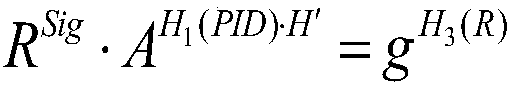Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
199 results about "Node authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
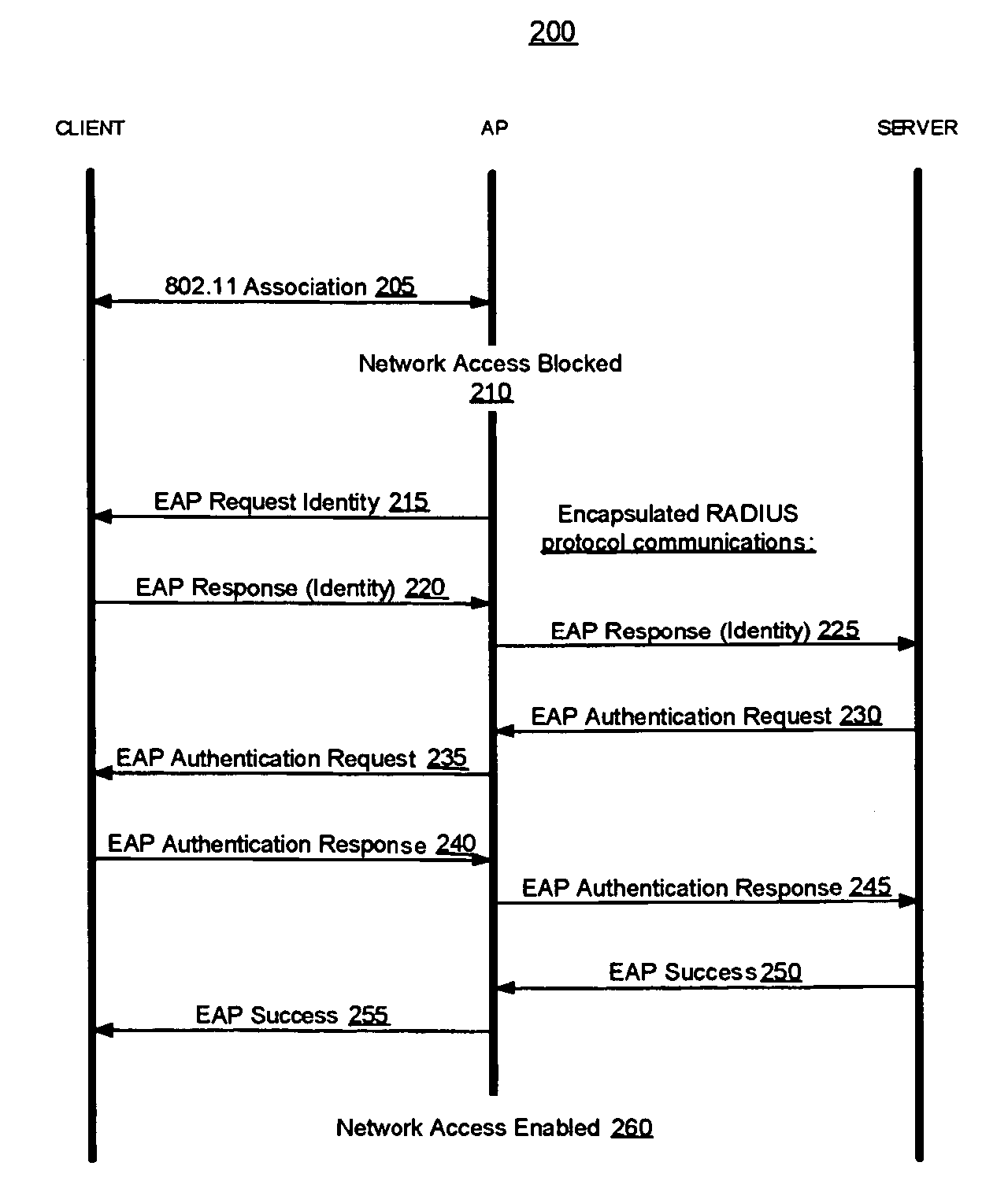
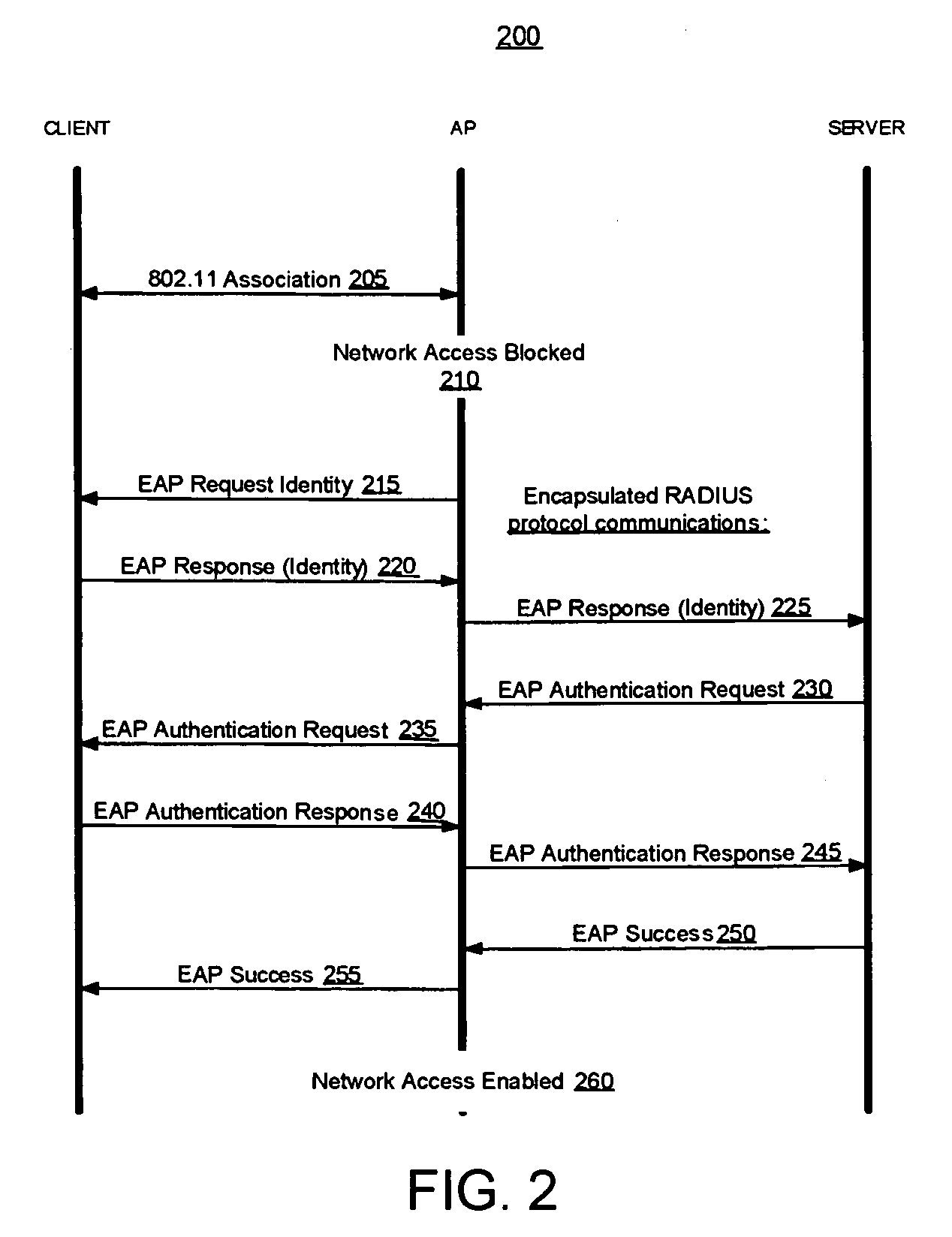
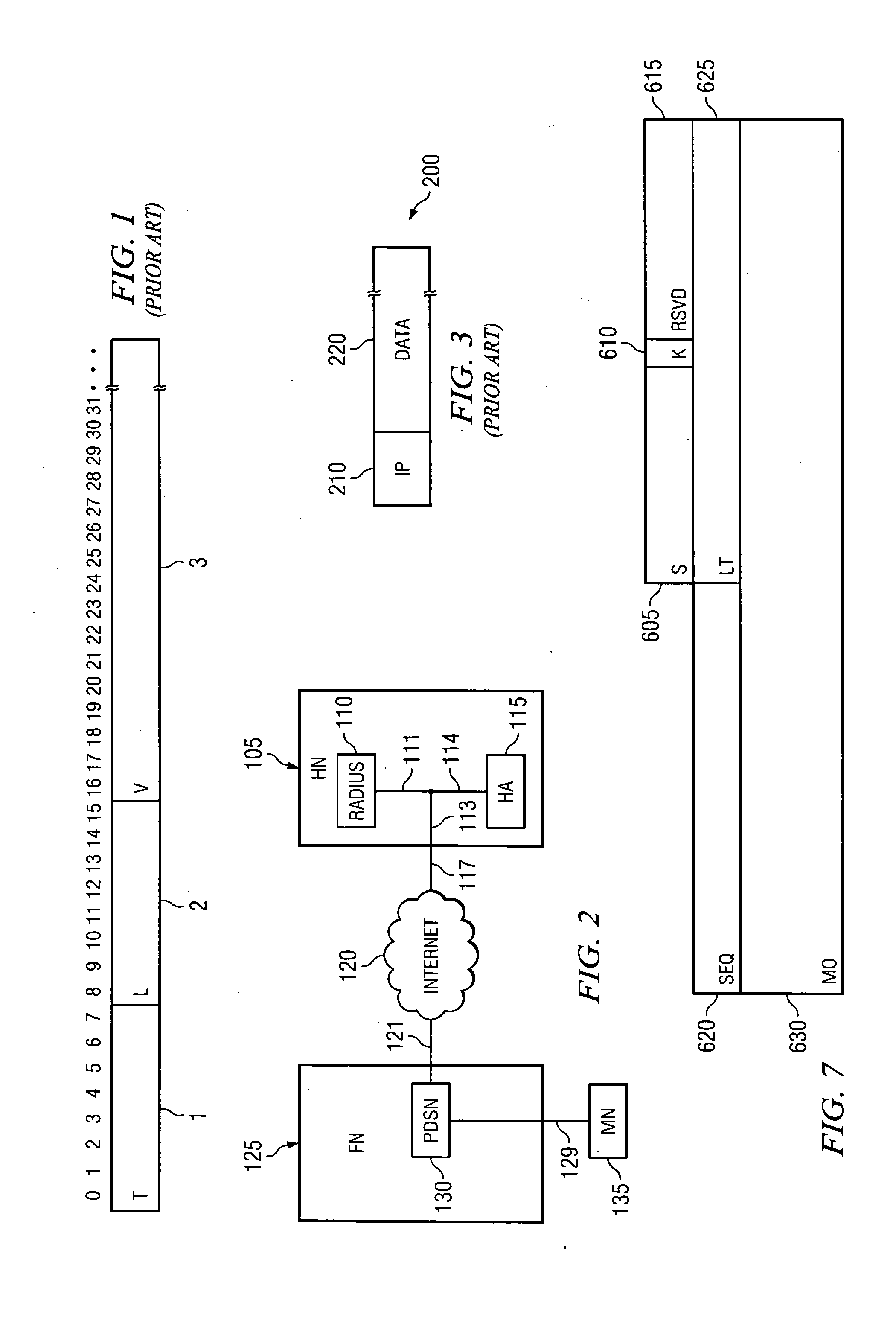
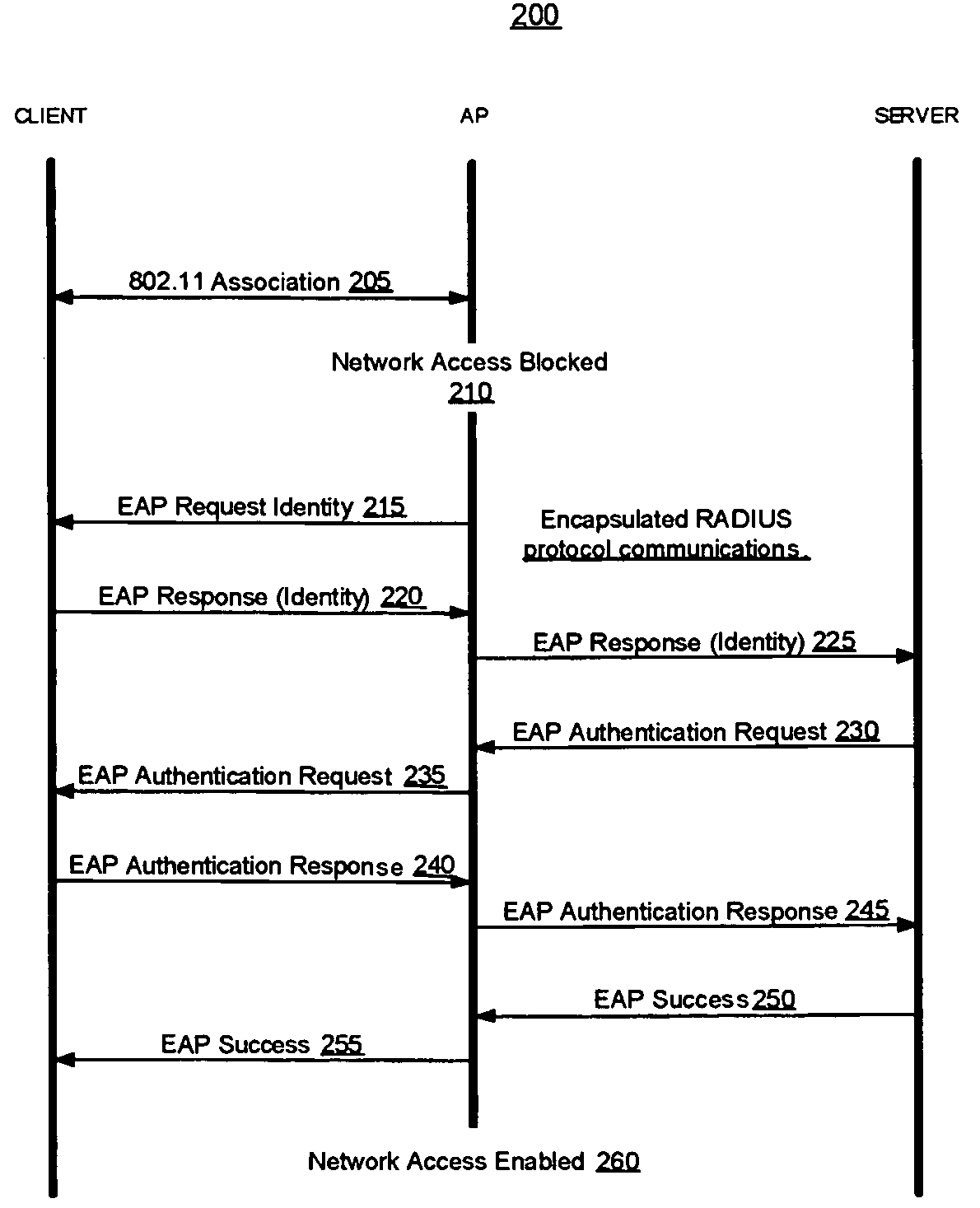
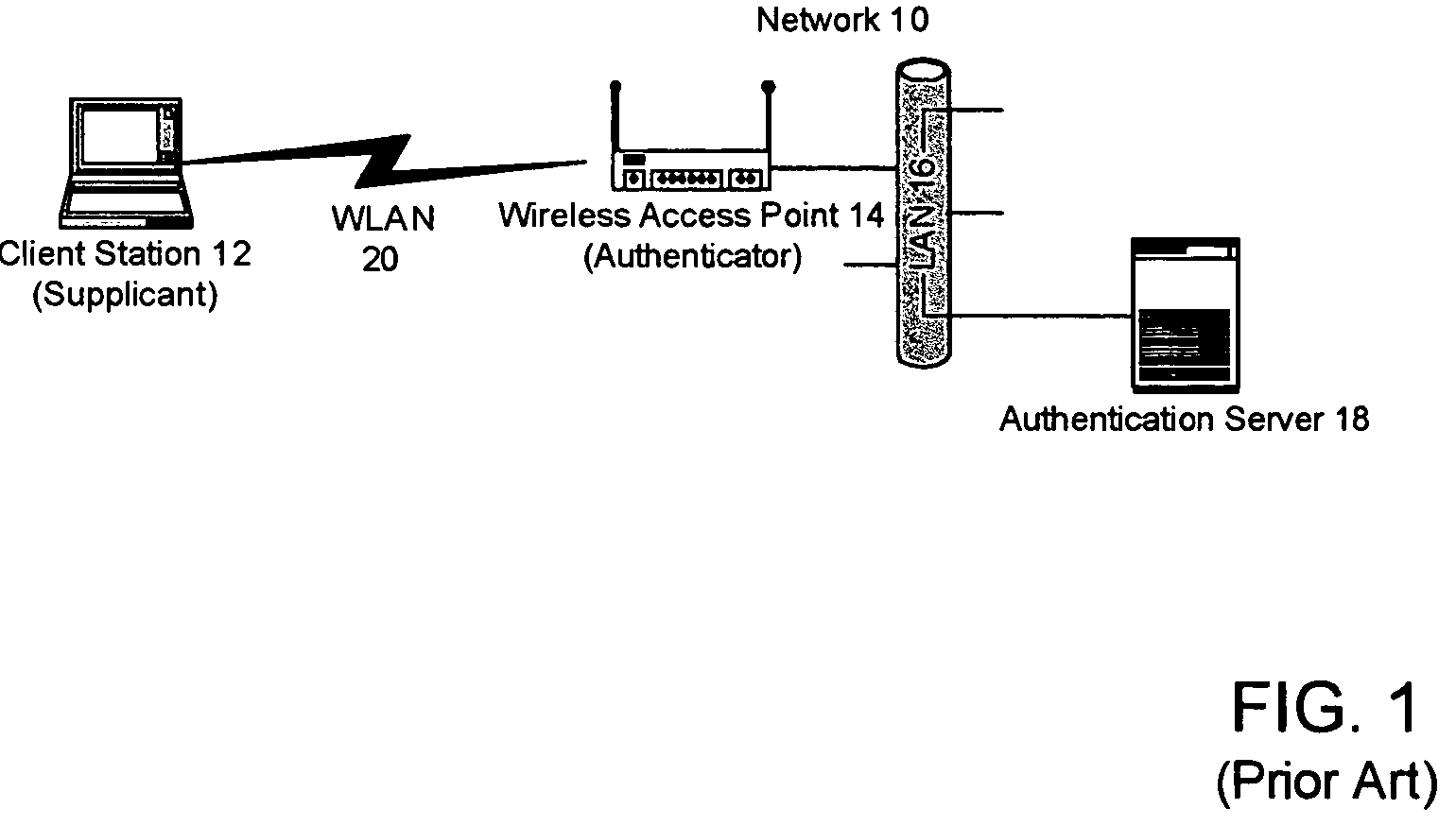
Methods and systems of remote authentication for computer networks
InactiveUS20050021979A1Computer security arrangementsSecret communicationUnique identifierAuthentication server
As part of a network node authentication process, a MAC address or other globally unique identifier of an access point through which the network node will access a computer network is transmitted in an EAP or other authentication message to an authentication server to uniquely identify the access point to the authentication server.
