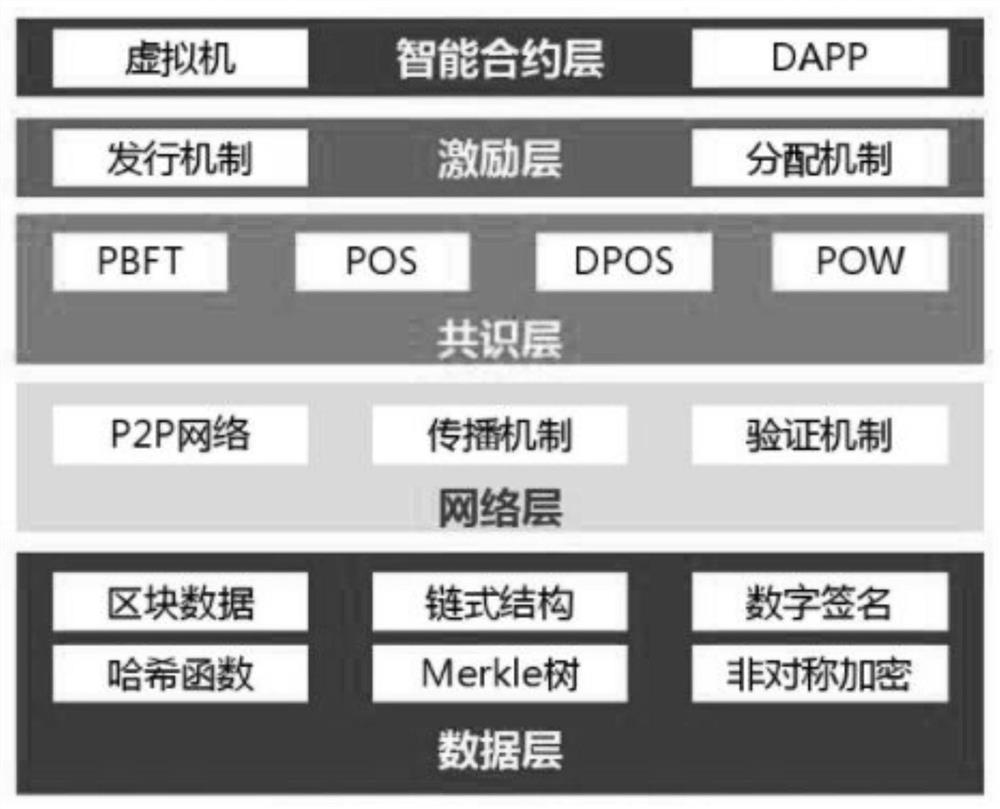
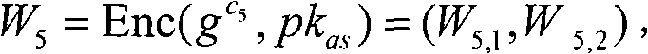Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
176results about How to "Cannot be tampered with" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
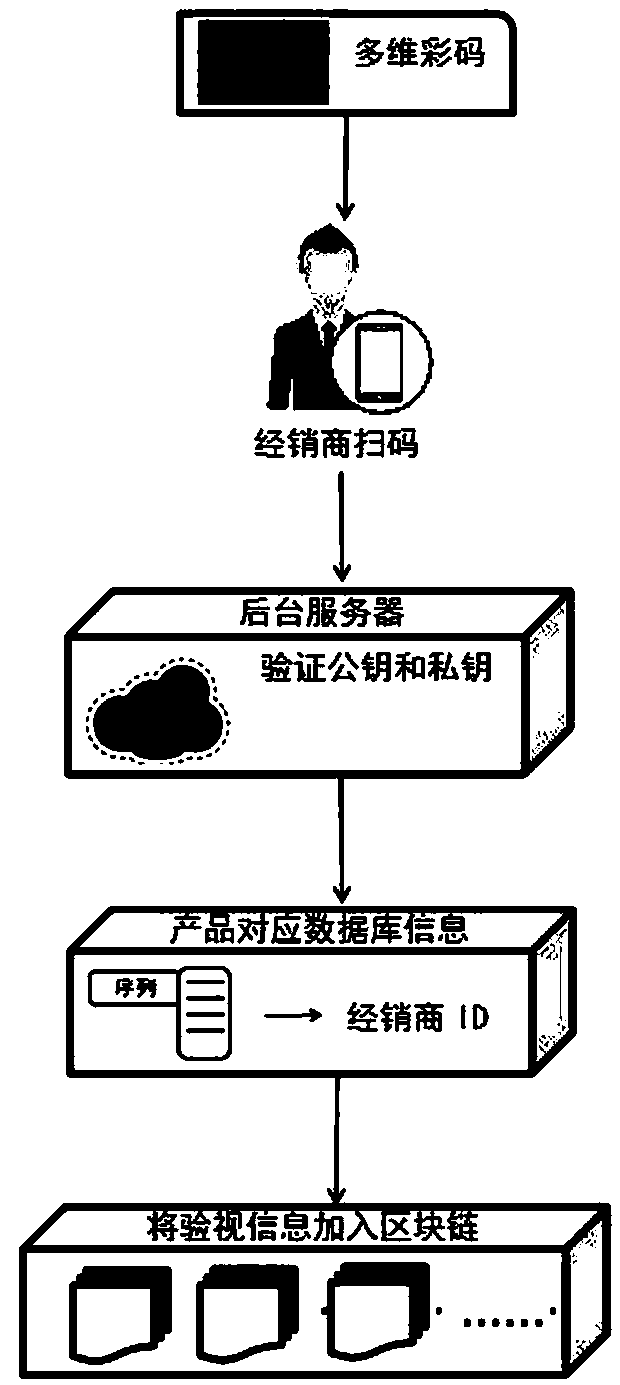
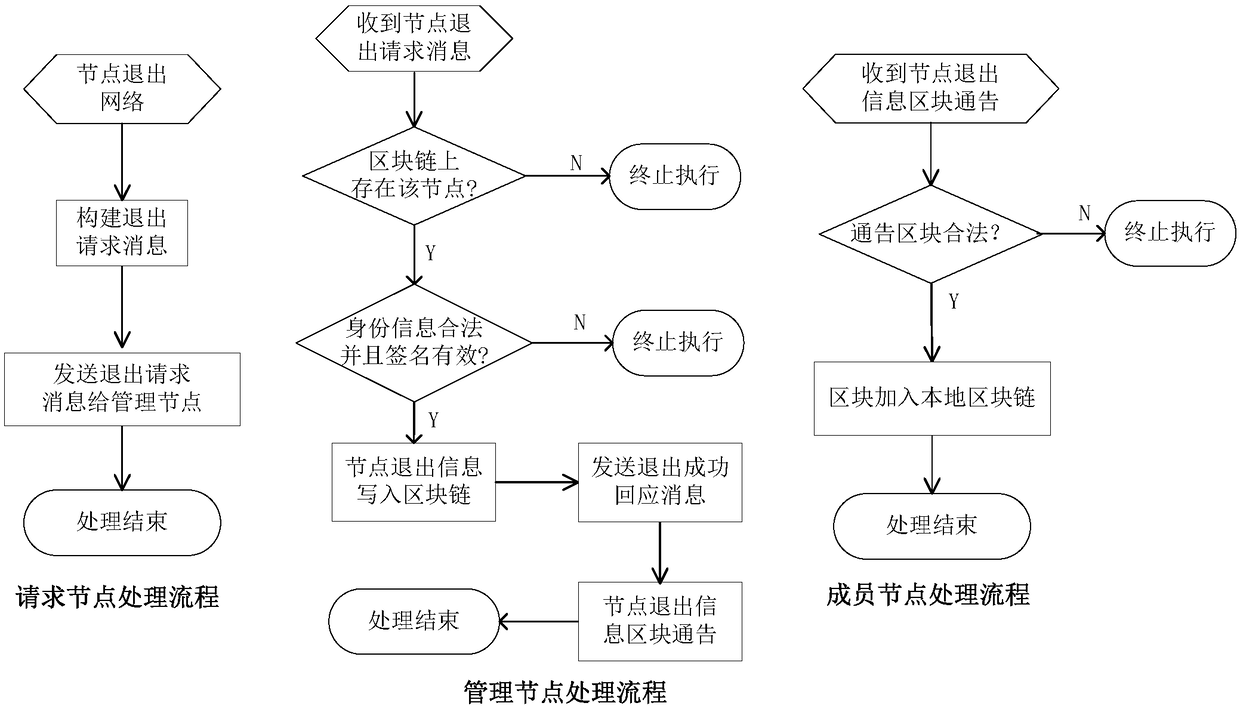
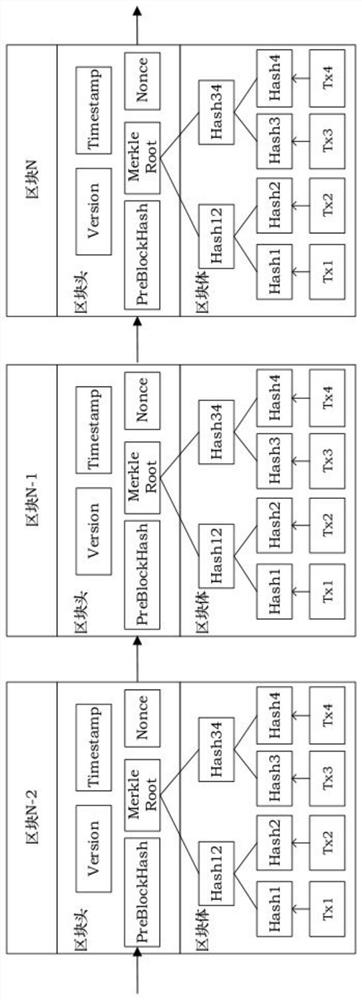
Authentication method and device based on blockchain
InactiveCN106790253AImprove the ability of hackingImprove accuracyUser identity/authority verificationProtocol authorisationDigital assetBlockchain
The invention discloses an authentication method and device based on a blockchain. The method comprises the following steps: generating a roll-out private key for transferring digital assets through the blockchain and a corresponding roll-out public key according to a random number; carrying out coding treatment on the roll-out public key, and generating a roll-in address; carrying out digital signature on the basis of the roll-out private key, a transferring numerical value of the digital assets to be transferred and the roll-in address; acquiring digital asset transferring data on the basis of the transferring numerical value, the roll-in address, the digital signature and the roll-out public key; and broadcasting the digital asset transferring data into the blockchain so that the digital asset transferring data are subjected to first-grade authentication by an authentication side, or are subjected to multi-grade authentication by a server side and the authentication side jointly after first-grade authentication is finished. Therefore, by the embodiment, hacker attack ability can be improved, and safety requirements of data and transaction in a blockchain open environment can be met.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院
Digital certificate management method and device and electronic equipment
ActiveCN107508680AImprove securityCannot be tampered withCryptography processingUser identity/authority verificationKey signatureBlockchain
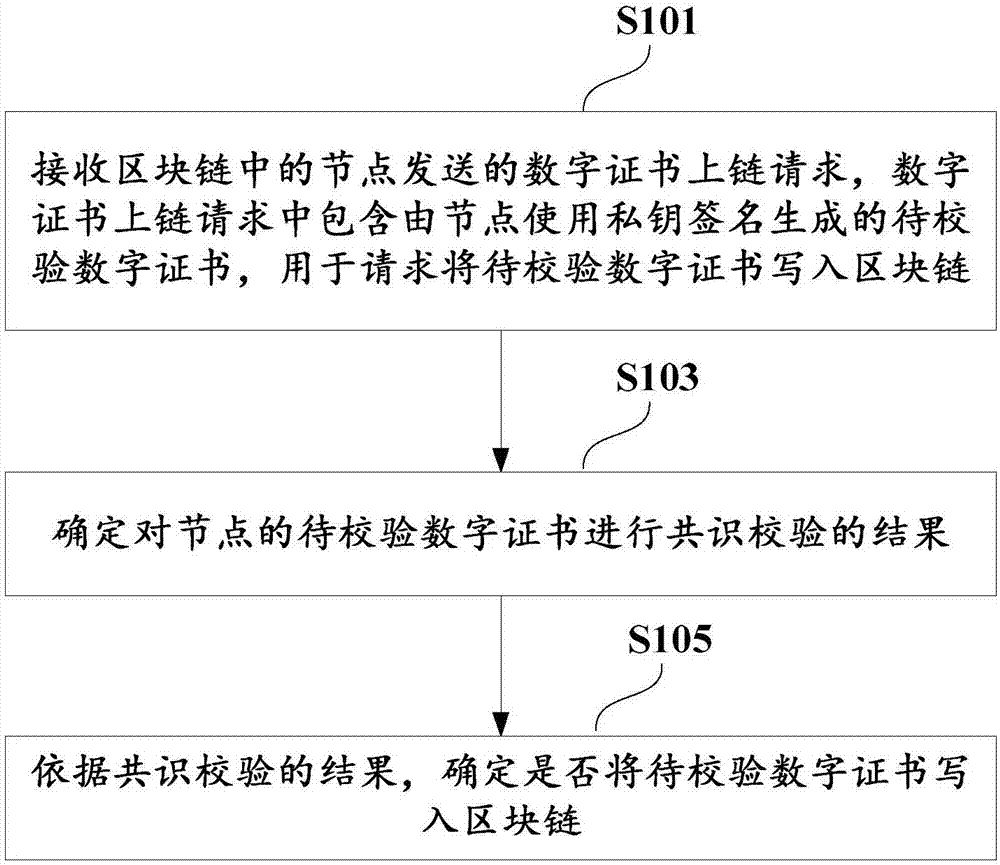
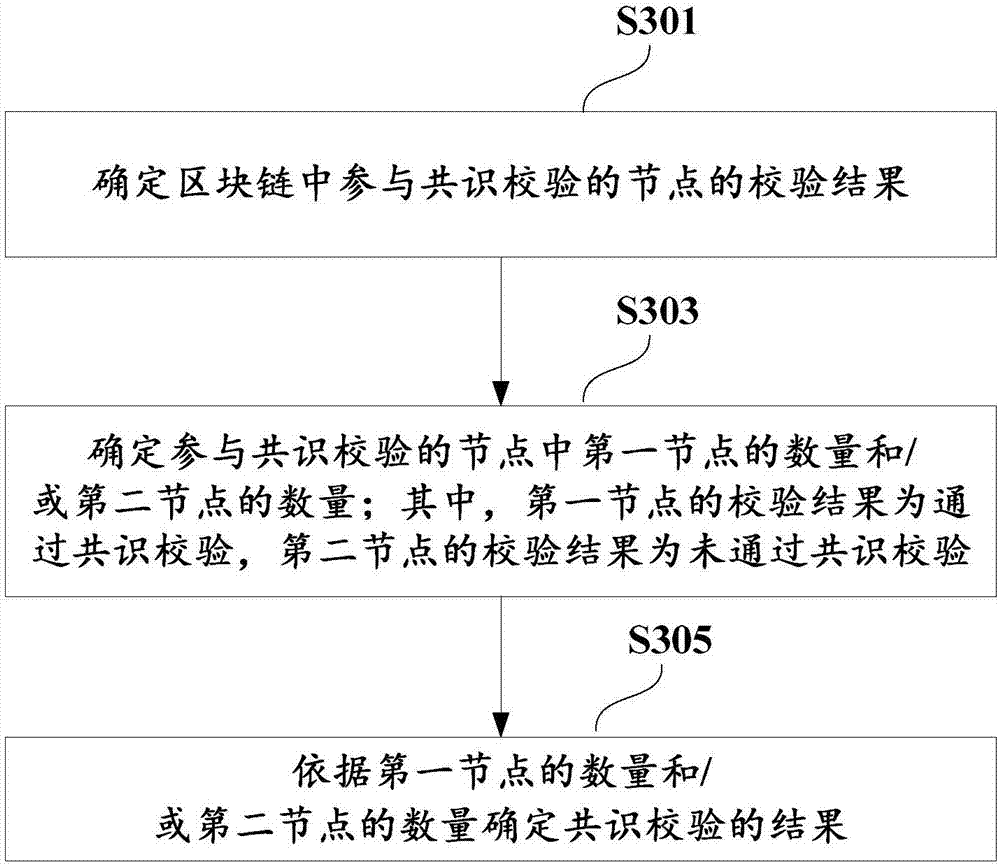
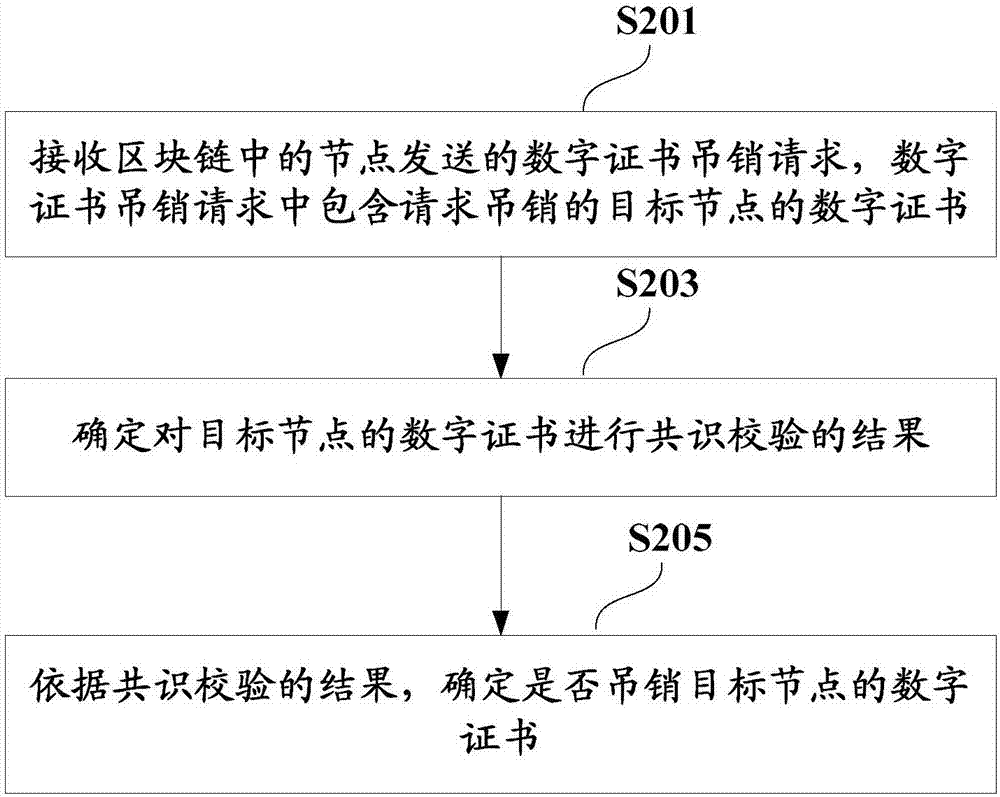
The application discloses a digital certificate management method which comprises the steps of: receiving a digital certificate uplink request sent by a node in a block chain, wherein the digital certificate uplink request comprises a to-be-checked digital certificate generated by the node by using a private key signature and is used for requesting to write the to-be-checked digital certificate into the block chain; determining a result of carrying out consensus checking on the to-be-checked digital certificate of the node; and according to the result of consensus checking, determining whether to write the to-be-checked digital certificate into the block chain. The application further discloses a corresponding device, electronic equipment and the like.
