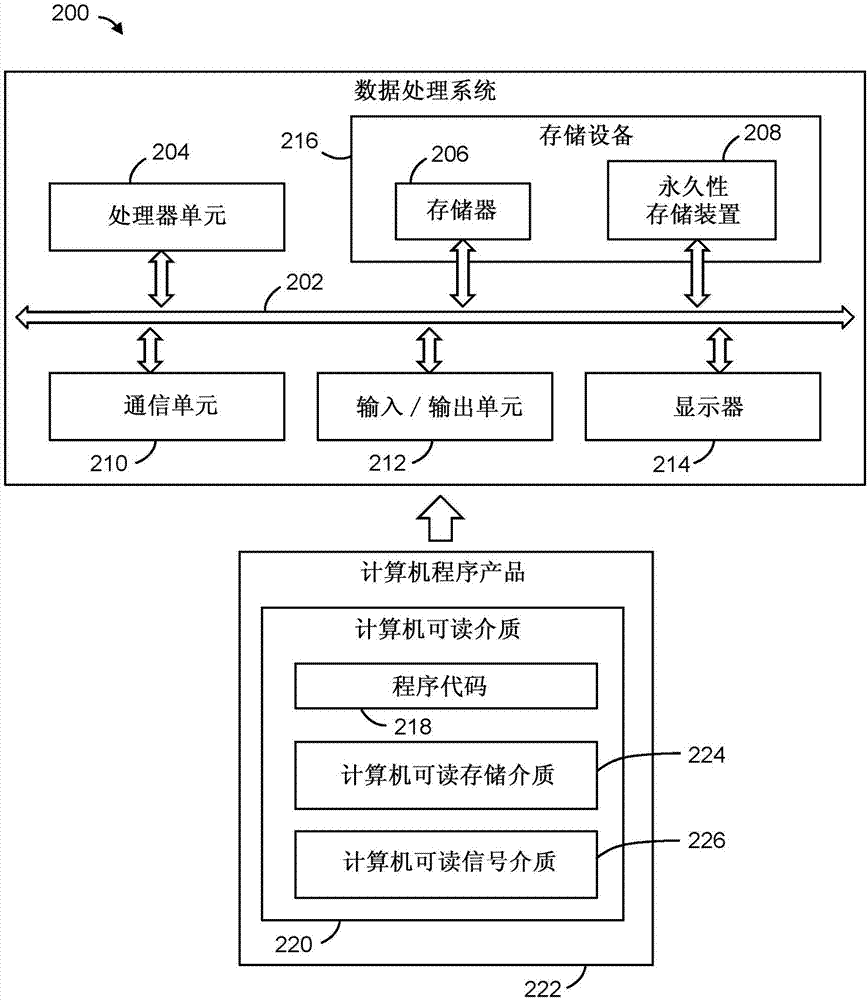
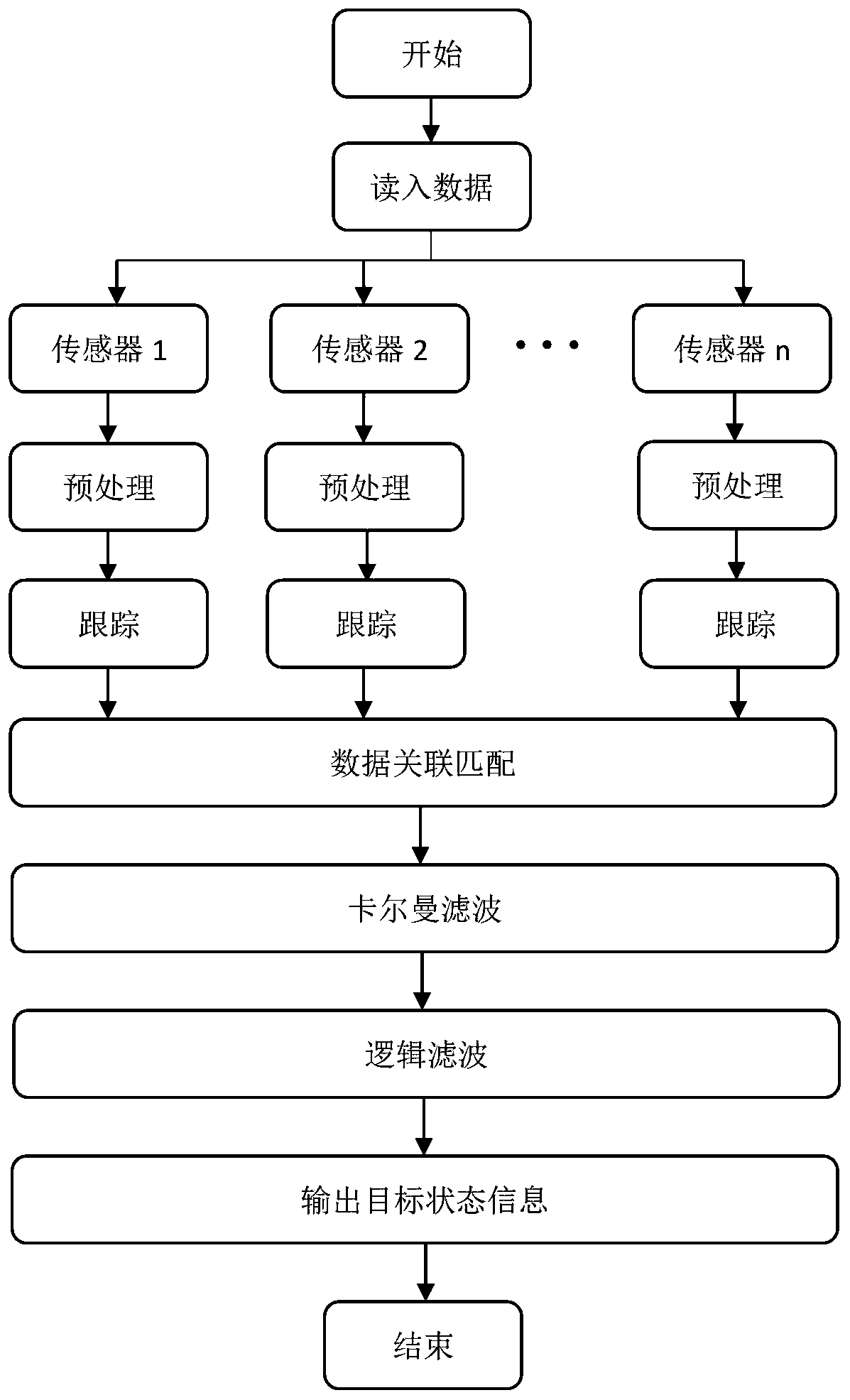
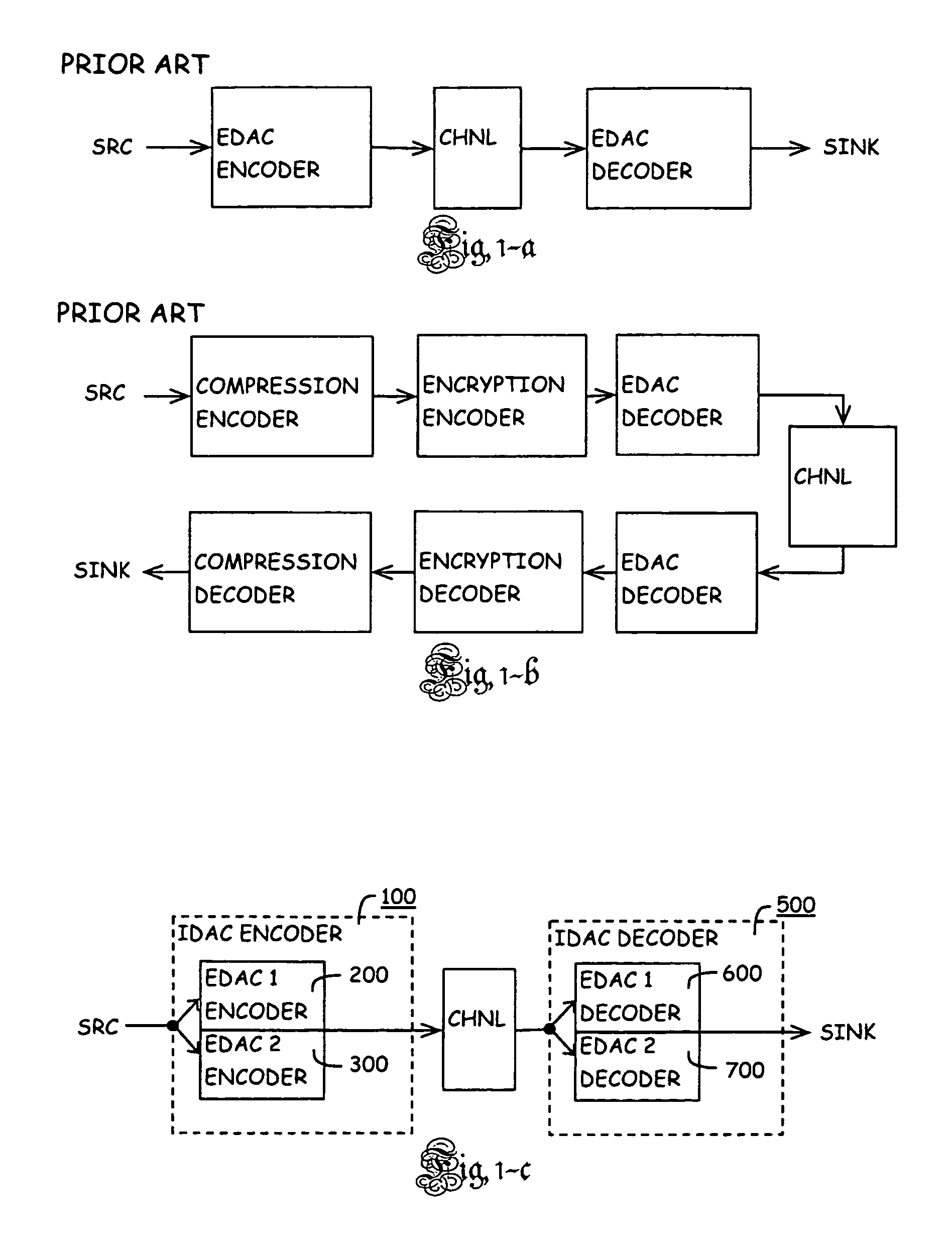
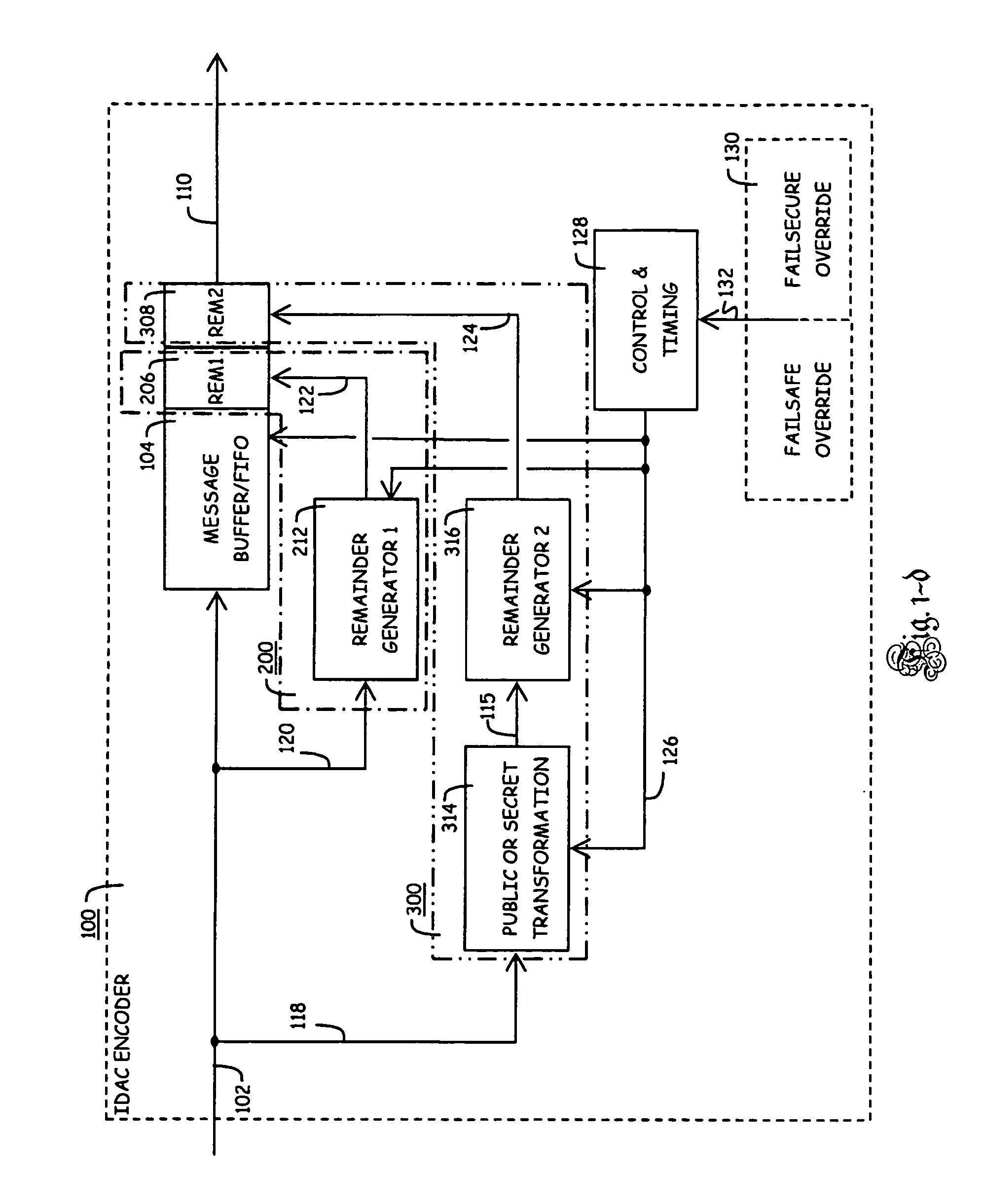
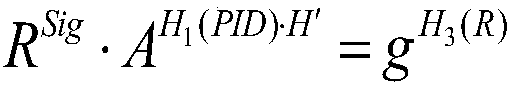Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
82 results about "Information assurance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information assurance (IA) is the practice of assuring information and managing risks related to the use, processing, storage, and transmission of information or data and the systems and processes used for those purposes. Information assurance includes protection of the integrity, availability, authenticity, non-repudiation and confidentiality of user data. It uses physical, technical, and administrative controls to accomplish these tasks. While focused predominantly on information in digital form, the full range of IA encompasses not only digital, but also analog or physical form. These protections apply to data in transit, both physical and electronic forms, as well as data at rest in various types of physical and electronic storage facilities. IA is best thought of as a superset of information security (i.e. umbrella term), and as the business outcome of information risk management.
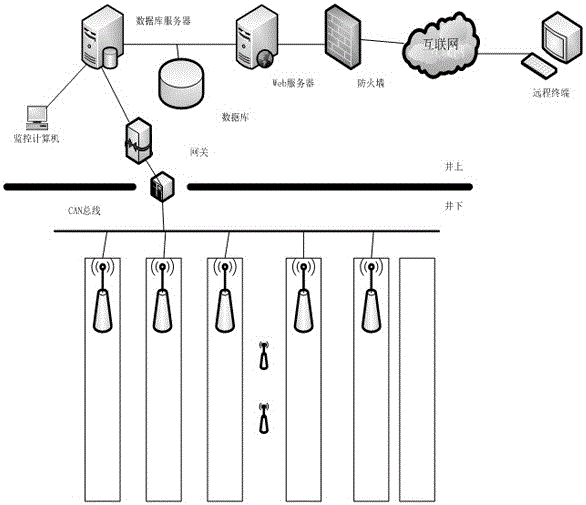
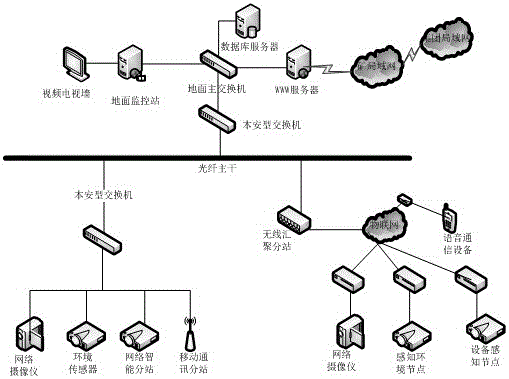
Coal mine safety integrated monitoring system based on Internet of Things
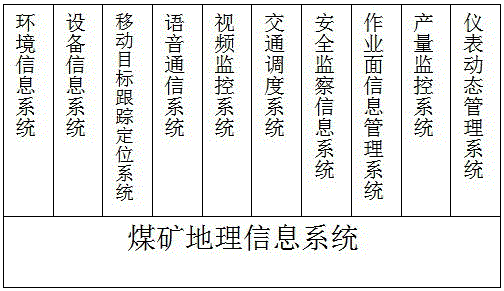
A coal mine safety integrated monitoring system based on the Internet of Things comprises an environment information system, an equipment information system, a mobile target tracking and positioning system, a voice communication system, a video monitoring system, a traffic dispatching system, a safety supervision information system, a working plane information management system, a yield monitoring system, a dynamic meter management system, a safety prewarning and decision supporting system and a rescue information assurance system. Nodes of the Internet of Things are installed to a coal mine tunnel, relevant equipment and workers, the nodes of the Internet of Things are connected with relevant sensors and actuating equipment, and objects, needing to be monitored, of an underground coal mine are connected with the Internet according to a unified agreement, so that the coal mine safety integrated monitoring system based on the Internet of Things is formed. The data information of the underground environment and equipment can be collected by every worker and underground equipment through the sensors carried with the workers and the underground equipment; besides, the state information of the workers and the underground equipment can be collected, so that intelligent recognition, positioning, tracking, monitoring and management are achieved.
