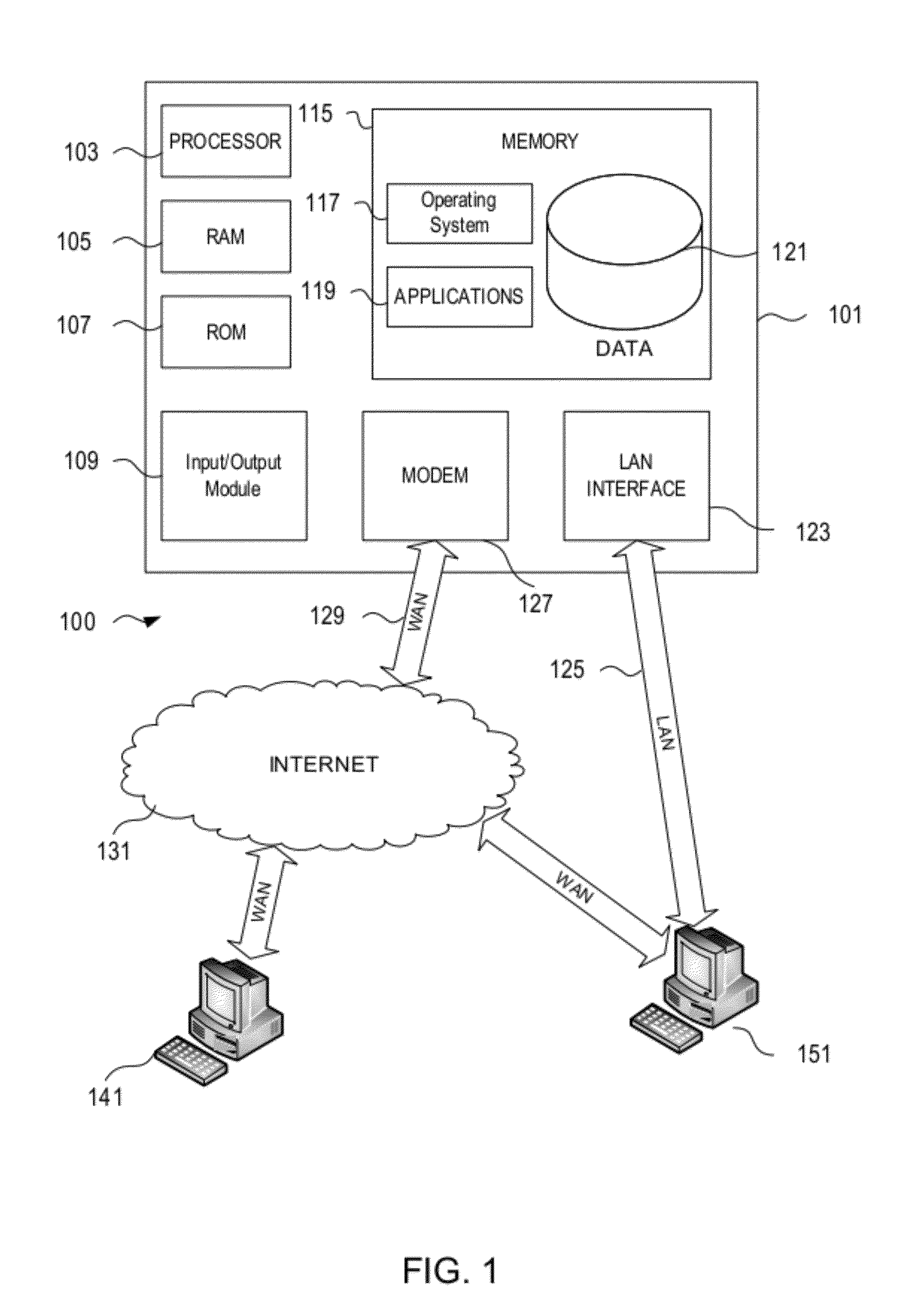
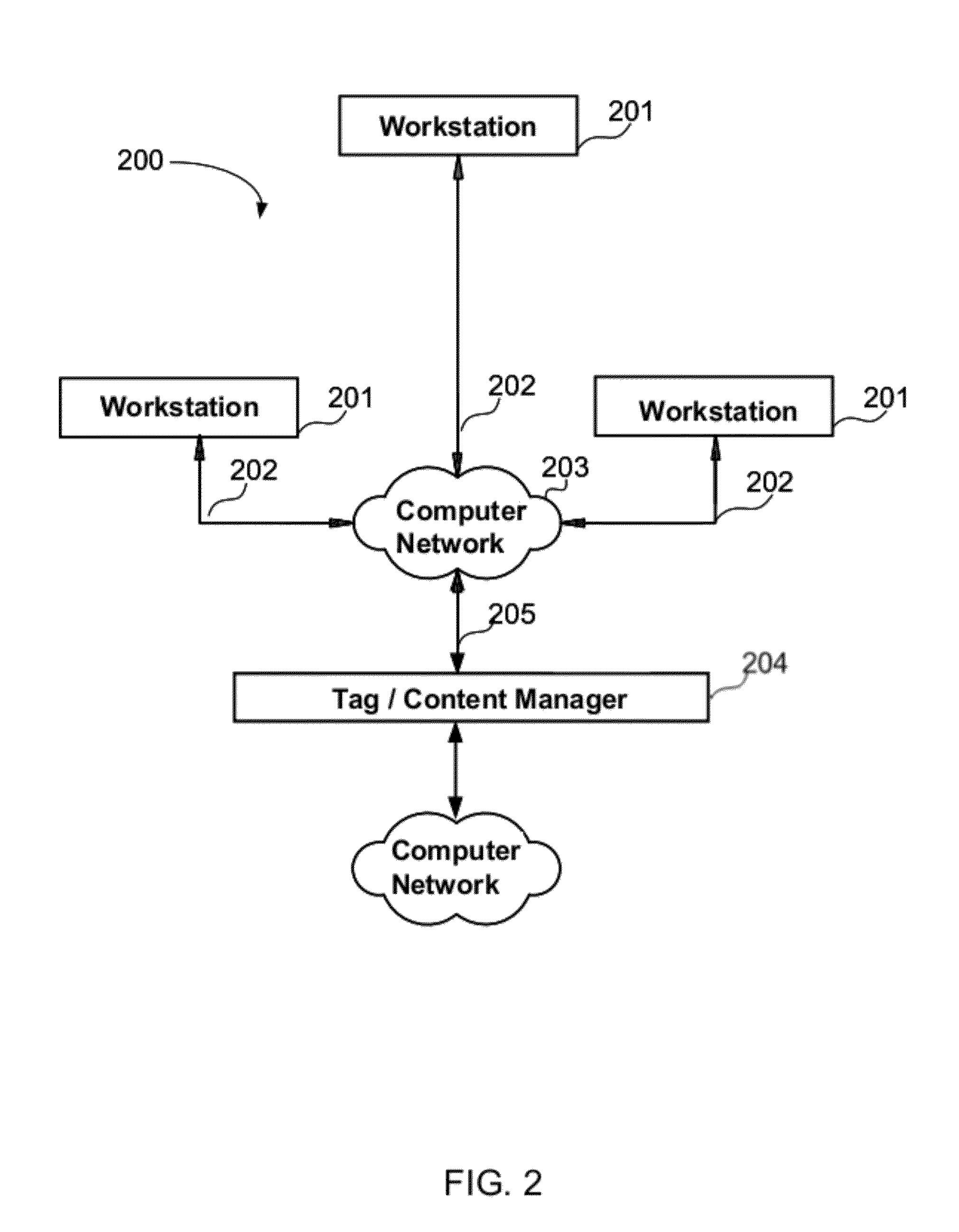
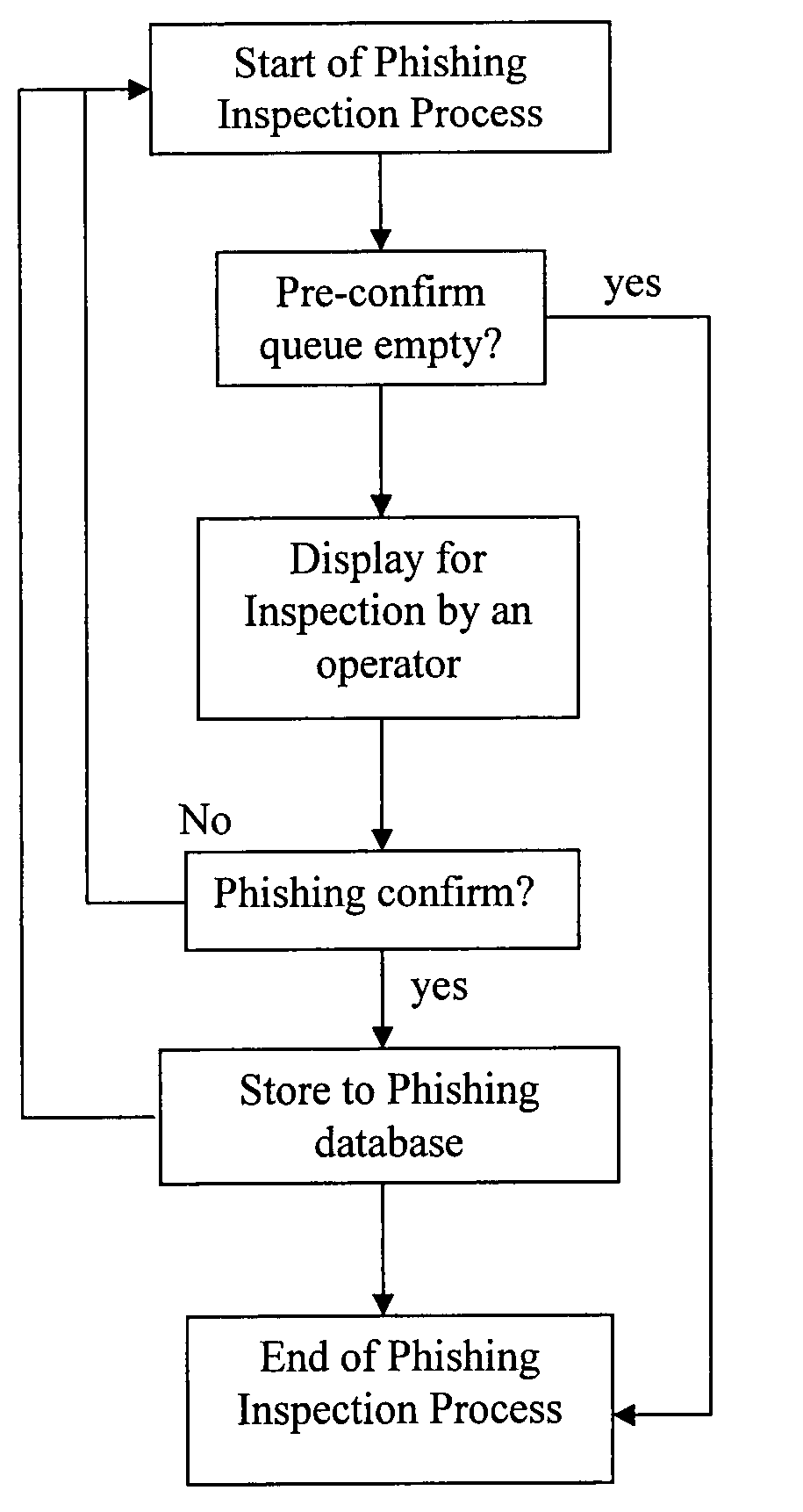
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
973 results about "Blacklist" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, a blacklist or blocklist is a basic access control mechanism that allows through all elements (email addresses, users, passwords, URLs, IP addresses, domain names, file hashes, etc.), except those explicitly mentioned. Those items on the list are denied access. The opposite is a whitelist, which means only items on the list are let through whatever gate is being used. A greylist contains items that are temporarily blocked (or temporarily allowed) until an additional step is performed.
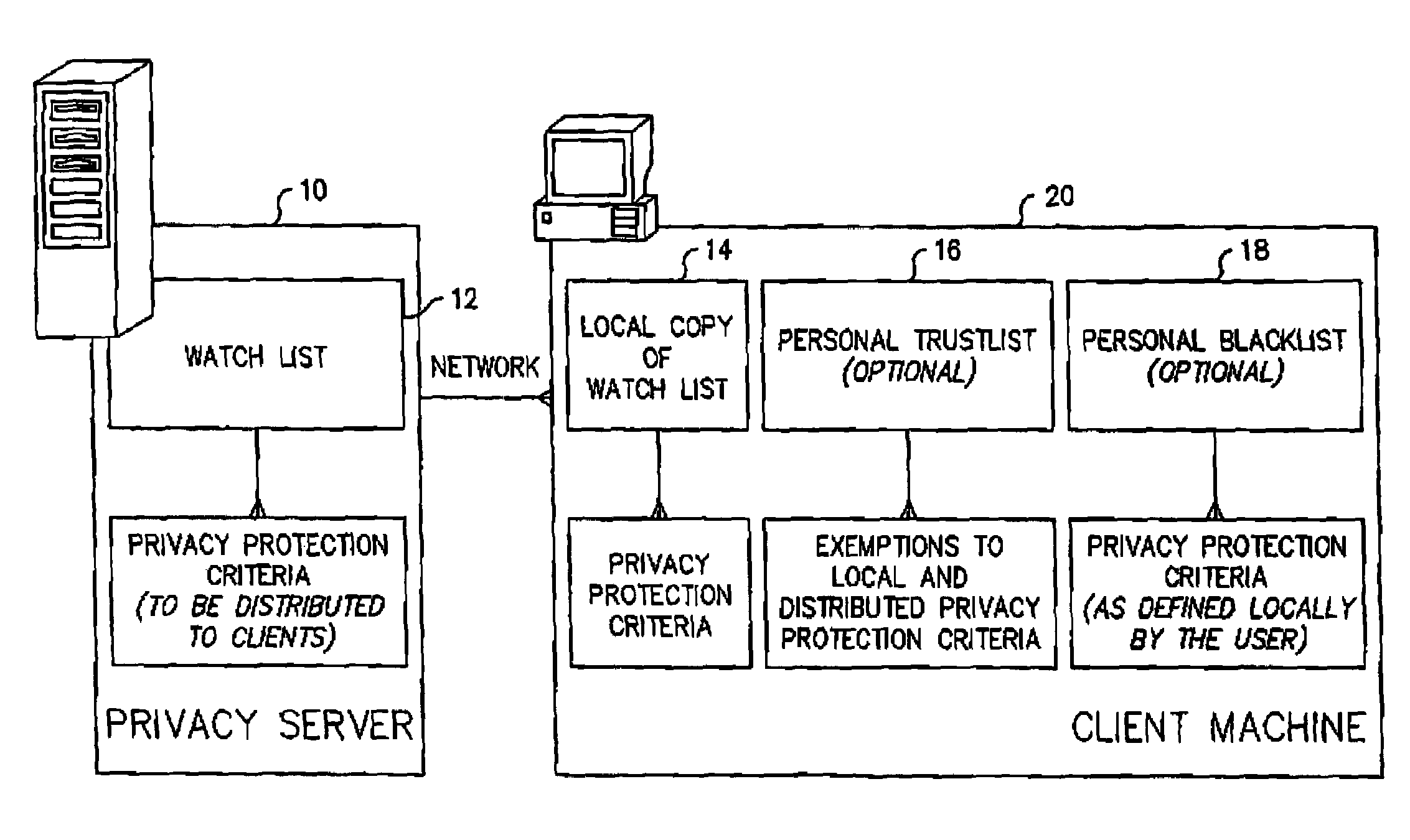
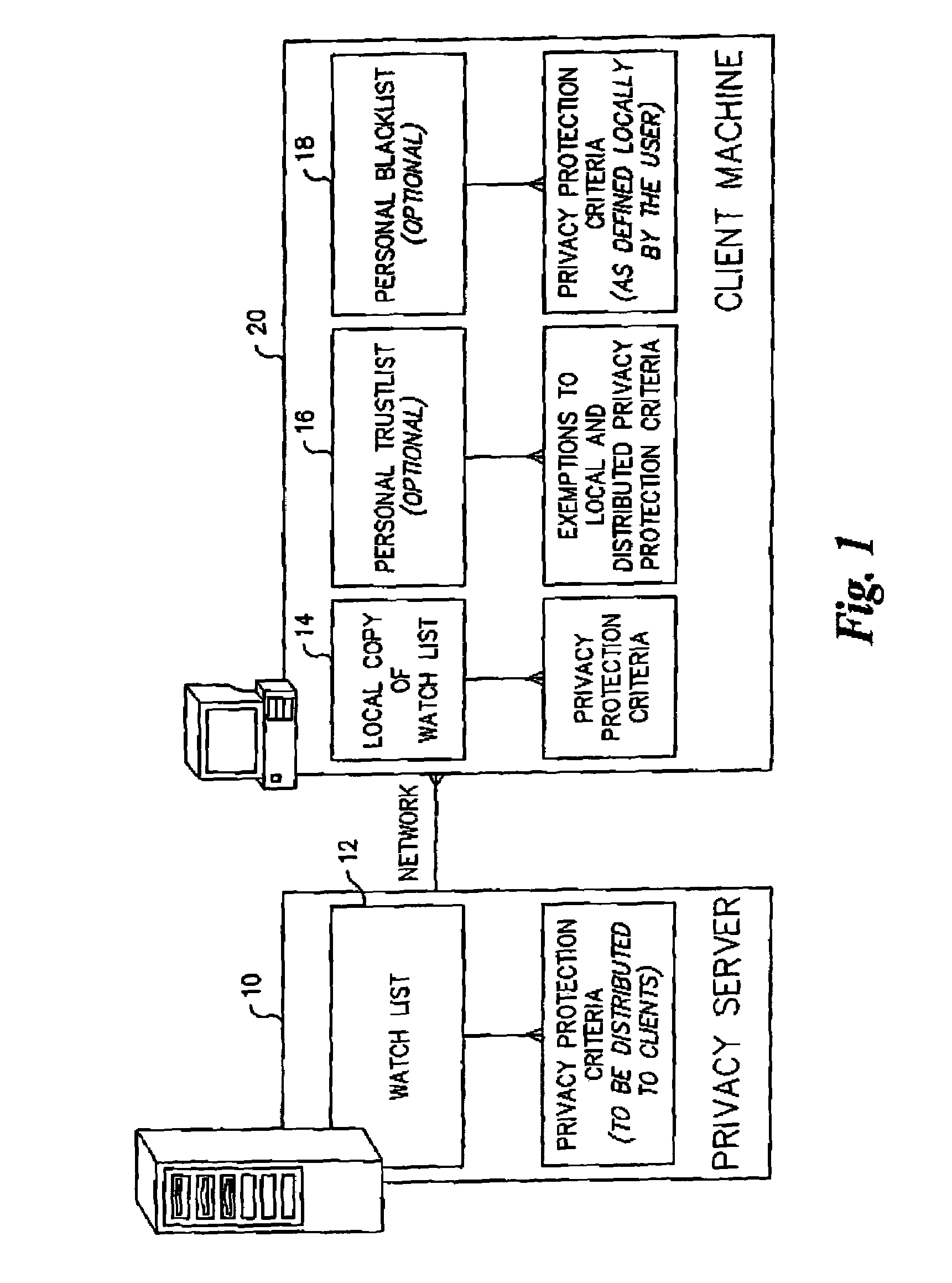
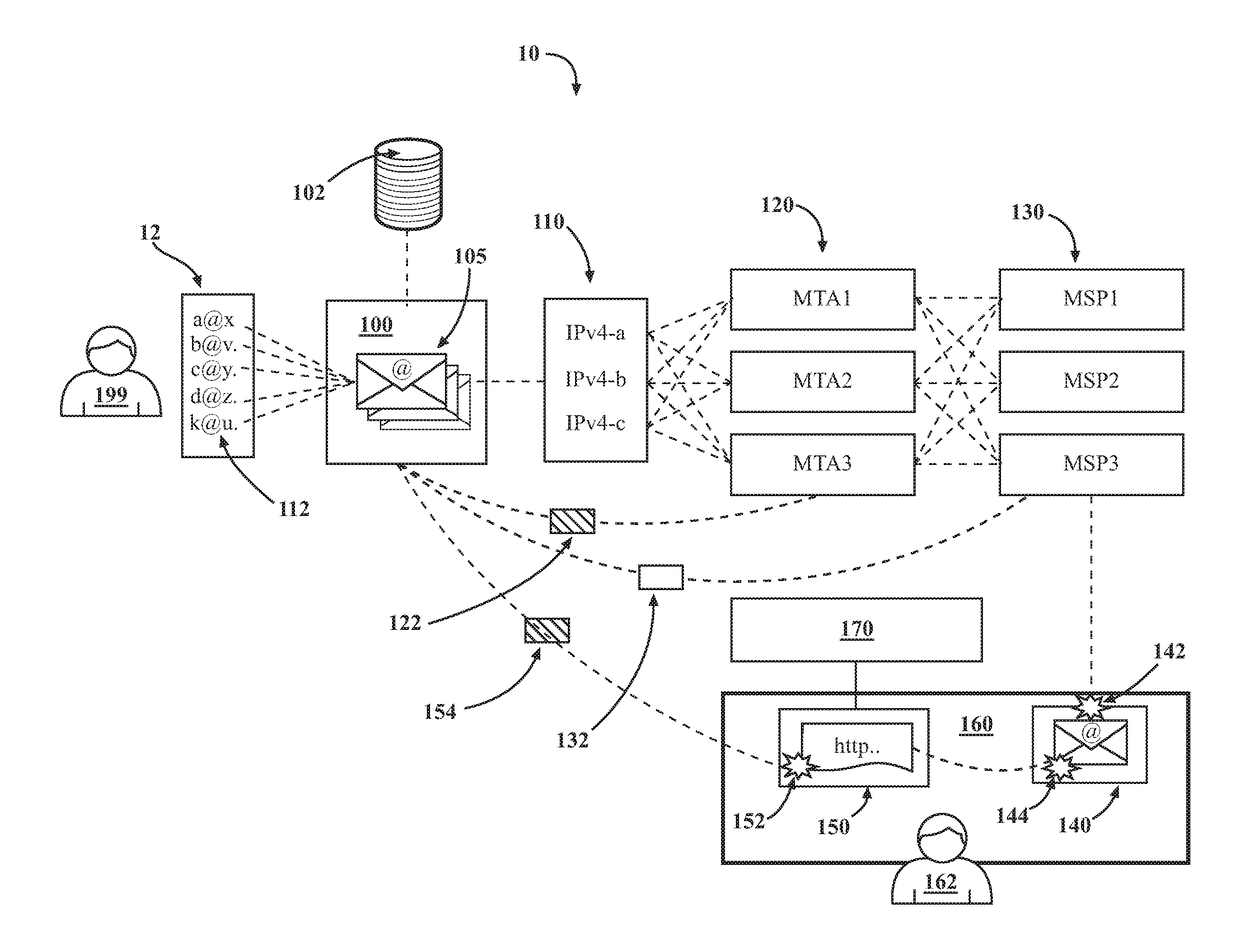
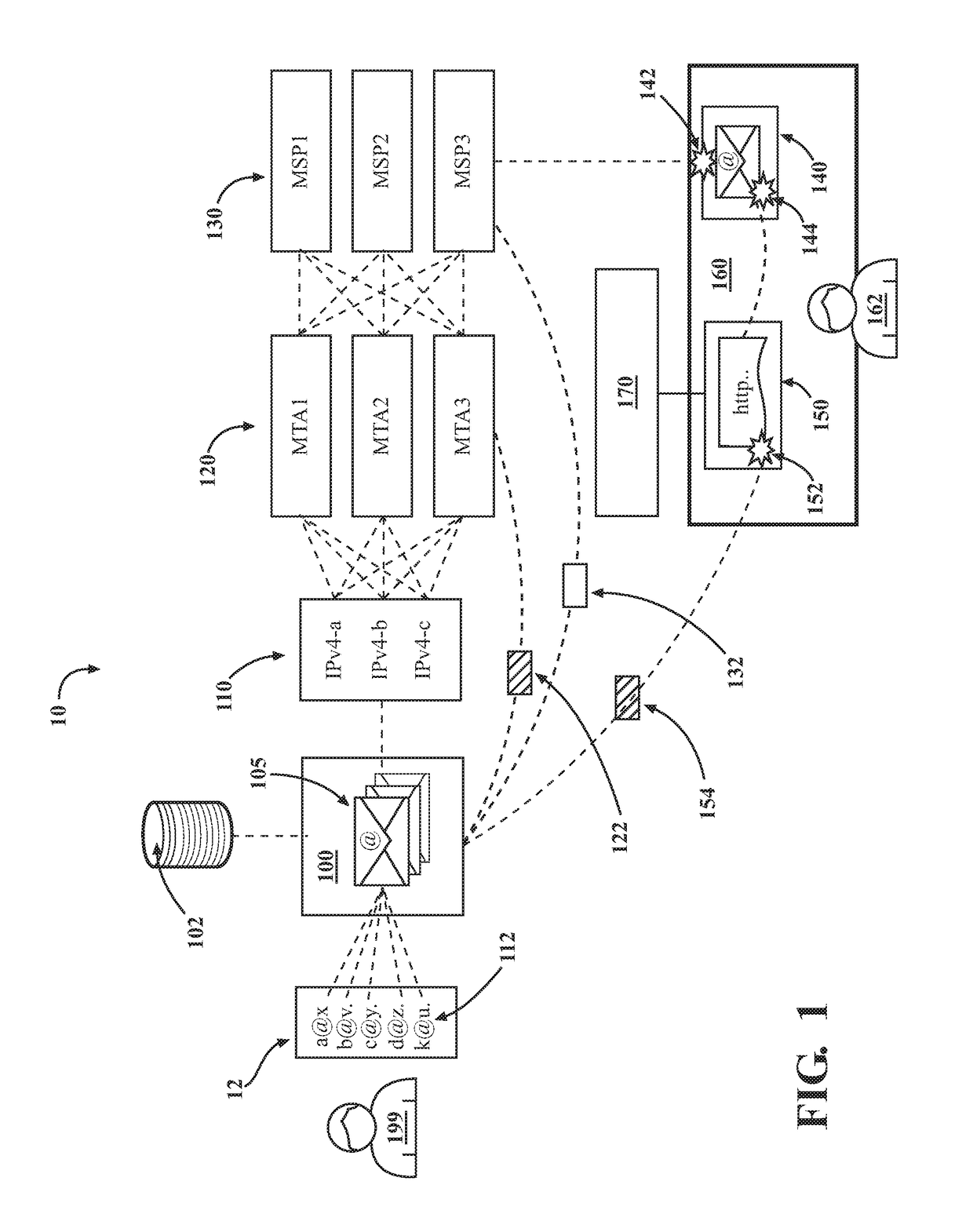
System and method for network administration and local administration of privacy protection criteria
InactiveUS7603356B2Computer security arrangementsSpecial data processing applicationsClient-sideContinuous mode
Cookie files received from cookie file sources (e.g., Internet websites) are screened based upon the recommendations of a service provider which downloads privacy protection criteria in the form of a “watch list” to a subscriber's client machine. A user-friendly interface allows the subscriber to optionally modify the watch list prior to it being used at the subscriber's client machine by assigning known cookie file sources to either a “trustlist” or a “blacklist.” A “composite list” is then generated and used by the client machine to screen cookie files. The subscriber receives updates from the service provider on either a periodic or “as-needed” basis using a “quick update algorithm.” A “privacy scanning algorithm” runs on the client machine and has two different modes of operation. The first is a continuous mode where unwanted cookie files are blocked from being stored at the client machine. The second is a periodic mode where the client machine is “scrubbed” of unwanted cookie files according to the privacy protection criteria.
