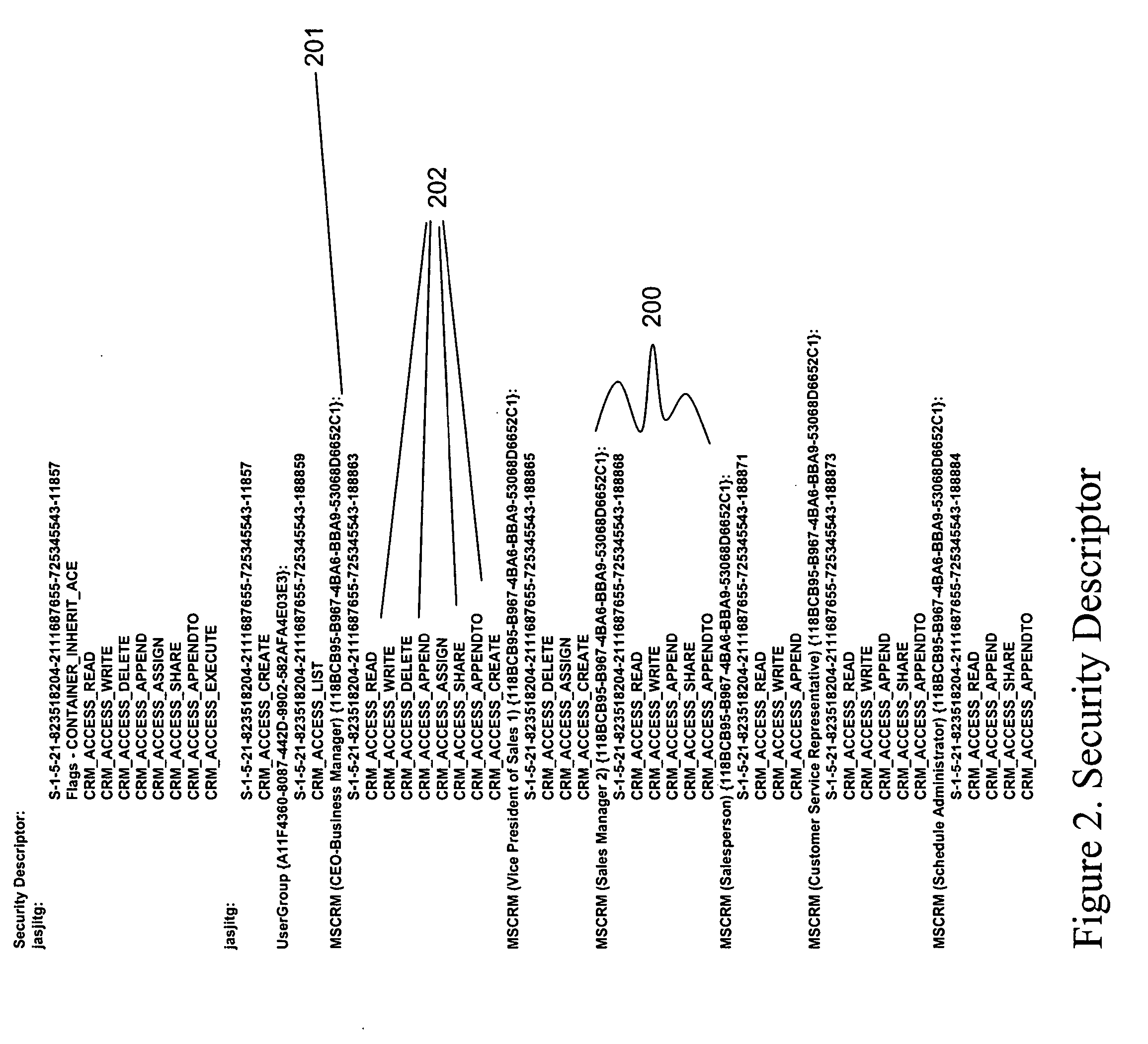
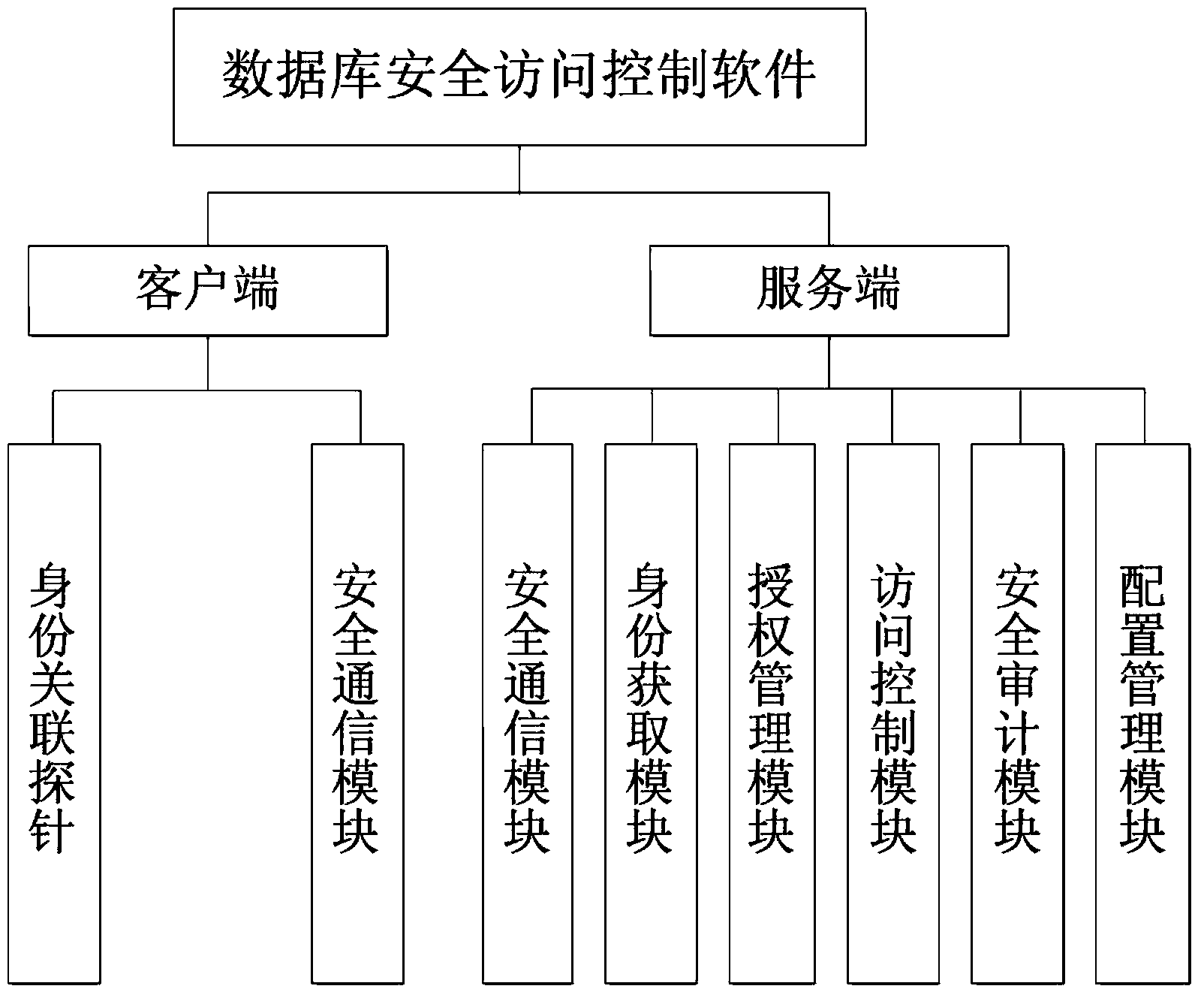
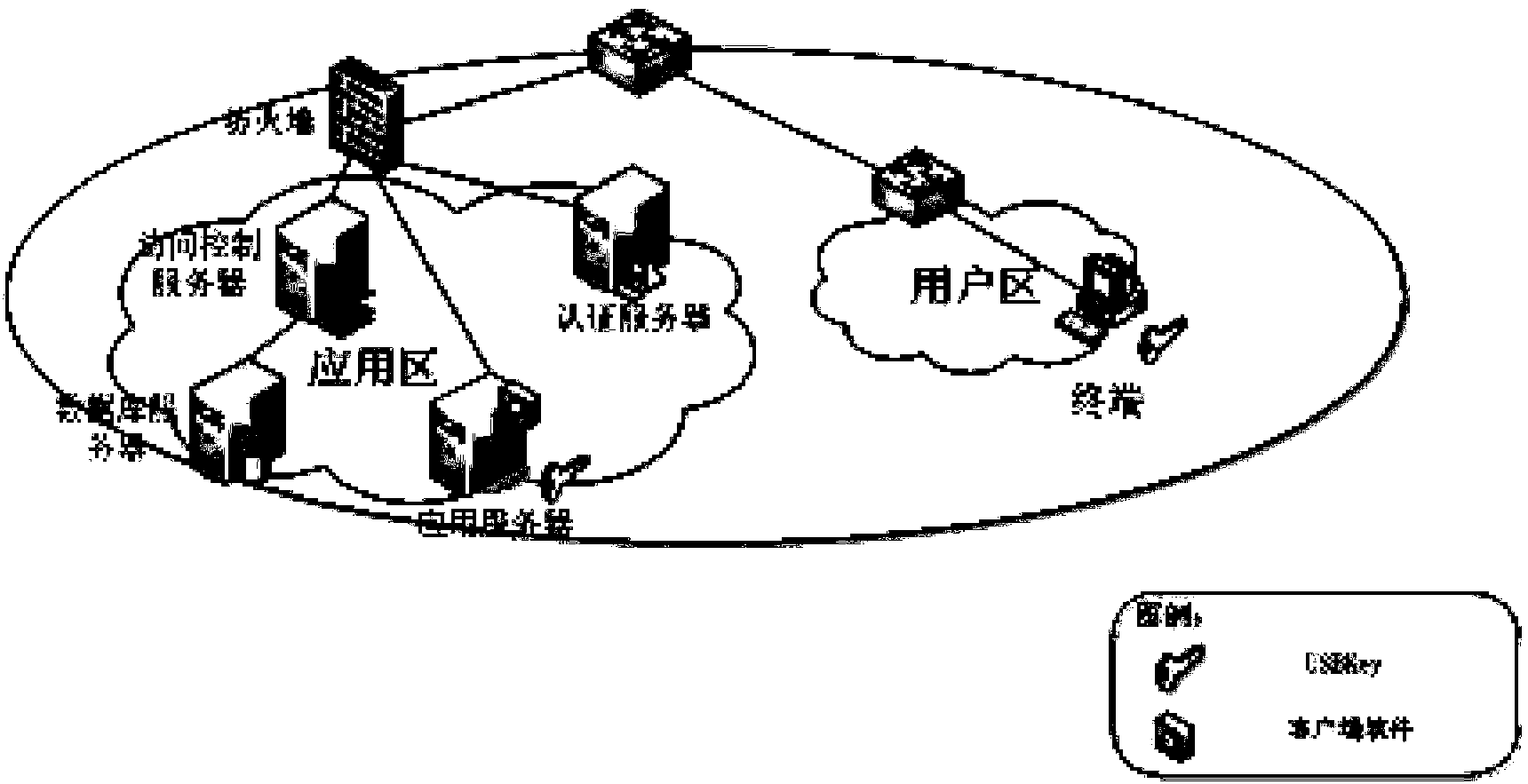
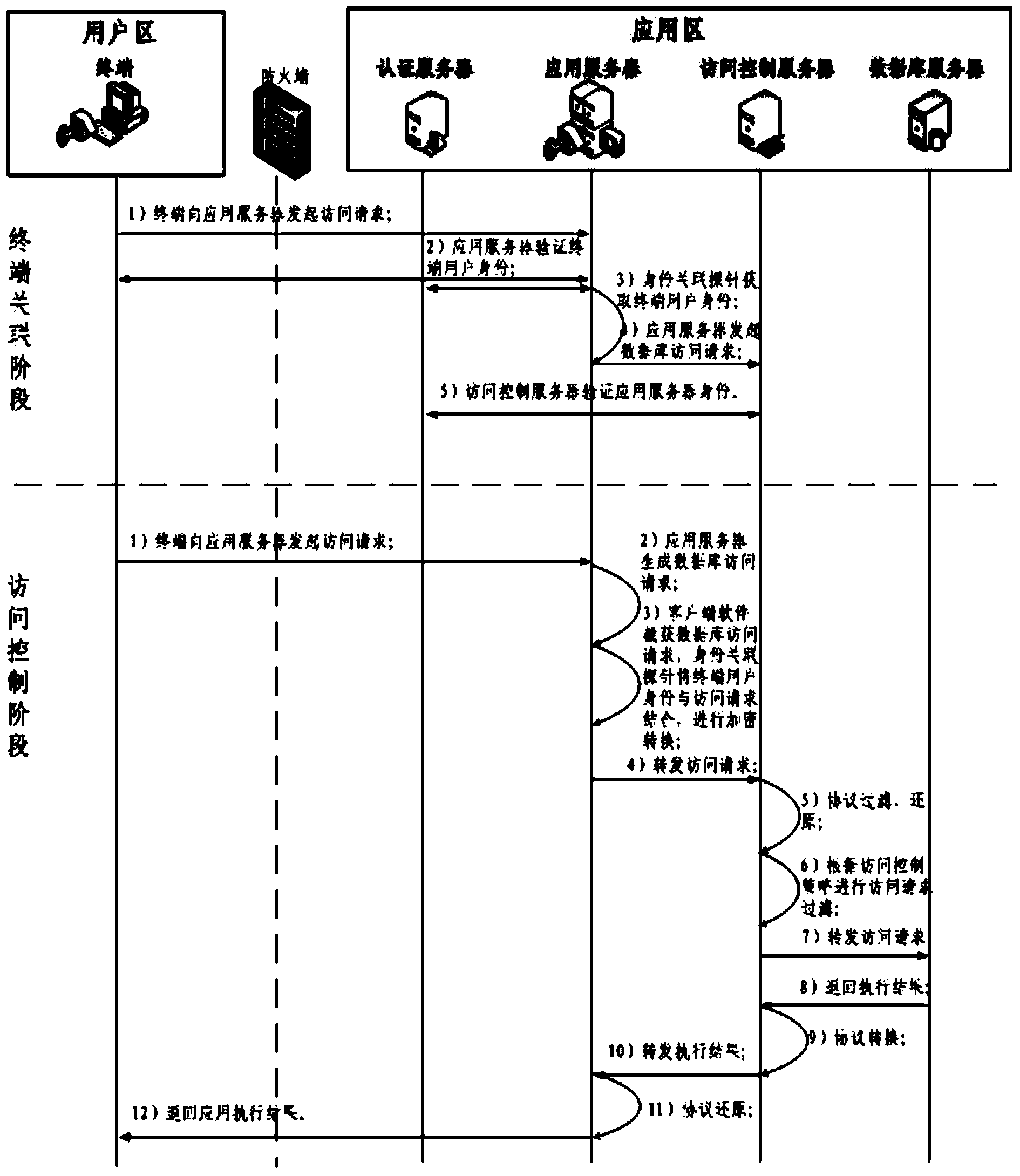
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
331 results about "Database security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Database security concerns the use of a broad range of information security controls to protect databases (potentially including the data, the database applications or stored functions, the database systems, the database servers and the associated network links) against compromises of their confidentiality, integrity and availability. It involves various types or categories of controls, such as technical, procedural/administrative and physical. Database security is a specialist topic within the broader realms of computer security, information security and risk management.
Database security via data flow processing
InactiveUS20110219035A1Easy to detectPreventing data flowDigital data information retrievalDigital data processing detailsComputer moduleData stream processing
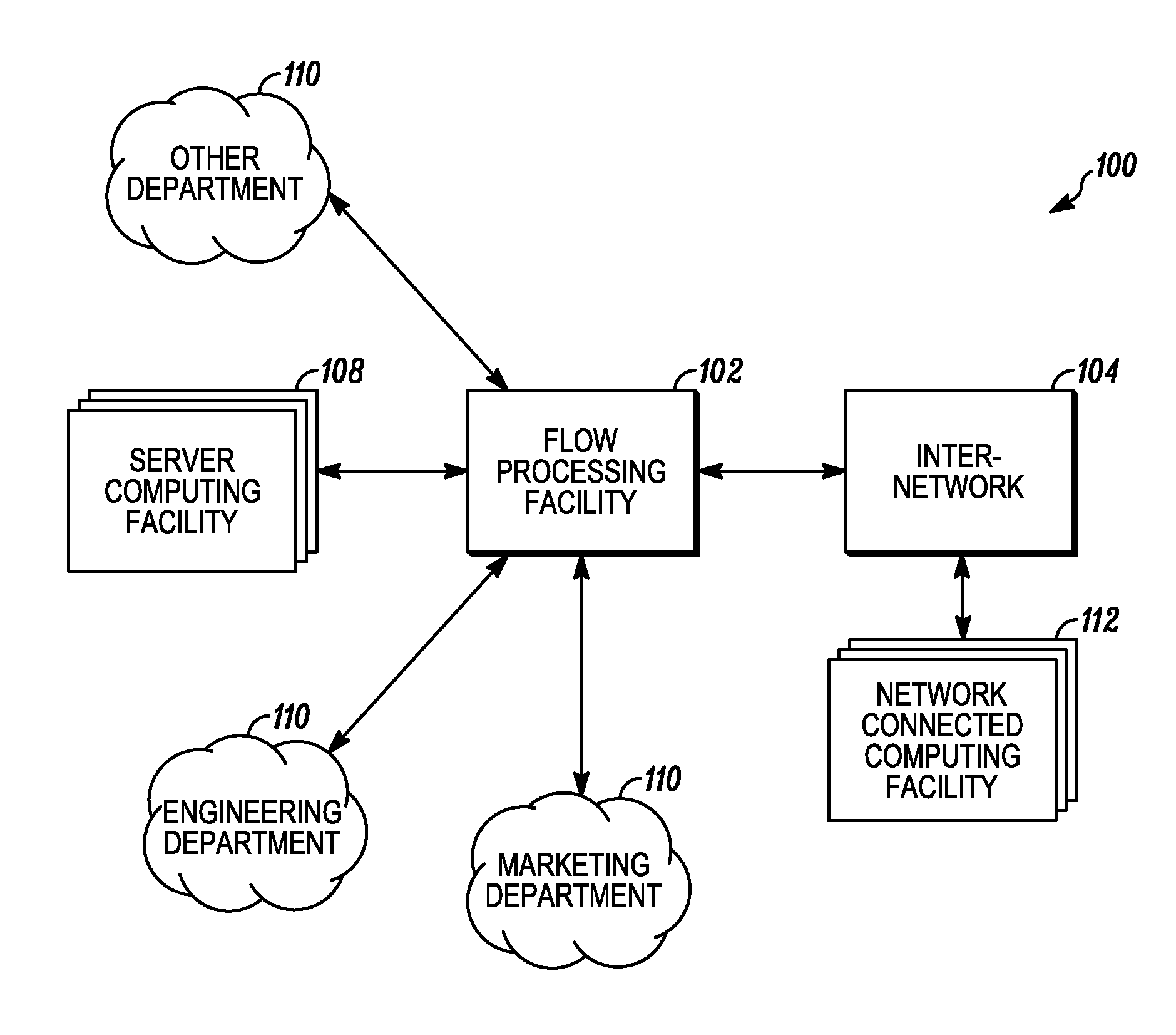
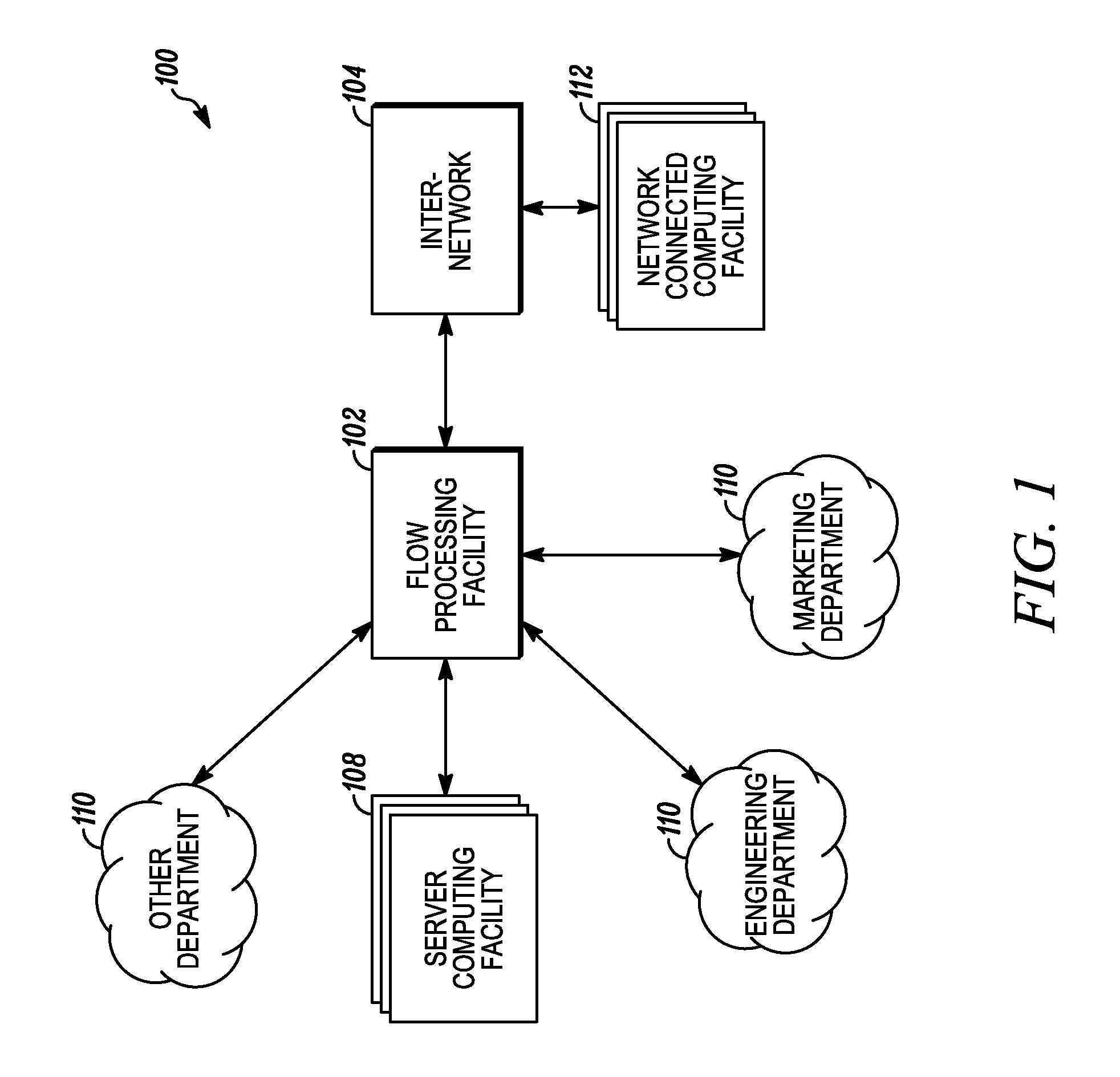
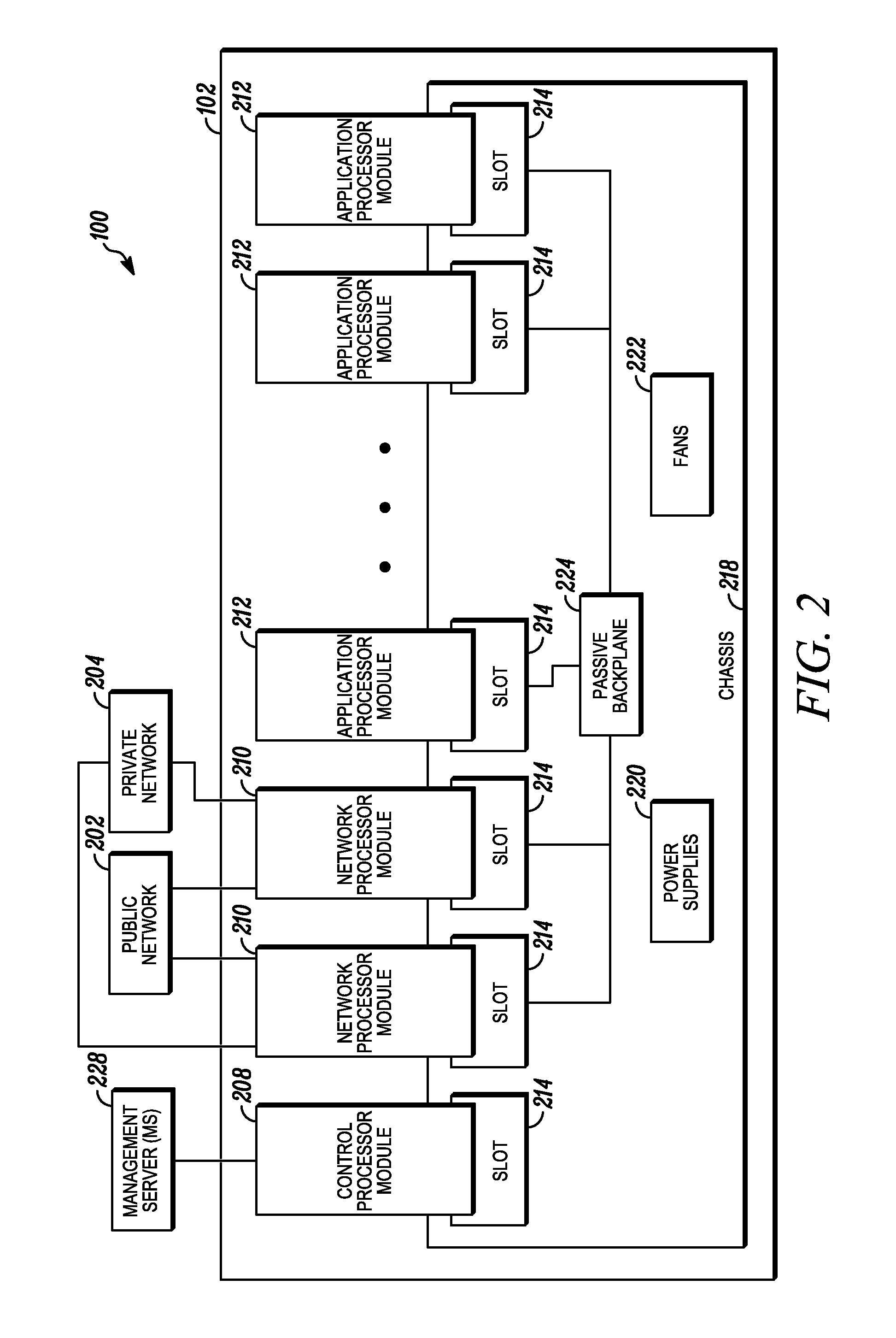
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
System and method for providing database security measures
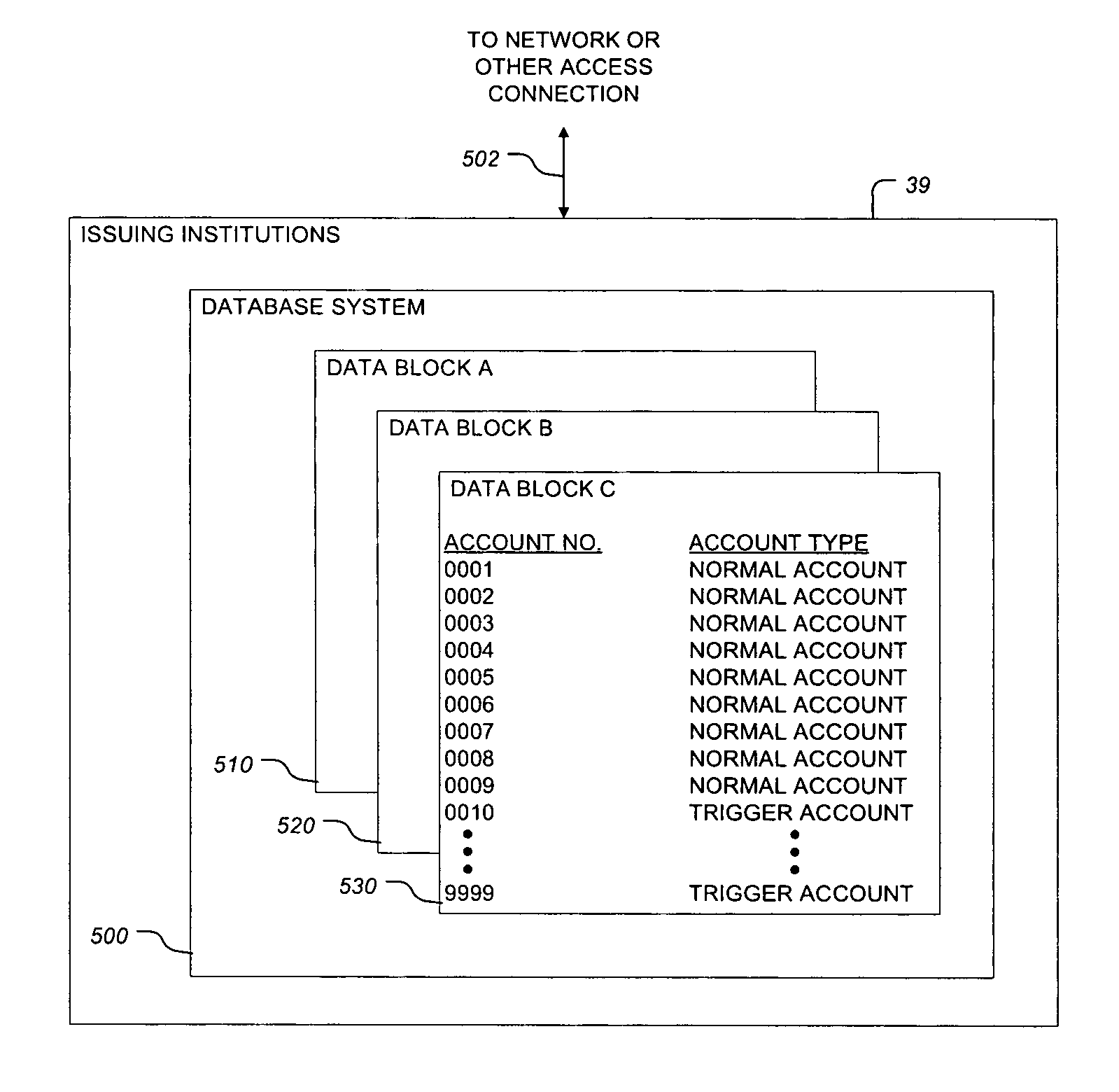
InactiveUS20060032909A1Increases arrest rateIncrease in arrest rateFinancePayment circuitsDatabase securityCard reader
A trigger card and system for preventing credit and debit card fraud is disclosed. The trigger card is adapted to be indistinguishable from typical credit cards and other cards issued by financial institutions. The system is adapted to receive signals when a standard card reader reads the trigger card. The system is further adapted to initiate an automated procedure to reduce fraud upon receipt of the signal indicating that the trigger card has been read by the card reader.
