Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
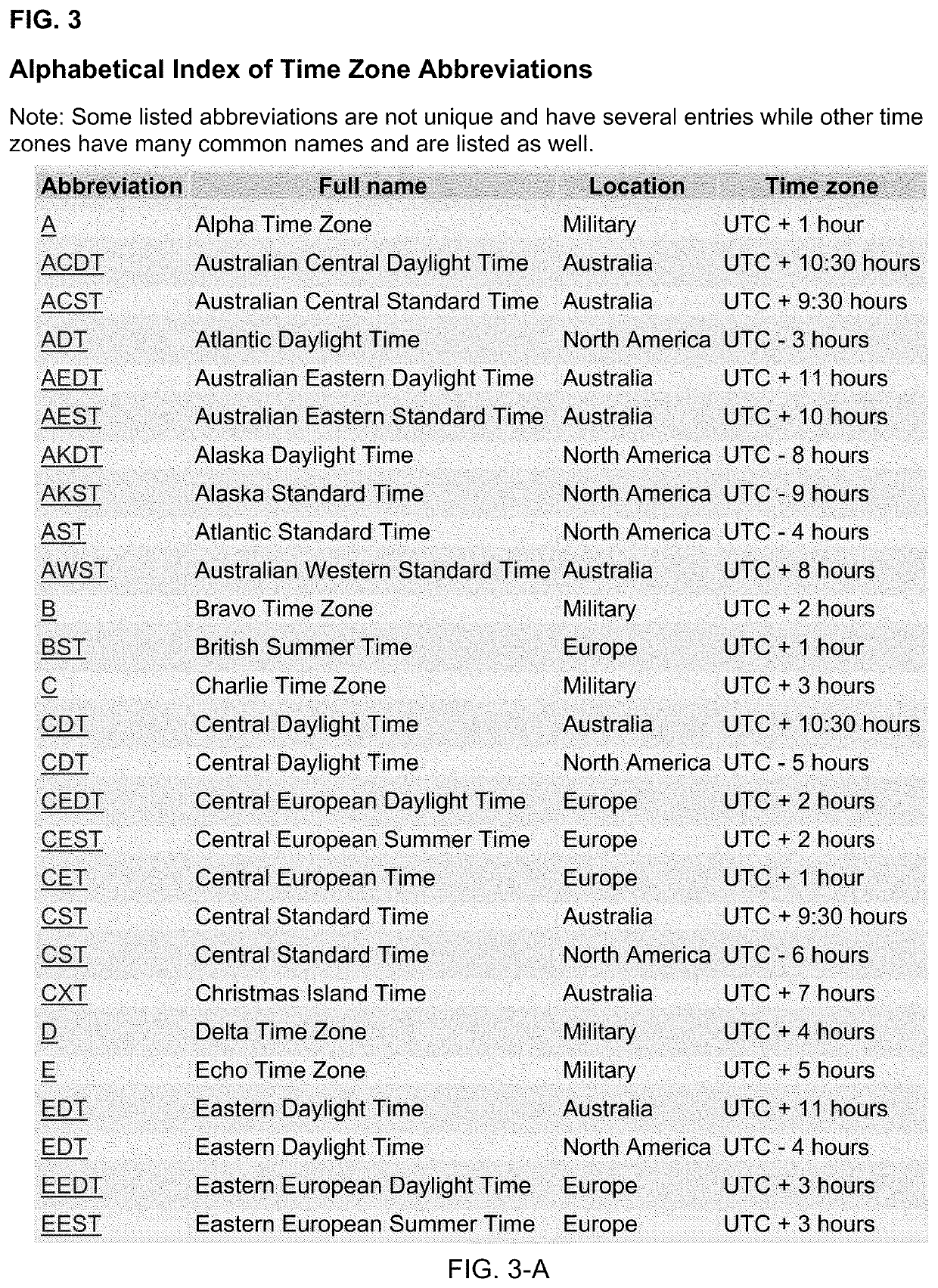
55 results about "Internet fraud" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Internet fraud is a type of fraud or deception which makes use of the Internet and could involve hiding of information or providing incorrect information for the purpose of tricking victims out of money, property, and inheritance. Internet fraud is not considered a single, distinctive crime but covers a range of illegal and illicit actions that are committed in cyberspace. It is, however, differentiated from theft since, in this case, the victim voluntarily and knowingly provides the information, money or property to the perpetrator. It is also distinguished by the way it involves temporally and spatially separated offenders.
Method and System for Identifying Users and Detecting Fraud by Use of the Internet
ActiveUS20110082768A1Accurate trackingAccurately and efficiently qualityTransmissionCommerceComputer usersInternet fraud
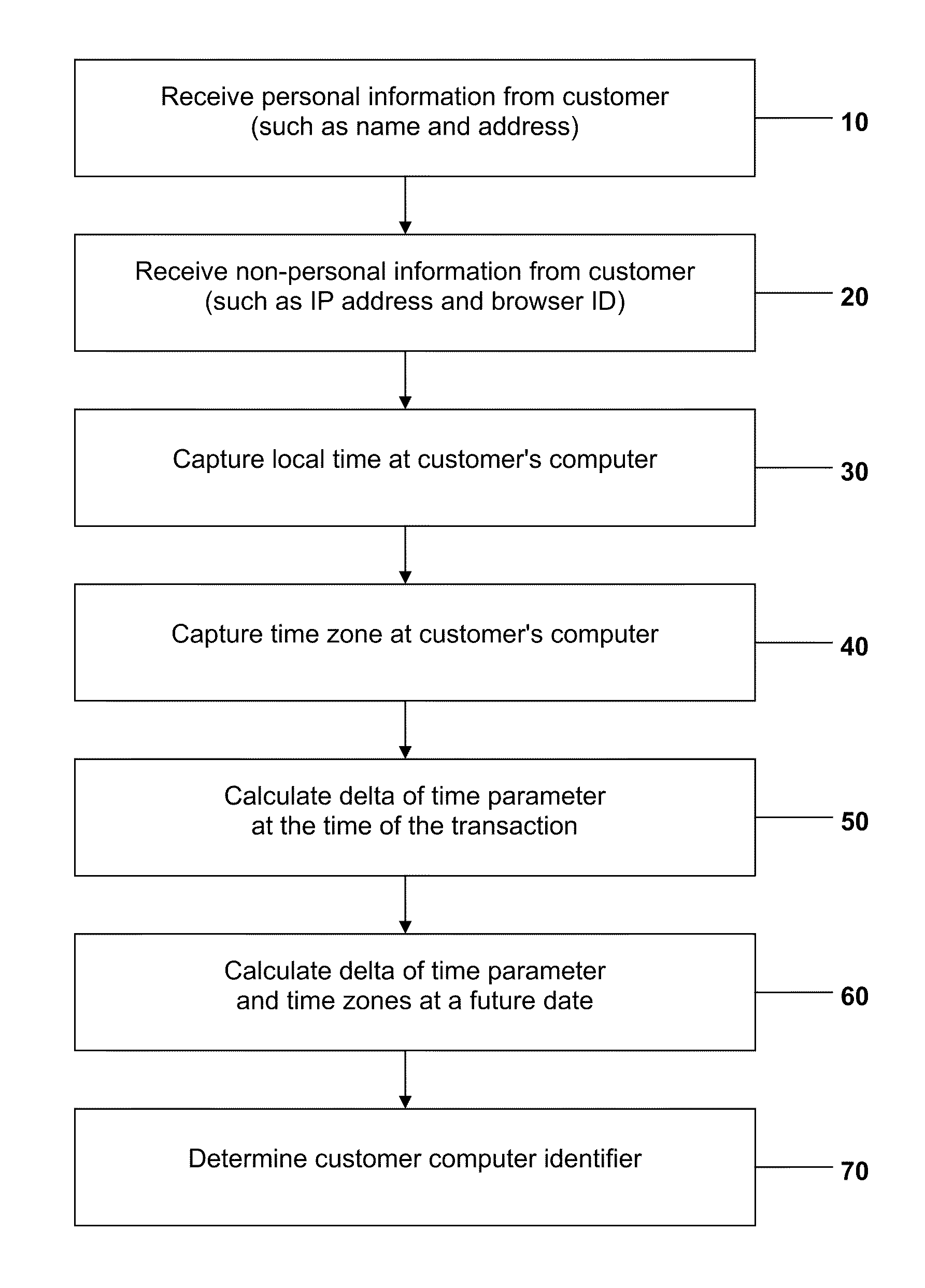
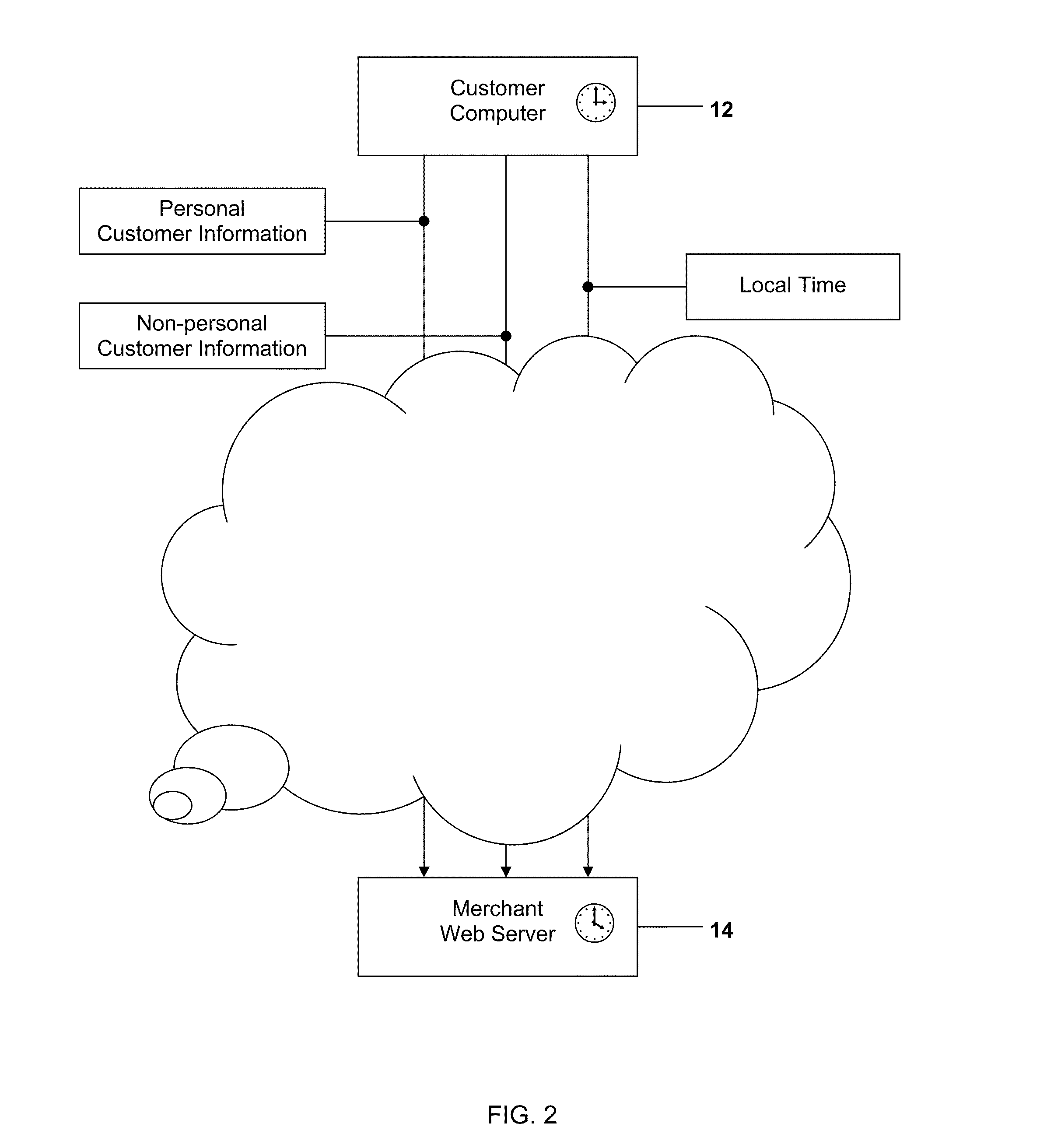
A method and system for detecting and preventing Internet fraud in online transactions by utilizing and analyzing a number of parameters to uniquely identify a computer user and potential fraudulent transaction through predictive modeling. The method and system uses a delta of time between the clock of the computer used by the actual fraudulent use and the potentially fraudulent user and the clock of the server computer in conjunction with personal information and / or non-personal information, preferably the Browser ID.
