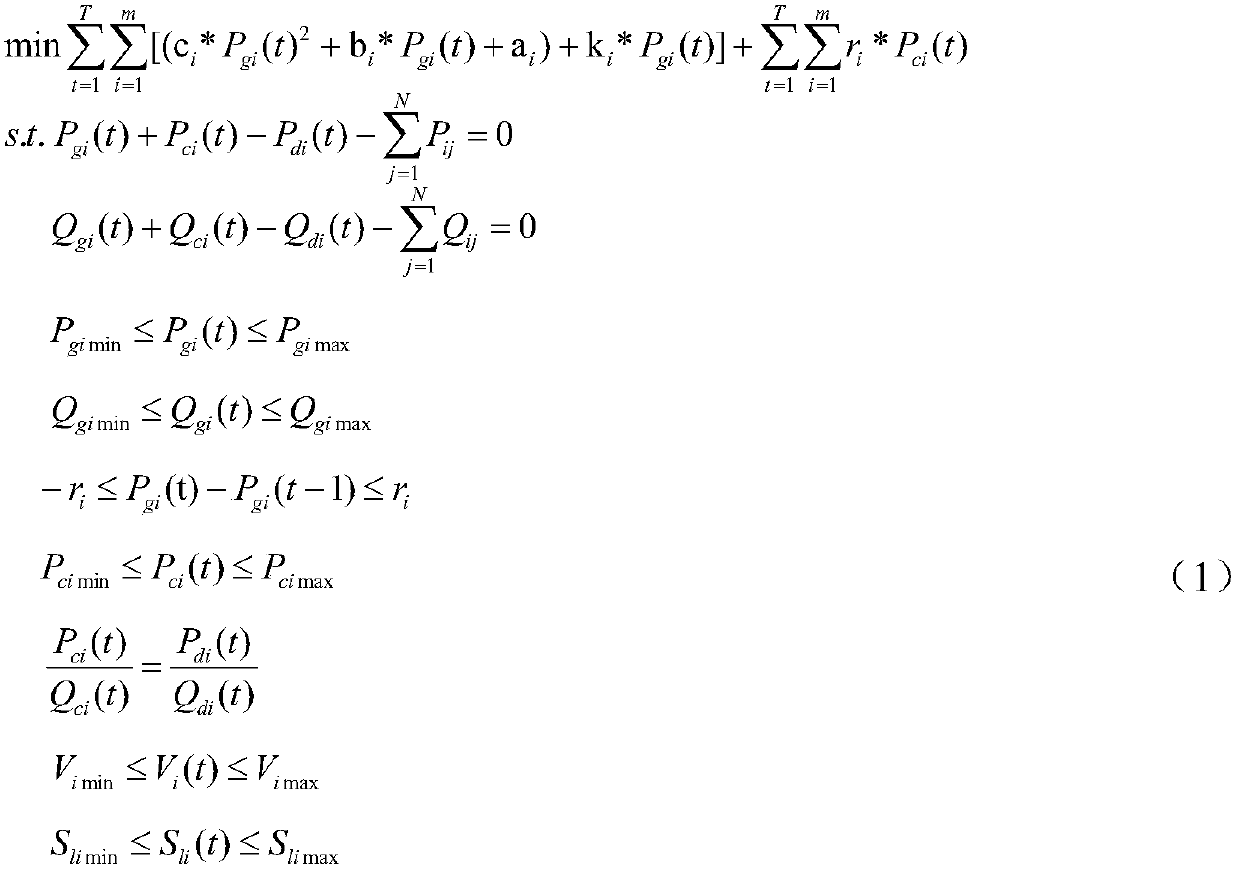Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
46results about How to "Improve risk assessment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
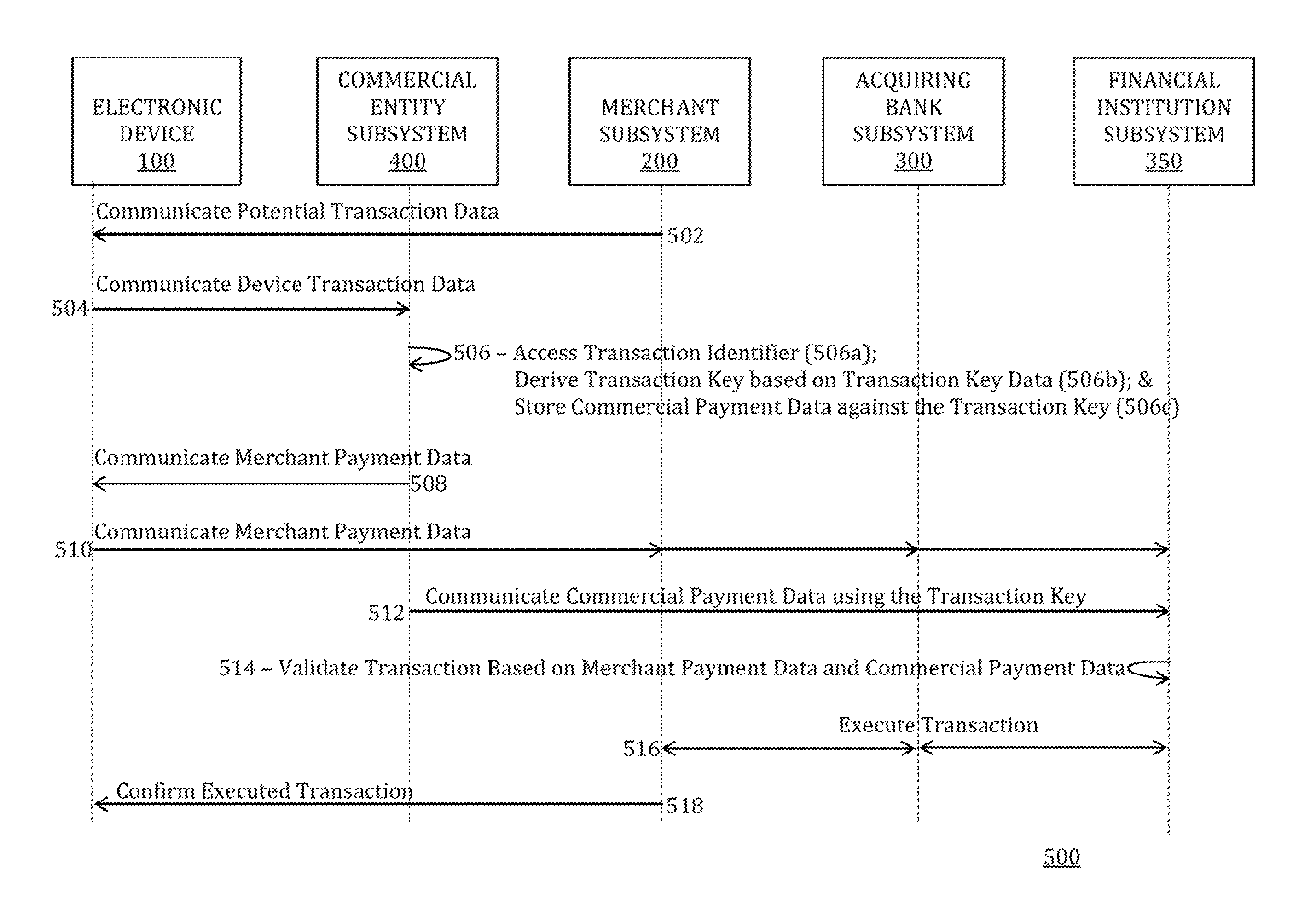
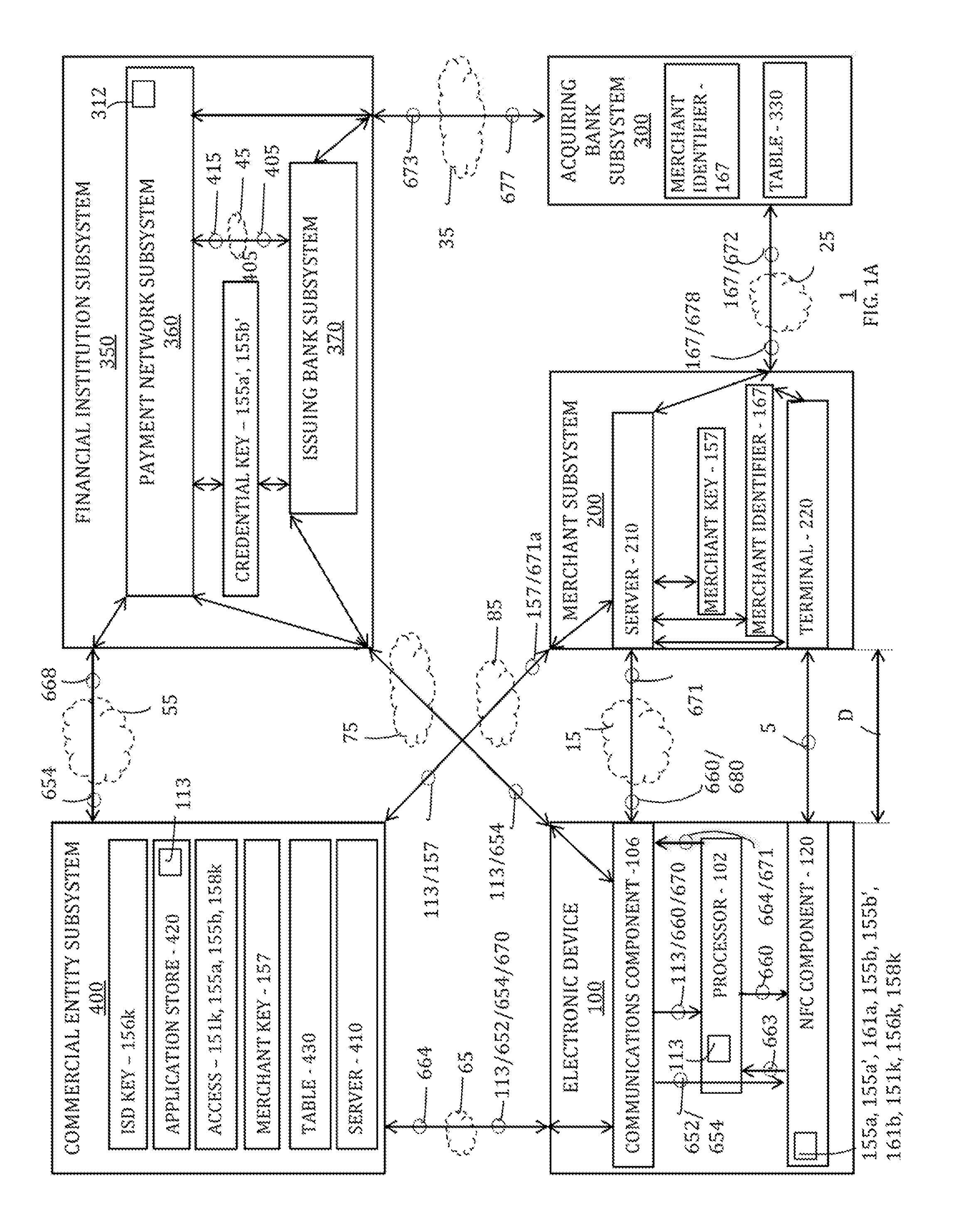
Multi-path communication of electronic device secure element data for online payments
ActiveUS20170011395A1Improve risk assessmentKey distribution for secure communicationCryptography processingTransaction dataFinancial transaction
Systems, methods, and computer-readable media for communicating electronic device secure element data over multiple paths for online payments are provided. In one example embodiment, a method includes, inter alia, at a commercial entity subsystem, receiving, from an electronic device, device transaction data that includes credential data indicative of a payment credential on the electronic device for funding a transaction with a merchant subsystem, accessing a transaction identifier, deriving a transaction key based on transaction key data that includes the accessed transaction identifier, transmitting, to one of the merchant subsystem and the electronic device, merchant payment data that includes a first portion of the credential data and the accessed transaction identifier, and sharing, with a financial institution subsystem using the transaction key, commercial payment data that includes a second portion of the credential data that is different than the first portion of the credential data. Additional embodiments are also provided.
Owner:APPLE INC
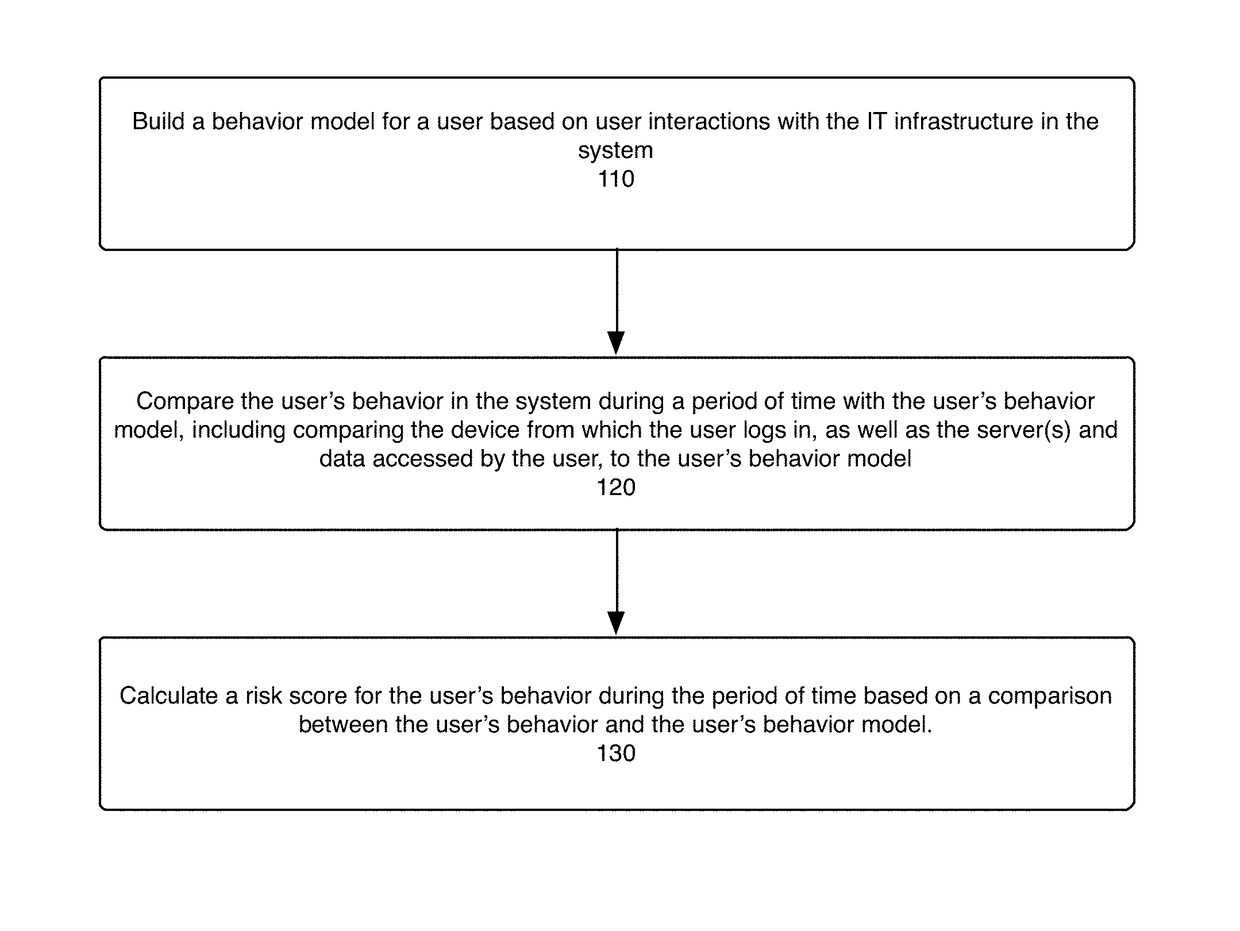
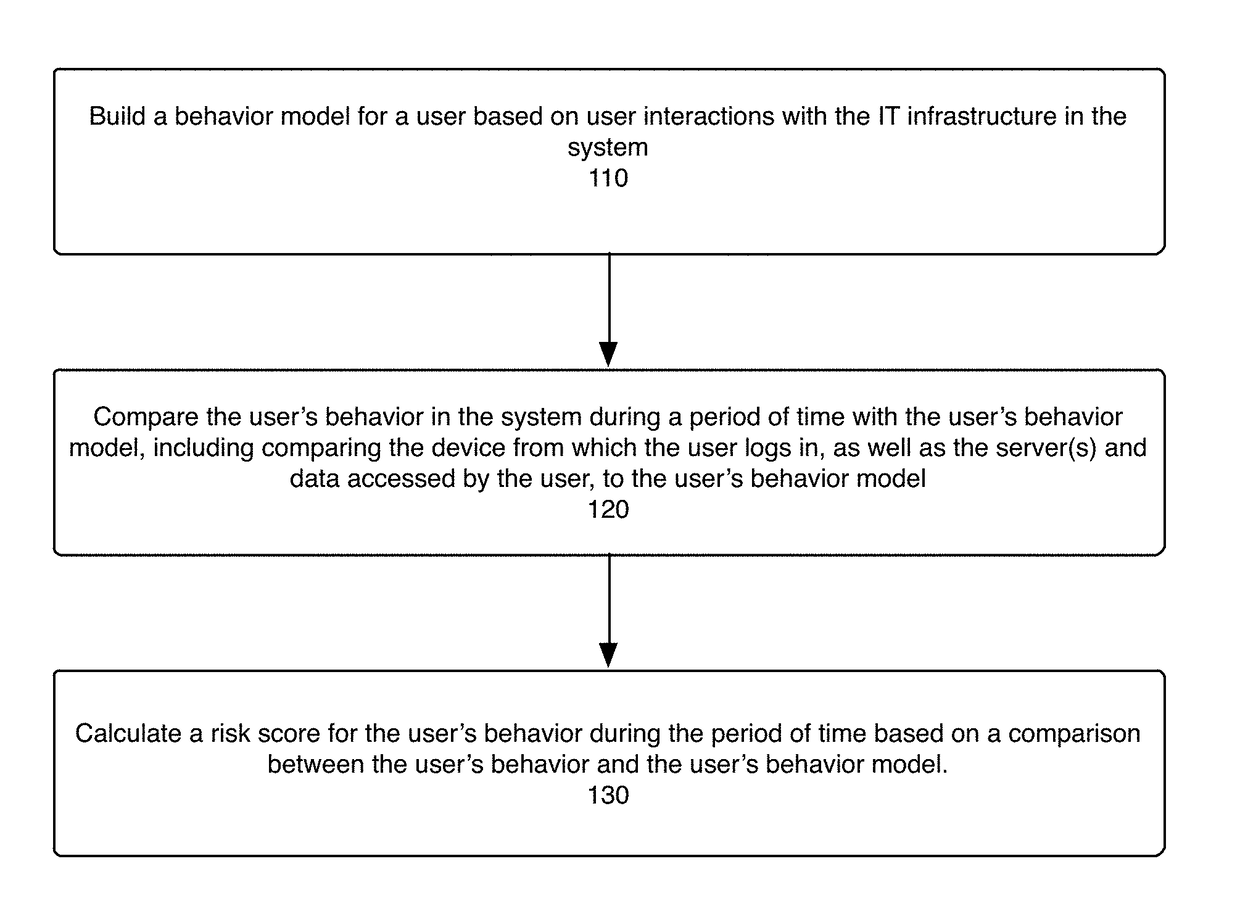
System, method, and computer program product for detecting and assessing security risks in a network
ActiveUS9798883B1Improve risk assessmentMemory loss protectionError detection/correctionClient-sideResource use
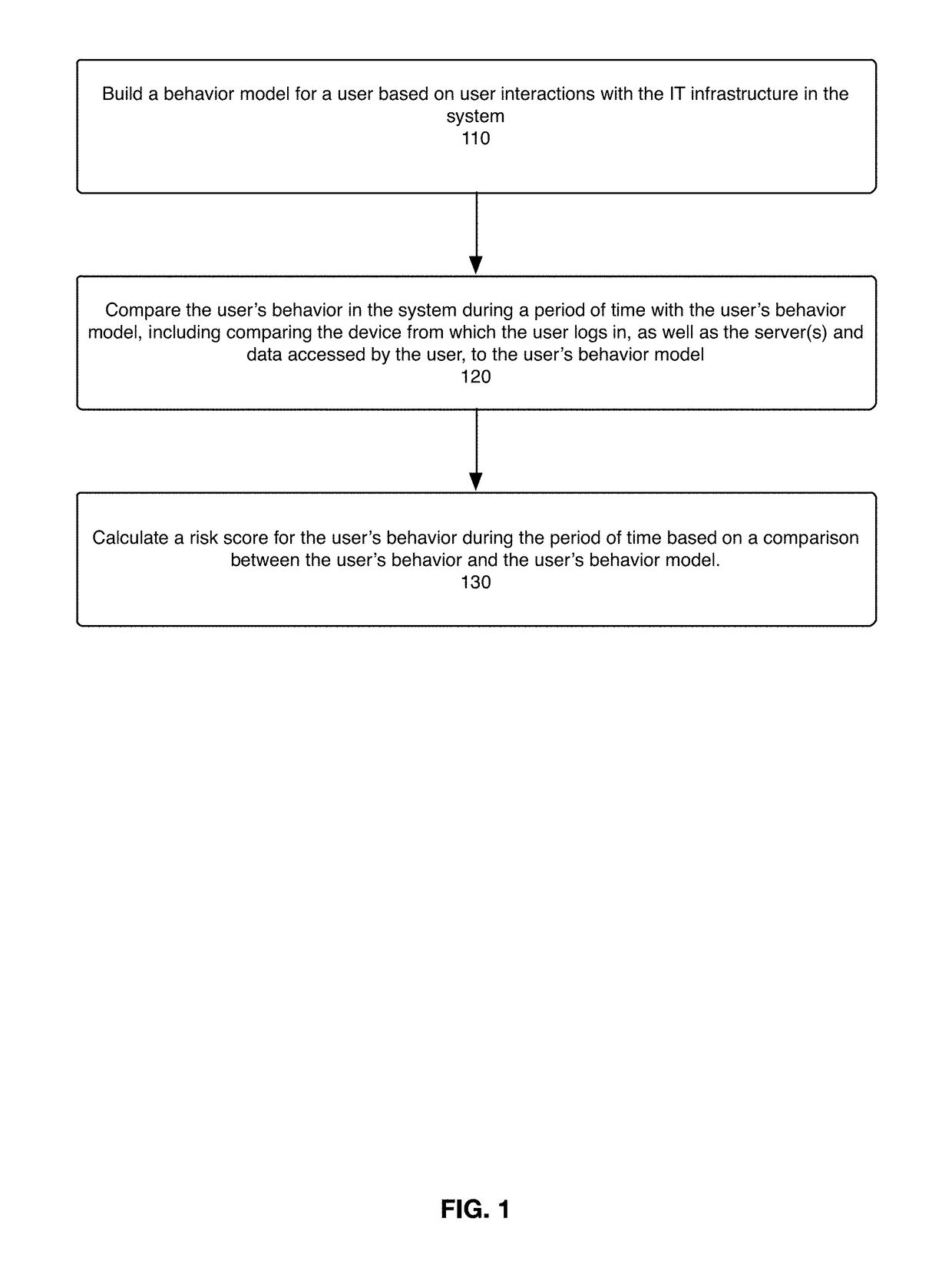
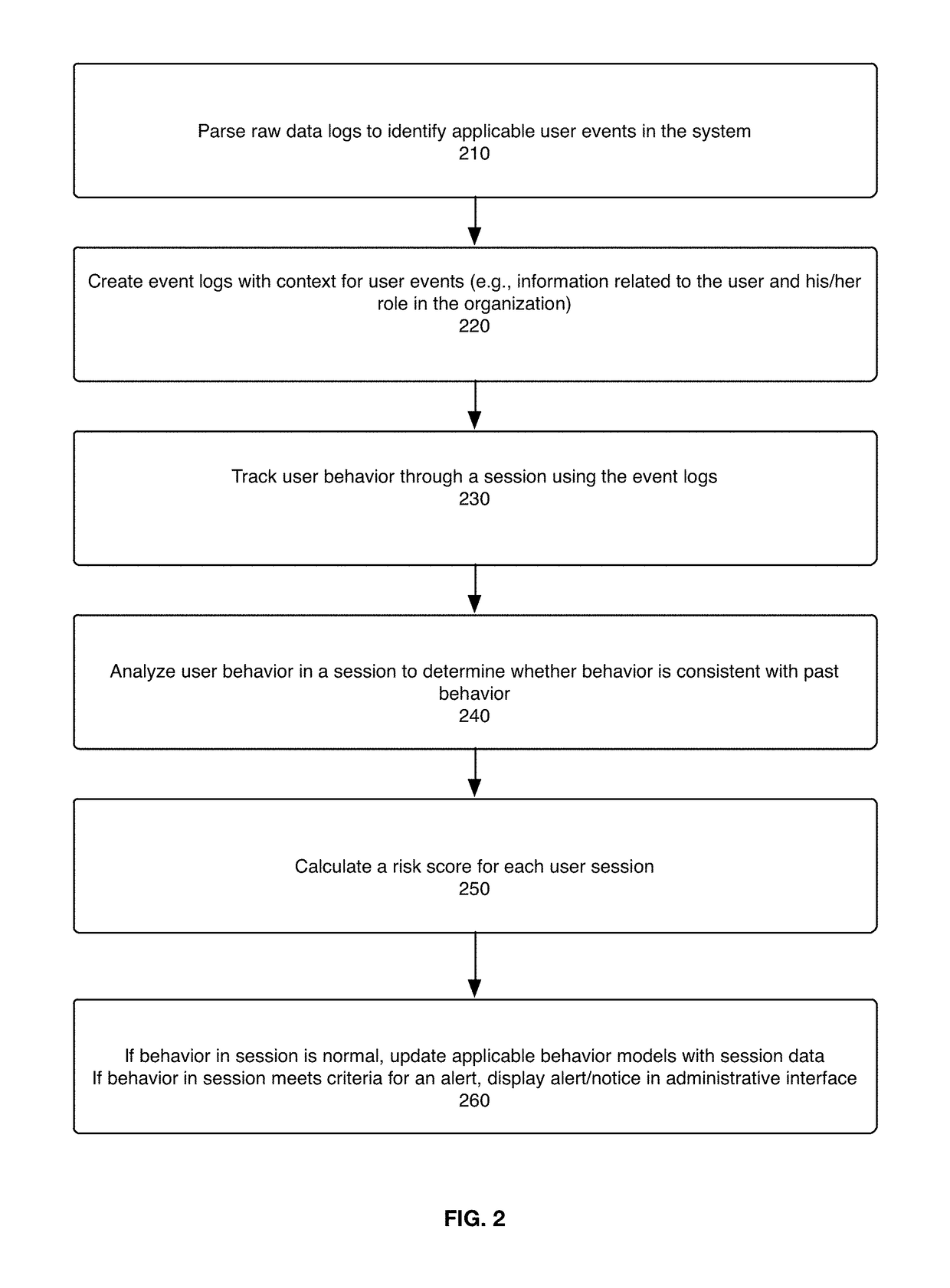
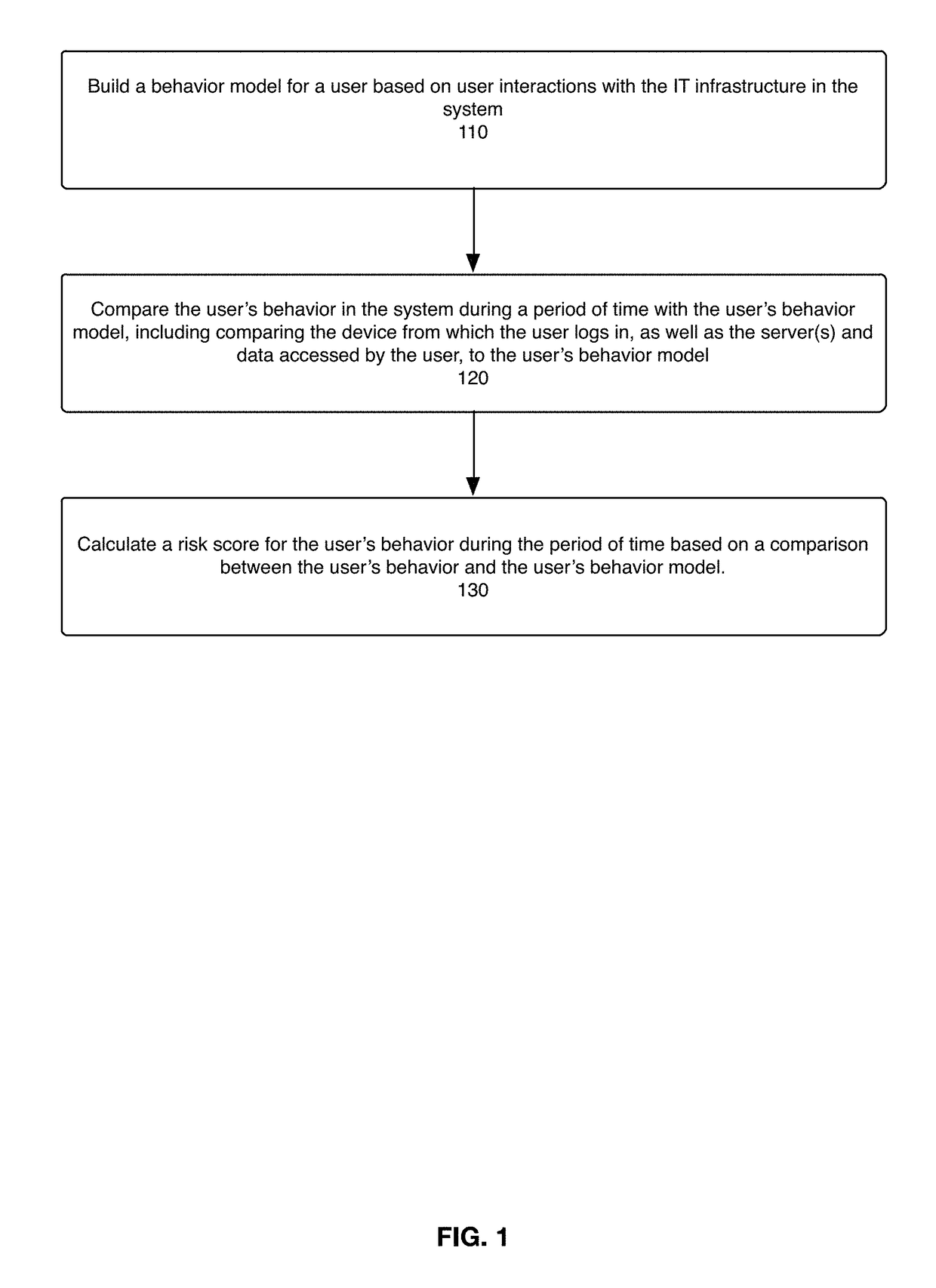
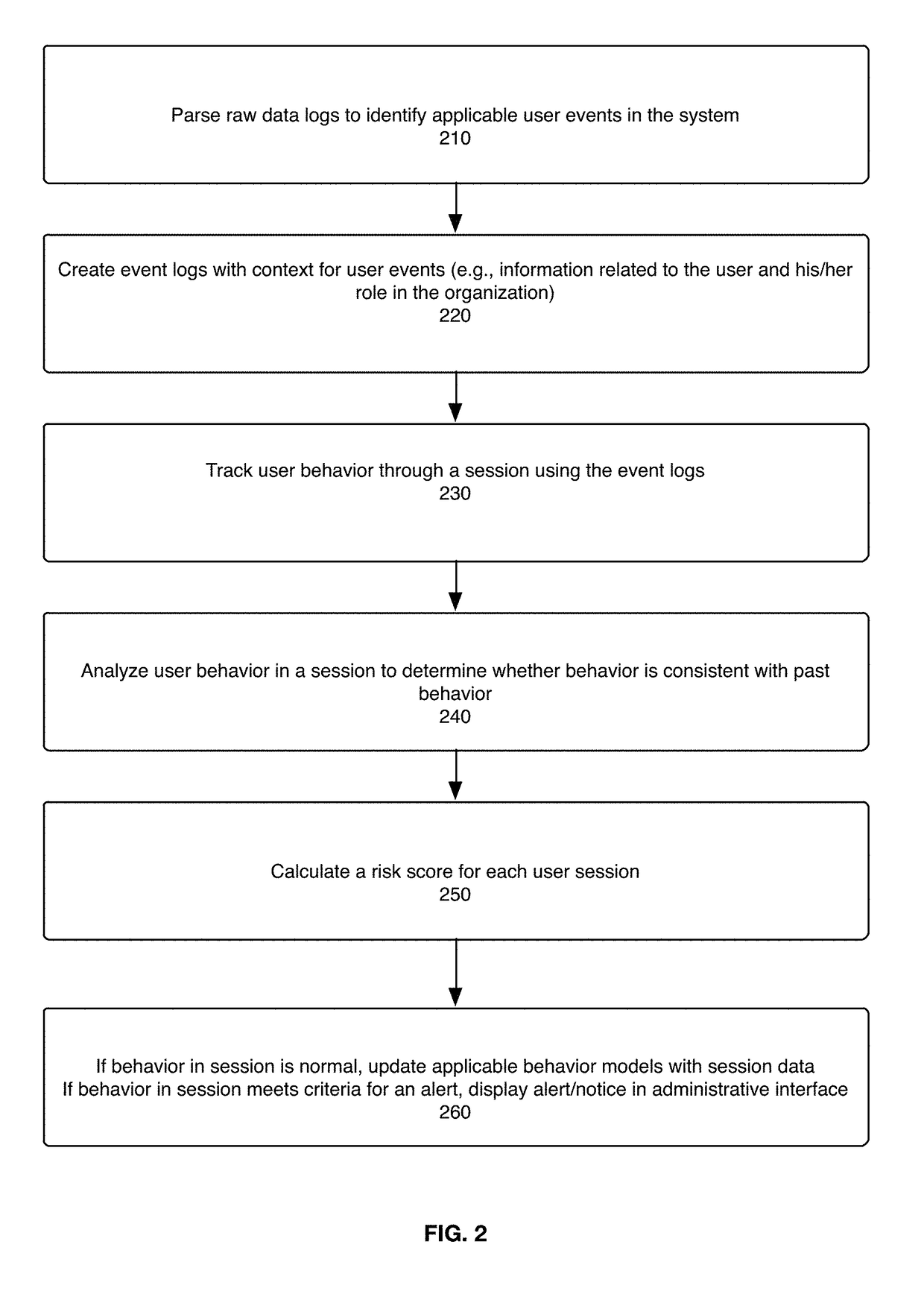
The present disclosure is directed to a system, method, and computer program for detecting and assessing security risks in an enterprise's computer network. A behavior model is built for a user in the network based on the user's interactions with the network, wherein a behavior model for a user indicates client device(s), server(s), and resources used by the user. The user's behavior during a period of time is compared to the user's behavior model. A risk assessment is calculated for the period of time based at least in part on the comparison between the user's behavior and the user's behavior model, wherein any one of certain anomalies between the user's behavior and the user's behavior model increase the risk assessment.