Owner:ASCENTIVE
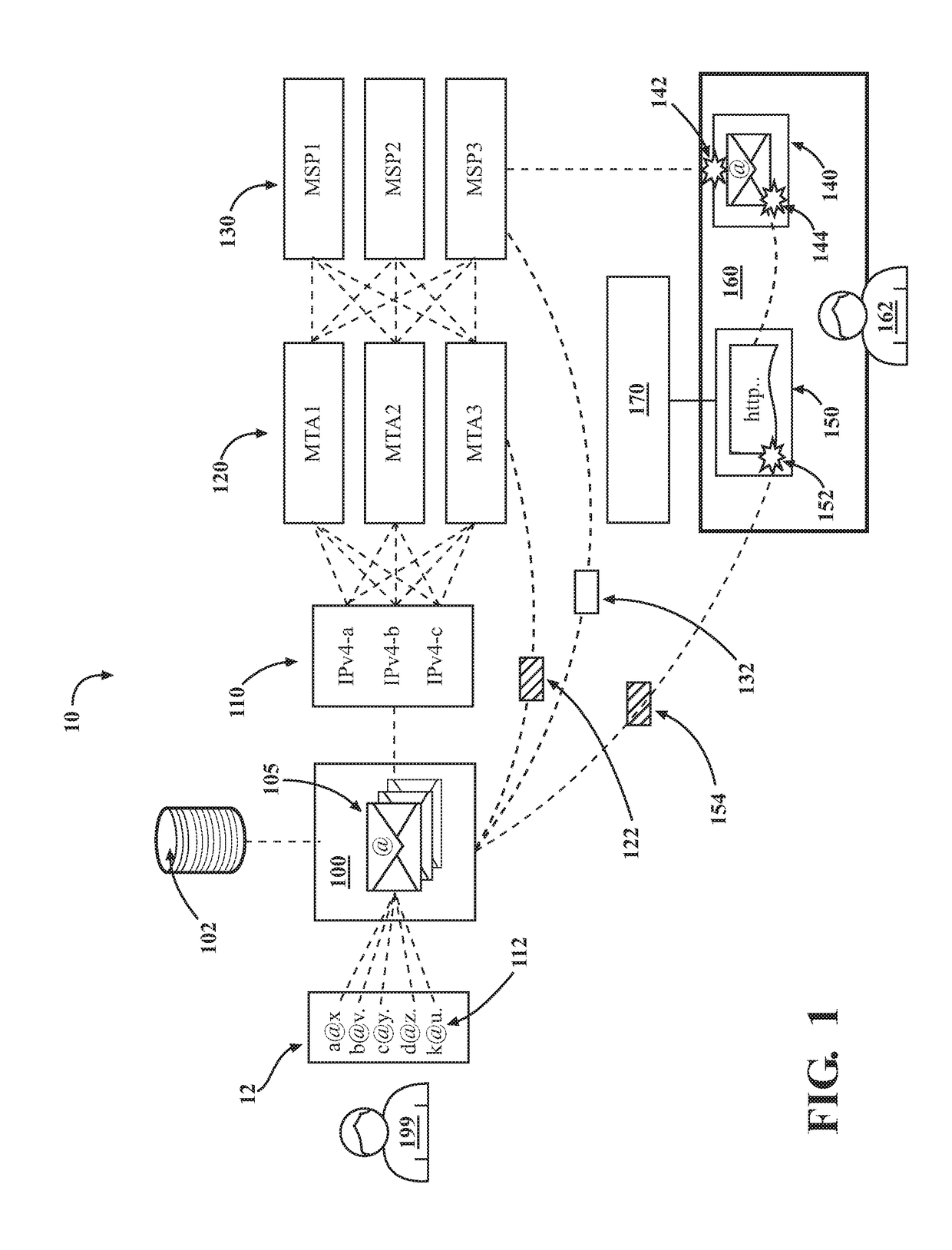
Introducing a new message source into an electronic message delivery environment
ActiveUS20180219830A1Reduce riskMaximizing numberMathematical modelsAdvertisementsMessage deliveryBlack list
Owner:HUBSPOT
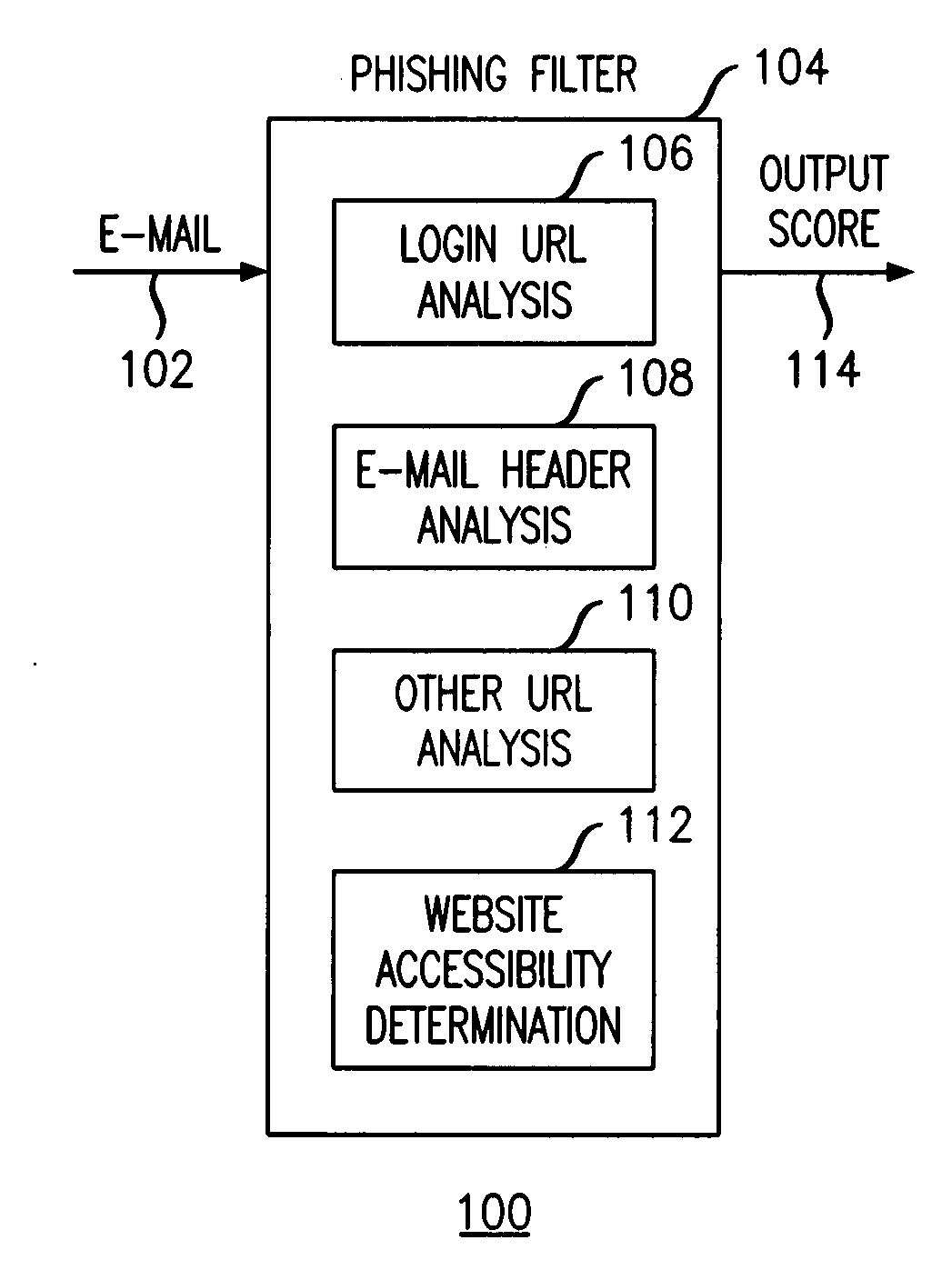
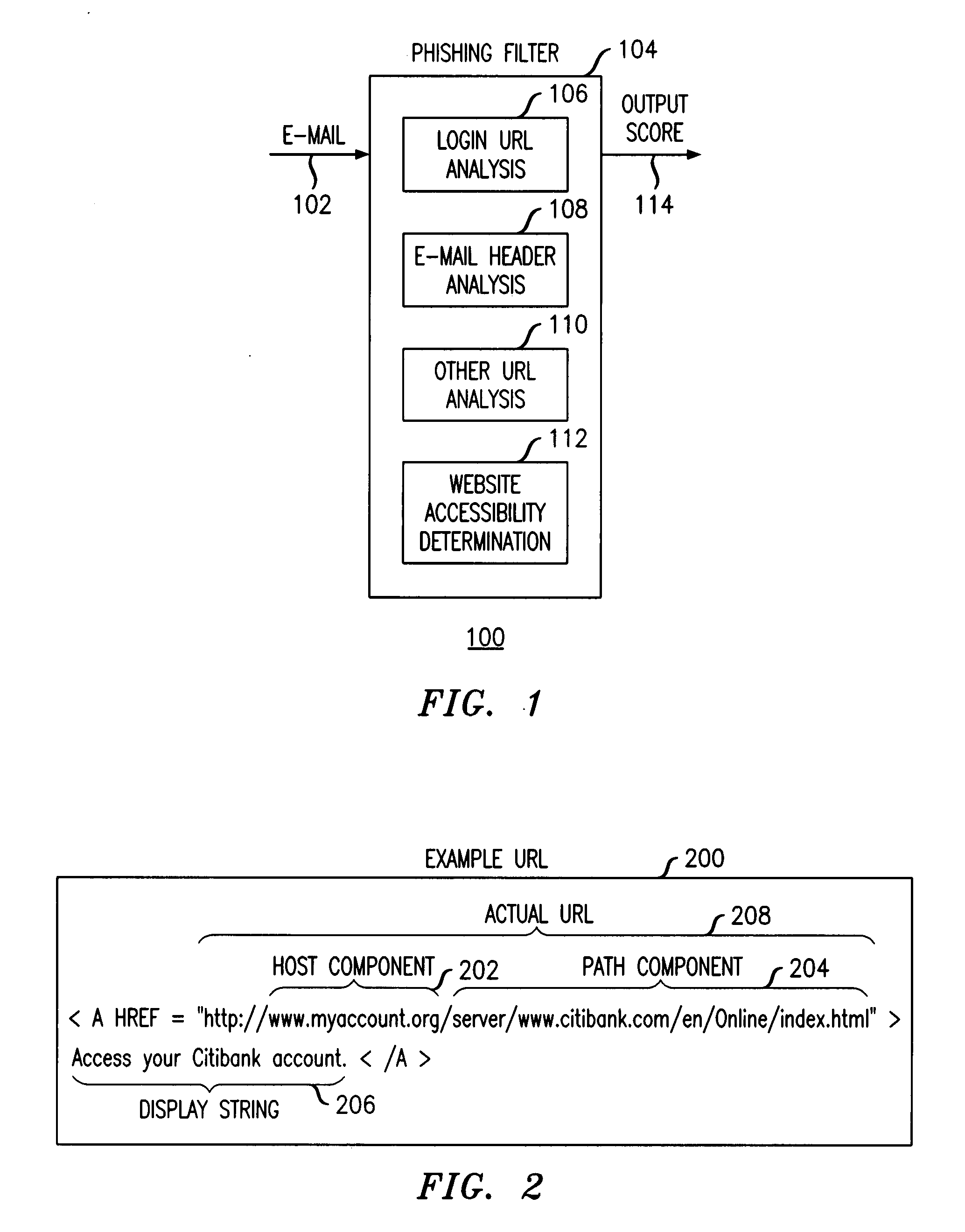
Method and apparatus for detecting phishing attempts solicited by electronic mail
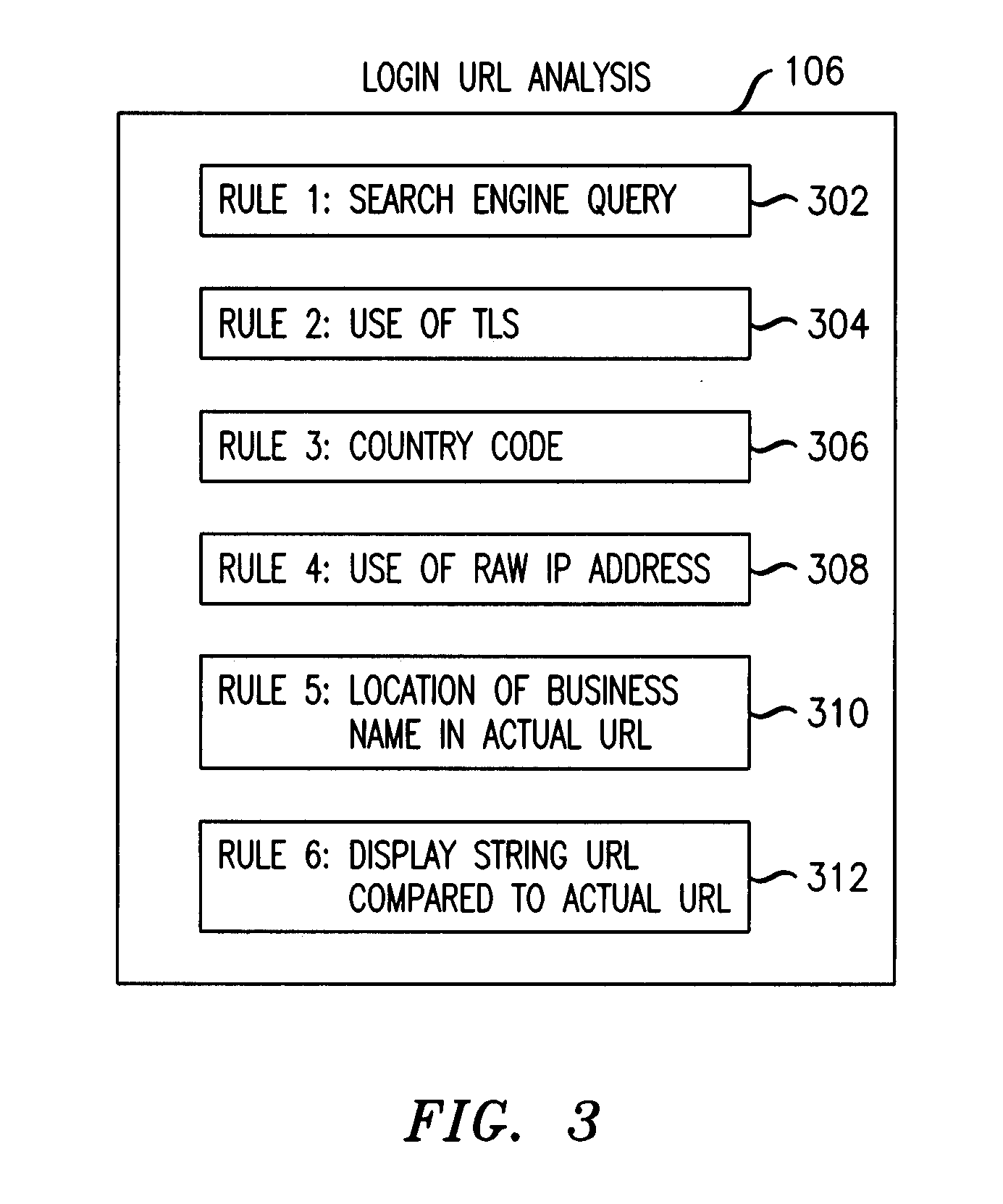
InactiveUS20090089859A1Digital data processing detailsUser identity/authority verificationKeyword analysisHeuristic
A phishing filter employs a plurality of heuristics or rules (in one embodiment, 12 rules) to detect and filter phishing attempts solicited by electronic mail. Generally, the rules fall within the following categories: (1) identification and analysis of the login URL (i.e., the “actual” URL) in the email, (2) analysis of the email headers, (3) analysis across URLs and images in the email other than the login URL, and (4) determining if the URL is accessible. The phishing filter does not need to be trained, does not rely on black or white lists and does not perform keyword analysis. The filter may be implemented as an alternative or supplemental to prior art spam detection filters.