Owner:THE 41ST PARAMETER
Block chain technology-based network digital identity authentication method
InactiveCN107181765AShorten confirmation timeAvoid the possibility of trending towards exclusive verificationUser identity/authority verificationDigital data protectionDigital identityInternet fraud
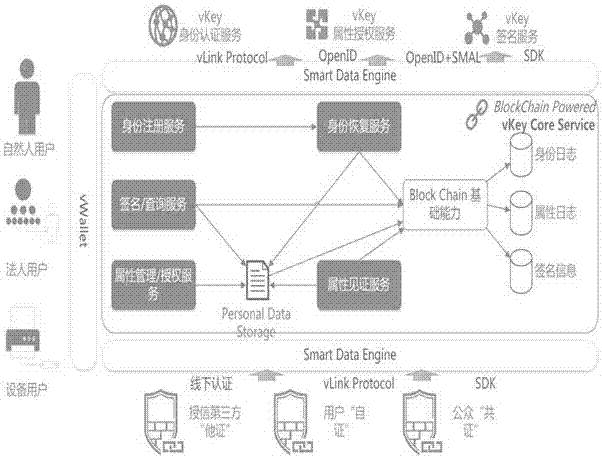
The present invention provides a block chain technology-based network digital identity authentication method. The method comprises the steps of 1) user registration: conducting the identity authentication service based on the vLink protocol, uploading a block chain if the identity of a user is legal, broadcasting the information of the user to the whole network by the block chain, and adding the information of the user into a corresponding block at each node, wherein blocks are mutually verified; 2) obtaining the information of the user, searching the information of the user through the vKey attribute authorization service, returning the user name, the gender and the age information of the user and returning a particular opened at the same time for distinguishing different users; 3) subjecting data to signature treatment during the digital identity authentication process based on the above block chain technology. According to the technical scheme of the invention, the personal data of a user are stored in a block chain, so that the occurrence of information leakage and internet fraud behaviors is radically avoided. The data security is ensured. During the data transmission process, the digital signature treatment is adopted. Therefore, the sensitive information is not tampered during the digital signature transmission process.
Owner:兰考同心互联数据管理有限公司
Method and system for identifying users and detecting fraud by use of the internet
ActiveUS7853533B2Accurate trackingAccurately and efficiently qualityRegistering/indicating working of machinesElectric unknown time interval measurementComputer usersInternet privacy
Owner:THE 41ST PARAMETER
Method and system for identifying users and detecting fraud by use of the internet
InactiveUS8862514B2Accurate trackingAccurately and efficiently qualityFinanceInternal/peripheral component protectionComputer usersInternet fraud
A method and system for detecting and preventing Internet fraud in online transactions by utilizing and analyzing a number of parameters to uniquely identify a computer user and potential fraudulent transaction through predictive modeling. The method and system uses a delta of time between the clock of the computer used by the actual fraudulent use and the potentially fraudulent user and the clock of the server computer in conjunction with personal information and / or non-personal information, preferably the Browser ID.
Owner:THE 41ST PARAMETER
Method and system for identifying users and detecting fraud by use of the internet
ActiveUS20090037213A1Accurate trackingAccurately and efficiently qualityInternal/peripheral component protectionPayment circuitsComputer usersInternet fraud
A method and system for detecting and preventing Internet fraud in online transactions by utilizing and analyzing a number of parameters to uniquely identify a computer user and potential fraudulent transaction through predictive modeling. The method and system uses a delta of time between the clock of the computer used by the actual fraudulent use and the potentially fraudulent user and the clock of the server computer in conjunction with personal information and / or non-personal information, preferably the Browser ID.
Owner:THE 41ST PARAMETER
Method and system for identifying users and detecting fraud by use of the internet
ActiveUS10999298B2Accurate trackingAccurately and efficiently qualityBuying/selling/leasing transactionsTransmissionPredictive modellingComputer users
A method and system for detecting and preventing Internet fraud in online transactions by utilizing and analyzing a number of parameters to uniquely identify a computer user and potential fraudulent transaction through predictive modeling. The method and system uses a delta of time between the clock of the computer used by the actual fraudulent use and the potentially fraudulent user and the clock of the server computer in conjunction with personal information and / or non-personal information, preferably the Browser ID.
Owner:THE 41ST PARAMETER
Method and system for recognizing internet fraud behavior
ActiveCN106453061AAccurate identificationQuick identificationData switching networksSpecial data processing applicationsInternet fraudData access layer
The invention discloses a method and a system for recognizing internet fraud behaviors. The method comprises the following steps: acquiring internet behavior information of a target object through a data access layer; recognizing a fraud behavior track related to fraud in the internet behavior information through a data preprocessing layer; integrating the fraud behavior track through a fraud prevention resource layer so as to obtain a fraud behavior integral value; determining whether the integral value exceeds a preset threshold or not through a service application layer, if the integral value exceeds the preset threshold, confirming that the target object has fraud behaviors. By adopting the method which is provided by the embodiment of the invention and is used for recognizing internet fraud behaviors, internet fraud behaviors can be accurately and rapidly recognized, and convenience can be brought to police departments to alarm and prevent internet fraud in advance.
Owner:RUN TECH CO LTD BEIJING
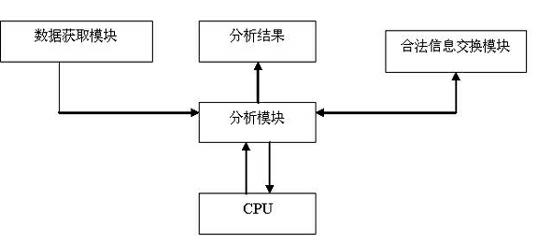
System and method for monitoring real data of website
InactiveCN102136973AGuarantee the legal right to knowComprehensive supervisionPlatform integrity maintainanceData switching networksInternet fraudInternet users
The invention discloses a system and a method for monitoring the real data of a website. The system at least comprises a data acquisition module, an authoritative information exchange module, an analysis module and a central processing unit (CPU), wherein the CPU is connected with the analysis module; the analysis module is connected with the data acquisition module and the authoritative information exchange module respectively; the data acquisition module and the authoritative information exchange module acquire the data of a browsed website or web page and the data published by an official or authoritative website or a database, and transmit the data to the analysis module; and the analysis module analyzes and compares the data to confirm the authenticity and legality of the browsed website or web page. By the system and the method, a reliable evaluation system is provided for Internet users to avoid the harms of fraudulent websites or web pages to the users; and questionable websites or web pages can be complained or reported to related supervision and control departments, and evaluation can be provided for a credit rating mechanism to suppress Internet fraud and illegal operations and safeguard lawful operations as well as customer rights.
Owner:乔永清
Fraud gang identification method based on network flow, controller and medium
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
Network fraud detection method and device thereof, electronic equipment and storage medium
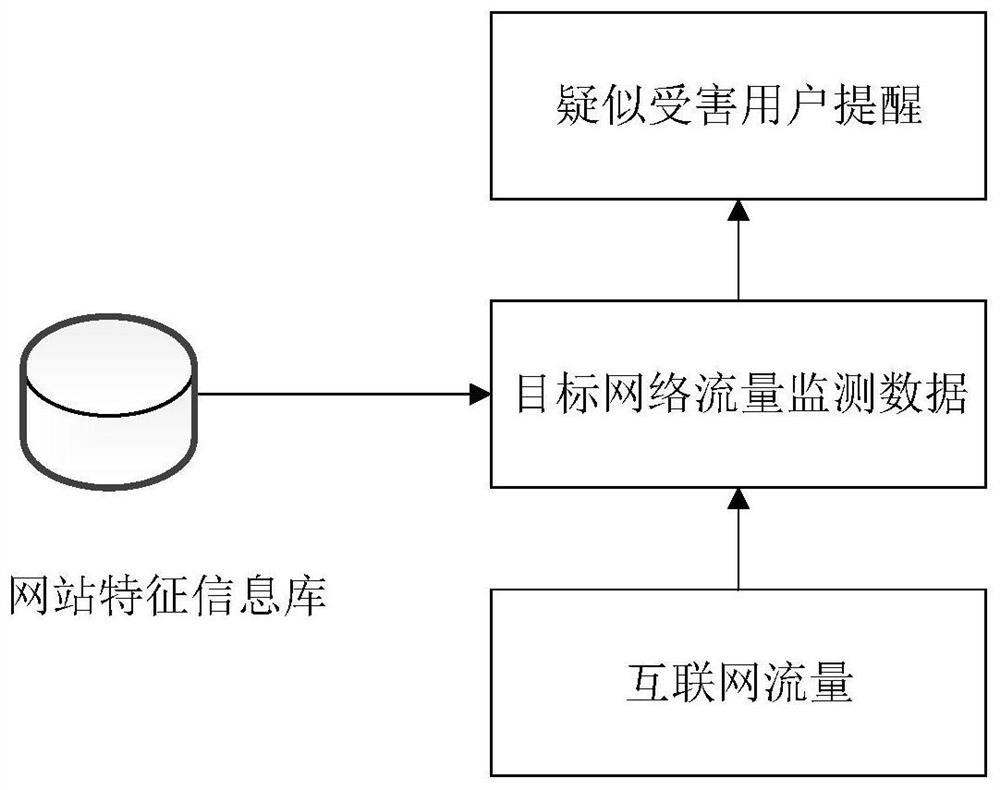
ActiveCN113098870ATroubleshoot technology identification issuesRealize pre-identificationData processing applicationsDatabase queryingWeb siteInformation repository
The invention discloses a network fraud detection method and a device thereof, electronic equipment and a storage medium. The method comprises the following steps: acquiring historical network interaction data of a victim in the case process in a target network fraud case, wherein the target network fraud case is a long-time multi-online interaction type fraud case; performing feature extraction on the historical network interaction data of each target network fraud case to form a website feature information base matched with at least one historical fraud website; acquiring network access data of at least one monitoring user in the monitoring time interval; and comparing the network access data with a website feature information base, and detecting suspected victim users whose number of times of accessing suspected fraud websites in a monitoring time interval exceeds a set threshold value; wherein the website feature information of the suspected fraud website and the website feature information of the historical fraud website meet preset similar conditions. According to the method, fraud cases can be identified in advance, so that the occurrence probability of the fraud cases is reduced.
Owner:EVERSEC BEIJING TECH
Method, device and equipment for carrying out early warning on abnormal webpage and/or APP
InactiveCN113067820AReduce sources of fraudTransmissionSecurity arrangementDomain nameComputer network
The invention discloses a method, device and equipment for carrying out early warning on abnormal webpages and / or APPs, and the method comprises the steps: obtaining a large amount of network fraud case data, generating fraud network features corresponding to network fraud according to the network fraud case data, and storing the fraud network features; regularly acquiring network features of the webpage and / or the APP; analyzing and comparing the network characteristics with pre-stored fraud network characteristics, and judging whether the webpage and / or the APP has a fraud risk or not; if it is detected that the fraud risk exists in the webpage and / or the APP, executing early warning operation. According to the embodiment of the invention, newly-registered domain names, distributed APPs and other resources can be collected from the Internet, feature comparison is carried out through report information, known fraud information and the like, potential high-risk sources are found in time, and related units are helped to carry out monitoring, early warning and blocking in time; and through mass data analysis, fraud sources can be effectively reduced, and property damage of common people can be reduced.
Owner:SHENZHEN ANLUO TECH CO LTD
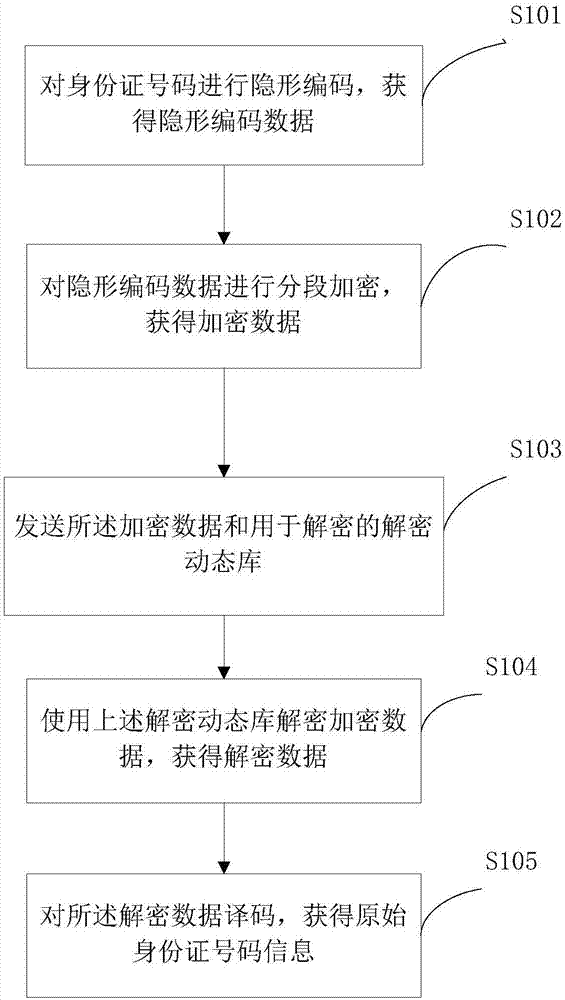
Identity card information transmission protection method and system
ActiveCN107172436AOpportunities decreaseReduce personalKey distribution for secure communicationDigital video signal modificationComputer hardwareInformation transmission
The invention provides an identity card information transmission protection method and system. The method comprises the following steps of S1, carrying out invisible coding on an identity card number, thereby obtaining invisibly coded data; S2, carrying out segmental encryption on the invisibly coded data, thereby obtaining encrypted data; S3, sending the encrypted data and a decryption dynamic library for decryption; S4, decrypting the encrypted data through utilization of the decryption dynamic library, thereby obtaining decrypted data; and S5, decoding the decrypted data, thereby obtaining original identity card number information. Through application of the method and the system, the lost identity card number can be encrypted and transmitted to various departments such as a financial institution, industrial and commercial registration, education, insurance and telecom; a lawbreaker can be effectively prevented from carrying out financial fraud, internet fraud and telephone fraud through utilization of an identity card of others; chances for a criminal to exploit are objectively reduced; and personal and social losses are reduced.
