Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
215 results about "Intelligence system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method for securing an enterprise computing environment
InactiveUS20180027006A1Process safetyKeep Content SafeMultiprogramming arrangementsComputer security arrangementsInternet privacyEnterprise computing
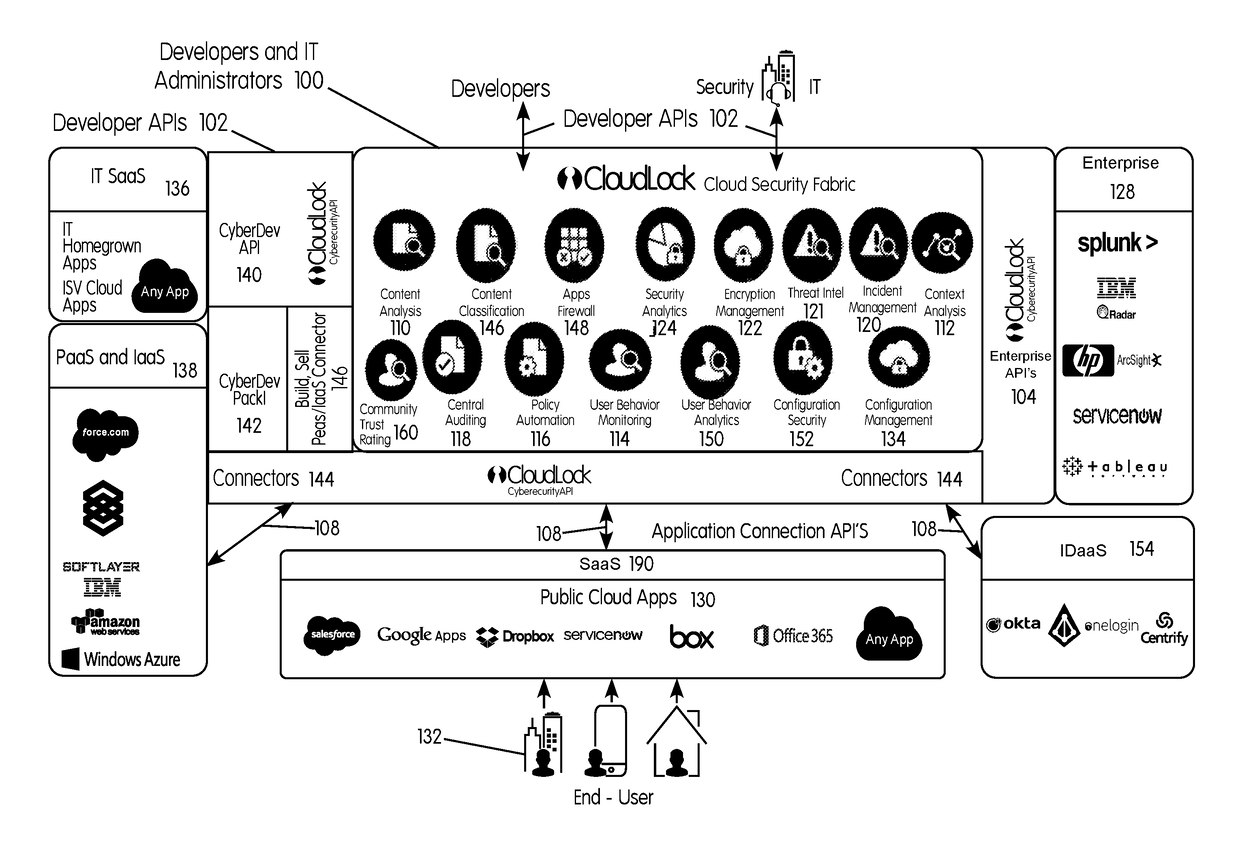
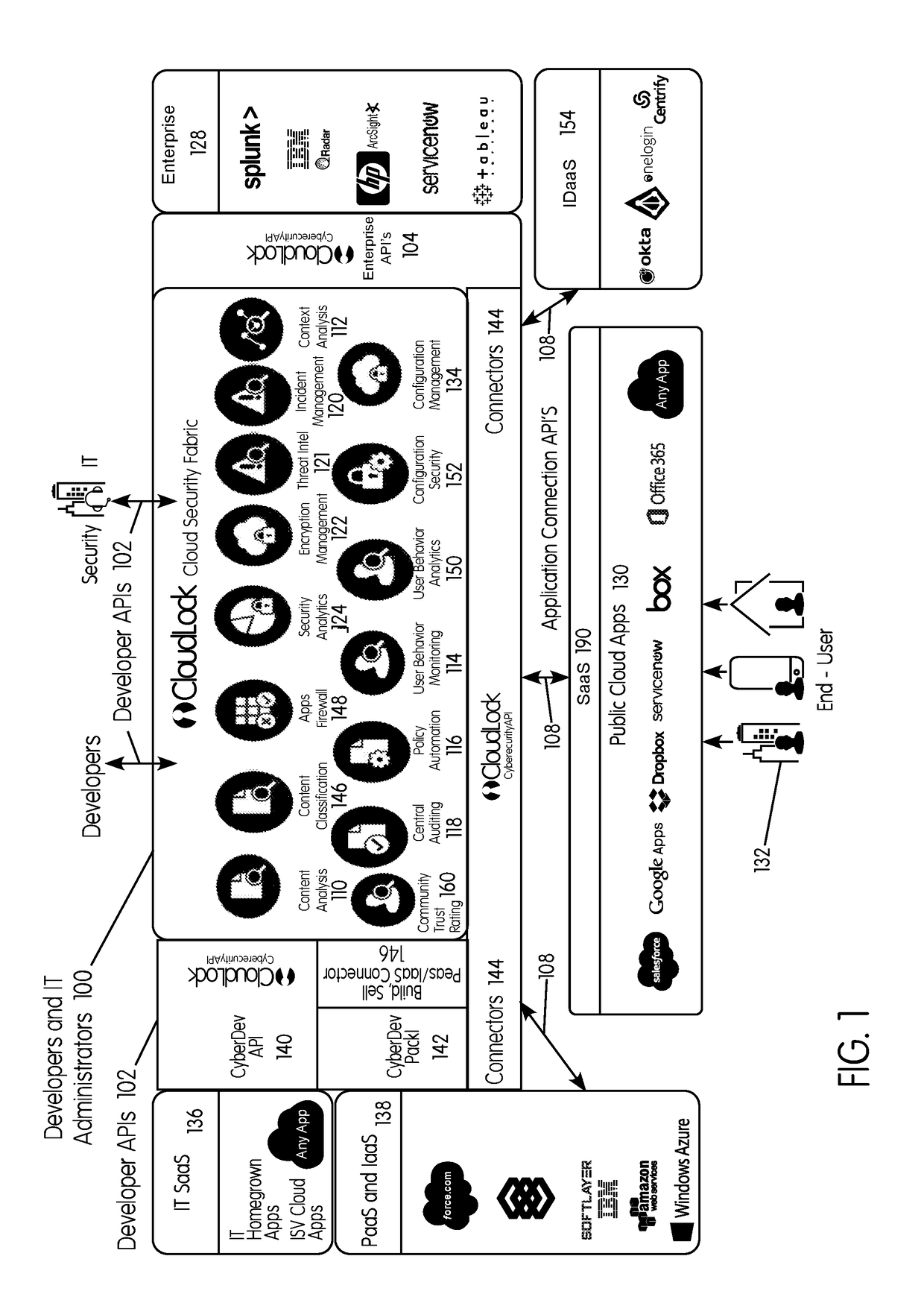
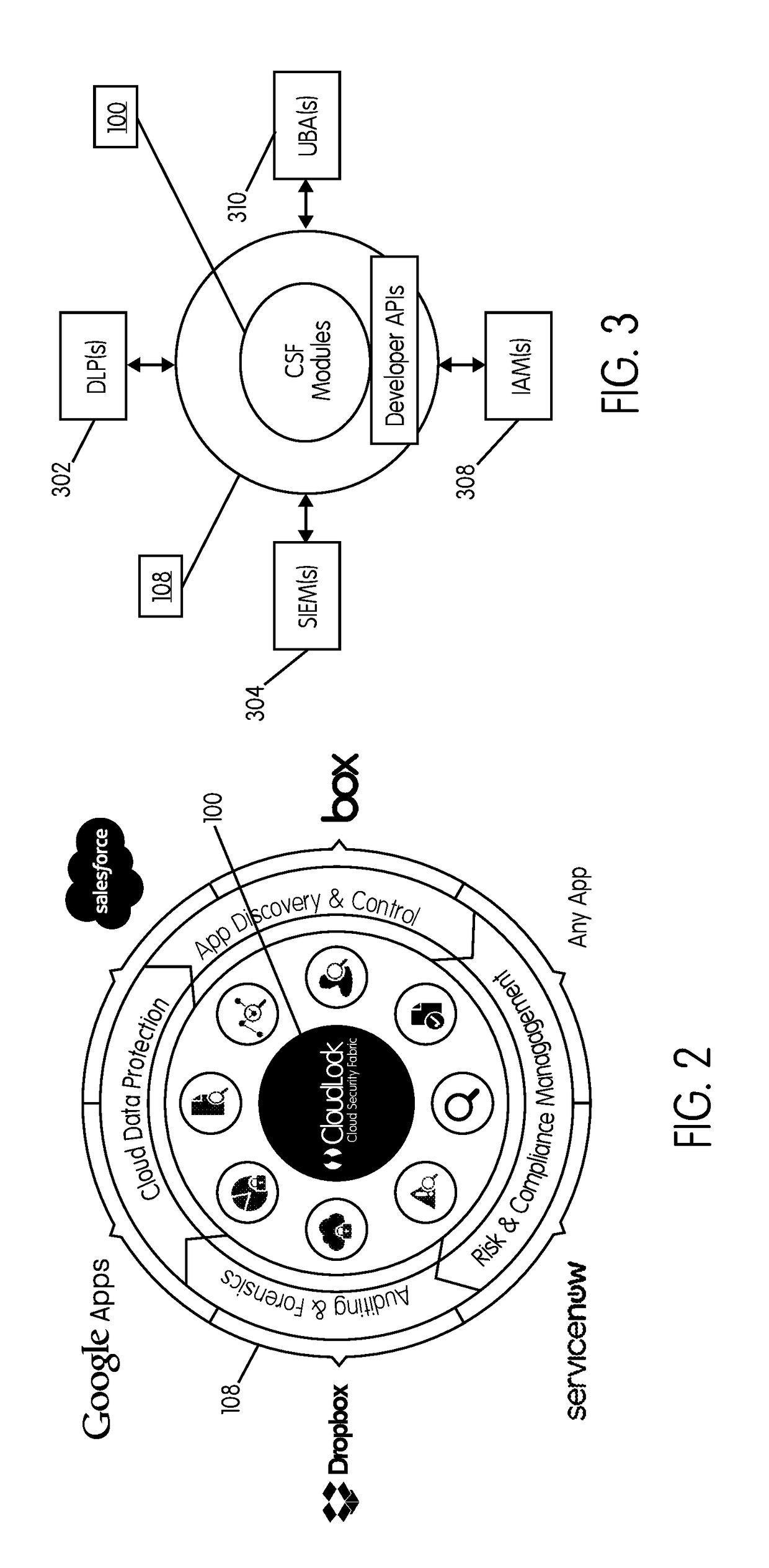
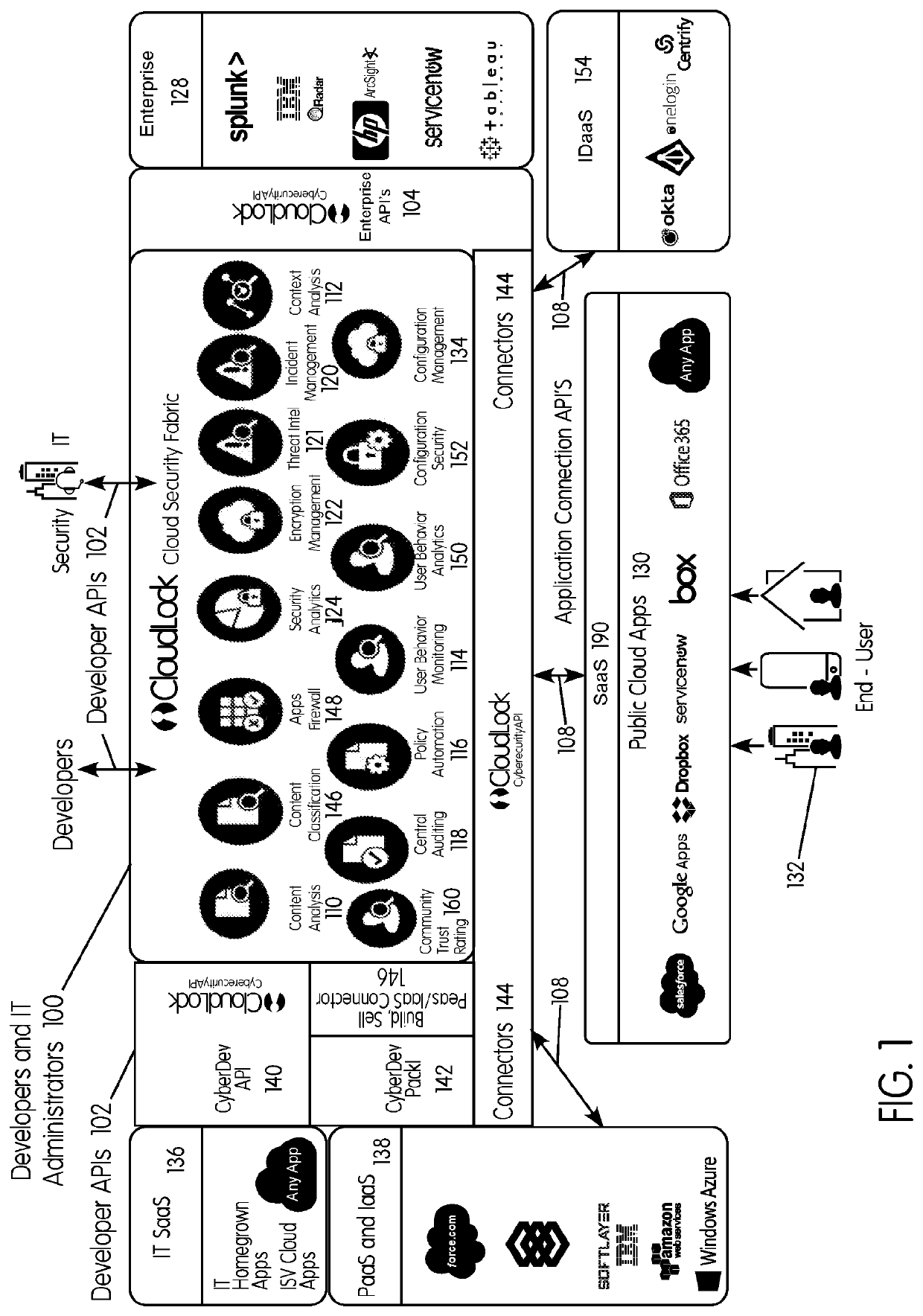
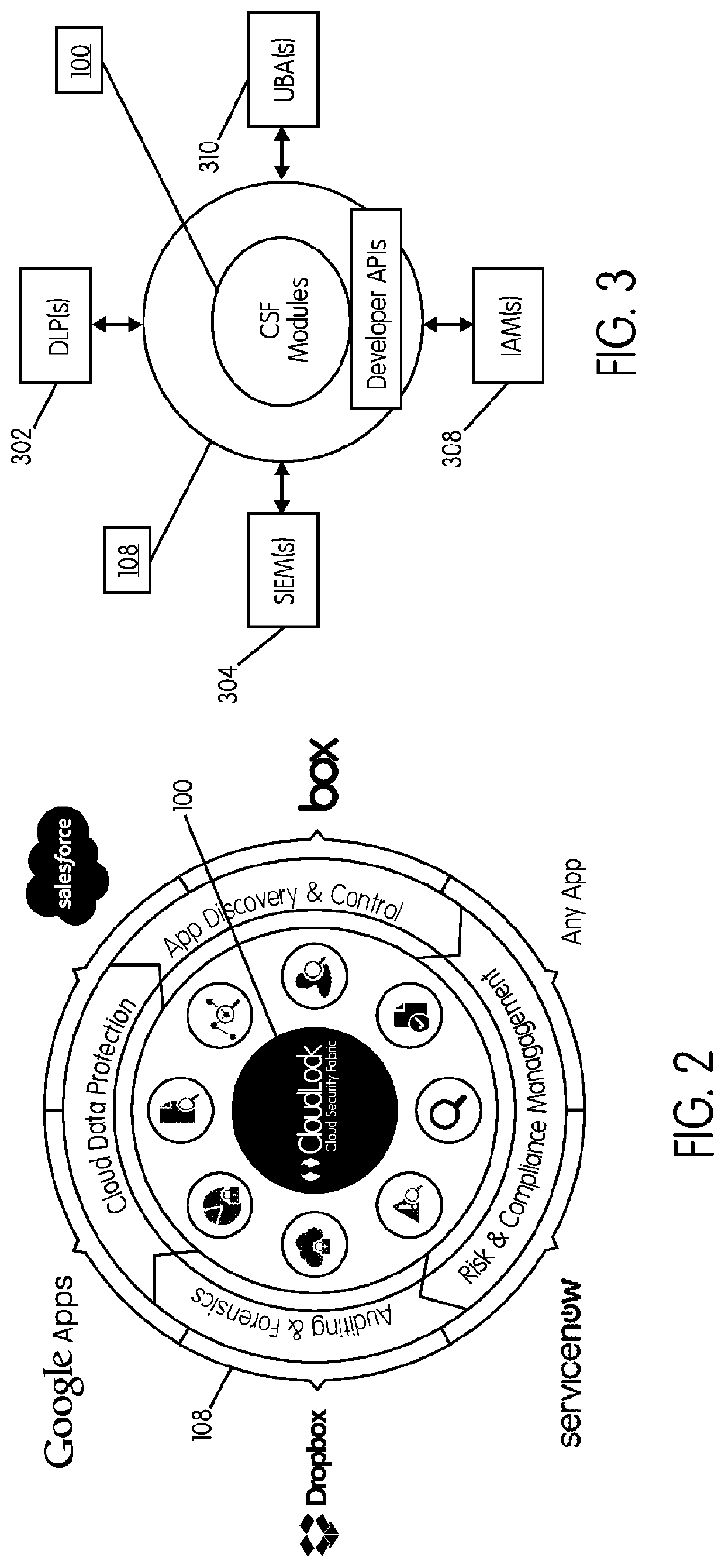
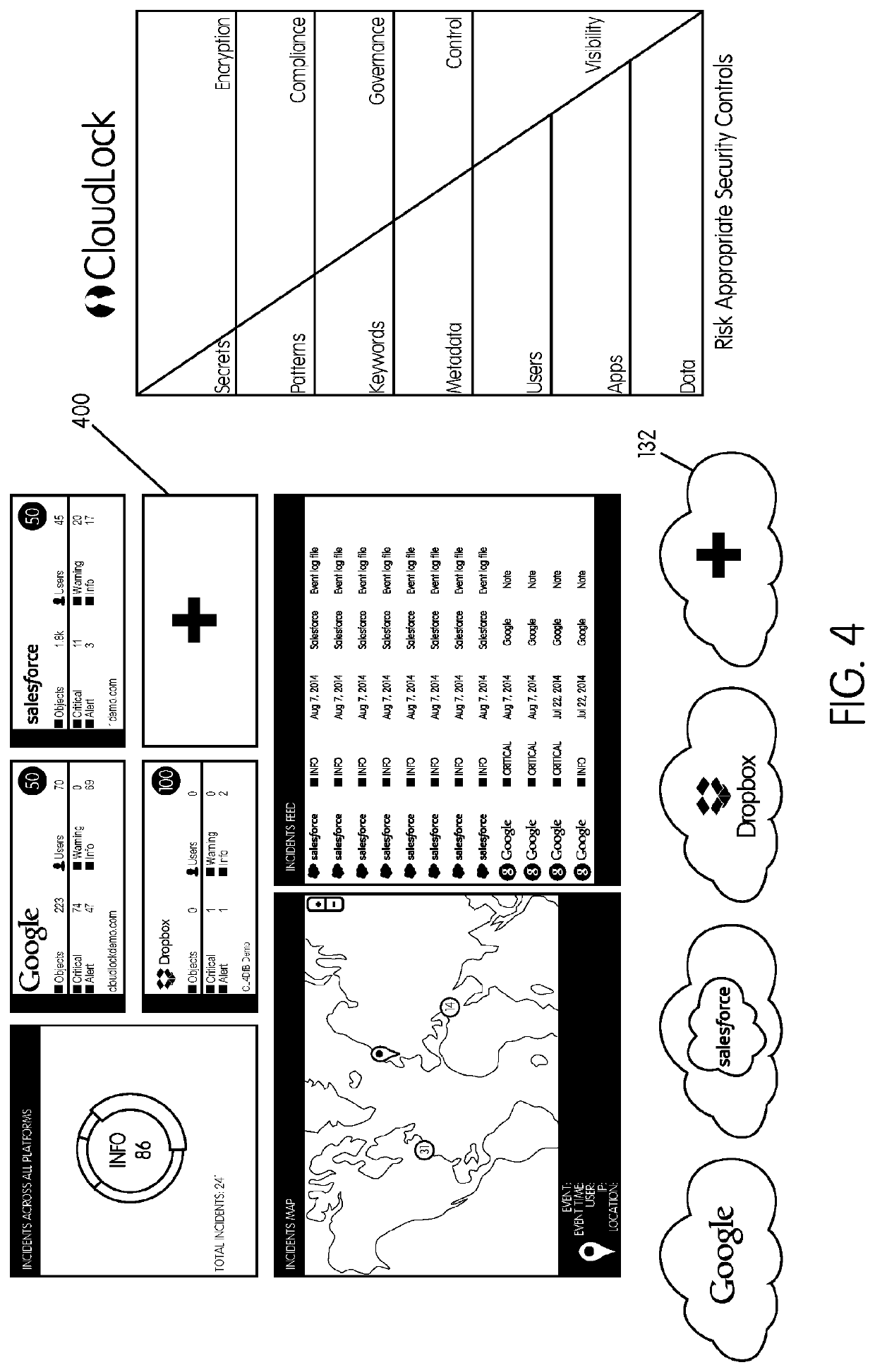
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CLOUDLOCK
System and method for securing an enterprise computing environment
InactiveUS20200137097A1Process safetyKeep Content SafeMultiprogramming arrangementsDigital data protectionBusiness enterpriseEnterprise computing
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CISCO TECH INC
Method for enabling risk management for sellers of items on internet auction sites
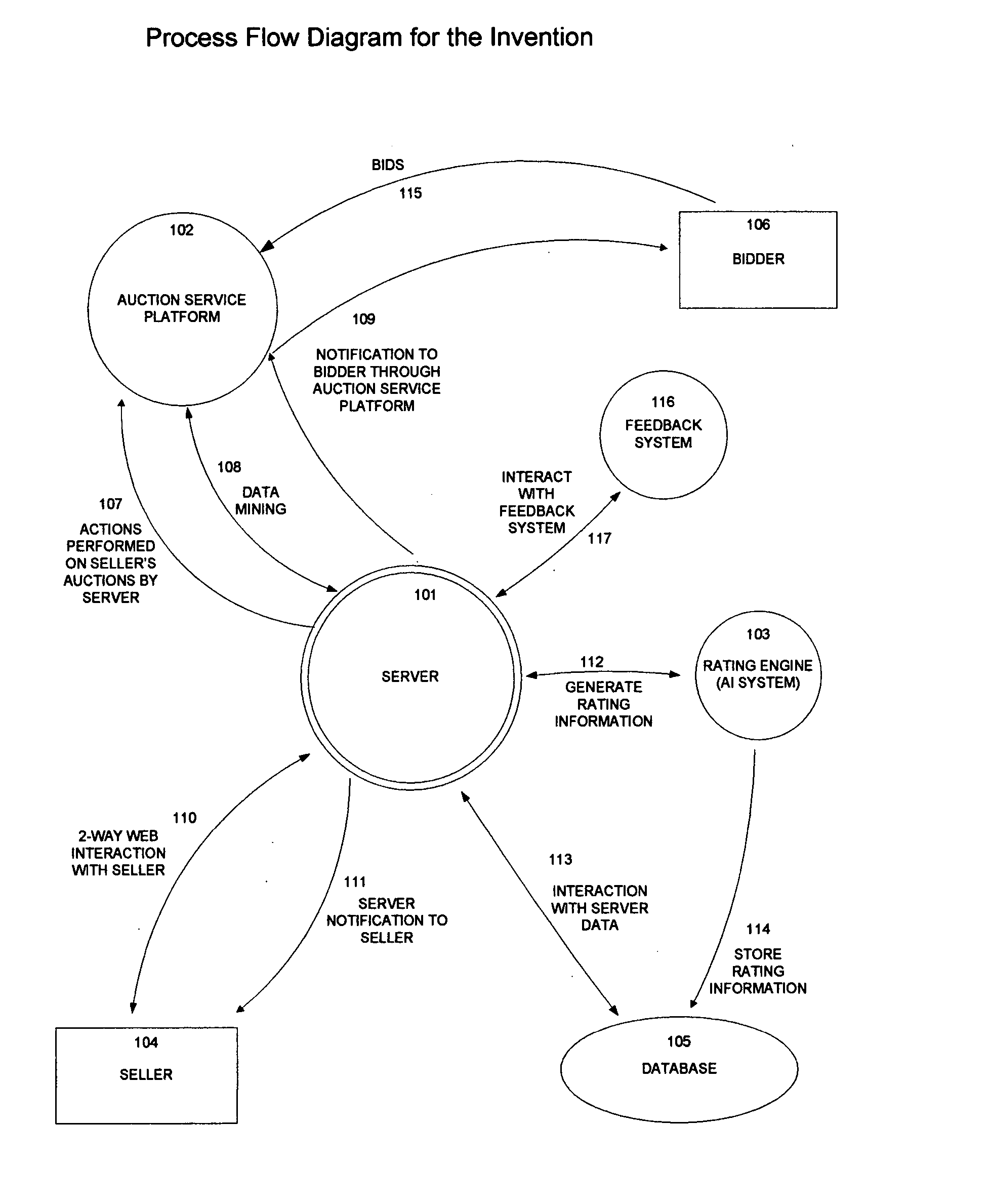
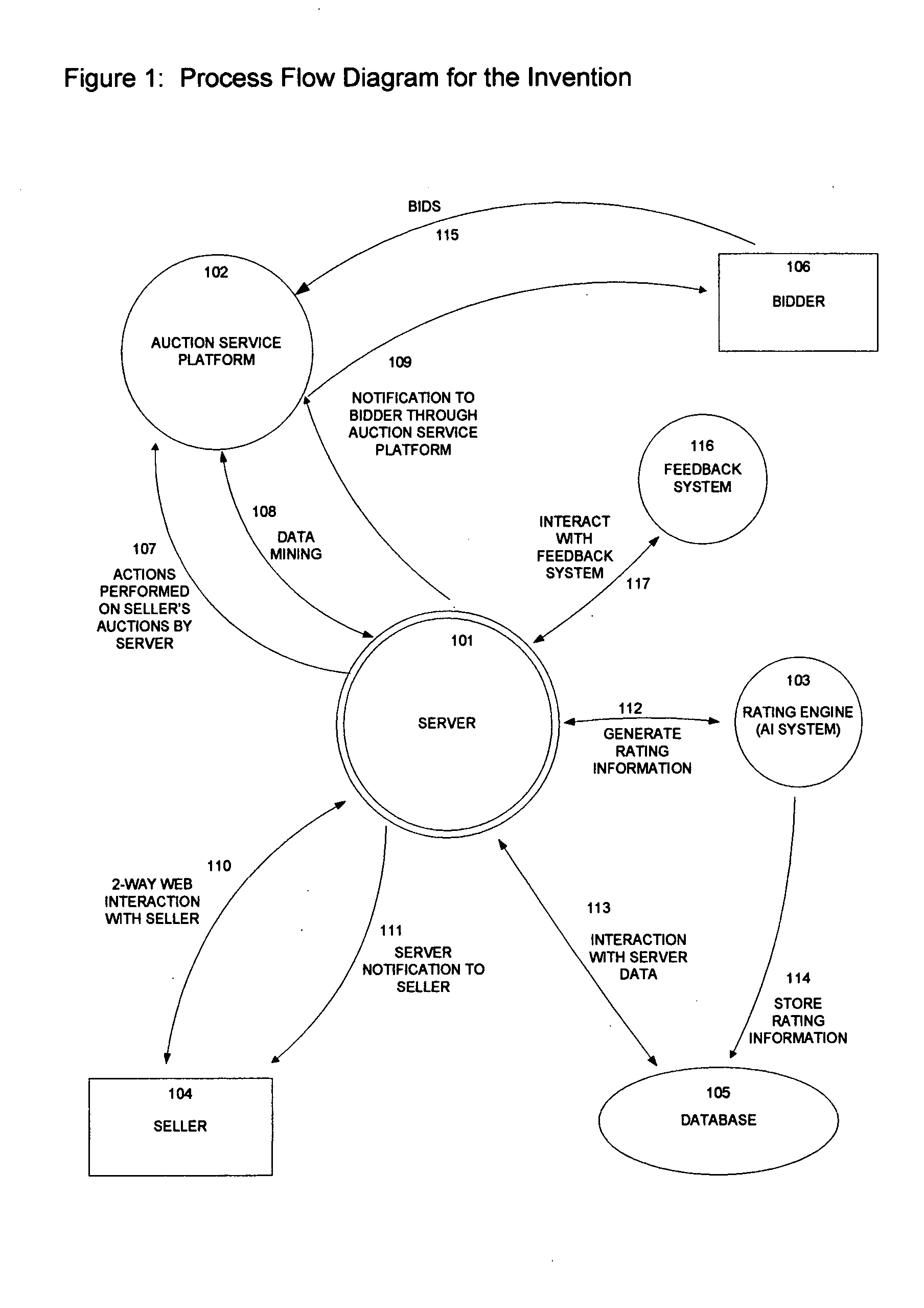
A method for enabling risk management for sellers of items on Internet auction sites with the steps of: Automatically detect new bids on auctions, Evaluate bidders on the basis of their past performance using an artifical intelligence system, Maintain on a central server rating information for bidders, Maintain on the central server a seller's preferences for dealing with bidders in each rating category, Based upon the rating act on the auction by: canceling bid, notifying seller, or accepting the bid, Based upon the bidder's country of registration notify the seller, Allow sellers to see all auctions with bidders on one screen, Allow sellers to see a list of other auctions where their bidders have placed bids, Automate auction fee refund processing, and Allow sellers to see a list of all pending and recently completed auction refund requests, allow anonymous reprisal-free bidder feedback.
