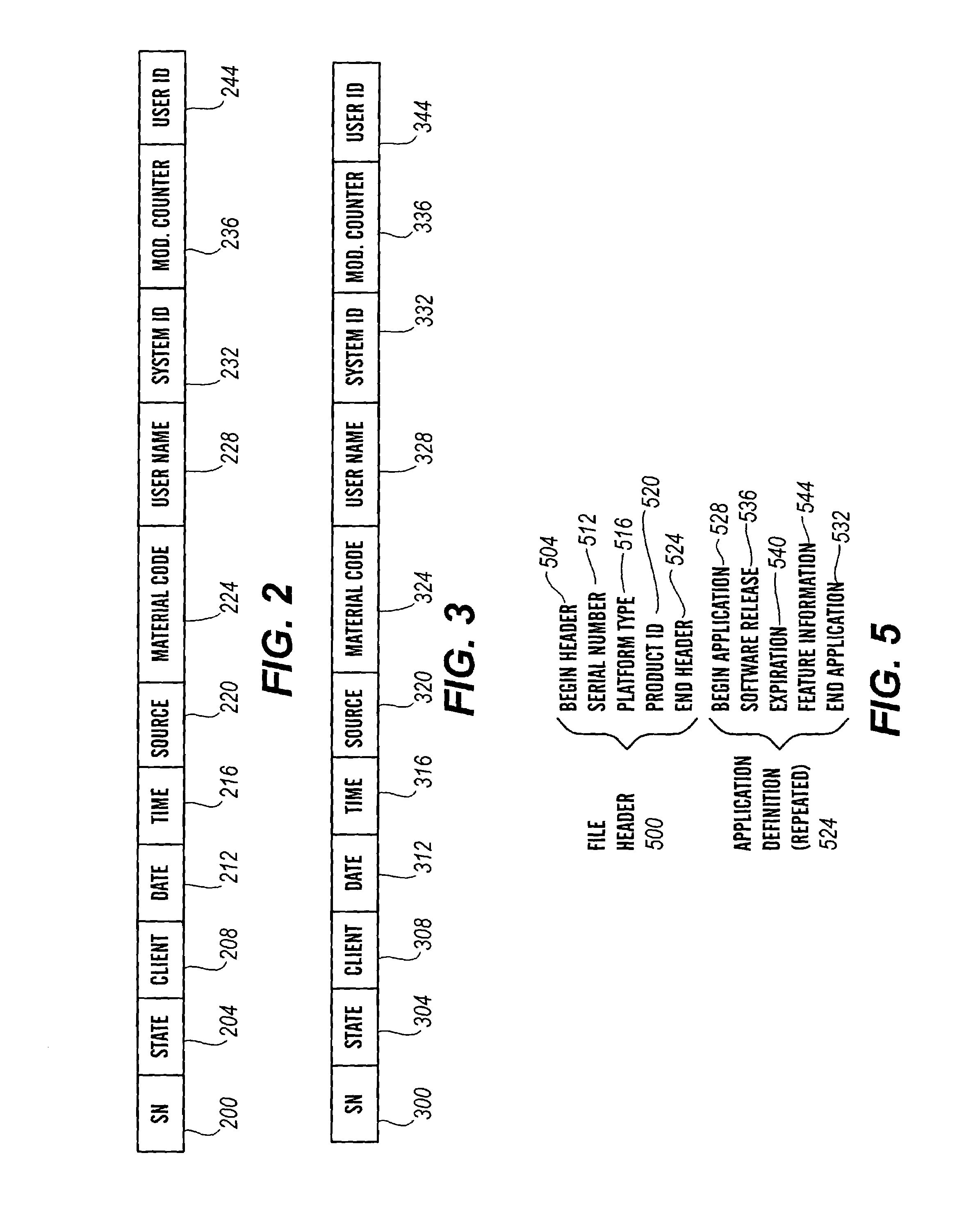
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
130results about How to "Prevent piracy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
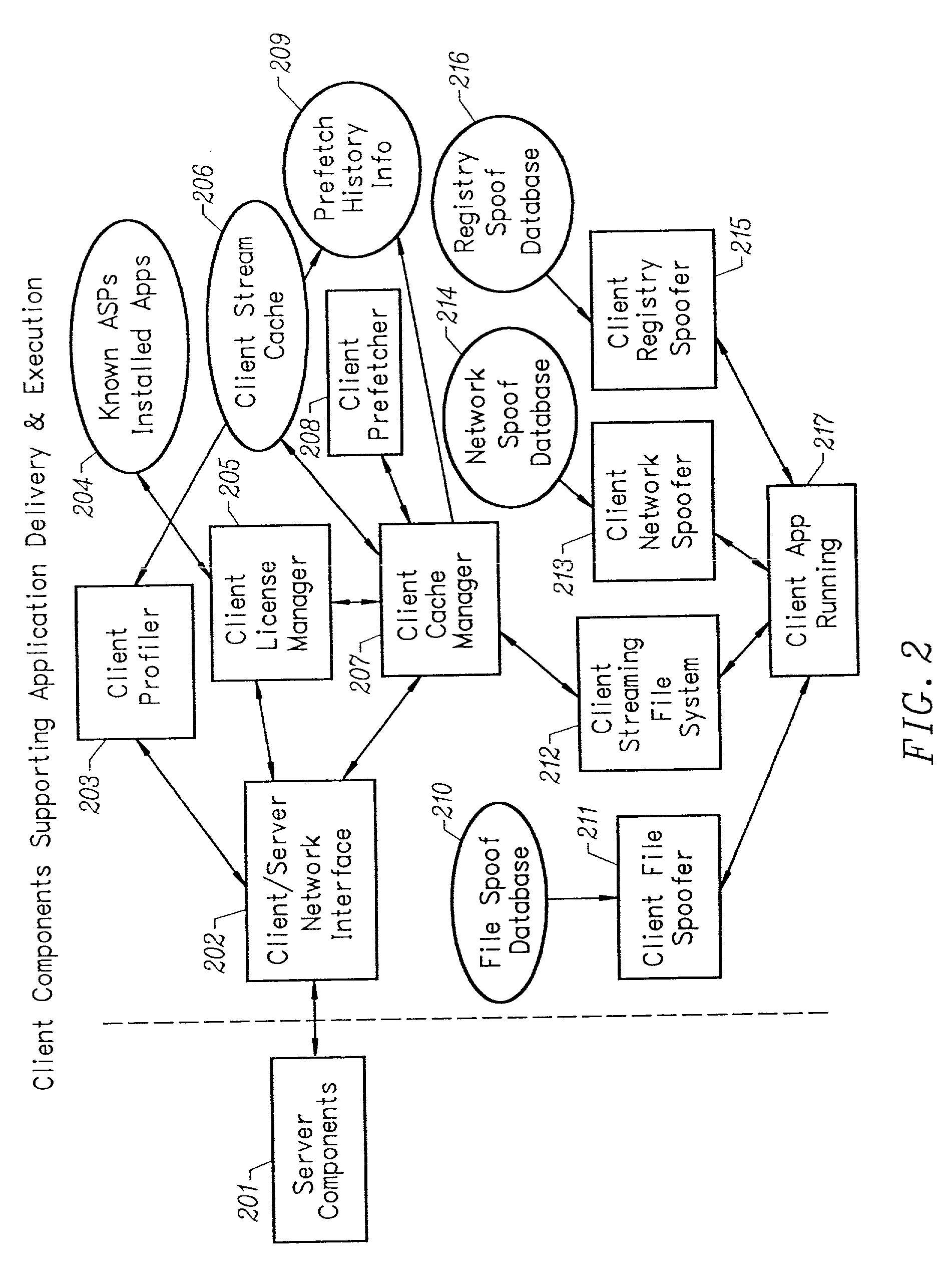
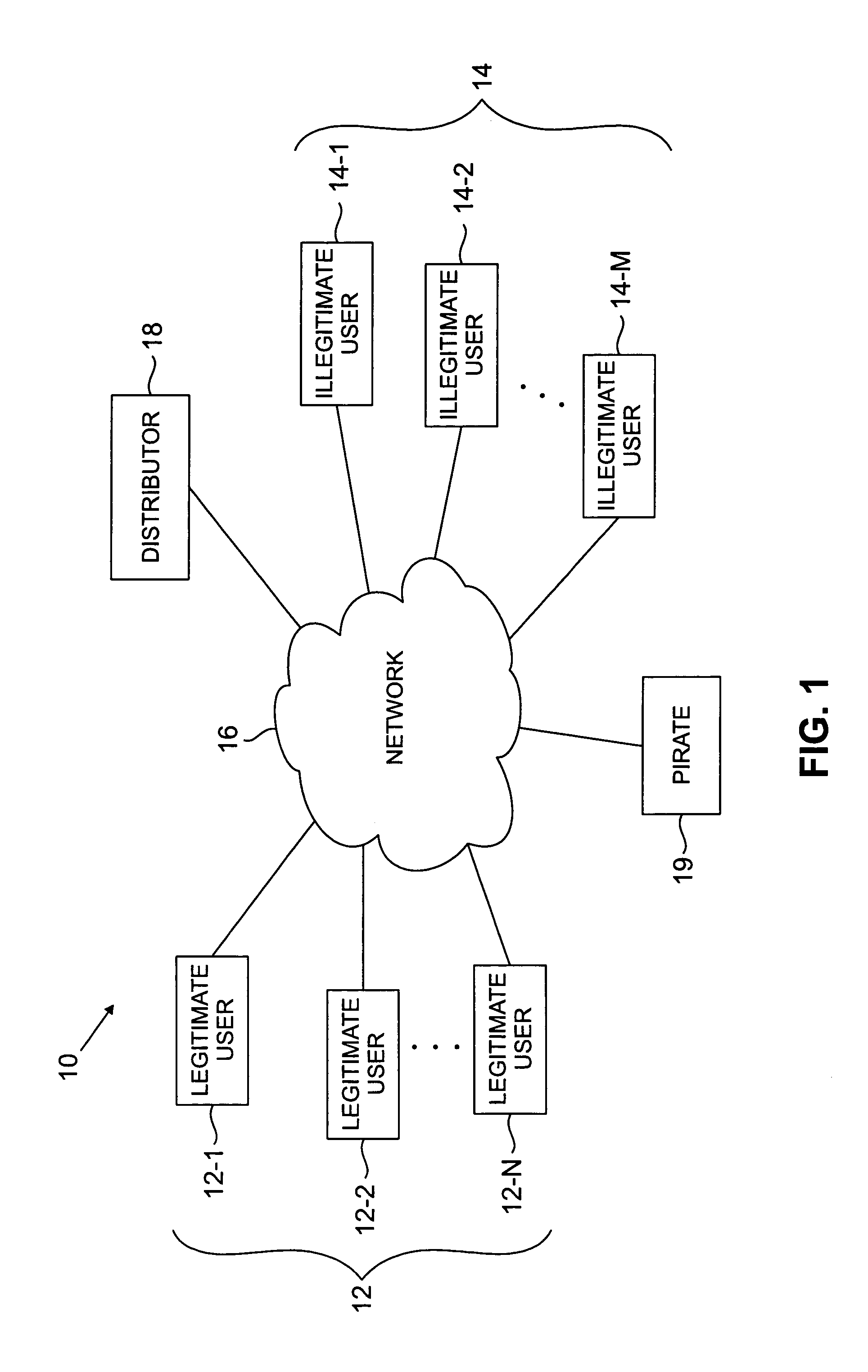
Anti-piracy system for remotely served computer applications
InactiveUS20020087883A1Prevent piracyMore decisionDigital data processing detailsHardware monitoringFile systemClient-side
An anti-piracy system for remotely served computer applications provides a client network filesystem that performs several techniques to prevent the piracy of application programs. The invention provides client-side fine-grained filtering of file accesses directed at remotely served files. Another technique filters file accesses based on where the code for the process that originated the request is stored. Yet another technique Identifies crucial portions of remotely served files and filters file accesses depending on the portion targeted. A further technique filters file accesses based on the surmised purpose of the file access as determined by examining the program stack or flags associated with the request. A final technique filters file accesses based on the surmised purpose of the file access as determined by examining a history of previous file accesses by the same process.
