Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
446 results about "Trustworthiness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
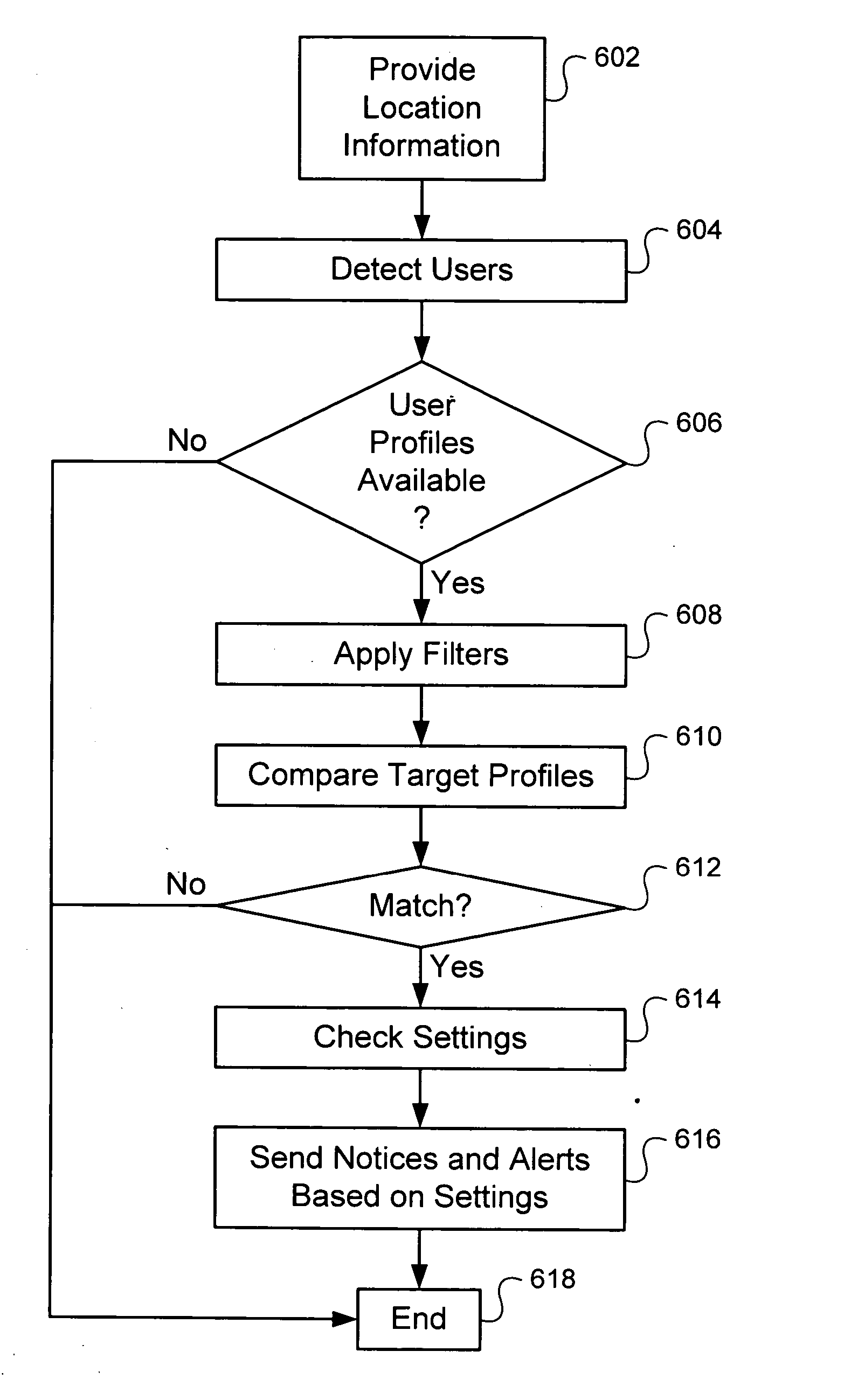
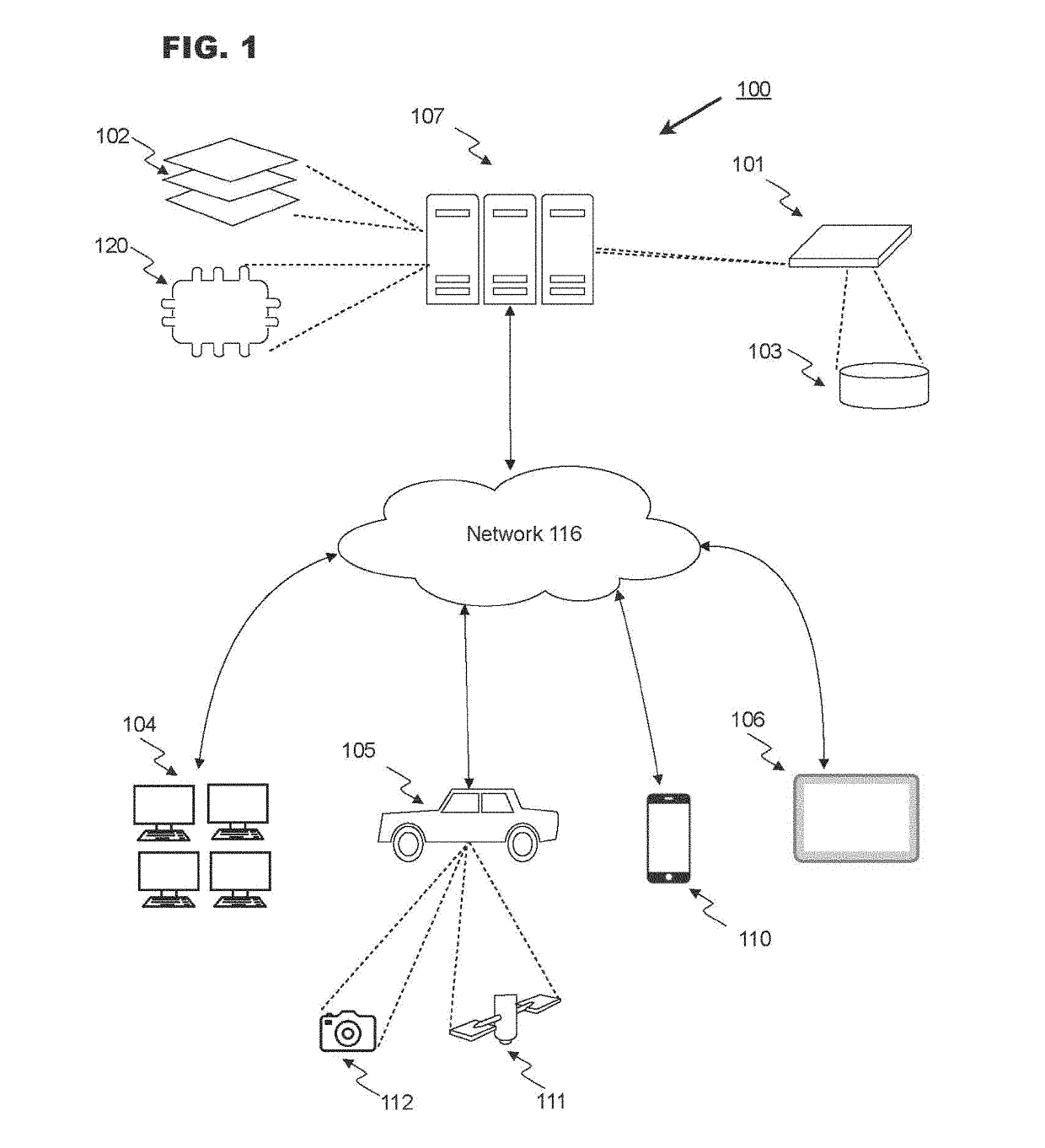
System and method for location based social networking
ActiveUS20060085419A1Quality improvementImprove trustworthinessDigital data information retrievalAdvertisementsPosition dependentSocial web
Systems and methods for social networking. Location-related data and other behavioral and exogenously generated characteristics are used to replace or supplement self-generated profiles in order to enhance the quality and trustworthiness of the matches made using the system and facilitate the inputting of profile information.
Owner:VERIZON PATENT & LICENSING INC
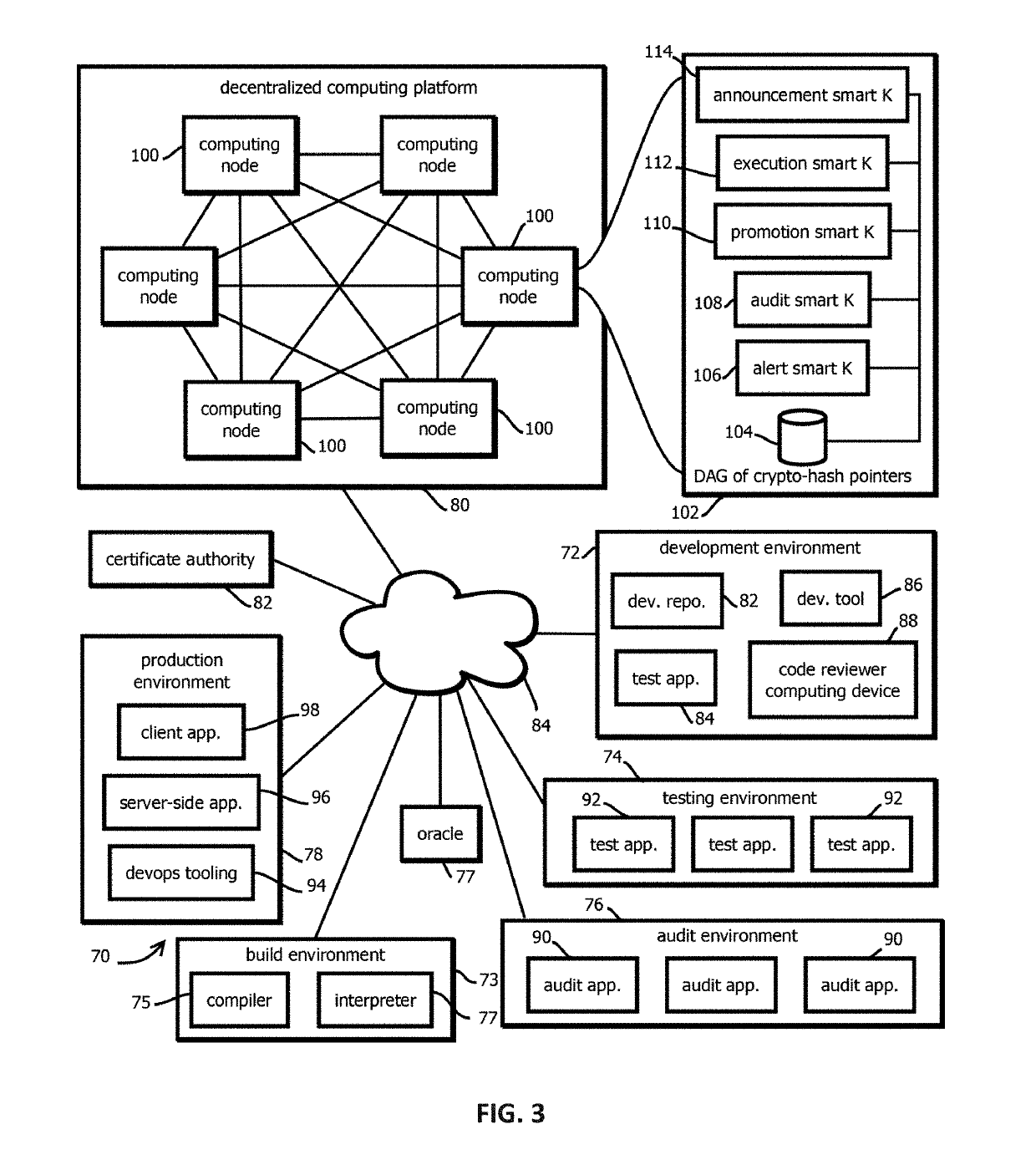
Systems and methods for threat identification and remediation
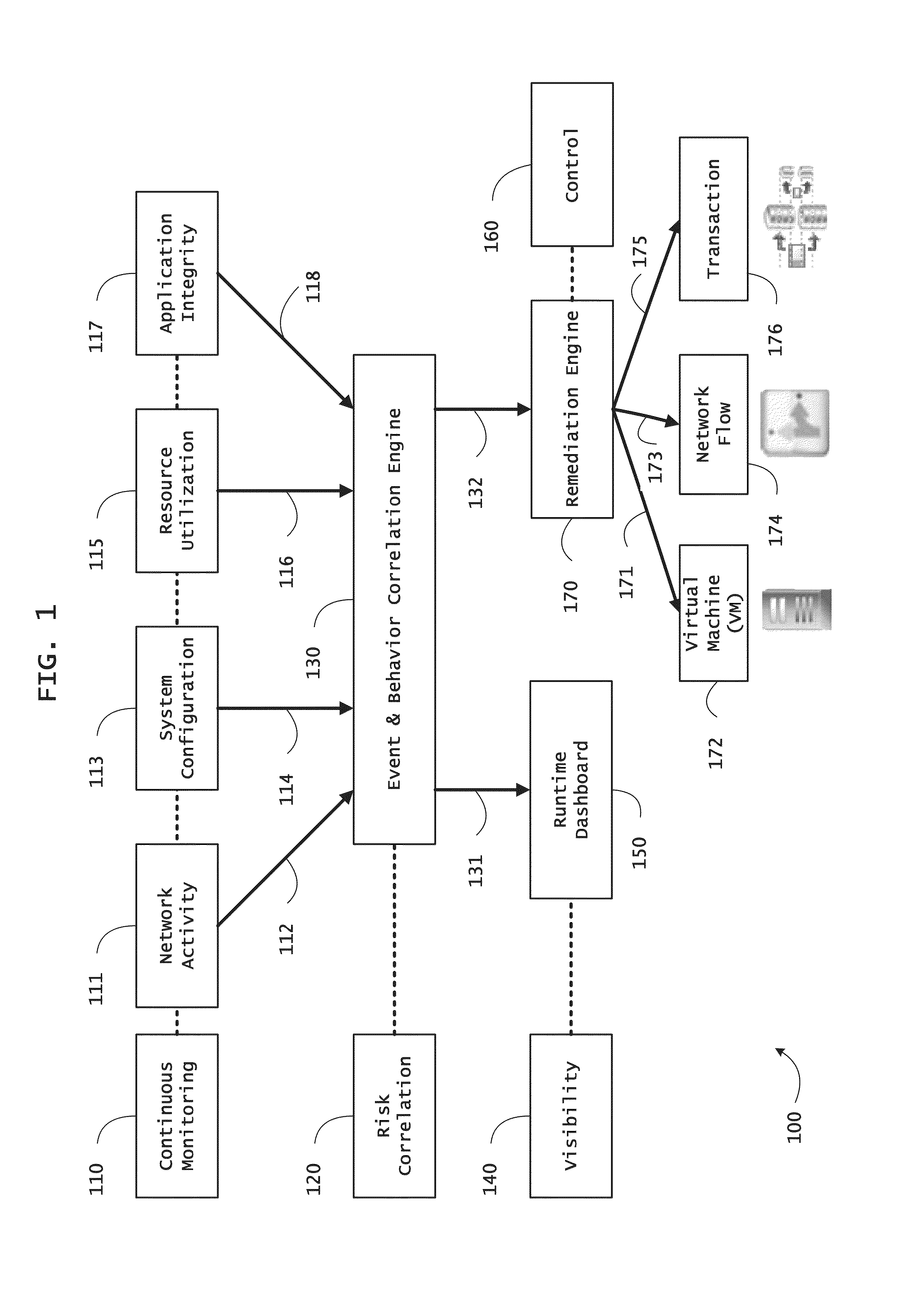
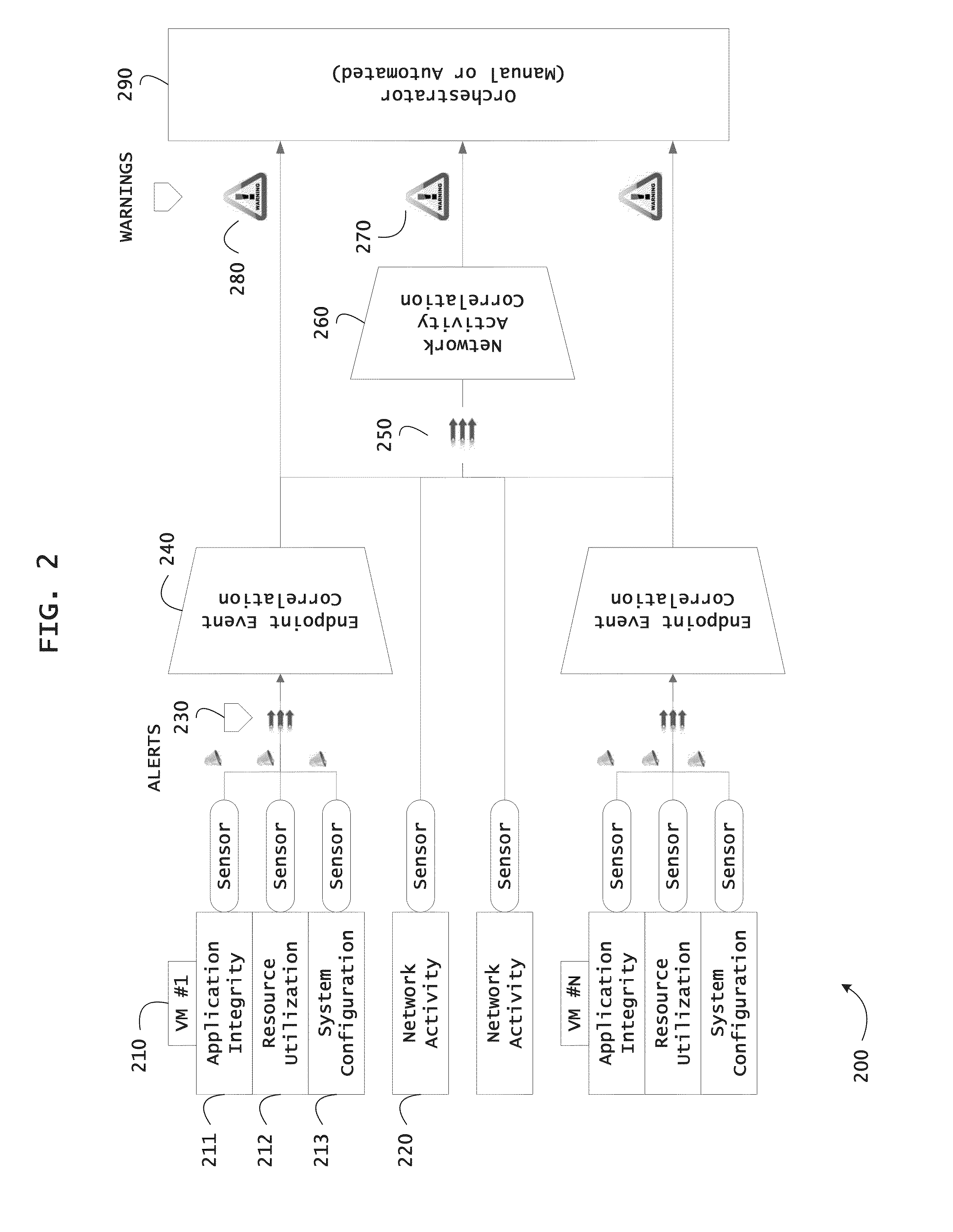
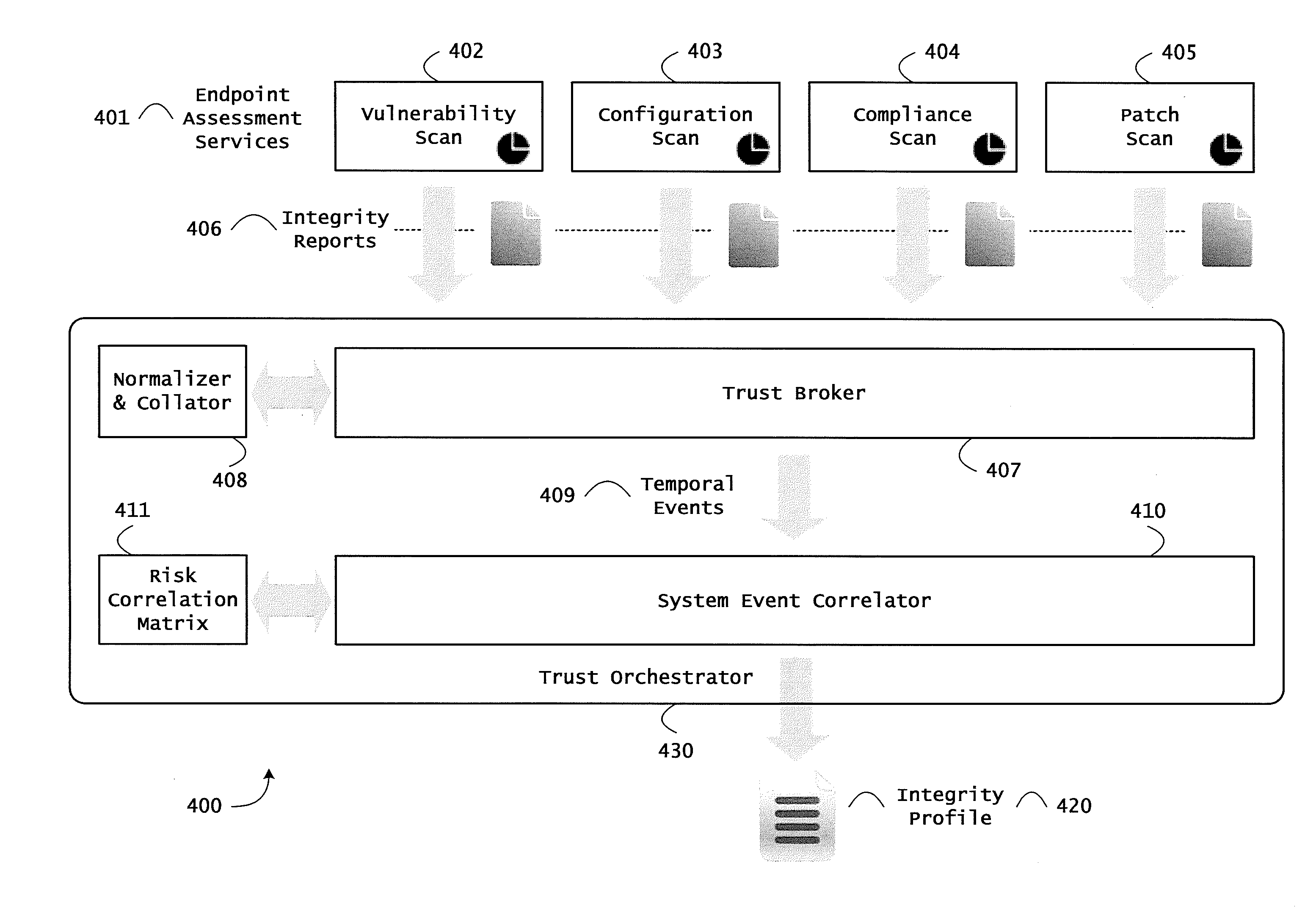
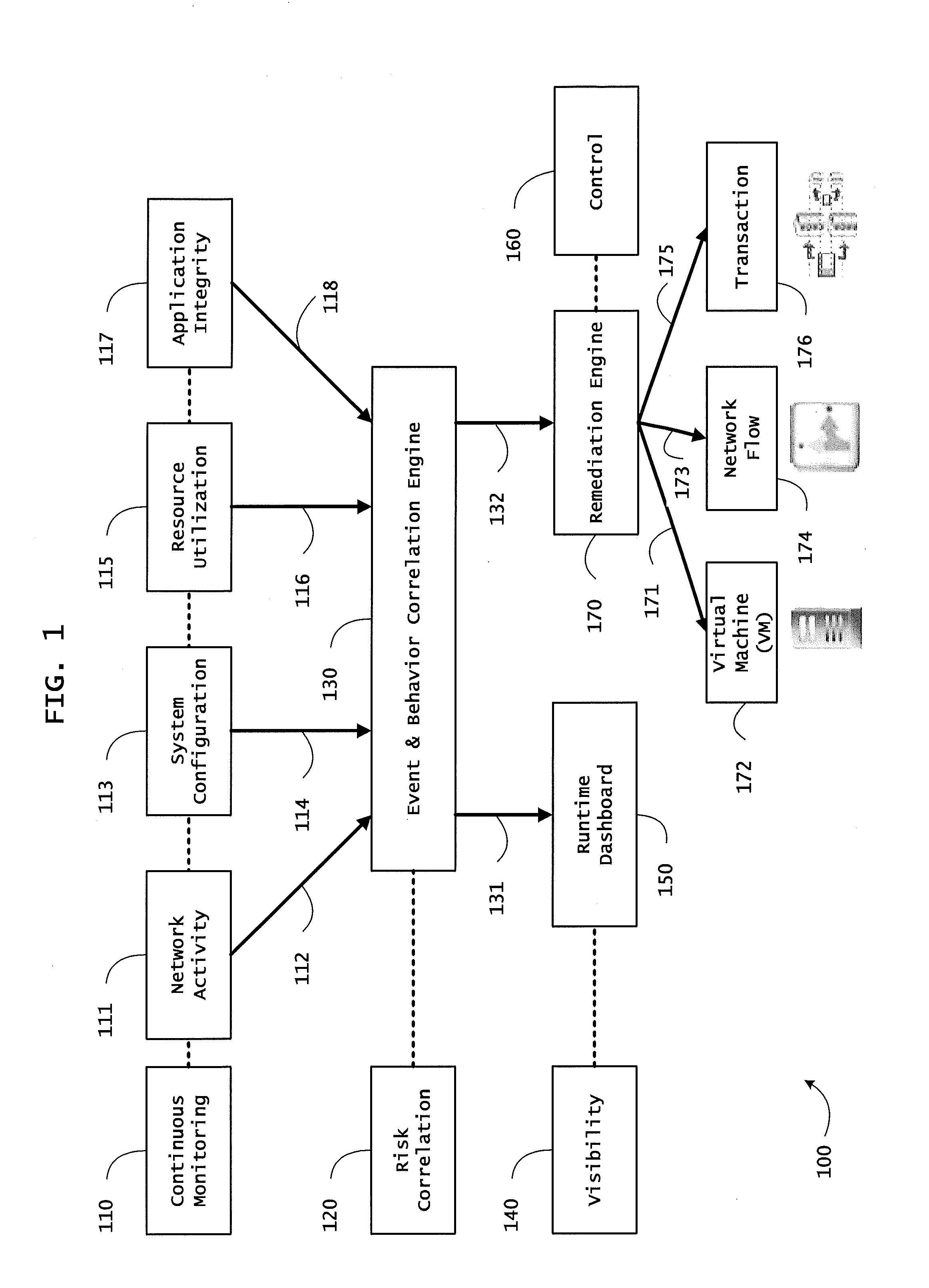
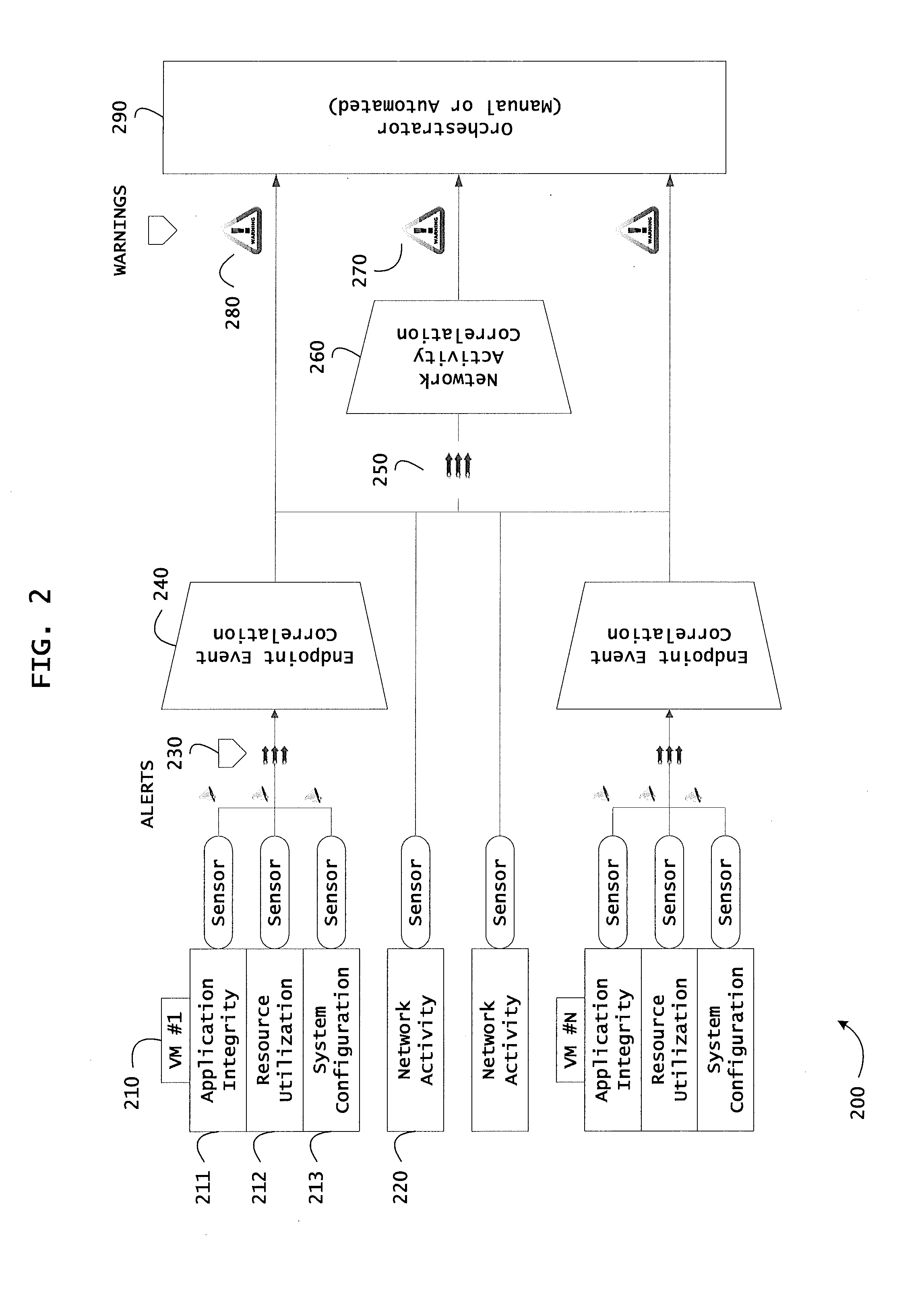
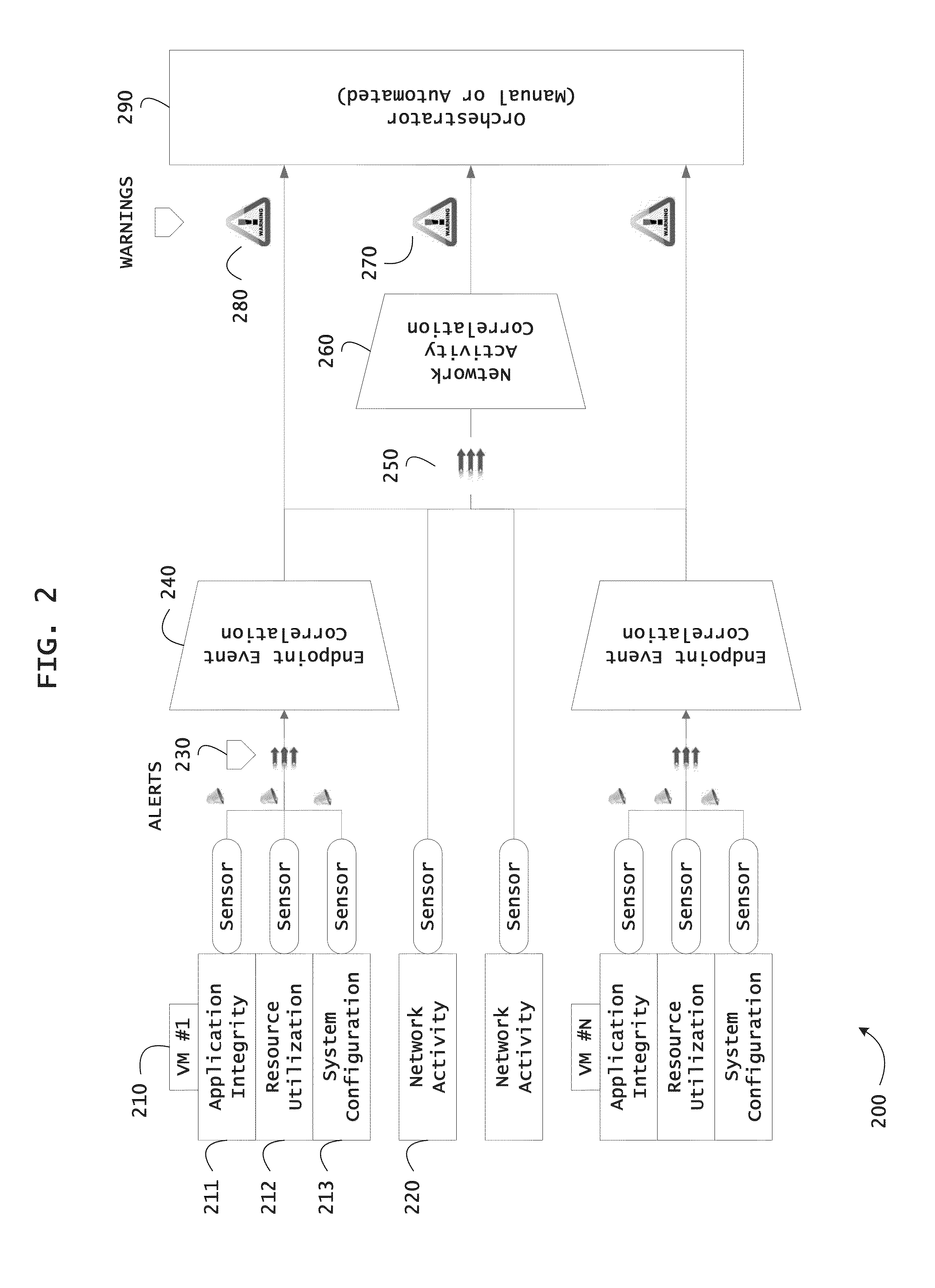
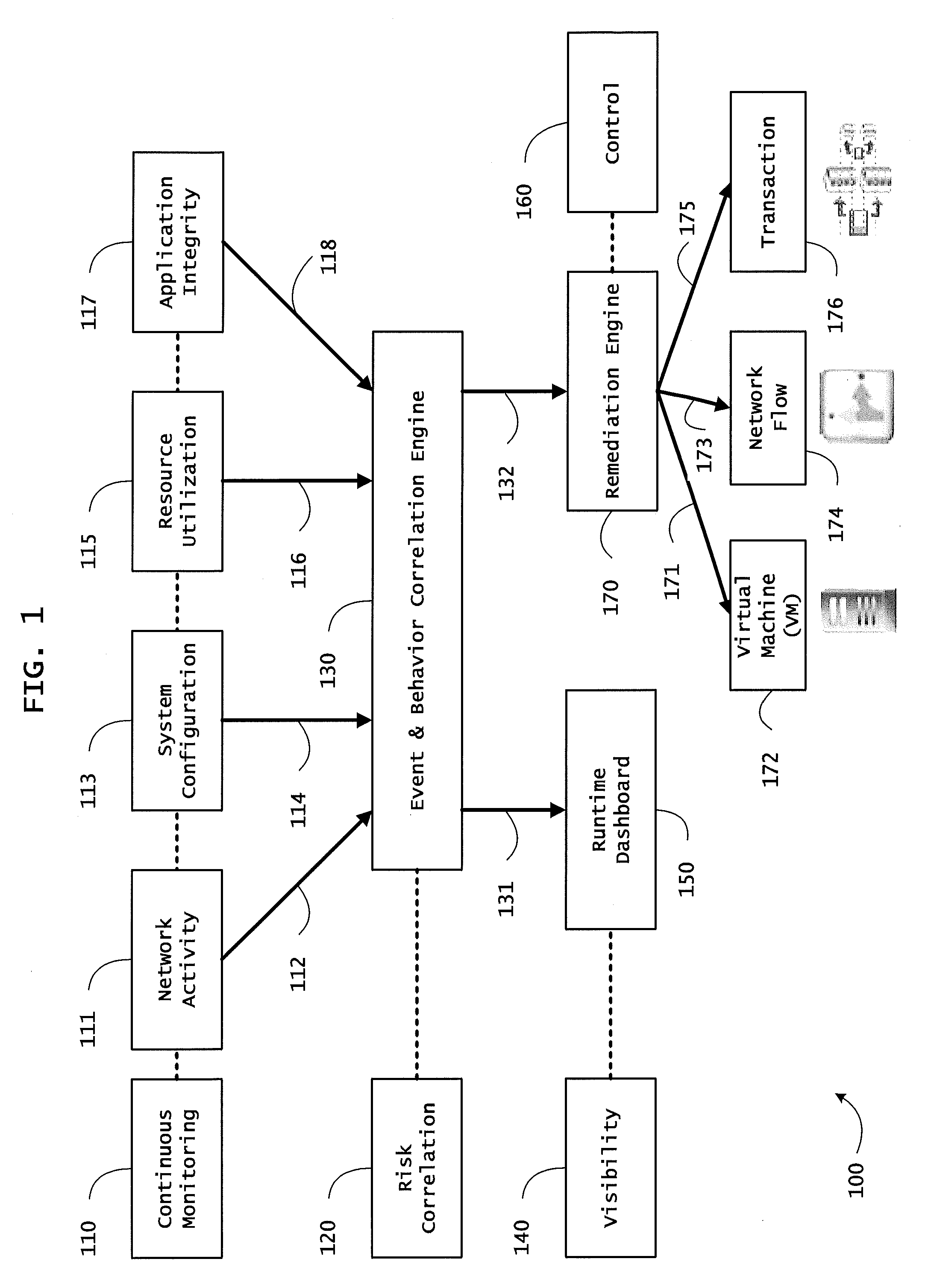