Owner:EXABEAM INC
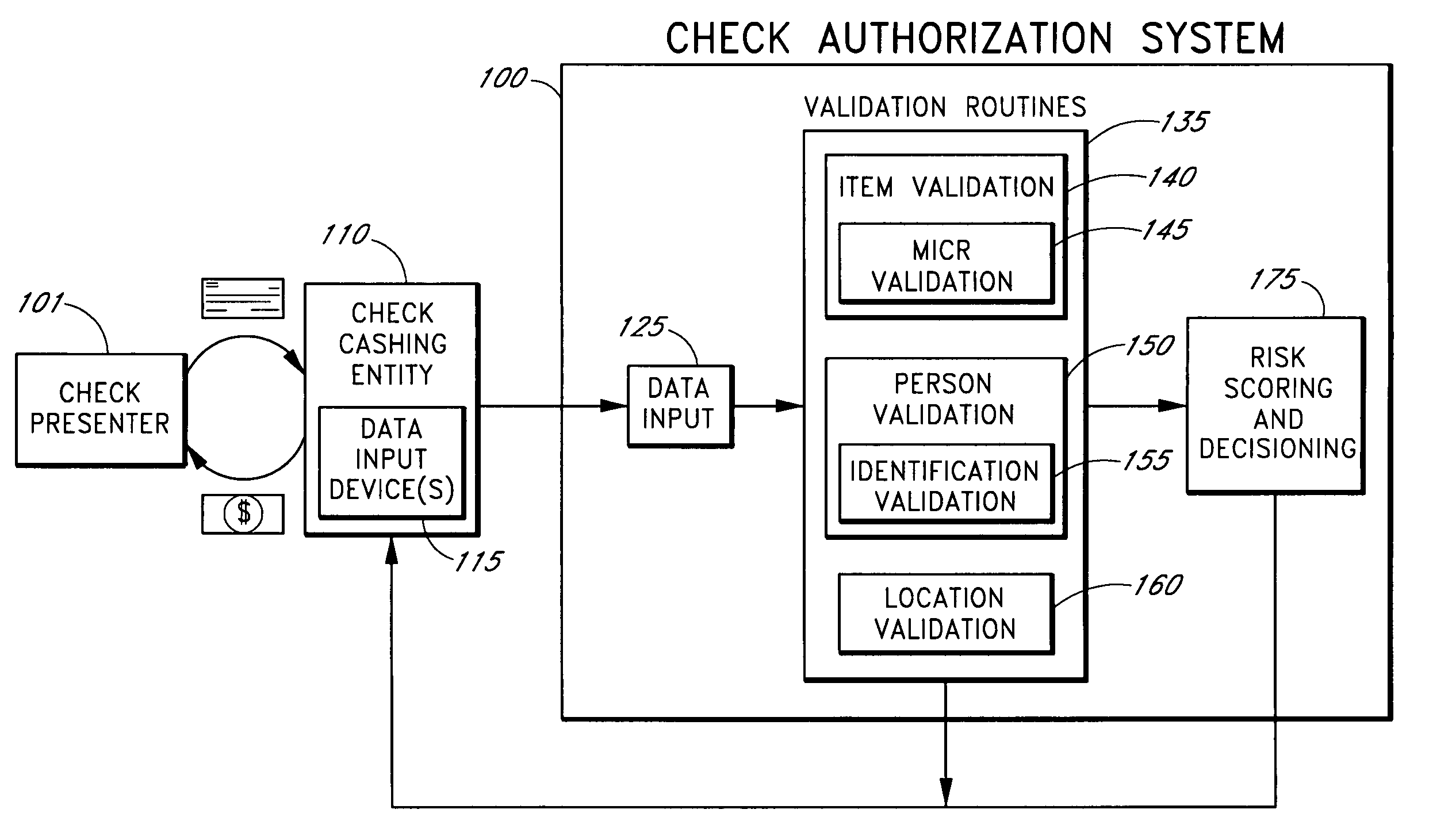
Systems and methods for identifying payor location based on transaction data
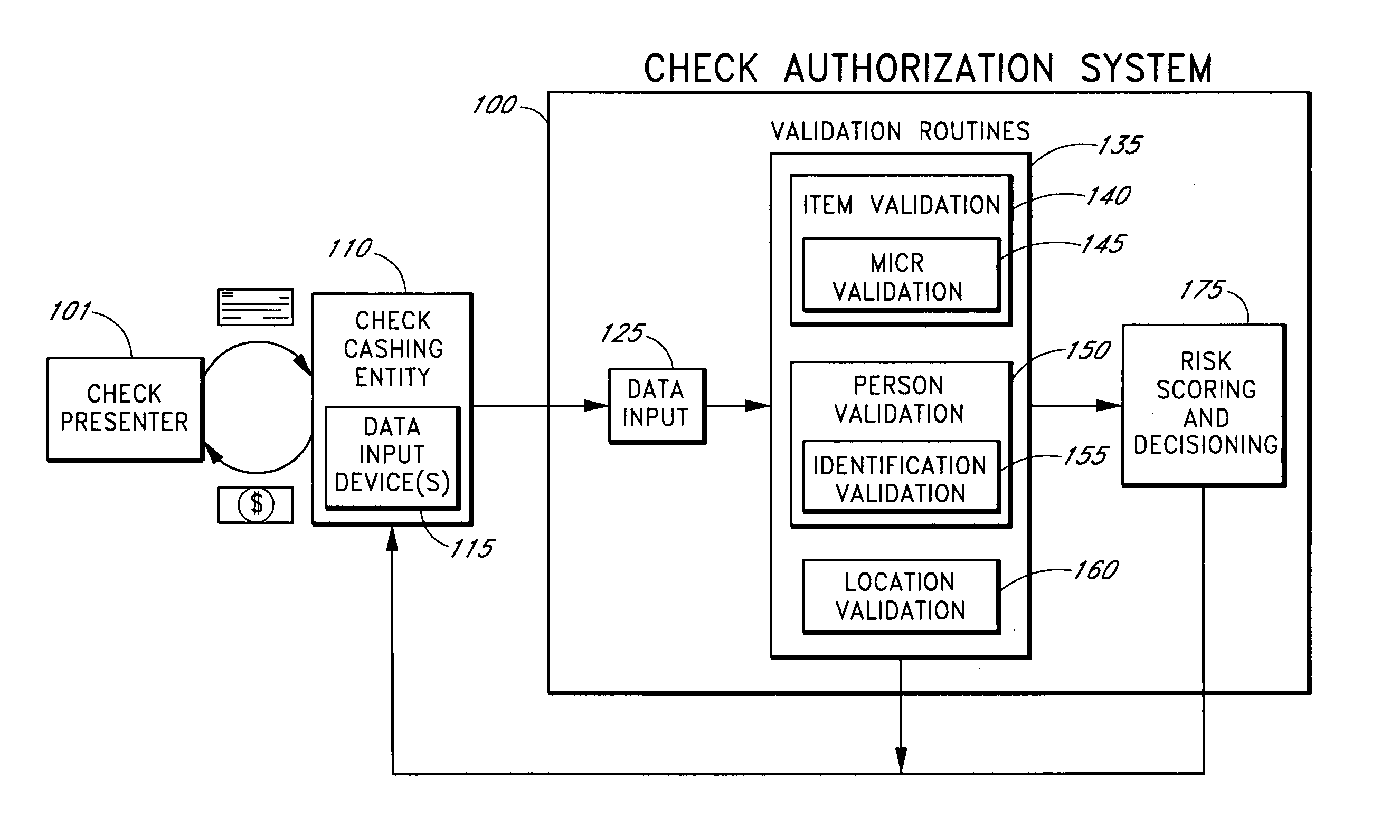
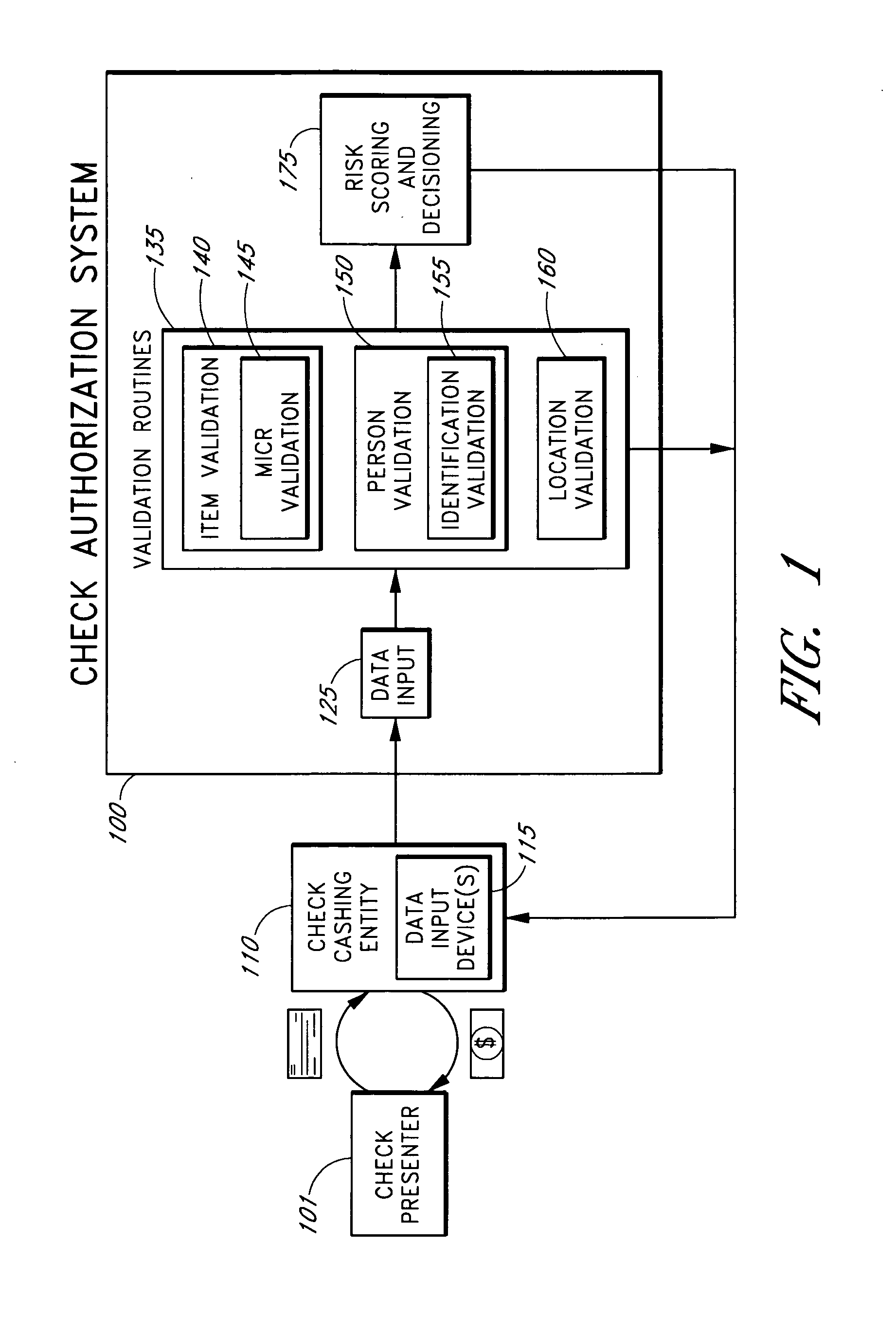
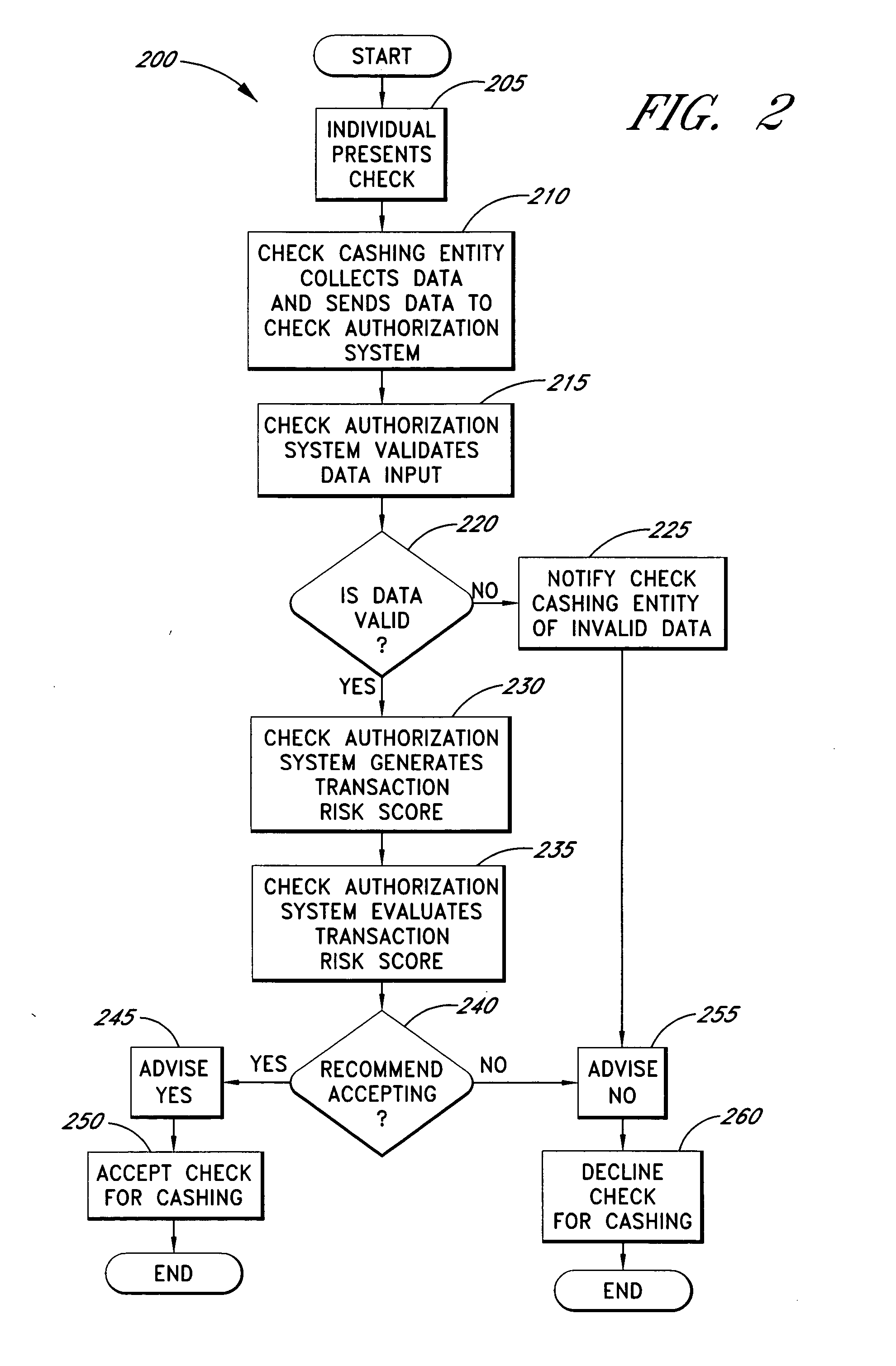
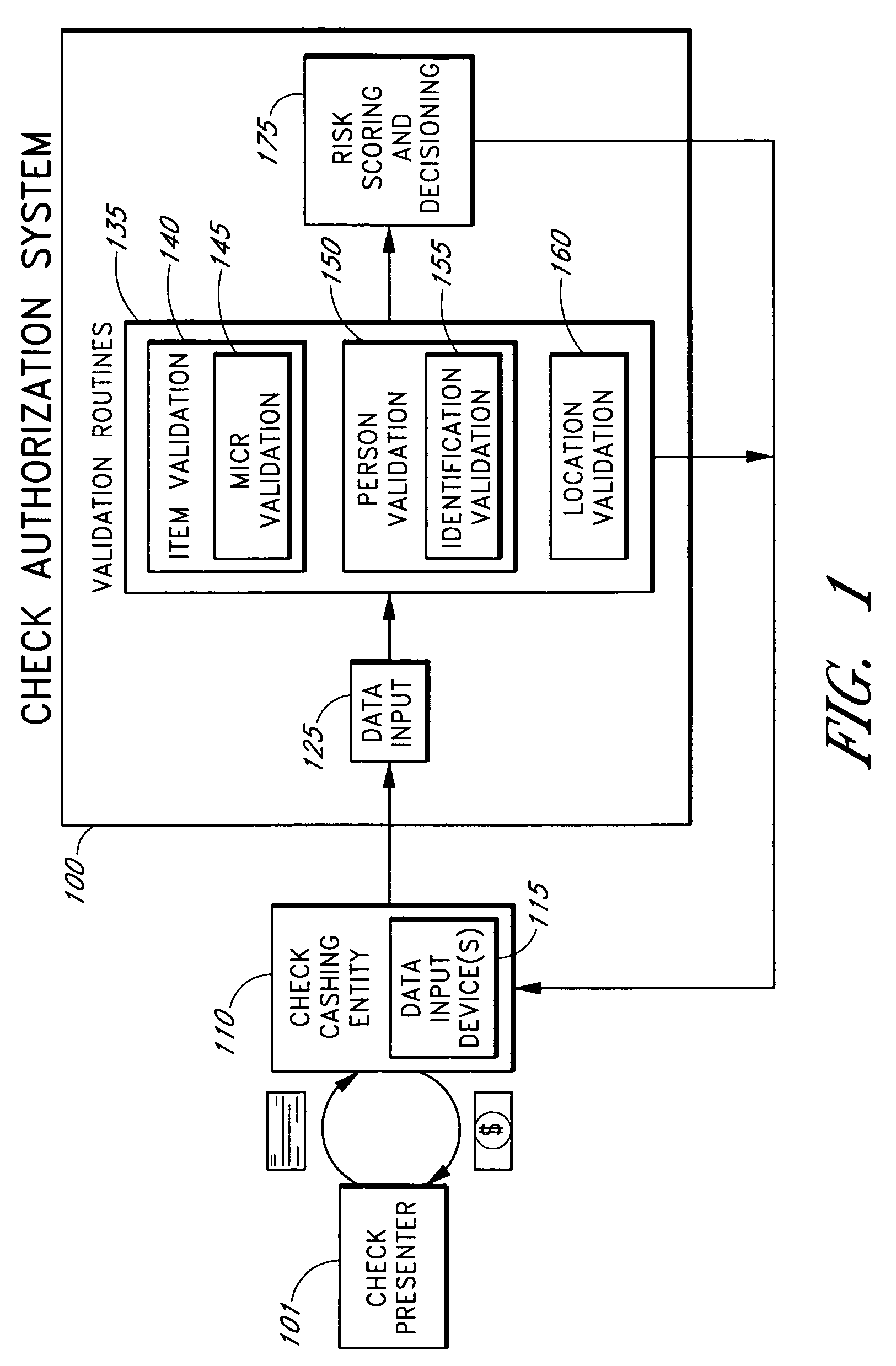
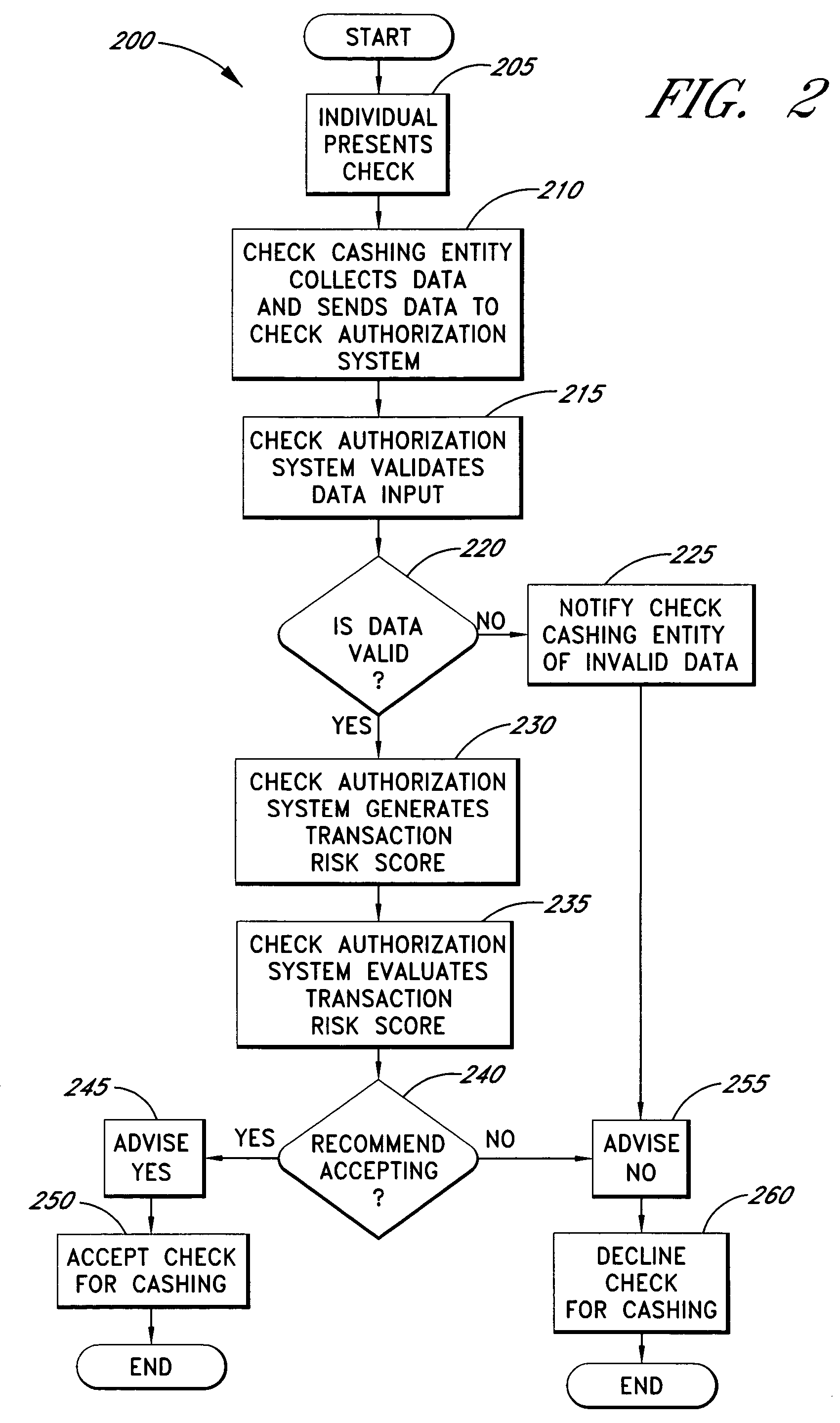
Systems and methods are described for building, maintaining, and using a repository of information about payors of second-party checks presented at a check-cashing entity for cashing. In various embodiments, the repository comprises stored information useful for determining the location of a payor of a second-party check. In one embodiment, information from the check that identifies an account on which the check is drawn, such as magnetic ink character recognition (MICR) line information from a paycheck, is used to access a repository of employer location information. In one embodiment, the payor location information is used to determine a proximity between the payor location and the check cashing entity location. In one embodiment, when a check is presented for which stored payor location information is not available, identifying information about the payor and / or the payor location is requested and is added to the repository.
