Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
147 results about "Enterprise computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
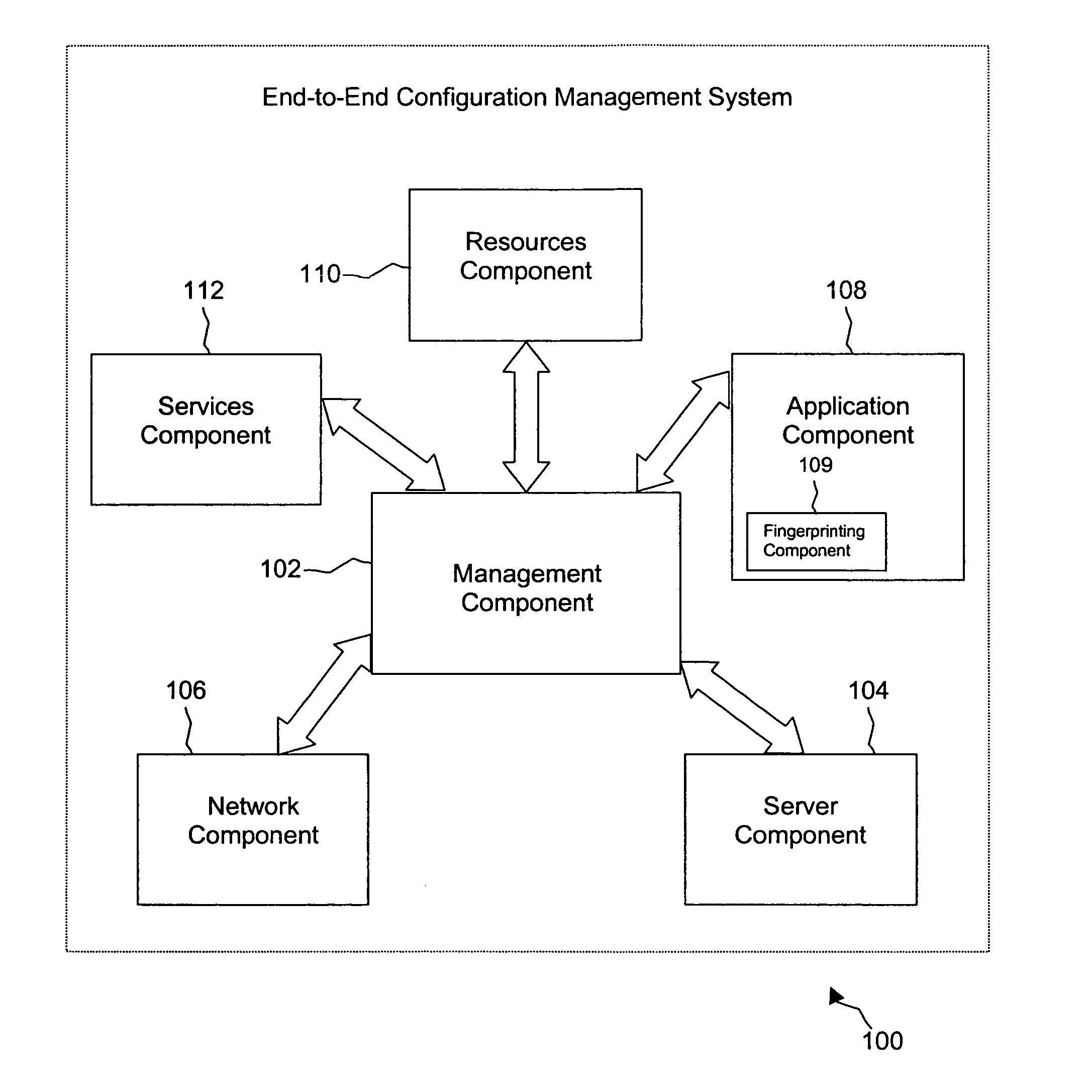
System and method for securing an enterprise computing environment
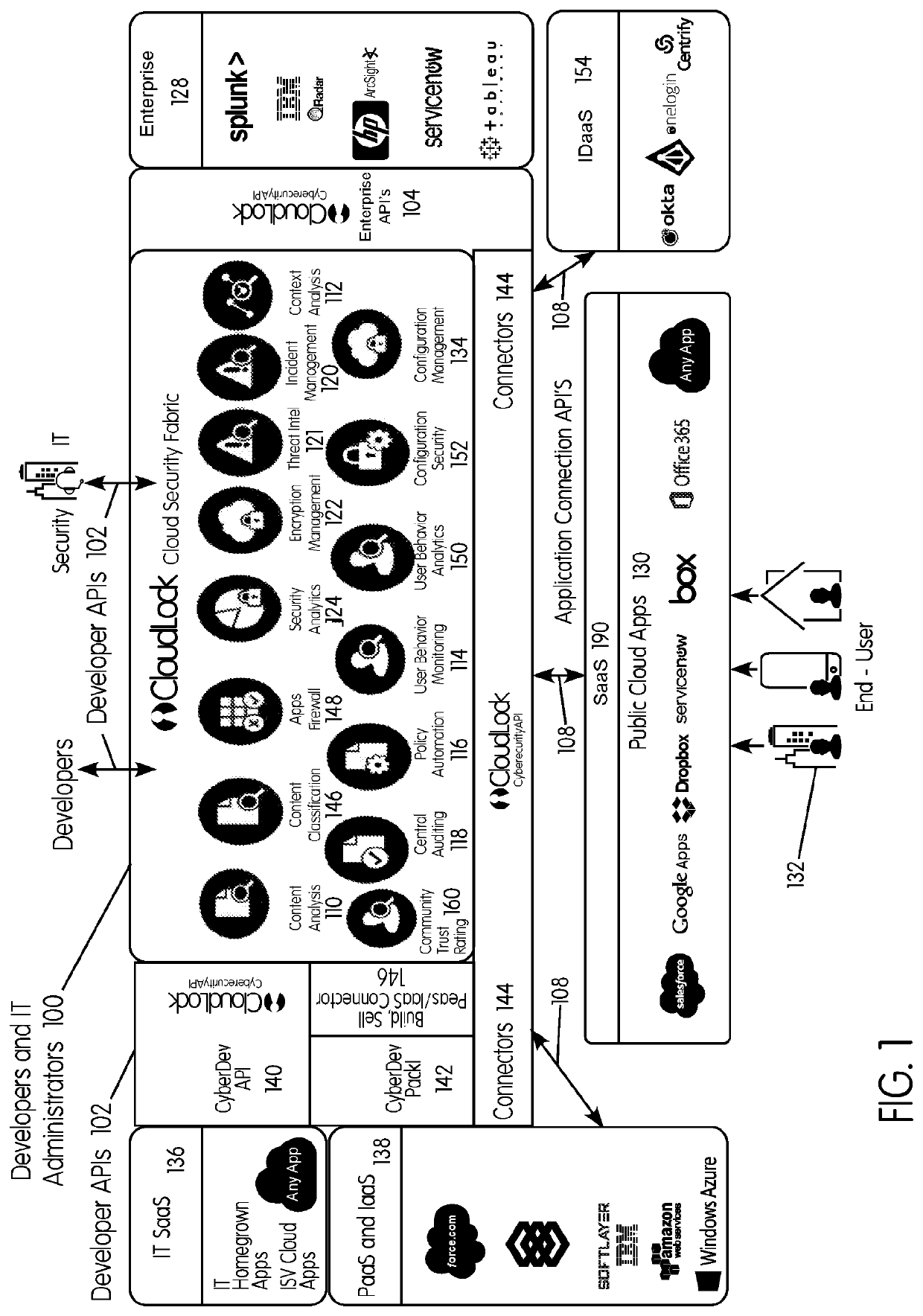
InactiveUS20180027006A1Process safetyKeep Content SafeMultiprogramming arrangementsComputer security arrangementsInternet privacyEnterprise computing
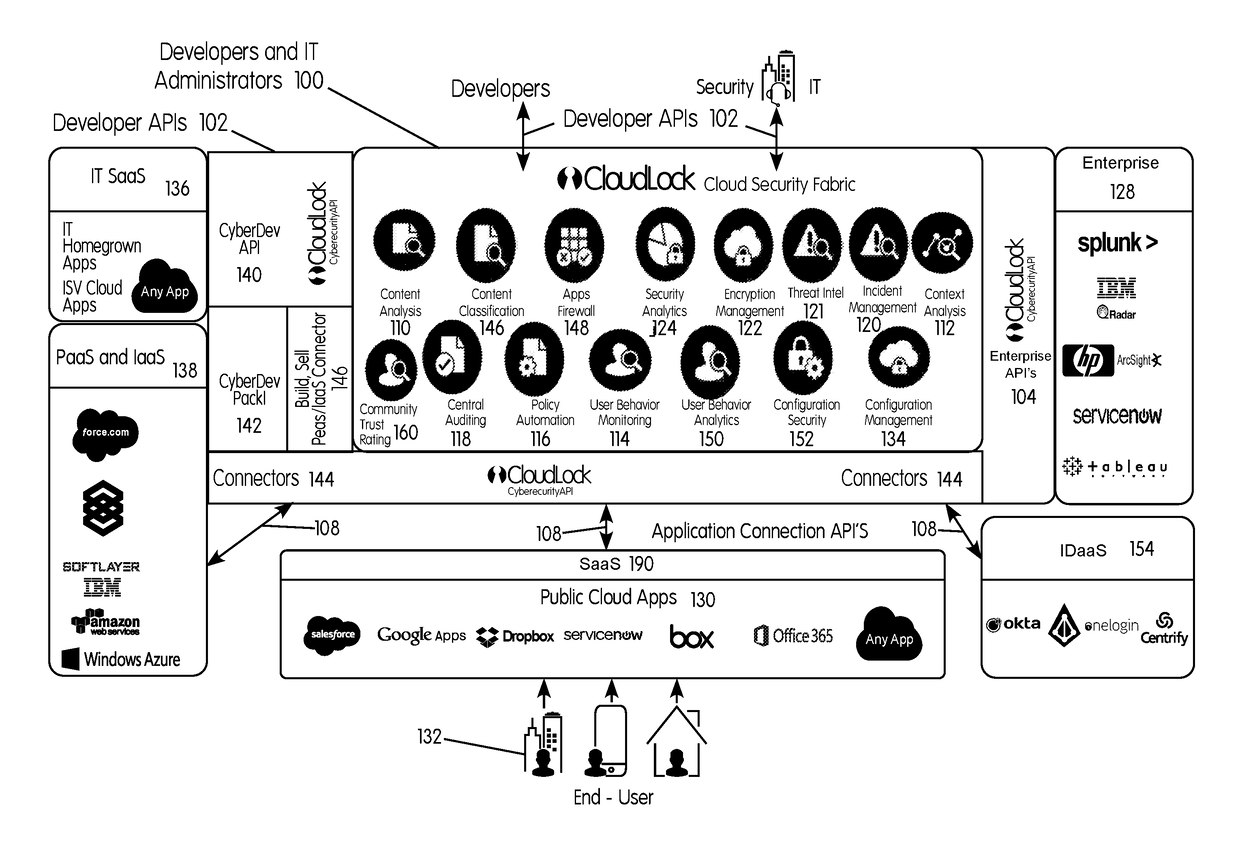
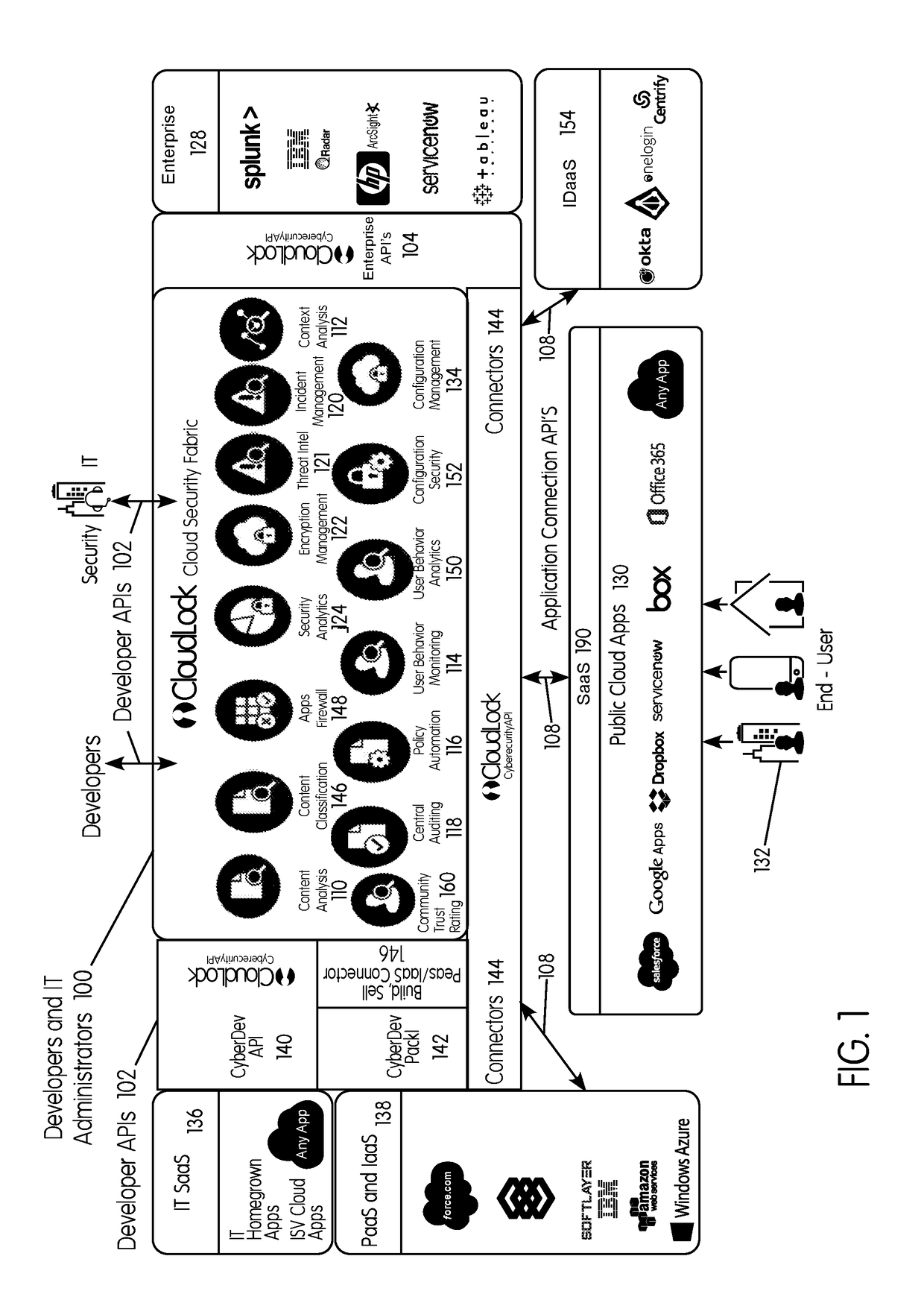
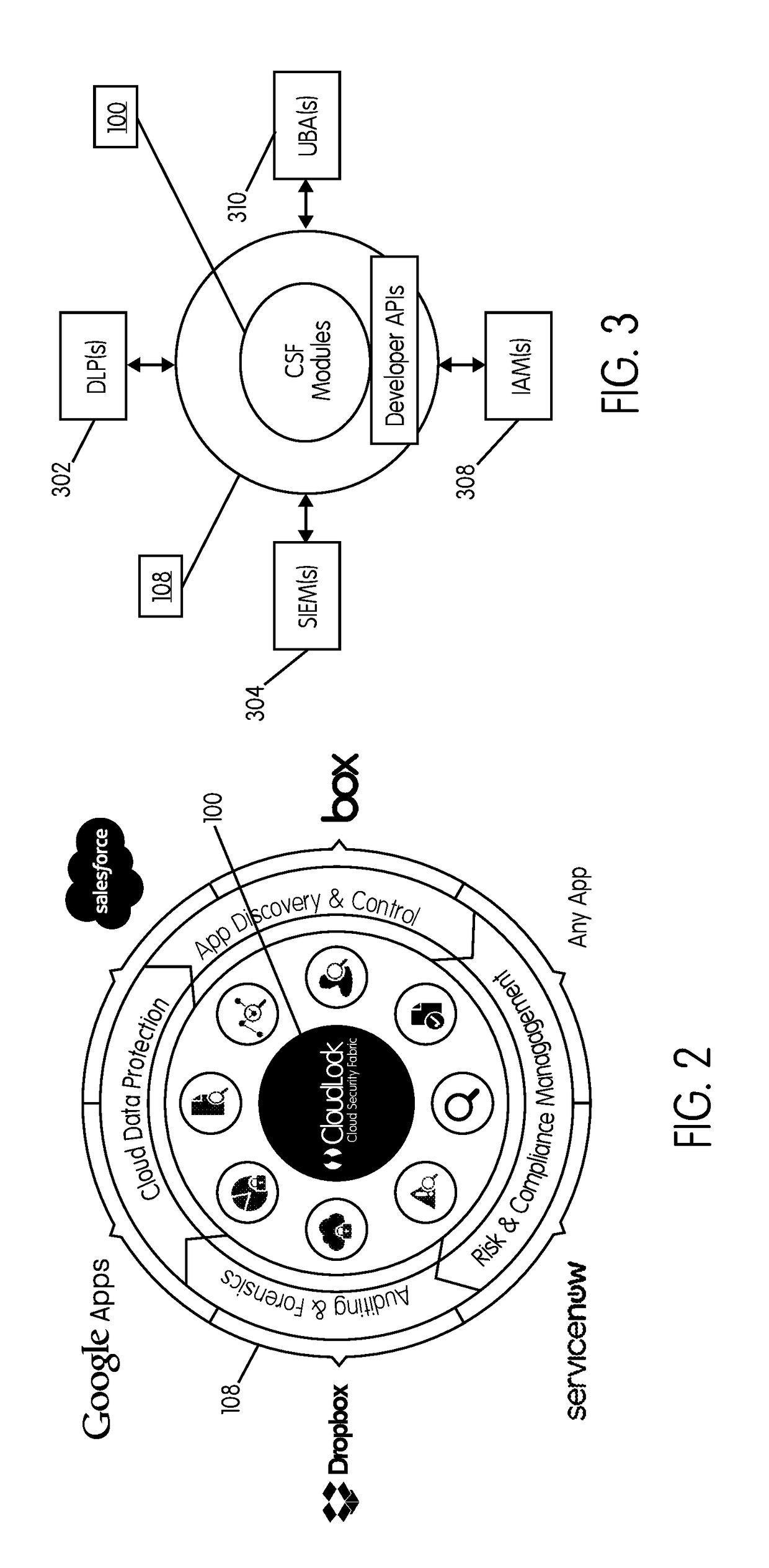
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CLOUDLOCK
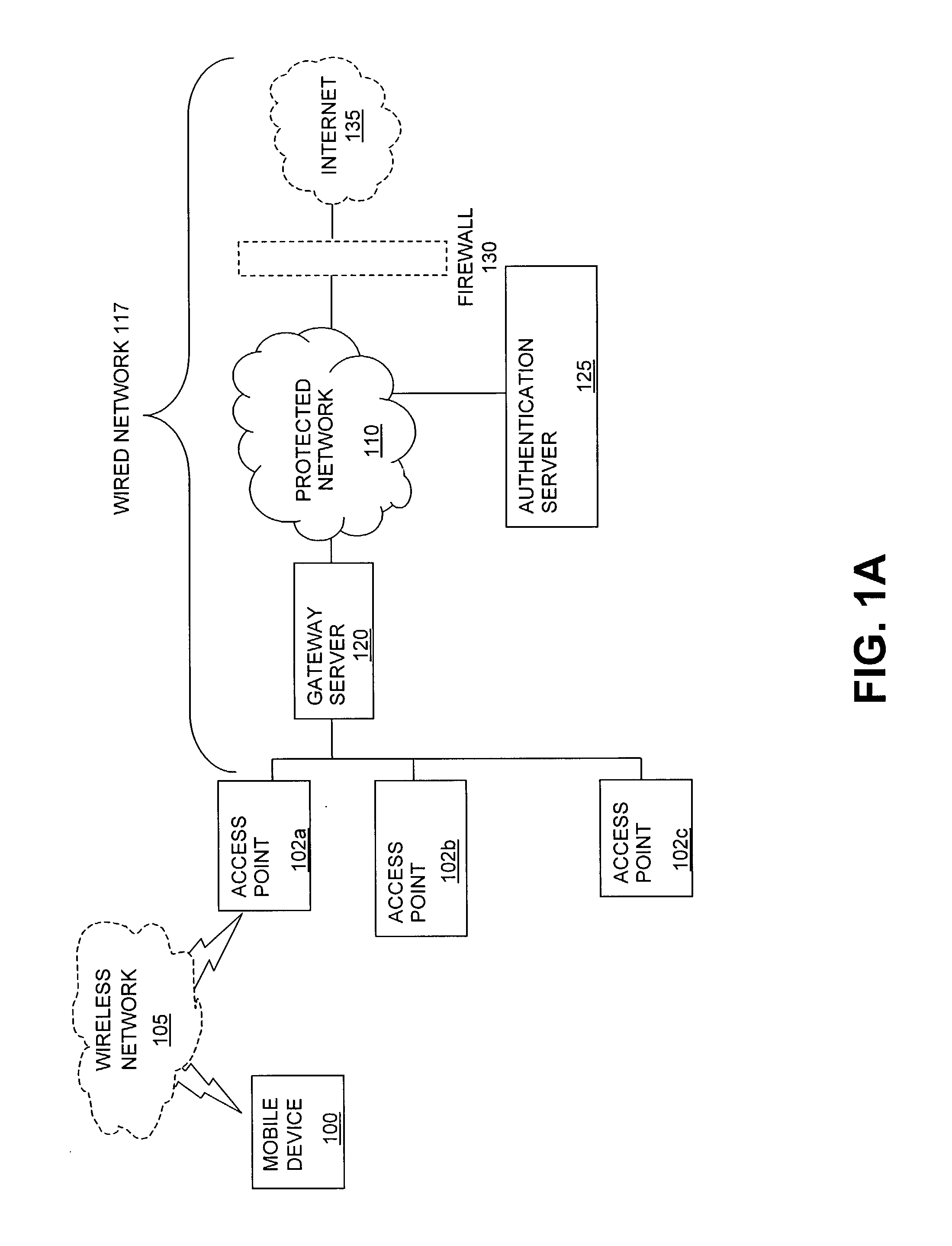
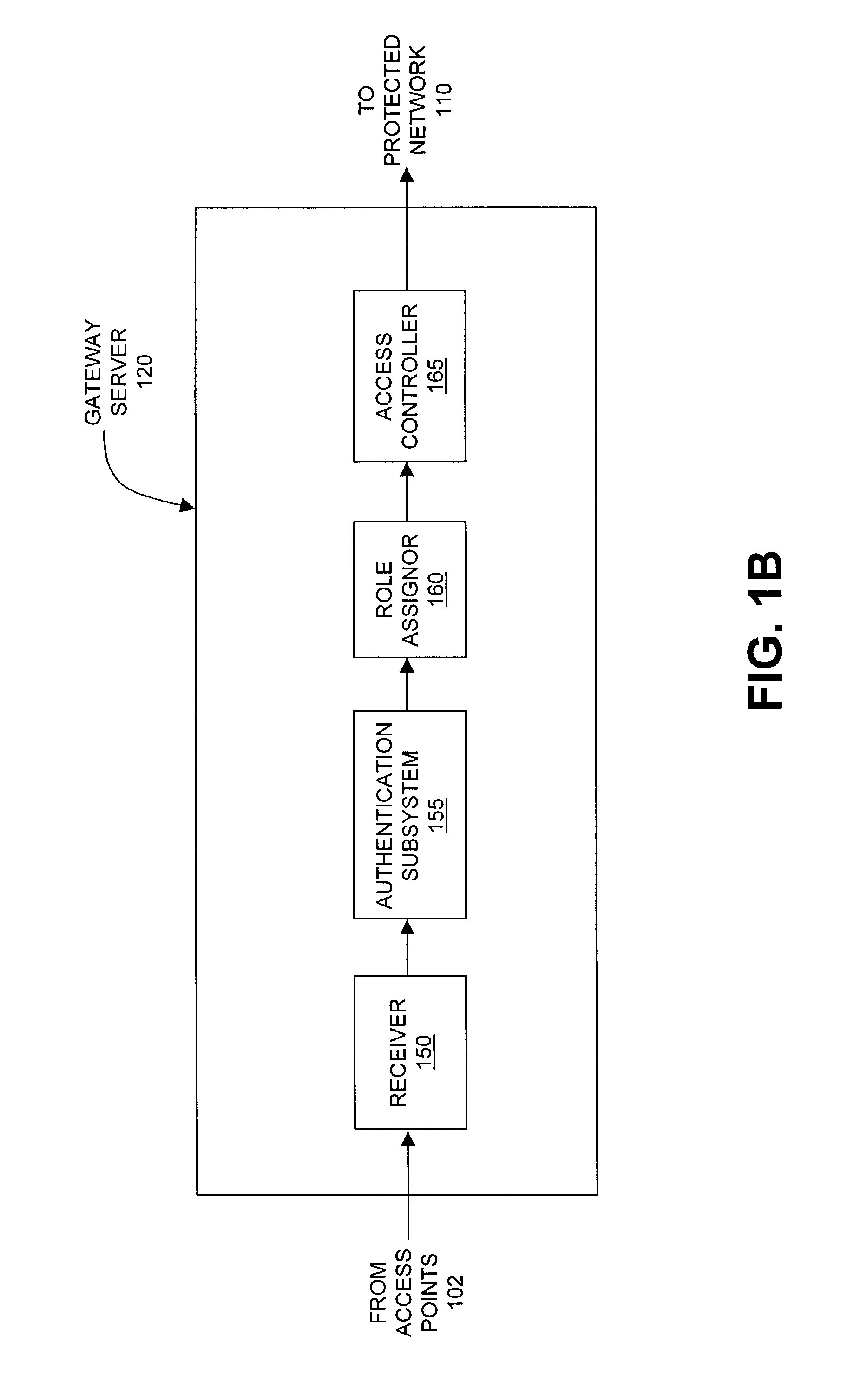
Method and system for managing data traffic in wireless networks
ActiveUS20030087629A1Reduce capacityEasy networkingError preventionUnauthorised/fraudulent call preventionEnterprise computingNetwork architecture
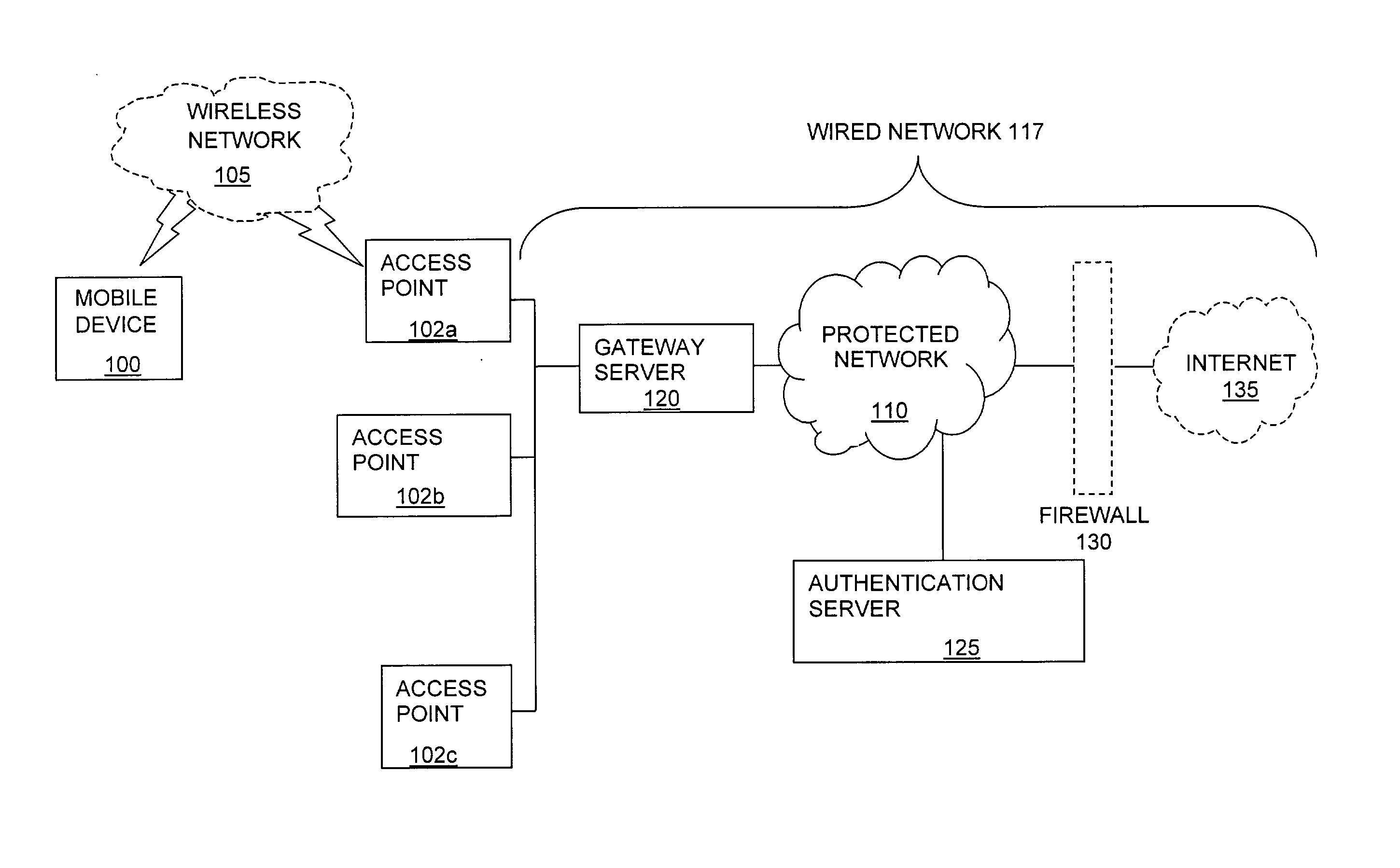
The present invention can be used to facilitate the integration of wireless capability provided by wireless access points into an enterprise computer network. A gateway server is interposed between wireless access points and protected networks to provide security and integration functions, for example, authentication, access control, link privacy, link integrity, and bandwidth metering in various embodiments. Use of such a gateway server allows substantial control to be gained over network access even with the use of relatively simple access points. In general, such a gateway server receives a request to access the protected network. An authentication subsystem of the gateway server authenticates the user, preferably by accessing an external authentication server and returns a role to the authenticated user. An access controller in the gateway server provides differential access to the protected network based on the user's assigned role. A multiple gateway servers can be connected together to form a mesh network architecture.
