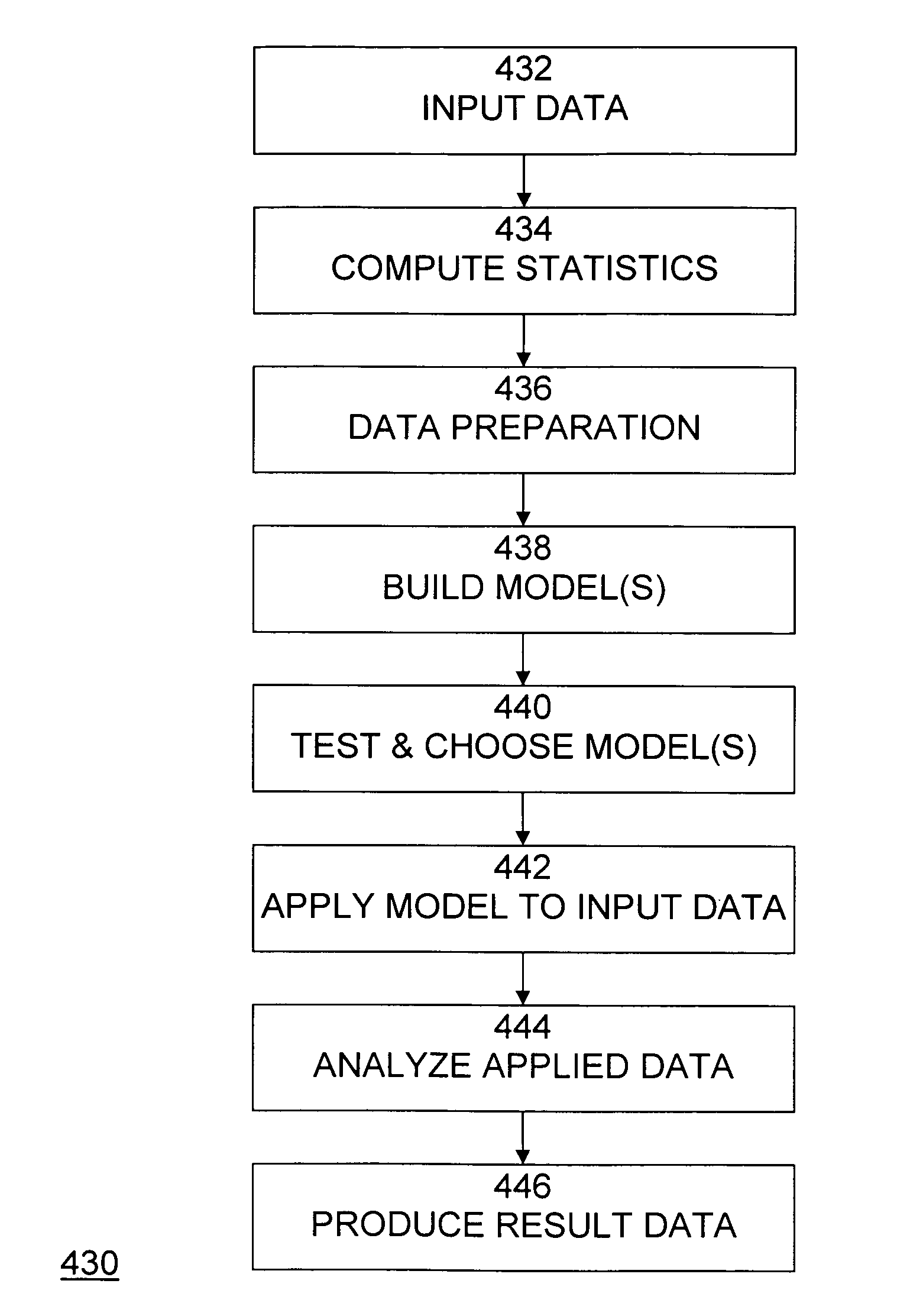
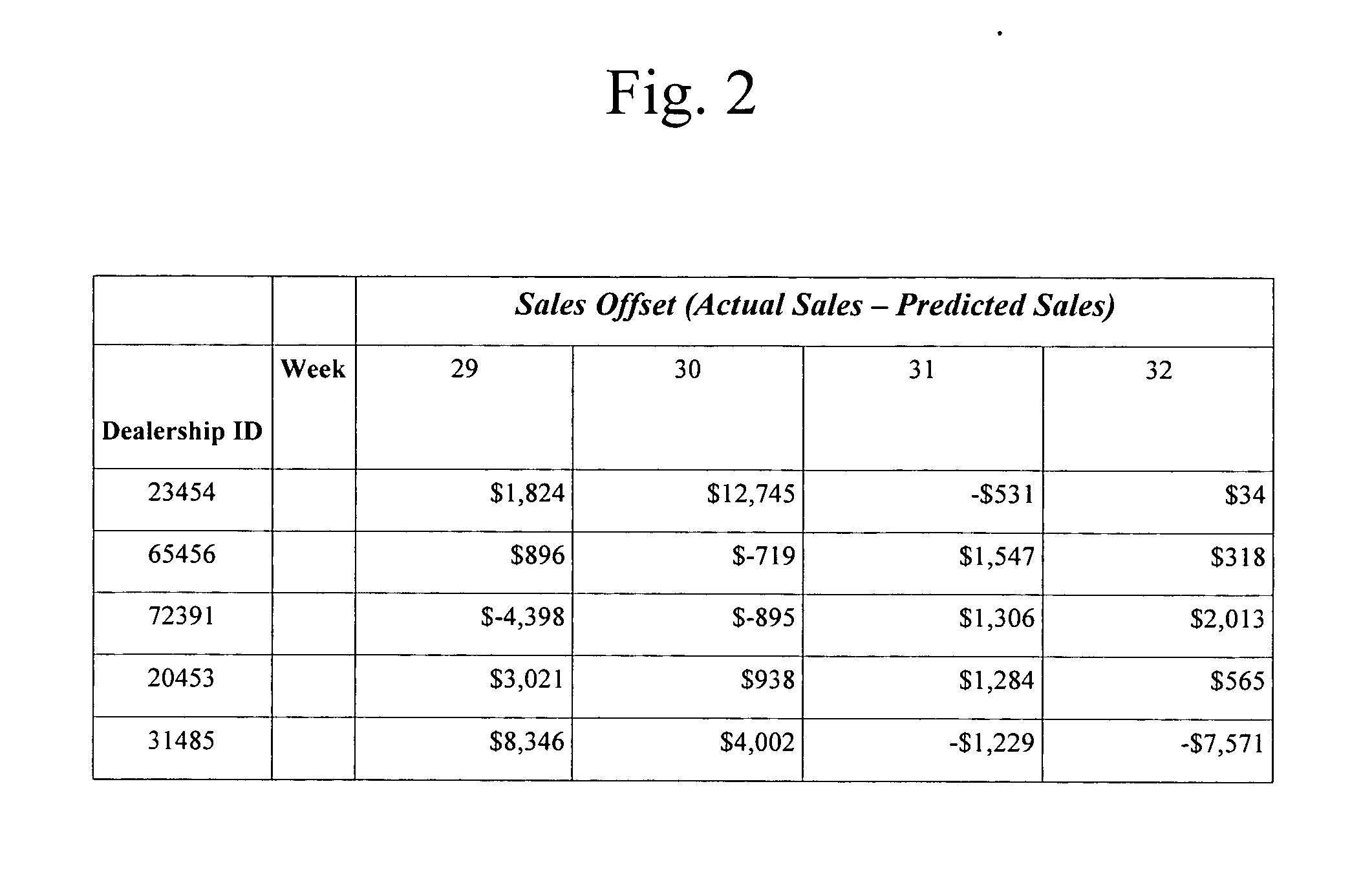
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1201 results about "Common method" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
There are three common methods that are used: straight-line, double-declining balance, and sum-of-the-years-digits. By far the most common is the straight-line method. This method spreads the costs evenly over the life of the asset.
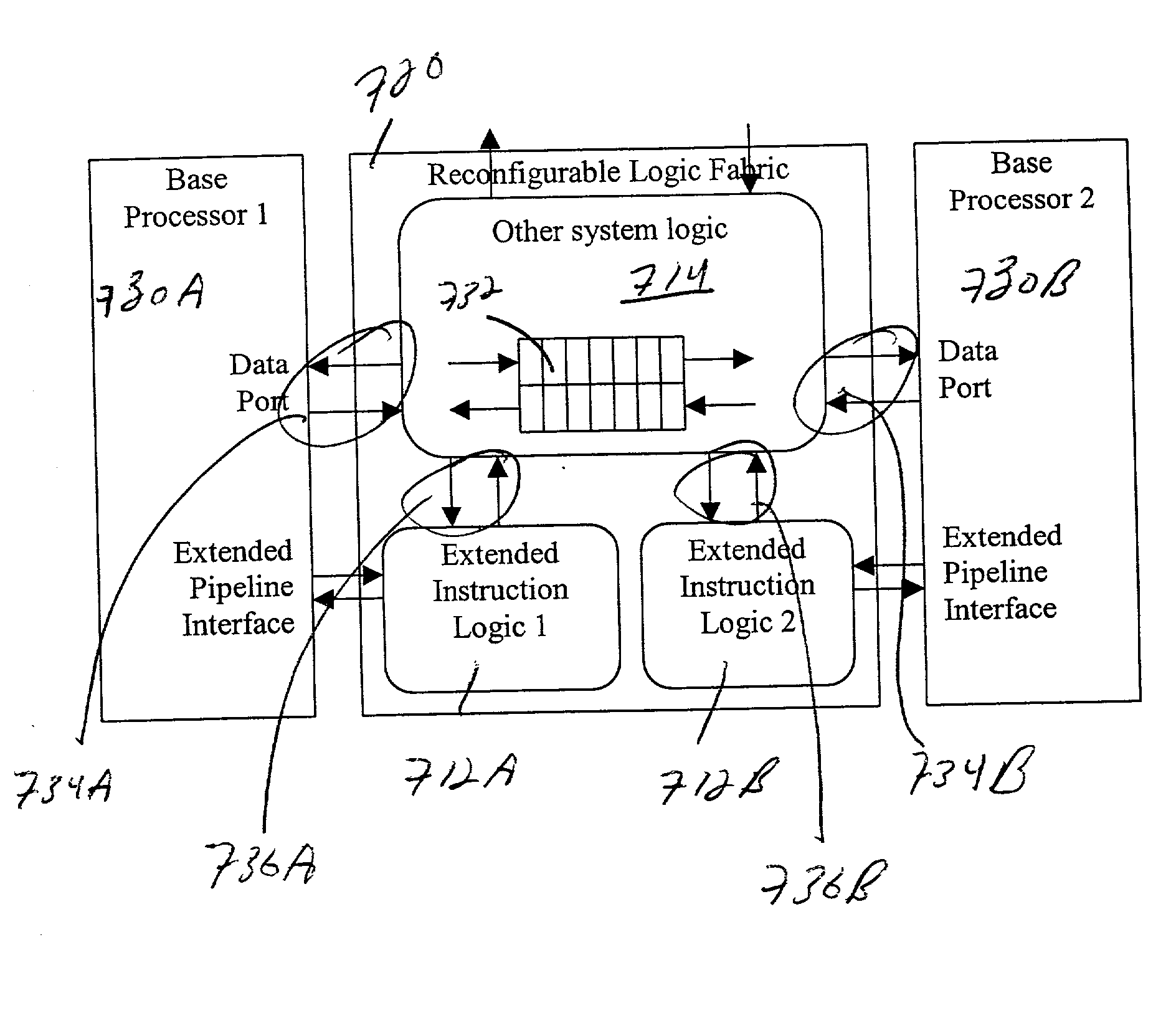
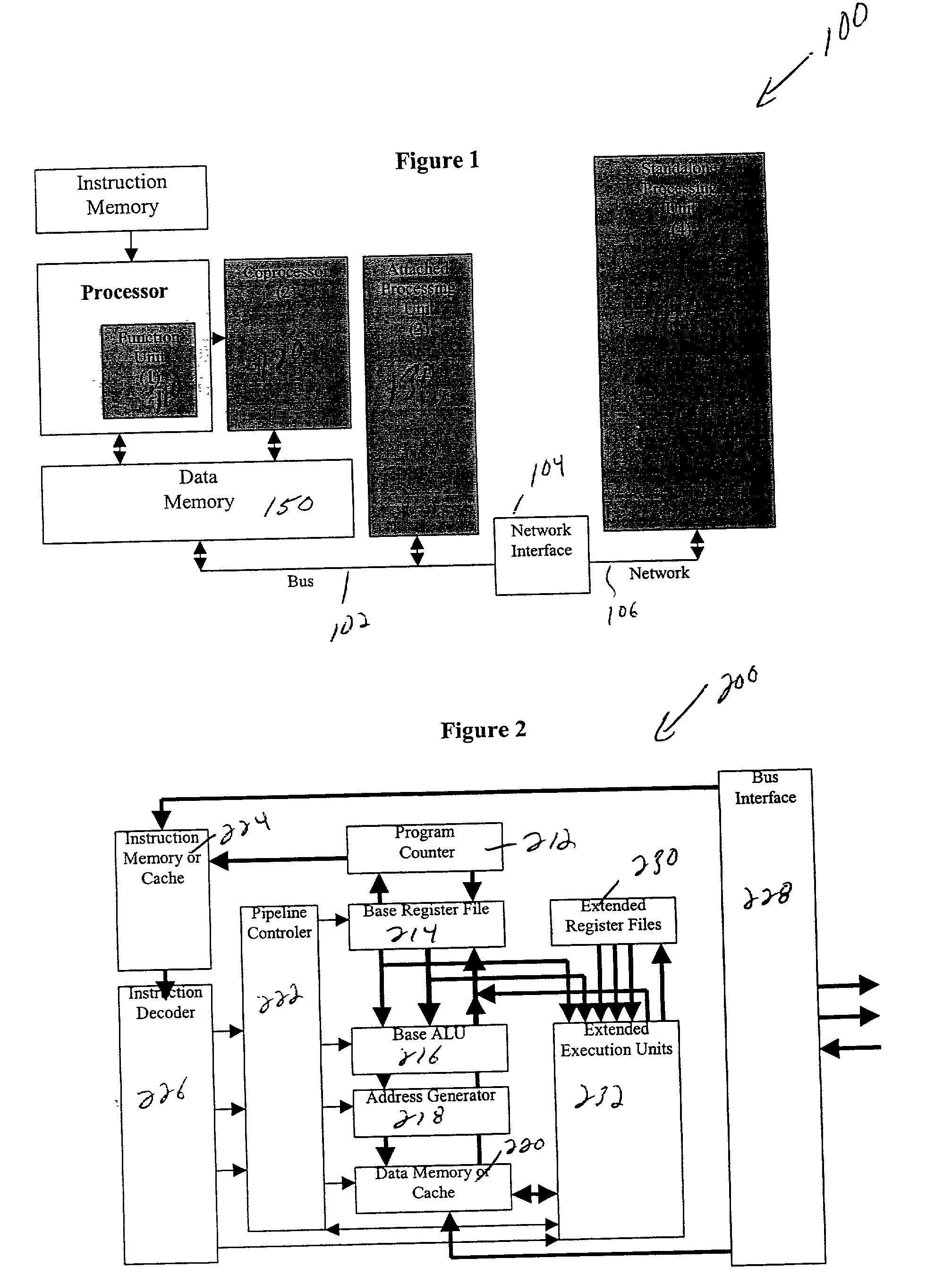
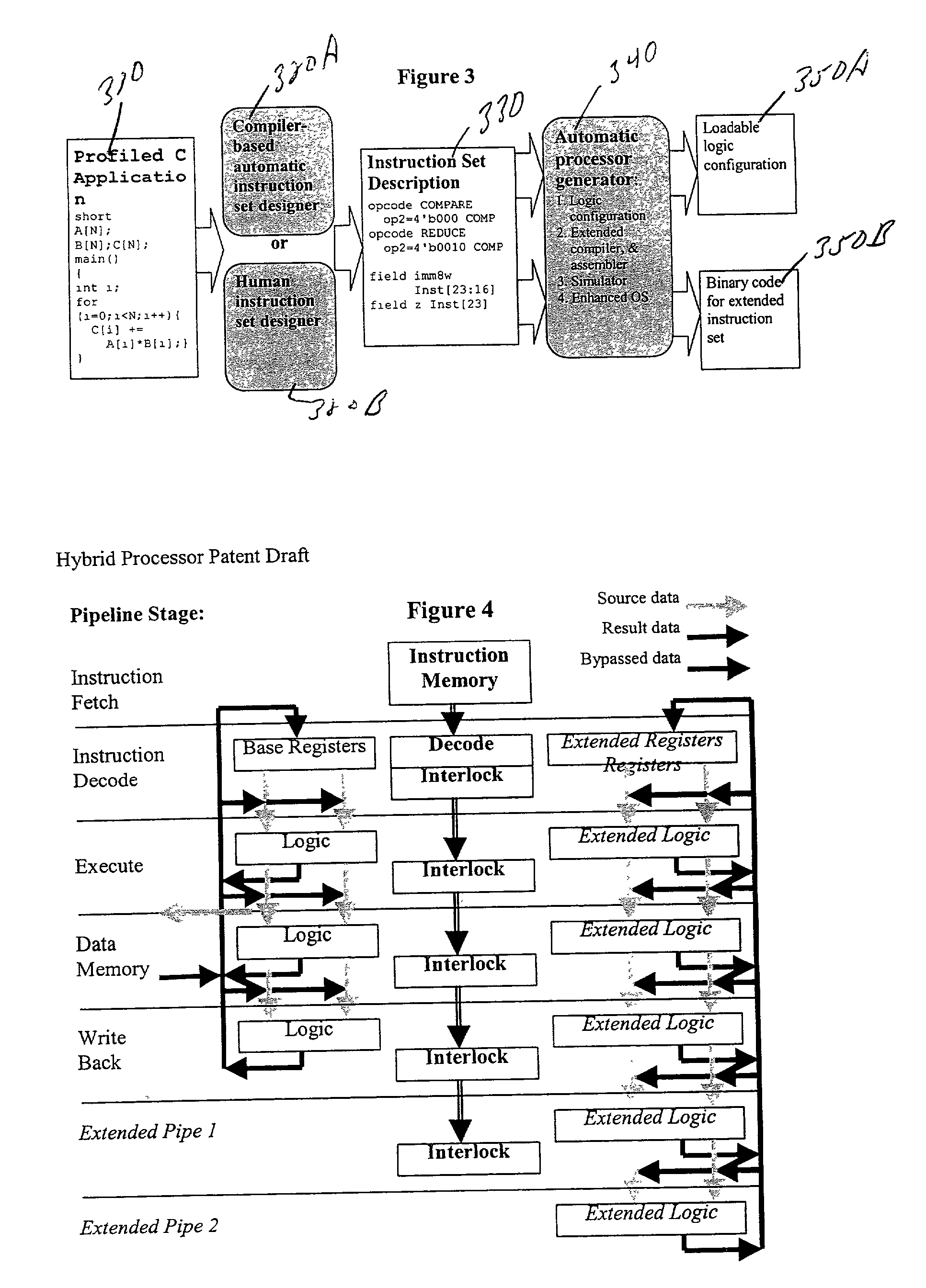
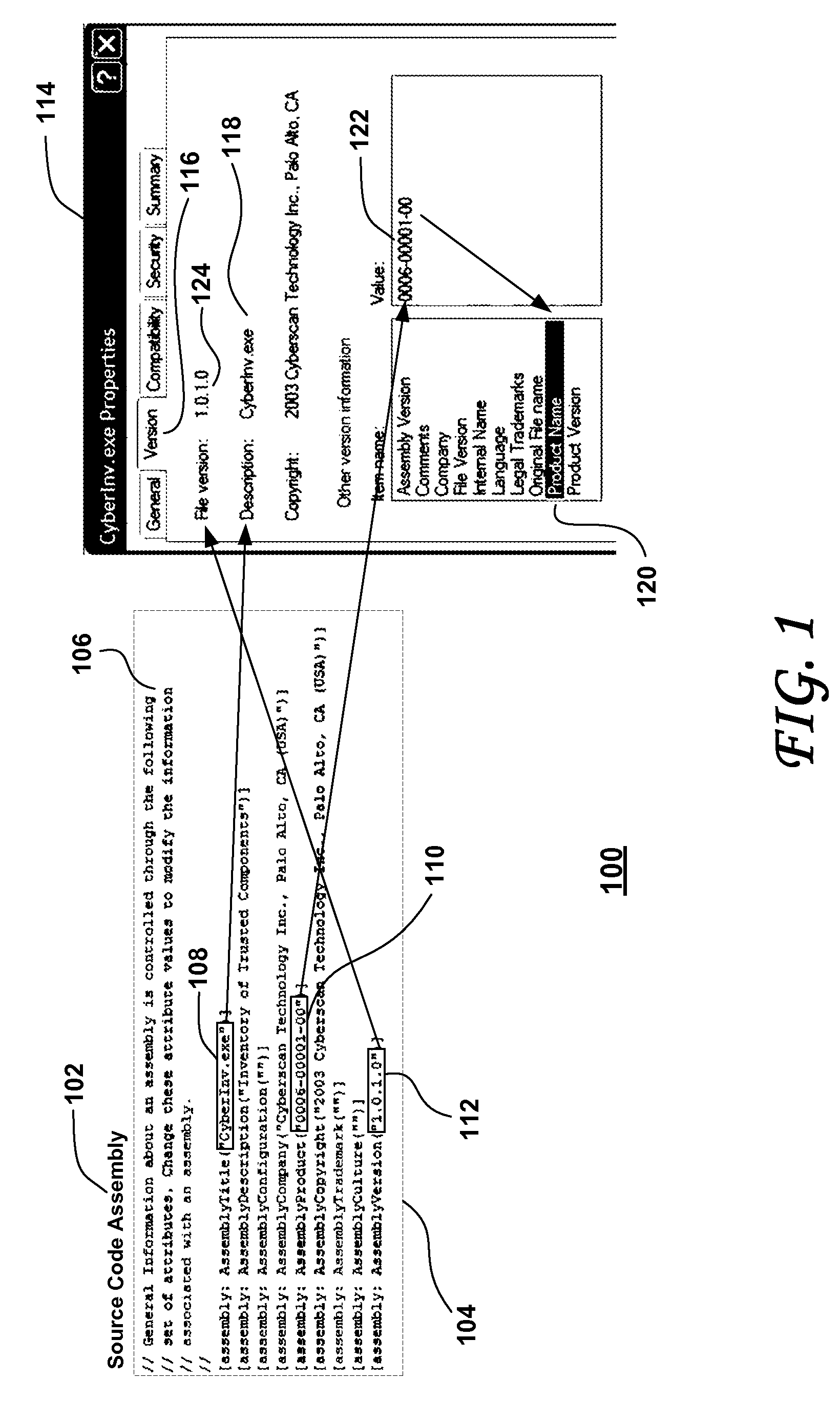
High-performance hybrid processor with configurable execution units
InactiveUS20050166038A1High bandwidthFlexibilityInstruction analysisConcurrent instruction executionHigh bandwidthLatency (engineering)
A new general method for building hybrid processors achieves higher performance in applications by allowing more powerful, tightly-coupled instruction set extensions to be implemented in reconfigurable logic. New instructions set configurations can be discovered and designed by automatic and semi-automatic methods. Improved reconfigurable execution units support deep pipelining, addition of additional registers and register files, compound instructions with many source and destination registers and wide data paths. New interface methods allow lower latency, higher bandwidth connections between hybrid processors and other logic.
Owner:TENSILICA
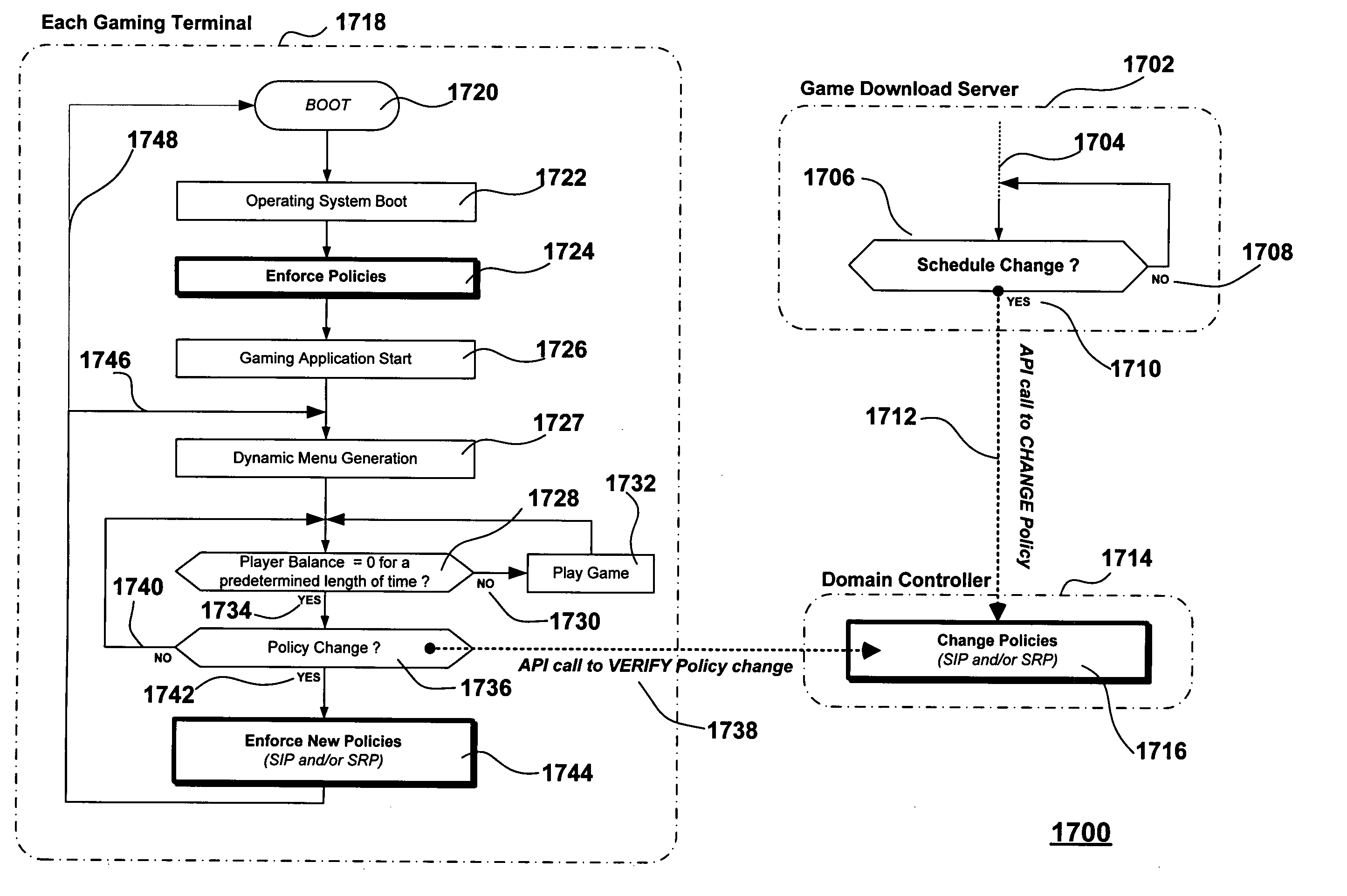
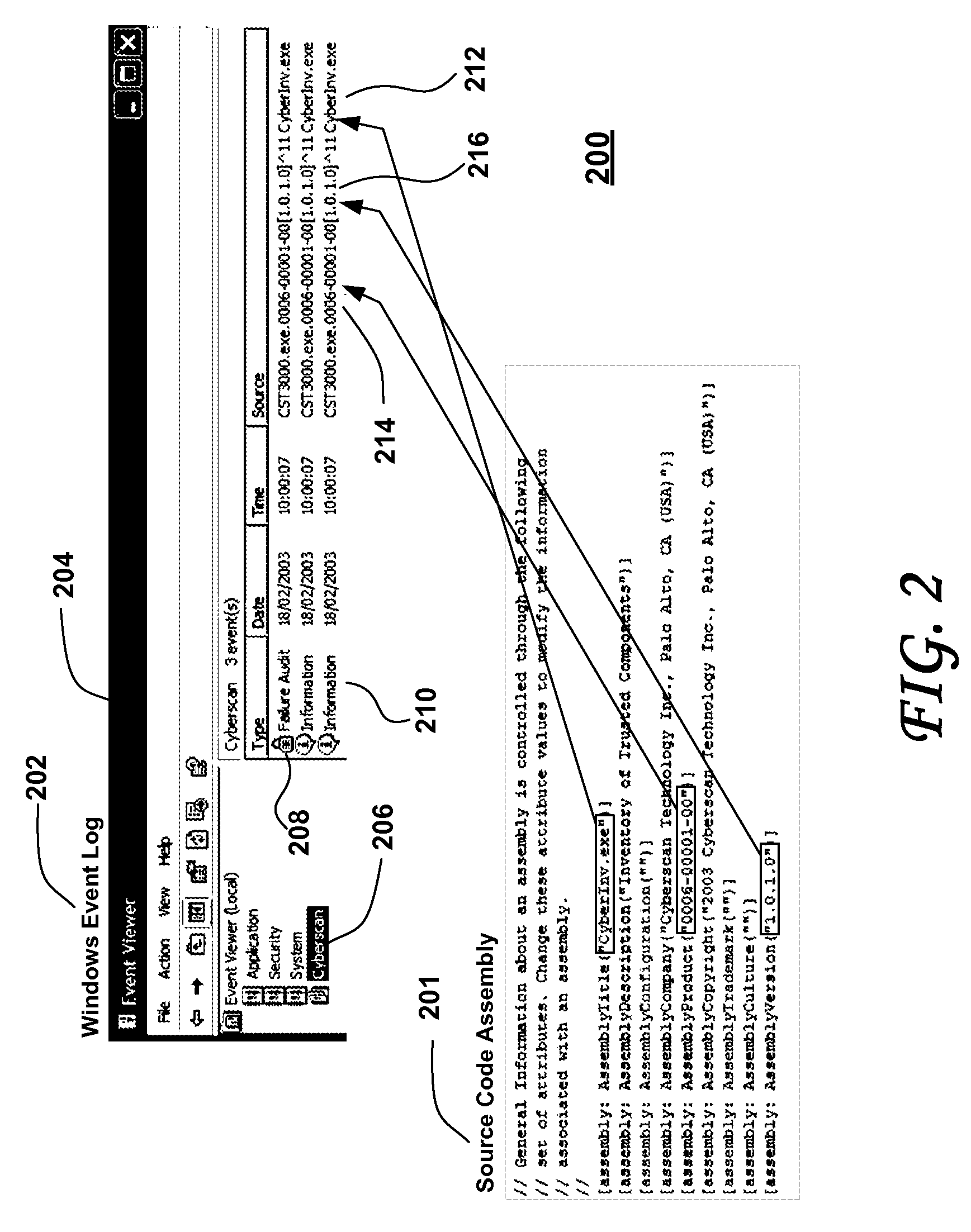
Dynamic configuration of a gaming system
ActiveUS20050223219A1Overcome limitationsUser identity/authority verificationUnauthorized memory use protectionCommon methodComputer hardware
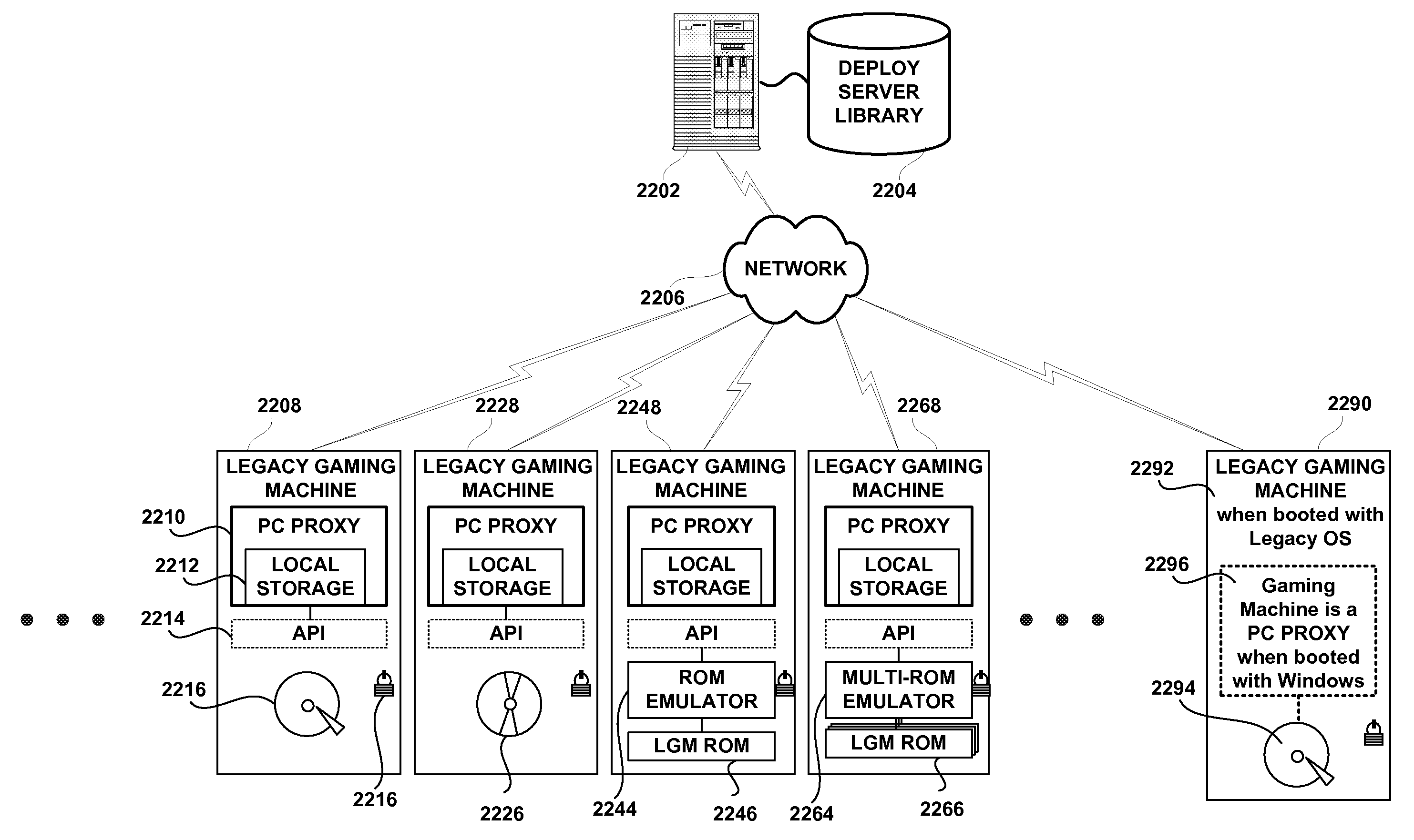
A universal method and system for downloading game software to legacy gaming machines. A gaming machine includes a locked enclosure; a first computing device disposed within the locked enclosure, the first computing device being programmed to enable game play of the gaming machine; a second computing device disposed within the locked enclosure of the gaming machine, the second computing device being configured for network access, and an interface between the first and the second computing devices. The second computing device is configured to receive game software components over the network that are compatible with (e.g., executable by) the first computing device but not compatible with (e.g., not executable by) the second computing device and to transfer the received game software components to the first computing device over the interface. The second computing device may include, for example, a PC. When the first computing device is a PC, it may be configured with dual-boot capability between two operating systems. When the first operating system is booted, game play may be enabled and when the second operating system is booted, game software components may be received over the network.