Owner:FIRST DATA
System and method for assessing compliance risk
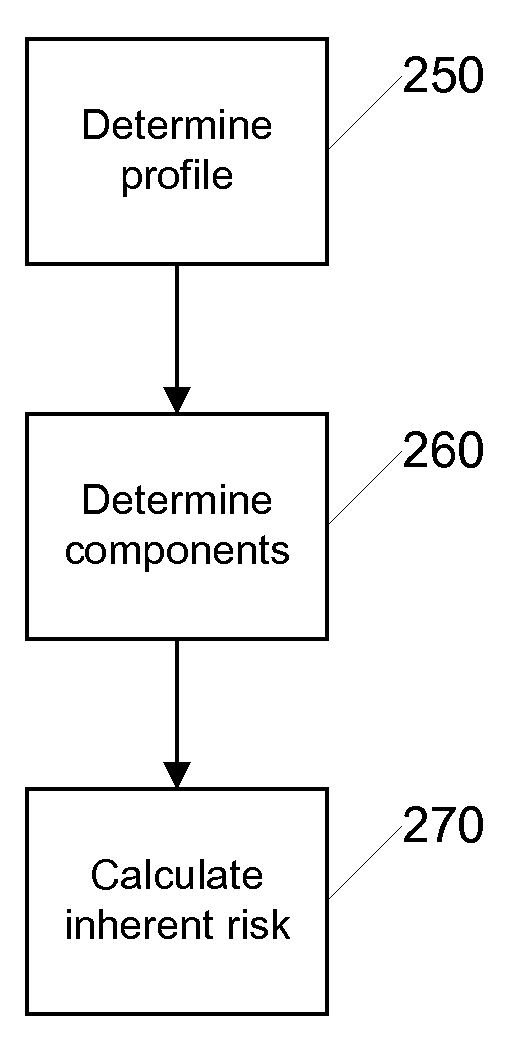
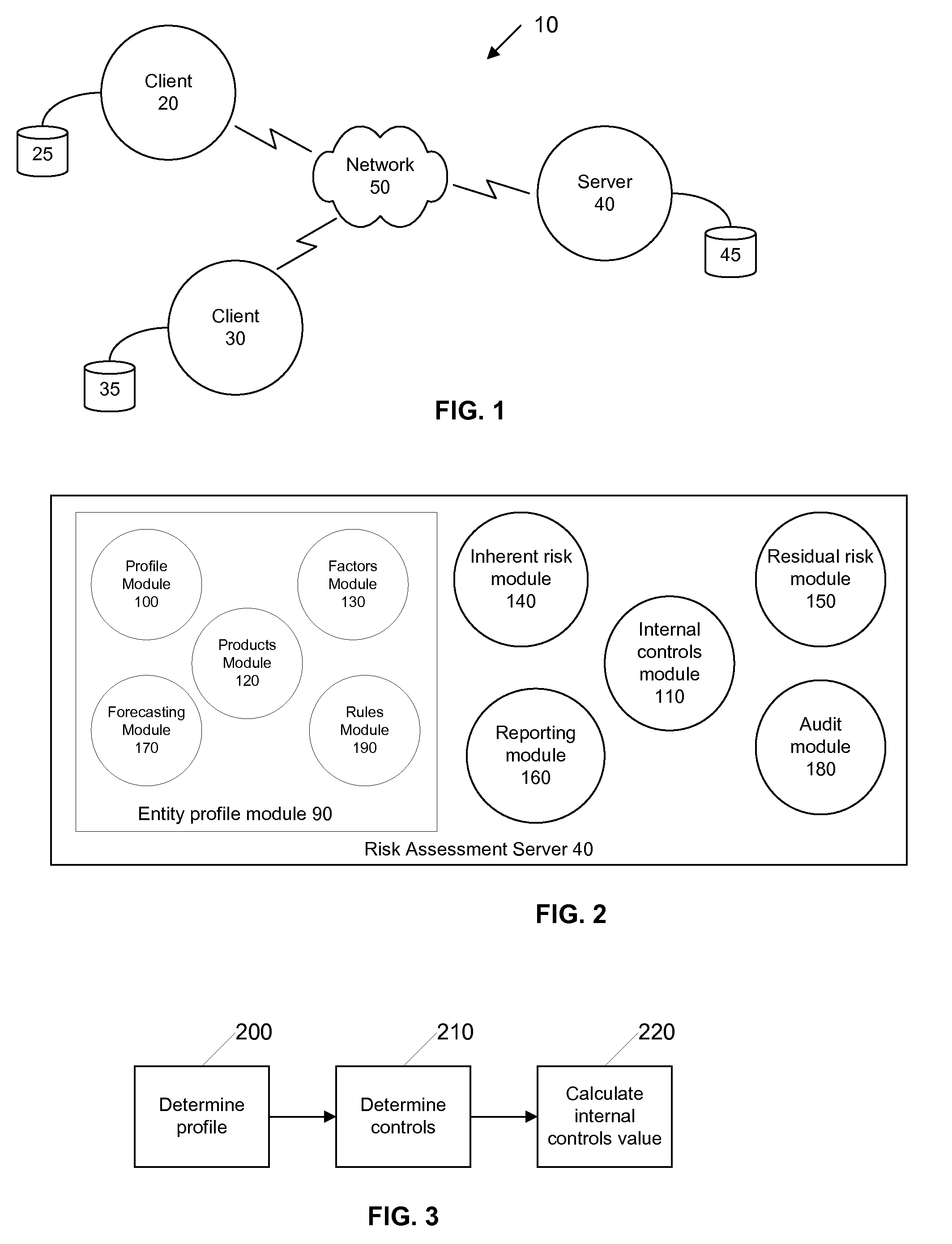
InactiveUS20090319420A1Improve risk assessmentAugment mitigation processFinanceEngineeringBusiness activities
Institutional risk is calculated by collecting information about the products and services offered by an institution and assigning a risk value to each product and service. Other aspects and components of an institution are also assigned risk values. The various risk values are calculated along with institutional controls that are in place to mitigate risk in order to determine an overall residual risk assessment for the entity. Forecasts can be made for an institution by adding new or subtracting current business activities and / or institutional controls and calculating an alternative overall residual risk assessment.
Owner:COMPLIANCE COACH
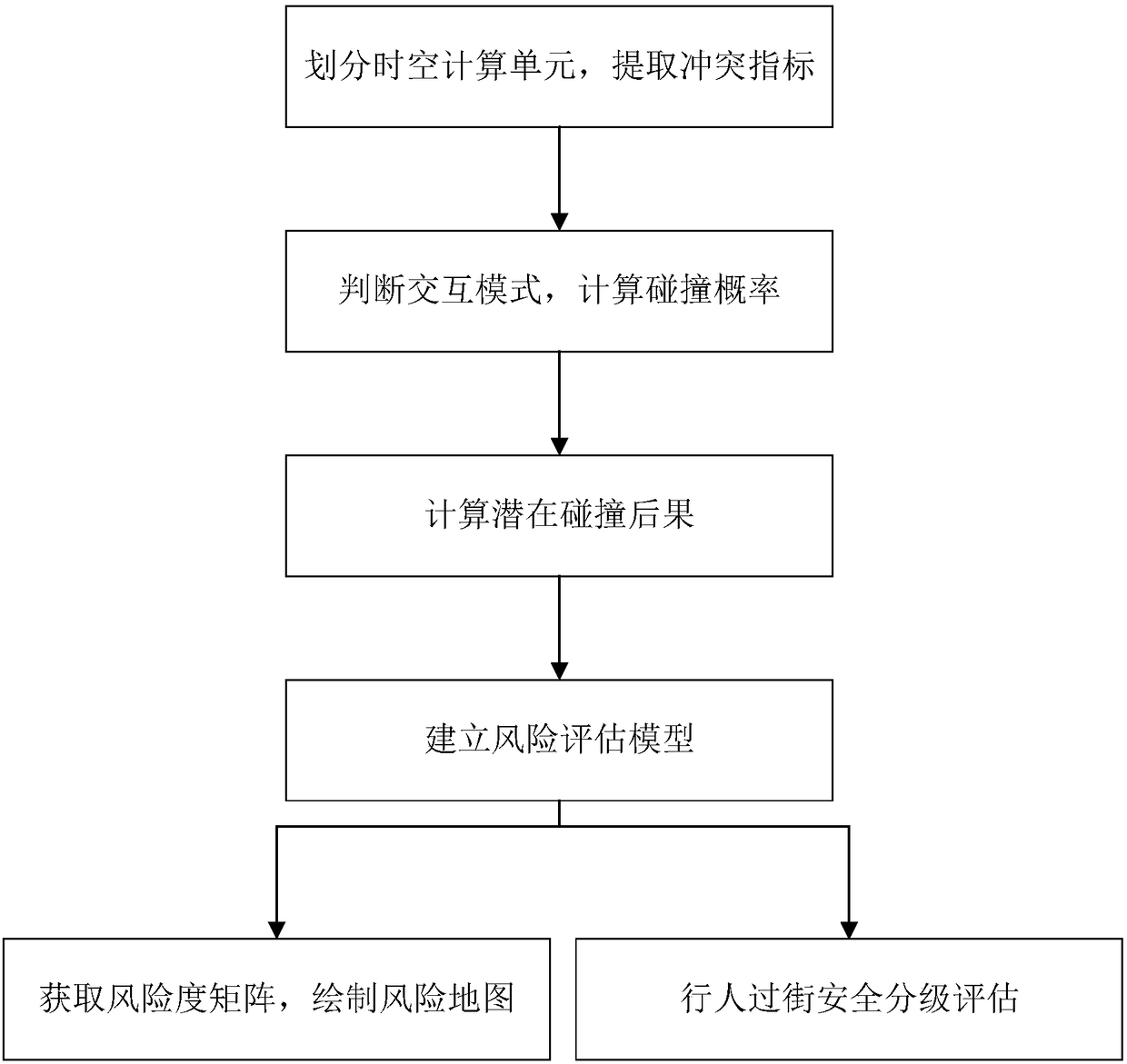
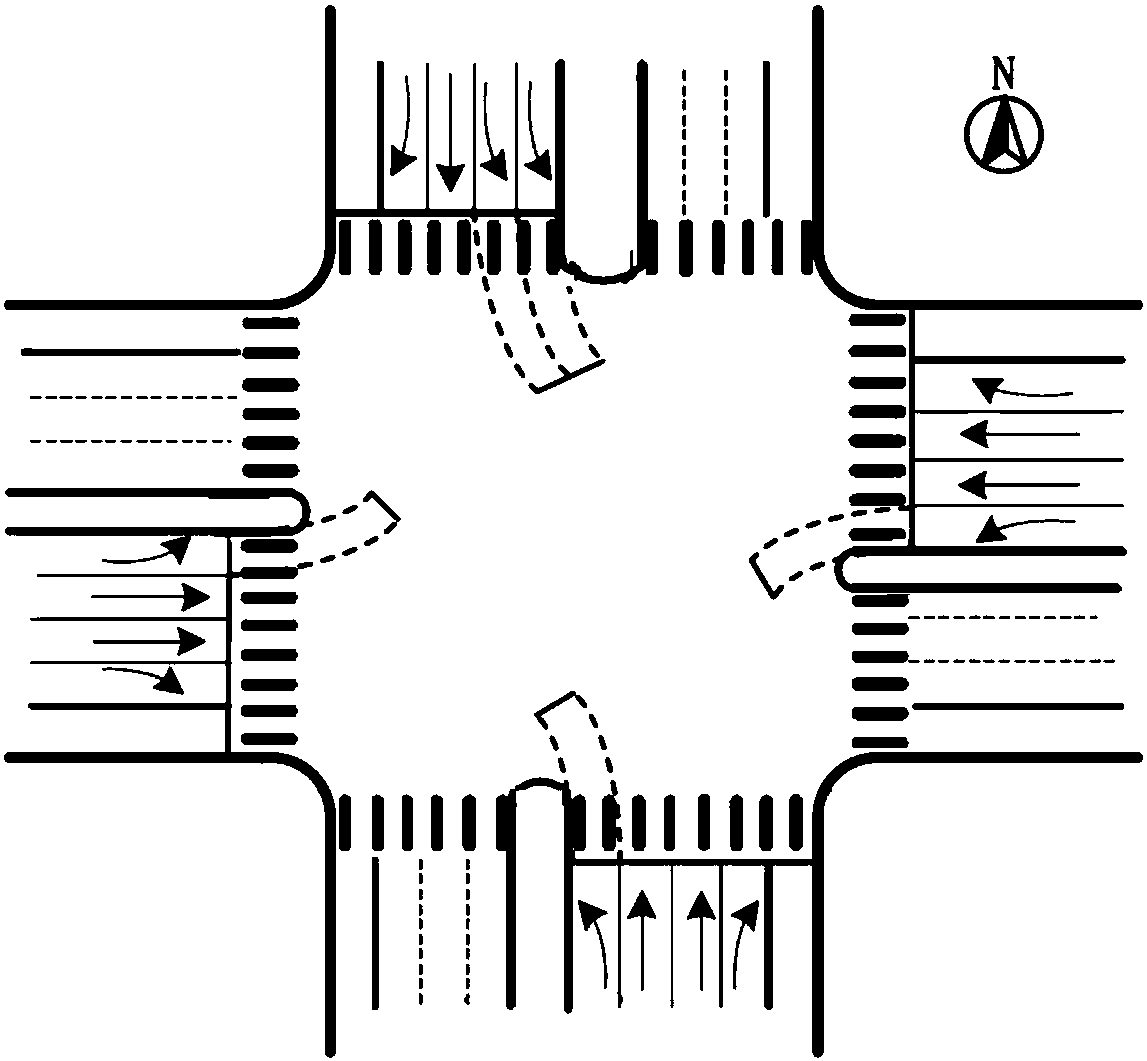
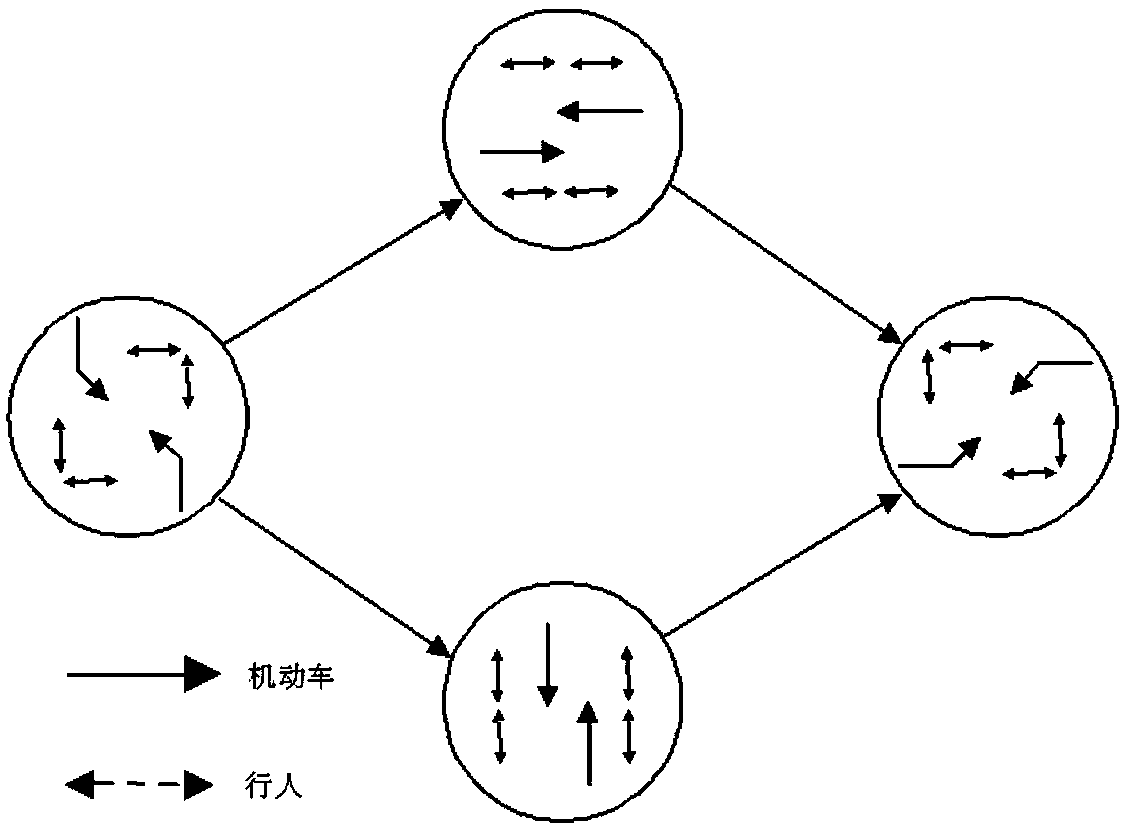
Method for assessing crossing risk of pedestrians at intersection on basis of trajectory data
ActiveCN108230676AAccurate risk calculationRealize graded evaluationDetection of traffic movementResourcesRisk levelRisk map
The invention relates to a method for assessing the crossing risk of pedestrians at an intersection on the basis of trajectory data. The method comprises the following steps of S1, extracting conflictindexes between motor vehicles and the pedestrians on the basis of the trajectory data; S2, identifying interactive modes of the pedestrians and motor vehicles on the basis of the extracted conflictindexes, and calculating potential collision probabilities between the pedestrians and motor vehicles according to different interaction modes; S3, calculating potential collision consequences of pedestrian-vehicle interaction events according to the vehicle types and vehicle speeds of the motor vehicles; S4, combining the collision probabilities with the potential collision consequences to createa risk assessment model; S5, according to a pedestrian crossing risk degree on each time and space calculation unit in the risk assessment model, obtaining a risk degree matrix and drawing a pedestrian crossing risk map according to the risk degree matrix; S6, combining an average pedestrian crossing risk degree in the risk assessment model with a subjective risk standard, dividing pedestrian crossing risk levels and conducting risk assessment. Compared with the prior art, the method has the advantages of comprehensive and accurate assessment and the like.
Owner:TONGJI UNIV
System, method, and computer program product for detecting and assessing security risks in a network
ActiveUS20180004961A1Improve risk assessmentPlatform integrity maintainanceTransmissionBusiness enterpriseEngineering
The present disclosure is directed to a system, method, and computer program for detecting and assessing security risks in an enterprise's computer network. A behavior model is built for a user in the network based on the user's interactions with the network, wherein a behavior model for a user indicates client device(s), server(s), and resources used by the user. The user's behavior during a period of time is compared to the user's behavior model. A risk assessment is calculated for the period of time based at least in part on the comparison between the user's behavior and the user's behavior model, wherein any one of certain anomalies between the user's behavior and the user's behavior model increase the risk assessment.
Owner:EXABEAM INC
Real-Time Visual Customer Support Enablement System and Method
InactiveUS20160037126A1Improving customer supportQuickly and easily acquireTwo-way working systemsData switching networksComputer terminalComputer science
Disclosed is a system and method for providing real-time visual customer support. In one embodiment, the present system is configured to enhance native phone communication by simultaneously being able to deliver one-way real-time visual streaming from the end consumer. In this way, the present invention allows businesses to participate in collaborative audio-visual communication during the very first customer contact over the phone.
Owner:LIVEGENIC
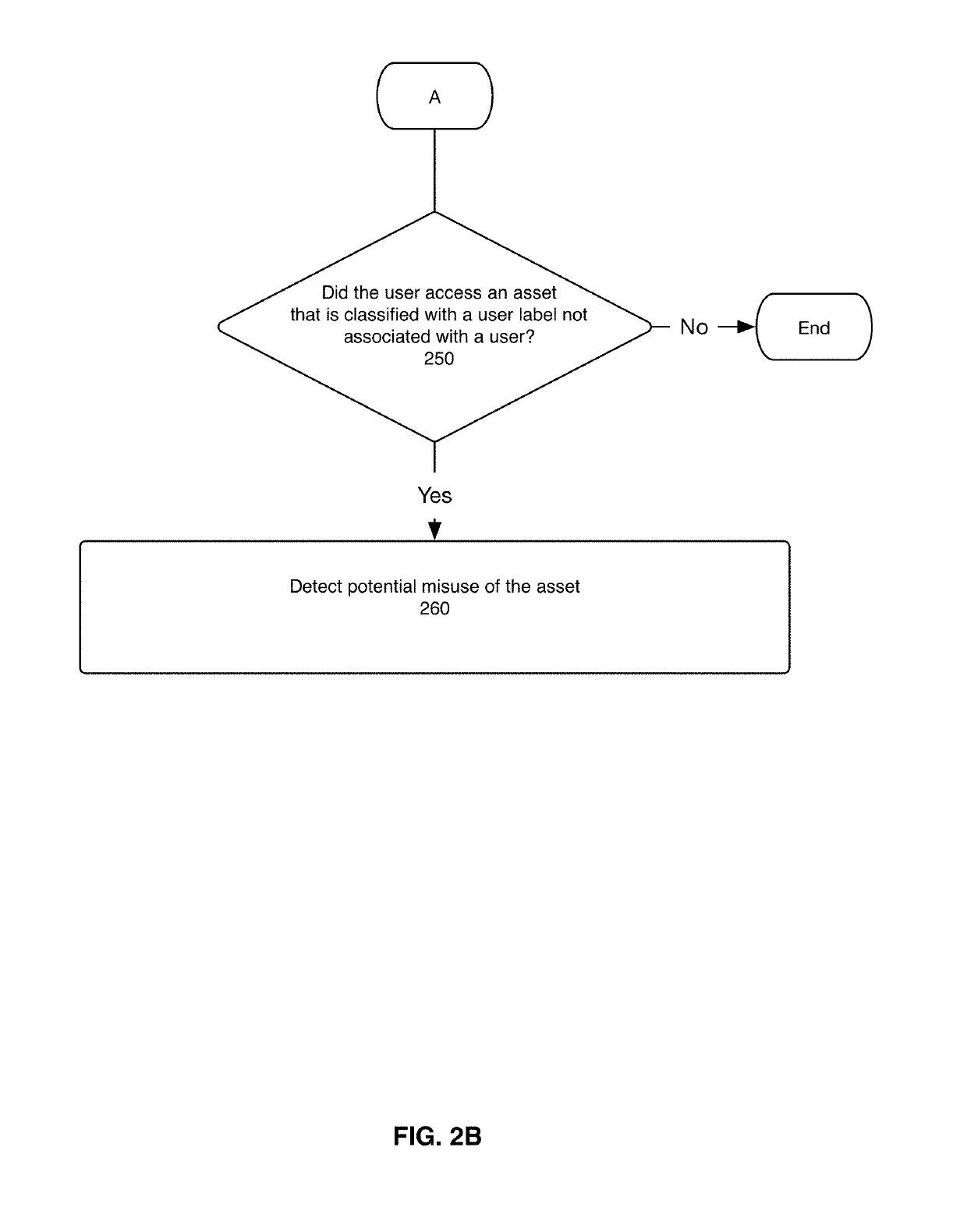
System, method, and computer program for classifying monitored assets based on user labels and for detecting potential misuse of monitored assets based on the classifications
ActiveUS10496815B1Improve risk assessmentRelational databasesOffice automationLearning basedComputer program
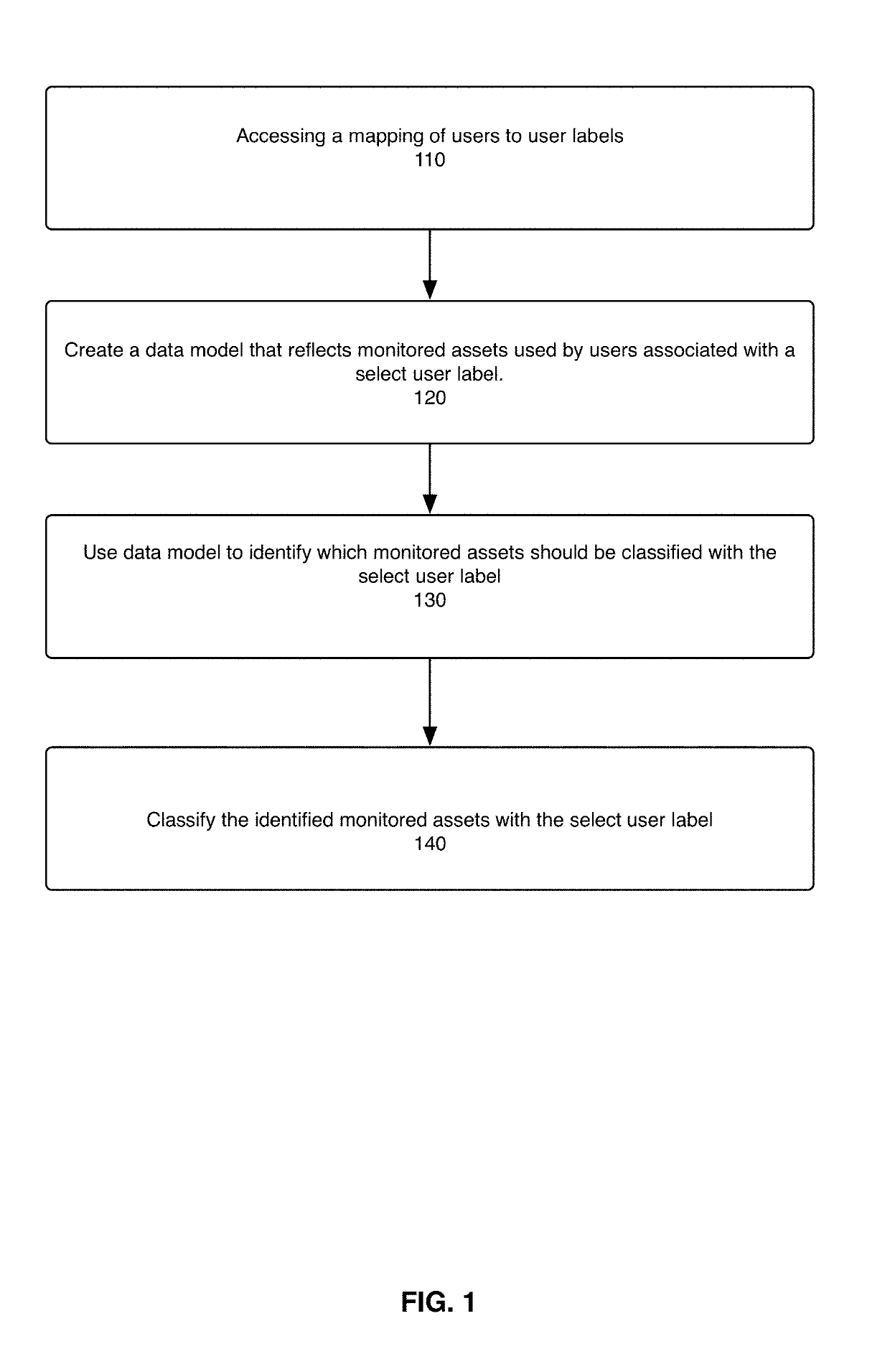
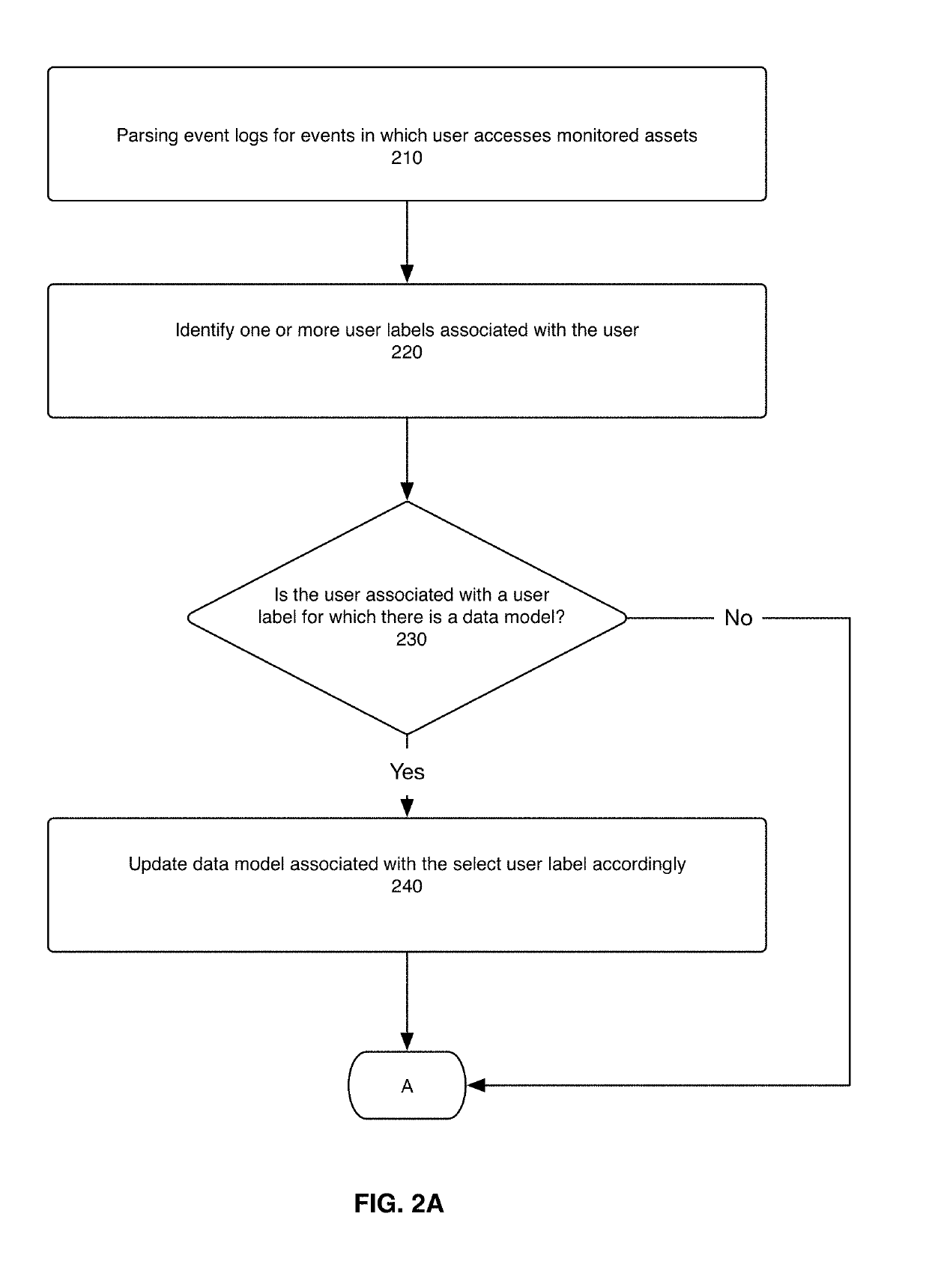
The present disclosure describes a system, method, and computer program for classifying monitored assets based on user labels and for detecting potential misuse of monitored assets based on said classifications. Machine-learning-based modeling is used to classify one or more types of monitored assets with a select user label. A data model is created that reflects monitored assets used by users associated with the select user label. Each a time a user with the select user label accesses an applicable type of monitored asset, the data model is updated to reflect the event. The data model is used to classify one or more monitored assets with the select user label. If a user without the select user label uses a monitored asset classified with the select user label, a potential misuse of the monitored asset is detected.