Owner:BEIJING GZT NETWORK TECH
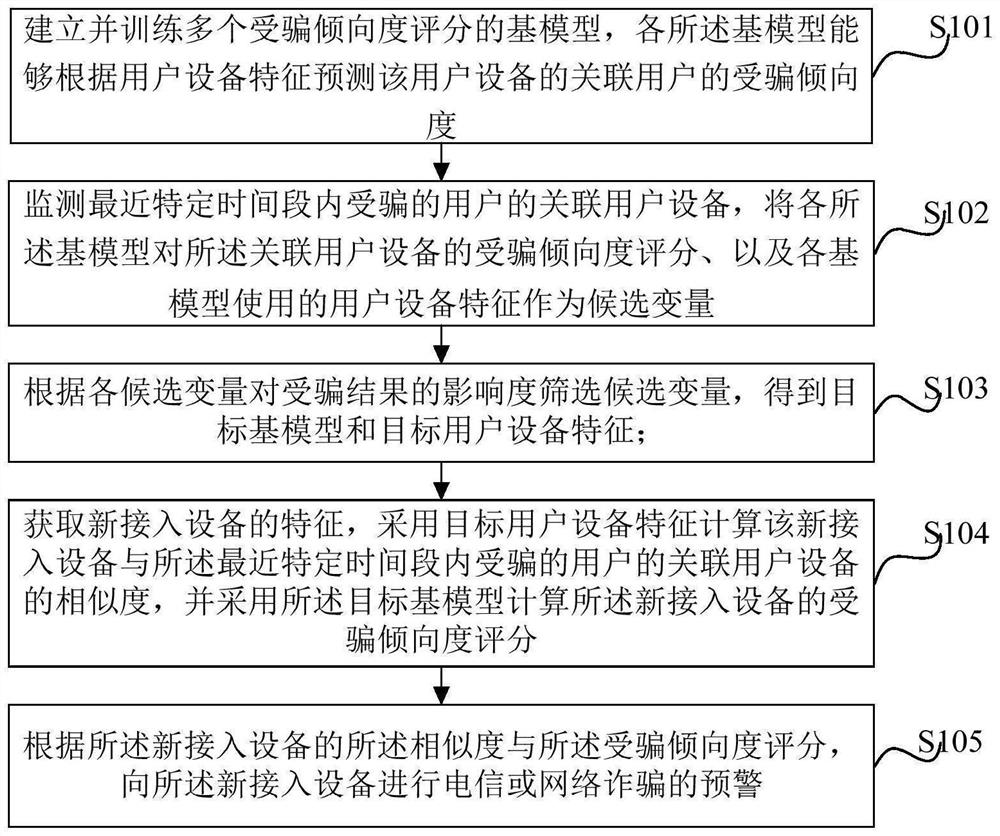
Early warning method and device for network fraud, and computer equipment
PendingCN113627566AEarly warning and accurate judgmentImprove classification accuracyCharacter and pattern recognitionNeural architecturesInternet fraudEngineering
The invention provides an early warning method and device for network fraud, and computer equipment. The method comprises the following steps: establishing and training a plurality of base models for cheating tendency score, wherein each base model is used for predicting the cheating tendency of an associated user of user equipment; monitoring associated user equipment of a deceived user in a recent specific time period, and determining candidate variables; screening the candidate variables according to the influence degree of each candidate variable on the deceived result to obtain a target base model and target user equipment characteristics; obtaining features of a new access device, and carrying out similarity and cheating tendency score calculation; and carrying out early warning of telecommunication or network fraud according to the similarity of the new access equipment and the deceiving tendency score. Compared with the prior art, whether telecommunication or network fraud early warning is carried out on the new access equipment or not can be accurately judged, and a user can be reminded in advance to avoid telecommunication or network fraud.
Owner:SHANGHAI QIYUE INFORMATION TECH CO LTD
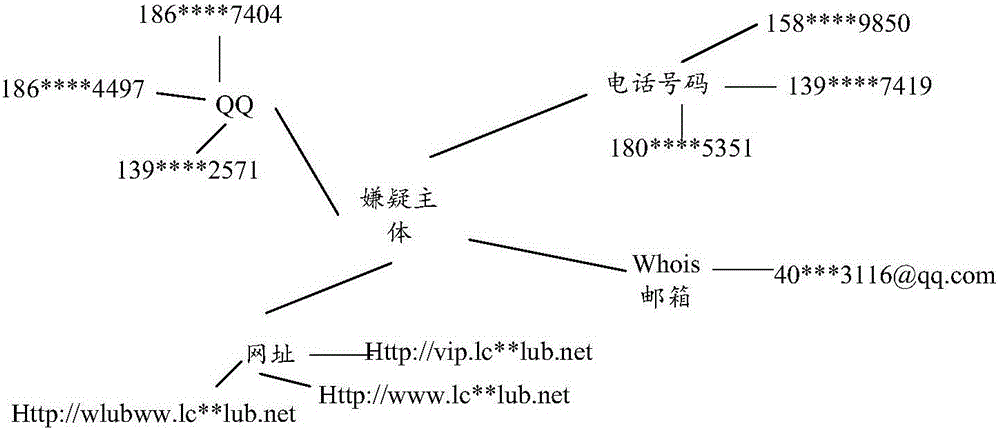
Method and device for processing information
ActiveCN106157215AQuick fixImprove case handling efficiencyData processing applicationsInternet fraudData mining
The invention discloses a method and a device for processing information, relates to the technical field of Internet, and aims to solve a problem that the efficiency, of the conventional network security department, in determining the identity of a suspect subject is low. The method provided by the invention comprises the following steps: acquiring offence reporting information reported by different users; searching for the same suspect clue information in different offence reporting information; associating the offence reporting information containing the same suspect clue information to generate a suspect information graph, wherein the suspect information graph is used for displaying all suspect clue information of the same suspect subject. The method and the device provided by the invention are applied to the process of processing network fraud information.
Owner:北京鸿享技术服务有限公司
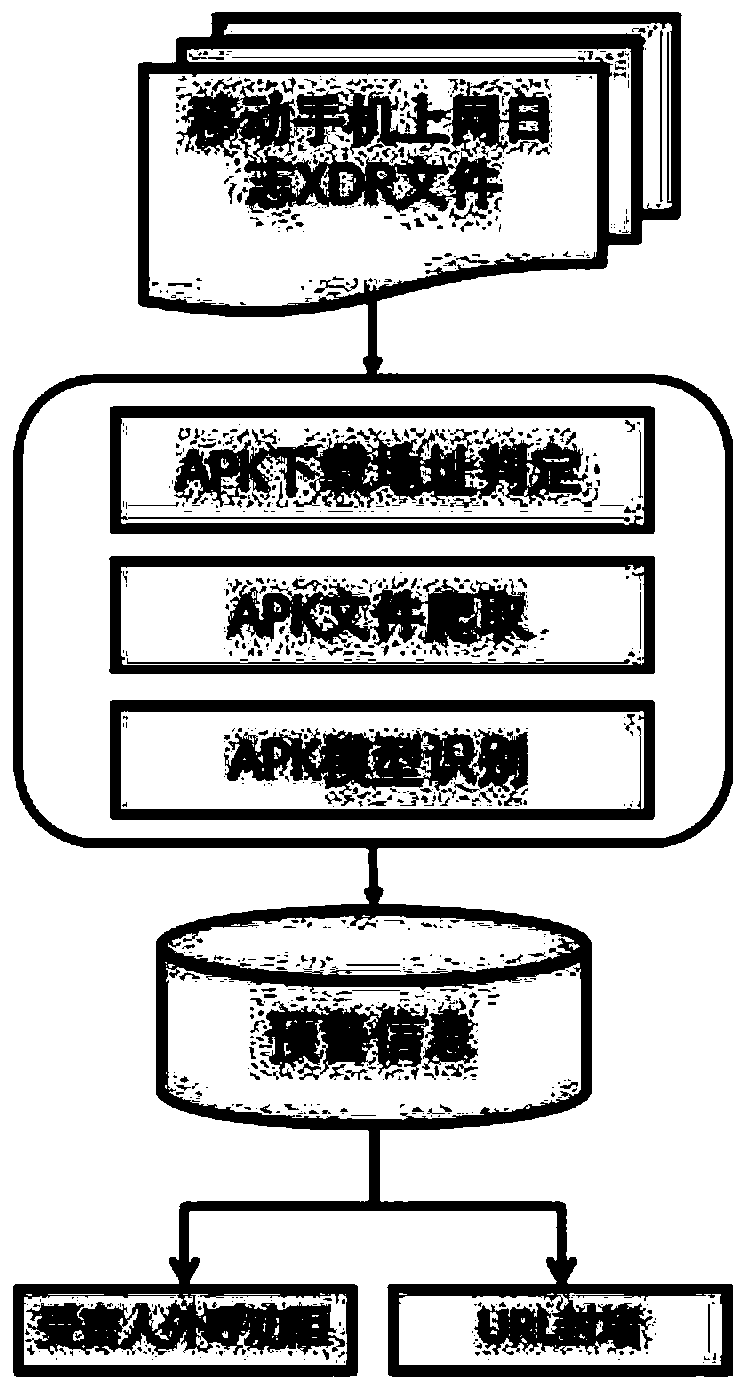
Method for identifying Internet fraud APK
The invention discloses an Internet fraud APK recognition method. The method comprises the following steps of S1, obtaining an Internet log XDR file of a mobile phone; s2, judging an APK downloading address in the XDR file, or crawling the APK file, or identifying and classifying the APK model; s3, if the APK suspected fraud APK is obtained, analyzing the victim; and S4, outputting a background URL and a victim number corresponding to the suspected fraud APK, blocking the URL and outbound persuasion of the victim, and otherwise, neglecting the URL and the victim number. According to the method, multiple technical means are used, the actual situation is combined, the user internet log XDR file is analyzed, fraud APPs are recognized from different perspectives, early warning is carried out,and the possibility of property loss of victims is reduced.
