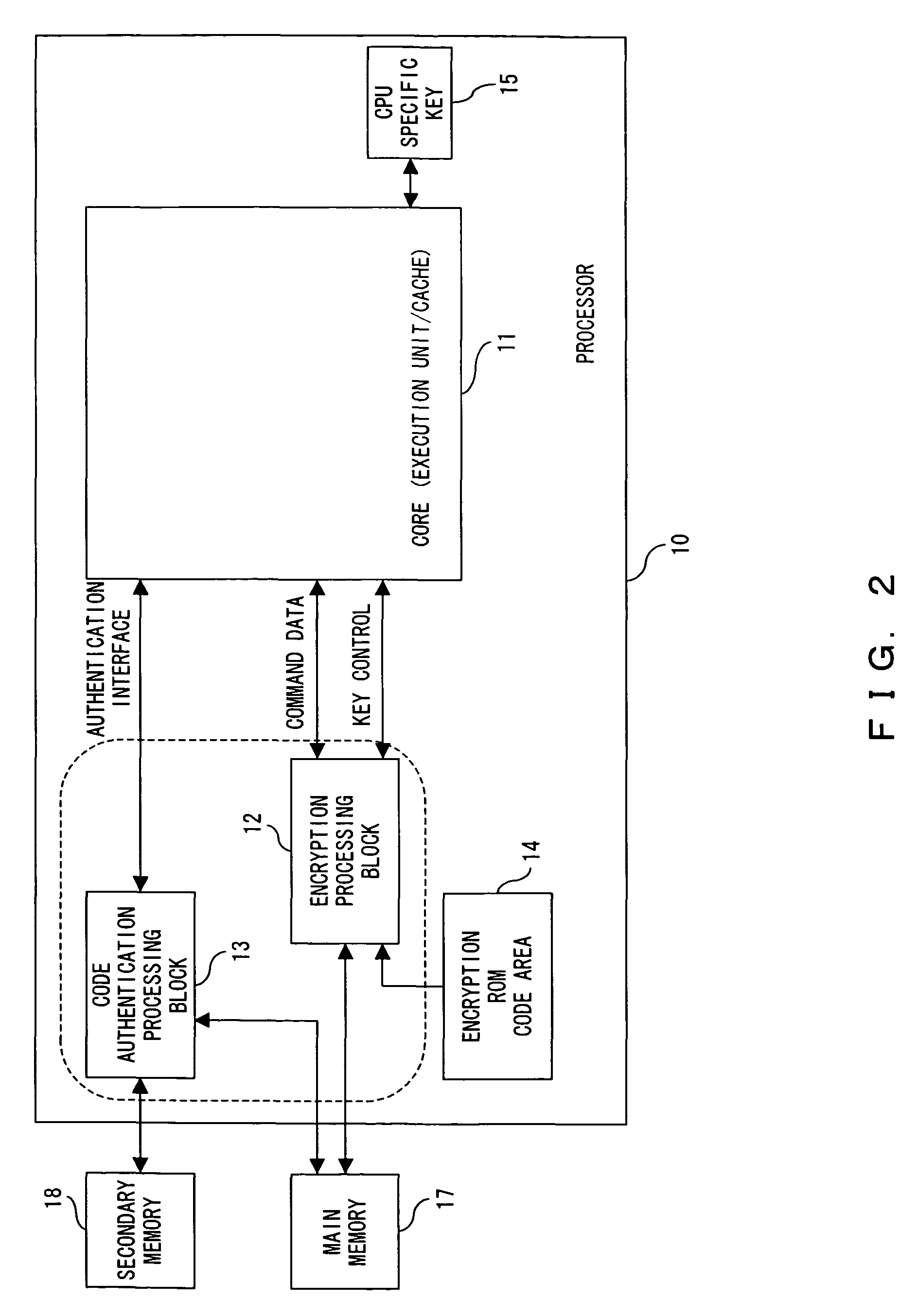
Secure processor system without need for manufacturer and user to know encryption information of each other
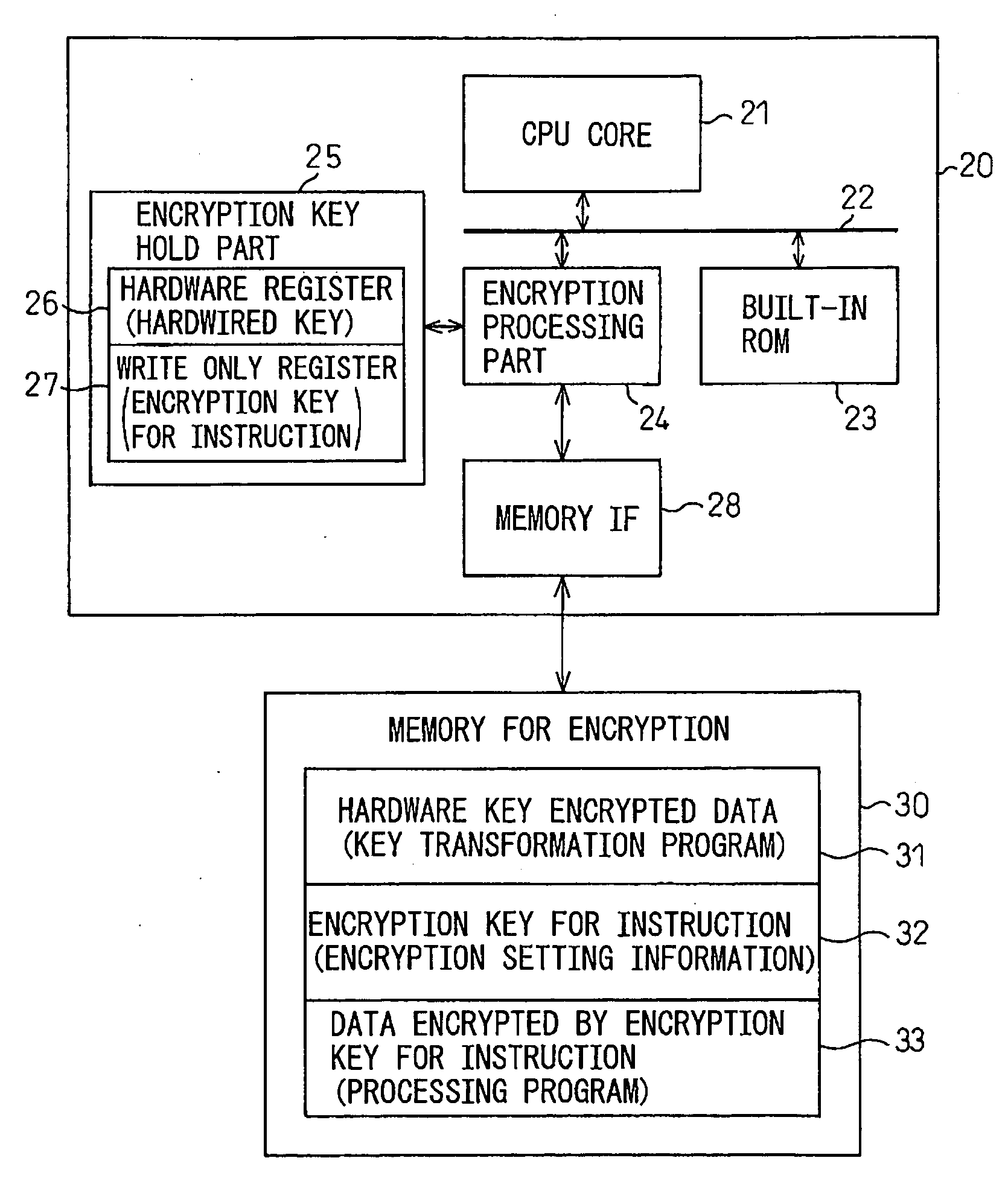
InactiveUS20080205651A1Key distribution for secure communicationPublic key for secure communicationProcessor registerSecure cryptoprocessor
A secure processor system capable of improving the security of processor processing by the addition of minimum modules without the need for a manufacturer and a user to know encryption information of each other has been disclosed. The secure processor system includes a secure processor having a CPU core that executes a instruction code, an encryption key hold part that holds a processor key, and an encryption processing part that encrypts or decrypts data input / output to / from the core with a processor key and a memory, and the encryption key hold part includes a hardware register that holds a hardwired encryption key, a write only register that stores an encryption key for instruction to be input and holds the stored encryption key for instruction so that it cannot be read, and the encryption key hold part outputs a hardware encryption key as a processor key at the time of activation and outputs a command encryption key as a processor key after a encryption key for instruction is written.
Owner:FUJITSU SEMICON LTD
Implementing instruction set architectures with non-contiguous register file specifiers
ActiveUS20120265967A1Effectively concatenatingInstruction analysisDigital computer detailsProcessing InstructionProcessor register
There are provided methods and computer program products for implementing instruction set architectures with non-contiguous register file specifiers. A method for processing instruction code includes processing an instruction of an instruction set using a non-contiguous register specifier of a non-contiguous register specification. The instruction includes the non-contiguous register specifier.
Owner:IBM CORP
Processor for executing instruction codes of two different lengths and device for inputting the instruction codes
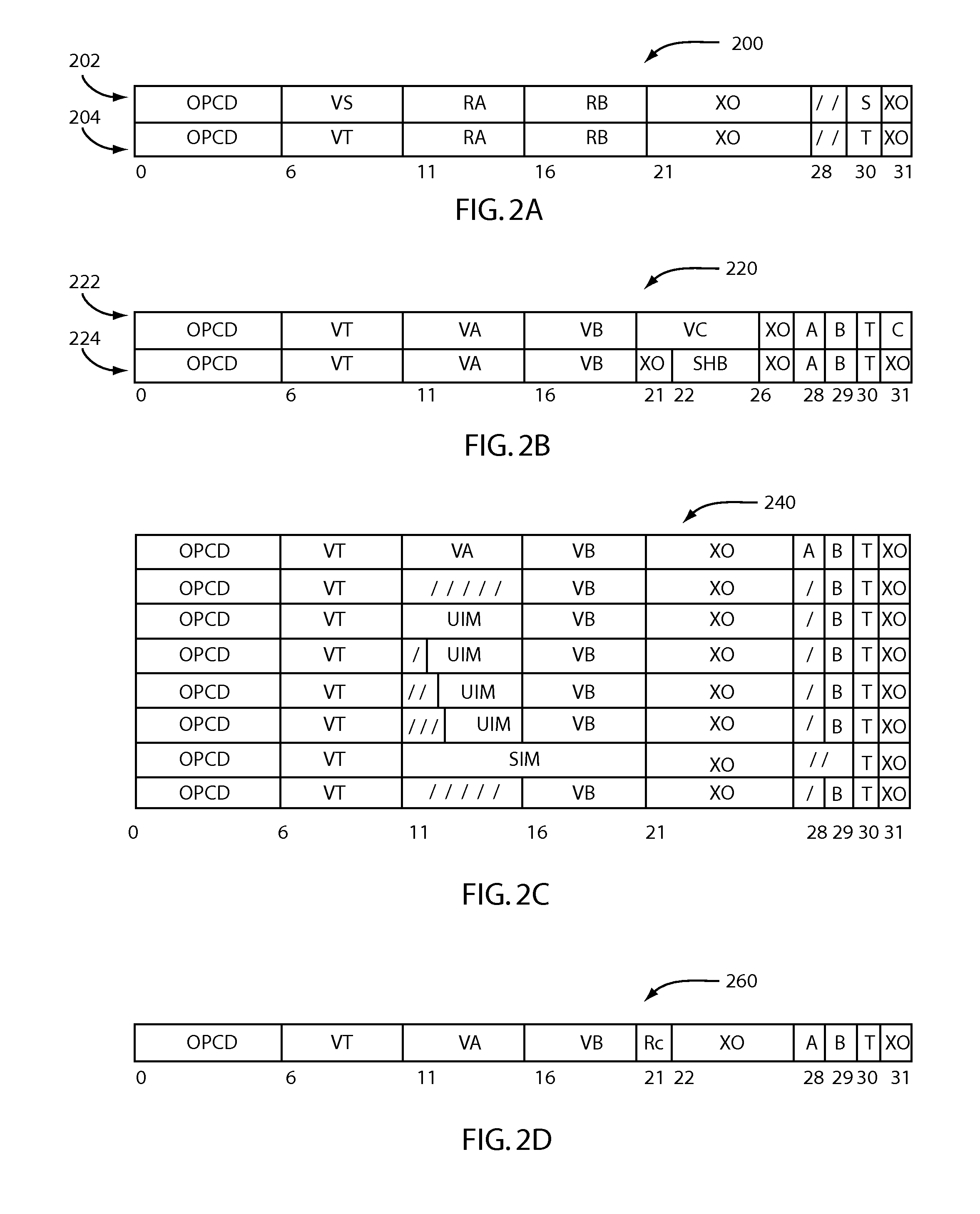
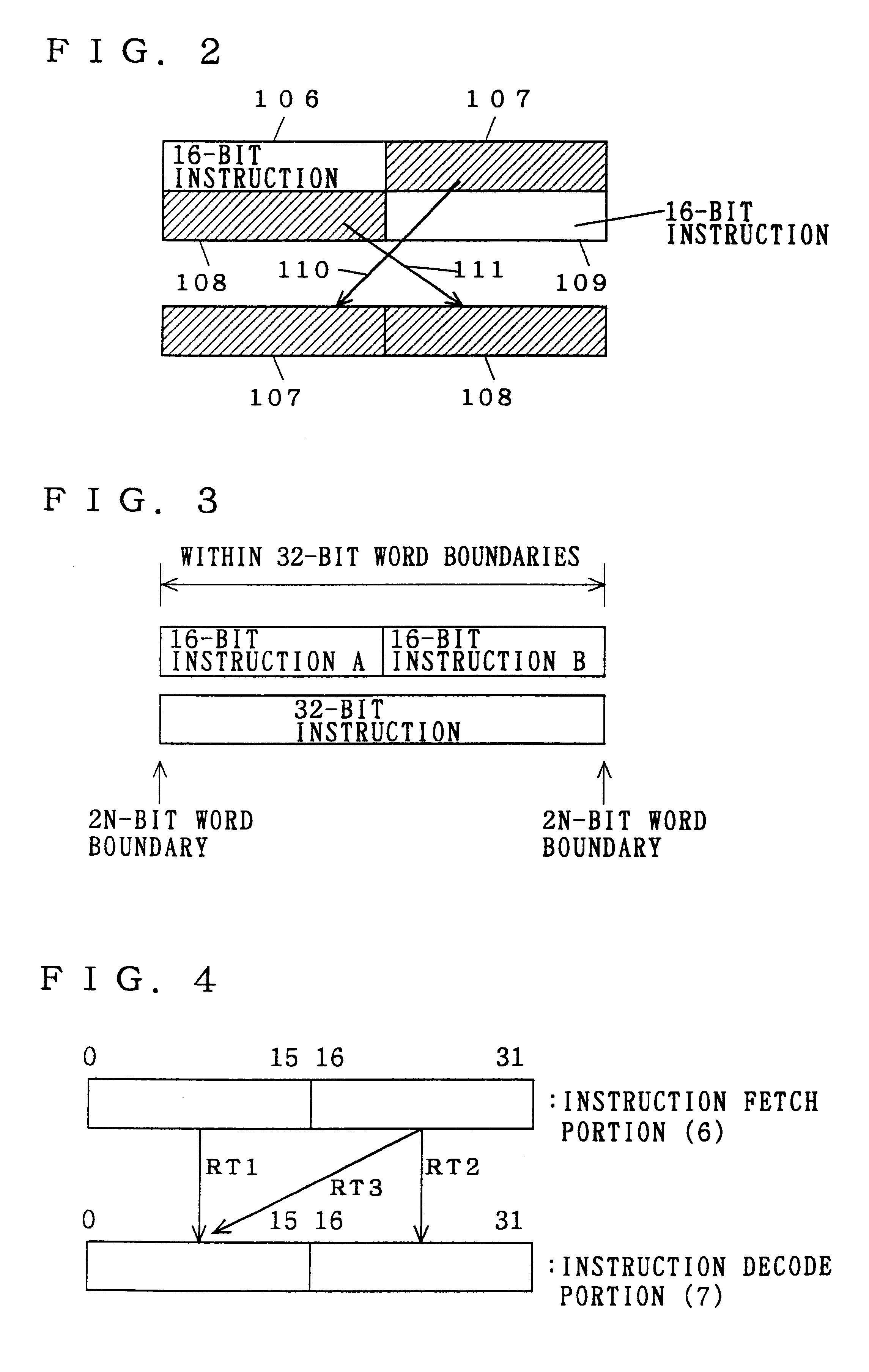
InactiveUS6209079B1Small sizeSmall amountInstruction analysisDigital computer details16-bitParallel computing
For a processor having instruction codes of two instruction lengths (16 bits and 32 bits), methods of locating the instruction codes are limited to two types: (1) two 16-bit instruction codes are stored within 32-bit word boundaries, and (2) a single 32-bit instruction code is stored intactly within the 32-bit word boundaries. A branch destination address is specified only on the 32-bit word boundary. The MSB of each instruction code serves as a 1-bit instruction length identifier for controlling the execution sequence of the instruction codes. This provides two transfer paths from an instruction fetch portion to an instruction decode portion within the processor, achieving reduction in code side and in the amount of hardware and, accordingly, the increase in operating speed.
