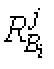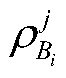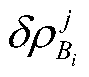Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2519 results about "Information leakage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
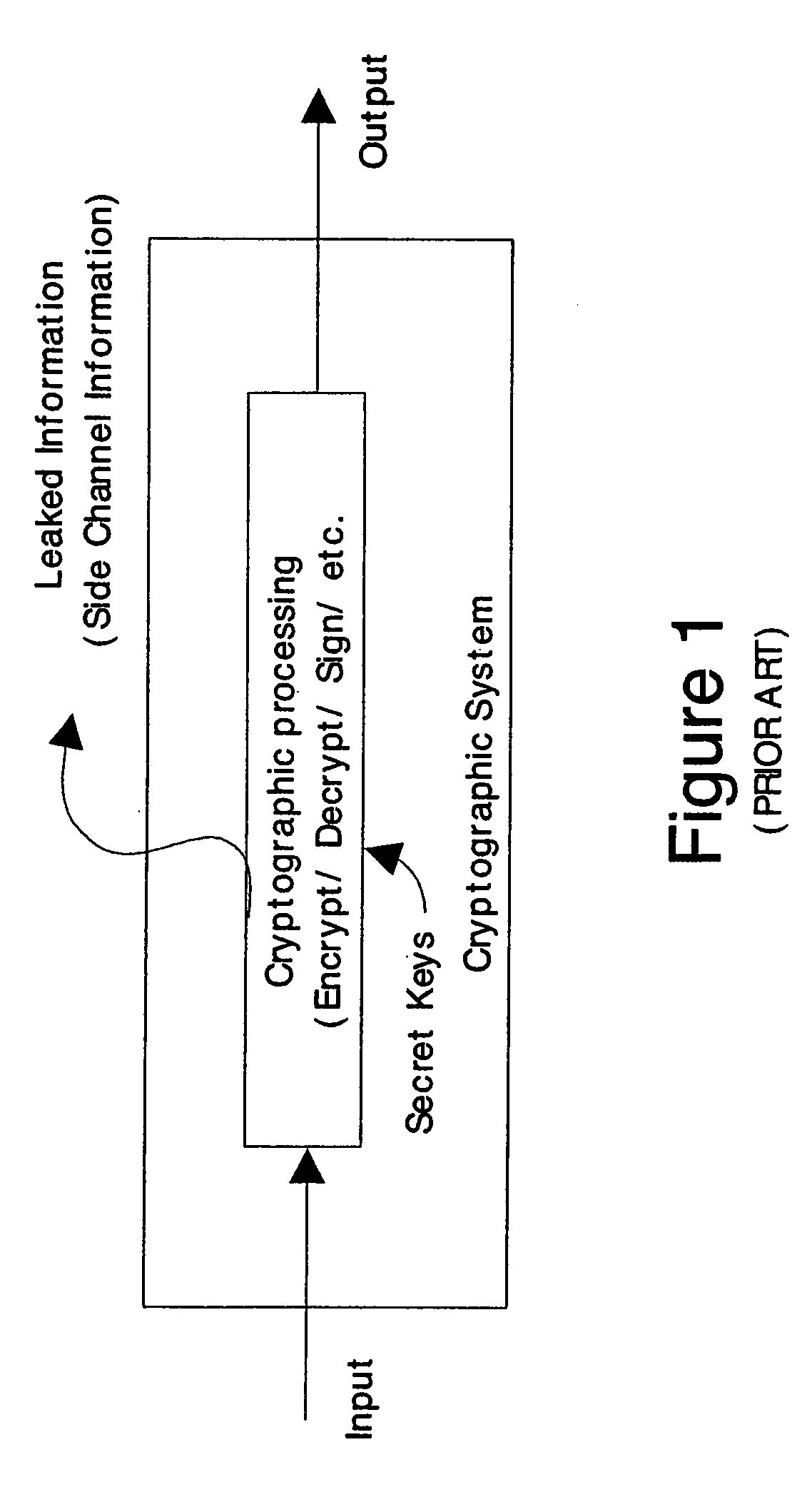
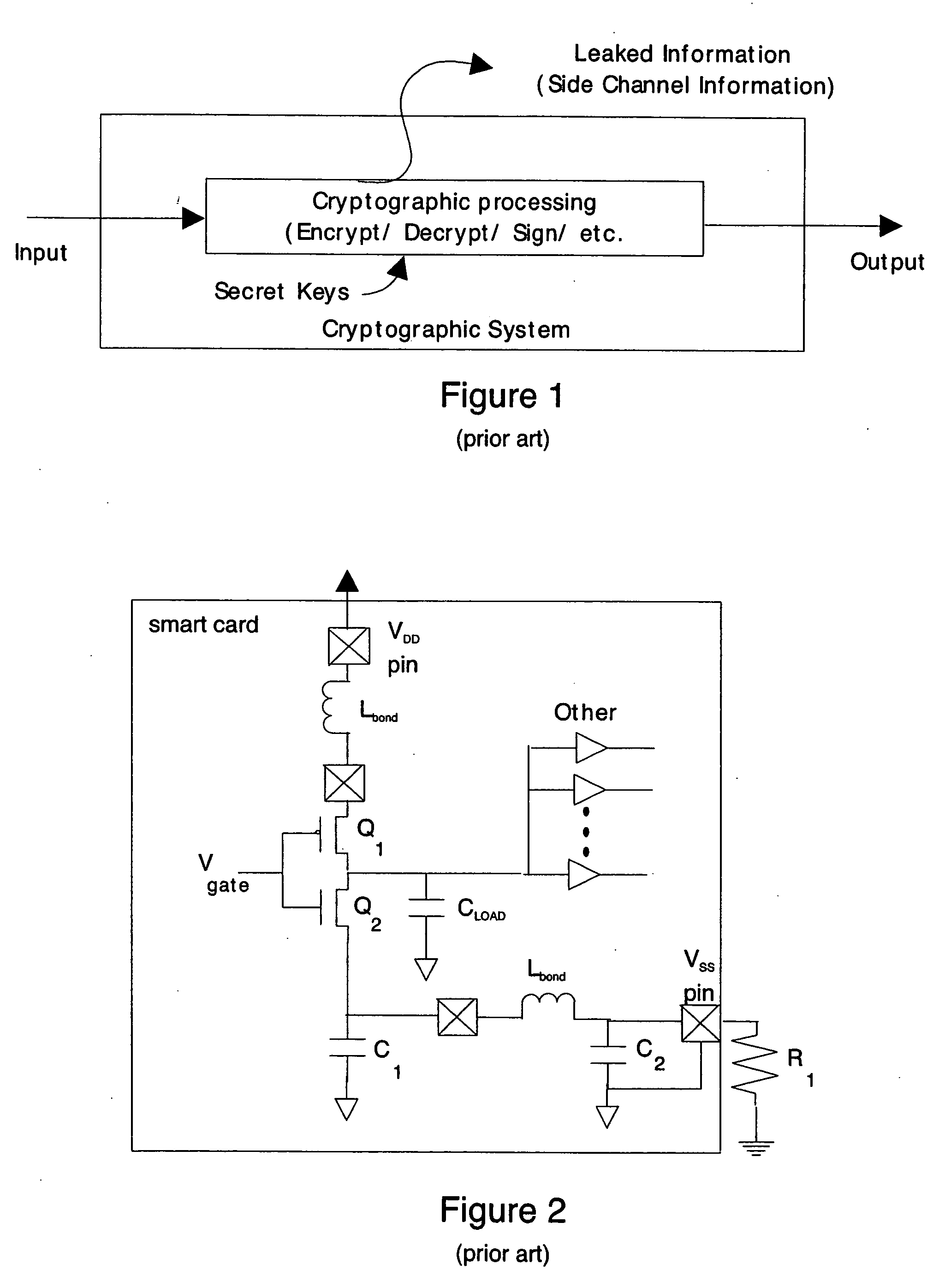
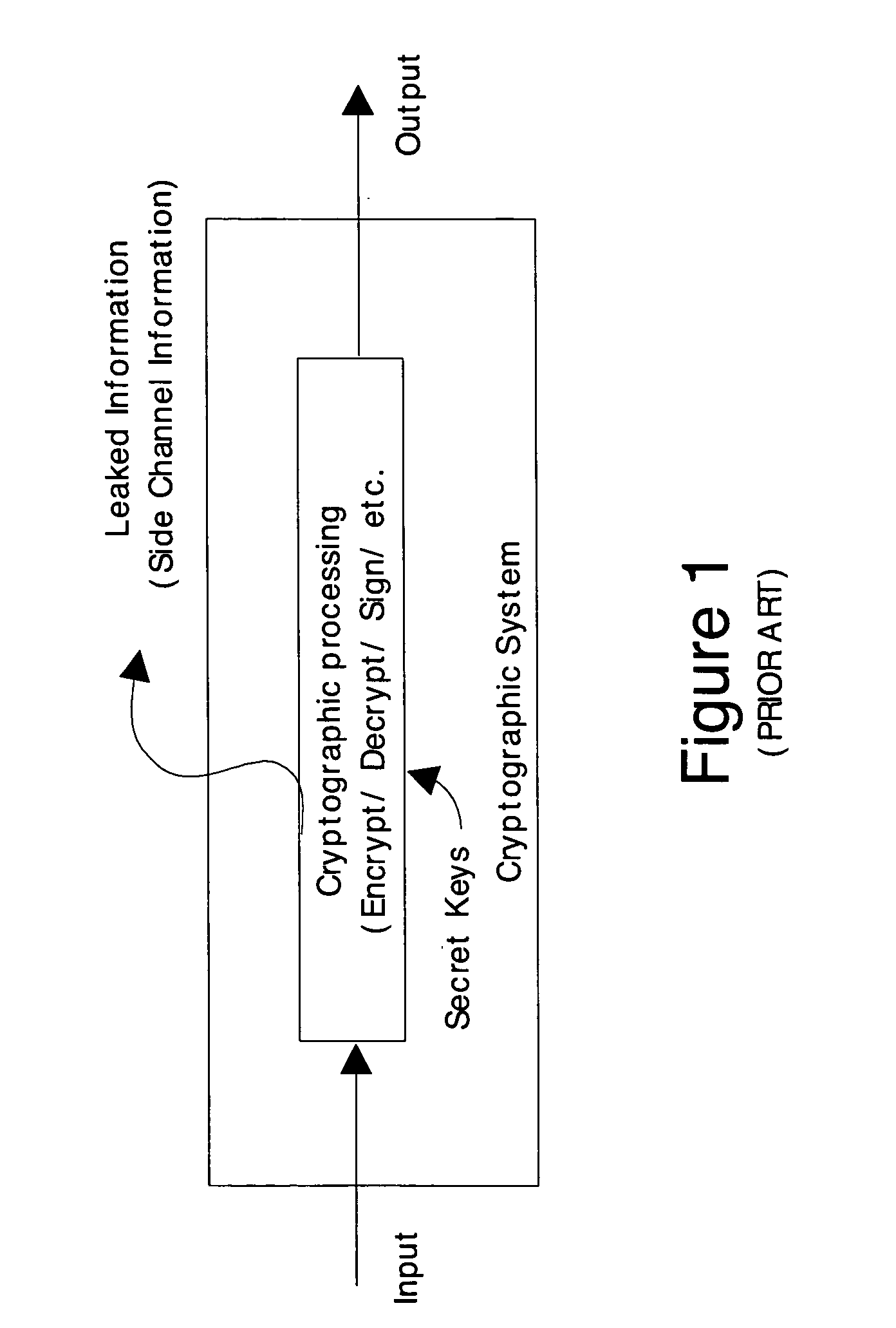
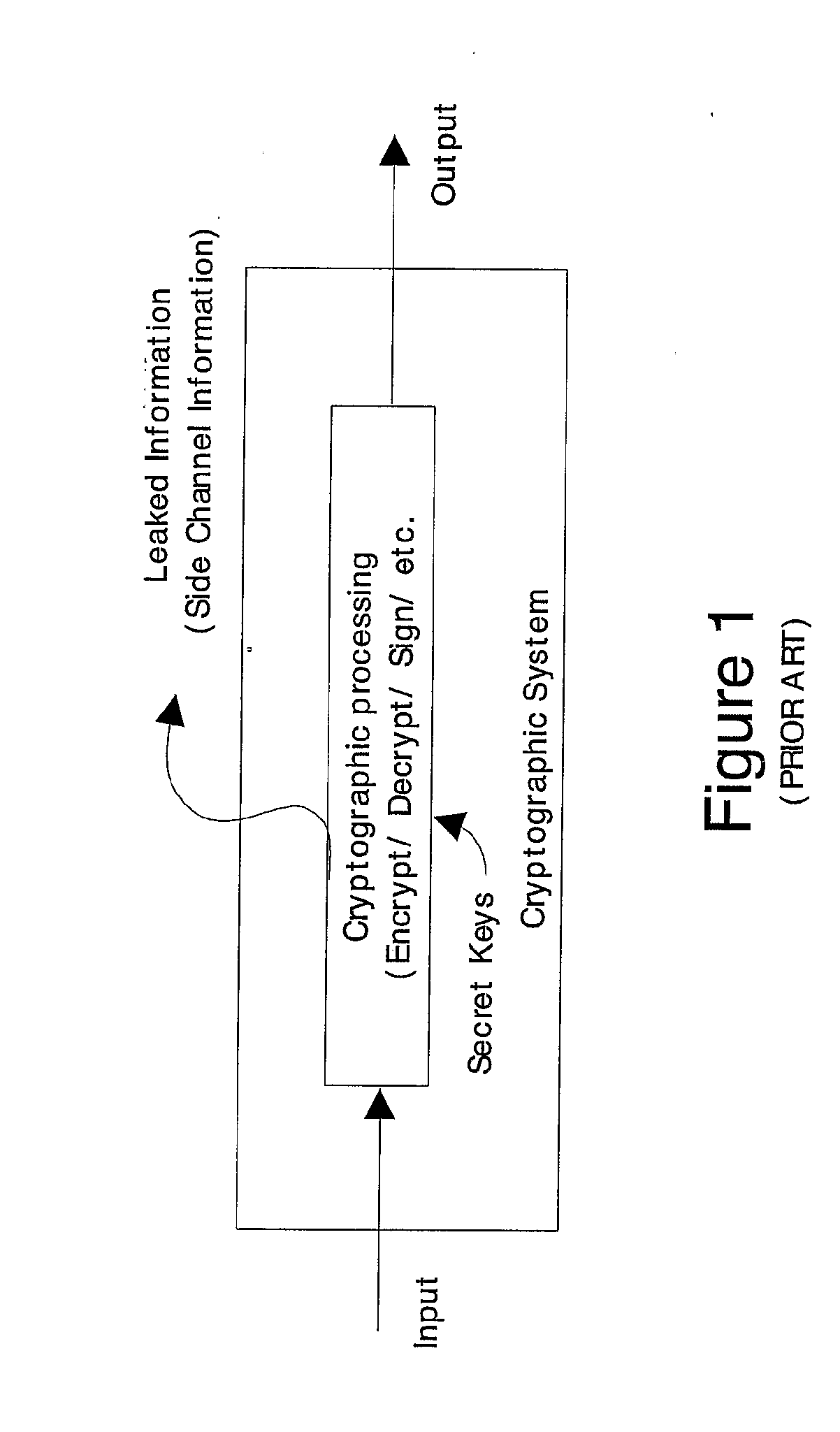
Information leakage happens whenever a system that is designed to be closed to an eavesdropper reveals some information to unauthorized parties nonetheless. For example, when designing an encrypted instant messaging network, a network engineer without the capacity to crack encryption codes could see when messages are transmitted, even if he could not read them. During the Second World War, the Japanese for a while were using secret codes such as PURPLE; even before such codes were cracked, some basic information could be extracted about the content of the messages by looking at which relay stations sent a message onward. As another example of information leakage, GPU drivers do not erase their memories and thus, in shared/local/global memories, data values persist after deallocation. These data can be retrieved by a malicious agent.
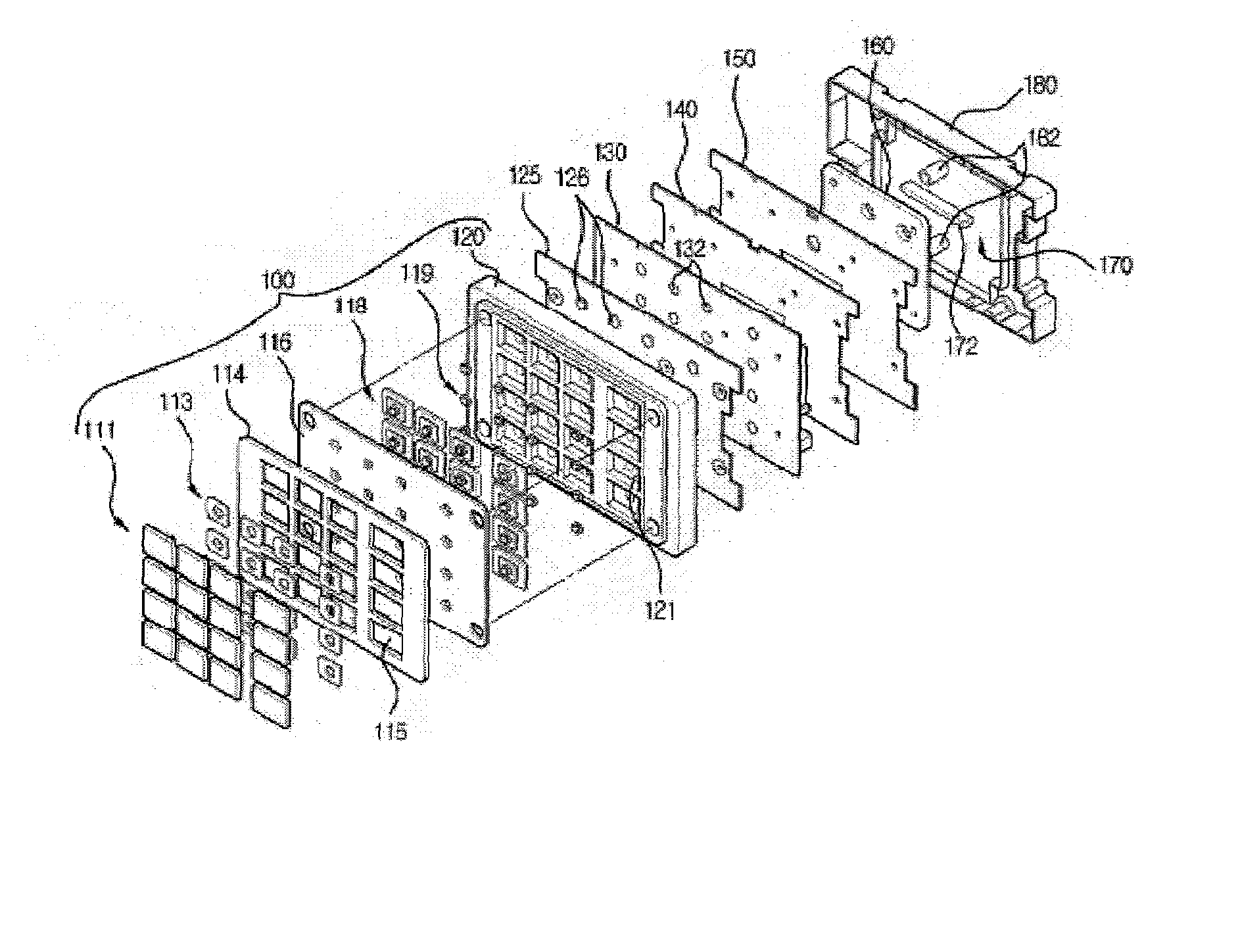
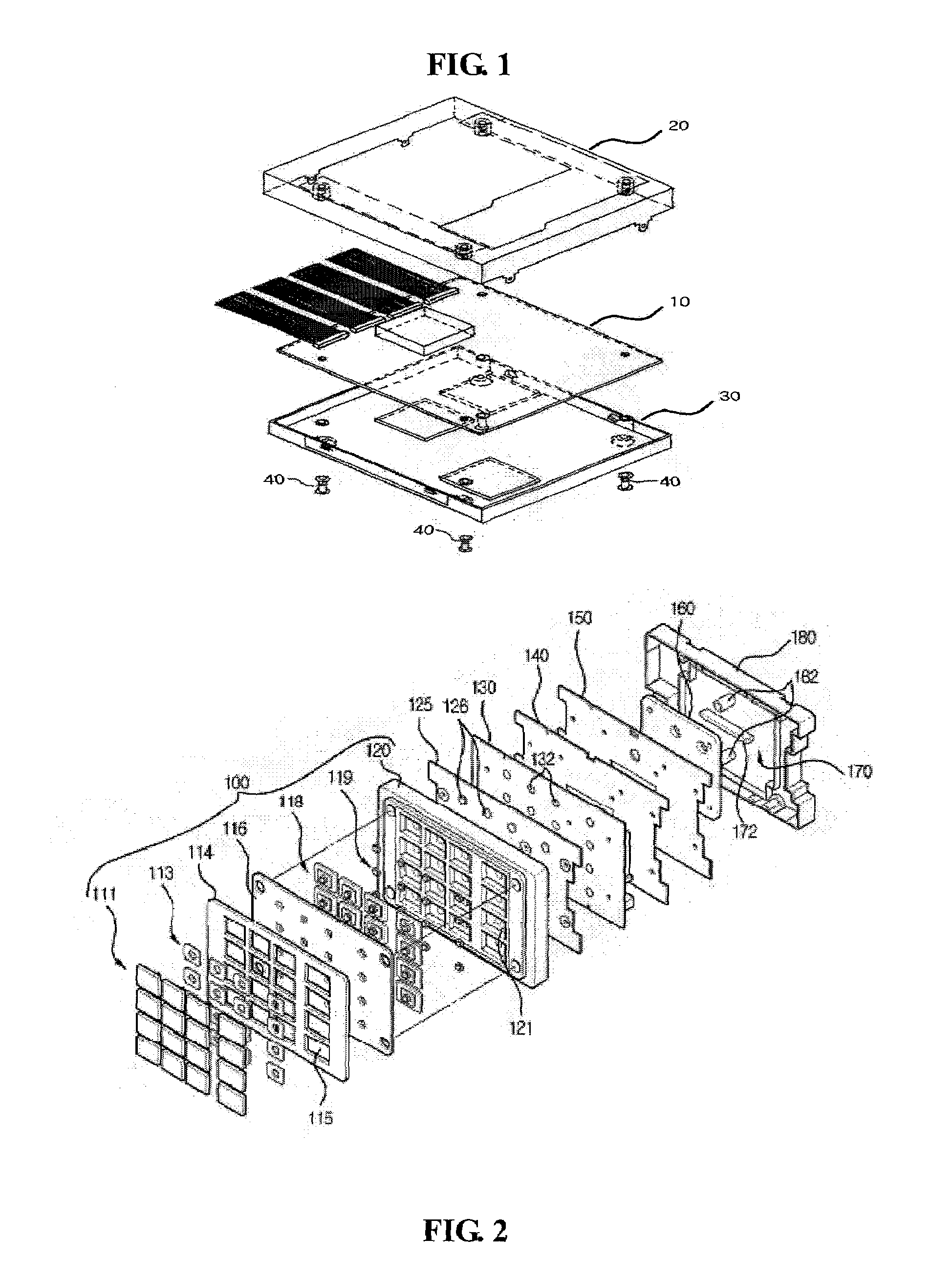
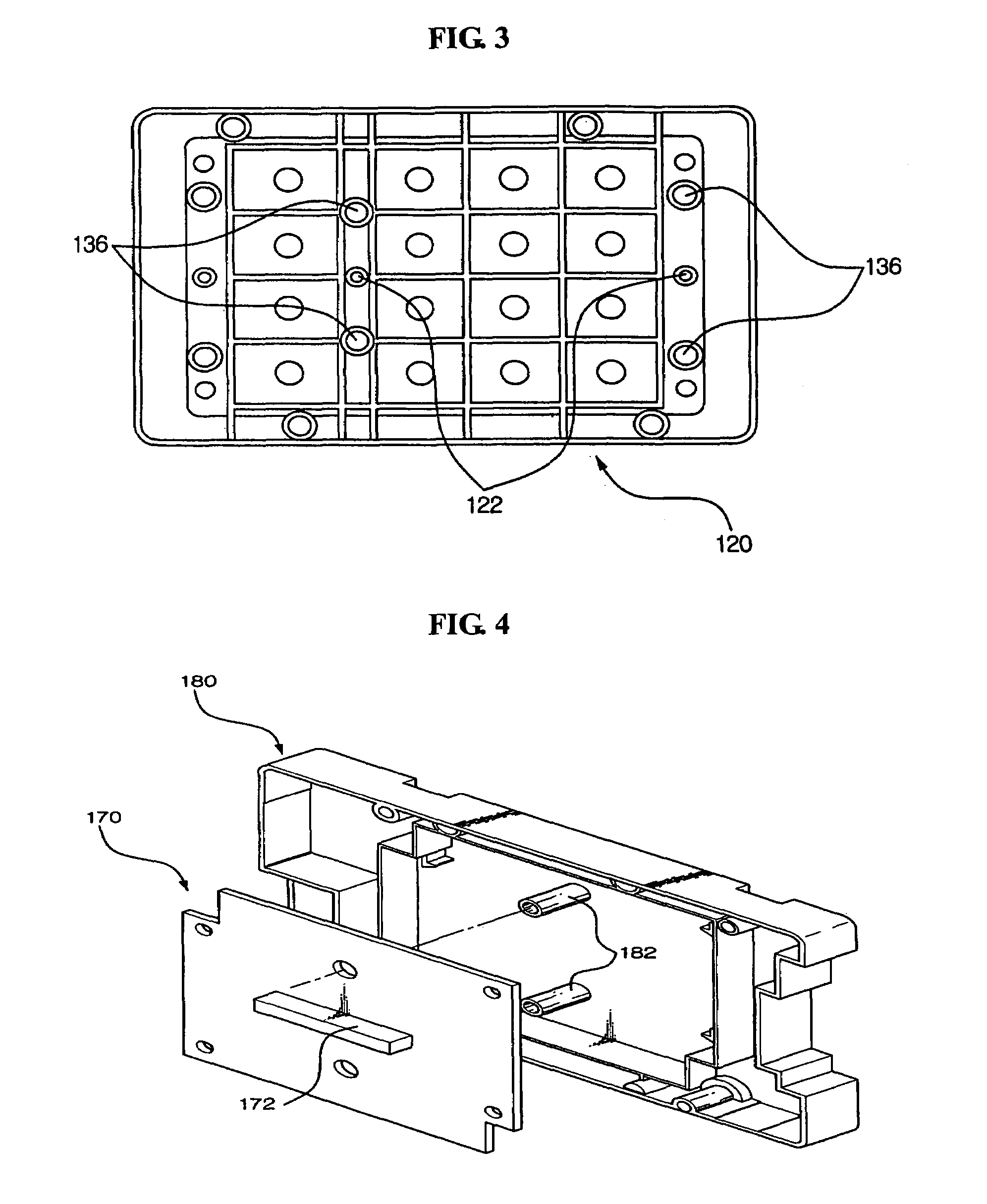
Tamper resistant pin entry apparatus
ActiveUS7238901B2Prevent leakagePrevent penetrationComplete banking machinesEmergency casingsPasswordElectric power system
Disclosed is a tamper resistant PIN entry apparatus for input of a key and for encryption of a password in a cash transaction machine. The PIN entry apparatus supplies the electric power to a memory of an electric circuit section, in such a manner that a first rod and a second rod of a rear case connect contacts of a key scan board, wherein the first rod is protruded on the rear of a key module including a button provided substantially on the front of the key module and the second rod of the rear case is coupled with the rear of the key module. At this time, in case that the rear case is removed from the key module or damaged, thereby changing the location of any one of the first and the second rods at the contact, the electric circuit section detects the event and destroys the memory itself physically. Otherwise, the electric circuit section makes information stored in the memory physically or softwarely unreadable, thereby preventing the leakage of the information.