Owner:SEEGAR MARK
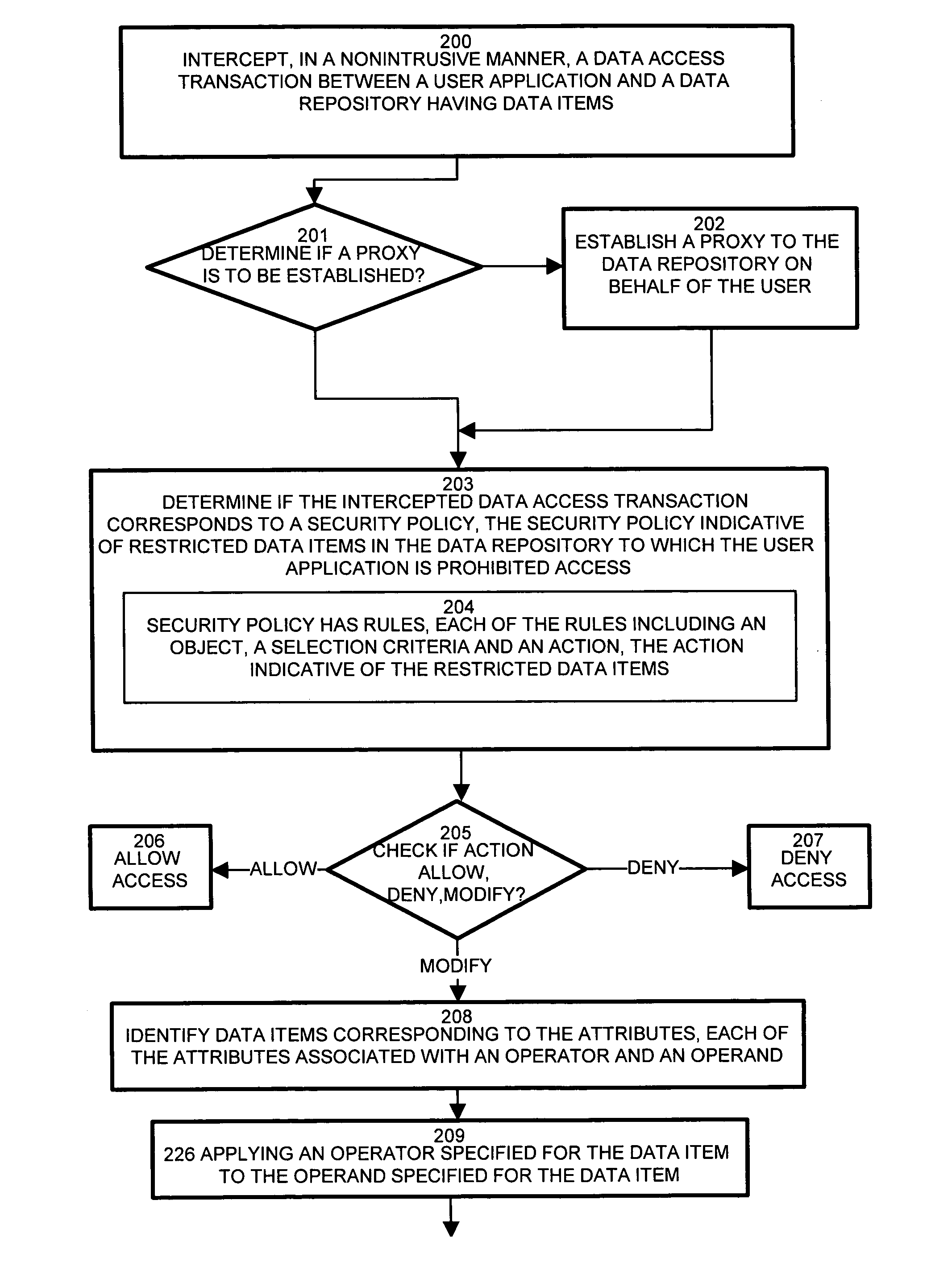
System and methods for nonintrusive database security
InactiveUS7437362B1Reduce the burden onOvercome deficienciesDigital data processing detailsComputer security arrangementsRelational databaseData access
Typical conventional database security scheme mechanisms are integrated in either the application or database. Maintenance of the security scheme, therefore, such as changes and modifications, impose changes to the application and / or database. Configurations of the invention employ a security filter for intercepting database streams, such as data access transactions, between an application and the a data repository, such as a relational database. A security filter deployed between the application and database inspects the stream of transactions between the application and the database. The security filter, by nonintrusively interrogating the transactions, provides a content-aware capability for seamlessly and nondestructively enforcing data level security. A security policy, codifying security requirements for the users and table of the database, employs rules concerning restricted data items. The filter intercepts transactions and determines if the transaction triggers rules of the security policy. If the transactions contain restricted data items, the security filter modifies the transaction to eliminate the restricted data items.
Owner:IBM CORP
Mandatory access control label security
ActiveUS20080010233A1Ease of administrationEnsure effective implementationDigital data processing detailsComputer security arrangementsData setDatabase security
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises a plurality of datasets, each dataset including a plurality of data, and a plurality of database objects, each object having a security label comprising a security classification of the object, at least one database session, the database session having a security label indicating a security classification of the database session, wherein, the database system is operable to allow or deny access to data to a database session based on a security label of a database object and on a security label of the database session.
Owner:ORACLE INT CORP
System and methods for adaptive behavior based access control
InactiveUS7506371B1Reliable indicatorFast to computeDigital data processing detailsUnauthorized memory use protectionData accessDatabase security
Owner:IBM CORP
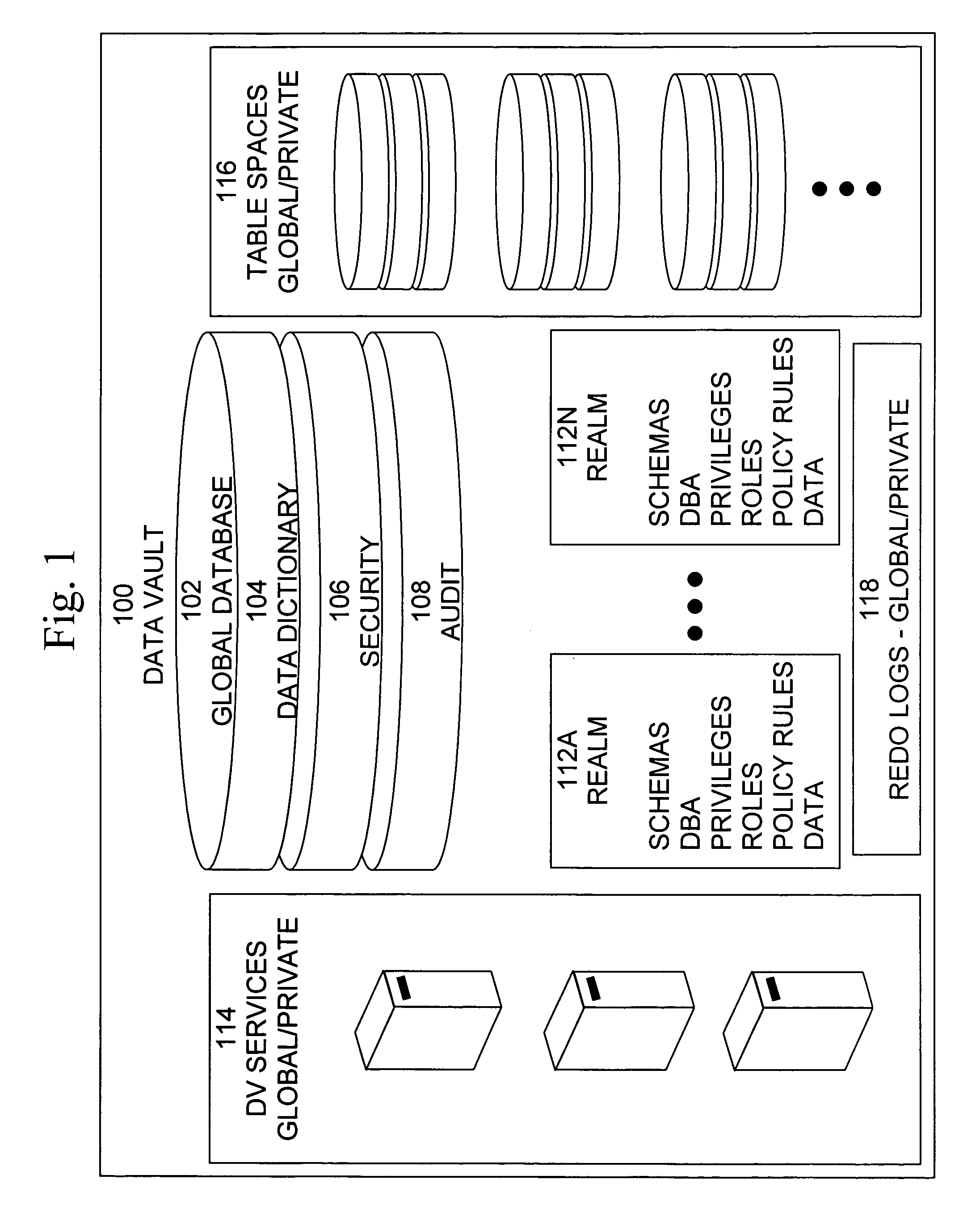
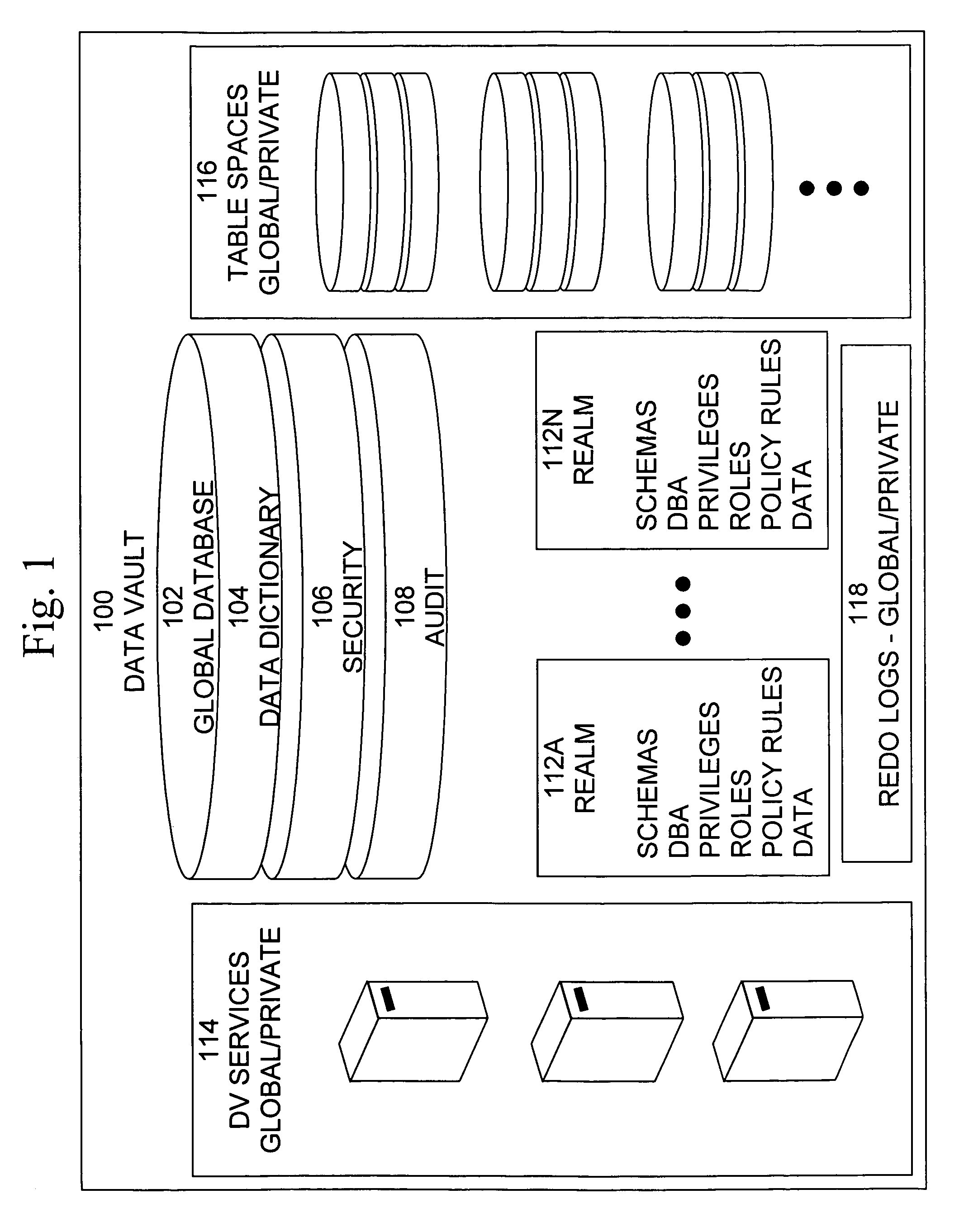
Cross-domain security for data vault
ActiveUS20060248599A1Ease of administrationEnsure effective implementationDigital data processing detailsUser identity/authority verificationDatabase securitySecurity level
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system communicatively connected to a plurality of network domains, each network domain having a level of security, the database system comprises at least one database accessible from all of the plurality of network domains, the database comprising data, each unit of data having a level of security and access control security operable to provide access to a unit of data in the database to a network domain based on the level of security of the network domain and based on the level of security of the unit of data.
Owner:ORACLE INT CORP
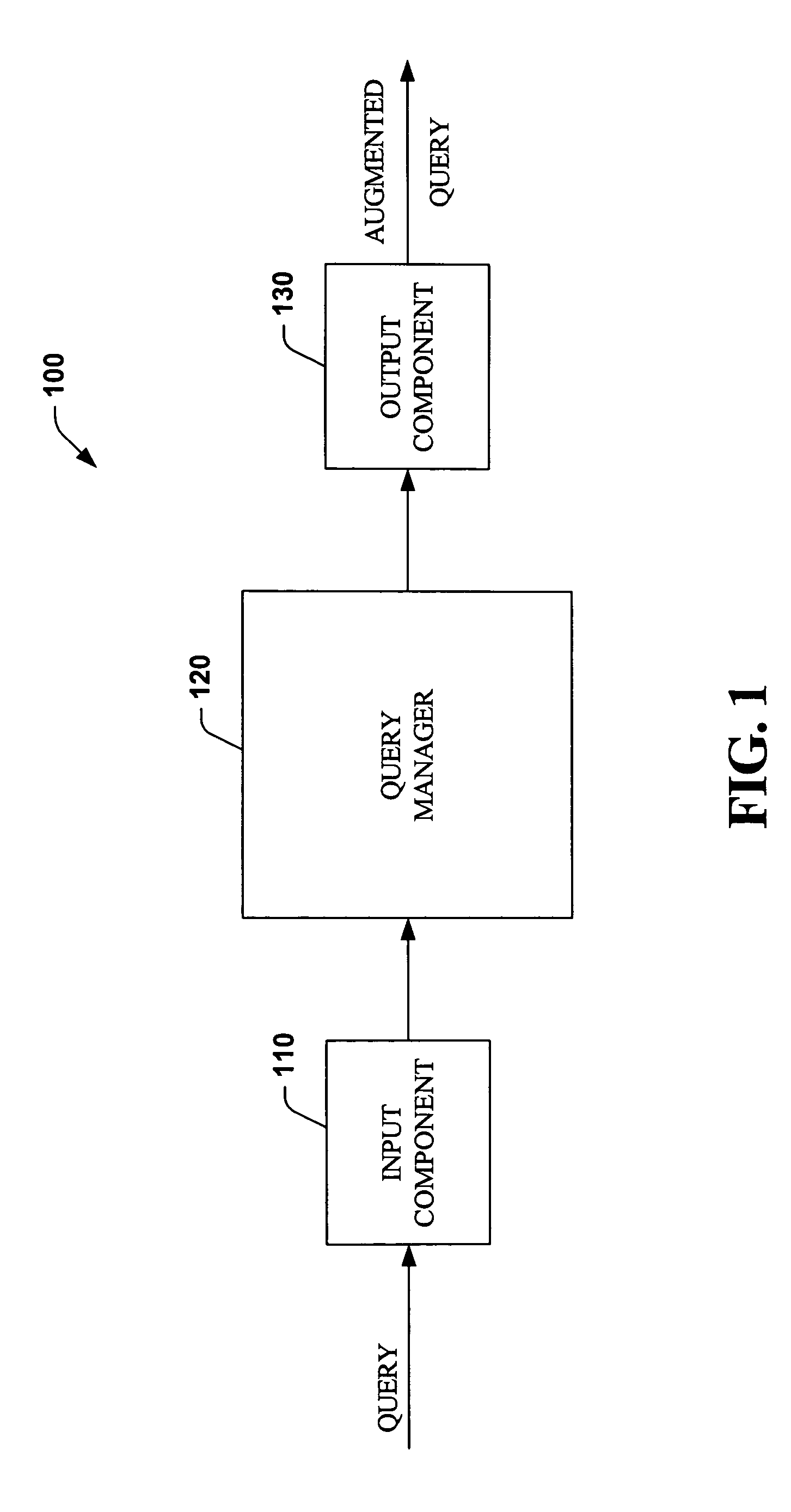
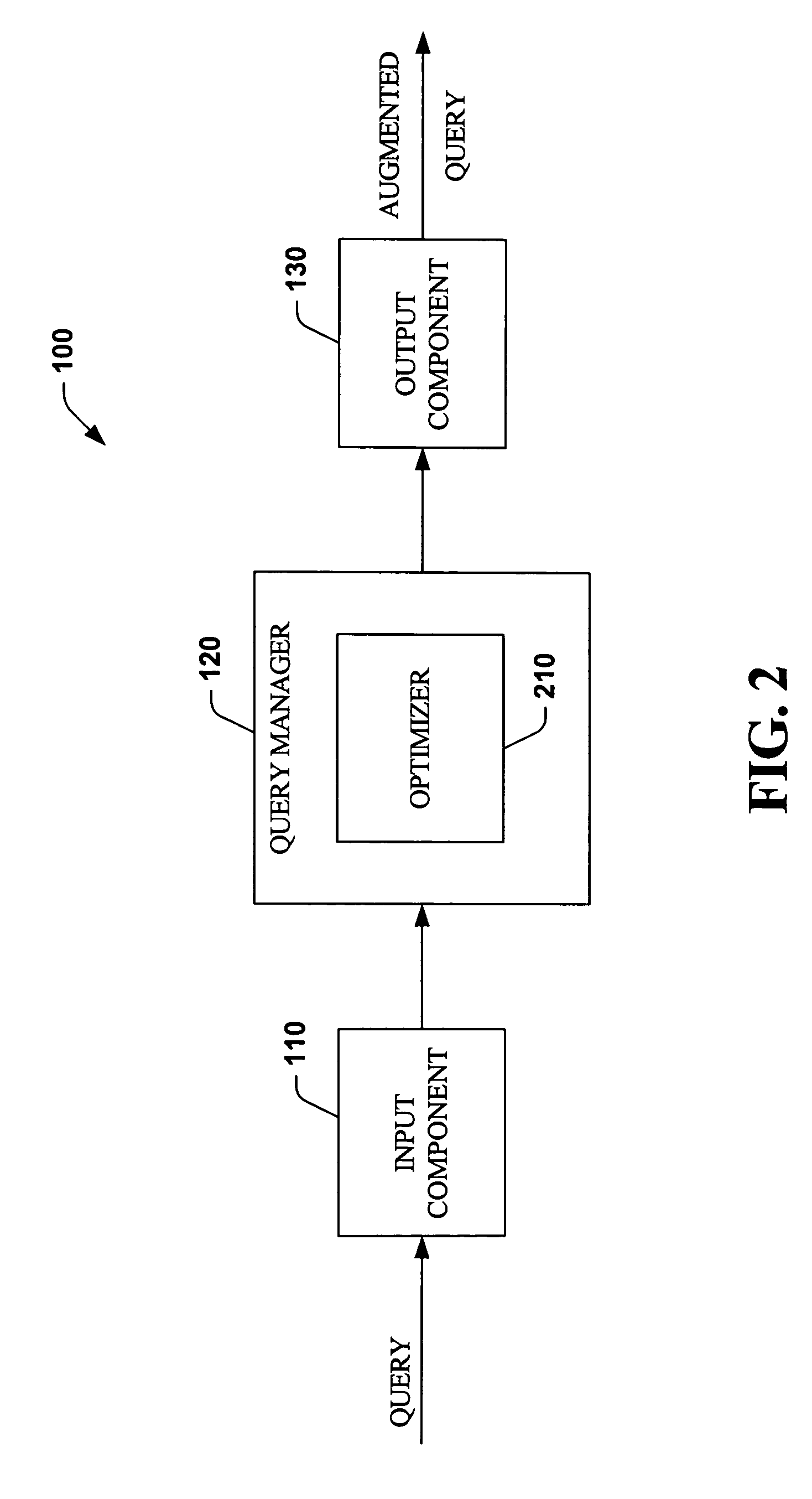
Systems and methods that optimize row level database security
ActiveUS20050177570A1Improve securityEnhanced syntaxDigital data processing detailsCheck valvesDatabase securityBoolean expression
The systems and methods of the present invention facilitate database row-level security by utilizing SQL extensions to create and associate named security expressions with a query initiator(s). Such expressions include Boolean expressions, which must be satisfied by a row of data in order for that data to be made accessible to the query initiator. In general, a query is augmented with security expressions, which are aggregated and utilized during querying rows of data. The systems and methods variously place security expressions within a query in order to optimize query performance while mitigating information leaks. This is achieved by tagging security expressions as special and utilizing rules of predicate to pull or push non-security expressions above or below security expressions, depending on the likelihood of a non-security being safe, as determined via a static and / or dynamic analysis.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods that optimize row level database security
ActiveUS7661141B2Facilitate row-level securityEnhanced syntaxDigital data processing detailsCheck valvesDatabase securityData bank
The systems and methods of the present invention facilitate database row-level security by utilizing SQL extensions to create and associate named security expressions with a query initiator(s). Such expressions include Boolean expressions, which must be satisfied by a row of data in order for that data to be made accessible to the query initiator. In general, a query is augmented with security expressions, which are aggregated and utilized during querying rows of data. The systems and methods variously place security expressions within a query in order to optimize query performance while mitigating information leaks. This is achieved by tagging security expressions as special and utilizing rules of predicate to pull or push non-security expressions above or below security expressions, depending on the likelihood of a non-security being safe, as determined via a static and / or dynamic analysis.