Owner:HUAYANG COMM TECH CO LTD
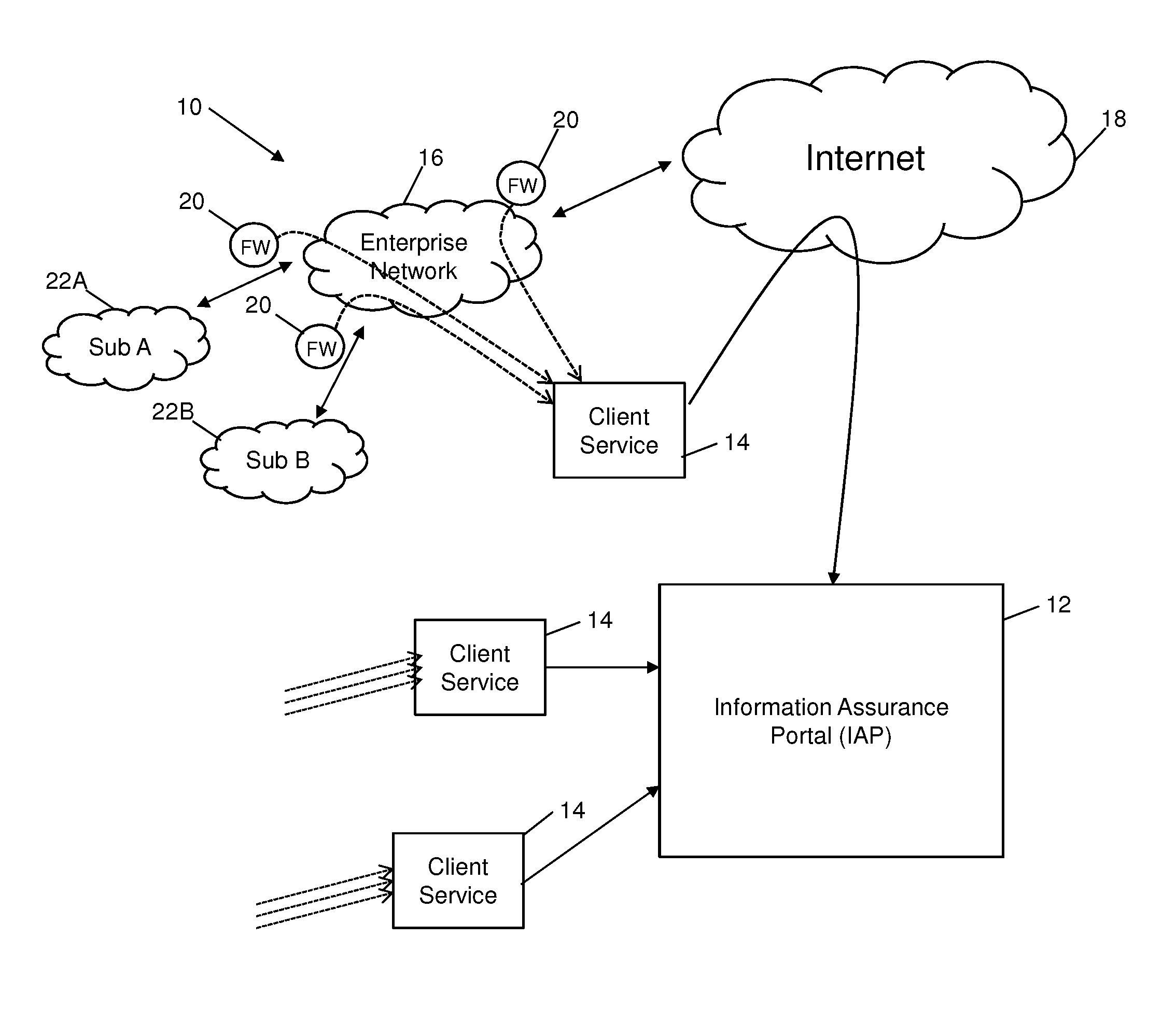
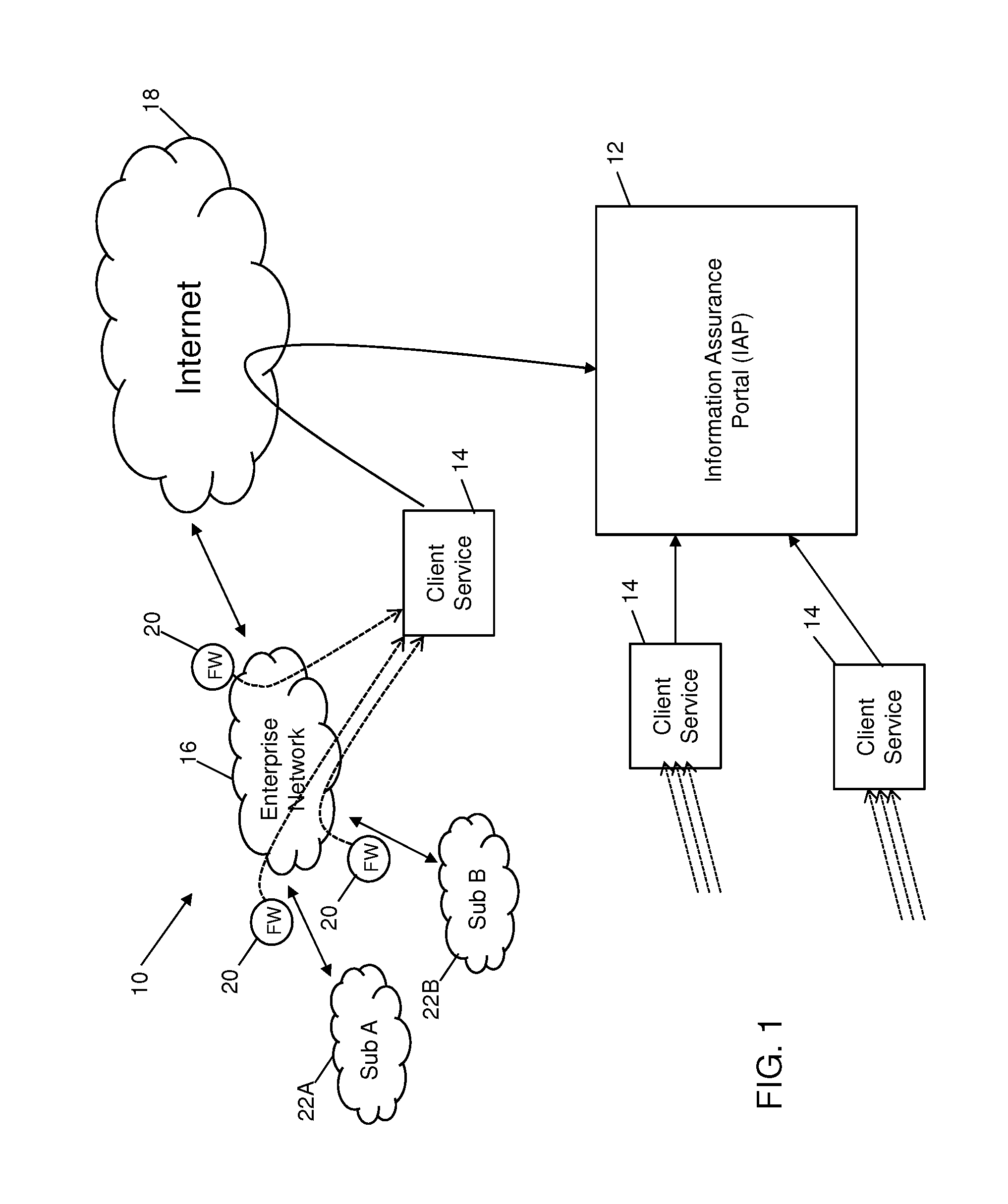
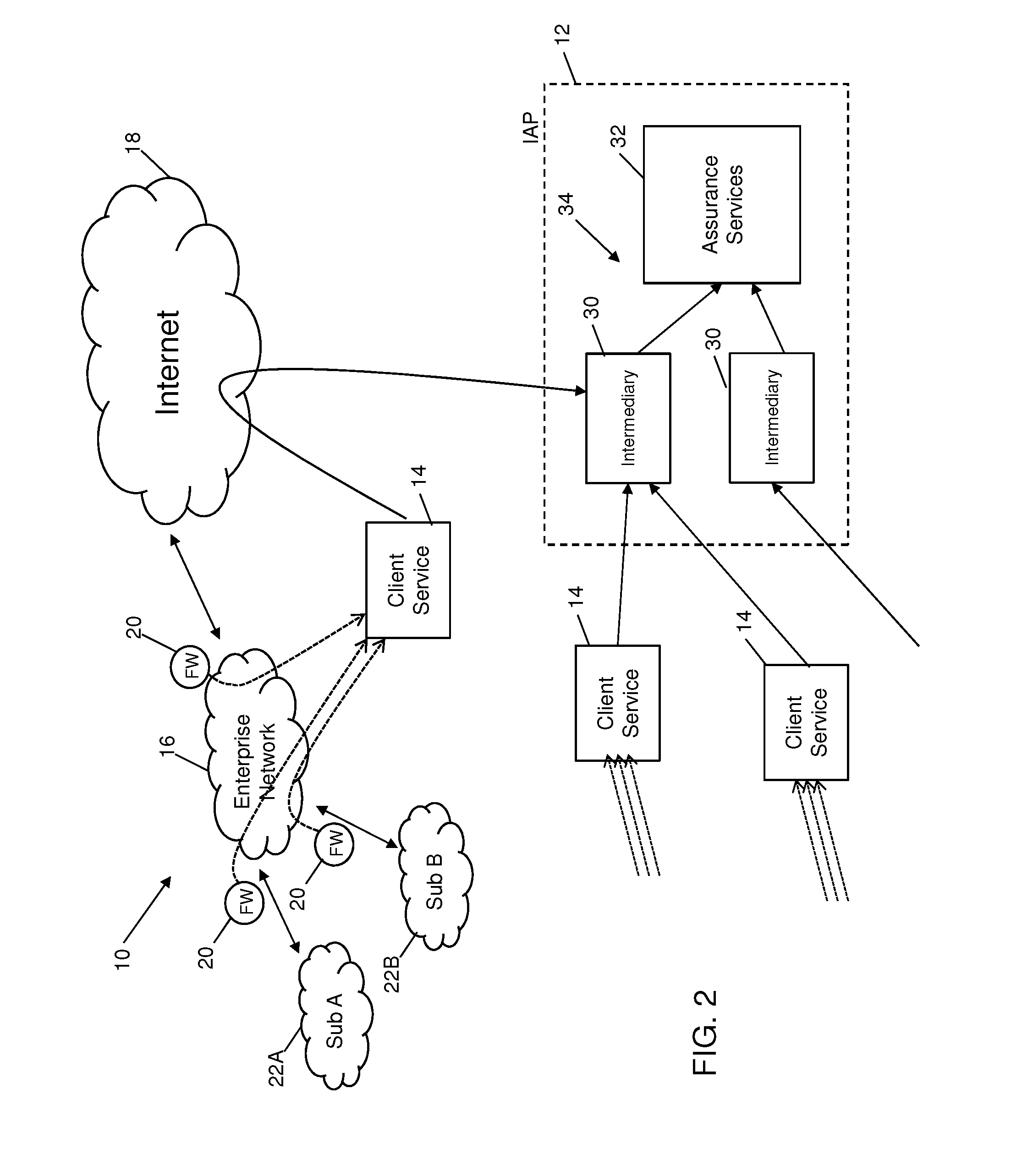
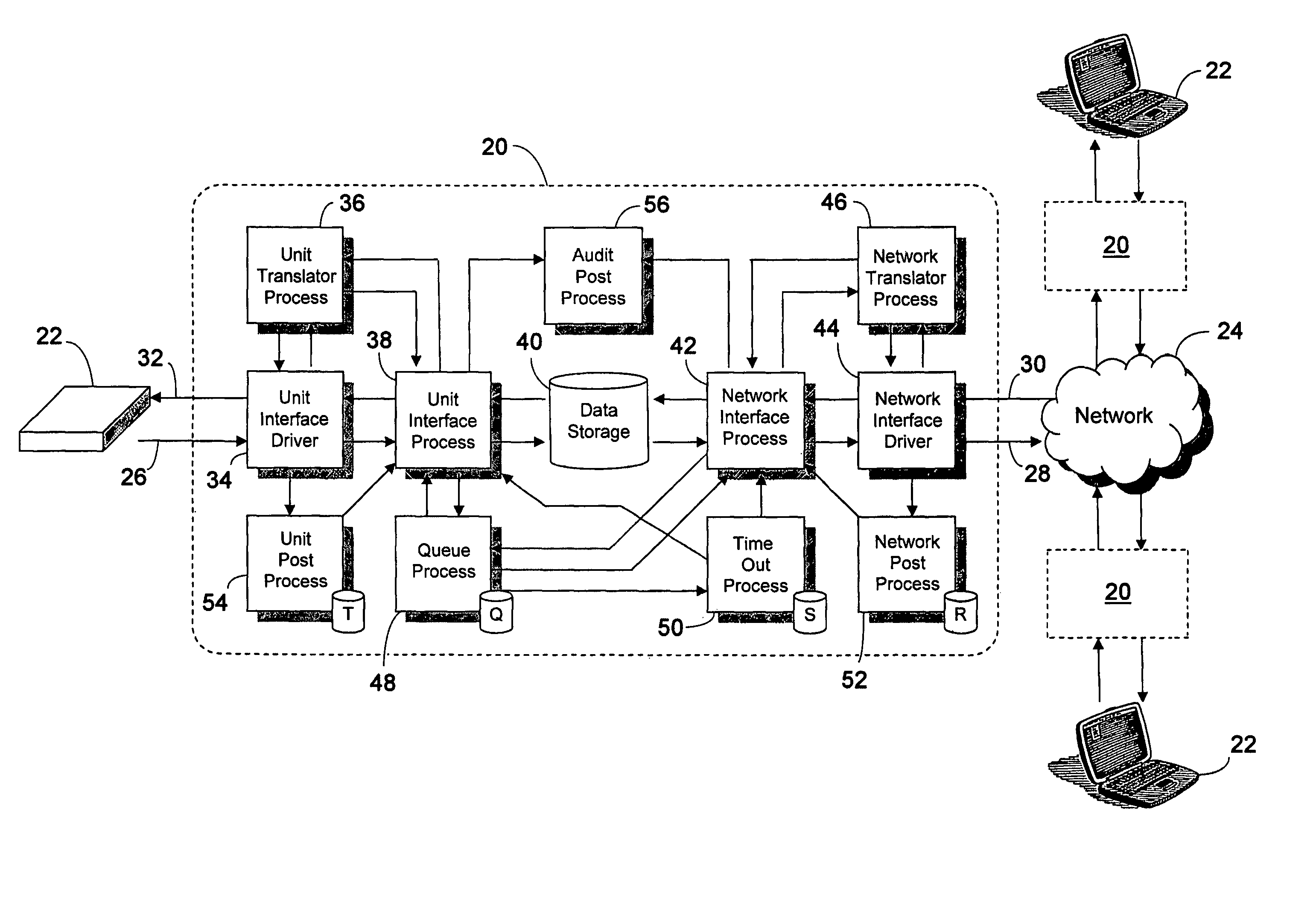
System and method for monitoring data in a client environment
InactiveUS20150347751A1Memory loss protectionError detection/correctionCloud baseInformation assurance
Systems and methods are provided which enable client environments, such as corporate and government enterprises, to adopt an integrated, strategic approach to governance, risk and compliance. The systems described herein provide a “cloud-based” information security service that provides such enterprises with round-the-clock visibility into security issues and risks across the enterprise. An advanced security information and event management system, also referred to as an information assurance portal (IAP), is described, which enables client customers to select various services such as threat and vulnerability management, asset classification and tracking, and business threat and risk assessments through a software-as-a-service portal.
Owner:SECCURIS INC
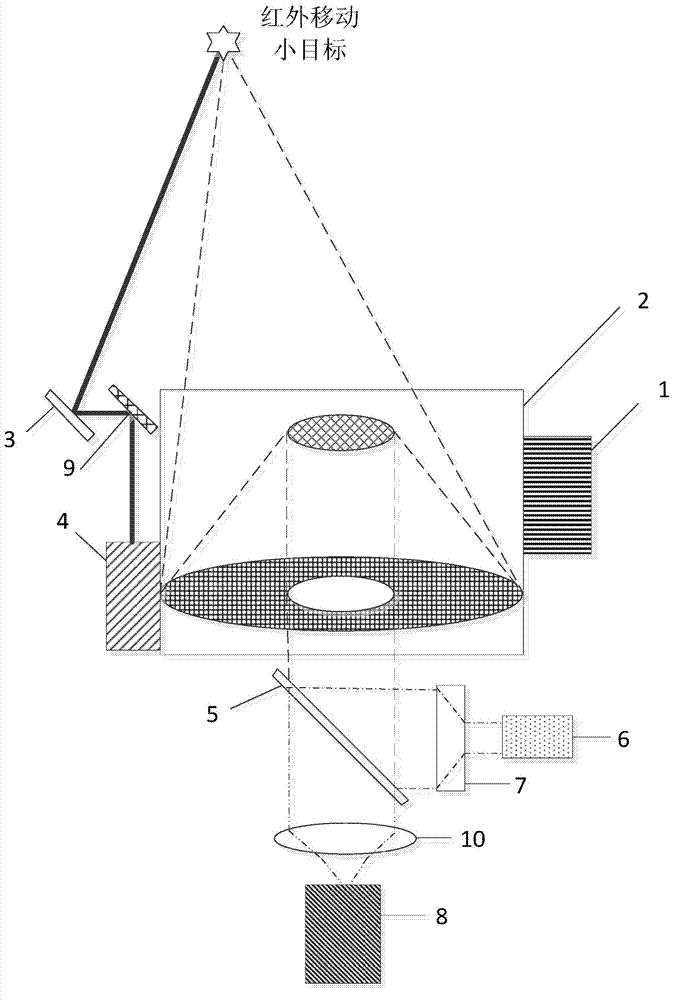
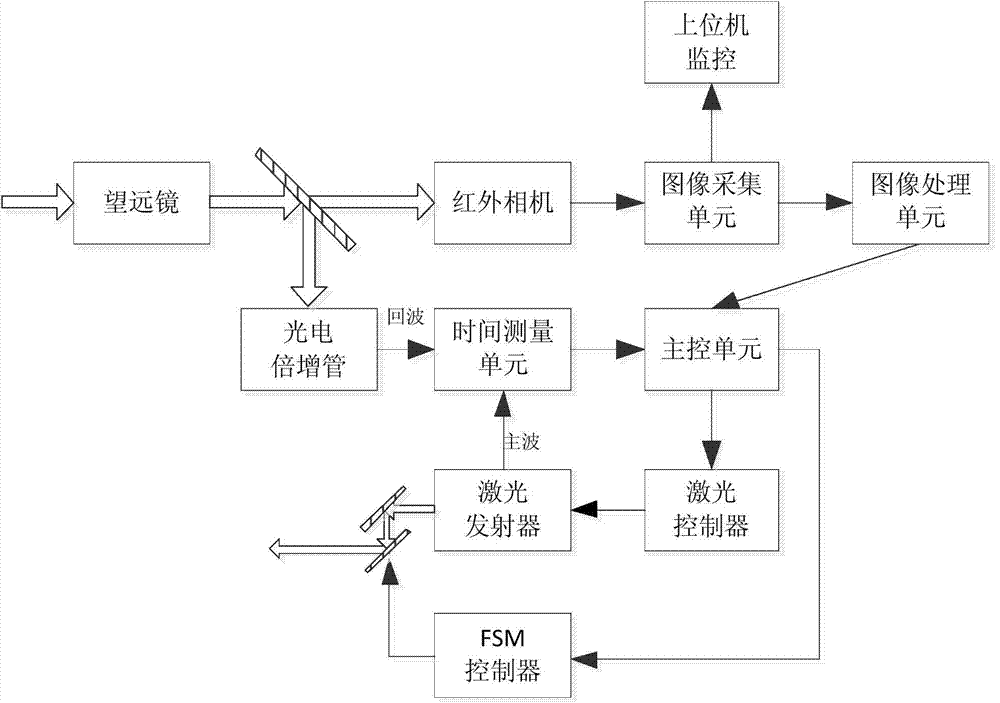
Infrared and laser compound detection system
ActiveCN103499818ARich detection informationOptical detectionElectromagnetic wave reradiationThree dimensional measurementPhotomultiplier
The invention discloses an infrared and laser compound detection system, which can realize stable tracking on an infrared moving target and accurate pointing on laser, and realize distance measurement on a target. The system is provided with a fold-back type common-caliber optical receiving head part, infrared rays and laser are separated by using a color separation filter, a small movable target is imaged through an infrared camera, coarse tracking of a two-dimensional rotary table and refined adjusting of a quick deflecting mirror are controlled according to a target centroid position, and emitted laser is accurately pointed to the target. A photomultiplier receives a laser echo signal, and target distance information is worked out according to a laser emission principal wave signal and the echo signal. The system can be carried on an onboard platform, a missile-borne platform and a satellite platform, realizes three-dimensional measurement on an infrared target, and provides information assurance for an aggregate decision.