Owner:NAUTILUS HYOSUNG
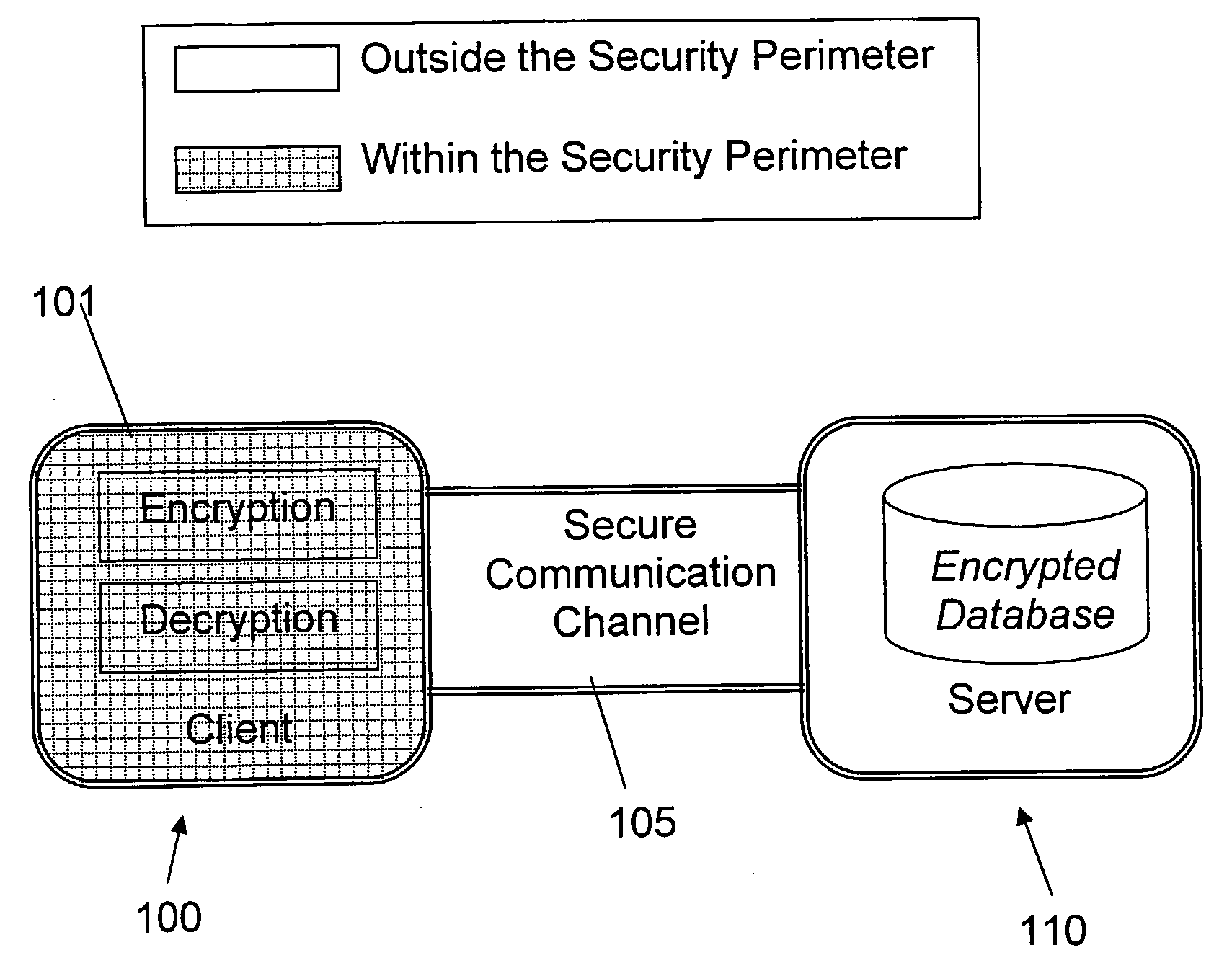
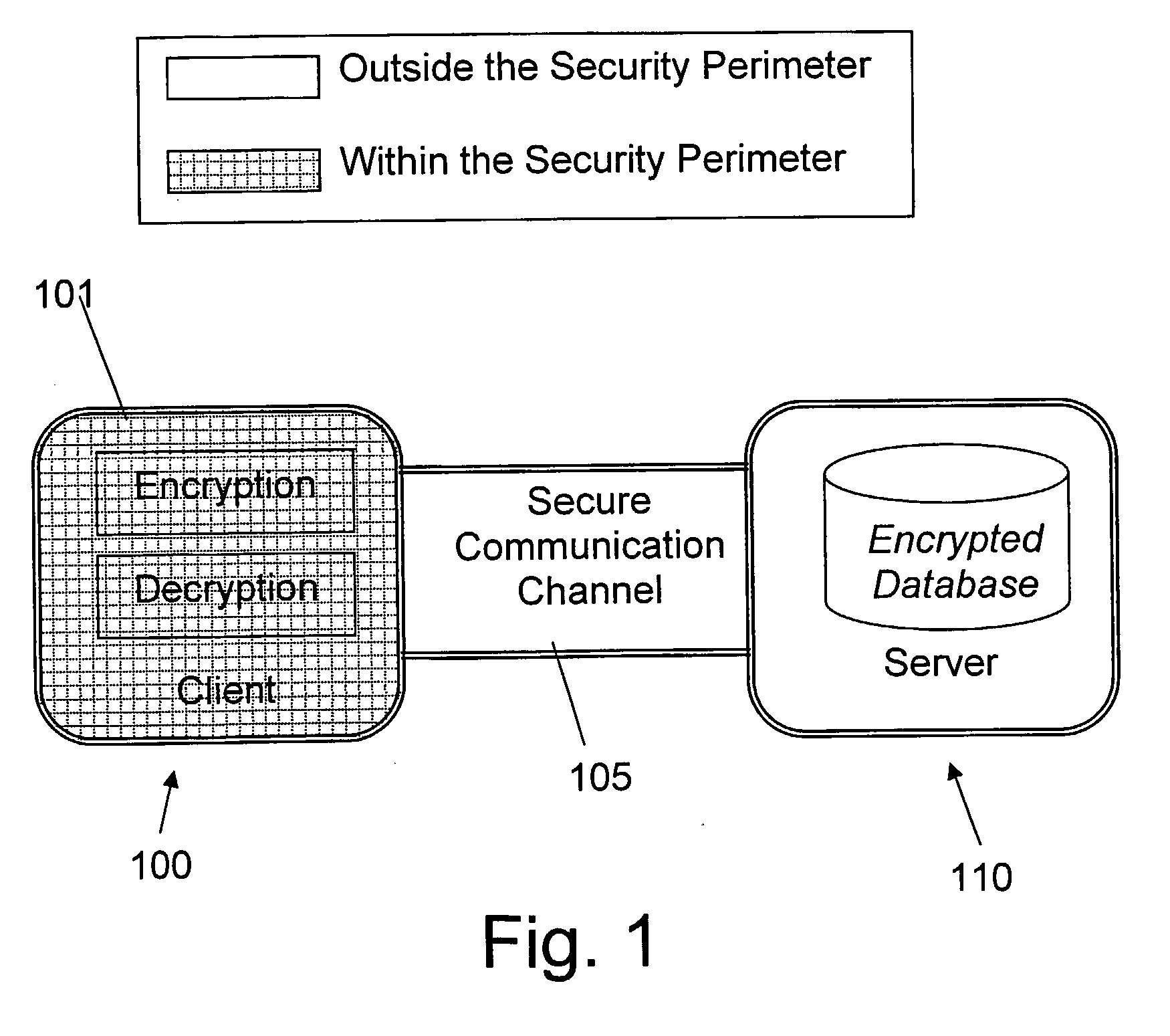
Structure Preserving Database Encryption Method and System
ActiveUS20080133935A1Easy accessAvoid contactKey distribution for secure communicationMultiple keys/algorithms usageDatabase indexMulti user environment
A database encryption system and method, the Structure Preserving Database Encryption (SPDE), is presented. In the SPDE method, each database cell is encrypted with its unique position. The SPDE method permits to convert a conventional database index into a secure one, so that the time complexity of all queries is maintained. No one with access to the encrypted database can learn anything about its content without the encryption key. Also a secure index for an encrypted database is provided. Furthermore, secure database indexing system and method are described, providing protection against information leakage and unauthorized modifications by using encryption, dummy values and pooling, and supporting discretionary access control in a multi-user environment.
Owner:BEN GURION UNIVERSITY OF THE NEGEV
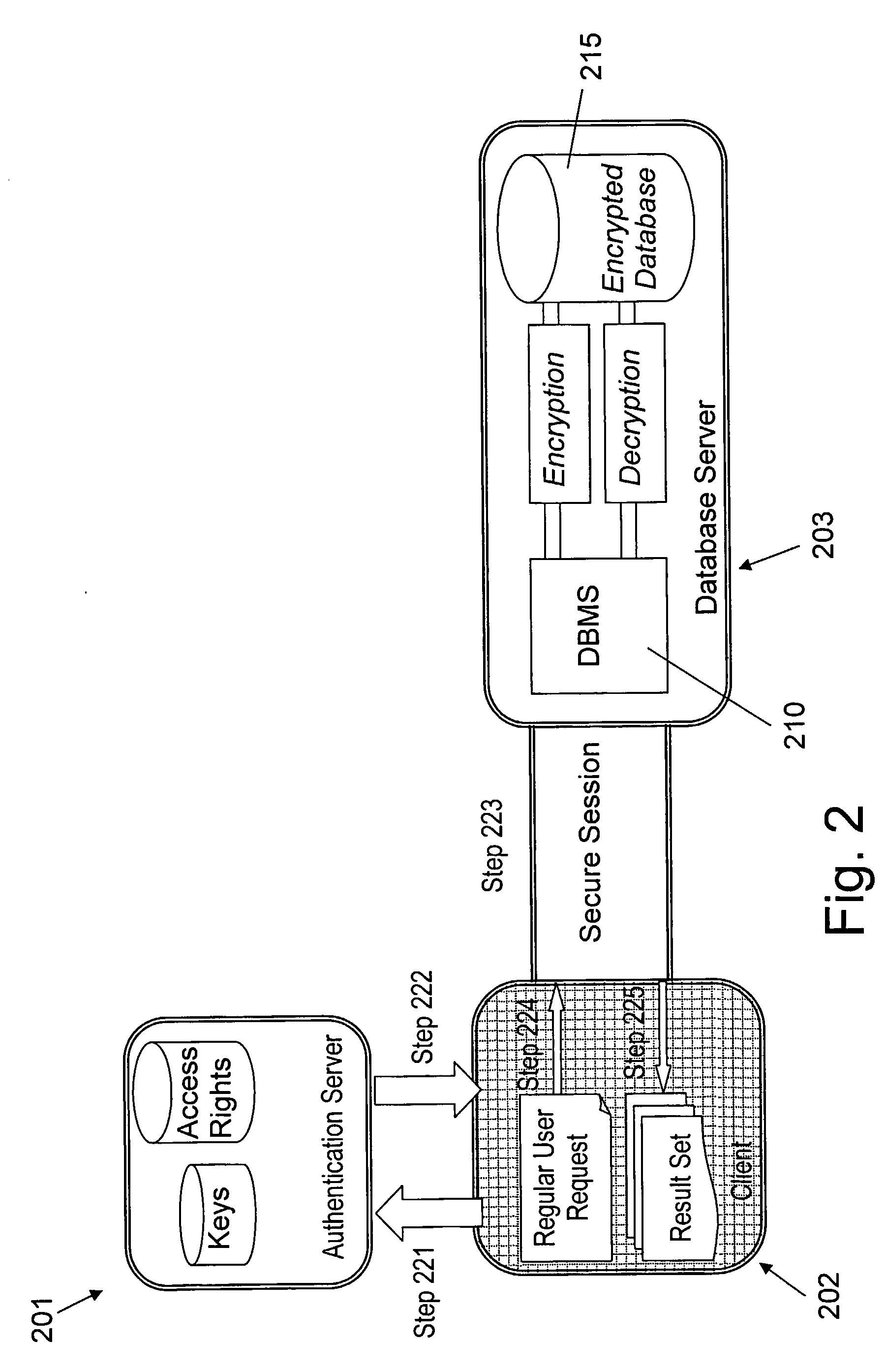
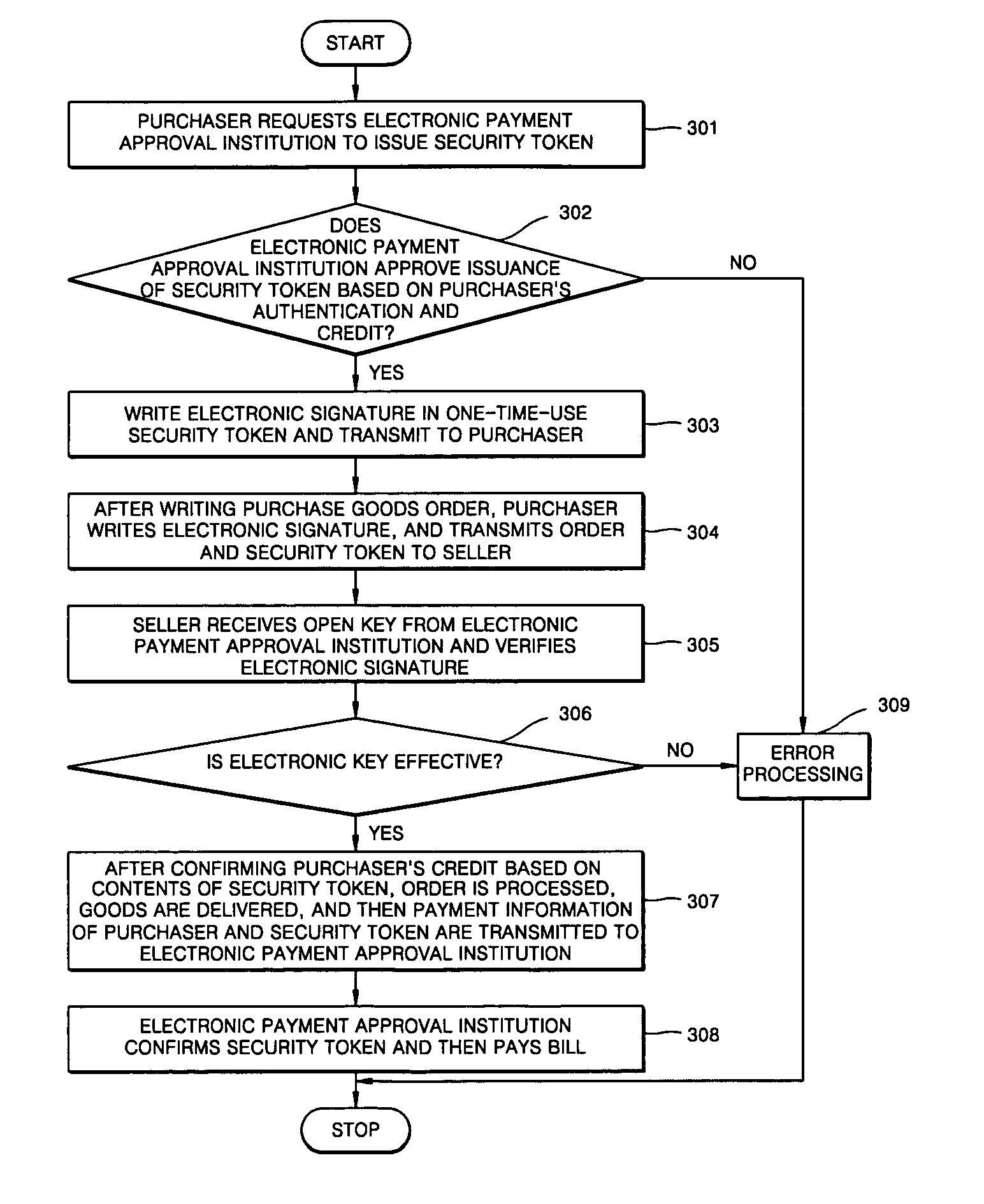
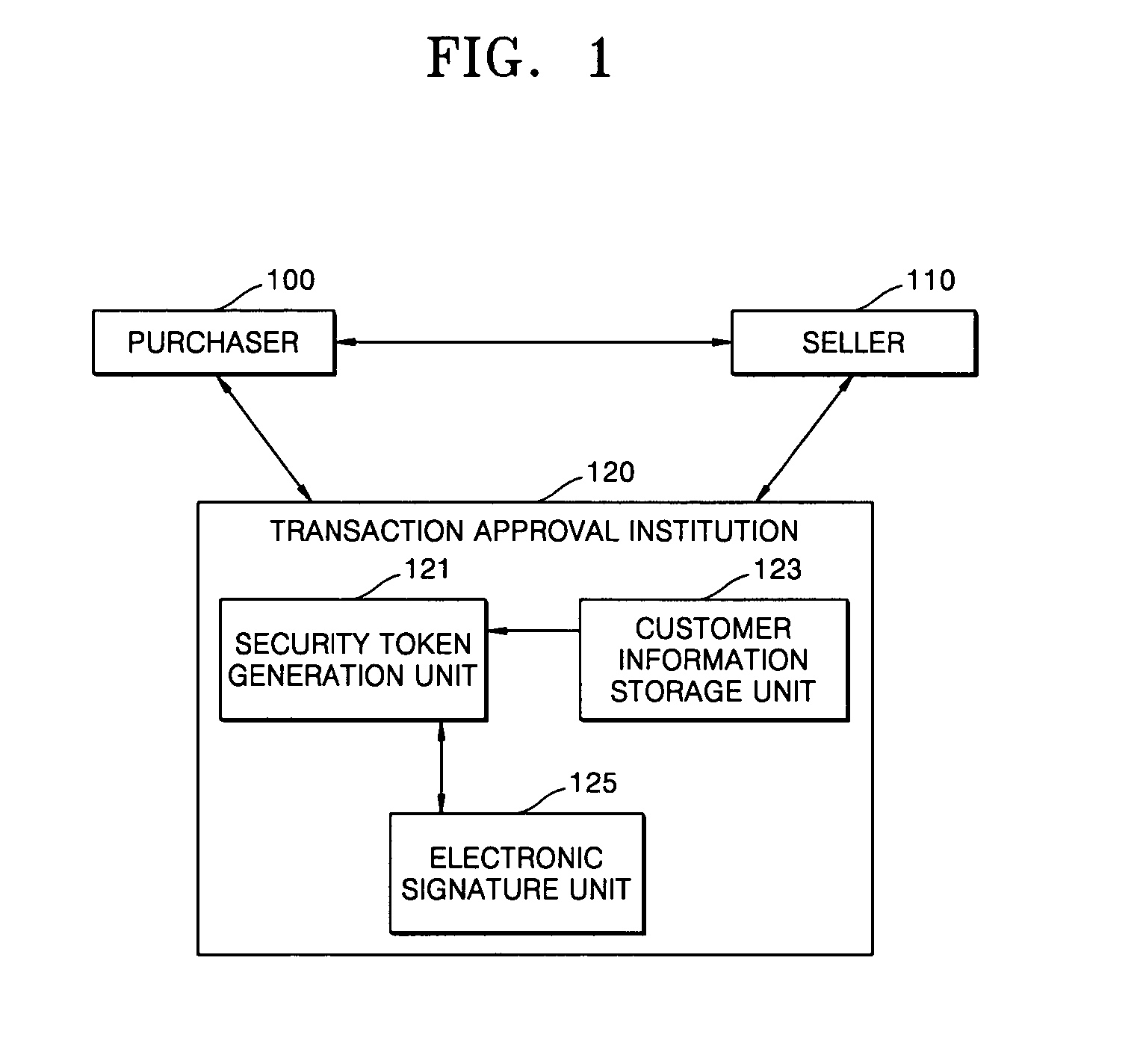
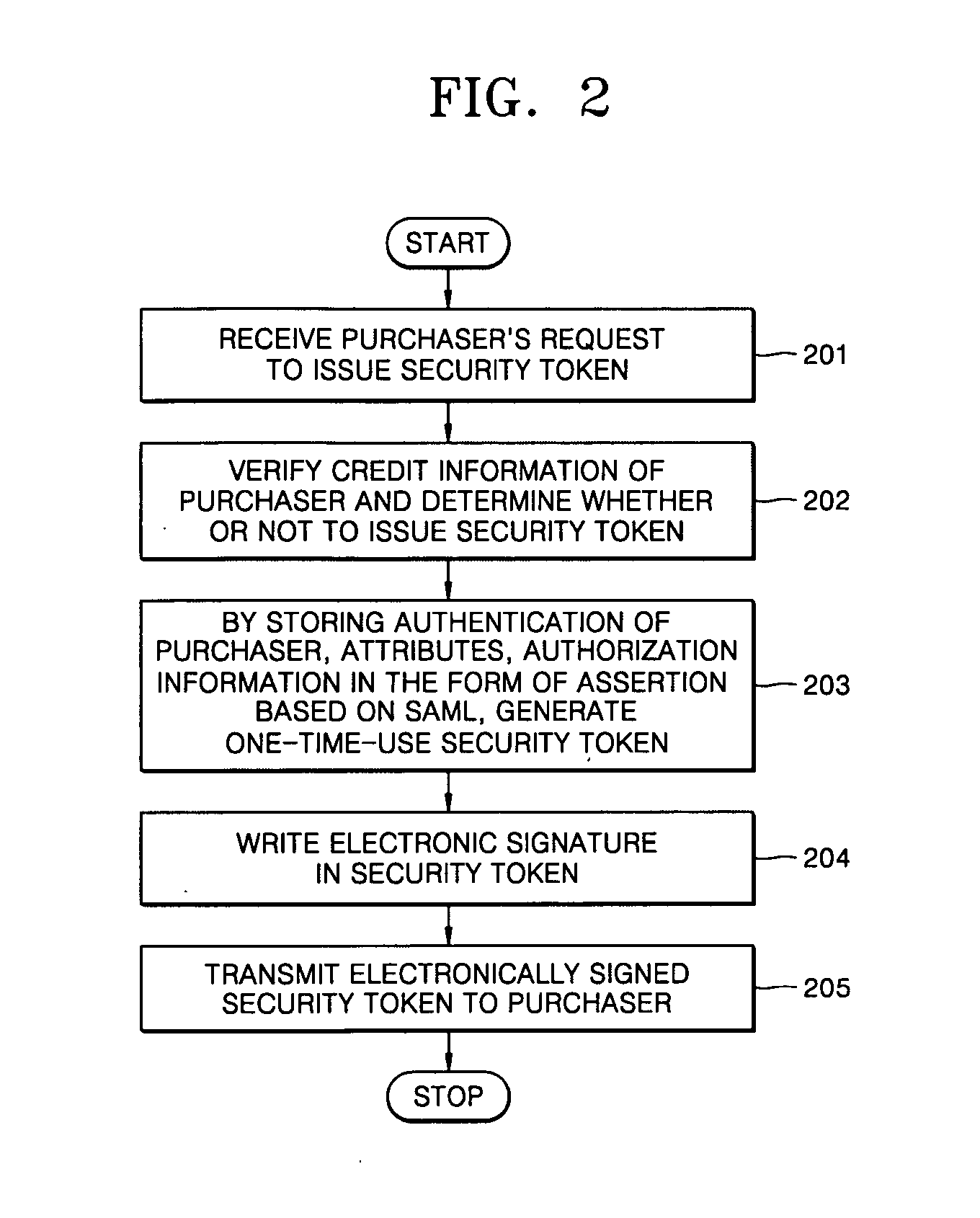
Method for electronic commerce using security token and apparatus thereof
InactiveUS20050097060A1Securing communicationPayments involving neutral partyConfidentialityExtensible markup
A method for electronic commerce using a security token and an apparatus thereof are provided. The electronic commerce method using a security token comprises a transaction approval institution generating a security token based on a security assertion markup language (SAML), using credit information of a purchaser who requests to issue a security token, and transmitting the security token to the purchaser; the purchaser writing an electronic signature on an order and transmitting the order together with the security token to a seller; the seller verifying the received order and security token, and then delivering goods according to the order to the purchaser; and the transaction approval institution performing payment for the seller and the purchaser. The method can solve the problems of personal information leakage and privacy infringement that may happen when a purchaser sends his personal information to a seller for electronic commerce. Since the token is one-time-use data, even if a security token sent is counterfeited or stolen, the loss can be minimized. In addition, by writing an extensible markup language (XML) electronic signature in the security token, authentication, integrity, and non-repudiation for a transmitted message can be guaranteed and through simple object access protocol (SOAP) security technology, confidentiality is maintained.
Owner:ELECTRONICS & TELECOMM RES INST
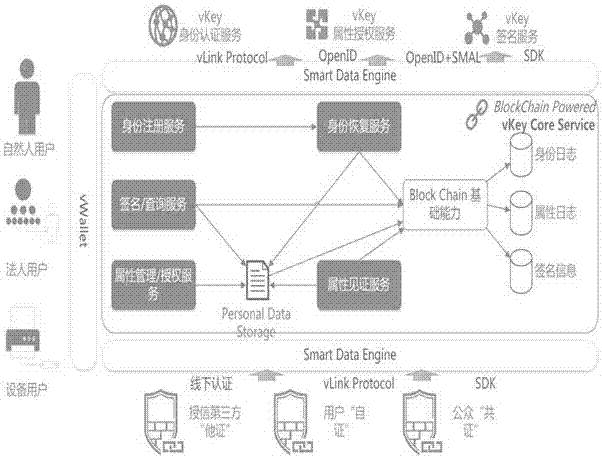
Block chain technology-based network digital identity authentication method