Owner:MCAFEE LLC
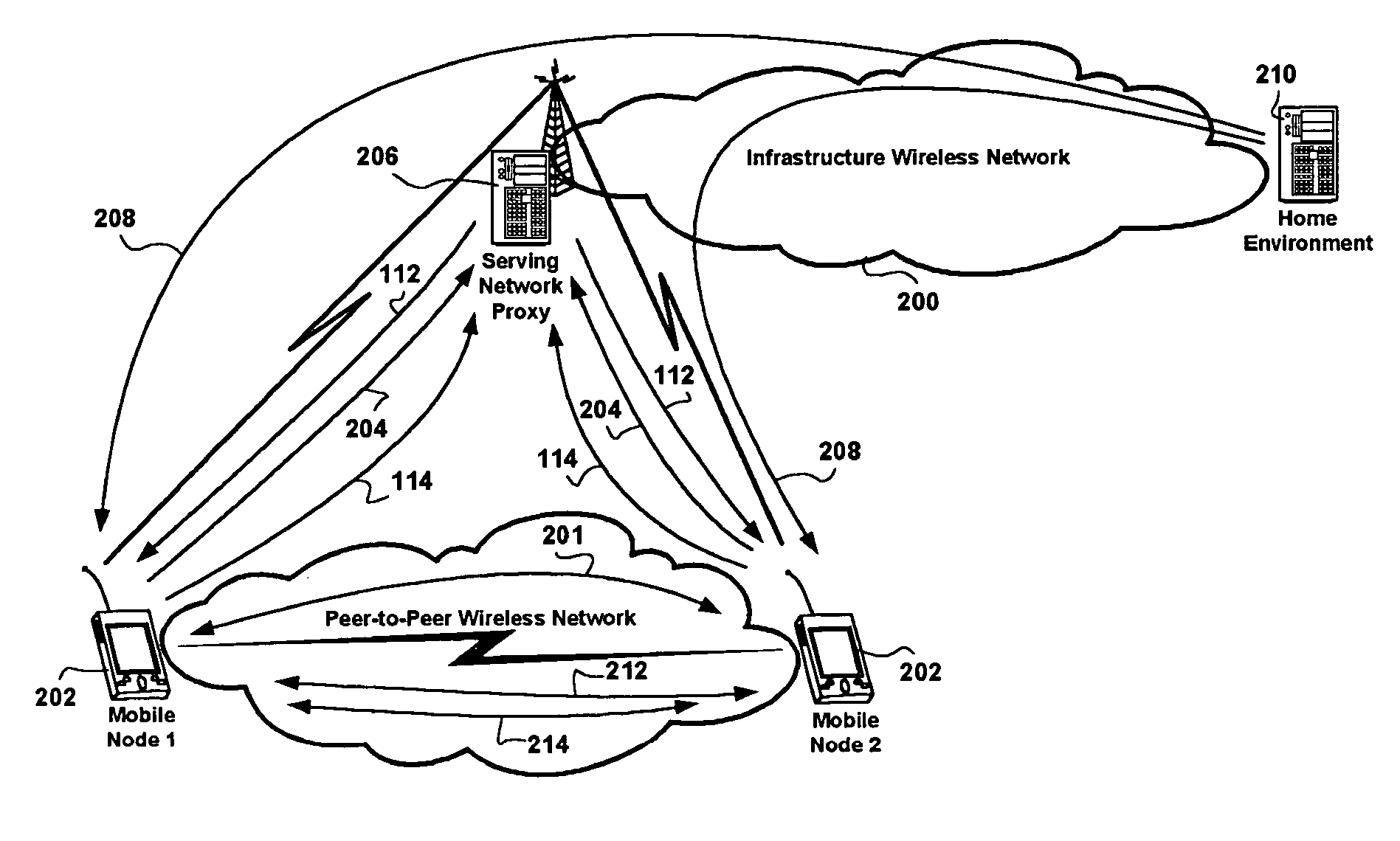
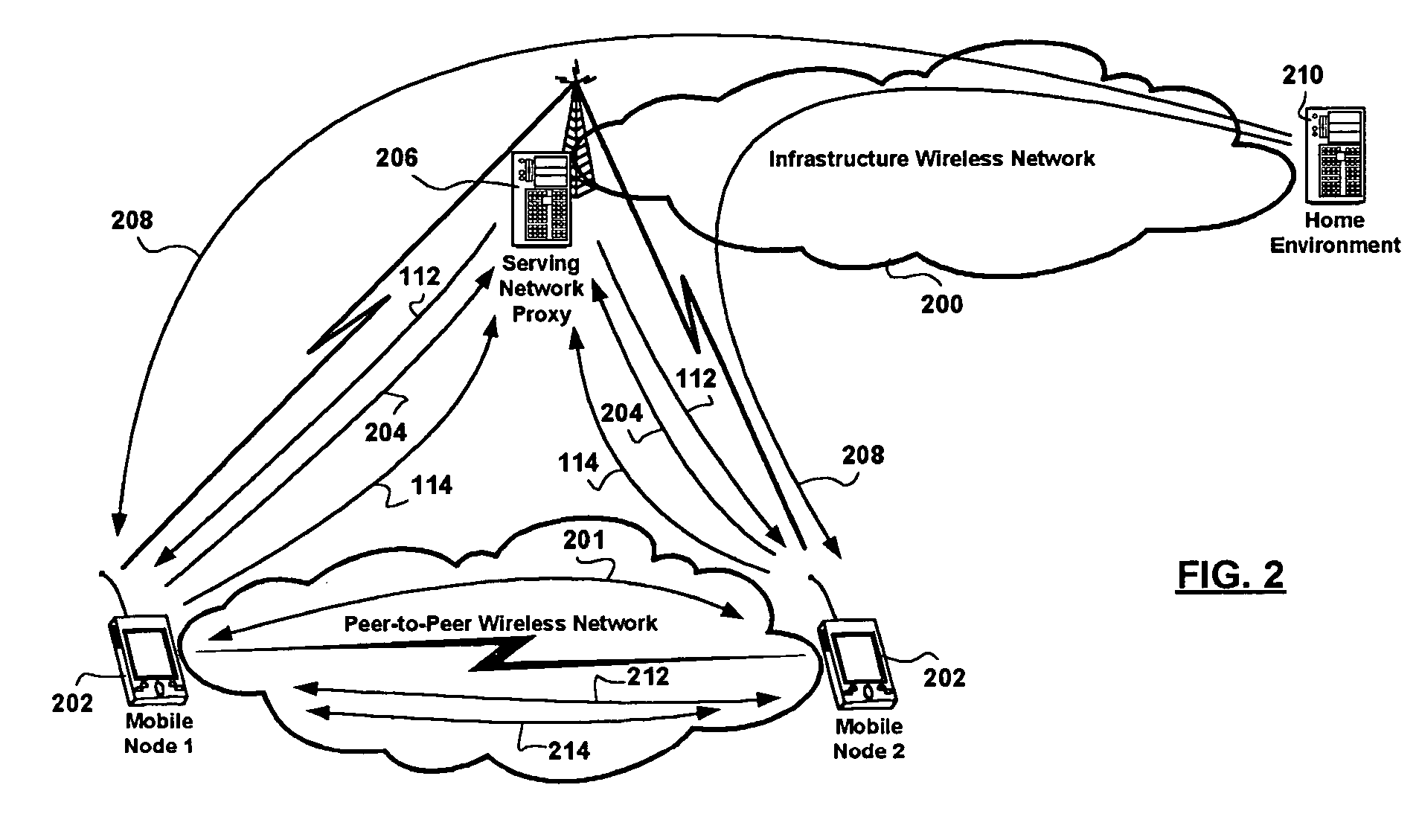
Method of authenticating a mobile network node in establishing a peer-to-peer secure context between a pair of communicating mobile network nodes
ActiveUS20060087999A1Near-field transmissionUnauthorised/fraudulent call preventionSecure communicationSecret code
Methods for authenticating peer mobile network nodes for establishing a secure peer-to-peer communications context in an ad-hoc network are presented. The methods include accessing wireless infrastructure network entities at low bandwidth and for a short time duration to obtain cryptographic information regarding a peer mobile network node for the purpose of establishing secure peer-to-peer communications therewith ad-hoc network. Having received cryptographic information regarding a peer mobile network node, the method further includes challenging the peer network node with a challenge phrase derived from the cryptographic information received, receiving a response, and establishing a secure communications context to the peer mobile network node based on the validity of the received response. Advantages are derived from addressing security threats encountered in provisioning ad-hoc networking, by leveraging wireless infrastructure network security architecture, exemplary deployed in UMTS / GSM infrastructure networks, enabling seamless mobile network node authentication through the existing UMTS and / or GSM authentication infrastructure, while pervasively communicating with peer mobile network nodes in an ad-hoc network.
Owner:ALCATEL LUCENT SAS
Internet connection service method, system, and medium for mobile nodes
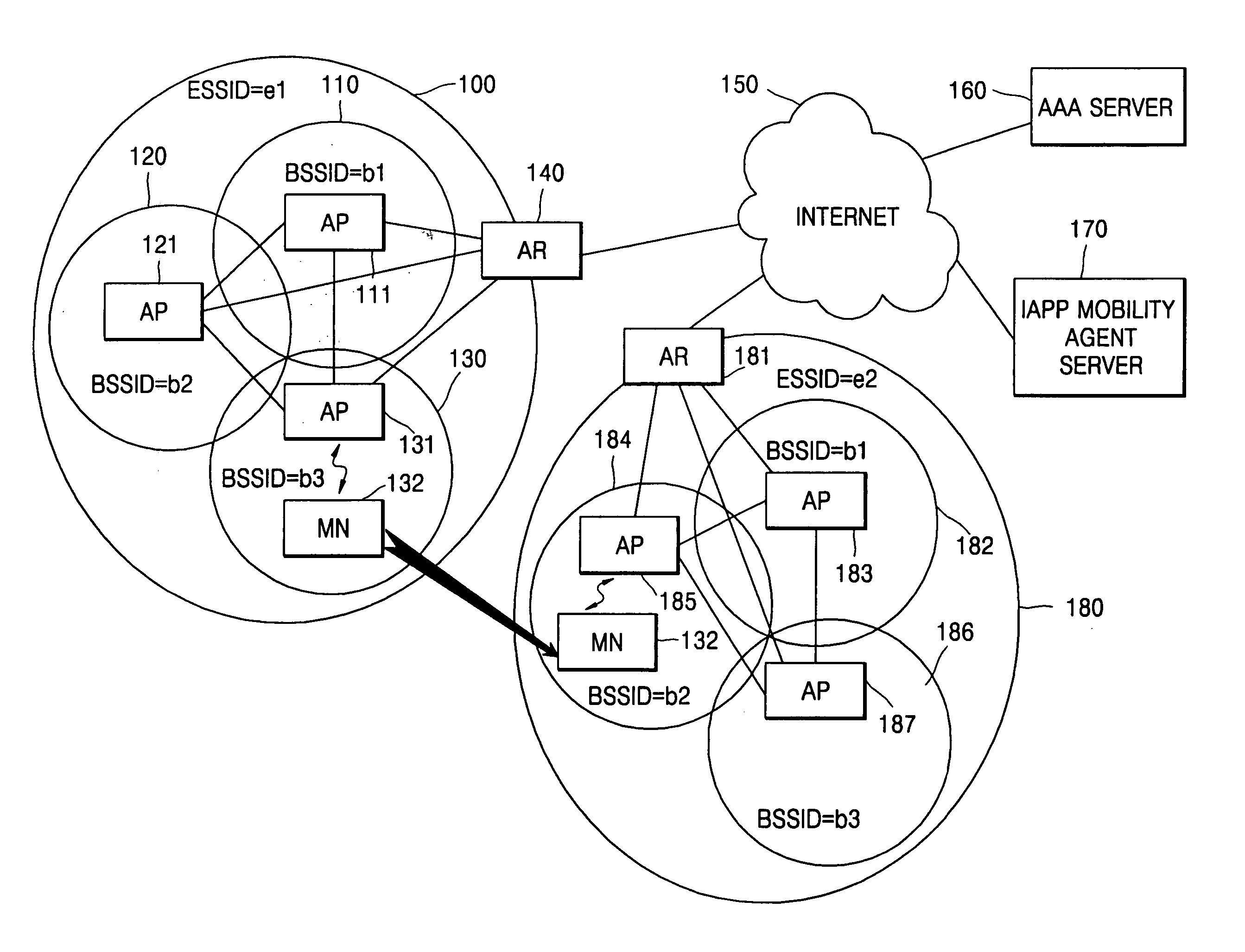
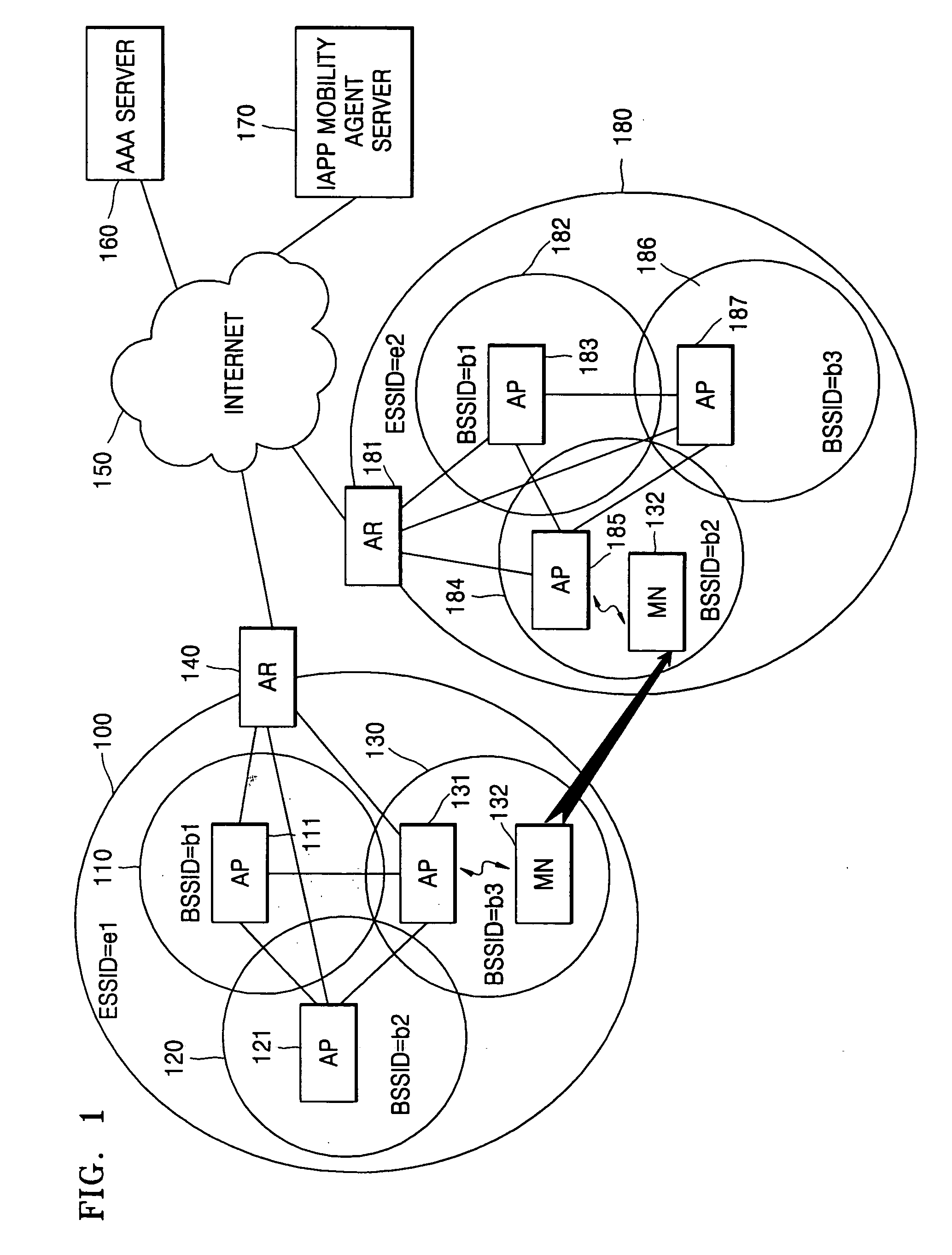
InactiveUS20050220048A1Quick switchSimple processData switching by path configurationWireless network protocolsInter-Access Point ProtocolThe Internet
An Internet connection service method, system, and medium used with mobile nodes. The Internet connection service method, system, and medium can switch a mobile node between network service areas having different extended service set identifiers (ESSIDs) by simplifying a process of re-authenticating a mobile node. The Internet connection service method includes: receiving an inter-access point protocol (IAPP) message containing authentication information on the mobile node from an access point (AP) of a network service area, to which the mobile node currently belongs; and transmitting the IAPP message to an AP of at least one network service area having different identification information from the network service area, to which the mobile node currently belongs.
Owner:SAMSUNG ELECTRONICS CO LTD
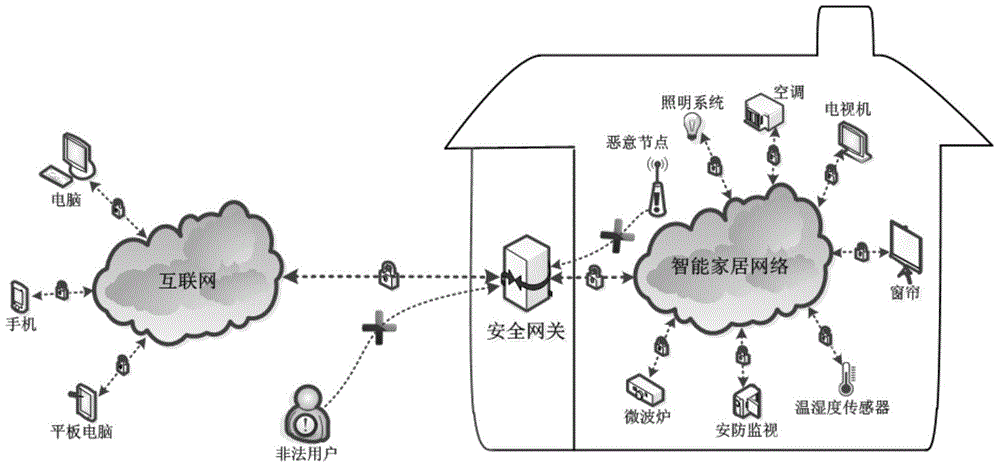
Internet of Things smart home security gateway system
ActiveCN104580233AEnhanced defense against attacksRealize free decouplingUser identity/authority verificationNetwork connectionsThe InternetSecure authentication
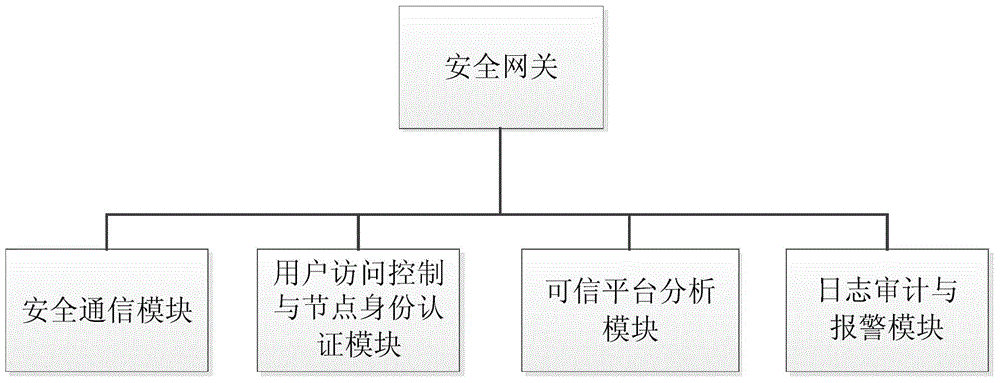
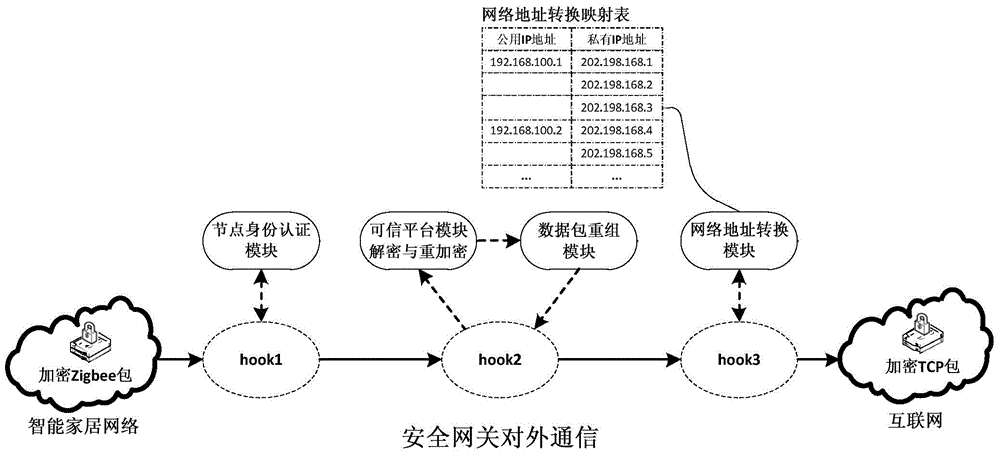
The invention relates to an Internet of Things smart home security gateway system. The system comprises a user side, a security gateway and a terminal node. The user side and the terminal node each comprise a data encrypting / decrypting module used for encrypting / decrypting a sent control order and received data through a preset encrypting program on a remote client side or the terminal node; the security gateway comprises a safety communication module, a user access control and node identity authentication module, a credible platform module and a log audit and alarm module; the safety communication module achieves data safety filtering, reconstructing and forwarding and guarantees safety of the bi-direction transmission; the credible platform module is used for achieving system safety authentication, user behavior credibility analysis, data sealing storage and free decoupling and can be independently maintained and upgraded; the log audit and alarm module is used for recording user access and node authentication behaviors, carrying out safety audit on the operation of viewing logs and giving a timely alarm for an abnormal phenomenon found in the gateway system safety monitoring process. By means of the Internet of Things smart home security gateway system, the safety performance of a smart home system and the running efficiency of a gateway can be improved, and a safety guarantee is provided for Internet of Things smart home.