Owner:BLUESOCKET
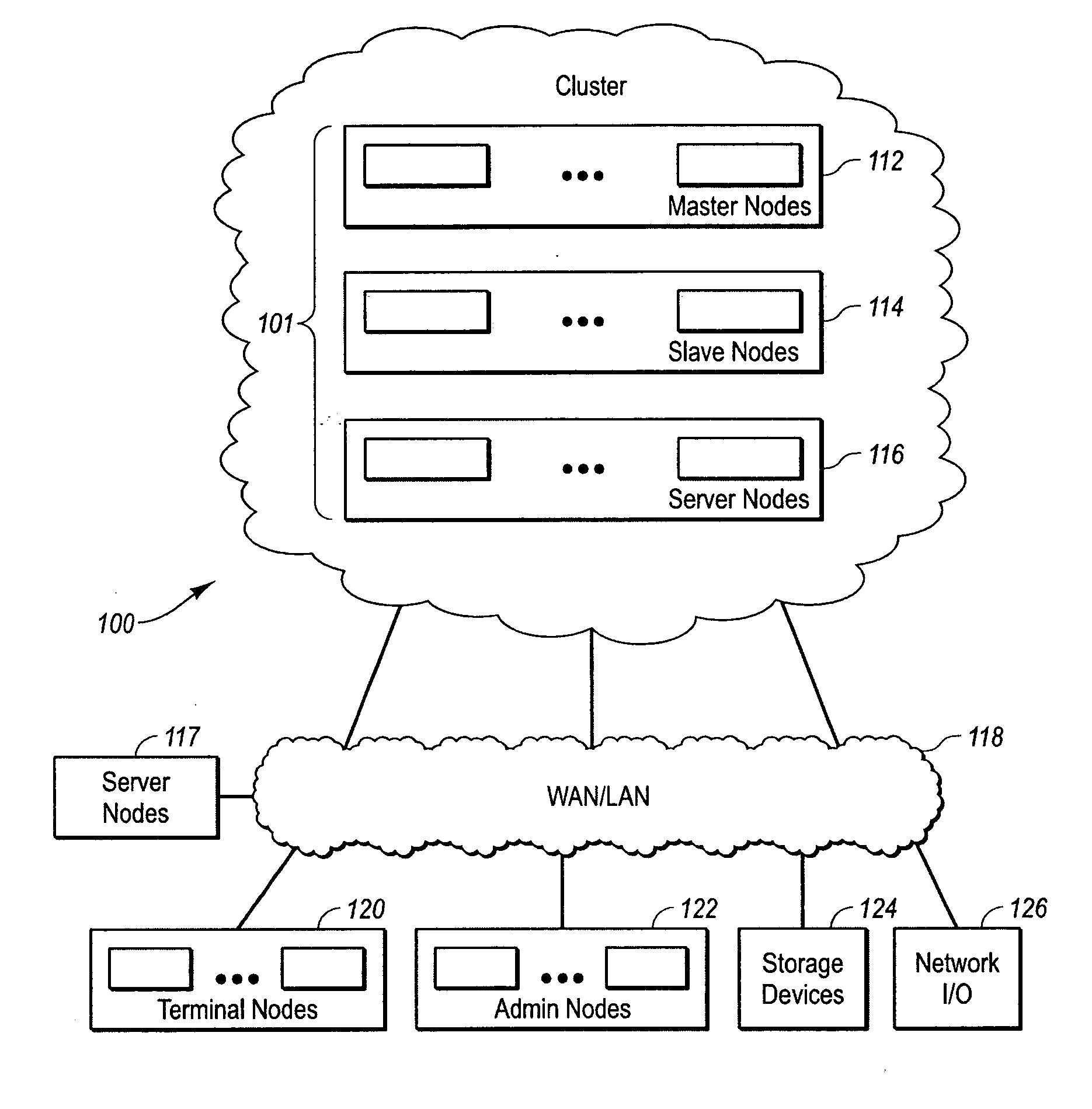
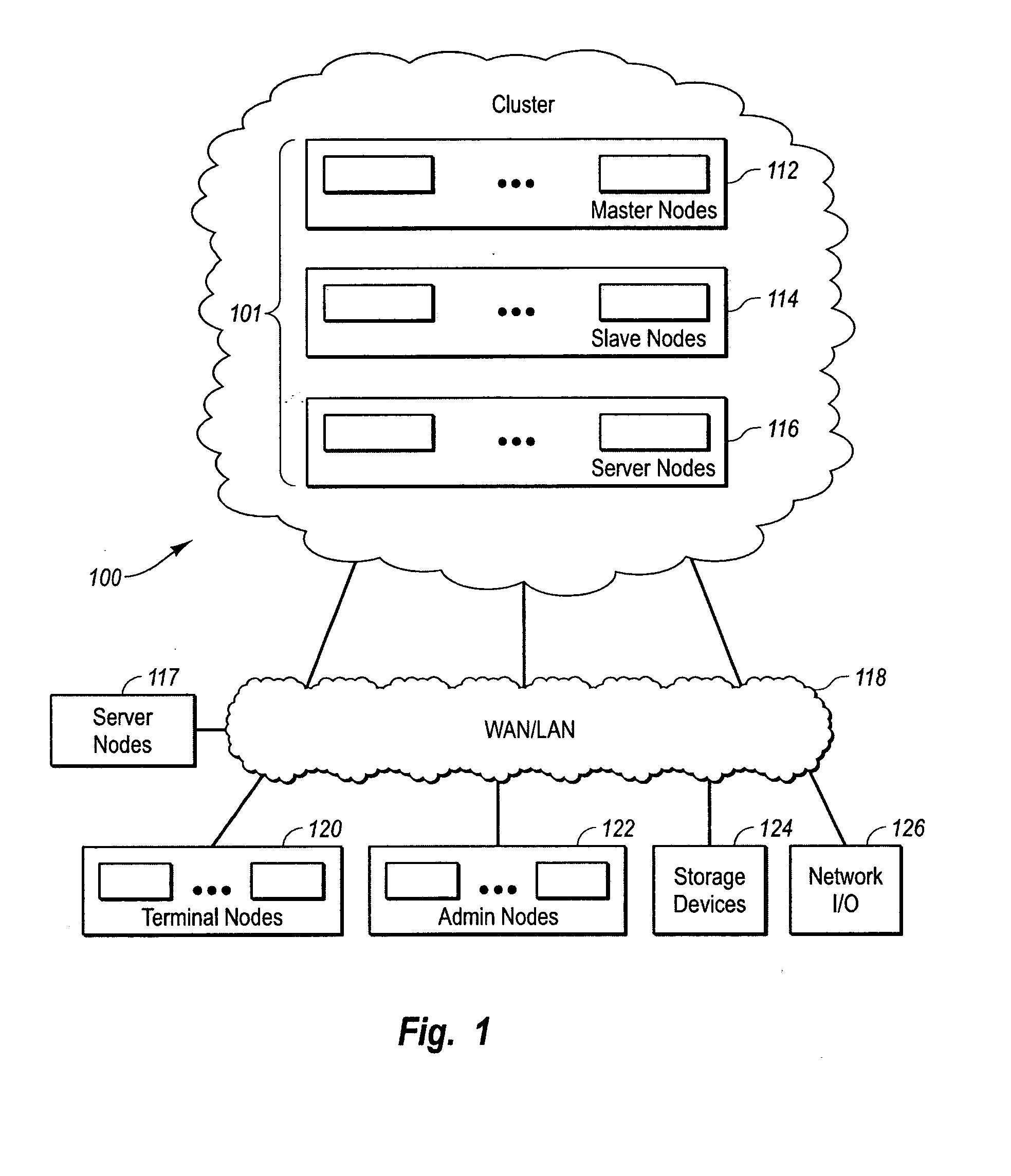
Clustered computer system with centralized administration
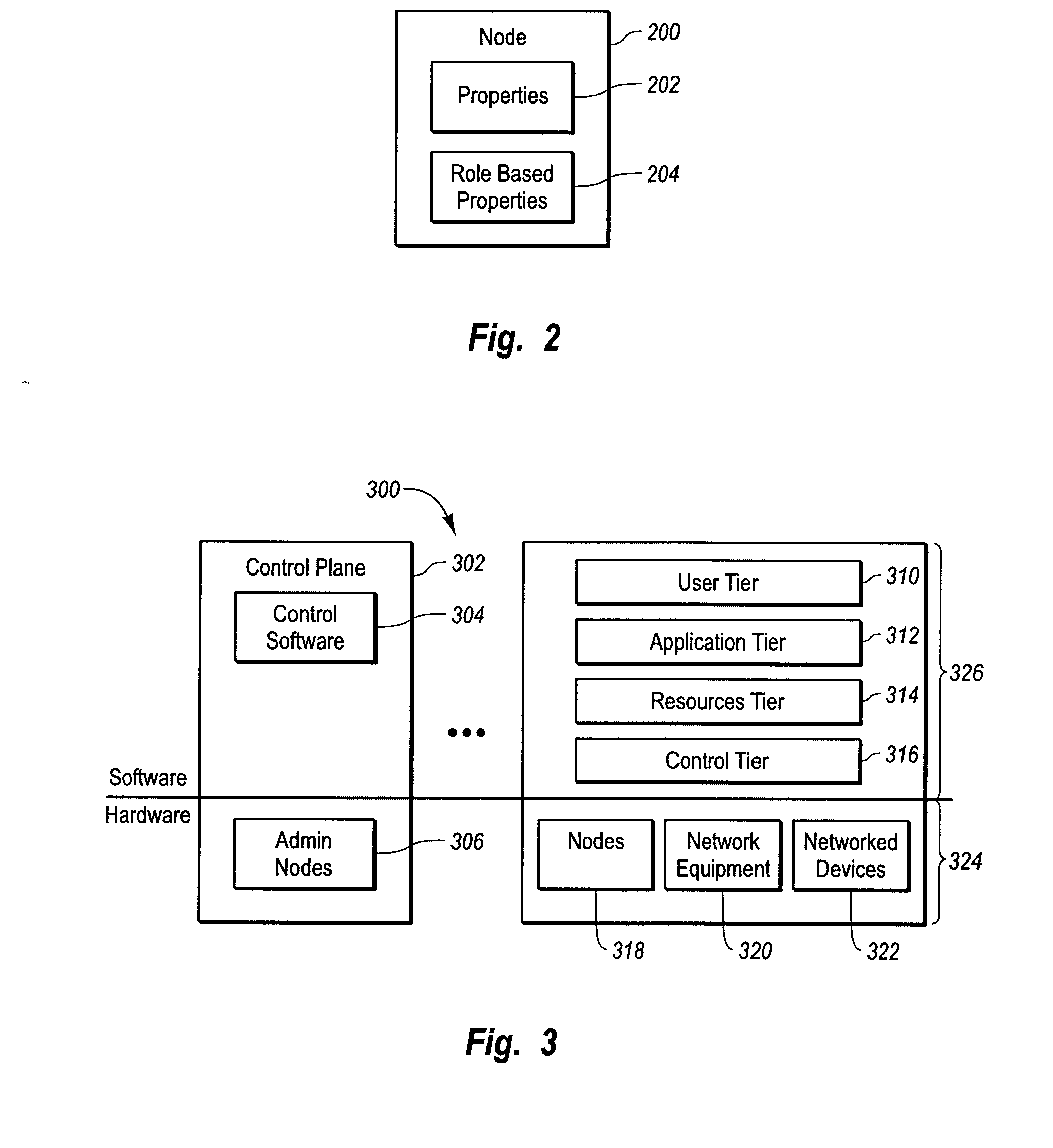
InactiveUS20060053216A1Digital computer detailsComputer security arrangementsOperational systemComputer cluster
Systems and methods for a computer cluster and for conducting user sessions in a managed enterprise computer network. A cluster includes multiple inter-connected nodes with specific roles. Master nodes administer and monitor slave nodes and the slave nodes are used to conduct user sessions with users through terminal nodes that provide an interface to the cluster. The cluster also may include server nodes that provide network services. Master nodes also control admittance to the cluster of external nodes and sub-clusters. Admin nodes form a control plane used to control and administer the cluster through the master nodes. The cluster provides a virtual environment for the user session that is built from at least an operating system image, an application image and other data needed for the user session.
Owner:METAMACHINIX
System and method for securing an enterprise computing environment
InactiveUS20200137097A1Process safetyKeep Content SafeMultiprogramming arrangementsDigital data protectionBusiness enterpriseEnterprise computing
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CISCO TECH INC
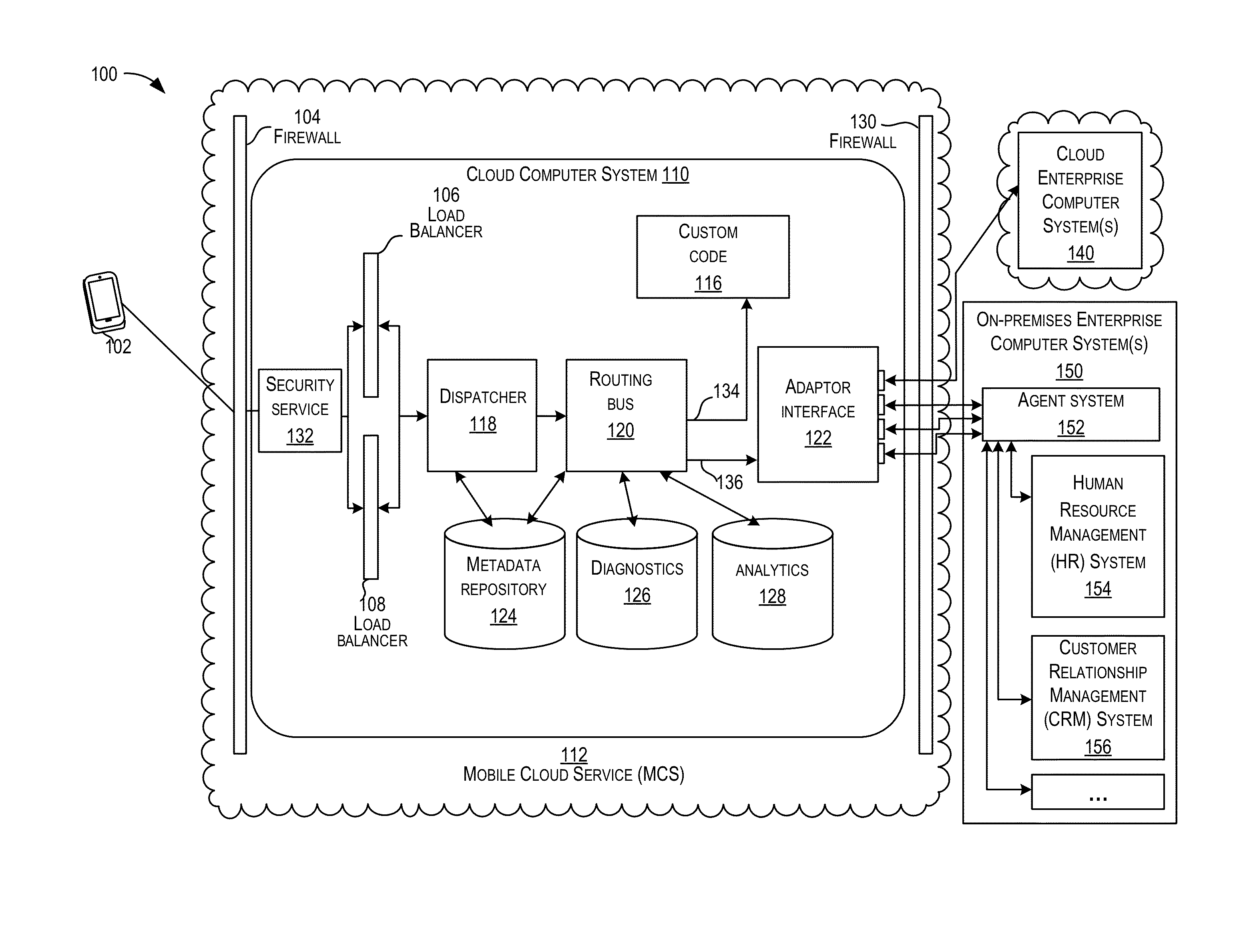
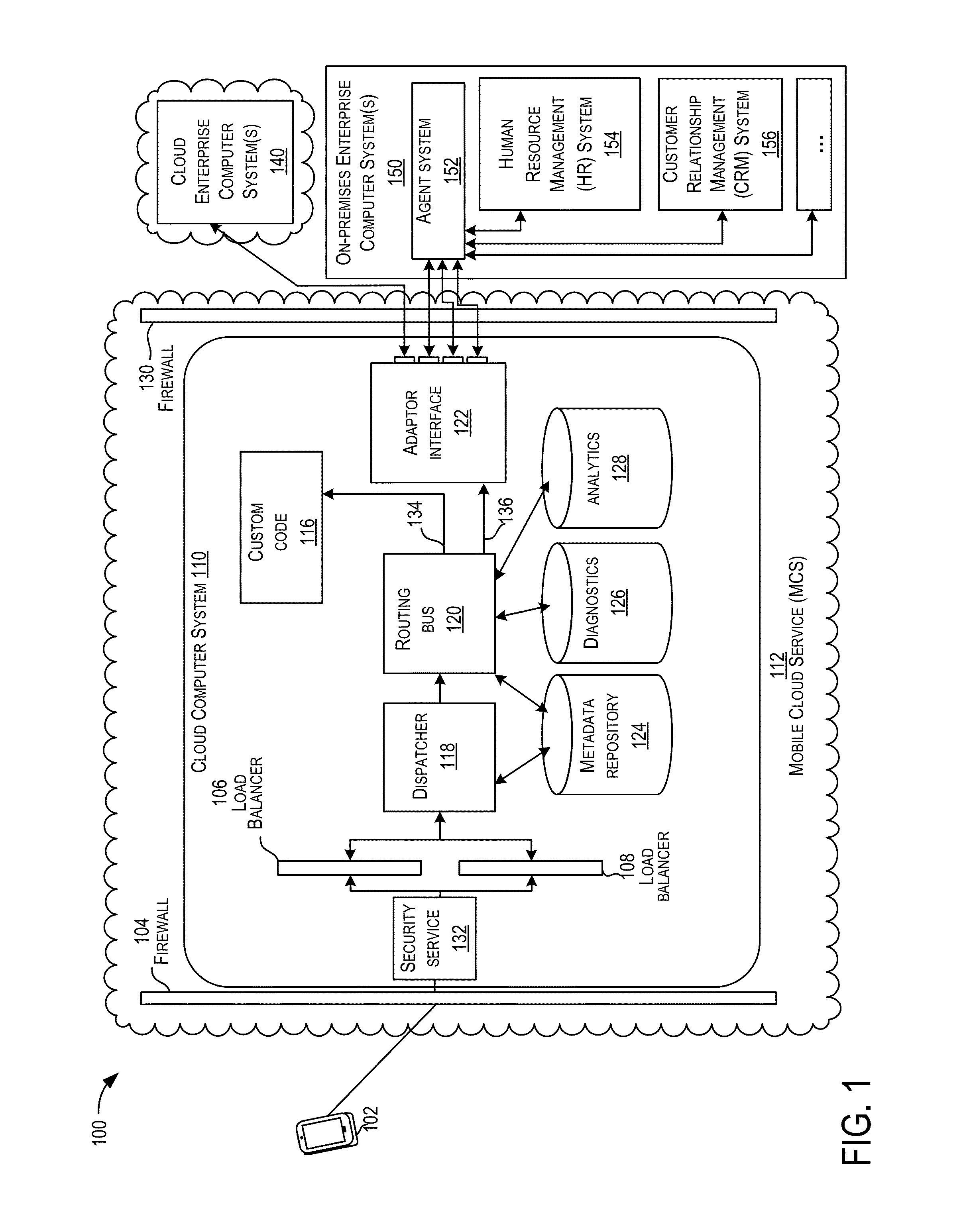
Mobile cloud service architecture
ActiveUS20150229638A1Facilitate communicationDigital data processing detailsInformation formatMobile cloudBusiness enterprise
Techniques are described for implementing a cloud computer system to facilitate communication between a computing device (e.g., a mobile computing device) and enterprise computer systems. In certain embodiments, the cloud computer system may receive, from a computing device, a request for a service provided by an enterprise computer system. The cloud computer system may determine security authentication of a user for the requested service. A security protocol may be determined for a requested enterprise computer system and a security token may be generated for the request according to the determined security protocol. The request may be sent to the requested enterprise computer system. In some embodiments, security authentication for a request to an enterprise computer system may be determined based on previous authentication. The cloud computer system may be configured to communicate with several different enterprise computer systems according to their supported protocols (e.g., communication protocol and / or security protocol).
Owner:ORACLE INT CORP
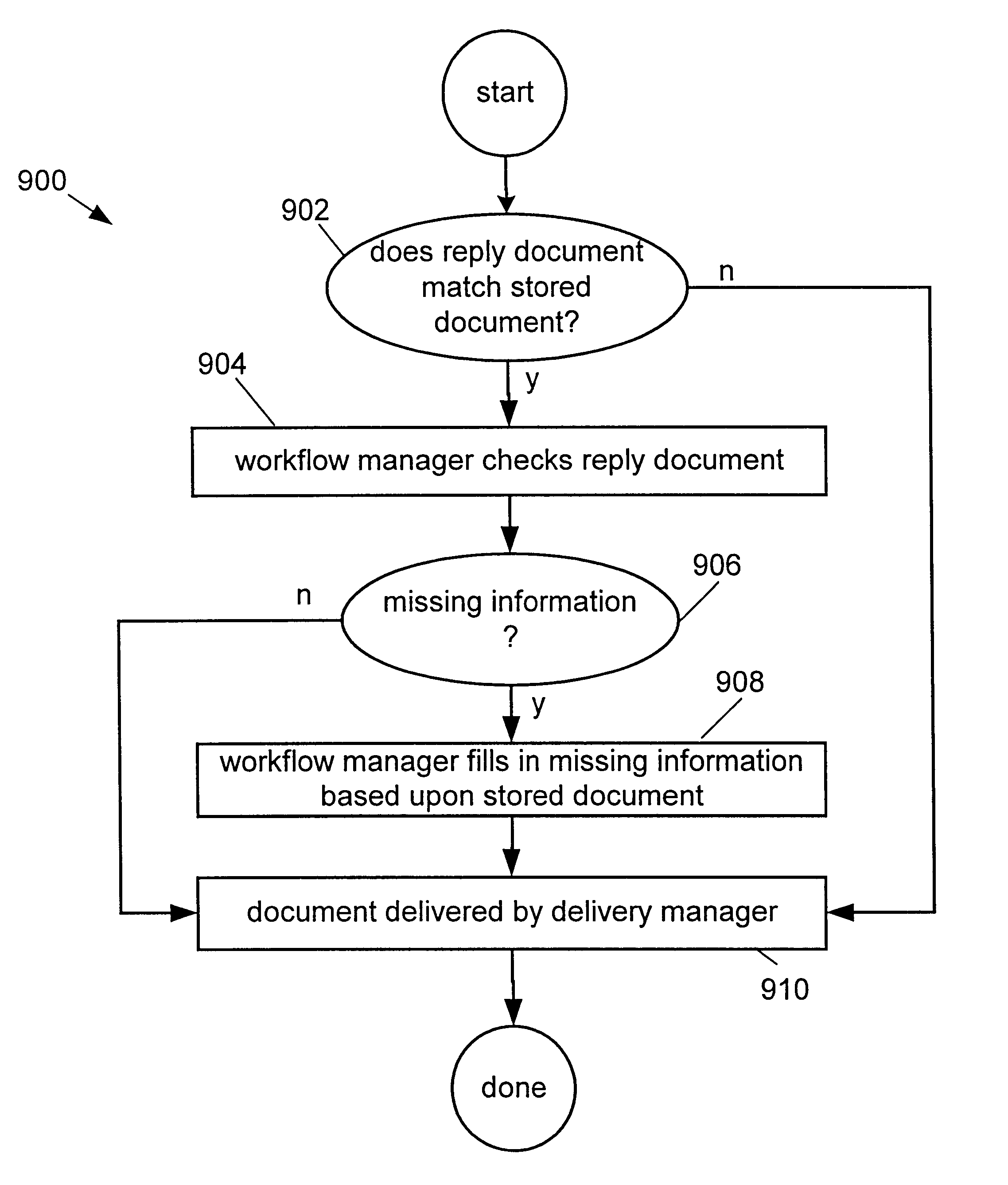
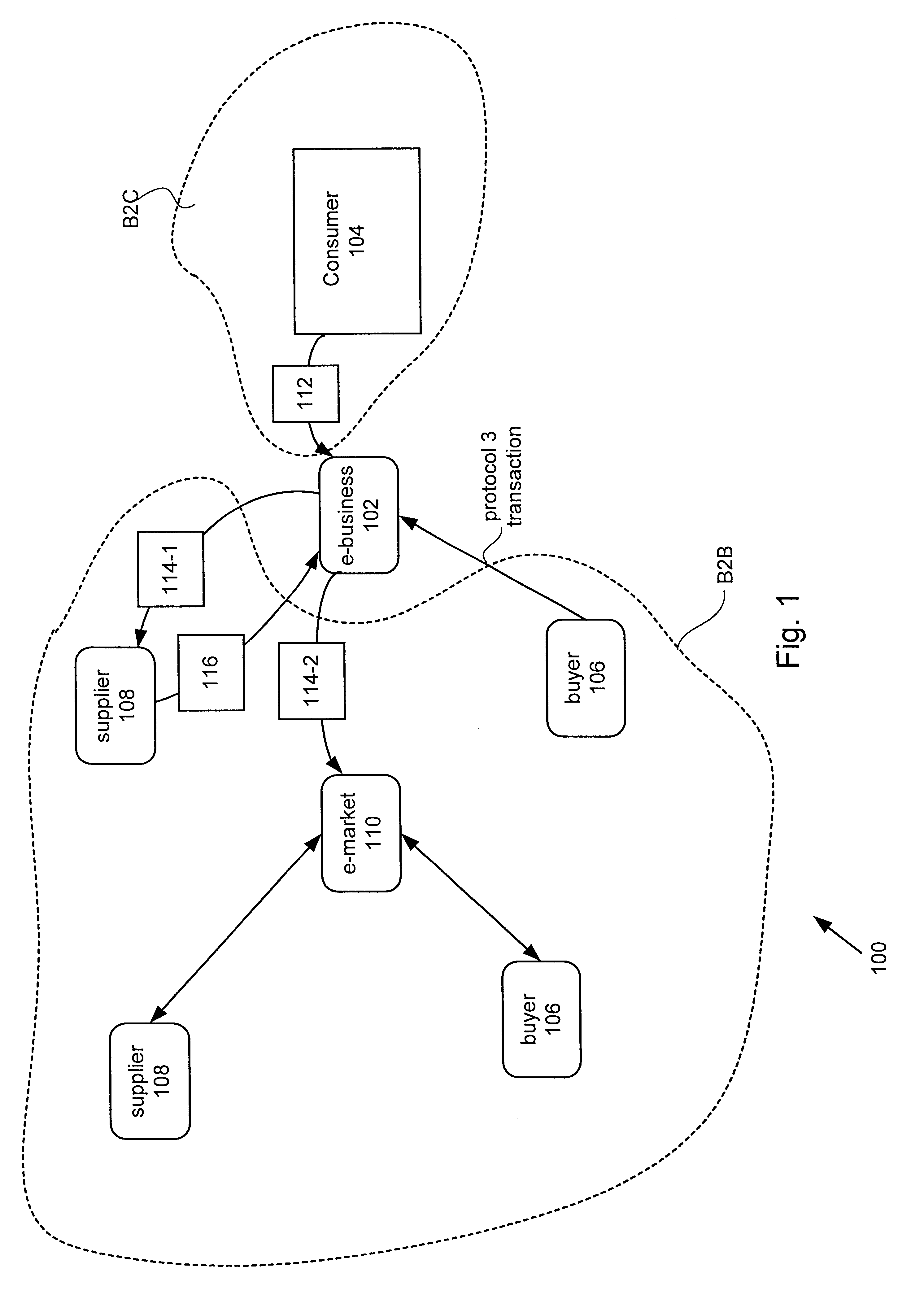
Techniques for preventing information loss in a business to business message in an enterprise computer system
InactiveUS6687848B1Error prevention/detection by using return channelError detection/correctionBusiness-to-businessEnterprise computing
A method of maintaining informational integrity of a business to business (B2B) message in a distributed e-business environment is described. A sent message is stored a selected portion of which is flagged. A corresponding response message is then compared to the stored sent message. Based upon the comparing, when the response message matches the stored sent message, if a portion of the response message corresponding to the flagged portion is determined to be substantially missing, then the missing portion of the response message is replaced.