Owner:ALCATEL-LUCENT USA INC
Detection and minimization of false positives in anti-malware processing
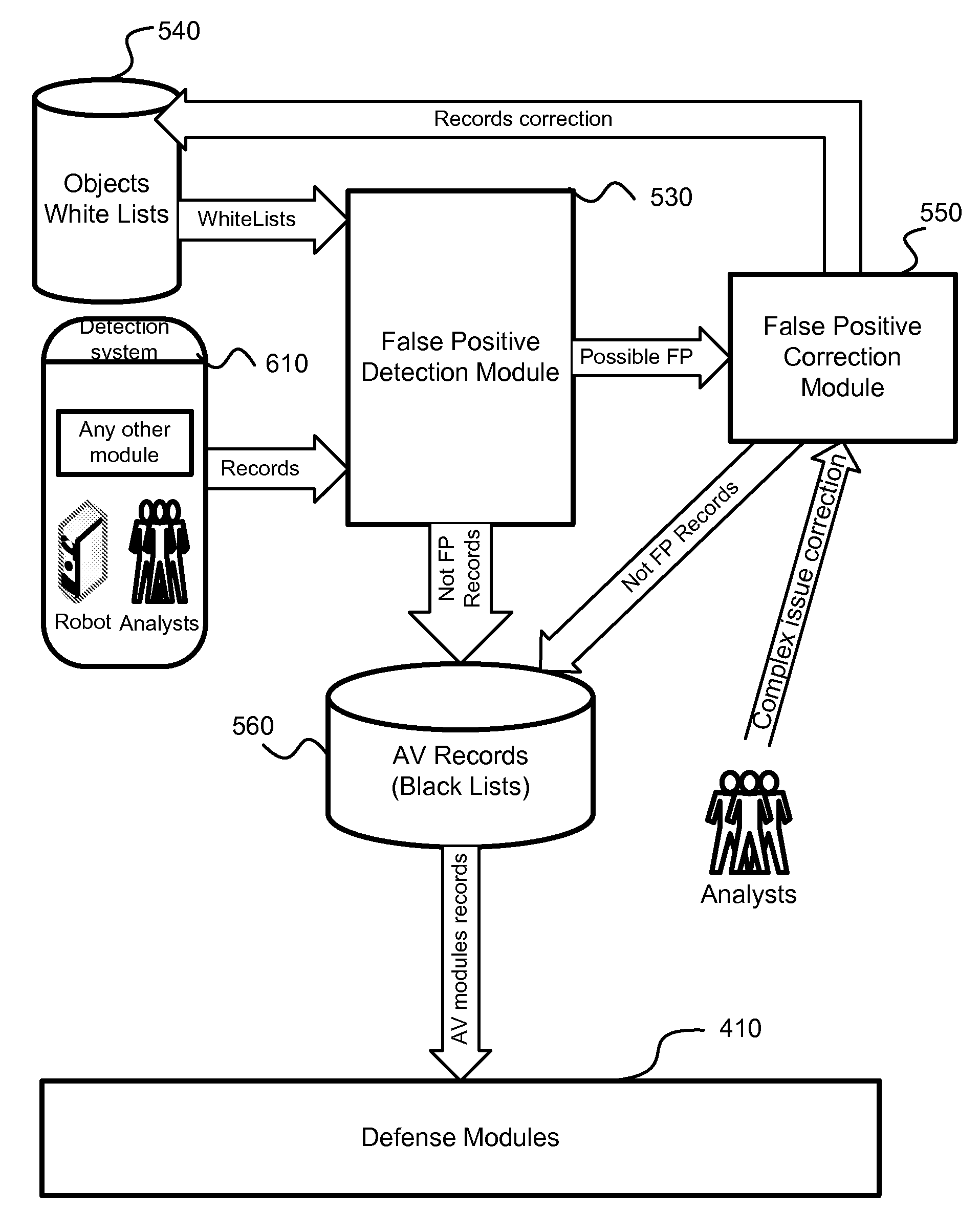
ActiveUS7640589B1Eliminate disadvantagesMemory loss protectionError detection/correctionAnti virusMalware
A system, method and computer program product for detection of false positives occurring during execution of anti-malware applications. The detection and correction of the false positives is implemented in two phases, before creation of new anti-virus databases (i.e., malware black lists) or before creation of new white lists, and after the anti-virus databases or new white lists are created and new false positives are detected. The system calculates a probability of detection of a certain potential malware object. Based on this probability, the system decides to either correct a white list (i.e., a collection of known clean objects) or update a black list (i.e., a collection of known malware objects). A process is separated into a several steps: creation and update (or correction) of white lists; creation and update of black lists; detection of collisions between these lists and correction of black lists or white lists based on the detected collisions.
Owner:AO KASPERSKY LAB
Quality-based routing of electronic messages
ActiveUS20180219818A1Mitigating cross-impactEasy to compareMathematical modelsAdvertisementsSpammingElectronic information
Owner:HUBSPOT
Online privacy management
ActiveUS8261362B2Simple processDigital data processing detailsAnalogue secracy/subscription systemsData streamClient-side scripting
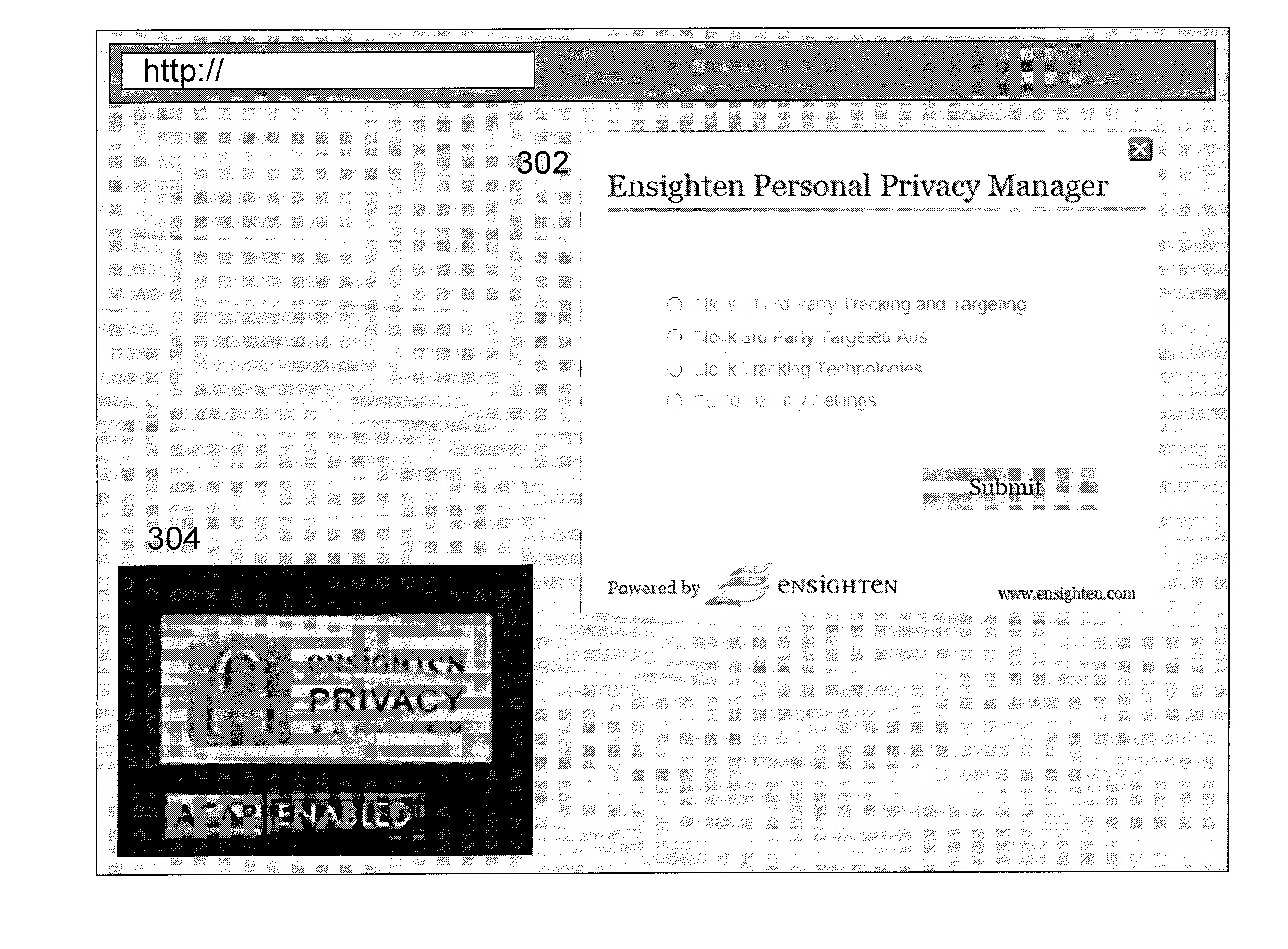
A privacy management system (PMS) is disclosed for a Chief Privacy Officer (CPO) or other user to use in monitoring and / or controlling in realtime the flow of data (e.g., outflow) about the user and his / her online experience. The PMS may provide a dashboard displaying a whitelist and / or blacklist indicating what destinations / sources are blocked or allowed. The PMS includes browser-client scripting code and may also include a PMS-certified verification icon for display on webpages being monitored / controlled in realtime by the PMS.
Owner:ENSIGHTEN
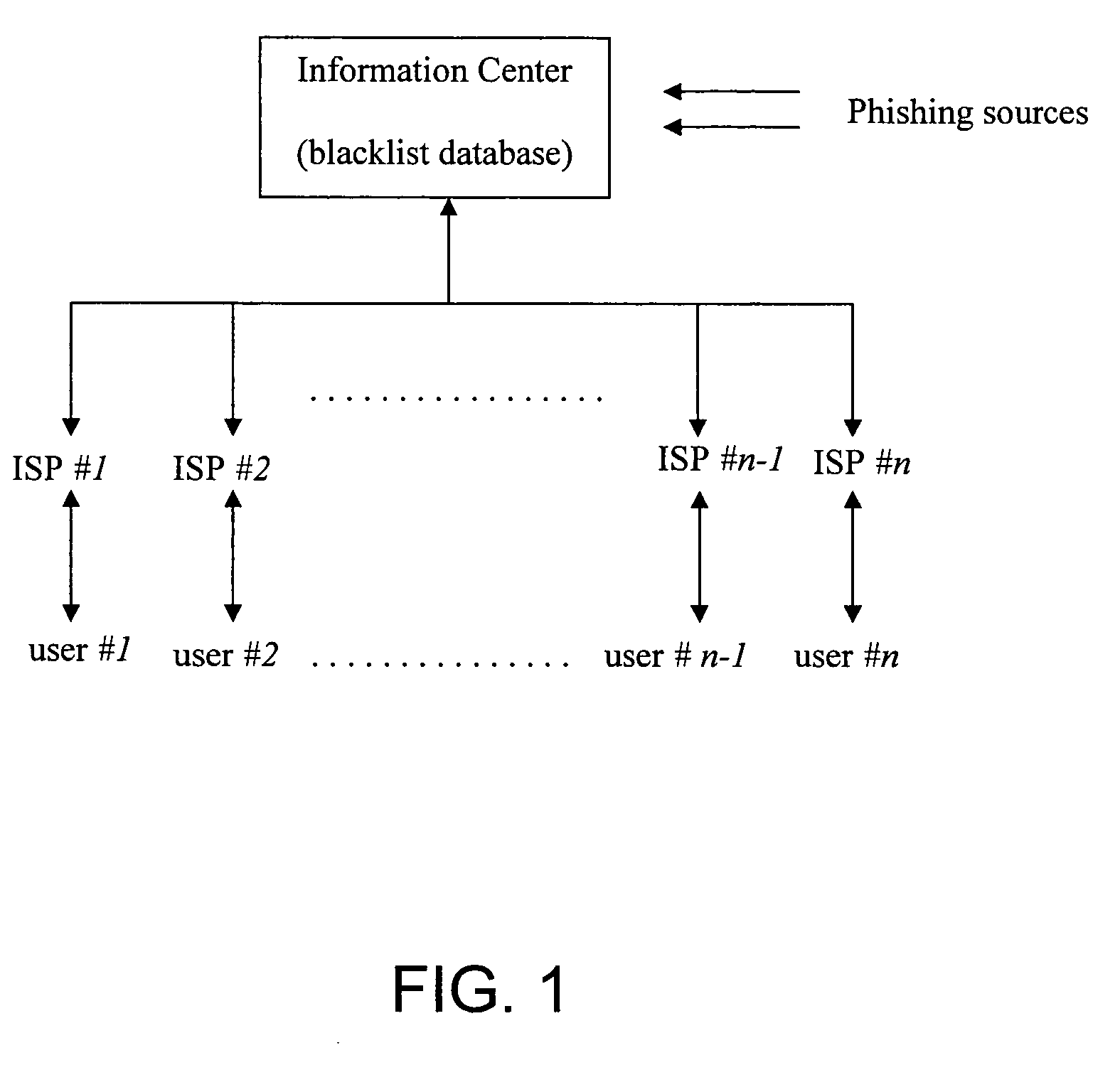
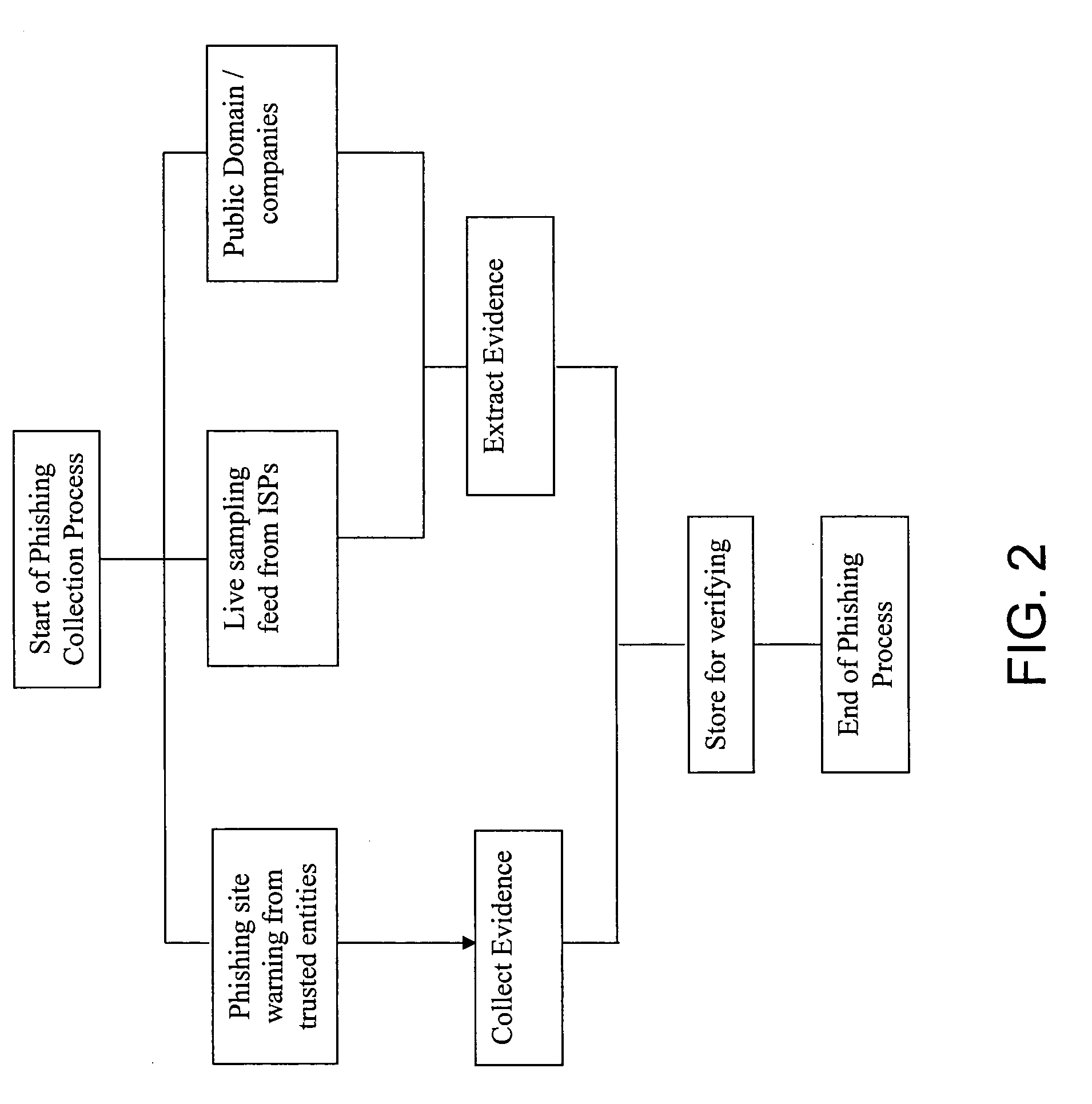
Jurisdiction-wide anti-phishing network service
InactiveUS20060095955A1Prevent theftPrevent users from being deceivedDigital data processing detailsUser identity/authority verificationWeb sitePhishing
An anti-phishing method includes the steps of establishing an information center having a blacklist database, wherein the information center is liaising with at least an Internet service provider (ISP) through a communication network; collecting a plurality of phishing sources to be stored in the blacklist database to form a plurality of blacklist items therein; and sending the blacklist sources to the Internet service provider such that when a user of the Internet service provider tries to access a website source which matches with one of the blacklist items, the user receives a warning signal to inform the user that the website address is the phishing source.
Owner:MAIL PROVE
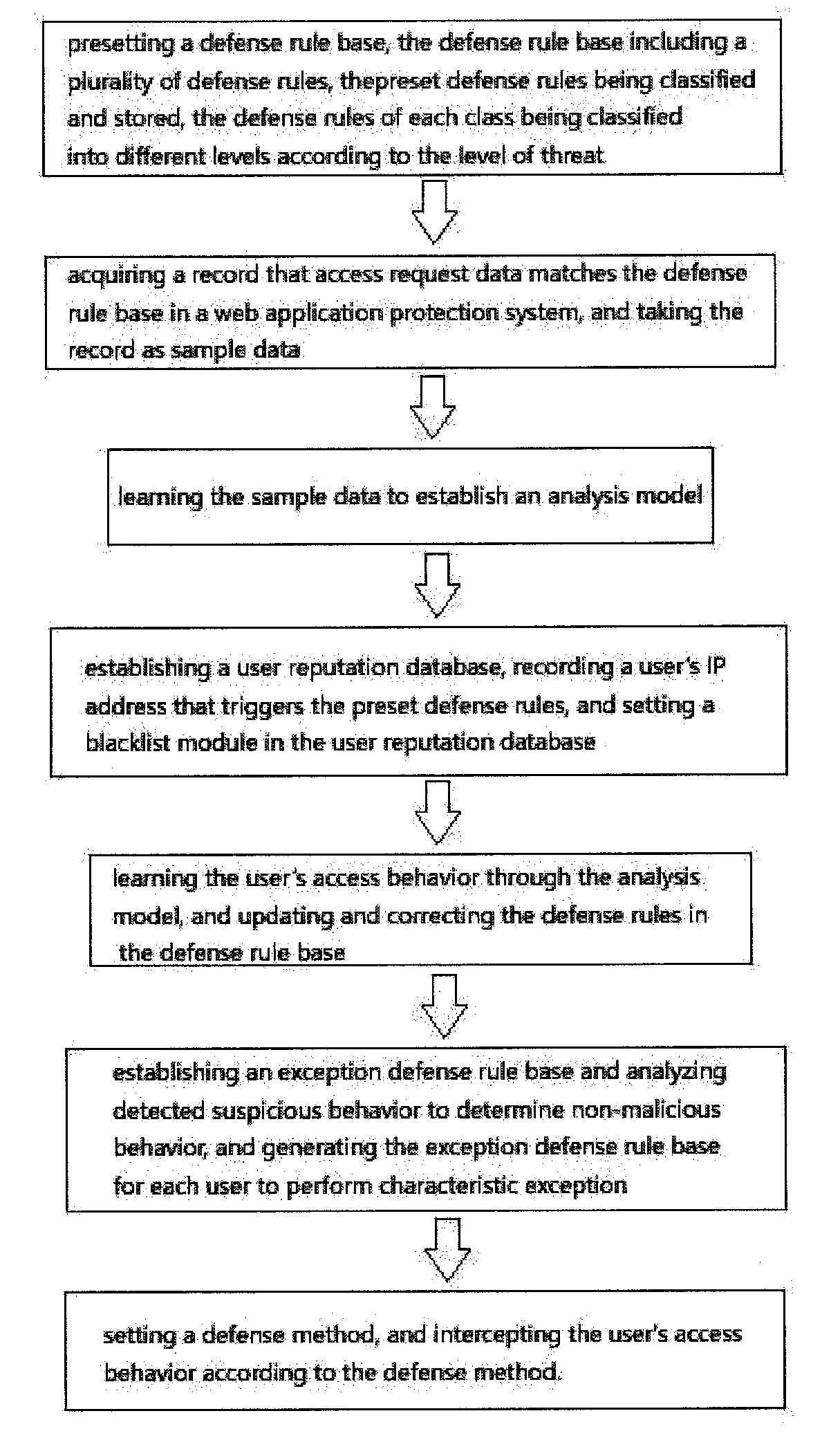
Method for web application layer attack detection and defense based on behavior characteristic matching and analysis
ActiveUS20180262521A1High false alarm rateLow efficiencyMathematical modelsTransmissionWeb serverApplication software
A method for web application layer attack detection and defense based on behavior characteristic matching and analysis includes presetting a defense rule base, the defense rule base including a plurality of defense rules; acquiring a record that access request data matches the defense rule base in a web application protection system and taking the record as sample data; learning the sample data to establish an analysis model; establishing a user reputation database and setting a blacklist module in the user reputation database; learning the user's access behavior through the analysis model and updating and correcting the defense rules in the defense rule base; establishing an exception defense rule base; and setting a defense method and intercepting the user's access behavior according to the defense method. By intelligently learning the user's behavior, threat behavior can be identified and intercepted quickly to ensure the security of the web server.