Owner:RENESAS ELECTRONICS CORP
Method and apparatus for changing microcode to be executed in a processor
InactiveUS6691308B1Runtime instruction translationGeneral purpose stored program computerComputer architectureEngineering
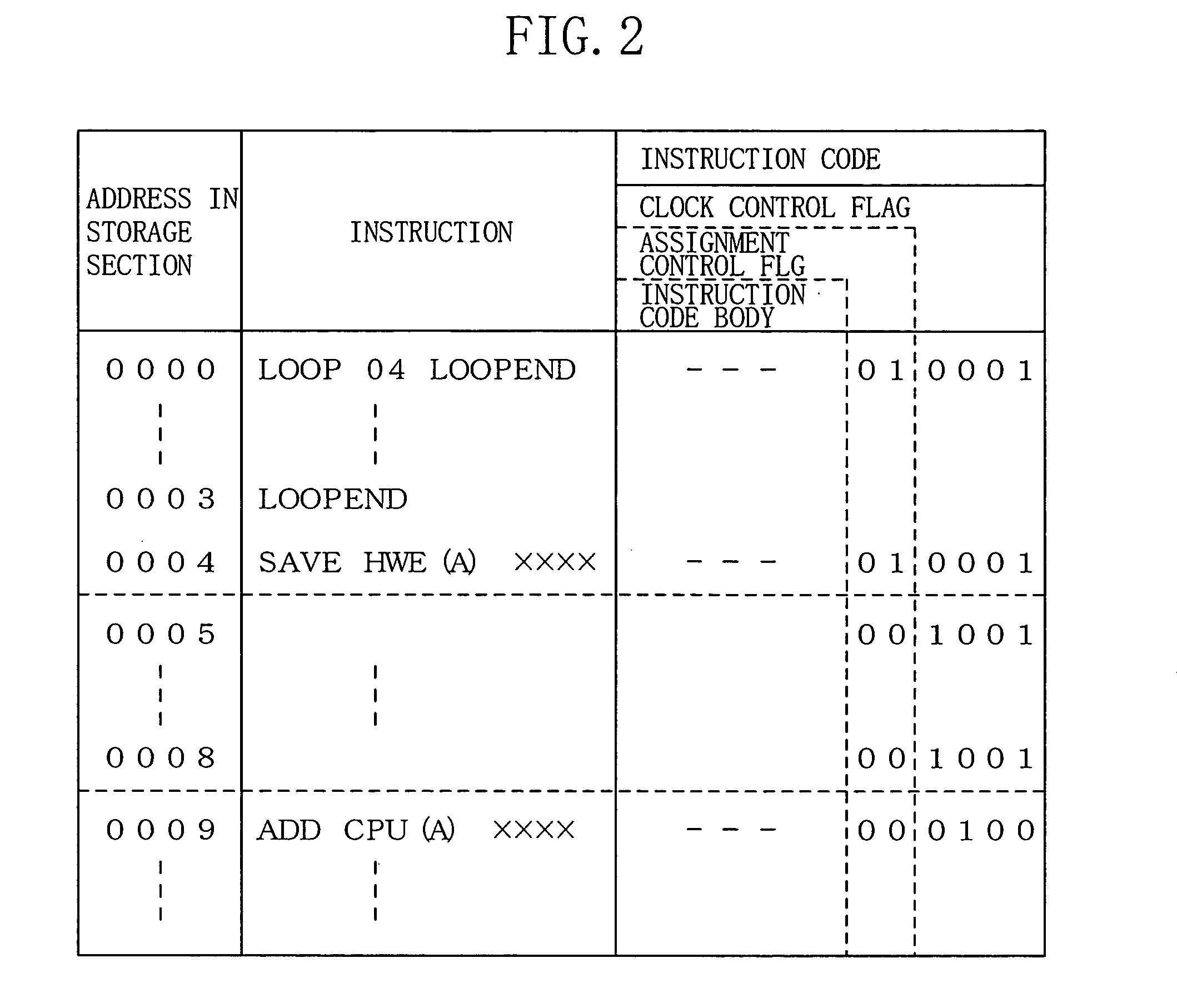
A Central Processing Unit (CPU) hotpatch circuit compares the run-time instruction stream against an internal cache. The internal cache stores embedded memory addresses with associated control flags, executable instruction codes, and tag information. In the event that a comparison against the current program counter succeeds, then execution is altered as required per the control flags. If no comparison match is made, then execution of the instruction that was accessed by the program counter is executed.
Owner:MICROELECTRONIC INNOVATIONS LLC
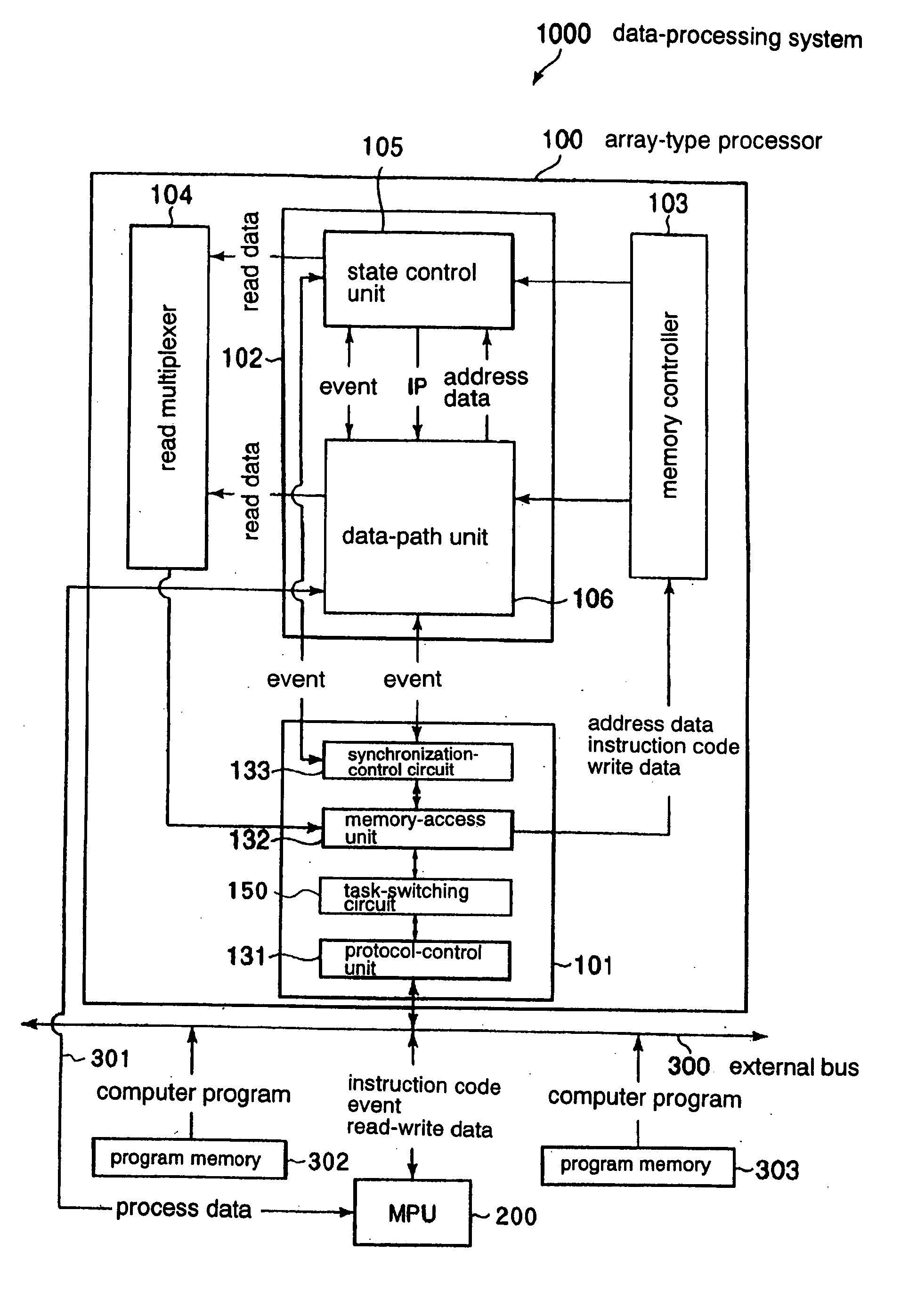
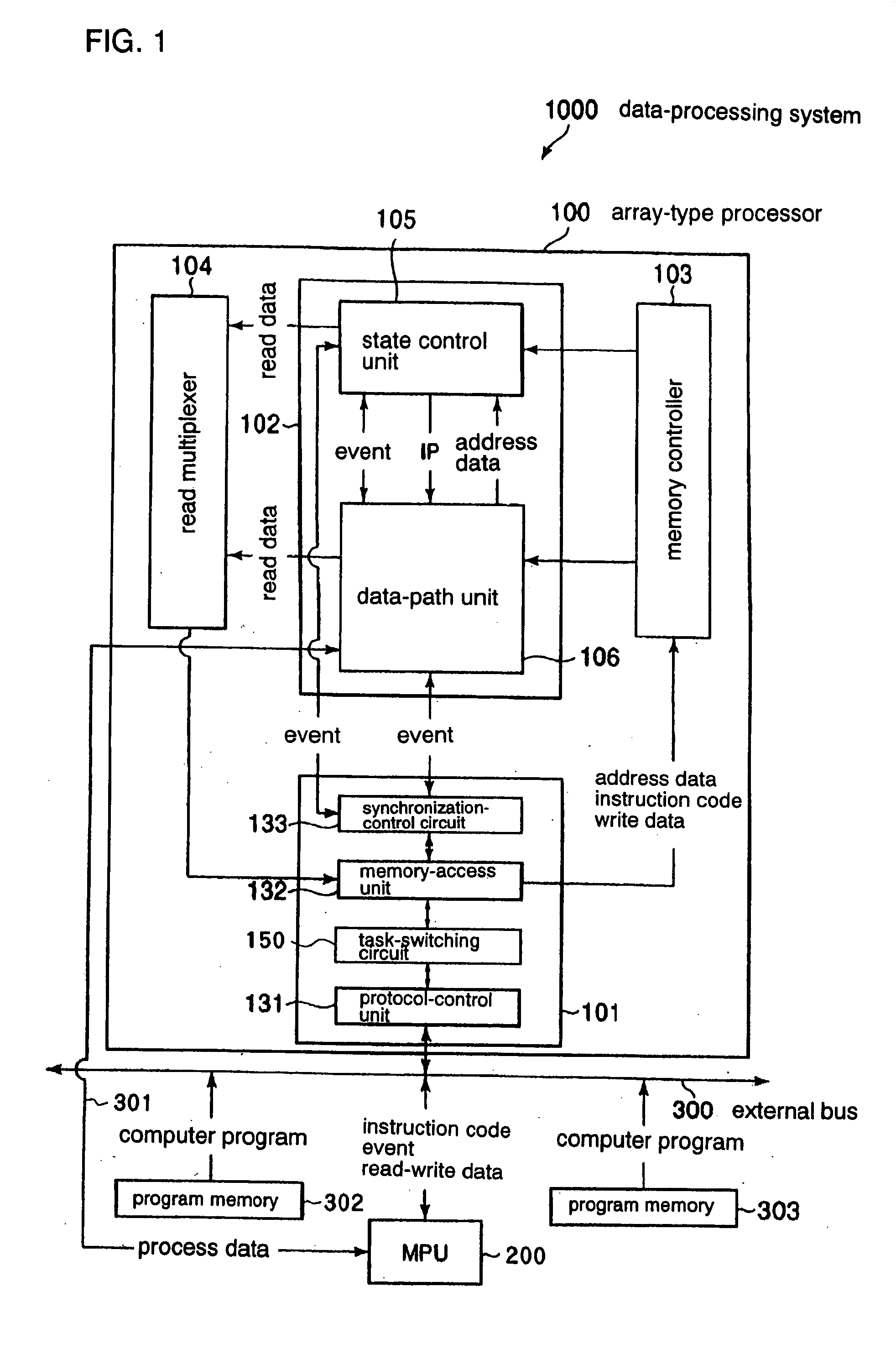
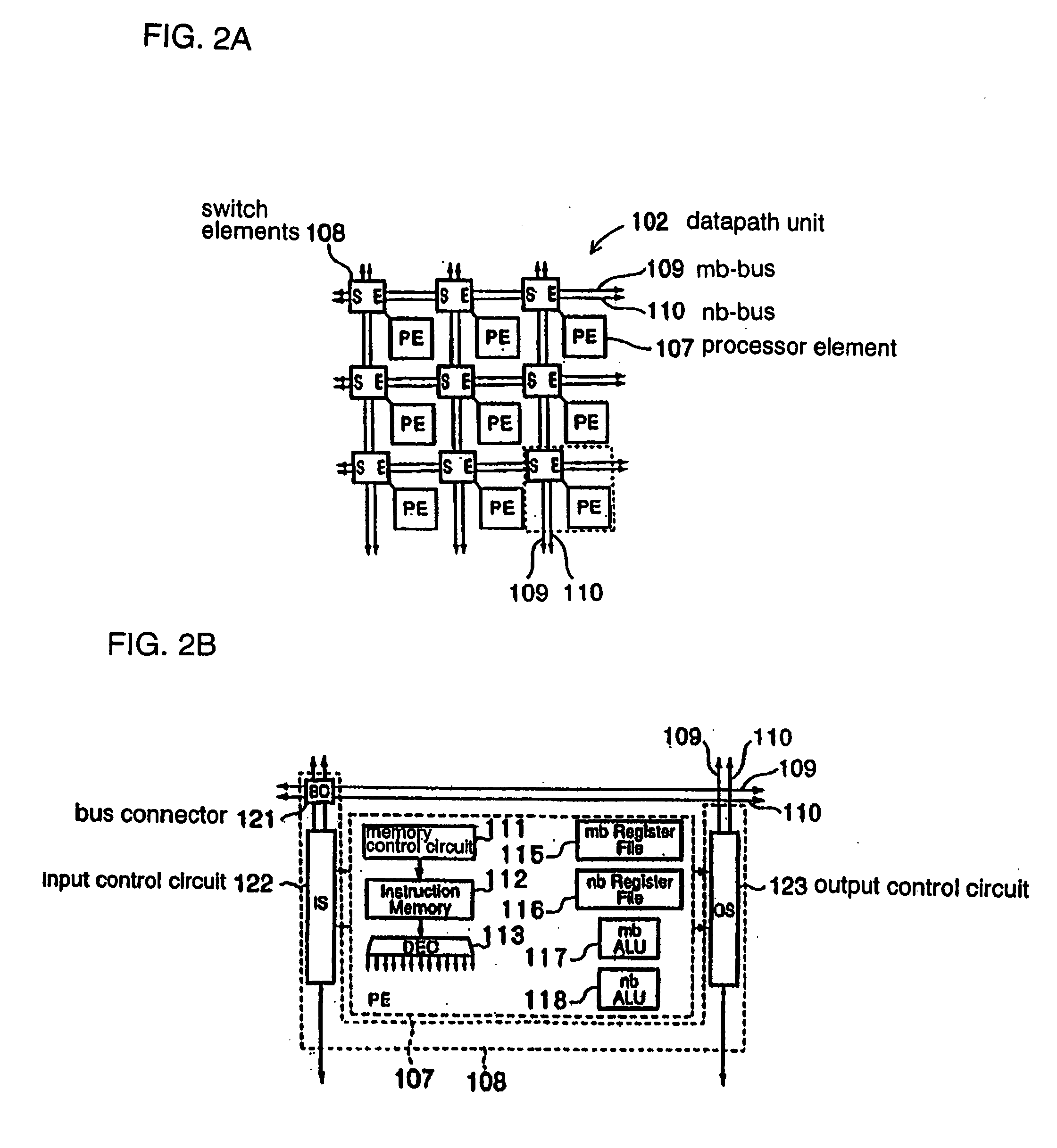
Array-type computer processor
InactiveUS20050172103A1Single instruction multiple data multiprocessorsSpecific program execution arrangementsParallel computingComputer program
An array-type computer processor obtains data of a predetermined number of cooperative partial instruction codes, and operates with temporarily holding only a predetermined number of data-obtained instruction codes, from an external program memory which stores data of a computer program. Every time the operations with the temporarily-held instruction codes are complete, the subsequent instruction codes are data obtained, so that the operation according to a computer program can be performed even if the data volume of the computer program is over the storage capacity.
Owner:RENESAS ELECTRONICS CORP +1
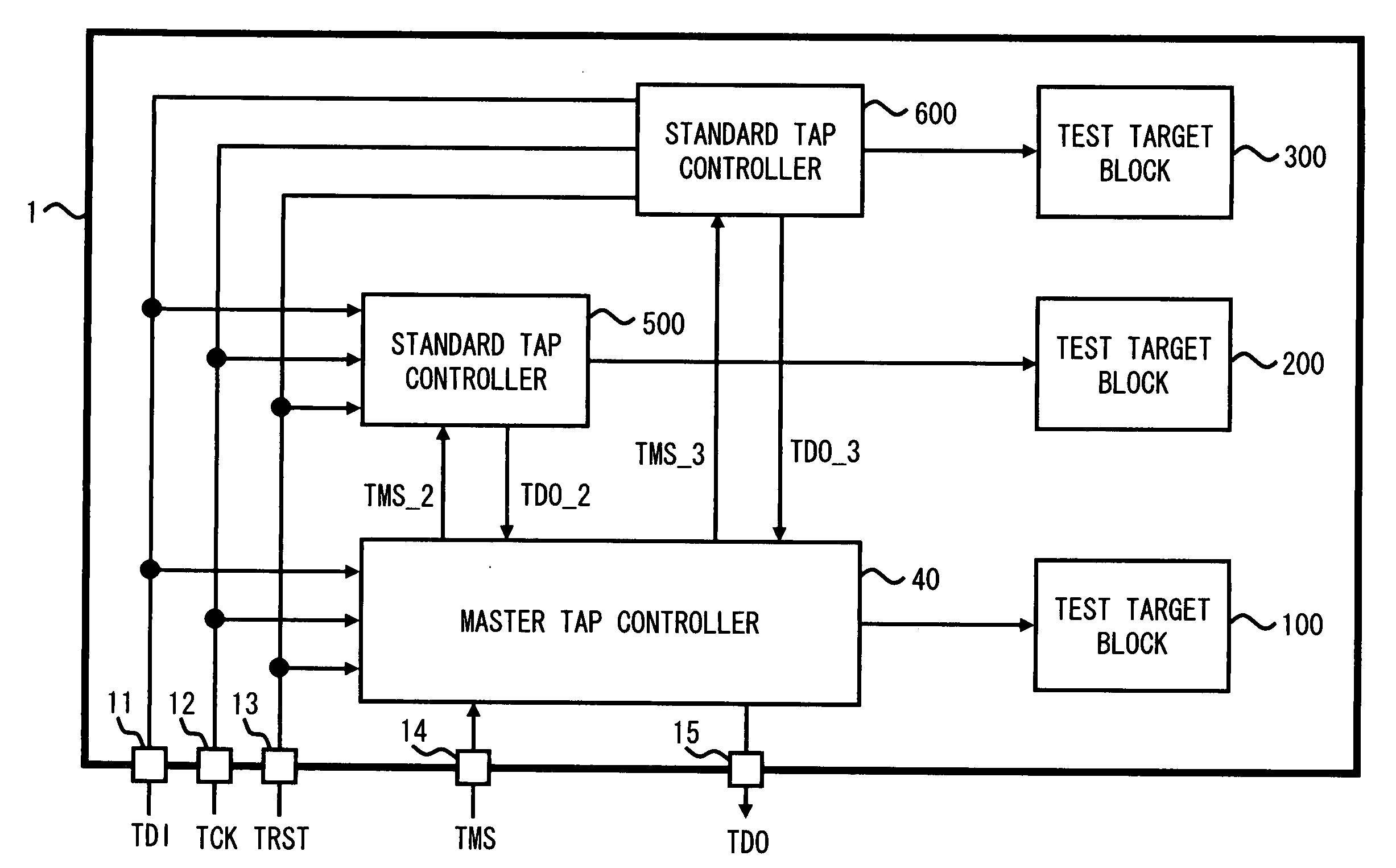
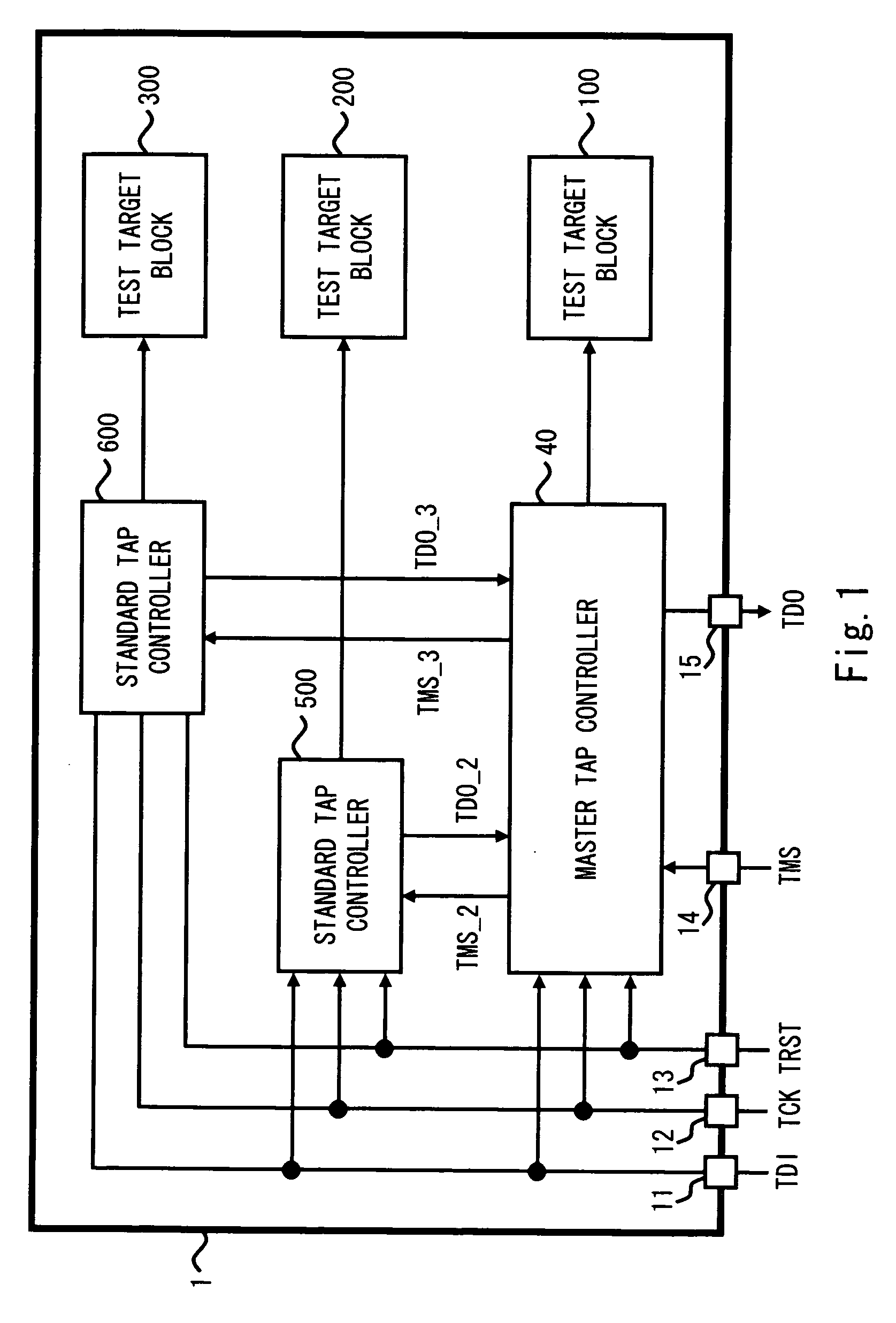
Test circuit
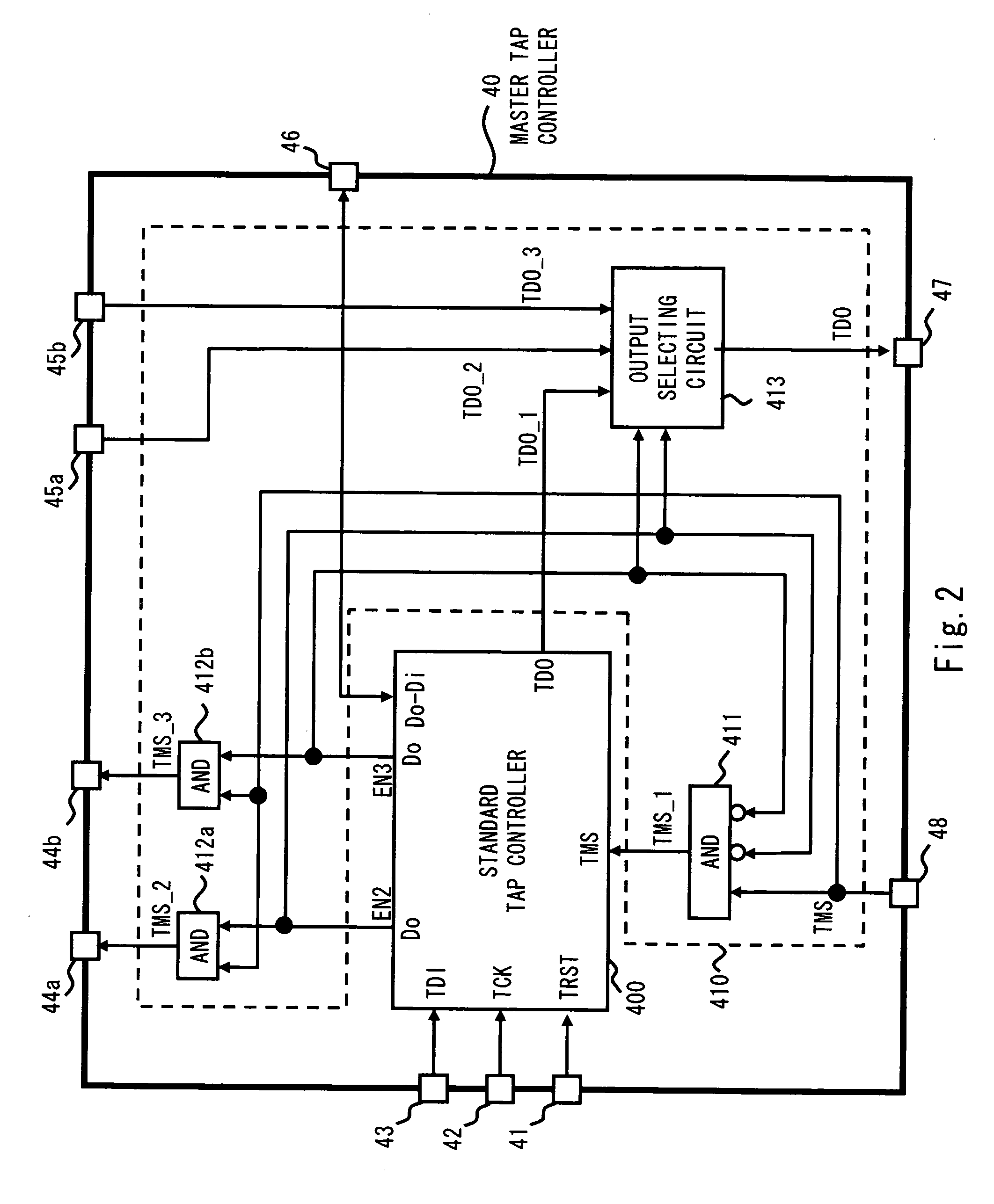