Owner:上海欣方智能系统有限公司 +1
Network fraud identification method and system based on knowledge graph
PendingCN113641827ABig amount of dataReduce crime ratesData processing applicationsNatural language data processingThird partyGraph spectra
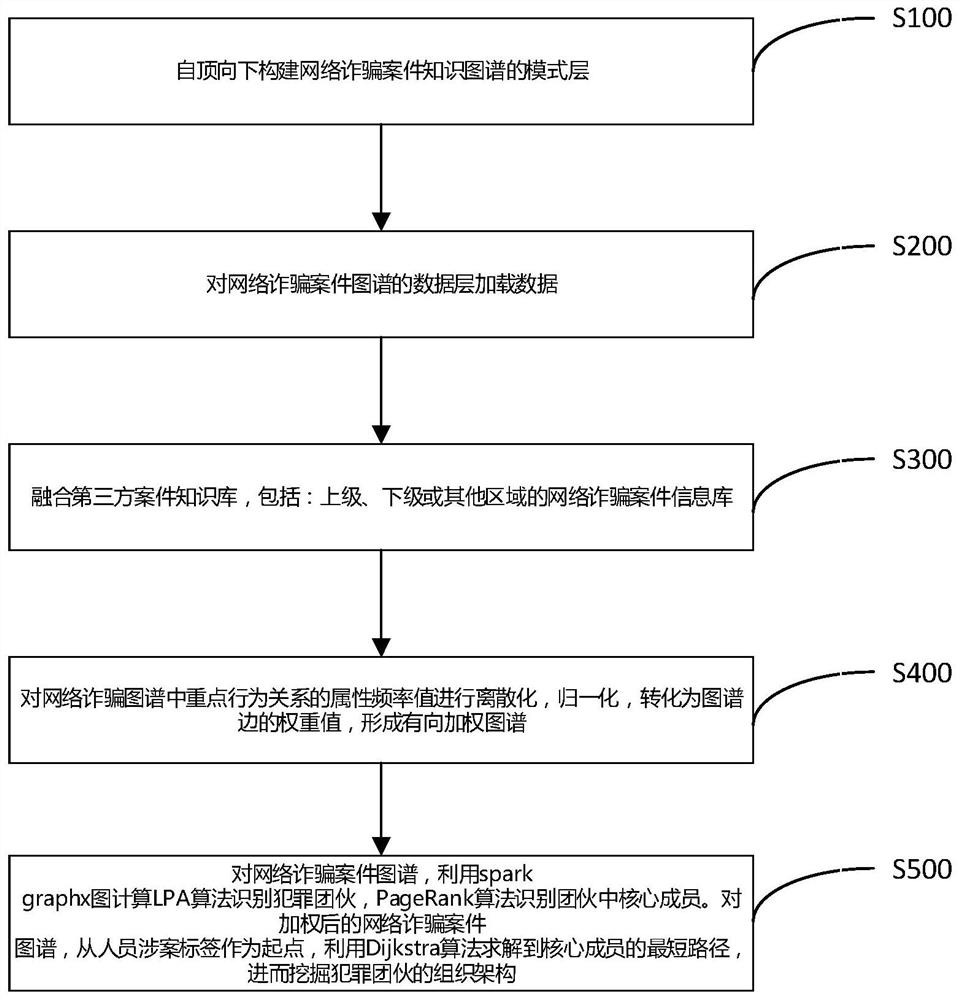
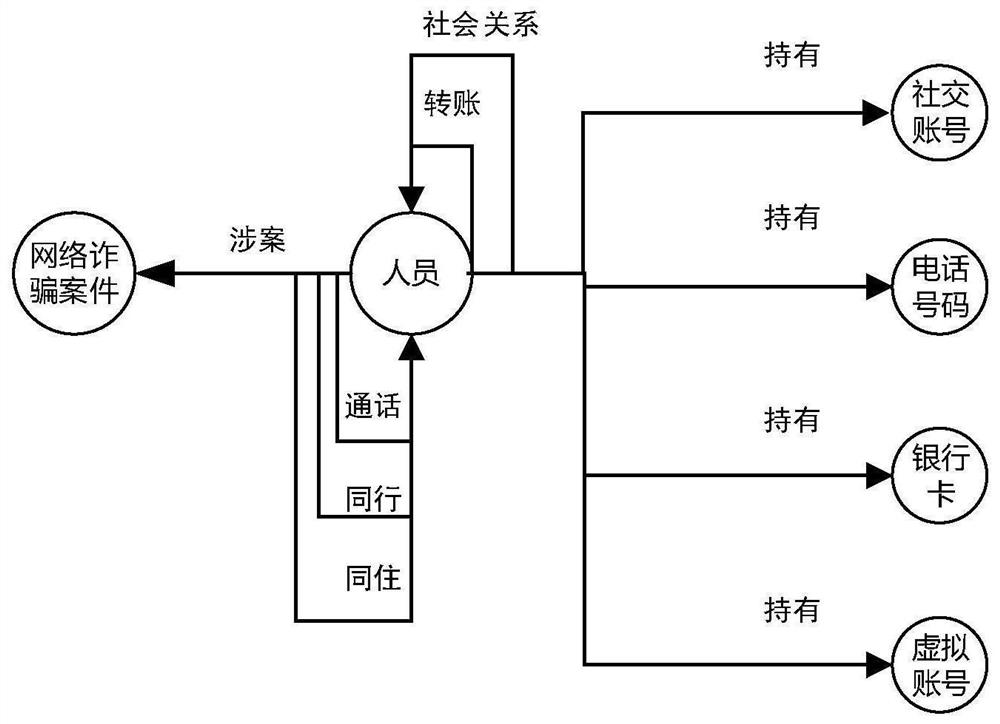
The invention belongs to the technical field of knowledge graph application, and particularly provides a network fraud identification method and system based on a knowledge graph, and the method comprises the steps: constructing a mode layer of a network fraud knowledge graph from top to bottom; loading data to the data layer of the network fraud knowledge graph; based on the constructed network fraud knowledge graph, fusing a third-party knowledge base in a data layer, and expanding the data volume of the data layer of the network fraud knowledge graph; discretizing and normalizing attribute frequency values of key behavior relationships in the network fraud knowledge graph, and converting the attribute frequency values into weight values of graph edges; and based on a network fraud case graph, by utilizing a spark graphics graph and an LPA algorithm, identifying a criminal gang, and then by utilizing a PageRank algorithm, identifying core members in the gang. The network fraud case and the criminal gang can be effectively organized through entities, relationships and attributes by using the strong relevance of the knowledge graph. The case detection efficiency is improved, and the occurrence rate of network fraud cases is reduced.
Owner:武汉众智数字技术有限公司
A detection method for network fraud information
ActiveCN109104429AReduce adverse effectsReduce lossesTransmissionSecurity arrangementInternet fraudNetwork link
The invention provides a detection method for network fraud information, comprising an information extraction server, a fraud information detection cloud platform and a communication network. When theinformation extraction server receives the information sent by the user, a network link, a telephone number or a bank account number, which may contain fraudulent content, is extracted from the network link, the telephone number or the bank account number, and the suspected fraudulent information is called, then the suspected fraudulent information is detected to determine whether the fraudulentinformation exists or not, and if so, the user is notified, otherwise the suspected fraudulent information is sent to the fraudulent information detection cloud platform. The fraud information detection cloud platform further detects the suspected fraud information to determine whether there is fraud. The fraud information detection cloud platform transmits the detected result to the information extraction server, and the information extraction server sends the result to the user. The invention can reduce adverse influence or loss caused by various network fraud information to smart phone users, personal computer users and the like, thereby providing an effective network fraud prevention mode.
Owner:GUANGDONG UNIV OF PETROCHEMICAL TECH
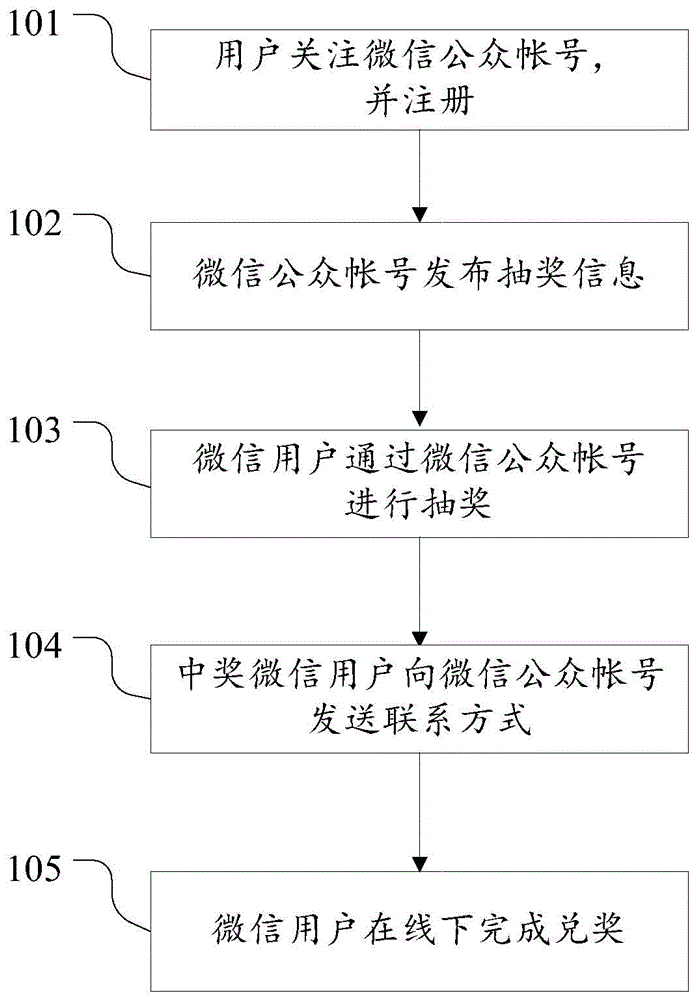
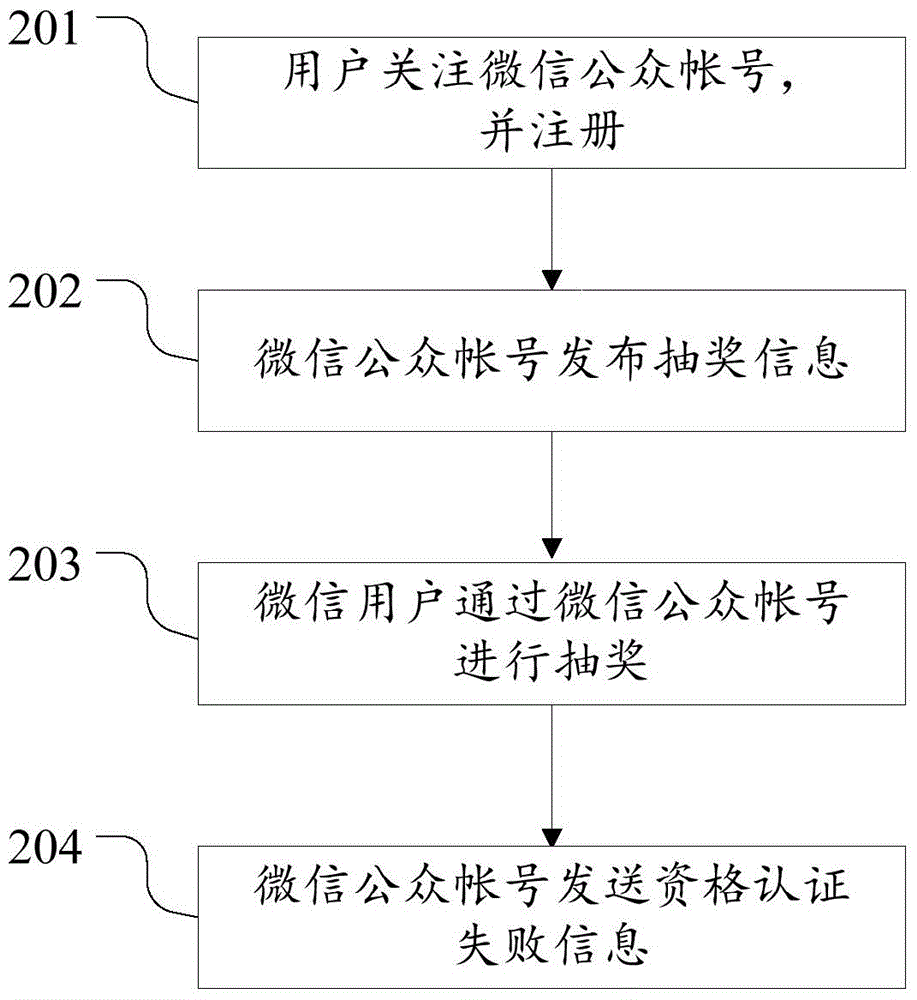
Internet lottery drawing method and system
The invention discloses an internet lottery drawing method and system. The method comprises the following steps of a WeChat user follows a WeChat public account and carries out registration; the WeChat public account posts lottery drawing activity information; the WeChat user draws a lottery through the WeChat public account; the WeChat public account sends winning information to the won WeChat user; the won WeChat user sends contact information to the WeChat public account; the WeChat user finishes getting a prize offline; a WeChat public platform is connected with a database to manage the WeChat user who participates in lottery drawing; and the WeChat public account provides an activity participating page to realize the information interaction of merchants and users. By use of the technical scheme of the invention, since an internet lottery drawing activity is carried out on the WeChat platform, the characteristics of being cheap and convenient of the internet can be performed, internet fraud and merchant fraud can be avoided, and the safety of internet lottery drawing is improved.
