Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1068results about How to "Improve trust" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Methods, systems and devices for packet watermarking and efficient provisioning of bandwidth
ActiveUS7287275B2Speeding routingFine granularityError preventionFrequency-division multiplex detailsData streamNetwork packet
Disclosed herein are methods and systems for transmitting streams of data. In one embodiment, a method comprises the steps of: receiving a stream of data; organizing the stream of data into a plurality of packets; generating a packet watermark associated with the stream of data; combining the packet watermark with each of the plurality of packets to form watermarked packets; and transmitting at least one of the watermarked packets across a network. The present invention also relates to: receiving at least one packet that has been transmitted across a network; analyzing at least one packet for a watermark; and authenticating the at least one packet using at least a portion of the watermark. The present invention also relates to generating packet watermarks and packet watermark keys.
Owner:WISTARIA TRADING INC
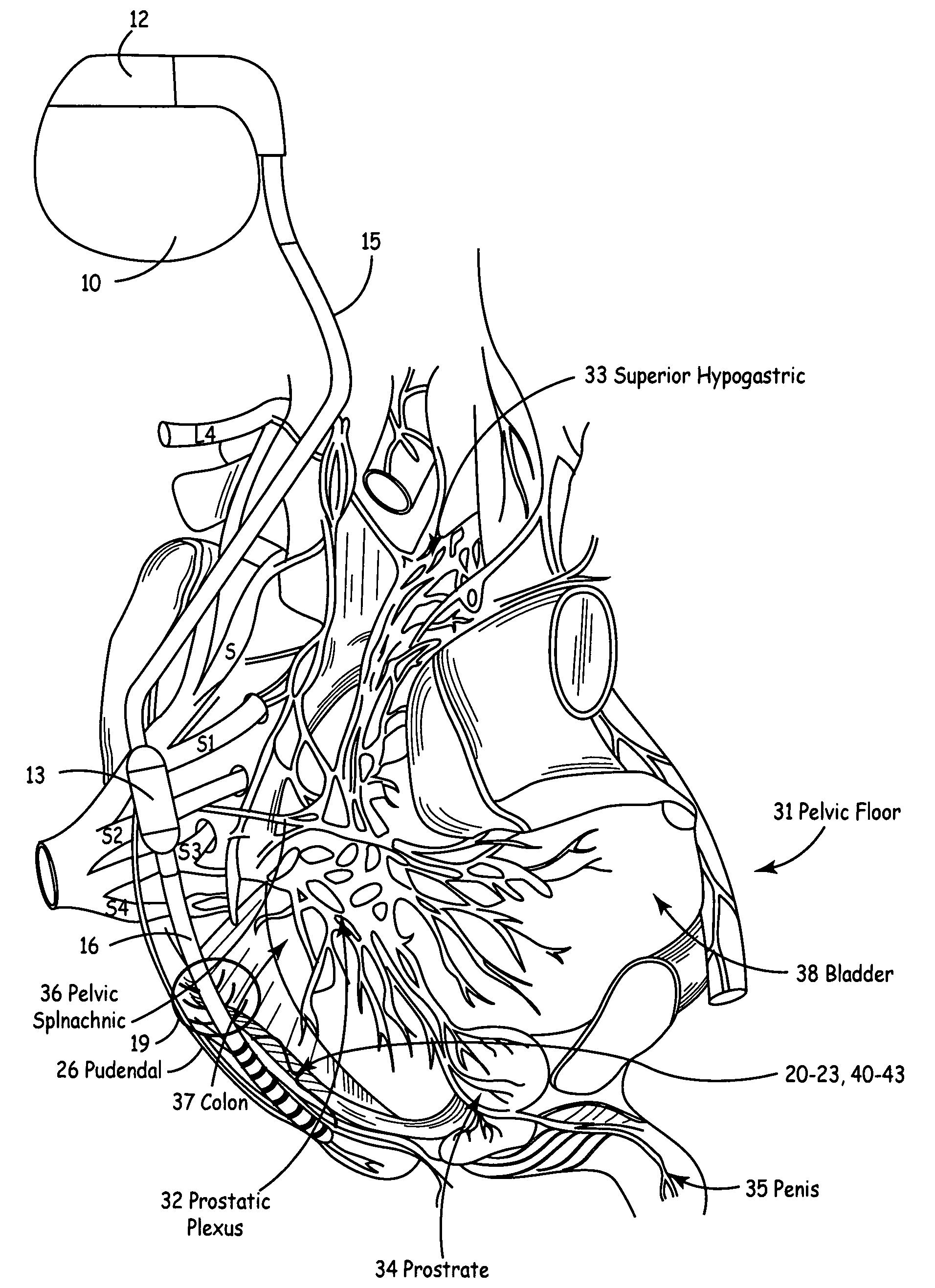
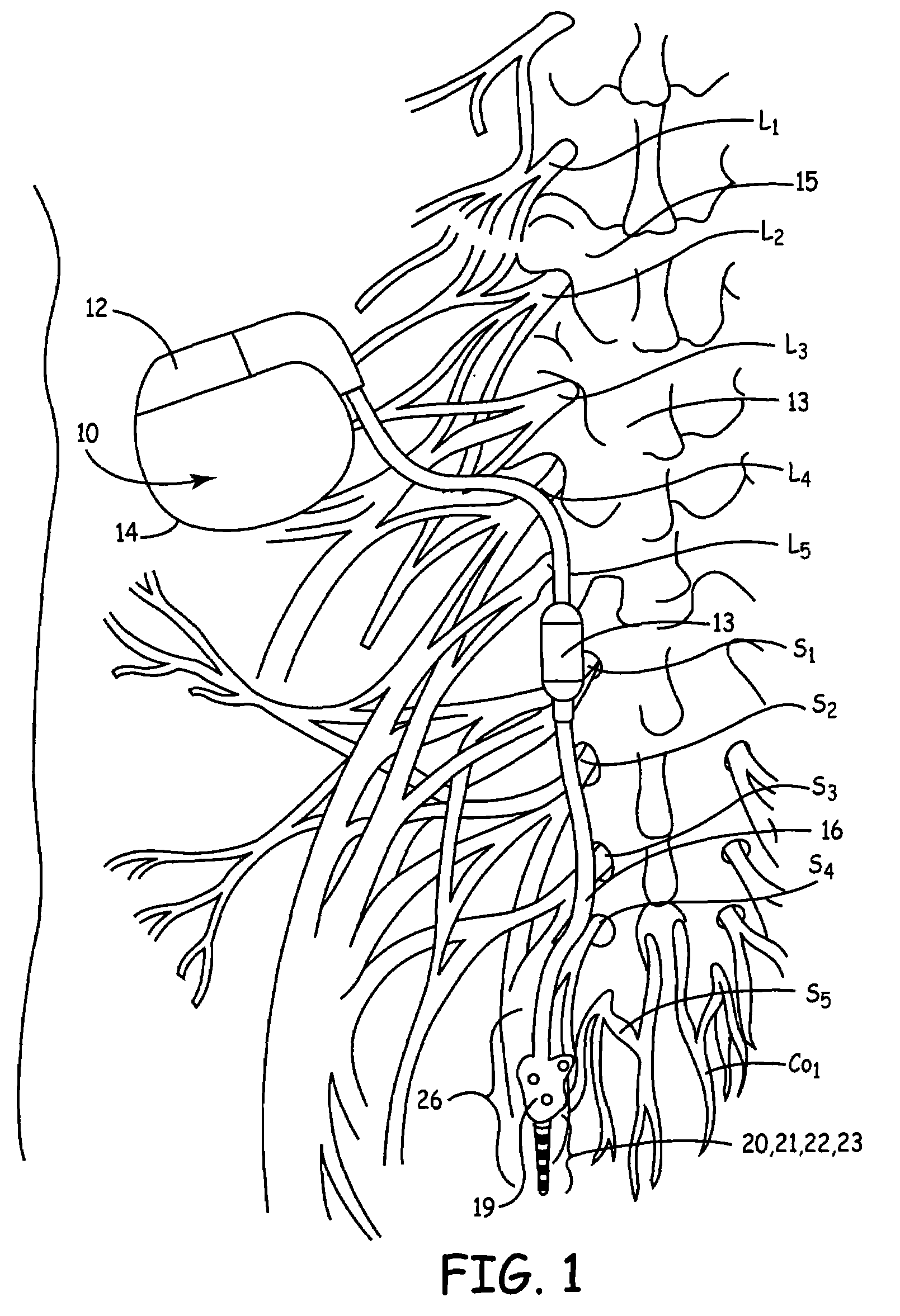
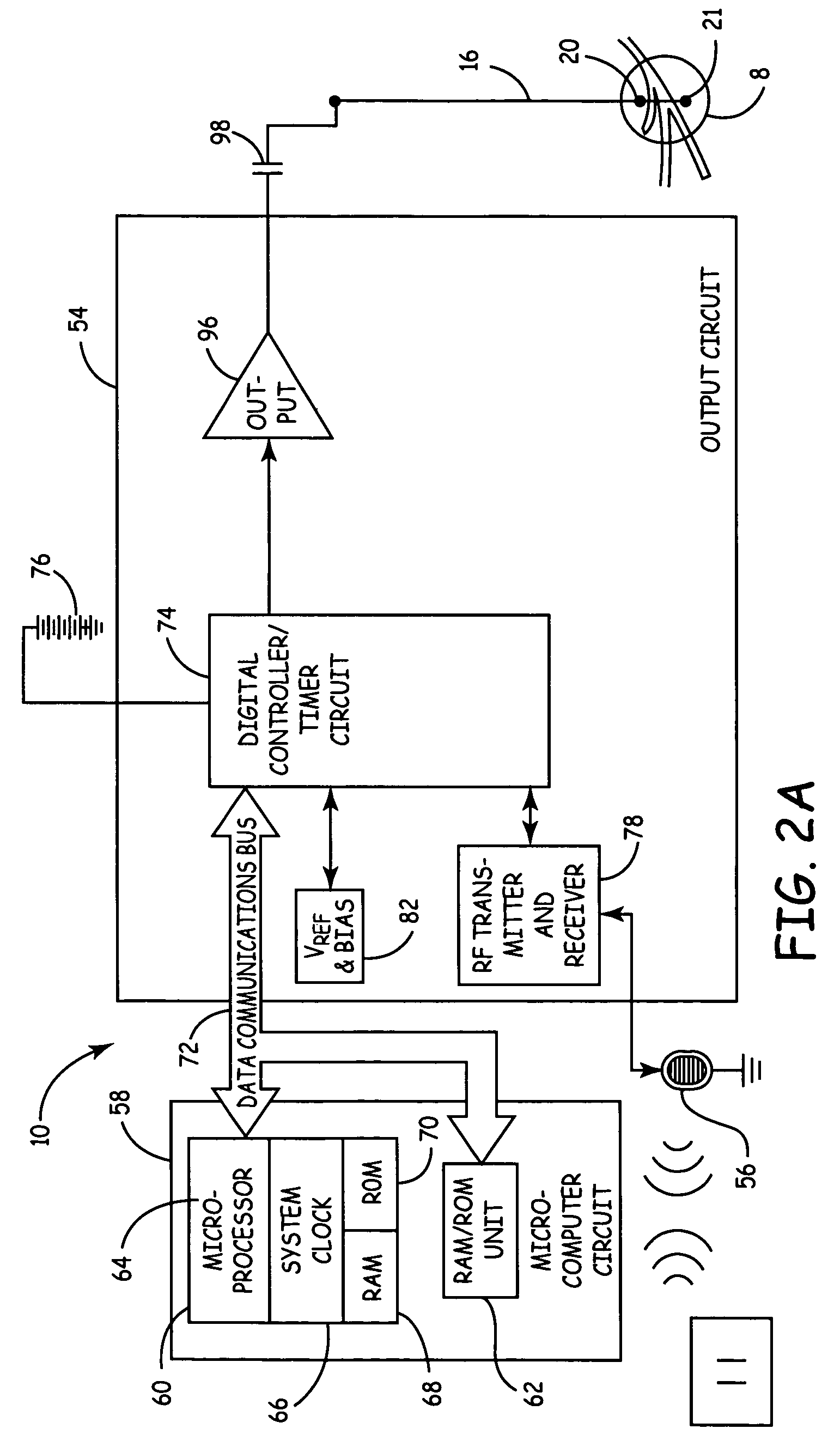
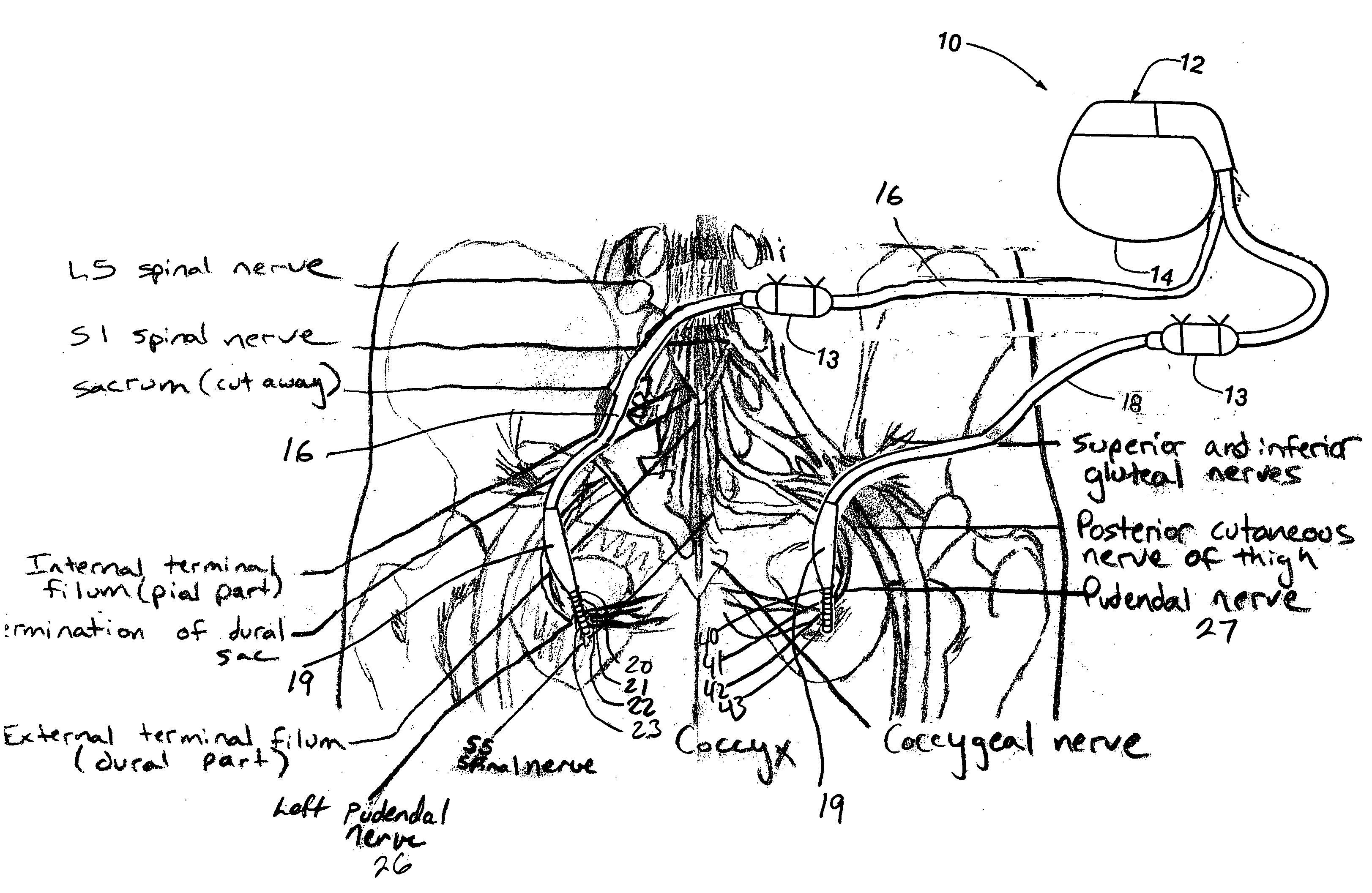
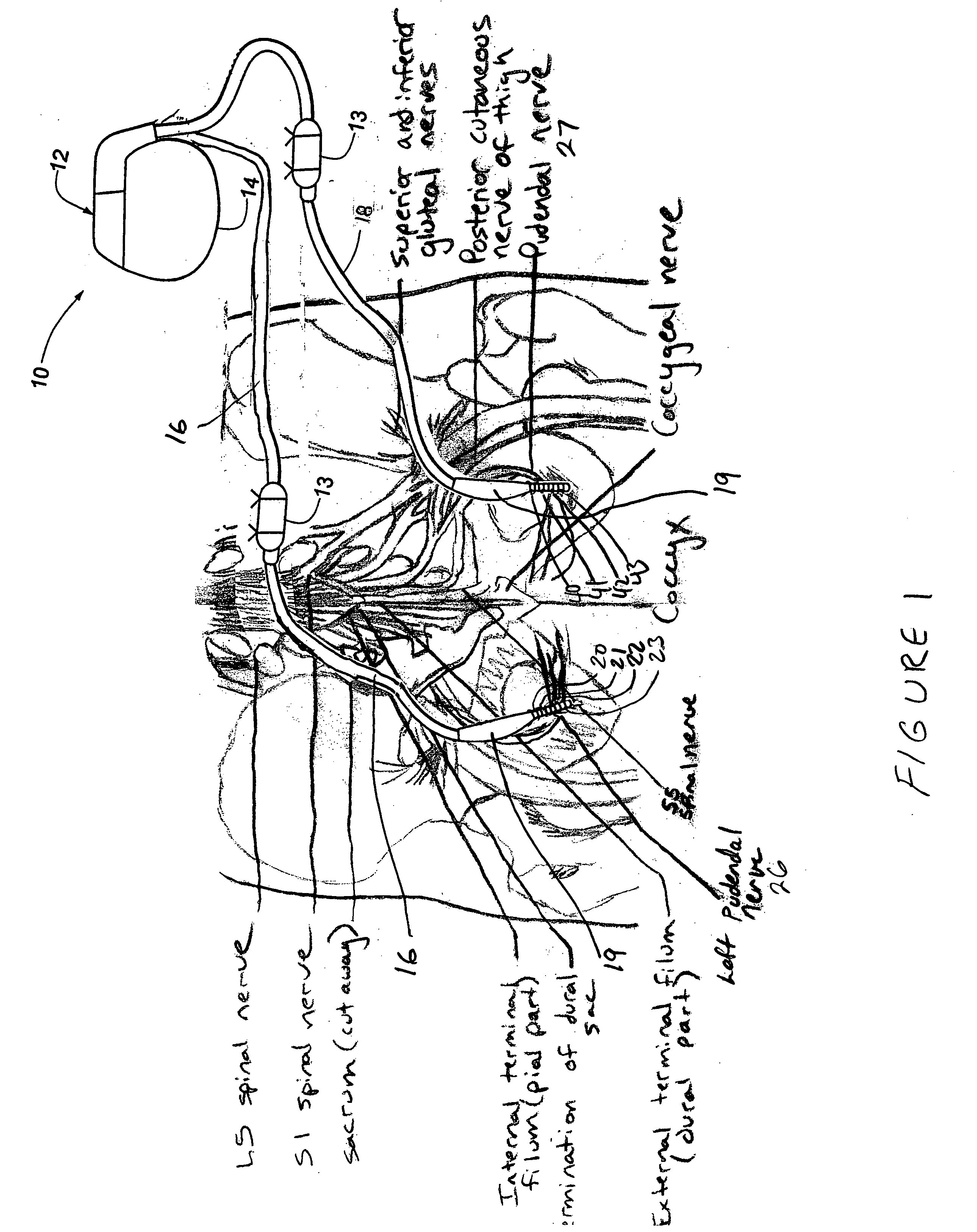
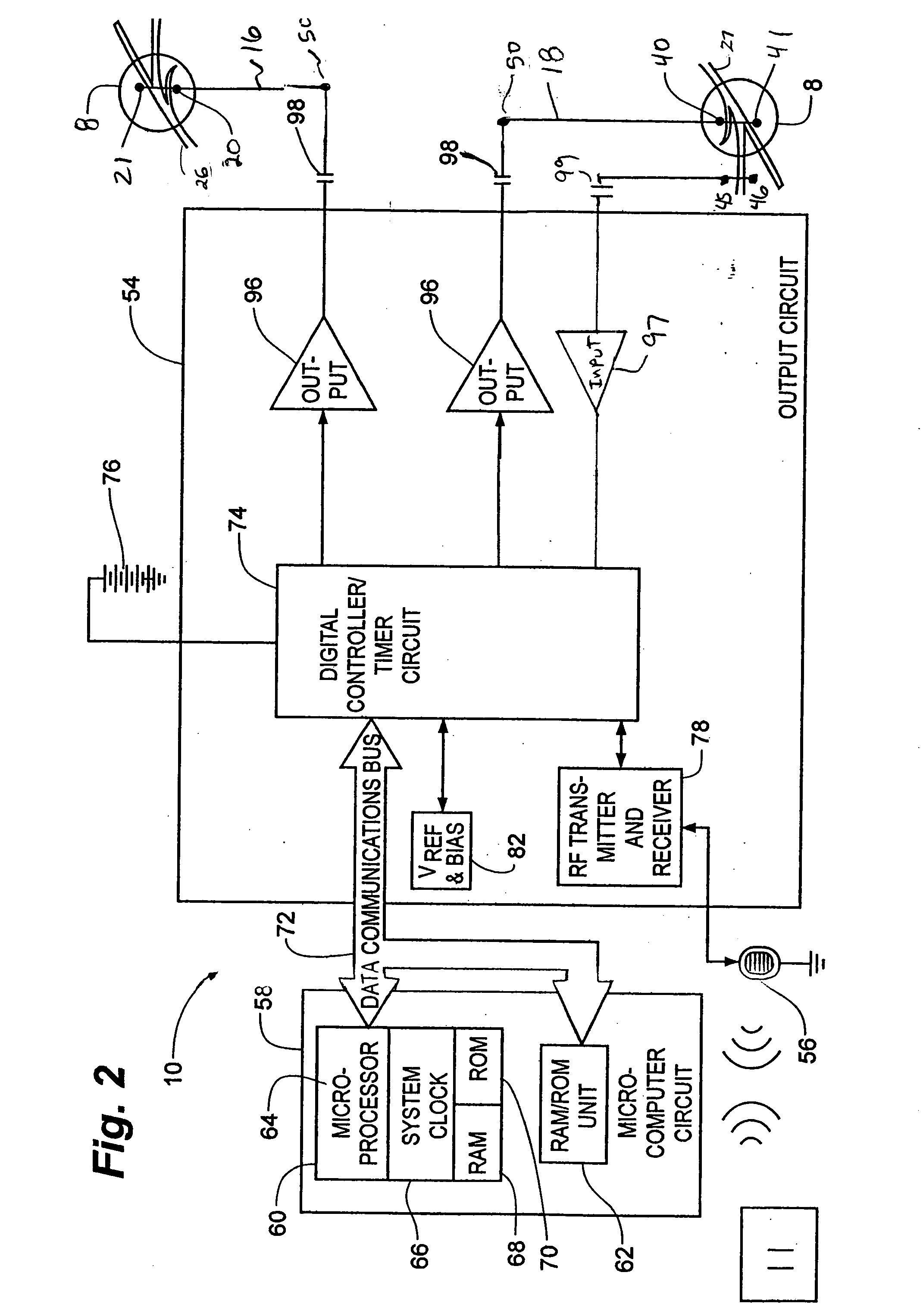
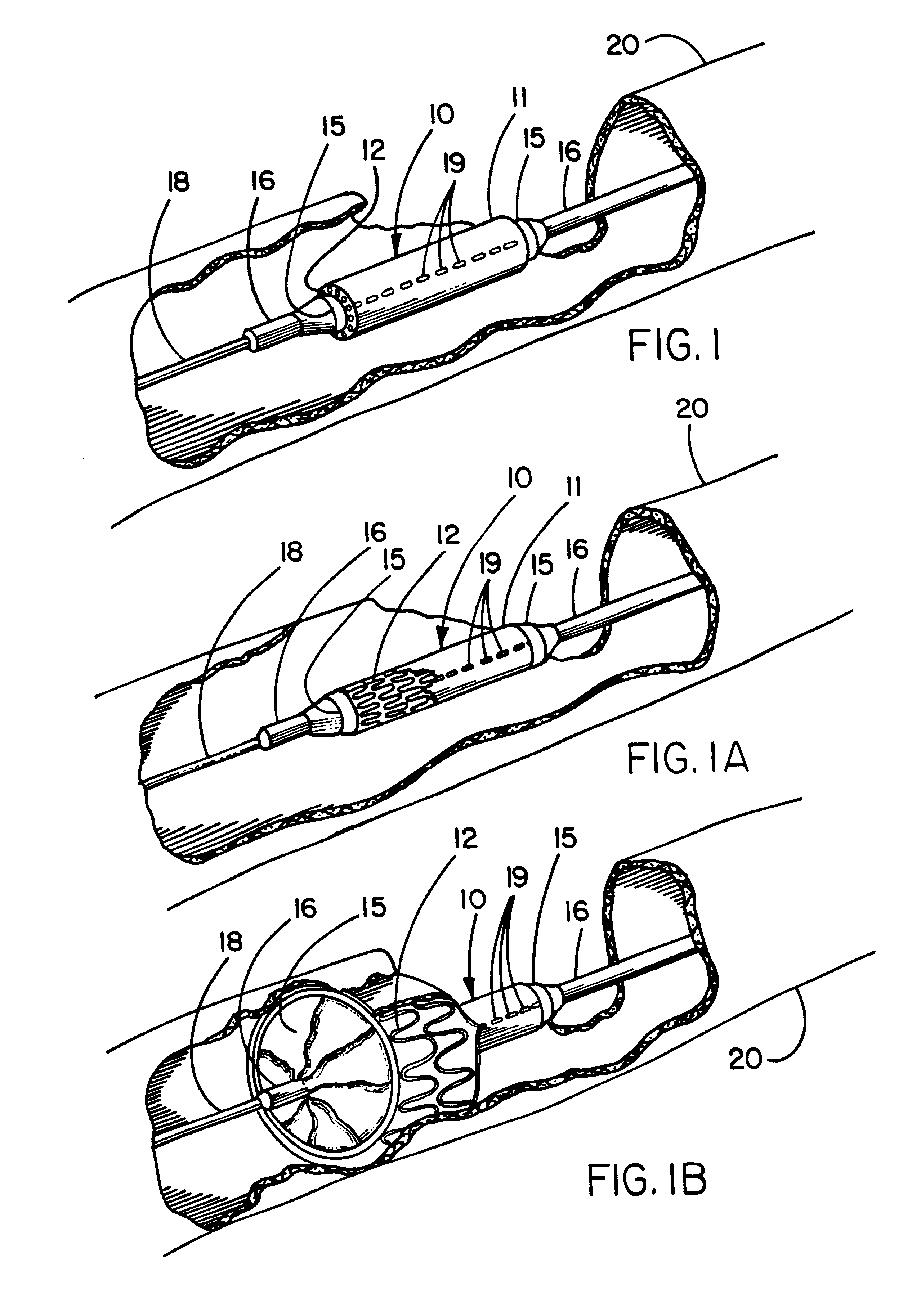
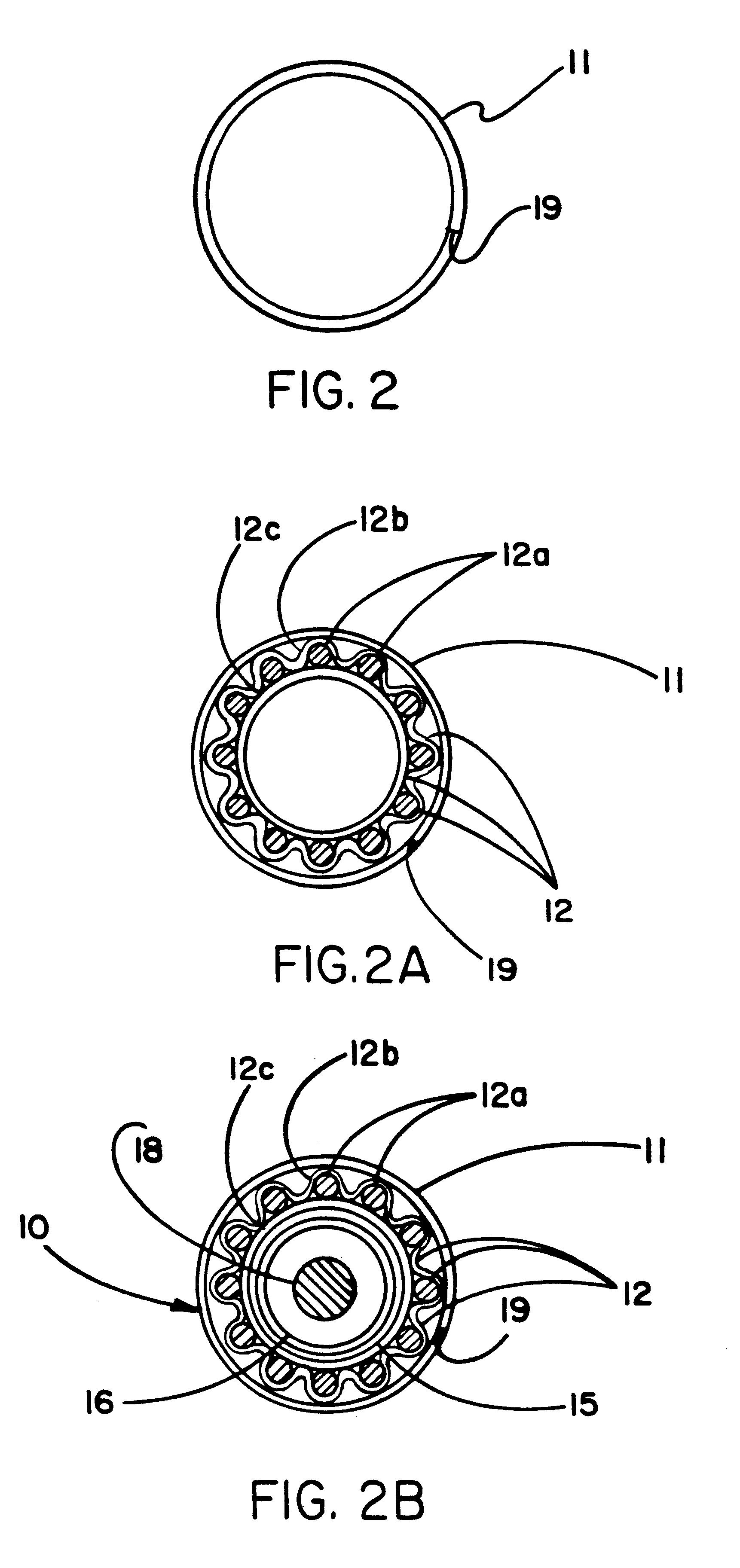
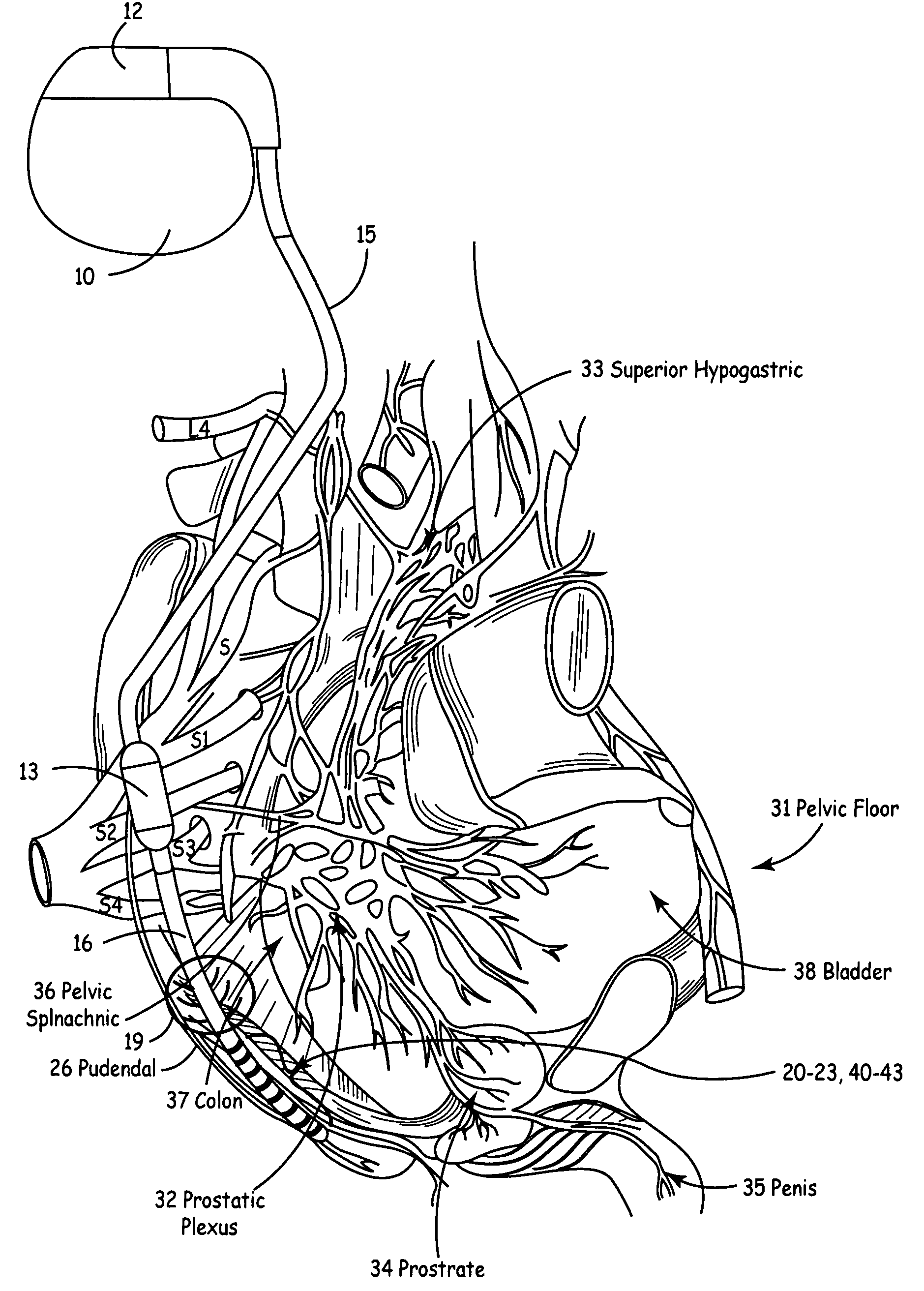
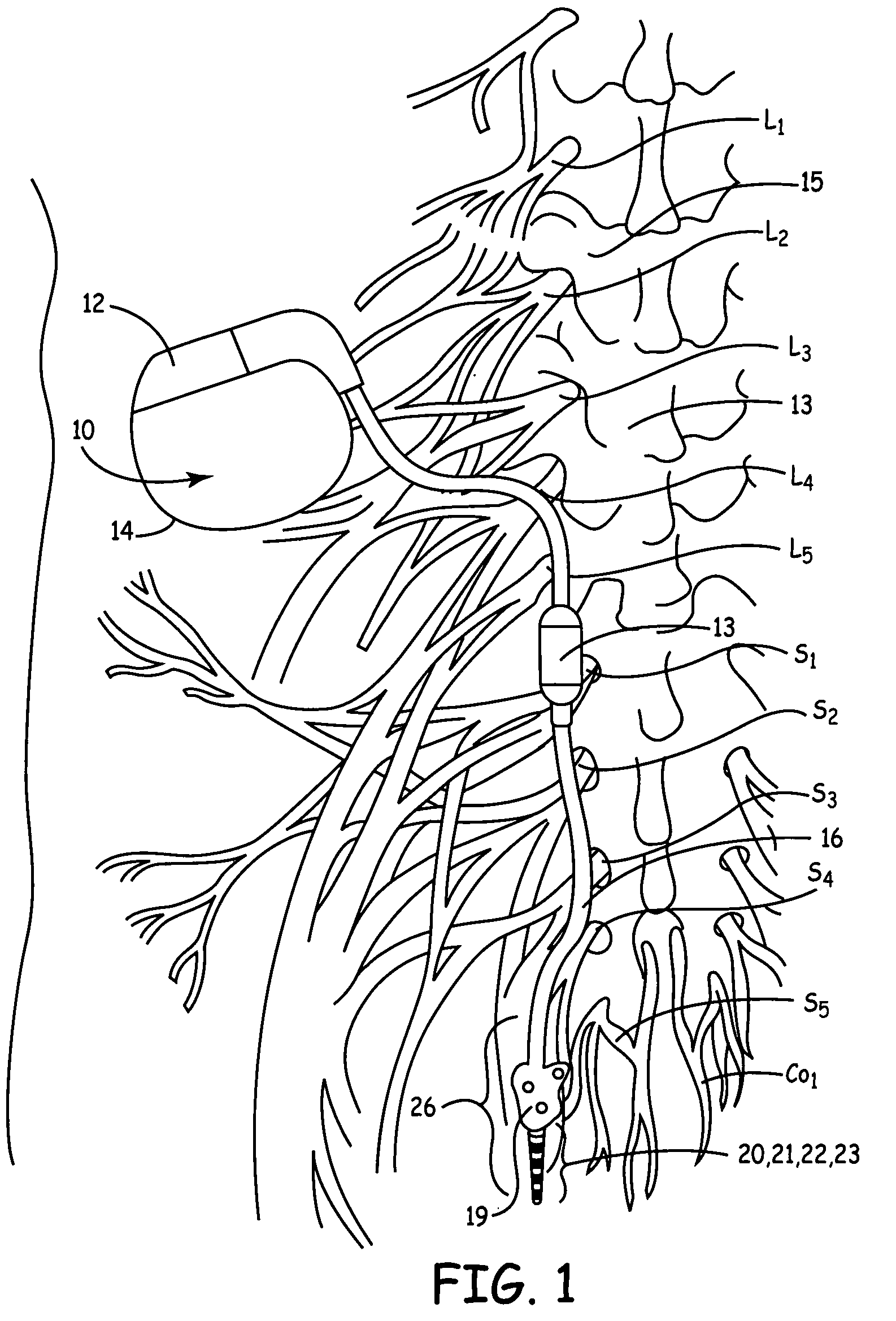
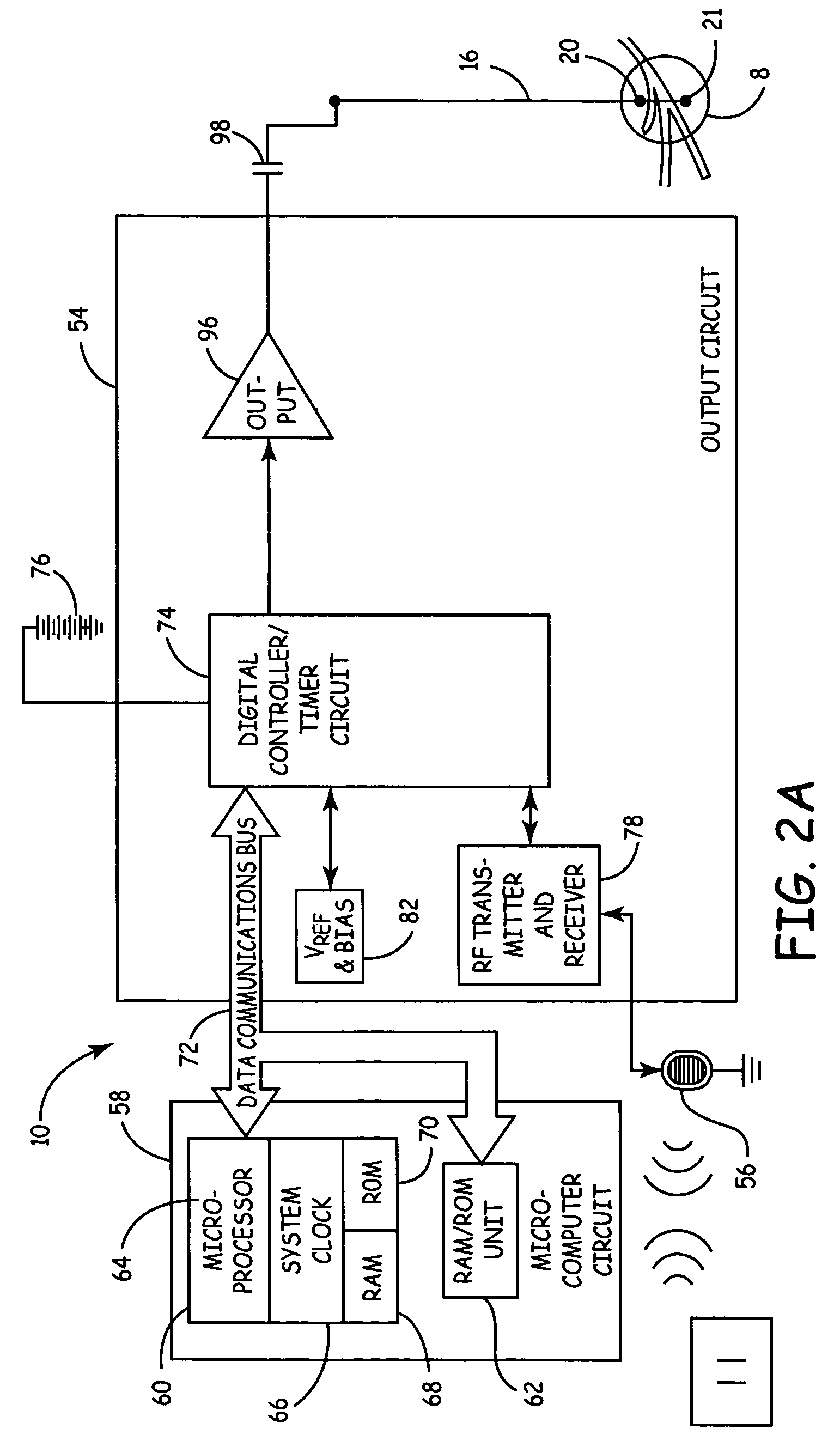
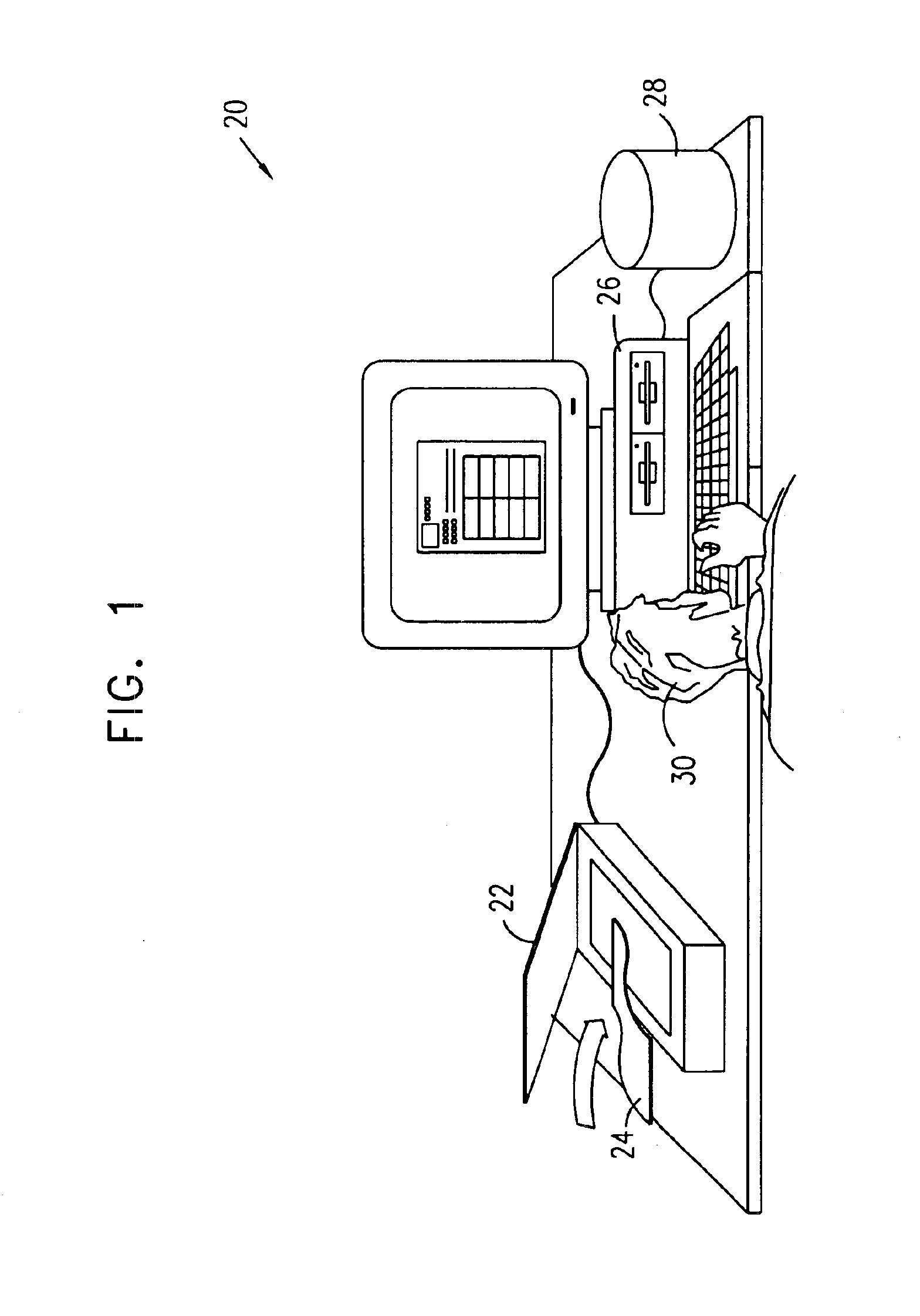
Method, system and device for treating disorders of the pelvic floor by means of electrical stimulation of the pudendal and associated nerves, and the optional delivery of drugs in association therewith
ActiveUS7328068B2Undesirable side effects of sacral nerve stimulation may be avoided or minimizedUndesirable side-effectDigestive electrodesGenital electrodesDiseaseProstatalgia
Described are implantable devices and methods for treating various disorders of the pelvic floor by means of electrical stimulation of the pudendal or other nerves, and optional means for delivering drugs in association therewith. A method of precisely positioning and implanting a medical electrical lead so as to provide optimal stimulation of the pudendal nerve or a portion thereof is also described. Placement of a stimulation lead next to or on the pudendal nerve may be performed using conventional prior art techniques through gross anatomical positioning, but usually does not result in truly optimal lead placement. One method of the present invention utilizes neurophysiological monitoring to assess the evoked responses of the pudendal nerve, and thereby provide a method for determining the optimal stimulation site. Additionally, one or more electrical stimulation signals are applied, and optionally one or more drugs are infused, injected or otherwise administered, to appropriate portions of a patient's pelvic floor and pudendal nerve or portions thereof in an amount and manner effective to treat a number of disorders, including, but not limited to, urinary and / or fecal voiding dysfunctions such as constipation, incontinence disorders such as urge frequency and urinary retention disorders, sexual dysfunctions such as orgasmic and erectile dysfunction, pelvic pain, prostatitis, prostatalgia and prostatodynia.
Owner:MEDTRONIC INC
Method, system and device for treating various disorders of the pelvic floor by electrical stimulation of the left and right pudendal nerves
InactiveUS20040193228A1Directly and effectively stimulatingUndesirable side effects of sacral nerve stimulation may be avoided or minimizedElectrotherapyDiseaseProstatalgia