Owner:SHANGHAI INST OF TECHNICAL PHYSICS - CHINESE ACAD OF SCI
Visibility identification system based on meteorological observation and road camera shooting and application method
InactiveCN110188586AImprove use valueLow costCharacter and pattern recognitionStill image data indexingSurveillance cameraInformation assurance
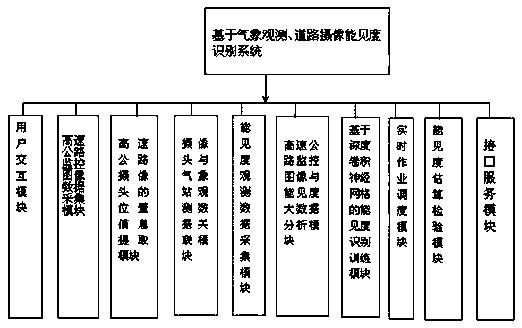
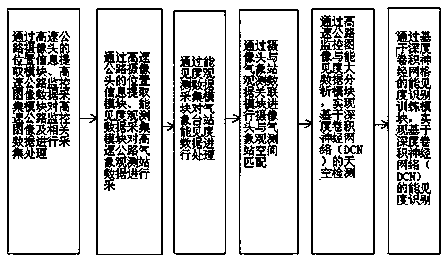
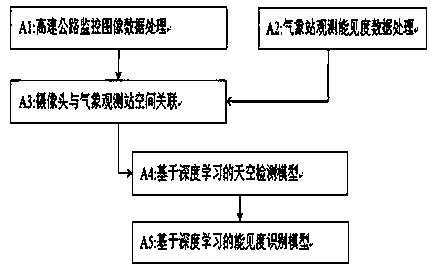
The invention discloses a visibility identification system based on meteorological observation and road camera shooting. The system includes a user interaction module, a highway monitoring image dataacquisition module, a highway camera position information extraction module, a camera and meteorological station observation data association module, a visibility observation data acquisition module,a highway monitoring image and visibility big data analysis module, a visibility recognition training module based on a deep convolutional neural network, a real-time operation scheduling module, a visibility estimation and inspection module and an interface service module. According to the system, highway camera shooting data is taken as an object, and through machine learning and an artificial intelligence technology, under the combined action of related software, the road visibility information is extracted from the high-speed monitoring image in a full-automatic mode, effective monitoringof sudden agglomerate fog of the bureau can be achieved, monitoring information is provided for passing of heavy fog weather of a road, the utilization value of a monitoring camera is increased, and afavorable information guarantee is provided for reducing traffic meteorological disasters induced by heavy fog.
Owner:象谱信息产业有限公司
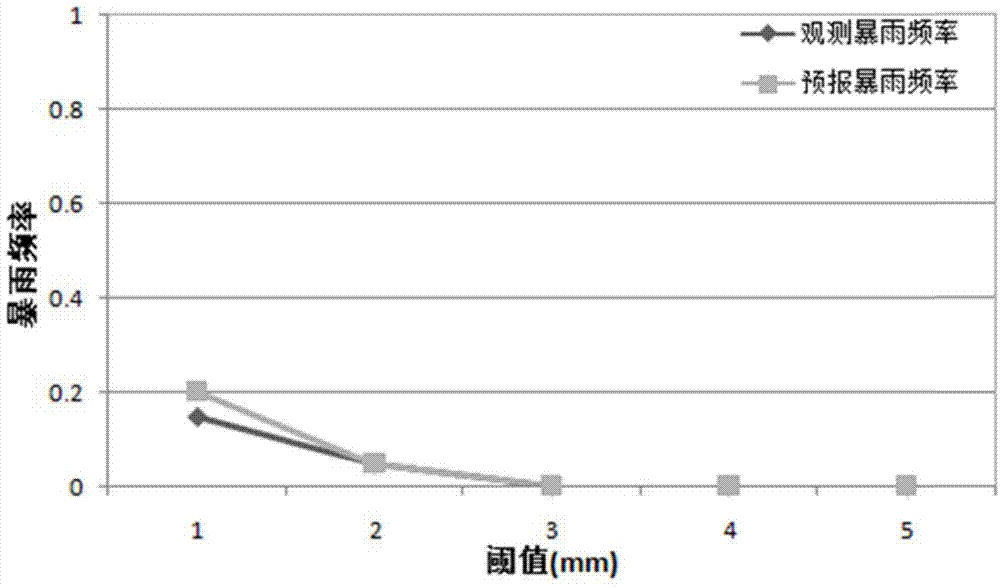
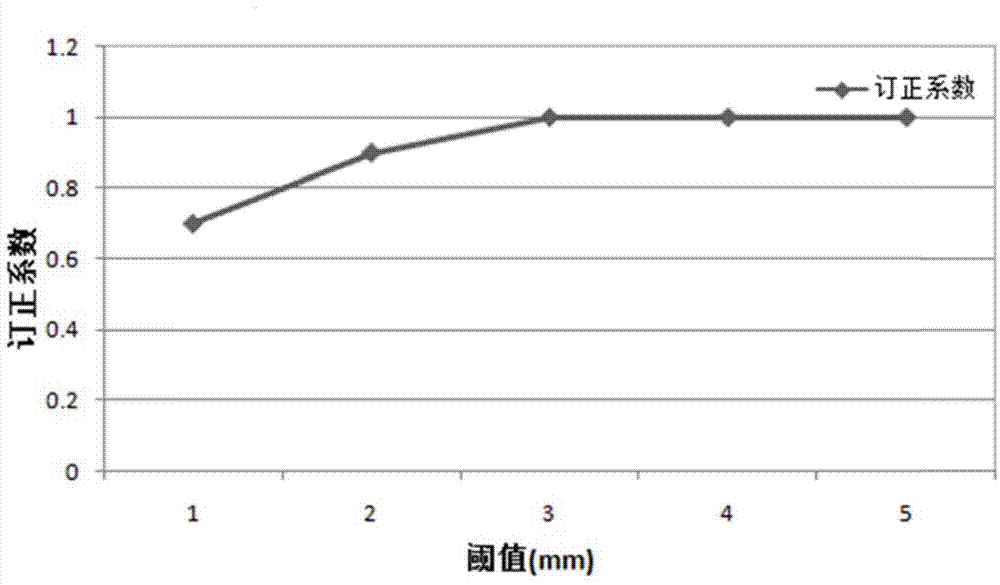
Dynamic-modification-combined storm rainfall fine alarming method for power grid zone
InactiveCN104851051AImprove the effect of early warningAccurately reflect the situationData processing applicationsPower gridPower equipment
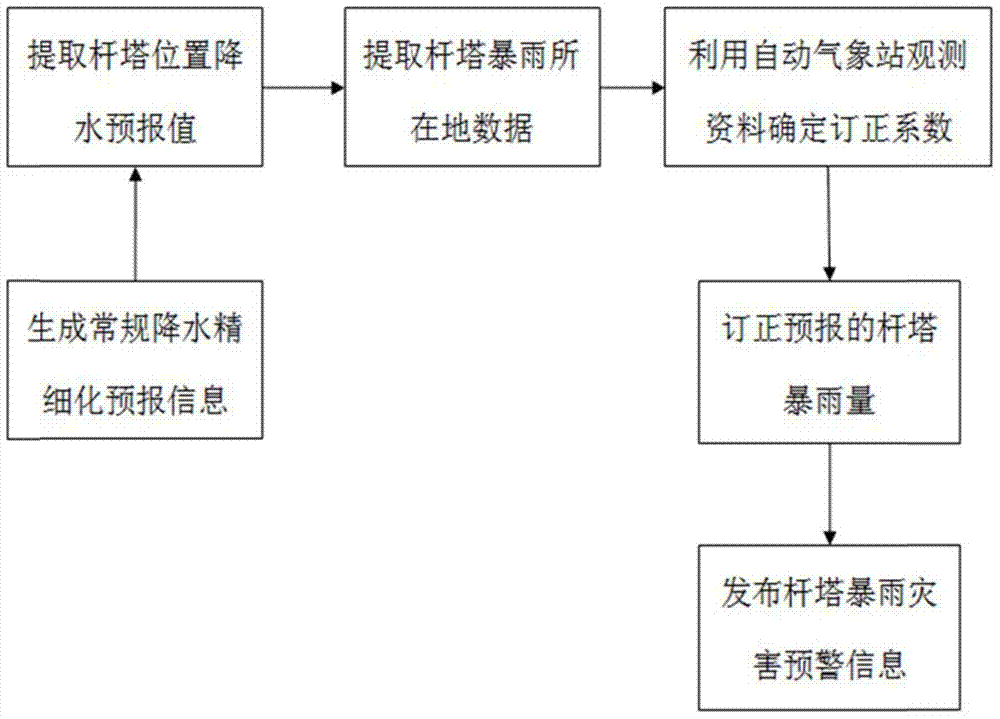
The invention discloses a dynamic-modification-combined storm rainfall fine alarming method for a power grid zone. The method includes an S1 step of forecasting local precipitation amount, generating forecasting information and extracting forecast values of precipitation at tower positions of a power grid; an S2 step of extracting position information of towers of the power grid meeting condition for rainstorms and storm rainfall information; an S3 step of determining correcting indexes by utilizing history observational data of a meteorological station and corresponding forecast information, correcting the forecast values of precipitation at the tower positions of the power grid of the current date according to the correcting indexes and acquiring the final forecast result; and an S4 step of making priory forecast of power equipment according to the final forecast result and publishing rainstorm disaster early warning information for the towers of the power grid. By adopting the method provided by the invention, accuracy of the storm rainfall forecast value of the current date is improved effectively, so that an effective information guarantee is made for rainstorm disaster early warning.
Owner:STATE GRID CORP OF CHINA +3
System and method for information assurance based on thermal analysis techniques
InactiveUS8091093B2Improve performanceImprove securityDigital computer detailsTransmissionComputer scienceInformation assurance
Systems and methods for network security are disclosed. Embodiments of the present invention include a scalable, real-time solution to complement existing security systems and detect unusual activity. Embodiments of the present invention leverage the scale and complexity of networks and use the principles of statistical physics and thermodynamics to define thermal properties like entropy, temperature and energy for network states and changes in the properties as packets move through the network.
Owner:EQUILIBRIUM NETWORKS
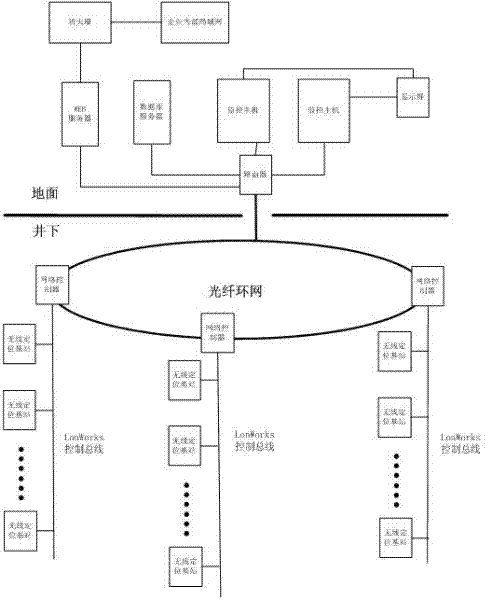
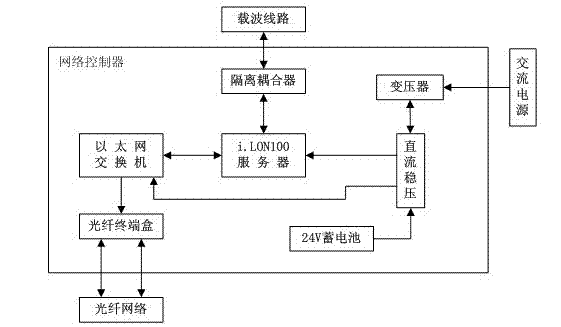
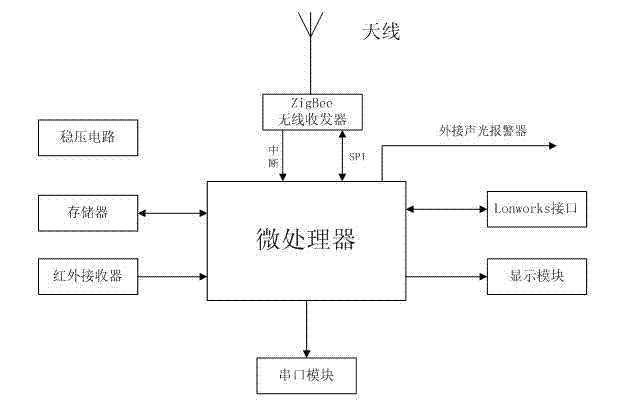
Coal mine worker positioning and managing system based on ZigBee technology
InactiveCN102418560AIncrease transfer rateImprove effective working timeMining devicesNetwork controlEngineering
The invention discloses a coal mine worker positioning and managing system based on a ZigBee technology. When a worker with an identification card passes through a working coverage of a wireless positioning base station, the identification card actively sends worker code information to the wireless positioning base station; the wireless positioning base station receives the information sent by the identification card and transmits the information to a network controller through a LonWork control bus; the network controller sends the data to a ground control center network through an Ethernet; and the ground control center network acquires and processes the information, and displays the information to a manager in real time. By the coal mine worker positioning and managing system, the real-time supervising ability of a coal mine manager and superior supervising departments on a running condition of a coal mine is improved; and powerful information insurance and support are supplied to rescuers after an accident happens.
Owner:CHANGSHU RES INSTITUE OF NANJING UNIV OF SCI & TECH +1
Lightweight authentication method for supporting anonymous access of heterogeneous terminal in edge computing scene
ActiveCN111371730AImplement anonymous authenticationRealize traceabilityKey distribution for secure communicationUser identity/authority verificationEdge computingTerminal equipment
The invention provides a lightweight authentication method for supporting anonymous access of a heterogeneous terminal in an edge computing scene. According to the invention, a pseudo identity is created for each terminal device by using a cloud platform to hide the real identity information of the terminal device; meanwhile, malicious terminal equipment can be traced back; the invention disclosesa method for authenticating an access edge computing node of terminal equipment. The edge computing node can verify the legality of the identities of all accessed devices under the condition of not communicating with the cloud platform; according to the method and the device, the real identity information of the terminal cannot be learned, the identity privacy of the terminal equipment is guaranteed, the access authentication efficiency is improved, common threats such as replay attacks can be resisted, the safety and reliability of the whole edge computing system are enhanced, and the problem of access authentication of the terminal equipment with limited resources in an edge computing scene is solved.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
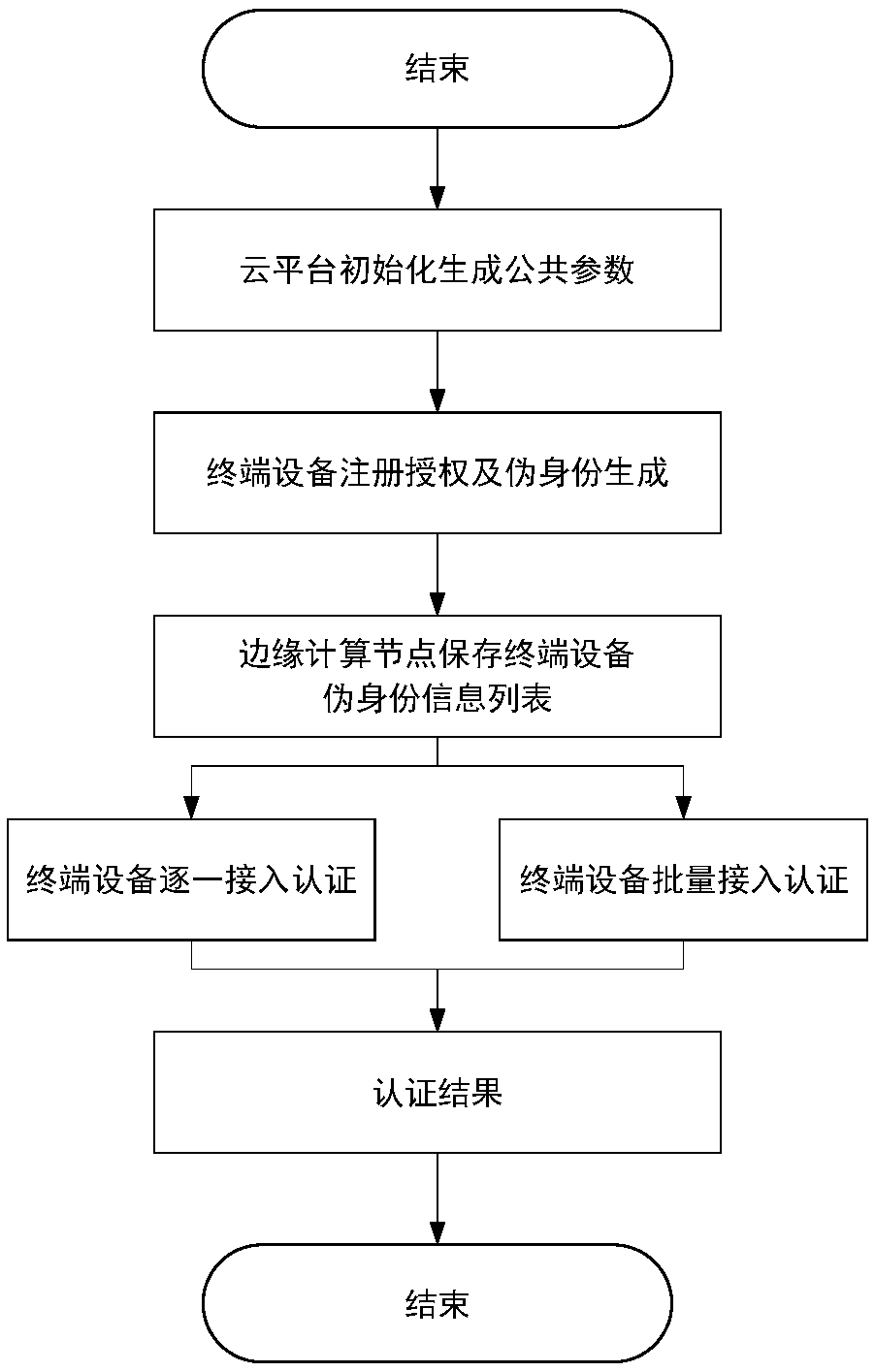
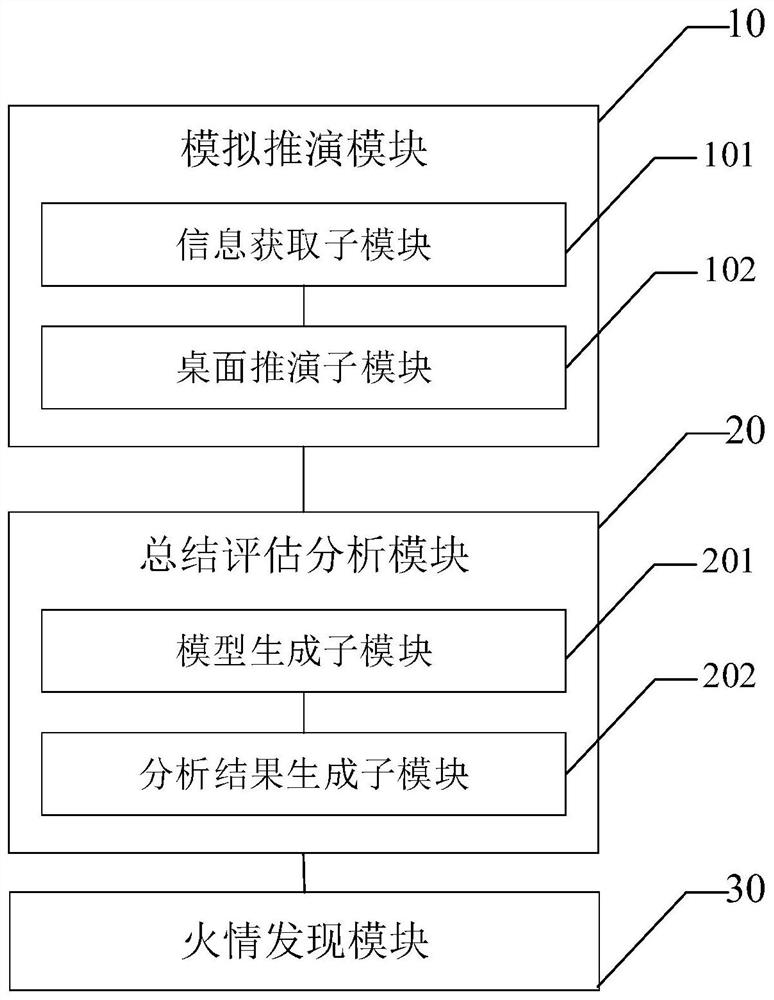
Forest fire emergency drill evaluation and analysis system and method and computer equipment
ActiveCN112530119AConvenient reviewImproving the ability to deal with forest fire emergency rescueCosmonautic condition simulationsData processing applicationsData informationFire - disasters
The invention discloses a forest fire emergency drill evaluation and analysis system and method and computer equipment, the system comprises a summary evaluation and analysis module and a simulation deduction module, the simulation deduction module comprises an information acquisition sub-module used for acquiring spatial geographic position information, fire information, fire rescue team information and guarantee reserve material information; a desktop deduction sub-module used for constructing a forest fire emergency drill scene according to the information and determining a forest fire spreading path according to a preset forest fire spreading model; generating a fire suppression scheme and a personnel rescue scheme according to the forest fire emergency drill scene and the forest firespreading path; a summary, evaluation and analysis module which comprises a model generation sub-module which is used for obtaining real data information of the whole drilling process and generating adrilling data model through an electronic sand table and a visual display system; and an analysis result generation sub-module which is used for generating a forest fire emergency drill evaluation analysis result according to the drill data model and a preset drill evaluation standard.