Owner:ADVANCED NEW TECH CO LTD
Identity authentication method based on block chain, authentication server and user terminal
ActiveCN106453407ACannot be tampered withImprove securityTransmissionProtocol authorisationAuthentication systemSmart contract
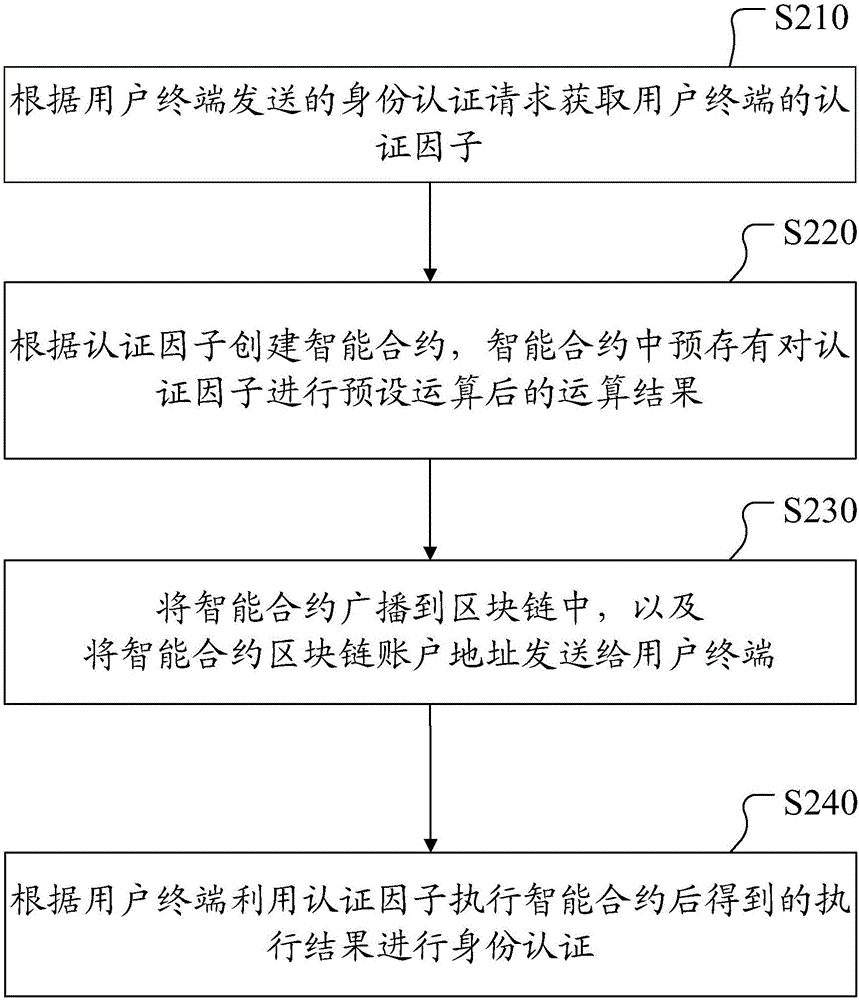
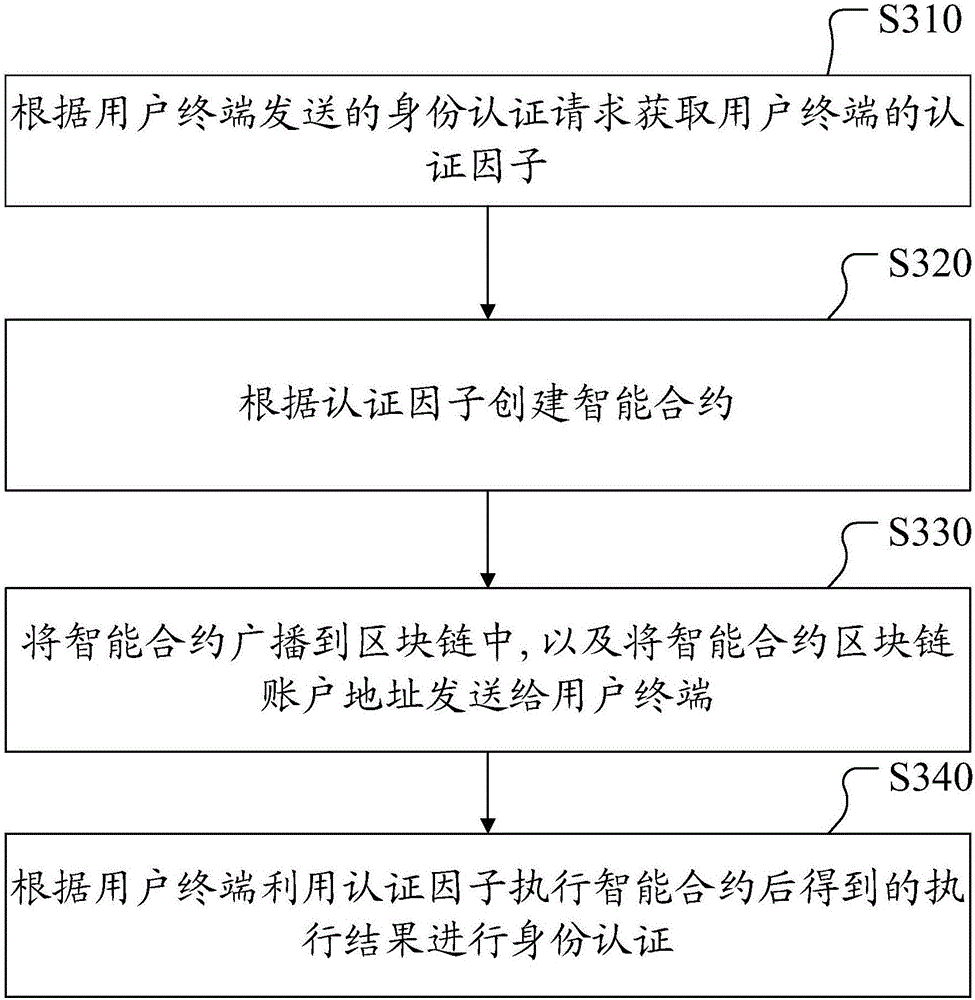
The embodiment of the application discloses an identity authentication method based on a block chain, an authentication server and a user terminal, and belongs to the technical field of identity identification. The method comprises the steps of: according to an identity authentication request sent by the user terminal, acquiring an authentication factor of the user terminal; according to the authentication factor, creating a smart contract, wherein an operation result obtained after a preset operation is carried out on the authentication factor is pre-stored in the smart contract; broadcasting the smart contract into the block chain, and sending a smart contract block chain account address to the user terminal; and according to an execution result obtained after the user terminal executes the smart contract by utilizing the authentication factor, carrying out identity authentication, wherein when the execution result is matched with the operation result, success of identity authentication is confirmed, and when the execution result is not matched with the operation result, failure of identity authentication is confirmed. Therefore, the identity authentication method in the embodiment of the application has very high safety.
Owner:JIANGSU PAYEGIS TECH CO LTD
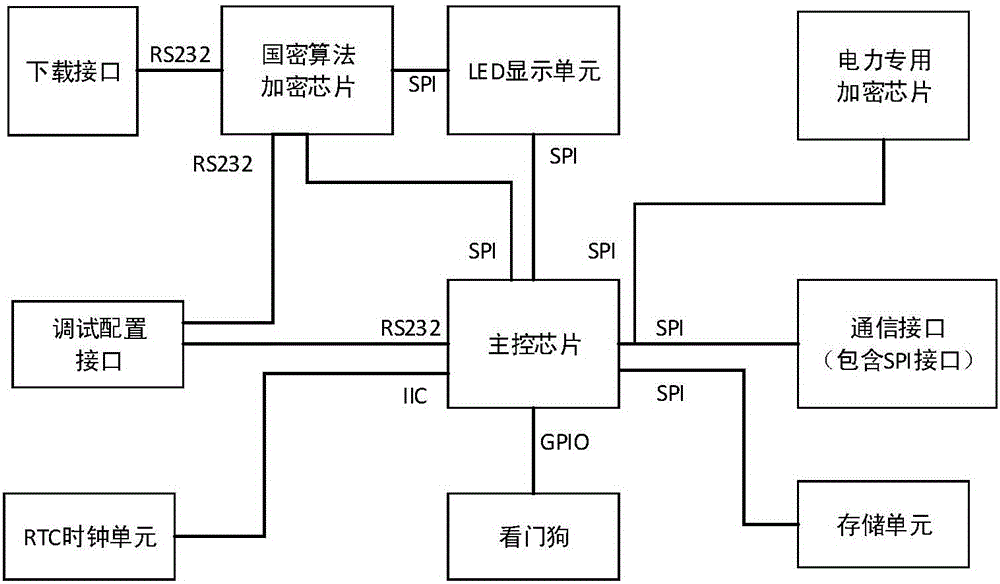
Security encryption authentication module for power distribution terminal communication and method thereof
InactiveCN105871873ASpeed up encryption/decryption timeReduce dependenceKey distribution for secure communicationUser identity/authority verificationCommunication interfaceCommunications security
The invention discloses a security encryption authentication module for power distribution terminal communication and a method thereof. The security encryption authentication module comprises a main control chip, a commercial code algorithm encryption chip, a communication interface and a storage unit; the main control chip is connected with the commercial code algorithm encryption chip, the communication interface and the storage unit and receives message information of a front-end processor of a distribution master station and a distribution terminal through safe interface software of the distribution terminal to overall manages the other modules, and the commercial code algorithm encryption chip encrypts or decrypts the message information received by the main control chip. The special encryption chip is adopted in the security encryption authentication module, response speed is increased, and dependence on a CPU and an internal storage is reduced. Besides, communication security is greatly improved by means of bidirectional authentication of verifying each other's identity between the security encryption authentication module and a distribution security interaction gateway.
Owner:STATE GRID CORP OF CHINA +4
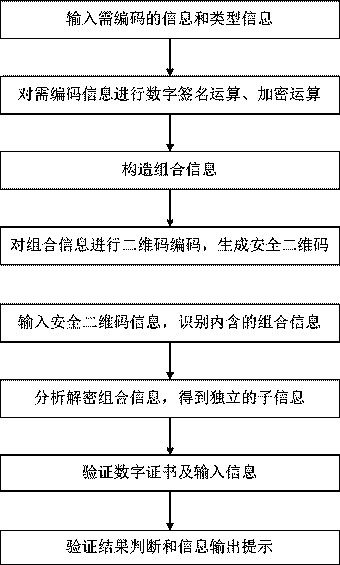
Construction verification method and device capable of verifying security two-dimensional code offline
ActiveCN106452756AEasy to useCannot be tampered withKey distribution for secure communicationUser identity/authority verificationInformation analysisEffective time
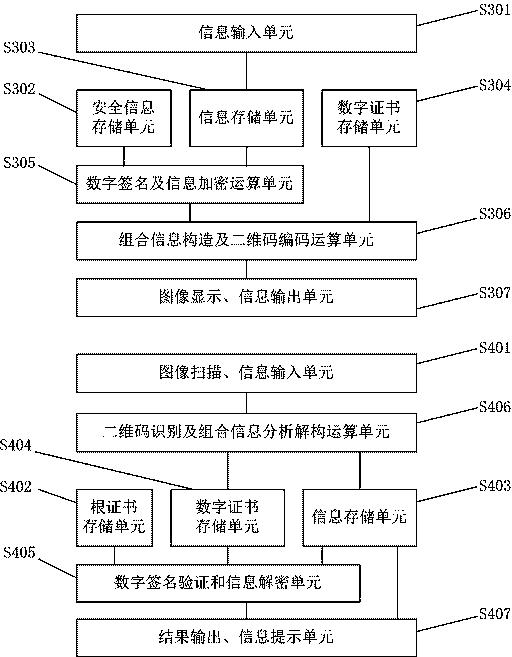
Embodiments of the invention provide a construction verification method and device capable of verifying a security two-dimensional code offline. The method comprises the following steps of inputting information that needs coding and type information, carrying out digital signature operation and encryption operation on the input information according to an information release type, constructing combination information, and encoding to generate a security two-dimensional code which can be verified off-line according to a two-dimensional code coding rule; inputting the information of the security two-dimensional code and identifying included combination information and type information, analyzing and decoding the combination information to obtain independent sub-information according to the type information of the two-dimensional code, and verifying digital certificate effectiveness information, a digital signature of the input information and an effective time limit of the input information; and if all verifications pass, showing that the offline verification of the security two-dimensional code is correct and the coding information source of the security two-dimensional code is credible, otherwise showing that the information release source of the security two-dimensional code is incredible. The method and the device have the beneficial effects that the security two-dimensional code cannot be tampered, counterfeited and denied, the public or private information can be released, and the integrity of the information of the security two-dimensional code and the authenticity of the source can be verified offline without a network connection.
Owner:王栋
Commodity tracing method and system based on blockchains
ActiveCN108305083AAchieving Zero-Cost JoiningJoin flexibleFinanceCo-operative working arrangementsParallel computingService networks
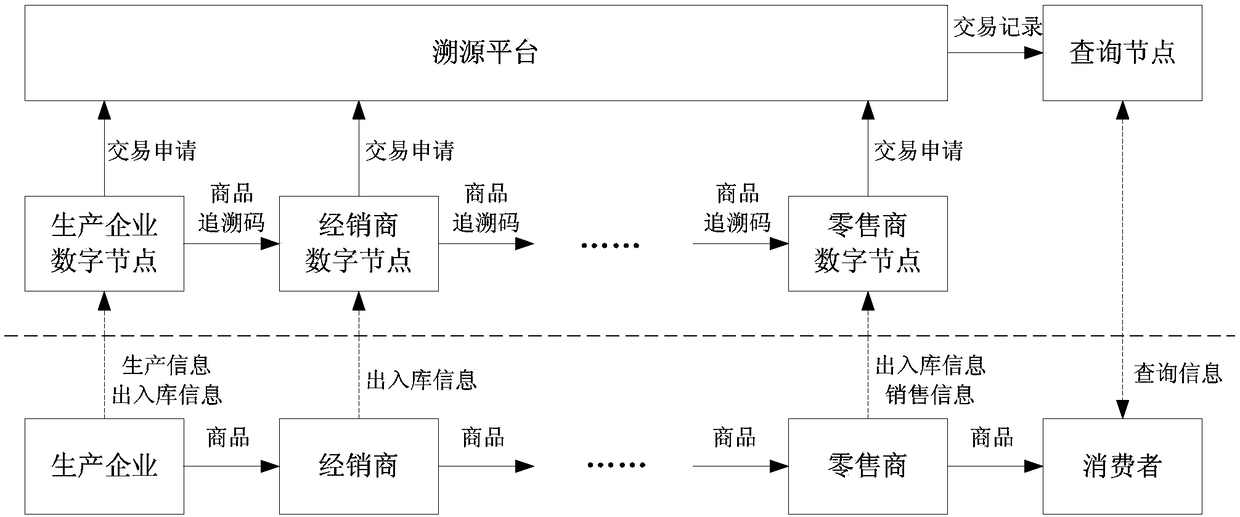
The invention discloses a commodity tracing method and system based on blockchains. The method includes: a plurality of equivalent service nodes form a decentralized service network used for recordinga detailed process of circulation of commodity tracing codes as block data; and production enterprises, and dealers and retailers at all levels are regarded as different categories of user nodes connected to a service platform, tracing code data related thereof is obtained and saved, and related business operations are performed. Each commodity is endowed with a unique commodity tracing code, when the commodity is circulated between the dealers, the tracing code data is circulated between the user nodes of the dealers, the circulation process of the commodity tracing codes is traced, and thetracking of the commodity circulation process is accomplished. The system is used for implementing the method. The method and the system are advantageous in that the principle is simple, the operationis simple, and the problem of commodity tracing can be basically solved.