Owner:IGT
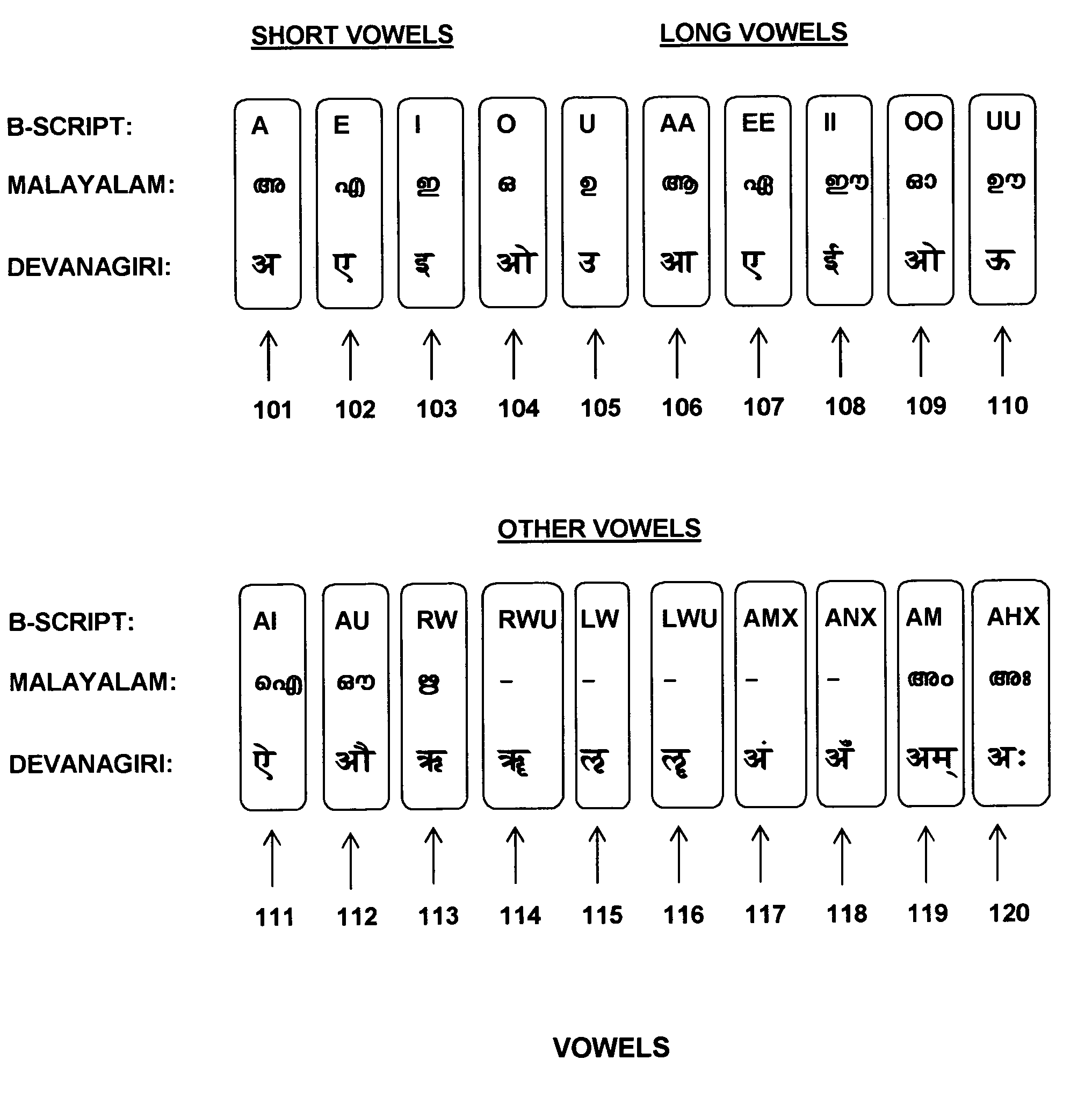
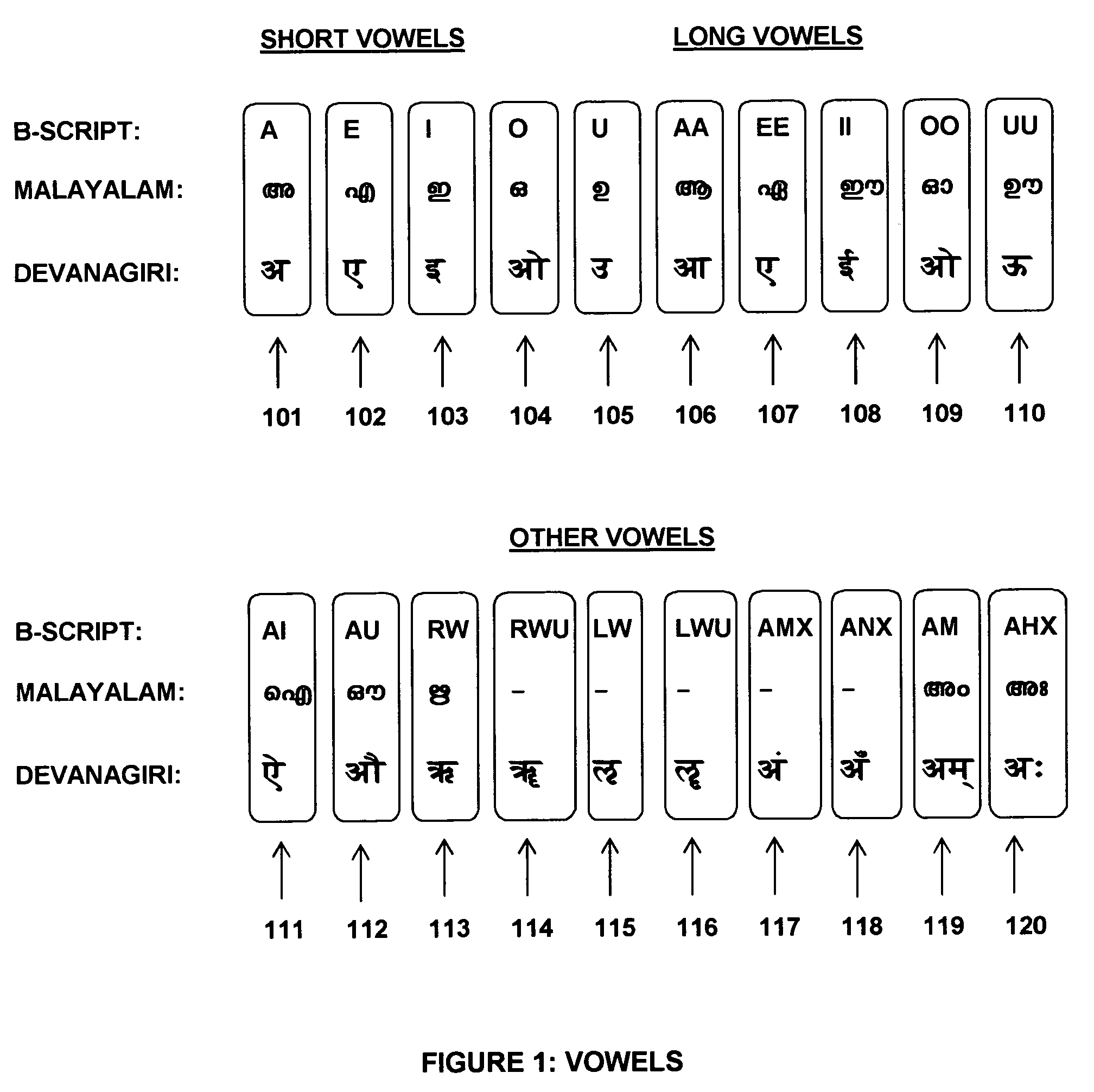
System and method for writing Indian languages using English alphabet
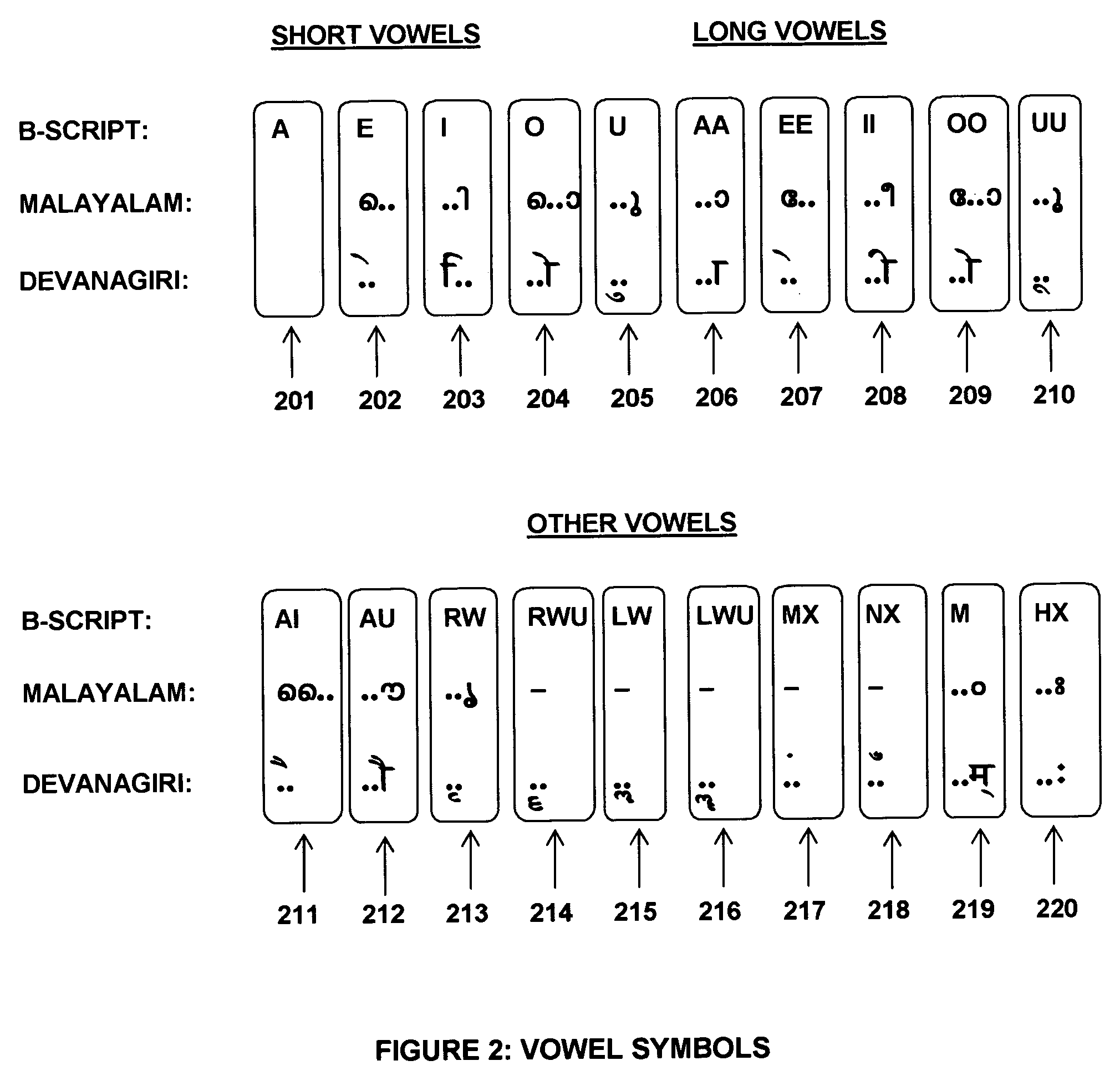
ActiveUS7177794B2Uniform phonetic representationSimple processNatural language translationSpecial data processing applicationsEnglish charactersMalayalam
A system and method for writing Indian languages using the English writing scheme is provided that includes specifying a script using the English alphabet to represent the various characters and character combinations in various Indian languages. The specified script follows the writing conventions of English. This script is based on how the Indian languages are spoken and rules are specified to facilitate mapping the sounds represented in English characters to the native language in its written form. This common method is intended for writing Hindi and related languages, such as Sanskrit, Marathi, and Gujarathi, and Bengali and somewhat distant, but closely related Dravidian languages, such as Malayalam, Tamil, Kannada, and Telegu.
Owner:MANI BABU V +1
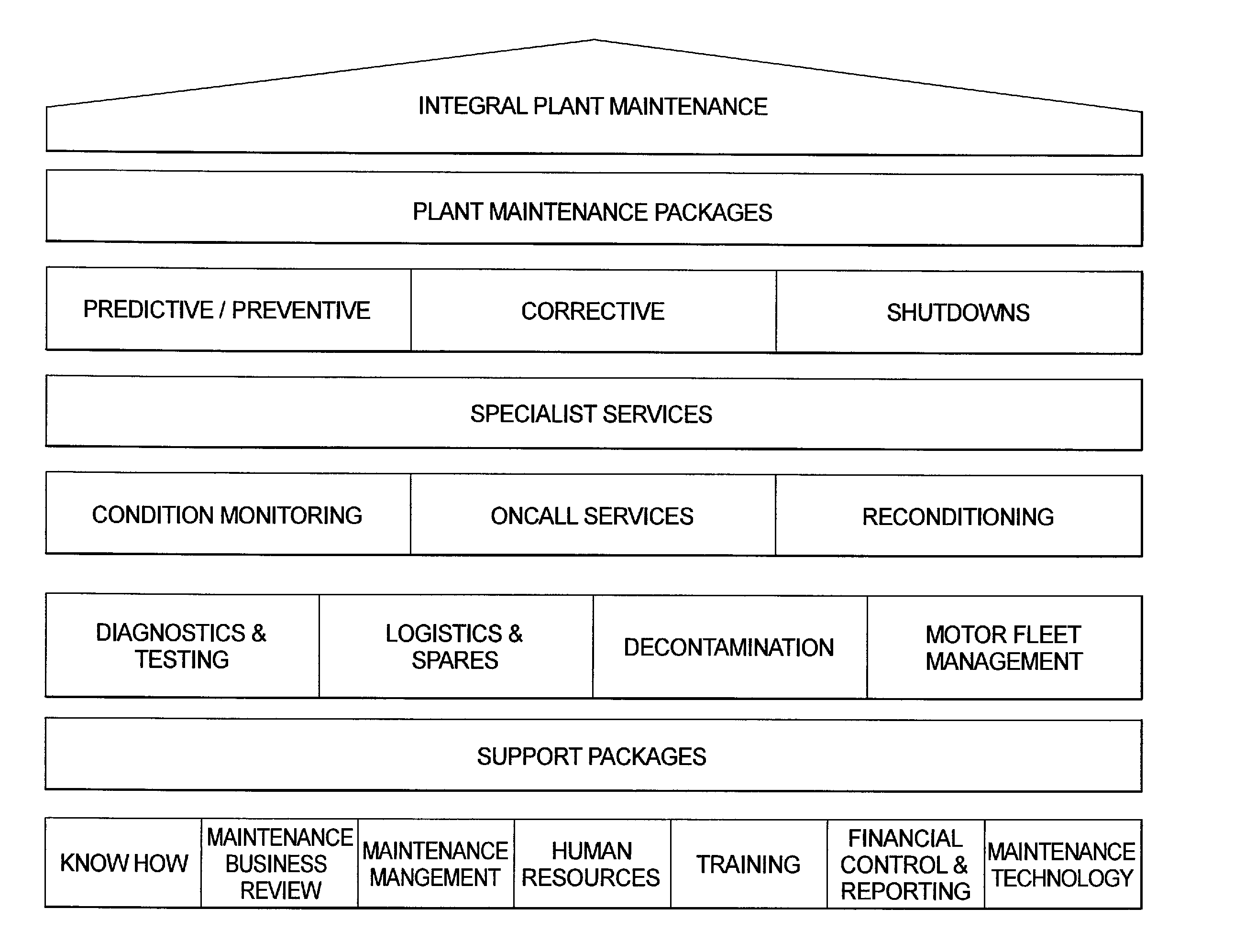
Method of providing maintenance services
The method of providing includes providing an assessment of the maintenance and technical service needs of a plant, as broadly defined, and recommending services for outsourcing selected from a menu of services. The services are modular and may be mixed and matched to a customized fit with the needs of the plant. Categories of services are directed to technical services, motor maintenance, electro-mechanical services, etc. A generic approach to all plant maintenance provides a framework in which to offer the services. Services are offered throughout the life cycle of a plant. Particular industries are targeted for outsourced services.
Owner:SIEMENS AG
Data-centric automatic data mining
ActiveUS20060136462A1Ease of use and stabilityIncrease flexibilityData processing applicationsRelational databasesQuality dataData source
Owner:ORACLE INT CORP
Universal game download system for legacy gaming machines using ROM and NVRAM emulation
ActiveUS20060160626A1Extended service lifeUser identity/authority verificationUnauthorized memory use protectionComputer hardwareGame play
A universal method and system for downloading game software to ROM based legacy gaming machines, activating selected games and providing new services. The method includes a ROM emulator for replacing the game program image and an NVRAM emulator for swapping the game context and critical meters accordingly. The method includes detection of the state of the current game activity such as to activate a new game only at an authorized time, when no player is playing a game or is carded-in for example. The system includes emulation of the original peripherals fitted to the legacy gaming machine such as to offer extended functionality and services. The universal method and system therefore prolongs the useful life of legacy machines which otherwise would be prematurely retired.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
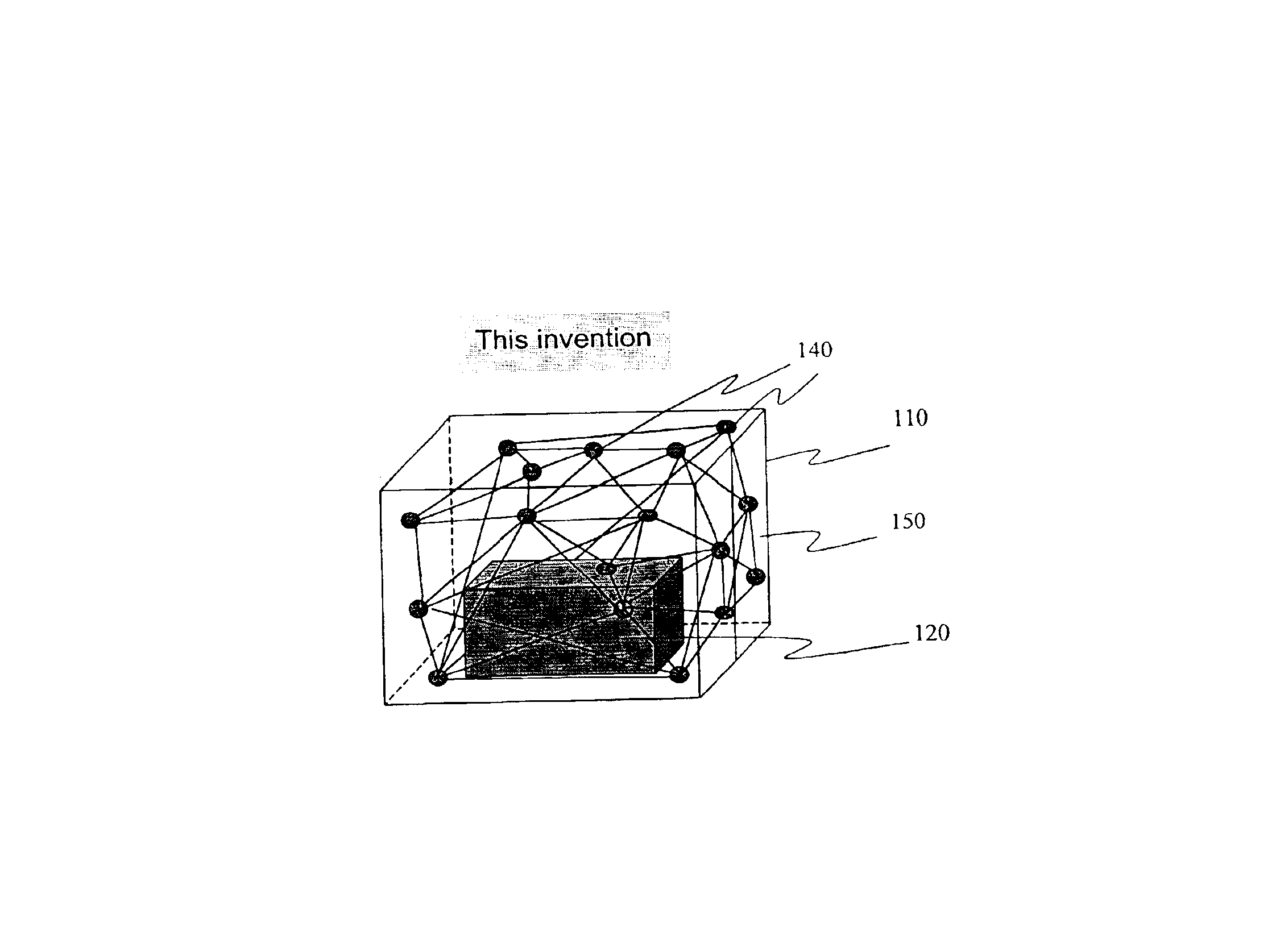
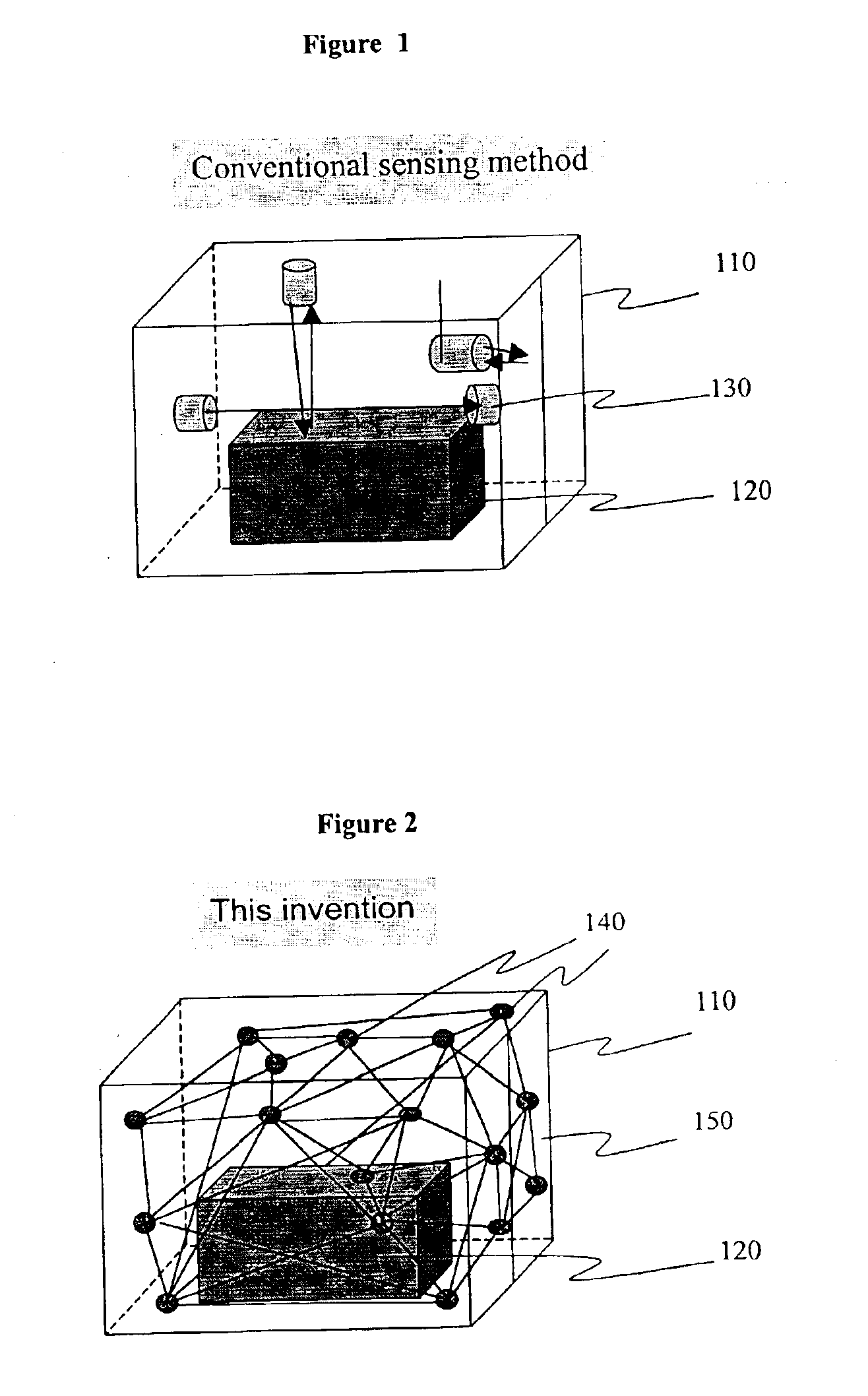
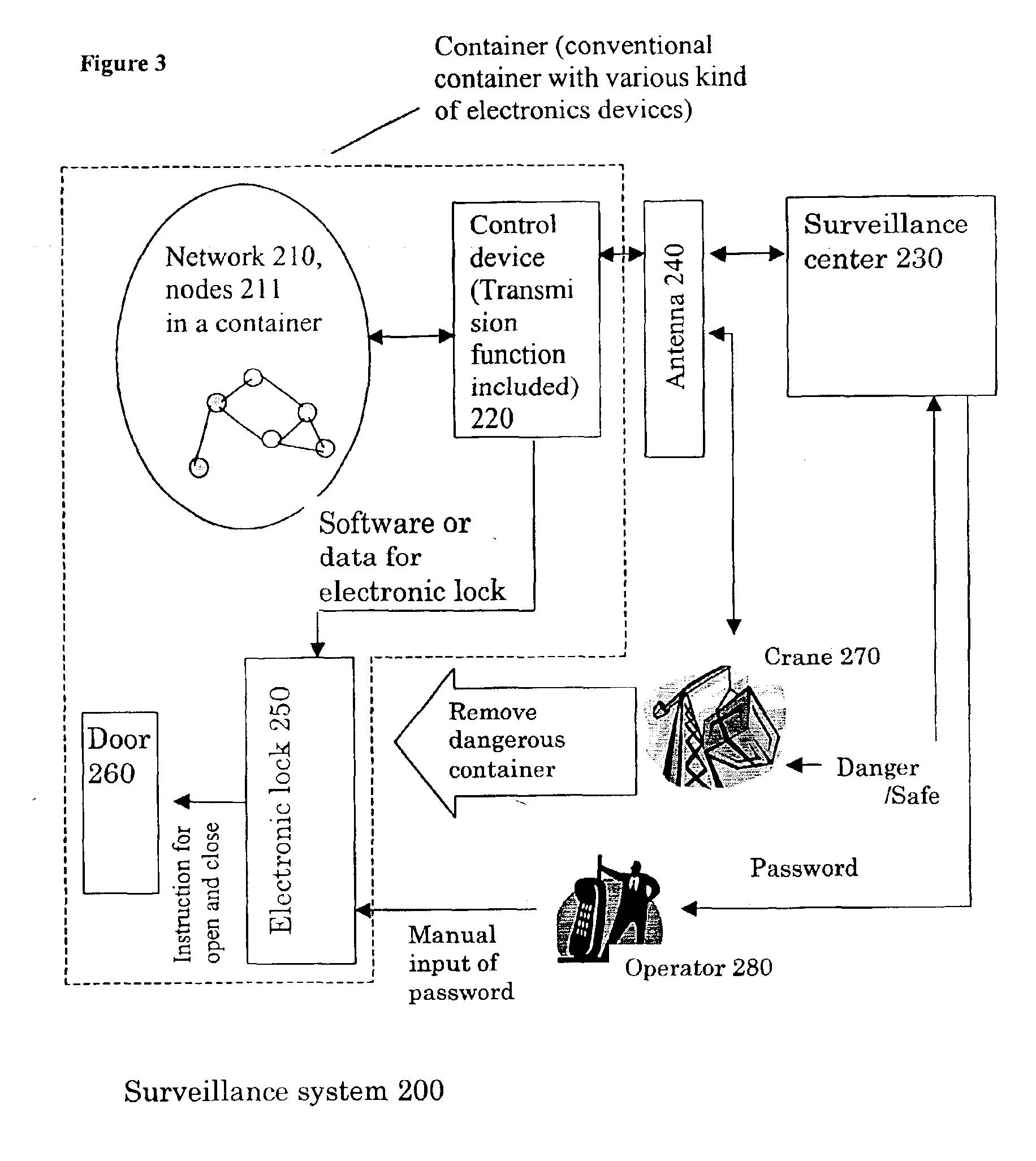
State surveillance system and method for an object and the adjacent space, and a surveillance system for freight containers
InactiveUS6879257B2Attacked easilyStrategy is hamperedDigital computer detailsElectric/electromagnetic visible signallingNODALCommunication unit
The objective of the present invention is to detect, using a universal method, any “movement” inside of the object being monitored, while maintaining the security of a container. The movement inside of the object to be monitored includes 1) a human movement when a human enters into a container to be monitored, 2) a movement to bring a foreign article in, 3) a movement to take cargo out. To achieve the objective, this invention uses the concept of a so-called “inside-seal”. In actual configuration, a plurality of communication units (communication nodes) are installed on the walls of the container. These communication units have a predetermined powered communication capability and form a communication network communicating with each other. A communication status between each node and all of the other nodes provided in the network, and a network graph matrix is generated which defines the nodal relationship between the nodes. Since the matrix is determined not only by the property of the object to be monitored, but also by the spatial condition within the container, it is possible to detect even a small change in the space. According to the first preferred embodiment, each node transmits a low power electric wave which can reach only neighboring nodes, and each node can transmit data to remote nodes only by relaying the data to the neighboring nodes. The relaying counts (HOP counts) of each node to communicate with all of the other nodes are obtained, and based on these relaying counts, a network graph matrix is generated which defines the relaying counts to communicate between all nodes. According to the second preferred embodiment, each node transmits UWB waves to all of the other nodes, which can reach to all of the other nodes, and the distances between all the nodes are measured and a network graph matrix between all the nodes is generated.