Owner:EXABEAM INC
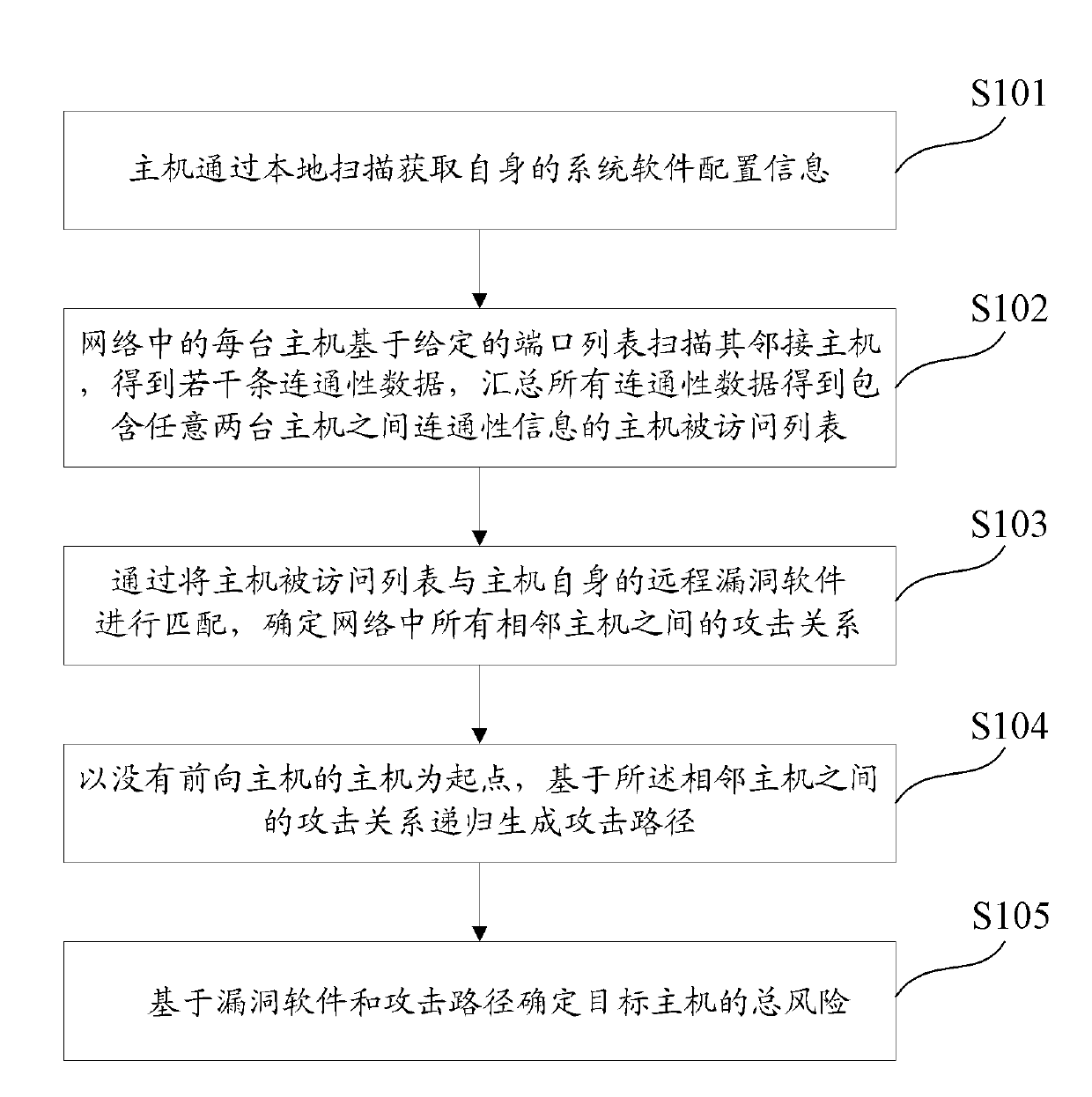
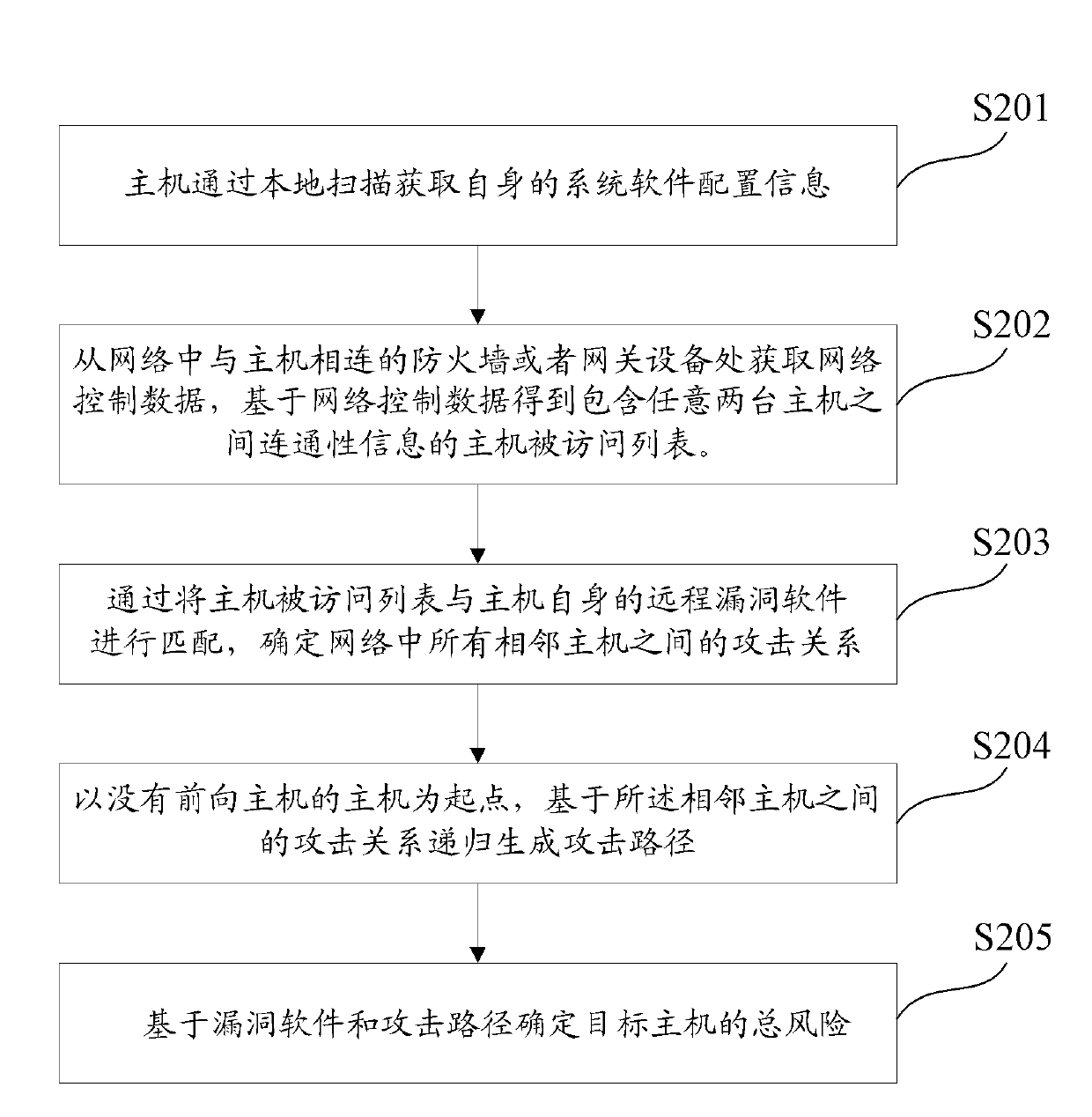
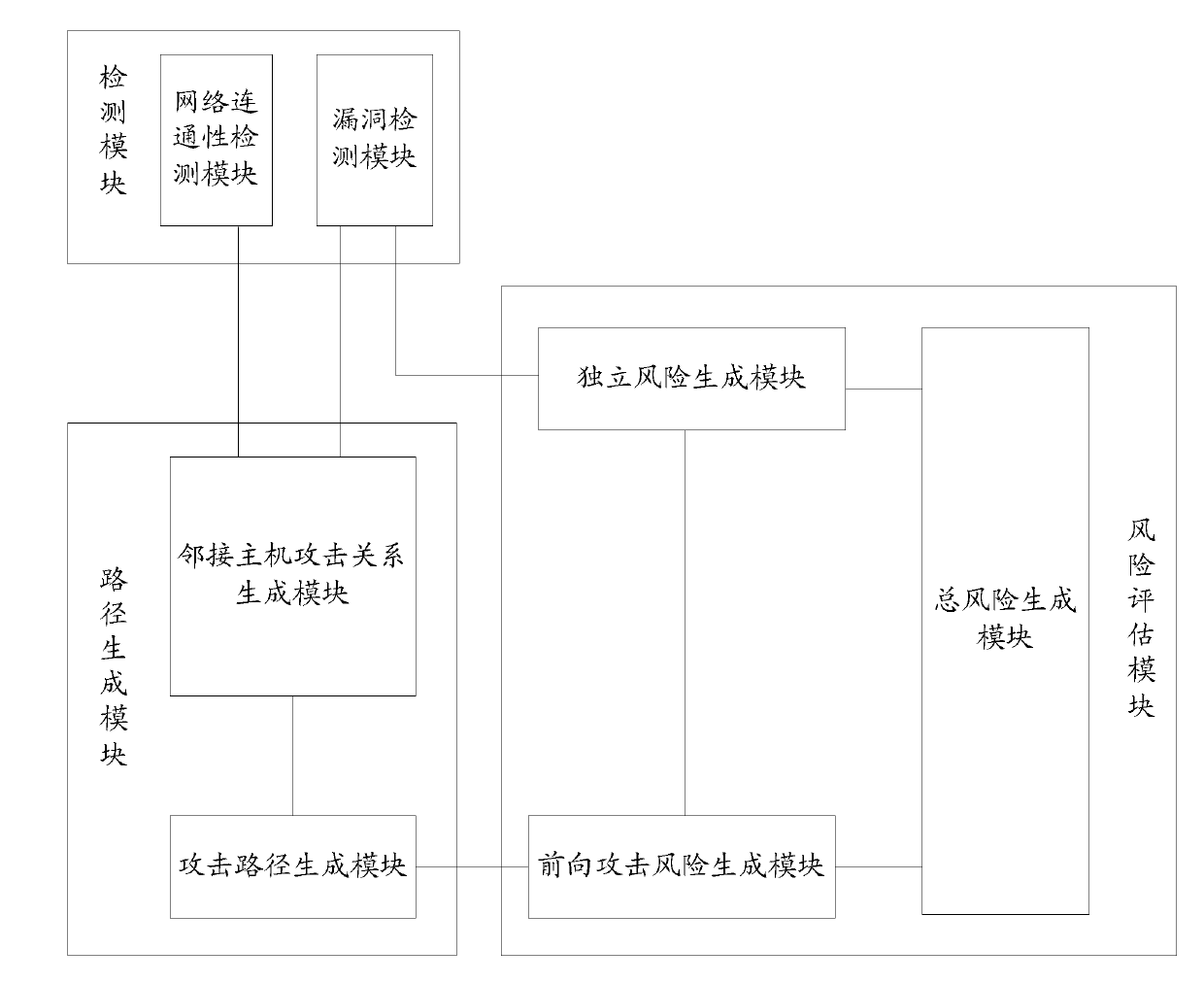
Host risk evaluation method and device
InactiveCN102170431AImprove risk assessmentComprehensive assessmentTransmissionTotal riskRisk evaluation
The invention discloses a host risk evaluation method and a host risk evaluation device. The method comprises the following steps of: detecting the bug information and network connectivity information of all hosts in a network; determining an attack path in the network according to the bug information and the network connectivity information; and determining the total risk of any target host based on the bug information and the attack path. In the method and the device, the thought of actively and dynamically evaluating potential bugs and risks by the attack path is put forward for the first time, so that host risk evaluation is more perfect, and effects are more ideal. Own bugs of the host and threats from the attack path in the network are combined, so the potential risks of the host can be explored more deeply.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
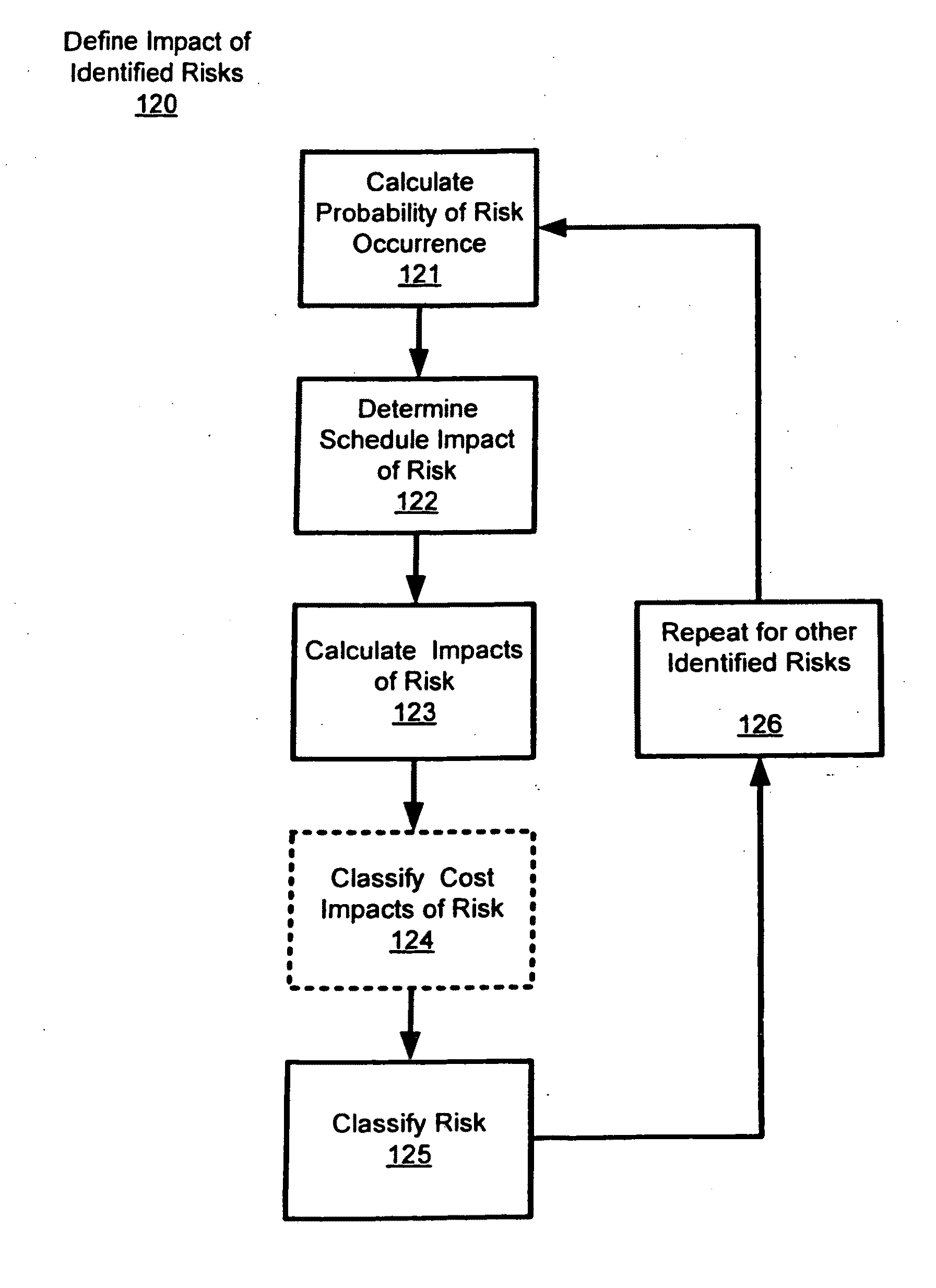
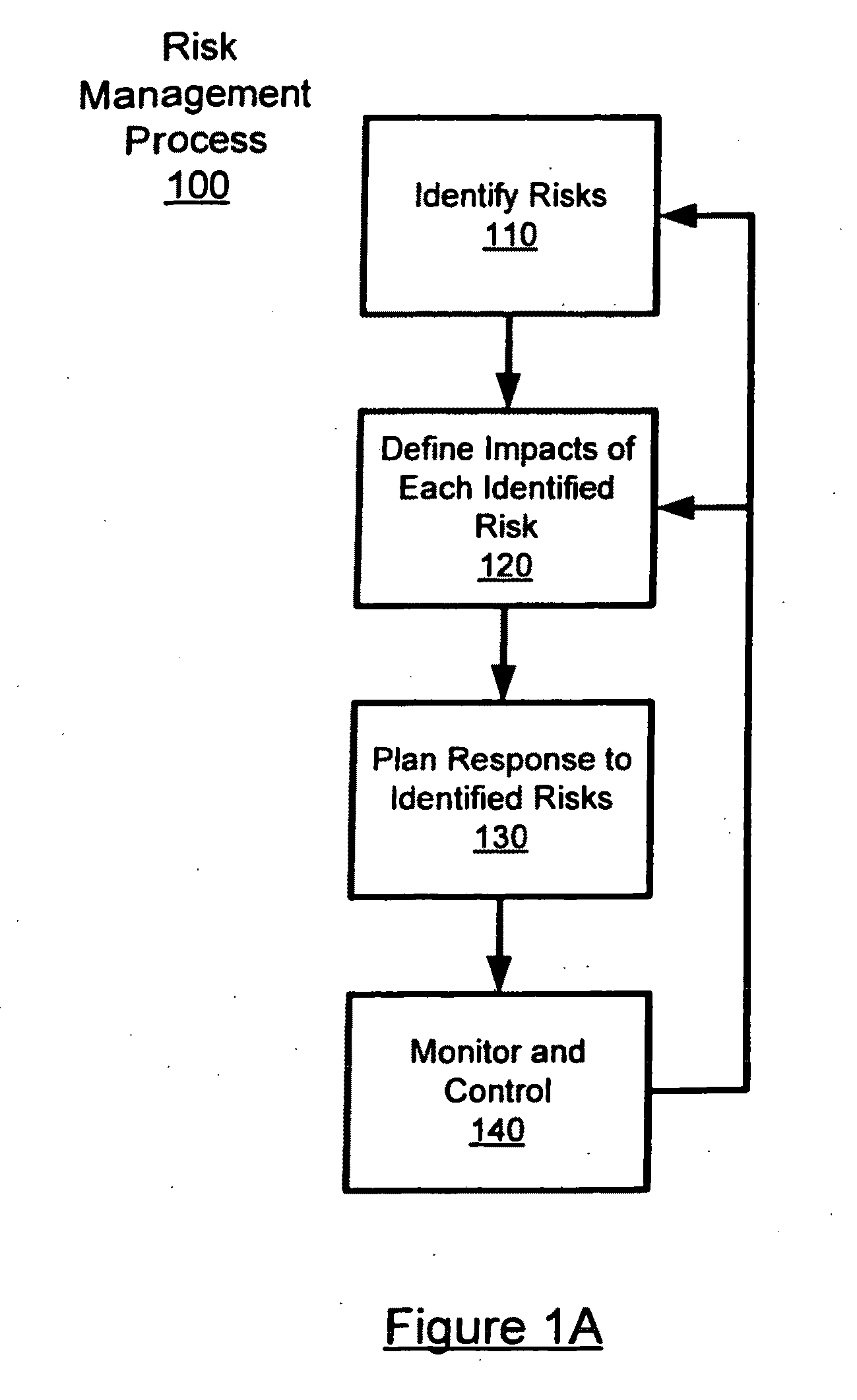
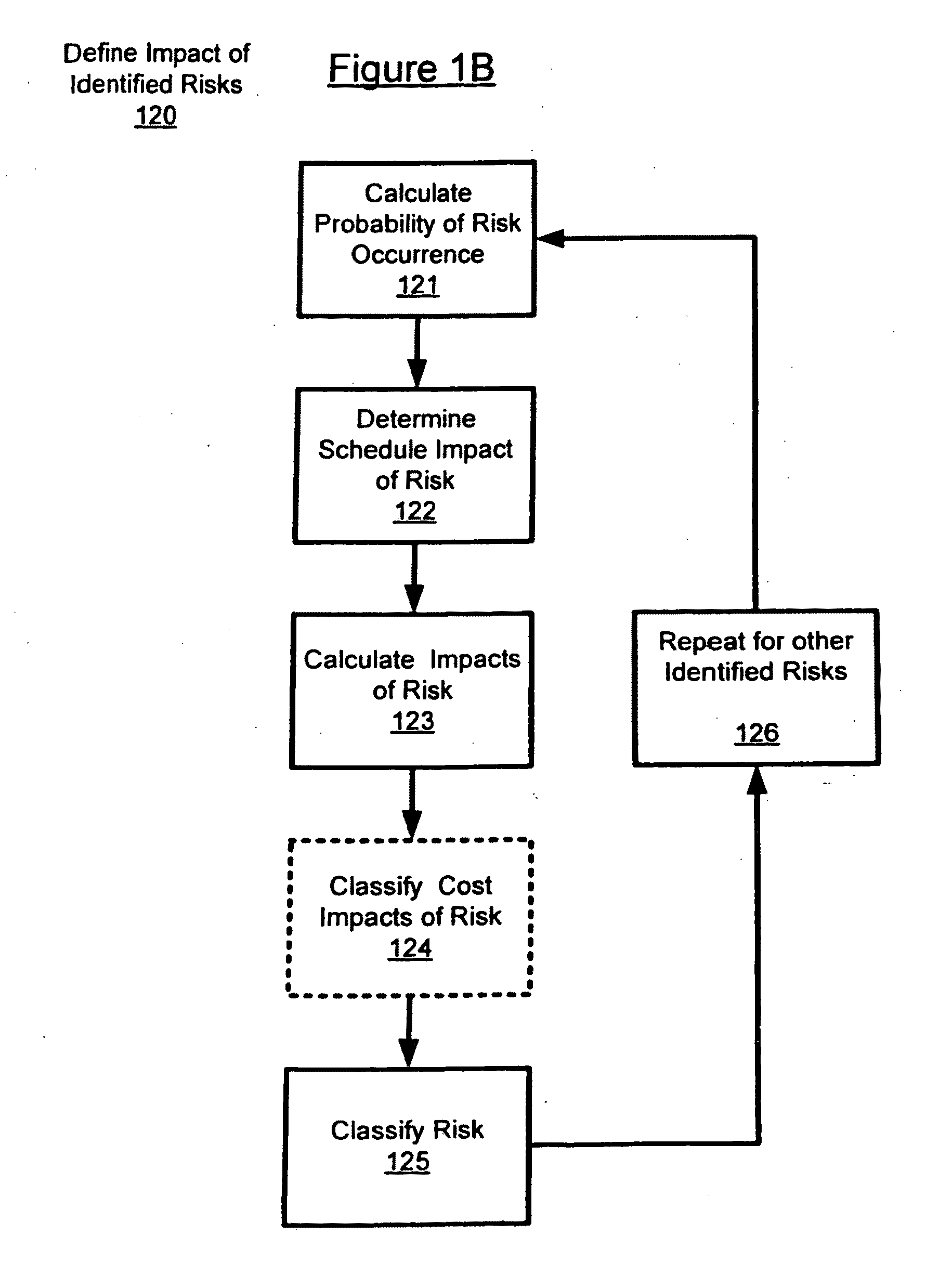
Semi-quantitative risk analysis
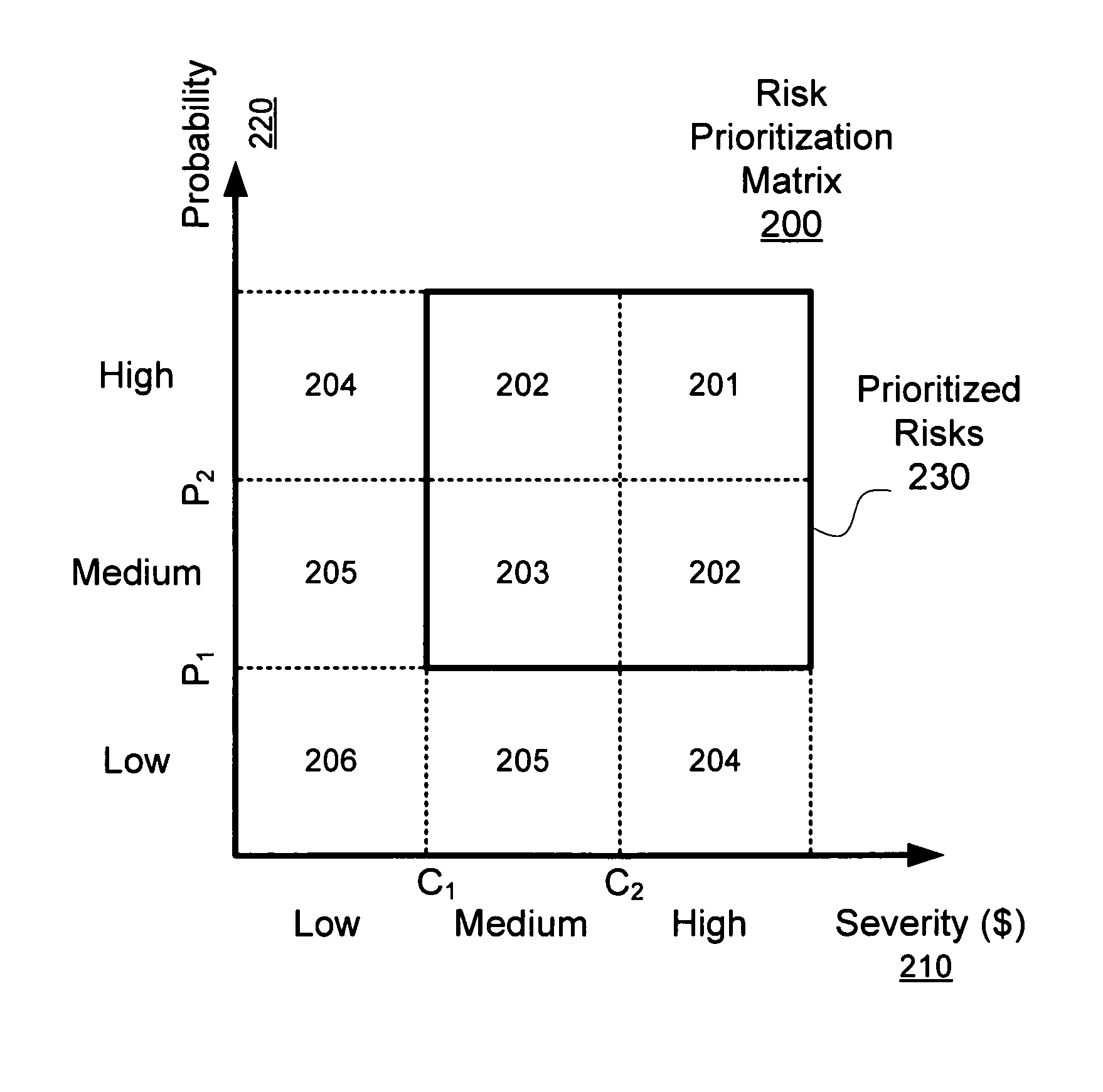
ActiveUS7769684B2Improve risk assessmentImprove productivityFinanceResourcesDecision makerManagement process
A semi-quantitative analysis on the risk management process increases the possibility of performing an accurate risks comparison, making easier the identification of which risks shall be prioritized and shall receive the greatest mitigation efforts. Specifically, the semi-quantitative risk analysis enables an improved risks comparison for evaluating the consequences of each risk considering its impacts on the project's Net Present Value (NPV), reflecting the project's cash flow at different times. The use of such method makes the prioritization process more efficient, helping the managers and other personnel involved on the process to focus their efforts to the most critical risks for the project's success. In this sense, the risk management process becomes more efficient and better able to provide better support to the project decision makers.