Owner:张国忠
Public key infrastructure system based on block chain, and certificate management method thereof
ActiveCN107769925ASafe and efficient managementImprove efficiencyUser identity/authority verificationDomain nameE infrastructure
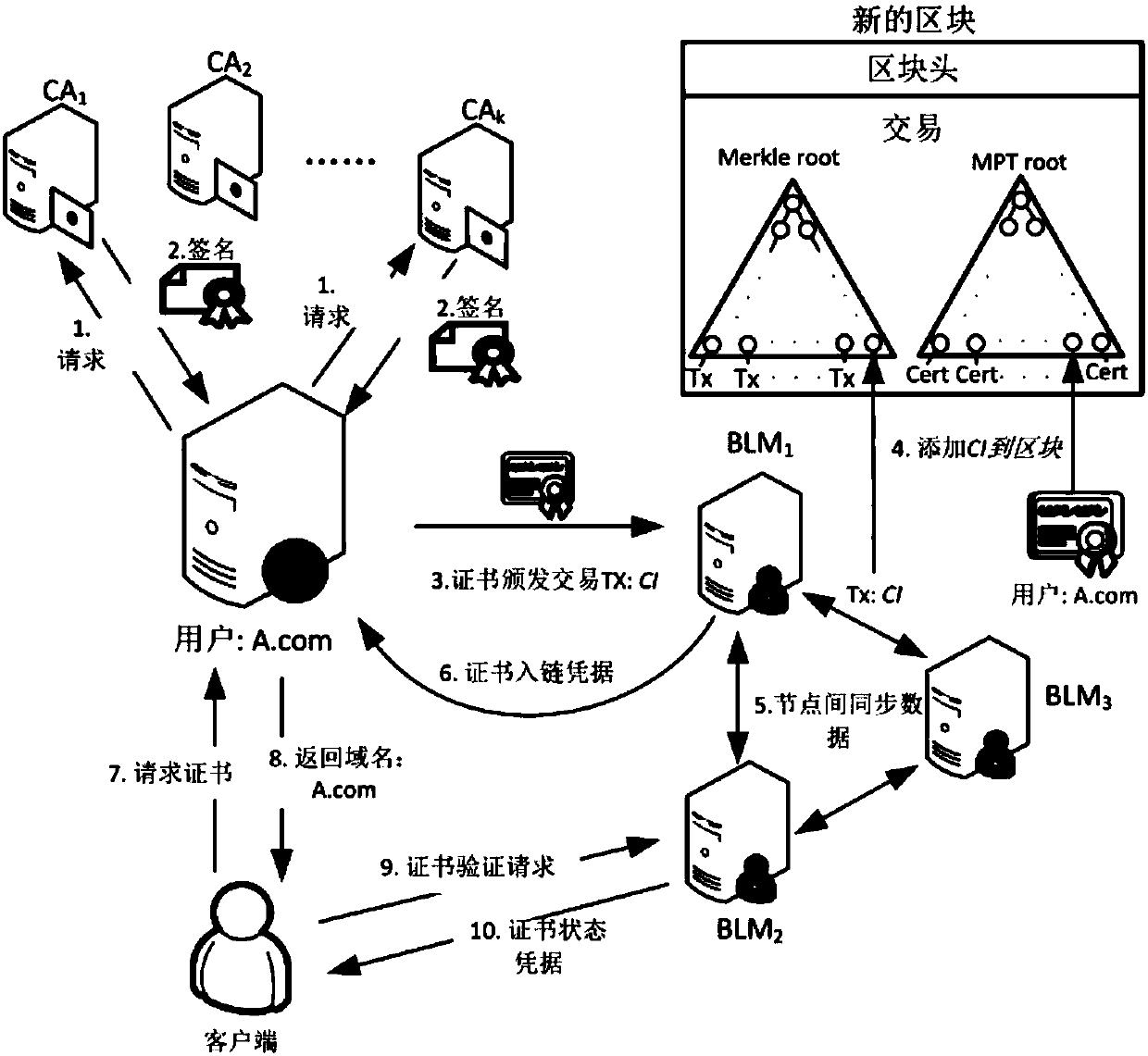
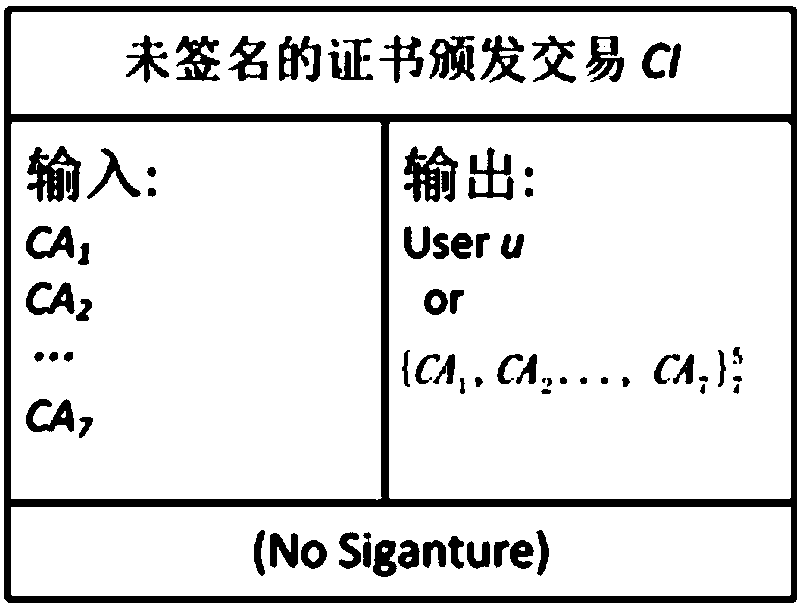
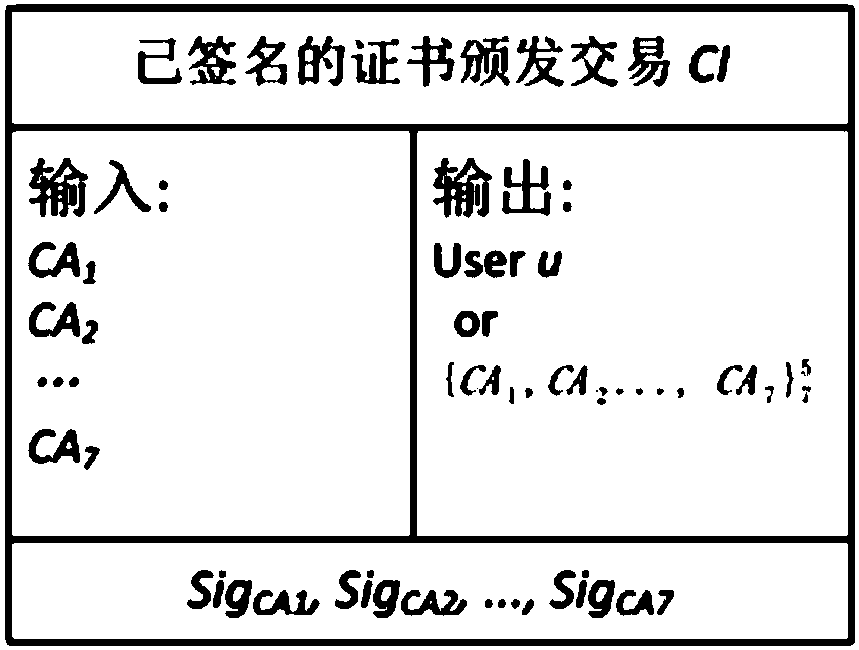
The invention relates to a public key infrastructure system based on a block chain, and a certificate management method thereof. The public key infrastructure system comprises a user u, a plurality ofCAs, a plurality of block chain maintainers BLM, a block chain and a client, the user u sends a signature request to the plurality of CAs, the plurality of CAs separately perform signature and feed back the same to the user u; the user u merges the signatures in a singed certificate issue affair and sends the same to the block chain maintainers BLM; the block chain maintainers BLM verify and store the signatures in candidate blocks of the block chain, and send proves of existence of the singed certificate issue affair CI-signed to the user u; and the client requests a certificate from the user u, the user u replies the domain name and the block chain maintainers BLM, and the client sends a query and verification request to the block chain maintainers BLM to query the state of the certificate and make response. By adoption of the public key infrastructure system, simple, convenient and efficient management of the certificates are achieved, and the problem of single point fault of CA can be avoided.
Owner:SHANDONG UNIV
Block chain privacy protection system and method based on homomorphic encryption
InactiveCN109840771AImprove confidentialityCannot be tampered withFinanceDigital data protectionEncrypted functionPrivacy protection
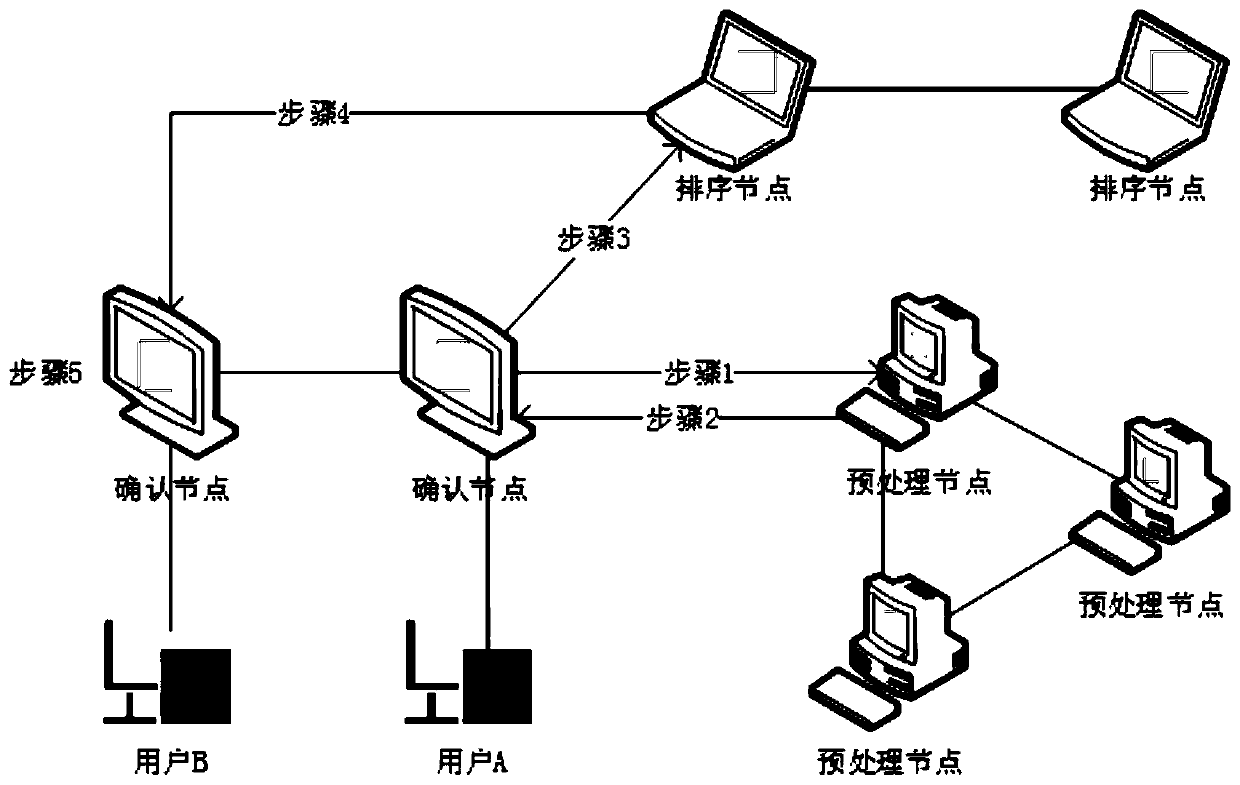
The invention provides a block chain privacy protection system and method based on homomorphic encryption. The privacy protection system comprises an authentication center which is used for carrying out identity verification, issuing a certificate and periodically checking an account book; The block chain nodes are used for collecting transactions, verifying the transactions, sorting the transactions and generating blocks; Wherein the block chain nodes comprise a preprocessing node, a confirmation node and a sorting node; And a user: one user corresponds to one confirmation node. According tothe block chain privacy protection system and method based on homomorphic encryption provided by the invention, the block chain privacy protection scheme can realize transaction information confidentiality; The blockchain privacy protection scheme can ensure that the transaction information cannot be tampered; The blockchain privacy protection scheme can ensure transaction legality; The re-encryption function in the blockchain privacy protection scheme is secure.
Owner:XIDIAN UNIV
Game data partition storage method based on block chain hash addressing and re-encryption
ActiveCN109327512AImprove securityImprove privacyUser identity/authority verificationVideo gamesStructure of Management InformationEncryption
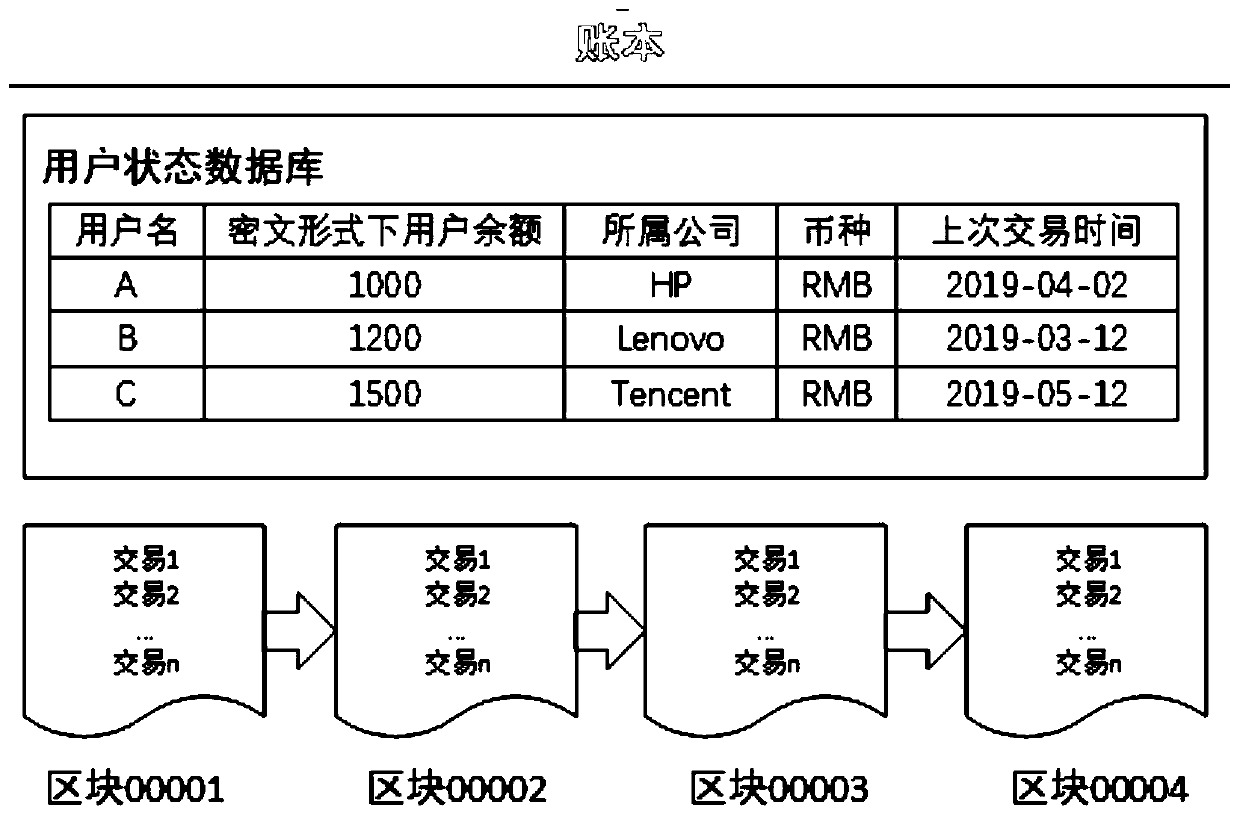
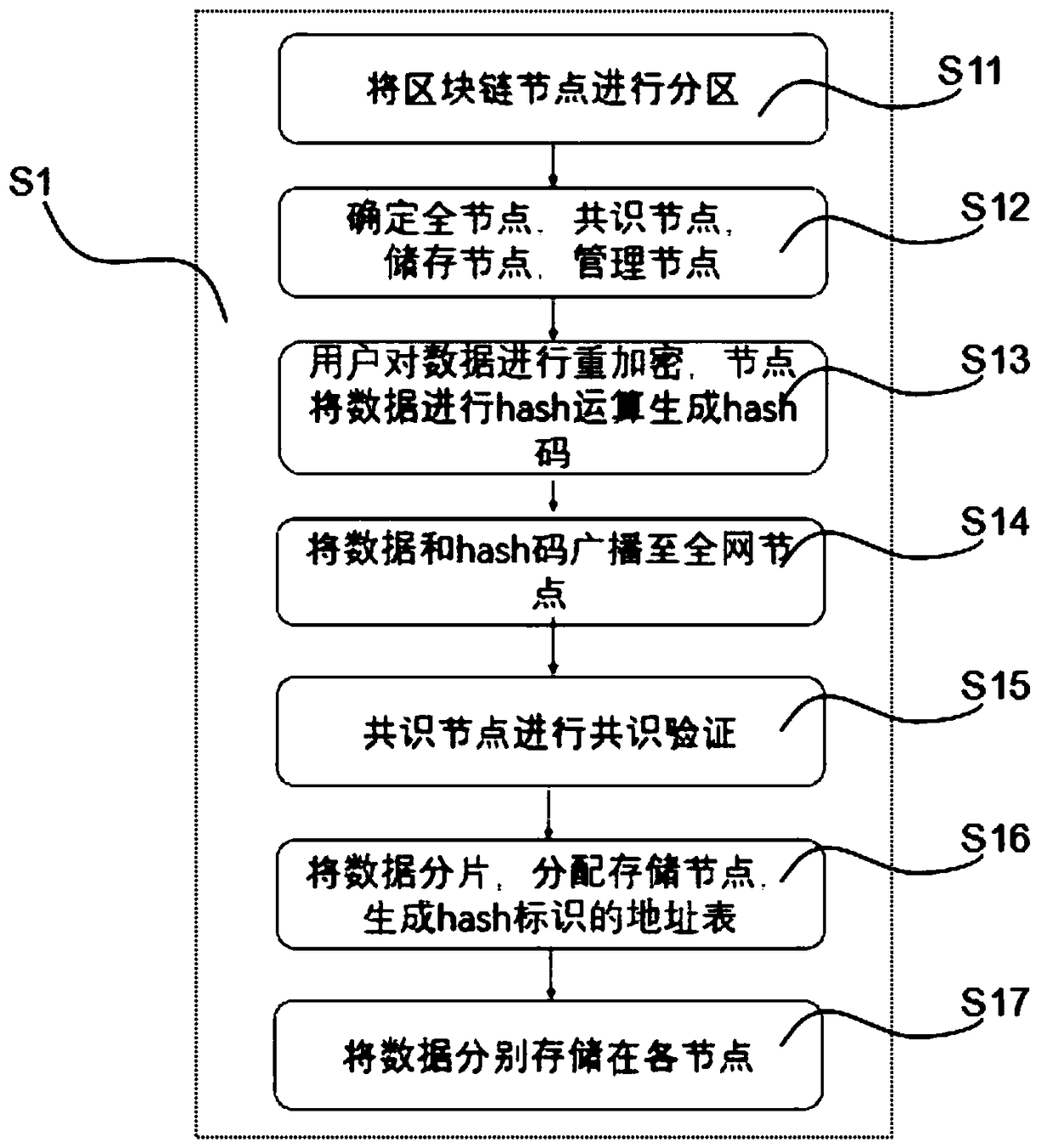
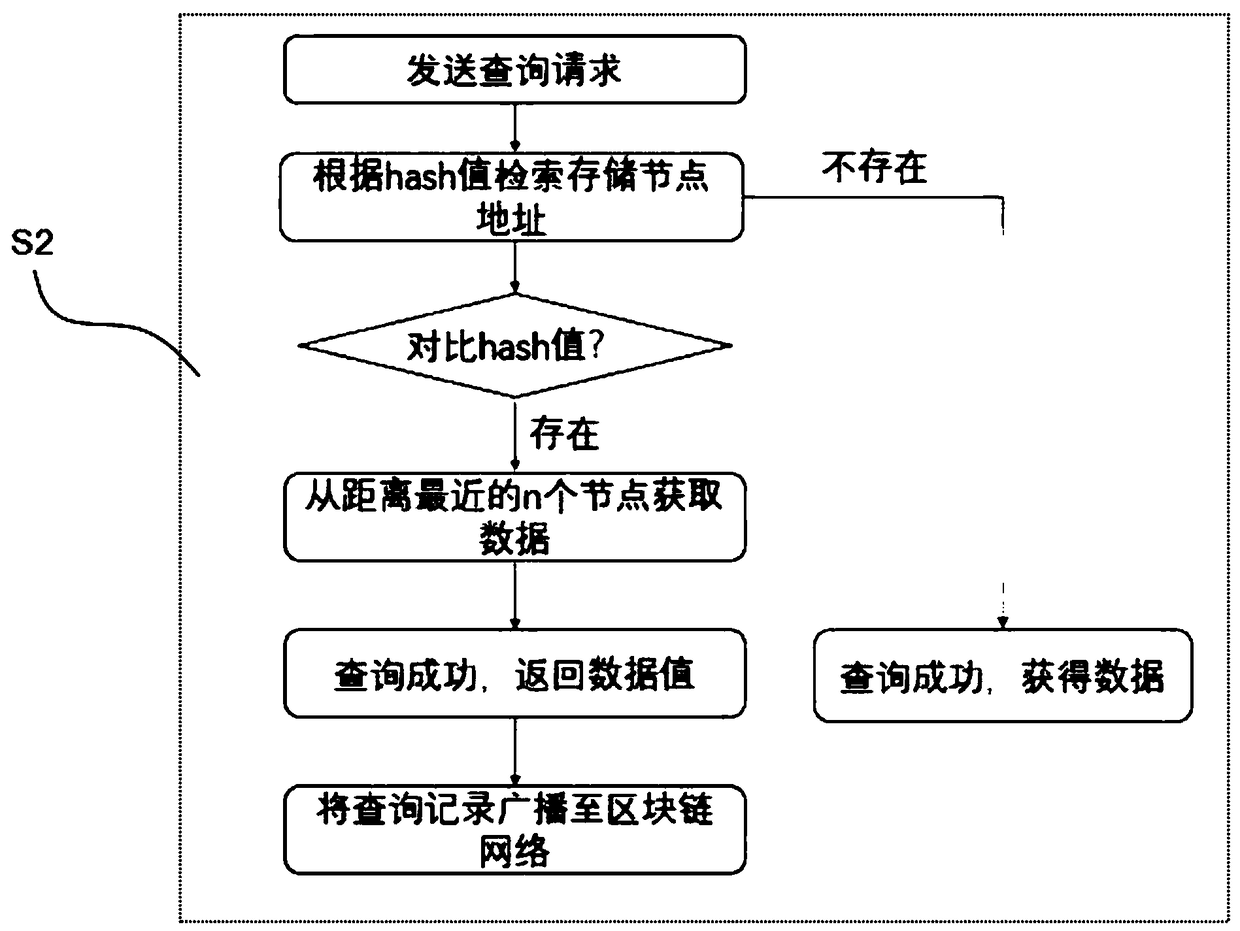
The invention relates to a game data partition storage method based on block chain hash addressing and re-encryption. The method comprises a data partition storage step and a data check step, whereinthe data partition storage step specifically comprises: partitioning block chain nodes into a full node, a consensus node, a storage node and a management node; performing hash operation on the node data to generate hash code; broadcasting the hash codes to nodes throughout the network; performing consensus verification by using hash values; generating a storage address table corresponding to thehash values; and respectively storing the data on the nodes according to the generated storage address table corresponding to the hash values. According to the game data partition storage method basedon block chain hash addressing and re-encryption, by performing fragmentation and partition storage on the data, the data have m pieces of redundancy, the stored data are fragmented, so that the dataprivacy is improved, and the nodes are classified, and different nodes are responsible for different functions, thereby reducing the resource waste, and the hierarchical node structure improves the scalability and the pluggability of the architecture.