InactiveCN107181765AShorten confirmation timeAvoid the possibility of trending towards exclusive verificationUser identity/authority verificationDigital data protectionDigital identityInternet fraud
The present invention provides a block chain technology-based network digital identity authentication method. The method comprises the steps of 1) user registration: conducting the identity authentication service based on the vLink protocol, uploading a block chain if the identity of a user is legal, broadcasting the information of the user to the whole network by the block chain, and adding the information of the user into a corresponding block at each node, wherein blocks are mutually verified; 2) obtaining the information of the user, searching the information of the user through the vKey attribute authorization service, returning the user name, the gender and the age information of the user and returning a particular opened at the same time for distinguishing different users; 3) subjecting data to signature treatment during the digital identity authentication process based on the above block chain technology. According to the technical scheme of the invention, the personal data of a user are stored in a block chain, so that the occurrence of information leakage and internet fraud behaviors is radically avoided. The data security is ensured. During the data transmission process, the digital signature treatment is adopted. Therefore, the sensitive information is not tampered during the digital signature transmission process.
Owner:兰考同心互联数据管理有限公司
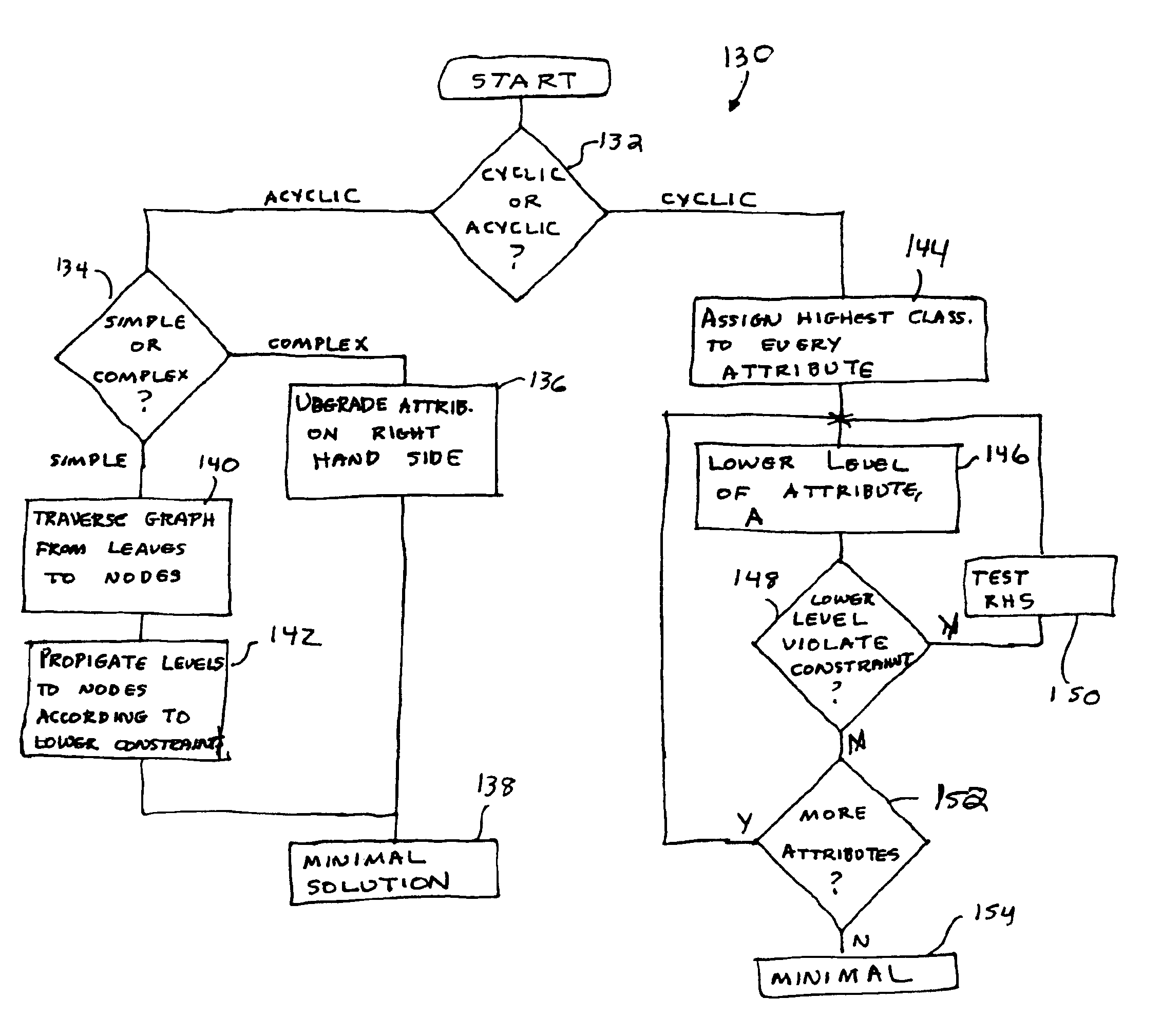
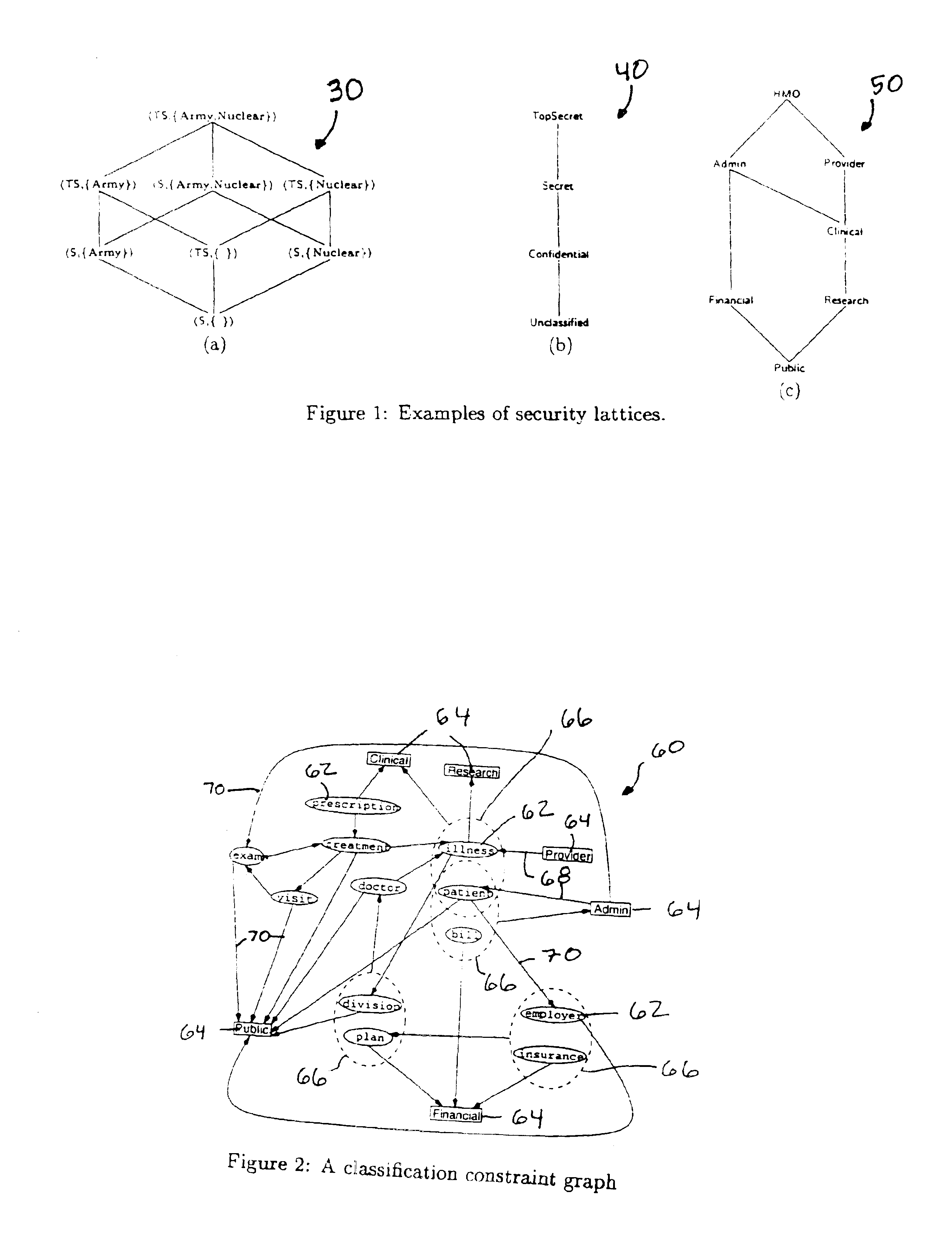
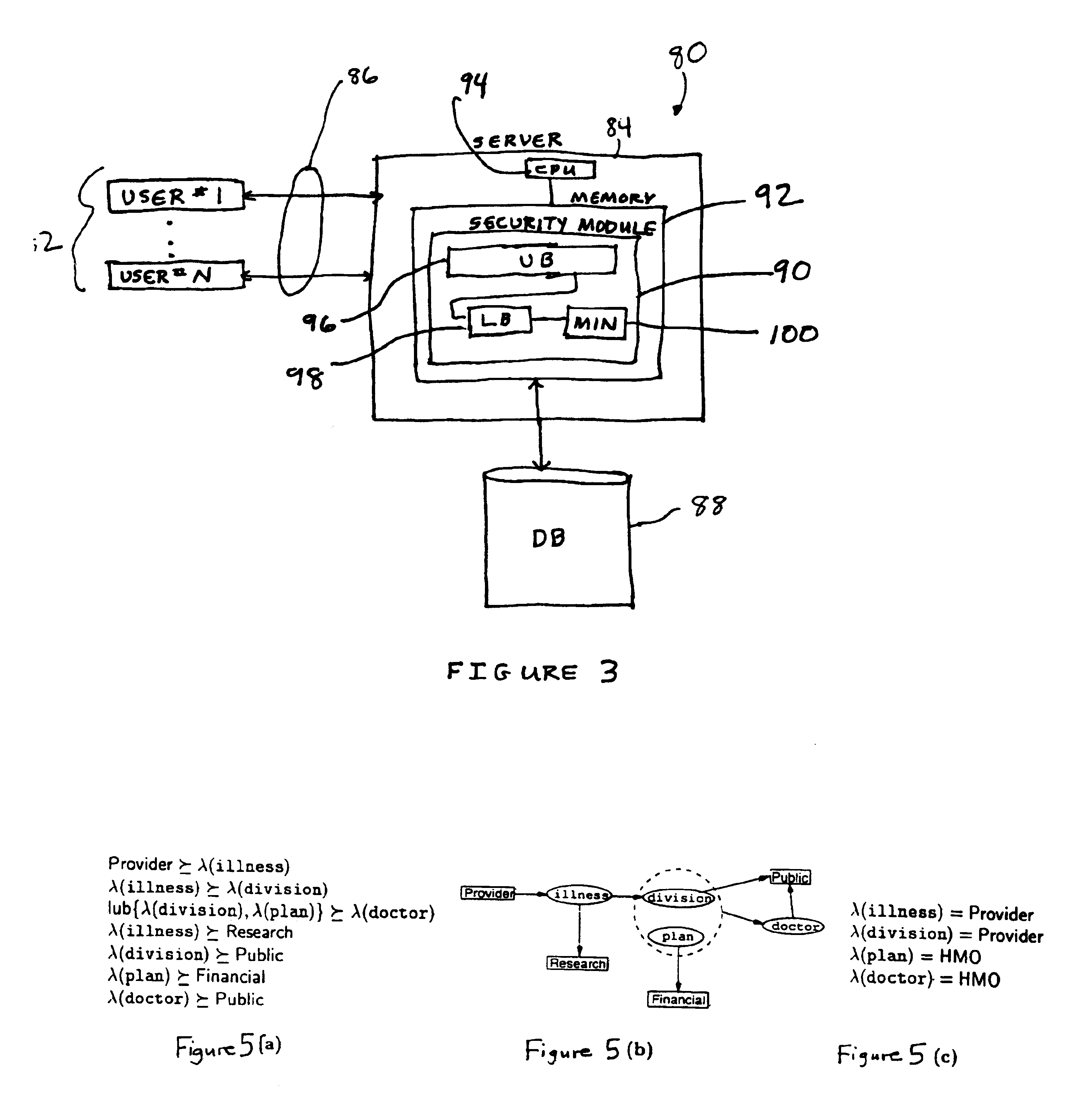
Lattice-based security classification system and method
InactiveUS6922696B1Avoids overclassifyingDecrease overclassificationData processing applicationsDigital computer detailsInformation repositoryRelevant information
Despite advances in recent years in the area of mandatory access control in database systems, today's information repositories remain vulnerable to inference and data association attacks that can result in serious information leakage. Without support for coping against these attacks, sensitive information can be put at risk because of release of other (less sensitive) related information. The ability to protect information disclosure against such improper leakage would be of great benefit to governmental, public, and private institutions, which are, today more than ever, required to make portions of their data available for external release. In accordance with the invention, a solution to the problem of classifying information by enforcing explicit data classification as well as inference and association constraints is provided. We formulate the problem of determining a classification that ensures satisfaction of the constraints, while at the same time guaranteeing that information will not be unnecessarily overclassified.