Owner:MOLBASE SHANGHAI BIOTECH CO LTD
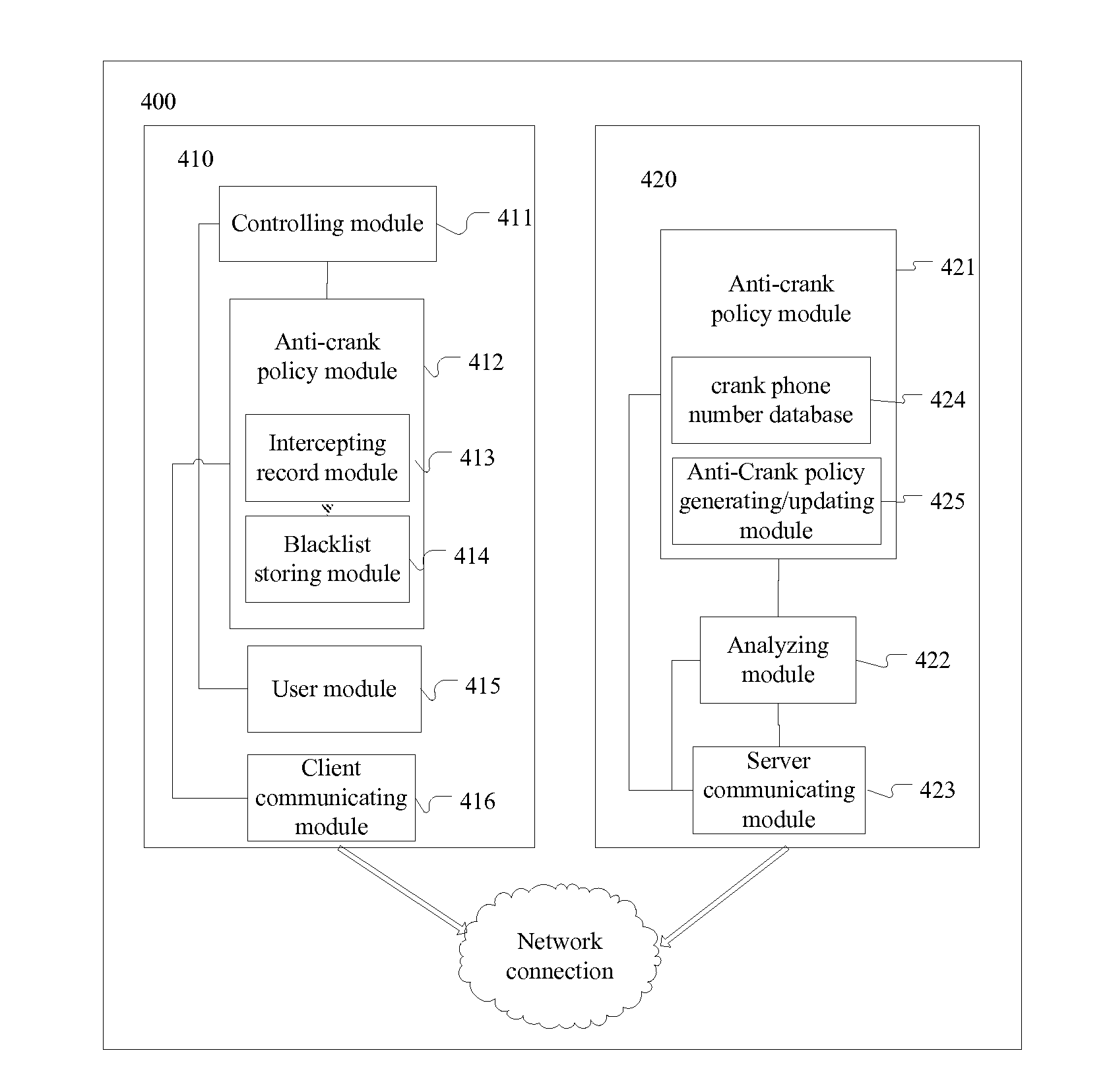
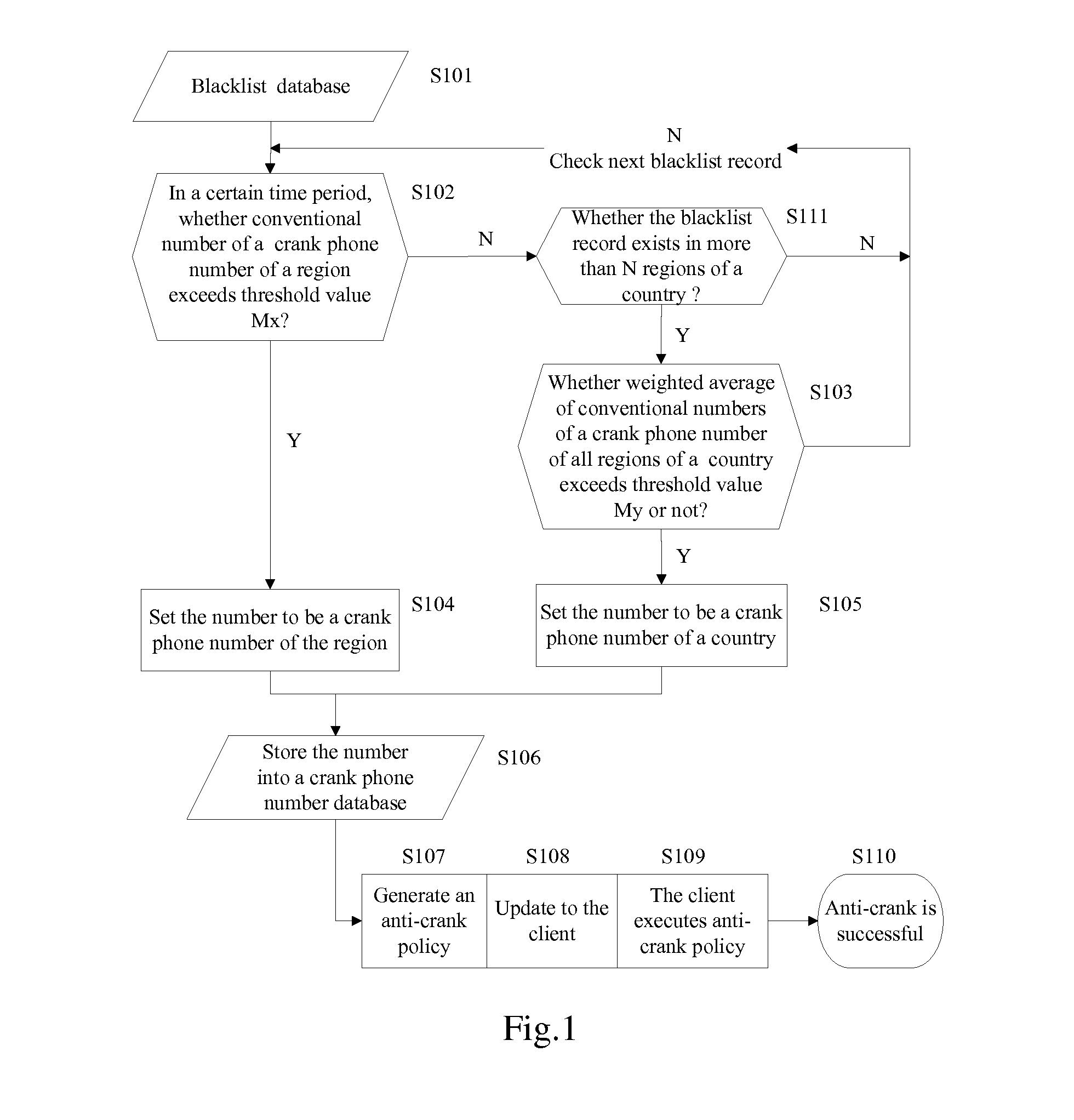
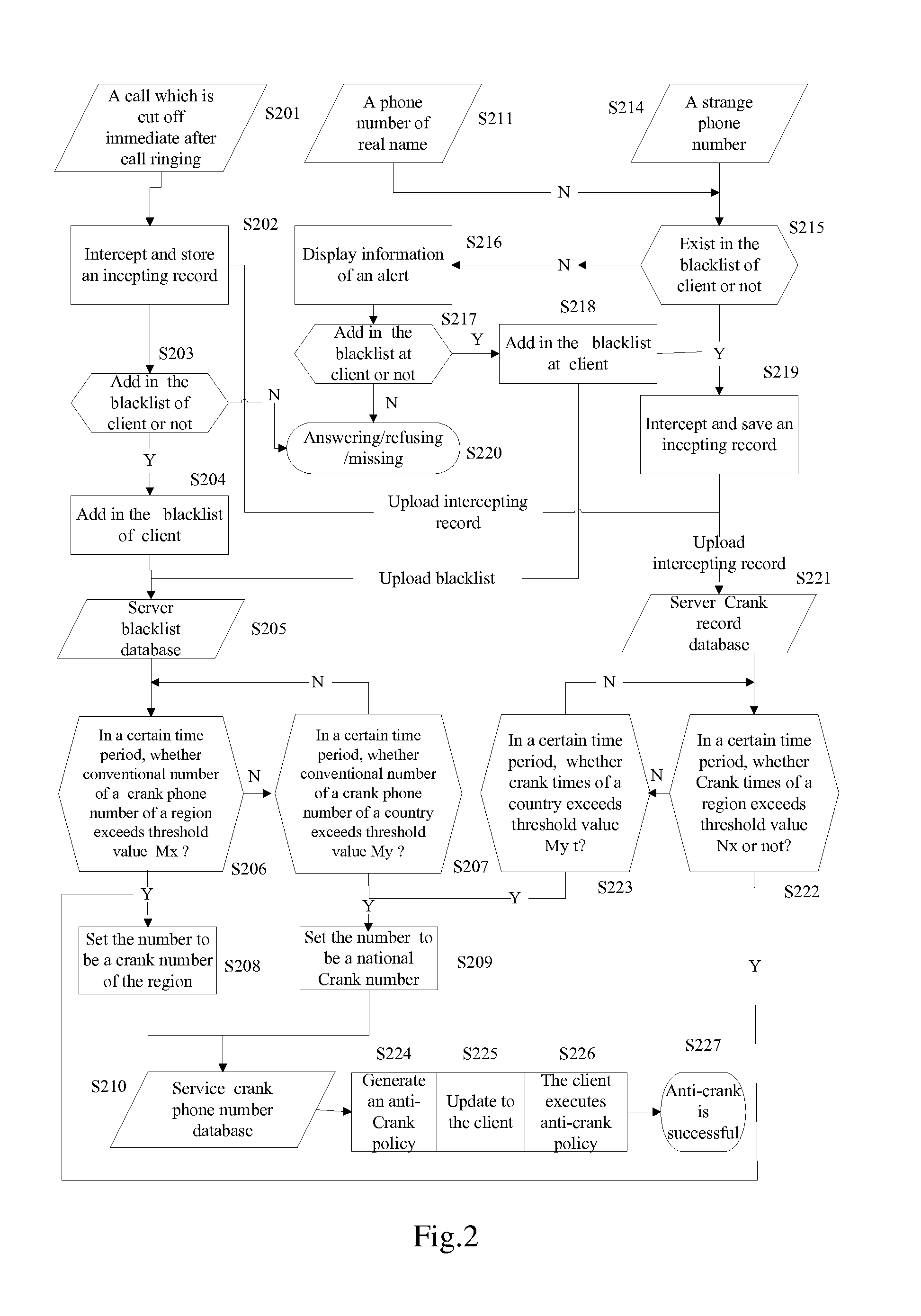
Method for blocking crank calls by using cloud computing and a system thereof
InactiveUS20120309365A1Increase quantityNot be correctSpecial service for subscribersCalling susbscriber number recording/indicationCloud computingEngineering
The present disclosure provides a method for blocking crank calls by using cloud computing and a system thereof. In the method, a client(s) uploads a blacklist to a server; the server makes statistic according to blacklist data uploaded by the client(s) and determines a particular phone number be a crank phone number, generates an anti-crank policy and updates the generated anti-crank policy to the client(s); when receiving a call or a message from the crank phone number, the client executes the anti-crank policy.
Owner:NETQIN MOBILE BEIJING
Methods and systems for data traffic based adaptive security
The present disclosure relates to traffic monitoring through one or more access control servers configured configured for (i) routing server resource request messages to resource server(s), (ii) extracting information identifying a target server resource from data packets corresponding to one or more received server resource request messages, and (iii) selectively transmitting the received server resource request message to a resource server. The security server(s) is configured to receive a server resource request message data extracted from a server resource request message and initiate a first security response, wherein the initiated first security response is dependent on analysis of the server resource request message data. Responsive to identifying an indicator of compromise or that an originating terminal corresponding to the server resource request is identified within a blacklist, the first security response comprises non-transmission of at least one server resource request message by the access control server to a resource server.
Owner:PING IDENTITY
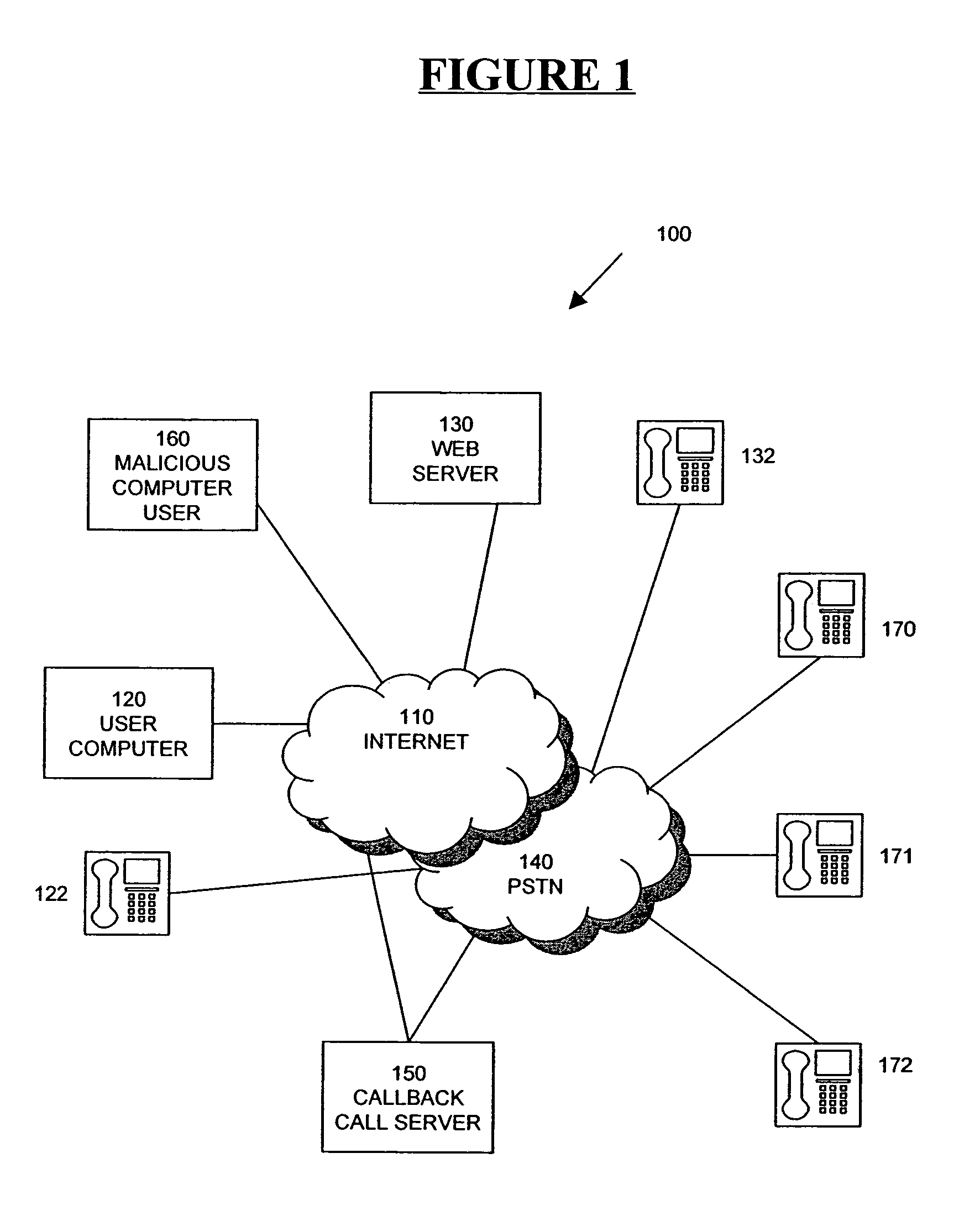
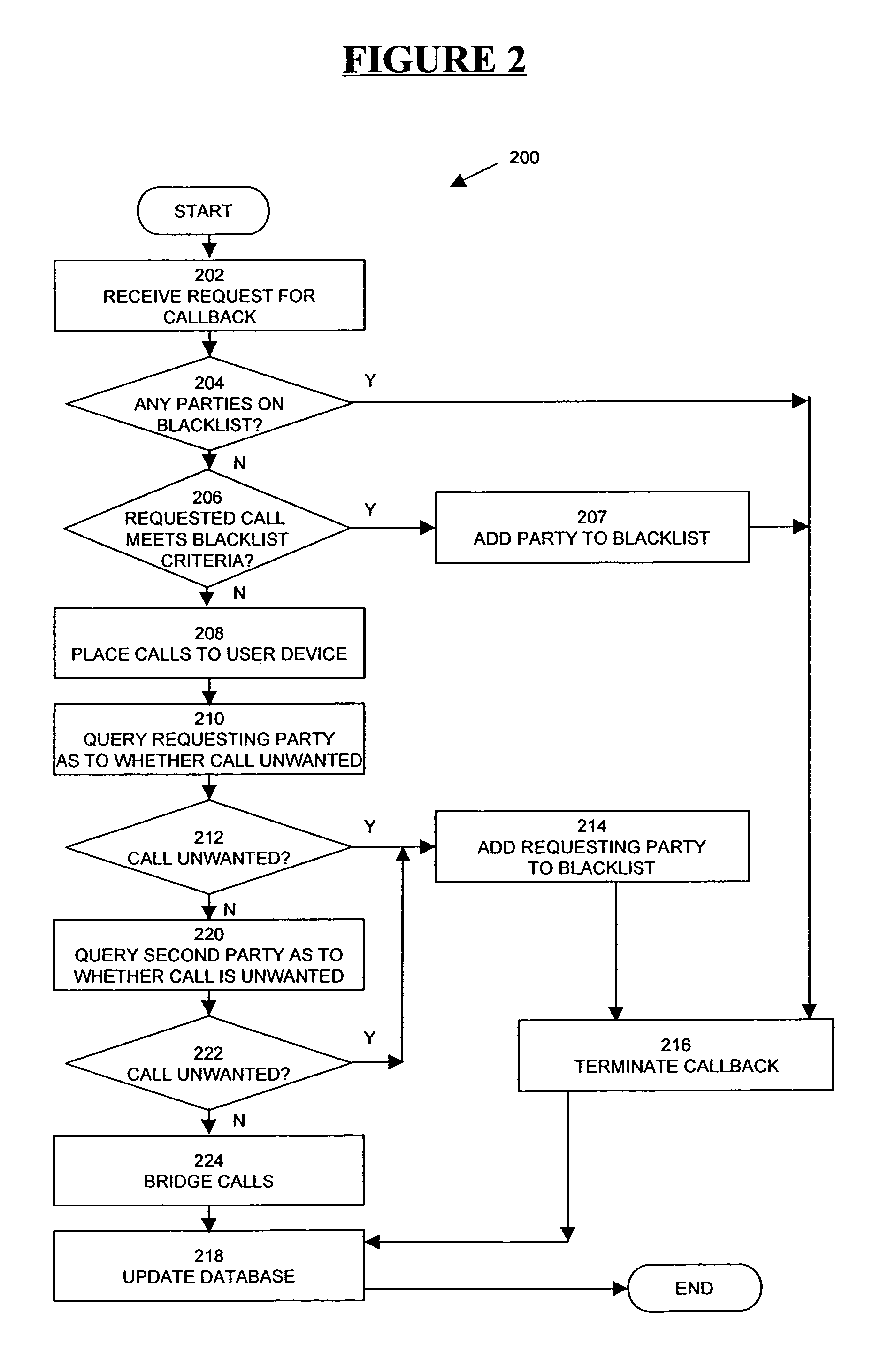
Method and apparatus for the prevention of unwanted calls in a callback system
ActiveUS7315518B1Prevent unwanted callsMultiplex system selection arrangementsSpecial service provision for substationTelecommunicationsUser device
In one method and apparatus for blocking unwanted calls in a callback system, parameters associated with a callback request (e.g., the user device to which the call is to be directed, the IP address from which the request originated or an identifier of the source computer from which the callback request originated, the party from whom the call is requested) are tracked for each call. A decision to automatically block the requested callback is made based on one or more criteria based on a combination of these parameters, which may be a total over a period of time. In a second method, one or both of the parties to the callback is queried as to whether the callback is unwanted and, if so, one or more parameters associated with the request are blacklisted.
Owner:ORACLE OTC SUBSIDIARY
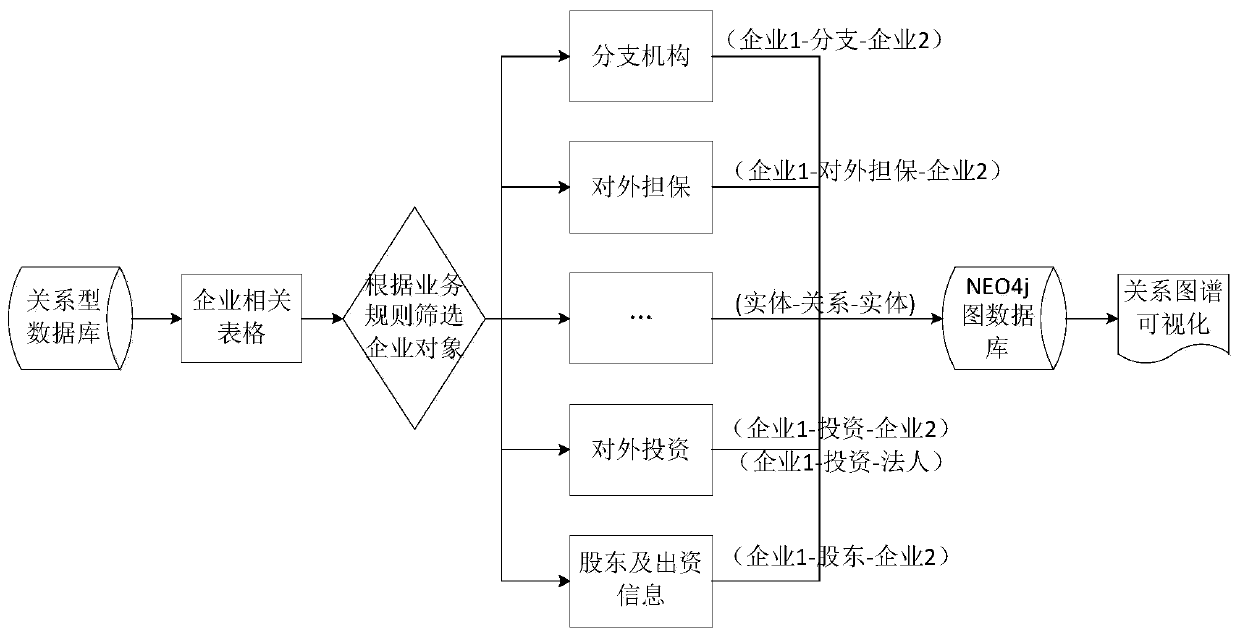
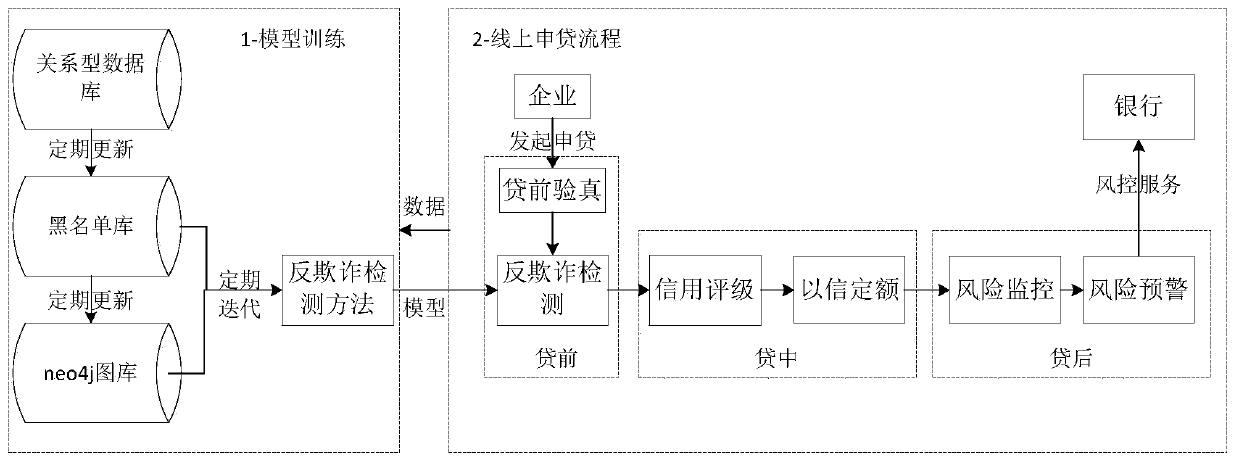
Label propagation anti-fraud detection method and system based on enterprise relation map
ActiveCN110223168AMany applicable scenariosStrong theoretical basisDatabase updatingFinanceComplex networkDatabase object
The invention discloses a label propagation anti-fraud detection method and system based on an enterprise relation map, belongs to the field of financial credit, and aims to solve the technical problem of how to effectively analyze complex network data to discover valuable information and further mine fraud risks embodied by complex network relations, and the method comprises the following steps of: s1, establishing an enterprise blacklist library; s2, constructing a relational graph: screening related tables and fields listed in the relational graph in a relational database, and extracting arelational database object entity and an entity relationship; and S3, performing anti-fraud detection on the enterprise based on the self-built blacklist library and the enterprise relationship graph:based on blacklist library identification relationship graph blacklist nodes, extracting blacklist node connection subgraphs, identifying fraud enterprise nodes in the connection subgraphs by applying a label propagation algorithm, and estimating the enterprise anti-fraud probability. The system comprises an enterprise blacklist library establishment unit, a relation graph construction unit and an anti-fraud detection unit.