Owner:广东微链科技有限公司
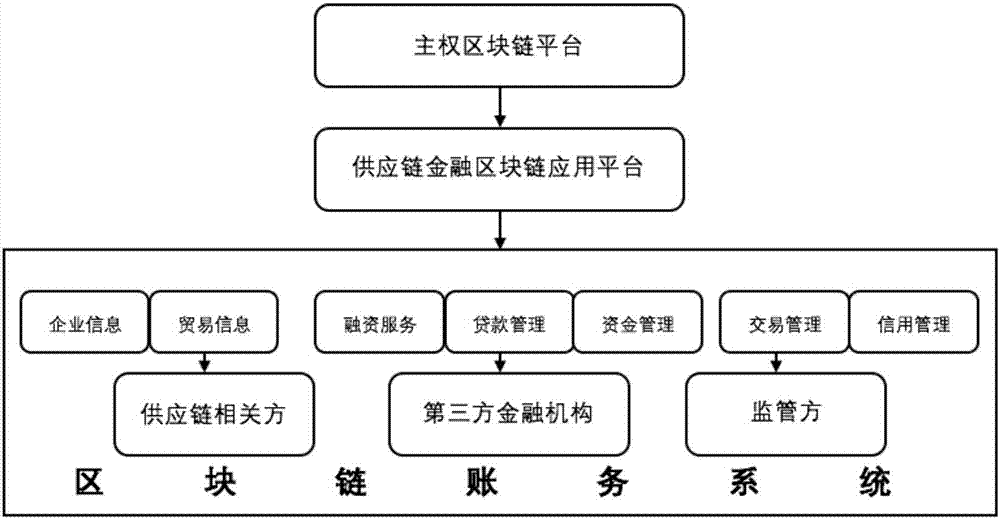
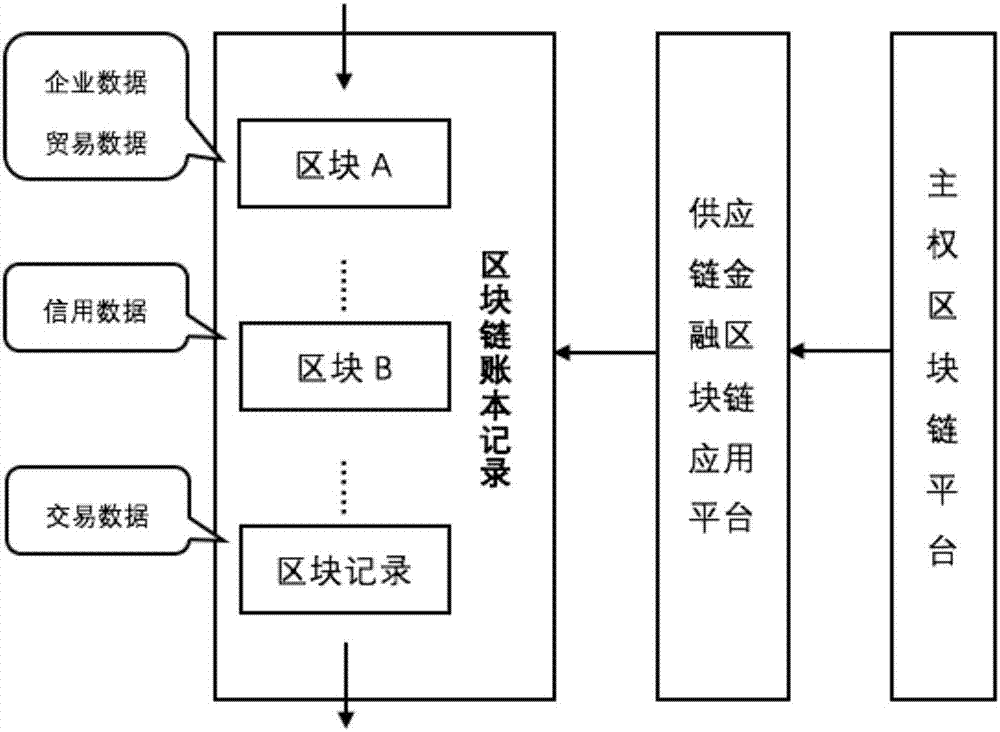
Supply chain finance block chain application method based on sovereign block chain
The invention discloses a supply chain finance block chain application method based on a sovereign block chain technology. The invention relates to a block chain field and especially relates to a sovereign block chain field. By using the method, problems that supply chain financing rate is low; a supply chain can not high-efficiently achieve a credit function; and a supply chain finance ecosphere cooperation development is restricted are solved. In the invention, based on the sovereign block chain technology, a block chain application platform suitable for China supply chain finance is constructed so that safety and traceability of supply chain finance application are increased. Mutual trust is established and transaction cost is reduced. Productivity of each node of a whole supply chain and a fund utilization rate are increased. A supervision node is provided for a supervision mechanism and whole process links of the supply chain finance are supervised.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
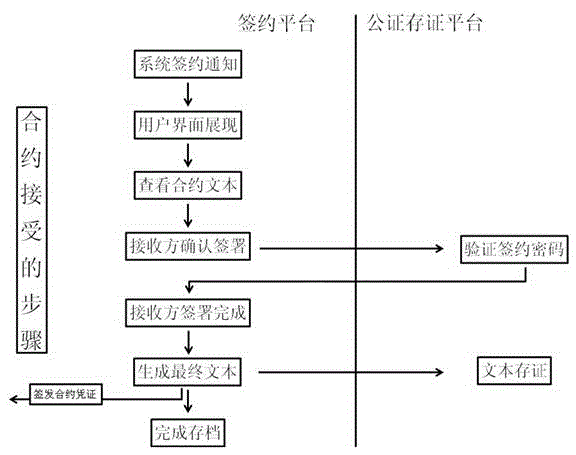
Electronic contract signing method based on the internet
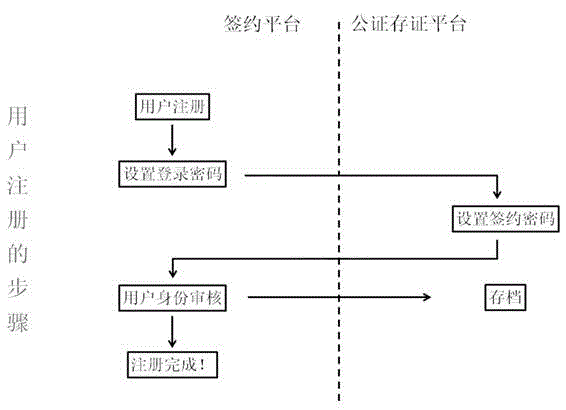
ActiveCN105635169ASolve the problem of confirming the authenticity of meaning expressionCannot be tampered withOffice automationBuying/selling/leasing transactionsThird partyElectronic contracts
The invention discloses an electronic contract signing method based on the internet. After a user registers information, a signing request is initiated; a contract text is directly uploaded to a server for text deposition; the server targets to a notarization and deposition platform; the notarization and deposition platform sends the deposited text contract to a signing platform for signing; a contrast receiver is informed of the singing by the signing platform; after confirming the signing, the receiver skips to the notarization and deposition platform for verification; after the verification is successful, the receiver returns to the signing platform for signing; and filing is carried out. According to the method provided by the invention, the signing platform and the notarization and deposition platform are separated; because of the intervention of a notarization mechanism, the original two-party relationship is changed into a three-party relationship; the data exchange generated by the signing behavior of the user is no longer generated between the user and the signing platform and is deposited by the third party notarization and deposition platform in real time; the three parties cooperate mutually and restrict mutually; and the user rights and interests are ensured.
Owner:江苏慧世联网络科技有限公司
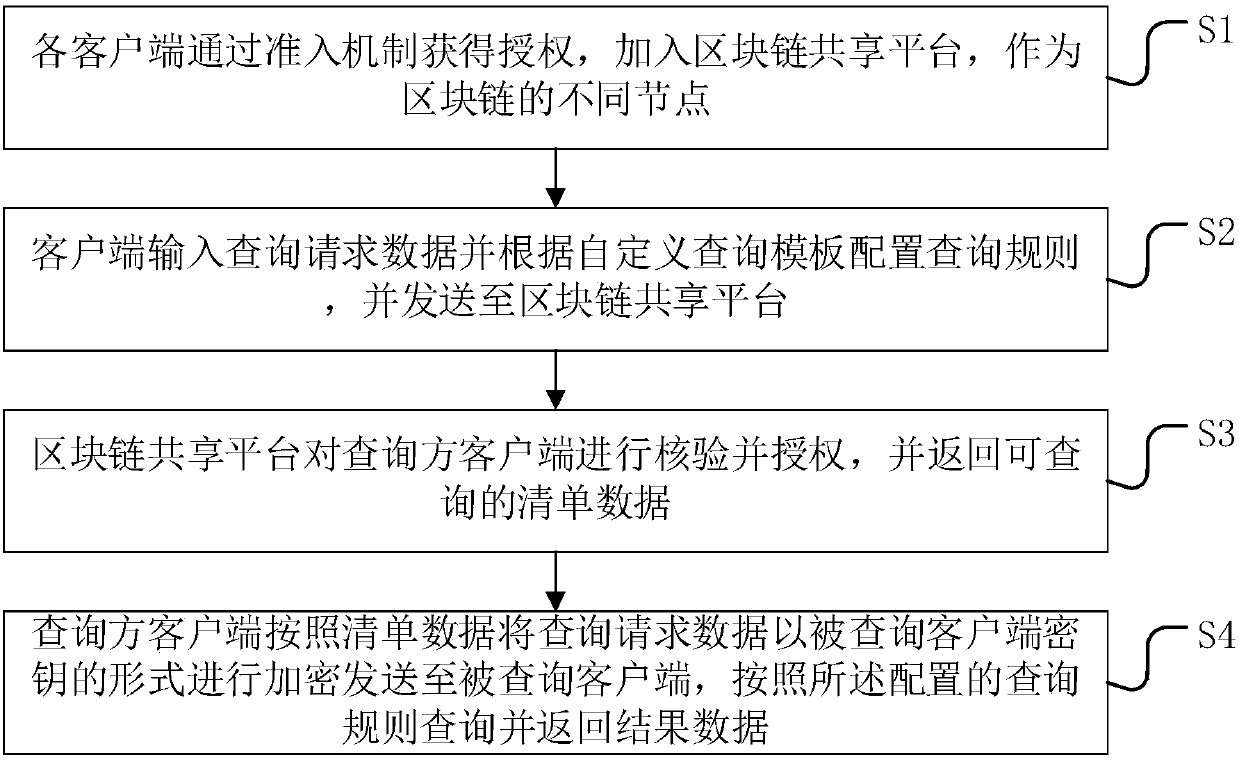
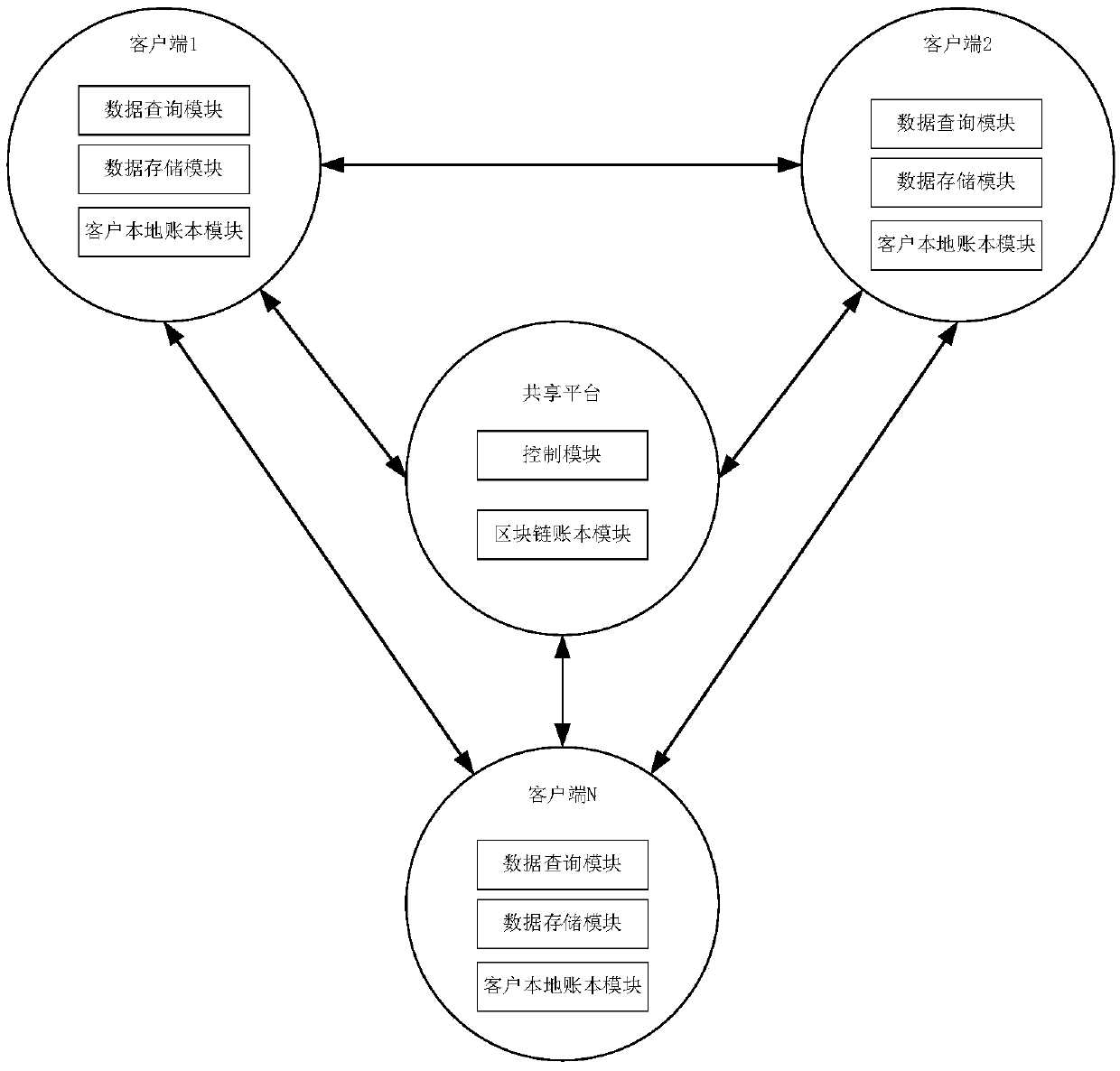
Financial institution user data sharing method and system based on a block chain technology
The invention provides a financial institution user data sharing method and system based on a block chain technology, and the method comprises the steps: S1, enabling each client to obtain authorization through an admission mechanism, and adding the authorization into a block chain sharing platform to serve as different nodes of a block chain; S2, enabling the client to input query request data and configures a query rule according to a user-defined query template; S3, enabling the block chain sharing platform to verify and authorize the query party client, and return inquirable list data; AndS4, enabling the query party client to encrypt the query request data in the form of a queried client key according to the list data, and querie and return result data according to the configured query rule. According to the method, financial platform user data sharing is achieved, desensitization, encryption and other technologies are adopted for multiple protection, original data cannot be checked, and the safety and integrity of the data cannot be affected; Based on the blockchain technology, a distributed transaction account book is co-built, and query information is accurately recorded and cannot be tampered.
