Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
92 results about "Vulnerability management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Vulnerability management is the "cyclical practice of identifying, classifying, prioritizing, remediating, and mitigating" software vulnerabilities. Vulnerability management is integral to computer security and network security, and must not be confused with Vulnerability assessment.
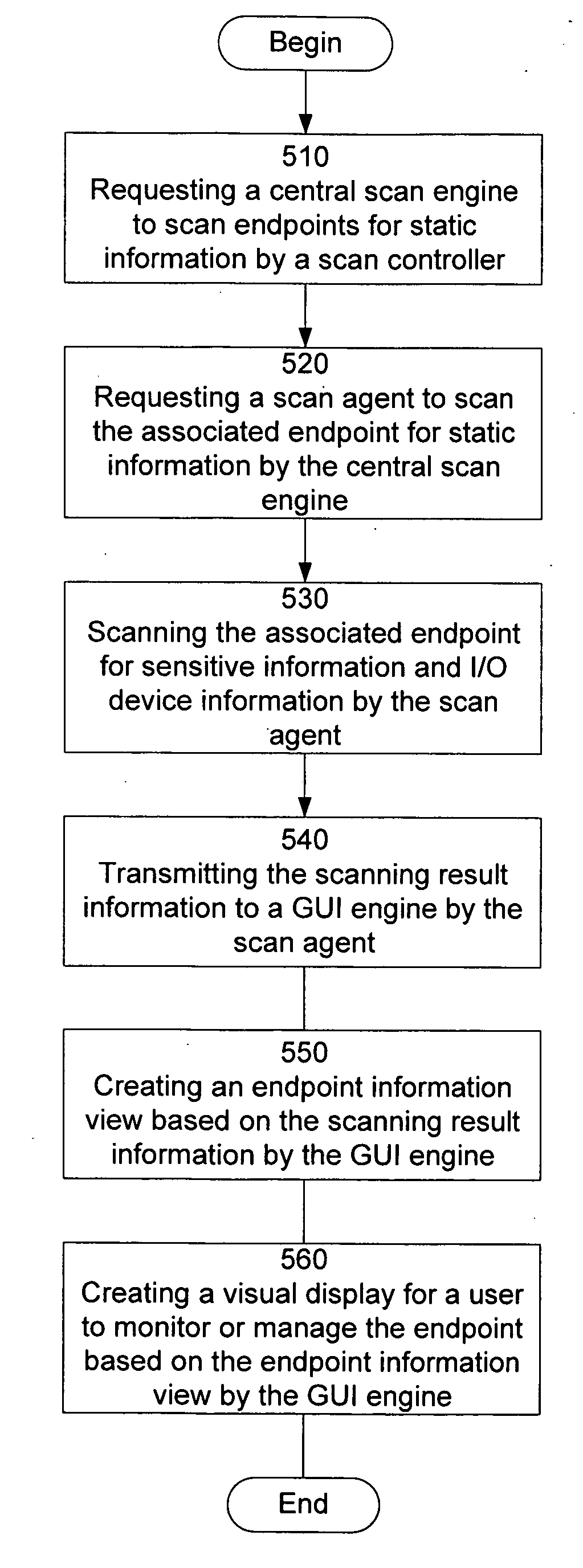
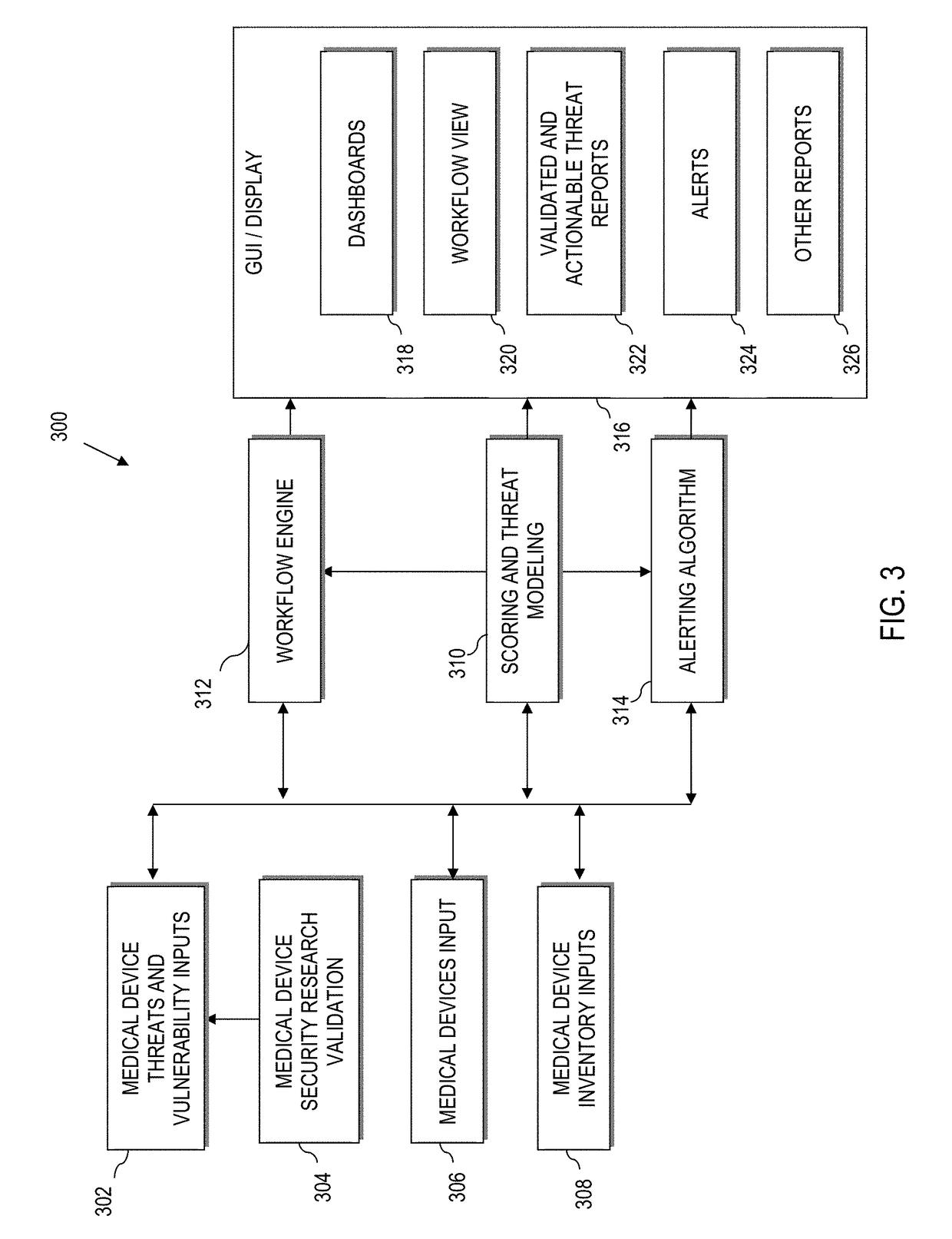
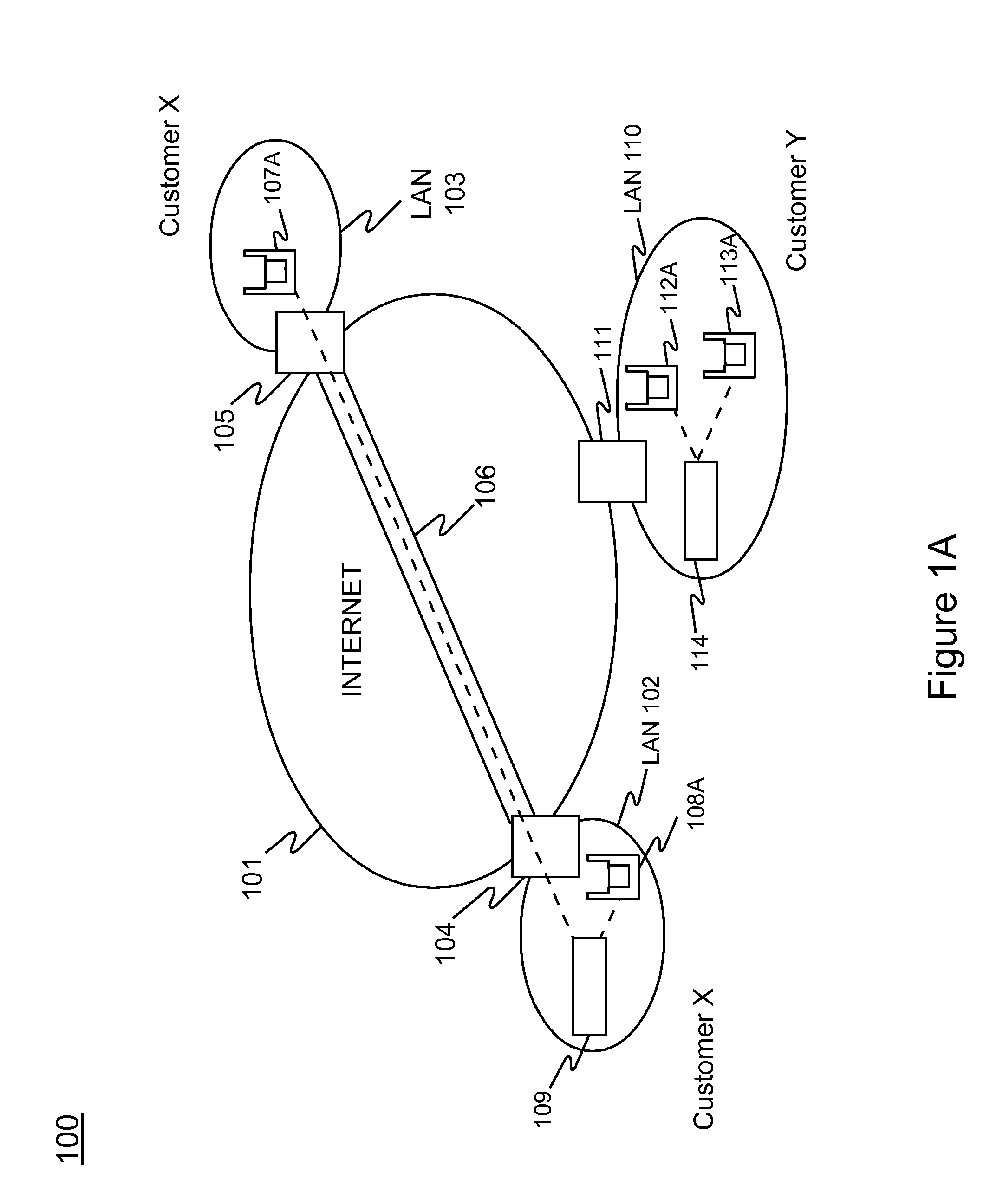
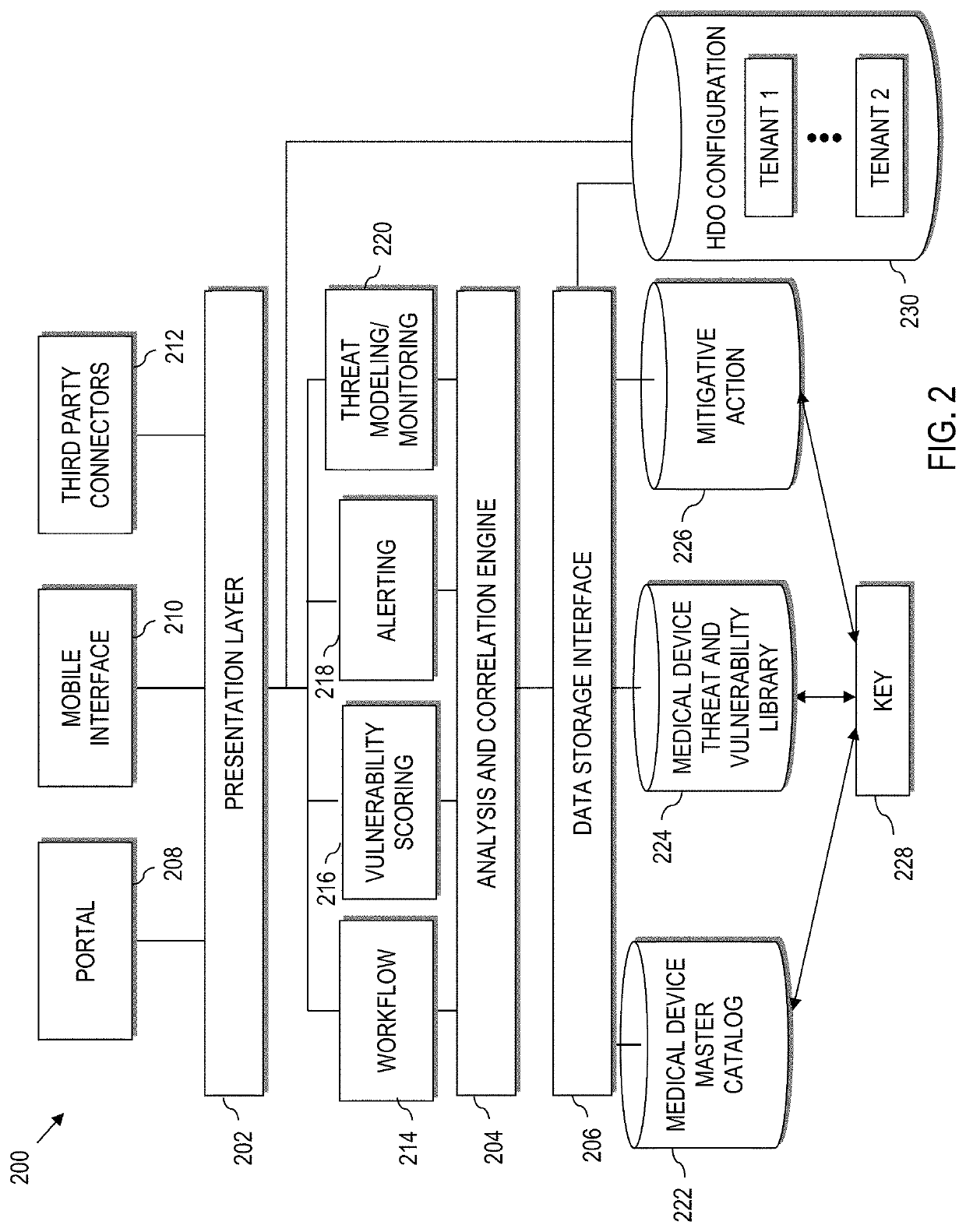
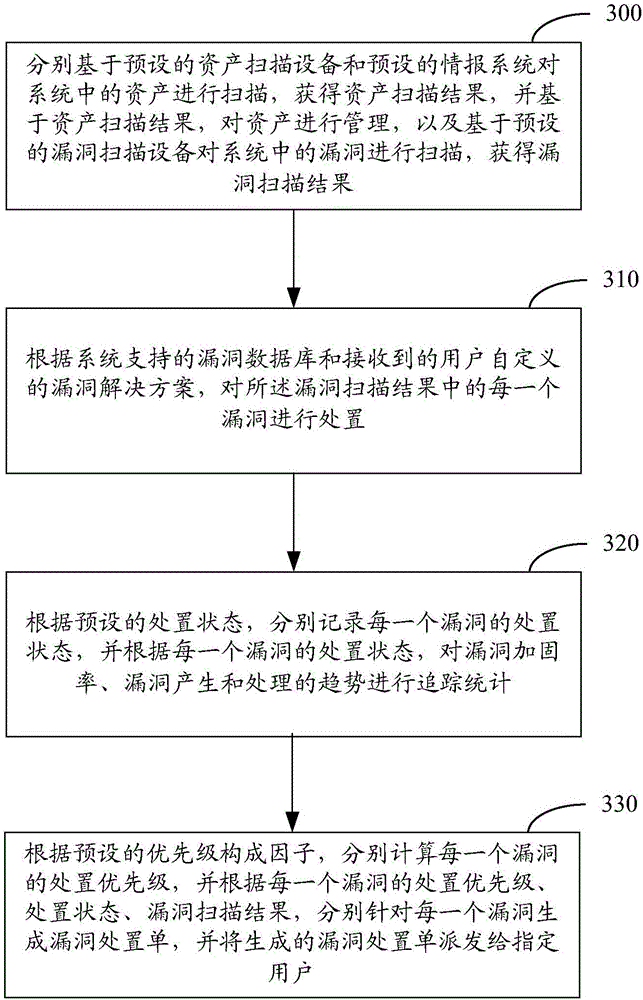
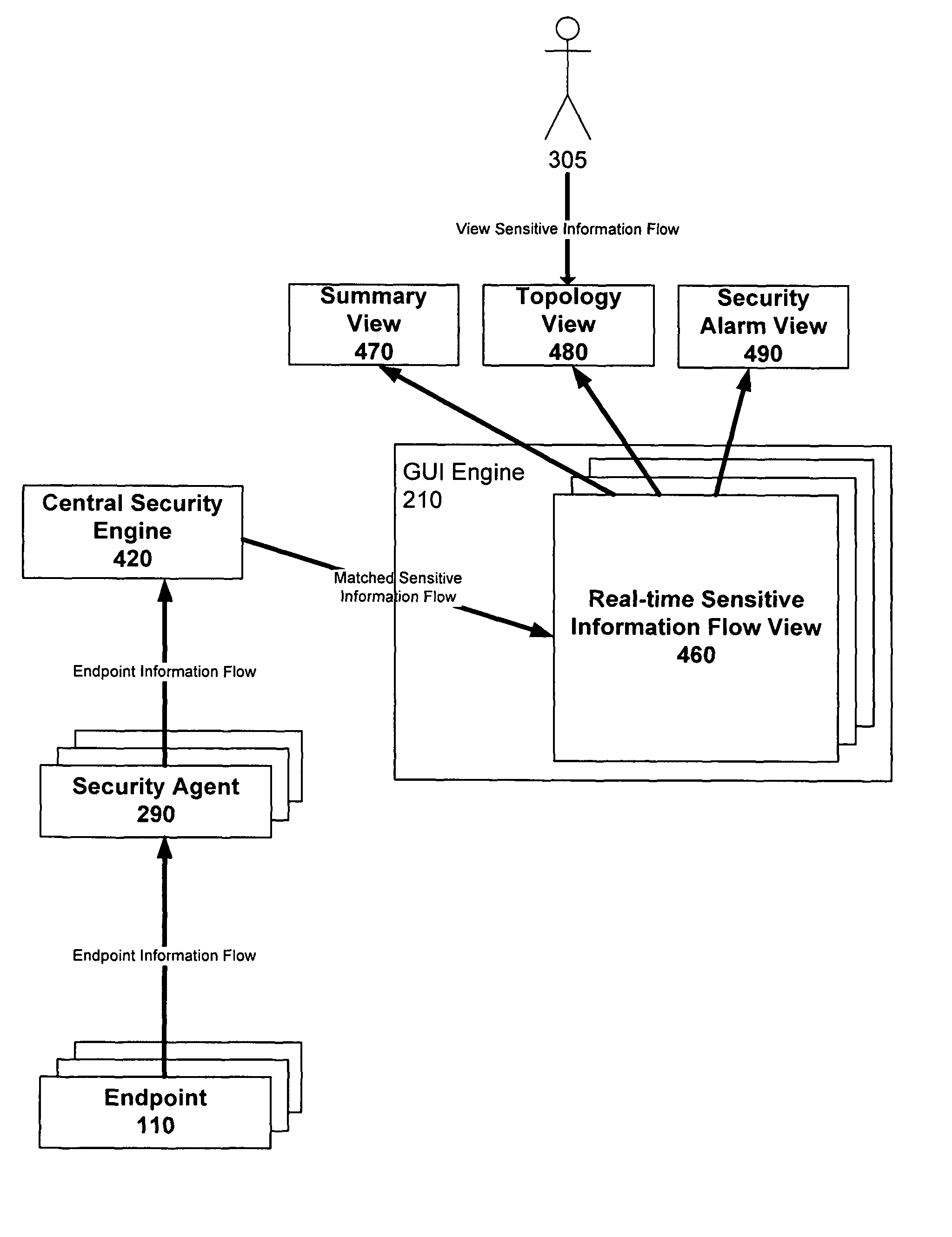
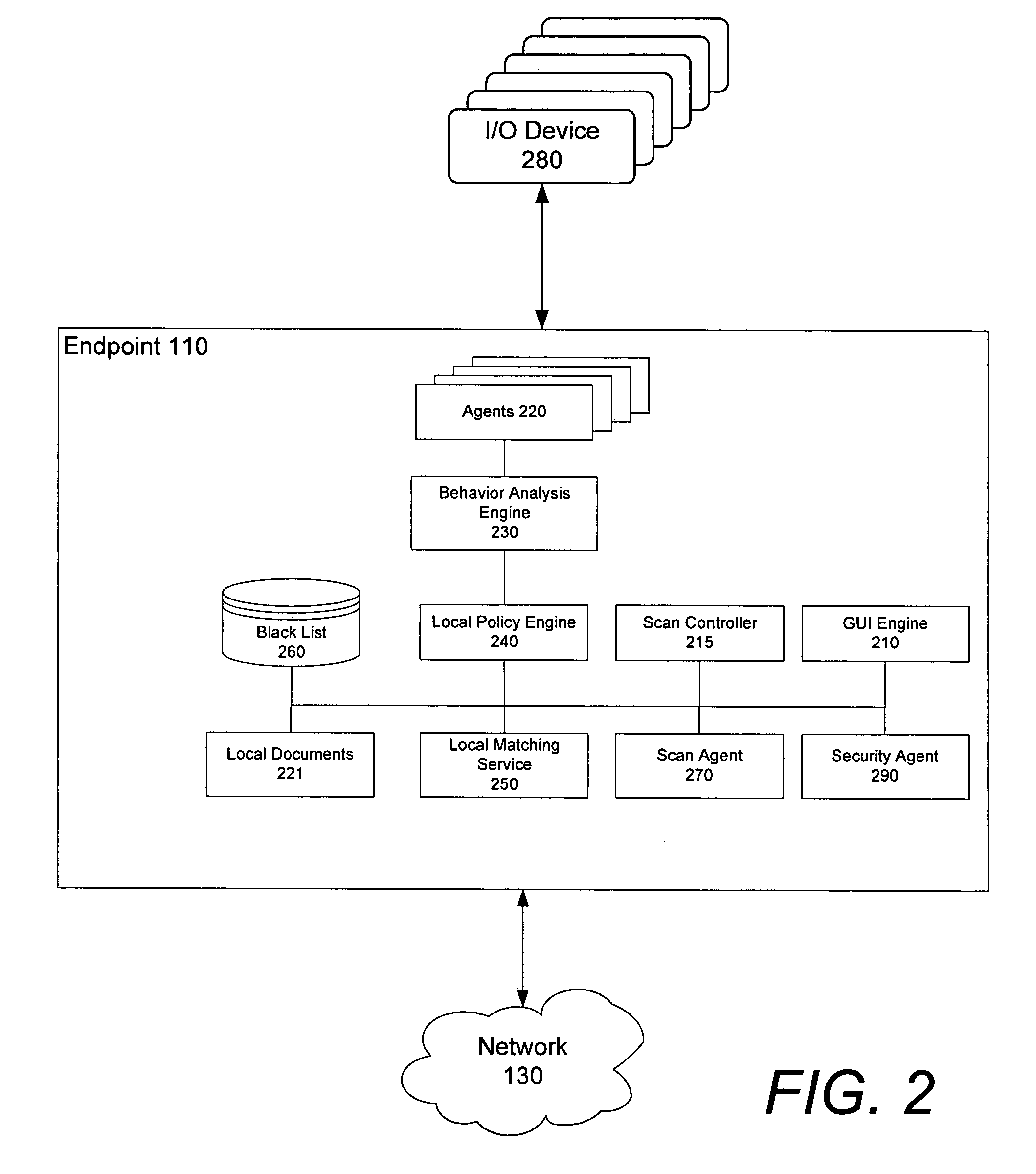
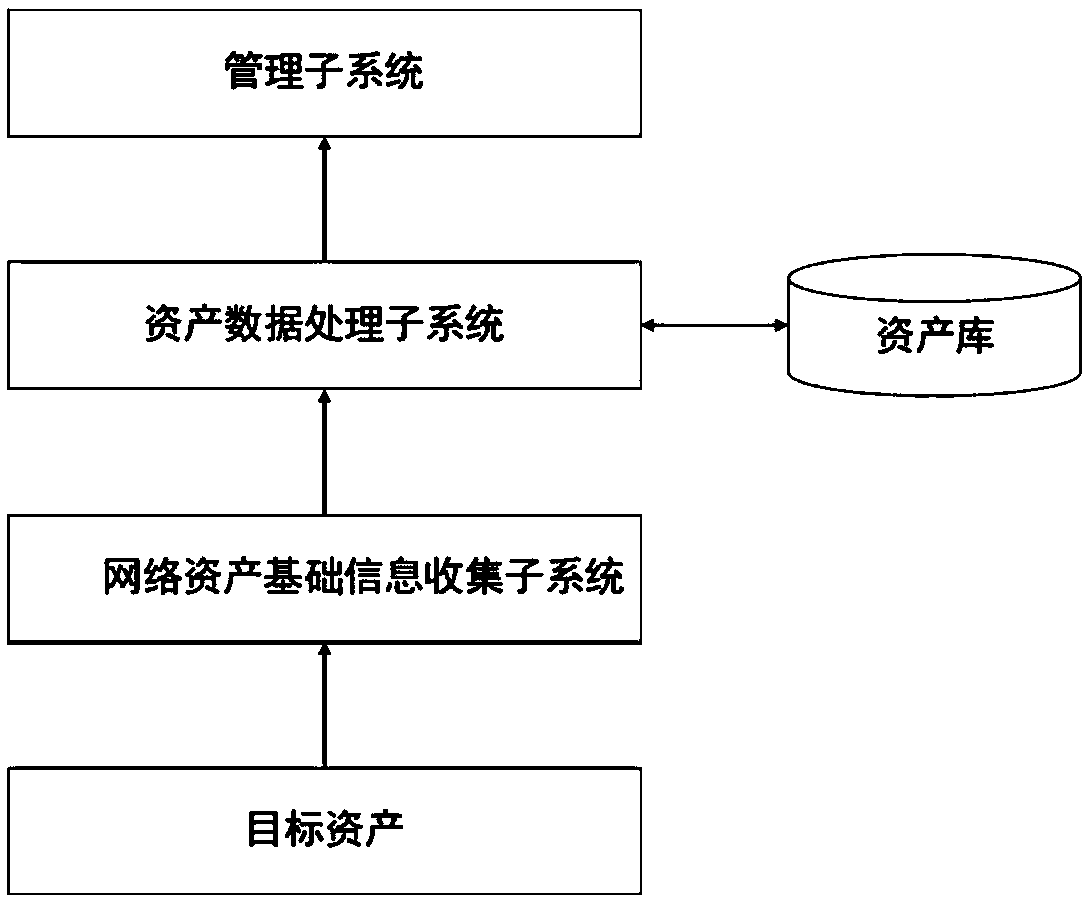
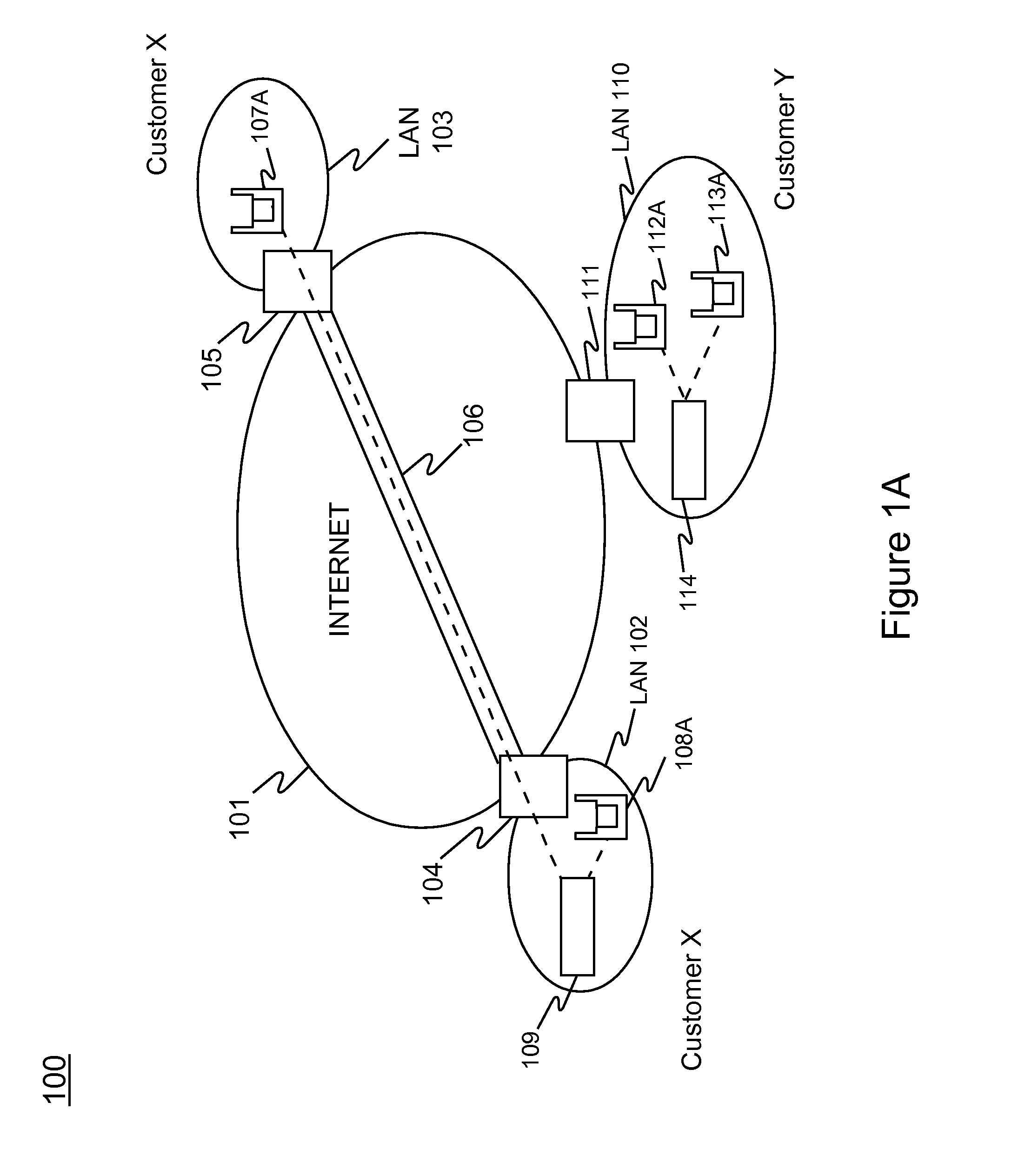
Graphical user interface based sensitive information and internal information vulnerability management system
ActiveUS20060272024A1Rapid assessmentEasy to identifyMemory loss protectionDigital data processing detailsTime informationGraphical user interface testing
A system and method provides a graphical user interface (GUI) for users to monitor and manage sensitive information within an enterprise network. The GUI can provide users with information, such as the presence of input / output devices (I / O device), the location of documents containing sensitive information (sensitive documents), and the status of local security policy. The GUI can also provide users with real-time information, such as the occurrence of local security policy violations, the life-cycle of sensitive documents, and the sensitive information dynamic flow within the enterprise network.