Owner:SRI INTERNATIONAL
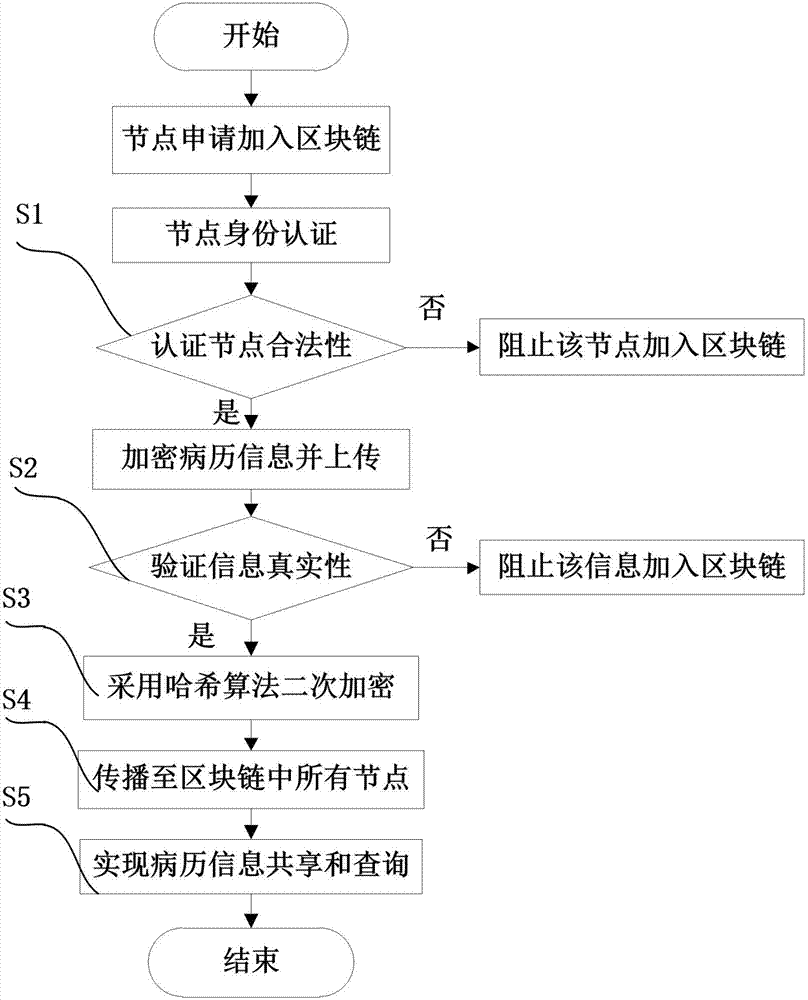
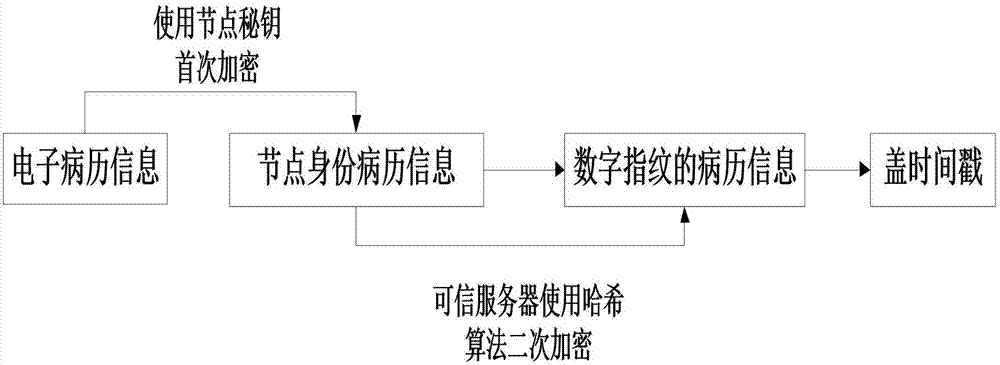
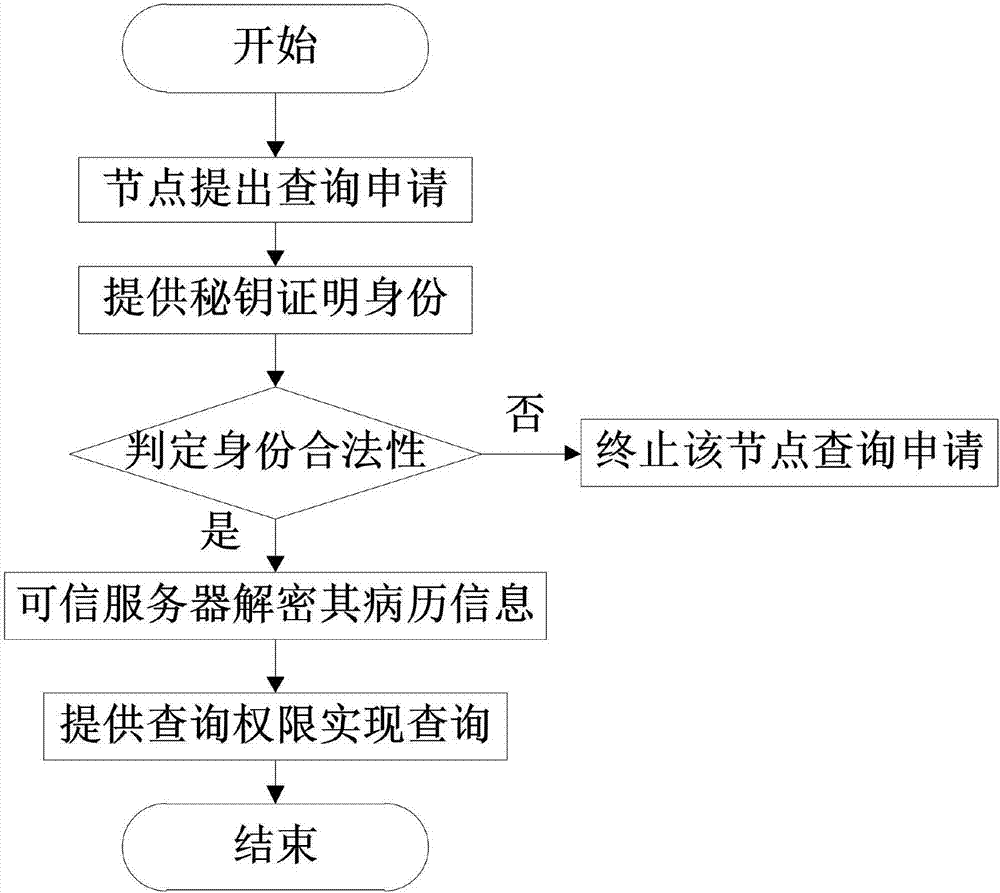
Sharing query method of electronic medical records based on block chain technology
InactiveCN107579979AAchieve sharingShared query implementationUser identity/authority verificationSpecial data processing applicationsMedical recordTimestamp
The invention discloses a sharing query method of electronic medical records based on block chain technology. The method comprises the following steps: a user node applies to join a block chain and sends identity authentication information, registers the identity information and allocates a pair of keys for encrypting electronic medical record information after legal authentication; meanwhile performing bidirectional verification on the encrypted electronic medical record information, and uploading the electronic medical record information passing the bidirectional verification to the block chain for the sharing query of the whole electronic medical record information; performing SHA256 hash algorithm secondary encryption on the real electronic medical record information by a trusted server to generate a segment of uploaded digital fingerprint of electronic evidence, and adding a corresponding timestamp for preventing electronic medical record tampering or information leakage; and storing the electronic medical records after twice encryption in the sharing query block chain, and uploading the same to the cloud; and providing a key by a remote node for identity proving, obtaining the electronic medical records in the sharing query block chain, and decrypting the electronic medical records by the trusted server.
Owner:CHENGDU UNIVERSITY OF TECHNOLOGY
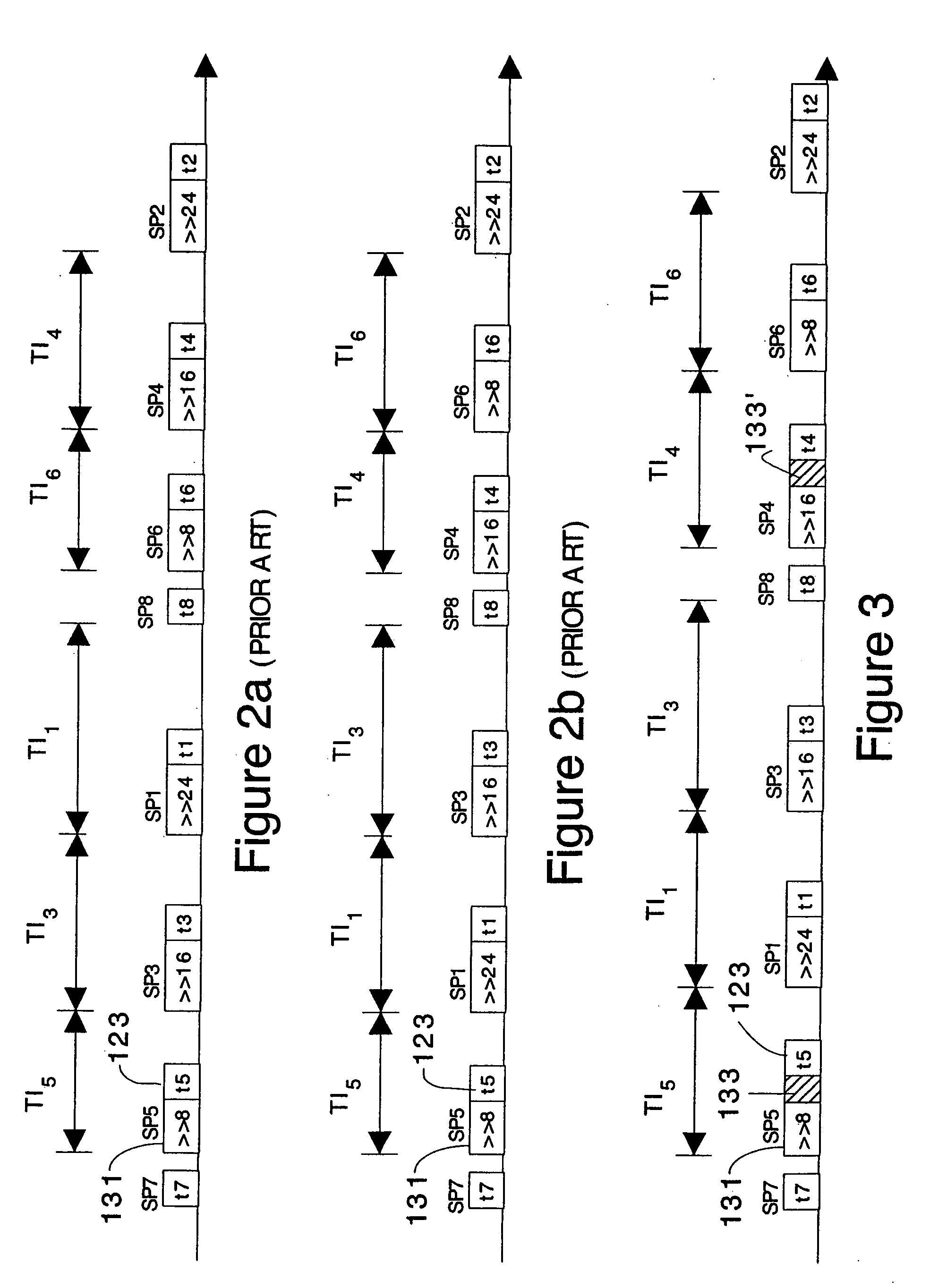
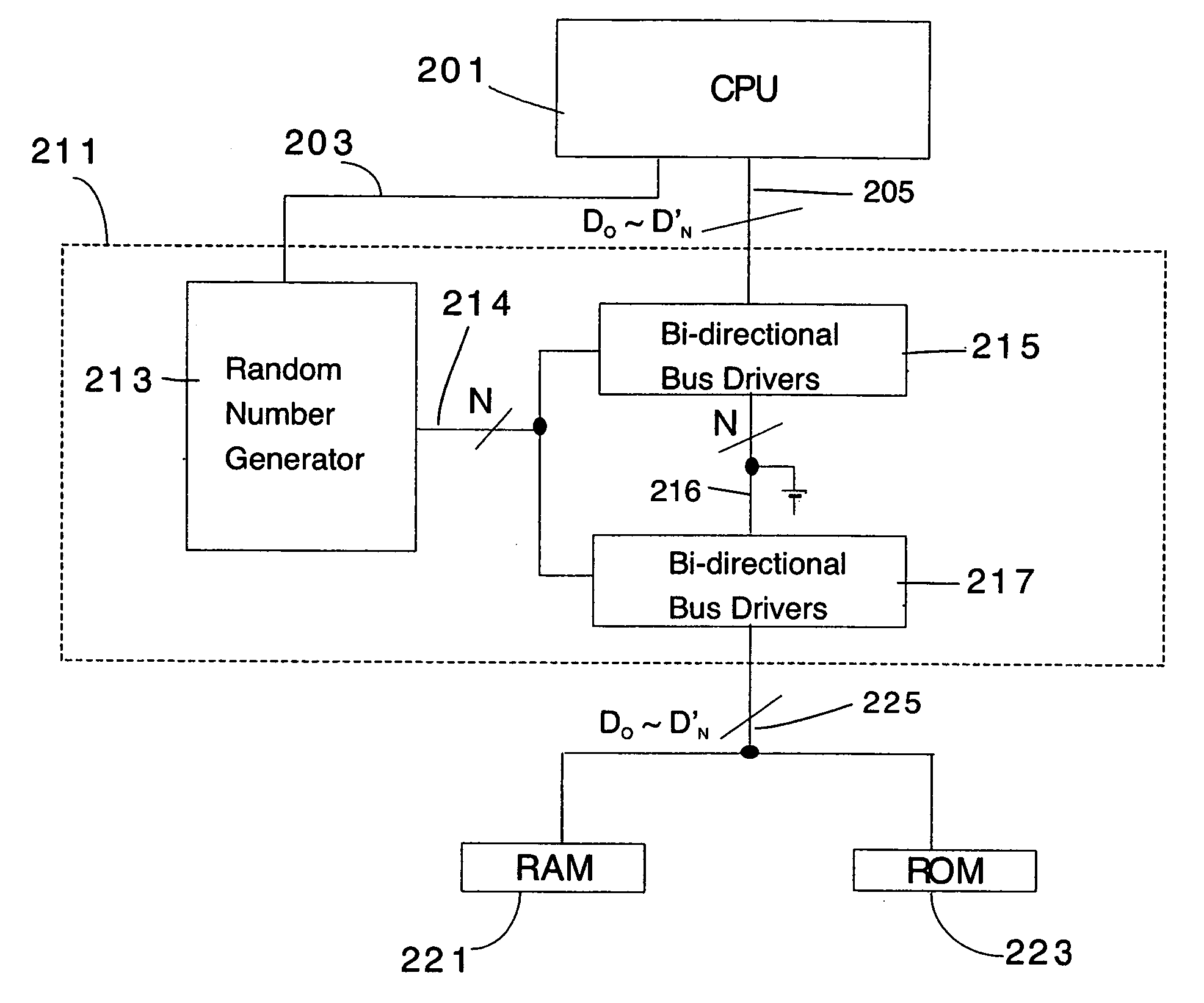
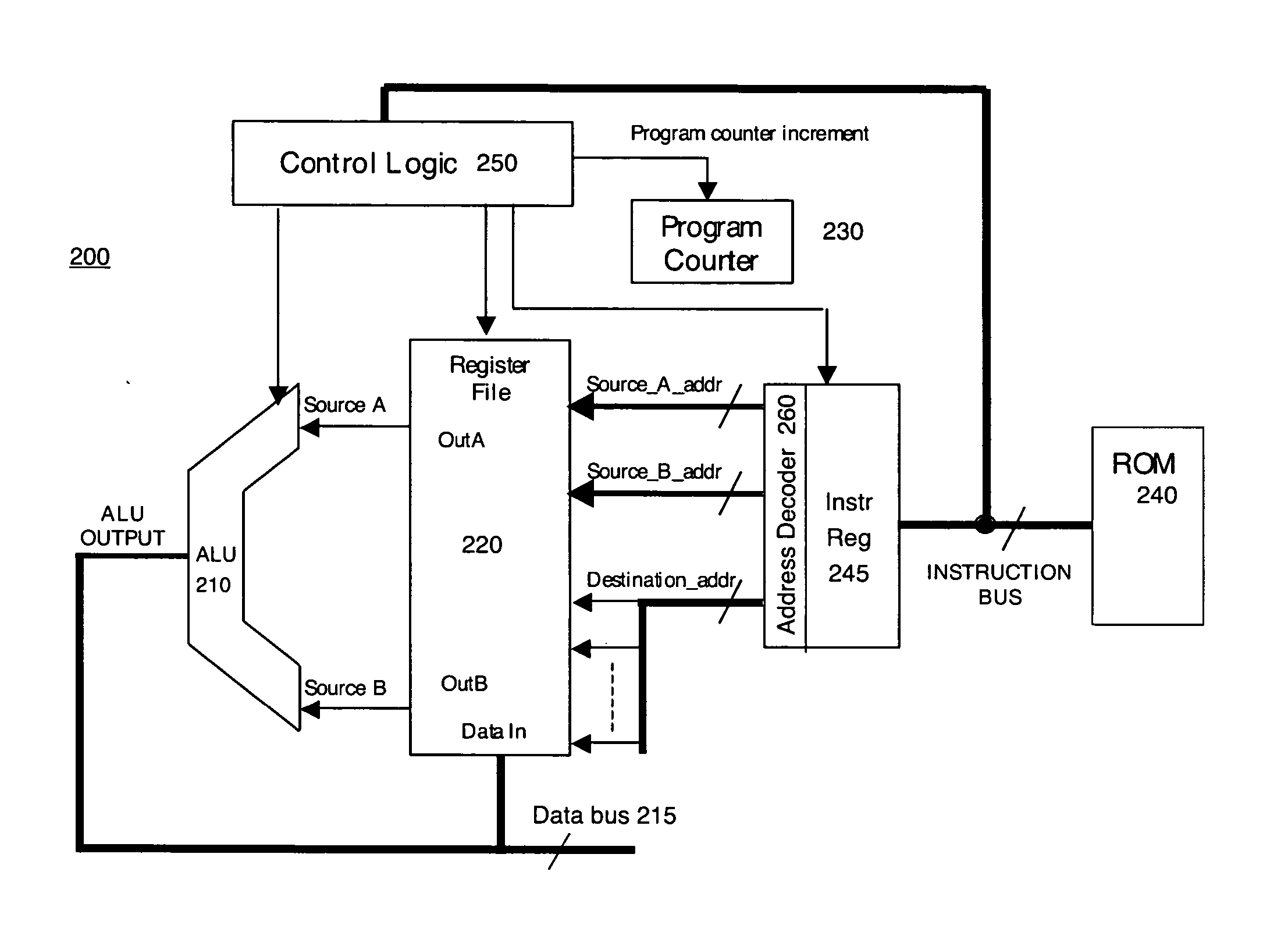
Cryptographic architecture with random instruction masking to thwart differential power analysis
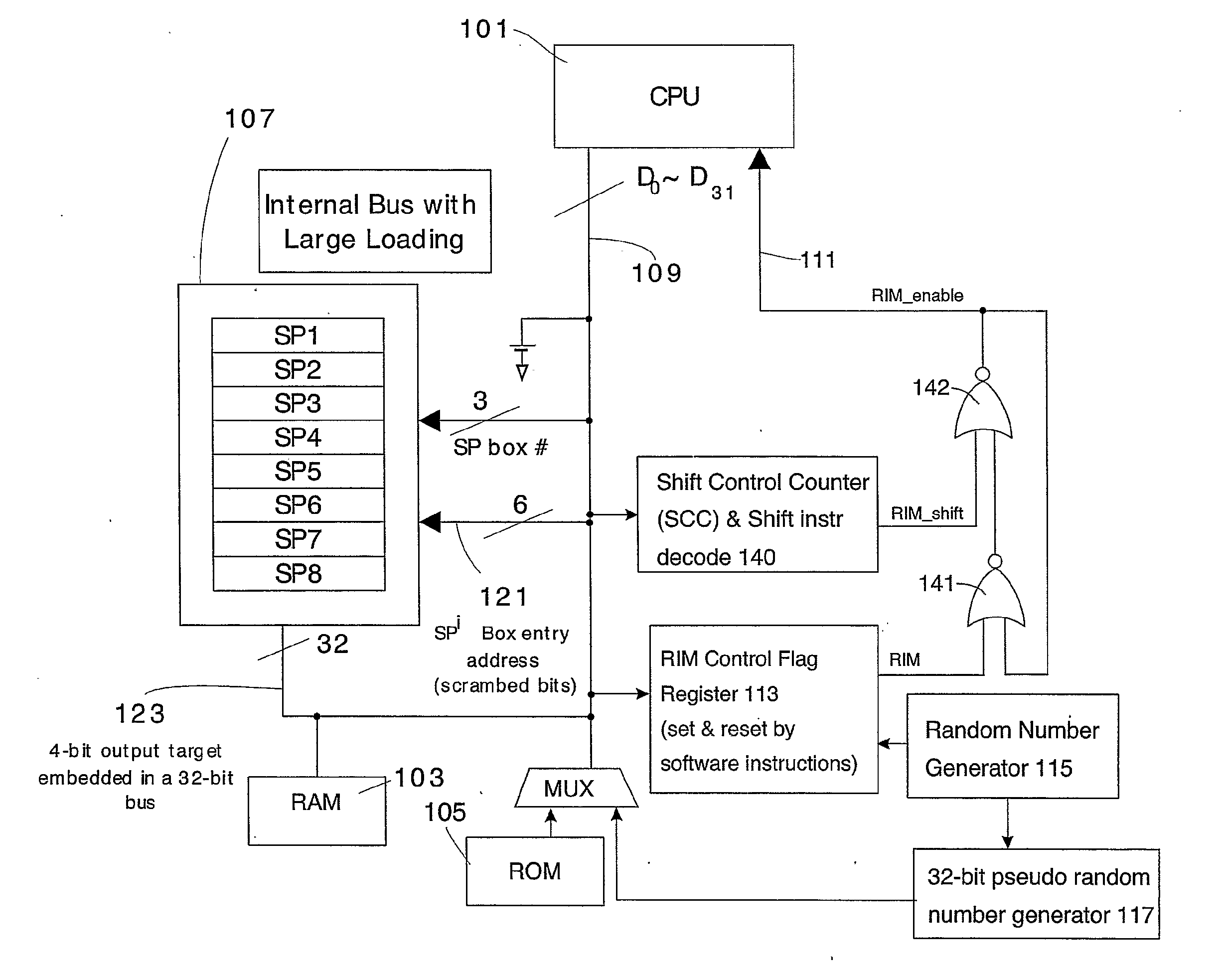
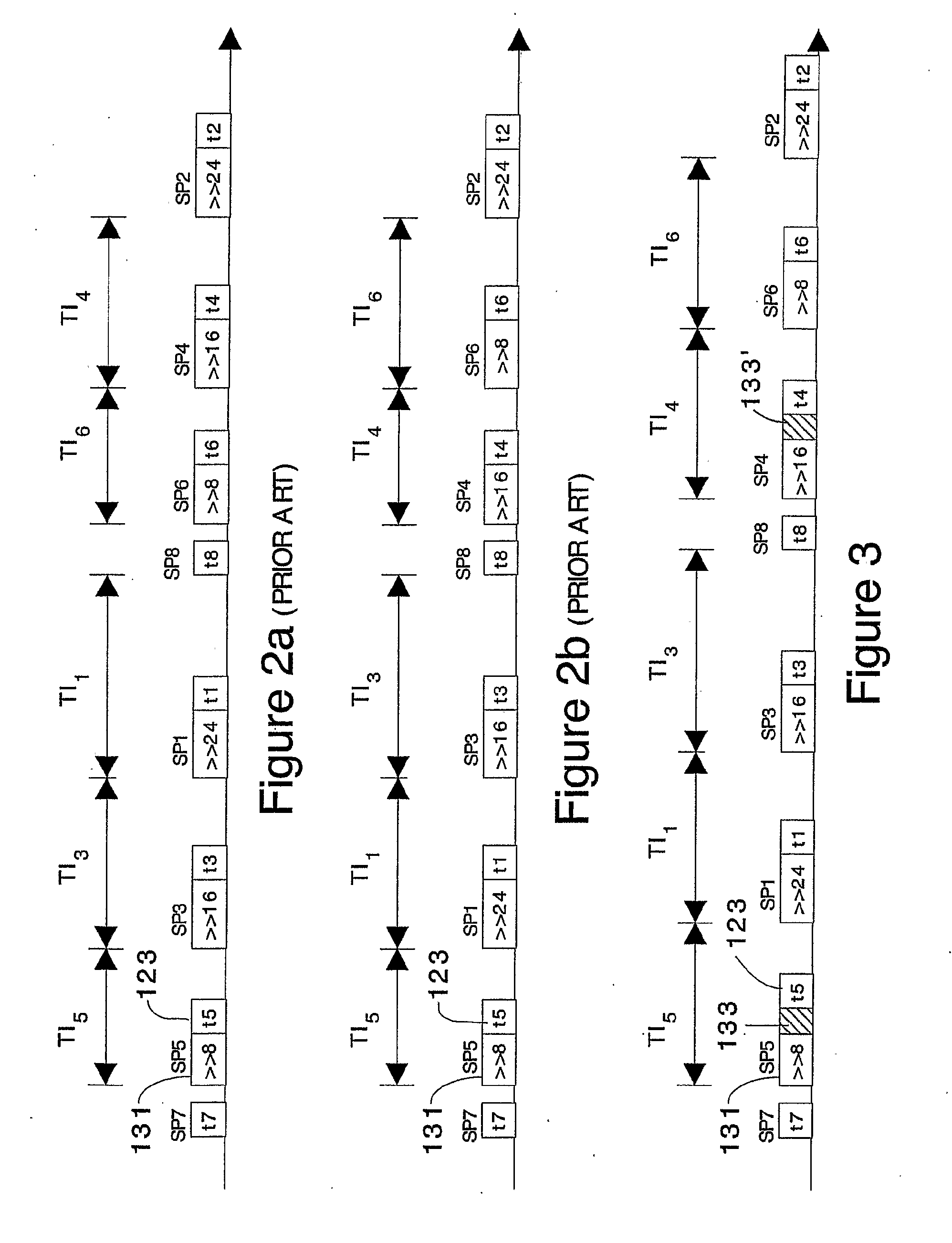
ActiveUS20050271202A1Memory loss protectionEncryption apparatus with shift registers/memoriesComputer hardwarePower analysis
An apparatus and method for preventing information leakage attacks that utilize timeline alignment. The apparatus and method inserts a random number of instructions into an encryption algorithm such that the leaked information can not be aligned in time to allow an attacker to break the encryption.