Owner:青岛中瑞云数科技有限公司
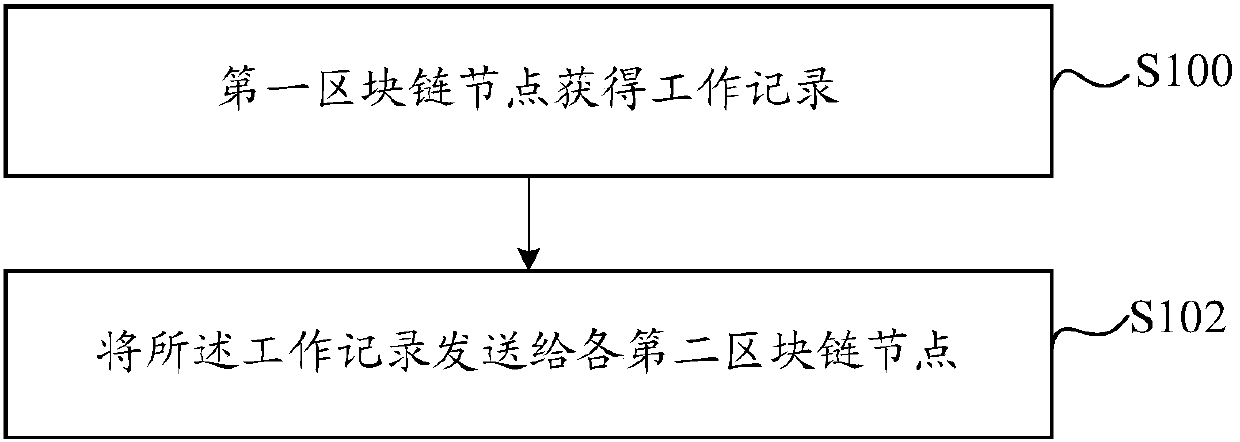
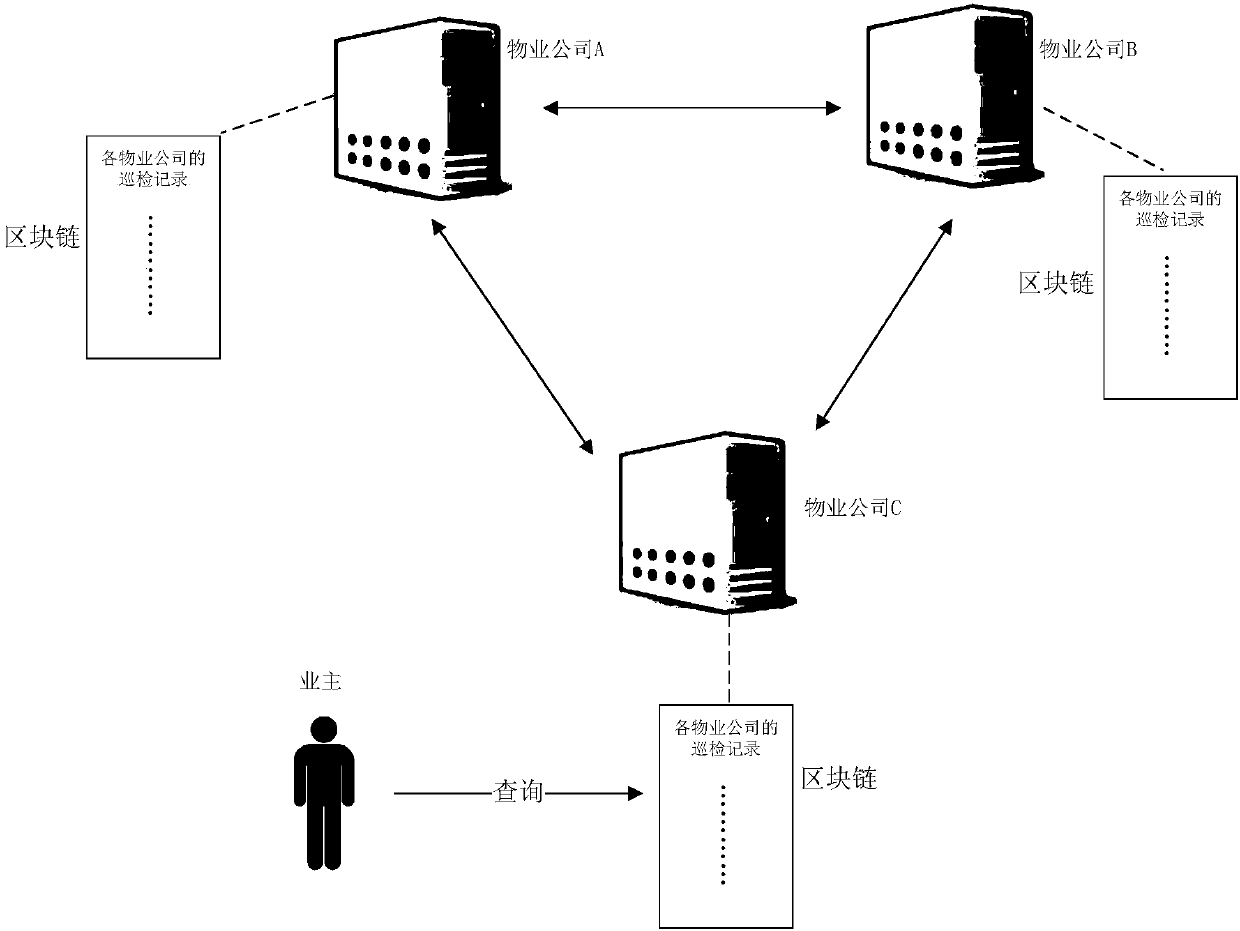
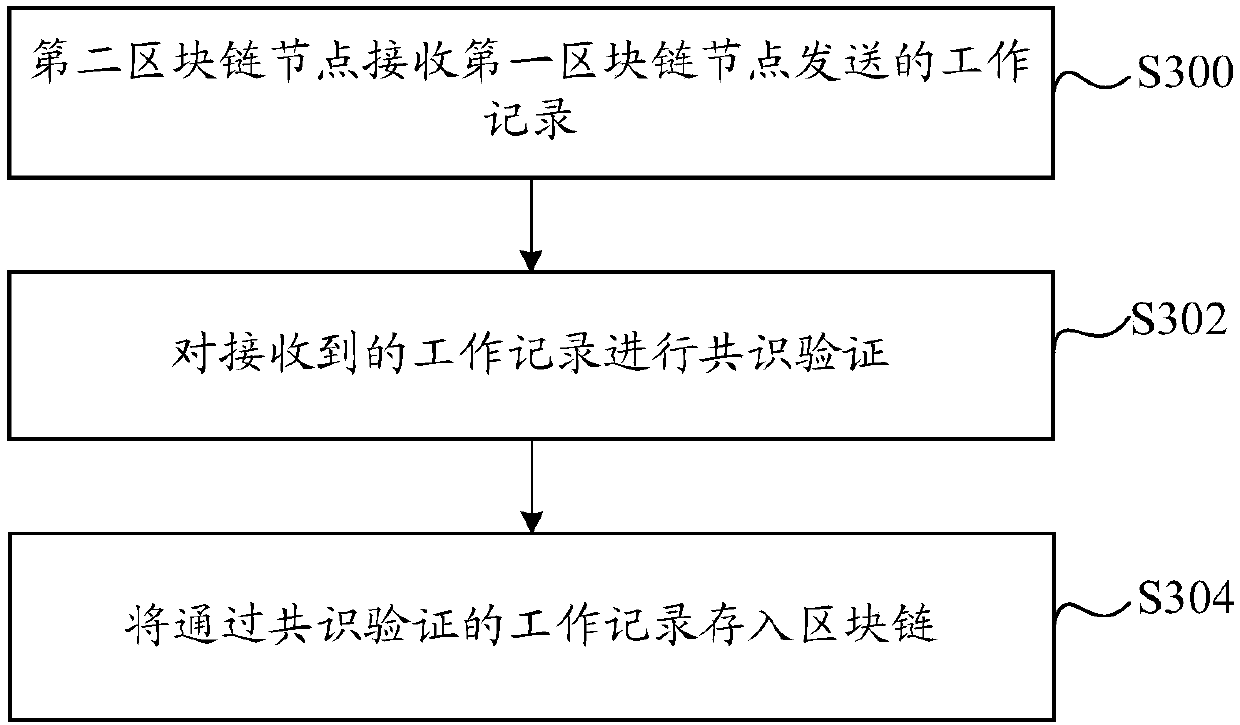
Method and device for storing work record
The embodiment of the invention discloses a method and a device for storing work record. In the embodiment of the invention, a first block chain node transmits the obtained work record to each secondblock chain node to perform consensus verification, and each second block chain node stores the work record into a block chain if the consensus verification is passed.
Owner:ADVANCED NEW TECH CO LTD
A wine product traceability anti-counterfeiting system and method based on a block chain
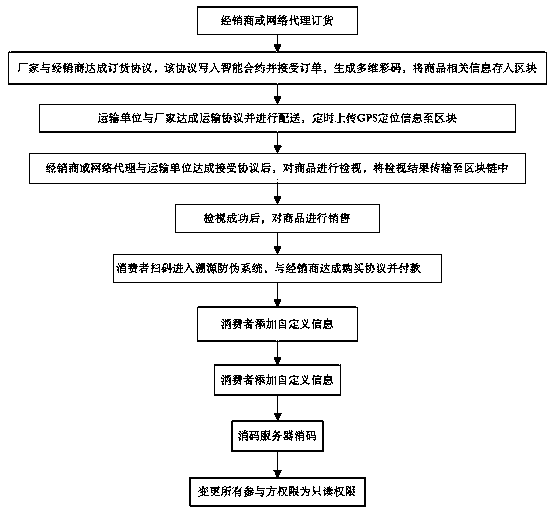
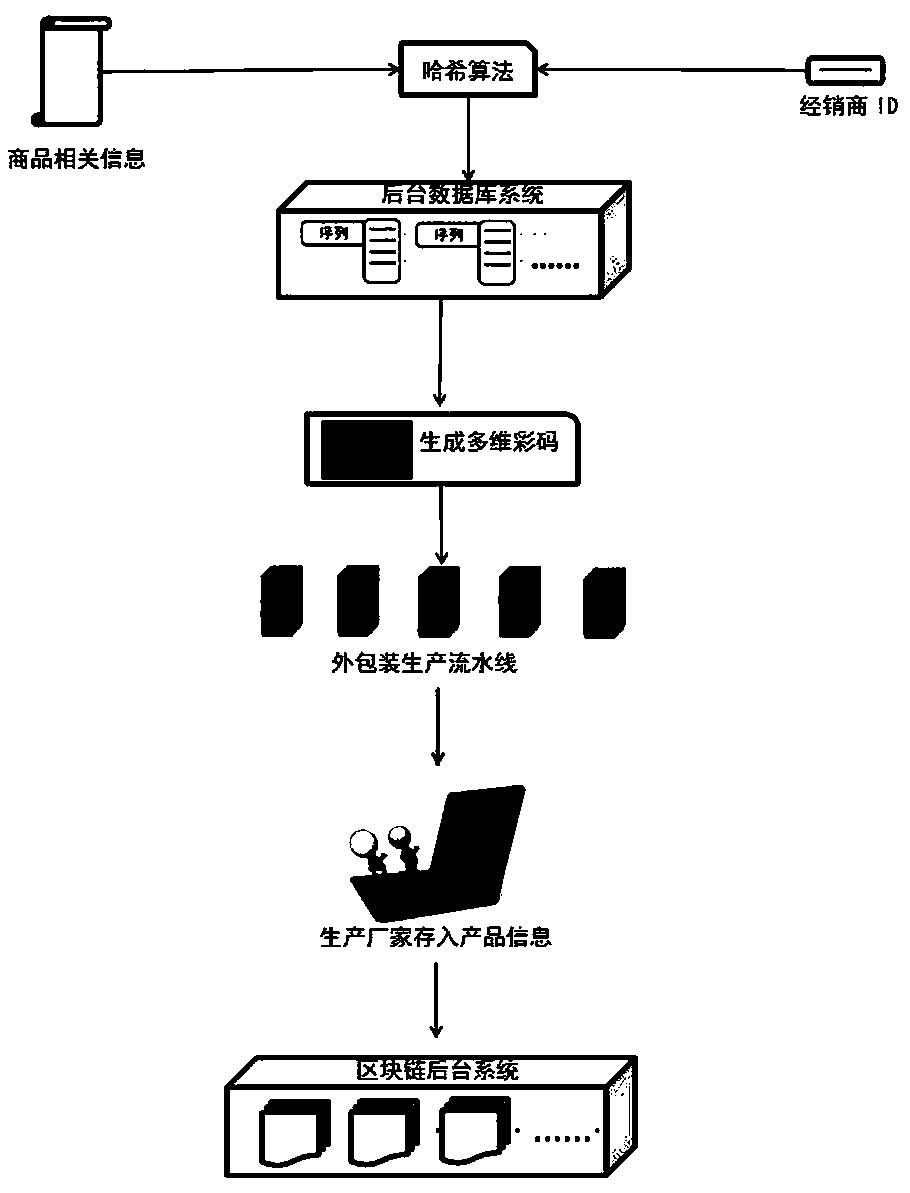
ActiveCN109345264AComplete traceability and anti-counterfeiting systemPut an end to the behavior of dropping packagesFinanceCommerceDigital signatureProduct traceability
The invention discloses a wine product traceability anti-counterfeiting system and method based on a block chain, including certificating dealer qualification, ordering, generating multi-dimensional color code, and carrying out transportation and distribution, dealer verification and consumer verification processes, obtaining public and private keys after qualification certification of all participants, enabling the upper level participants and the lower level participants to jointly reach a basic agreement, after both parties digitally sign with the private keys, writing the basic agreement into an intelligent contract, and distributing the intelligent contract to each node; transferring the right to modify the information of the batch of liquor products to the next level of participants;after the user-defined information is successfully added, using the system to start the cancellation server to cancel the code, wherein the permission is read-only and traceable. The system and the method can solve the problems of goods switching and the like in links of packaging, transportation, sales and the like.