Owner:SUN MICROSYSTEMS INC
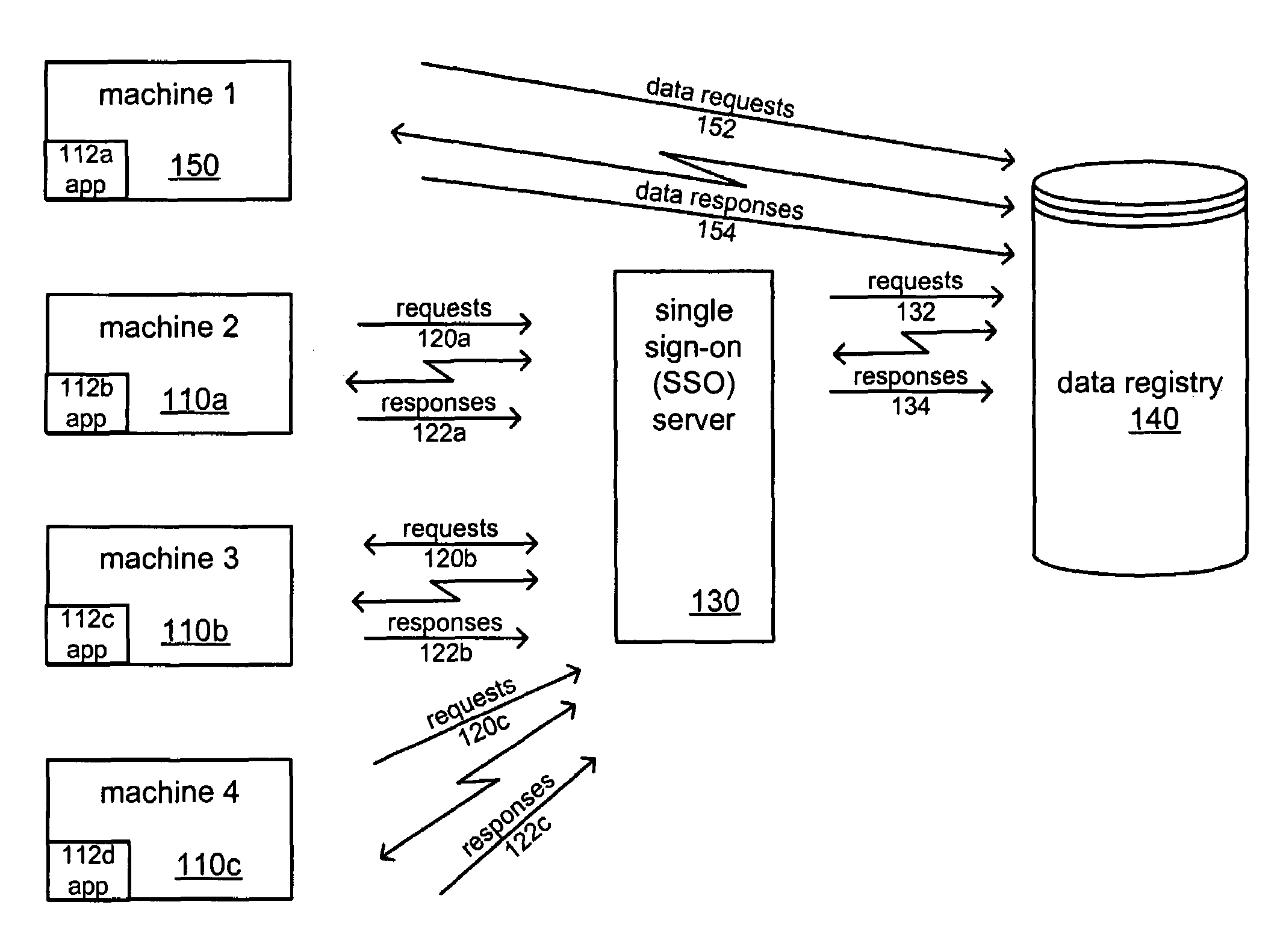
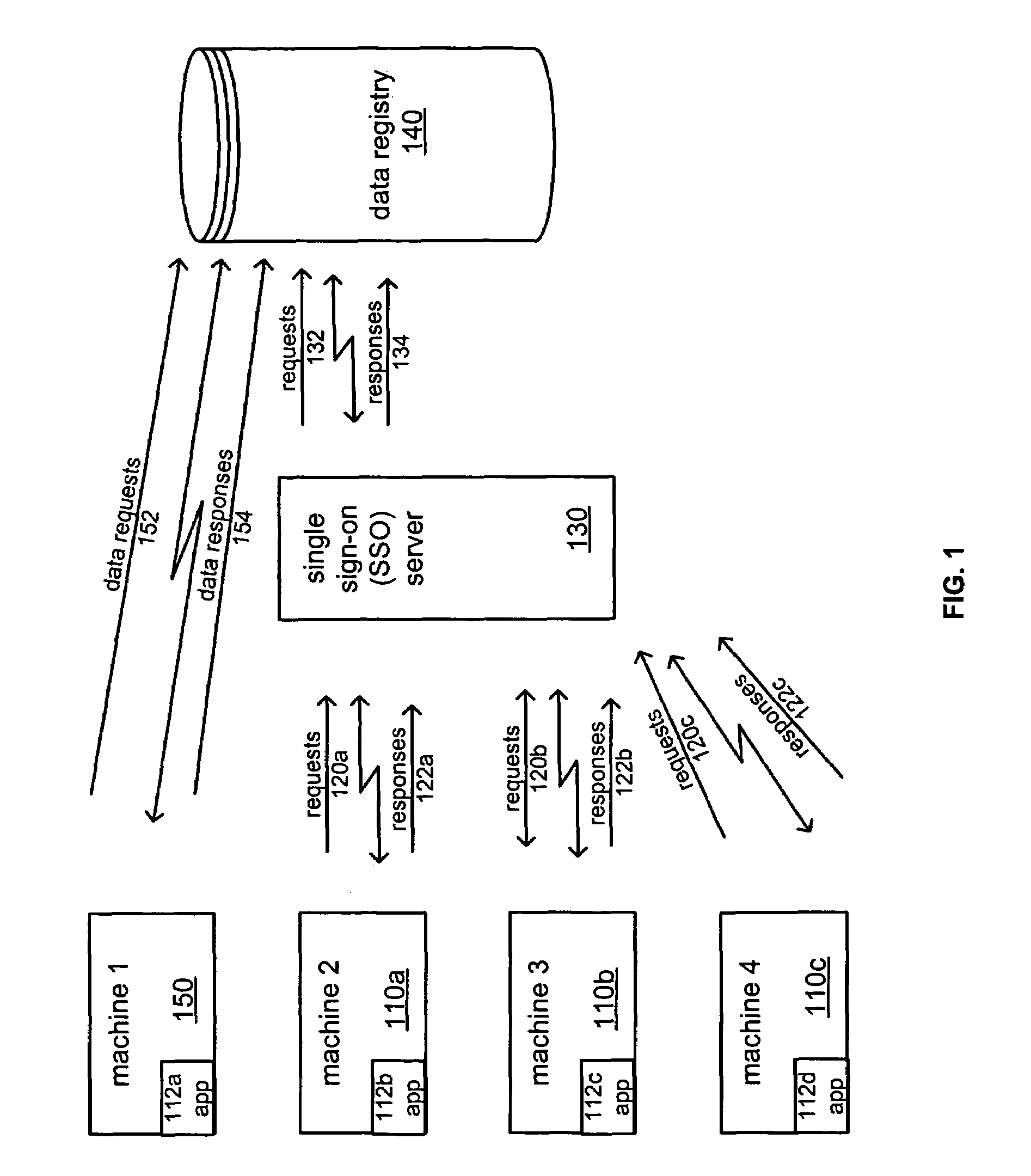
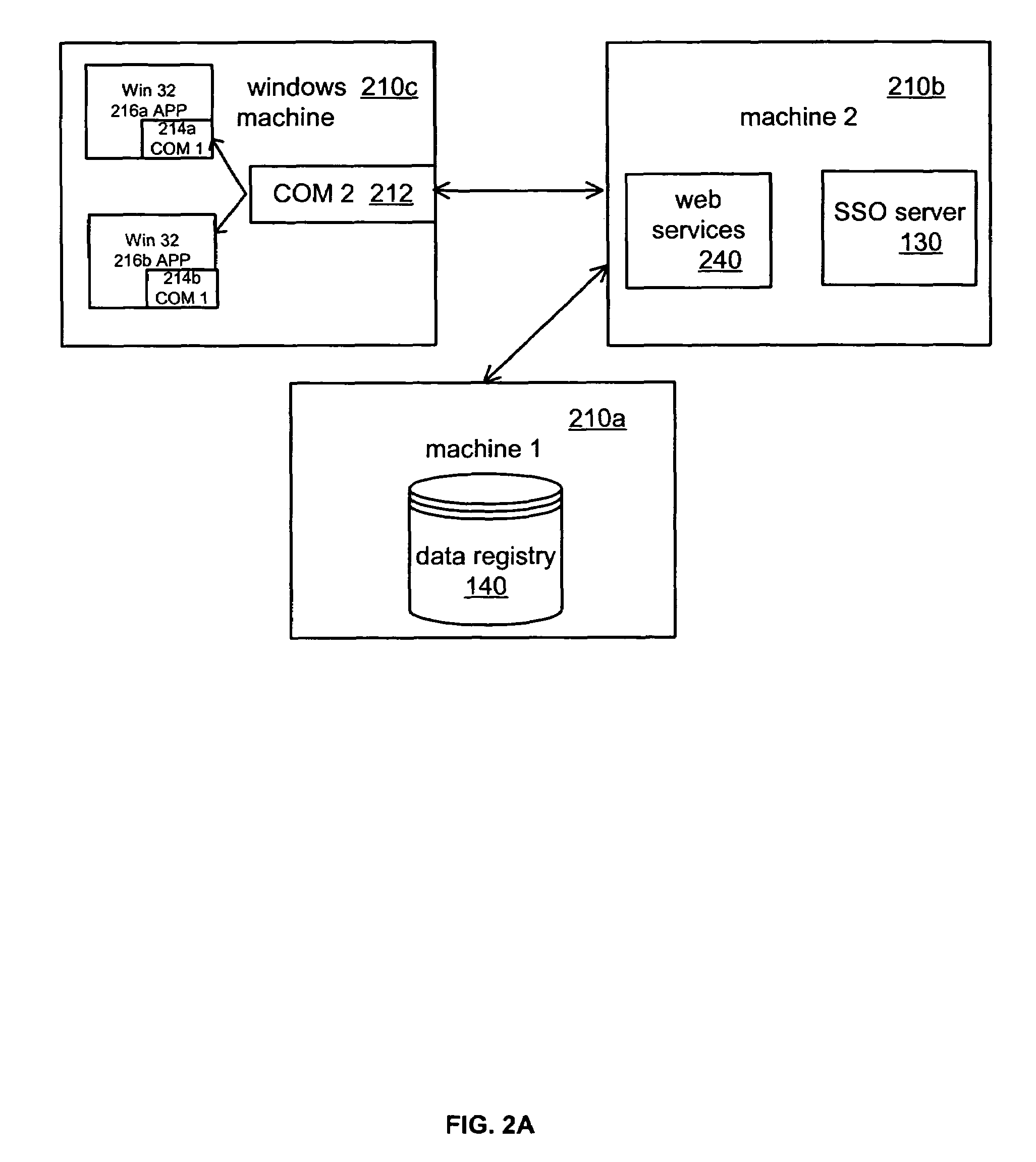
Cross-platform single sign-on data sharing
ActiveUS7509672B1Digital data processing detailsMultiple digital computer combinationsEnterprise computingApplication software
Systems and methods of authentication and data sharing across applications and platforms based on a single authentication are described. The systems and methods allow a user, based on a single log on to an application, to be automatically logged on to other applications and to fetch and store preference, state, and setting data across enterprise computing systems that include multiple computing platforms and applications. A data registry stores authentication and non-authentication data. An interface for automatically executing authentication transactions for the applications and facilitating the share of non-authentication data is also provided. The non-authentication data is user configurable to provide flexible application support across the enterprise, such as through the preservation of state information, preferences, settings, and application data across multiple computers.
Owner:BMC SOFTWARE
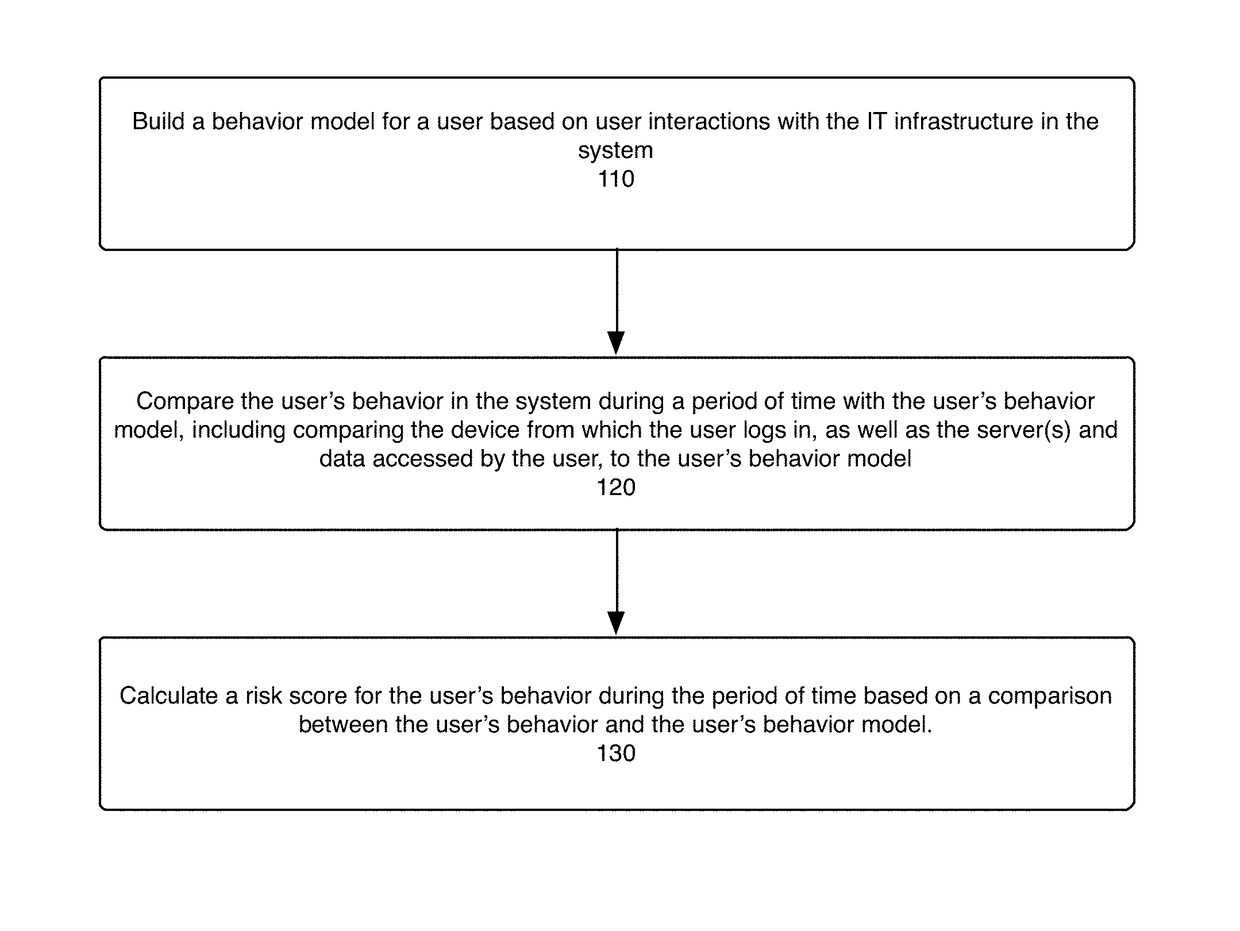
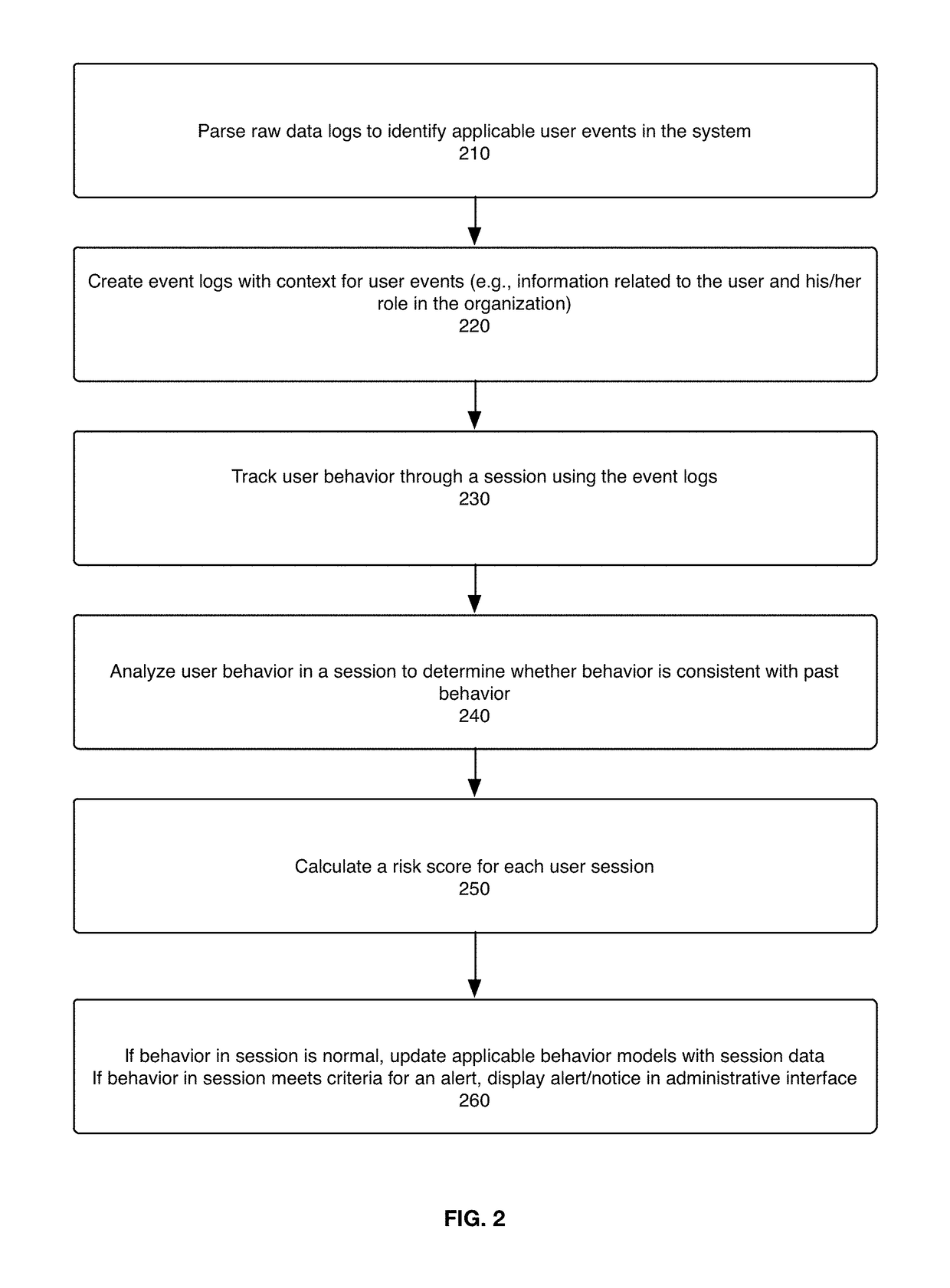
System, method, and computer program product for detecting and assessing security risks in a network
ActiveUS9798883B1Improve risk assessmentMemory loss protectionError detection/correctionClient-sideResource use
The present disclosure is directed to a system, method, and computer program for detecting and assessing security risks in an enterprise's computer network. A behavior model is built for a user in the network based on the user's interactions with the network, wherein a behavior model for a user indicates client device(s), server(s), and resources used by the user. The user's behavior during a period of time is compared to the user's behavior model. A risk assessment is calculated for the period of time based at least in part on the comparison between the user's behavior and the user's behavior model, wherein any one of certain anomalies between the user's behavior and the user's behavior model increase the risk assessment.
Owner:EXABEAM INC
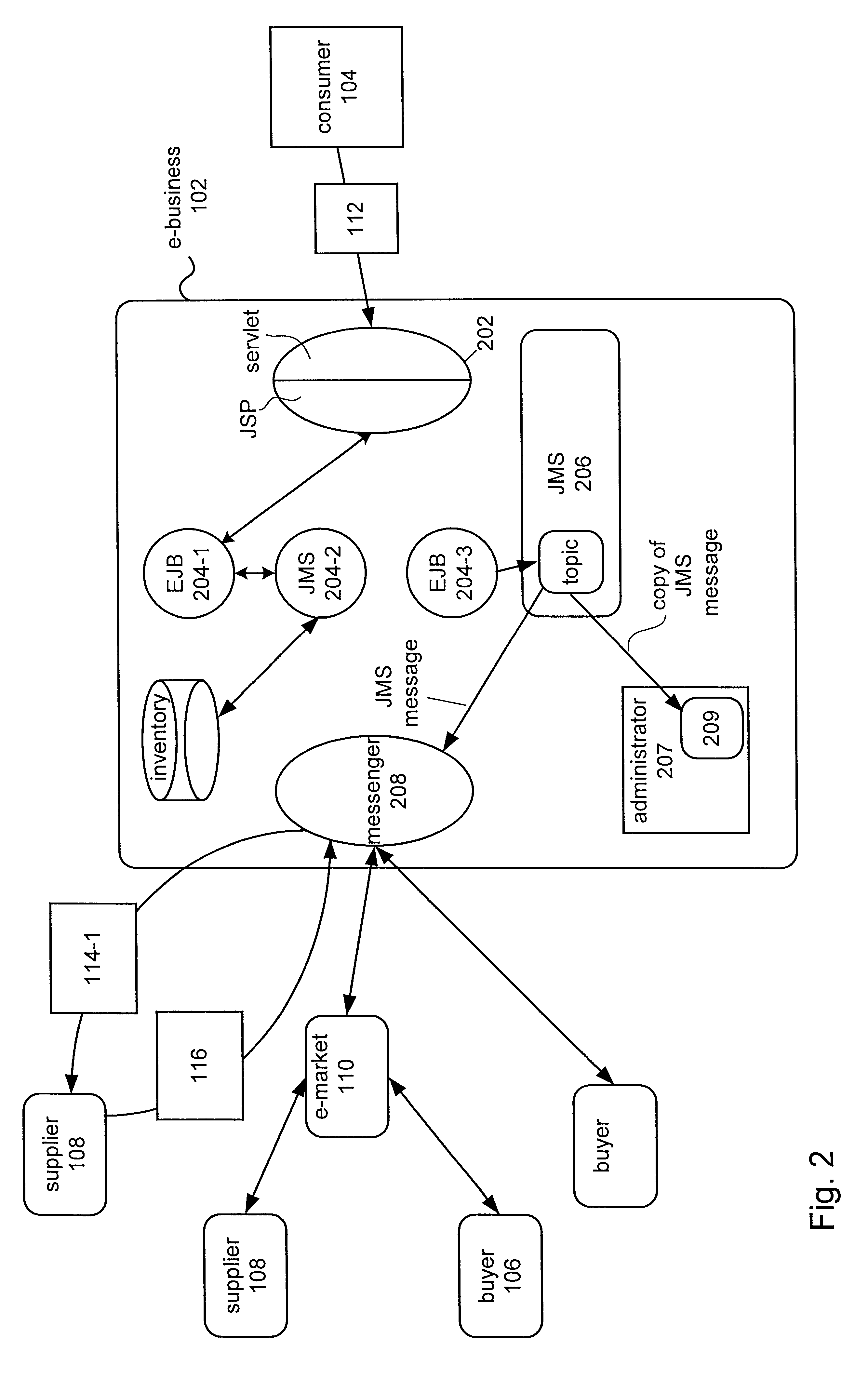
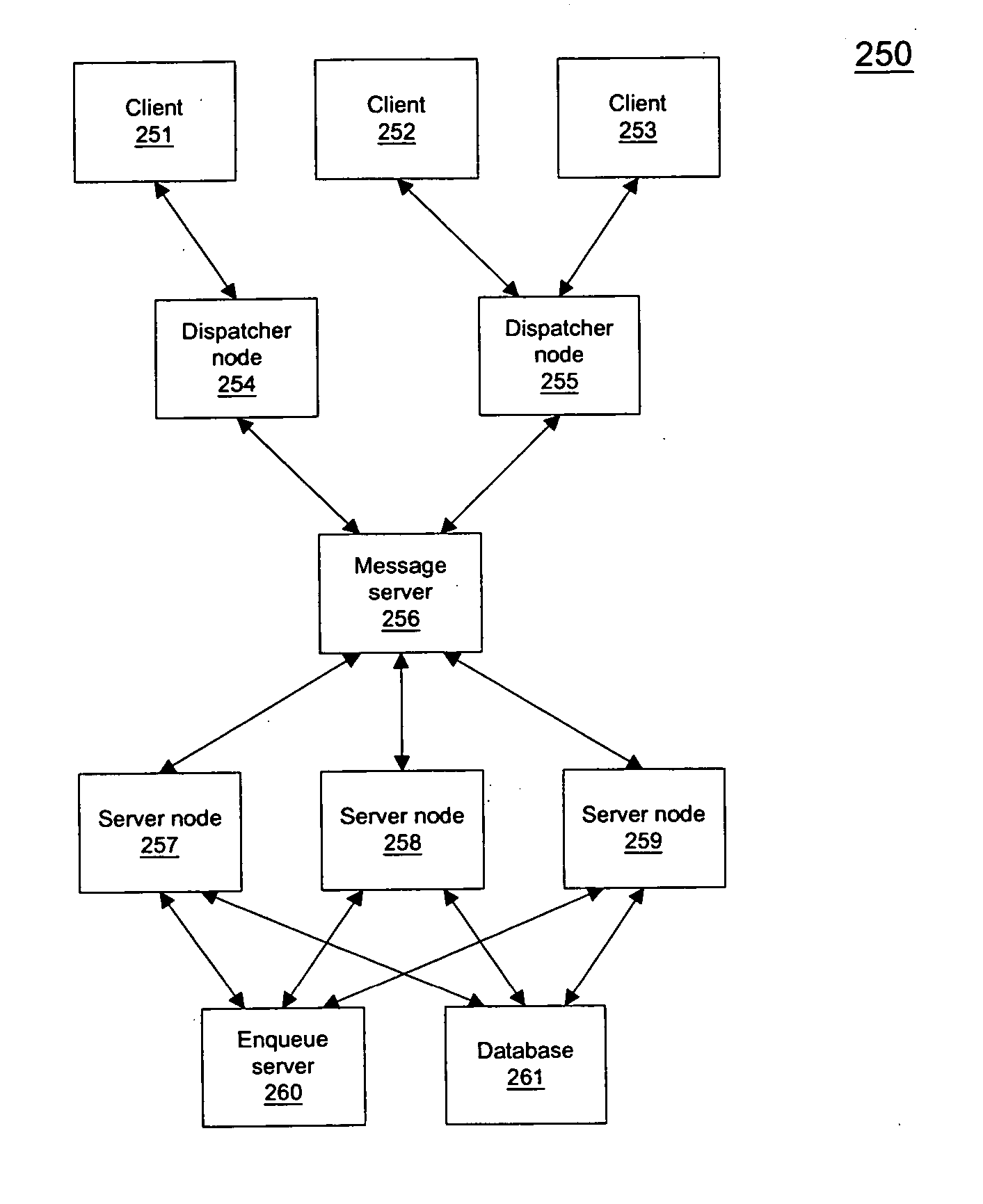
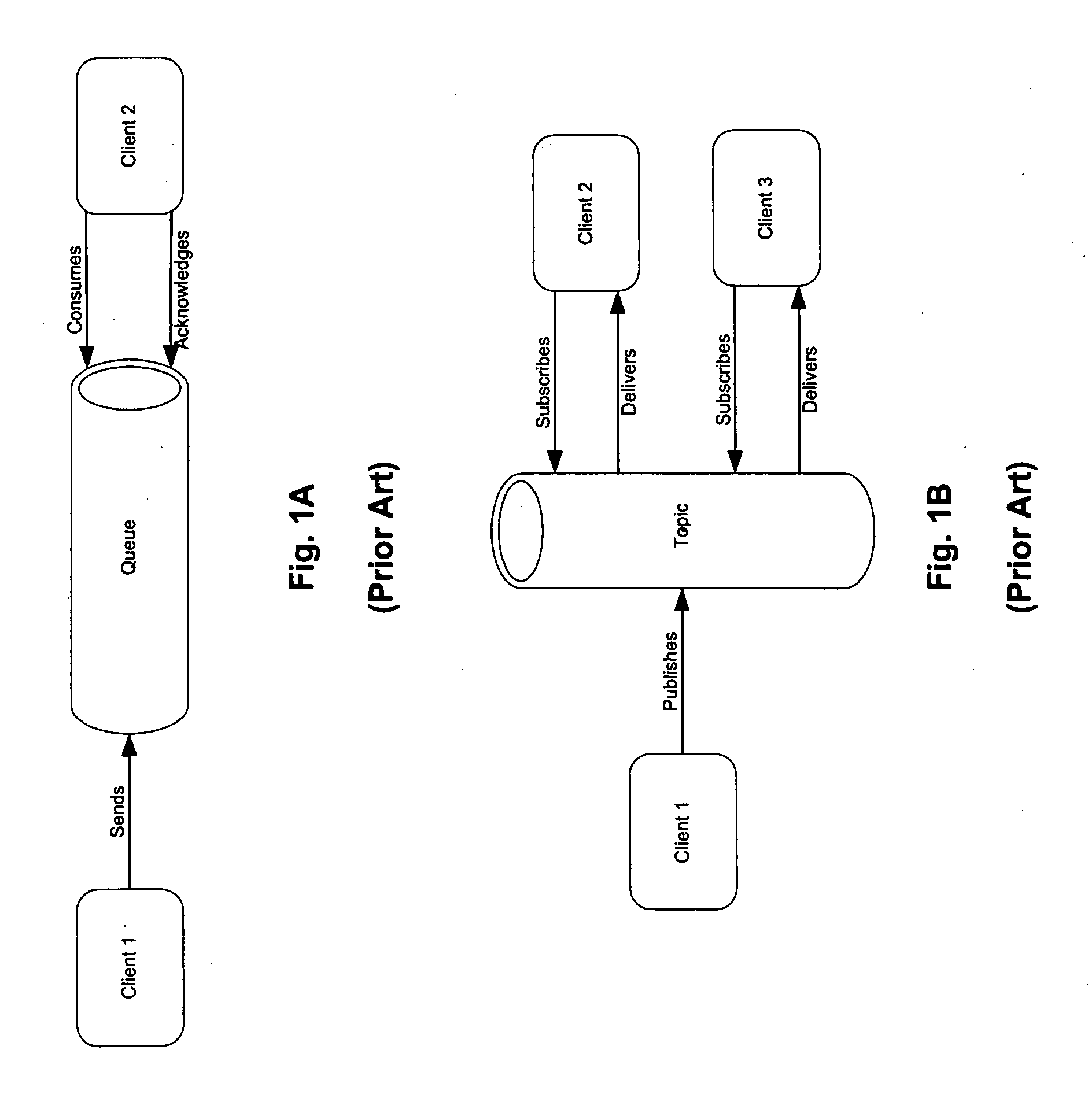
Delivering messages in an enterprise messaging system using message selector hierarchy
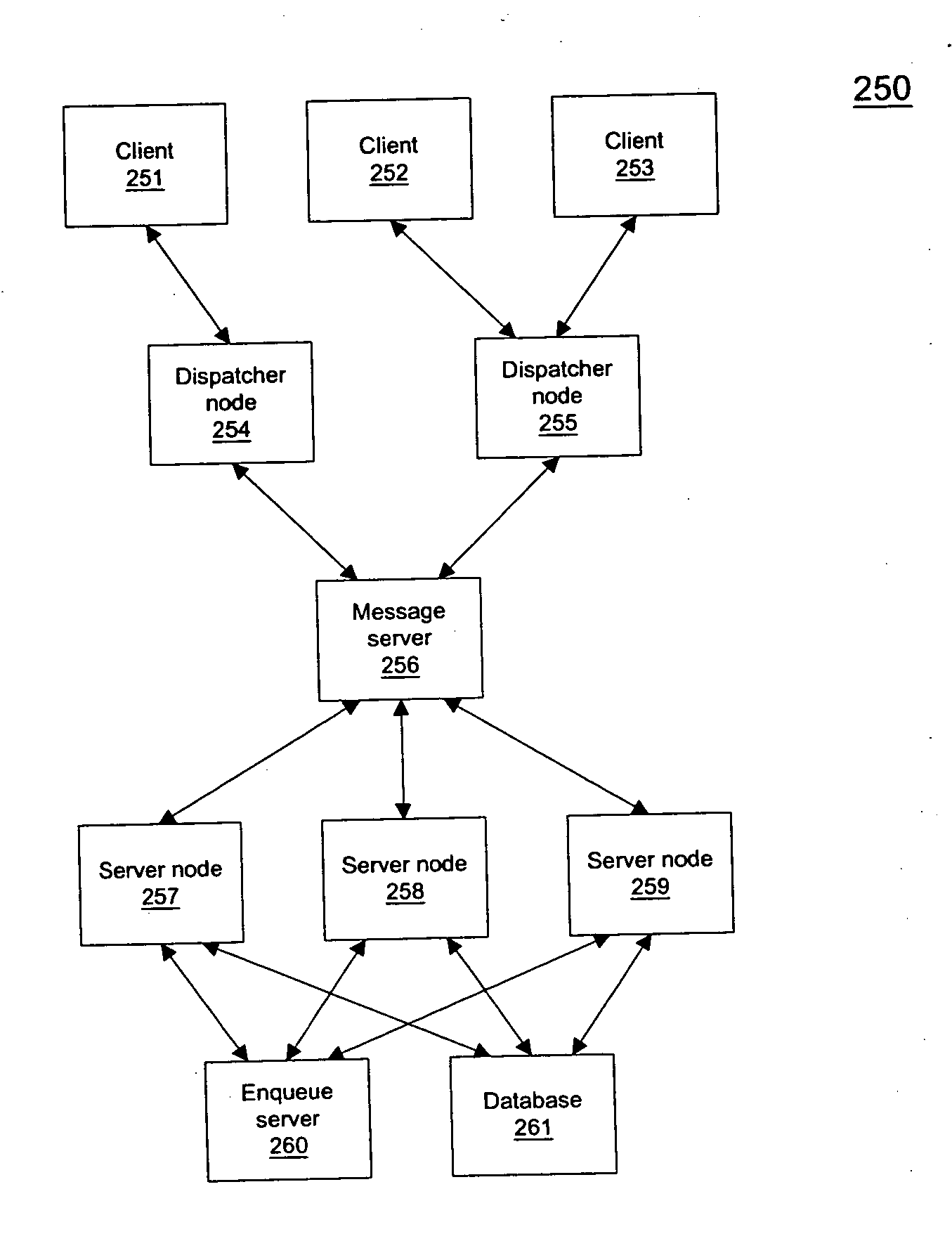
Methods and apparatuses for delivering enterprise messages in an enterprise computing environment are described herein. In one embodiment, an exemplary process is provided to determine, at a first node hosting a topic published by a producer, one or more groups of subscribers subscribing to the topic based on similarity of the subscribers. For each of messages associated with the topic, the respective message is delivered once to a second node associated with one of the one or more groups of the subscribers, where the second node distributes the respective message to each of the subscribers of the respective group individually without again invoking the first node. Other methods and apparatuses are also described.