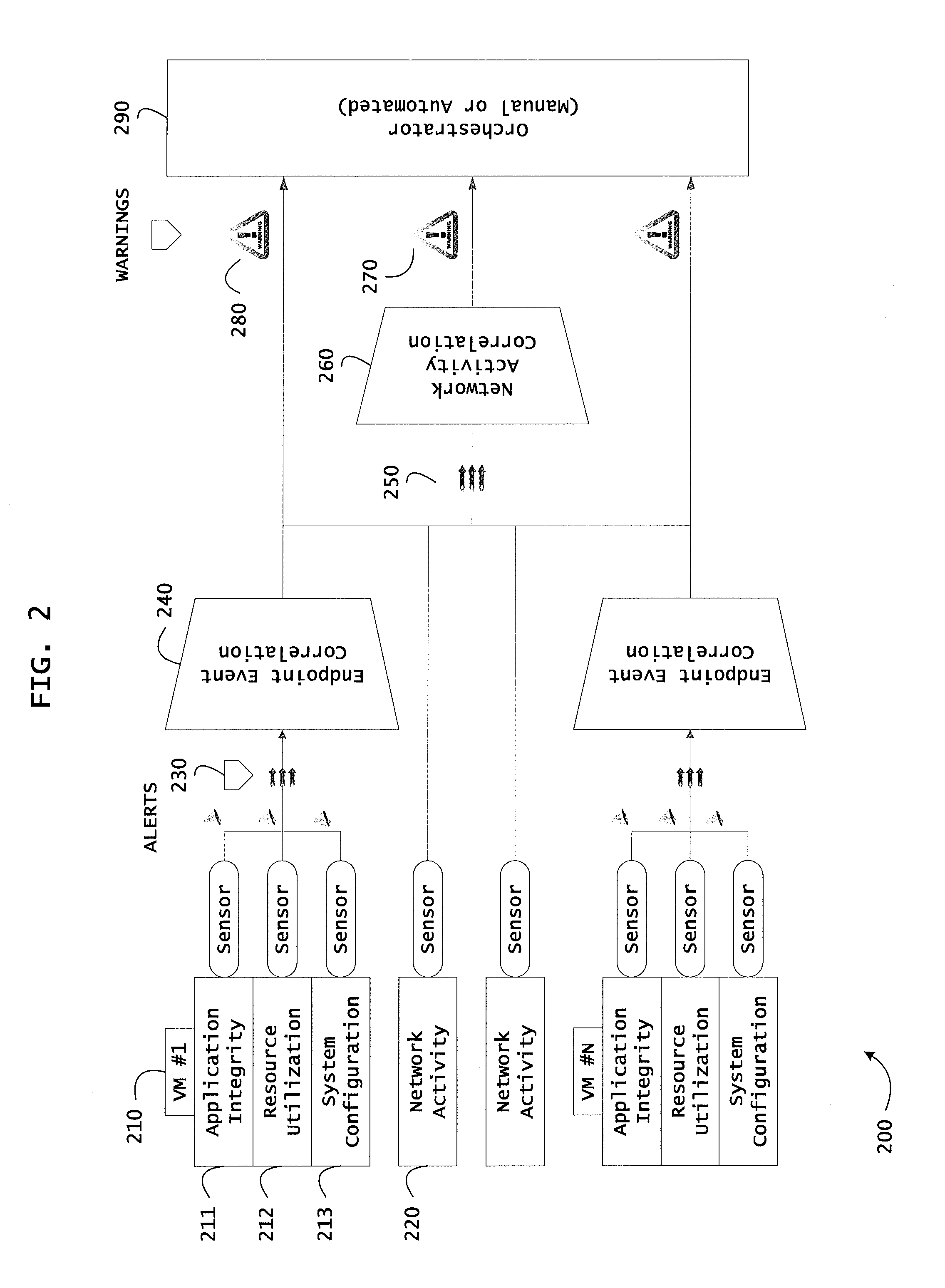
ActiveUS20130298244A1Memory loss protectionError detection/correctionOrchestrationApplication software
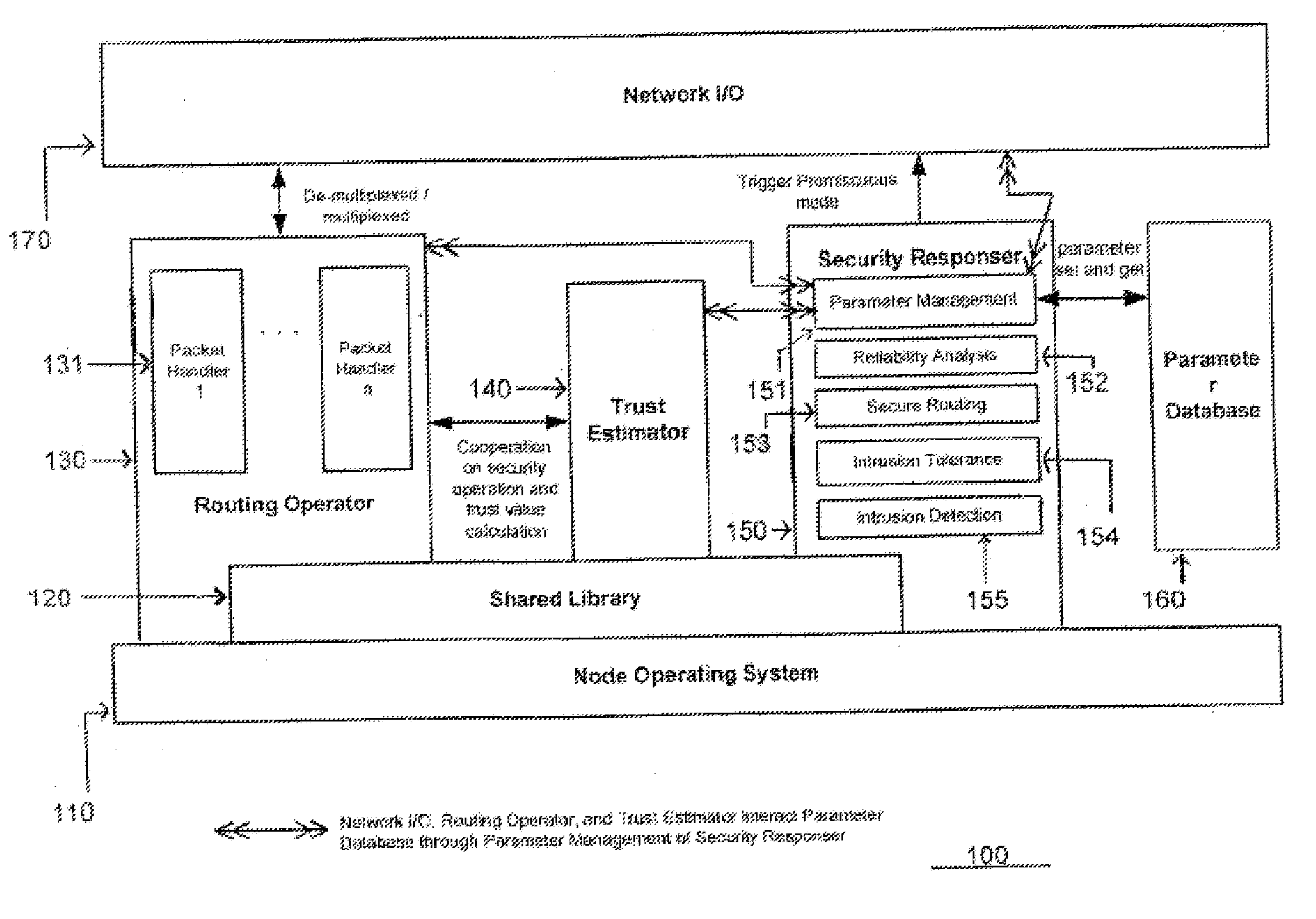
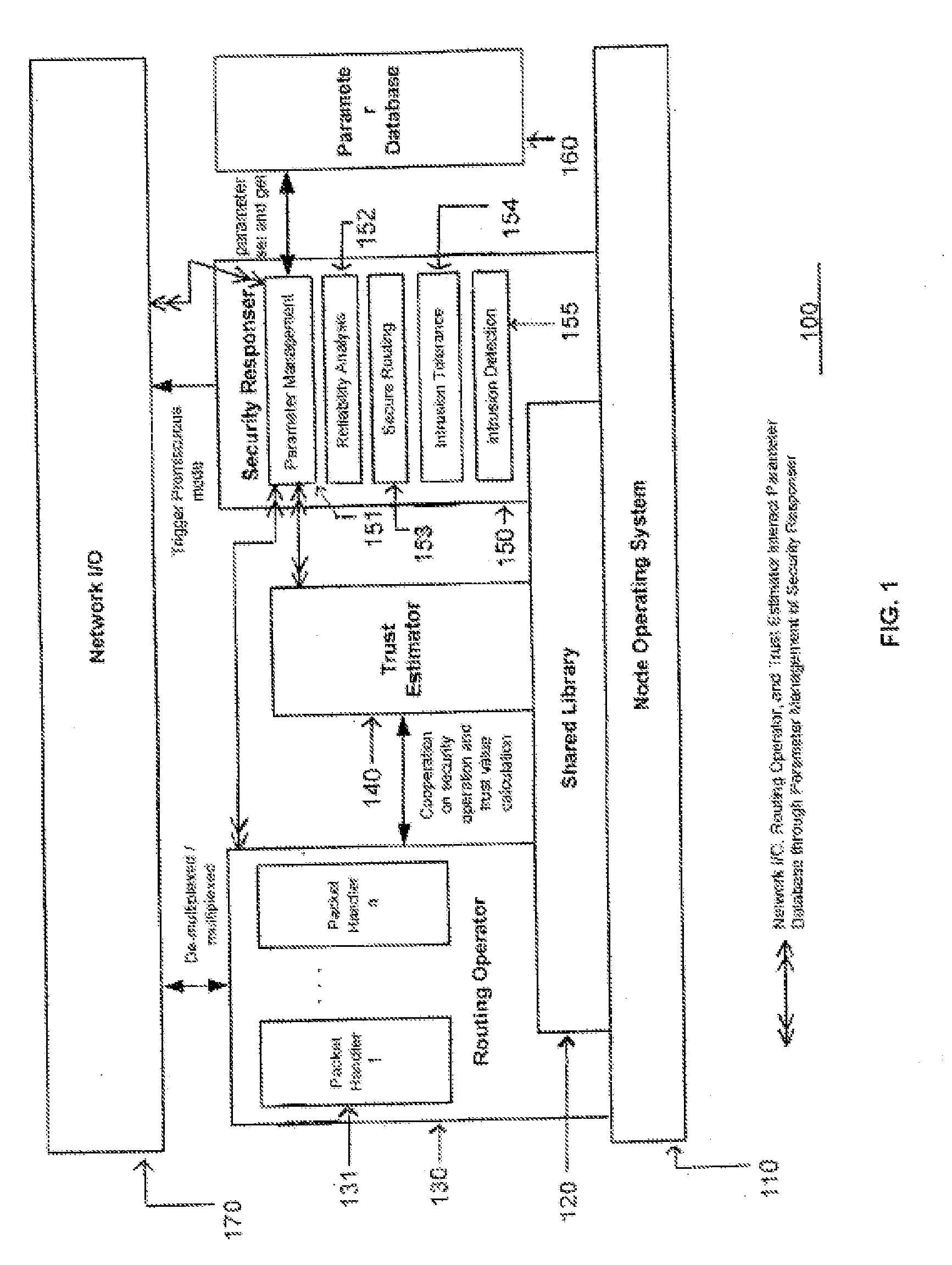
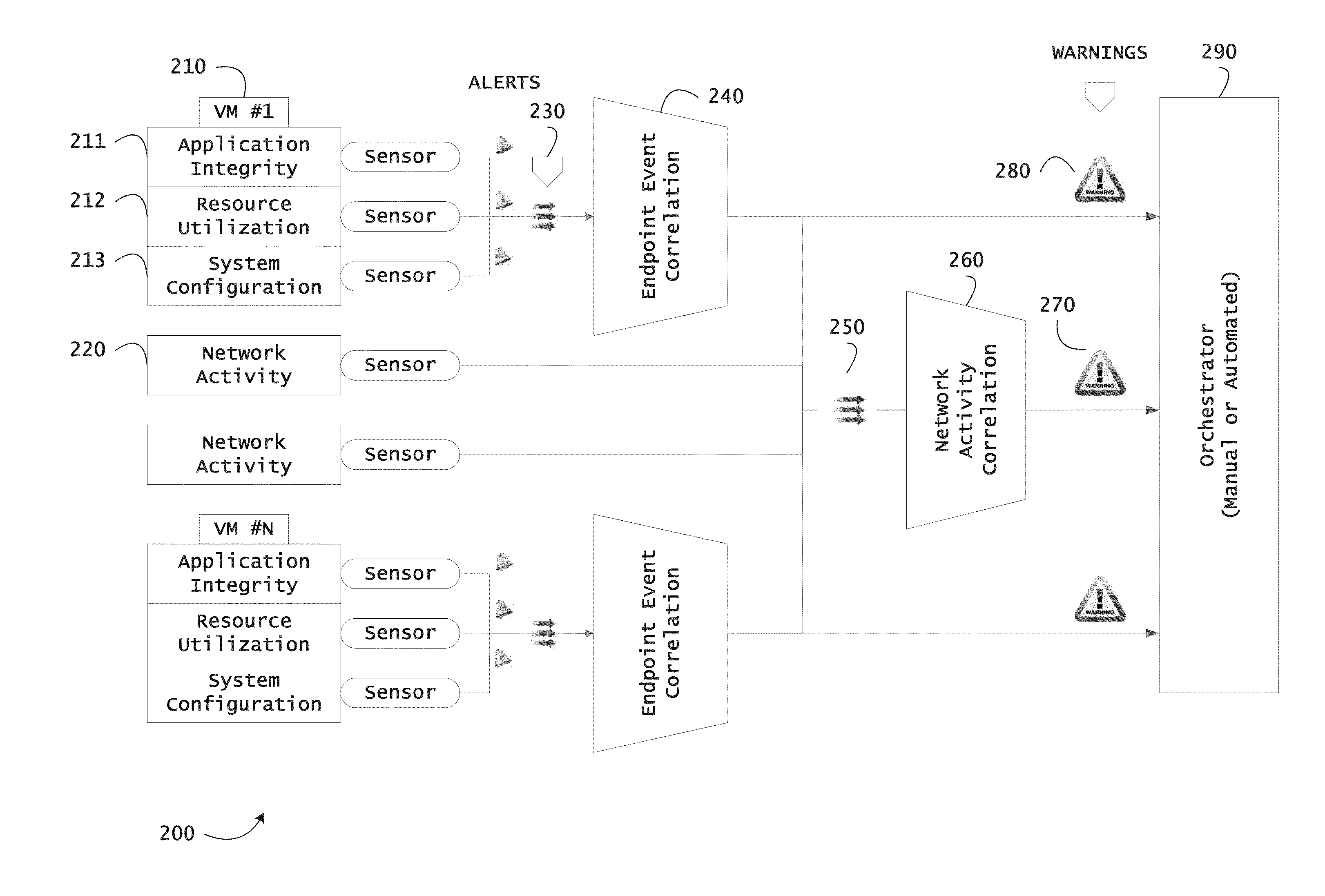
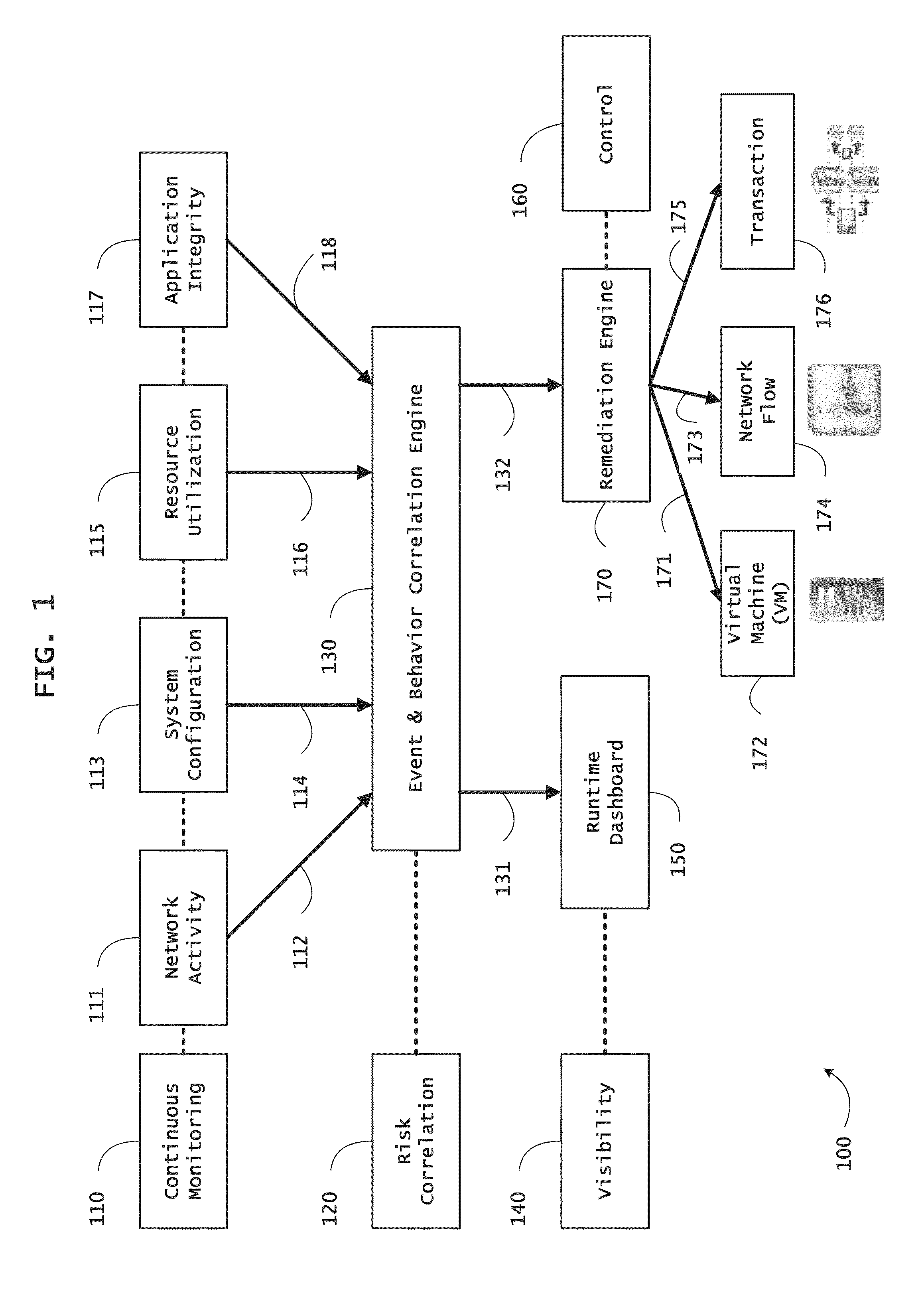
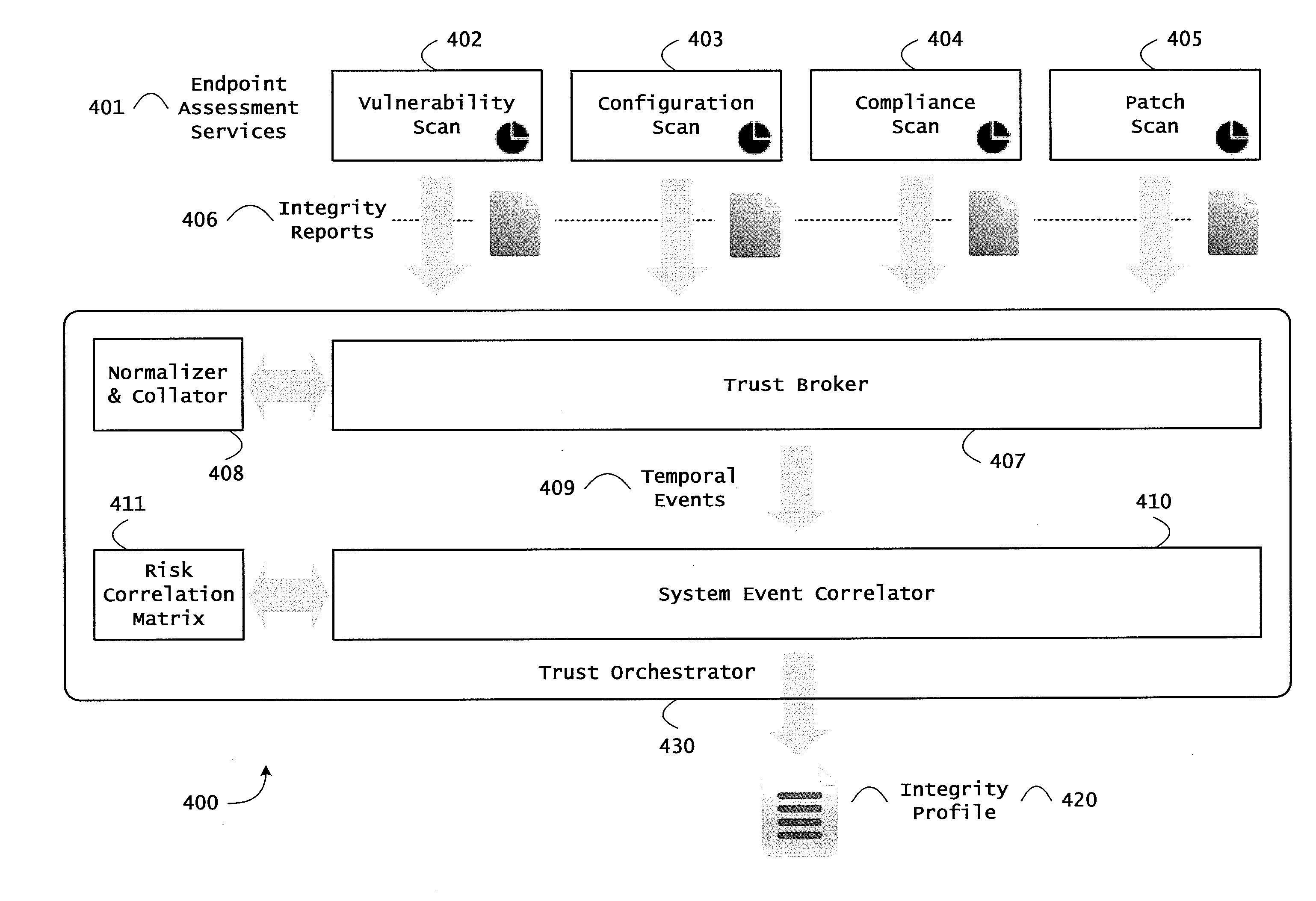
Instrumented networks and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Systems and methods for threat identification and remediation for computing platforms based upon reconnaissance-based intelligence correlation and network / application monitoring are disclosed. In an embodiment, a method provides runtime operational integrity of a system by receiving: a dynamic context including endpoint events; and network endpoint assessments. The method generates temporal events based on the network endpoint assessments and correlates the endpoint events and temporal events before generating an integrity profile for the system. In another embodiment, flow level remediation is provided to isolate infected or compromised systems from a computing network fabric using a network trust agent, an endpoint trust agent, and a trust orchestrator.
