Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
11061 results about "Information technology" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information technology (IT) is the use of computers to store, retrieve, transmit, and manipulate data, or information, often in the context of a business or other enterprise. IT is considered to be a subset of information and communications technology (ICT). An information technology system (IT system) is generally an information system, a communications system or, more specifically speaking, a computer system – including all hardware, software and peripheral equipment – operated by a limited group of users.
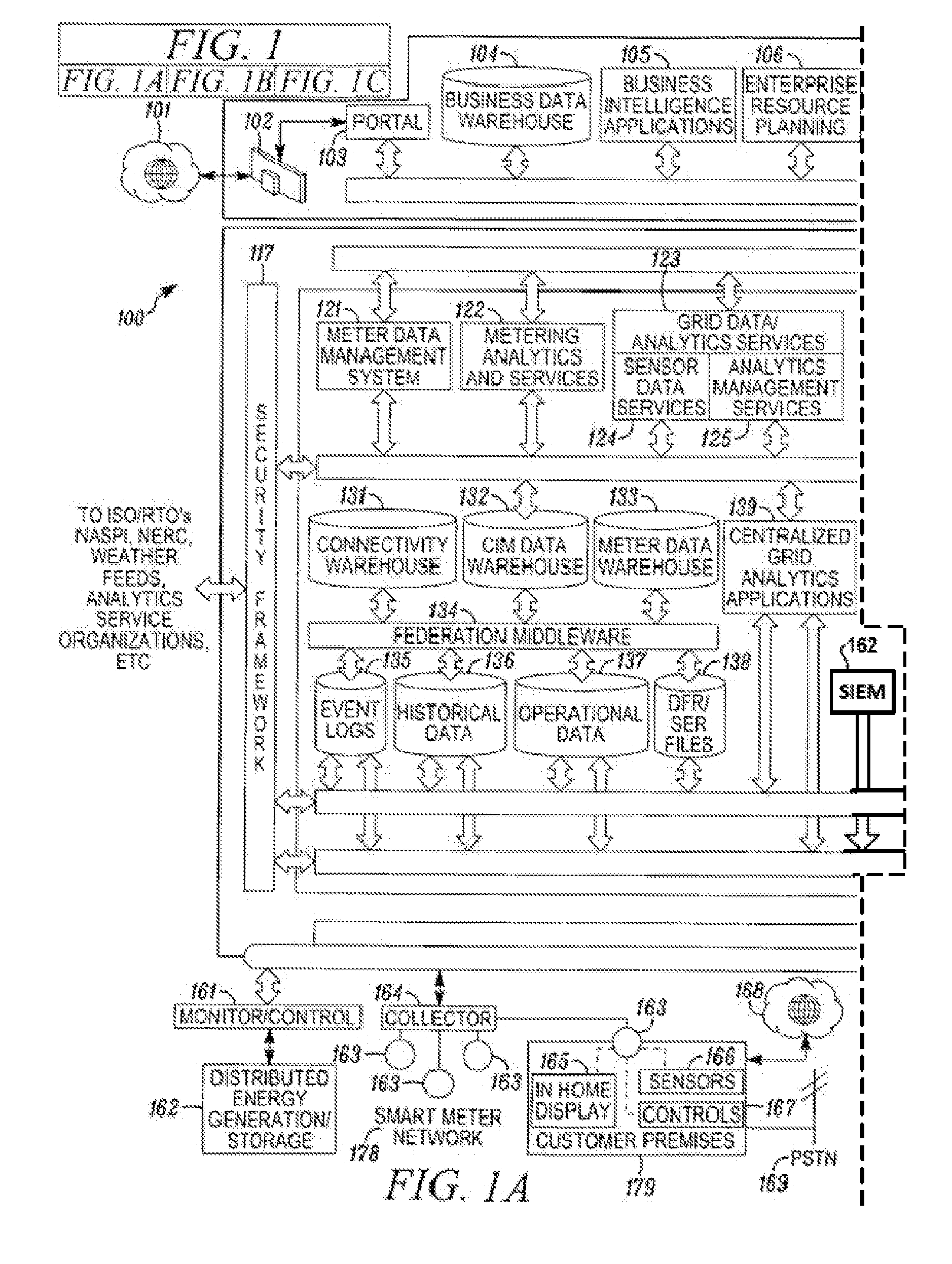
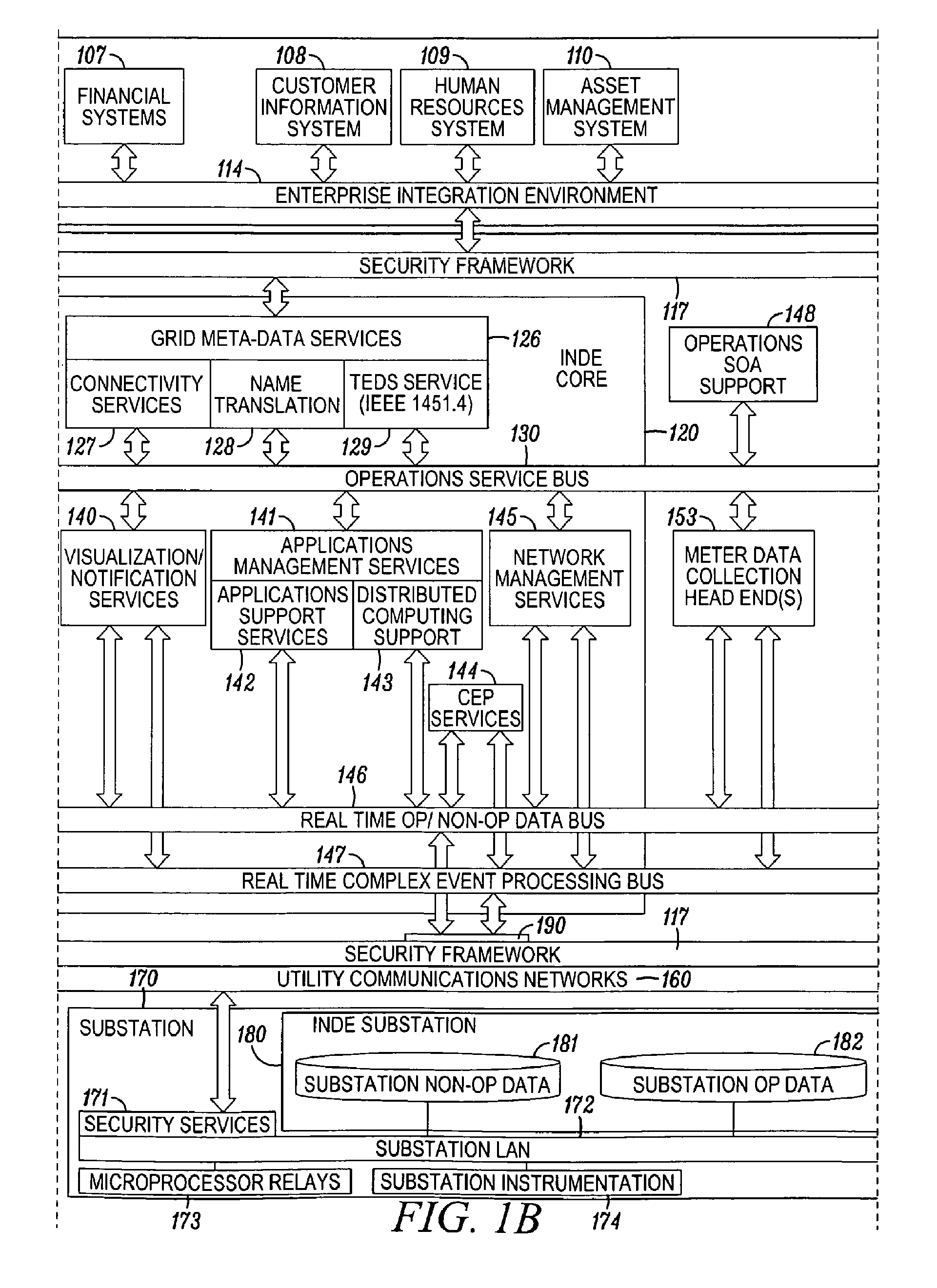
System and method for securing an enterprise computing environment
InactiveUS20180027006A1Process safetyKeep Content SafeMultiprogramming arrangementsComputer security arrangementsInternet privacyEnterprise computing
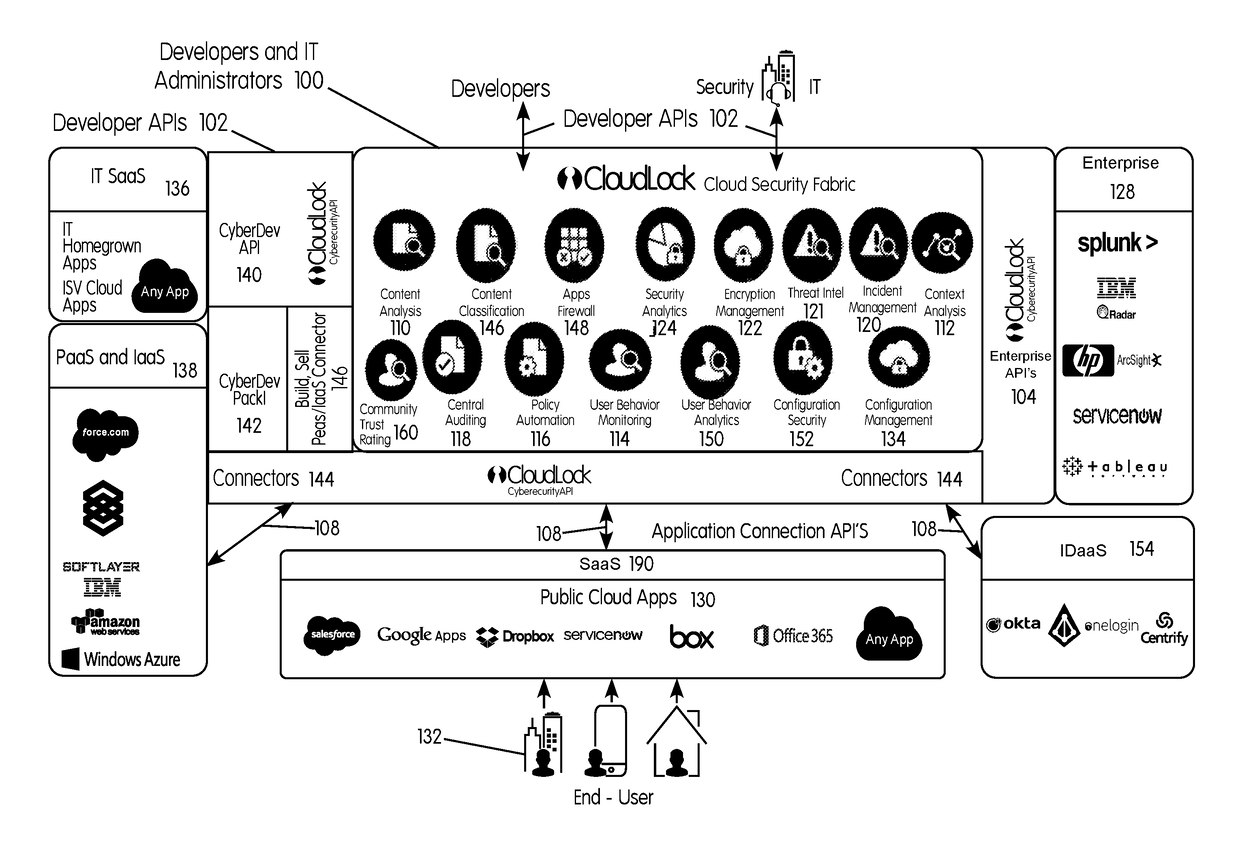
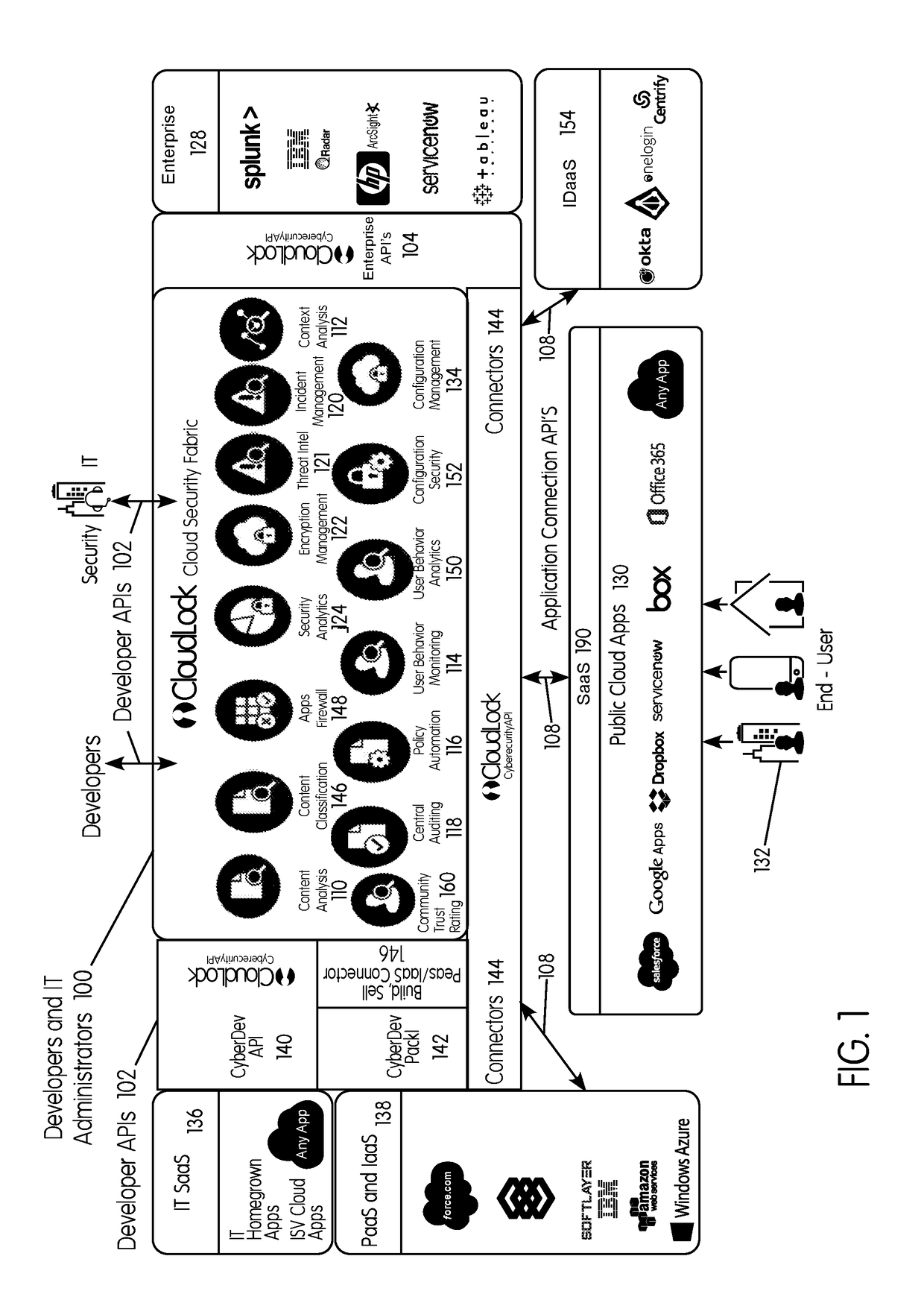
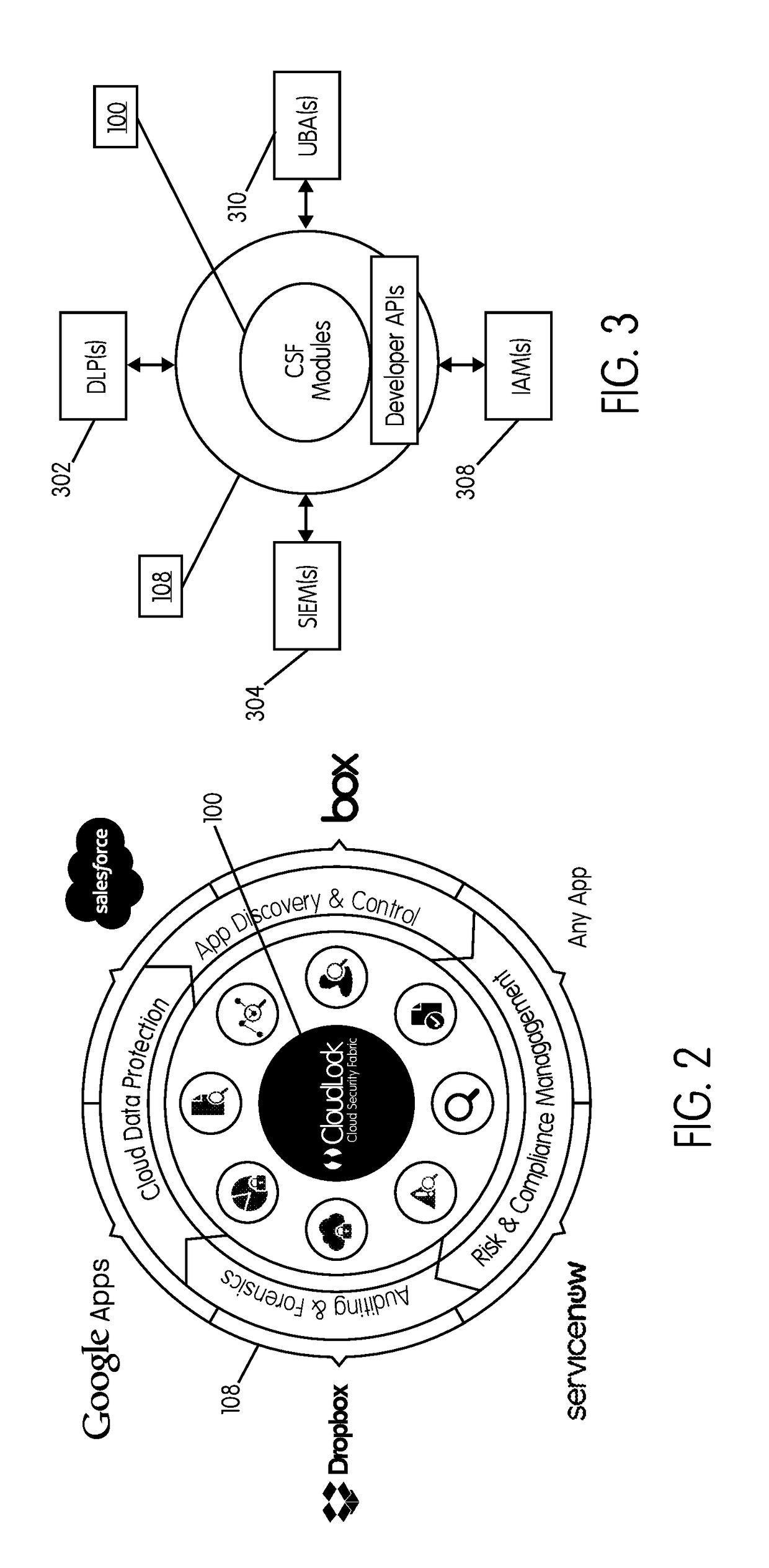
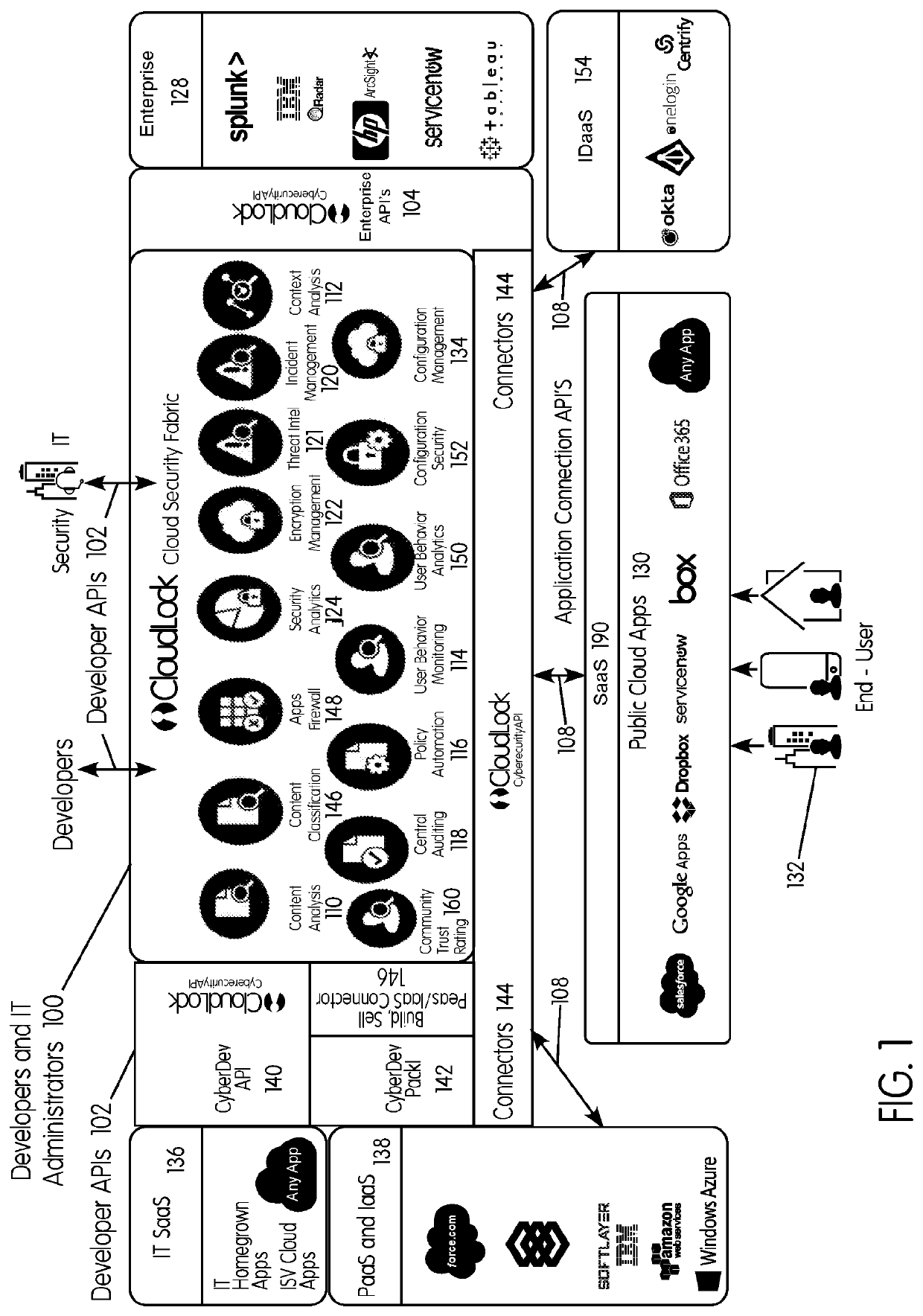
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CLOUDLOCK
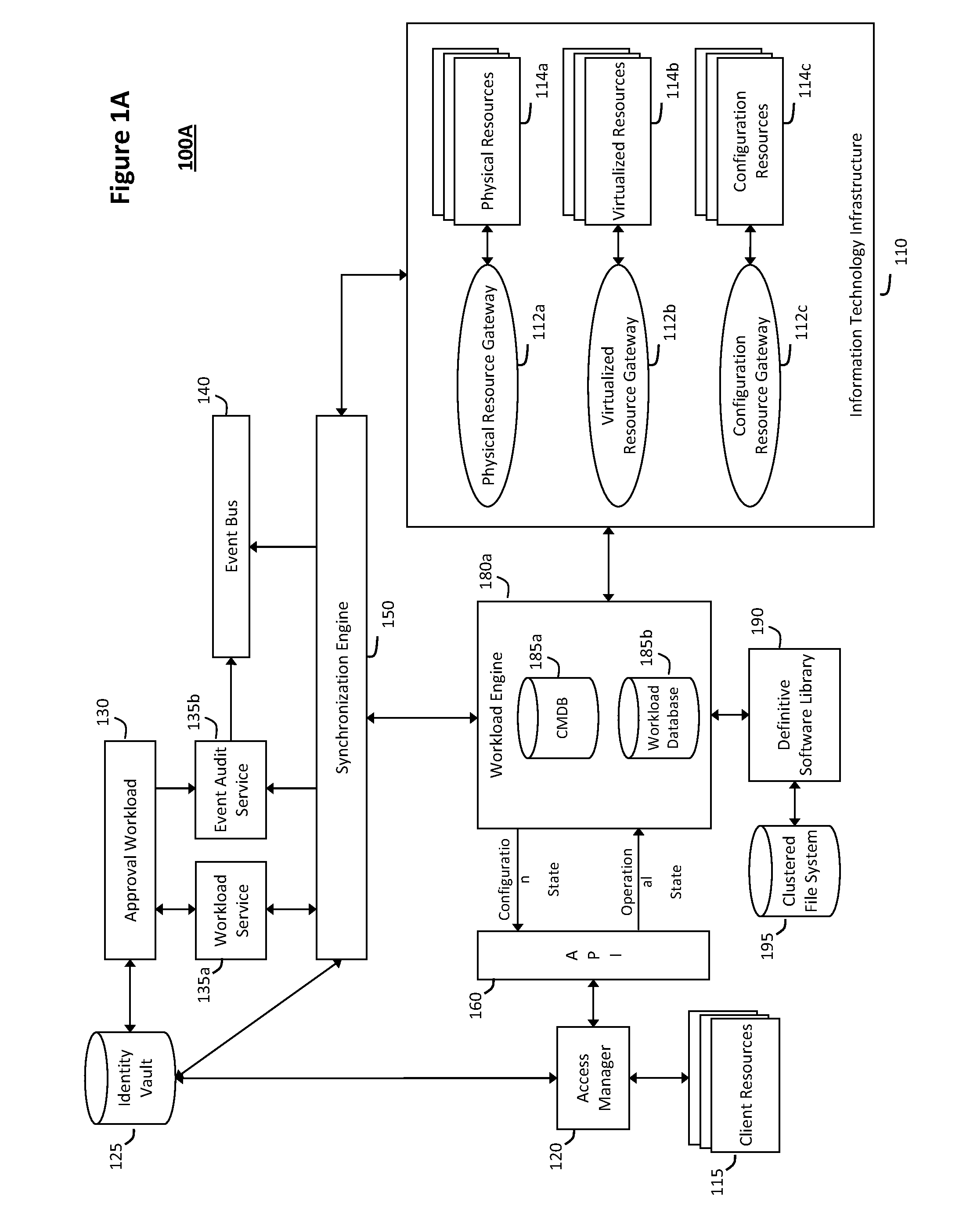
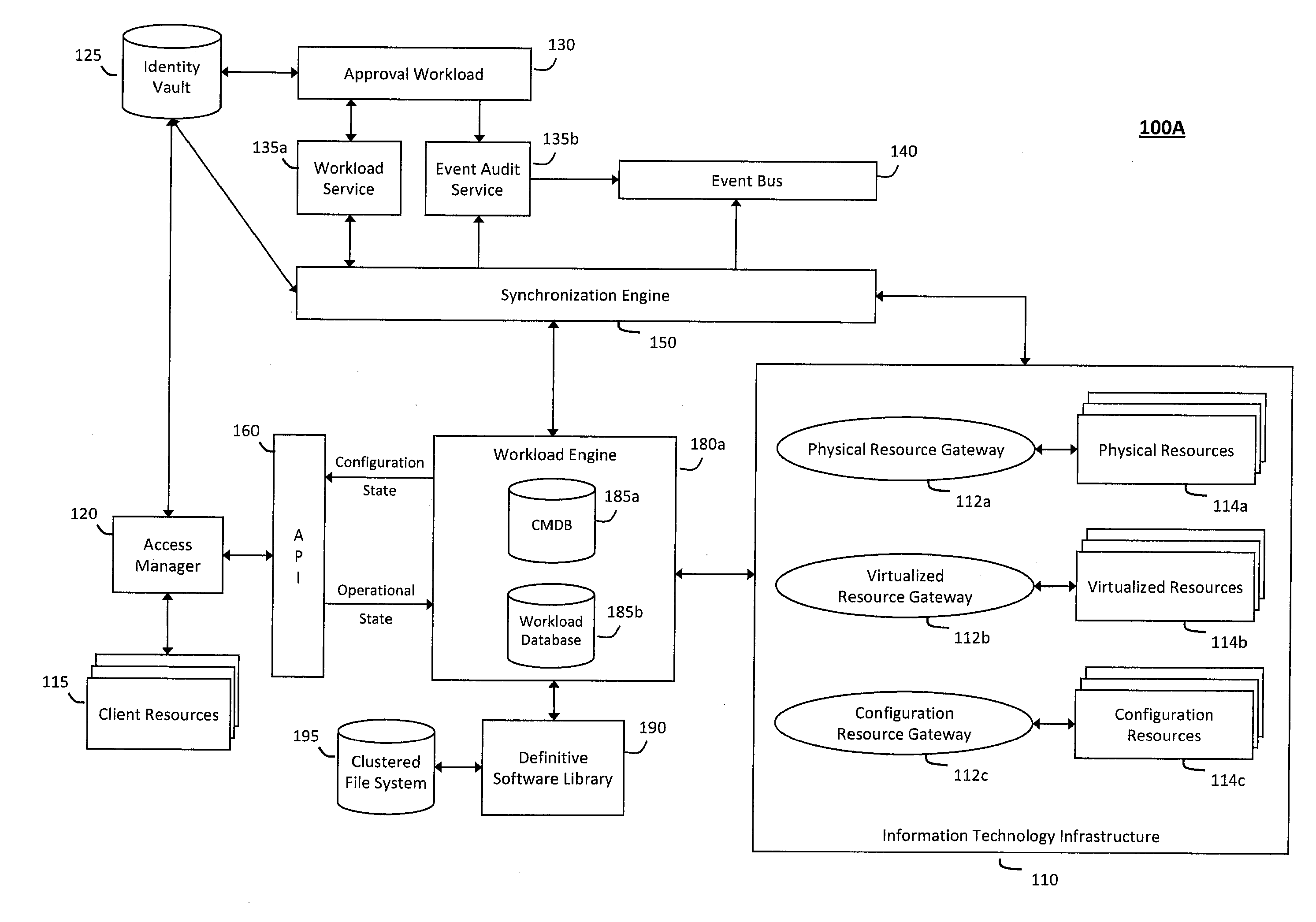
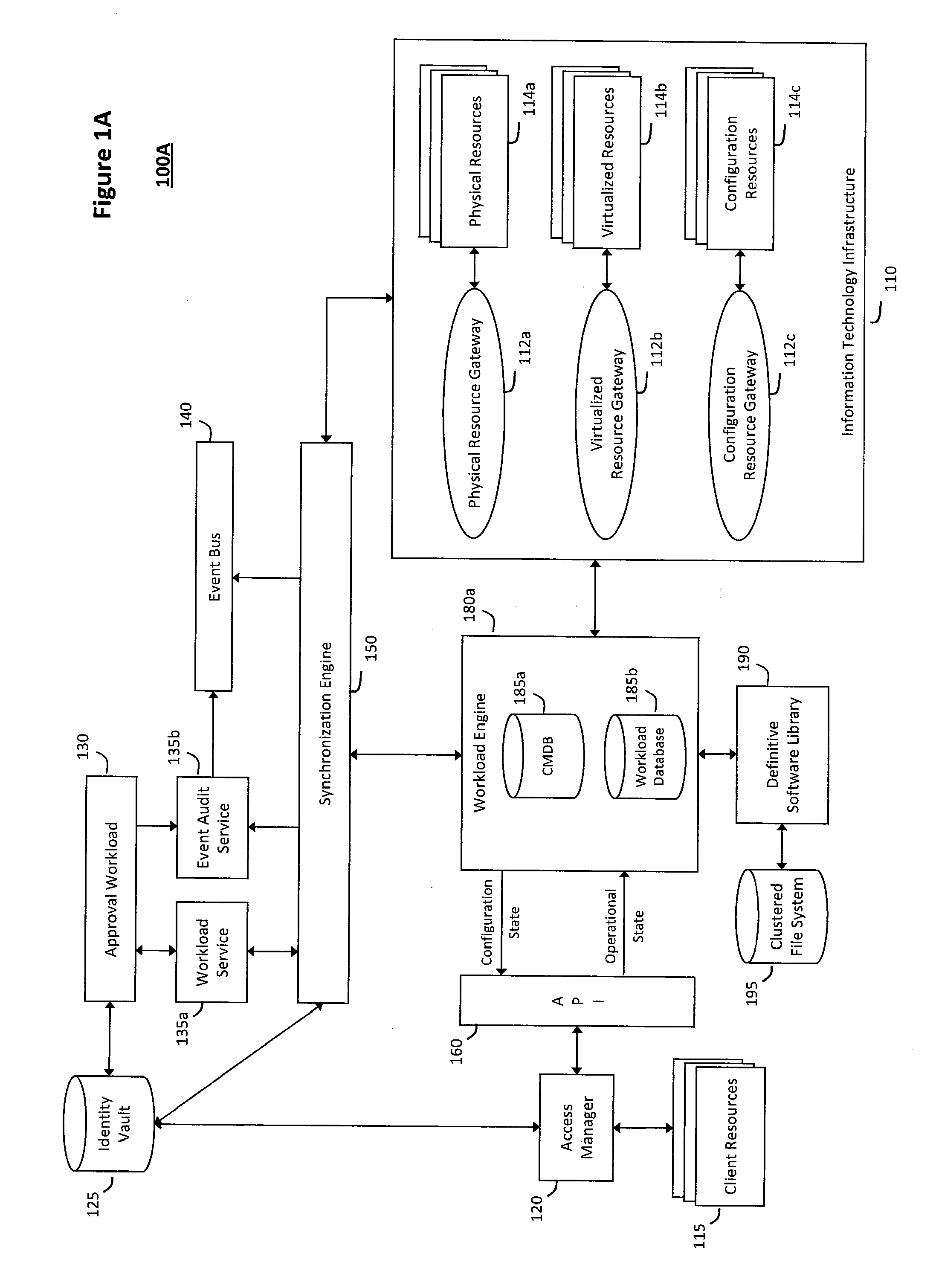
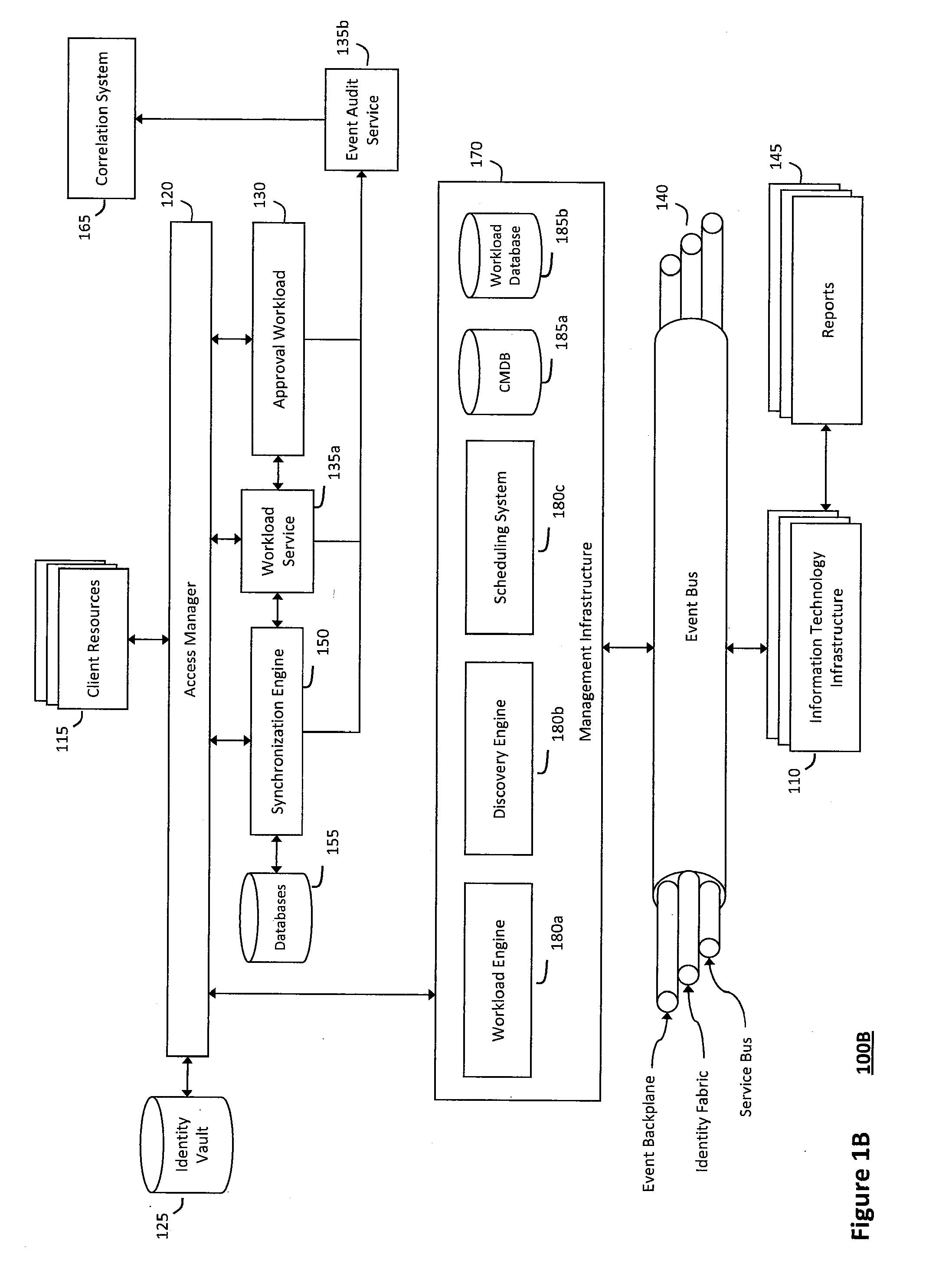
System and method for intelligent workload management
ActiveUS20110125894A1Free computational resourceAgile and flexible managementDigital data processing detailsUser identity/authority verificationAuthentication serverService-oriented architecture
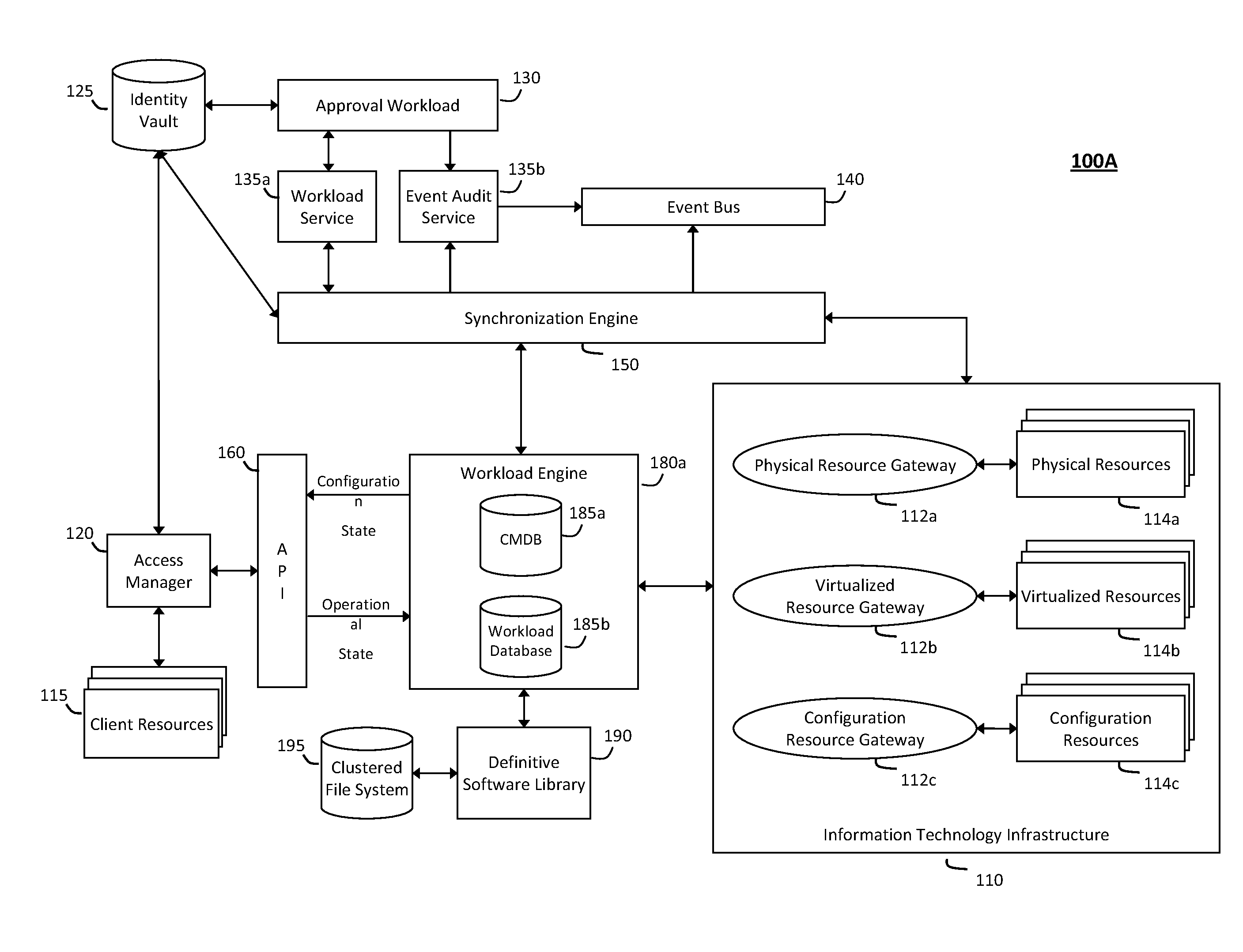
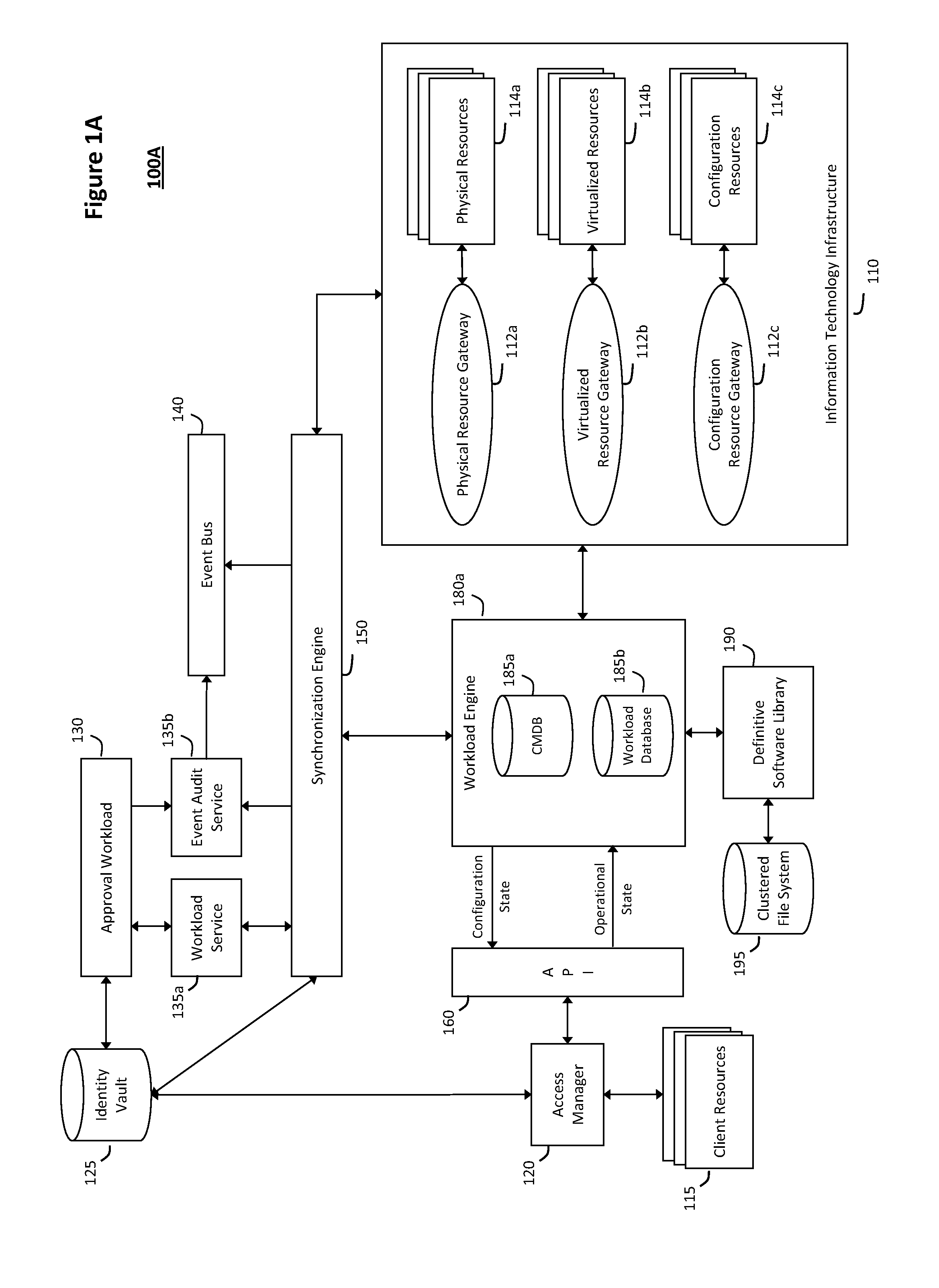
The system and method for intelligent workload management described herein may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads, wherein the management threads may converge information for managing identities and access credentials, enforcing policies, providing compliance assurances, managing provisioned and requested services, and managing physical and virtual infrastructure resources. In one implementation, an authentication server may generate authentication tokens defining access credentials for managed entities across a plurality of authentication domains, wherein the authentication tokens may control access to resources in an information technology infrastructure. For example, a management infrastructure may create service distributions for the managed entities, which may include virtual machine images hosted on physical resources. Further, the authentication tokens may be embedded in the service distributions, whereby the embedded authentication tokens may control access to the resources in the information technology infrastructure.