Owner:OMRON CORP MANAGEMENT CENT OF AMERICA INC +1
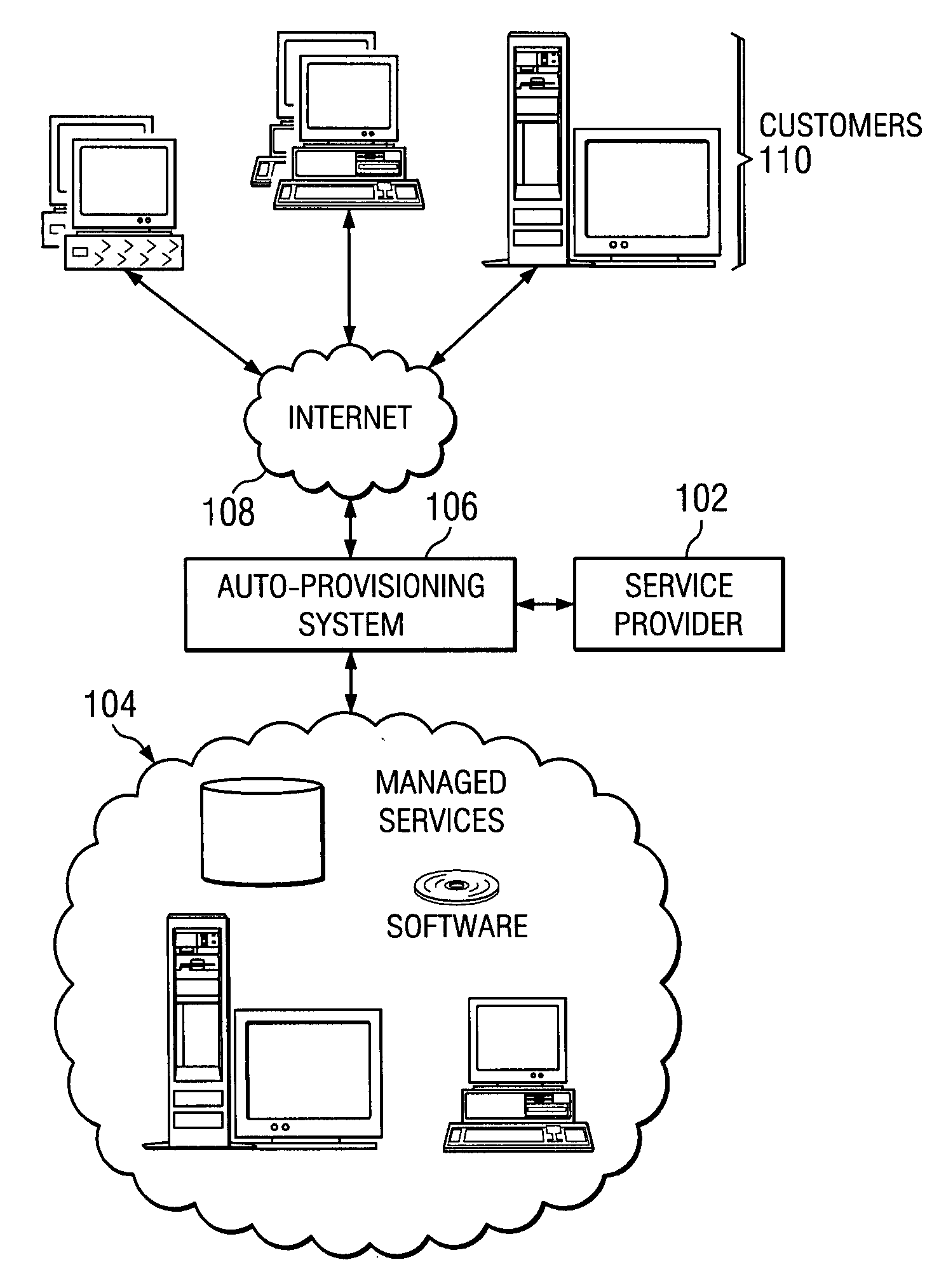
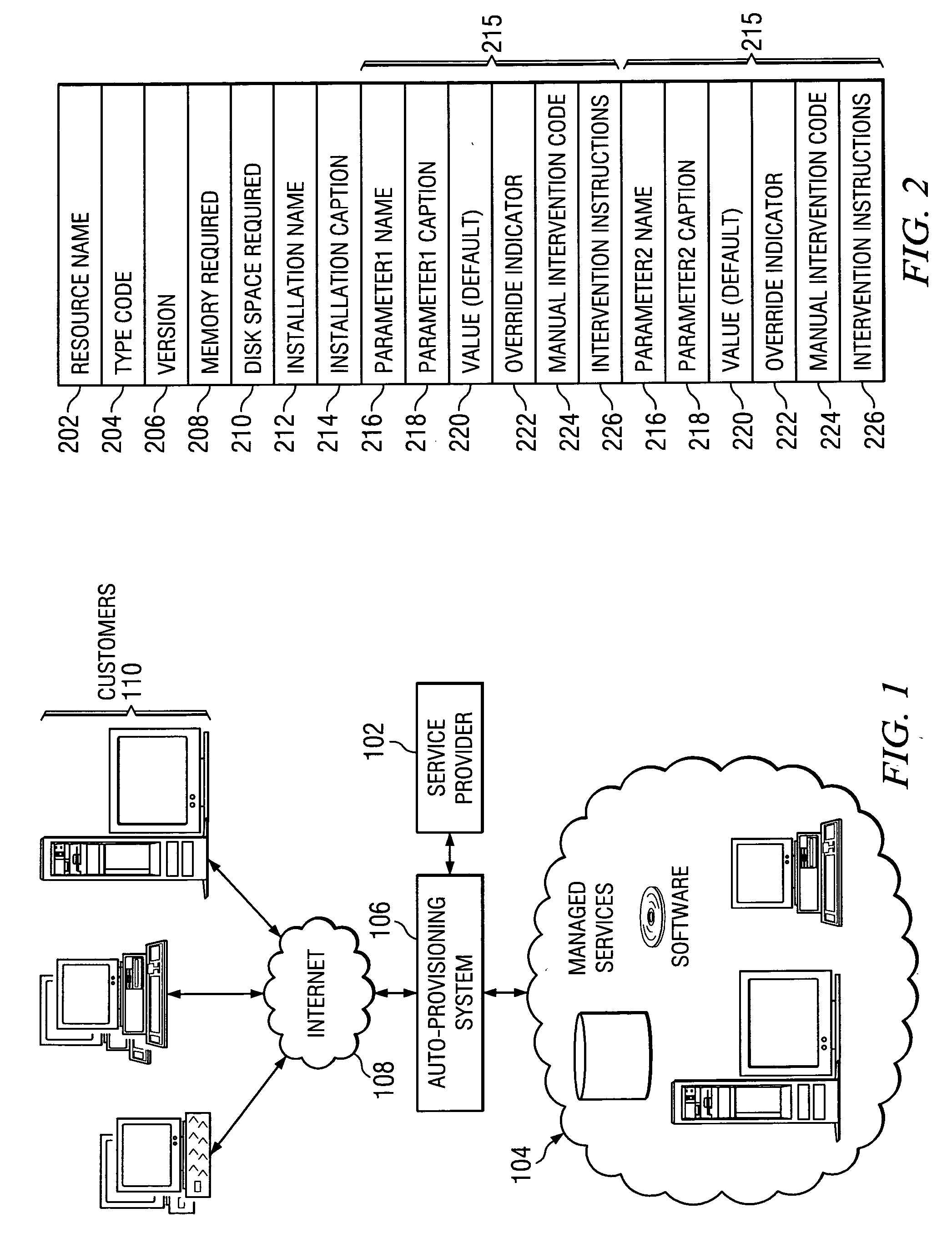
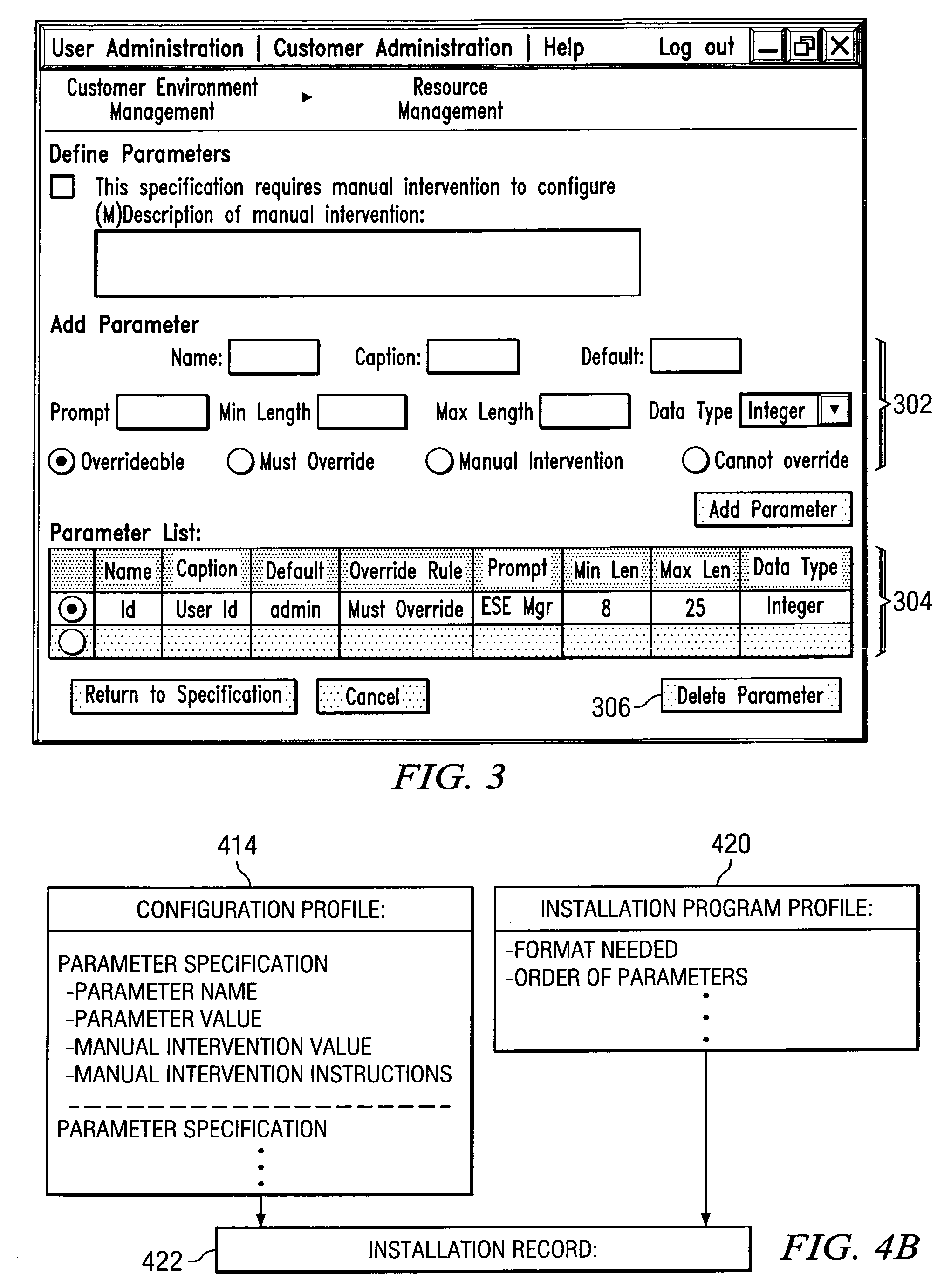
Generic method for defining resource configuration profiles in provisioning systems
InactiveUS20050050175A1Digital computer detailsSpecific program execution arrangementsConfigfsComputer science
A generic method and model for capturing and storing configuration profiles for each resource in a provisioning system. As a resource is utilized in a specific environment, the configuration values can be changed as needed to reflect different stages in the life cycle of the resource, such as configuration, and modification.
Owner:IBM CORP
Multiple-wavelength spectroscopic quantitation of light-absorbing species in scattering media
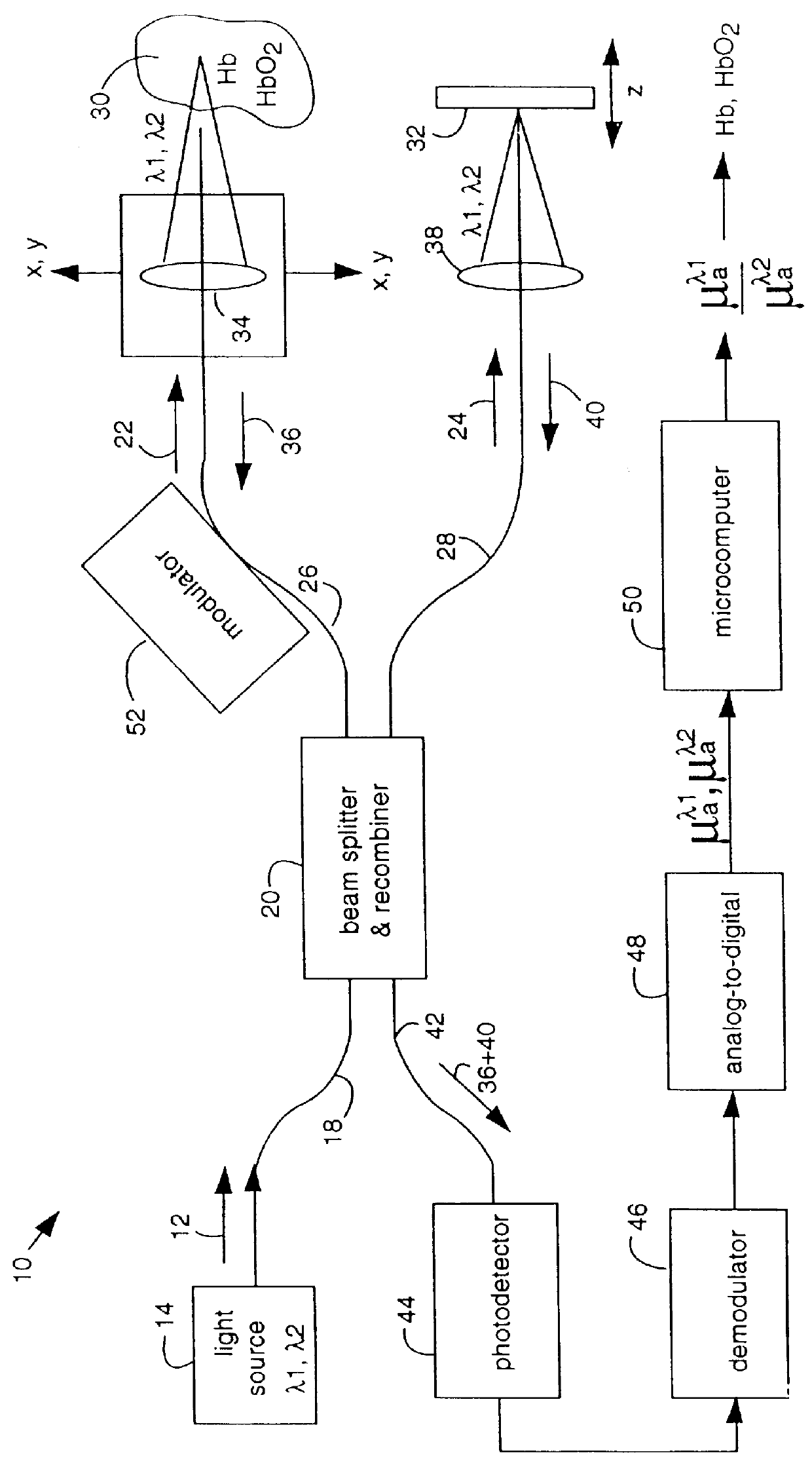
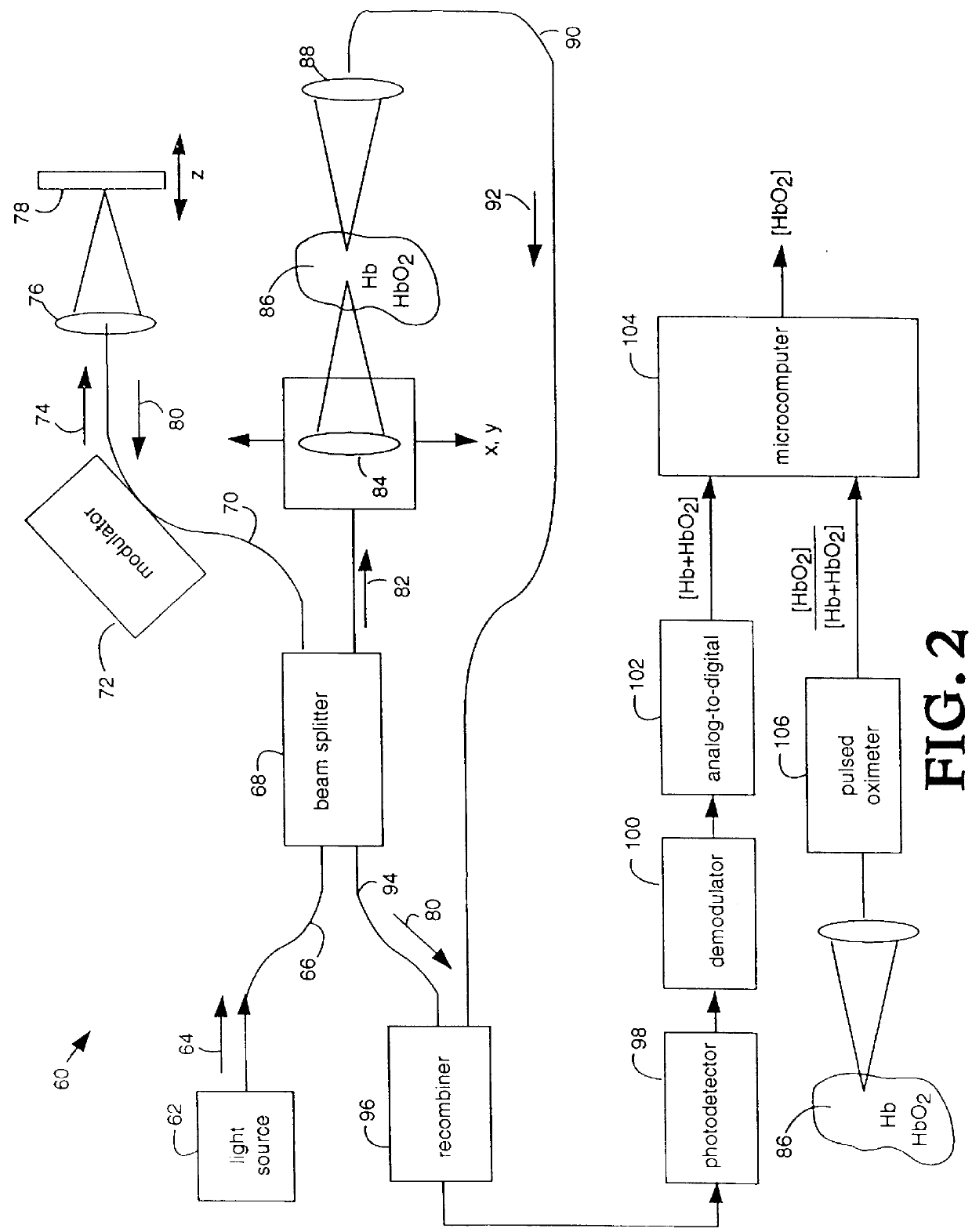
InactiveUS6015969ASimplified determinationRadiation pyrometryPhotoelectric discharge tubesFiberMultiwavelength spectroscopy
An oxygen concentration measurement system for blood hemoglobin comprises a multiple-wavelength low-coherence optical light source that is coupled by single mode fibers through a splitter and combiner and focused on both a target tissue sample and a reference mirror. Reflections from both the reference mirror and from the depths of the target tissue sample are carried back and mixed to produce interference fringes in the splitter and combiner. The reference mirror is set such that the distance traversed in the reference path is the same as the distance traversed into and back from the target tissue sample at some depth in the sample that will provide light attenuation information that is dependent on the oxygen in blood hemoglobin in the target tissue sample. Two wavelengths of light are used to obtain concentrations. The method can be used to measure total hemoglobin concentration [Hb.sub.deoxy +Hb.sub.oxy ] or total blood volume in tissue and in conjunction with oxygen saturation measurements from pulse oximetry can be used to absolutely quantify oxyhemoglobin [HbO.sub.2 ] in tissue. The apparatus and method provide a general means for absolute quantitation of an absorber dispersed in a highly scattering medium.