Owner:TAASERA LICENSING LLC
Systems and methods for using reputation scores in network services and transactions to calculate security risks to computer systems and platforms
ActiveUS20130298192A1Memory loss protectionError detection/correctionMathematical CalculusInternet privacy
Instrumented networks, computer systems and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Methods and systems are disclosed for calculating security risks by determining subject reputation scores. In an embodiment, a system receives a query for a reputation score of a subject, initiates directed queries to external information management systems to interrogate attributes associated with the subject, and analyzes responses. The system receives a hierarchical subject reputation score based on a calculus of risk and returns a reputation token. In another embodiment, a method provides real time attestation of a subject's reputation to a service provider using an endpoint trust agent, and a trust orchestrator comprising a reputation broker and a trust broker.
Owner:TAASERA LICENSING LLC
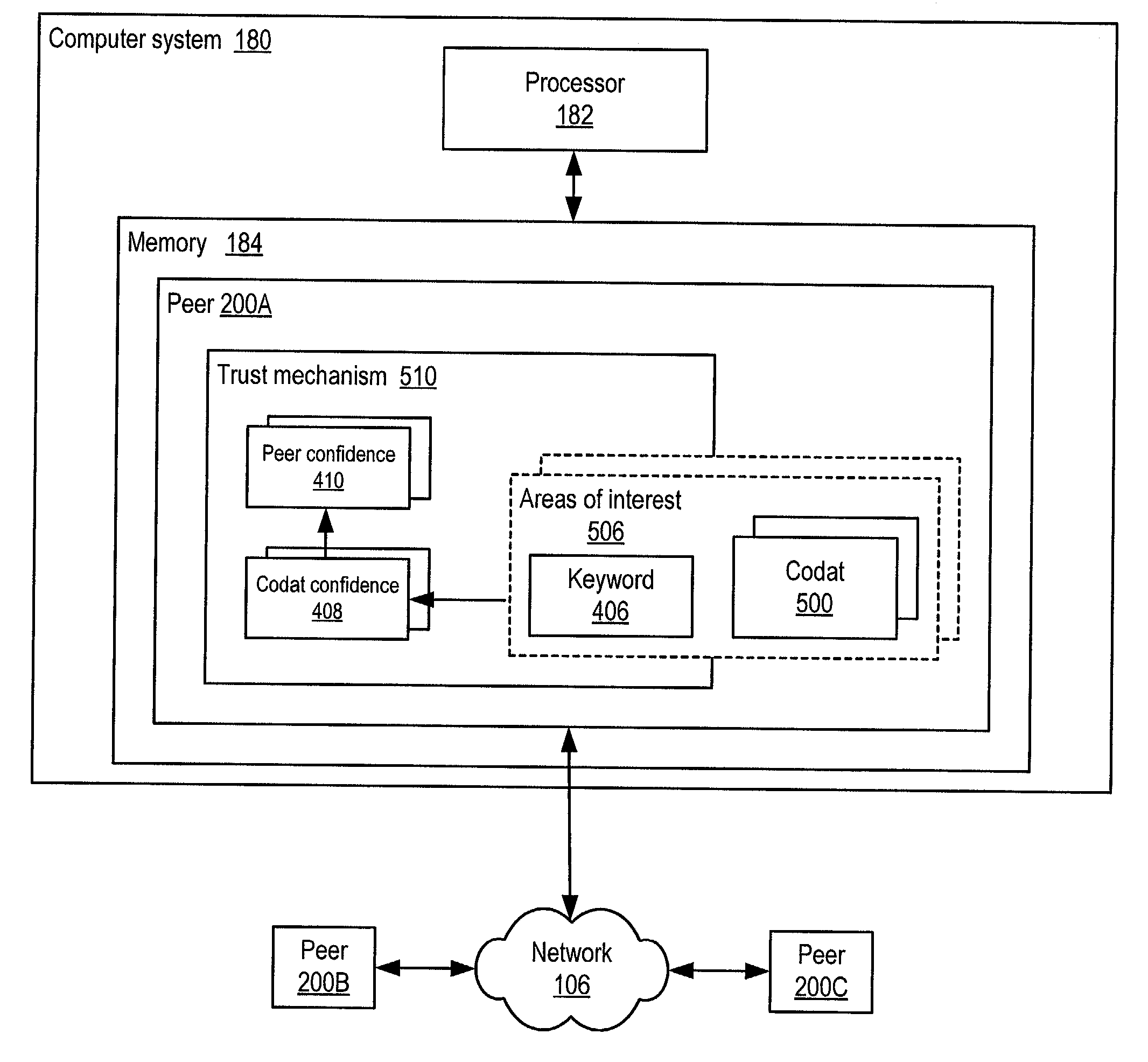
Propagating and updating trust relationships in distributed peer-to-peer networks
ActiveUS20030055898A1Multiprogramming arrangementsMultiple digital computer combinationsInternet privacyTrust relationship
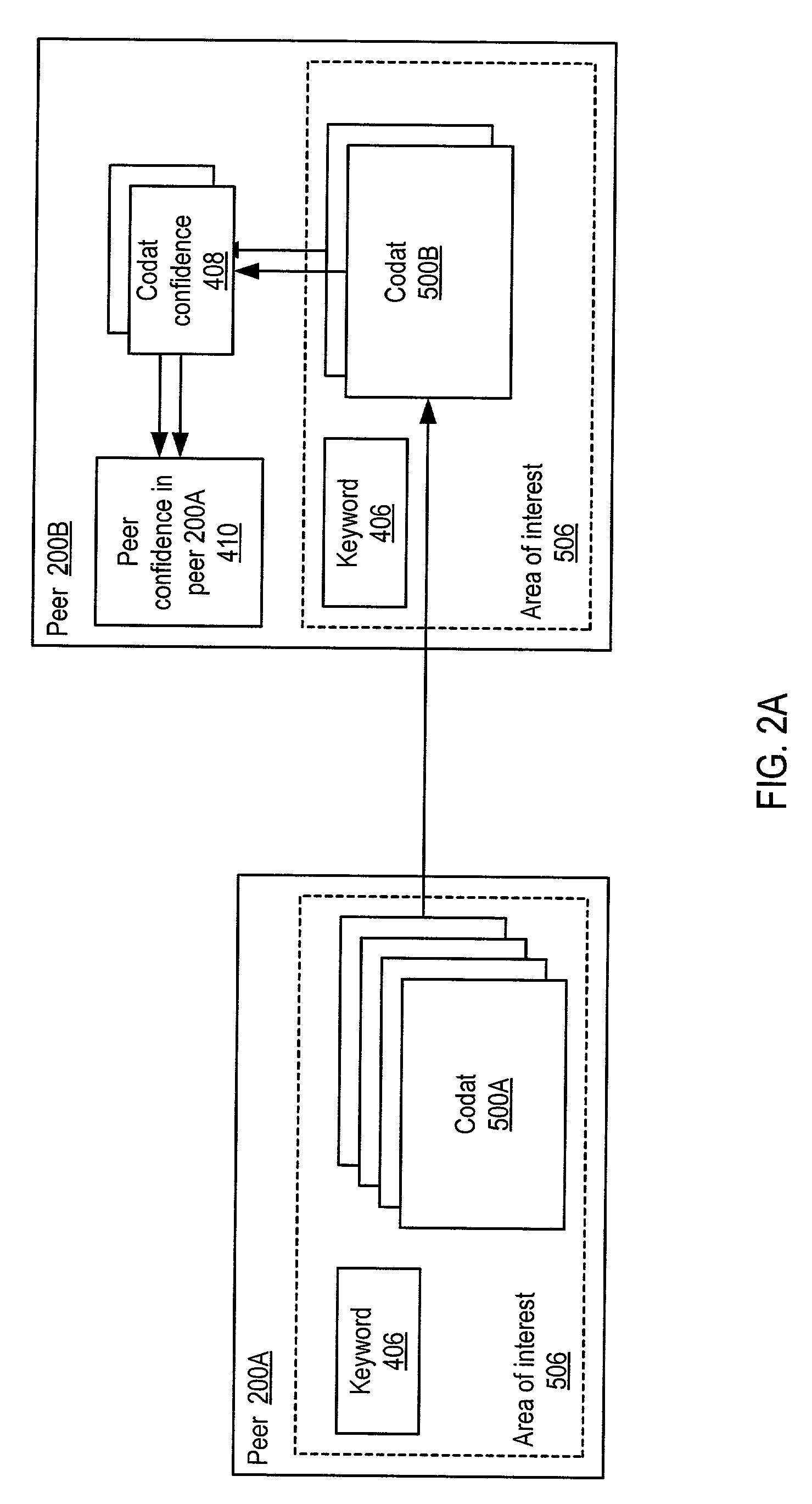
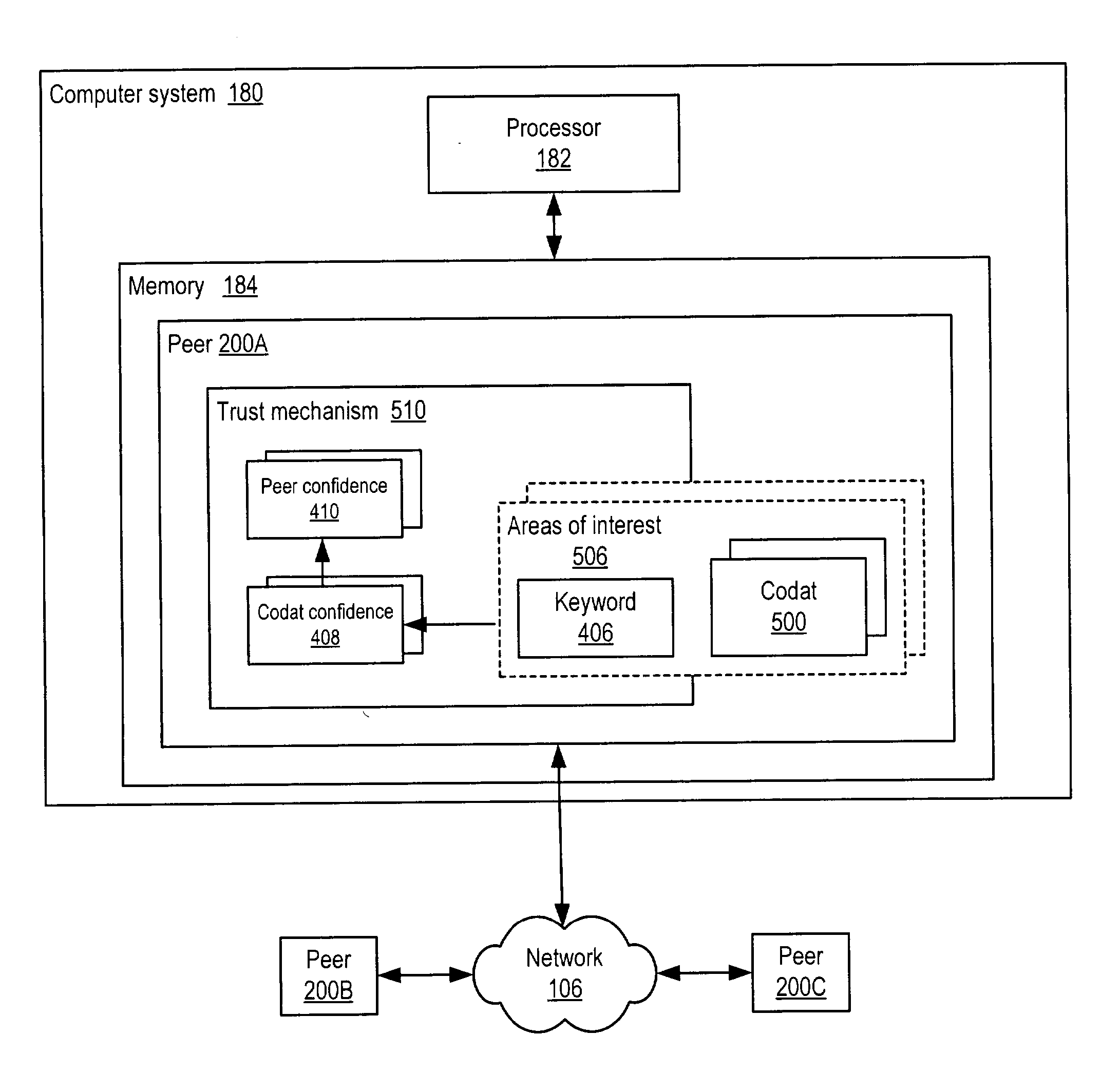
System and method for representing and rate the trustworthiness of peers as providers of content and data (codats) relevant to the peers' interests. In one embodiment, trust may be propagated through transaction pipes (paths) along which codats located in a search for codats relevant to an area of interest may be accessed by the requestor. In some embodiments, the trust a peer has in another peer as a provider of codats may be a function of the trust values of the provider peer and all other peers on a path. If there are multiple paths, trust in the provider peer may be an average of the trust values for all the paths. Trust in a provider peer may be used to determine confidence in codats provided by the peer. Embodiments may provide mechanisms for feeding back trust information to the providing peer and for propagating trust information to other peers.
Owner:ORACLE INT CORP
Wireless sensor network and adaptive method for monitoring the security thereof
InactiveUS20080084294A1Data taking preventionNetwork topologiesWireless mesh networkWireless sensor networking
The present invention relates to a sensor network having node architecture for performing trust management of neighboring sensor nodes, and to an adaptive method for performing trust management of neighboring sensor nodes for monitoring security in the sensor network. The sensor network includes a base station and a plurality of sensor nodes for reporting sensed information packets to the base station through radiofrequency signals relayed by other sensor nodes. A judge sensor node may have a trust estimator in its node architecture to evaluate trustworthiness of a neighboring suspect sensor node by determining a personal reference and receiving personal references from jury sensor nodes. Based on the trustworthiness of the suspect, the judge may modify a route for transmitting packets to the base station.
Owner:ELECTRONICS & TELECOMM RES INST
Systems and methods for providing mobile security based on dynamic attestation
ActiveUS20130298242A1Memory loss protectionError detection/correctionMobile securityApplication software
Instrumented networks, machines and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects (including mobile devices) and applications on the instrumented target platform. Methods and systems are disclosed for dynamic attestation of mobile device integrity based upon subject reputation scores. In an embodiment, a method scores trustworthiness of a mobile device based on reputation scores for users associated with the device and / or a device reputation score. The method generates runtime integrity alerts regarding execution anomalies for applications executing on the device, calculates risks based on a ruleset, and determines a calculus of risk for the device. The method sends endpoint events comprising data and content of the integrity warnings to a trust orchestrator, which generates an integrity profile based on the endpoint events.
Owner:TAASERA LICENSING LLC
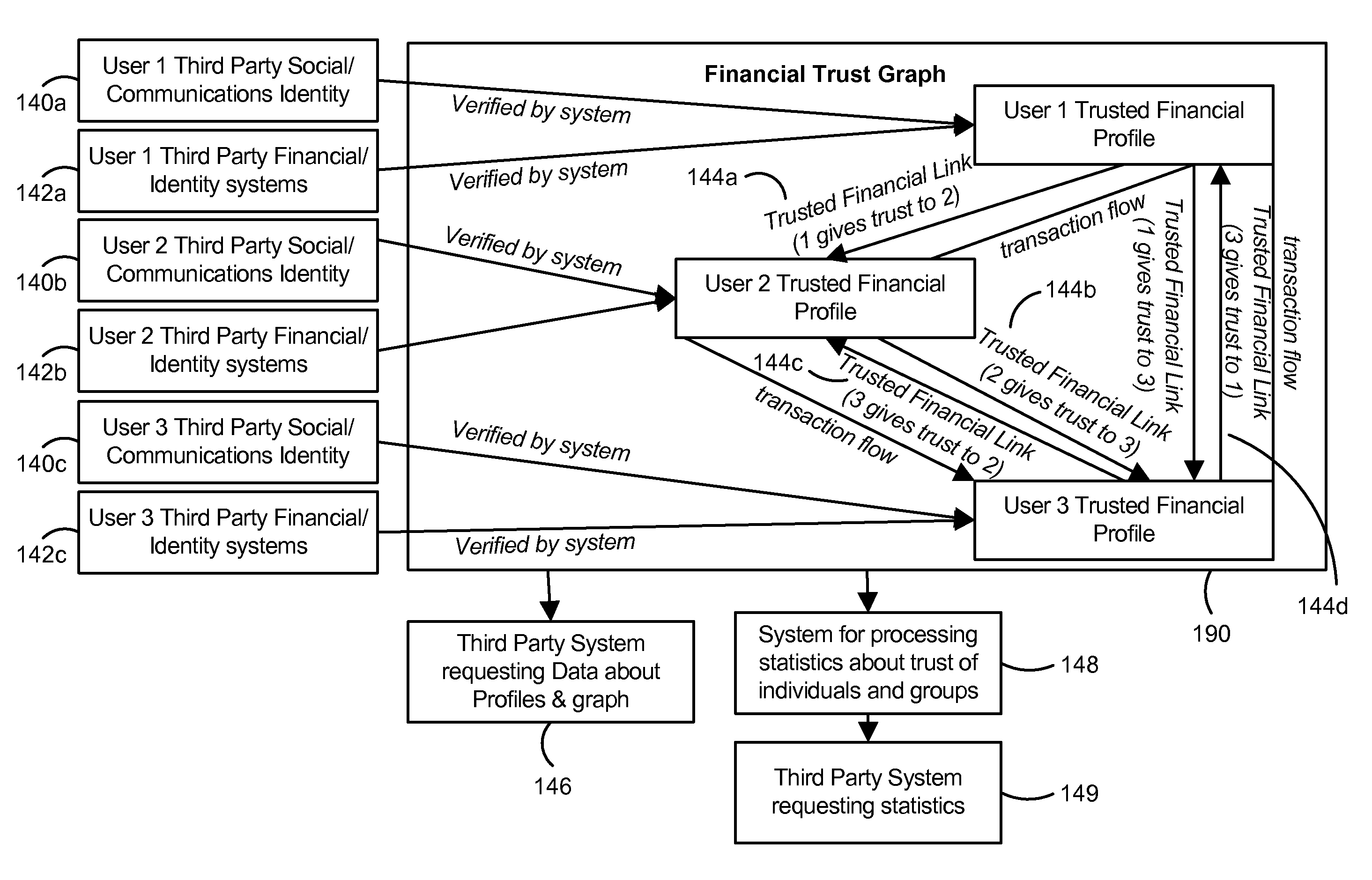
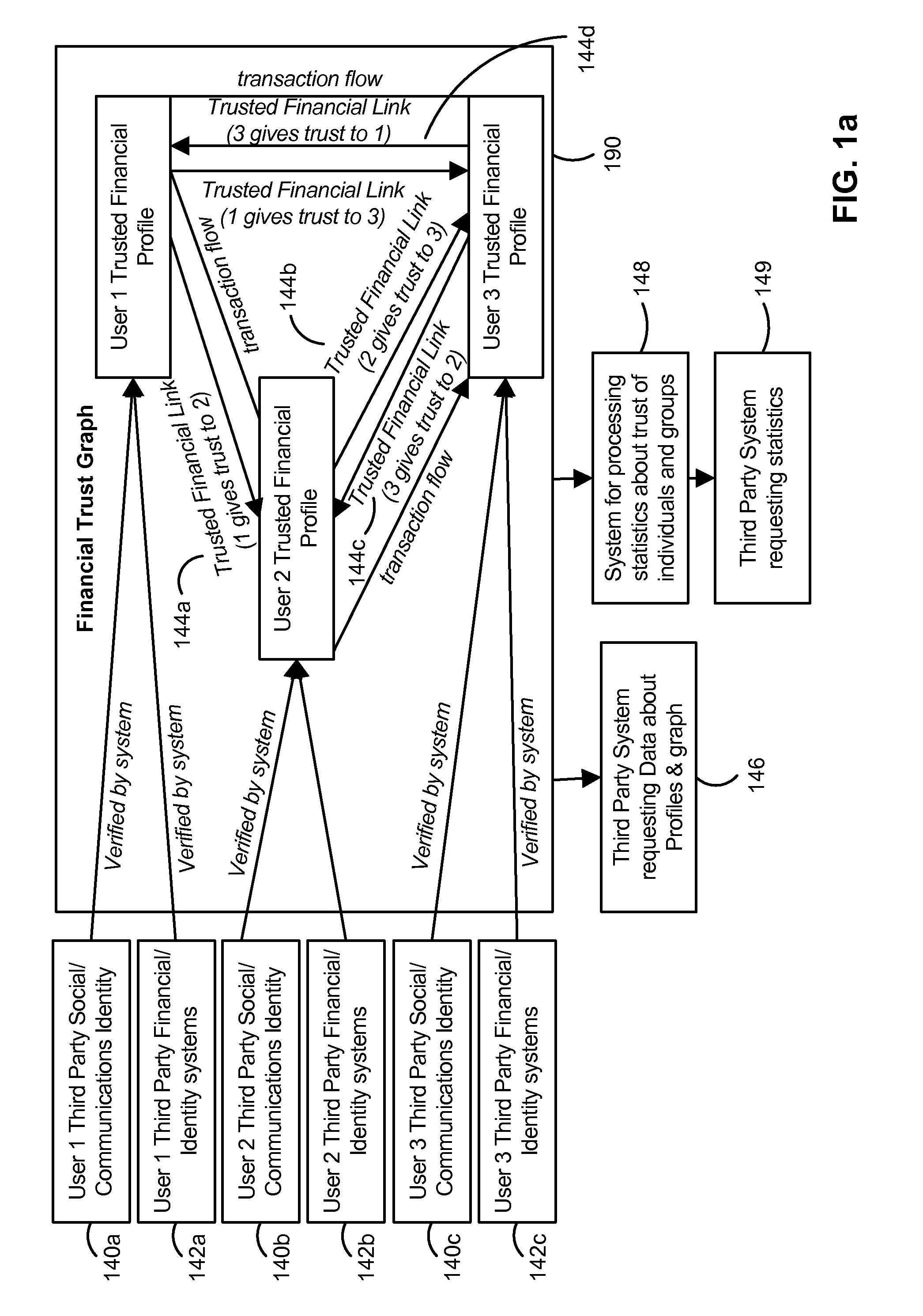
Trust Based Transaction System
A configuration for more efficient electronic financial transactions is disclosed. Users input personal and financial information into a system that validates the information to generate trusted financial profiles. Each user can establish trusted financial links with other users. The trusted financial link provides a mechanism for the user to allow other users to withdraw money from the link provider account. The data from these relationships and the financial data flowing through the system enable a measure of trustworthiness of users and the trustworthiness of all interactions in the system. The combination of trusted financial profiles, trusted financial links, and financial transactions between users create a measurable financial trust graph which is a true representation of the trusting economic relationships among the users. The financial trust graph enables a more accurate assessment of the creditworthiness and financial risk of transactions by users with little or no credit or transaction history.
Owner:PAYPAL INC
Online identity tracking
InactiveUS20060230039A1Ease of evaluationFacilitate of entityTransmissionSpecial data processing applicationsDomain nameOnline identity
Embodiments of the invention provide novel systems, software and methods for gathering information about online entities and for identifying, evaluating and scoring such entities. Merely by way of example, the trustworthiness of an online entity, such as a domain, can be evaluated based information known about other online entities (e.g., the owner of the domain, other domains) associated with that domain. In an aspect of the invention, for example, publicly-available data (and, in some cases, other data) can be obtained and correlated to reveal previously-unknown associations between various online entities, despite, in some cases, the attempts of those entities to obscure such associations. This can facilitate the evaluation of such entities. For instance, if a new domain is registered, there generally is little basis on which to evaluate the trustworthiness of that domain (other than facially-apparent characteristics, such as the domain name itself), since it has not yet begun operating. By ascertaining the domain's association with other online entities, however, information known about the reputation and / or behavior of those entities can be used to inform an evaluation of the domain.