Owner:BEERY PETER DOUGLAS +1
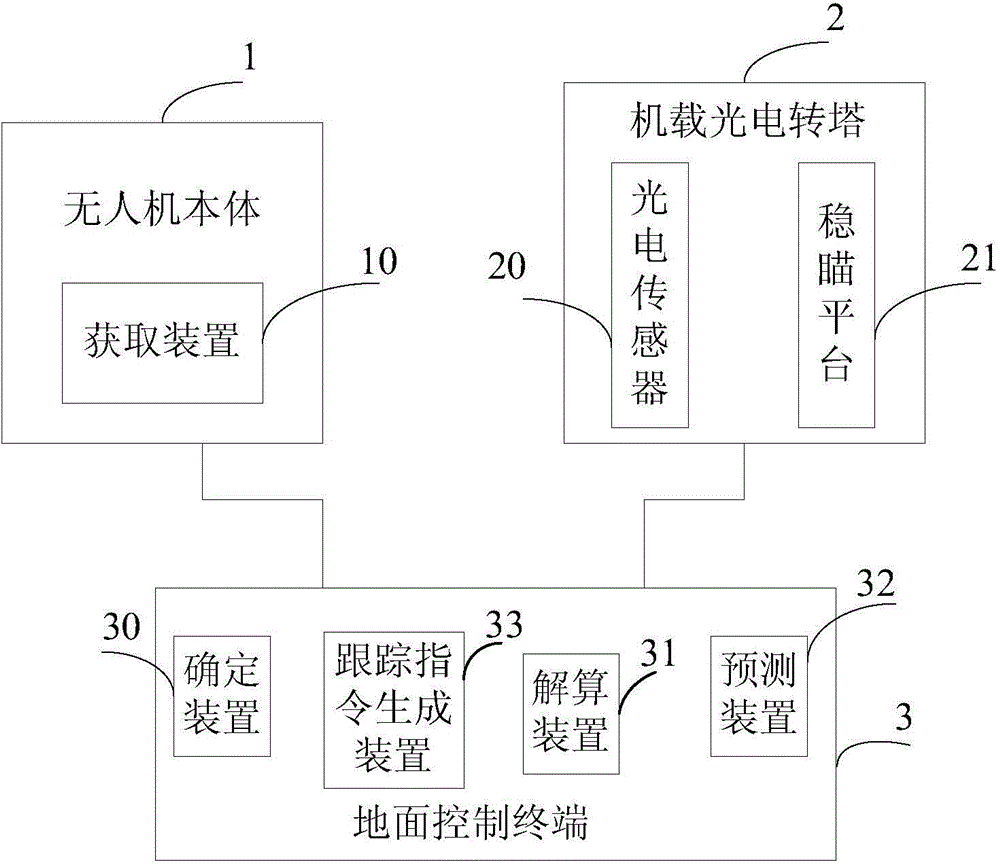
Unmanned aerial vehicle system and method for dynamically positioning ground moving target
ActiveCN103604427AMeet initial alignment requirementsHigh positioning accuracyNavigation instrumentsTarget-seeking controlLongitudeUncrewed vehicle
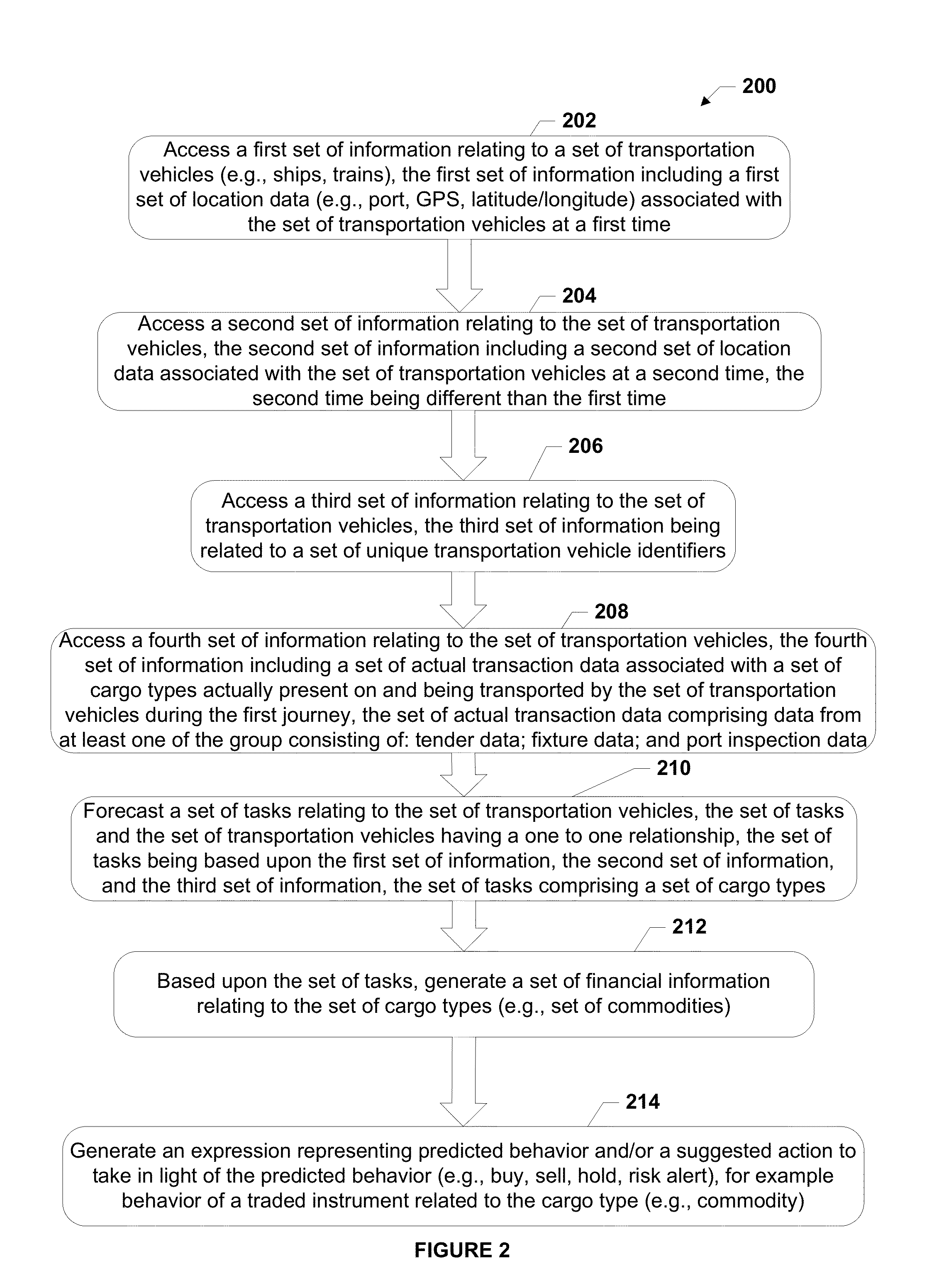
The invention discloses an unmanned aerial vehicle system and a method for dynamically positioning a ground moving target, belonging to the fields of unmanned aerial vehicle system application and the like. The unmanned aerial vehicle system comprises an unmanned aerial vehicle body, a vehicle-mounted photoelectric rotating tower and a ground control terminal, wherein the unmanned aerial vehicle body comprises an acquisition device, the vehicle-mounted photoelectric rotating tower comprises a photoelectric sensor and a sight-stabilizing platform, and the ground control terminal comprises a determining device, a trace command generating device, a resolving device and a predicting device. According to the technical scheme provided by the invention, geographical coordinate information including latitude, longitude and the like of a tracked ground moving target can be output in real time, the original geographical coordinate information can be accurately and quickly fitted, the moving trend of the ground moving target can be predicted and evaluated, and the original geographical coordinate information can be screened to realize display and prediction of the track of the moving target; the positioning accuracy acquired by the unmanned aerial vehicle system and the method approaches that of static positioning and can meet requirements for initial alignment of weapons including artilleries and the like, and the probability of fusion processing of an unmanned aerial vehicle intelligence system and an entire-army intelligence gathering network is provided.