Owner:ENDEAVORS TECH
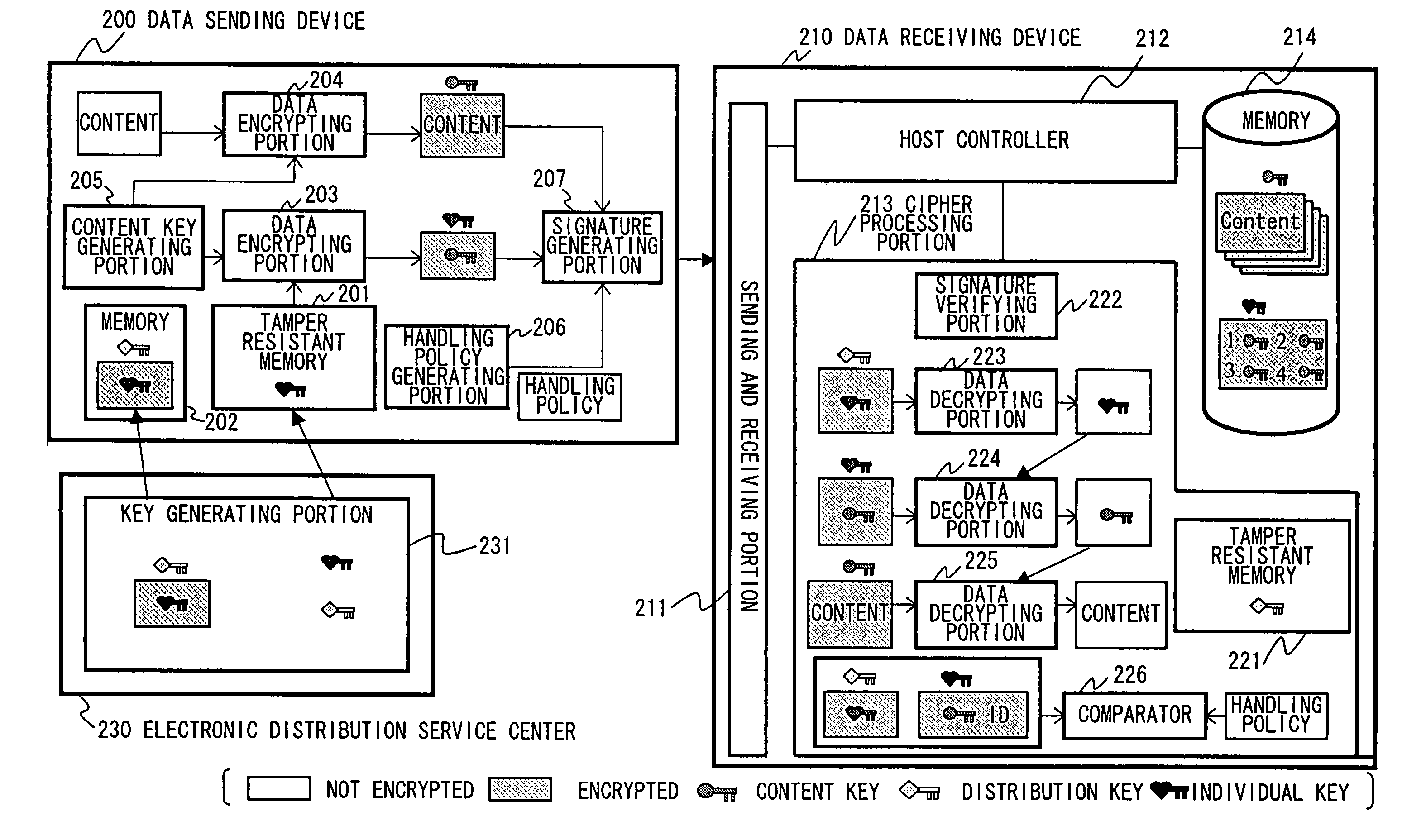
Information transmission system, transmitter, and transmission method as well as information reception system, receiver and reception method
InactiveUS7099479B1Prevent piracySimple configurationKey distribution for secure communicationUnauthorized memory use protectionInformation transmissionInformation seeking
Owner:SONY CORP
Multimedia platform synchronizer
InactiveUS8015200B2Reduce pressureReduce problemsTelevision system detailsElectrophonic musical instrumentsComputer hardwareComputerized system
Owner:SEIFLEIN PHIL +1
Information sending system, information sending device, information receiving device, information distribution system, information receiving system, information sending method, information receiving method, information distribution method, apparatus, sending method of information receiving device, playback method of apparatus, method of using contents and program storing medium
InactiveUS20060168451A1Improve usabilityPrevent piracyKey distribution for secure communicationUser identity/authority verificationComputer hardwareDistribution method
Owner:SONY CORP
Network, system and method for distributing digital media
InactiveUS20070036303A1Prevent piracyPrevent theftCable networksInterconnection arrangementsComputer networkSet top box
A network, a system and a method distribute digital media from a substation and / or a server to a set-top box of a subscriber. The digital media is requested, is accessed and / or is transferred from the substation and / or the server to the set-top box via one or more nodes and / or one or more node clusters. The subscriber may utilize an interactive means in conjunction with the set-top box to access, to request, to receive and / or to display the digital media via a communication medium and / or a connection line. One or more nodes and / or one or more node clusters connect a central office to the substation. The digital media is stored in a server farm of the central office which is accessed by one or more nodes and / or one or more node clusters. The digital media is transmitted and / or is distributed to the set-top box via the communication medium, the connection line one or more of the nodes and / or one or more of the node clusters. The subscriber access, displays and / or views the digital media via the set-top box, a display monitor, one or more input devices and / or one or more output devices.
Owner:APPLE INC
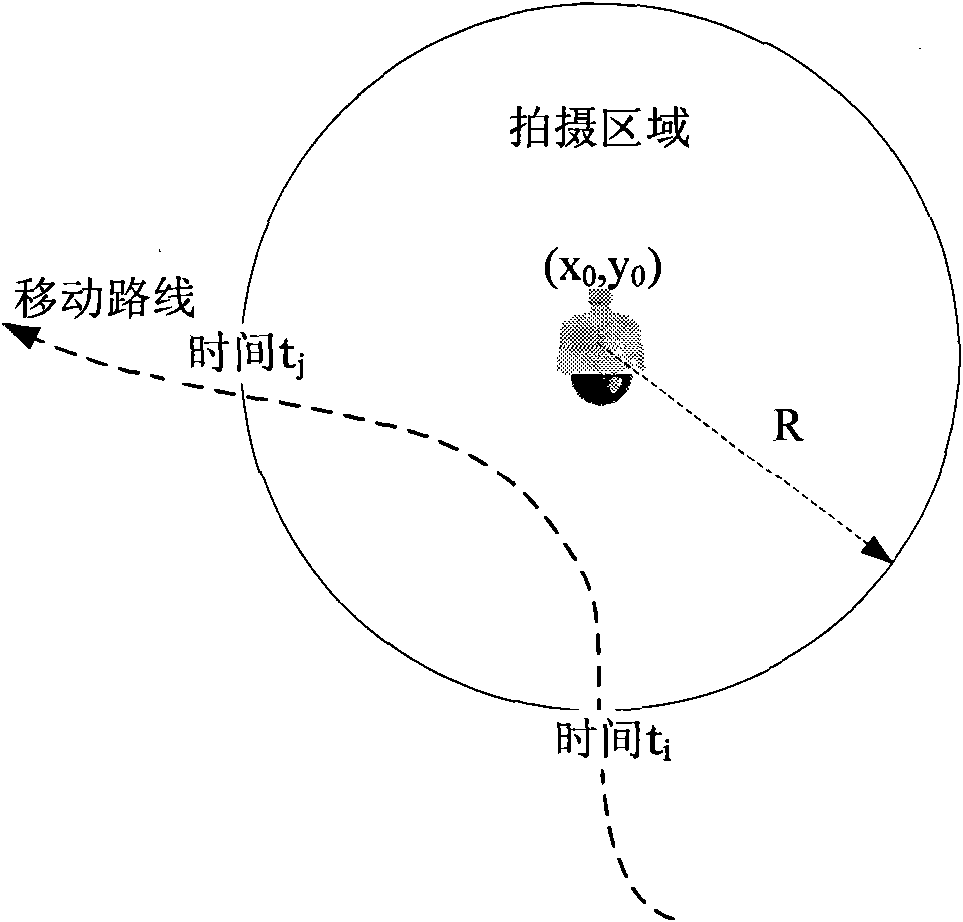
Multimedia integration method based on user trajectory
ActiveCN101867730AStrong commemorative significancePrevent piracyTelevision system detailsColor television detailsPersonalizationMedia content
The invention discloses a multimedia integration method based on user trajectory, which comprises the following steps: 1, establishing an index structure of space region data in the scene; 2, establishing an index structure for monitoring the video data; 3, collecting the user moving trajectory; 4, receiving user-shot picture data; 5, searching multimedia content according to the user moving trajectory; and 6, integrating the multimedia content. With the user moving trajectory in the scene as a centre, the new digital content is formed by associating with the relevant multimedia data. The user behaviour track is realized in the security field, the invention has wide application in the aspects, such as creating a personalized tourist commemorative video in a scenery area.
Owner:WUXI YUNQUE TECH CO LTD
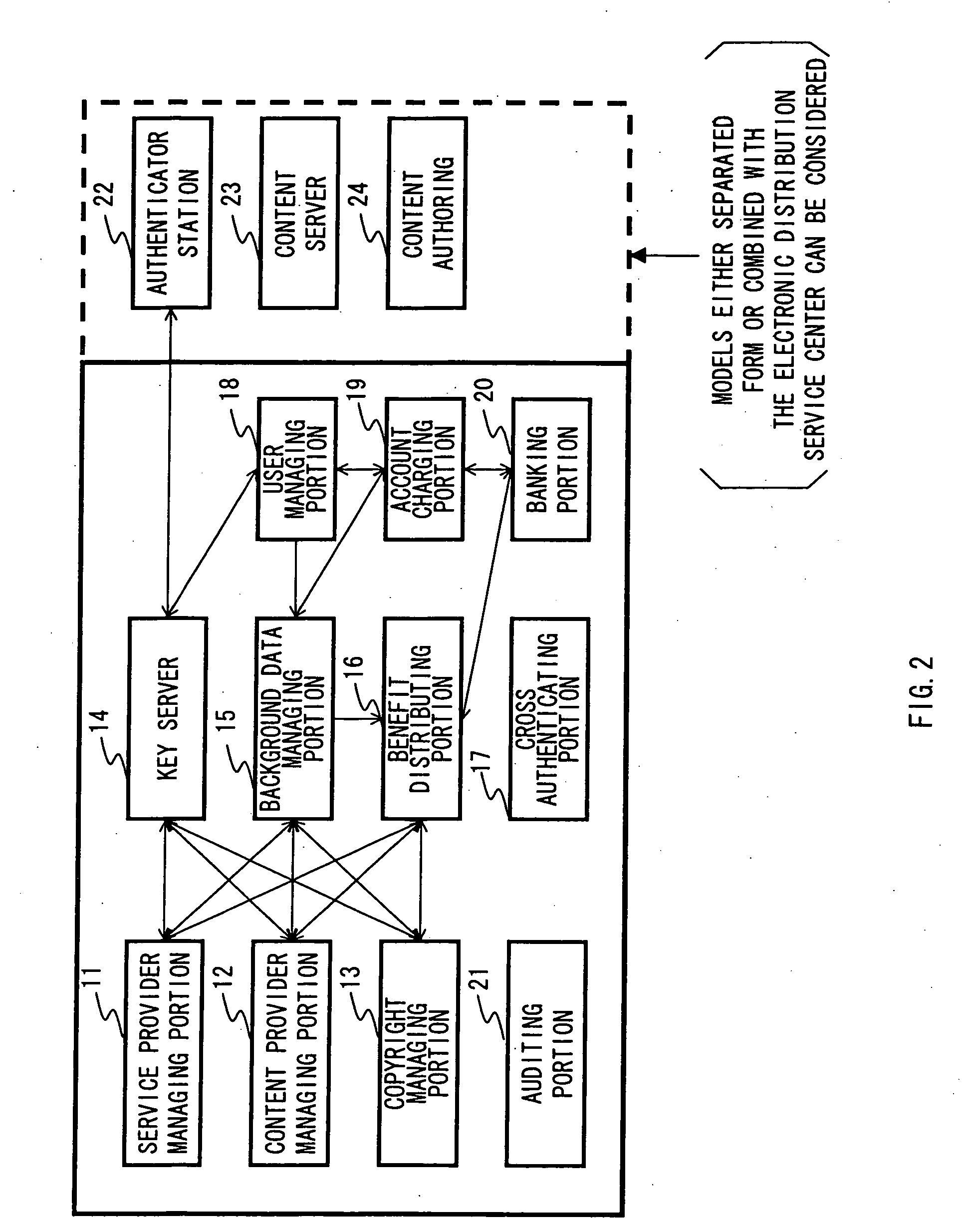
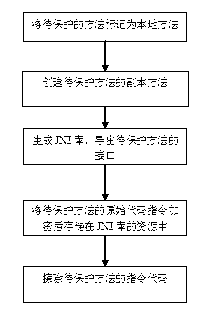
License file serial number tracking
ActiveUS7228567B2Protect and control actuationEffectively piracyDigital data processing detailsUser identity/authority verificationUnique identifierComputer science
A system for monitoring licensing eligibility of a computational component, the computational component being associated with a unique identifier, is provided. The system comprises (i) an input and / or interface 120 operable to receive a request to authorize operation of at least part of the computational component; (ii) a memory, such as licensing database 128, comprising licensing database information associated with the identifier, the information comprising a licensing state indicator; and (iii) an activator, such as remote feature activator 112, operable to (a) authorize operation of the at least part of the computational component when the licensing state indicator has a first state and (b) not authorize operation of the at least part of the computational component when the licensing state indicator has a second state other than the first state.