Owner:重庆中邮信科集团股份有限公司
Method for a Dynamic Perpetual Encryption Cryptosystem
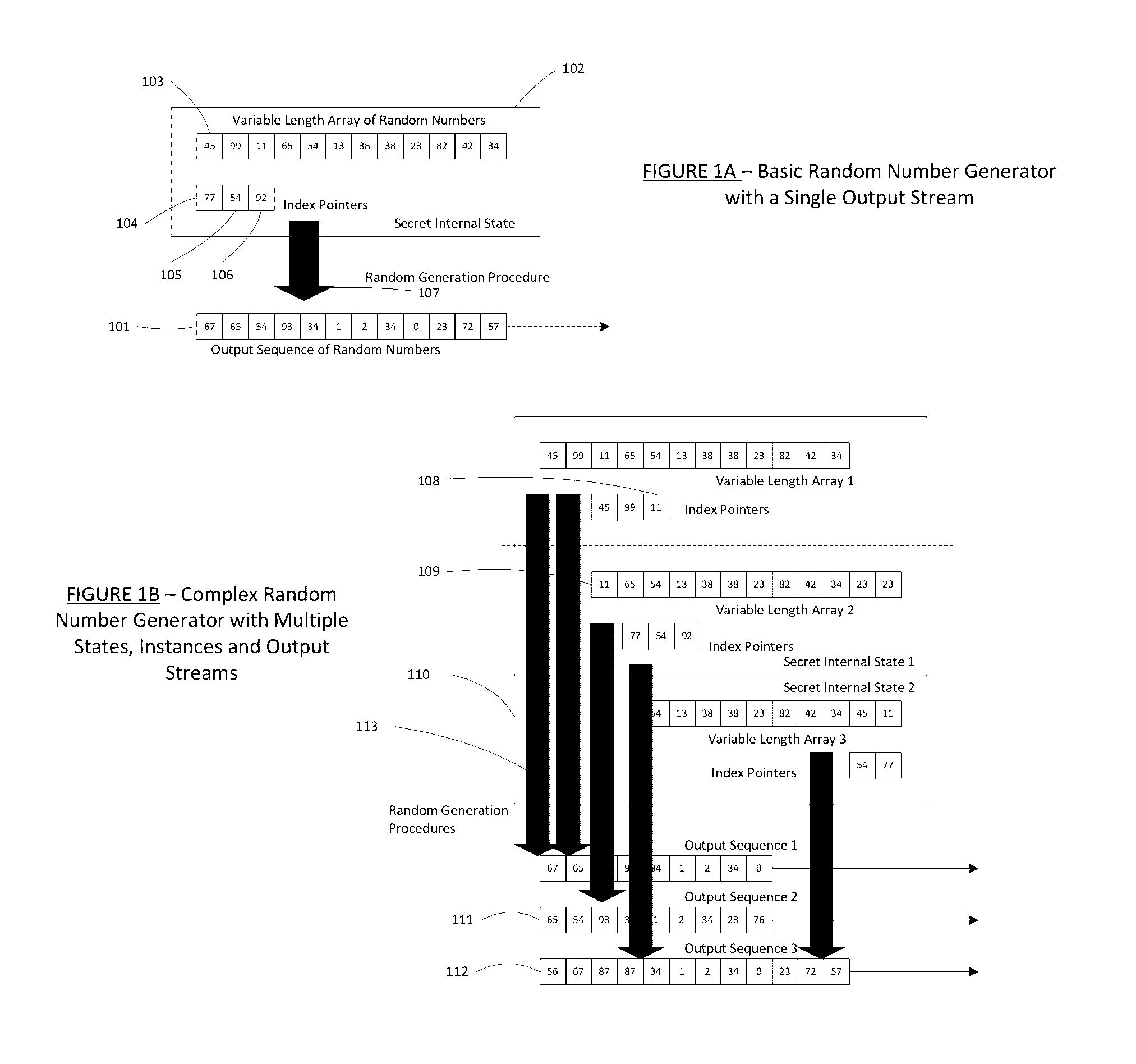
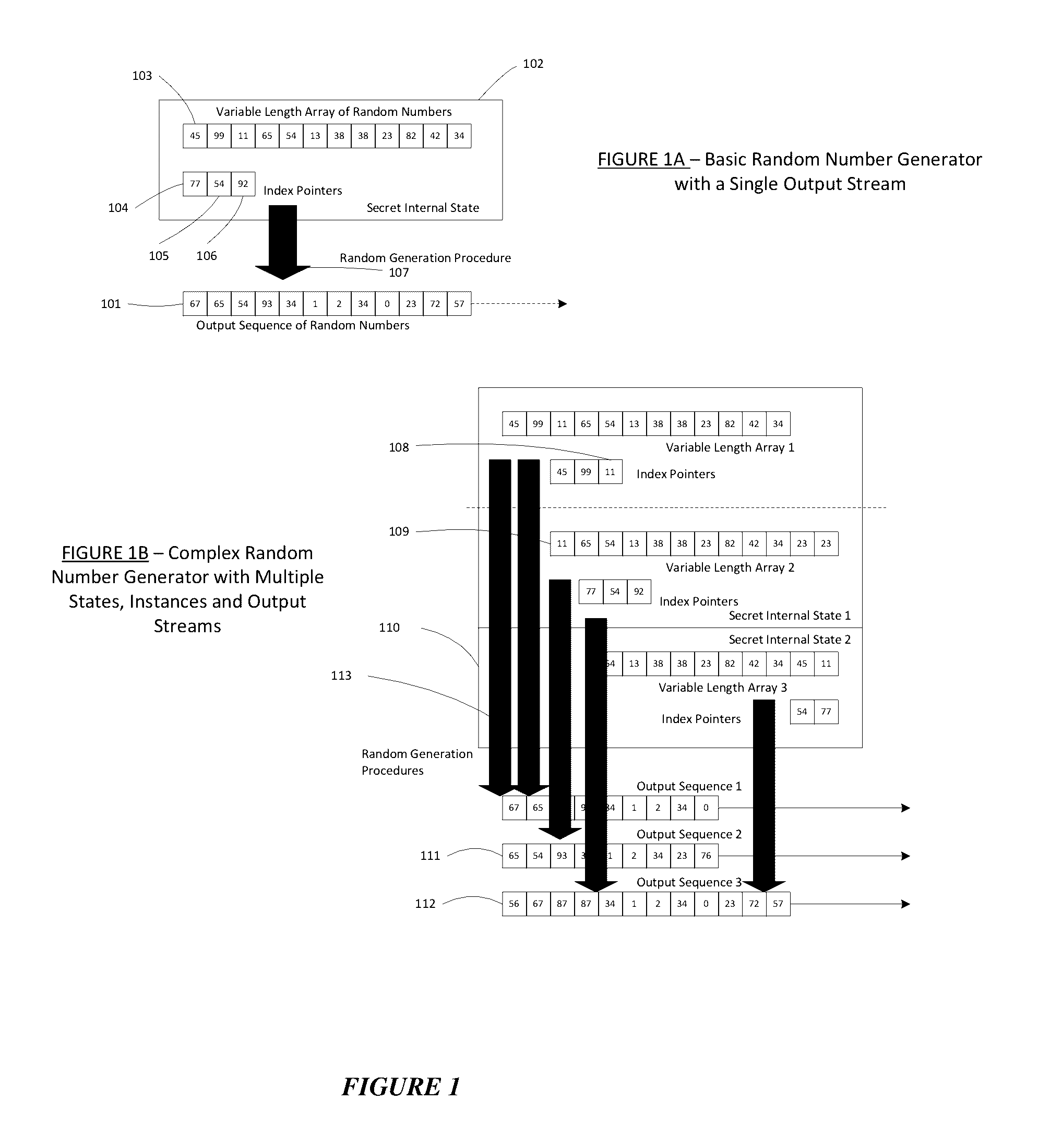
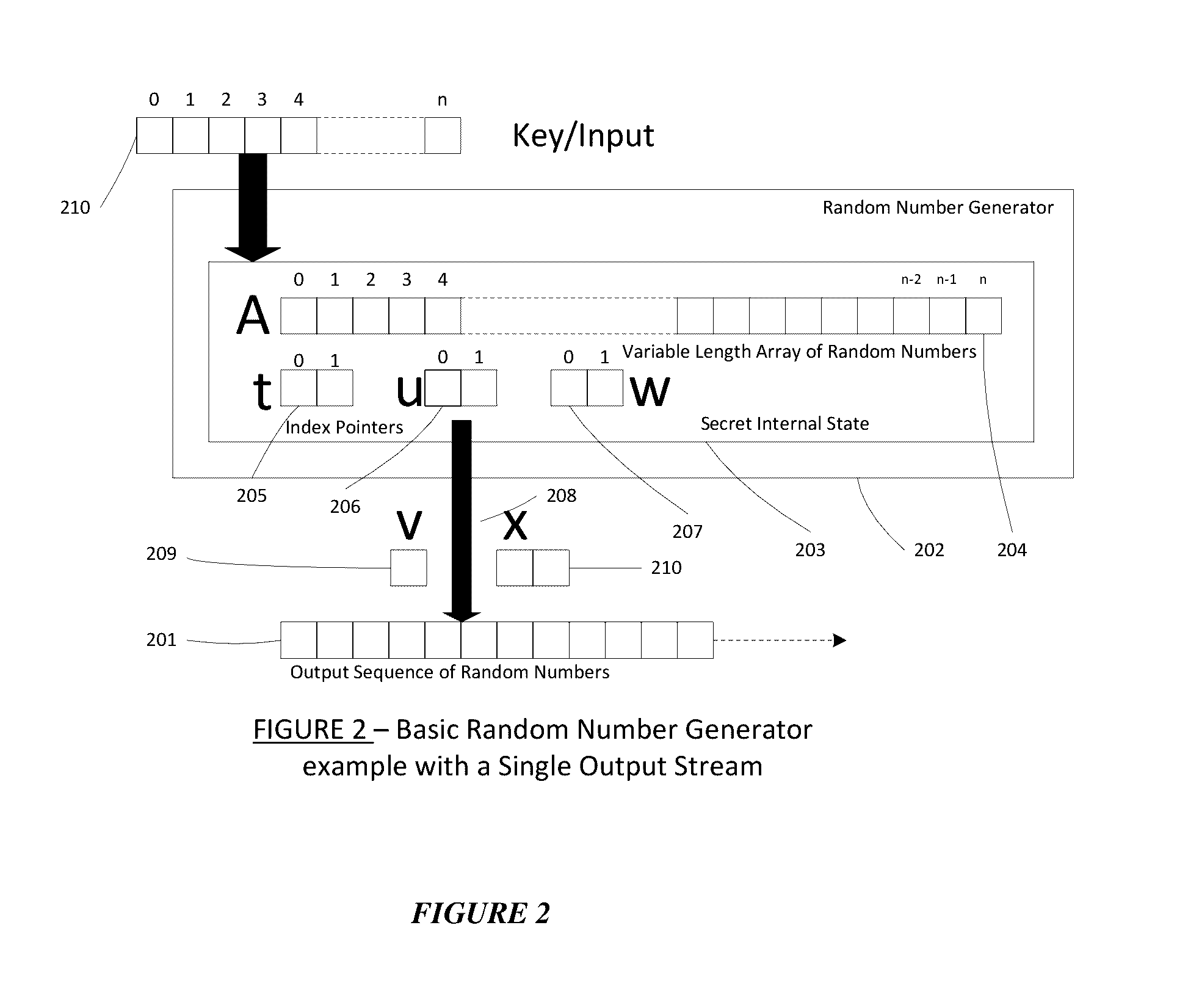
A dynamic computer communication security encryption method or system using an initial seed key and multiple random number generators of a specific design, whereby a sequence of independent random entropy values is produced by one set of random number generators and encrypted along with the message stream using the initial seed key, or the output of a second set of random number generators initialized with the initial seed key, and following the subsequent transmission of the variable encrypted entropy / message block, the entropy values are used to symmetrically or identically augment or increase the current uncertainty or entropy of the cryptosystem at both the sender and the receiver, prior to the next encryption block operation. The encryption process effectively entailing the use of multiple encryption ciphers, and the entropy augmentation process entailing the encryption or application of various logical mathematical operations on the already dynamic but deterministic internal state values of the second set of random number generators, effectively altering their deterministic outputs in a random probabilistic manner.Random length message value sequences from one or more data sources is combined with one or more random length entropy value sequences from an independent source, following which the entropy “updates” may also be used to alter, or change any cryptosystem variable, value or component in a randomly determined manner. In addition, whilst ensuring synchronization, the random entropy sequences also serve to “pollute” the cipher-stream and thereby hinder most current forms of cryptanalysis, whilst simultaneously injecting additional entropy into the cryptographic system and allowing for its propagation to affect any connected system nodes, and thereby introducing unpredictable entropy into the system pseudorandom number generator outputs, and thereby ensuring the perpetual generation of unpredictable random numbers.Super-encryption mechanics are independent of the user data, simple, fast and efficient, and can incorporate compression, error correction and asymmetric encryption authentication routines. But most importantly, super-encryption ensures resistance to brute force attacks (not possible to verify if a message was even sent), an ability to exceed “perfect secrecy” requirements, and an improvement on previous super-encipherment design, since overhead can be dramatically reduced from 100% overhead.Communication links previously established by system nodes with central authorities may be used for secure node authentication and registration, whilst allowing the central authority to broker and synchronize communication channels and providing mutual authentication and other security functions between the system nodes.
Owner:FIGUEIRA HELDER SILVESTRE PAIVA
Method and apparatus for resilient end-to-end message protection for large-scale cyber-physical system communications
InactiveUS20140129838A1Reduce overheadCompromising scalabilityKey distribution for secure communicationUser identity/authority verificationEnd to end securityPhysical system
To address the security requirements for cyber-physical systems, embodiments of the present invention include a resilient end-to-end message protection framework, termed Resilient End-to End Message Protection or REMP, exploiting the notion of the long-term key that is given on per node basis. This long term key is assigned during the node authentication phase and is subsequently used to derive encryption keys from a random number per-message sent. Compared with conventional schemes, REMP improves privacy, message authentication, and key exposure, and without compromising scalability and end-to-end security. The tradeoff is a slight increase in computation time for message decryption and message authentication.
Owner:WSOU INVESTMENTS LLC
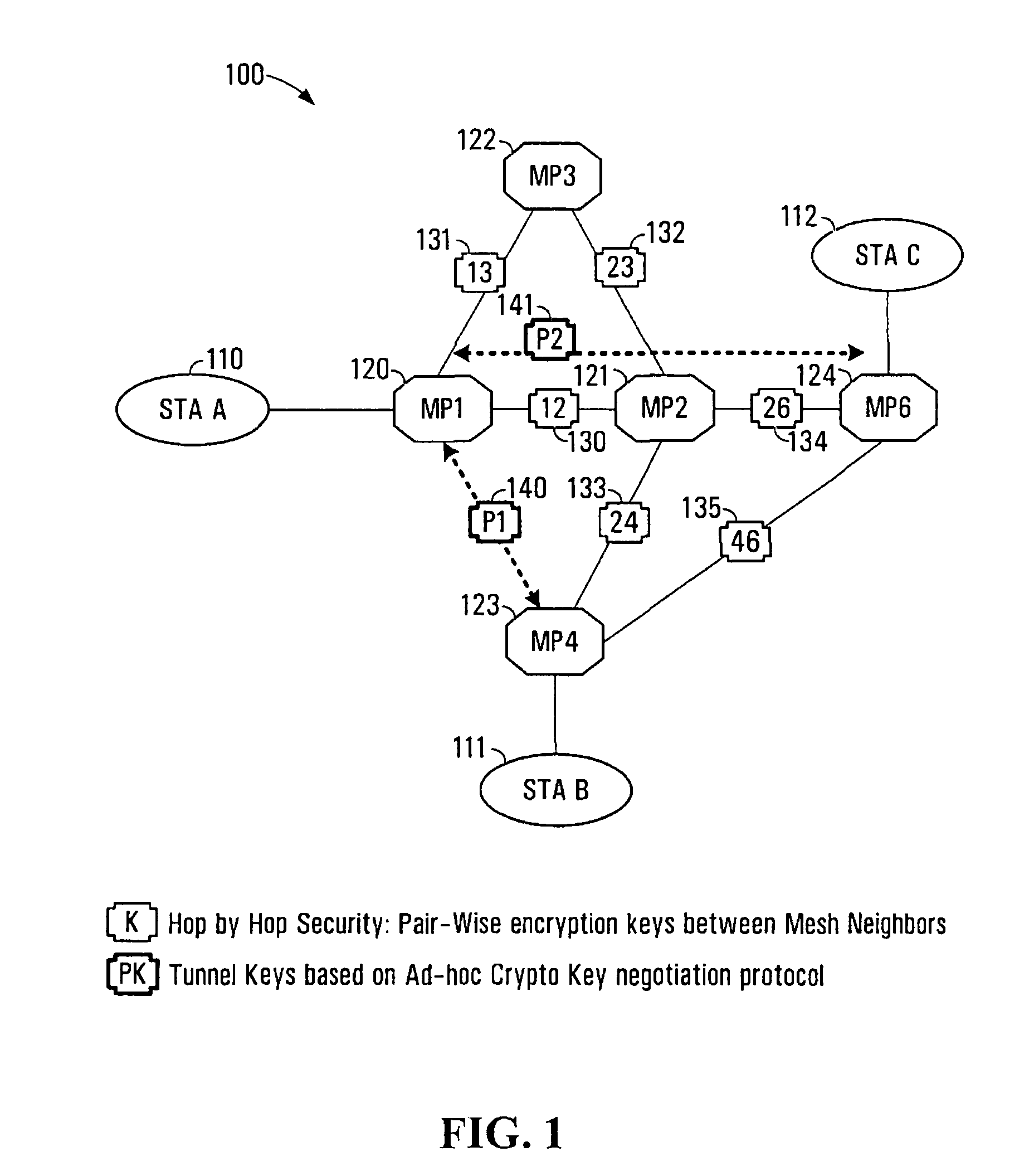
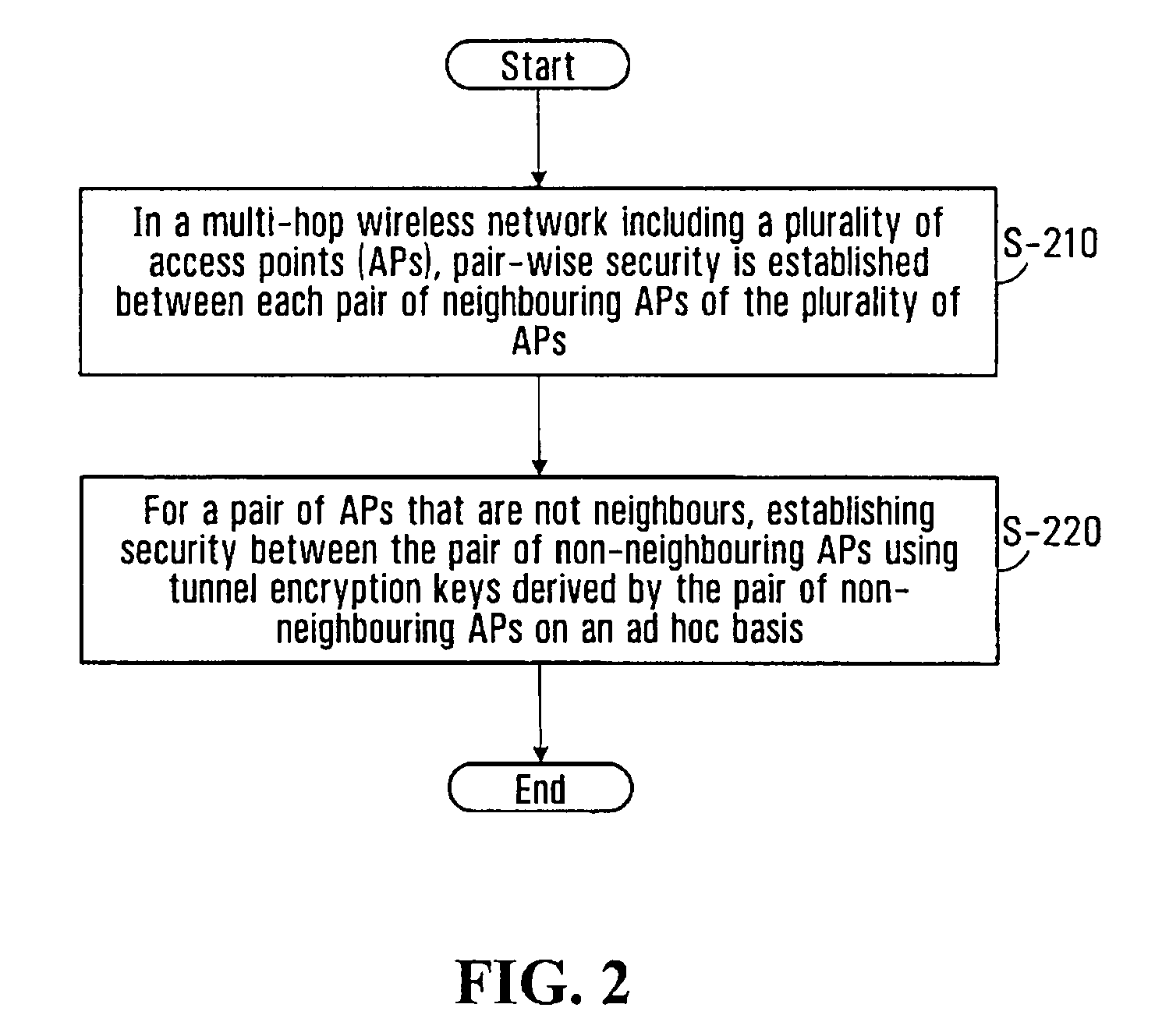
System and method for secure wireless multi-hop network formation
ActiveUS20080016338A1Synchronising transmission/receiving encryption devicesUser identity/authority verificationNode authenticationEncryption
The present invention provides methods and devices for a security architecture for use in wireless multi-hop networks. A method for implementing pair-wise encryption key establishment, network node authentication and determining tunnel encryption keys is provided in a following manner. In a multi-hop wireless network including a plurality of network nodes, pair-wise security is established between pairs of neighbouring network nodes of the plurality of network nodes. For example, pair-wise security is established in the form of temporal pair-wise encryption keys. Following establishment of pair-wise security between pairs of neighbouring network nodes, for a pair of network nodes that are not neighbours, tunnel security is established between the pair of network nodes using tunnel encryption keys derived by the pair of network nodes on an ad hoc basis. The tunnel encryption keys are used to form the connection between non-neighbouring network nodes so as to avoid the hop-by-hop encryption / decryption used in conventional multi-hop wireless systems.