A test circuit including a TAP controller specified in IEEE (Institute of Electrical and Electronics Engineers) 1149 and a test access port includes a first controller including a selecting circuit and a first TAP controller, the selecting circuit generating an internal TMS signal in accordance with TMS signal and selecting an output destination of the internal TMS signal in accordance with a selection signal, and the first TAP controller changing internal state based on the internal TMS signal, testing corresponding test target block in accordance with instruction code for test, and generating the selection signal in accordance with instruction code for selection, and a second controller including a second TAP controller changing internal state based on the internal TMS signal and testing corresponding test target block in accordance with the instruction code for test.
Owner:RENESAS ELECTRONICS CORP
System for automatically locating and manipulating positions on an object
A system for automatically locating positions on an object and uniquely identifying the object employing an electronic tag positioned in or on the object. The system utilizes a plurality of sensors to locate the electronic tag and identify the object, and triangulation techniques to locate positions on the object where the object may be manipulated according to instructions coded with respect to the positions. Advantageously, the present invention may be used for automatically locating specimens on a microscope slide without regards to their positions on the slide, and for uniquely labeling a microscope slide.
Owner:TAFAS TRIANTAFYLLOS P +1
Method for protecting JAVA application programs in Android system
ActiveCN102708322APrevent piracyProgram/content distribution protectionSpecific program execution arrangementsApplication softwareJava classes
The invention relates to the field of computer safety, in particular to a method for protecting application programs in an Android system. By carrying out encryption transformation on a plurality of method instruction codes of JAVA objects to be protected, encrypted method codes are subjected to real-time decryption operation according to the calling requirement when the programs operate, so that the application programs are difficult to subject to decompilation and static analysis, and therefore, the effective protection on the JAVA programs in the Android system is implemented.