Owner:ACCENTURE GLOBAL SERVICES LTD
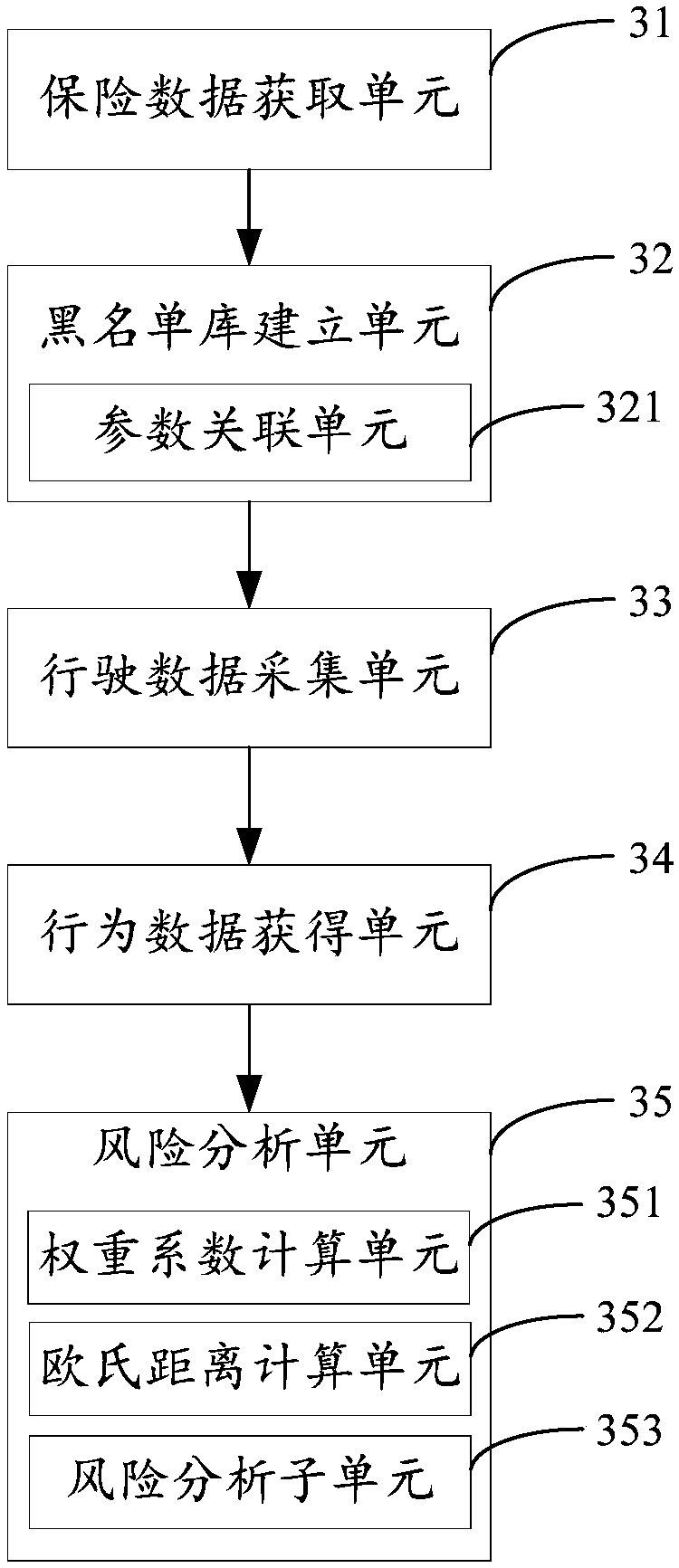
Driving behavior risk assessment method, device, equipment and storage medium
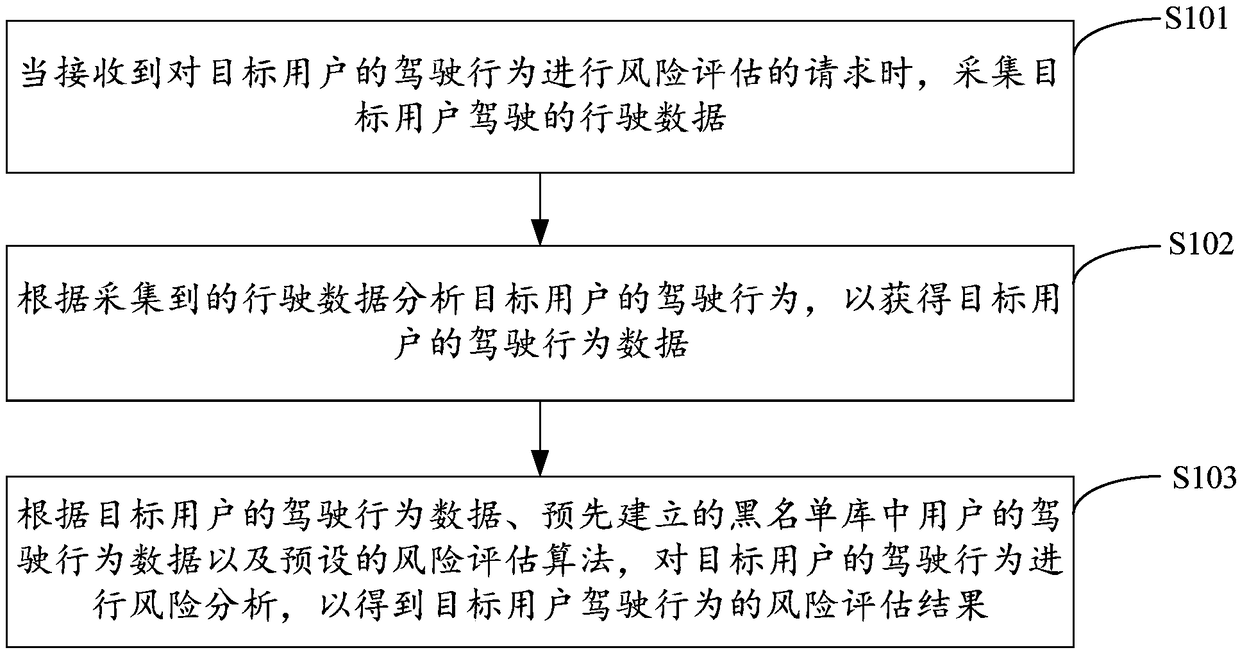
PendingCN108446824AImprove premium accuracyImprove risk assessmentFinanceResourcesData-drivenBlack list
The invention is applicable to the technical field of data processing, and provides a driving behavior risk assessment method, device, equipment, and a storage medium. The method comprises that when arequest for carrying out risk assessment on the driving behavior of the target user is received, acquiring the driving data driven by the target user; analyzing the driving behavior of the target user according to the acquired driving data so as to obtain the driving behavior data of the target user, according to the driving behavior data of the target user, the driving behavior data of a user ina pre-established blacklist library and a preset risk assessment algorithm, carrying out the risk analysis on the driving behavior of the target user to obtain the risk assessment result of the driving behavior of the target user, so that the risk assessment of the commercial insurance of the vehicle is more complete and scientific, and the insurance accuracy of the vehicle are further improved.
Owner:SHENZHEN SEG SCI NAVIGATIONS CO LTD
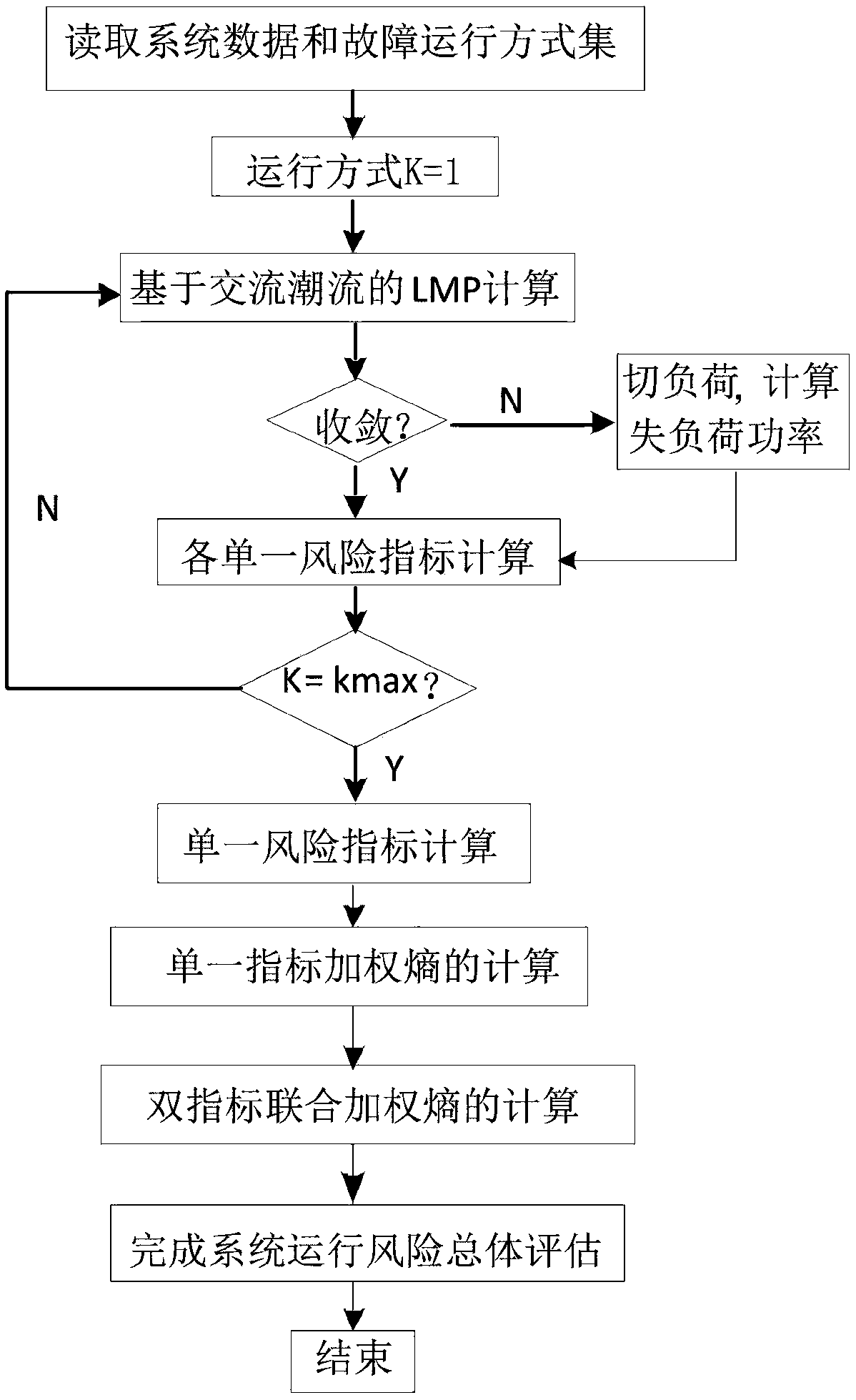
Power grid risk analysis method based on node marginal electricity prices
InactiveCN109636113AThe evaluation results are close to realityProtect interestsResourcesSystems intergating technologiesNODALElectricity price
The invention relates to a power grid risk analysis method based on a node marginal electricity price, and belongs to the field of power grids. The method calculates the marginal electricity price andthe output of the generator based on the original dual-point internal point method optimal power flow model, and solves the single risk evaluation index under the high-risk N-3 fault operation statethrough the nonlinear programming method, and further calculates the joint entropy index. Comprehensive risk assessment of the grid. The method uses the power load data of a city for one month to scanthe high-risk N-3 line fault scenario, so that the risk assessment can consider most of the possible situations, and the result is closer to reality; the comprehensive risk index solved includes thedouble index. Combined weighted entropy, this indicator takes into account the combined influence of power flow distribution, load loss and congestion severity on grid risk level and self-organized criticality, which makes up for the lack of individual indicator analysis.
Owner:GUIZHOU POWER GRID CO LTD
Systems and methods for identifying payor location based on transaction data
ActiveUS7783563B2Improve risk assessmentReduce riskFinanceMarketingInformation repositoryTransaction data
Systems and methods are described for building, maintaining, and using a repository of information about payors of second-party checks presented at a check-cashing entity for cashing. In various embodiments, the repository comprises stored information useful for determining the location of a payor of a second-party check. In one embodiment, information from the check that identifies an account on which the check is drawn, such as magnetic ink character recognition (MICR) line information from a paycheck, is used to access a repository of employer location information. In one embodiment, the payor location information is used to determine a proximity between the payor location and the check cashing entity location. In one embodiment, when a check is presented for which stored payor location information is not available, identifying information about the payor and / or the payor location is requested and is added to the repository.
Owner:FIRST DATA
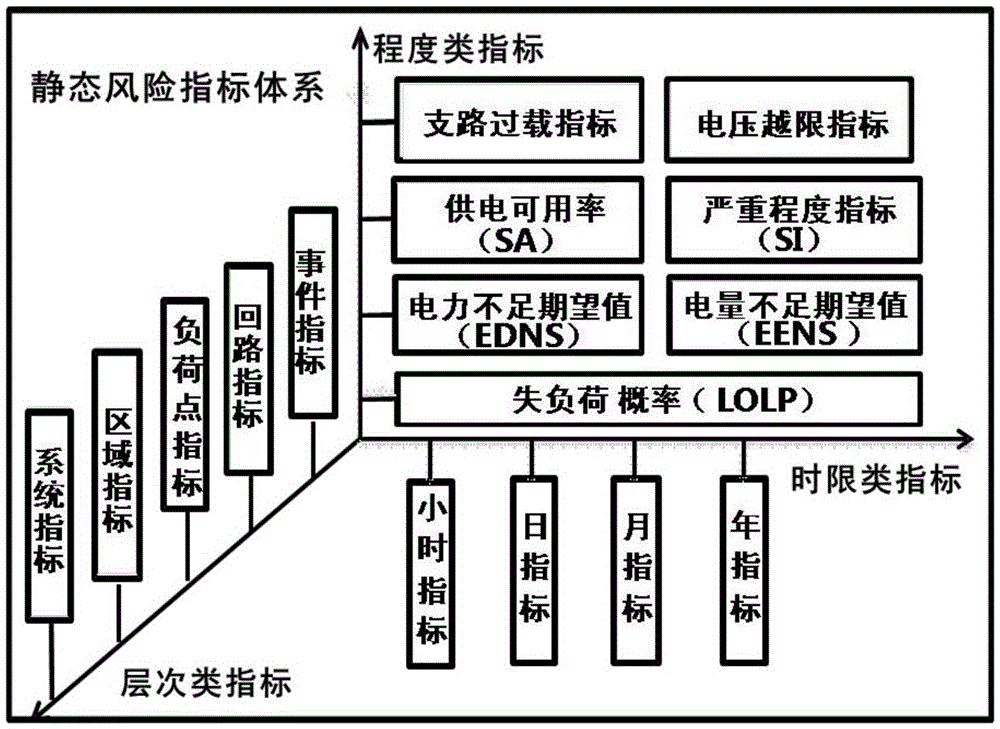
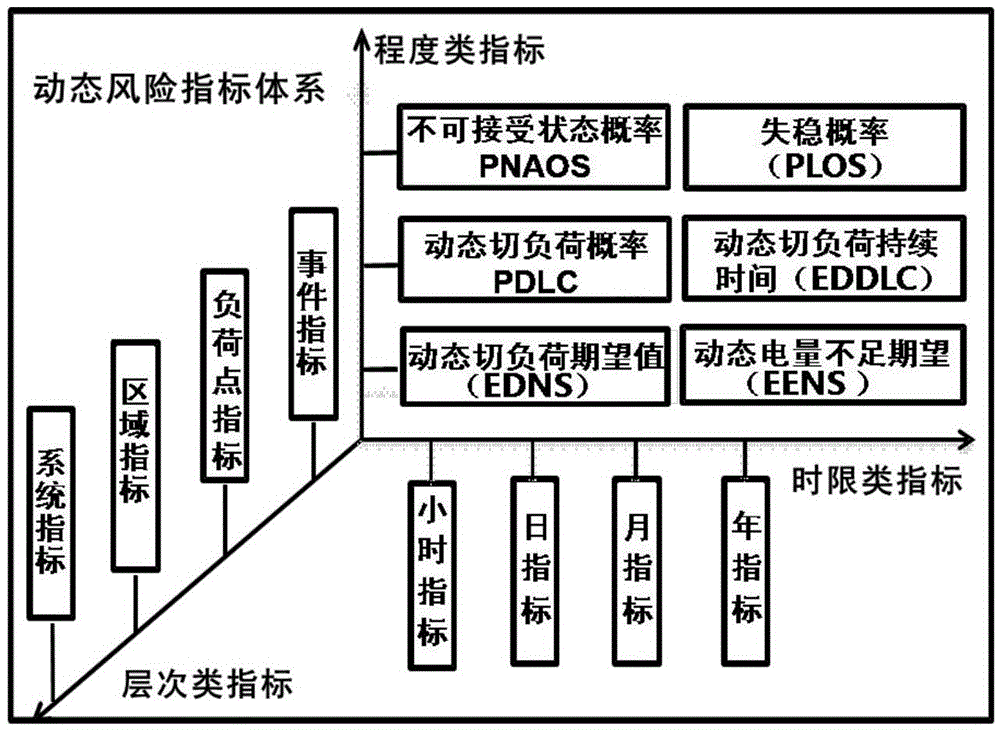
Risk evaluation method comprehensively taking regard of system adequacy and system security
InactiveCN106815770AImprove risk assessmentStart fastData processing applicationsTransient stateSource Data Verification
The invention relates to a risk evaluation method comprehensively taking regard of system adequacy and system security. The method comprises steps that an evaluation object is determined; data verification is carried out; static and transient total fault intelligent scanning for a power grid is respectively carried out; risk evaluation is carried out; risk evaluation indexes are determined. The method is advantaged in that static risk evaluation based on static safety analysis and dynamic risk evaluation based on transient stabilization are realized, evaluation and analysis are more comprehensively carried out, a convenient operation mode and form display are provided for a user, and the method is mainly utilized to serve power grid operation mode, programming, scheduling and national security quality supervision departments.
Owner:CHINA ELECTRIC POWER RES INST +2
Risk assessment method based on consumption loan scene, and system implementation
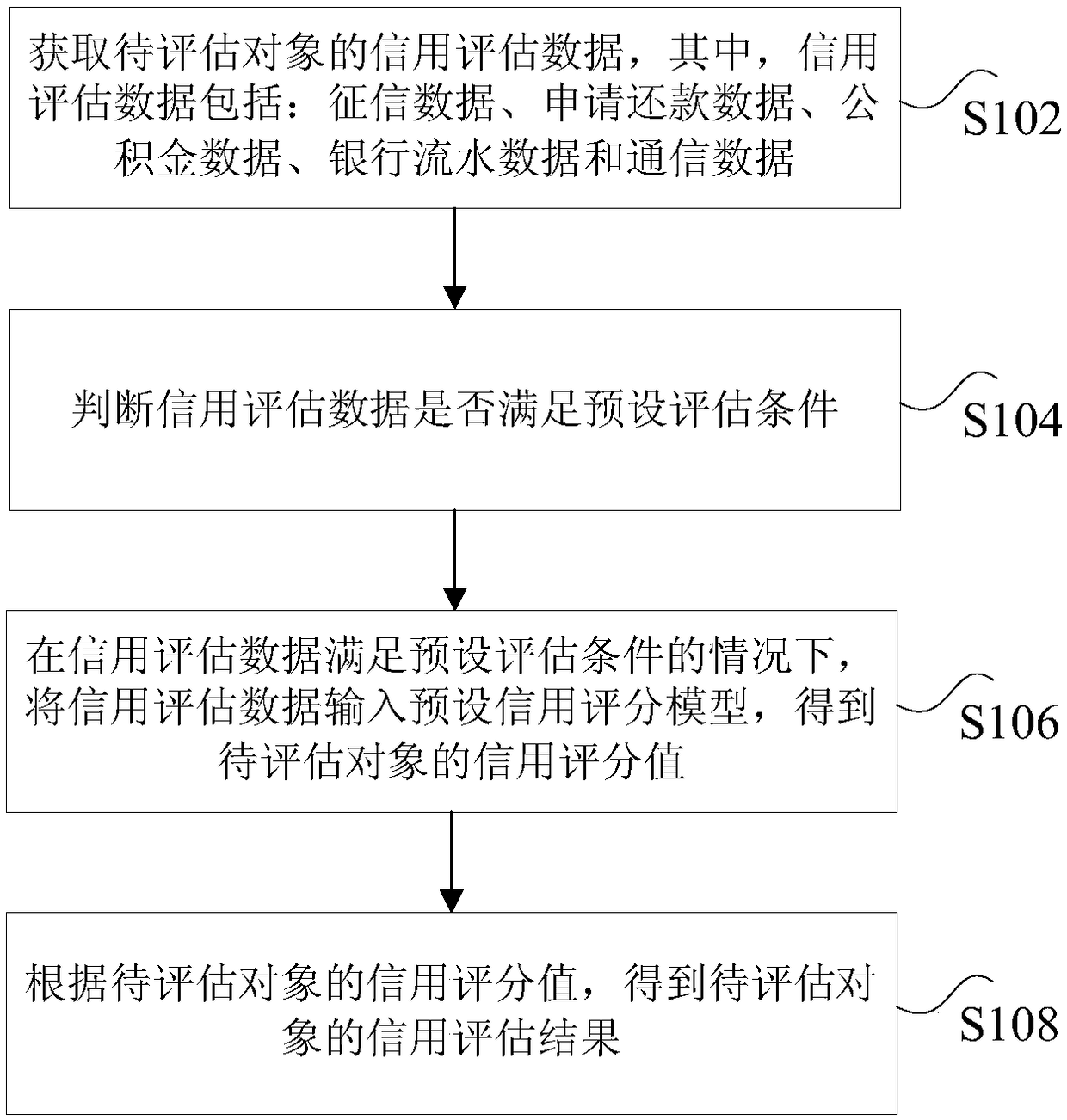
The invention discloses a risk assessment method based on a consumption loan scene, and system implementation. The method comprises the steps: obtaining credit assessment data of a to-be-assessed object, wherein the credit assessment data comprises credit data, application repayment data, accumulation fund data, account statement data, and communication data; judging whether the credit assessmentdata meets a preset assessment condition or not; inputting the credit assessment data into a preset credit scoring model under the condition that the credit assessment data meets the preset assessmentcondition, and obtaining a credit score of the to-be-assessed object, wherein the credit score is used for representing the income state and consumption capability of the to-be-assessed object; and obtaining a credit assessment result of the to-be-assessed object according to the credit score of the to-be-assessed object. The method solves a technical problem that the single assessment dimensionof a risk assessment method of a consumption load scene causes the low accuracy of an assessment result in the prior art.
Owner:广州越秀金融科技有限公司
Electronic monitoring system and electronic monitoring method based on active-passive fusion
ActiveCN106548251ARealize three-dimensional supervisionMeet needsForecastingMarine craft traffic controlOriginal dataElectron
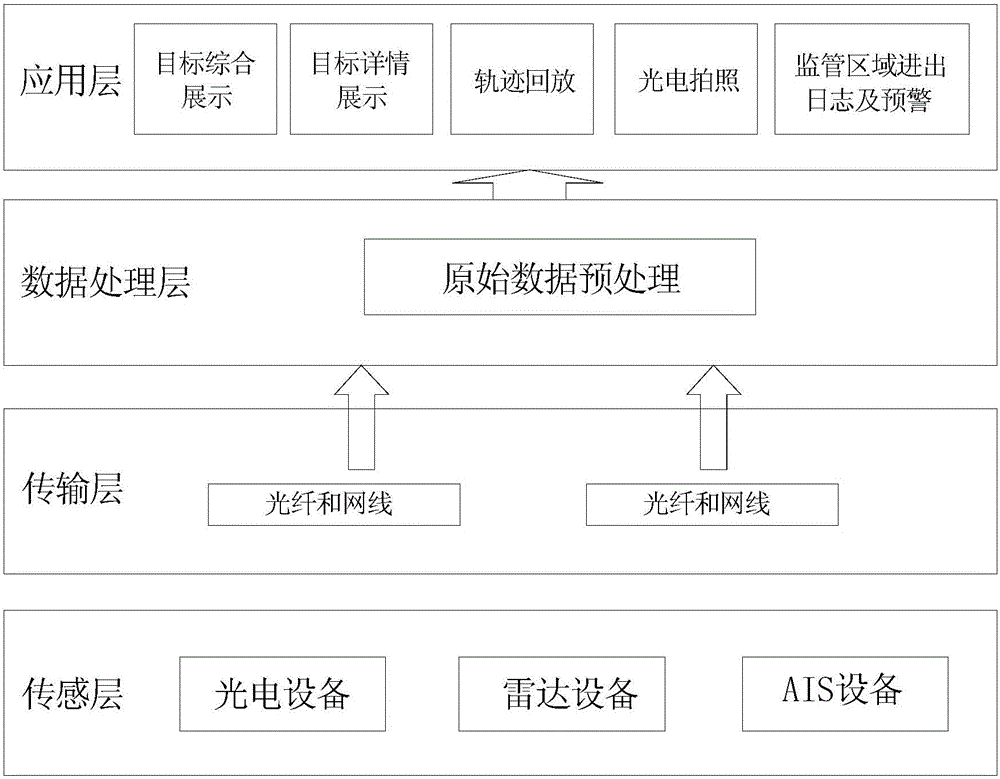
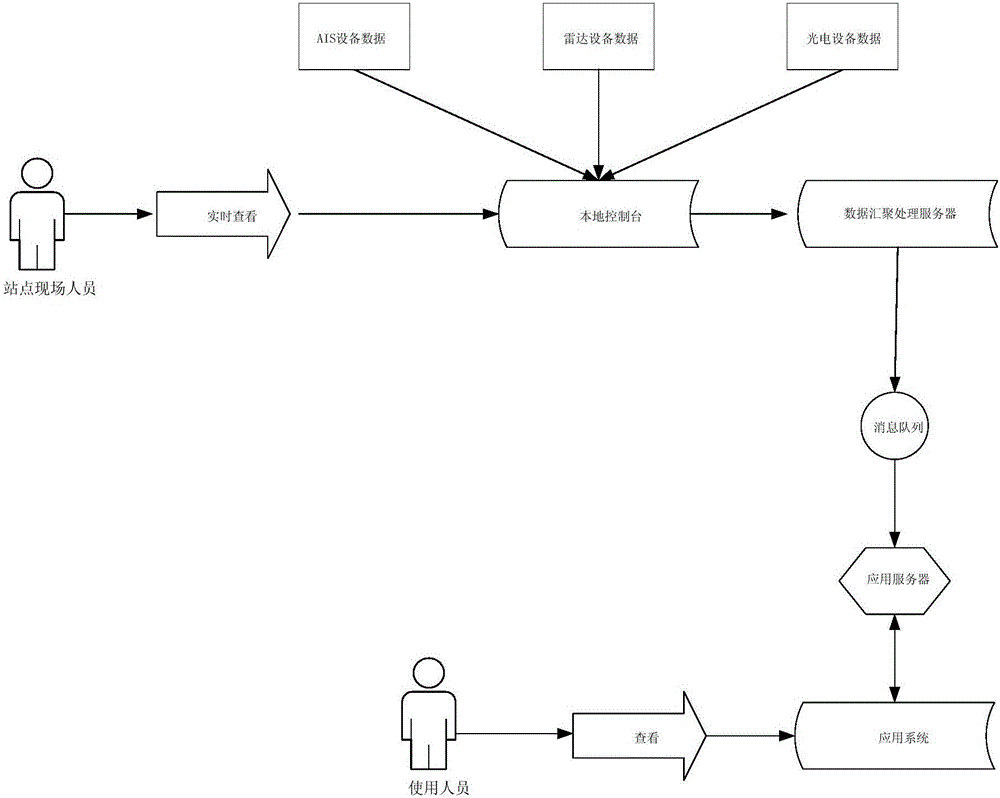
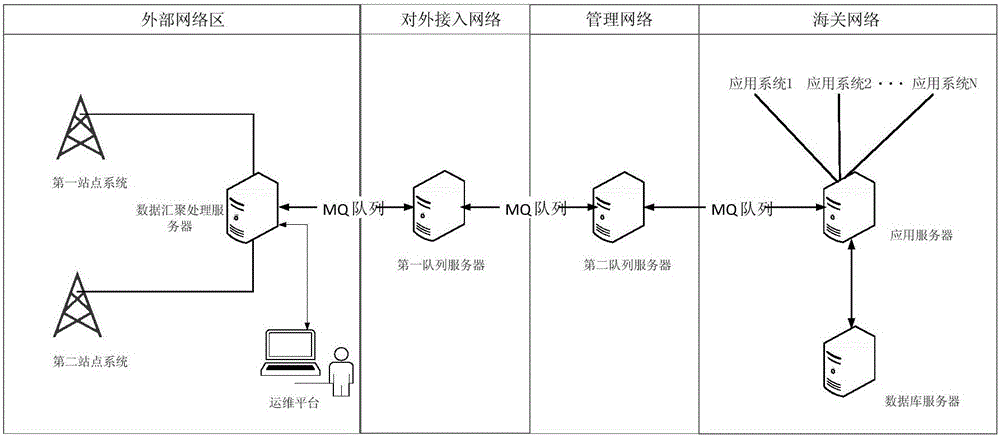
The invention discloses an electronic monitoring system and an electronic monitoring method based on active-passive fusion. The system comprises a sensing layer, a transport layer, a data processing layer, and an application layer. The sensing layer is used for collecting signals of a target through AIS equipment, radar equipment and photovoltaic equipment and converting the signals collected by the AIS equipment, the radar equipment and the photovoltaic equipment into original data. The transport layer is used for performing data exchange and command communication and transmitting the original data converted by the sensing layer to the data processing layer through an optical fiber and a network. The data processing layer is used for preprocessing the original data converted by the sensing layer and storing the data in a database to provide a source data support for the application layer. The application layer is used for realizing comprehensive display and detailed display of the target. A powerful support and a decision aid are provided for customs logistics monitoring and vehicle regulation. Pilot construction is implemented from the angle of filling the customs technology gap and innovating the technology application.