Owner:MICROSOFT TECH LICENSING LLC
Extensible, customizable database-driven row-level database security
InactiveUS20060136361A1Easy to handleDigital data information retrievalComputer security arrangementsDatabase securityData model
The method and system of the claims decomposes an organization structure into a set of mapping objects, where each mapping object represents an affiliation between entities of an organization. Each object in the data model is associated with an owner by designating a set of ownership affiliation attributes for each object. A set of privileges is assigned to an affiliation and access is checked based on a user's affiliation to an object and a user's privilege depth. Single privilege checking is performed only as a last resort for special, infrequent situations.
Owner:MICROSOFT TECH LICENSING LLC
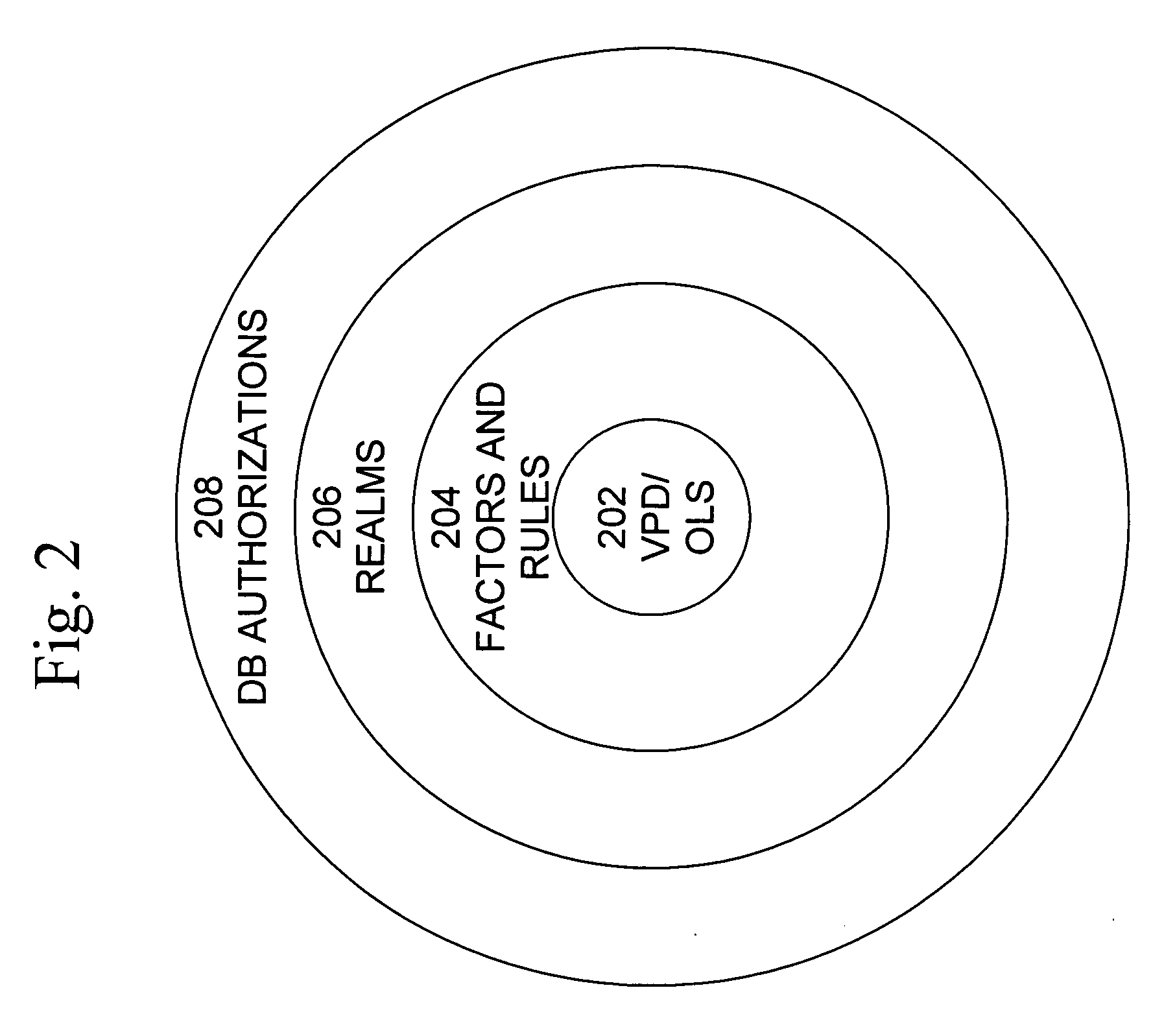
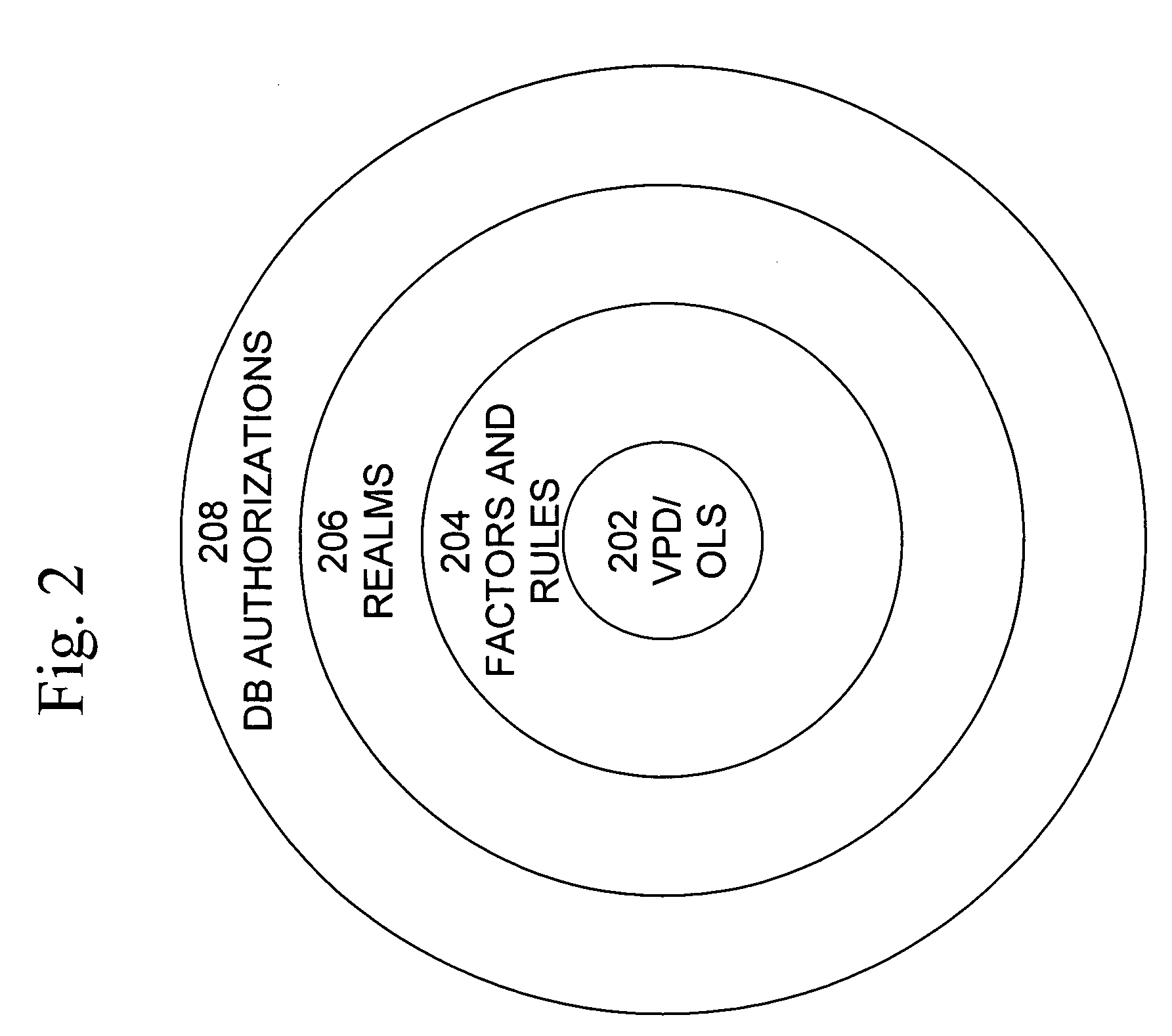
Mandatory access control base
ActiveUS20060248083A1Ease of administrationEnsure effective implementationComputer security arrangementsSpecial data processing applicationsData accessDatabase security
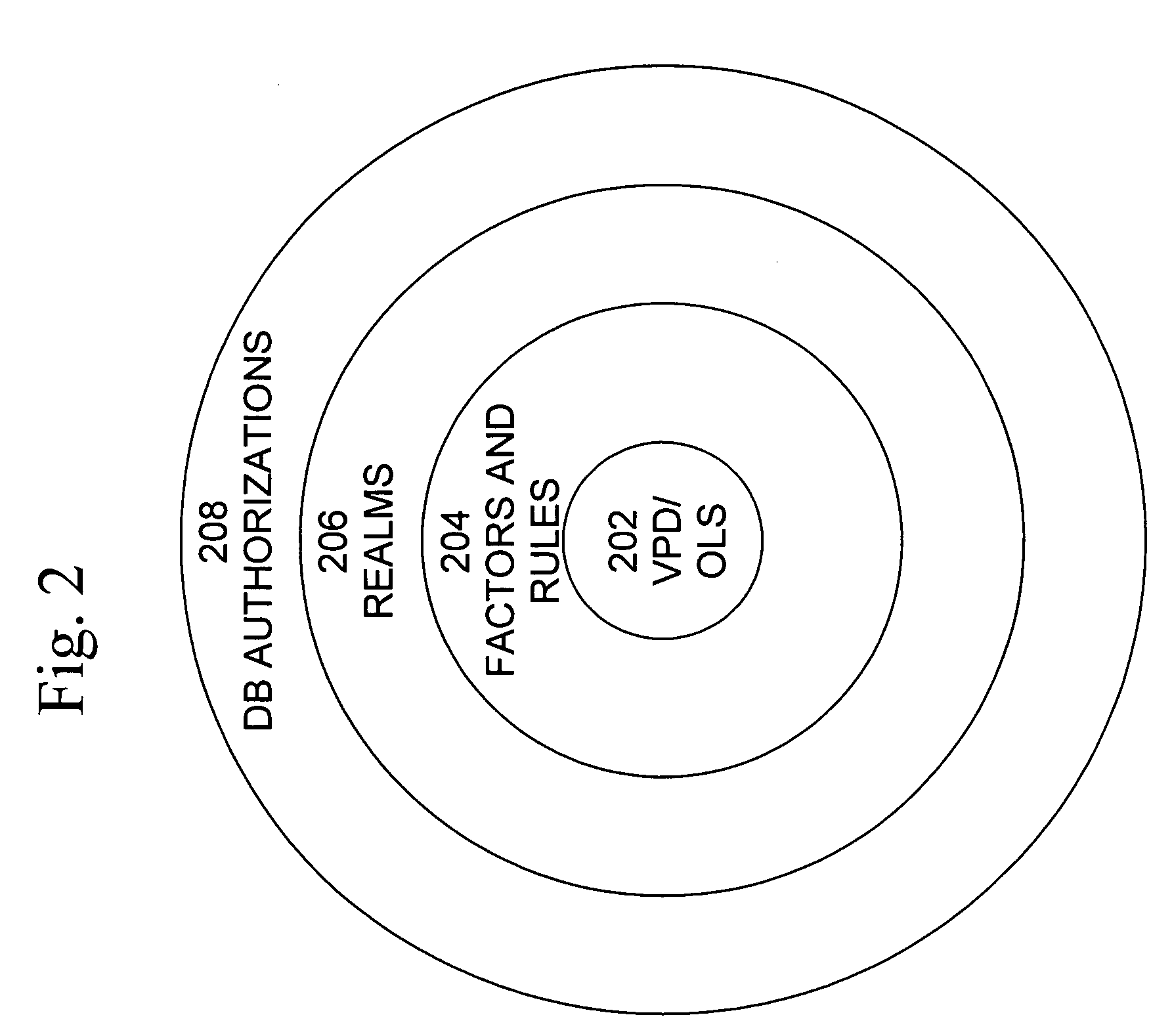
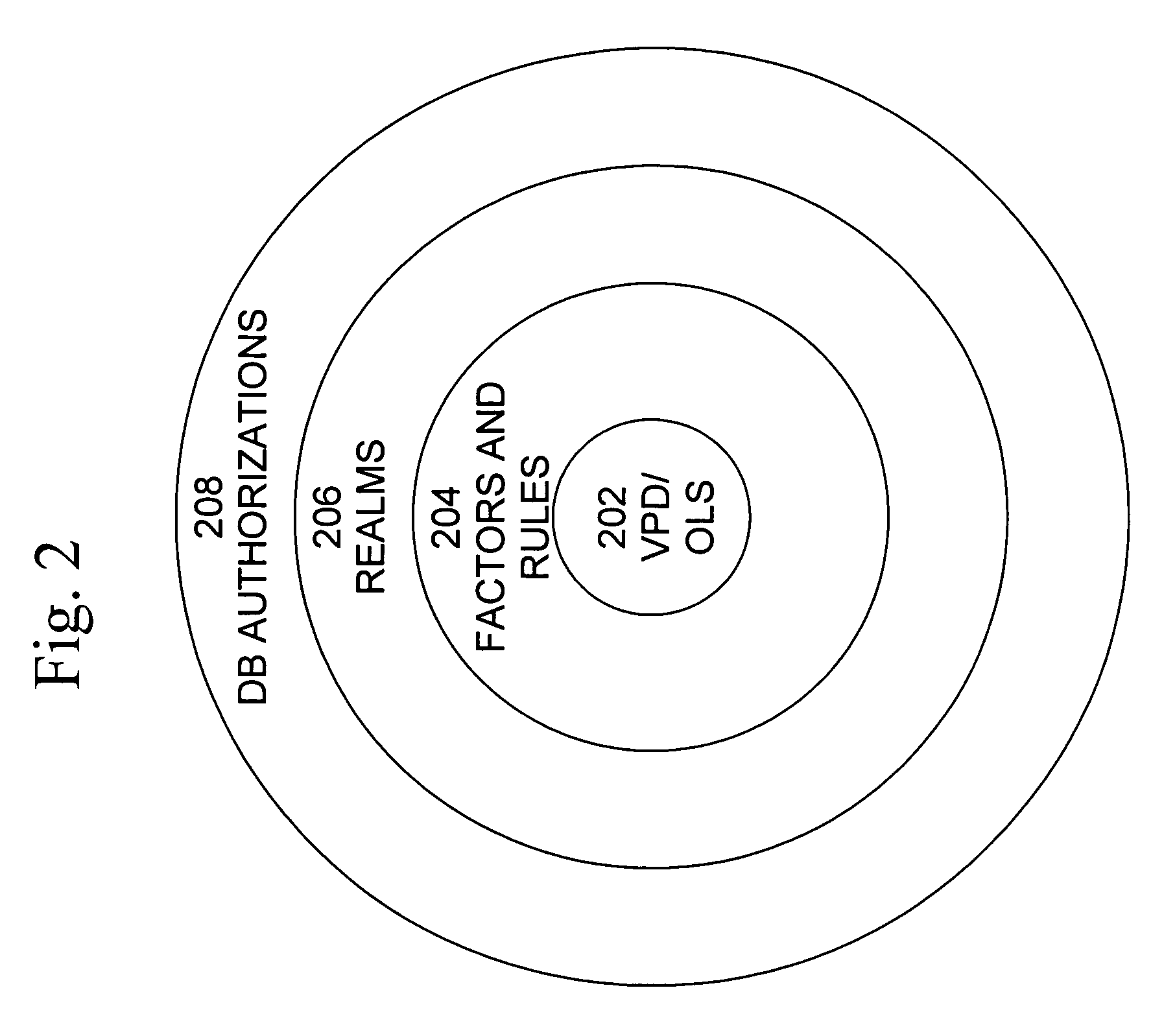
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises database objects having a level of security, factors representing a characteristic of a user of the database system, rules defining a limitation on operation of the database system by the user based on at least some of the plurality of factors and based on attributes of data to be operated on, including the level of security of the database object, and a plurality of realms defining a privilege of the user relative to a schema, the database system is operable to grant or deny access to data to a user based on the factors, the rules satisfied by the factors and the attributes of the data, and the realm associated with the user.
Owner:ORACLE INT CORP
Vulnerability management system based on multi-engine vulnerability scanning association analysis
ActiveCN108737425AMeet safety construction requirementsEfficient and accurate executionTransmissionVulnerability managementOperational system
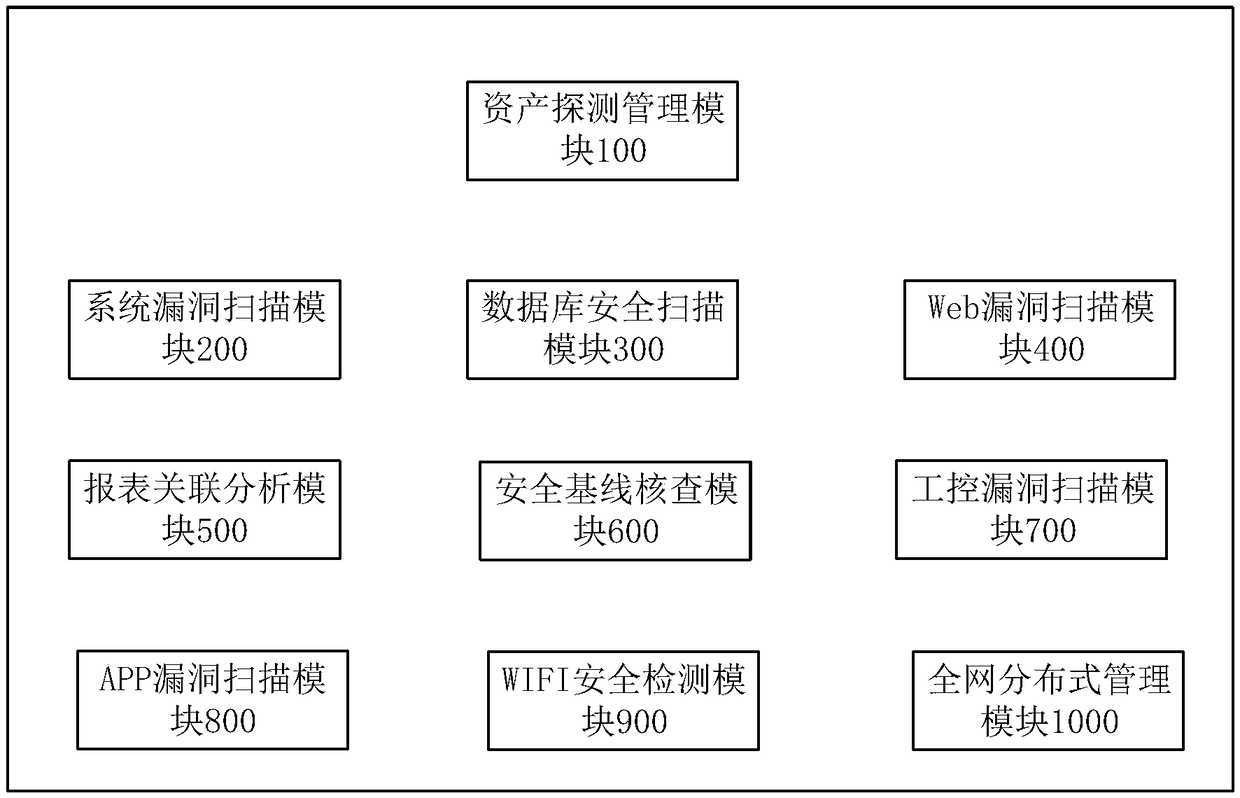
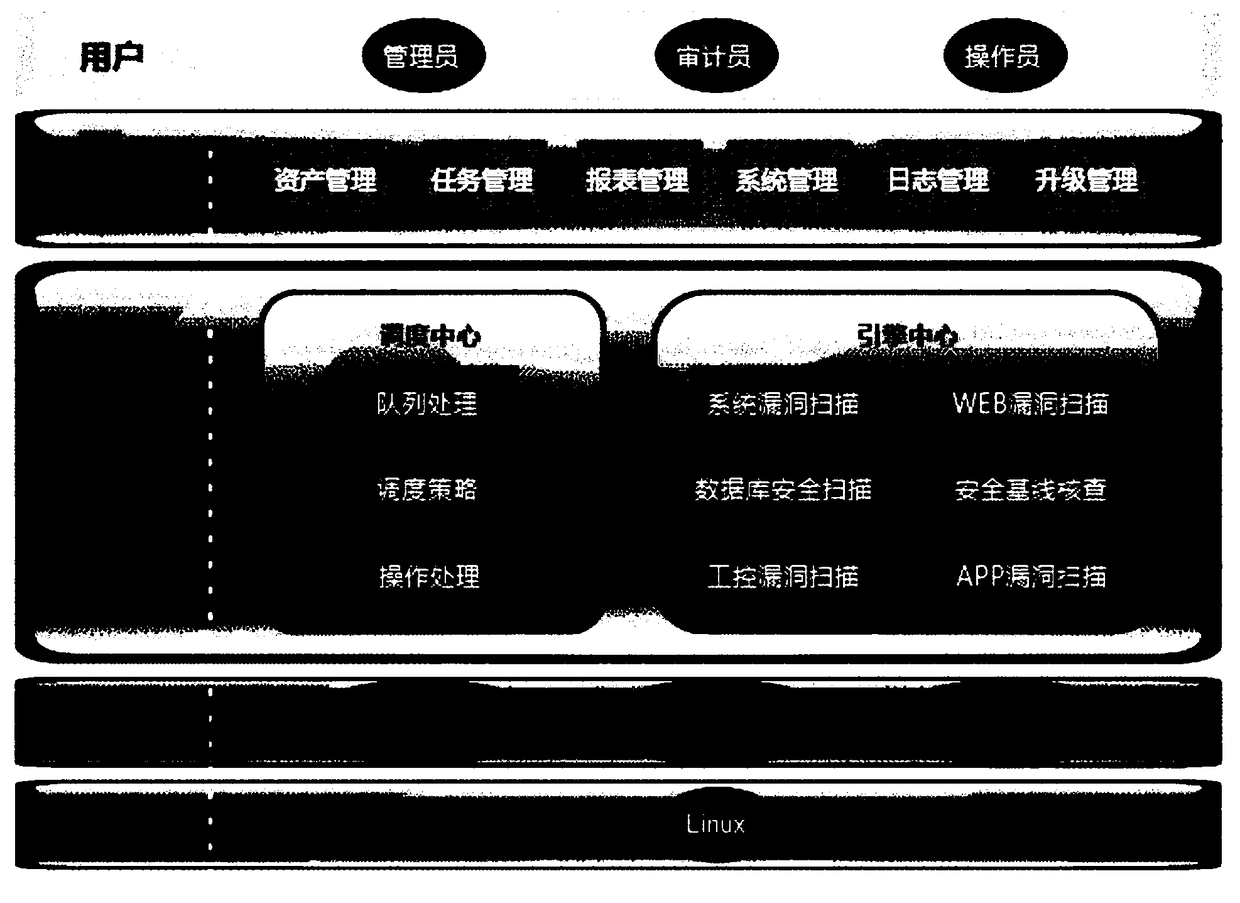
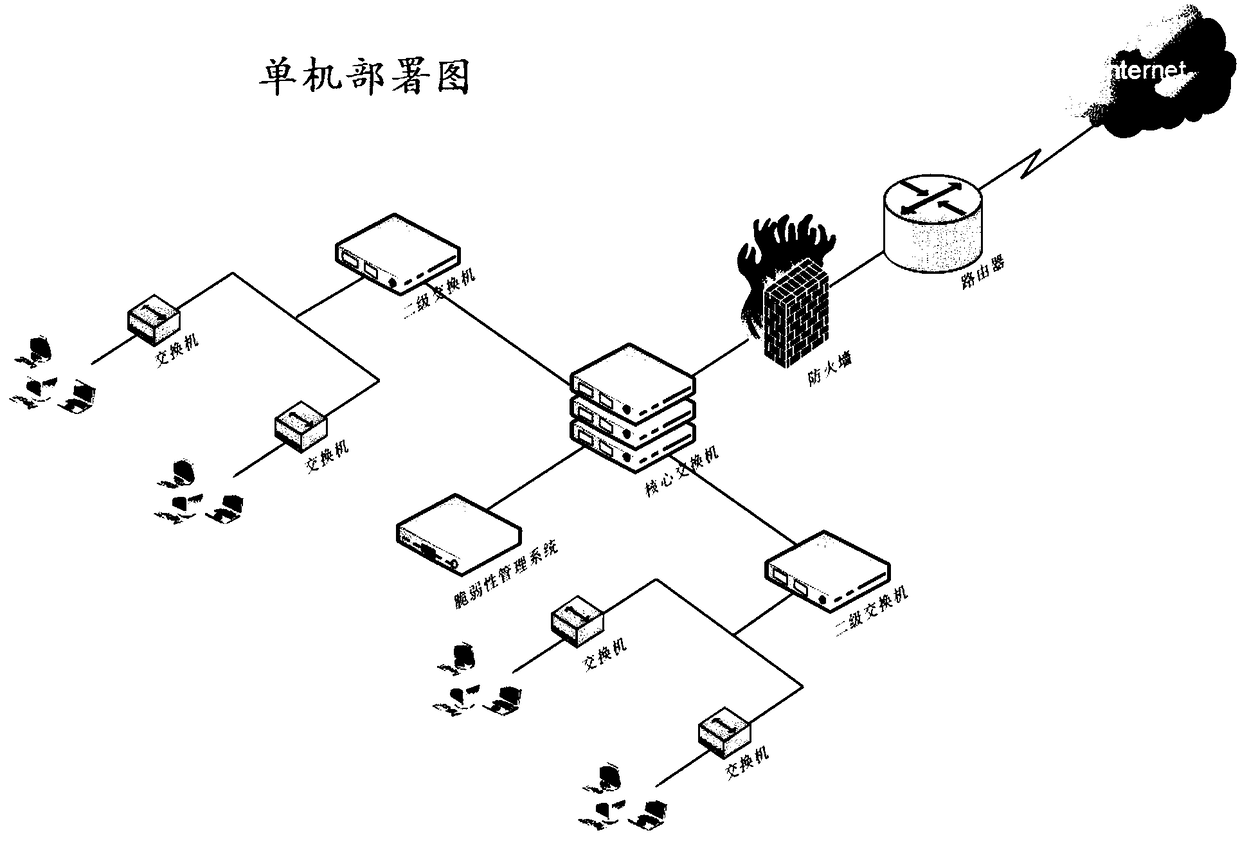
The invention provides a vulnerability management system based on multi-engine vulnerability scanning association analysis. The vulnerability management system comprises: an asset detection managementmodule used for detecting asset information in a scanning network; a system vulnerability scanning module used for performing vulnerability scanning and analysis on a network device, an operating system, application service and a database according to the asset information, and supporting intelligent service identification; a Web vulnerability scanning module used for automatically parsing data according to the asset information, scanning the data, verifying a discovered WEB vulnerability, and recording a test data packet discovered by vulnerability scanning; a database security scanning module; a security baseline verification module; an industrial control vulnerability scanning module; an APP vulnerability scanning module; a WIFI security detection module; a report association analysismodule; and a whole-network distributed management module. The vulnerability management system provided by the invention can perform association analysis on a detection result and a compliance libraryof information security level protection to generate a level protection evaluation report that meets the specification requirements, and the security requirements of different customers are comprehensively met.