Owner:BEIJING SENSESHIELD TECH
Variable register and immediate field encoding in an instruction set architecture
ActiveUS20100287359A1Suppresses increase in code sizeSpecific costInstruction analysisDigital computer detailsOperation modeApplication software
A method and apparatus provide means for compressing instruction code size. An Instruction Set Architecture (ISA) encodes instructions compact, usual or extended bit lengths. Commonly used instructions are encoded having both compact and usual bit lengths, with compact or usual bit length instructions chosen based on power, performance or code size requirements. Instructions of the ISA can be used in both privileged and non-privileged operating modes of a microprocessor. The instruction encodings can be used interchangeably in software applications. Instructions from the ISA may be executed on any programmable device enabled for the ISA, including a single instruction set architecture processor or a multi-instruction set architecture processor.
Owner:ARM FINANCE OVERSEAS LTD
Data processing circuit with target instruction and prefix instruction
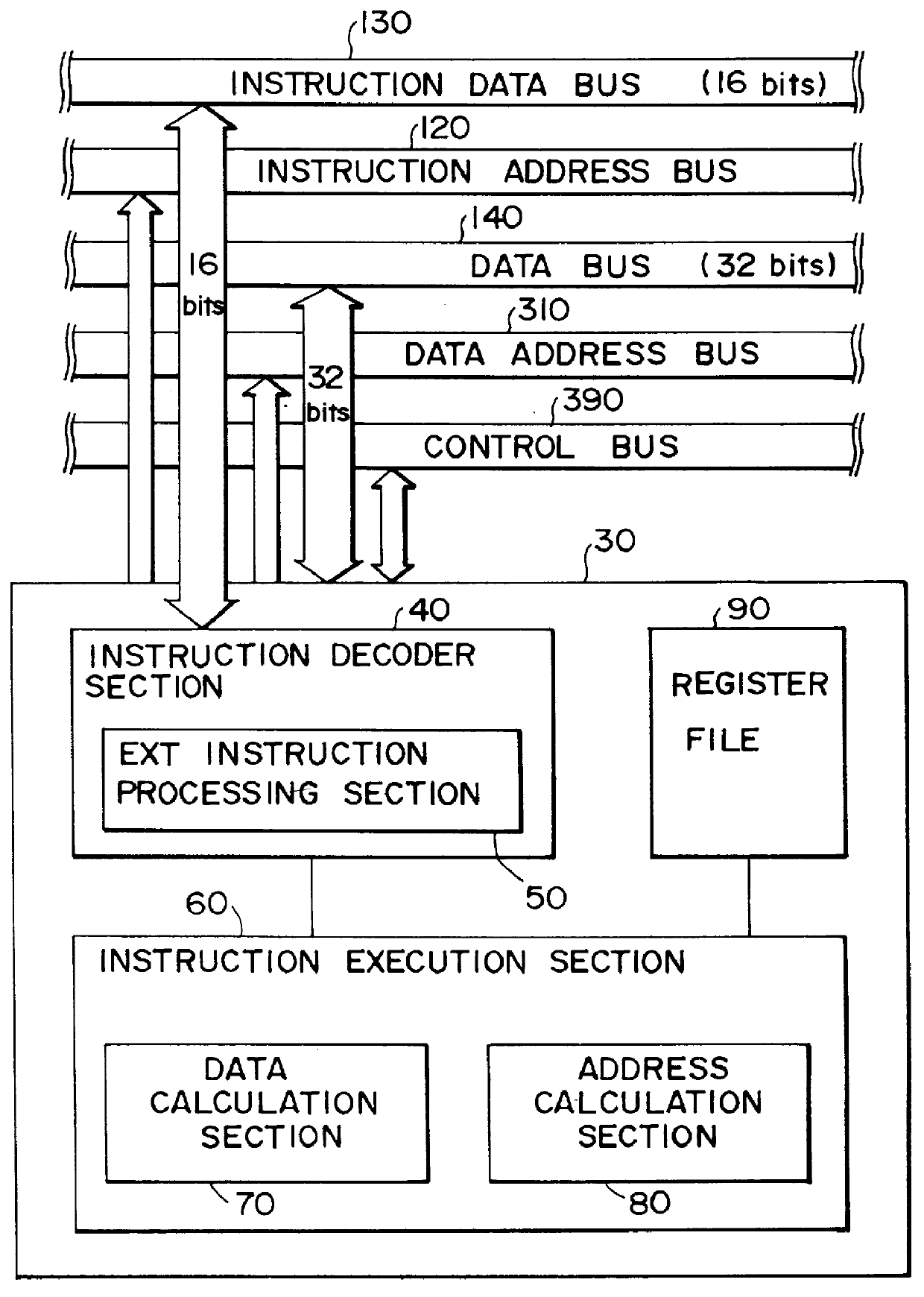
InactiveUS6167505AEasy to operateSimple structureInstruction analysisDigital computer detailsRegister fileInstruction code
A certain target instruction and a prefix instruction for expanding the function of that target instruction are input to the present data processing circuit. The data processing circuit analyzes the thus-input instruction code and performs the processing necessary for the execution of that instruction. The data processing circuit comprises an instruction decoder section, a register file, and an instruction execution section that executes the instruction based on operational details of the instruction analyzed by the instruction decoder section. The instruction decoder section comprises an ext instruction processing section that processed the expansion of immediate data from the prefix instruction.