Owner:GUANGDONG SOUTHERN COAST TECHNOLOGY SERVICE CO LTD
System and method for providing enterprise wide data security
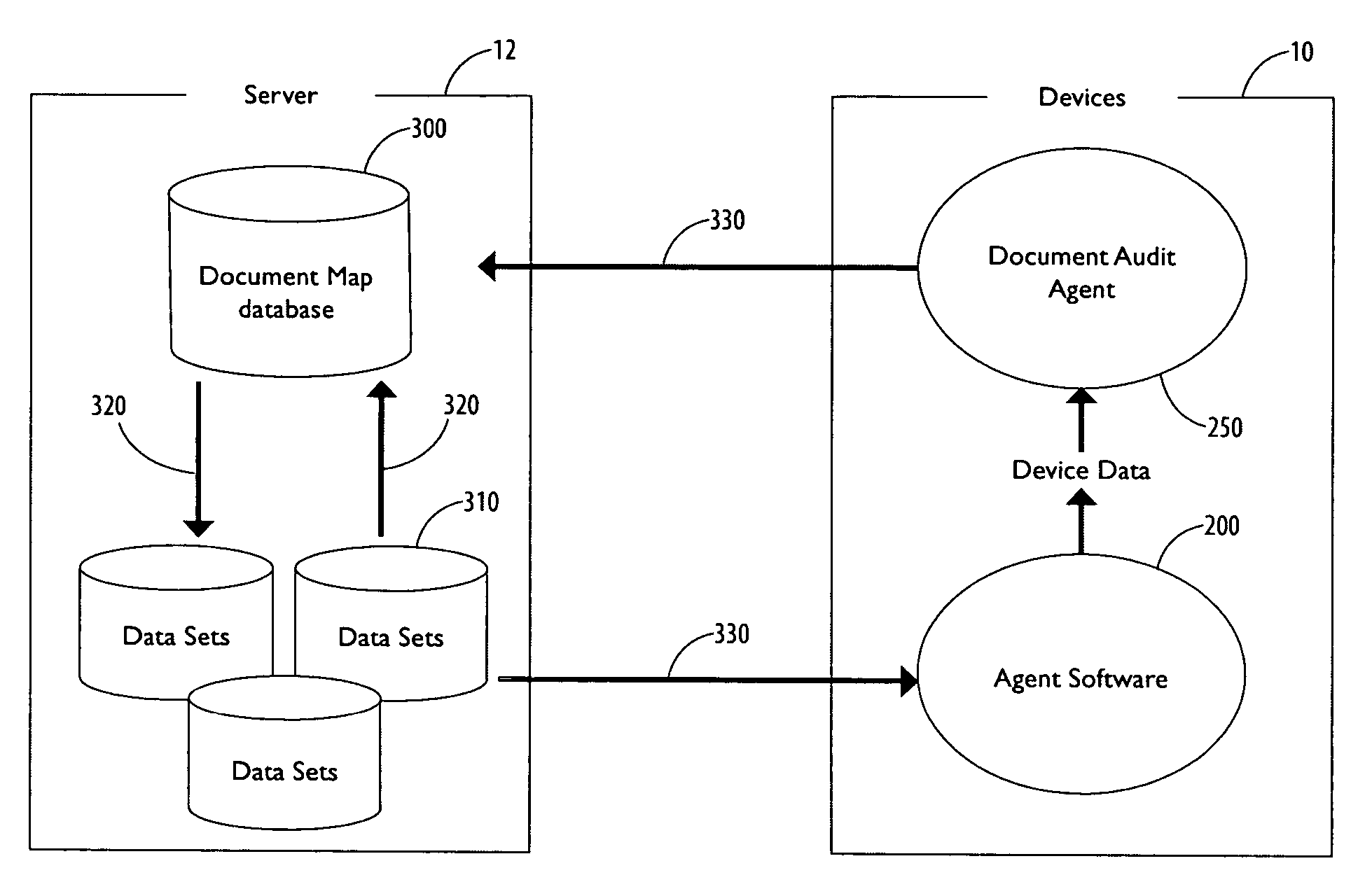
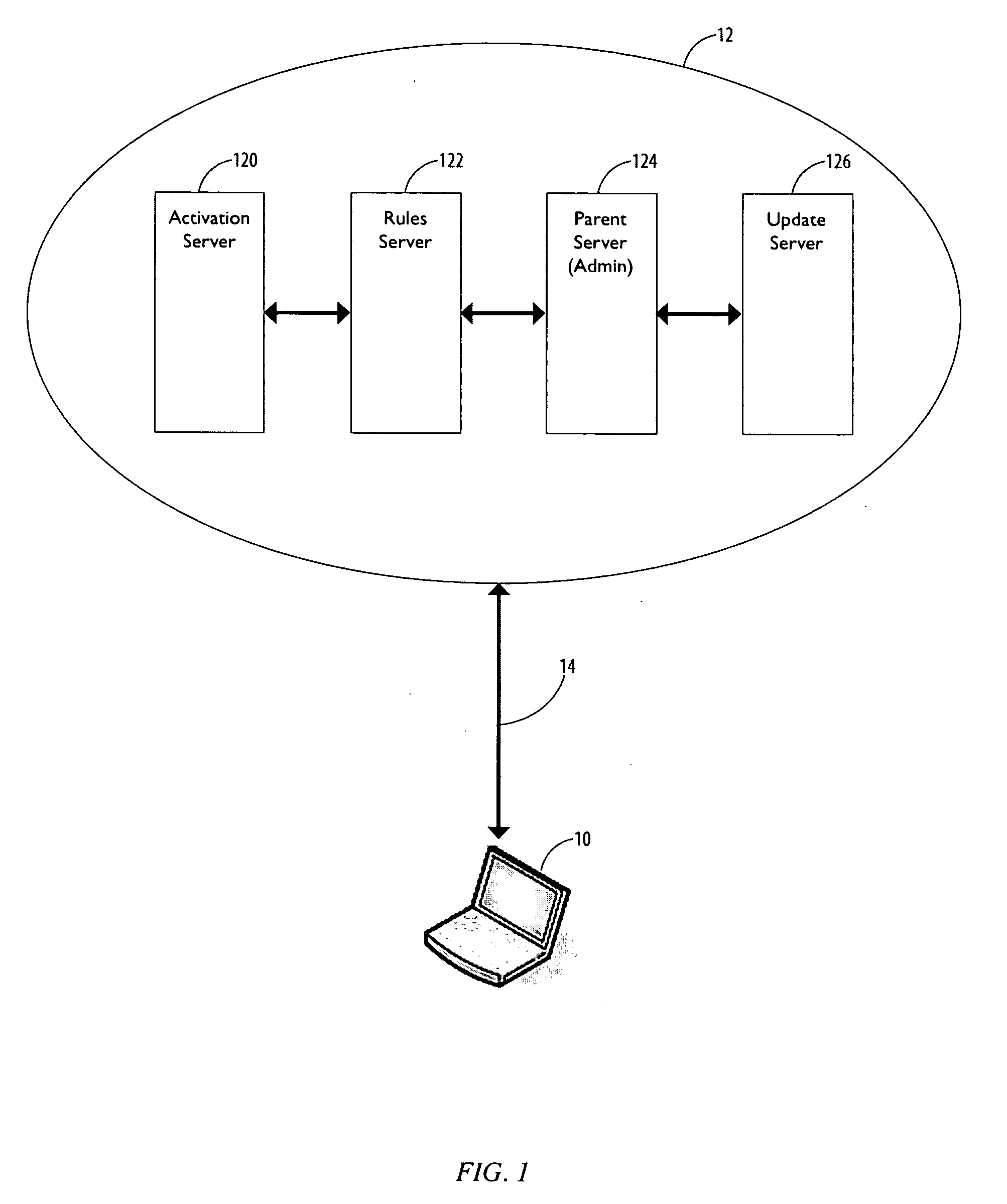
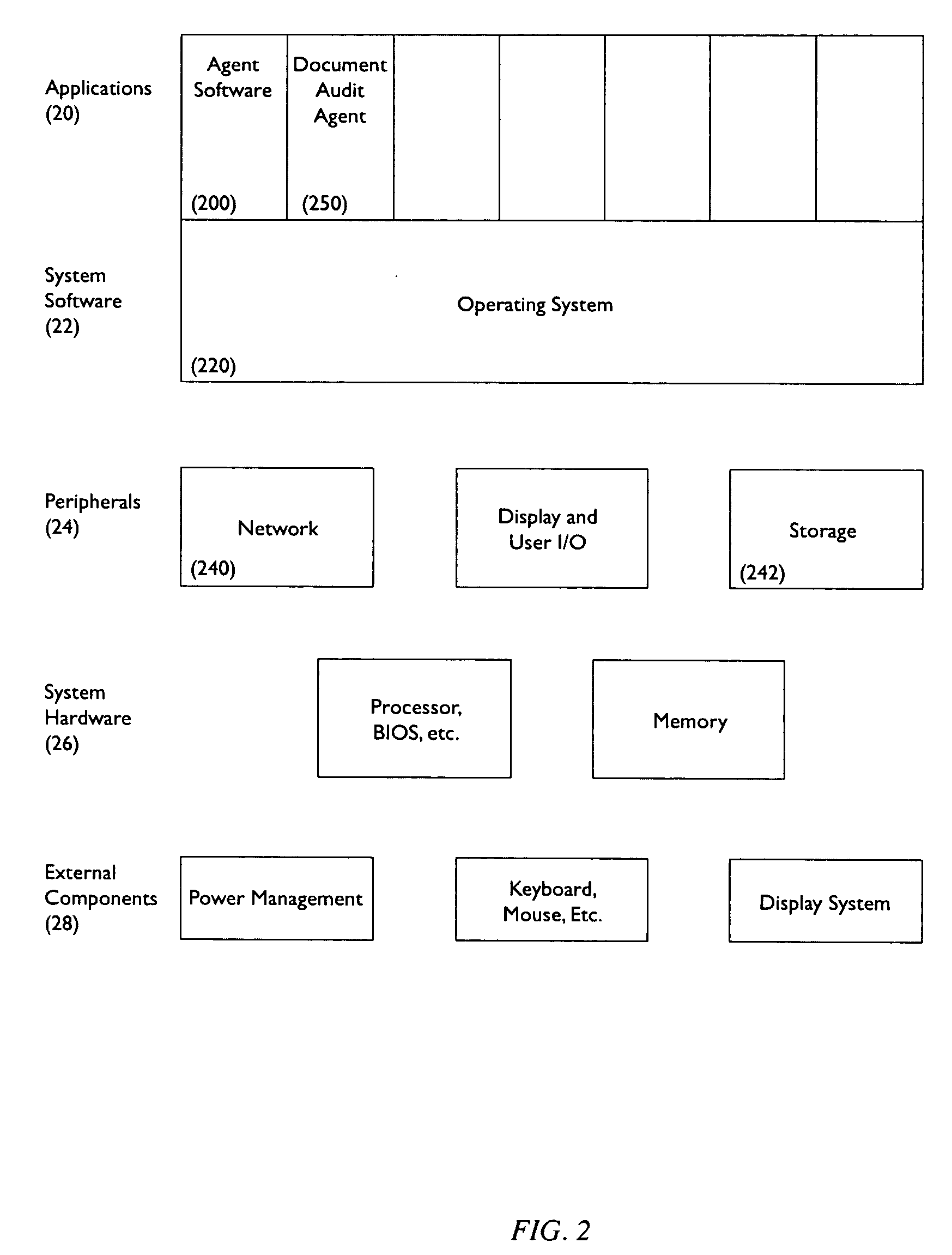
InactiveUS20060238802A1Improve risk assessmentGreat disclosureComputer security arrangementsDigital output to print unitsData setPaper document
A system of securing data stored on a portable electronic device and an associated method are disclosed. The system includes a server machine coupled to the portable electronic device, the server machine comprising a plurality of data sets adaptively coupled to a document map database, the document map database storing a document catalog provided by a document audit agent residing on the portable electronic device, the portable electronic device further comprising a rules agent operable to execute security rules associated with each of the plurality of data sets.
Owner:HANAY JOHN W +3
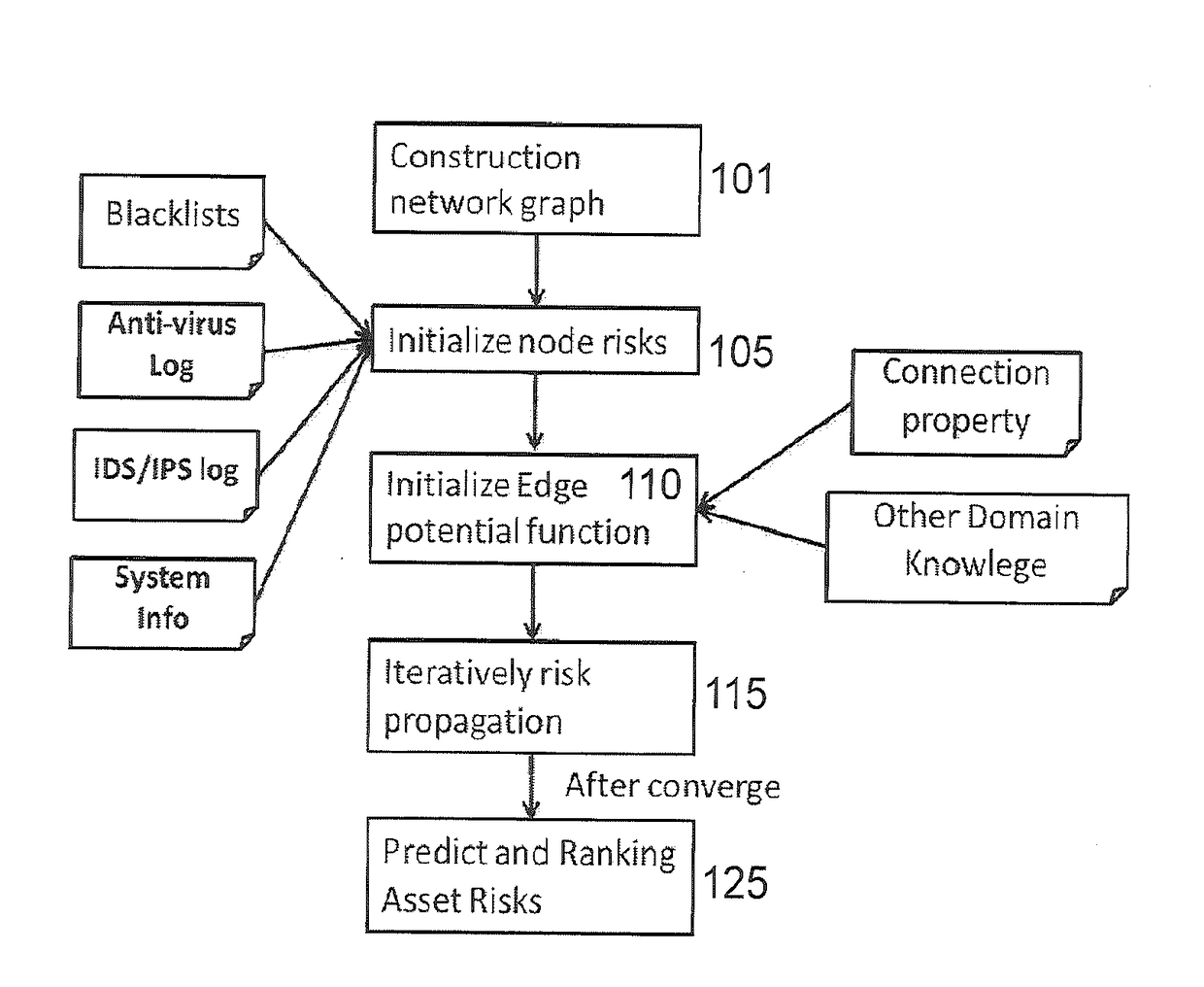
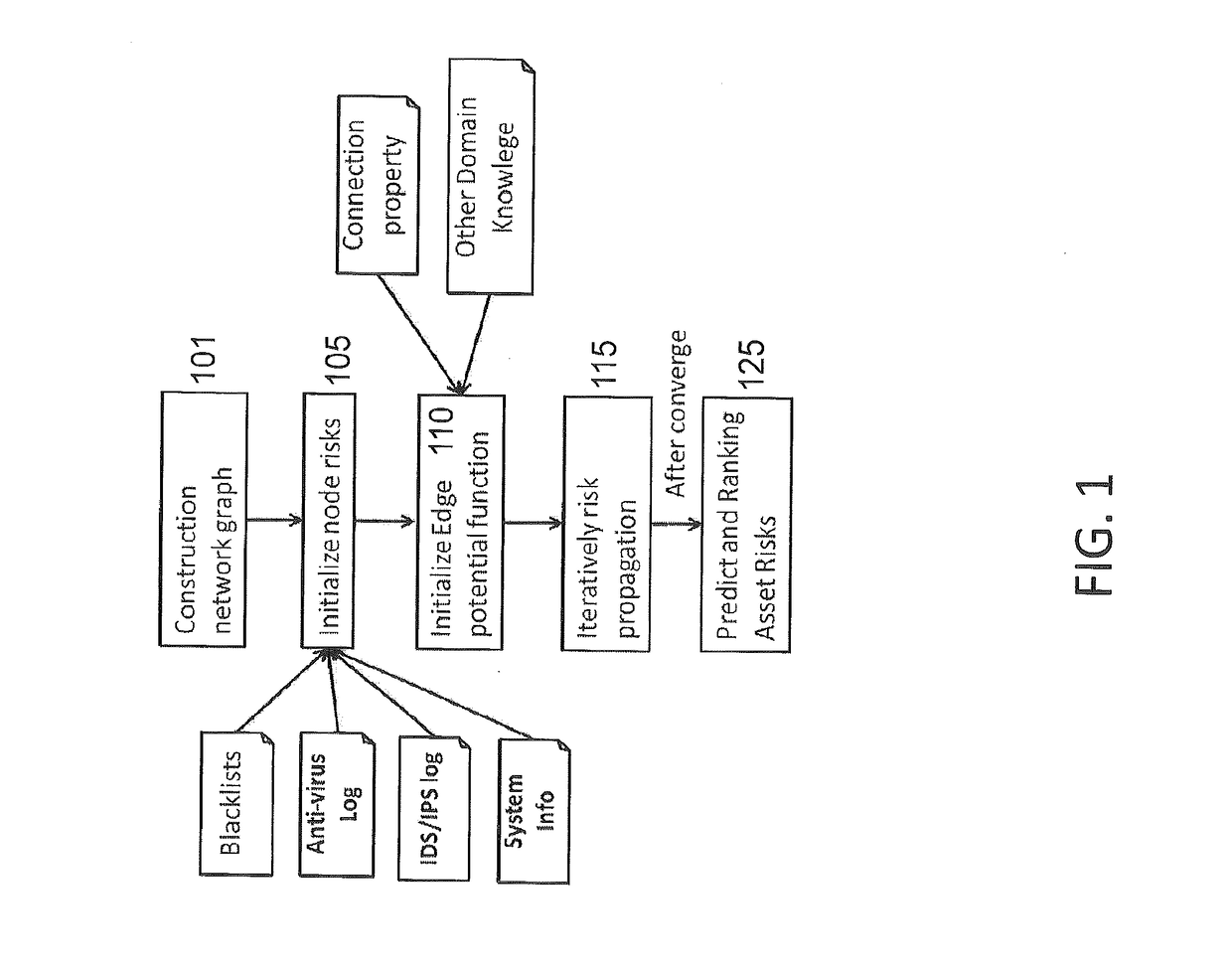
Cognitive scoring of asset risk based on predictive propagation of security-related events
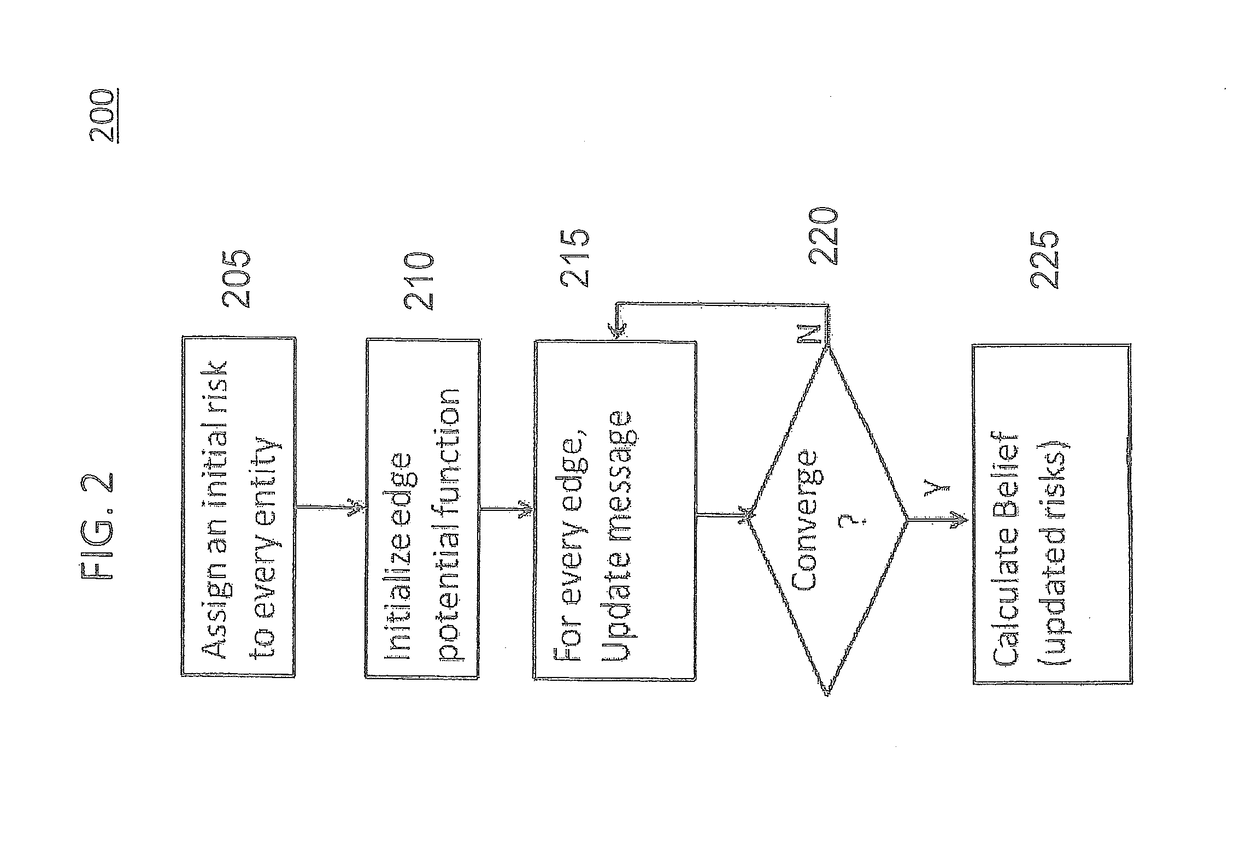
InactiveUS20180285797A1Improve risk assessmentEfficient disseminationResourcesAlgorithmBelief propagation
A method (and system) of scoring asset risk including modeling an interdependence of risks of a plurality of entities within a network by modeling the network as a graph connecting different entities, the different entities are selected from a group of a user, a device, a credential, a high-value asset, and an external server, the graph being defined as a set of vertices comprising the user, the device, the credential, the high-value asset, and the external server and a set of edges represented by an N-by-N adjacency matrix with each pair of the entities sharing a relationship and applying a Belief Propagation (BP) algorithm for solving the inference problem over the graph by inferring the risk from the entities own properties and surrounding entities with the shared relationship in the adjacency matrix, the Belief Propagation algorithm obtains risk information related to each entity of the plurality of entities.
Owner:IBM CORP
Individualized disease risk level analyzing method based on conventional factor
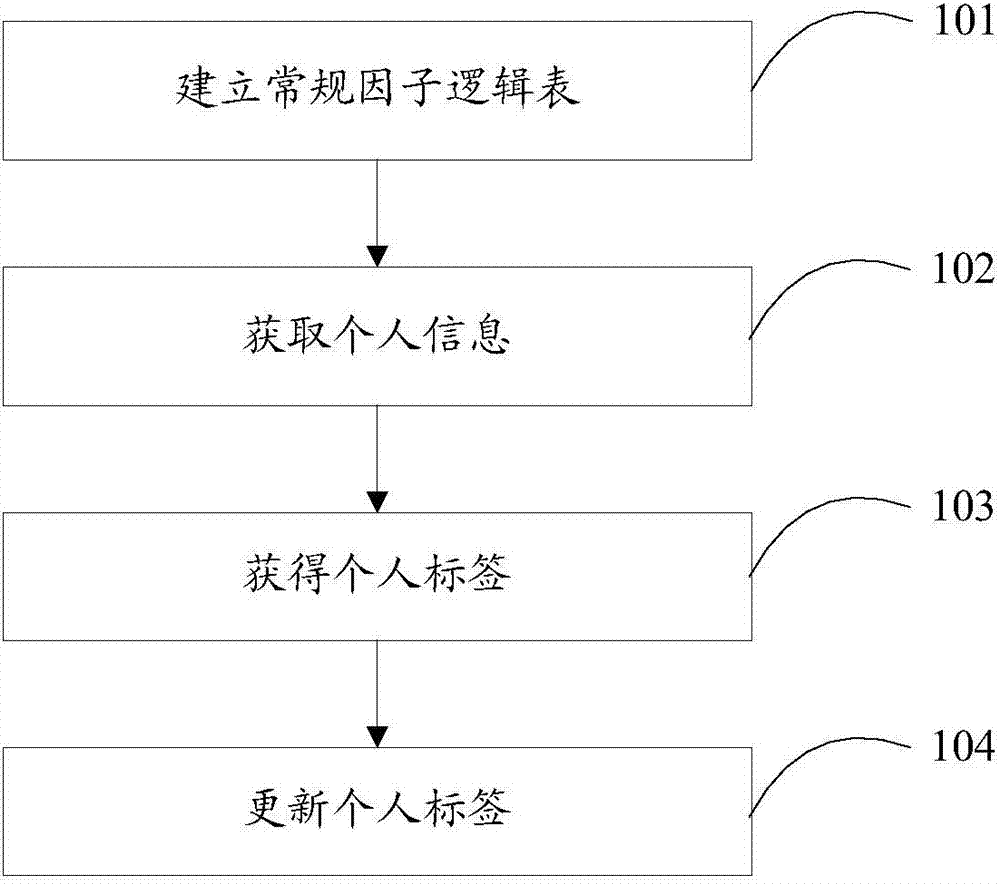
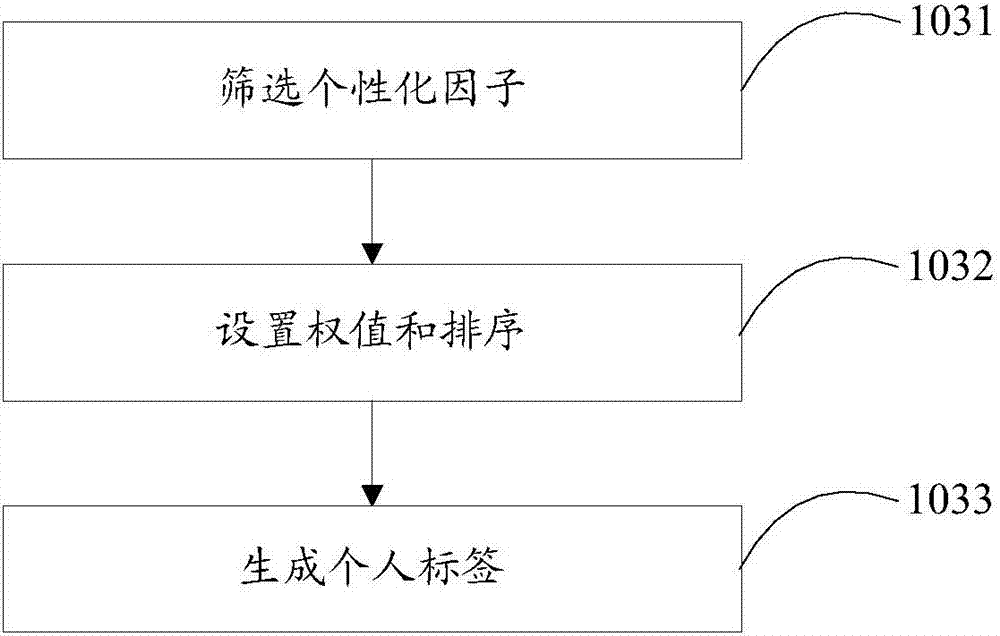
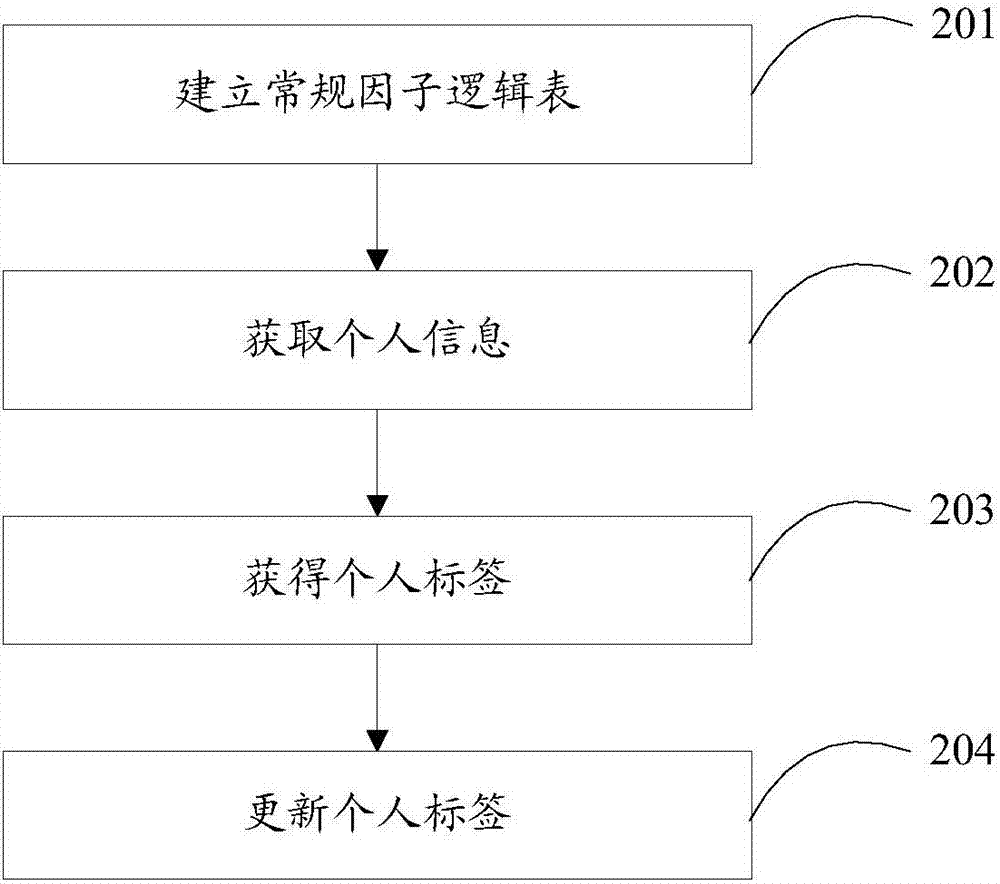
InactiveCN107301326AThe result is accurateResults and real-timeSpecial data processing applicationsMedical emergencyPersonalization
The invention discloses an individualized disease risk level analyzing method based on a conventional factor. The method comprises the following steps: establishing a conventional factor logic table according to medical information and big data information and adjusting in real time according to the update of the medical information and / or the big data information; obtaining personal information; screening out individualization factors and setting weights thereof; sorting the individualization factors according to the weights to obtain a personal label, wherein the personal label comprises an initial disease group, and the initial disease group comprises at least one disease name and a risk level corresponding to the disease name; obtaining personal updated information and obtaining a personal updated label according to the personal updated information, wherein the personal updated label comprises an updated disease group, and the updated disease group comprises at least one disease name and a risk level corresponding to the disease name; when the updated disease group and the initial disease group comprise the same disease name, the updated disease group comprises the change trend of the same disease name. The method disclosed by the invention has relatively high individuality and real-time property and higher accuracy.
