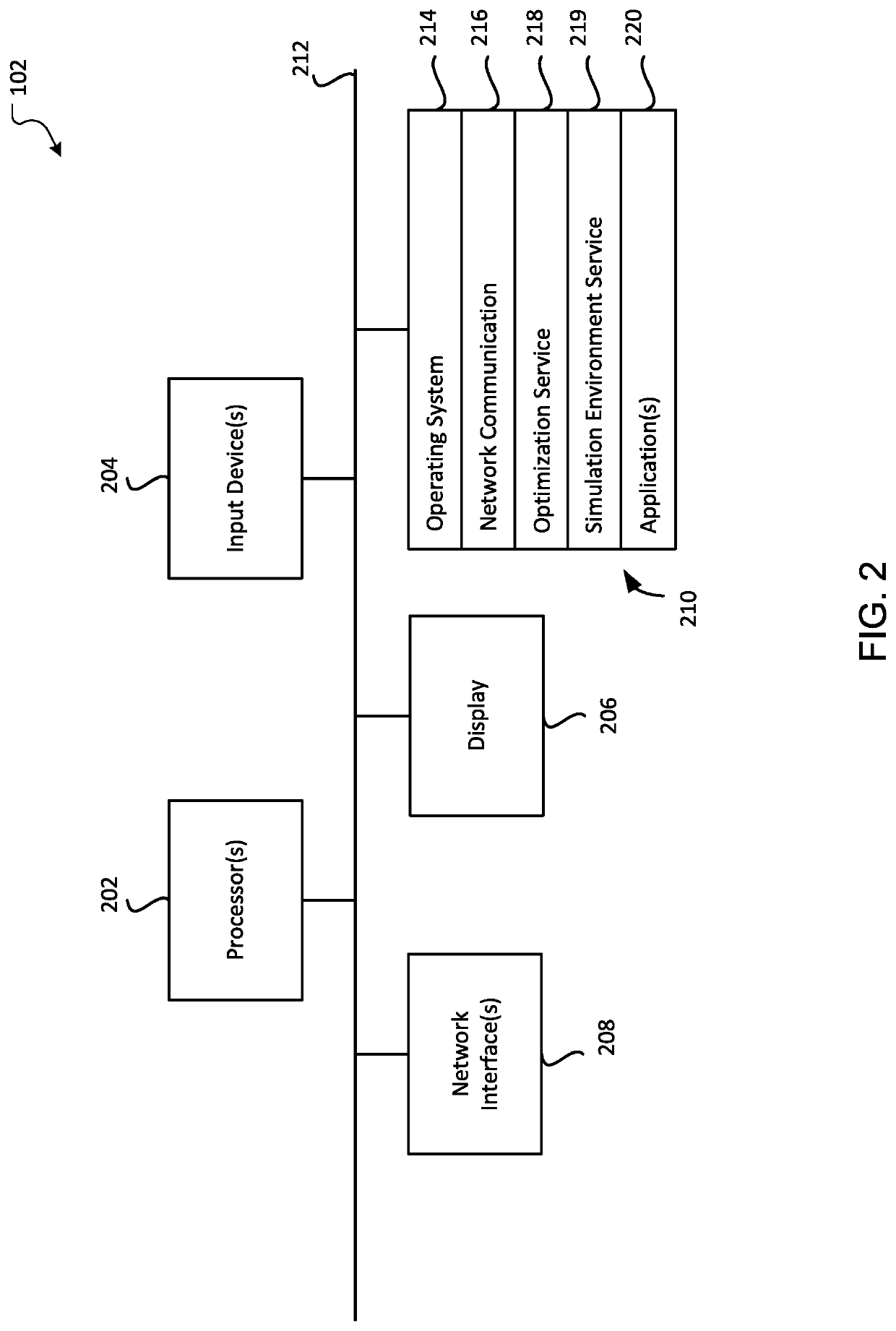
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
150 results about "Application profile" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In the information sciences, an application profile consists of a set of metadata elements, policies, and guidelines defined for a particular application. The elements may come from one or more element sets, thus allowing a given application to meet its functional requirements by using metadata from several element sets - including locally defined sets. For example, a given application might choose a subset of the Dublin Core that meets its needs, or may include elements from the Dublin Core, another element set, and several locally defined elements, all combined in a single schema. An application profile is not complete without documentation that defines the policies and best practices appropriate to the application.
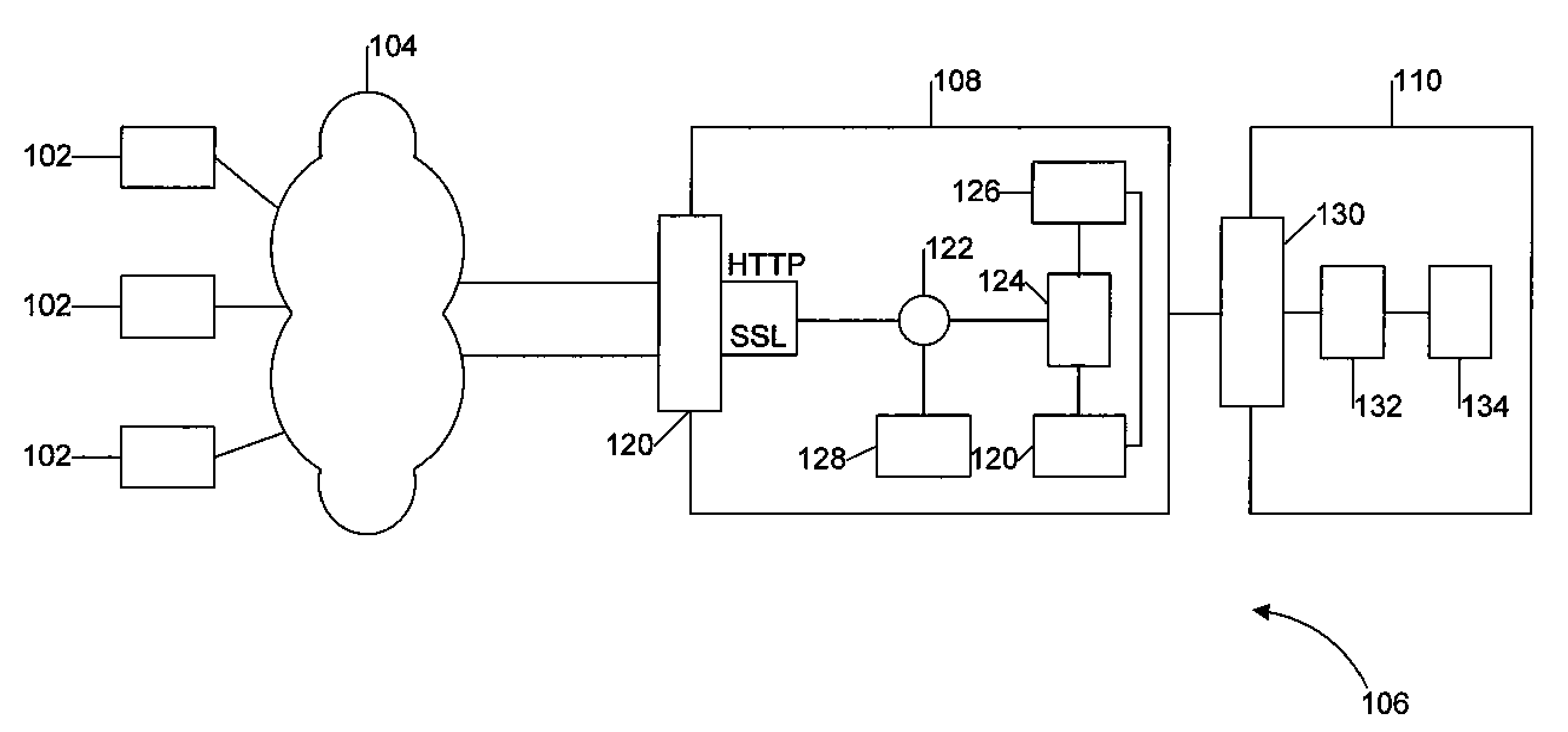
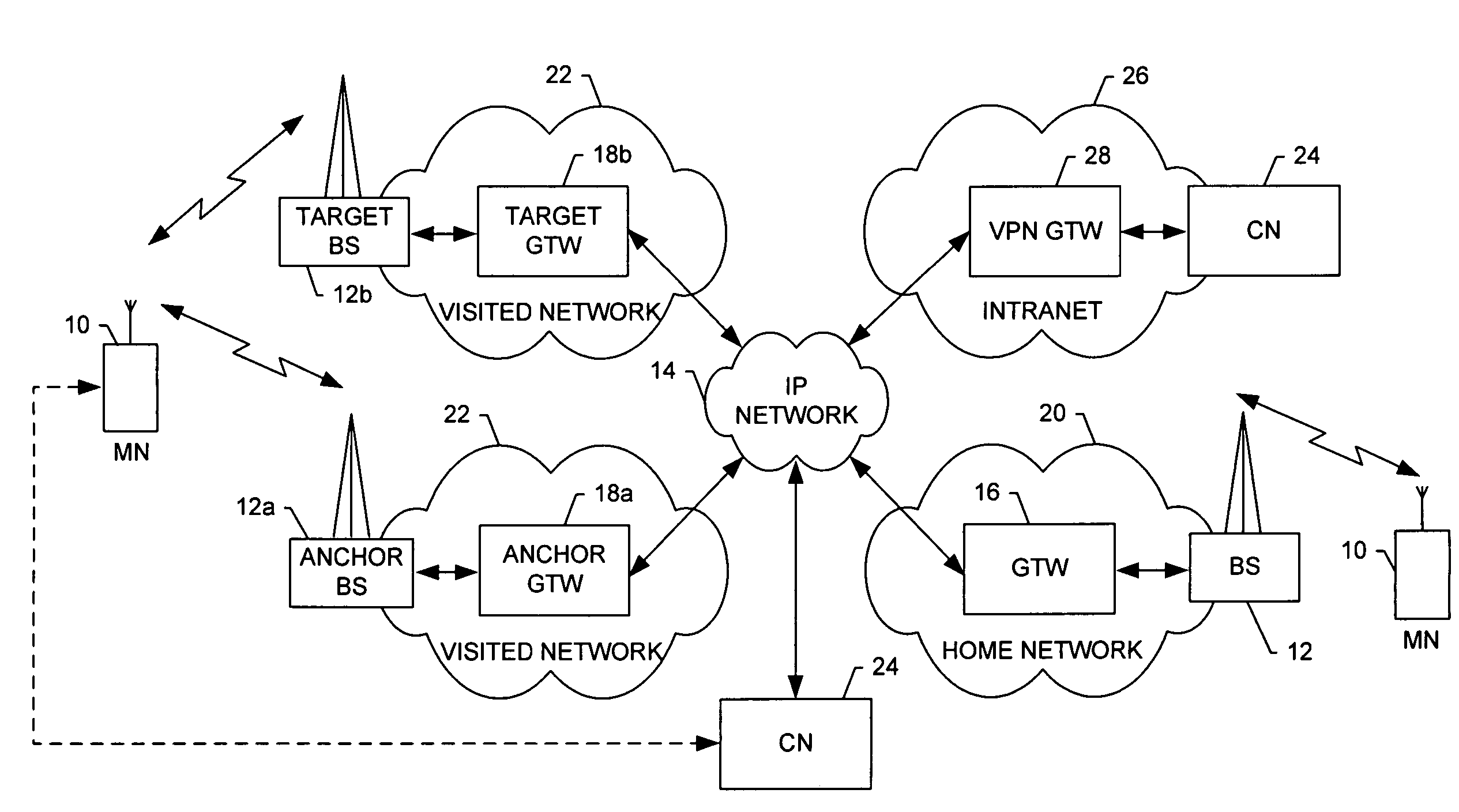
System and method of preventing web applications threats
InactiveUS20080034424A1Avoid attackMemory loss protectionError detection/correctionTraffic capacityWeb application
A system and method for protection of Web based applications are described. An agent is included in a web server such that traffic is routed through the agent. A security module is also in communication with the agent. The agent receives information about the application profile, and patterns of acceptable traffic behavior, from the security module. The agent acts as a gatekeeper, holding up suspicious traffic that does not match the pattern of acceptable traffic behavior until the suspicious traffic has been analyzed by the security module. Using the agent, malicious traffic can dropped before it can reach the application, or the user can be logged out, or both.
Owner:TRUSTWAVE HOLDINGS
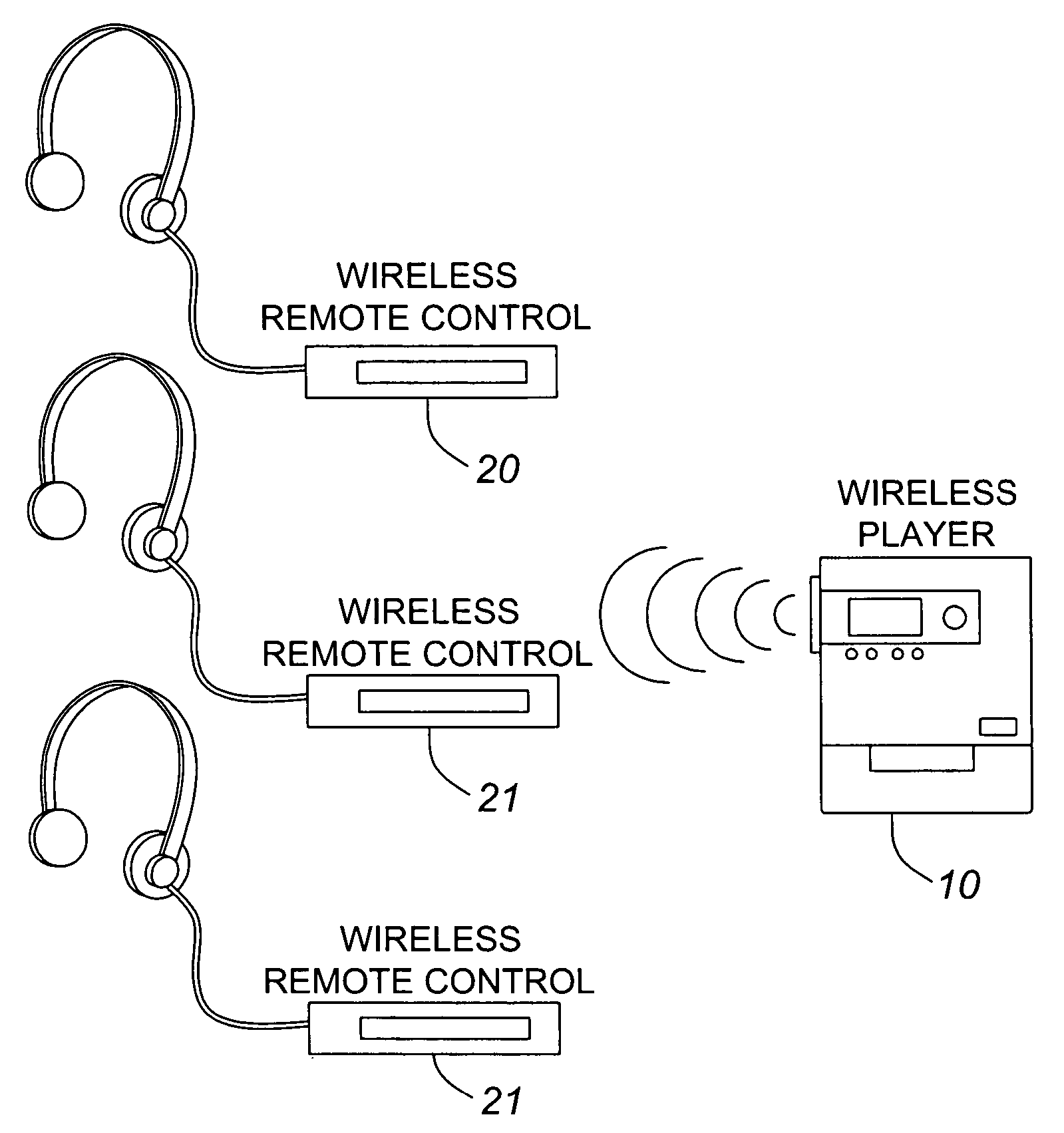
Apparatus and method for wireless audio network management
InactiveUS20060205349A1Telemetry/telecontrol selection arrangementsNetwork topologiesData streamRemote control
Electronic apparatus and method are provided for management of communications between channel master (e.g. audio player), responding device (e.g. remote control / headphones) and, optionally, passive devices (e.g. headphones) wirelessly connected in a wireless audio network. The channel master transmits, and the responding device receives, audio signals and network management information. Profile negotiation means communicates application profiles for the devices, establishing at least one application profile which is common to them and designating a selected, common application profile for use in associating the devices. Channel selection means selects a channel for the communications using an ordered selection of channels (PCS) obtained from scanning the channels for idle channels and ordering the scanned channels according to priority based on channel quality. Normalized control and status interfaces establish interoperability between devices which use different data streams to communicate in the network.
Owner:KLEER SEMICON CORP
System and method for automatic application profile and policy creation
A system is provided for configuring an application for operation onboard a mobile node that includes a plurality of communication interfaces for accessing a plurality of types of networks. The system includes a network entity that can send a request for an application-specific profile for operating an application onboard the mobile node, the request including information identifying the application. In response, a profile server can create / retrieve an application-specific profile based upon the request. The application-specific profile includes one or more application-specific preferences and / or one or more application-specific settings, where at least one of the application-specific preference(s) and / or setting(s) can be interpreted into one or more policy rules capable of at least partially controlling selection of one or more of the communication interfaces of the mobile node during operation of the application. The application can thereafter be configured at least partially based upon the application-specific profile independent of user input.
Owner:RPX CORP
Network-independent profiling of applications for automatic partitioning and distribution in a distributed computing environment
InactiveUS6983463B1Multiprogramming arrangementsTransmissionDistributed Computing EnvironmentParallel computing
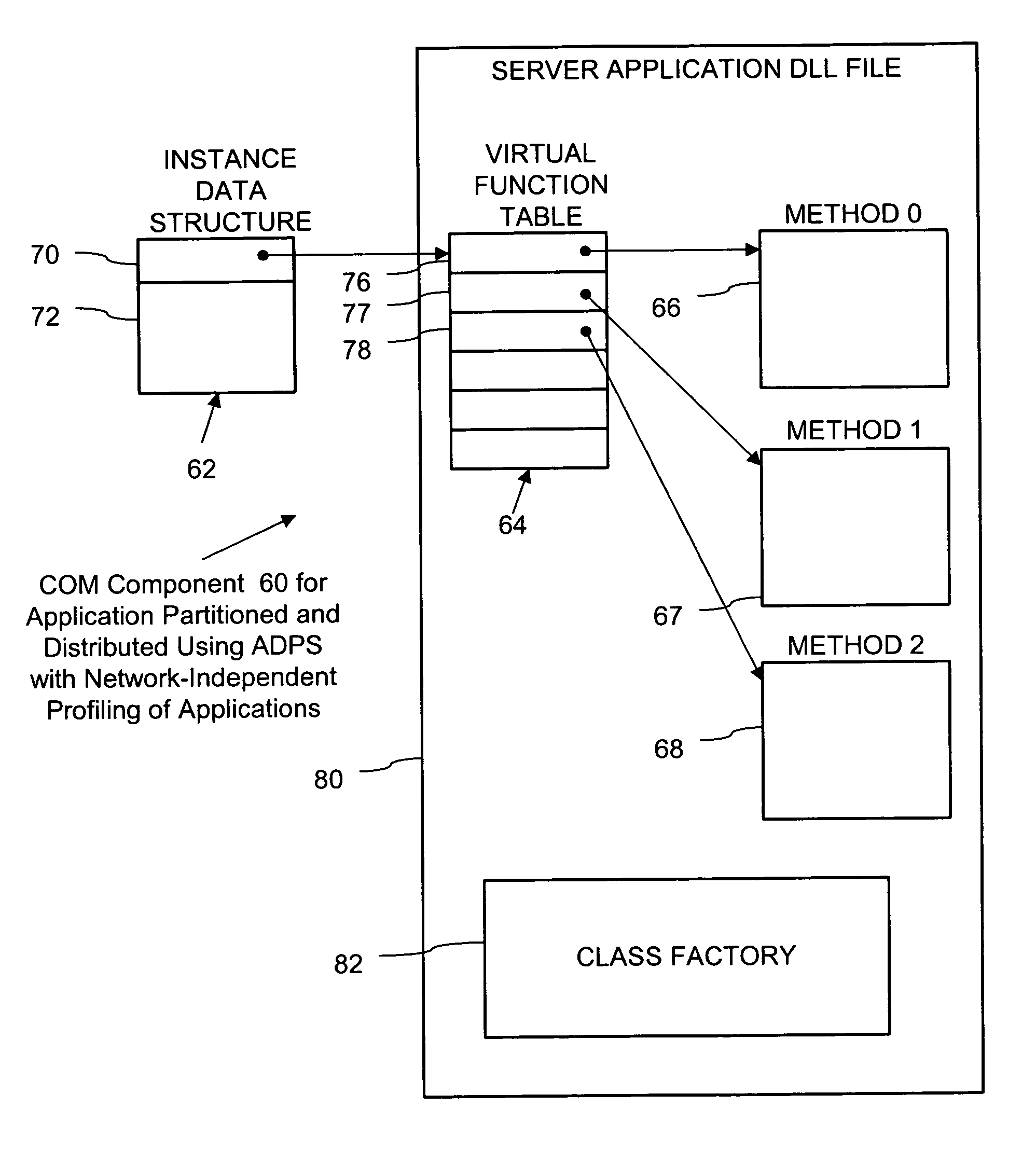
An instrumentation system profiles an application using structural metadata description of the application. Units (such as COM objects) of the application have strongly-typed, binary-standard interfaces, and are profiled, for example, using an executable file and DLLs for the application. A structural metadata description of the application includes compiled, interface-level type information used to identify and measure interaction between units of the application. For example, the type information is produced by analyzing IDL information. Profiling results in an application profile that includes description of the static relationships and / or dynamic interactions between units of the application. The application profile is combined with a network profile that describes a distributed computing environment. Analysis of the result yields a distribution plan, which, for example, reduces costs associated with communication between the units. During execution, units of the application are distributed through the distributed computing environment according to the distribution plan.