Owner:MARKMONITOR
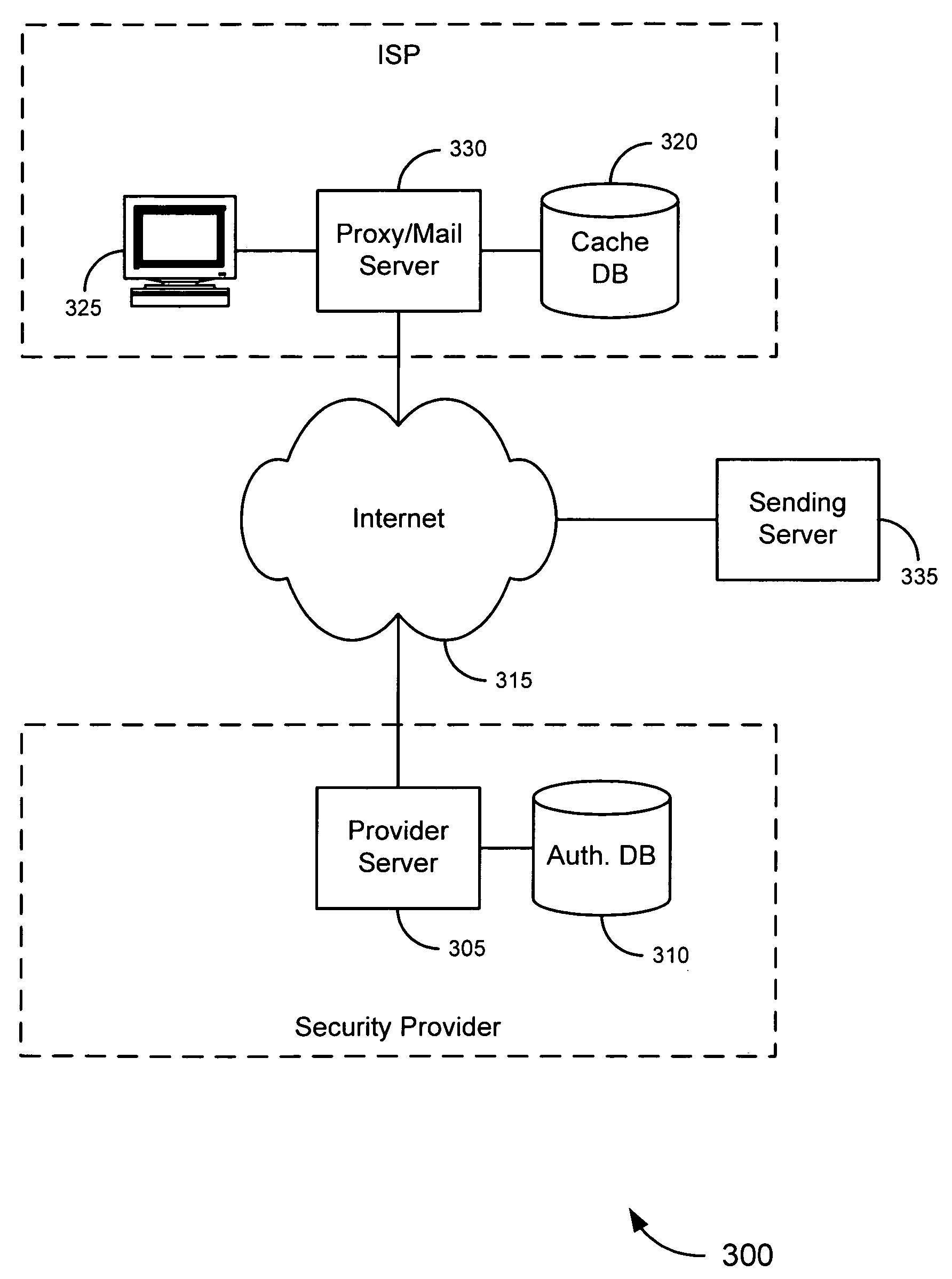
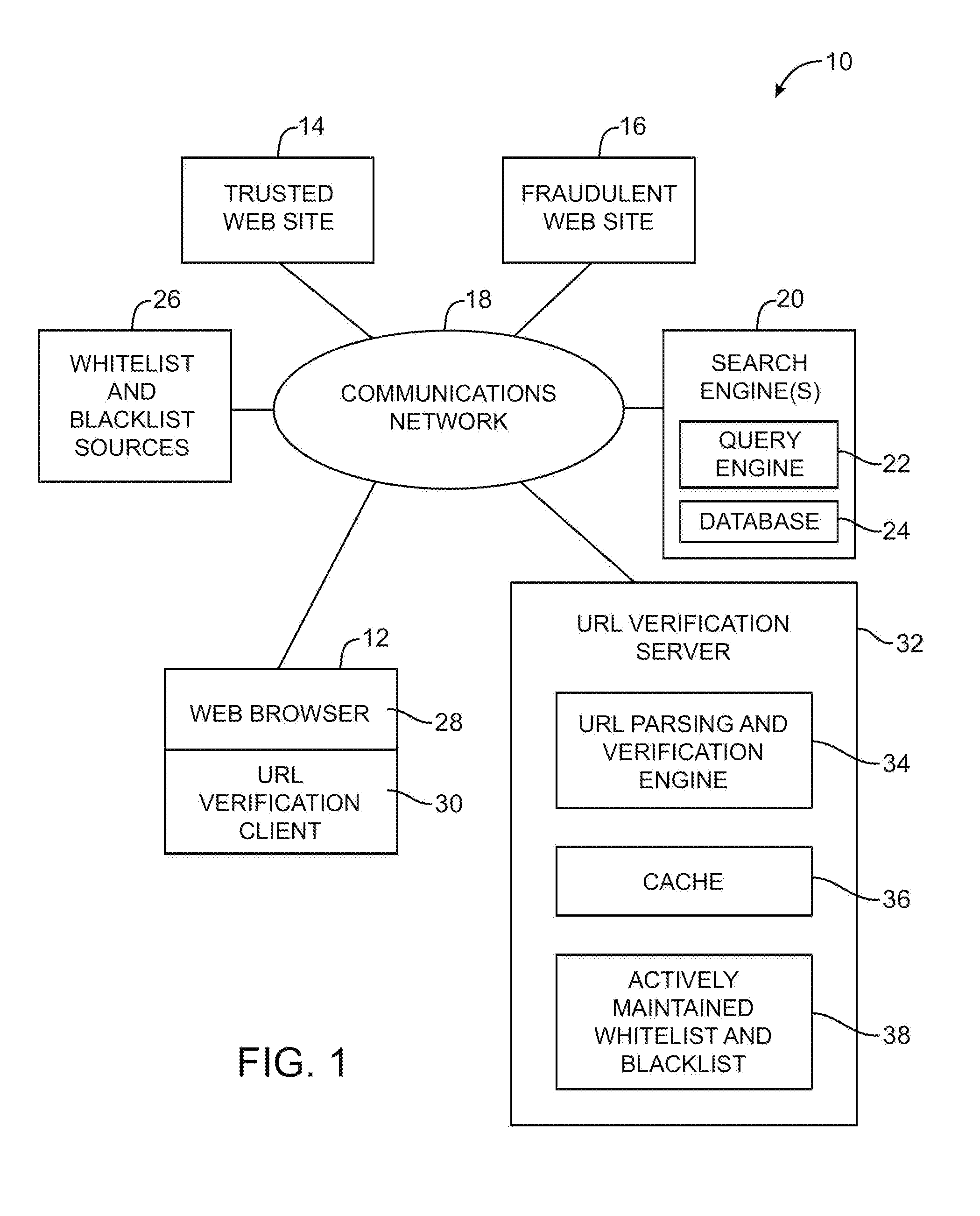
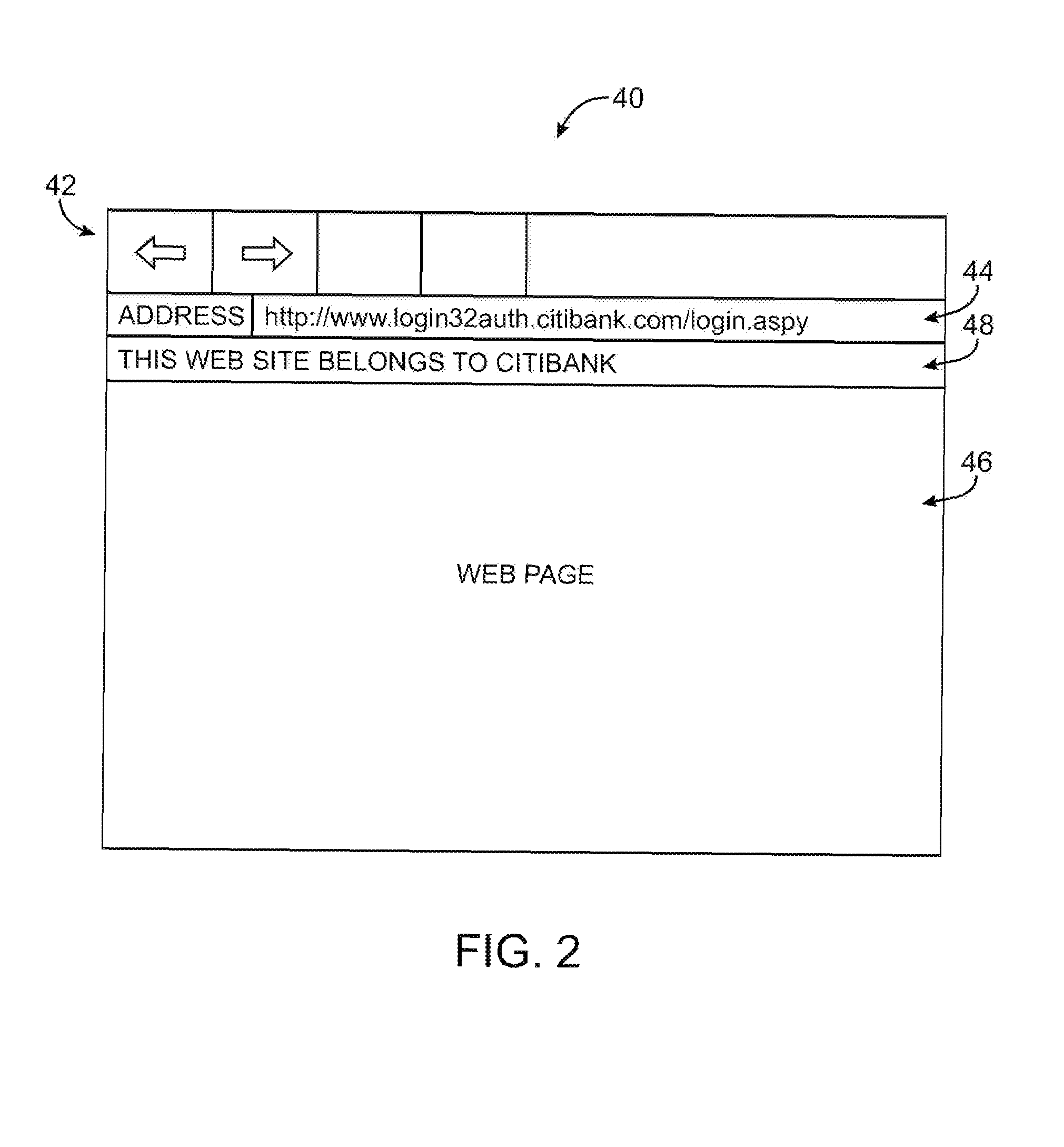
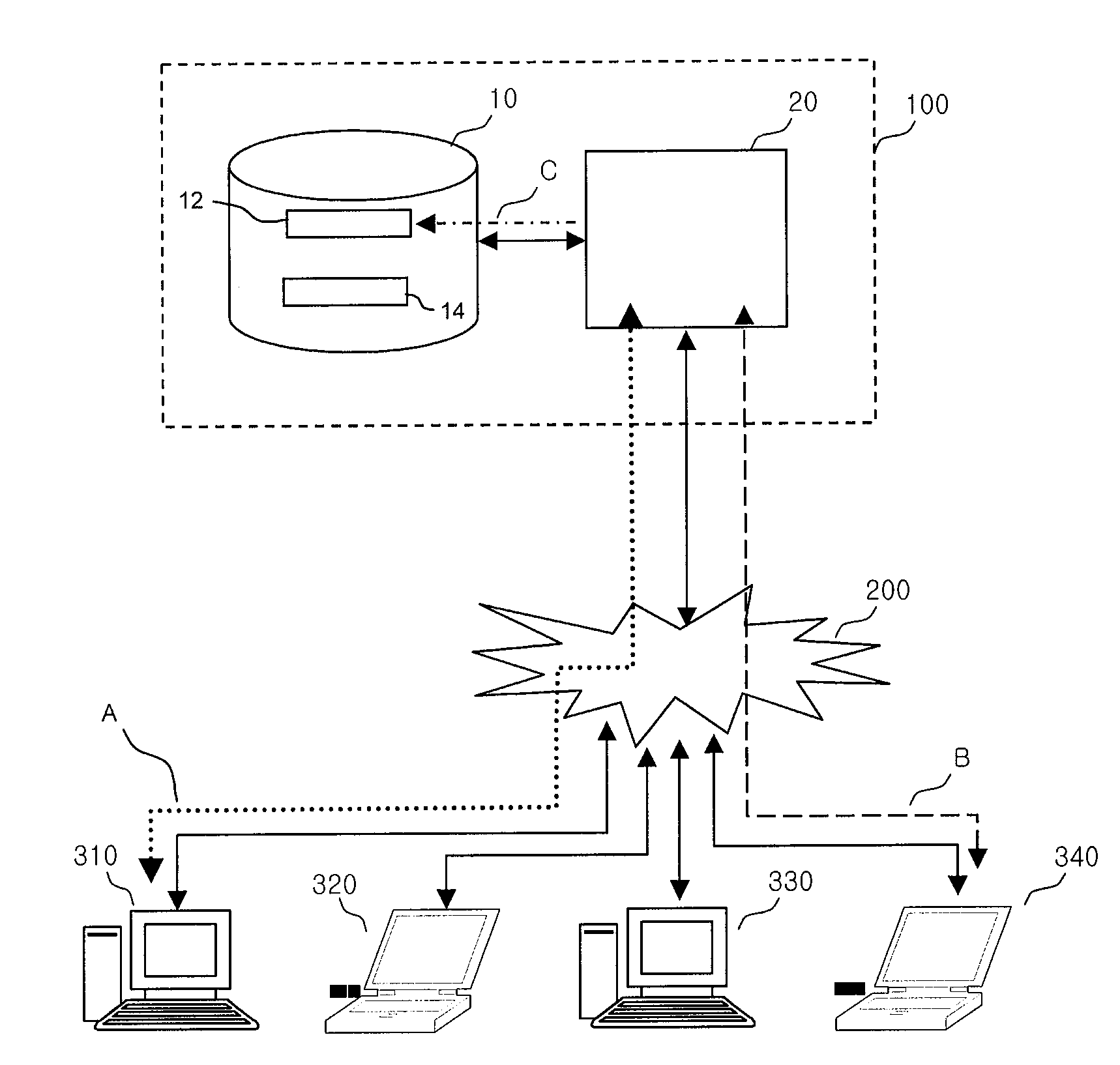
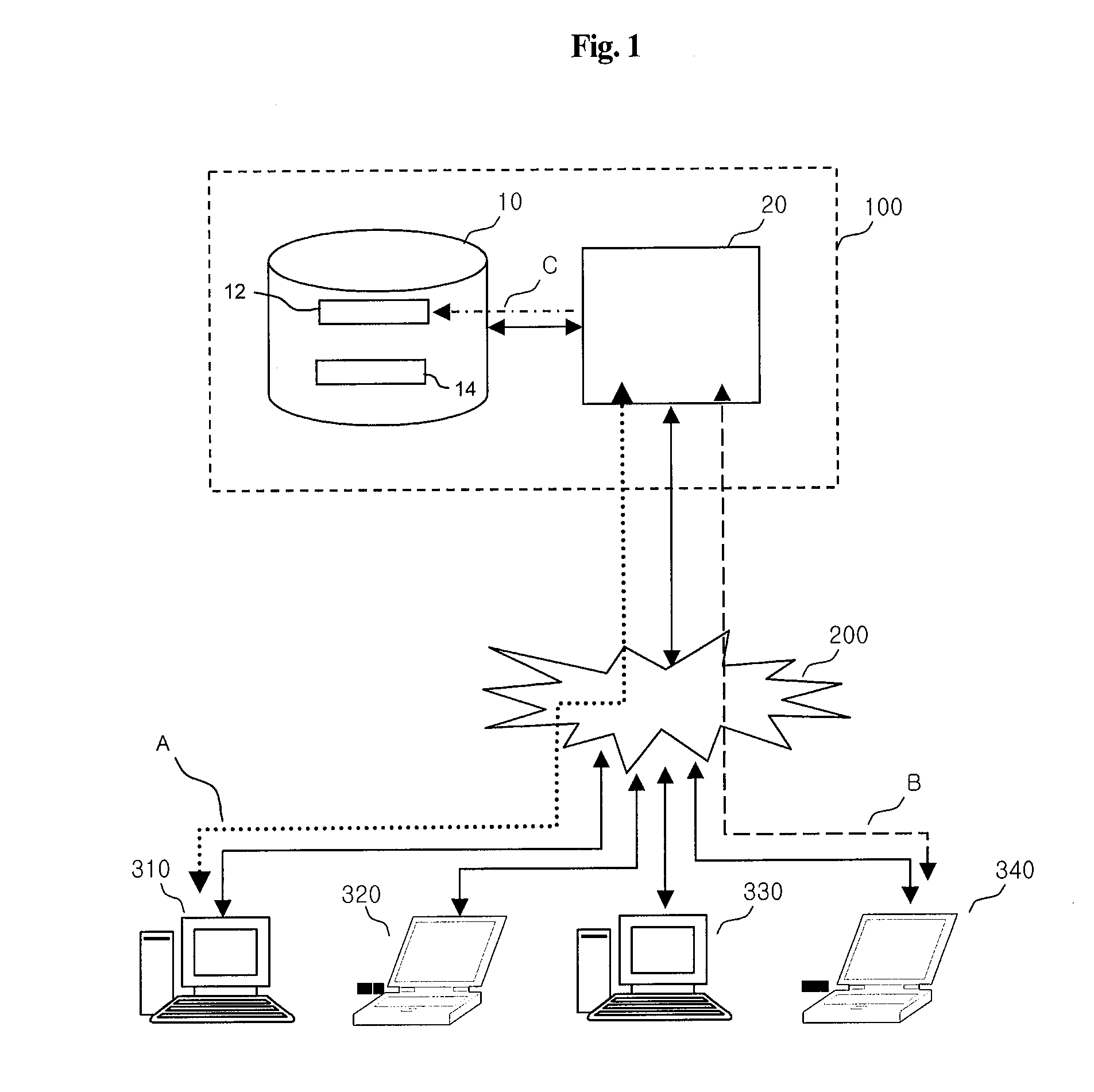
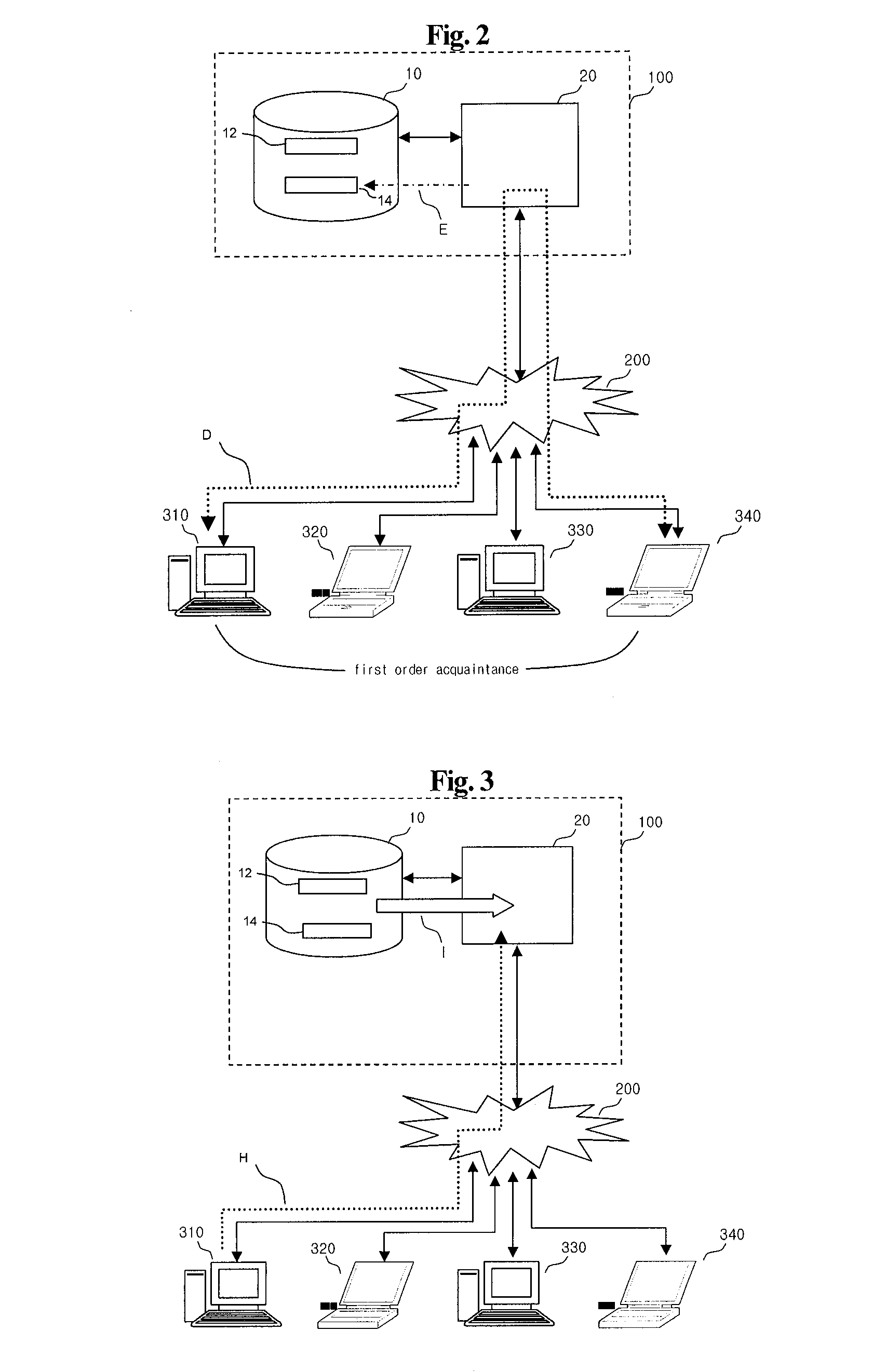
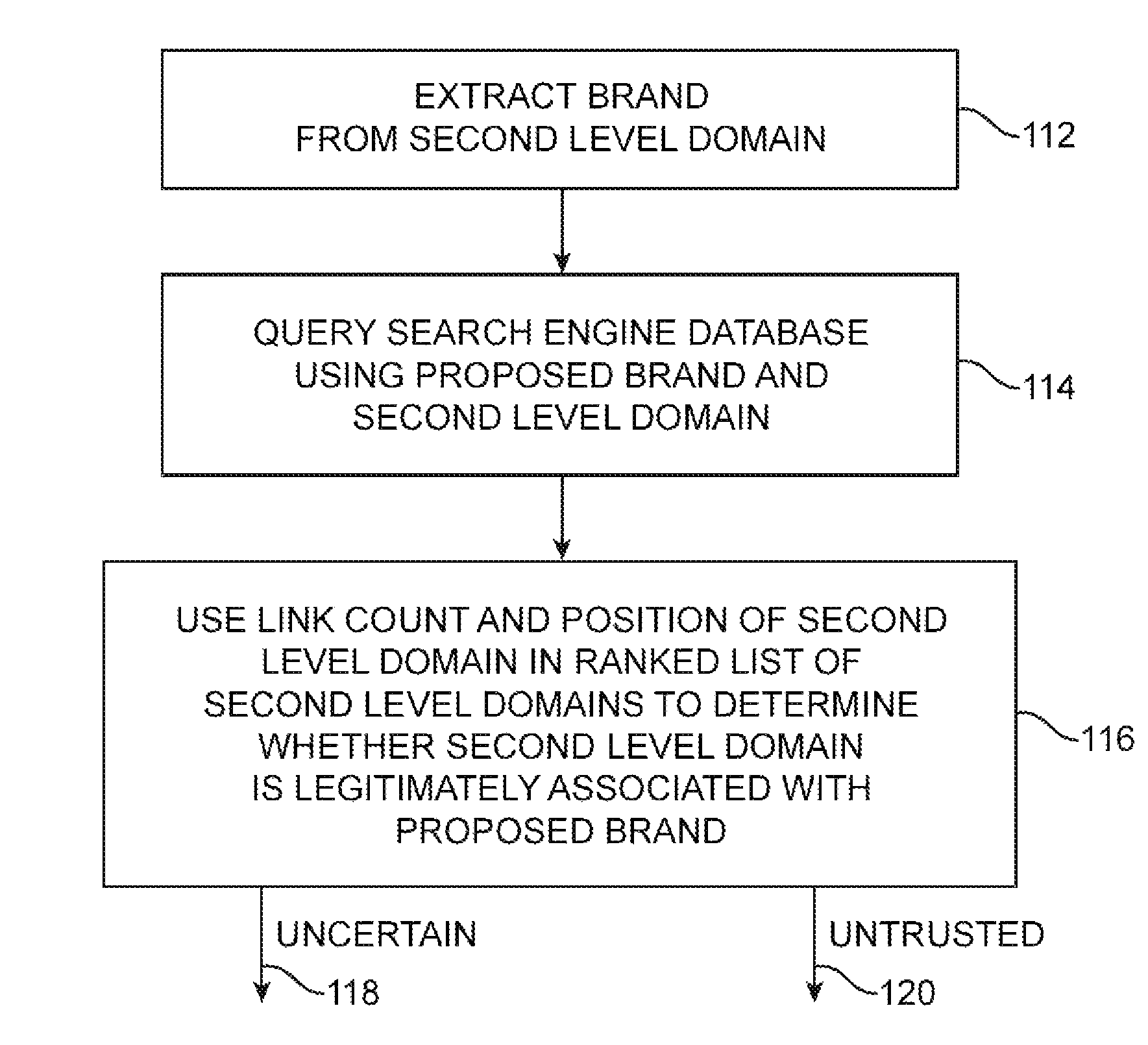
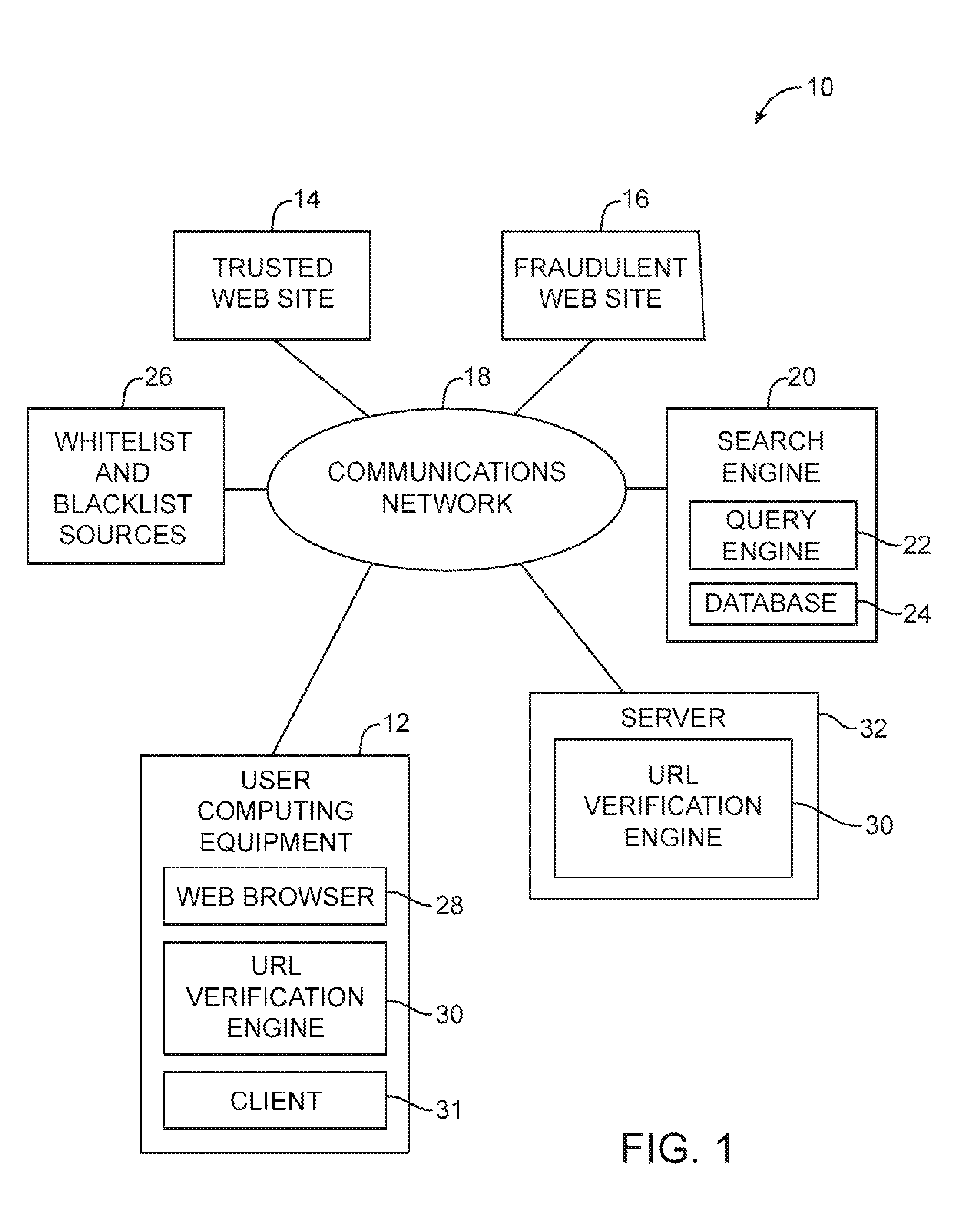
Server-based universal resource locator verification service
A URL verification service is provided that is used to evaluate the trustworthiness of universal resource locators (URLs). As a user browses the world wide web, a URL verification client captures a URL associated with a web page of unknown authenticity. The URL verification client transmits the captured URL to a URL verification server. The URL verification server compares the URL to actively maintained whitelist and blacklist information. The server also uses the URL and a user-supplied or automatically-extracted brand to query a search engine. The URL verification server processes the response of the search engine to the search engine queries and the results of cache and whitelist and blacklist comparisons to determine whether the captured URL is legitimately associated with the brand. The results of the URL evaluation process are transmitted from the URL verification server to the URL verification client, which notifies user.