Owner:TAIYUAN UNIV OF TECH
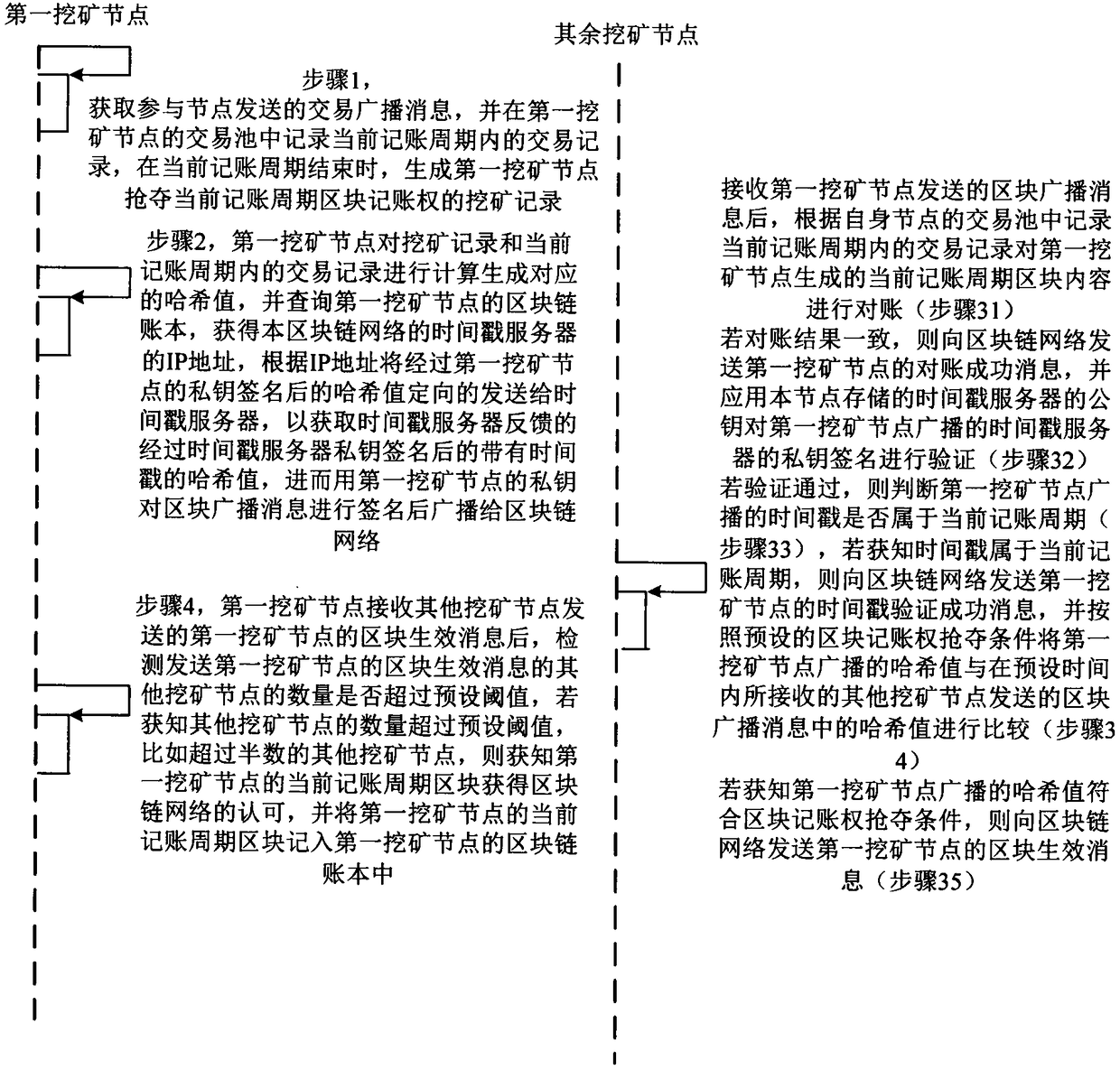
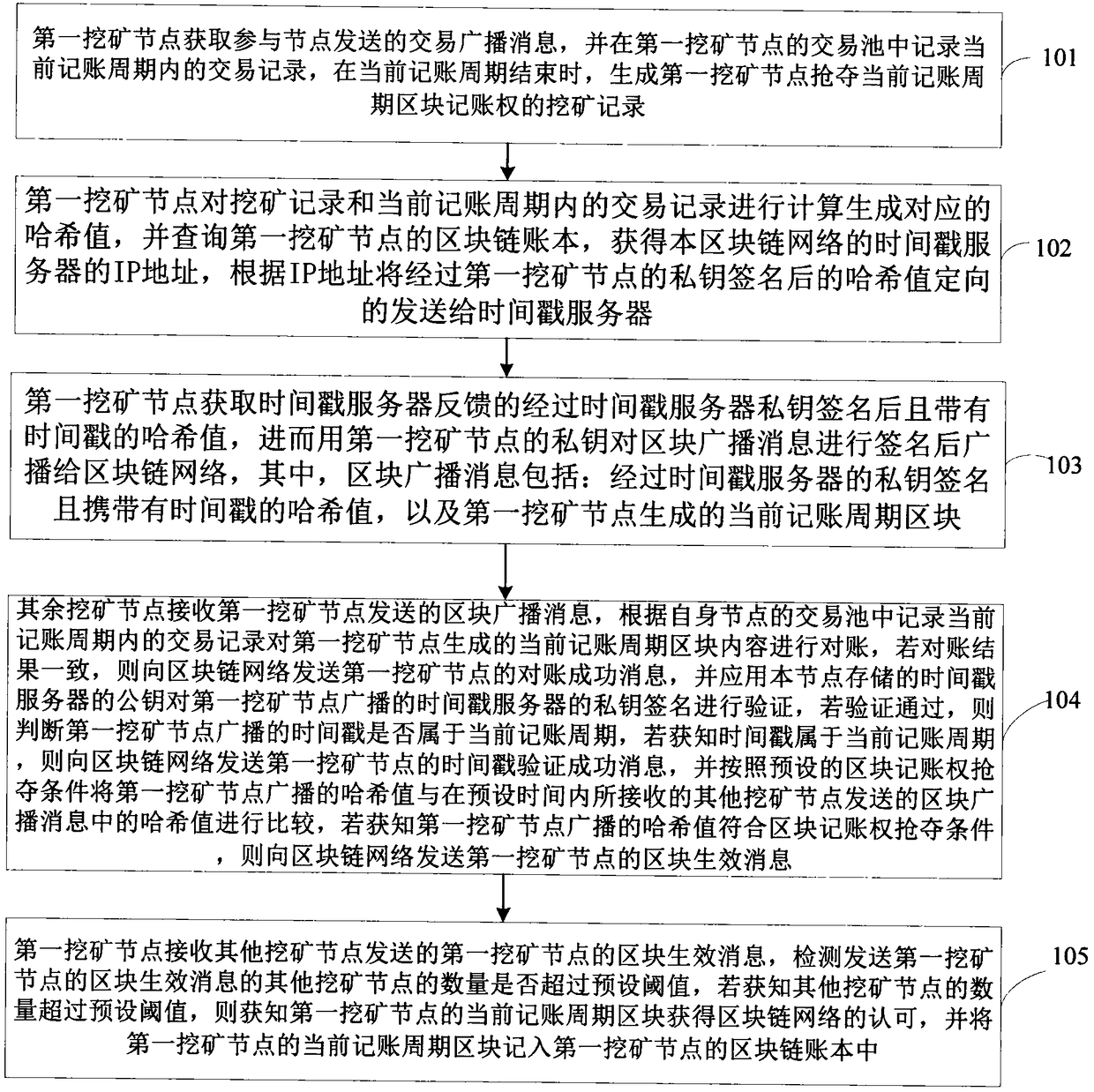
Accounting method and system for block chain network
The invention discloses an accounting method and system of a block chain network, wherein, the method comprises the following steps: a first mining node obtains a transaction broadcast message sent bya participating node, records a transaction record in a current bookkeeping cycle in a transaction pool, and generates a mining record of robbing the block bookkeeping right in the current bookkeeping cycle; the mining node obtains a transaction broadcast message sent by the participating node, and records the transaction record in the transaction pool; the first mining node generates a corresponding hash value according to the mining record, directionally sends the hash value to the timestamp server for timestamp marking according to the IP address of the timestamp server, and then signs theblock broadcast message with the private key of the first mining node and broadcasts the message to the block chain network. The remaining mining nodes verify according to the block broadcast messagesent by the first mining node, and send the block effective message of the first mining node to the block chain network through the back; the current billing cycle block of the first mining node is recorded in the block chain ledger of the first mining node. Thus, a low-cost, reliable and fair accounting rights contention method is provided.
Owner:全链通有限公司
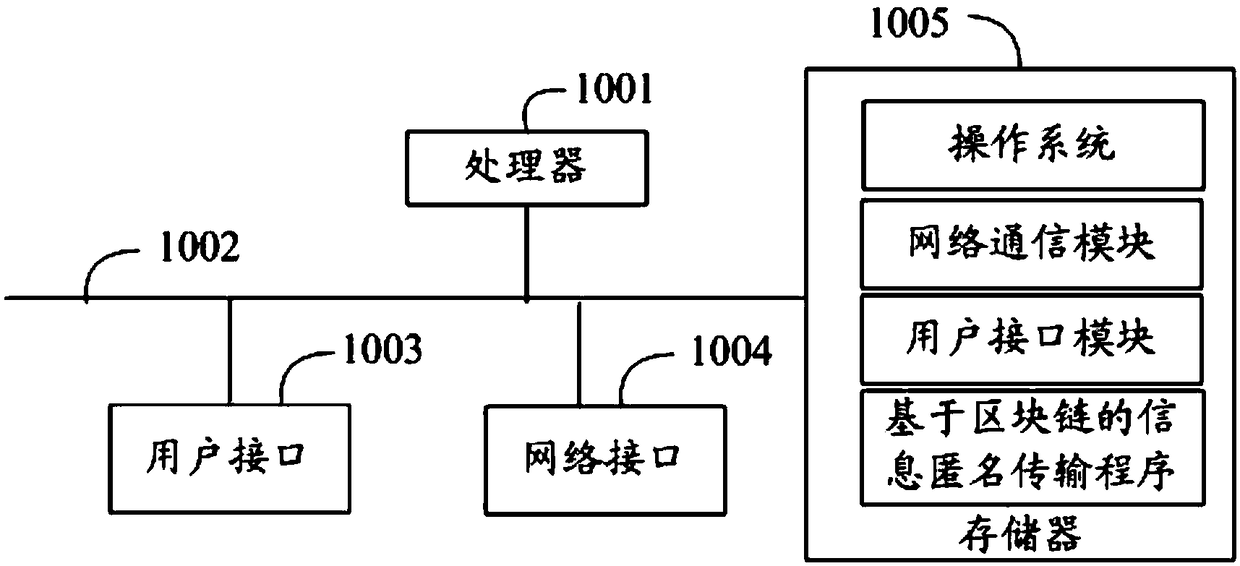
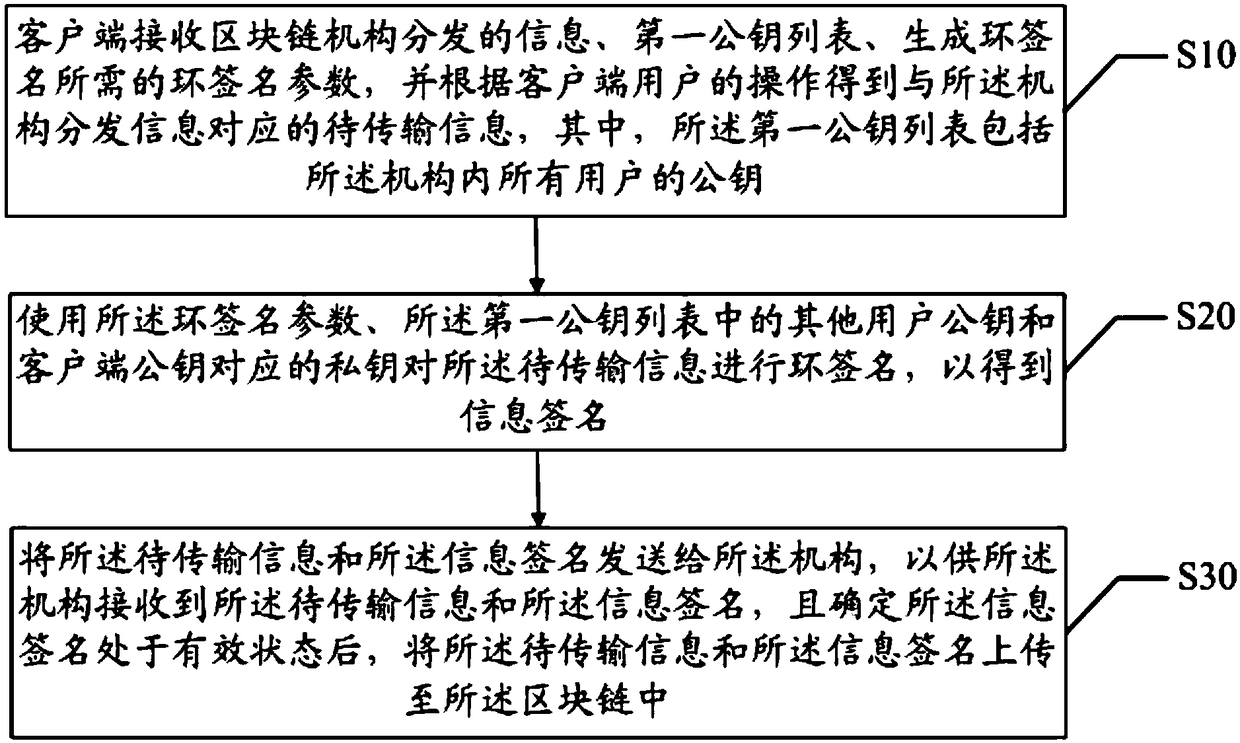
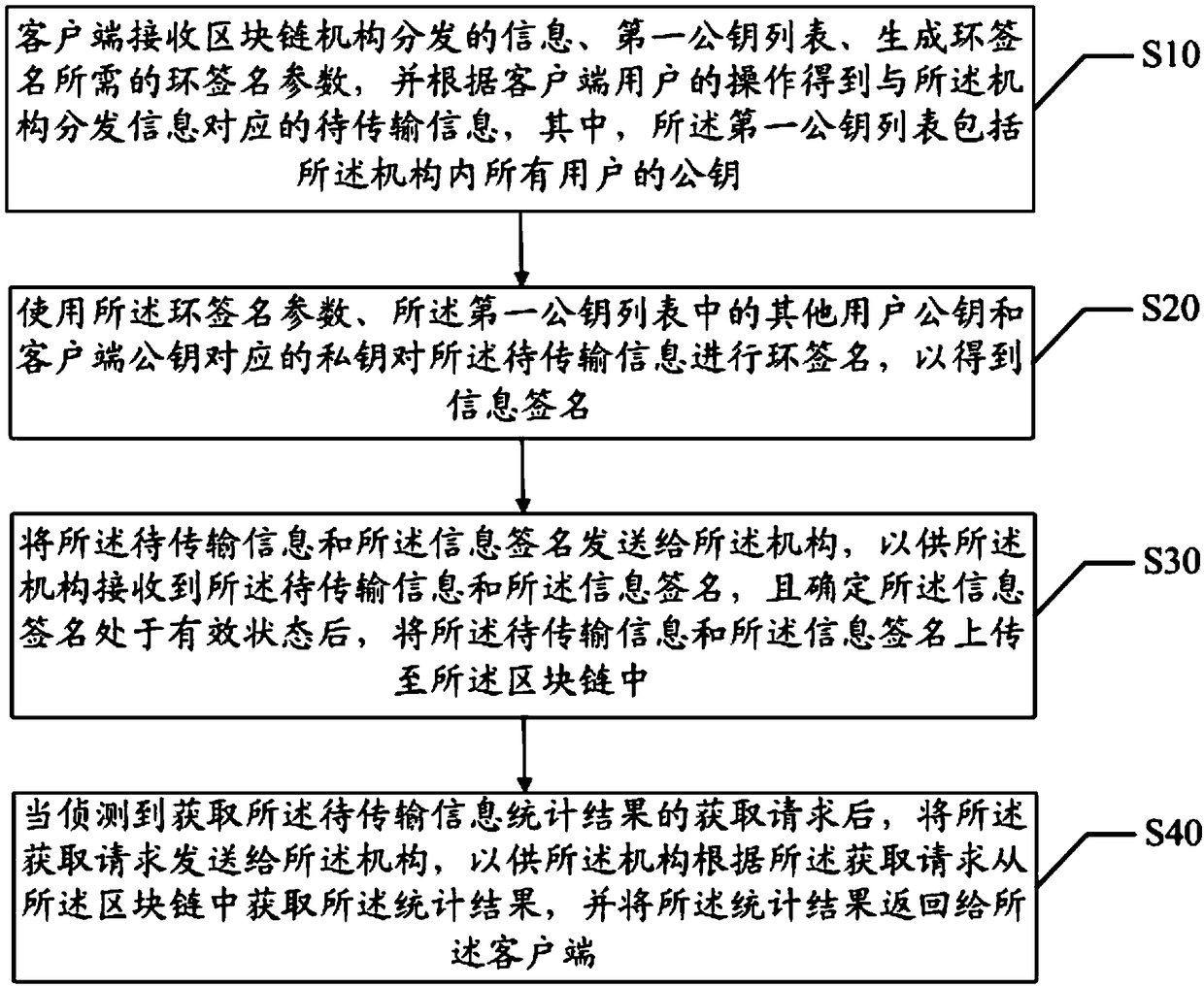
Blockchain-based anonymous information transmission method and device, and readable storage medium
ActiveCN108768992ARealize transmissionRealize anonymous transmissionUser identity/authority verificationInformation transmissionRing signature
The invention discloses a blockchain-based anonymous information transmission method and device, and a readable storage medium. The method comprises the following steps: receiving, by a client, information distributed by a blockchain mechanism, a first public key list and a ring signature parameter required for generating a ring signature, and obtaining information to be transmitted correspondingto the information distributed by the mechanism according to the operation of a user of the client; performing ring signature on the information to be transmitted by using the ring signature parameter, other user pubic keys in the first public key list and a private key corresponding to the public key of the client to obtain an information signature; and sending the information to be transmitted and the information signature to the mechanism, so that the mechanism, receives the information to be transmitted and the information signature and uploads the information to be transmitted and the information signature to a blockchain after determining that the information signature is in an effective state. By adoption of the blockchain-based anonymous information transmission method and device disclosed by the invention, the anonymous information transmission is realized; and by writing the information to be transmitted and the corresponding information signature into the blockchain, the non-tampering of the information to be transmitted is achieved by the characteristics of the blockchain.