Owner:HRL LAB
Methods and apparatus for self-adaptive, learning data analysis
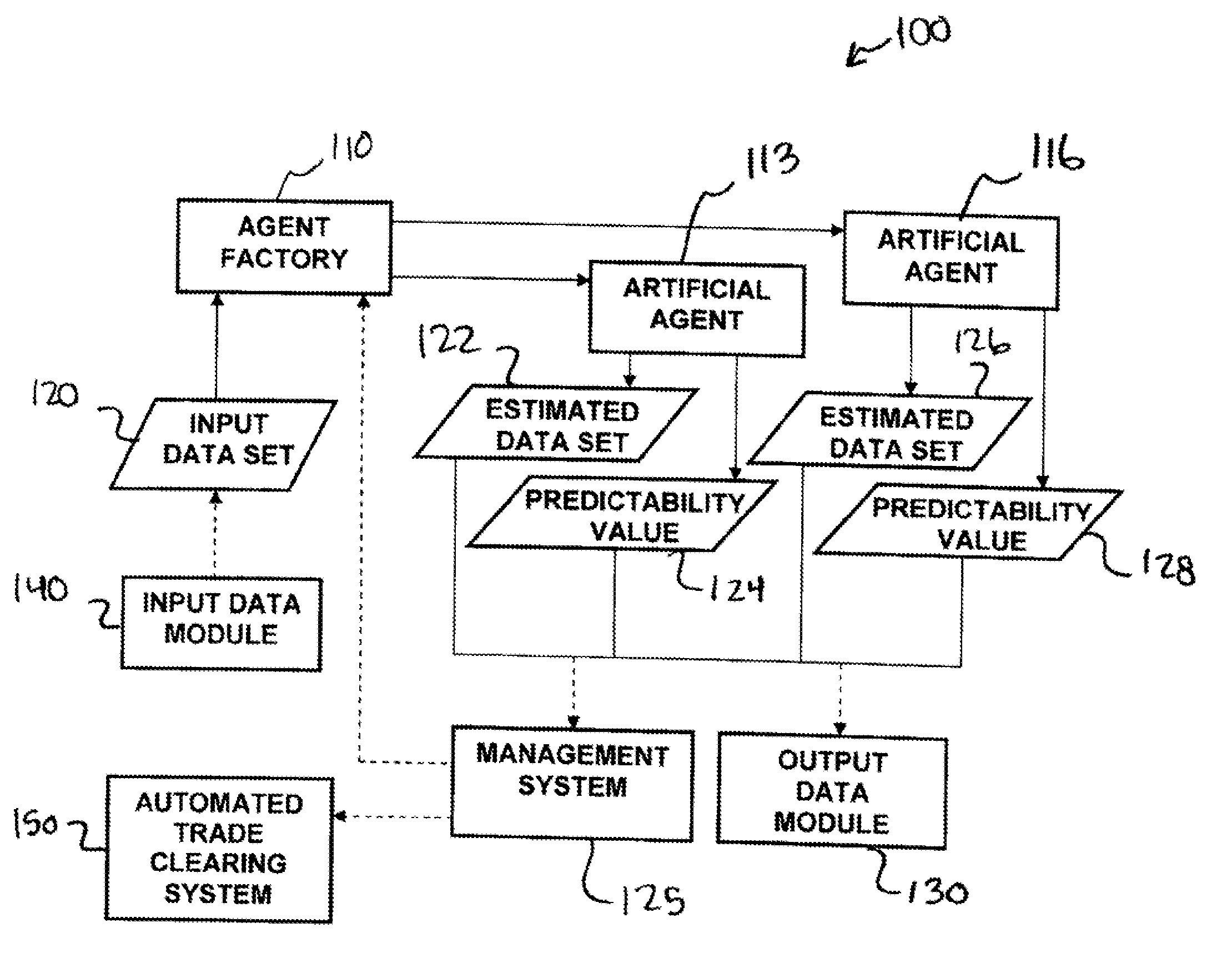
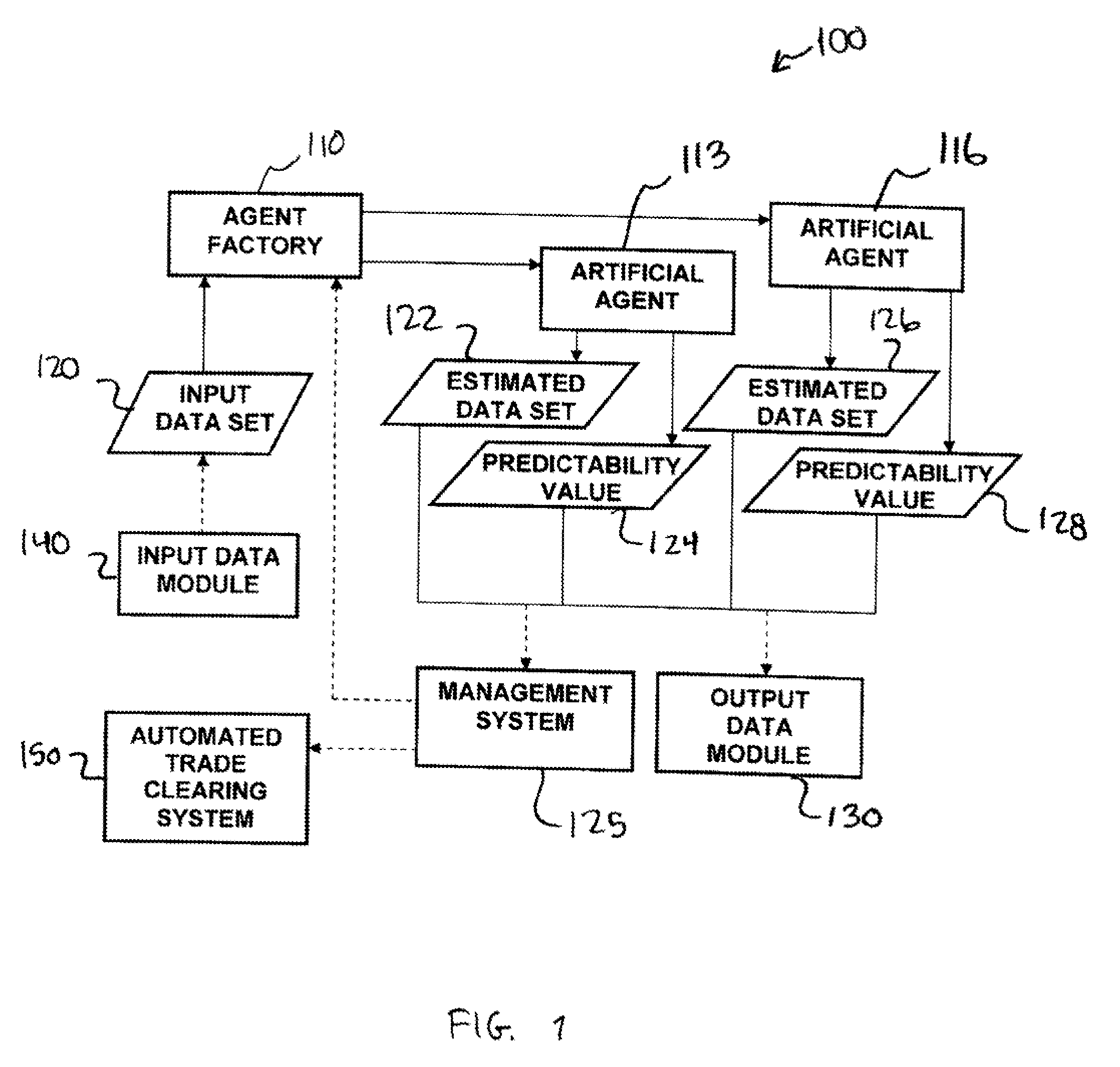
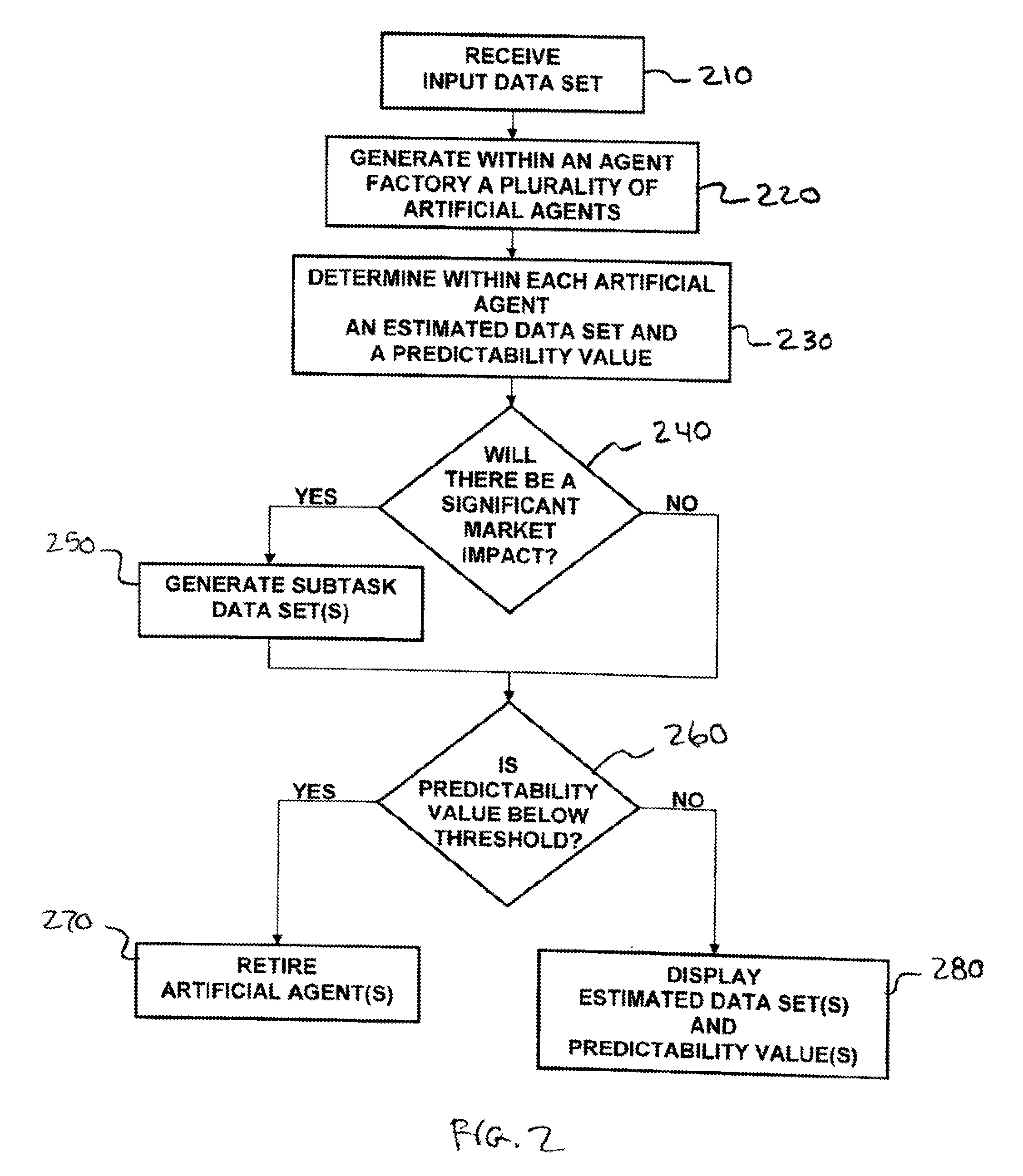
Methods and apparatus for analyzing financial data generally includes a predictive modeling system. The predictive modeling system may include an artificial agent responsive to an input data set. The artificial agent may produce an estimated data set including a market conditions data set. The market conditions data may include an estimate of at least one of liquidity of a market, strategy of a counterparty, and an effect of information leakage. The artificial agent may determine a predictability value for the estimated data set. The predictive modeling system may also include an agent factory responsive to the input data set. The agent factory may generate an artificial agent in response to the input data set.
Owner:ADAPTIV TECH
Universal method and universal system for performing safety testing on Android application programs
InactiveCN104484607AReduce false alarm ratePlatform integrity maintainanceApplication softwareSafety testing
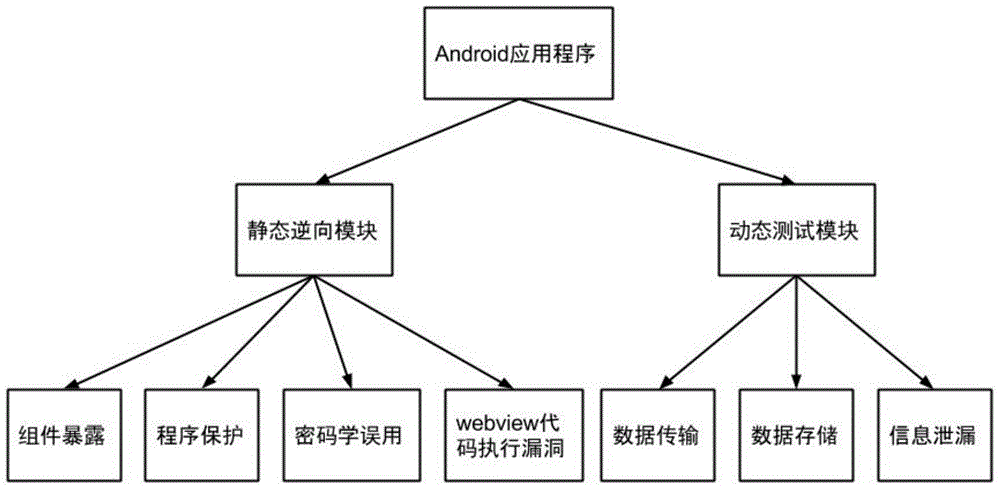
The invention discloses a universal method and a universal system for performing safety testing on Android application programs. The universal method comprises the following steps of unpacking and decompiling a to-be-tested program to obtain an XML (extensive markup language) source code; then, through static analysis on configuration files and the code of the to-be-tested program, performing vulnerability detection and safety testing on the aspects of component exposed vulnerability, cryptology misuse, webview code execution vulnerability and code protection; then, performing actual running on the to-be-tested program, and configuring a network detection environment; finally, performing dynamic analysis, and performing dynamic vulnerability detection and the safety testing on three aspects of information leakage, data transmission safety and data storage safety, thus obtaining a vulnerability detection and safety testing report. According to the universal method and the universal system disclosed by the invention, by performing a static analysis and dynamic analysis combination mode on an optional Android application program and through a series of steps of detection and estimation, safety flaws and potential safety hazards existing in the aspects of design and implementation of the application program can be finally given out.
Owner:SHANGHAI JIAO TONG UNIV +1
Method and apparatus for multiplication in Galois field, apparatus for inversion in Galois field and apparatus for AES byte substitution operation
InactiveUS20050283714A1Avoid attackEncryption apparatus with shift registers/memoriesError detection/correctionByteComputer science
A method and apparatus for multiplication in a Galois field. The method of multiplication in a Galois field (GF) for preventing an information leakage attack by performing a transformation of masked data and masks in GF(2n) includes: receiving a plurality of first and second masked input data, a plurality of first and second input masks and an output mask; calculating a plurality of intermediate values by performing a multiplication of the plurality of masked input data and the plurality of input masks in GF(2n); and calculating a final masked output value by performing an XOR operation of the intermediate values and the output masks.
Owner:SAMSUNG ELECTRONICS CO LTD
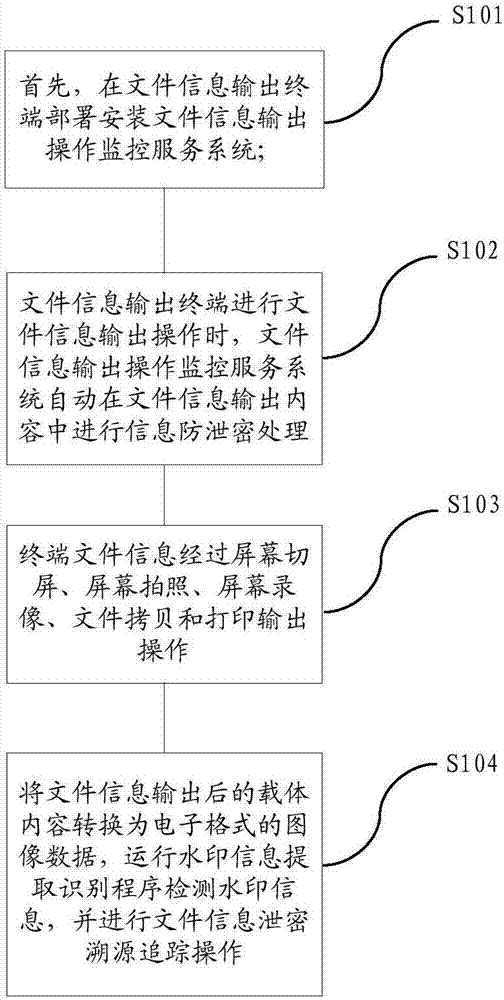
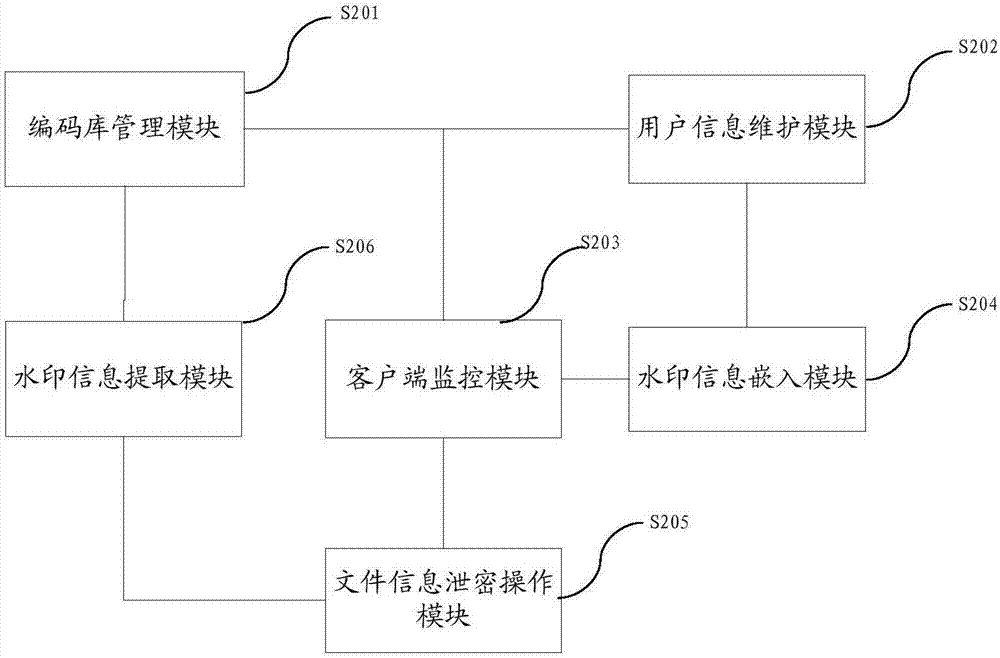
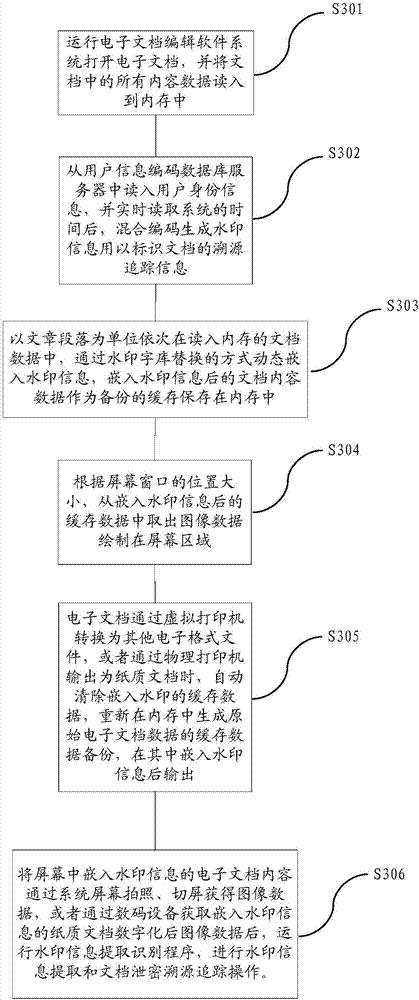
File information output anti-leakage and tracing method and system
ActiveCN107423629AImprove visual effectsDoes not affect normal readingText processingDigital data protectionMonitoring systemComputer terminal
The invention relates to a file information output anti-leakage and tracing method and system. The method comprises the steps of deploying a file information output operation monitoring service system in a file information output terminal; when the file information output terminal performs file information output operation, automatically performing information anti-leakage processing in file information output contents by the file information output operation monitoring system, wherein the anti-leakage processing includes the addition of invisible watermark information; performing one or more of screen switching, screen shooting, screen video recording, file copying and printout operations on file information of the file information output terminal; and converting carrier contents after file information output into image data in an electronic format, running a watermark information extraction identification program to detect the watermark information, and performing file information leakage tracing operation. According to the method and the system, the technical difficult problem of tracing after leakage of screen shooting and printout modes of the file information output terminal can be solved on the premise of not influencing the visual effect of right reading of users.