Owner:北斗云谷(北京)科技有限公司
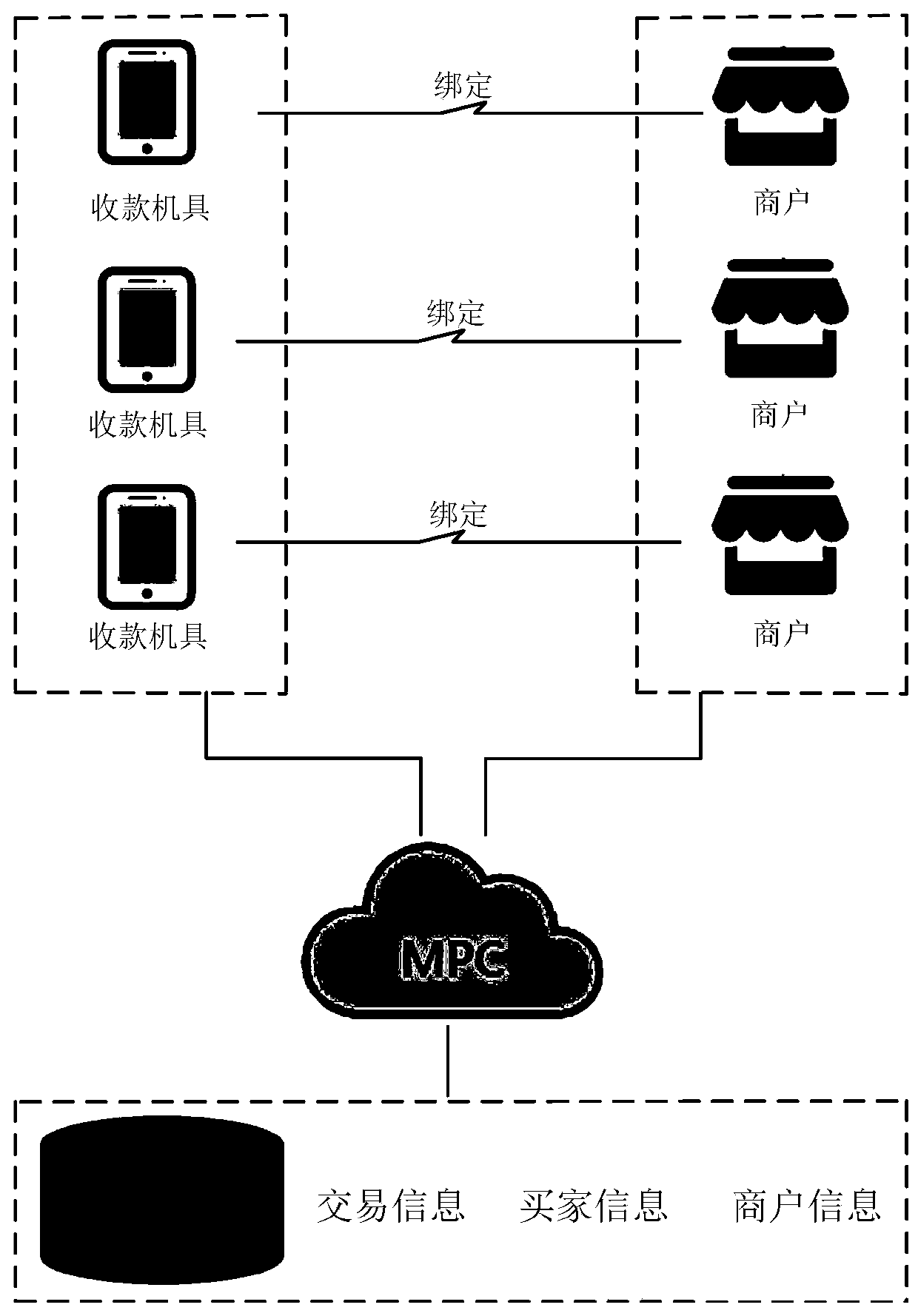
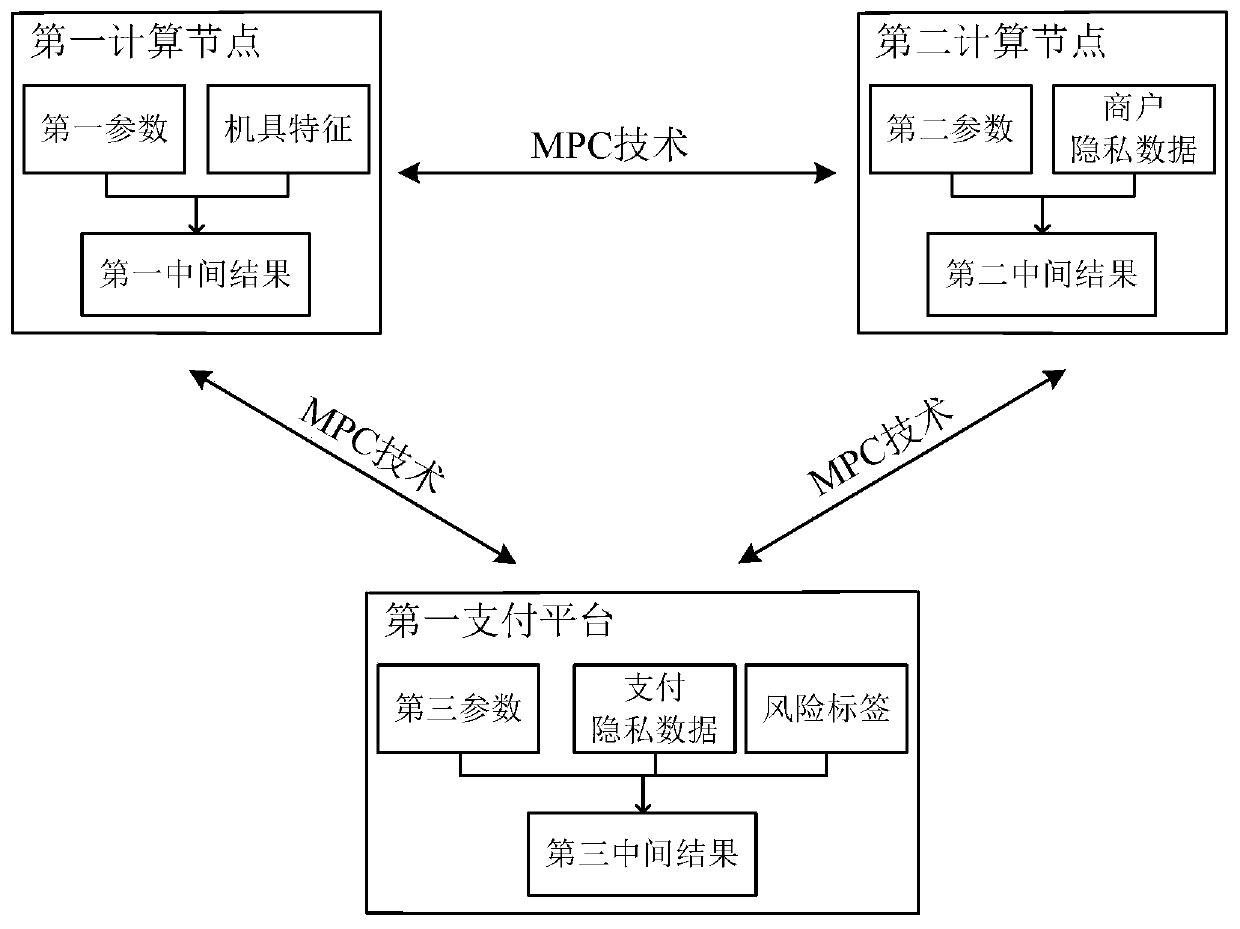
Method and device for multi-party joint training of risk assessment model for IoT machine
The embodiment of the invention provides a method for multi-party joint training of a risk assessment model for an IoT machine. The multiple parties comprise a machine end computing node, a merchant end computing node and a payment platform computing node which are used for respectively storing machine privacy data of a plurality of machines, binding merchant privacy data of a plurality of merchants of the plurality of machines and payment privacy data related to the plurality of merchants, and respectively maintaining partial parameters in the risk assessment model. In addition, the payment platform computing node also stores a machine risk tag. According to the method, a machine tool end computing node and a merchant end computing node determine an intermediate computing result based onstored private data and maintained partial parameters, and a payment platform computing node computes the intermediate computing result based on the stored private data, the maintained partial parameters and labels. And then, the three parties provide respective calculated intermediate calculation results based on a secure multi-party calculation MPC technology, determine training loss, and then respectively adjust partial maintained model parameters.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Database security risk assessment system
ActiveCN113505371AMaintain accuracyAbility to assessCharacter and pattern recognitionPlatform integrity maintainanceDatabase securityWeb server
The invention discloses a database security risk assessment system. The system comprises a risk assessment engine, a server-side SQL (Structured Query Language) abnormal risk assessment module, an intranet node SQL abnormal risk assessment module, a basic risk assessment module, a vulnerability library and a historical assessment recording module, the risk assessment engine is used for scheduling the server-side SQL exception risk assessment module, the intranet node SQL exception risk assessment module and the basic risk assessment module and respectively executing server-side SQL exception risk assessment of the first round, intranet node SQL exception risk assessment of the second round and basic risk assessment of the last round, the vulnerability library is used for storing known database vulnerabilities and web server vulnerability, and the historical assessment recording module is used for storing evaluation history record data. According to the system, database security risk assessment is more comprehensive and objective.
Owner:SICHUAN UNIV
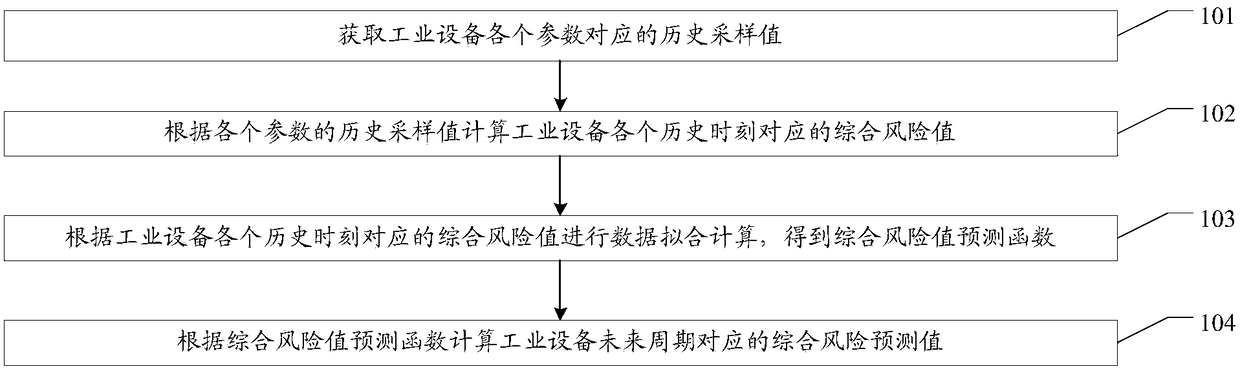
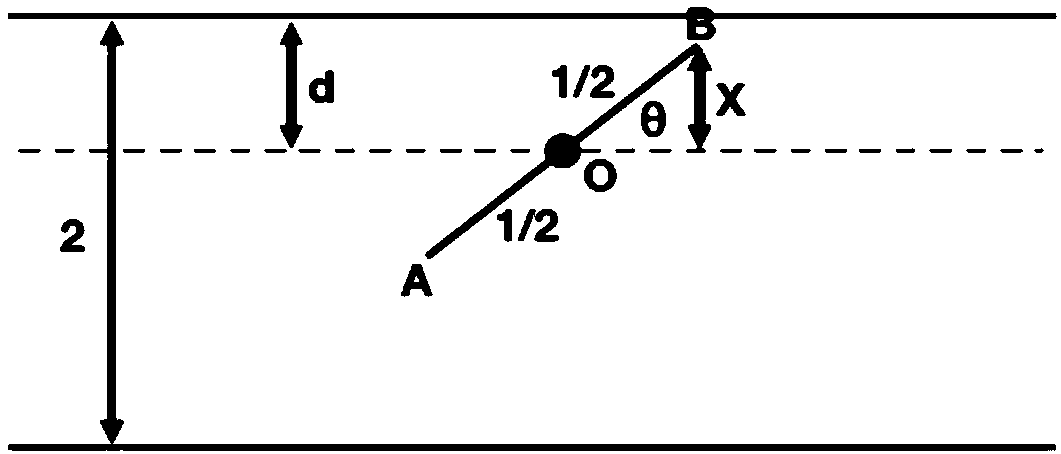
Industrial equipment risk analysis method, system and related equipment
ActiveCN109284908AImprove risk assessmentImprove reliabilityResourcesIndustrial equipmentAnalysis method
An embodiment of the present invention provides an industrial equipment risk analysis method, system, and related equipment for synthetically predicting a comprehensive risk value and a probability ofa risk occurrence of an industrial equipment in combination with one or more parameter indices. The method of the embodiment of the invention comprises the following steps: acquiring the historical sampling values corresponding to each parameter of the industrial equipment; calculating a comprehensive risk value corresponding to each historical moment of the industrial equipment according to thehistorical sampling value of each parameter; carrying out data fitting calculation according to the comprehensive risk value corresponding to each historical time of the industrial equipment, and obtaining a comprehensive risk value prediction function; calculating a comprehensive risk prediction value corresponding to a future cycle of the industrial equipment according to the comprehensive riskprediction function.
Owner:MIXLINKER NETWORKS INC
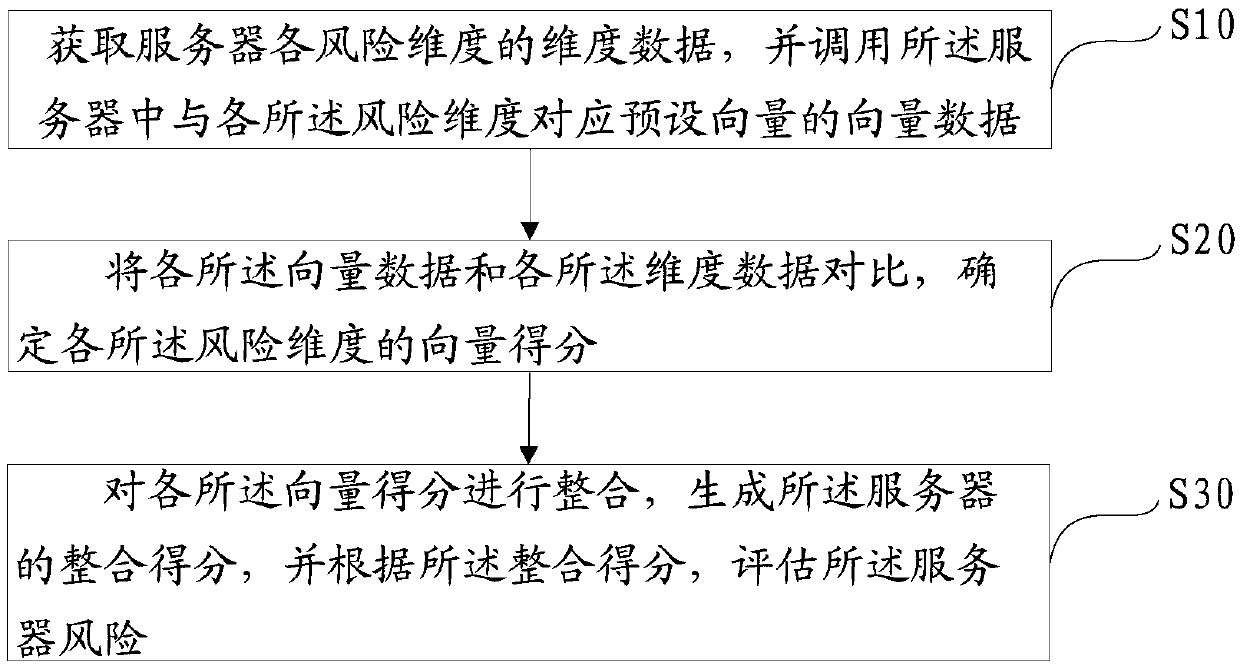
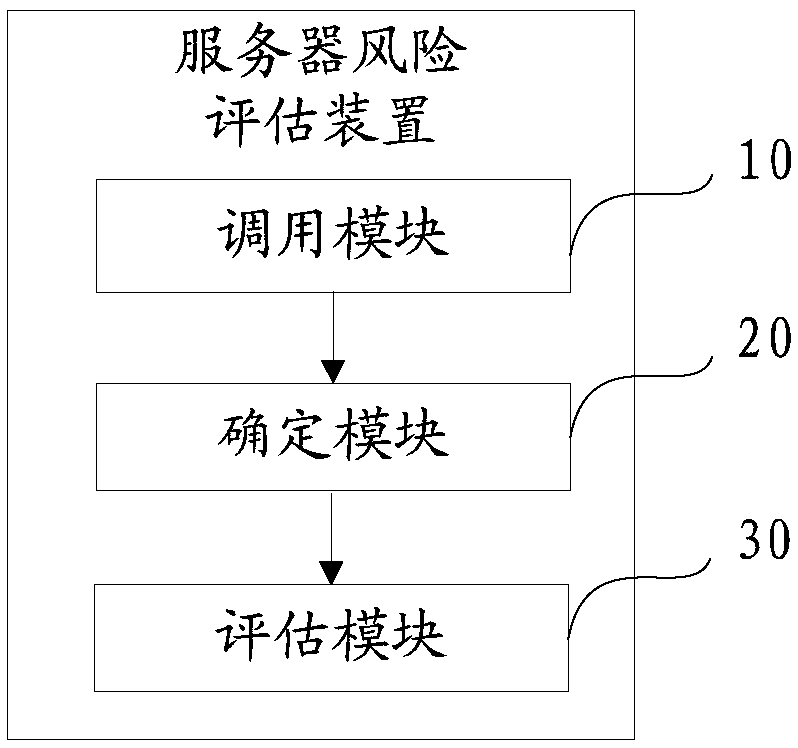
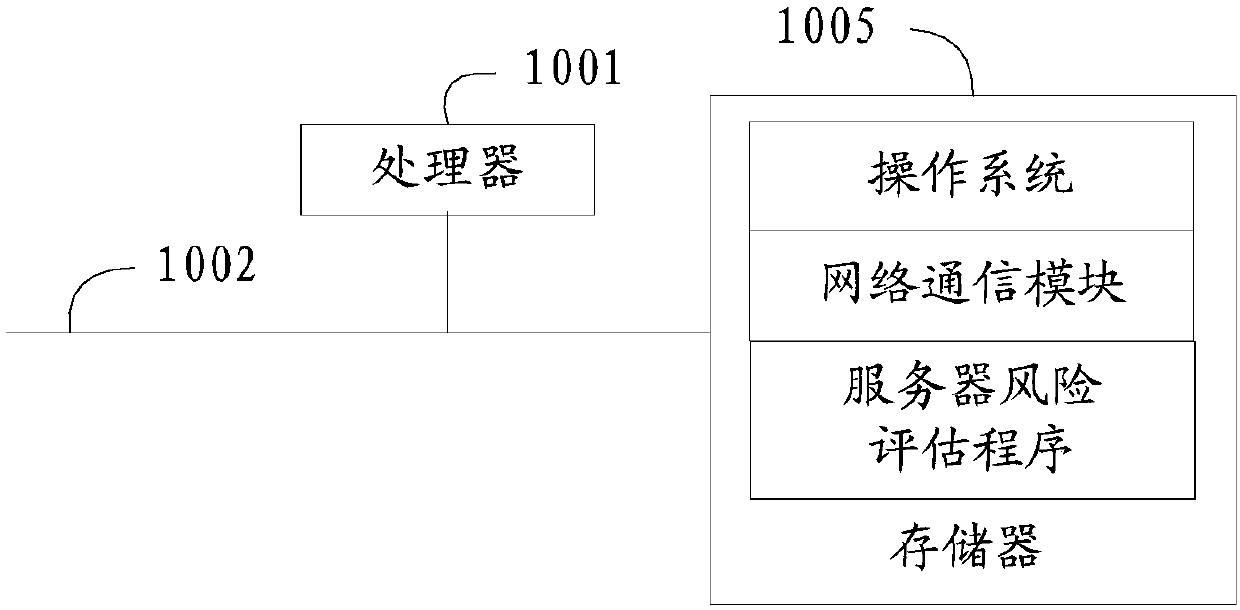
Server risk assessment method, device and equipment and computer readable storage medium
PendingCN109670314AImprove risk assessmentImprove accuracyPlatform integrity maintainanceResourcesComputer scienceRisk assessment
The invention discloses a server risk assessment method, device and equipment and a computer readable storage medium, and the method comprises the steps of obtaining the dimension data of each risk dimension of a server, and calling the vector data of a preset vector corresponding to each risk dimension in the server; comparing the vector data with the dimension data, and determining a vector score of each risk dimension; and integrating the vector scores to generate an integrated score of the server, and evaluating the server risk according to the integrated score. According to the scheme, the risk of dimension data reflecting all aspects of the server is evaluated through a plurality of preset vectors, and an integrated score is generated; and the overall risk of the server is evaluatedaccording to the integration score, so that the risk evaluation of the server is more comprehensive, and the risk evaluation accuracy is improved to ensure that each information asset in the server isin a safe environment.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Semi-quantitative risk analysis
A semi-quantitative analysis on the risk management process increases the possibility of performing an accurate risks comparison, making easier the identification of which risks shall be prioritized and shall receive the greatest mitigation efforts. Specifically, the semi-quantitative risk analysis enables an improved risks comparison for evaluating the consequences of each risk considering its impacts on the project's Net Present Value (NPV), reflecting the project's cash flow at different times. The use of such method makes the prioritization process more efficient, helping the managers and other personnel involved on the process to focus their efforts to the most critical risks for the project's success. In this sense, the risk management process becomes more efficient and better able to provide better support to the project decision makers.
Owner:ACCENTURE GLOBAL SERVICES LTD
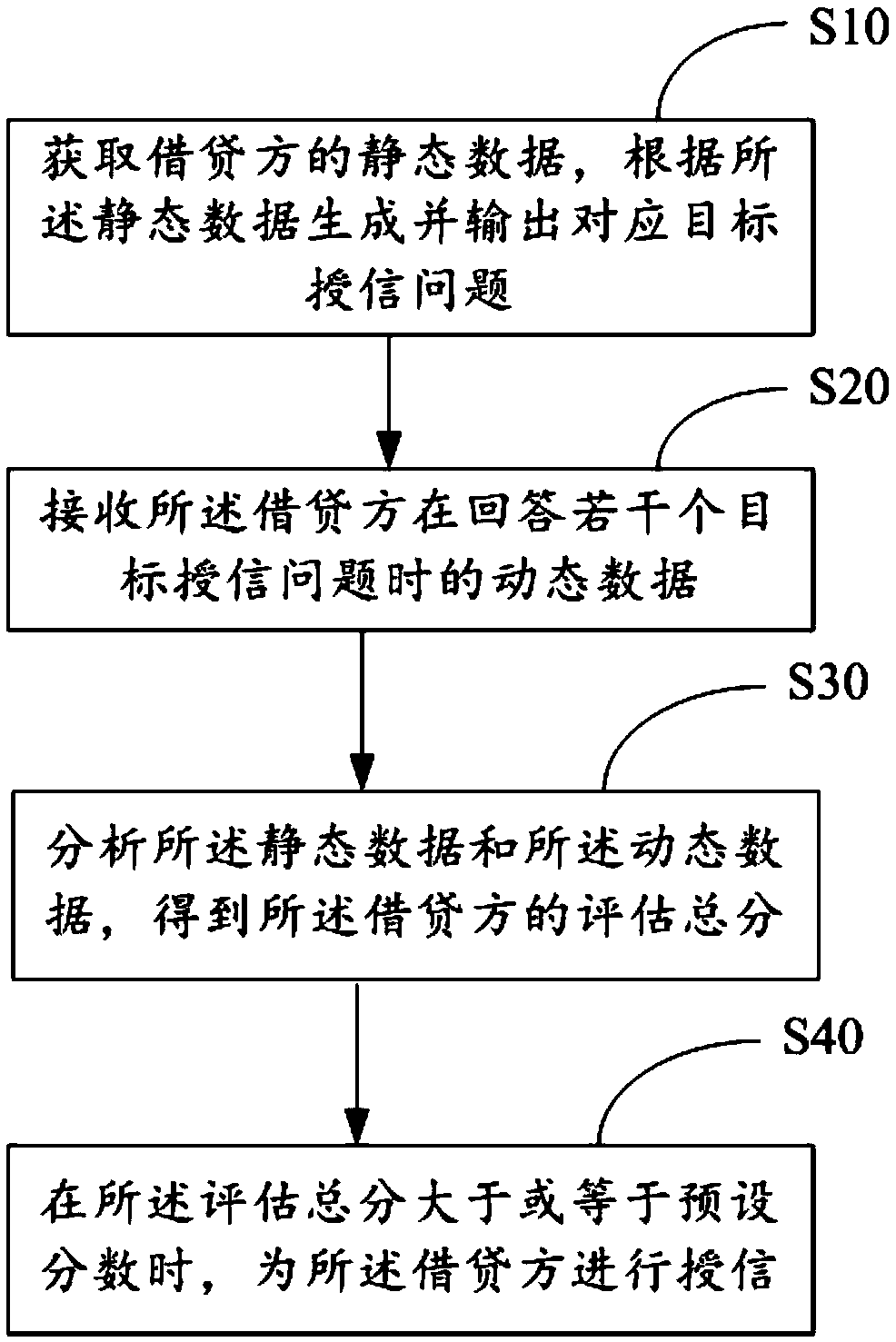
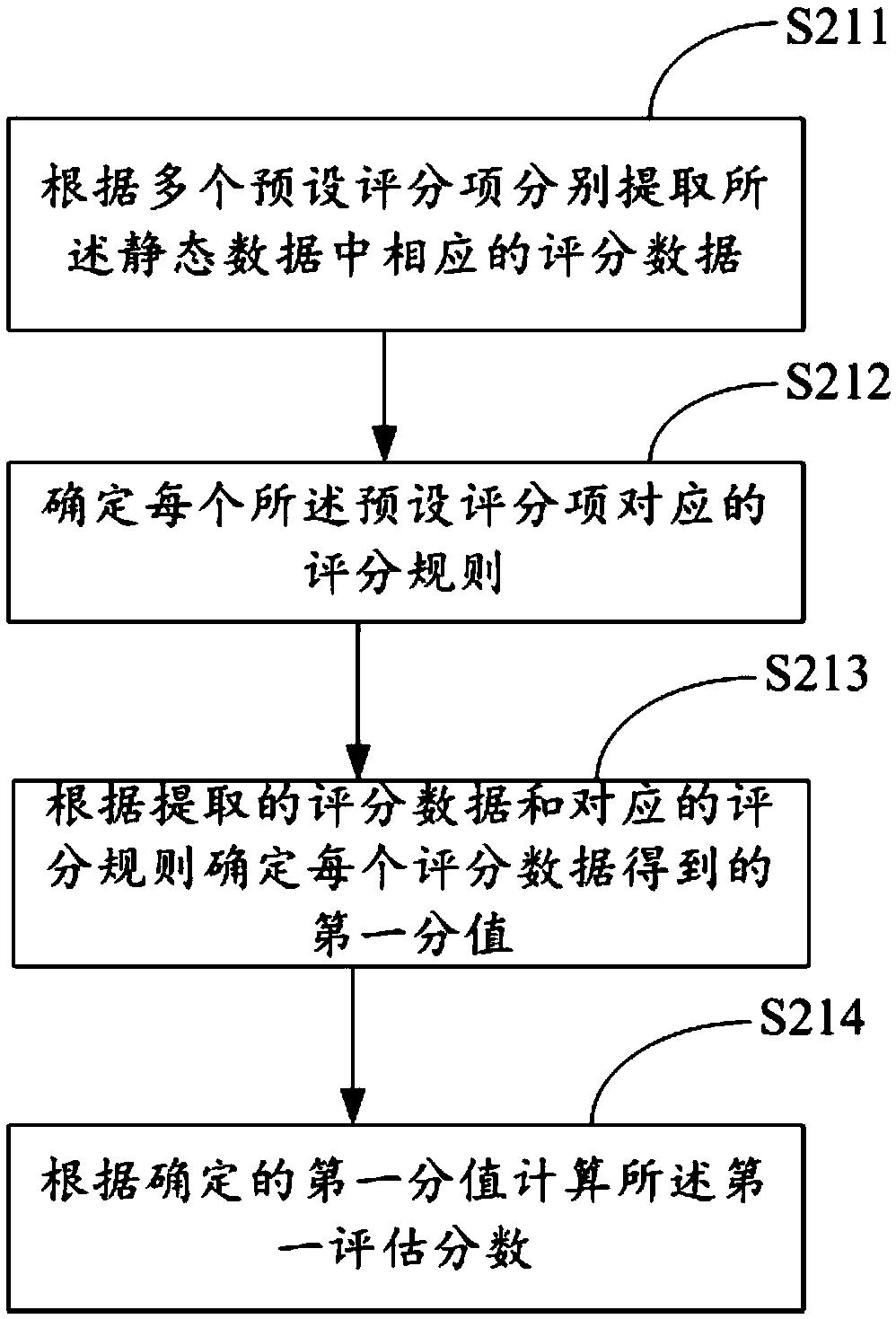
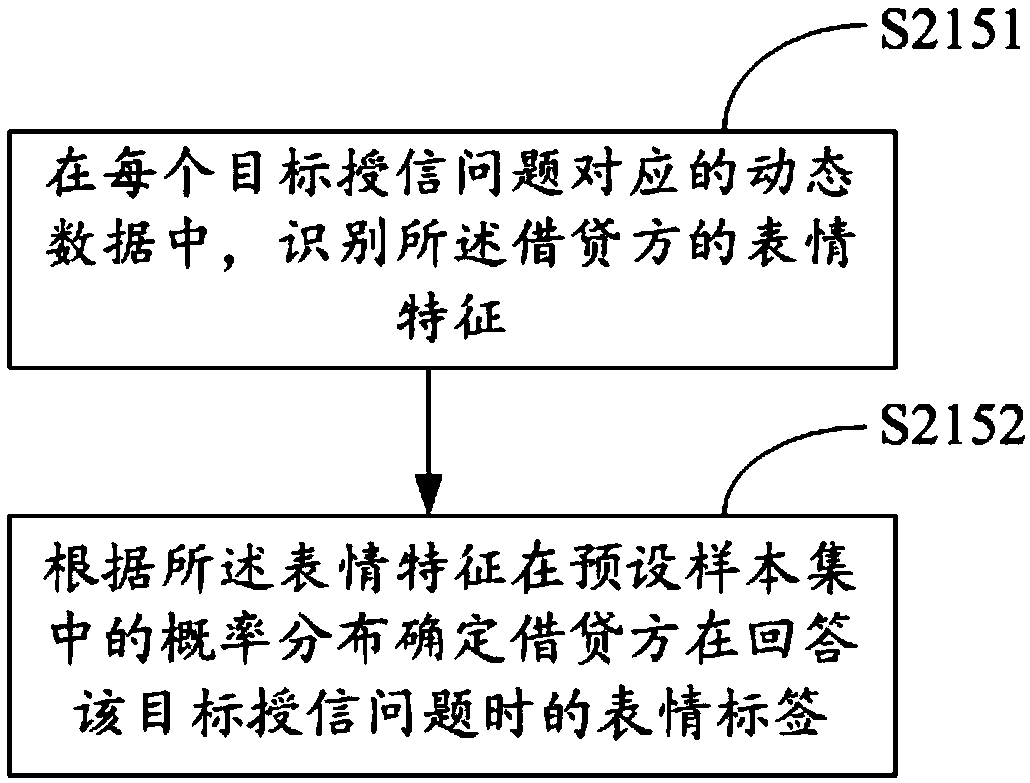
Loan credit granting platform and credit granting method thereof, credit granting equipment and readable storage medium