Owner:TREND MICRO INC
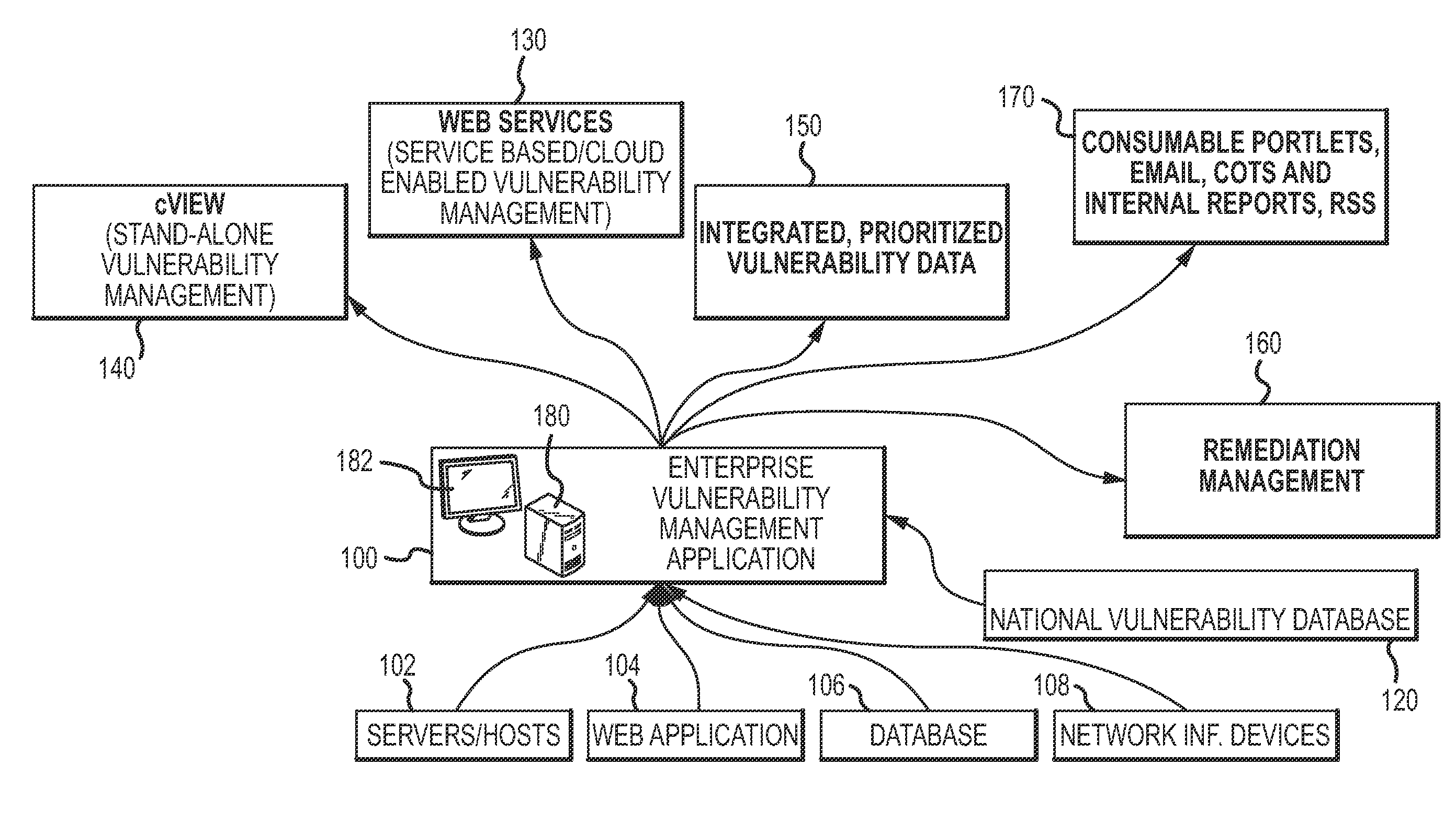
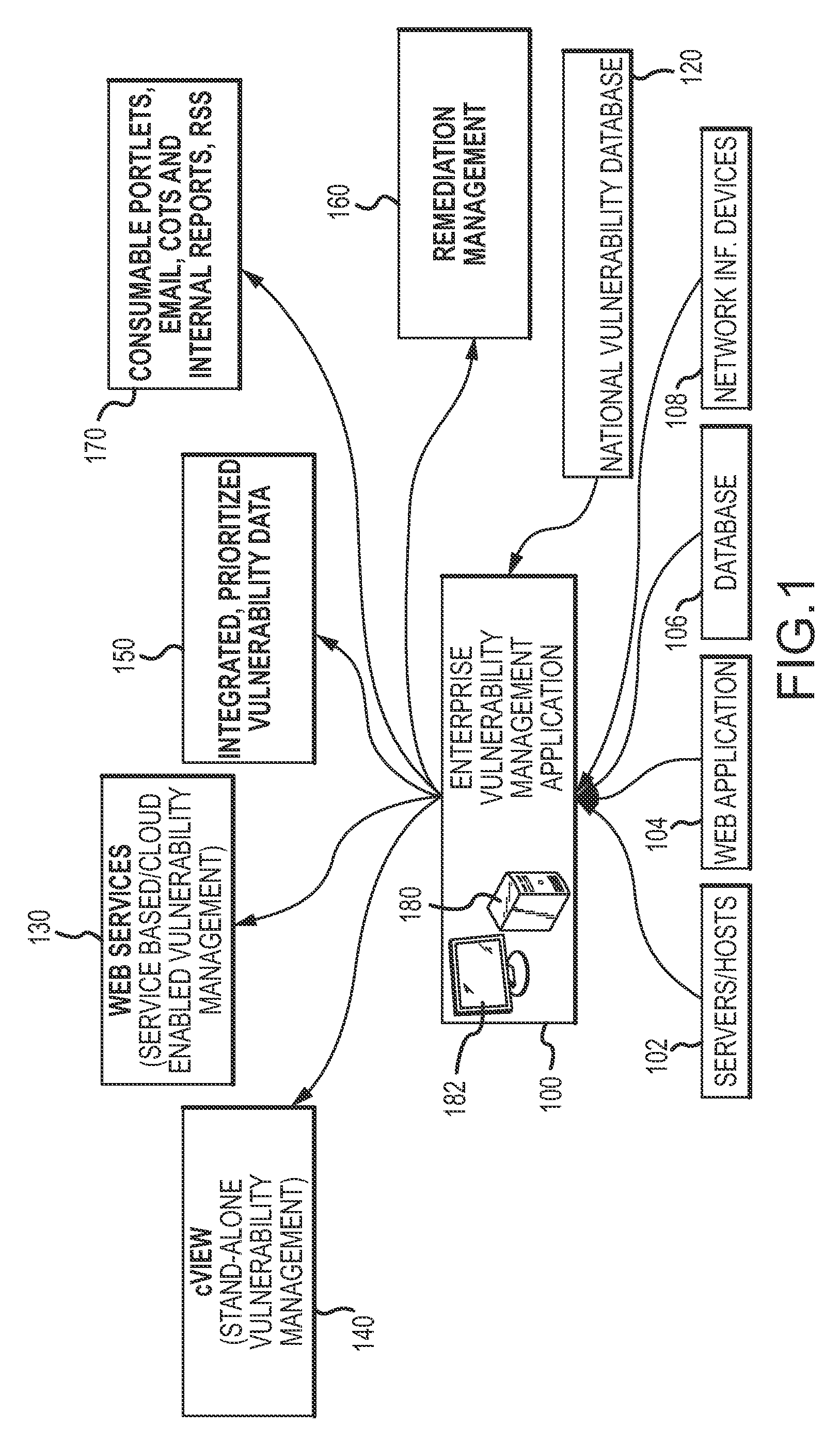
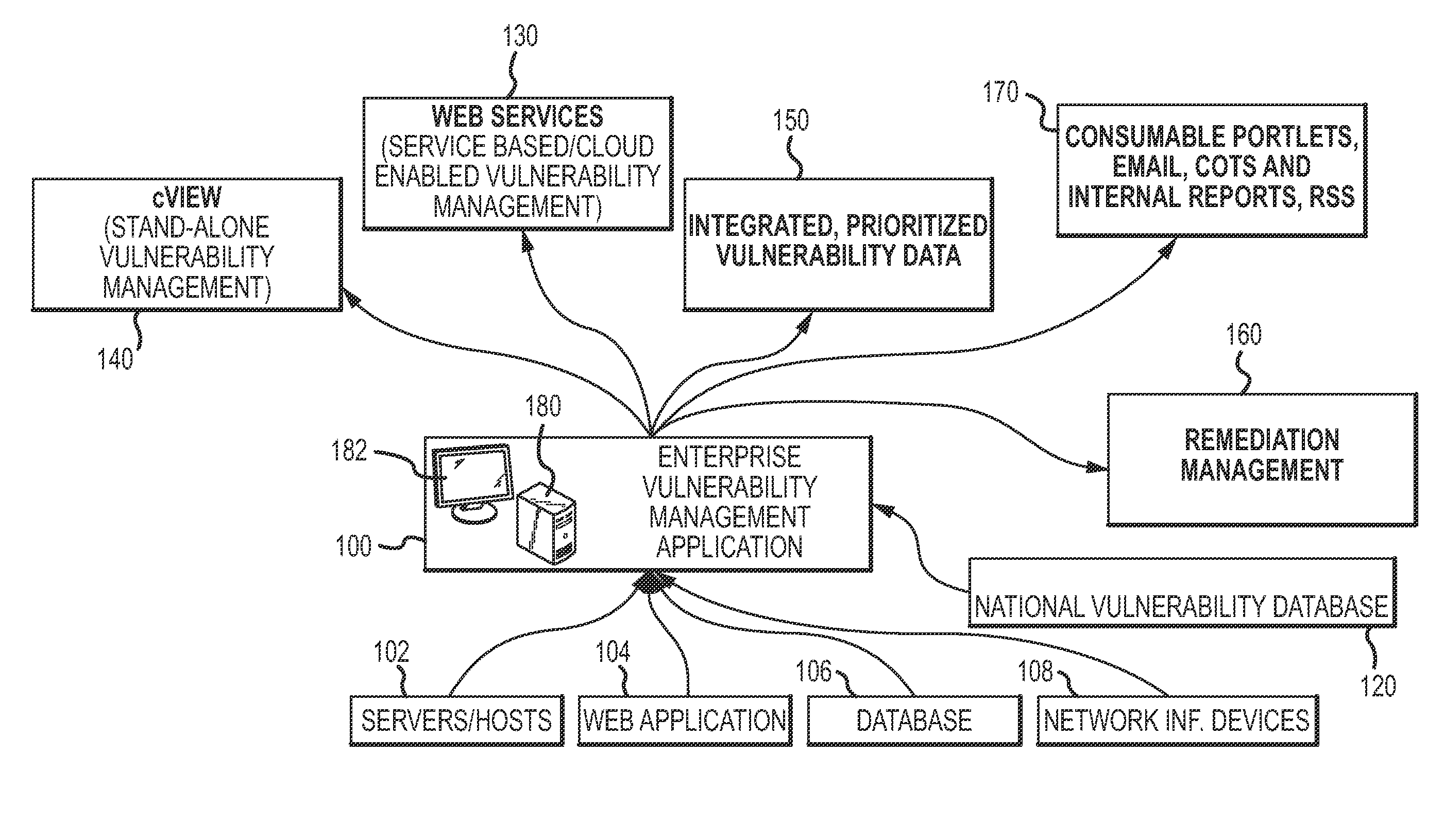
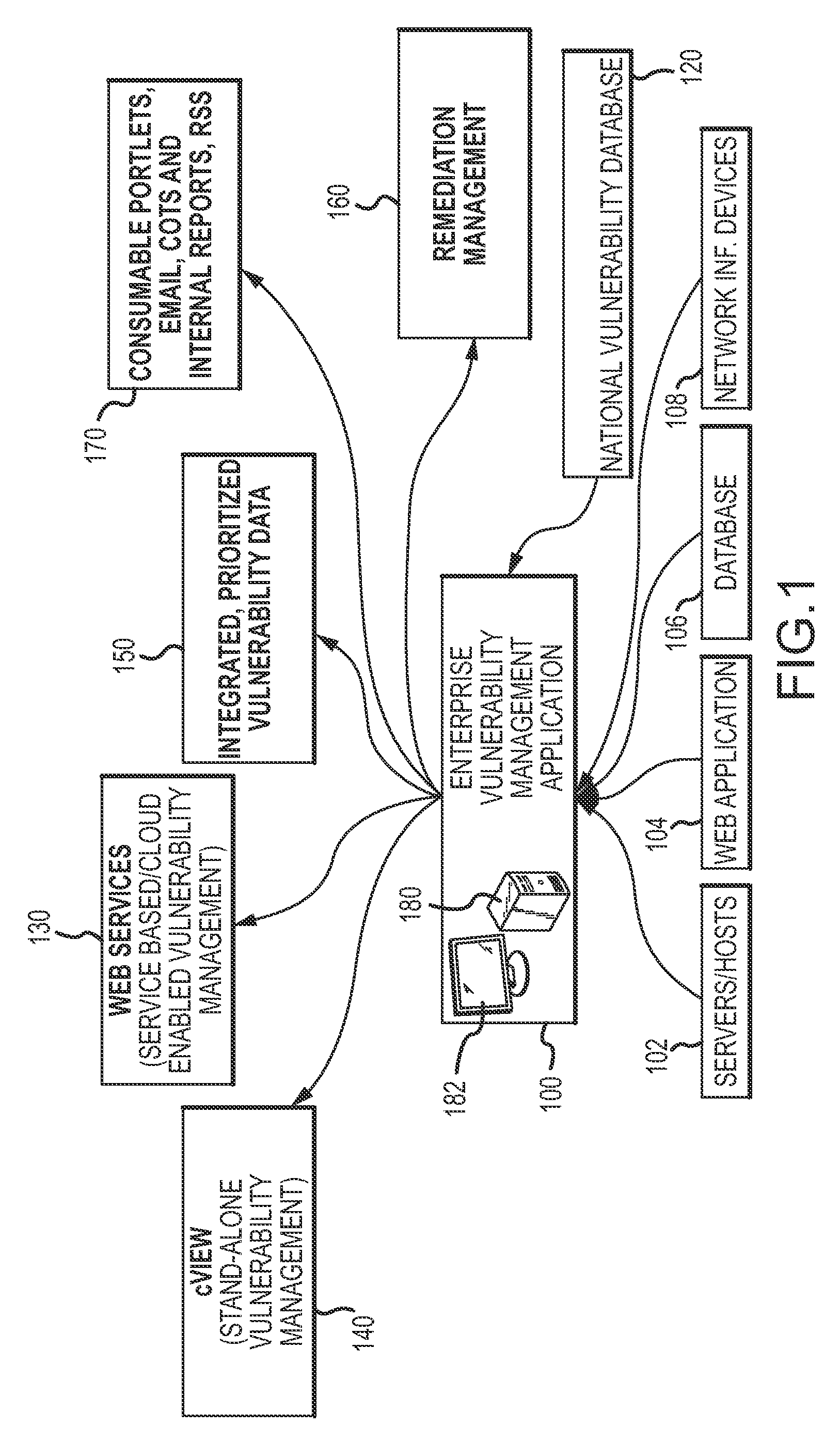
Enterprise vulnerability management
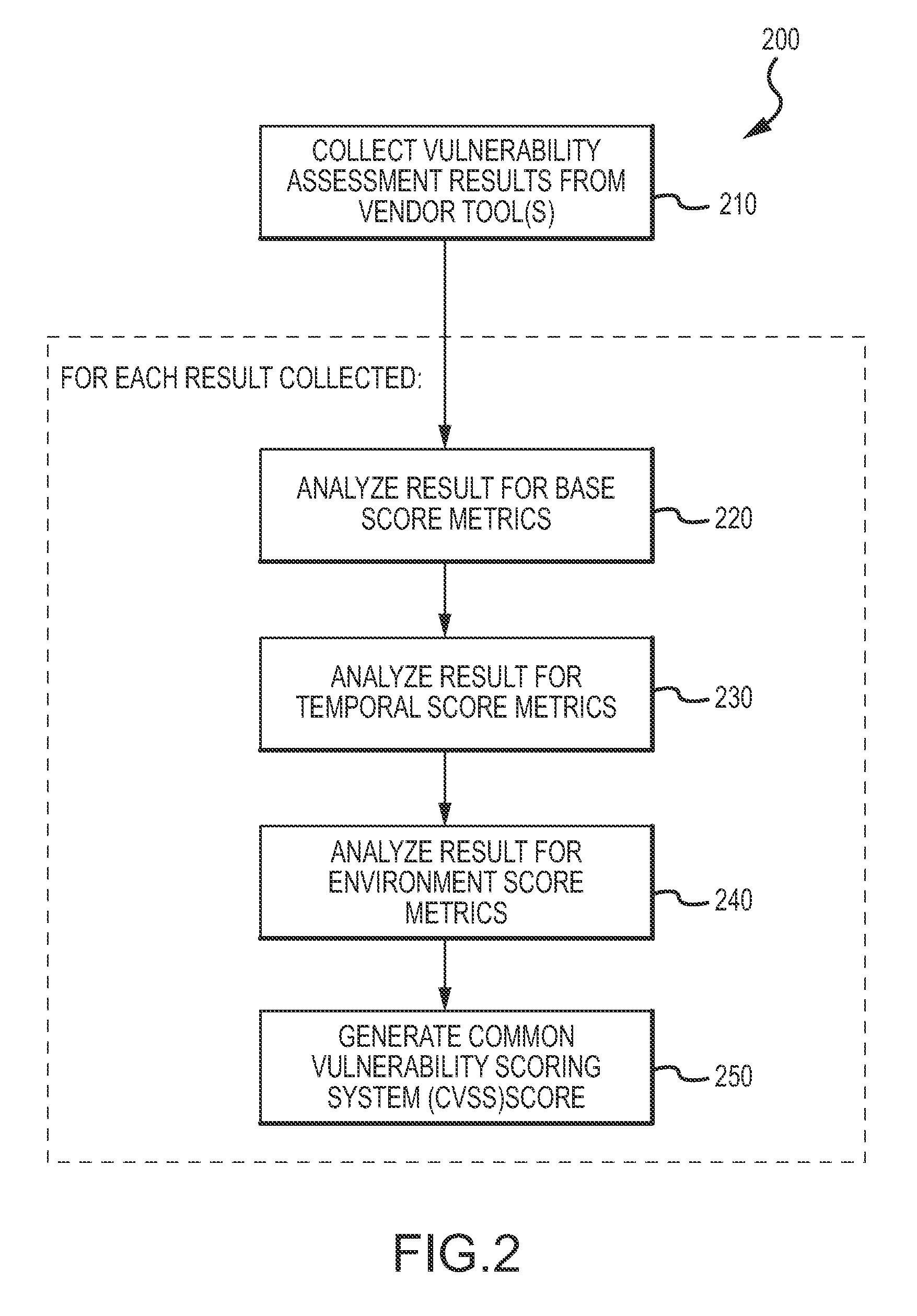
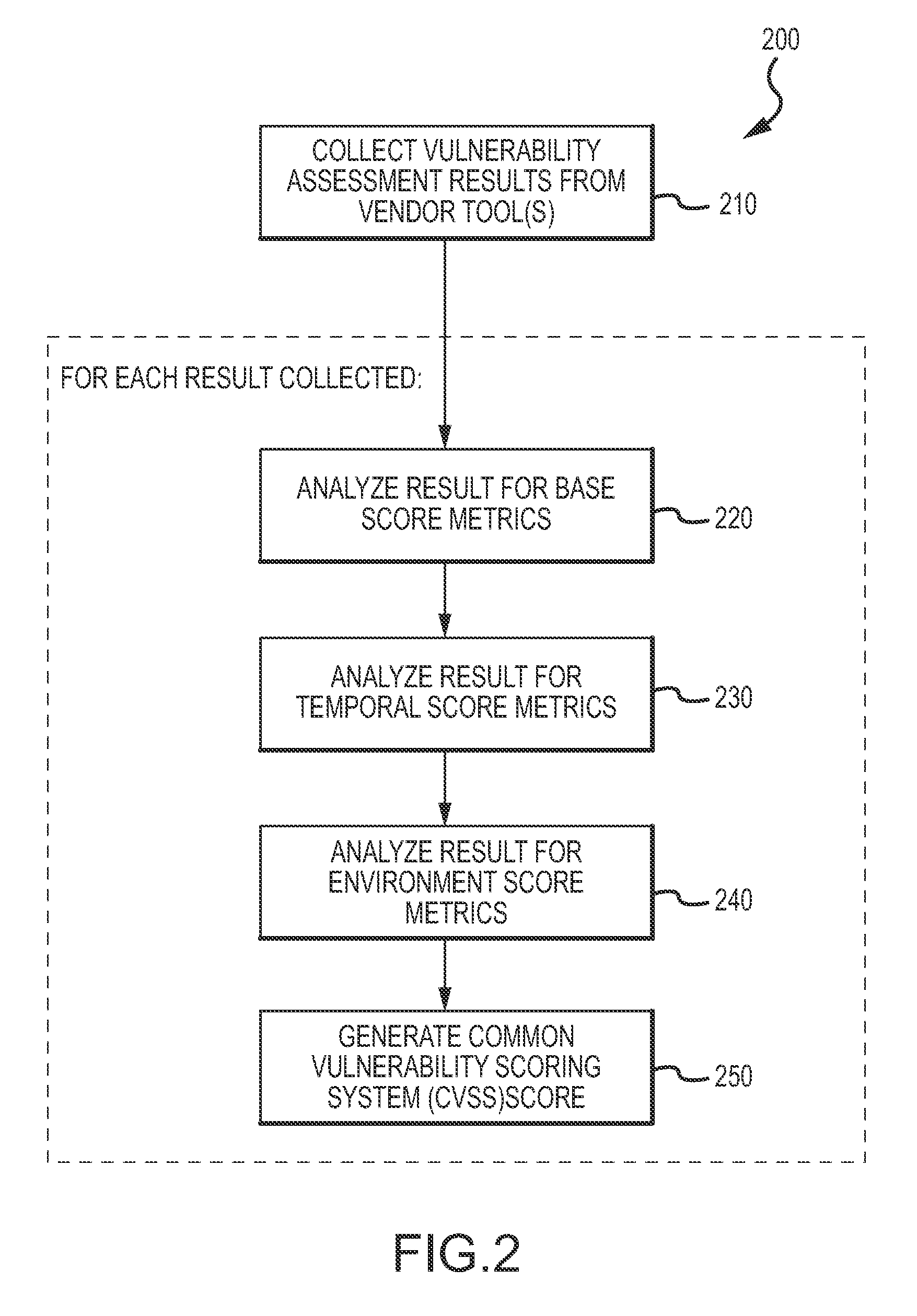
ActiveUS20120304300A1Fast data analysisEasy to addMemory loss protectionError detection/correctionVulnerability managementRemedial action
An enterprise vulnerability management application (EVMA), enterprise vulnerability management process (EVMP) and system. In one embodiment, the EVMP may include executing computer software code on at least one computer hardware platform to receive login information from a user, inventory current information technology assets of the enterprise, conduct vulnerability scanning of the inventoried information technology assets, analyze vulnerability correlation and prioritization of the information technology assets, remediate one or more vulnerabilities of the information technology assets, and report to the user about the vulnerabilities and remediation undertaken. As part of the analysis, one or more vulnerability scores such as, for example, Common Vulnerability Scoring System (CVSS) scores, may be generated from base score metrics, temporal score metrics and environment score metrics.
Owner:LEIDOS INNOVATIONS TECH INC
Device vulnerability management
ActiveUS20180351987A1Suitable for implementationWeb data indexingComputer security arrangementsVulnerability managementComputer science
A computer-implemented process of remediating device security vulnerabilities is carried out by determining identifications of electronic devices associated with an entity and calculating, for each device, a security cyber-vulnerability score. For instance, the cyber-vulnerability score is calculated by generating a device cyber-vulnerability score based upon known threats and vulnerabilities, generating a device level cyber-vulnerability score by augmenting the generated device cyber-vulnerability score based upon at least one device level parameter, generating an environmental cyber-vulnerability score, and computing an overall cyber-vulnerability score based upon the device level cyber-vulnerability score and the environmental cyber-vulnerability score. The computer-implemented process also comprises prioritizing the electronic devices based upon the computed overall cyber-vulnerability score, identifying whether a patch is available for at least one electronic device, and initiating a remediation / mitigation workflow to patch at least one electronic device.