Owner:李晓妮
Cryptographic bus architecture for the prevention of differential power analysis
InactiveUS20050273630A1Encryption apparatus with shift registers/memoriesDigital data processing detailsComputer hardwarePower analysis
An apparatus and method for preventing information leakage attacks through a polarized cryptographic bus architecture. The polarized cryptographic bus architecture randomly changes the polarity of the target bit such that the leaked information cannot be consistently averaged to yield statistical key material. Further, to increase the prevention of information leakage attacks, a set of dual rails is used to write data to a given register bit.
Owner:HRL LAB
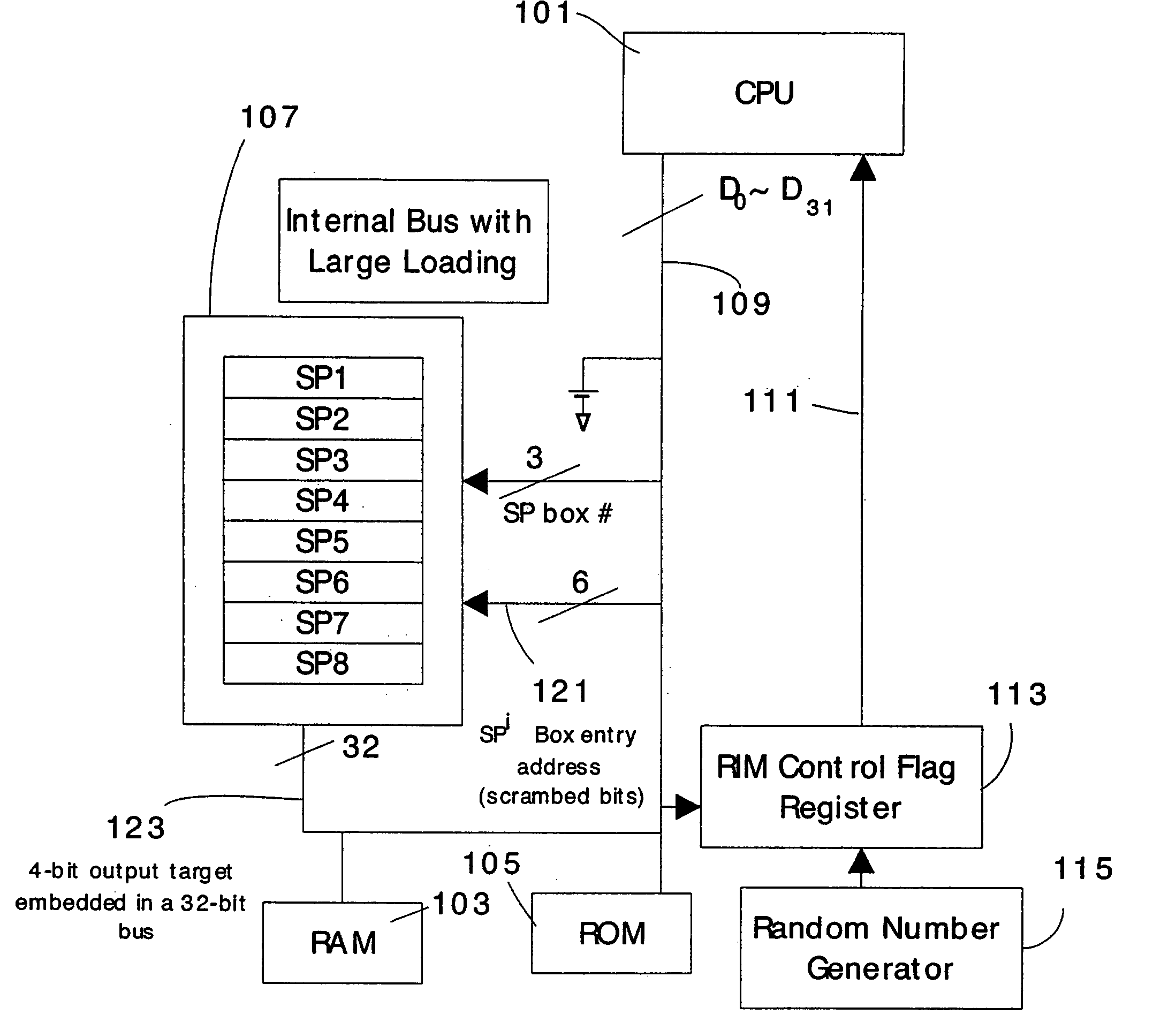
Systems and methods providing wear leveling using dynamic randomization for non-volatile memory
InactiveUS20120324141A1Increased durabilityLow costMemory architecture accessing/allocationMemory adressing/allocation/relocationPhase-change memoryOperational system
Systems and methods for dynamically remapping elements of a set to another set based on random keys. Application of said systems and methods to dynamically mapping regions of memory space of non-volatile memory, e.g., phase-change memory, can provide a wear-leveling technique. The wear leveling technique can be effective under normal execution of typical applications, and in worst-case scenarios including the presence of malicious exploits and / or compromised operating systems, wherein constantly migrating the physical location of data inside the PCM avoids information leakage and increases security; wherein random relocation of data results in the distribution of memory requests across the physical memory space increases durability; and wherein such wear leveling schemes can be implemented to provide fine-grained wear leveling without overly-burdensome hardware overhead e.g., a look-up table.
Owner:GEORGIA TECH RES CORP
Method and apparatus for detecting leakage of sensitive information
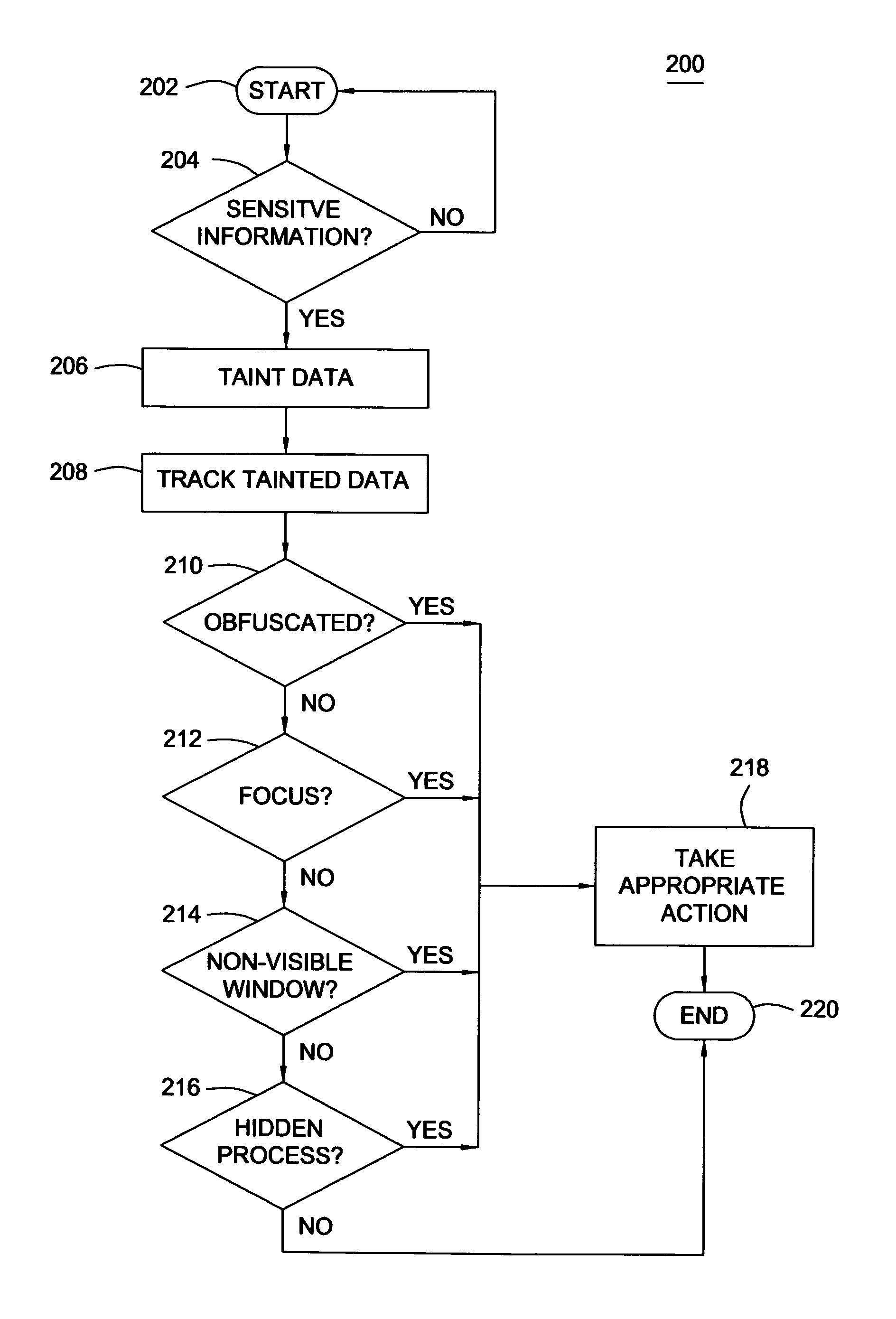
ActiveUS8127360B1Avoid Sensitive Information LeakageMemory loss protectionError detection/correctionInternet privacyComputerized system
A method and apparatus for preventing leakage of sensitive information from a computer is described. The method includes identifying data entered into the computer system as sensitive data, tainting the sensitive data with at least one taint bit to form a tainted data, tracking the tainted data within the computer system and identifying at least one condition that compromises the security of the tainted data. The system is a computer system including taint analysis software for identifying data entered into the computer system as sensitive data, tainting the sensitive data with at least one taint bit to form a tainted data, tracking the tainted data within the computer system and identifying at least one condition that compromises the security of the tainted data.
Owner:CA TECH INC
Nano foamed concrete, reinforced insulation wallboard and preparation method of reinforced insulation wallboard
ActiveCN103359997AAvoid interferenceAvoid pollutionBuilding componentsFoam concreteAdditive ingredient
The invention belongs to the field of building materials and construction technologies and relates to nano foamed concrete, a reinforced insulation wallboard and a preparation method of the reinforced insulation wallboard. The nano foamed concrete disclosed by the invention is prepared from the following ingredients in parts by weight: 100 parts of cement, 0.1-5 parts of desulfurized oil coke ash residue, 0.012 part of waterproofing agent, 10-30 parts of fly ash, 0.1-6 parts of superplasticizer, 50-200 parts of water, 1-20 parts of foamer and 0.01-5 parts of nano wave absorbing agent. Thus, when a wallboard product, prepared by embedding steel wire meshes in the nano foamed concrete disclosed by the invention, is applied nearby airports, docks, navigation marks, television stations and receiving stations or applied to concrete-based retaining walls of electromagnetic wave interference preventing scientific research departments, precise instrument plants and information leakage prevention high-grade buildings of national confidential units and the like, the most basic physical, mechanical, heat preservation and heat insulation properties are guaranteed on one hand, and the wallboard product has the capabilities of lowering noise and insulating sound on the other hand.
Owner:QINGDAO TECHNOLOGICAL UNIVERSITY
High shielding effect information leakage preventing glass
InactiveCN1482853AContainment leakImprove visibilityMagnetic/electric field screeningScreening apparatusHuman bodySheet film
The invention discloses a glass for prevention of information leakage which comprises glass, metal mesh and polycarbonate film, wherein two layers of polycarbonate films are arranged on each side of the metal mesh, a layer of glass is adhered on the outboard of the polycarbonate film by thermal compression bonding to form a unitary. The invention can effectively prevent information leakage, and diminishes the possible injury by the electromagnetic wave to the human body. íí
Owner:北京安方电磁屏蔽技术开发中心
Cryptographic CPU architecture with random instruction masking to thwart differential power analysis
InactiveUS20050273631A1Memory loss protectionEncryption apparatus with shift registers/memoriesComputer hardwarePower analysis
An apparatus and method for preventing information leakage attacks that utilize timeline alignment. The apparatus and method inserts a random number of instructions into an encryption algorithm such that the leaked information can not be aligned in time to allow an attacker to break the encryption.
Owner:HRL LAB
Blockchain-based FIDO authentication method, apparatus and system
ActiveCN108064440AImprove securityReduce the likelihood of being attackedUser identity/authority verificationUser equipmentComputer science
The present disclosure relates to a blockchain-based FIDO authentication method, apparatus and system. The method comprises the following steps: an initial authentication request sent by a piece of user equipment is received by a first application service, an authentication request is sent to the user equipment, wherein the authentication request includes a challenge value. After the user equipment uses an authentication private key to sign the challenge value, a FIDO server receives the authentication response sent by the user equipment through the first application service, and the authentication response includes a challenge value signature, and then the FIDO obtains an authentication public key corresponding to the authentication private key from the blockchain, and the challenge valuesignature in the authentication response is verified using the authentication public key. The method solves the problems that the FIDO system in the prior art is vulnerable to information leakage, tampered or failed, and the security of the FIDO system is improved.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
Cryptographic architecture with instruction masking and other techniques for thwarting differential power analysis
ActiveUS20070180541A1Encryption apparatus with shift registers/memoriesVolume/mass flow measurementComputer hardwarePower analysis
Owner:HRL LAB
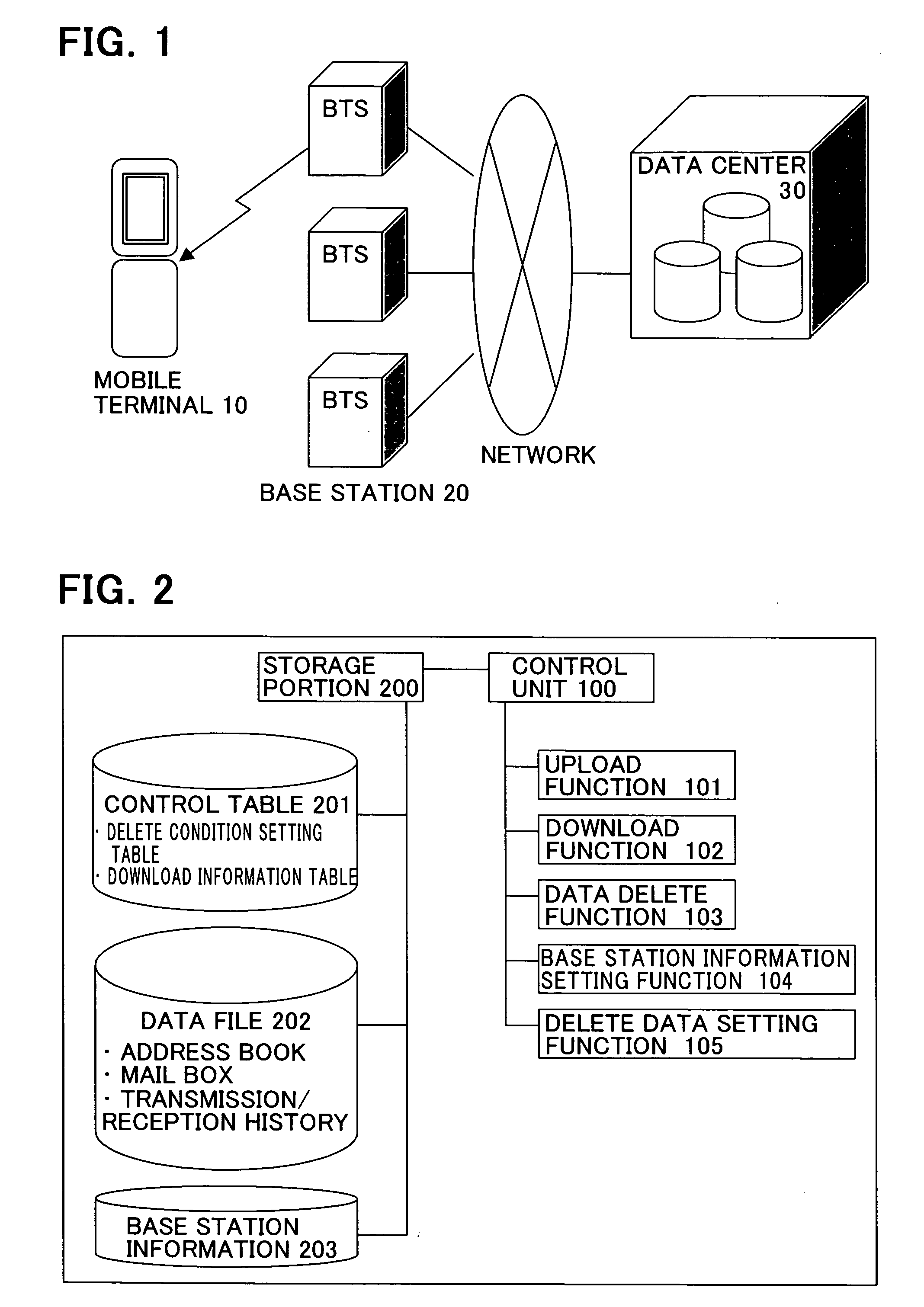
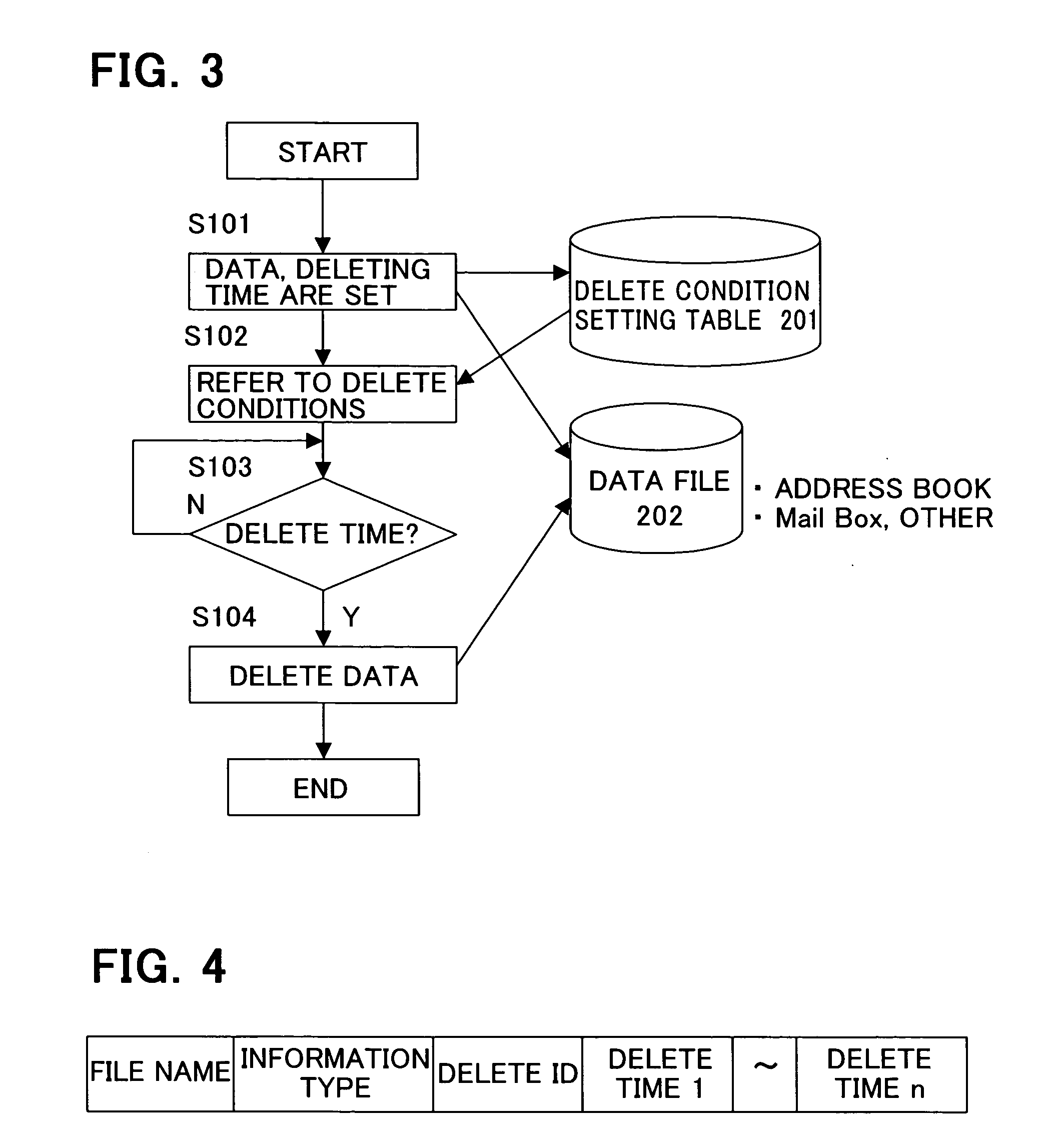
Mobile terminal with data delete function
InactiveUS20070077925A1Reduce riskPrevent leakageUnauthorised/fraudulent call preventionSpecial service for subscribersComputer scienceInformation leakage
To prevent information leakage due to the loss of a mobile terminal, when various delete conditions that are set in advance in the mobile terminal are satisfied, data is deleted by control performed by the mobile terminal itself. By allowing the mobile terminal to perform control of deleting data instead of allowing an outside system such as a network to perform the control of deleting the data, it is possible to reduce the risk that the information leaks out to a third person when the network cannot perform the control or during a period of time between when the mobile terminal is lost and when the loss of the mobile terminal is noticed. Moreover, by saving the data to be deleted in another computer device by uploading the data onto, for example, a server on the network so that the data can be recovered, leakage of the information from the mobile terminal can be prevented without hampering the convenience for the user.