Owner:SAP AG
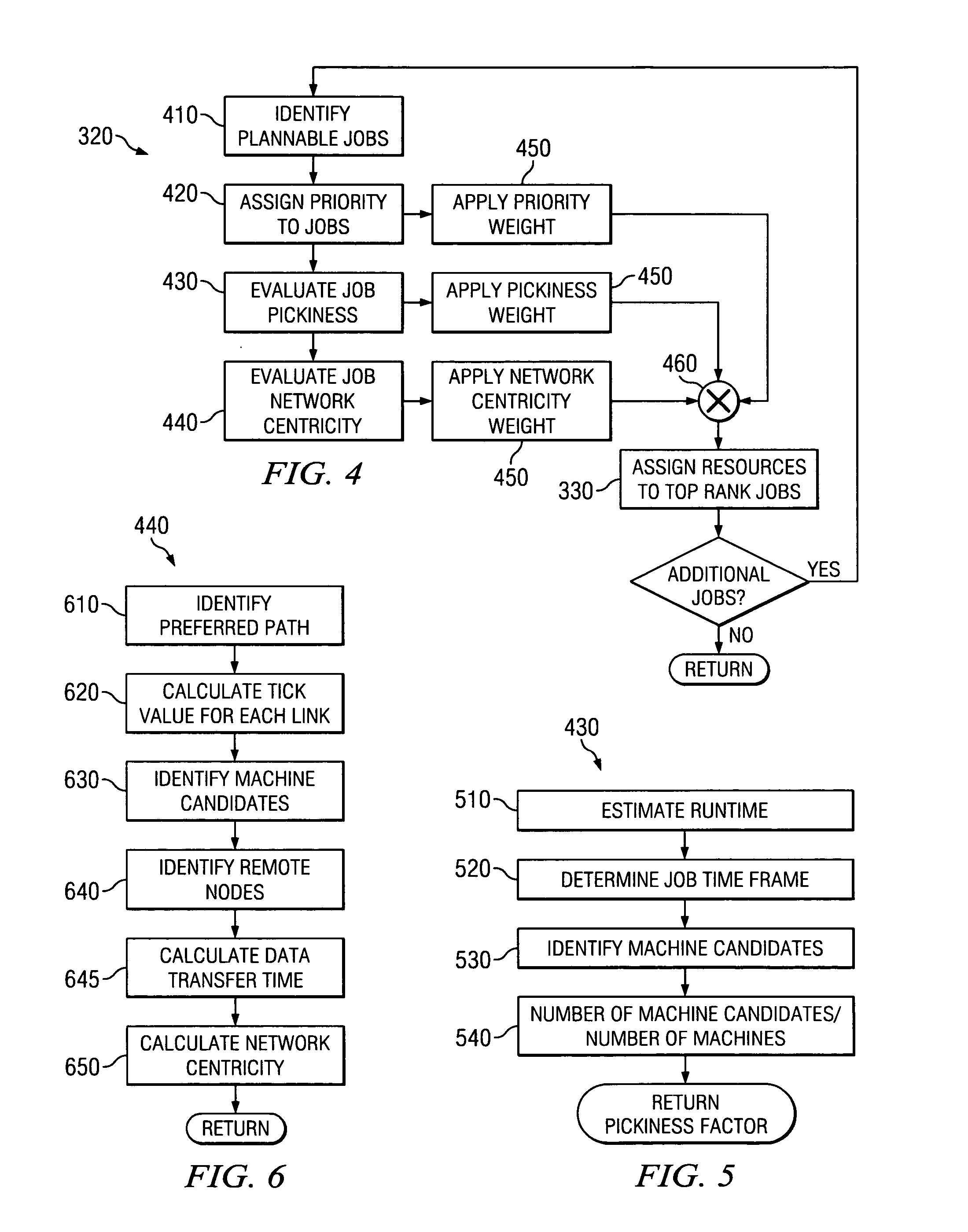
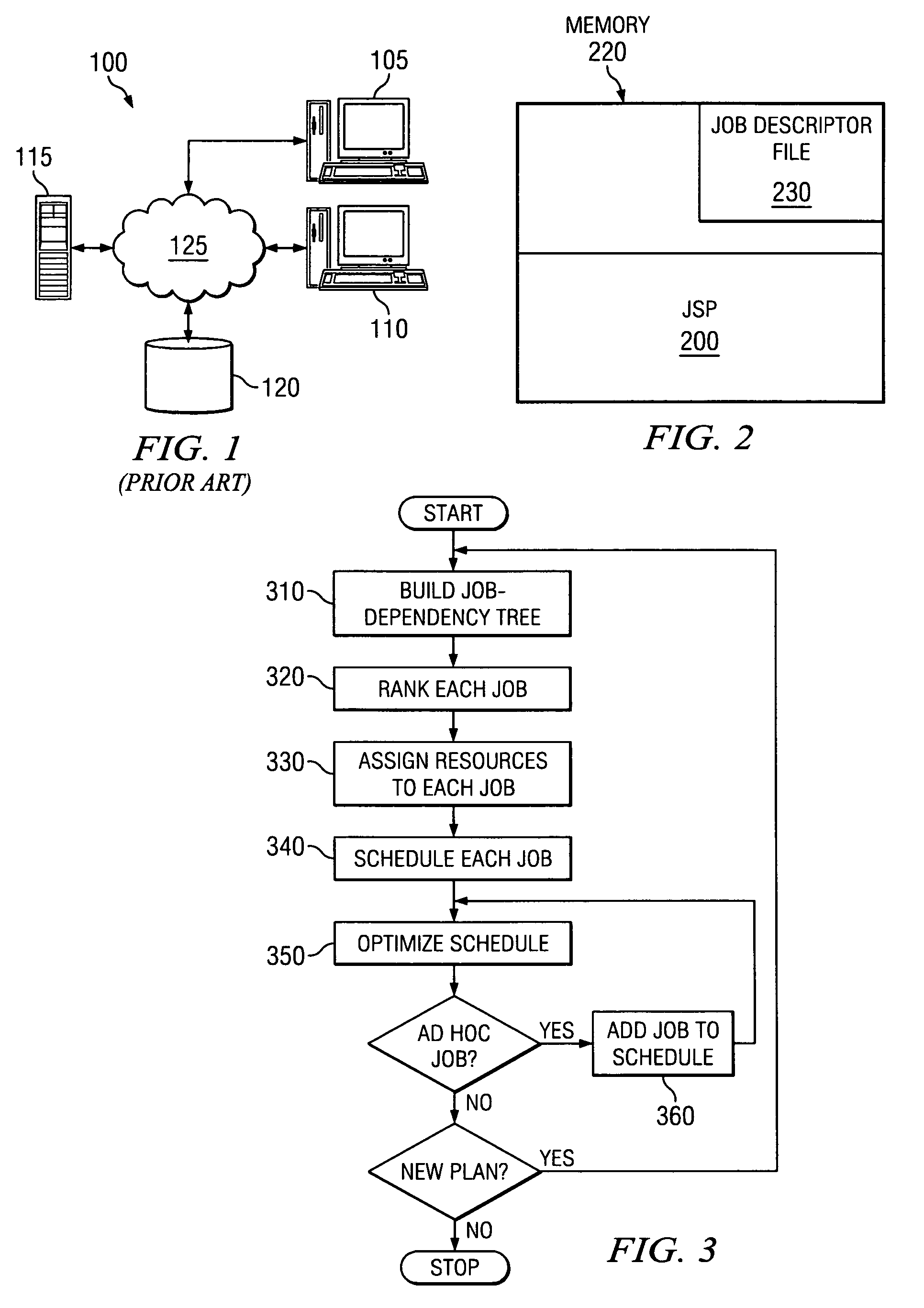
Jobstream planner considering network contention & resource availability
InactiveUS20060218551A1Good flexibilityImprove efficiencyMultiprogramming arrangementsMultiple digital computer combinationsWork planningEnterprise computing
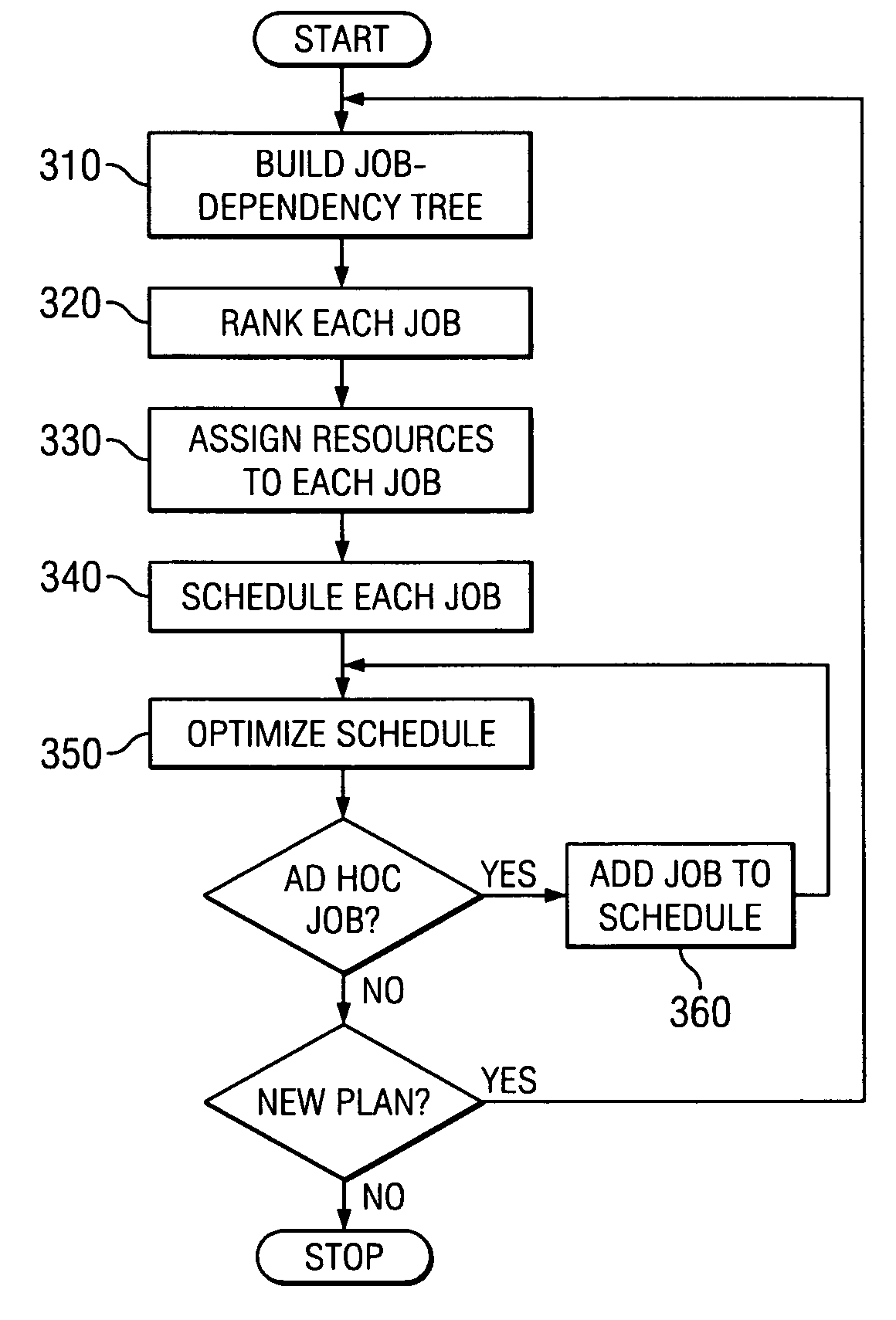
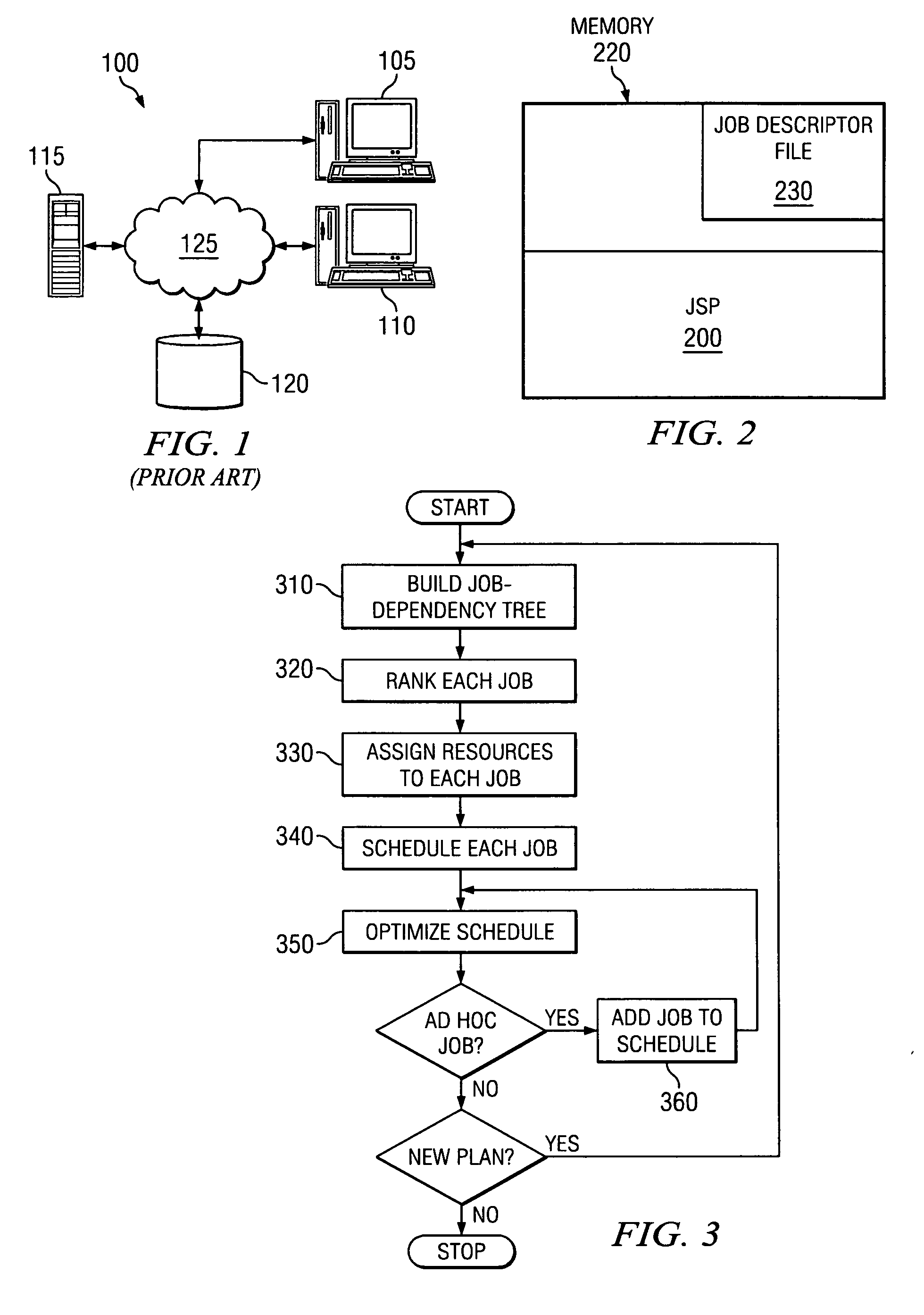
Disclosed is a computer-implemented planning process that aids a system administrator in the task of creating a job schedule. The process treats enterprise computing resources as a grid of resources, which provides greater flexibility in assigning resources to jobs. During the planning process, an administrator or other user, or software, builds a job-dependency tree. Jobs are then ranked according to priority, pickiness, and network centricity. Difficult and problematic jobs then are assigned resources and scheduled first, with less difficult jobs assigned resources and scheduled afterwards. The resources assigned to the most problematic jobs then are changed iteratively to determine if the plan improves. This iterative approach not only increases the efficiency of the original job schedule, but also allows the planning process to react and adapt to new, ad-hoc jobs, as well as unexpected interruptions in resource availability.
Owner:KYNDRYL INC
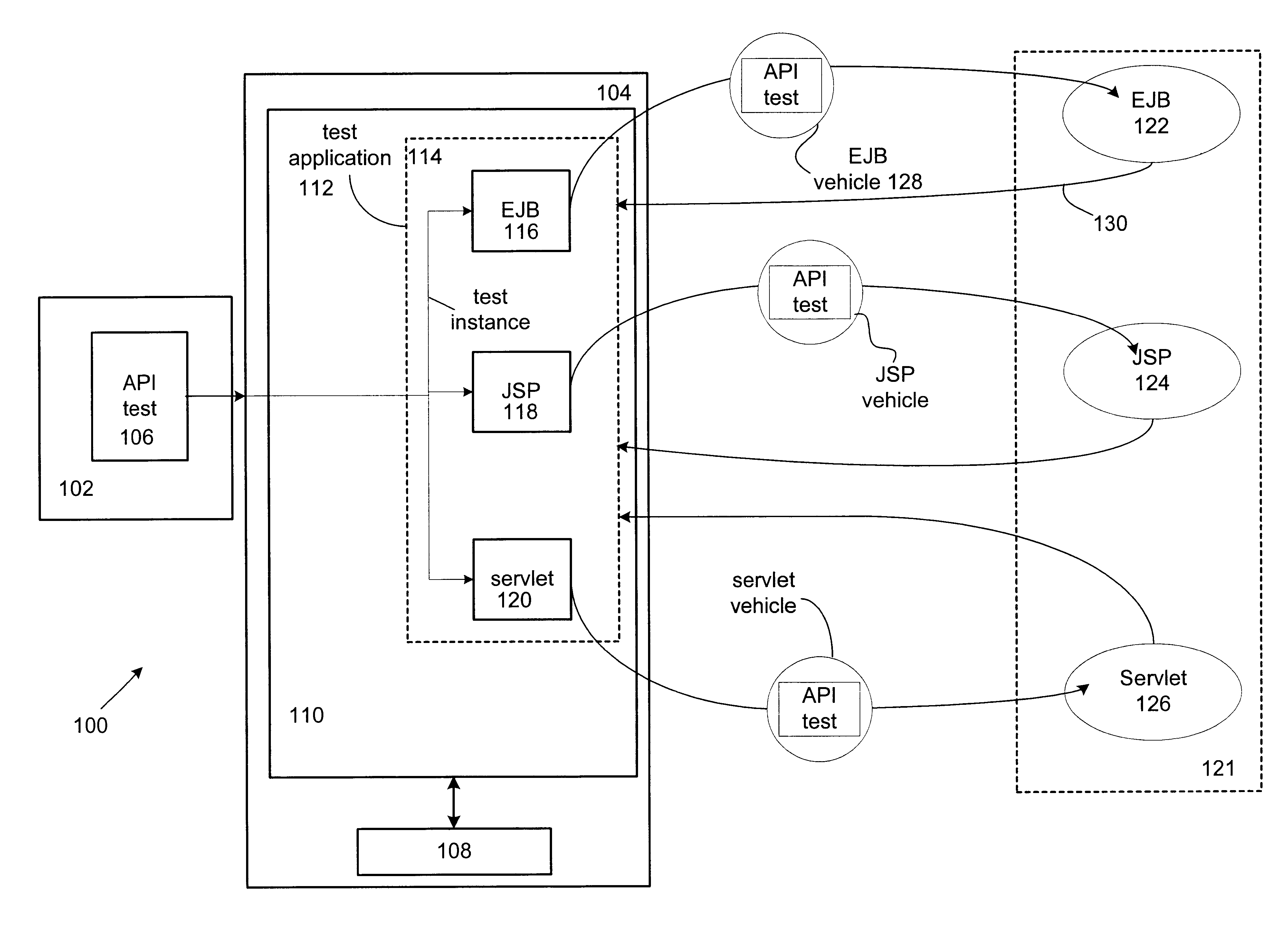
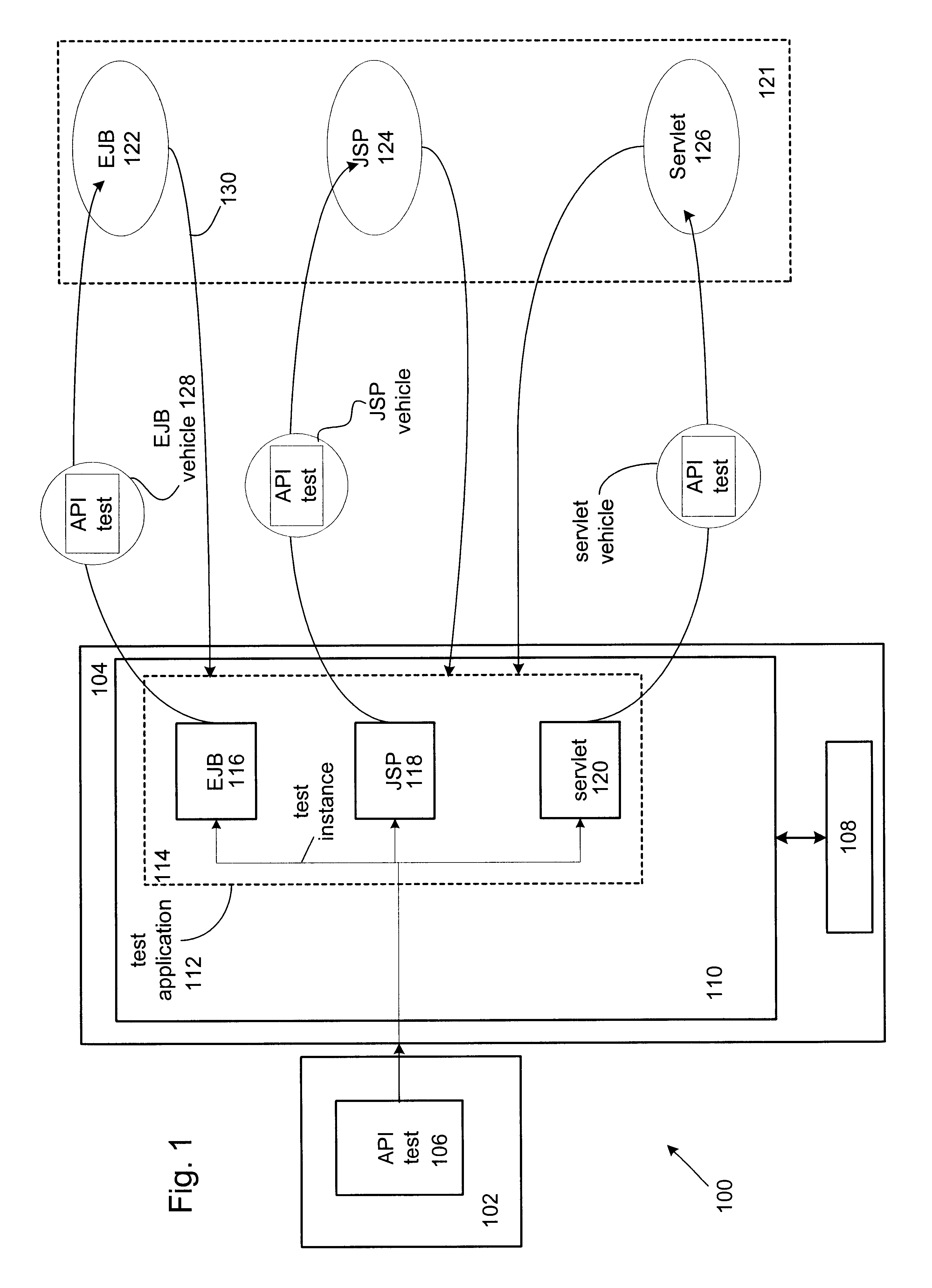
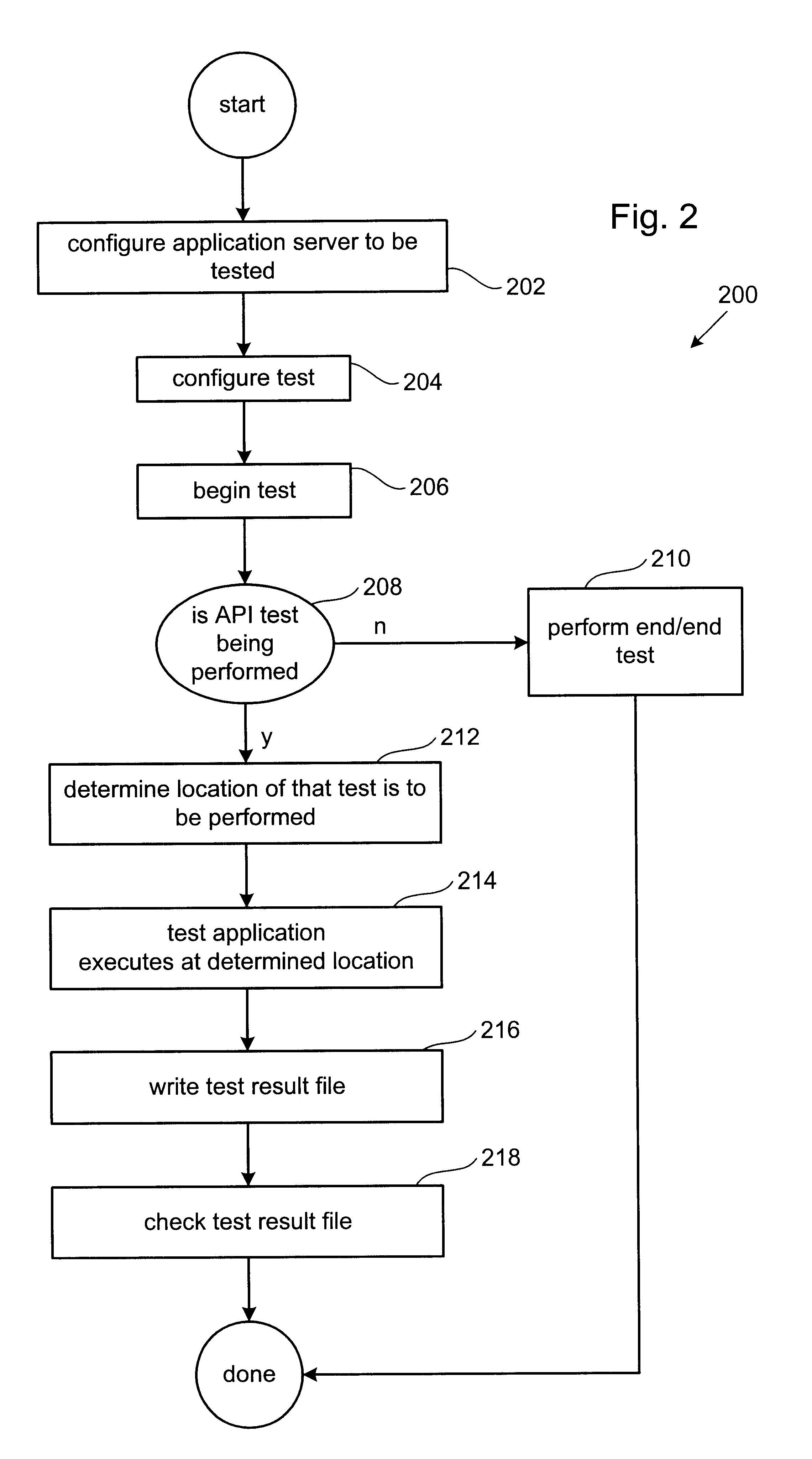
Distributed component testing in an enterprise computer system
A method of automatically performing a component test at any number of locations in a distributed environment is disclosed. In general, in order to assure compatibility of the various components in an enterprise computing system, a service test is created as part of a compatibility test suite and passed to a test application server having a test application program. The test application program includes a generic vehicle class that includes a plurality of vehicle class invokers each of which is used to implement each of the object types that are run in each of a plurality of containers. During the build process of the CTS, each service test is automatically packaged with each of the appropriate vehicle classes so that each can be deployed into and run within the associated container.