Owner:LAWRENCE LIVERMORE NAT SECURITY LLC
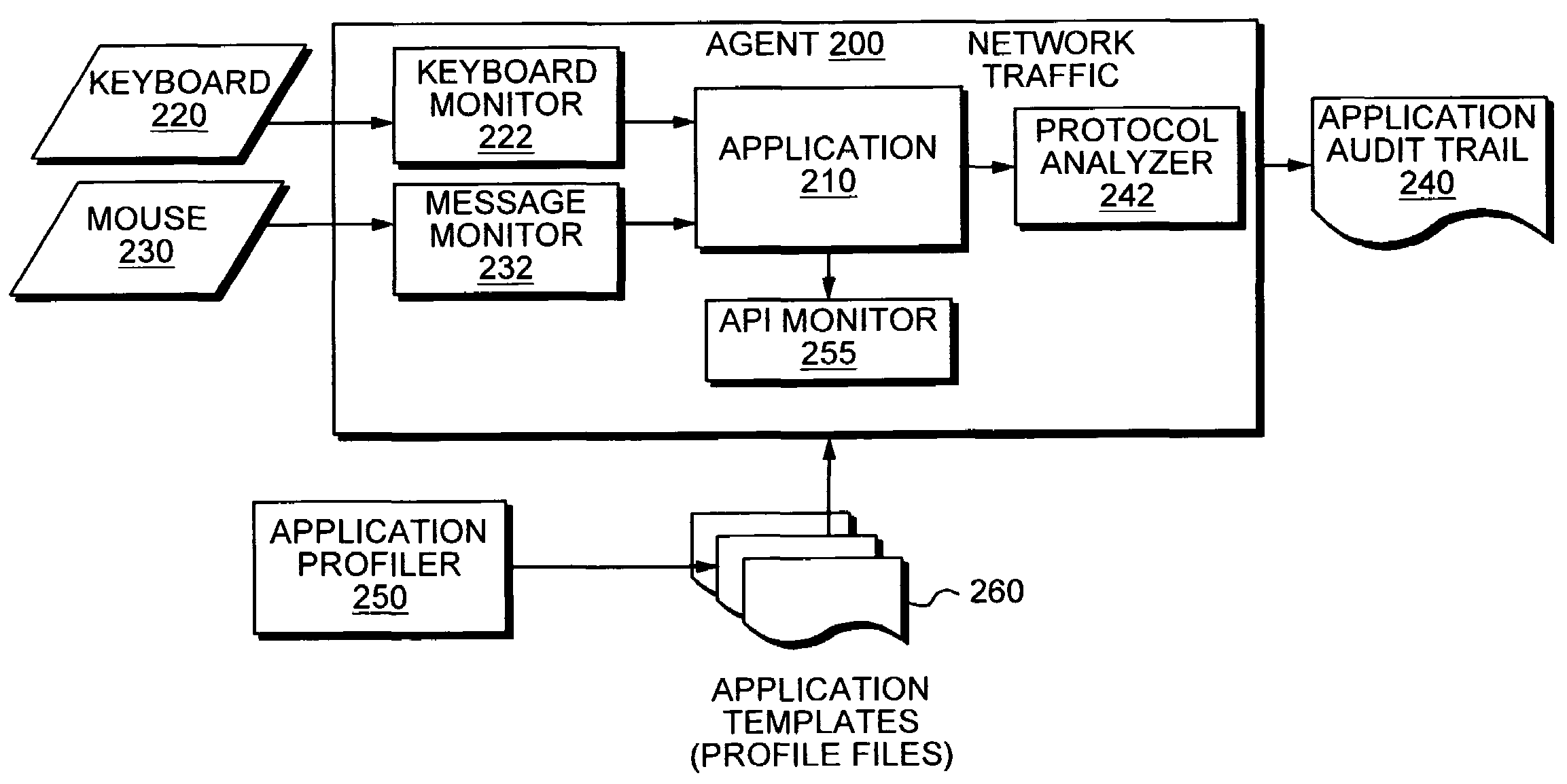
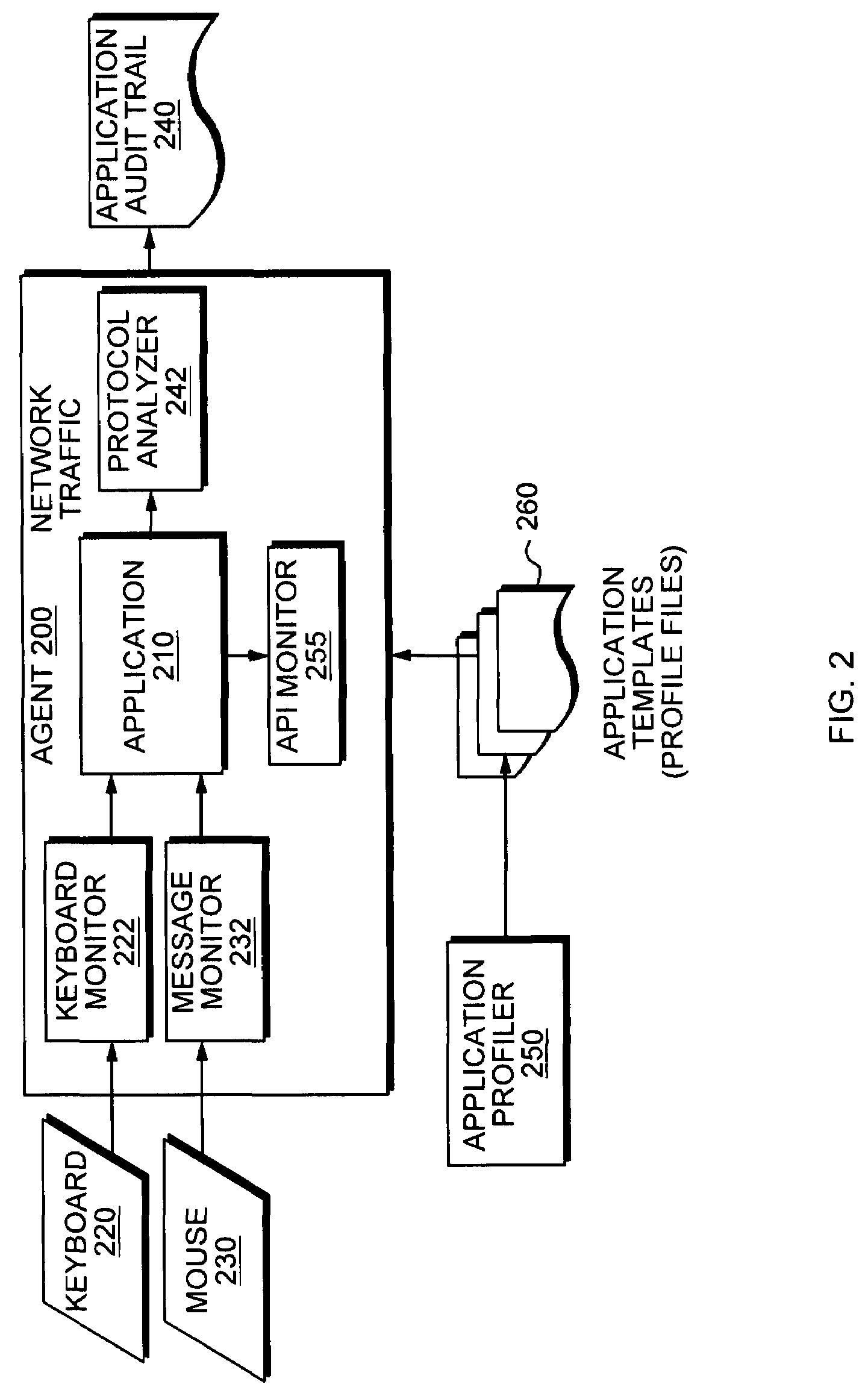
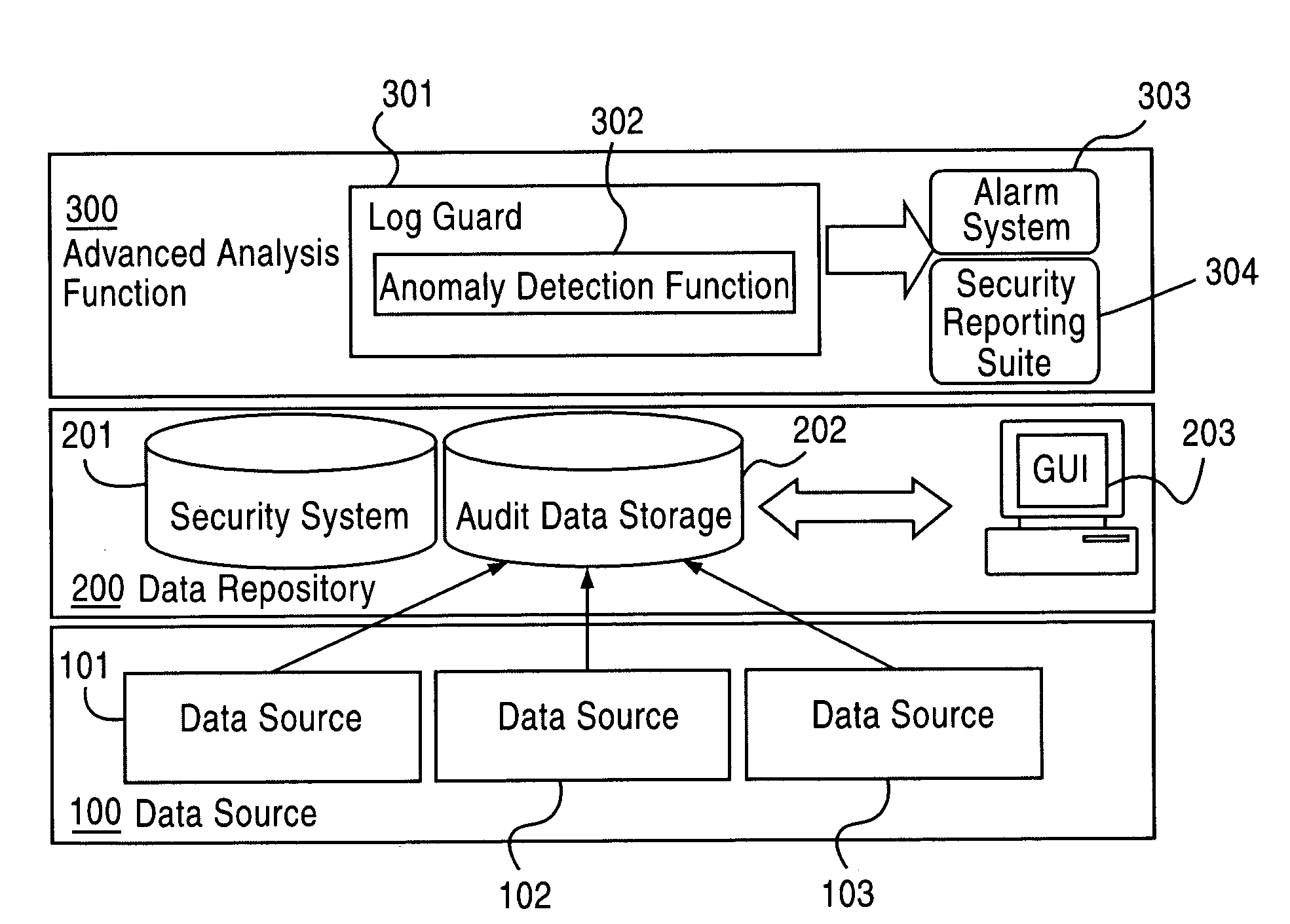
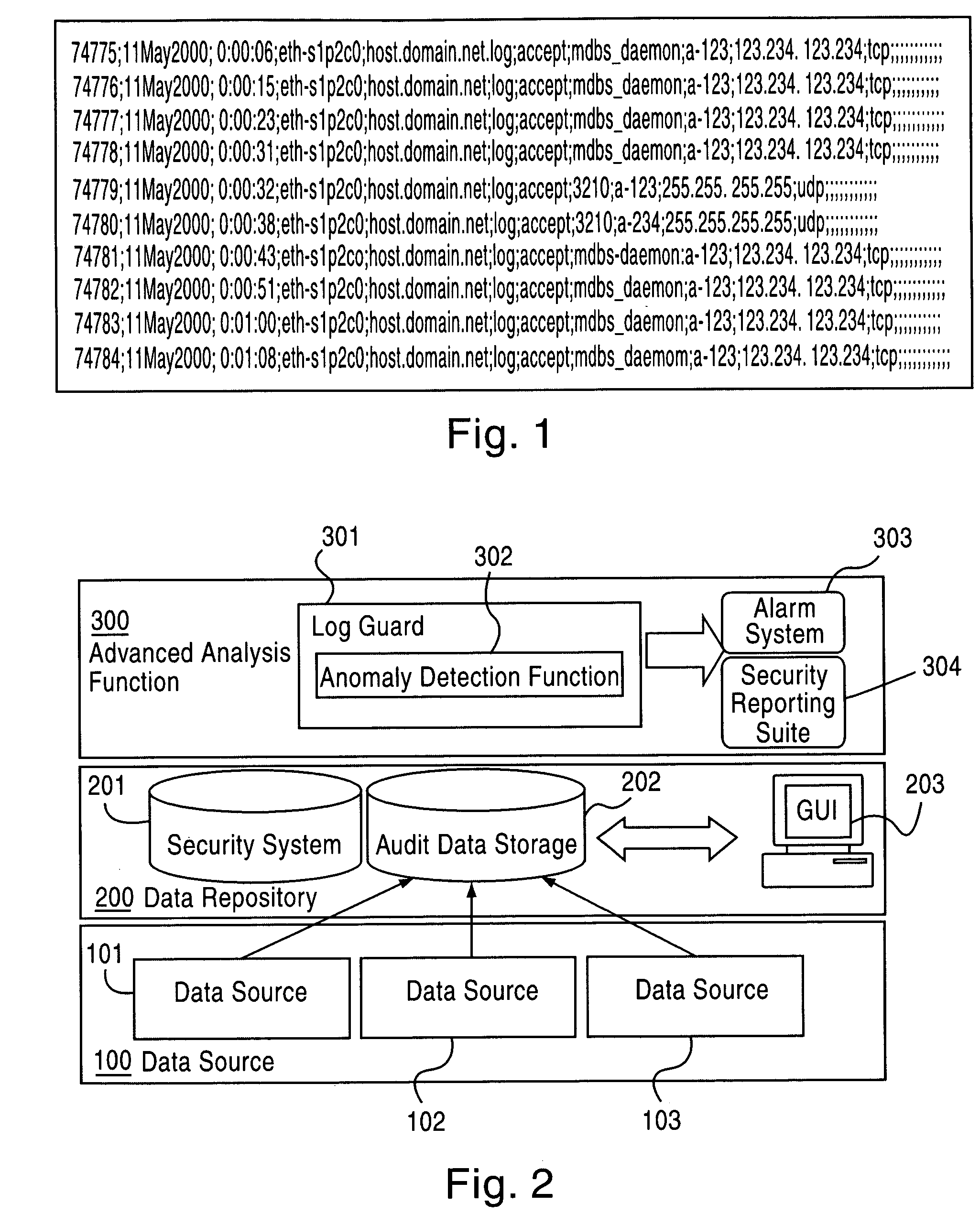
Application instrumentation and monitoring
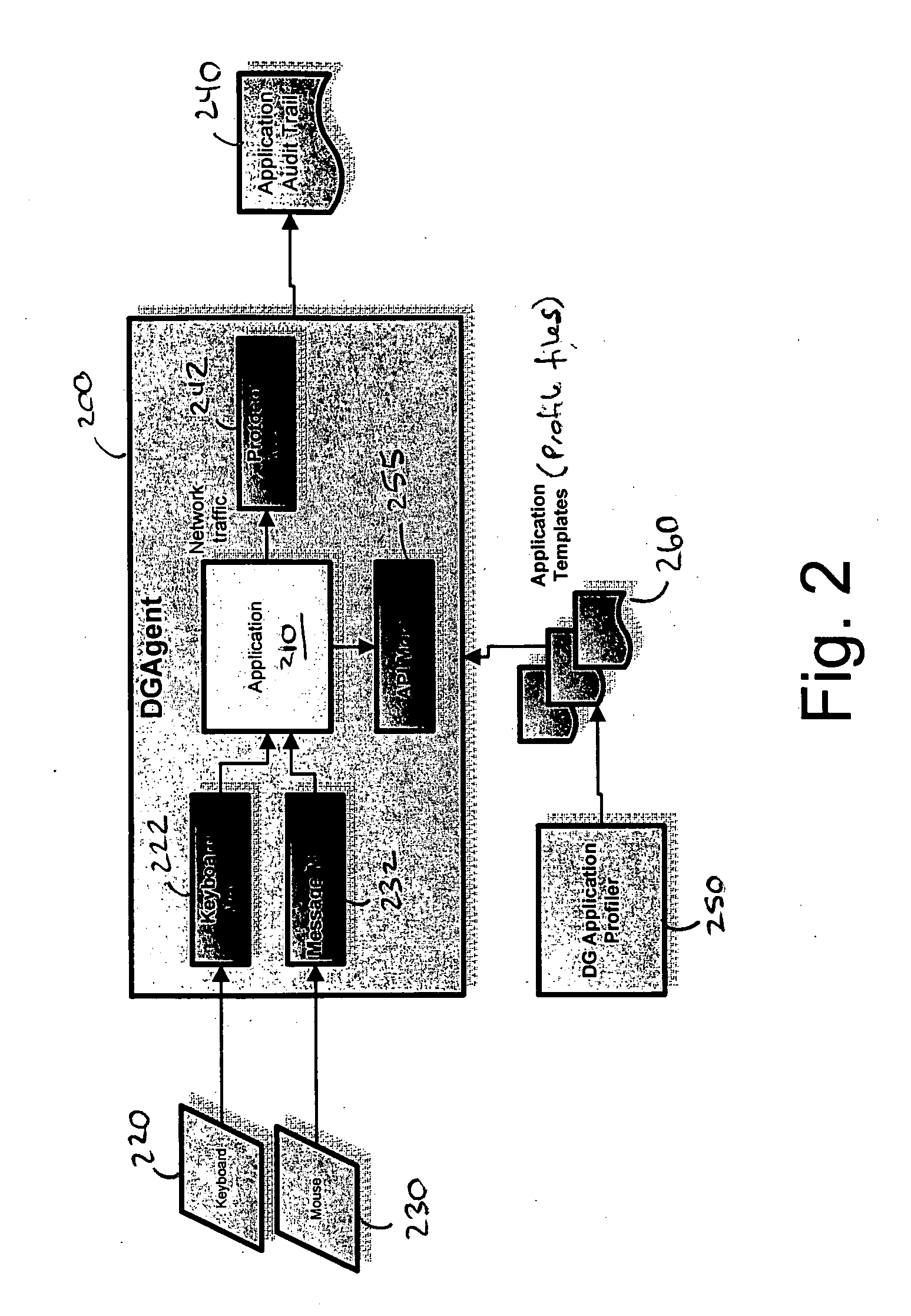
ActiveUS7496575B2Cost effectiveAvoid the needDigital data processing detailsDigital computer detailsApplication softwareData store
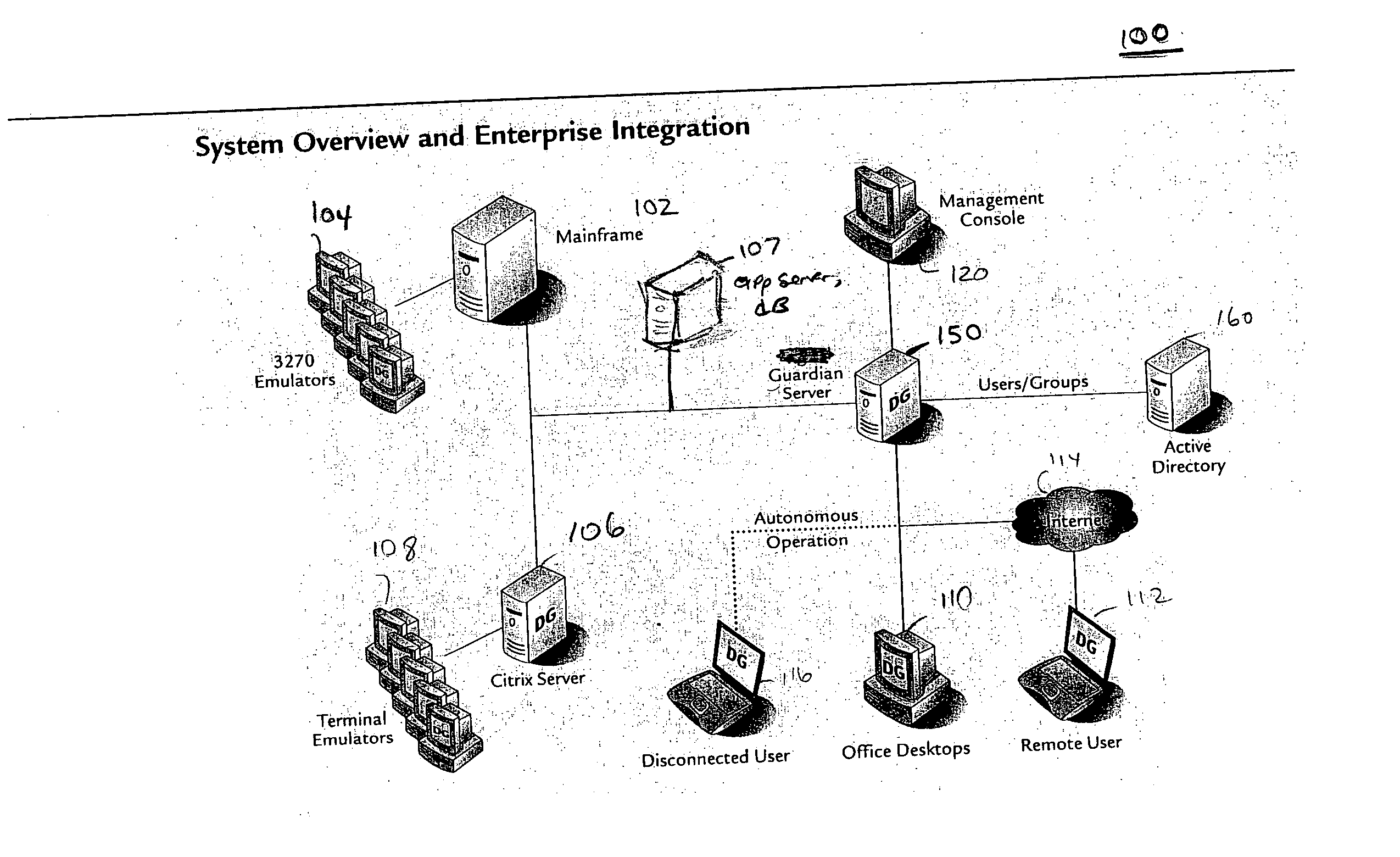
A data processing application logging, recording, and reporting process and infrastructure. Compliance with regulatory directives such as HIPAA, internal organizational and corporate, personal information privacy, and other security policies can thus be enforced without the need to recode legacy application software. In one preferred embodiment, a core agent process provides “listener” functionality that captures user input events, such as keyboard and mouse interactions, between a user and a legacy application of interest. The agent obtains instructions for how to deal with such events, accessing information that describes the application's behavior as already captured by an application profiler tool. Keyboard and mouse data entry sequences, screen controls and fields of interest are tagged during application profiling process. This data is stored in application profile developed for each mode of a legacy application. The technique can be implemented in various Information Technology (IT) environments including mainframe / terminal applications and / or client / server applications. Thus, full coverage of “fat” client, “thin” client, and legacy “mainframe” applications can be provided with a common approach across an enterprise.
Owner:DIGITAL GUARDIAN LLC
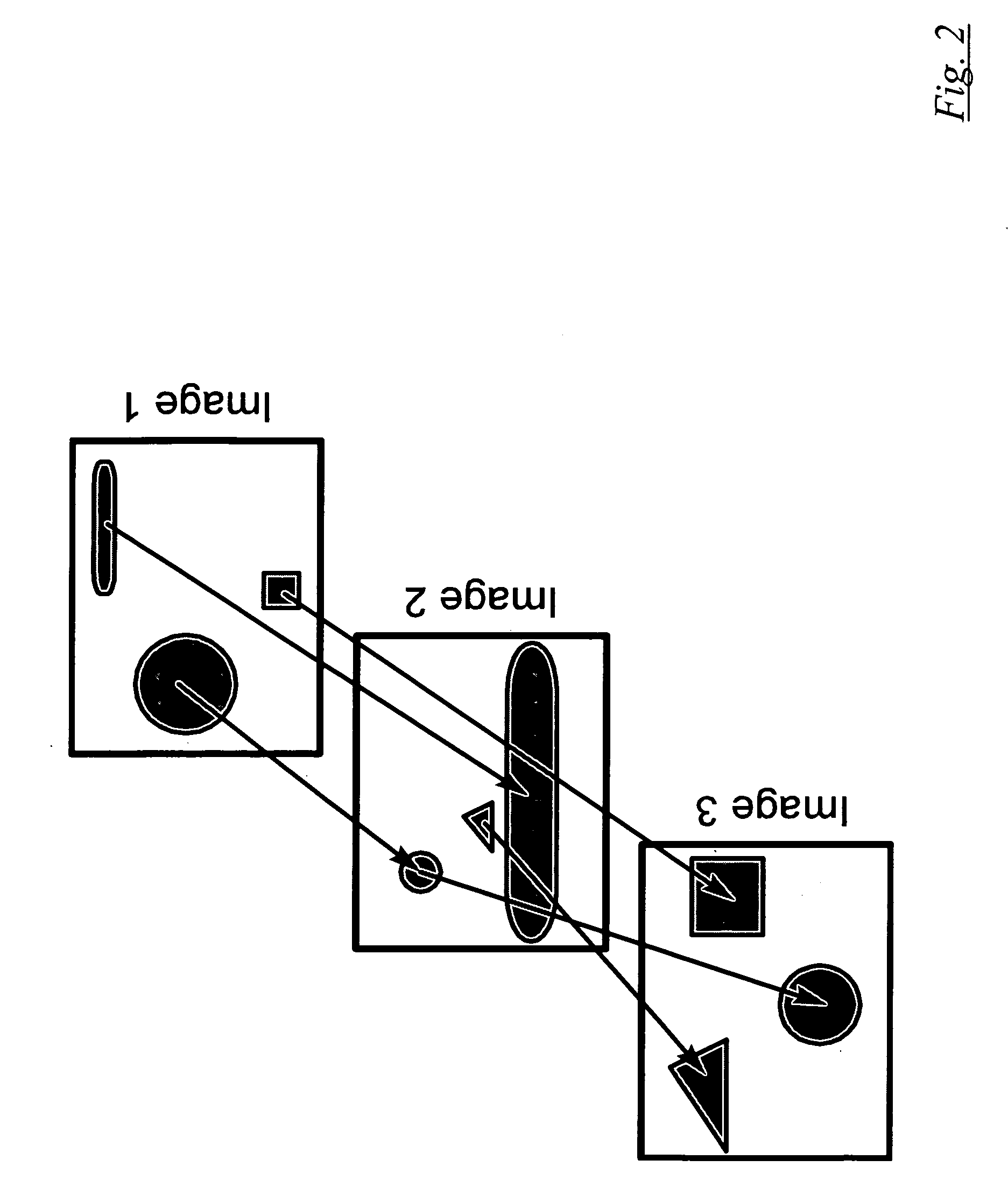
Method, system and computer program for interactive spatial link-based image searching, sorting and/or displaying
ActiveUS20080069480A1Effective registrationEfficient use ofCharacter and pattern recognitionStill image data indexingApplication softwareFast methods
A web-based application provides more accurate and clearer methods of searching, sorting, and displaying a set of images stored in a database. A first aspect of the present invention is the method by which image data is stored. Typical content-based systems use colour information, whereas the present invention uses an image-location tagging method. A second aspect of the present invention is the method by which the set of images are sorted in relevancy. Tag data of the images allows for a new and fast method of searching through an entire set. A third aspect of the present invention is the method by which the sorted images are displayed to the user. Instead of the common method of just displaying the images in a rectangular array, where each image is the same size, the web-based application positions and sizes each image based on how relevant it is.
Owner:AARABI PARHAM +1
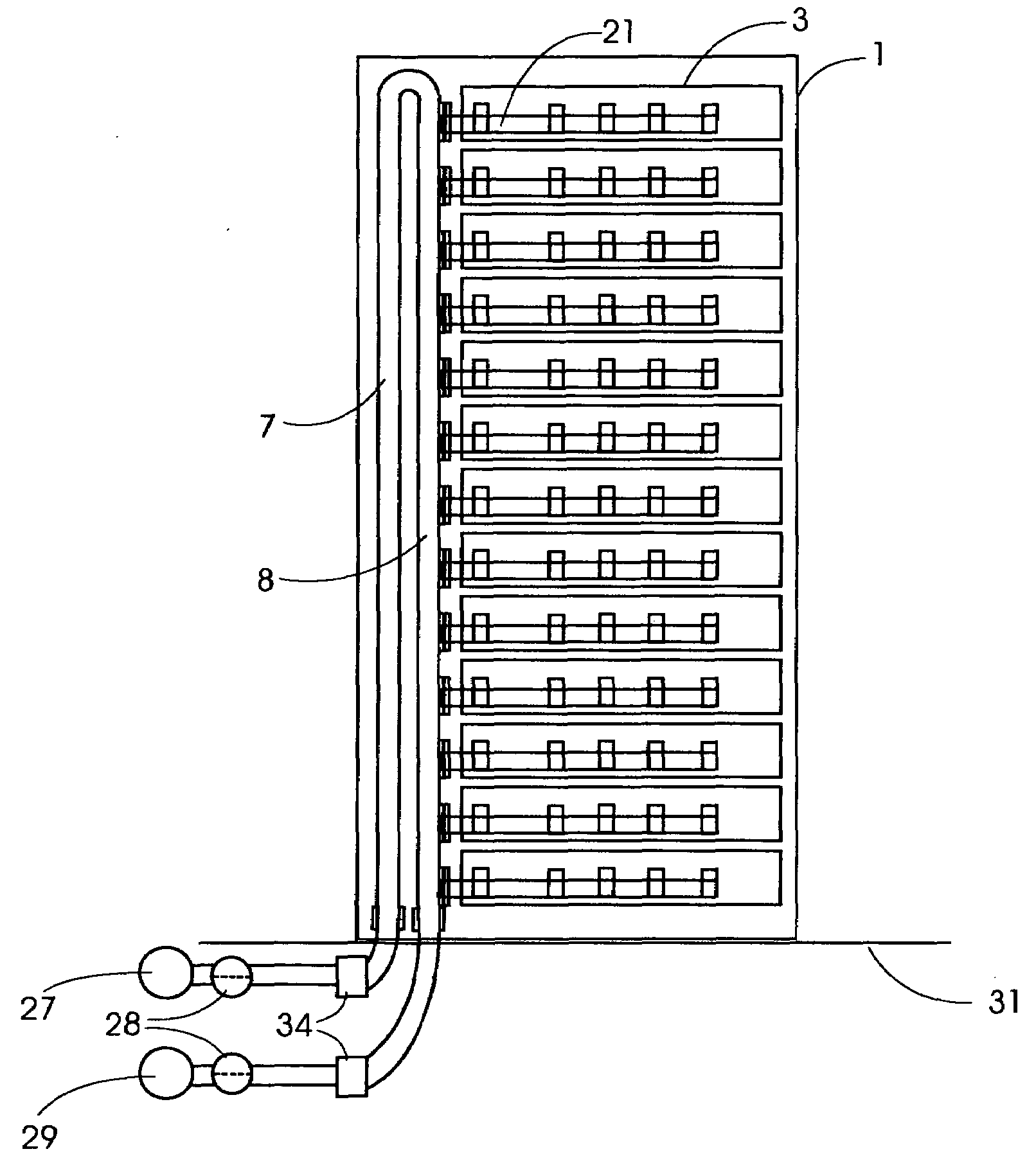
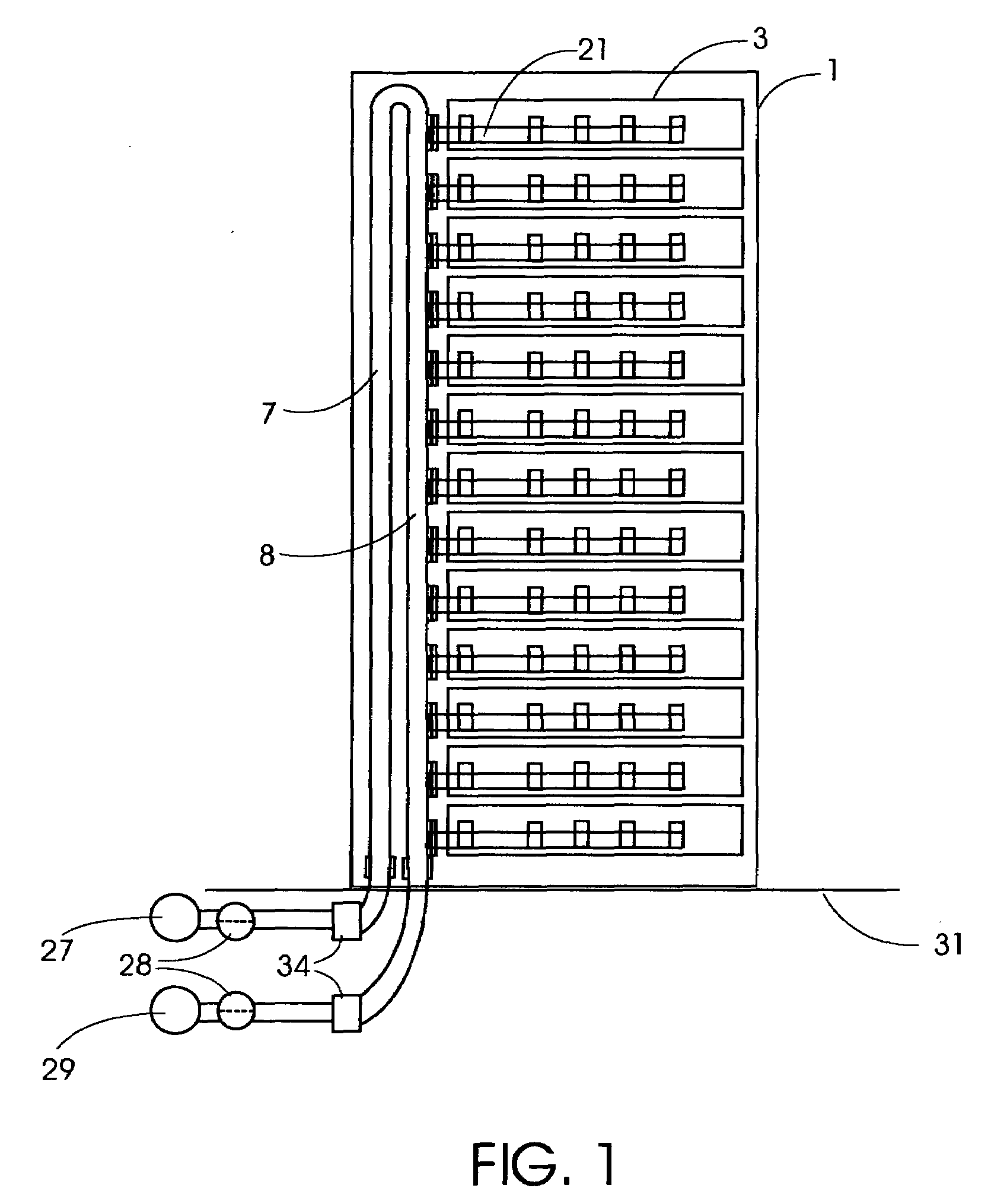
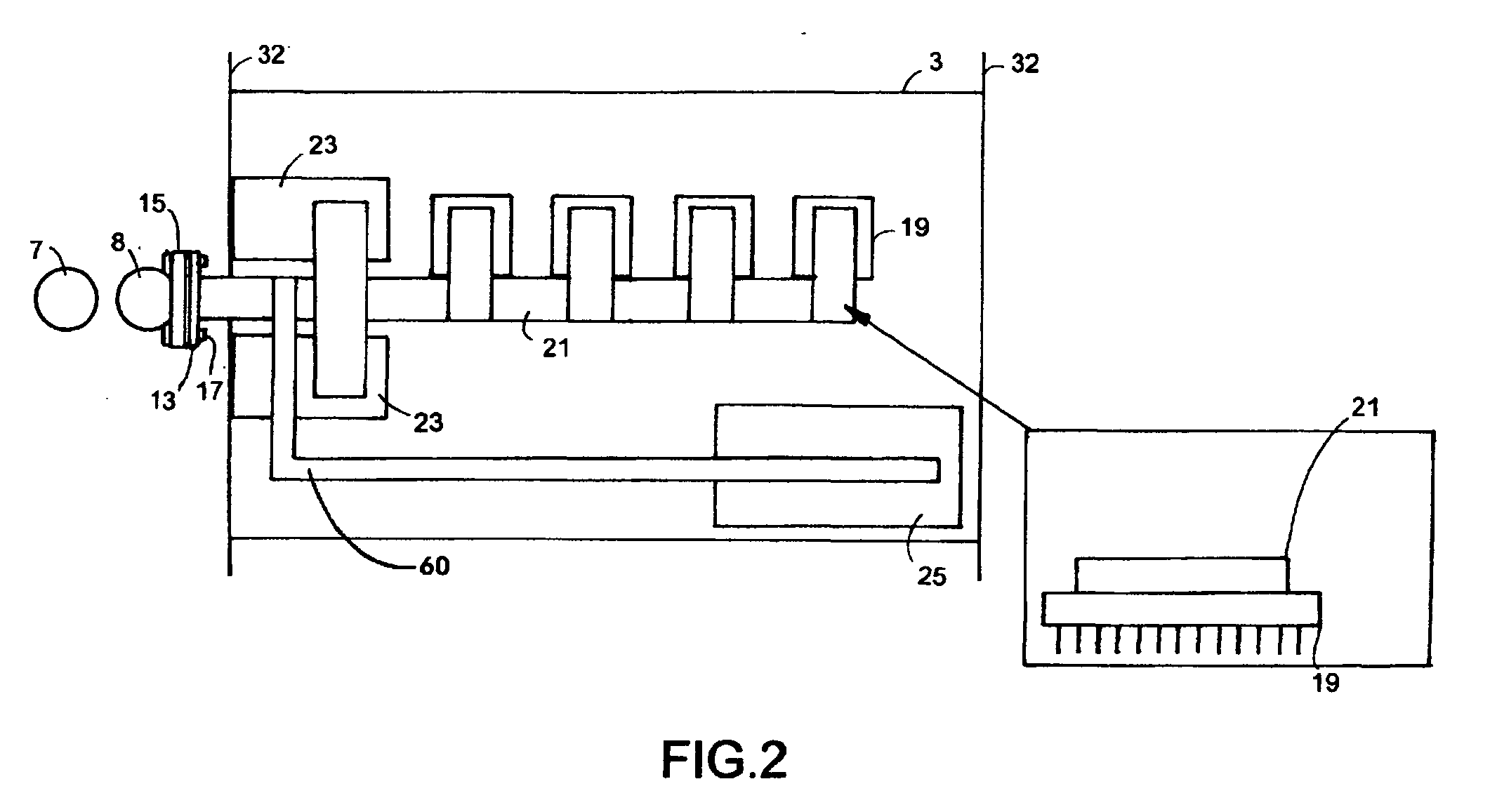
High efficiency heat removal system for rack mounted computer equipment
InactiveUS20090262495A1Minimize energy usageEfficient transportDomestic cooling apparatusDigital data processing detailsHeat conductingEngineering
An efficient method of heat removal from rack mounted computer equipment, network gear and other electronic equipment, consisting of solid heat conducting components in direct contact with the heat generating sources. In particular, this invention is primarily focused on the ability to efficiently and effectively cool computer equipment in standard computer rack cabinets.This invention utilizes a design that retains the general existing form factor of the rack mounted computer equipment, but uses direct contact heat transfer to a metal heat transfer conduit (Copper, Aluminum or other metal or efficient heat conducting material) contained within the computer equipment chassis. Furthermore, it is thermally coupled to an external rack mounted solid-to-fluid heat exchanger as an efficient method of heat transfer and removal. This is much more efficient than air as heat transfer medium which it the common method of heat removal from existing standardized rack mounted computer equipment.This invention covers the design of the heat transfer components within the chassis of rack mounted computer server and the heat transfer system components external to the server within rack enclosure, as well as the external cooling system components necessary to connect to existing fluid based heat transfer and removal systems and processes.