Owner:MICRO FOCUS SOFTWARE INC
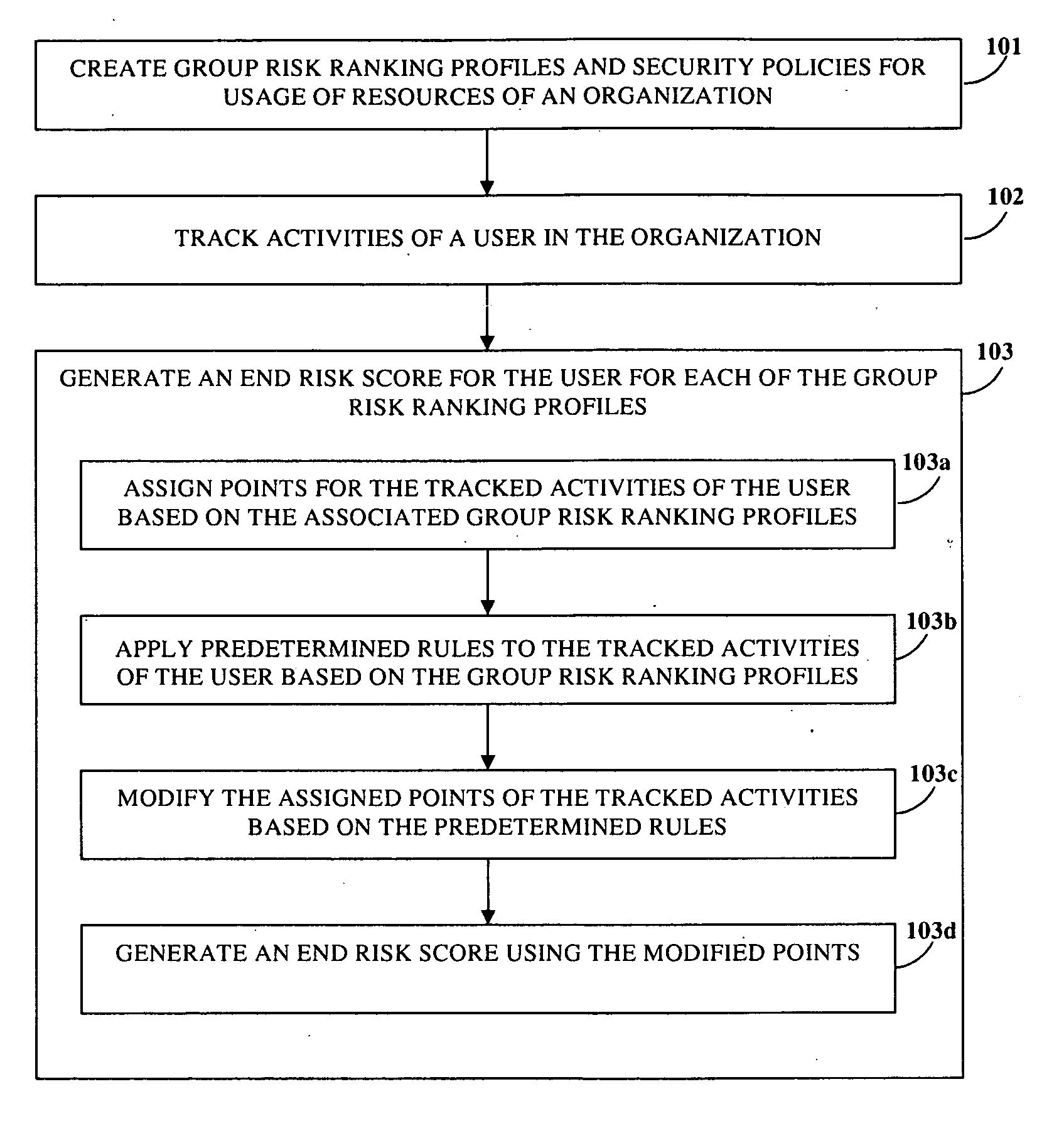
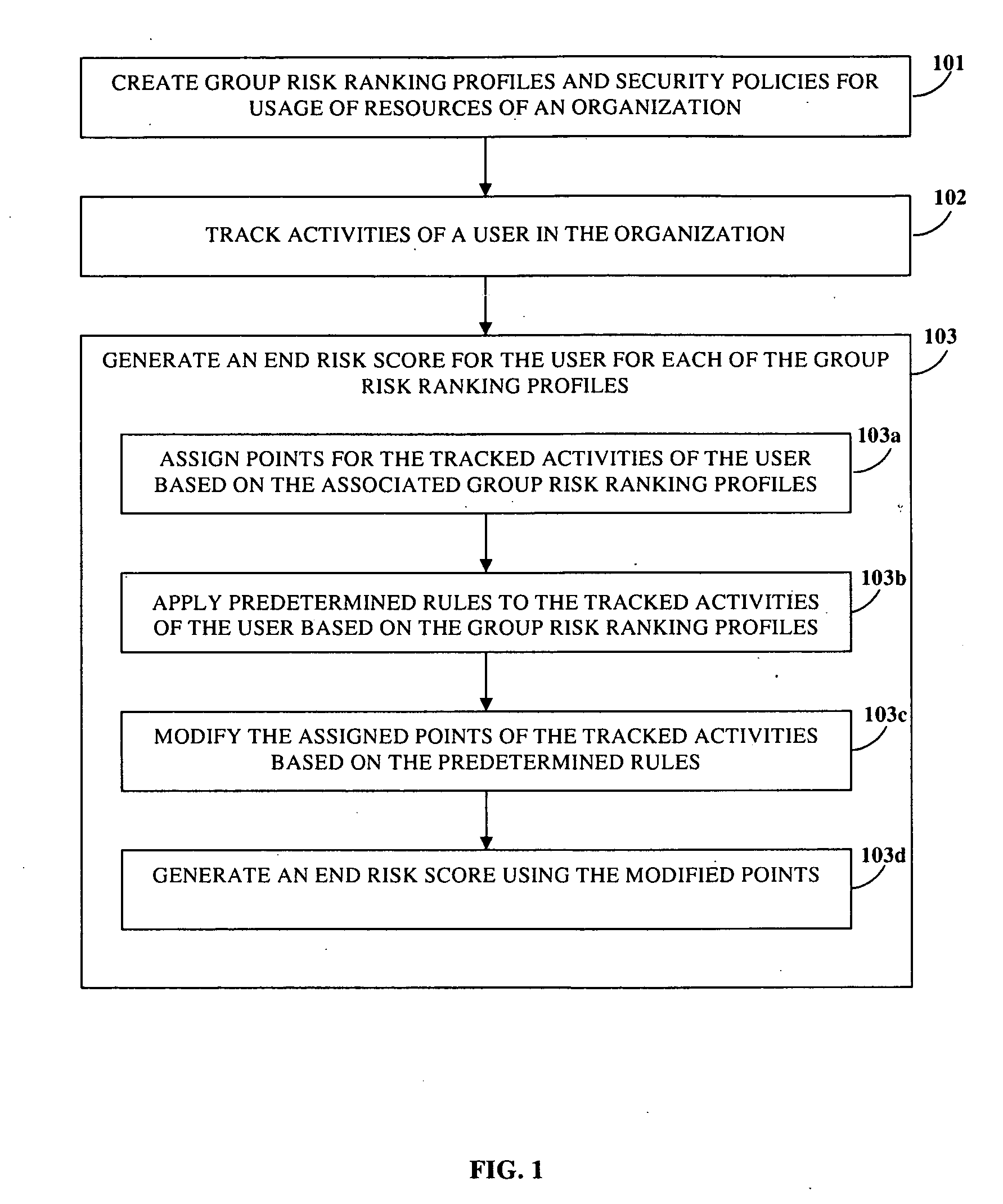
Risk Scoring Based On Endpoint User Activities
InactiveUS20100125911A1Minimize further violationMemory loss protectionError detection/correctionRisk rankingApplication software
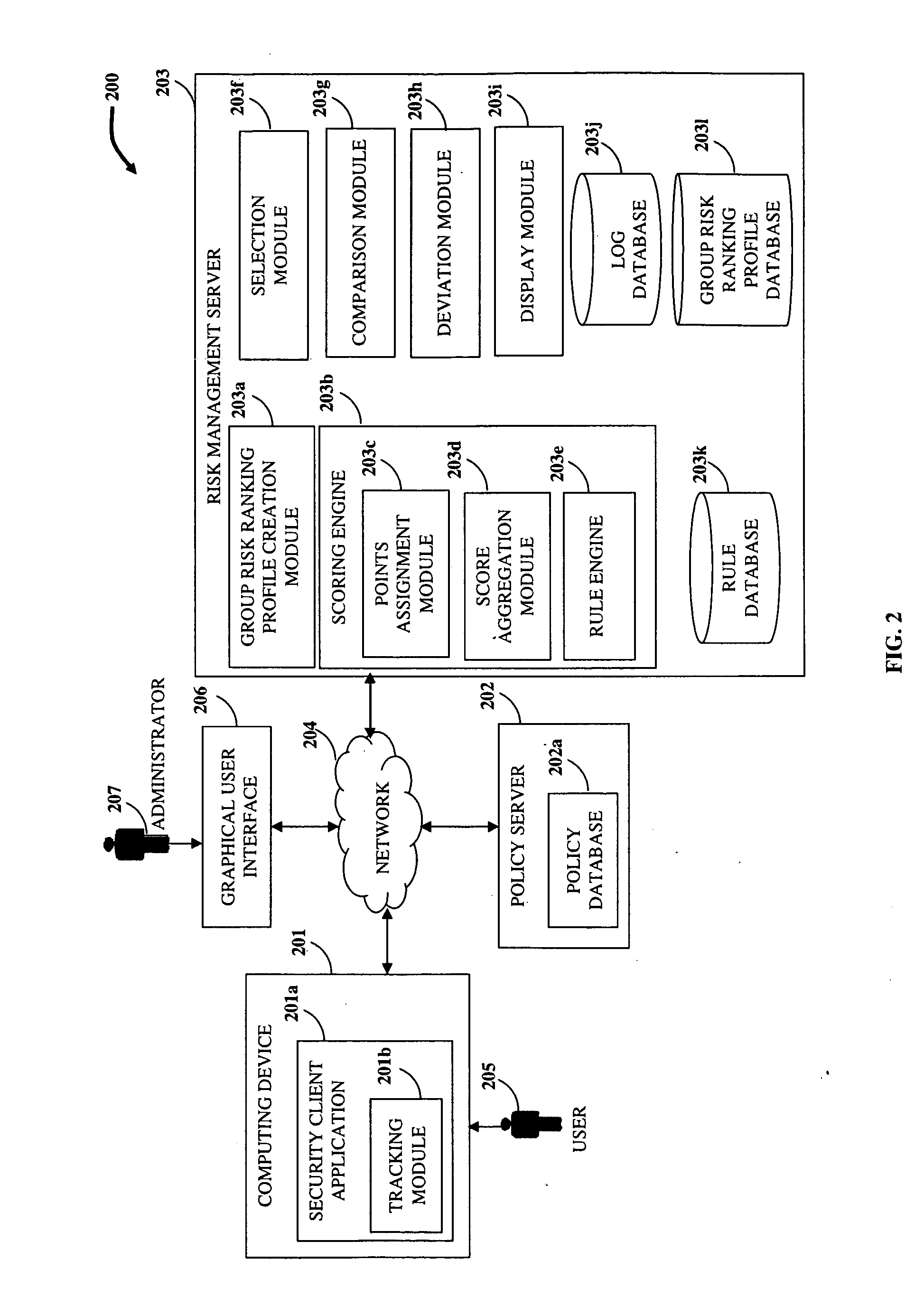
Disclosed herein is a computer implemented method and system for ranking a user in an organization based on the user's information technology related activities and arriving at an end risk score used for determining the risk involved in activities performed by the user and for other purposes. Group risk ranking profiles and security policies for usage of the organization's resources are created. The user is associated with one or more group risk ranking profiles. A security client application tracks the user's activities. Points are assigned to the user's tracked activities based on each of the associated group risk ranking profiles. The assigned points are aggregated to generate a first risk score. The assigned points of the user's tracked activities are modified at different levels based on predefined rules. The modified points are aggregated to generate the end risk score which is used for compliance and governance purposes, optimizing resources, etc.
Owner:CISCO TECH INC
Method and system for providing context awareness
InactiveUS20030182394A1Easy accessInstruments for road network navigationMultiple digital computer combinationsContext awarenessData mining
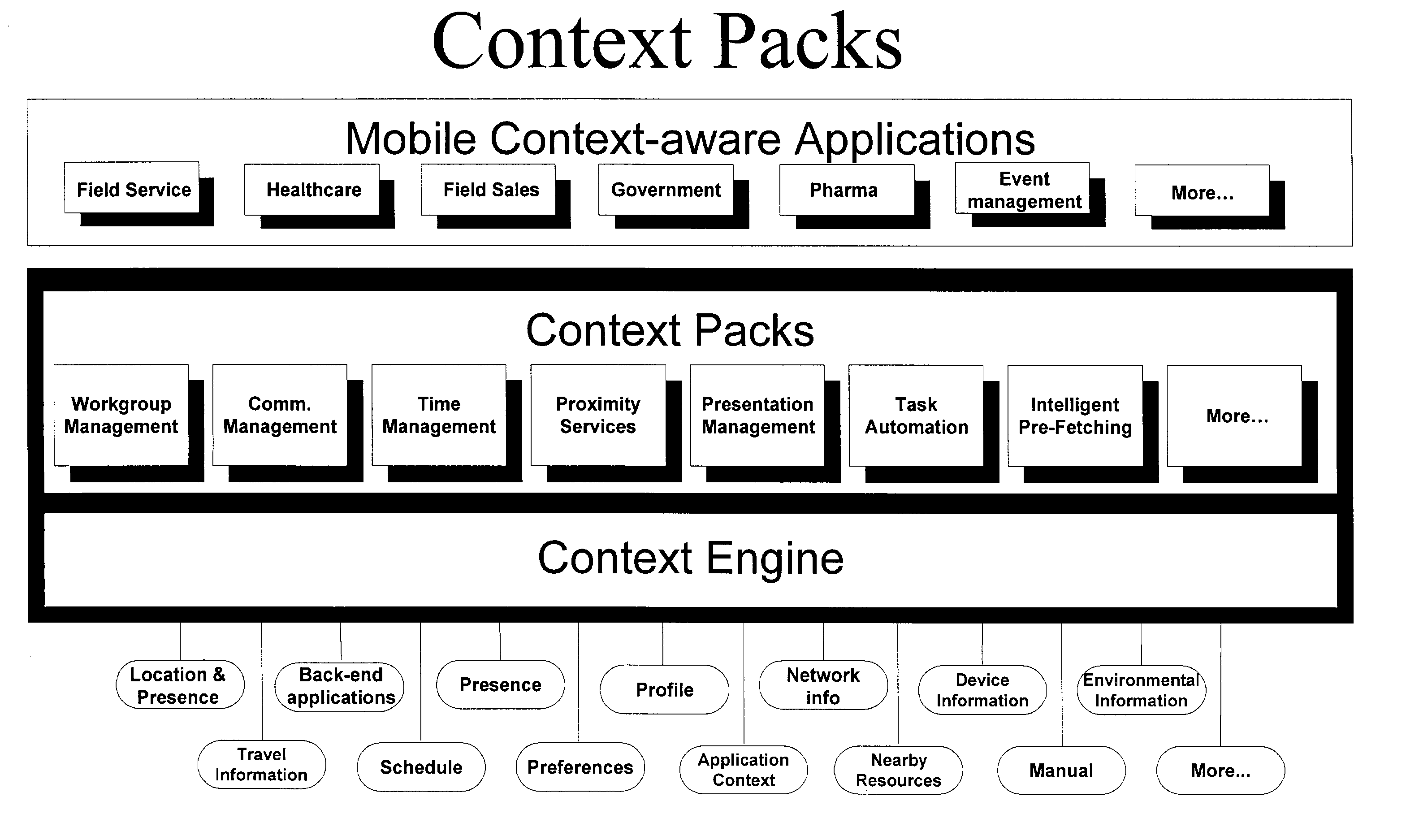
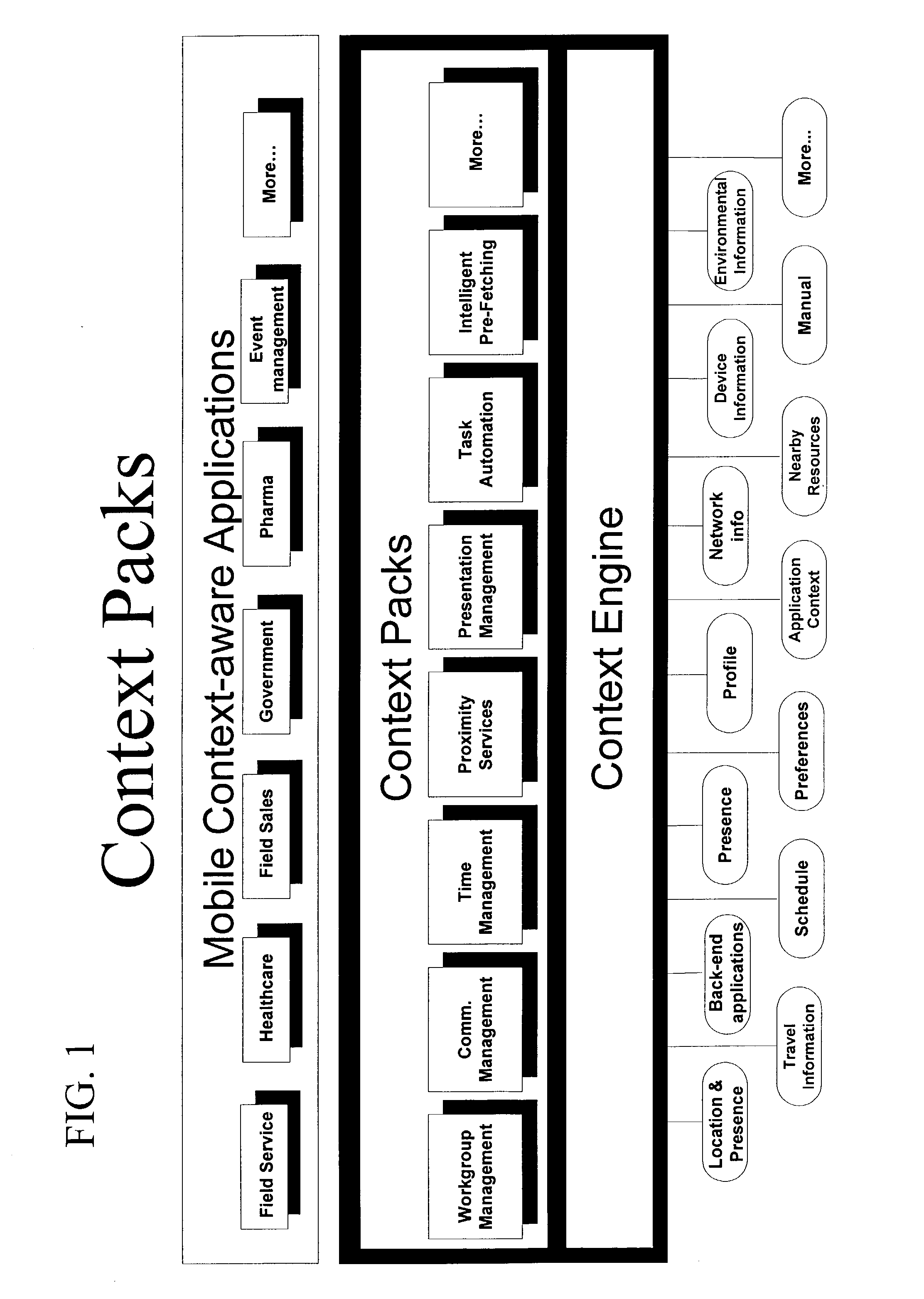
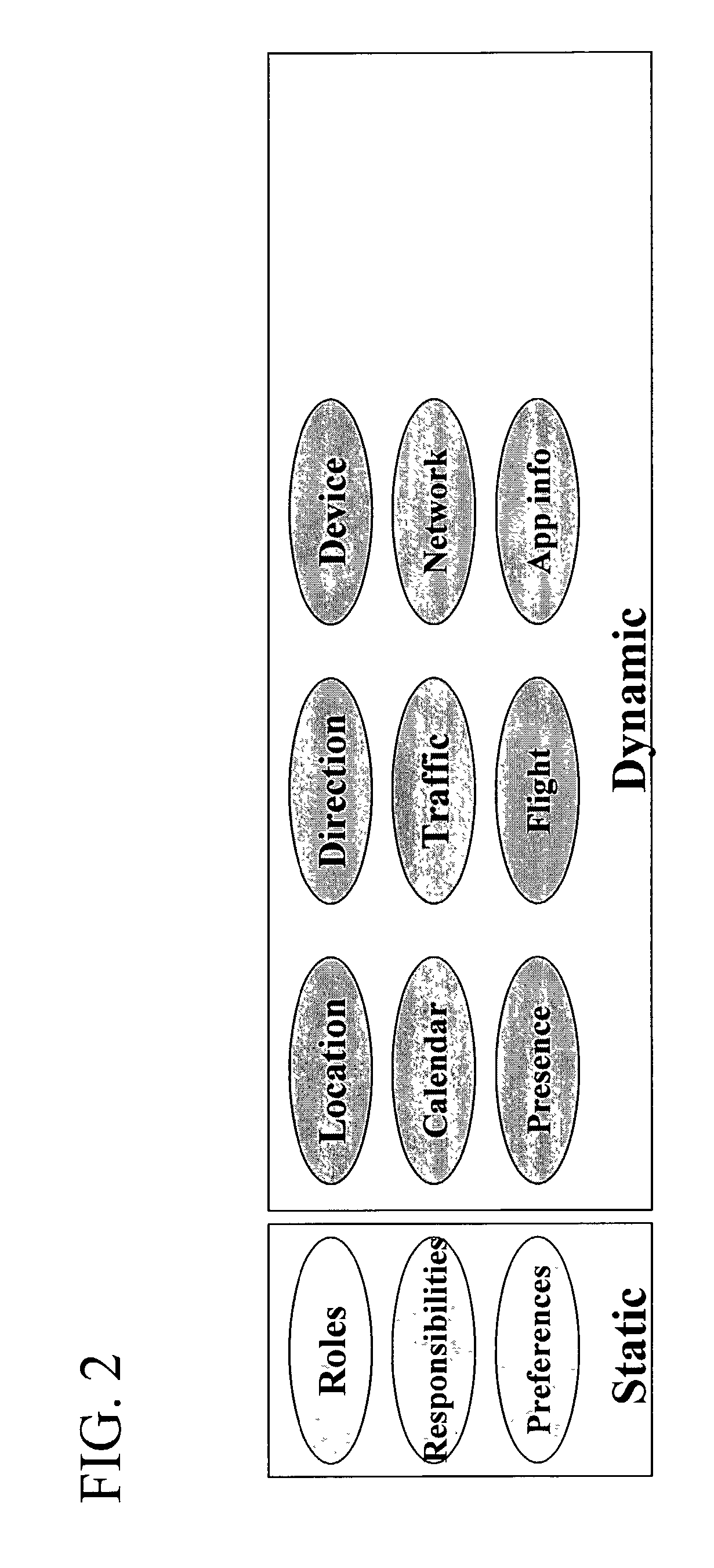
A method and system for providing context information, systems, and actions for a range of information technology platforms and interfaces. Context includes the aggregate knowledge about a user's situation and intent. Included in the system are tiers of features for enabling context awareness, including a collection tier, analysis tier, and action / effect tier. Information relating to entities, which are the elements that are included in the system, such as users and communication devices, along with states and relationships, is identified and accessed by a context engine, which obtains the information from sensors and interpreters for the information. In one application tier, the context engine is used with any set of entities, states, and relationships. Another application tier, referred to as "context packs," includes preset sets of entities, states, and relationships identified for predetermined applications.