Owner:ORACLE INT CORP
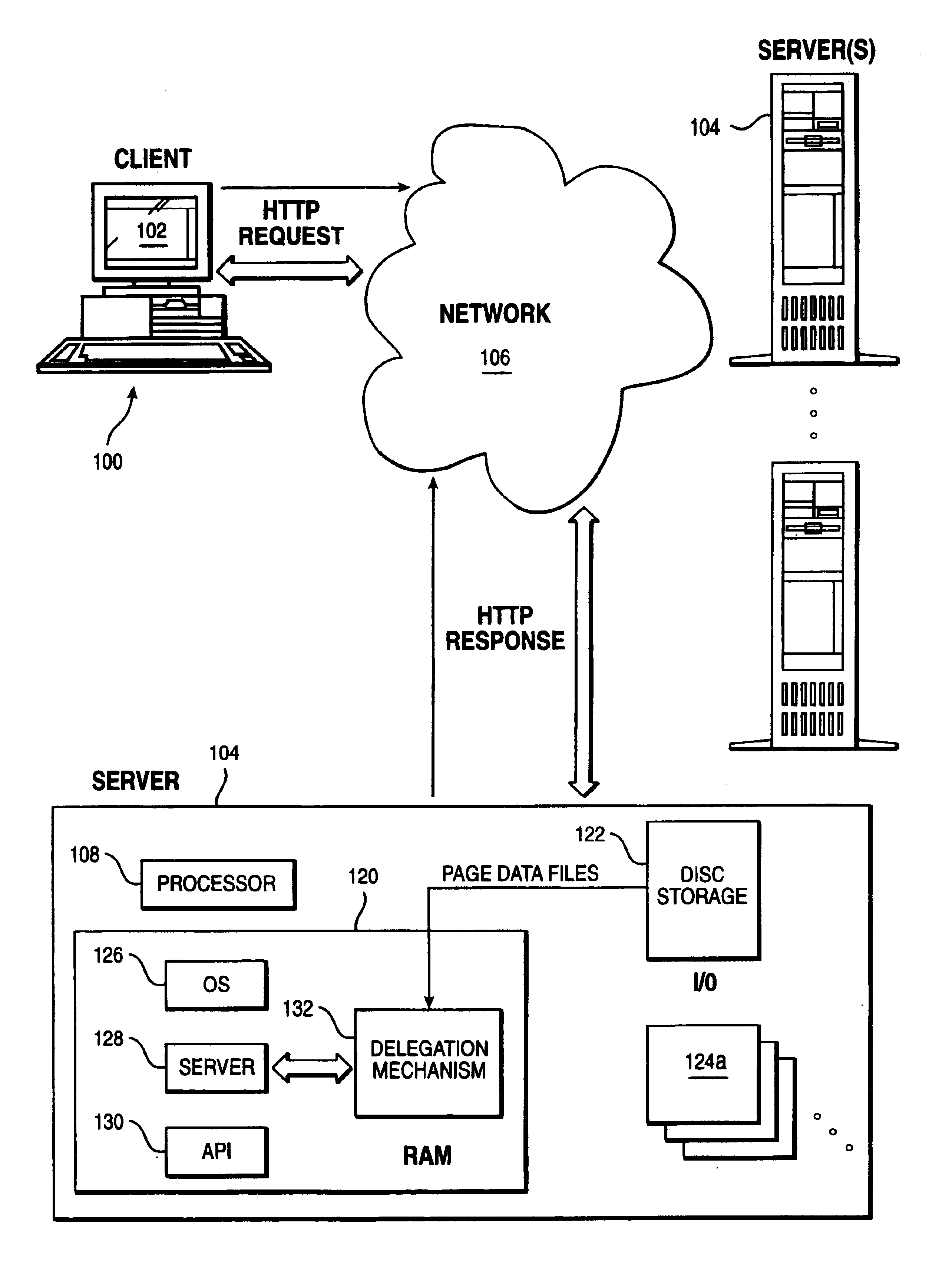
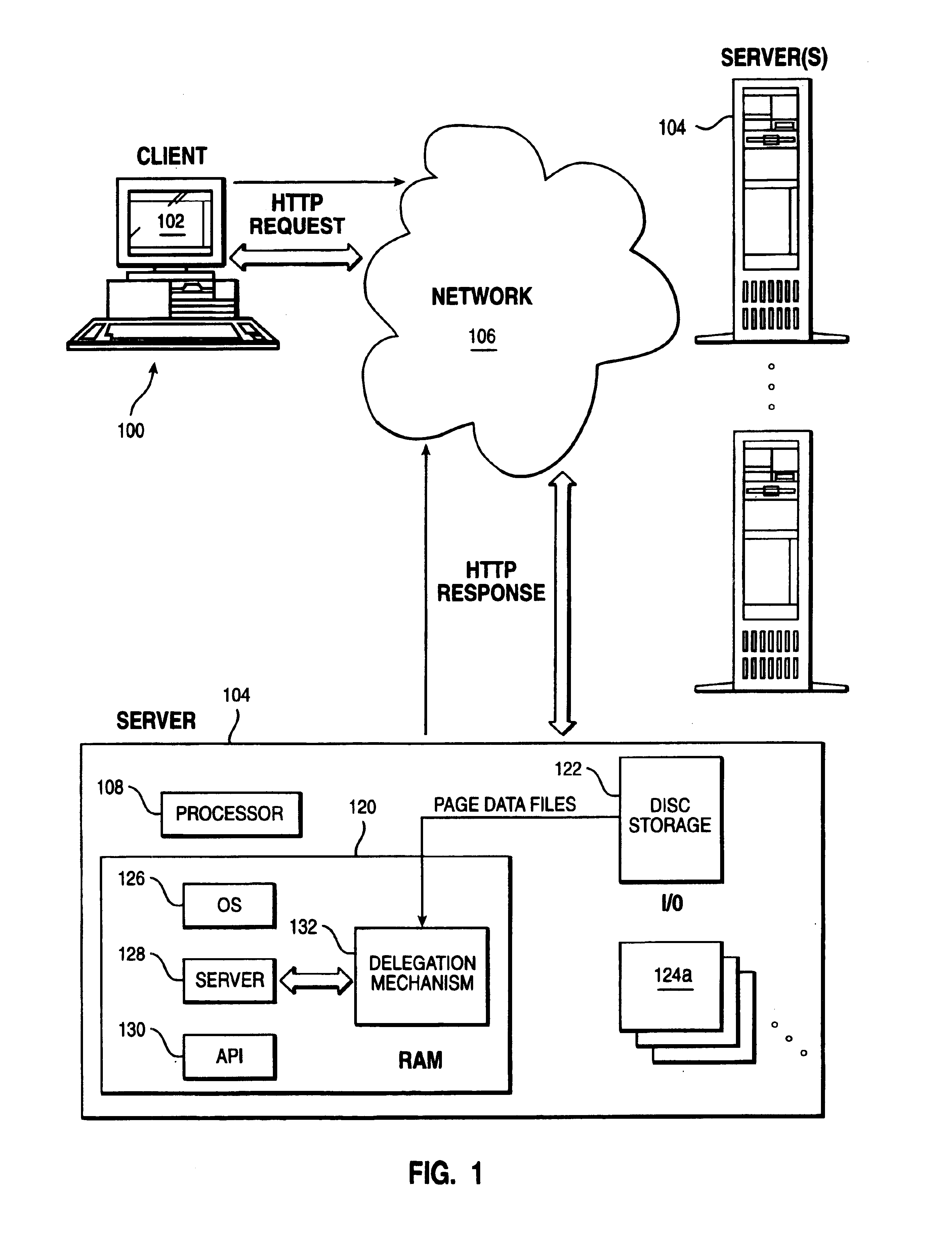
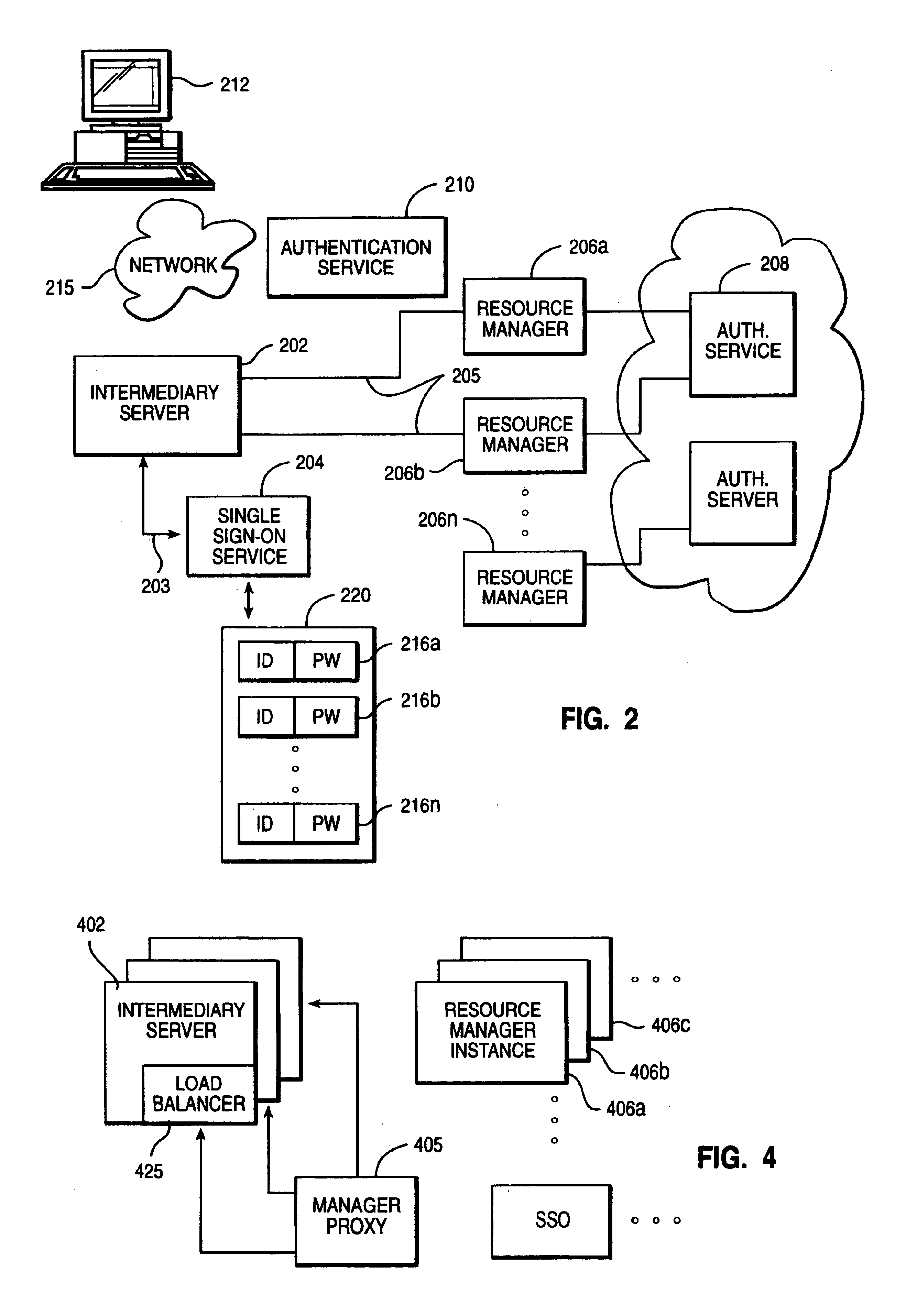
Method of enabling an intermediary server to impersonate a client user's identity to a plurality of authentication domains
InactiveUS7039714B1Multiple digital computer combinationsTransmissionEnterprise computingResource management
An enterprise computing environment such as a corporate web portal includes an intermediary server, a sign on service, and one or more backend enterprise systems managed by resource managers. Before or after user primary logon, which establishes a user primary account identity, the intermediary server uses its own identity to authenticate to the sign on service its right to retrieve user secondary account identities with respect to the backend enterprise systems. Retrieved secondary account identities are then used by the intermediary server to perform user secondary logons to respective resource managers in the environment. The intermediary server also manages the passing of resource requests and associated replies between the user and the resource managers.
Owner:IBM CORP
Methods and apparatuses for processing messages in an enterprise computing environment
ActiveUS20050256931A1Special service provision for substationMultiple digital computer combinationsMultiple deliveryEnterprise computing
Methods and apparatuses for processing enterprise messages are described herein. In one embodiment, an exemplary process is provided to maintain multiple delivery policies of multiple subscription sessions of a subscriber subscribing a topic published by a producer, wherein at least one policy is different from a remainder of the delivery policies. The messages associated with the topic are delivered according to substantially all the delivery policies of the subscription sessions including the at least one different delivery policy. Other methods and apparatuses are also described.
Owner:SAP AG
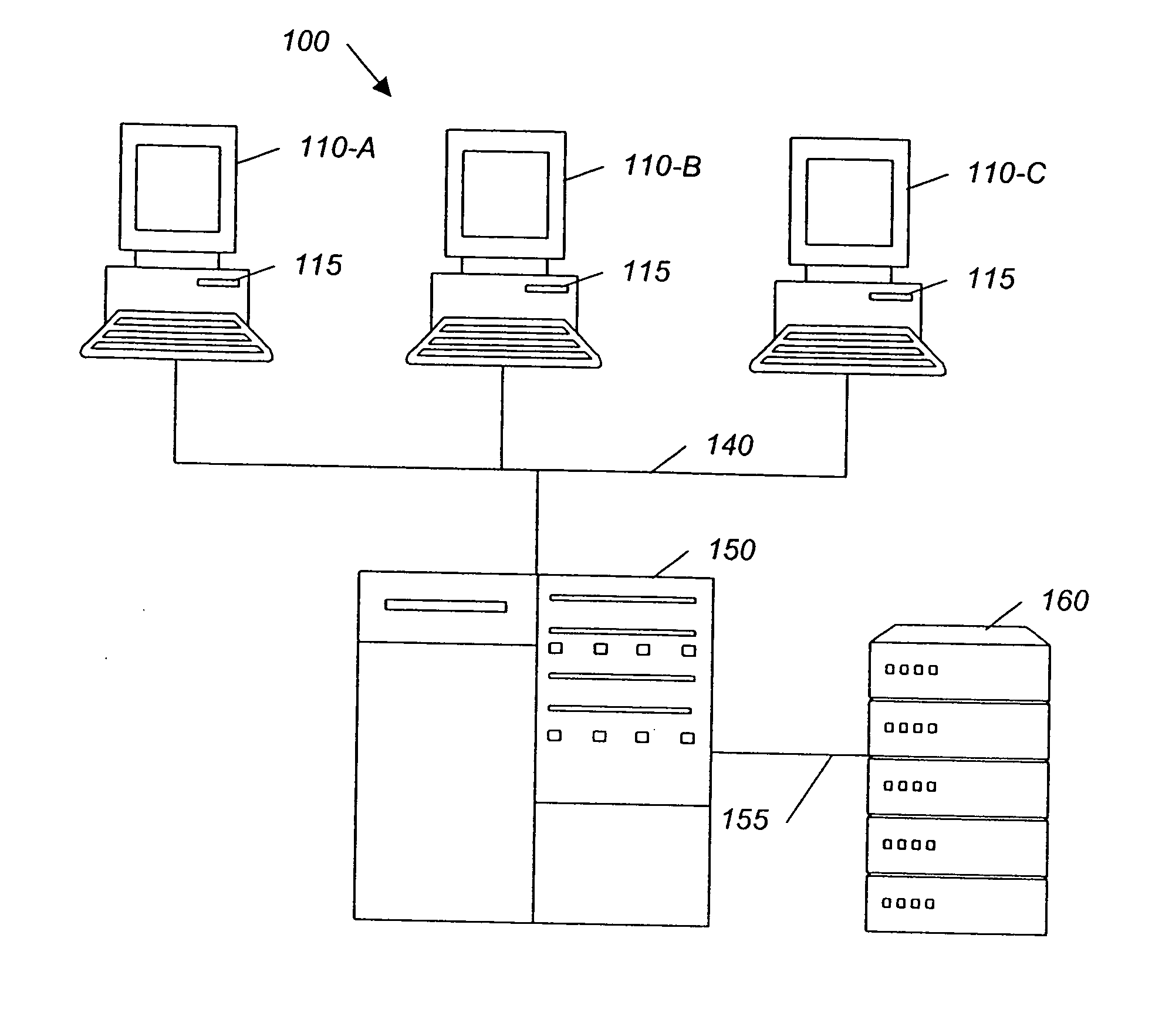
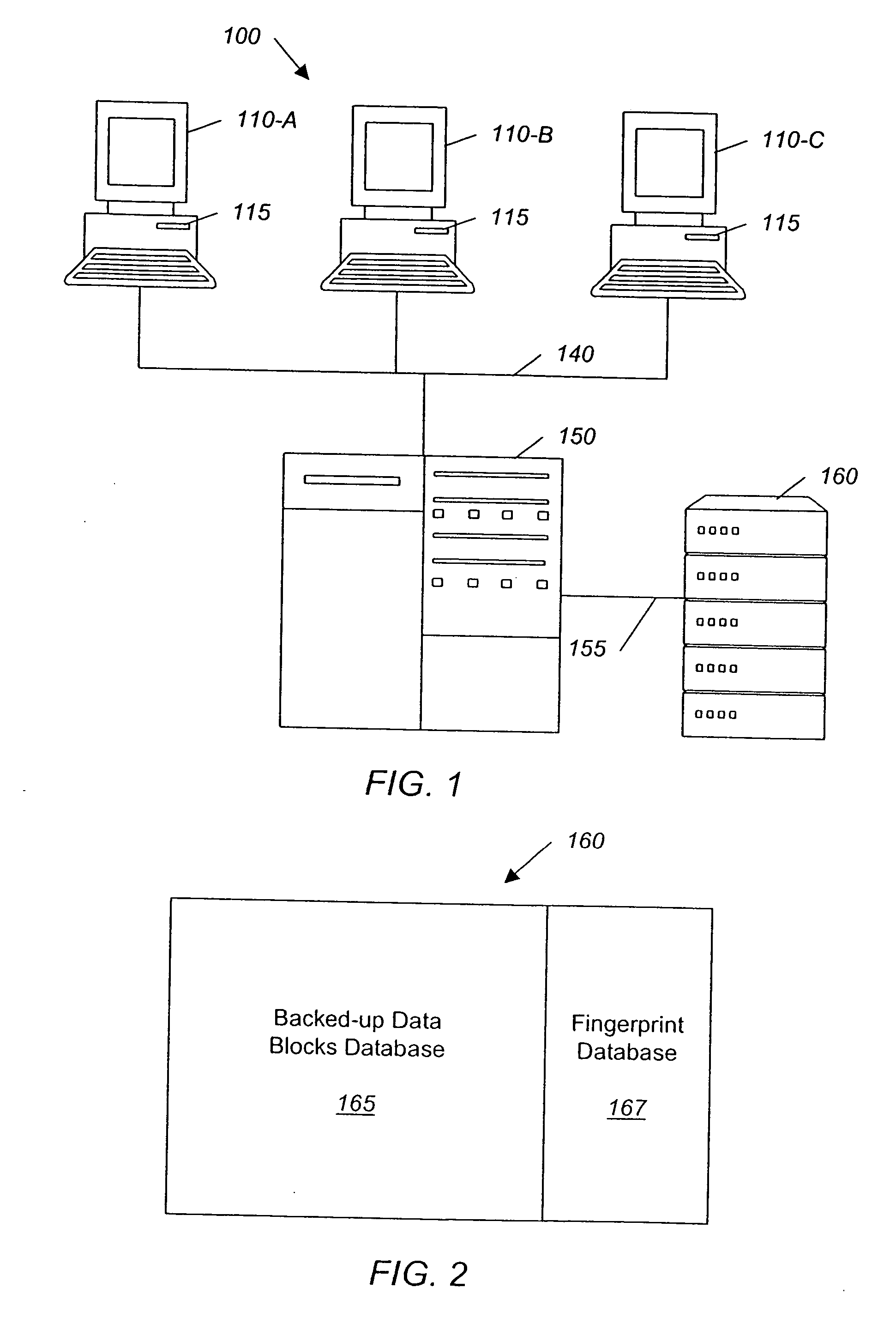
System and method for backing up data
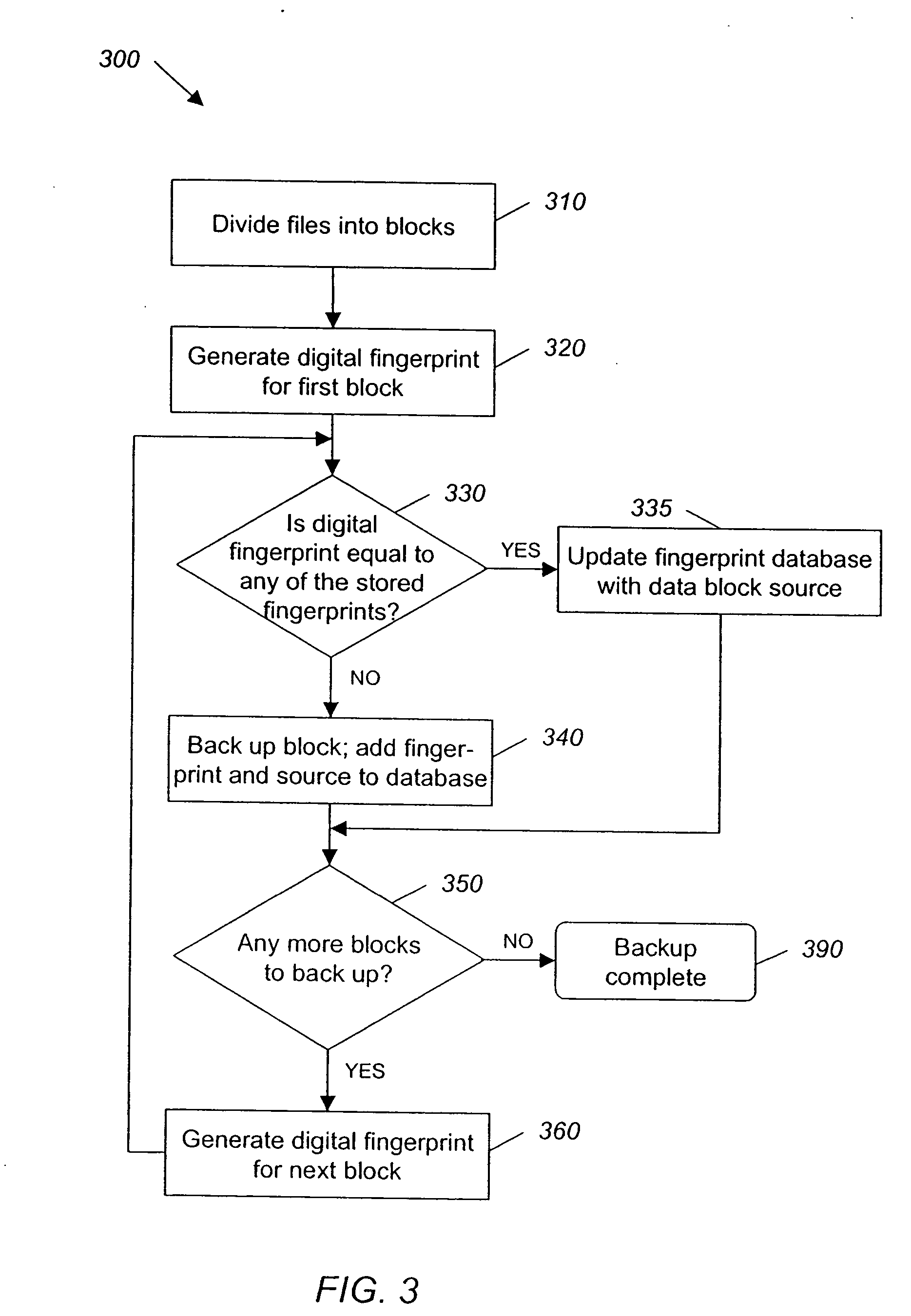
InactiveUS20060218644A1Inefficiency of the Shnelvar patent can be avoidedAvoid inefficiencyDigital data processing detailsCamera focusing arrangementEnterprise computingTheoretical computer science
A method is provided to audit license restrictions of a computer program in an enterprise computing environment. In one example, a digital fingerprint is generated of at least one file in the computer program using a substantially collision-free algorithm, and a digital fingerpring is generated for each file on each computer in the enterprise using the substantially collision-free algorithm. The digital fingerprints from the enterprise files are compared with the digital fingerprint of the computer program file, and the number of fingerprint matches is counted. Another method is provided for inventorying a computer program in an enterprise computing environment. In examples of both methods, a file may be divided into data blocks and a digital fingerprint may be generated for each data block.
Owner:FALCONSTOR
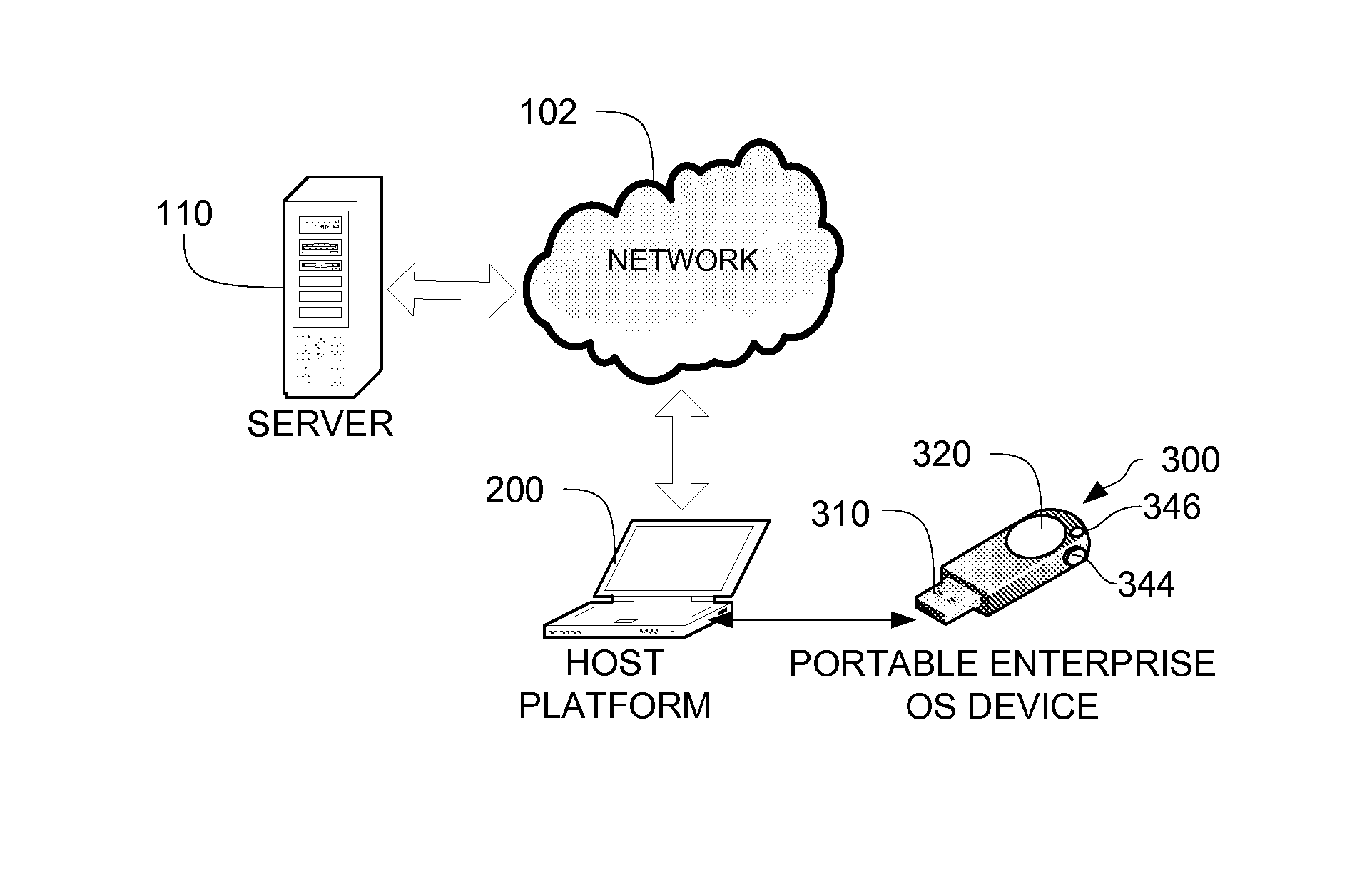
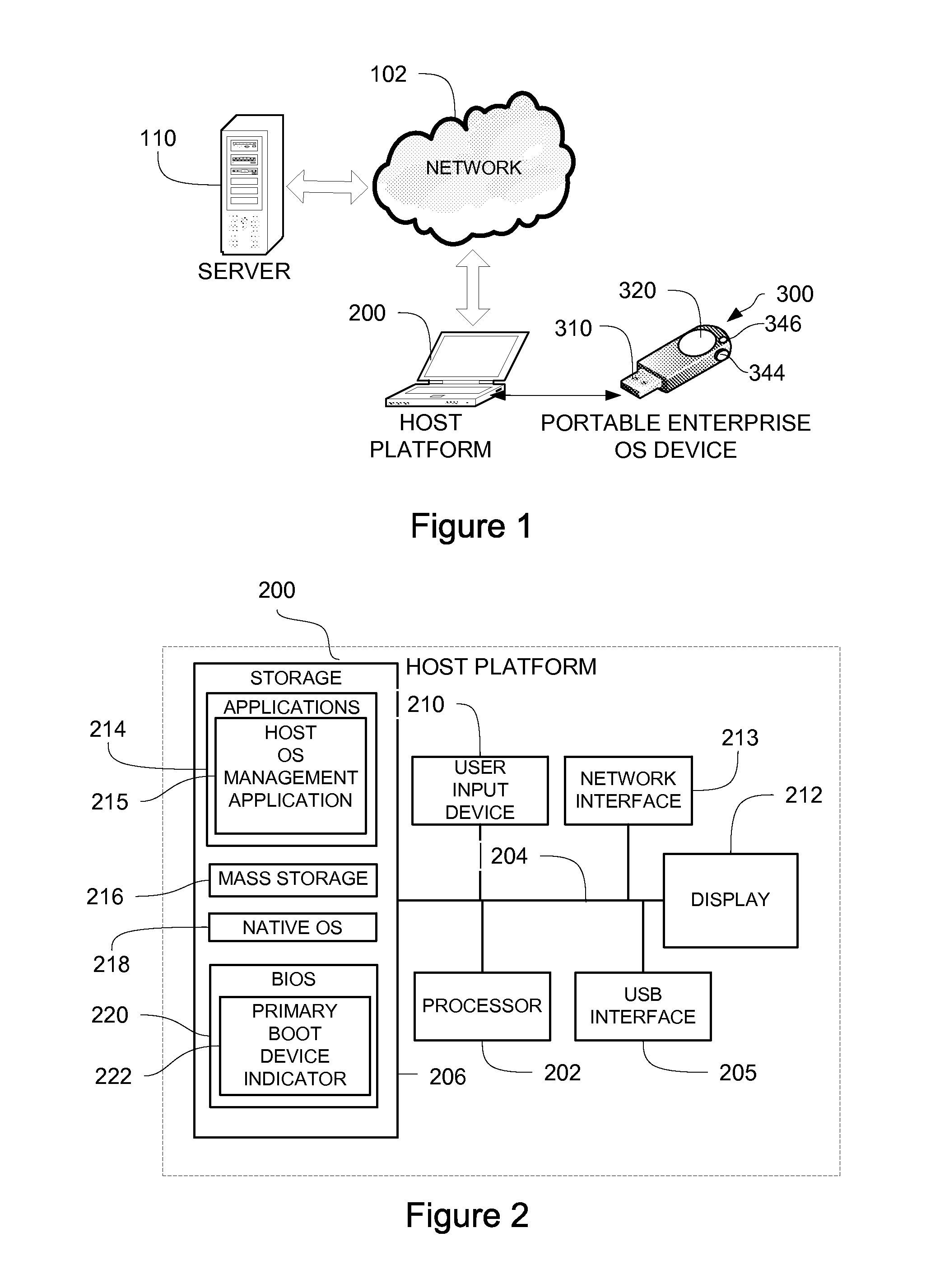
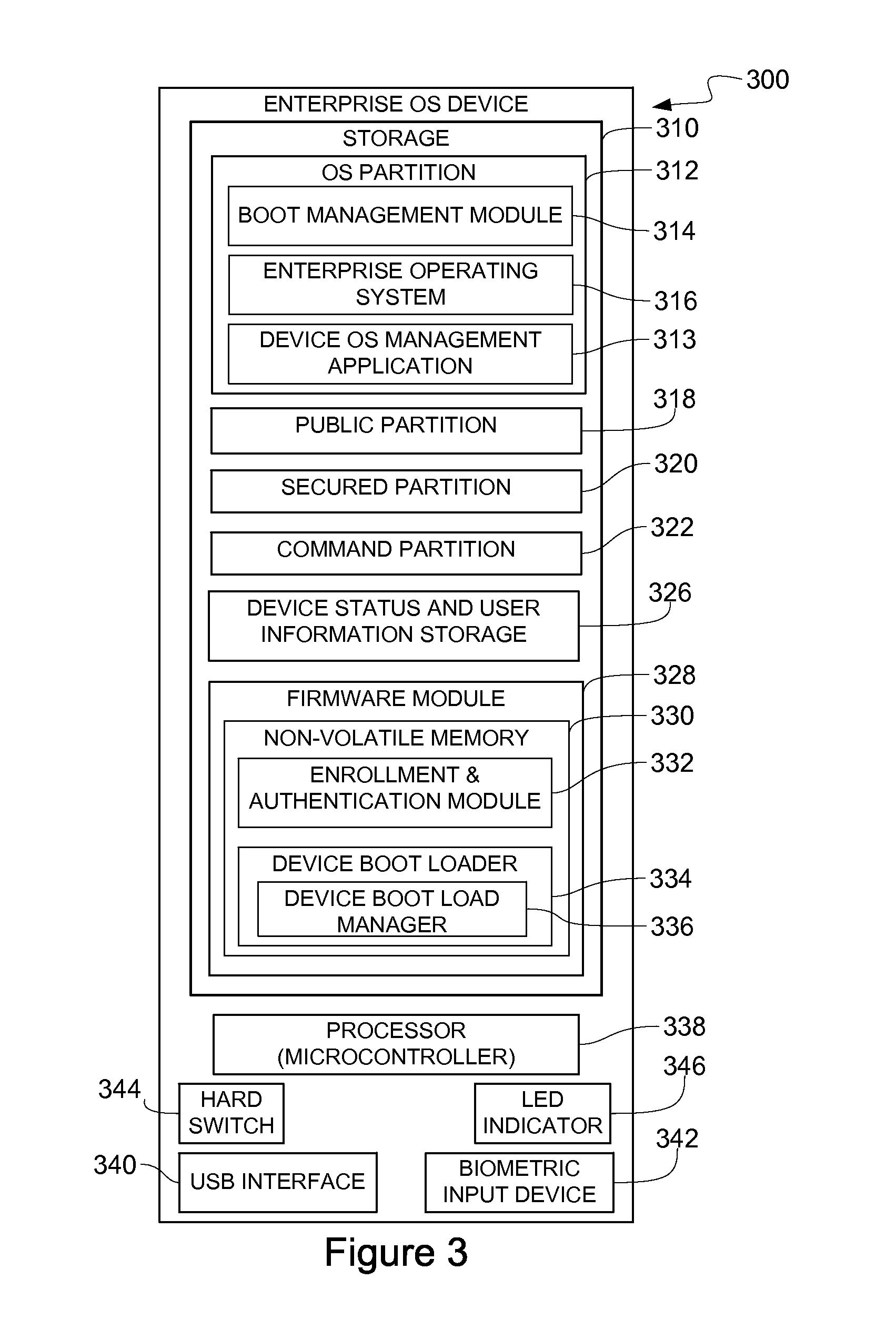
Portable, secure enterprise platforms
InactiveUS20140101426A1Improve securityPrevent unauthorized accessDigital computer detailsDigital data authenticationProgram managementComputer module
A portable, secure enterprise computing platform is provided by a device having a storage or memory, including a firmware module, a processor and an interface for interfacing with a host platform. The interface may be a USB interface and the device may have the form factor of a USB thumb drive. The storage may include a public partition, secure partition, operating system partition and command partition. A boot load manager in the firmware module causes the processor to load an operating system on the operating system partition and selectively enables access to the operating system by the host platform. The operating system partition may be formatted as a CDFS device such that the host platform recognizes the device as a bootable CD drive. The device provides for secure booting to the operating system partition by the host platform, without risk of corruption or malware from the host platform. A user may select from multiple operating systems. Multiple devices may be managed by a policy management application, which may assign groups of users and applications to one or more devices across an enterprise.