Owner:NEUDORFER JULIUS
Method of administering software components using asynchronous messaging in a multi-platform, multi-programming language environment
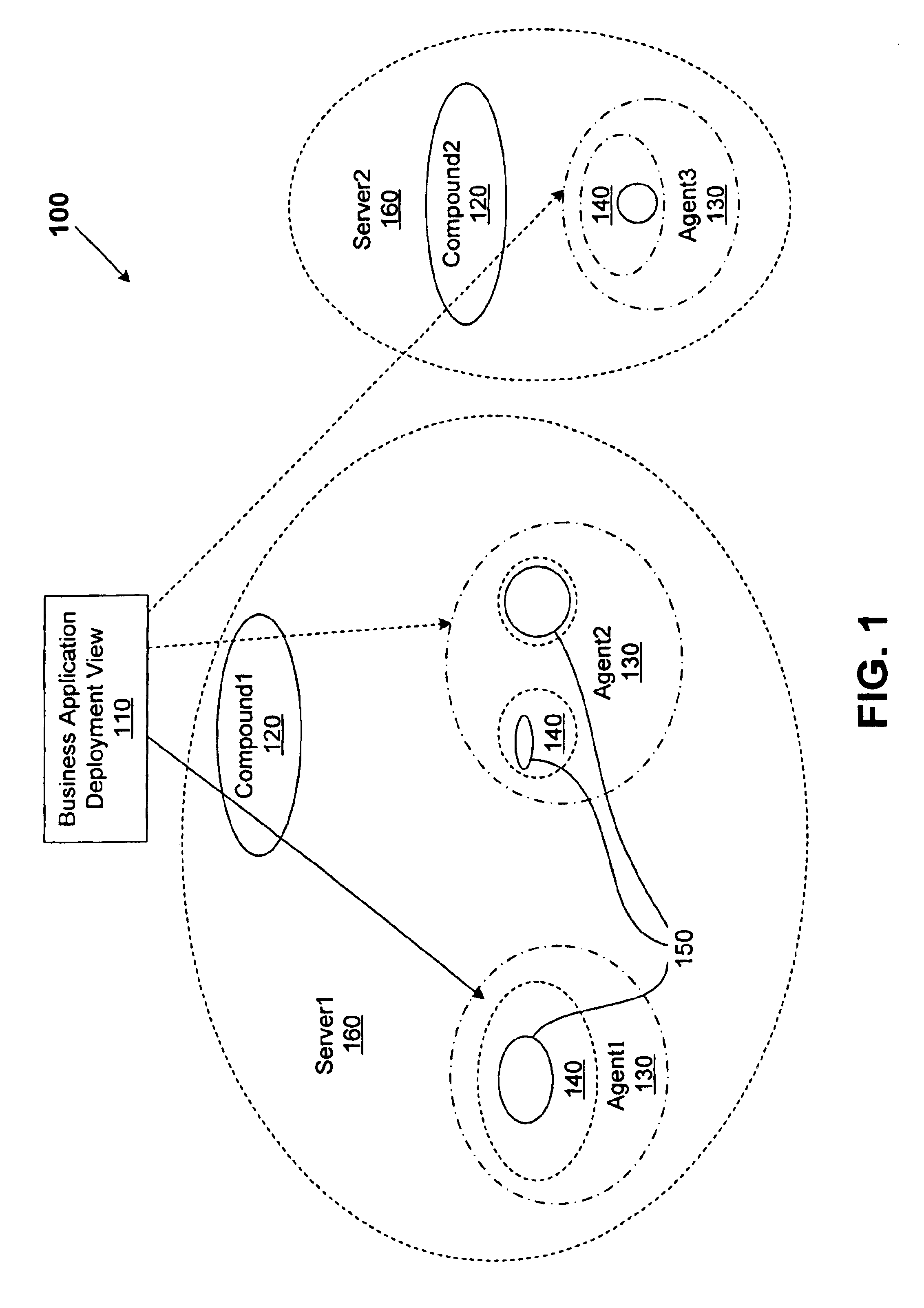
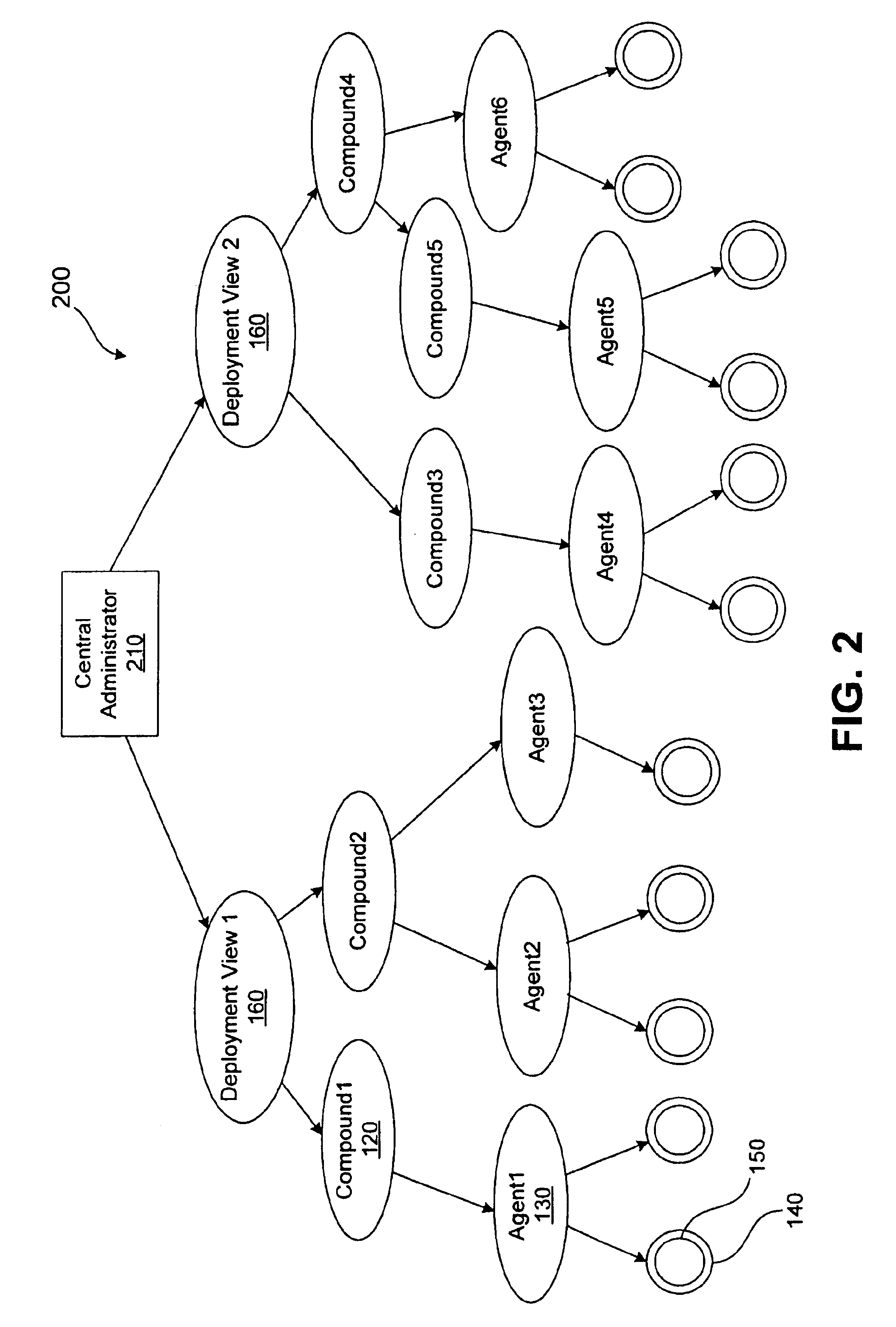
A method for performing life cycle management of business software applications and their components across a multiple-platform, multiple-language network. The method takes advantage of the inheritance properties of object-oriented programming (OOP) by developing all components of a business application from a set of base classes, thus deploying a common set of methods across all application components. The Central Administrator then determines when a need to reconfigure one or more components of the business application has arisen. The Central Administrator then modifies or replaces existing components of the business application or installs entirely new components over the network without end user interaction. In one embodiment of the present invention, the Central Administrator is aided by a set of Distributed Administrators located on each virtual node server / host computer of a business application operating over a network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method for insertion and overlay of media content upon an underlying visual media
InactiveUS20080101456A1Good flexibilityComplicate the architecture necessaryTelevision system detailsColor television with pulse code modulationProgram segmentVideo bitstream
An improved system and method for enabling the insertion, overlay, removal or replacement of sequential or concurrent targeted program segments and / or visual icons in a video bitstream without modifying the fidelity of the underlying visual media. The present invention provides for a wide variety of supplemental enhancement information fields which permit the use of data updates that are synchronous with delivered video content. The present invention offers a generic approach to program insertion and iconic overlay that covers a wide range of use-cases and applications, without necessarily transmitting the visual content to be inserted as part of the underlying visual media stream.
Owner:NOKIA CORP
Application instrumentation and monitoring
ActiveUS20060123101A1Cost effectiveAvoid the needDigital computer detailsComputer security arrangementsApplication softwareData store
A data processing application logging, recording, and reporting process and infrastructure. Compliance with regulatory directives such as HIPAA, internal organizational and corporate, personal information privacy, and other security policies can thus be enforced without the need to recode legacy application software. In one preferred embodiment, a core agent process provides “listener” functionality that captures user input events, such as keyboard and mouse interactions, between a user and a legacy application of interest. The agent obtains instructions for how to deal with such events, accessing information that describes the application's behavior as already captured by an application profiler tool. Keyboard and mouse data entry sequences, screen controls and fields of interest are tagged during application profiling process. This data is stored in application profile developed for each mode of a legacy application. The technique can be implemented in various Information Technology (IT) environments including mainframe / terminal applications and / or client / server applications. Thus, full coverage of “fat” client, “thin” client, and legacy “mainframe” applications can be provided with a common approach across an enterprise.
Owner:DIGITAL GUARDIAN LLC
SIP-based VoIP traffic behavior profiling
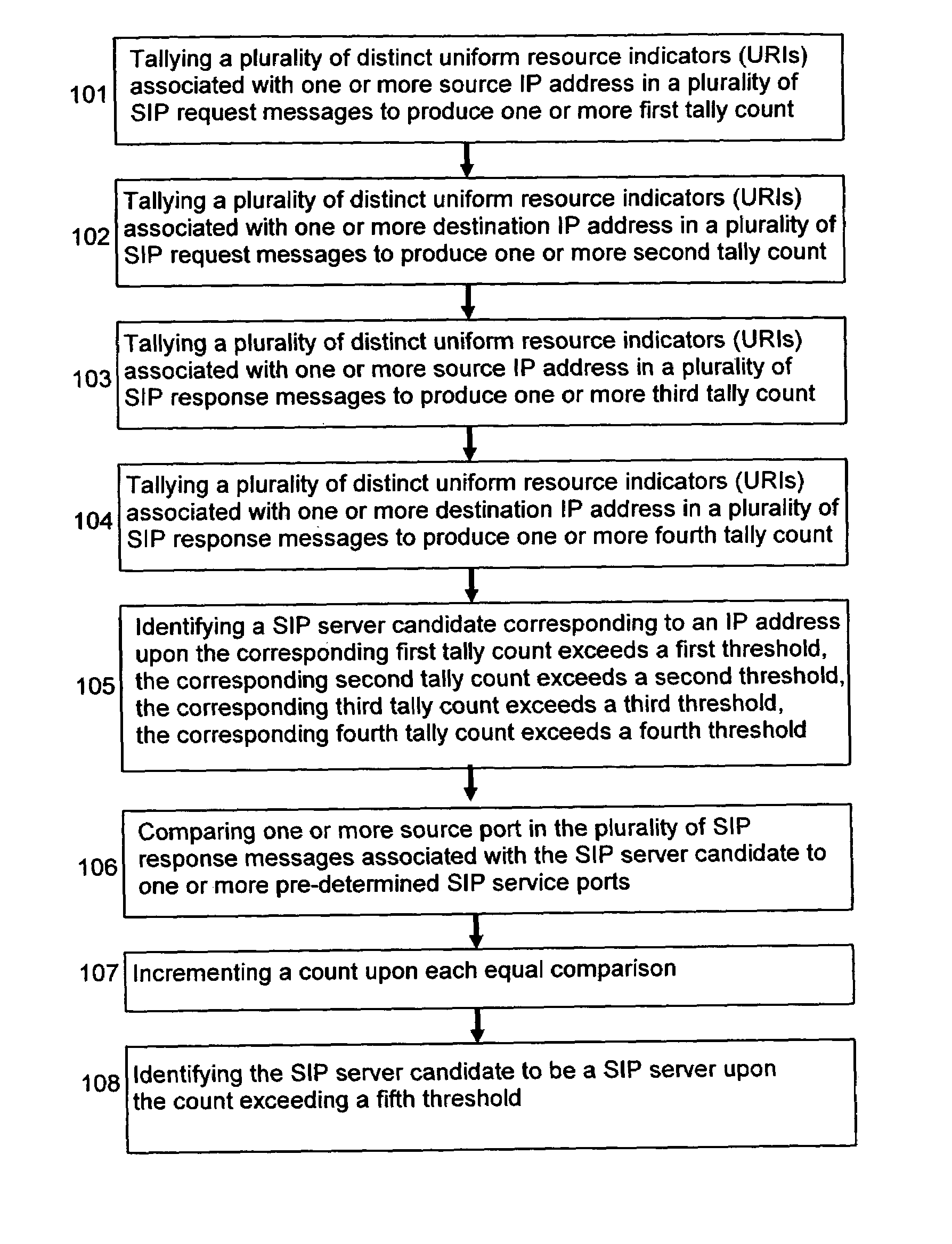
ActiveUS7441429B1Accurate diagnosisPrecise processPinsError preventionTraffic capacityAnalysis method
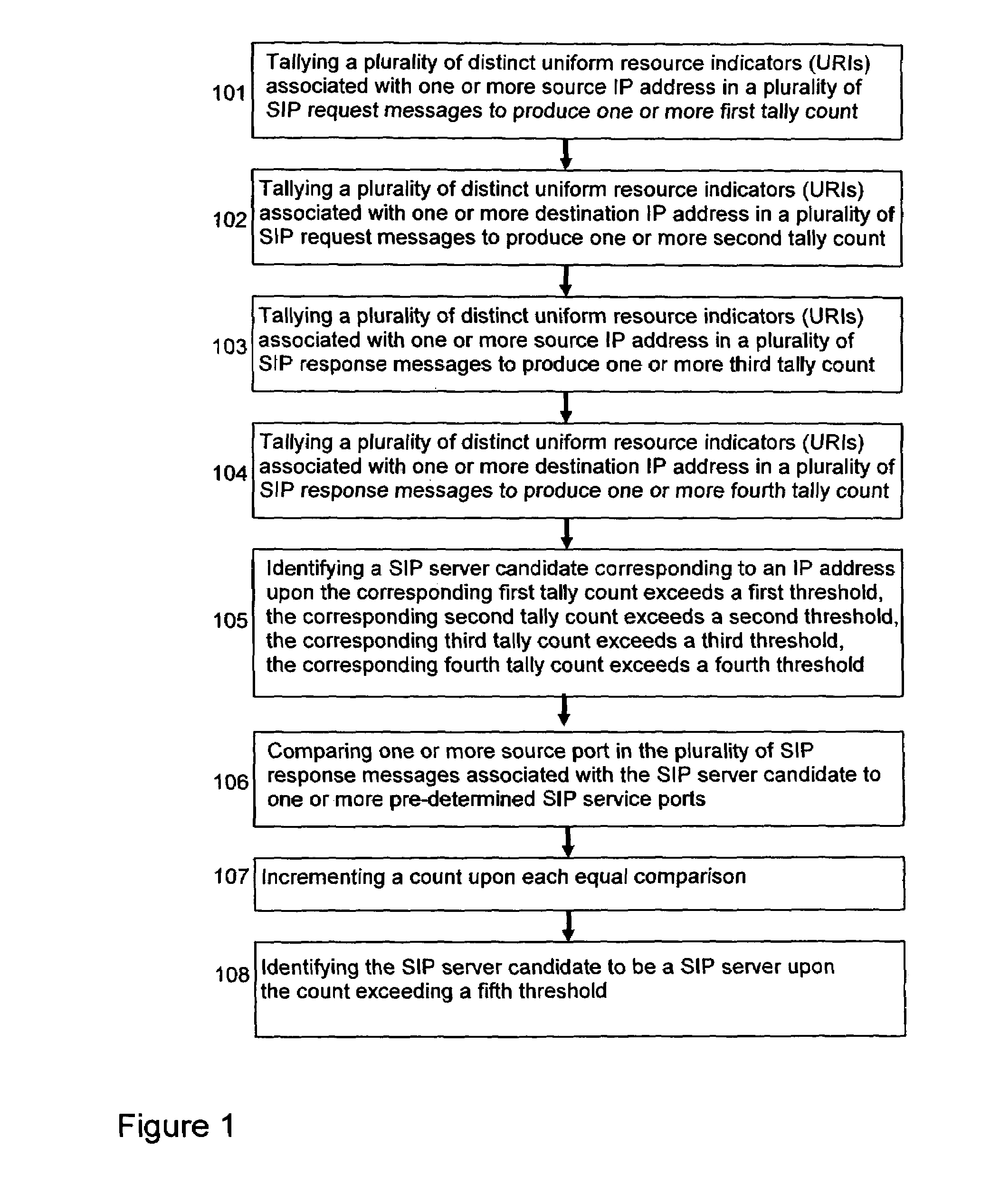
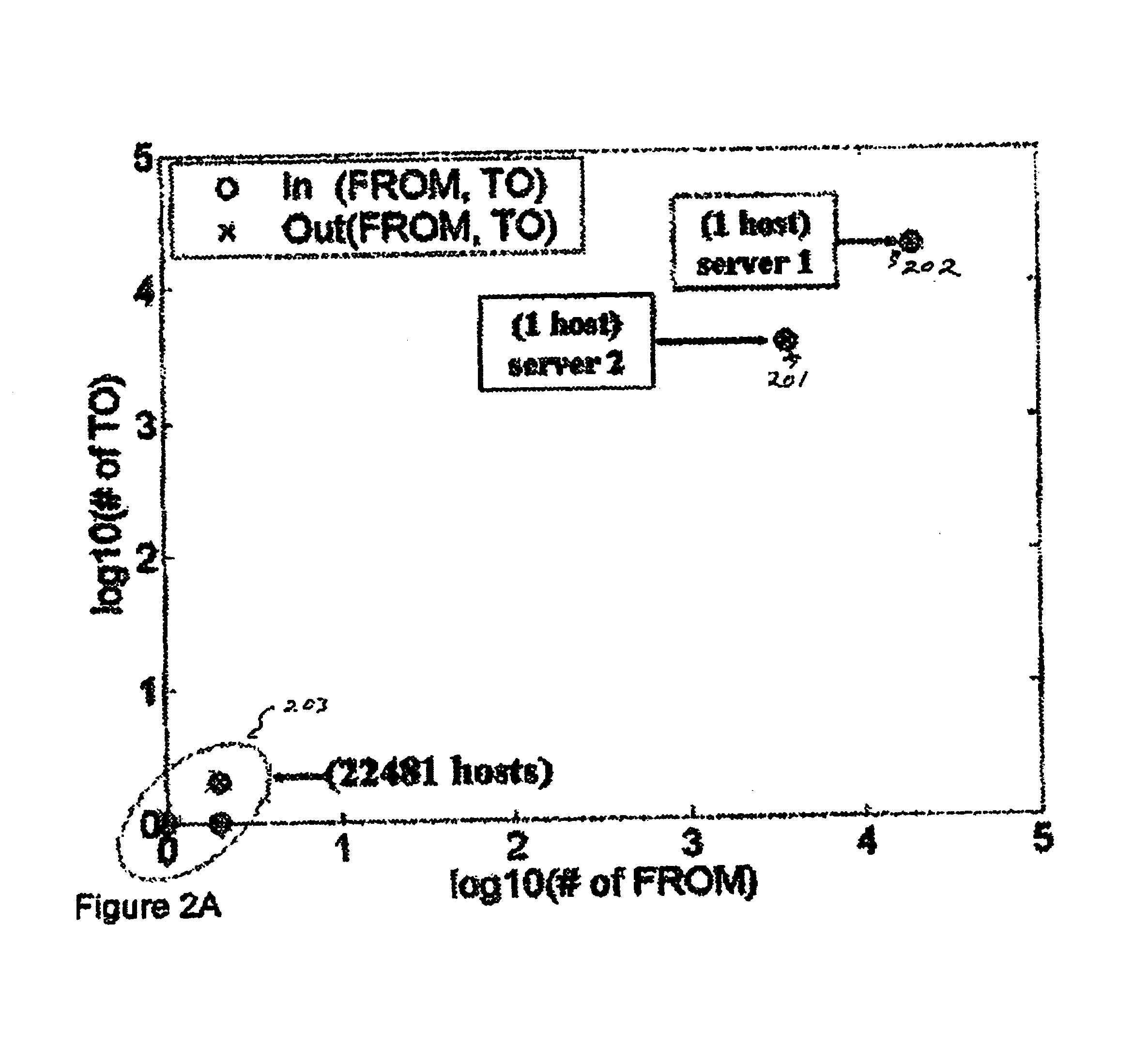
With the widespread adoption of SIP-based VoIP, understanding the characteristics of SIP traffic behavior is critical to problem diagnosis and security protection of VoIP services. A general methodology is provided for profiling SIP-based VoIP traffic behavior at several levels: SIP server host, server entity (e.g., registrar and call proxy) and individual user levels. Using SIP traffic traces captured in a production VoIP network, the characteristics of SIP-based VoIP traffic behavior in an operational environment is illustrated and the effectiveness of the general profiling methodology is demonstrated. In particular, the profiling methodology identifies anomalies due to performance problems and / or implementation flaws through a case study. The efficacy of the methodology in detecting potential VoIP attacks is also demonstrated through a test bed experimentation.
Owner:THE BOEING CO
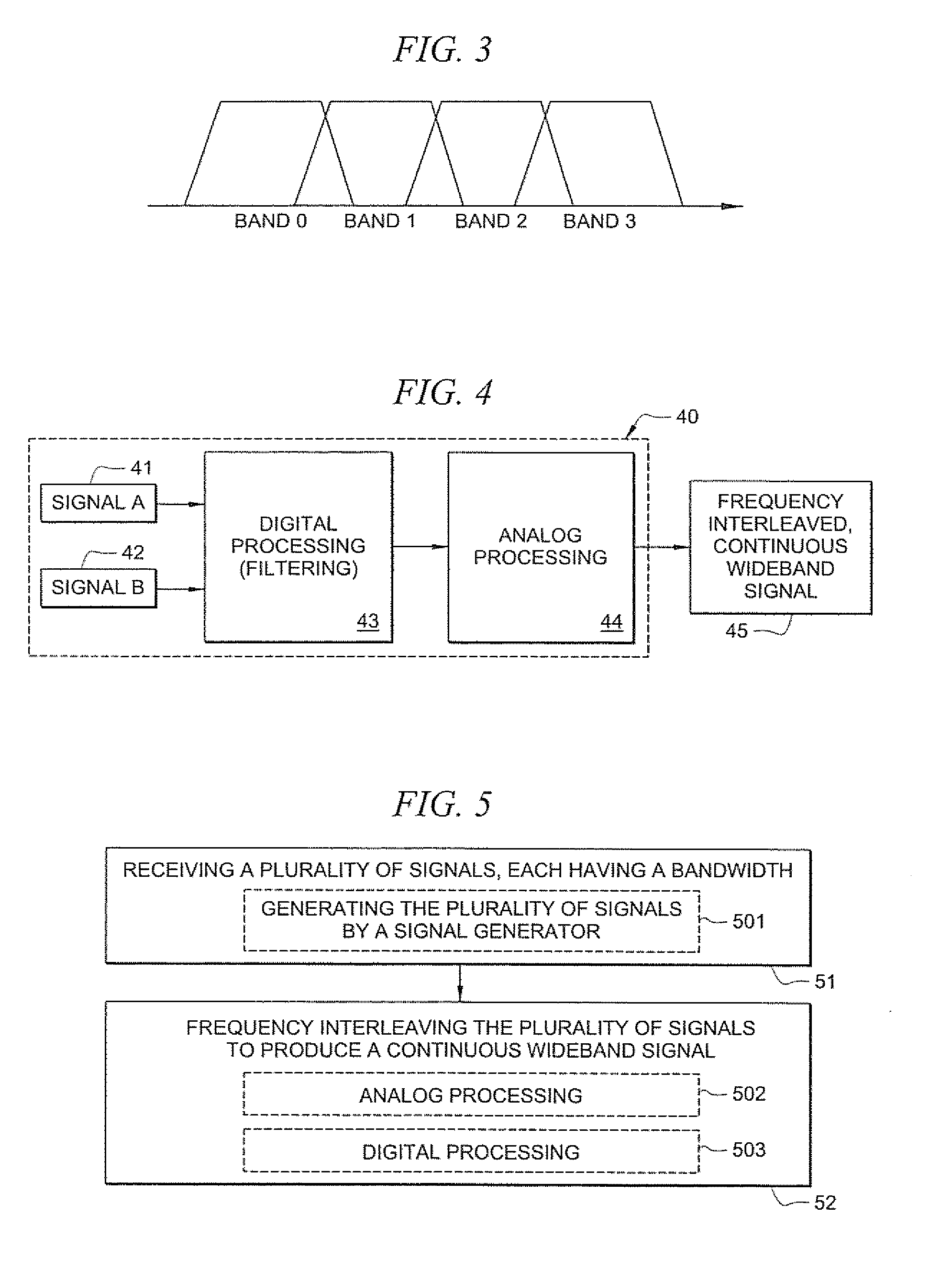
Frequency interleaving method for wideband signal generation
InactiveUS20090052556A1Improve fidelityAvoiding “ spectral hole ”Electric signal transmission systemsTransmissionDigital signal processingEngineering
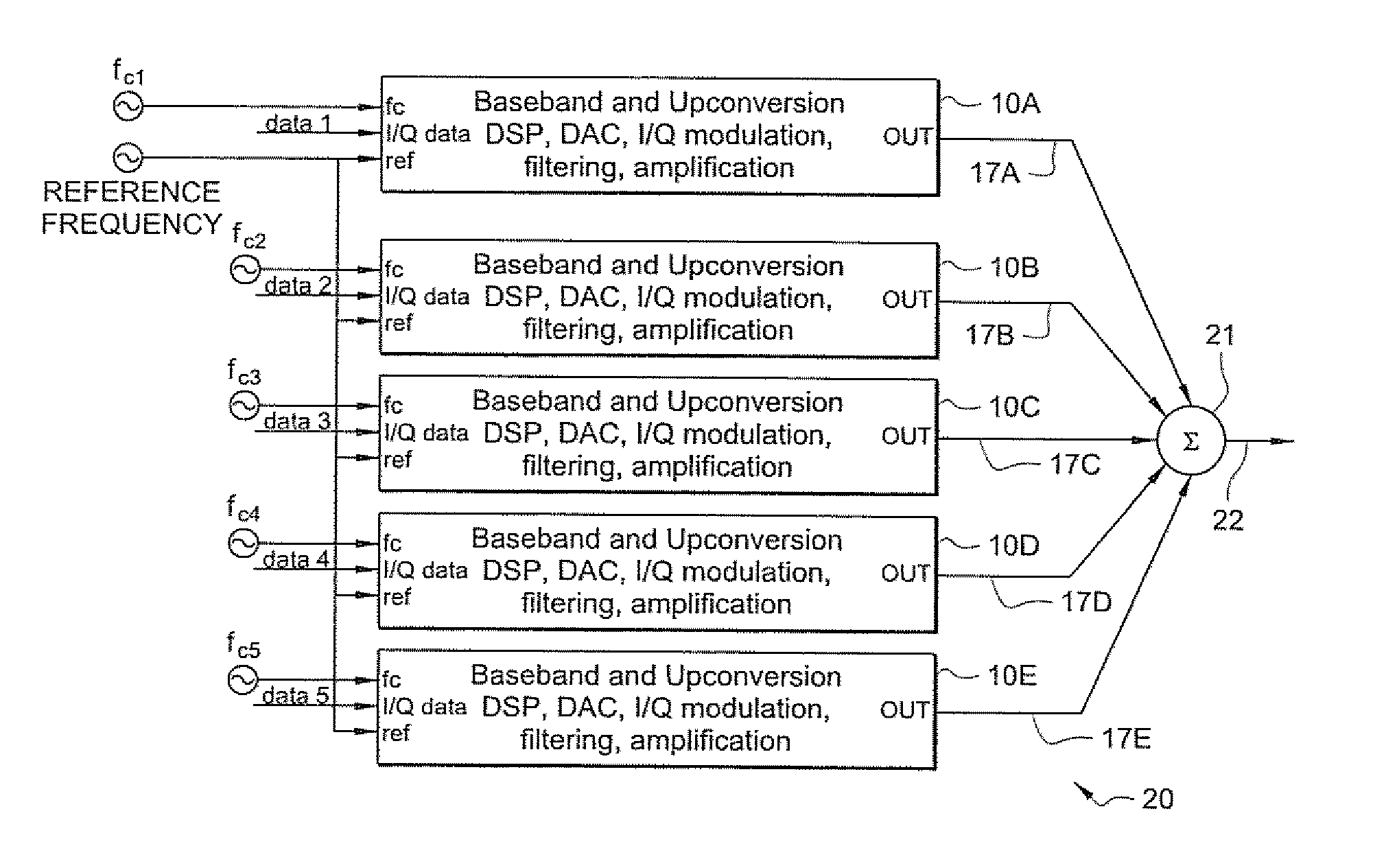
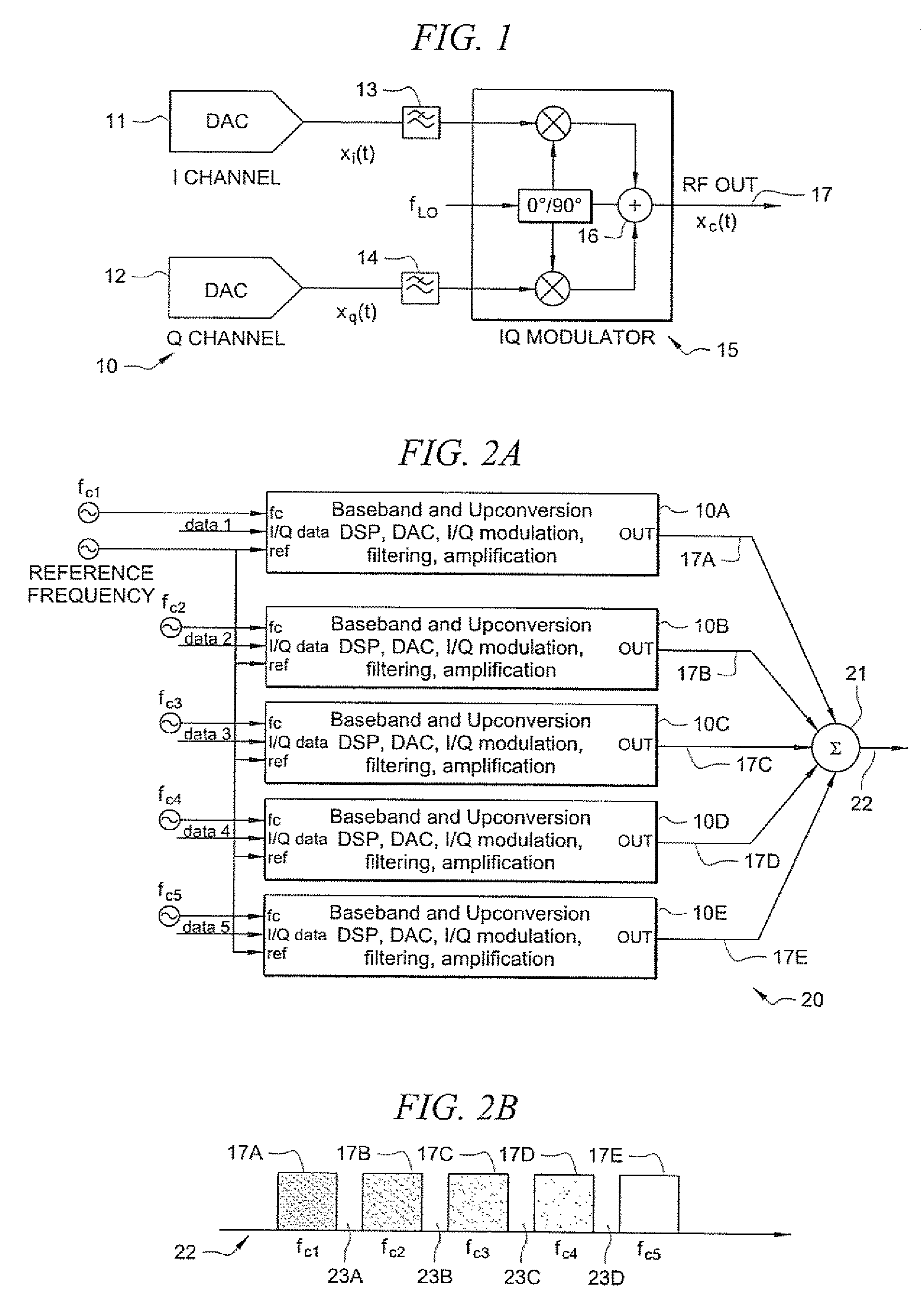
Wideband signal generation systems and methods are provided which employ frequency interleaving for generating wideband signals. A general method increases a digitally synthesized signal's bandwidth by frequency interleaving multiple digitally synthesized signal sources of narrower bandwidth. Frequency interleaving creates a continuous wideband signal by summing multiple narrower band signals that overlap in frequency. According to certain embodiments, digital signal processing (DSP) and analog mixing are used to create the multiple narrower band signals such that a high fidelity, continuous wideband signal is produced when the multiple narrower band signals are summed.