Owner:MEDITECHSAFE INC
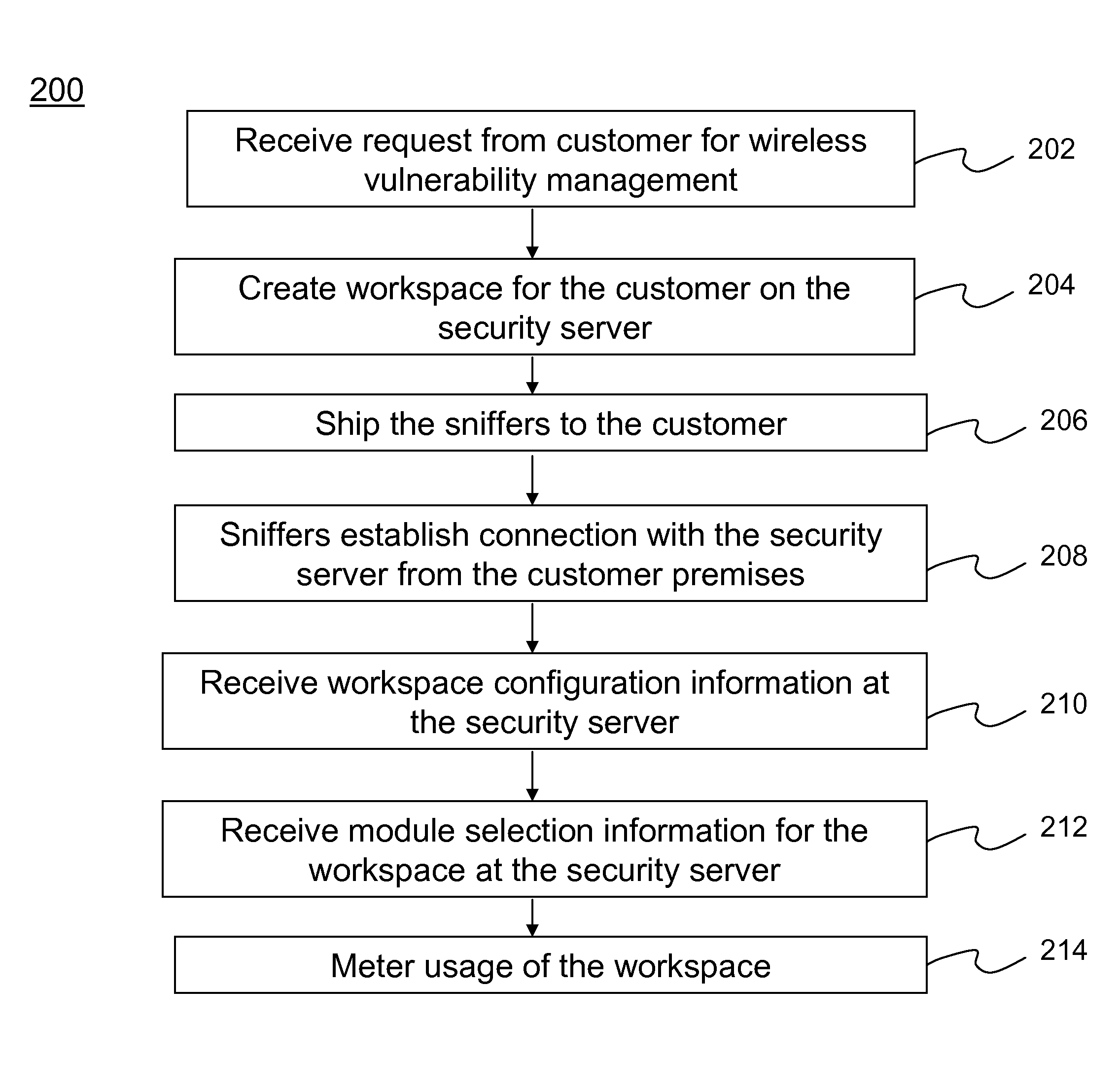
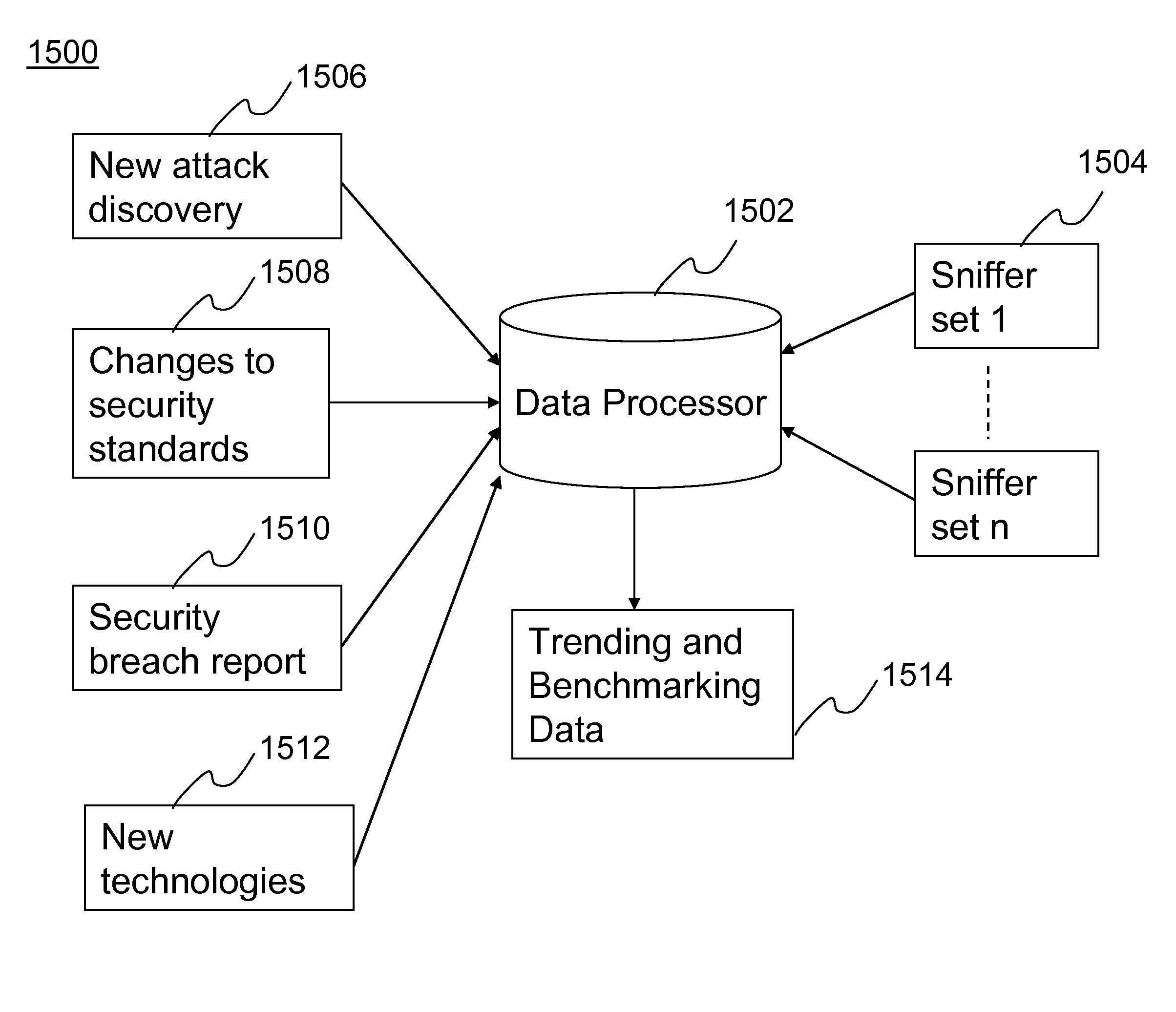
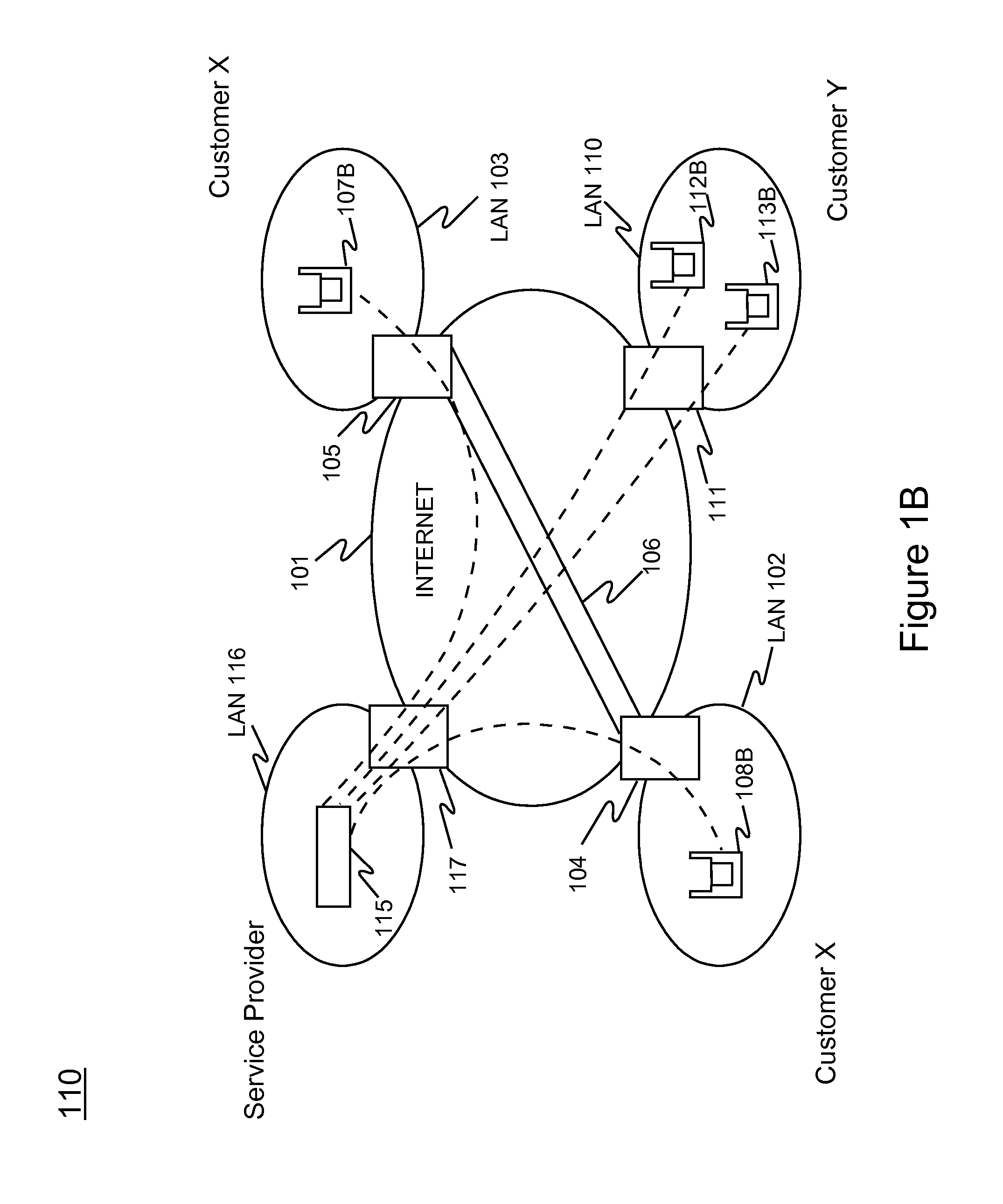
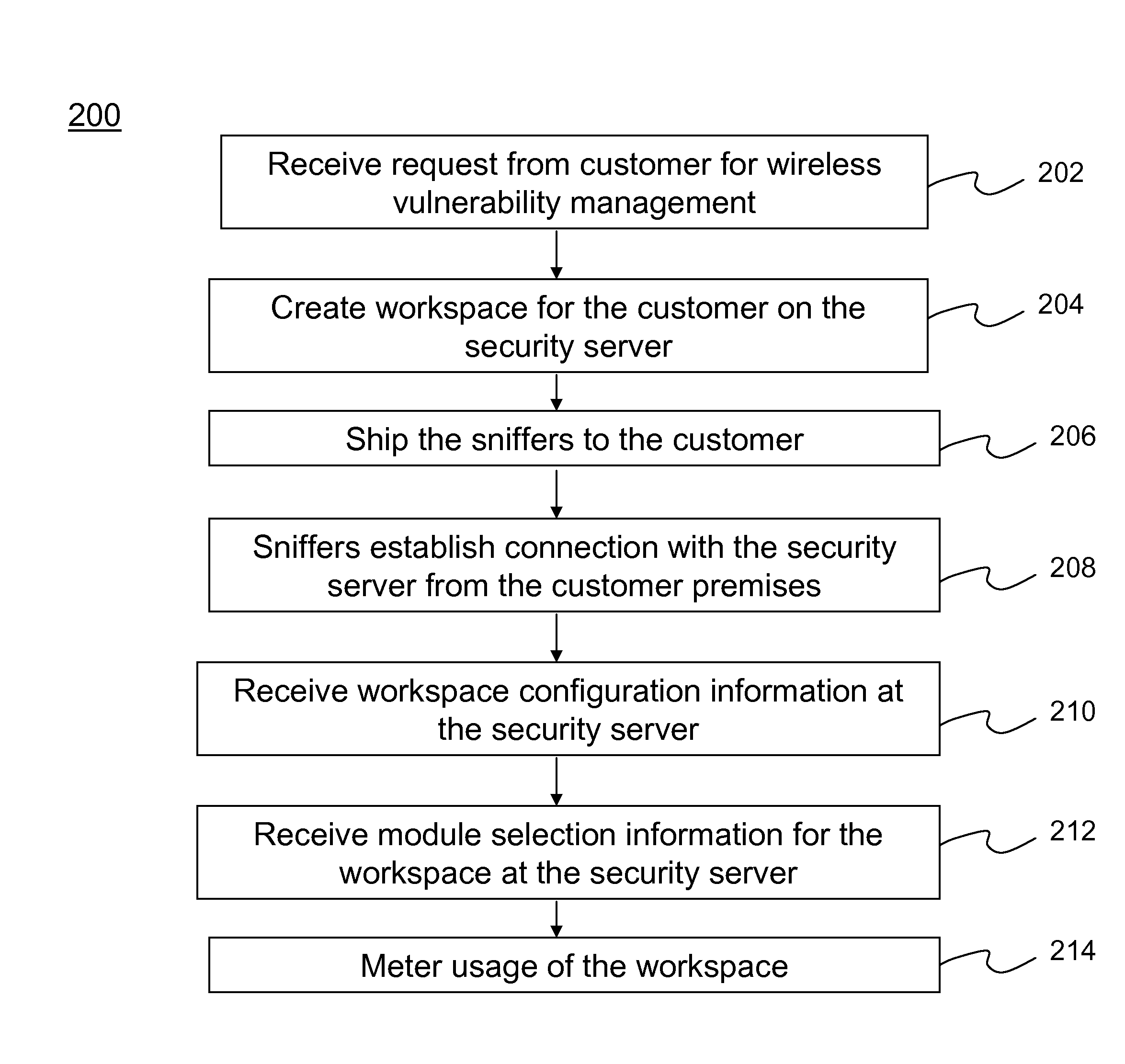
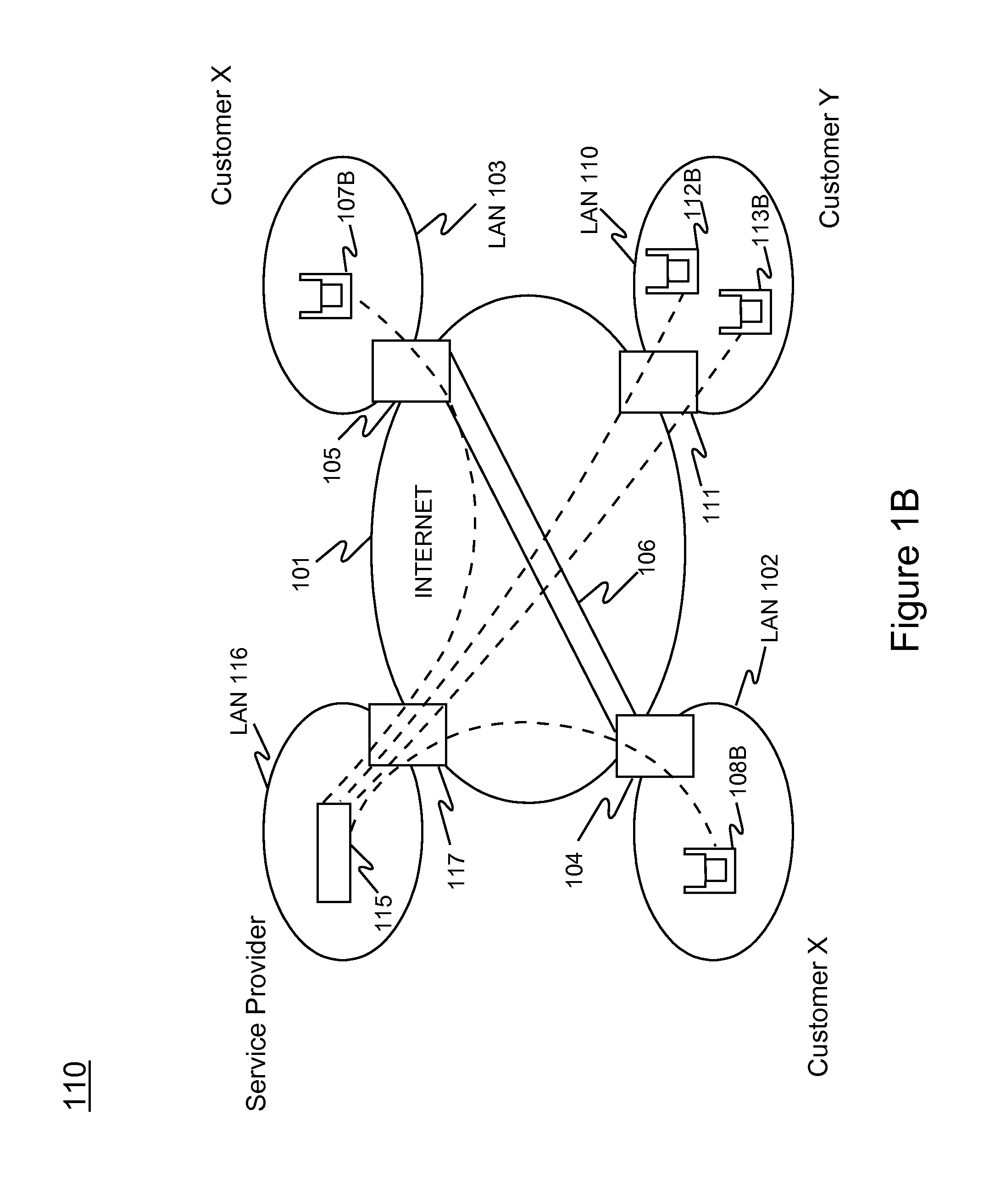
Method and system for providing wireless vulnerability management for local area computer networks
ActiveUS20090119776A1Reduce overheadEasy to customizeMemory loss protectionDigital computer detailsVulnerability managementComputer network
A Software-as-a-Service (SaaS) based method for providing wireless vulnerability management for local area computer networks. The method includes providing a security server being hosted by a service provider entity to provide analysis of data associated with wireless vulnerability management for a plurality of local area computer networks of a plurality of customer entities, respectively. The method includes creating a workspace for wireless vulnerability management for a customer entity on the security server and receiving configuration information associated with the workspace. The method also includes supplying one or more sniffers to the customer entity. The method includes receiving at the security server information associated with wireless activity monitored by the one or more sniffers at premises of the customer entity and processing the received information within the workspace for the customer entity using the security server. The method includes metering usage of the workspace for wireless vulnerability management for the customer entity.
Owner:ARISTA NETWORKS
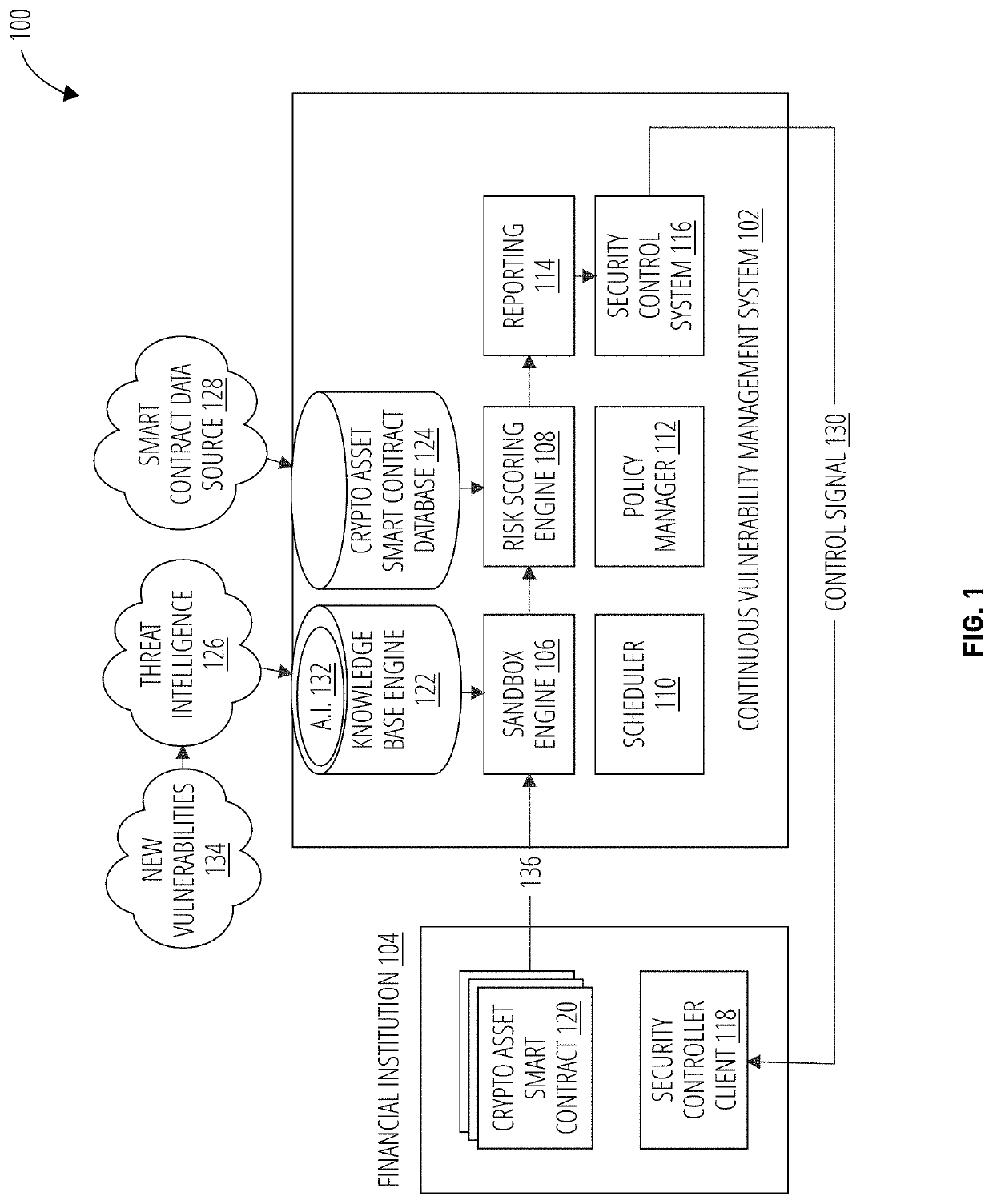
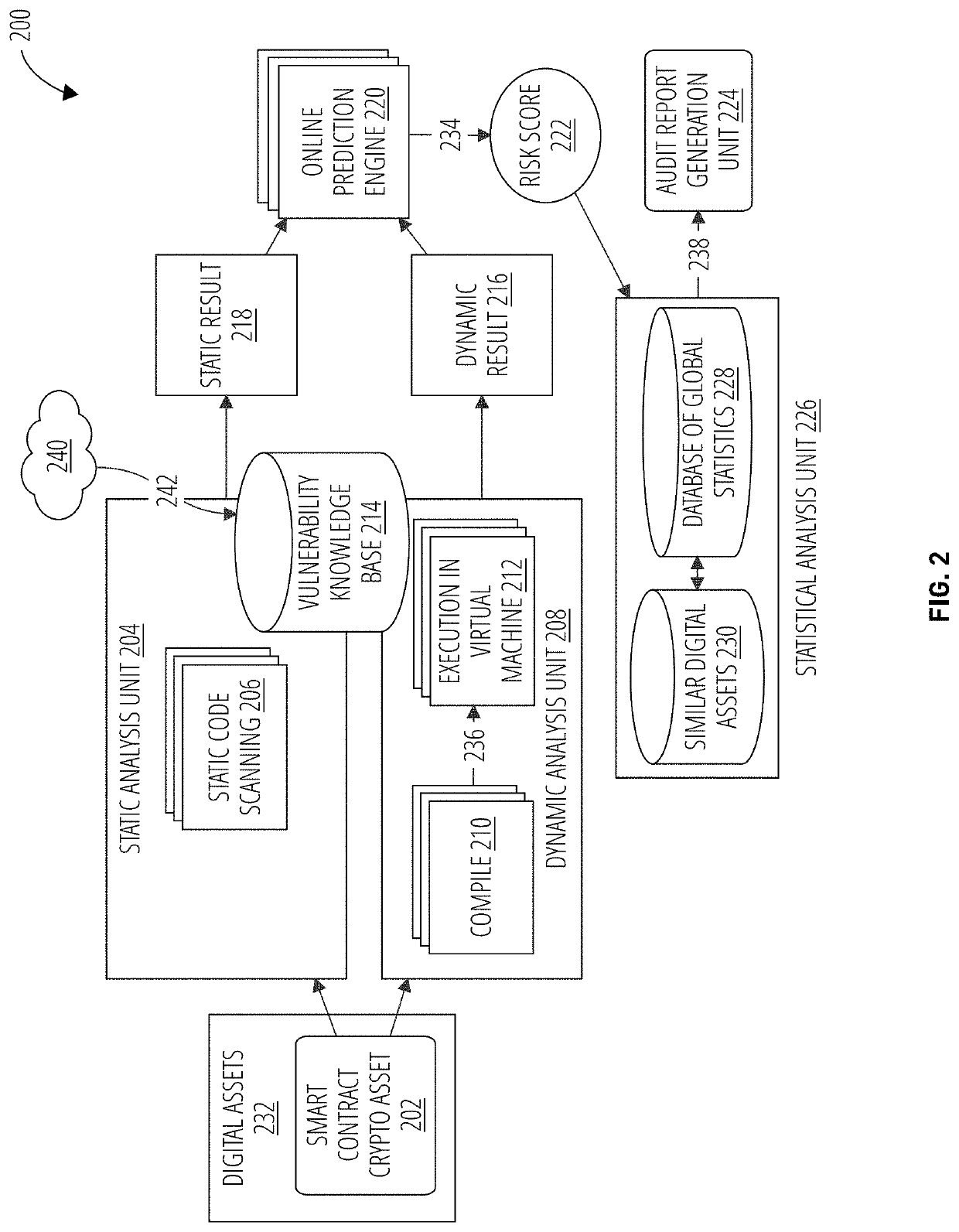
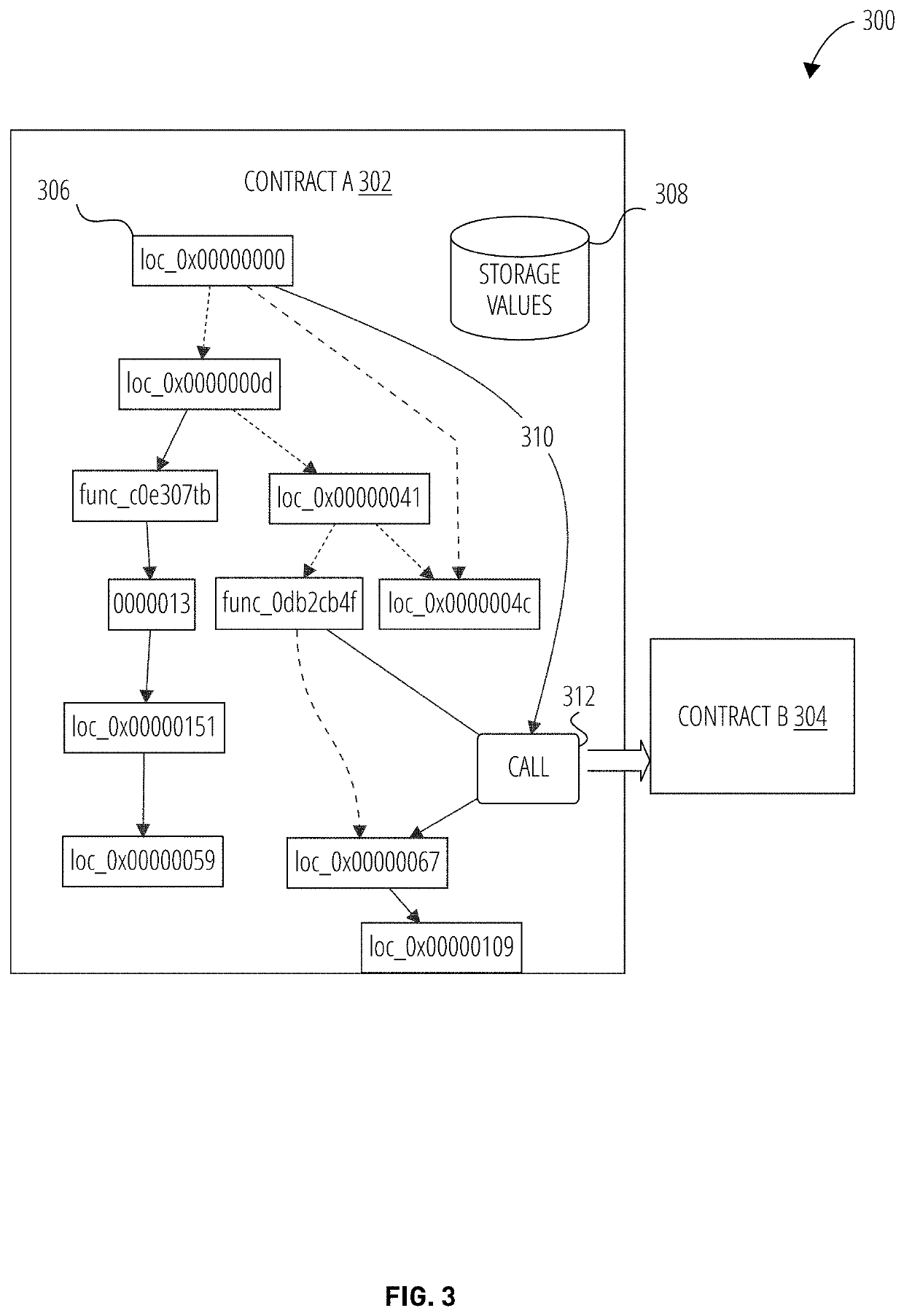
Continuous vulnerability management system for blockchain smart contract based digital asset using sandbox and artificial intelligence
ActiveUS20210110047A1Database distribution/replicationPayment protocolsStatistical analysisReliability engineering
A continuous vulnerability management system for identifying, analyzing, protecting, and reporting on digital assets is disclosed. The continuous vulnerability management system comprises a sandbox engine configured to scan digital assets for vulnerabilities, including a static analysis unit for static code scanning, a dynamic analysis unit for analyzing compiled code, and a statistical analysis unit for processing a risk score and generating an audit report. A knowledge base is also disclosed, including a knowledge base engine configured to acquire information related to new vulnerabilities to digital assets. A risk scoring engine is configured to analyze sandbox engine outcomes and assign a risk score to each vulnerable asset. A security control system is configured to act on an identified vulnerable asset based on the risk score assigned to the identified vulnerable asset.
Owner:ANCHAIN AI INC
Hosted vulnerability management for wireless devices
InactiveUS20100100930A1Reduce overheadEasy to customizeNetwork topologiesComputer security arrangementsVulnerability managementClient-side
A method, a multi-tenant security server apparatus and associated system for securing wireless communication of devices. The method includes transferring security policy configuration information from the security server to wireless devices. The method also includes ascertaining compliance of wireless activity of the wireless devices with the security policy configuration using client software modules installed on the wireless devices.