Owner:RYNGLER OREN +5
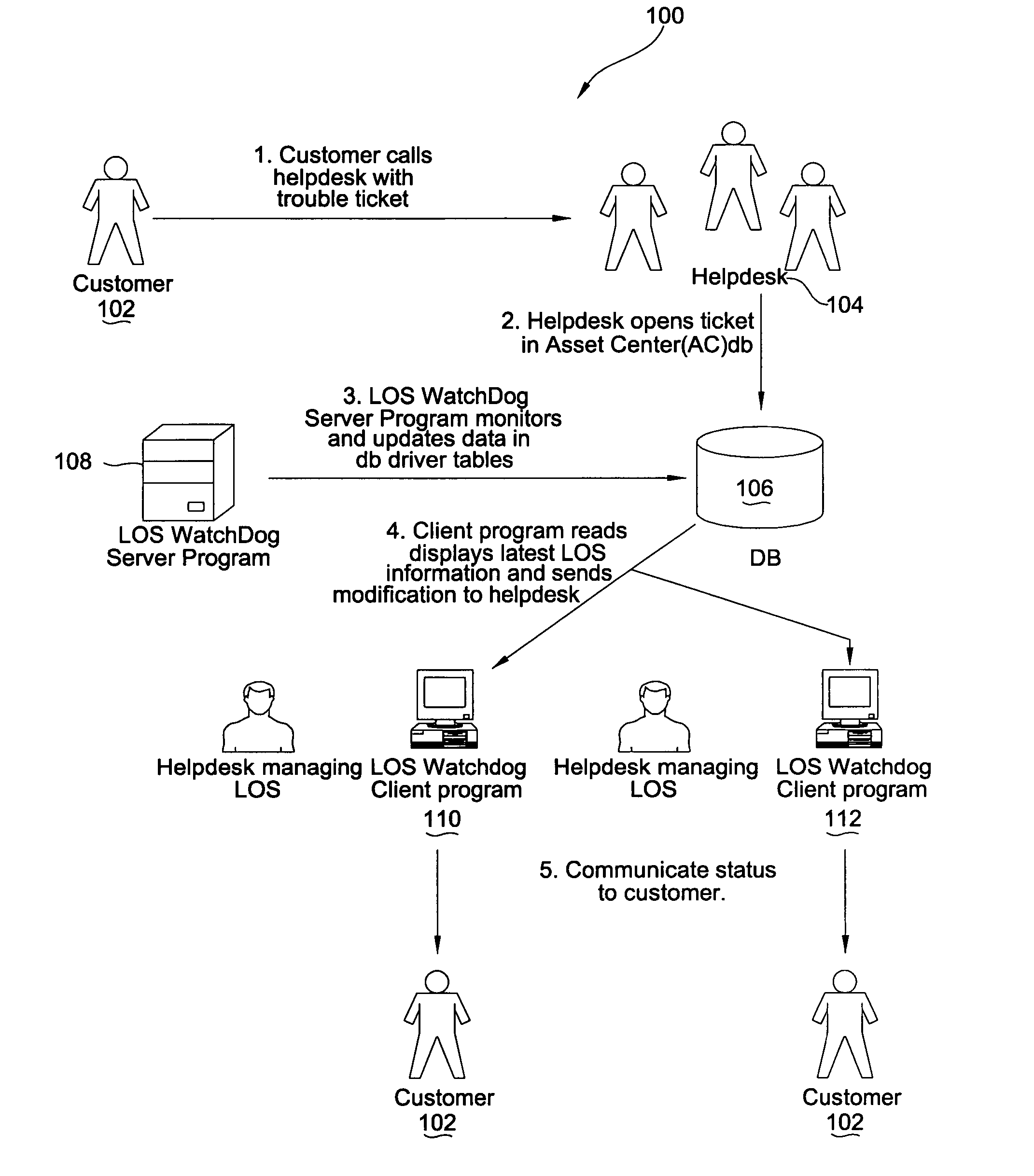
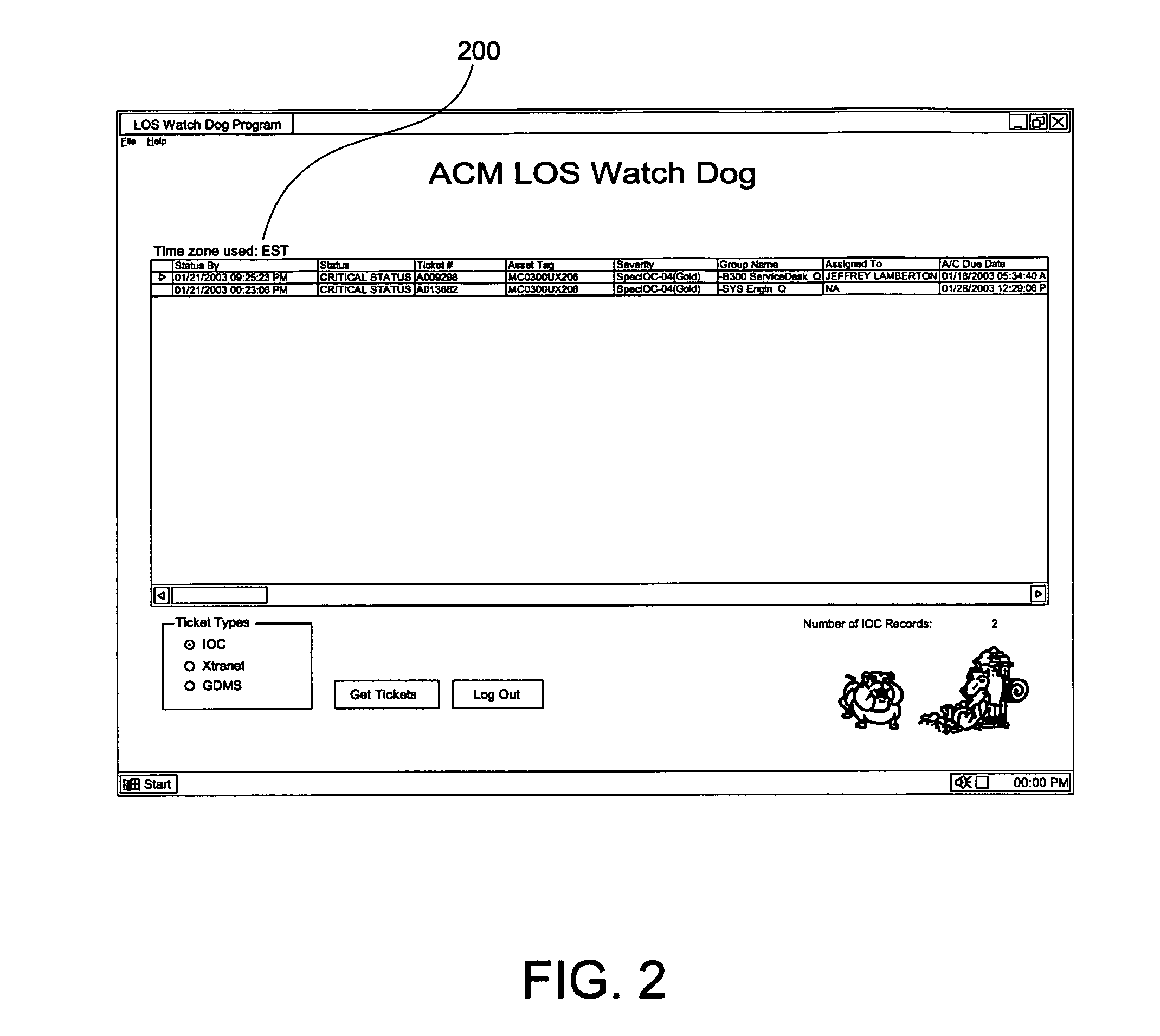
Information technology service request level of service monitor
A method, system, and computer program product for monitoring service tickets for information technology (IT) service providers to ensure that levels of service regarding resolving problems identified by a customer are met is provided. In one embodiment, a monitoring server inspects a service ticket in a database to determine a deadline for when a problem associated with the service ticket must be resolved. The server then determines a deadline approaching alert time. This deadline approaching alert time is a time at which a help desk user must be notified that the deadline for resolving the problem must be met is approaching. The server then alerts the help desk user that the deadline for resolving the problem is approaching when the deadline approaching alert time is reached. If the problem is not resolved by the deadline, the server periodically alerts the help desk user when times for status updates, which have been specified by a level of service agreement for updating the customer of the status of resolution of problems that have past deadline, are approaching, thereby ensuring that the IT provider meets its obligations to the customer.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
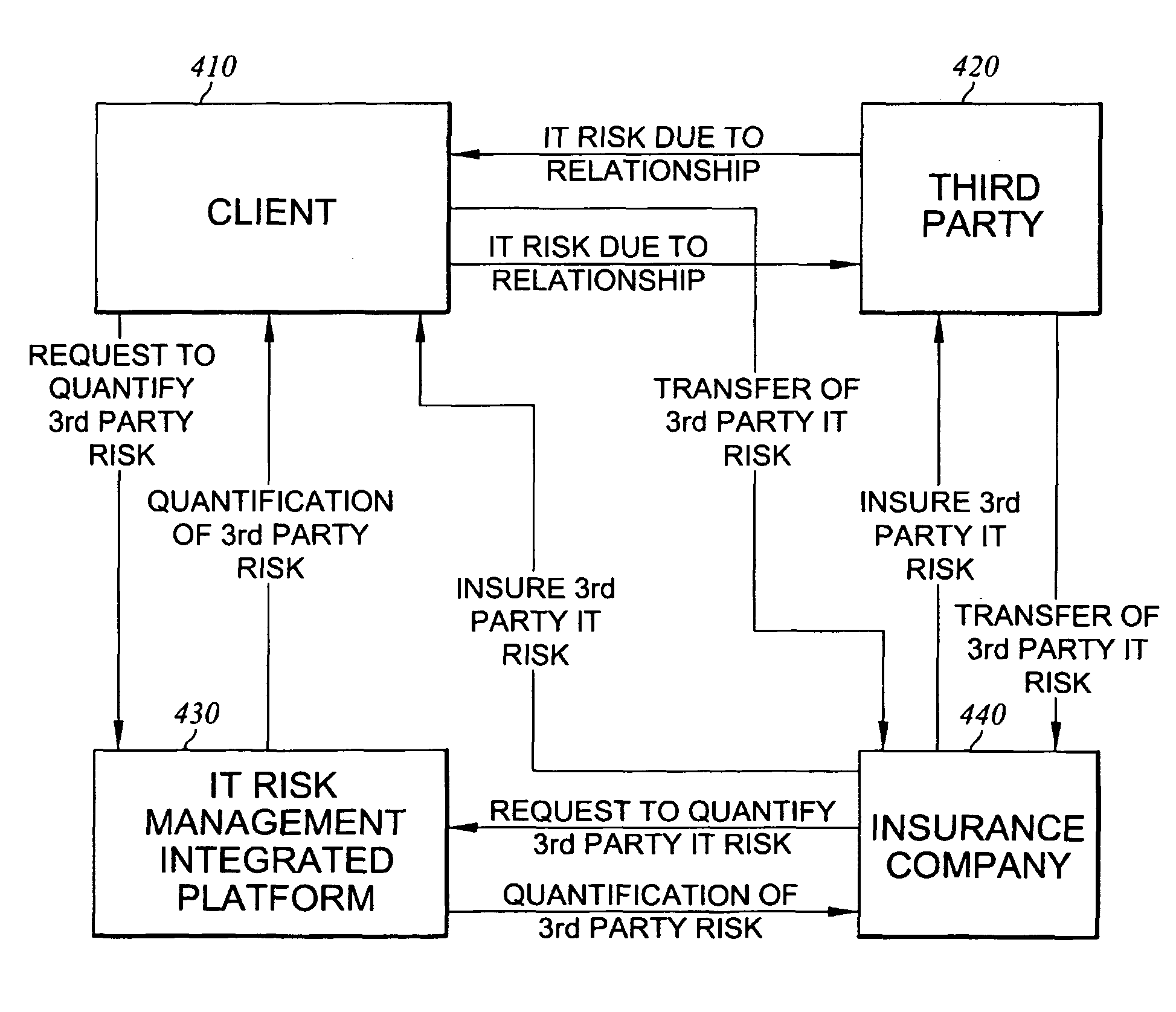
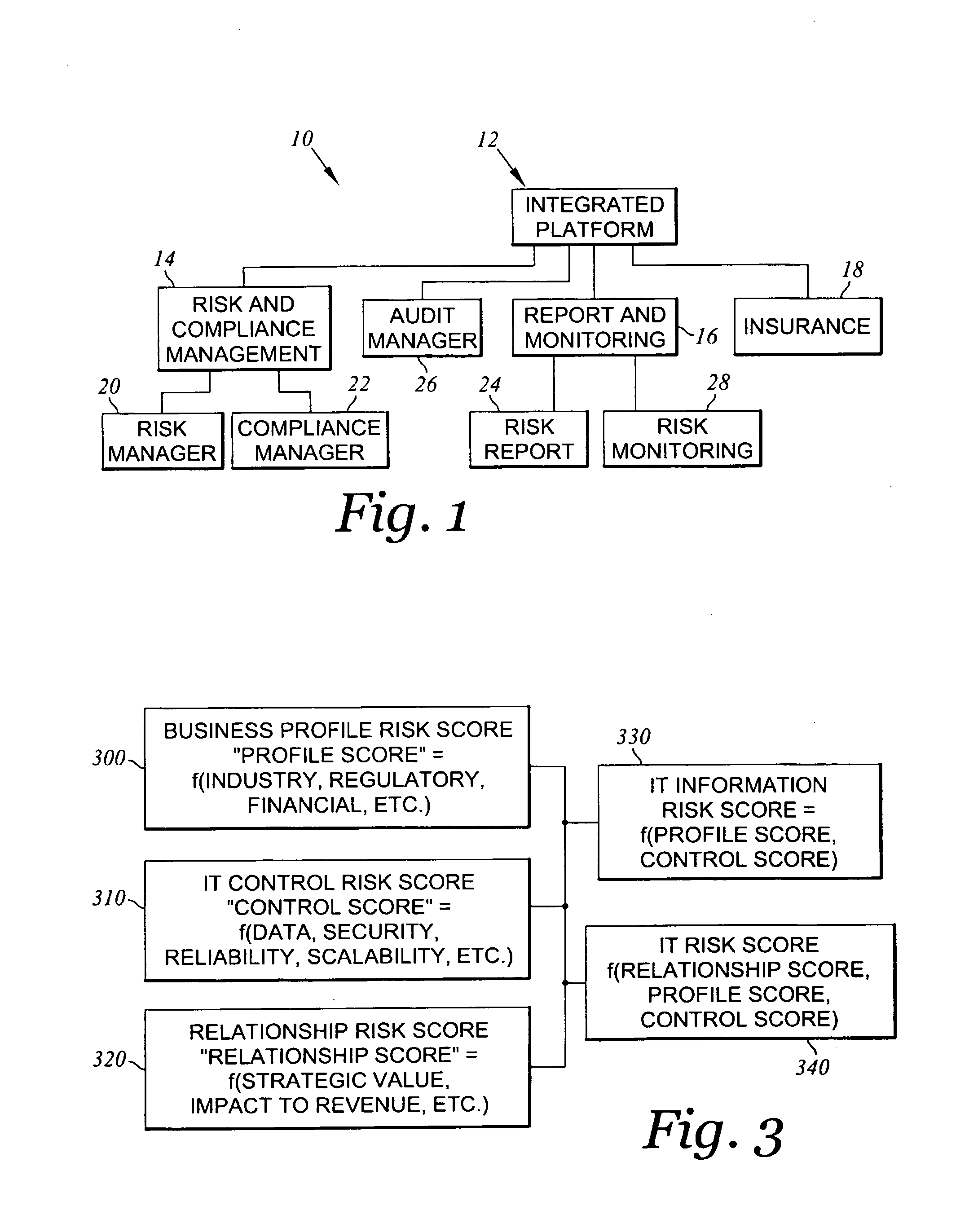
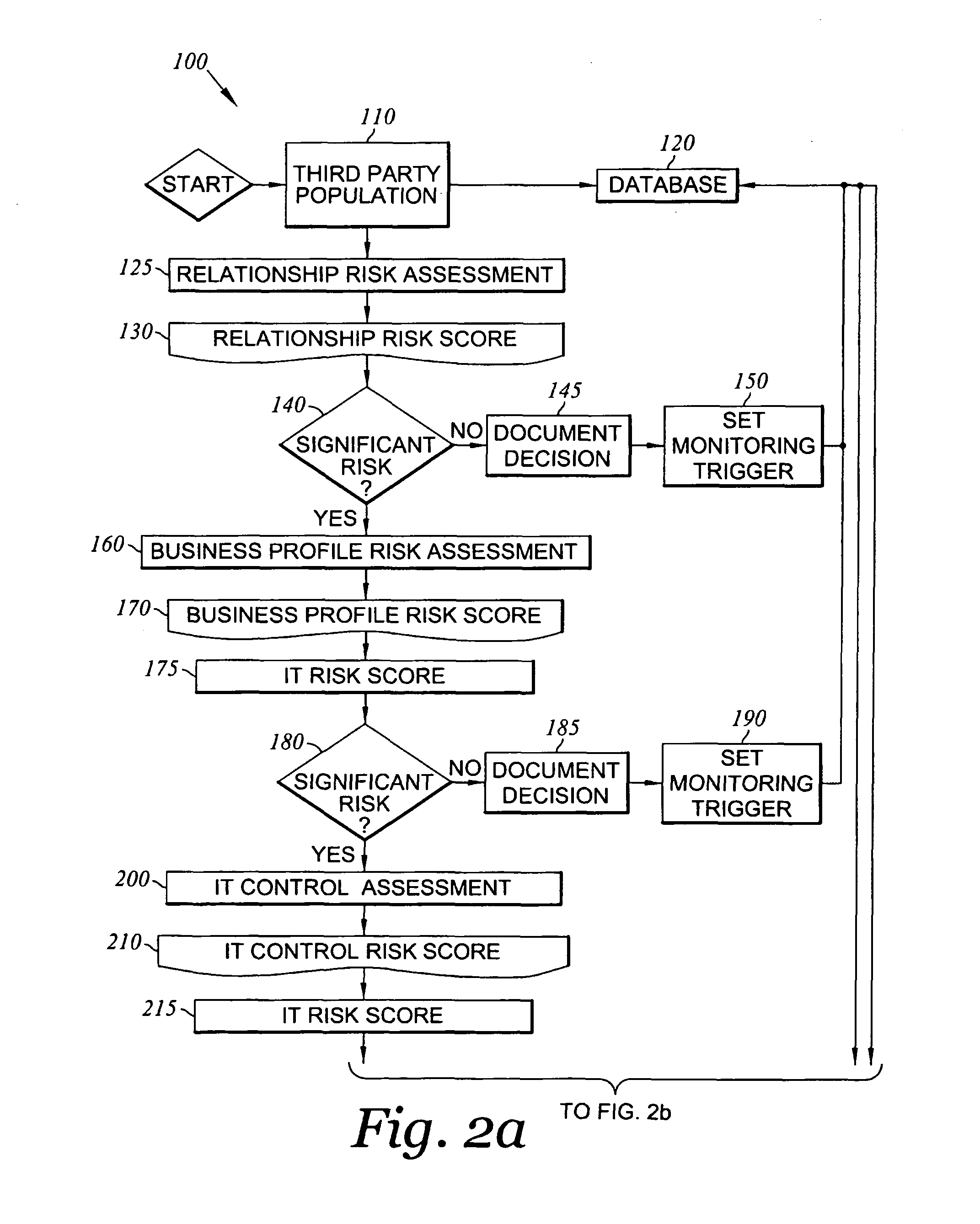
Method and system for assessing, managing, and monitoring information technology risk
A method for information technology (IT) and information asset risk assessment of a business relationship between a client and a third party. The method includes establishing a database. The database includes a plurality of IT information risk factors. The database is configured to receive IT risk information. The IT risk information is associated with the plurality of IT information risk factors. The plurality of IT information risk factors includes a subset of relationship risk factors. The subset of relationship risk factors are utilized for evaluating the business relationship risk between the client and the third party. The method also includes receiving IT risk information corresponding to the subset of relationship risk factors. The method continues with generating a relationship risk score. The relationship risk score is determined in response to evaluating the subset of relationship risk factors using the IT risk information corresponding to the subset of relationship risk factors.
Owner:OPTIV SECURITY INC
System and method to provide secure navigation to resources on the internet
InactiveUS6381579B1Quick changeBuying/selling/leasing transactionsResourcesWeb browserManagement tool
Provide an electronic-business-to-electronic-business portal that organizes the access to extended business applications. A method allows end users to access a server using standard Web browsers, and then view their own customized menu of applications. Enhanced security and administrative tools allow this portal to be shared throughout enterprises and across supply chains, providing secure access to collaborative applications by business partners and suppliers. Access to specific applications is granted to authorized users and teams, within and outside of a company. Real-time, on-line registration of users allows for rapid changes in teams and projects. Users can be added, deleted, or have access levels altered to reflect changes in the makeup of teams. Provide a common infrastructure for application administration, security management, and directory use, which can help reduce information technology (IT) costs and speed solution deployment.
Owner:TWITTER INC
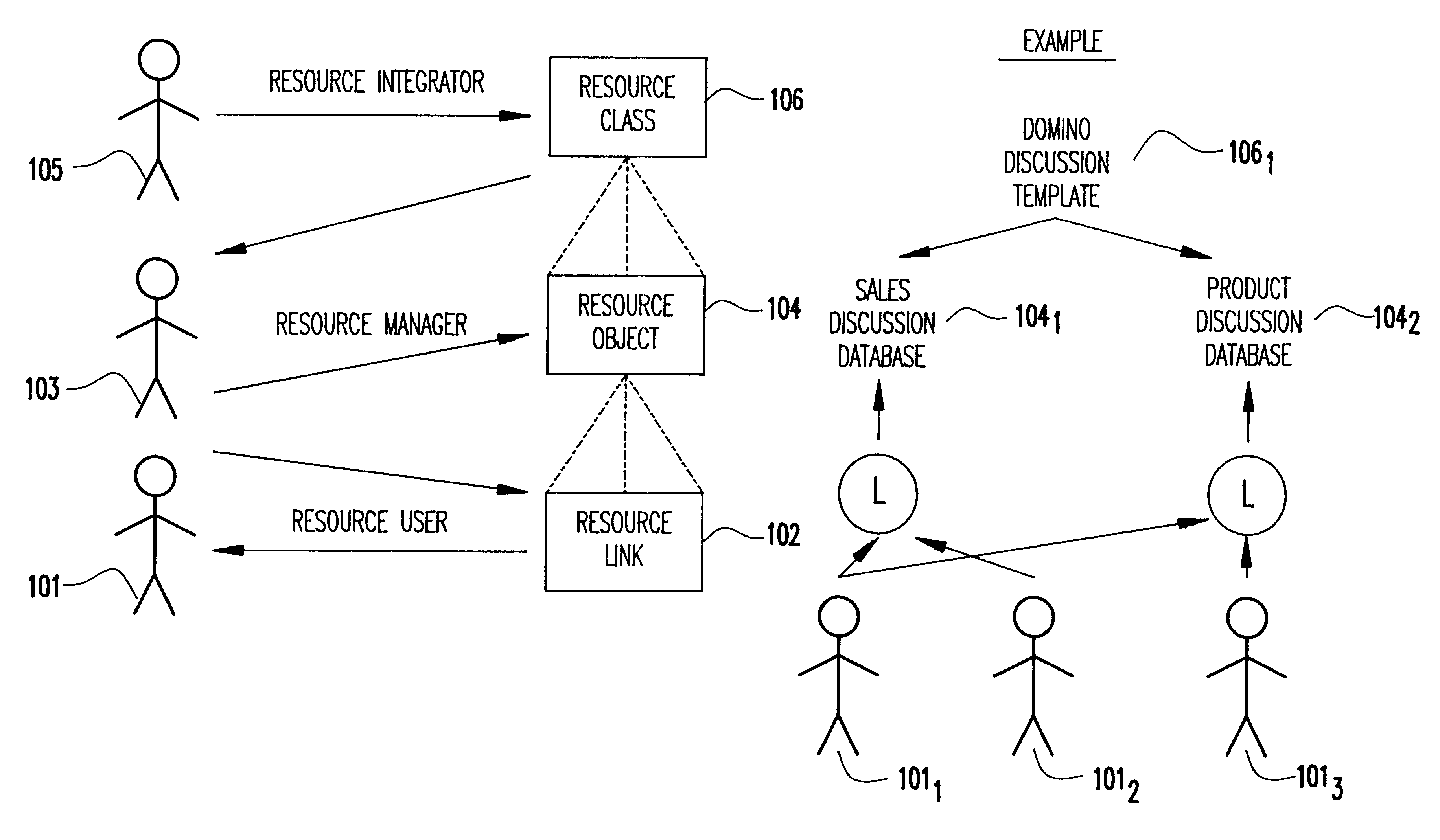
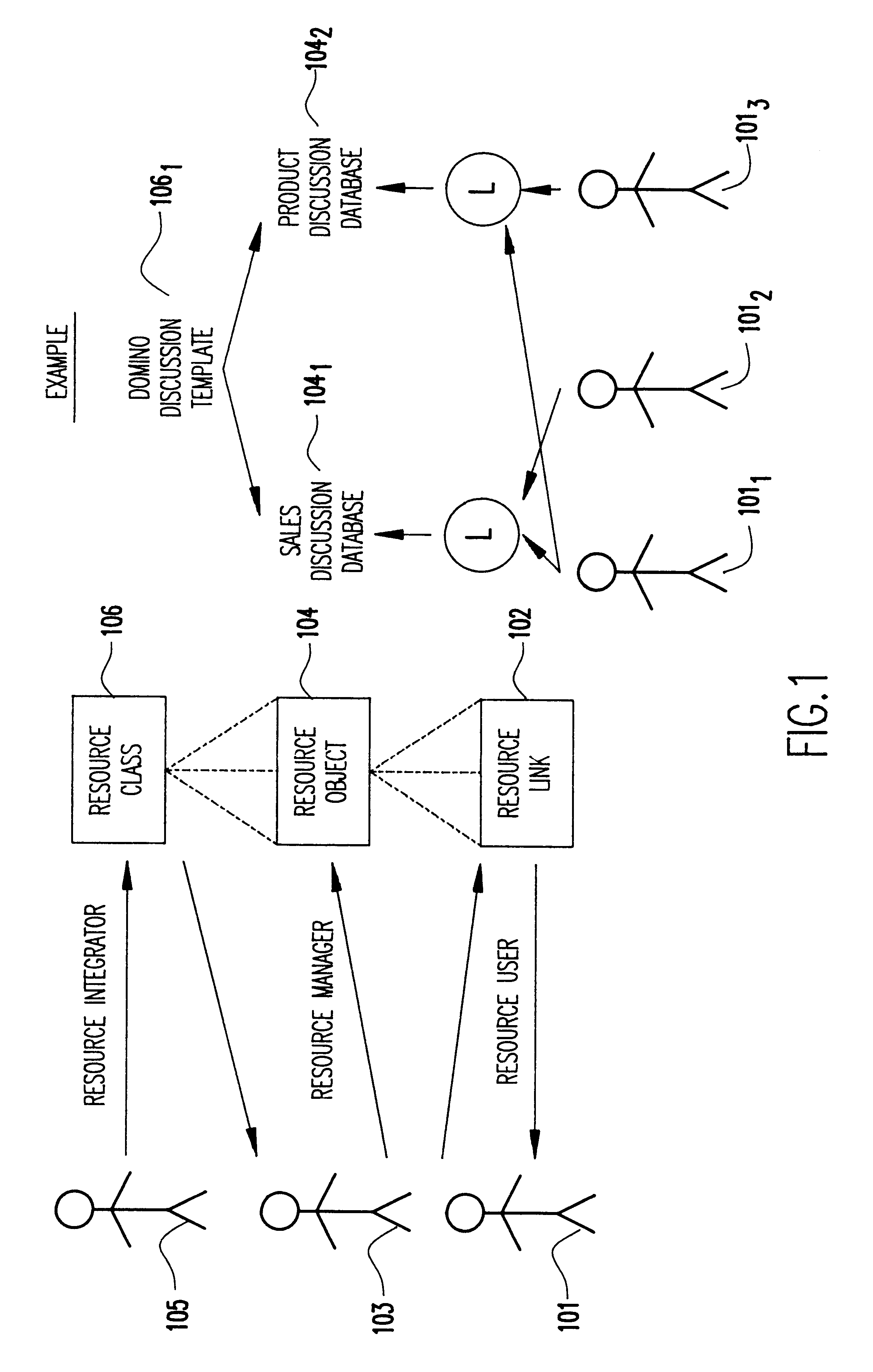
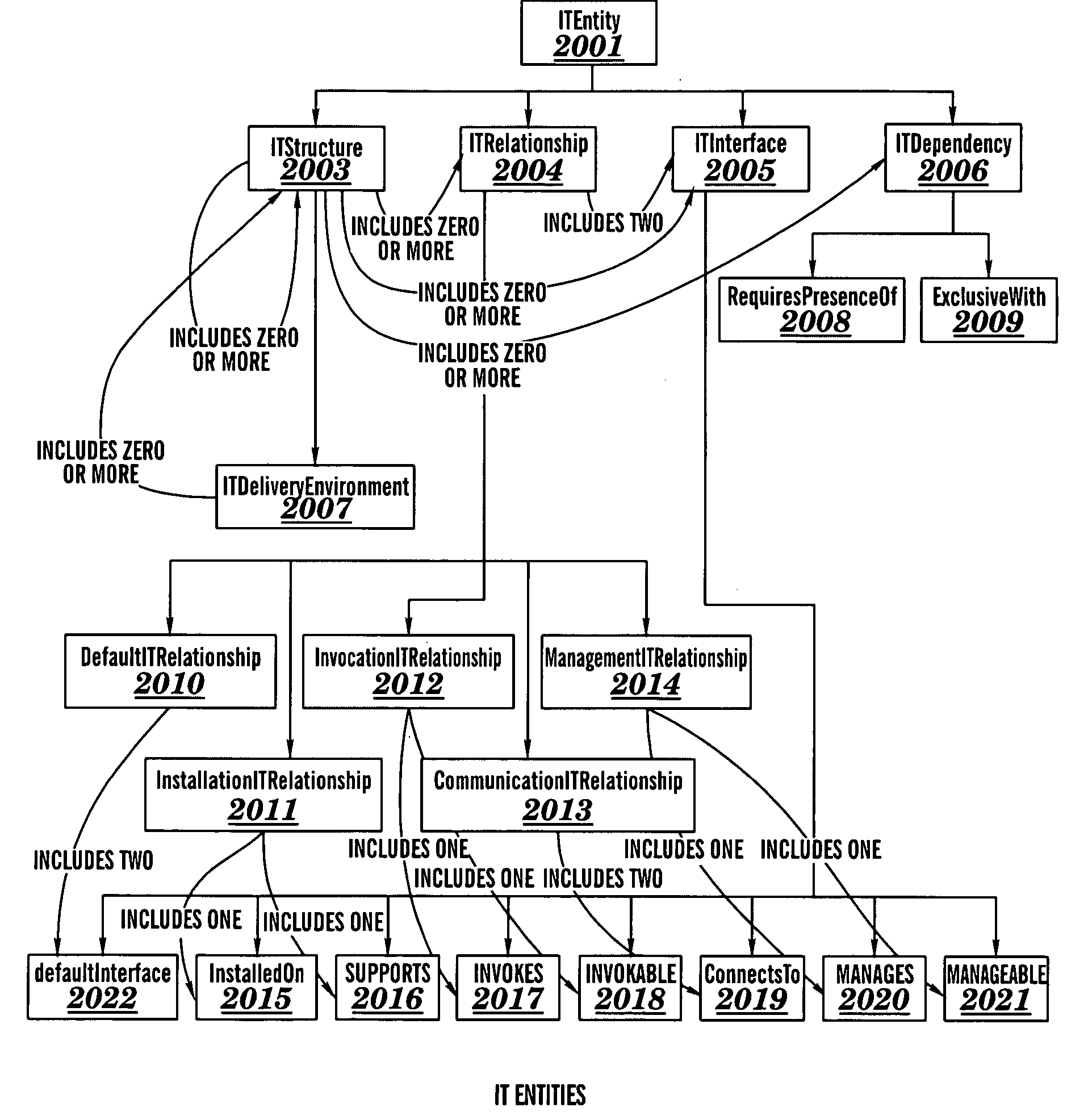
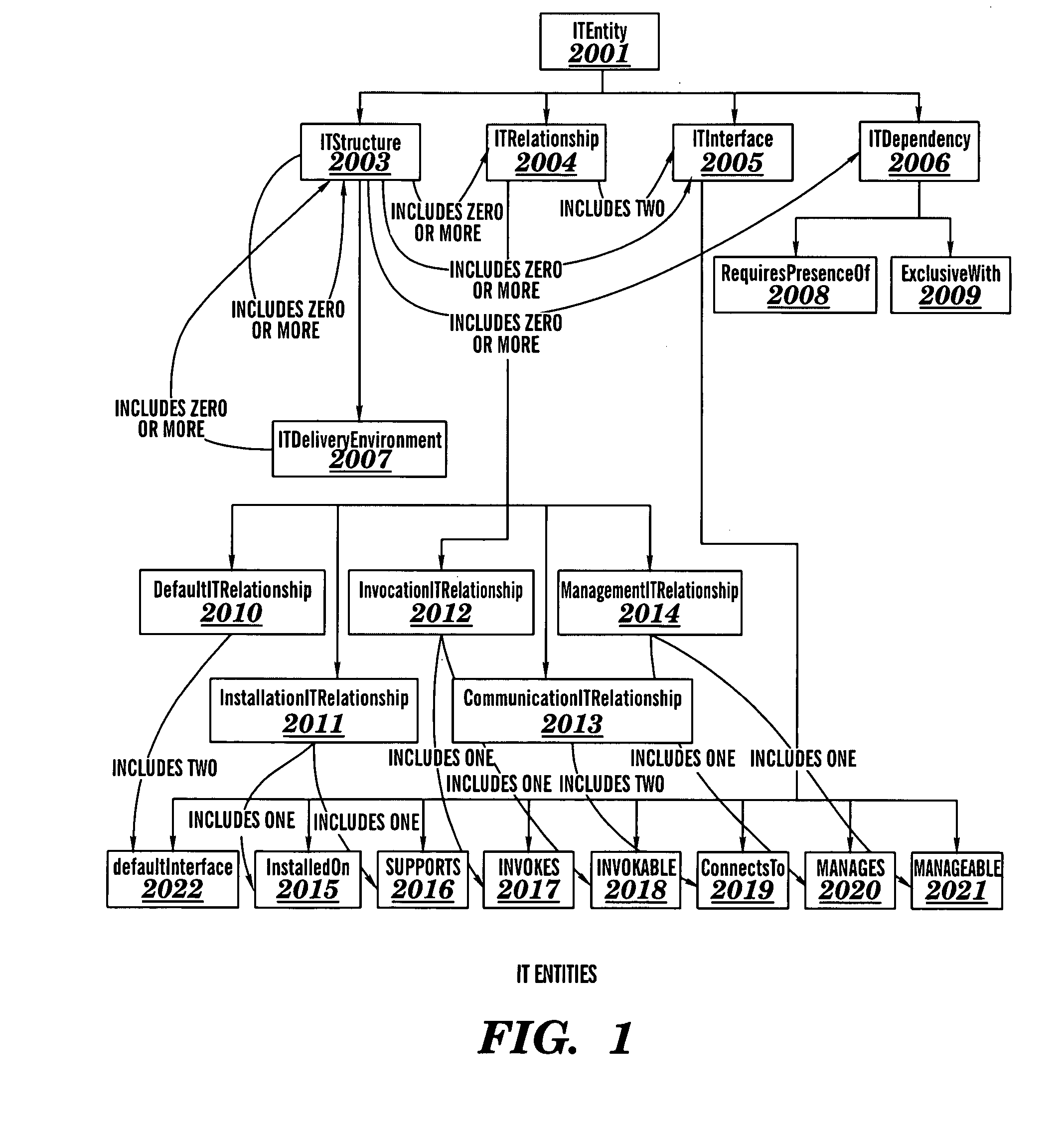
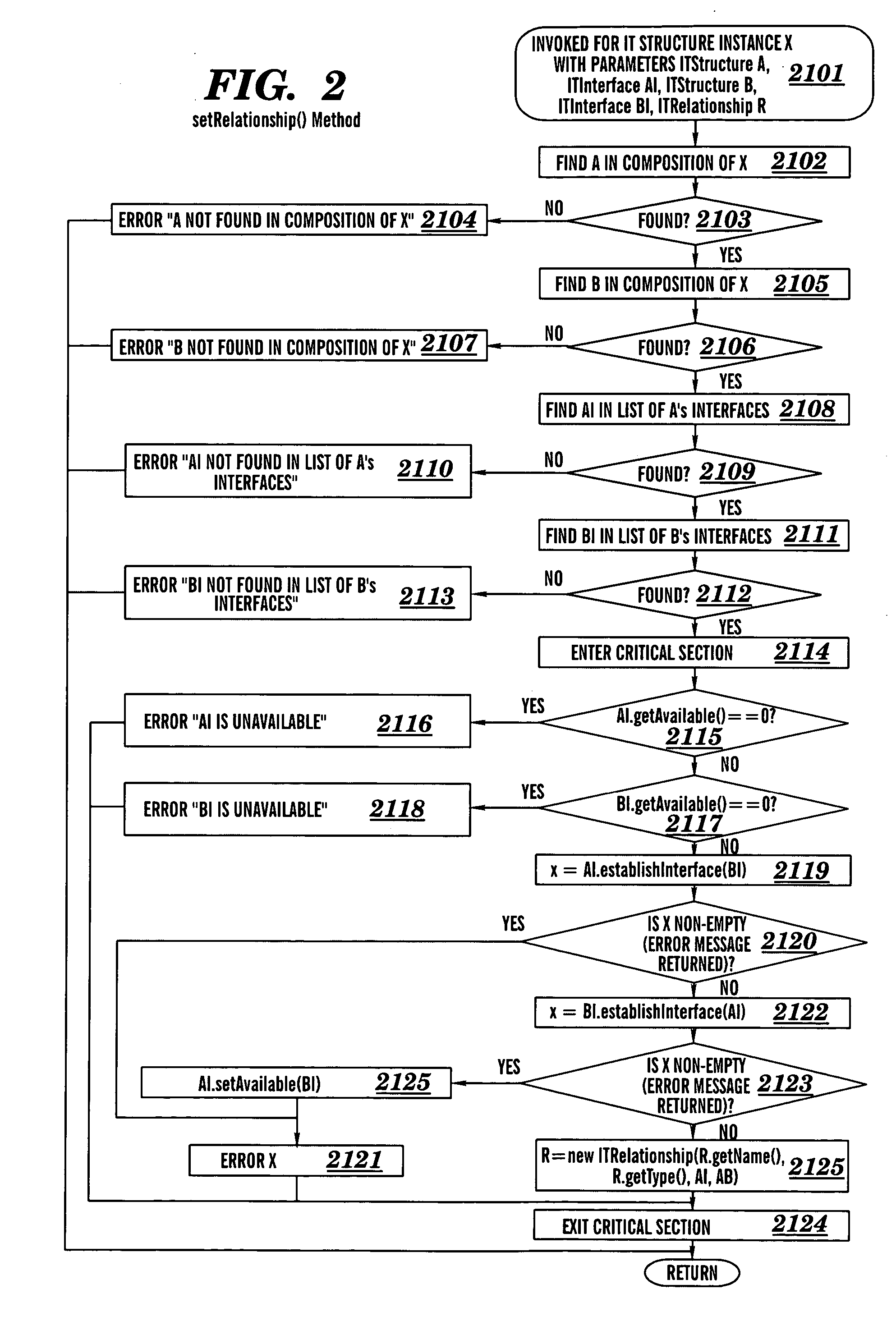
Object management system supporting the use of application domain knowledge mapped to technology domain knowledge
InactiveUS6226792B1Easy to browseThrough simpleSoftware reuseSpecific program execution arrangementsCatalogingAssociate - relationship
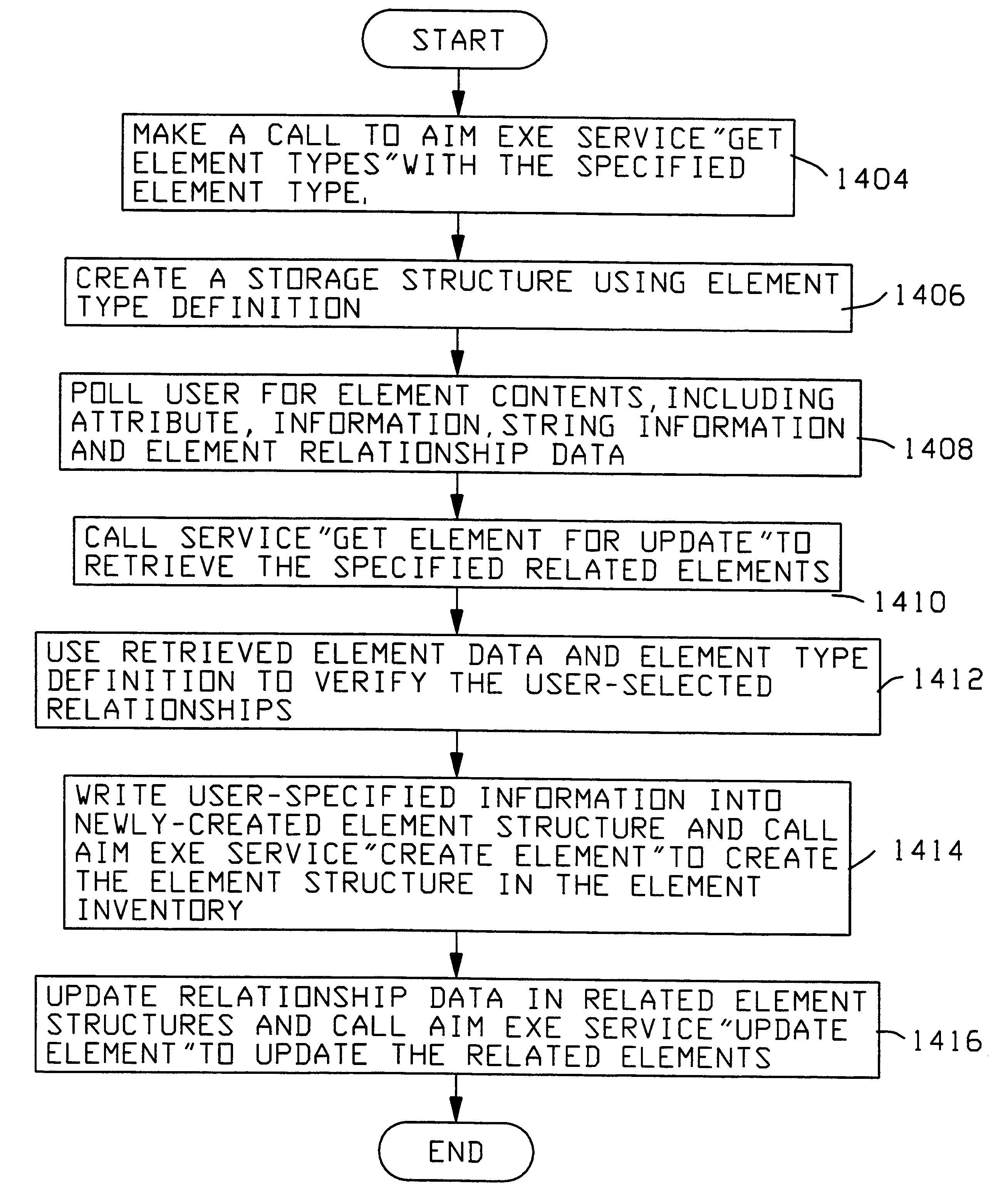
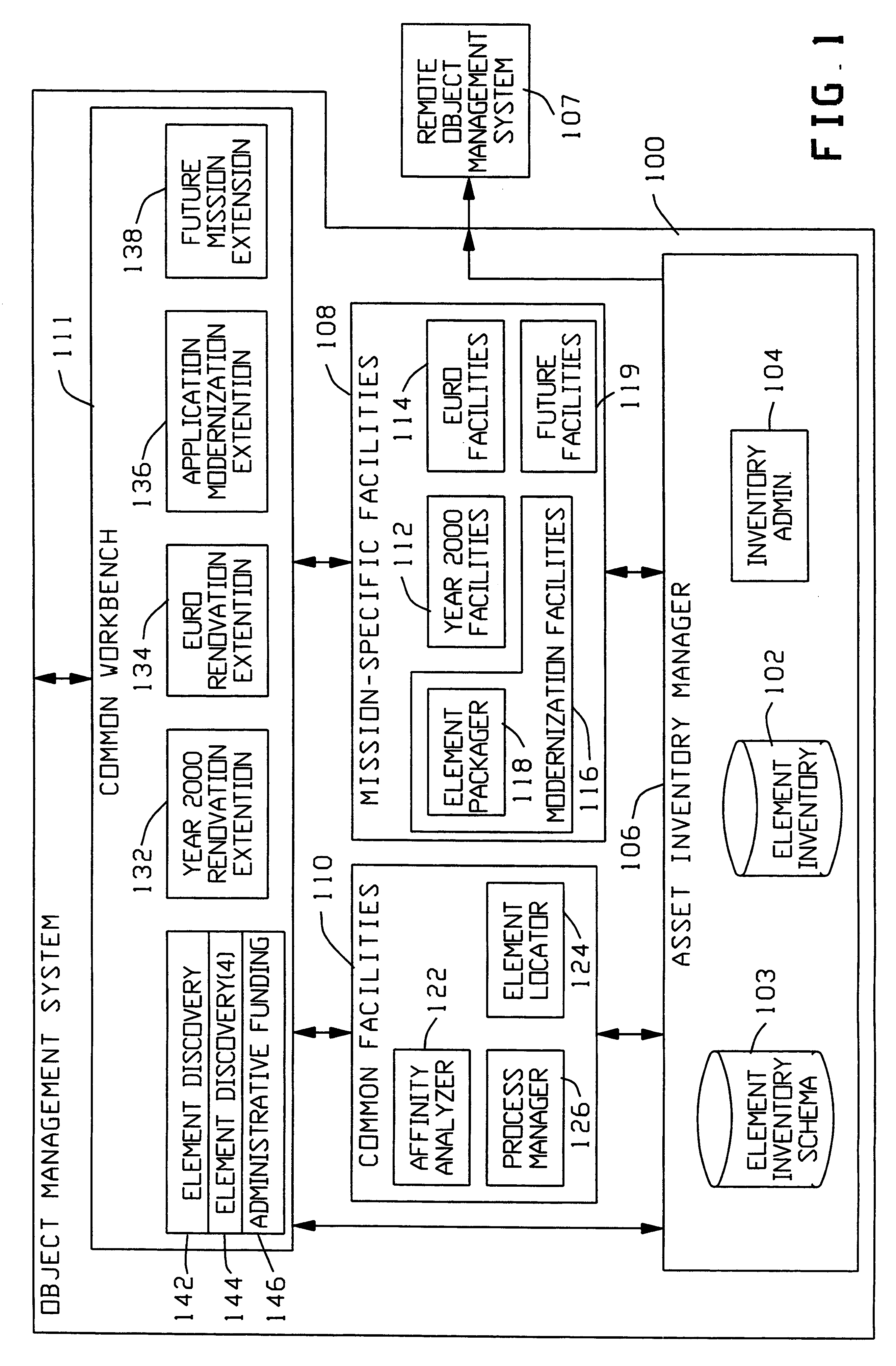