Owner:KEYSIGHT TECH
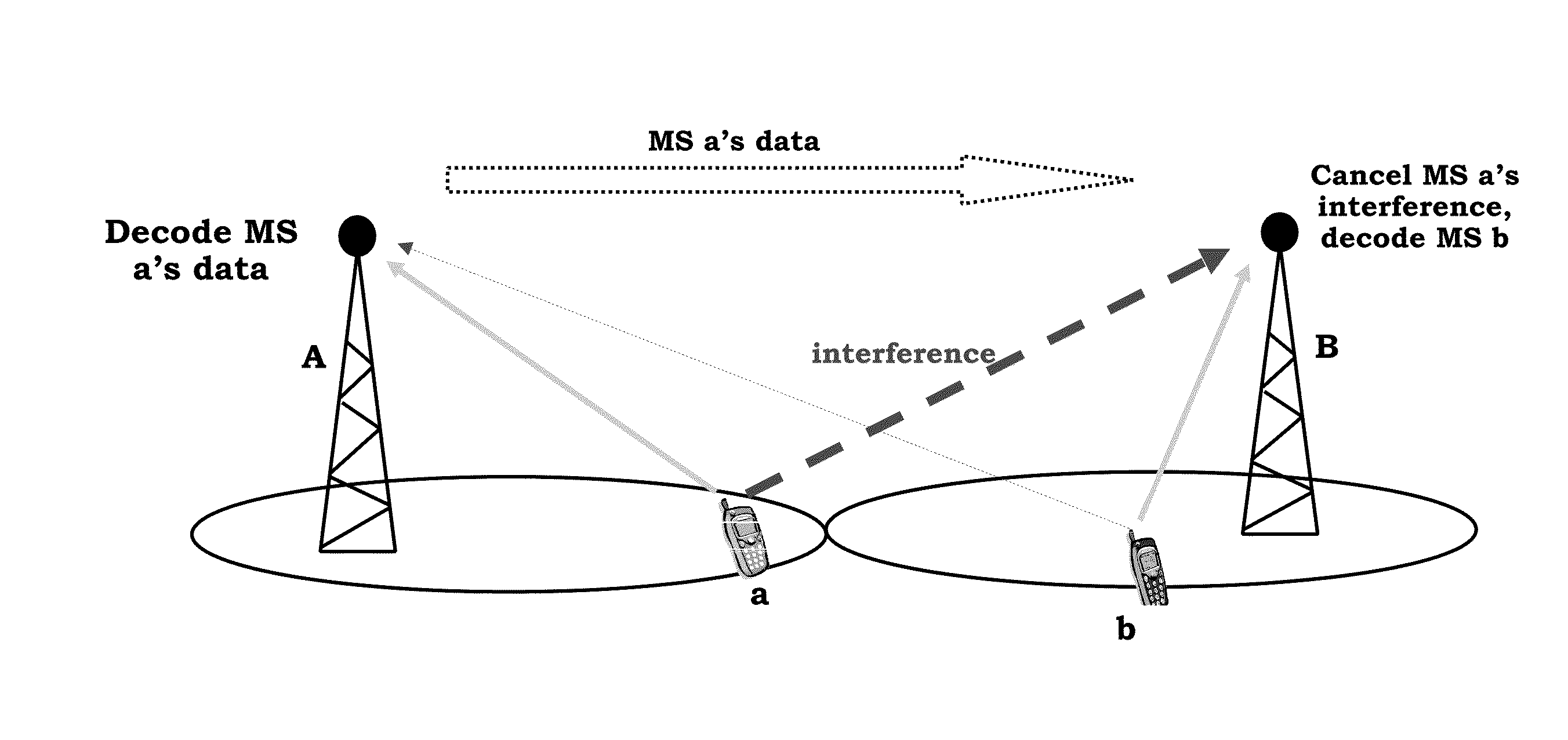
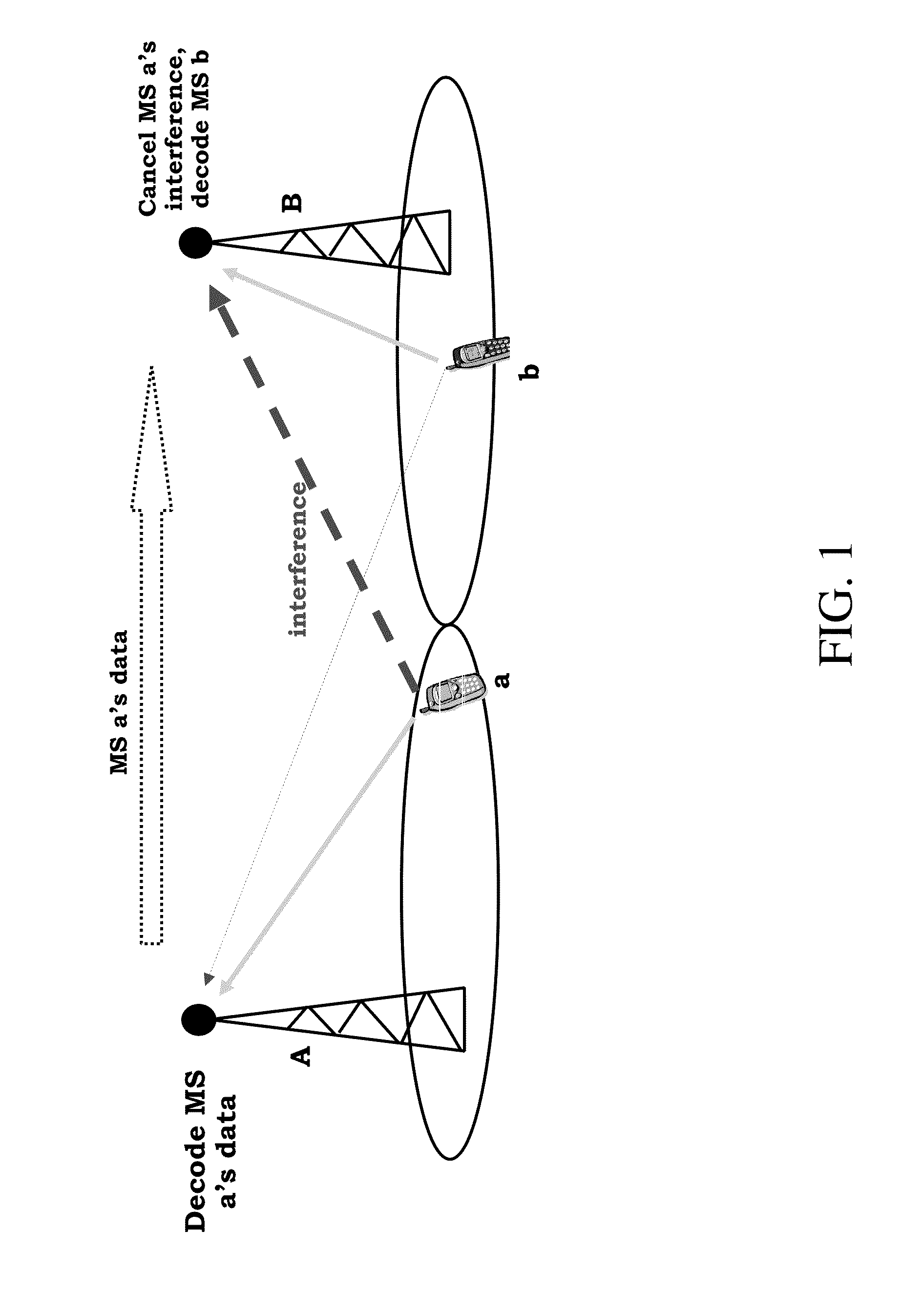
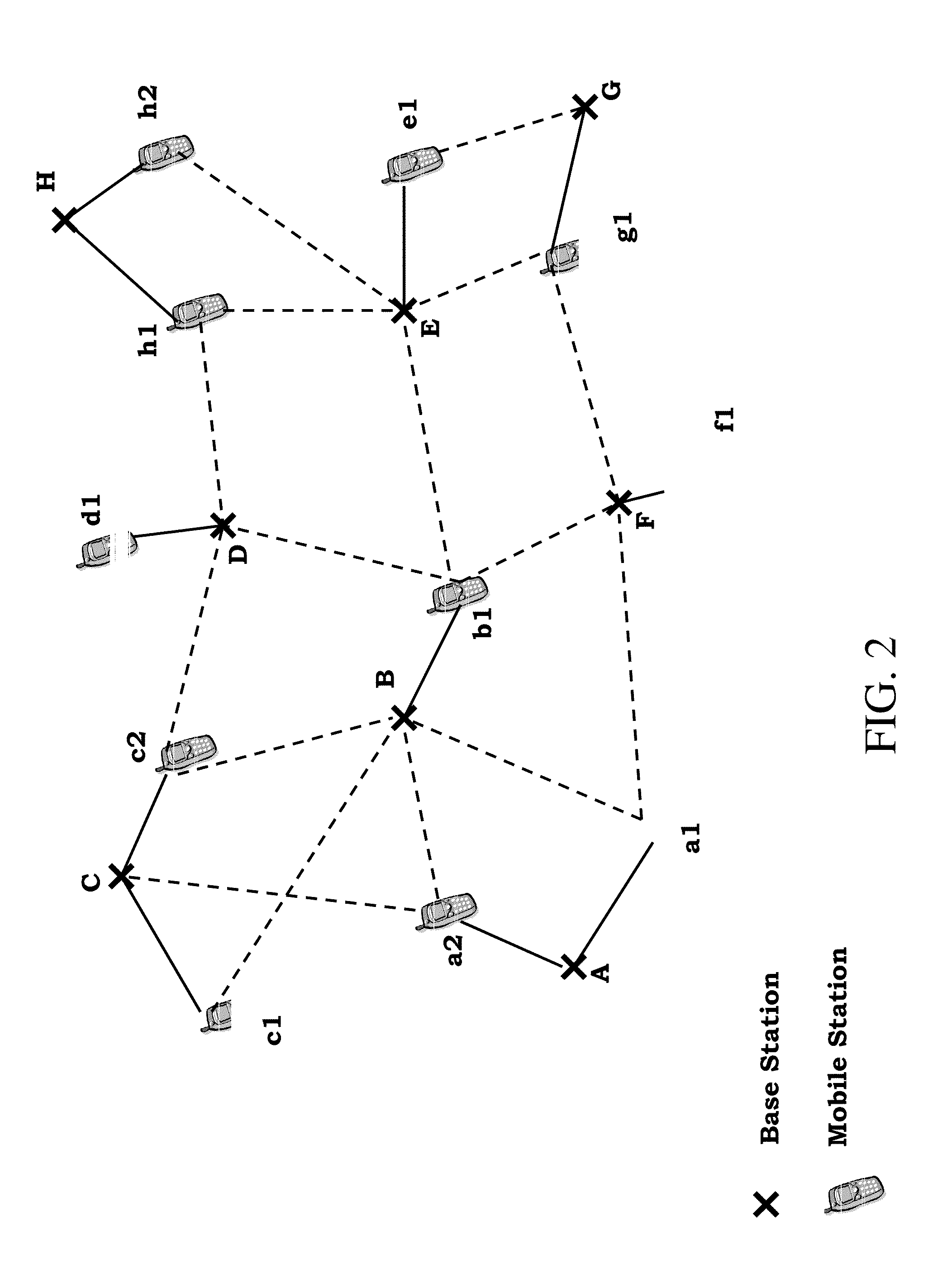
Opportunistic Network Interference Cancellation For Wireless Networks
InactiveUS20110124289A1Modulated-carrier systemsInter user/terminal allocationWireless mesh networkEngineering
Embodiments are described herein to provide improvements to known network interference cancellation techniques. One general approach involves a receiver attempting to decode (801) a received signal which includes signaling from a wireless device transmission and at least one interfering transmission. If the receiver is unsuccessful in attempting to decode the received signal, decoded signaling that corresponds to the interfering transmission is requested (802). The receiver then uses the decoded signaling to decode (803) the received signal.
Owner:ALCATEL LUCENT SAS
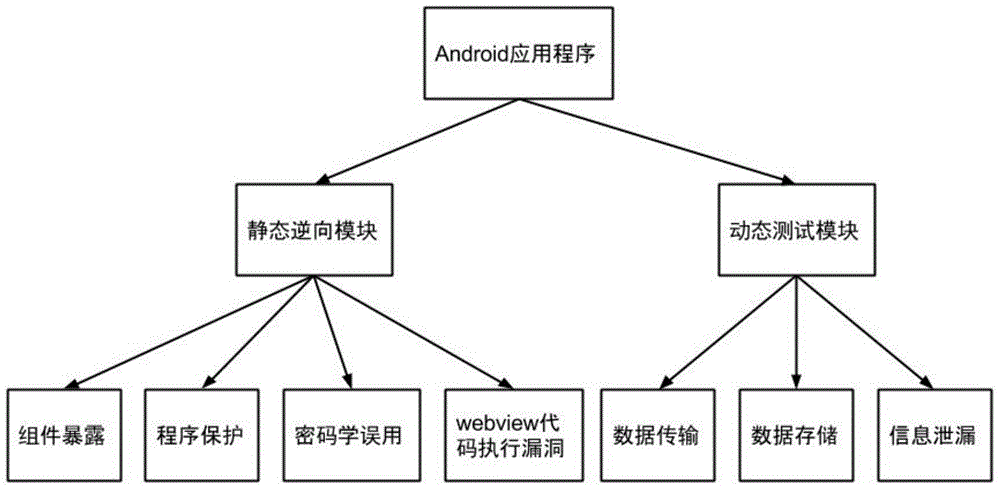
Universal method and universal system for performing safety testing on Android application programs
InactiveCN104484607AReduce false alarm ratePlatform integrity maintainanceApplication softwareSafety testing
The invention discloses a universal method and a universal system for performing safety testing on Android application programs. The universal method comprises the following steps of unpacking and decompiling a to-be-tested program to obtain an XML (extensive markup language) source code; then, through static analysis on configuration files and the code of the to-be-tested program, performing vulnerability detection and safety testing on the aspects of component exposed vulnerability, cryptology misuse, webview code execution vulnerability and code protection; then, performing actual running on the to-be-tested program, and configuring a network detection environment; finally, performing dynamic analysis, and performing dynamic vulnerability detection and the safety testing on three aspects of information leakage, data transmission safety and data storage safety, thus obtaining a vulnerability detection and safety testing report. According to the universal method and the universal system disclosed by the invention, by performing a static analysis and dynamic analysis combination mode on an optional Android application program and through a series of steps of detection and estimation, safety flaws and potential safety hazards existing in the aspects of design and implementation of the application program can be finally given out.
Owner:SHANGHAI JIAO TONG UNIV +1
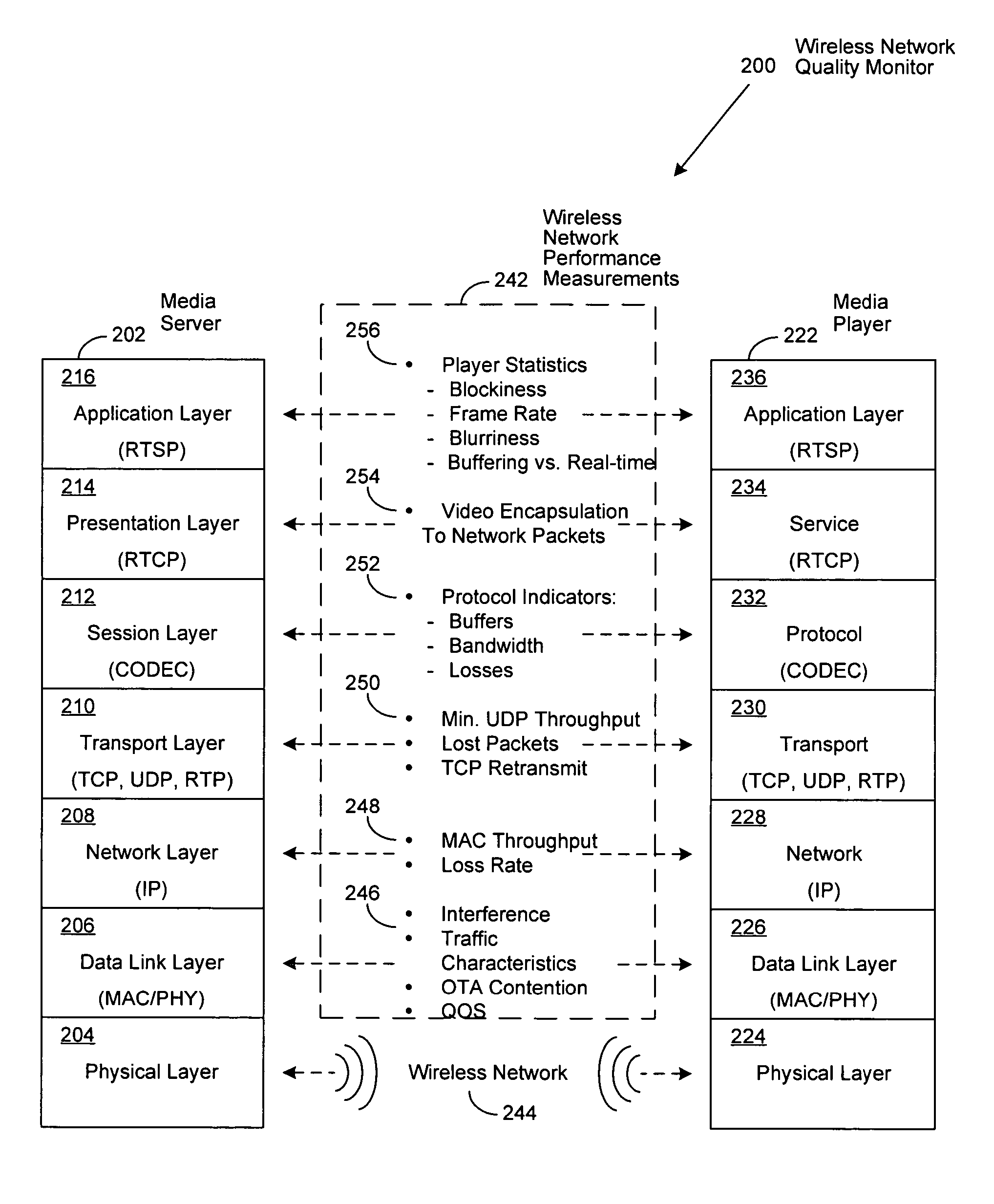
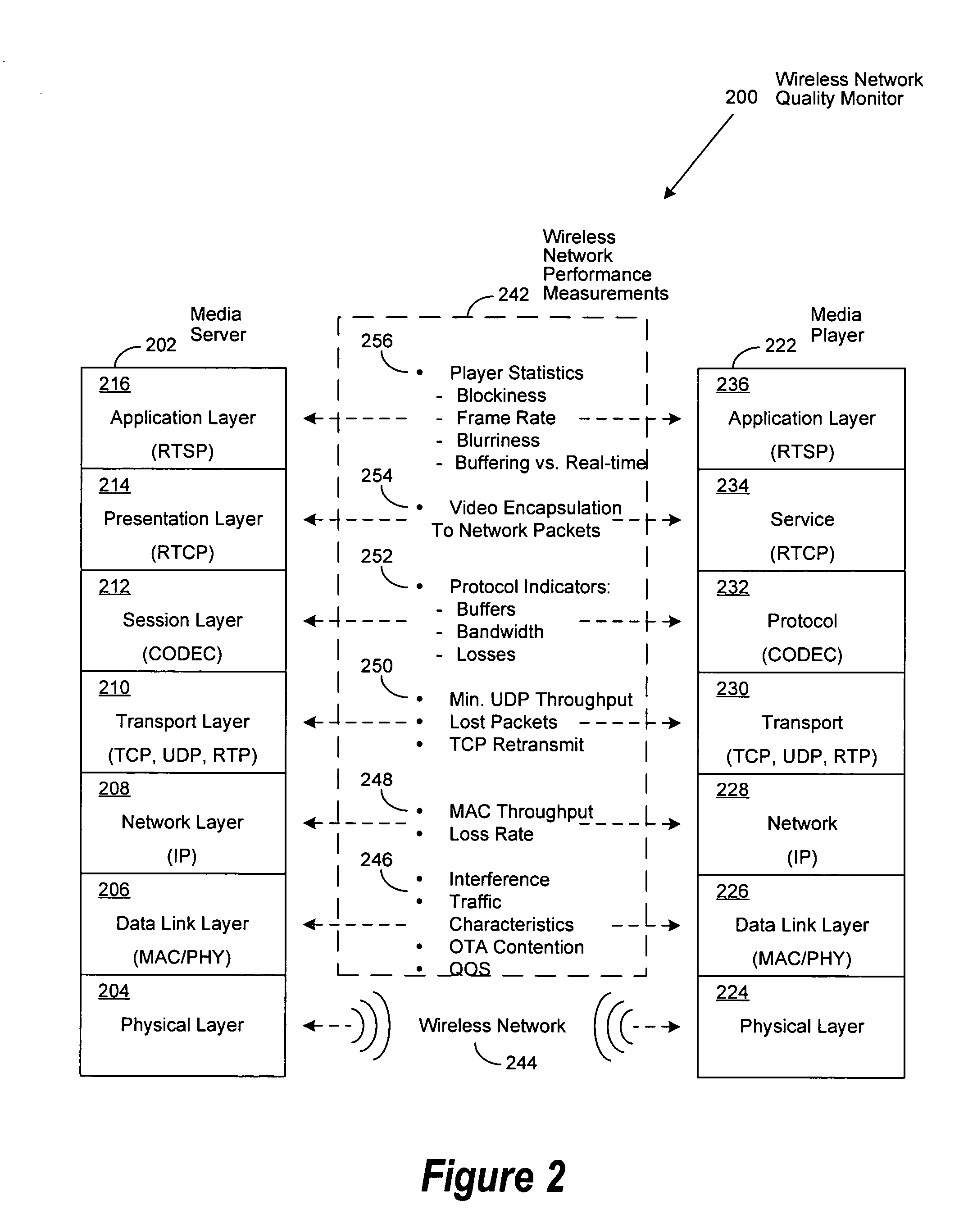
System and method to predict the performance of streaming media over wireless links
ActiveUS20070180106A1Multiple digital computer combinationsTransmissionStatistical analysisVideo quality
An improved system and method for predicting streaming media performance through the use of real-time wireless network performance measurements and statistical analysis, combined with a generalized methodology for comparing digital media quality before and after transmission. Network performance parameters of a benchmark media stream, such as throughput and signal strength, are measured for predetermined wireless network ranges and correlated to the introduction of various artifacts such as but not limited to, blurring, blockiness, and jerkiness, affecting streaming video quality. In various embodiments of the invention, network throughput and signal strength measurements of a received media stream can be processed by an algorithm and correlated to previously collected benchmark measurements to predict the resulting audio and video quality as experienced by a user.