Owner:AIRTIGHT NETWORKS
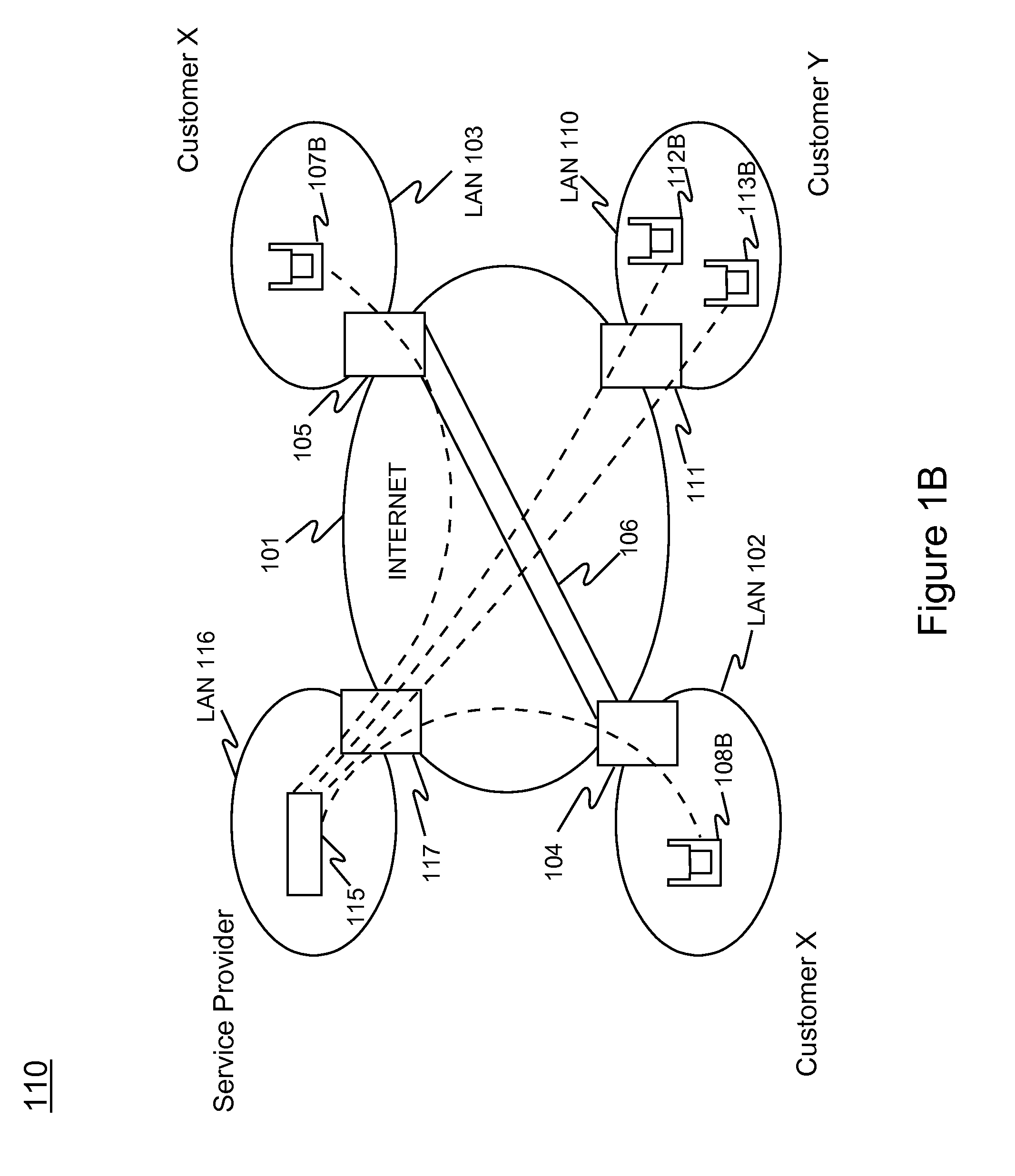
Method and system for Synchronized Policy Control In A Web Services Environment
ActiveUS20080098453A1Digital data processing detailsUser identity/authority verificationVulnerability managementService-level agreement
Policy controls for Web service resource objects in a hierarchical resource space are loosely coupled so that policy changes are applied and enforced across the objects. This technique ensures that different policies are not applied unintentionally to the same resource (for example, one at the Web services entry level, and the other at the resource level). By synchronizing the object in the manner described, neither the entity that deploys the application nor the security administrator need to be aware of the differences between the various types of requests that occur within a Web services environment. In a representative embodiment, resource objects are linked within a hierarchical resource space to provide synchronized policy control, where the policy is an audit policy, a quality-of-service (QoS) policy, a service level agreement (SLA) policy, a governance policy, a compliance policy, a patch management / vulnerability management policy, a user management policy, or a rights management policy.
Owner:IBM CORP
Vulnerability management system based on multi-engine vulnerability scanning association analysis
ActiveCN108737425AMeet safety construction requirementsEfficient and accurate executionTransmissionVulnerability managementOperational system
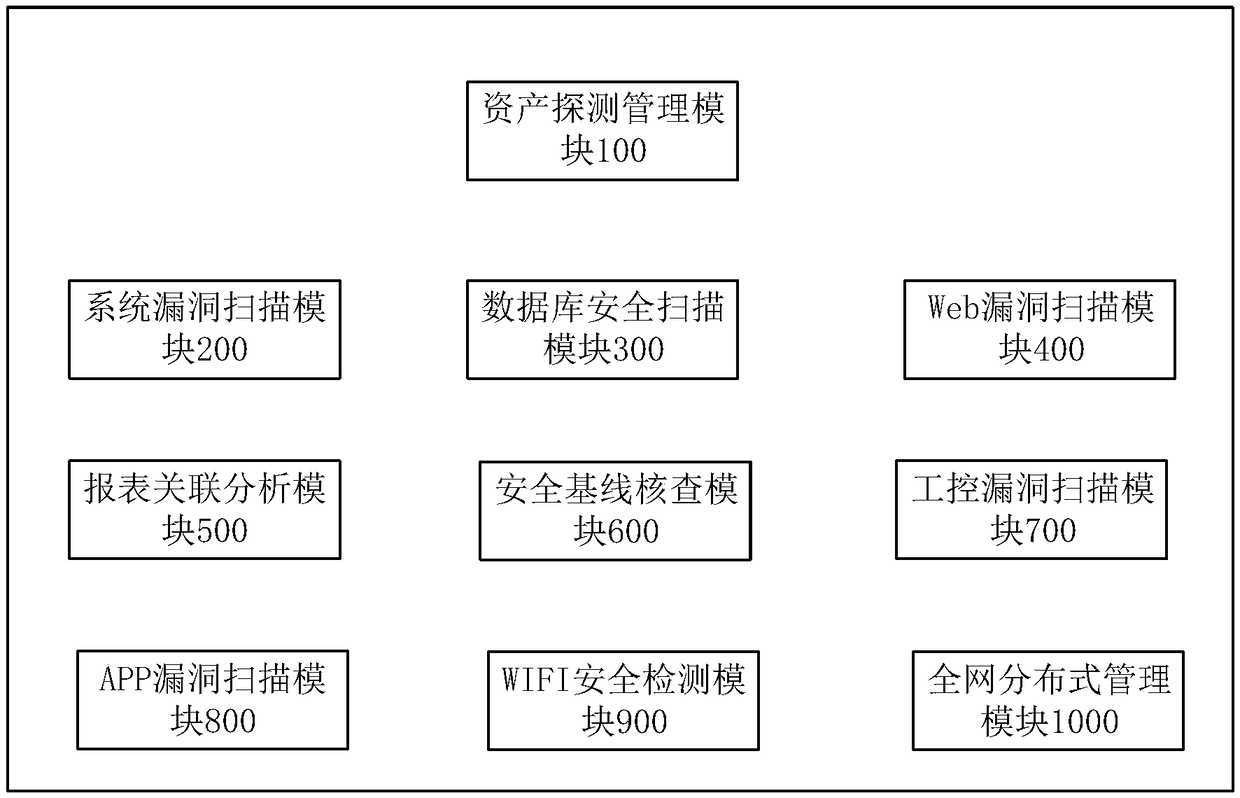
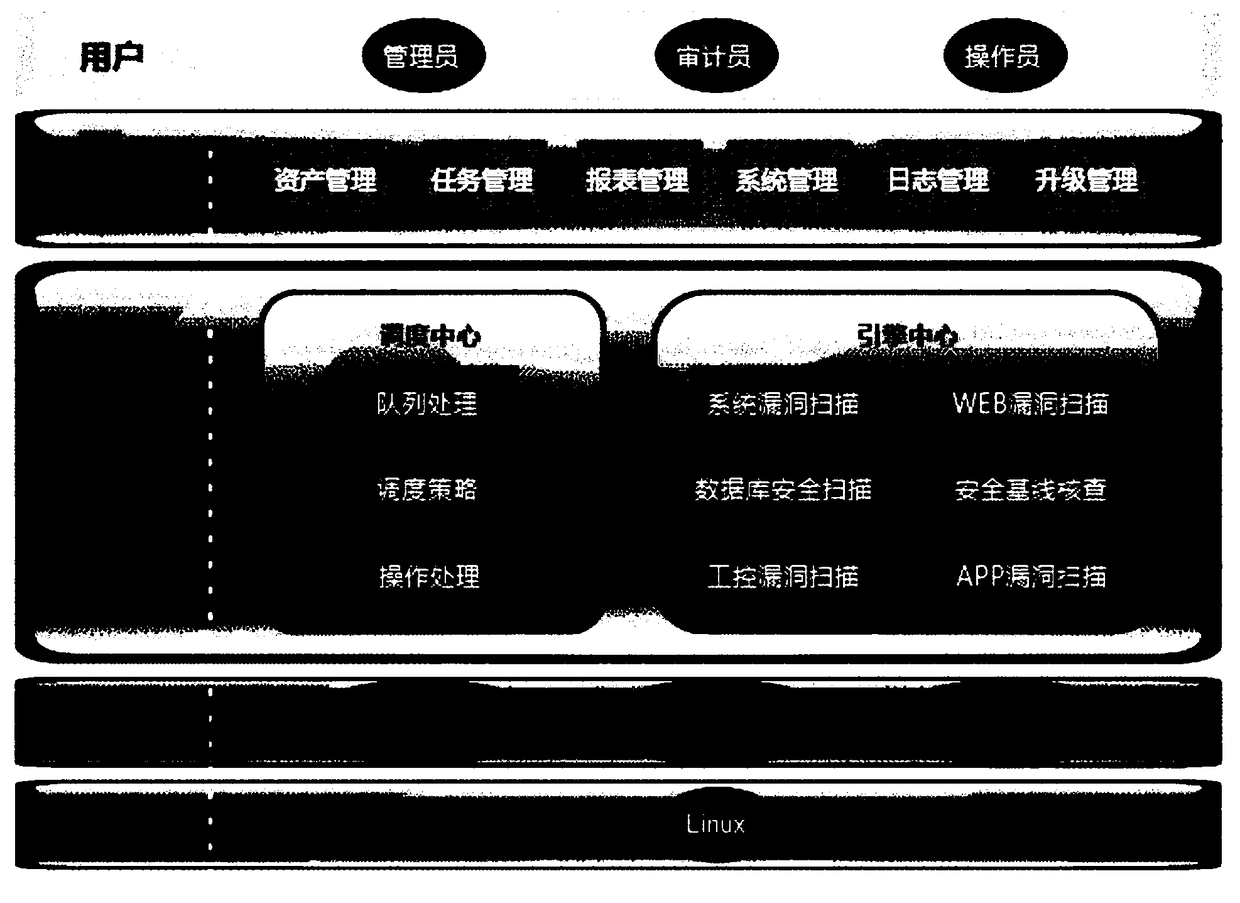
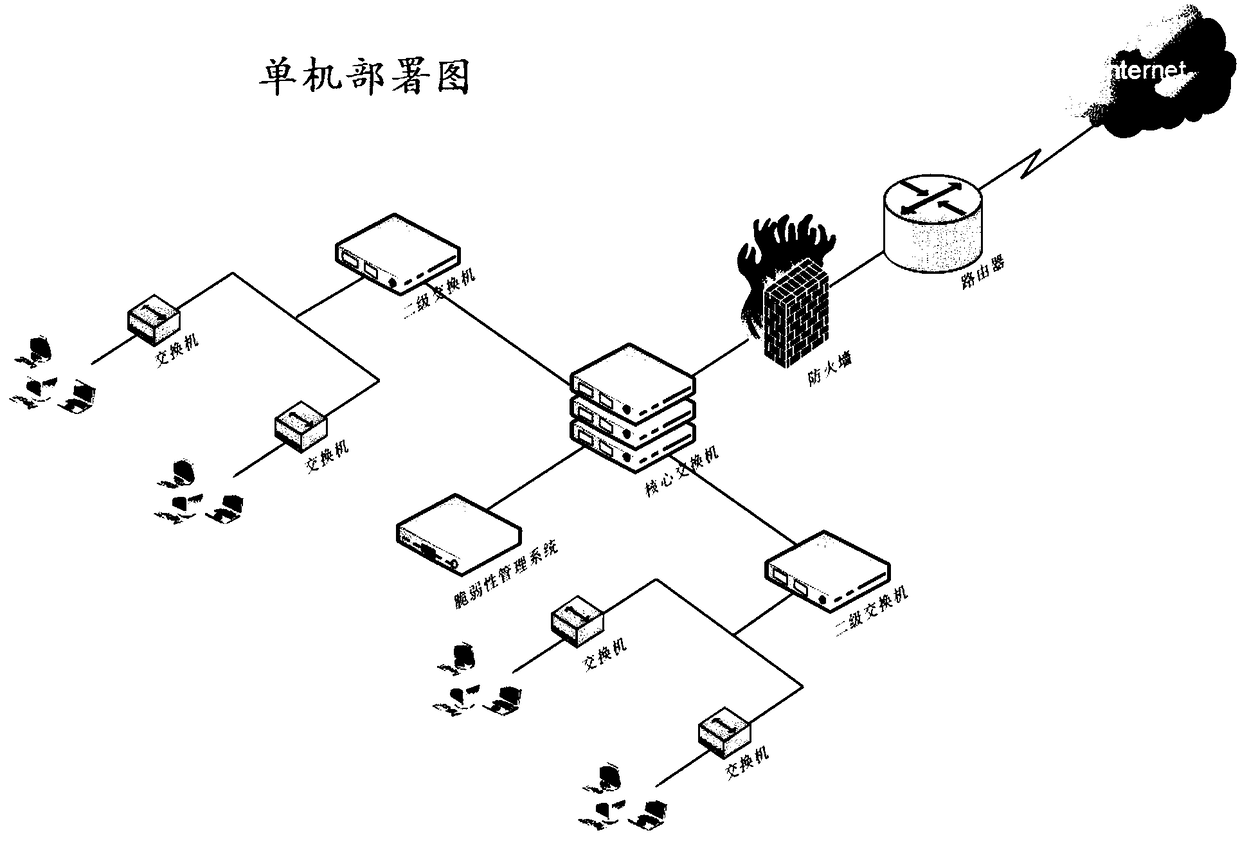
The invention provides a vulnerability management system based on multi-engine vulnerability scanning association analysis. The vulnerability management system comprises: an asset detection managementmodule used for detecting asset information in a scanning network; a system vulnerability scanning module used for performing vulnerability scanning and analysis on a network device, an operating system, application service and a database according to the asset information, and supporting intelligent service identification; a Web vulnerability scanning module used for automatically parsing data according to the asset information, scanning the data, verifying a discovered WEB vulnerability, and recording a test data packet discovered by vulnerability scanning; a database security scanning module; a security baseline verification module; an industrial control vulnerability scanning module; an APP vulnerability scanning module; a WIFI security detection module; a report association analysismodule; and a whole-network distributed management module. The vulnerability management system provided by the invention can perform association analysis on a detection result and a compliance libraryof information security level protection to generate a level protection evaluation report that meets the specification requirements, and the security requirements of different customers are comprehensively met.
Owner:北京凌云信安科技有限公司
Device vulnerability management
ActiveUS10992698B2Web data indexingPlatform integrity maintainanceVulnerability managementEngineering
A computer-implemented process of remediating device security vulnerabilities is carried out by determining identifications of electronic devices associated with an entity and calculating, for each device, a security cyber-vulnerability score. For instance, the cyber-vulnerability score is calculated by generating a device cyber-vulnerability score based upon known threats and vulnerabilities, generating a device level cyber-vulnerability score by augmenting the generated device cyber-vulnerability score based upon at least one device level parameter, generating an environmental cyber-vulnerability score, and computing an overall cyber-vulnerability score based upon the device level cyber-vulnerability score and the environmental cyber-vulnerability score. The computer-implemented process also comprises prioritizing the electronic devices based upon the computed overall cyber-vulnerability score, identifying whether a patch is available for at least one electronic device, and initiating a remediation / mitigation workflow to patch at least one electronic device.
Owner:MEDITECHSAFE INC
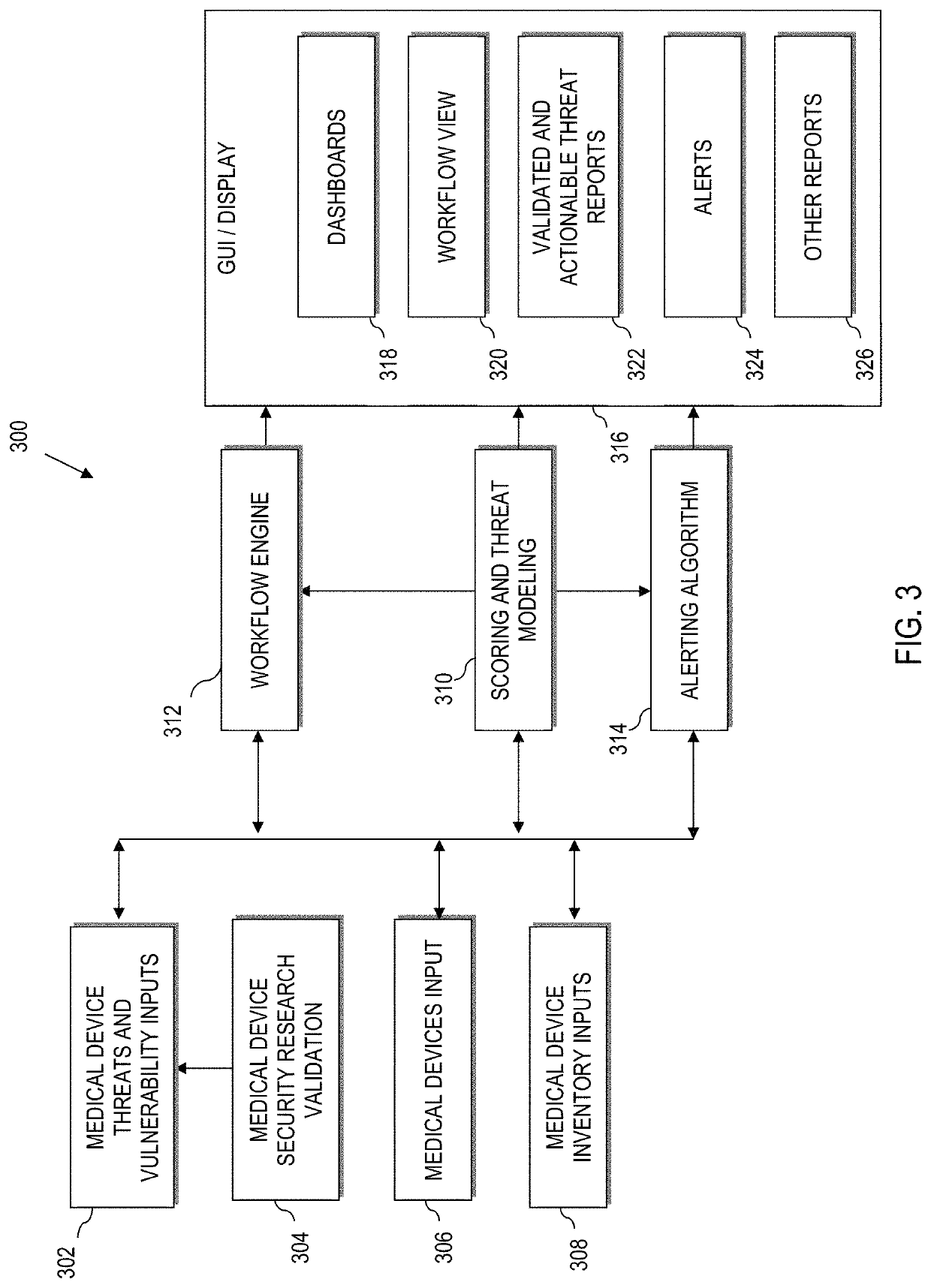
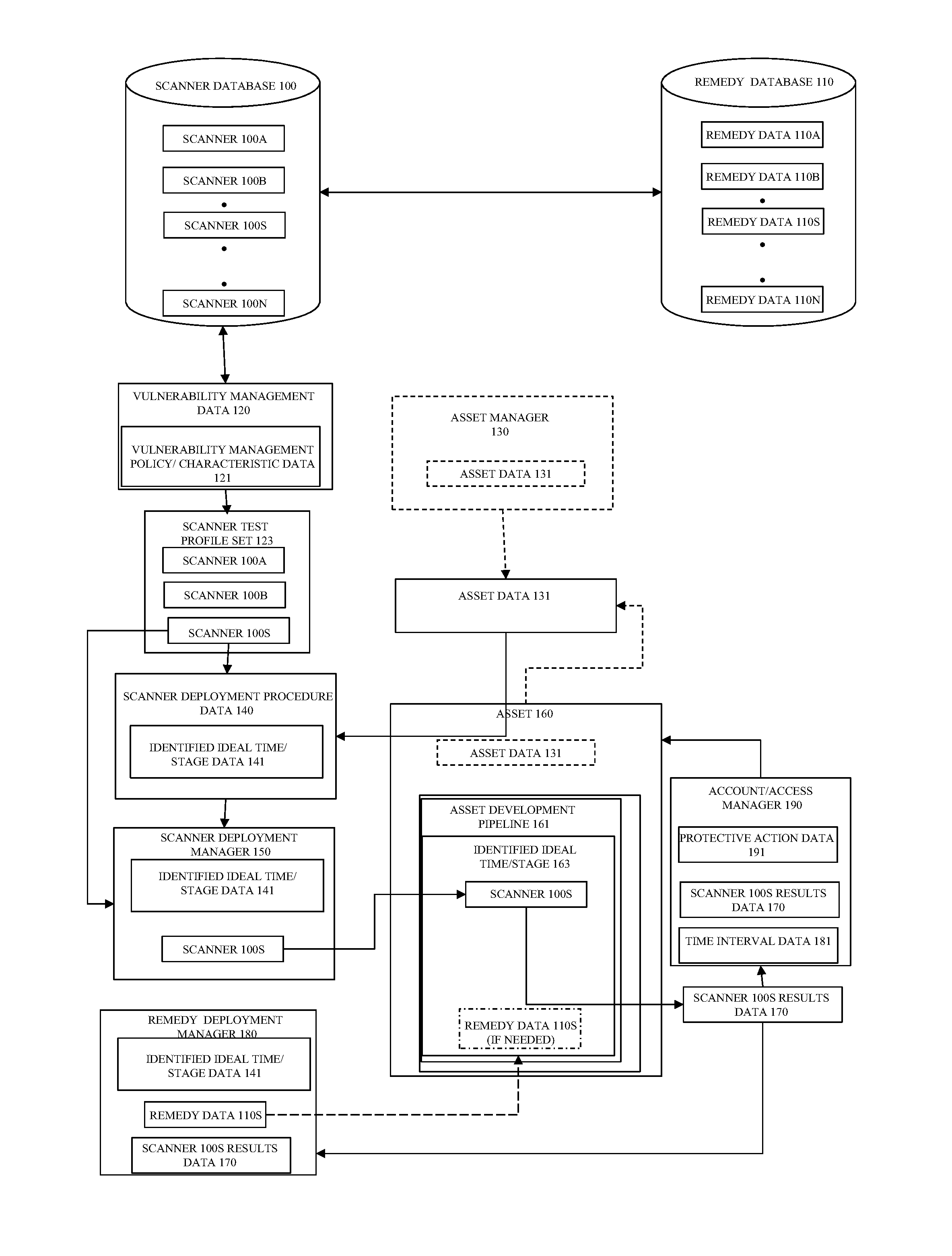
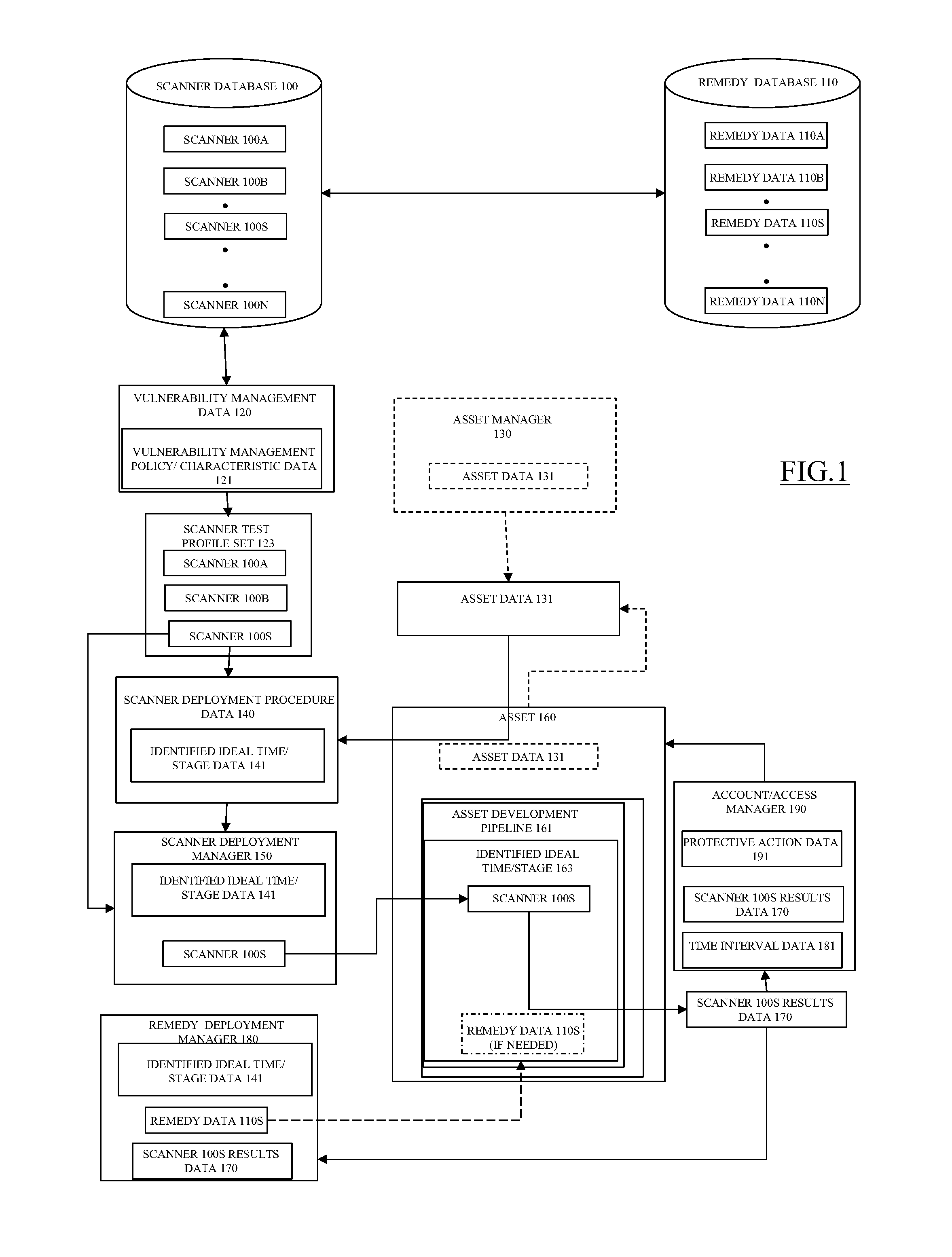
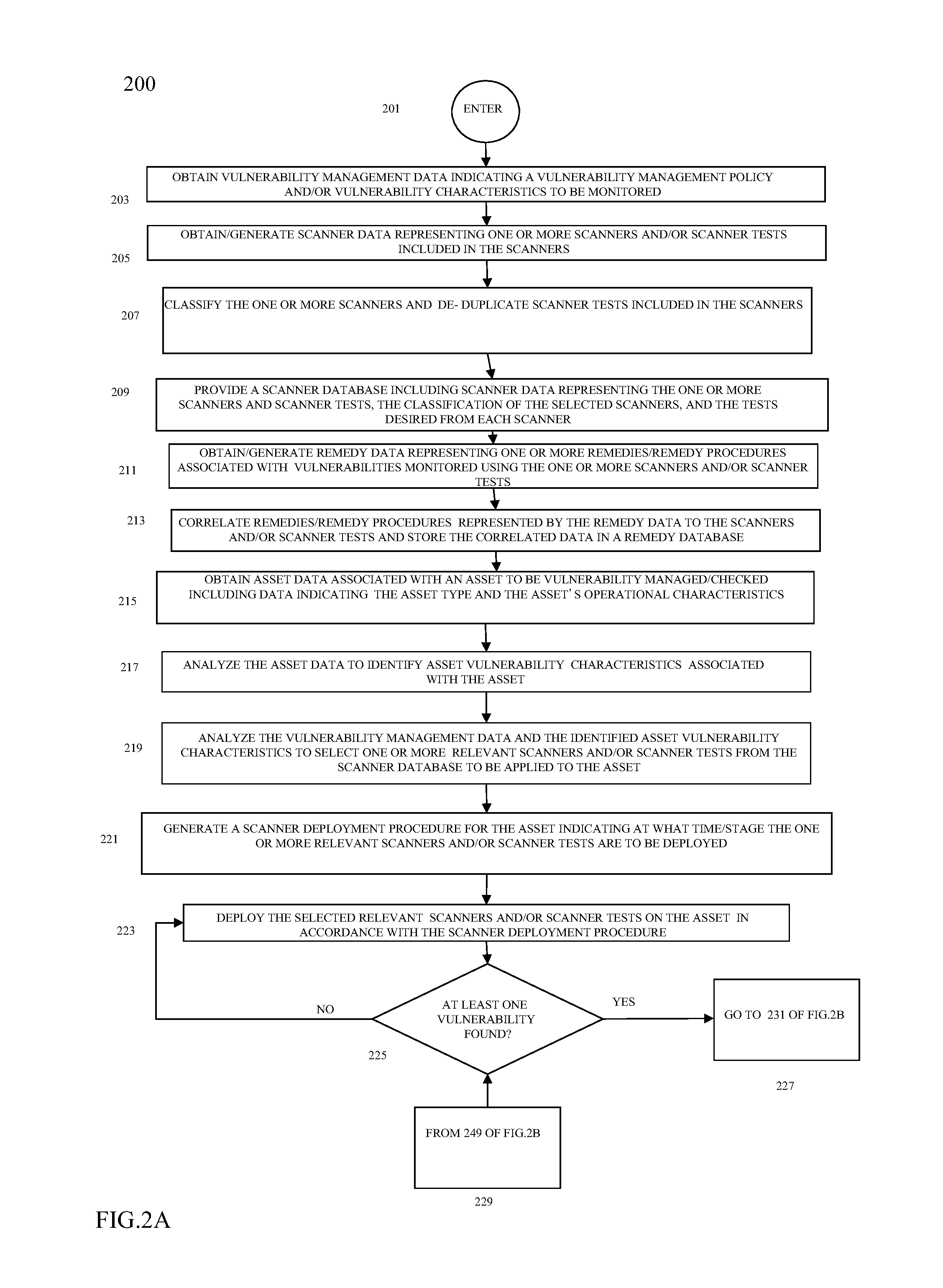
Method and system for dynamic and comprehensive vulnerability management
ActiveUS20150106939A1Reduce vulnerabilityMemory loss protectionError detection/correctionVulnerability managementRemedial action
One or more relevant scanners used to identify asset vulnerabilities are identified, obtained, and logically arranged for deployment on an asset in accordance with a vulnerability management policy and a scanner deployment policy such that the relevant scanners are deployed at, or before, a determined ideal time to minimize the resources necessary to correct the vulnerabilities, if found. The relevant scanners are then automatically deployed in accordance with the scanner deployment policy and, if a vulnerability is identified, one or more associated remedies or remedy procedures are applied to the asset. At least one of the one or more relevant scanners are then re-deployed on the asset to determine if the identified vulnerability has been corrected and, if the vulnerability is not corrected at, or before, a defined time, protective measures are automatically taken.