Owner:MICROSOFT TECH LICENSING LLC
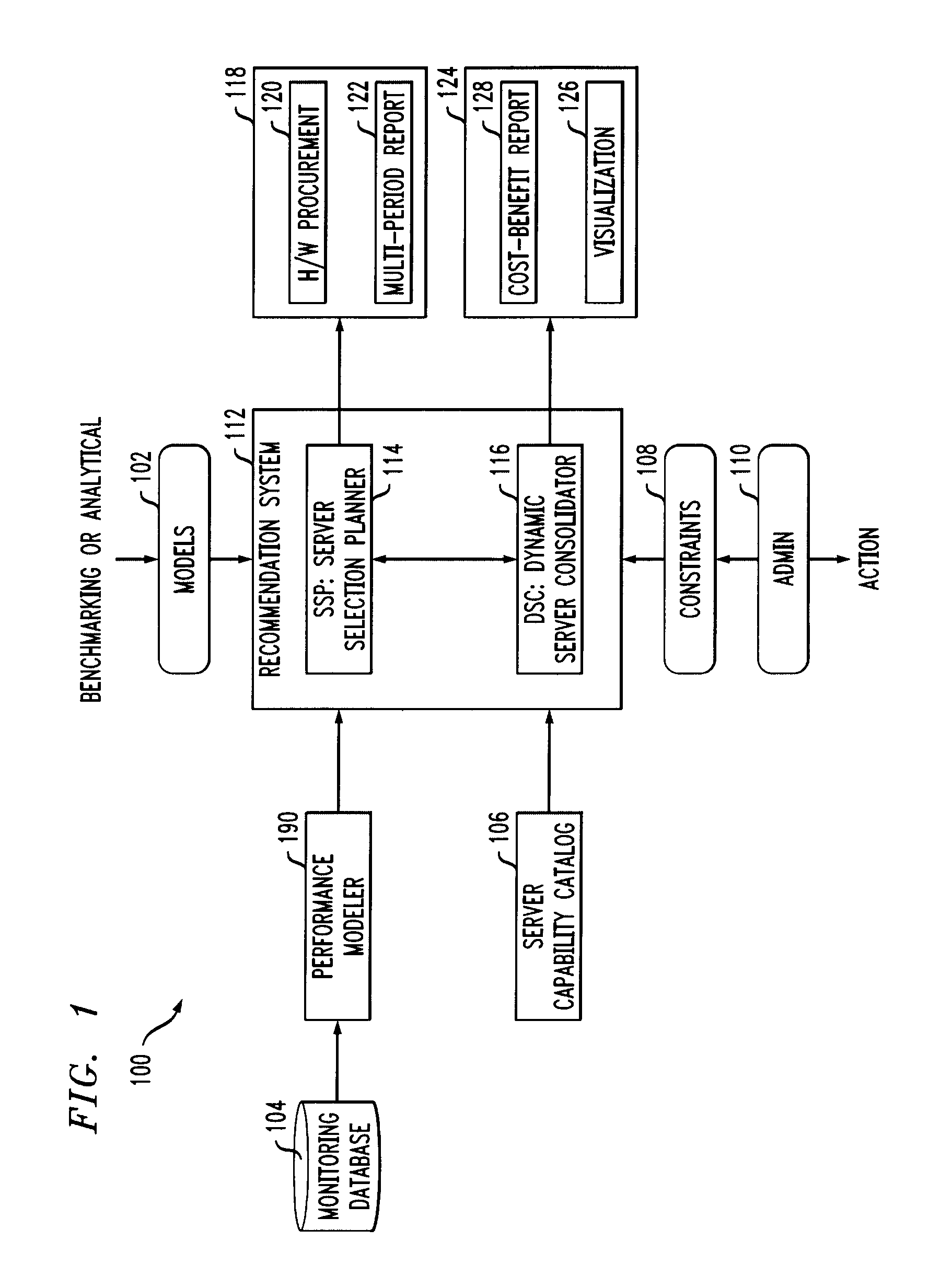
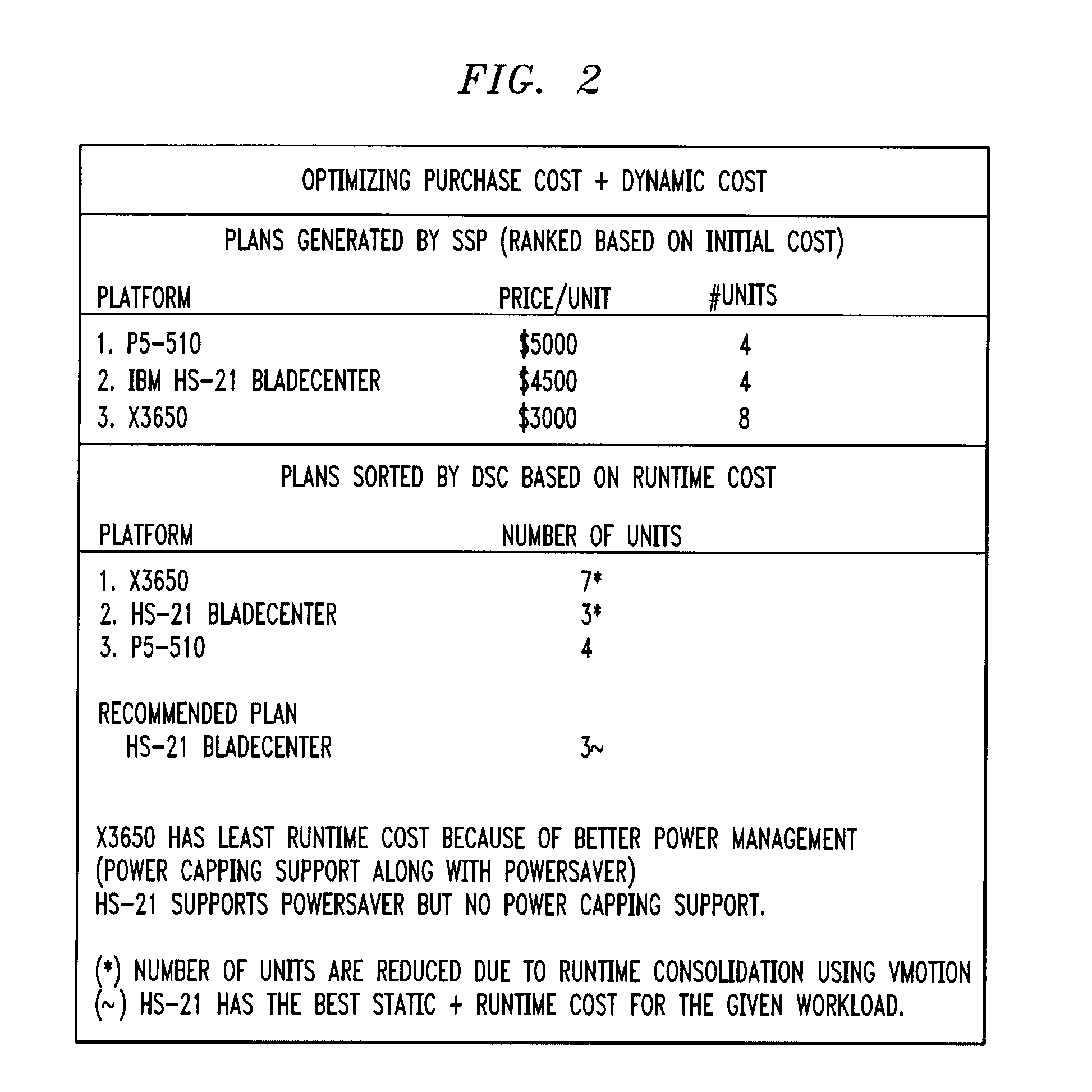
Method, system and computer program product for server selection, application placement and consolidation
InactiveUS20100005173A1Lower acquisition costsGood specificationMultiprogramming arrangementsMultiple digital computer combinationsBin packing problemRecommendation service
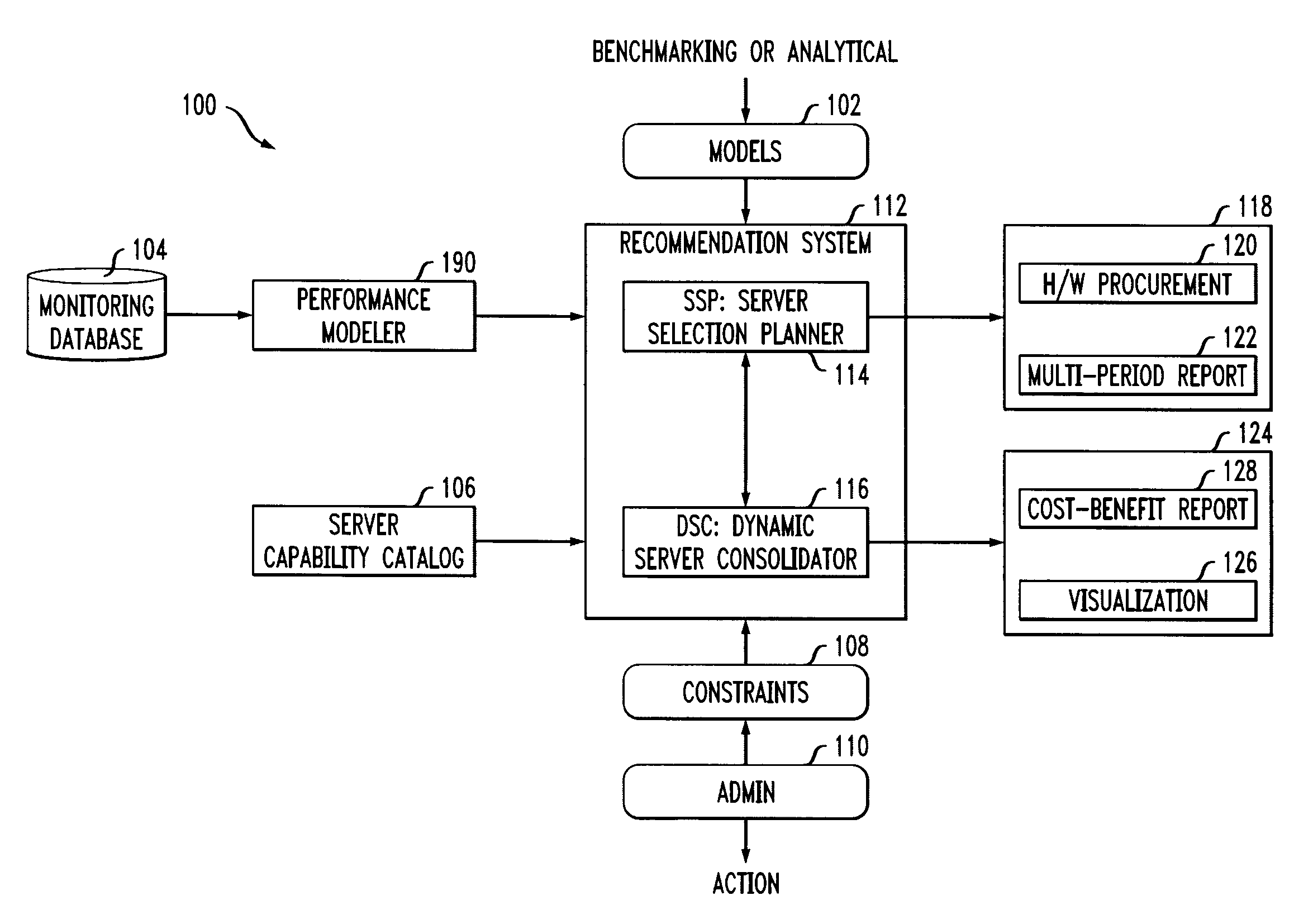
A plurality of application profiles are obtained, for a plurality of applications. Each of the profiles specifies a list of resources, and requirements for each of the resources, associated with a corresponding one of the applications. Specification of a plurality of constraints associated with the applications is facilitated, as is obtaining a plurality of cost models associated with at least two different kinds of servers on which the applications are to run. A recommended server configuration is generated for running the applications, by formulating and solving a bin packing problem. Each of the at least two different kinds of servers is treated as a bin of a different size, based on its capacity, and has an acquisition cost associated therewith. The size is substantially equal to a corresponding one of the resource requirement as given by a corresponding one of the application profiles. Each of the applications is treated as an item, with an associated size, to be packed into the bins. The bin packing problem develops the recommended server configuration based on reducing a total acquisition cost while satisfying the constraints and the sizes of the applications.
Owner:IBM CORP
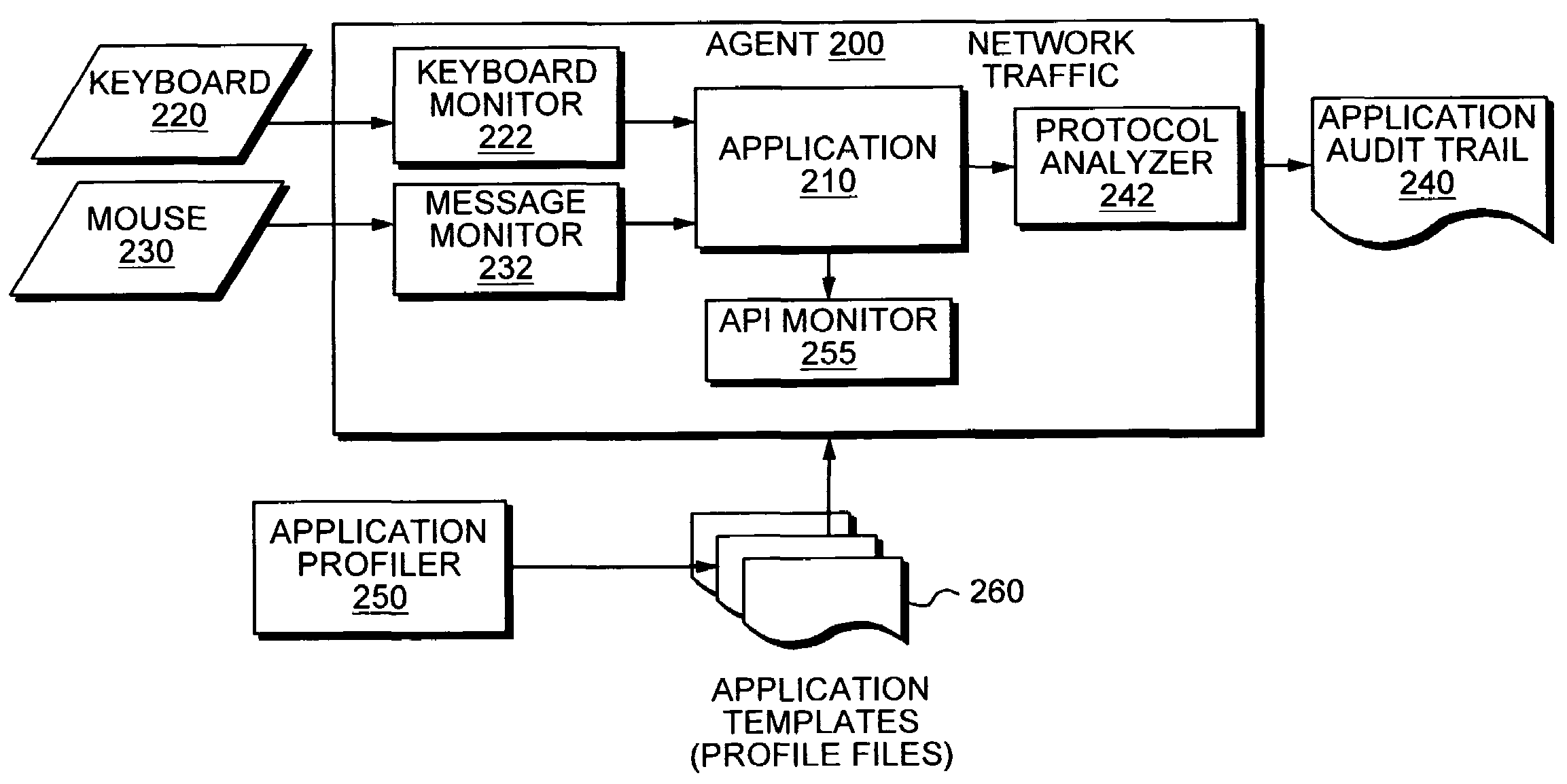
Application instrumentation and monitoring
ActiveUS7496575B2Cost effectiveAvoid the needDigital data processing detailsDigital computer detailsApplication softwareData store
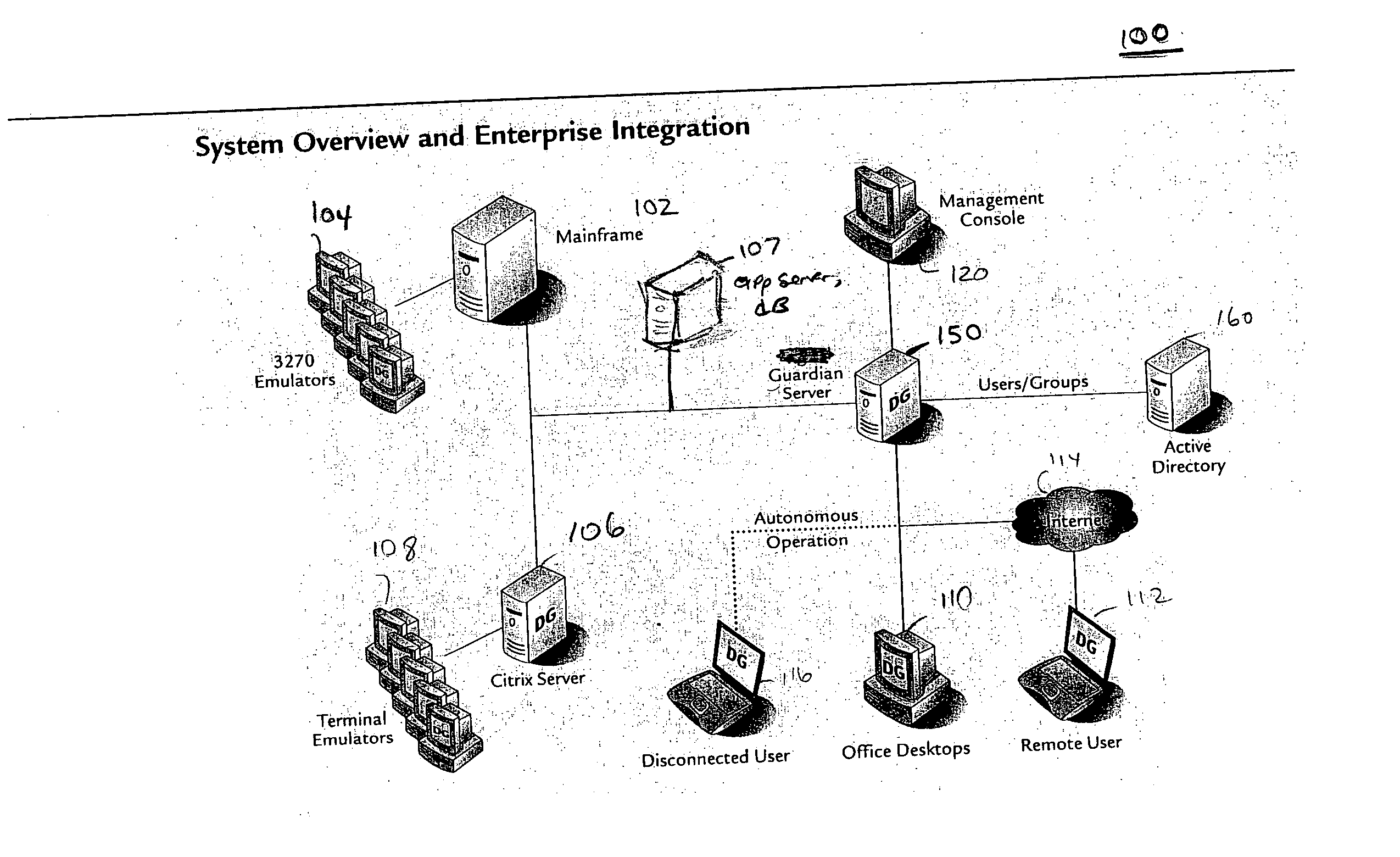
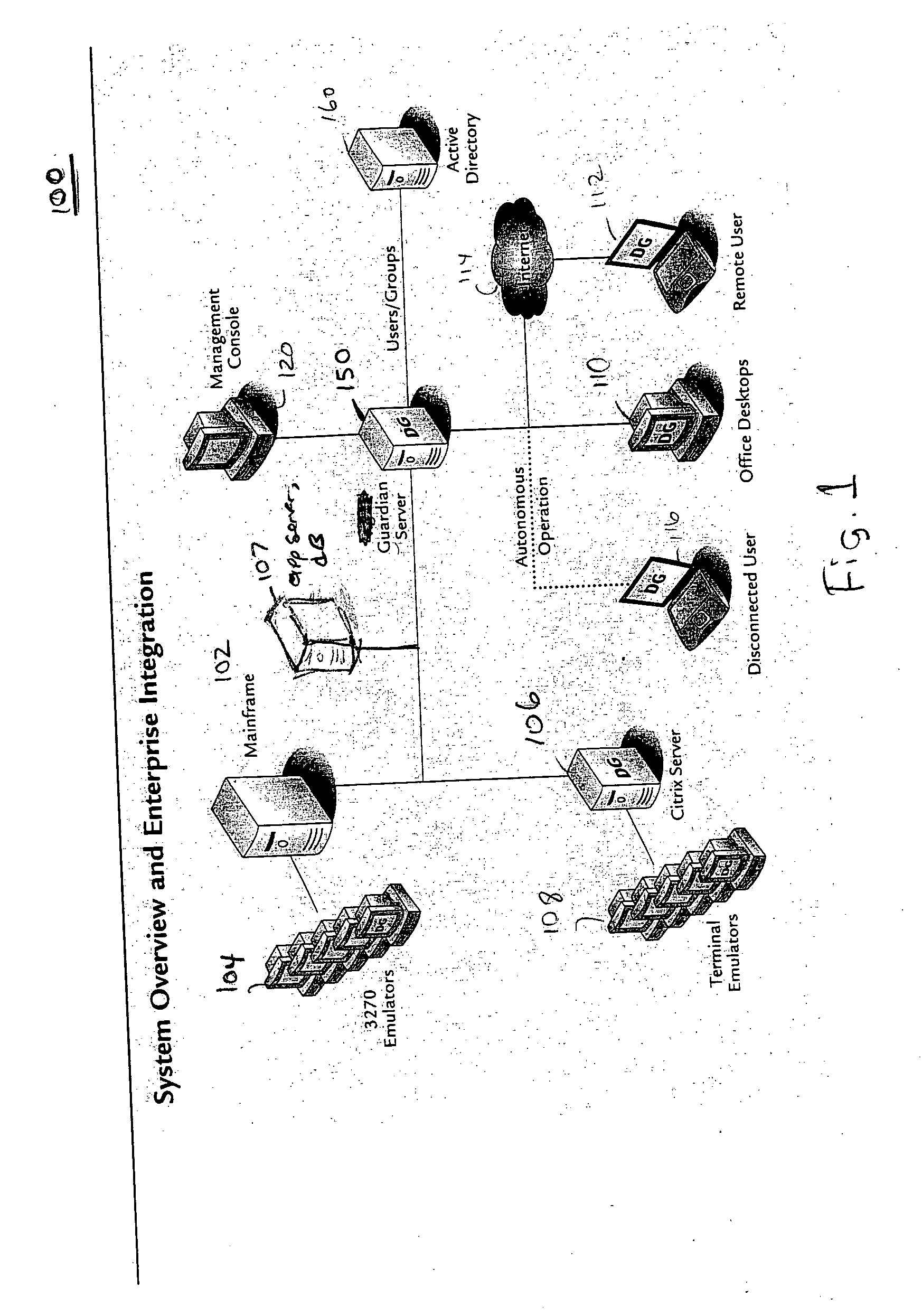
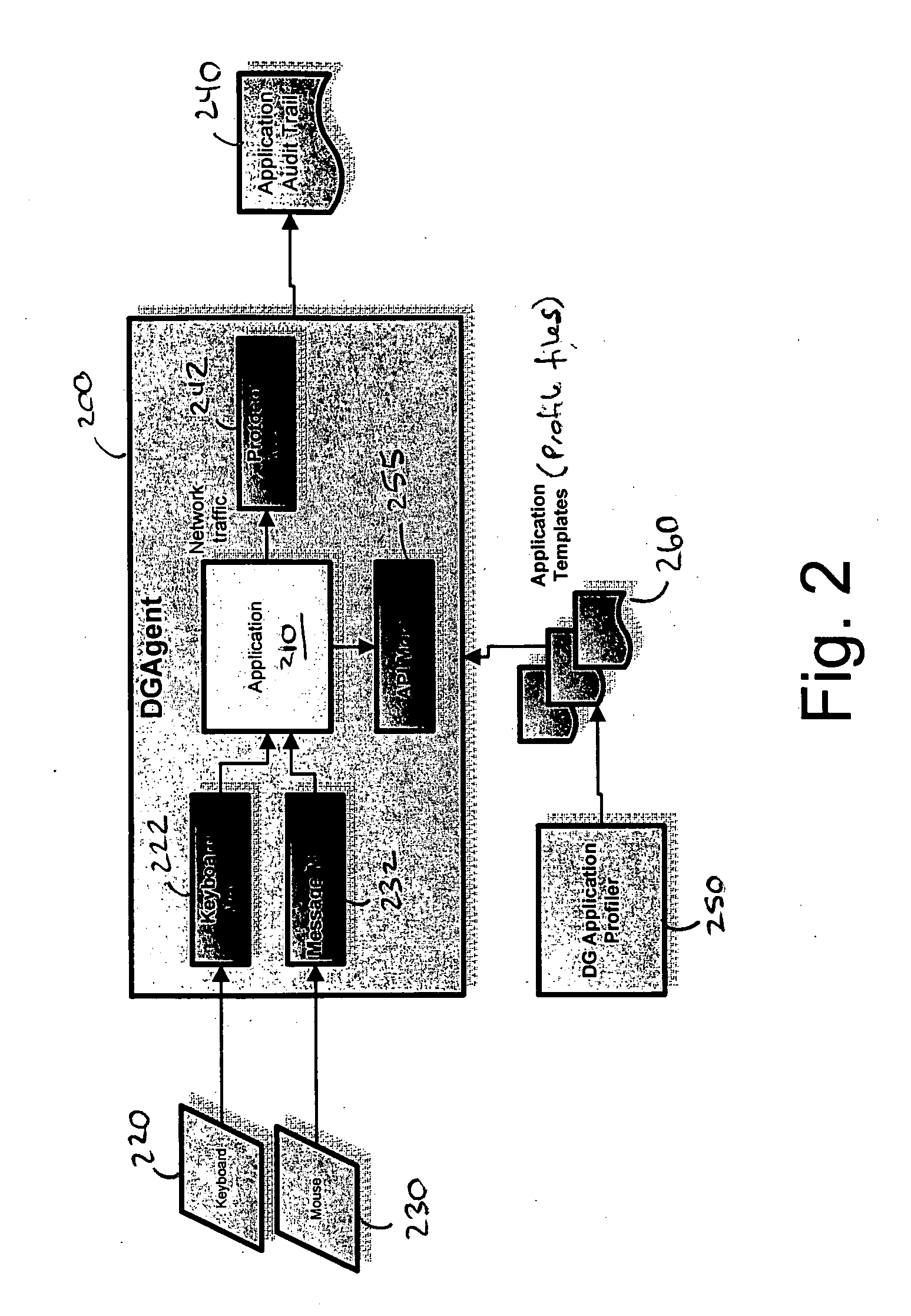
