Lightweight authentication method for supporting anonymous access of heterogeneous terminal in edge computing scene
A lightweight authentication and edge computing technology, applied in user identity/authority verification and key distribution, can solve the problems of not supporting anonymity and the authentication system being overwhelmed, and achieve the effect of improving the efficiency and privacy of identity authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be described in detail below in conjunction with the accompanying drawings.
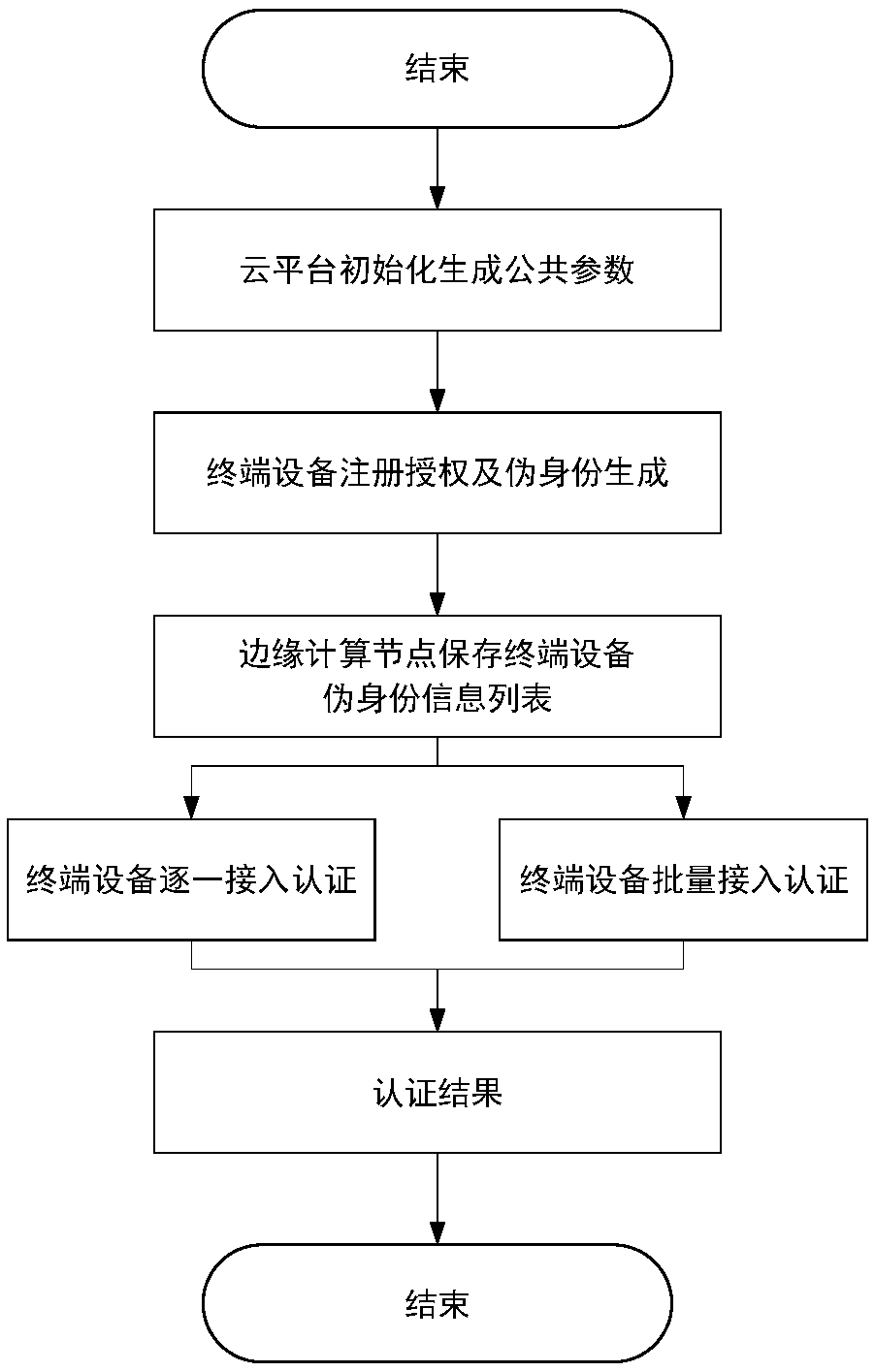
[0038] Such as figure 1 As shown, the terminal lightweight access authentication mechanism supporting anonymity in the edge computing scenario includes three entities, namely the cloud platform, edge computing nodes and terminal devices. The cloud platform is responsible for issuing disguised identity information for each terminal device, and the edge Computing nodes can perform identity authentication on connected terminal devices.
[0039] Such as figure 2 As shown, a lightweight authentication mechanism that supports anonymous access of heterogeneous terminals in an edge computing scenario includes the following steps:
[0040] 1) Initialization stage: the cloud platform will first initialize and generate its own public-private key pair and master key information, and then use the master key information to calculate and publicize public parameter information, w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com