Owner:北京凌云信安科技有限公司
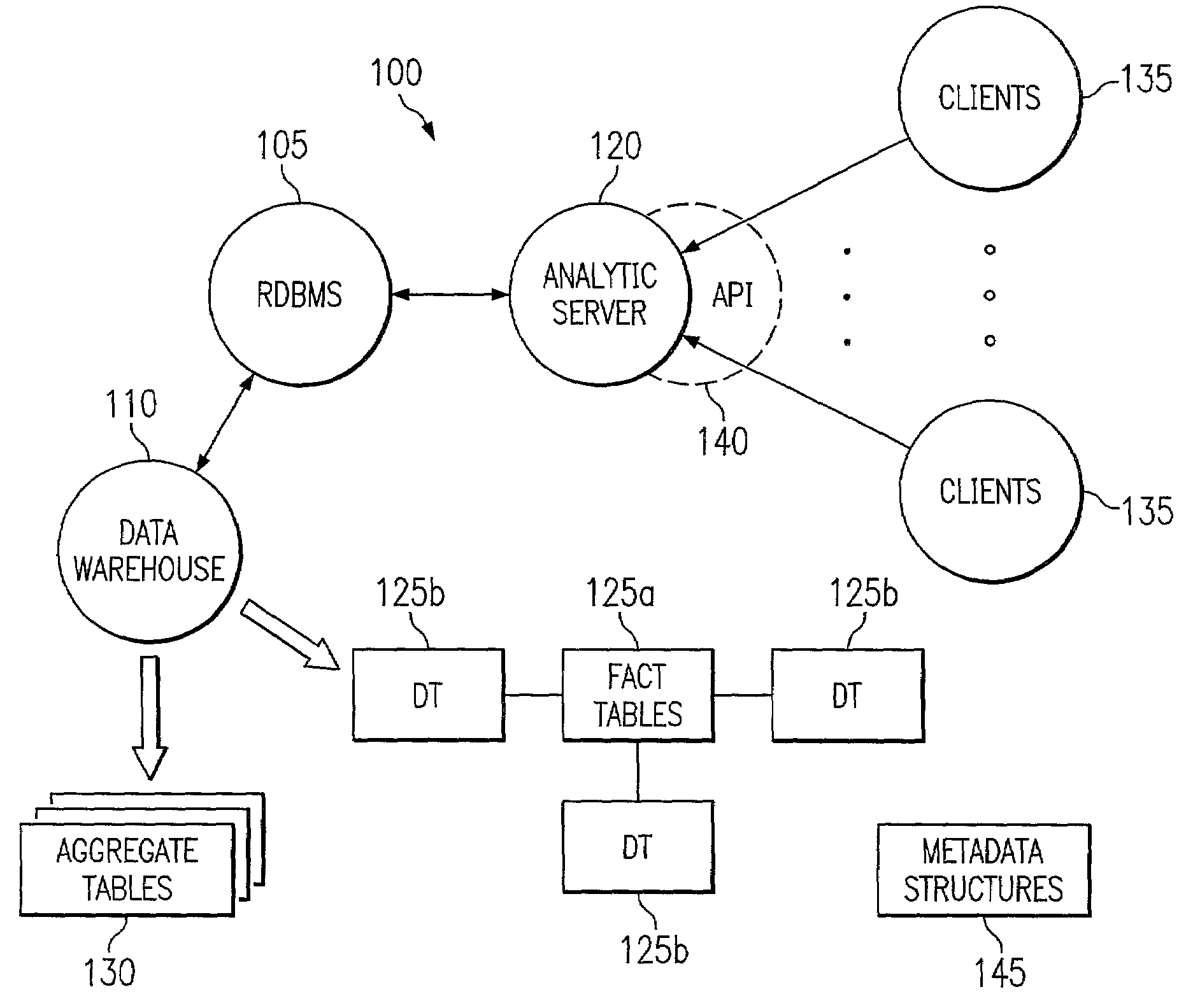
Database security
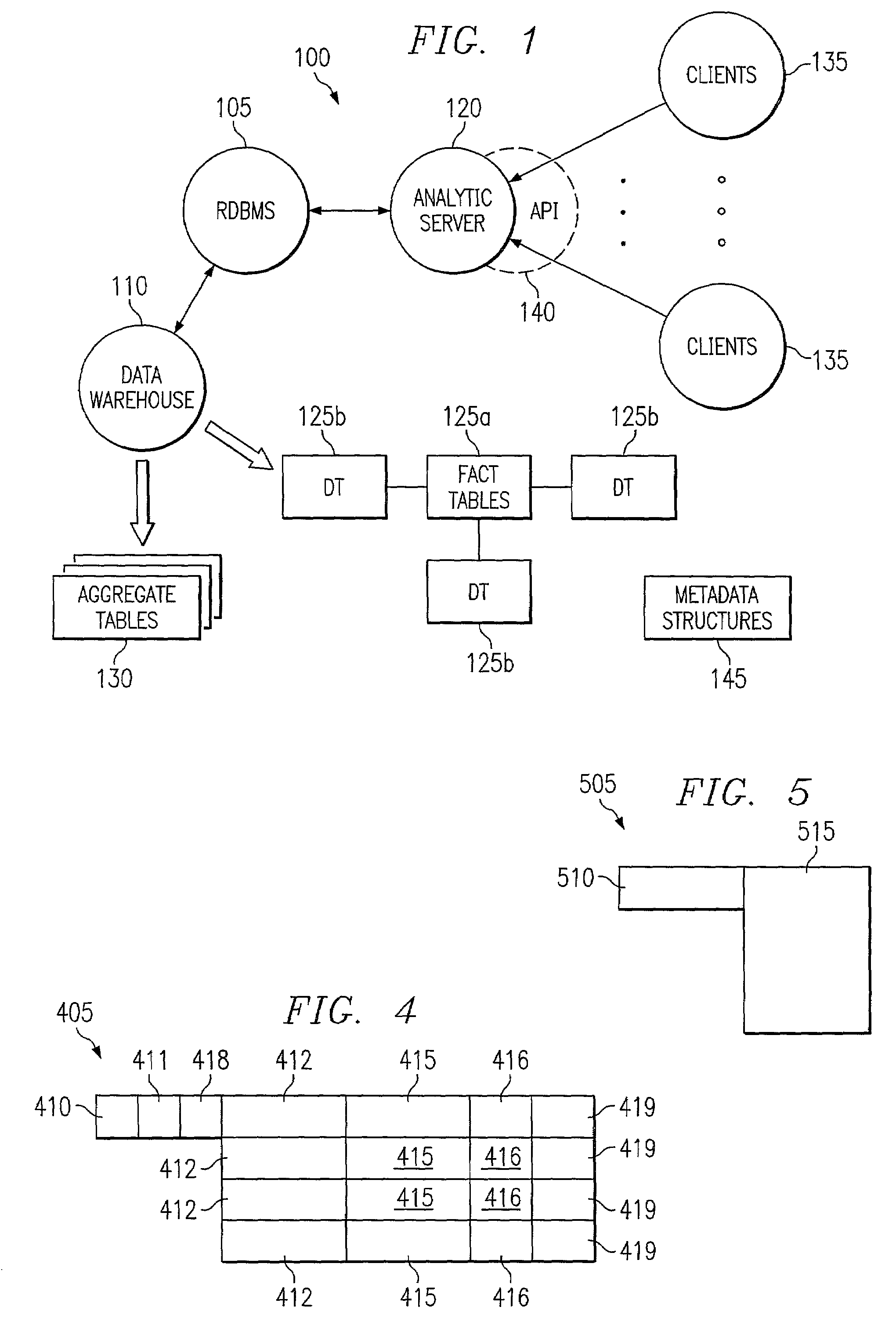
InactiveUS7167859B2Efficient accessEasy to calculateData processing applicationsDigital data processing detailsComputation complexityDatabase security
Disclosed is a system, method, and apparatus for calculating metrics by using hierarchical level metadata to describe the various structures within the database. The hierarchical level metadata permit calculation of complex metrics by an analytical server which would otherwise be difficult or impossible. As a result of the way that the analytical server calculates the metrics, slicing and drilling are supported. Additionally, dimension and fact level security are also supported.
Owner:ORACLE INT CORP
Systems and methods that specify row level database security
ActiveUS7711750B1Consumes spaceReduce disadvantagesDigital data processing detailsComputer security arrangementsClustered dataContext data
The present invention specifies database security at a row level and, optionally, at a column and table level. The systems and methods cluster one or more sets of rows with similar security characteristics and treat them as a named expression, wherein clustered data is accessed based on associated row-level security. The systems and methods specify a syntax that invokes row(s), column(s) and / or table(s) security via programming statements. Such statements include arbitrary Boolean expressions (predicates) defined over, but not restricted to table columns and / or other contextual data. These statements typically are associated with query initiators, incorporated into queries therefrom, and utilized while querying data. Rows of data that return “true” when evaluated against an aggregate of associated security expressions are said to “satisfy” the security expressions and enable access to the data stored therein. Such security expressions can be created and invoked via the Structured Query Language (SQL) database programming language.
Owner:MICROSOFT TECH LICENSING LLC
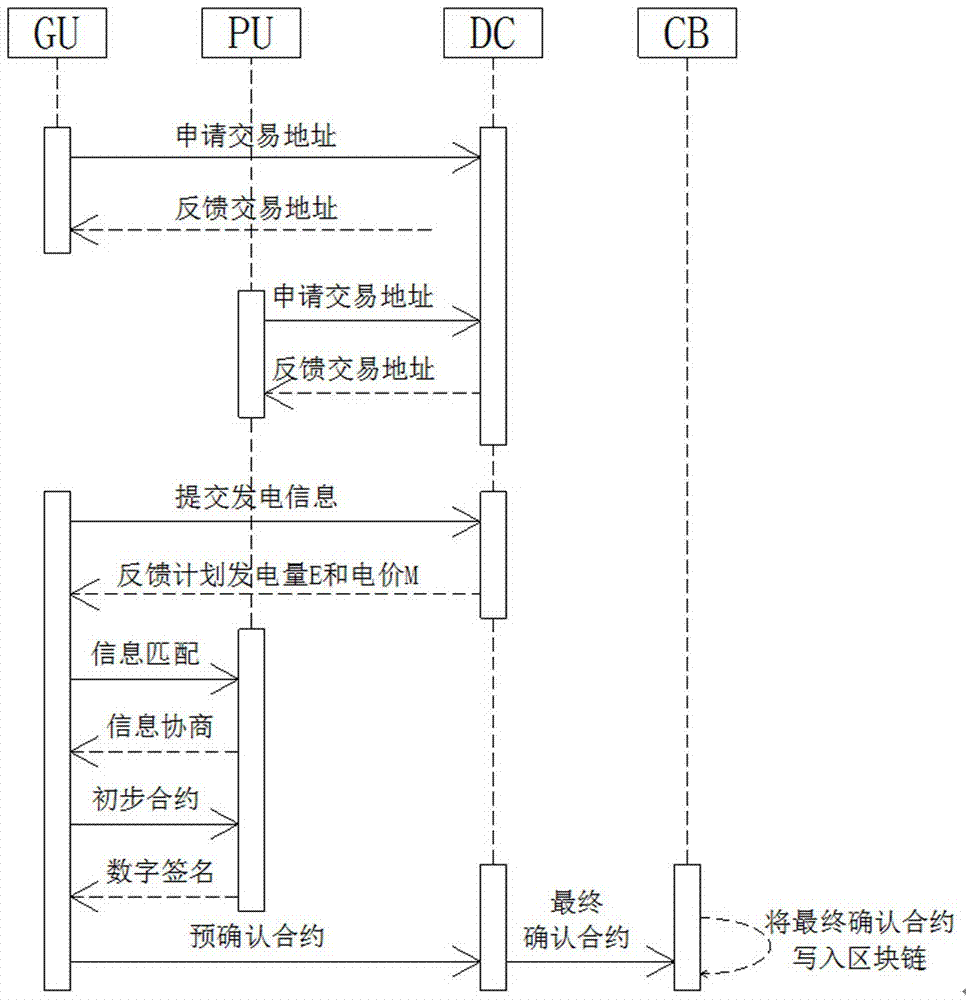
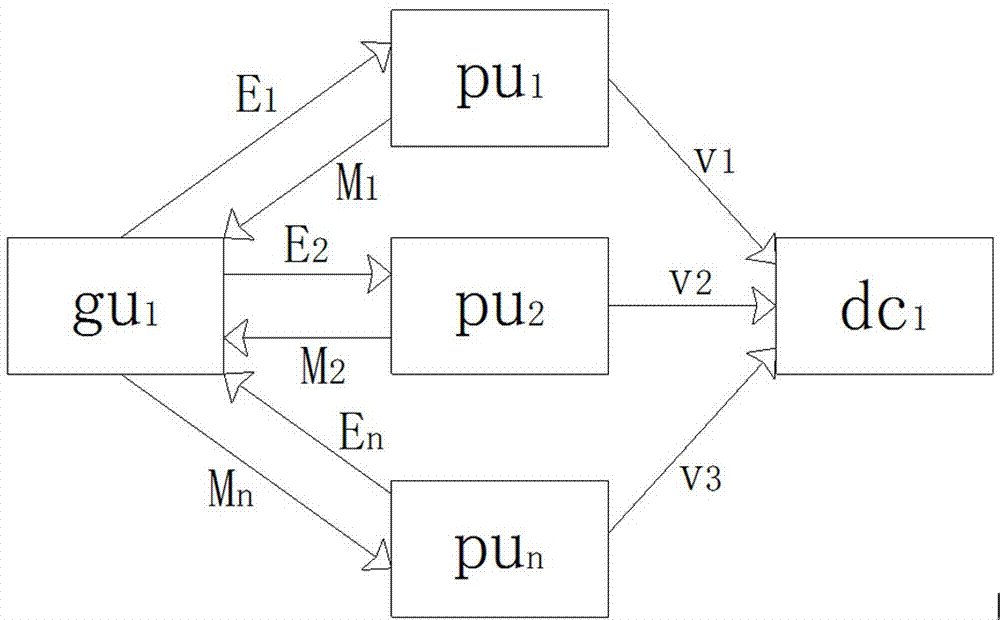
Distributed energy transaction authentication method based on alliance block chain
InactiveCN107423978AConvenient transaction supervisionEasy data traceabilityProtocol authorisationTransaction dataInformation transparency
The invention relates to a distributed energy transaction authentication method based on an alliance block chain. For the data security problem of a distributed energy source during the transaction authentication process, a distributed energy transaction authentication model based on the alliance chain technology, a related TCA transaction authentication algorithm and an ET-Pos interest proving method are provided. the method is provided based on the data encryption of the block chain technology, the time stamp, the distributed consensus and other means, and the traditional energy transaction system is optimized. Therefore, the security of a transaction center database, the user information privacy, the capacity mismatching of multiple units and the like are well solved. The safety, the information transparency and the automatic authentication level of distributed energy transaction data are improved.
Owner:ZHENGZHOU UNIV
Dynamic auditing
ActiveUS20060248084A1Ease of administrationEnsure effective implementationDigital data processing detailsComputer security arrangementsDatabase securitySecurity level
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises a plurality of database objects, each database object having a level of security, a plurality of factors, each factor representing a characteristic of a user of the database system, at least one database session of the user in the database, the database session having a level of security, the user connected to the database with a network domain, each network domain having a level of security, wherein the database system is operable to grant or deny access to the data to a user based on the factors associated with the user, based on the level of security of the data, based on the level of security of the database session, and based on the level of security of the network domain.
Owner:ORACLE INT CORP
Mandatory access control label security
ActiveUS7831570B2Ease of administrationEnsure effective implementationDigital data processing detailsComputer security arrangementsData setData access
A secure database appliance leverages database security in a consistent framework provides consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises a plurality of datasets, each dataset including a plurality of data, and a plurality of database objects, each object having a security label comprising a security classification of the object, at least one database session, the database session having a security label indicating a security classification of the database session, wherein, the database system is operable to allow or deny access to data to a database session based on a security label of a database object and on a security label of the database session.
Owner:ORACLE INT CORP
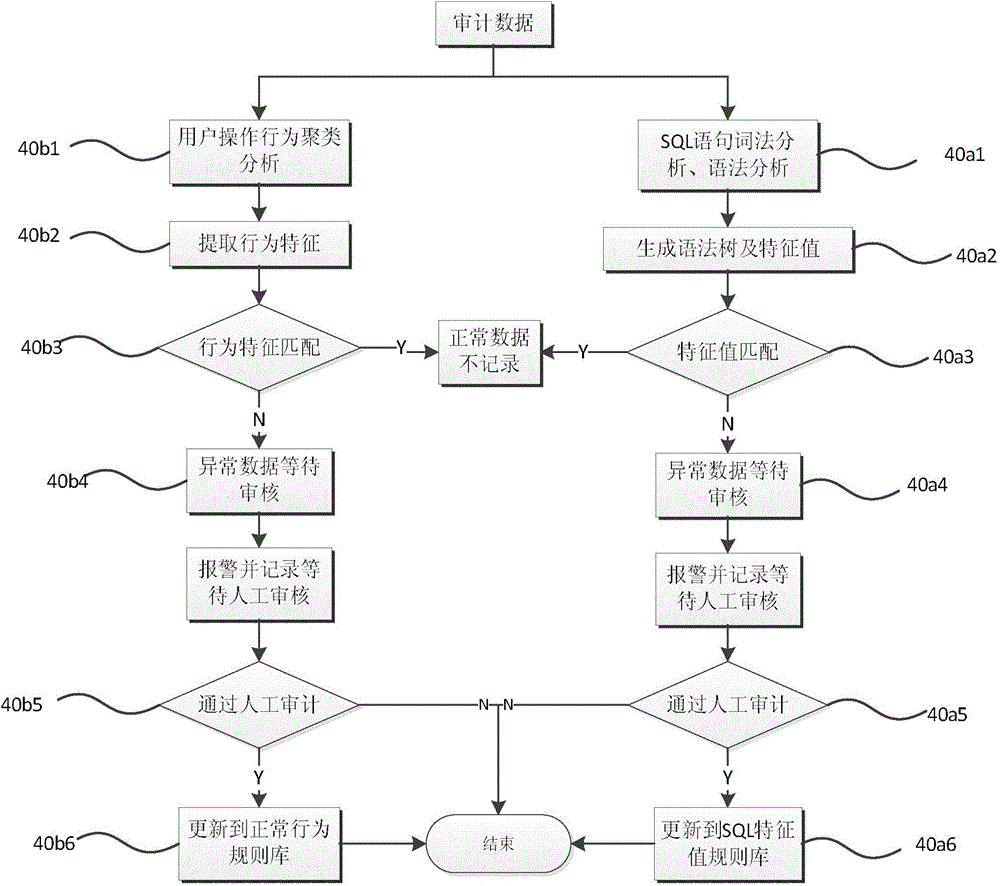
Database security auditing method
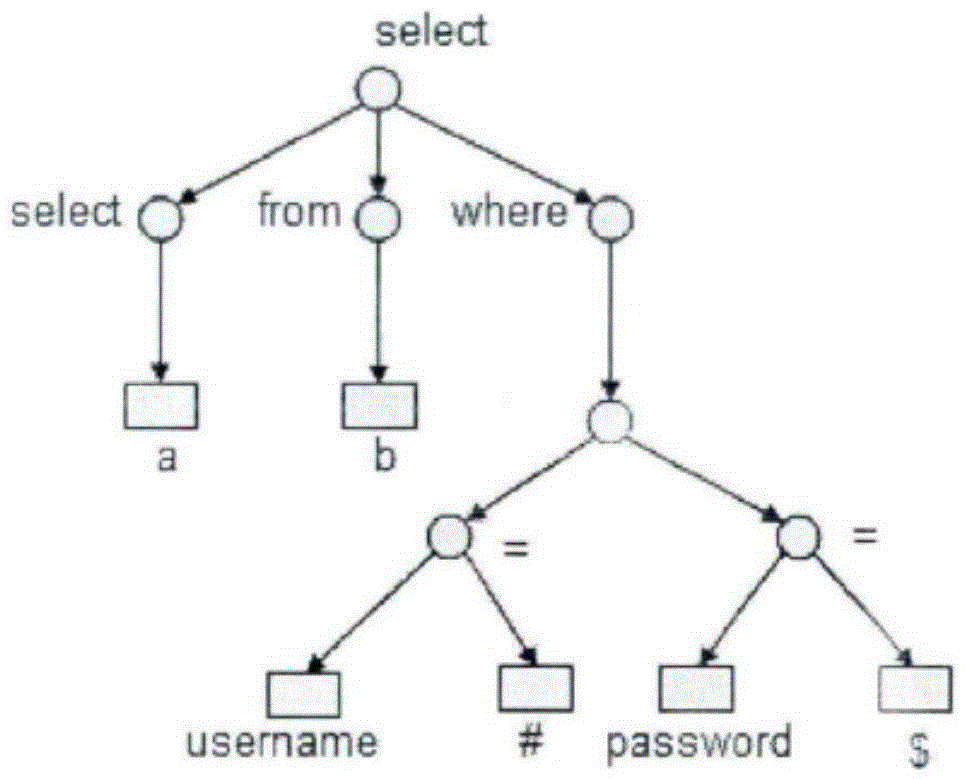
InactiveCN104484474APreventive actionsDiscover usability in timePlatform integrity maintainanceSpecial data processing applicationsSQL injectionNetwork Communication Protocols
The invention relates to a database security auditing method which comprises the following steps: acquiring database network communication data; parsing a database network communication protocol; carrying out self-learning digging on audit rules; detecting database risk event invasion; evaluating database user permissions; tracking the three-layer correlation of a primary user. The database security auditing method can be used for auditing and monitoring a database in real time, so that the automatic assessment, audit, protection and invasion detection operation can be realized; the method can be used for preventing, recording and tracking the complete database operation behavior so as to help an administrator to find out the internal safety problems of unauthorized use, privilege abuse, permission theft and the like of the database in time; furthermore, after the method is used, the outside attacks such as SQL (structured query language) injection and the like can be avoided.