Owner:TVM BEIJING TECH
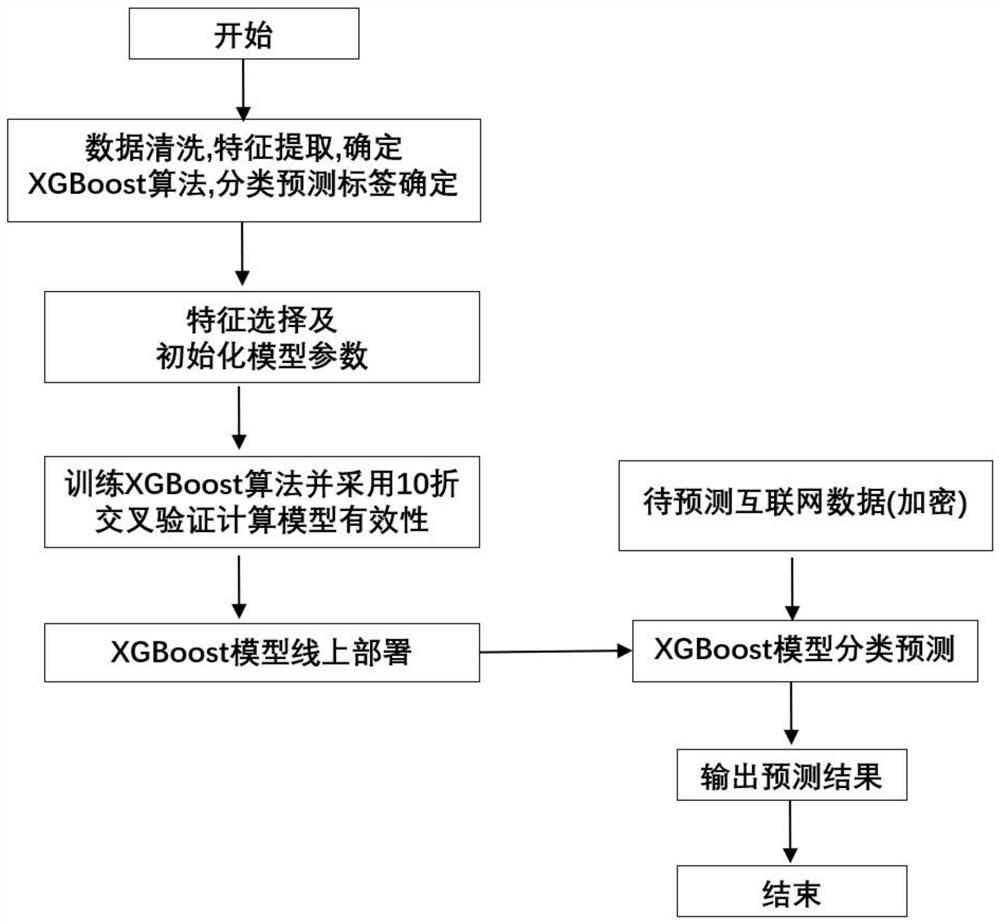
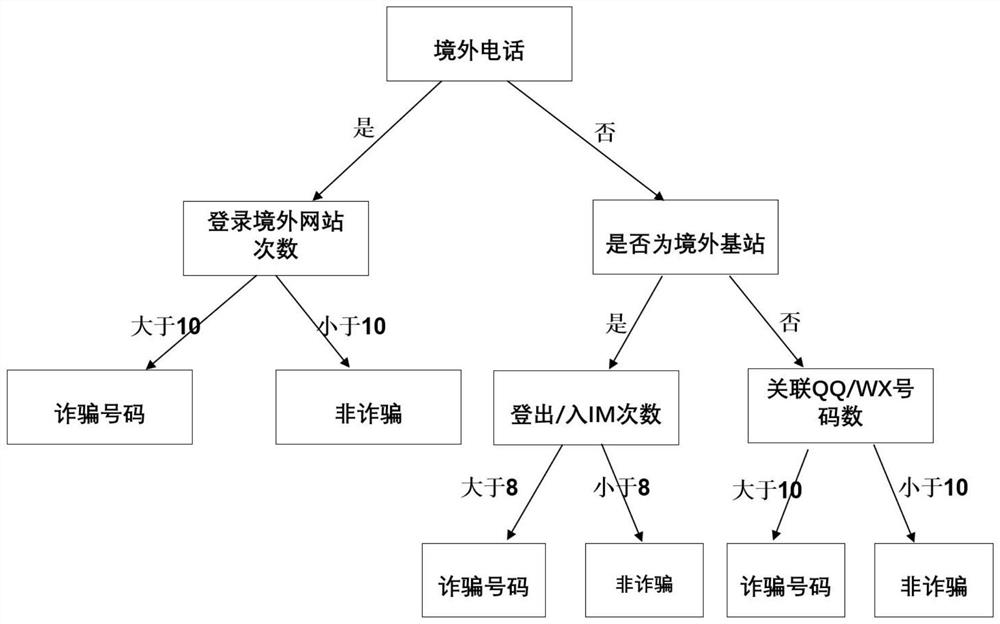
Telecommunication internet fraud identification method based on XGBoost algorithm
PendingCN112464058ASolve misjudgmentSolve case problems such as missed judgmentsEnsemble learningForecastingData setAlgorithm
The invention discloses a telecommunication Internet fraud identification method based on an XGBoost algorithm. The method comprises the following steps: carrying out encryption processing on originaltelecommunication Internet data; processing mobile phone internet surfing and position moving data, and extracting internet data internet surfing features; sampling the feature data set by adopting KMeans downsampling to form a final data set; initializing model parameters, performing verification by using the test set, calculating the accuracy, recall rate and F1 score of the model, and evaluating the model; obtaining an optimal XGBoost model, and serializing and storing the model through adoption of picks in a server; carrying out deserialization on the model by using picks, and constructing an API by using a Flask framework; and when the call record arrives, inputting the data into the XGBoost prediction model, and returning a result after model prediction. By adopting the XGBoost machine learning algorithm, telecommunication internet fraud can be accurately recognized, and the problems of misjudgment, missed judgment and other cases in the public security case judgment process areeffectively solved.
Owner:上海欣方智能系统有限公司 +1
Method, website or product capable of preventing person transferring money to remote place from being cheated
InactiveCN107292627AReduce the worry of fraudulent remittanceImprove trustCommerceInternet fraudInternet privacy
The invention relates to a method, a website or a product capable of reducing fraud for remitters to different places. Nowadays, when people buy products or services online, they are extremely afraid of being cheated by some online scammers when sending money. After the money is sent, they cannot get the products or services promised by the other party, so these problems will appear on the Internet. One of the reasons is that the remitter does not recognize the payee at all. Once the remittance is cheated, they have to report the case to the public security department, and there is not even a photo of the other party. This makes the public security department solve such cases. It is also difficult. The method, website, and product provided by the present invention can greatly help people prevent remittance fraud, and even if remittance fraud occurs, it can provide some convenience for the Ministry of Public Security to solve the case.
Owner:王国起
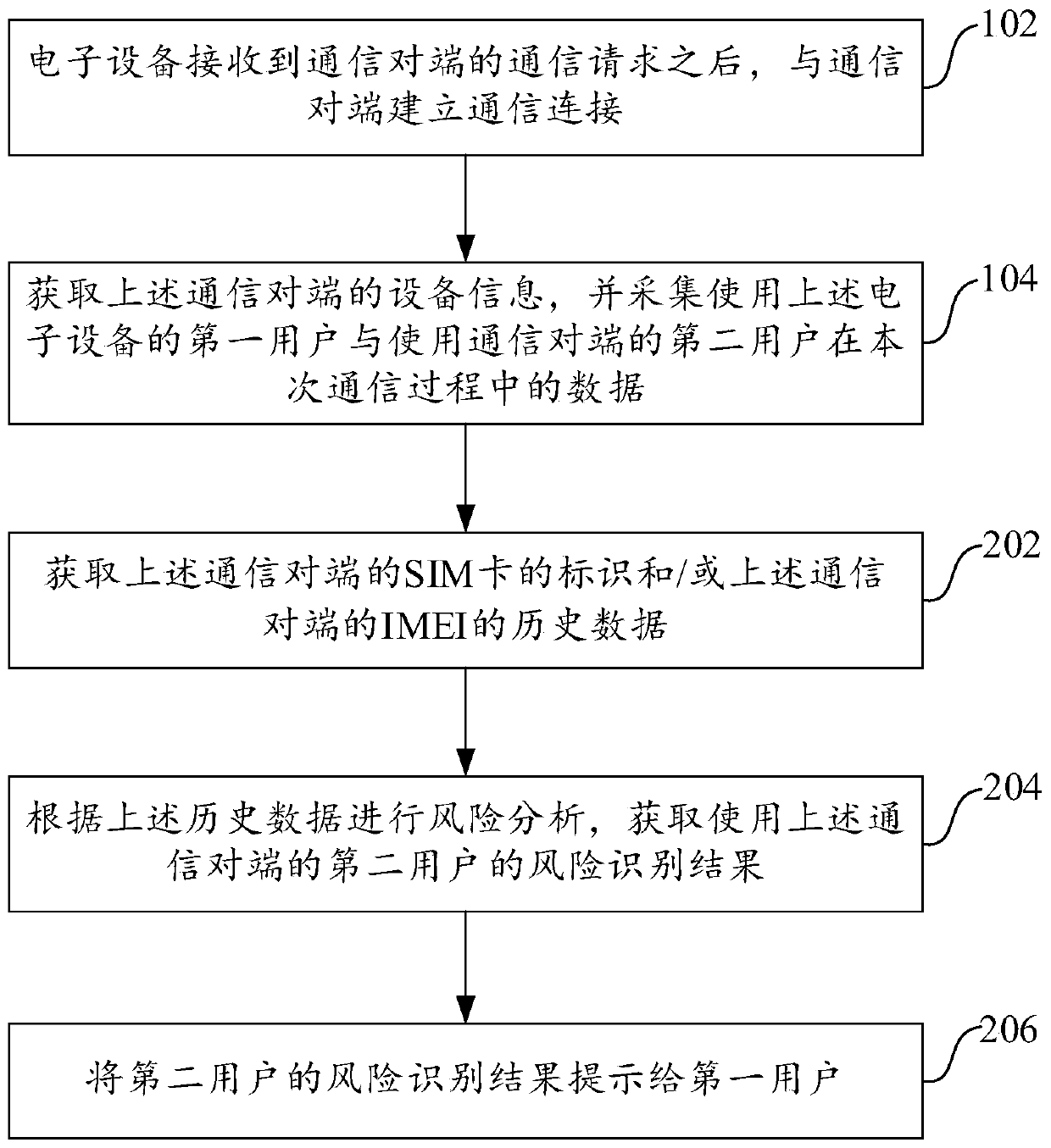
Communication network fraud identification method and apparatus, and electronic device
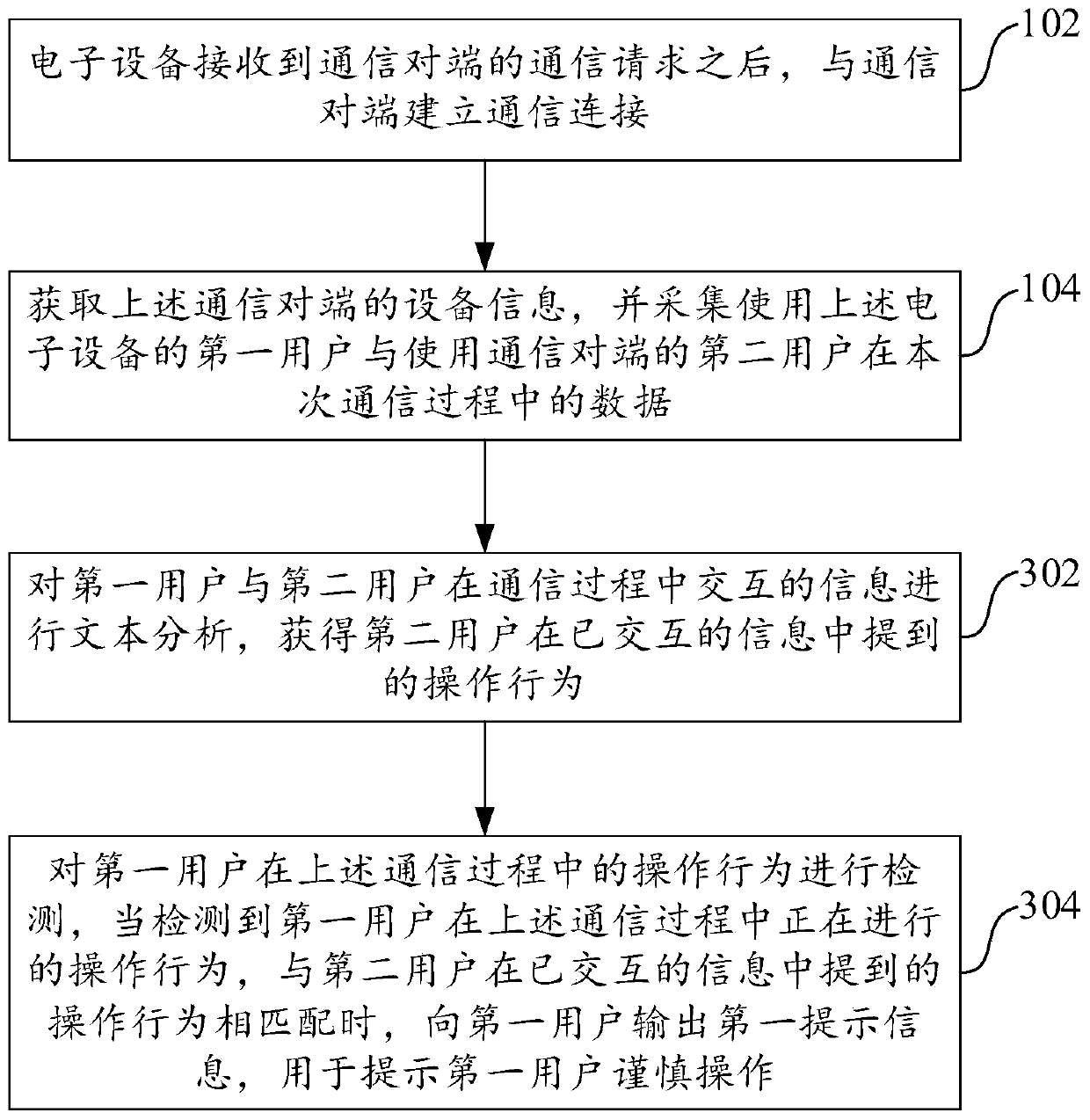
ActiveCN111601000APrevent being cheatedRealize risk management and controlSupervisory/monitoring/testing arrangementsComputer networkInternet fraud
Embodiments of the invention provide a communication network fraud identification method and apparatus, and an electronic device. The invention discloses a communication network fraud identification method. The electronic devicereceives a communication request of a communication opposite terminal, and then establishes communication connection with a communication opposite terminal; then, the electronic deviceacquires equipment information of the communication opposite terminal; thedata of a first user is acquired by using the electronic device and a second user using the communication opposite terminal in the communication process; risk analysis is carried out according to the equipment information of the opposite communication terminal; text analysis, environment analysis and voiceprintrecognition are carried out according to the collected data; and finally, according to a risk analysis result, a and / or the prompt information is output to the first user according to the results of the text analysis, the environment analysis and the voiceprint recognition, so that the information output by the communication opposite terminal in the communication process can be recognized and prompted at the first time when the two communication parties begin to communicate, and accompanying risk management and control are realized.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Third-party-based verified information non-leakage data integrity and source verification method