Owner:浪潮卓数大数据产业发展有限公司
Method and system for grading detection and prompt of fishing website
InactiveCN102769632AGuarantee the safety of useTransmissionSpecial data processing applicationsWhitelistPhishing
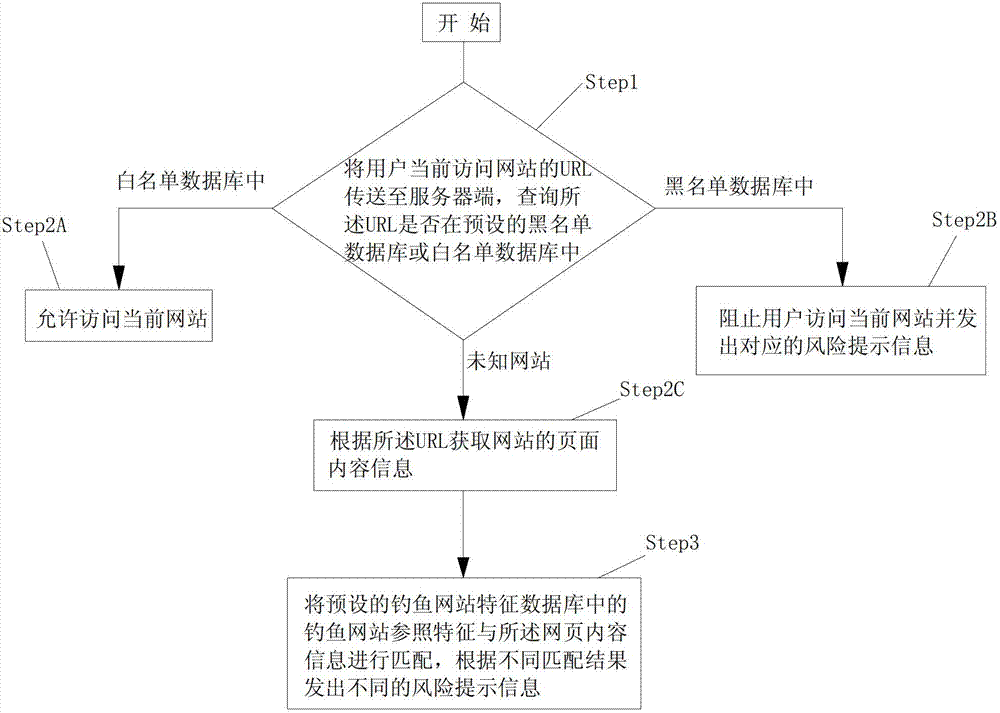
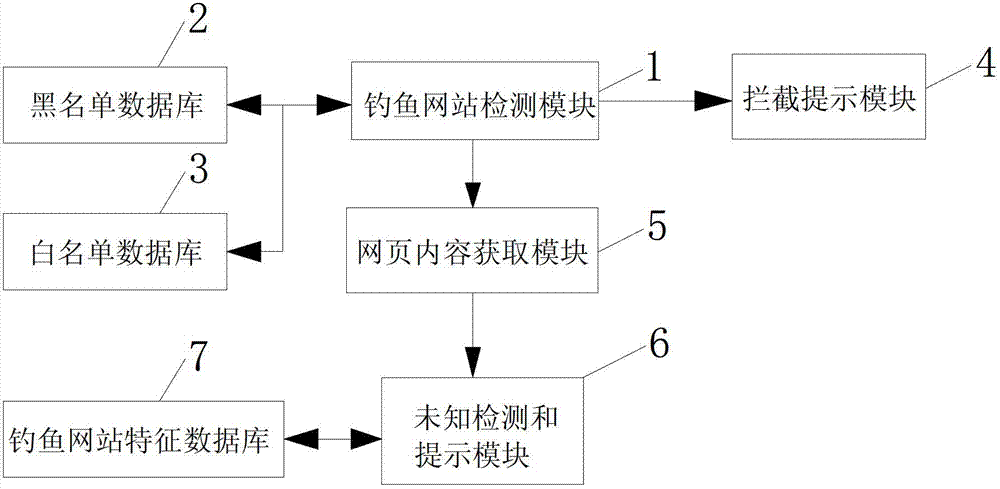
The invention belongs to the technical field of computer defense and particularly discloses a method and a system for grading detection and prompt of a fishing website. The method includes transmitting uniform resource locator (URL) of a user current visit website to a server end, searching whether the URL is in the preset blacklist database or a white list database, allowing users to visit the current website if the URL in the white list database, preventing the users from visiting the current website and transmitting corresponding risk prompt information if the URL is in the blacklist database, obtaining page content information according to the URL if the URL is not in the blacklist database or the white list database, matching phishing website reference characteristics in a preset phishing website characteristic database with webpage content information and transmitting different risk prompt information according to different matching results. Risk prompt with different grades can be given according to characteristics of different websites, so that using safety of users can be further guaranteed.
Owner:ZHUHAI JUNTIAN ELECTRONICS TECH +3
Vehicle remote assistance mode
ActiveUS20180004214A1Instruments for road network navigationNavigational calculation instrumentsEngineeringAuxiliary system
Systems and method are provided for controlling a vehicle. In one embodiment, a method includes calculating, via a router of a vehicle system that accesses road map data, at least one route to a destination based on the road map data, thereby producing route solution data. The vehicle system enters a remote assistance mode in response to remote assistance decision data received from a blockage arbiter of the vehicle system. In the remote assistance mode, the method includes determining, via the router, at least one road segment of the road map data that is permitted to be blacklisted, thereby producing permitted blacklist data. The method includes transmitting the permitted blacklist data and the route solution data, via a vehicle communications module of the vehicle system, to a remote vehicle assistance system. The method includes updating, via the router, the road map data to exclude at least one blacklisted road segment defined by the permitted blacklist data.
Owner:GM GLOBAL TECH OPERATIONS LLC
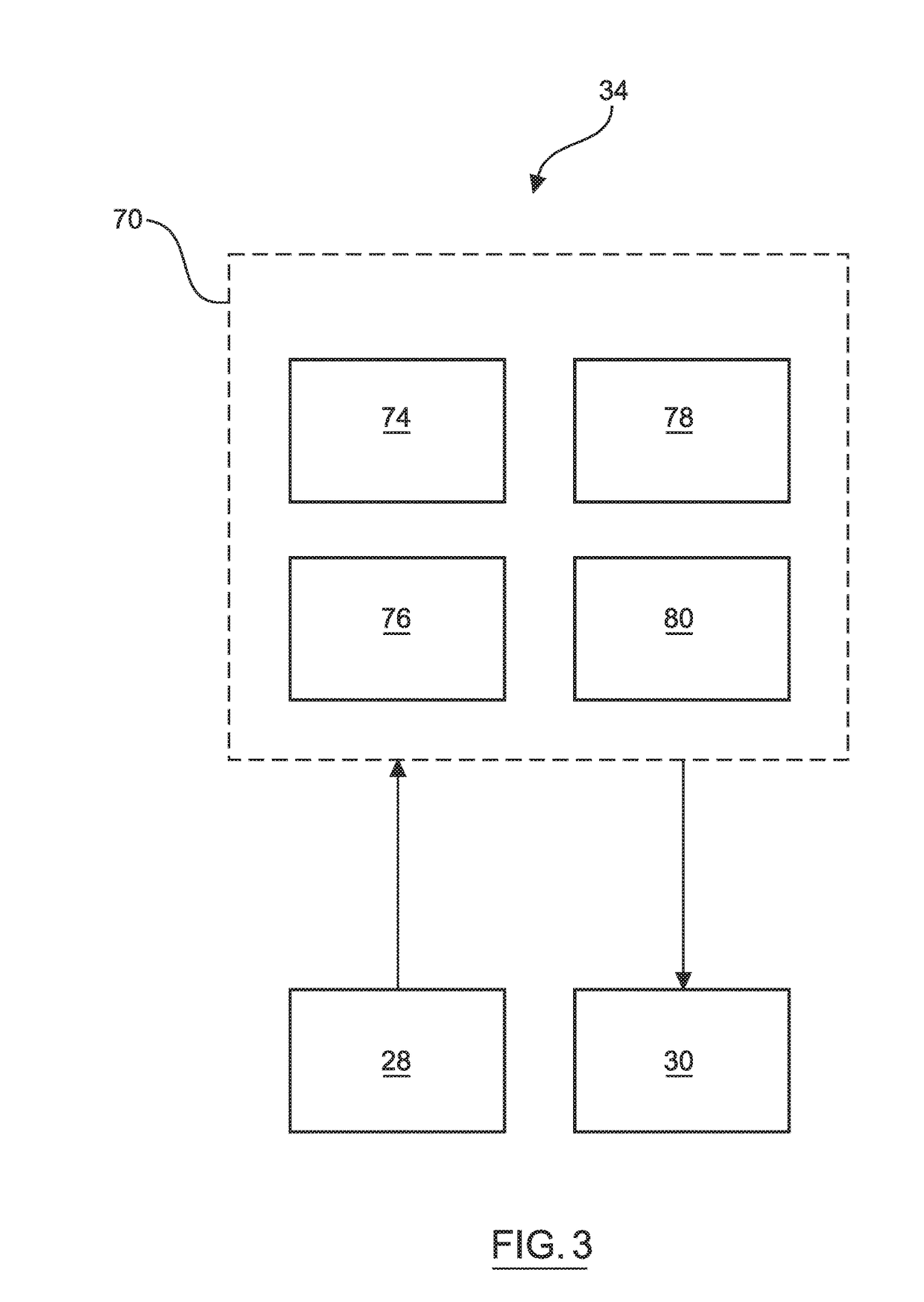
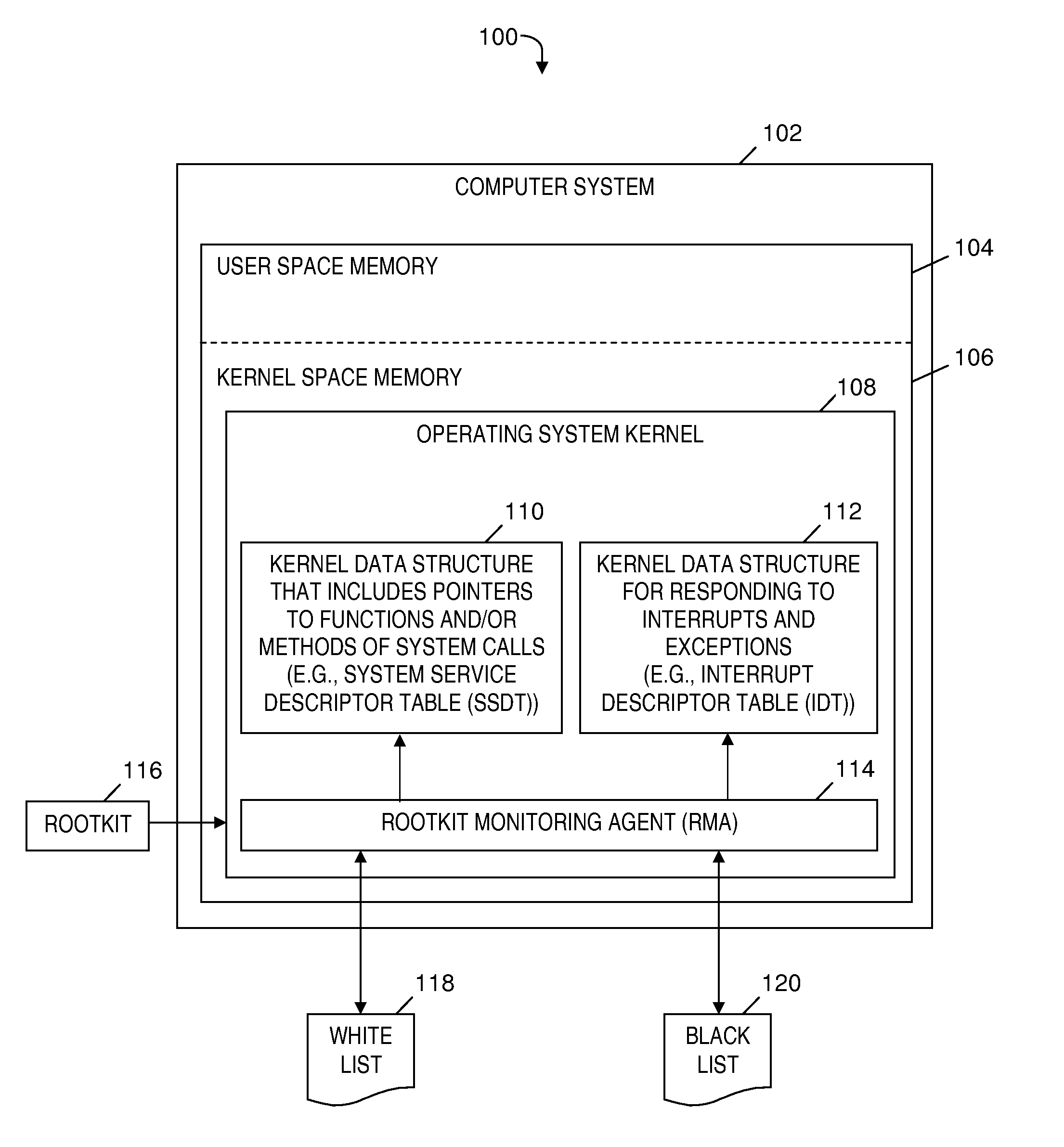
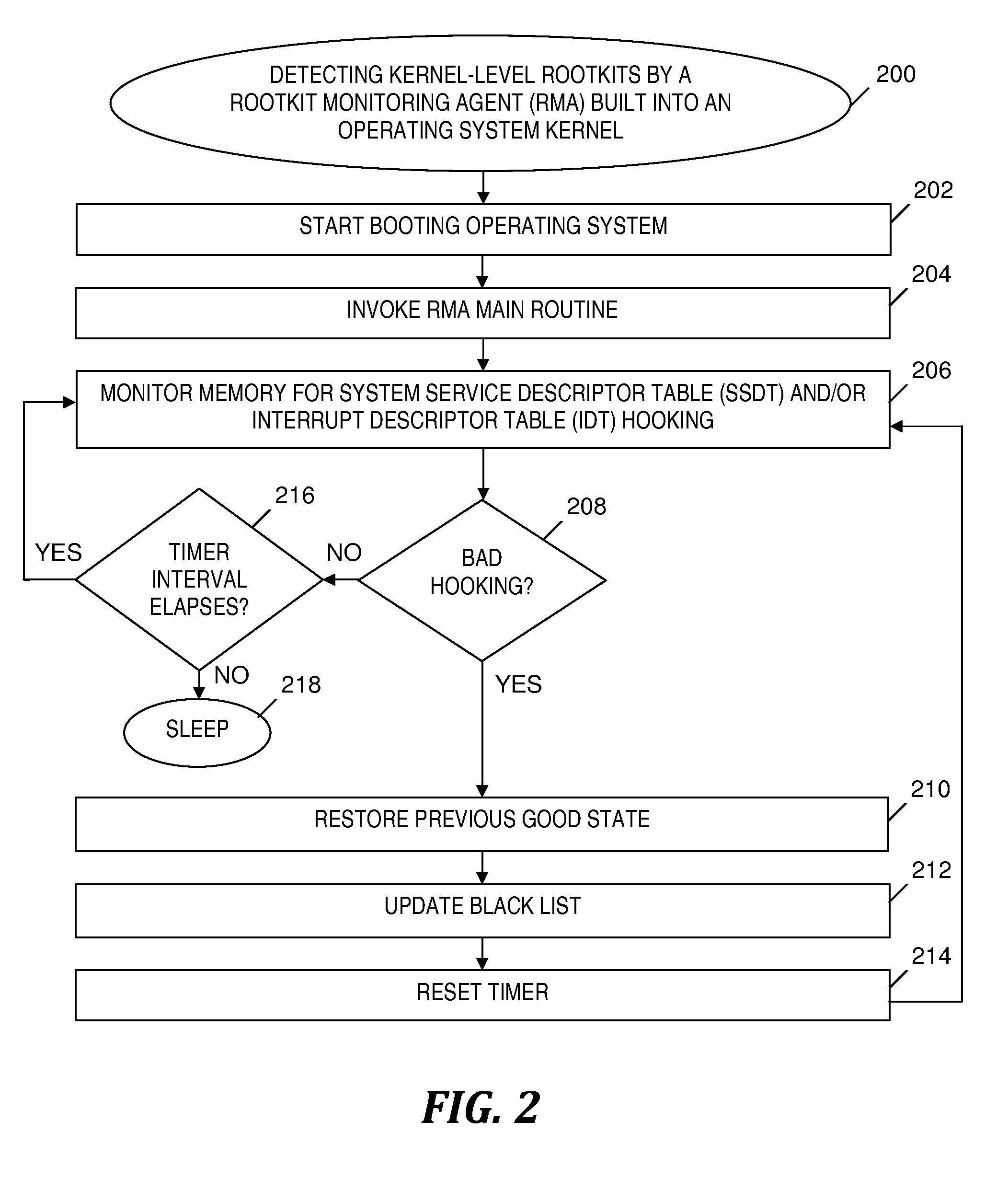
Rootkit monitoring agent built into an operating system kernel
InactiveUS20120054868A1Avoid negative effectsMemory loss protectionUnauthorized memory use protectionWhitelistRootkit
A rootkit monitoring agent (RMA) built into an operating system (OS) kernel for detecting a kernel-based rootkit and preventing subsequent effects of the rootkit. The RMA is activated as a kernel process subsequent to the OS initialization and stores a good state of OS kernel data structures including the System Service Descriptor Table (SSDT) and Interrupt Descriptor Table (IDT). The RMA monitors the SSDT and IDT and detects that a hook previously stored in the good state is changed by an installation of suspect software. The RMA determines the suspect software is a kernel-based rootkit by determining a whitelist does not indicate the changed hook. The RMA restores the changed hook to its good state. The RMA updates a blacklist to reference the changed hook.
Owner:IBM CORP
A method for defending against denial of service attacks based on cloud computing platform
ActiveCN102291390ATroubleshoot Denial of Service AttacksDenial of service attack defenseTransmissionAttackInternet privacy
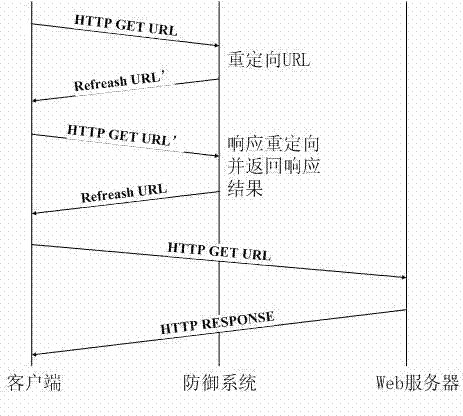
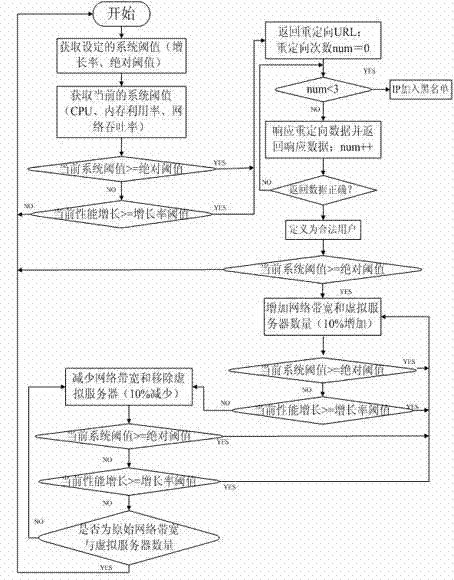
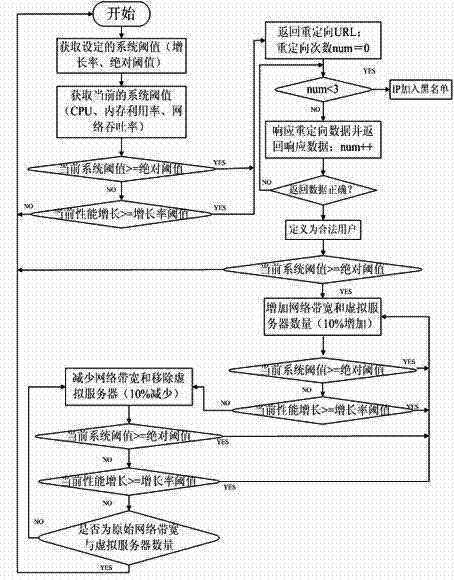
The invention relates to a method for defending against a denial of service attack based on a cloud computation platform, which solves the problem of the HTTP (HyperText Transfer Protocol) denial of service attack on a concrete application. A CPU (Central Processing Unit), a network throughput rate and the like are analyzed to determine whether the denial of service attack exists, and after the existence of an attack behavior is determined, access data is first intercepted; access users are subjected to redirected accesses, and identifying code technology with 4-digit random numbers / letters plus mathematical problems with fixed answers is adopted at Cookie; meanwhile, the number of the redirected accesses is defined to discriminate a legal user from an attacker, and therefore, the IP of the attacker is added to a blacklist, and is banned from accessing so as to filter the attacker; as for the attacks which are disguised as the legal user and continue to attack a server, the inherent elastic performance of the cloud computation platform is utilized to dynamically increase a network bandwidth and the number of virtual servers; and after a system is stabilized, an original system state is recovered, the bandwidth is recovered, and the virtual servers are removed so as to effectively defending against the denial of service attack.
