Web page tamper prevention device based on web server cache matching and method thereof
A server cache and server technology, applied in electrical components, transmission systems, etc., can solve problems such as damaging corporate image and interests, achieve the effects of improving security, overcoming low detection efficiency, and preventing hackers from tampering with web pages
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
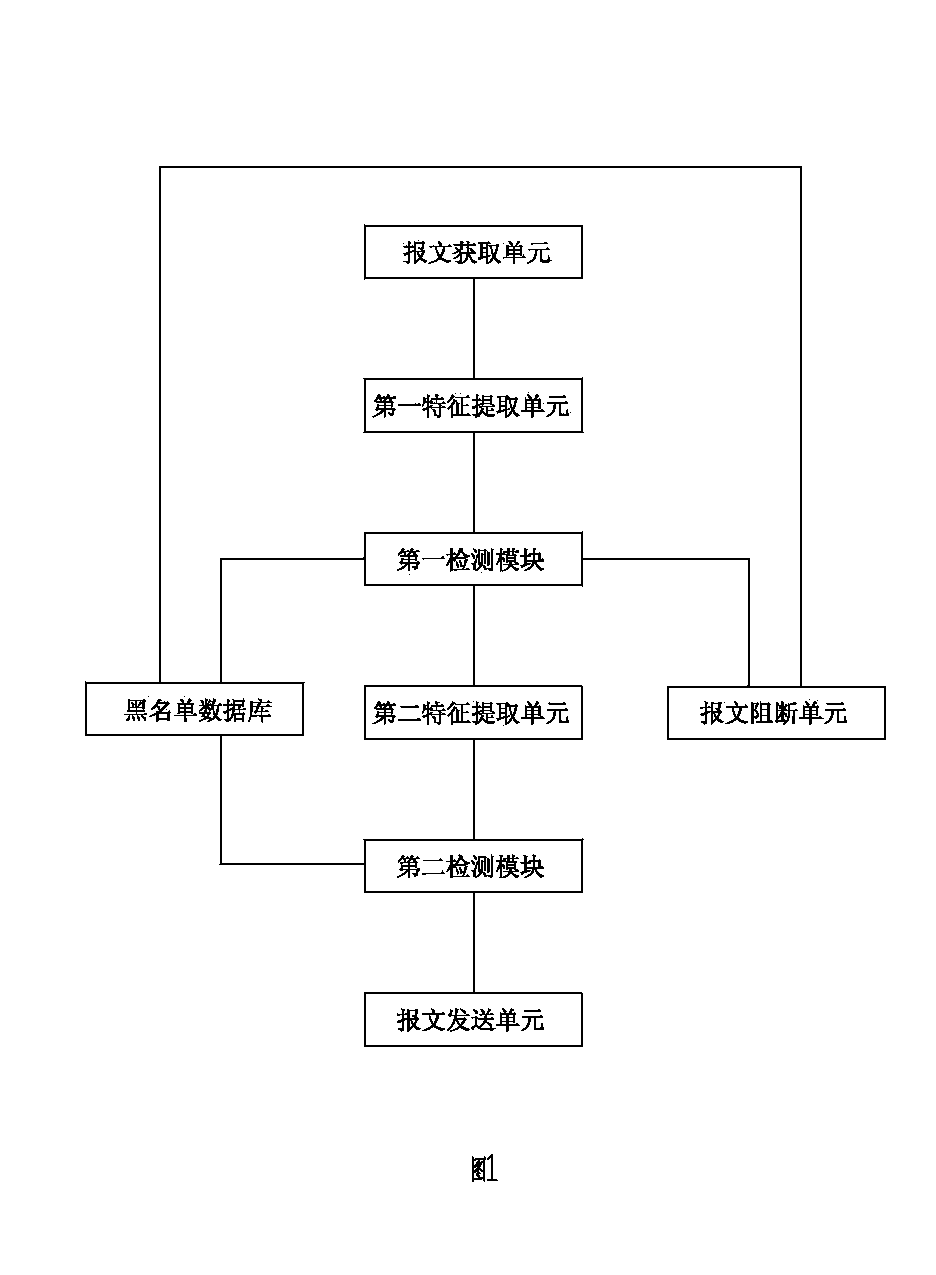
[0039] Embodiment 1: as attached figure 1 As shown, the webpage anti-tampering device based on web server cache matching includes:
[0040] A message obtaining unit, configured to obtain an IP response message sent by the web server to the client;
[0041] The first feature extraction unit is used to perform feature value extraction on the data in the IP response message that is easy to inject into the Trojan horse process and tamper process, to obtain the first feature value;
[0042] The first detection module, which performs fuzzy matching processing, detects whether the first feature value sent by the first feature extraction unit matches the blacklist database feature value; if so, judges that the detected webpage is a tampered webpage; if not, sends a detection signal To the second detection module; the fuzzy matching process extracts SQL injection, XSS cross-site scripting, CSRF cross-site request forgery and other behavioral features in the webpage according ...