Owner:INTUIT INC
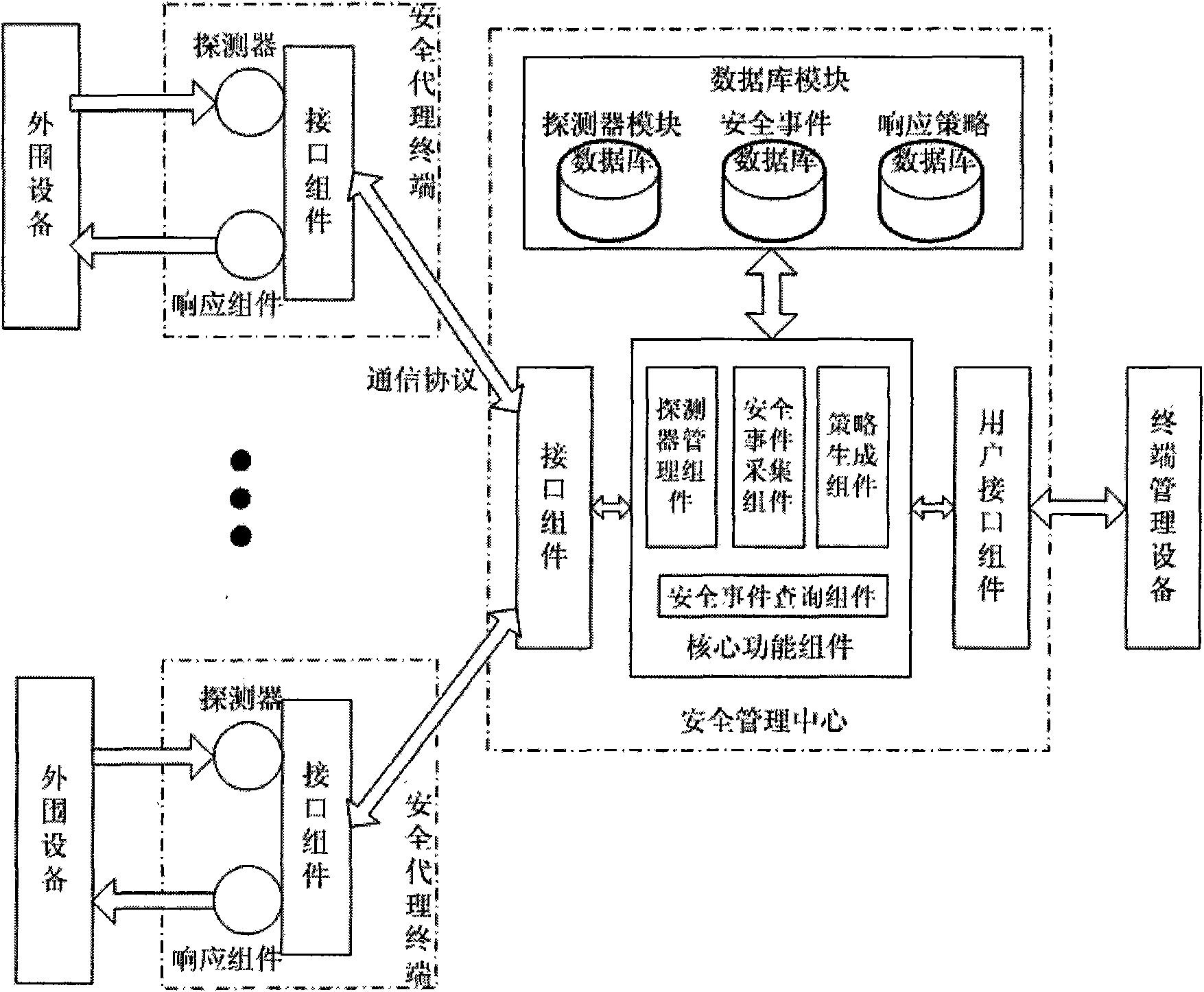
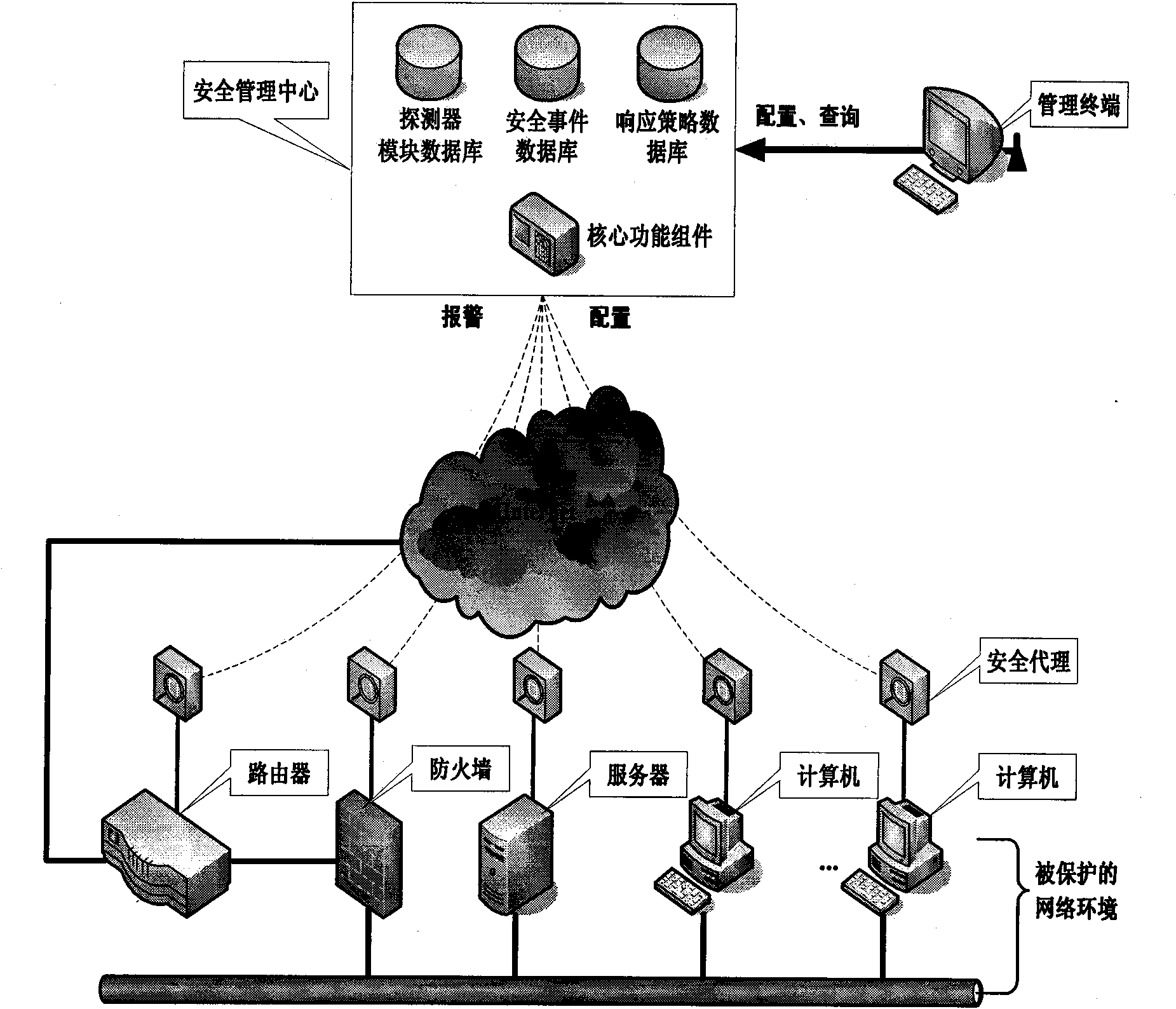
System and method for managing security of general network
InactiveCN101582883AImprove general performanceIncrease opennessData switching networksDistributed securityProtection system
The invention discloses a system and a method for managing security of a general network, and mainly overcomes the defects of poor openness and expansibility and weak functional completeness existing in the prior network security management system. The system mainly comprises peripheral equipment, a security agent terminal, a security management center and terminal management equipment, wherein the security management center applies security technology of network access control, intrusion detection, virus detection and vulnerability management to the security agent terminal through an interface component, a data base module and a user interface component; and under the unified management and control, all security technology is mutually complemented and matched to detect and control network behaviors, so that a distributed security protection system structure in which security strategies are under central management and the security detection is separately distributed is formed. The system and the method have the advantages of flexible configuration, easy expansion, good openness, support of the different level management, and suitability for the security management and protection of the computer network in governments, colleges and universities, and large- and medium-sized enterprises.
Owner:XIDIAN UNIV
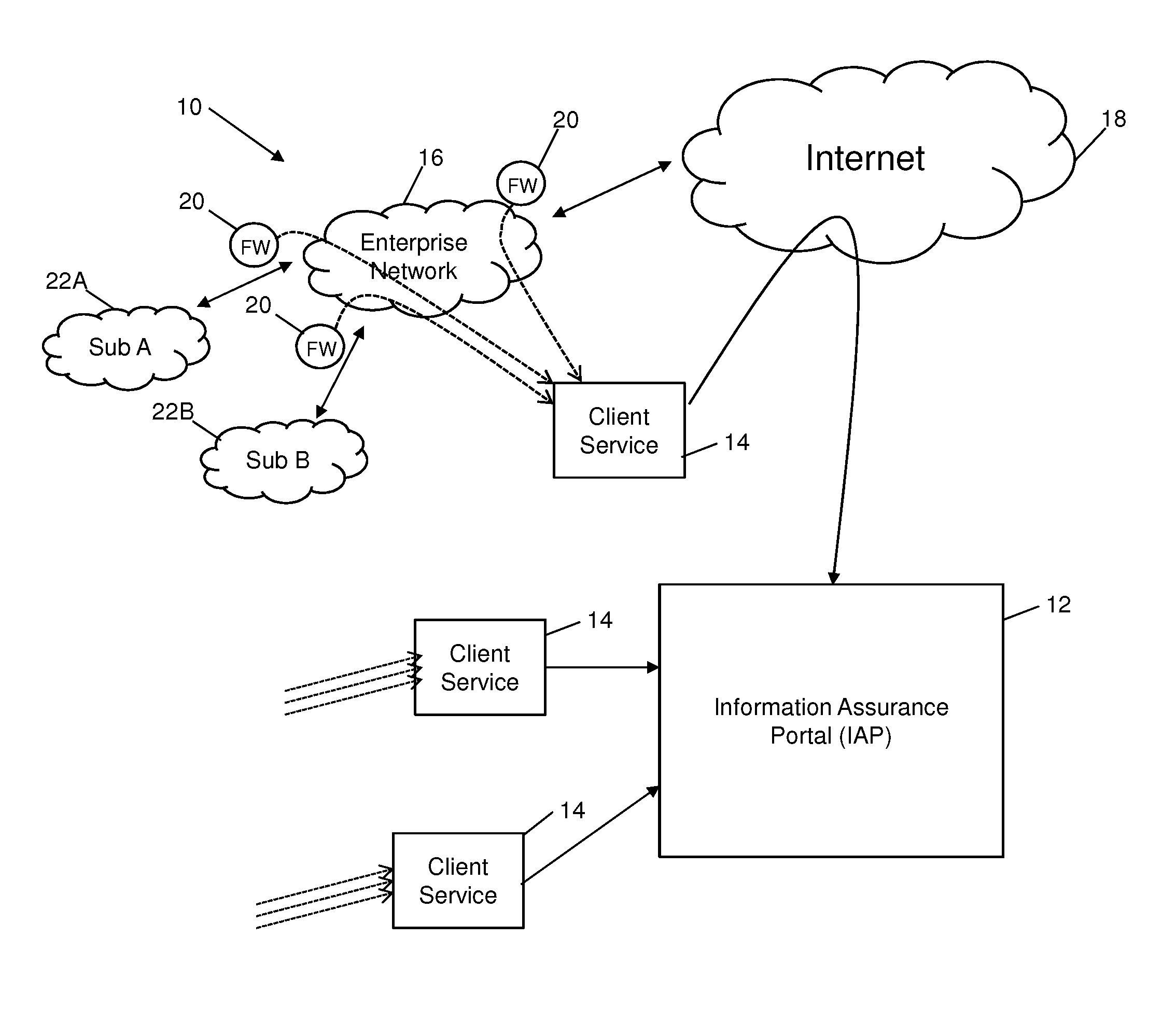
System and method for monitoring data in a client environment
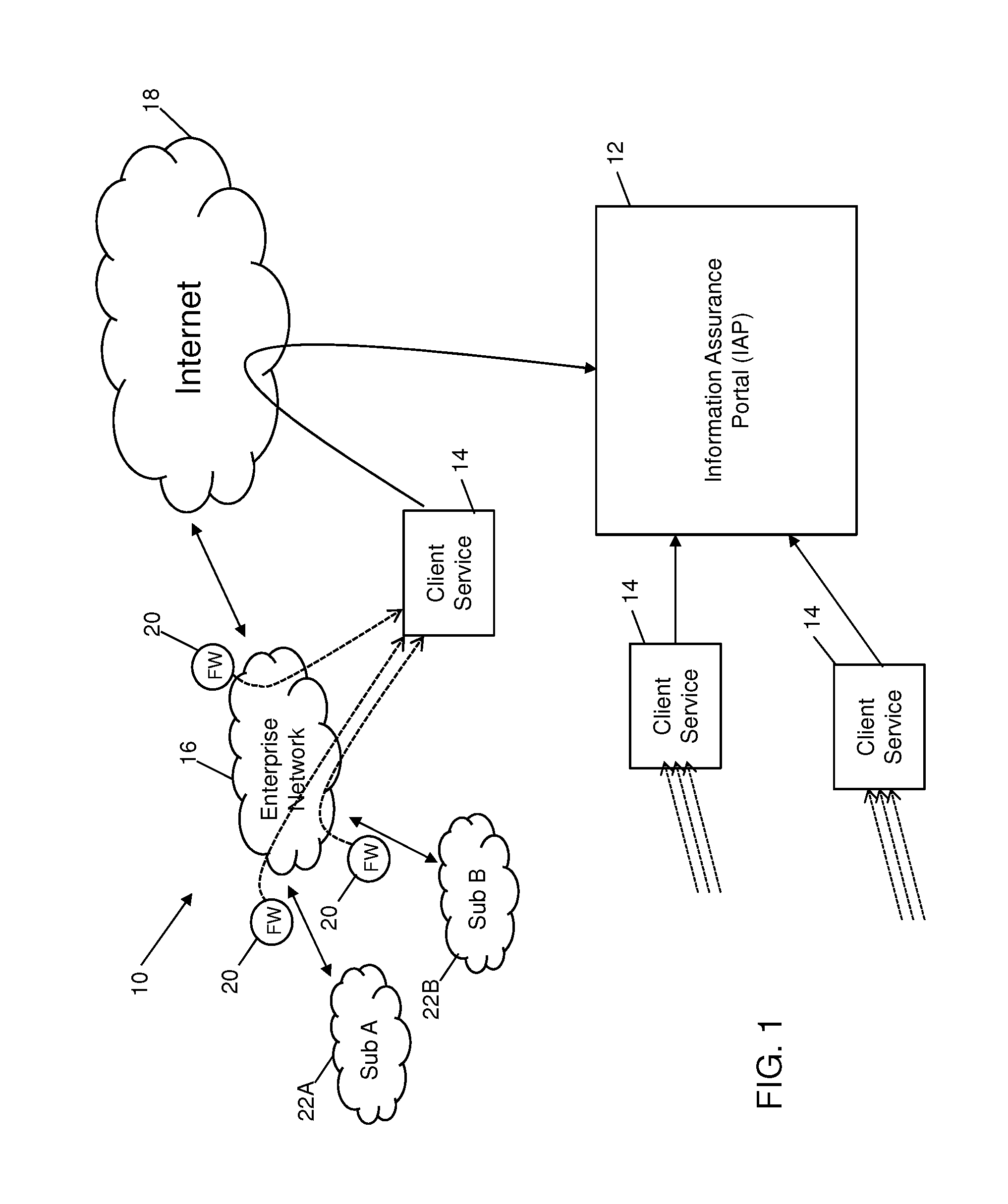
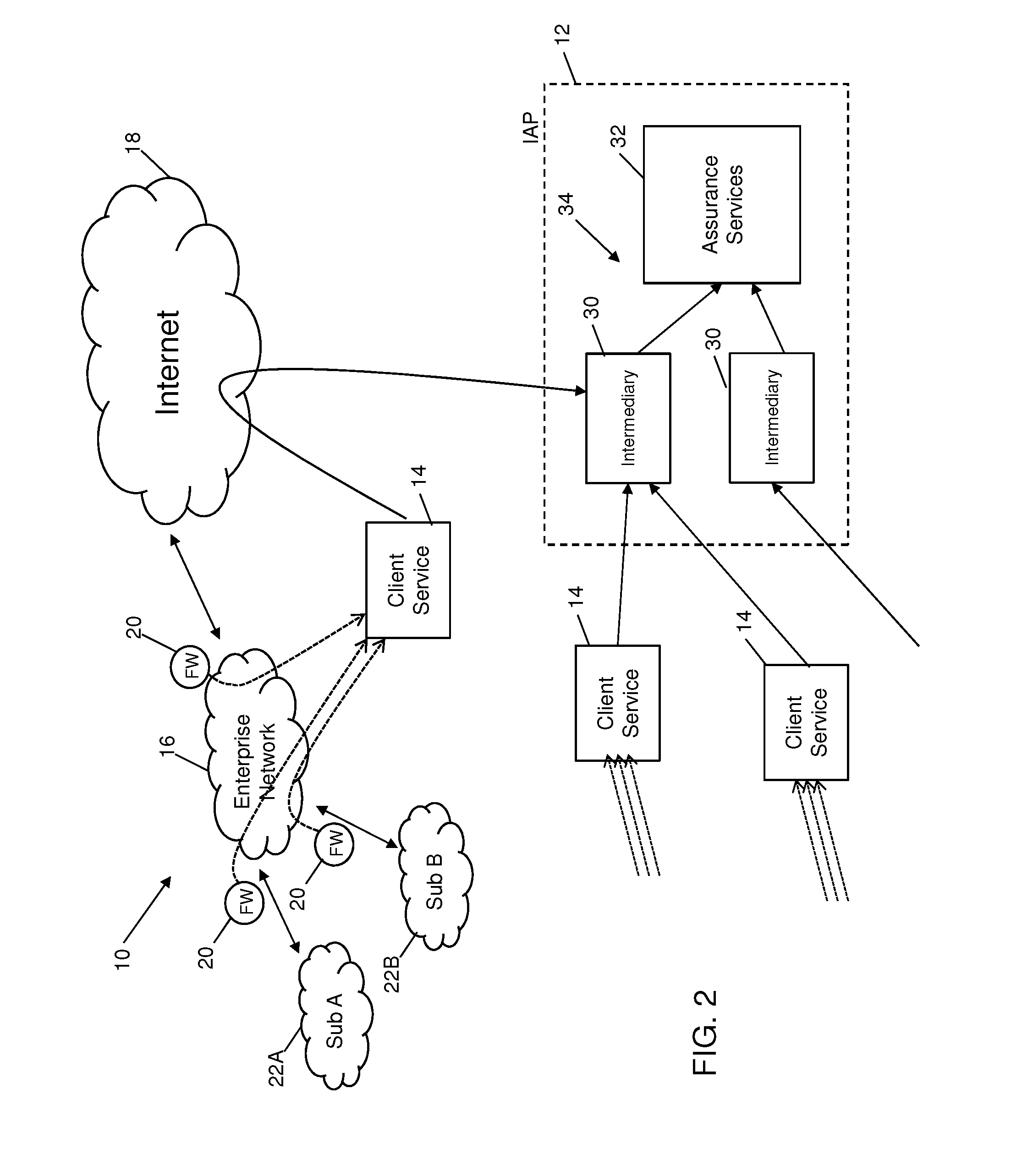
InactiveUS20150347751A1Memory loss protectionError detection/correctionCloud baseInformation assurance
Systems and methods are provided which enable client environments, such as corporate and government enterprises, to adopt an integrated, strategic approach to governance, risk and compliance. The systems described herein provide a “cloud-based” information security service that provides such enterprises with round-the-clock visibility into security issues and risks across the enterprise. An advanced security information and event management system, also referred to as an information assurance portal (IAP), is described, which enables client customers to select various services such as threat and vulnerability management, asset classification and tracking, and business threat and risk assessments through a software-as-a-service portal.
Owner:SECCURIS INC
Method and system for providing wireless vulnerability management for local area computer networks
InactiveUS20120185390A1Customization processReduce overheadDigital data processing detailsUser identity/authority verificationVulnerability managementComputer network
A Software-as-a-Service (SaaS) based method for providing wireless vulnerability management for local area computer networks. The method includes providing a security server being hosted by a service provider entity to provide analysis of data associated with wireless vulnerability management for a plurality of local area computer networks of a plurality of customer entities, respectively. The method includes creating a workspace for wireless vulnerability management for a customer entity on the security server and receiving configuration information associated with the workspace. The method also includes supplying one or more sniffers to the customer entity. The method includes receiving at the security server information associated with wireless activity monitored by the one or more sniffers at premises of the customer entity and processing the received information within the workspace for the customer entity using the security server. The method includes metering usage of the workspace for wireless vulnerability management for the customer entity.