Described are implantable devices and methods for treating various disorders of the pelvic floor by means of electrical stimulation of the pudendal and sacral nerves, or portions thereof, and optional means for delivering drugs in association therewith. Two or more electrical stimulation regimes are applied on a continuous, alternating, intermittent or other basis to the sacral and pudendal nerves, and optionally one or more drugs are infused, injected or otherwise administered, to appropriate portions of a patient's pelvic floor and pudendal nerve and / or sacral nerve, or portions thereof, in an amount and manner effective to treat a number of disorders, including, but not limited to, urinary and / or fecal voiding dysfunctions such as constipation, incontinence disorders such as urge frequency and urinary retention disorders, sexual dysfunctions such as orgasmic and erectile dysfunction, pelvic pain, prostatitis, prostatalgia and prostatodynia.
Owner:GERBER MARTIN T
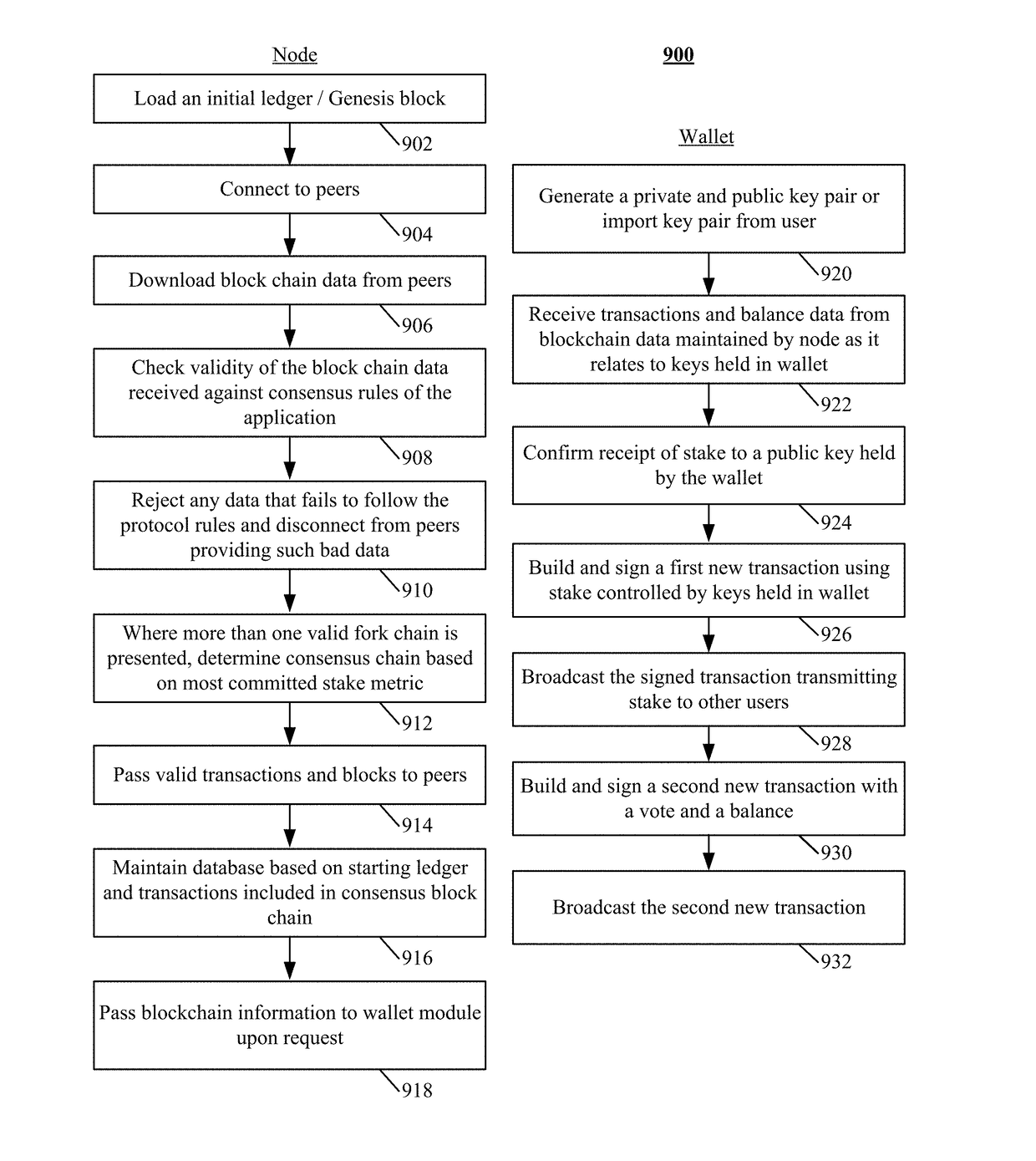
Consensus system for tracking peer-to-peer digital records
ActiveUS9875510B1Improve trustReduce overheadComplete banking machinesFinanceDigital recordingData Corruption
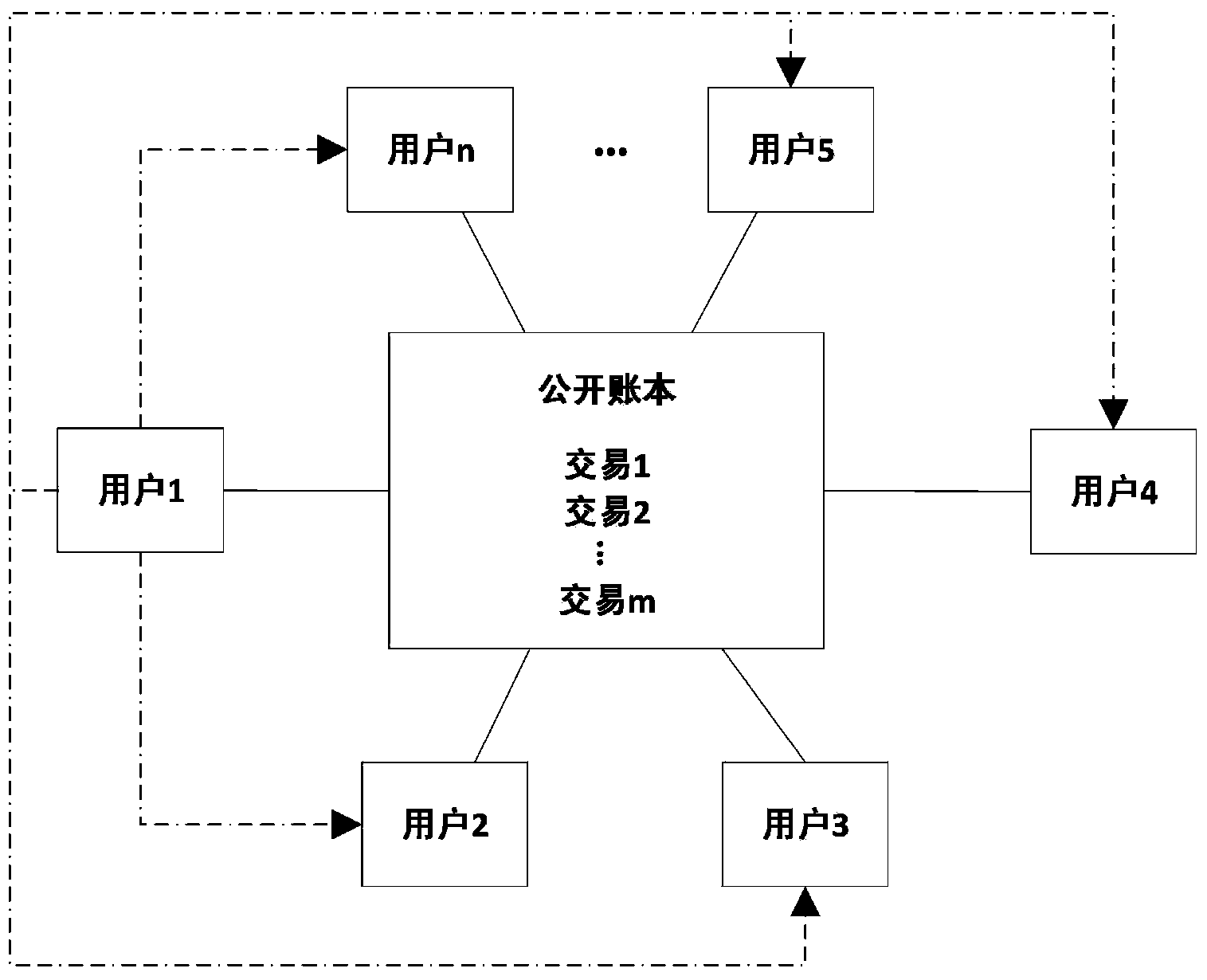
The disclosure describes a peer-to-peer consensus system and method for achieving consensus in tracking transferrable digital objects. The system achieves consensus on a shared ledger between a plurality of peers and prevents double spending in light of network latency, data corruption and intentional manipulation of the system. Consensus is achieved and double spending is prevented via the use of the most committed stake metric to choose a single consensus transaction record. A trustable record is also facilitated by allowing stakeholders to elect a set of trusted non-colluding parties to cooperatively add transactions to the consensus record. The voting mechanism is a real-time auditable stake weighted approval voting mechanism. This voting mechanism has far reaching applications such as vote directed capital and providing a trusted source for data input into a digital consensus system. The system further enables digital assets that track the value of conventional assets with low counterparty risk.
Owner:KASPER LANCE
User public key address binding, searching and verifying method and system based on crypto currency open account book technology
ActiveCN104320262AImprove convenienceImprove securityUser identity/authority verificationPayment architectureDigital currencyDependability
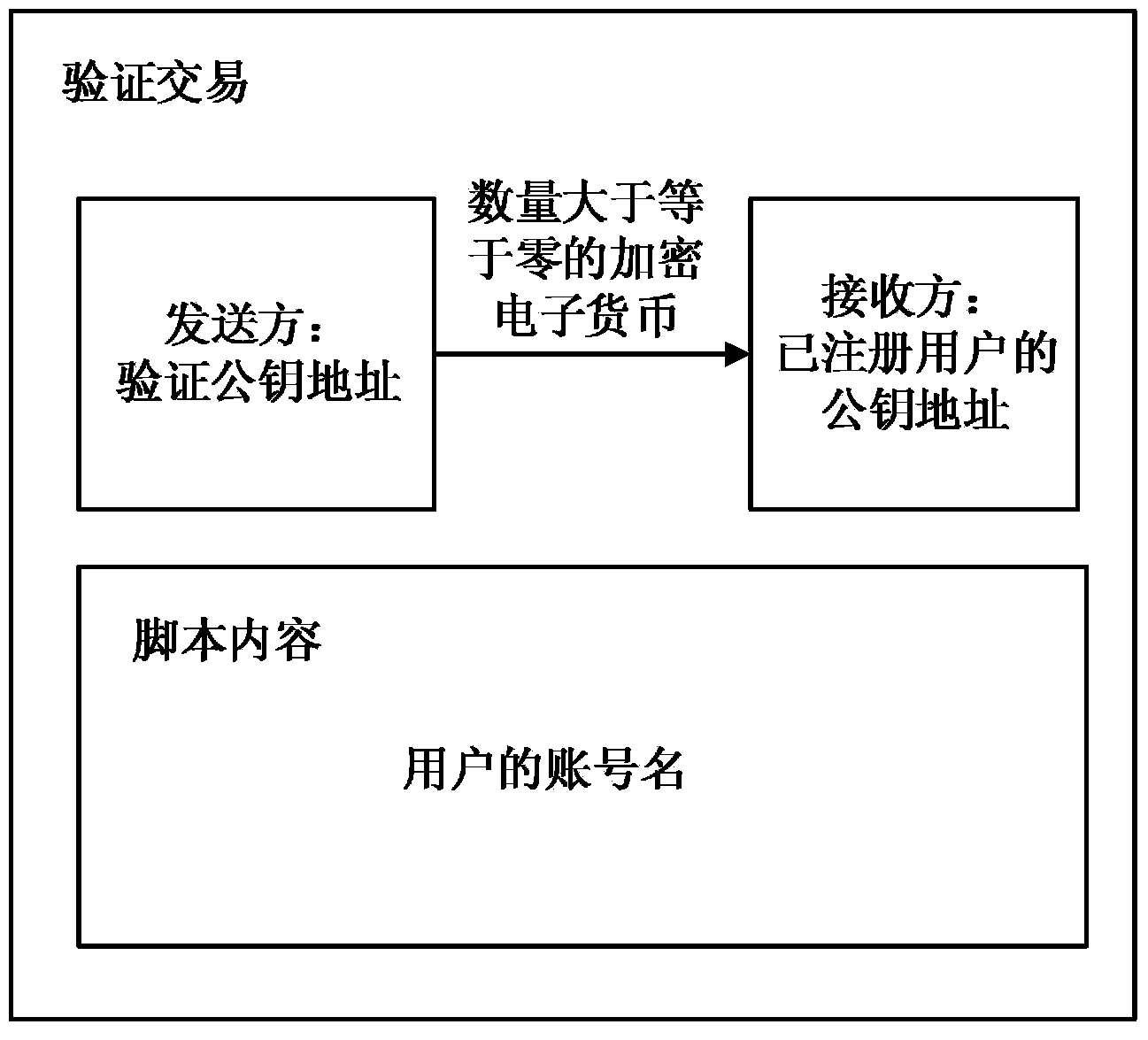
The invention discloses a user public key address binding, searching and verifying method and system based on the crypto currency open account book technology. The user public key address binding, searching and verifying method is characterized by comprising the following steps that (1) verification public key addresses are published to users in a crypto currency network; (2) an account name registration request of one user is received, and the public key address of the user is received; (3) crypto currency is sent to the public key address of the crypto currency of the registered user through a private key address corresponding to the verification public key address and used as a verification transaction, and it is set that additional information or script content of the verification transaction contains the account number of the user, wherein the amount of the crypto currency is greater than or equal to zero; (4) query requests from other users in the crypto currency network are received, and the public key address of the registered user is fed back according to the query requests. The user public key address binding, searching and verifying method and system can substantially improve the availability, convenience, safety and reliability of crypto currency transactions, and protect the users against economic losses caused by the situation that the public key addresses are tampered with and used illegally.