Owner:NANJING UNIV OF POSTS & TELECOMM
Online Privacy Management
ActiveUS20120284801A1Simple processDigital data processing detailsAnalogue secracy/subscription systemsData streamClient-side scripting
Owner:CHEQ AI TECH (2018) LTD
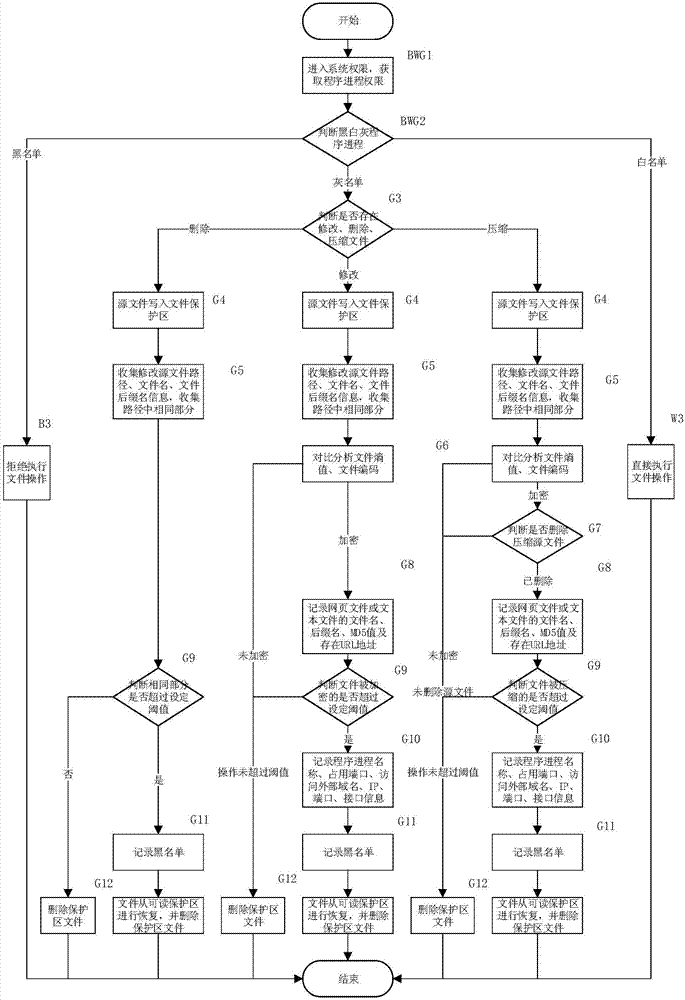
Method and system of preventing files from being damaged by malicious operation behaviors
InactiveCN107506642AReduce risk frequencyEffective identification of malicious operationsDigital data protectionPlatform integrity maintainanceBlack listEncryption
The invention discloses a method and a system of preventing files from being damaged by malicious operation behaviors. if a process of deleting the file exists, the process is released if the process is a white-list process, is directly blocked if the process is a black-list file reading or writing operation process, and is suspended if the process is a gray-list process, and released after backing up the file to a readable protected area is completed; if a process of modifying the file exists, the process is released if the process is a white-list process, is directly blocked if the process is a black-list process, and is suspended if the process is a gray-list process, and released after backing up the file to the readable protected area is completed; and if an encryption / compression encryption operation exists, whether operation frequency of a process for the file in a preset time exceeds a set threshold value is judged, and if yes, it is determined that the operation is a suspected malicious file operation behavior. According to the technical solution of the invention, the malicious file operation behaviors can be effectively identified, and risk frequency of maliciously deleting and modifying important files can be reduced at the same time.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
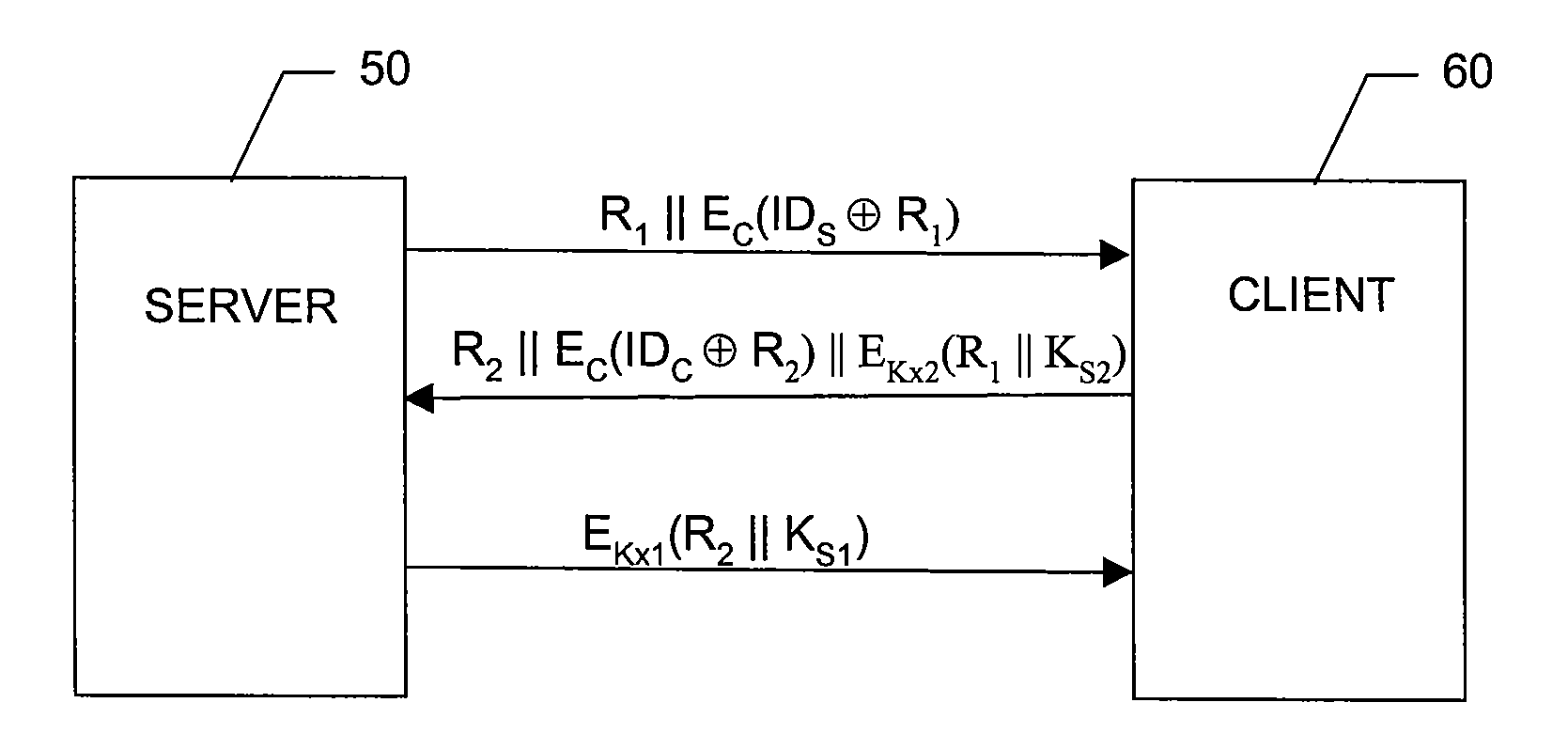
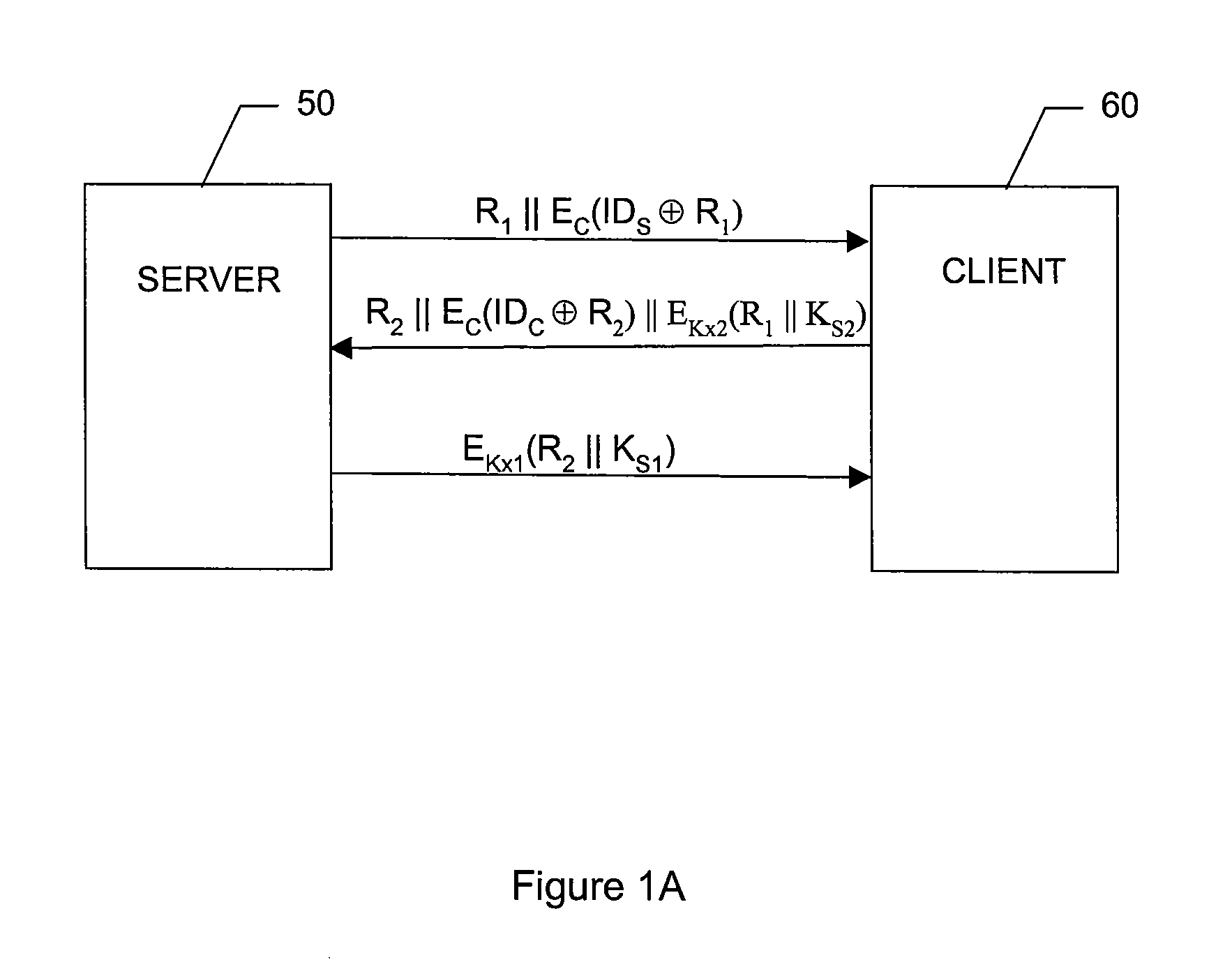
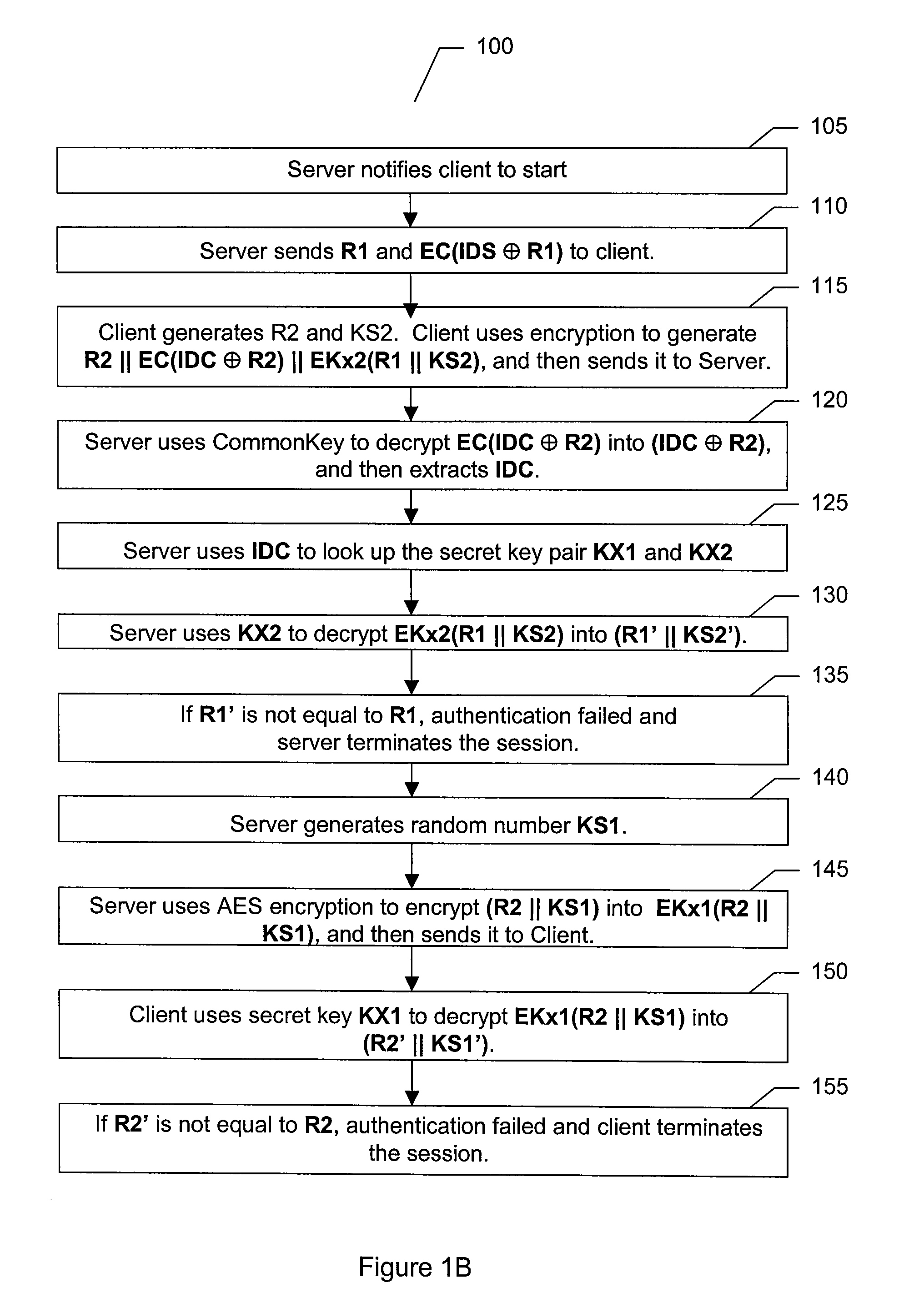
Content protection system
InactiveUS20080046731A1Secure deliveryCommunication is interceptedUser identity/authority verificationTelevision systemsClient-sideComputer security
A content protection system for securely delivering audio / video data from a content server to a content client through an unsecured channel is disclosed. For each session, the content protection system comprises two phases. The first phase is client-server mutual authentication and session key establishment. In this phase, the content server and the content client verify each other's legitimacy, and at the same time exchange information so that both server and client can calculate or derive the same session key. In the second phase, audio / video data is encrypted with the session key in the content server, and then decrypted with the session key in the content client. If a version of server or client is found to be compromised, its ID will be put into a blacklist.
Owner:COREL CORP
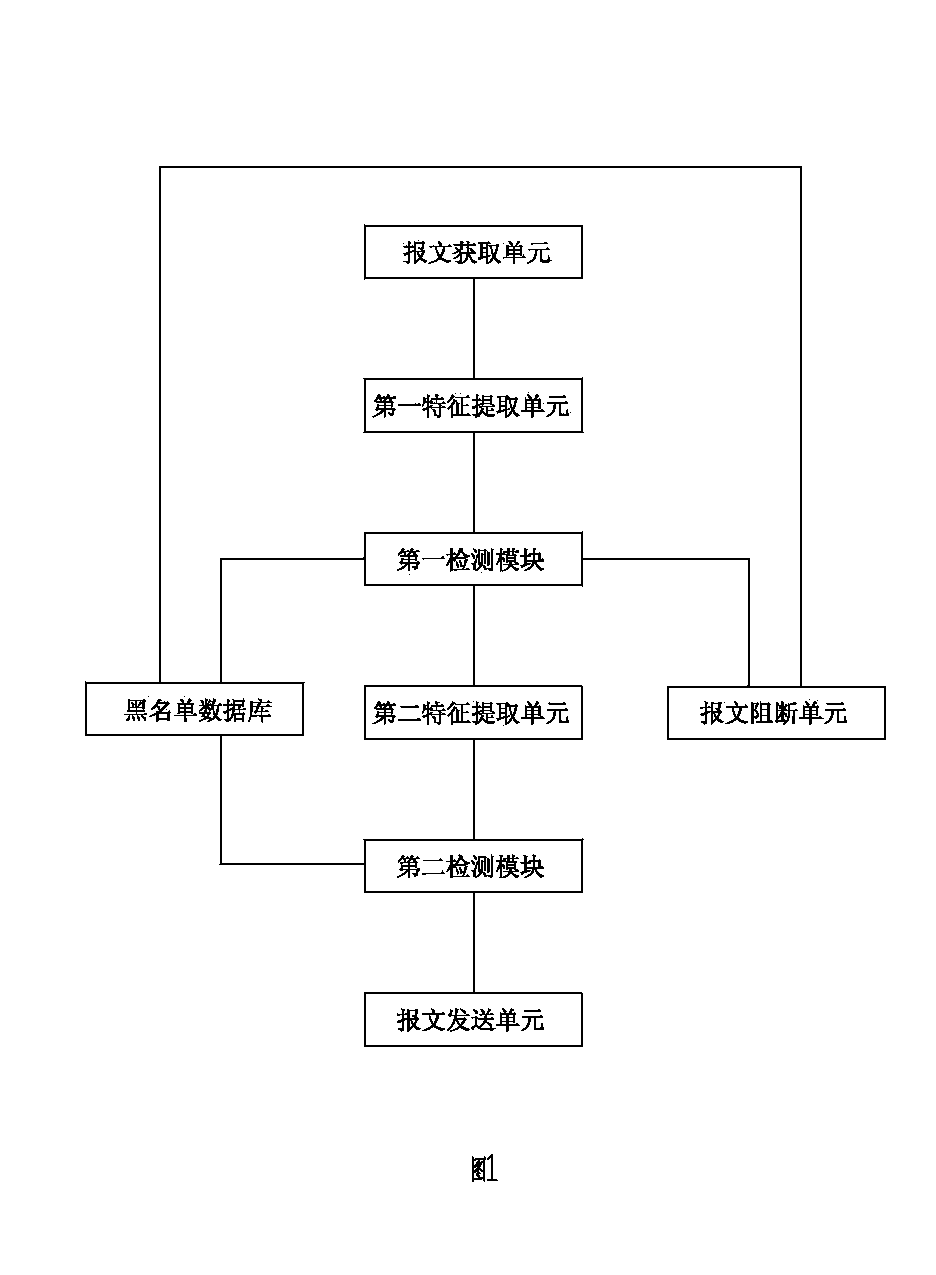
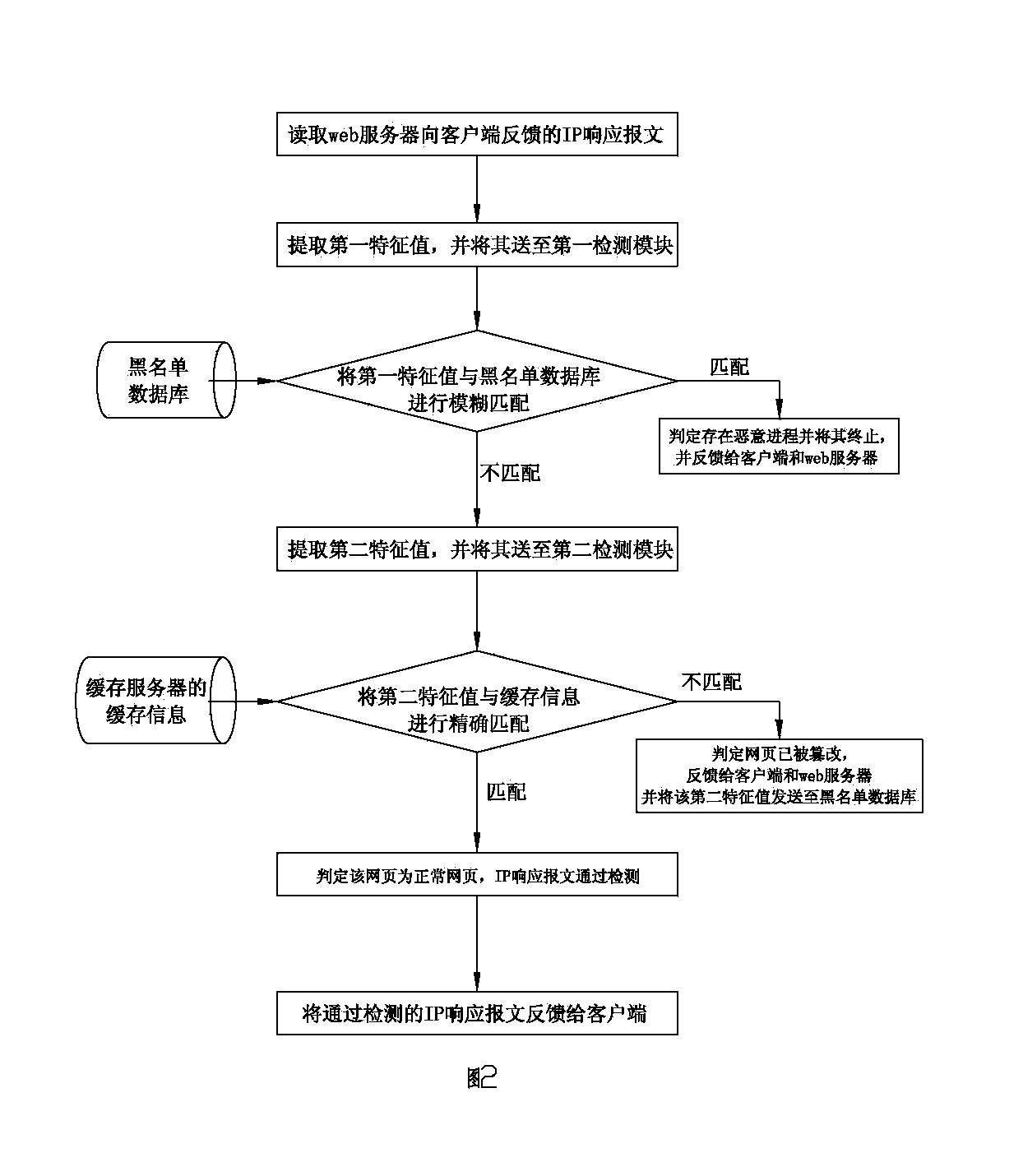
Web page tamper prevention device based on web server cache matching and method thereof
ActiveCN103929440AOvercoming Tamper Detection InefficienciesImprove securityTransmissionWeb siteEngineering
The invention relates to the technical field of electric power industry information web page tamper prevention, in particular to a web page tamper prevention device based on web server cache matching and a method of the device. According to the web page tamper prevention device based on web server cache matching, a feature value of a suspected Trojan program in an IP response message is extracted, whether the feature value is matched with a black list database or not is judged through fuzzy matching, then the feature values of all information of an accessed web page are extracted to be precisely matched with web server cache data, and whether a web page accessed by a client side is tampered or not is judged. Fuzzy matching processing is carried out through a first detection module, the Trojan program and other malicious programs in the web page are detected, precise matching processing is carried out through a second detection module, the feature values of all the information of the accessed web page are compared with the web server cache data, the problem that existing web page tamper detection efficiency is low is solved, the web page can be effectively prevented from being tampered by a blacker, and website safety is greatly improved.