Owner:DELL PROD LP
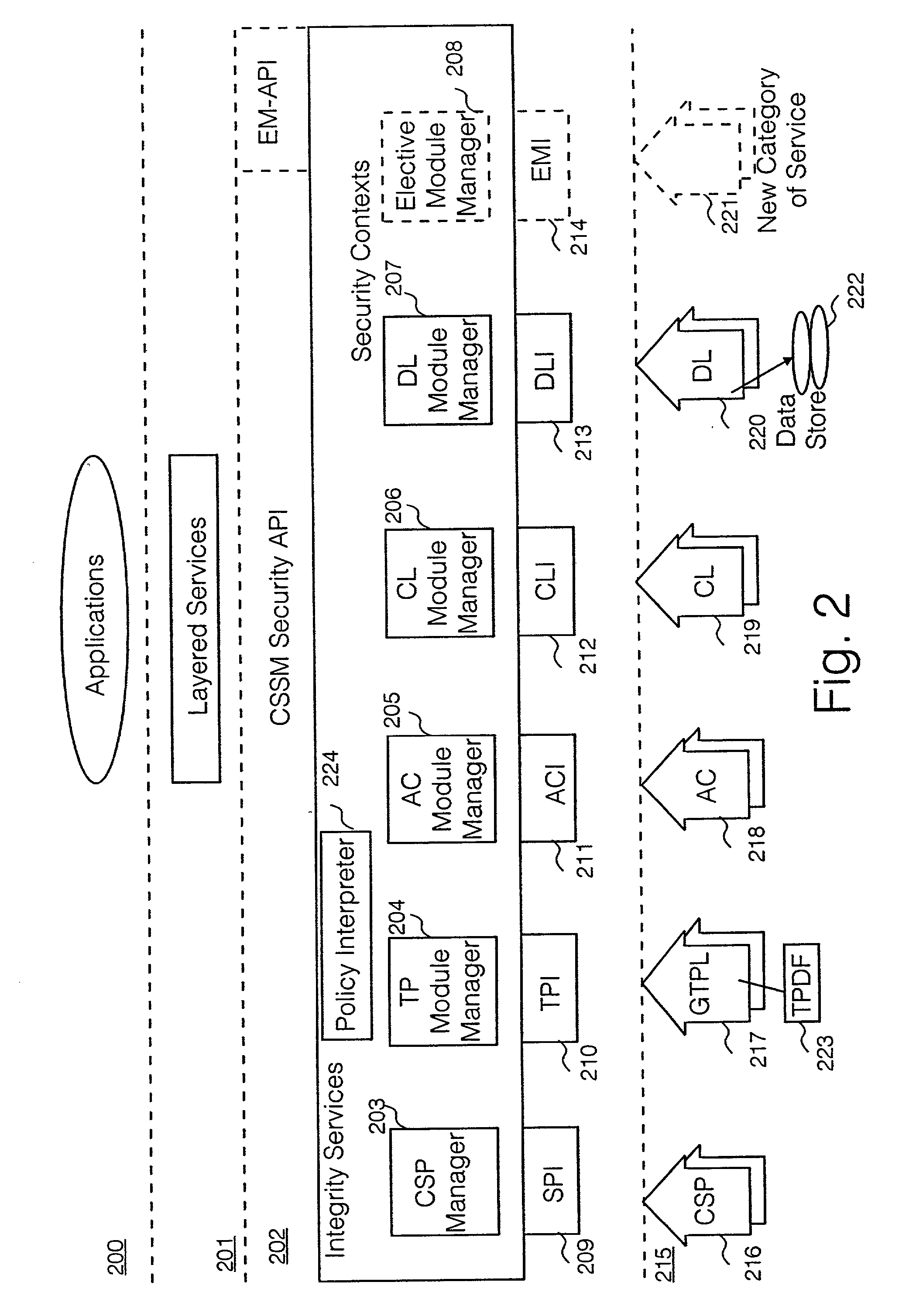
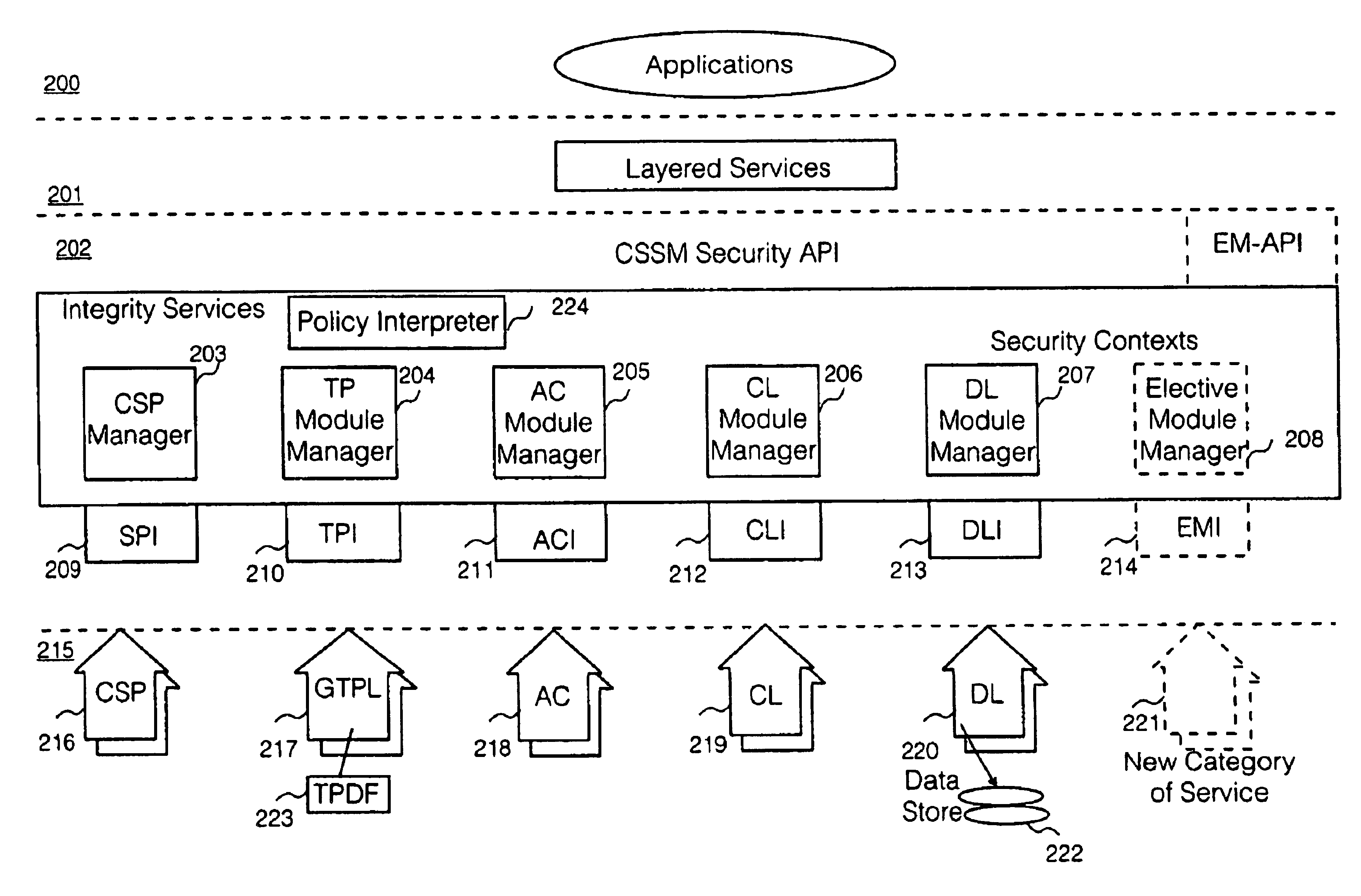
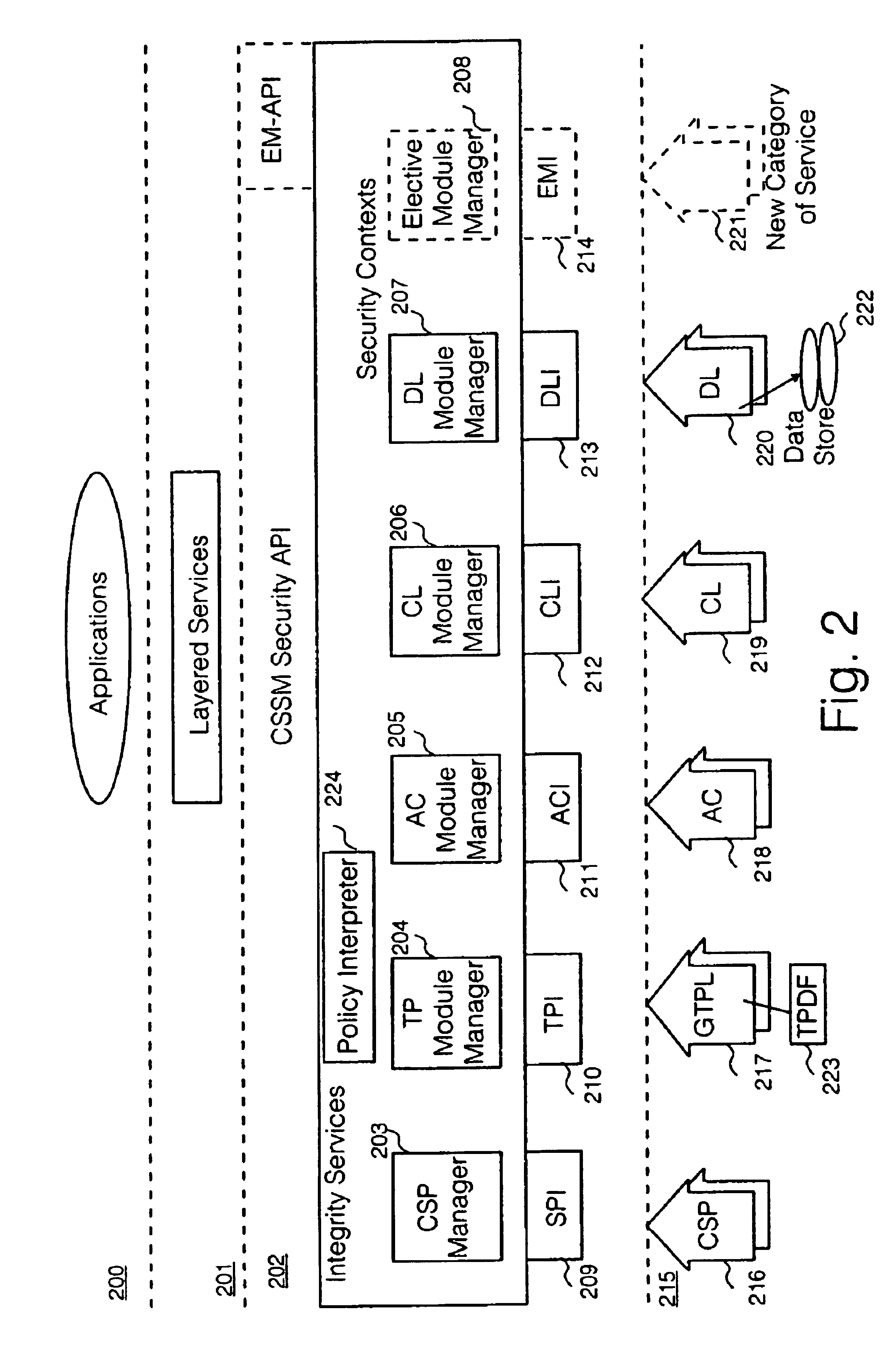
Security policy applied to common data security architecture
InactiveUS20010018746A1Digital data processing detailsUser identity/authority verificationHard codingSemantics
An improved architecture is provided, based upon the prior art common data security architecture, with the modification of adding in a generic trust policy library (217) at an add-in security modules layer (215) and a policy interpreter (224) at a common security services manager layer (202), so that individual users may provide sets of trust policies in the form of a trust policy description file (223), which uses a generic policy description language provided by the architecture. The architecture provides a generic method of incorporating trust policies into a computing platform in a manner which avoids a prior art problem of the semantics of trust policies which are hard-coded in prior art trust policy modules (117). The architecture also improves management flexibility. In the present disclosure, a generic policy description language is provided, which enables different users to define the semantics of a plurality of trust policies.
Owner:HEWLETT PACKARD DEV CO LP
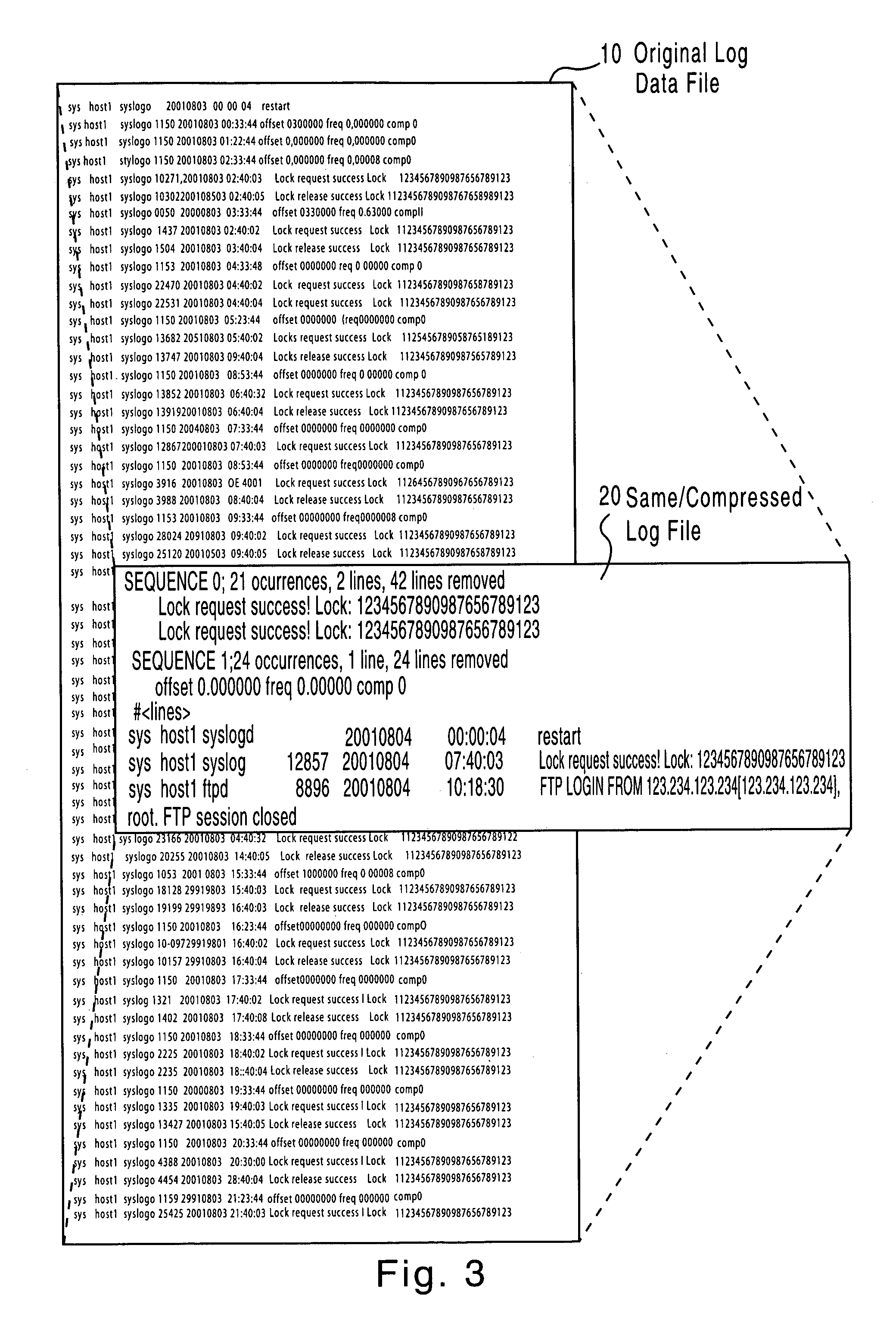
Method and apparatus for compressing log record information
InactiveUS7778979B2Intuitive monitoringLower requirementDigital data processing detailsHardware monitoringMonitoring systemData mining
The present invention relates to a method and apparatus for compressing a log record information provided e.g. to a monitoring system. Frequent patterns in the log information are detected and, then, redundant frequent patterns whose value or record combination is a subset of a value or record combination of another one of said detected frequent patterns are removed. Accordingly, a general method is provided which can be applied to all event logs arising from communication networks or other monitoring systems. The detection of frequent patterns is only based on value or record combinations and is thus independent of the specific application. On the other hand, the size of the stored log files can be decreased remarkably while remaining readable for human beings.
Owner:RPX CORP
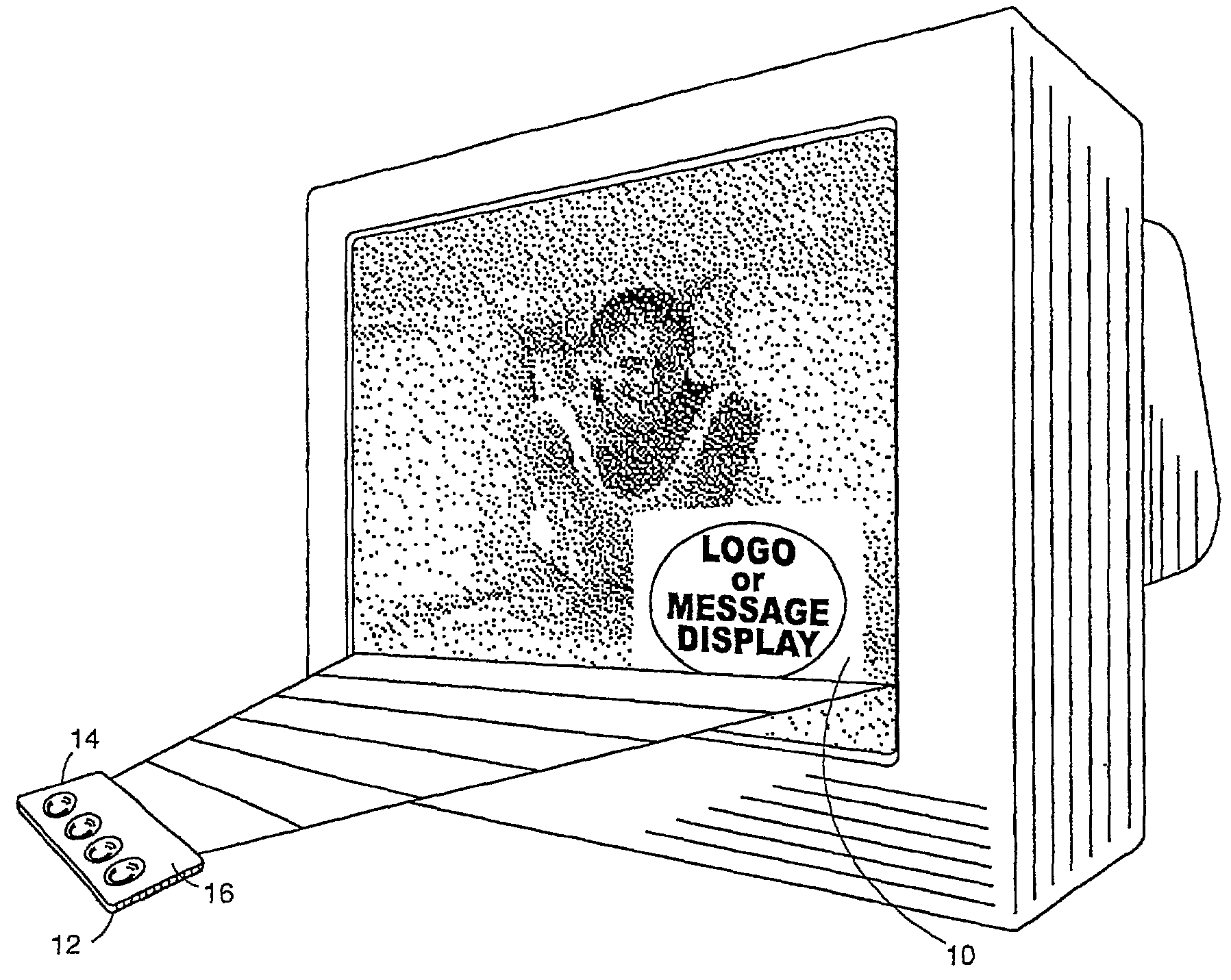
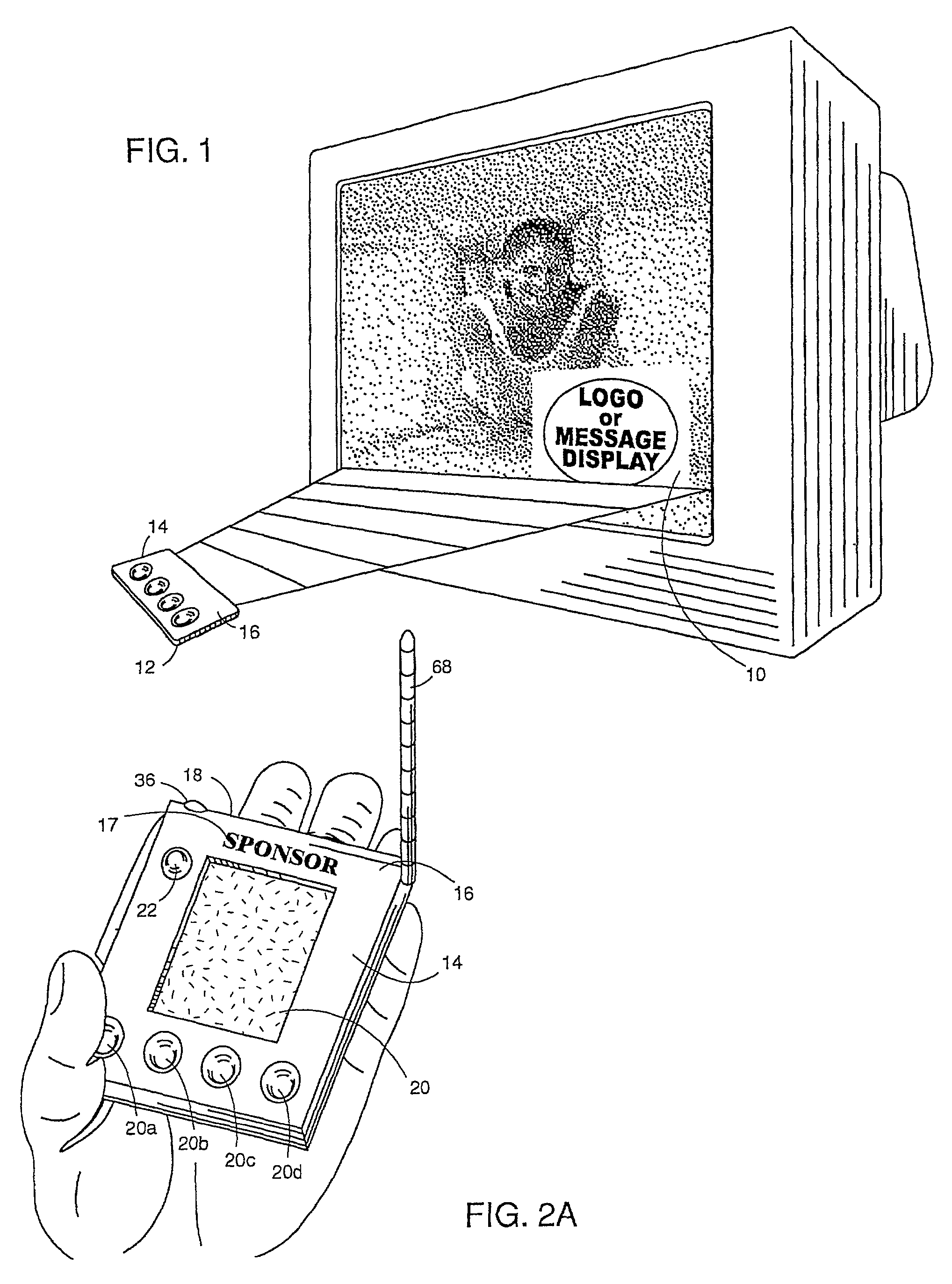
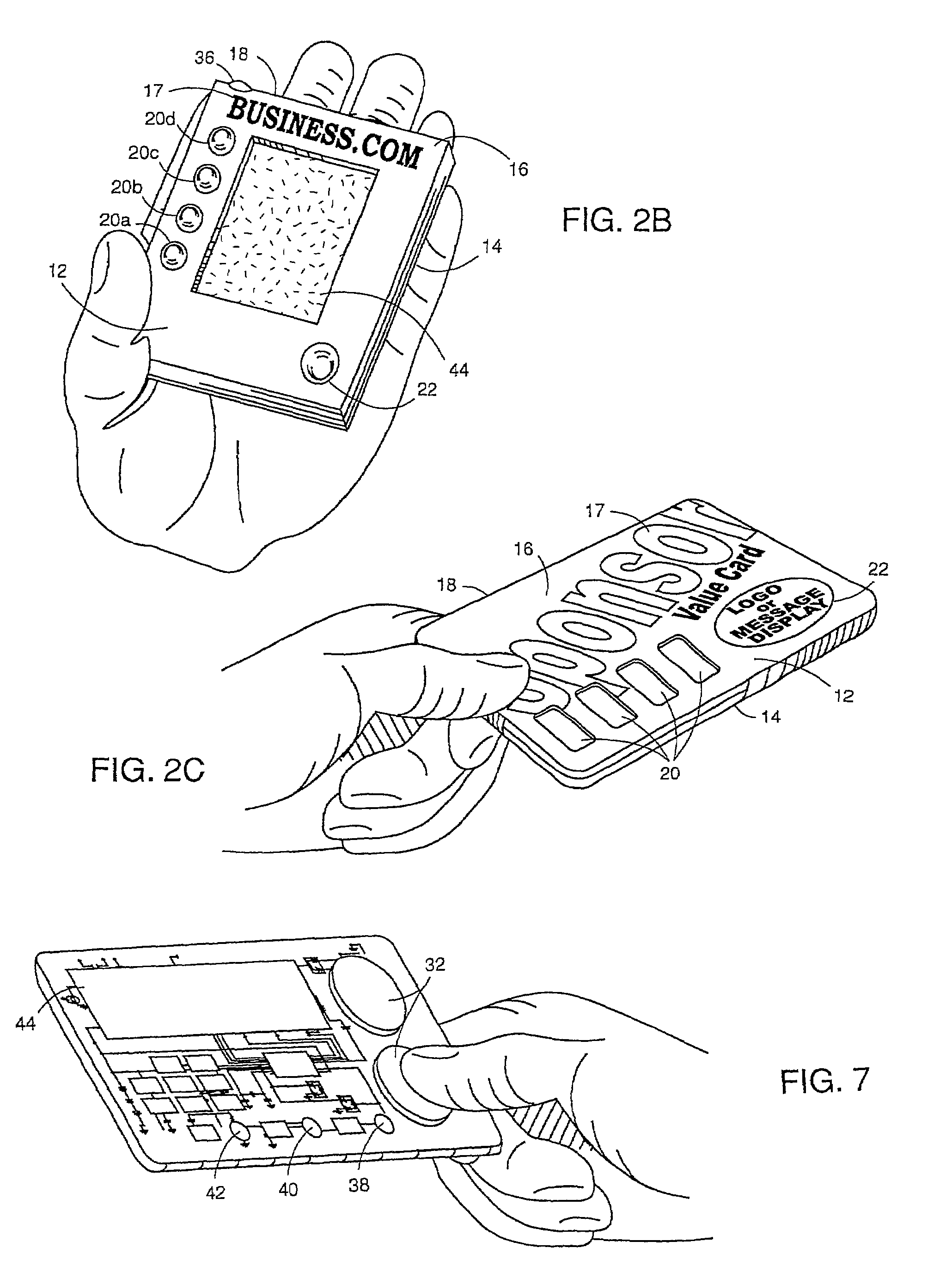
Universal methods and device for hand-held promotional opportunities
ActiveUS7213254B2Cost effectiveBrand efficientAnalogue secracy/subscription systemsTwo-way working systemsDisplay deviceHand held
A system is described for deriving benefits from the reception and processing of composite video signals from a display device 10 by a hand-held device 12, such as a smart card, personal digital assistant (“PDA”), or mobile phone. Video signals are modulated with auxiliary data creating composite video signals. The users directs the hand-held device 12 toward display device 10 by placing leading edge 18 in the path of the video signal. The composite video signals are then transmitted to and received by a hand-held device 12. Aiming light 24 and / or audio transducer 34 alert the user of hand-held device 12 that auxiliary data is being received. The auxiliary data is then utilized by hand-held device 12. In other embodiments of hand-held device 12, the auxiliary data is received from a decoder box, which in turn transmits the information to device 12 by RF which may be received by the RF antenna 68 of the device.The user receives benefits such as promotional opportunities resulting from the reception of the auxiliary data. Such opportunities are expressed on visual display 20, which may include a series of lights 20a, 20b, 20c, and / or 20d, or an LCD 44. The lights and LCD provide promotional opportunities which may be redeemable and conventional stores or via the Internet. Hand-held devices 12 are outfitted with a PCMCIA interface 70 or wireless Internet access to obtain such promotional activities on the Internet.Hand-held device 12 may have housing 14 in various shapes to promote various promotional opportunities. On front surface 16 of the hand-held device may have indication of a sponsor 17.
Owner:ADVOCADO INC
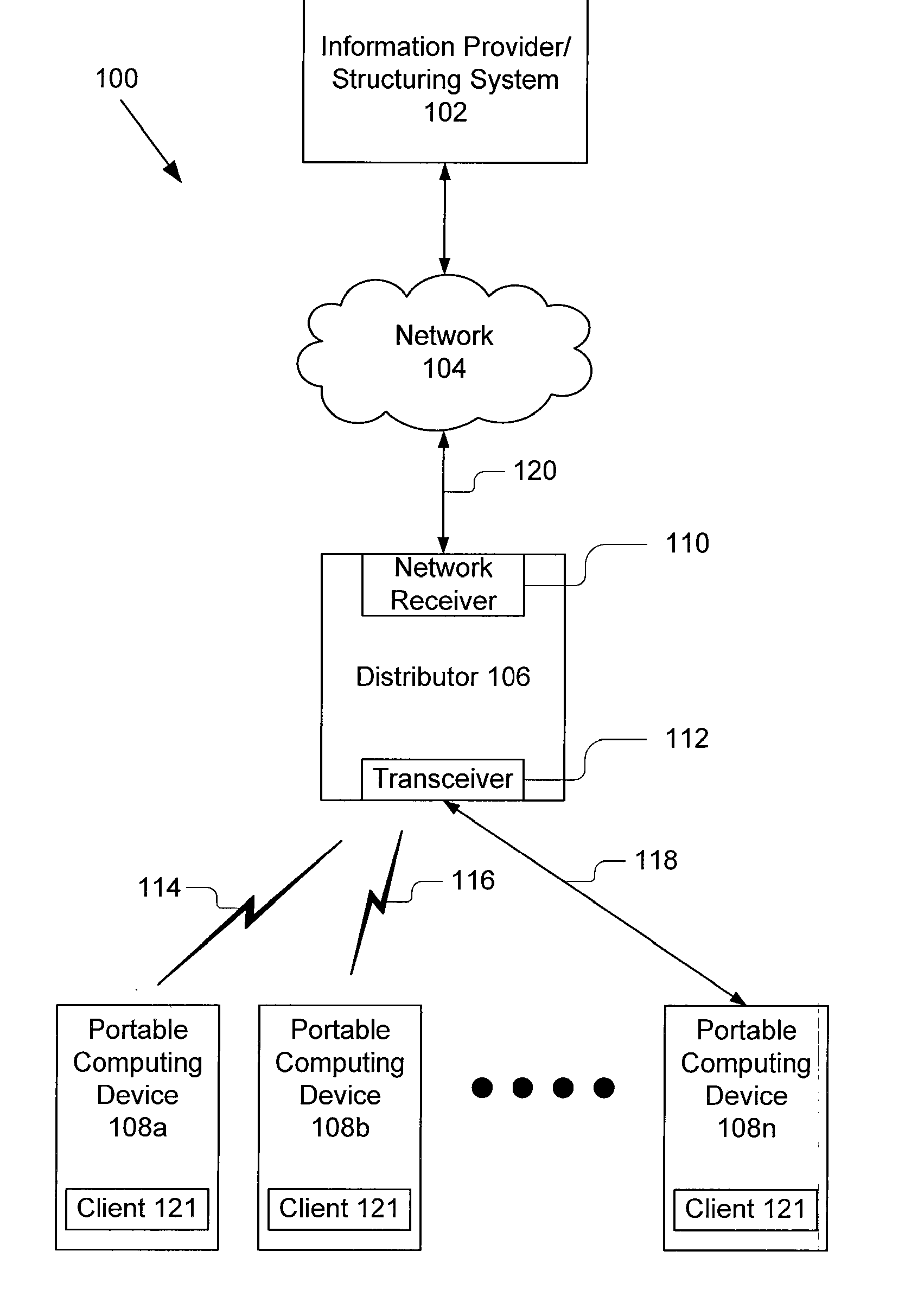
Device-aware content delivery
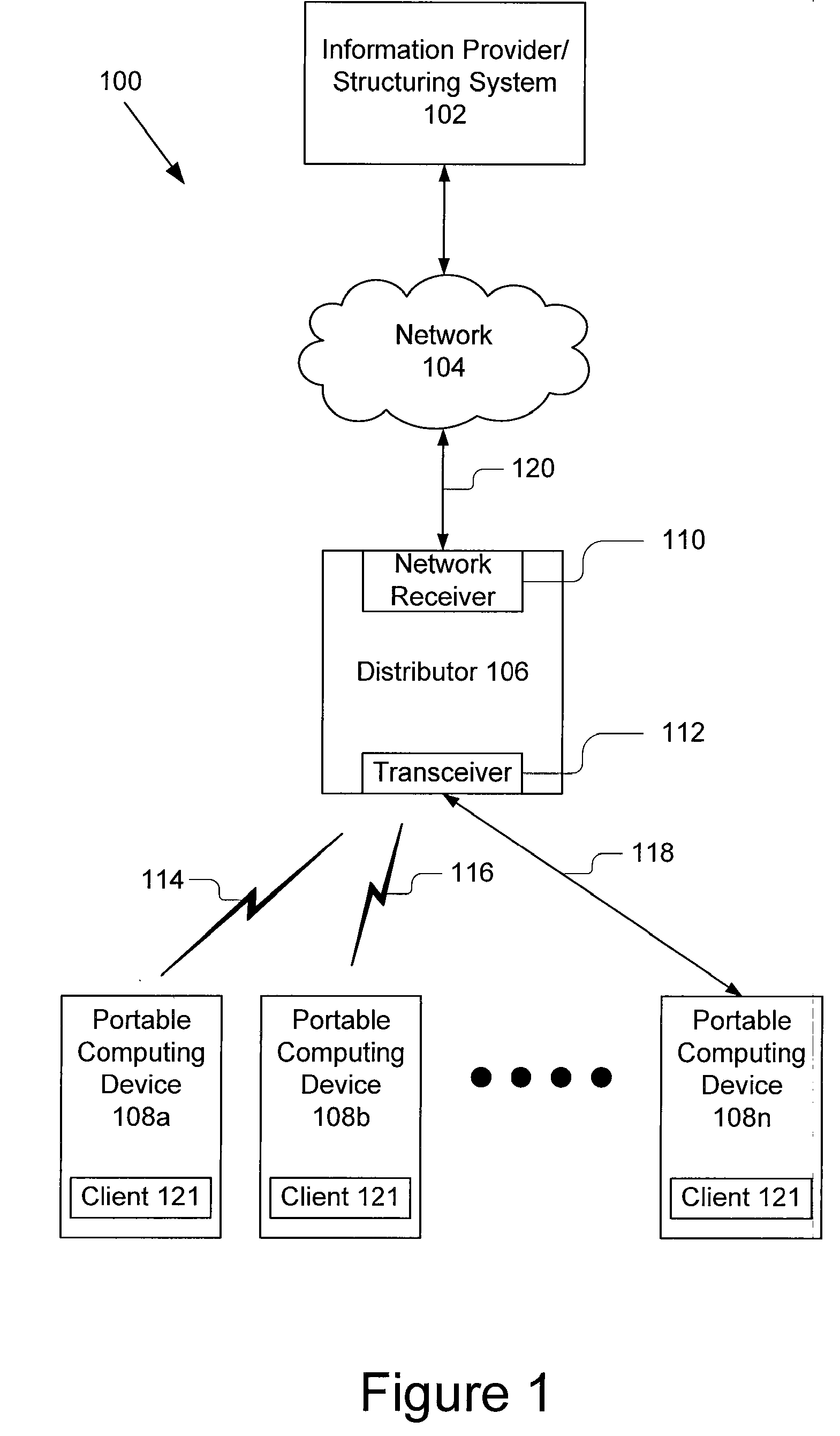
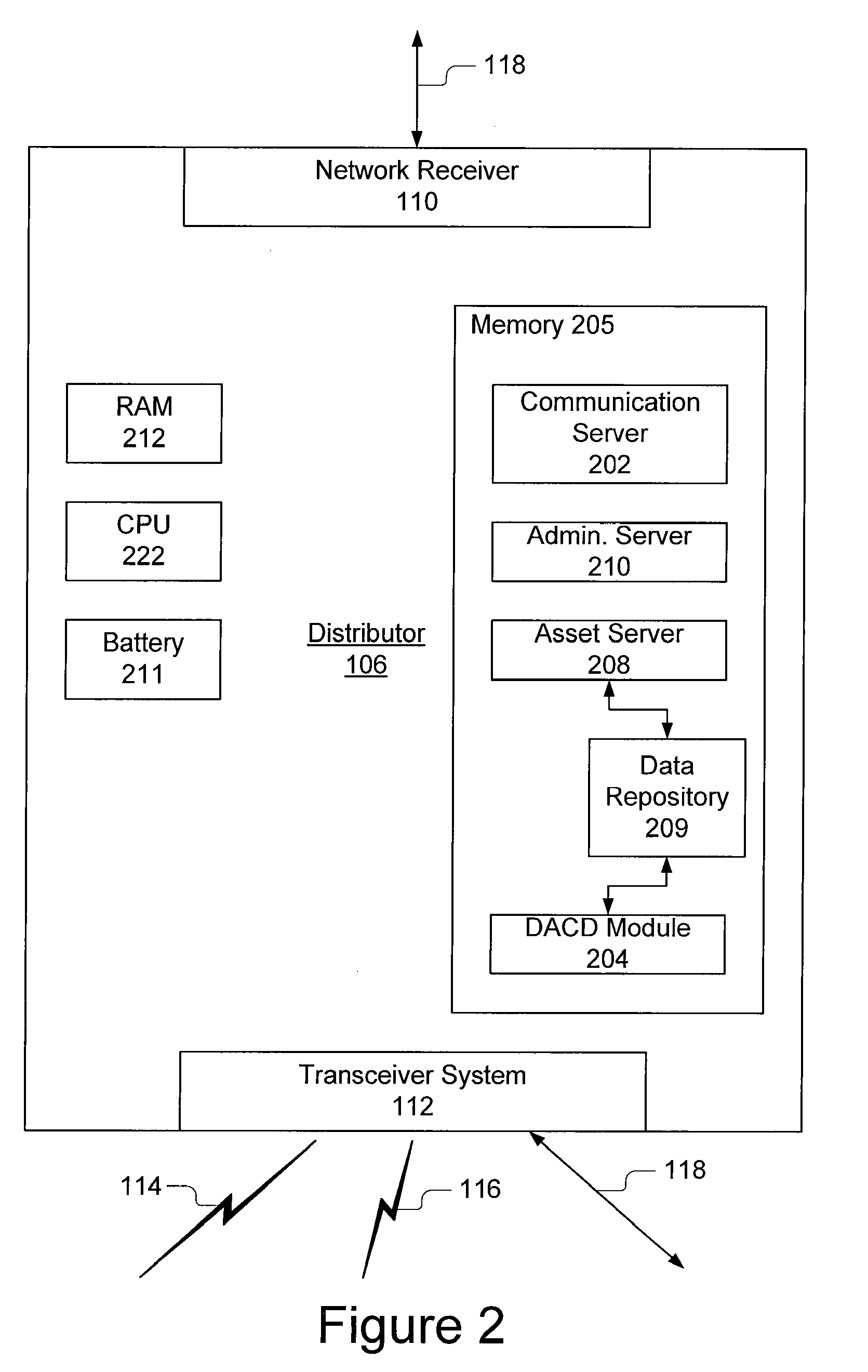
InactiveUS20070130626A1Overcome limitationsLink editingDigital data processing detailsDevice typeDistributor
A system for device-aware content delivery includes a distributor and a database. The distributor includes modules for determining the type of portable computing device and delivering content that is operable on the specific type of portable computing device and uses the unique capabilities of the identified portable computing device. The database includes different profiles for different portable computing devices and gives information that allows those portable computing devices to be identified by type and distinguished from each other portable computing devices during a discovery or interrogation phase. The database also stores different versions of content adapted for operation on specific device types, such that once the device type has been identified, the matching content can be sent to the portable computing device, installed and executed. The matching content is programmatic action specific to the portable computing device. The present invention also includes a number of novel methods including: a method device-aware content delivery, a general method for automatically determining a device type, a method for determining device type using a Bluetooth® protocol and a method for determining a device type using an infrared device access protocol.