Owner:APPLE INC
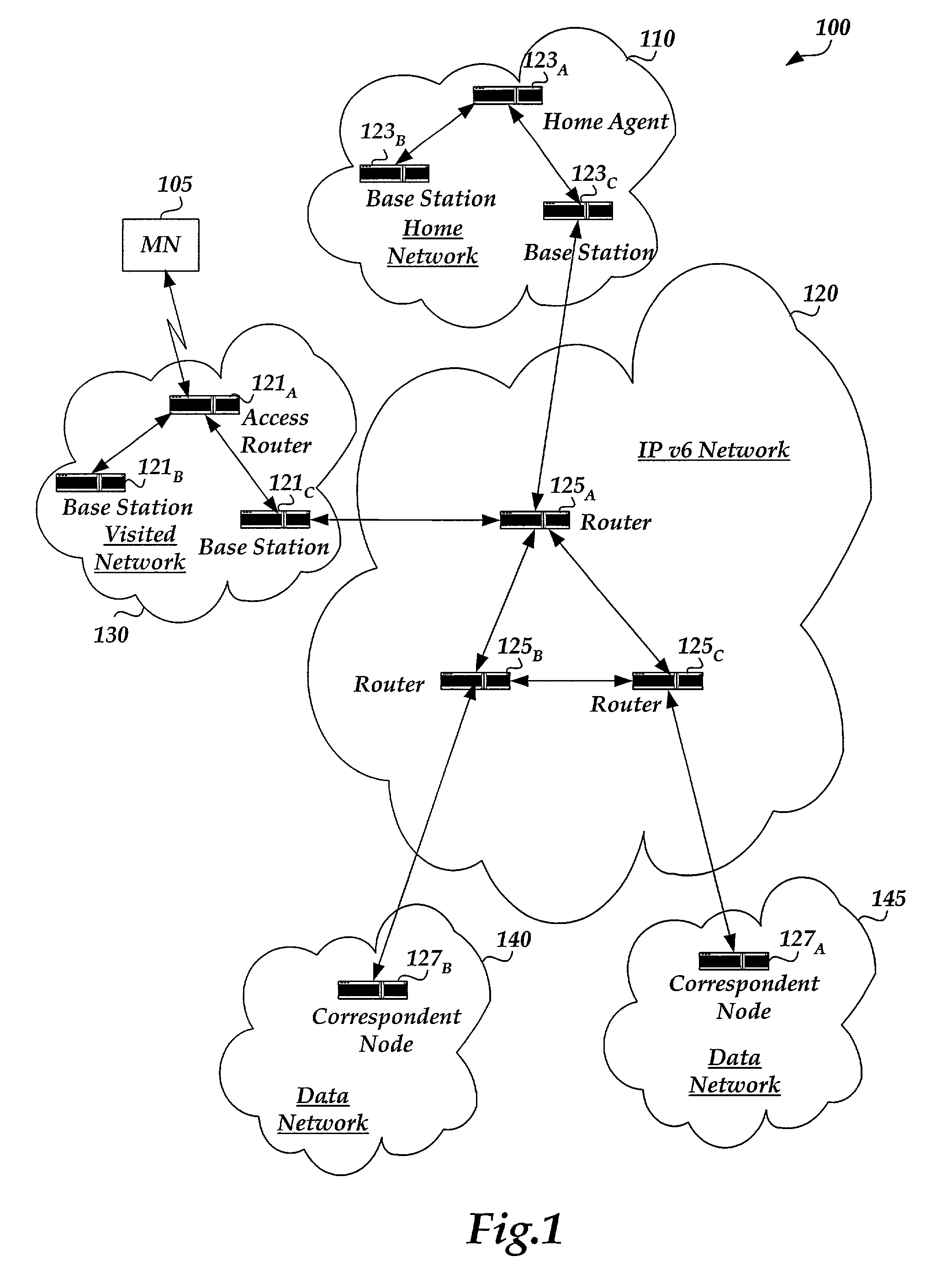
Mobile IPv6 authentication and authorization baseline
ActiveUS20050237983A1User identity/authority verificationData switching by path configurationAuthorizationNode authentication
The invention consists of an authentication protocol for the Home Agent to authenticate and authorize the Mobile Node's Binding Update message. Two new mobility options compatible with RADIUS AAA are used to exchange a shared secret between the Home Agent and the Mobile Node so the Mobile Node can be authenticated. A Mobile Node-AAA authenticator option is added to the Binding Update message. The Home Agent generates the Mobile Node-AAA authenticator as a shared secret that it communicates as authentication data to the RADIUS AAA server on the home network. The RADIUS AAA server authenticates the communication and generates an Access-Accept message with a Mobile Node-Home Agent authenticator option. After receipt at the Home Agent, a Binding Update message with the Mobile Node-Home Agent authenticator option is transmitted from the Home Agent to the Mobile Node to use as an authenticator.
Owner:MICROSOFT TECH LICENSING LLC
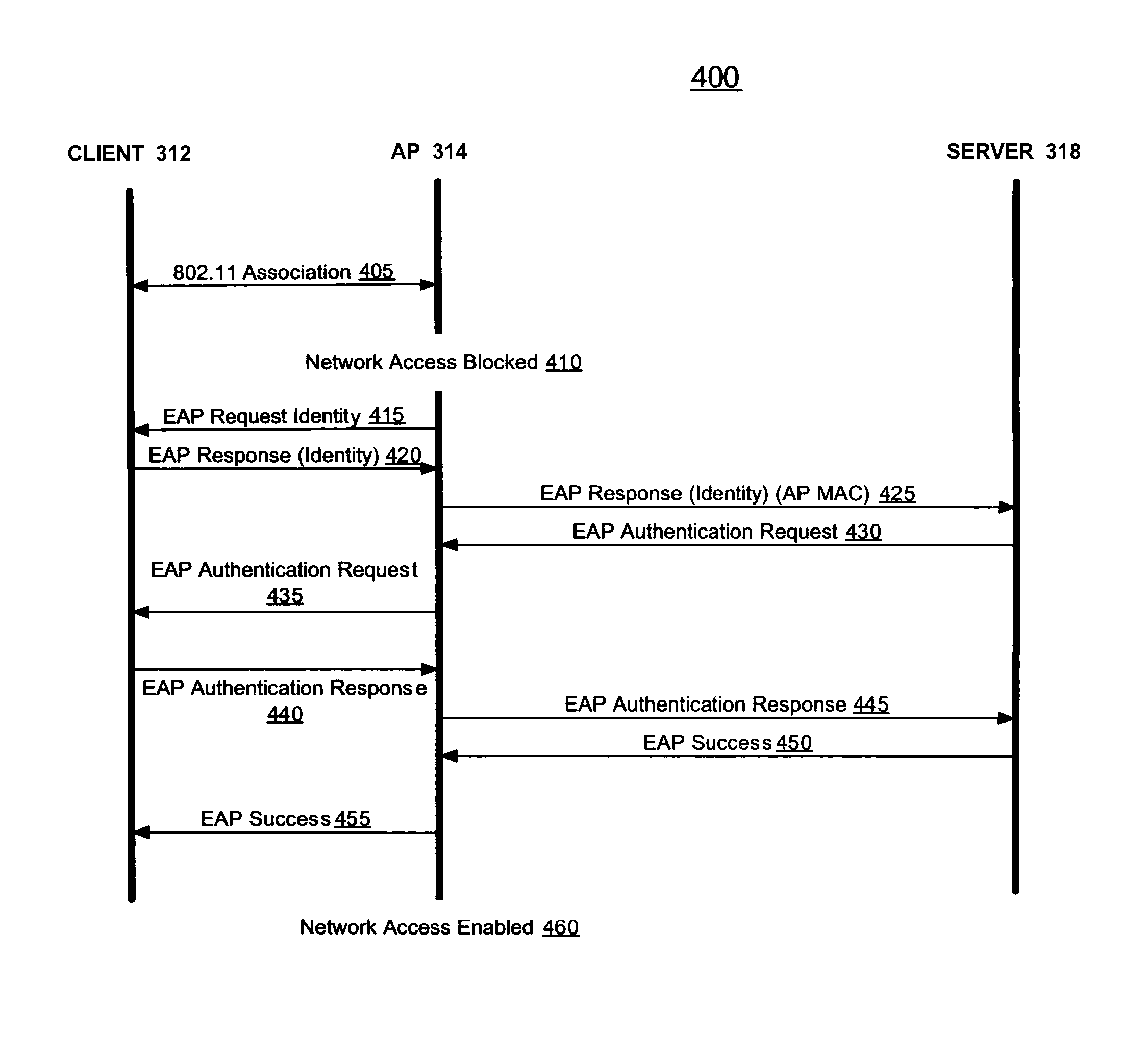
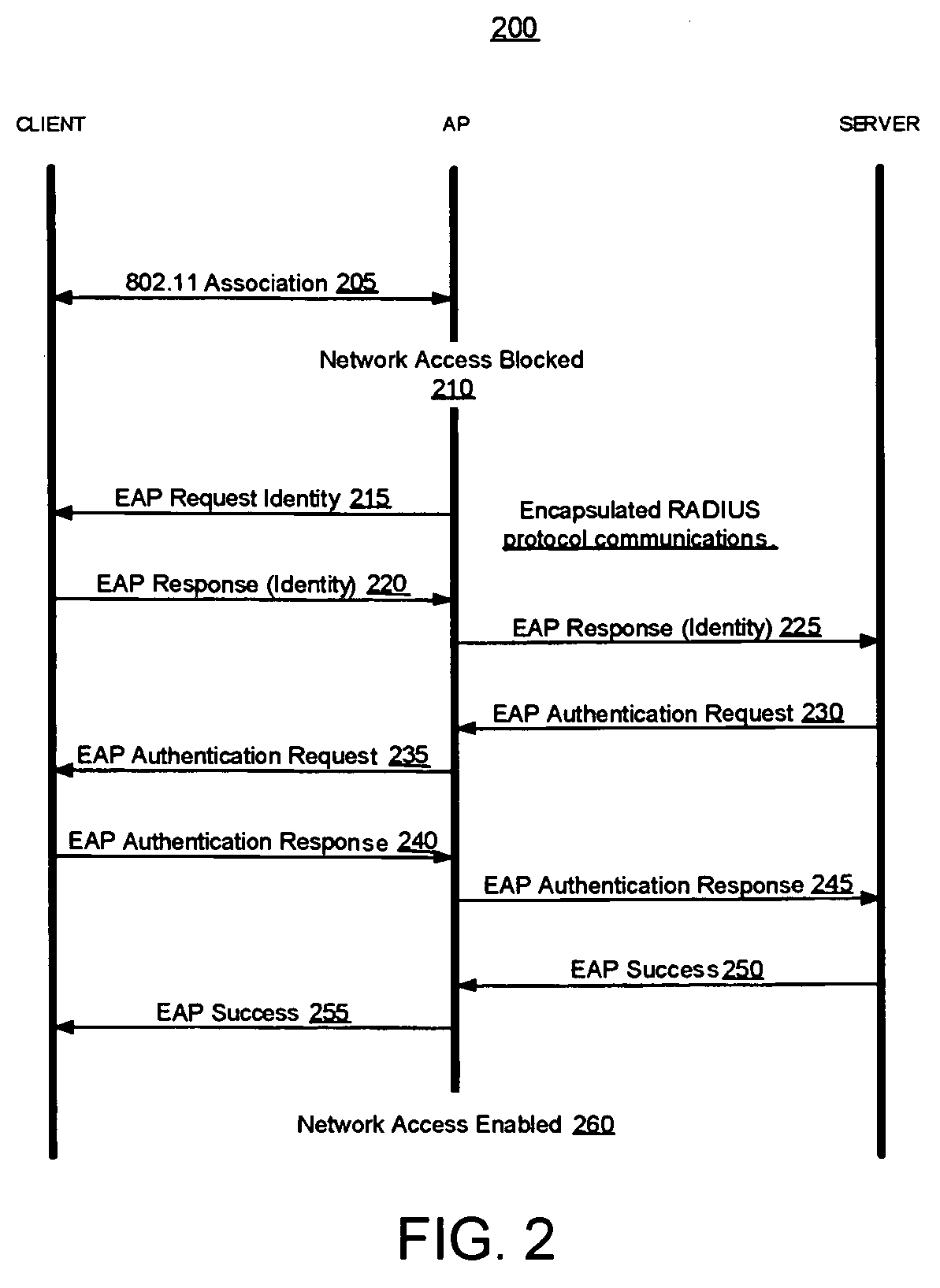
Methods and systems for fallback modes of operation within wireless computer networks
ActiveUS8555344B1Authentication process will failDigital data processing detailsError detection/correctionAuthentication serverWireless computing
Described herein are systems and methods for fallback operation within WLANs that rely on remote authentication procedures. When a primary network node authentication process fails, fallback access control parameters associated with a secondary network node authentication process are exchanged between a network node and an authentication server, wherein the secondary network node authentication process allows the network node to access other resources of a computer network.
Owner:MCAFEE LLC
Method of authenticating a mobile network node in establishing a peer-to-peer secure context between a pair of communicating mobile network nodes
ActiveUS7974234B2Near-field transmissionUnauthorised/fraudulent call preventionSecure communicationSecurity context
Methods for authenticating peer mobile network nodes for establishing a secure peer-to-peer communications context in an ad-hoc network are presented. The methods include accessing wireless infrastructure network entities at low bandwidth and for a short time duration to obtain cryptographic information regarding a peer mobile network node for the purpose of establishing secure peer-to-peer communications therewith ad-hoc network. Having received cryptographic information regarding a peer mobile network node, the method further includes challenging the peer network node with a challenge phrase derived from the cryptographic information received, receiving a response, and establishing a secure communications context to the peer mobile network node based on the validity of the received response. Advantages are derived from addressing security threats encountered in provisioning ad-hoc networking, by leveraging wireless infrastructure network security architecture, exemplary deployed in UMTS / GSM infrastructure networks, enabling seamless mobile network node authentication through the existing UMTS and / or GSM authentication infrastructure, while pervasively communicating with peer mobile network nodes in an ad-hoc network.
Owner:ALCATEL LUCENT SAS
Authentication method and apparatus in a communication system
ActiveUS20120204027A1User identity/authority verificationSecurity arrangementCommunications systemAuthentication server
An authentication method and apparatus in a communication system are provided. In a method for authenticating a first node at a second authentication server in a communication system comprising the first node registered to a first authentication server and a second node registered to the second authentication server, an authentication request message requesting authentication of the first node is received from the second node, the authentication request message is transmitted to the first authentication server, and upon receipt of an authentication success message indicating successful authentication of the first node from the first authentication server, the authentication success message is transmitted to the second node.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for secure wireless multi-hop network formation
ActiveUS7881474B2Synchronising transmission/receiving encryption devicesUser identity/authority verificationSelf-organizing networkNode authentication
The present invention provides methods and devices for a security architecture for use in wireless multi-hop networks. A method for implementing pair-wise encryption key establishment, network node authentication and determining tunnel encryption keys is provided in a following manner. In a multi-hop wireless network including a plurality of network nodes, pair-wise security is established between pairs of neighboring network nodes of the plurality of network nodes. For example, pair-wise security is established in the form of temporal pair-wise encryption keys. Following establishment of pair-wise security between pairs of neighboring network nodes, for a pair of network nodes that are not neighbors, tunnel security is established between the pair of network nodes using tunnel encryption keys derived by the pair of network nodes on an ad hoc basis. The tunnel encryption keys are used to form the connection between non-neighboring network nodes so as to avoid the hop-by-hop encryption / decryption used in conventional multi-hop wireless systems.
Owner:APPLE INC
Methods and systems of remote authentication for computer networks
InactiveUS7673146B2Computer security arrangementsSecret communicationUnique identifierAuthentication server
As part of a network node authentication process, a MAC address or other globally unique identifier of an access point through which the network node will access a computer network is transmitted in an EAP or other authentication message to an authentication server to uniquely identify the access point to the authentication server.
Owner:MCAFEE LLC
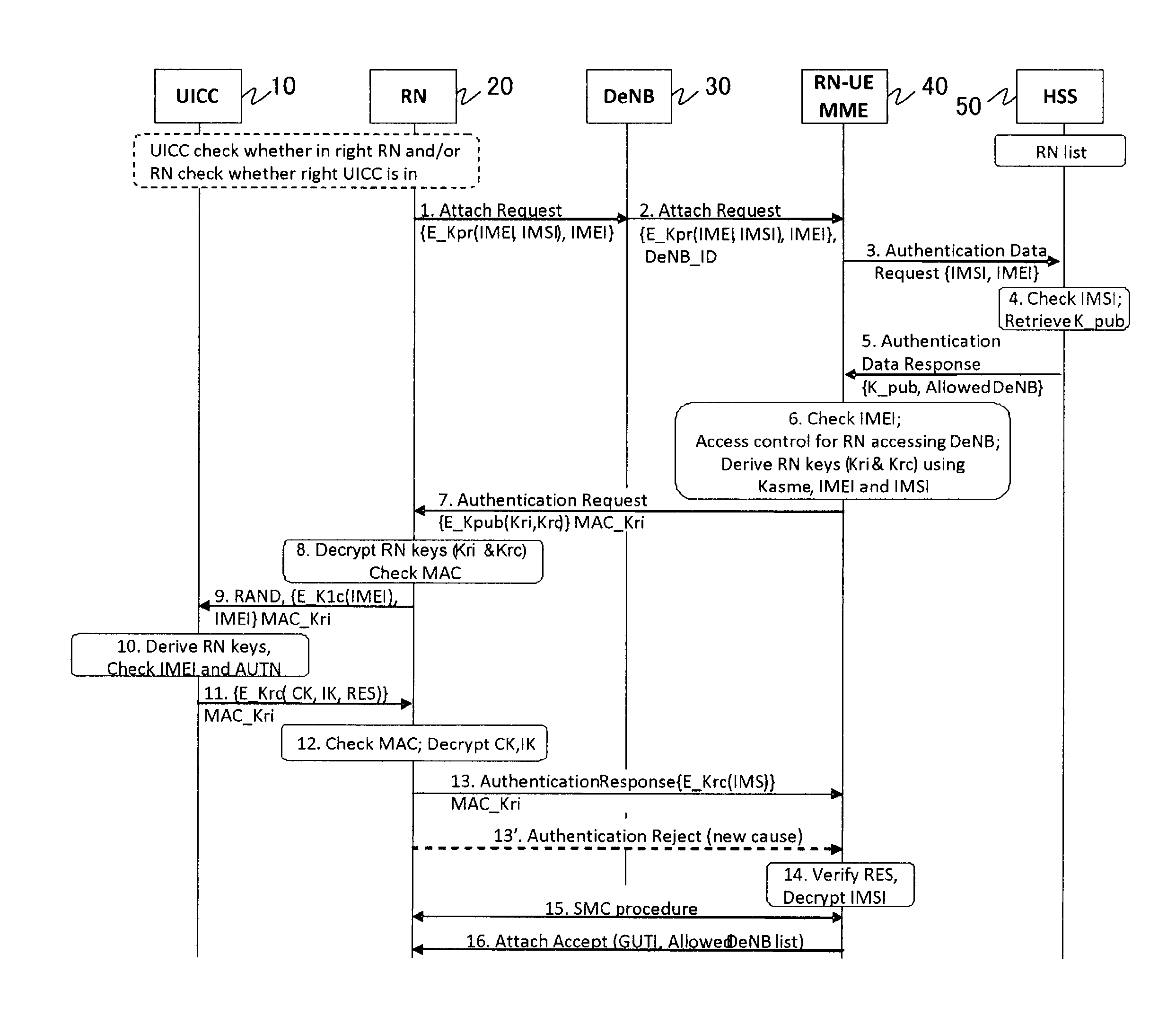
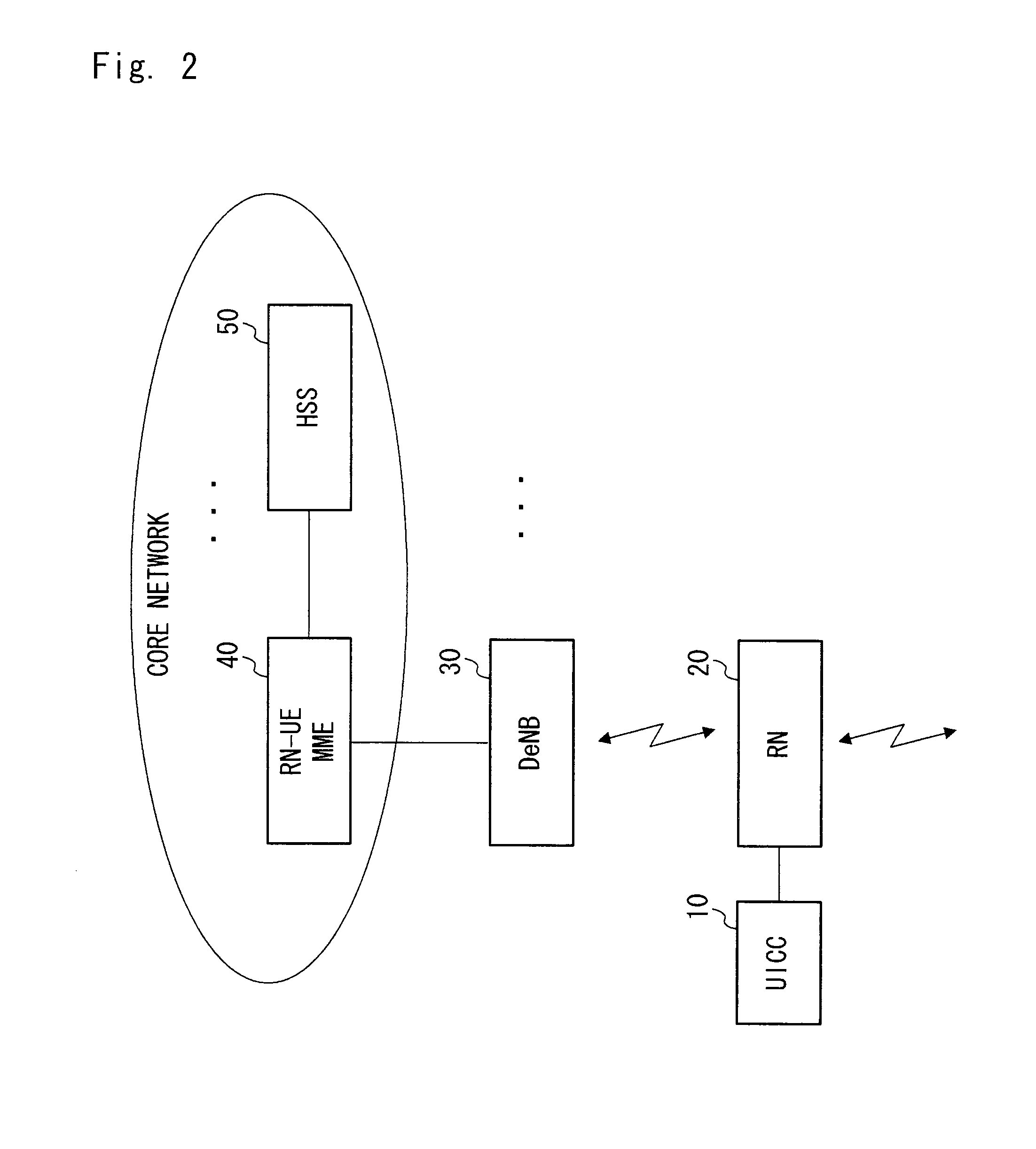
Relay node device authentication mechanism
InactiveUS20130163762A1Avoid misuseSignalingNetwork topologiesSecret communicationMutual authenticationNode authentication
A solution of relay node authentication is proposed. The solution includes mutual authentication of relay node and relay UICC, mutual authentication of relay node and network, secure channel establishment between relay UICC and relay node. AKA procedure in TS 33.401 is re-used so that no extra NAS message is needed. IMEI is sent to network in the initial NAS message, according to which MME-RN can retrieve RN's public key from HSS, and perform access control for DeNB. MME-RN will generate a session key based on IMSI, IMEI and Kasme, and encrypt it by RN's public key and send it to RN. UICC will also generate the same key and thus RN can authenticate both UICC and network. When the key or other parameters sent between UICC and RN do not match, UICC or RN will send Authentication Reject message with a new cause to inform network.