Owner:SHENZHEN URBAN PUBLIC SAFETY & TECH INST CO LTD
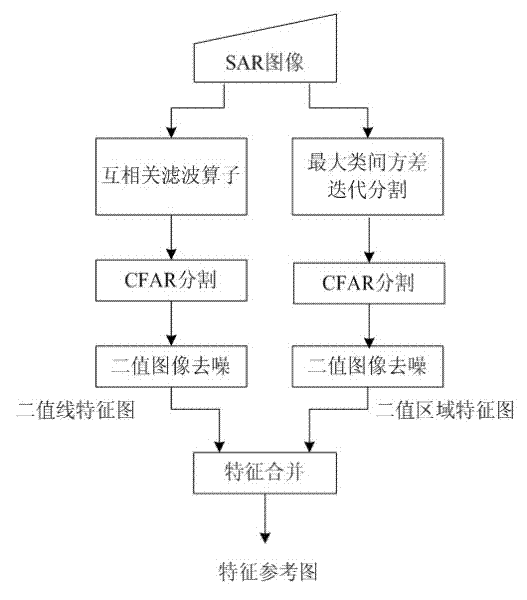
Radar scene matching feature reference map preparation method based on satellite SAR (synthetic aperture radar) images
InactiveCN102175993ATimely supportAccurate supportCharacter and pattern recognitionRadio wave reradiation/reflectionReference mapNatural satellite
The invention provides a radar scene matching feature reference map preparation method based on satellite SAR (synthetic aperture radar) images. The method comprises the following steps: respectively extracting line features and region features from an orthographic SAR image to obtain a binary line feature map and a binary region feature map; and combining the two feature maps to obtain the radar scene matching feature reference map. The method for preparing the radar matching feature reference map based on the SAR images has a good effect, small calculation amount, good real-time performance and low information assurance requirements, and can be effectively applied in the radar matching reference map preparation field.
Owner:HUAZHONG UNIV OF SCI & TECH
Real time monitoring apparatus for human body gait motion energy consumption
InactiveCN101219050ASimple structureReduce testing costsMuscle exercising devicesHuman bodyMeasurement device
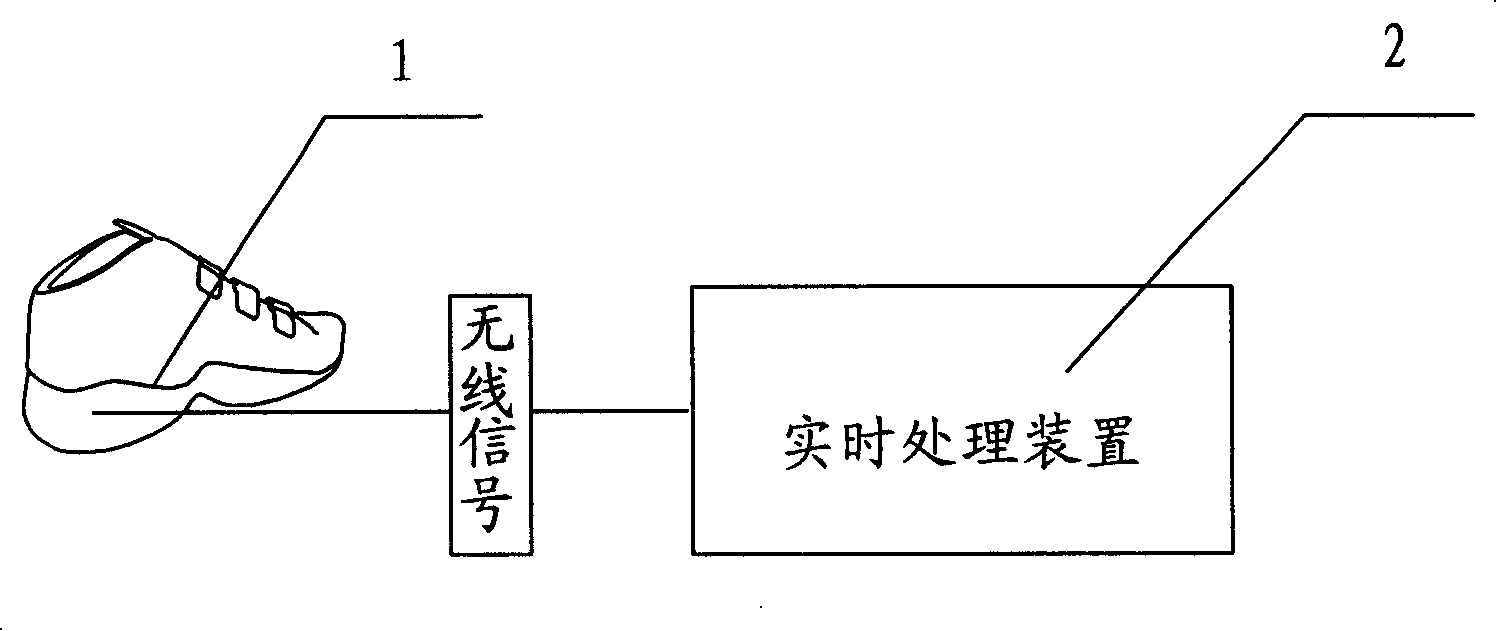
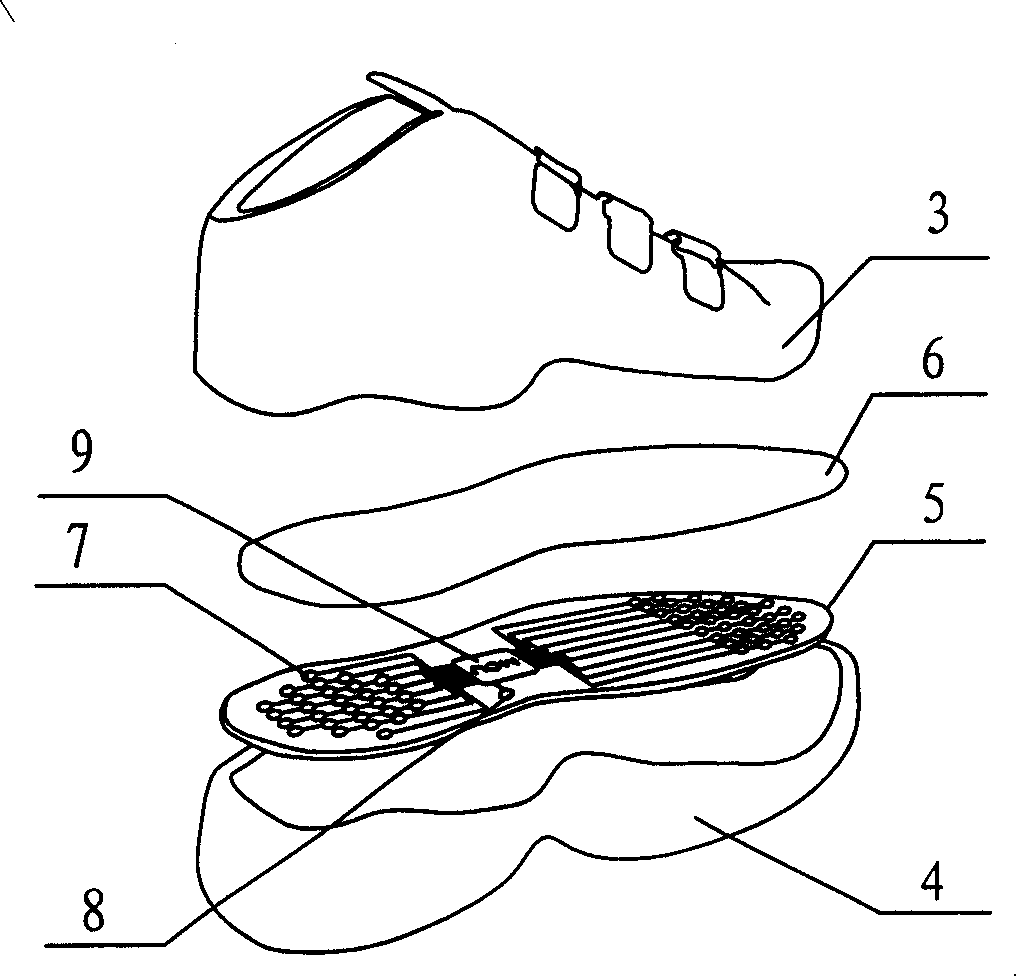
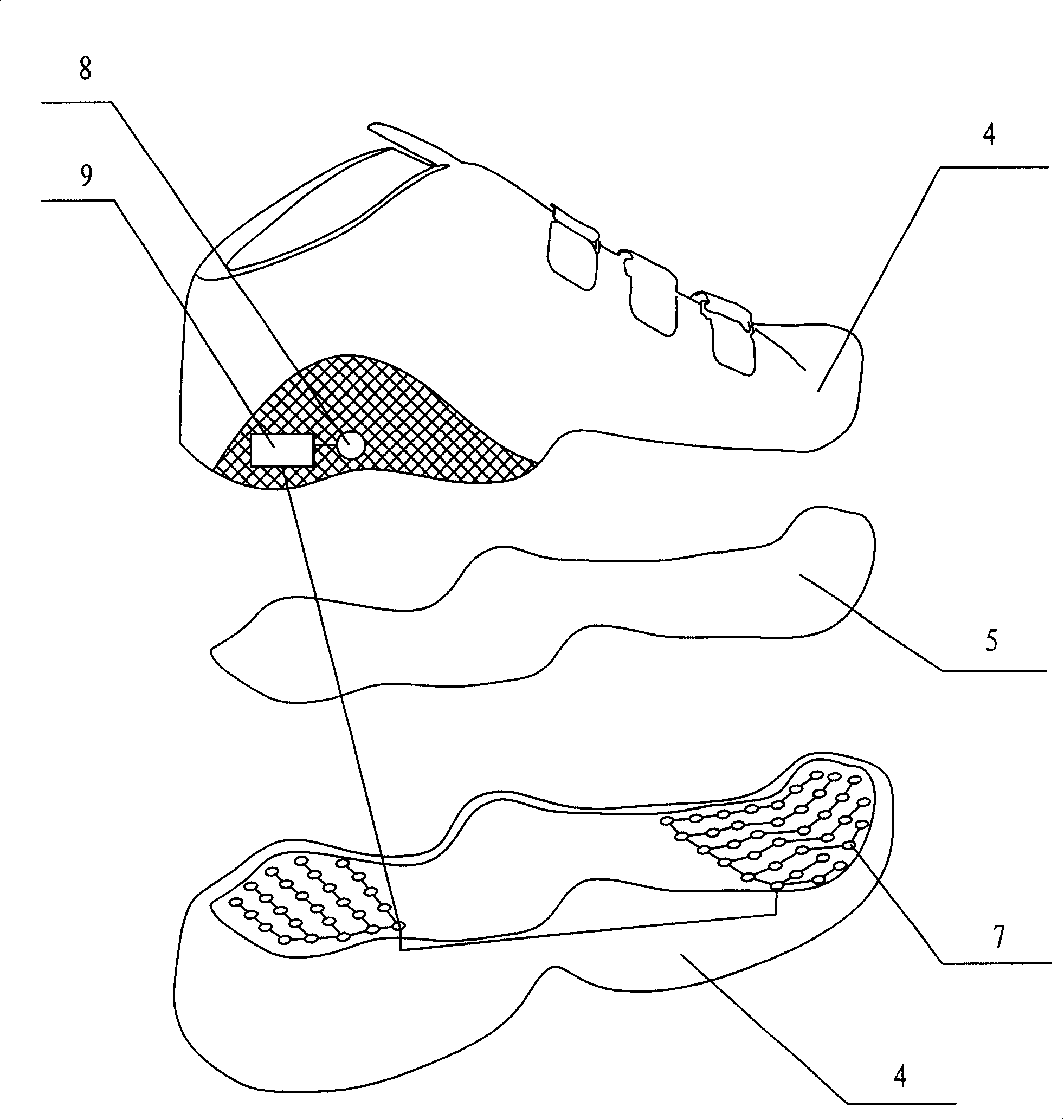
The invention relates to a human body motion measurement, in particular to a real-time monitoring device for monitoring energy consumption of human body gait motion. The purpose of noninvasively monitoring human body gait motion states and energy consumption can be realized by the system. The device comprises gait motion measuring shoes and a gait signal processing device; the measuring device of the gait motion measuring shoes and gait signal real-time processing device are wirelessly connected with each other. The invention has the benefit effects that 1. the invention has a simple structure and low measuring cost; 2. characteristics of human gait can be measured conveniently, noninvasively and real-timely through the sole movement of the foot, thereby providing information assurance for measuring human body energy consumption and building mathematical model for the energy consumption of human body gait; 3. personalized motion instruction can be made quickly through a measuring signal receiving and processing device.