The invention discloses a loan credit granting method, which comprises the following steps of: obtaining static data of a borrower, and generating and outputting a corresponding target credit grantingproblem according to the static data; receiving dynamic data of the creditor when the creditor answers a plurality of target credit granting questions; analyzing the static data and the dynamic datato obtain a total evaluation score of the creditor; and when the total evaluation score is greater than or equal to a preset score, credit granting is carried out on the debtor. The invention furtherdiscloses a loan credit extension platform, loan credit extension equipment and a readable storage medium. According to the method, the accuracy of risk assessment of the borrowing and lending users is improved, the risk of borrowing and lending is reduced, and unnecessary economic loss of a financial platform is avoided.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
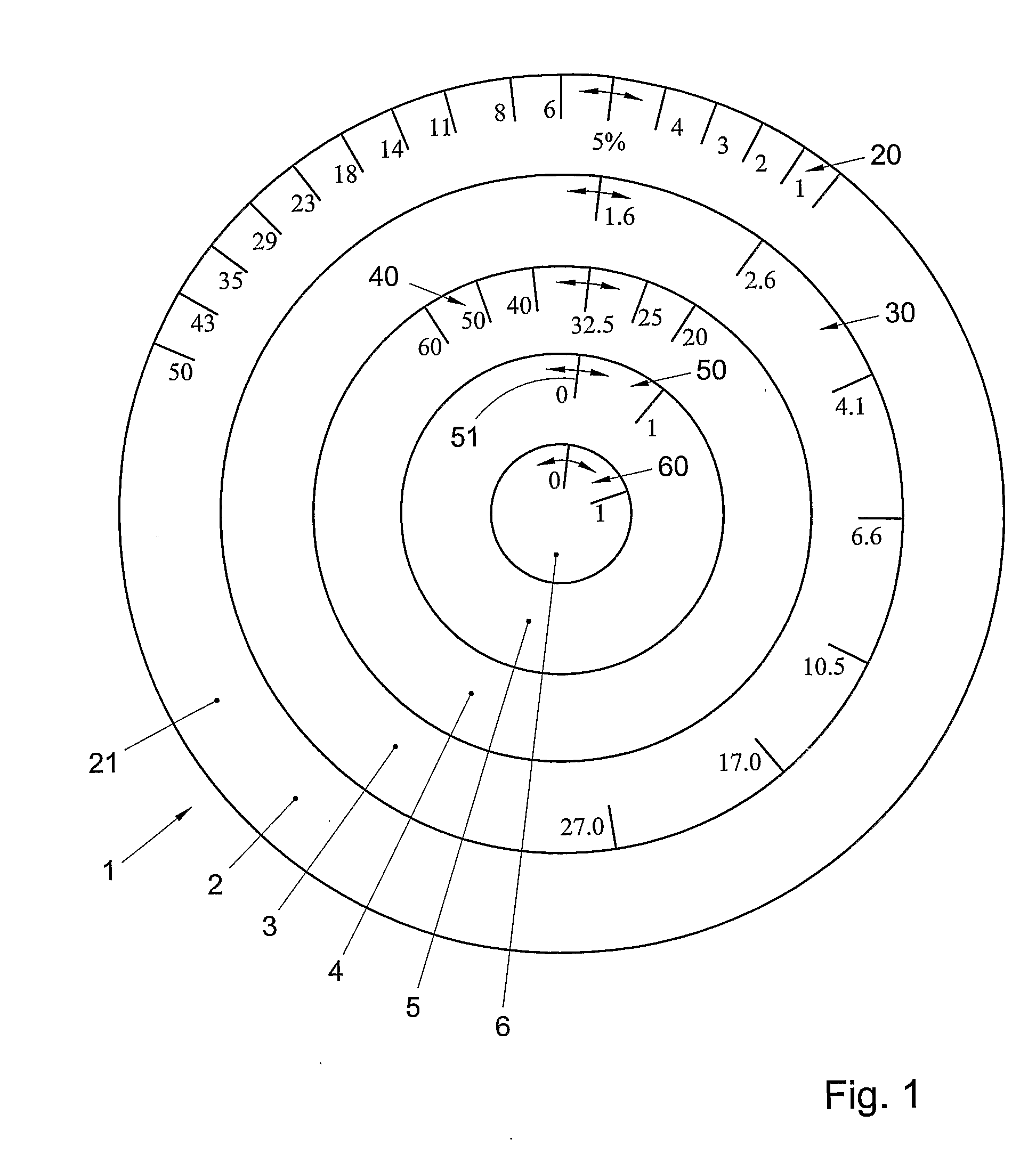
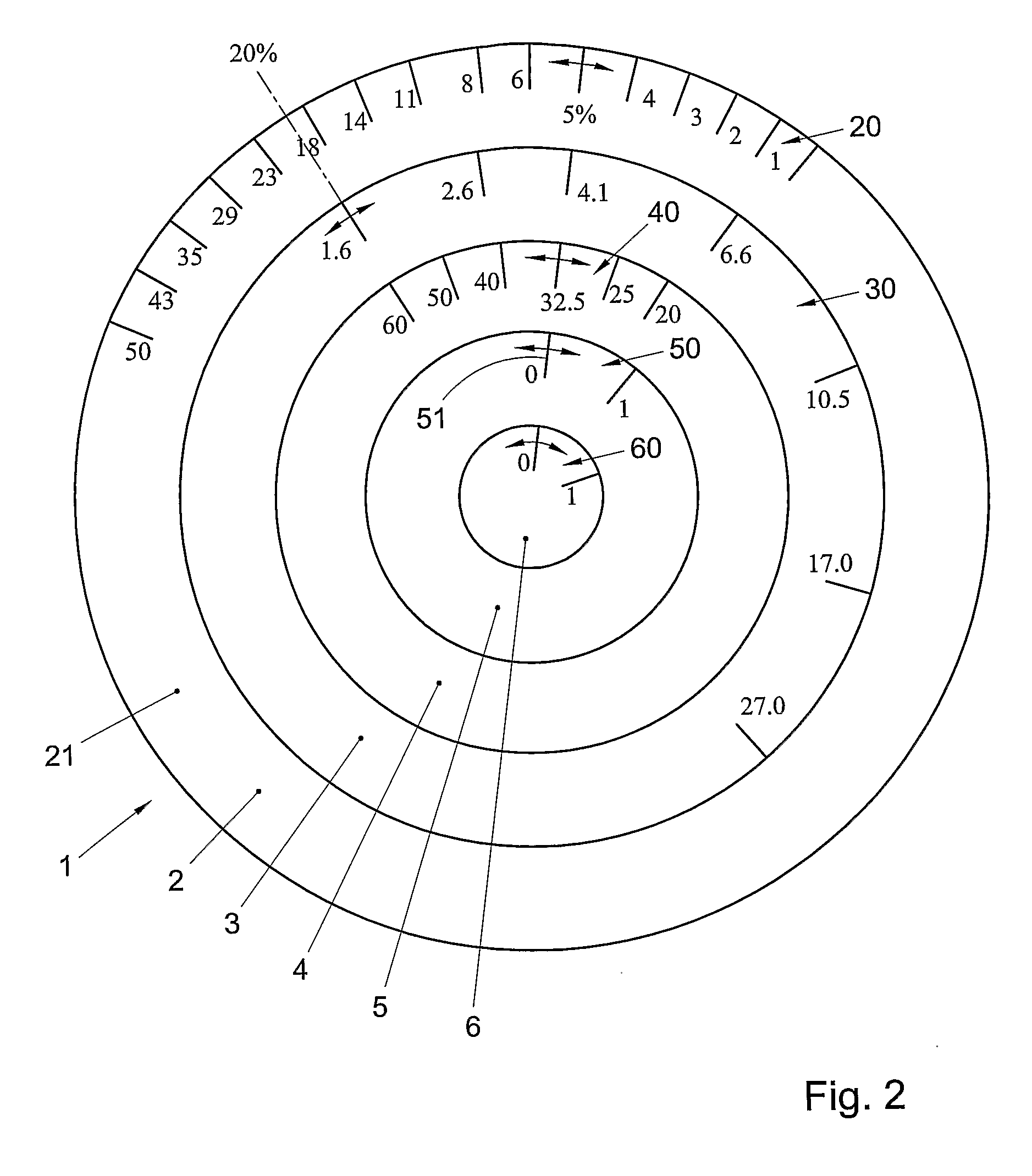
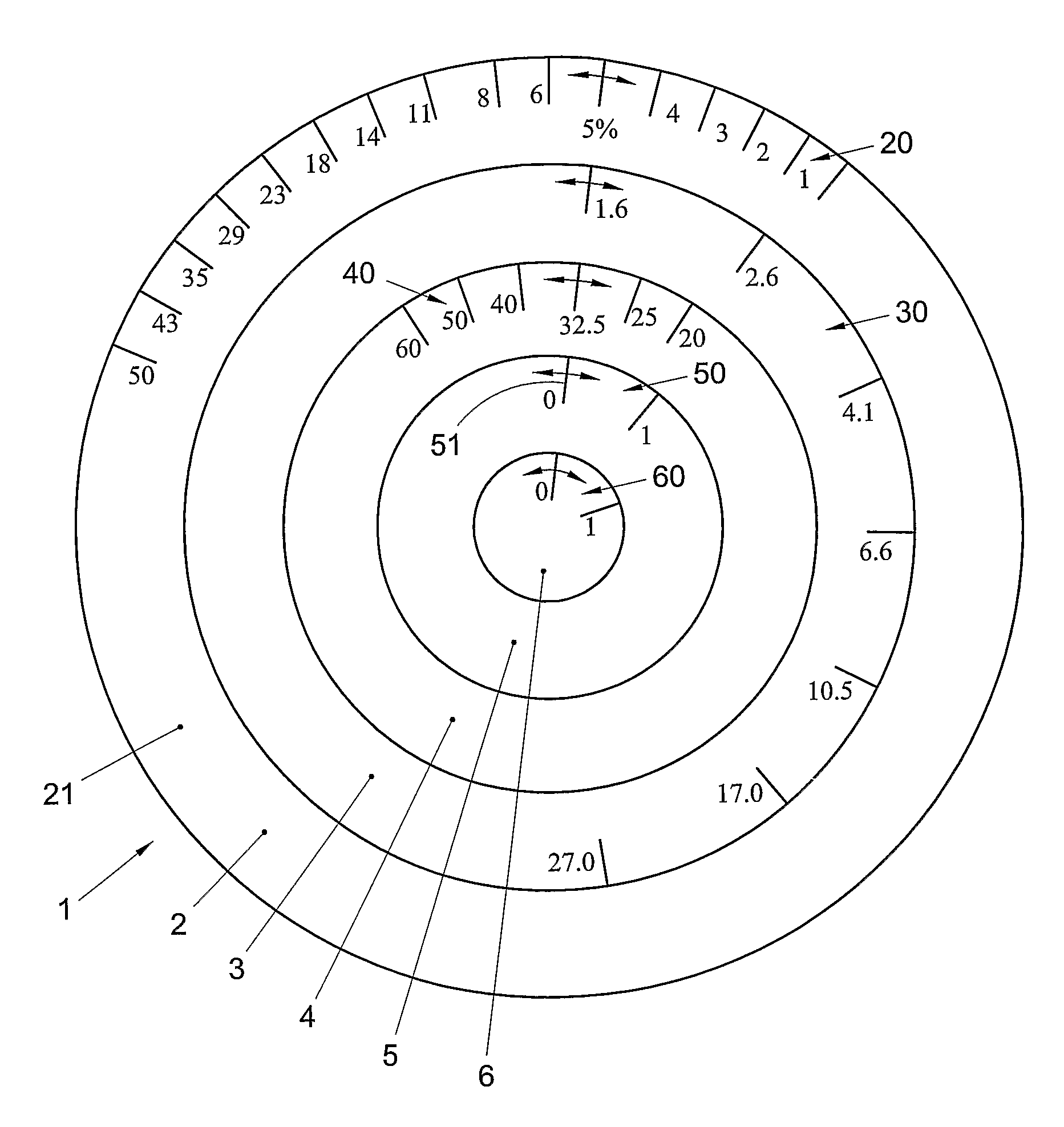
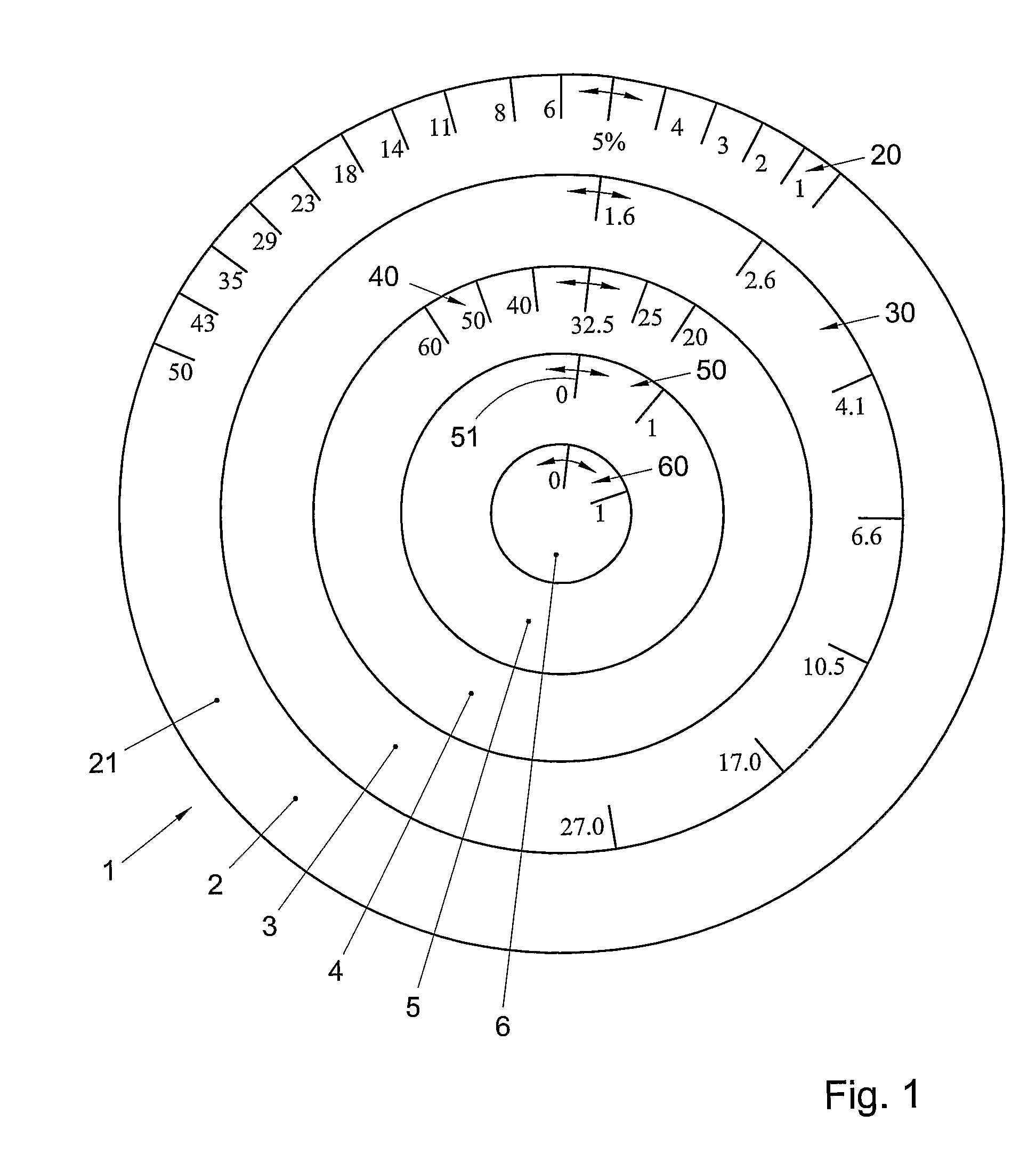
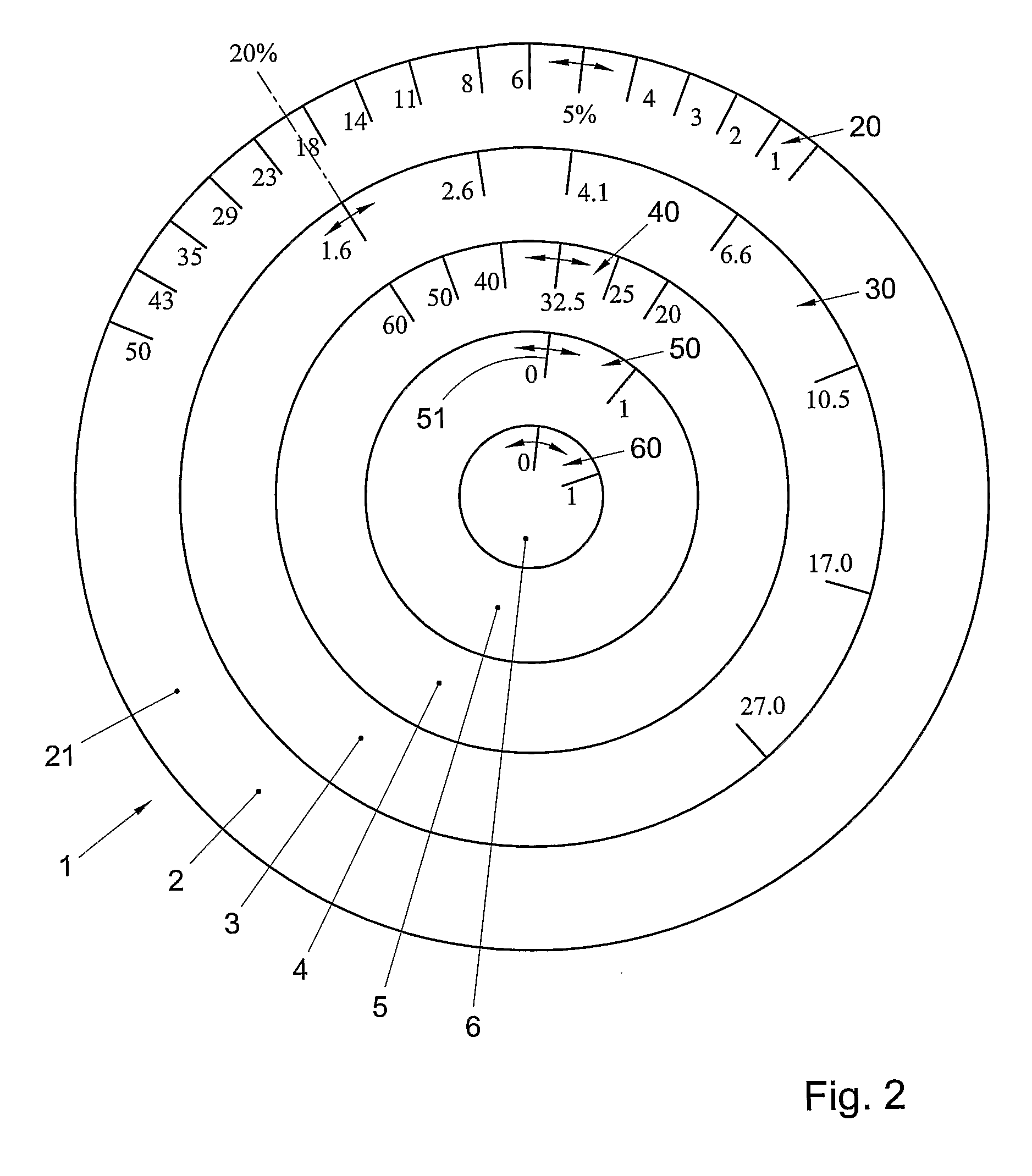
Data storage device and method for determining the dependency of the risk for prostate cancer, device and method for indicating a risk for a disease of an individual
InactiveUS20090212551A1Low costSuffers riskOther printing matterHand manipulated computer devicesDiseaseMedicine
A data storage device comprises a memory in which a collection of prostate cancer screening data is stored. The screening data is obtained from a selection of the general male population without medical pre-selection. A device for indicating a risk for a disease of an individual, comprises an indicator for indicating a determined value for said risk. The indicator comprises a risk scale representing a range of values of said risk, and at least one dialler for entering a value of a diagnostic parameter of an individual. The dialler comprises a parameter scale representing a range of values of said diagnostic parameter. The dialler is movable with respect to said indicator such that when a parameter value on said parameter scale is selected, an associated risk value is indicated on said risk scale according to a predetermined mathematical relationship
Owner:STICHTING WETENSCHAPPELIJK ONDERZOEK PROSTAATKANKER SWOP
Data storage device and method for determining the dependency of the risk for prostate cancer, device and method for indicating a risk for a disease of an individual
InactiveUS8087576B2Low costSuffers riskHand manipulated computer devicesOther printing matterDiseaseMedicine
A data storage device comprises a memory in which a collection of prostate cancer screening data is stored. The screening data is obtained from a selection of the general male population without medical pre-selection. A device for indicating a risk for a disease of an individual, comprises an indicator for indicating a determined value for said risk. The indicator comprises a risk scale representing a range of values of said risk, and at least one dialler for entering a value of a diagnostic parameter of an individual. The dialler comprises a parameter scale representing a range of values of said diagnostic parameter. The dialler is movable with respect to said indicator such that when a parameter value on said parameter scale is selected, an associated risk value is indicated on said risk scale according to a predetermined mathematical relationship.
Owner:STICHTING WETENSCHAPPELIJK ONDERZOEK PROSTAATKANKER SWOP
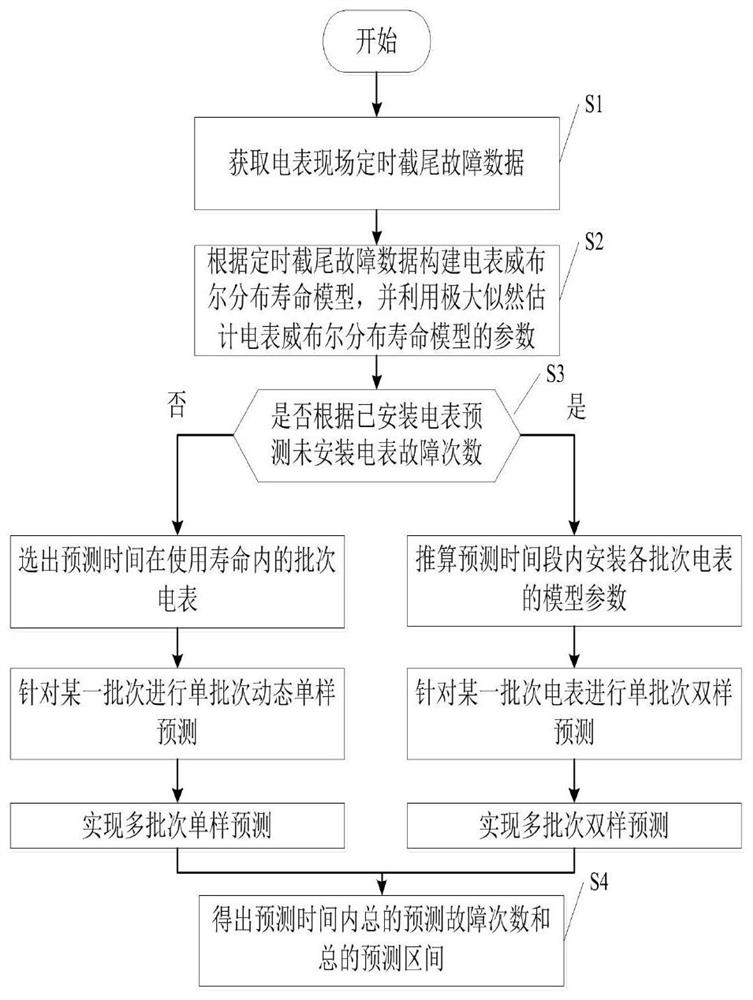
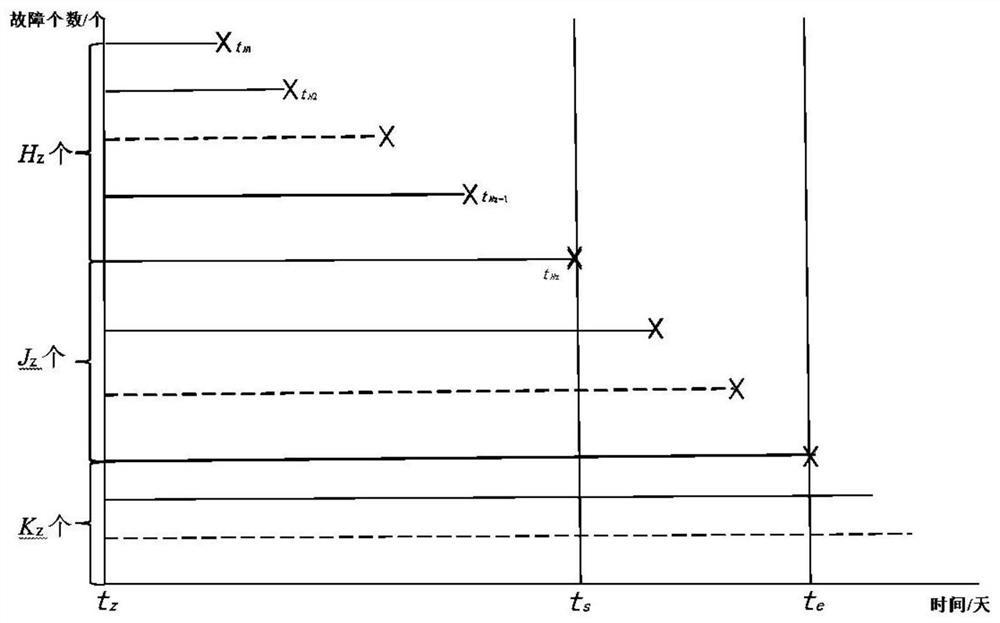
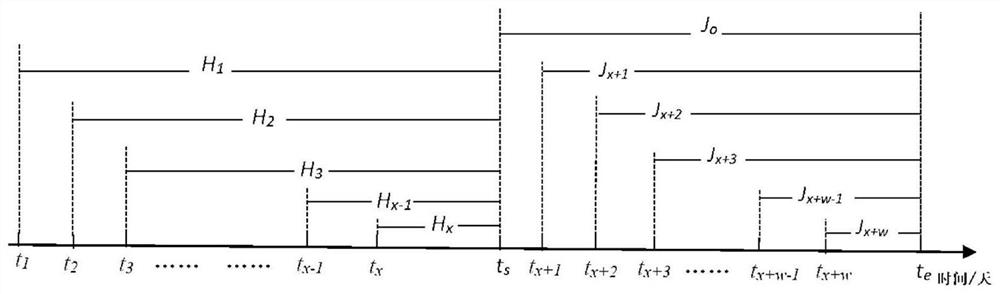
Electric meter fault frequency prediction method and system
PendingCN113887778AImproved Lifetime PredictionImprove risk assessmentForecastingDesign optimisation/simulationData predictionElectric energy
The invention combines field fault data to predict the number of faults in a future time period, improves the prediction accuracy by introducing the advantage ratio, is beneficial to solving the problem of pre-judging the faults of the electric energy meters in advance, and thus discovers the possible fault number change trend of the same batch of intelligent electric energy meters in the future interval in advance. The full-life-cycle management and control capability of a power grid company on life prediction, risk evaluation and management decision-making of the intelligent electric energy meter is improved. The possible fault frequency change trend of the same batch of intelligent electric energy meters in the future interval can be found in advance, technical support can be provided for the aspects of operation maintenance, batch rotation, hidden danger investigation and the like of the electric energy meters in the future time period, and the full-life-cycle management and control capacity of a power grid company on life prediction, risk evaluation and management decision making of the intelligent electric energy meters is improved.
Owner:国网山东省电力公司营销服务中心(计量中心) +2
Methods of computing pericardial and abdominal fat and methods for motion compensation
ActiveUS9965592B2Increased riskImprove risk assessmentMedical simulationHealth-index calculationPhysical therapyPericardium
Owner:UNIV HOUSTON SYST
Multi-dimensional software security risk assessment method based on CVSS
InactiveCN114065223AGuaranteed discretizationDiversity guaranteedPlatform integrity maintainanceEvaluation resultData set
The invention discloses a multi-dimensional software security risk assessment method based on CVSS. The problem that a CVSS measurement assessment standard cannot accurately and comprehensively evaluate vulnerability risk levels is solved. The method comprises the following implementation steps: acquiring software vulnerability data; analyzing vulnerability data and integrating into a data set; readjusting the weight of the relative importance measurement index; optimizing a distribution scheme of the measurement indexes in the influence; adding vulnerability type measurement indexes; adding utilization time probability measurement in the risk score; obtaining a risk assessment result by using the risk assessment formula. Relative importance weight distribution is carried out on measurement indexes in influence, vulnerability measurement indexes are added in availability measurement, and time utilization probabilities are added in risk scores. Compared with a traditional evaluation method, the method has more accurate scoring standards, more comprehensive evaluation factors and more dimensional evaluation results. The method is used for risk assessment of software vulnerabilities.
Owner:XIAN TECHNOLOGICAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com