Owner:STATE GRID CORP OF CHINA +1
A system for filtering spam in Internet and its implementation method
InactiveCN101087259AImprove intelligenceEfficient Learning EvolutionOffice automationData switching networksHuman useOperational system
The invention relates to a system and method to filter the wasted mails on internet. At present there is a lot of wasted mails, human use keywords to filter it, build black name list, and set regulation to prevent, but the result is unobvious, hard to maintain, high requirement for professional skill. The invention consists of hardware, software which is installed on hardware and supported network, the software includes Linux operating system, analyzing engine for wasted mails, extended black name list, internet library and management interface. The periphery supporting network includes complain device for wasted mails, analyzing system for wasted mails, which can work as transparent gateway before LAN or mail sever, take over MX interface to work before mail sever. The method includes the hardware connection, telnet management, management of wasted mails and anti-waste setting, and the operation is convenient, easy to maintain, high identifying rate, high stability, low misjudgment rate, and plug and play.
Owner:SHENZHEN DUHU NETWORK TECH
Multi-stage phishing website detection method and detection system based on supervised learning
ActiveCN109510815AReduce testing costsAccurate identificationCharacter and pattern recognitionTransmissionSupervised learningUniform resource locator
The invention relates to a multi-stage phishing website detection method and detection system based on supervised learning. A first detection layer performs phishing website judgment based on a blacklist database or a white list database, the to-be-detected website is directly output if the website is matched with the blacklist database or the white list database; or a second detection layer extracts features of the to-be-detected website URL and constructs a classifier model to perform detection according to the URL features of the known phishing website; if the website is detected as a suspicious website, a third detection layer downloads the page of the to-be-detected website to acquire the page content features, and the classifier model is constructed according to the known phishing website content features so as to perform the detection; an output end outputs the result that to-be-detected website is the phishing website or the normal website, and adds the data to the blacklist database and the white list database. The primary black-white list judges the known website and reduces the detection cost; the secondary URL detects and distinguish the clear phishing website or the normal website; and the third-stage page content detection identifies the suspicious website of the secondary detection, the judgment result is precise; an identification result is accurate, and the detection time is short.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD +1
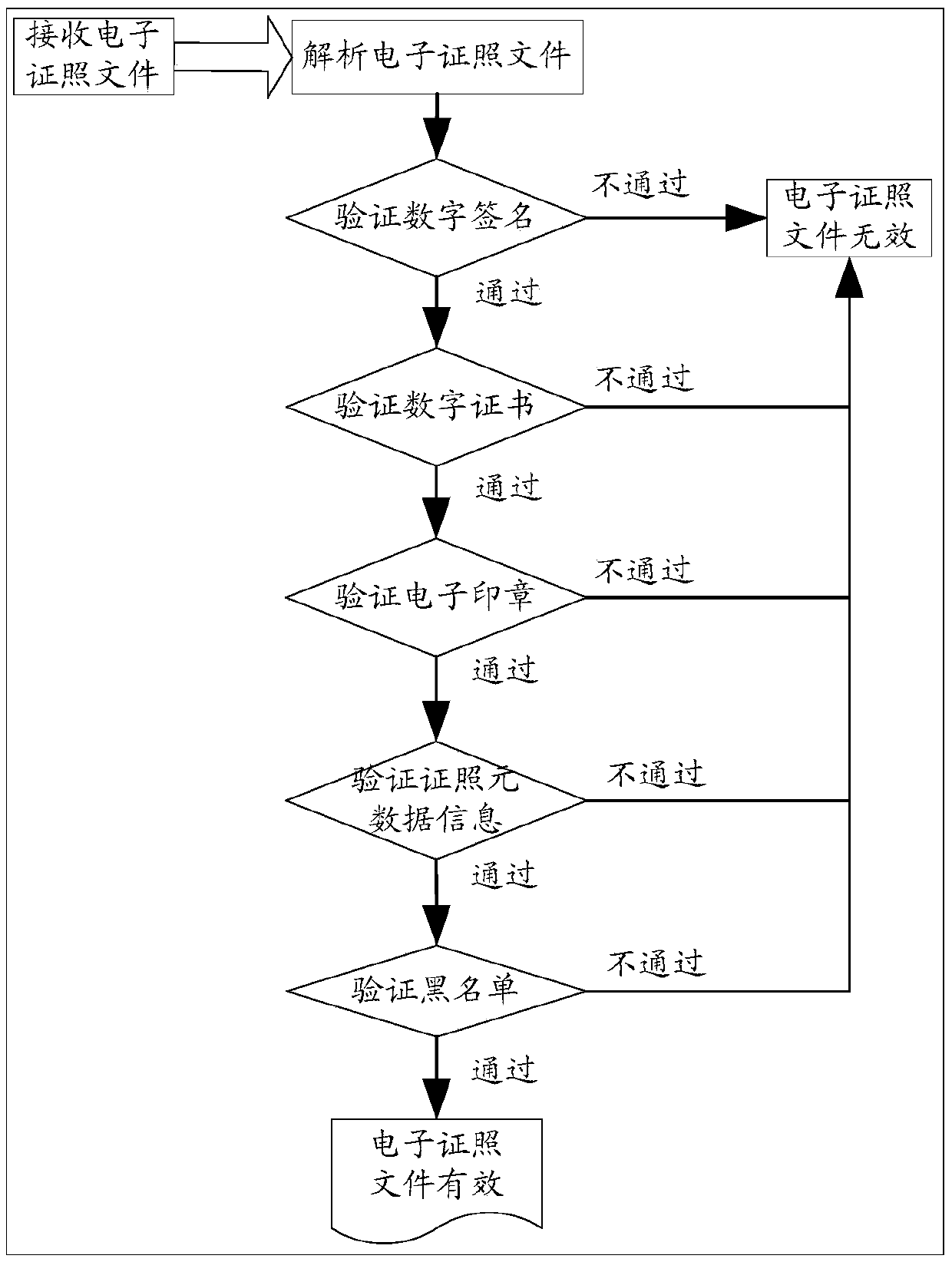
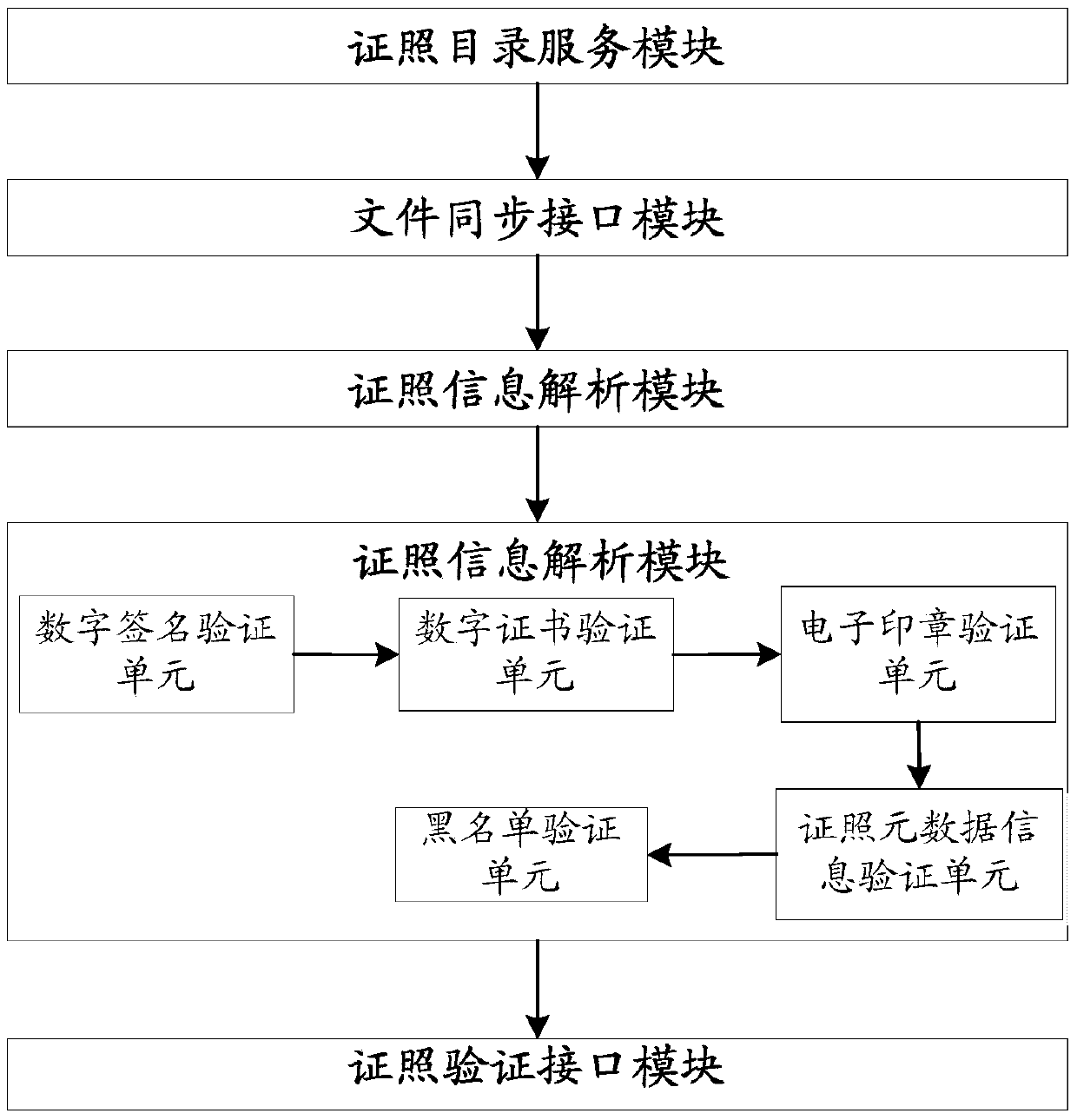
E-government internal network electronic certificate authentication method and system
InactiveCN105512570AIn line with the construction conceptDigital data protectionData informationDigital signature
The invention provides an e-government internal network electronic certificate authentication method. 1, Electronic certificate data is generated in dependence on an electronic certificate, and is stored to an electronic certificate database; 2, the identity of one side requesting to be verified is authenticated, after the authentication is passed, the electronic certificate file is submitted to an authentication server side; 3, the obtained electronic certificate file is loaded, after invalid files are filtered, the filtered electronic certificate file is resolved, a digital signature, a digital certificate, an electronic seal, certificate meta-data information and a blacklist are obtained after the resolving process, and are synchronized with the electronic certificate database; 4, the digital signature, the digital certificate, the electronic seal, the certificate meta-data information and the blacklist are verified; 5, the verification result is obtained and is returned to the side requesting to be verified. The invention provides an e-government internal network electronic certificate authentication system. The e-government internal network electronic certificate authentication method and system provide an authentication mechanism for cooperative application of electronic certificates among government departments.
Owner:LINEWELL SOFTWARE
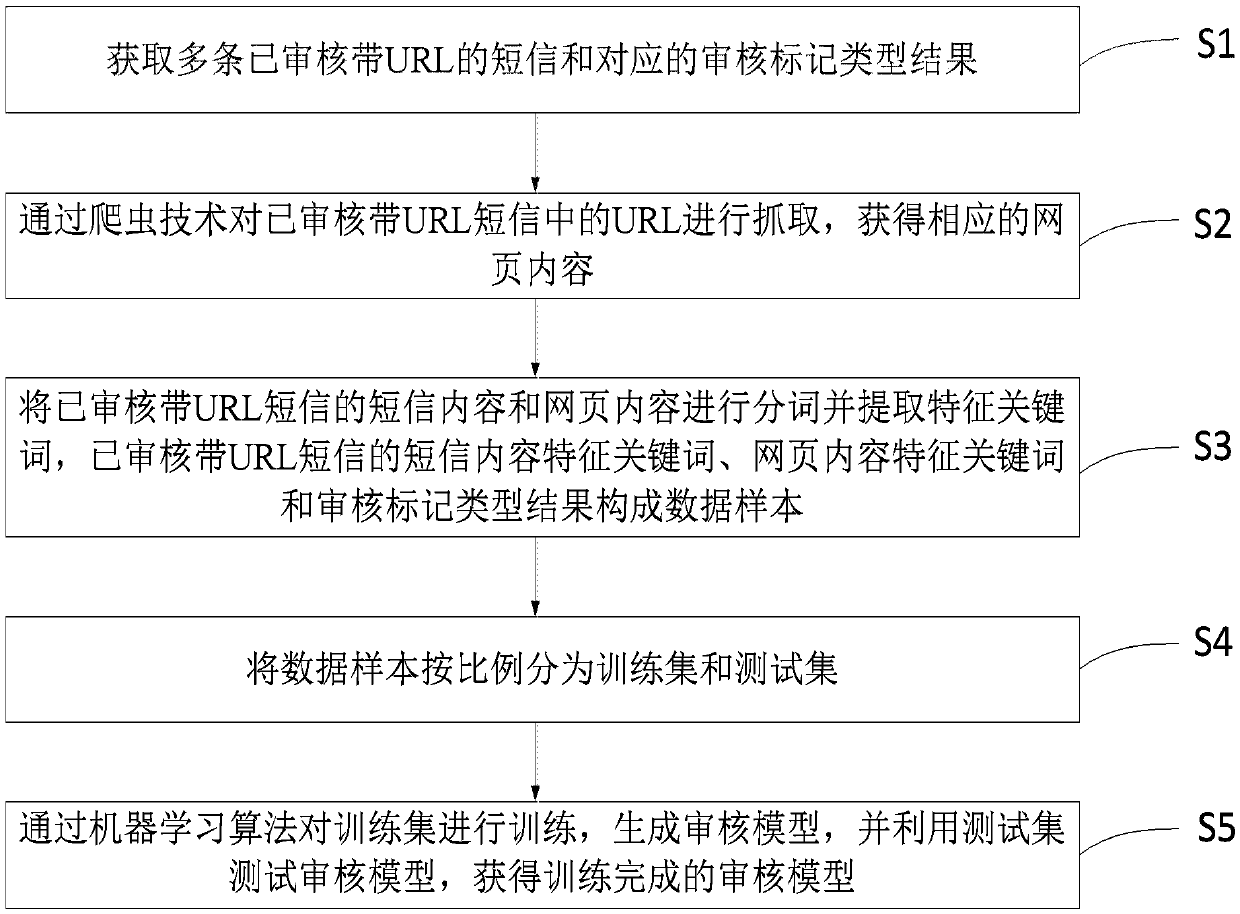
Short message auditing system and method, and method for constructing short message auditing model
ActiveCN107612893AImprove accuracyFine-grained audit interceptionMessaging/mailboxes/announcementsTransmissionPersonalizationEngineering
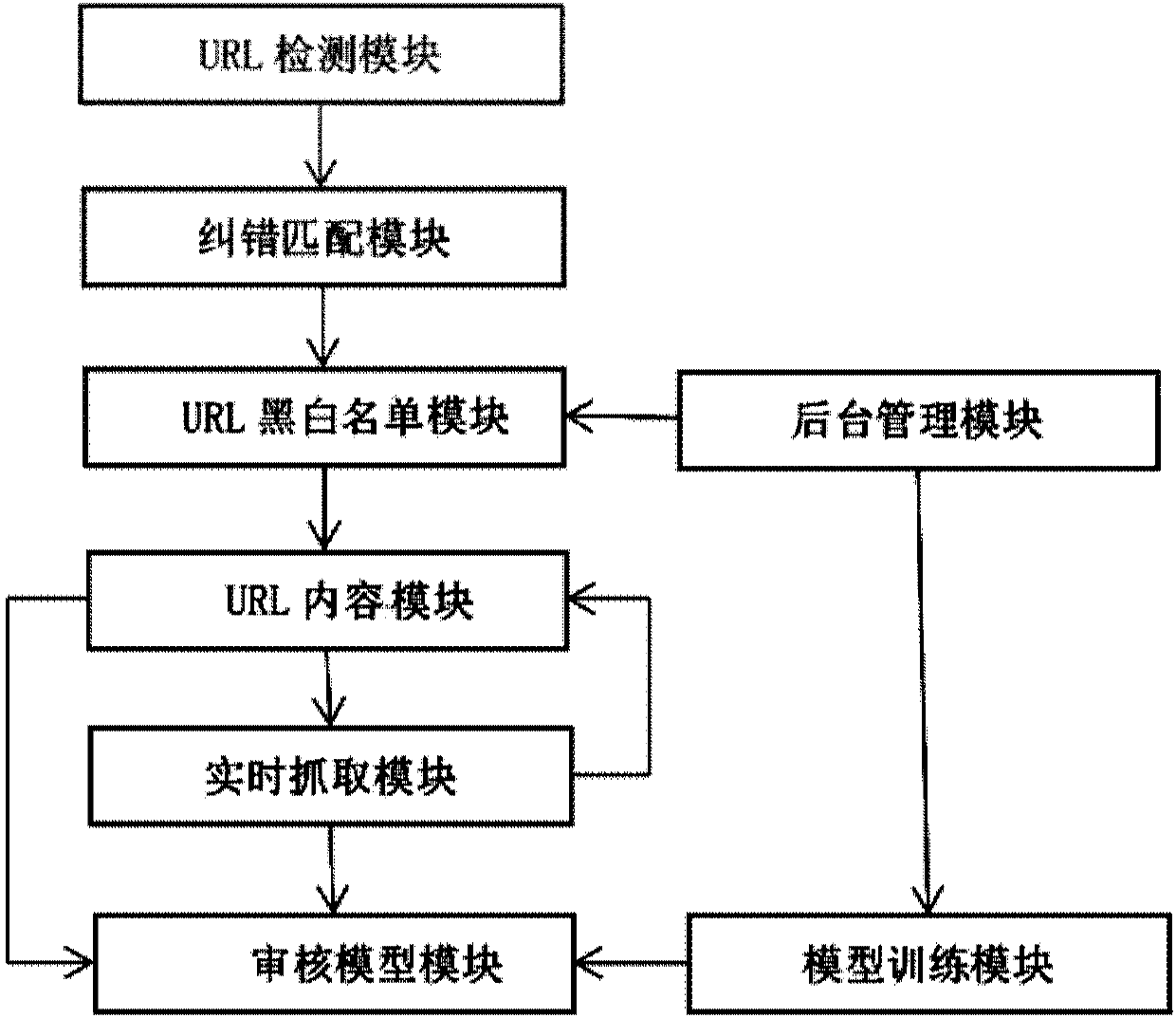
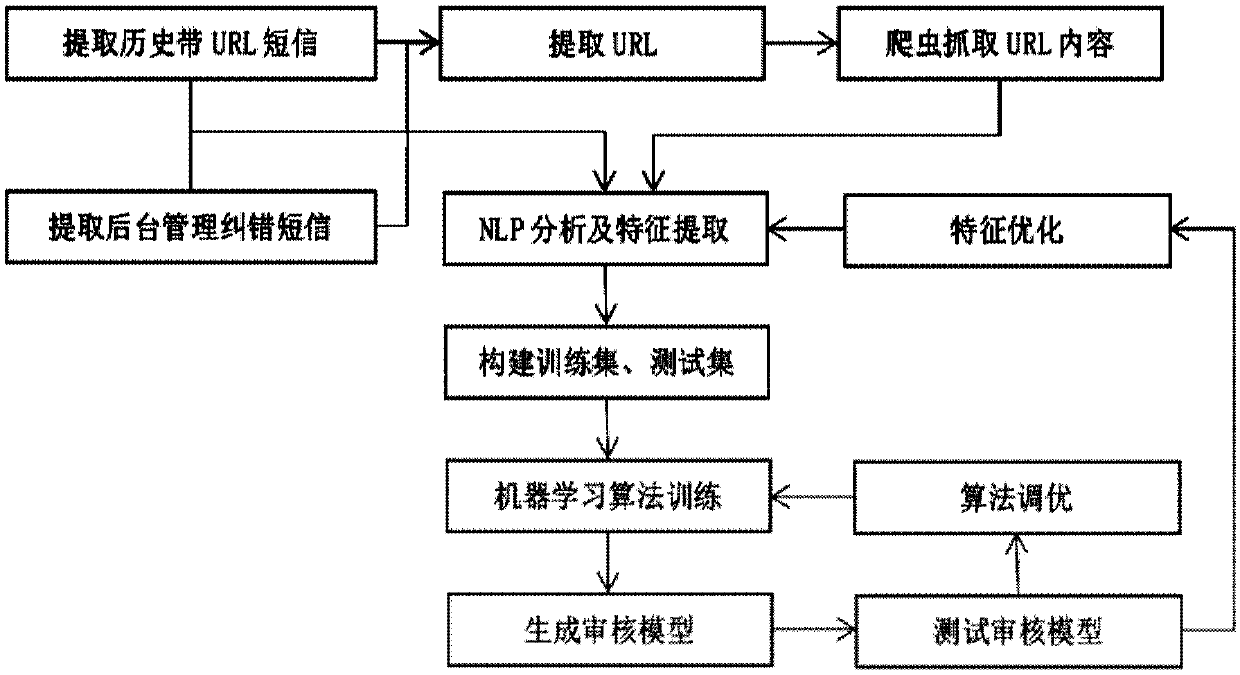
The invention provides a short message auditing system and method, and a method for constructing a short message auditing model. The auditing system includes a URL detection module, an error correction matching module, a URL blacklist and white list module, a URL content module, a real-time capture module, an auditing model, a model training module and a background management module. The auditingmethod comprises the following steps: capturing the URL in a short message by using the crawler technology in real time, modeling by combining the contents of the short message with webpage contents,and classifying the properties of to-be-audited short message contents via a machine learning algorithm, and finally determining to release or intercept the short message. Compared with the traditional auditing method according to the short message contents and the URL, the auditing method has the advantages of greatly improving the accuracy, shortening the URL by short URL service during the auditing, an performing personalized auditing according to different URL after skipping instead of single manner just like that in the traditional manner.