Owner:SEIKO EPSON CORP
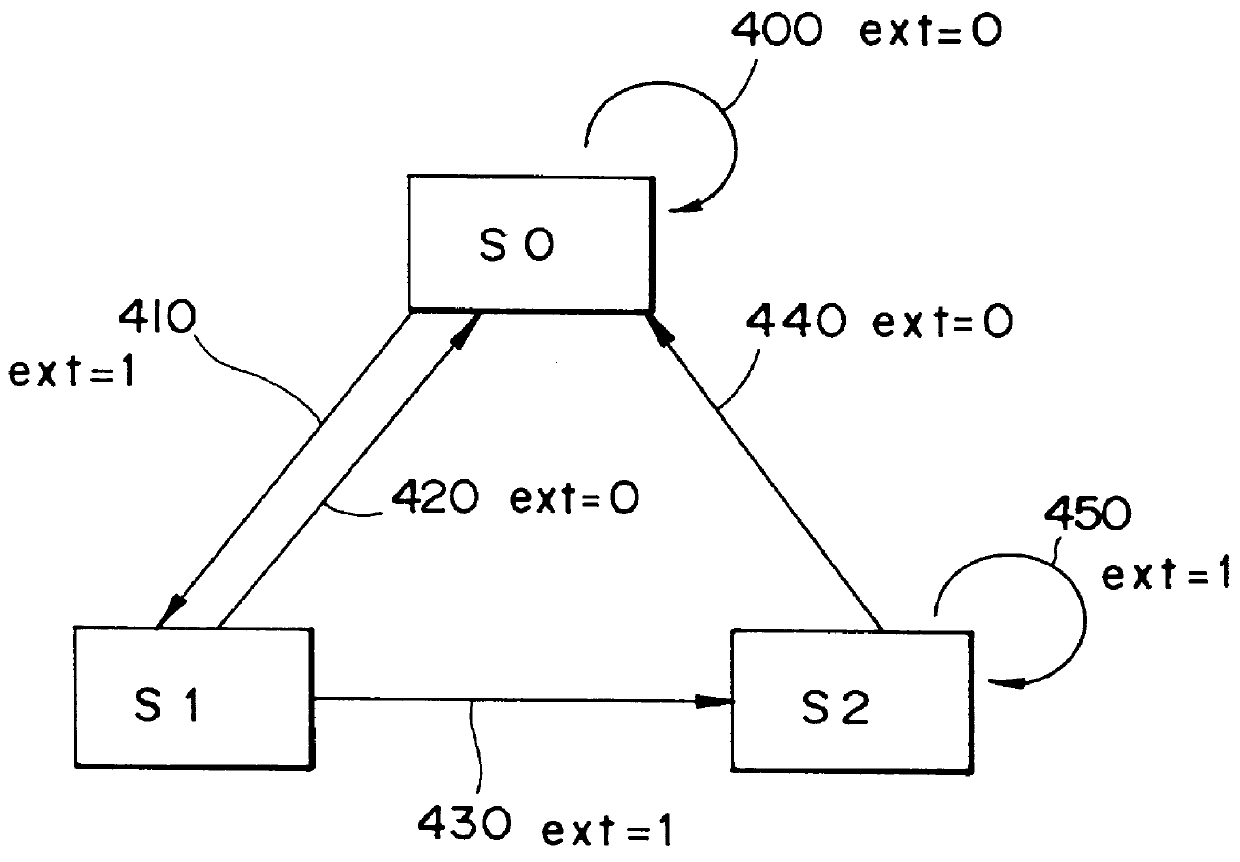
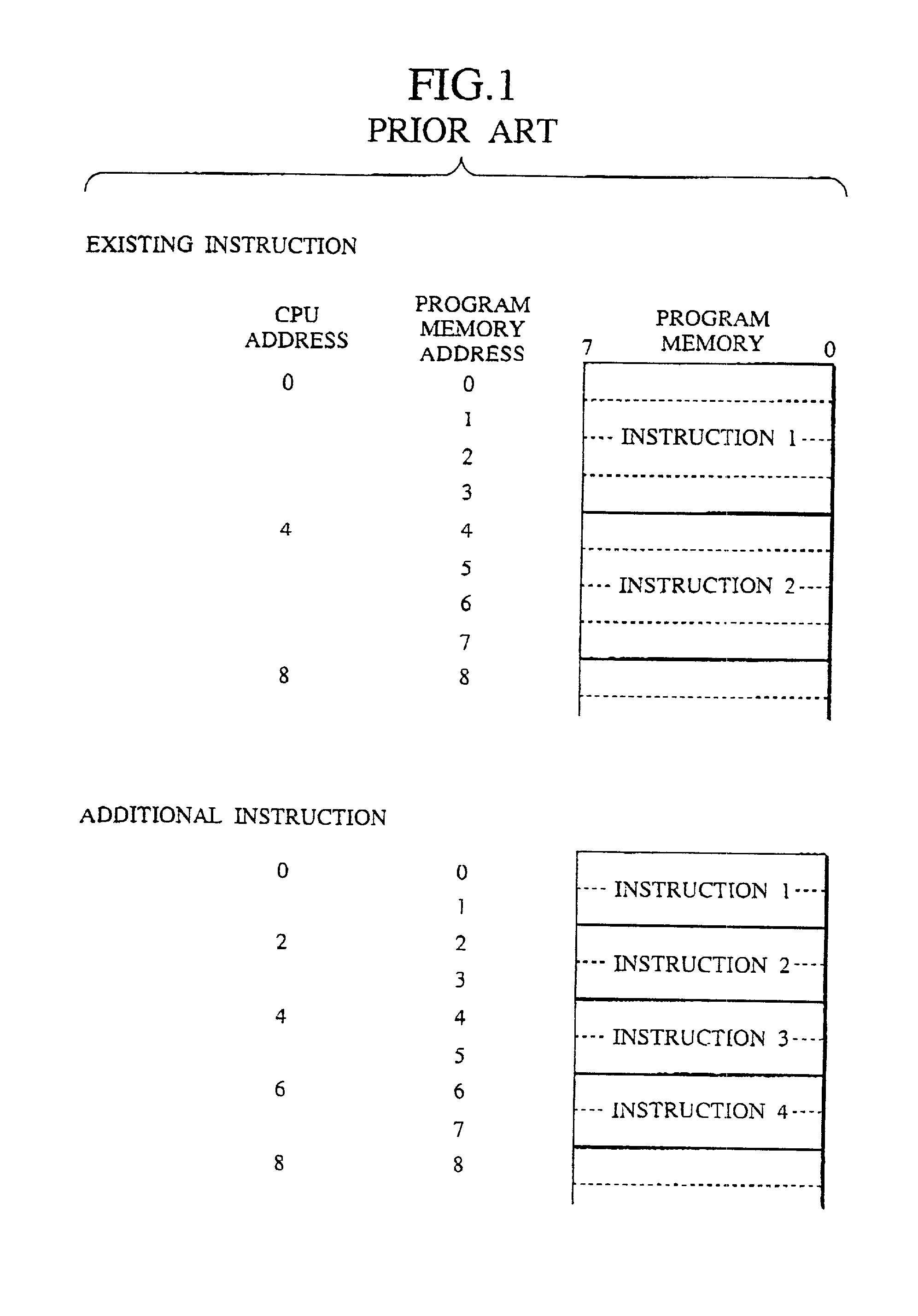
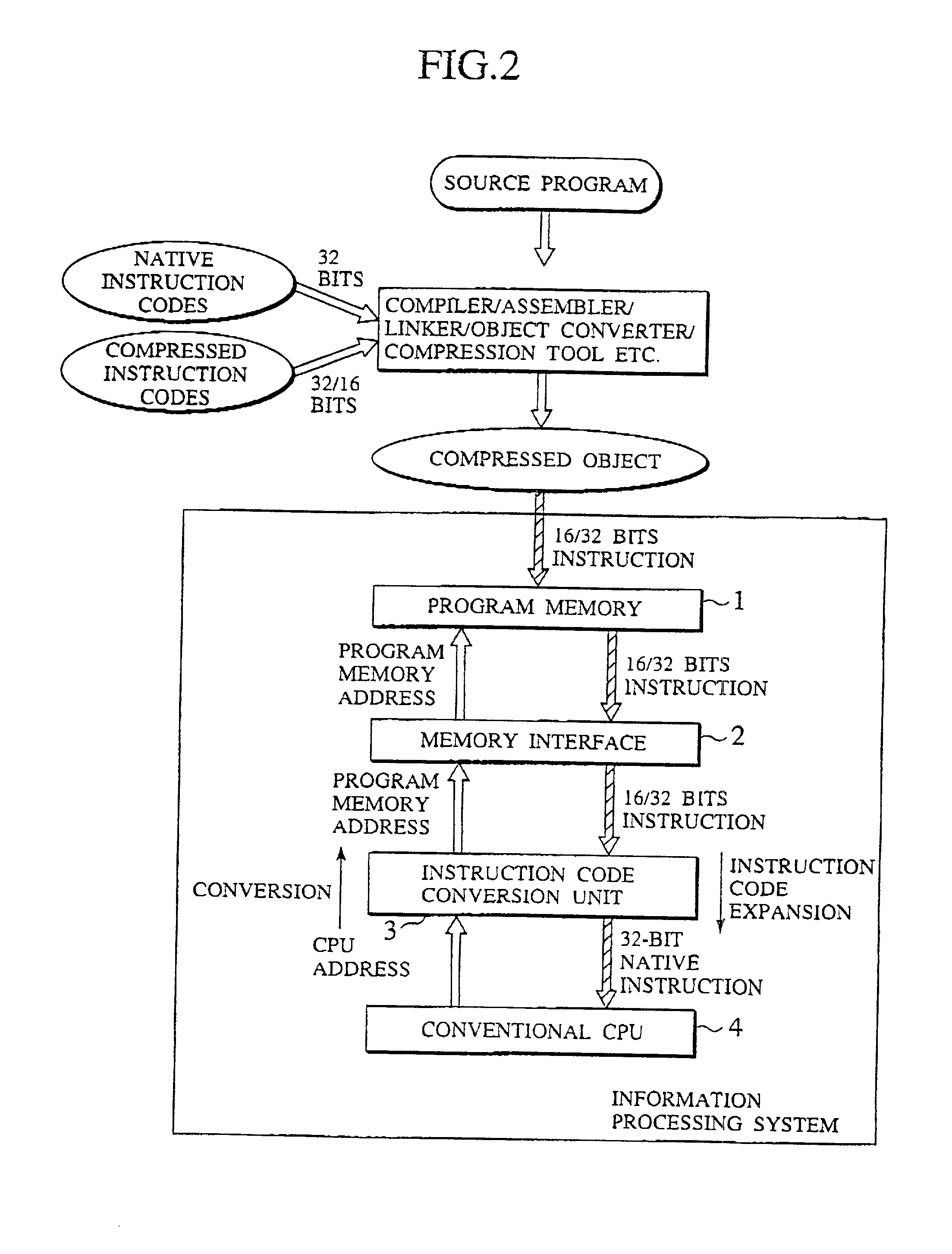
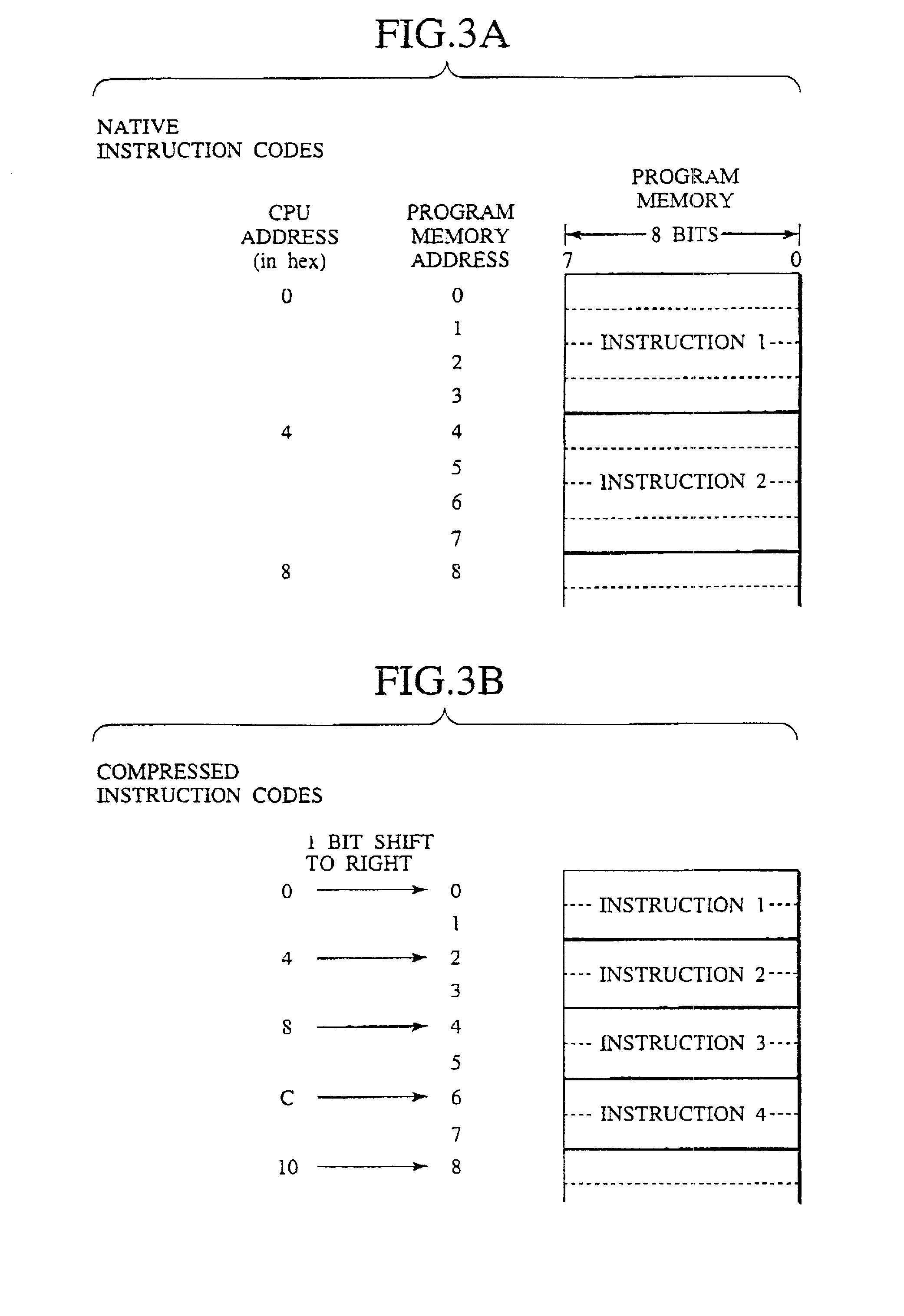
Instruction code conversion unit and information processing system and instruction code generation method
InactiveUS20010013093A1Digital computer detailsNext instruction address formationInformation processingParallel computing
An instruction code conversion unit, an information processing system provided with the instruction code conversion unit and an instruction code generation method for generating instruction codes which are converted by the instruction code conversion unit are described. The efficiency of coding of the program is improved by making use of an existing processor as selected is used without modification. An instruction code conversion unit performs conversion of the address of a native instruction code to the address of the corresponding compressed instruction code in a program memory by shifting the address of the native instruction code as outputted from the processor to the right by one bit.