Owner:AVAYA INC
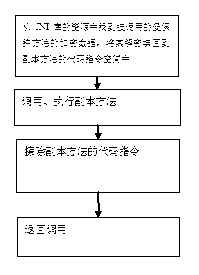
Method for protecting JAVA application programs in Android system
ActiveCN102708322APrevent piracyProgram/content distribution protectionSpecific program execution arrangementsApplication softwareJava classes
The invention relates to the field of computer safety, in particular to a method for protecting application programs in an Android system. By carrying out encryption transformation on a plurality of method instruction codes of JAVA objects to be protected, encrypted method codes are subjected to real-time decryption operation according to the calling requirement when the programs operate, so that the application programs are difficult to subject to decompilation and static analysis, and therefore, the effective protection on the JAVA programs in the Android system is implemented.
Owner:BEIJING SENSESHIELD TECH
Method for the server side processing of user interactions with a web-browser
InactiveCN1835507AAllow interactionData exchange compactWeb data retrievalTransmissionWeb applicationWeb browser
The present invention relates to a method and system for client-side interacting with a server-side web application in a web-based client-server environment, in which a client-side web browser is used as a user interface for displaying web pages sent by the web application within a browser application frame and for converting events triggered by one or more user actions within said application frame into a request directed to said server-side web application, wherein an executable program object for example a Java Script is used at the client side as a part of the client-side web application user interface.
Owner:IBM CORP
Method for transmitting data with digital watermark access control and devices therefor
InactiveUS20030026421A1Prevent piracyData processing applicationsUser identity/authority verificationDigital watermarkingAccess control
Process of transmission of information with access control as a digital watermark. The access control information is inserted into the scrambled data in the form of a digital watermark. On reception, the digital watermark is extracted from the received data, the access control information is recovered, and the received data are unscrambled if access is authorized. Application particularly to the transmission of images.
Owner:FRANCE TELECOM SA +1
Software aging method and apparatus for discouraging software piracy
InactiveUS7003110B1Discourages unauthorized useIncreasing tracingKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareSoftware
A software program is configured in accordance with a software aging process such that one or more files generated by the program are at least partially encrypted using a cryptographic key associated with a current time interval for which the files are generated. The cryptographic key may be a symmetric key used for both encryption and decryption operations, such that cryptographic key used for encryption in a given interval is also required to decrypt files encrypted during that interval. Periodic updates of the software program are provided to a legitimate user of the software program, with a given one of the updates including a different cryptographic key associated with a subsequent time interval. The cryptographic key associated with a particular one of the time intervals may be common to each of a set of legitimate copies of the software program that have received the corresponding version of the periodic update. The variation of the cryptographic keys from one interval to another discourages unauthorized use of the software program by deliberately requiring both legitimate and illegitimate users to request unusually frequent updates, thereby substantially increasing the tracing and prosecution risks borne by software pirates.
Owner:ALCATEL-LUCENT USA INC
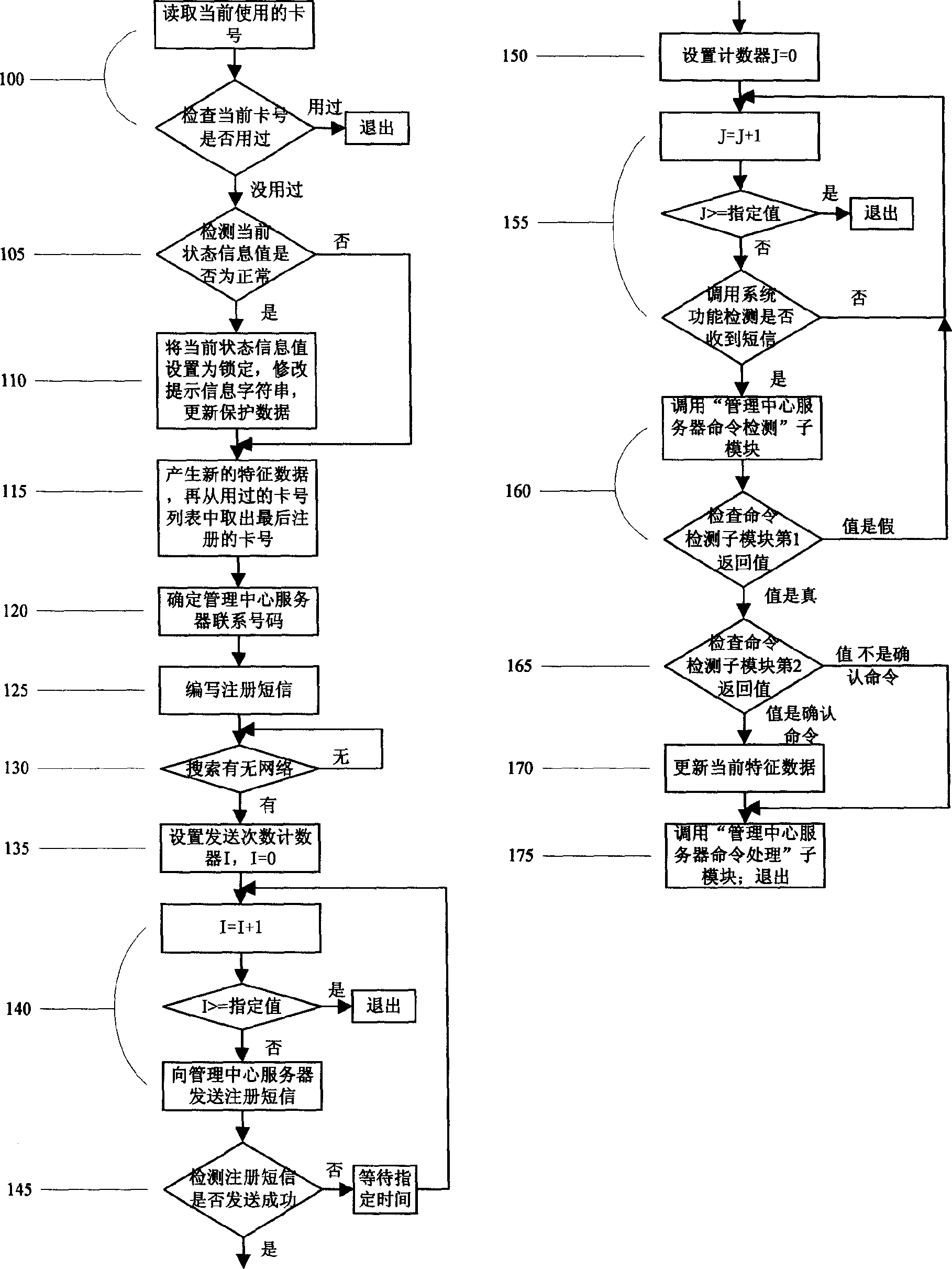
System and method for preventing software and hardware with communication condition/function against embezzlement
InactiveCN1764106APrevent cheatingPrevent smugglingComputer security arrangementsSecurity arrangementClient-sideWeb server
The system to prevent stealing of the soft / hard ware with communication function comprises: the terminal soft / hard ware with an ID number, the server of management center to store basic and register information of every ID number, a WEB server, a client for after service with terminal soft / hard ware, and the communication network between client and servers. Wherein, the terminal hardware sends register information to management server and obtains returned ACK demand to start work. This invention can send lock demand to terminal soft / hard ware to disable opposite function and track communication number to anti false.
Owner:乔超
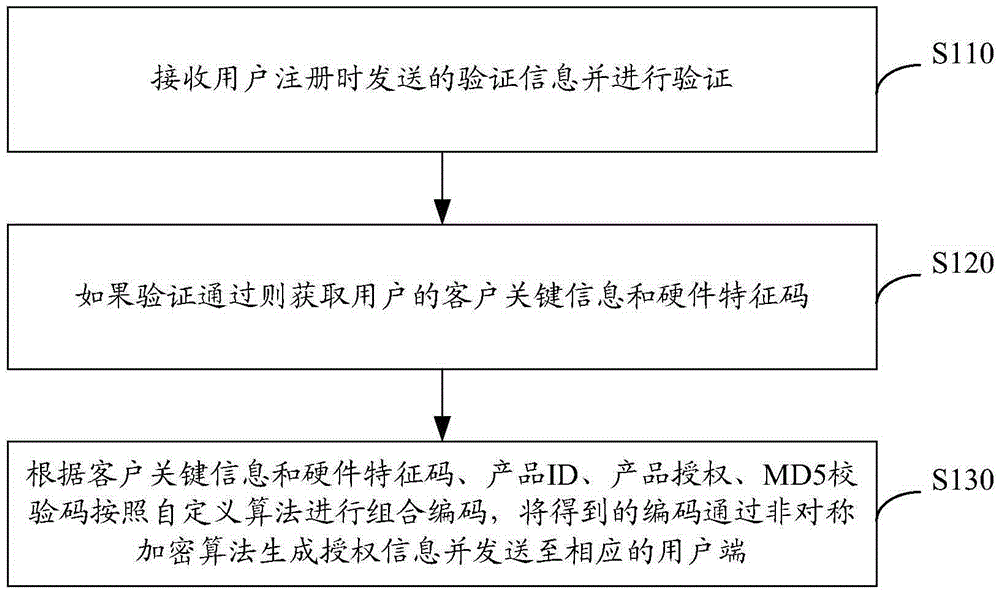
Software protecting, authorizing and registering method
ActiveCN104700002APrevent piracyAvoid business lossProgram/content distribution protectionFeature codeAuthorization
The invention discloses a software protecting, authorizing and registering method. The software protecting, authorizing and registering method comprises the following steps: receiving verification information sent out during user registration and verifying; if the verification is successful, obtaining client key information and hardware feature codes of a user; carrying out integrated coding in accordance with custom arithmetic and according to the client key information and the hardware feature codes, product ID, product authorization and MD5 check codes, generating authorization information by obtained codes through asymmetric cryptographic algorithm and sending the authorization information to a corresponding user side. The method provided by the invention can protect product intellectual property, limit unauthorized use of software products, can effectively prevent piracy and avoid business loss, further can support rich and flexible authorized packaging and pricing mechanisms, can achieve high efficiency and low cost software distributing and delivering, and further can be used for comprehensive analysis to software product selling, marketing and customer conditions.
Owner:航天信息软件技术有限公司
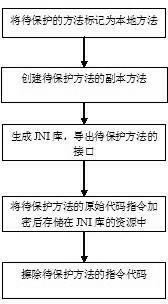
Android platform executable program encrypting method
ActiveCN103914637APrevent tamperingPrevent piracyProgram/content distribution protectionComputer hardwareOperational system
The invention provides an Android platform executable program encrypting method. The Android platform executable program encrypting method comprises the steps of, firstly, packaging APK (Android package) files into encrypted APK files through a package tool; secondly, performing run-time encryption and decryption in a mode of API (application programming interface) interception and replacement. The Android platform executable program encrypting method can avoid decompilation, tempering and pirate of APKs, thereby protecting the interests of program developers.