Embodiment 2
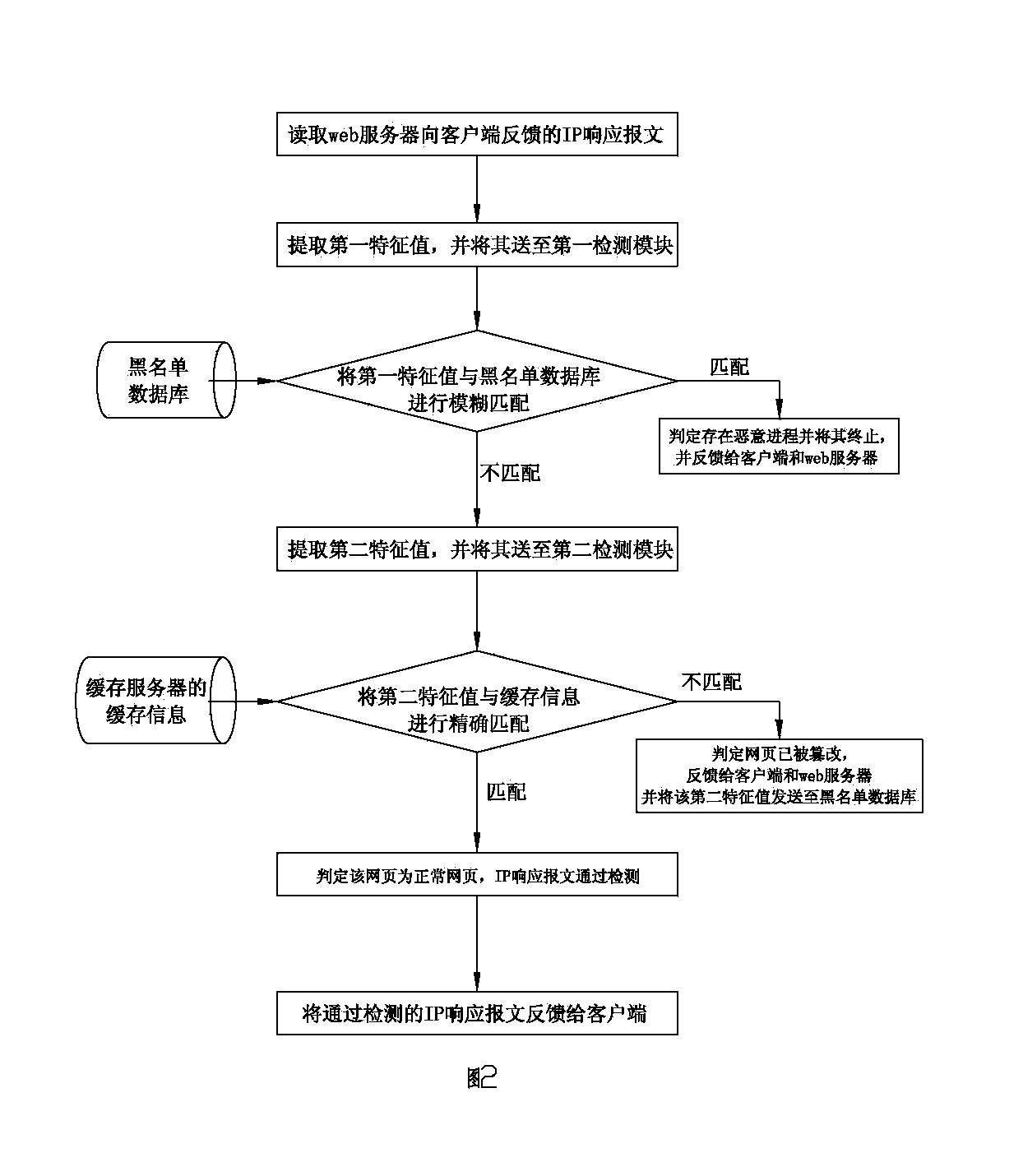
[0052] Embodiment 2: as attached figure 2 As shown, the webpage anti-tampering method using the above-mentioned webpage anti-tampering device comprises the following steps:
[0053] The first step: read the IP response message fed back by the web server to the client, and obtain the web page characteristic data of the web server;
[0054] The second step: extracting the feature value of the data at the place where the Trojan horse process and the tampering process are easy to be injected into the IP response message as the first feature value;
[0055] Step 3: performing fuzzy matching processing on the first characteristic value and the blacklist database;
[0056] If the result of the fuzzy matching process is that the first feature unit matches the blacklist database, then it is determined that there is a malicious process in the client webpage and the process is terminated, and feedback to the client prompts that the webpage has been maliciously tampered with, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com