Owner:AIRTIGHT NETWORKS
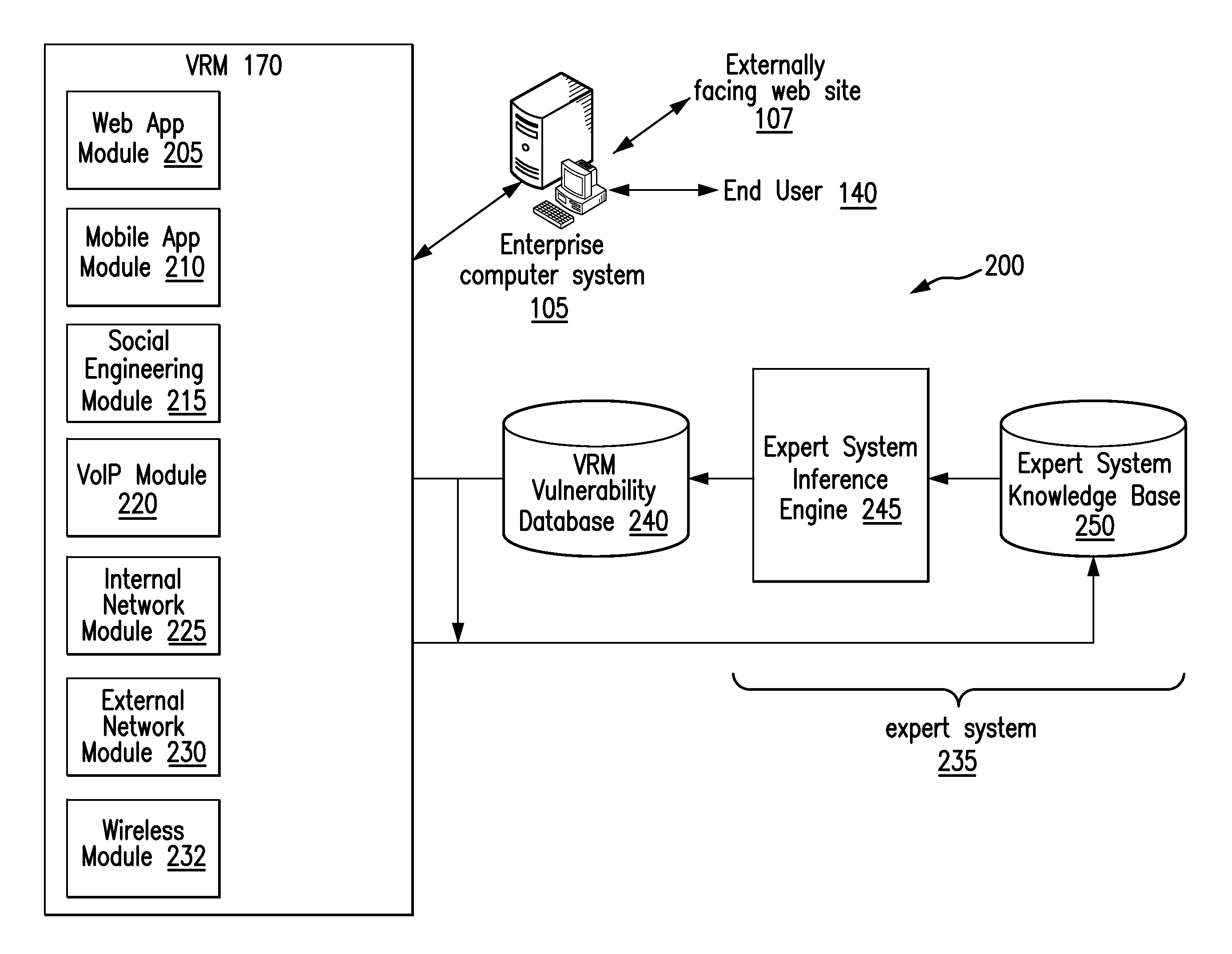
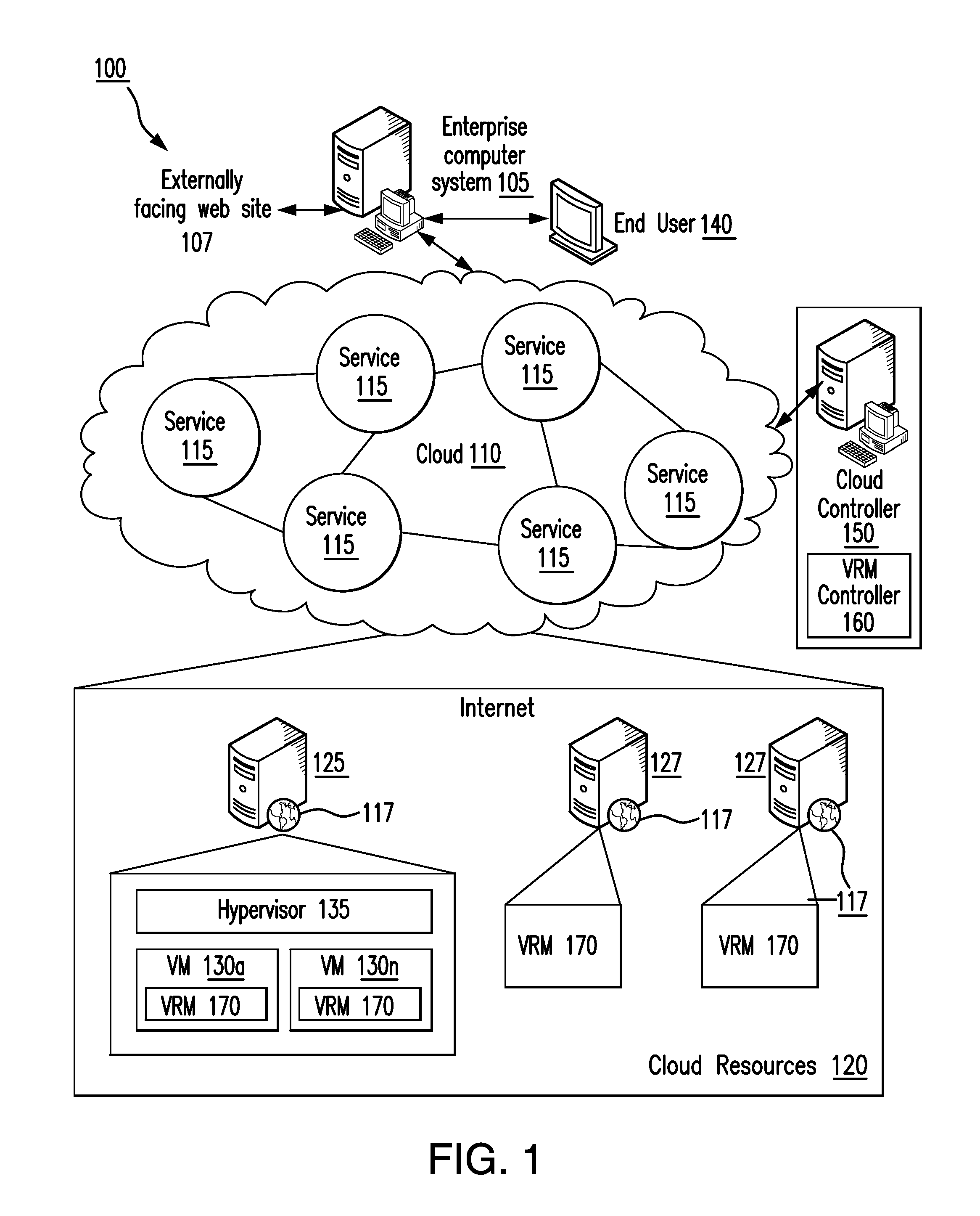
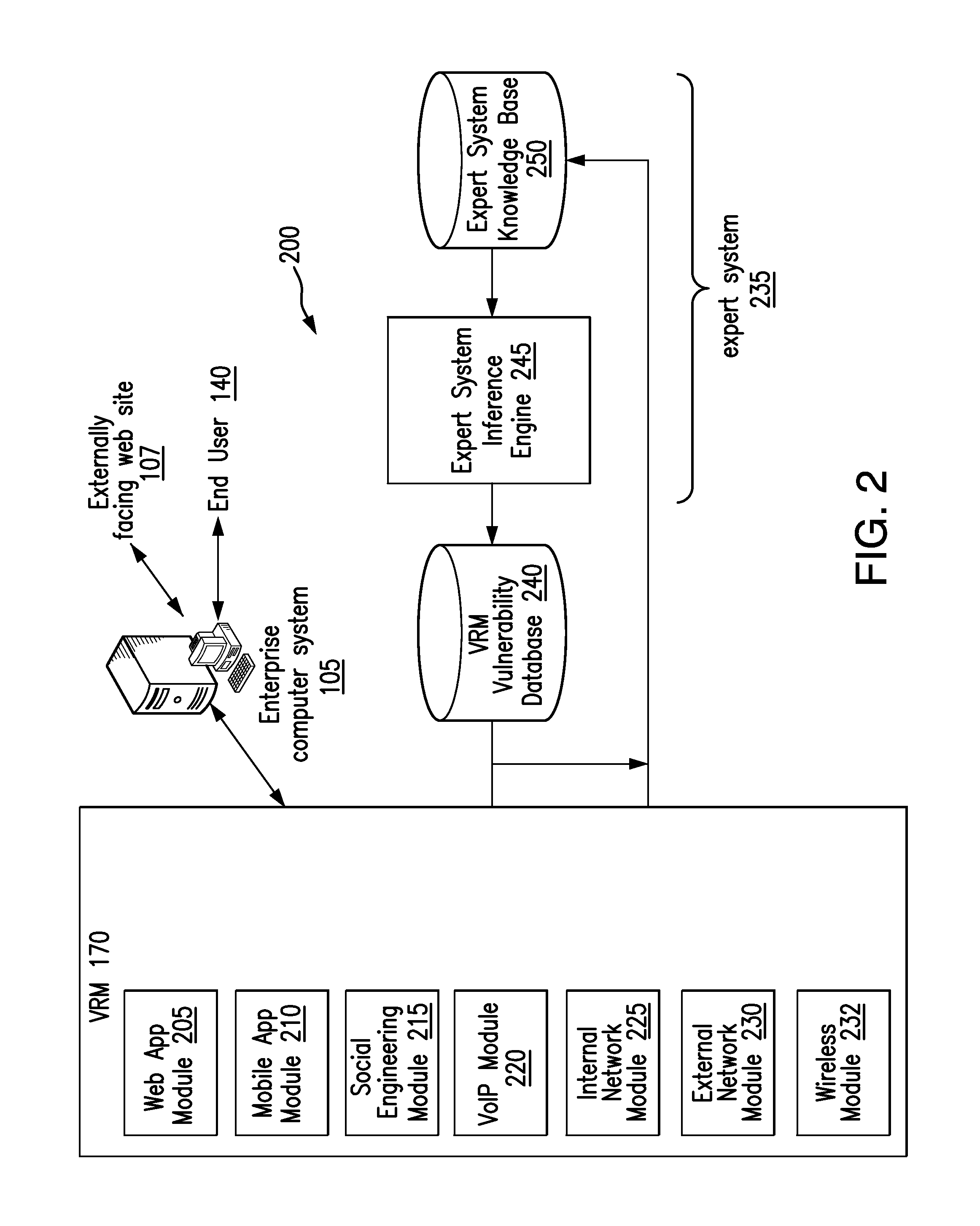
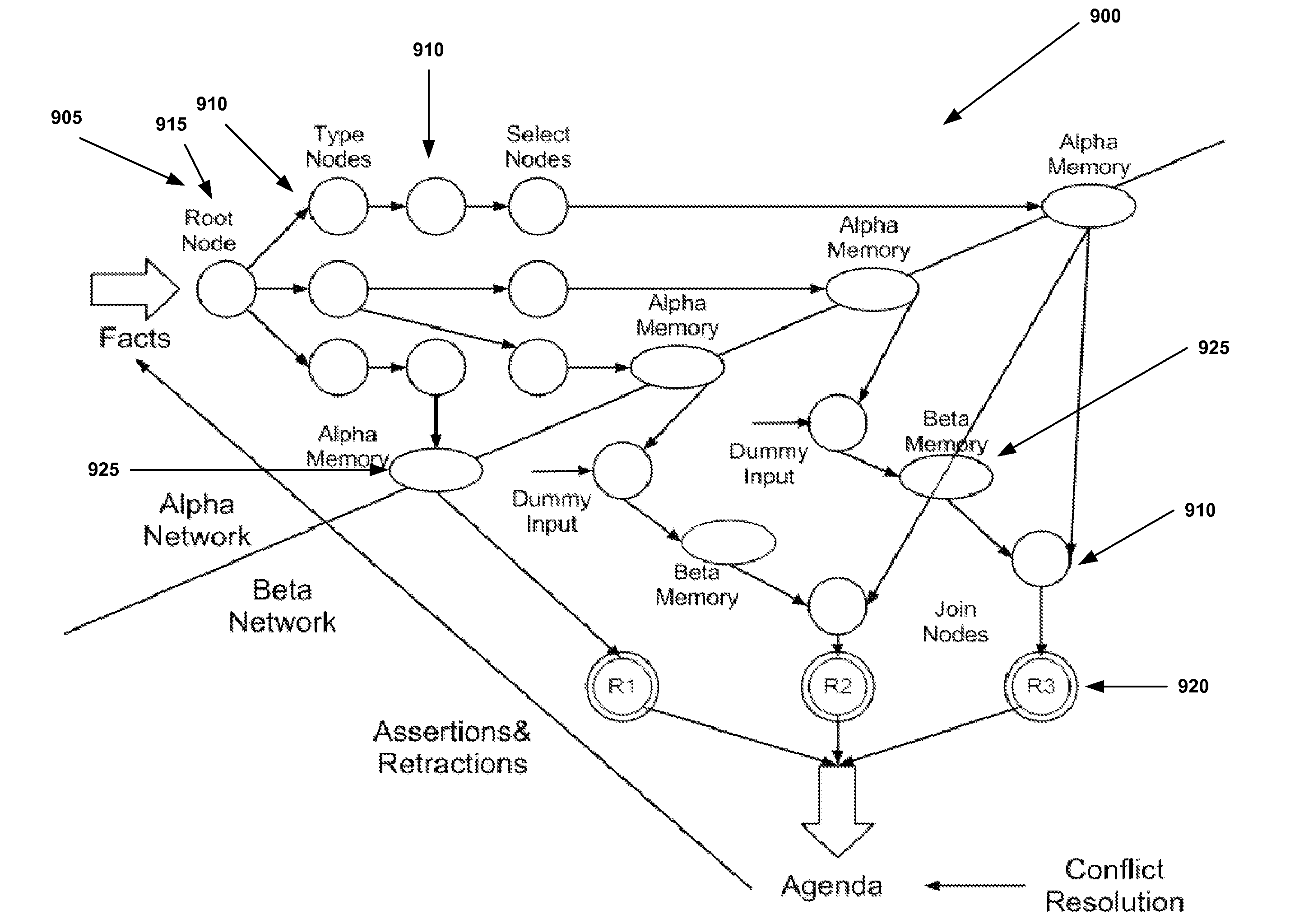
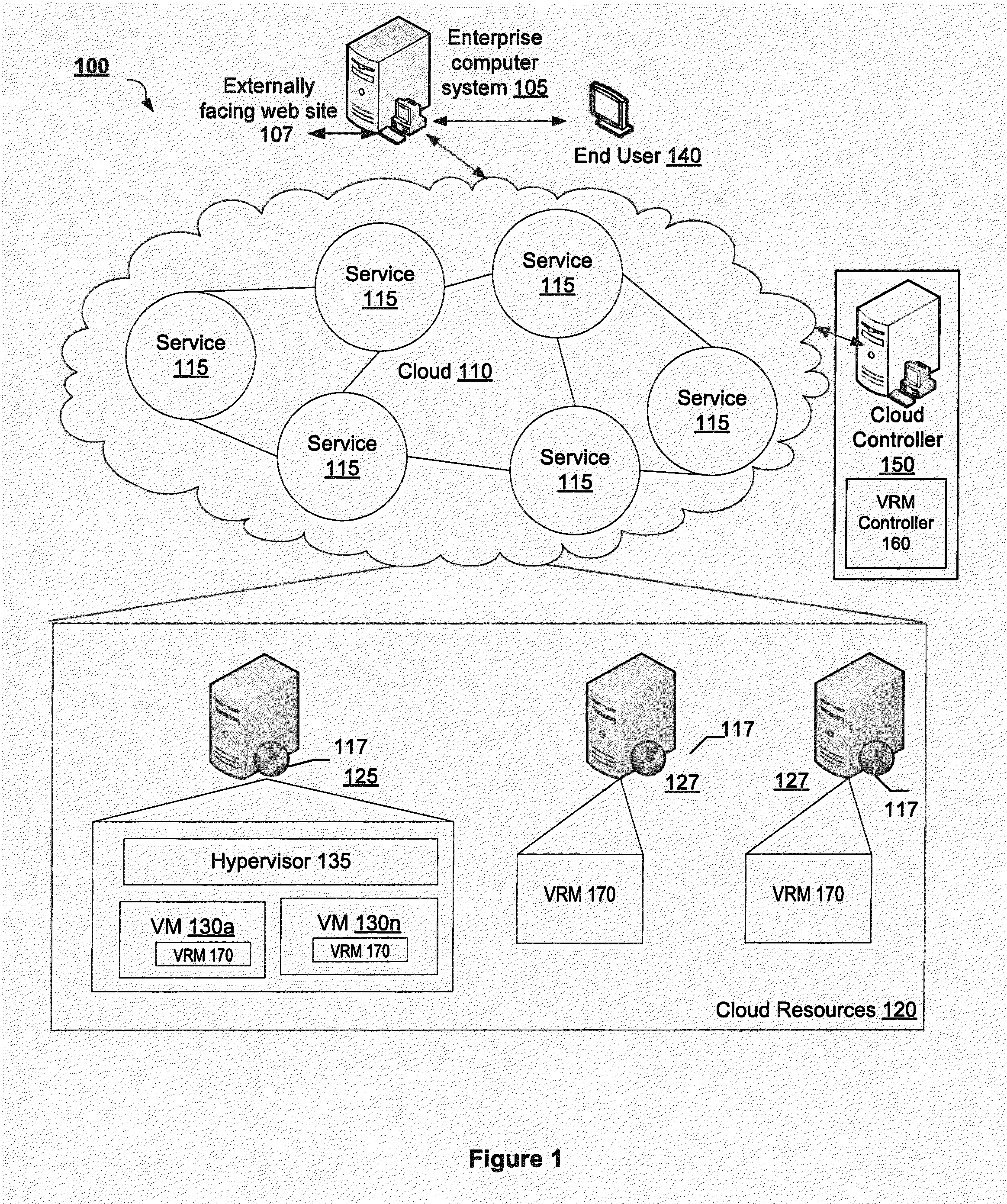
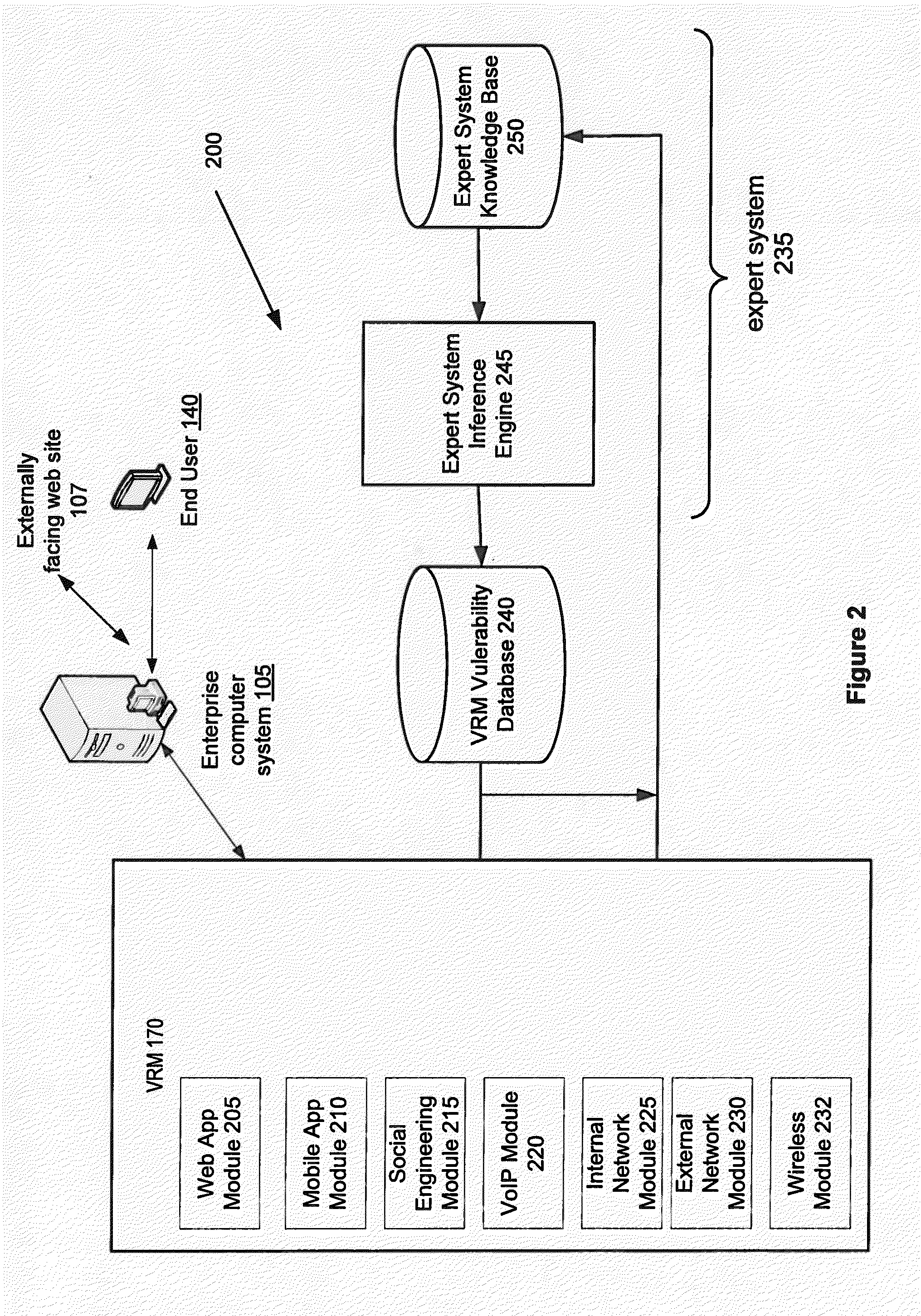
Expert system for detecting software security threats
An instance of a vulnerability risk management (VRM) module and a vulnerability management expert decision system (VMEDS) module are instantiated in a cloud. The VMEDS module imports scan results from a VRM vulnerability database and saves them as vulnerabilities to be reviewed in a VMEDS database. The VMEDS module converts vulnerabilities into facts. The VMEDS module builds a rule set in the knowledge base to verify whether certain vulnerabilities are false positives. Rules related to a vulnerability are received in plain English from a web-based front-end application. The VMEDS module tests each rule against all of the facts using the Rete algorithm. The VMEDS module executes the action associated with the rule derived from the Rete algorithm. The VMEDS module stores the results associated with the executing of the action in the VMEDS database and forwards the results to the VRM module.
Owner:NOPSEC
Method and system for providing wireless vulnerability management for local area computer networks
InactiveUS20090119741A1Reduce overheadEasy to customizeFinanceComputer security arrangementsVulnerability managementService provision
A Software-as-a-Service (SaaS) based method for providing wireless vulnerability management for local area computer networks. The method includes providing a security server being hosted by a service provider entity to provide analysis of data associated with wireless vulnerability management for a plurality of local area computer networks of a plurality of customer entities, respectively. The method includes creating a workspace for wireless vulnerability management for a customer entity on the security server and receiving configuration information associated with the workspace. The method also includes supplying one or more sniffers to the customer entity. The method includes receiving at the security server information associated with wireless activity monitored by the one or more sniffers at premises of the customer entity and processing the received information within the workspace for the customer entity using the security server. The method includes metering usage of the workspace for wireless vulnerability management for the customer entity.
Owner:AIRTIGHT NETWORKS
Expert system for detecting software security threats
ActiveUS20140047545A1Memory loss protectionError detection/correctionVulnerability managementDecision system
An instance of a vulnerability risk management (VRM) module and a vulnerability management expert decision system (VMEDS) module are instantiated in a cloud. The VMEDS module imports scan results from a VRM vulnerability database and saves them as vulnerabilities to be reviewed in a VMEDS database. The VMEDS module converts vulnerabilities into facts. The VMEDS module builds a rule set in the knowledge base to verify whether certain vulnerabilities are false positives. Rules related to a vulnerability are received in plain English from a web-based front-end application. The VMEDS module tests each rule against all of the facts using the Rete algorithm. The VMEDS module executes the action associated with the rule derived from the Rete algorithm. The VMEDS module stores the results associated with the executing of the action in the VMEDS database and forwards the results to the VRM module.
Owner:NOPSEC
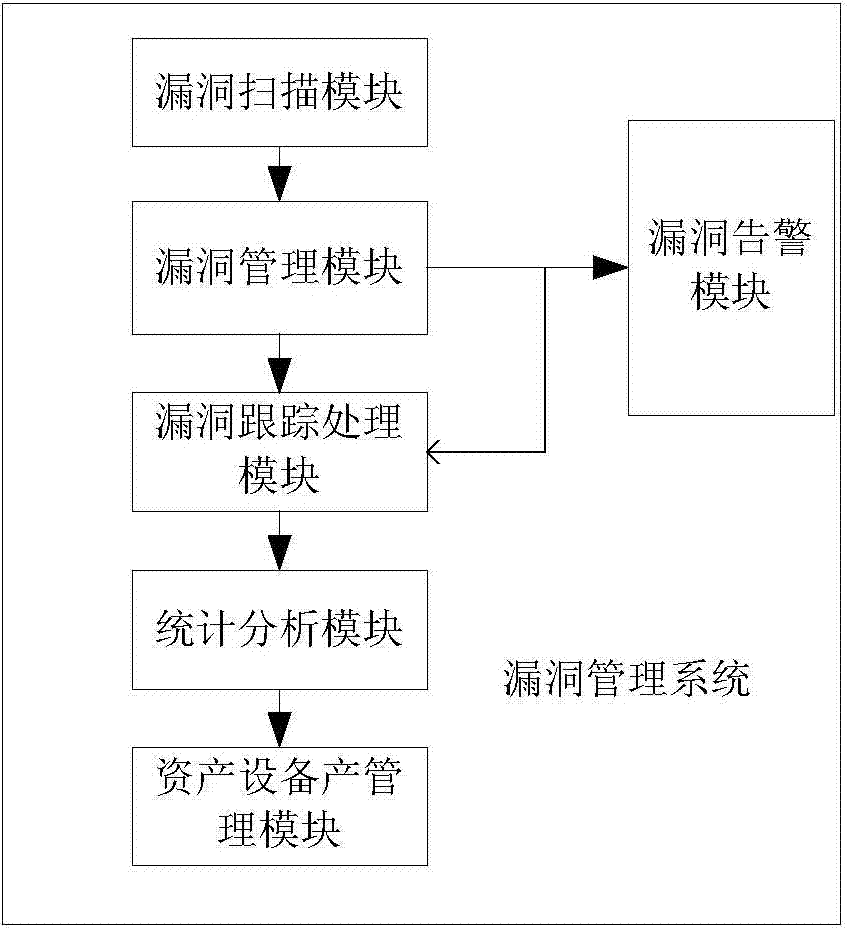
Vulnerability management system and vulnerability management method
ActiveCN106790190ADiscover comprehensiveSolve the problem that Internet assets cannot be accurately discoveredTransmissionVulnerability managementManagement efficiency
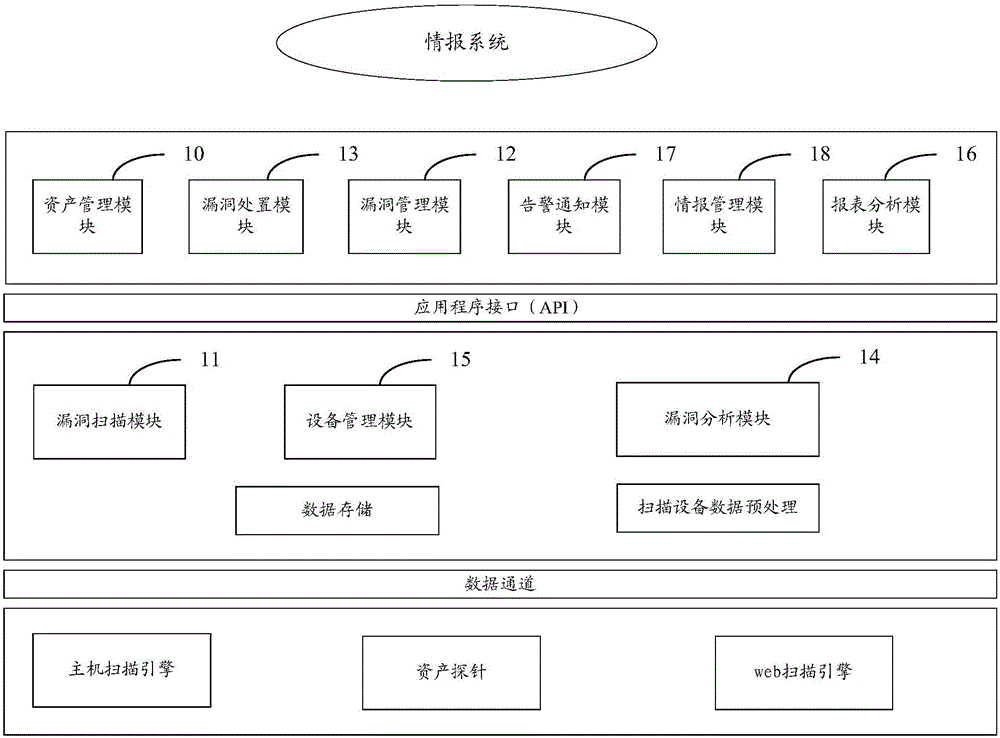
The invention relates to the field of information security, and in particular to a vulnerability management system and a vulnerability management method. The vulnerability management system comprises an asset management module, a vulnerability scanning module, a vulnerability management module, a vulnerability processing module and a vulnerability analyzing module; all assets including public network assets and vulnerability can be comprehensively found by the asset management module and the vulnerability scanning module; analysis, trace and management of the vulnerability are realized by the vulnerability analyzing module, the vulnerability processing module and the vulnerability management module, so that the vulnerability management system has the effects that detailed record and trace can be carried out on the assets and the vulnerability, security conditions of the assets and the vulnerability in the system also can be evaluated and the management efficiency of the assets and the vulnerability in the system is improved.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Graphical user interface based sensitive information and internal information vulnerability management system
ActiveUS8140664B2Rapid assessmentEasily identify and assessMemory loss protectionError detection/correctionTime informationOutput device
Owner:TREND MICRO INC
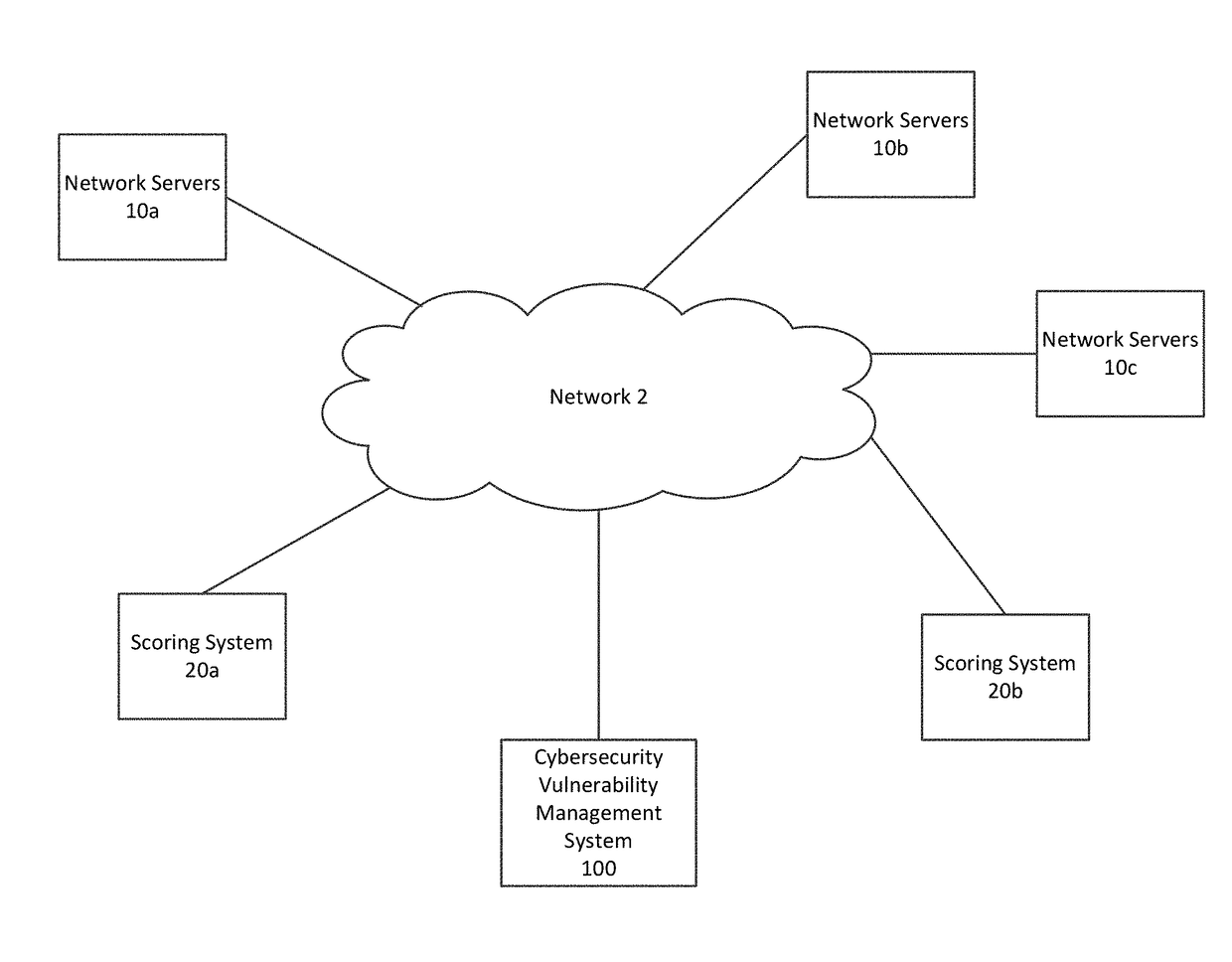
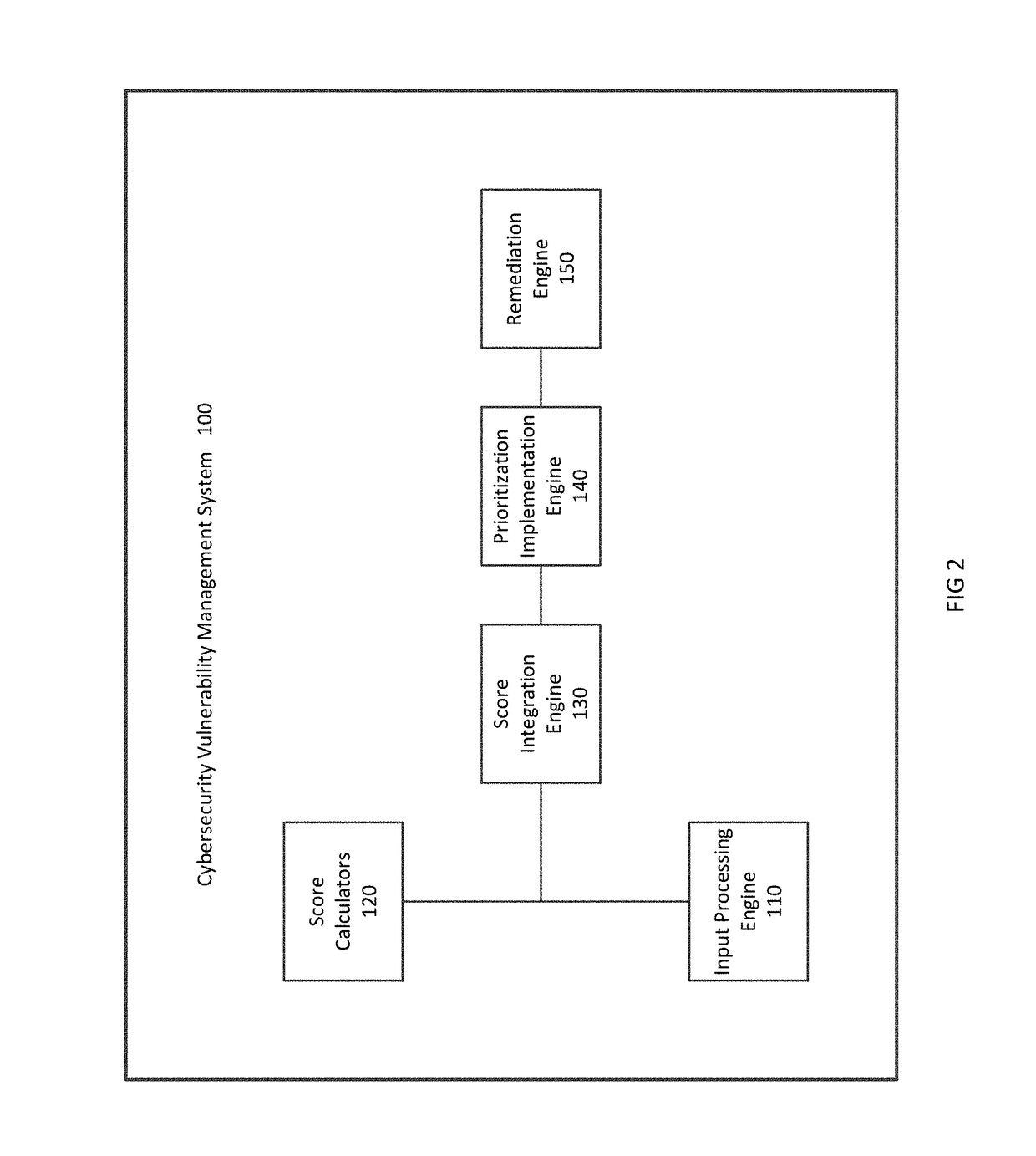
Cybersecurity Vulnerability Management System and Method
A method and system are provided for managing cybersecurity vulnerabilities of resources within at least one network. The method includes collecting data including application risk rank and network location. The method further includes determining a vulnerability score for vulnerabilities of the resources and determining a severity score based on the application risk rank and network location. The method additionally includes integrating the vulnerability score and the severity score to create a two-dimensional risk ranking and prioritizing remediation of the vulnerabilities based on the two-dimensional risk ranking.