Owner:NANJING DUNLEI NETWORK TECH CO LTD
Database access control method on basis of multi-strategy integration
ActiveCN104484617AEnsure safetyQuick Action SupportDigital data protectionElectronic systemsRole-based access control
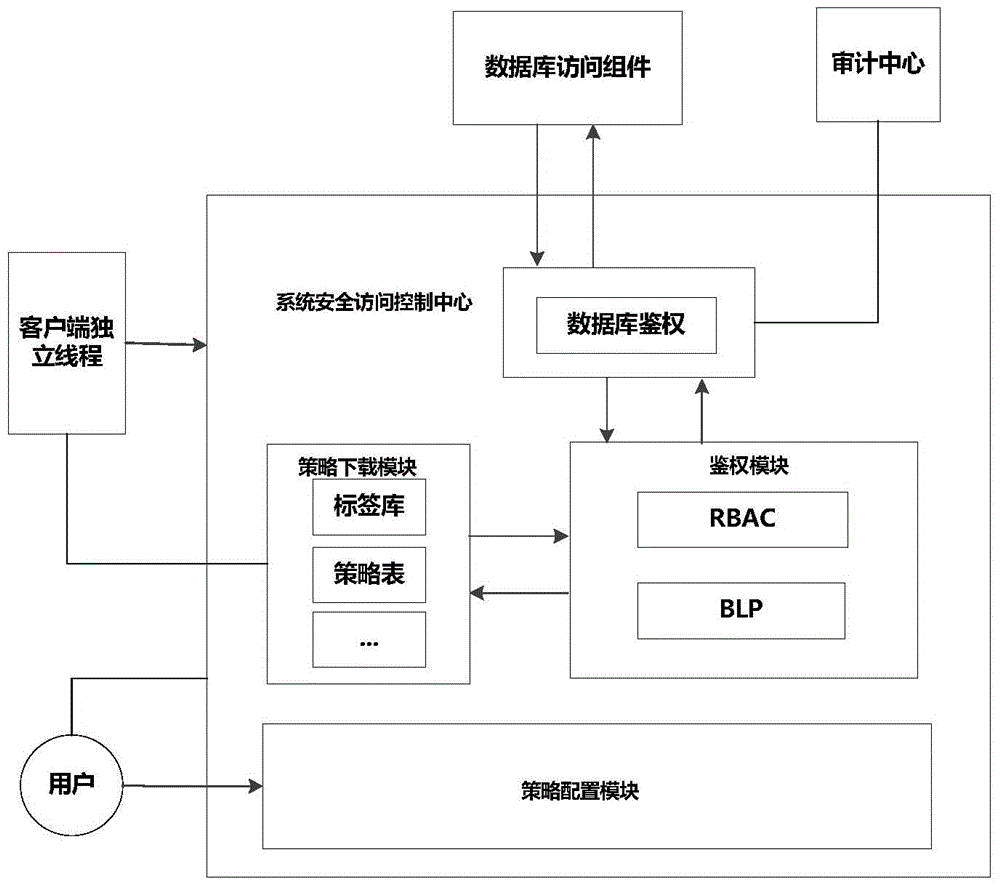
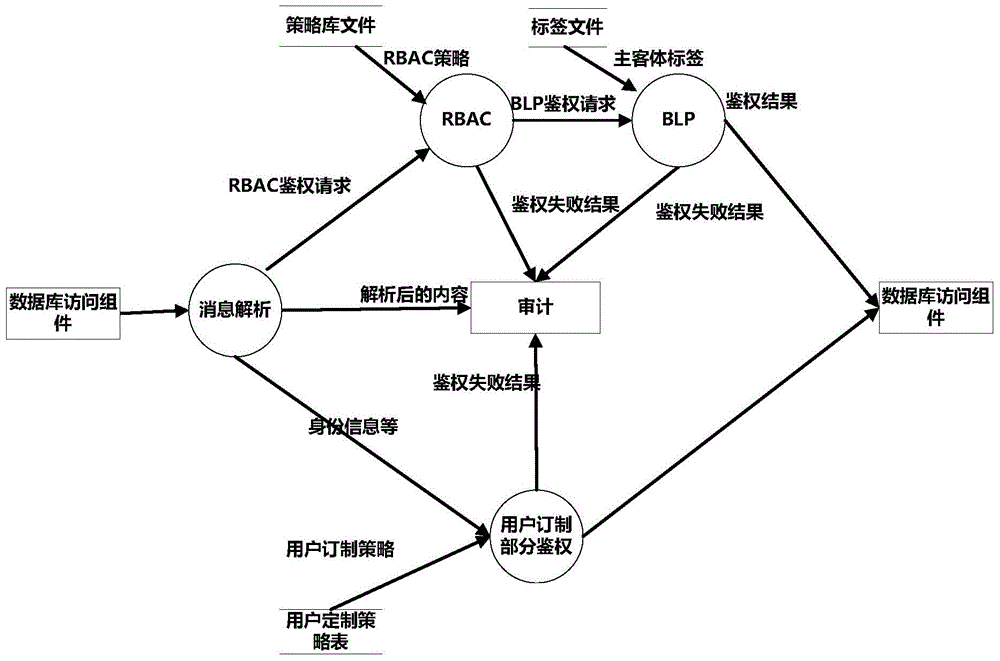
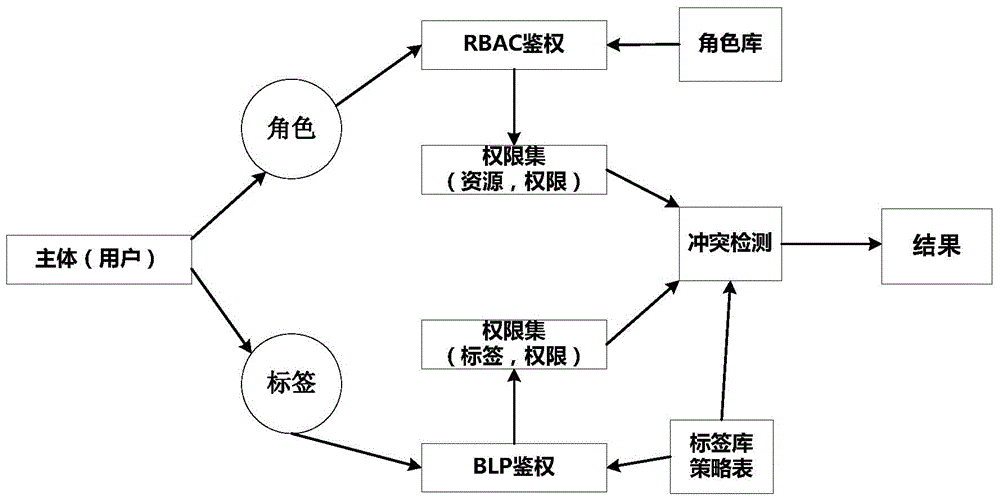
The invention provides a database access control method on the basis of multi-strategy integration. The database access control method aims to solve widespread problems in the aspect of security access to databases of comprehensive electronic systems. The database access control method includes enabling an RBAC (role-based access control) module to judge whether roles corresponding to users have access permission corresponding to required-to-be-accessed database tables or not; denying access if the roles do not have the access permission; enabling a BLP (Bell-La Padula) module to judge operation permission of the users for fields in the required-to-be-accessed database tables if the roles have the access permission. The database access control method has the advantages that various security levels of information in databases can be assuredly effectively accessed, the security of the databases can be protected on table levels and even field levels, permission of subjective bodies and objective bodies can be effectively customized according to actual conditions, and corresponding access control strategies can be provided for the subjective bodies of the different roles.
Owner:AVIC NO 631 RES INST
Database security access control method and system
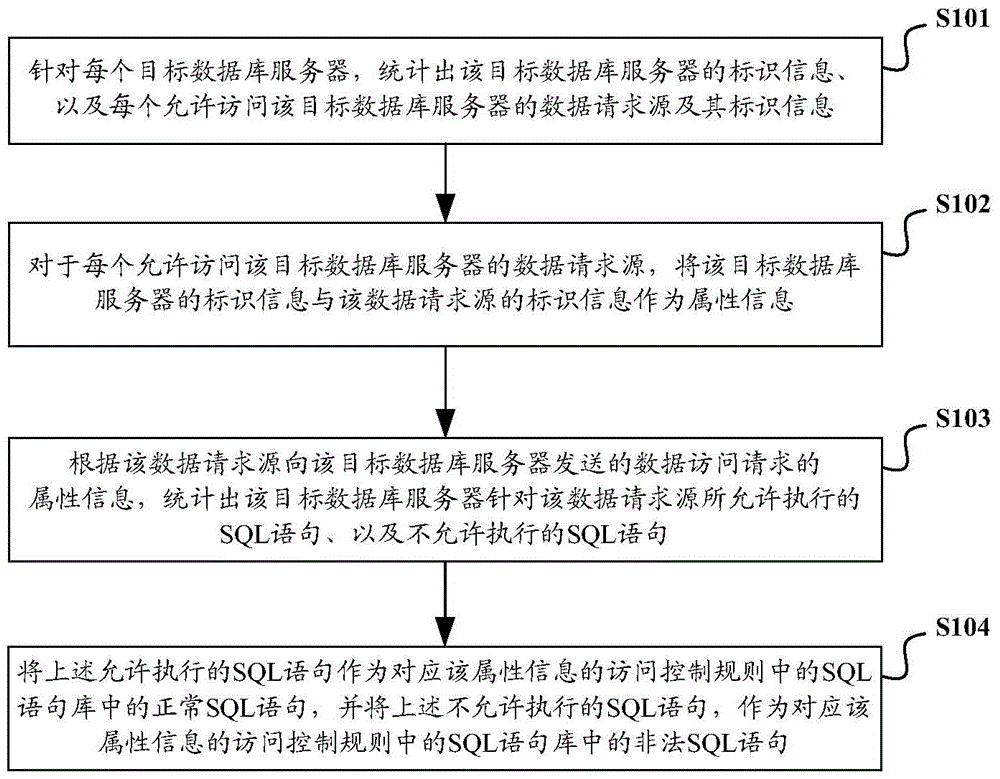
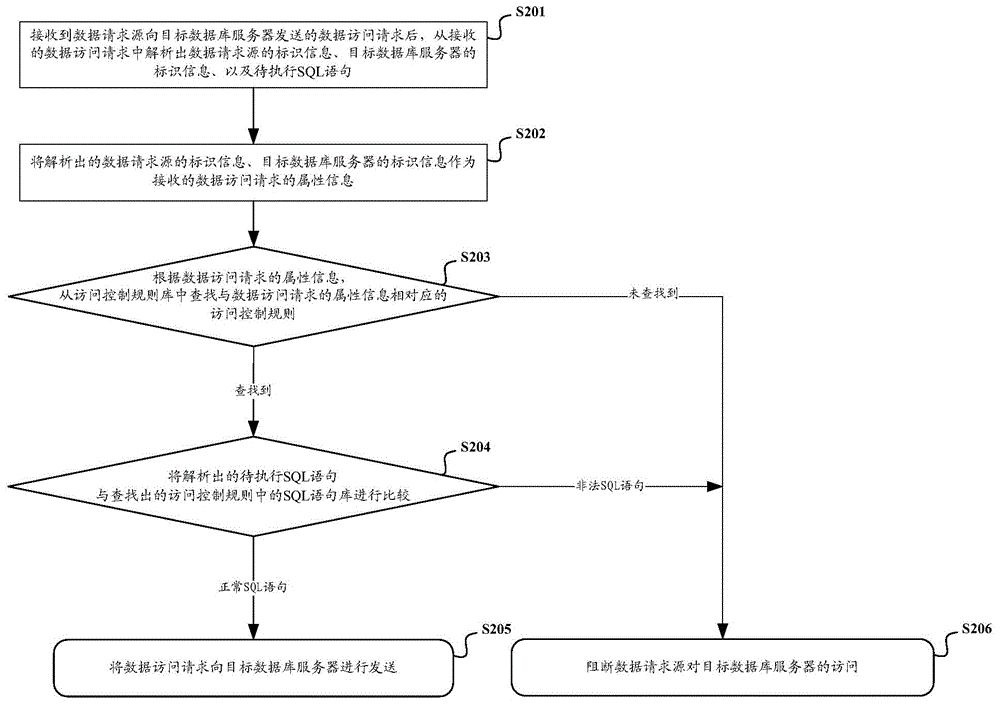
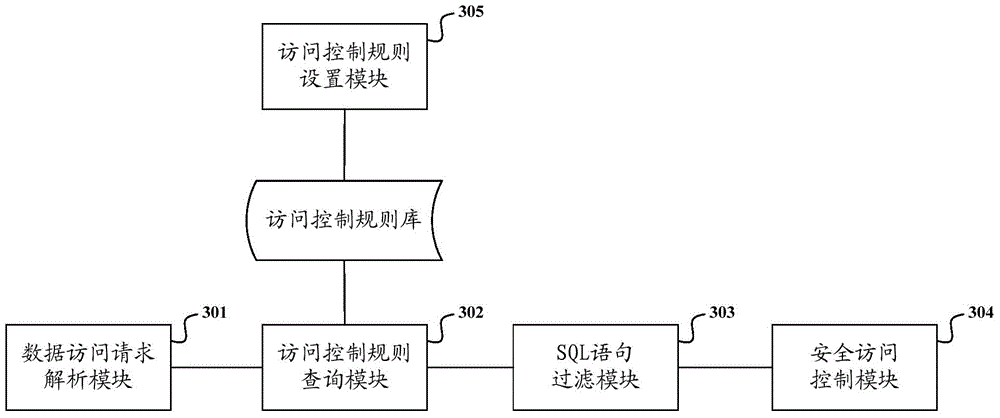
InactiveCN104008349AHigh strengthDigital data protectionSpecial data processing applicationsSQL injectionDatabase server
The invention discloses a database security access control method and system. The method comprises the steps of: analyzing a to-be-executed SQL (Structured Query Language) statement in a data access request sent from a data request source to a target database server and analyzing label information of the data request source and label information of the target database server to serve as attribute information of the data access request; comparing the to-be-executed SQL statement with an SQL statement library in an access control rule after the access control rule corresponding to the attribute information is found in the access control rule library based on the attribute information; if the comparison result is that the to-be-executed SQL statement is an illegal SQL statement in the SQL statement library, interdicting the access of the data request source to the target database server. By the application of the database security access control method and system, SQL injection attacks can be prevented, and security control intensity of a database system is enhanced.
Owner:STATE GRID CORP OF CHINA +3
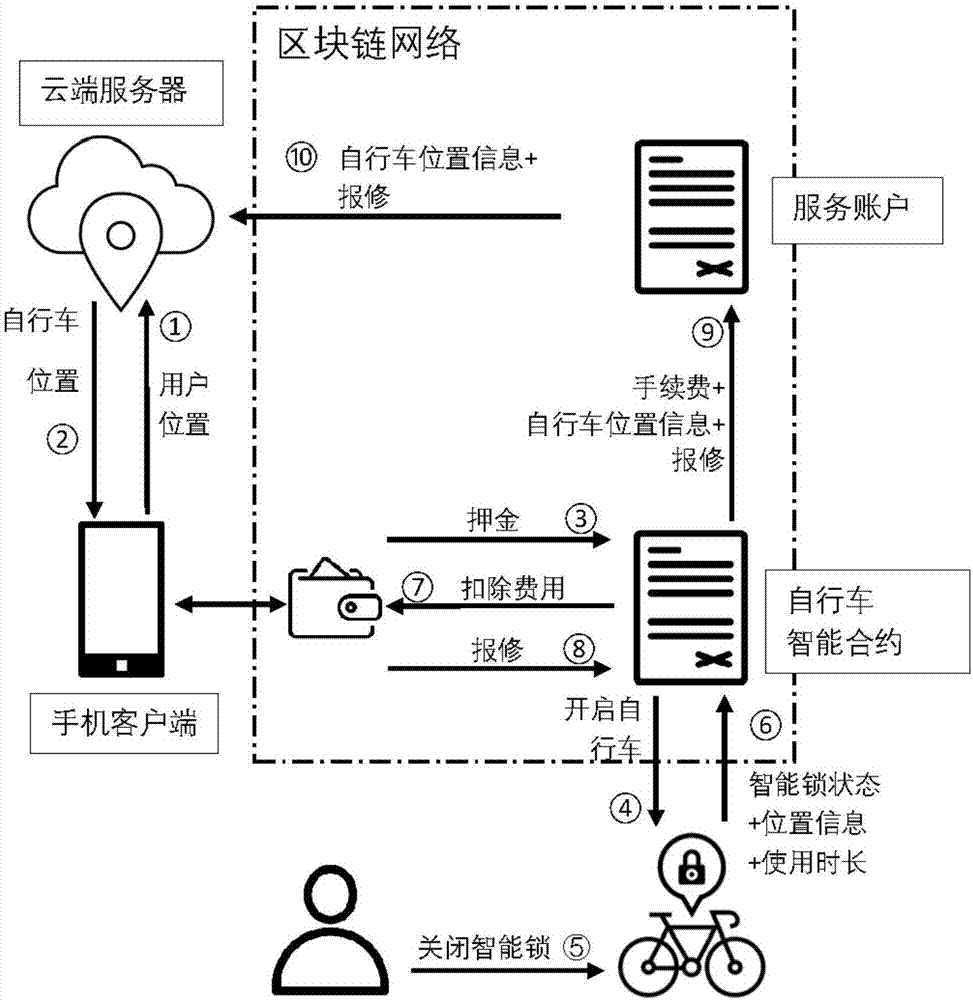
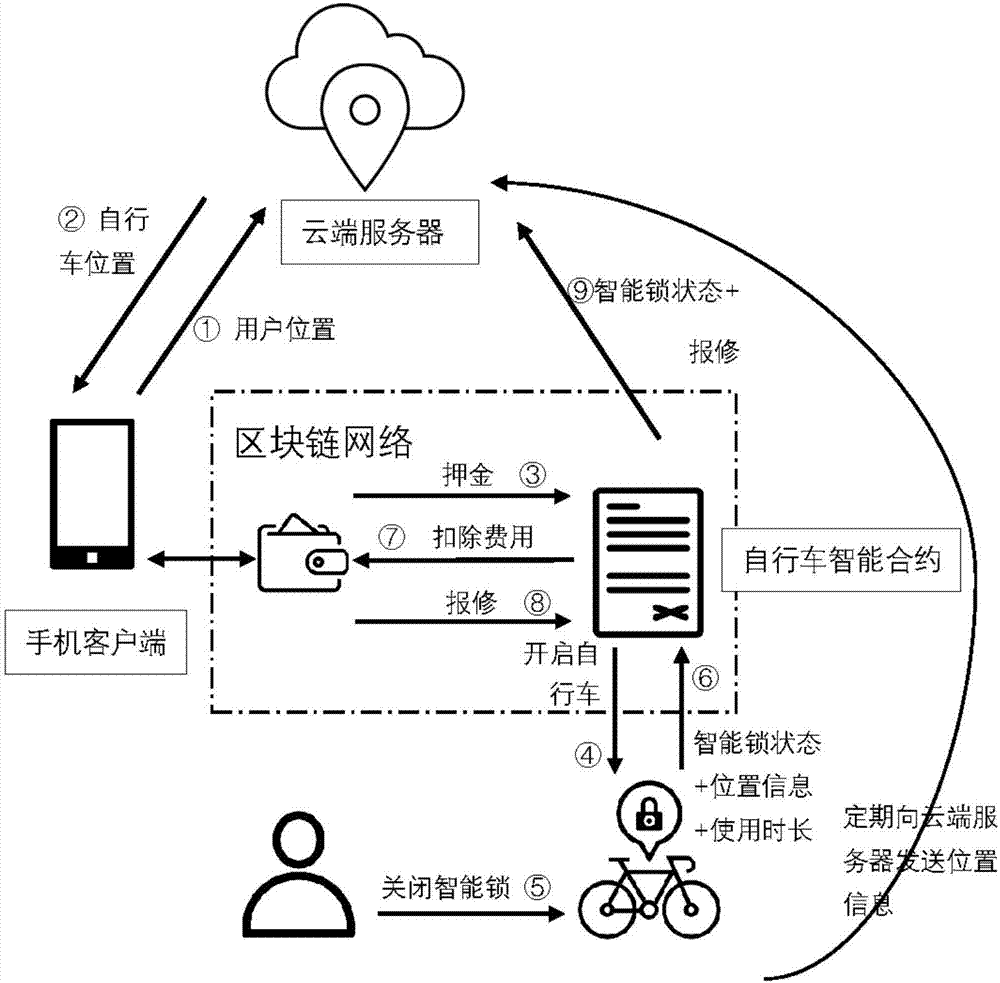
End-to-end bike sharing system and method based on blockchain
ActiveCN107993359AEnsure safetyLow costApparatus for meter-controlled dispensingTransmissionThird partyBike sharing
The invention discloses an end-to-end bike sharing system and method based on blockchain. The system comprises a system administrator, a cloud server, bike owners, bike users and a blockchain network;the blockchain network contains accounts, bike smart contracts and nodes; there is no need for the bike users to download multiple different applications any more, after registration, deposits are paid to the bike smart contracts, the blockchain network does not contain third parties, and the users only need to apply to the bike smart contracts when the deposits need to be returned, so that the phenomenon of difficult deposit returning is effectively avoided; the payment process does not rely on third-party payment software, so that needed commission charge is effectively reduced. Transactioninformation is stored by the nodes in the blockchain network together, each node stores all transaction data in the network totally redundantly, and once the data in one node is tampered with, othernodes raise objections, so that a whole database is high in safety, and private security of the bike users and the bike owners can be protected.