An object management system is providing for managing, cataloging, and discovering various potentially reusable code and data components that exist within an Information Technology (IT) platform, and which each have well-defined interfaces with other components. For each of these re-usable code and data components, an associated software object called an "asset element" is created that describes the associated component. Relationships are created between various asset elements to represent the relationships existing between the software components. Other software objects called "locator elements" are created that each describes an application concept or sub-concept. This application concept or sub-concept is associated with a problem solved by the code and data components within the IT platform. Relationships are created between the various locator elements to correlate the concepts and sub-concepts to software constructs represented by asset elements. The object management system further supports various object discovery tools capable of identifying locator elements associated with a particular concept. These locator elements and the associated relationships may then be efficiently traced to identify related asset elements and the associated software and code constructs. This provides an efficient concept-based search mechanism for the code constructs. Other tools are provided for creating, modifying, and deleting the elements. A model may be used to define the various types of relationships and elements that may exist within the system, thereby simplifying the various tools needed to support element creation, modification, deletion, and traversal.
Owner:UNISYS CORP
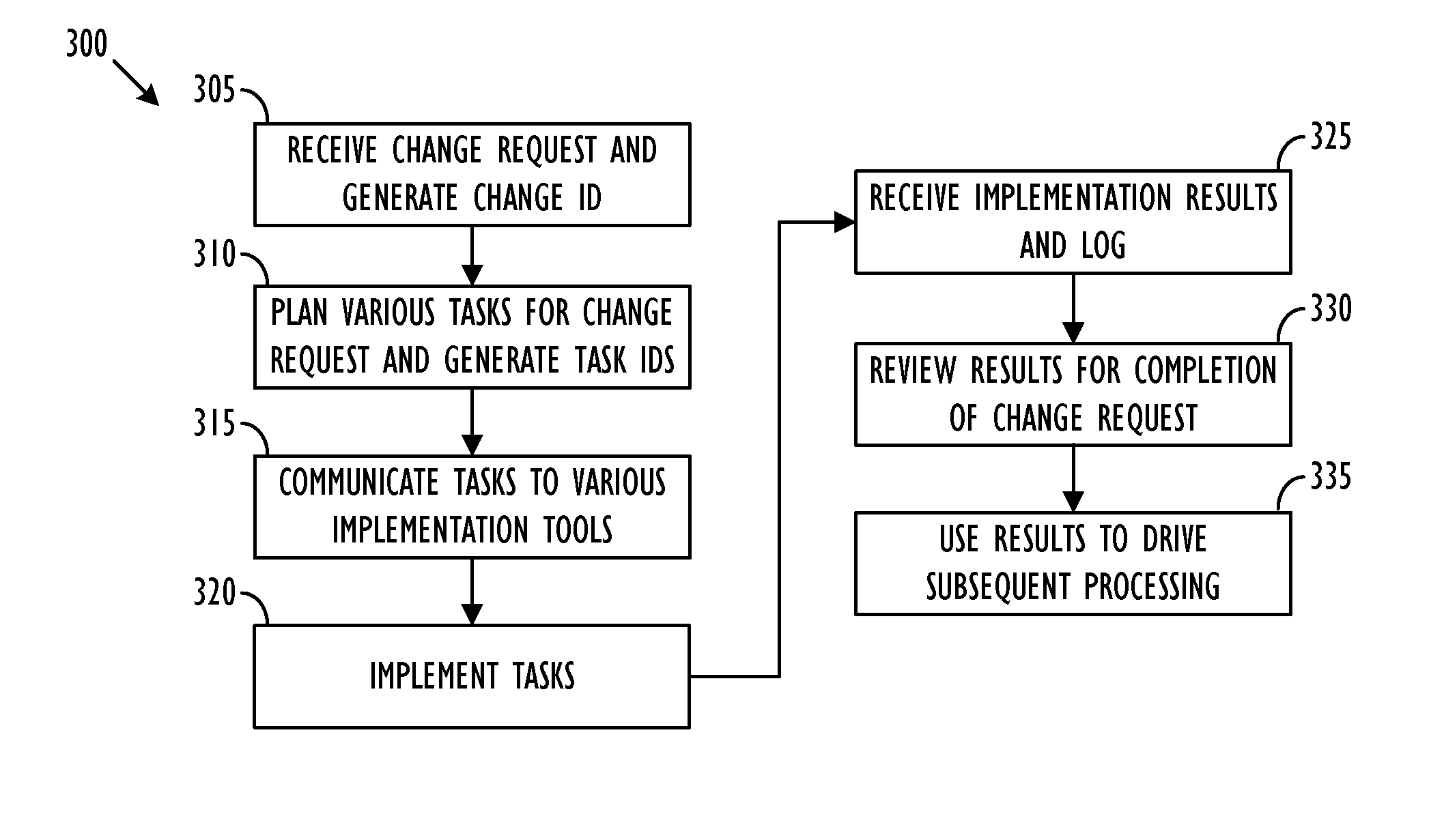
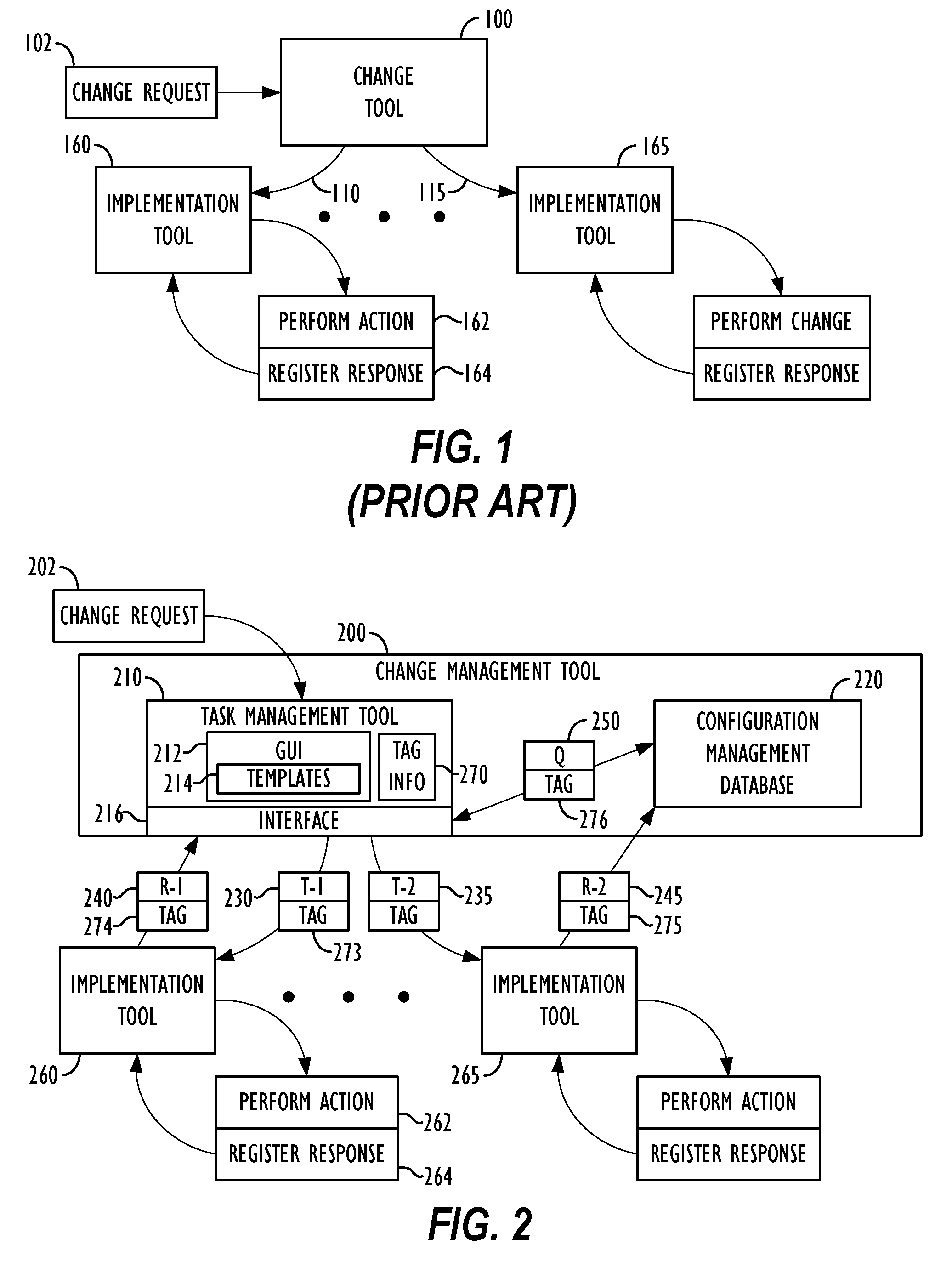
Bi-directional communication between change management tool and implementation tools
ActiveUS8887133B2Version controlSpecific program execution arrangementsChange managementManagement tool
Owner:BMC SOFTWARE
System and Interface For Monitoring Information Technology Assets
ActiveUS20100229096A1Retain controlStandardize the interfaceInput/output for user-computer interactionError preventionApplication softwareApplication service provider
An application service provider (ASP)-based interface and system for analyzing performance and costs of respective enterprise information technology assets from the correlation of metrics data of enterprise SNMP-enabled devices.
Owner:DYNATRACE
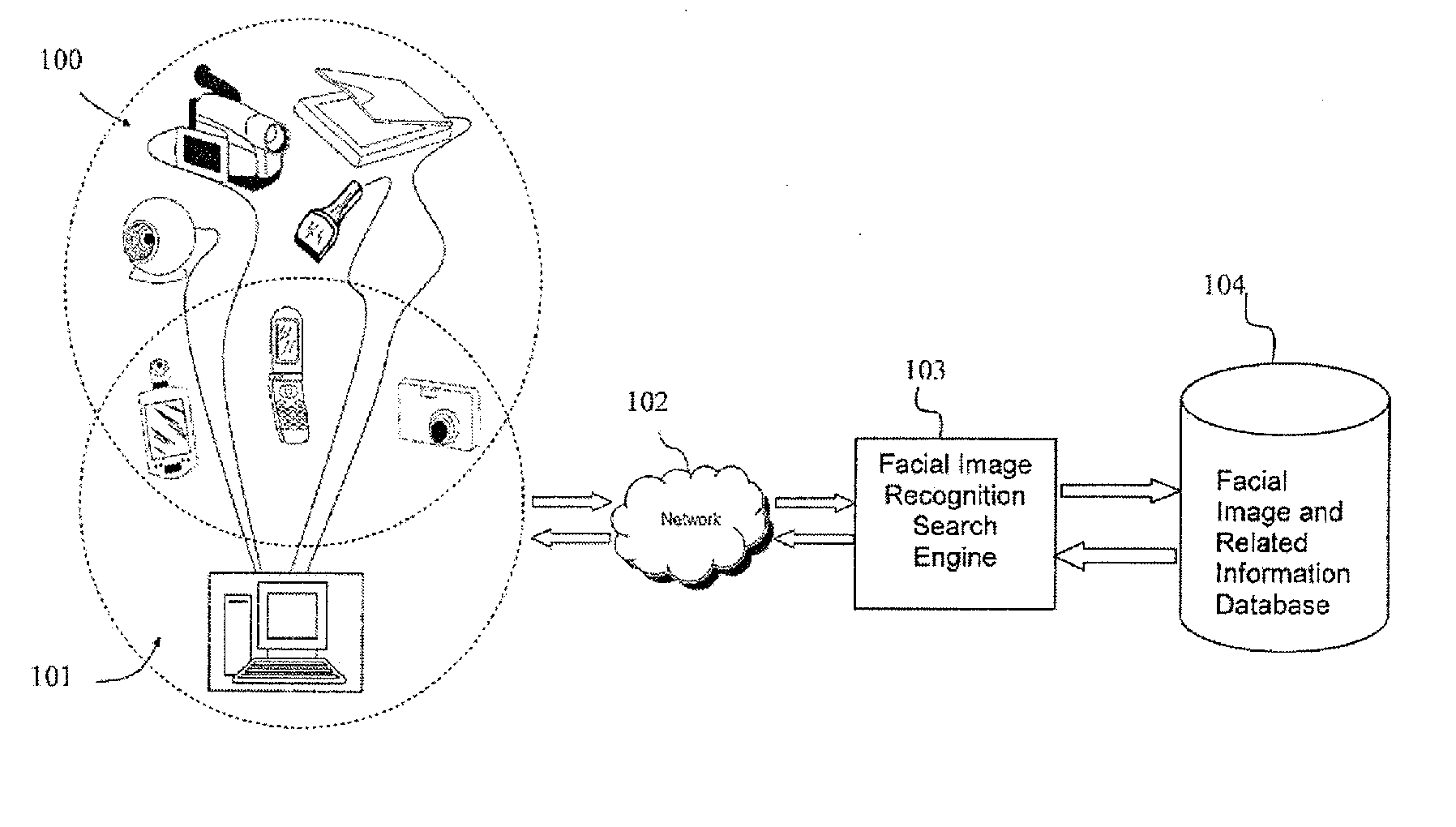
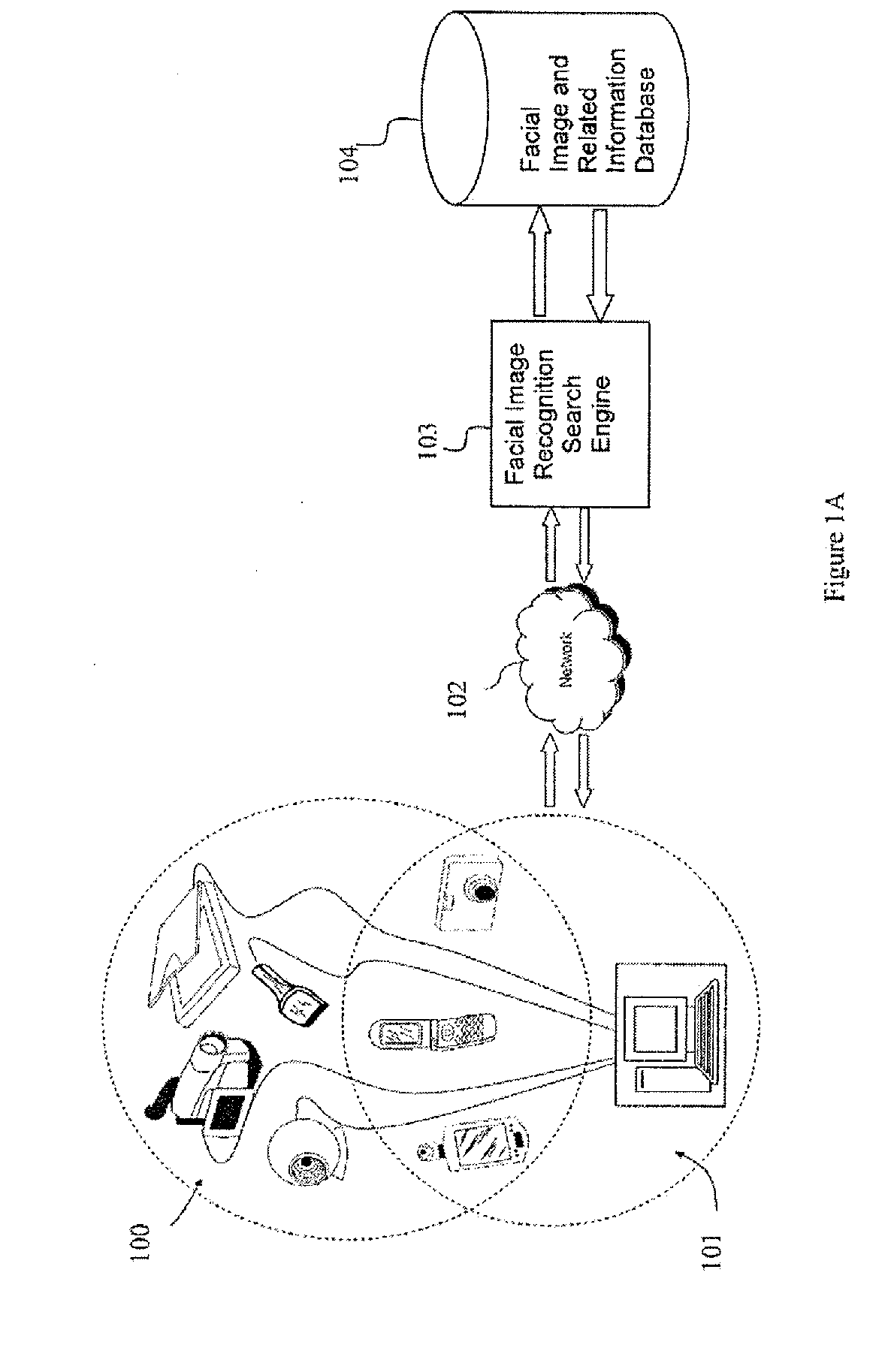
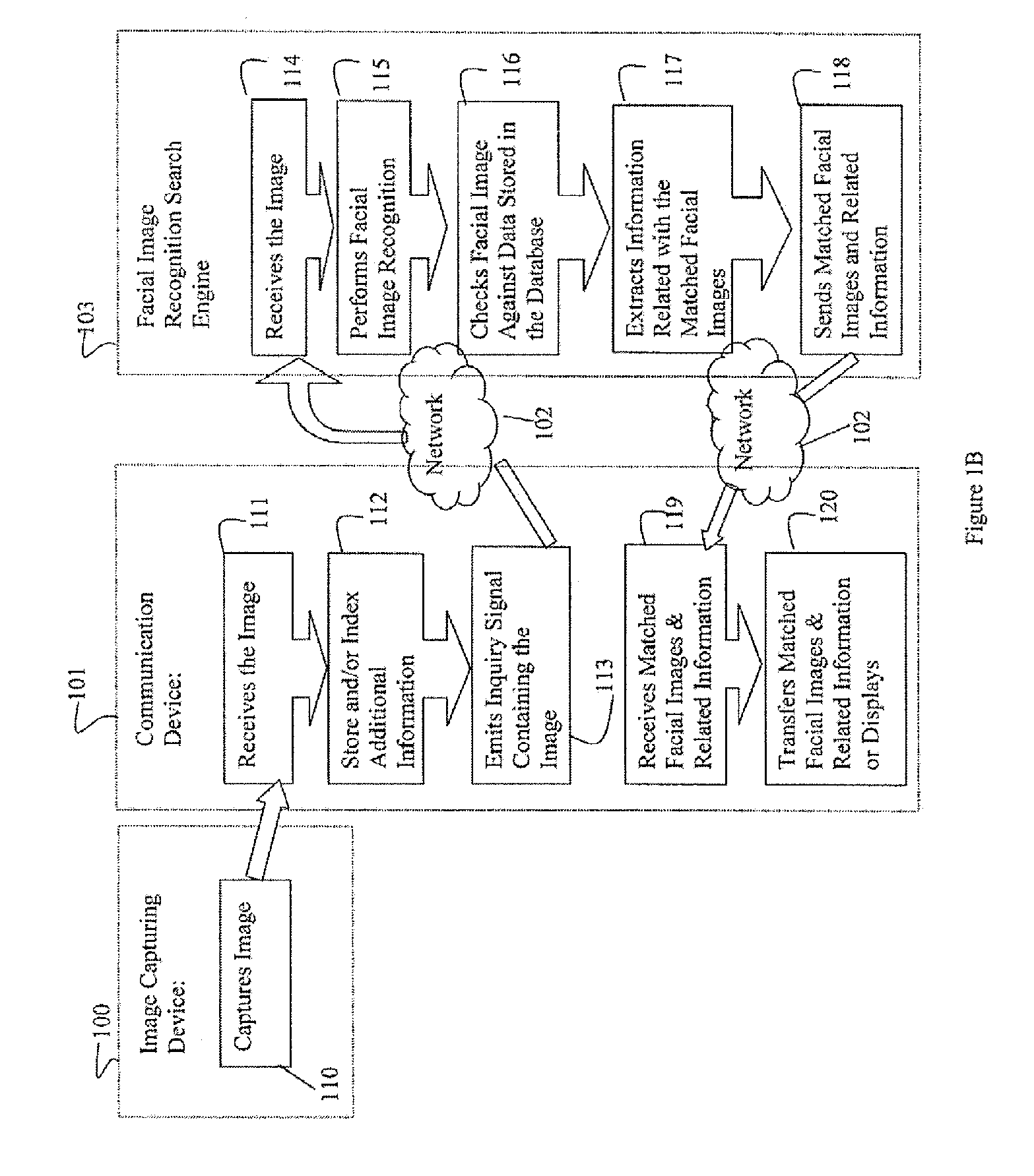
Photo Automatic Linking System and method for accessing, linking, and visualizing "key-face" and/or multiple similar facial images along with associated electronic data via a facial image recognition search engine
ActiveUS20070172155A1Quick searchEnhanced and improved organization, classification, and fast sorts and retrievalDigital data information retrievalCharacter and pattern recognitionHealth professionalsWeb crawler
The present invention provides a system and method for input of images containing faces for accessing, linking, and or visualizing multiple similar facial images and associated electronic data for innovative new on-line commercialization, medical and training uses. The system uses various image capturing devices and communication devices to capture images and enter them into a facial image recognition search engine. Embedded facial image recognition techniques within the image recognition search engine extract facial images and encode the extracted facial images in a computer readable format. The processed facial images are then entered for comparison into at least one database populated with facial images and associated information. Once the newly captured facial images are matched with similar “best-fit match” facial images in the facial image recognition search engine's database, the “best-fit” matching images and each image's associated information are returned to the user. Additionally, the newly captured facial image can be automatically linked to the “best-fit” matching facial images, along with comparisons calculated, and / or visualized. Key new use innovations of the system include but are not limited to: input of user selected facial images for use finding multiple similar celebrity look-a-likes, with automatic linking that return the look-a-like celebrities' similar images, associated electronic information, and convenient opportunities to purchase fashion, jewelry, products and services to better mimic your celebrity look-a-likes; health monitoring and diagnostic use by conveniently organizing and superimposing periodically captured patient images for health professionals to view progress of patients; entirely new classes of semi-transparent superimposed training your face to mimic other similar faces, such as mimic celebrity look-a-like cosmetic applications, and or facial expressions; intuitive automatic linking of similar facial images for enhanced information technology in the context of enhanced and improved organization, classification, and fast retrieval objects and advantages; and an improved method of facial image based indexing and retrieval of information from the web-crawler or spider searched Web, USENET, and other resources to provide new types of intuitive easy to use searching, and / or combined use with current key-word searching for optimized searching.