Digital rights protection method based on block chain technology
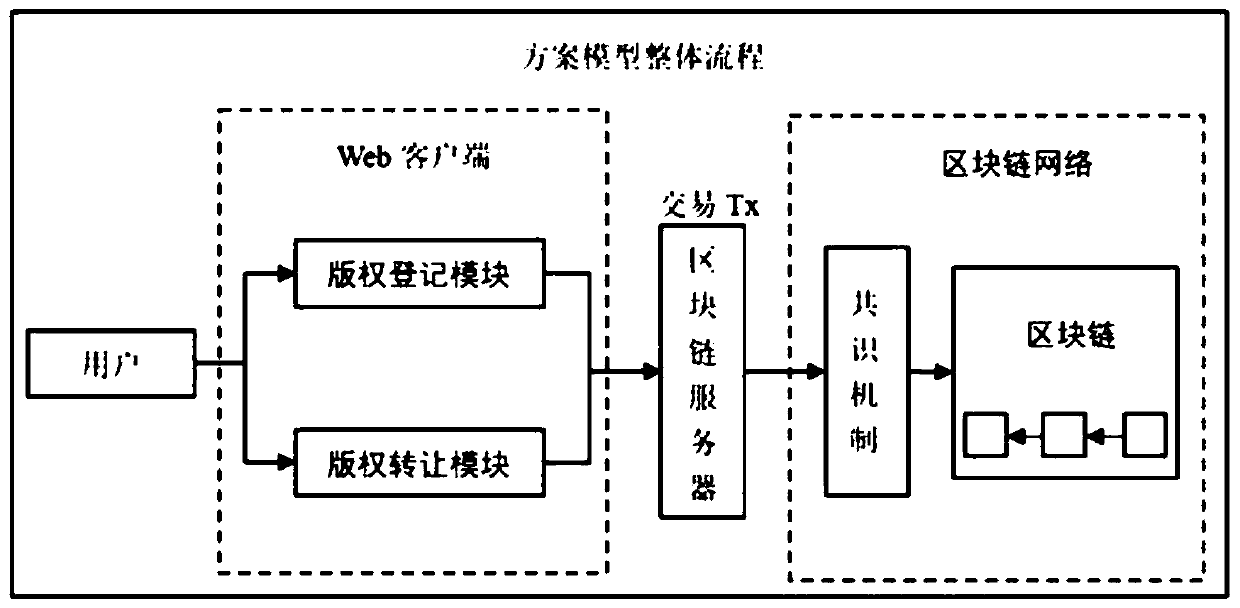
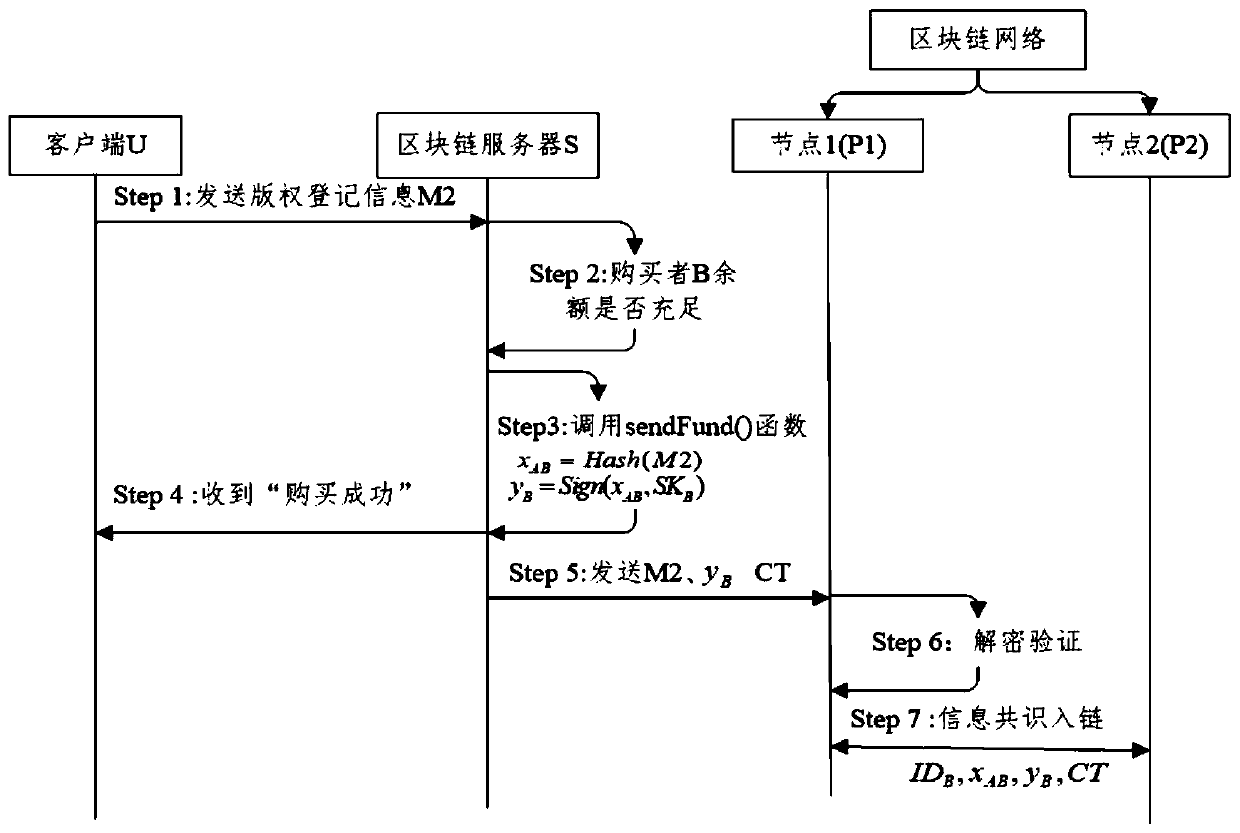
InactiveCN110968842AEnable secure storageRealize immutableUser identity/authority verificationProgram/content distribution protectionInternet privacyEngineering
The invention discloses a digital copyright protection method based on a block chain technology. The digital copyright protection method comprises a digital copyright protection model based on the block chain technology and a copyright protection protocol. The digital copyright protection model comprises a user, a Web client, a block chain server and a block chain network. A user registers and identifies through the Web client, generated transaction information Tx is processed through the block chain server, and information consensus is carried out through a consensus mechanism of the block chain network; the copyright protection protocol comprises a digital copyright registration sub-protocol and a digital copyright transfer sub-protocol. Information leakage cannot be caused even if the scheme is attacked; according to the method and the system, piracy and copying behaviors of the digital works are prevented, malicious users cannot perform camouflage attacks, piracy infringement behaviors can be solved, the real uniqueness of the digital works is ensured, and the calculation cost of a Simhash (locality sensitive hash) algorithm is greatly reduced.
Owner:NANTONG UNIVERSITY
Method and apparatus for inhibiting the piracy of motion pictures
InactiveUS8018569B2Prevent piracyQuality improvementTelevision system detailsProjectorsDigital videoPhase shifted
A method and apparatus to inhibit the piracy of motion pictures in theaters by taking advantage of the frame rate discrepancies between film (or digital) display and video camcorders. By alternating specific image display intervals and, shuttering cadences, or with digital video projectors commanding a similar modified display via the digital projector's blanking and display capabilities, so that the projected images occur in a random and / or phase shifted manner, objectionable distortions are produced in an illicitly captured video image, while being invisible to theatrical viewers. In addition, various serrated, slit, multi-quadrant or spotted patterns may be used on mechanical shutters, or simulated on digital displays, to further degrade the quality of illicitly captured video by pirates in theaters.
Owner:MAXIVISION CINEMA TECH
Method and system for encryption protection of video files
InactiveCN102693386ACopyright protectionPrevent leakageProgram/content distribution protectionComputer hardwareAuthorization
The invention discloses a method and a system for encryption protection of video files. The method includes firstly, encrypting the video files by the default encryption algorithm; secondly, storing the encrypted video files and file IDs (identities) to an authorization center, and generating a certificate; thirdly, sending the identity of a user to the authorization center to be verified, and requesting the certificate of the video files after the encrypted documents are acquired by a terminal; and fourthly, acquiring the certificate by the terminal after verification passes, and decrypting and playing the encrypted video files by utilizing a secret key included in the certificate. By the method and the system for encryption protection of the video files, protection of copyrights of digitized audio and video program contents can be reinforced, safe propagation of digitized video contents is guaranteed, and piracy is avoided.
Owner:北京网尚数字电影院线有限公司
Copyright protection method and device for STB (set top box) middleware
InactiveCN102867138ADetermine the usage feeAvoid piracyDigital data authenticationSelective content distributionMedia access controlSet top box
Owner:SHENZHEN COSHIP ELECTRONICS CO LTD
Design method for interactive server integrated with copyright management and its network structure
InactiveCN101175094AFaster and easier transferProtection of rights and interestsData switching by path configurationSecuring communicationNetwork architecturePersonal account
A design method and network architecture for an integrated copyright management mutual server belong to the computer field. The network architecture includes an authority server: providing copyright customization services; the Peer side applies to the authority server for purchase, and the authority server deducts fees and issues authority certificates; certificate server: issues identity certificates to P2P clients; user server: responsible for providing user login verification , password modification, personal account recharge service; multiple user nodes; database server: provide data storage support function, used to support intelligent nodes and authority servers, provide network information, user information data storage, query analysis. In this design method, DRM is built into a module of P2P downloading software; the DRM module is divided into applying for a personal identity certificate; viewing the authority list; purchasing authority certificate; these three parts interact with the authority server and the certificate server. The invention realizes high-speed download and upload in the P2P network, and also integrates the DRM authentication and decryption function.
Owner:COMMUNICATION UNIVERSITY OF CHINA
Software installation control method and system based on cloud computing
InactiveCN104700025AEasy to deployGood for version controlComputer security arrangementsProgram loading/initiatingHuman–machine interfaceCloud systems
The invention provides a software installation control method and system based on cloud computing, relates to the technical field of cloud systems, wherein the method comprises the following steps: obtaining a user equipment identifier or a user identifier; querying the software installation authority of the user equipment identifier or the user identifier, obtaining a software identifier matched with the authority of the user equipment identifier or the user identifier; transmitting the software identifier to user equipment corresponding to the user equipment identifier or the user identifier, displaying the software identifier by the user equipment through a human-machine interface; responding a selection instruction input by the user through the human-machine interface, determining a software data packet designated according to the selection instruction, and transmitting the software data packet to the user equipment. According to the invention, the installation software is managed in a unified way on a server side, the corresponding installation authority is set for the terminal equipment or user identifier, so as to avoid the piracy, viruses and other risks caused by personal download and installation, and help IT support departments of enterprises to deploy and manage the software.
Owner:GUANGDONG MICROCLOUD TECH INC
System and apparatus for digital rights management of content and accessibility at various locations and devices
InactiveUS20080115197A1Reduce loadPrevent contentDigital data processing detailsMultiple digital computer combinationsVirtualizationNetwork management
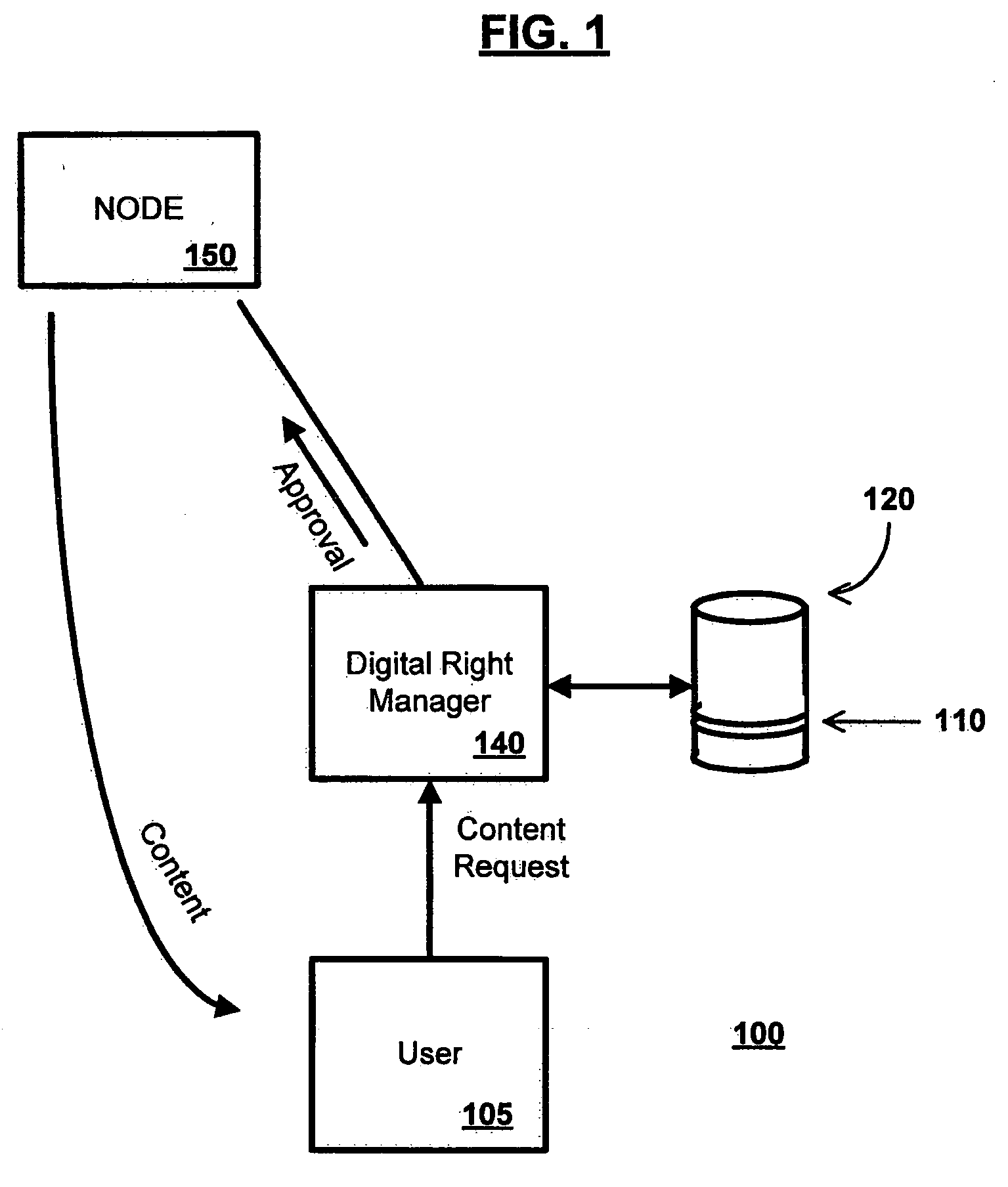
An active virtual environment for the identification and distribution of content and other resources according to digital rights. A network of brokers manage and provide access to a nodes containing virtualized set of resources and services. The resources and services are granted to requesting users who have appropriate licensed rights (or have accounts sufficient to pay for those rights upon request). A digital rights manager is configured to approve requests based on existing rights and / or approve request based on an appropriately configured account with sufficient balance or credit to acquire those rights when requested. The user requests are made from user devices connected to a world-wide network.