Owner:JPMORGAN CHASE BANK NA
Distributed asset identification and change awareness method and system for implementing vulnerability management
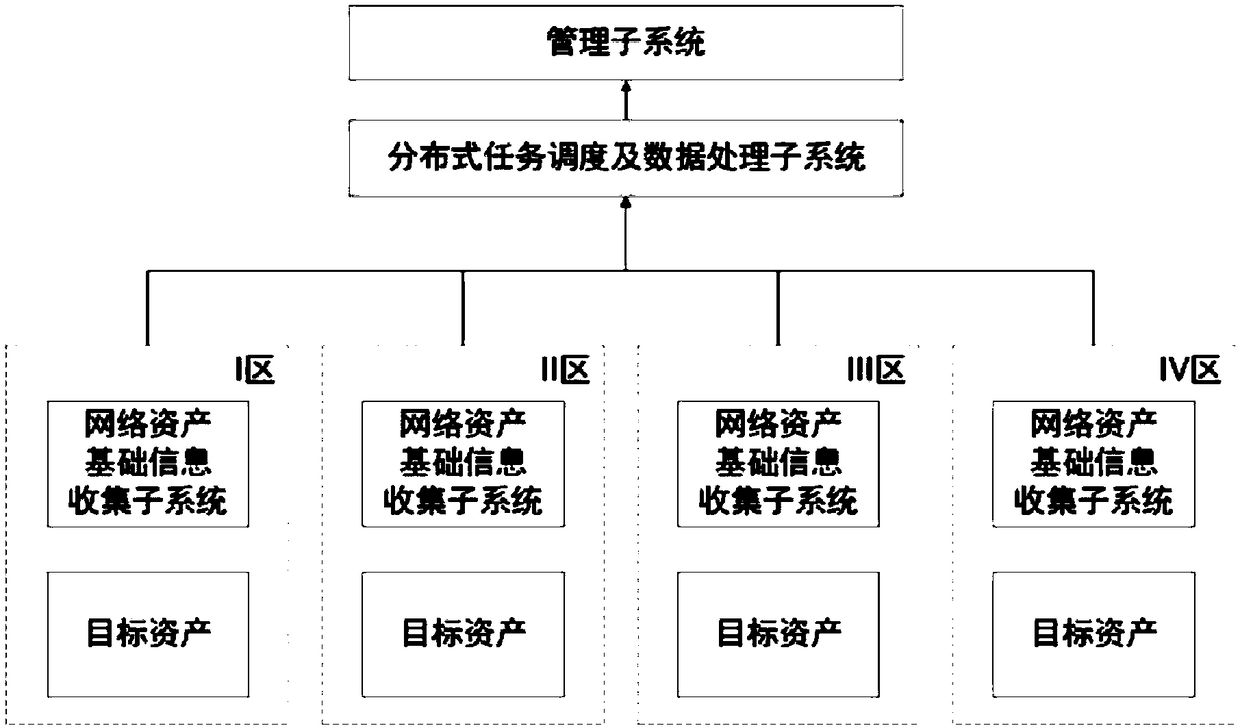
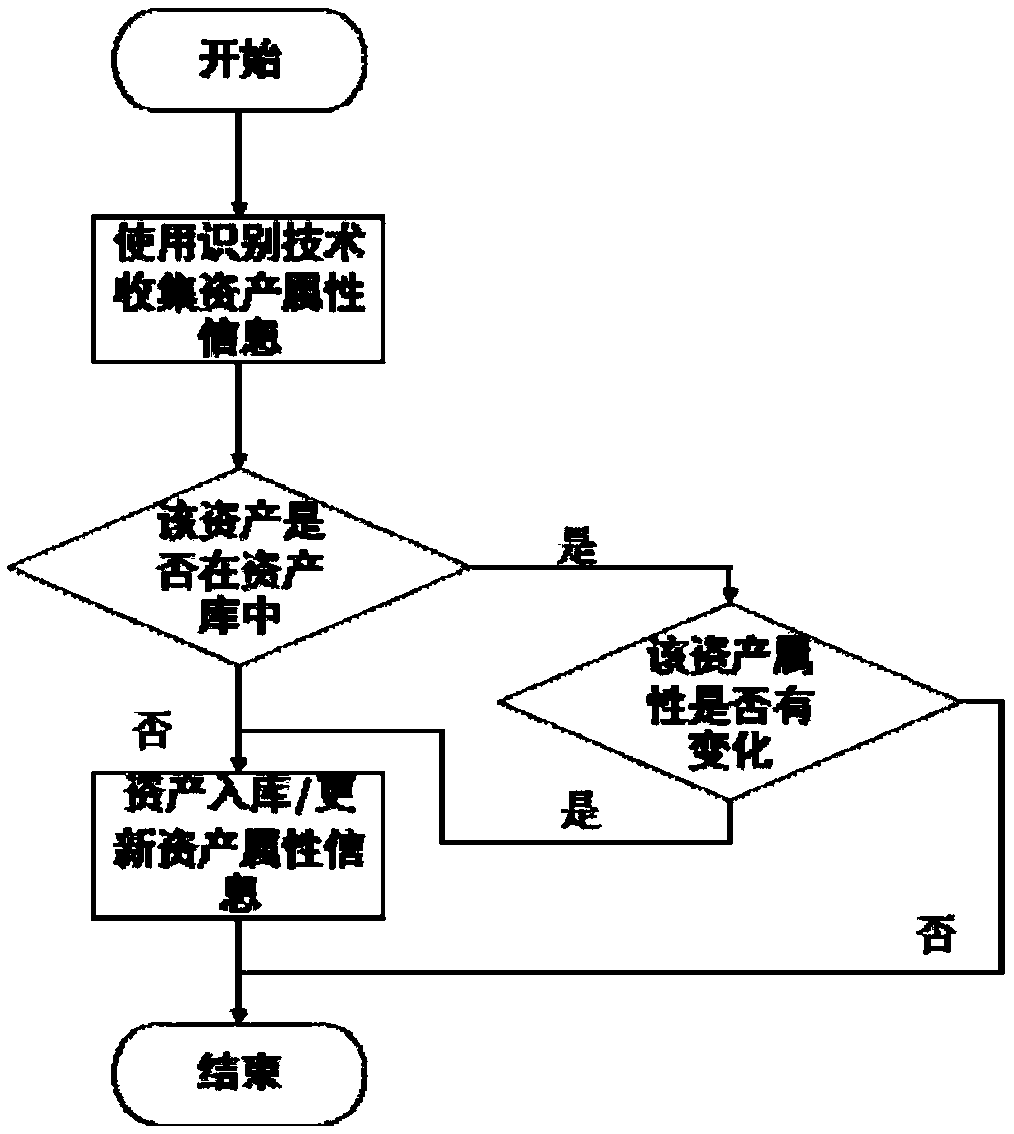
InactiveCN108769064AIncreased cyber riskImproving the Accuracy of Vulnerability AssessmentsTransmissionVulnerability managementInformation Harvesting
A distributed asset identification and change awareness system for implementing vulnerability management includes a plurality of network asset information collection subsystems distributed in different regions and a distributed task scheduling and data processing subsystem, wherein tasks are decomposed based on a distributed architecture and allocated to appropriate resources through the task scheduling, task distribution and processing are realized for a plurality of nodes, and asset information detection and sensing are distributedly performed; the network asset information collection subsystems collect asset information of the networked active host; the data processing part of the distributed task scheduling and data processing subsystem obtains the asset information of the networked active host from the network asset information collection subsystems, and compares the asset information with the confirmed asset attribute information stored in the asset library to realize the automatic update of the asset information for the networked surviving host in the asset library. Vulnerability information is collected though vulnerability scanning, which may quickly treat and fix securityvulnerabilities in networked information systems.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
Hosted vulnerability management for wireless devices
InactiveUS20130007837A1Reduce overheadEasy to customizeNetwork topologiesTransmissionVulnerability managementClient-side
A method, a multi-tenant security server apparatus and associated system for securing wireless communication of devices. The method includes transferring security policy configuration information from the security server to wireless devices. The method also includes ascertaining compliance of wireless activity of the wireless devices with the security policy configuration using client software modules installed on the wireless devices.
Owner:AIRTIGHT NETWORKS
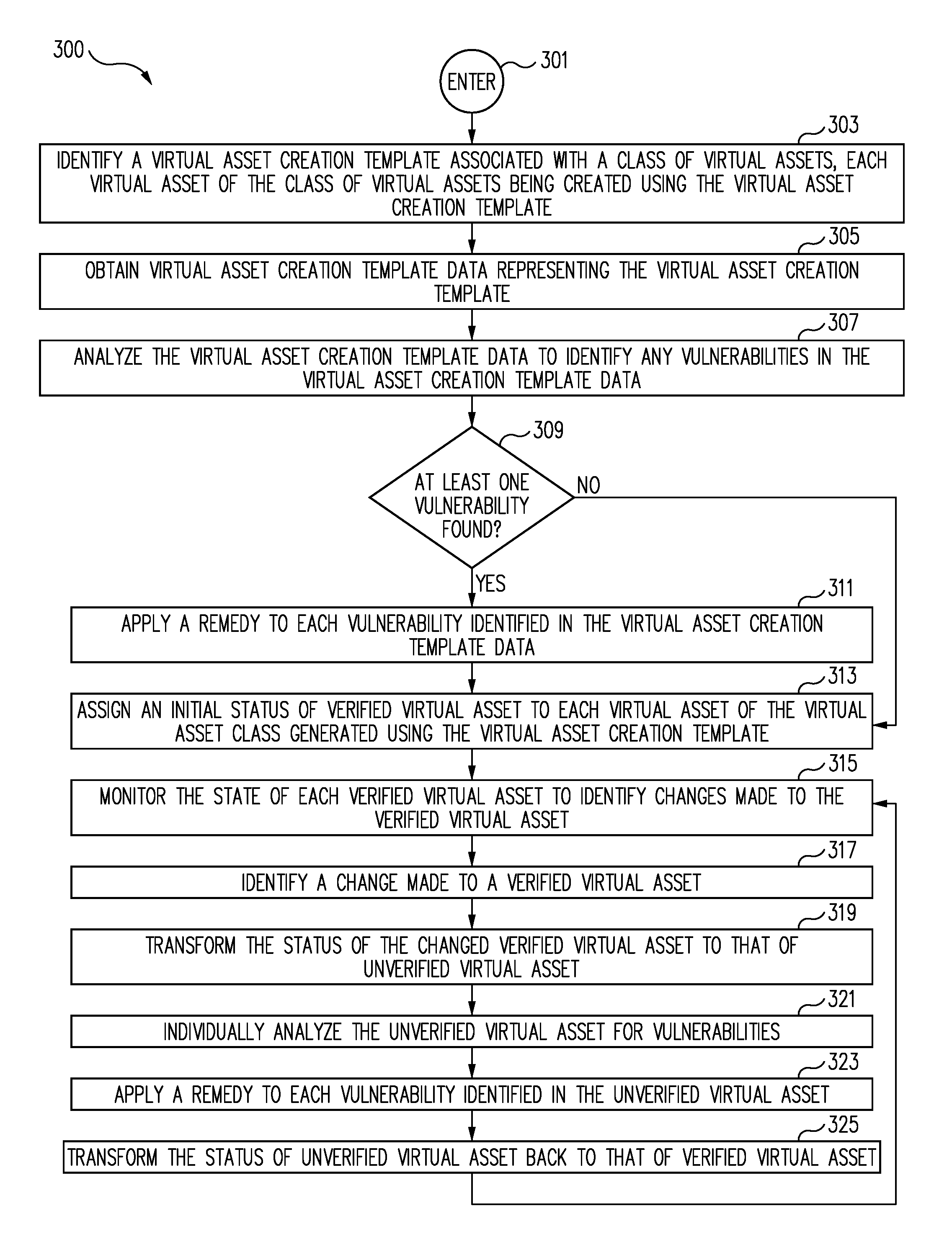
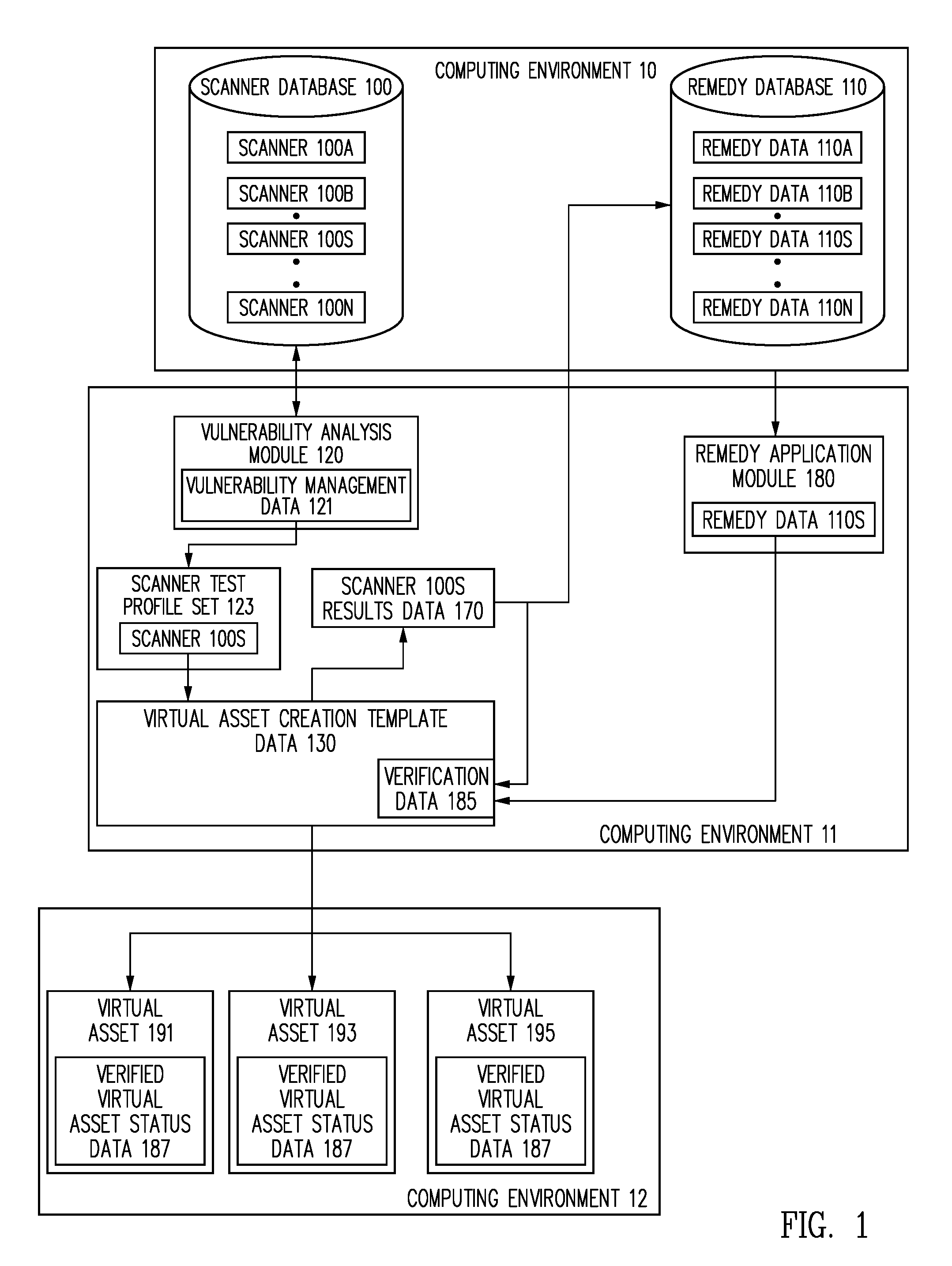
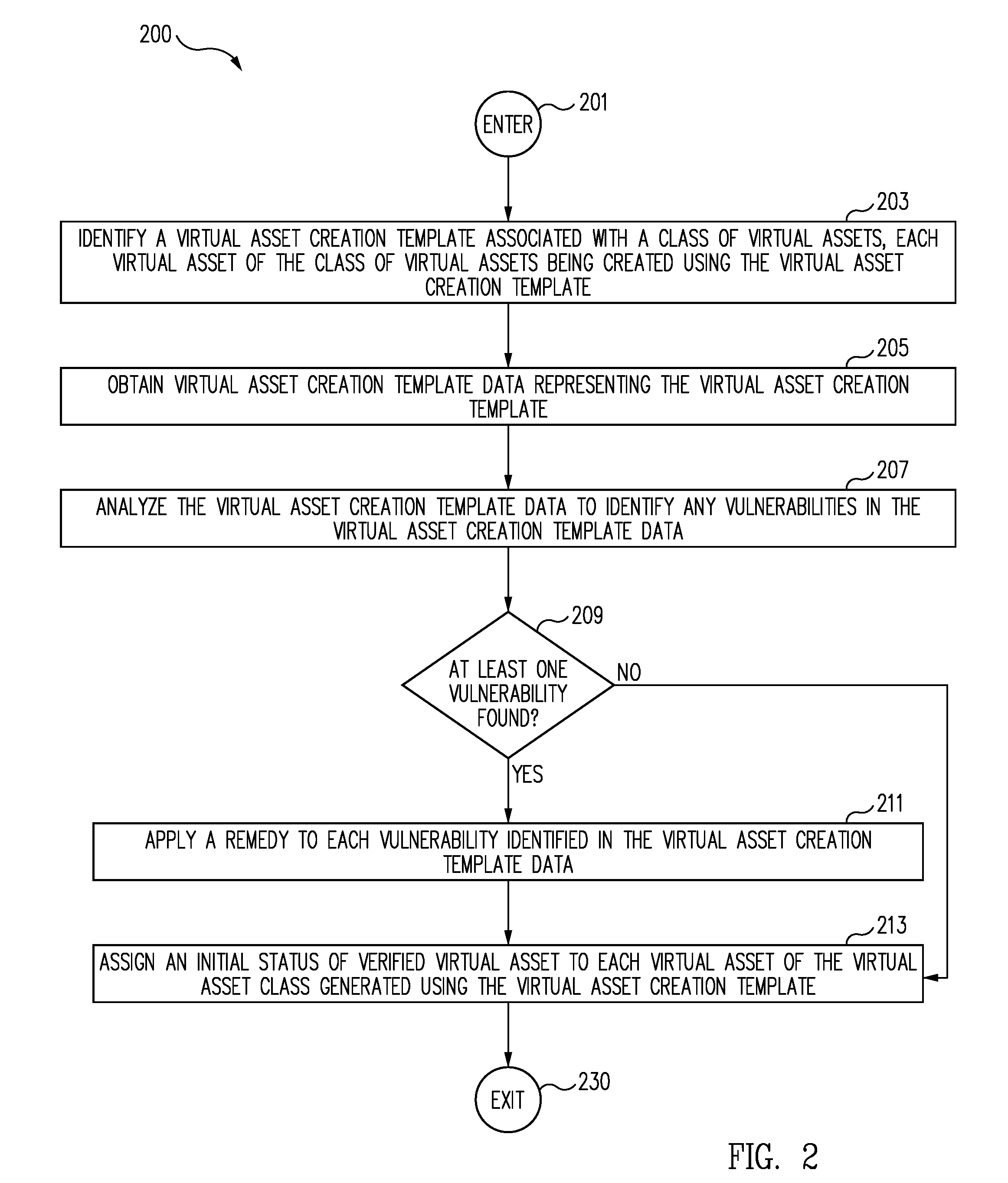
Method and system for providing an efficient vulnerability management and verification service
ActiveUS9298927B2Unauthorized memory use protectionPlatform integrity maintainanceVulnerability managementSoftware engineering
A virtual asset creation template associated with a class of virtual assets is identified and analyzed to identify any vulnerabilities in the virtual asset creation template. If one or more vulnerabilities are identified in the virtual asset creation template, an appropriate remedy for each identified vulnerability identified in the virtual asset creation template is applied. If no vulnerability is identified in the virtual asset creation template, or once each vulnerability identified in the virtual asset creation template is remedied, each virtual asset of the virtual asset class generated using the virtual asset creation template is assigned an initial status of verified virtual asset.
Owner:INTUIT INC
Enterprise vulnerability management
ActiveUS8789192B2Easy to addIncrease capacityMemory loss protectionError detection/correctionVulnerability managementRemedial action
Owner:LEIDOS INNOVATIONS TECH INC
Method and system for providing wireless vulnerability management for local area computer networks
ActiveUS8032939B2Customization processReduce overheadMemory loss protectionUnauthorized memory use protectionVulnerability managementComputer network
A Software-as-a-Service (SaaS) based method for providing wireless vulnerability management for local area computer networks. The method includes providing a security server being hosted by a service provider entity to provide analysis of data associated with wireless vulnerability management for a plurality of local area computer networks of a plurality of customer entities, respectively. The method includes creating a workspace for wireless vulnerability management for a customer entity on the security server and receiving configuration information associated with the workspace. The method also includes supplying one or more sniffers to the customer entity. The method includes receiving at the security server information associated with wireless activity monitored by the one or more sniffers at premises of the customer entity and processing the received information within the workspace for the customer entity using the security server. The method includes metering usage of the workspace for wireless vulnerability management for the customer entity.
Owner:ARISTA NETWORKS
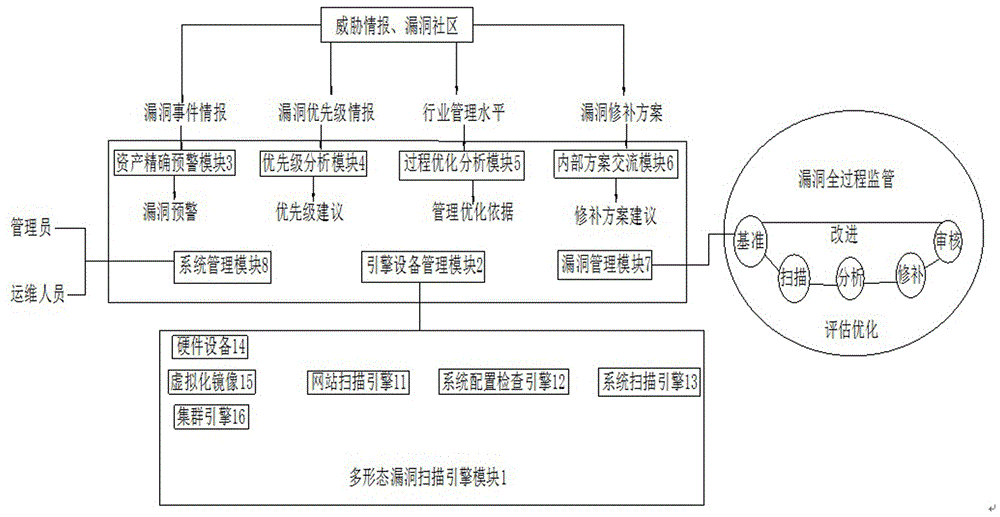
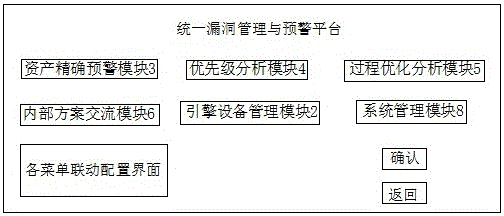
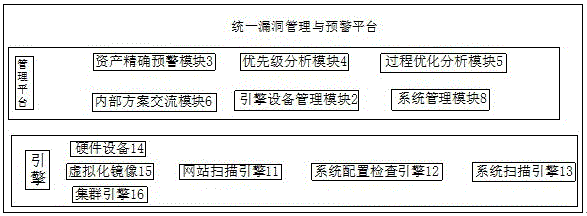
Vulnerability scanning and threat intelligence based unified vulnerability management and warning platform
InactiveCN106453432ASituation to reduce scanningReduce manual workloadTransmissionVulnerability managementPower utility
The invention discloses a vulnerability scanning and threat intelligence based unified vulnerability management and warning platform. The platform comprises a multi-form vulnerability scanning engine module, an engine equipment management module, an accurate asset warning module, a priority analysis module, a process optimization analysis module, an internal plan communication module, a vulnerability management module and a system management module. Through a unified management mode, multiple lower multi-mode vulnerability scanning engines are subjected to unified dispatching, task issue and result return, asset statistic information and external intelligence information can be combined to realize threat warning of assets in the corporate scope, the platform can be used in the corporate information internal-external network single-network environment as well as in information internal-external network province, city and county cascade environment, the advantages of the platform in the longitudinal cascade or transverse distribution network environment can be reflected more fully, and integrated defense in electric power company information security is realized.