Owner:安徽中科晶格技术有限公司
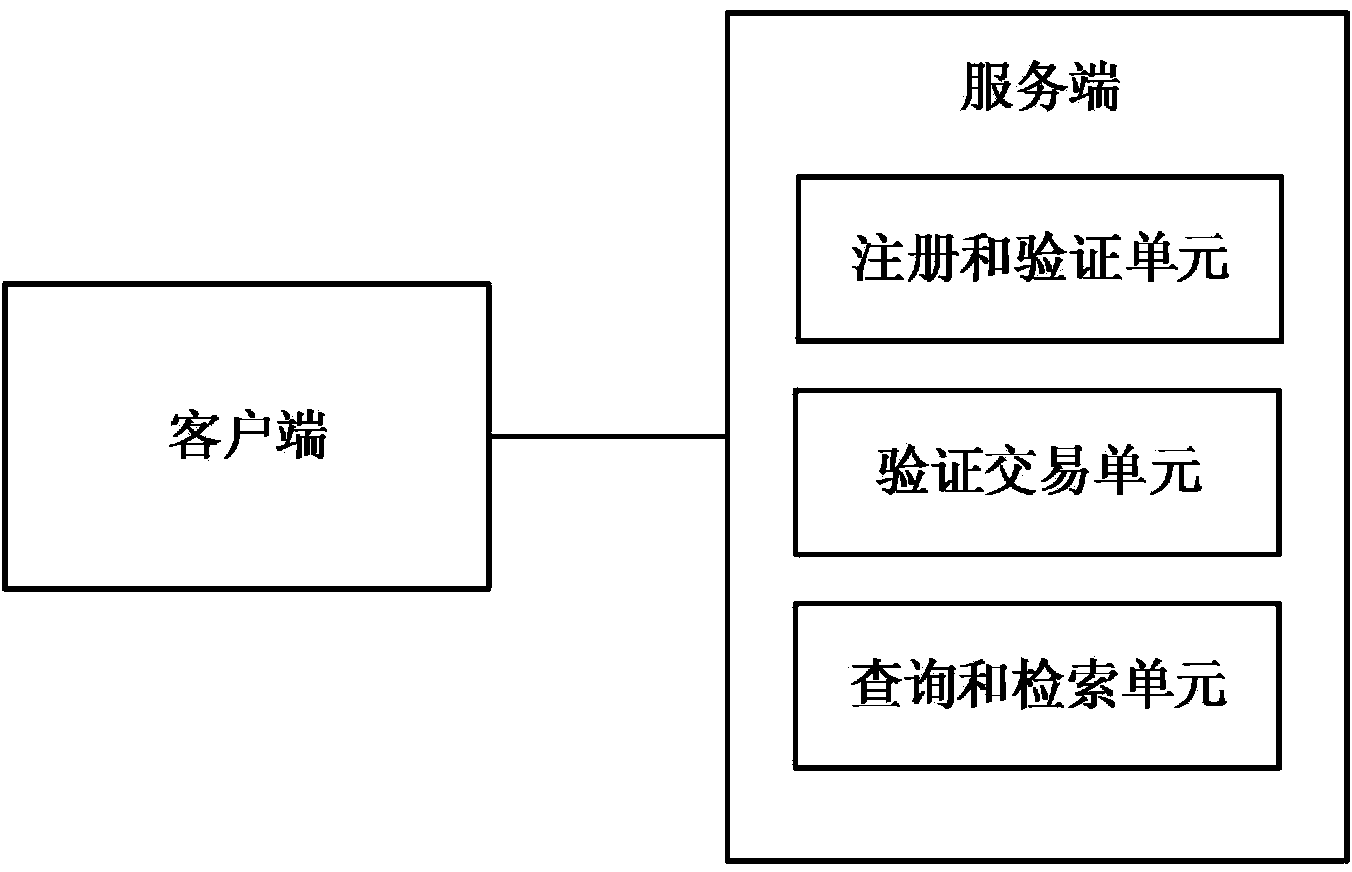
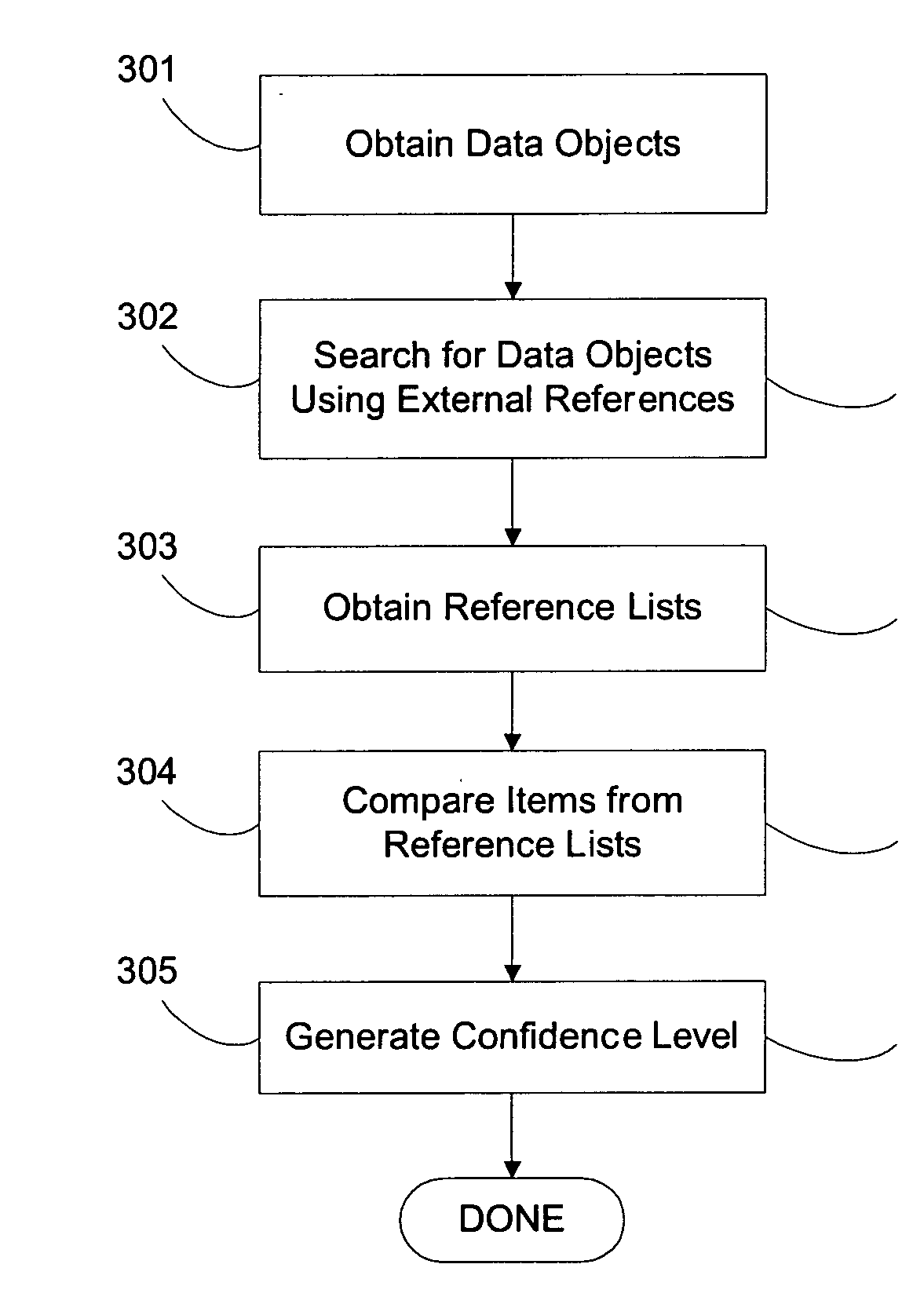
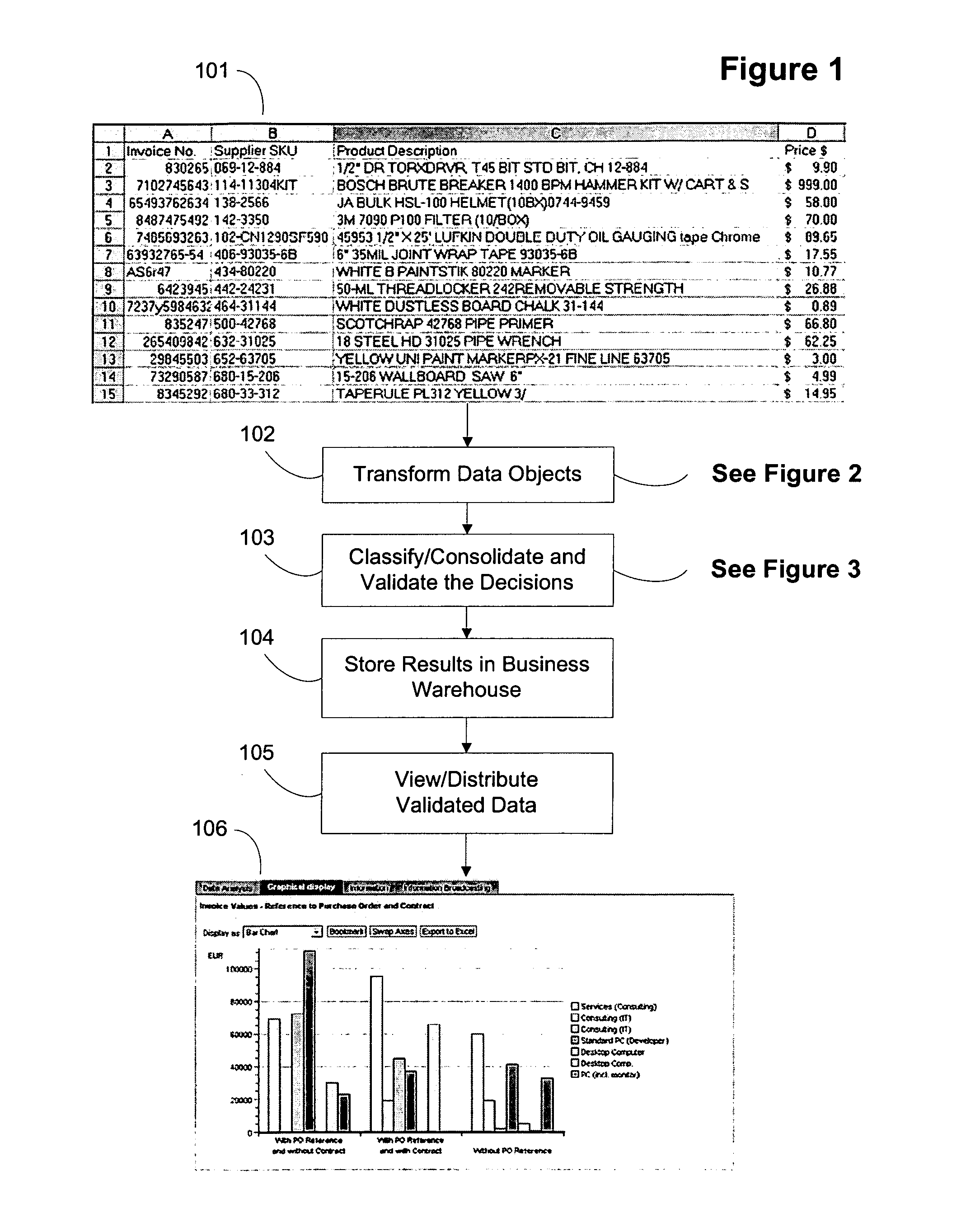
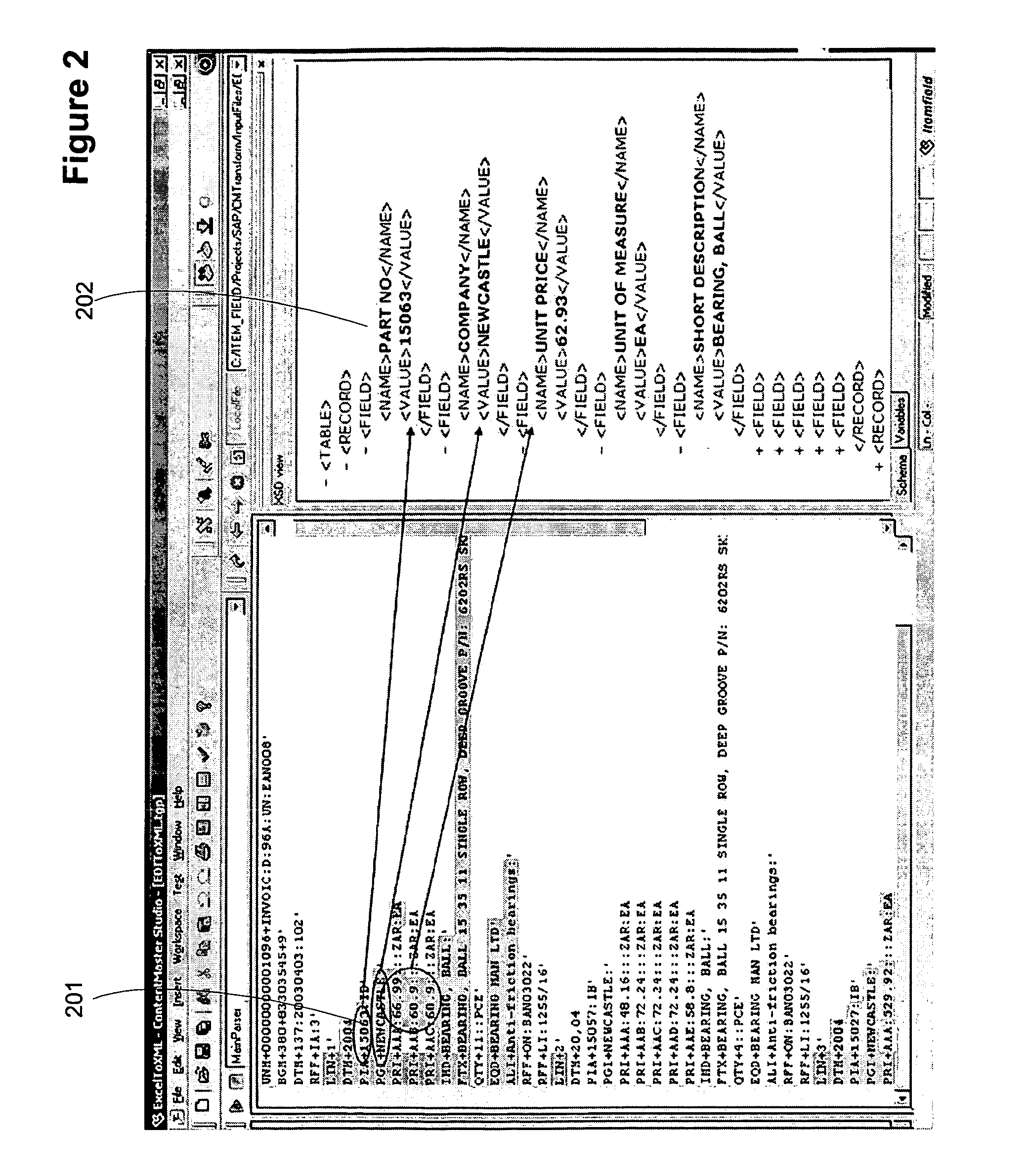
System and method for using external references to validate a data object's classification / consolidation
ActiveUS20070162414A1Improve trustTake substantial amountDigital data information retrievalDigital data processing detailsOriginal dataExternal reference
A computer system and method for validating data object classification and consolidation using external references. The external references may be web pages, product catalogs, external databases, URLs, search results provided by a search engine or subsets or combinations of any of these to validate a classification or consolidation of records. Embodiments validate a data object classification or consolidation decision by searching external data sources, such as databases, the Internet etc. for references to the transactional data object and determining a confidence level based on the original data object and the unstructured information reference, URL, or search result for example. Decisions may be verified or denied based on the comparison of the external references related to each data object. Embodiments of the invention save substantial labor in validating business data objects and make data more reliable across enterprise systems.
Owner:SAP AG
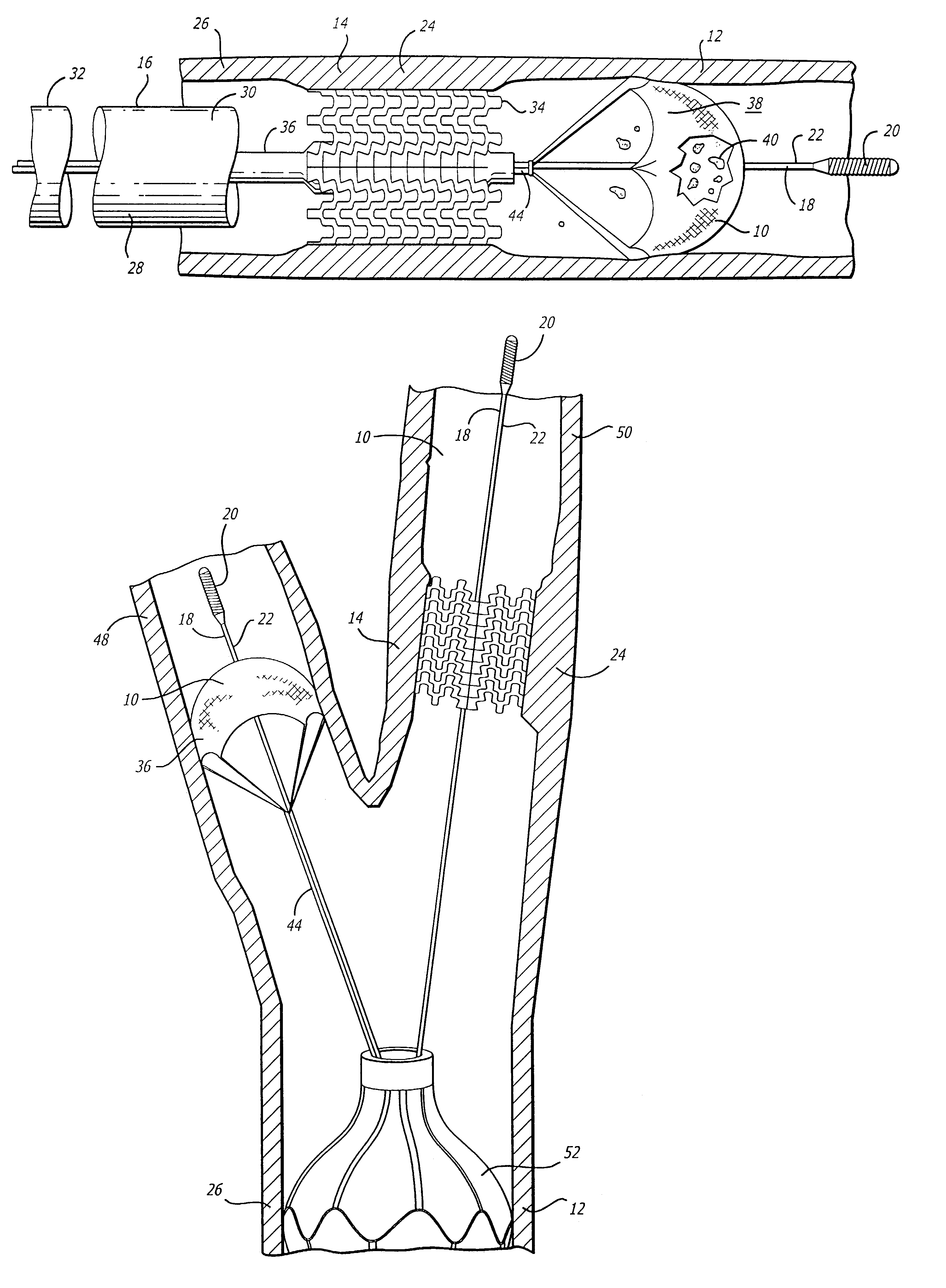
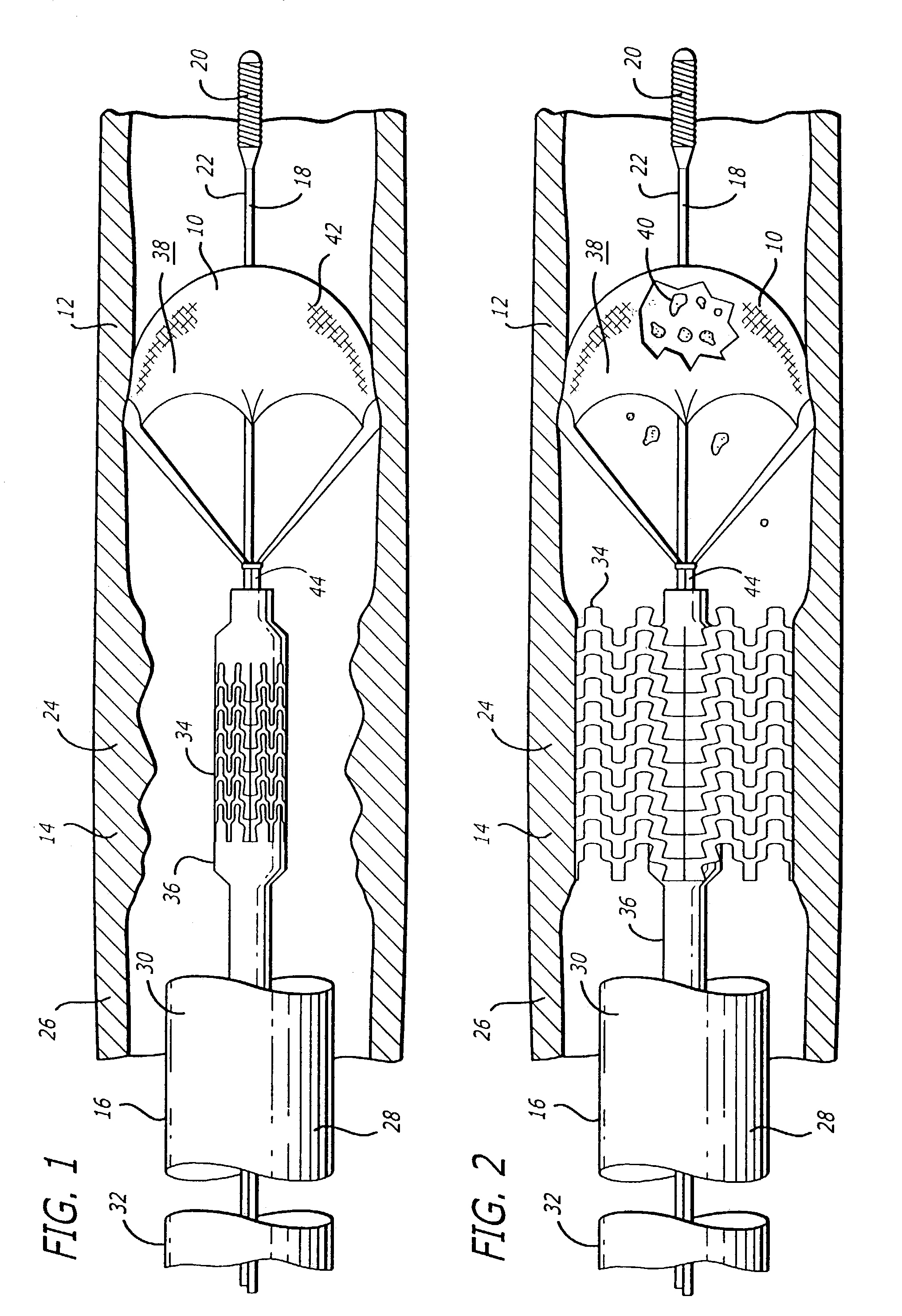
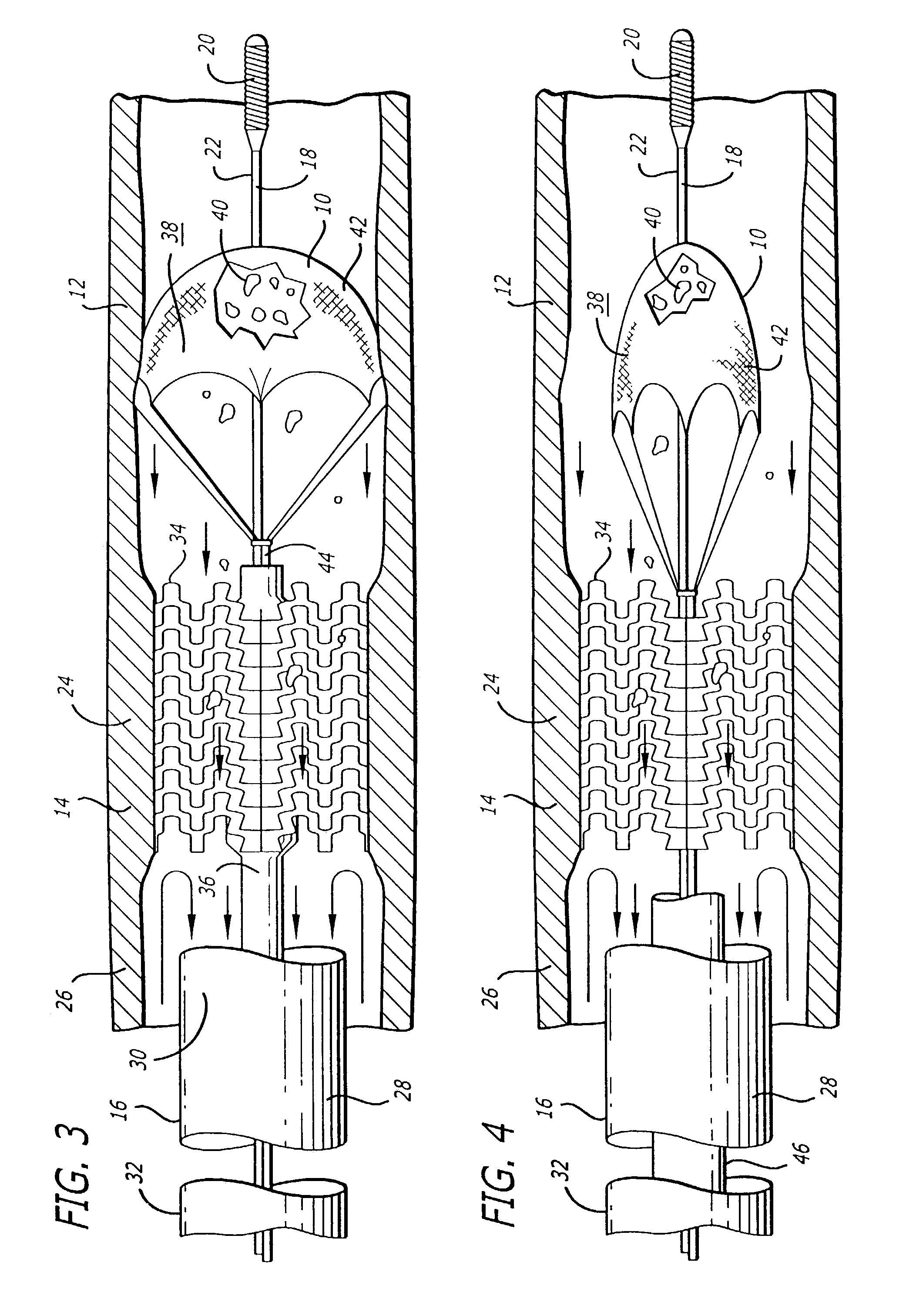
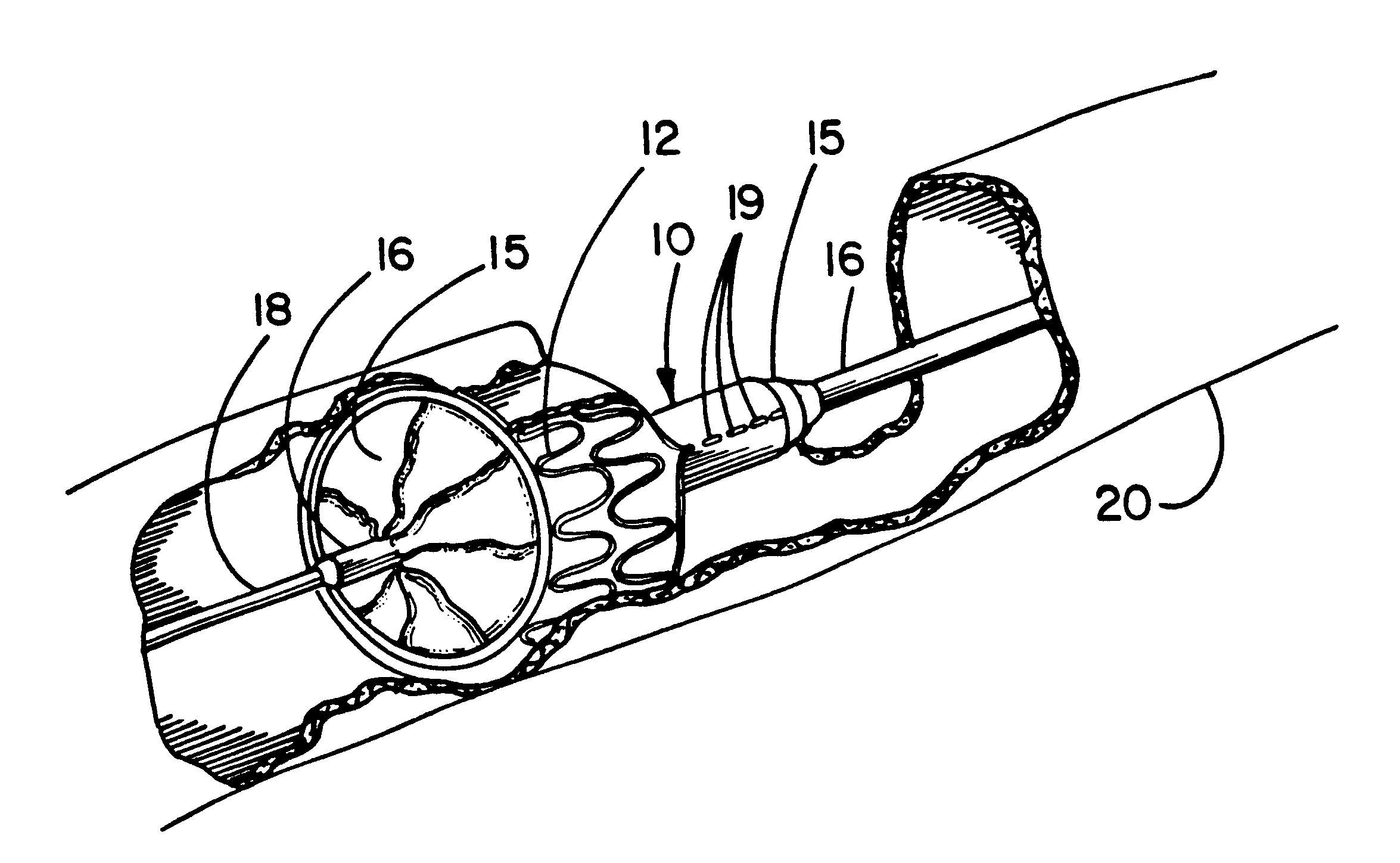
Vessel occlusion device for embolic protection system
A system used in a blood vessel when an interventional procedure is being performed in a stenosed or occluded region, which is capable of capturing embolic material which may be released into a blood vessel during a therapeutic interventional procedure at the site of a lesion in the blood vessel. The system is adapted to be utilized in a collateral blood supply system adapted to enable the flow of blood to bypass the blood vessel upon blocking thereof and to enable the reverse flow of blood through the blood vessel upon unblocking thereof. The system includes a guide wire, including a distal end, adapted to be positioned in a blood vessel relative to an interventional procedure site. A guide catheter, including a distal end, is adapted to enable the interventional procedure to be performed, and to be inserted over the guide wire and through a patient's vasculature to a position in the blood vessel relative to the interventional procedure site. An occluding device for occluding and blocking a blood vessel at a location relative to the interventional procedure site is adapted to be positionable at a location relative to he interventional procedure site, to be expandable so as to prevent and block the flow of blood past the occlusion, and to enable the capture of embolic material which may be released into the blood in the blood vessel during the therapeutic interventional procedure, and to be contracted to unblock the blood vessel and enable the recovery of captured embolic material.