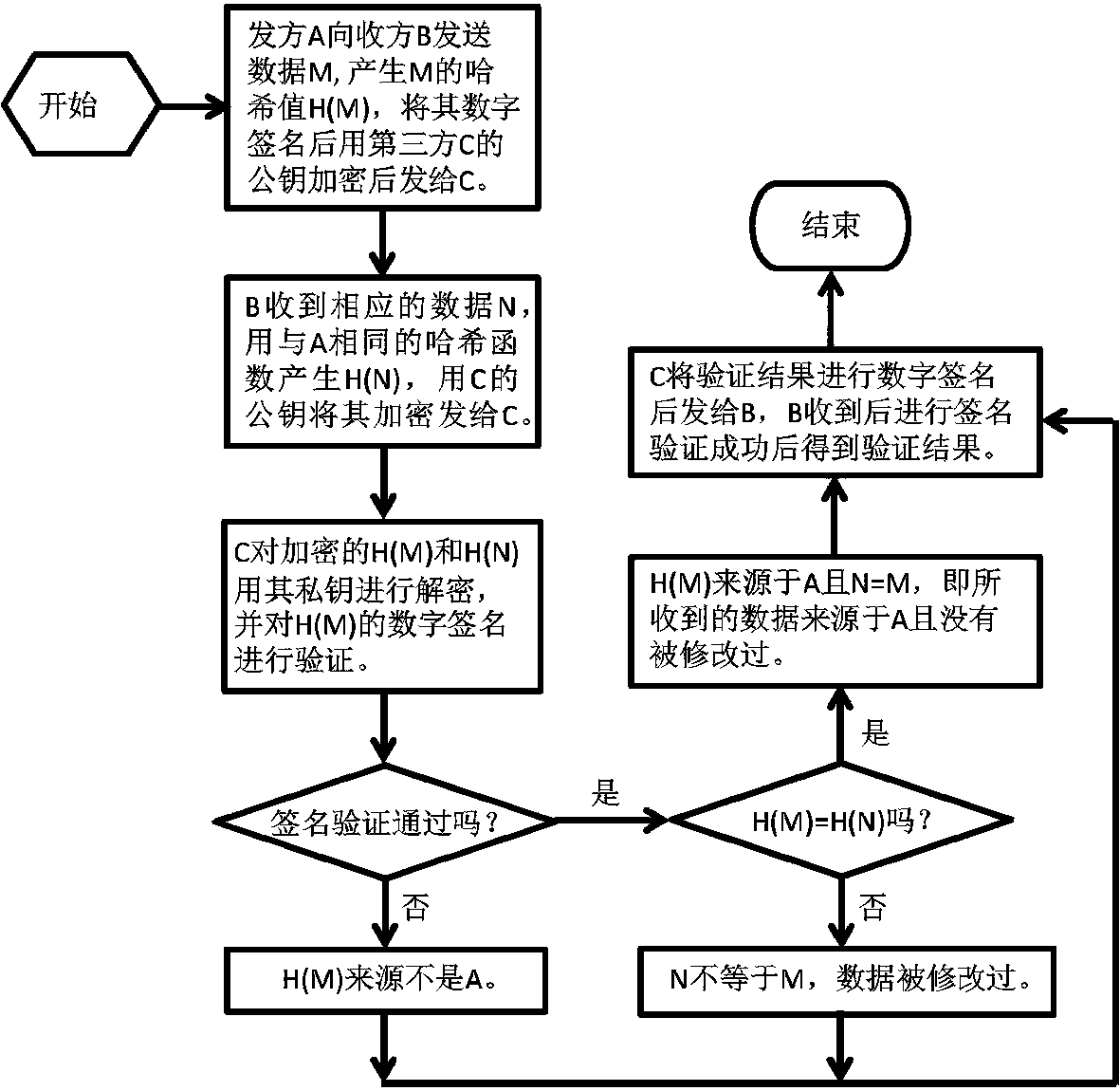
ActiveCN108768958ASource and Integrity VerificationEnsure safetyEncryption apparatus with shift registers/memoriesUser identity/authority verificationData OriginKey exchange
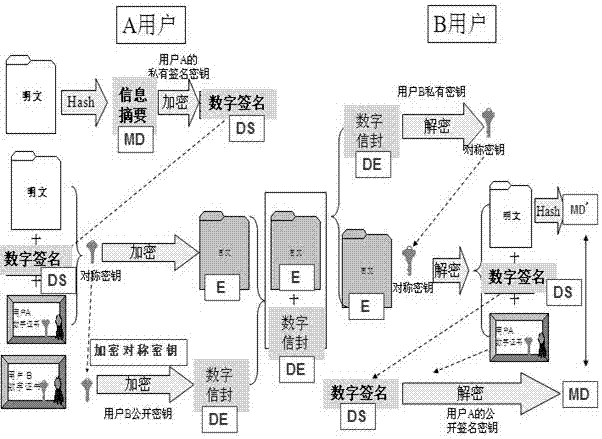
The invention provides a third-party-based verified information non-leakage data integrity and data source verification method which comprises a third-party-based verified information non-leakage dataintegrity and source verification method in a simple mode, a third-party-based verified information non-leakage data integrity and source verification method in a key exchange mode and a third-party-based verified information non-leakage data integrity and source verification method in a secure communication mode, wherein the third-party-based verified information non-leakage data integrity and source verification method in the simple mode is used for a case that verified and transmitted data is a cleartext, a sender does not encrypt the data and a receiver also does not need to decrypt the received data; according to the third-party-based verified information non-leakage data integrity and source verification method in the key exchange mode, on the basis of the simple mode, key securitytransmission is further provided for the sender and the receiver so as to support more secure communication between the sender and the receiver; and according to the third-party-based verified information non-leakage data integrity and source verification method in the secure communication mode, on the basis of the simple mode, the verified and transmitted data is a ciphertext. Acquired information can be used for identity verification of both the sender and the receiver, and two users who do not know public keys of opposite parties are allowed to verify an integrity and a source of data sentbetween the users, and the third-party-based verified information non-leakage data integrity and source verification method can be used for defending internet frauds and establishing an authoritativeinformation release and verification platform.
Owner:SHANGHAI MARITIME UNIVERSITY
Identity authentication method and system
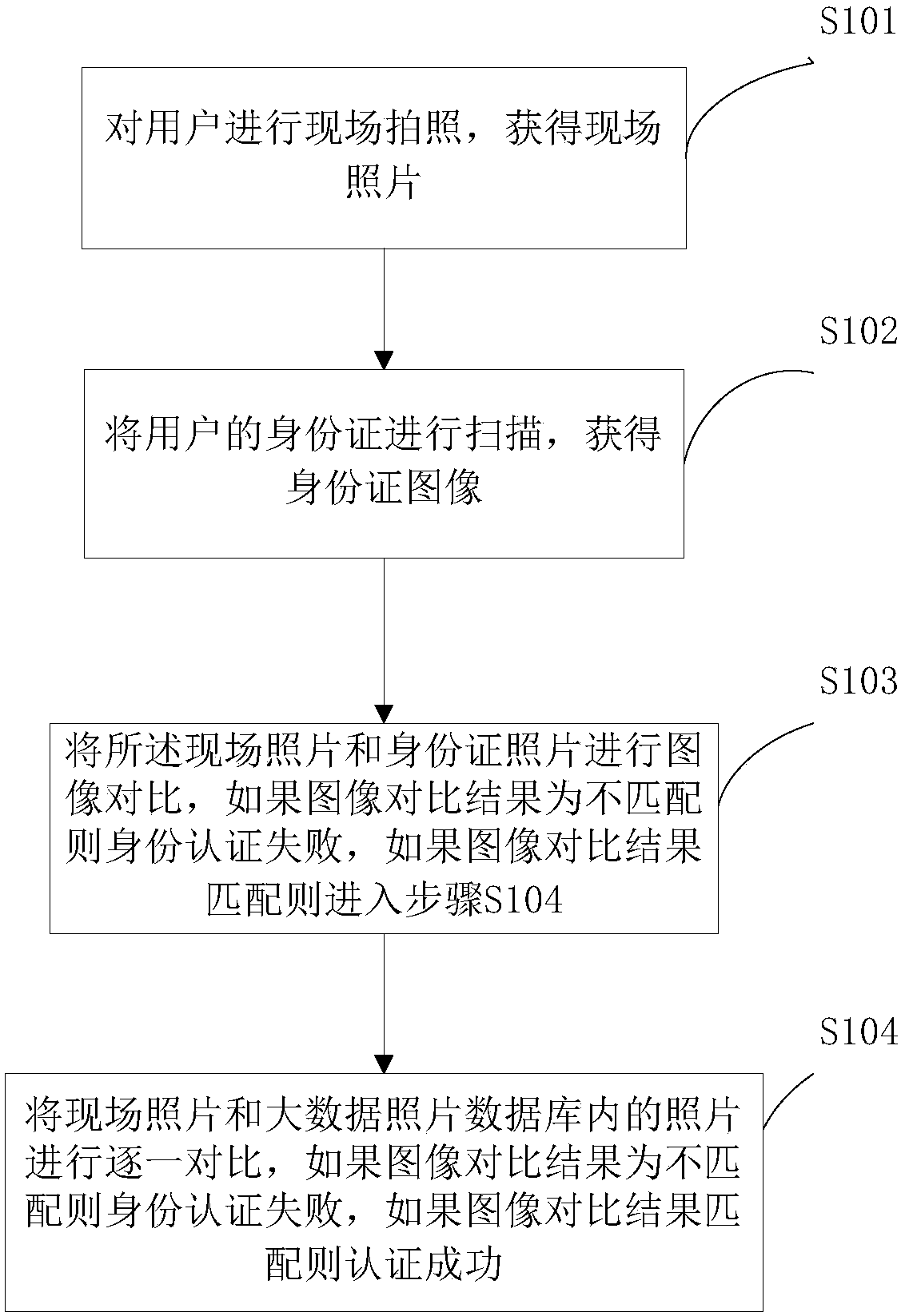
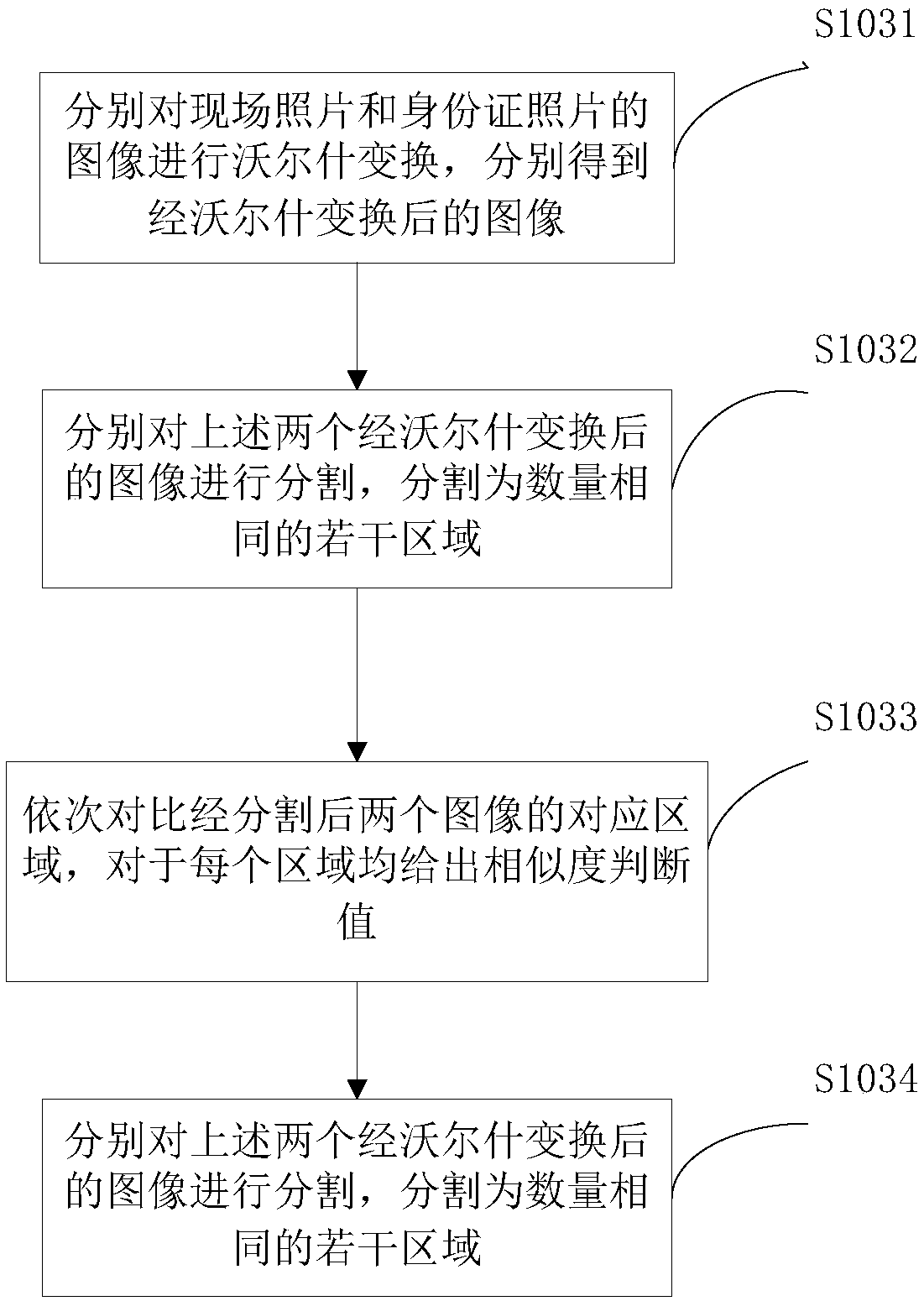
InactiveCN108171113AOpportunities decreaseReduce personalCharacter and pattern recognitionInternet privacyInternet fraud
The invention provides an identity authentication method and system. The method comprises the following steps of 1, performing site photography on a user to obtain a site photo; 2, scanning an identity card of the user to obtain an identity card image; 3, performing image comparison on the site photo and the identity card image, and if an image comparison result is that the site photo is not matched with the identity card image, indicating that identity authentication fails, otherwise, entering the step 4; and 4, comparing the site photo with photos in a big data photo database one by one, andif an image comparison result is that the site photo is not matched with the photos in the big data photo database, indicating that the identity authentication fails, otherwise, indicating that the identity authentication succeeds. Through the method and the system, personal identity authentication can be effectively performed; lawbreakers can be effectively prevented from performing financial fraud, internet fraud and phone fraud by utilizing identity cards lost by others; the exploitable opportunities of criminals are objectively reduced; and the personal and social loss is reduced.