Owner:VR REHAB INC +2
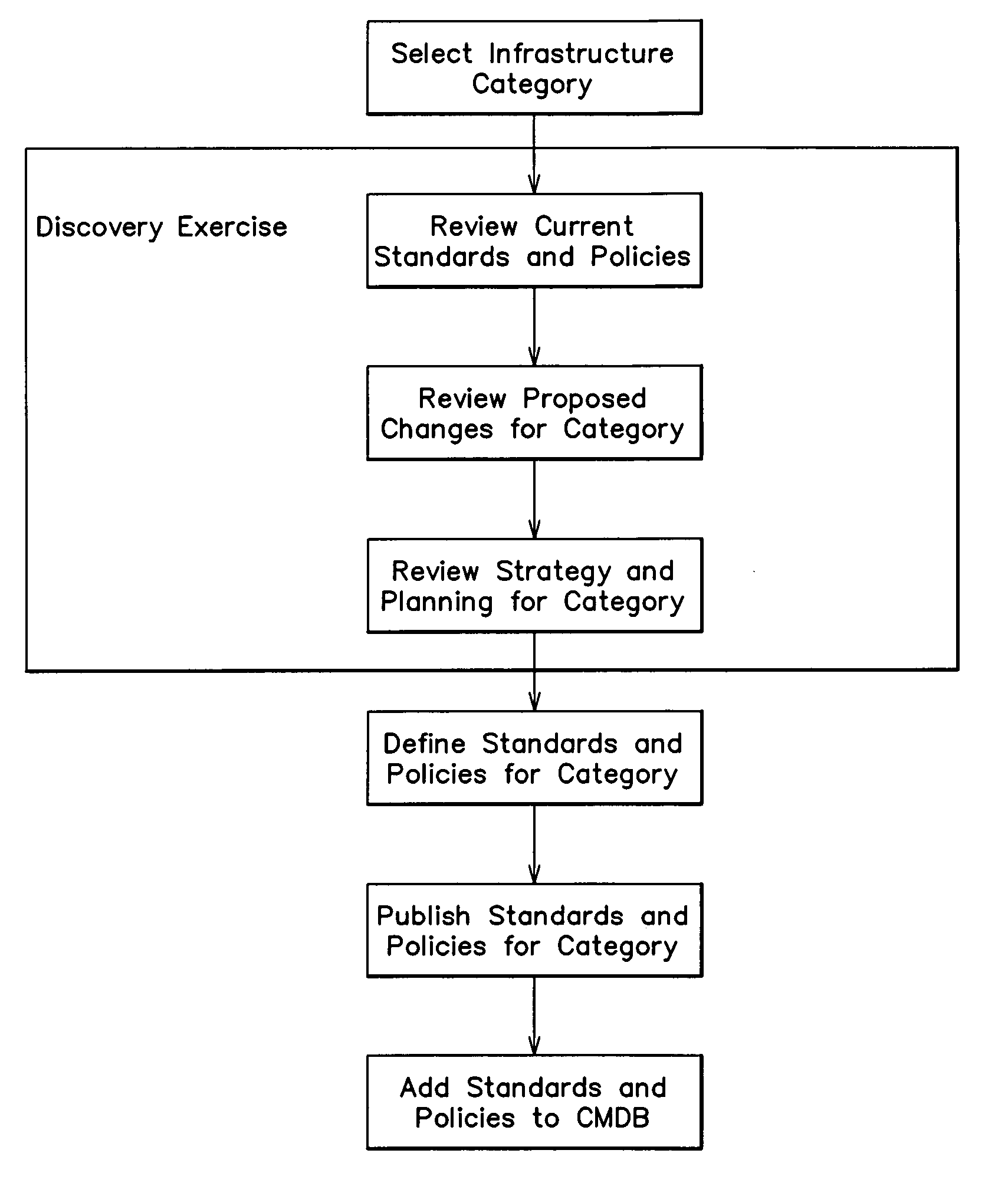
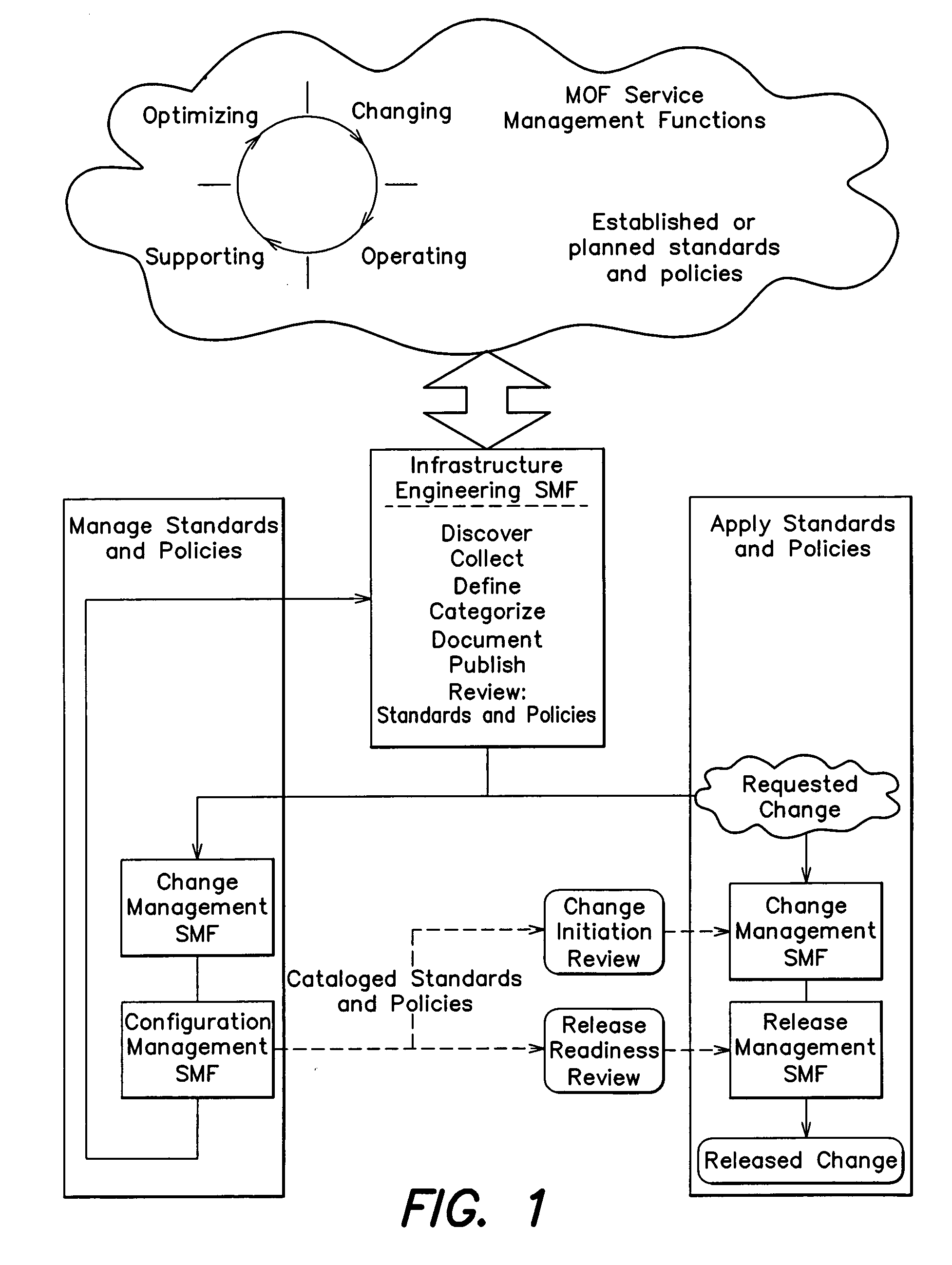
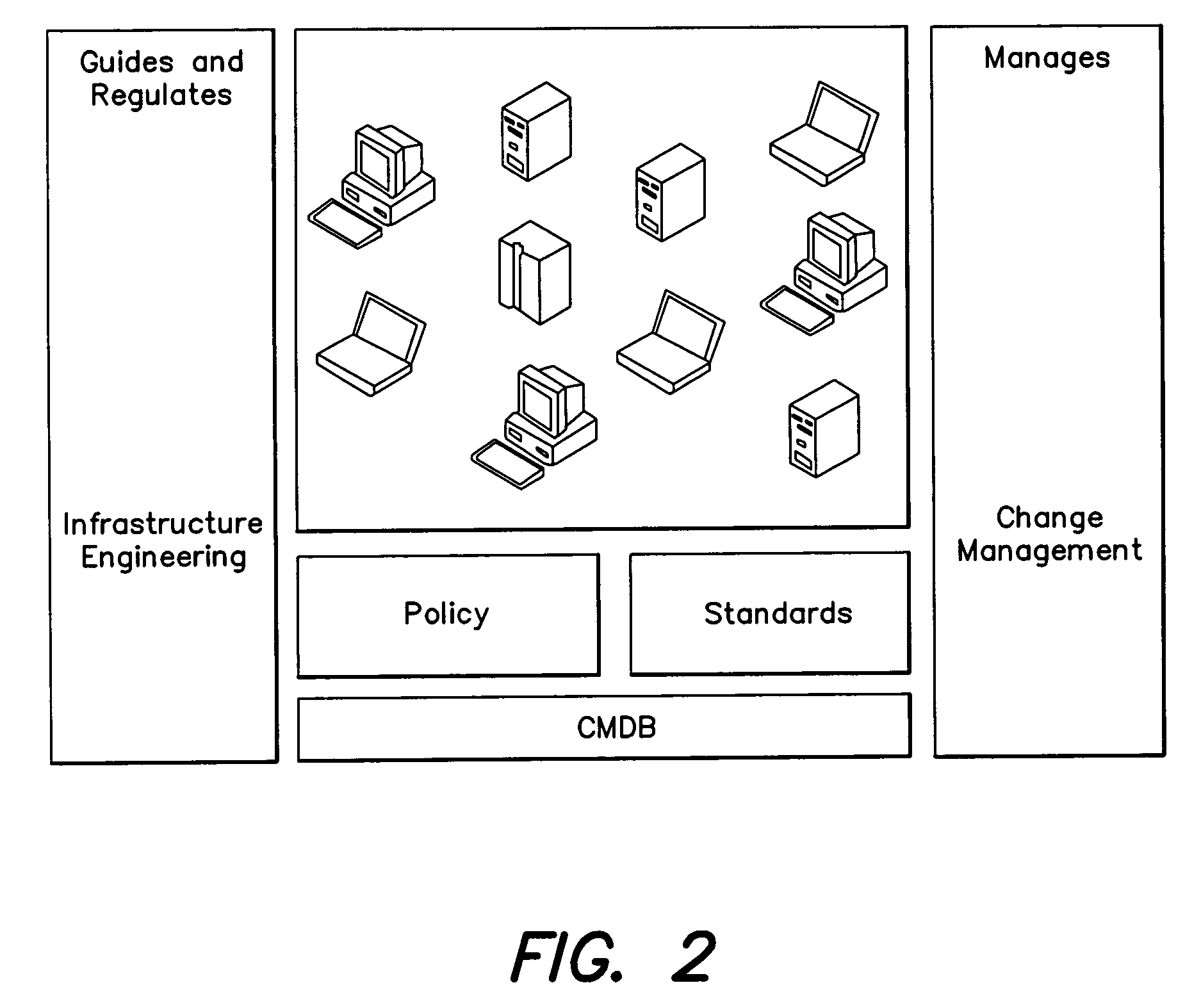
Methods for managing standards
One embodiment is directed to a method of instructing at least one operator in a best practices implementation of a standards facility for managing at least one standard in an information technology (IT) environment comprising a plurality of standards to be managed, the IT environment being managed in accordance with at least some aspects of the Microsoft Operations Framework (MOF), the at least some aspects of the MOF comprising a change management service management function (SMF) that documents, assesses the impact of, approves, schedules and reviews changes in the IT environment and a configuration management SMF that identifies and documents components of the IT environment and relationships between them. The method comprises an act of: (A) instructing the at least one operator to treat the at least one standard as a configuration item so that changes to the at least one standard are managed in accordance with the change management SMF and so that the at least one standard is tracked in accordance with the configuration management SMF.
Owner:MICROSOFT TECH LICENSING LLC
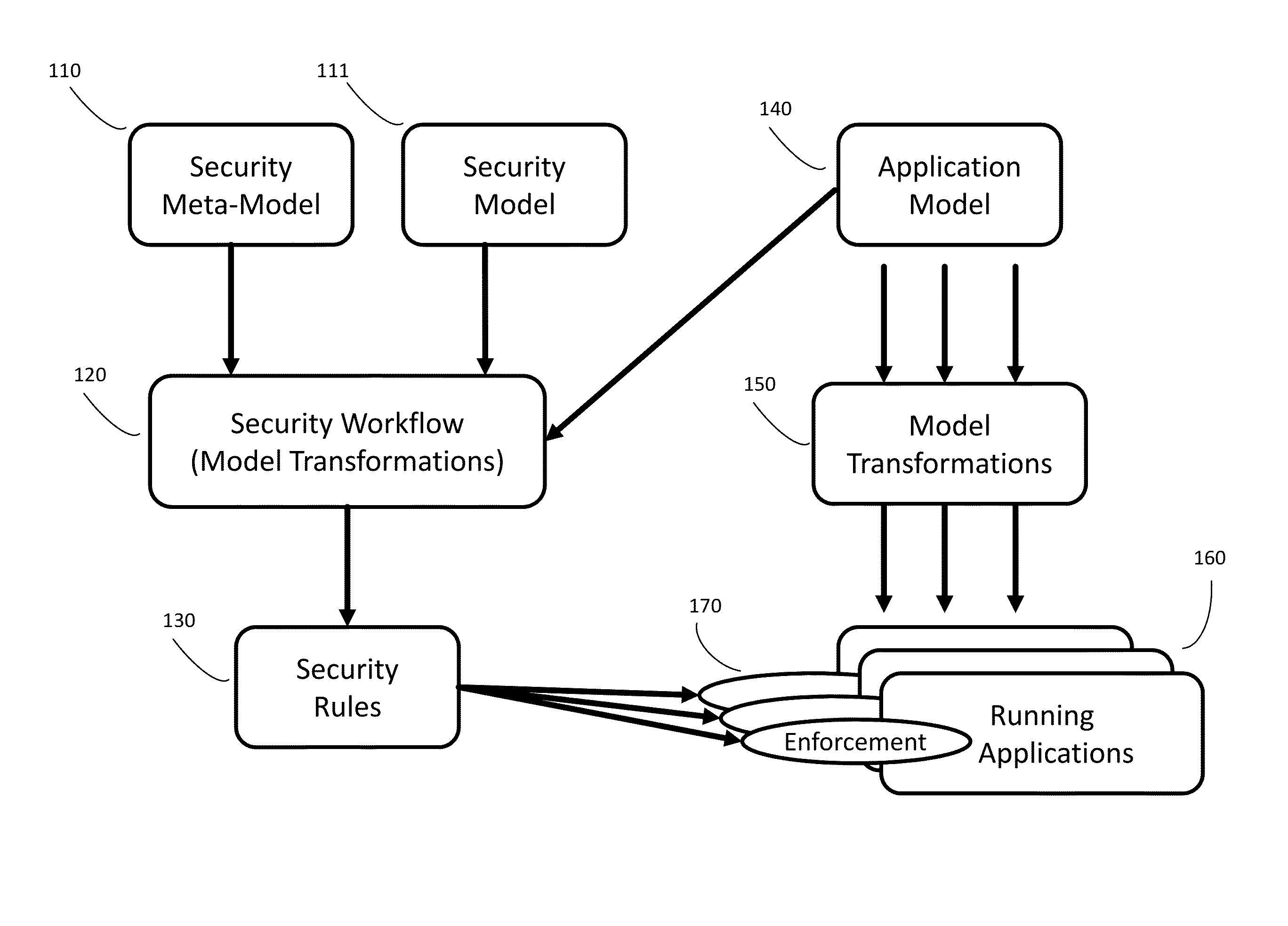
Automated and adaptive model-driven security system and method for operating the same
ActiveUS20150269383A1Platform integrity maintainanceTransmissionSecurity systemReliability engineering
A system and method for managing implementation of policies in an information technologies system receives at least one policy function, at least one refinement template and at least one available policy function from the at least one memory, receives a policy input indicating a high-level policy for the IT system where the policy input is compliant with the at least one policy function and is received in a format that is not machine-enforceable at an enforcement entity of the IT system, based on the received policy input, automatically or semi-automatically generates a machine-enforceable rule and / or configuration by filling the at least one refinement template, where the machine-enforceable rule and / or configuration includes the at least one available policy function and being compliant with the received policy input, and distributes the machine-enforceable rule and / or configuration to the at least one memory of the IT system or another at least one memory to thereby enable implementation of the policies.
Owner:OBJECT SECURITY
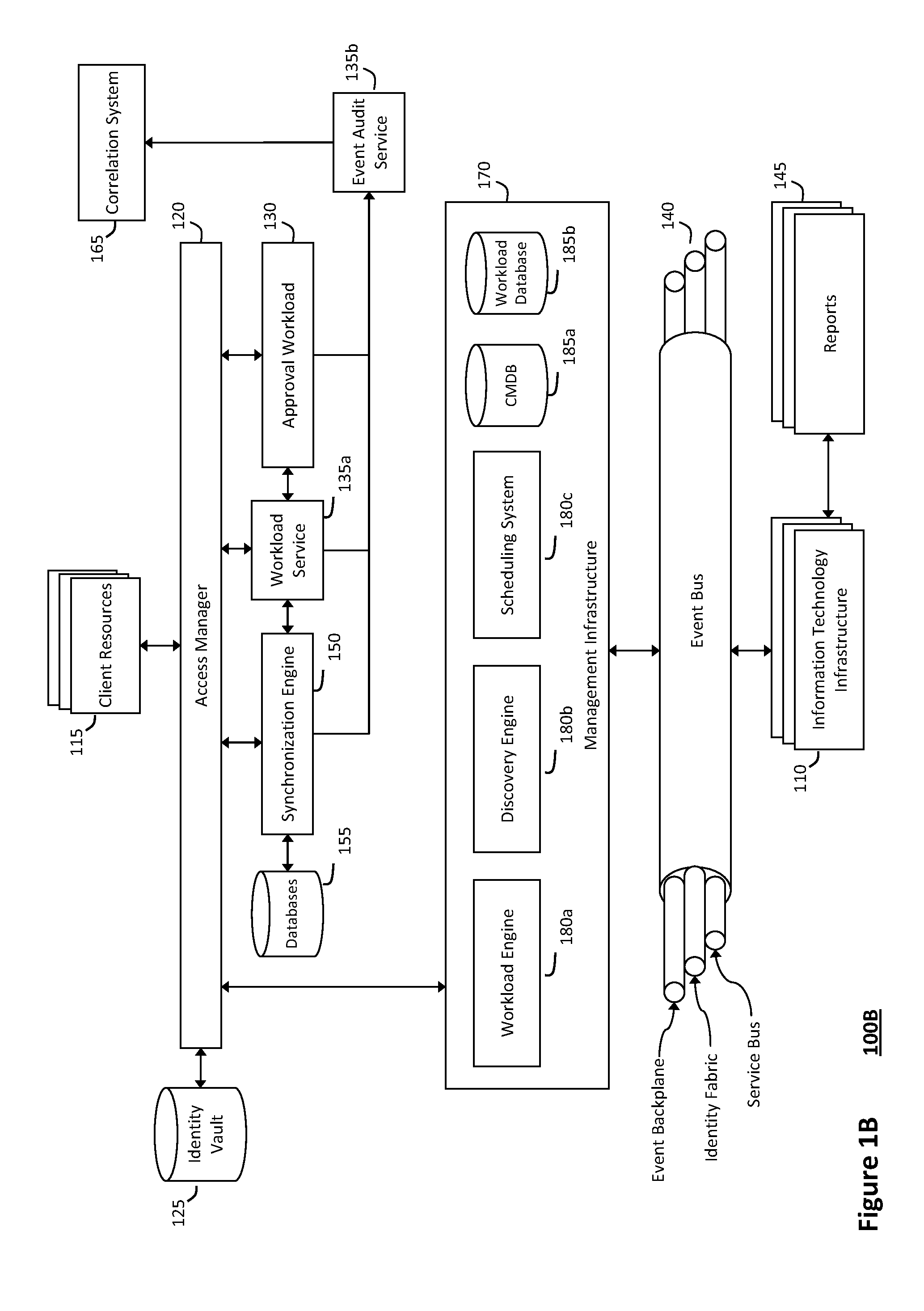
System and method for providing annotated service blueprints in an intelligent workload management system
InactiveUS20110126207A1Free computational resourceAgile and flexible managementMultiprogramming arrangementsDigital data authenticationService blueprintService-oriented architecture
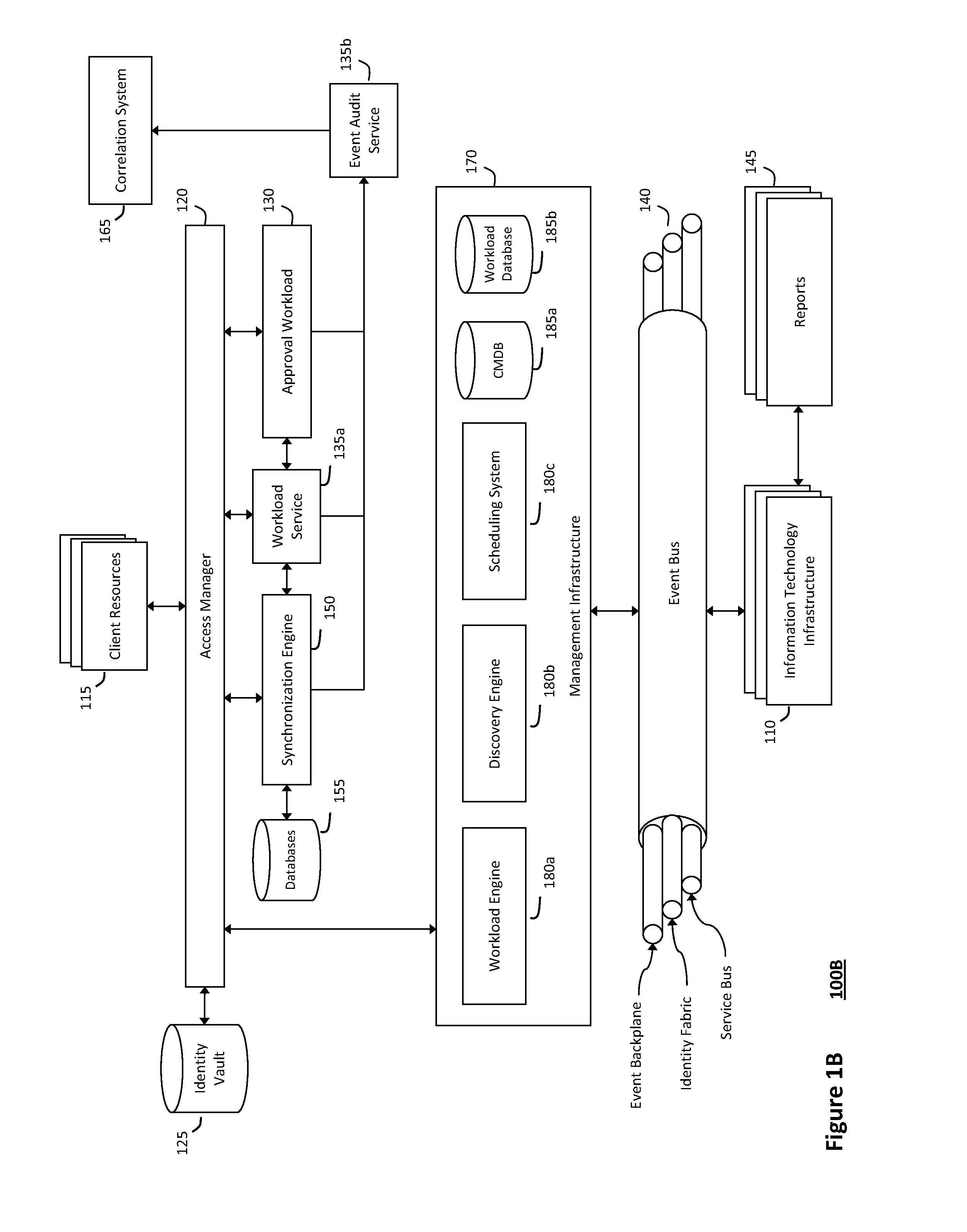
The system and method described herein for providing annotated service blueprints in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for creating annotated service blueprints to provision and manage tessellated services distributed within an information technology infrastructure. For example, in response to a request to provision a service, a service blueprint describing one or more virtual machines may be created. The service blueprint may then be annotated to apply various parameters to the virtual machines, and the annotated service blueprint may then be instantiated to orchestrate the virtual machines with the one or more parameters and deploy the orchestrated virtual machines on information technology resources allocated to host the requested service, thereby provisioning the requested service.