Owner:CHINA ACAD OF AEROSPACE AERODYNAMICS
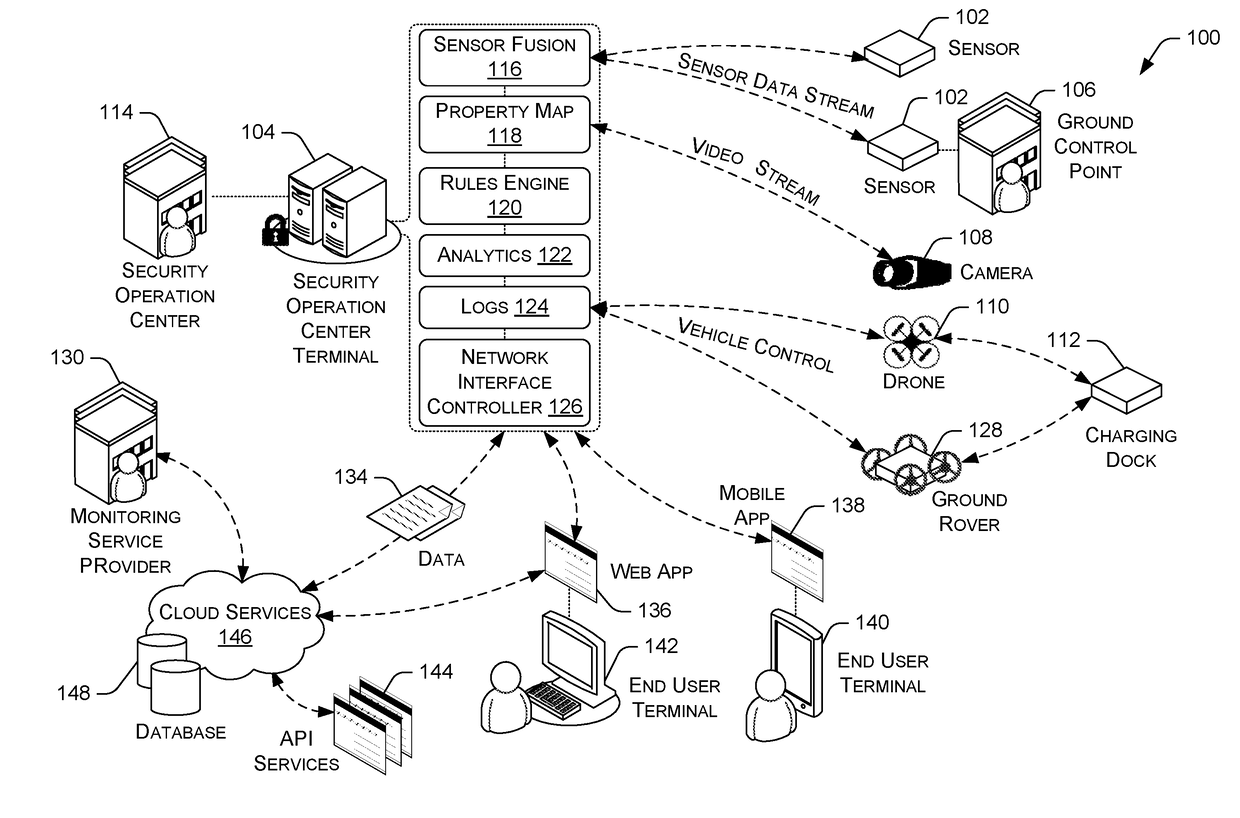
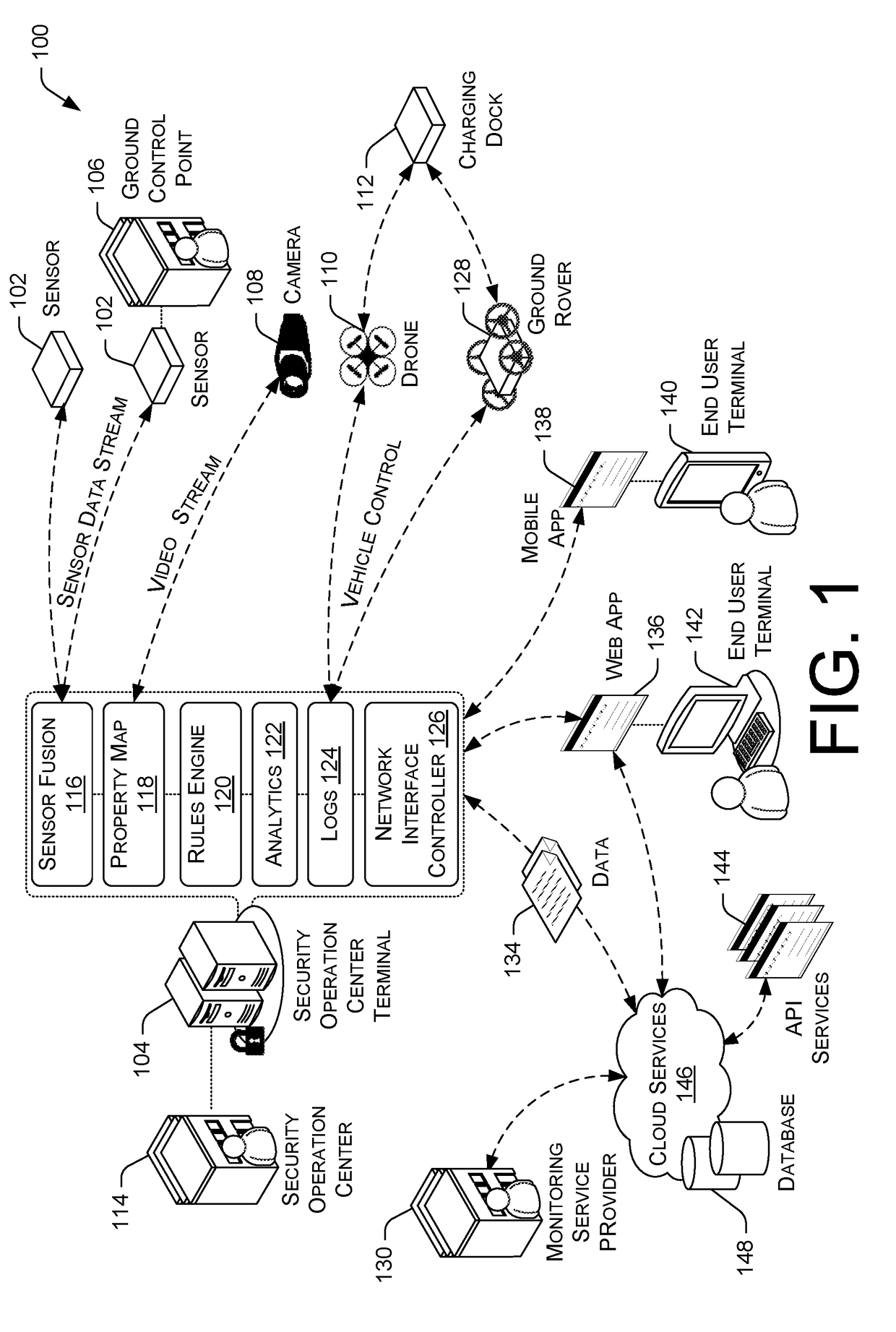
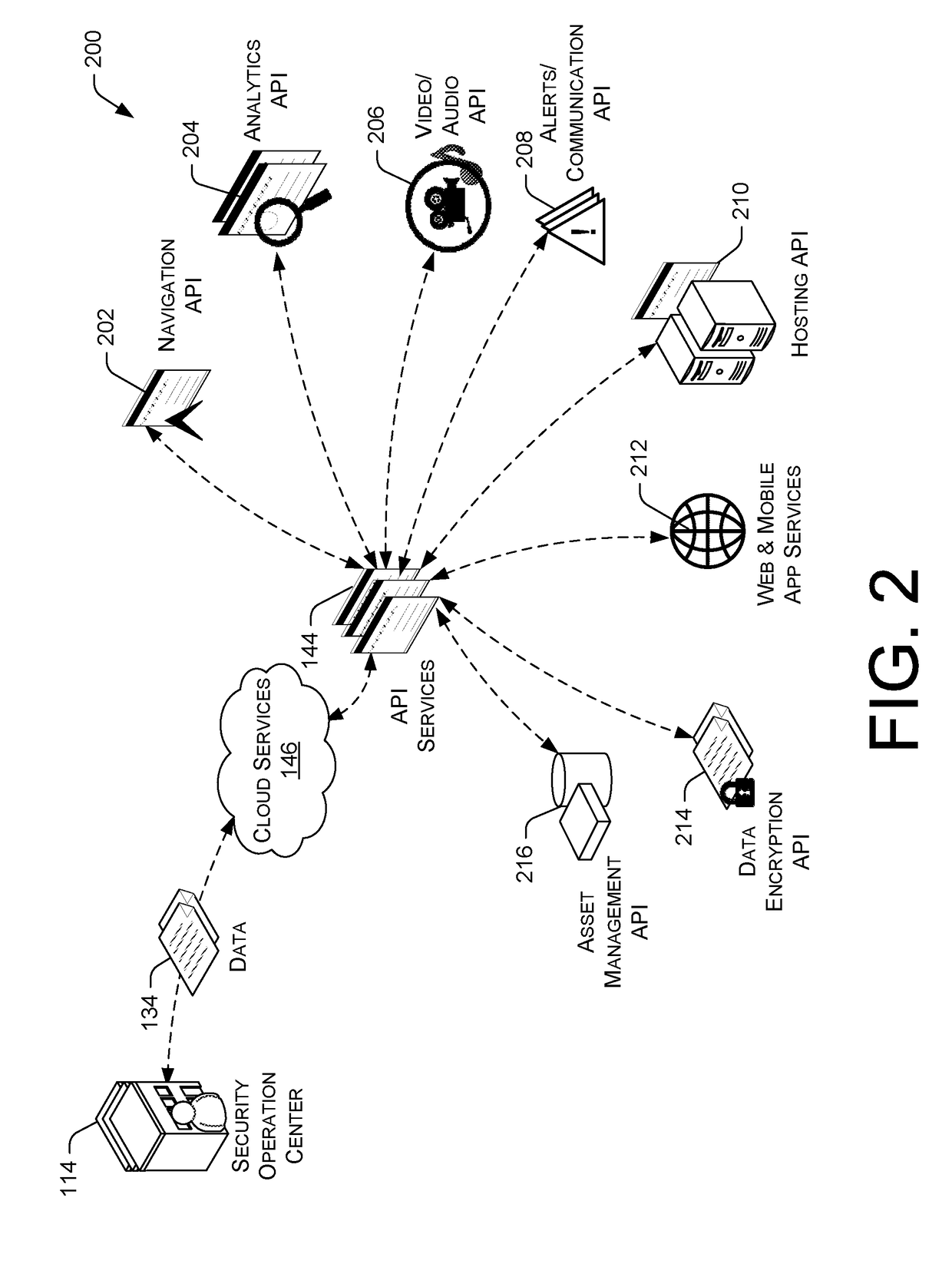
Total Property Intelligence System
ActiveUS20180211115A1Multiple keys/algorithms usagePublic key for secure communicationPhysical securityApplication software
A total property security system may be implemented to conduct security and surveillance operations. The system includes security operations centers that are connected to one or more sensors and vehicles for collecting and transmitting surveillance data to a database hosted on cloud services. The collected surveillance data is analyzed in order to automatically deploy security measures and / or recommend courses of action using a rules engine that can be configured to client-specific or user-specific security needs. The cloud services can provide a set of application program interface services that can act on the surveillance operations center. Sensor fusion data and other surveillance data can be also transmitted to vetted monitoring service providers on a subscription basis to provide physical security services to the area within the property perimeter. During the subscription period, the selected monitoring service providers can obtain time-based encryption token for accessing surveillance data.
Owner:KLEIN MATIAS
System for Inventory Management
Systems and methods related to a store intelligence system can include a plurality of end-point devices associated with a product shelf configured to display product, and a plurality of hubs each positioned adjacent to one or more of the plurality of end-point devices. One or more of the plurality of end-point devices can be configured to detect and transmit inventory information to a predetermined adjacent hub of the plurality of hubs or to receive and display price information or product information from a predetermined hub of the plurality of hubs. Each of the hubs can be configured to receive inventory information from one or more of the plurality of endpoint devices, provide alerts, transmit inventory information to a network, receive price information and product information, and transmit the price information and product information to one or more of the plurality of end-point devices.
Owner:RTC IND
Dynamic gathering of social media content
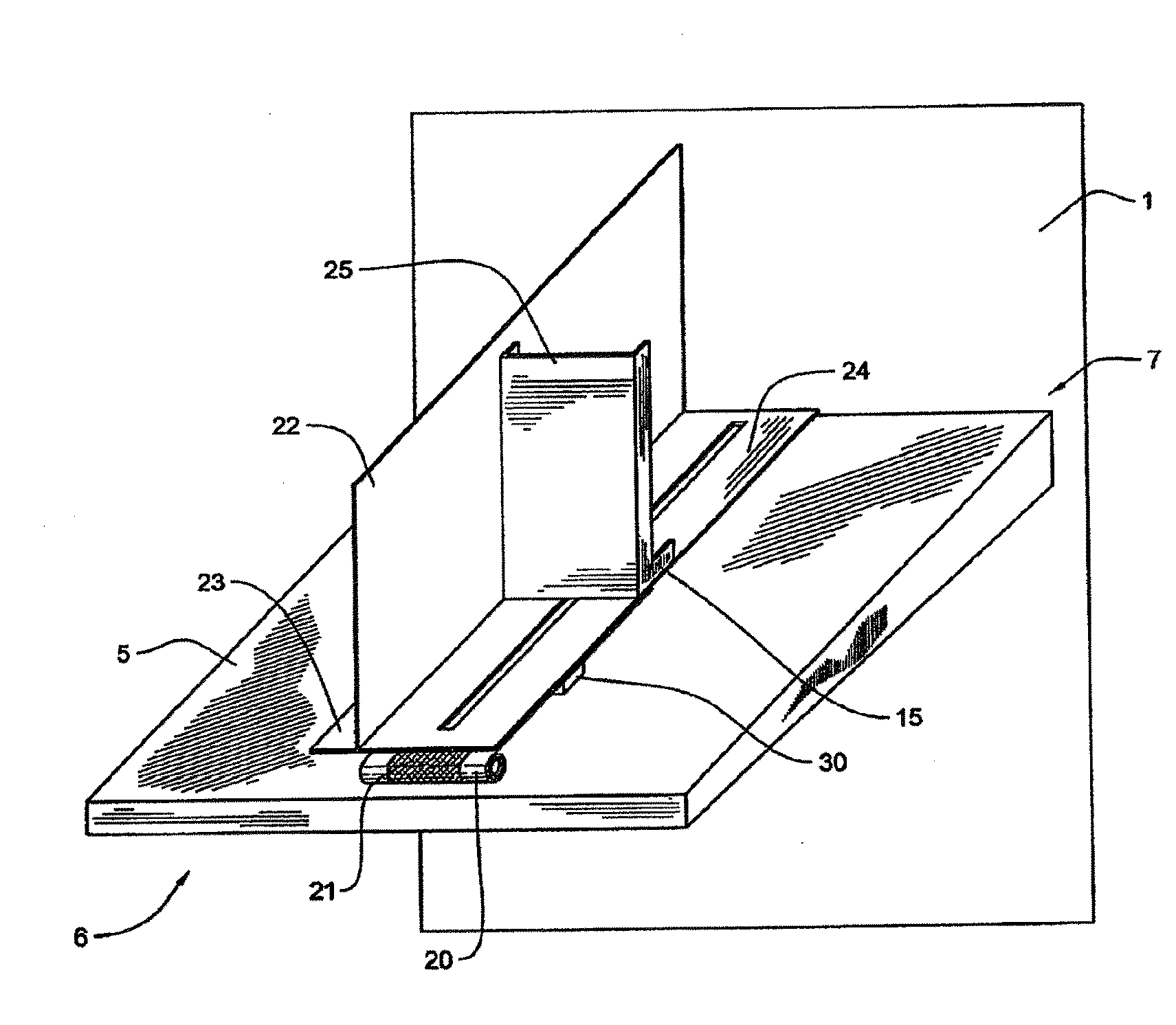
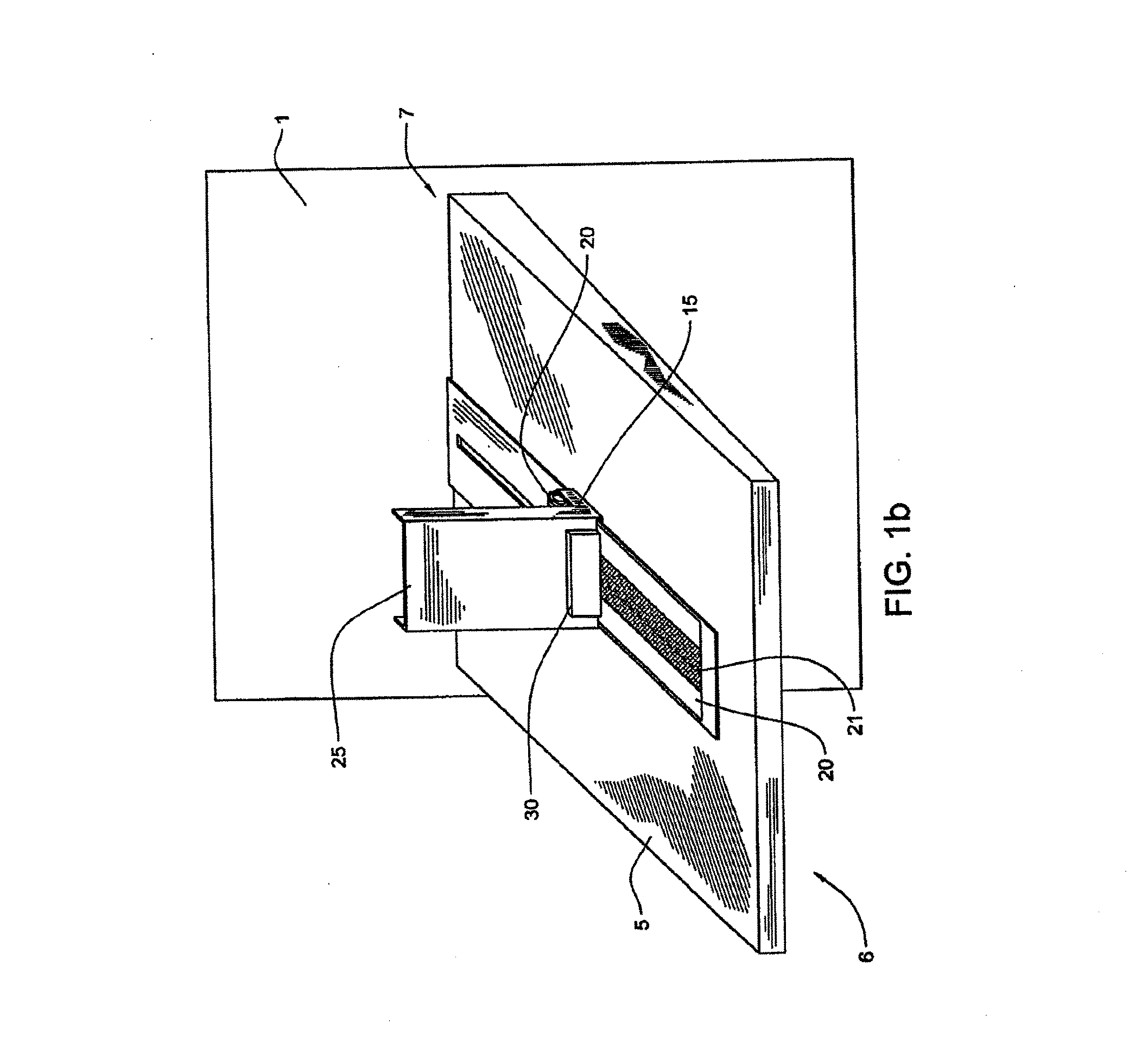
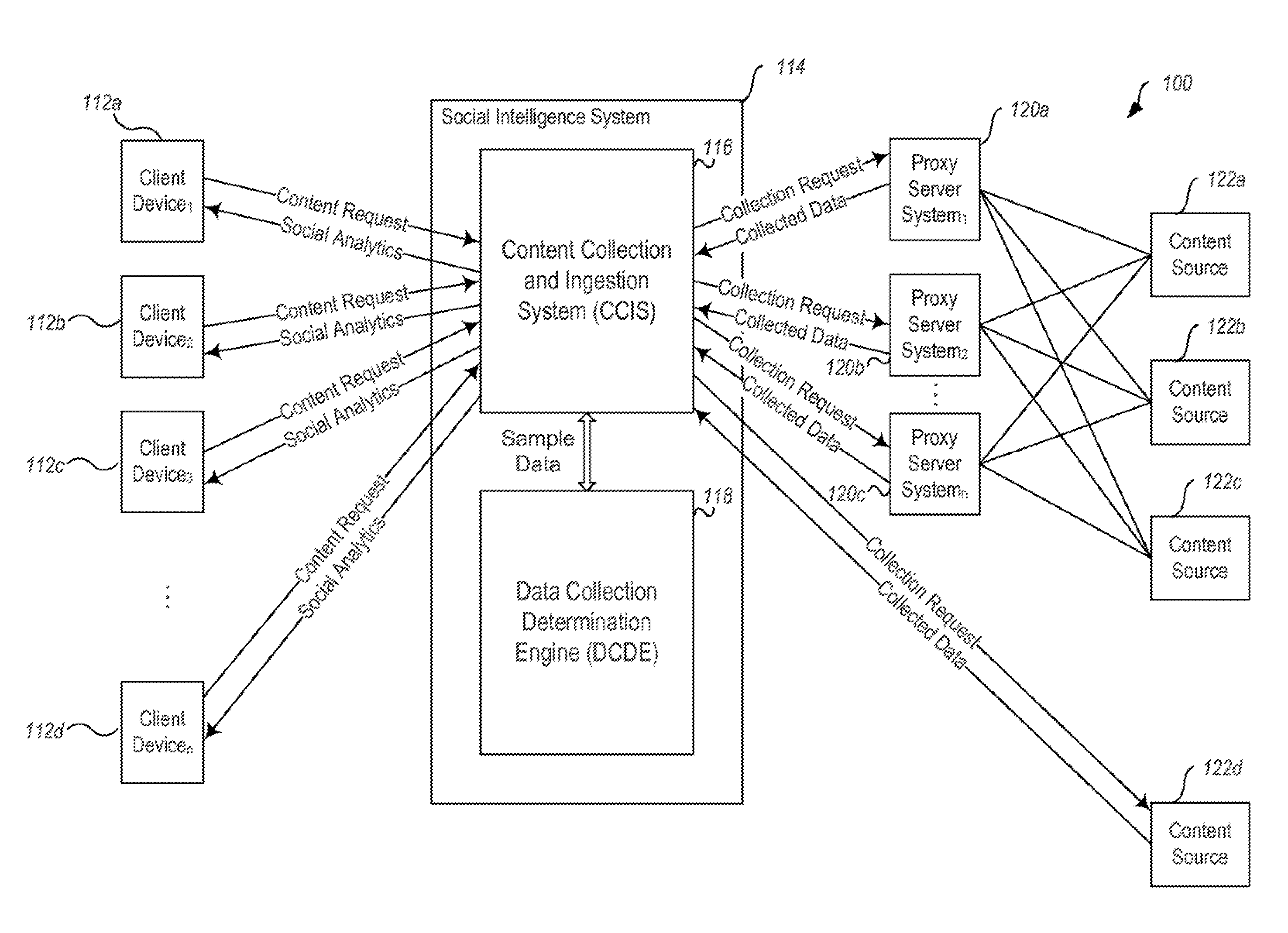
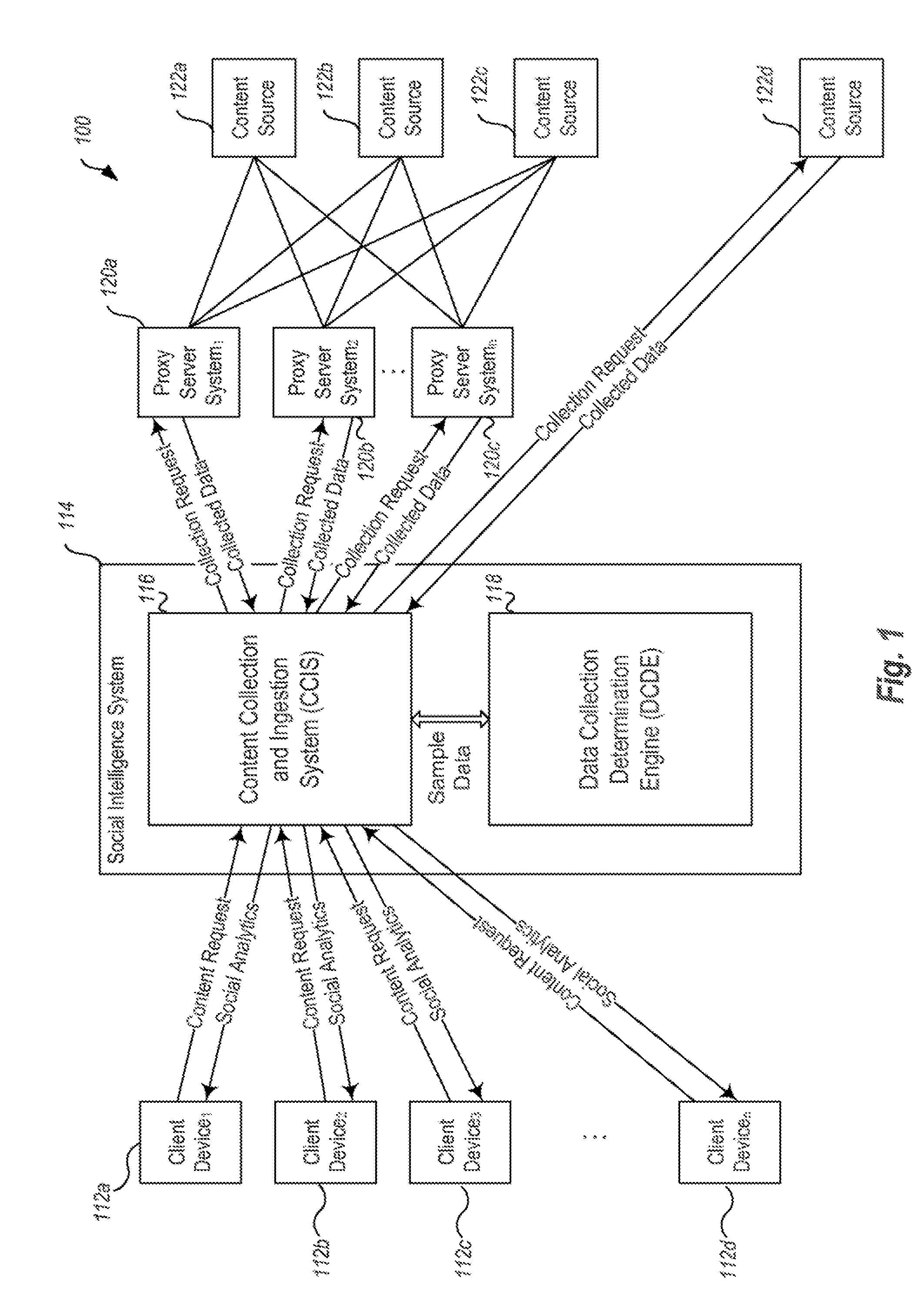
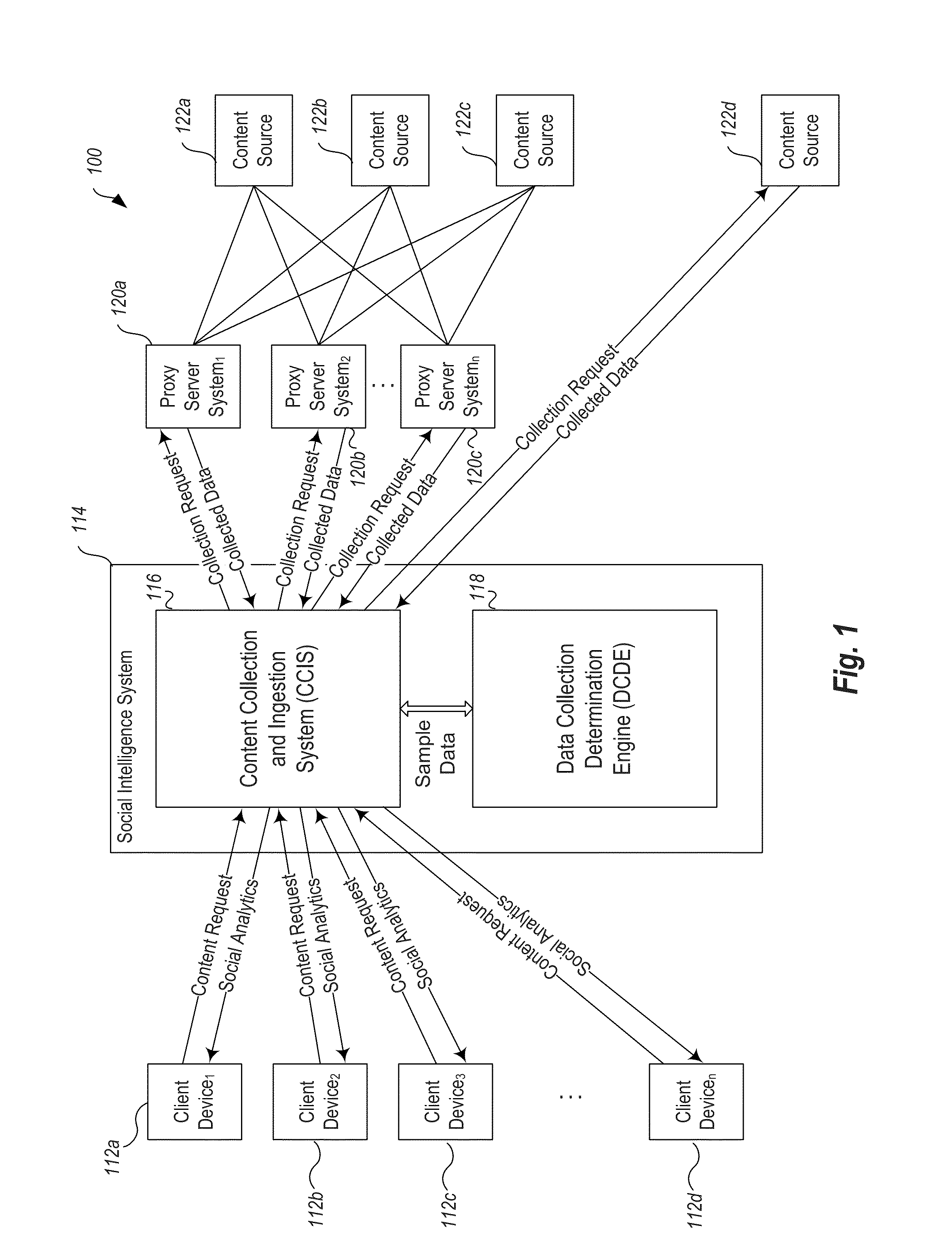
Methods, techniques, and systems for gathering social media content are provided. Some embodiments provide a Social Intelligence System (“SIS”) configured to provide dynamic search capability of a content source by using a proxy server system as an intermediary between the SIS and the content source. The SIS may then dynamically determine a rate at which it searches for content based on a rate of change or predicted change of a particular content source. Dynamically determining a rate allows the SIS to track a particular topic or series of topics over time, while only searching for content on the topic at the most optimal time periods to reduce overall cost.
Owner:CISION US INC
Method and system for an integrated incident information and intelligence system
ActiveUS20060235833A1Emergency connection handlingConnection managementTelecommunications networkData source