Owner:AMGEN INC
Design method of inter-operation system
InactiveCN1945531AImprove interoperabilityAdd supportMultiprogramming arrangementsSpecific program execution arrangementsOperational systemApplication software
This invention belongs to the technical field of computer operating systems, particularly in relation to a design method of the software, which will run interoperability in a single operating system, but at first this software ran in many operating systems. The design method of this invention is a single-core model structure with multi-interfaces, it founds a core service system with coordinate different operating system, which bases on the new invented core; when running apply program, it will distinguish this program belonging to which type of operation system's program according reading the head of file to check the type or format of this file, and then transfer relevant core service, thereby it settle the problem of interoperability of single operation system. The space interoperability system redesigned, reintegrated, redeveloped basing on opening original code, can run the program from Windows and Linux operation system synchronously. The realization of this interoperability technology doesn't only reduce the cost, but also has a better practicability and spread applied worth.
Owner:刘金刚
Security monitor system for cable TV network
InactiveCN1396771APrevent political conspiracyPrevent stealingPulse modulation television signal transmissionTransmission monitoringNetwork terminationAudio power amplifier
A safety monitor system for cable TV network is composed of station equipment and user's network terminals. The station equipment consists of mixer and cable TV transmitter. The user's network terminals comprise trunk amplifiers, user's amplifiers, intelligent branch distributors and user's TV receiver sets. The mixer is connected via FM broadcast modulator to an encoder for transmitting synchronizing signals of encrypted data.
Owner:NANJING UNIV OF POSTS & TELECOMM
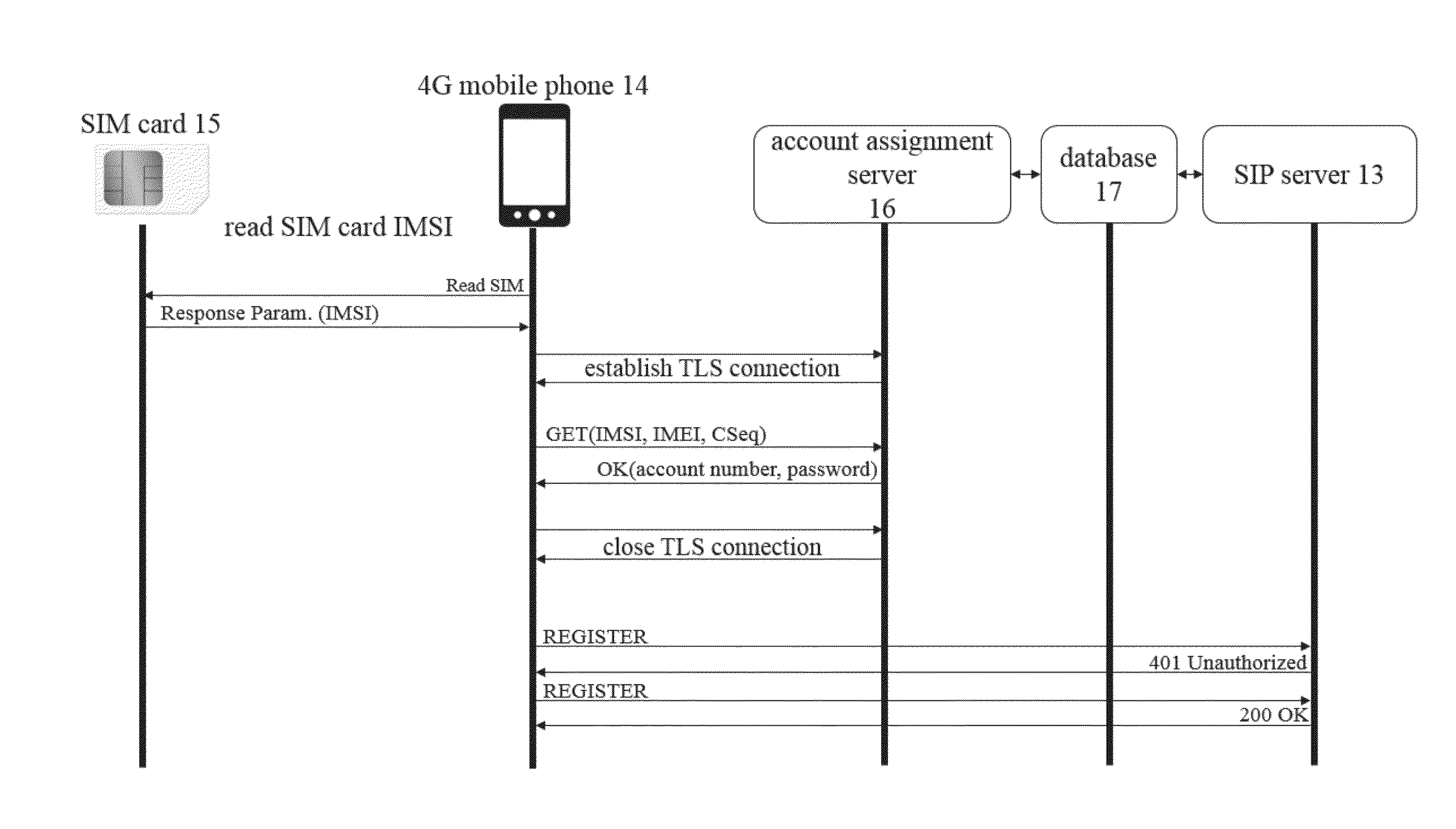
AUTHENTICATION METHOD OF VoLTE
InactiveUS20150350899A1Prevent piracyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications securityPassword
The present invention provides VoIP authentication in 4G VoLTE, and also provides an extra authentication method of VoLTE for achieving communication security. The key point of the extra authentication method of VoLTE is: when a 4G mobile phone is turned on for the first time, a security registration sequence number will be random generated by the 4G mobile phone, and sent with IMSI and IMEI through TLS to an account assignment server for comparison and storage. Thereafter the account assignment server sends an account and a password in a database corresponding to IMSI to the 4G mobile phone, and then the 4G mobile phone conducts VoIP authentication with a SIP server for standby or communication.
Owner:NAT TAIPEI UNIV OF TECH
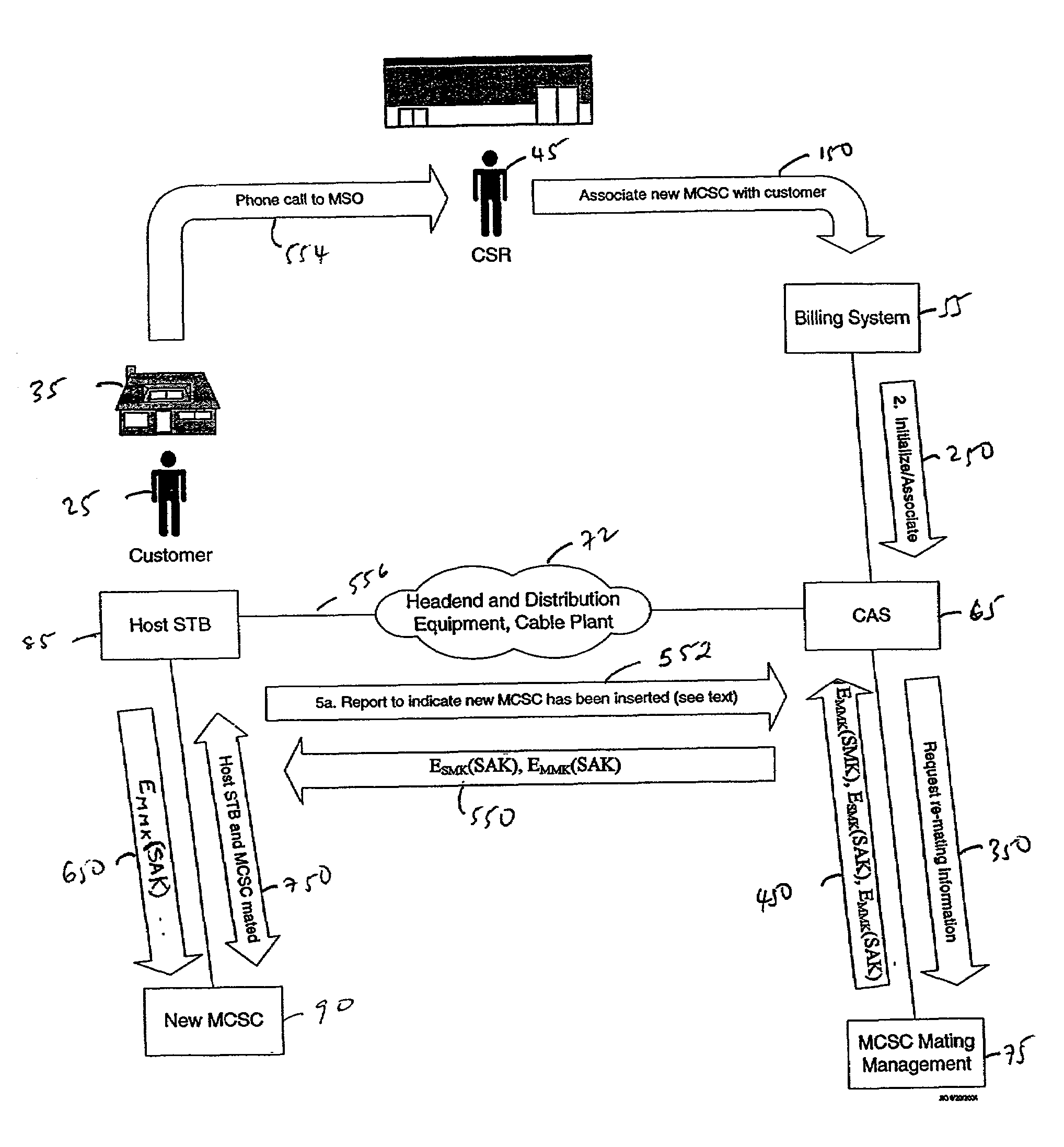
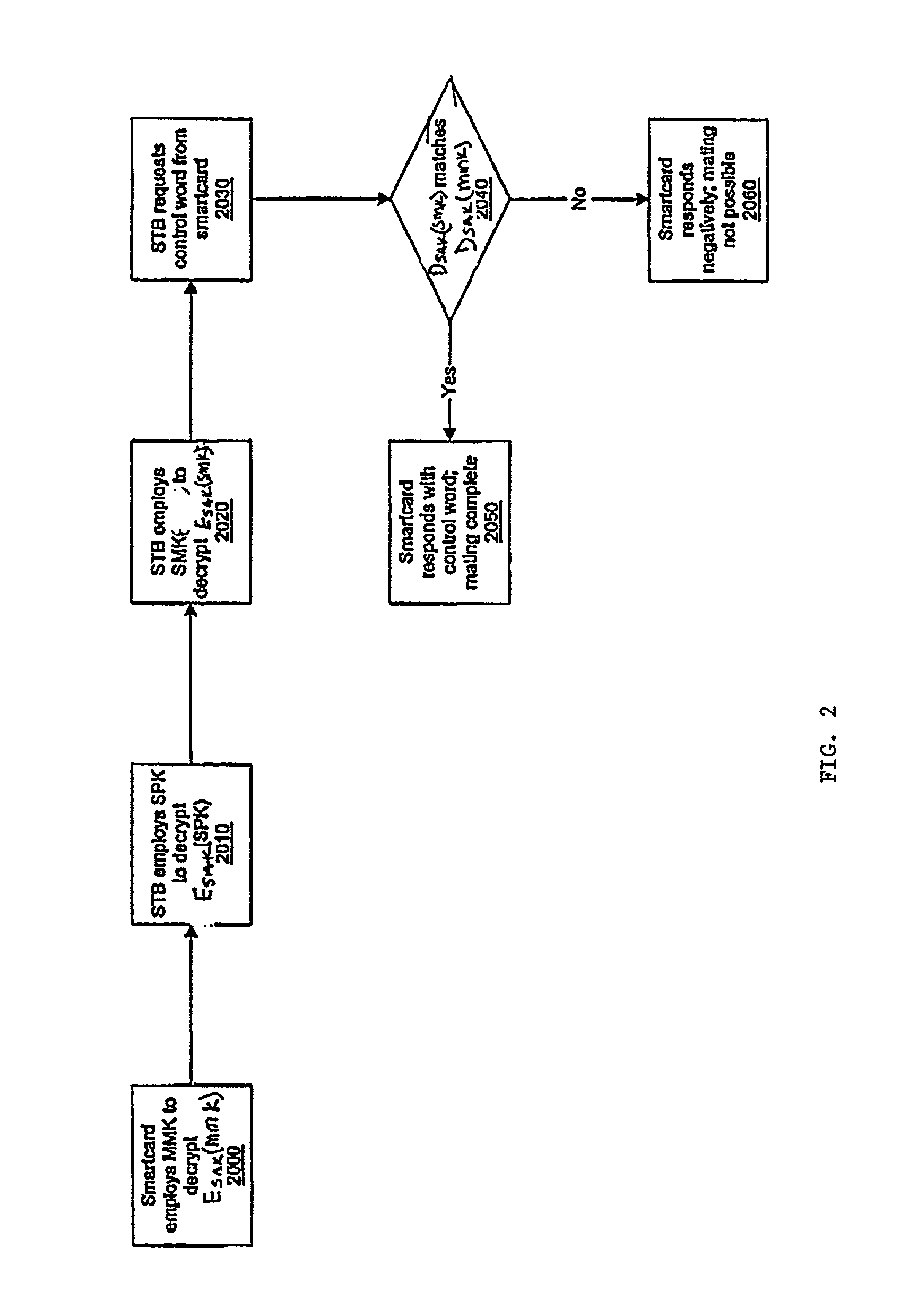
Smart card mating protocol
InactiveUS7305555B2Prevent piracySecure transmissionKey distribution for secure communicationFinanceDigital contentNumber content
A system is described for uniquely mating components of a communication network such as a smartcard and a set-top box. When mated, the smartcard and set-top box are tied together and have a single identity. Further, the smartcard operates properly only when inserted into an authorized set-top box. Exchanges of information between both components are secured by encryption and authentication to guard against piracy of the exchanged information. The system provides the same authentication key to the set-top box and the smartcard. This key is used for authenticating communication between the set-top box and the smartcard. First, the authentication key is encrypted by a set-top box mating key. The set-top box employs this mating key to decrypt the authentication key. After it is derived, the authentication key is stored in the set-top box's memory. Further, the same authentication key is encrypted by a smartcard mating key. Thereafter, the smartcard employs the smartcard mating key to extract the authentication key. The clear authentication key is stored in the smartcard's memory as well. In this manner, the authentication key is used for securing all communication between the set-top box and the smart-card. For example, the set-top box may request control words from the smartcard. Only after authenticating the request, are the control words for decrypting digital content provided to the set-top box. If the smartcard authentication key is different from the set-top box key, the request for control words is denied.