Owner:ZHEJIANG UNIV
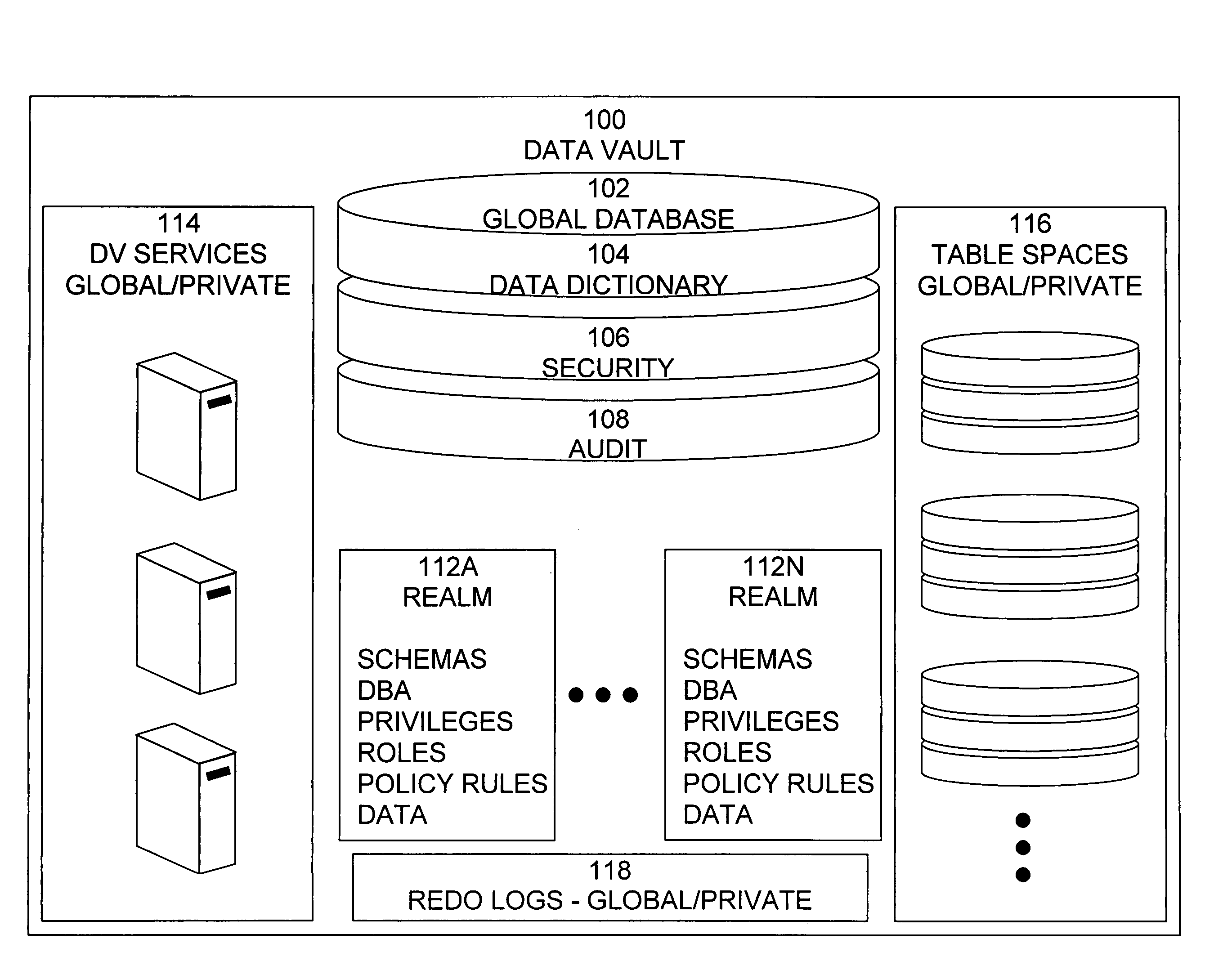
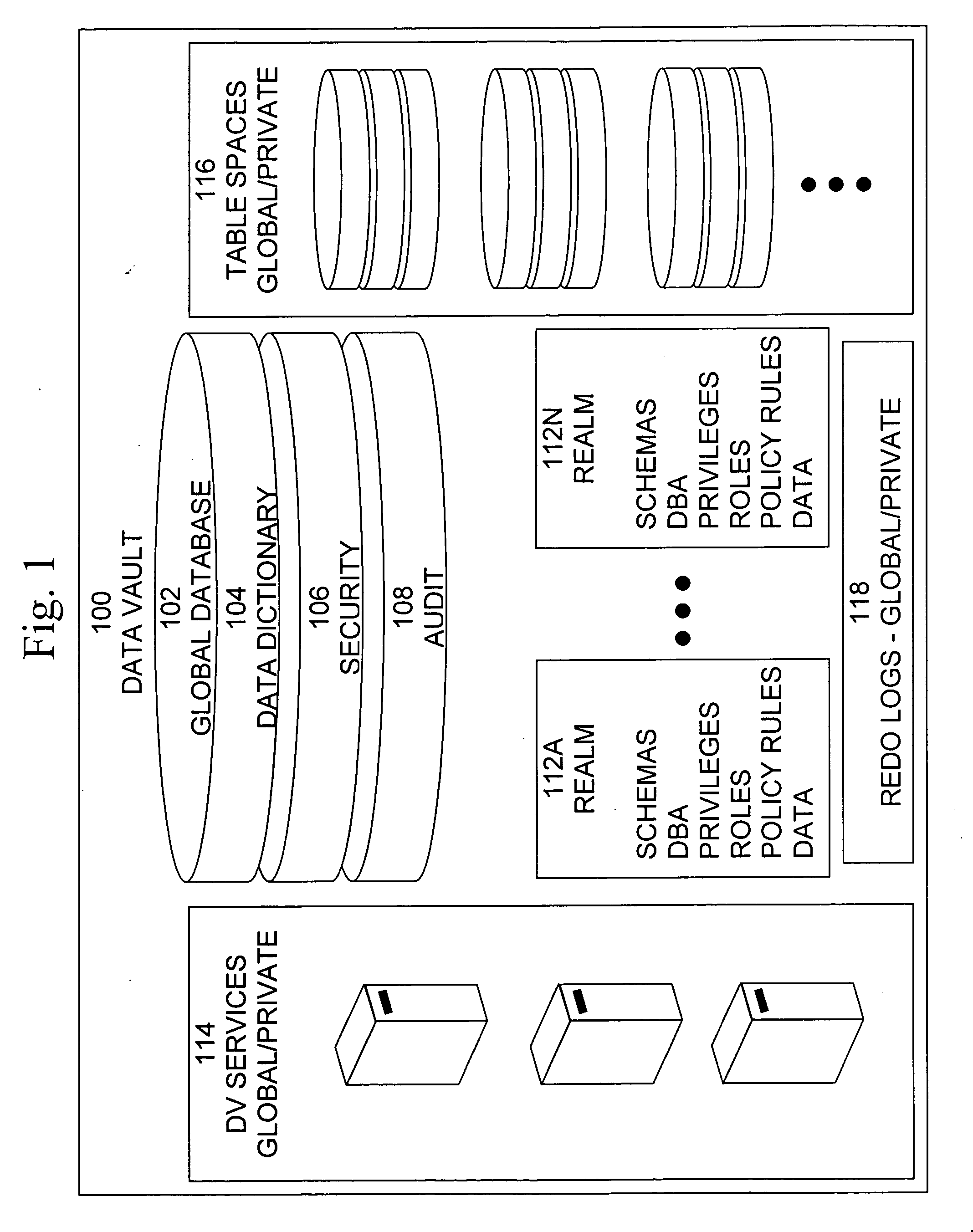
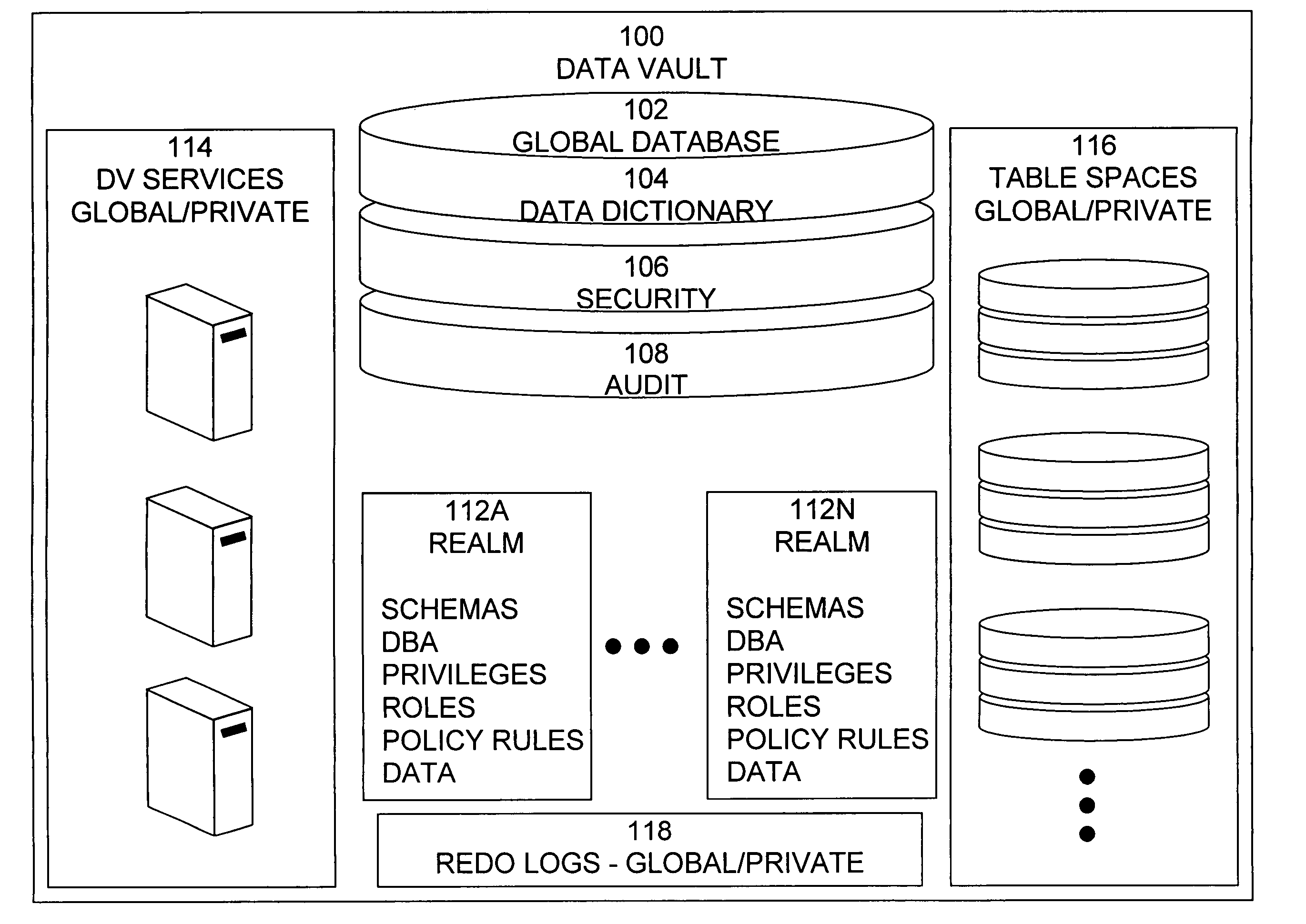
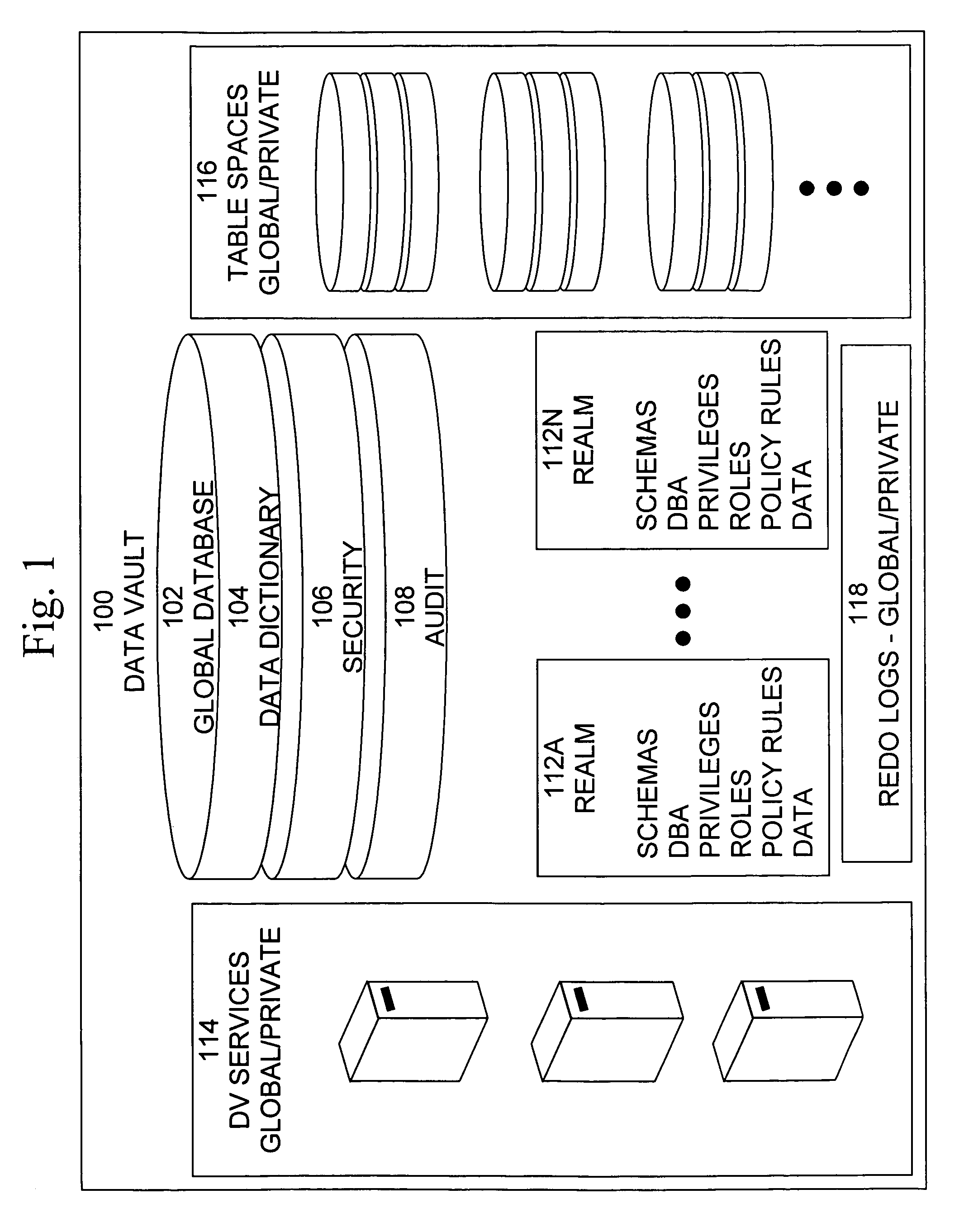
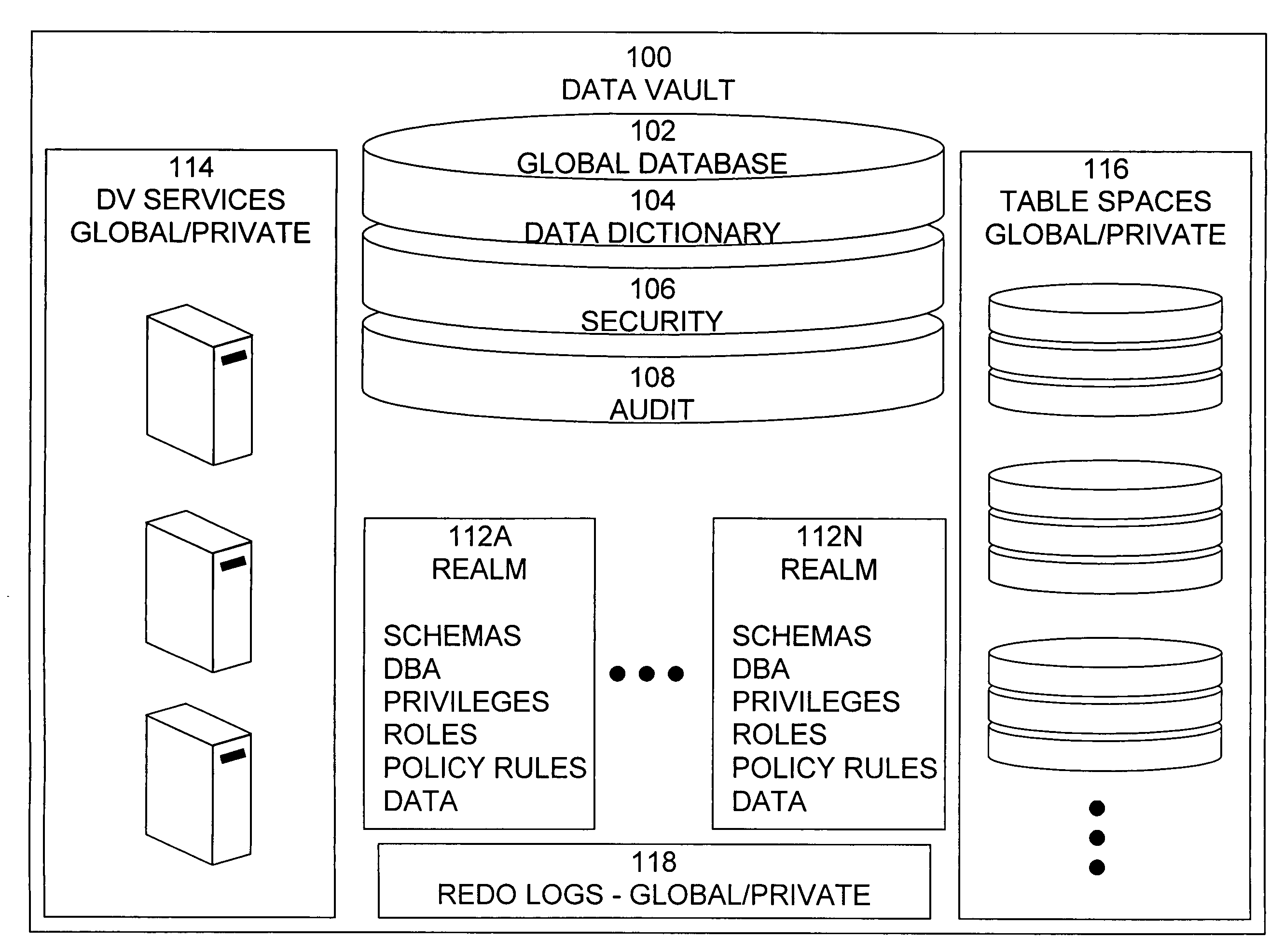
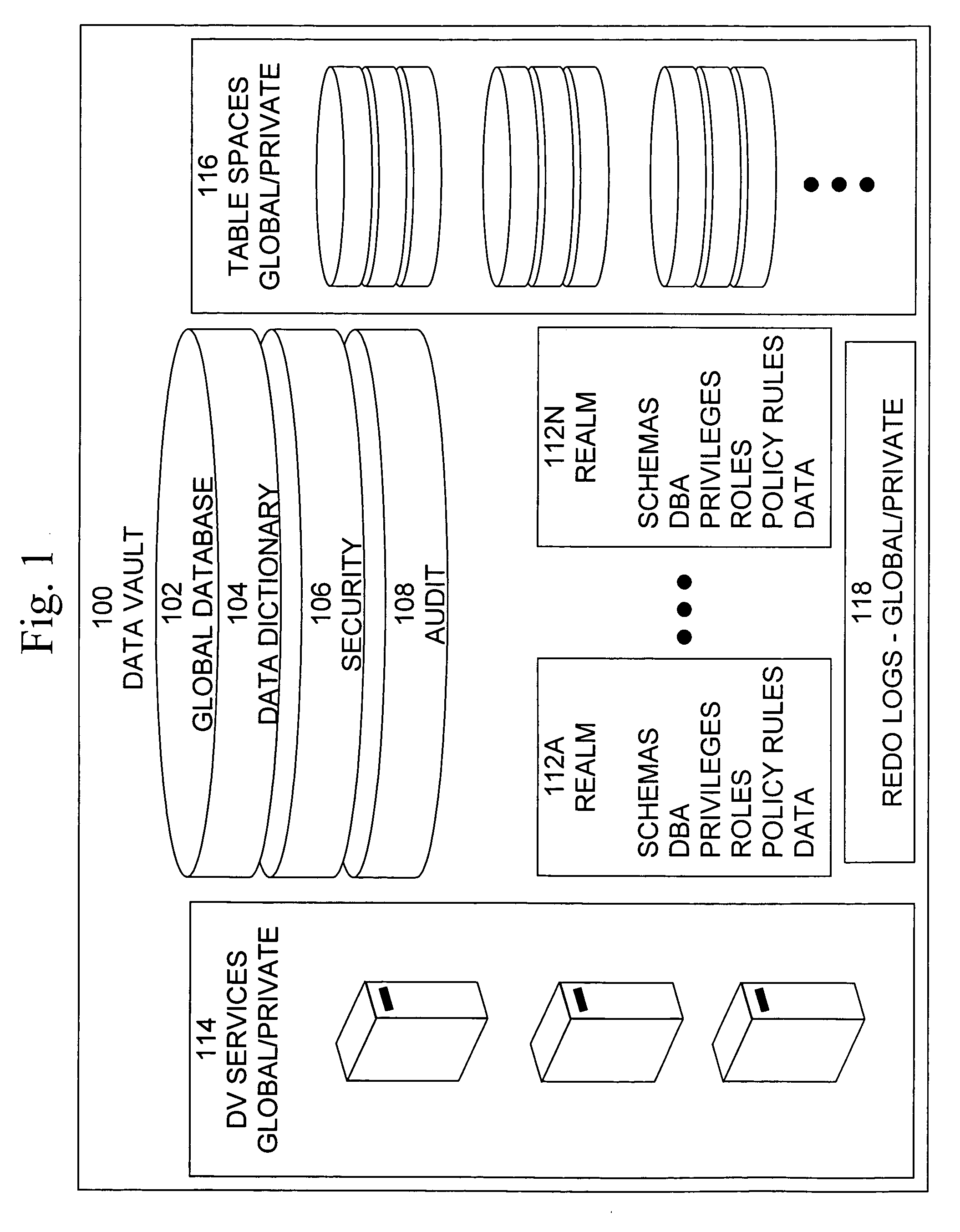
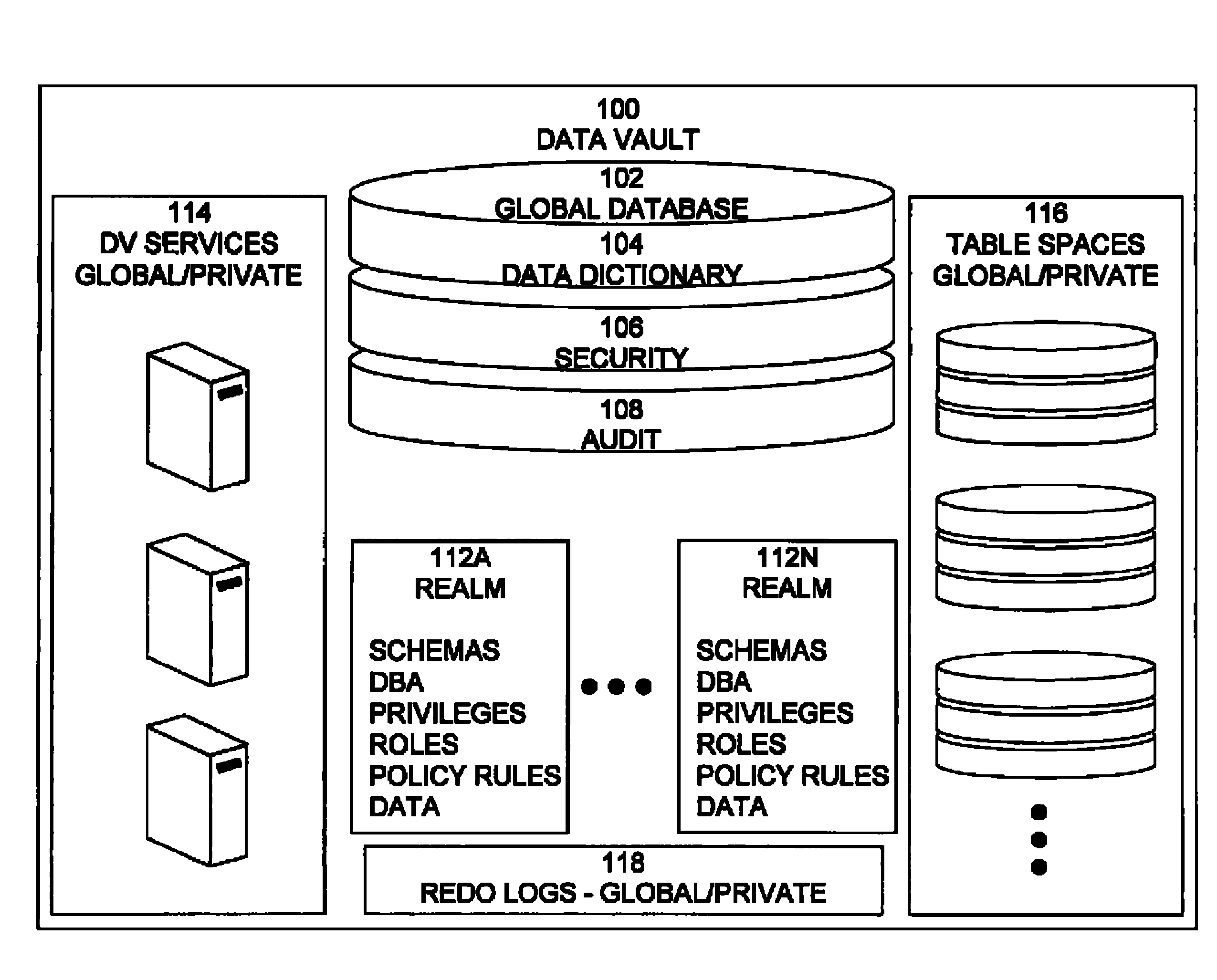
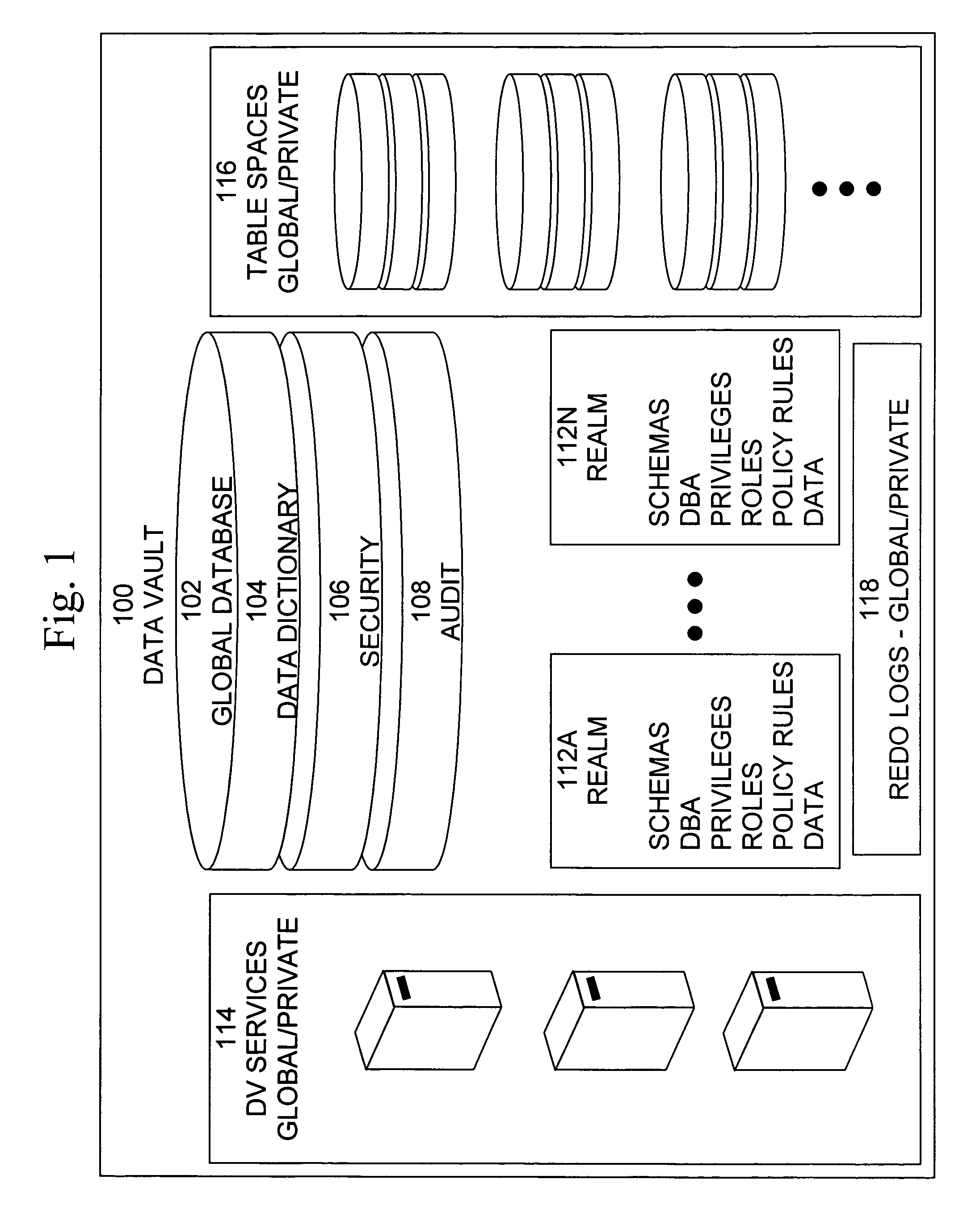
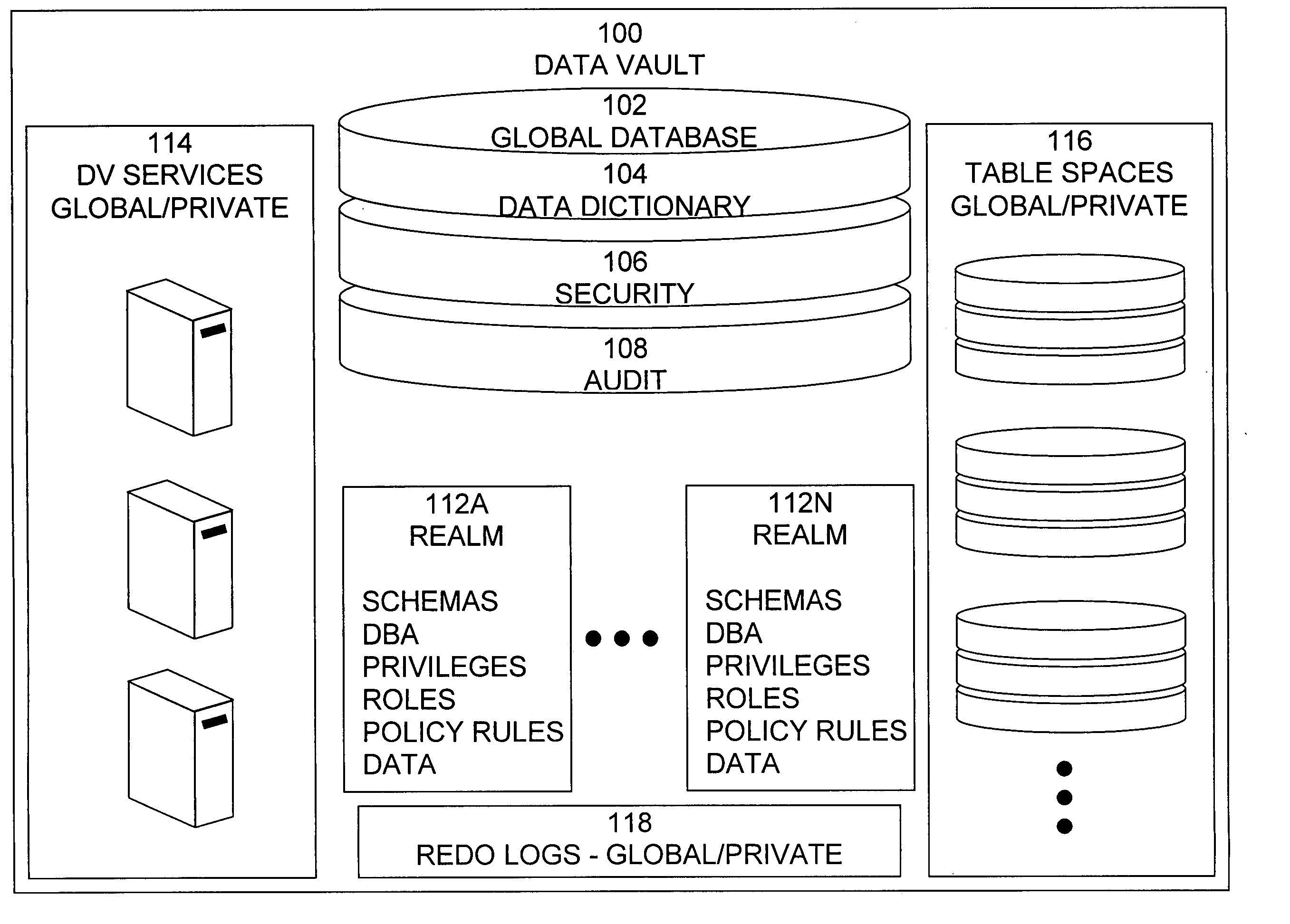
Data vault
ActiveUS20060248085A1Ease of administrationEnsure effective implementationDigital data processing detailsComputer security arrangementsDatabase securitySecurity level
A secure database appliance leverages database security in a consistent framework providwa consistent, flexible, and adaptable security using mandatory access controls in addition to user and role based security for access control and accountability. A database system comprises a plurality of database objects, each database object having a level of security, a plurality of factors, each factor representing a characteristic of a user of the database system, at least one database session of the user in the database, the database session having a level of security, the user connected to the database with a network domain, each network domain having a level of security, wherein the database system is operable to grant or deny access to the data to a user based on the factors associated with the user, based on the level of security of the data, based on the level of security of the database session, and based on the level of security of the network domain.