Owner:ABBOTT CARDIOVASCULAR
Deployment system for intraluminal devices
InactiveUS6899727B2Facilitate removalFacilitate fluoroscopic visualizationStentsBlood vesselsProsthesisBiomedical engineering
A constraining sheath for use around an endoprosthesis (e.g., a stent device, with or without a graft covering), which may be a balloon expandable endoprosthesis but more preferably is a self-expanding prosthesis. The endoprosthesis is coaxially enclosed within the constraining sheath, which is an outer, disruptable, preferably implantable tubular sheath, preferably made of ePTFE. The constraining sheath and endoprosthesis are preferably mounted together as an assembly on an angioplasty balloon for delivery. Deployment of the endoprosthesis entails inflating the angioplasty balloon to a pressure sufficient to disrupt or break the constraining sheath in a prescribed fashion, thereby allowing a self-expanding endoprosthesis to spontaneously deploy. The constraining sheath of ePTFE may be attached to the endoprosthesis and implanted along with the device, or alternatively attached to the balloon catheter shaft and removed with the balloon catheter.
Owner:WL GORE & ASSOC INC
Method, system and device for treating disorders of the pelvic floor by means of electrical stimulation of the pudenal and associated nerves, and the optional delivery of drugs in association therewith
ActiveUS20050113877A1Reduce traumaAvoid damageDigestive electrodesArtificial respirationDiseaseProstatalgia
Described are implantable devices and methods for treating various disorders of the pelvic floor by means of electrical stimulation of the pudendal or other nerves, and optional means for delivering drugs in association therewith. A method of precisely positioning and implanting a medical electrical lead so as to provide optimal stimulation of the pudendal nerve or a portion thereof is also described. Placement of a stimulation lead next to or on the pudendal nerve may be performed using conventional prior art techniques through gross anatomical positioning, but usually does not result in truly optimal lead placement. One method of the present invention utilizes neurophysiological monitoring to assess the evoked responses of the pudendal nerve, and thereby provide a method for determining the optimal stimulation site. Additionally, one or more electrical stimulation signals are applied, and optionally one or more drugs are infused, injected or otherwise administered, to appropriate portions of a patient's pelvic floor and pudendal nerve or portions thereof in an amount and manner effective to treat a number of disorders, including, but not limited to, urinary and / or fecal voiding dysfunctions such as constipation, incontinence disorders such as urge frequency and urinary retention disorders, sexual dysfunctions such as orgasmic and erectile dysfunction, pelvic pain, prostatitis, prostatalgia and prostatodynia.
Owner:MEDTRONIC INC
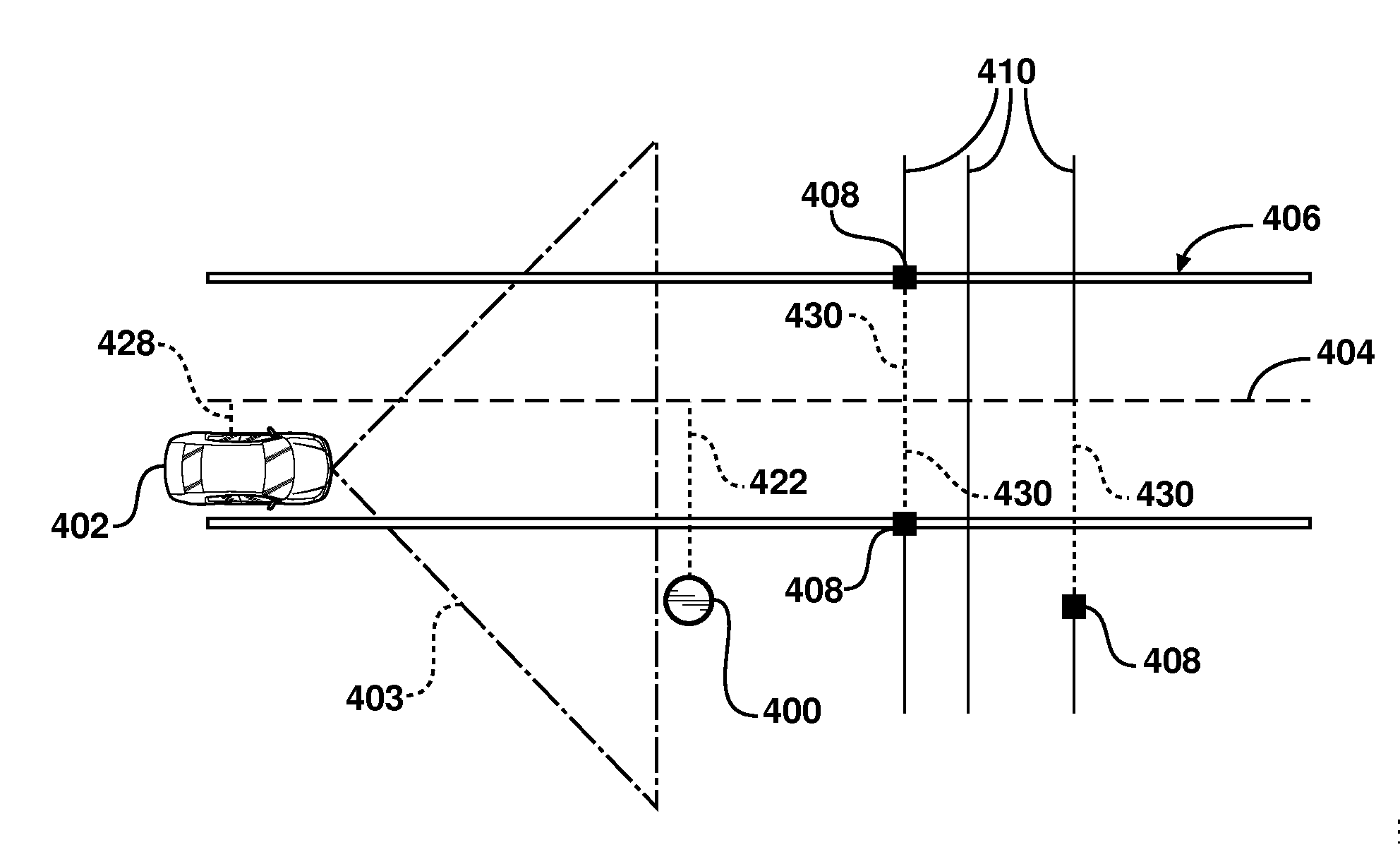
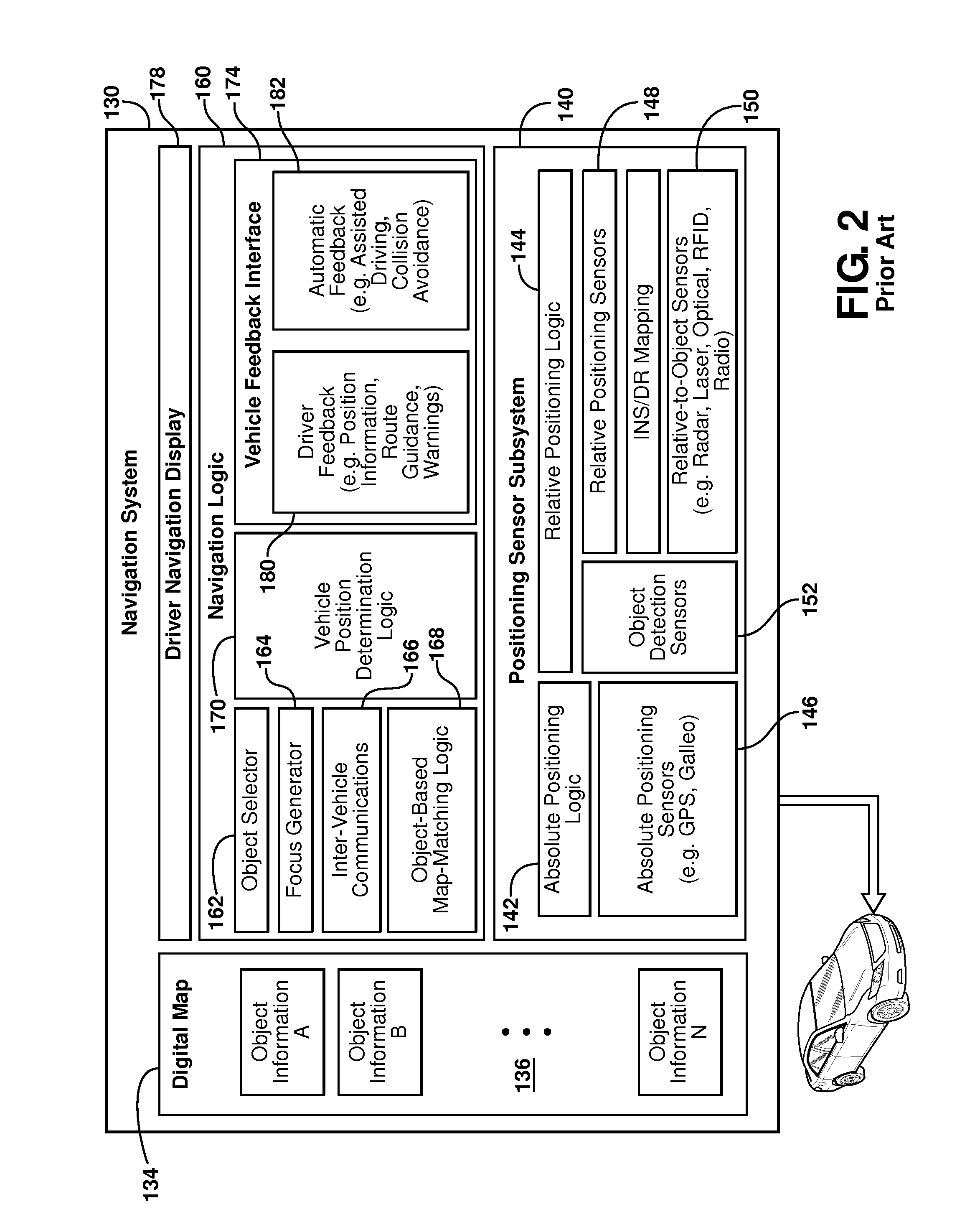
System and method for vehicle navigation using lateral offsets
ActiveUS20120271540A1Enhanced driver assistance featureSimple calculationInstruments for road network navigationAnti-collision systemsRadarLaser scanning
A navigation system for use in a vehicle (402). The system includes an absolute position sensor, such as GPS, in addition to one or more additional sensors, such as a camera, laser scanner, or radar. The system further comprises a digital map or database that includes records for at least some of the vehicle's surrounding objects (400). These records can include relative positional attributes with respect to a reference axis (404). As the vehicle (402) moves, sensors sense the presence of at least some of these objects (400), and measure the vehicle's relative position to those objects. This information is used to determine the vehicle's instantaneous lateral offset (428) relative to the reference axis (404), and support features such as enhanced driving directions, collision avoidance, or automatic assisted driving. The system also allows new objects (408, 414) to be attributed using relative positioning, and thereby factored into the enhanced navigation features.
Owner:TOMTOM POLSKA
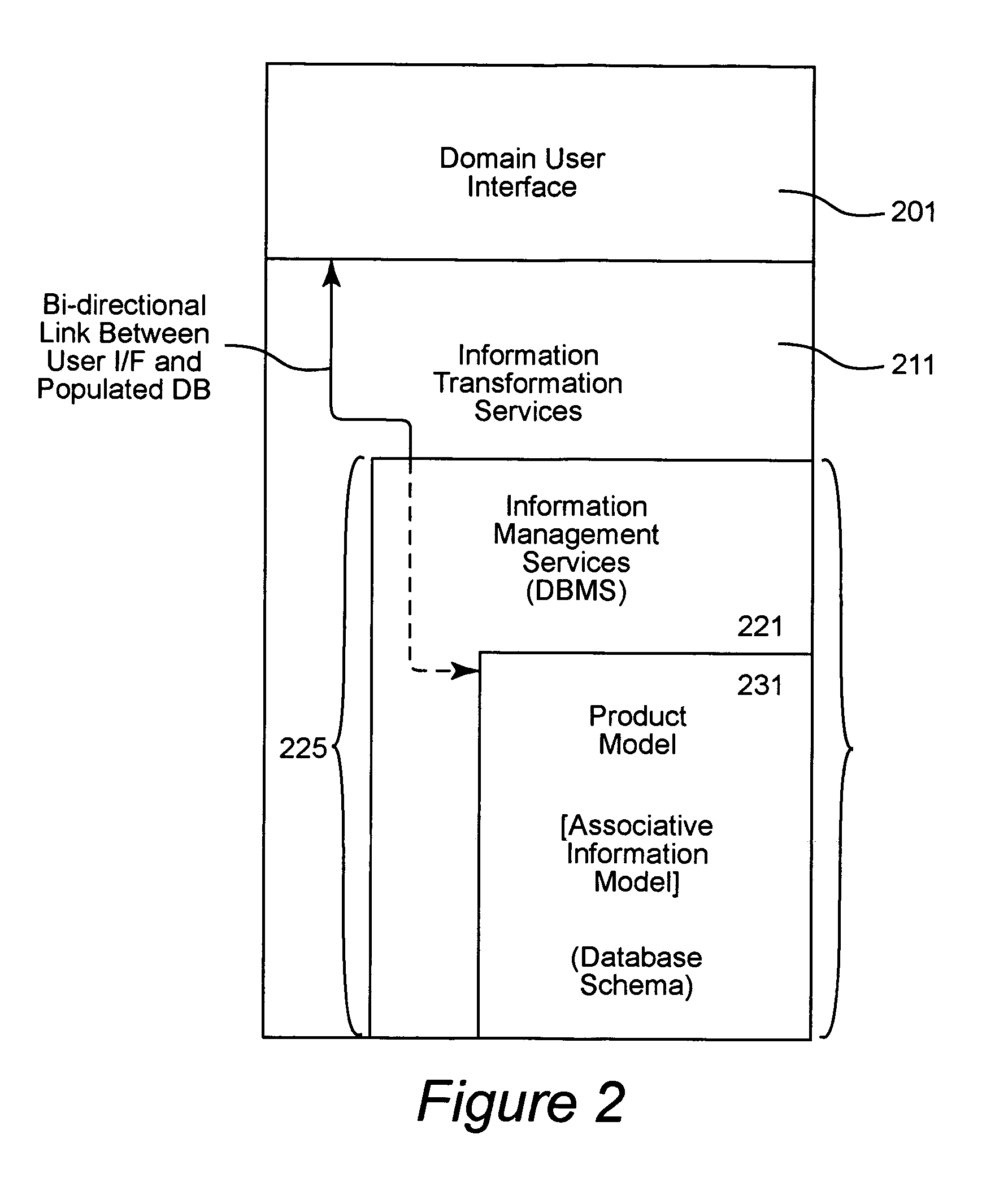
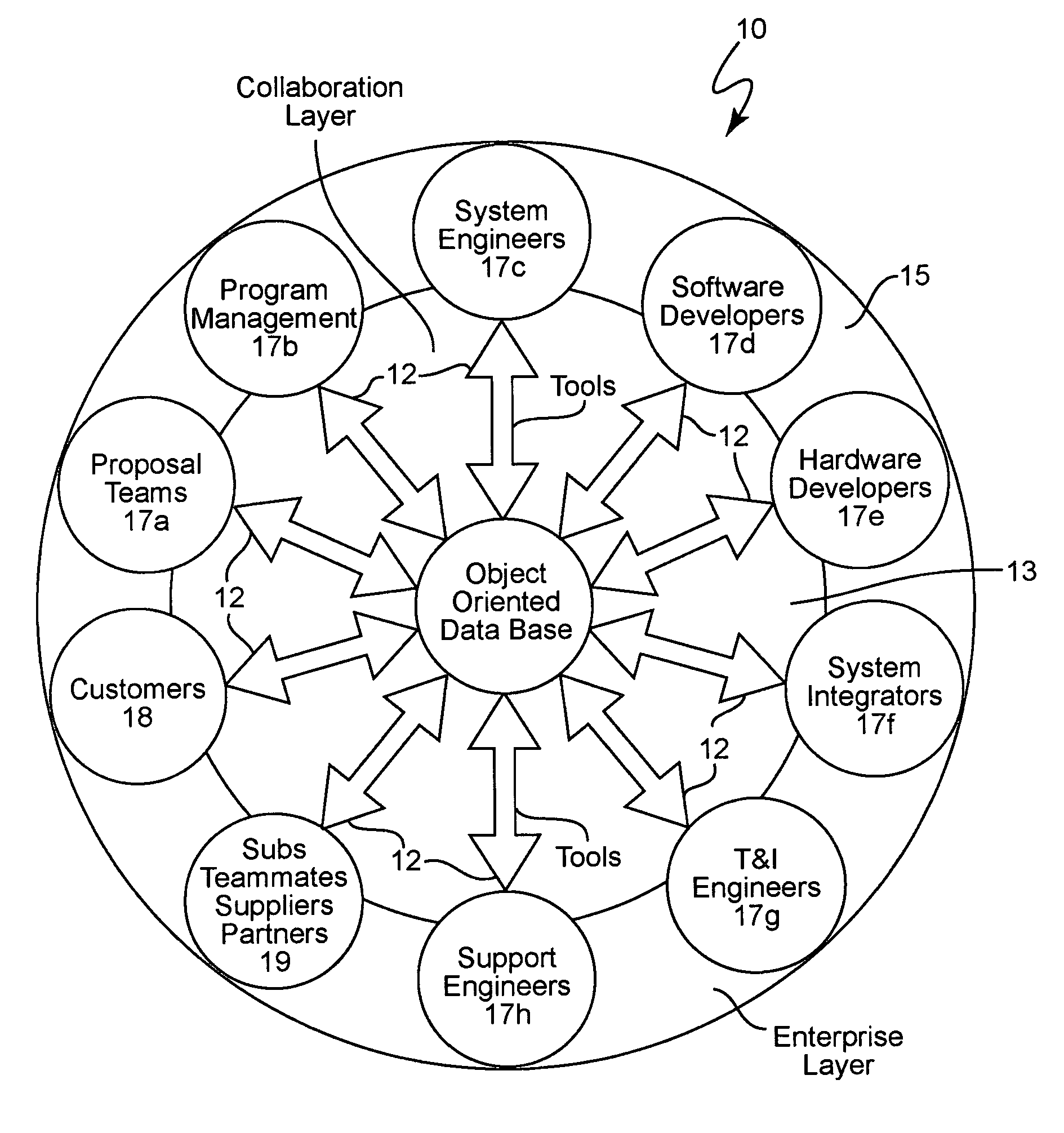
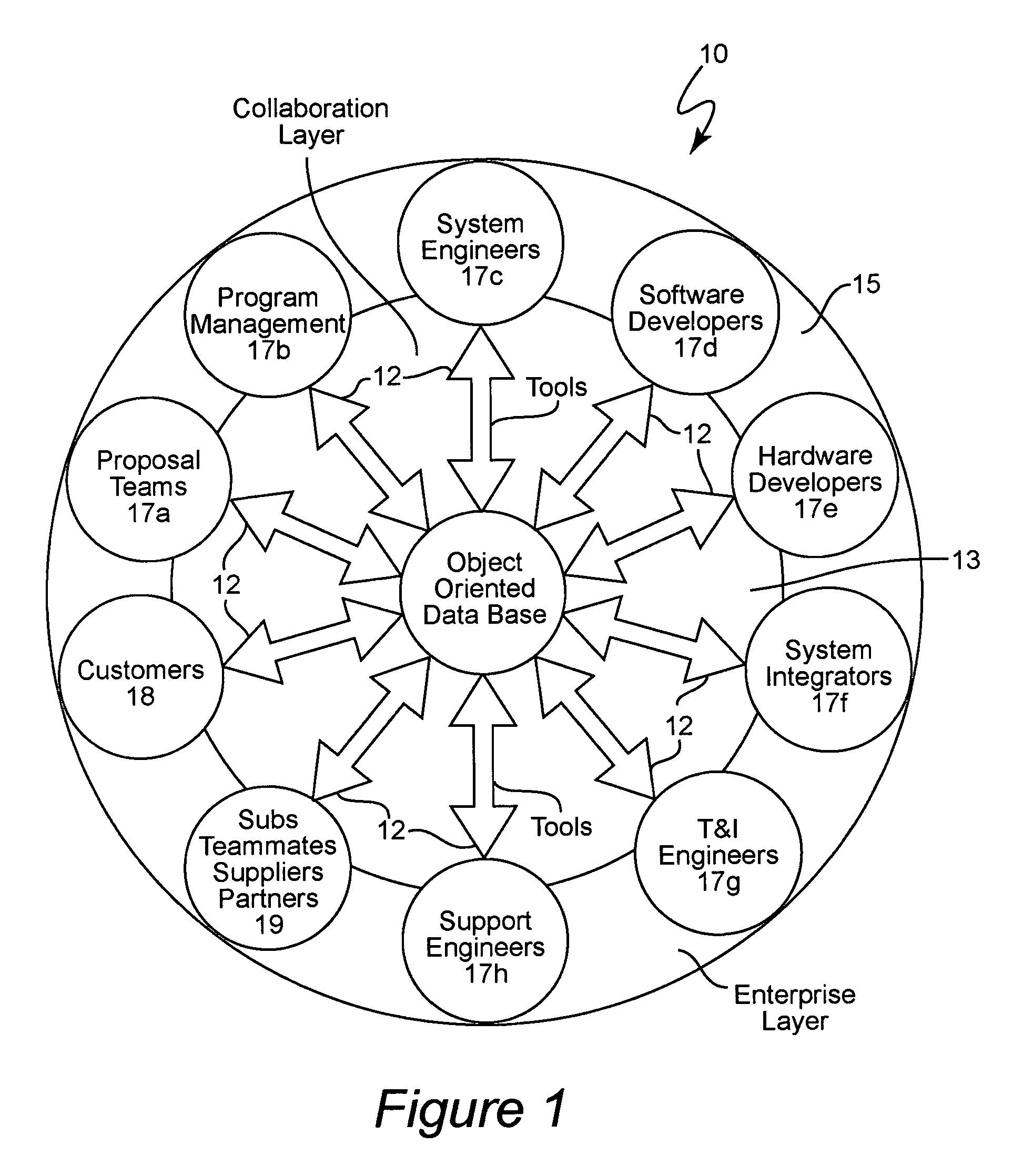
Product catalog for use in a collaborative engineering environment and method for using same
InactiveUS6959268B1Easy to useImprove visibilityMultiple digital computer combinationsOffice automationInformation dispersalSubject-matter expert
A collaborative engineering environment (CEE) enables the effective capture, management, communication, and exploitation of all product related information to a project team. The systematic employment of this information offers substantial improvements in productivity, cost savings, cycle time reductions, product integrity, and lifetime supportability of the system. Advanced CEE capabilities exploit and leverage the engineering, architectural and technological expertise of enterprise subject matter experts (domain experts) across multiple complex systems development and integration activities. The CEE provides a tightly coupled process automation using reusable product elements for coupling information with engineering processes and ensuring adherence to repeatable and traceable engineering processes. A product catalog provides a single information management point for intrinsic complex product characteristics and facilitates the propagation of that information to engineering teams incorporating the complex product into their system designs. The intrinsic complex product characteristics are augmented with implementation specific information to fully describe the complex product in the system design.