Owner:GOOGLE TECH HLDG LLC
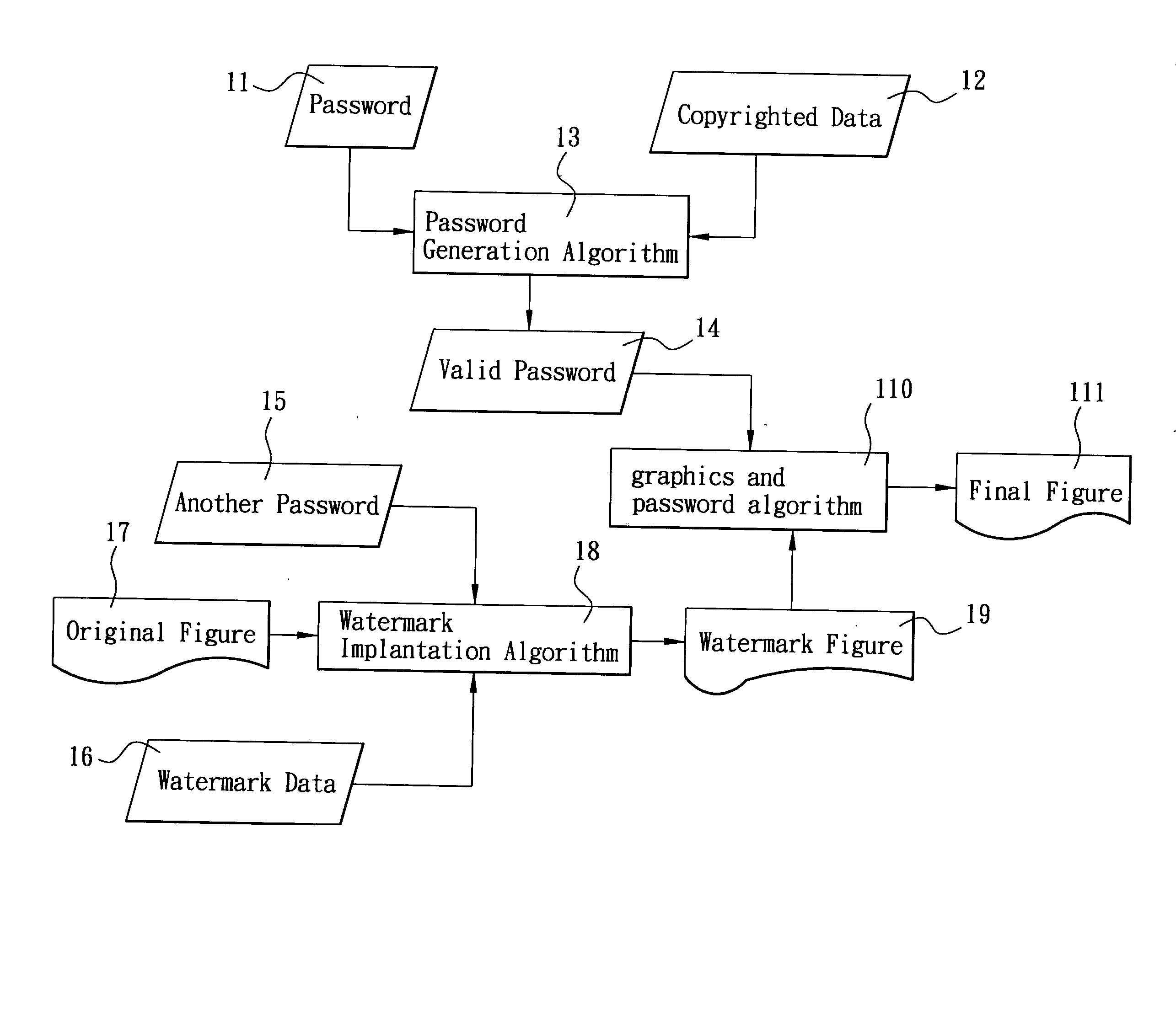
Method of protecting copyright of digital video work
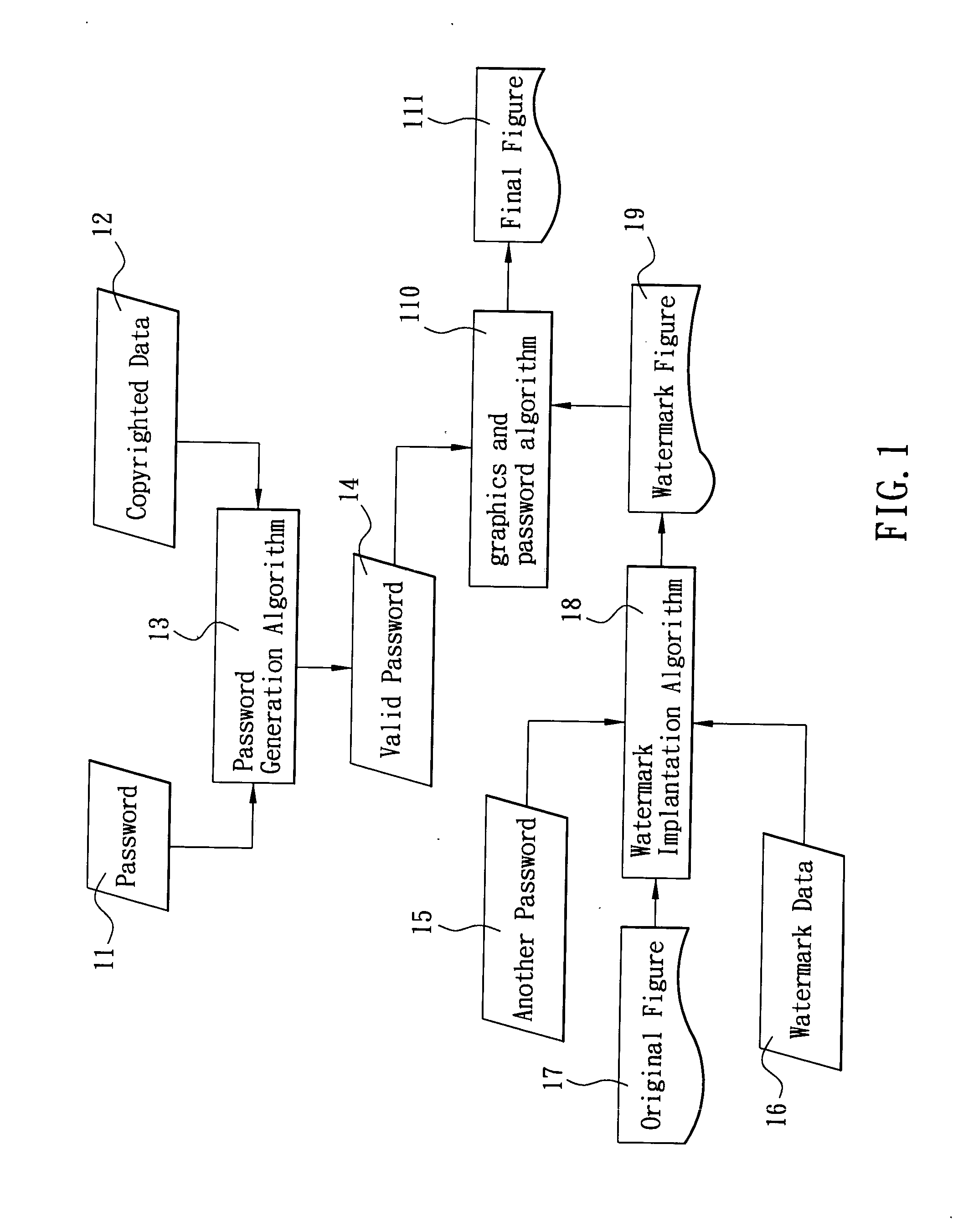
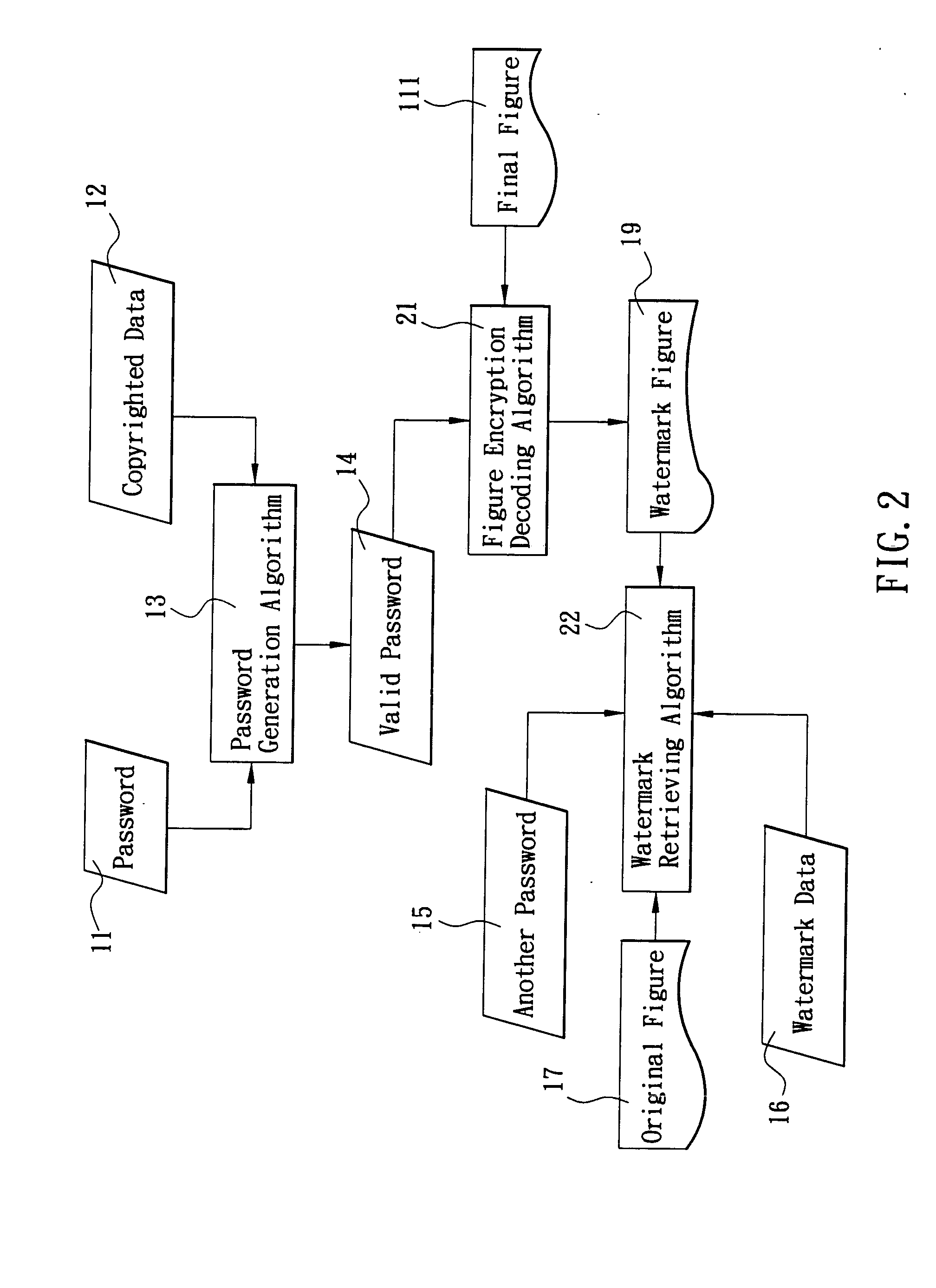
ActiveUS20050069129A1Prevent piracyStrong evidencePulse modulation television signal transmissionUnauthorized memory use protectionDigital videoComputer graphics (images)
This invention discloses a method of protecting copyright of a digital video work by using a digital password technology and a digital watermark technology to prevent the unauthorized use of a digital video work. Such method adds a password into two color matrixes of such video work in advance, so that when such video work is published on the Internet, it can be played by a specified player. As long as a user enters the correct password into the specified player, a full visual effect of such video work can be obtained. If other players are used to play such video work, only partial gray-scale visual effect can be obtained. Users must request or buy a specific player and a password from the distributor of such video work to play the complete information to prevent piracy.