Owner:QWIKKER
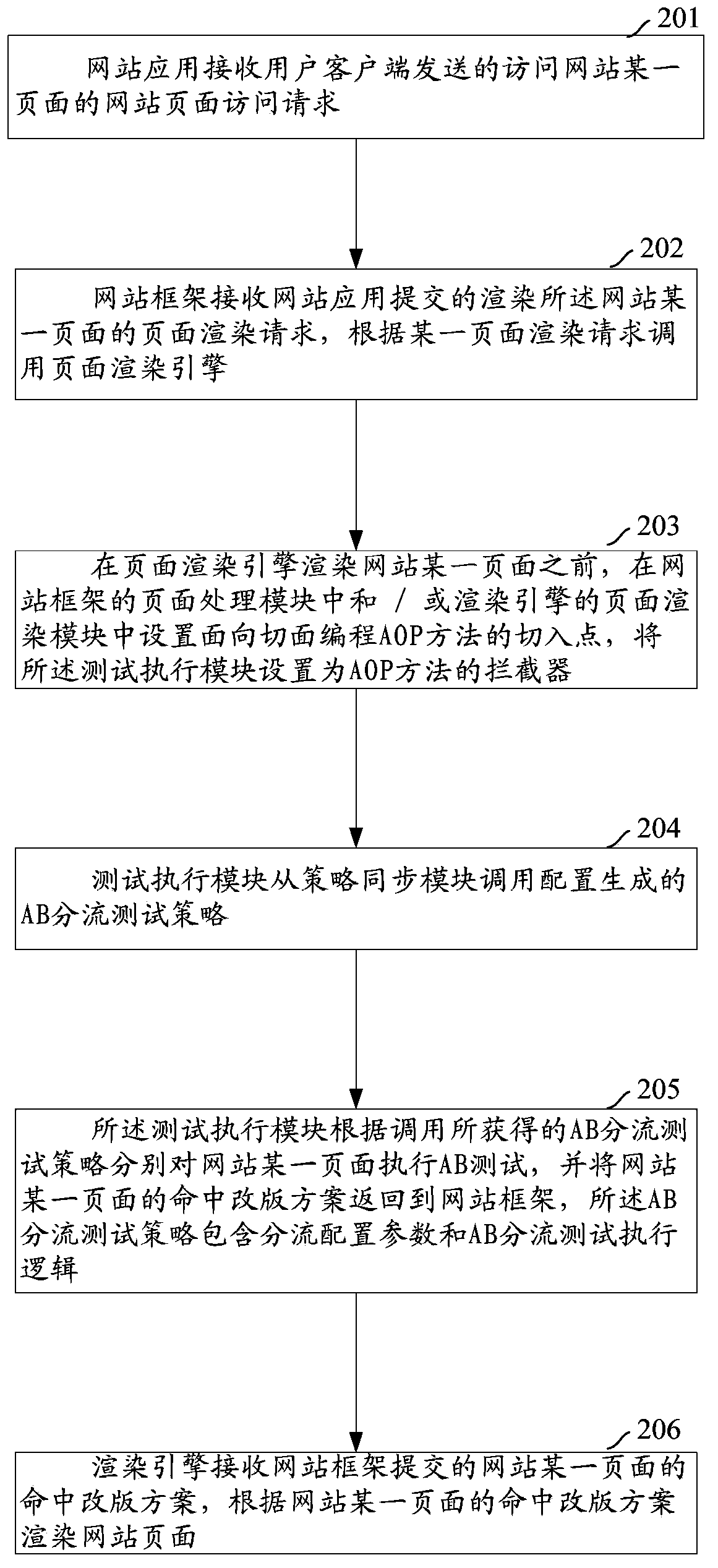
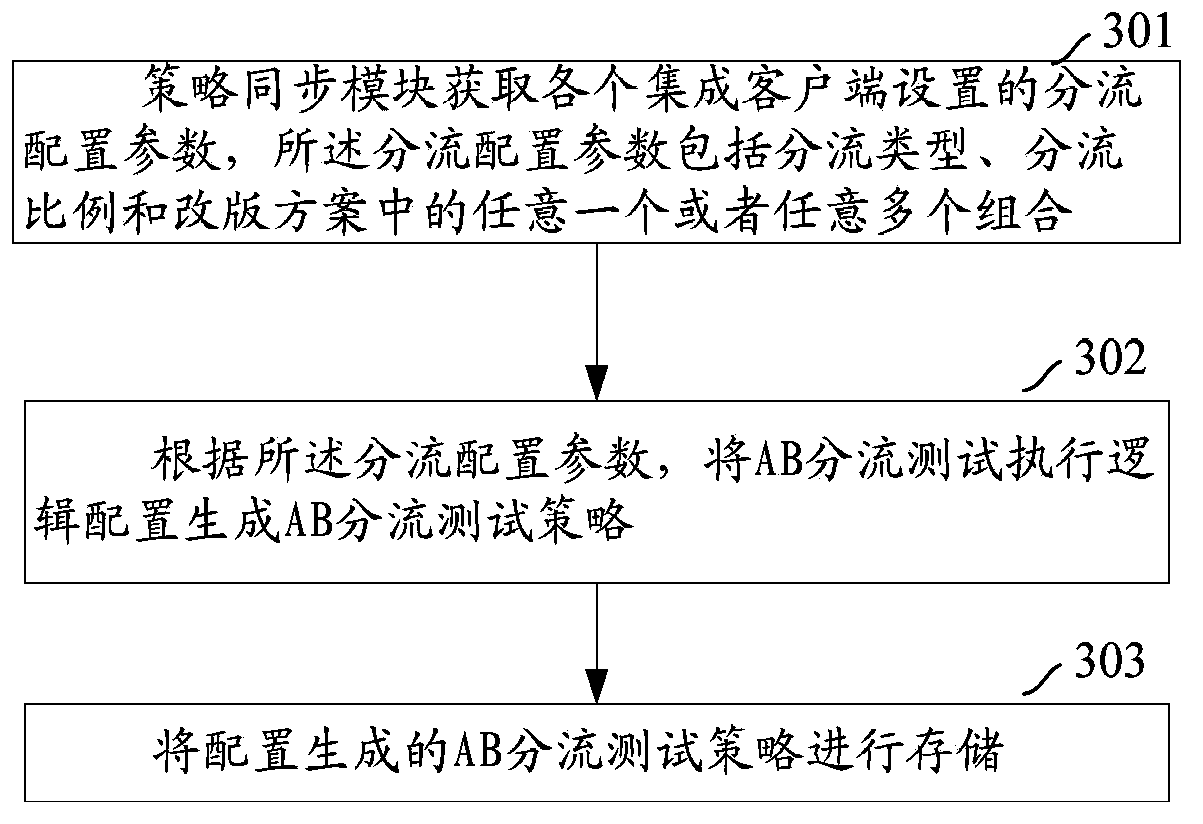
Multi-version parallel test method for web pages and server
The invention discloses a multi-version parallel test method for web pages and a server. A web framework receives a page rendering request which is submitted by a web application for rendering a certain page of the web; before a page rendering engine renders the certain page of the web, a page processing logic is skipped from a page processing module of the web framework and / or a page rendering module of the rendering engine to the same test execution module for executing AB test on the certain page of the web, and a selected reversion scheme of the certain page of the web is returned to the web framework; the web page is rendered according to the selected reversion scheme of the certain page of the web. A high-efficiency and flexible general method for multi-version parallel test of the web page and a system are realized and are suitable for different web frameworks and different rendering engines; the problem of system invasion caused by multi-version parallel test is solved; the multi-version parallel test execution logic can be reused and is convenient to expand; a test strategy can be flexibly adjusted and can dynamically take effect instead of being issued.
Owner:ALIBABA GRP HLDG LTD
Security policy applied to common data security architecture
InactiveUS6941471B2Digital data processing detailsUnauthorized memory use protectionHard codingSemantics
An improved architecture is provided, based upon the prior art common data security architecture, with the modification of adding in a generic trust policy library (217) at an add-in security modules layer (215) and a policy interpreter (224) at a common security services manager layer (202), so that individual users may provide sets of trust policies in the form of a trust policy description file (223), which uses a generic policy description language provided by the architecture. The architecture provides a generic method of incorporating trust policies into a computing platform in a manner which avoids a prior art problem of the semantics of trust policies which are hard-coded in prior art trust policy modules (117). The architecture also improves management flexibility. In the present disclosure, a generic policy description language is provided, which enables different users to define the semantics of a plurality of trust policies.
Owner:HEWLETT PACKARD DEV CO LP
Universal method for submitting gaming machine source code software to a game certification laboratory
InactiveUS20060122937A1Data processing applicationsUser identity/authority verificationOperational systemGeneral purpose computer
A universal computer-implemented method for submitting source code to an authorized game certification laboratory. Initial source code and subsequent source code patches may be transferred from the manufacturer's software development environment into the laboratory's software development environment in a controlled fashion using packaging installation technology normally used for deploying software applications. The packaging technology contains automation actions for automating the synchronization and / or management of the source code and related files between the two software development environments. The entirety of the source code or any source code patch sequence may be removed by executing the corresponding uninstall function. The package containing the original source code or the source code patch sequences and related files may be code signed such as to provide persistent proof of origin which may be verified at any time. The method may be implemented under any operating system such as Microsoft Windows, Linux, UNIX and Apple Mac OS without the laboratory having to learn a complex source code configuration management software.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
Method for planting edible fungi and producing artificial grass peat by using cabo
The invention provides a comprehensive utilization method for planting edible fungi and producing artificial grass peat by using waste cabo generated in a tobacco threshing redrying plant as main raw materials. Raw materials forming culture materials are as follows: 60-100 parts of cabo and 1-5 parts of lime or / and plaster; and 1-40 parts of accessories also can be added. A bag cultivation methodis perfectly selected for a planting process, comprising the steps of dosing, bagging, sterilizing, inoculating, culturing and the like. After the harvest, waste residue of the culture materials containing the cabo is directly crushed to be in a puffy fiber, scrap, or powder state , or is crushed after being fermented and decomposed, and then is dried to obtain the artificial grass peat product. The artificial grass peat is mixed with packing materials such as perlite, roseite and the like to obtain plant culture substrate. The invention has centralized and stable raw materials so as to be beneficial to the massive production; the production cost is 1 / 3 lower than the common method; the planted edible fungi is large and thick, green and safe; and the artificial grass peat is prepared by the waste residue so as to realize high-efficiency comprehensive utilization of the waste cabo.
Owner:ZHENGZHOU UNIV
Secure enterprise network
ActiveUS20050193427A1Prevent and restrict unauthorized accessPreserve availabilityDigital data processing detailsDigital computer detailsUser authenticationData traffic
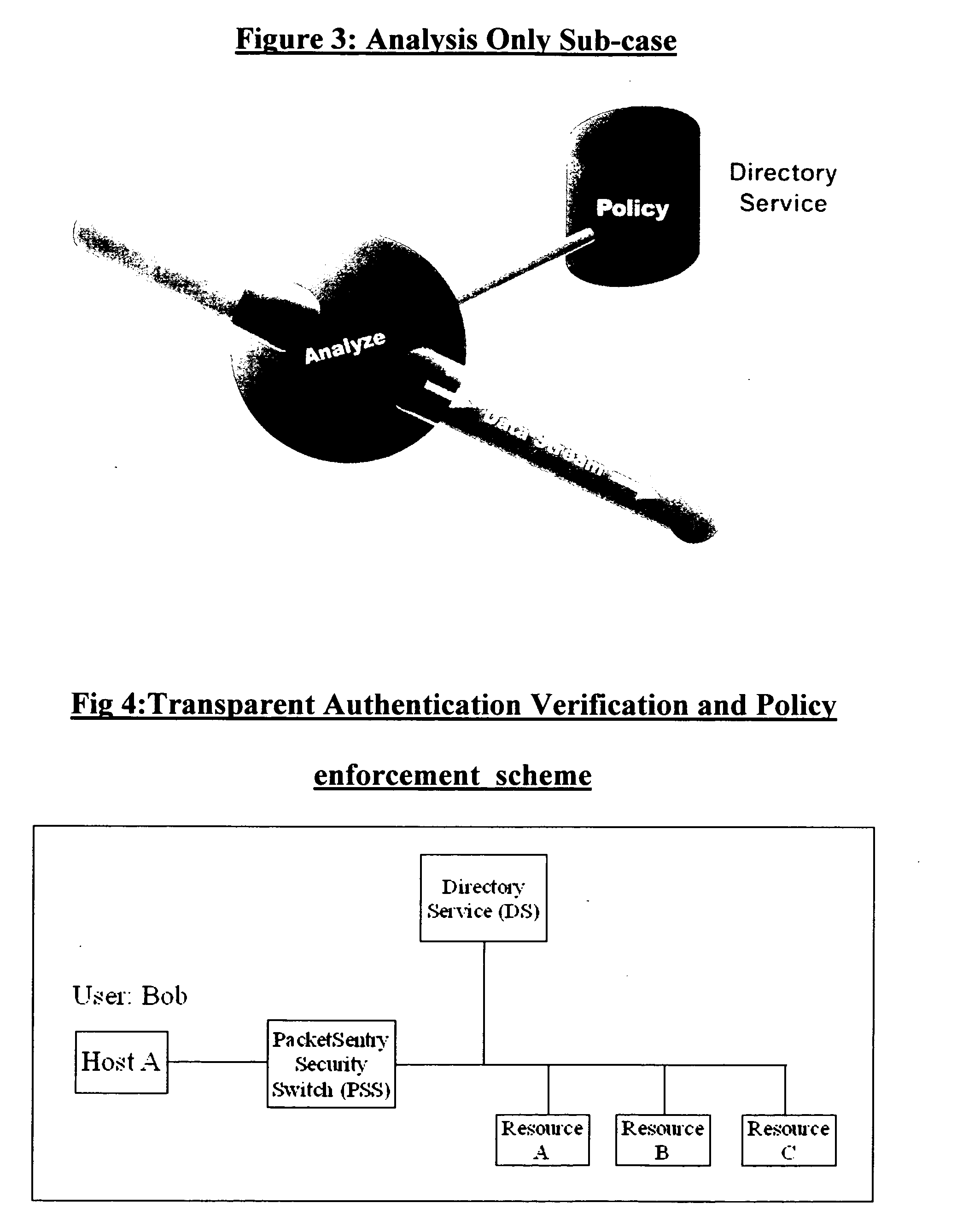
What is proposed is a method of implementing a security system (Packet Sentry) addressing the internal security problem of enterprises having a generalized approach for inferential determination and enforcement of network policy with directory service based group correlation with transparent authentication of the connected customer and the policy enforcement inside the network. The security system enables the network to analyze and enforce policy using any bit or bits in a stream or a packet, conduct Flow Vector analysis on the data traffic, provide Application Monitoring, Normalization and user authentication validation. The system enables the network to implement Group relationship Analysis and correlation using combination of Network inferences and Directory service data resulting in generation of Group norms using statistically significant relationships. These will provide a more secure enterprise environment where data security levels can be enforced and the usage monitored effectively in the infrastructure.
Owner:VMWARE INC
Falling-down detection device and method
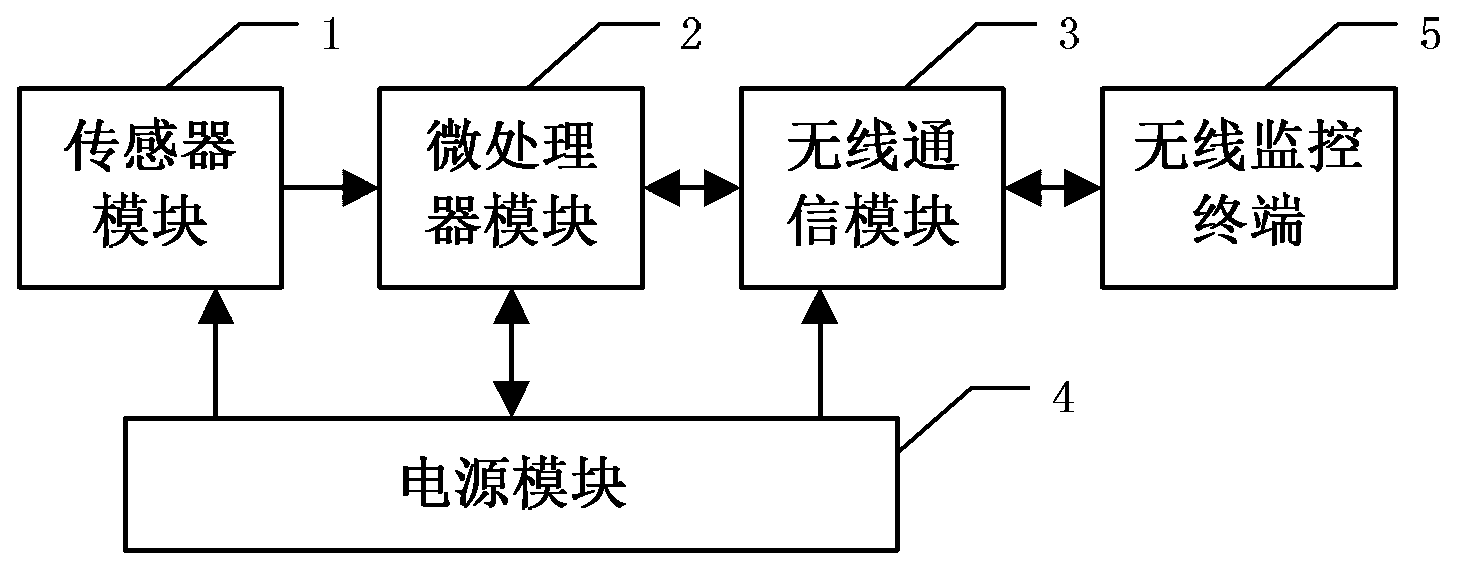
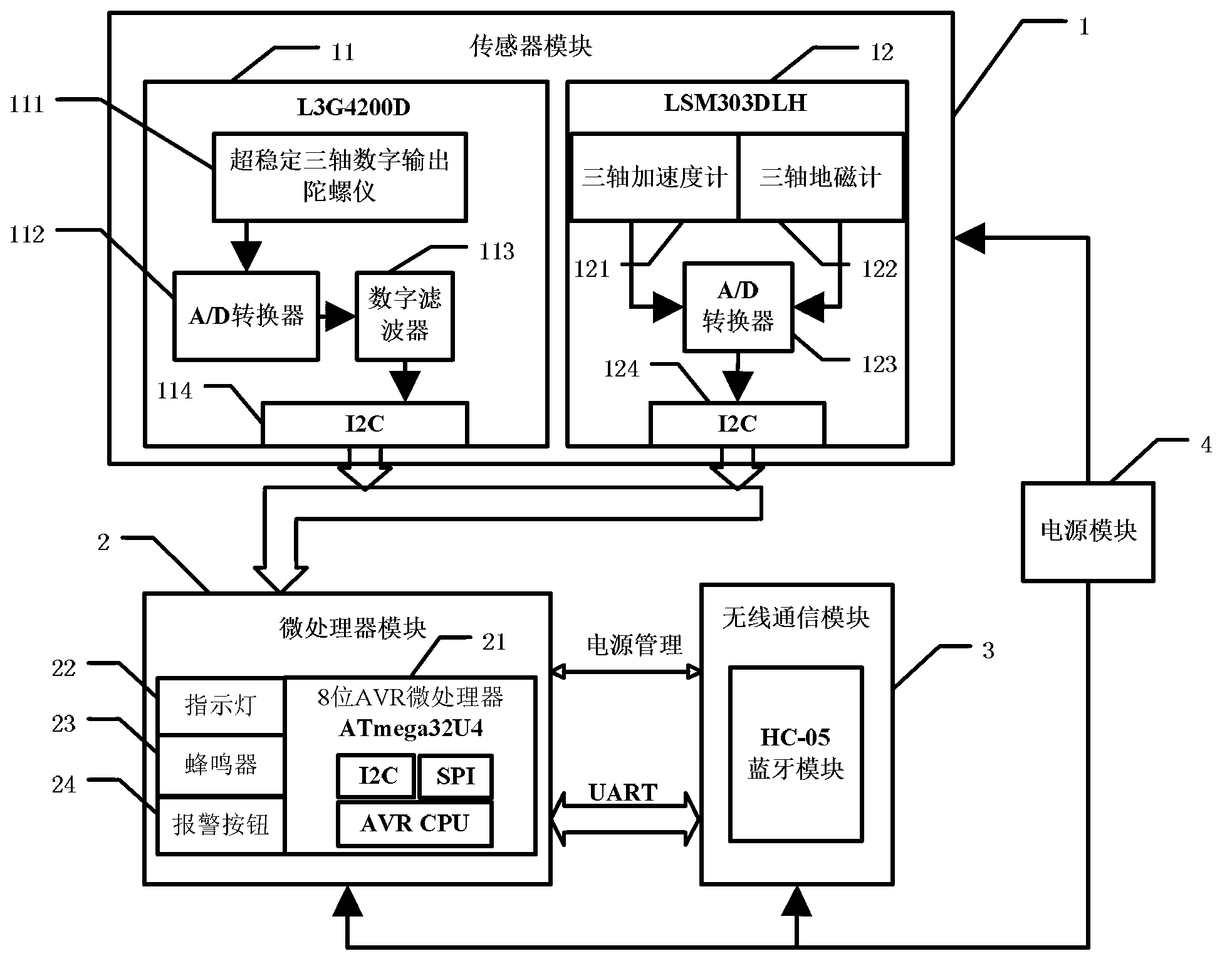
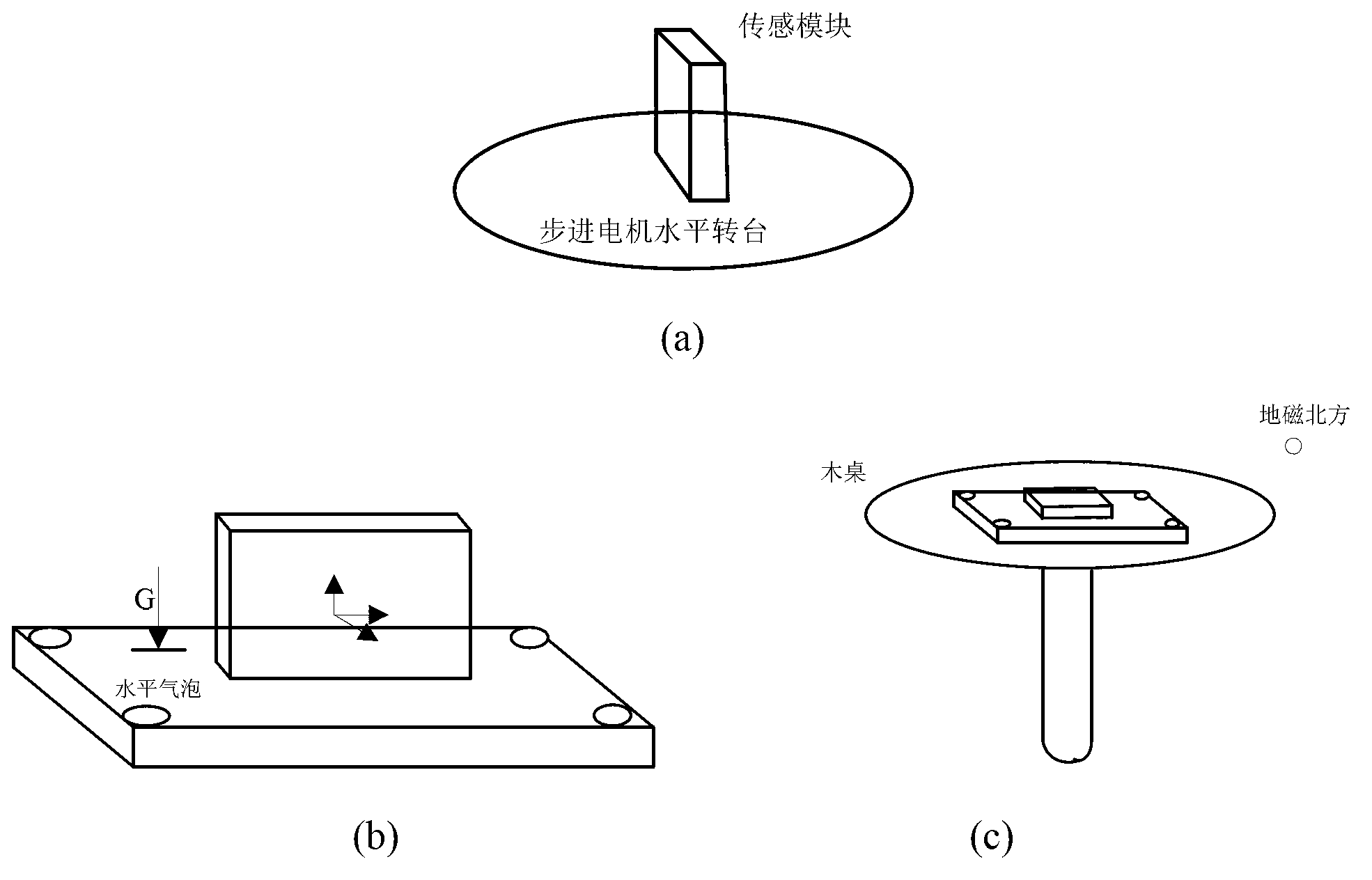
ActiveCN103308069AAccurate final attitude angleReduce false alarm rateTransmission systemsNavigation instrumentsGyroscopeAccelerometer
The invention discloses a falling-down detection device and method. A gyroscope, an accelerometer and a magnetometer are respectively used for measuring to obtain angular speed data, accelerated speed data and terrestrial magnetism data; the angular speed data are utilized to solve a basic posture angle, and the accelerated speed data and the terrestrial magnetism data are utilized to carry out noise self-adapted Kalman fusion filtering on the basic posture angle to obtain a final posture angle. The angular speed data and the accelerated speed data are used tor carrying out movable and static state judgment on a user; when the user is static, whether the user lies down or not is judged according to the posture angle; if the user lies down, conscious / unconscious screening and falling-down stress assessment of lying-down movement is carried out to judge whether the user falls down or not in a combined manner; when the user falls down, an alarm is sent out. According to the falling-down detection device and method disclosed by the invention, the obtained posture angle is more accurate than that obtained by using a common method; meanwhile, the conscious / unconscious screening and the falling-down stress assessment are used for carrying out combined judgment so that a falling-down judging result is accurate and the false alarm rate is reduced.
Owner:北京福瑞思达信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com