Owner:FUJITSU LTD
Apparatus and method for providing controlling service for IoT security
ActiveUS20160352685A1Information leakageMinimize spreadingWireless commuication servicesData switching networksData packIot gateway
The present invention provides a technology for controlling an IoT gateway command control based packet, preemptively blocking information leakage by detecting / blocking command not allowed through a DB updated by automatically learning new commands recognized based thereon in real-time, determining whether they correspond to each other through search / comparison in each pattern DB corresponding thereto and selectively processing the corresponding packet according to the determined result, generating a session table based on the processed result and determining whether there is an abnormal act by checking a predetermined item, and blocking access to IoT server of abnormal packet by performing a policy according to packet blocking rule management flow.
Owner:WINS CO LTD
Identity authentication system and method based on electronic identification card
ActiveCN104994114AProtect identity privacyImprove reliabilityUser identity/authority verificationElectronic identificationOnline identity
The invention provides an identity authentication system and method based on an electronic identification card. The identity authentication system comprises an intelligent terminal, an operator server, a network identity authentication center and an application platform. The intelligent terminal is used for storing a first temporary secret key only associated with the electronic identification card of a user, and generating to-be-authenticated encryption information and first encryption information. The operator server is used for acquiring the first encryption information, authenticating the first encryption information preliminarily, and then generating second encryption information. The network identity authentication center is used for acquiring the second encryption information, generating a second temporary secret key and authenticated encryption information, and comparing the to-be-authenticated encryption information with the authenticated encryption information so as to realize authentication of the user identity. The application platform is connected with a secret key server. The application platform sends an authentication request and is used for acquiring a result of user identity authentication from the operator server. The first temporary secret key is stored in a safe area of the intelligent terminal, so that the user does not need to carry a hardware carrier and are not worry about risks, such as information leakage and so on when in online payment or online identity authentication.
Owner:尤磊
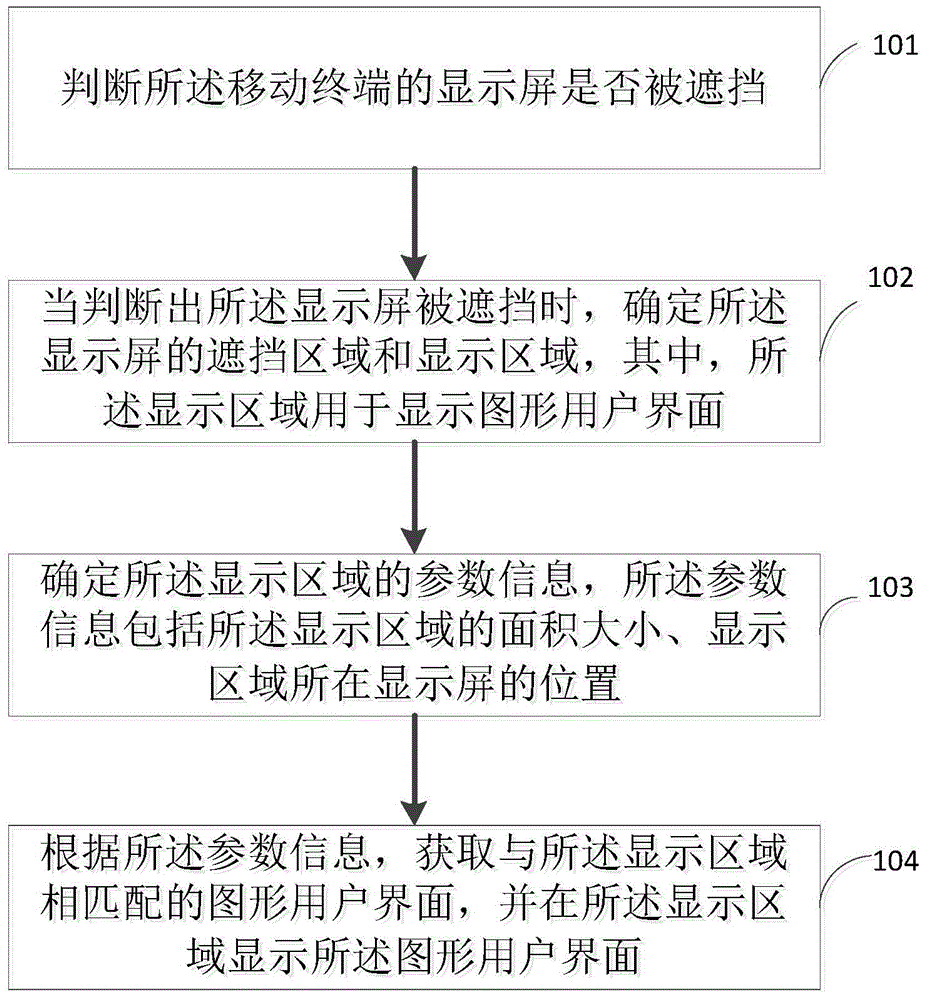
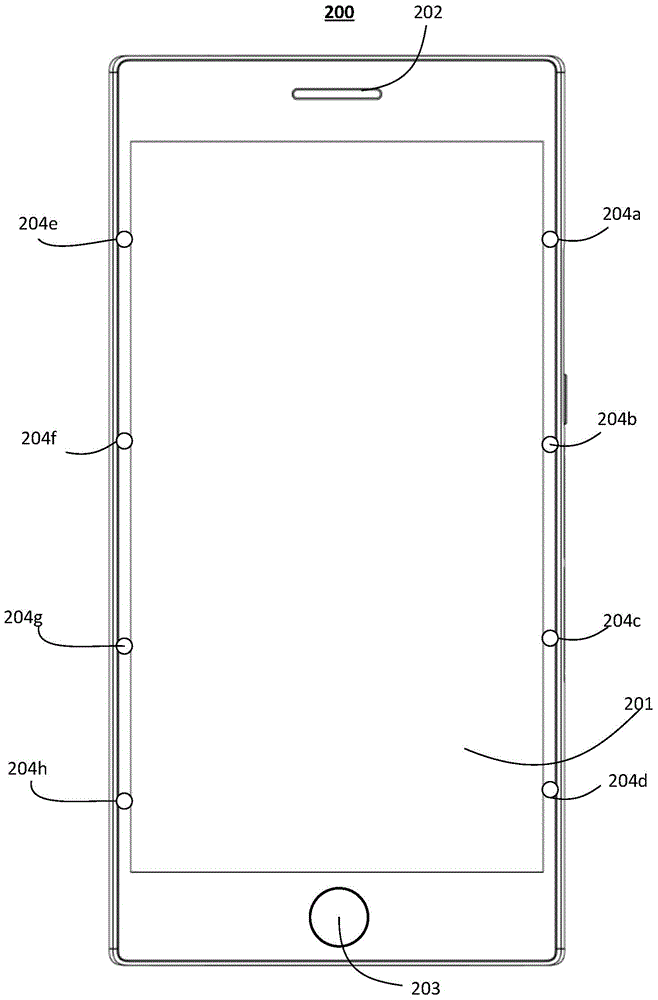
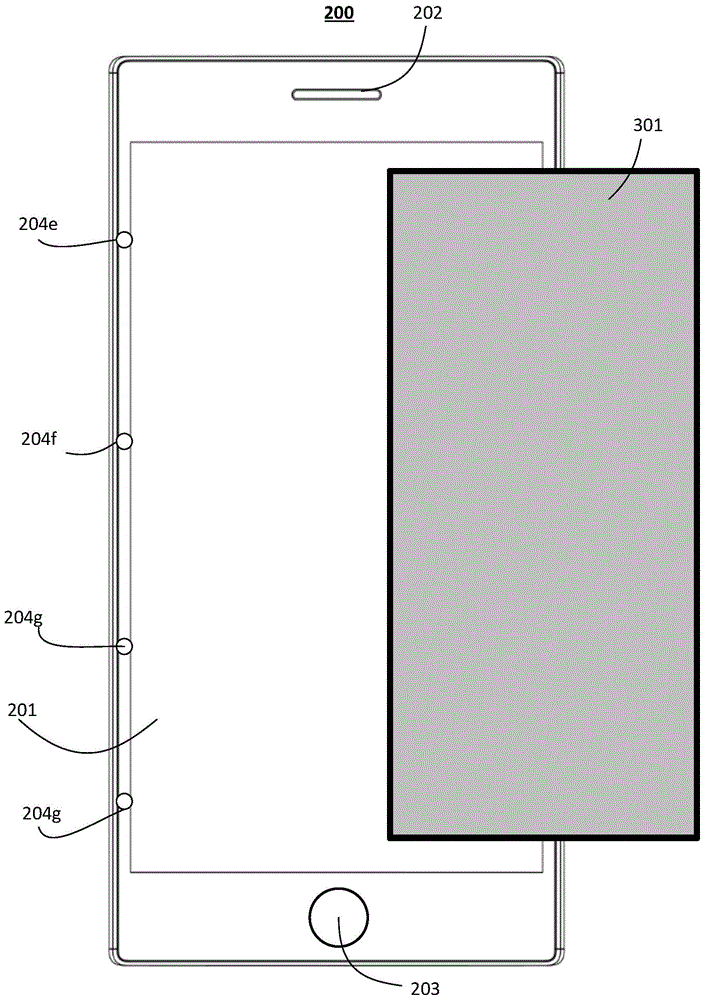
Display method of graphical user interface, and mobile terminal
ActiveCN105808040AReduce the possibility of leaksImprove privacyDigital data processing detailsDevices with sensorGraphicsMobile data terminal
The embodiment of the invention provides a display method of a graphical user interface, and a mobile terminal, and relates to the field of data processing. The method specifically comprises the following steps: judging whether the display screen of the mobile terminal is blocked or not; when a judgment result shows that the display screen is blocked, determining the blocking area and the display area of the display screen, wherein the display area is used for displaying the graphical user interface; determining the parameter information of the display area, wherein the parameter information comprises the area size of the display area and the position of the display screen where the display area is positioned; and according to the parameter information, obtaining the graphical user interface matched with the display area, and displaying the graphical user interface in the display area. The embodiment of the invention judges whether the touch screen of the mobile terminal is blocked or not, when the touch screen is blocked, the graphical user interface is displayed in the display area, the graphical user interface can be only displayed in the display area of the display screen without full-screen display, information leakage possibility is reduced, and privacy is good.
Owner:HUAWEI DEVICE CO LTD
BDS/GPS high-accuracy positioning method
InactiveCN105929424AOvercome the safety hazards of leakageSolve potential safety hazardsSatellite radio beaconingObservation dataSatellite observation
The invention discloses a BDS / GPS high-accuracy positioning method, relating to the field of satellite navigation. The method includes establishing a virtual reference station, acquiring the common-view satellite ephemeris and the satellite observation data received by a reference station Bi and a roving station M, and acquiring the geometry distance between the satellite and the reference station Bi; acquiring the pseudo range correction number of the reference station Bi; interpolating the pseudo range correction number of the virtual reference station by means of an algorithm of inverse distance to a power; interpolating the pseudo range correction number of the roving station by the roving station by means of an algorithm of inverse distance to a power; correcting the satellite pseudo range observation data received by the roving station by means of the pseudo range correction number of the roving station; and establishing a roving station satellite pseudo range observation equation to obtain the accurate coordinate of the roving station to complete the positioning. According to the invention, the safety hidden troubles of information leakage of the reference station because a multi-reference difference positioning method in the prior art must use the accurate coordinate of the reference station can prevented, and high-accuracy positioning is obtained.
Owner:CHINESE ACAD OF SURVEYING & MAPPING
Secret information delivery system and secret information delivery method
InactiveUS20100049966A1Prevent leakageUser identity/authority verificationUnauthorized memory use protectionComputer accessData shipping
Owner:ORICOM
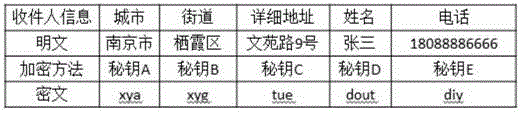
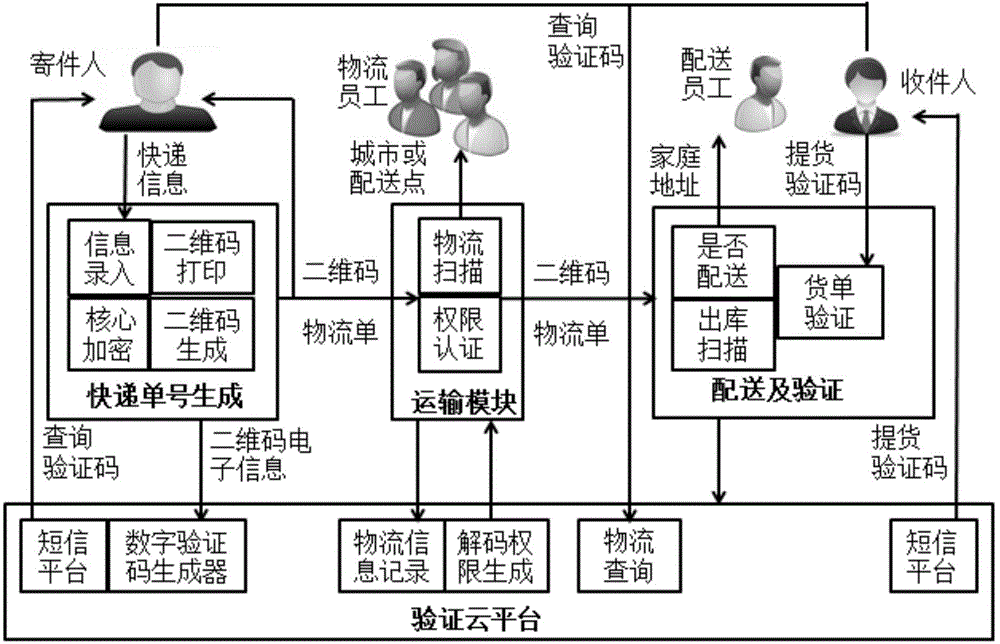
Logistics personal information privacy protection system based on multilayer-encrypted two-dimensional code
ActiveCN104933371APrevent leakageImplement query authentication mechanismDigital data protectionRecord carriers used with machinesLogistics managementPrivacy protection