Owner:MICRO FOCUS LLC
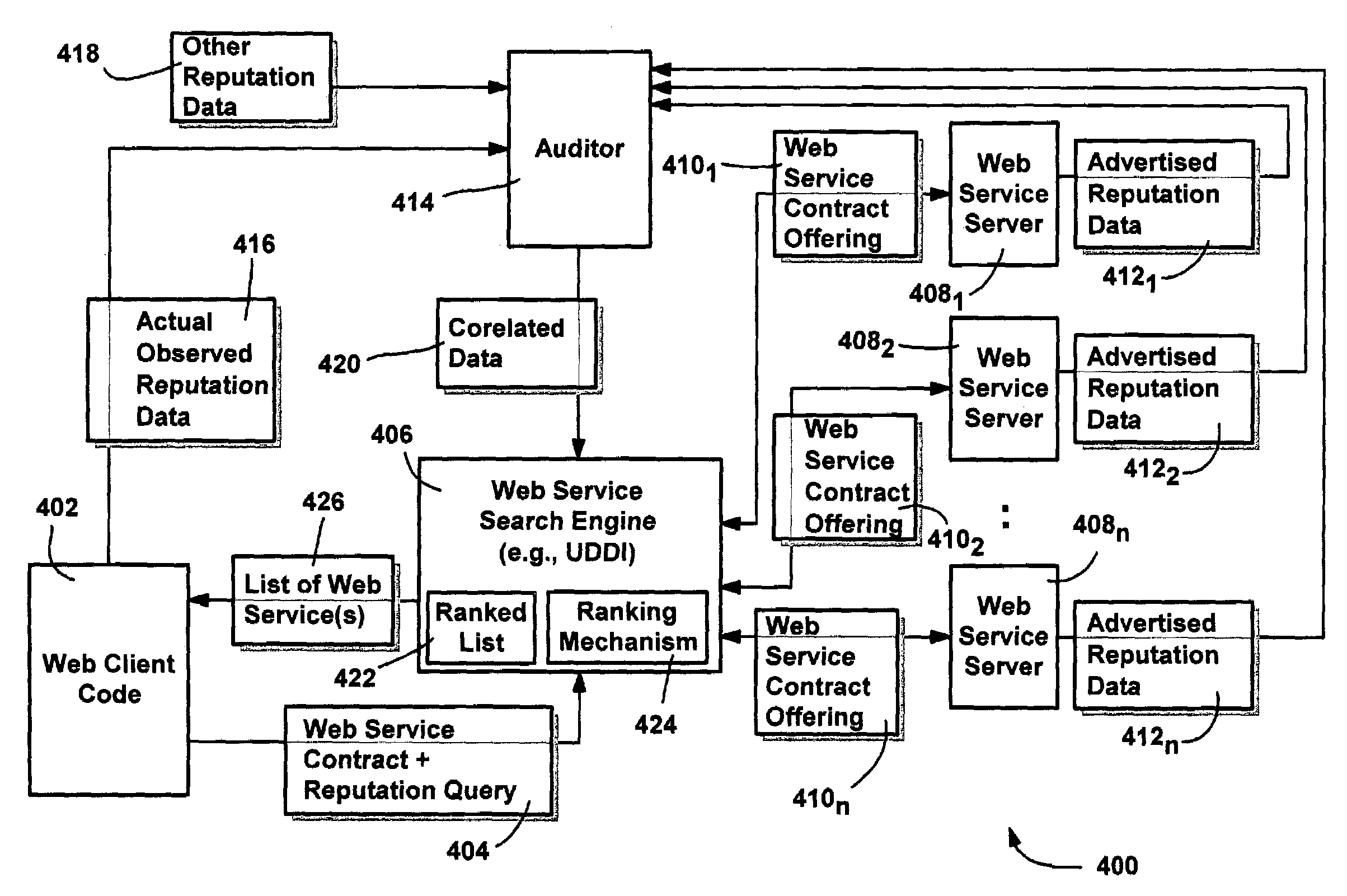
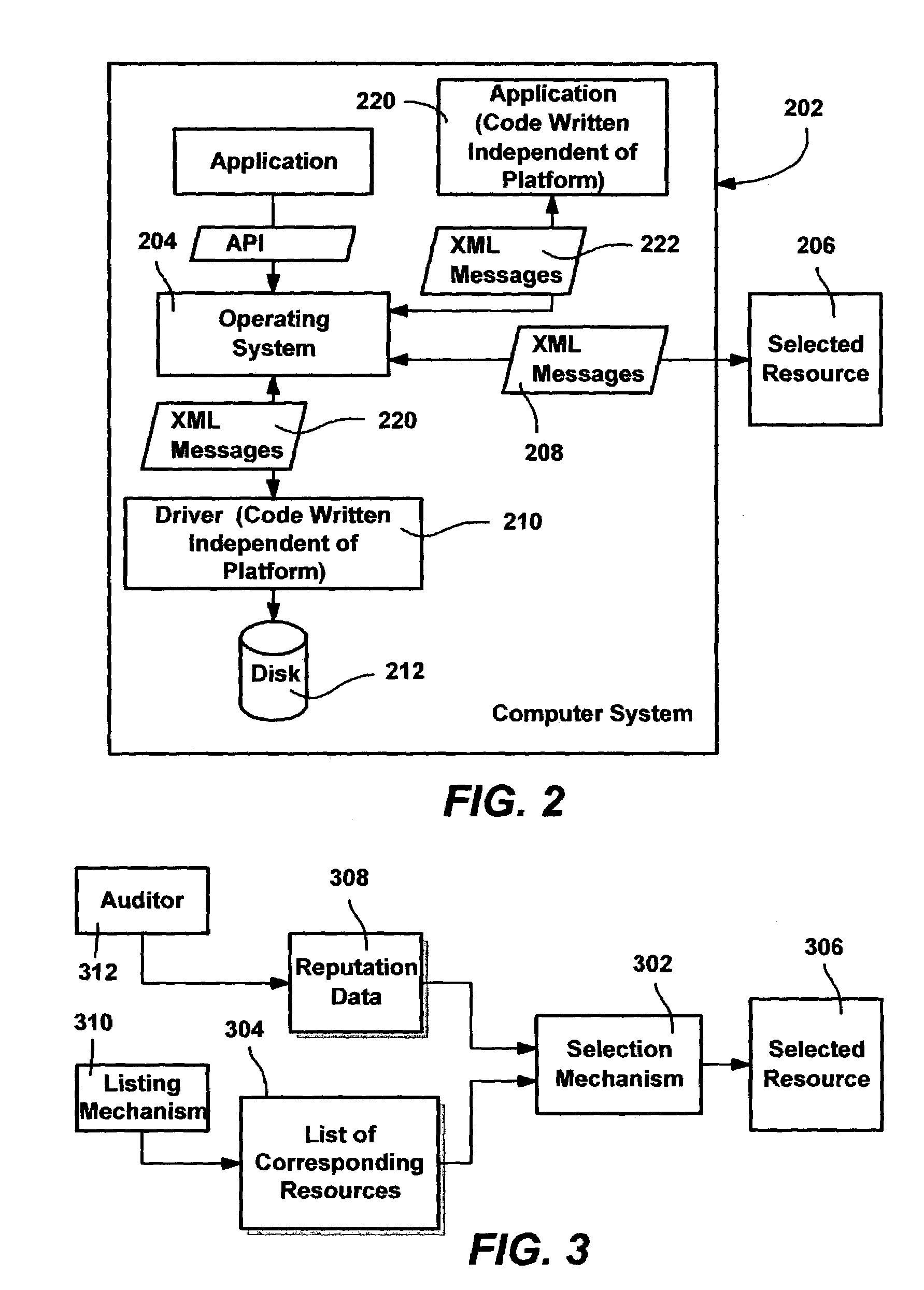
Reputation system for web services
InactiveUS7467206B2Good reputationScale downWeb data indexingNatural language data processingWeb serviceThe Internet
A system and method for automating the web service selection based on reputation information, to help negotiate a contractual web service binding between a client and a server. Reputation information may be schematized into behavioral attributes such as web service responsiveness, web service latency, web service uptime, cost data, business solvency and other trustworthiness and business-related data. Some of the reputation data may be empirically determined, and provided by an independent or other trusted auditor. In one implementation, a client queries a search engine, which returns a ranked list of web services, with the ranking based on reputation scores computed for each web service as collected by an auditor. Clients may provide computational data to weigh the attributes separately. A corporate internet can maintain reputation data for web services to act as an auditor, and a web service server can also execute trusted code to act as an auditor.
Owner:MICROSOFT TECH LICENSING LLC
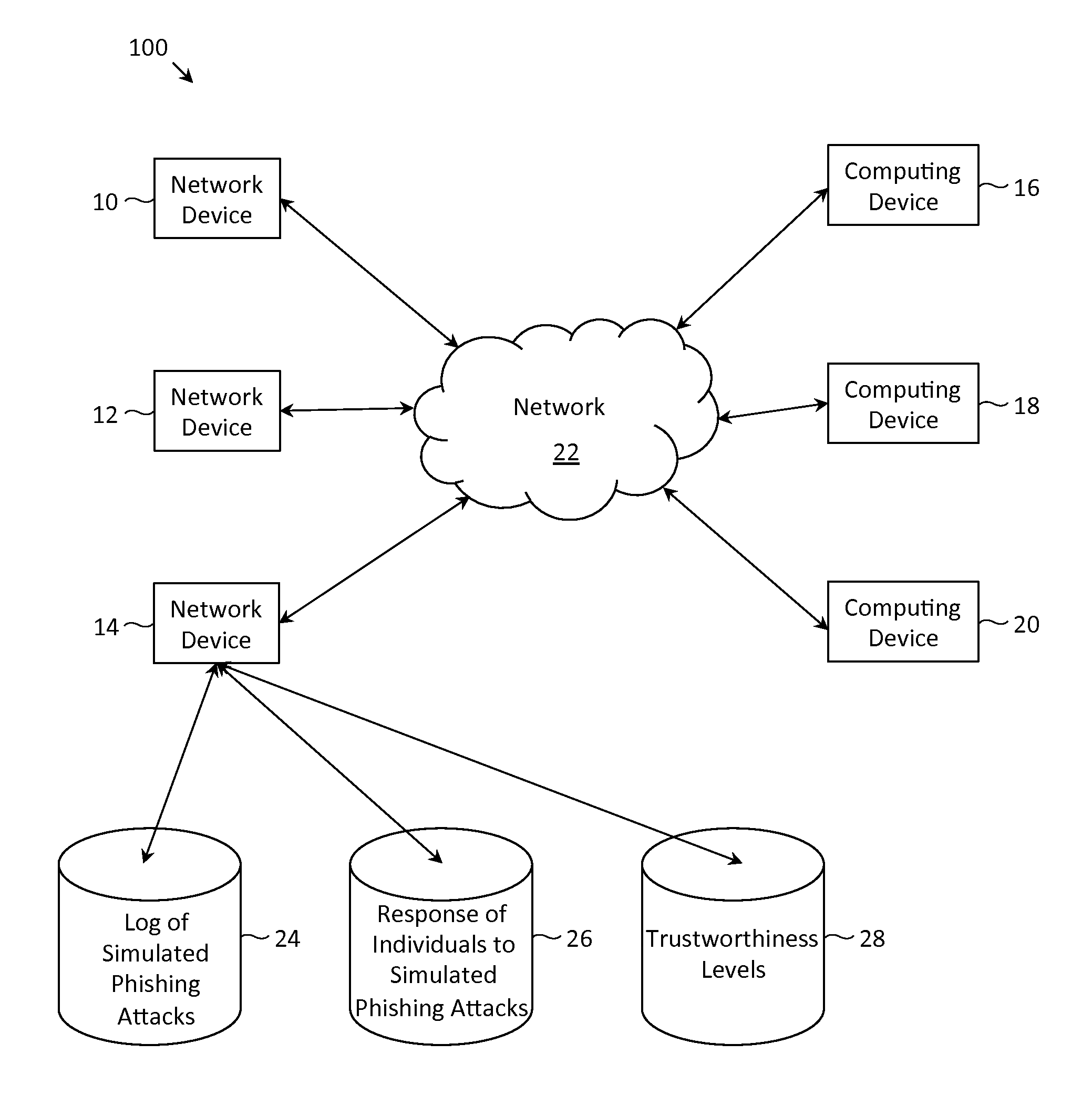
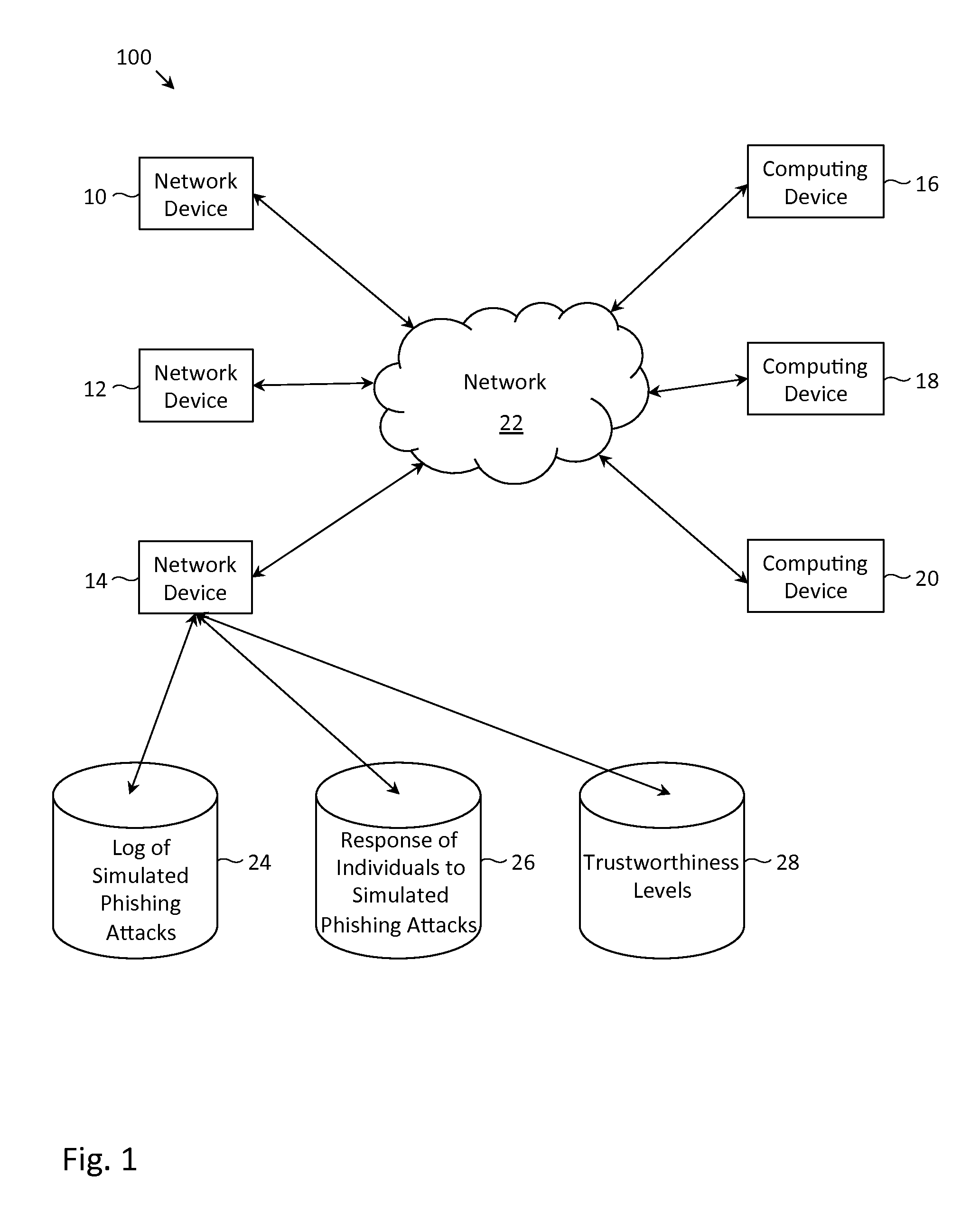
Collaborative phishing attack detection
ActiveUS8719940B1Reduce the possibilityMemory loss protectionError detection/correctionComputer networkRanking
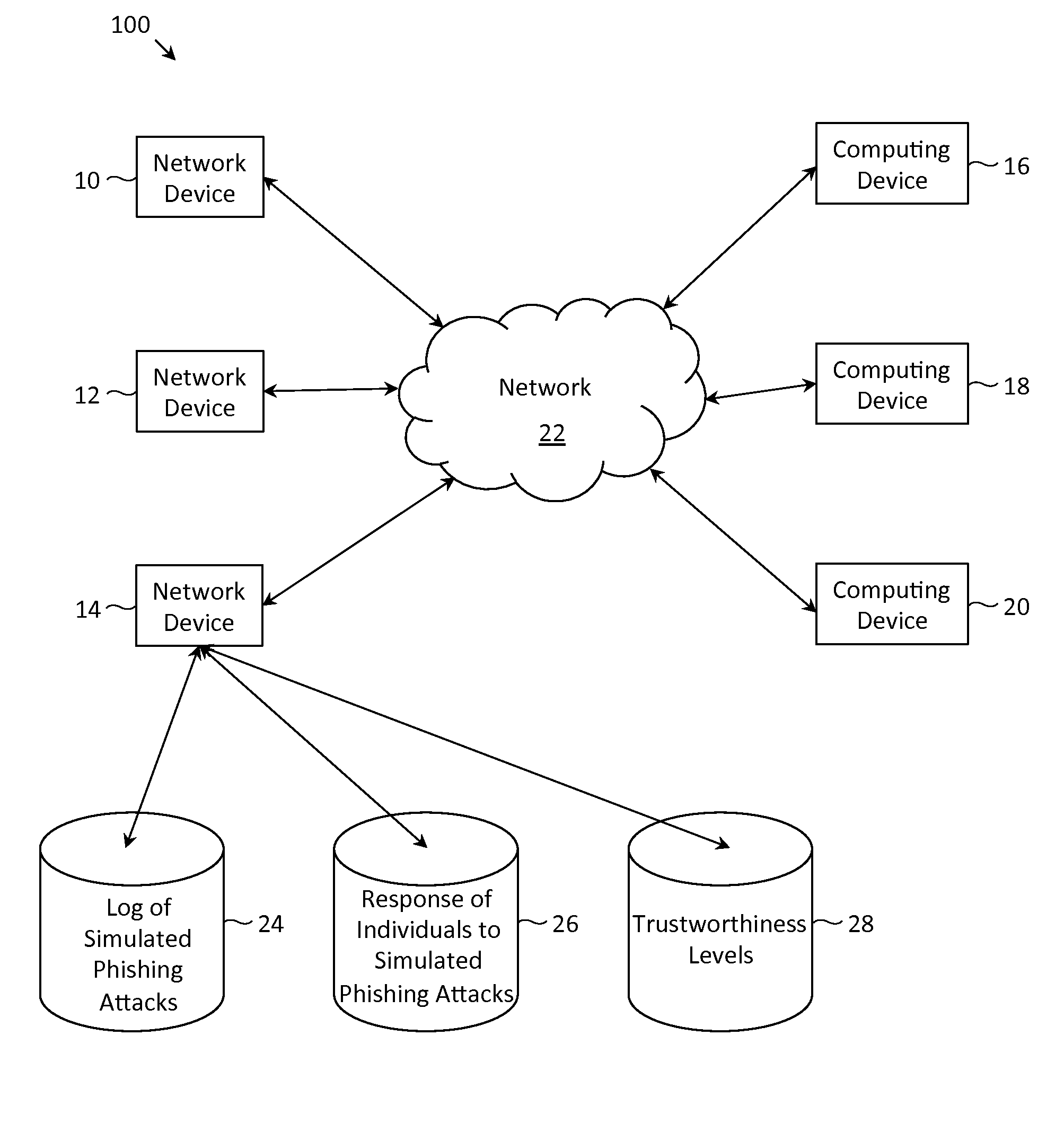
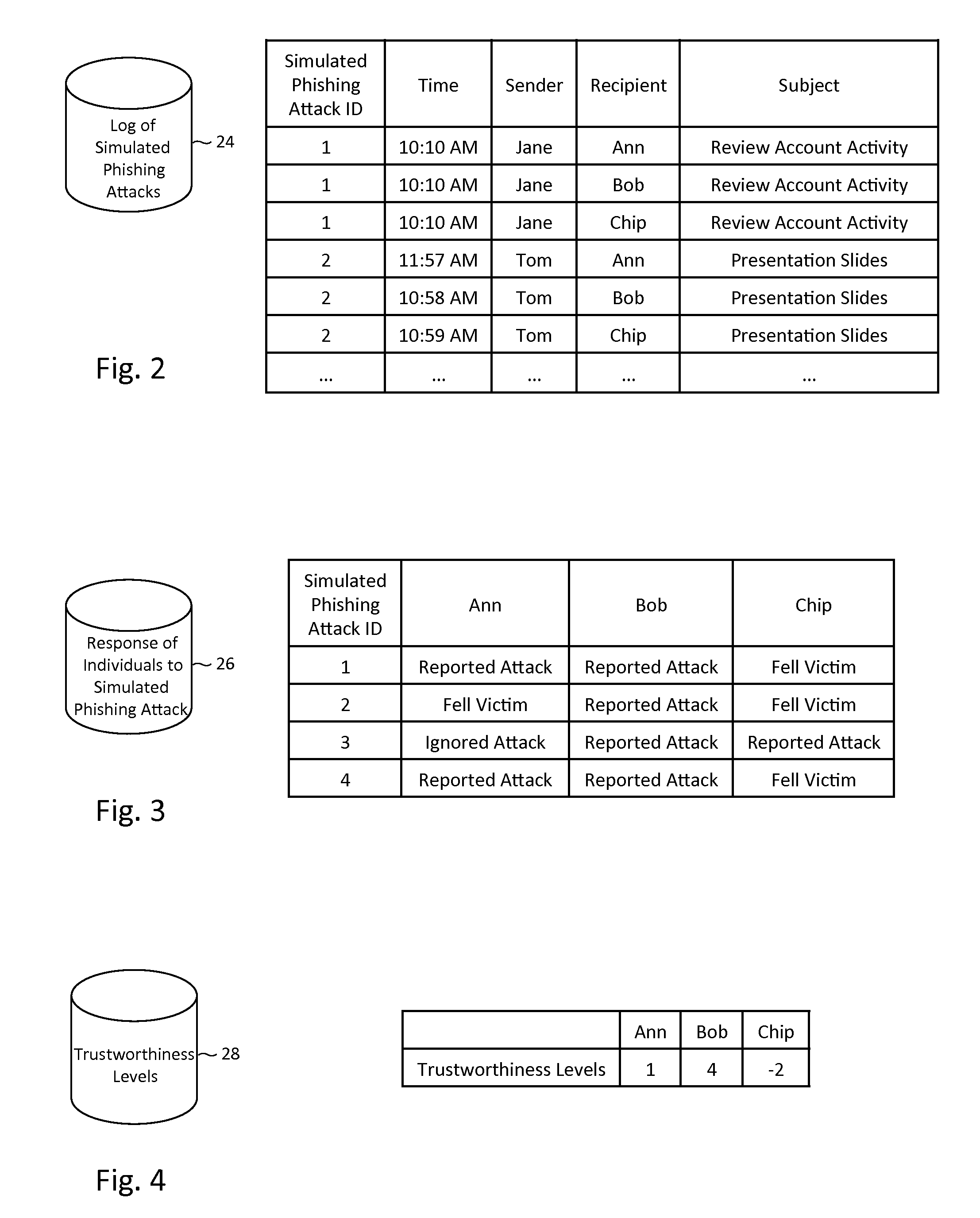
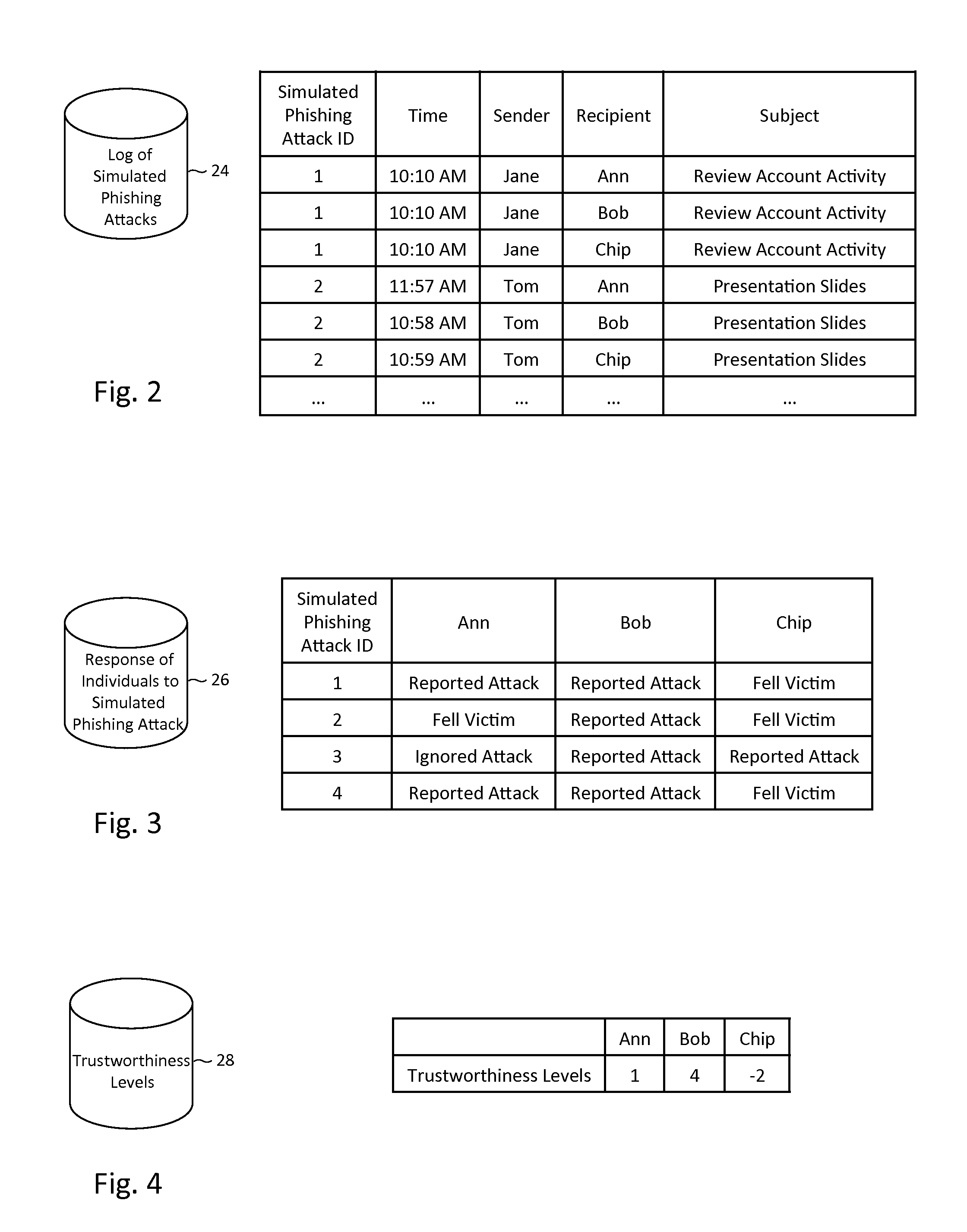
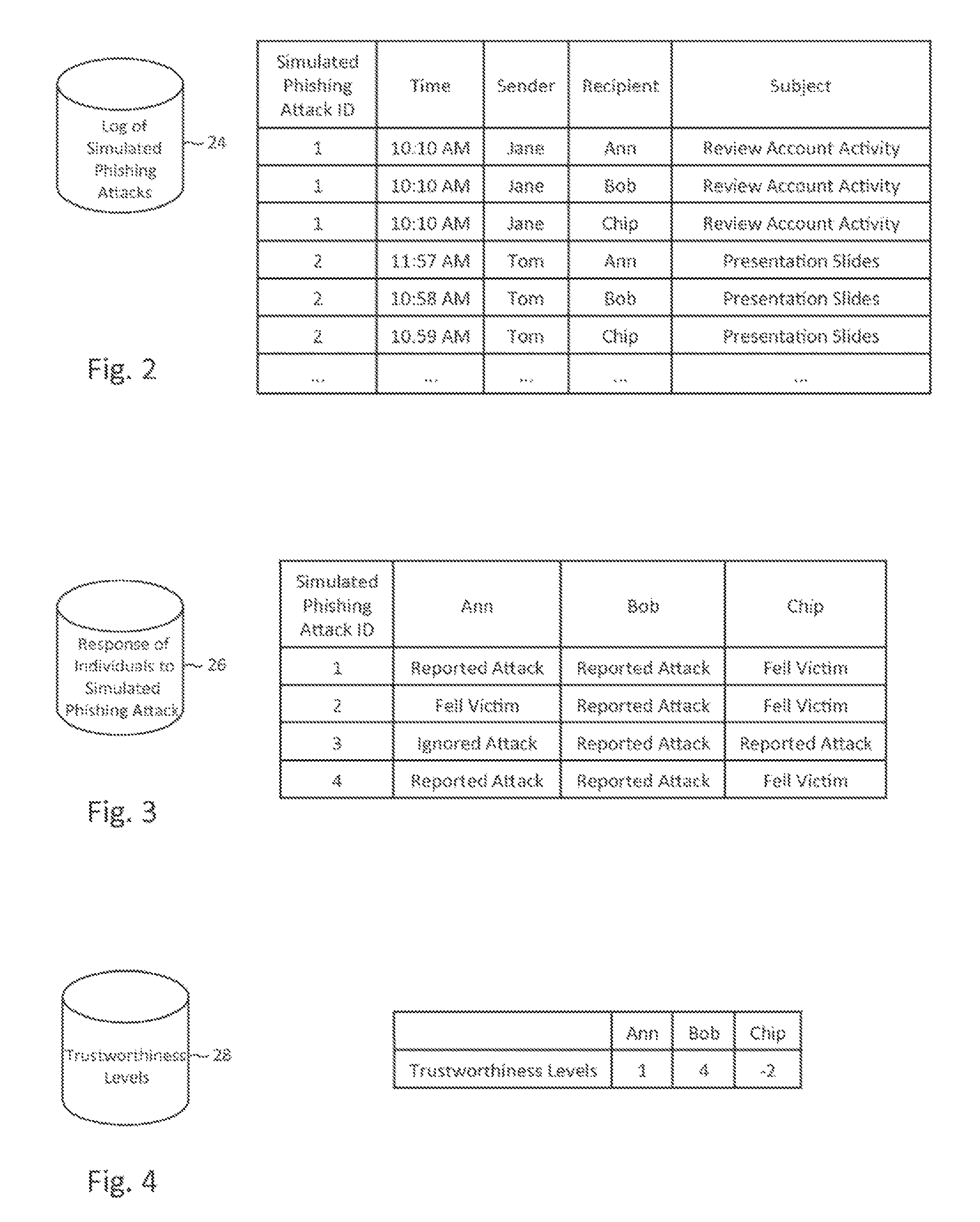
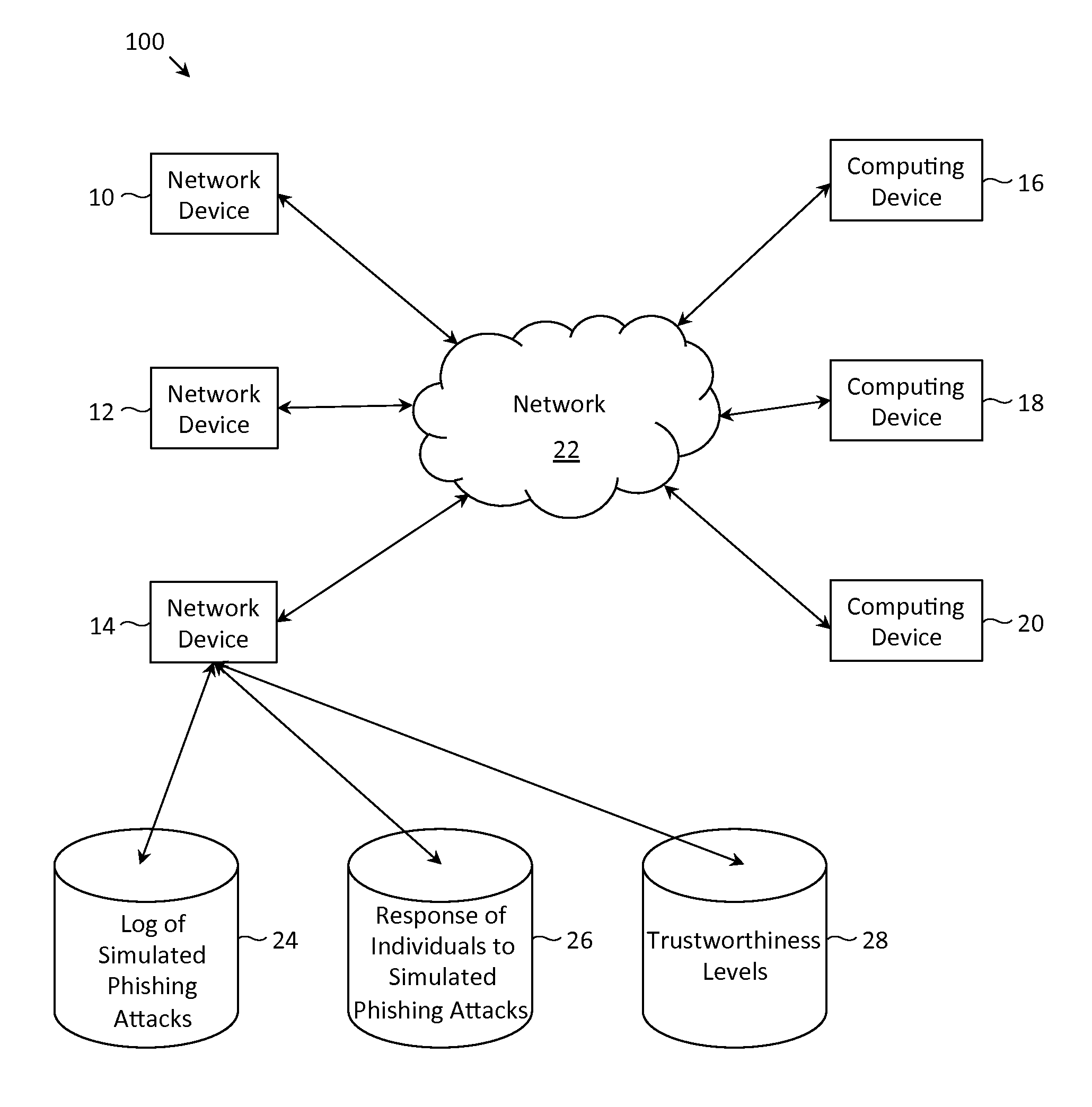
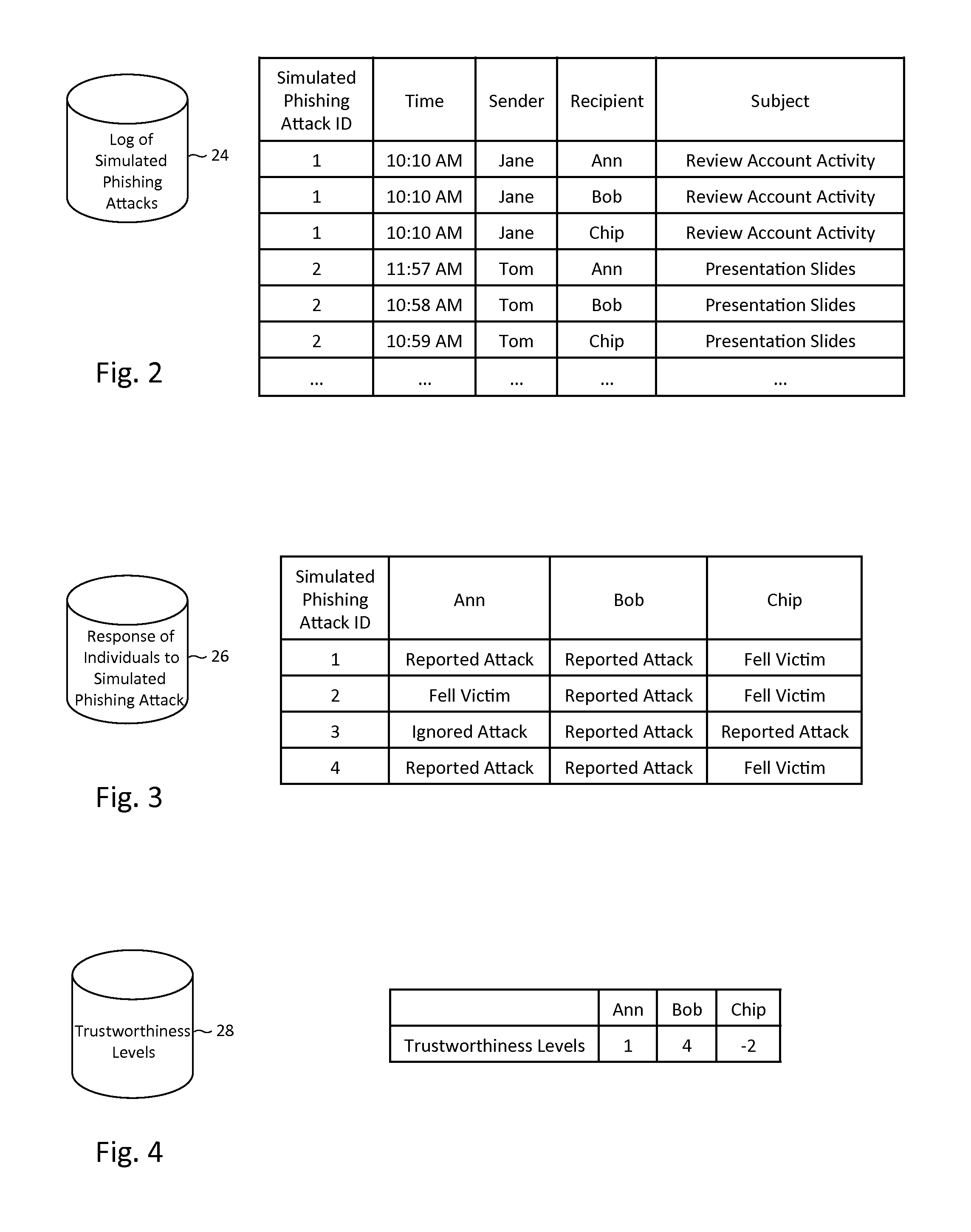
Described herein are methods, network devices and machine-readable storage media for detecting whether a message is a phishing attack based on the collective responses from one or more individuals who have received that message. The individuals may flag the message as a possible phishing attack, and / or may provide a numerical ranking indicating the likelihood that the message is a possible phishing attack. As responses from different individuals may have a different degree of reliability, each response from an individual may be weighted with a corresponding trustworthiness level of that individual, in an overall determination as to whether a message is a phishing attack. A trustworthiness level of an individual may indicate a degree to which the response of that individual can be trusted and / or relied upon, and may be determined by how well that individual recognized simulated phishing attacks.
Owner:COFENSE INC
Systems and methods for using reputation scores in network services and transactions to calculate security risks to computer systems and platforms
ActiveUS8776180B2Memory loss protectionDigital data processing detailsMathematical CalculusInternet privacy
Owner:TAASERA LICENSING LLC
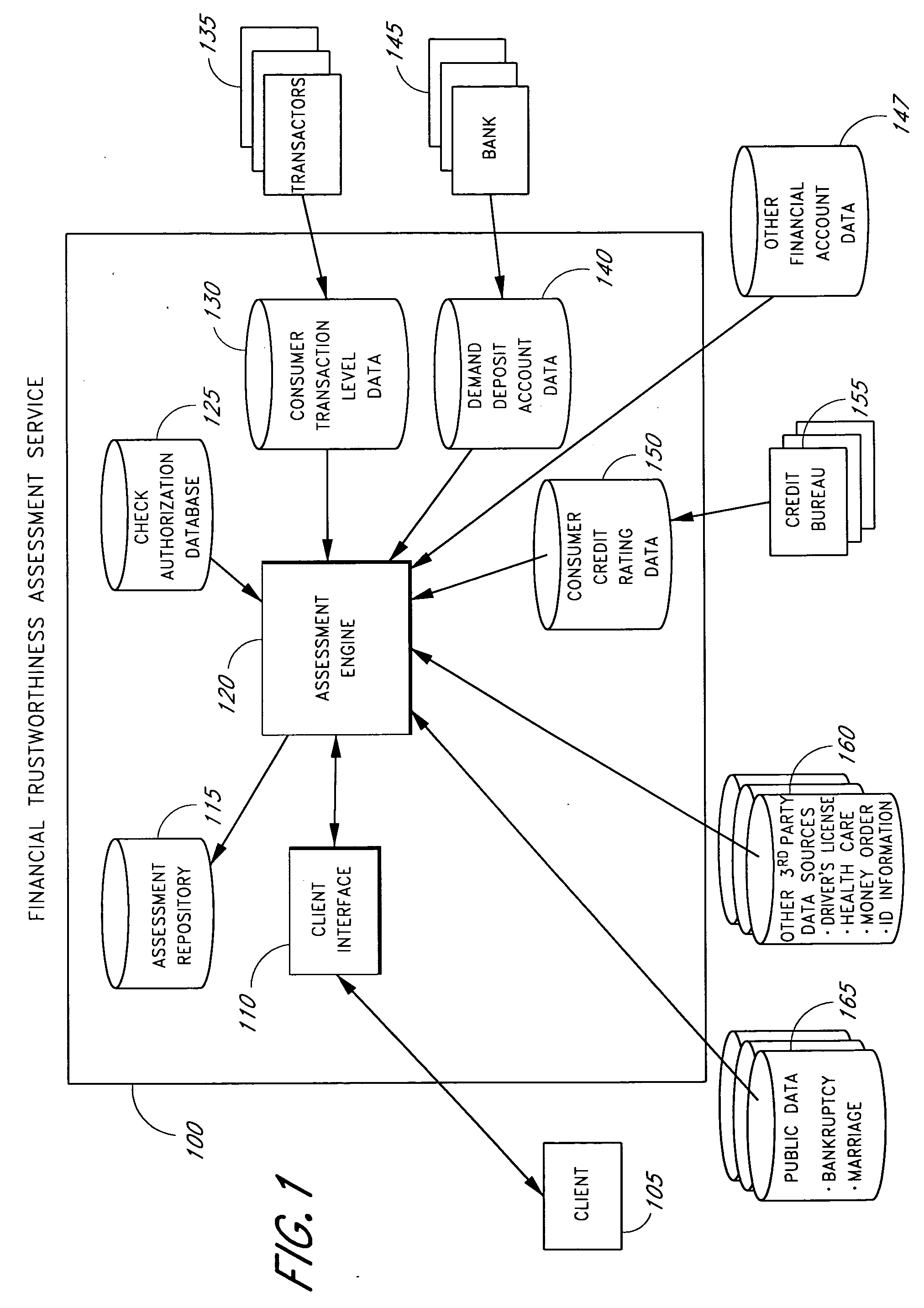
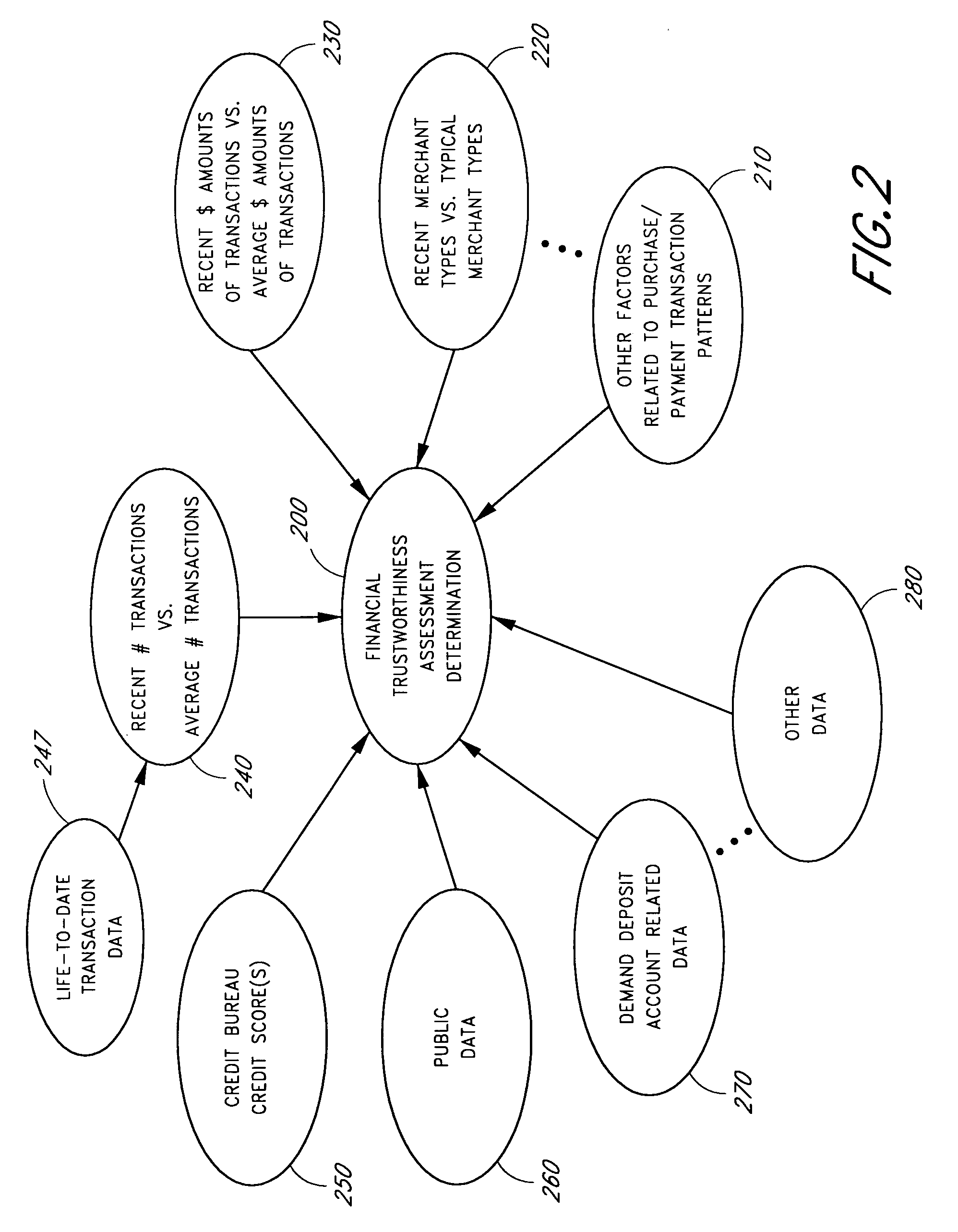
Systems and methods for performing a financial trustworthiness assessment
InactiveUS20080059364A1Accurately reflectQuick identificationFinancePayment architectureThird partyDeposit account
Systems and methods are described in connection with a financial trustworthiness assessment service that provides an assessment of an individual's financial trustworthiness that is not necessarily on credit bureau information. The financial trustworthiness assessment is based, at least in part, on transaction-level financial information associated with the individual, as well as on other data associated with the individual that may be financially-based or otherwise indicative, alone or in conjunction with other data, of financial trustworthiness. For example, the assessment may be based at least in part on information from one or more repositories of information, including, but not limited to a check authorization database, a demand deposit account database, a consumer credit rating database, public data (such as bankruptcy and marriage records), department of motor vehicle records, and other third party data sources.
