System and method for constructing trusted node network
A node network and node technology, applied in the system and system field of building a trusted node network, can solve the problems of complex management and application, data forgery and tampering, and increase maintenance costs, and achieve low management and application costs and strong scalability. and flexibility, low management costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
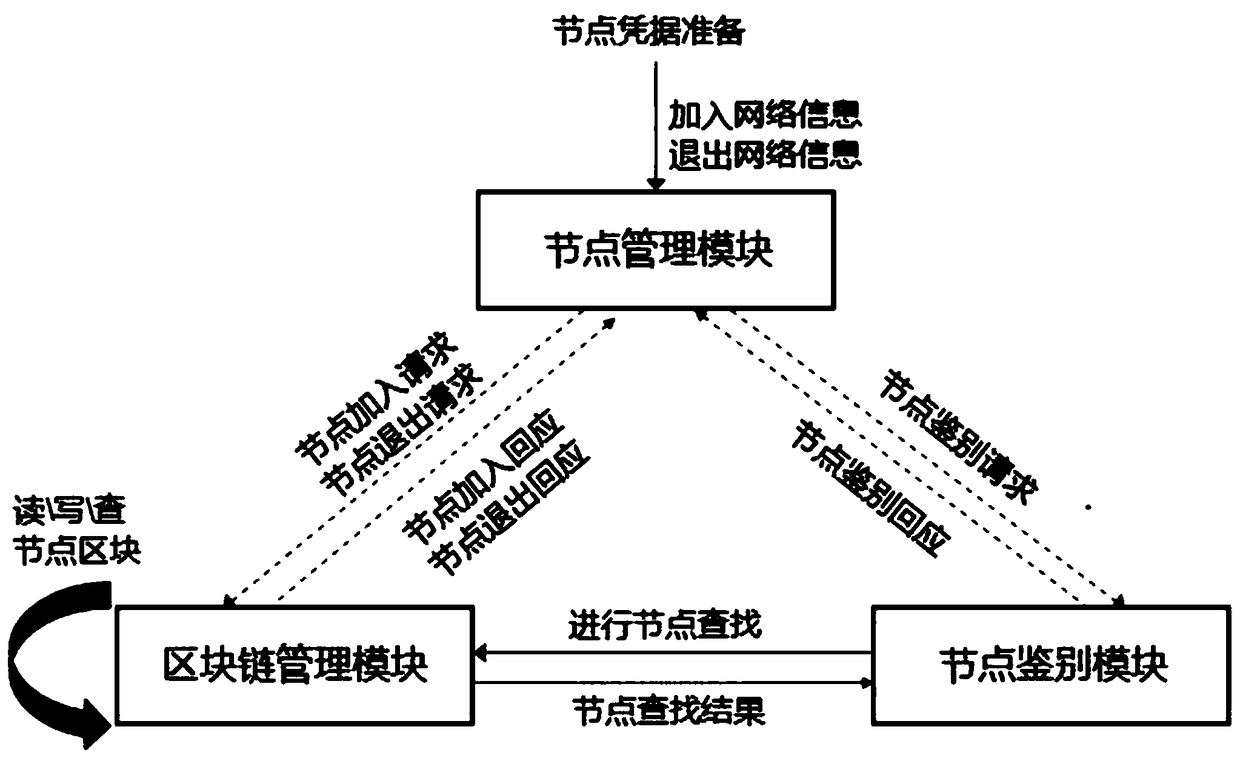
[0044] Embodiment 1: see figure 1 , a system for building a trusted node network, the system includes a block chain management module, a node management module and a node identification module;
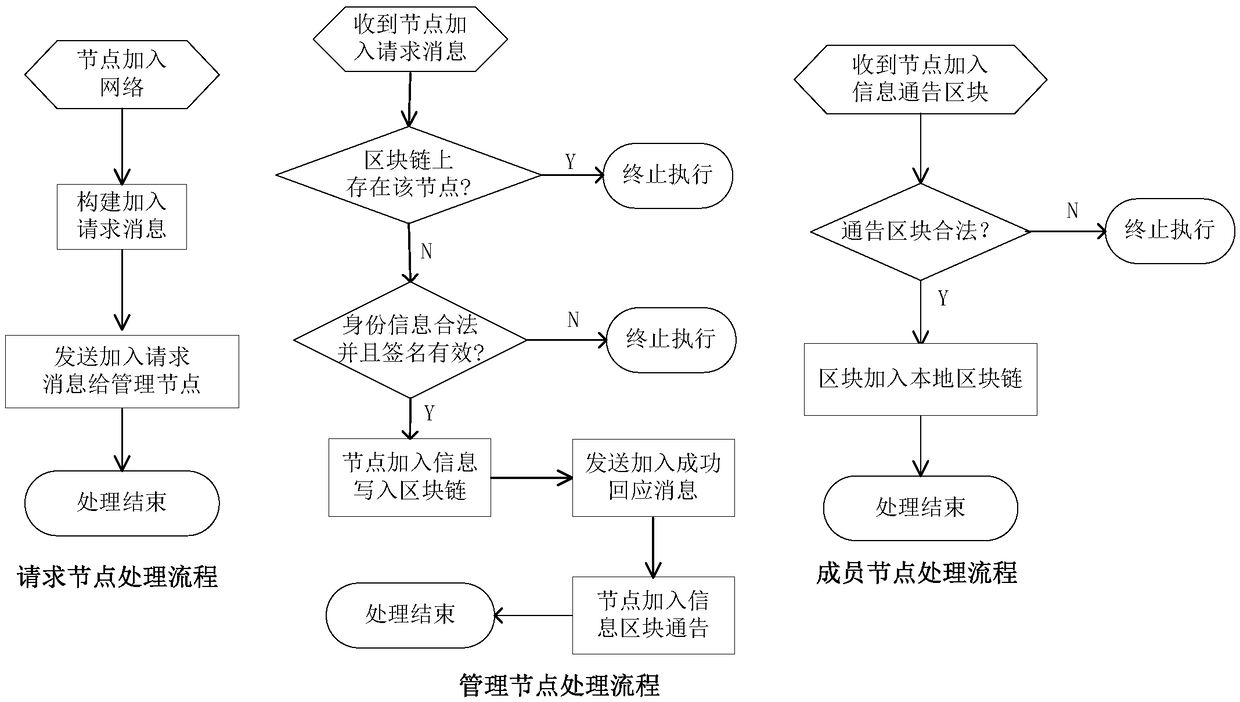
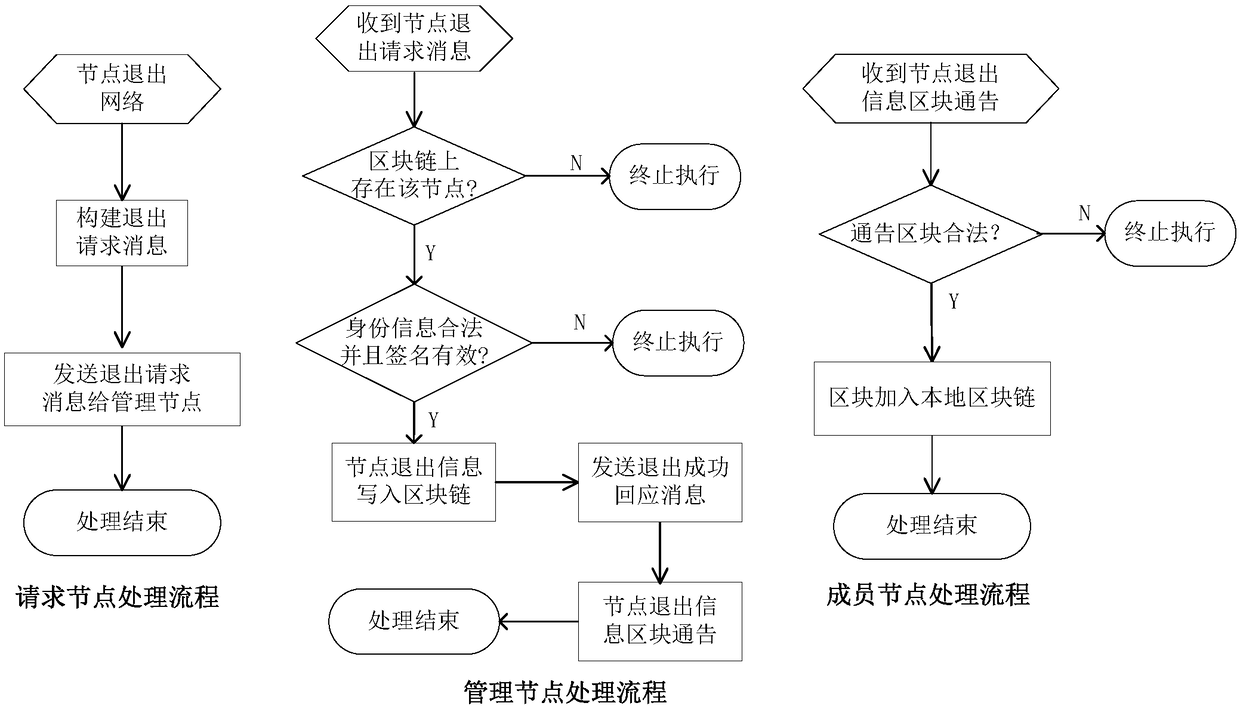
[0045] The blockchain management module is responsible for the management of node member information on the blockchain, that is, reading, writing, and checking the node information of the blockchain, as well as the management of the node's blockchain read and write authority; the node management module is responsible for the node members on the blockchain The joining, exiting, node network member information management, etc.; the node identification module is responsible for identifying the credibility of other nodes on the blockchain communicating with the node.
[0046] The details of the node network are as follows. The trust system of the trusted node network is jointly established and maintained by the node group through blockchain technology. The blockchain system is composed of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com