Providing a system and method for identifying and characterizing incidents. The system and method can receive information from telecommunications networks or other information providers that may trigger generating an Incident Record. The Incident Record may further be analyzed to characterize the type of incident. This further analysis may include retrieving data from multiple data sources to support the application of rules used to characterize the incident. Additionally, analyses from multiple incidents may be combined if determined to relate to a single event.
Owner:AIRSAGE INC
Reconfigurable spam detection system based on global intelligence
InactiveUS20090063371A1Content analysis accurateDelayed informationDigital computer detailsDigital dataSpammingEngineering
Owner:FORTINET
Methods and systems for managing supply chain processes and intelligence
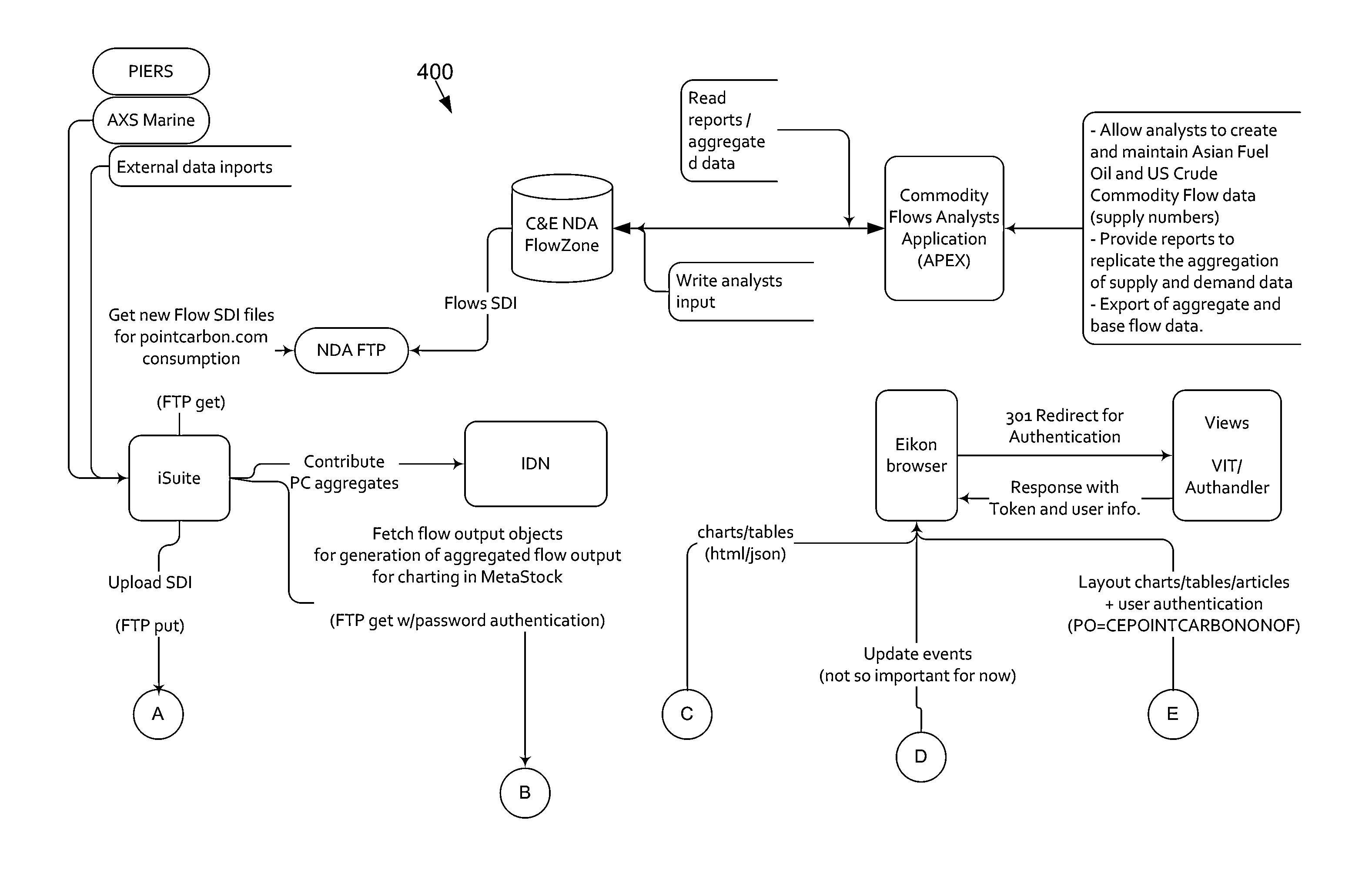
A Global Supply Chain Intelligence system (“GSCI”) adapted to predict, discover and verify commodity trade flows. Creating and maintaining a dataset that tracks real and near real-time commodity flows as they happen as an input to the GSCI. The dataset used in a business intelligence process within the GSCI to arrive at an output, such as a predicted price behavior, a price alert, a risk alert, etc. A Commodity Flow Intelligence (CFI) component that collects and analyzes information with the timeliness, detail and accuracy required to track, forecast and predict supply and demand imbalances at the discrete flow level to aid market participants in making operational trading and investment decisions, for example, in connection with a financial services system or offering providing enhanced data and tools to promote market transparency.
Owner:THOMSON REUTERS GLOBAL RESOURCES UNLIMITED CO
Homeland intelligence systems technology "H-List"
InactiveUS20090115603A1High detection sensitivityHigh selectivitySemiconductor/solid-state device detailsSurgeryFiberEngineering
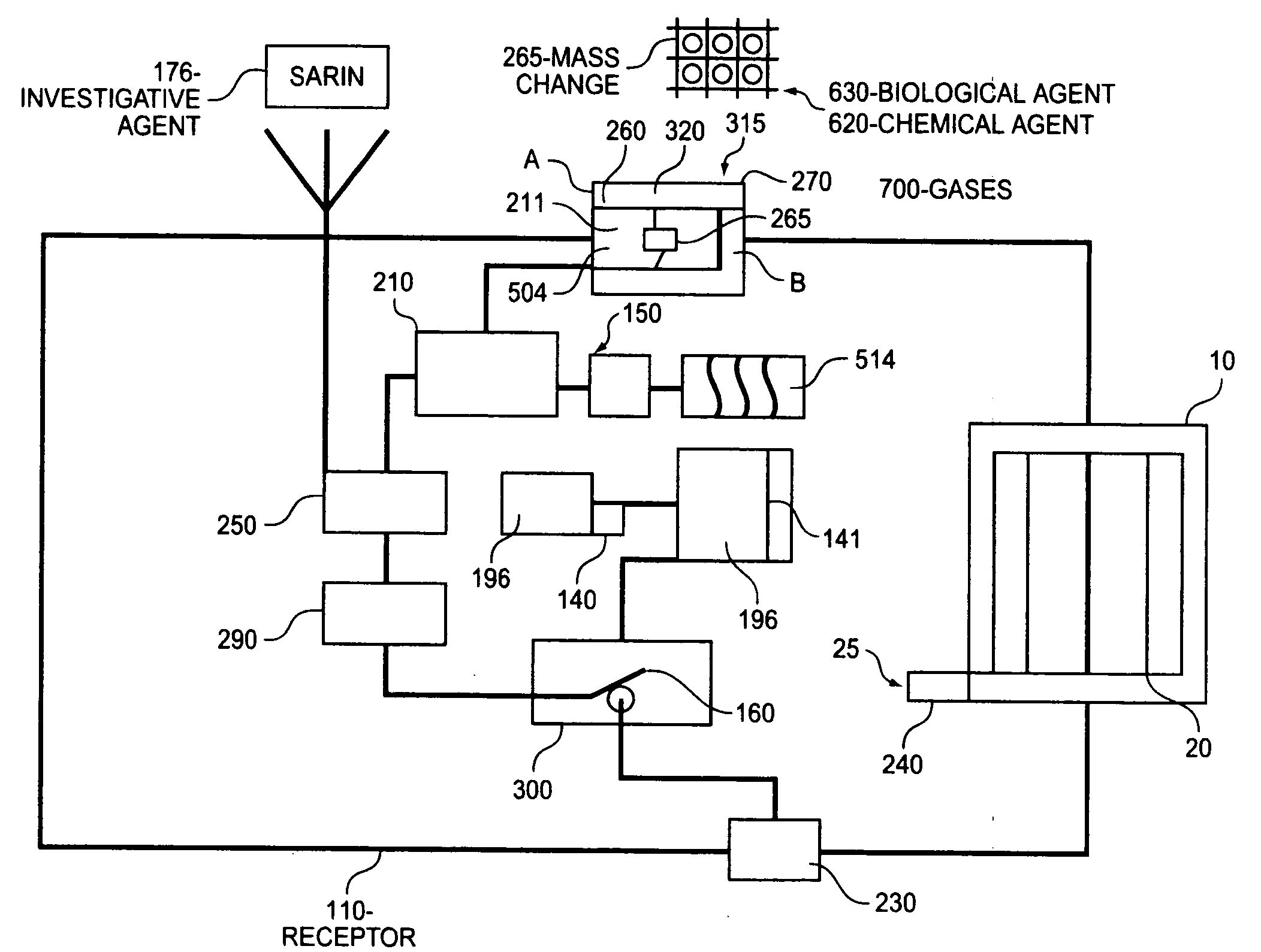
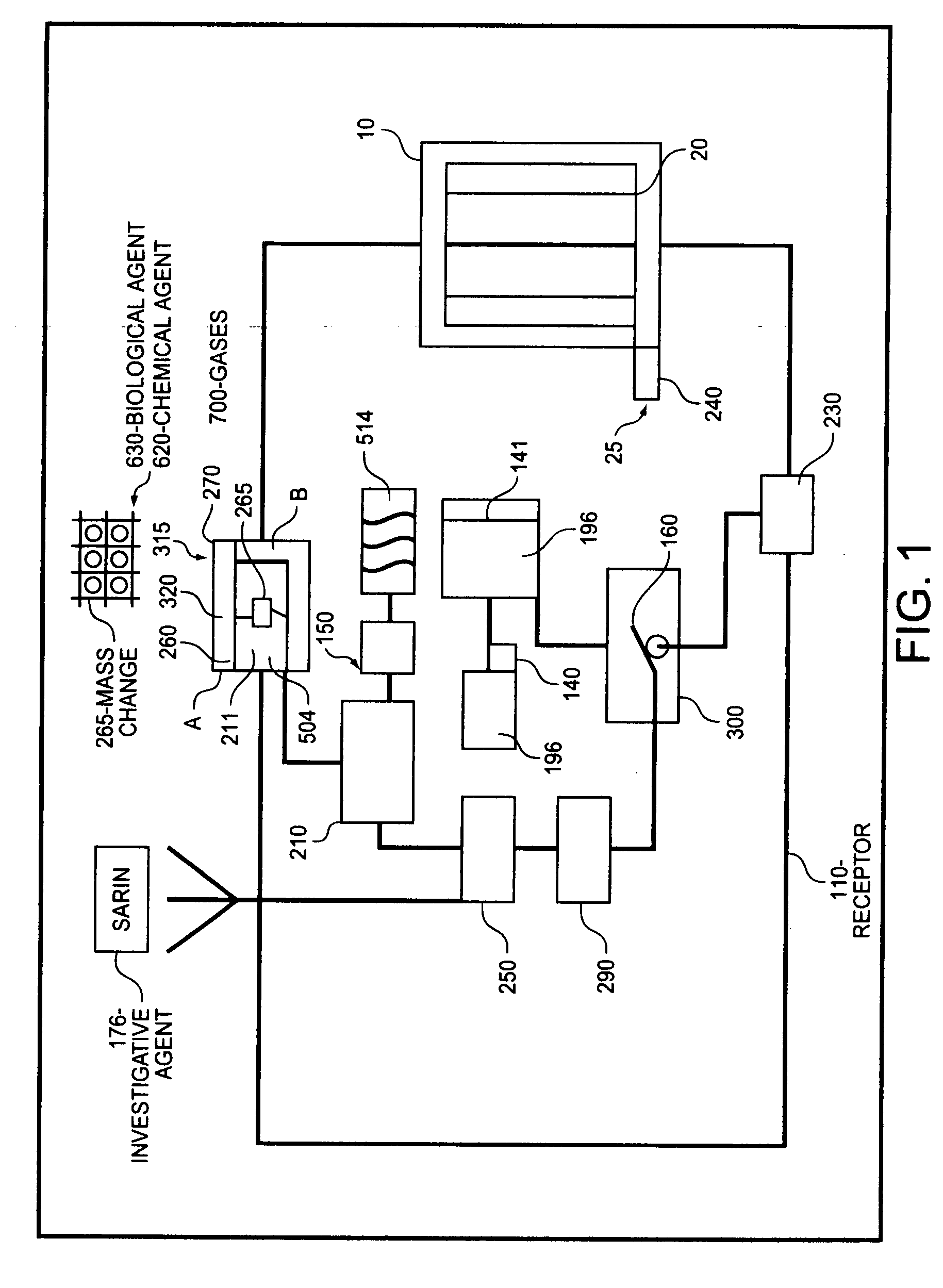
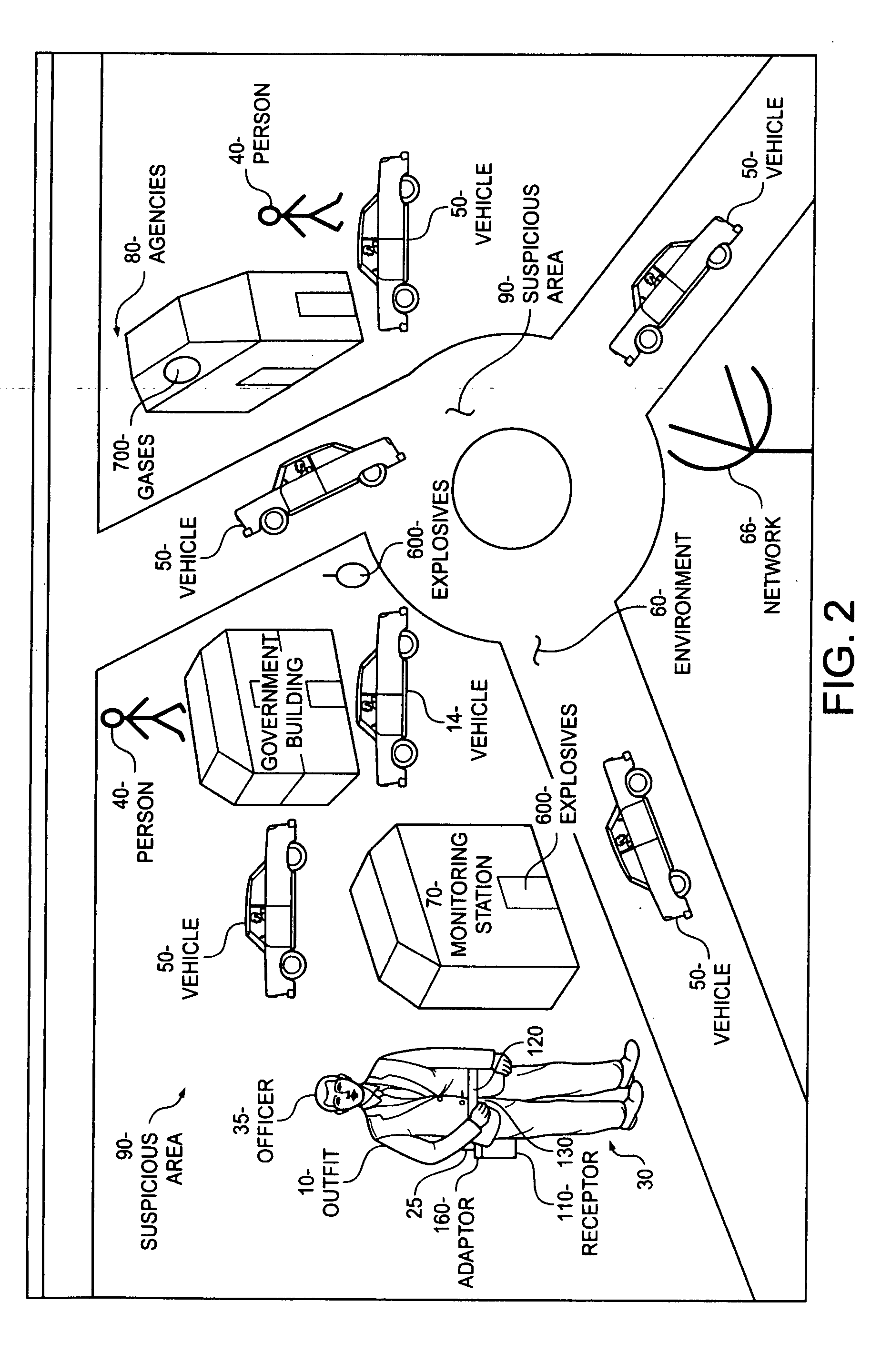
Homeland Intelligence Systems Technology “H-LIST” comprises nano-sensors embedded in a silicon substrate and etched / fused in a micro-fibered material alloyed with miniaturized steel responsive to preventing bullet penetration and to enable effective detection platform on an outfit for monitoring suspicious terrorist activities and for tracking biological and chemical gases, and explosives, including weapons of mass destruction and physiological conditions of personnel. H-LIST comprises plurality sensors on an outfit worn by an officer, a security officer, a bus driver, hostesses, Doctors, civil establishment hospital patients and the like, for sensing deadly gases, explosives, and physiological conditions in a defined area A receptor is operatively configured and worn proximate to the outfit responsive for empowering the sensors and for receiving / analyzing detection signal communications wirelessly indicative of the presence of a sensed agent, whereby detected signals are transported wirelessly to a central security monitoring station, enabling communication with first responders and backup security personnel or agents to the vicinity of the detection. The sensors are multifunctional and coded to recognize wavelike pattern of gases and explosives traveling through the wave, enabling the outfit and the receptor to be operable and process the portion of the detection signal to determine the detection type and / or whether there is a concealed object by conducting a test in which a first characteristic of a first dielectric constant associated with a person is determined, and a second characteristic of a second dielectric constant associated with the concealed object and or weapons of mass destruction is determined to expedite data transmission and communication to first responders.