A data processing application logging, recording, and reporting process and infrastructure. Compliance with regulatory directives such as HIPAA, internal organizational and corporate, personal information privacy, and other security policies can thus be enforced without the need to recode legacy application software. In one preferred embodiment, a core agent process provides “listener” functionality that captures user input events, such as keyboard and mouse interactions, between a user and a legacy application of interest. The agent obtains instructions for how to deal with such events, accessing information that describes the application's behavior as already captured by an application profiler tool. Keyboard and mouse data entry sequences, screen controls and fields of interest are tagged during application profiling process. This data is stored in application profile developed for each mode of a legacy application. The technique can be implemented in various Information Technology (IT) environments including mainframe / terminal applications and / or client / server applications. Thus, full coverage of “fat” client, “thin” client, and legacy “mainframe” applications can be provided with a common approach across an enterprise.
Owner:DIGITAL GUARDIAN LLC
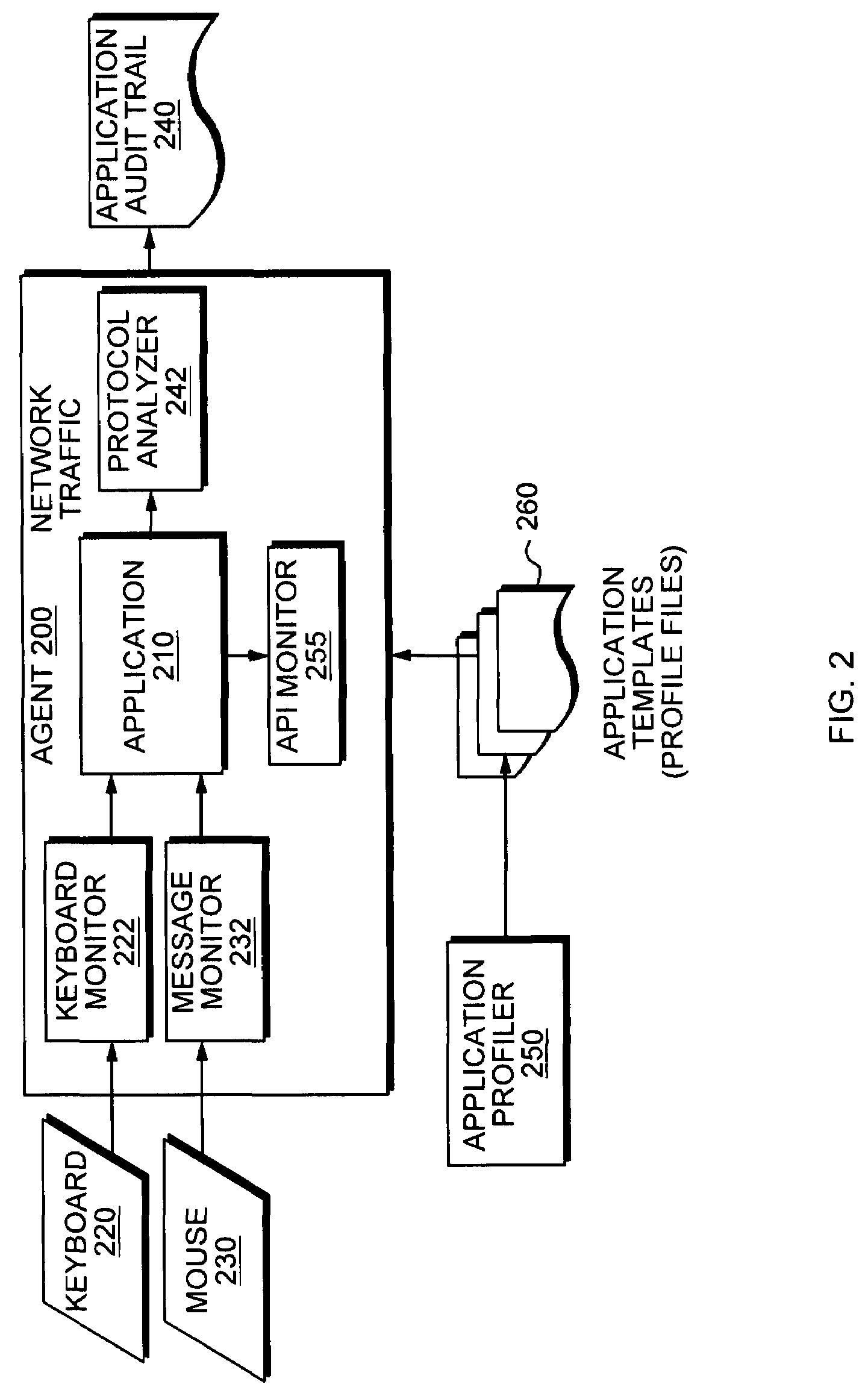
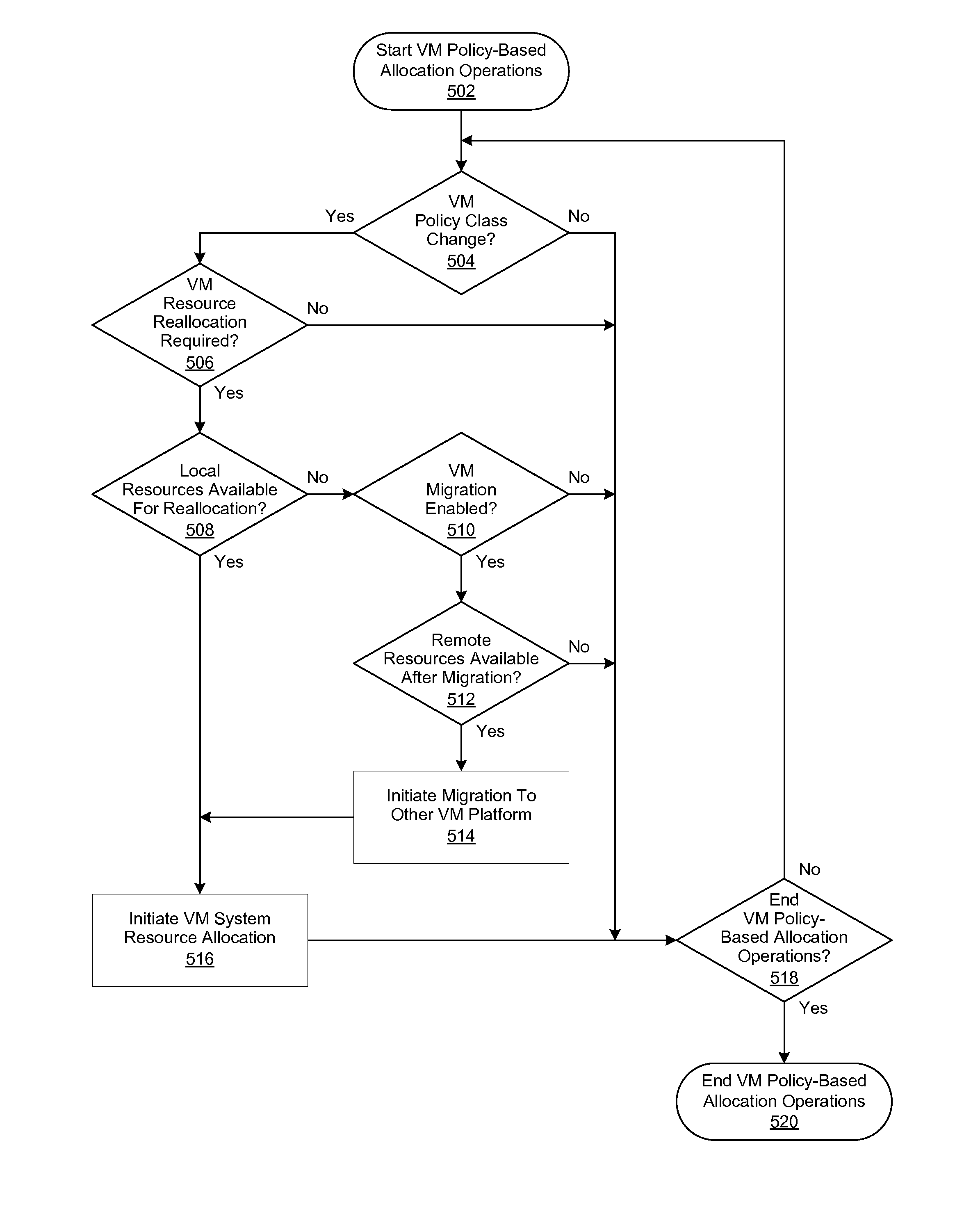
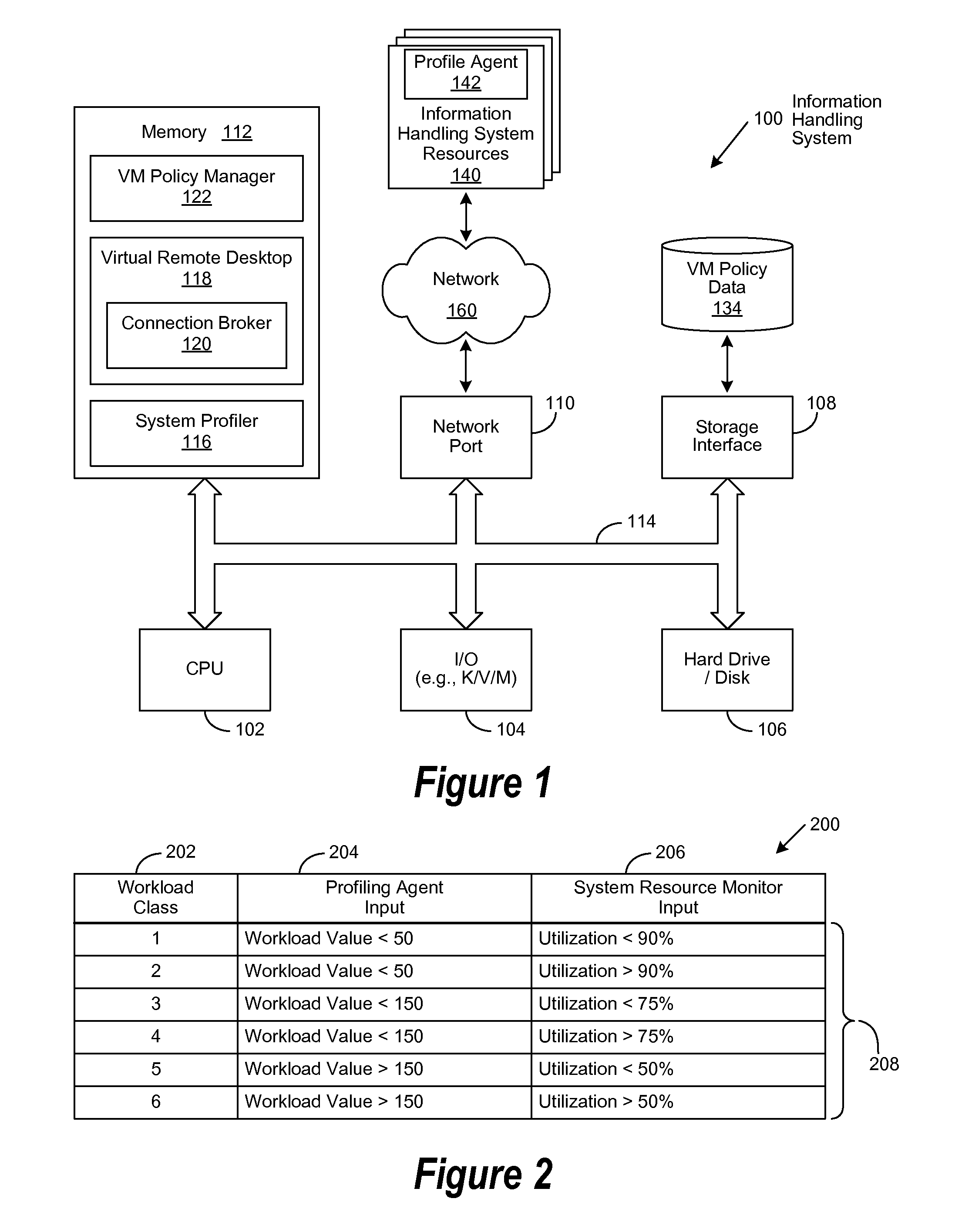
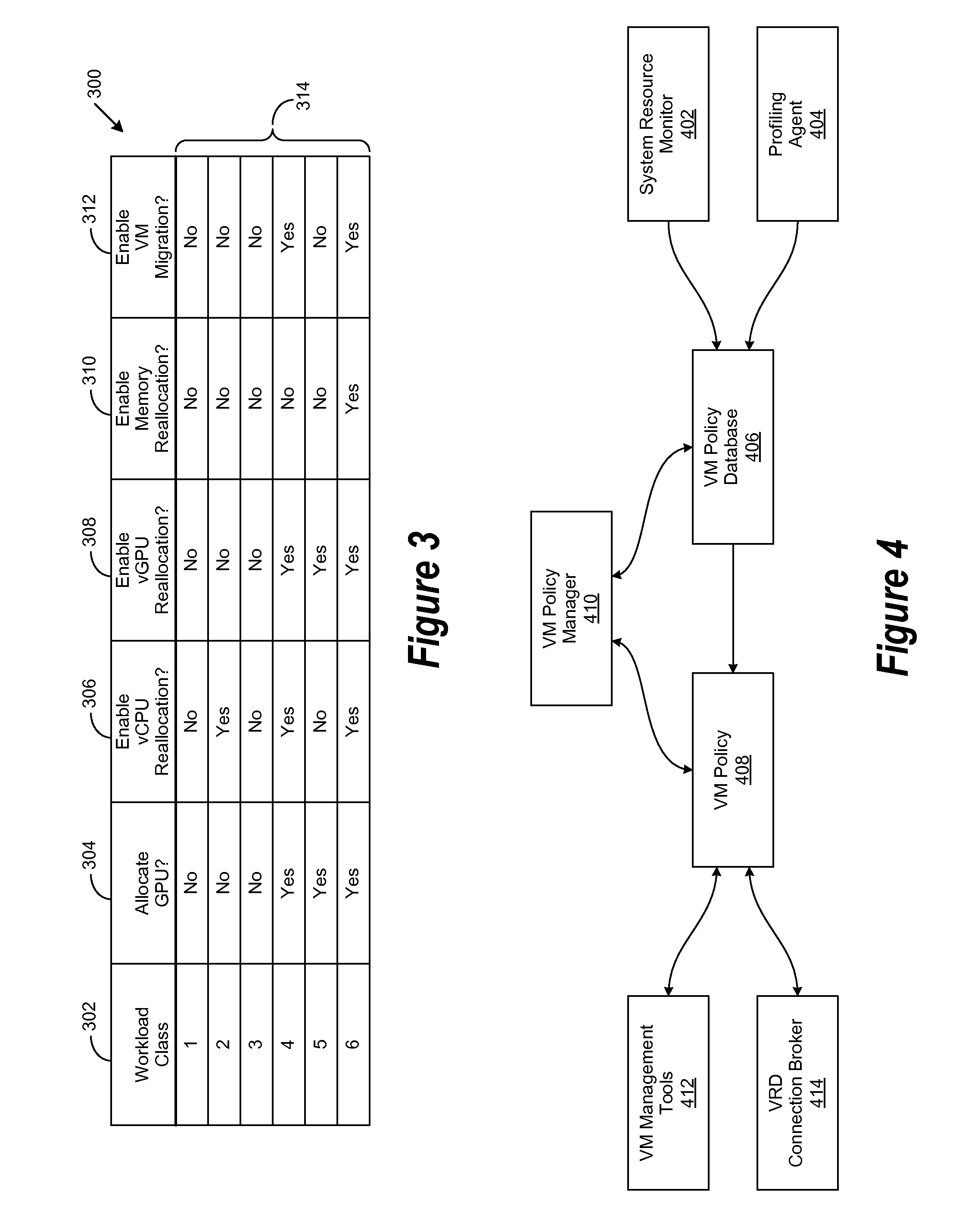
Application Profile Based Provisioning Architecture For Virtual Remote Desktop Infrastructure
ActiveUS20110083131A1Multiprogramming arrangementsSoftware simulation/interpretation/emulationWorkload profilingResource utilization
A system, method, and computer-readable medium are disclosed for automatically allocating resources to a virtual machine. Expected workload profile data and application utilization data corresponding to a software application associated with a virtual machine (VM) is collected by an application profiling agent. Resource utilization data corresponding to the utilization of resources associated with the execution of the software application is collected by a system resource monitor. The expected workload profile data, the application utilization data, and the resource utilization data are then processed to determine a virtual machine workload class, which is then used to determine a corresponding VM policy. Data associated with the VM policy then processed to generate VM resource allocation instructions, which are in turn processed to provision the VM.