Owner:KK TOSHIBA
Video image processing with remote diagnosis and programmable scripting
ActiveUS20070046821A1Television system detailsColor signal processing circuitsNetwork connectionImaging analysis
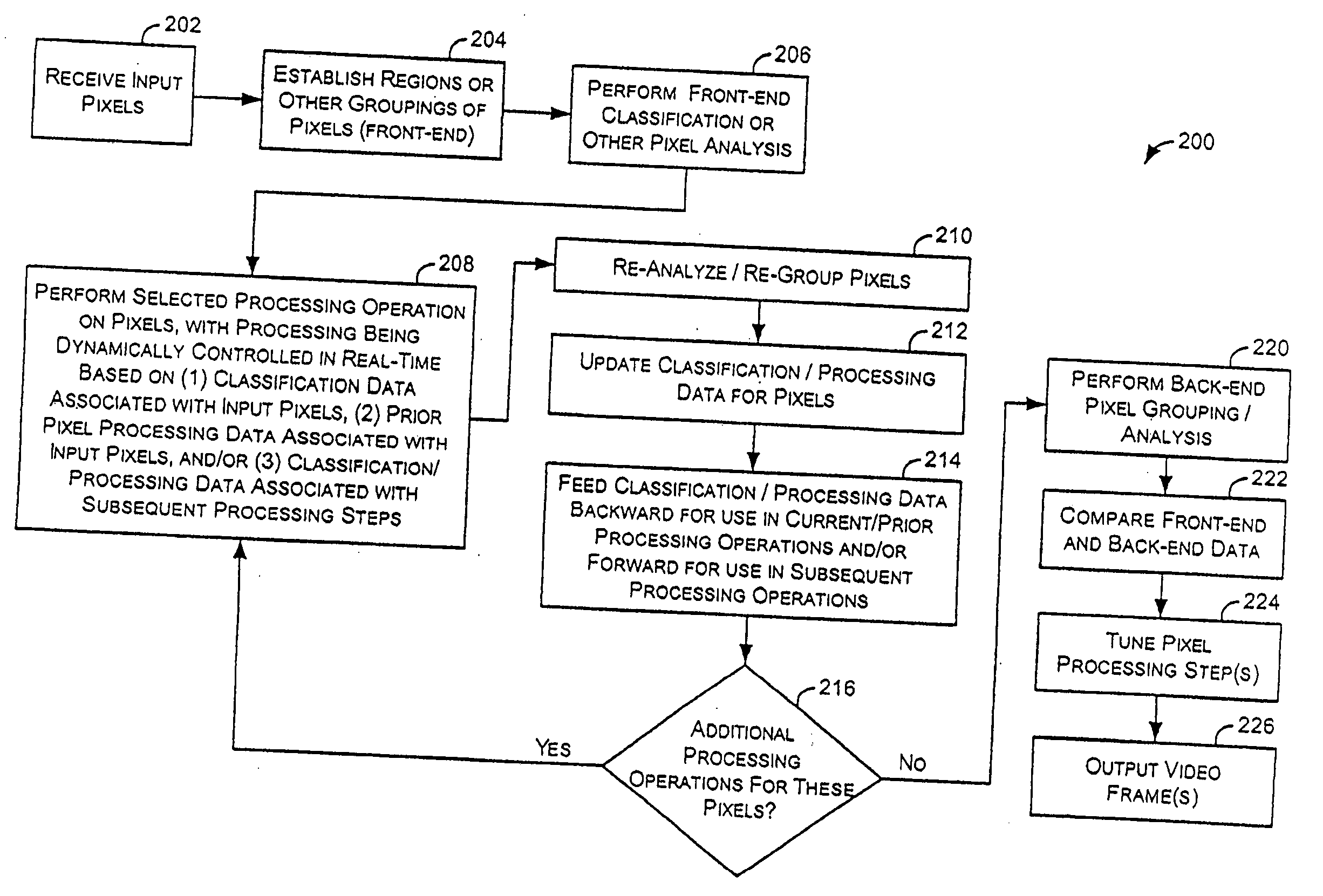
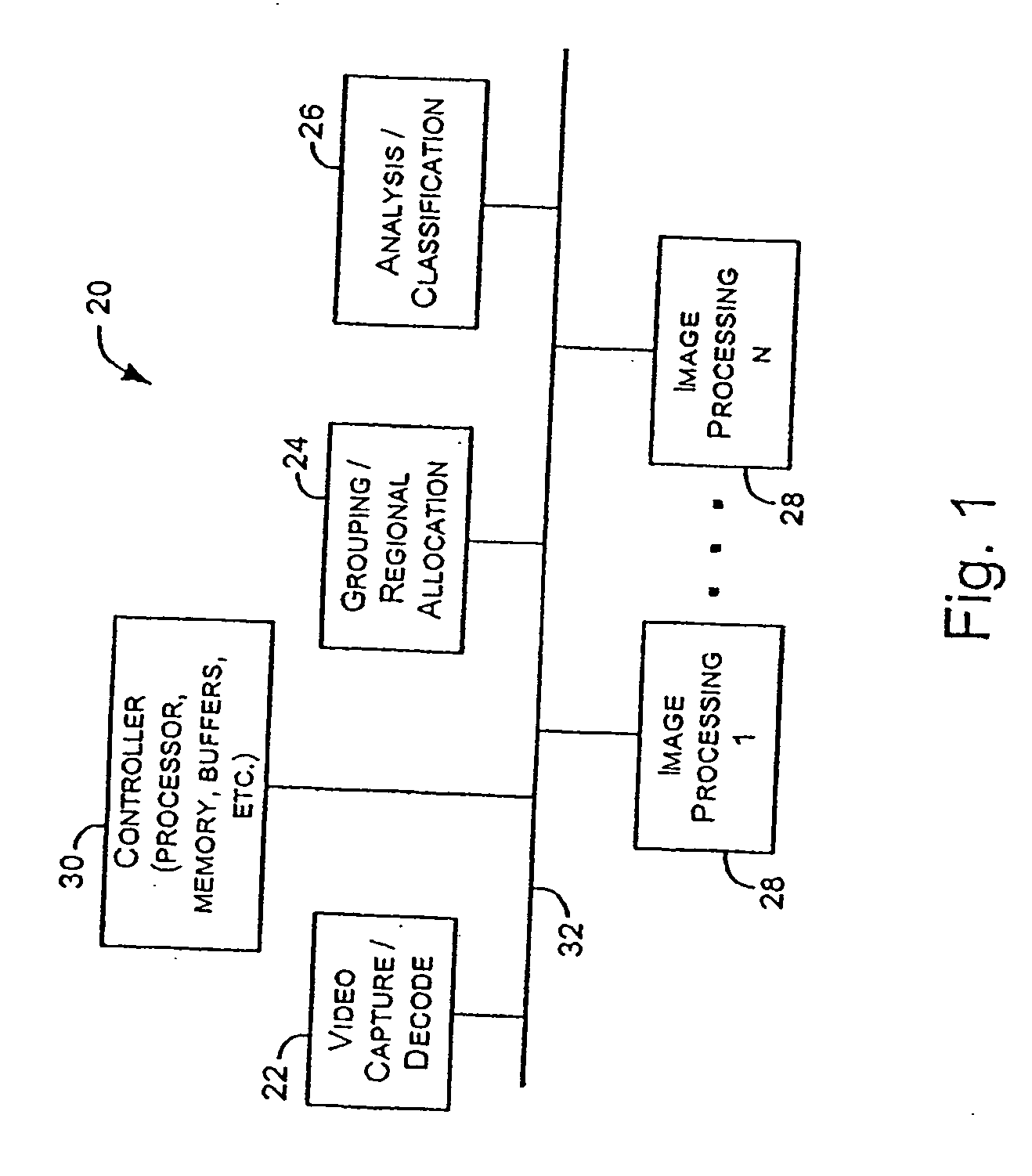
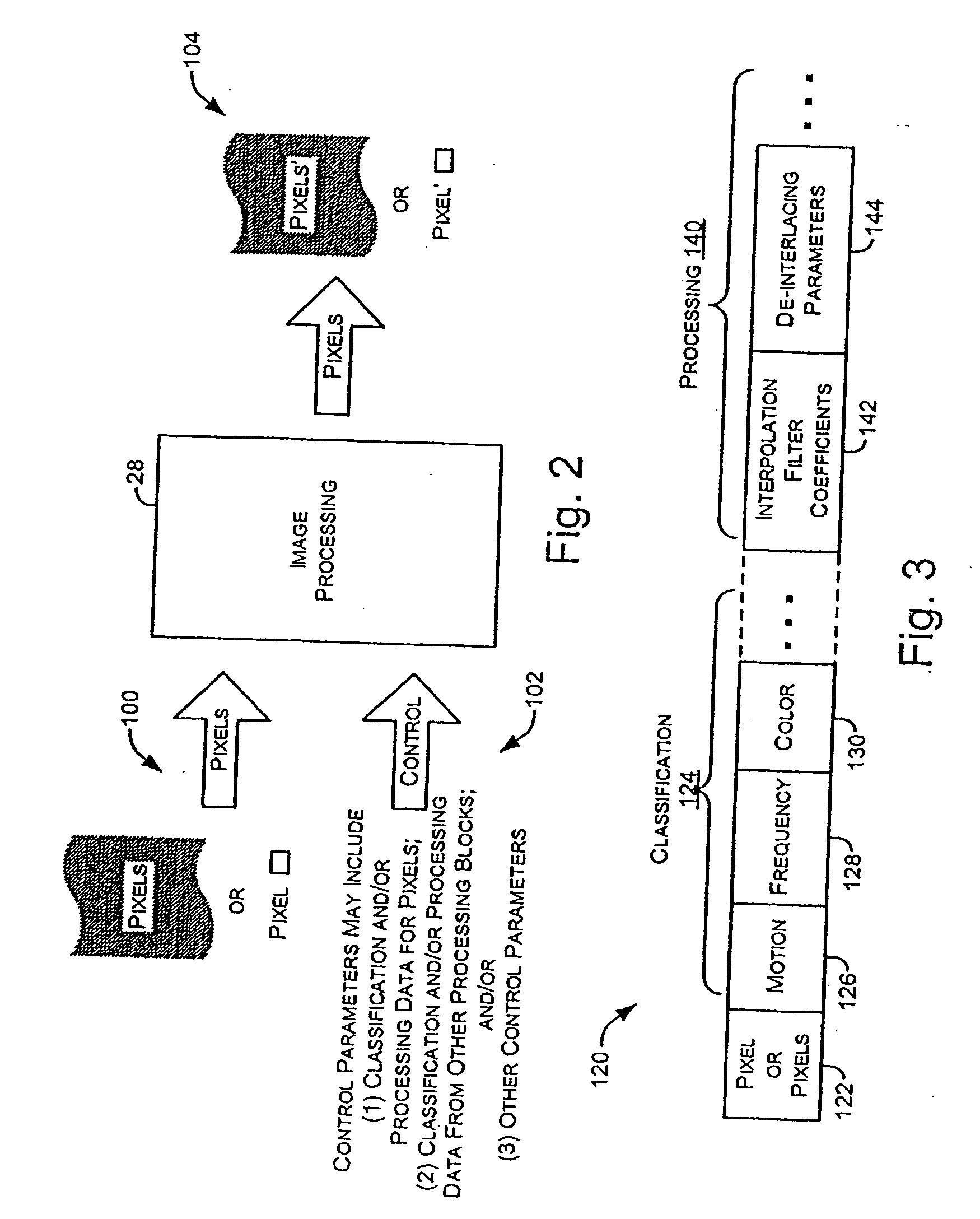
This document discusses, among other things, systems and methods for receiving a local input video signal, processing the video signal, and providing a processed video signal to a local digital television display panel. A communications port includes an Ethernet or other communications network connector for allowing access to the video signal processing system by a remote device. This allows a remote user to remotely diagnose, debug, and even modify operation of the video signal processing system. In certain examples, this involves downloading a Lua script that can take partial or complete control over operation of the video signal processing system from resident instruction code. In certain examples, the video signal processing system includes pipelined image analysis or processing stages. Video signal data intermediate to such processing, or the processed video signal being provided to the local display can be communicated to the remote user.
Owner:NVIDIA CORP
Cross-ledger transfers between distributed ledgers
ActiveUS20190188711A1Block valueCryptography processingTelephonic communicationDistributed computingThroughput
The presently-disclosed solution provides cross-ledger transfers between distributed ledgers to achieve highly-scalable transaction throughput. Disclosed are methods and instruction code for writing a cross-ledger transfer in a way that effectively transfers value from a source distributed ledger to a target distributed ledger while preventing double spending of the value. This results in the transformation of the ledgers in that the total value in the source ledger is decreased by the transferred value while the total value in the target ledger is increased by the same amount. Also disclosed are system architectures that utilize cross-ledger transfers between multiple distributed ledgers to achieve highly-scalable transaction throughput. Also disclosed are computer apparatus configured to implement cross-ledger transfers between distributed ledgers. Other embodiments and features are also disclosed.