Owner:TABE JOSEPH AKWO
Relevance based digital building
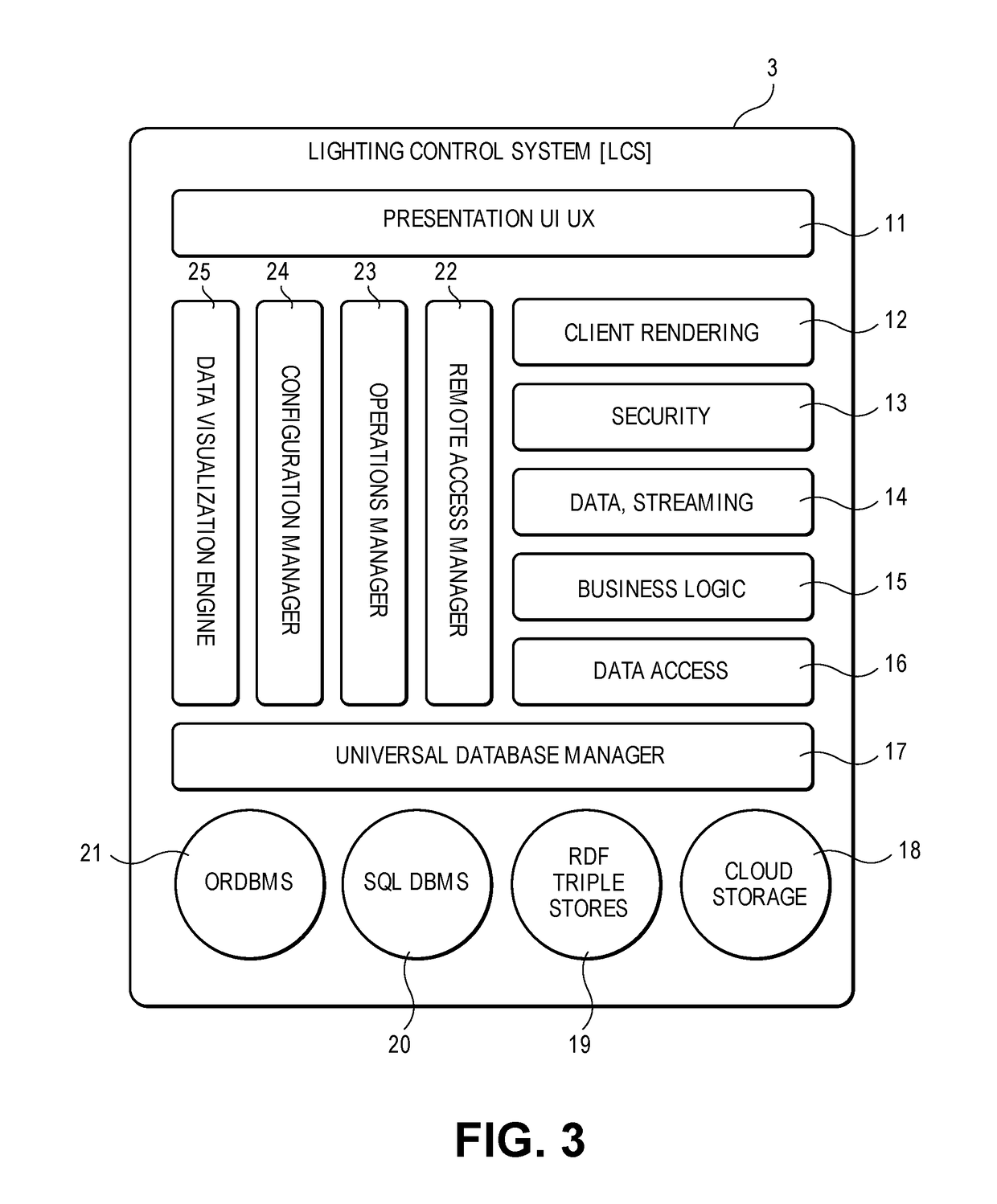
InactiveUS20180188712A1High activityHigh evolutionProgramme controlData processing applicationsNetwork structureREMS Stakeholder
The Relevance Based Digital Building [RBDB] invention describes a method and apparatus consisting of a hardware and software environment that creates a relevance based digital building intelligence system. RBDB defines a Network Lighting System [NLS] that delivers the network fabric for an array of intelligent luminaries configured with Internet of Things [IoT] devices. Layered on the NLS network fabric is a Digital Building Intelligence information architecture that enables the building to become Self-Aware with Digital Personas. The building can manage many of its own needs through operational optimization, Machine to Machine [M2M] and machine to stakeholder interactions. RBDB allows the stakeholders associated with the building to take on a multiplicity of digital personas enabling high relevance interactions with the building and each other through these digital intelligence representations. The digital building adapts to the occupants (stakeholders) preferences and requirements and empowers he interaction between individuals (stakeholders) and their environment (Digital Building Intelligence).
Owner:MACKAY MICHAEL T
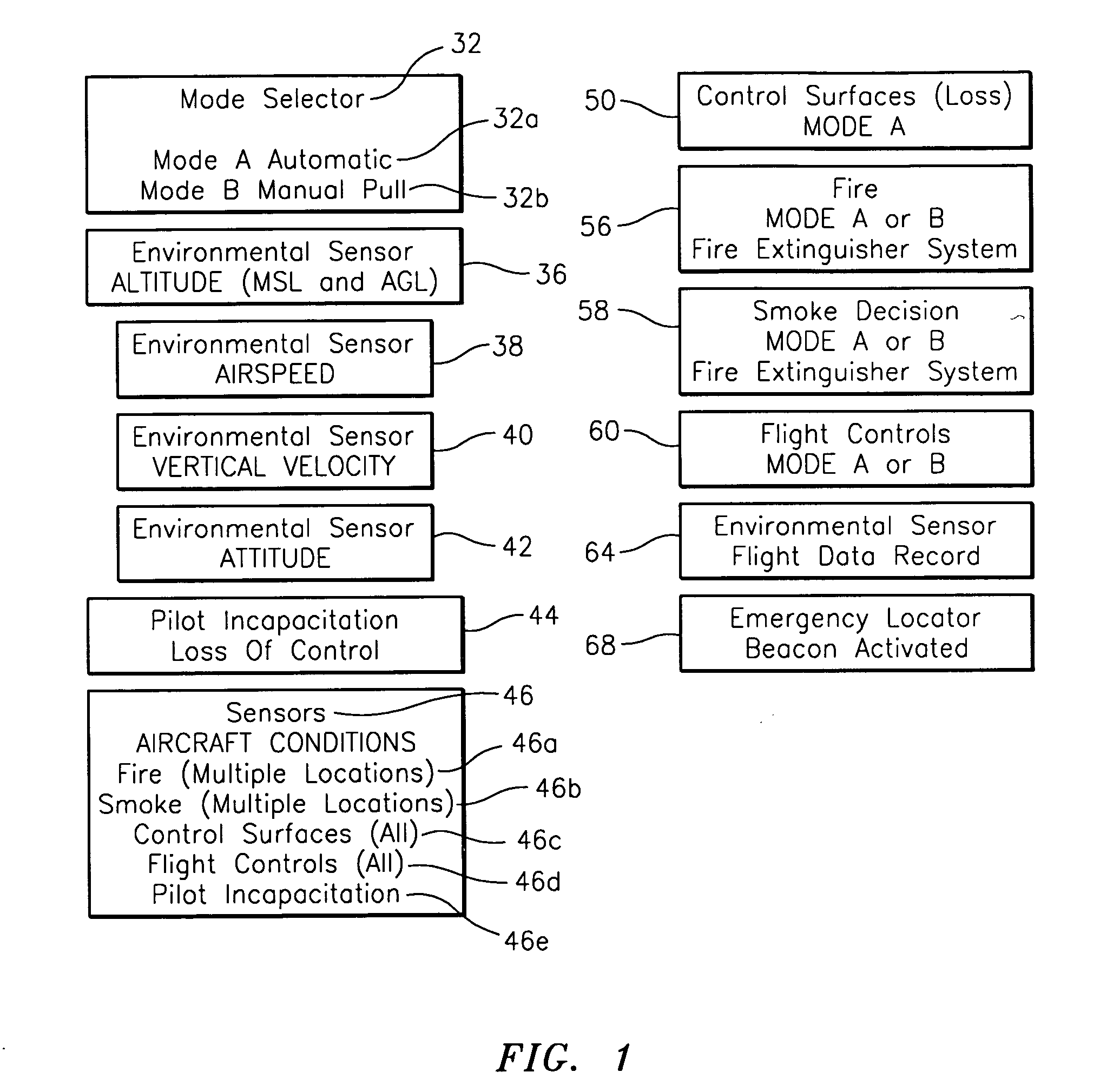
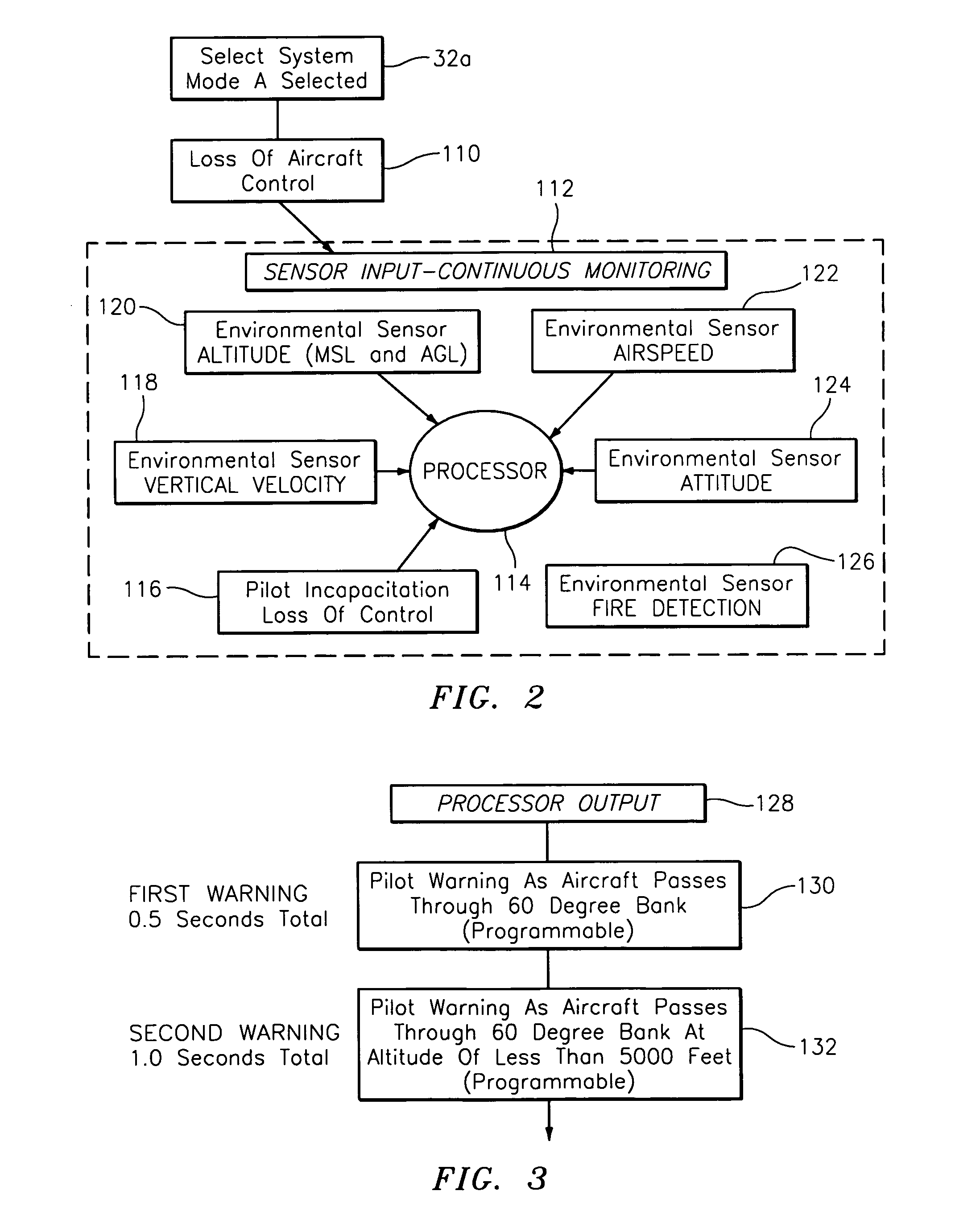
Smart recovery system
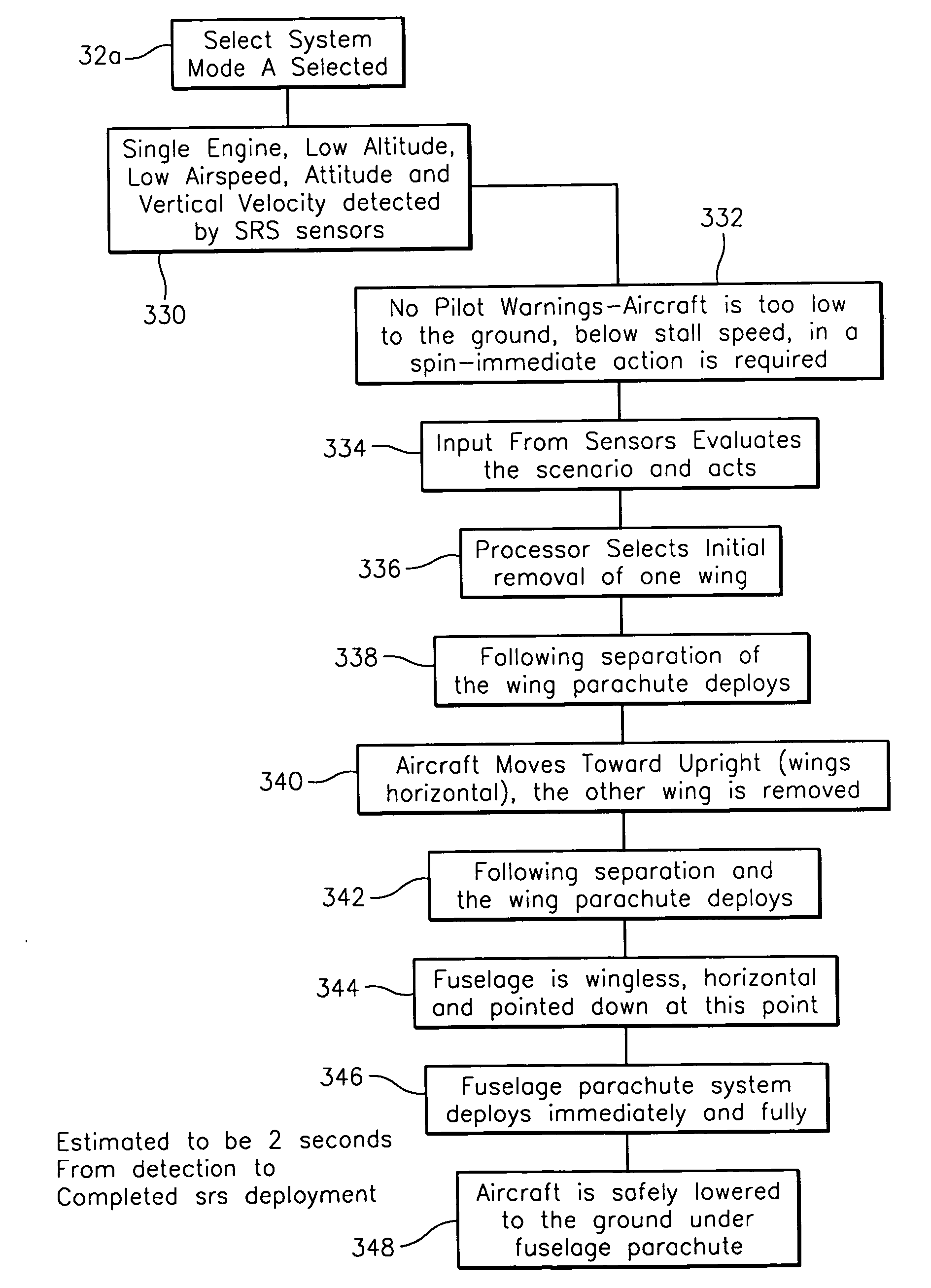
ActiveUS20100004803A1Shorten speedSlow downAnalogue computers for trafficAircraft controlOn boardSmart system
This invention relates to an intelligence system on board an aircraft that detects an emergency, assesses the situation, and then acts on the situation in a pre-determined manner.