Owner:FIRST DATA
Location-based verification for predicting user trustworthiness
ActiveUS10255602B2Improve securityFinanceLocation information based serviceFinancial transactionData mining
Owner:OPERR TECH INC
Propagating and updating trust relationships in distributed peer-to-peer networks
ActiveUS7203753B2Multiprogramming arrangementsMultiple digital computer combinationsInternet privacyTrust relationship
System and method for representing and rate the trustworthiness of peers as providers of content and data (codats) relevant to the peers' interests. In one embodiment, trust may be propagated through transaction pipes (paths) along which codats located in a search for codats relevant to an area of interest may be accessed by the requestor. In some embodiments, the trust a peer has in another peer as a provider of codats may be a function of the trust values of the provider peer and all other peers on a path. If there are multiple paths, trust in the provider peer may be an average of the trust values for all the paths. Trust in a provider peer may be used to determine confidence in codats provided by the peer. Embodiments may provide mechanisms for feeding back trust information to the providing peer and for propagating trust information to other peers.
Owner:ORACLE INT CORP
Methods for encouraging charitable social networking
A method of encouraging charitable donations by individuals who are members of a social network is disclosed. A user creates a member account by supplying user identity data from the user and creates a campaign, wherein the created campaign is associated with one or more charities and a financial goal. The user sends invitation to one or more members or non-members and the one or more members or non-members may accept or decline the user's invitation. The one or more members are given the option to donate any amount of money to a charity to post comments about the user, where the monetary value of the donation is associated with the comments posted such that a higher amount donated represents a higher trustworthiness of the comments. The one or more members or non-members may support the campaign by donating money to the one or more charities to help reach the financial goal. One or more user weight values are calculated based at least on a total volume of members or non-members who support the campaign by donating money to the one or more charities and / or a total monetary value of the money donated by the one or more members or non-members, where the one or more user weight values represent reliability of a user's reputation.
Owner:STAY AWAKE INC
Representing trust in distributed peer-to-peer networks
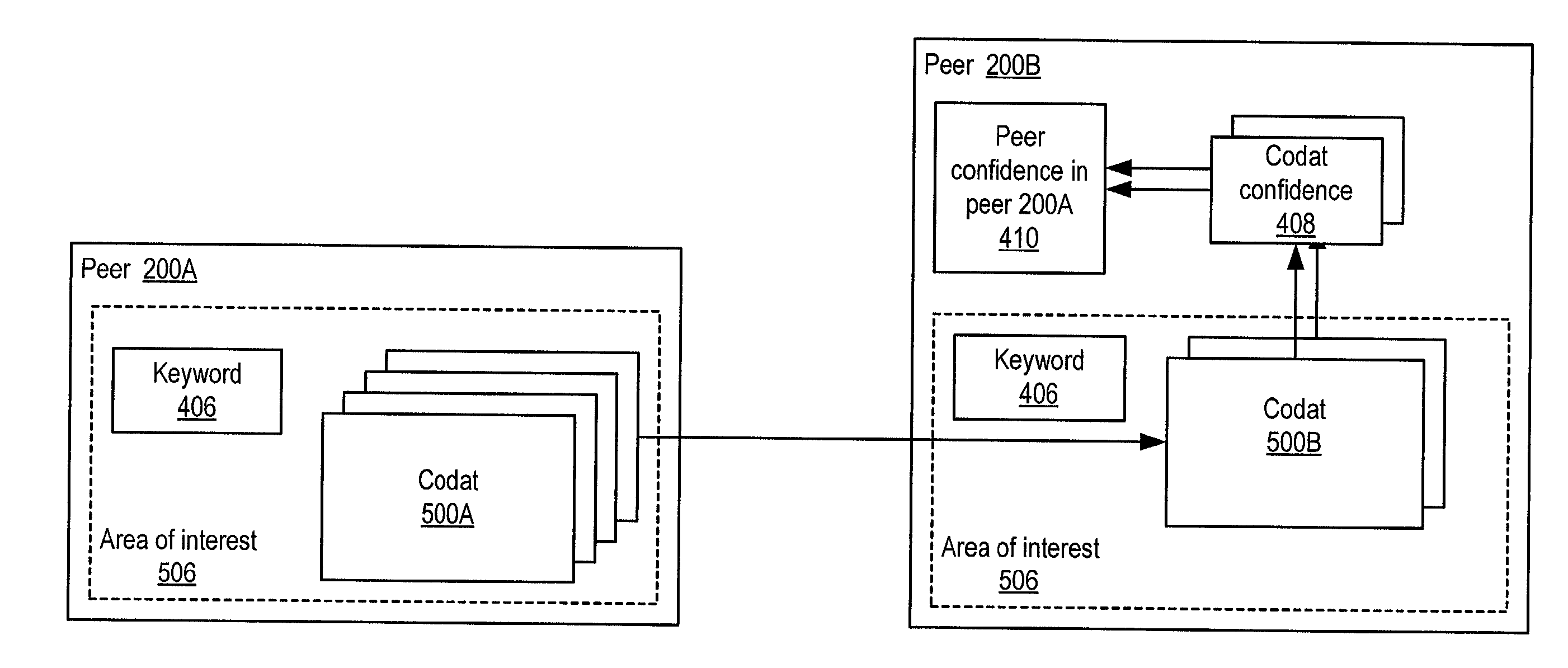
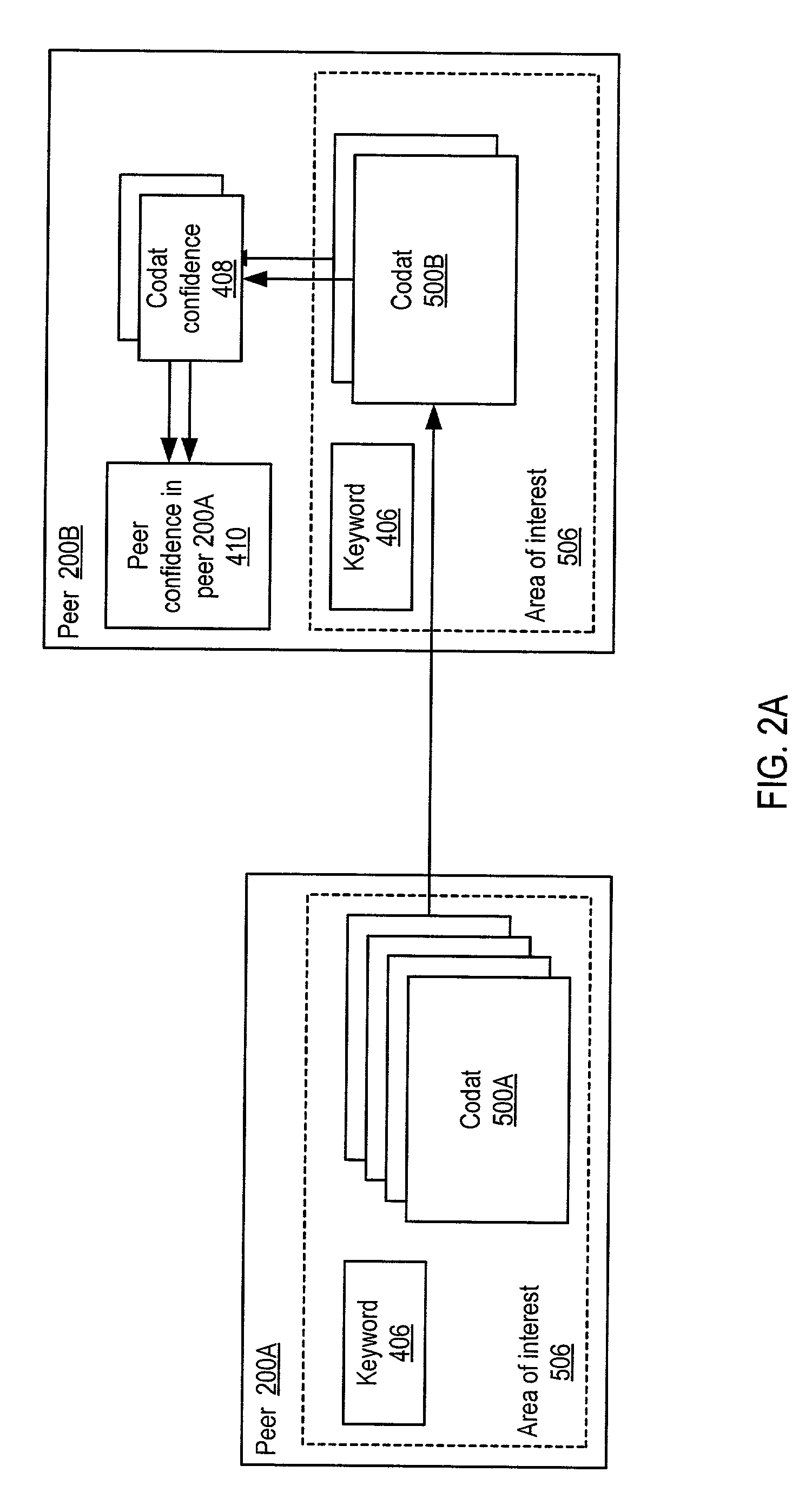
ActiveUS20030055894A1Multiprogramming arrangementsMultiple digital computer combinationsInformation feedbackPeer-to-peer
Embodiments may provide mechanisms for representing trust between peers or systems in decentralized networking environments including peer-to-peer networking environments. Trust may include both direct trust between two peers and trust in a pipeline of peers along which codat may be passed. Embodiments may provide a mechanism for a peer to represent and rate the trustworthiness of other peers as providers of codat relevant to the peer's interest. To evaluate trust in another peer as a provider of codats in the area of interest, trust may be represented with two components, confidence and risk. Embodiments may provide mechanisms for measuring the components and determining trust from the components. Embodiments may also provide mechanisms for feeding back trust information to the providing peer and for propagating trust information to other peers.