Owner:TBCASOFT INC
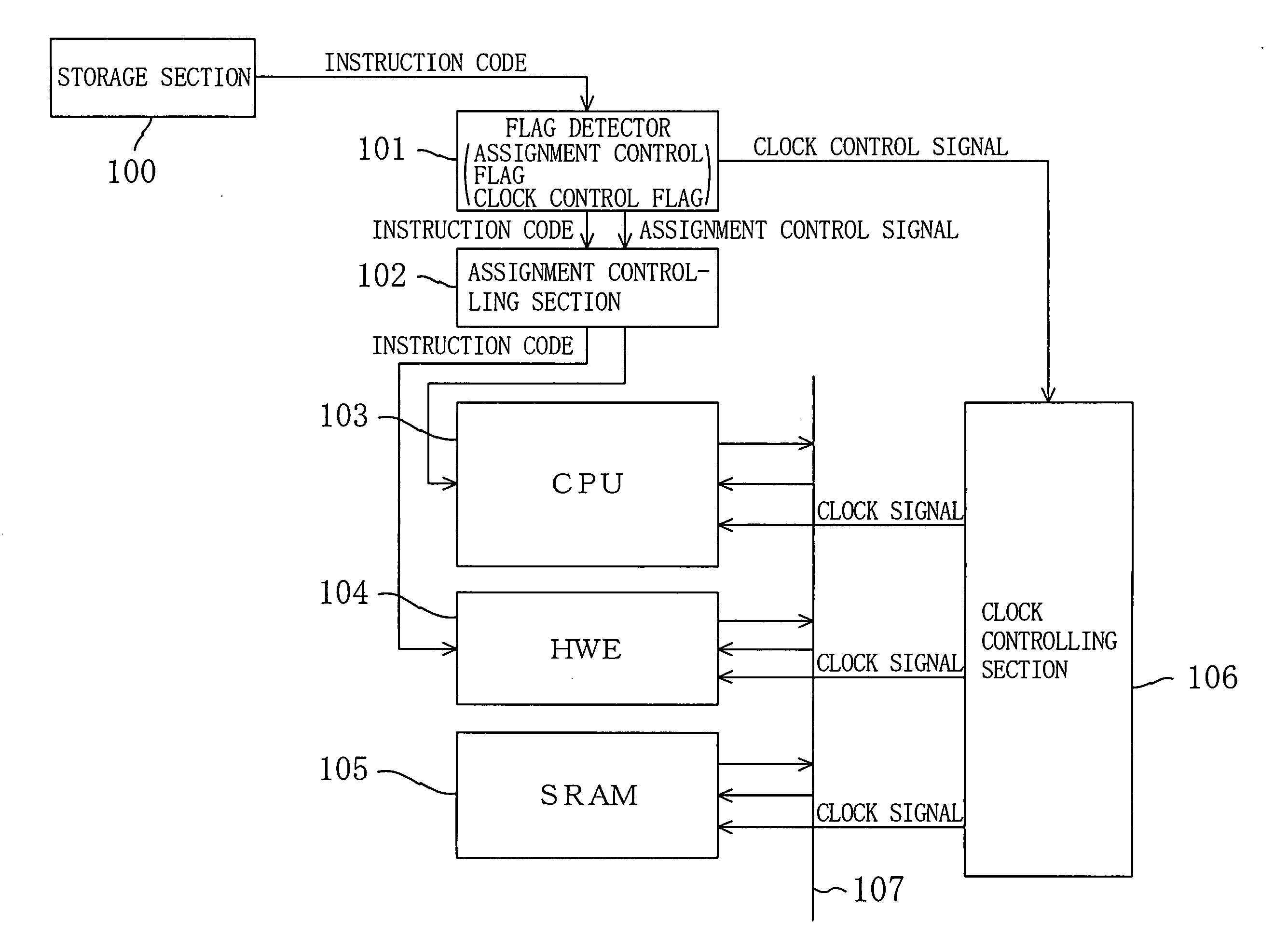
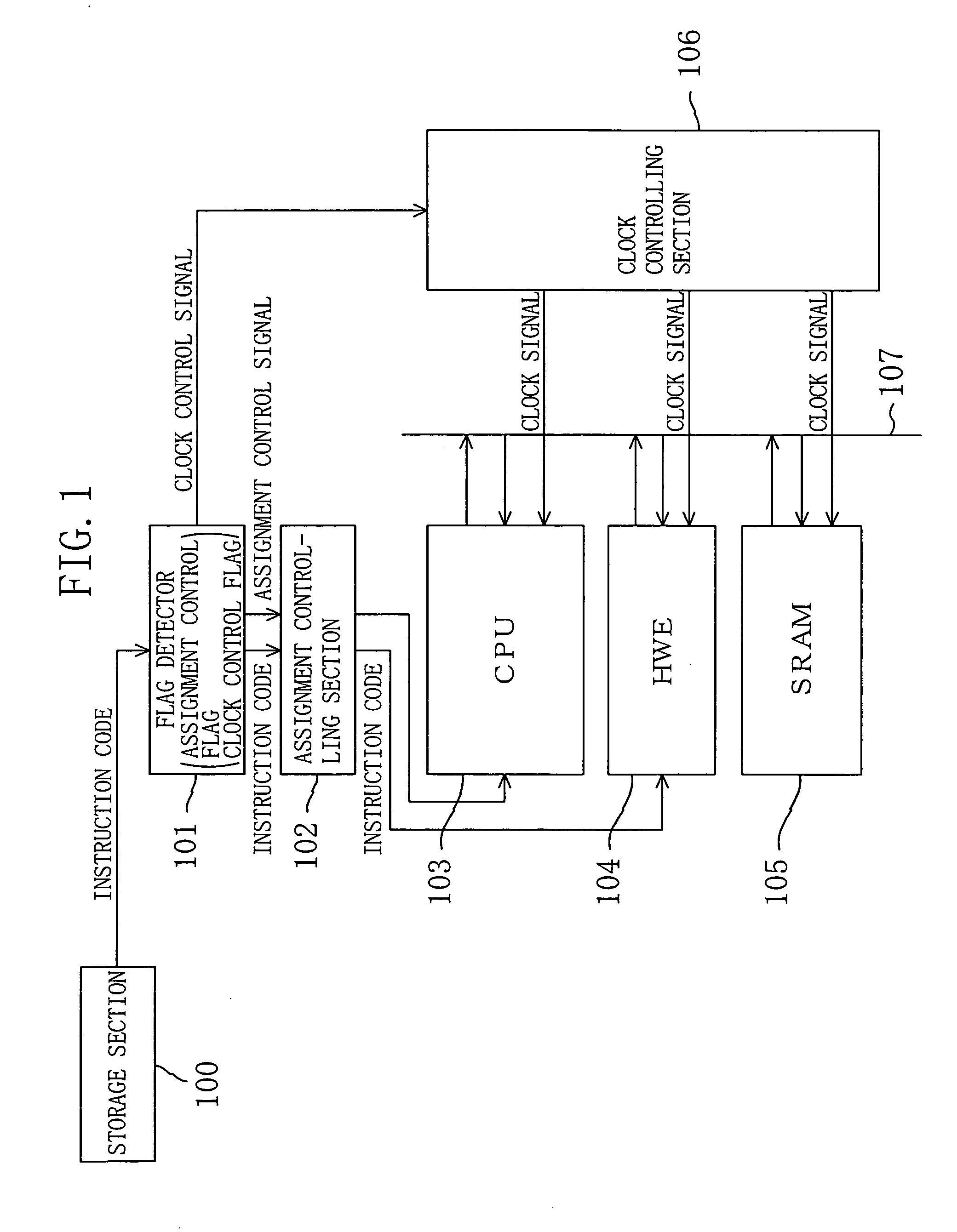
Processor system, instruction sequence optimization device, and instruction sequence optimization program
ActiveUS20050102560A1Reduce power consumptionMaintenanceEnergy efficient ICTError detection/correctionControl signalInstruction sequence
To reduce power consumption of a processor system including a plurality of processors without degradation of the processing ability, a CPU detects mode setting information added to instruction code and outputs a clock control signal and a power supply voltage control signal to a clock controlling section and a power supply voltage controlling section, respectively. When a plurality of processing engines execute an instruction in parallel, clock signals with a frequency lower than a predetermined frequency and power supply voltages lower than a predetermined voltage are supplied. As a result, power consumption is reduced and the processing ability is maintained by the parallel execution.
Owner:SOCIONEXT INC
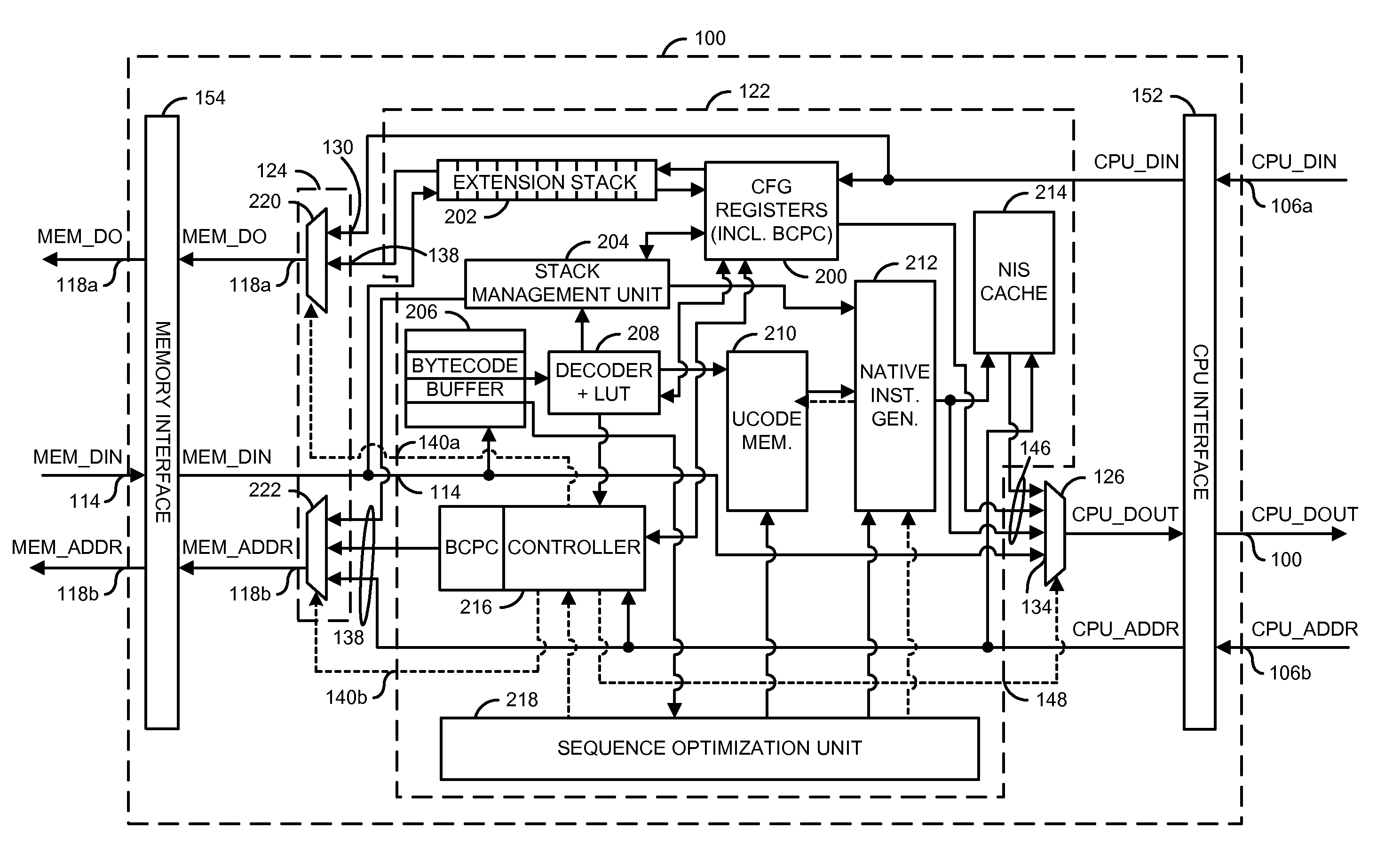
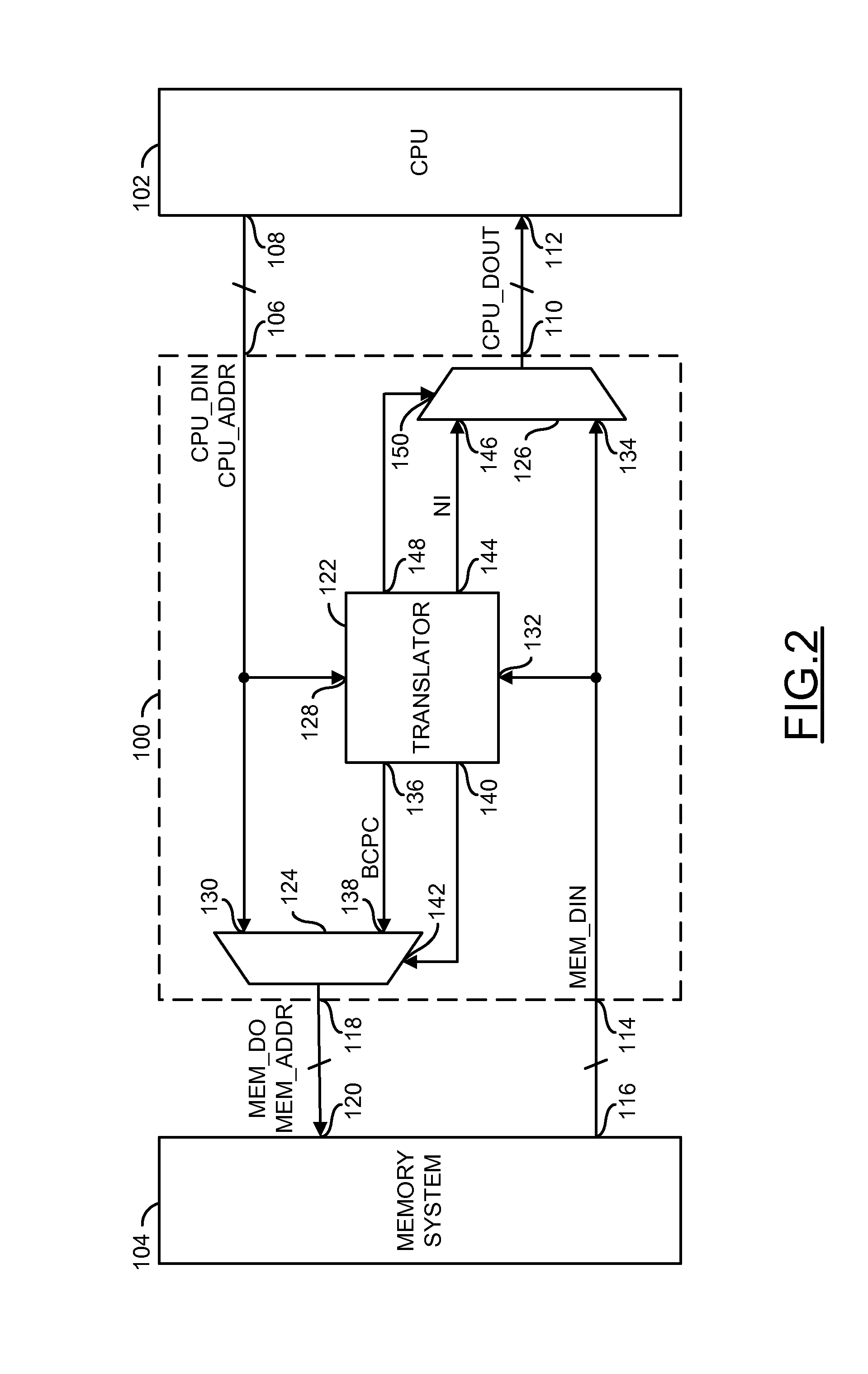
Microcode based hardware translator to support a multitude of processors
InactiveUS7873814B1Fast executionRuntime instruction translationDigital computer detailsMicrocodeInstruction set
An apparatus comprising a circuit configured to translate instruction codes of a first instruction set into sequences of instruction codes of a second instruction set that emulate a functionality of the instruction codes of the first instruction set.