Owner:BEIJING GZT NETWORK TECH
Anti-communication network fraud identification method based on feature classification
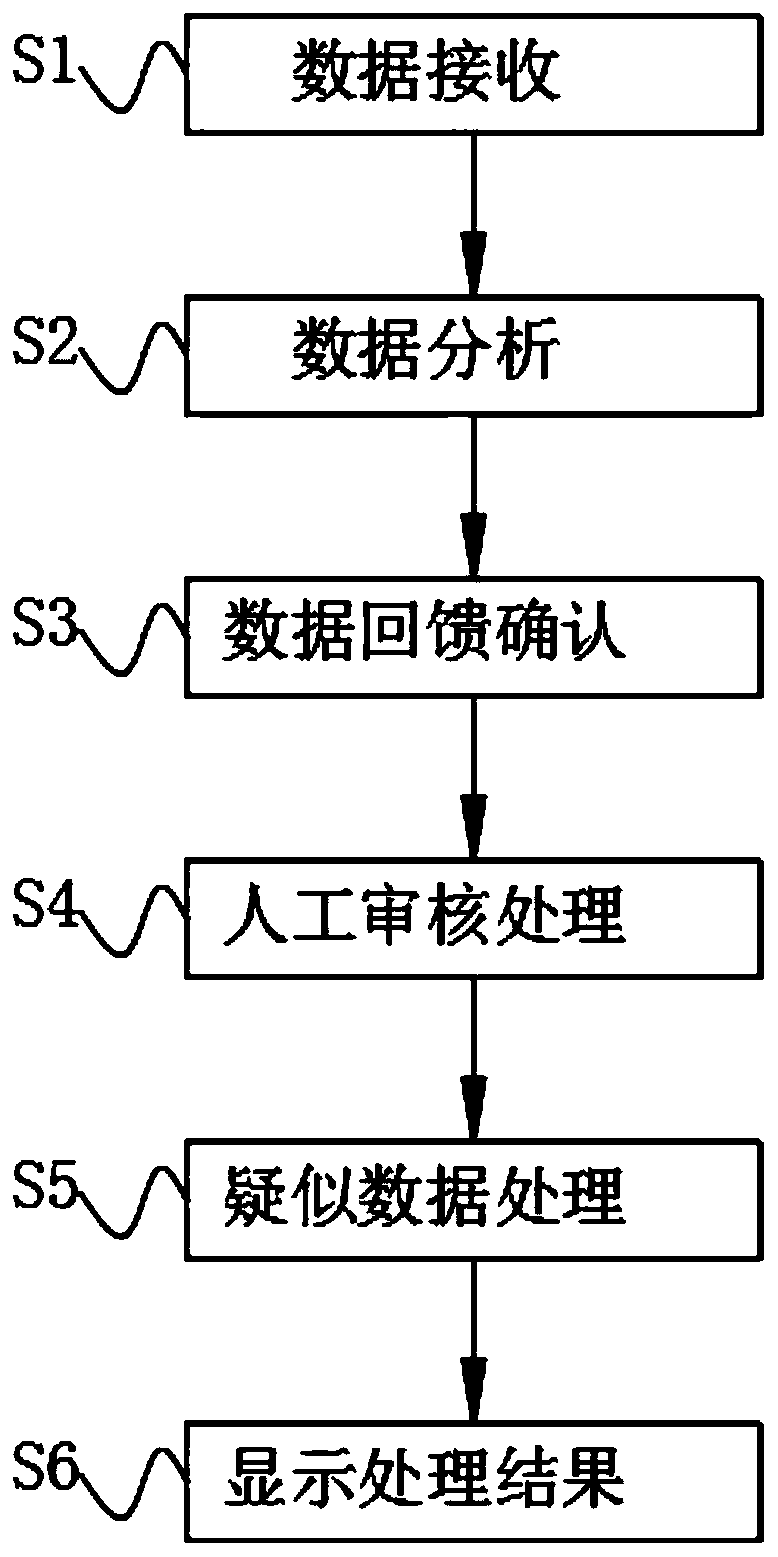
PendingCN111539747AAvoid receivingIntercept and controlCharacter and pattern recognitionCommerceComputer networkInternet fraud
The invention discloses an anti-communication network fraud identification method based on feature classification, and relates to the technical field of anti-communication network fraud, and the method comprises the following steps: S1, data receiving; S2, data analysis; S3, data feedback confirmation; S4, performing manual auditing processing; S5, processing suspected data; and S6, processing result displaying, wherein, in the step S1, the data acquisition device internally comprises a data acquisition unit, a data processing unit and a CPU interface, the CPU interface is electrically connected with the data acquisition unit, and the data acquisition unit is electrically connected with the data processing unit. According to the method, the network fraud data can be better intercepted andcontrolled, the identification degree of the network fraud data is higher, external personnel are effectively prevented from receiving the network fraud, the unstored fraud data can be transmitted into the big database to be stored, an operator can match the next group of fraud data conveniently, and the identification and interception efficiency is improved.
Owner:贵州索讯科技有限公司
Electronic data comprehensive evidence storage method and evidence storage system
InactiveCN111885085AProtect economic assetsEffective Evidence CollectionDigital data protectionDigital data authenticationData synchronizationCloud systems
The invention discloses an electronic data comprehensive evidence storage method. The method comprises the following steps: S10, an identity verification request: carrying out identity compliance andsecurity verification on a user individual; S20, requesting data preservation: analyzing certificate storage data pre-collected by a user individual in the data certificate storage request in a business execution process, encrypting the certificate storage data by an electronic data certificate storage background service, generating a unique identifier, and storing the unique identifier into a database; and S30, evidence storage cloud data synchronization: synchronizing the evidence storage data preserved to the database in the step S20 to an electronic data evidence storage cloud system. Theinvention further discloses an electronic data comprehensive evidence storage system which comprises an electronic data evidence storage application program, a data evidence storage background servicesystem and an electronic data evidence storage cloud system. Key data in internet telecommunication network fraud can be stored in the data storage cloud system, a victim can be helped to fix electronic data at the first time, and the storage data can be quickly synchronized to related public security organizations.
Owner:上海弘连网络科技有限公司
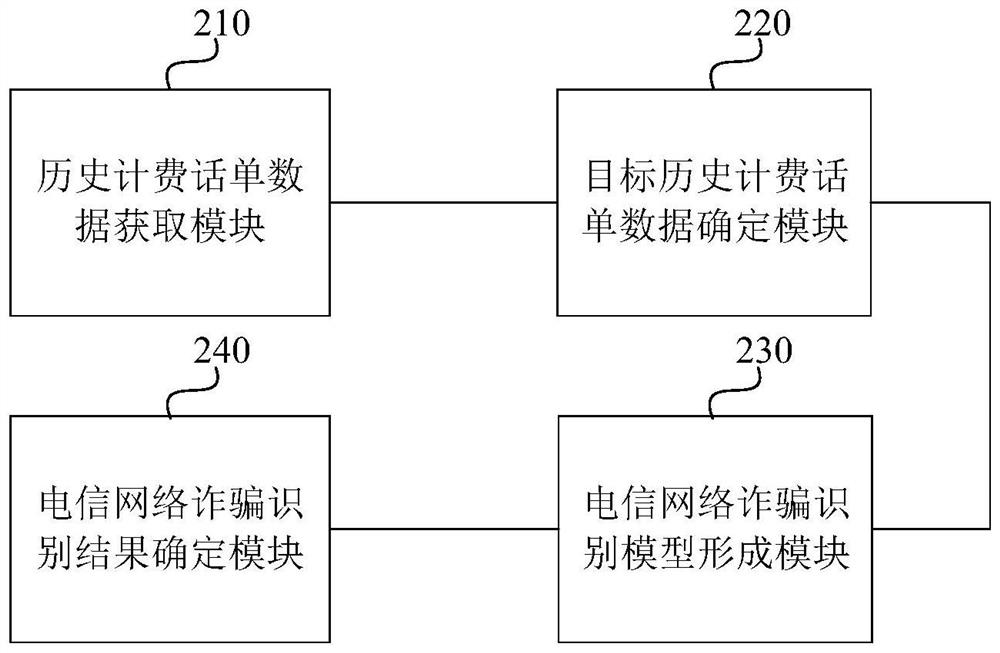
Telecommunication network fraud identification method and device, equipment and storage medium
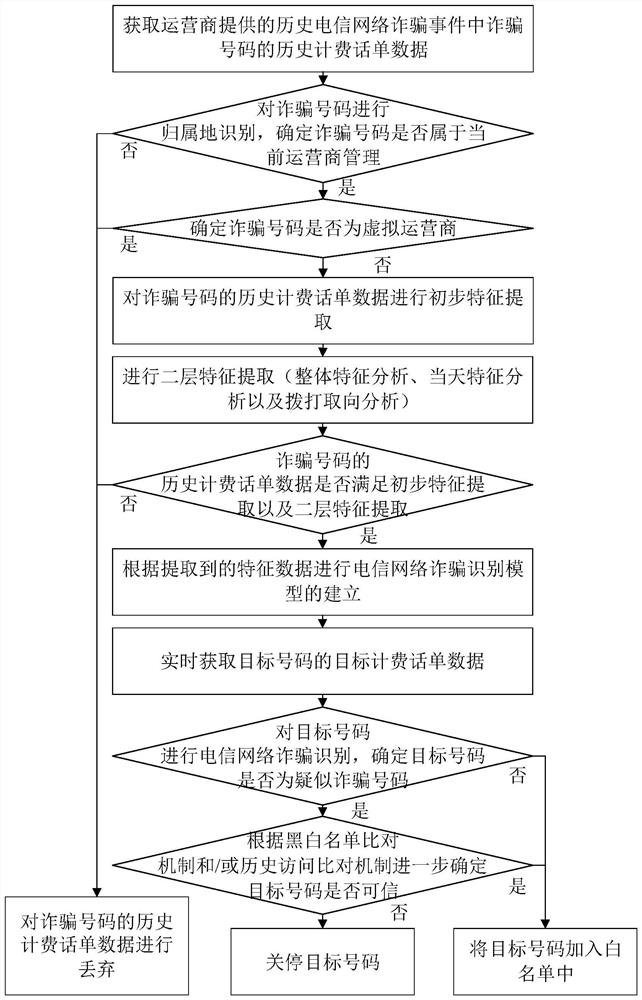
PendingCN114169438ASolving recognition problemsAvoid lostDigital data information retrievalCharacter and pattern recognitionTicketTelecommunications network
The technical scheme of the embodiment of the invention discloses a telecommunication network fraud identification method and device, equipment and a storage medium. The method comprises the following steps: acquiring historical charging ticket data of a fraud number in a historical telecommunication network fraud event; performing feature extraction on the historical charging ticket data, and determining target historical charging ticket data meeting a preset telecommunication network fraud type; forming a telecommunication network fraud identification model according to feature data matched with a preset telecommunication network fraud type in the target historical charging ticket data; and obtaining target charging ticket data of the target number in real time, and inputting the target charging ticket data into the telecommunication network fraud recognition model to obtain a telecommunication network fraud recognition result of the target number. According to the method, the telecommunication network fraud can be detected in advance, so that the loss caused by the telecommunication network fraud is avoided.
Owner:EVERSEC BEIJING TECH
Segmentation word-taking method and system for social text
ActiveCN114021564AThe segmentation result is accurateDatabase updatingNatural language data processingText recognitionInternet fraud
The invention discloses a segmentation word-taking method and system for a social text, and belongs to the technical field of social text processing. In order to solve the problem that in the prior art, a social text involved by a person engaged in network fraud cannot be accurately segmented, the system comprises a text preprocessing module, an N-gram lexicon creating module, a word segmentation function module and an N-gram lexicon updating module. According to a self-defined word segmentation function in the word segmentation module, accurate word segmentation is carried out on text information, a certain updating period is set, and new data generated during the updating period is used for updating an N-gram word bank, so that the word segmentation accuracy is improved. Aiming at the strong and distinct language style of the chat information of the people engaged in the network fraud and the huge difference between the chat information and the traditional chat content, a text recognition and segmentation technology with own characteristics is formed according to different types of corpora, and accurate segmentation and word extraction are performed on the text.