Owner:ORACLE INT CORP
Collaborative phishing attack detection
ActiveUS9398038B2Reduce the possibilityUser identity/authority verificationComputer security arrangementsComputer networkInternet privacy
Owner:COFENSE INC
Collaborative phishing attack detection
ActiveUS9325730B2Reduce the possibilityTransmissionInput/output processes for data processingComputer networkRanking
Described herein are methods, network devices and machine-readable storage media for detecting whether a message is a phishing attack based on the collective responses from one or more individuals who have received that message. The individuals may flag the message as a possible phishing attack, and / or may provide a numerical ranking indicating the likelihood that the message is a possible phishing attack. As responses from different individuals may have a different degree of reliability, each response from an individual may be weighted with a corresponding trustworthiness level of that individual, in an overall determination as to whether a message is a phishing attack. A trustworthiness level of an individual may indicate a degree to which the response of that individual can be trusted and / or relied upon, and may be determined by how well that individual recognized simulated phishing attacks.
Owner:COFENSE INC
Collaborative phishing attack detection
ActiveUS20140230061A1Reduce the possibilityMemory loss protectionError detection/correctionComputer networkRanking
Described herein are methods, network devices and machine-readable storage media for detecting whether a message is a phishing attack based on the collective responses from one or more individuals who have received that message. The individuals may flag the message as a possible phishing attack, and / or may provide a numerical ranking indicating the likelihood that the message is a possible phishing attack. As responses from different individuals may have a different degree of reliability, each response from an individual may be weighted with a corresponding trustworthiness level of that individual, in an overall determination as to whether a message is a phishing attack. A trustworthiness level of an individual may indicate a degree to which the response of that individual can be trusted and / or relied upon, and may be determined by how well that individual recognized simulated phishing attacks.
Owner:COFENSE INC
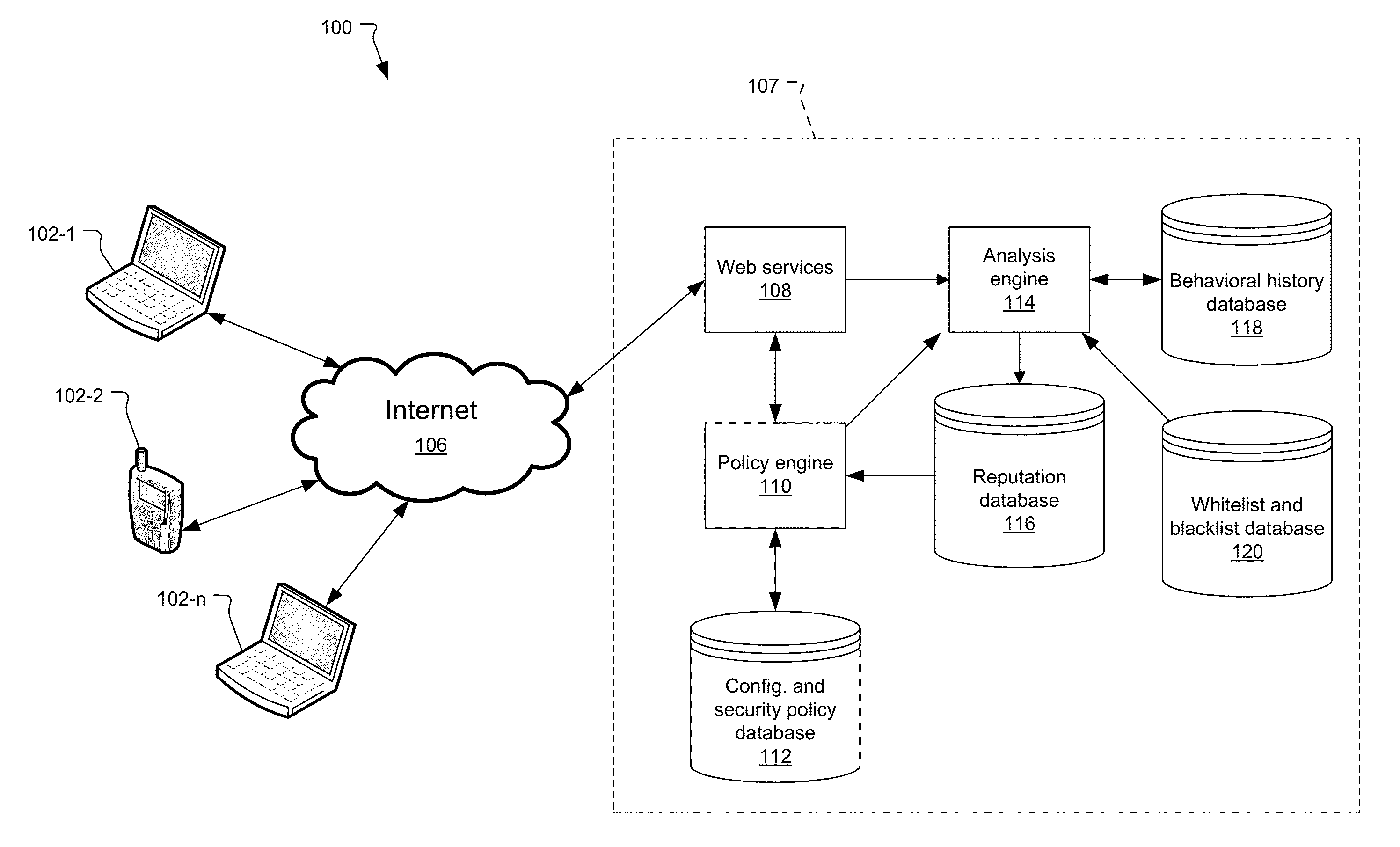
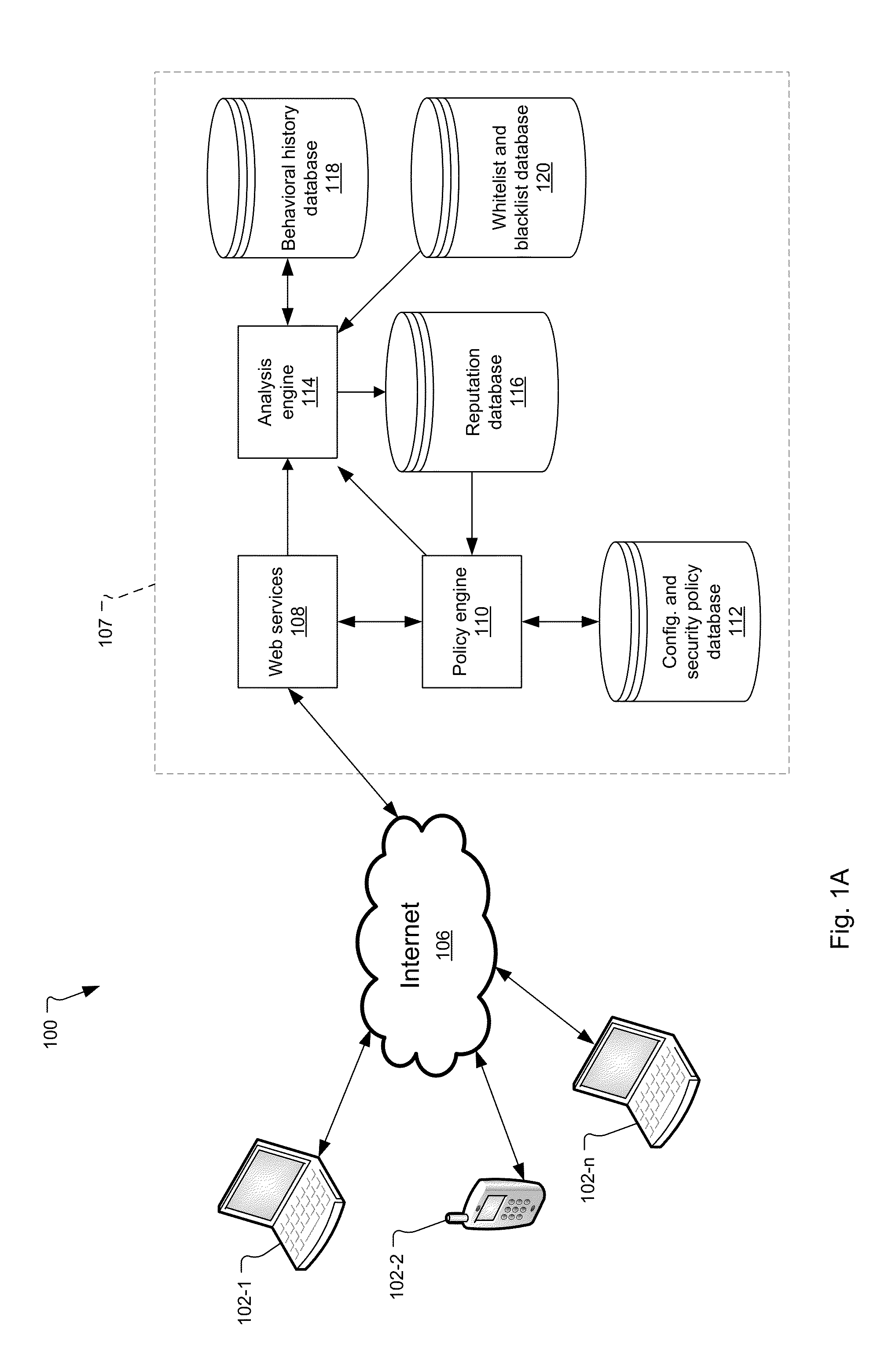
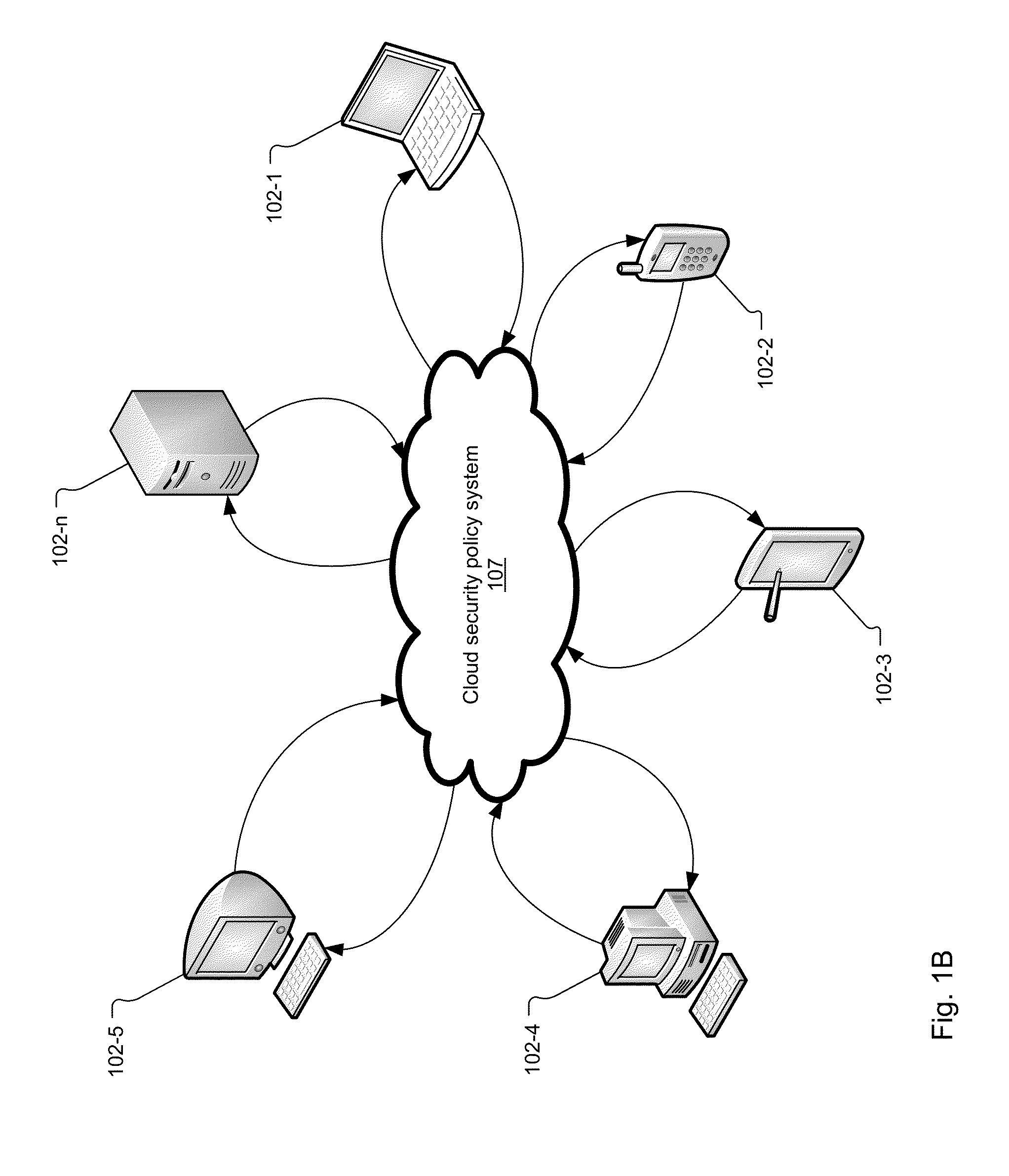
Security Policy Deployment and Enforcement System for the Detection and Control of Polymorphic and Targeted Malware
The present system and method pertain to the detection of malicious software and processes such as malware. A cloud security policy system receives hashes and behavioral information about applications and / or process executing on user devices. The cloud security policy system records this information and then evaluates the trustworthiness of the hashes based on the information received from the user devices to provide a security policy for the applications and / or processes. The security policy is sent from the cloud security policy system to user devices to be applied by the user devices.
Owner:CARBON BLACK
Execution smart contracts configured to establish trustworthiness of code before execution
InactiveUS20190305957A1User identity/authority verificationProgram documentationSmart contractTrustworthiness
Provided is a process that includes: determining whether to execute a software asset based on trust records documenting provenance of the software asset published to a blockchain, wherein determining whether to trust the software asset comprises: accessing the trust record, verifying the trust record has not been tampered with subsequent to publishing, verify that a hash digest based on the software asset matches a hash digest associated with the trust record and published to the blockchain; verifying that trust assertions of the trust record are cryptographically signed by trusted entities specified by entity criteria, and verifying that the trust assertions satisfy execution criteria.
Owner:CA TECH INC
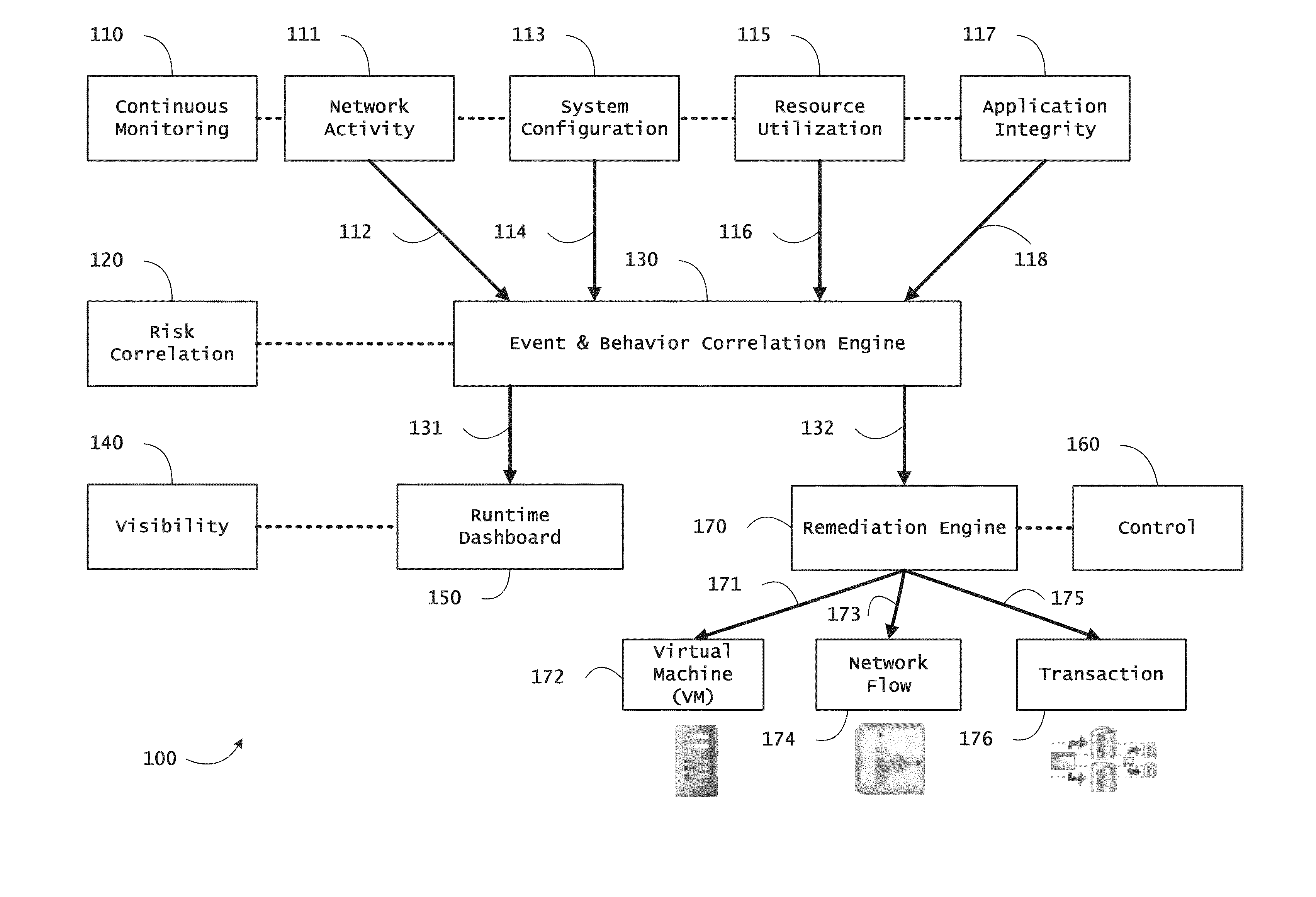
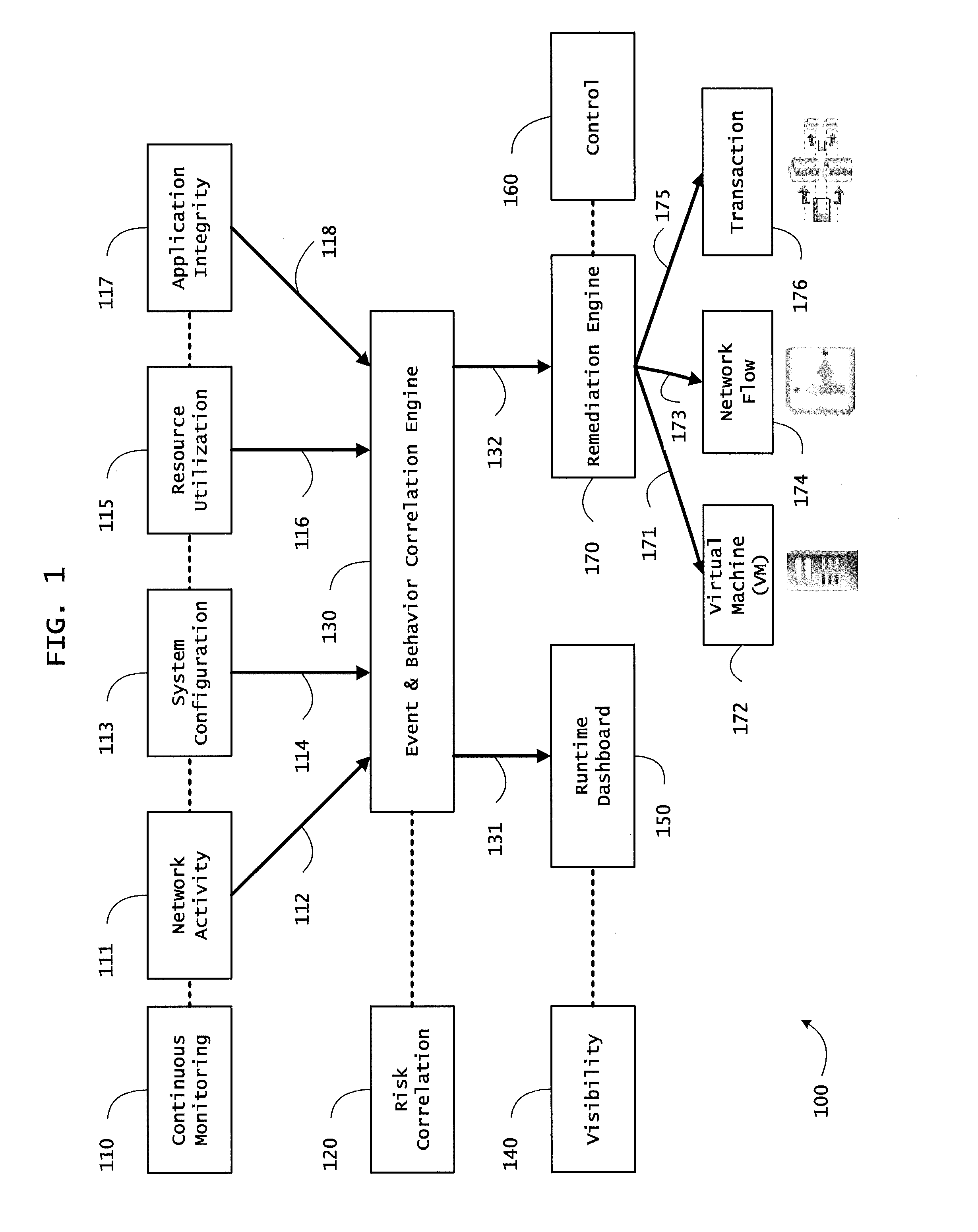
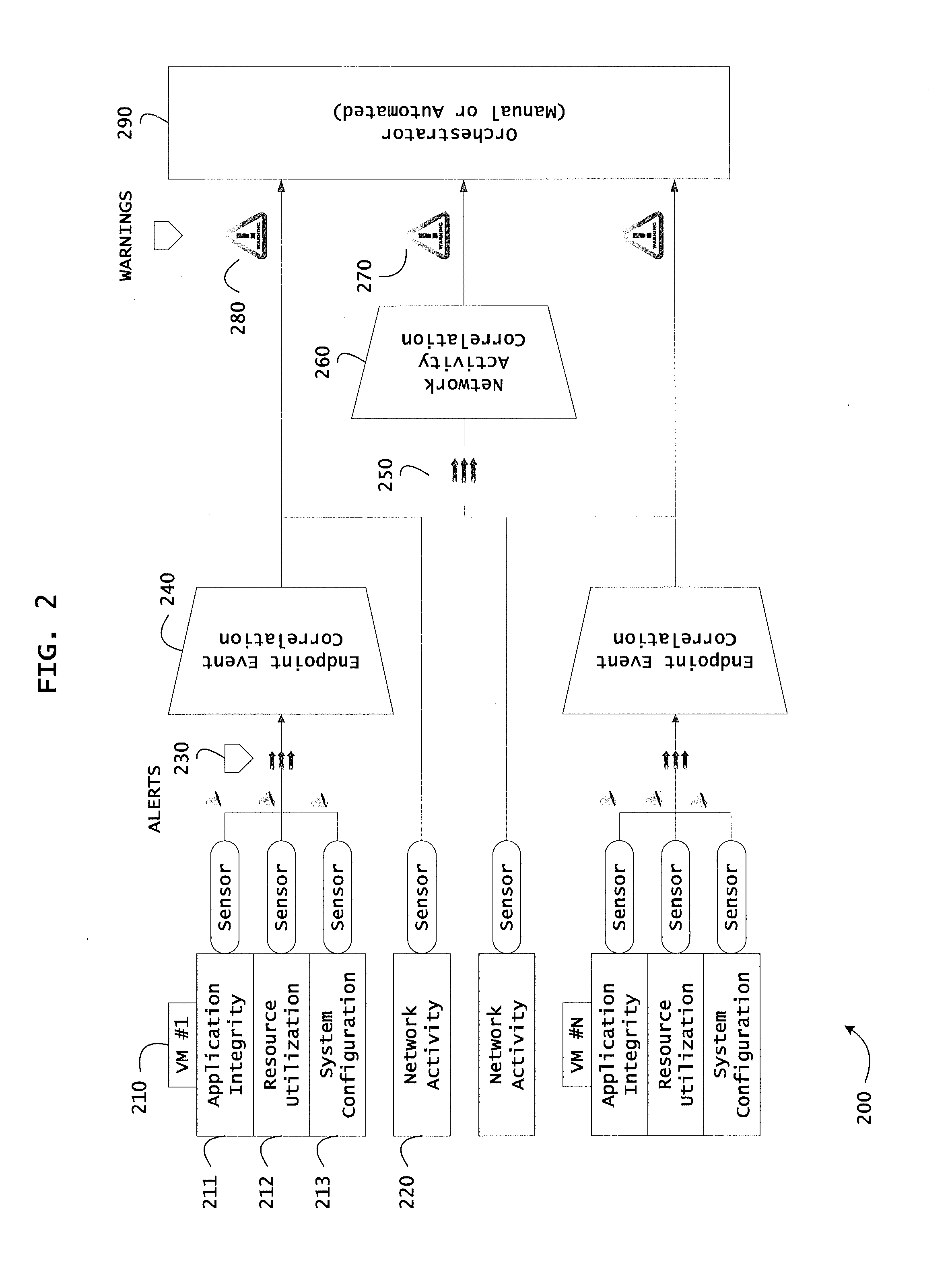
Systems and methods for network flow remediation based on risk correlation
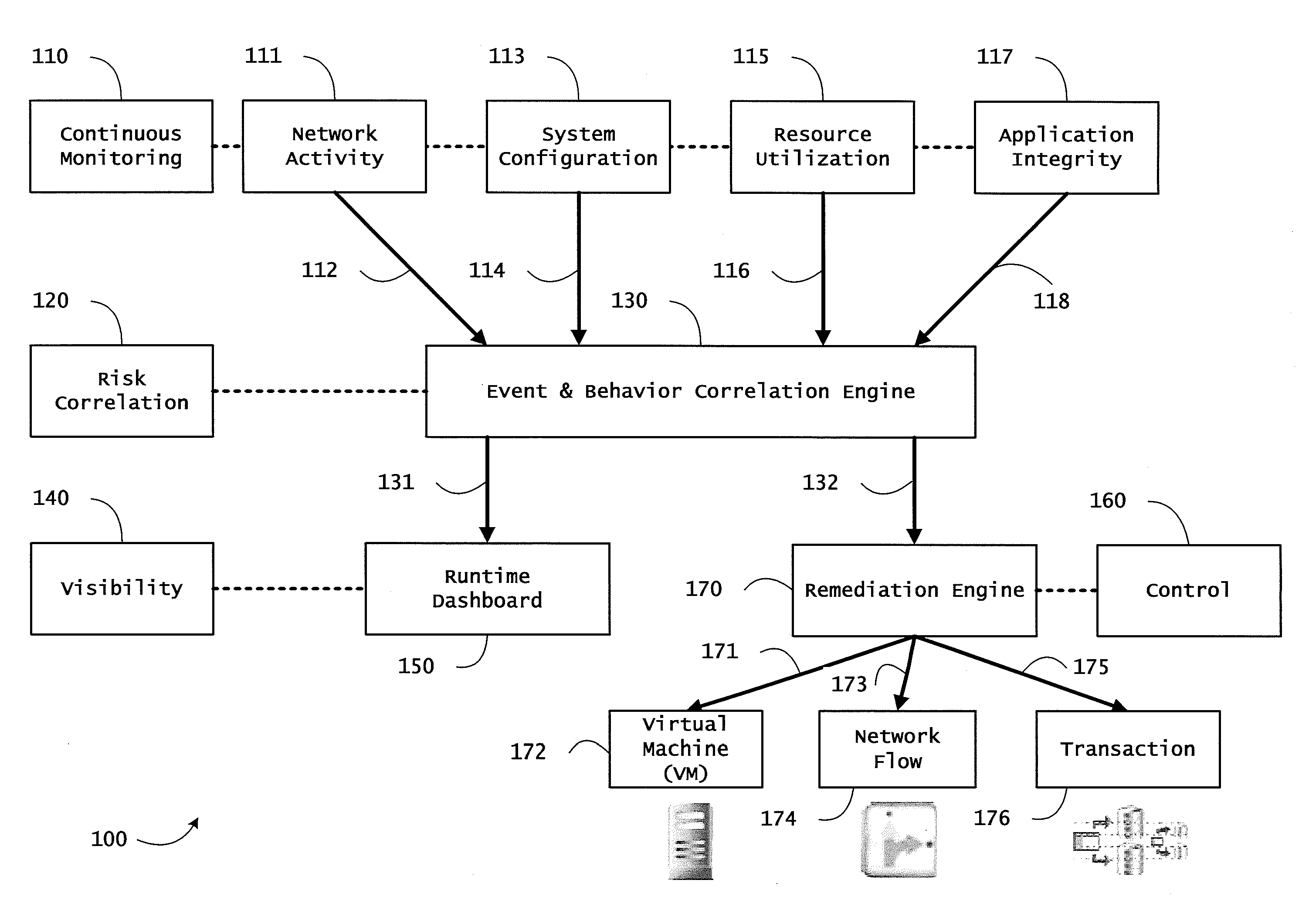
ActiveUS20130298230A1Memory loss protectionError detection/correctionResource utilizationSystem configuration
Instrumented networks and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Methods and systems are disclosed for network flow and device / platform remediation in response to reconnaissance-based intelligence correlation based on network monitoring, to accomplish network flow remediation and device / platform remediation. In an embodiment, a system receives system warnings and endpoint threat intelligence. The system correlates risk based on inputs from sensory inputs that monitor network activity, system configuration, resource utilization, and device integrity. The system then performs a calculus of risk on a global security context including endpoint assessment reports and sends system warnings based upon the endpoint threat intelligence. The system includes a remediation engine for receiving real time directives to control the device.