Owner:李祥臣
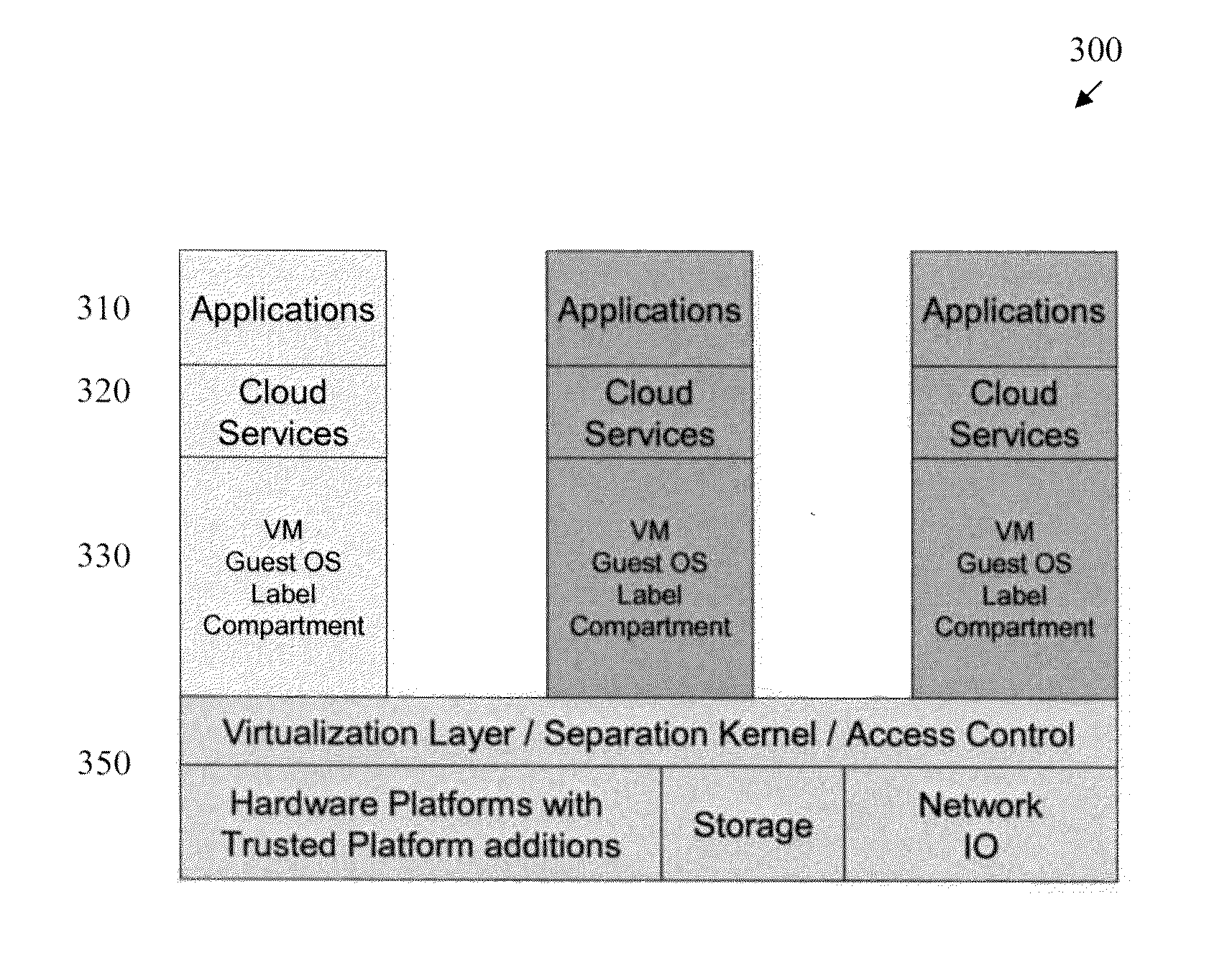
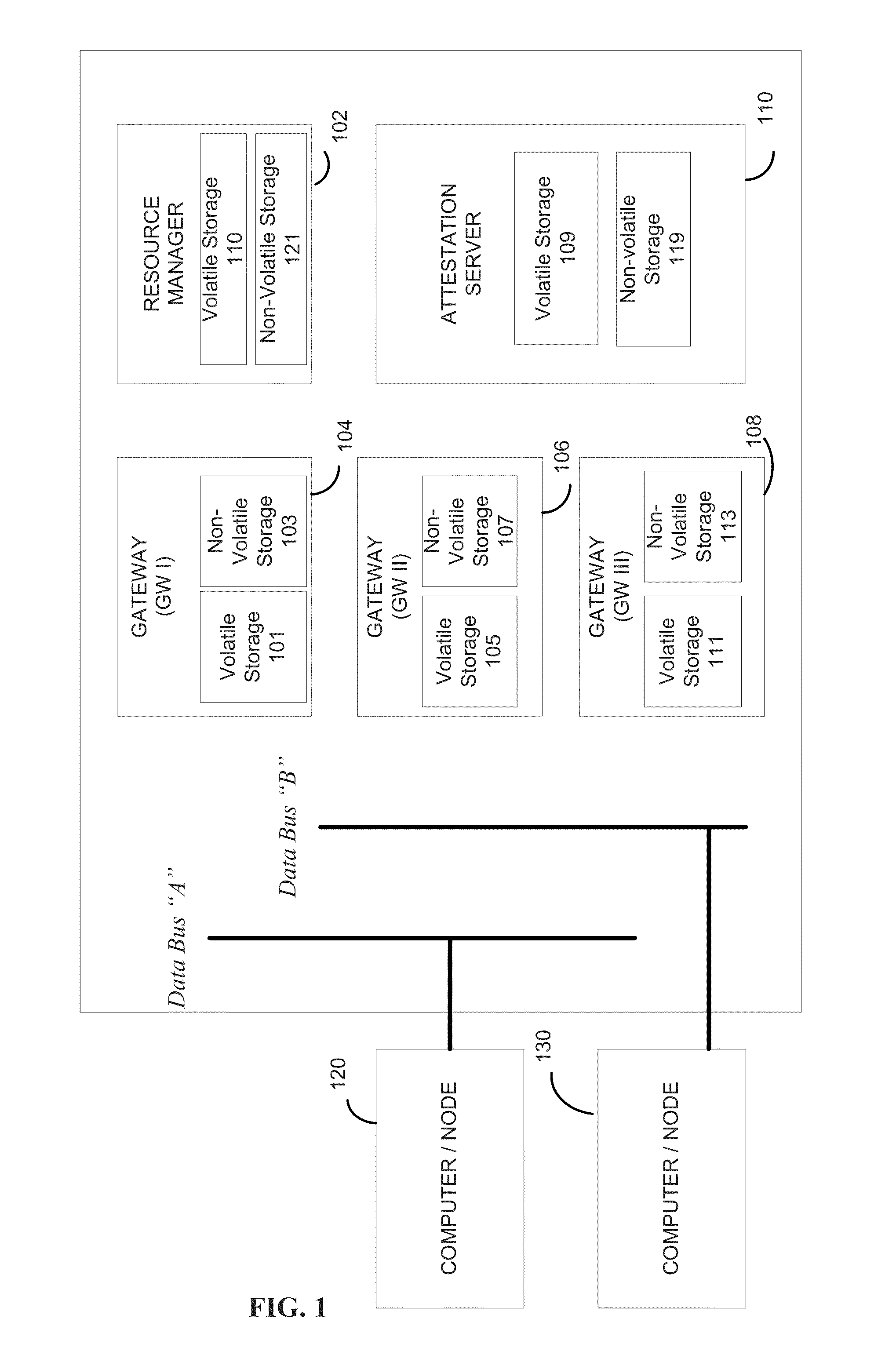
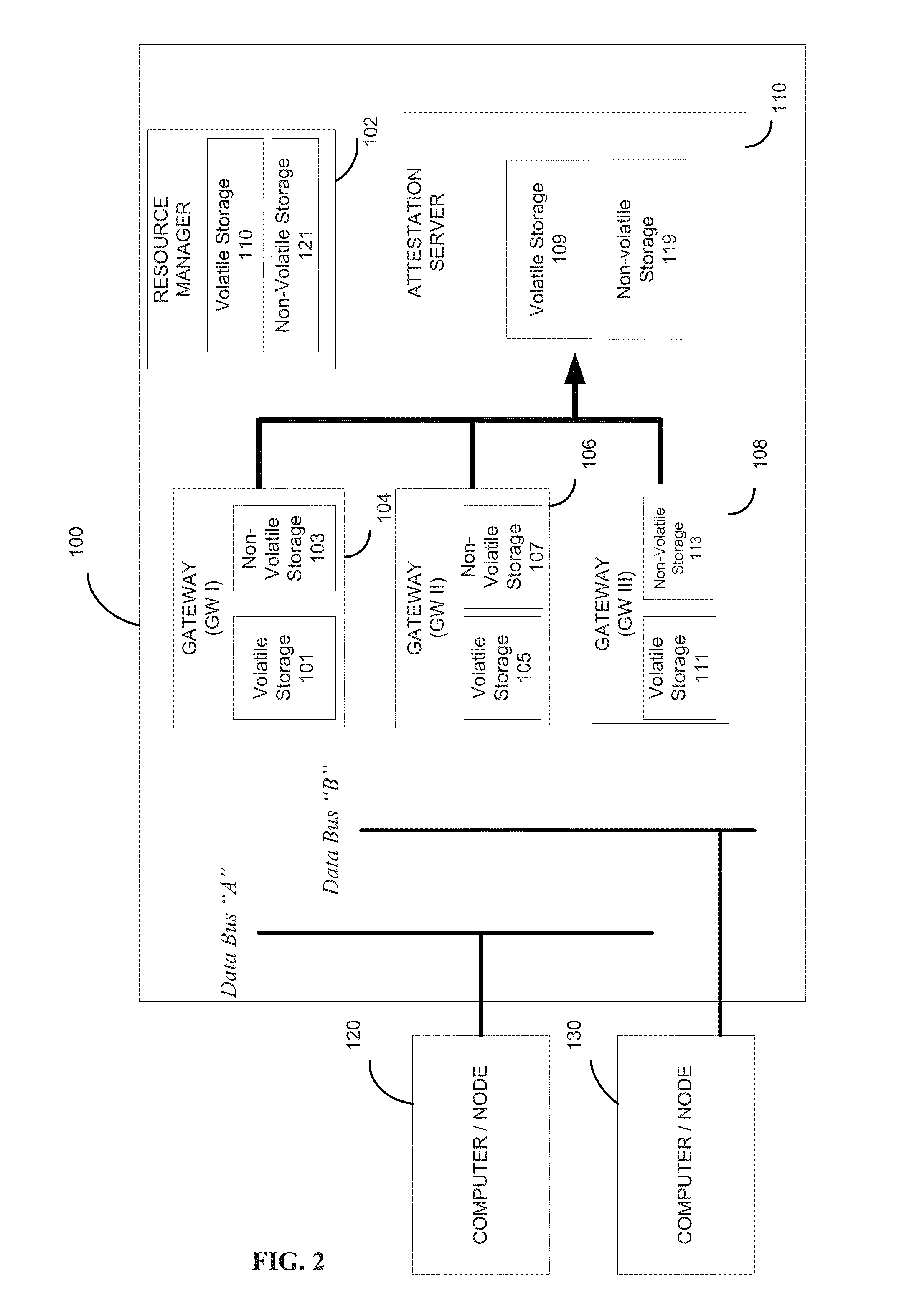
Methods and apparatus for information assurance in a multiple level security (MLS) combat system
InactiveUS20130276133A1Prevent tamperingMemory loss protectionDigital data processing detailsOperational systemData access
Methods and apparatus are provided for information assurance in a multiple level security (MLS) combat system. A plurality of tasks are executed, where at least one of the tasks requiring a transition from a first security level to a second security level. At least one of the tasks are executed on a cloud computing system; and a kernel is employed to prevent a leakage of data between at least two of the tasks. The cloud computing system comprises a virtualization layer and provides one or more operating systems, as well as interface access control to data. The kernel provides a mechanism for the transition from the first security level to the second security level. The kernel optionally tags one or more data records with a security classification to allow one or more classification levels to be segregated for role-based data access.
Owner:RITE SOLUTIONS
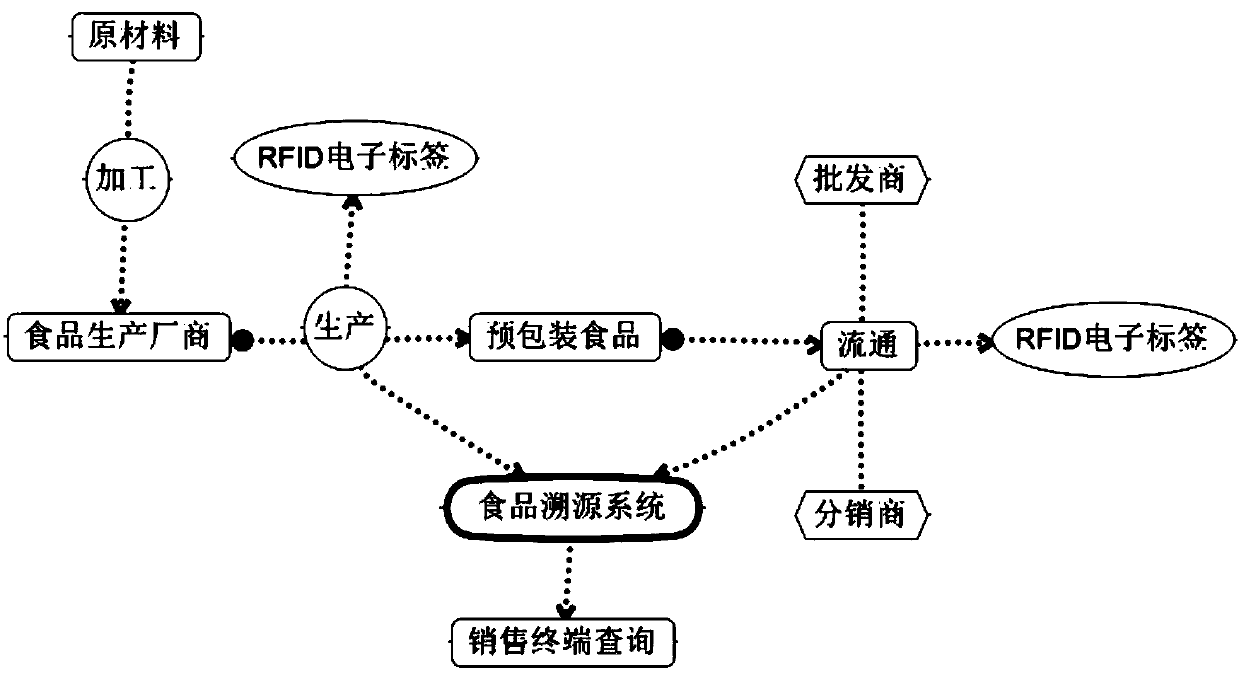
Pre-packaged food supervision system based on RFID technology
InactiveCN103793782AEnsure safetySatisfy the right to knowCo-operative working arrangementsResourcesRelevant informationComputer terminal
The invention aims at providing a pre-packaged food supervision system based on an RFID technology, and the system can provide information assurance to a food production and whole process. The pre-packaged food supervision system includes a pre-packaged module, an RFID electronic tag, an electronic tag identification module, and a computer terminal and food traceability system. First of all, in a production process, food is packaged with the pre-packaged module; the RFID electronic tag is inserted into the pre-packaged module; the RFID electronic tag is written with related information of the food; in a transportation process, information of the whole process is stored in the RFID electronic tag; in a sales process, a consumer can choose the food to buy according to information displayed by the electronic tag identification module and information displayed by the computer terminal; and in an after-sale process, when a problem emerges, the food traceability system on the computer terminal can be used to comprehensively detect in which link the problem lies and to correct the problem. According to the invention, the RFID electronic tag method is used to realize the quality supervision and trace in the whole process.
Owner:QINGDAO ZHONGKE SOFTWARE
Method and system for securely managing application transactions using cryptographic techniques
InactiveUS7941668B2User identity/authority verificationMultiple digital computer combinationsCredit cardApplication software
A method and system for secure managing transactions between application devices over a network. The present invention provides a method and system for receiving data from an application device, such as computer workstation, ATM, credit card point-of-sale terminal, or application software, and transferring that data securely over a network to a recipient application device. The method and system provide secure cryptographic key and enterprise management of embedded, standalone and tightly coupled information assurance components.
Owner:INNOVE
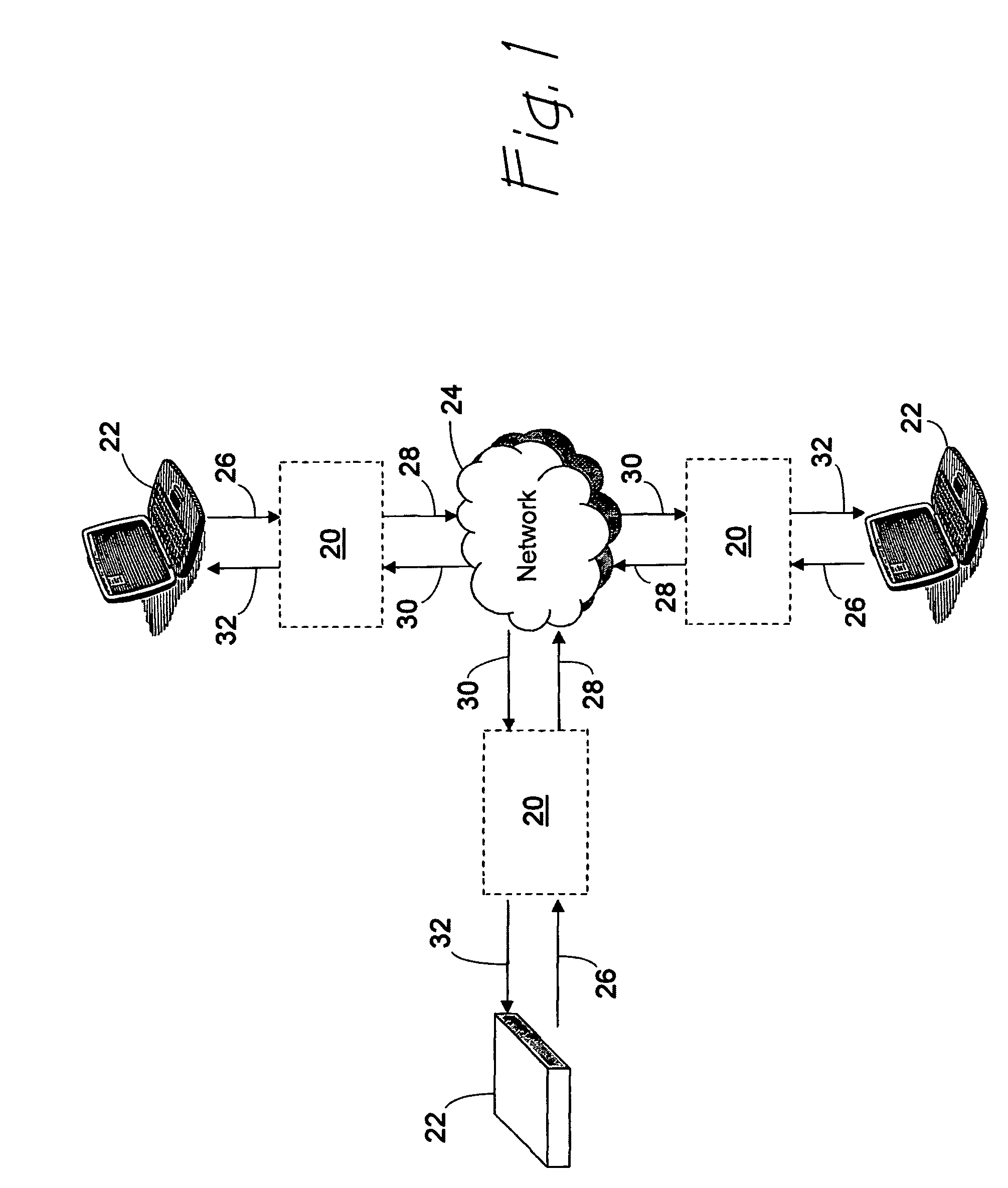
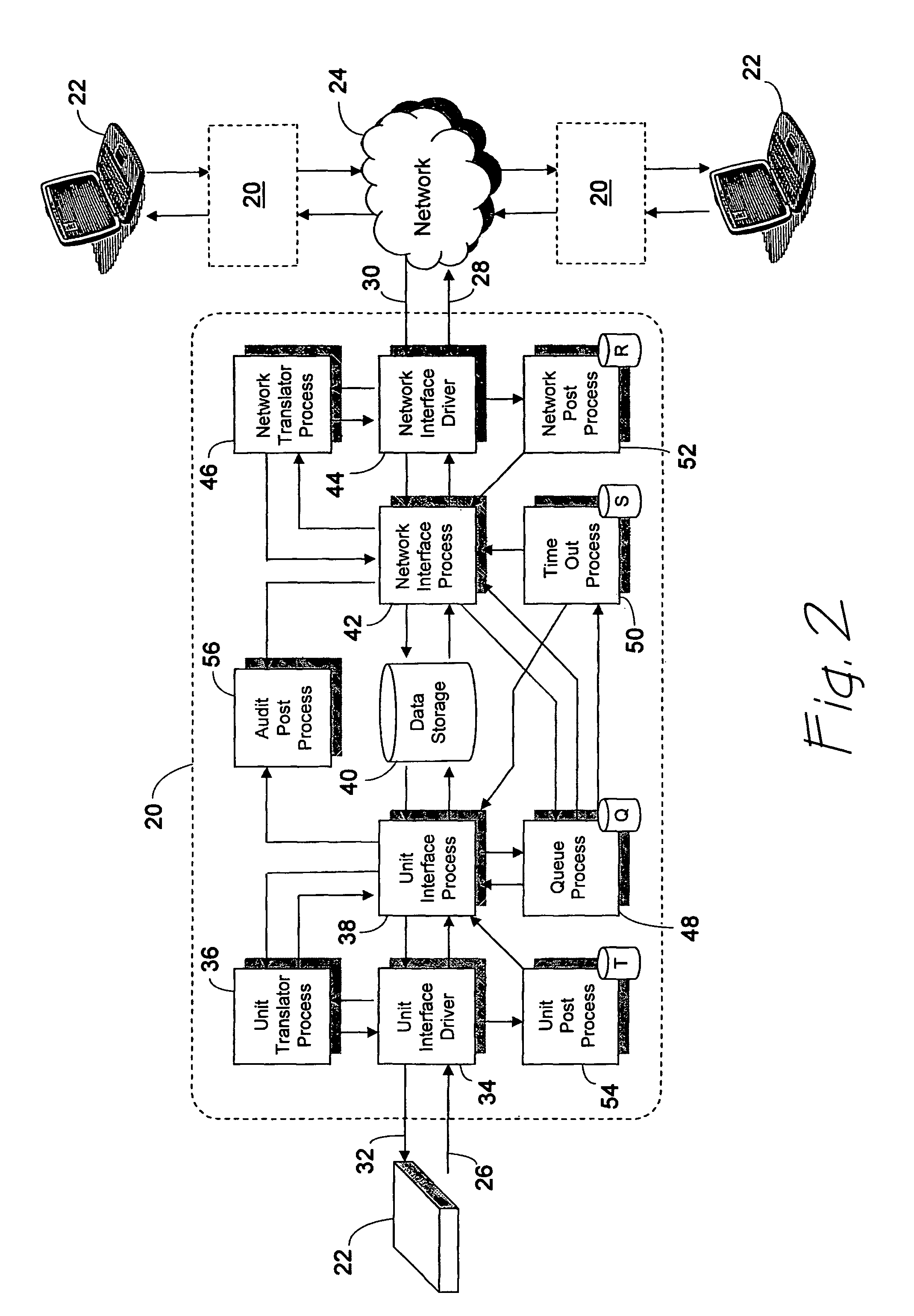
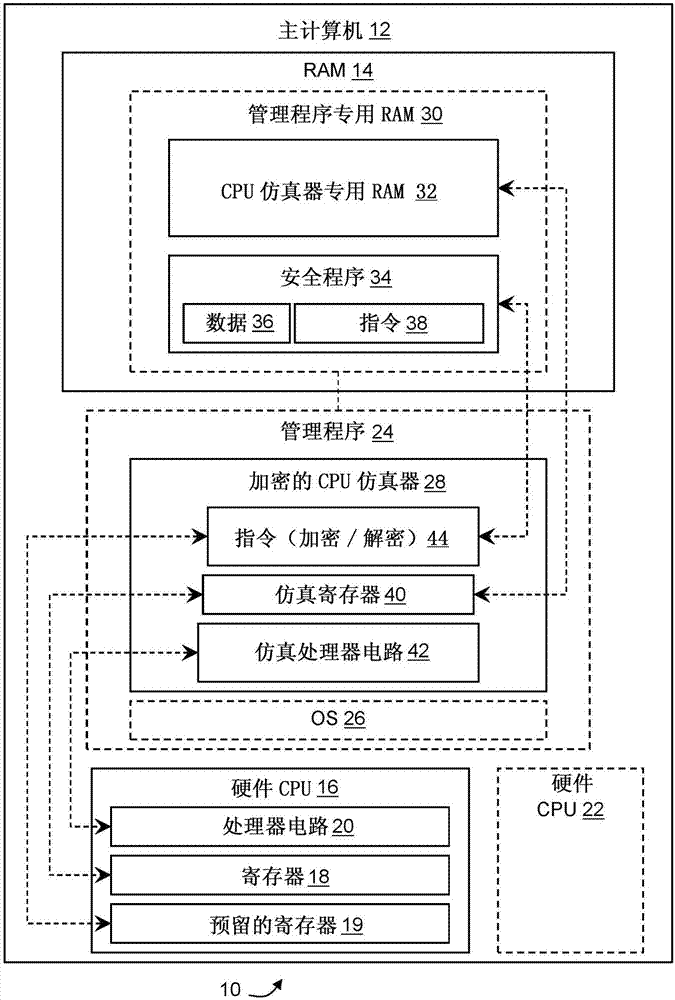
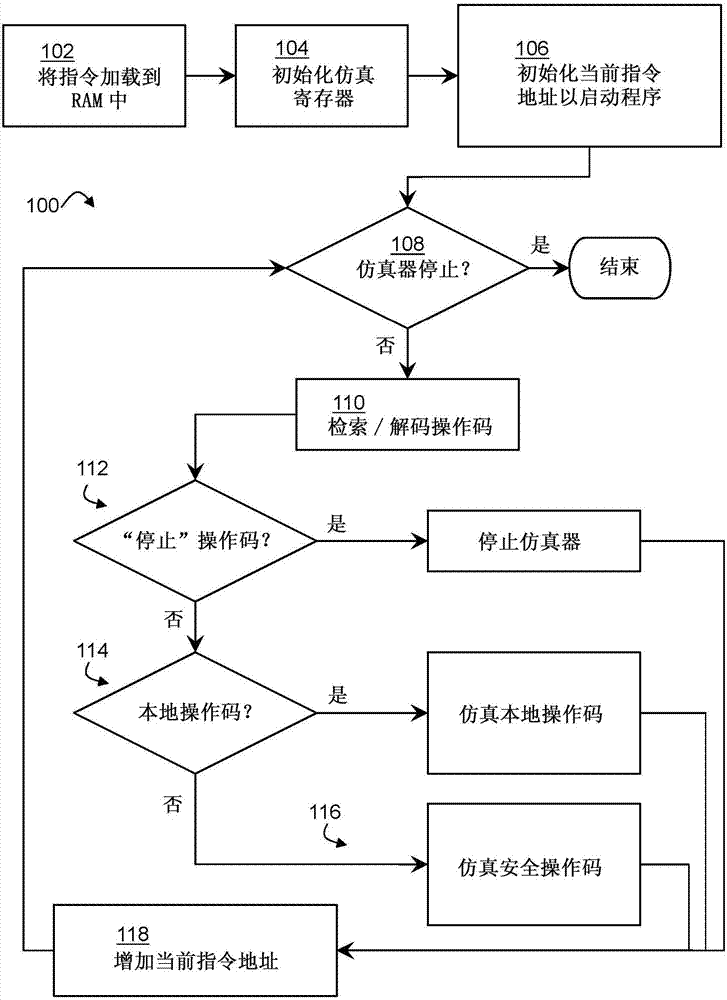
Information assurance system for secure program execution
ActiveCN107346401ADigital data protectionInternal/peripheral component protectionStatic random-access memoryRandom access memory
An information assurance system for secure program execution is disclosed. The enhanced information assurance system may comprise an improved computer (12) including a central processing unit (CPU) (16) emulator configured to extend the available machine instruction set. The CPU emulator may be configured to emulate machine language instructions taken from a nonnative set of secure opcodes. The CPU emulator may ensure that instructions and data (36) in a random access memory (RAM) (14) remain encrypted at all times when in RAM, for example by storing the instructions (38) and data (36) in CPU registers (18) when decrypted on an as-needed basis.