Owner:MSI SECURITY
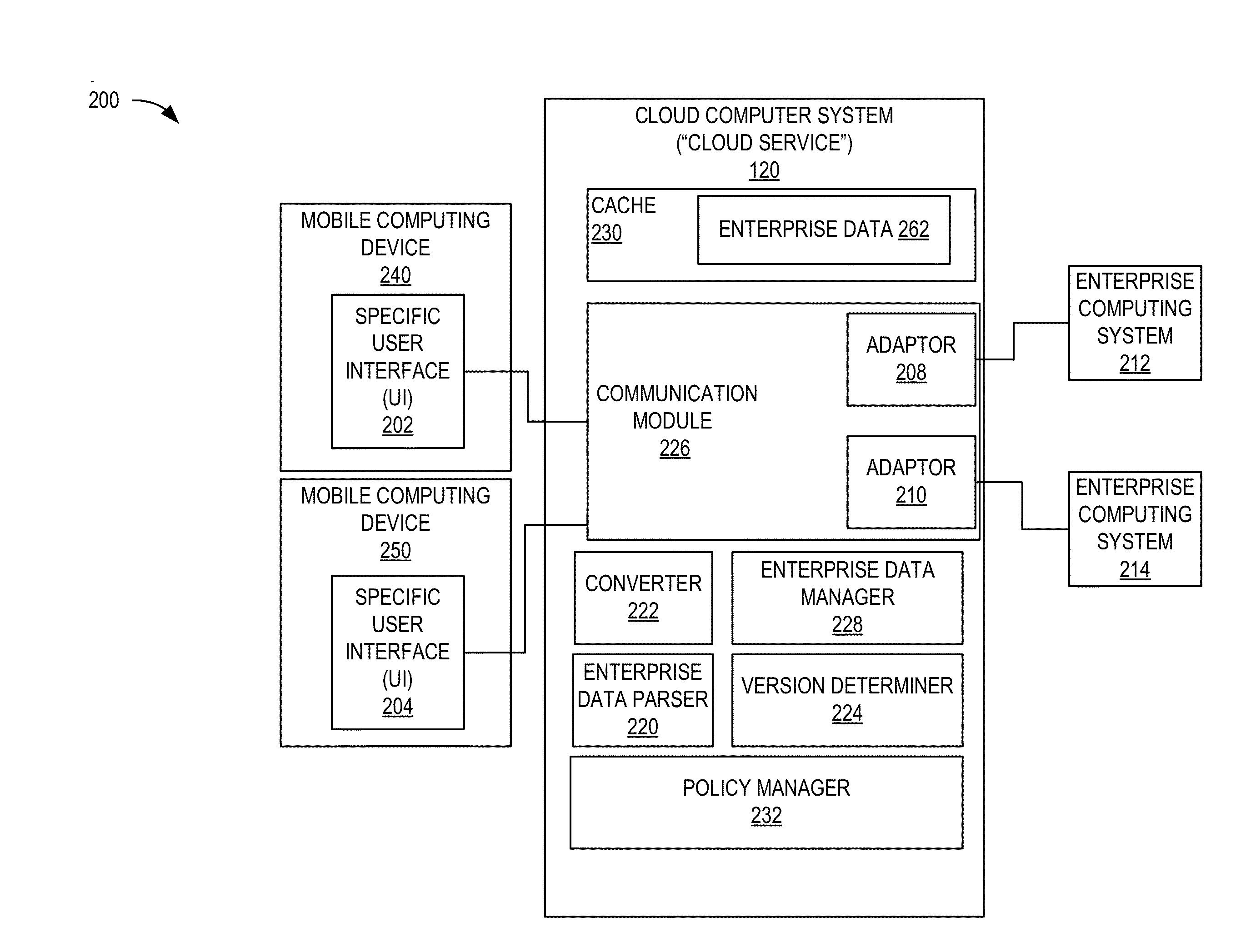
Infrastructure for synchronization of mobile device with mobile cloud service
ActiveUS20150278245A1Good synchronizationEasy to identifyDigital data information retrievalDigital data processing detailsHuman resource managementMobile cloud
Techniques are described for implementing a cloud computer system (e.g., “a cloud service”) for facilitating the synchronization of enterprise data between mobile computing devices and enterprise computing systems (e.g., human resource management systems, business management systems, or the like). The cloud service may convert enterprise data received from different enterprise computing systems to a format that can be managed and updated easily by mobile computing devices. The converted format may enable distinct information to be easily identified. The enterprise data may be associated with policy information and version information to manage synchronization of the enterprise data. In some embodiments, the cloud service may manage synchronization with mobile computing devices based on classification of a communication connection the mobile computing devices have to a wireless network. The communication connection may be used to determine a manner for synchronizing enterprise data between the mobile computing devices and the cloud computer system.
Owner:ORACLE INT CORP
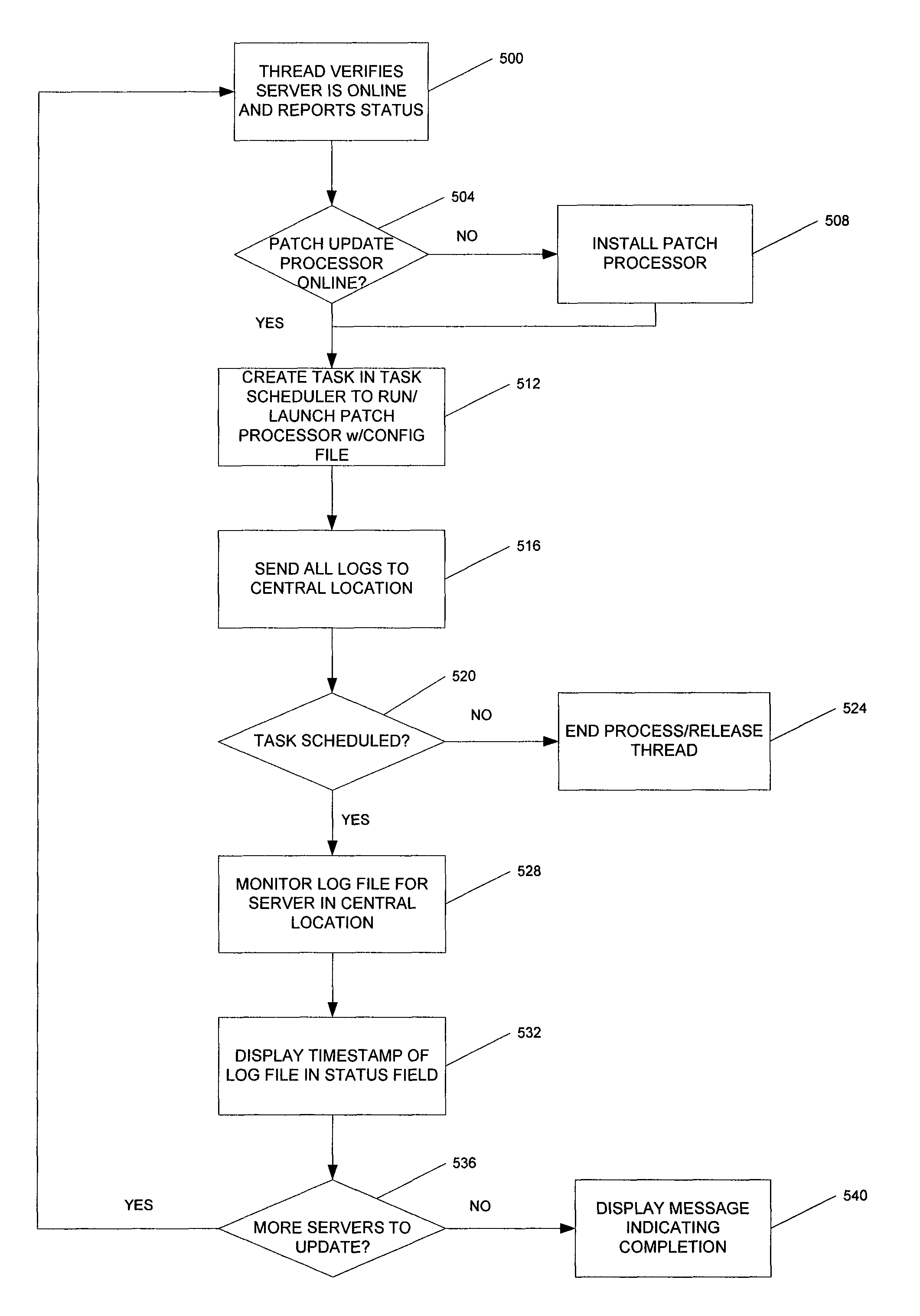
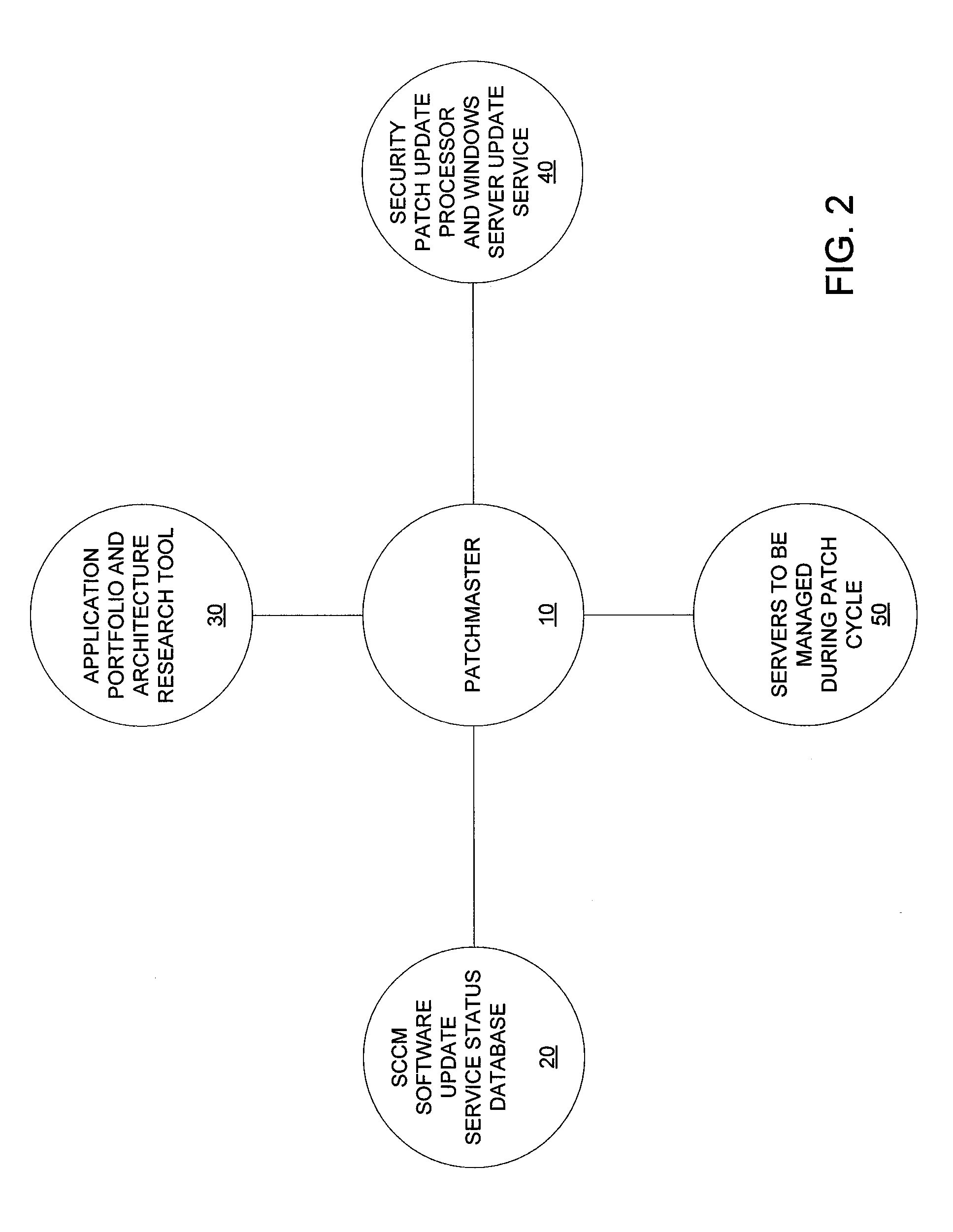
Patch cycle master records management and server maintenance system
ActiveUS8296756B1Reduce gapSoftware engineeringSpecific program execution arrangementsBusiness enterpriseEnterprise computing
A method, system, and computer readable storage medium for managing the deployment of software patch updates on a plurality of computers in an enterprise computer network during a patch cycle wherein each computer receives and installs periodic software patch updates automatically. An inventory is maintained of the computers in a central database that stores a status of each computer for each patch during the patch cycle. The computers are filtered into at least one filter group and a list of computers in the filter group is displayed along with the status for each patch. The status of each patch is verified and displayed for each computer in the filter group. A controlled software patch update is performed for each non-compliant computer in the filter group. A controlled reboot of each computer in the filter group is performed following the completion of the software patch updates for the patch cycle.
Owner:SOUTHERN COMPANY SERVICES
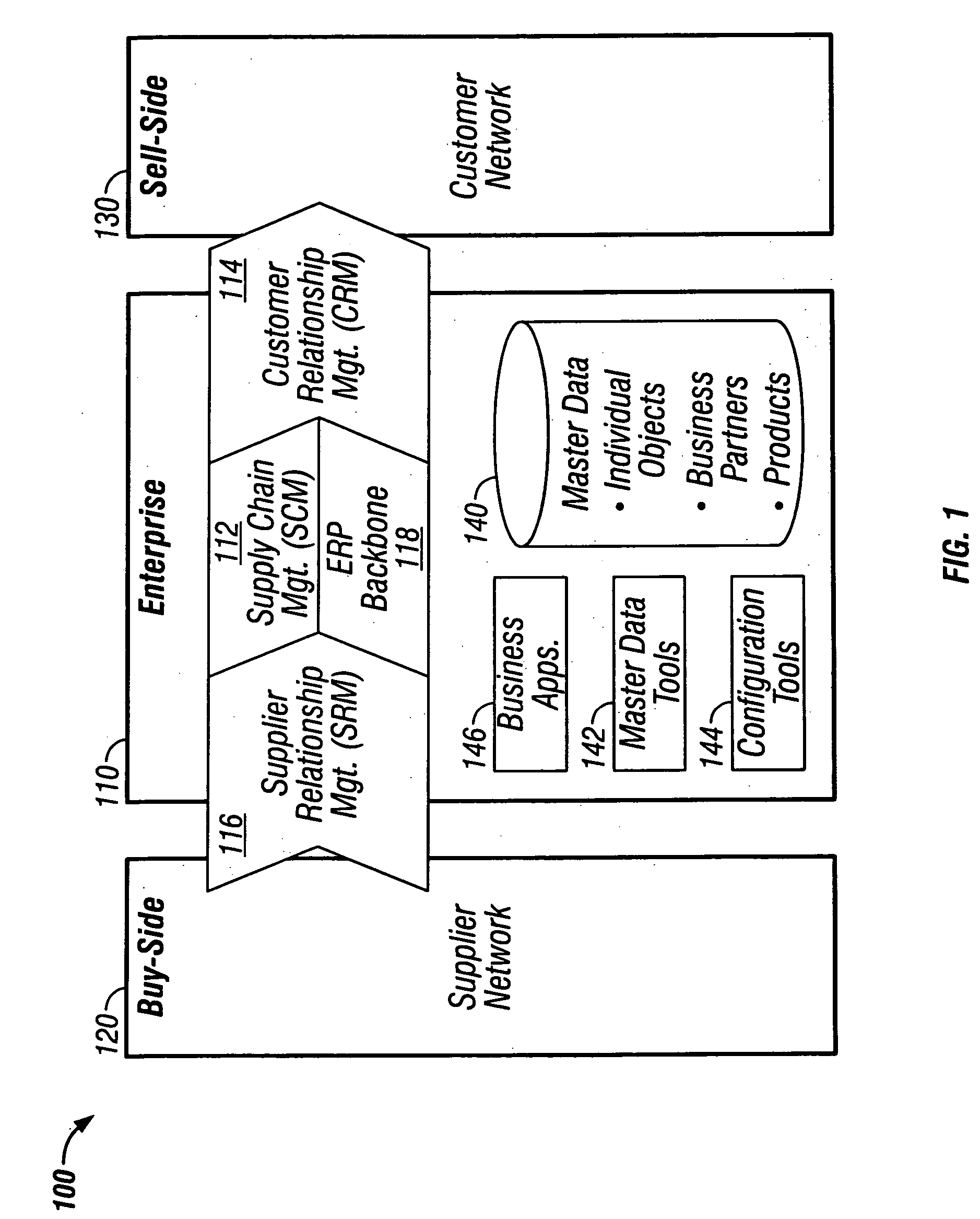
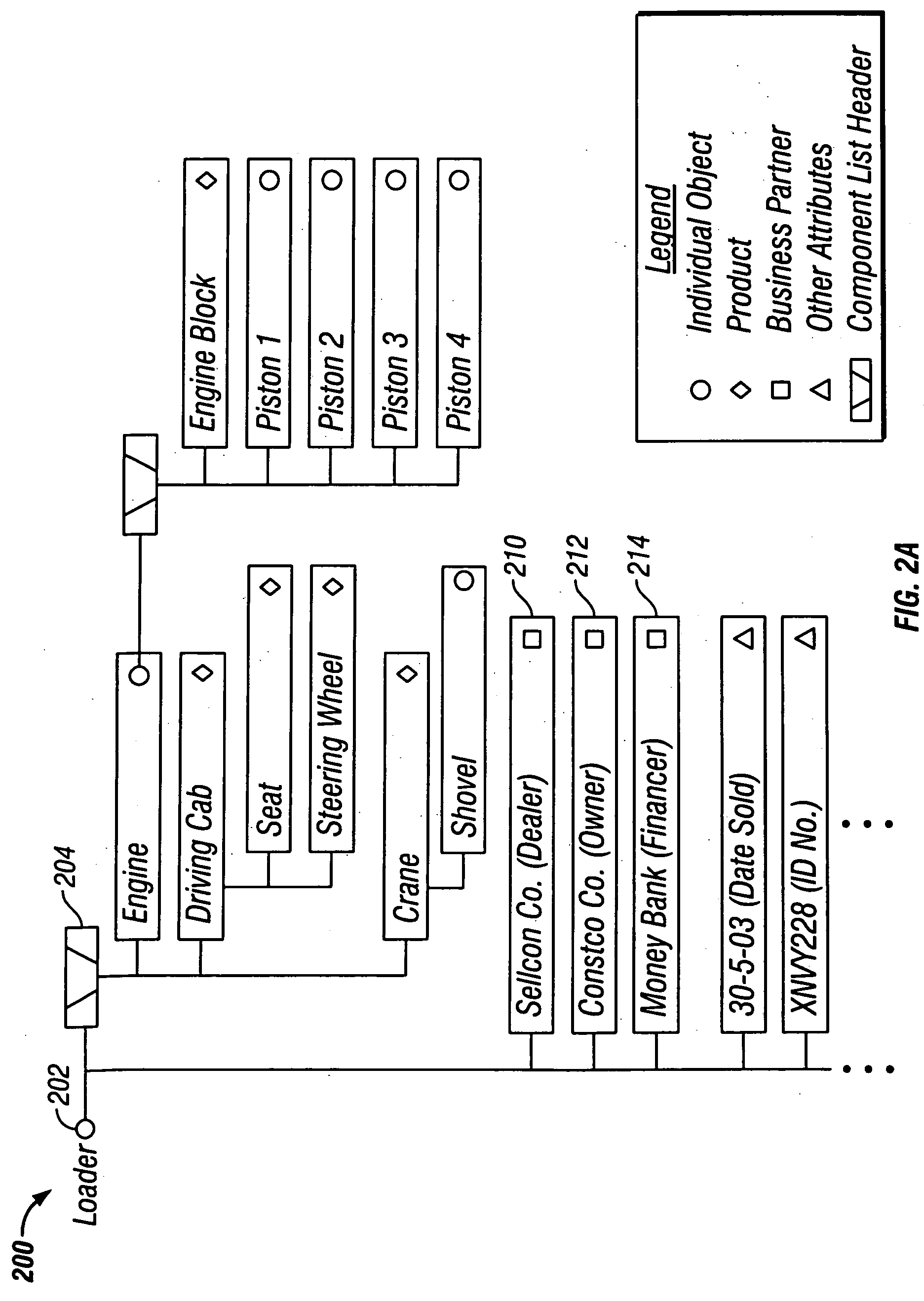
Modeling the life cycle of individual data objects
ActiveUS20050010504A1Highly configurableIncrease valueComplete banking machinesHand manipulated computer devicesEnterprise computingGeneric Product
Techniques are provided for individual data objects in an enterprise computing system, where the individual data objects represent unique assets of a family of assets. The individual data objects are used in addition to business partner master data, and also in some cases in addition to generic product master data. The individual data objects are configurable such that attributes for an individual data object change over the lifetime of the unique asset to which the individual data object pertains. Techniques for modeling the lifecycle of an individual object family are described. Techniques also are provided for an integration framework that integrates a software application with an individual object that is used or altered by the software application.
Owner:SAP AG
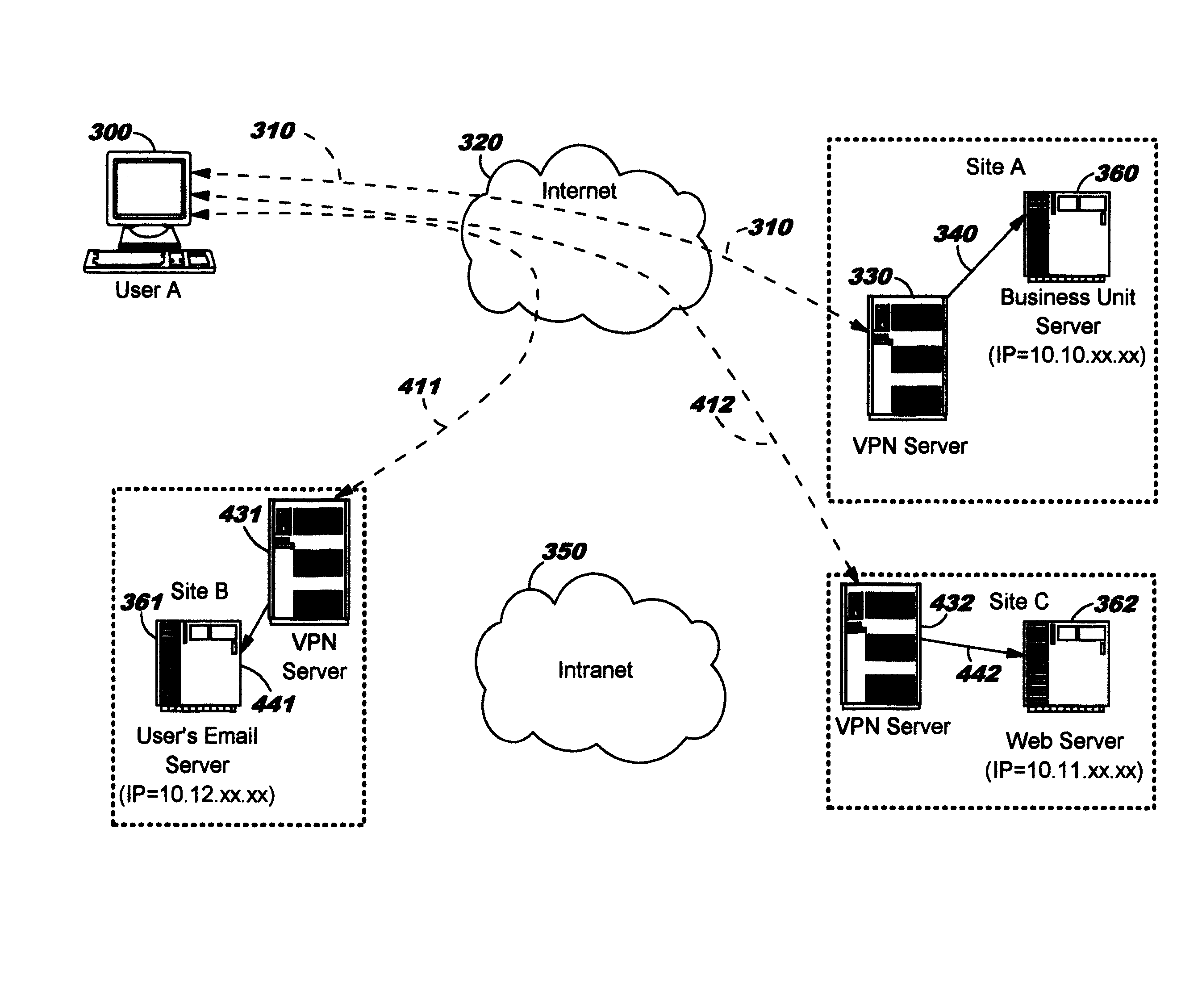
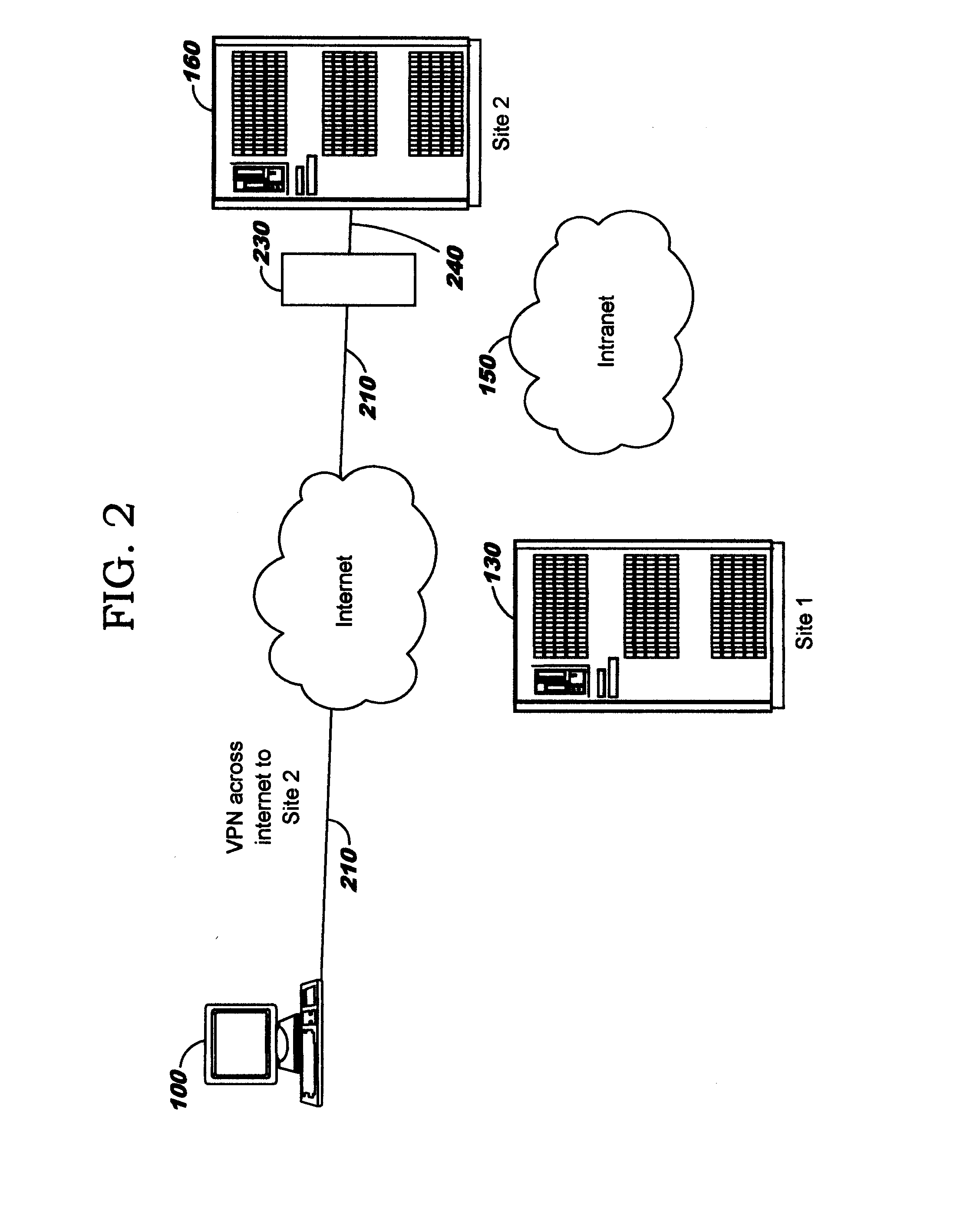
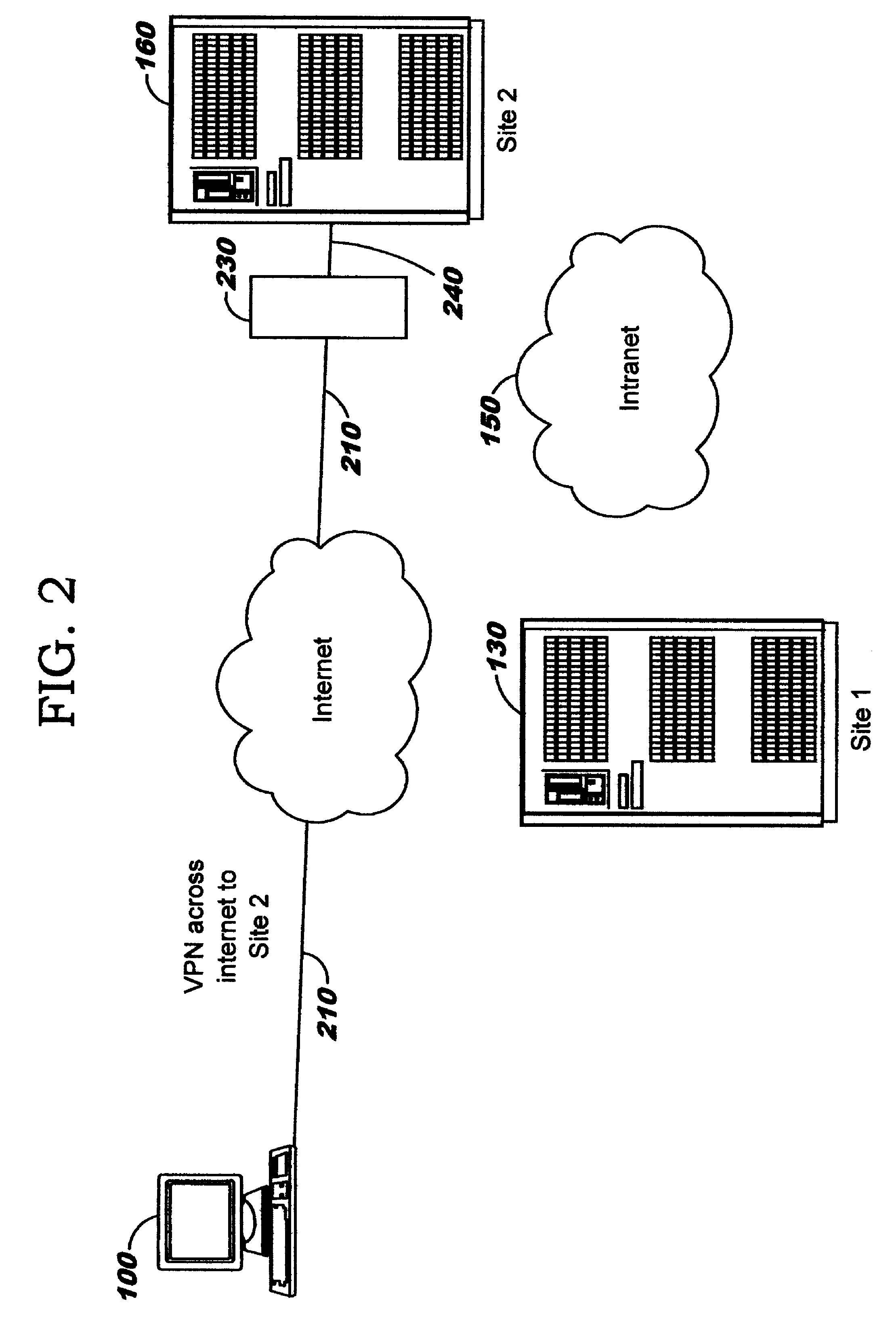
Dynamic Network Tunnel Endpoint Selection
ActiveUS20110083174A1Digital data processing detailsMultiple digital computer combinationsLeast costEnterprise computing
Dynamically selecting an endpoint for a tunnel into an enterprise computing infrastructure. A client dynamically selects a gateway (which may alternatively be referred to as a boundary device or server) as a tunnel endpoint for connecting over a public network (or, more generally, an untrusted network) into an enterprise computing infrastructure. The selection is made, in preferred embodiments, according to least-cost routing metrics pertaining to paths through the enterprise network from the selected gateway to a destination host. The least-cost routing metrics may be computed using factors such as the proximity of selectable tunnel endpoints to the destination host; stability or redundancy of network resources for this gateway; monetary costs of transmitting data over a path between the selectable tunnel endpoints and destination host; congestion on that path; hop count for that path; and / or latency or transmit time for data on that path.