Owner:AVAGO TECH INT SALES PTE LTD
Control method for intelligent appliance
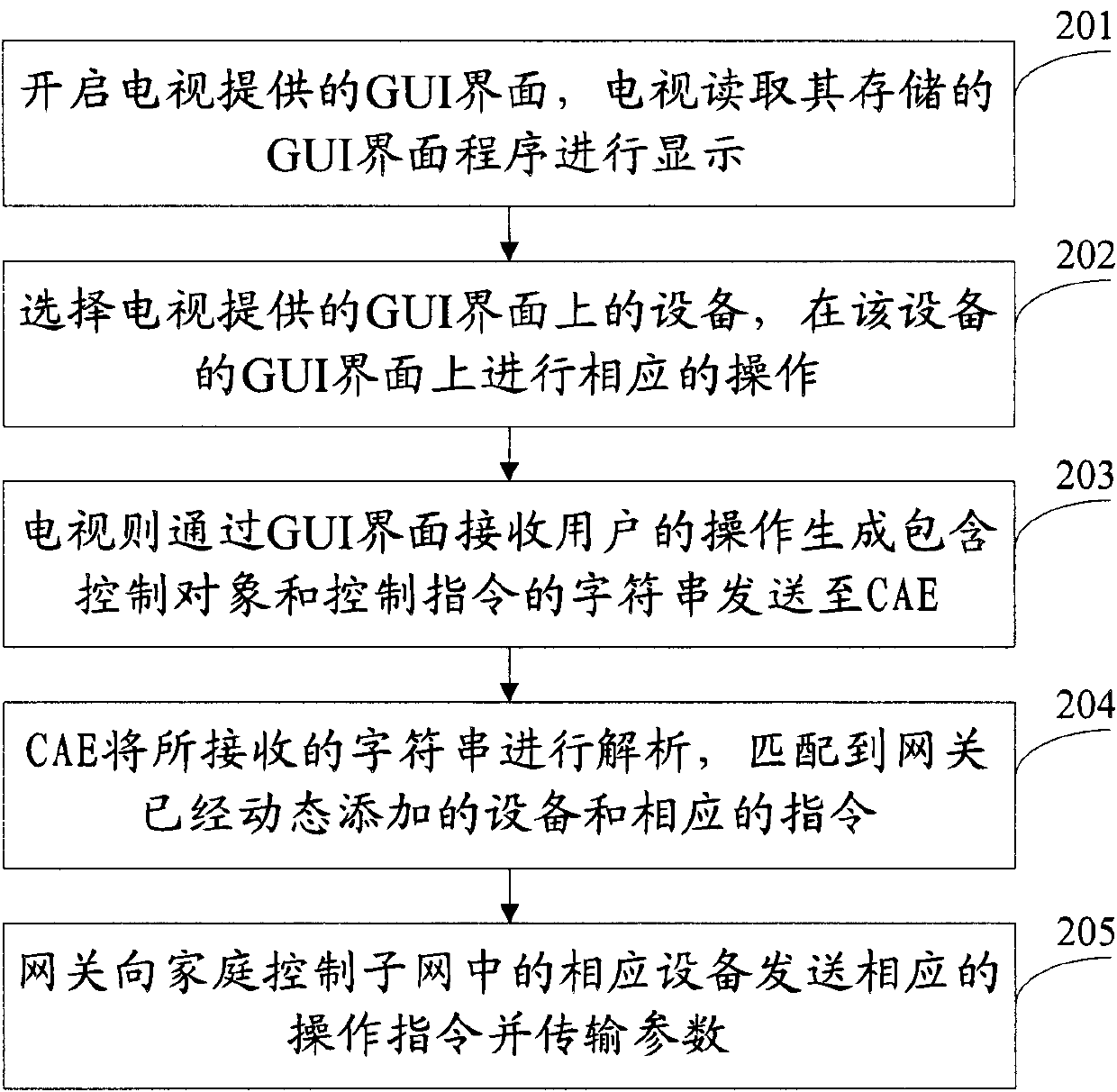
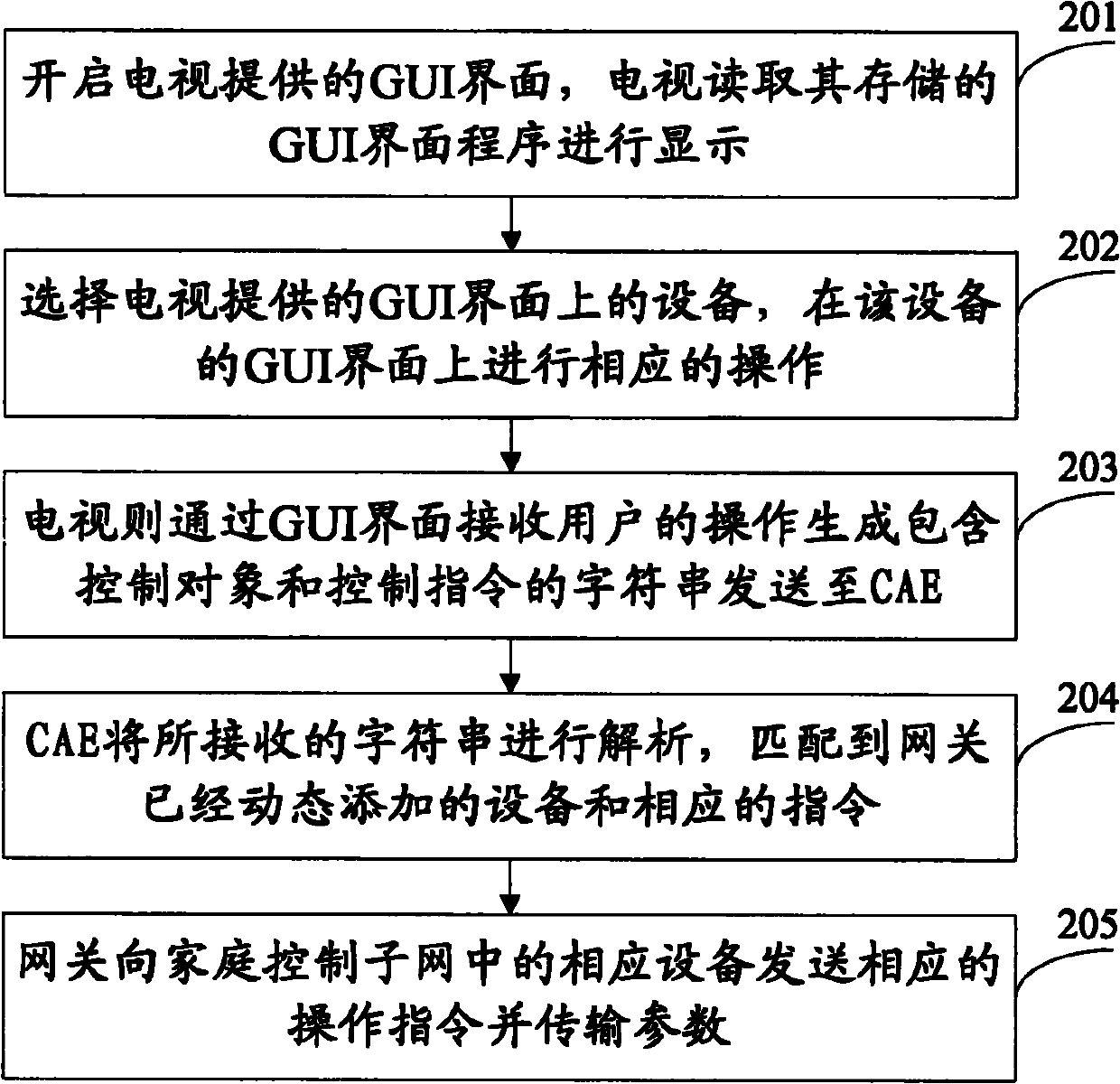
ActiveCN101908989AHigh resolutionPixel heightTelevision system detailsColor television detailsInternet applianceLoose coupling
The invention provides a control method for an intelligent appliance. The method comprises the following steps that: A, a TV set reads and displays a program of a GUI interface stored by the TV set, and receives operation of a user on a control interface of the intelligent appliance in the GUI interface through a remote controller; B, a character string which contains a control target and a control instruction is generated; C, a core application engine (CAE) module matches the character string with an equipment index number and a corresponding instruction index number which are acquired from a gateway by the core application engine (CAE) module and dynamically added by the gateway and sends the equipment index number and the corresponding instruction index number to the gateway; and D, the gateway acquires the corresponding address and instruction code of the intelligent appliance by matching according to the received equipment index number and instruction index number and sends the corresponding instruction code to the address so as to control the intelligent appliance. The control method can provide high-resolution and high-pixel images to a user, realize the loose coupling between the GUI interface and specific equipment and simplify operation of GUI writing of a user.
Owner:HAIER GRP CORP +1
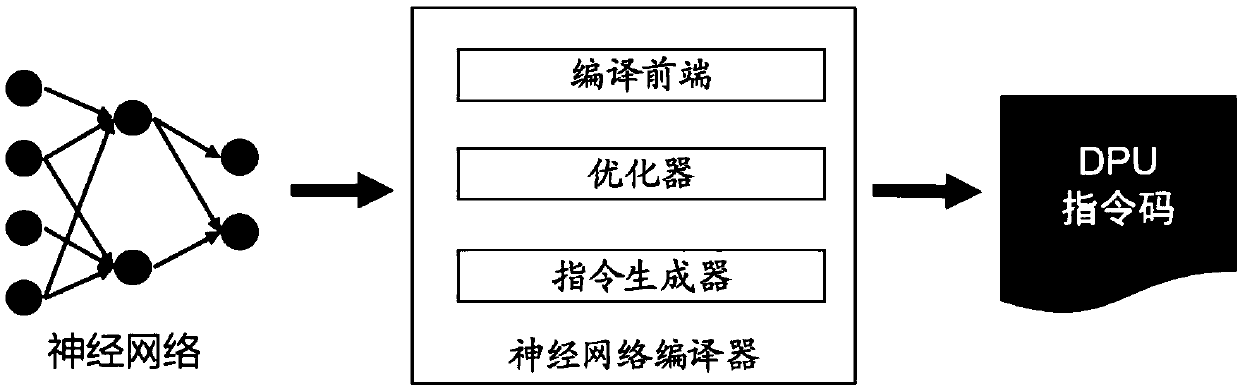
Neural network compiler architecture and compiling method
ActiveCN110766147AEasy to optimizeImprove targetingNeural architecturesPhysical realisationComputer architectureGranularity
The invention provides a neural network compiler architecture and method. The compiler architecture comprises: a calculation graph construction module which is used for constructing a universal firstintermediate representation based on inputted different types of model files, wherein the first intermediate representation is in a graph form; a calculation graph optimization module which is used for carrying out graph optimization on the first intermediate representation to obtain a second intermediate representation in a graph form; and an instruction generation module which is used for carrying out scheduling optimization on the second intermediate representation to obtain a fine-grained third intermediate representation, and compiling the third intermediate representation into an instruction code executed on the hardware platform based on the hardware platform. The modules in the compiler architecture are matched with various intermediate representations with different granularitiesand attributes, so that various deep learning frameworks and rear-end hardware platforms can be handled with extremely high expandability and compatibility, and efficient and accurate code optimization capability is provided.
Owner:XILINX INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com