Owner:DELL PROD LP
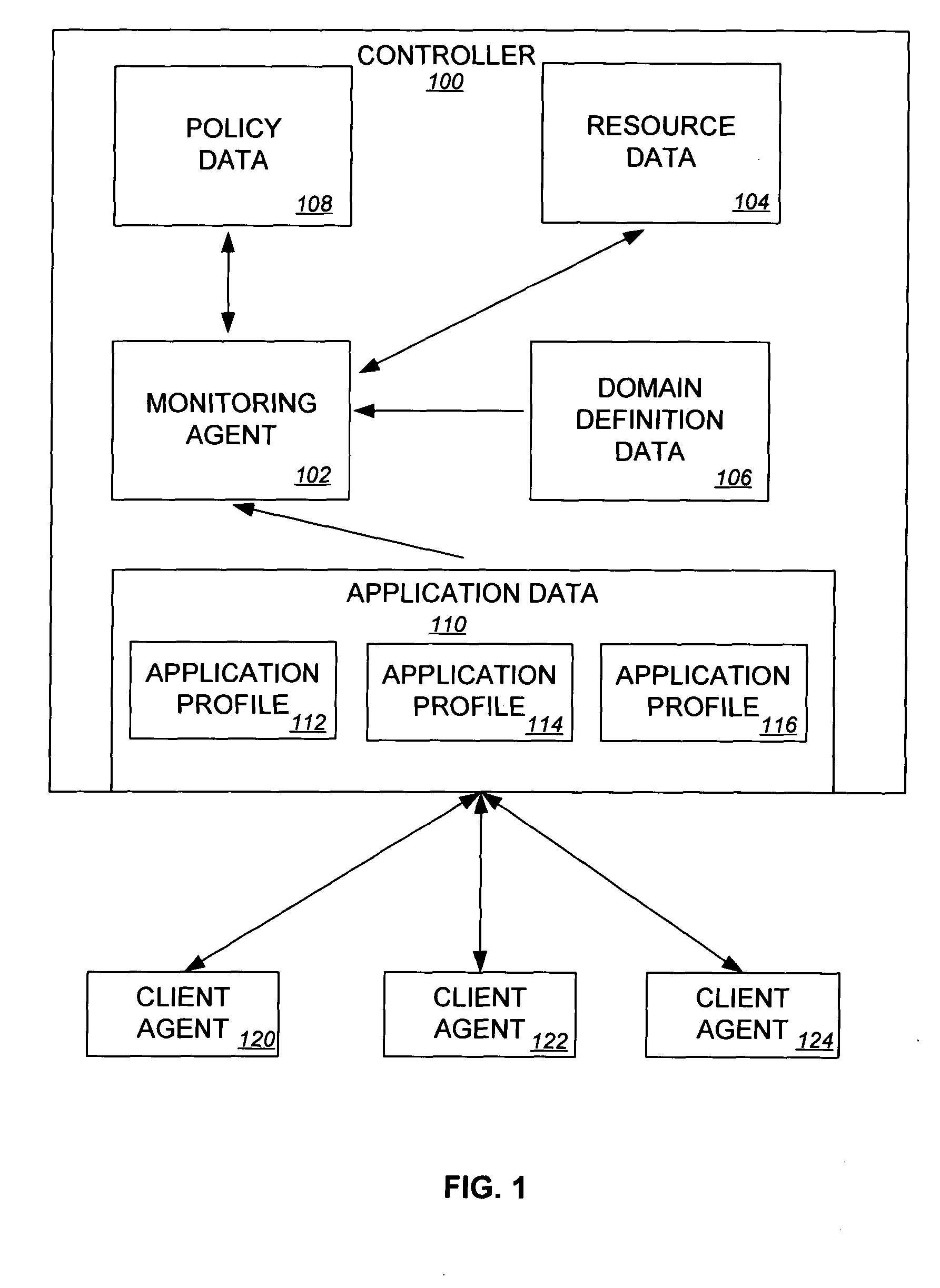
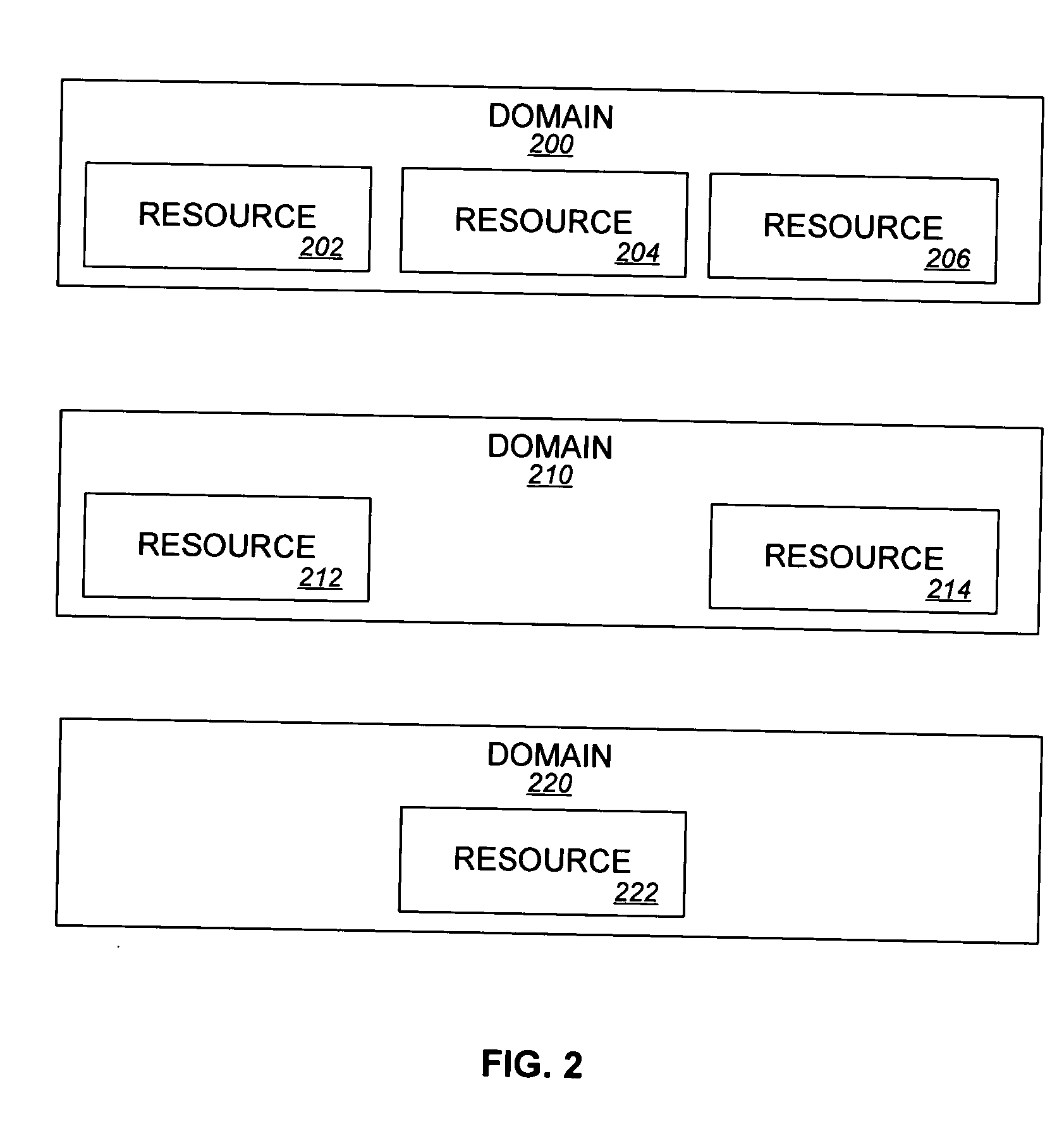
Systems and methods for monitoring resource utilization and application performance
ActiveUS7581224B2Hardware monitoringMultiprogramming arrangementsResource utilizationApplication software
Owner:GOOGLE LLC
Mobile application security and management service
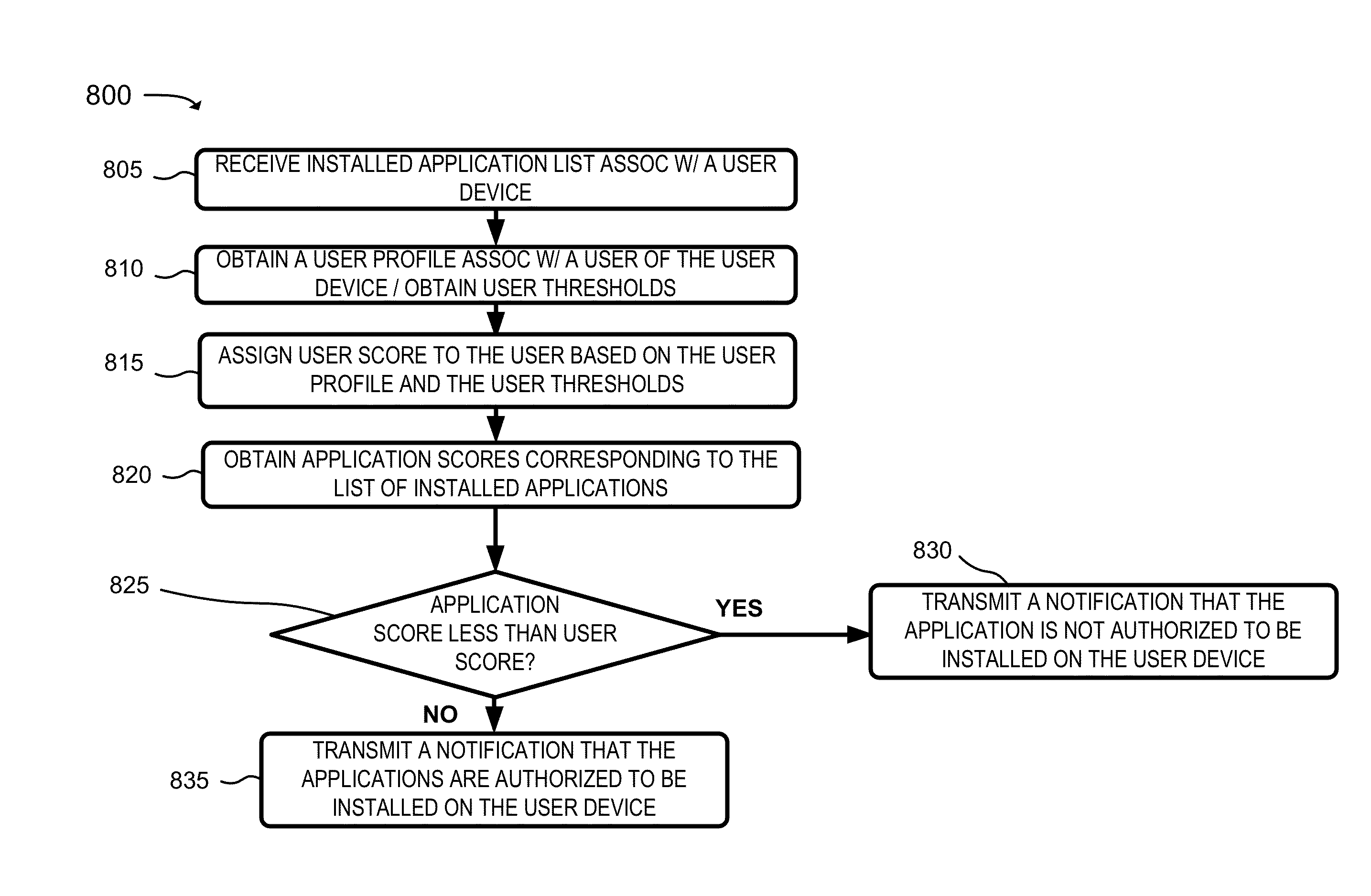
A system is configured to receive a list of applications installed on a user device; obtain application profiles that identify risk levels associated with the applications; obtain a user profile that identifies a job level, security risk level, or an access level to confidential information associated with the user of the user device; identify a highest risk level authorized for the user device based on whether the job level is greater than a first threshold, the security risk level is greater than a second threshold, or the access level is greater than a third threshold; determine whether any of the risk levels are greater than the highest risk level; and transmit a notification that one of the applications is to be removed from the user device when one of the risk levels, associated with the one of the applications, is greater than the highest risk level.
Owner:VERIZON PATENT & LICENSING INC
Profile based capture component
An indexing system in a computer system may include applications, a capture processor, a queue, a search engine, and a display processor. The indexing system captures events of user interactions with the applications. Events are queued and if indexable, indexed and stored for user access through the search engine. Capture components in the capture processor can include a keyboard capture component that processes user keystrokes to determine events. A display capture component captures event data from windows associated with the applications. Display event data can be captured on a polling schedule or based on state changes of window elements. To determine target applications and window applications of interest application profiles and window profiles can be used.
Owner:GOOGLE LLC
Application instrumentation and monitoring
ActiveUS20060123101A1Cost effectiveAvoid the needDigital computer detailsComputer security arrangementsApplication softwareData store
A data processing application logging, recording, and reporting process and infrastructure. Compliance with regulatory directives such as HIPAA, internal organizational and corporate, personal information privacy, and other security policies can thus be enforced without the need to recode legacy application software. In one preferred embodiment, a core agent process provides “listener” functionality that captures user input events, such as keyboard and mouse interactions, between a user and a legacy application of interest. The agent obtains instructions for how to deal with such events, accessing information that describes the application's behavior as already captured by an application profiler tool. Keyboard and mouse data entry sequences, screen controls and fields of interest are tagged during application profiling process. This data is stored in application profile developed for each mode of a legacy application. The technique can be implemented in various Information Technology (IT) environments including mainframe / terminal applications and / or client / server applications. Thus, full coverage of “fat” client, “thin” client, and legacy “mainframe” applications can be provided with a common approach across an enterprise.
Owner:DIGITAL GUARDIAN LLC
Distributed firewall security system that extends across different cloud computing networks
An application profile is provided to manage security of an application deployed across two or more cloud computing networks. A user can define in the application profile first and second server groups, a cloud chamber as including the first and second server groups, and a computing flow to the cloud chamber. A firewall rule is generated based on the computing flow. The firewall rule is distributed to the first server group of the cloud chamber. A copy of the firewall rule is distributed to the second server group of the cloud chamber. The first server group is in a first cloud computing network that is provided by a first cloud provider. The second server group is in a second cloud computing network that is provided by a second cloud provider, different from the first cloud provider.