Owner:NEC CORP
Method and system for securing mobile IPv6 home address option using ingress filtering
InactiveUS6973086B2Data switching by path configurationWireless network protocolsIp addressNode authentication
The invention provides for disabling communication at the access router on a visited network that supports mobile IP v6 and the home address destination option. Until a home agent or a correspondent node authenticates the home IP address of the mobile node and the access router verifies this address, the mobile node is unable to communicate with other resources over the visited network. If the home IP address included in a binding acknowledgement message is verified by the access router and affirmatively compared to the state of a corresponding binding update message from the mobile node, the access router enables subsequent messages to be communicated over the visited network between the mobile node and other resources.
Owner:NOKIA SOLUTIONS & NETWORKS OY
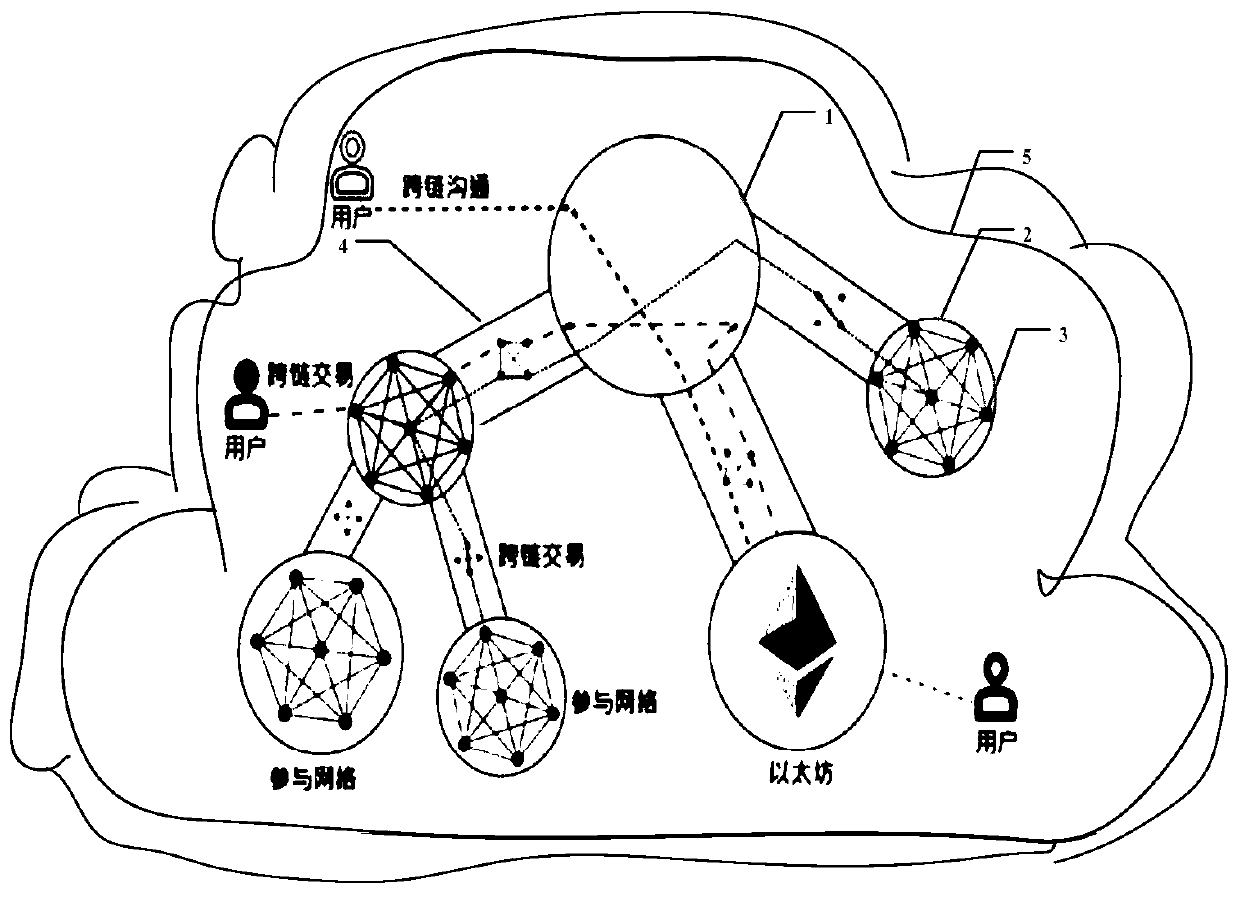
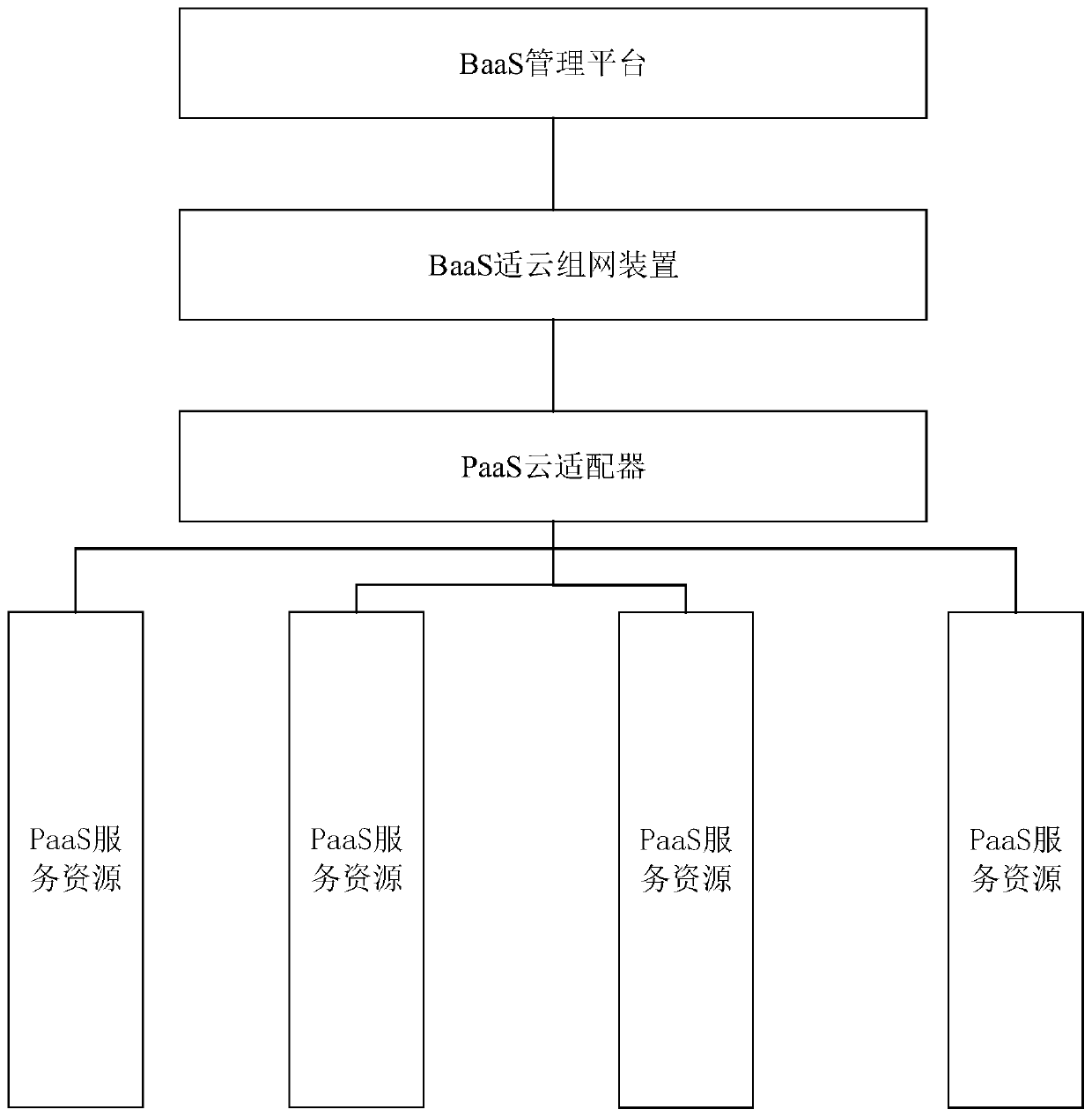
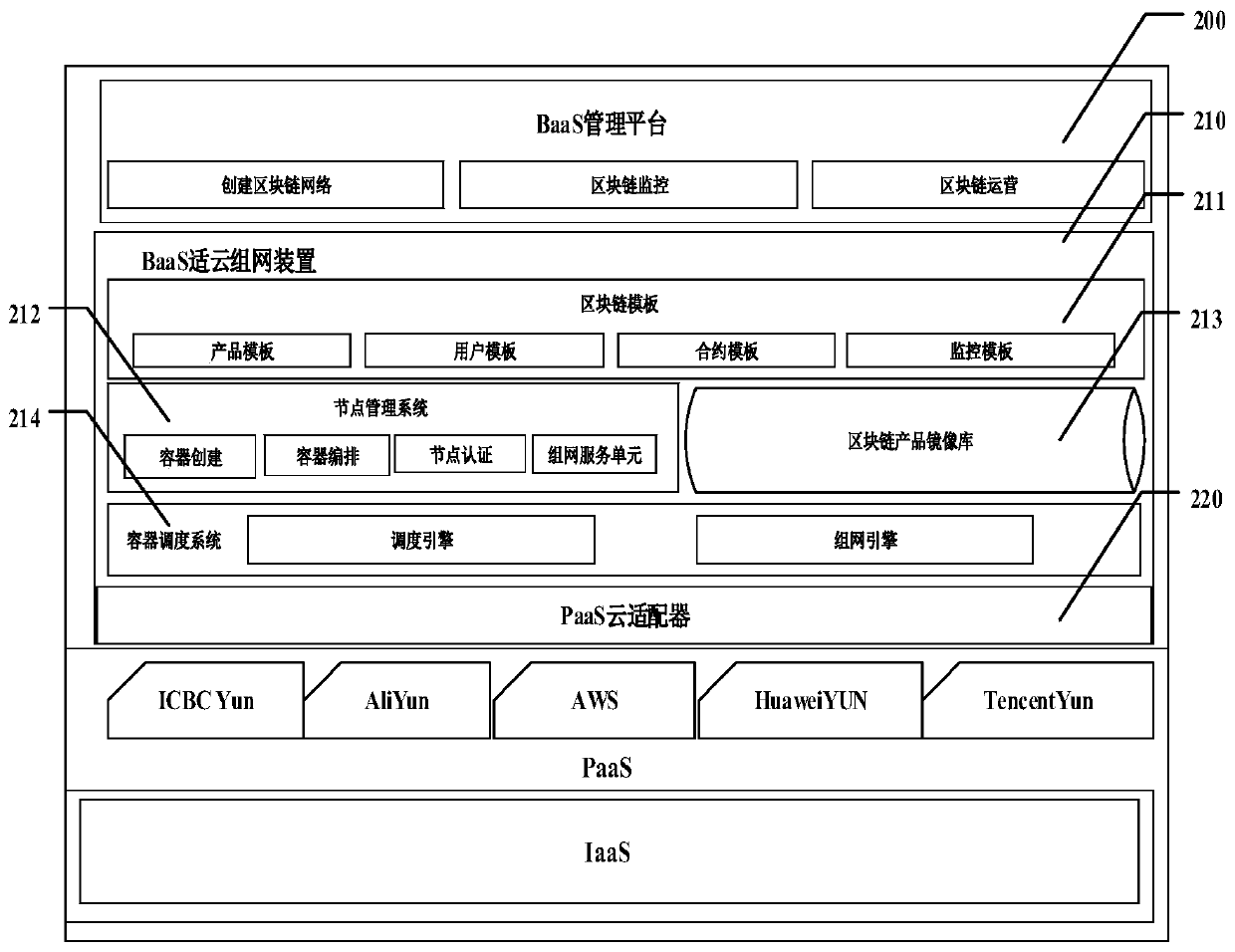
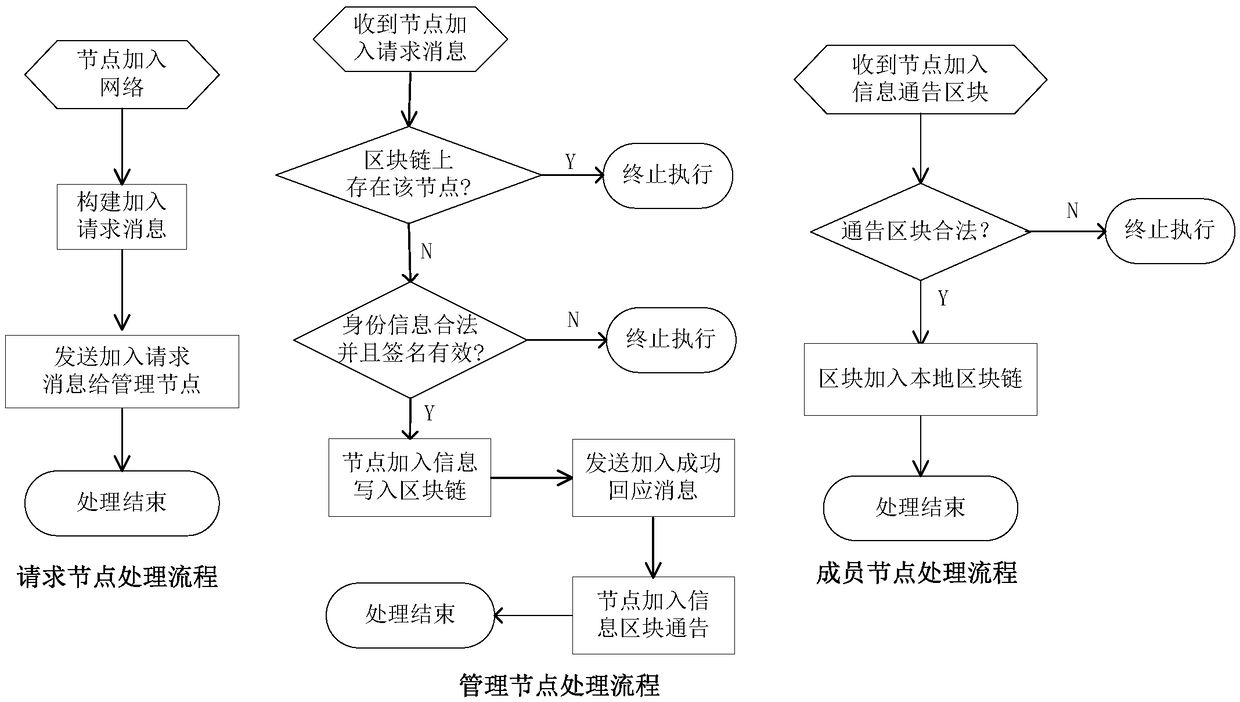
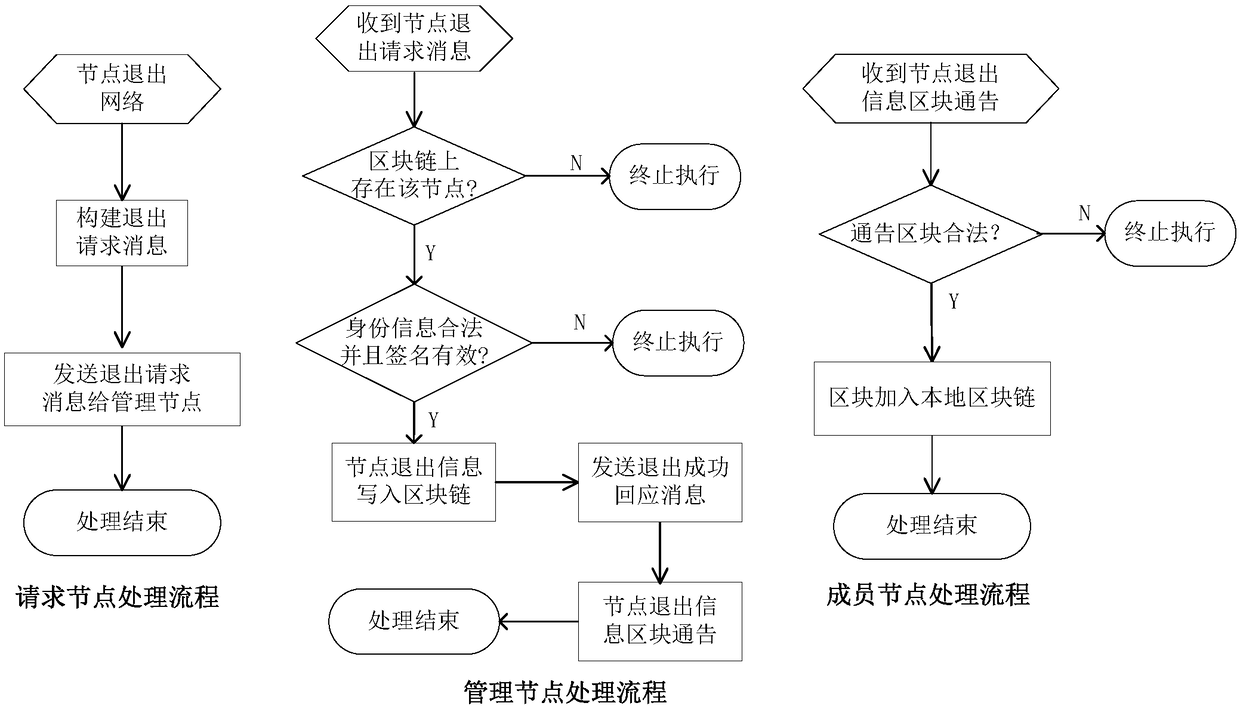
Cloud-based blockchain dynamic networking system and cloud-based block chain dynamic networking method
ActiveCN110417896ACreate flexible and secureGuaranteed flexibilityDatabase distribution/replicationData switching networksData synchronizationCloud base
The invention discloses a cloud-based blockchain dynamic networking system and method, and the method specifically comprises the steps of enabling a BaaS management platform to store the information of trusted nodes, and provide a query service of a trusted node list for the outside; querying a local trusted node list through a BaaS platform, and setting a networking request instruction accordingto the returned trusted node list; executing a container creation instruction, and deploying the blockchain node into the container to form a new node; sending a node authentication request to the newnode, and sending an encryption authentication mode and trusted node network information in a request message; after receiving the authentication request, the new node performs node authentication, and sends signature information and network information to the trusted node in a message form; adding a new node to the trusted node to send node adding success information to the new node; sending a node adding instruction to the new node, and adding credible node information to send node adding success information to the credible node after the new node receives the request; and after receiving the node adding success message, enabling the trusted node to start data synchronization.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Method for key management and node authentication of sensor network
ActiveCN101699891ARealize confidential communicationSave resourcesKey distribution for secure communicationUser identity/authority verificationSecure communicationNetwork deployment
Owner:CHINA IWNCOMM
Fine grained access control for wireless networks
InactiveUS7788705B2Digital data processing detailsUnauthorized memory use protectionWireless mesh networkAuthentication server
As part of a network node authentication process access control parameters that define the network node's ability to access other resources accessible through a computer network are provided by an authentication server (e.g., a RADIUS server) to an access point through which the network node is seeking to gain access to the computer network.