Owner:LOCKHEED MARTIN CORP
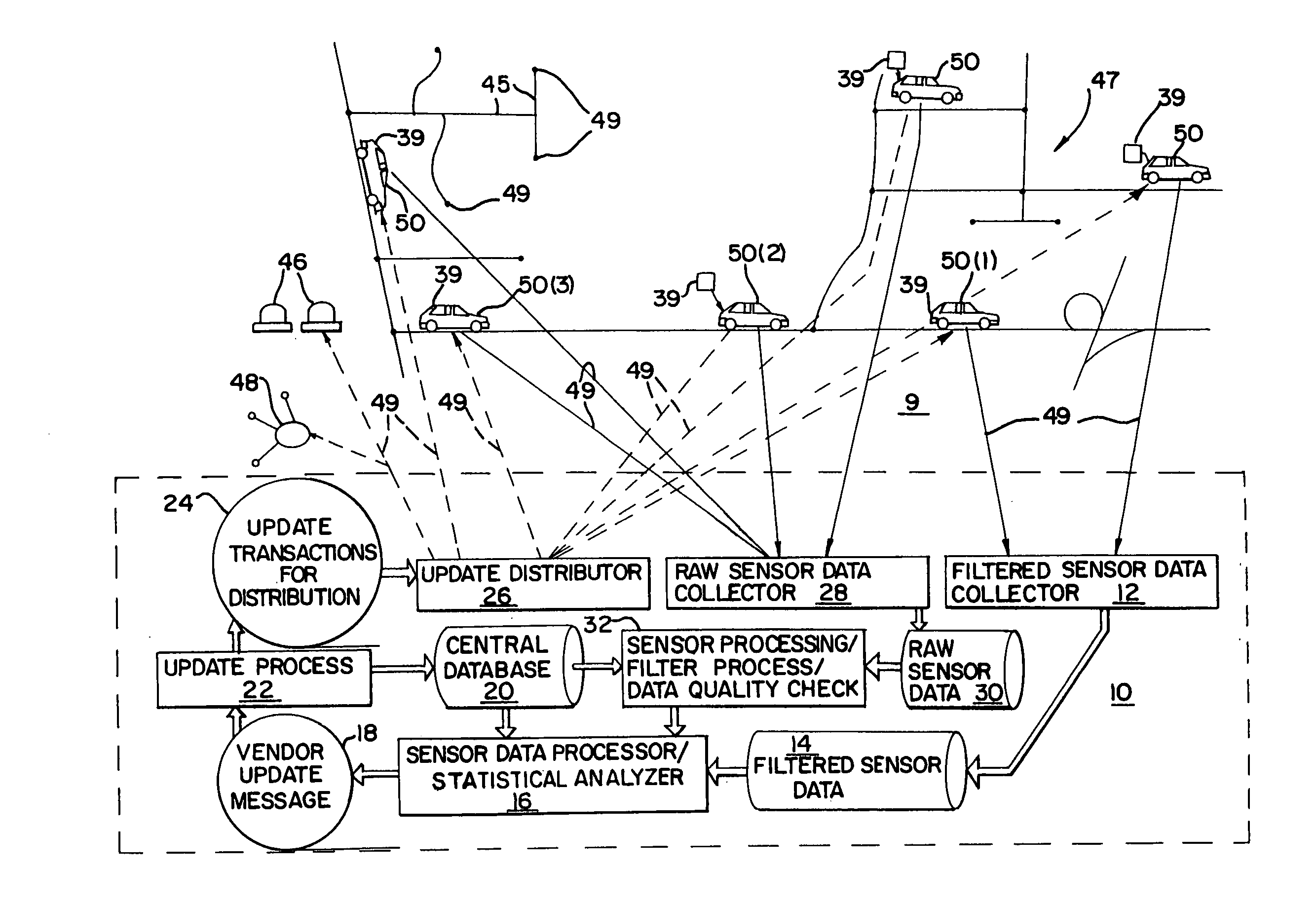
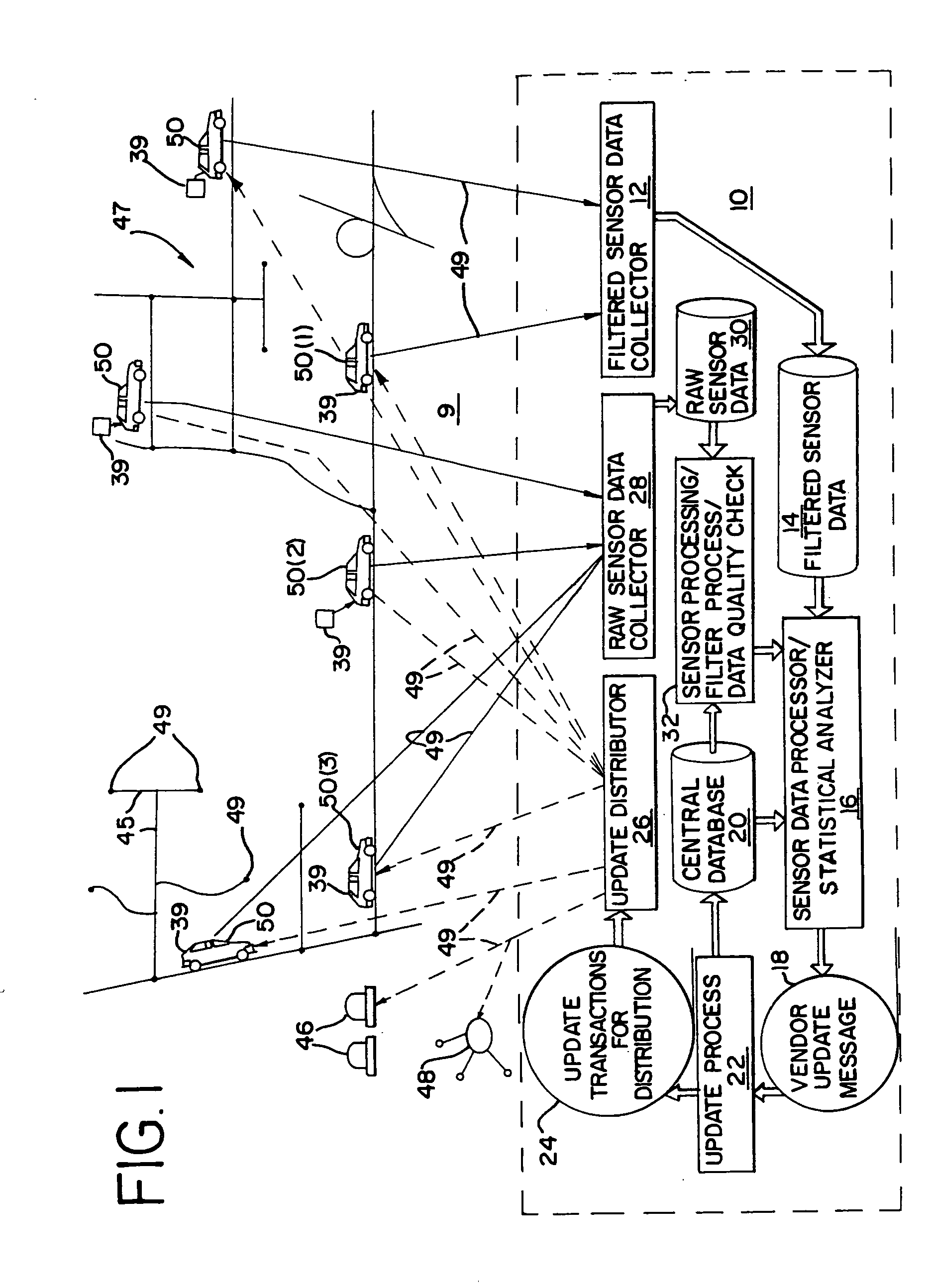
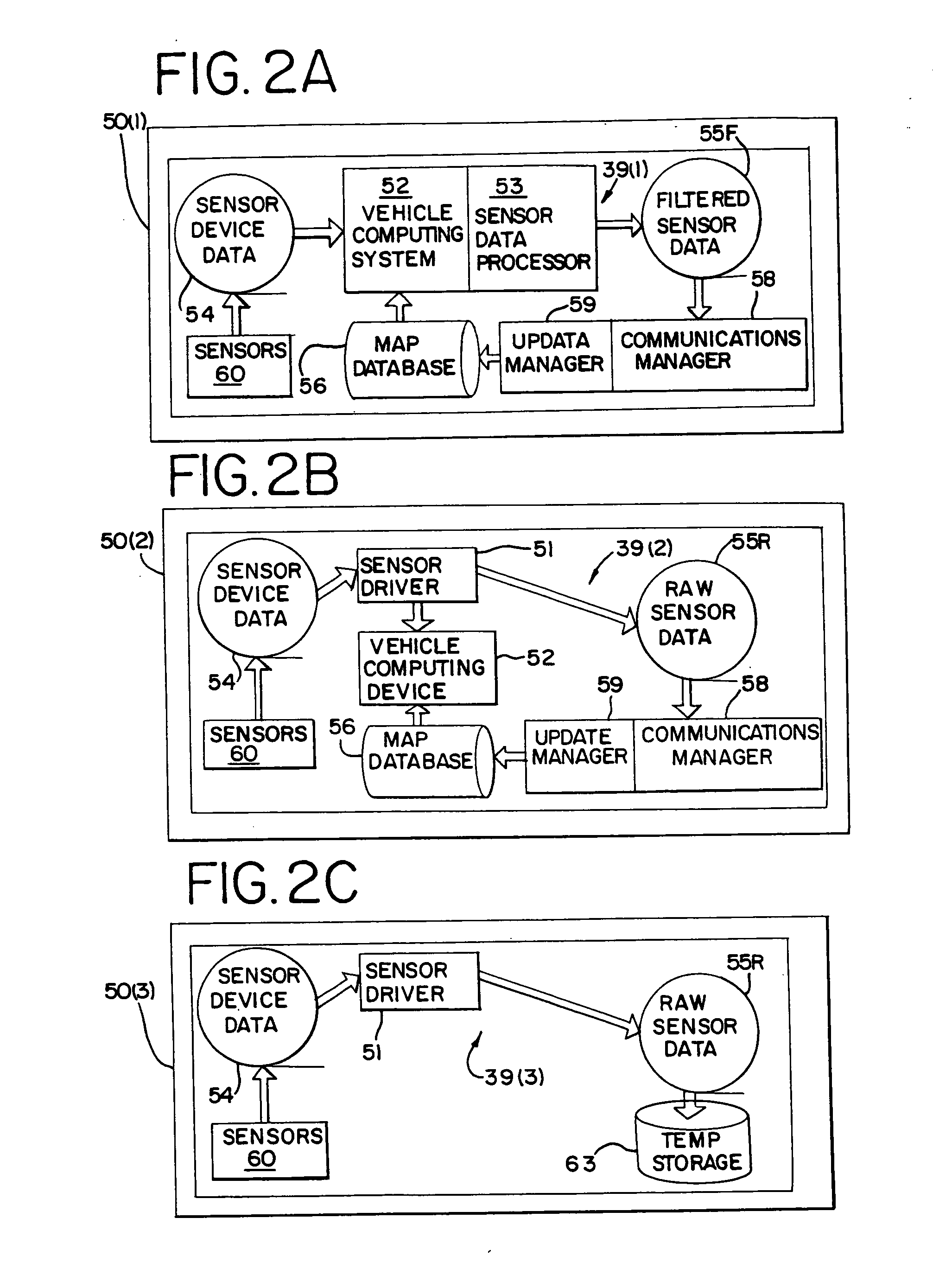
System and method for updating, enhancing, or refining a geographic database using feedback
InactiveUS20050149259A1Improve trustInstruments for road network navigationArrangements for variable traffic instructionsData matchingNavigation system
A method for updating a geographic database is disclosed. Data collecting equipment is installed in each of a plurality of vehicles each of which also has a navigation system. The data collection equipment is used to collect data while the vehicles are being driven along roads by their respective users. In addition, a method for assigning a confidence level to geographic data is disclosed. The confidence level is assigned to the geographic data as an attribute. In addition, a method for determining a position of a vehicle by sensing roadside structures is disclosed. Data indicating positions of roadside structures are contained in a geographic database. By matching positions of sensed roadside structures to data in the geographic database that indicates the positions of the structures, the position of the vehicle while traveling can be determined.
Owner:HERE GLOBAL BV
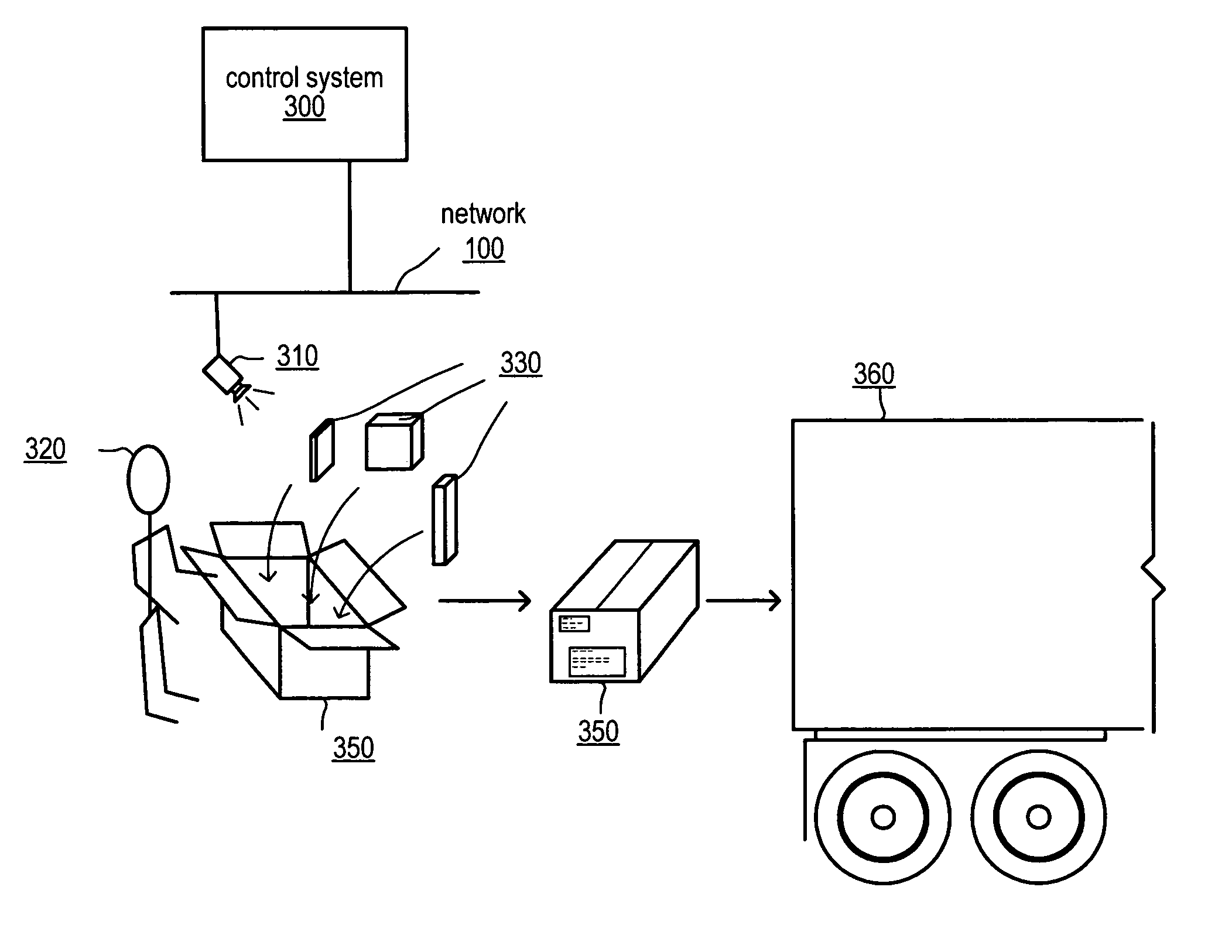
System and method for visual verification of order processing
One or more images of items for an order being processed at processing station of an order fulfillment center may be captured and associated with the order. Alternatively, a short video clip may be captured of the order being packaged. An electronic notification that the order has been processed may be sent to a customer associated with the order. The electronic notification may include a reference to one or more of the captured images or video clips. The customer may use a reference included in the notification to view the captured images. The customer may view captured images to verify that the order has been correctly processed. The captured images may include images of the items being packaged for shipment and may show the shipping address on the package allowing the customer to verify that indeed it is his package in the images.
Owner:AMAZON TECH INC
Operation of trusted state in computing platform
ActiveUS7302698B1Improve trustSimple taskDigital data processing detailsUser identity/authority verificationOperational systemModem device
A computing entity comprises a trusted monitoring component having a first processing means and a first memory means, the trusted monitoring component being a self-contained autonomous data processing unit, and a computer platform having a main processing means and a main memory area, along with a plurality of associated physical and logical resources such as peripheral devices including printers, modems, application programs, operating systems and the like. The computer platform is capable of entering a plurality of different states of operation, each state of operation having a different level of security and trustworthiness. Selected ones of the states comprise trusted states in which a user can enter sensitive confidential information with a high degree of certainty that the computer platform has not been compromised by external influences such as viruses, hackers or hostile attacks. To enter a trusted state, references made automatically to the trusted component, and to exit a trusted state reference must be made to the trusted component. On exiting the trusted state, all references to the trusted state are deleted from the computer platform. On entering the trusted state, the state is entered in a reproducible and known manner, having a reproducible and known configuration which is confirmed by the trusted component.
Owner:META PLATFORMS INC
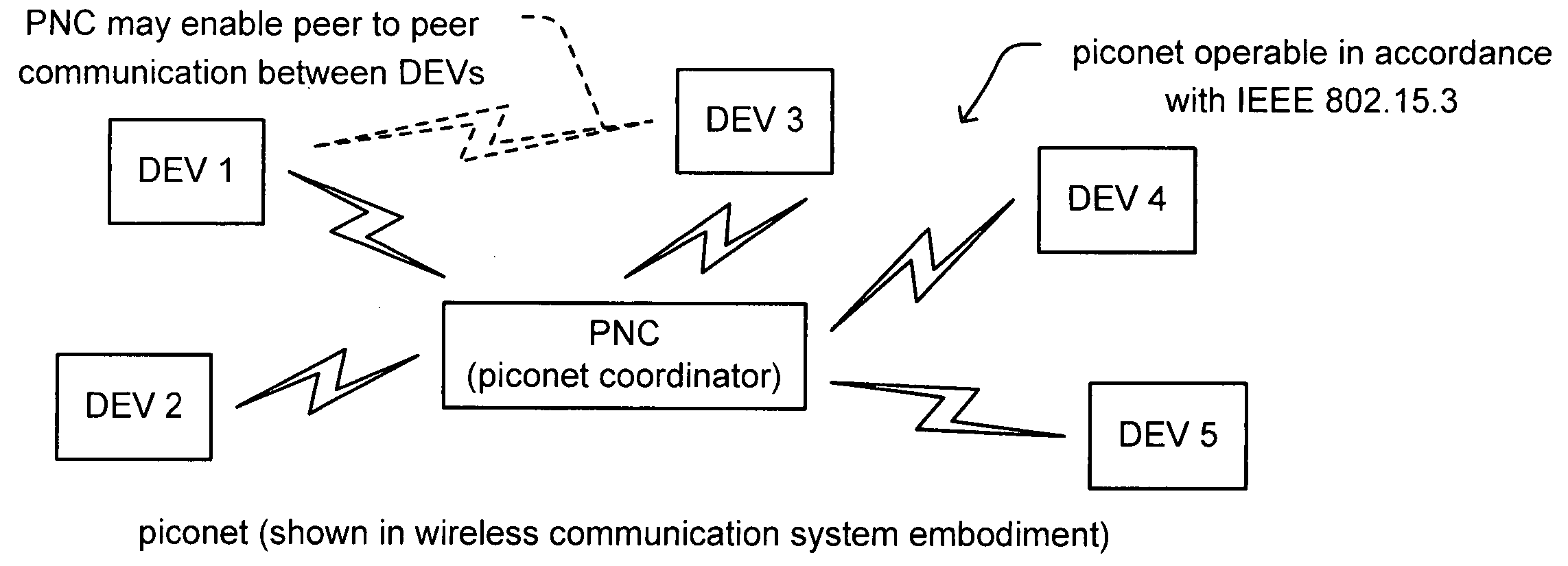
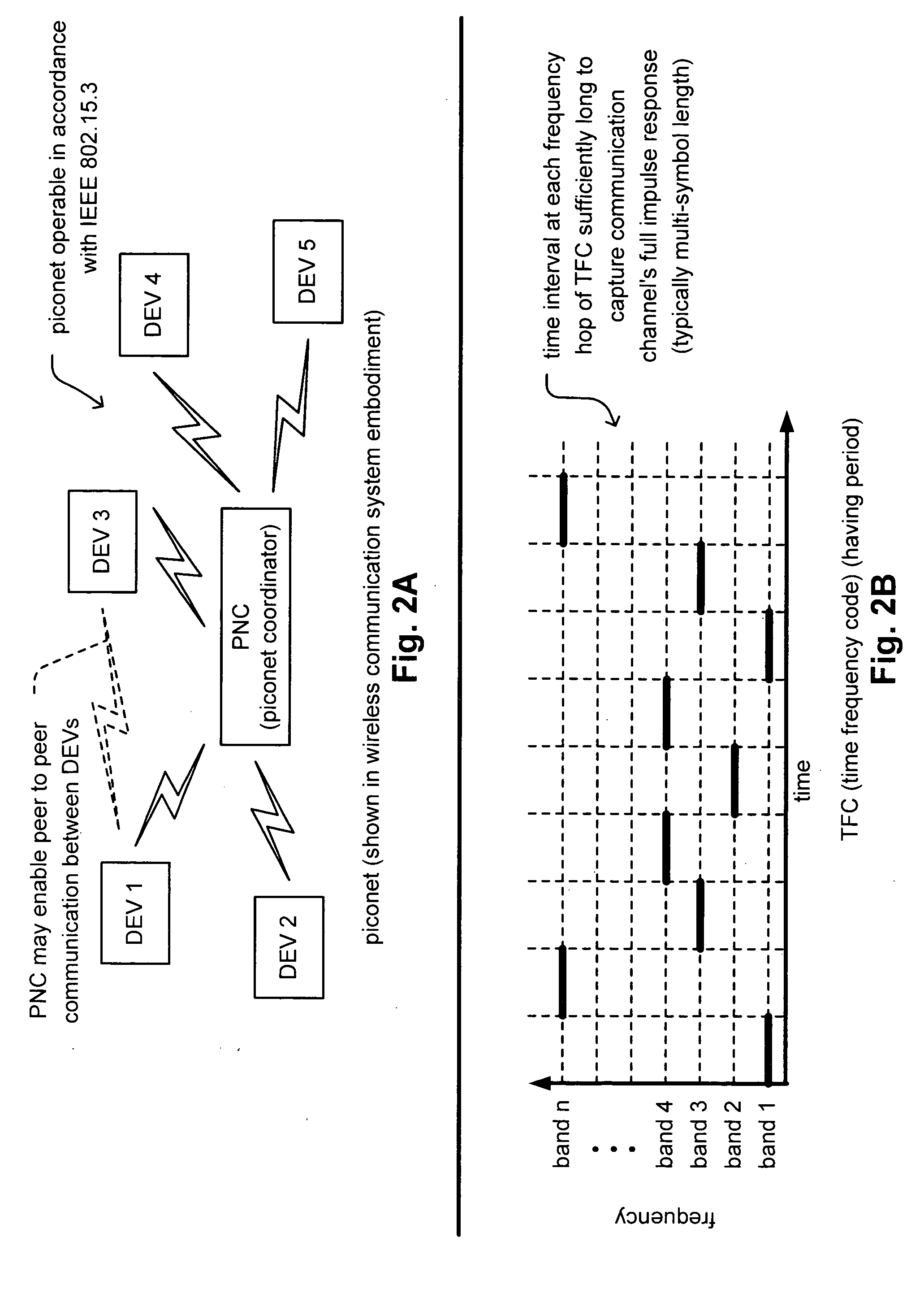
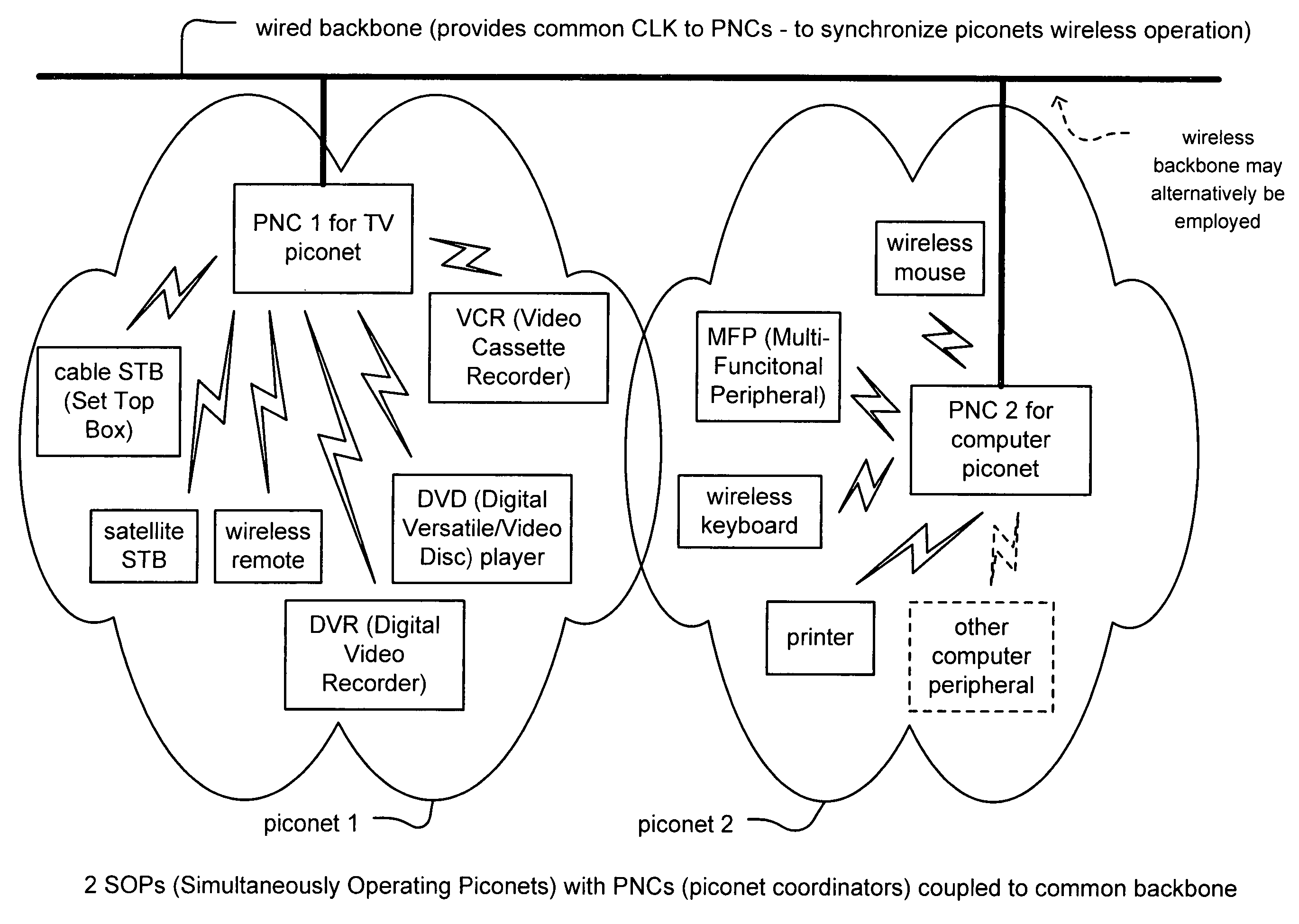
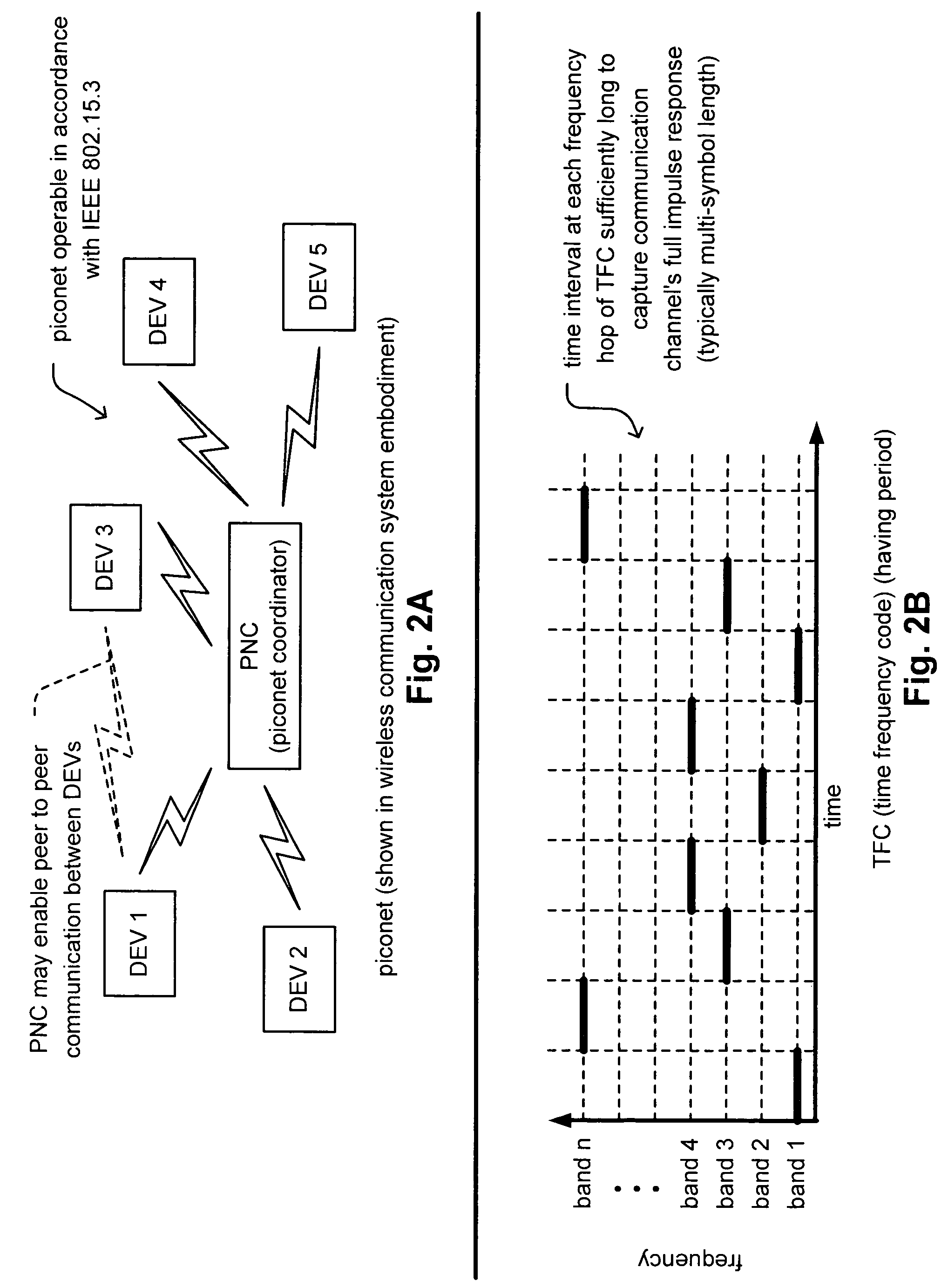
Synchronized UWB piconets for SOP (Simultaneously Operating Piconet) performance
ActiveUS20050090200A1Improve overall utilizationImprove trustSynchronisation arrangementSynchronisation information channelsTime division multiple accessEngineering
Synchronized UWB piconets for SOP (Simultaneously Operating Piconet) performance. A common backbone (either wired or wireless) is employed that provides a common CLK (clock signal) to all of the various PNCs (piconet coordinators) of various piconets that may operate within a sufficiently close region such that interference could undesirably occur. By providing a very reliable CLK signal from a common backbone to all of the PNCs of the various piconets operating within a substantially close proximity to one another, very precise synchronization may be ensured for all of the communications performed therein. The various piconets may then even operate using TDMA (Time Division Multiple Access)—whose performance would be substantially compromised without effective synchronization. In addition, combined TFC (time frequency code) and TDMA may also be employed to support the communications therein thereby providing even another degree of orthogonality that provided by TDMA alone.