Owner:成都无糖信息技术有限公司
Network fraud number detection method and system, storage medium and terminal equipment
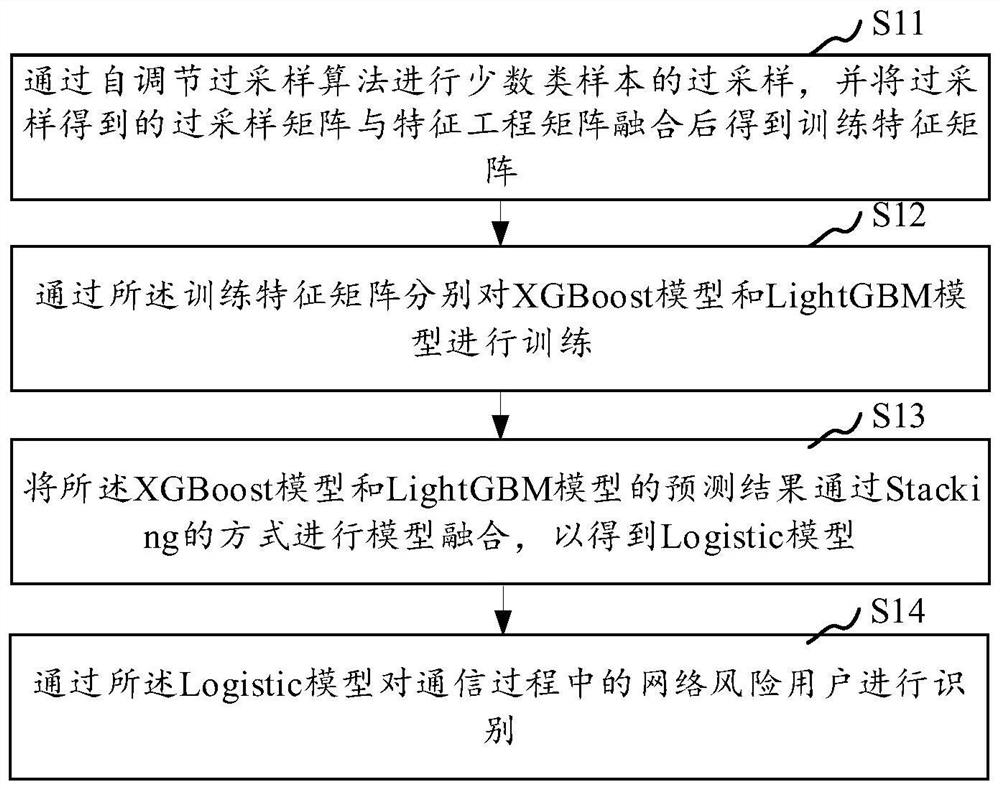
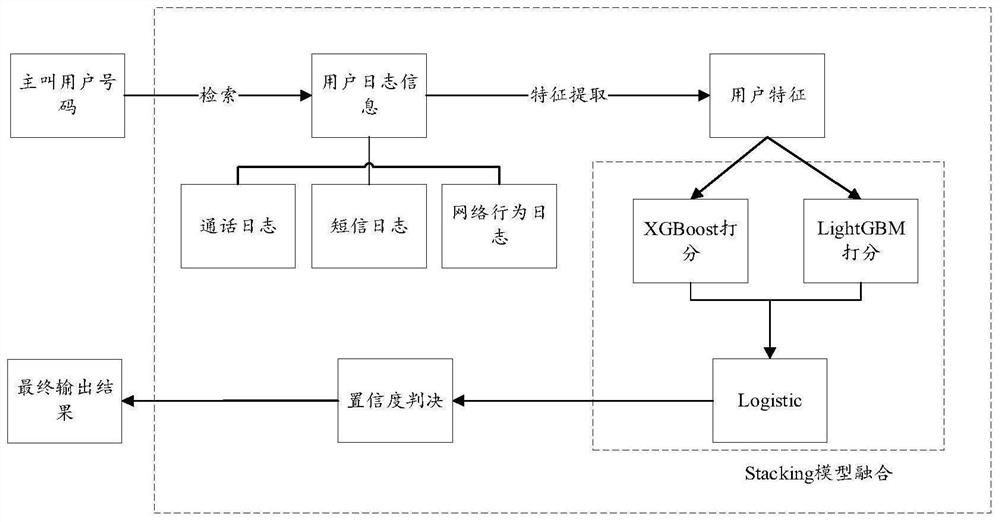
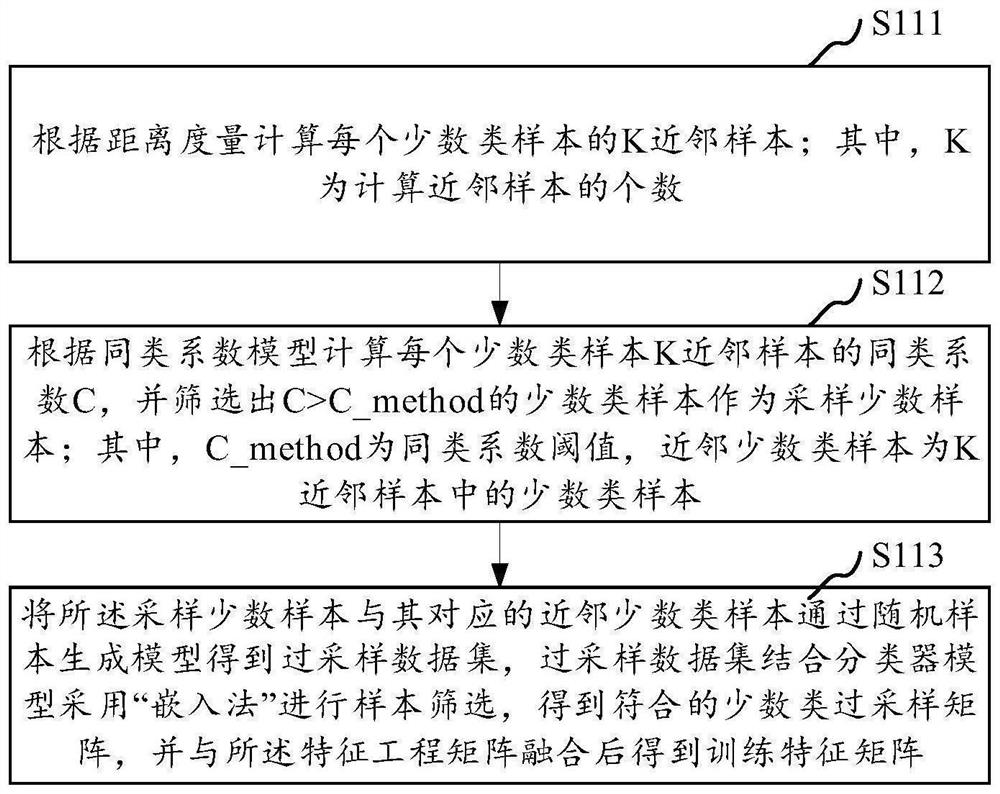
PendingCN113591924AImprove accuracyImprove robustnessSupervisory/monitoring/testing arrangementsCharacter and pattern recognitionInternet fraudTerminal equipment
The invention relates to a network fraud number detection method, and the method comprises the steps: firstly designing corresponding features for information fraud behaviors, carrying out the feature extraction of a user behavior log, constructing an original feature matrix, and carrying out the data preprocessing; then, according to the unbalance degree of the proportion of normal users and risk users in the original feature matrix after data preprocessing, carrying out minority class sample oversampling by adopting a self-adjusting oversampling algorithm, and reconstructing a training set; then carrying out pre-training, feature importance evaluation and feature screening through an XGBoost model; then, carrying out model training on the reconstructed feature matrix by using an XGBoost model and a LightGBM model; and finally, improving the model performance through a Stacking multi-model fusion mode, obtaining a two-layer model Logistic, and completing a mobile network risk user identification model. According to the invention, the accuracy and robustness of fraud number identification in network communication can be improved, and the actual application requirements are met.
Owner:中山大学新华学院
Internet financial risk control system with child-mother type double-key verification
PendingCN110009506AMinimize payment riskPrevent financial fraudFinanceDigital data authenticationRisk ControlInternet fraud
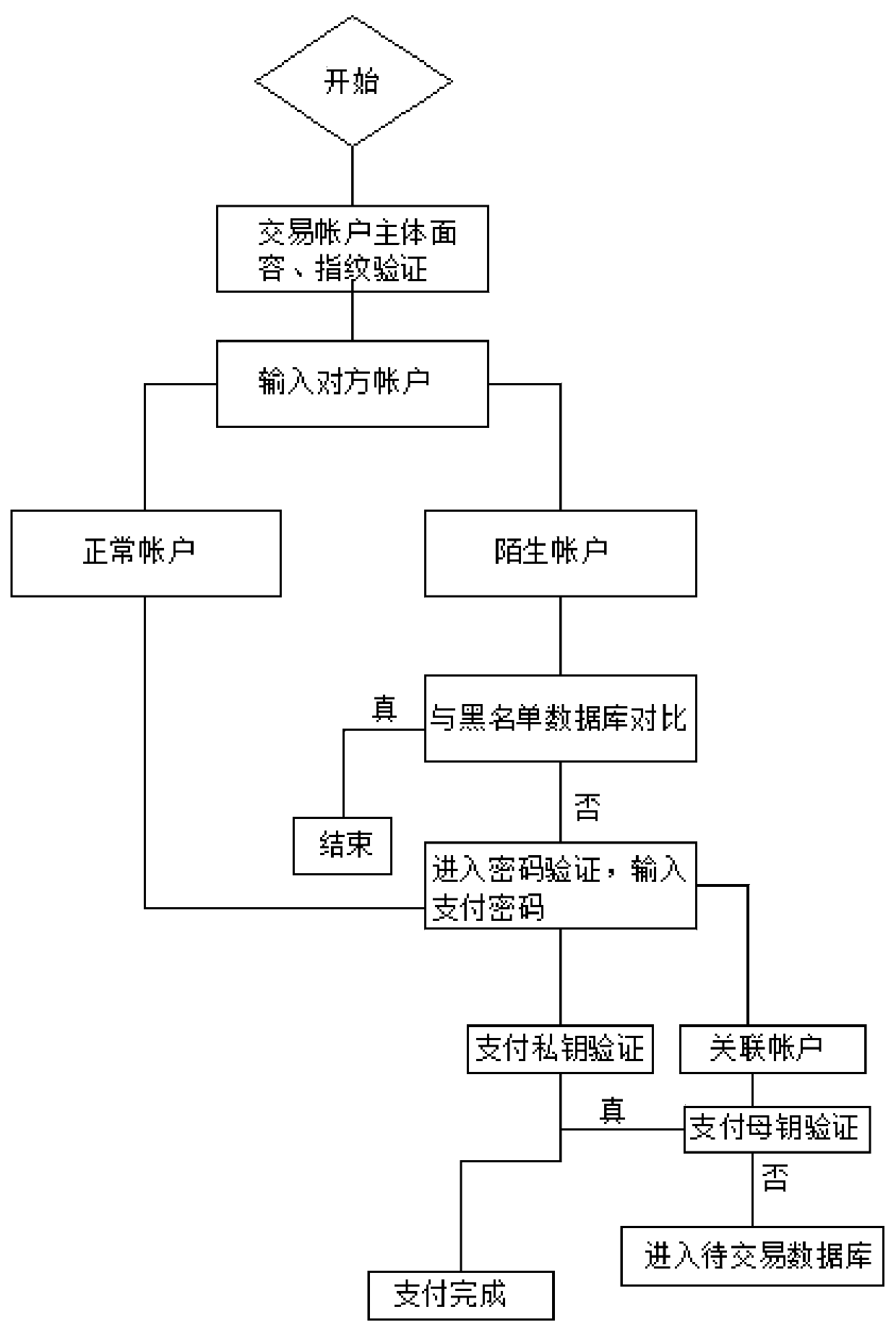
The invention relates to the technical field of internet finance, in particular to an internet financial risk control system. The following steps are adopted: 1, in a network transaction, a transaction account main body adopts identity information real-name registration, a mobile phone account is a transaction payment sub-account, and a digital password and a fingerprint password are set to form apayment private key; an associated account is required to be registered, the associated account takes a mobile phone account as registration, and a verification code received by the mobile phone account is a payment mother key; 2, after the network transaction is completed, for an initial transaction account, a payment platform is entered firstly when strange account electronic payment is carriedout, and face appearance and fingerprint verification is carried out; according to the invention, by setting double associated accounts and combining private key payment and mother key payment, the linkage of three parties for strange accounts is realized, and the payment risk is minimized, so that financial fraud, network fraud and the like are effectively prevented, and the risk management andcontrol of financial payment are realized.
Owner:山东经贸职业学院
Implementation method and system for intercepting network fraud calls based on IMS (IP Multimedia Subsystem)
PendingCN113766065ACut off in real timeInterconnection arrangementsSpecial service for subscribersInternet fraudEngineering
The invention discloses an IMS (IP Multimedia Subsystem) network-based fraud call interception implementation method, which comprises the following steps: at a fraud call interception platform side, receiving a first call triggered by an IMS network, storing call parameters carried by the first call, wherein the call parameters comprise a calling number, a called number and a call identifier; and when an interception request from an external system is received, querying the stored call parameters according to at least one or any combination of a calling number and a called number carried by the request, and if the stored call parameters are queried, sending a disconnection signaling to the IMS network so as to enable the first call to be disconnected. According to the invention, fraud phone monitoring and interception can be carried out on the call based on the IMS network, communication can be cut off in real time, and new business services can be provided for users.
Owner:上海欣方智能系统有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com