Owner:INVENTEC APPLIANCES CORP
Hierarchical watermark adding method and system
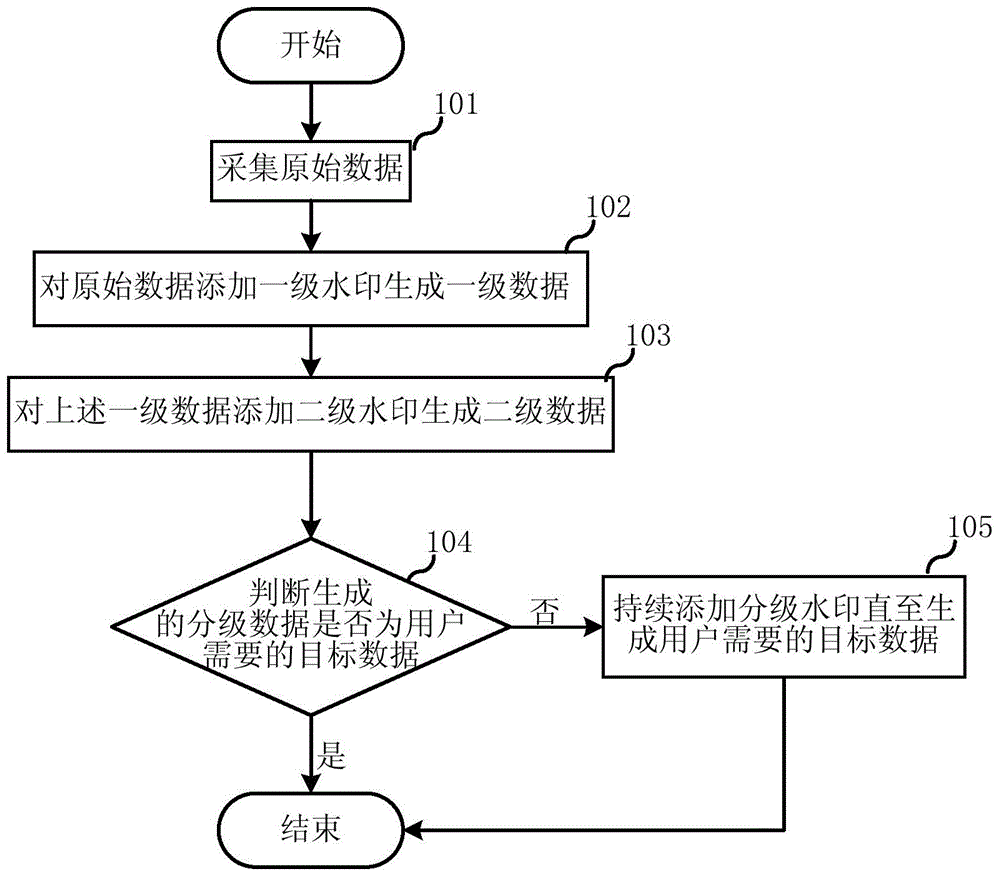
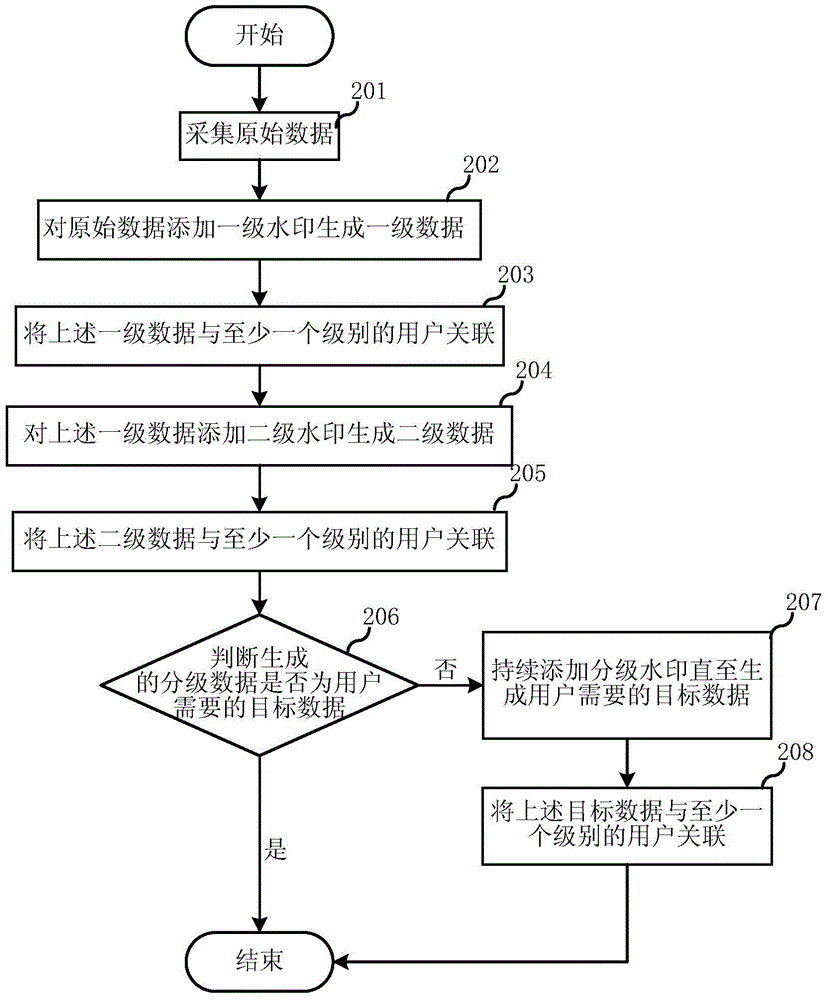
InactiveCN104917989AIncrease the difficulty of tamperingAvoid infringementTelevision system detailsColor television detailsOriginal dataData mining
The invention belongs to the watermark technical field and discloses a hierarchical watermark adding method and system. The method includes the following steps that: watermarks of at least two levels are added into acquired original data, so that target data required by a user can be generated; and in a process in which the watermarks of at least two levels are added into the acquired original data, and after the addition of watermarks of each level in the watermarks of at least two levels is completed, the watermarks of each level are correlated to hierarchical data which are generated after the addition of the watermarks of each level is completed. Compared with the prior art, the hierarchical watermarks are added into the original data, so that the original data additionally have watermarks of several levels equivalently, and protection of the copyright of the original data can be better benefitted, and infringement and piracy can be prevented.
Owner:EQUES TECH
Cloud platform dynamic watermark generation system and control method thereof
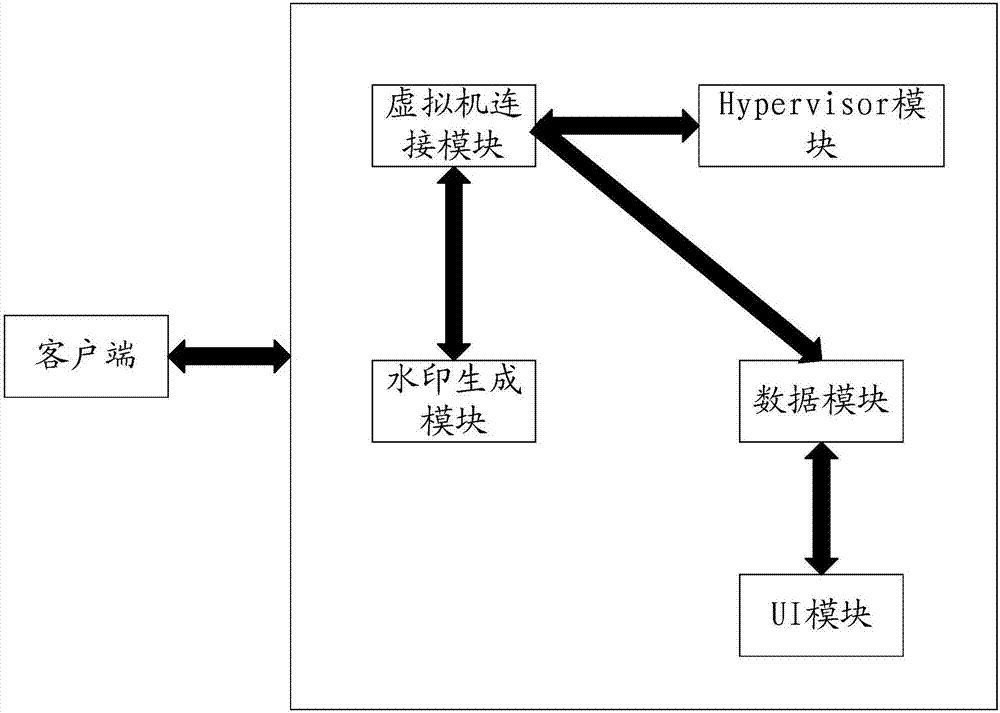
InactiveCN107038355APrevent piracyStrong practical valueInternal/peripheral component protectionProgram/content distribution protectionClient-sideVirtual machine
The invention relates to a cloud platform dynamic watermark generation system and a control method thereof. The system comprises a virtual machine connection module, a watermark generation module in bidirectional connection with the virtual machine connection module and a data module in unidirectional connection with the virtual machine connection module, wherein the watermark generation module is also in unidirectional connection with the data module; the watermark generation module generates a dynamic watermark according to basic information, stored in the data module, of a virtual machine and dynamic watermark generation switch and static watermark configuration information selection, and the dynamic watermark is interposed into to-be-sent data flow through the virtual machine connection module; and the virtual machine connection module can also immediately notify the watermark generation module to generate a new dynamic watermark according to specific information of a client to adapt to the client connected with the virtual machine connection module. Through the cloud platform dynamic watermark generation system and the control method thereof, watermarks can be dynamically generated according to different virtual machine configuration information, and copyright protection can be realized when the dynamic watermarks are interposed into the data flow sent to the client by the virtual machine.