Owner:BEIJING BAIWU TECH CO LTD
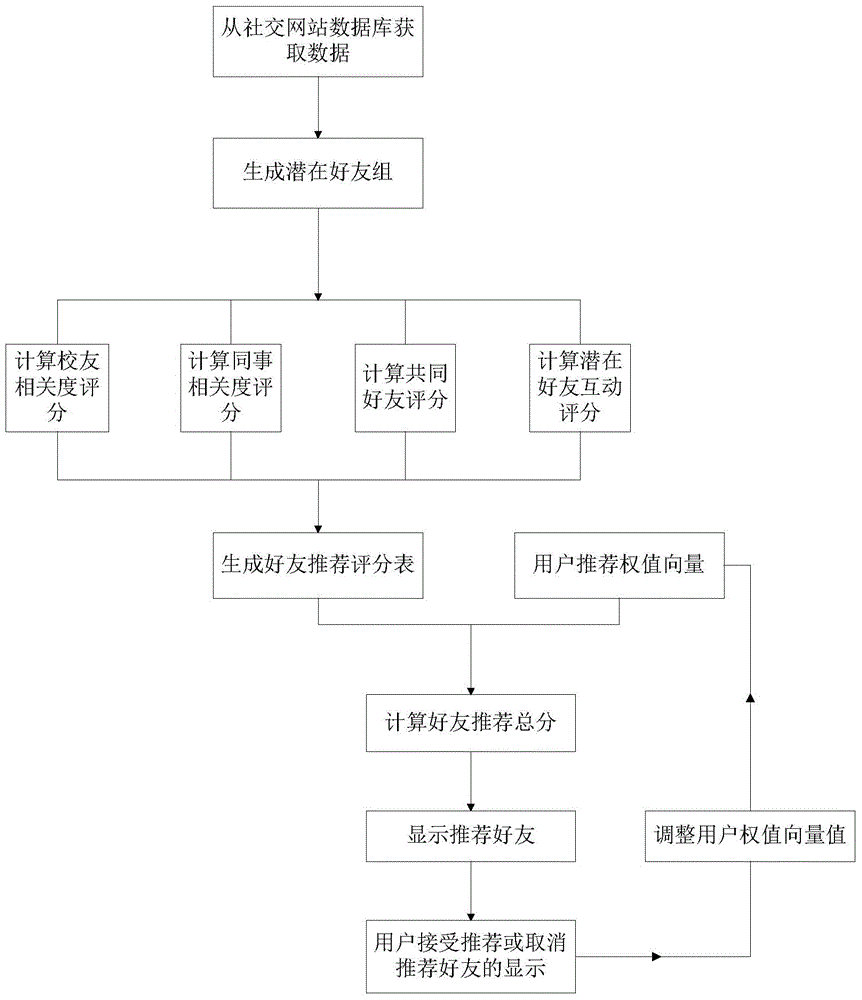
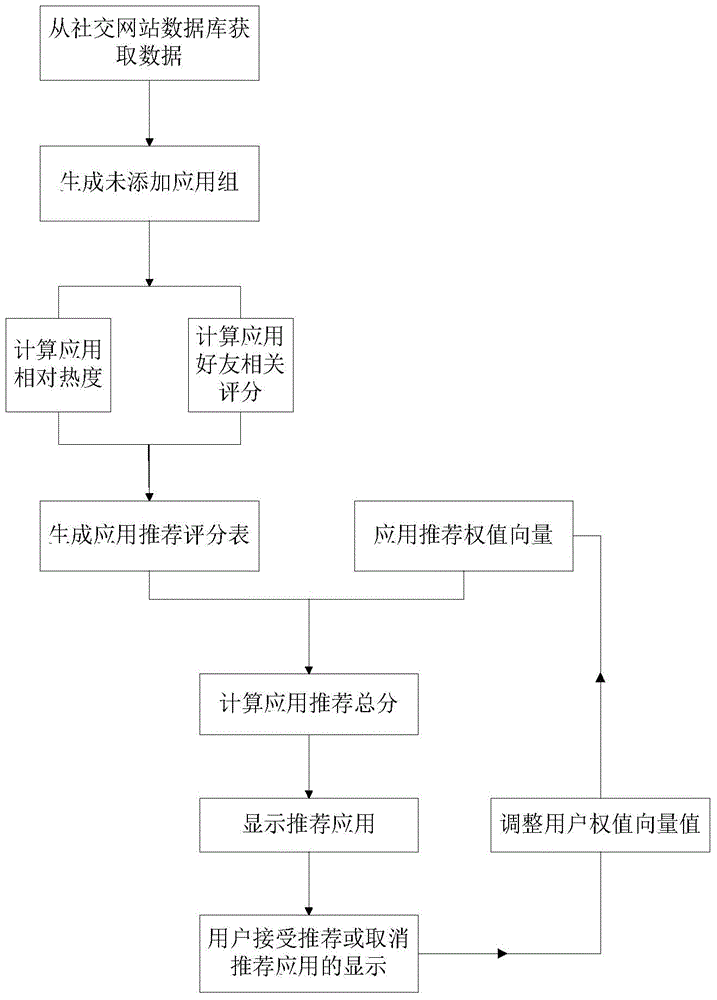
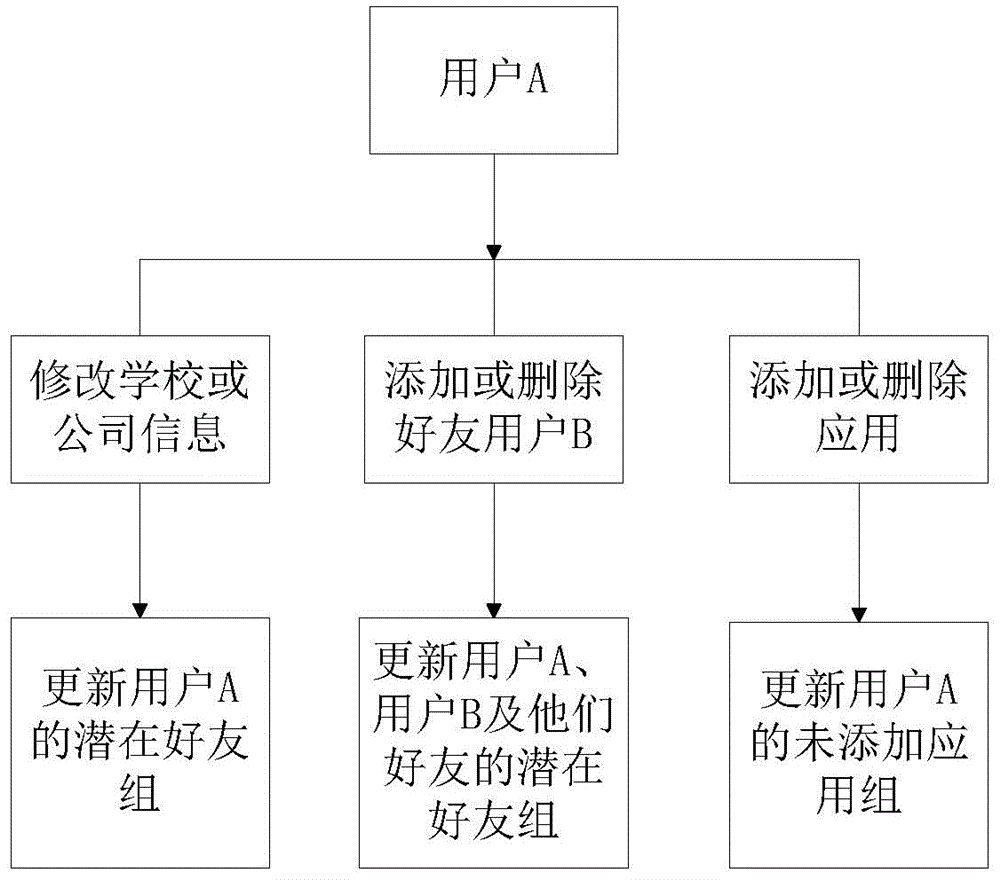
Personalized recommendation method and system for friends and applications
ActiveCN104156392APrecise filtering and recommendation effectAvoid the influence of recommendation effectSpecial data processing applicationsPersonalizationIdle time
The invention provides a personalized recommendation method and system for friends and applications. The method comprises the steps that A, a recommendation score S is calculated; B, recommended content is displayed according to the recommendation score; C, a recommendation weight vector is adjusted according to feedback information about the recommended content from a user; D, the recommended content is updated according to the adjusted user recommendation weight vector. The personalized recommendation method and system have the advantages that the application range is wider, recommendation results are more accurate, the calculating speed is higher, calculation at idle time is achieved, a blacklist mechanism is adopted, the accuracy of information recommendation can be effectively improved, calculation cost is saved, and a good recommendation effect is achieved.
Owner:CETC CHINACLOUD INFORMATION TECH CO LTD
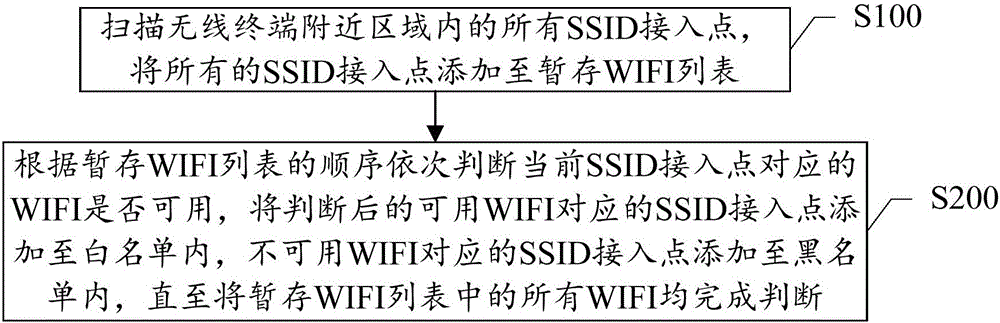
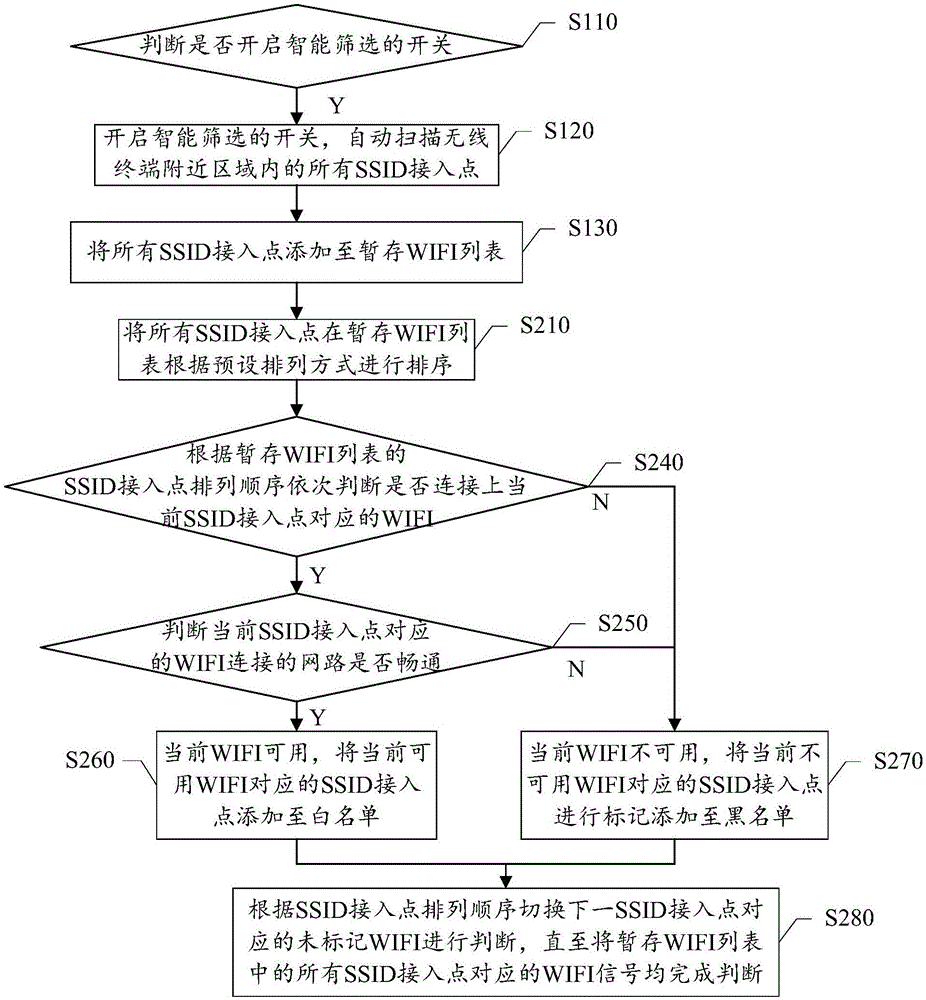
Method for intelligently screening SSID access point and wireless terminal
InactiveCN106412910AIntelligent managementAssess restrictionSecurity arrangementEngineeringWhitelist
The invention discloses a method for intelligently screening an SSID access point and a wireless terminal. The method comprises: S100, all SSID access points in a nearby region of a wireless terminal are scanned and are added to a temporary WIFI list; S200, according the sequence in the temporary WIFI list, whether WIFI corresponding to a current SSID access point is available is determined, the SSID access point corresponding to the available WIFI after determination is added to a white list, and SSID access point corresponding to the non-available WIFI is added into a black list, and the operation is executed until all WIFIs in the temporary WIFI list are determined. Therefore, intelligent SSID identification for availability in a wireless region is realized; and the WIFI and the non-available WIFI that correspond to the available SSID are screened and automatic classification is realized.
Owner:PHICOMM (SHANGHAI) CO LTD
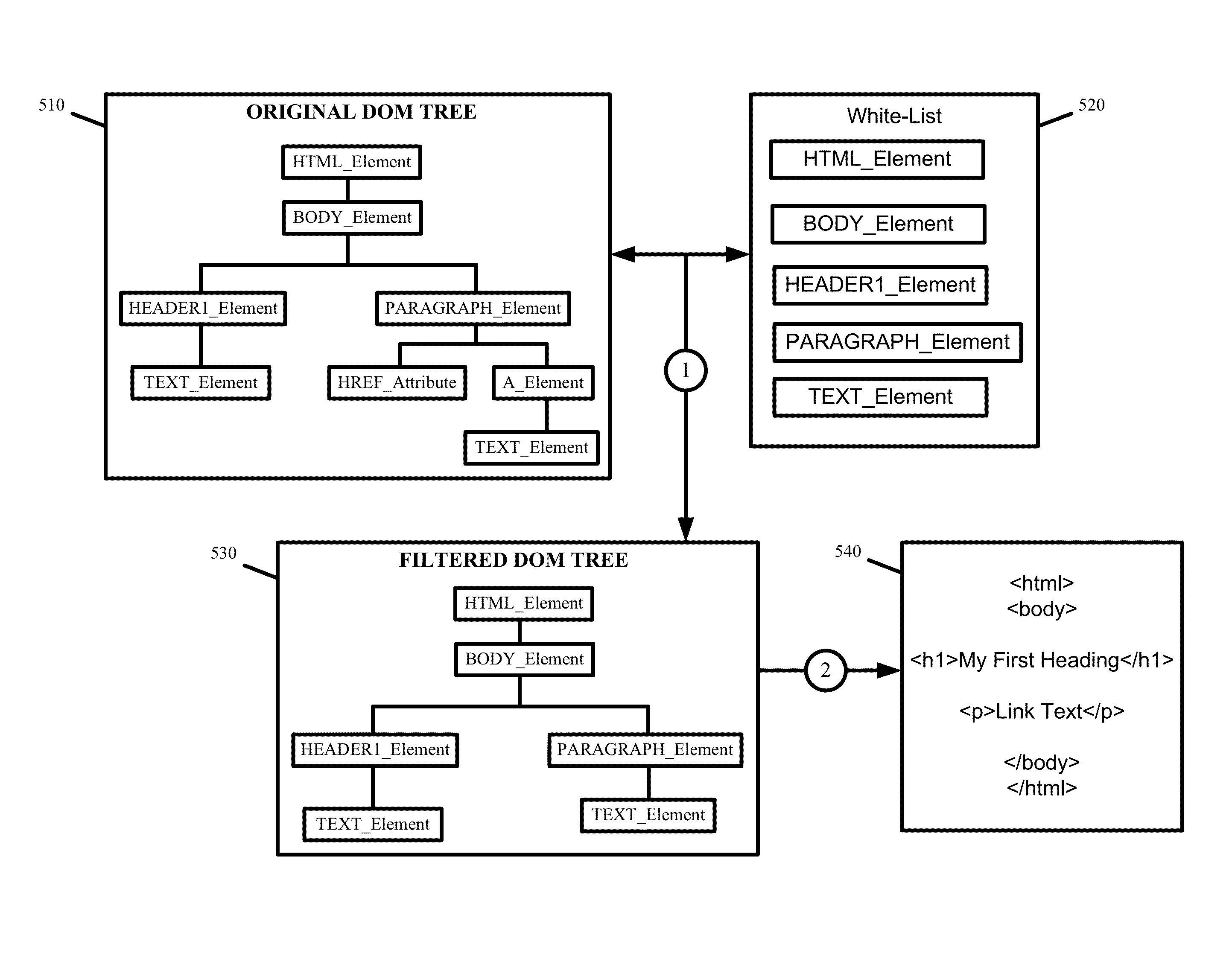
White-list firewall based on the document object model
ActiveUS8601565B1Great security flexibilityIncreased complexityComputer security arrangementsMultiple digital computer combinationsComponent Object ModelDocumentation
Some embodiments provide firewalls and methods for guarding against attacks by leveraging the Document Object Model (DOM). The firewall renders the DOM tree to produce a white-list rendering of the data which presents the non-executable elements of the data and, potentially, outputs of the executable elements of the data without the executable elements that could be used to carry a security threat. Some embodiments provide control over which nodes of the DOM tree are included in producing the white-list rendering. Specifically, a configuration file is specified to white-list various nodes from the DOM tree and the white-list rendering is produced by including the DOM tree nodes that are specified in the white-list of the configuration file while excluding those nodes that are not in the white-list. Some embodiments provide a hybrid firewall that executes a set of black-list rules over white-listed nodes of the DOM tree.
Owner:EDGIO INC +1
Mitigating abuse in an electronic message delivery environment
ActiveUS20180219820A1Reduce riskMaximizing numberAdvertisementsOffice automationMessage deliveryBlack list
Owner:HUBSPOT
Malicious website protection method based on OpenFlow protocol
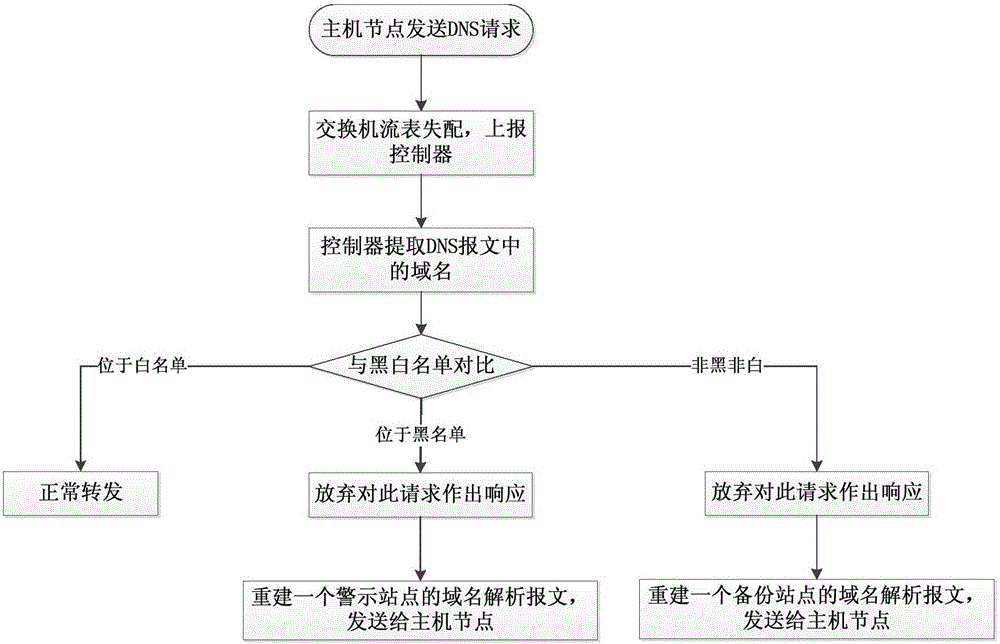
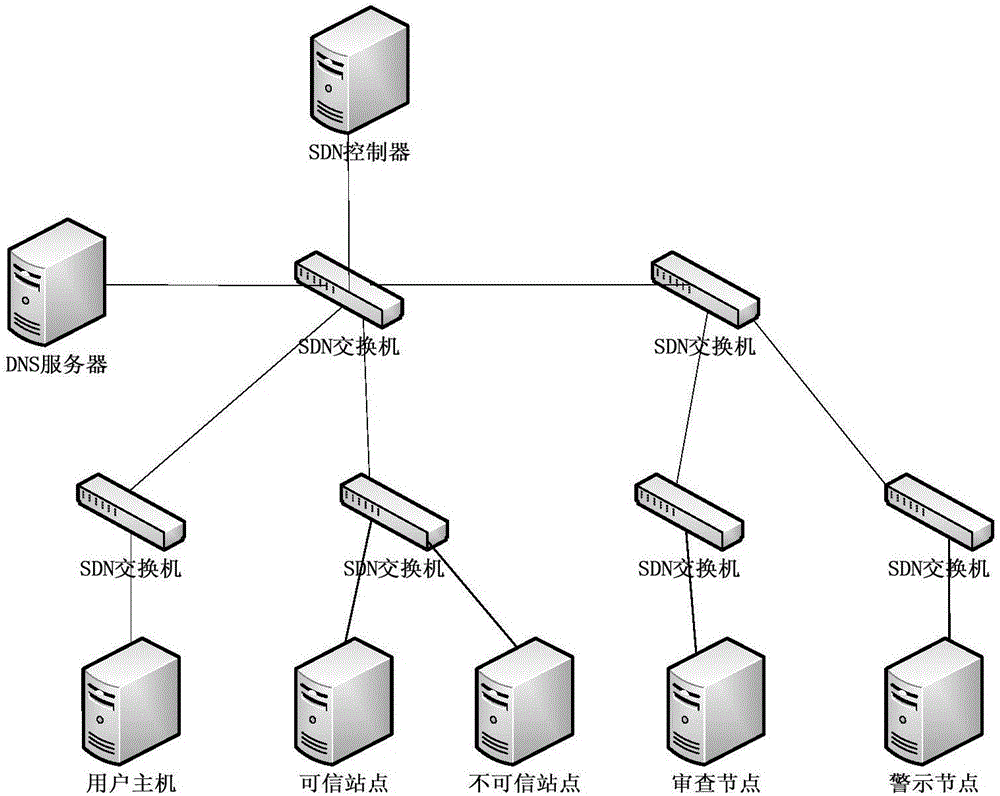
InactiveCN105119930APrevent cheatingEliminates the hassle of installing firewall softwareTransmissionDomain nameEnd system
This invention discloses a malicious website protection method based on an OpenFlow protocol. The method comprises the following steps: based on the structure and the characteristic of SDN (Self-Defending Network), domain name resolution messages sent by an end system are transmitted to a controller through the OpenFlow protocol; performing security check to the messages in a controller module and making a processing decision. The method provided by the invention can be mainly applied to the environments such as SDN structured enterprise network and campus network. Domain names in the domain name resolution messages are firstly extracted from the controller end; then the domain names are compared with a blacklist and a whitelist in the controller by applying the domain name fuzzy matching algorithm; and a specific processing operation is performed to a domain name resolution request by using the comparing result. By adopting the method of the invention, the visit of a terminal to the malicious website can be examined and separated effectively, and simultaneously, a phishing website with similar domain name also can be detected; furthermore, the security policy of the controller can be conveniently changed in the SDN-based network structure.
Owner:NANJING UNIV OF SCI & TECH
Managing electronic messages with a message transfer agent
ActiveUS20180219819A1Mitigating cross-impactEasy to compareMathematical modelsAdvertisementsSpammingEngineering
Owner:HUBSPOT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com