Owner:WEBANK (CHINA)
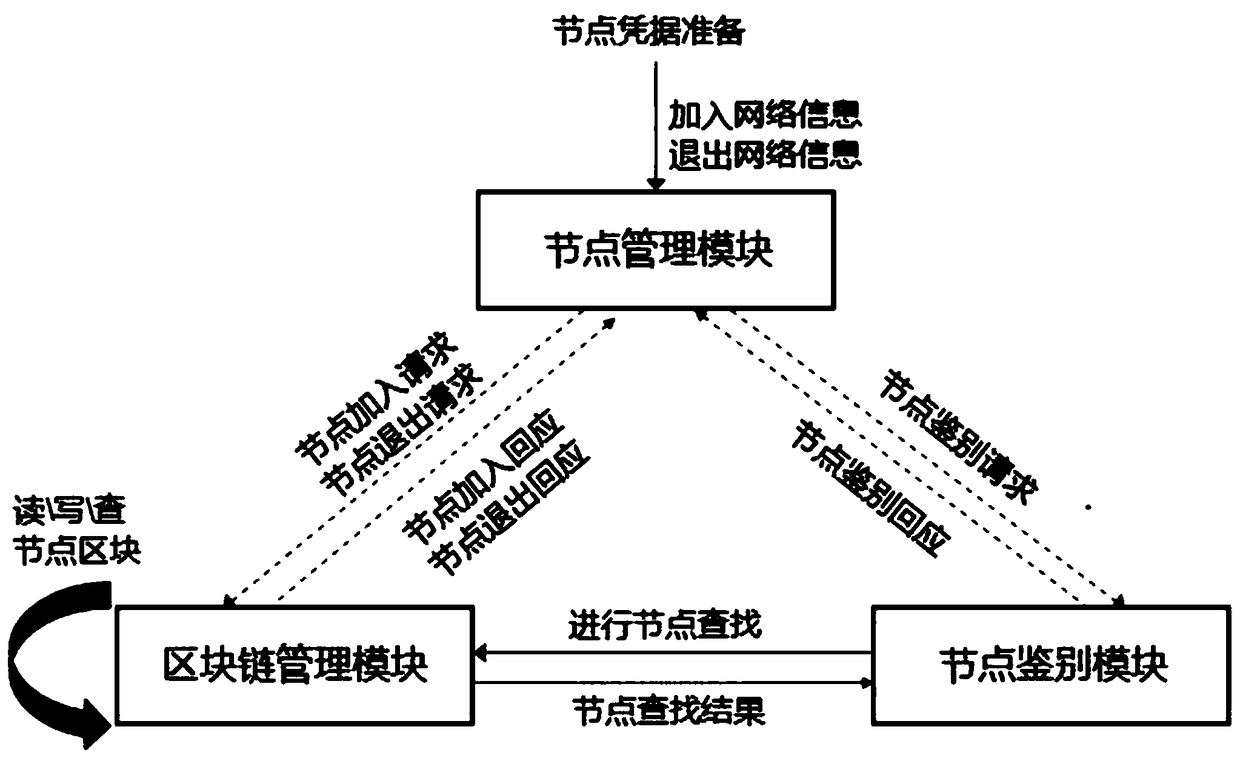
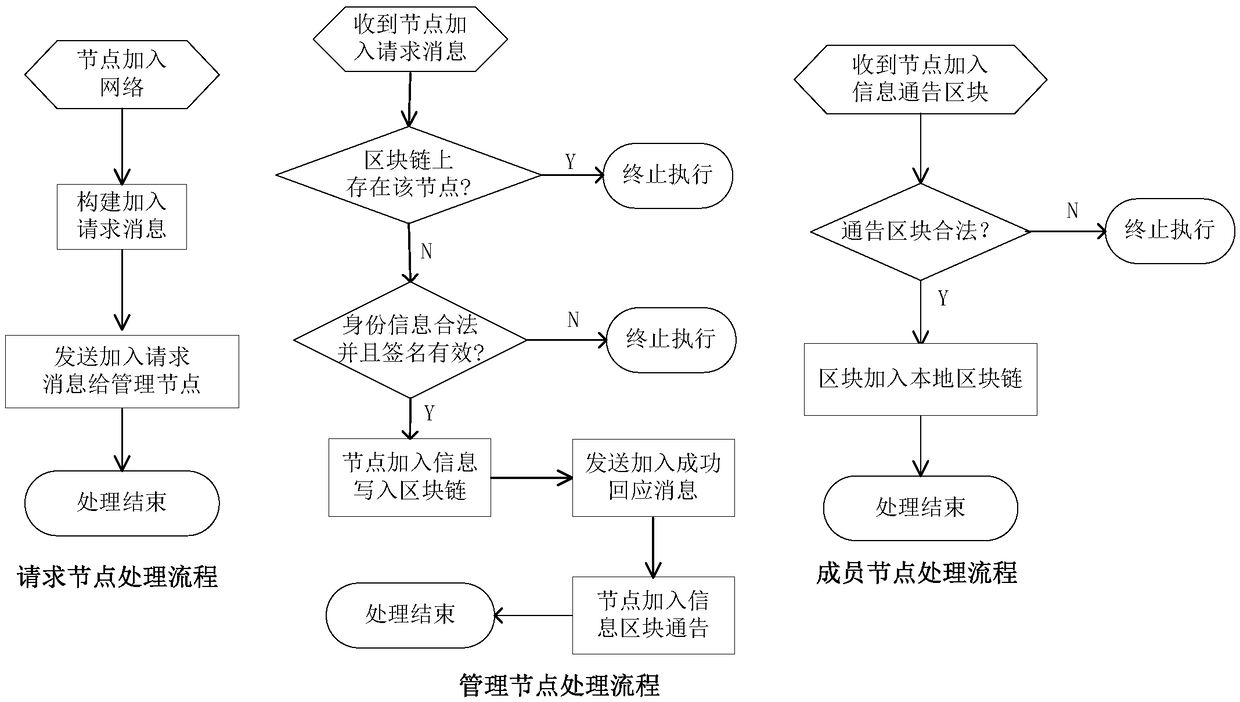
System and method for constructing trusted node network
ActiveCN109104415AImprove flexibilityIncrease elasticityUser identity/authority verificationTrusted systemNode authentication
The invention relates to a system for constructing a trusted node network. The system comprises a block chain management module, a node management module and a node identification module. Block chainmanagement module is responsible for the management of node member information on the block chain, that is, read, write, look up the node information of the block chain, as well as the read and writeprivileges management of the node block chain; the node management module is responsible for the joining and exiting of the node members on the block chain and the information management of the node network members. The node authentication module is responsible for authenticating the trustworthiness of other nodes on the block chain communicating with the node. The technical scheme is a decentralized trust system and peer-to-peer identity authentication mechanism based on block chain and public key technology, which is used to construct a trusted and controlled node network, and solve the security problems of single point failure, DoS attack, forgery and tampering in the centralized mechanism. There is no centralized trust and authority center in the technical scheme. What the new technical scheme establishes is a decentralized, distributed trust system and admittance mechanism maintained by the network node group.
Owner:JIANGSU FEIBO SOFTWARE TECH
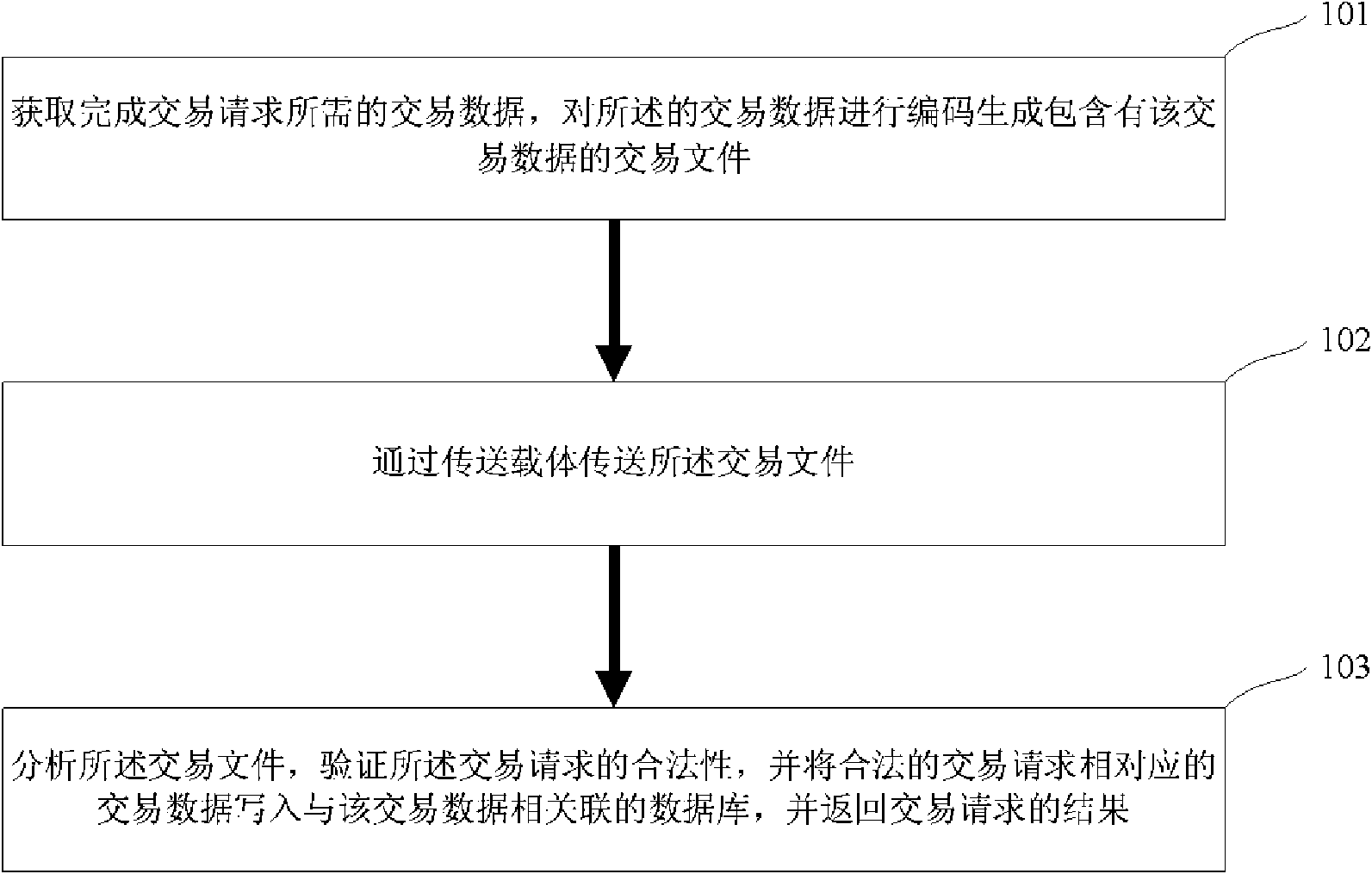
Method and system for processing electronic transaction request
InactiveCN101593338AResolve incomplete changesImprove securityUser identity/authority verificationCommerceComputer network technologyTransaction data
The invention belongs to the technical filed of computer network, and relates to a method and a system for processing an electronic transaction request. The method for processing the electronic transaction request comprises the following steps: acquiring transaction data required by finishing the transaction request; encoding the transaction data to generate a transaction document containing the transaction data; transmitting the transaction document by a transmission carrier; analyzing the transaction document; verifying the validity of the transaction request; writing the transaction data related with the valid transaction request into an account capital database; and returning the result of the transaction request. The transaction data comprises transaction information and a first electronic signature representing the identity of transaction requesters. The method and the system have the characteristics of high safety, convenience and quickness.
Owner:CHINA MERCHANTS BANK
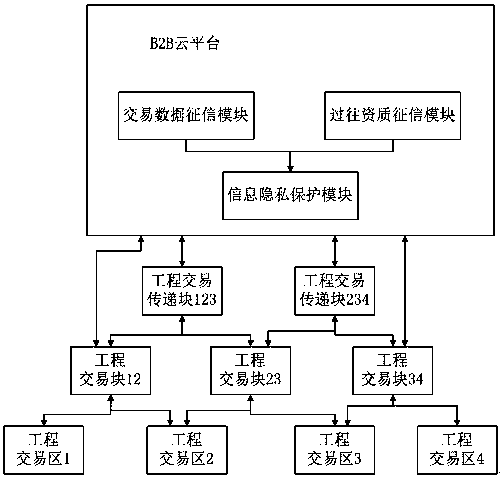
Intelligent engineering network transaction data management system based on block chain
ActiveCN107609844ACannot be tampered withUser identity/authority verificationPayment protocolsAccess networkTransaction data
Provided is an intelligent engineering network transaction data management system based on a block chain, belonging to the field of intelligent engineering. The system comprises a B2B cloud platform,a plurality of engineering transaction areas and a plurality of engineering transaction blocks, and each engineering transaction block is arranged between any two engineering transaction areas where the transaction is generated; each engineering transaction block is provided with a linkage of a corresponding transaction area, each engineering transaction block is in data sharing with a B2B cloud platform; the B2B cloud platform comprises a transaction data credit investigation module for obtaining the transaction data on the engineering transaction blocks; and a previous qualification credit investigation module is used for obtaining the qualification credit investigation data through an external access network or the engineering transaction blocks. By adopting the B2B platform and the block chain technology, the transaction information of each link of the intelligent engineering is real and reliable and cannot be tampered; and the obtained credit investigation information is complete,reliable and safe.
Owner:易信(厦门)信用服务技术有限公司