Owner:OWTWARE (SHANGHAI) TECHNOLOGY LIMITED
Method and device for protecting program source
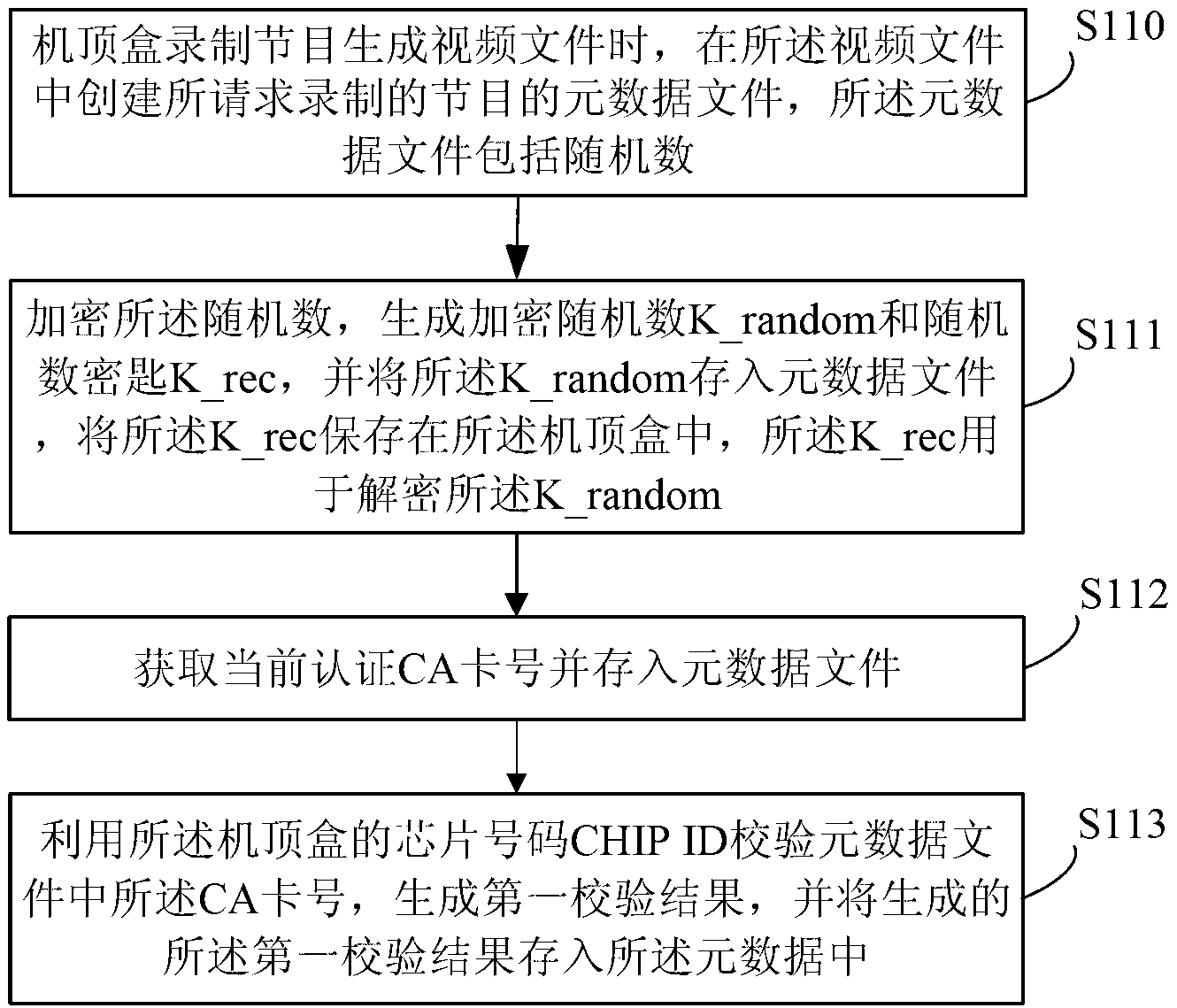
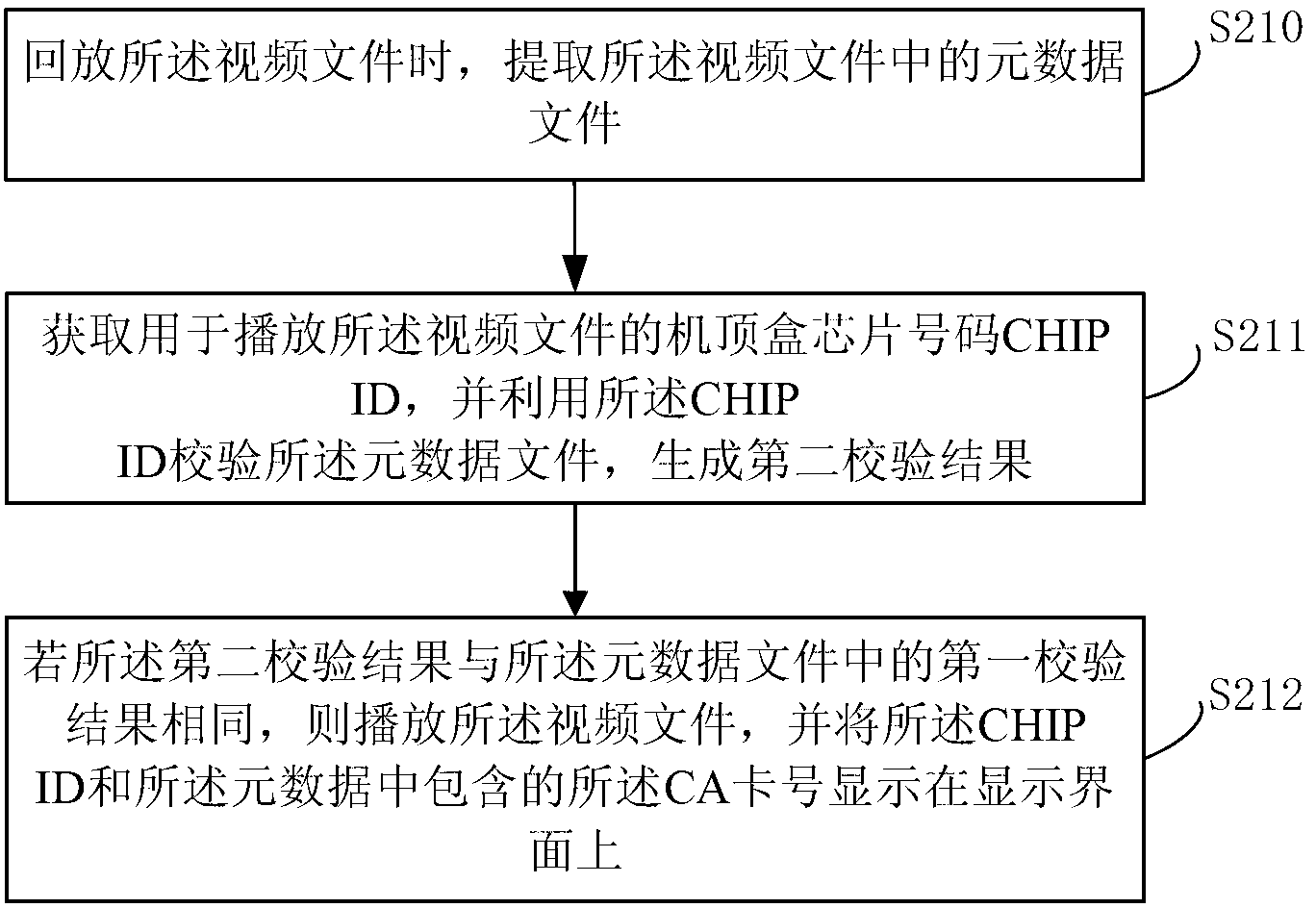
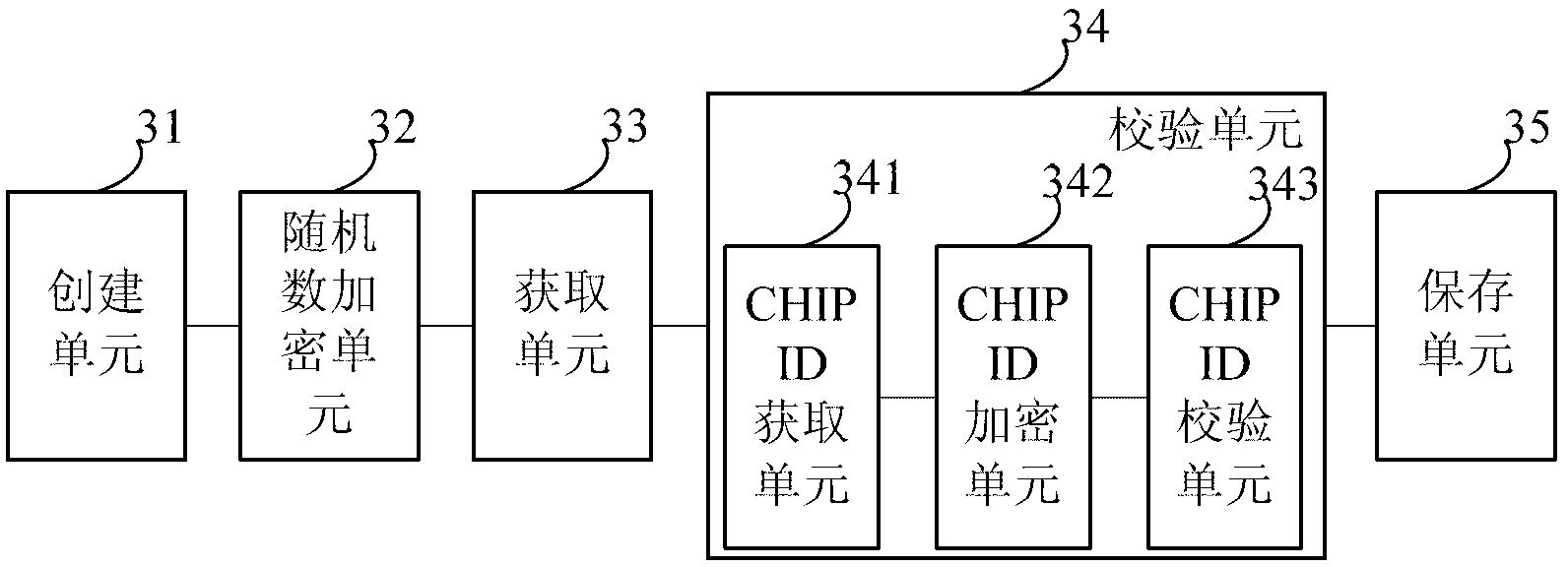
The embodiment of the invention provides a method and a device for protecting a program source. The method comprises the following steps of: creating a metadata file of a program requested to be recorded in a video file when a set-top box records the program to generate the video file, wherein the metadata file comprises a random number; encrypting the random number, generating an encrypted random number K_random and a random number key K_rec, storing the K_random into the metadata file, and storing the K_rec into the set-top box, wherein the K_rec is used for decrypting the K_random; acquiring a current certificate authority (CA) card number, and storing the current CA card number into the metadata file; and checking the CA card number in the metadata file by utilizing a chip number CHIP ID of the set-top box, generating a first check result, and storing the generated first check result into the metadata file. According to the embodiment of the invention, the method for protecting the program source is improved, so that a certificate card number of the program and the chip number of the set-top box can be accurately acquired when the program is discovered to be pirated, and a video pirating user can be tracked.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
Optical disk safety management method and device
InactiveCN101826354AStrengthen security managementPrevent leakageRecord information storageRecording signal processingCD-ROMComputer science
The invention discloses optical disk safety management method and device. In the optical disk safety management method, the optical disk safety management device reads a chip identification number of a safety chip packaged on an optical disk; the optical disk safety management device acquires the chip identification number burned in the optical disk and read by a CD-ROM device; if the chip identification number burned in the optical disk is identical with the chip identification number of the safety chip, the optical disk safety management device sends a burning instruction or a reading instruction to the CD-ROM device to encrypt data to be burnt or decrypt data to be read, otherwise, the optical disk safety management device instructs the CD-ROM device to stop running. The optical disk safety management device compares the chip identification number of the safety chip with the chip identification number burned in the optical disk, thereby facilitating the safety management on the optical disk and realizing special disk for special use; an institution needed to be secreted realizes the management on each optical disk in the institution, thereby avoiding divulging a secret; and a merchant can also avoid pirating.
Owner:WUHU ZHENHUA RONGKE INTELLIGENT TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com