Owner:ORACLE INT CORP
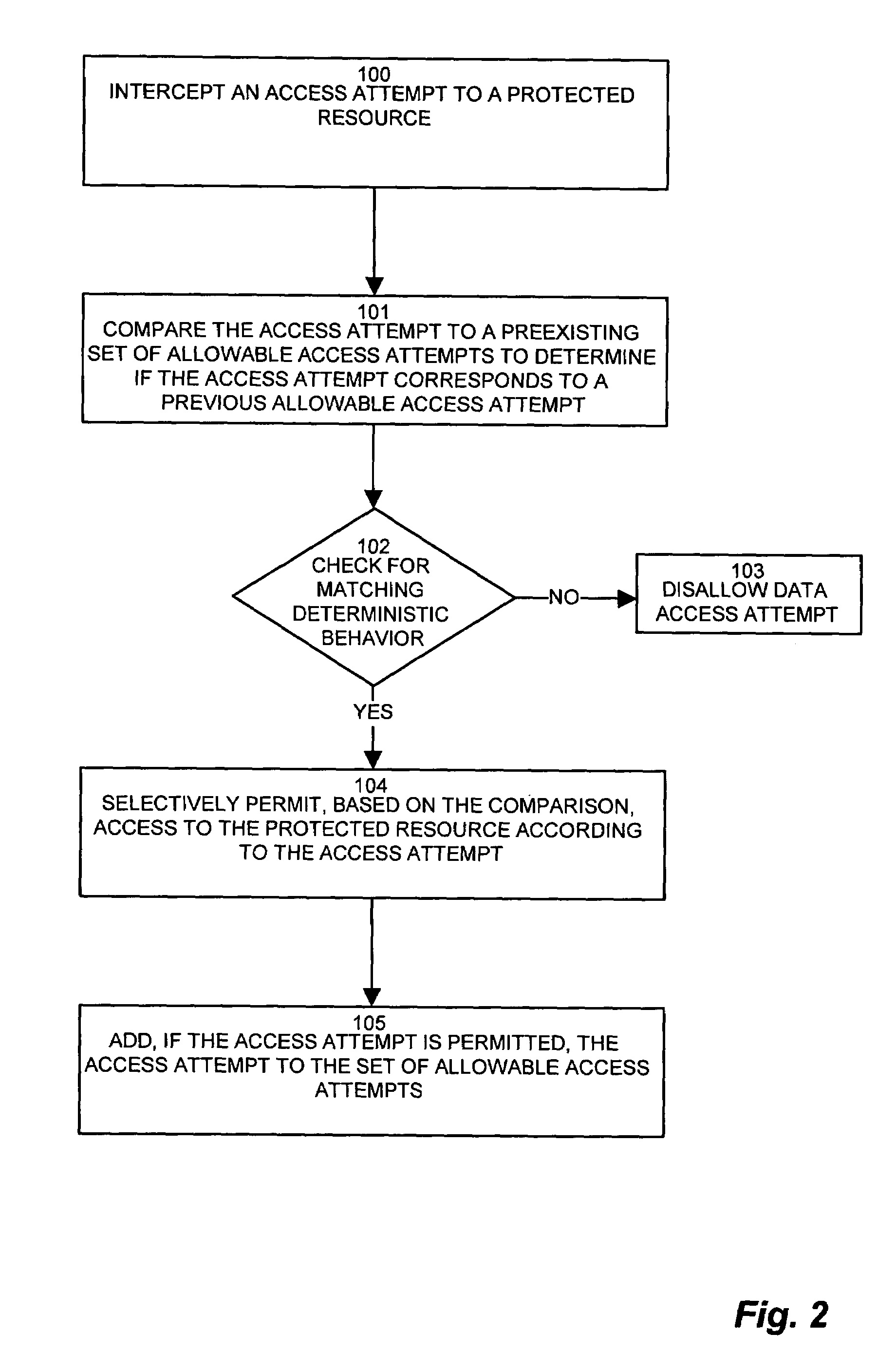
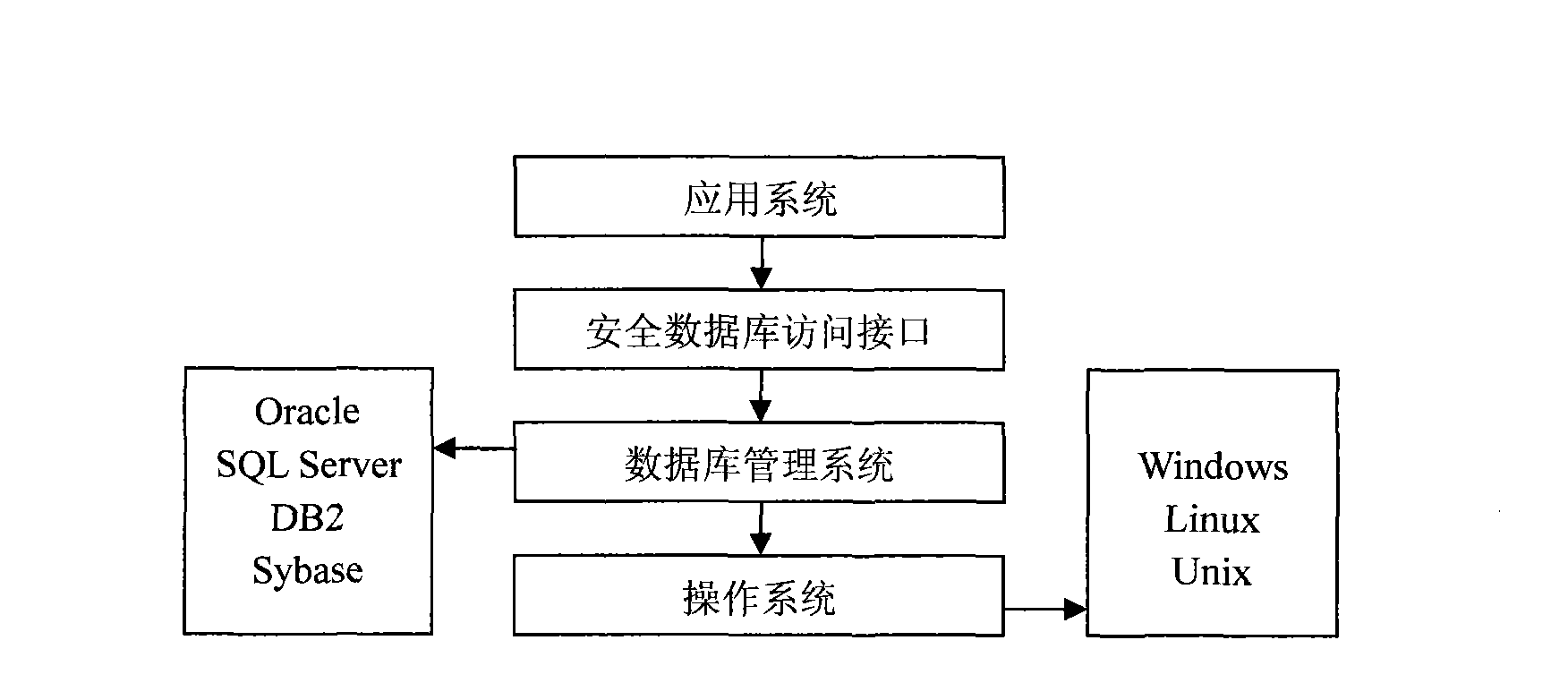
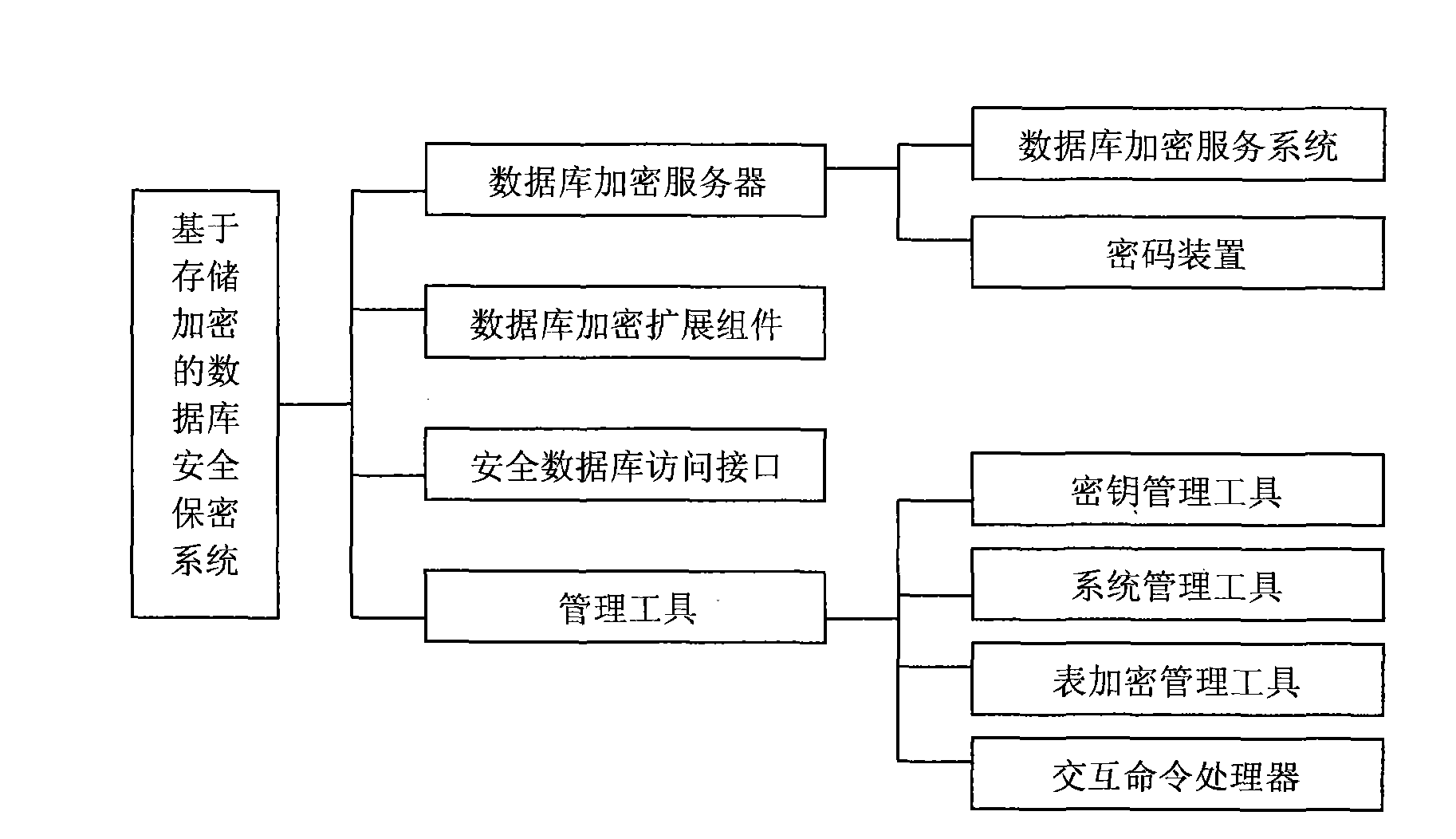
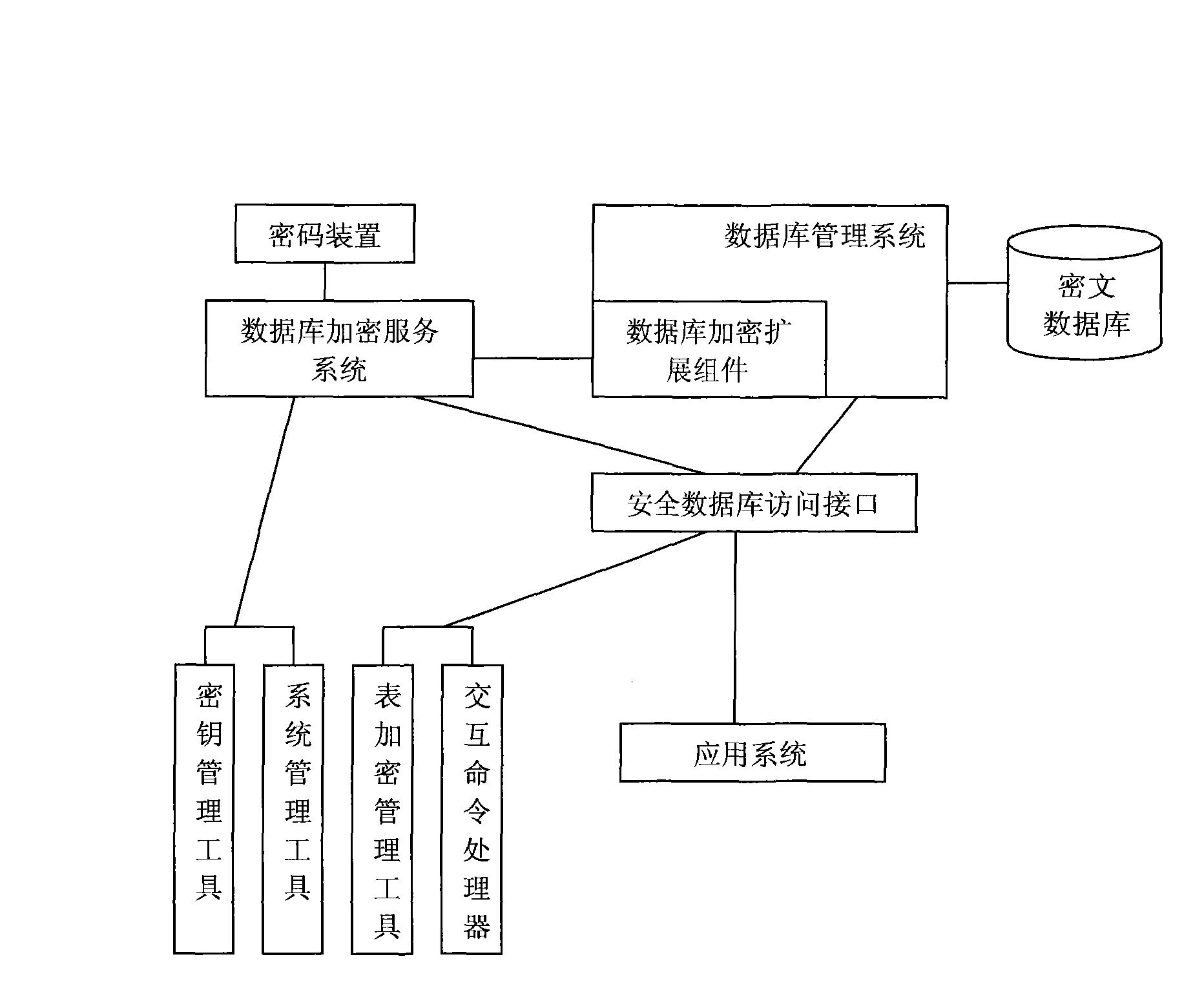
Database security system based on storage encryption
ActiveCN101639882AImplement encapsulationAchieve isolationDigital data protectionSpecial data processing applicationsManagement toolInterface standard
The invention provides a database security system based on storage encryption, comprising a database encryption server, a database encryption expansion component, a safe database access interface anda management tool. A database encryption service system encrypts and decrypts all data in the database security system and intensively applies safety control and management; the database encryption expansion component connects with the database encryption service system and a database management system and calls a cipher service function of the database safety service system to encrypt and decryptroutine data; the safe database access interface provides safe and transparent database access support to an application system; the management tool is used for safety configuration management by management personnel. The database security system provides an interface standard conforming to database access, supports transparent encryption and decryption of routine data and big data object, and screens complex details realizing the security function of the database for the application system.
Owner:HUAZHONG UNIV OF SCI & TECH +1
Database security auditing method and system and computer readable storage medium
InactiveCN109885554AExpand coverageImprove recognition accuracyDigital data authenticationTransmissionWorkloadOperational behavior
A database security auditing method comprises the following steps of obtaining a database message in traffic; carrying out unpacking analysis on the message; executing a preset auditing strategy according to the obtained operation behavior of the database account through analysis, and generating an auditing log; and generating an early warning report for the operation behavior violating the auditing strategy according to the auditing log, and storing the auditing log and the early warning report. According to the database security auditing method, different auditing strategies are formulated for different operation behaviors, so that the coverage range of abnormal operation behaviors of a database in the express industry is expanded; the identification accuracy of the sensitive informationis improved, and the machine learning mode greatly reduces the workload of manual audit and improves the working efficiency.
Owner:SF TECH
Method and system to issue an electronic visa of a foreign visitor at a country's foreign consular premises
InactiveUS7118027B2Reduce fraud and other misuse.Payment architectureSecret communicationComputer hardwareComputer number format
This invention integrates with a country's customs and immigration system to issue an electronic visitor's visa, and to validate periodically, electronically a visitor's visa within the country's borders. A computer-encoded visa card is created and issued to the visitor at the country's overseas consulate. Pertinent visa application information is embedded in the issued card. Cryptographic technology is used with the card to maintain privacy, as well as to reduce fraud and other misuse. The card is used as the visitor's official identification document whilst in the country. During the visitor's stay, at specified intervals, the visitor registers with self-service kiosks, which are placed at various locations within the country. The kiosks are securely integrated with the customs and immigration database.
Owner:SUSN LESTER
Database safety access control method based on independent authorization
ActiveCN104166812AImprove securityDigital data authenticationSpecial data processing applicationsLoose couplingDatabase security
The invention discloses a database safety access control method based on independent authorization, and belongs to the field of database safety. The designing thought that the method is in loose coupling with a database system is adopted, access control on the basis of users instead of database accounts is realized by binding database access behaviors with a USBKey, and control and audit can be conducted on behaviors of terminal users by correlating the database access behaviors and the terminal users. Advanced access control is introduced for conducting analyzing and monitoring on database access statements, therefore, database attack behaviors are shielded, insider operation behaviors are controlled and audited, and information loss caused by the database attacking behaviors can be reduced. By repackaging database access requests, monitoring and sniffing attacks are avoided. According to the technology, by adding the means of identity authentication, access control and safety transmission which are independent from a database management system, safety enhancing of a heterogeneous database management system under multiple platforms is realized on the premise that the usage mode of an existing application system is not changed.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND +1
Database security structure