Owner:ZENTERA SYST
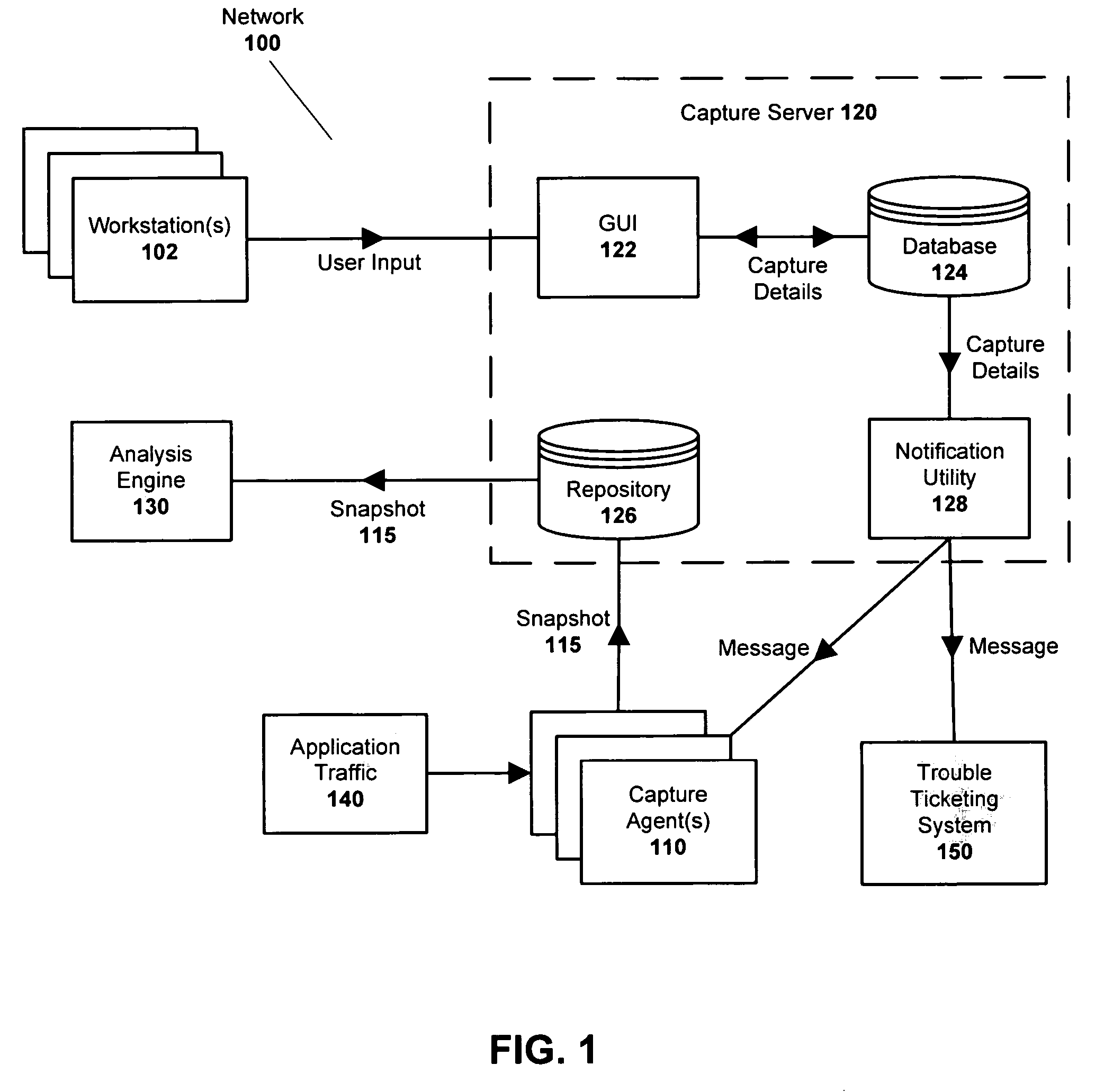
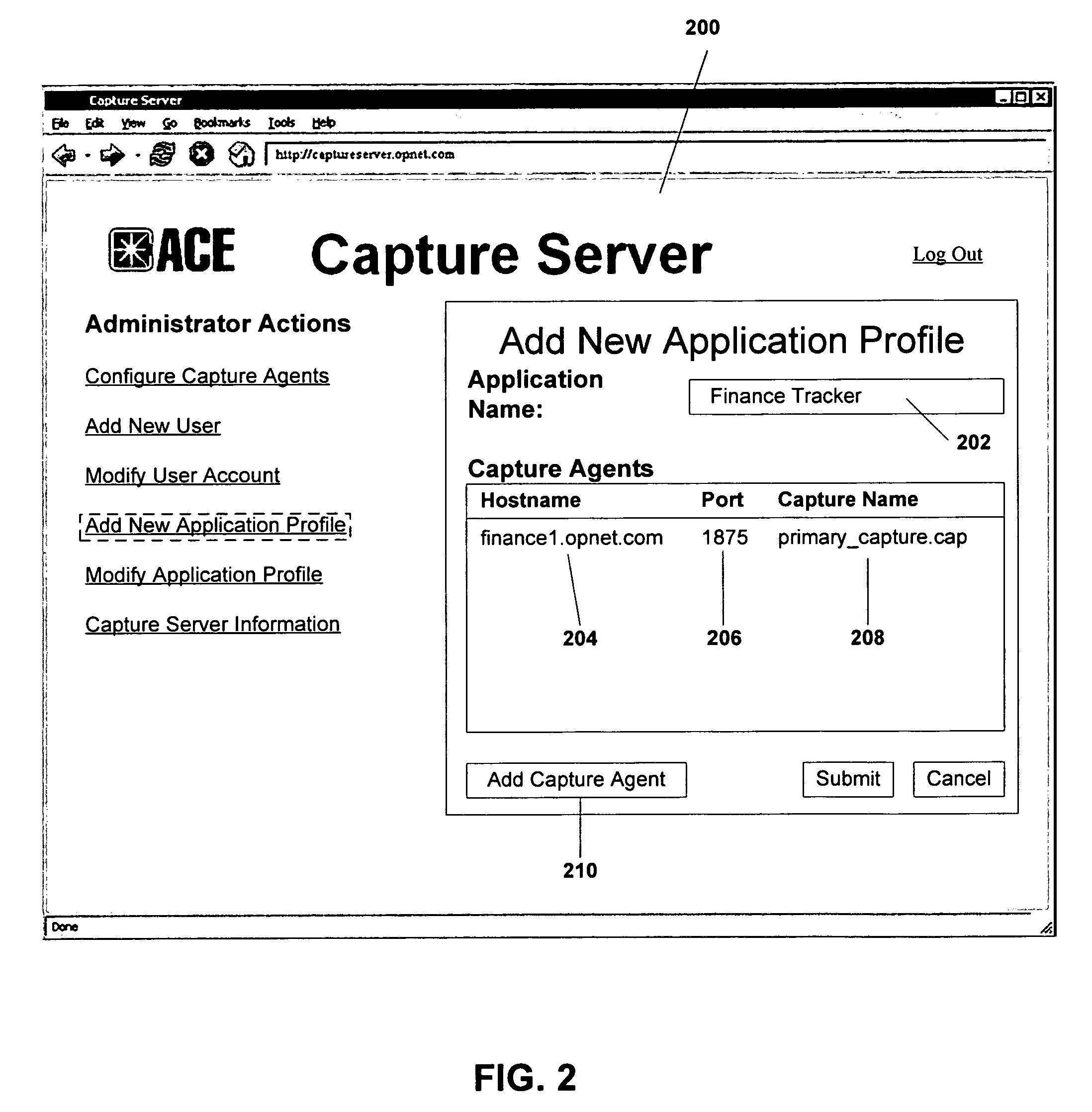
Managing captured network traffic data
ActiveUS20070067450A1Quick fixFully testedDigital computer detailsData switching networksTraffic capacityApplication software
A system and method for managing captured network traffic data is provided. The invention comprises a plurality of capture agents, each being configured to capture the network traffic associated with one or more applications. Each application is associated with one or more capture agents according to an application profile that is stored and maintained in a capture server. When analysis of an application's network traffic is required, the capture server contacts the corresponding capture agents according to the application profile. The capture server then effects the identification and archiving of the network traffic that corresponds to a user-defined capture condition. A database at the capture server maintains a record that associates the corresponding network traffic with the user-defined capture condition such that the corresponding network traffic can later be retrieved and analyzed using an analysis engine.
Owner:RIVERBED TECH LLC
Method For Software Program Synchronization
ActiveUS20080215758A1Change operabilityMultiple digital computer combinationsDigital data authenticationSoftwareComputer program
A method, devices, and a computer program for synchronizing one or more software programs from a first device (D100) to a second device (D200) are disclosed. The method comprises the steps of creating (100) an application profile indicating one or more software programs on the first device (ID100) and indicating one or more software program providing nodes (SN 100,SN200) from which said one or more software programs are obtainable, providing (200) the application profile to a synchronization manager (SM 100), identifying (300) by the synchronization manager (SM 100) the one or more software programs and the one or more software program providing nodes (SN100,SN200) according to the application profile, requesting (400) by the synchronization manager (SM 100) the one or more software program providing nodes (SN 100,SN200) to transfer the one or more software programs, and transferring (500) the one or more software programs from the one or more software program providing nodes (SN 100,SN200) to the second device (D200).
Owner:TELEFON AB LM ERICSSON (PUBL)
System and method for automatic application profile and policy creation
ActiveUS7263353B2Service provisioningRadio/inductive link selection arrangementsCommunication interfaceUser input
A system is provided for configuring an application for operation onboard a mobile node that includes a plurality of communication interfaces for accessing a plurality of types of networks. The system includes a network entity that can send a request for an application-specific profile for operating an application onboard the mobile node, the request including information identifying the application. In response, a profile server can create / retrieve an application-specific profile based upon the request. The application-specific profile includes one or more application-specific preferences and / or one or more application-specific settings, where at least one of the application-specific preference(s) and / or setting(s) can be interpreted into one or more policy rules capable of at least partially controlling selection of one or more of the communication interfaces of the mobile node during operation of the application. The application can thereafter be configured at least partially based upon the application-specific profile independent of user input.
Owner:RPX CORP
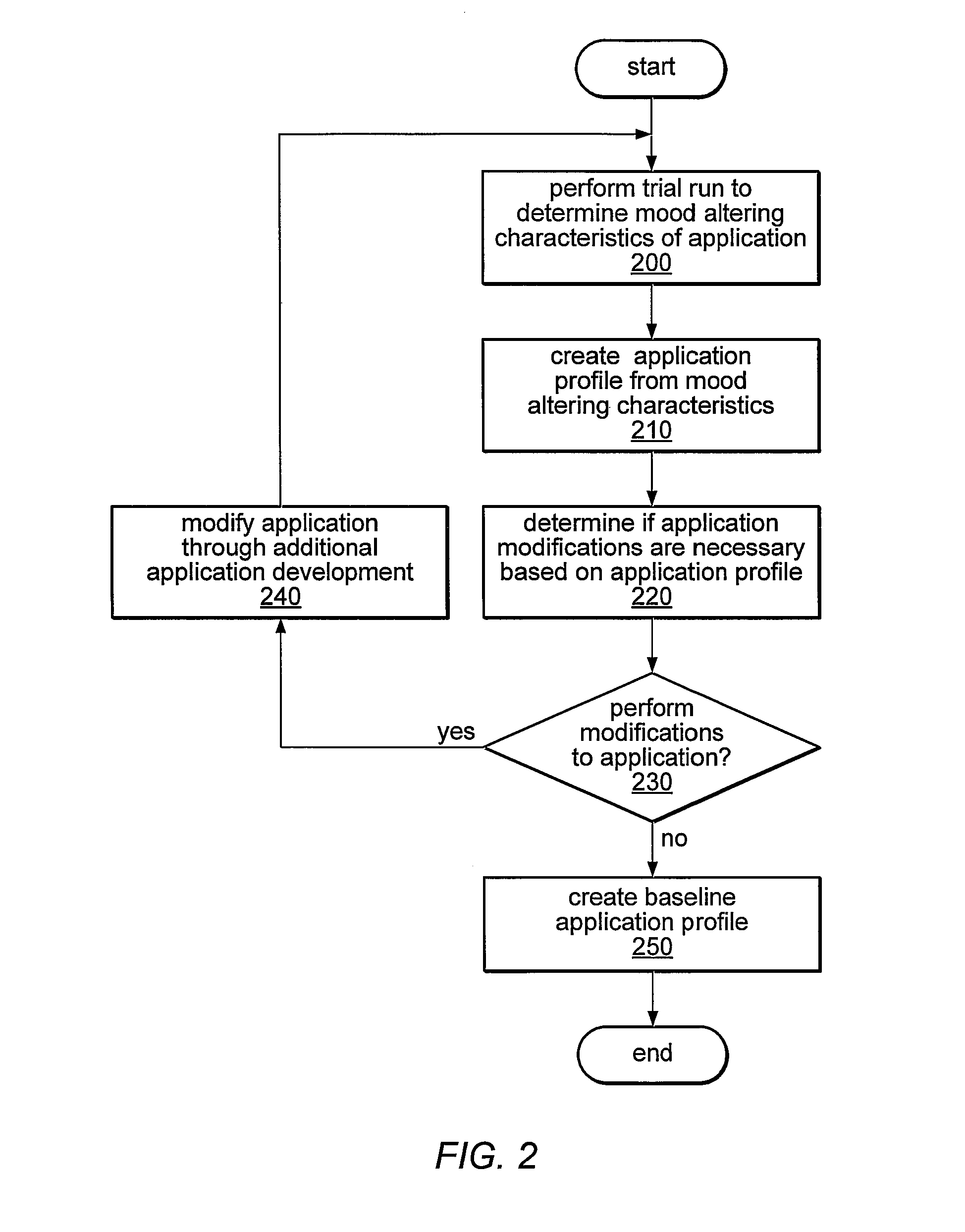
System and method for adapting software elements based on mood state profiling
ActiveUS7930676B1More context informationProgram loading/initiatingSpecial data processing applicationsApplication softwareMood state
Owner:INTUIT INC
Systems and methods for monitoring resource utilization and application performance
ActiveUS20050022185A1Digital computer detailsHardware monitoringResource utilizationMultiple applications
Systems and methods are disclosed for monitoring application performance. In one embodiment, the system comprises resource data including information on a plurality of resources, the resources including a plurality of computers, application data including one or more application profiles, each application profile having a performance profile and a resource profile, the resource profile including resource utilization information. The system further comprises policy data including one or more application performance policies and one or more resource utilization policies, and a monitoring agent to monitor the application data for compliance with the policy data.
Owner:GOOGLE LLC
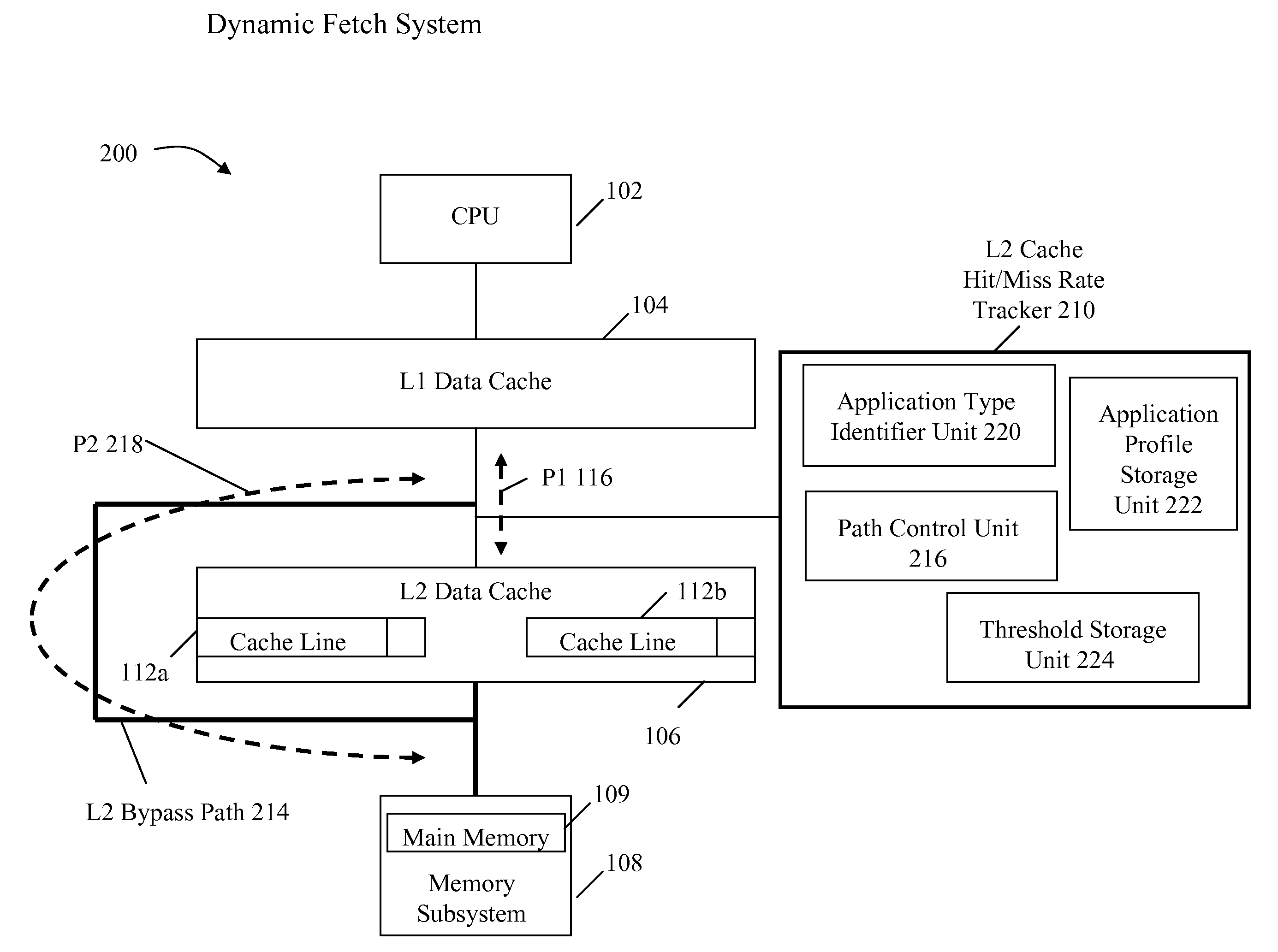
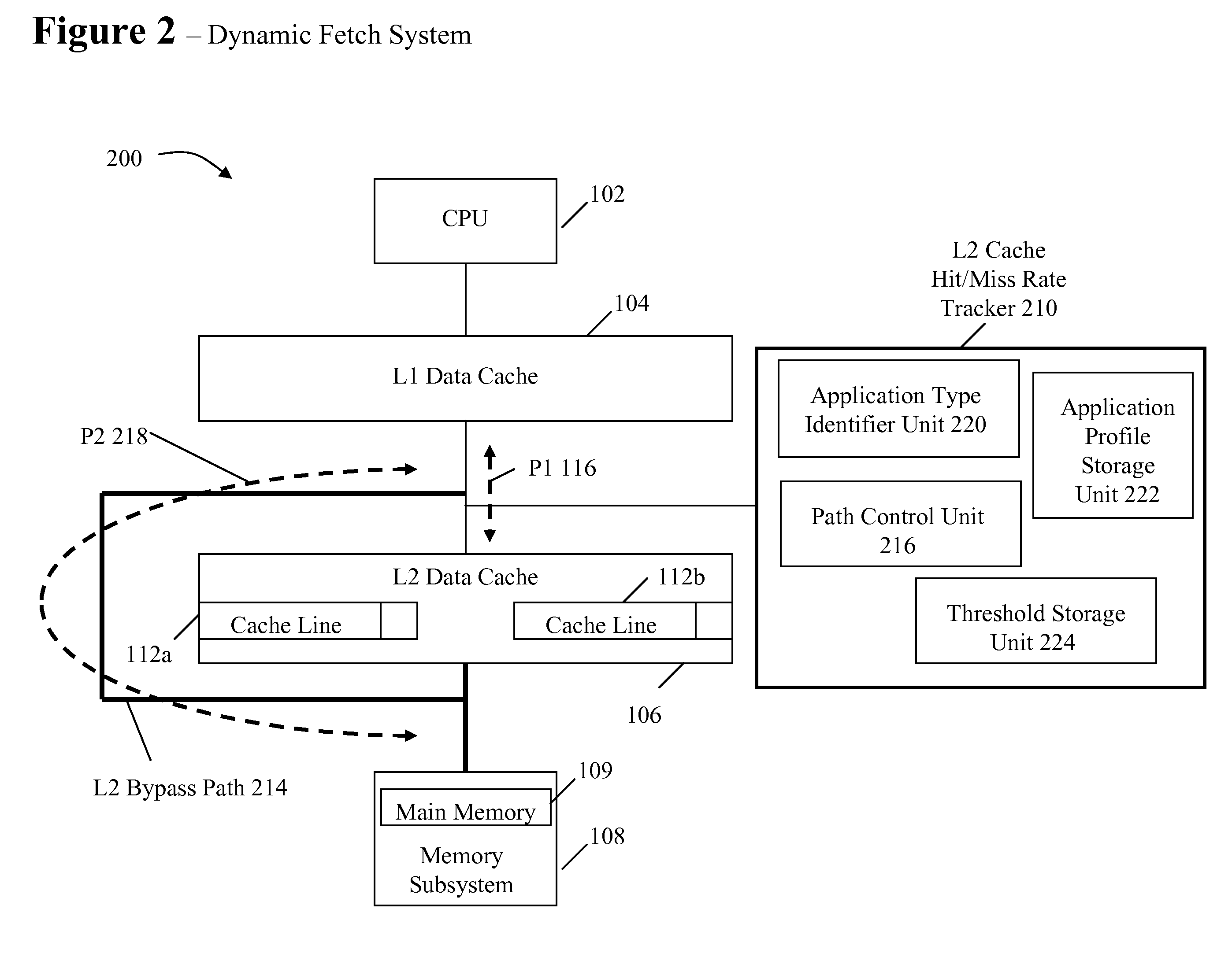
System and method for dynamically selecting the fetch path of data for improving processor performance
InactiveUS20090037664A1Improve system performanceImprove latencyMemory adressing/allocation/relocationData accessParallel computing
A system and method for dynamically selecting the data fetch path for improving the performance of the system improves data access latency by dynamically adjusting data fetch paths based on application data fetch characteristics. The application data fetch characteristics are determined through the use of a hit / miss tracker. It reduces data access latency for applications that have a low data reuse rate (streaming audio, video, multimedia, games, etc.) which will improve overall application performance. It is dynamic in a sense that at any point in time when the cache hit rate becomes reasonable (defined parameter), the normal cache lookup operations will resume. The system utilizes a hit / miss tracker which tracks the hits / misses against a cache and, if the miss rate surpasses a prespecified rate or matches an application profile, the hit / miss tracker causes the cache to be bypassed and the data is pulled from main memory or another cache thereby improving overall application performance.