Owner:AVAGO TECH INT SALES PTE LTD
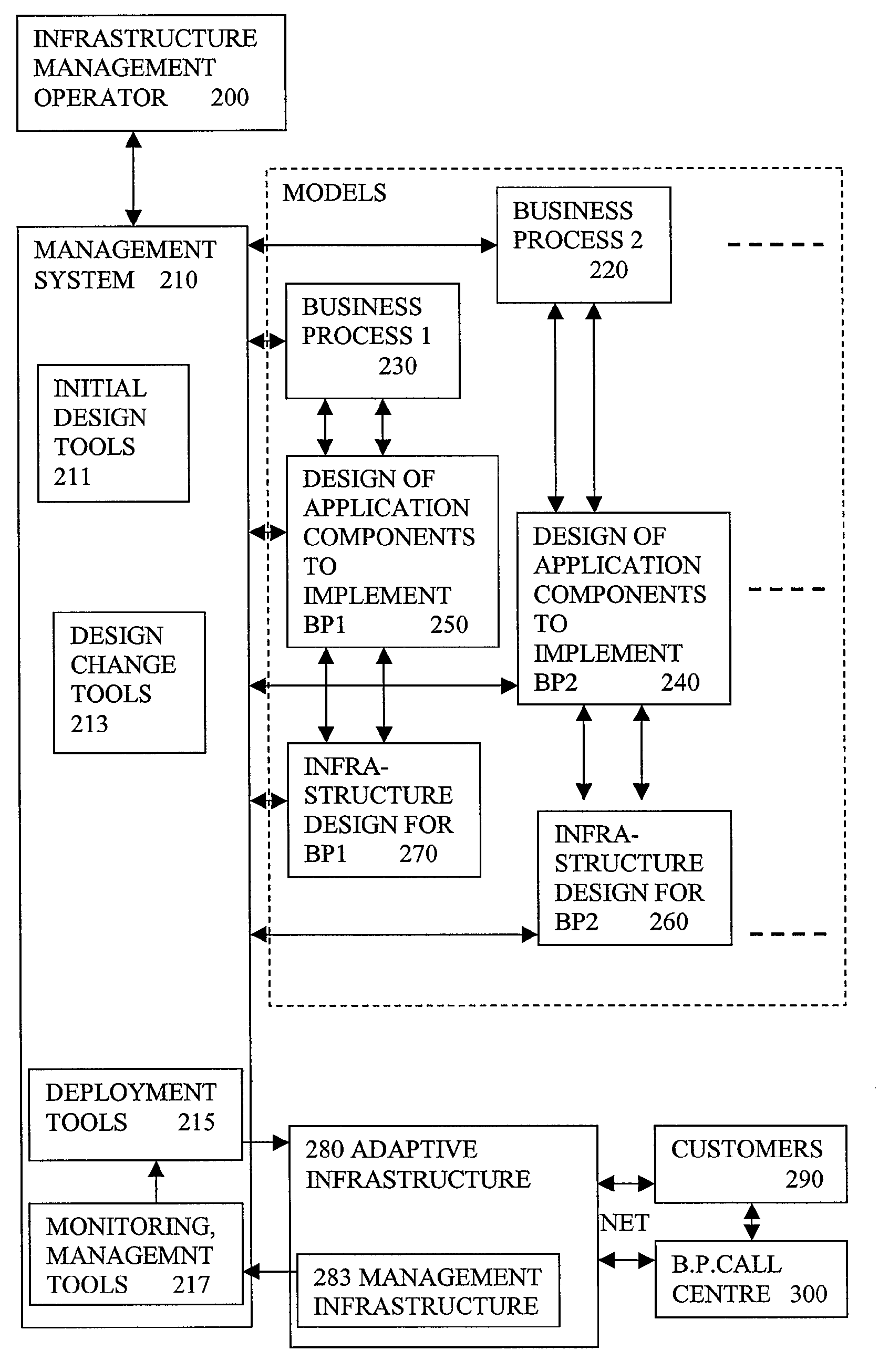
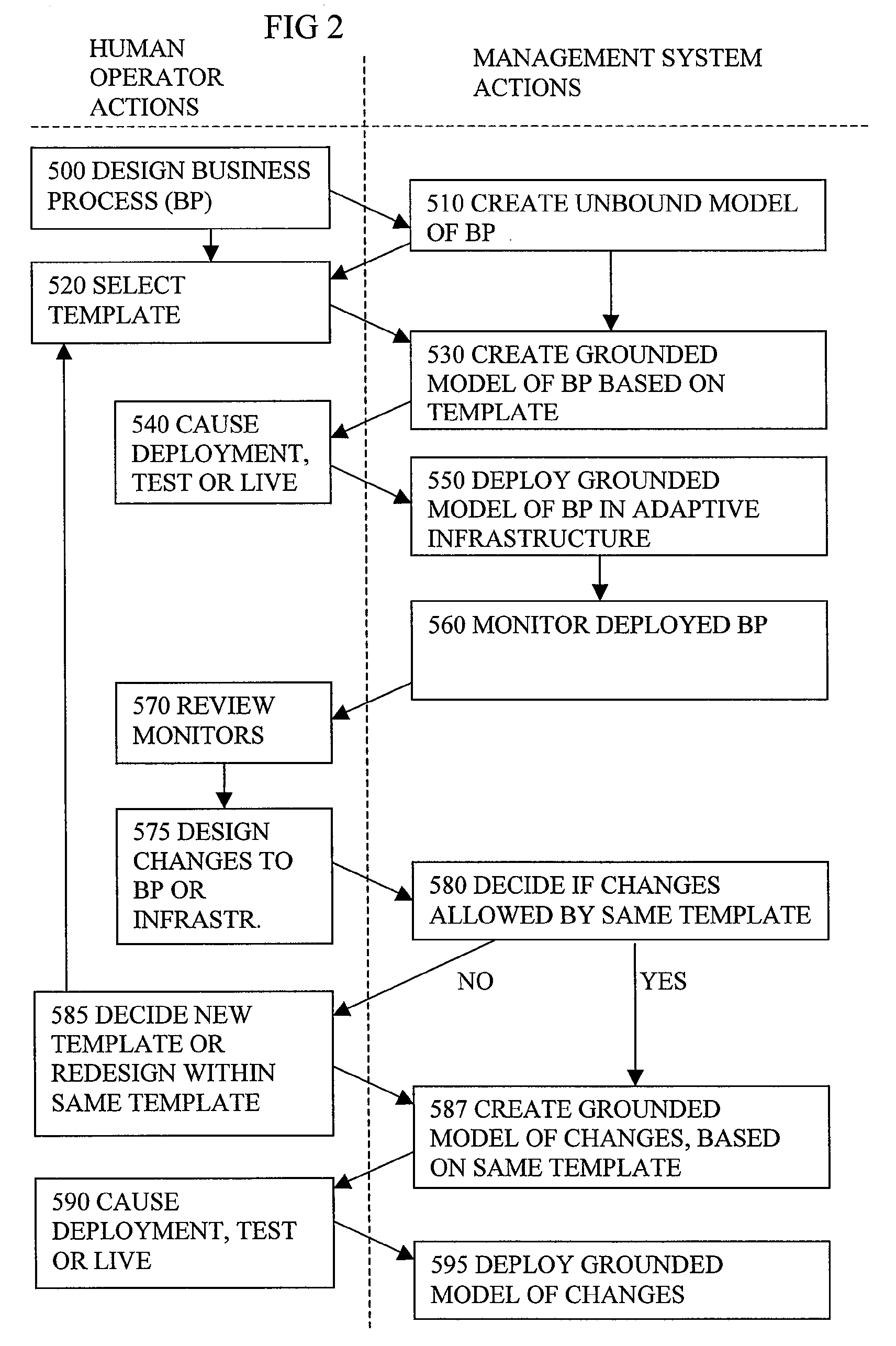
Model Based Deployment Of Computer Based Business Process On Dedicated Hardware
A method of automated deployment managed by a service provider, of a computer based business process, involves generating a model (730) of the business process including a design of computing infrastructure, and deploying the model on hardware (770) dedicated to the enterprise, with an interface for the service provider to enable ongoing management of the deployed process by the service provider. Having dedicated hardware means the location of the hardware can be arranged to suit the enterprise. This means limitations such as bandwidth or latency of WAN links, can be addressed by choosing the location of the dedicated hardware appropriately. Trust of security can also be increased compared to that of the shared data centres. The automated model driven deployment can help enable the service provider to provide such deployments on different types of hardware. The need for the enterprise to maintain specialist expertise in house is reduced.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Methods, systems and devices for packet watermarking and efficient provisioning of bandwidth
InactiveUS20080005572A1Fine granularityEffective distributionError preventionFrequency-division multiplex detailsData streamDigital signature
Disclosed herein are methods and systems for transmitting streams of data. The present invention also relates to generating packet watermarks and packet watermark keys. The present invention also relates to a computerized system for packaging data for transmission to a user. The system may utilize computer code to generate a bandwidth rights certificate that may include: at least one cryptographic credential; routing information for the transmission; and, optionally, a digital signature of a certificate owner; a unique identification code of a certificate owner; a certificate validity period; and pricing information for use of bandwidth. The present invention also relates to an electronic method and system for purchasing good and services by establishing an account whereby a customer is credited with a predetermined amount of bandwidth usage, and then charges are assessed against the account in an amount of bandwidth usage which corresponds to the agreed upon purchase value for the selected item.
Owner:WISTARIA TRADING INC
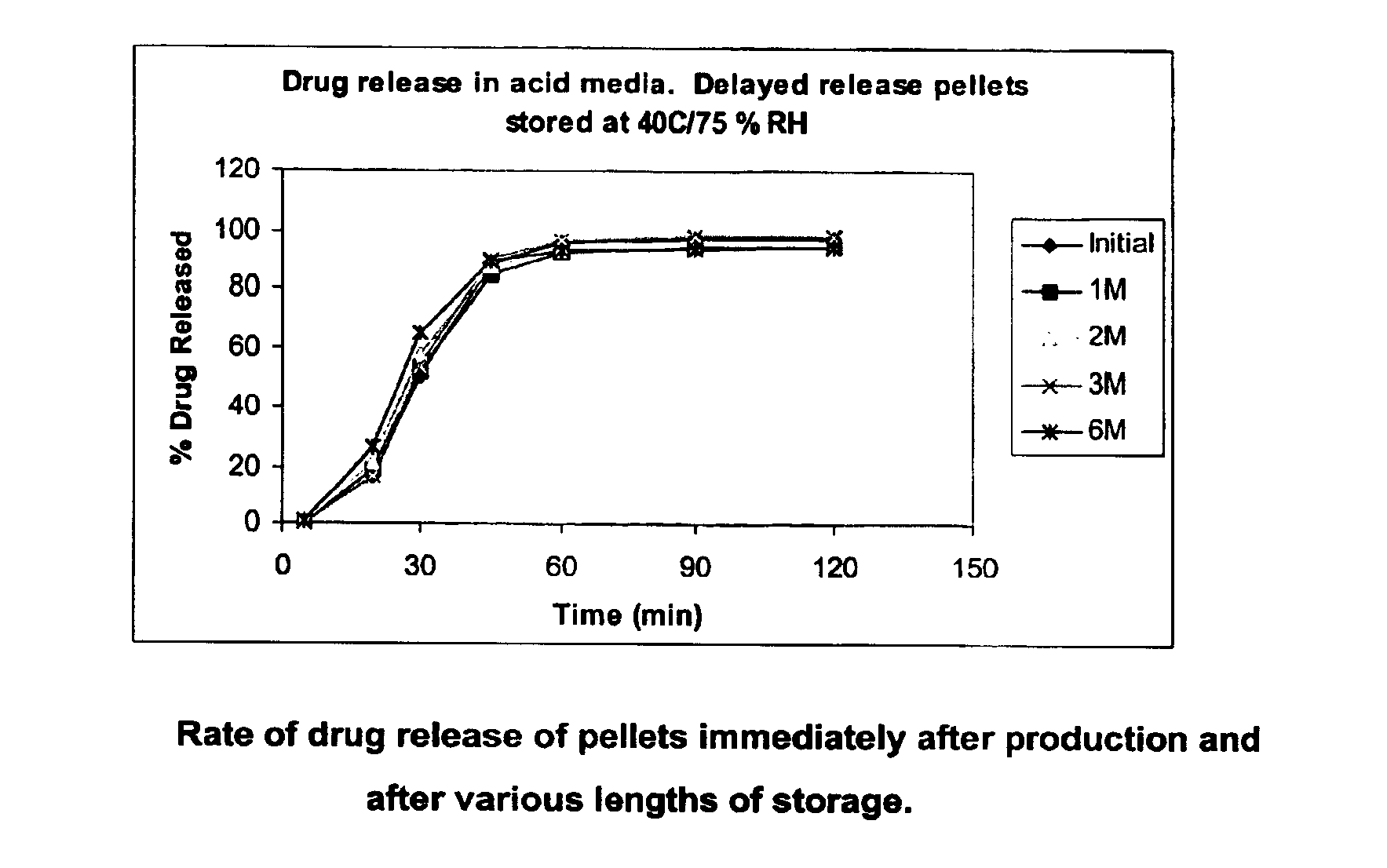
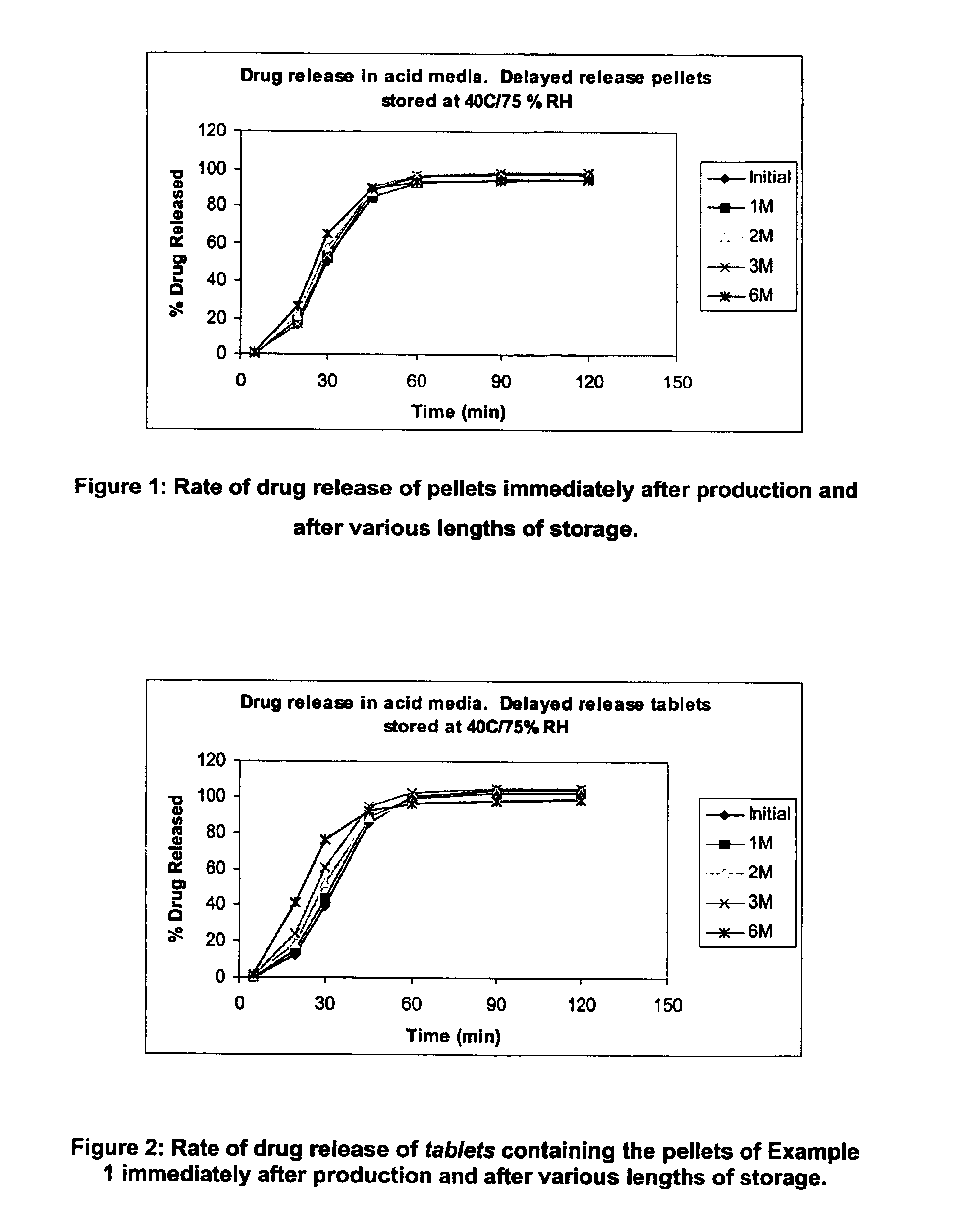
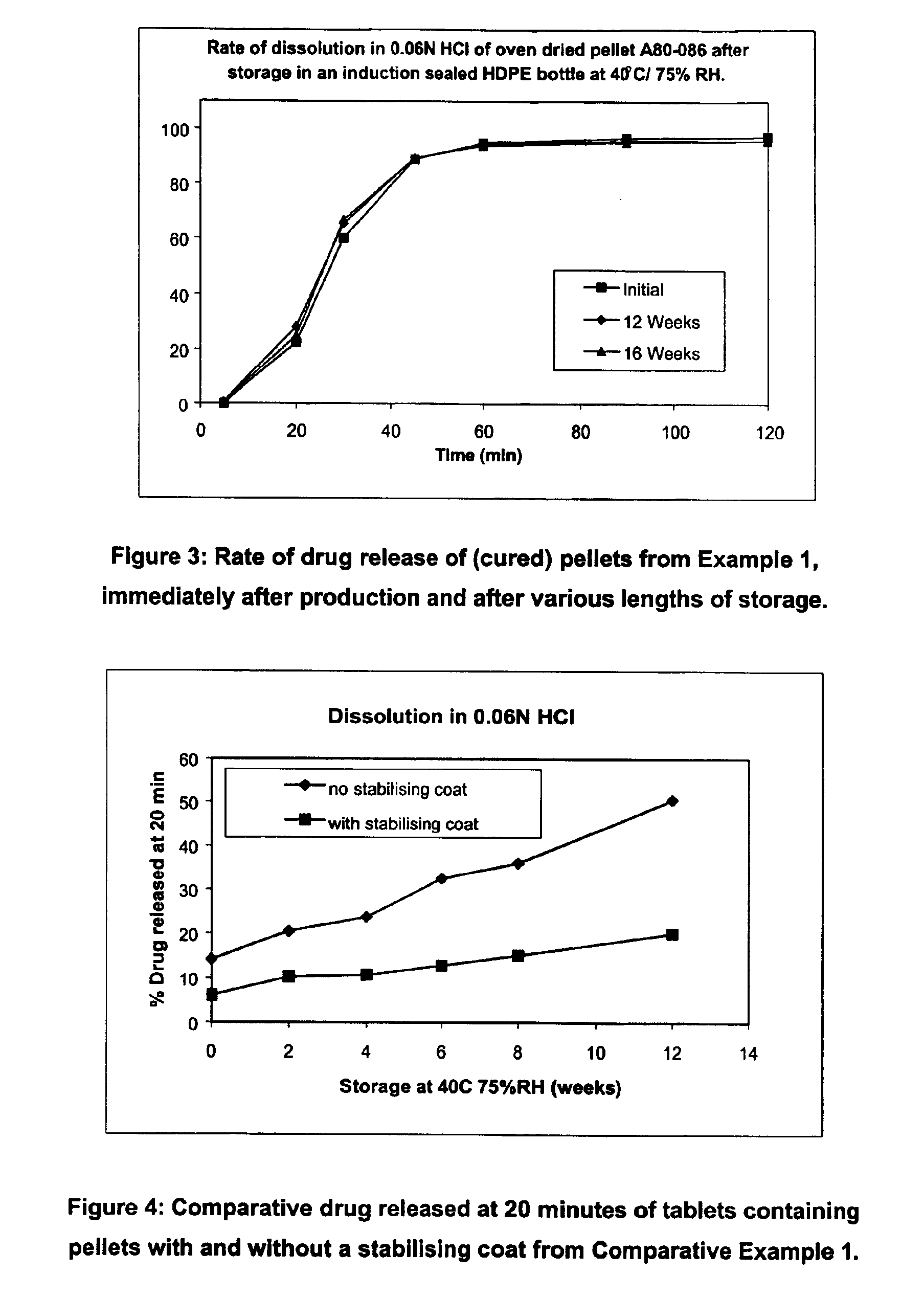
Modified release coated drug preparation
InactiveUS6958161B2Extension of timeImprove trustBiocideTetracycline active ingredientsDissolutionBULK ACTIVE INGREDIENT
A modified release preparation having one or more coated core elements, each core element including an active ingredient and having a modified release coating, wherein a stabilising coat is provided between each core element and its modified release coating so that, upon in vitro dissolution testing, the amount of active ingredient released at any time on a post-storage dissolution profile is within 40 percentage points of the amount of active ingredient released at any time on a pre-storage dissolution profile.
Owner:MAYNE PHARMA INT
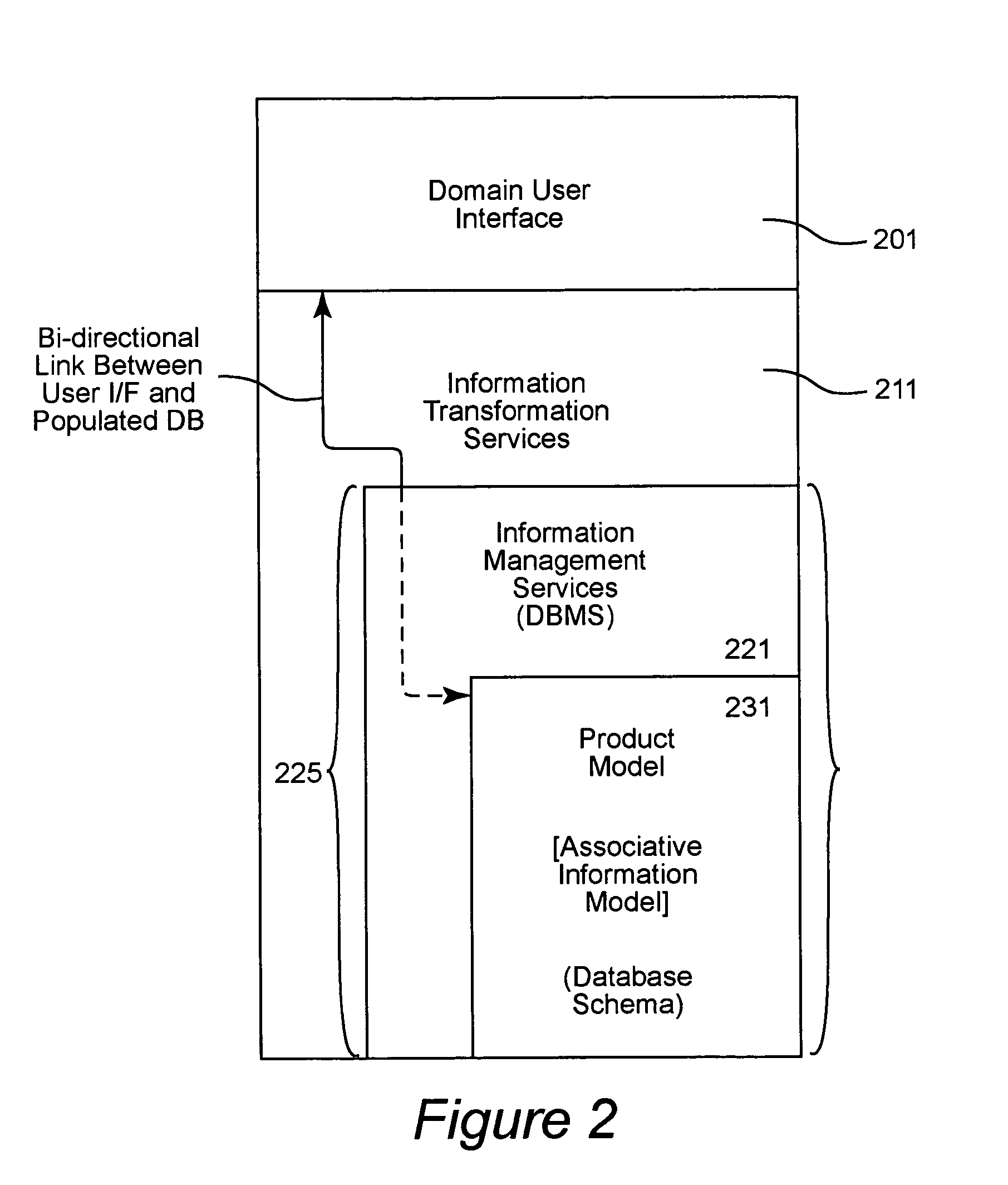
Internet based product data management (PDM) system
InactiveUS6961687B1Defect informationImprove visibilityMultiple digital computer combinationsSound input/outputSystems designApplication software
An integrated product data environment for system design and optimization, e.g., a Collaborative Engineering Environment (CEE). The CEE provides a multi-disciplinary engineering team with immediate access to all relevant product information. It is an enterprise system at the program as well as the company levels, managing product information as a program and corporate asset. Product-centric collaborative capabilities for the CEE are provided by extending the functionality of a commercial Product Data Management (PDM) System. Emerging web-centric commercial-off-tho-shelf (COTS) PDM capabilities, object-oriented technologies, associated rapid application development environments, sophisticated engineering toolsets, and COTS computing and communications technologies have been leveraged to establish the CEE for the complex electronic systems integration domain. The CEE offers substantial improvements in productivity, cost savings, cycle time reductions, product integrity and lifetime support of a system.
Owner:LOCKHEED MARTIN CORP
System and method for establishing historical usage-based hardware trust
InactiveUS7174454B2Improve trustPromote recoveryDigital data processing detailsUser identity/authority verificationThird partyPassword
Establishing trust according to historical usage of selected hardware involves providing a usage history for a selected client device; and extending trust to a selected user based on the user's usage history of the client device. The usage history is embodied as signed statements issued by a third party or an authentication server. The issued statement is stored either on the client device, or on an authentication server. The usage history is updated every time a user is authenticated from the selected client device. By combining the usage history with conventional user authentication, an enhanced trust level is readily established. The enhanced, hardware-based trust provided by logging on from a trusted client may eliminate the necessity of requiring secondary authentication for e-commerce and financial services transactions, and may also be used to facilitate password recovery and conflict resolution in the case of stolen passwords.
Owner:MICROSOFT TECH LICENSING LLC
Automatic template and field definition in form processing
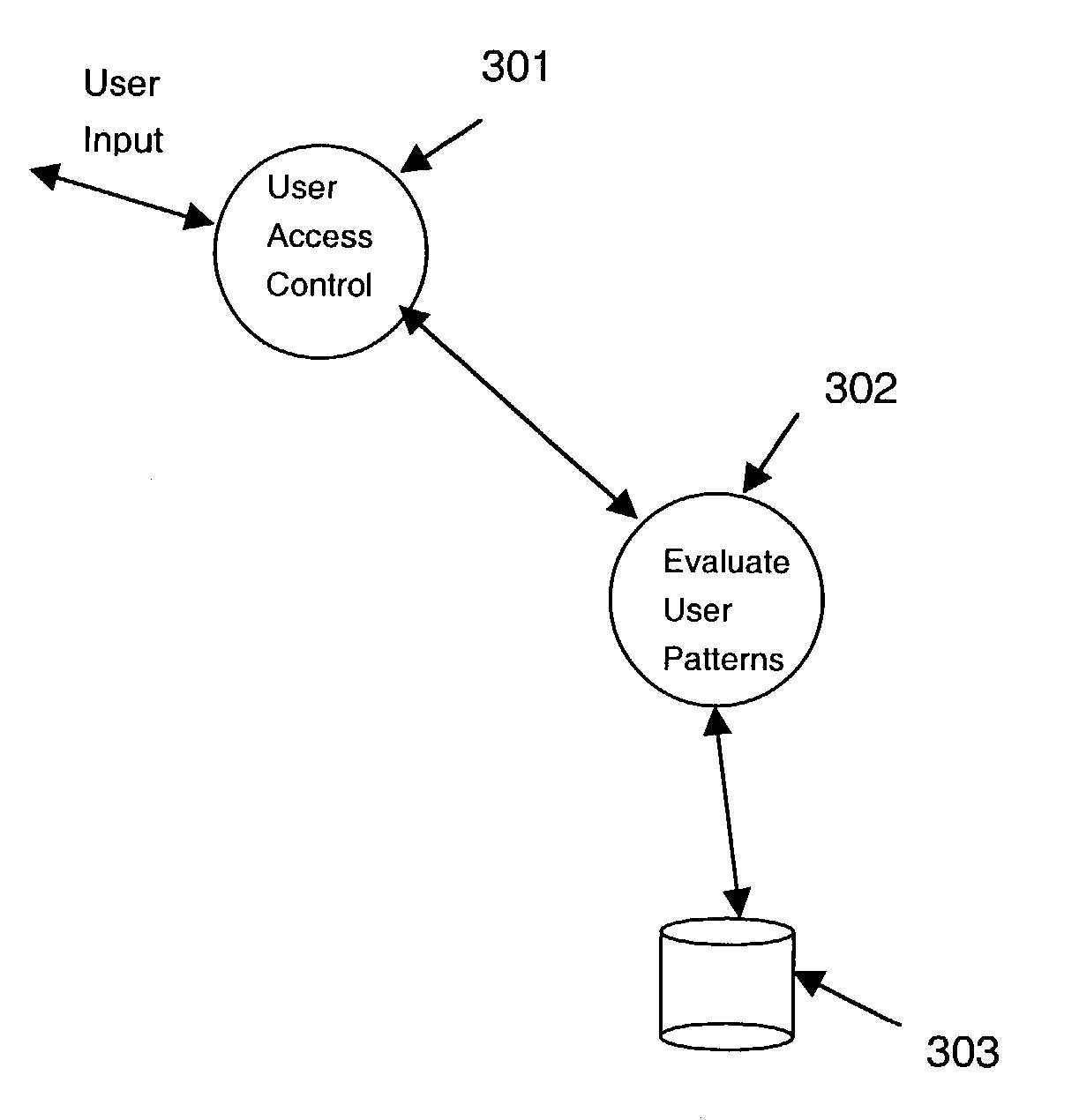
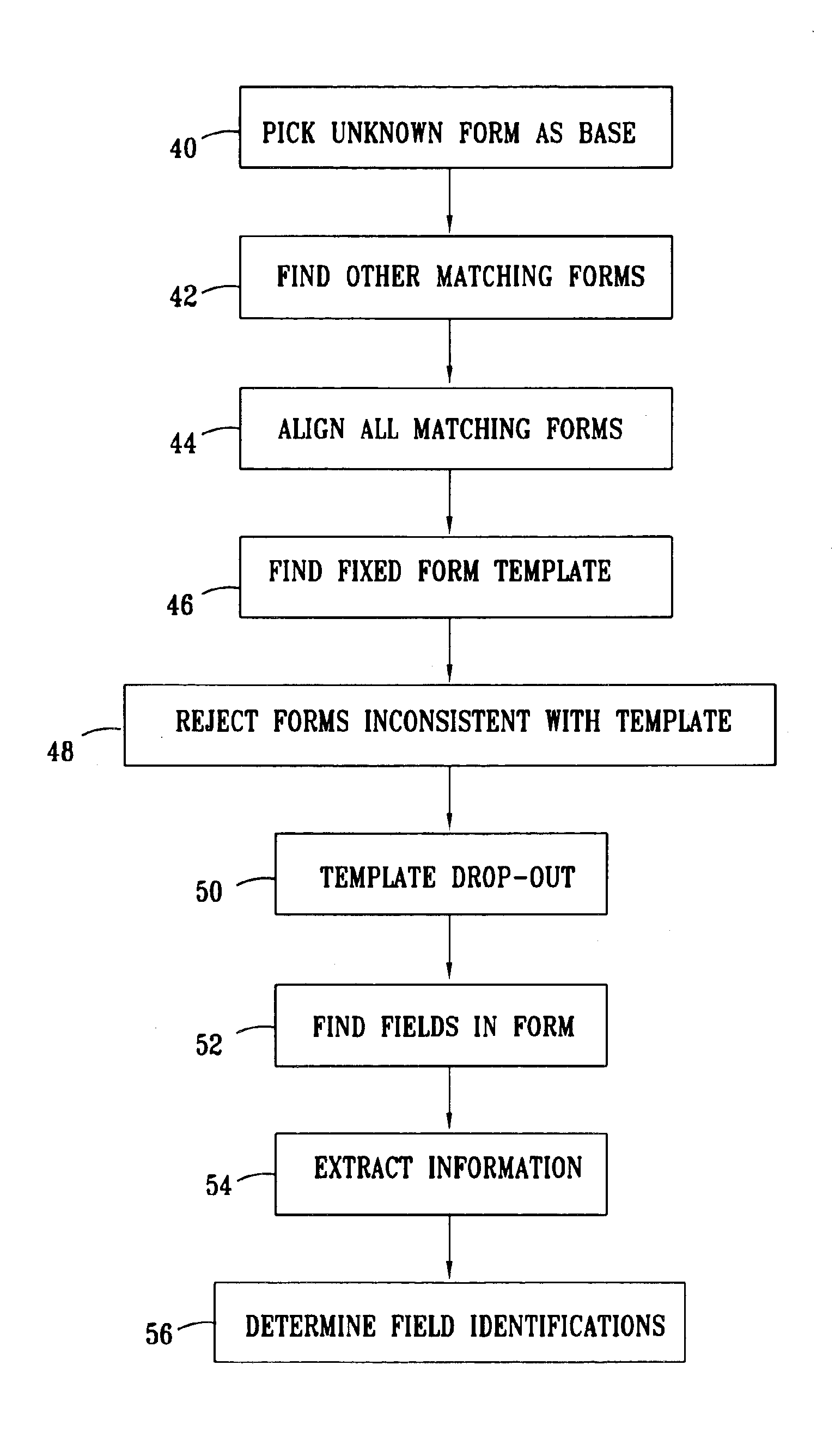
InactiveUS6886136B1Improve trustDigital data processing detailsCharacter and pattern recognitionPattern recognitionComputer graphics (images)
A method for processing a plurality of input images containing variable content that is filled into respective, fixed templates. The method includes comparing the images to collect a group of the images having a high degree of similarity therebetween, and combining the images in the group so as to distinguish the variable content from a fixed portion common to a preponderant number of the images in the group. The fixed portion is processed to reconstruct the fixed template that is common to at least some of the images among the preponderant number, and information is extracted from the images using the reconstructed template.