The invention discloses a privacy protection system based on a two-dimensional code multilayer encryption technology for personal information in a logistics process. A two-dimensional code encryption technology and a layered extraction technology are combined in order to solve the problem of leakage of logistics platform personal information. The privacy protection system mainly comprises a two-dimensional code layered encryption printing module of a sending service department, a layered two-dimensional code decryption information extraction scanning module for use in a logistics transfer process, and a personal information verification module of a logistics distribution end. Through adoption of the privacy protection system, a logistics information inquiry authentication mechanism is implemented, and the contradiction between address information leakage and incapability of inquiring after encryption in logistics number inquiry is solved.
Owner:NANJING UNIV OF POSTS & TELECOMM
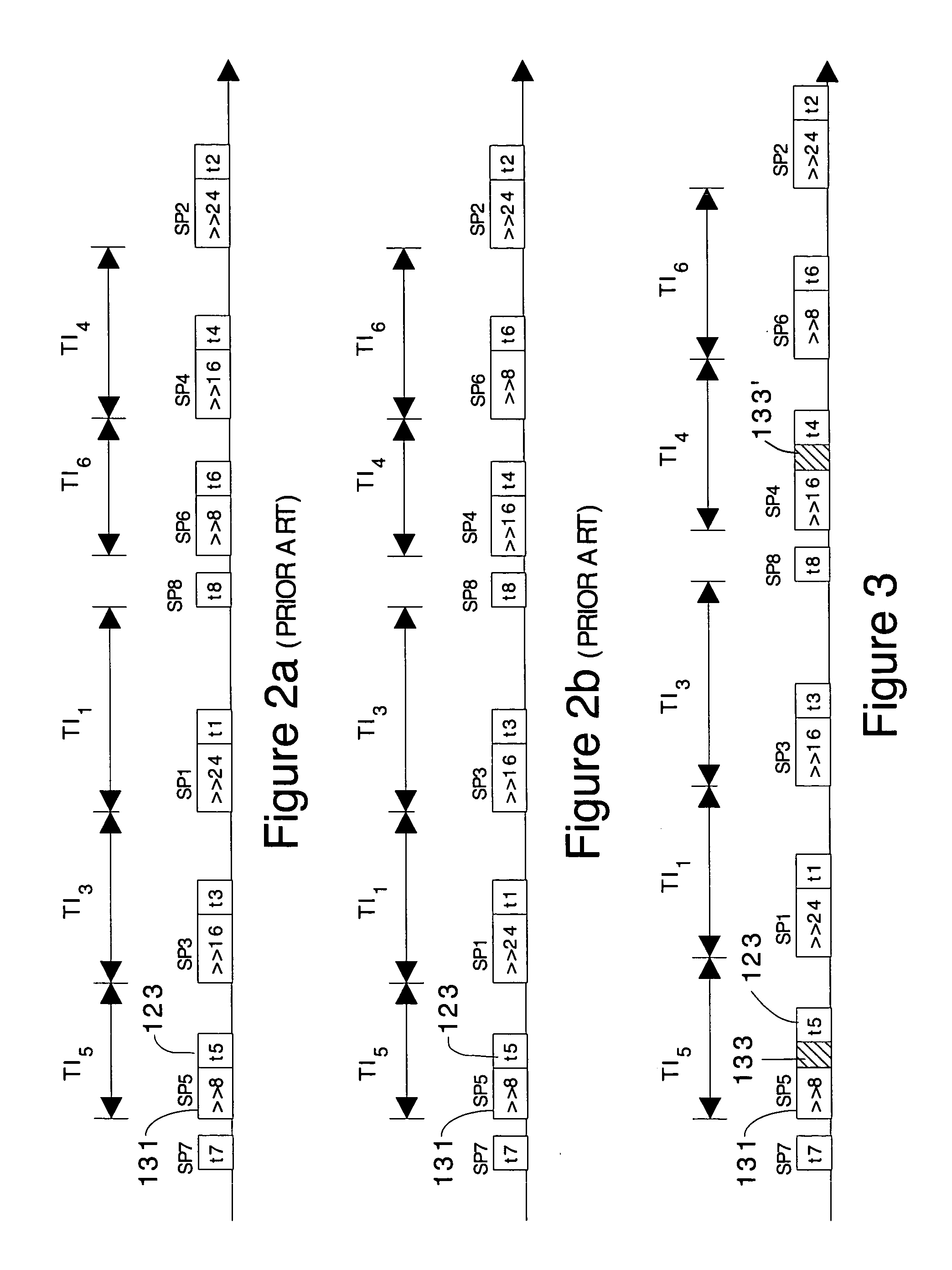
Cryptographic computation using masking to prevent differential power analysis and other attacks
InactiveUS7668310B2Easy to convertInhibition of informationEncryption apparatus with shift registers/memoriesComputer security arrangementsPlaintextPower analysis
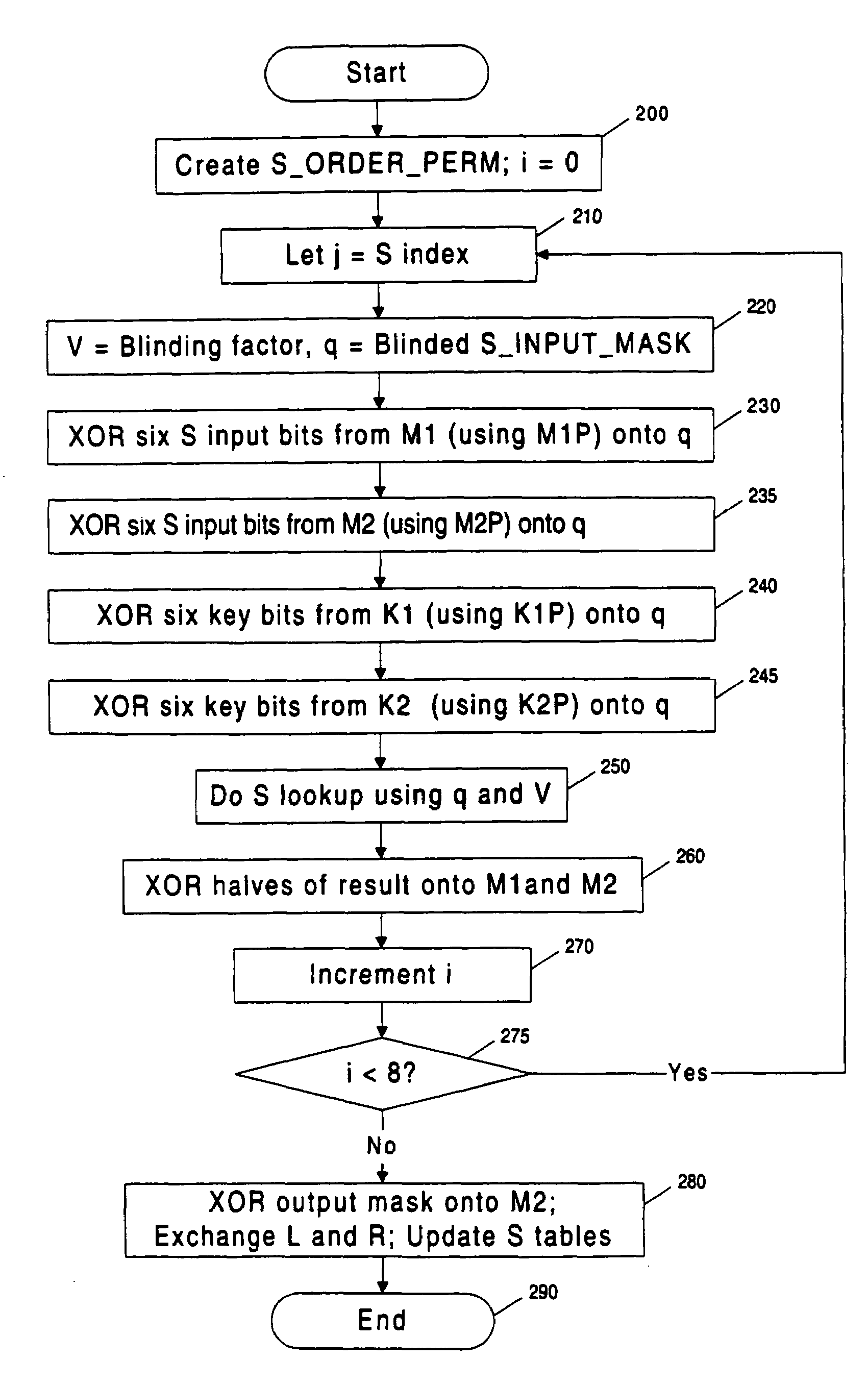
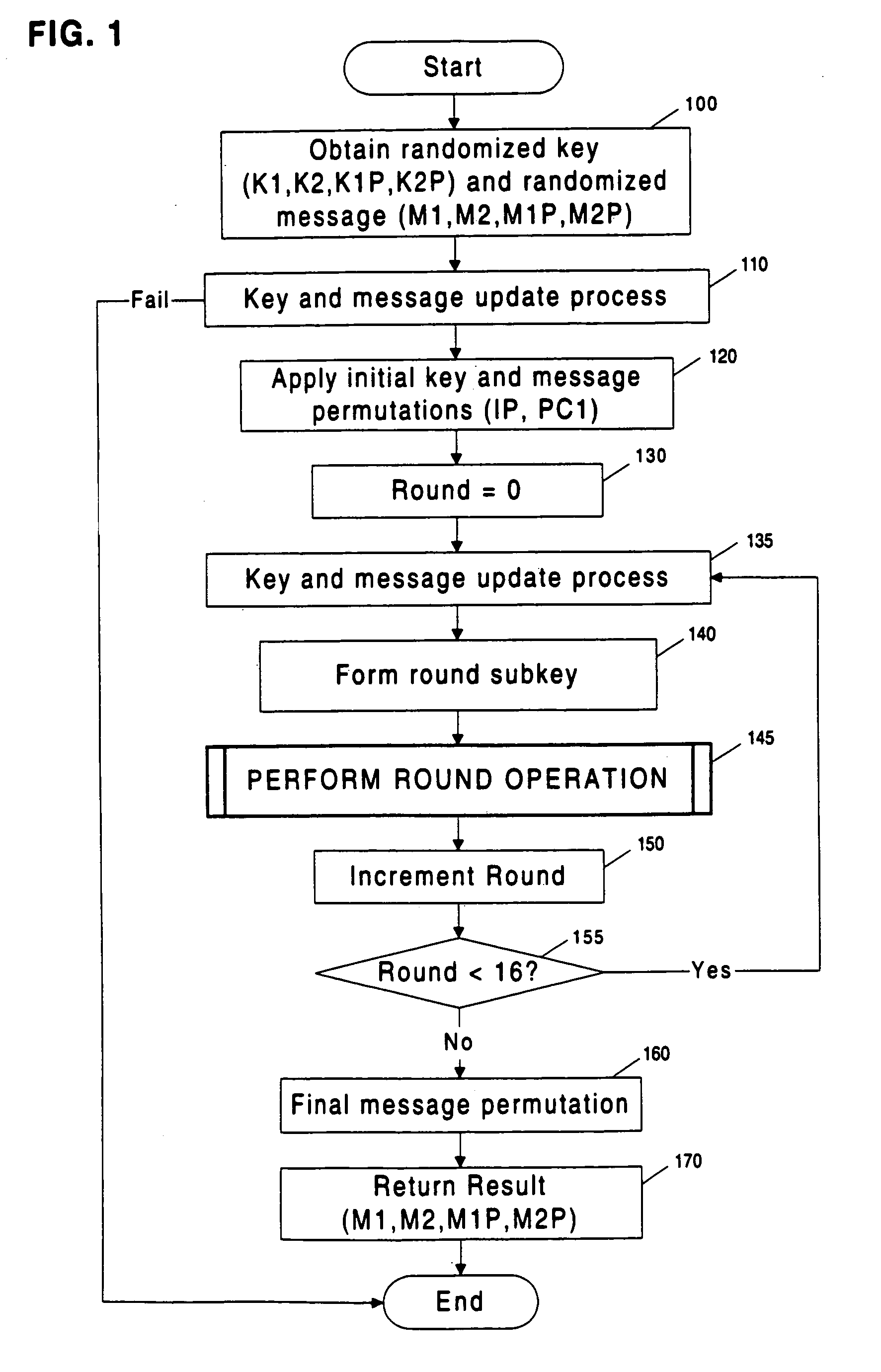
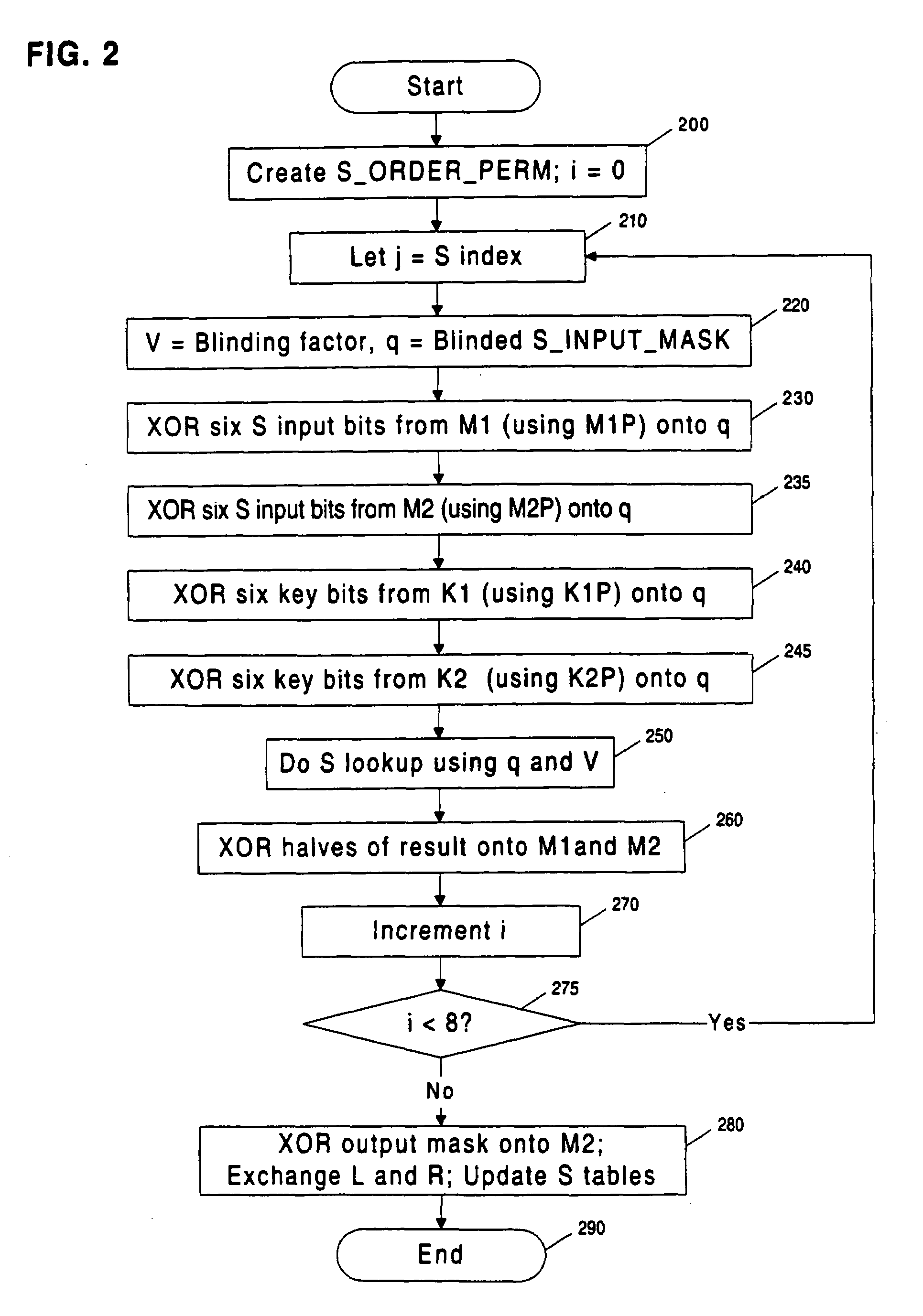
Methods and apparatuses are disclosed for improving DES and other cryptographic protocols against external monitoring attacks by reducing the amount (and signal-to-noise ratio) of useful information leaked during processing. An improved DES implementation of the invention instead uses two 56-bit keys (K1 and K2) and two 64-bit plaintext messages (M1 and M2), each associated with a permutation (i.e., K1P, K2P and M1P, M2P) such that K1P{K1} XOR K2P {K2} equals the “standard” DES key K, and M1P{M1} XOR M2P{M2} equals the “standard” message. During operation of the device, the tables are preferably periodically updated, by introducing fresh entropy into the tables faster than information leaks out, so that attackers will not be able to obtain the table contents by analysis of measurements. The technique is implementable in cryptographic smartcards, tamper resistant chips, and secure processing systems of all kinds.
Owner:CRYPTOGRAPHY RESEARCH
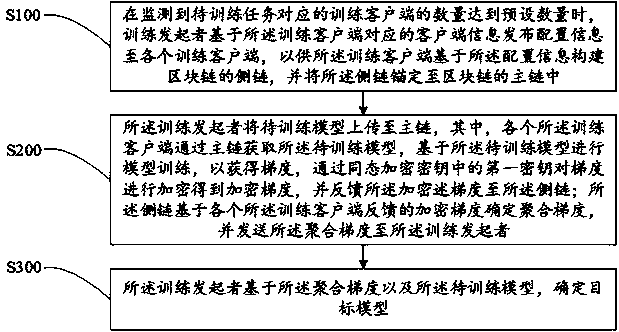
Federated modeling method, device and equipment based on block chain, and storage medium
ActiveCN111552986AAccuracy has no effectAccuracy impactDigital data protectionNeural architecturesModelSimPrivacy protection
The invention discloses a federated modeling method, device and equipment based on a block chain, and a storage medium. The method comprises the following steps: a training initiator issues configuration information to all training clients based on client information corresponding to the training clients when the number of the training clients is monitored to reach a preset number; the training initiator uploads a to-be-trained model to a main chain; and the training initiator determines a target model based on aggregation gradient and the to-be-trained model. Modeling of federated learning isrealized through the block chain; on the premise of protecting the privacy of federated learning data, the accuracy of federated learning is not affected, the training effect and model precision of federated learning are improved, model parameters such as gradients in transmission do not need to be modified, and the balance between privacy protection of the model parameters such as gradients andmodel convergence or model precision is achieved; and information leakage can be completely prevented, so the safety of data samples in federated learning is improved.
Owner:PENG CHENG LAB +1
Two-dimensional barcode-based logistics industry personal information privacy protection system and method
InactiveCN103401676ATroubleshoot access rights assignmentsPrevent leakageLogisticsSecuring communicationProtection systemInformation privacy
The invention discloses a two-dimensional barcode-based logistics industry personal information privacy protection system. The system comprises a key distribution and management system, a database, a first PC (Personal Computer) side logistic management system, a first two-dimensional barcode generation and reading module, a first two-dimensional barcode reading module, a first mobile phone delivery terminal, a first mobile phone number hiding module, a third PC side logistic management system, a third two-dimensional barcode generation and reading module, a third two-dimensional barcode reading module, a third mobile phone delivery terminal and a third mobile phone number hiding module, wherein the first PC side logistic management system is positioned at a letter sending site; and the third PC side logistic management system is positioned at a receiving site. According to the two-dimensional barcode-based logistic personal information privacy protection scheme design, the two-dimensional barcode technology and an encryption technology are applied to the logistics industry to try to solve the problem of personal information leakage. The functions such as two-dimensional barcode generation and reading, sensitive information encryption protection, and key distribution and management are realized, and the problem of privacy information leakage is solved better.
Owner:NAVAL UNIV OF ENG PLA
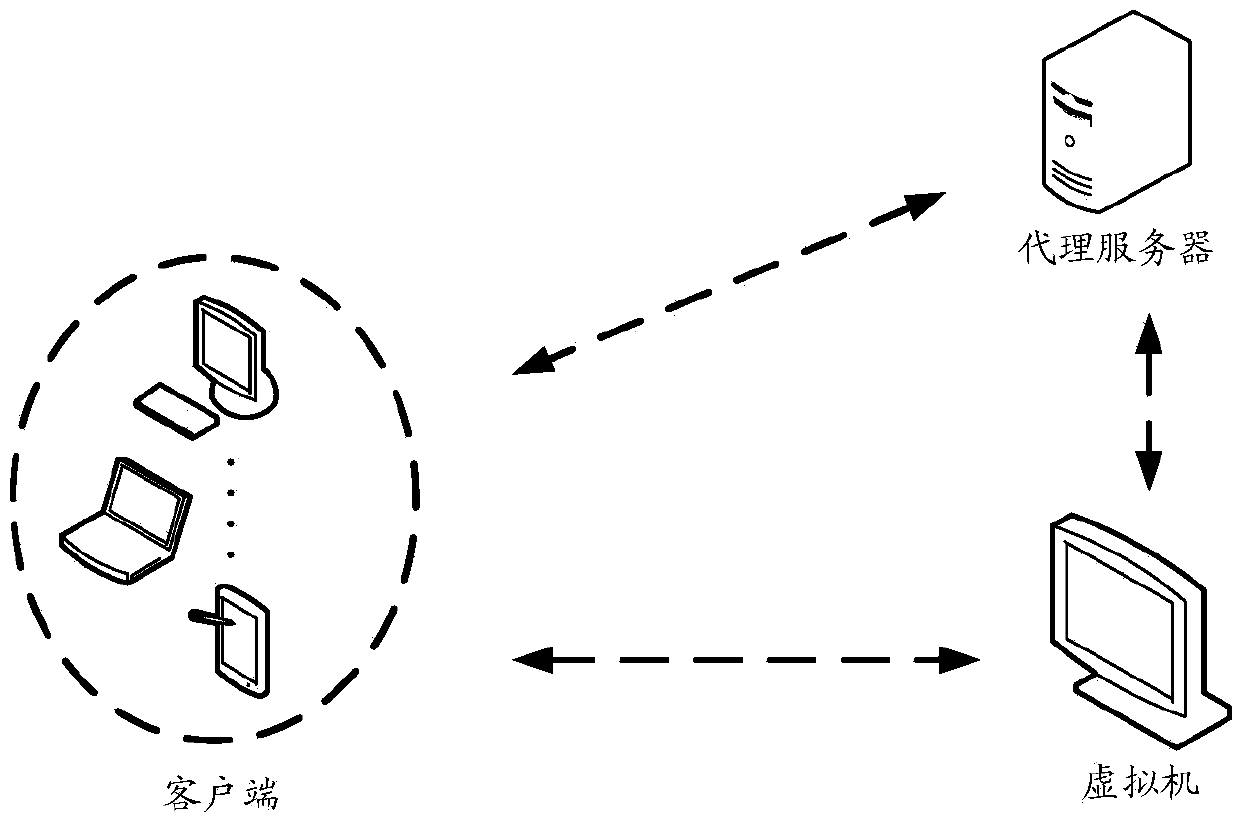
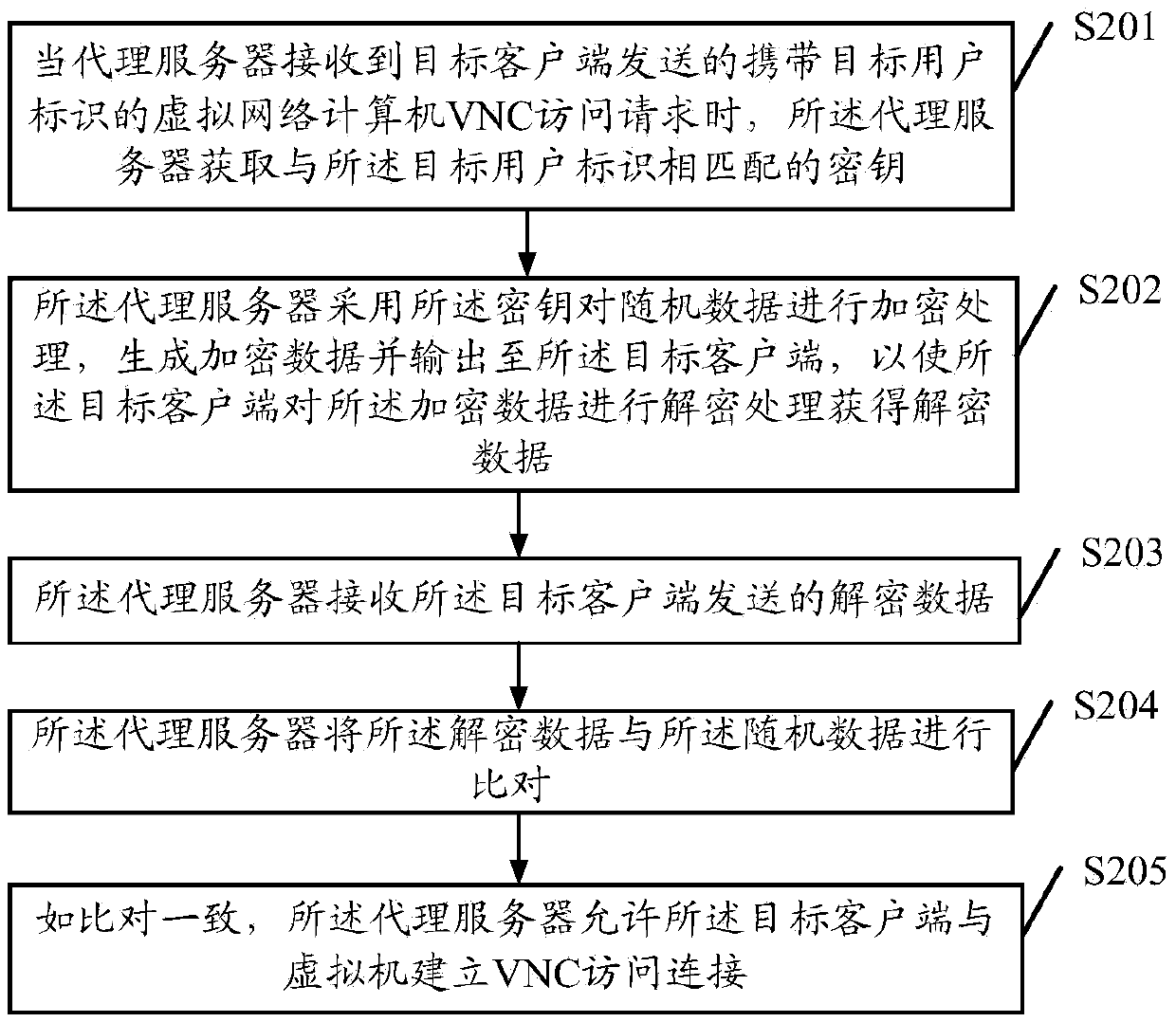
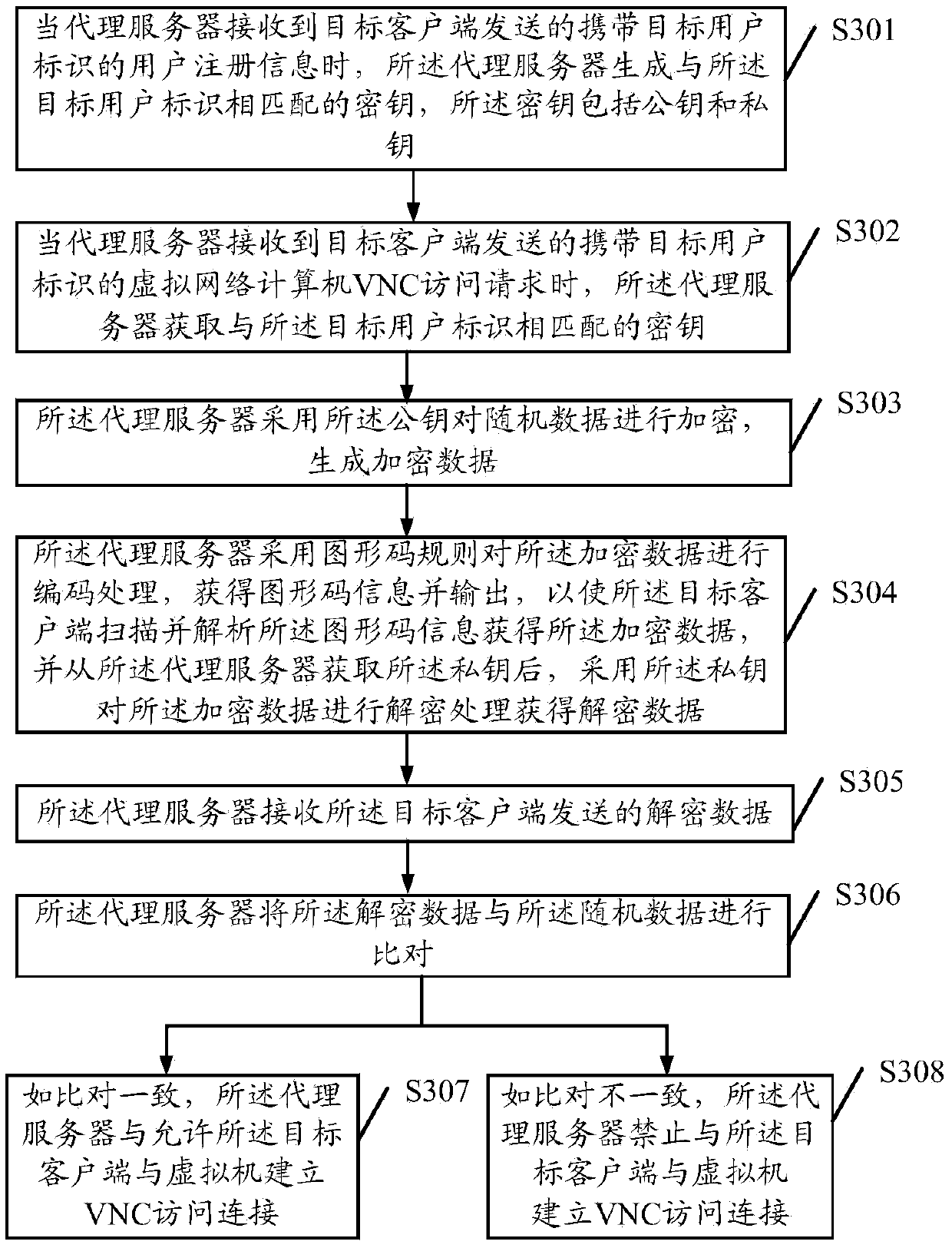
Remote access method, agent server and client end
The embodiments of the invention disclose a remote access method, an agent server and a client end, wherein the method comprises the steps that: when the agent server receives a virtual network computer VNC access request carrying a target user identifier; and sent by a target client end, the agent server obtains a secret key matched with the target user identifier; the secret key is utilized for carrying out encryption processing on random data, and encrypted data is generated and output to the target client end so as to enable the target client end to carry out decryption processing on the encrypted data and obtain decrypted data; the encrypted data sent by the target client end is received; the encrypted data is compared with the random data; and if the encrypted data is consistent with the random data, the target client end is allowed to establish a VNC access connection with a virtual machine. According to the embodiments of the invention, invalid VNC access caused by information leakage is voided, the information leakage risk is reduced, and the safety of the VNC access is improved.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com