Owner:IBM CORP
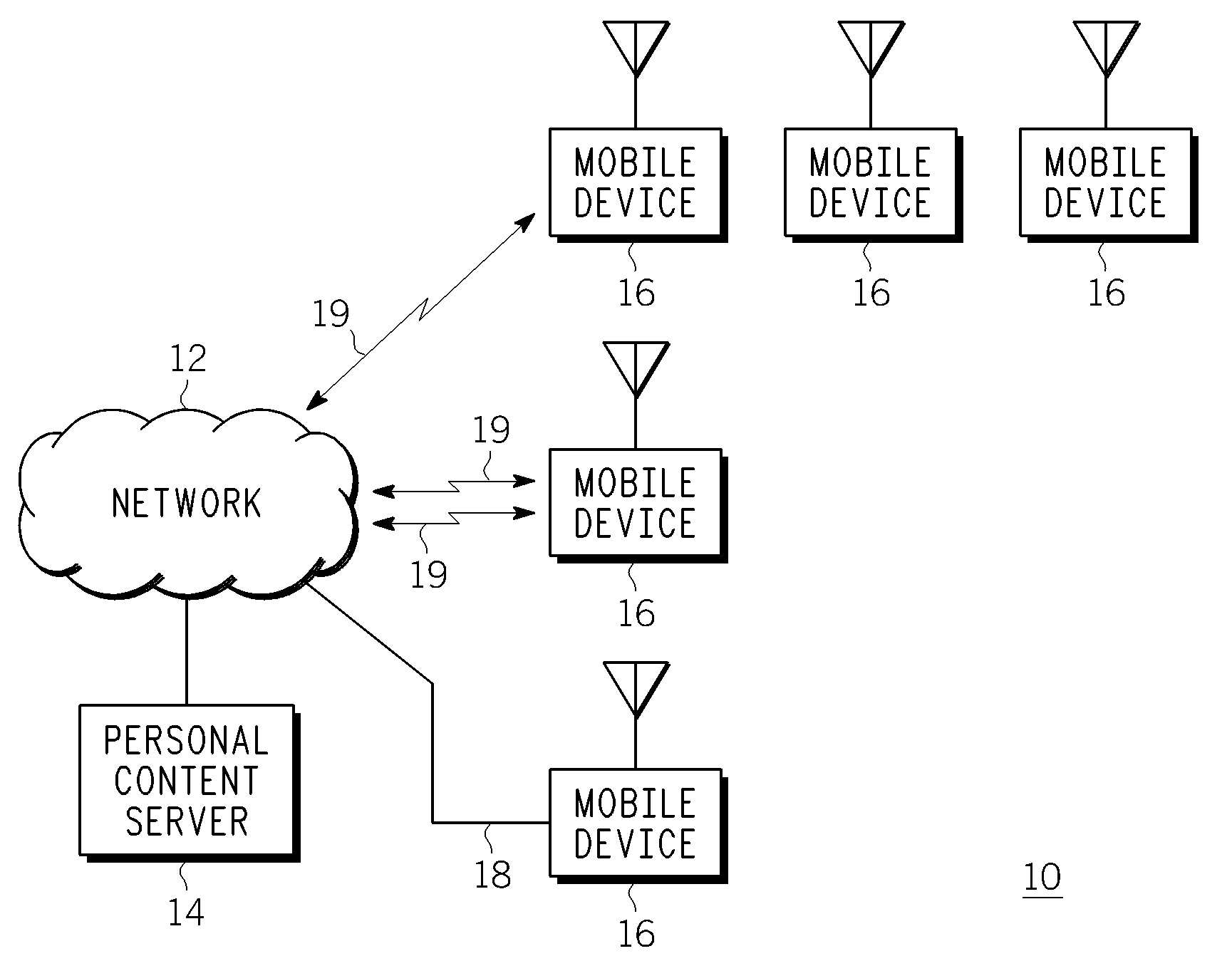
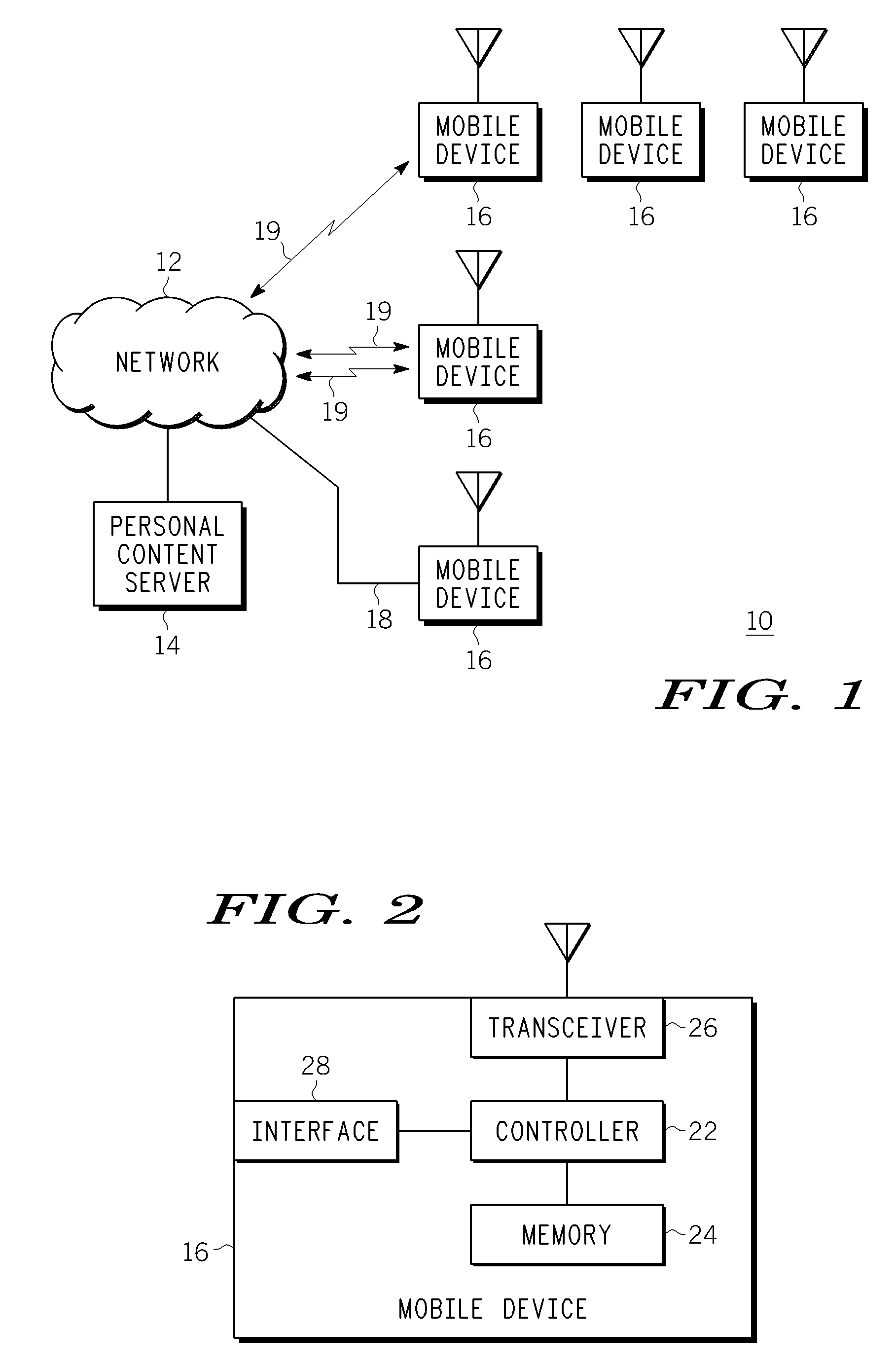
Method, Device and System for Accessing Mobile Device User Information
InactiveUS20080233977A1Radio/inductive link selection arrangementsWireless commuication servicesInternet privacyMobile device
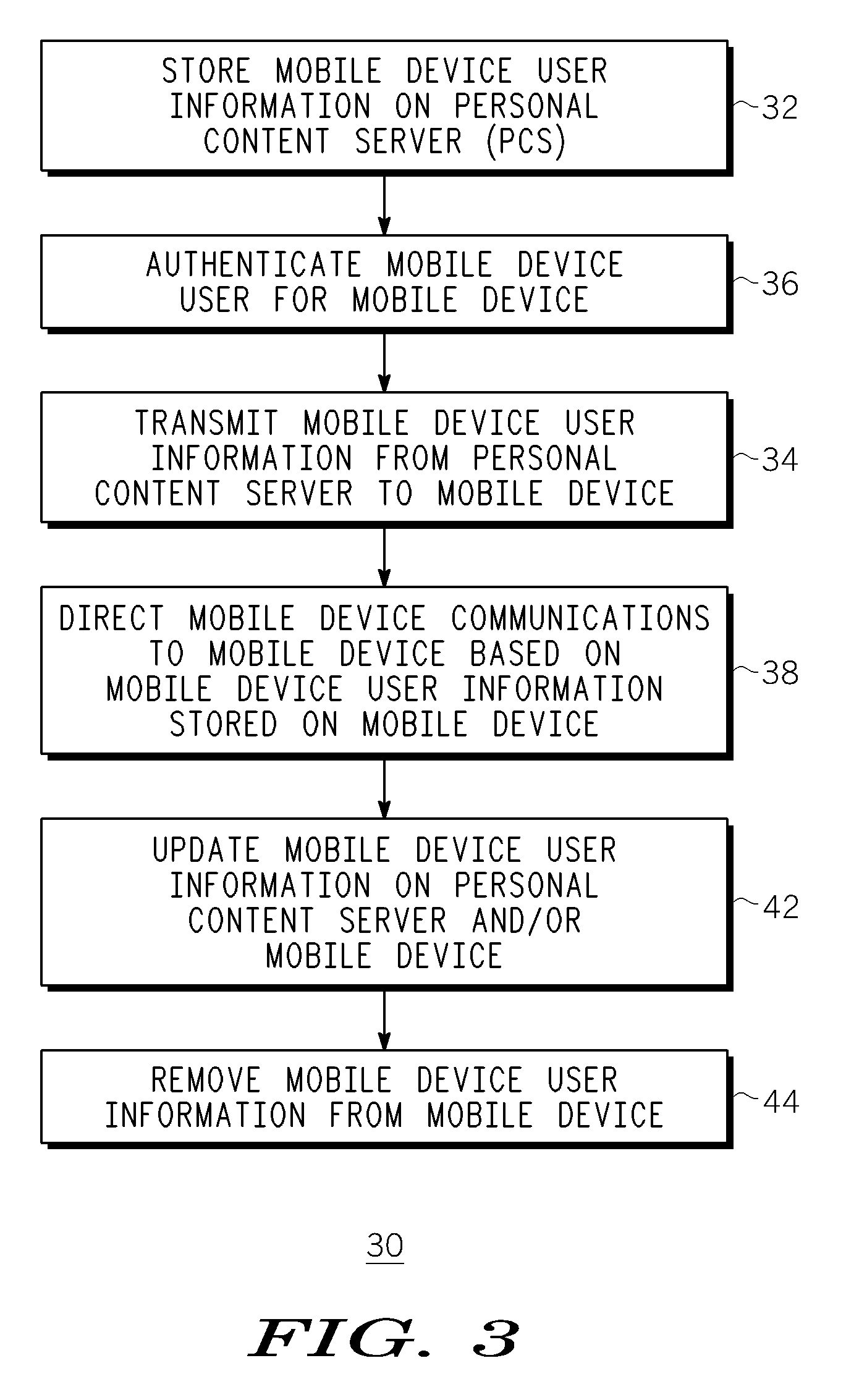
A method, device and system for accessing mobile device user information. A Personal Content Server (PCS) is used to store mobile device user information for one or more mobile device end users. The mobile device user information can be accessed and downloaded, via a communication network, to one or more mobile devices in an appropriate manner, e.g., wirelessly or via a wired connection between the mobile device and the communication network. The mobile device user information allows one or more end users to operate at least one mobile device according to their respective user preferences. The method can include authenticating an end user before allowing user information to be downloaded to the end user's mobile device, and updating user information between the mobile device and the PCS. Mobile device user information can include user identity information, personal preferences, subscription information and application profile information.
Owner:GOOGLE TECH HLDG LLC
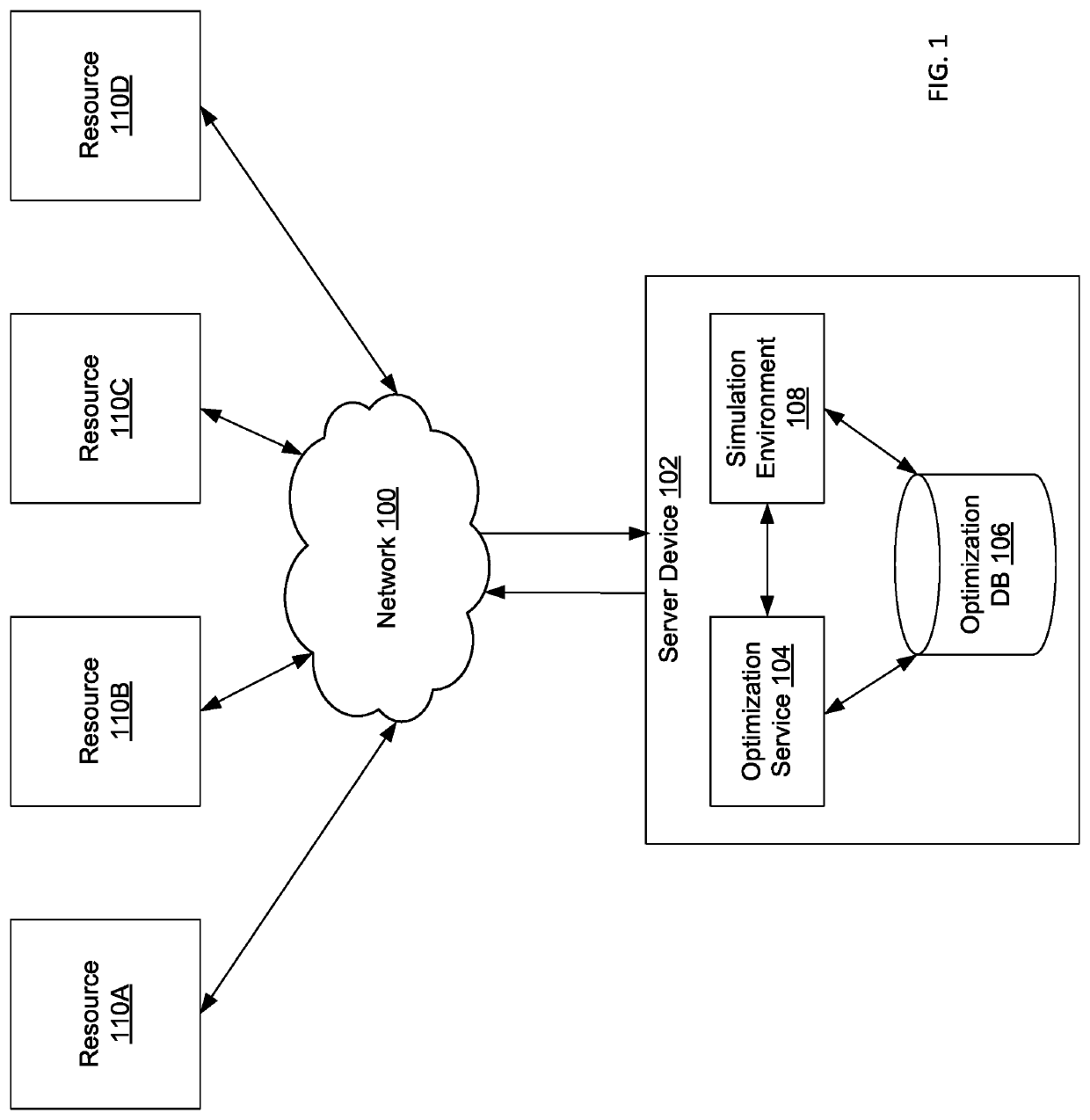
Cloud infrastructure optimization
ActiveUS20200110691A1OptimizationResource allocationHardware monitoringTest performanceApplication procedure
A processor may receive at least one test application corresponding to an application profile. The processor may simulate the at least one test application in a non-production environment for a plurality of infrastructure configurations to generate a plurality of test performance results. The processor may evaluate the plurality of test performance results to identify an optimal infrastructure configuration from among the plurality of infrastructure configurations for the application profile. The processor may apply the optimal infrastructure configuration to an application corresponding to the application profile that is deployed in a production environment.