Owner:IBM CORP
Methods, systems and devices for packet watermarking and efficient provisioning of bandwidth
ActiveUS20080005571A1Fine granularityEffective distributionUser identity/authority verificationDigital data protectionComputer networkDigital signature
Disclosed herein are methods and systems for transmitting streams of data. The present invention also relates to generating packet watermarks and packet watermark keys. The present invention also relates to a computerized system for packaging data for transmission to a user. The system may utilize computer code to generate a bandwidth rights certificate that may include: at least one cryptographic credential; routing information for the transmission; and, optionally, a digital signature of a certificate owner; a unique identification code of a certificate owner; a certificate validity period; and pricing information for use of bandwidth. The present invention also relates to an electronic method and system for purchasing good and services by establishing an account whereby a customer is credited with a predetermined amount of bandwidth usage, and then charges are assessed against the account in an amount of bandwidth usage which corresponds to the agreed upon purchase value for the selected item.
Owner:WISTARIA TRADING INC
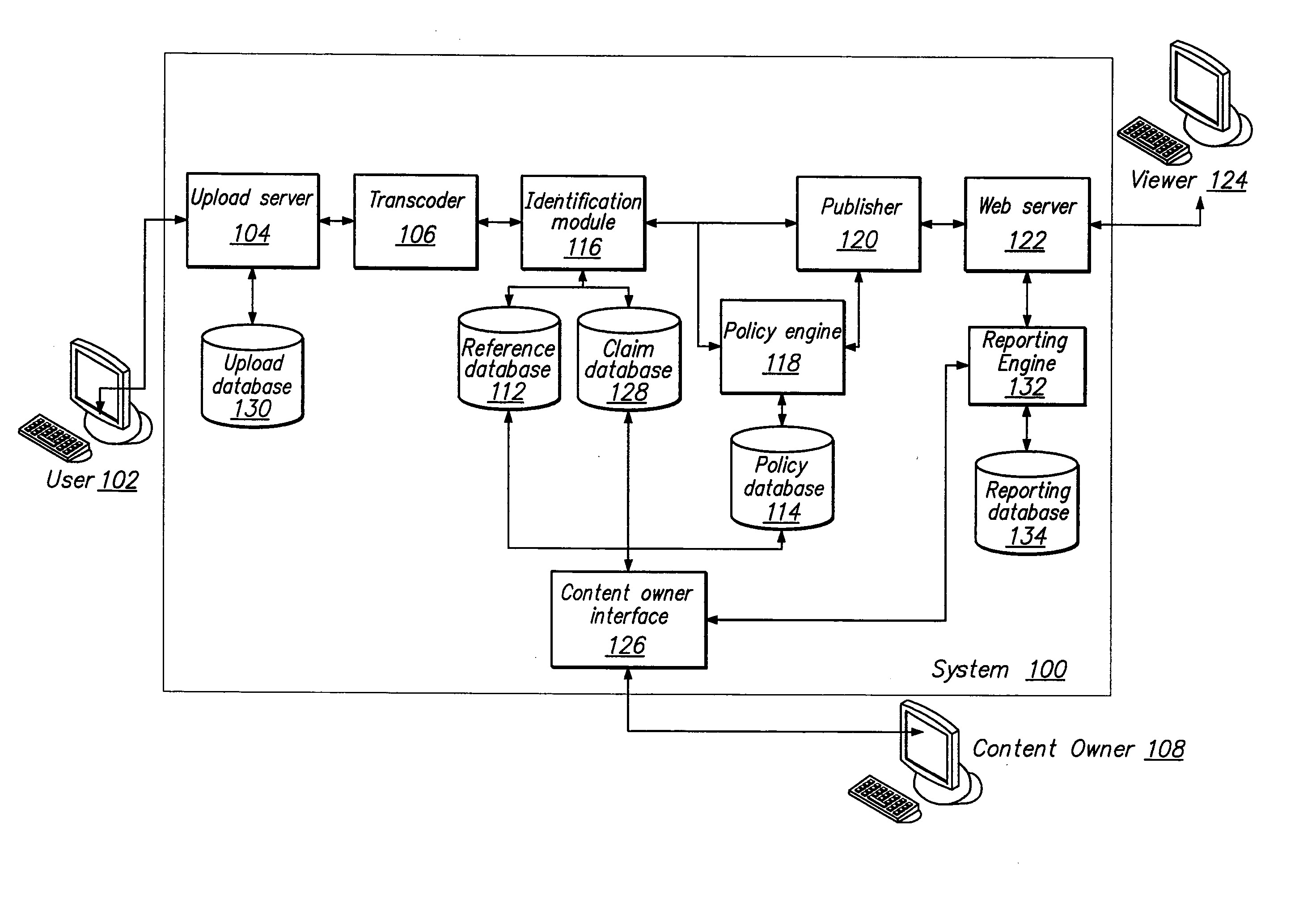
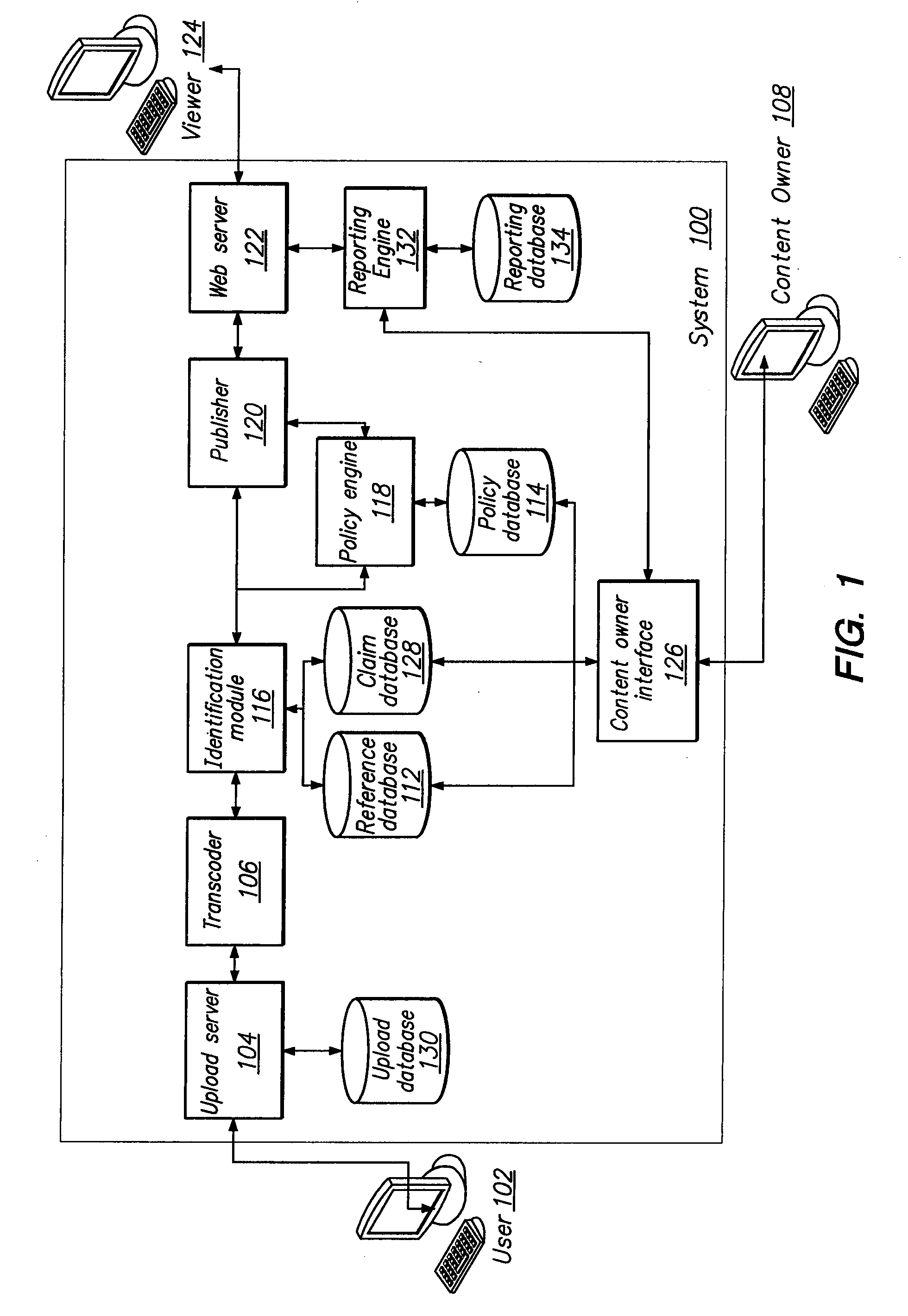
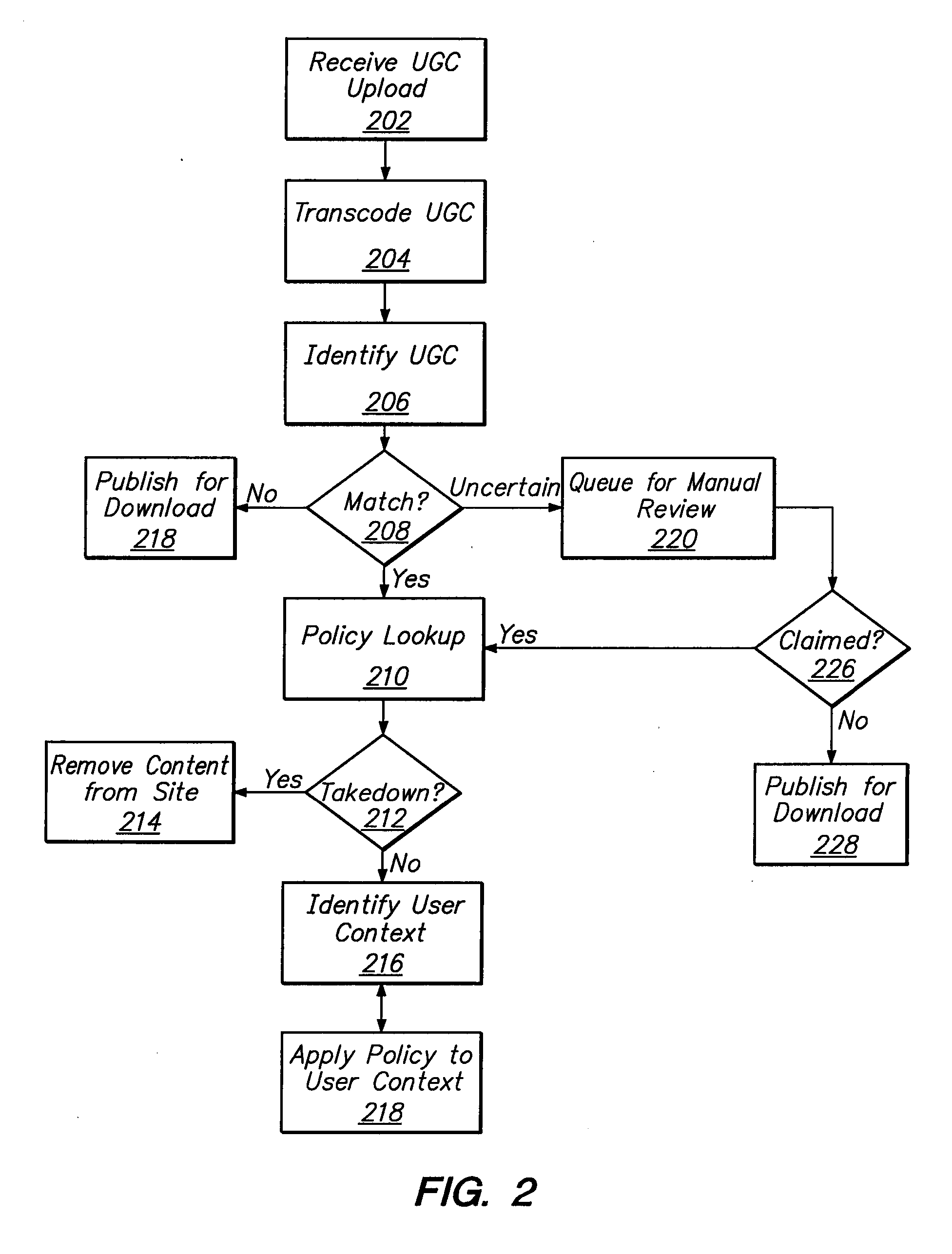
Content Management System
InactiveUS20080109369A1Improve trustAvoid distributingAdvertisementsDigital data protectionDigital contentNumber content
Content rights holders provide digital content to a hosting site to be used as reference content. The content owner specifies a policy for each digital content item, indicating how that content may be used on the site when uploaded by someone other than the content owner. An identification module compares the uploaded content against reference content. If the content matches reference content, the specified policy for that reference content is applied to the uploaded content. Policy options provided by the content owner include tracking the content to see how it is viewed, preventing the content from being distributed on the site, and allowing the content to be displayed in a revenue-sharing environment. In one embodiment, if the identification module matches the uploaded content to a reference item but the match does not have a sufficiently high level of confidence, the suggested match is queued for review by the content owner.
Owner:GOOGLE LLC
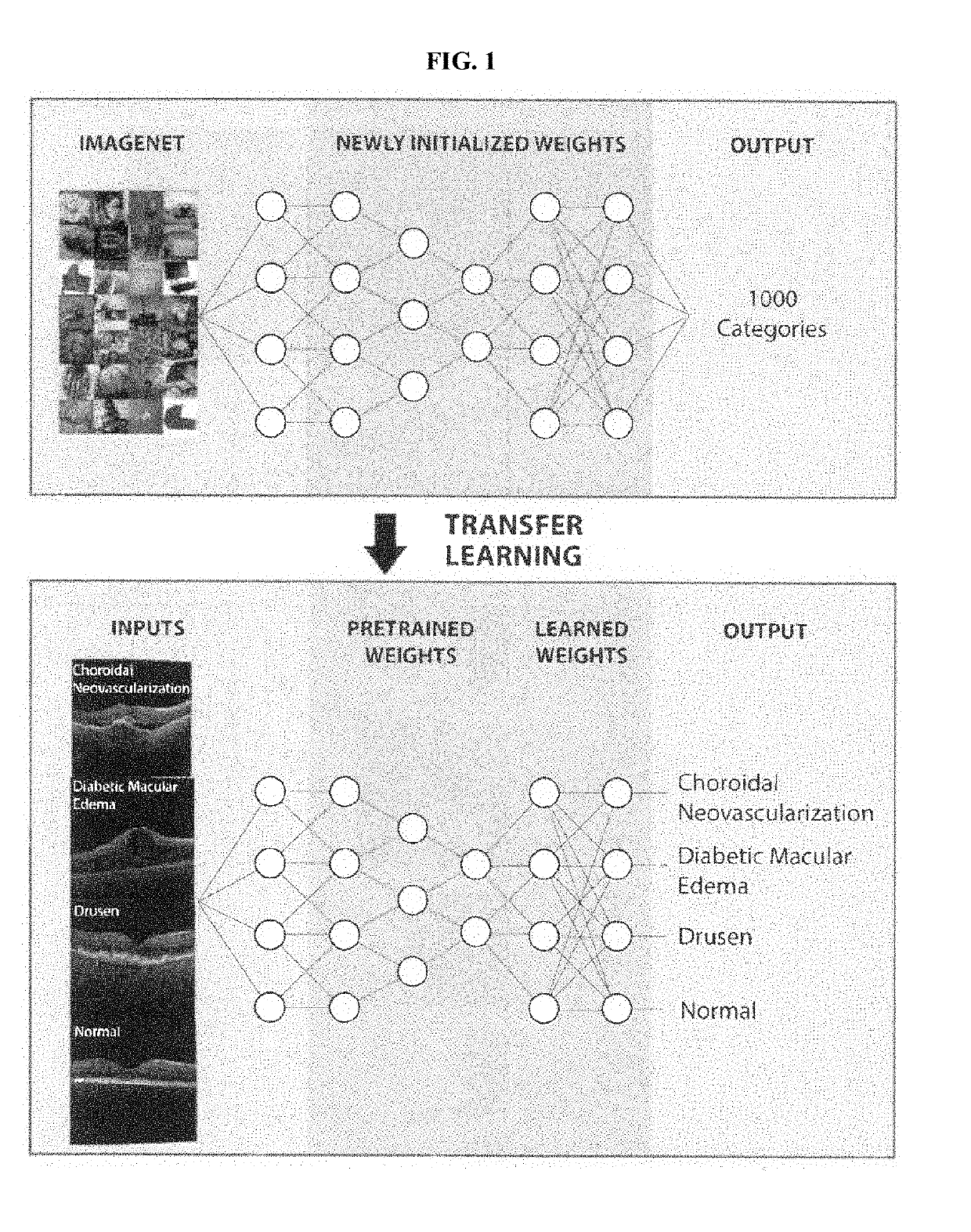
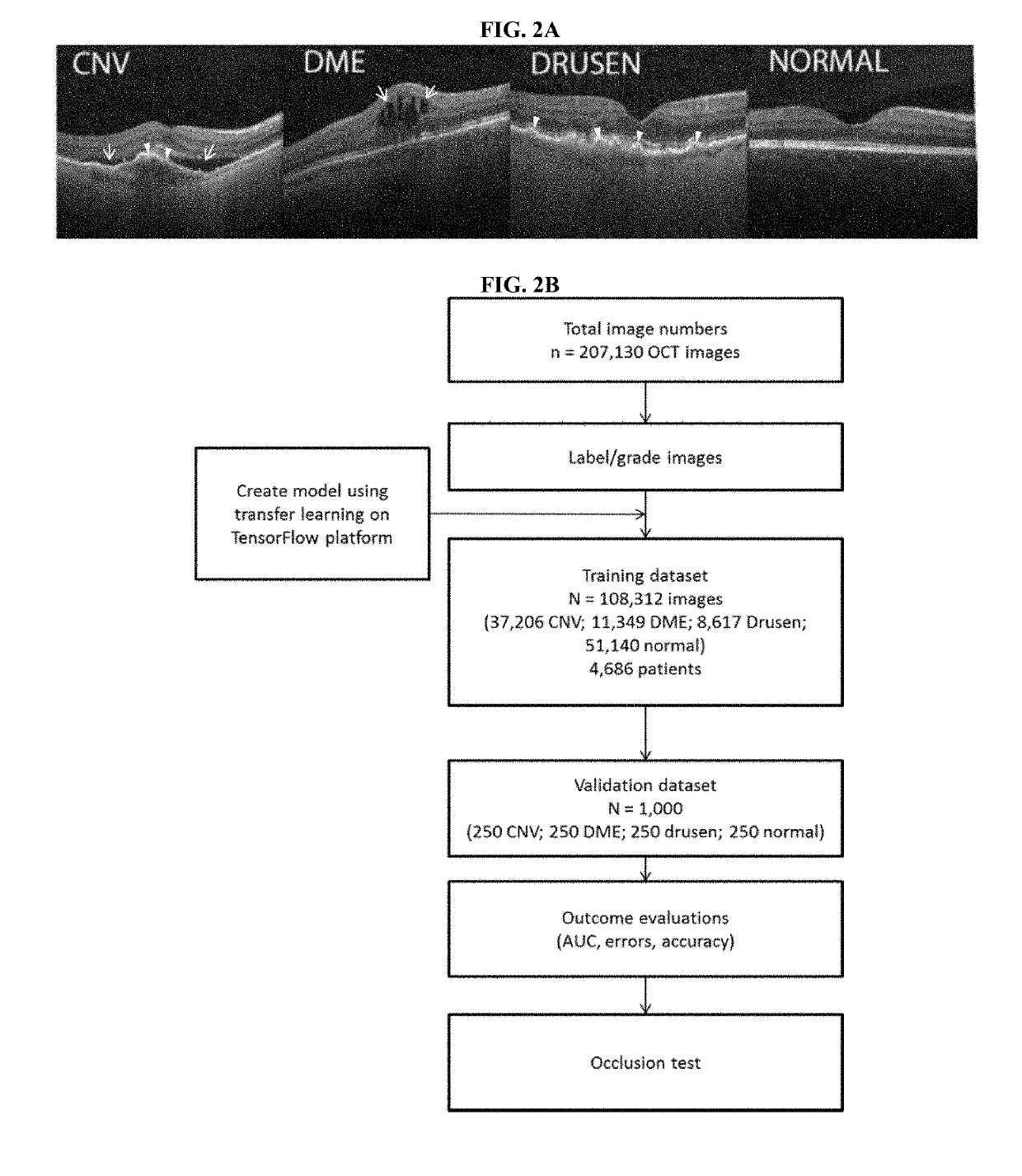
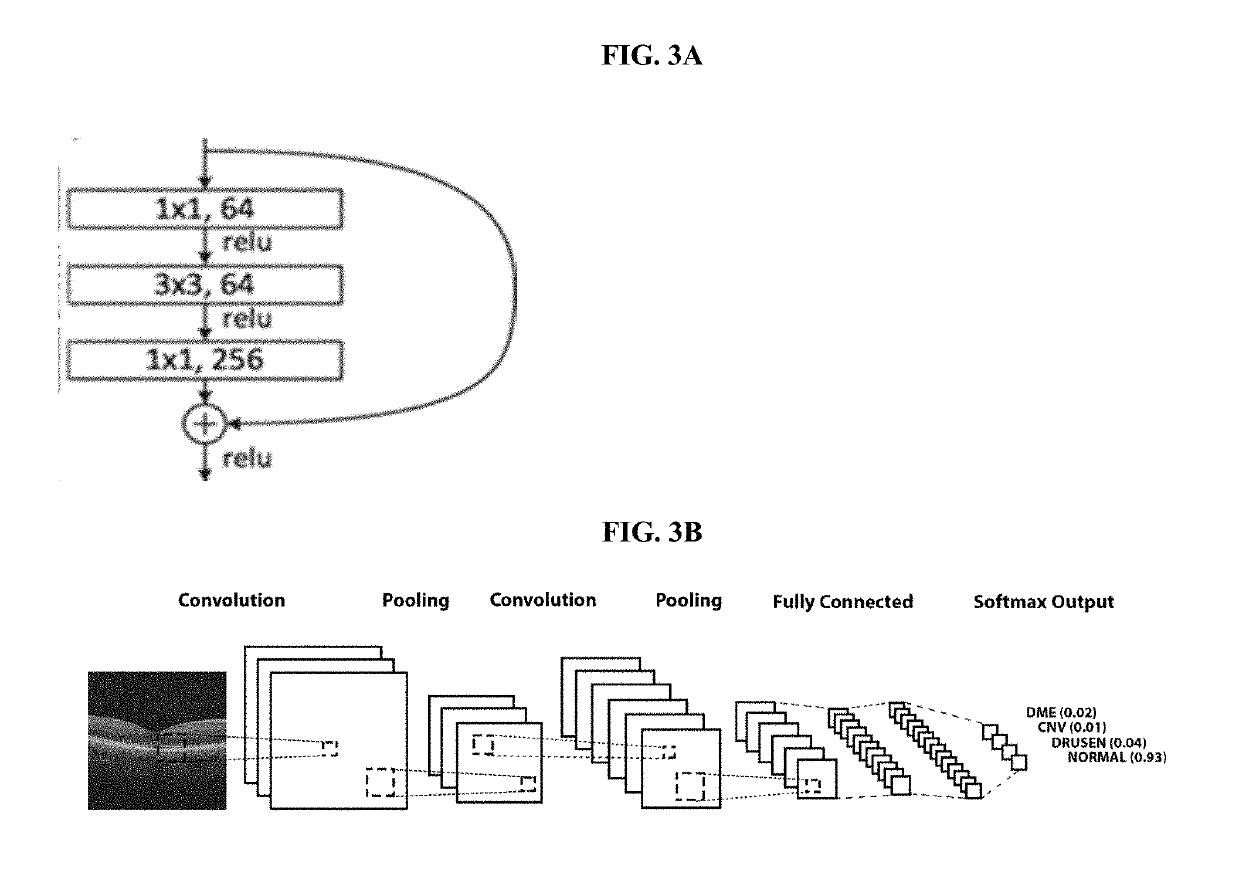
Deep learning-based diagnosis and referral of ophthalmic diseases and disorders
ActiveUS20190110753A1Efficient analysisLess computing powerMedical imagingEvaluation of blood vesselsDiseaseLearning based
Disclosed herein are systems, methods, devices, and media for carrying out medical diagnosis of ophthalmic diseases and conditions. Deep learning algorithms enable the automated analysis of ophthalmic images to generate predictions of comparable accuracy to clinical experts.