Owner:A10 NETWORKS
Dynamic network tunnel endpoint selection
ActiveUS7992201B2Facilitate communicationMultiple digital computer combinationsProgram controlLeast costEnterprise computing
Dynamically selecting an endpoint for a tunnel into an enterprise computing infrastructure. A client dynamically selects a gateway (which may alternatively be referred to as a boundary device or server) as a tunnel endpoint for connecting over a public network (or, more generally, an untrusted network) into an enterprise computing infrastructure. The selection is made, in preferred embodiments, according to least-cost routing metrics pertaining to paths through the enterprise network from the selected gateway to a destination host. The least-cost routing metrics may be computed using factors such as the proximity of selectable tunnel endpoints to the destination host; stability or redundancy of network resources for this gateway; monetary costs of transmitting data over a path between the selectable tunnel endpoints and destination host; congestion on that path; hop count for that path; and / or latency or transmit time for data on that path.
Owner:A10 NETWORKS
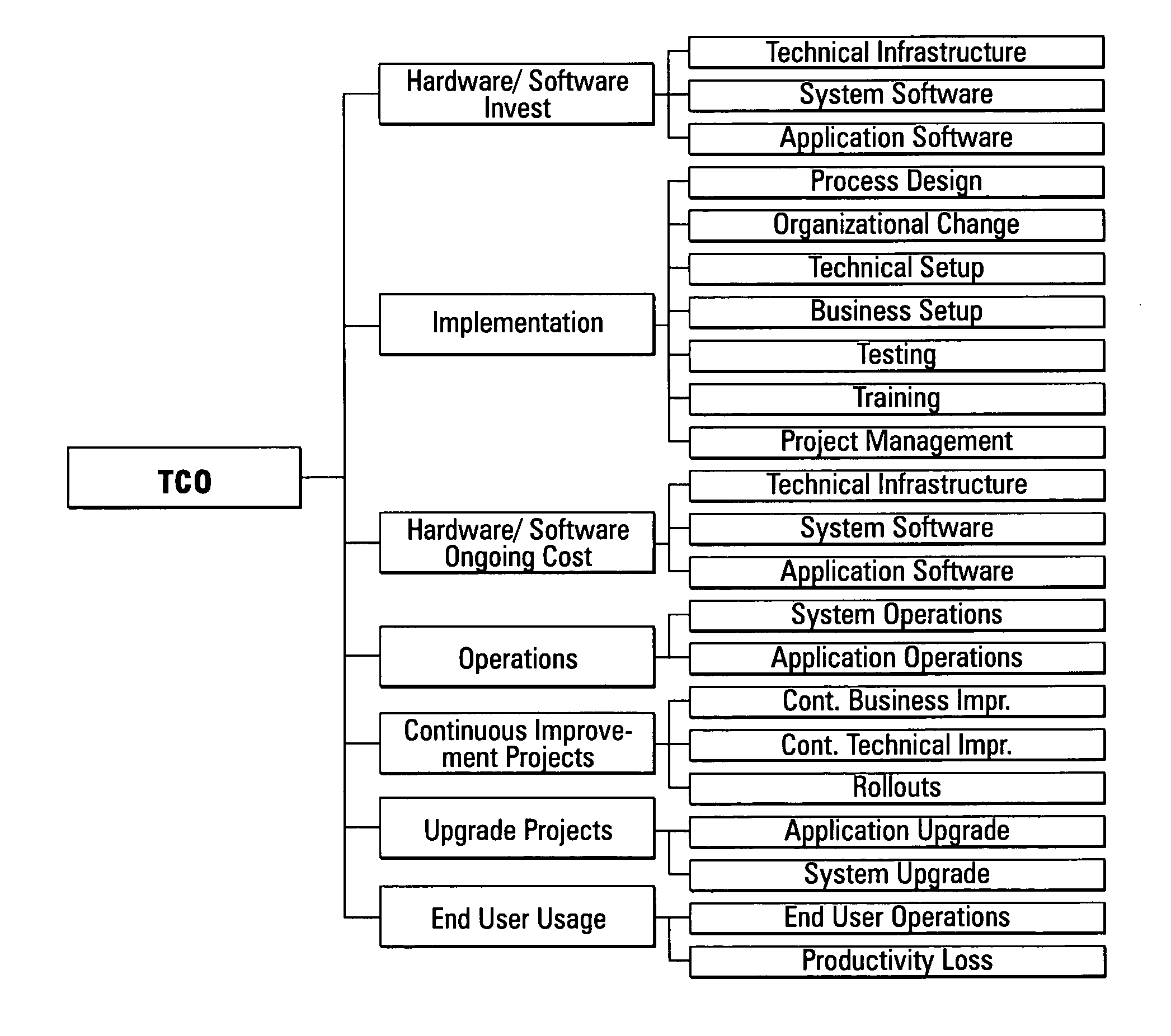
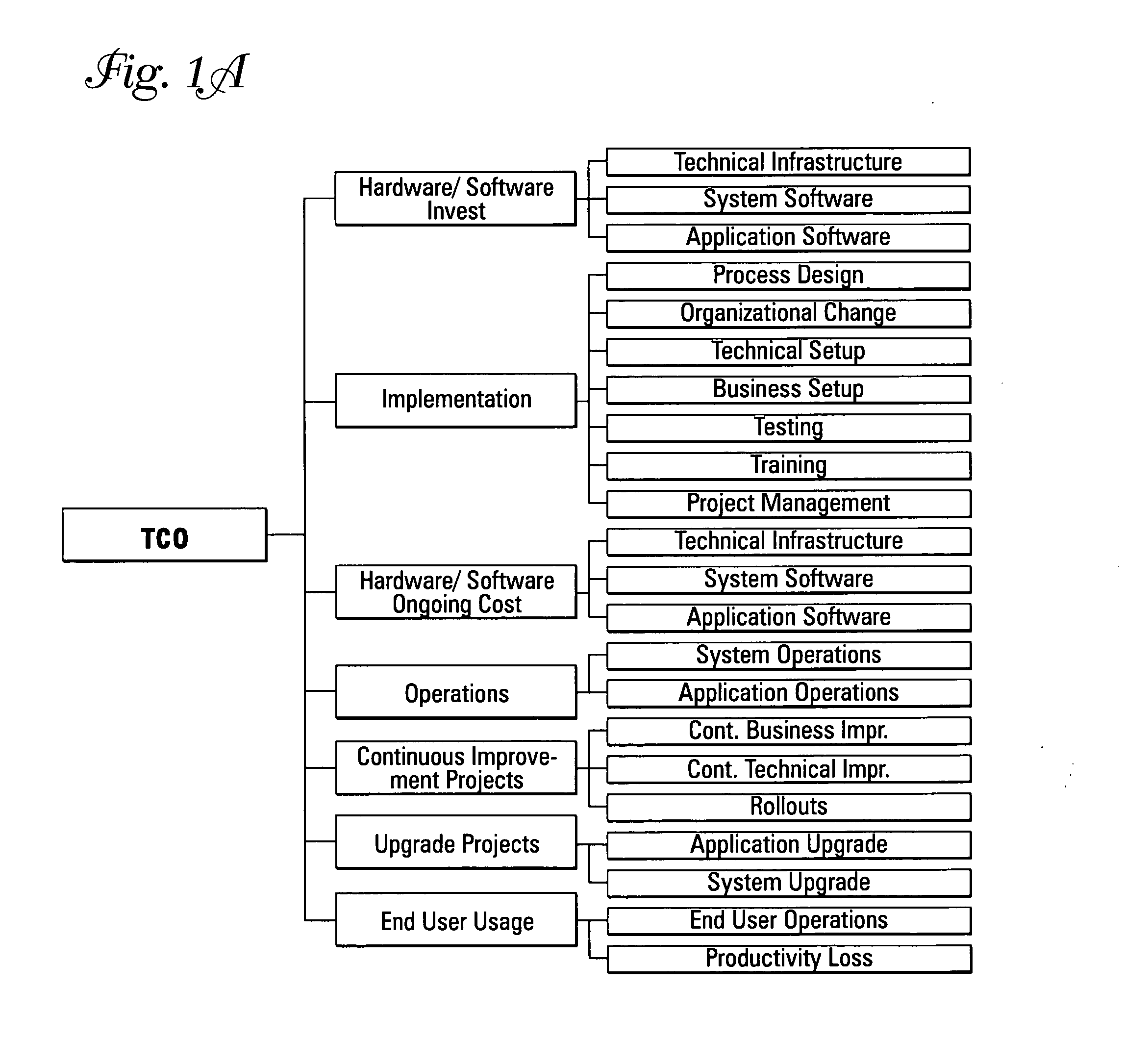
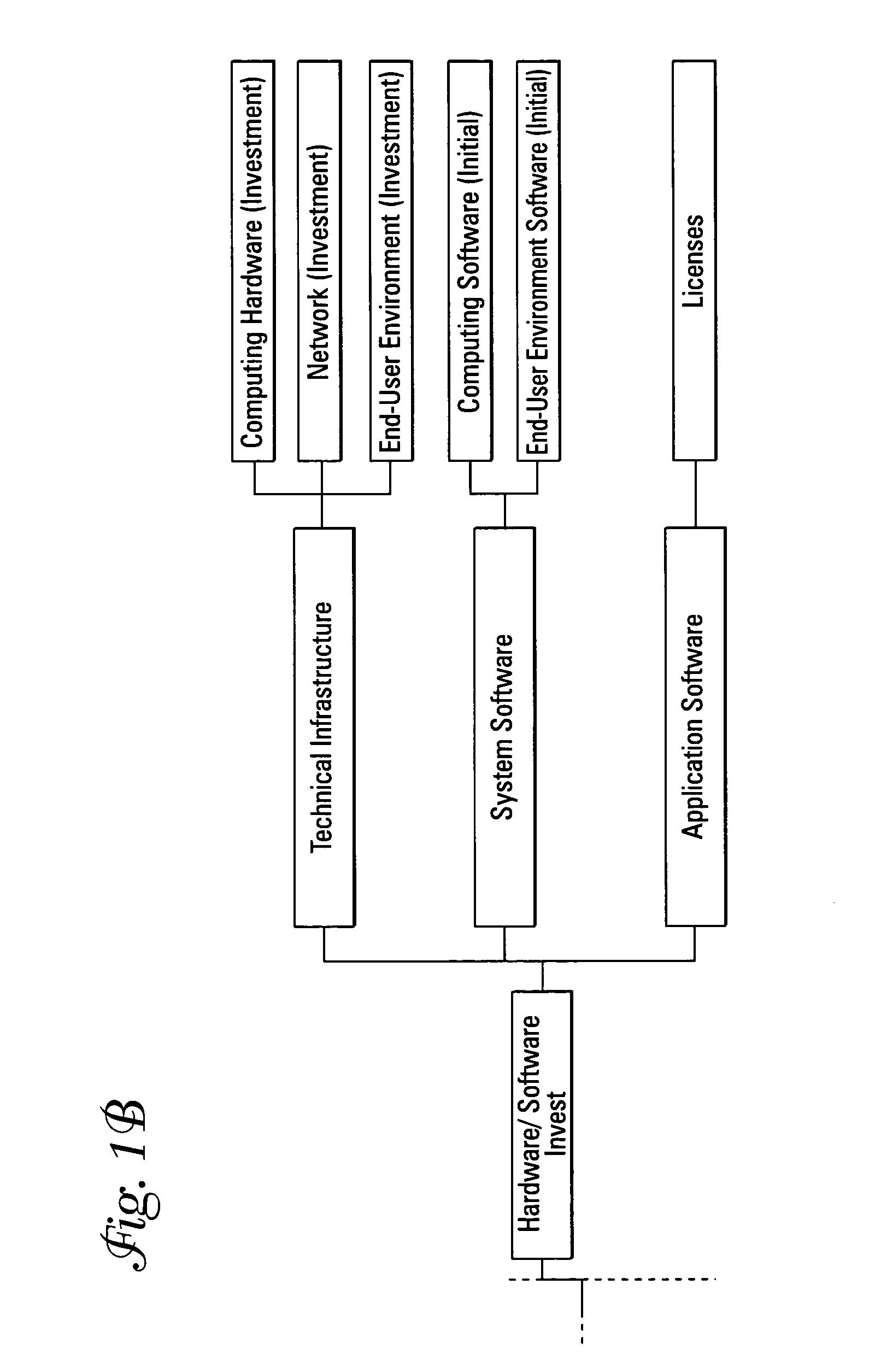
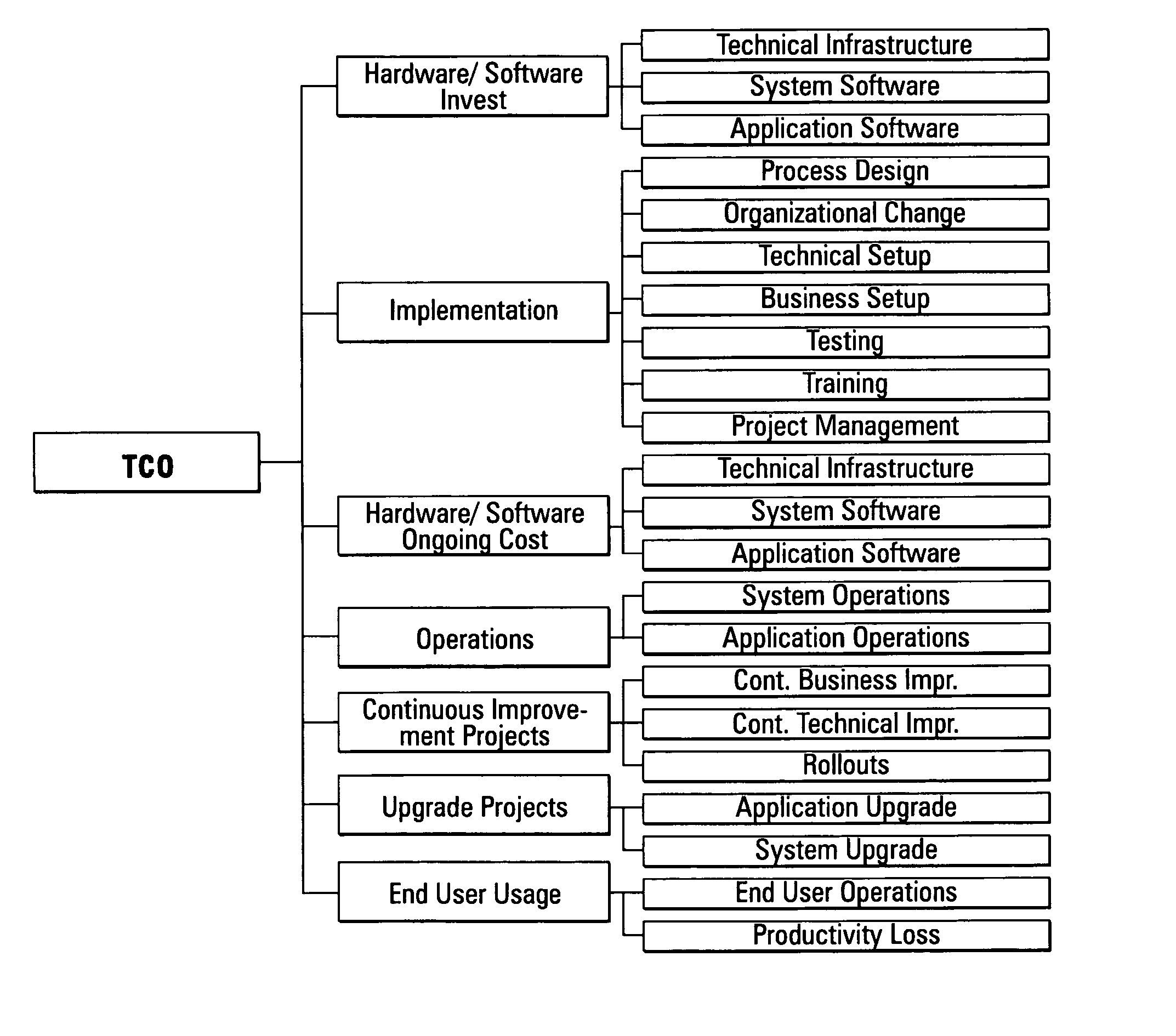
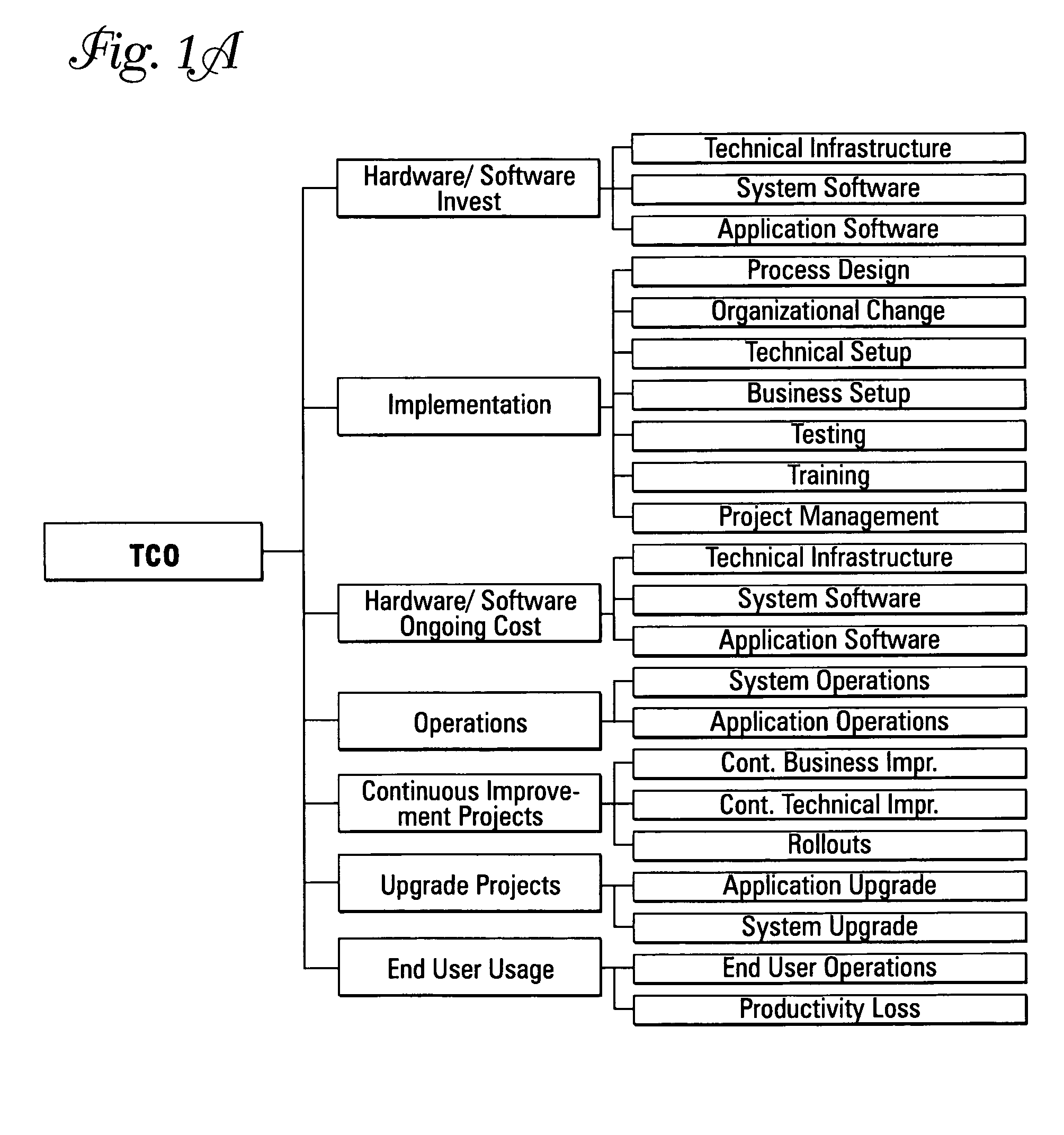
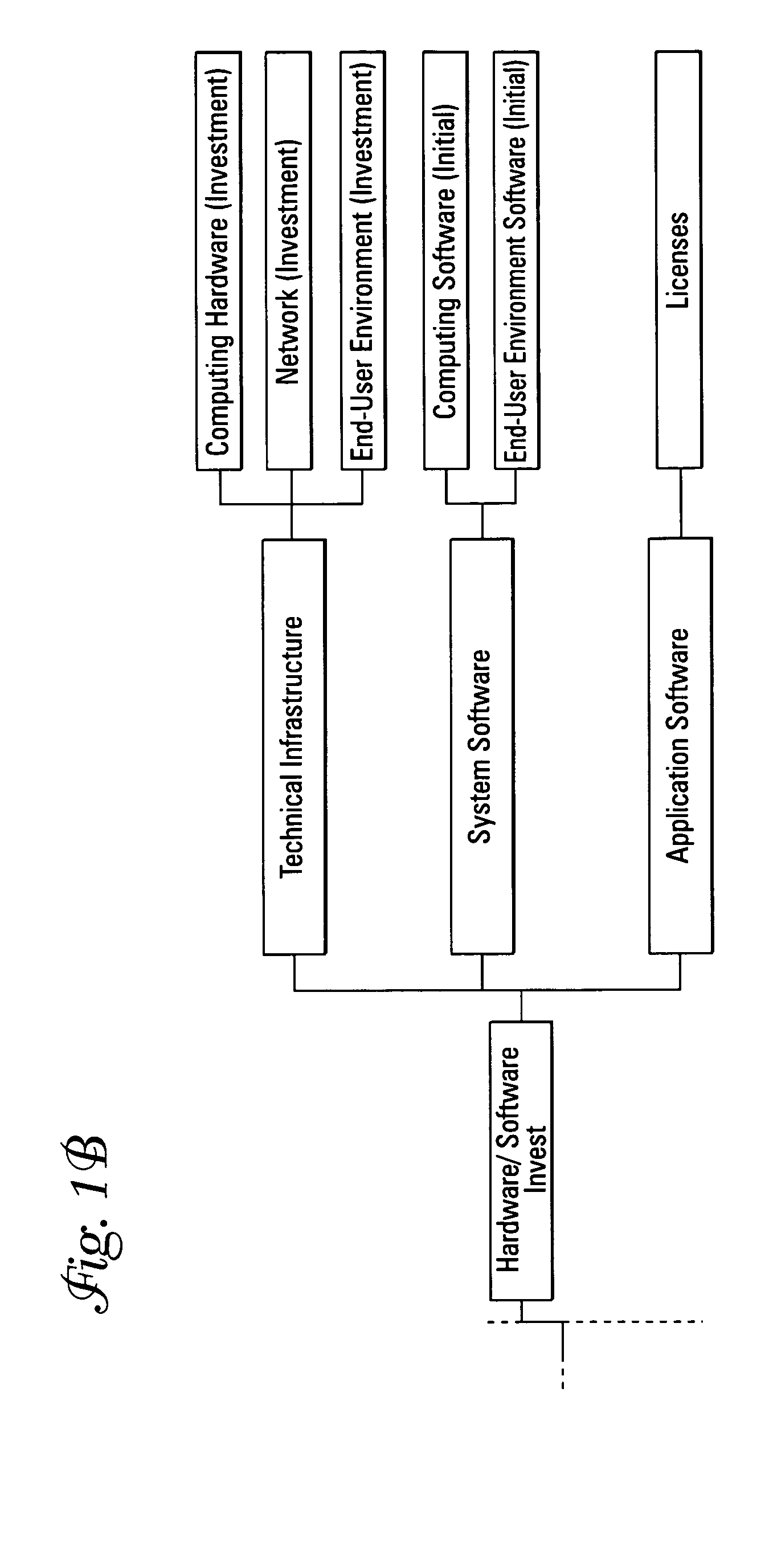
Computing systems that capture cost information for total cost of ownership analyses
InactiveUS20050071348A1Digital data processing detailsOffice automationEnterprise computingComputing systems
An enterprise computing system is provided that has computing components that each perform a specified computing function for the enterprise. The computing components also have electronic database storage capability that stores data aligned with a predefined model that defines costs to be considered in a total cost of ownership analysis. The enterprise computing system also has a computing component that extracts the stored data aligned with the total cost of ownership data model, and that uses the extracted data to provide an electronic aggregation of costs associated with owning the enterprise computing system.
Owner:SAP AG
Integrated fingerprinting in configuration audit and management
ActiveUS8051298B1Memory loss protectionUnauthorized memory use protectionEnterprise computingSoftware engineering
A system and computer implemented method for identifying active applications in an enterprise computing system is provided. The method includes defining a plurality of fingerprints for an application. A first fingerprint is related to a directory structure associated with the application. A second fingerprint is related to checking memory of at least some of the enterprise computing systems for data related to the application. The method includes searching the enterprise computing system for at least one fingerprint. The method includes when a fingerprint is found, identifying the application associated with the fingerprint as active.