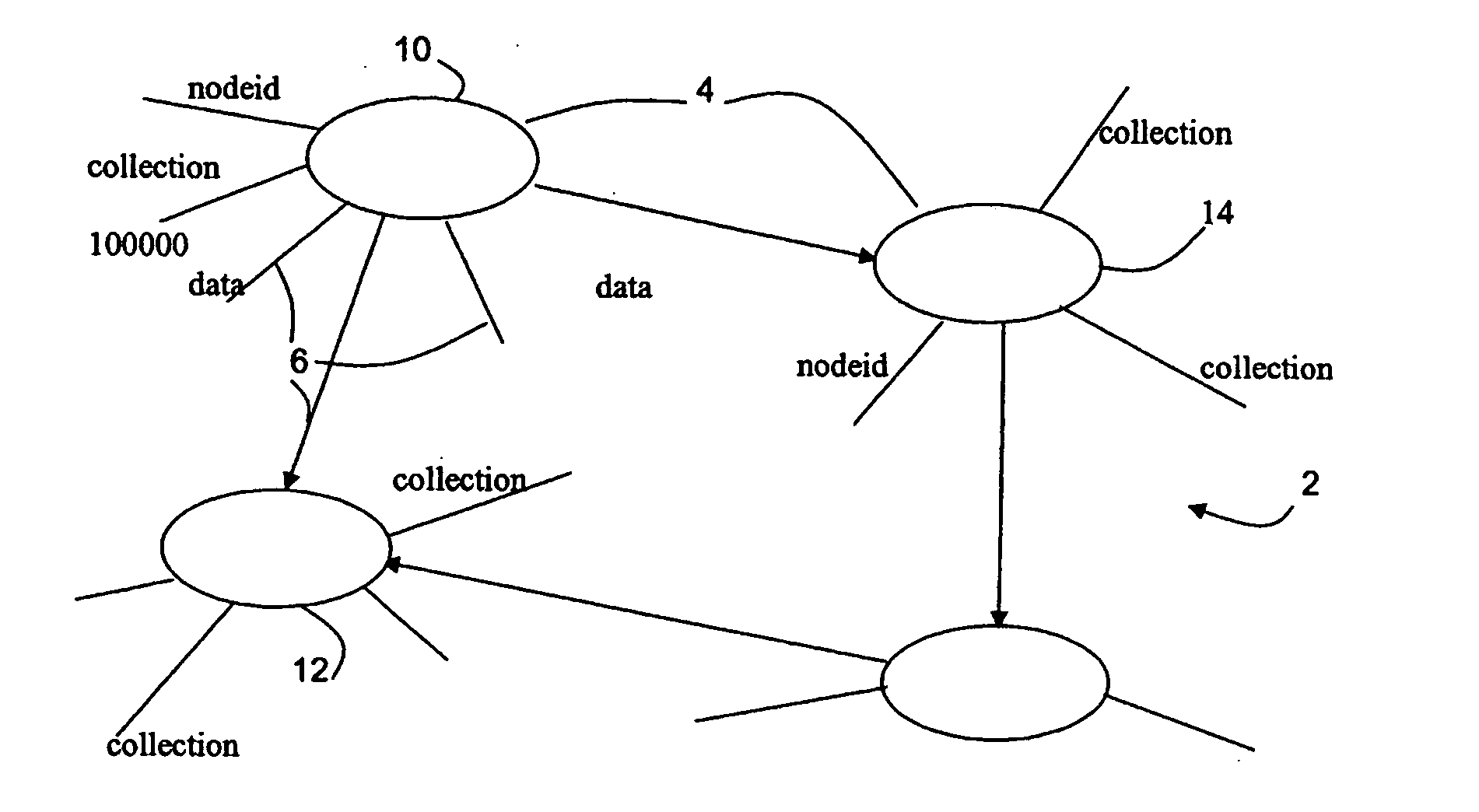
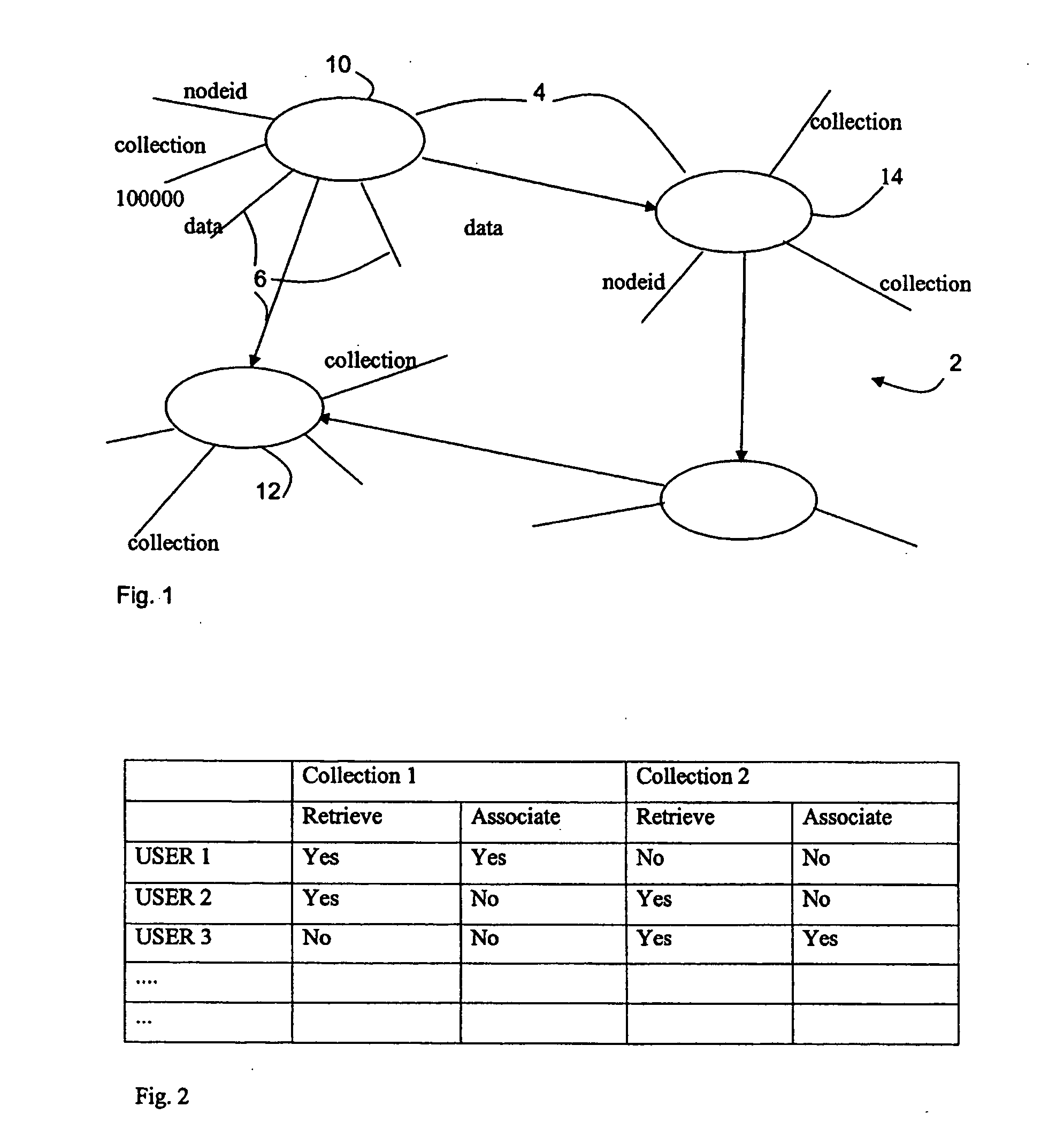
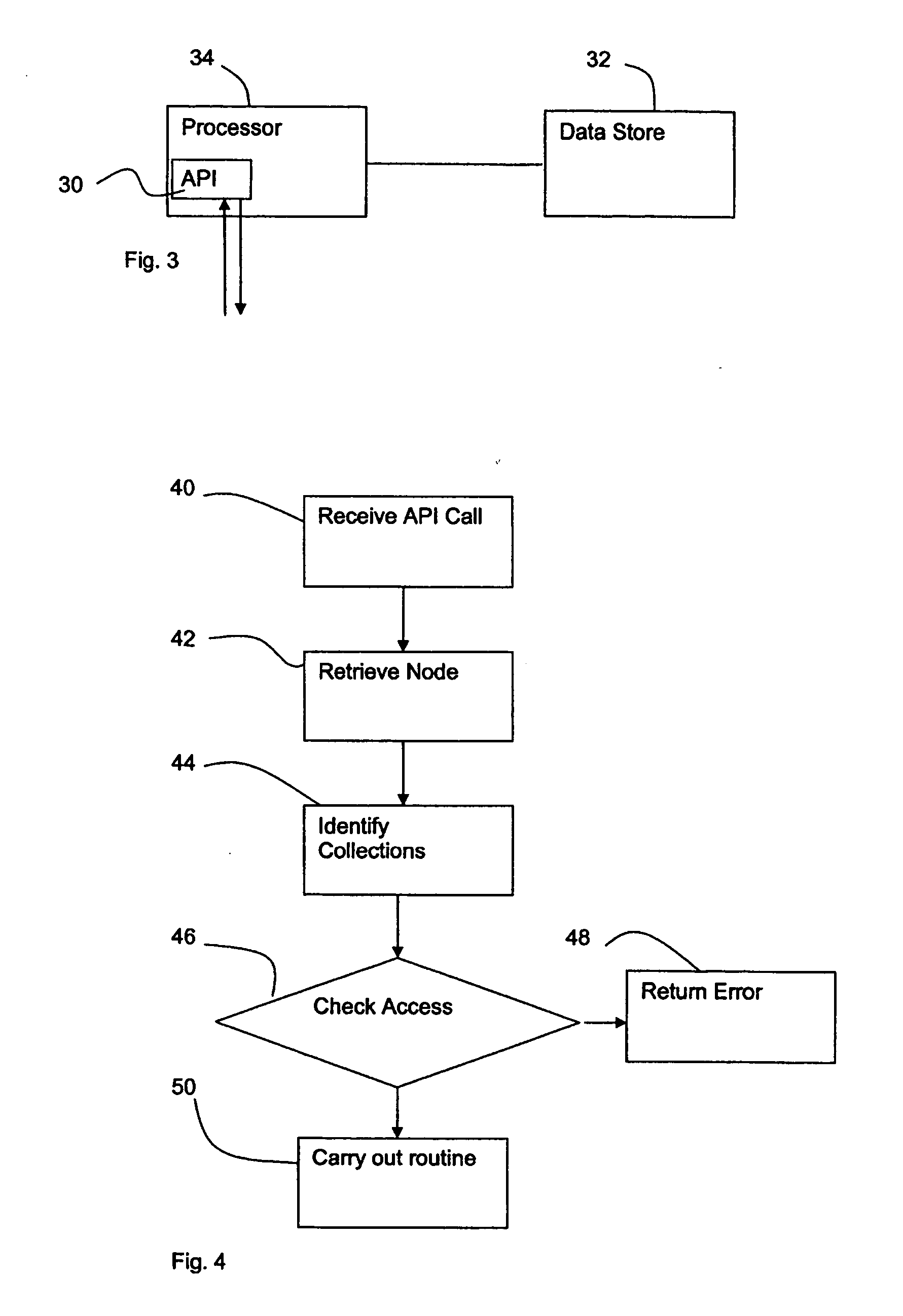
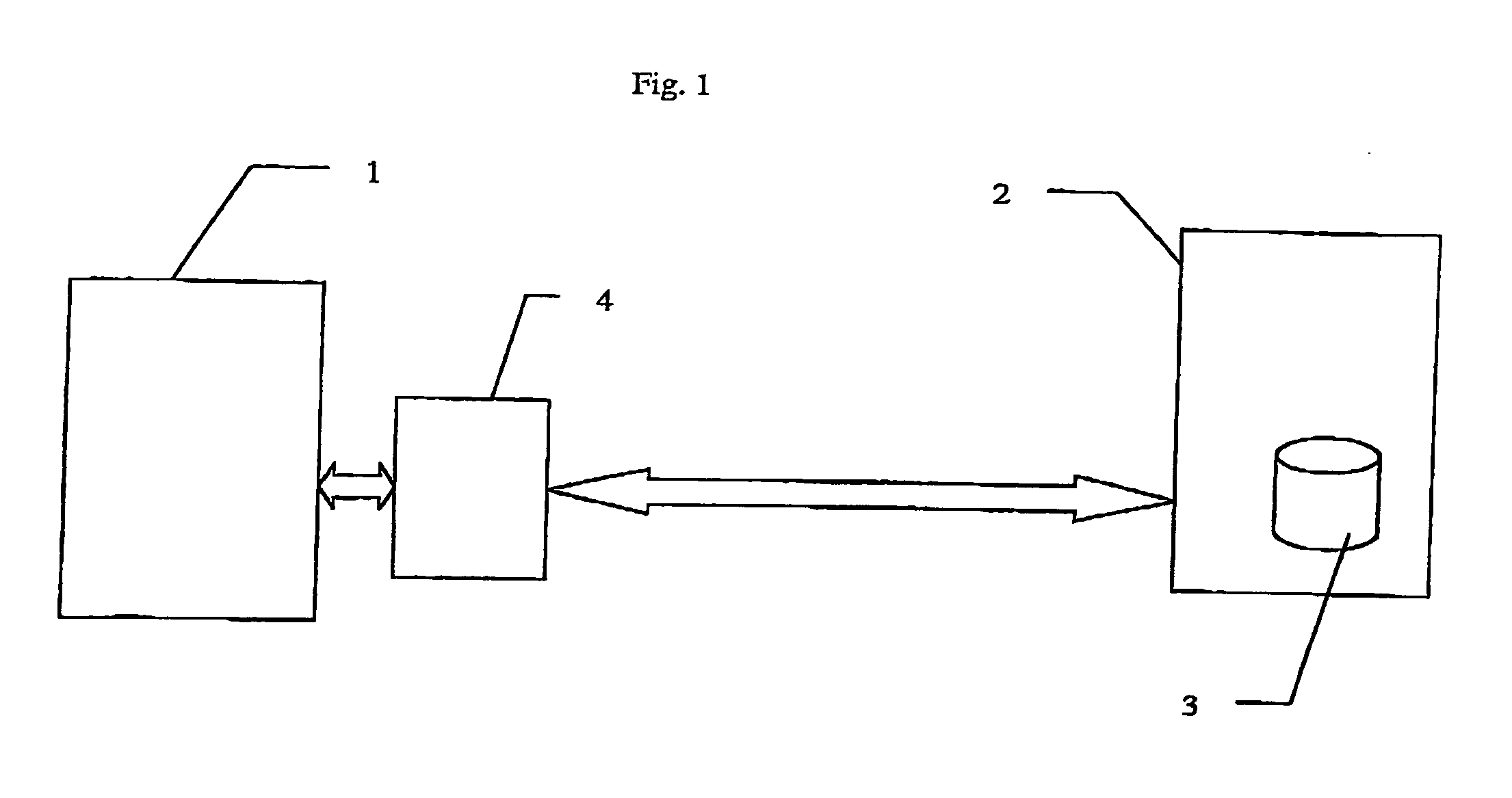
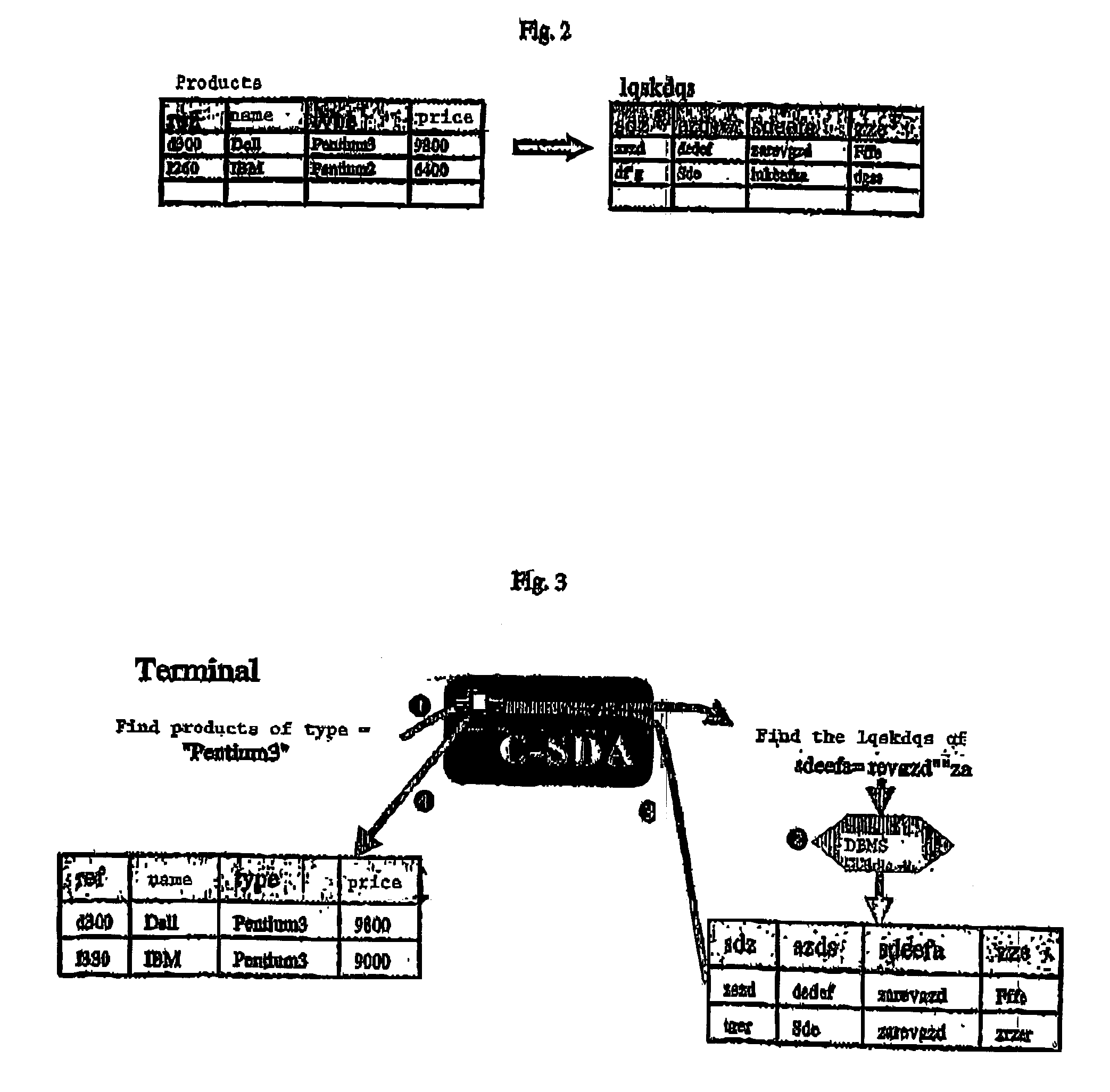
InactiveUS20060230042A1Digital data processing detailsComputer security arrangementsSemi-structured dataDatabase security
A database security structure that may be used for semistructured databases assigns each node 4 of a database to a collection. For each collection, create rights, retrieve rights, associate rights and dissassociate rights are provided to one or more users, the rights being assigned in common for all nodes of the collection. Users can only carry out the task if they have the appropriate rights. In this way, a flexible database security structure is provided that can deliver appropriate security for different elements of a semistructured database.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Database auditing system and database auditing method
InactiveCN104090941ARealize audit automatic learningEasy to detectDigital data protectionSpecial data processing applicationsData miningFalse detection
The invention provides a database auditing system which comprises a database statement auditing module and a database user behavior auditing module. The database statement auditing module is used for analyzing collected auditing data, obtaining an SQL statement and detecting the obtained SQL statement. The database user behavior auditing module is used for analyzing the collected auditing data, obtaining user behavior and detecting the user behavior. The invention further relates to an auditing method based on the database auditing system. According to the database auditing system and the database auditing method, universality is high, detection efficiency is high, maintenance is convenient, a rule base is updated continuously to ensure that the false detection rate is reduced, the requirements for database safety of different users can be practically met, and the system and the method have the wide application prospect in the database auditing industry.
Owner:北京华电天益信息科技有限公司
Mandatory access control base
ActiveUS7593942B2Ease of administrationEnsure effective implementationComputer security arrangementsSpecial data processing applicationsData accessDatabase security
Owner:ORACLE INT CORP
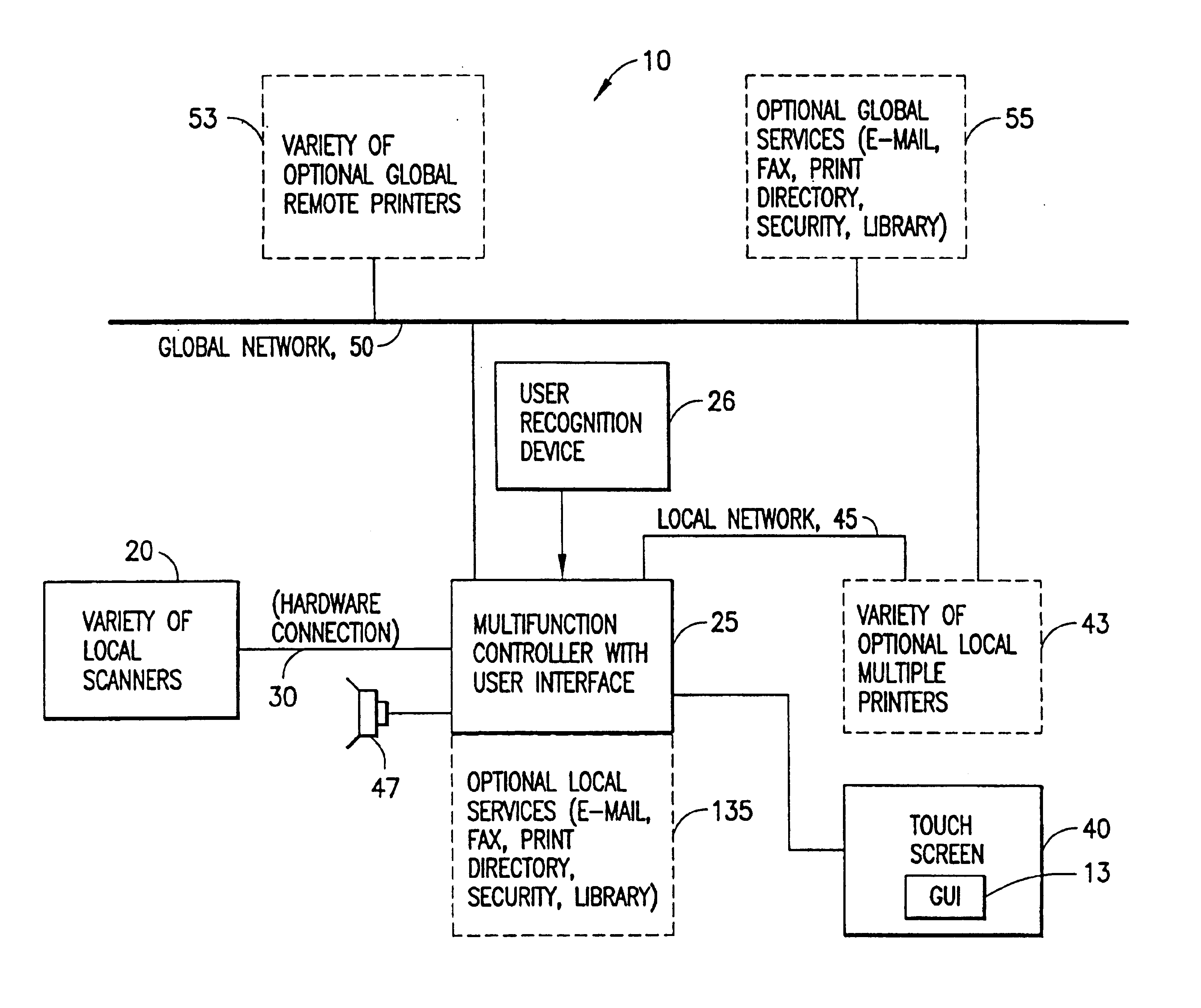
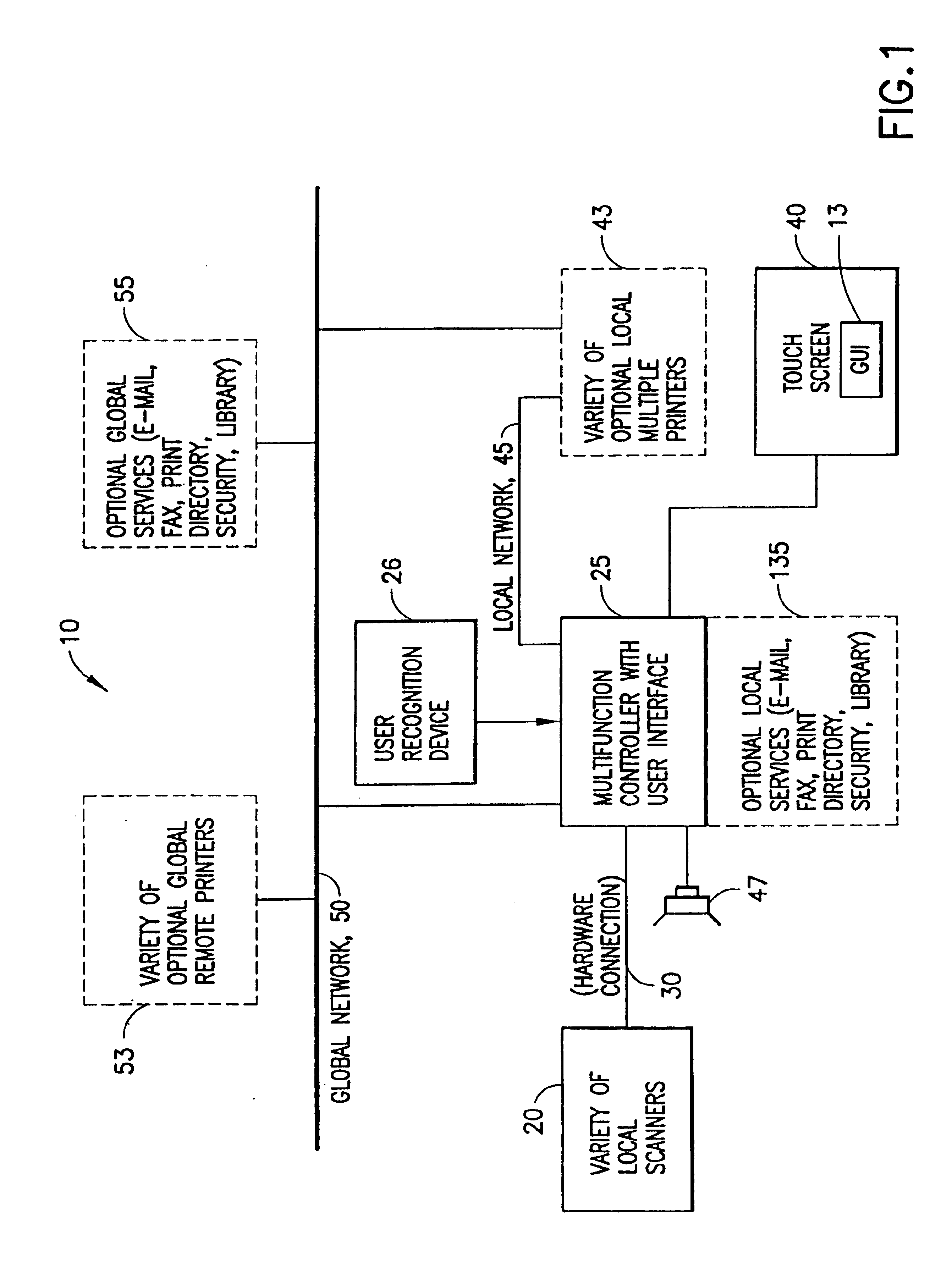
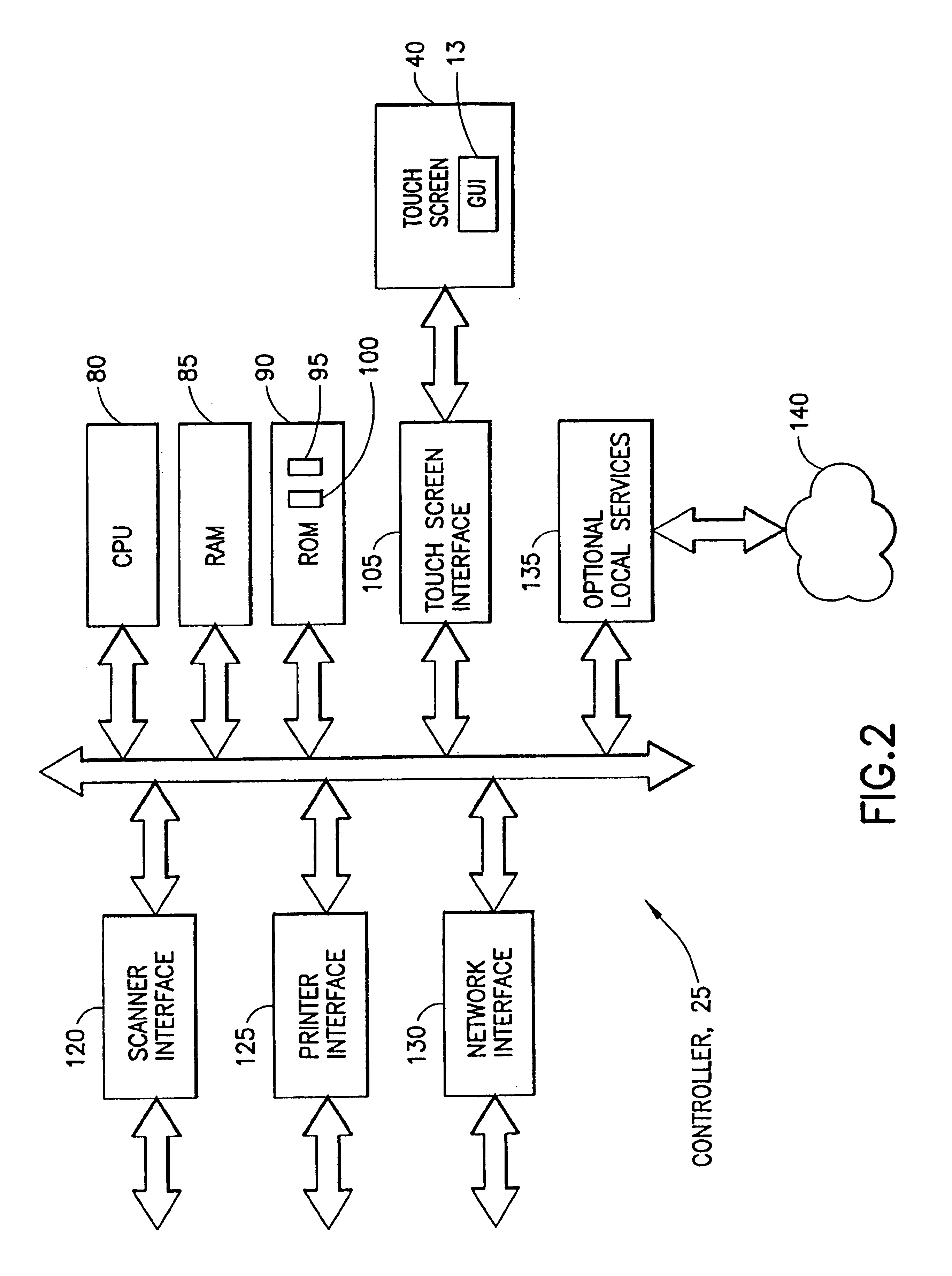
Remote database support in a multifunction office device
InactiveUS6867876B1Good user interfaceExpand accessSpecial service provision for substationDigitally marking record carriersFacsimileMultiple function
A multifunction device includes a multifunction controller, a first interface for receiving input data from a document source and a second interface for outputting processed input data to at least one printer, and a third interface for coupling to a global data communications network for receiving current document data, as well as up to date recipient contact information therefrom. An interface is provided to control the operation of the multifunction device, including controlling access to and searching of remote databases coupled to the global data communications network. The remote databases can include, by example, a database of forms, a security database, and a directory database. The interface can control the operation of the multifunction device for accessing and searching a database containing the recipient contact information for sending at least one of a facsimile or an e-mail that contains processed input data.
Owner:RICOH KK
Method for making databases secure
InactiveUS20050044366A1Digital data information retrievalDigital data processing detailsDatabase securityEncryption system
A secure management system for confidential database including a server having at least one computer equipped with an operating system, a database storage and a communication system, at least one host computer equipment unit including a communication system with the server and a system for constructing queries and processing results of queries, a security system to make secure the exchanges between the client equipment unit and the server, wherein the security system includes a secure hardware support connected to the client equipment unit and a microprocessor for encryption of attributes of the queries issued by the client equipment unit and decryption of responses issued by the server, a memory for recording intermediary results, a memory for recording the operating system and wherein the server records encrypted data; and a method for secure management of a database including construction of a query including at least one attribute, encrypting attributes by a calculator integral with an individual security device linked to a client equipment unit, interrogating a database containing data encrypted with a similar encryption system as those used during the preceding step, returning a response contains data corresponding to attributes of the query, and decryption of the data by the calculator of an individual security device prior to transmitting them to host equipment.
Owner:PUCHERAL PHILIPPE +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com