Owner:MICRO FOCUS SOFTWARE INC
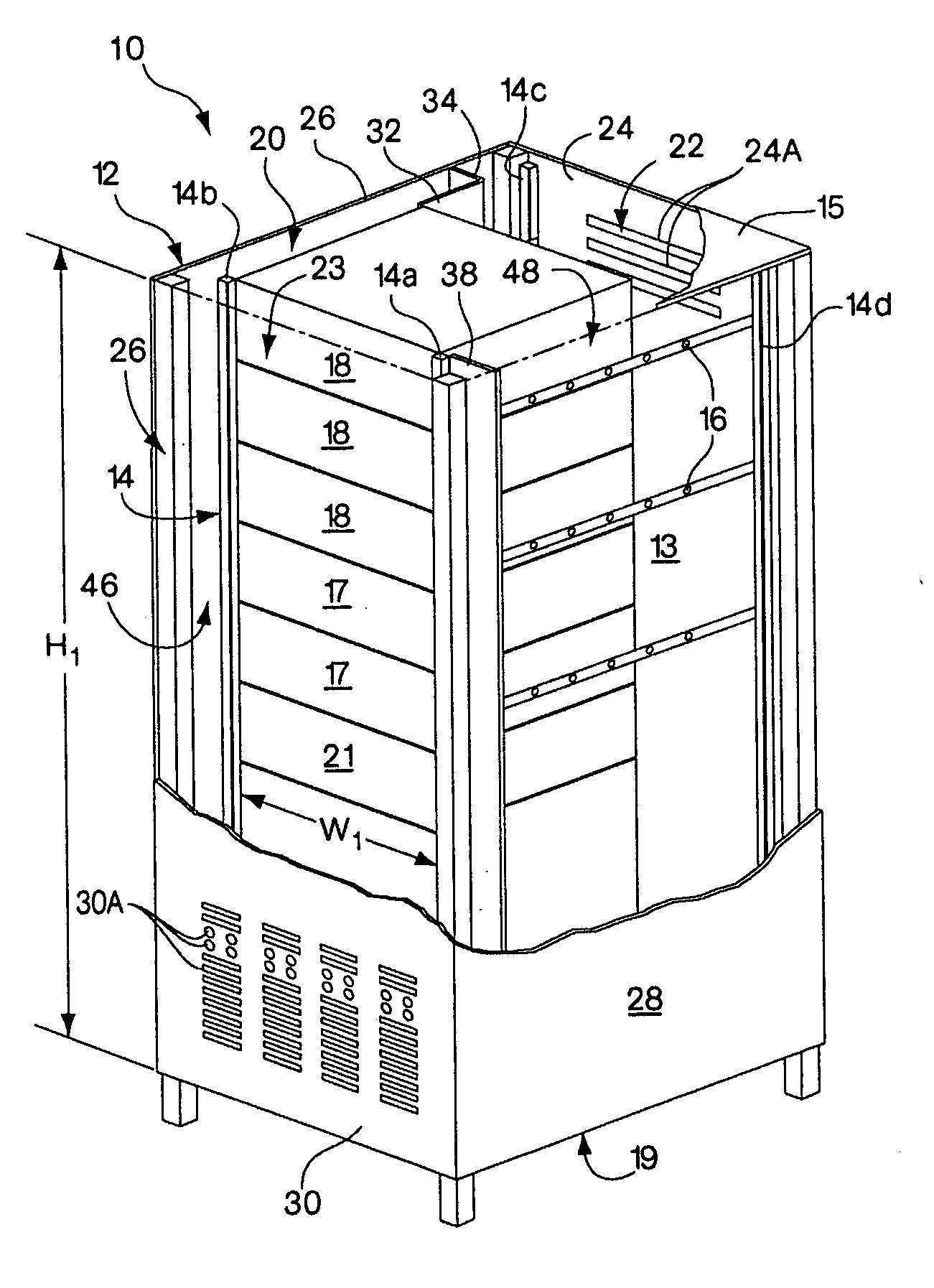
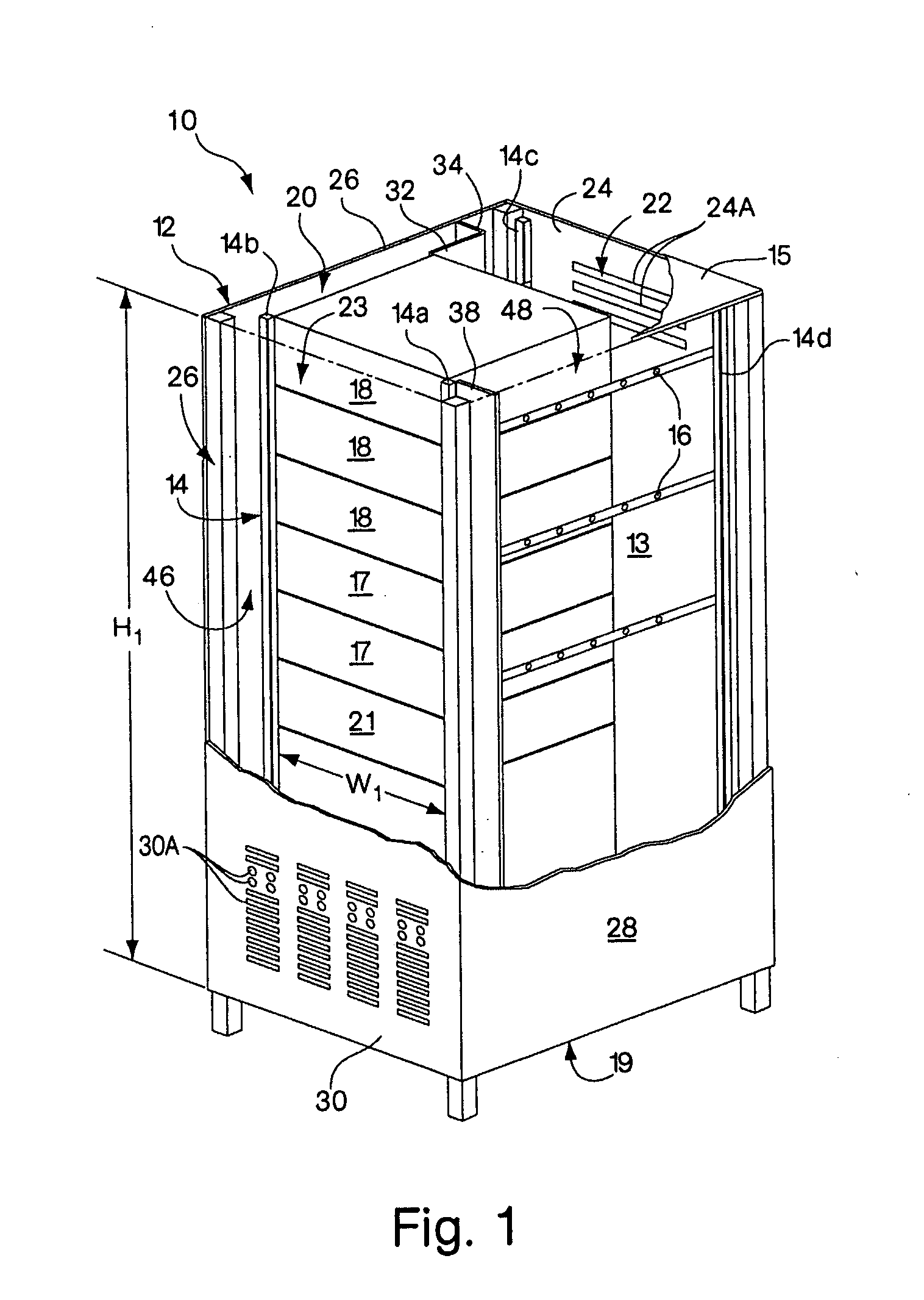
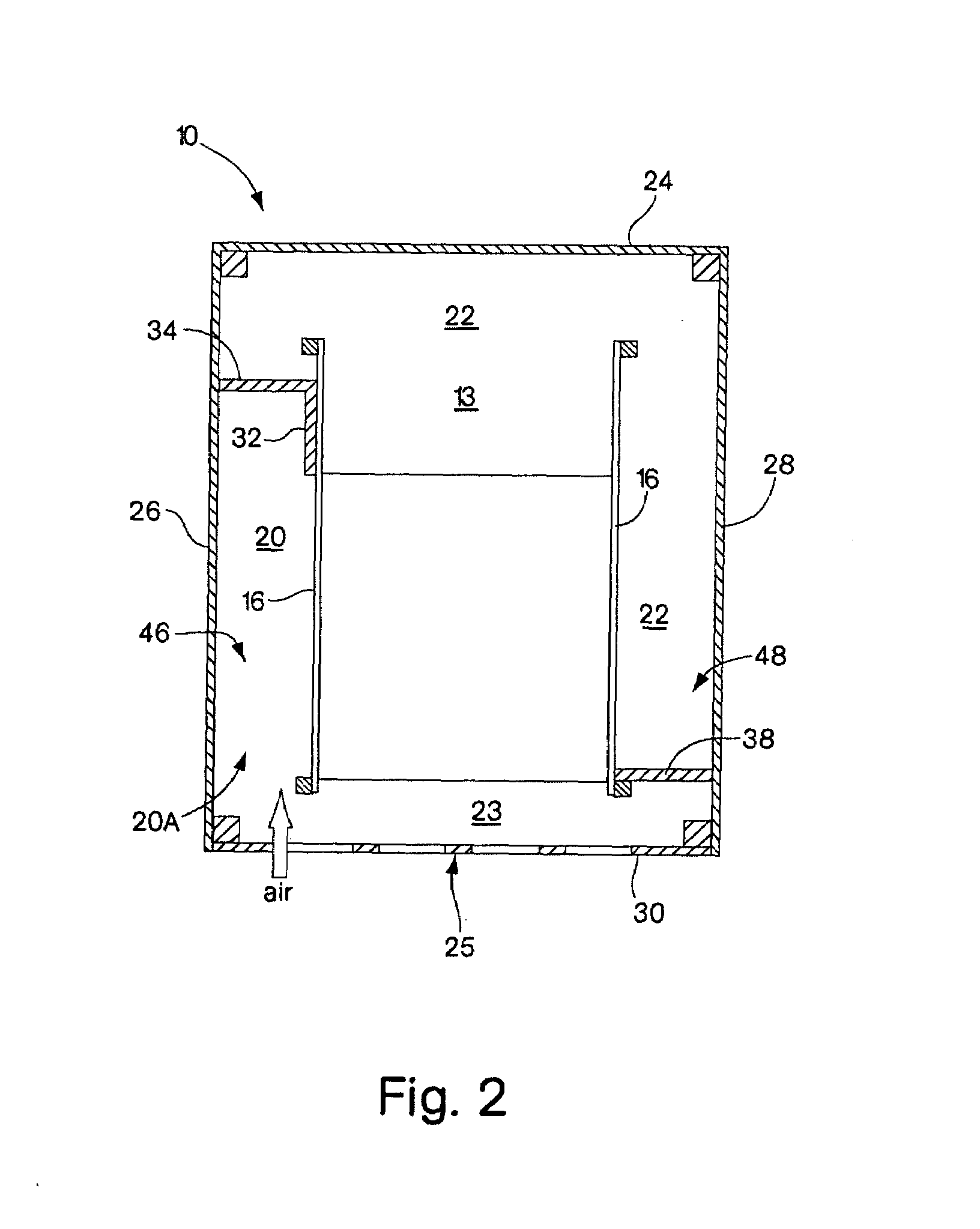
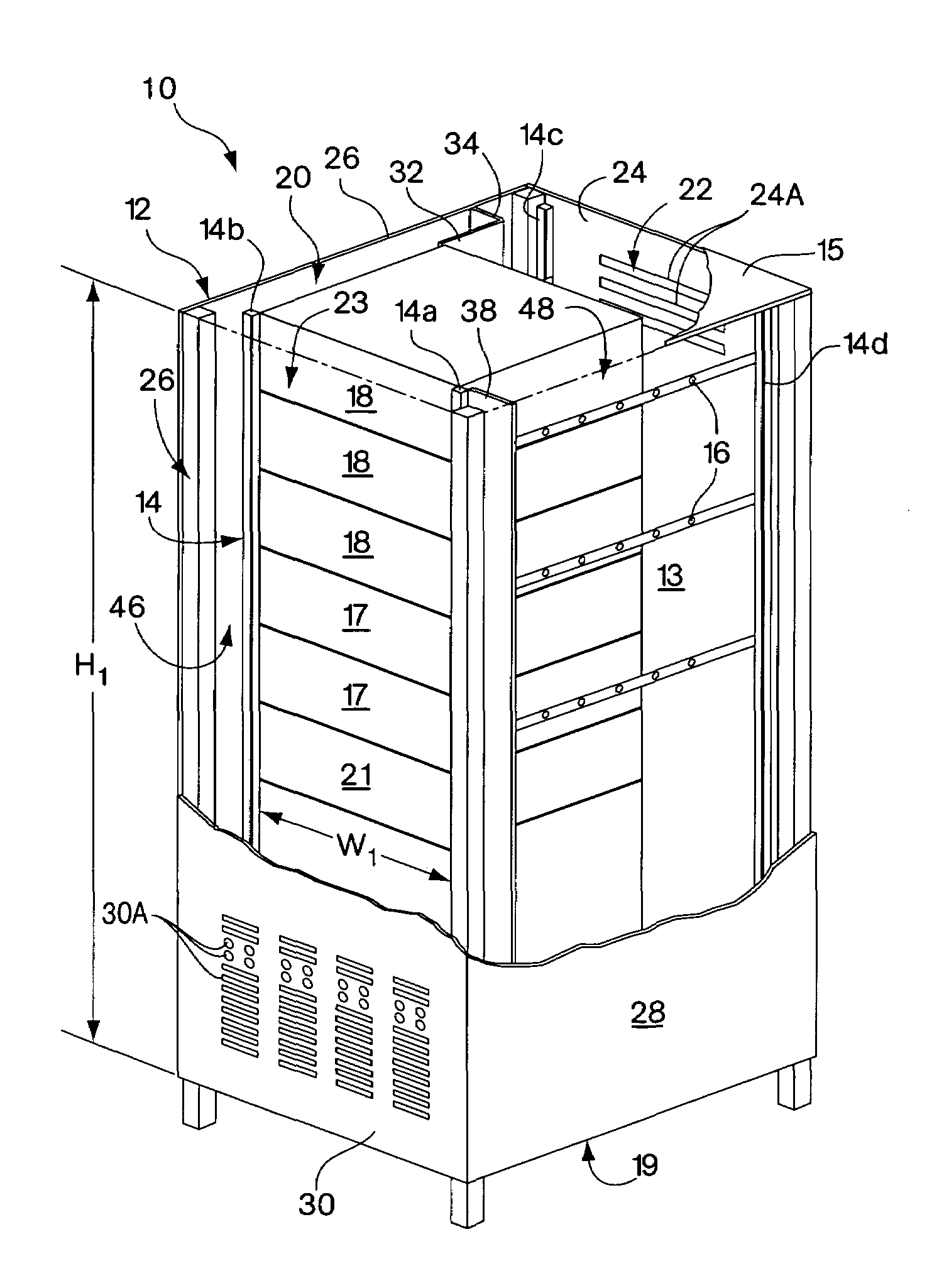
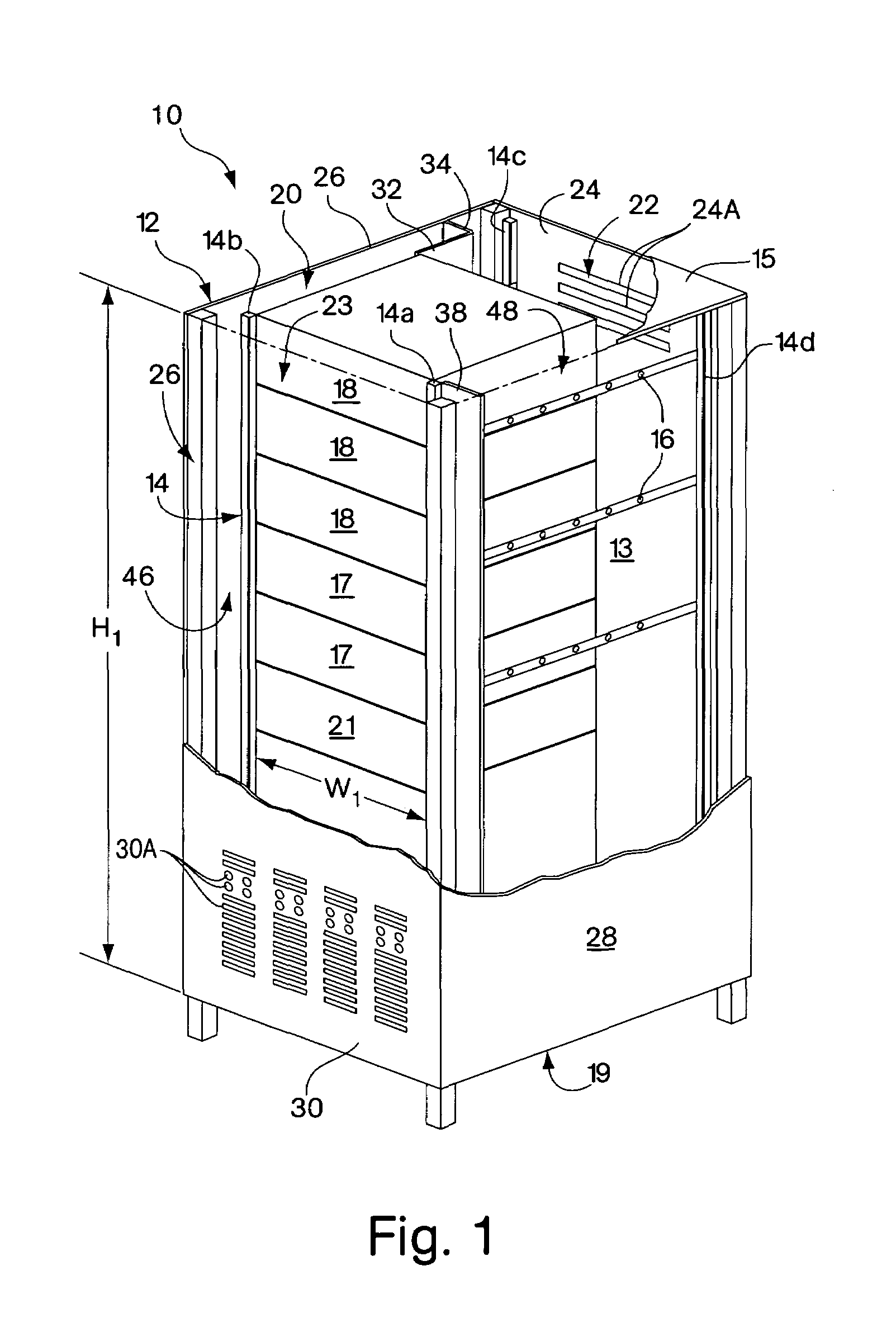
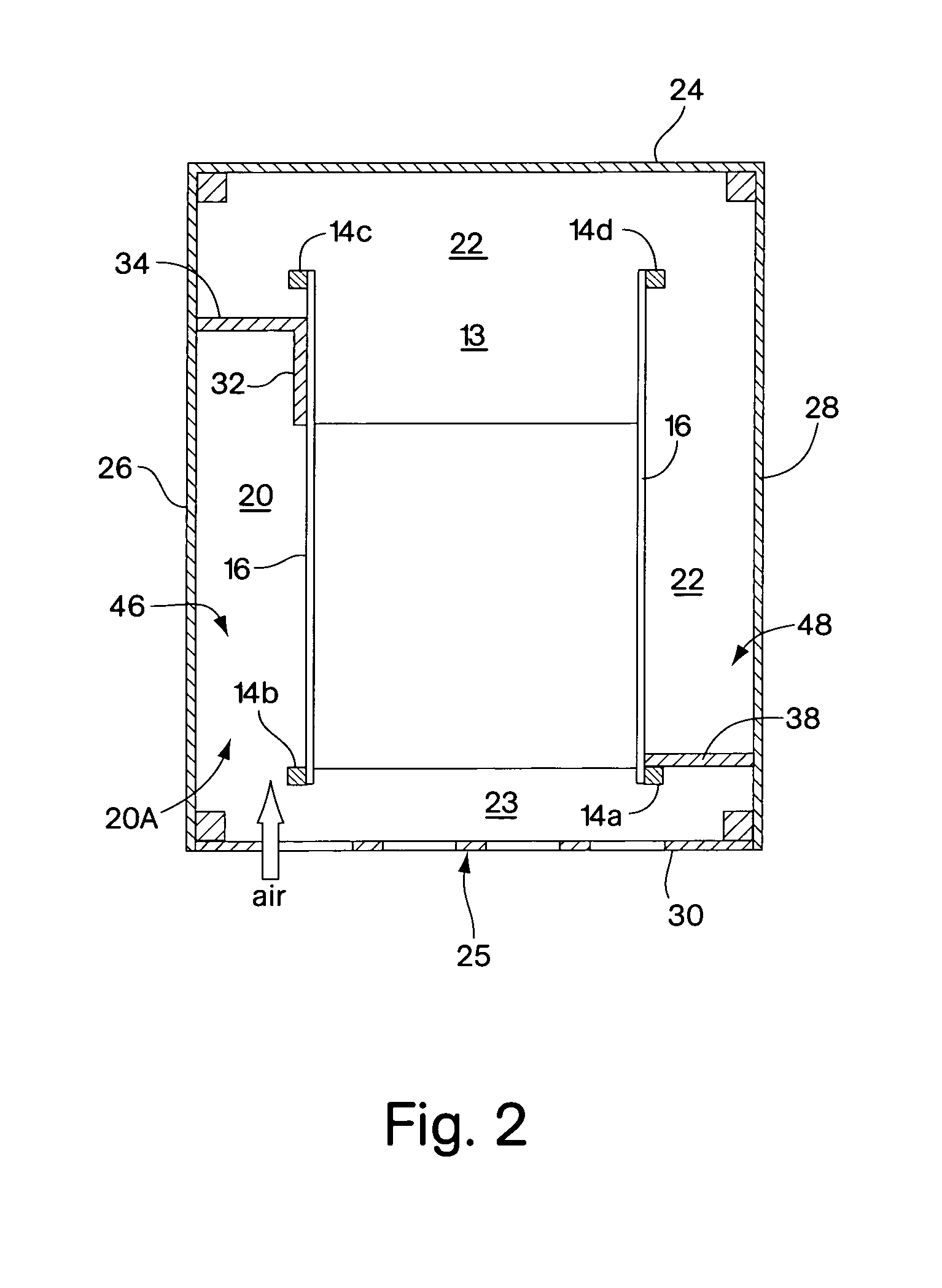
Rack enclosure
ActiveUS7112131B2Avoid overall overheatingPrevent air lossSemiconductor/solid-state device detailsSolid-state devicesData centerTelecommunications equipment
An enclosure is provided for housing electronic equipment that accommodates the different cooling and ventilating requirements of different types of equipment. The enclosure is constructed and arranged to support cooling airflow in a front-to-back configuration through the enclosure and in a side-to-side configuration from one side to an opposite side of the enclosure. The enclosure can thereby provide within a single enclosure means cooling air for components using front-to-back airflow for cooling, such as information technology (IT) equipment, and for components using side-to-side airflow, such as certain types of telecommunications equipment. The enclosure can thereby support a mix of IT and telecommunications equipment, providing flexibility and adaptability in network room and data center configuration. The enclosure is further configured to separate intake air used by equipment for cooling from exhaust air vented by equipment into its interior during operation. As a result, the enclosure promotes sufficient equipment cooling and prevents / minimizes equipment overheating.
Owner:AMERICA POWER CONVERSION CORP
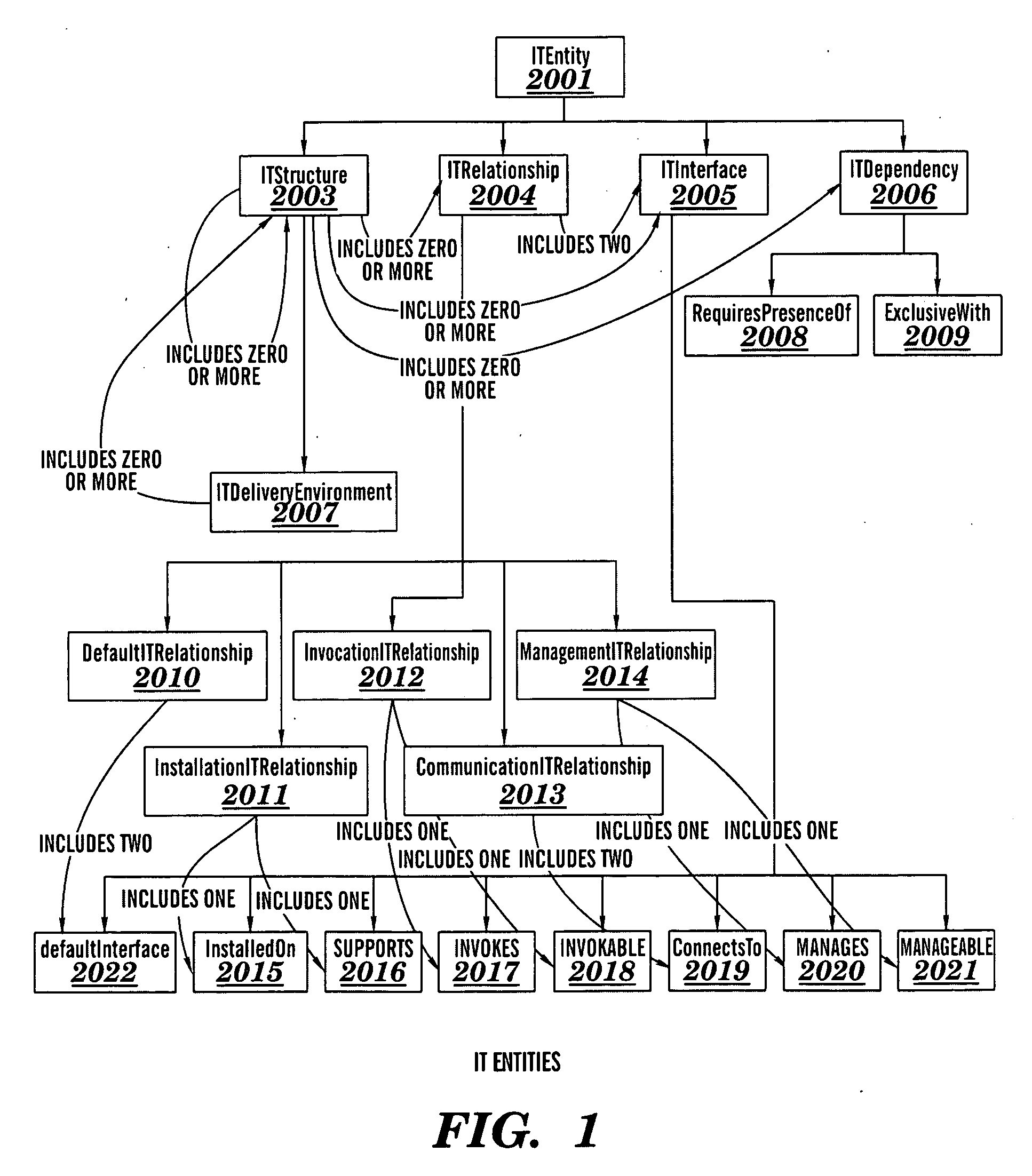
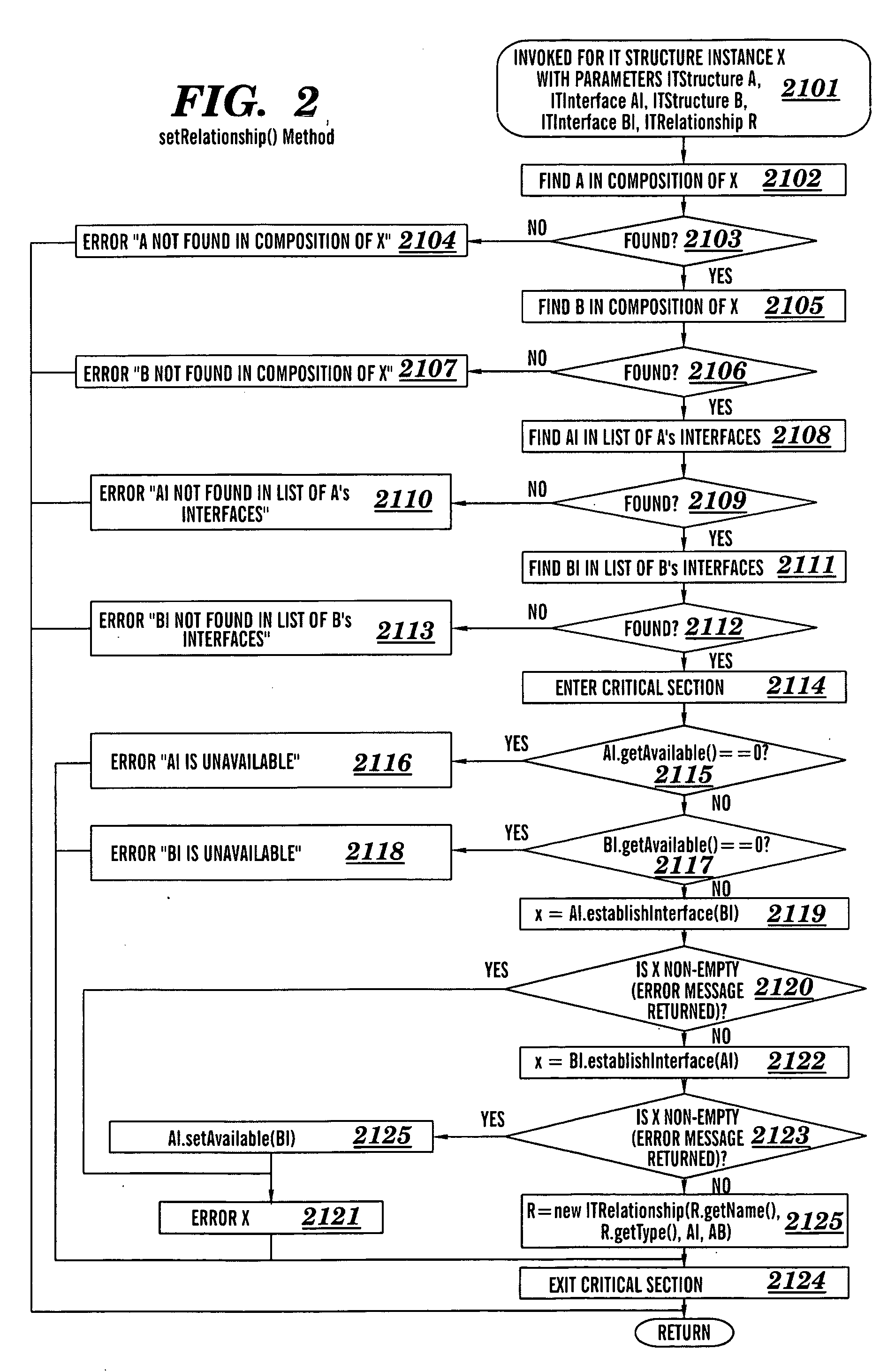
Optimization of aspects of information technology structures
InactiveUS20090204693A1Low costFinanceMultiprogramming arrangementsComputerized systemControl parameters
A computer system and computer program product for optimizing an aspect of an Information Technology (IT) structure of an IT system. The aspect of the IT structure is optimized with respect to at least one control parameter. The IT structure includes a plurality of elements. Each element independently is a hardware element, a software element, or a combination of a hardware element and a software element. Each control parameter has a value that is specific to each element of the IT structure.
Owner:KYNDRYL INC
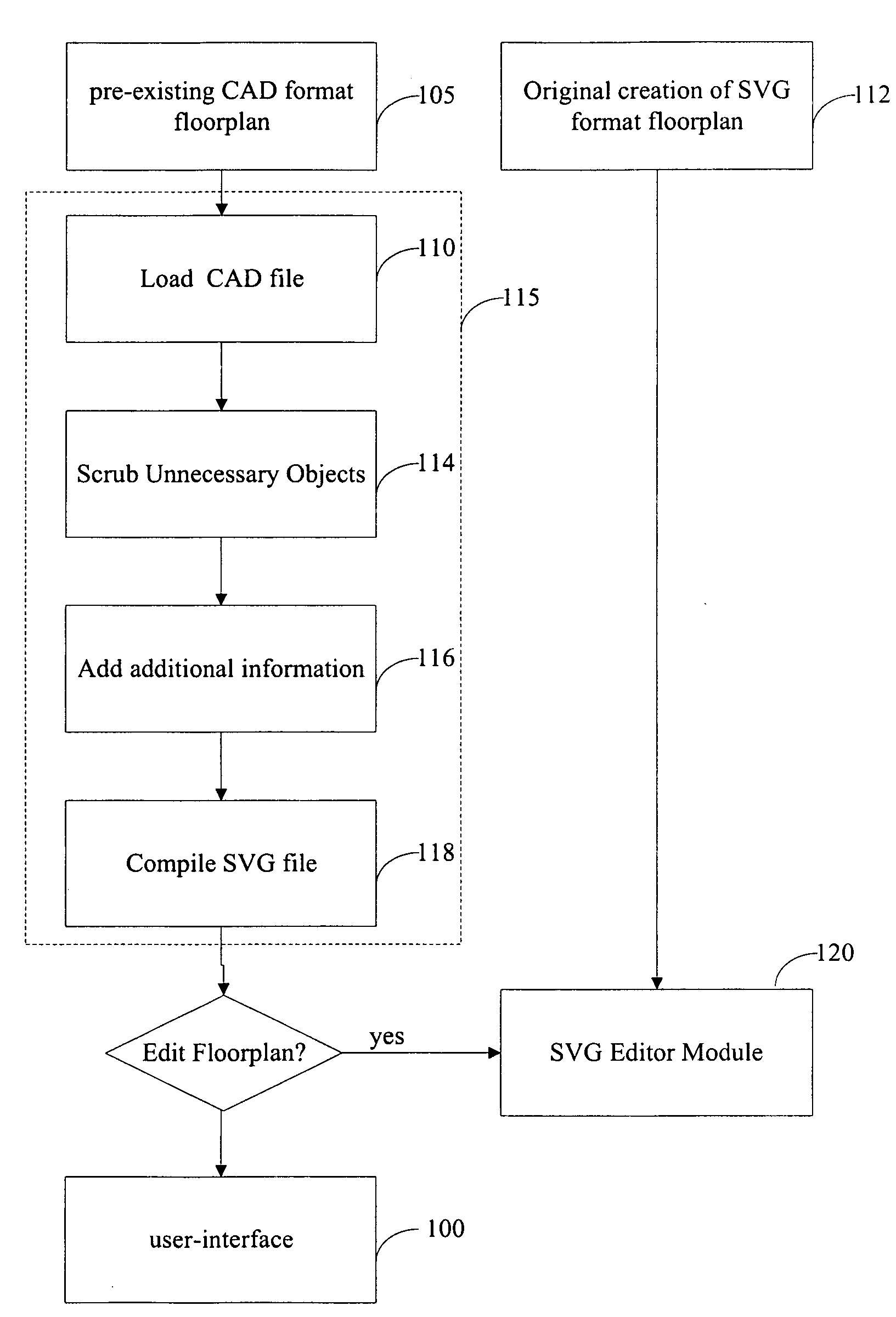
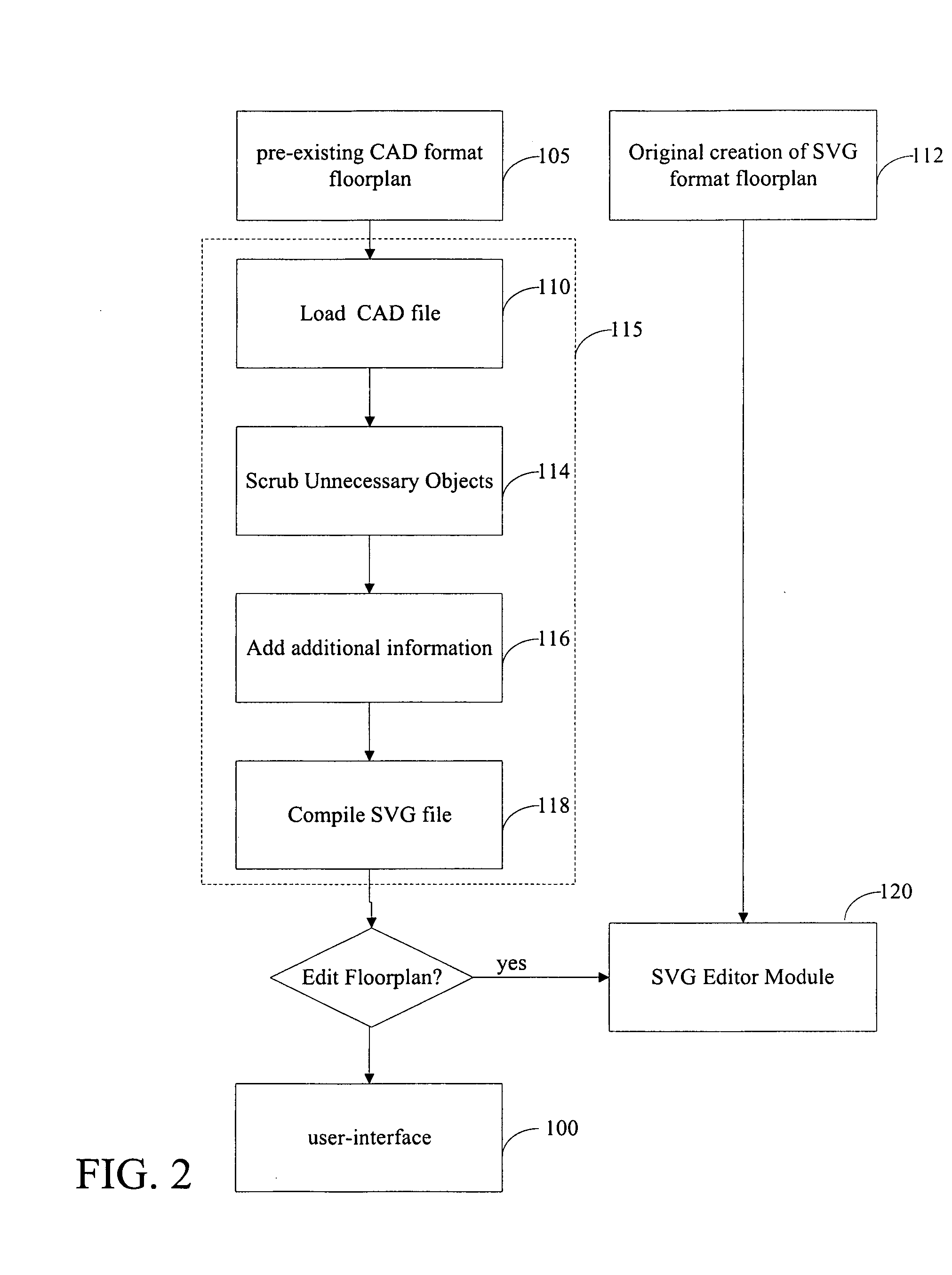
Office management solution
InactiveUS20080183483A1Special trainingGeometric CADSpecial data processing applicationsDrag and dropRelational database
A spatial database interface for generally managing assets in a graphical user environment is disclosed, in the particular context of a CAOM office management software solution for managing office facilities inclusive of office layouts (equipment, furniture, information technology assets and other assets) and basic human resources within a physically-defined office space. The software is a web-based custom map application that links a relational database to an SVG or browser rendering format layout map that shows physical locations and relationships among people, rooms and other assets. It imposes a graphical user interface for point-and-click identification of the assets, reporting and reconfiguration (for “what-if” scenarios), and drag-and-drop manipulation of the assets. The software is resident on a web-enabled server hosted by an application service provider. The assets are associated with asset data stored in a web-enabled database and are linked to corresponding visual icons represented on the layout map by embedded HTML elements such as IFrames. All asset data is stored in the database, and robust searching, analysis and reporting capabilities are provided to employ the data.