Owner:MANFREDI DARIO P +1
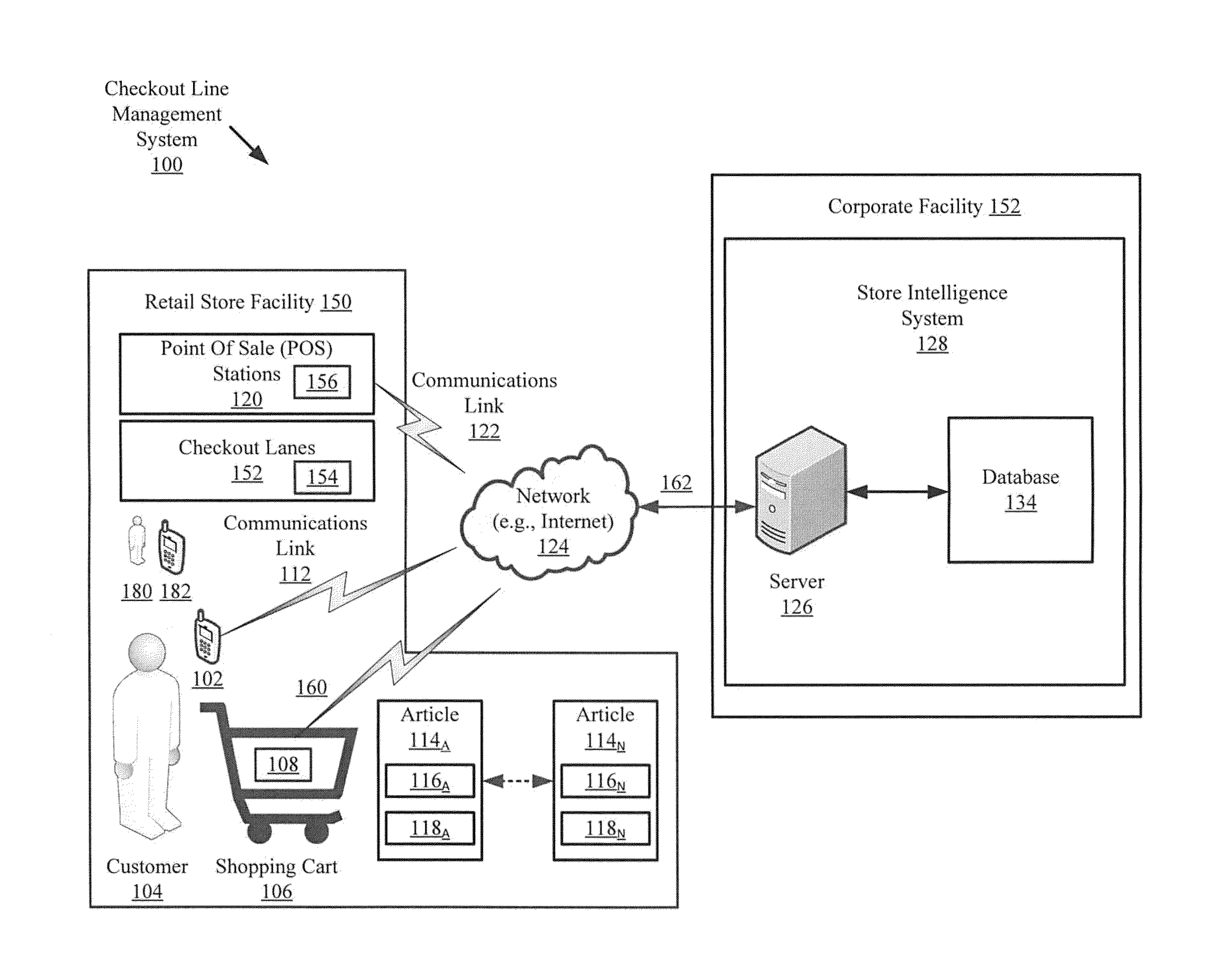
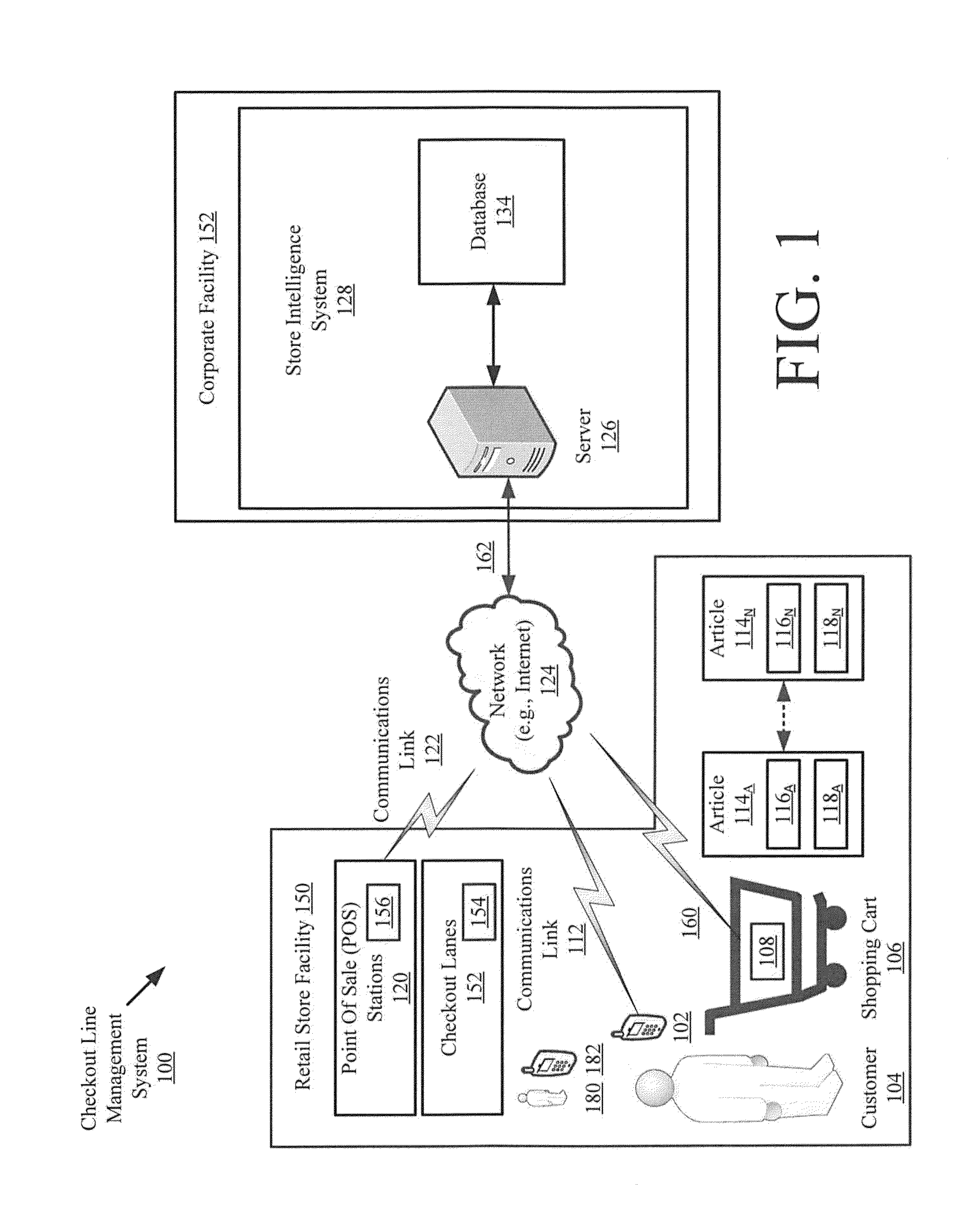
Systems and methods for retail line management
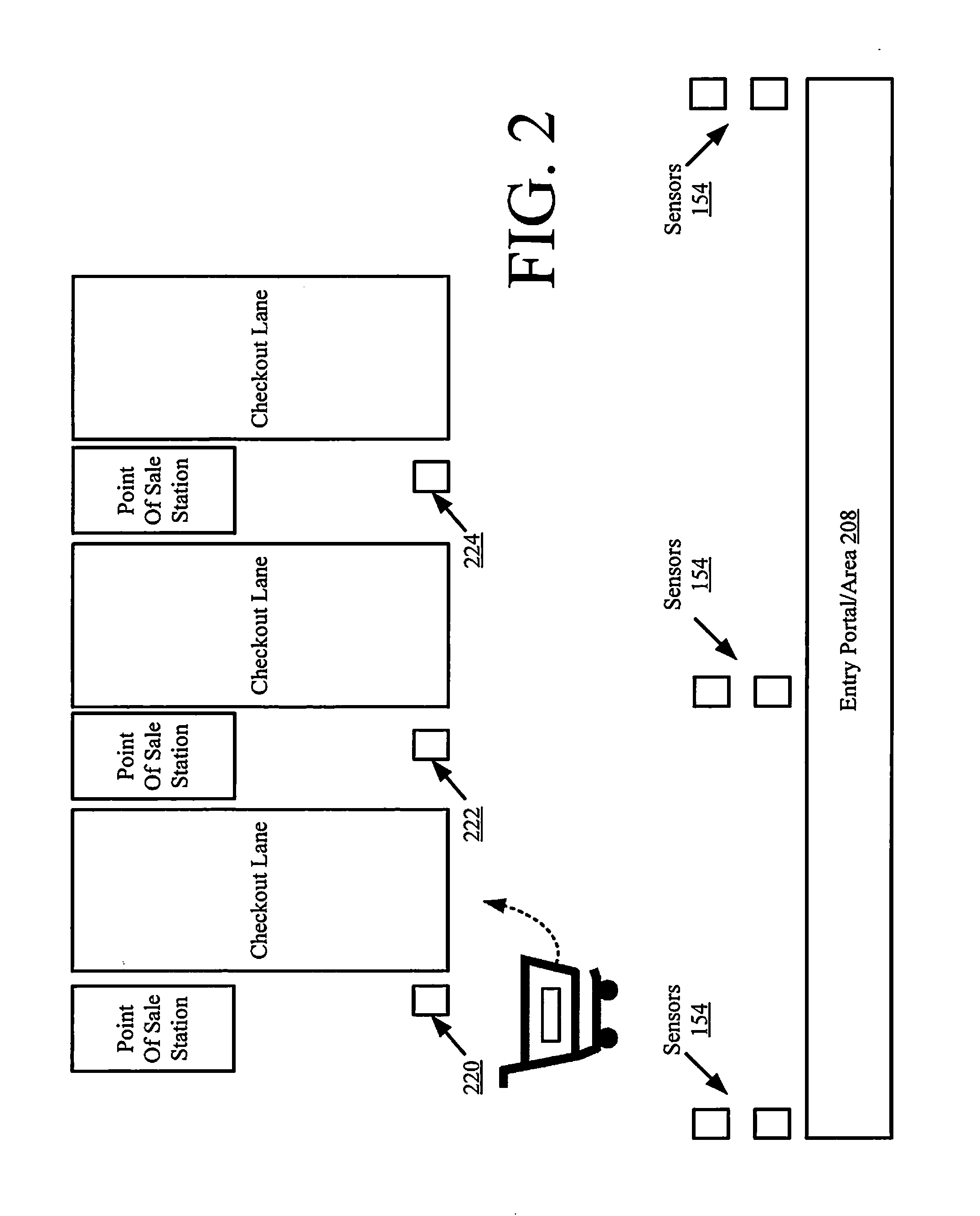
InactiveUS20140236653A1Improve shopping experienceChecking apparatusCash registersLine managementSmart system
Systems (100) and methods (100) for managing checkout line efficiency of a retail store. The methods involve electronically obtaining, by a store intelligence system (128), first data indicating an efficiency of each checkout lane of a plurality of checkout lanes (152) and second data indicating a total number of shopping carts (106) in each checkout lane and / or a total number of articles within each shopping cart. A checkout lane recommendation is then generated by the store intelligence system for a customer (104) based at least on the first data and / or the second data. The checkout lane recommendation is communicated from the SIS to a mobile communication device (102) in the possession of the customer.
Owner:TYCO FIRE & SECURITY GMBH
Composite self-healing system
InactiveUS20100119704A1Improve survivabilityFunction increaseLayered productsLaminationSelf-healingDielectric
An advanced reflexive structure system is disclosed. The reflexive system mimics the pain withdrawal reflex on which the human body relies. The reflexive system incorporates a continuous health and performance monitoring system via an embedded dielectric film, an adaptive composite structure based on shape memory composite material, and an intelligence system which will be interfaced with both the health / performance sensors and the adaptive structure. When activated shape memory polymer will recover its structural integrity via shape recovery and a reptation healing process. These features enable the use of SMP as an adaptive structure in the proposed reflexive system. The development of a reflexive system for structures will enable increased safety and security and demonstrate a better understanding of integrated performance systems. This reflexive technology could find immediate implementation on all current and future systems and future implementation on platforms such as the International Space Station, Lunar, and Martian habitats.
Owner:CORNERSTONE RES GROUP
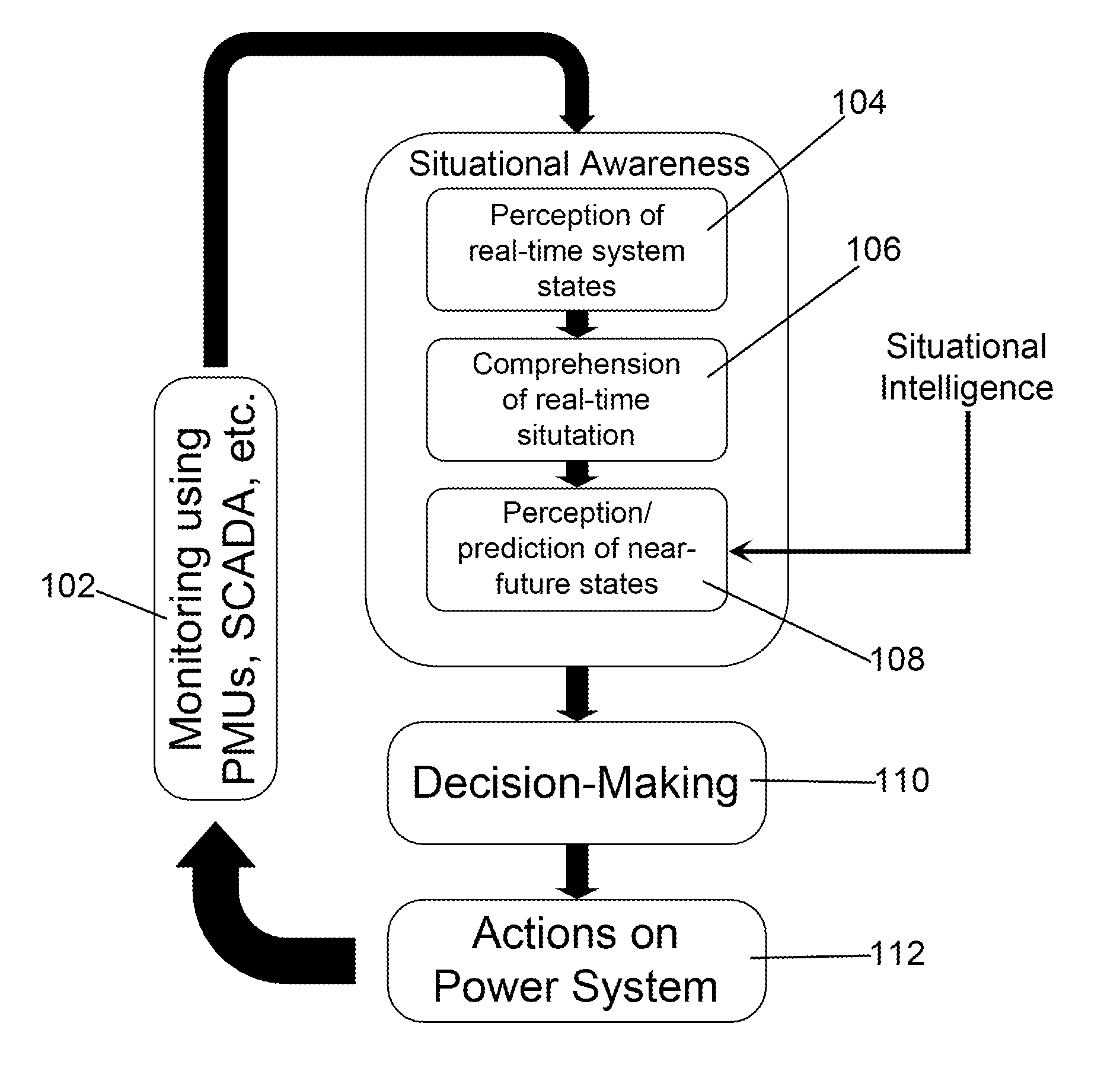
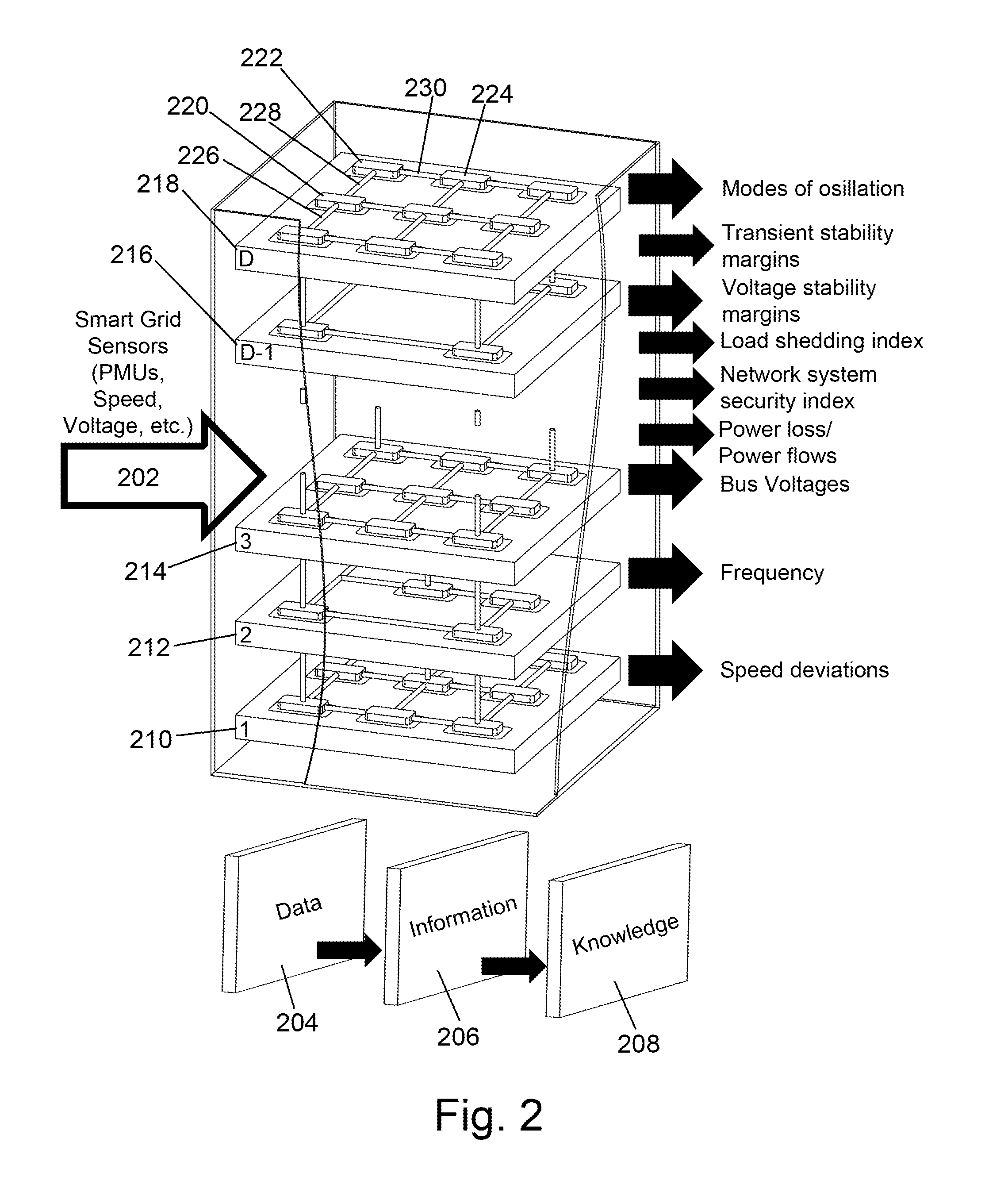
Situational Awareness / Situational Intelligence System and Method for Analyzing, Monitoring, Predicting and Controlling Electric Power Systems
ActiveUS20140148962A1Change in stateImprove integrityMechanical power/torque controlLevel controlInformation layerAutomatic control
A system and method for modeling, controlling and analyzing electrical grids for use by control room operators and automatic control provides a multi-dimensional, multi-layer cellular computational network (CCN) comprising an information layer; a knowledge layer; a decision-making layer; and an action layer; wherein each said layer of said CCN represents one of a variable in an electric power system. Situational awareness / situational intelligence is provided therefrom so that the operators and grid control systems can make the correct decision and take informed actions under difficult circumstances to maintain a high degree of grid integrity and reliability by analyzing multiple variables within a volume of time and space to provide an understanding of their meaning and predict their states in the near future where these multiple variables can have different timescales.