Owner:CAPITAL ONE SERVICES
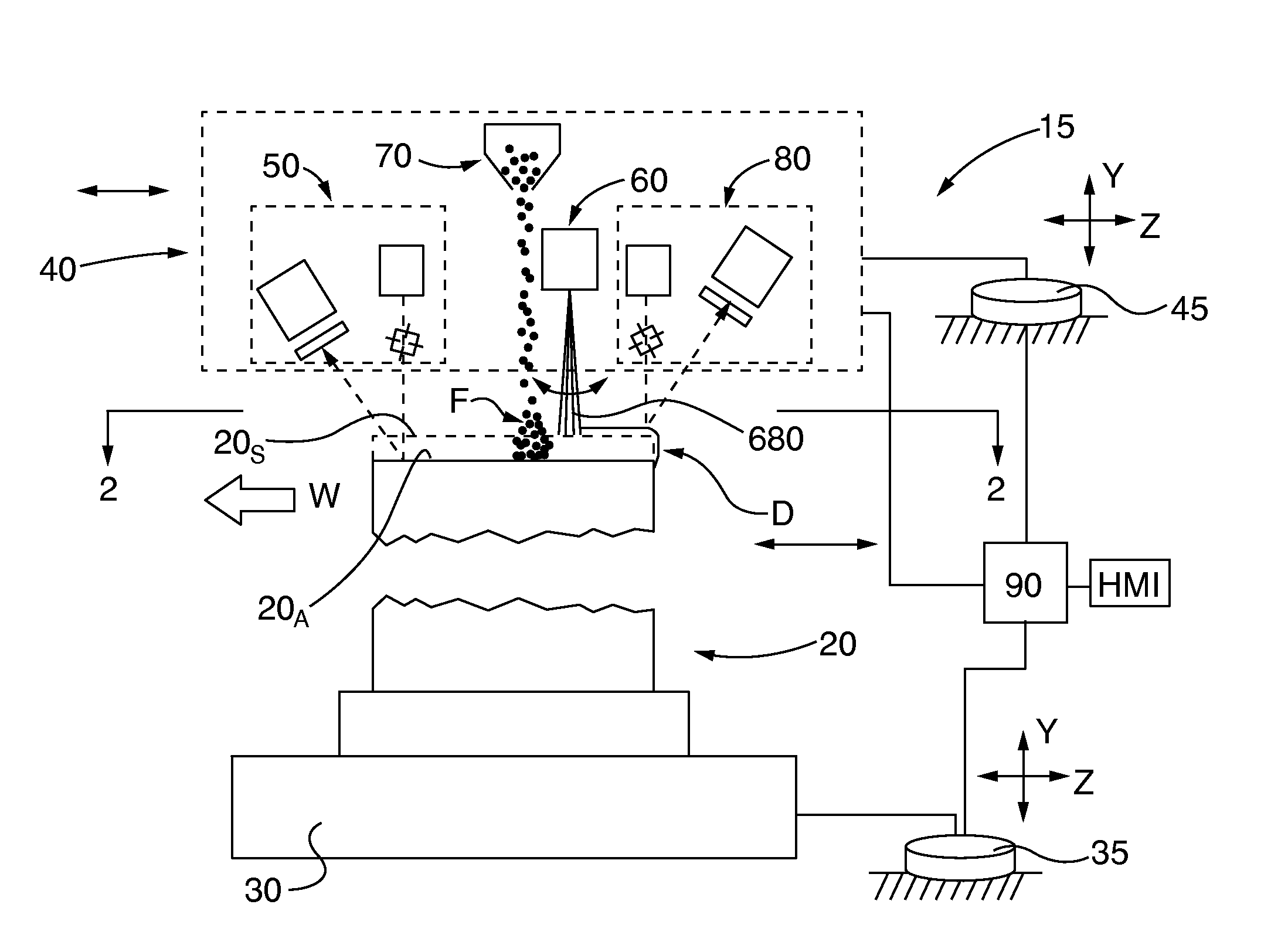
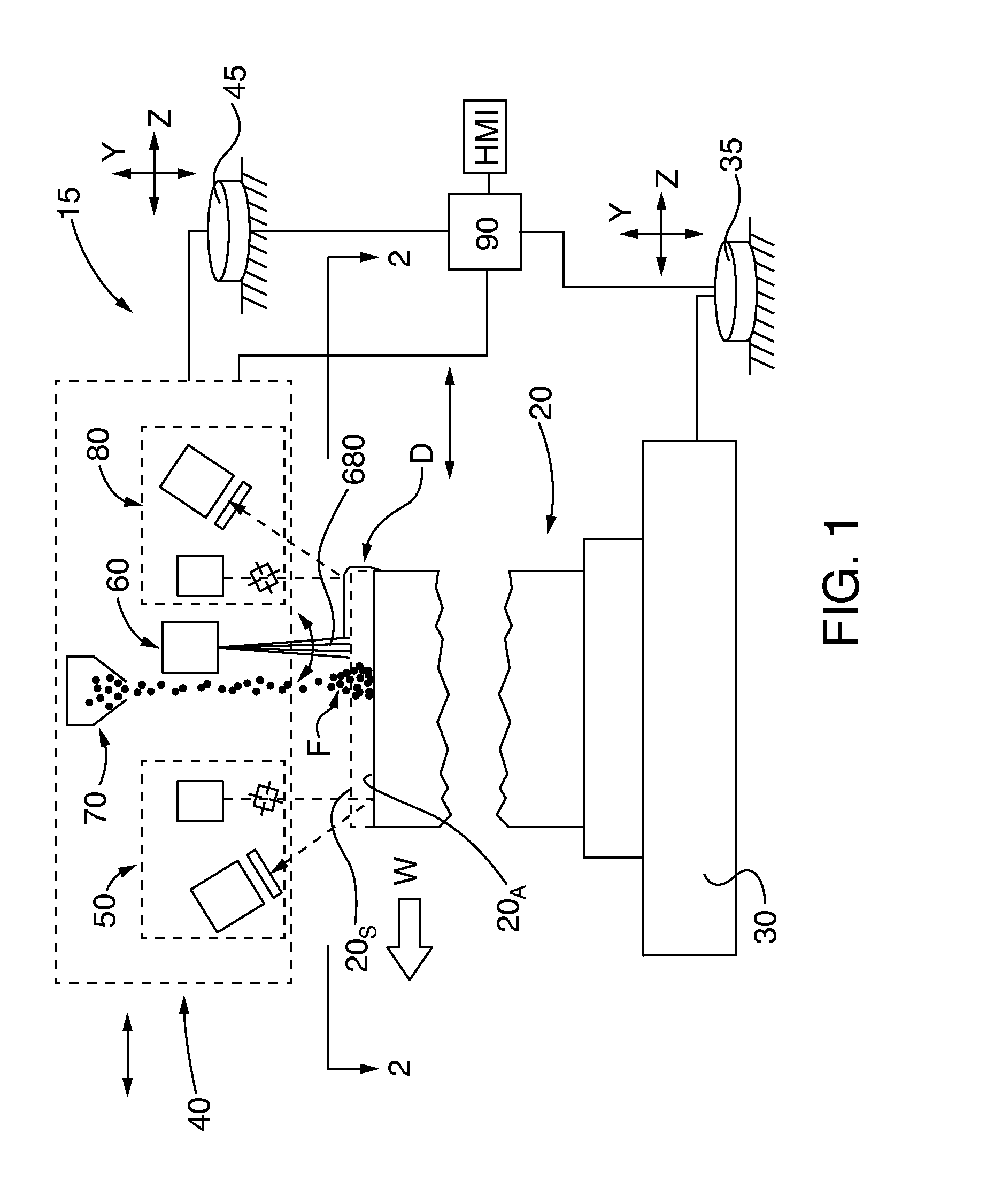
Method for automated superalloy laser cladding with 3D imaging weld path control
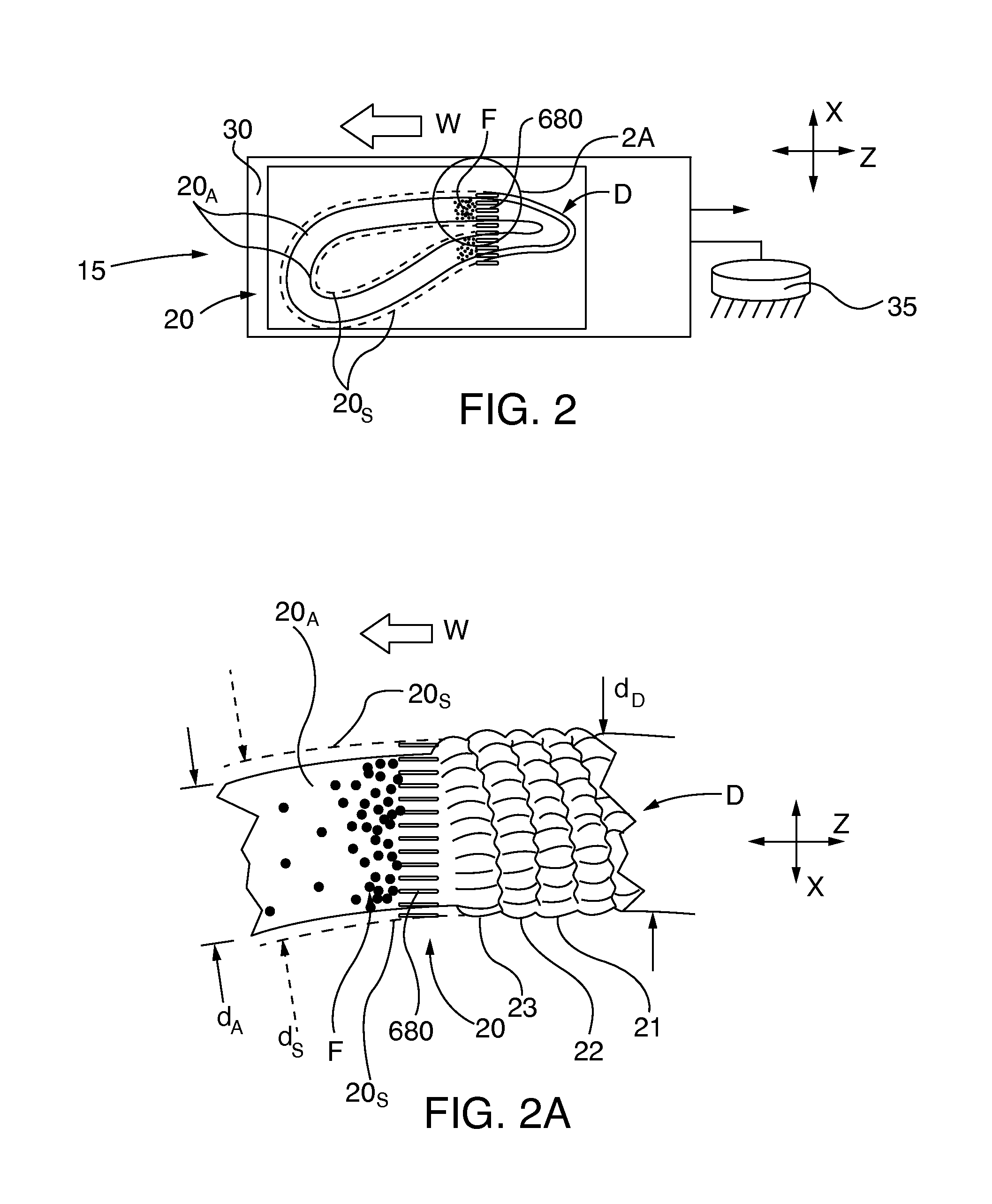
Superalloy components, such as service-degraded turbine blades and vanes, are clad by laser beam welding. The welding / cladding path, including cladding application profile, is determined by prior, preferably real time, non-contact 3D dimensional scanning of the component and comparison of the acquired dimensional scan data with specification dimensional data for the component. A welding path for cladding the scanned component to conform its dimensions to the specification dimensional data is determined The laser welding apparatus, preferably in cooperation with a cladding filler material distribution apparatus, executes the welding path to apply the desired cladding profile. In some embodiments a post-weld non-contact 3D dimensional scan of the welded component is performed and the post-weld scan dimensional data are compared with the specification dimensional data. Preferably the welding path and / or cladding profile application are modified in a feedback loop with the pre- and / or post-welding 3D dimensional scanning.
Owner:SIEMENS ENERGY INC
Method for fault-injection test based on virtual machine
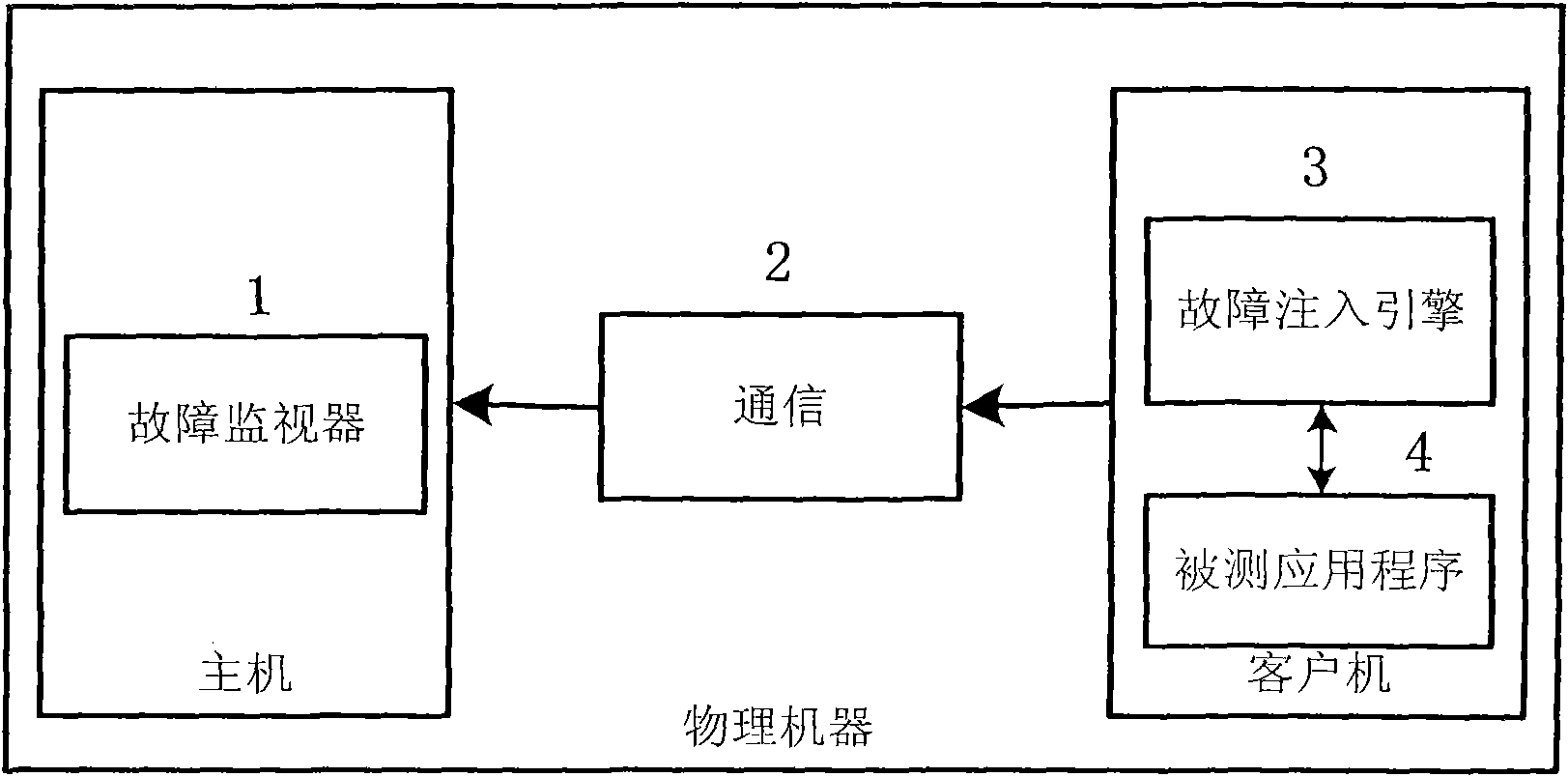
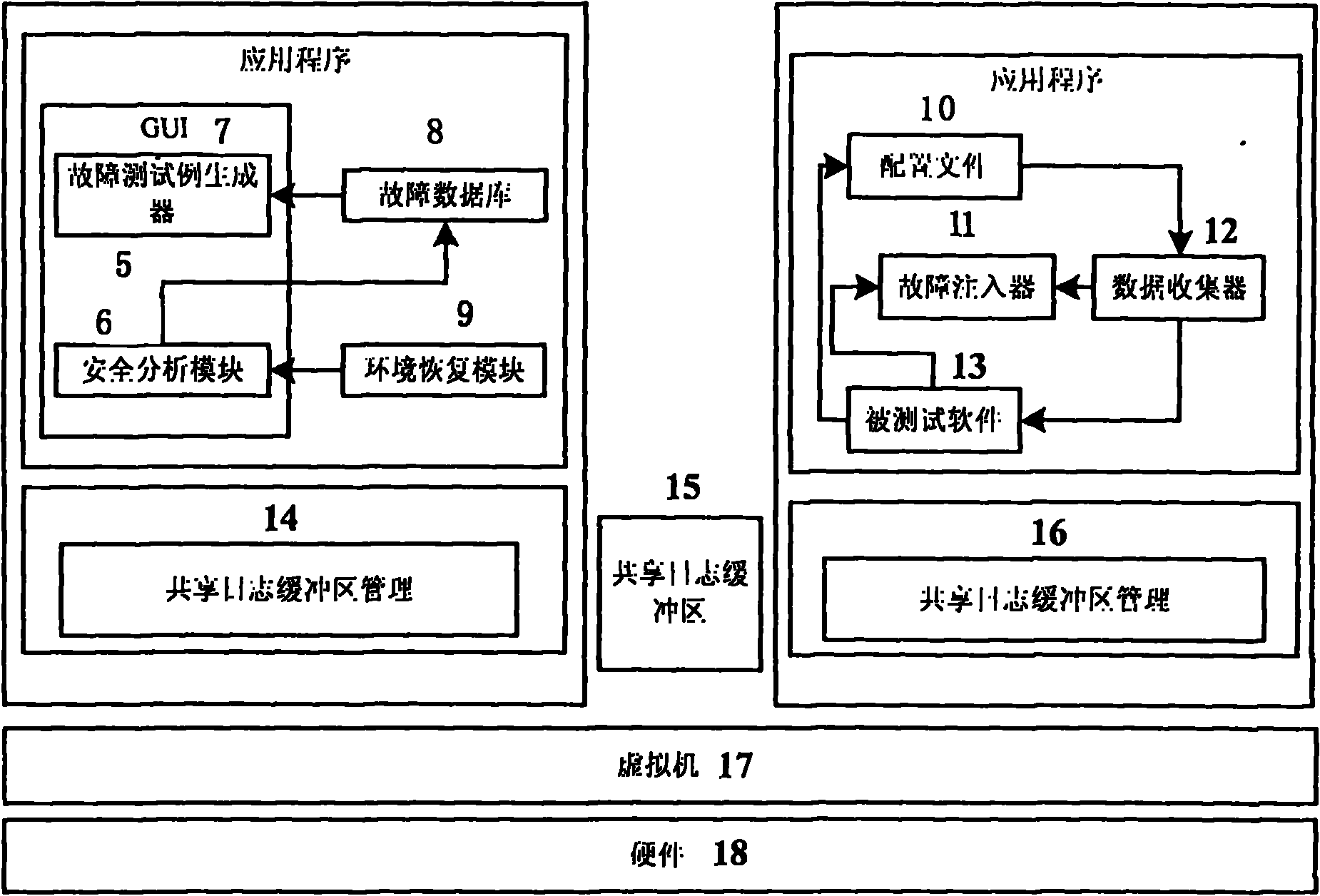
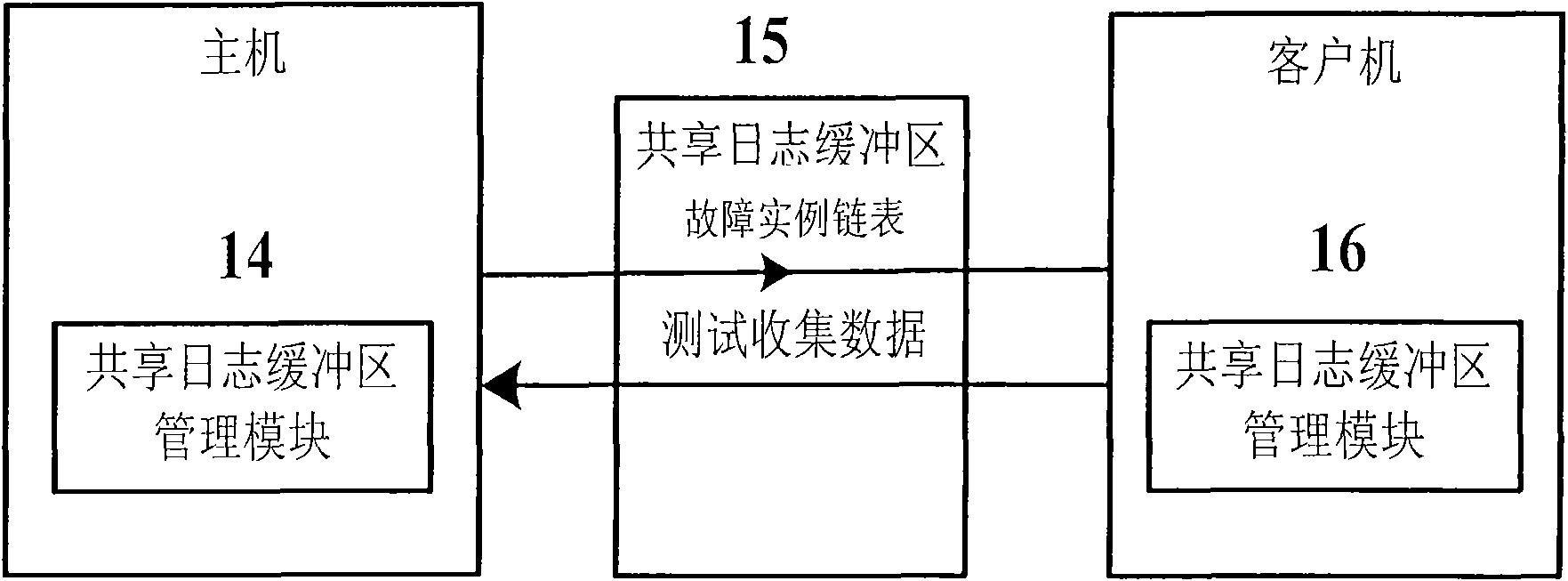
The invention provides a method for using a virtual machine to improve the performance in software-testing based on fault injection. Based on the EAI (environment-application interaction) model put forward by WENLIANG DU, Syracuse University (US), the fault injection is carried out on the interaction point of the application program and the environment thereof in the invention to disturb the environment and further test the software vulnerability, thus reducing the semantic difference between the injected fault and the actual fault, reducing the number of test cases and respectively achieving the two functional parts of the test tool at the host and guest of the virtual machine; and based on the shared files between the virtual machine and the guest, and the backup and recovery mechanism of the virtual machine, the invention can improve the robustness and flexibility of the test tool. The tool generated by the method comprises an application program configuration file (10), a fault test case generator (5), a security analysis module (6), a graphical user interface (7), an environment recovery module (9), a fault injector (11) and a data collector (12), wherein the tool further comprises software (13) to be tested and shared memory auxiliary modules (14), (15) and (16) of the virtual machine for sharing the data related to the tests. The method of the invention is capable of effectively detecting and simulating the security breaches in the software and improving the security of the software.
Owner:曾凡平 +2
Managing captured network traffic data
A system and method for managing captured network traffic data is provided. The invention comprises a plurality of capture agents, each being configured to capture the network traffic associated with one or more applications. Each application is associated with one or more capture agents according to an application profile that is stored and maintained in a capture server. When analysis of an application's network traffic is required, the capture server contacts the corresponding capture agents according to the application profile. The capture server then effects the identification and archiving of the network traffic that corresponds to a user-defined capture condition. A database at the capture server maintains a record that associates the corresponding network traffic with the user-defined capture condition such that the corresponding network traffic can later be retrieved and analyzed using an analysis engine.
Owner:RIVERBED TECH LLC
System and method for managing ota provisioning applications through use of profiles and data preparation
ActiveUS20120174189A1Service provisioningDigital data processing detailsOriginal dataComputer terminal
A method using a non-transitory processor for providing an application product including receiving an application profile, a key profile, a secure element (SE) profile, and a mobile terminal profile; establishing a link between the received profiles, in which the link is established for assembling the application product; and applying a limitation to the application product, in which the applied limitation determines whether the application product is accessible to a user. A method using a non-transitory processor for data preparation in a Trusted Service Manager (TSM) including receiving data from a service provider, in which the received data is in a Data Grouping Identifier (DGI) format or a raw data format; and processing the data using at least one of a logical data preparation and a physical data preparation.