Owner:THE BOEING CO
Unmanned driving technology perception fusion method based on mining area environment
ActiveCN111551938AGuaranteed stabilityGuaranteed reliabilityCharacter and pattern recognitionElectromagnetic wave reradiationMultiple sensorEngineering
The invention discloses an unmanned driving technology perception fusion method based on a mining area environment, and the method employs a plurality of sensors as data sources, and guarantees the stability and reliability of perception information through employing a multi-sensor fusion technology for a special driving environment of a mining area. Various sensors are used for collecting vehiclesurrounding environment information, complementation is conducted according to different sensor characteristics based on the multi-sensor fusion principle, more accurate sensing information can be obtained, the sensing accuracy is improved, and therefore the unmanned mine card vehicle can adapt to the complex mining area environment in the using process, and work is completed safely and efficiently. Obstacle information is obtained by using different sensors; the feature information weight is obtained by calculating the information entropy, the matching matrix is optimized, and the matching precision is improved, so obstacle information and tracking target information extracted in a severe mining area environment are more accurately matched, more accurate driving environment information is obtained, and the safety and fluency in the whole driving process are guaranteed.
Owner:北京踏歌智行科技有限公司
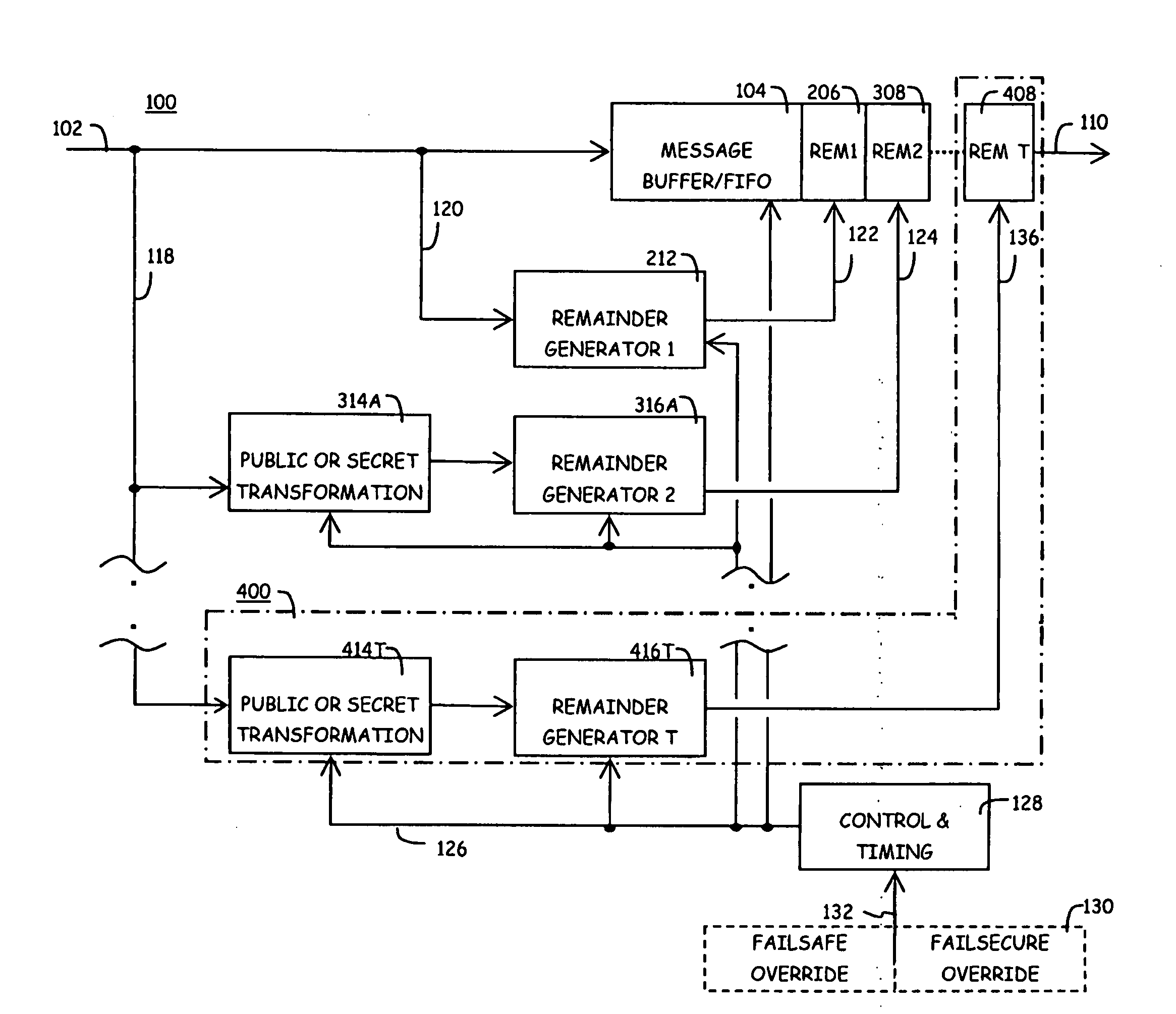
Method of identifying and protecting the integrity of a set of source data
A method of identifying and protecting the integrity of a set of source data which produces and combines an identification signature with a detection and correction remainder and extends the existing capability of some information assurance methods.
Owner:LRDC SYST
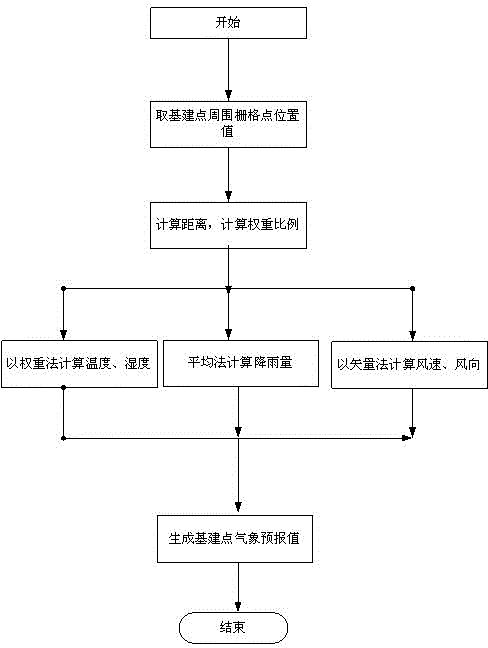
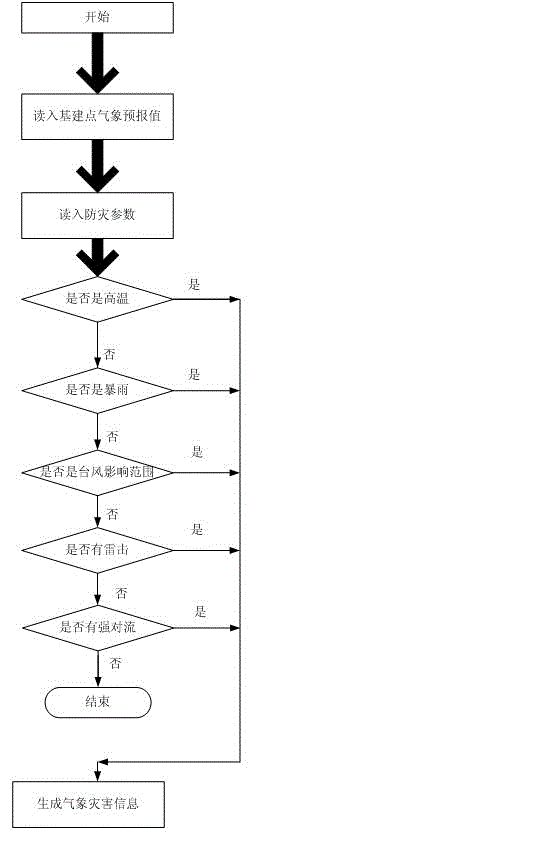
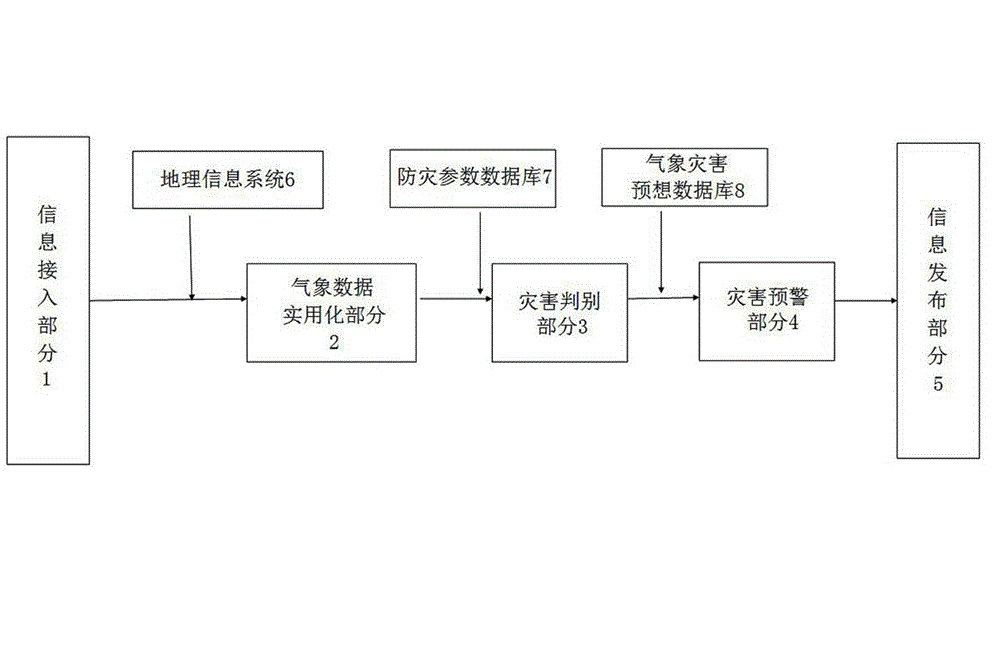
Electric capital construction meteorological disaster warning method based on refined weather forecast information and system
The invention discloses an electric capital construction meteorological disaster warning method based on refined weather forecast information. The electric capital construction meteorological disaster warning method based on refined weather forecast information includes receiving the refined weather forecast information, calculating corresponded weather forecast value from the refined weather forecast information based on the geographic position of a capital construction, comparing a meteorological environment value to a disaster prevention parameter threshold value and generating meteorological disaster information, querying disaster prevention strategy information from a disaster prevention expectation data base based on the meteorological disaster information and sending meteorological disaster warning information and disaster prevention strategy information. The invention further provides a warning system for the meteorological disaster warning method. With the help of refined weather forecast information and through rasterized data calculation, a meteorological environment around a specific capital construction project construction site can be forecasted and early warned in a relatively exact mode and powerful information assurance of weather forecast aspect can be provided for the safe and smooth conduction of the electric construction.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +2
Method of Identifying and Protecting the Integrity of a Set of Source Data
ActiveUS20130019140A1Verify integrityJoint error correctionCode conversionInformation assuranceOperating system
A method of identifying and protecting the integrity of a set of source data which produces and combines an identification signature with a detection and correction remainder and extends the existing capability of some information assurance methods.
Owner:LRDC SYST
Cyber isolation, defense, and management of a inter-/intra- enterprise network
InactiveUS20120304290A1Memory loss protectionError detection/correctionDemarcation pointTraffic capacity
Methodologies, tools and processes for the cyber isolation, defense, and management of an inter- / intra-enterprise network utilizing NSA-approved Type-1 encryptors to first completely isolate all HardNet fixed and mobile participants from the logical internet. Secondly, to enable inter-corporation traffic exchange while maintaining the established security barrier. Next, to create a network demarcation point through which all traffic shall enter or exit HardNet, and through which all traffic shall be inspected with DoD grade cyber security and information assurance (IA) capabilities. Effective net end result is a weapons-grade cyber security shield and cyber management capability for the business, educational, non-profit, governmental and all other enterprises.
Owner:MCPHAIL LON DANIEL
Balanced retractable whole water pressure drilling and cutting device for soft and hard stratums
ActiveCN108590509APrecision DrillingEffective drillingConstructionsBorehole drivesControl systemSludge
The invention provides a balanced retractable whole water pressure drilling and cutting device for soft and hard stratums and belongs to the technical fields of underground construction rock and earthmass drilling and cutting and underground construction disaster preventing and reducing. The balanced retractable whole water pressure drilling and cutting device includes a power system, a sensing system, a control system, a pressurization system, a balanced retractable system, a sludge discharging system, a supporting and protecting system, a pressure pipeline system and a drilling and cuttingsystem. The device can provide ultrastrong high water pressure to be used as a drilling and cutting power source, and the different soft and hard stratums can be accurately drilled and cut; the drilling and cutting force applied into the hard earth stratum area of a drilling and cutting head is controlled in a quantitative mode and is increased at real time, the drilling and cutting force in the soft earth stratum area can be kept constant, and the stability and accuracy of whole drilling and cutting construction are guaranteed; and the drilling and cutting force in the soft and hard stratumsof the different areas can be fed back quickly in a quantitative mode and information assurance is provided for ensuring that deviation of pile positions does not occur during the underground construction drilling and cutting construction.
Owner:ZHEJIANG UNIVERSITY OF SCIENCE AND TECHNOLOGY
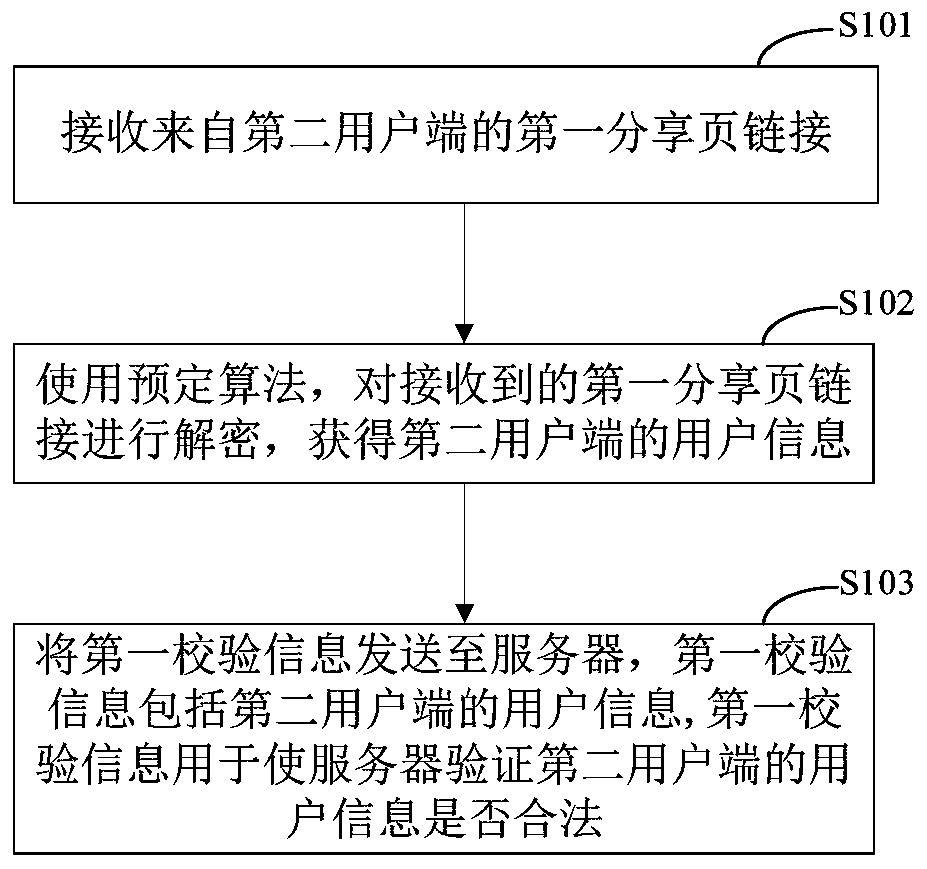
Information sharing method and device, electronic equipment and storage medium
ActiveCN110889124AImprove securityEnsure safetyDigital data protectionDigital data authenticationInformation processingInformation sharing
The invention discloses an information sharing method and device, electronic equipment and a storage medium, and relates to the field of internet information processing. The specific implementation scheme is as follows: receiving a first sharing page link from a second user side; encrypting the first sharing page link, wherein the first sharing page link comprises user information of the second user side; decrypting the received first sharing page link by using a predetermined algorithm to obtain user information of a second user side; sending the first verification information to a server, wherein the first verification information comprises user information of the second user side, and the first verification information is used for enabling the server to verify whether the user information of the second user side is legal or not. According to the embodiment of the invention, the user information is sent only when the first user side and the second user side are both normal user sides, so that the user information is prevented from being intercepted by malicious programs, and the user information security is guaranteed.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Method and system for securely managing application transactions using cryptographic techniques
InactiveUS20070011459A1User identity/authority verificationMultiple digital computer combinationsCredit cardNetwork management application
A method and system for secure managing transactions between application devices over a network. The present invention provides a method and system for receiving data from an application device, such as computer workstation, ATM, credit card point-of-sale terminal, or application software, and transferring that data securely over a network to a recipient application device. The method and system provide secure cryptographic key and enterprise management of embedded, standalone and tightly coupled information assurance components.