Owner:CLEMSON UNIVERSITY
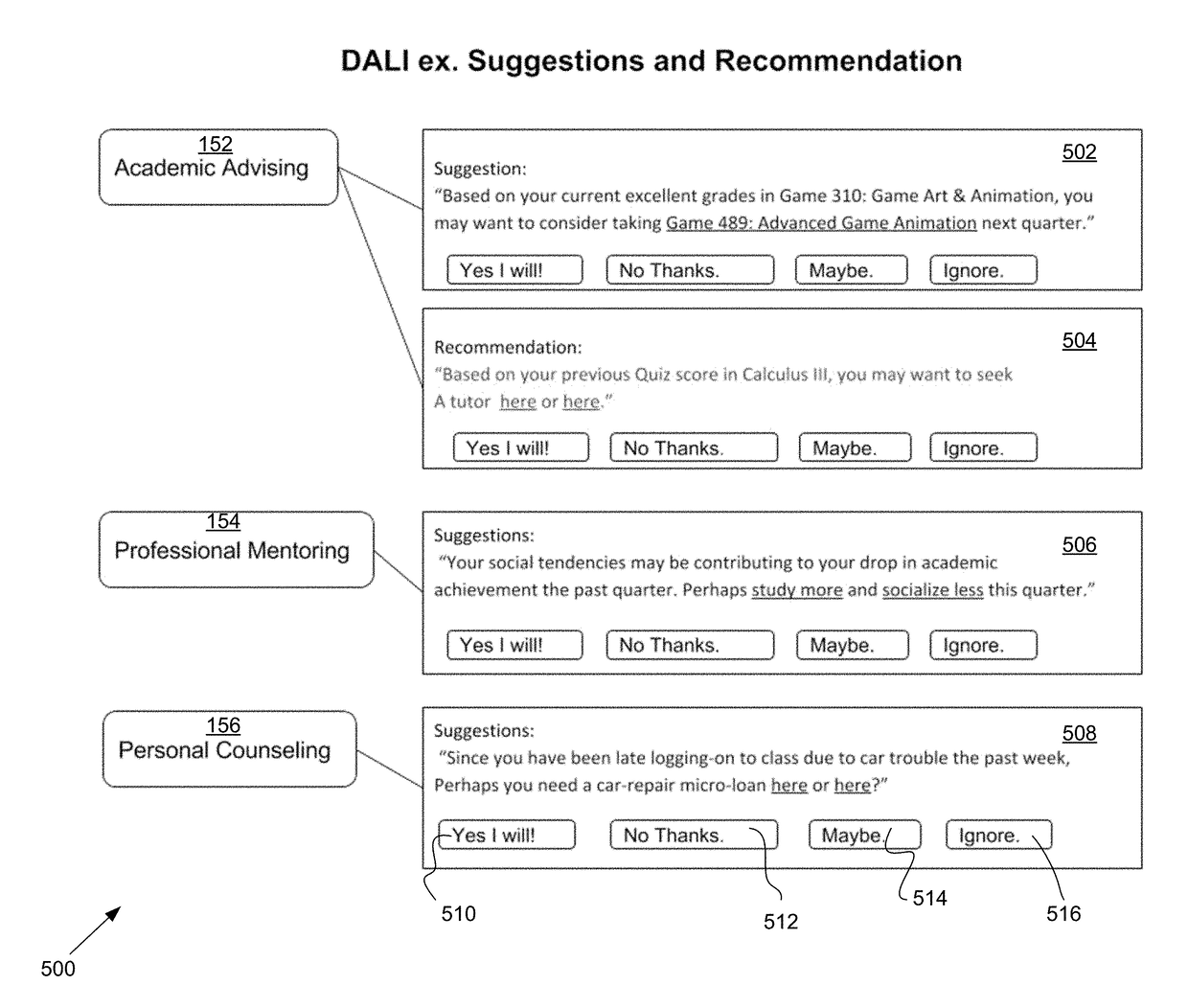
Deep academic learning intelligence and deep neural language network system and interfaces
InactiveUS20180247549A1Enhanced student learning environmentImprove efficiencySemantic analysisProbabilistic networksLearning basedLanguage network
A knowledge acquisition system and artificial cognitive declarative memory model to store and retrieve massive student learning datasets. A Deep Academic Learning Intelligence system for machine learning-based student services provides monitoring and aggregating performance information and student communications data in an online group learning course. The system uses communication activity, social activity, and the academic achievement data to present a set of recommendations and uses responses and post-recommendation data as feedback to further train the machine learning-based system.
Owner:SCRIYB LLC
Cable fault detection
ActiveUS7725295B2Level controlEmergency protective arrangements for automatic disconnectionElectric power systemCable fault location
A cable fault detection component (168) receives input data indicative of a fault in an electrical power system. The component (168) analyzes the input data to determine if the fault is indicative of a temporary or self-clearing cable fault and generates corresponding output data (276). In one implementation, the cable fault detection component (168) is implemented as a software module which operates on a computer (105) of a substation intelligence system (104).
Owner:HITACHI ENERGY SWITZERLAND AG
Supply chain intelligence search engine
InactiveUS20170039500A1Data augmentationEnhanced analyticsWeb data indexingResourcesData setDecision taking
A Global Supply Chain Intelligence system (“GSCF”) configured as a supply chain intelligence search engine adapted to predict, discover and verify commodity trade flows. Creating and maintaining a dataset that tracks real and near real-time commodity flows as they happen as an input to the GSCI. The dataset used in a business intelligence process within the GSCI to arrive at an output, such as a predicted price behavior, a price alert, a risk alert, etc. A Commodity Flow Intelligence (CFI) component that collects and analyzes information with the timeliness, detail and accuracy required to track, forecast and predict supply and demand imbalances at the discrete flow level to aid market participants in making operational trading and investment decisions, for example, in connection with a financial services system or offering providing enhanced data and tools to promote market transparency.
Owner:REFINITIV US ORG LLC
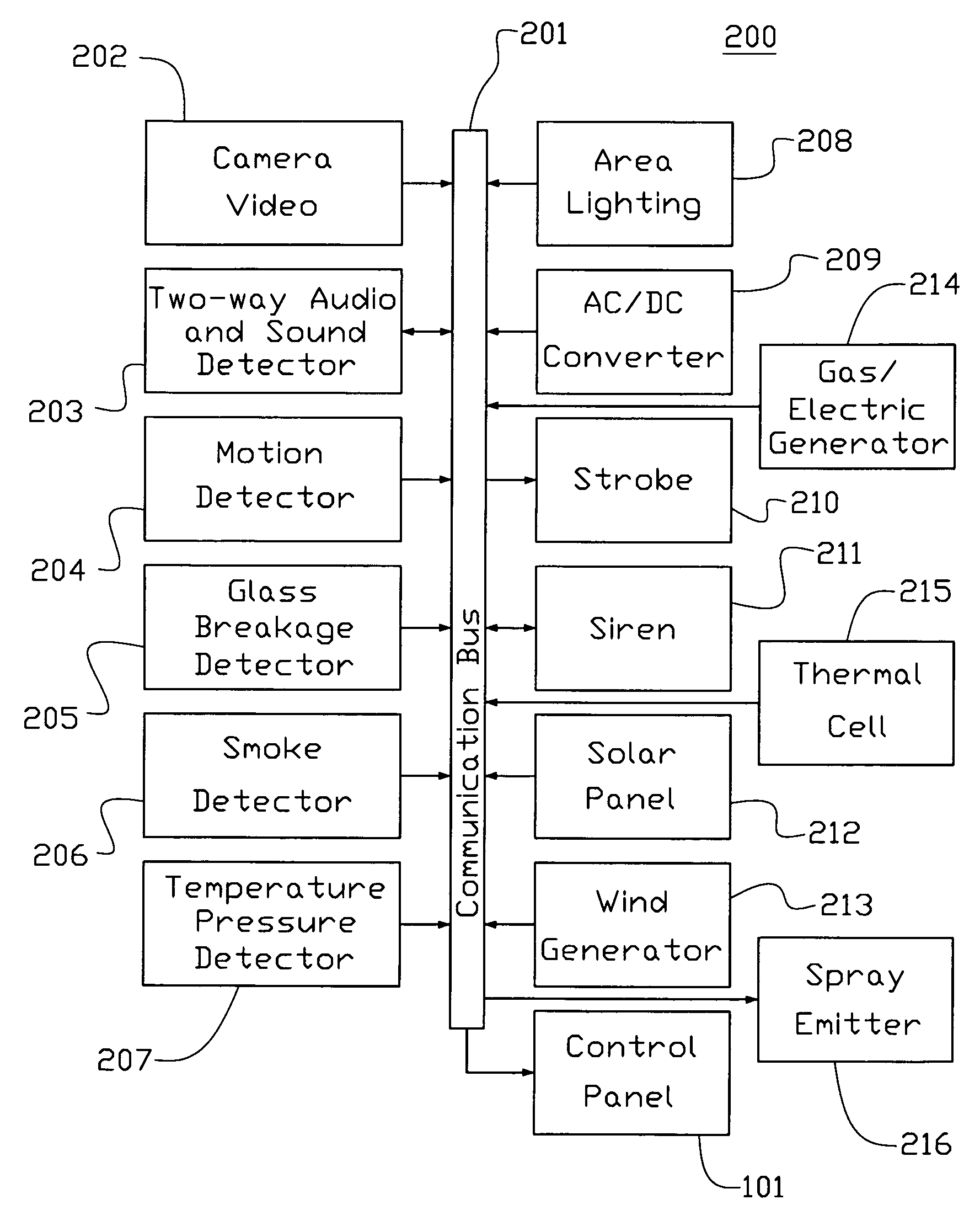
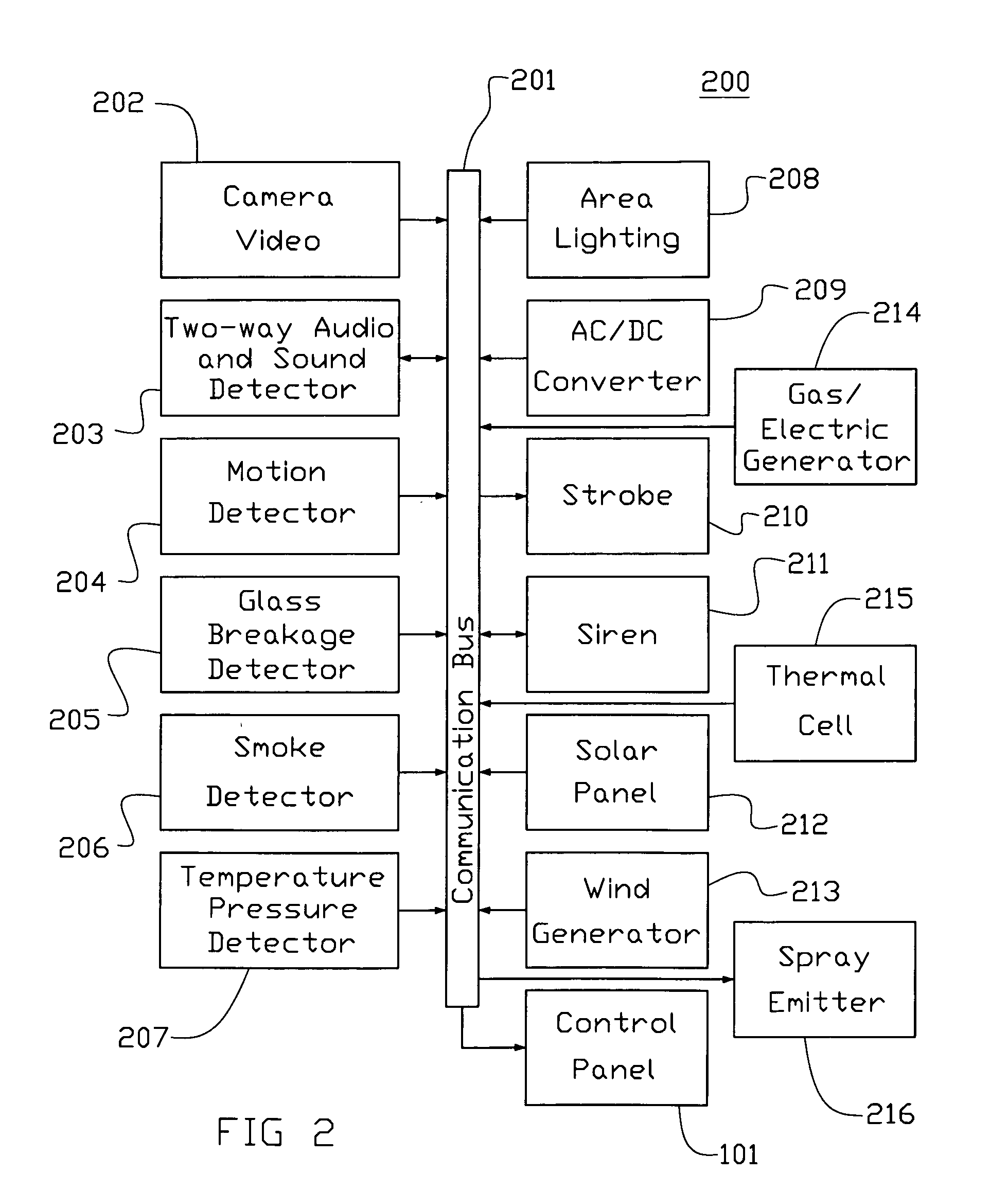
Method for detecting events at a secured location
InactiveUS20090122144A1Alarms with smoke/gas/colored-powderClosed circuit television systemsSmart systemTransmission network
A method for detecting events / activities at a secured location in which the security method may include an operator and / or determination application for supervising the location, and a transmission network for transceiving data indicative of determined activities of the secured location, wherein the determination application and the operator can initiate a deter device in response to adverse activities. The determination application of the security method may include an intelligence system for distinguishing between normal and adverse conditions. The method may also include an application for the transfer of activity data to a storage device in which operator(s) may access the stored data.
Owner:LATHAM JOEL PAT +5
Dynamic gathering of social media content
Methods, techniques, and systems for gathering social media content are provided. Some embodiments provide a Social Intelligence System (“SIS”) configured to provide dynamic search capability of a content source by using a proxy server system as an intermediary between the SIS and the content source. The SIS may then dynamically determine a rate at which it searches for content based on a rate of change or predicted change of a particular content source. Dynamically determining a rate allows the SIS to track a particular topic or series of topics over time, while only searching for content on the topic at the most optimal time periods to reduce overall cost.
Owner:CISION US INC
Attack intention recognition method based on Bayesian network inference
InactiveCN102724199AImprove scalabilityThe calculation result is accurateTransmissionPattern recognitionClique tree
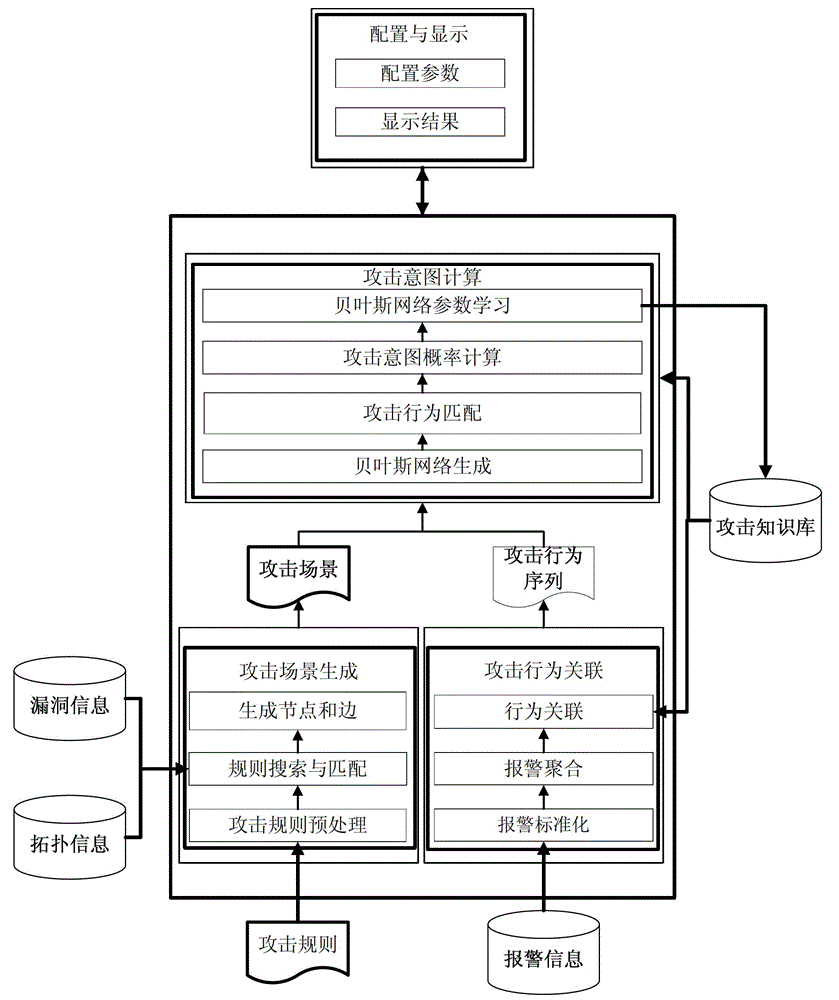
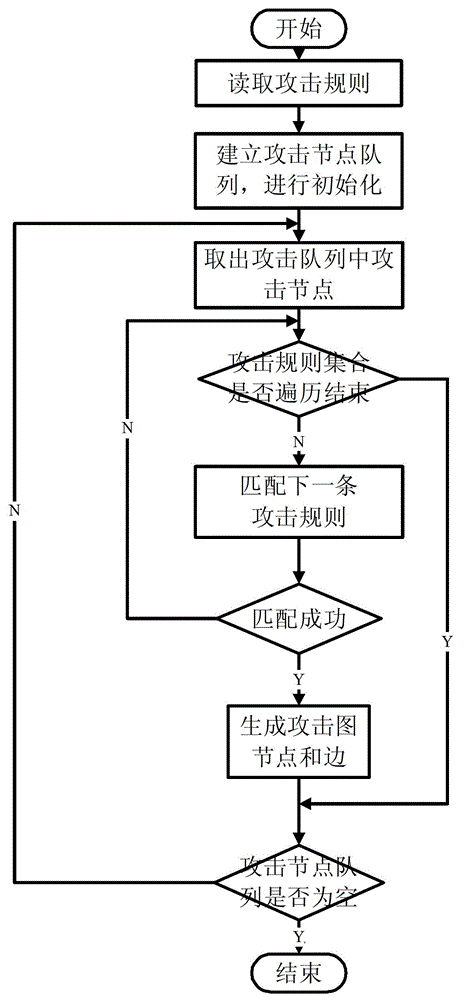
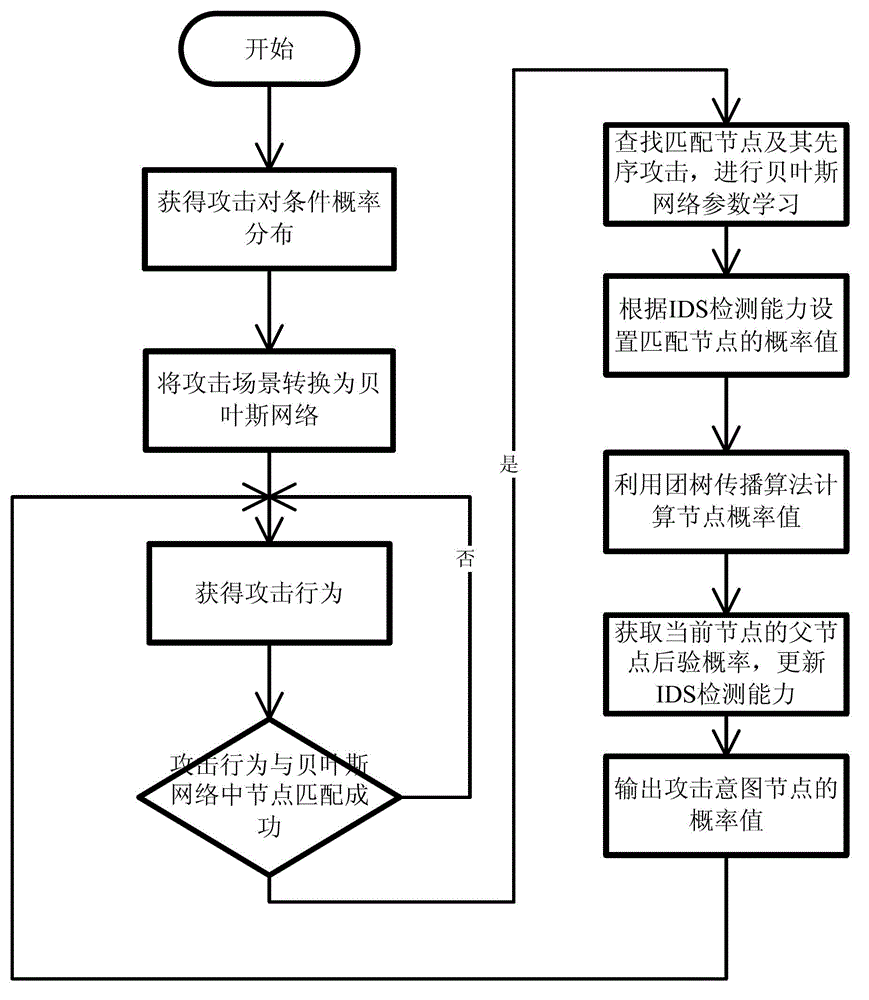
The invention provides an attack intention recognition method based on Bayesian network inference. The attack intention recognition method is applied to the attack intention recognition of an intelligence and decision-making oriented system with a parameter learning mechanism in computer network self-organizing operation (CNSOO). The method can enable an intelligence system to recognize the attack intention of an attacker by using IDS (Intrusion Detection System) alarm information according to given host vulnerability information, network topological information and attack knowledge base and supply the attack intention to a decision-making system as a decision-making basis in a CNSOO environment. The attack intention recognition process comprises the following steps of: generating attacking scenes, fusing and matching IDS alarm information, updating conditional probability distribution caused by attacking behaviors, calculating the probability of attack intention nodes by using a clique tree propagation algorithm in the Bayesian network inference, and updating Bayesian network parameters and IDS detection capability. The calculation parameters are updated according to calculation results and historical information, so that the calculation results can be more accurate.