Owner:MCAFEE LLC
System and method for constructing trusted node network
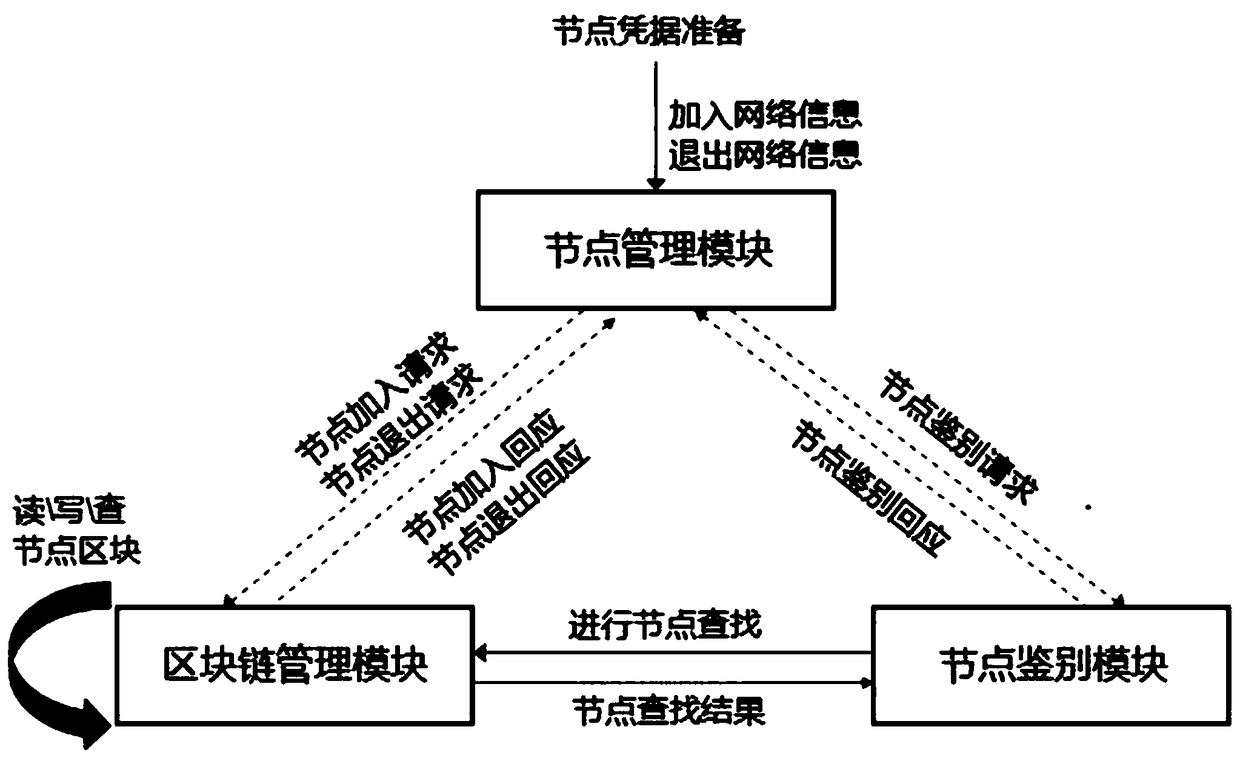
ActiveCN109104415AImprove flexibilityIncrease elasticityUser identity/authority verificationTrusted systemNode authentication
The invention relates to a system for constructing a trusted node network. The system comprises a block chain management module, a node management module and a node identification module. Block chainmanagement module is responsible for the management of node member information on the block chain, that is, read, write, look up the node information of the block chain, as well as the read and writeprivileges management of the node block chain; the node management module is responsible for the joining and exiting of the node members on the block chain and the information management of the node network members. The node authentication module is responsible for authenticating the trustworthiness of other nodes on the block chain communicating with the node. The technical scheme is a decentralized trust system and peer-to-peer identity authentication mechanism based on block chain and public key technology, which is used to construct a trusted and controlled node network, and solve the security problems of single point failure, DoS attack, forgery and tampering in the centralized mechanism. There is no centralized trust and authority center in the technical scheme. What the new technical scheme establishes is a decentralized, distributed trust system and admittance mechanism maintained by the network node group.
Owner:JIANGSU FEIBO SOFTWARE TECH
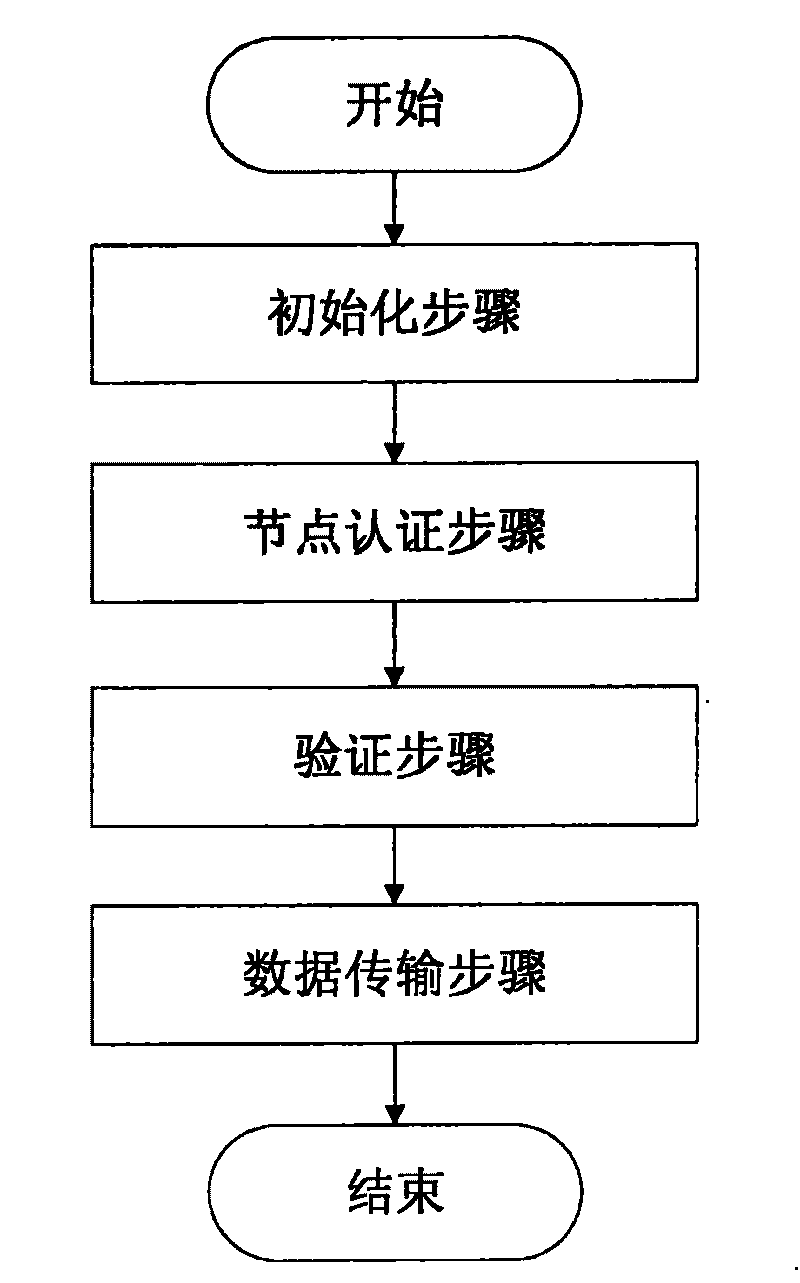
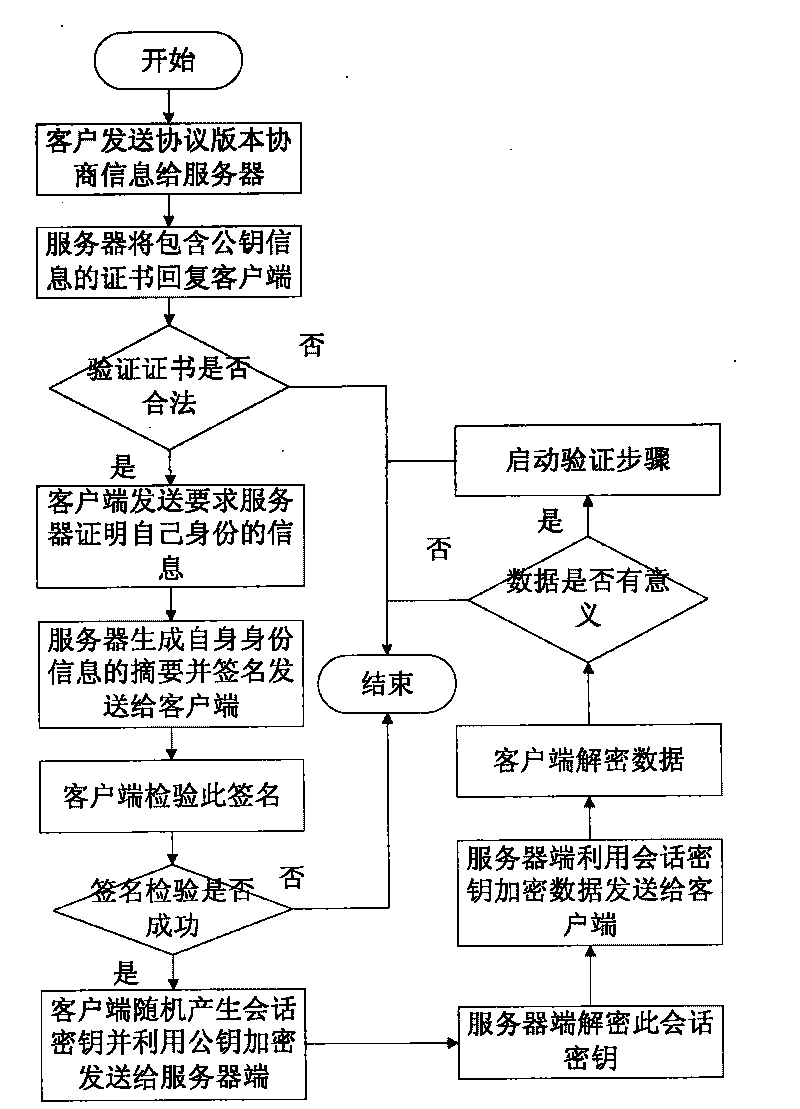
Computer remote security control method
ActiveCN101741860AGuaranteed legalityEnsure safetyUser identity/authority verificationInformation processingConfidentiality
The invention discloses a computer remote security control method, which belongs to a method for managing and controlling a computer network and aims to solve the problem that in the conventional control method, identity authentication and authority control of involved nodes and security control of an information transmission process are absent, and also to provide a complete set of security mechanism for remote control in an Internet environment. The computer remote security control method is used for a network information processing system consisting of a client node and a server node, which orderly comprises a step A of initialization, a step B of node authentication, a step C of verification and a step D of data transmission. The computer remote security control method has the advantages of effectively verifying the identities of the nodes and users involved in a remote control network and control authorities thereof, providing the security control for the access of the users, providing secure socket links for the encrypted transmission of various information and data, and greatly enhancing the confidentiality and security of the data transmission in the network environment, and is applied to remote control systems in the current complex, open and remote Internet environment.
Owner:HUAZHONG UNIV OF SCI & TECH
Key management and node authentication method for sensor network
ActiveUS20120300939A1Lower capability requirementsReduce storageKey distribution for secure communicationUser identity/authority verificationNetwork communicationNode authentication
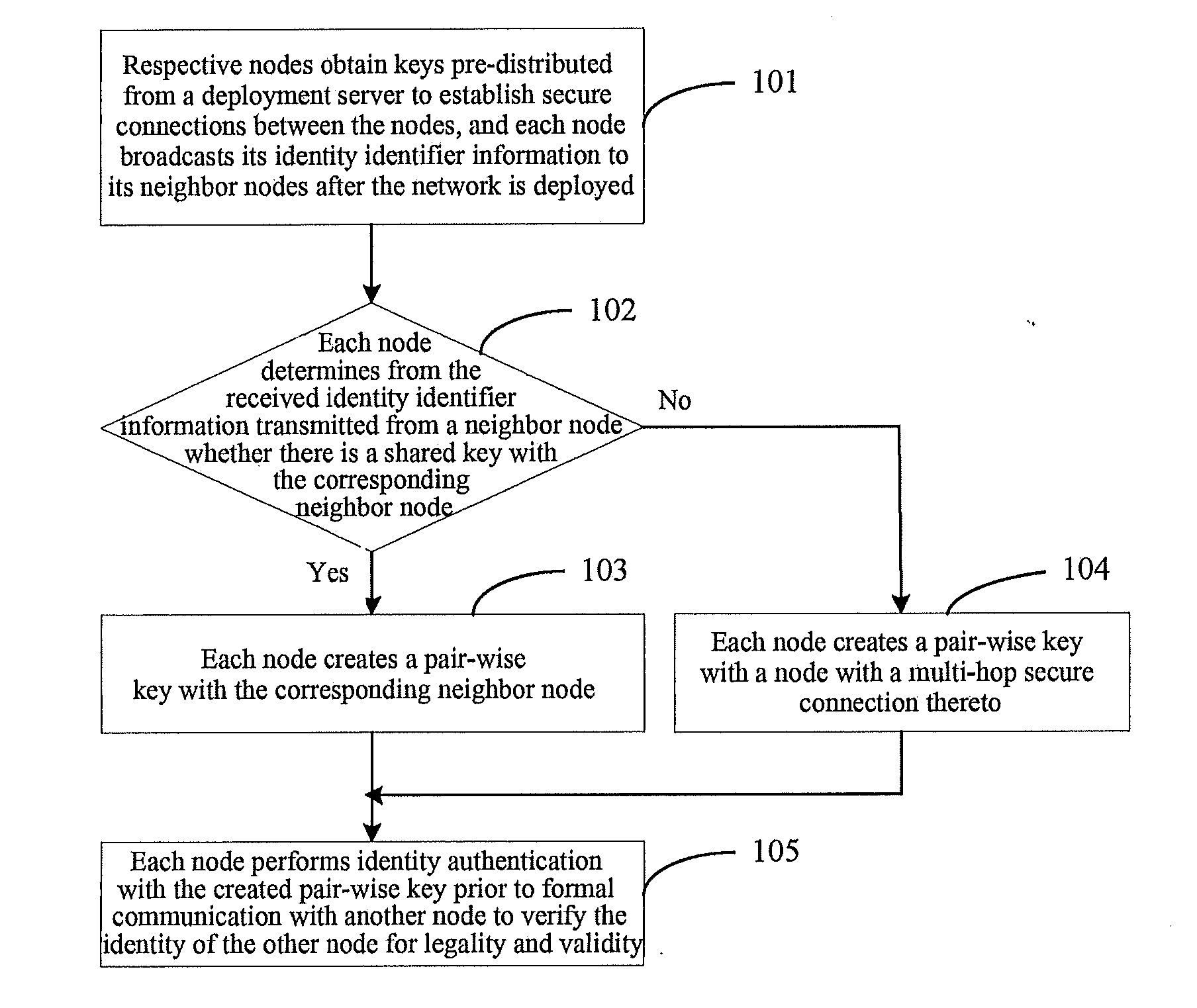
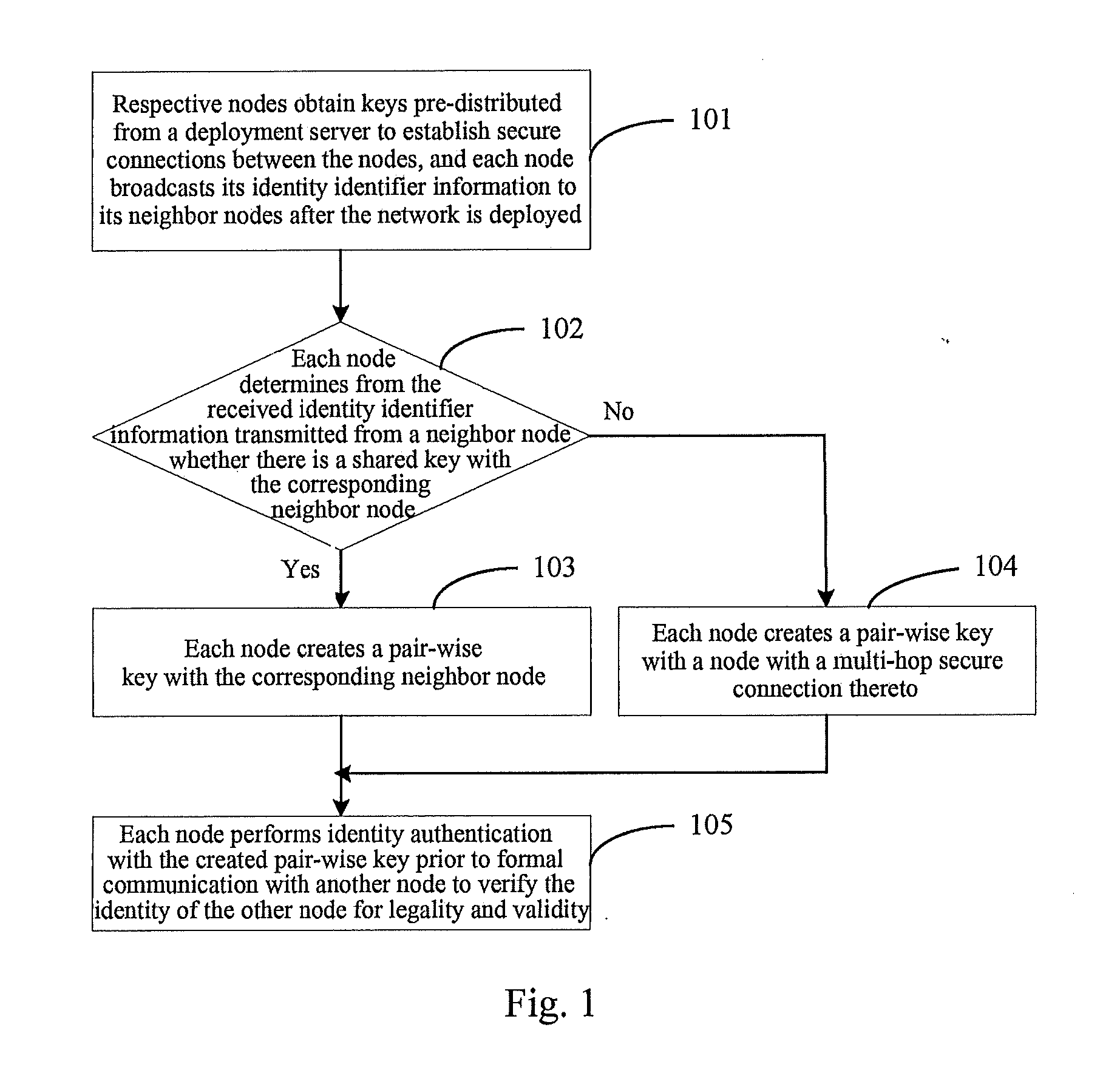
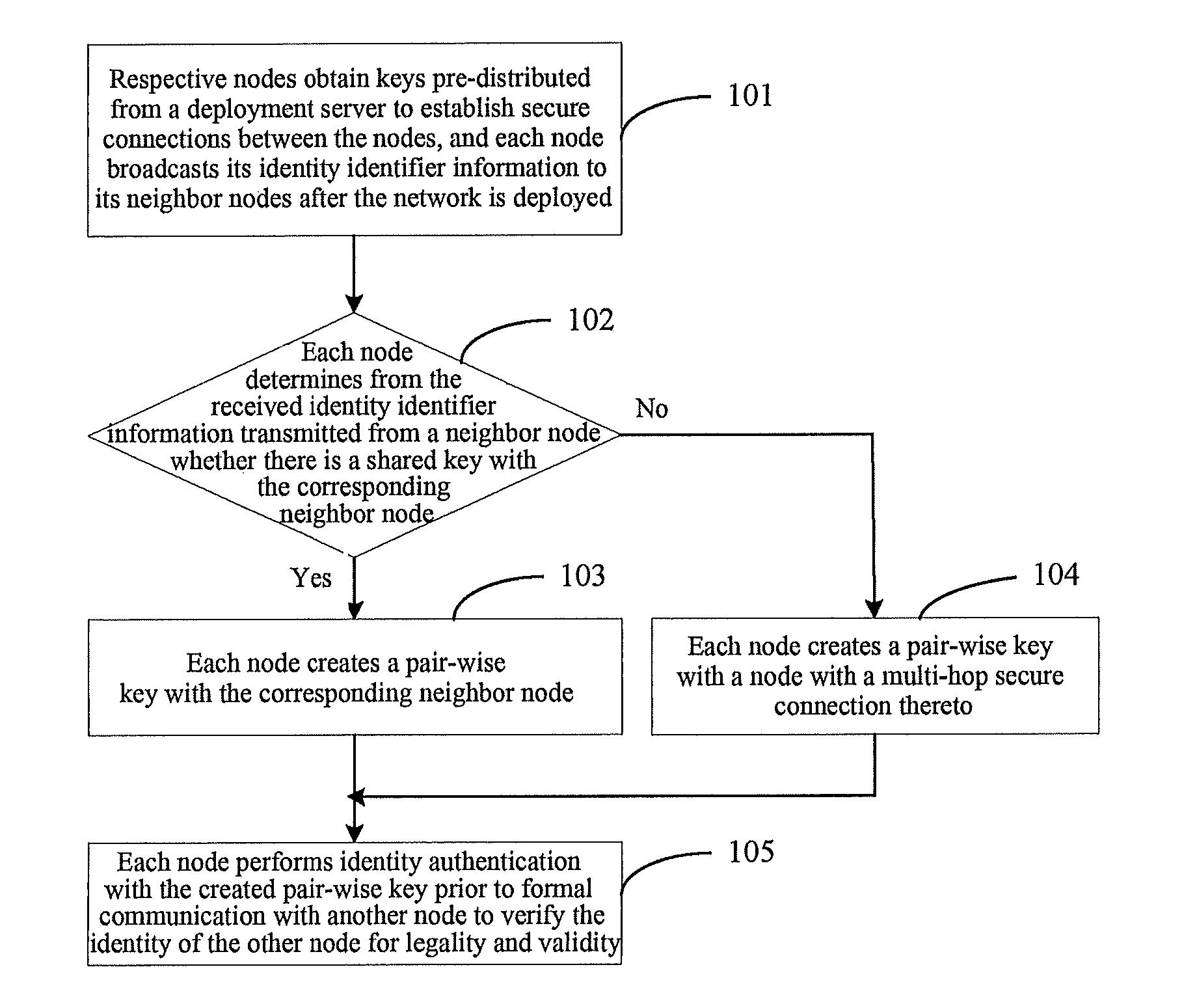
A key management and node authentication method for a sensor network is disclosed. The method comprises the following steps of: 1) keys pre-distribution: before deploying the network, communication keys for establishing security connection between nodes are pre-distributed to all of nodes by a deployment server. 2) Keys establishment: after deploying the network, a pair key for the security connection is established between nodes, which includes the following steps of: 2.1) establishment of shared keys: the pair key is established between neighbor nodes in which the shared keys are existed; 2.2) path keys establishment: the pair key is established between the nodes in which there is no shared keys but there is a multi-hop security connection. 3) Node identity (ID) authentication: before formally communicating between nodes, the identity is authenticated so as to determine the legality and the validity of the identity of the other. It is possible for effectively resisting attacks such as wiretapping, tampering, and replaying and the like for the network communication, realizing the secret communication between the nodes, effectively saving resources of the nodes of the sensor network, and prolonging the service lift of the sensor network in the method.