Owner:TAASERA LICENSING LLC
Online Social Network Management System and Method For Simulating Users to Build Various Faces of Relation
ActiveUS20080288612A1Patterns of online acquaintance relationships can be more diversifiedIncrease success rateOperating means/releasing devices for valvesDomestic plumbingSocial webComputer science
A system and method of managing a social network are disclosed. The method includes the step of recording the IDs and corresponding personal information of users who have subscribed to a service via a network, in a user DB; the step of recording corresponding relationships between the users and relationship indices R, reflecting the degrees of trustworthiness of the users having the corresponding relationships, in a relationship information DB; and the path search step of evaluating one or more paths based on the relationship indices R of respective links constituting the paths and providing evaluation results to a first user so that the first user can select an optimal path from among the paths existing between the first user and a second user on the social network constructed with the users used as nodes and the corresponding relationships of the users used as the links.
Owner:NHN CORP
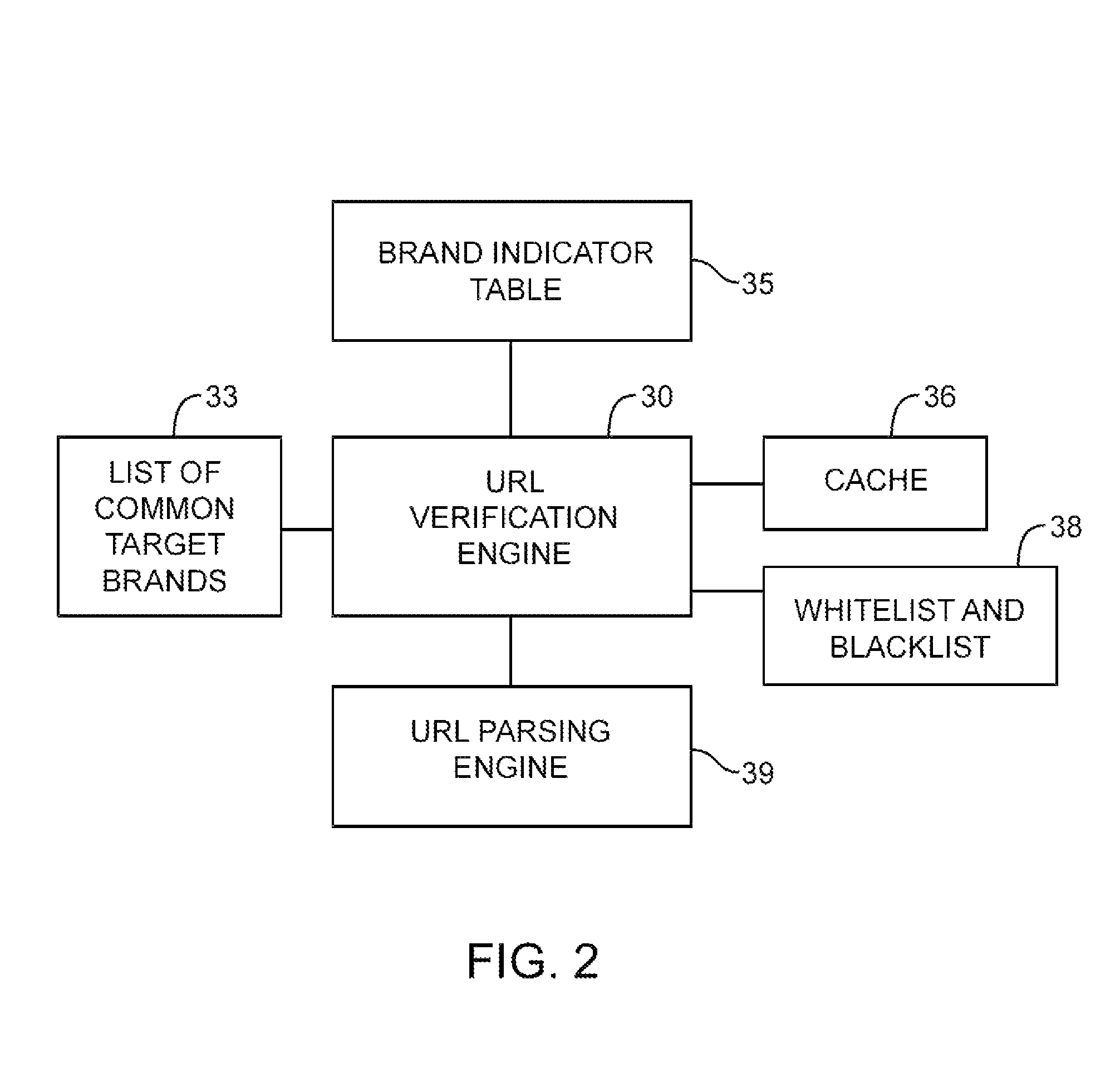
Universal resource locator verification service with cross-branding detection
ActiveUS8079087B1Memory loss protectionDigital data processing detailsThe InternetUniform resource locator
A URL verification service is provided that is used to evaluate the trustworthiness of universal resource locators (URLs). As a user browses the world wide web, the URL for a web page to which the user is browsing is evaluated. A brand and a second level domain portion may be extracted from the URL and used as search engine inputs in evaluating the trustworthiness of the URL. The content of the web page can also be analyzed. Page elements may be extracted from the web page and compared to page elements in a brand indicator table to identify page brands associated with the web page. The brand extracted from the URL is compared to the page brands to detect cross-branding. If cross-branding is detected, the URL verification service helps to prevent the user from submitting sensitive information over the internet.
Owner:MICRO FOCUS LLC
Selective Location Determination
ActiveUS20110250903A1Maximize accuracyStability of the locationPosition fixationWireless commuication servicesCell IDMedia access control
Methods, program products, and systems for selective location determination are described. A mobile device can determine a location of the mobile device using various techniques. When there is a conflict between the locations determined using different techniques, the mobile device can select a most trustworthy location from the locations, and designate the most trustworthy location as a current location of the mobile device. The mobile device can determine a first location of the mobile device (e.g., a coarse location) using a cell identifier (cell ID) of a cellular network. The mobile device can determine a second location of the mobile device (e.g., a fine location) using one or more media access control (MAC) addresses of a WLAN. The first location and second location can be associated with confidence values that can indicate trustworthiness of the first location and second location.
Owner:APPLE INC
Operation of trusted state in computing platform
ActiveUS7302698B1Improve trustSimple taskDigital data processing detailsUser identity/authority verificationOperational systemModem device
A computing entity comprises a trusted monitoring component having a first processing means and a first memory means, the trusted monitoring component being a self-contained autonomous data processing unit, and a computer platform having a main processing means and a main memory area, along with a plurality of associated physical and logical resources such as peripheral devices including printers, modems, application programs, operating systems and the like. The computer platform is capable of entering a plurality of different states of operation, each state of operation having a different level of security and trustworthiness. Selected ones of the states comprise trusted states in which a user can enter sensitive confidential information with a high degree of certainty that the computer platform has not been compromised by external influences such as viruses, hackers or hostile attacks. To enter a trusted state, references made automatically to the trusted component, and to exit a trusted state reference must be made to the trusted component. On exiting the trusted state, all references to the trusted state are deleted from the computer platform. On entering the trusted state, the state is entered in a reproducible and known manner, having a reproducible and known configuration which is confirmed by the trusted component.
Owner:META PLATFORMS INC
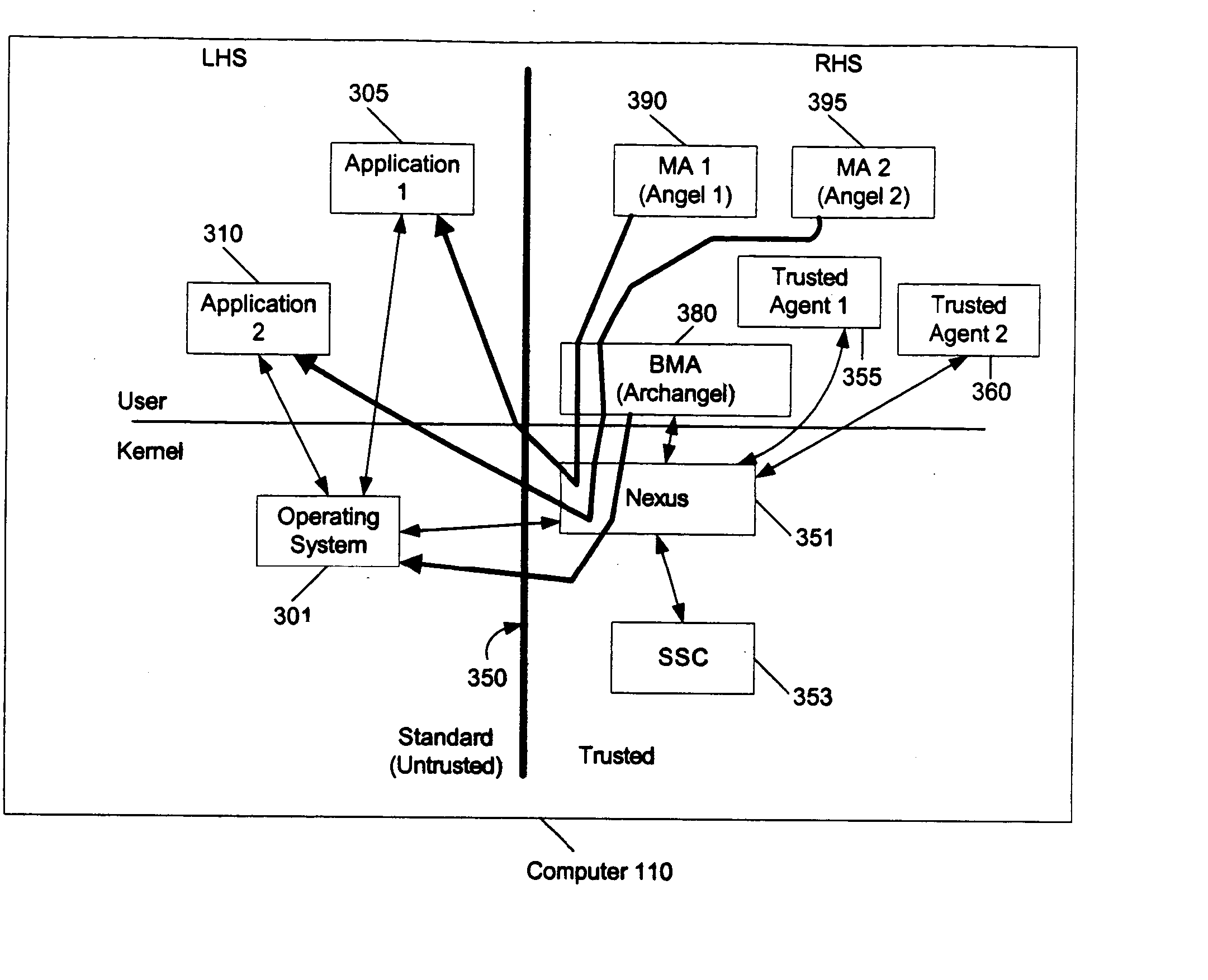
Projection of trustworthiness from a trusted environment to an untrusted environment
InactiveUS20050033980A1Digital data processing detailsDigital computer detailsOperational systemSafe operation
In a single machine that has entities running in an untrusted environment and entities running in a trusted environment, the trustworthiness of the entities in the trusted environment is projected to the entities in the untrusted environment. This is applicable, for example, to Microsoft®'s Next Generation Secure Computing Base (NGSCB), where a regular operating system (e.g., the Windows® operating system) hosts a secure operating system (e.g., the nexus).
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for authenticating an open system application to a portable IC device
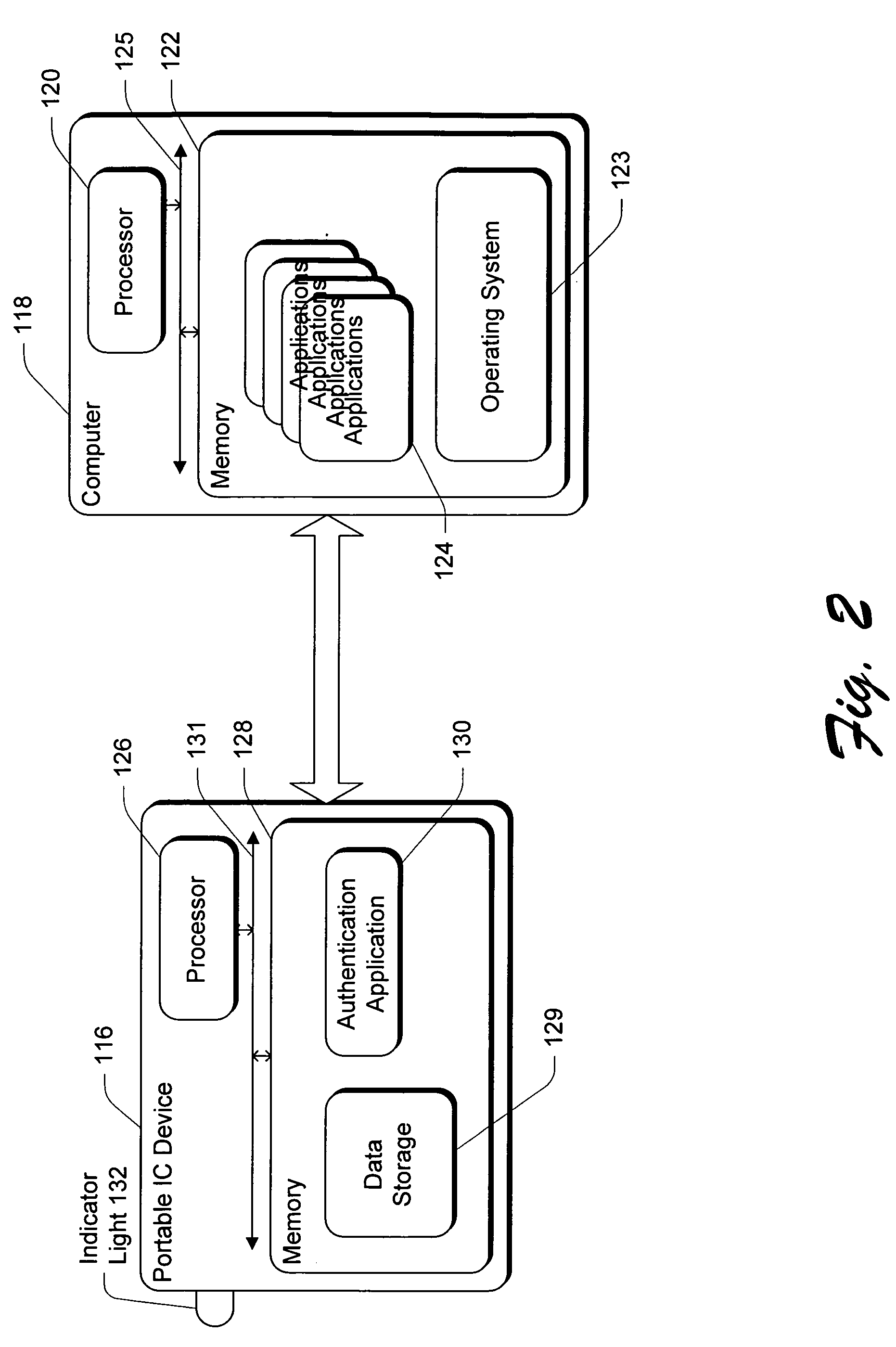
InactiveUS20060036851A1Specific access rightsUser identity/authority verificationSecure communicationApplication software
A secure communication channel between an open system and a portable IC device is established. An application running on the open system desiring access to the information on the portable IC device authenticates itself to the portable IC device, proving that it is trustworthy. Once such trustworthiness is proven, the portable IC device authenticates itself to the application. Once such two-way authentication has been completed, trusted communication between the open system and the portable IC device can proceed, and private information that is maintained on the portable IC device can be unlocked and made available to the application.
Owner:MICROSOFT TECH LICENSING LLC
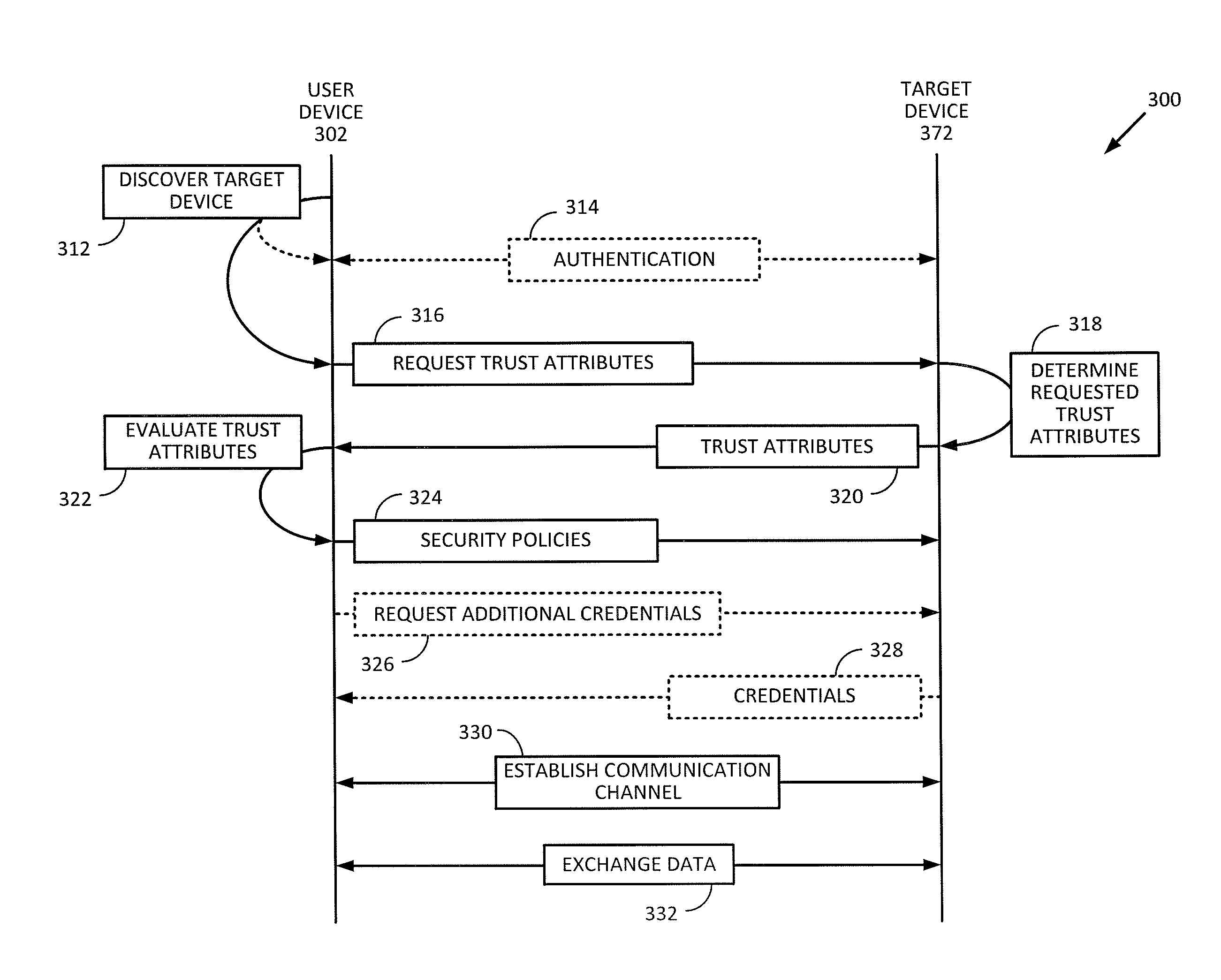
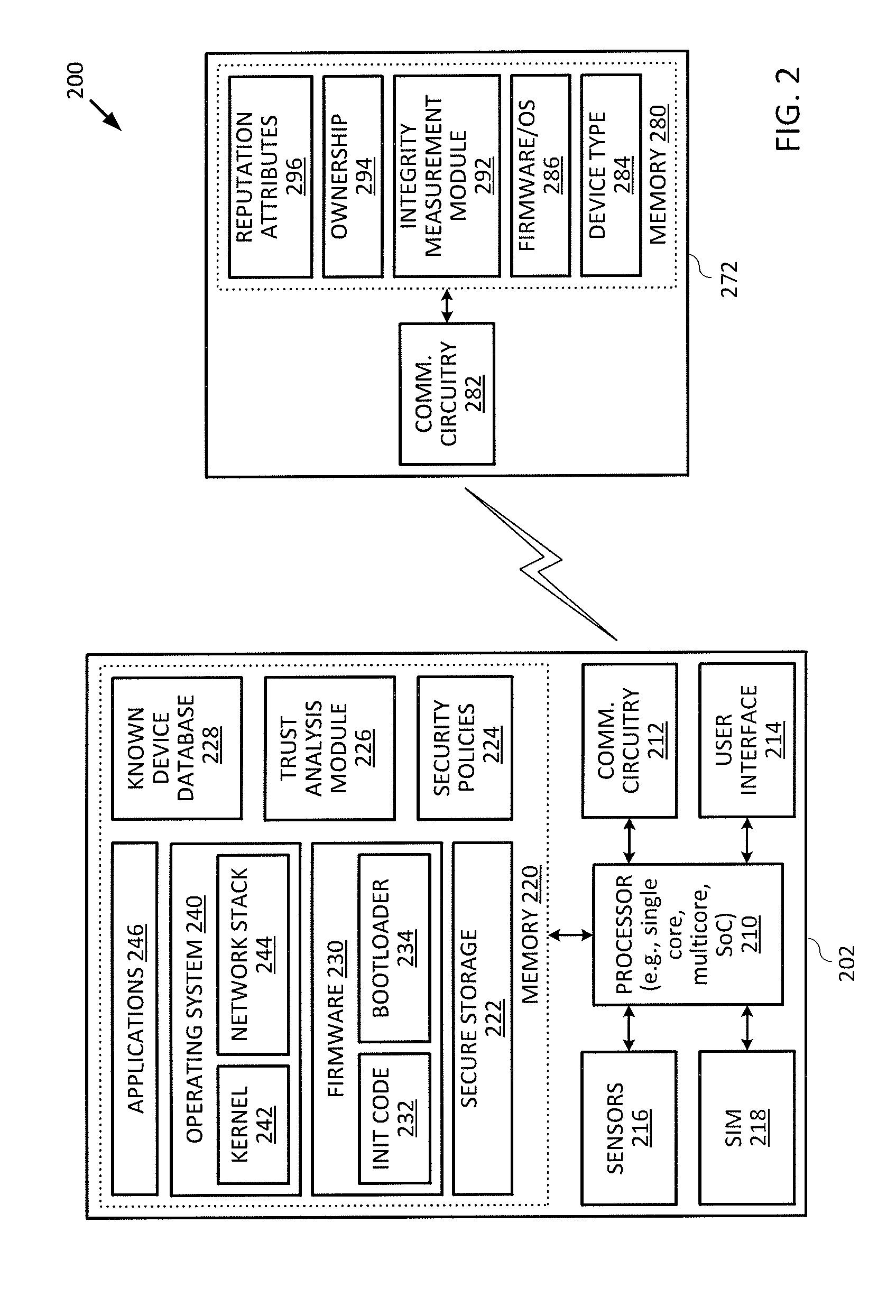
Device Communication Based On Device Trustworthiness
Techniques for assessing the trustworthiness of a target device that a user device is attempting to communicate with are described. A user device may request one or more trustworthiness attributes of a target device before exchanging data with the target device. The user device may receive the one or more trustworthiness attributes of the target device, and determine, based on the received one or more trustworthiness attributes of the target device, a set of one or more security policies to enforce on a communication channel used for exchanging data between the user device and the target device. A communication channel between the user device and the target device can then be established according to the set of one or more security policies.
Owner:VISA INT SERVICE ASSOC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com