Owner:INNOVE
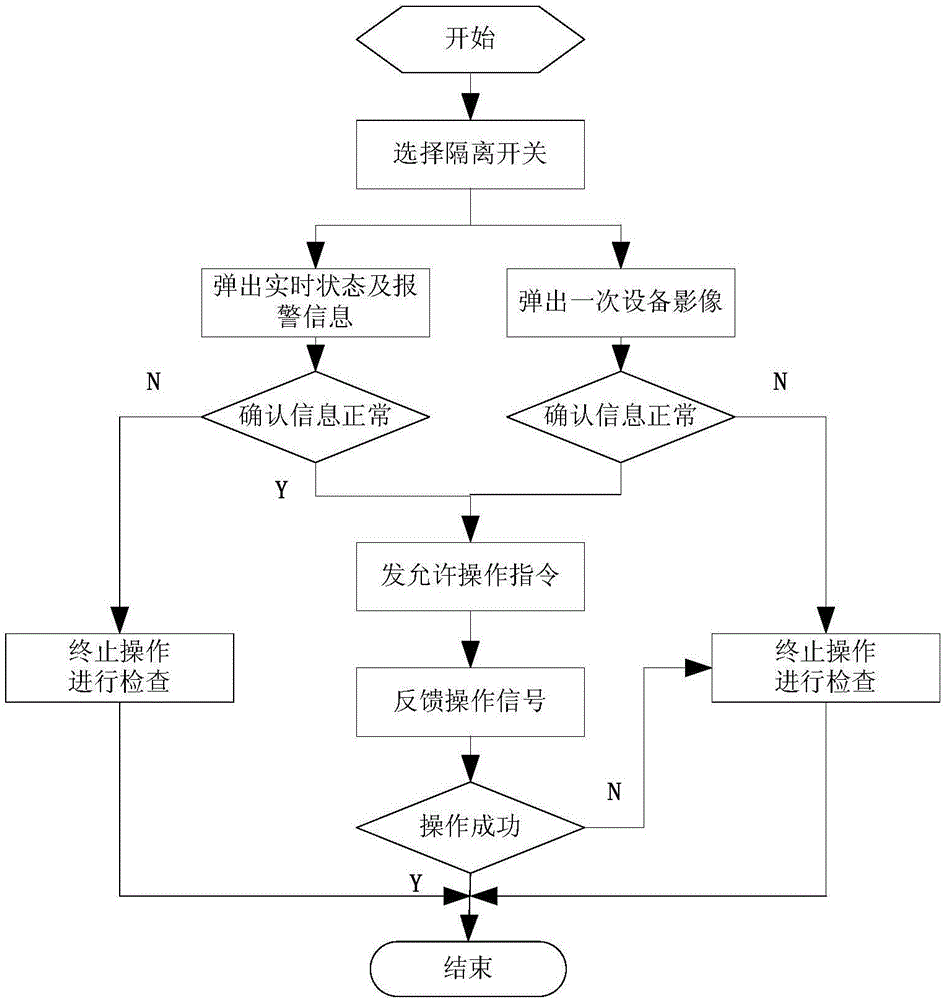
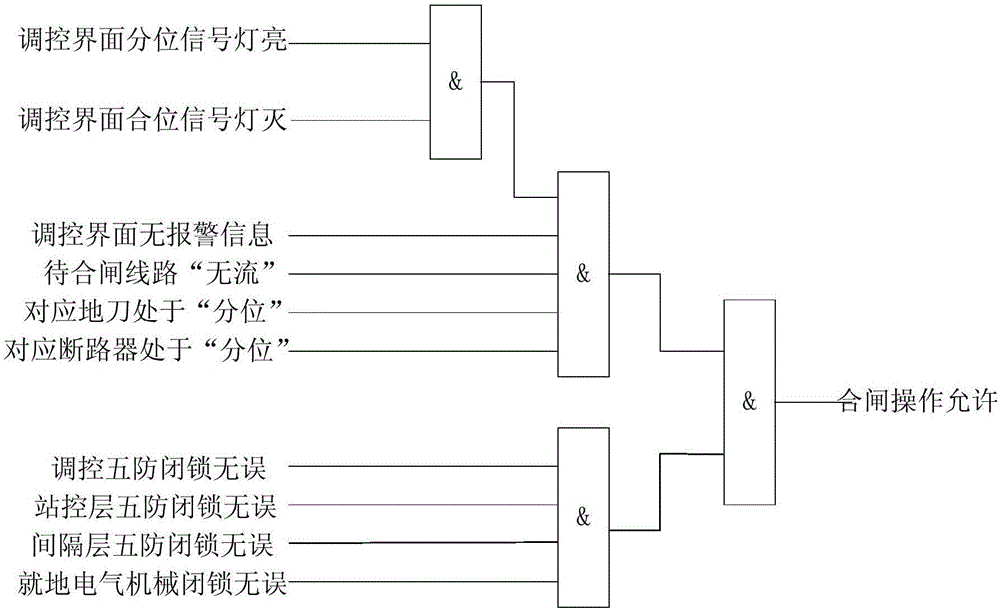
Remote switching operation method based on comprehensive visualization and anti-error topology analysis
ActiveCN106208372AEffective monitoringSafety Guarantee Operational SafetyCircuit arrangementsInformation technology support systemOperation modeDependability
The invention discloses a remote switching operation method based on comprehensive visualization and anti-error topology analysis, and belongs to the field of transformer substation dispatching control. Through the technical scheme, comprehensively visual online monitoring of an isolating switch is combined with a security protection technology based on four-layer anti-error topology, so that the security and reliability of remote operation projects of the isolating switch at a dispatching end are guaranteed. The method consists of two aspects, namely a visual operation mode and four-layer anti-error security assurance. Through the visual operation mode, reliable information assurance is supplied for the operation of the isolating switch, and the state of the isolating switch can be effectively monitored under an unattended condition; and through four-layer anti-error locking, the reliability of the operation is guaranteed, switching misoperation can be effectively avoided, and the security of the operation is guaranteed.
Owner:STATE GRID CORP OF CHINA +1
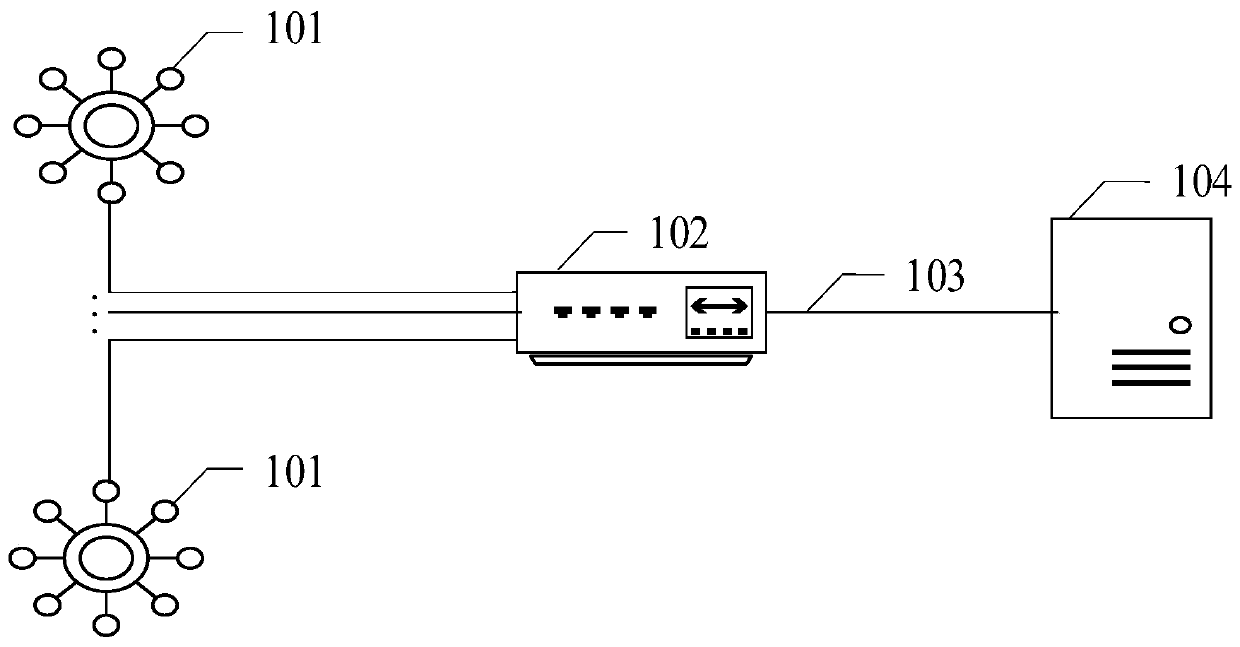
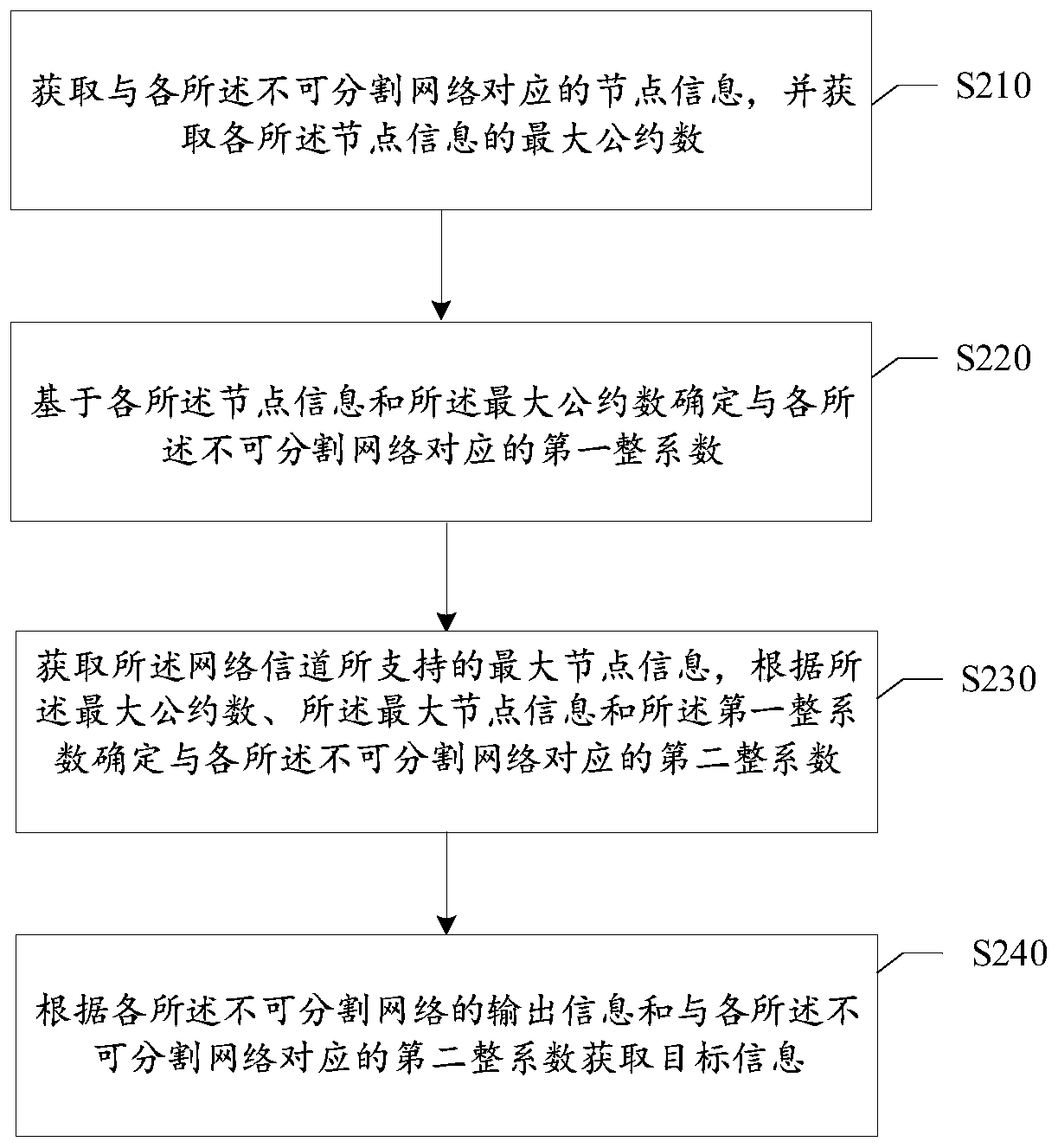
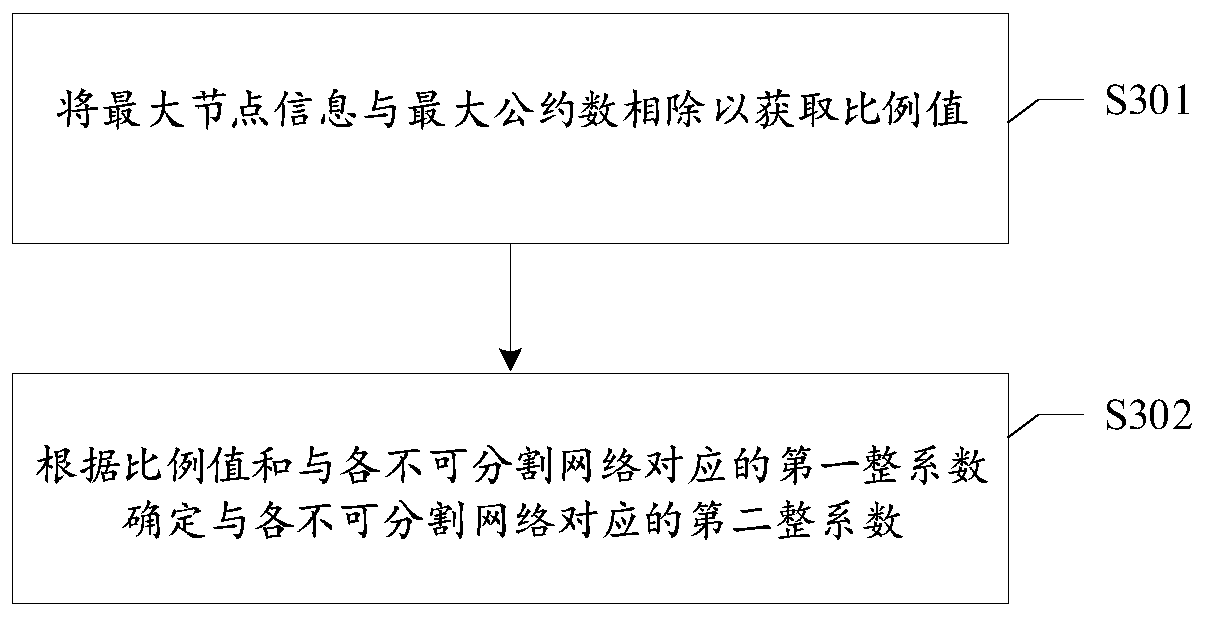
Network regulation and control method and device, network regulation and control system and electronic equipment
ActiveCN111327473AHigh precisionIntegrity guaranteedData switching networksComputer networkInformation support
The invention provides a network regulation and control method and device, is applied to a network regulation and control system, and relates to the field of network regulation and control. The network regulation and control system comprises a plurality of inseparable networks and network channels, and the inseparable networks are networks of which network structures and output information cannotbe segmented; the method comprises the following steps: acquiring node information corresponding to each inseparable network, and acquiring the greatest common divisor of each piece of node information; determining a first integer coefficient corresponding to each inseparable network based on each piece of node information and the greatest common divisor; obtaining maximum node information supported by a network channel, and determining a second integer coefficient corresponding to each inseparable network according to the greatest common divisor, the maximum node information and the first integer coefficient; and obtaining target information according to the output information of each inseparable network and the second integer coefficient corresponding to each inseparable network. According to the method and the device, the network information which has the maximum information amount and is embedded with the information of each inseparable network can be obtained, the integrity of theinformation is guaranteed, and the accuracy of the target information is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Secure layered iterative gateway
ActiveUS8973138B2Reduce attackReduce attack surfaceMemory loss protectionError detection/correctionOperational systemCyber-attack
In methods and a device for mitigating against cyber-attack on a network, a distributed intermediary device is placed into a network between computers or network nodes of the network to mitigate cyber-attacks between the computers or nodes of a network from remote systems. Threats are assessed by utilizing internal information assurance mechanisms of the device to detect such cyber-attacks without requiring external modification of the software and / or hardware of the computers or nodes of the network to be protected. The device prevents attacks at the platform level against the OS and network resources.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
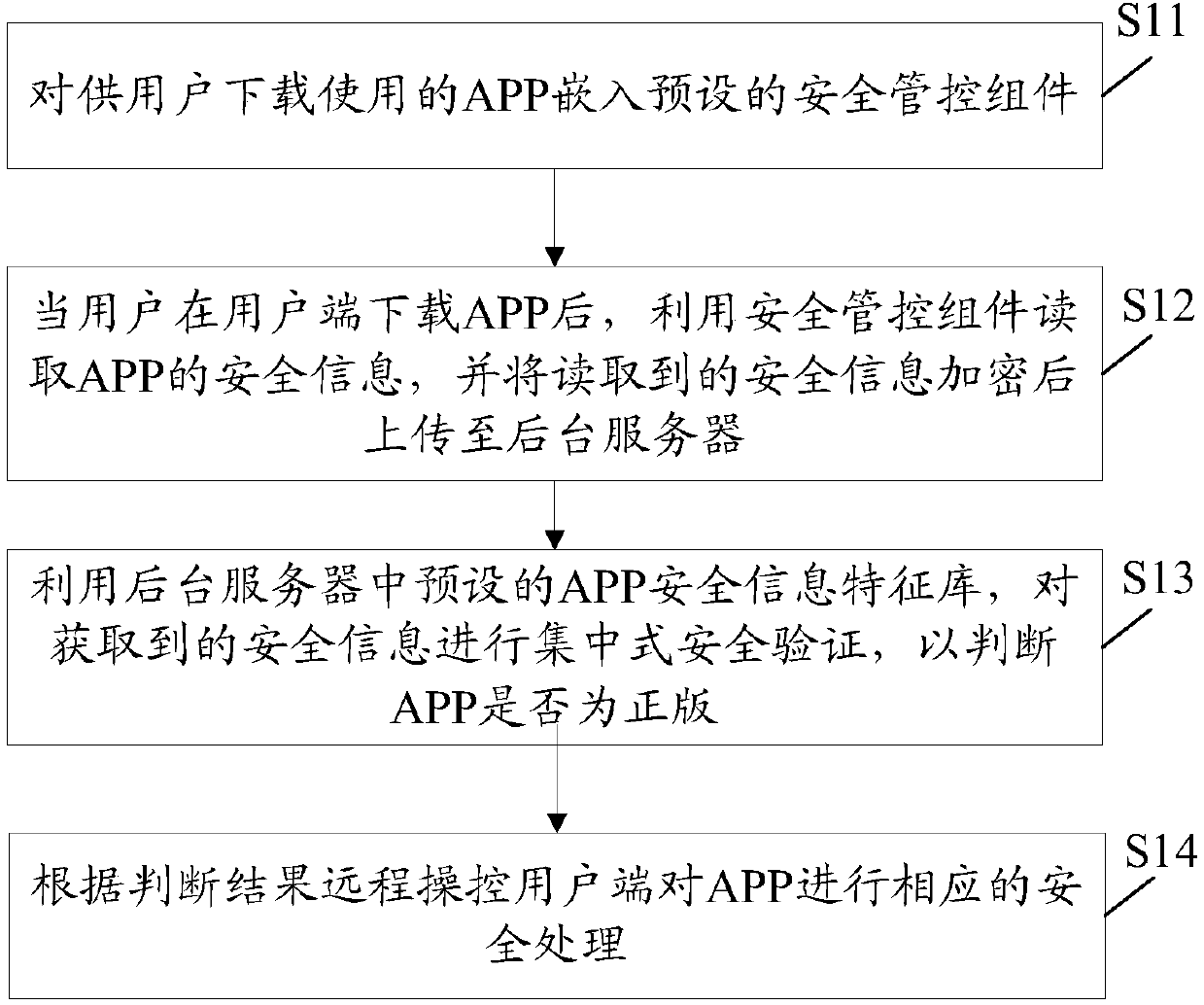
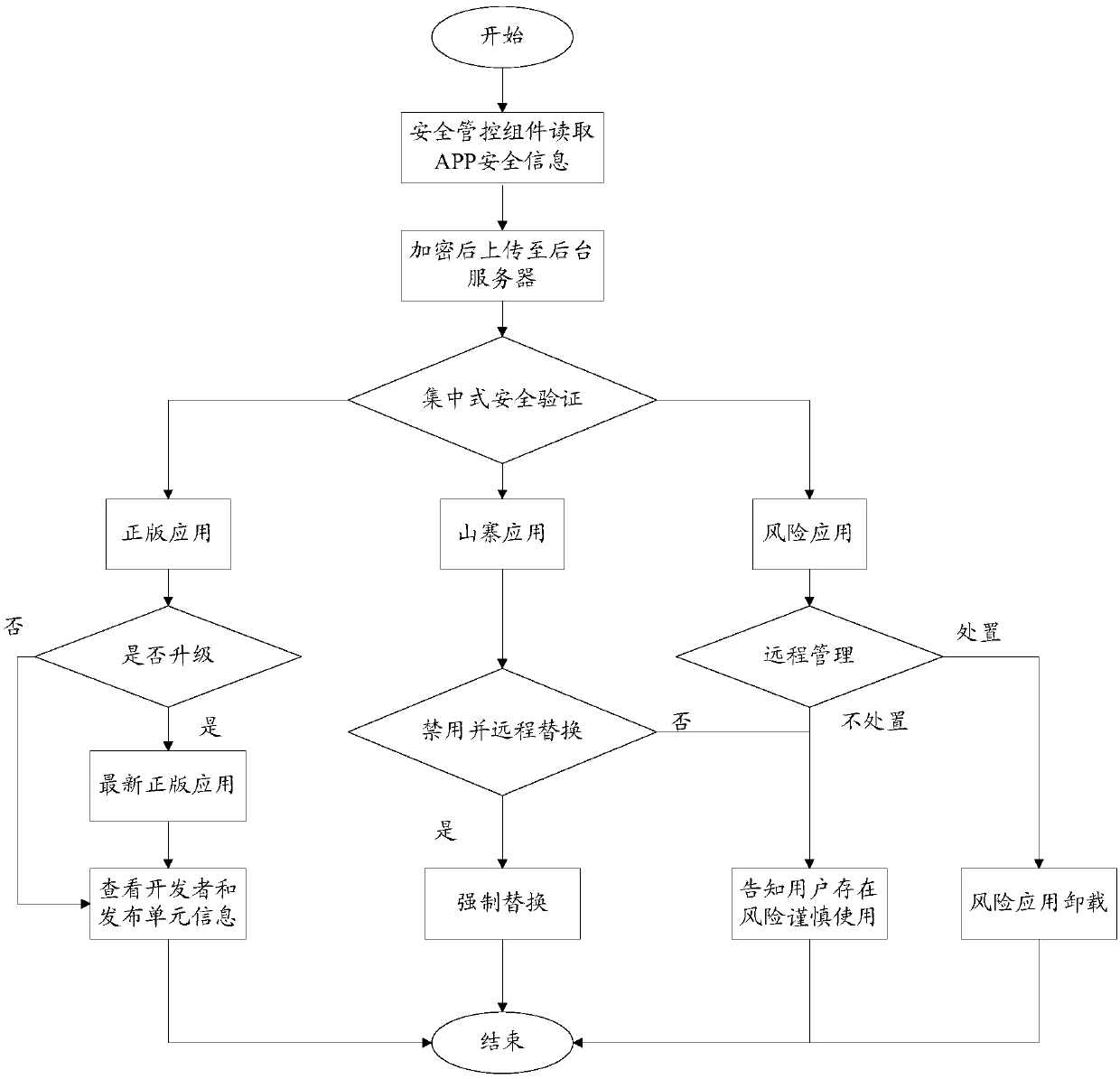
APP remote tracking protection method and system
InactiveCN109583157AEnsure safetyGuarantee authenticityProgram/content distribution protectionSafe handlingSecurity validation
The invention discloses an APP remote tracking protection method and system. The method comprises the following steps of: obtaining a sample; embedding A preset security management and control component into an APP downloaded and used by a user; downloading an APP at a user side by a user; the security management and control assembly is used for reading security information of the APP; The methodcomprises the steps of reading security information of an APP, encrypting the read security information, uploading the encrypted security information to a background server, carrying out centralized security verification on the obtained security information by utilizing a preset APP security information feature library in the background server to judge whether the APP is a genuine version or not,and remotely controlling a user side to carry out corresponding security processing on the APP according to a judgment result. On the premise that the original signature is not changed, the security information of the APP is obtained through the security control assembly and transmitted to the background server in an encrypted mode, the background server is used for conducting remote centralized security verification on whether the version of the APP is hillside or not, and the security, authenticity and reliability of the information are guaranteed through encryption transmission of the application information.