Owner:CHINA IWNCOMM
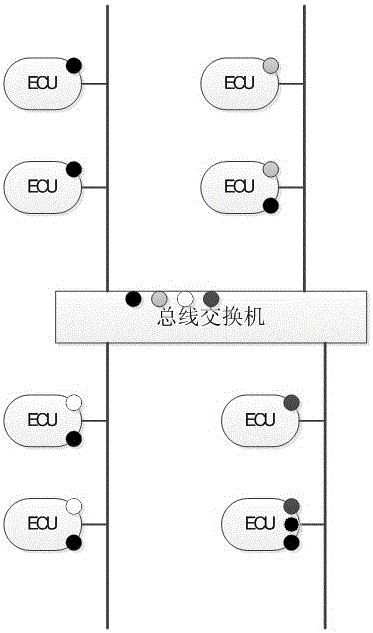
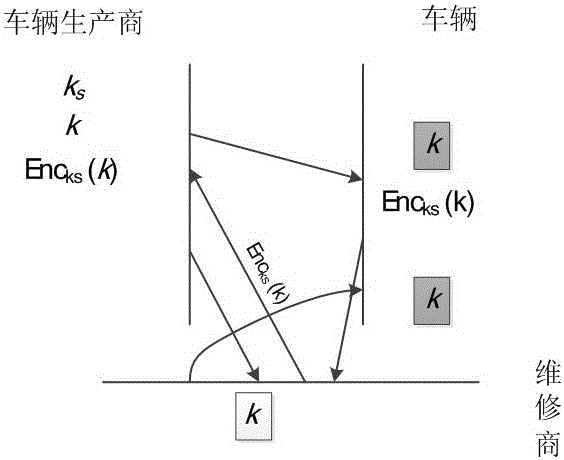
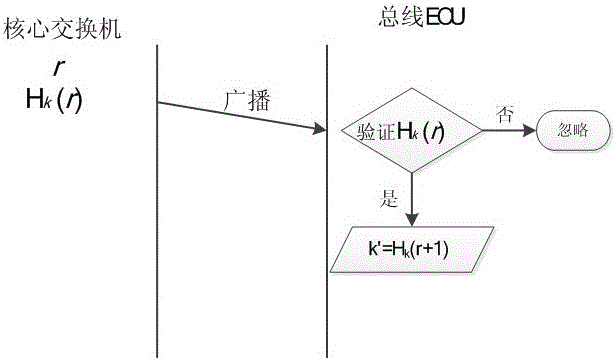
Authentication and access control method for CAN (Controller Area Network) bus
ActiveCN106453326AAchieve authenticationAchieve protectionBus networksArea networkCryptography protocols
The invention relates to an authentication and access control method for a CAN (Controller Area Network) bus, which is characterized by particularly comprising the following steps of: (1) completing functional partitioning of a vehicle system, and defining each function as a logic functional region; (2) based on functional partitioning of the vehicle system in the step (1), partitioning nodes of the vehicle system into each logic functional region according to functions to which the nodes belong; (3) based on partitioning of each node logic functional region in the step (2), allocating a secret key to each logic functional region; (4) based on each secret key in the step (3), generating a session secret key of the corresponding logic functional region after a vehicle is started up every time; (5) based on each session secret key in the step (4), completing authentication and encryption of CAN data, and based on each secret key in the step (3), implementing secret key resetting on updated nodes. According to the authentication and access control method disclosed by the invention, based on a cryptography technology, a node authentication and encryption protocol of the CAN bus is constructed by utilizing a cryptographic algorithm, and resource access control on the integral CAN bus is implemented.
Owner:CHINA FIRST AUTOMOBILE
Relay node authentication method, apparatus, and system
ActiveUS20120297474A1Ensure safetyDigital data processing detailsConnection managementSecurity domainNode authentication
Embodiments of the present invention disclose a relay node authentication method, apparatus, and system. The method provided in an embodiment of the present invention includes: sending, by a relay node, an authentication request message to a peer node, where the authentication request message includes a certificate of the relay node, so that the peer node authenticates the relay node according to the certificate of the relay node, where the peer node is a network side node or a security gateway in a security domain where the network side node is located; and receiving, by the relay node, an authentication response message sent by the peer node, where the authentication response message includes a certificate of the peer node, and authenticating the peer node according to the certificate of the peer node.
Owner:HONOR DEVICE CO LTD
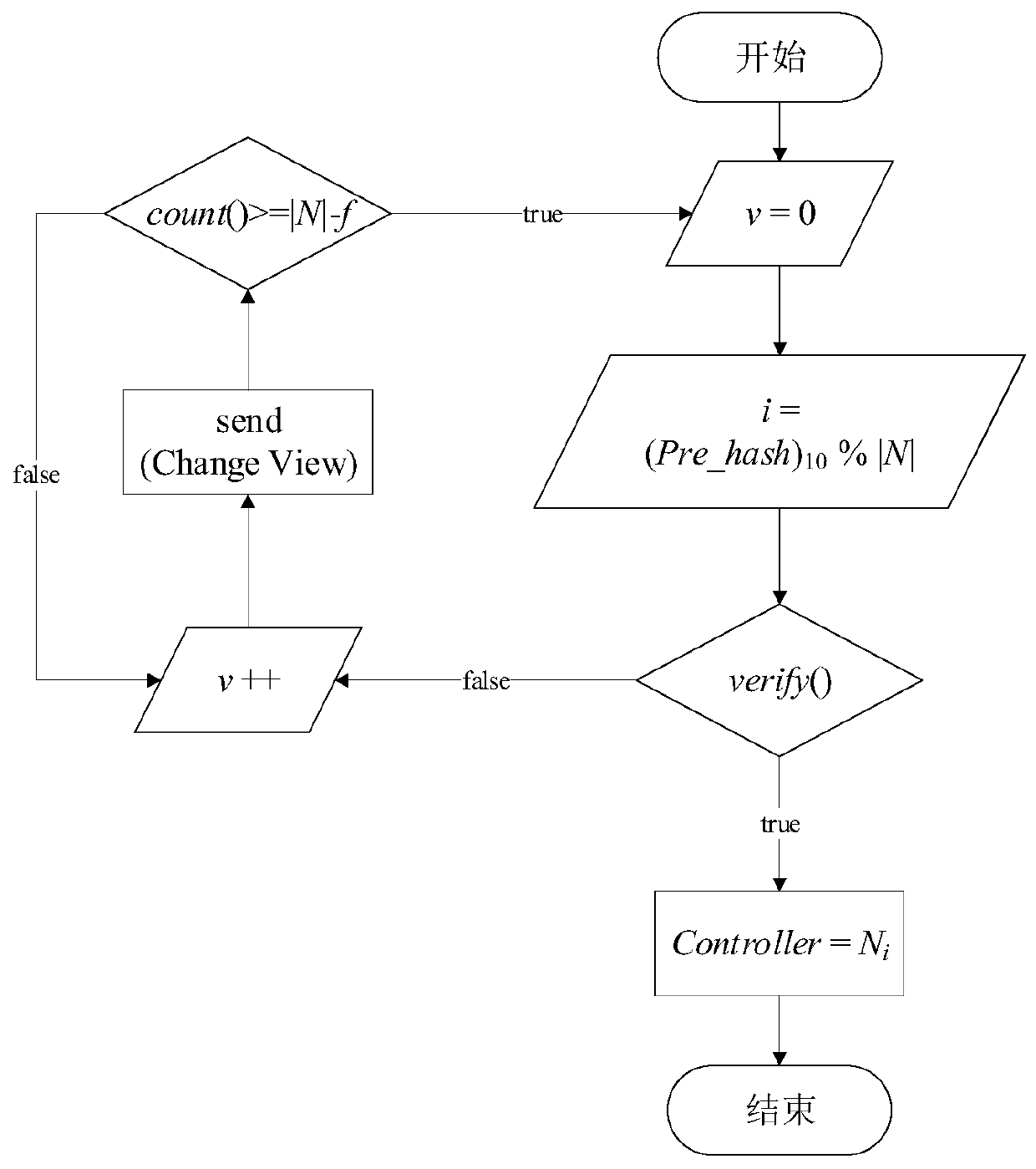
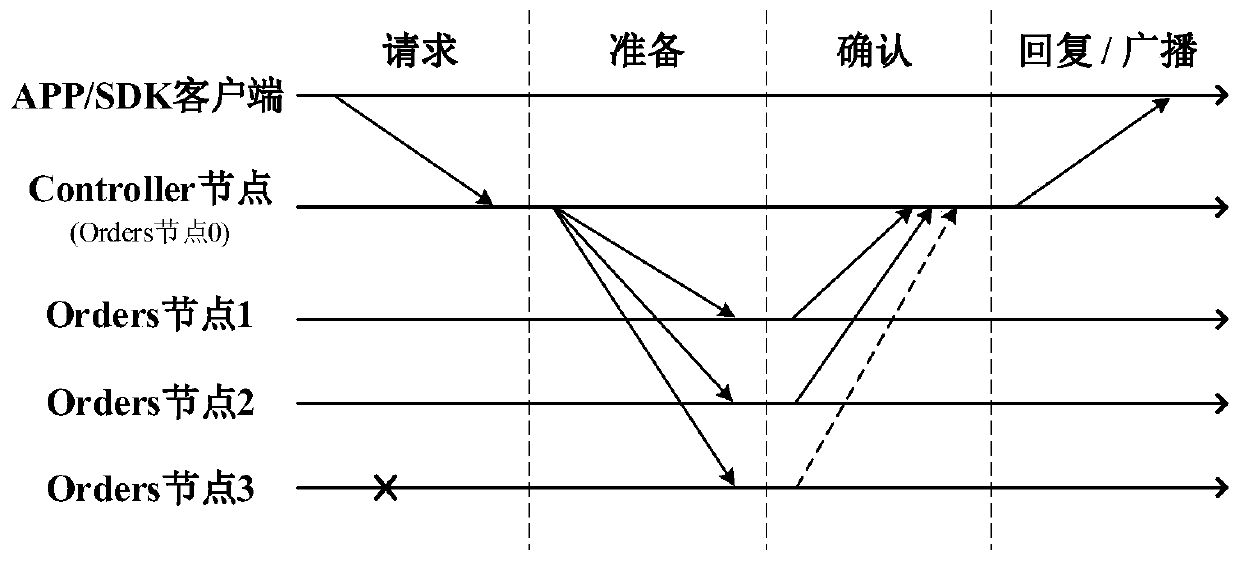
Block chain platform based on Meta-BFT consensus mechanism and implementation method
ActiveCN109981565AImprove throughputImprove consensus efficiencyTransmissionChain networkDistributed computing
The invention belongs to the technical field of block chain consensus algorithms, and particularly relates to a block chain platform based on a Meta-BFT consensus mechanism and an implementation method. The invention discloses a block chain platform of a Tolerant consensus mechanism and an implementation method. The block chain platform mainly comprises a Control node selection model, a Orders node, a Control node, a Peers node, a CA authentication center and an APP / SDK client. The method comprises the following steps: step S1, enabling the APP / SDK client to register / log in the CA authentication center; step S2, selecting the Control node from the Orders node according to the Control node selection model, and further enabling all the APP / SDK clients to only send a service request to the Control node; step S3, enabling a Controller node to order all transactions in the block chain network based on the Meta-BFT consensus mechanism and combine the ordered transaction combination to the block sturtcure and send a result to a Peers node; and step S4, after confirmation by the Peers node, returning the result to the APP / SDK client, and synchronizing information to the Orders node.
Owner:INST OF SOFTWARE APPL TECH GUANGZHOU & CHINESE ACAD OF SCI
Key management and node authentication method for sensor network
ActiveUS8913751B2Improve abilitiesConserve effectively resourceKey distribution for secure communicationUser identity/authority verificationNetwork communicationNode authentication
A key management and node authentication method for a sensor network is disclosed. The method comprises the following steps of: 1) keys pre-distribution: before deploying the network, communication keys for establishing security connection between nodes are pre-distributed to all of nodes by a deployment server. 2) Keys establishment: after deploying the network, a pair key for the security connection is established between nodes, which includes the following steps of: 2.1) establishment of shared keys: the pair key is established between neighbor nodes in which the shared keys are existed; 2.2) path keys establishment: the pair key is established between the nodes in which there is no shared keys but there is a multi-hop security connection. 3) Node identity (ID) authentication: before formally communicating between nodes, the identity is authenticated so as to determine the legality and the validity of the identity of the other. It is possible for effectively resisting attacks such as wiretapping, tampering, and replaying and the like for the network communication, realizing the secret communication between the nodes, effectively saving resources of the nodes of the sensor network, and prolonging the service lift of the sensor network in the method.