Owner:T MOBILE INNOVATIONS LLC
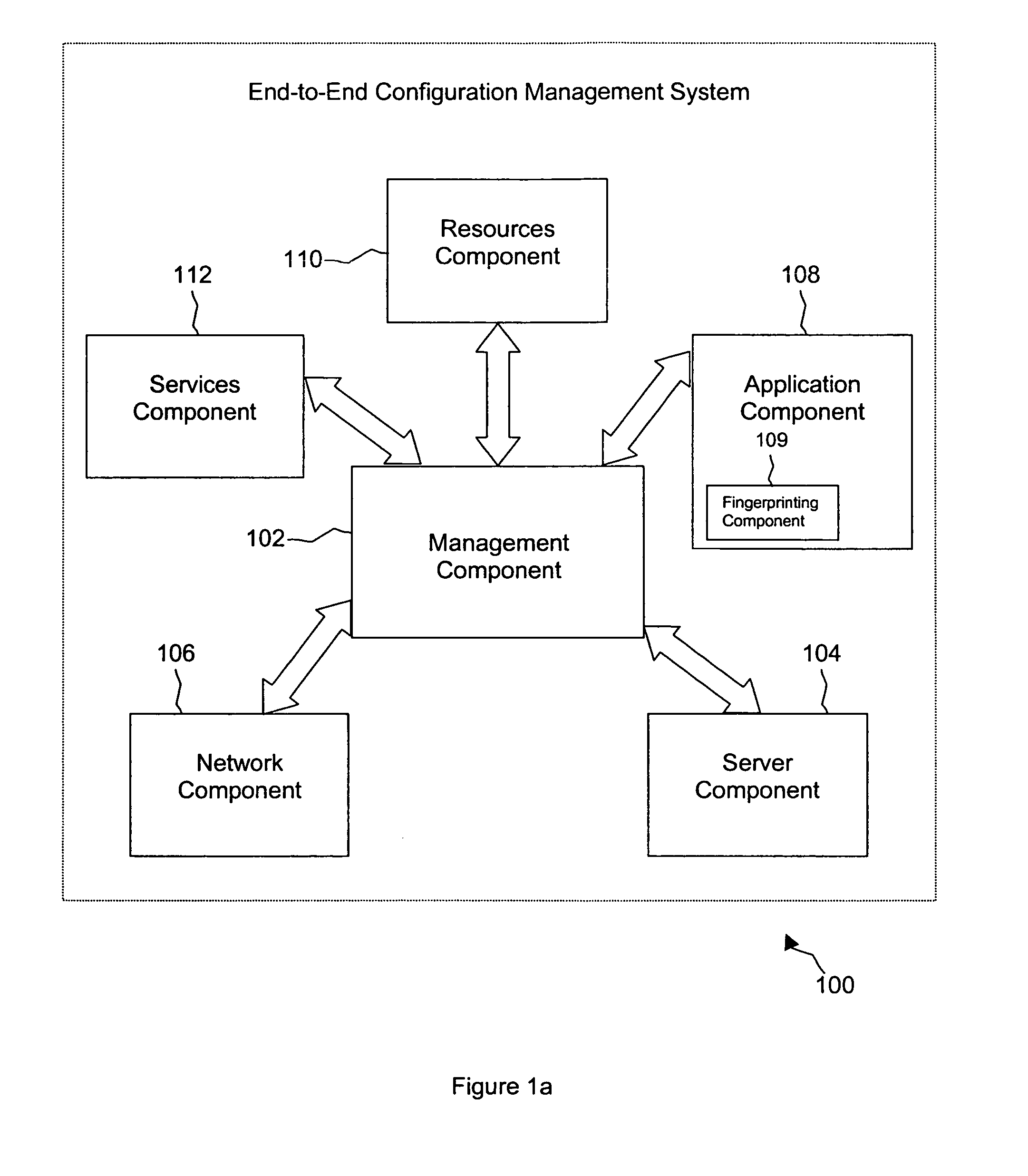
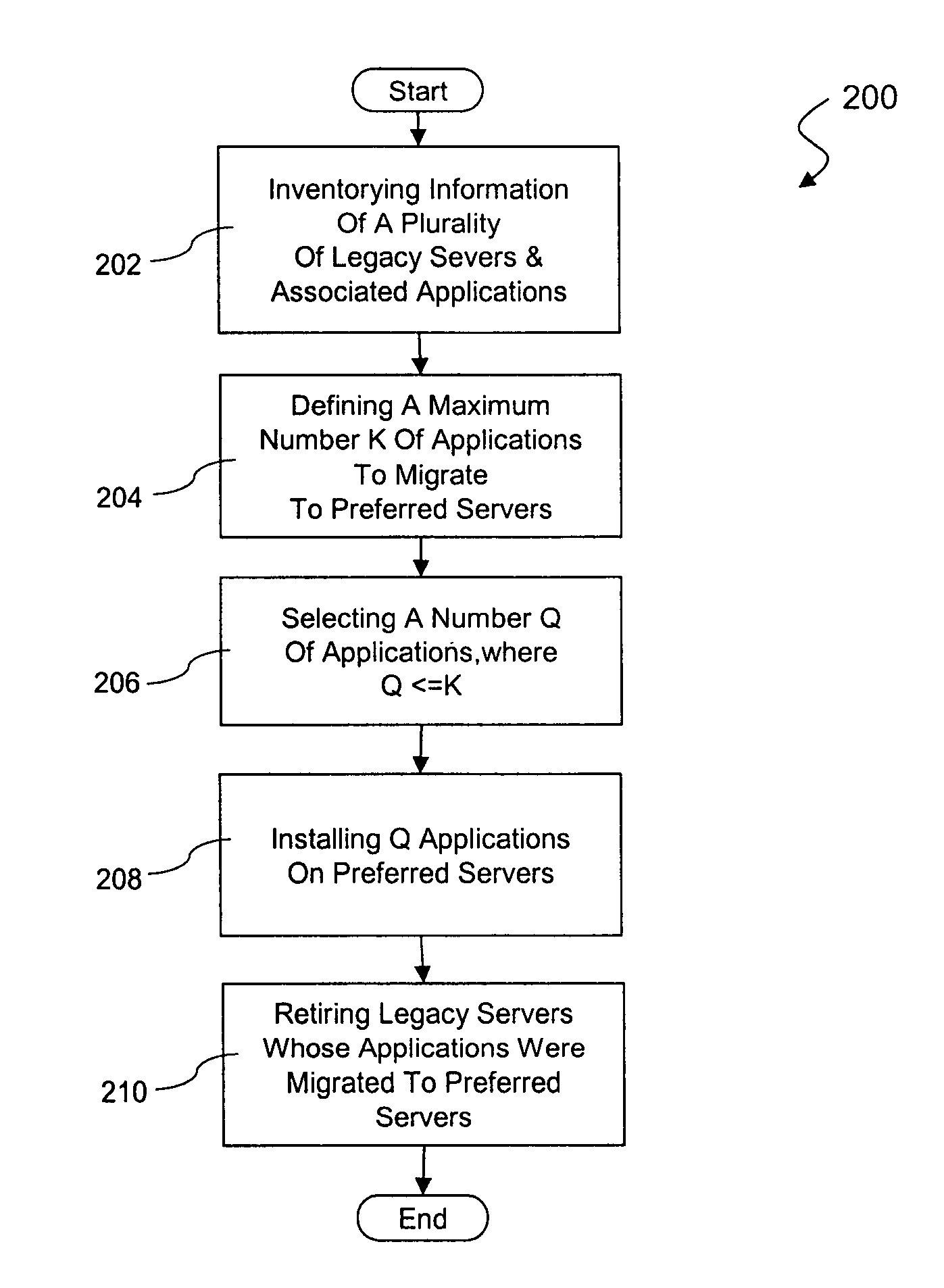
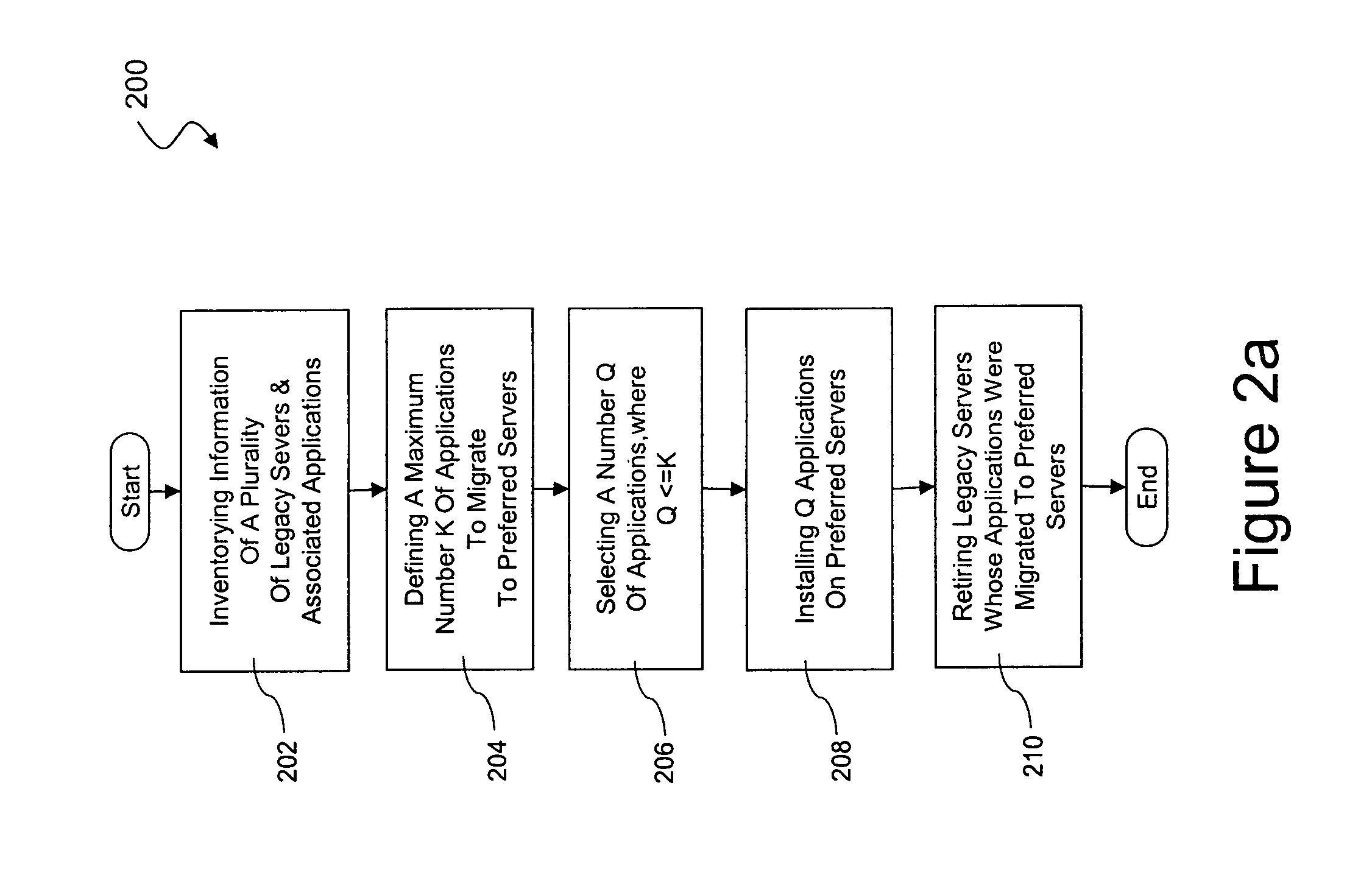
System and method of implementing major application migration
ActiveUS7818410B1Low criticalityIncrease the number ofDigital computer detailsProgram controlEnterprise computingApplication software
A method of managing migration in enterprise-computing systems is provided. The method includes inventorying information about each of a plurality of legacy servers and each of a plurality of applications, wherein the inventory information identifies the one or more applications installed on each of the legacy servers. The method includes defining a maximum number K of applications to migrate during a wave from the legacy servers to a plurality of preferred servers. The method also includes selecting a number Q of applications to migrate during the wave from the legacy servers to the preferred servers, where Q is less than or equal to K. The method further includes installing the Q applications on the preferred servers, and retiring the legacy servers whose applications have been migrated to the preferred server.
Owner:T MOBILE INNOVATIONS LLC
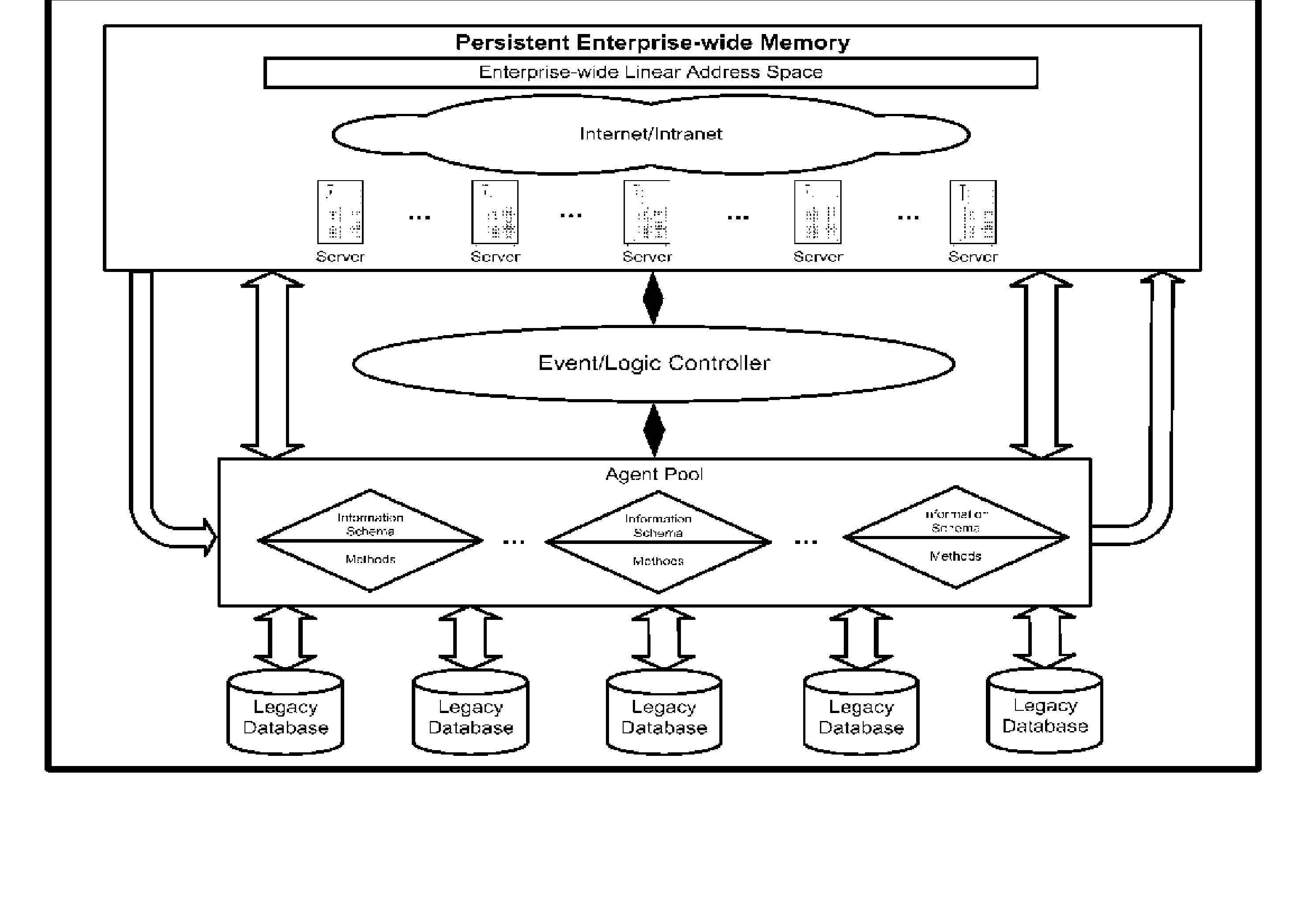
Virtual Enterprise Computer
InactiveUS20050049882A1Simplicity of implementationSimplified managementComputer controlBusiness ruleStraight-through processing
The Virtual Enterprise Computer (VEC) is a method for creating a single virtual, enterprise-wide computing environment consisting of a single, enterprise-wide persistent address space to uniquely identify and location enterprise data and intellectual assets, a single, enterprise-wide, persistent memory as a single source for all enterprise data, resources and intellectual assets, an enterprise-wide persistent knowledge repository that models the business enterprise by maintaining relationships between business processes, workflows, business rules, business metrics, data, resources, legacy systems and intellectual assets, self-aware agents encapsulating data and computer code, a real-time event / logic controller to manage the execution of agents eliminating data pollution and data duplication, conserving knowledge assets, creating an enterprise-wide collaboration environment, enhancing the flow and sharing of information and knowledge, permitting the arbitration of intellectual resources across the business enterprise, providing a foundation architecture and knowledge infrastructure to address numerous business initiatives including: the Seamless Business Enterprise the Real-Time Business Enterprise Enterprise Knowledge Management Single-View of the Business Enterprise Enterprise Application Integration Coherent Business Enterprise Straight-Through-Processing Collaborative Work Environments Mergers and Acquisitions Single View of Customers and Suppliers Enterprise Resource Planning Enterprise Business Processing Reengineering Business Intelligence intelligent Business Enterprise Optimized Business Enterprise Enterprise Business Modeling.
Owner:SAWKA WALTER A
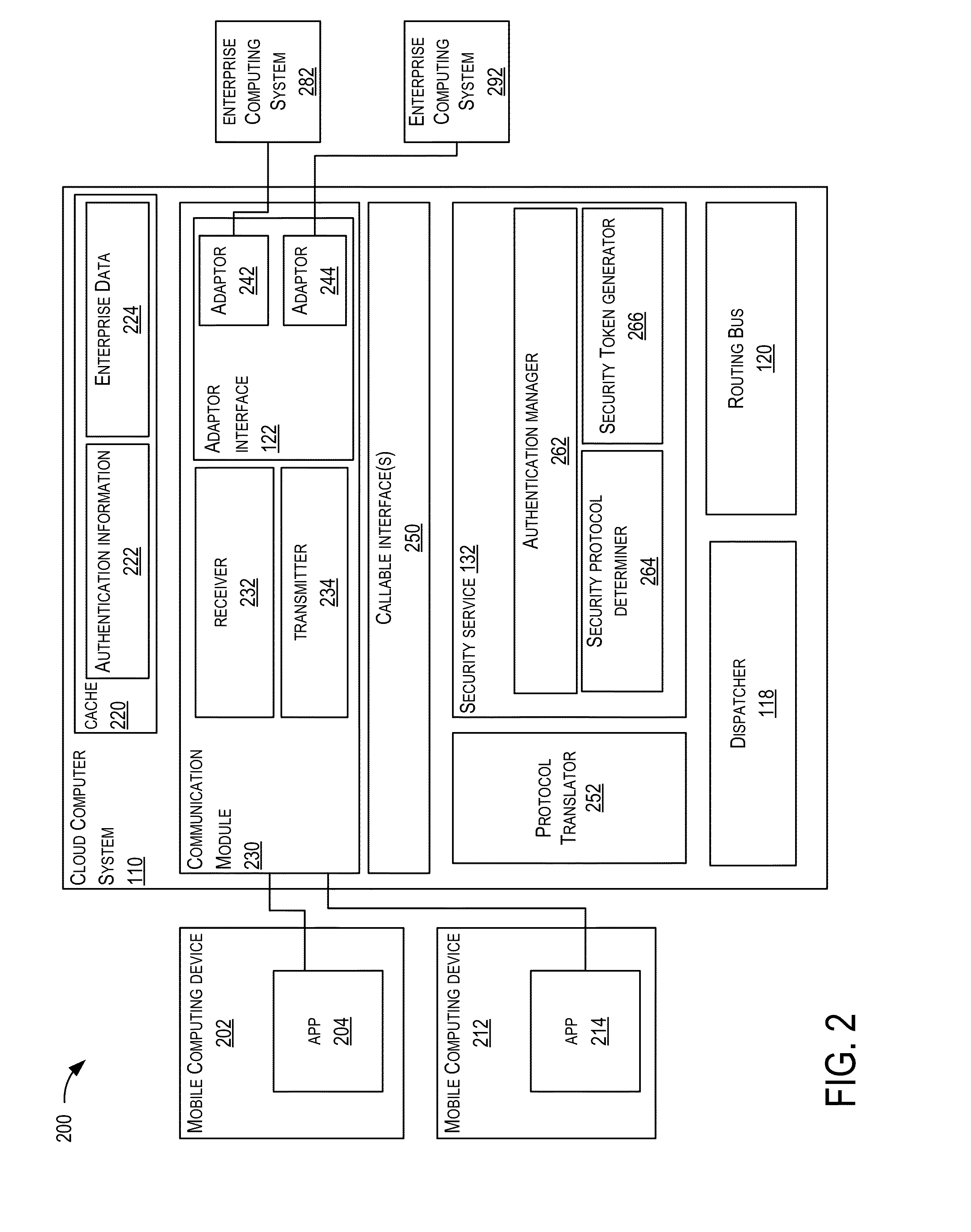
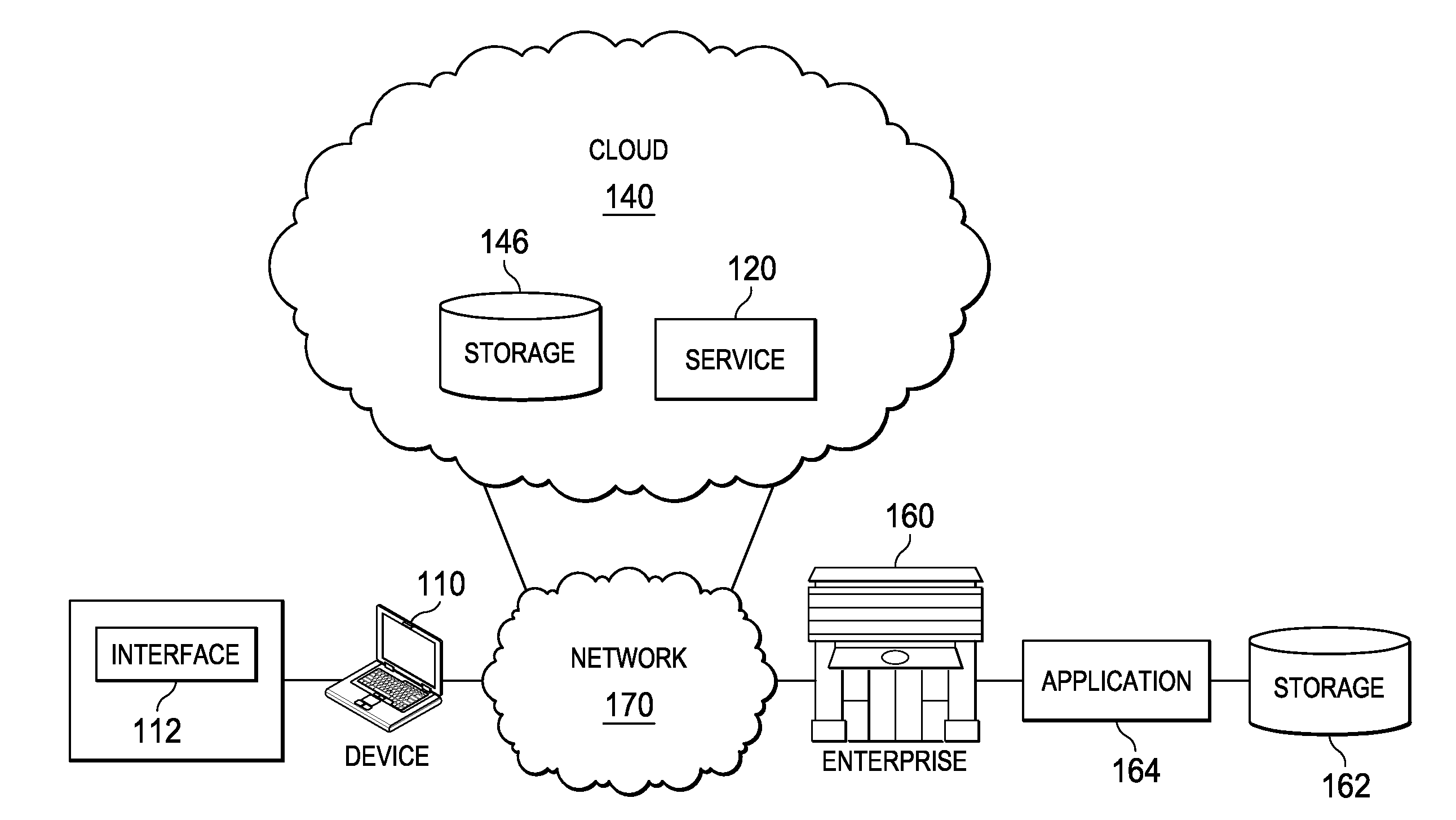
System and method for securing authentication information in a networked environment
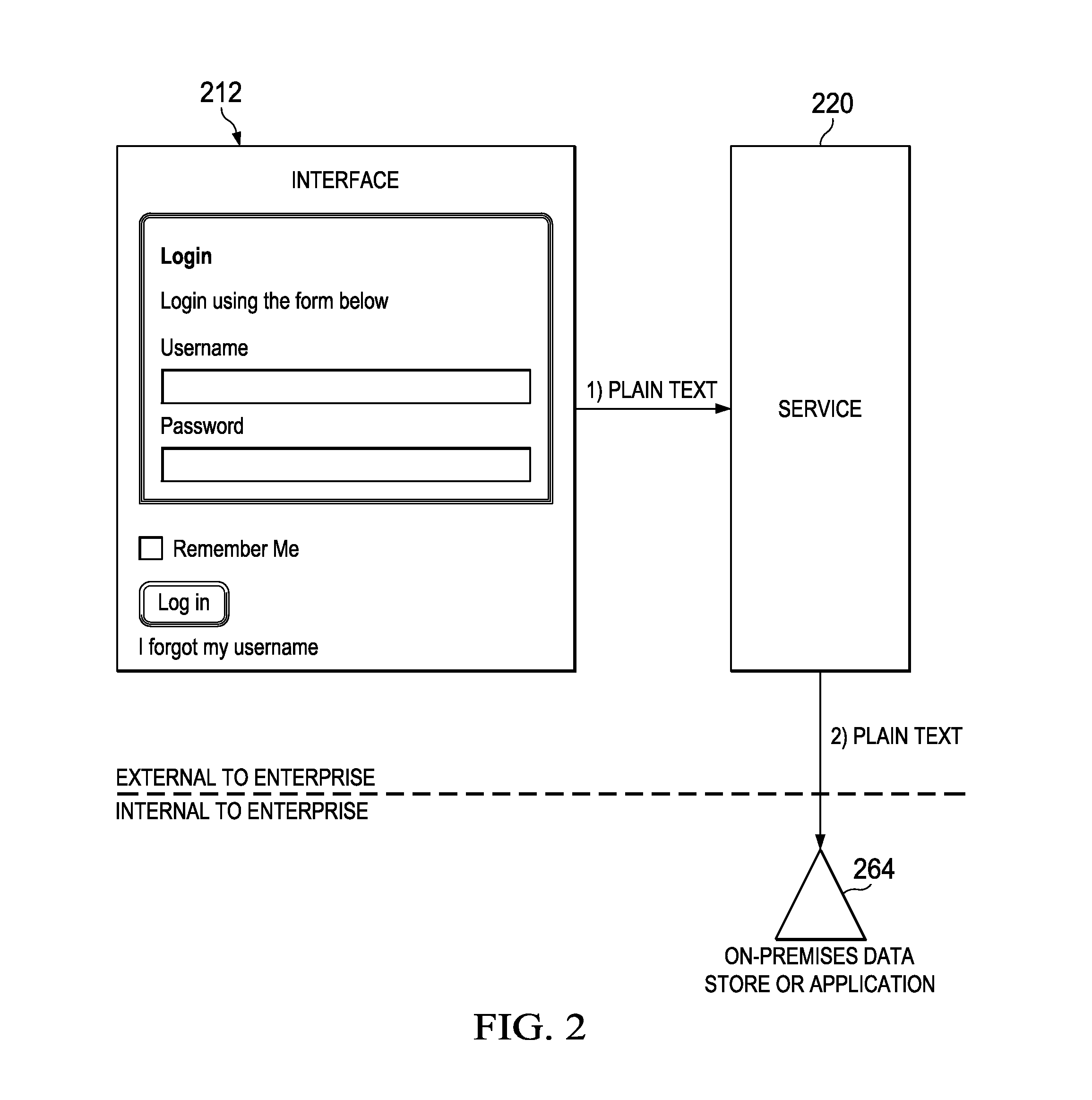
ActiveUS20150012751A1Public key for secure communicationUser identity/authority verificationCloud baseEnterprise computing
This disclosure is directed to systems and methods for securely communicating authentication information in a networked environment such as one involving a client device, a cloud based computing platform, and an enterprise computing environment. Some embodiments may include encrypting, by a client device using a public key, authentication information provided by a user. The encrypted authentication information is sent to a cloud based service which then sends it to an on-premises component residing behind a firewall of an enterprise. The on-premises component decrypts the authentication information using a private key, validates the authentication information, and returns the result to the cloud based service over a network. If validated, the cloud based service establishes a secure connection between the client device and the on-premises component such that the user can access the enterprise's content without the enterprise having to share the authentication information with the cloud based service.
Owner:SAILPOINT TECH INC
Jobstream planner considering network contention & resource availability
InactiveUS7406689B2Good flexibilityImprove efficiencyMultiprogramming arrangementsMultiple digital computer combinationsEnterprise computingDependency tree
Disclosed is a computer-implemented planning process that aids a system administrator in the task of creating a job schedule. The process treats enterprise computing resources as a grid of resources, which provides greater flexibility in assigning resources to jobs. During the planning process, an administrator or other user, or software, builds a job-dependency tree. Jobs are then ranked according to priority, pickiness, and network centricity. Difficult and problematic jobs then are assigned resources and scheduled first, with less difficult jobs assigned resources and scheduled afterwards. The resources assigned to the most problematic jobs then are changed iteratively to determine if the plan improves. This iterative approach not only increases the efficiency of the original job schedule, but also allows the planning process to react and adapt to new, ad-hoc jobs, as well as unexpected interruptions in resource availability.
Owner:KYNDRYL INC
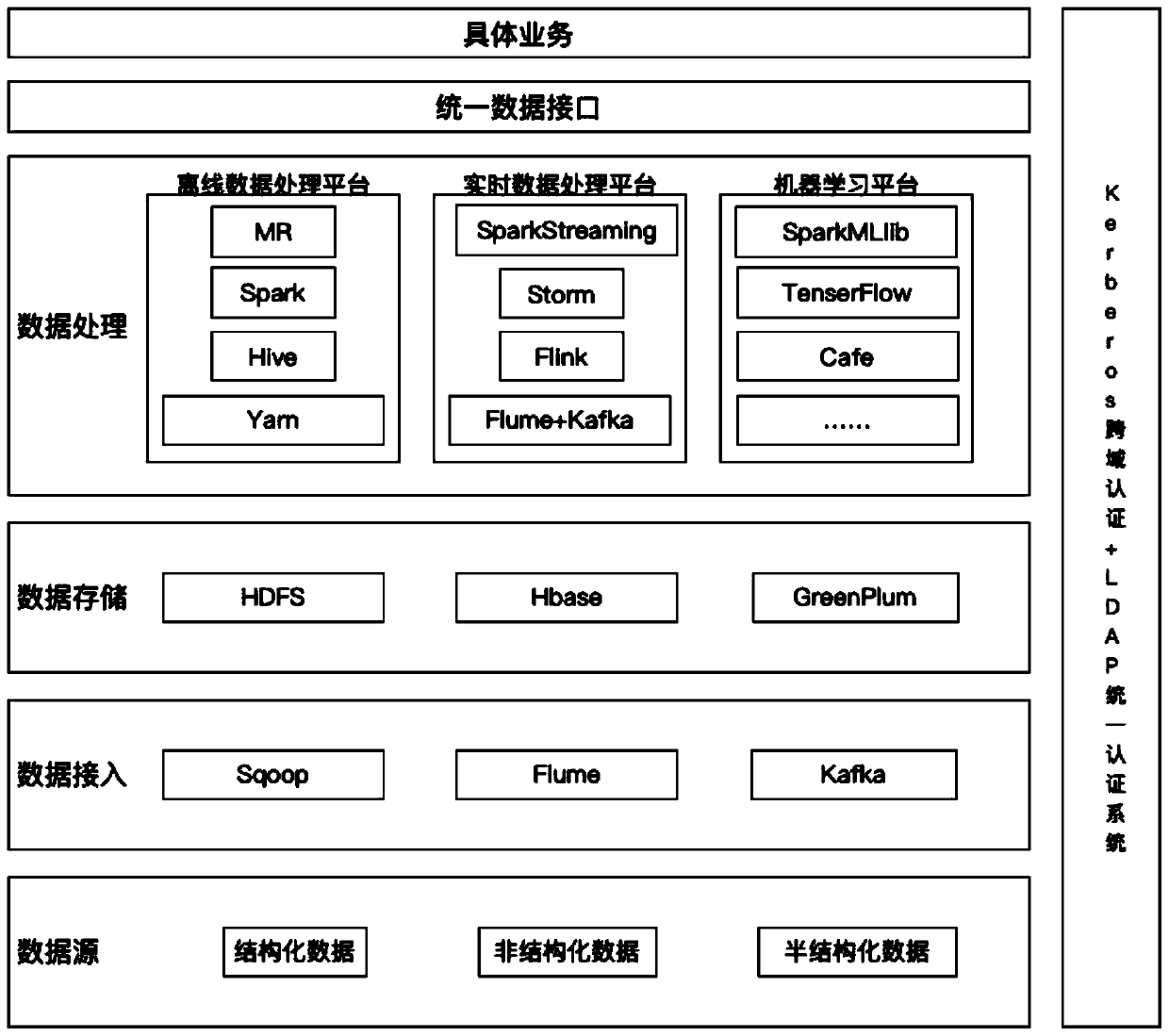
An enterprise-level big data platform architecture
InactiveCN109840253ADatabase queryingDatabase distribution/replicationData platformEnterprise computing
The invention relates to enterprise-level big data platform architecture, and aims to improve standardization and efficiency of big data processing, extraction, storage and data mining of enterprisesin actual production at low cost. The big data platform can run on expandable common hardware based on Hadoop, Spark, Hive, Hbase and other Apache open source projects, and a complete big data technical system is constructed and comprises a data storage platform, an offline computing platform, a real-time computing platform and a machine learning platform. And enterprise computing tasks under various complex conditions can be met. The platform further comprises a set of complete data processing standards such as data storage, data quality supervision and ETL process standards, and strategy schemes such as core data protection and data authority control so as to ensure data quality normalization and data asset safety.
Owner:BEIJING UNIV OF TECH
System and method for intelligent agents for decision support in network identity graph based identity management artificial intelligence systems
ActiveUS10523682B1Easy accessReduce computing burdenDigital data protectionArtificial lifeIntelligent designEnterprise computing
Systems and methods for embodiments of a graph based artificial intelligence systems for identity management are disclosed. Embodiments of the identity management systems disclosed herein may utilize a network graph approach to analyzing identities or entitlements of a distributed networked enterprise computing environment. Specifically, in certain embodiments, an artificial intelligence based identity governance systems may include an intelligent decision support agent to provide an approval or denial recommendation for an access request. To provide an approval or denial recommendation, the intelligent agent may utilize a classifier trained on historical certification data. The intelligent agent may utilize features which represent relevant signals to the approval or denial decision including features that may be associated with a network graph of the identities and entitlements of the enterprise computing environment.
Owner:SAILPOINT TECH INC
Assessing total cost of ownership for a computing system
A method and program product that when executed causes the method to be executed are provided. The method is included in performing a total cost of ownership analysis of an enterprise computing system. The method includes extracting, within an enterprise computing system, electronically stored data from predefined data source fields included in the enterprise computing system. The method also includes using the extracted data to provide an aggregation of electronically stored cost information that is structured in conformity with a predefined model that defines a cost structure for assessing total cost of ownership analysis for an enterprise computing system.
Owner:SAP AG
Systems and methods for event-based authentication
In one embodiment, a method is performed by a computer system. The method includes receiving a request to authenticate a user of an enterprise computing system. The method further includes, responsive to the request, selecting a set of previous user-initiated events of the user on the enterprise computing platform. Further, the method includes accessing user-specific event information related to the selected set of previous user-initiated events. In addition, the method includes generating, from at least a portion of the user-specific event information, a user-specific authentication sequence comprising a plurality of event-information requests. Additionally, the method includes administering the user-specific authentication sequence to the user, the administering comprising requiring the user to provide a valid response to each of the event-information requests as a precondition to successful authentication.
Owner:QUEST SOFTWARE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com