Owner:INFORMATION & COMMNUNICATION BRANCH STATE GRID JIANGXI ELECTRIC POWER CO +1
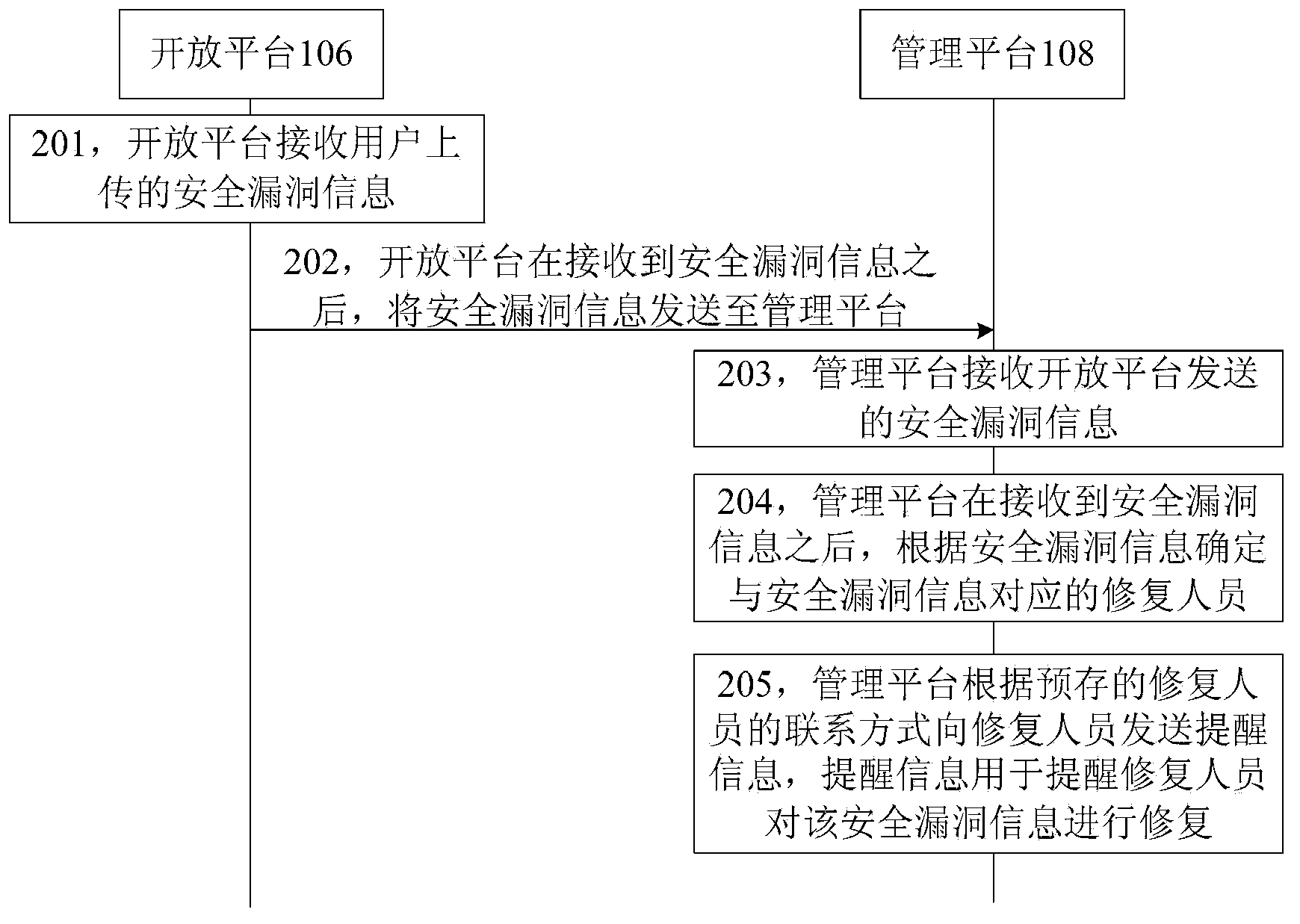
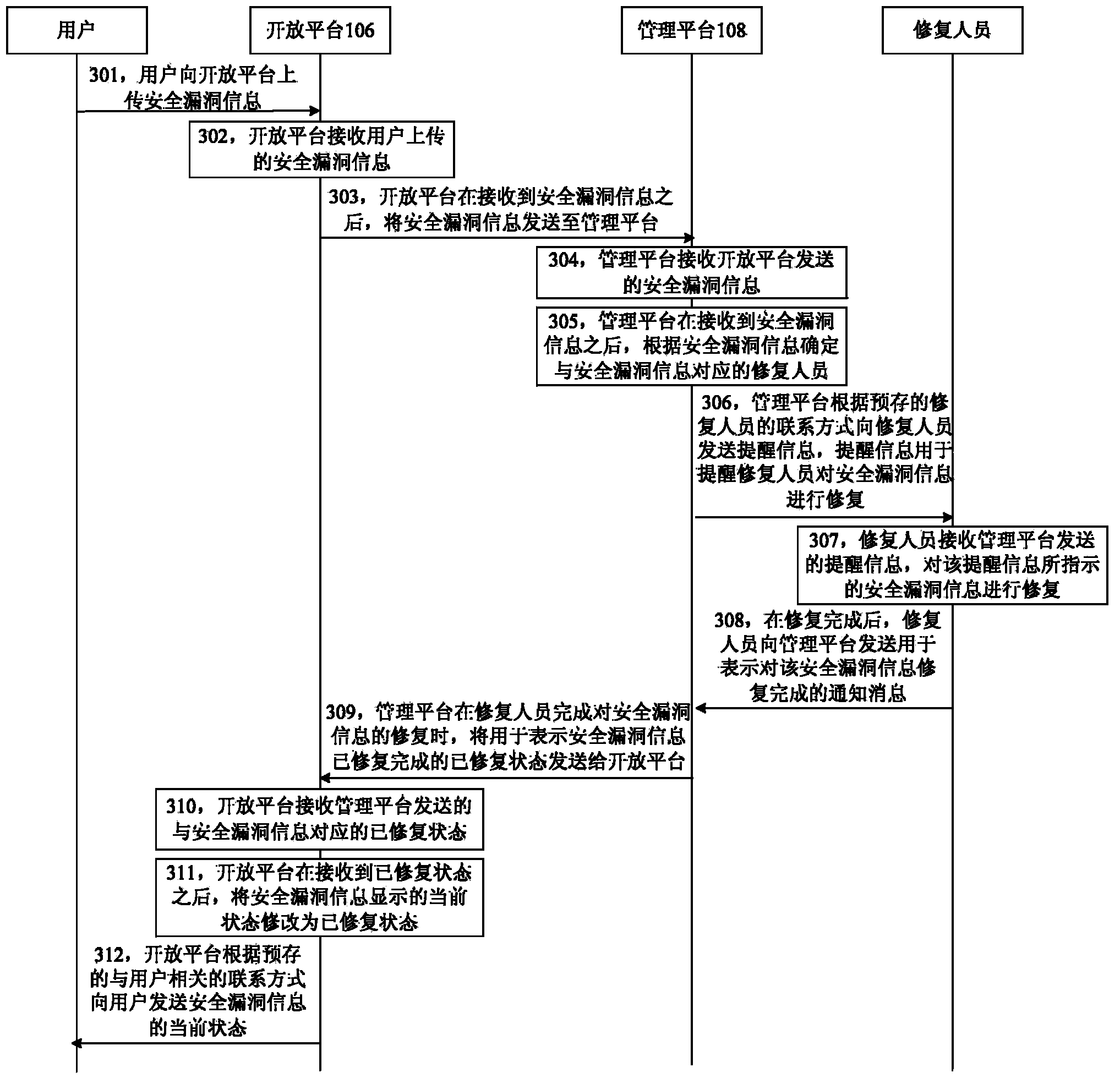
Security vulnerability management method and system and device
ActiveCN104346571AImprove work efficiencyPlatform integrity maintainanceProgram/content distribution protectionVulnerability managementDEVS
The invention discloses a security vulnerability management method and system and a device, and belongs to the technical field of computers. The method includes the steps of receiving security vulnerability information uploaded by a user, sending the security vulnerability information to a management platform so that the management platform can find a repairer corresponding to the security vulnerability information according to the security vulnerability information, and sending prompting information to the repairer, wherein the prompting information is used for prompting the repairer to repair the security vulnerability information. By sending the safety vulnerability information uploaded by the user to the management platform so as to find the repairer corresponding to the security vulnerability information through the management platform and prompting the repairer to repair the security vulnerability information, the problems that work is complex and efficiency is low when multiple pieces of information containing security vulnerability are manually sent to corresponding developers respectively by interface personnel in the prior art are solved, and the effects that the reported security vulnerability information can be managed in a unified mode and the work efficiency can be improved are achieved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Vulnerability management system and method
ActiveCN104778414AAssess security postureIdentify Weak LinksPlatform integrity maintainanceVulnerability managementRelevant information
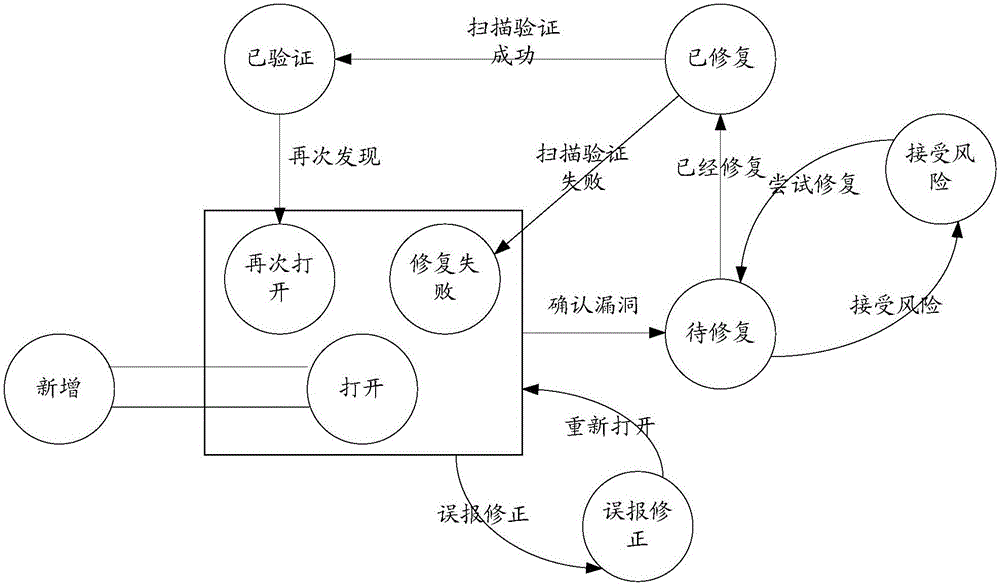
The invention discloses a vulnerability management system and method. The vulnerability management system comprises a vulnerability scanning module, a vulnerability management module, a vulnerability warning module, a vulnerability track processing module, a statistic analysis module and an asset equipment management module. Management control is conducted through vulnerability scanning, vulnerability warning, vulnerability management, vulnerability track processing, statistical analysis and asset equipment management. By the adoption of the vulnerability management system and method, all relevant information of vulnerability can be recorded in detail, tracking and tracing of the safety risk of a system device are facilitated, the safety condition of the whole network system can be effectively evaluated, the weak link in a network is identified, and then network security reinforcing work is guided.
Owner:GUANGZHOU WONFONE TECH
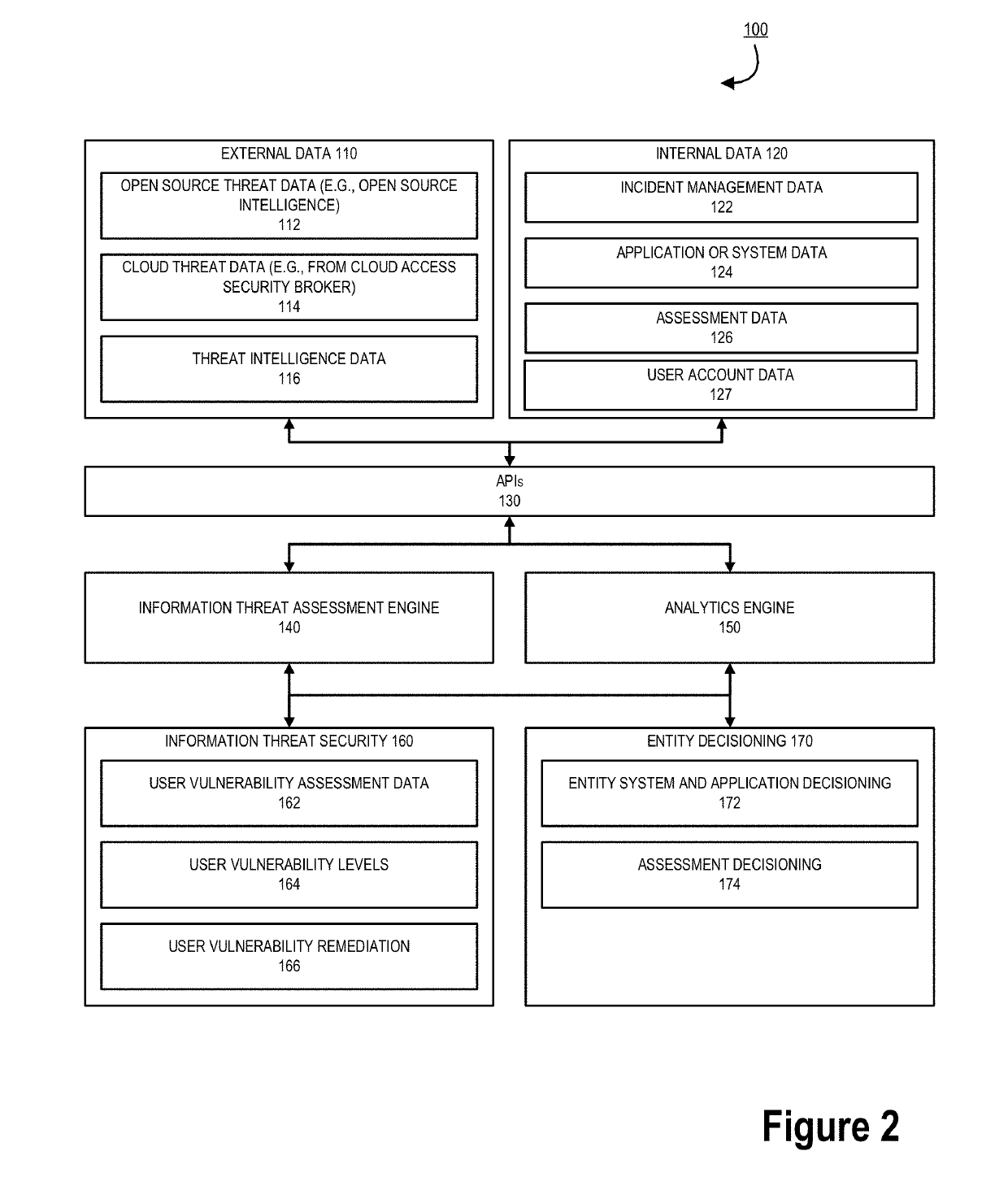
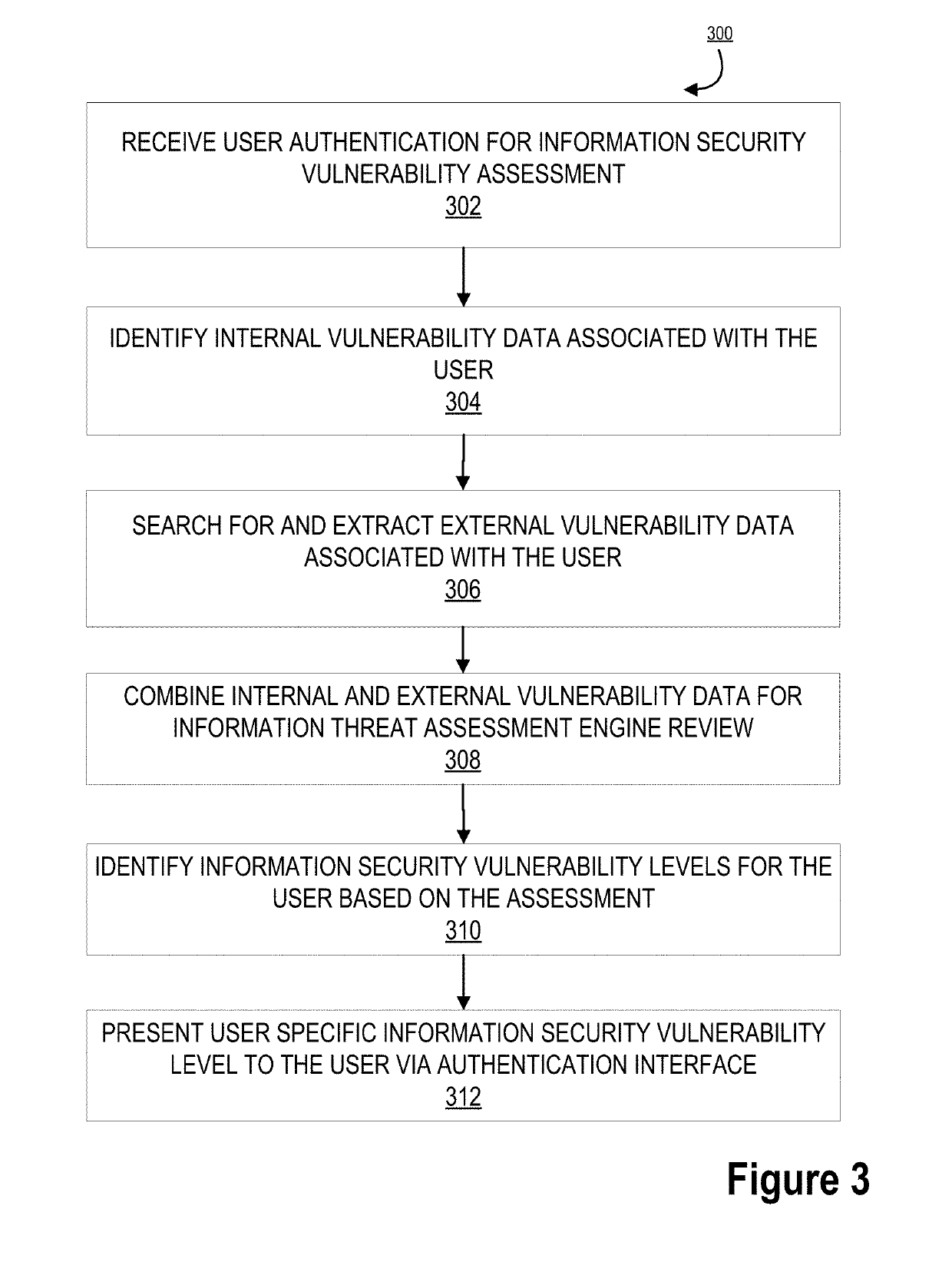
Information security vulnerability assessment system
ActiveUS20190166153A1Enhancing misappropriation assessmentAvoid future misappropriationDigital data protectionMachine learningVulnerability managementInternet privacy
Embodiments of the invention are directed to systems, methods, and computer program products for real-time generation and deployment of specific user information security vulnerability levels based on vulnerability assessments for the user. The invention utilizes a two-component system to detect security vulnerabilities for a user, generate a coherent vulnerability level for the user in real-time, and provides user specific mitigation actions depending on each user vulnerability assessment. The first component of the system is an information threat assessment engine, which identifies and / or receives external and internal data regarding users to determine information security threats. The second component is an analytics engine, which is configured to generate vulnerability levels and specific mitigation actions for the user based on threat patterning.
Owner:BANK OF AMERICA CORP
Method and devices of submitting vulnerability information
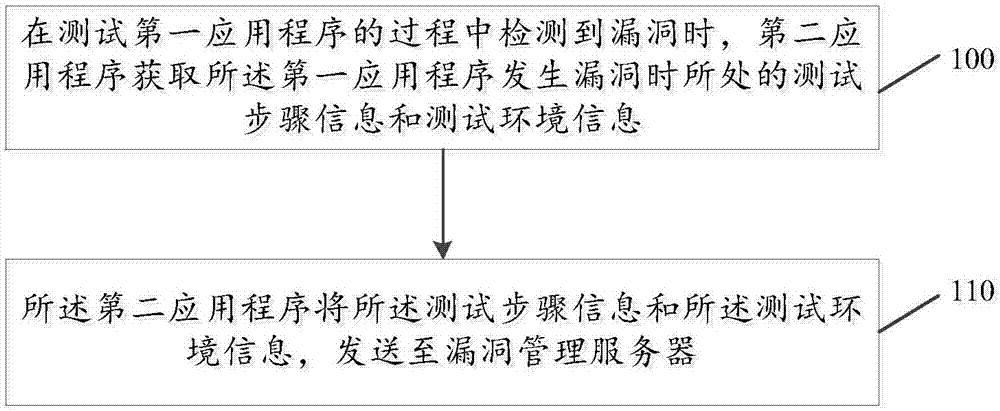
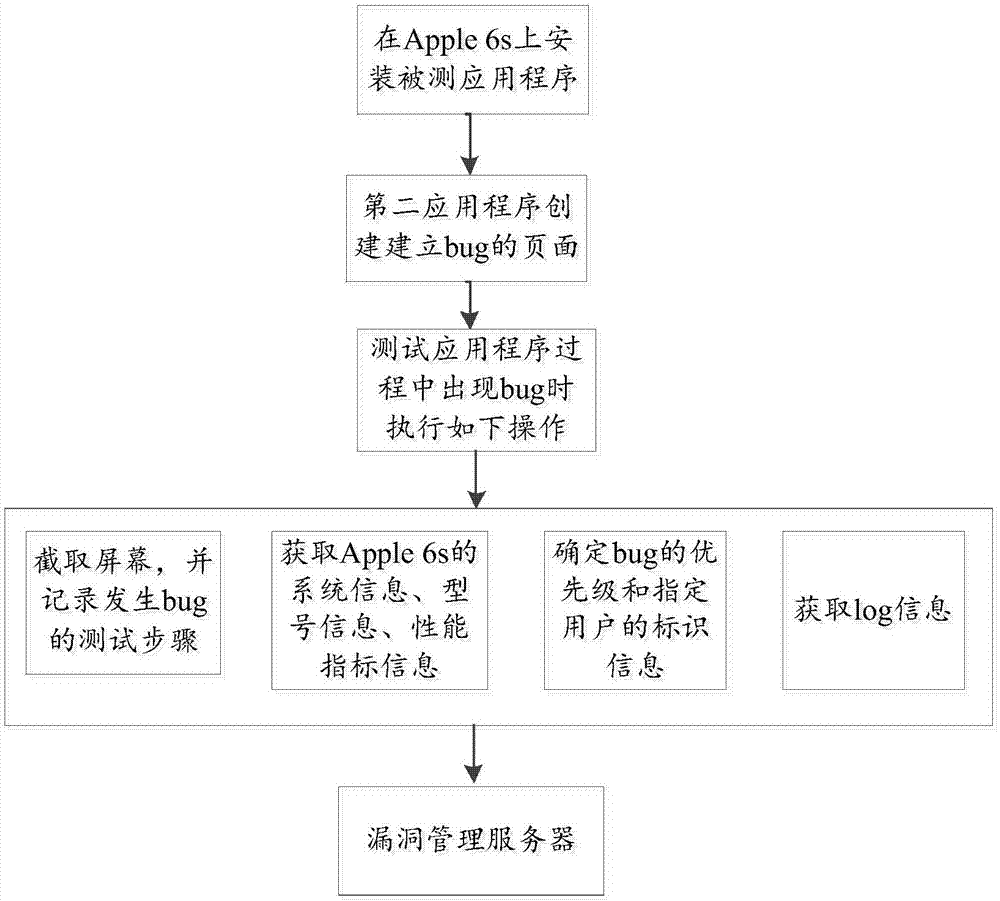
InactiveCN107368413AAvoid accuracyShorten the timeSoftware testing/debuggingVulnerability managementSoftware engineering
In the embodiment of the invention, a method of submitting vulnerability information is provided. The method includes: acquiring information of a test step and a test environment, where vulnerability of a first application program is located when the vulnerability occurs, by a second application program when the vulnerability is detected in a process of testing the first application program; and sending the test step information and the test environment information to a vulnerability management server by the second application program. In the solution, when the vulnerability is detected in the process of testing the first application program, the second application program acquires the information of the test step and the test environment where the vulnerability is located when the vulnerability occurs, and sends the same to the vulnerability management server, completely manual participation in the process by a tester is not needed, thus time consumed for submitting the vulnerability information can be reduced, and the efficiency can be improved; and at the same time, because operation is not completely manually carried out by the tester, the defect that submitted information is lower in accuracy and imperfect due to manual mistakes can also be avoided.
Owner:网易有道信息技术(北京)有限公司
Safe and efficient vulnerability management system
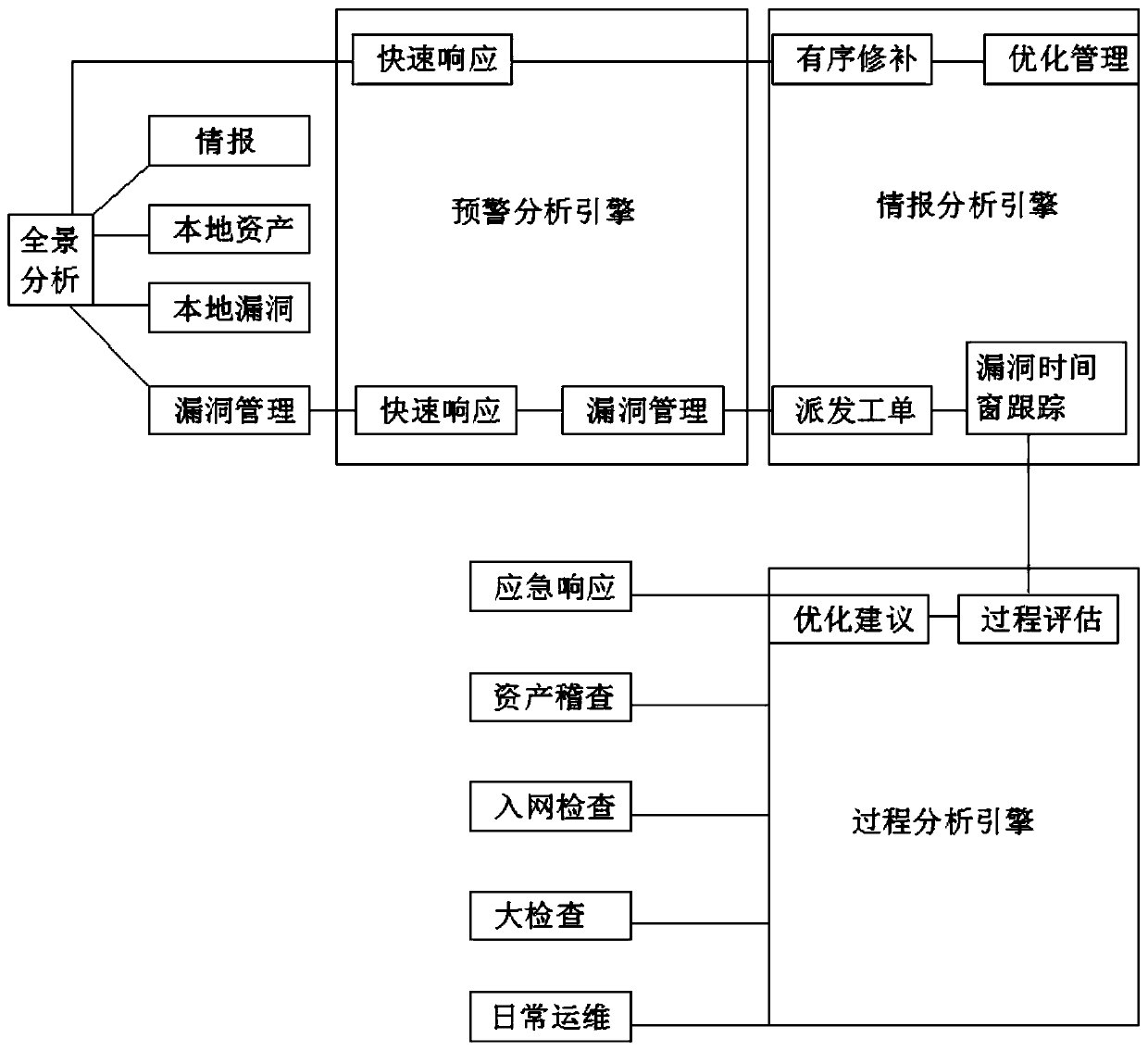
PendingCN111199042AQuick responseOrderly repairPlatform integrity maintainanceCollection systemThe Internet
The invention discloses a security and high-efficiency vulnerability management system, and relates to the technical field of vulnerability management,, in particular to a security and high-efficiencyvulnerability management system, a threat intelligence system and an internet intelligence intelligent collection system based on big data architecture, which are mainly used for uniformly integrating intelligence searched by company self-research, friend-merchant sharing, industry sharing and the internet, and sharing related intelligence to a third-party system or product according to industrycharacteristics. Te local threat and vulnerability management platform is mainly used for realizing Internet asset auditing, scanning engine centralized management and vulnerability management supportfunctions. According to the safe and efficient vulnerability management system, except for collecting and analyzing the risk data of the scanning missing product, other risk data can be imported forunified analysis, and the management capacity of quick response, ordered repair and continuous optimization is provided for the customer vulnerability management process in combination with local riskcontinuous monitoring and vulnerability management full-process management and control capacity.
Owner:CSG EHV POWER TRANSMISSION +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com