Owner:CHINA IWNCOMM
Lightweight authentication method for supporting anonymous access of heterogeneous terminal in edge computing scene
ActiveCN111371730AImplement anonymous authenticationRealize traceabilityKey distribution for secure communicationUser identity/authority verificationEdge computingTerminal equipment
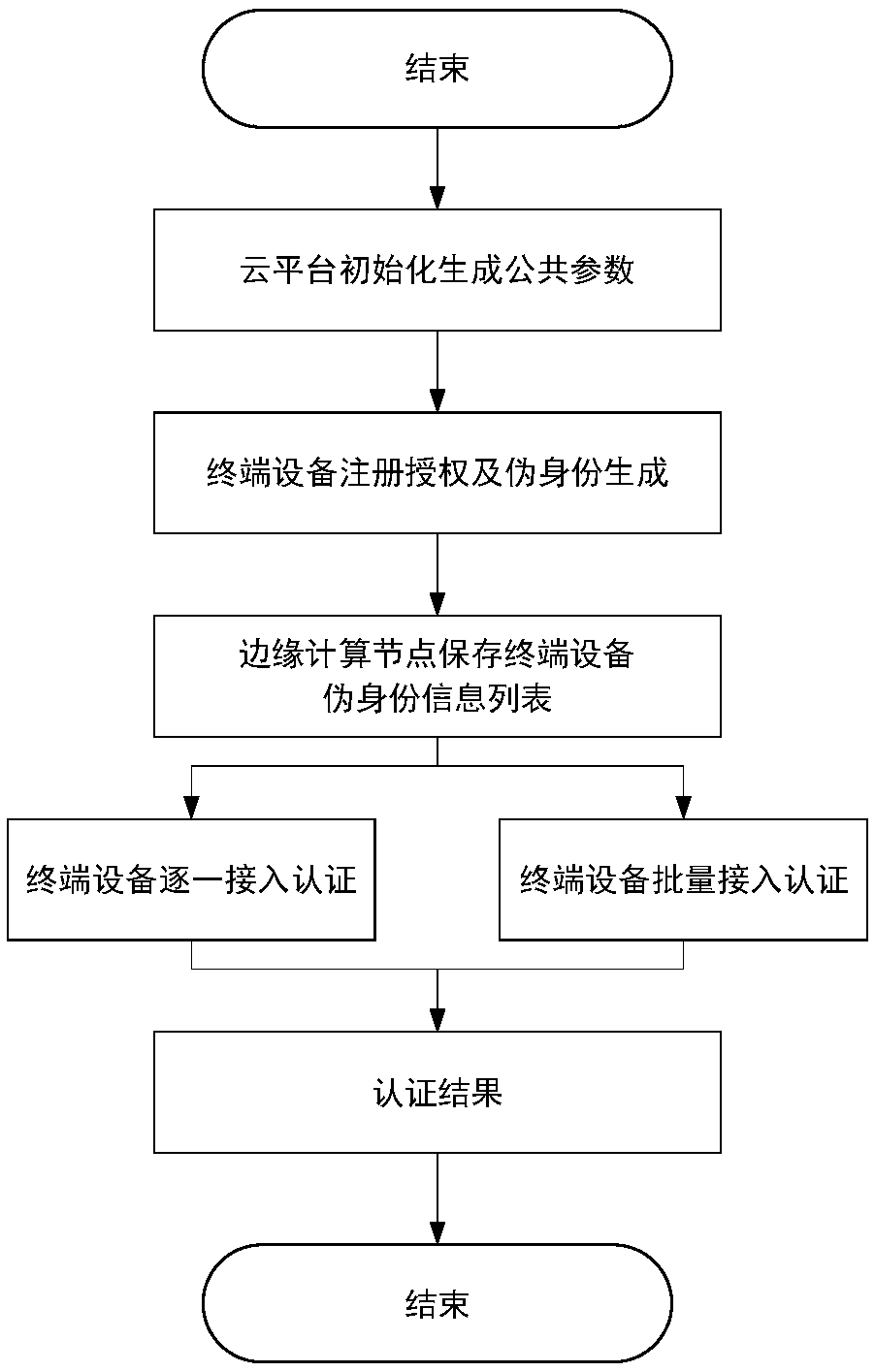
The invention provides a lightweight authentication method for supporting anonymous access of a heterogeneous terminal in an edge computing scene. According to the invention, a pseudo identity is created for each terminal device by using a cloud platform to hide the real identity information of the terminal device; meanwhile, malicious terminal equipment can be traced back; the invention disclosesa method for authenticating an access edge computing node of terminal equipment. The edge computing node can verify the legality of the identities of all accessed devices under the condition of not communicating with the cloud platform; according to the method and the device, the real identity information of the terminal cannot be learned, the identity privacy of the terminal equipment is guaranteed, the access authentication efficiency is improved, common threats such as replay attacks can be resisted, the safety and reliability of the whole edge computing system are enhanced, and the problem of access authentication of the terminal equipment with limited resources in an edge computing scene is solved.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Method and device for node authentication based on block chain network
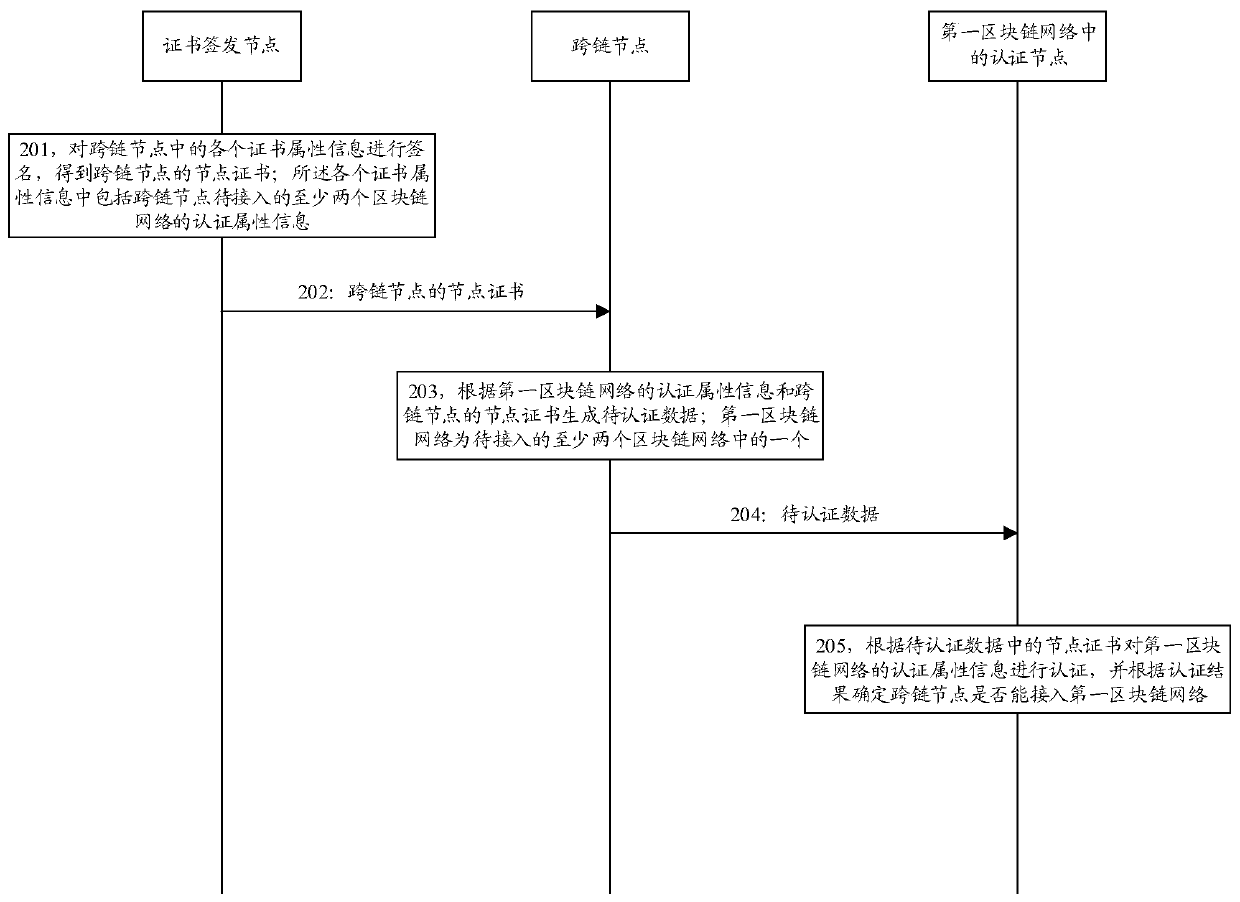
ActiveCN111131171AWon't leakEnsure safetyUser identity/authority verificationEngineeringChain network
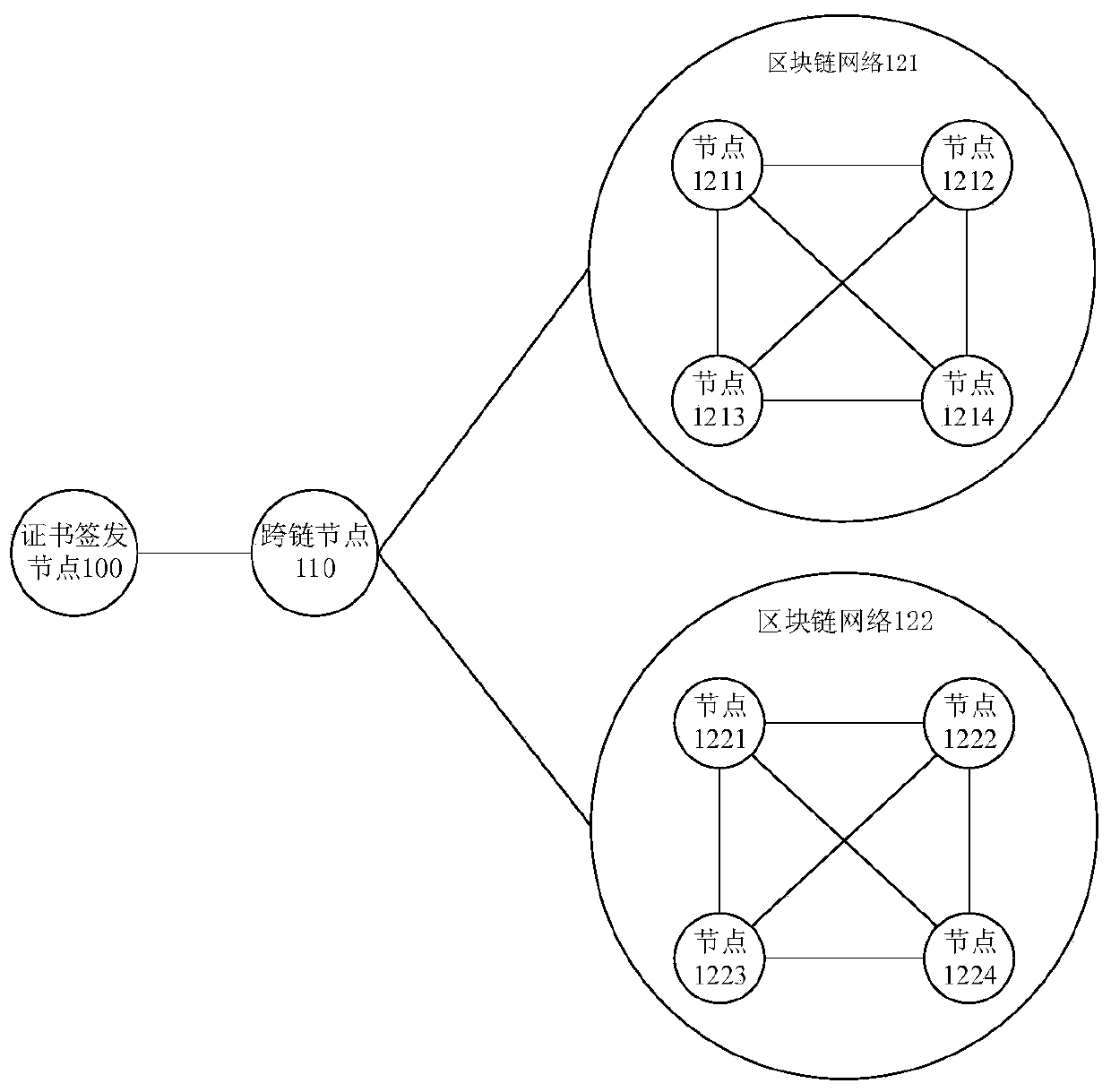
The embodiment of the invention discloses a method and a device for node authentication based on a block chain network. A certificate issuing node signs each piece of certificate attribute informationin a cross-chain node to obtain a node certificate, so that the cross-chain node generates to-be-authenticated data according to the authentication attribute information of a first block chain network and the node certificate, and sends the to-be-authenticated data to an authentication node in the first block chain network to enable the authentication node to perform authentication. The node certificate of the cross-chain node is obtained by signing authentication attribute information of at least two to-be-accessed block chain networks, so that the cross-chain node uses one node certificateto manage an authentication process of accessing multiple block chain networks by the cross-chain node, and the complexity of node certificate management and authentication can be reduced; and the authentication attribute information of other block chain networks cannot be leaked during authentication, so that the security of the authentication attribute information of each block chain network canbe ensured.
Owner:WEBANK (CHINA)
Network authentication
ActiveUS20150264040A1Optimize networkOvercomes drawbackDigital data processing detailsMultiple digital computer combinationsWeb authenticationOnline identity
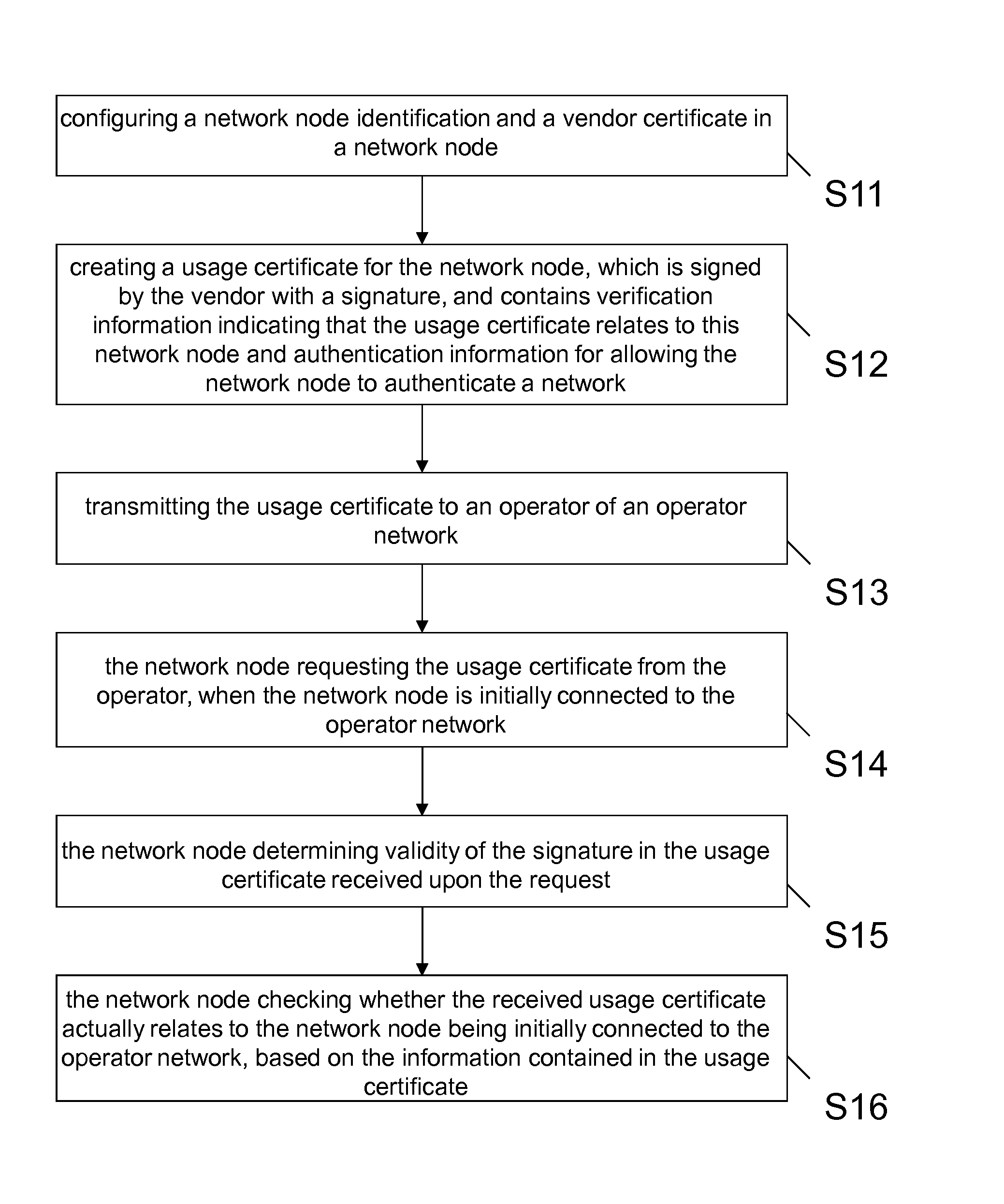
The present invention addresses apparatuses, methods and computer program product for providing improved authentication of a network by a network node. A network node identification and a vendor certificate are configured in a network node, a usage certificate is created for the network node, which is signed by the vendor with a signature, and contains verification information indicating that the usage certificate relates to this network node and authentication information for allowing the network node to authenticate a network, the usage certificate is transmitted to an operator of an operator network, the network node requests the usage certificate from the operator, when the network node is initially connected to the operator network, the network node determines validity of the signature in the usage certificate received upon the request, and the network node checks whether the received usage certificate actually relates to the network node being initially connected to the operator network, based on the information contained in the usage certificate.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Method of registering home address of a mobile node with a home agent
InactiveUS7636569B2Easy to deployLimited durationUnauthorised/fraudulent call preventionMultiple digital computer combinationsResponse processSecurity association
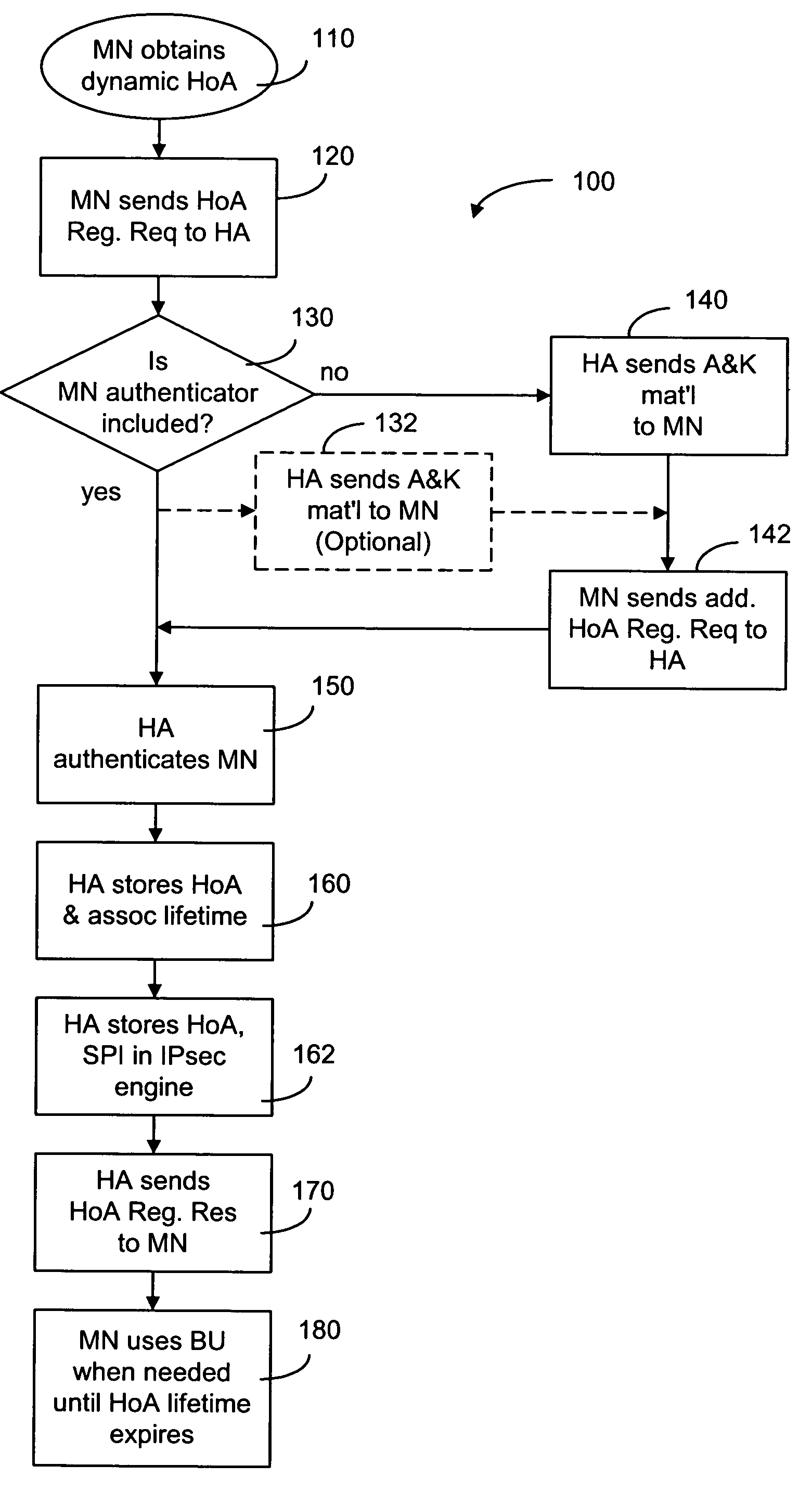
A method for registering a home address of a mobile node with a home agent in a network. Instead of using the home address of the mobile node as the key element in identifying the mobile node, the home agent uses the network access identity of the mobile node included in a registration request sent by the mobile node to the home agent in the registration process. Upon receiving the registration request, the home agent authenticates the mobile node by selecting the appropriate security association based on the network access identity. In response, the home agent may send Authentication and Key material to the mobile node so as to allow the mobile node to further provide the home agent with a mobile node authentication for use in a challenge-response procedure.
Owner:NOKIA CORP
A node access and node authentication method based on edge computing
ActiveCN109861828AGuaranteed reliabilityPrevent leakageKey distribution for secure communicationPublic key for secure communicationInternet Authentication ServiceAccess method
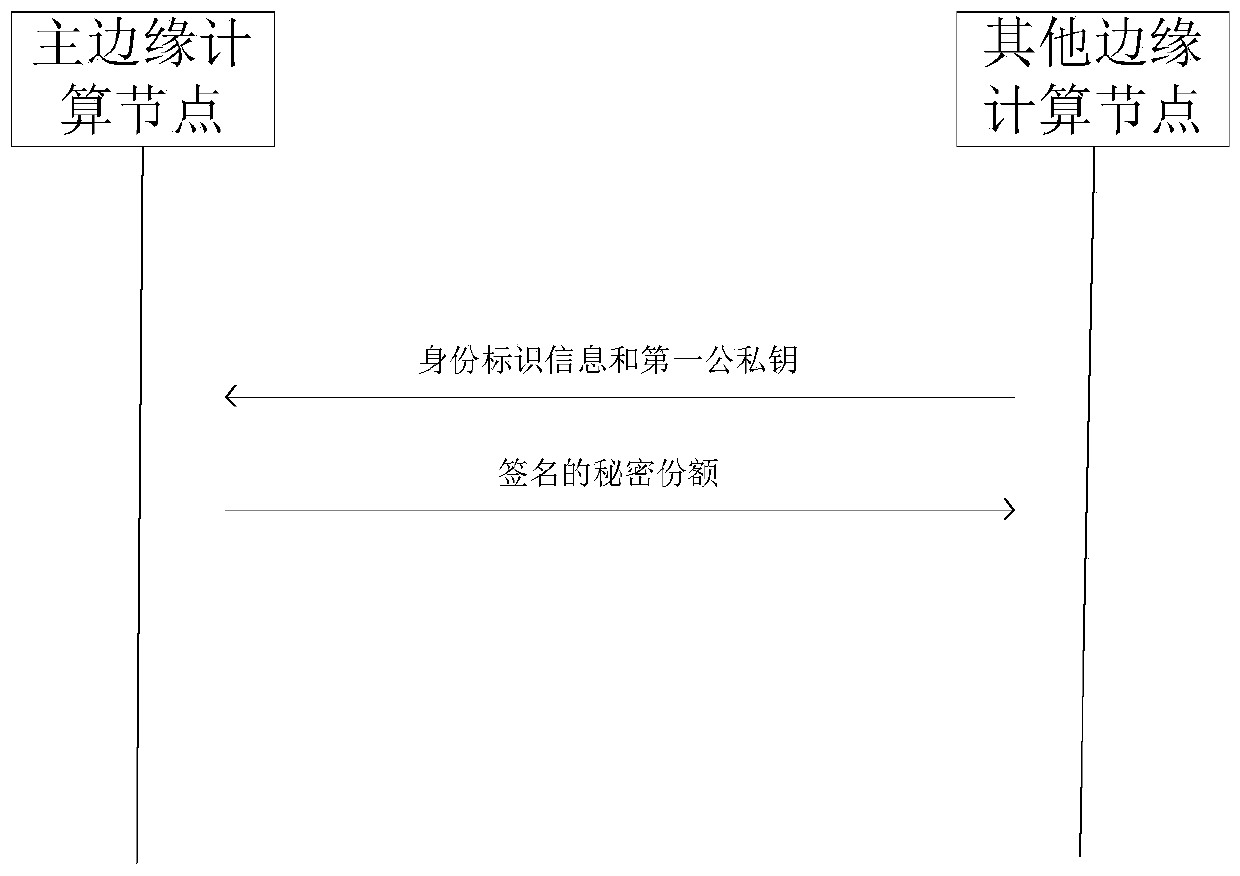
The invention discloses a node access and node authentication method based on edge computing. The access method comprises the following steps: receiving an authentication master key and a public parameter sent by a key generation server; Sending identity identification information to the main edge computing node and the key generation server; Receiving part of private key information generated bythe key generation server according to the authentication master key, the public parameters and the identity information; Calculating a first public and private key according to the public parameter,the identity identification information and part of private key information, and sending the first public and private key to the main edge computing node; And receiving a secret share signed by the main edge computing node according to the first public and private key, and taking the secret share as a certificate of access authentication. The access method solves the technical problem that user data and privacy are threatened due to the fact that edge equipment lacks identity authentication service in the prior art, meanwhile, the secret share of the generated signature is generated, the reliability of the secret share in the transmission process is guaranteed, and the safety and reliability of a whole edge computing system are enhanced.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com