Owner:卓望数码技术(深圳)有限公司
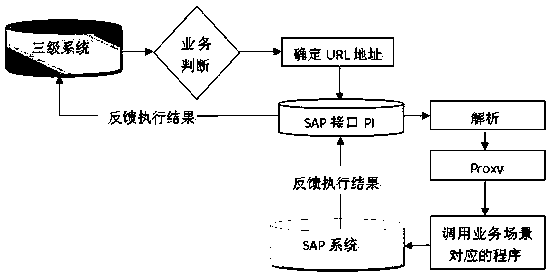
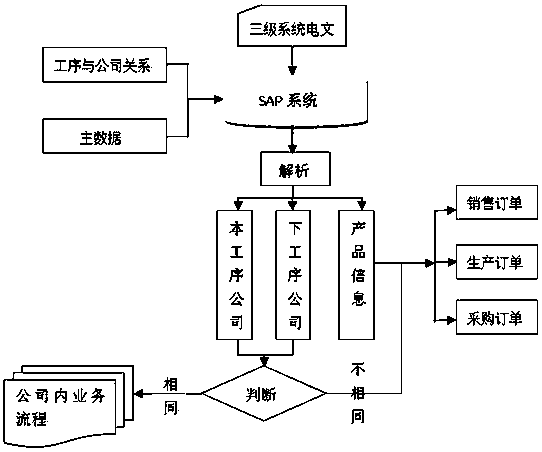
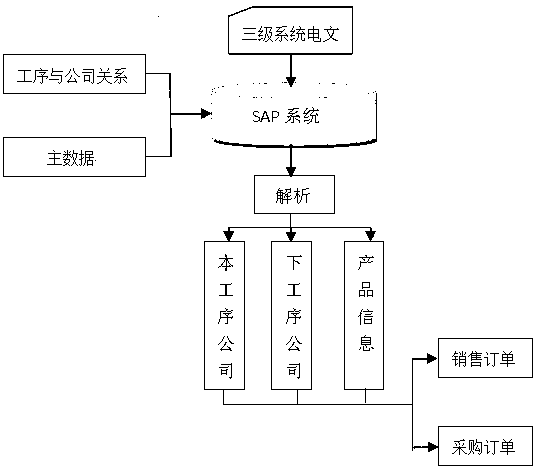
SAP-based method for automatically creating internal reciprocation business order in iron and steel industry
ActiveCN110322190AMeet business needsSimplify business operationsBuying/selling/leasing transactionsLogisticsLogistics managementTransaction service
The invention relates to an SAP-based iron and steel industry internal transaction service order automatic creation method, which comprises the steps of establishing a data platform in an SAP system,and providing a data basis for processing inter-company service circulation; setting a timing task in the SAP system, and achieving timing updating of the data platform; setting an interface specification for the SAP system to receive inter-company transaction service messages; analyzing the message information, and automatically creating an inter-company business order; and automatic monitoring business order creation between companies. According to the invention, dynamic creation of orders in a business exchange process between companies in an iron and steel enterprise group is realized; product information and company information in cross-company businesses are obtained by means of building a data platform, designing external interfaces and the like, accuracy and uniqueness of data in the logistics allocation process are guaranteed, meanwhile, wrong order data are automatically checked and processed through programs, business requirements are met, meanwhile, business operation is simplified, and working efficiency is improved.
Owner:TANGSHAN IRON & STEEL GROUP +1
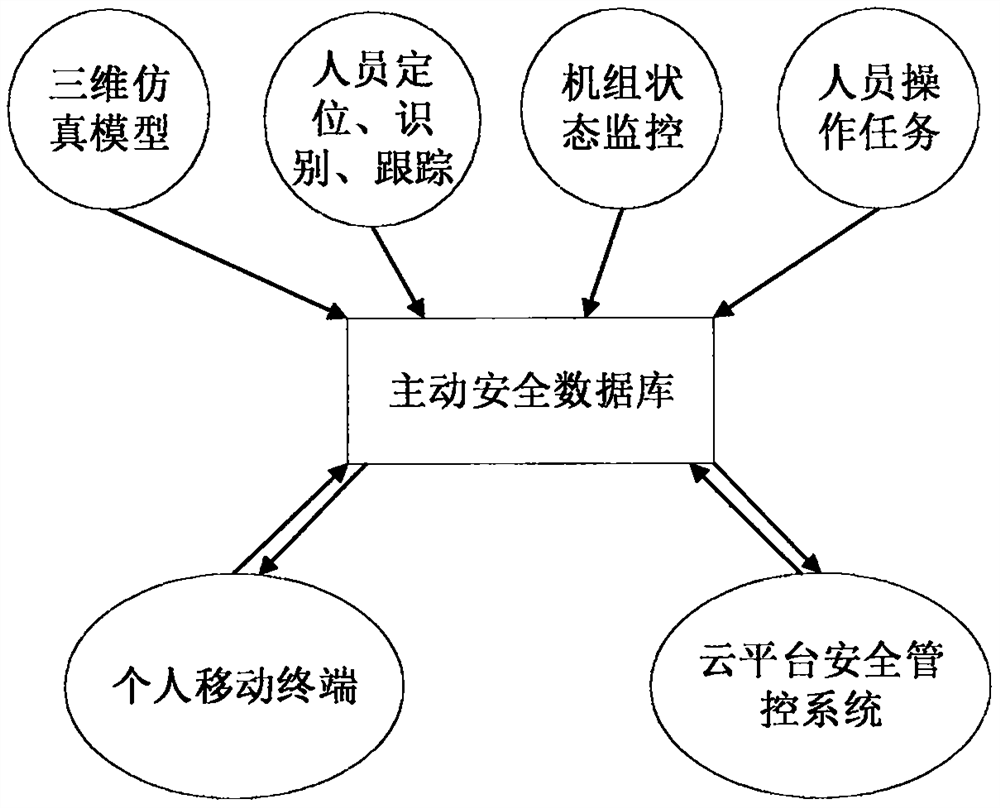
Complex environment intelligent safety management and control system based on multi-source data fusion
PendingCN111813841ARealize on-site monitoringImplement error correctionData processing applicationsDatabase management systemsDaily operationOnline and offline
The invention provides a complex environment intelligent security management and control system based on multi-source data fusion, which is applied to the field of electric power. According to the system, an on-site three-dimensional lightweight model is established, the position information of personnel, the working state of a unit and the operation content of monitoring personnel are positioned,and multi-source fusion of online and offline data, qualitative and quantitative data and the like is realized, so that an active safety database is established. According to the invention, online monitoring of a network cloud platform is supported, and task access of an intelligent mobile terminal is also supported. For a management layer, comprehensive information of the unit can be monitored in real time, and daily operation content can be audited; for on-site personnel, the state information of work and construction sites can be obtained in time, and the personal safety is guaranteed; forthe system, according to preset settings, bad states and misoperation can be prompted and alarmed in time, potential safety hazards are reduced, and the efficiency is improved.
Owner:华电忻州广宇煤电有限公司 +1
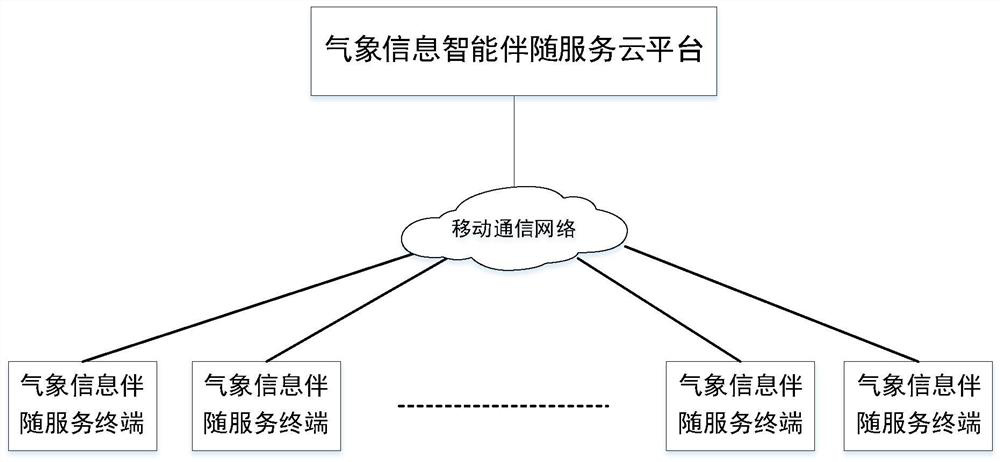
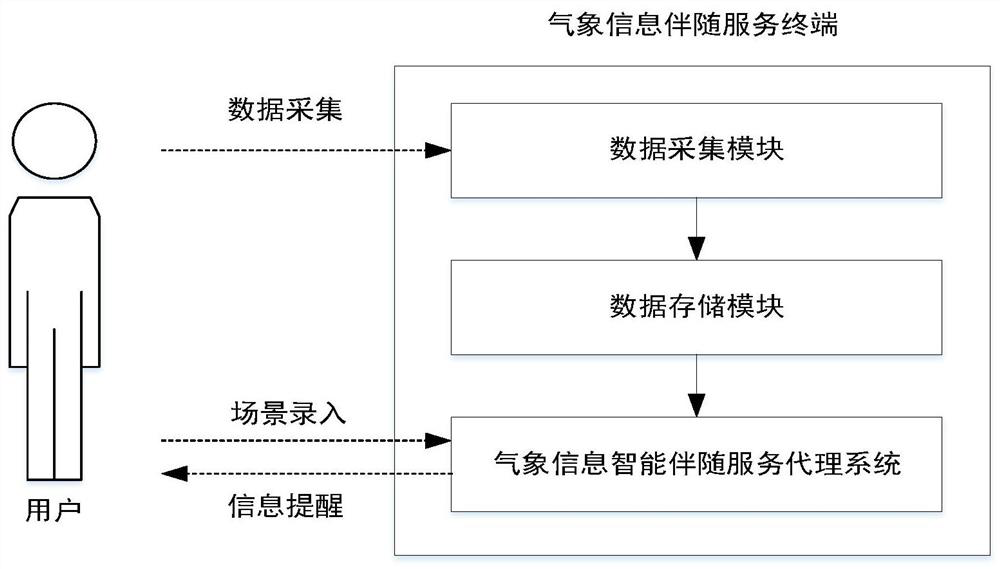
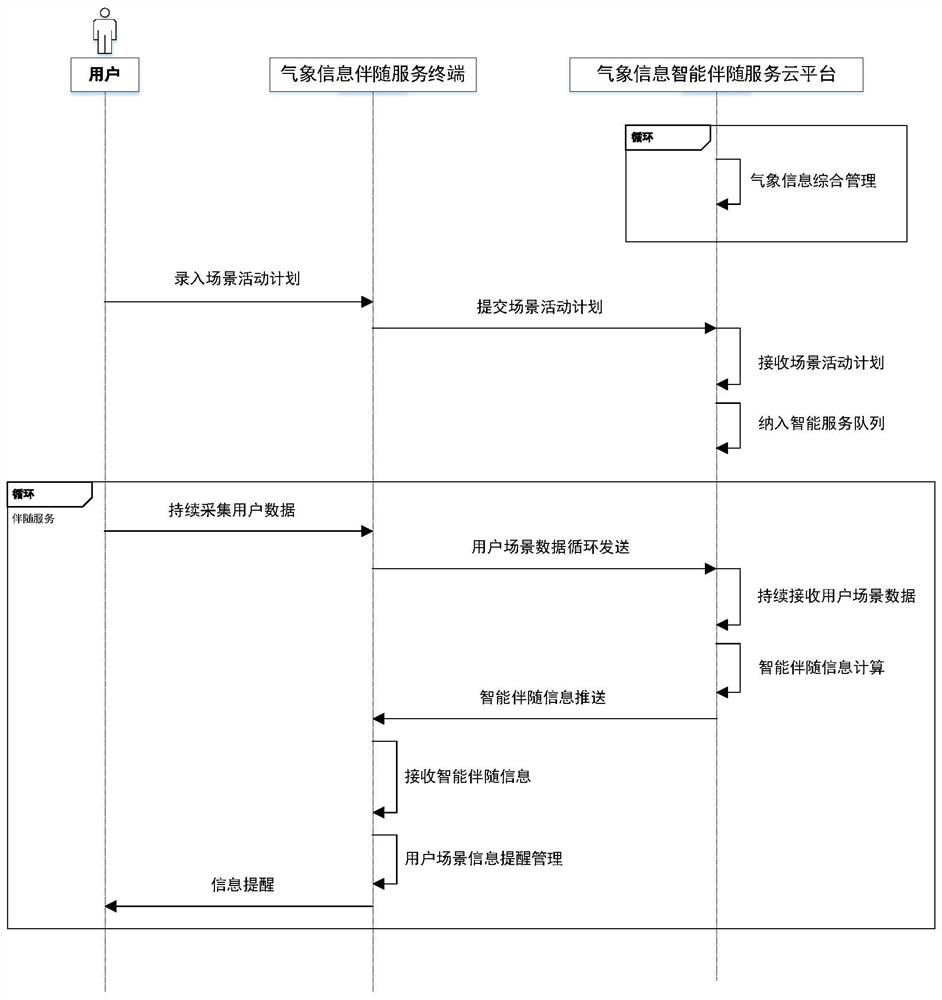
Multi-scene-oriented meteorological information intelligent accompanying service system and method
PendingCN114757584AReduce potential weather risksSafe completionOffice automationResourcesWeather riskActivity time
The invention discloses a multi-scene-oriented meteorological information intelligent accompanying service system and method, the system adopts a'cloud + end 'architecture, a cloud platform can monitor and sense the activity process of a user end in real time, and comprehensive reminding services such as meteorological information meeting the requirements of the scene are provided for the user end before, during and after the activity time period of the user end; the service content comprises weather live information, weather forecast information, weather risk early warning information and various important prompt information of activity scenes. By customizing the service, the user can timely and effectively obtain the meteorological environment information comprehensive service pushed by the cloud platform in a single scene or multiple scene activities, and effective information guarantee is provided for safely and efficiently completing the scene activities.
Owner:NAT UNIV OF DEFENSE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com