Owner:AITECH +1
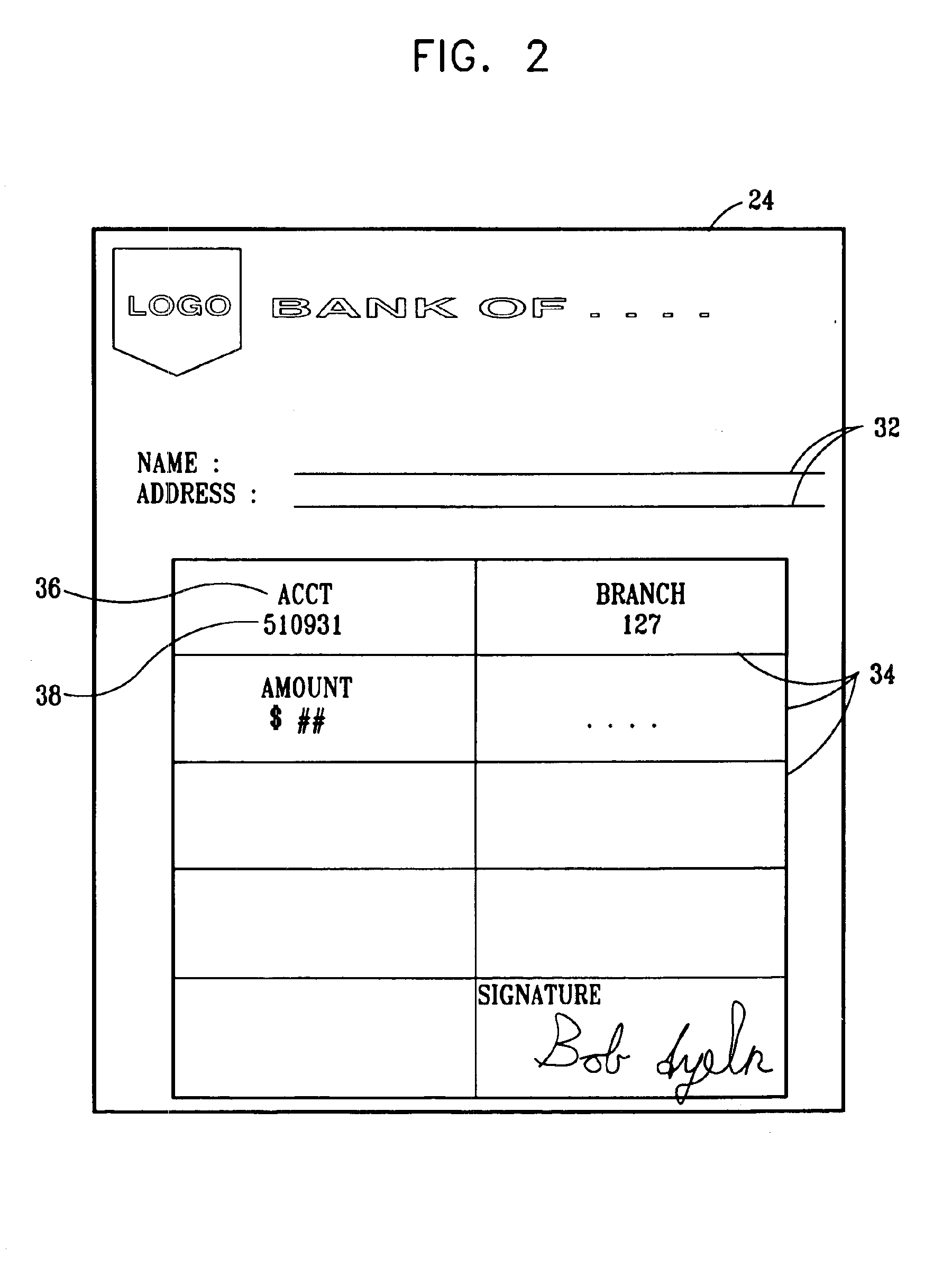
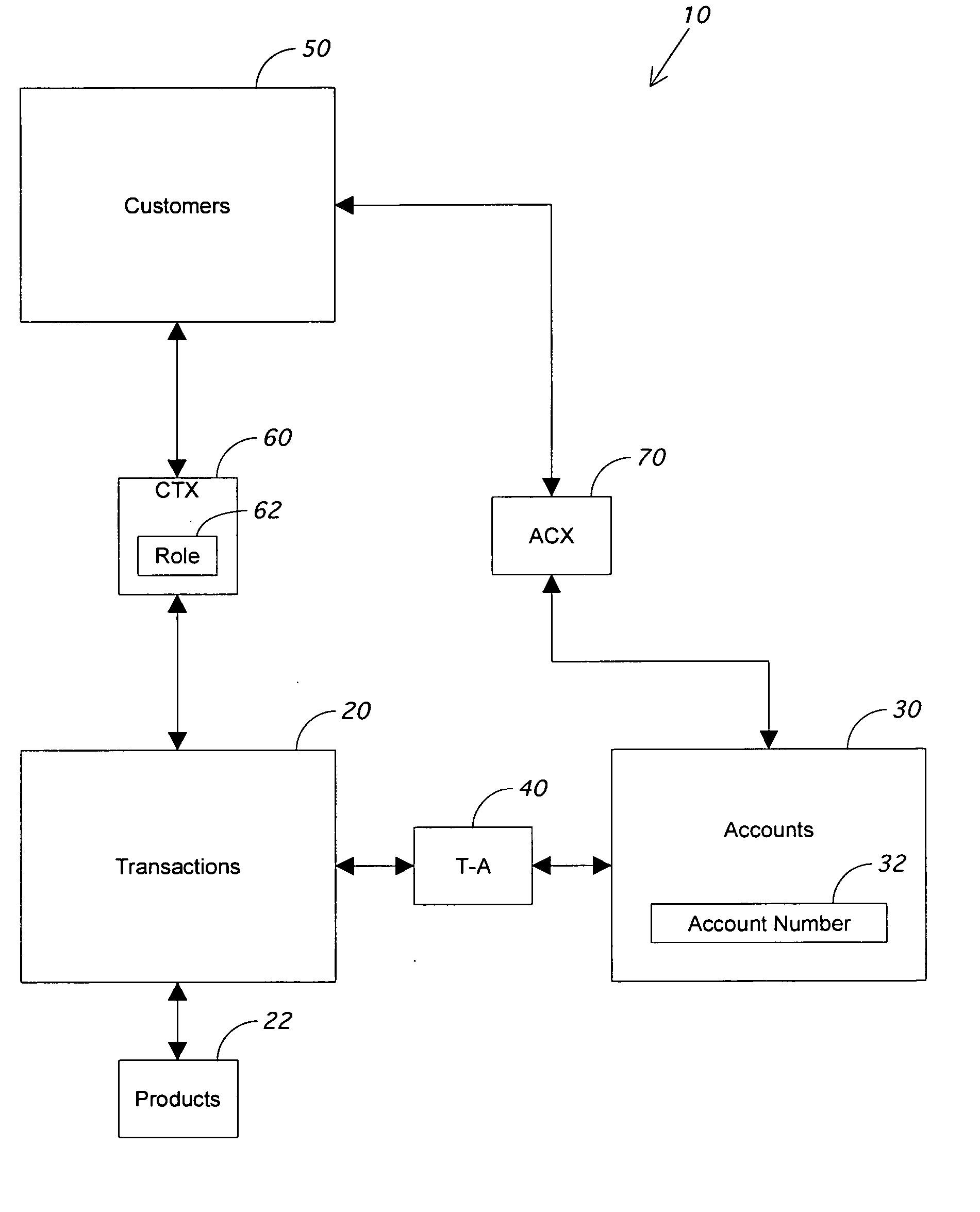
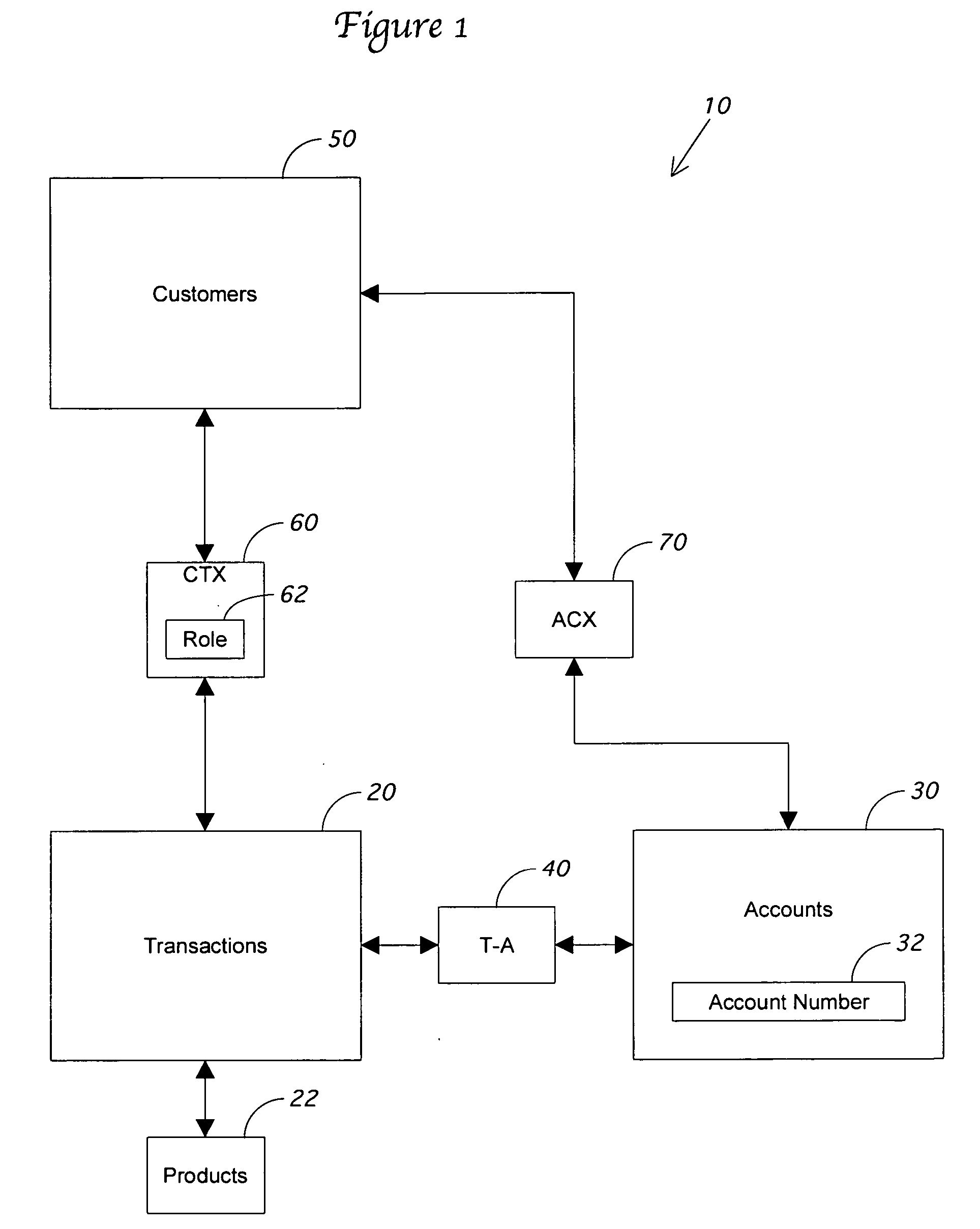
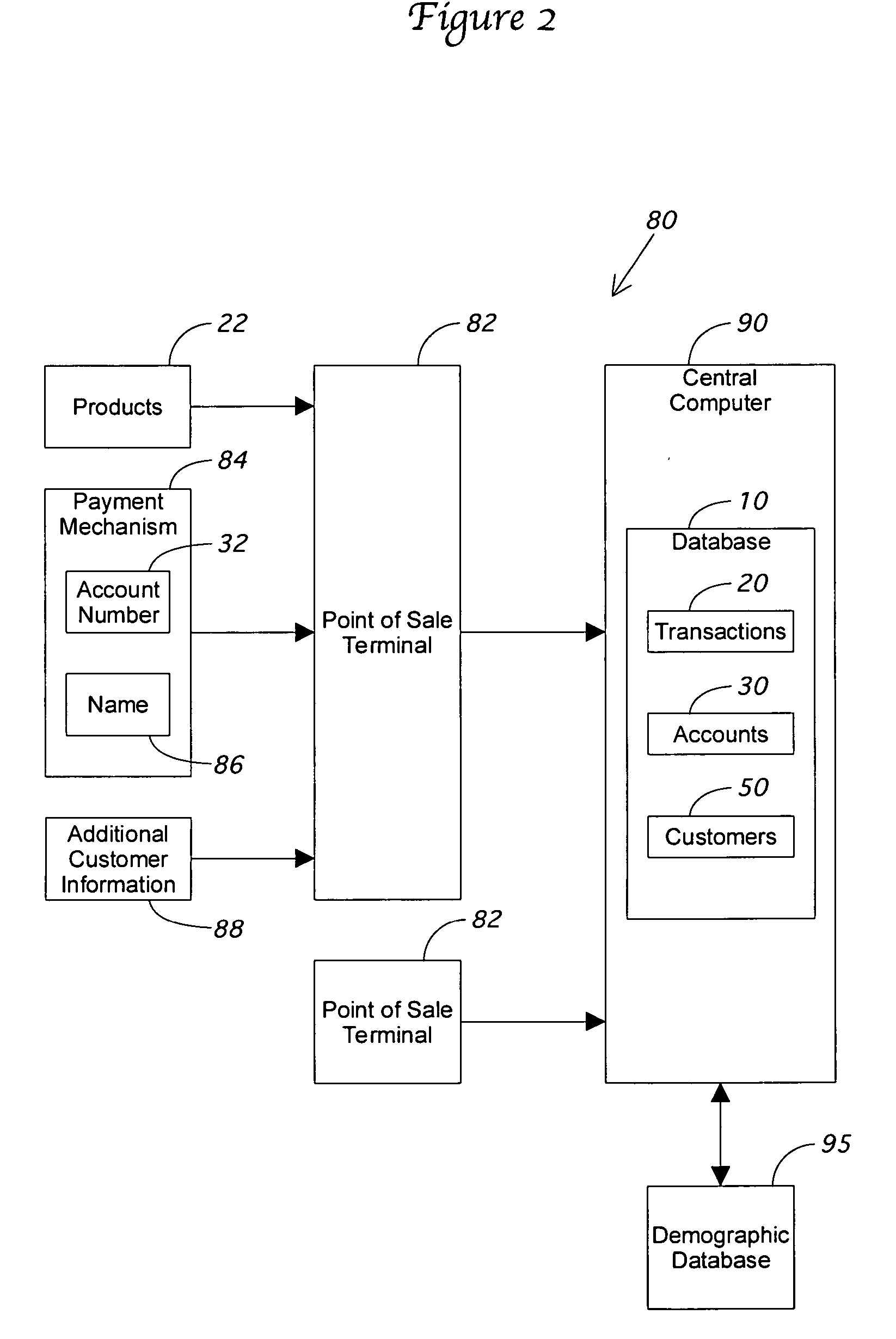
Indirect customer identification system and method
ActiveUS20060065716A1Improve trustPayment circuitsPoint-of-sale network systemsPaymentTransaction data
A database system and method is presented that updates a retail transaction database for each transaction by extracting a name from a payment mechanism. Associations already made between the customer records, the transactions database, and the payment account database are used in conjunction with the extracted name to create additional associations between customers and transactions and between customers and payment accounts. In addition, new customer records can be created by searching demographic databases using the reverse append name and data associated with the transaction already in the database.
Owner:BBY SOLUTIONS
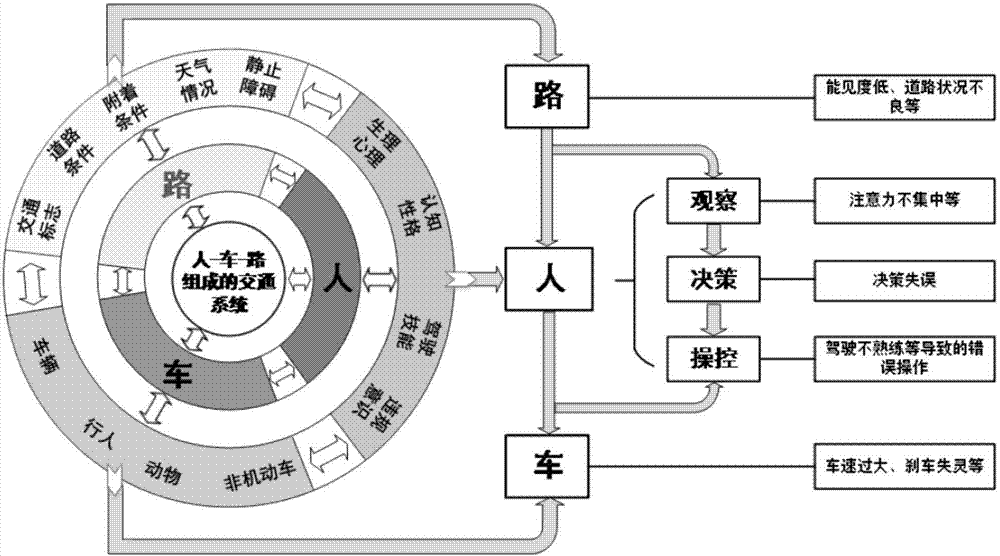
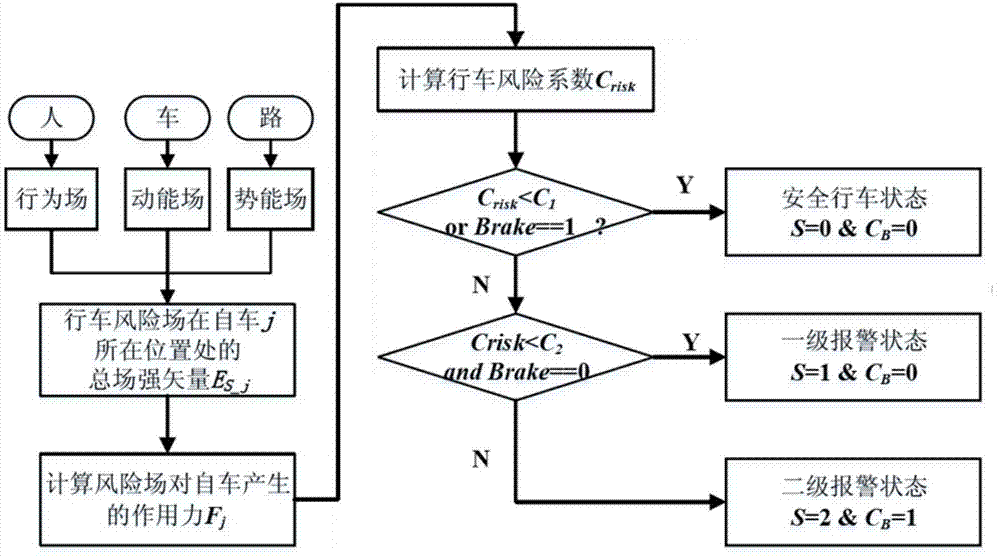
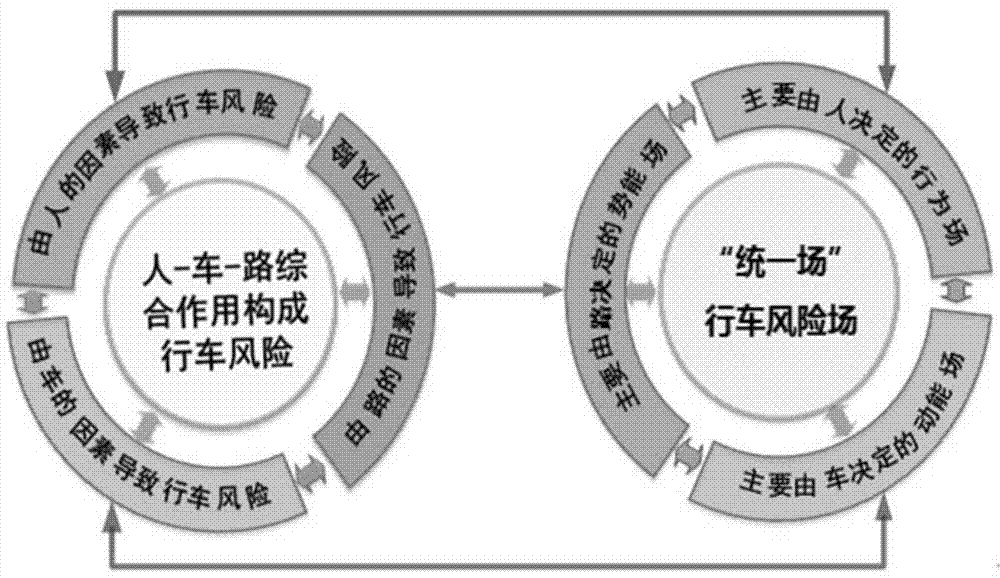
Travelling risk field-based automobile driving safety assistance method
ActiveCN104239741AAvoid interferenceAvoid confictSpecial data processing applicationsCar drivingMathematical model
The invention relates to a travelling risk field-based automobile driving safety assistance method which comprises the steps of (1) establishing a travelling risk field unified model according to the combined action of all factors of people, automobiles and roads in the ambient environment for the travelling risk; (2) establishing a self automobile travelling risk field model by building a mathematical model of the kinetic energy field, the potential energy field and the behavior field of objects in the ambient environment, and calculating the total field intensity of the travelling risk field of a self automobile; (3) calculating the acting force applied to the self automobile in the travelling risk field based on the total field intensity of the travelling risk field; (4) calculating the travelling risk factor of the self automobile according to the acting force applied to the self automobile in the travelling risk field, and carrying out safety assistance in the travelling process based on the risk factor. The method is suitable for decision of driving safety assistance in the complex environment and the route planning of an intelligent vehicle.
Owner:TSINGHUA UNIV
Synchronized UWB piconets for Simultaneously Operating Piconet performance
ActiveUS7433697B2Improve overall utilizationImprove trustSynchronisation arrangementSynchronisation information channelsTime division multiple accessEngineering
Synchronized UWB piconets for SOP (Simultaneously Operating Piconet) performance. A common backbone (either wired or wireless) is employed that provides a common CLK (clock signal) to all of the various PNCs (piconet coordinators) of various piconets that may operate within a sufficiently close region such that interference could undesirably occur. By providing a very reliable CLK signal from a common backbone to all of the PNCs of the various piconets operating within a substantially close proximity to one another, very precise synchronization may be ensured for all of the communications performed therein. The various piconets may then even operate using TDMA (Time Division Multiple Access)—whose performance would be substantially compromised without effective synchronization. In addition, combined TFC (time frequency code) and TDMA may also be employed to support the communications therein thereby providing even another degree of orthogonality that provided by TDMA alone.
Owner:AVAGO TECH INT SALES PTE LTD
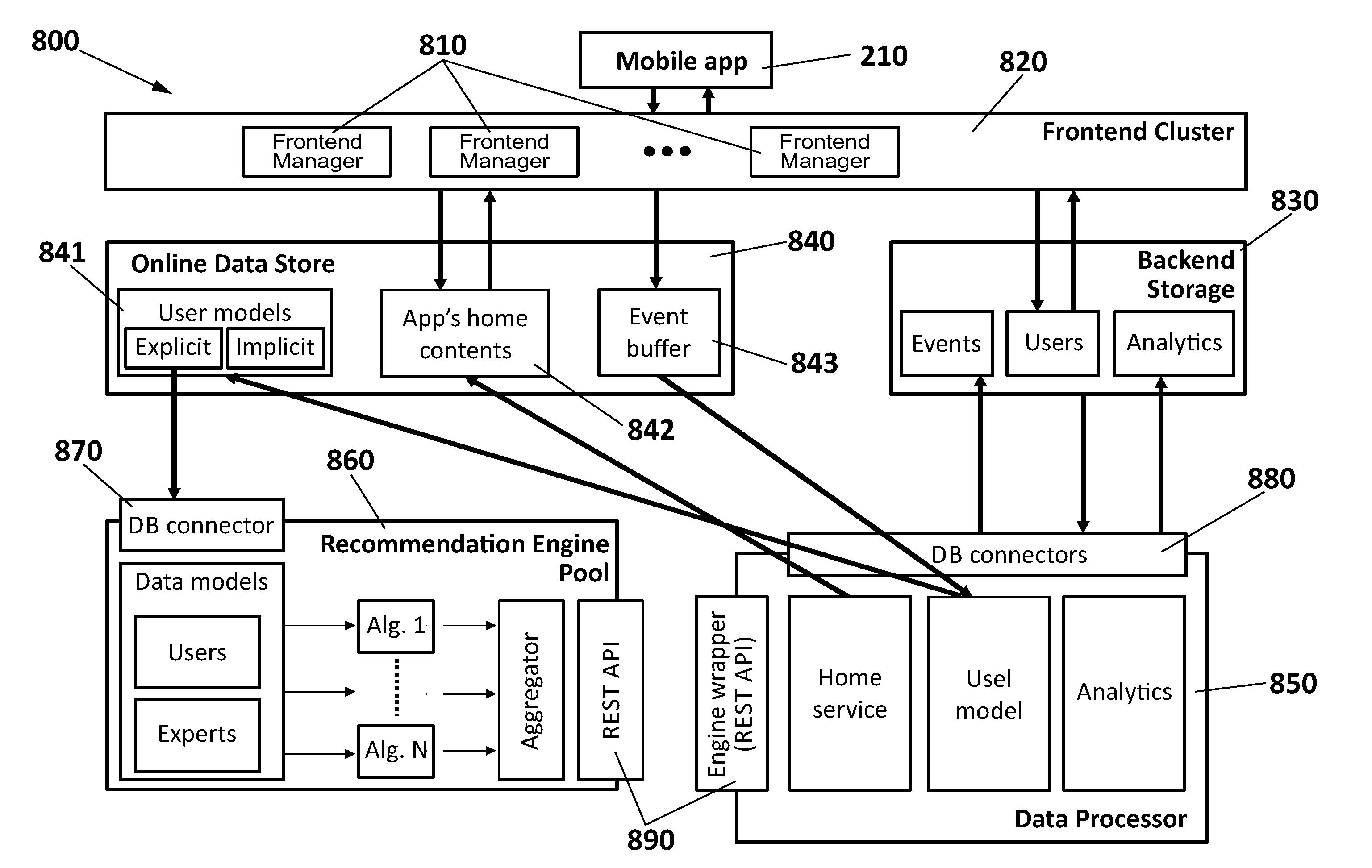
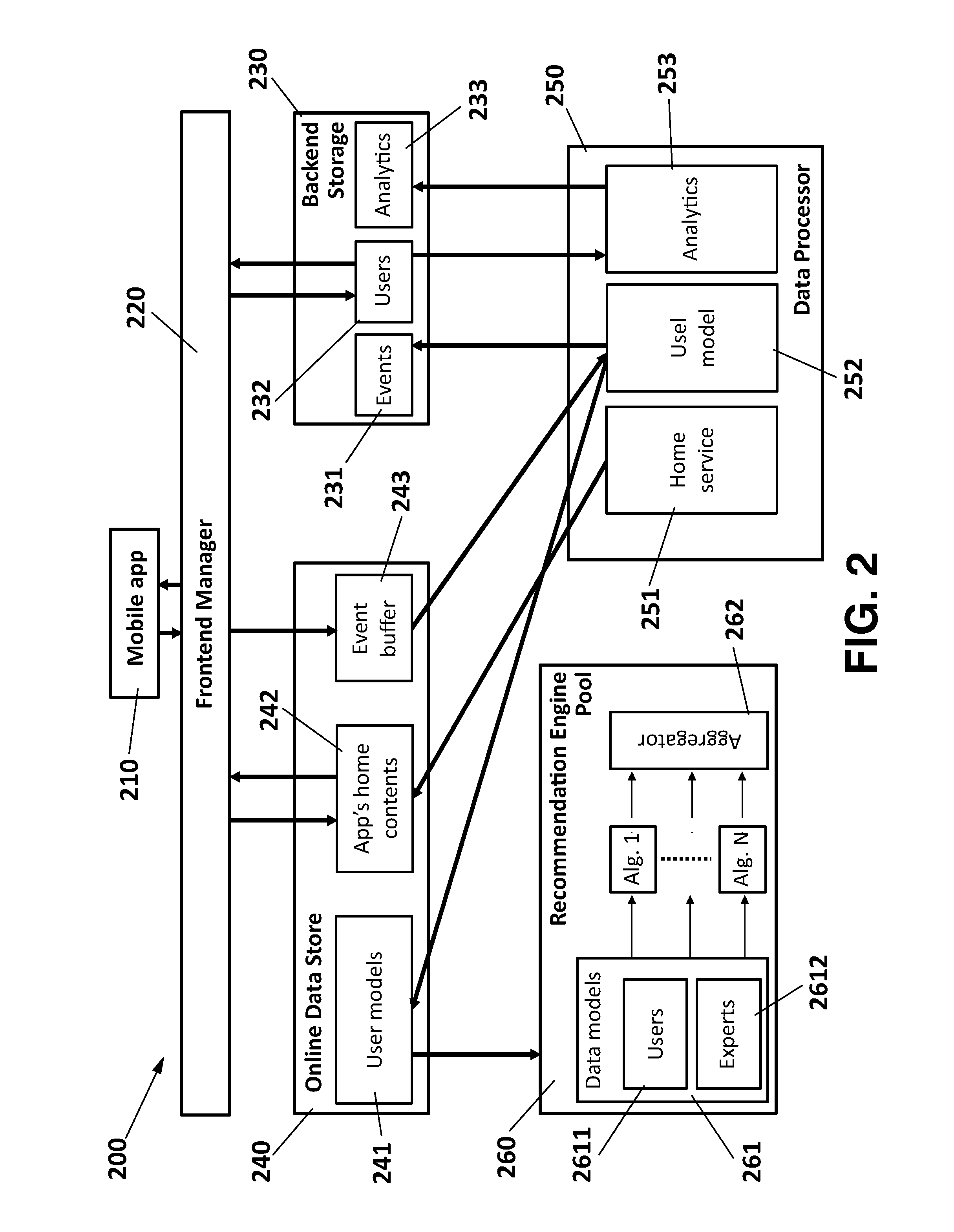
Method and system for providing multimedia content recommendations
InactiveUS20150120722A1Promote assimilationImprove trustDigital data information retrievalDigital data processing detailsApplication softwareClient-side
A system for providing content recommendations, including a frontend manager for receiving explicit events from a client application of a user and generating implicit events based upon additional user actions within the client application; a backend storage of data on events and users and an Online Data Store for the explicit events and the implicit events; a Data Processor for creating an explicit user model from the explicit events and an implicit user model from the implicit events; a pool of recommendation engines with one or more recommendation algorithms for receiving the explicit user model and assigning a ranked recommendation list of content items to the user as a result, and further including an aggregator controlled by the Data Processor for aggregating the ranked recommendation lists based on a user-dependent strategy, in order to obtain multiple content recommendation lists of ranked items to be delivered by the frontend server to the client application in a final arrangement, pull from the Online Data Store along with data on the content sources.
Owner:TELEFONICA DIGITAL ESPANA
System, device, and method for providing secure electronic commerce transactions
InactiveUS7404202B2Improve trustDigital data processing detailsUser identity/authority verificationE-commerceSerial code
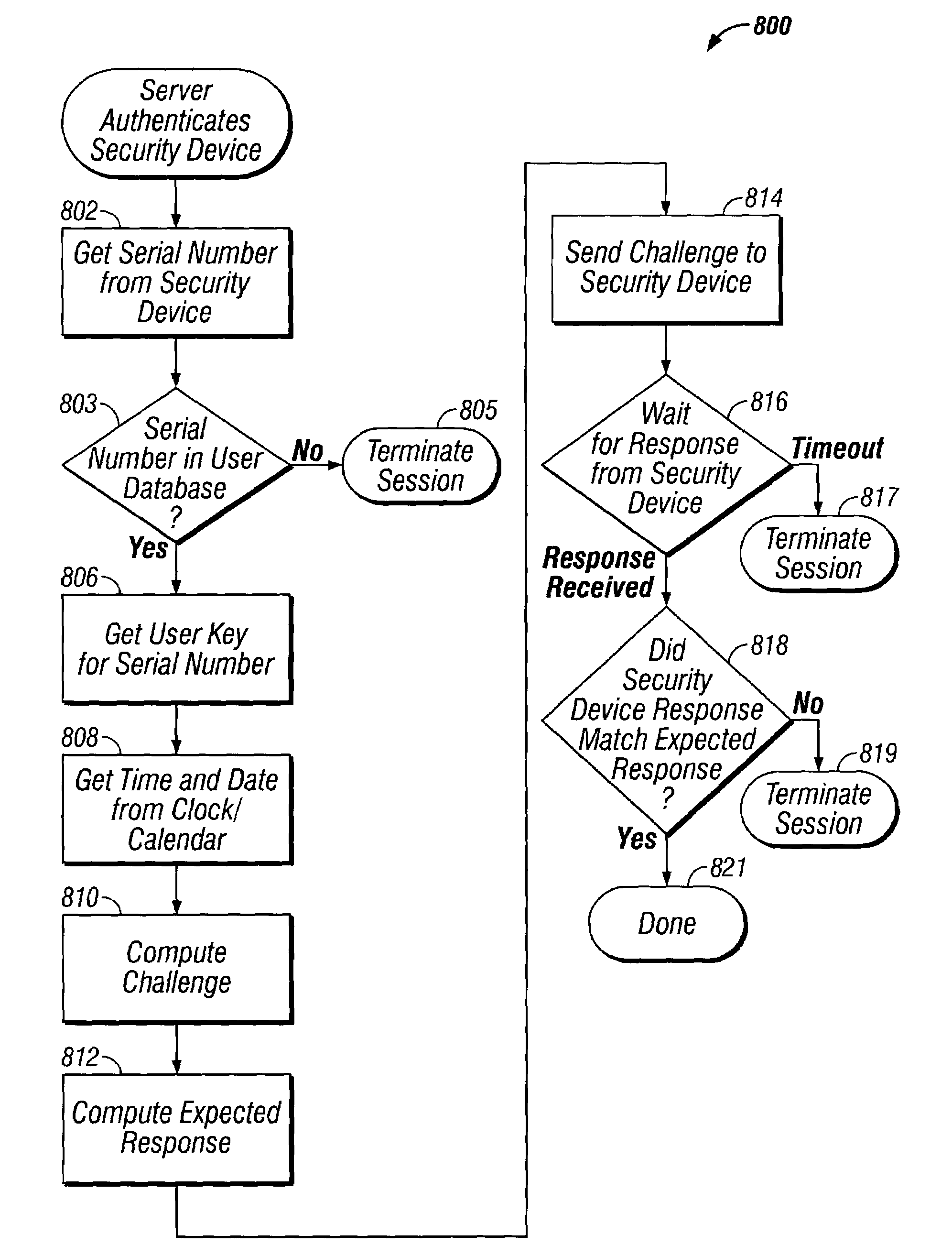
Disclosed is a security device coupled to a computing device, which is, in turn, coupled to a server through a computer network. The security device stores a serial number associated with the security device and a user key associated with the serial number. When the computing device attempts to log onto the server over the computer network, the server requests a serial number from the security device. If the serial number is stored within a user information database, the server obtains an associated user key and computes a challenge. Further, the server computes an expected response for the security device based on the associated user key. The server then sends the challenge to the security device over the computer network. If the server receives a response back from the security device that matches the expected response, the server will allow the computing device to log onto the server.
Owner:YAMAHA GUITAR GRP INC
System and method for establishing historical usage-based hardware trust
InactiveUS7849307B2Improve trustPromote recoveryDigital data processing detailsUser identity/authority verificationThird partyPassword
Establishing trust according to historical usage of selected hardware involves providing a usage history for a selected client device; and extending trust to a selected user based on the user's usage history of the client device. The usage history is embodied as signed statements issued by a third party or an authentication server. The issued statement is stored either on the client device, or on an authentication server. The usage history is updated every time a user is authenticated from the selected client device. By combining the usage history with conventional user authentication, an enhanced trust level is readily established. The enhanced, hardware-based trust provided by logging on from a trusted client may eliminate the necessity of requiring secondary authentication for e-commerce and financial services transactions, and may also be used to facilitate password recovery and conflict resolution in the case of stolen passwords.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com