Owner:BEIHANG UNIV
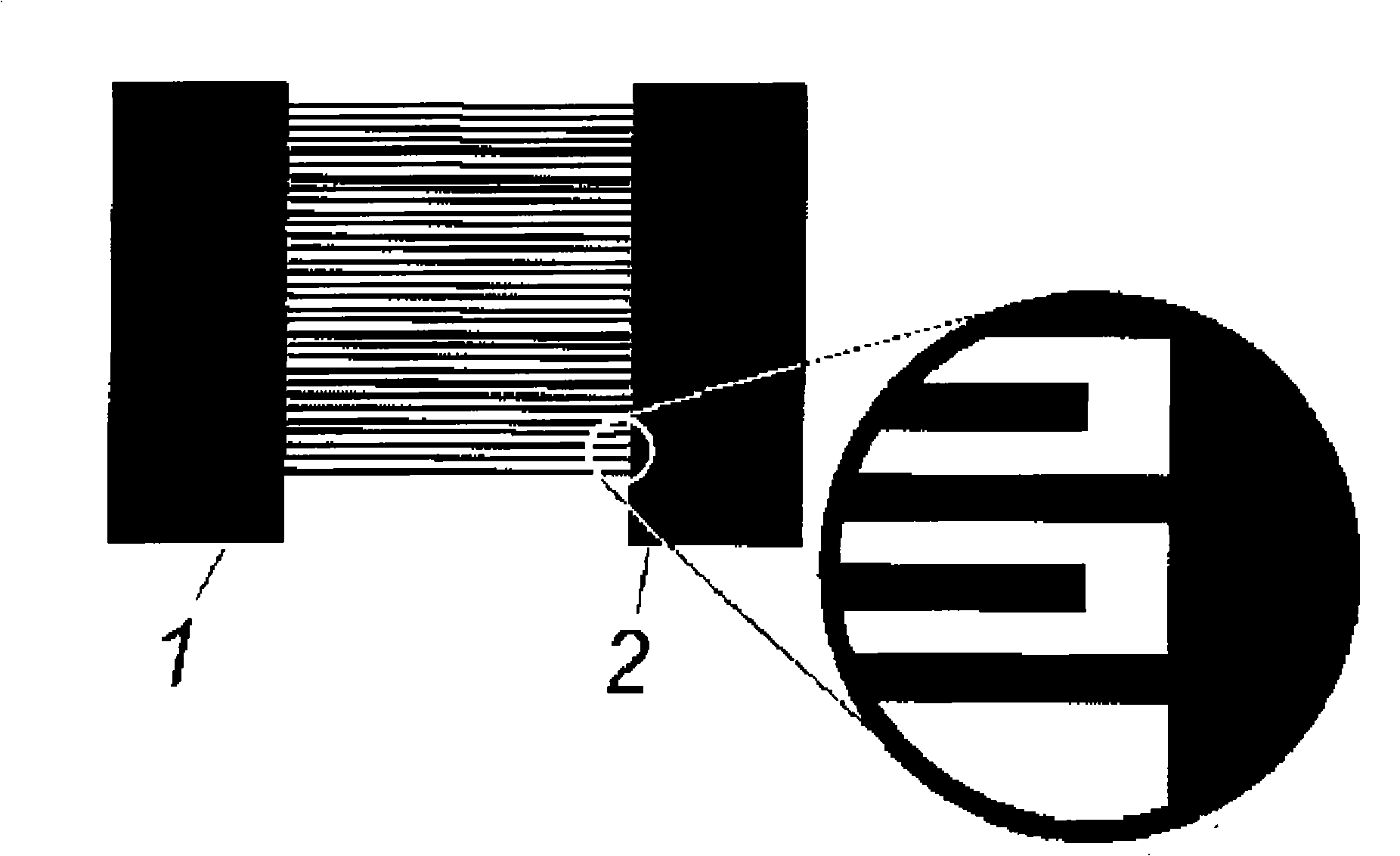
Poly-pyrrole minisize super capacitor based on MEMS technique and method for manufacturing the same
InactiveCN101325130AGood high current discharge performanceIncrease energy densityCapacitor electrolytes/absorbentsSecondary cellsSilicon matrixSolid state electrolyte
The invention discloses a polypyrrole minitype super capacitor in the range of the capacitor manufacturing technology based on MEMS technology and the preparation method thereof. The polypyrrole minitype super capacitor adopts the structure that a metal comb two-dimensional plane structure as a current collector is prepared on the surface of the silicon matrix by utilizing the micro-machining technology; a comb-shaped polypyrrole active electrode is prepared on the surface of the current collector by adopting the method of polypyrrole substance being prepared by the electric precipitation method; a layer of gel solid electrolyte is covered on the surface of the comb-shaped polypyrrole electrode and between a positive electrode and a negative electrode; and a layer of polyimide material is covered on the surface of the structure to accomplish the encapsulation of the minitype super capacitor. The MEMS-based manufacturing technology has the characteristic that the process is simple, and is suitable for mass manufacture. The minitype super capacitor has the advantages of small volume, high energy storage and stable performance, and is widely applicable to micro-robot electronic intelligence systems, chemical sensors, battlefield friend-or-foe identification devices, distributed type battlefield sensors and other fields.
Owner:TSINGHUA UNIV
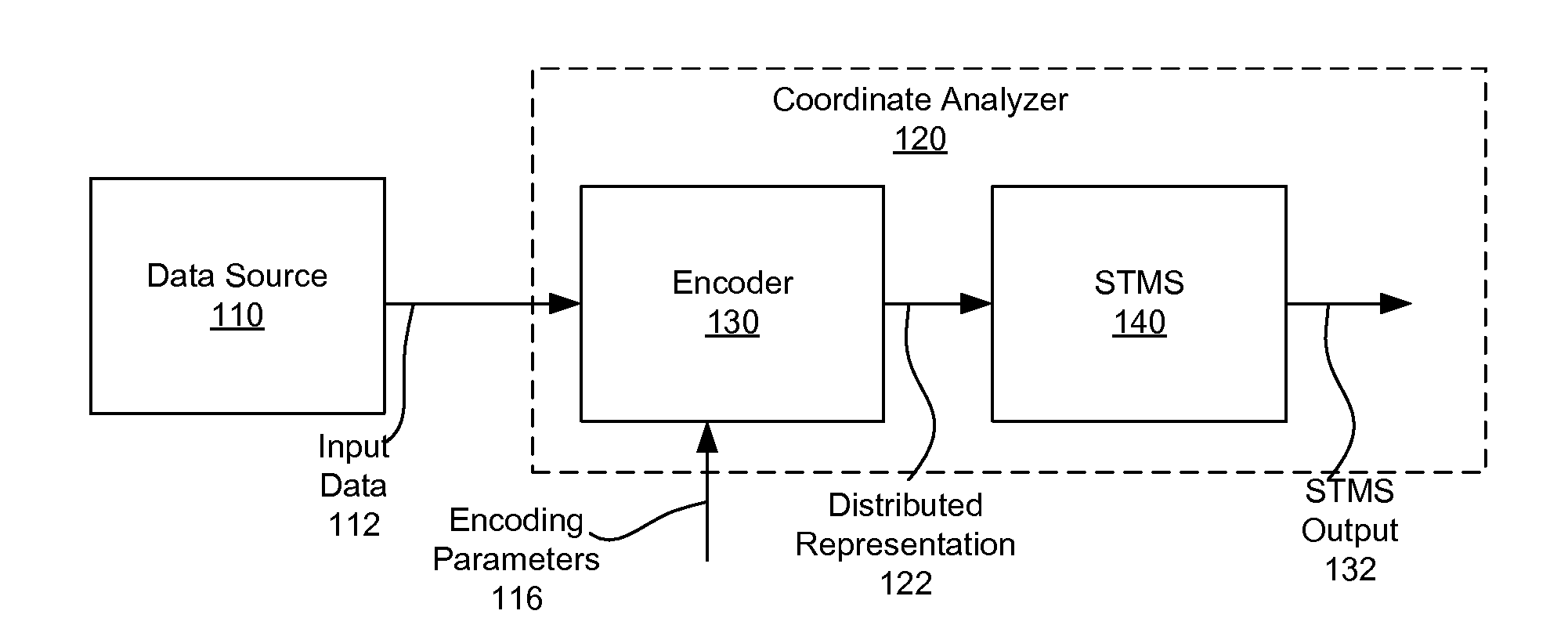
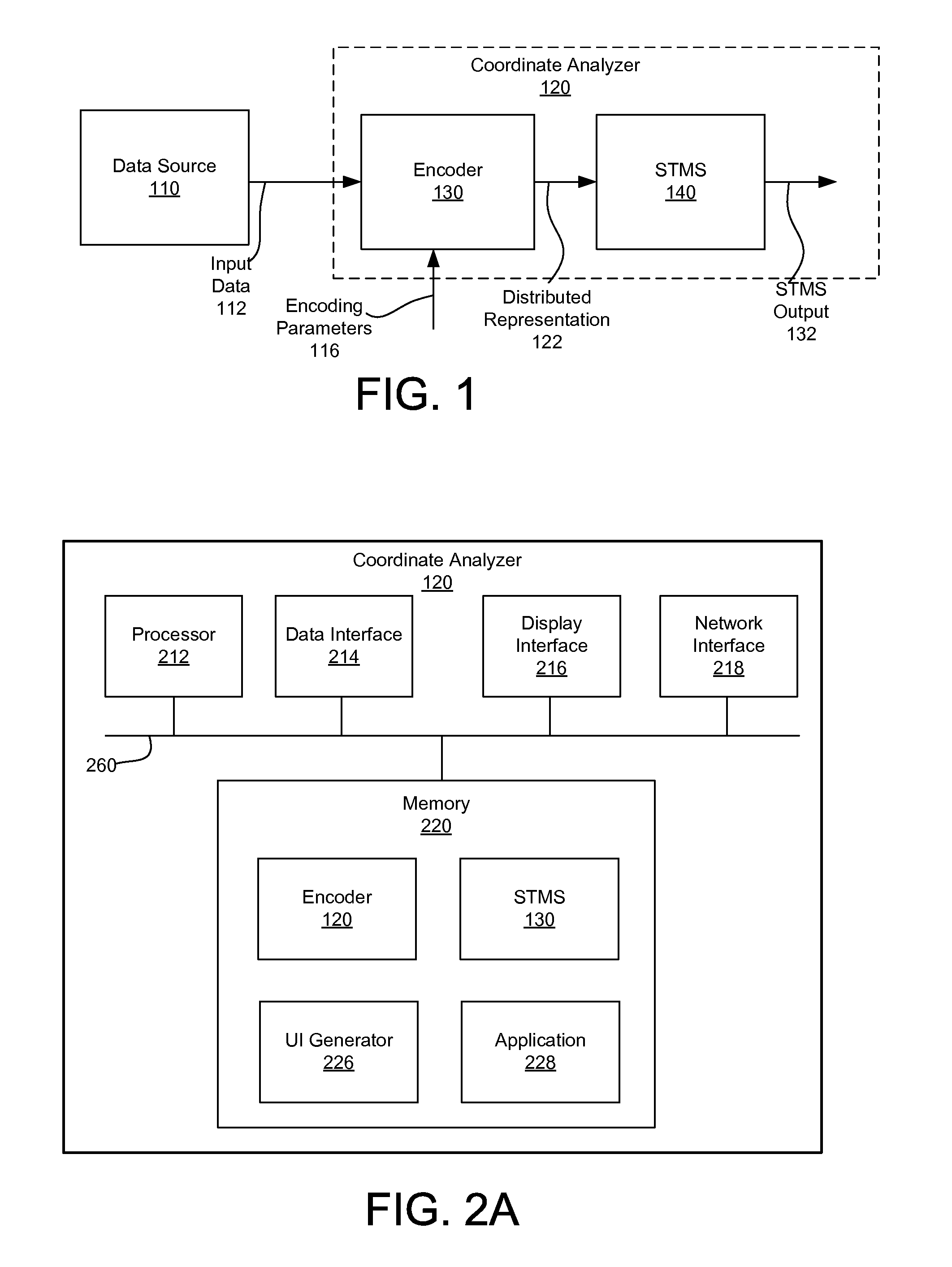
Sparse distributed representation of spatial-temporal data
InactiveUS20160217164A1Machine learningSpecial data processing applicationsCoordinate changeTemporal change
Coordinate data is encoded as a distributed representation for processing and analysis by a machine-intelligence system such as a hierarchical temporal memory system. Input coordinates represented in coordinate space having at least one dimension are obtained. The input coordinates change over time. A corresponding region around each of the input coordinates in the coordinate space is determined. A subset of coordinates within the corresponding region for each of the input coordinates is selected. A distributed representation for each of the input coordinates reflecting the selected subset of coordinates for each of the input coordinates is generated. The distributed representation may be provided to one or more processing nodes for detection of temporal sequences and spatial patterns. Based on discrepancies between predicted coordinate data and actual coordinate data, anomalies may be detected.
Owner:NUMENTA INC
Detecting, deterring security system
A security system used to detect, deter, and / or document security events and information from a secured area. The security system may include an intelligence system for distinguishing between false alarms and actual alarm events. The security system may also include multiple deter devices actionable upon detection of an actual alarm event. The security system may further include a security event data collection system that collects event or alarm data pertaining to security events either onsite or remote and a video / camera system that records images of security events.
Owner:LATHAM JOEL PAT +5
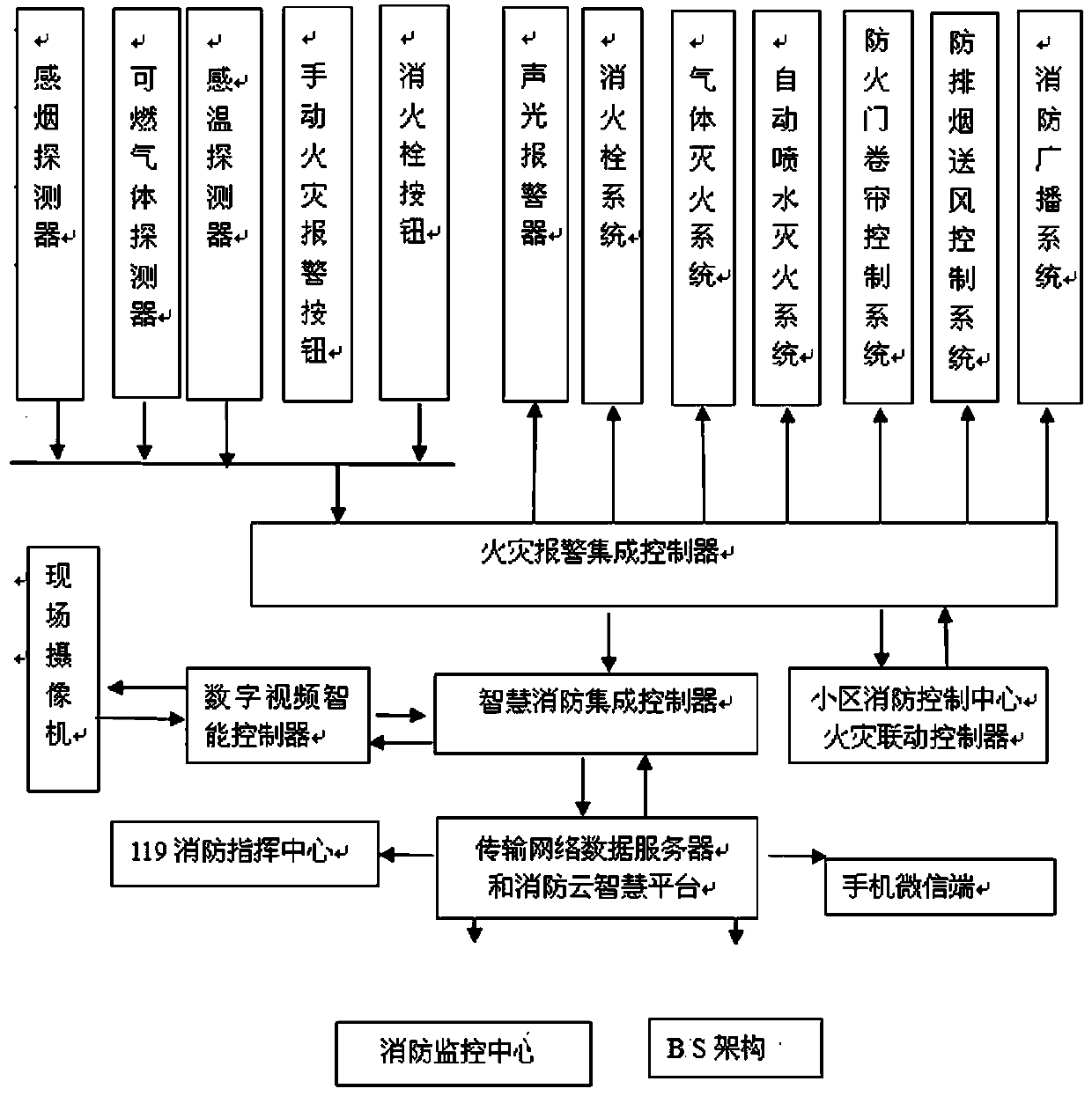
Building fire and security cloud intelligence integrated linkage system
InactiveCN110471361AProtect lifeAccurate informationProgramme controlComputer controlVideo monitoringData information
The invention belongs to the technical field of fire alarm systems and discloses a building fire and security cloud intelligence integrated linkage system. The building fire and security cloud intelligence integrated linkage system comprises an automatic fire alarm system, a digital network video monitoring system, an intelligent fire extinguishing and linkage control system, a fire cloud intelligence system and a data transmission service system, wherein the automatic fire alarm system is used for collecting original information of a field fire alarm system and converting the original information into an alarm signal; the digital network video monitoring system is used for dynamically obtaining field video image information by using a network camera in real time; the intelligent fire extinguishing and linkage control system is used for transmitting the information to a device end of performing fire extinguishing; the fire cloud intelligence system is used for carrying out integrated matching processing on the obtained alarm signal and video image information, feeding back the obtained alarm signal and video image information to the intelligent fire extinguishing and linkage control system to perform fire extinguishing operation, and uploading data information to a transmission network data server and a fire cloud intelligence platform; and the data transmission service systemis used for transmitting the information processed by the fire cloud intelligence system to a terminal operation system. According to the building fire and security cloud intelligence integrated linkage system, linked visual dynamic monitoring of a fire field, a field video and an automatic field fire alarm device and building fire and security cloud intelligence integrated linkage control of a terminal and the fire extinguishing performing end can be achieved.
Owner:CHINA SHANXI SIJIAN GRP
Artificial cognitive declarative-based memory model to dynamically store, retrieve, and recall data derived from aggregate datasets
InactiveUS20180240015A1Enhanced student learning environmentImprove efficiencySemantic analysisNeural architecturesLearning basedData set
A knowledge acquisition system and artificial cognitive declarative memory model to store and retrieve massive student learning datasets. The memory storage model enables storage and retrieval of massive data derived using multiple interleaved machine-learning artificial intelligence models to parse, tag, and index academic, communication, and social student data cohorts as applied to academic achievement. Artificial Episodic Recall Promoters assist recall of academic subject matter for knowledge acquisition. A Deep Academic Learning Intelligence system for machine learning-based student services provides monitoring and aggregating performance information and student communications data in an online group learning course. The system uses communication activity, social activity, and the academic achievement data to present a set of recommendations and uses responses and post-recommendation data as feedback to further train the machine learning-based system.
Owner:SCRIYB LLC
Real-time activity intelligence system and method
InactiveUS20050027574A1Office automationSpecial data processing applicationsContent analyticsData system
An activity intelligence system includes a channel of a communication, such as a packetized communications network, for example, the Internet. The communication includes data about which activity intelligence is desired. The system includes an interceptor for accessing particular desired data of the communication. A mapper of the system indexes the data so intercepted. A processor of the system performs an operation with the data. The operation can include any of a wide variety of possibilities, such as HTML content analysis, flag generation and response, statistical and business functions, and others. Conventional, customized or other applications can operate on and with the data for determining desired activity intelligence.
Owner:AGRAWAL PURUSHARTH +1
Cable fault detection
ActiveUS20090281740A1Electrical testingSpecial data processing applicationsElectric power systemCable fault location
A cable fault detection component (168) receives input data indicative of a fault in an electrical power system. The component (168) analyzes the input data to determine if the fault is indicative of a temporary or self-clearing cable fault and generates corresponding output data (276). In one implementation, the cable fault detection component (168) is implemented as a software module which operates on a computer (105) of a substation intelligence system (104).
Owner:HITACHI ENERGY SWITZERLAND AG
Joint combat system modeling method based on hyper-network theory and storage medium
The invention discloses a joint combat system modeling method based on a hyper-network theory. The mapping relationship between a physical entity and a model in the combat system is combined. Work division is carried out according to roles of action entities in joint operation to create system nodes. Different types of information flows are designed. A combat ring is created so that the requirements of different levels and different granularities of modeling are met according to a joint combat system; a coarse-grained and fine-grained joint combat system model is established and comprises a reconnaissance intelligence system model, a command and control system model, a firepower strike system model and a support guarantee system model, and a joint combat system dynamic model is constructedby combining a combat task, a time sequence and an organization structure transformation rule. The mapping relationship between the physical entity and the model in the joint operation system is fully considered, the network characteristics and the information characteristics in the joint operation system are highlighted, and the static and dynamic system modeling problem of the joint operation system is solved.
Owner:BEIJING HUARU TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com