Owner:MOZIDO CORFIRE - KOREA
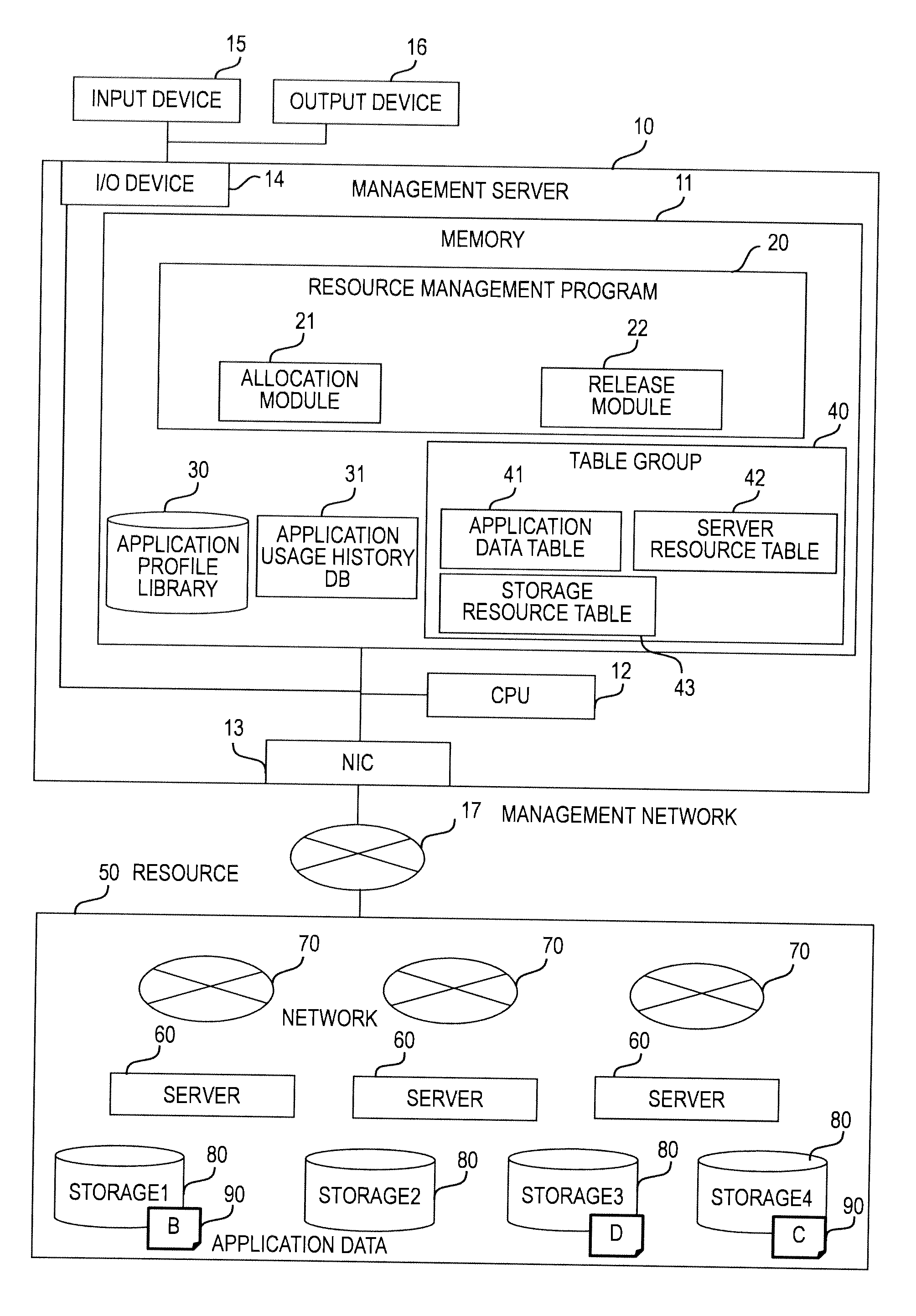
Computer system, management method of computer resource and program
InactiveUS20120179823A1Easy to operateEliminate troubleInput/output to record carriersResource allocationComputer resourcesDatasheet
Servers and a management server for managing a computer resource for a providing application constructed from storage connected to the servers receive an identifier of the application and a requested resource amount to assign to the application, refer to a application profile to identify the application and a system image corresponding to the identifier, and on the basis of the identifier, refer to a application usage history database and a application data table to acquire the number of times that the application has been used and the existence or non-existence of saved application data. If the usage is a reuse and there is saved application data, storage in which the application data has been saved is acquired from the application data table, and a combination of a server and storage which satisfies the requested resource amount and can access the application data is determined by referring to a resource table.
Owner:HITACHI LTD
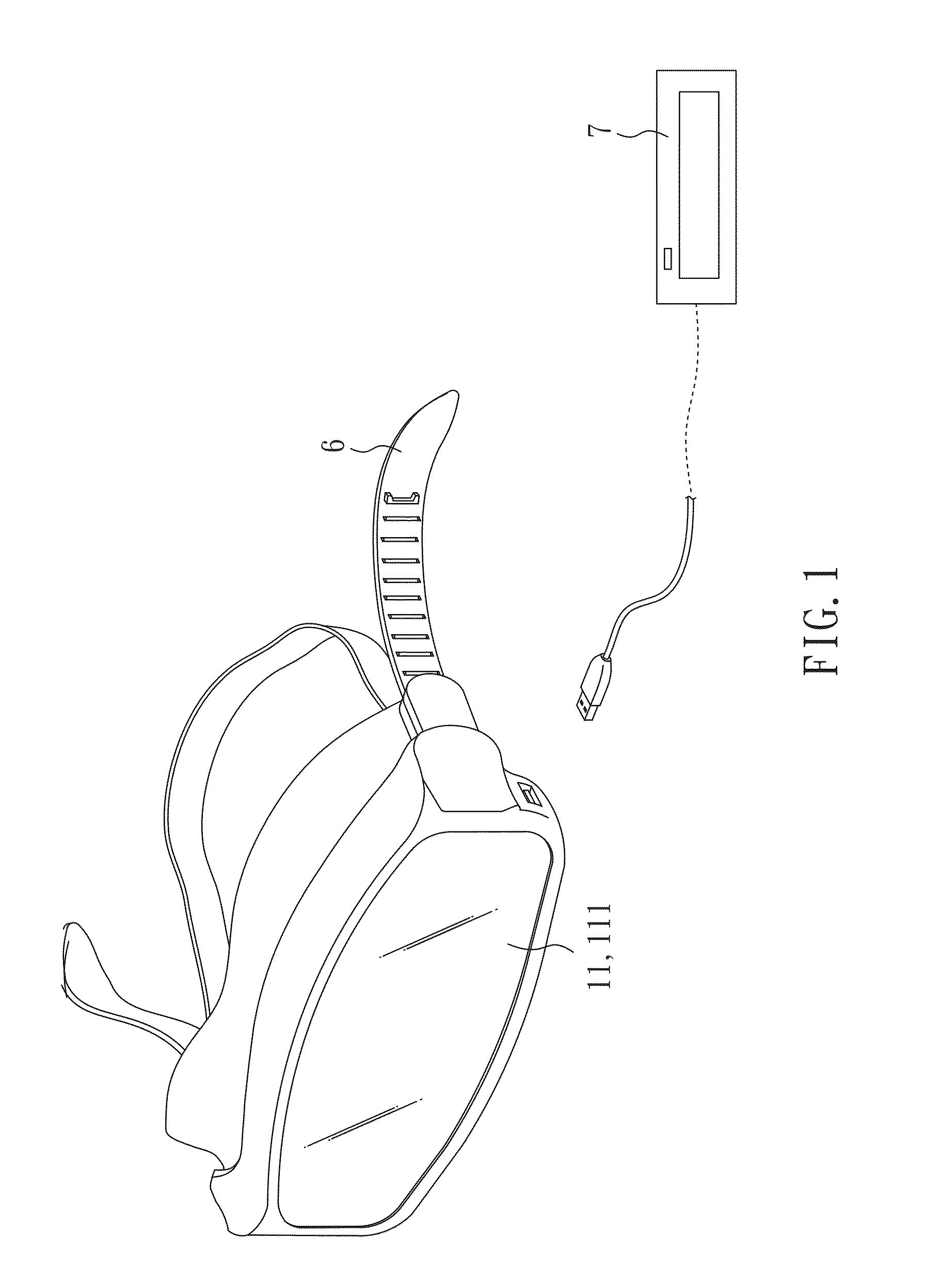
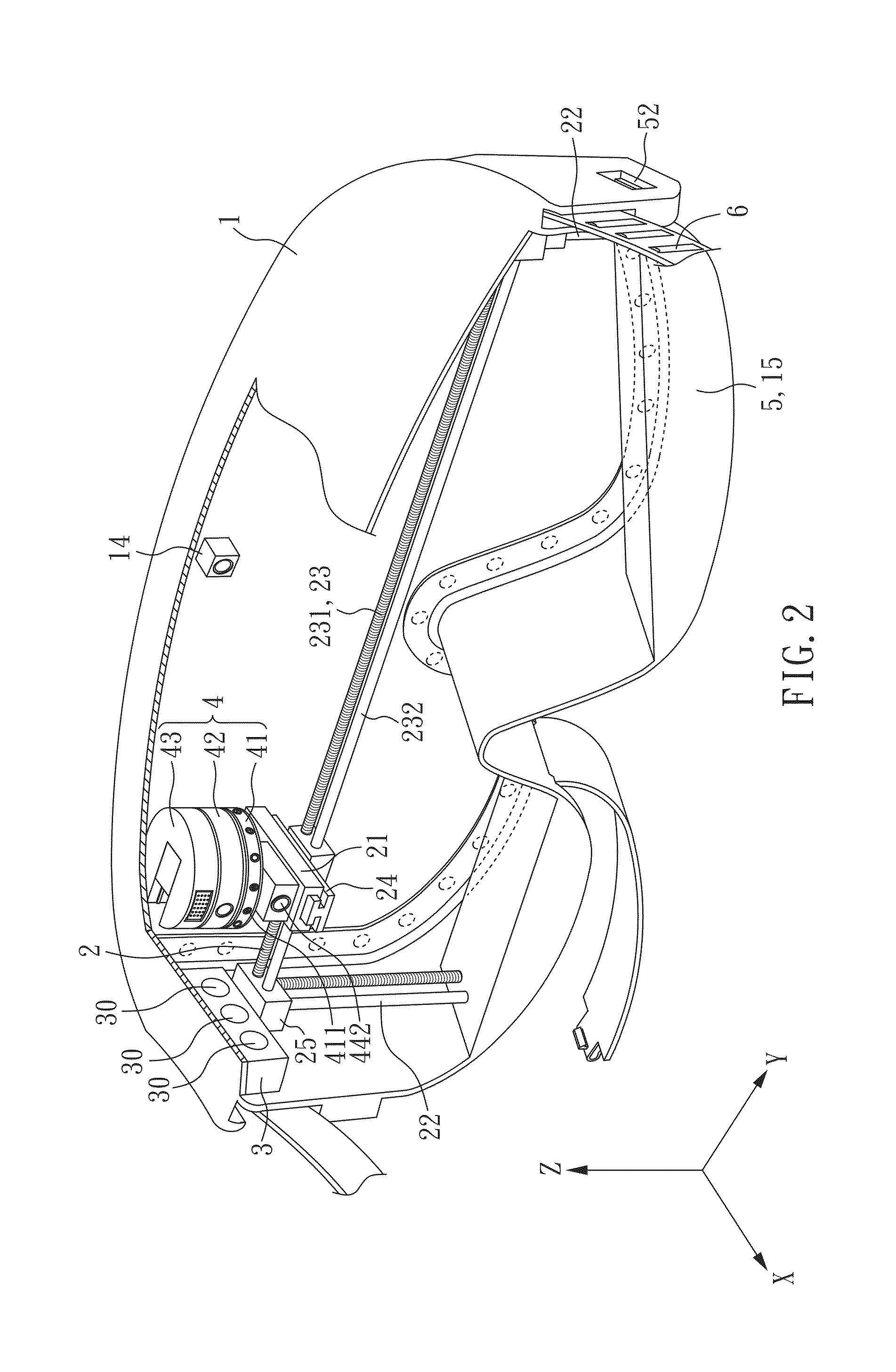
Eyes make-up application machine
InactiveUS20130216295A1Writing implementsPackaging toiletriesImage identificationApplication profile
An eye make-up application machine is provided, which includes a cosmetics provider in an eyeshade. The control device can control the cosmetics provider to move to a make-up application utility into position in order to spray or apply cosmetic materials to a contour corresponding to a human eye. Thus, the invention can provide an automatic make-up application utility for variously and accurately carrying out a makeup-application on eyes selected or emulated by one or more users. An eye contour image in the invention can be provided by an internal or external storage device or image recognition device. A plurality of makeup-application profiles can be provided by an internal or external storage device or be edited by the user as an option.
Owner:ZONG JING INVESTMENT
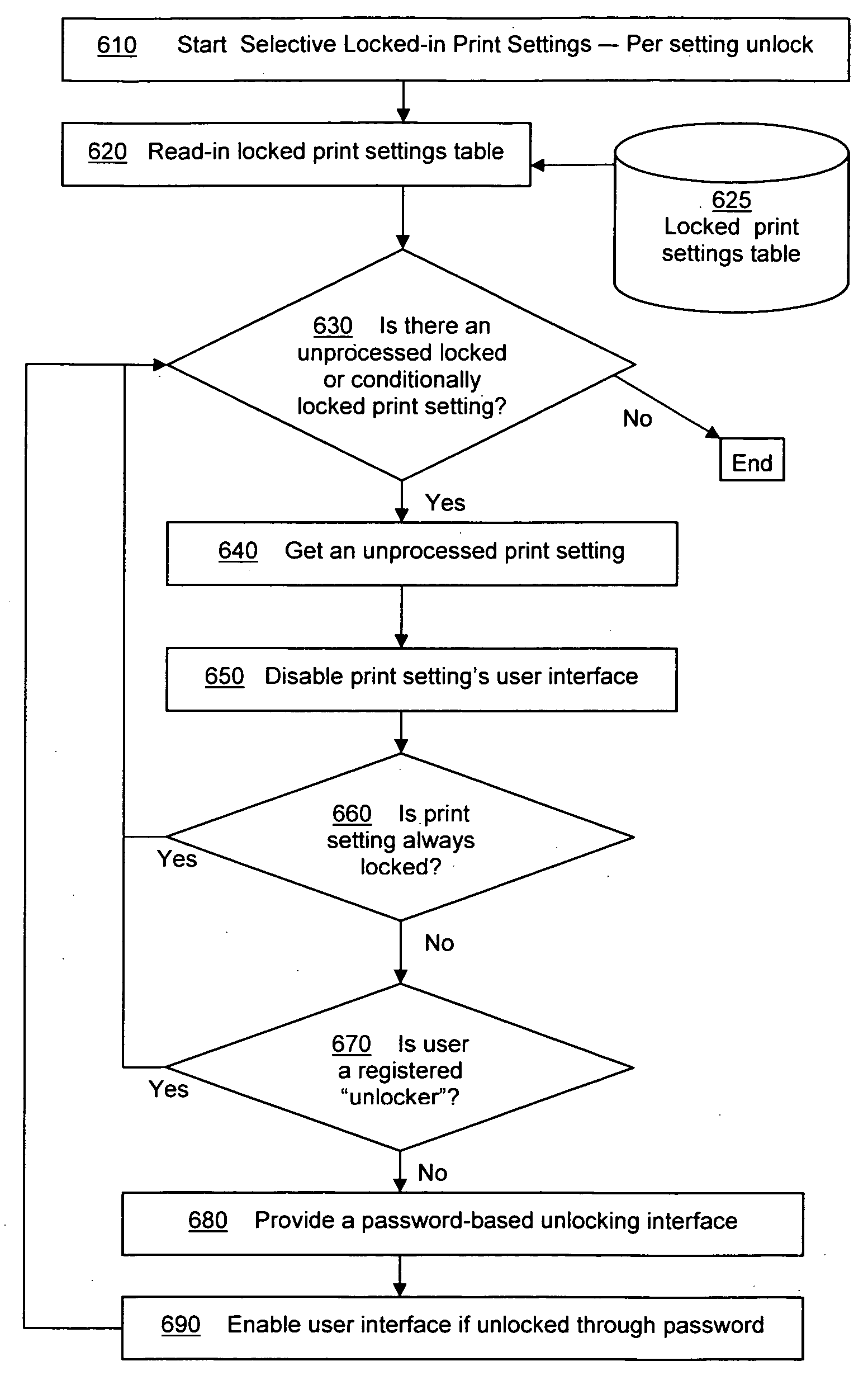
Application-based profiles of printer driver settings
InactiveUS20090128843A1Digitally marking record carriersDigital output to print unitsPasswordApplication software
A method for managing printer driver settings using application-based profiles, comprising: applying the print settings for the application using application-profile name table and print settings table, and applying selective lock-in print settings process based on the user's administrative privilege status. Profile generation by statistical tracking of use of printing features comprises recording application name and settings in effect for a print job into user's PC registry, the administrator collecting and analyzing this data for all relevant users, and specifying new profiles using this data. Methods also include the administrator's designating administrative status for users including registered unlockers, always locked and conditionally changeable settings, which are differentiated by special icons in GUI menus, password interface, merging of unlocking and change setting steps, monitoring of unlocking operations, administrator feedback and analysis for economical and efficient use of resources, special checkbox and list view GUI for aiding administrator analysis, and adding count tallies for application-settings combinations.
Owner:KYOCERA DOCUMENT SOLUTIONS DEV AMERICA +1
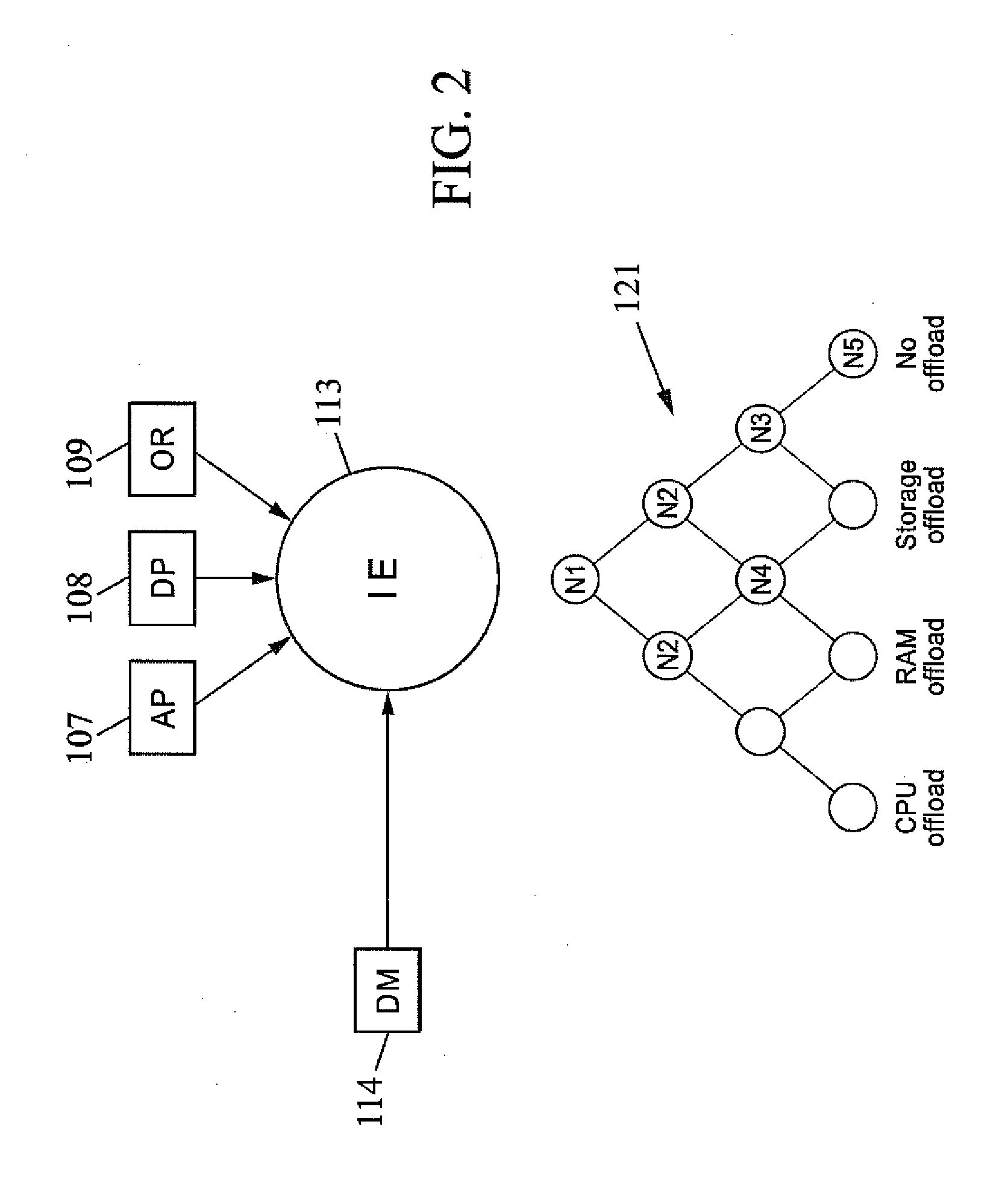
Method for allowing distributed running of an application and related device and inference engine
ActiveUS20120102098A1Avoid less flexibilityIncrease flexibilityMultiple digital computer combinationsProgram controlResource consumptionNetwork connection
Method for allowing distributed running of an application between a device and a server connected via a network. The method includes the following steps carried out by the device: obtaining a device profile including resource capacity characteristics of the device; obtaining an application profile including resource consumption characteristics of the application; obtaining device metrics relating to real-time resource usage with respect to the device; obtaining offload rules defining conditions under which an application is to be run at least in part on a server and / or on a device, the conditions involving device resource capacity, application resource consumption and device real-time resource usage; and making a decision by an inference engine to run the application at least in part on the server and / or on the device, by evaluating the offload rules applied to the device profile, application profile and device metrics.
Owner:FRANCE TELECOM SA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com