Owner:HART MARCIA A
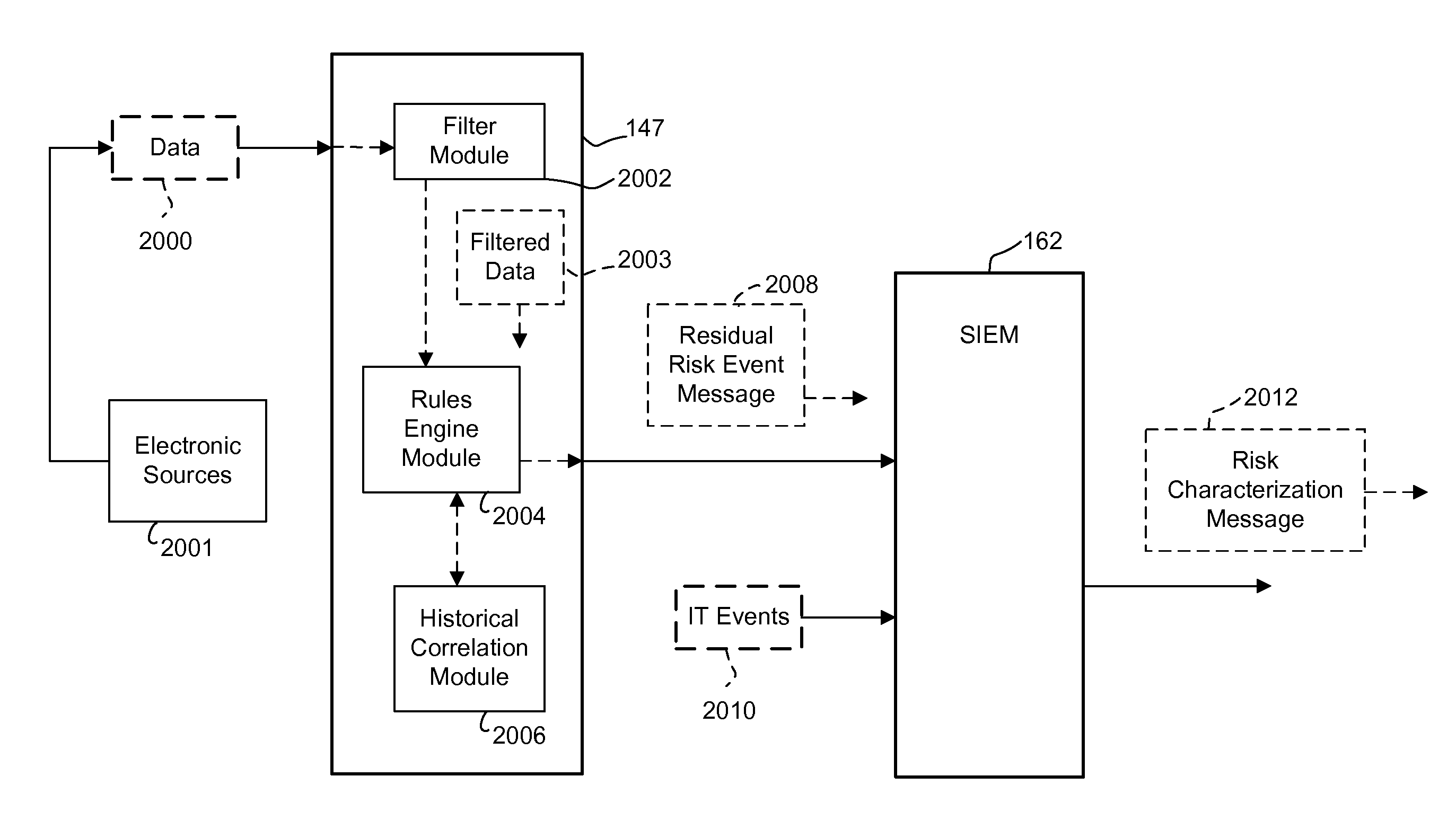
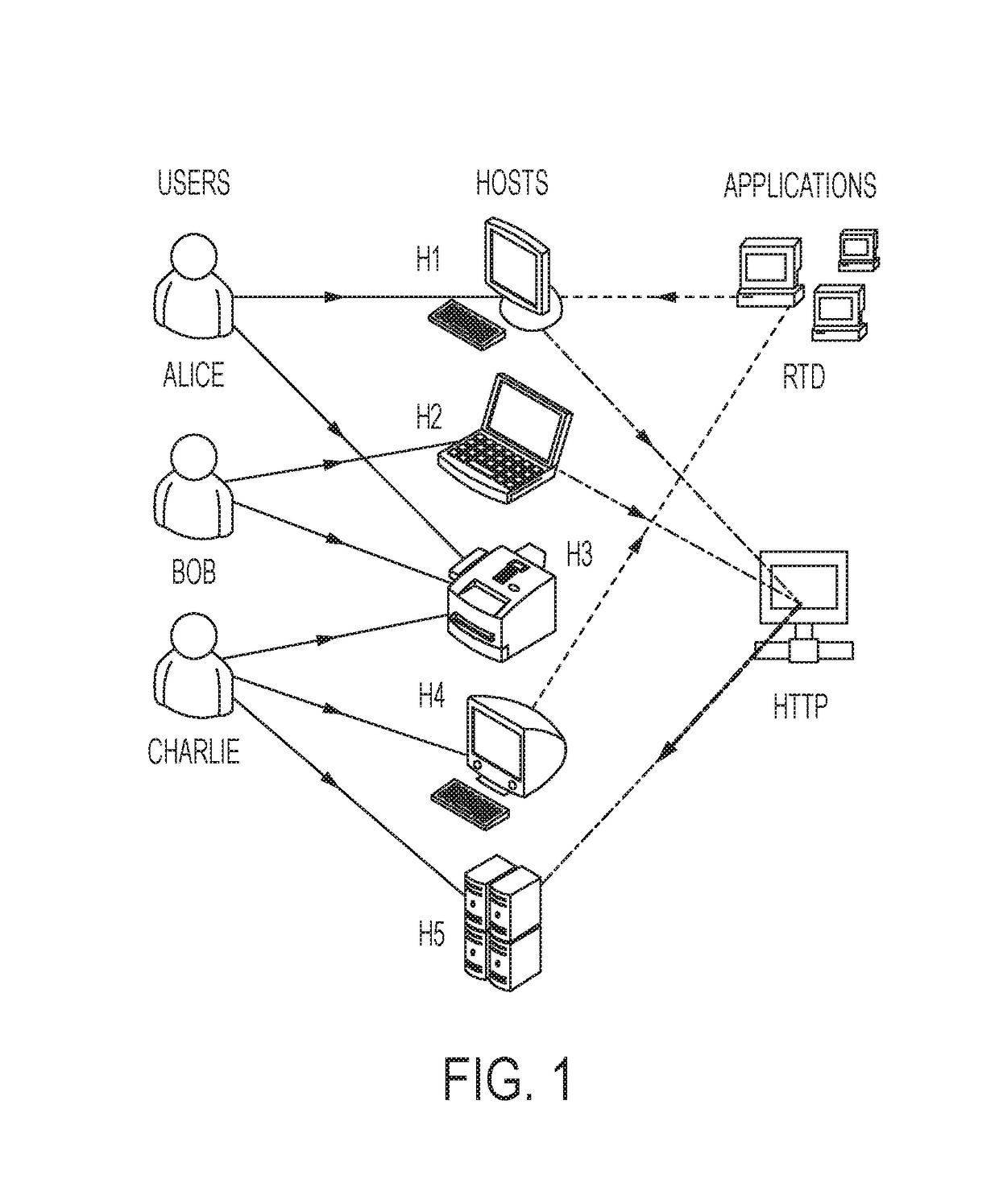
Malicious attack detection and analysis
A system for characterizing malicious activity in an intelligent utility grid system includes a system storage in which to store a database including a plurality of rules. A collector is operable to collect and store in the system storage information-technology (IT) data including IT-related activity from the intelligent grid system. A complex event processing (CEP) bus is operable to receive non-IT data including location-specific event data from a plurality of electronic sources, the CEP bus further operable to disregard the non-IT data failing to meet a predetermined level of relevance to one of a plurality of risk-related events. A processor is operable to apply the plurality of rules to the relevant non-IT data to: associate an undesired event with reference to the IT-related activity; and determine a probability that the undesired event is indicative of malicious activity. The processor further applies a risk characterization to the undesired event based on the probability and the IT-related activity.
Owner:ACCENTURE GLOBAL SERVICES LTD
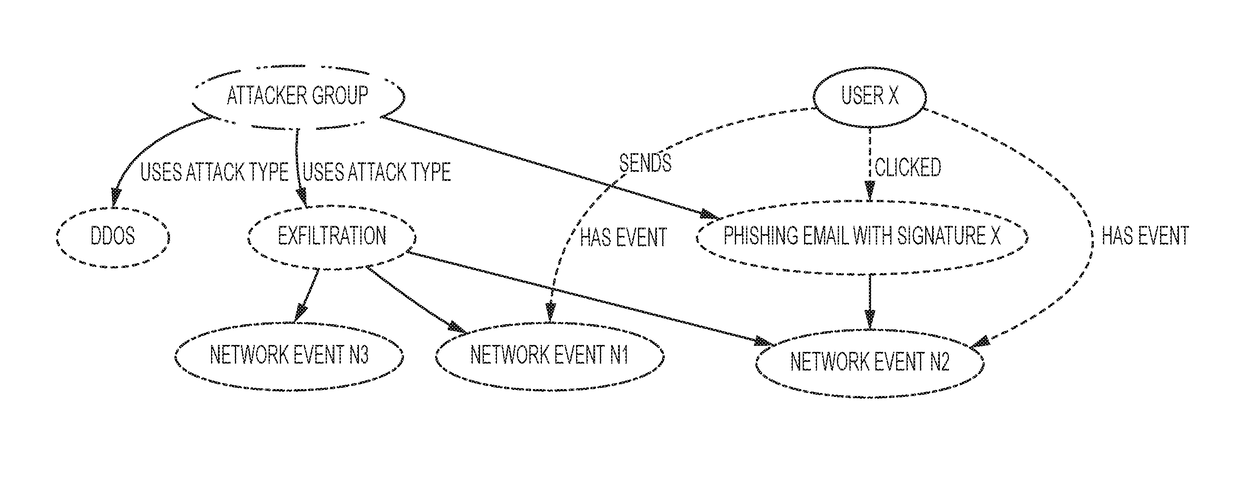
System and methods for automated detection, reasoning and recommendations for resilient cyber systems
ActiveUS20180103052A1Improve applicabilityLarge capacityDigital data information retrievalComputer security arrangementsElastic networkKnowledge extraction
A method for securing an IT (information technology) system using a set of methods for knowledge extraction, event detection, risk estimation and explanation for ranking cyber-alerts which includes a method to explain the relationship (or an attack pathway) from an entity (user or host) and an event context to another entity (a high-value resource) and an event context (attack or service failure).
Owner:BATTELLE MEMORIAL INST
System and method for securing an enterprise computing environment
InactiveUS20200137097A1Process safetyKeep Content SafeMultiprogramming arrangementsDigital data protectionBusiness enterpriseEnterprise computing
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CISCO TECH INC
System and method for managing information technology models in an intelligent workload management system
ActiveUS20110126047A1Free computational resourceAgile and flexible managementFault responseDigital computer detailsPlanned changeService-oriented architecture
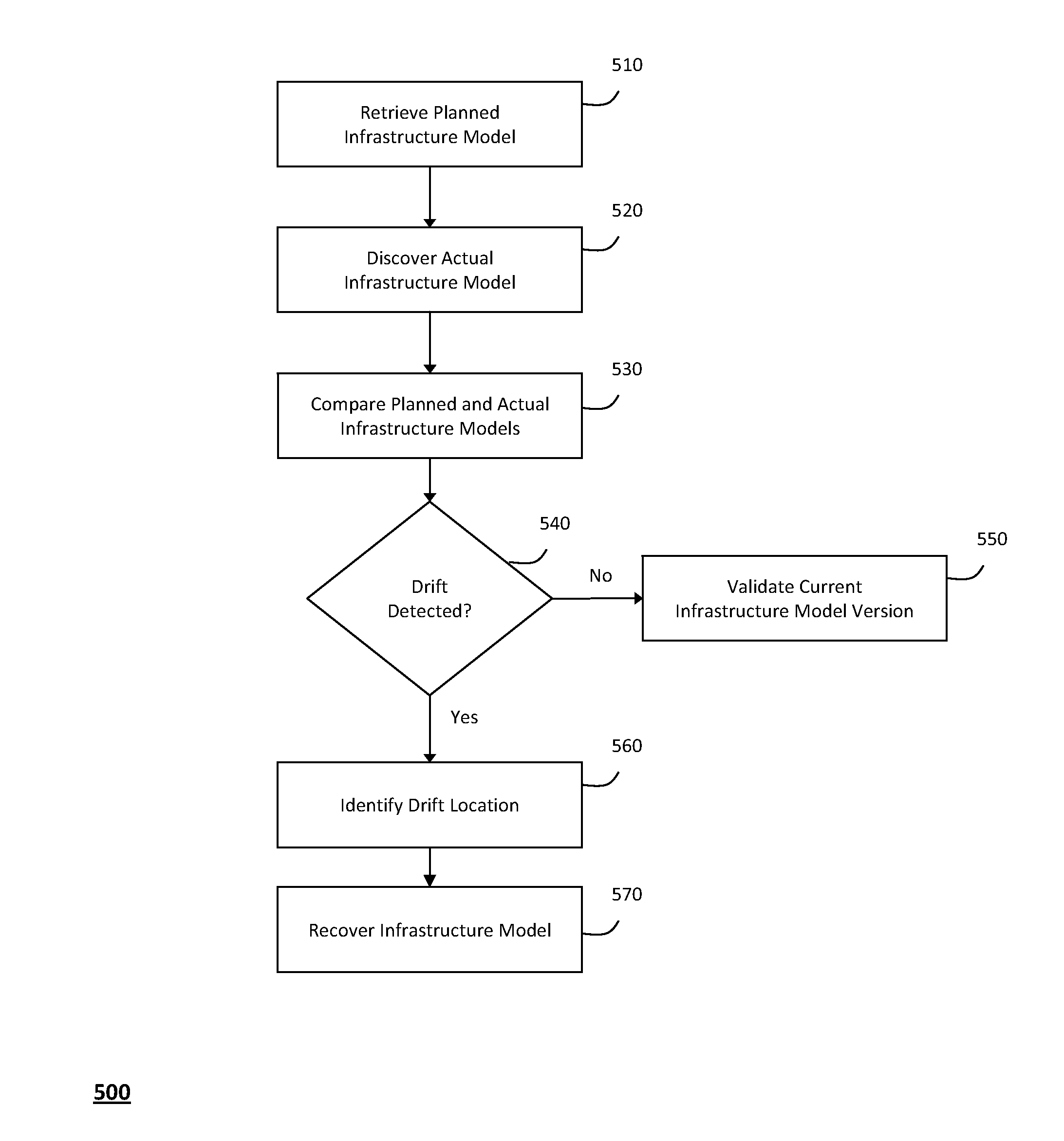
The system and method described herein for managing information technology models in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for managing planned changes and recovery processes for version-controlled snapshots of the information technology models. For example, a discovery engine may enrich models of an infrastructure with identity information obtained from an identity vault and the infrastructure itself, and a management infrastructure may then manage planned changes to the infrastructure model. In particular, the management infrastructure may construct implementation plans that coordinate interaction between managed entities to implement the planned changes, and may further detect drifts between operational states and planned states for the infrastructure models.
Owner:MICRO FOCUS SOFTWARE INC
Managing the computer collection of information in an information technology environment
InactiveUS20090172674A1Error detection/correctionMultiprogramming arrangementsDynamic managementTime frame
The collection of information in an Information Technology environment is dynamically managed. Processing associated with a batch of requests executed to obtain information is adjusted in real-time based on whether responses to the requests executed within an allotted time frame were received. The adjustments may include adjusting the time allotted to execute a batch of requests, adjusting the number of requests in a batch, and / or adjusting the execution priority of the requests within a batch.
Owner:IBM CORP
Methods for managing capacity
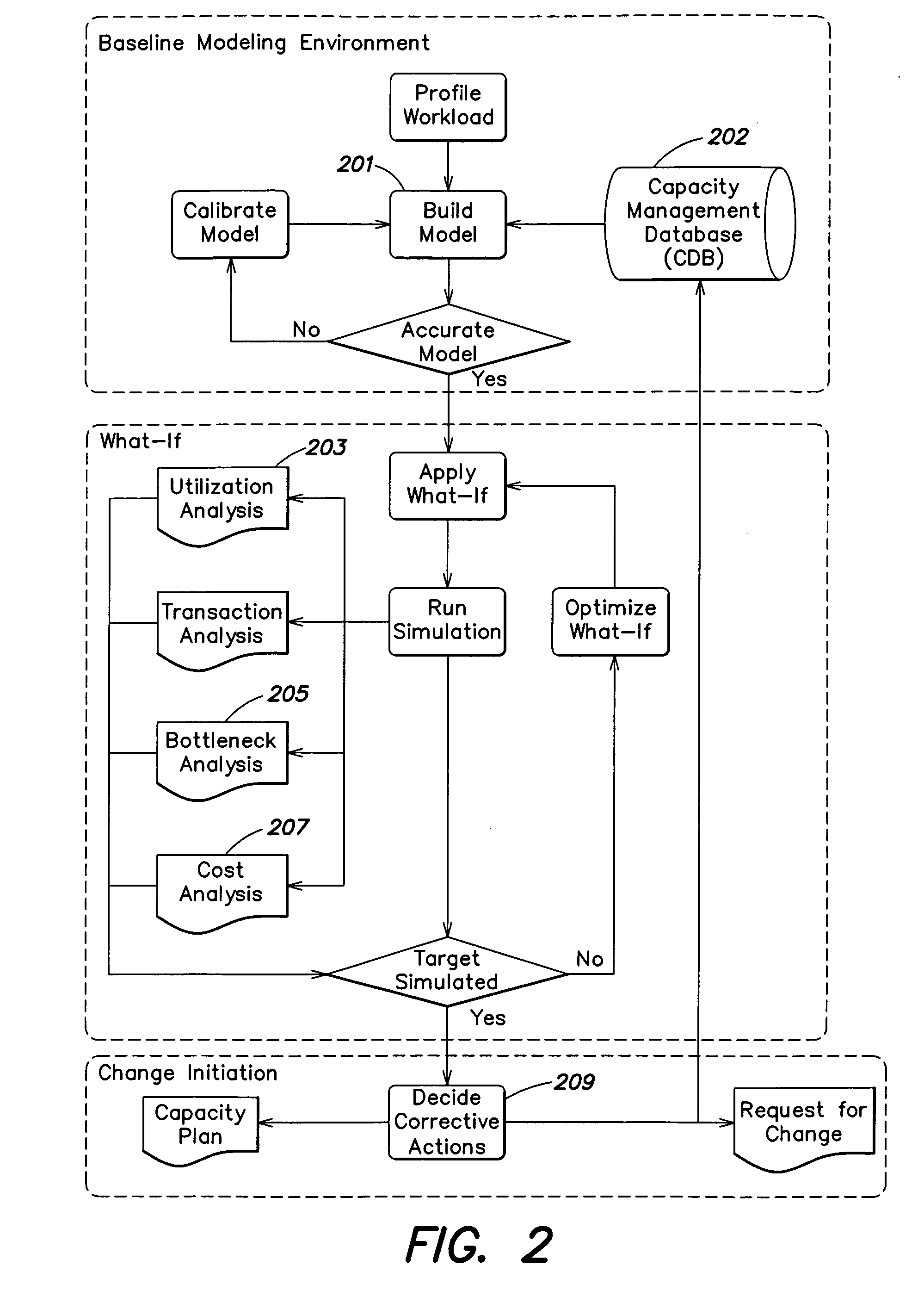
ActiveUS20060161884A1Error detection/correctionMultiple digital computer combinationsGood practiceComputer science
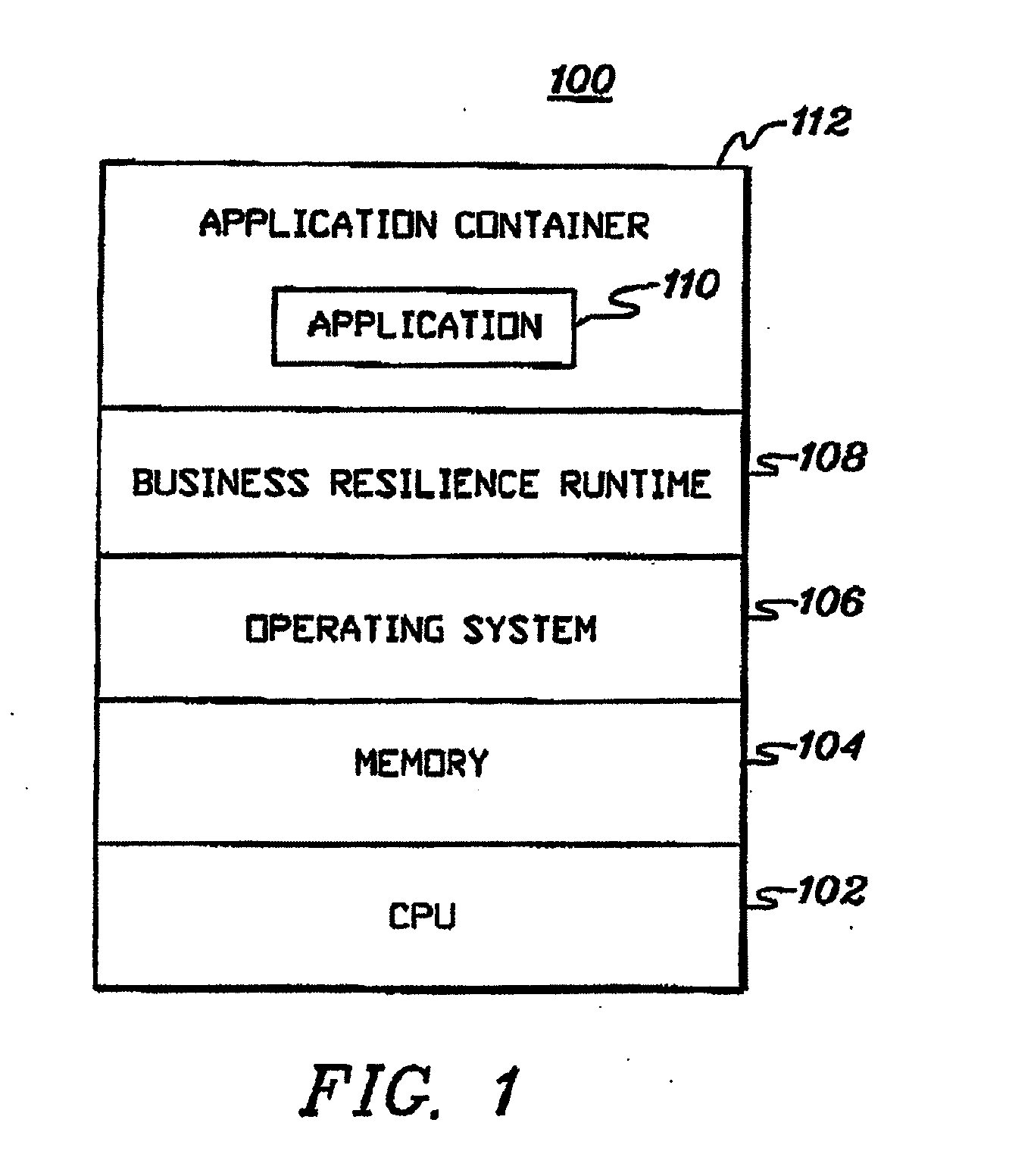
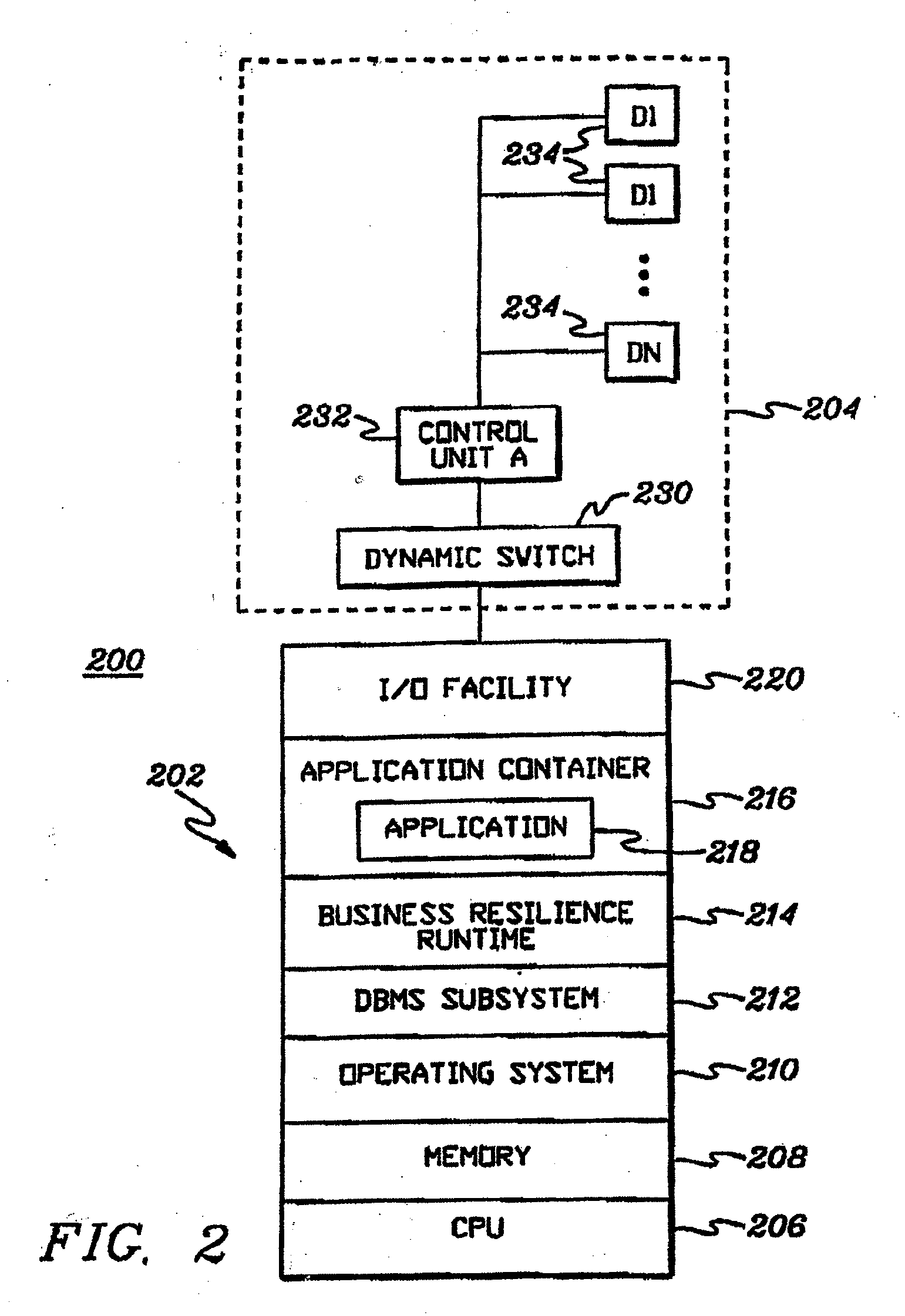
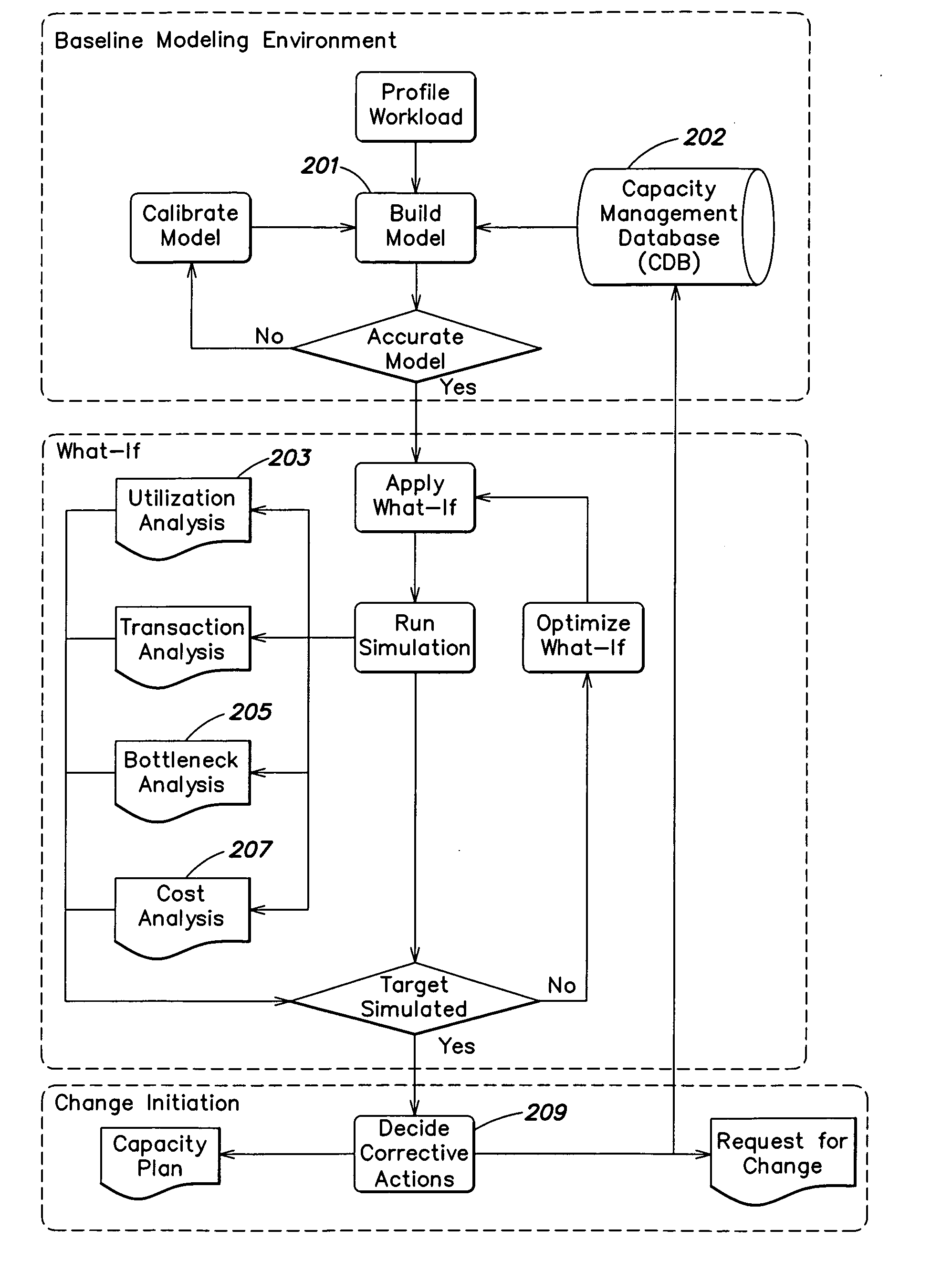
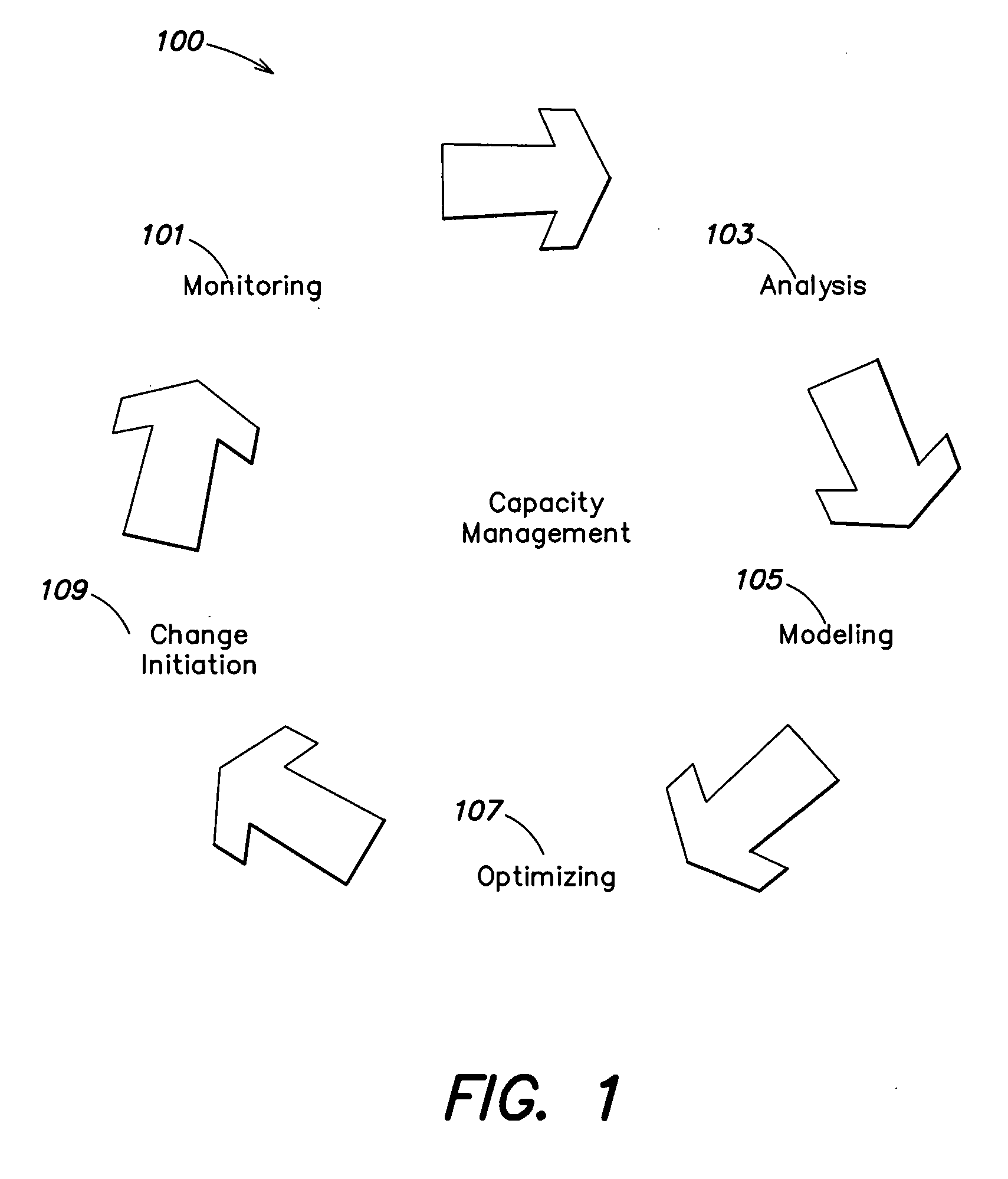
In one aspect, a method of instructing at least one operator in a best practices implementation of a process for managing resource capacity in an information technology (IT) environment is provided. The method comprising providing instructions to the at least one operator to perform acts of: (A) creating at least one model of at least some aspects of the IT environment; (B) analyzing the at least one model to determine cost information relating to the modeled IT environment; (C) applying at least one simulated use condition to the at least one model; (D) analyzing performance of the at least one model under the at least one simulated use condition to determine information relating to at least a utilization of resources in the modeled IT environment and to determine resources in the modeled IT environment that create performance bottlenecks in the modeled IT environment; and (E) modifying at least one aspect of the at least one model impacting resource capacity based on the information determined in (B) and / or (D).
Owner:MICROSOFT TECH LICENSING LLC
Coupling of a business component model to an information technology model
A method for managing a business. At least one relationship is determined between N business components (B1, B2, . . . , BN) and respective N costs (C1, C2, . . . , CN) and respective N values (V1, V2, . . . , VN) pertaining to the N business components. The N business components are a subset of M business components (B1, B2, . . . , BM) of a Component Based Model (CBM) of the M business components subject to M≧2 and N≦M. Determining the at least one relationship includes relating business components of the CBM with an Information Technology (IT) model of an IT system. The IT model includes abstract IT structures, virtual IT structures, real IT structures, or combinations thereof.
Owner:KYNDRYL INC
Rack enclosure
ActiveUS7033267B2Improve securityImprove protectionShow cabinetsKitchen cabinetsInformation technologyAirflow
An enclosure is provided for housing electronic equipment that accommodates the different cooling and ventilating requirements of different types of equipment. The enclosure is constructed and arranged to support cooling airflow in a front-to-back configuration through the enclosure and in a side-to-side configuration from one side to an opposite side of the enclosure. The enclosure can thereby provide within a single enclosure means cooling air for components using front-to-back airflow for cooling, such as information technology (IT) equipment, and for components using side-to-side airflow, such as certain types of telecommunications equipment. The enclosure can thereby support a mix of IT and telecommunications equipment, providing flexibility and adaptability in network room and data center configuration. The enclosure is further configured to separate intake air used by equipment for cooling from exhaust air vented by equipment into its interior during operation. As a result, the enclosure promotes sufficient equipment cooling and prevents / minimizes equipment overheating.
Owner:AMERICA POWER CONVERSION CORP
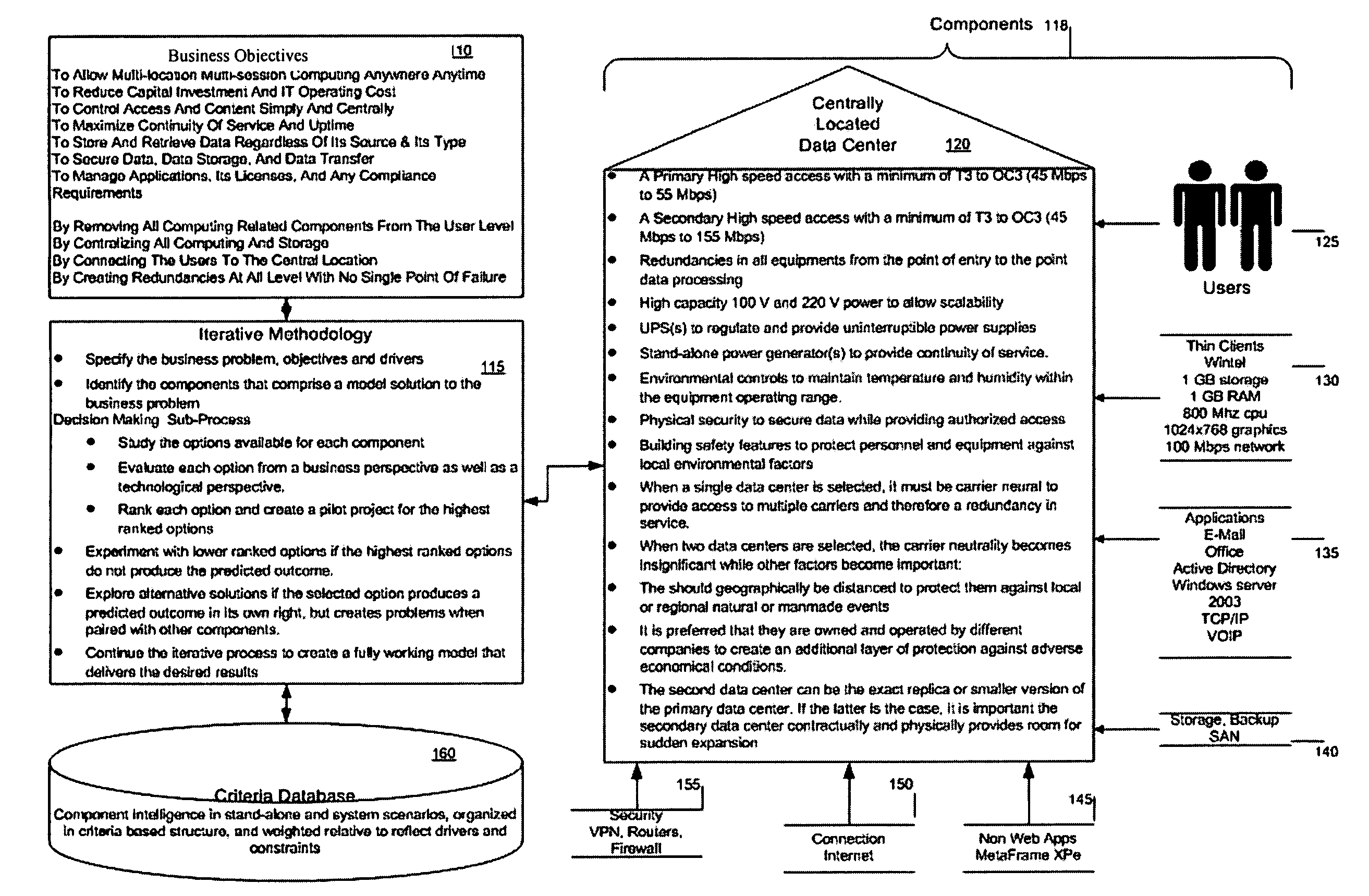
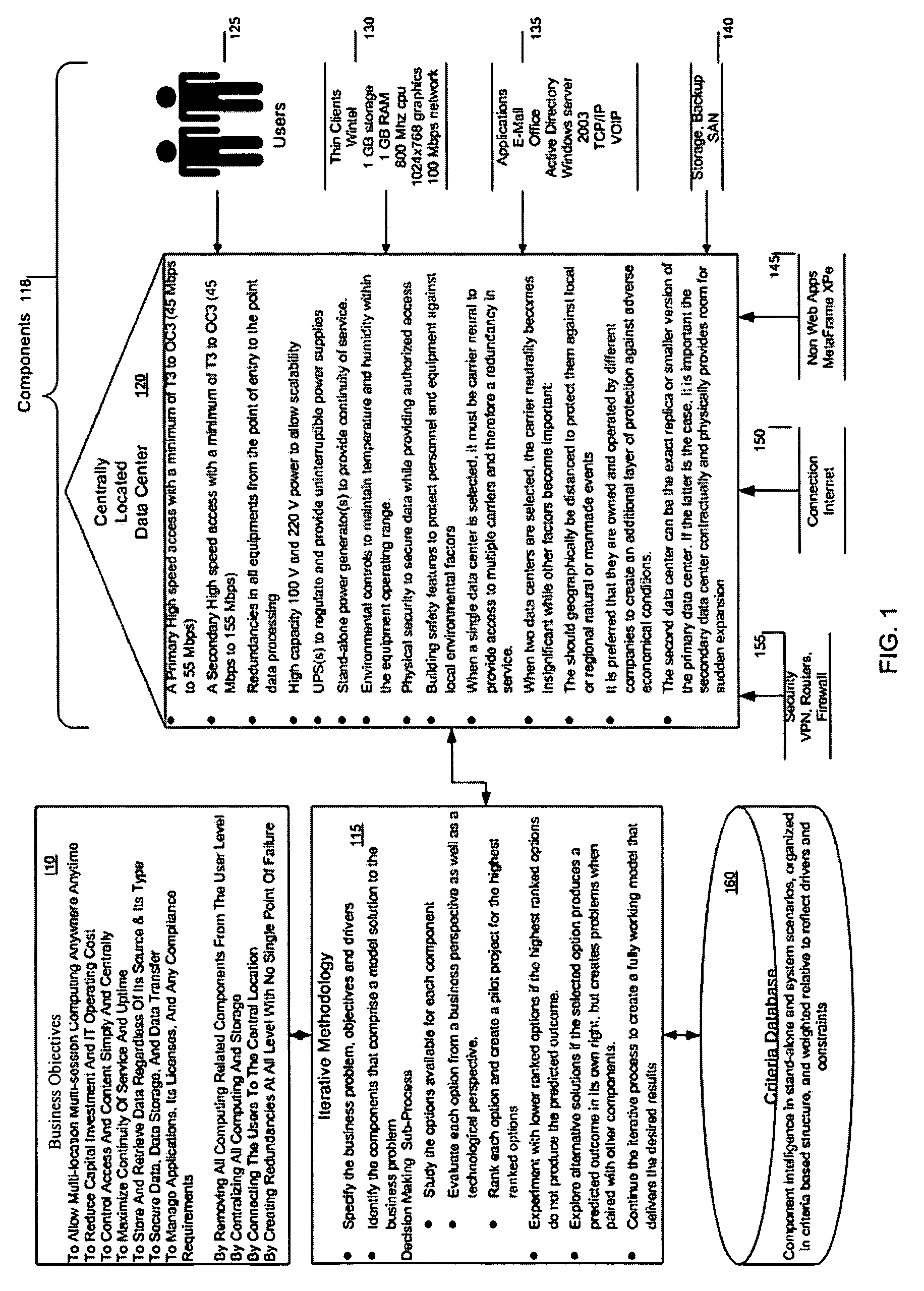
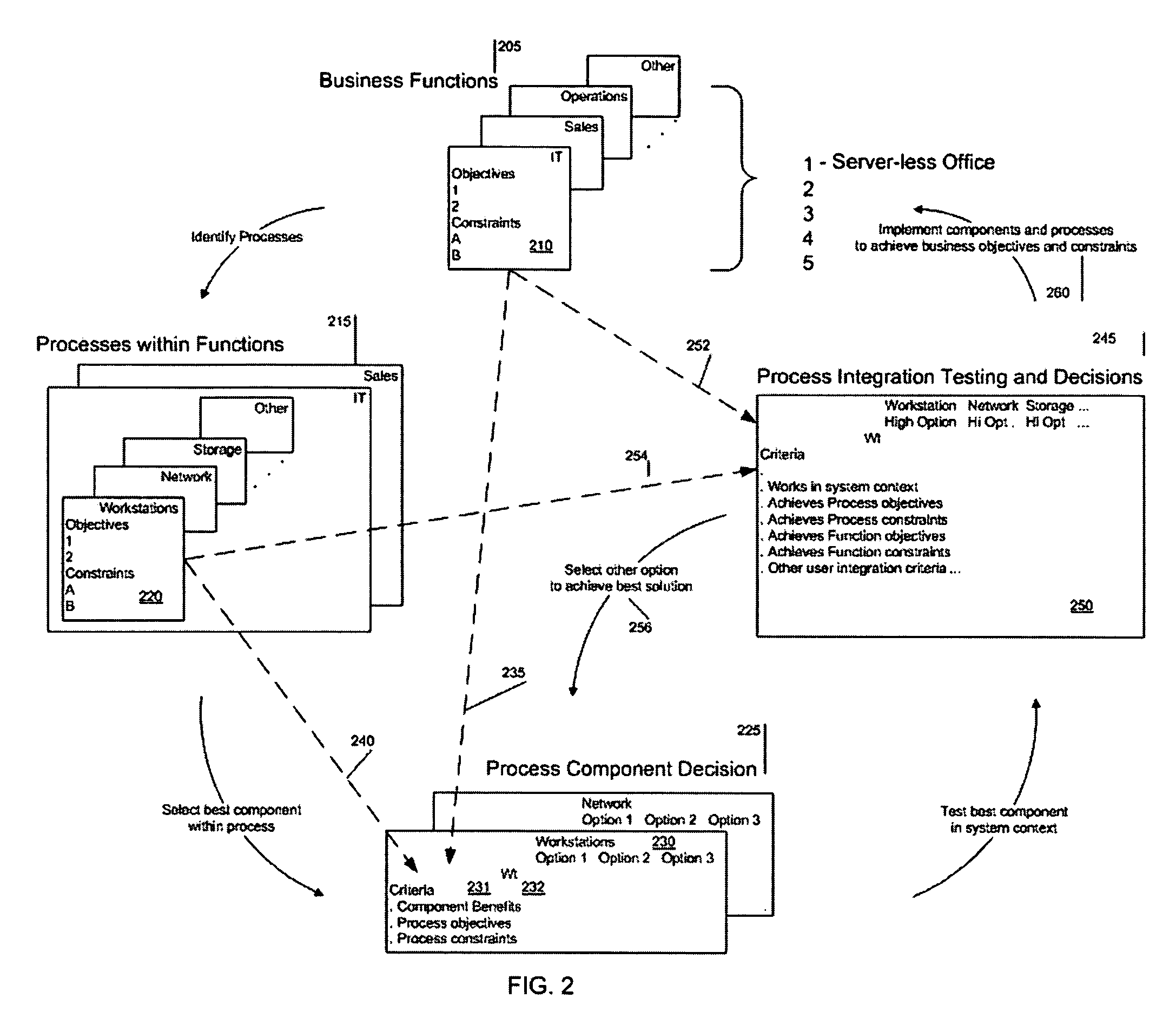
Method for a server-less office architecture
InactiveUS20050288961A1Easy to useImprove efficiencyDigital data authenticationOffice automationClient-sideFour component
A way is provided for architecting a server-less office that delivers anywhere anytime computing support to an organization. The server-less office comprises a plurality of information technology IT components selected based on business objectives and constraints associated with the business function of the organization to work together to deliver computing support functions to a plurality of end users who no longer have local computing support and may only have thin clients on their desks. A pre-determined server-less architecture is imposed by the present invention by including at least four architectural groupings of IT components that the organization must map the objectives and constraints of its business functions onto for IT component selection purposes. A local group is included in this minimum set of groups so that unique processing needs can be satisfied that are not met by the imposed pre-determined server-less office architectural groupings.
Owner:EPLUS CAPITAL
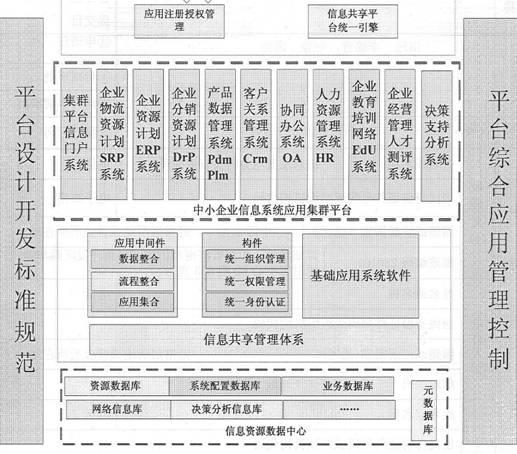
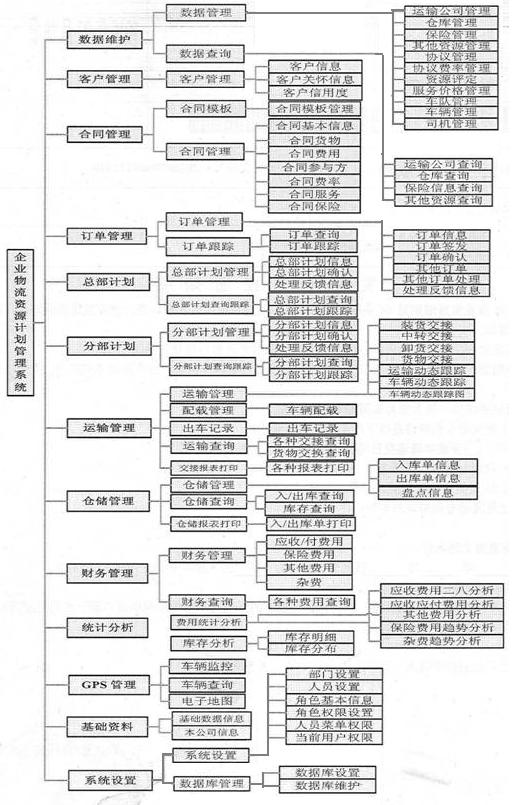
Informatization application cluster platform of small and medium enterprises
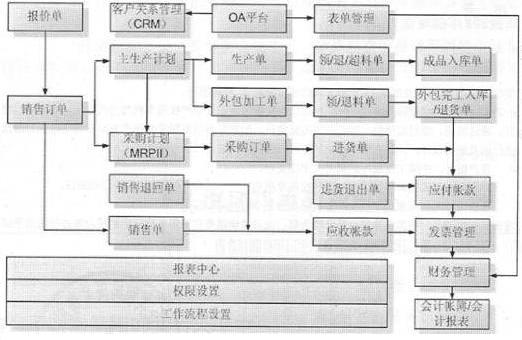
InactiveCN102324074ALow application costOptimal Management BottlenecksInstrumentsInformatizationCustomer relationship management
The invention discloses an informatization application cluster platform of small and medium enterprises. The informatization application cluster platform comprises a portal management system, an enterprise logistics supply chain resource planning management system, an enterprise resource planning management system, an enterprise distribution resource planning and supply chain management system, an enterprise customer relation management system, an enterprise collaborative working platform management system, an enterprise product data management and product life cycle management system, an enterprise human resource management system, an enterprise operating management talent assessment system, an enterprise educational training network platform integrated system and a decision supporting analysis system. The informatization application cluster platform of the small and medium enterprises has the advantages that: by real-time on-line application and management for a plurality of small and medium enterprises, the safety of the operation data of on-line enterprises can be guaranteed; the investment of economic and technical talents for the informatization application of the small and medium enterprises of China is greatly reduced; an enterprise management bottleneck is optimized; the information technology (IT) application cost of the enterprises is greatly saved; and the implementation of the informatization of the small and medium enterprises is simplified.
Owner:SHANDONG CENTONG TECH
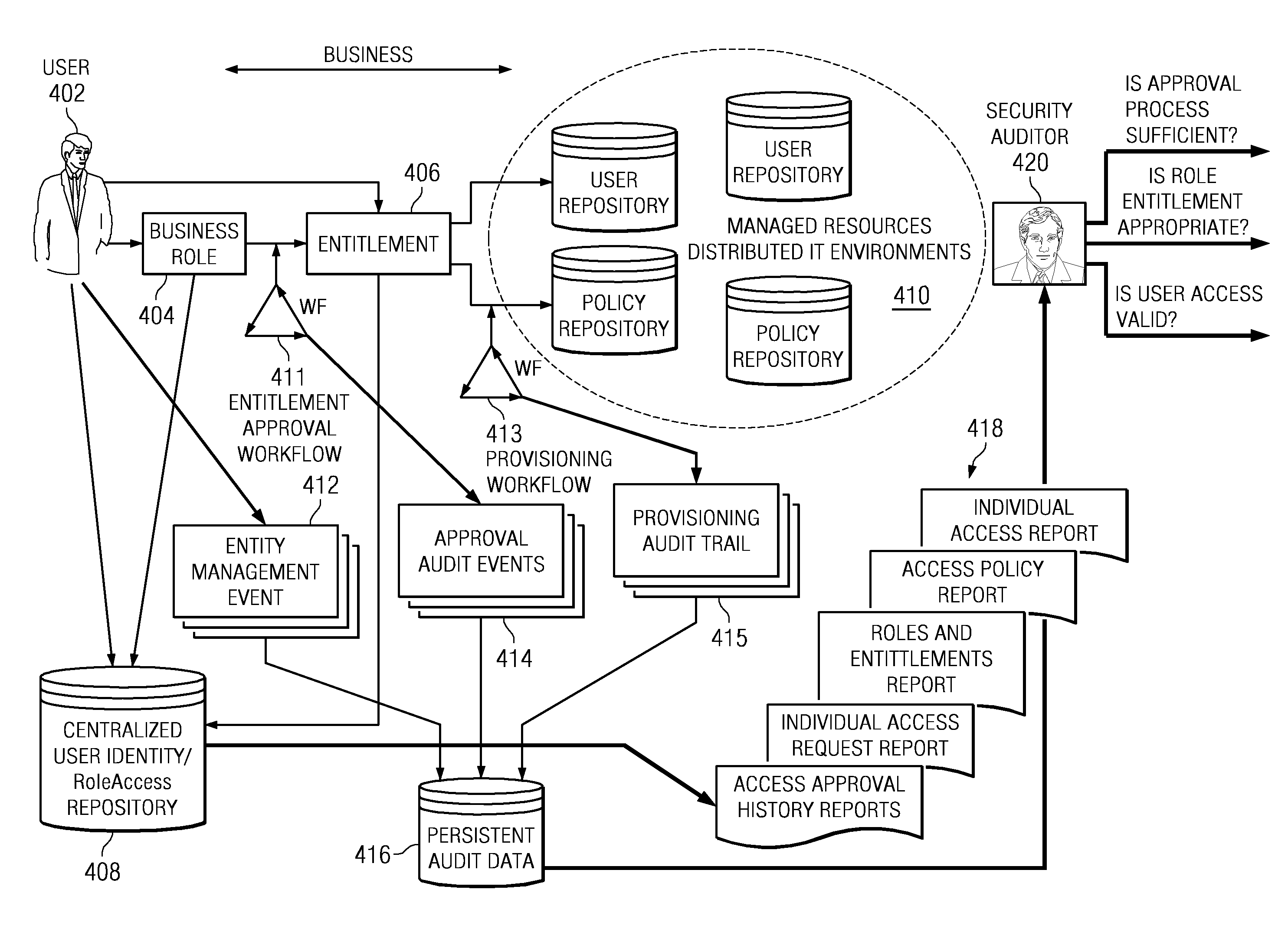
Managing user access entitlements to information technology resources
ActiveUS20090150981A1Digital data processing detailsUser identity/authority verificationData processing systemInterface layer
A computer implemented method, data processing system, and computer program product for logical management and provisioning of business applications within the framework of an identity management system. The illustrative embodiments providing an interface layer to map respective attributes, permissions, and resource accounts in a data repository needed to represent access to business applications via a managed service in the identity management system. The illustrative embodiments define user entitlements on a user account associated with the managed service. The illustrative embodiments provision user access to the business applications via the managed service in the identity management system upon user request.
Owner:SERVICENOW INC
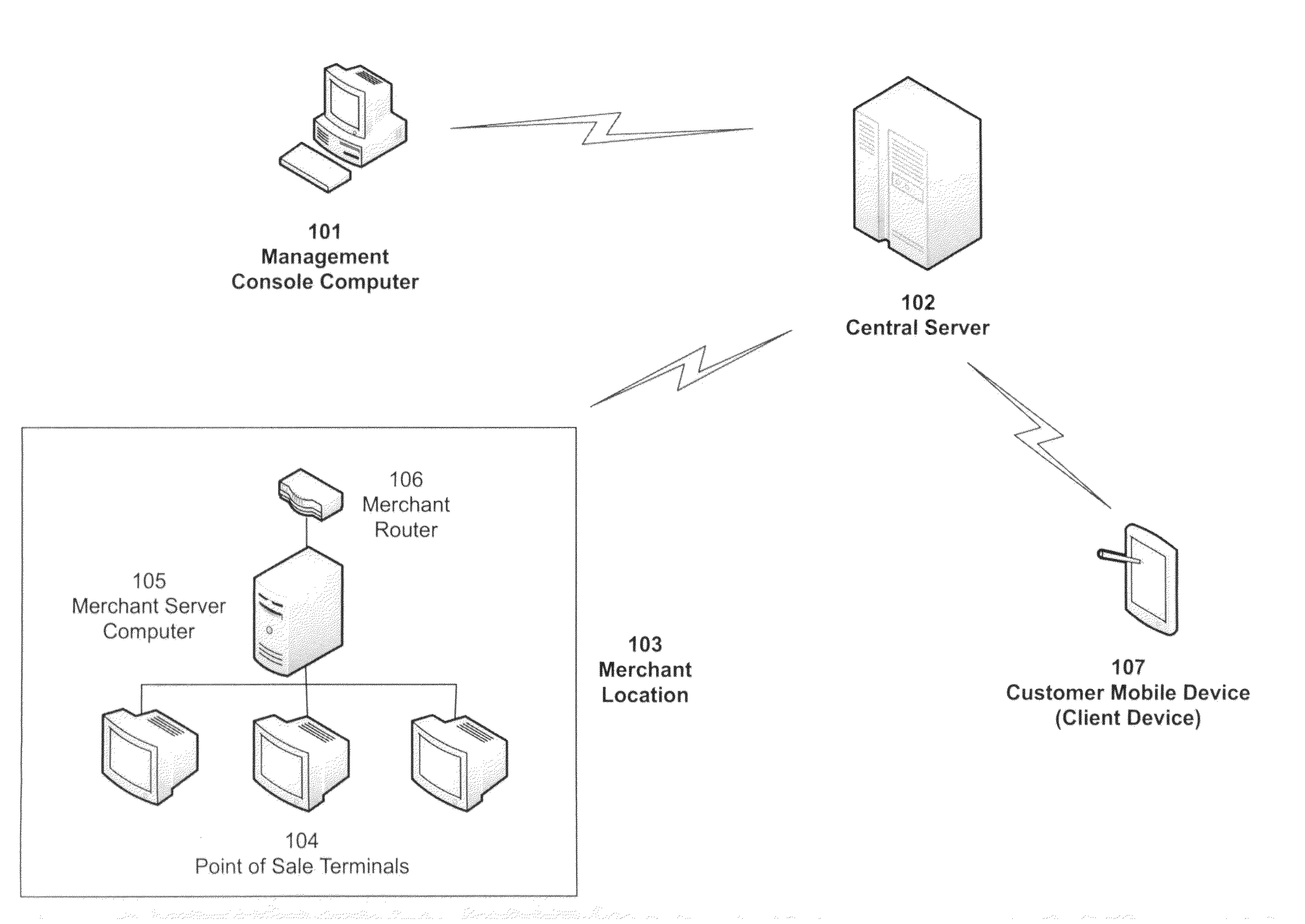
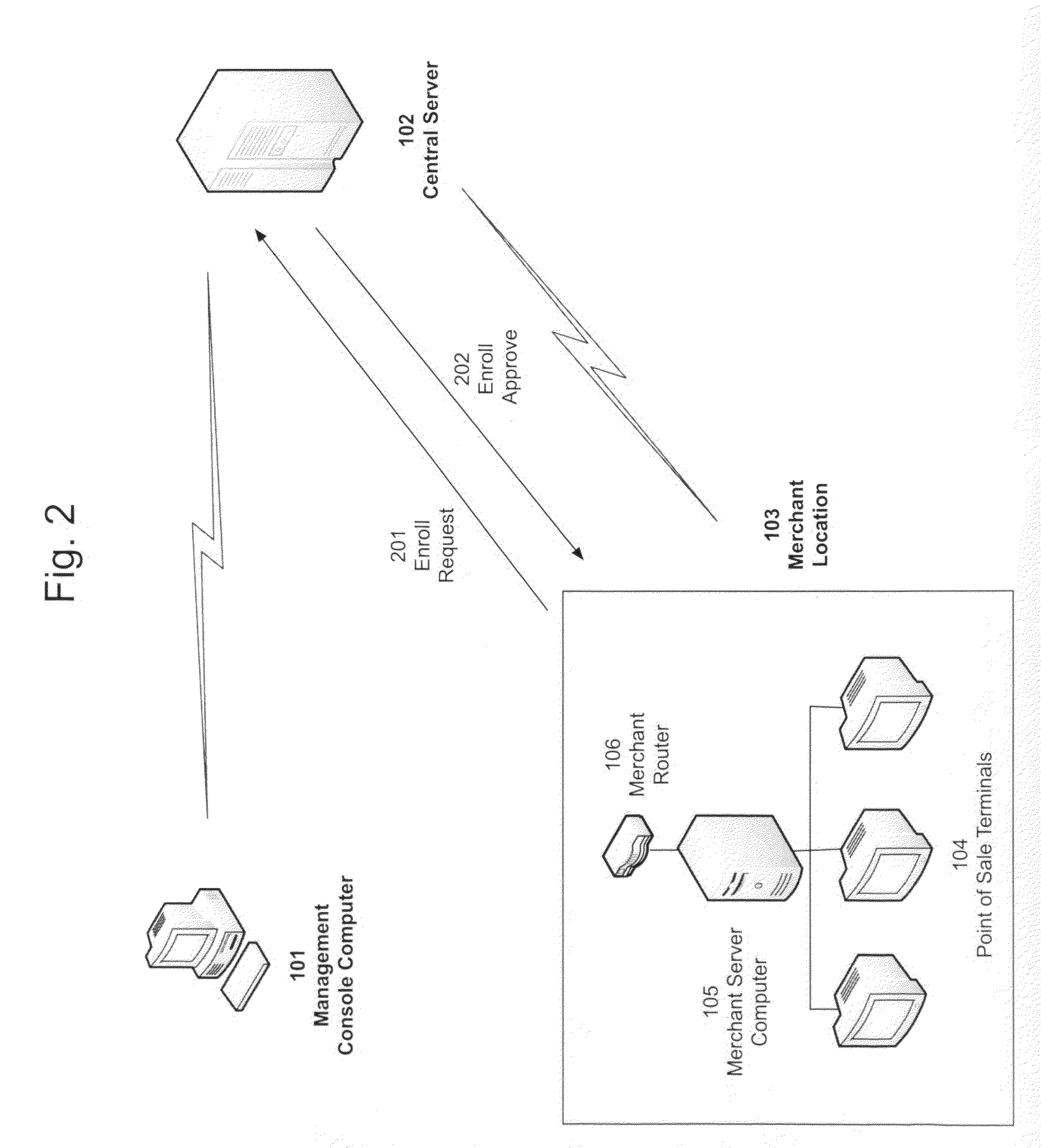
System for Interfacing a Client Device with a Point of Sale System
An information technology system taking the form of a management console, central server, point of sale system, software running on a point of sale system and software running on a customer's mobile phone. The software on the customer's mobile phone lets a customer interact with the point of sale system, allowing the customer to view a pending economic transaction, optionally add or remove items to the transaction, and pay for the transaction using payment information stored on the mobile phone.
Owner:ATX INNOVATION
System and Method for Forensic Identification of Elements Within a Computer System
ActiveUS20100030996A1Memory adressing/allocation/relocationComputer security arrangementsMemory forensicsComputer system design
A system and method for employing memory forensic techniques to determine operating system type, memory management configuration, and virtual machine status on a running computer system. The techniques apply advanced techniques in a fashion to make them usable and accessible by Information Technology professionals that may not necessarily be versed in the specifics of memory forensic methodologies and theory.
Owner:FIREEYE SECURITY HLDG US LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com