Credit data storage method and device, computer equipment and storage medium
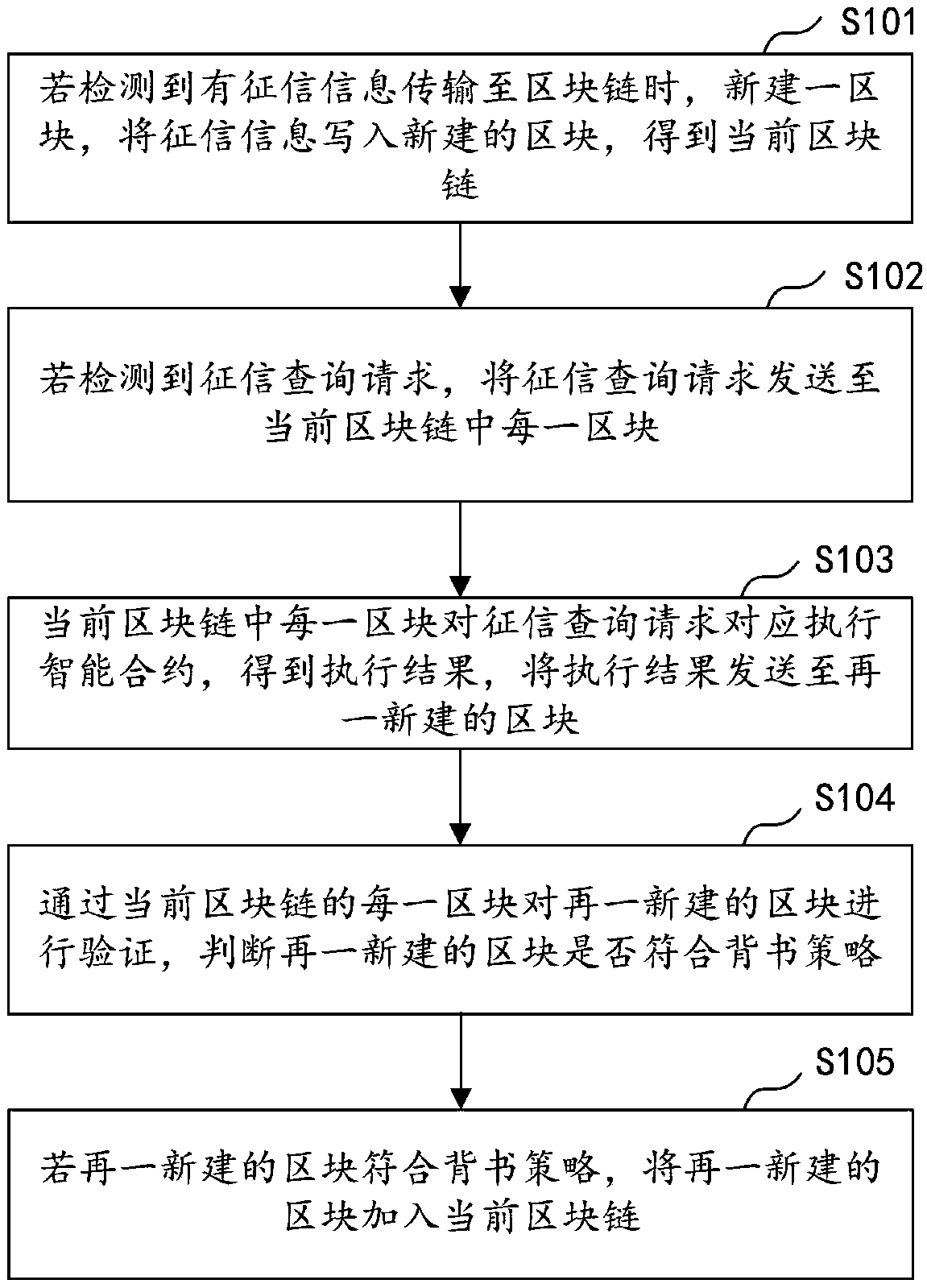
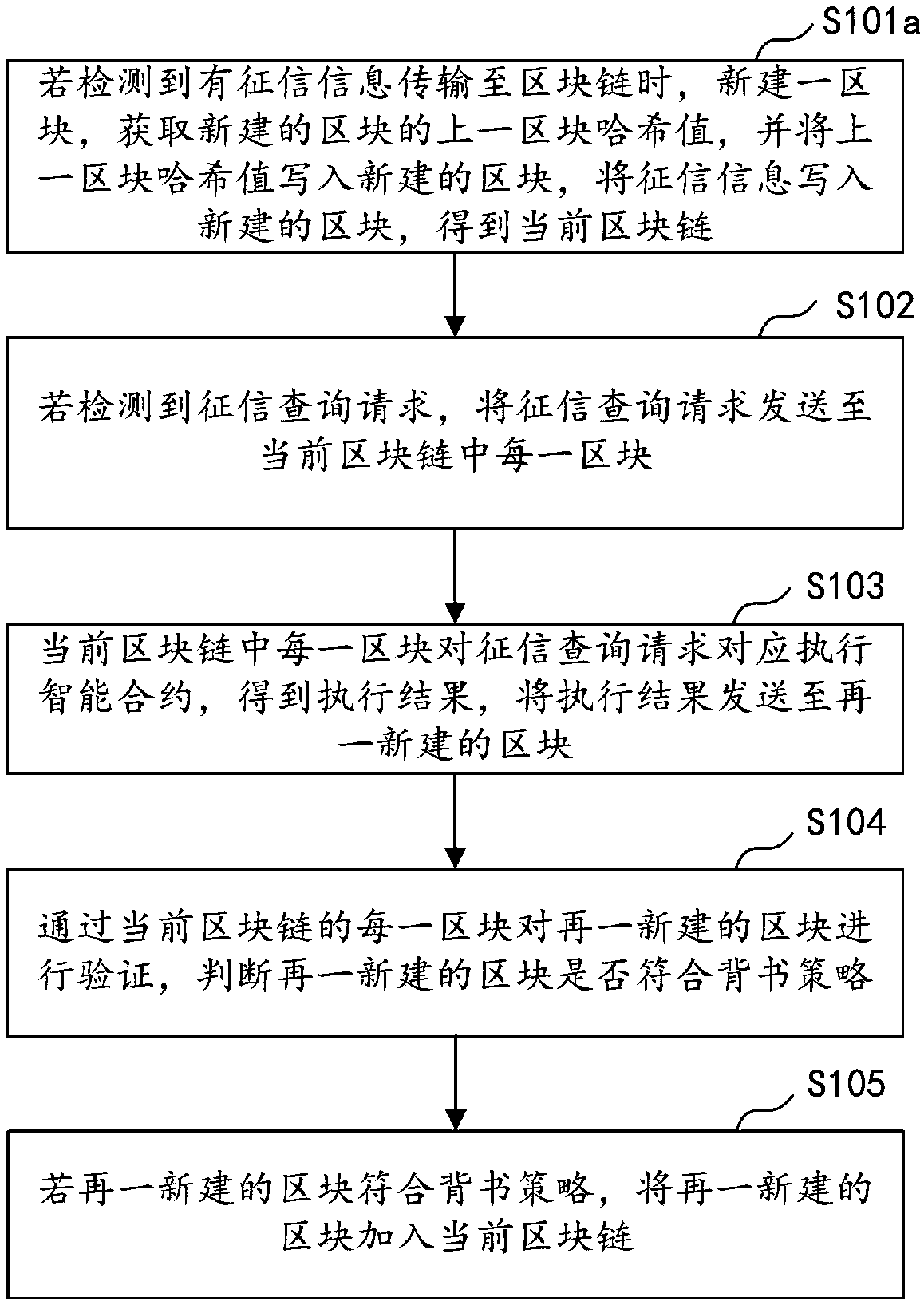
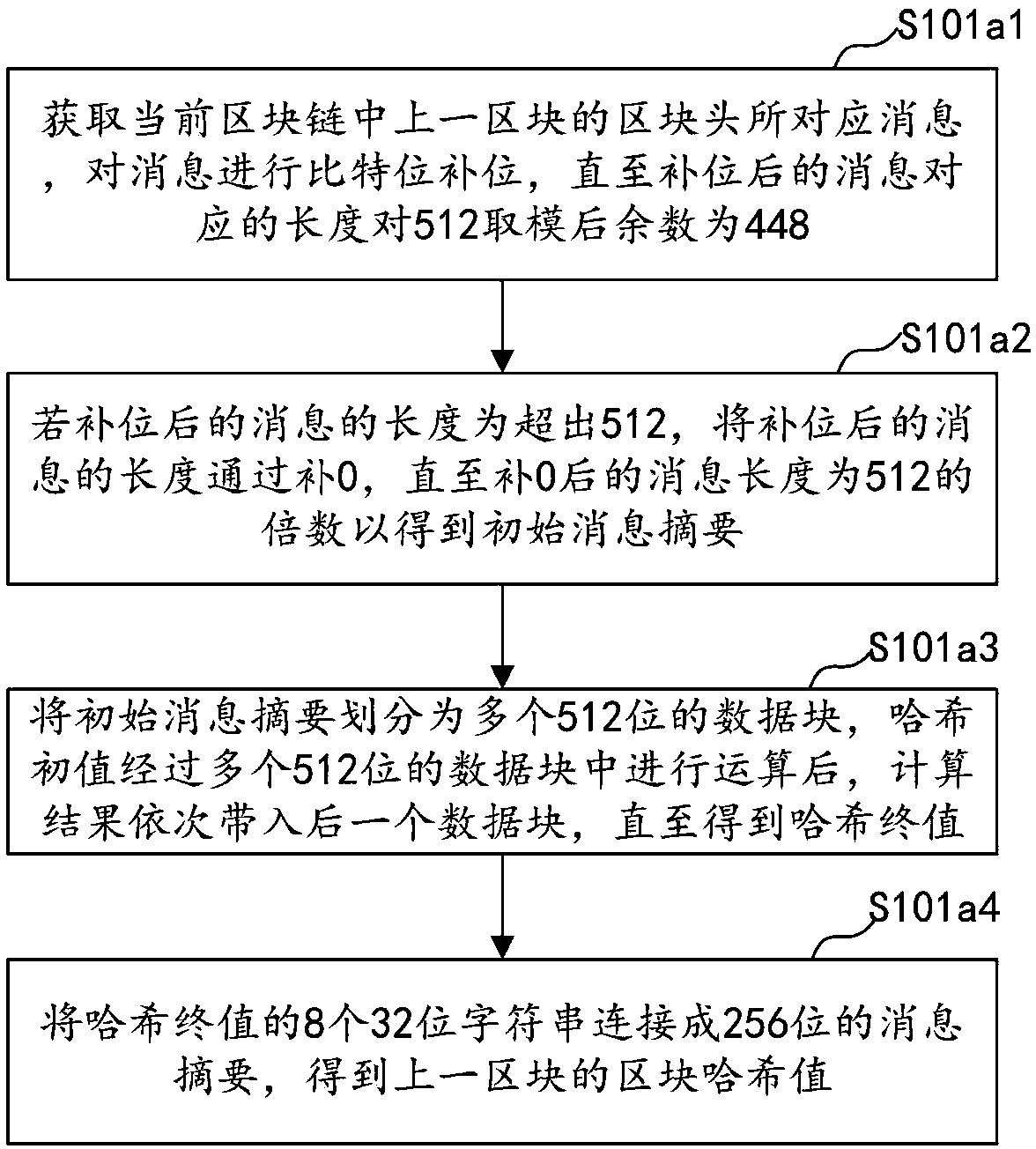
InactiveCN108717466ABig amount of dataStrong correlationSpecial data processing applicationsComputer equipmentInformation transfer
The invention discloses a credit data storage method, a credit data storage device, computer equipment and a storage medium. The method comprises the steps of newly constructing a block when detectingthat credit information is transferred to a block chain, and writing the credit information into the newly constructed block to obtain a current block chain; if a credit query request is detected, sending the credit query request to each block of the current block chain; enabling each block in the current block chain to correspondingly execute a smart contract for the credit query request to obtain an execution result, and sending the execution result to another newly constructed block; verifying the newly constructed block through each block in the current block chain to judge whether the newly constructed block conforms to an endorsement strategy; and if the newly constructed block conforms to the endorsement strategy, adding the another newly constructed block into the current block chain. With the method, the effects that the data size of the collected credit information is large, the correlation is relatively high and the data cannot be tampered are implemented, and the accuracyof the credit information is guaranteed.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
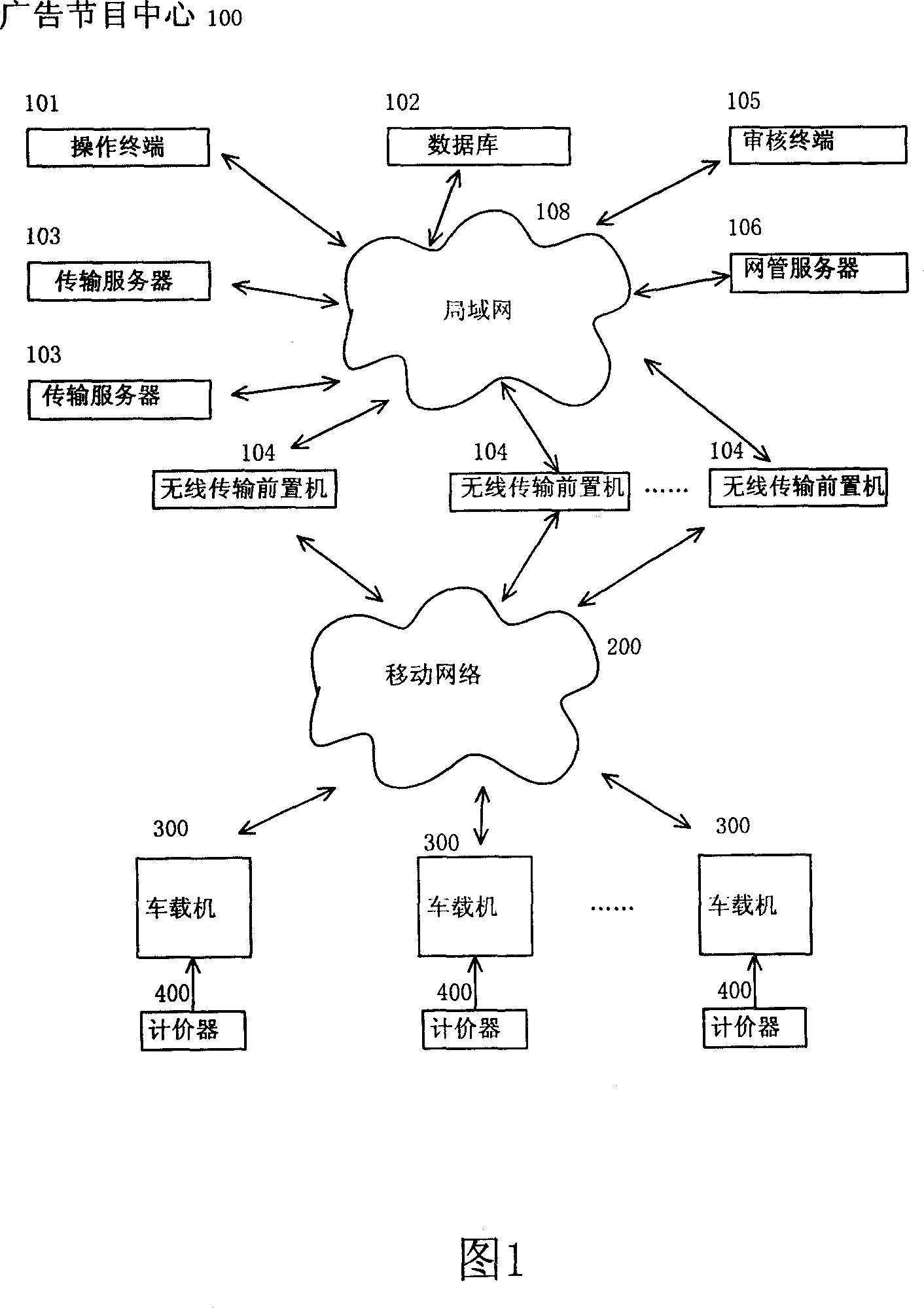
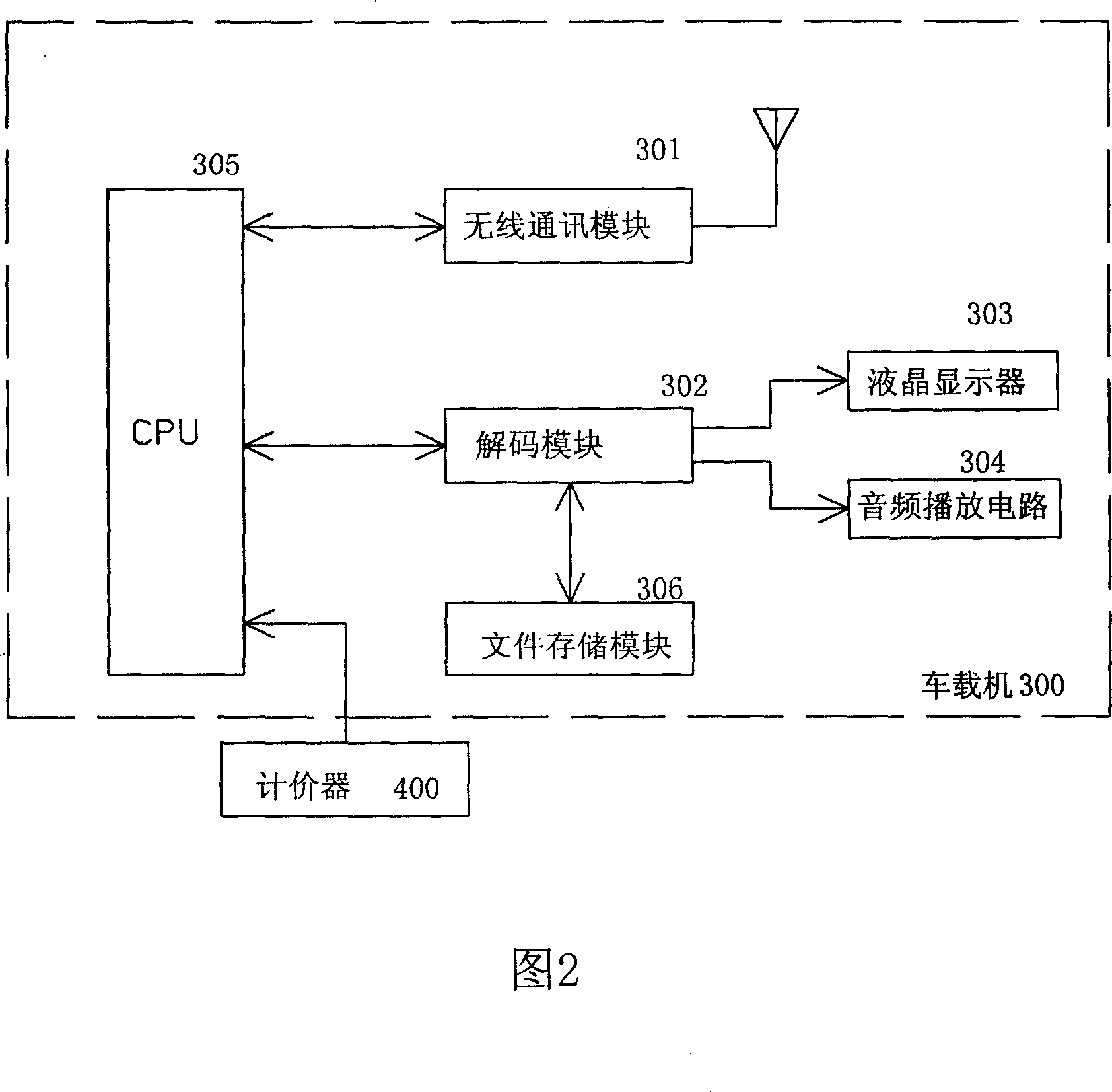
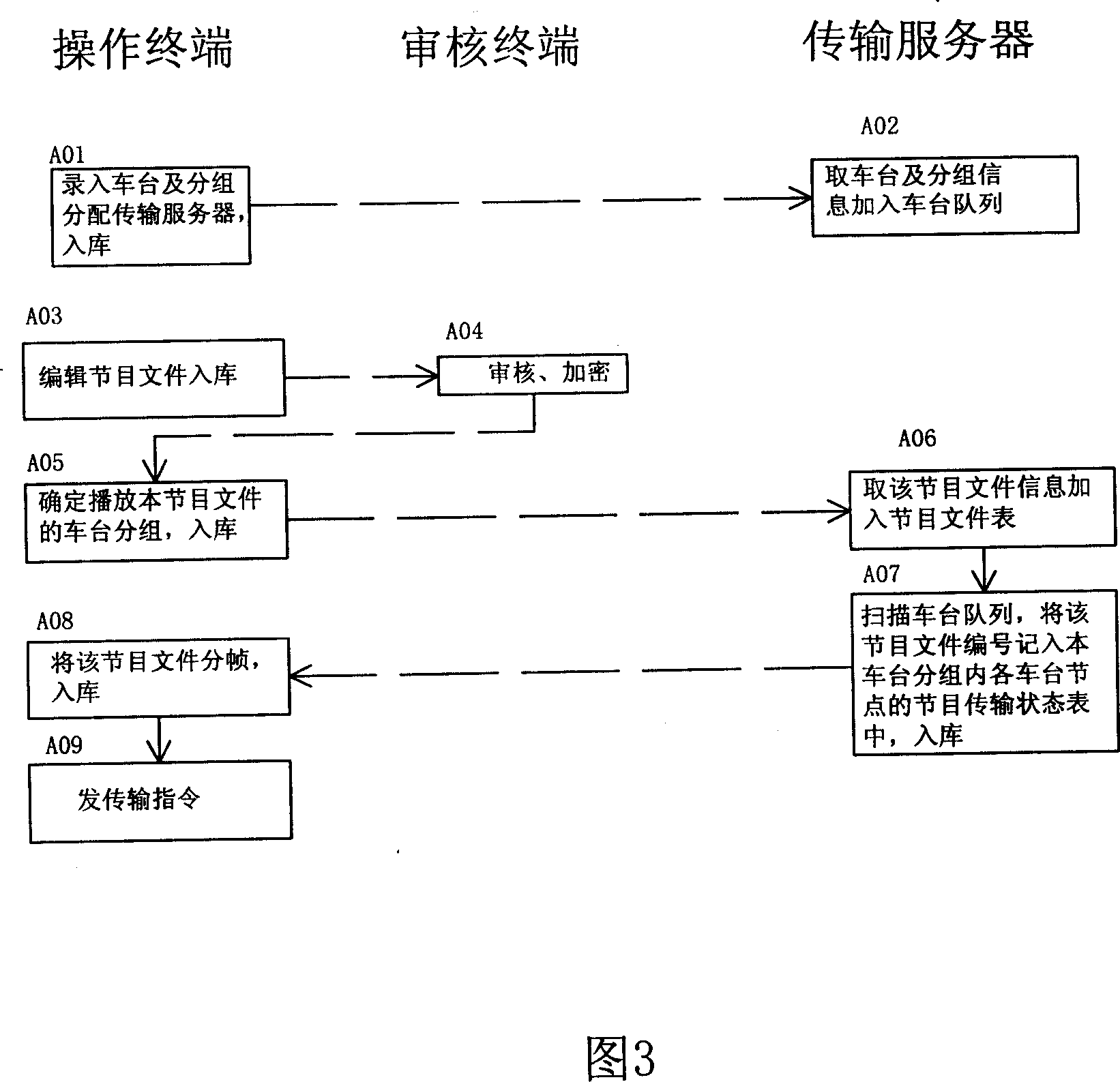
Method and system for issuing on-line advertisement on taxi
InactiveCN1984319AMeet the requirements of rigorHigh implementabilityClosed circuit television systemsMarketingVideo advertisingRadio networks
The invention relates to a method and system for providing advertising to the taxis through radio network. It comprises: grouping the taxis participating the network; the audio and video advertising program to be released is coded into stream media program and is allocated to the taxi group; editing program menu for each taxi group; after framing, using sliding window and multipath multi session approach to send down the program file to the relevant taxi group through internet or mobile communication network; the taxi receives and saves the advertising, and the price-marking weigher controls the play of program; when there is customer on the taxi, the advertising programs is played according to the program menu; when there is no customer on the taxi, the play of advertising program is ended.
Owner:XIAMEN YAXON NETWORKS CO LTD
Method for achieving data security communication by applying blockchain encryption technology
PendingCN111654364AAchieve deliveryAchieve sharingDatabase management systemsData stream serial/continuous modificationData transmissionInteraction device
The invention discloses a method for achieving data security communication by applying a blockchain encryption technology, and relates to the technical field of data encryption. According to the invention, a secure communication system comprising a data layer, a data encryption layer, a data network layer, a data transmission layer and a data application layer is constructed; a block chain technology is integrated into data communication, safe transmission of data is realized, the transmitted data can be shared and cannot be tampered, the encryption performance of the data is improved, remote,online and real-time acquisition and application of the data can be achieved through systematic construction, and a user can achieve application, management and monitoring of database data without going to the site personally. According to the invention, the ant colony algorithm is adopted; according to the characteristics of data communication and the requirements of interaction equipment, the optimization search of the encryption algorithm is carried out among the plurality of encryption units, so that a user can quickly find out the optimal value of the target data suitable for applicationfrom the plurality of encryption algorithms, and the efficiency and the data management capability of the encryption unit application algorithm are greatly improved.
Owner:重庆知翔科技有限公司
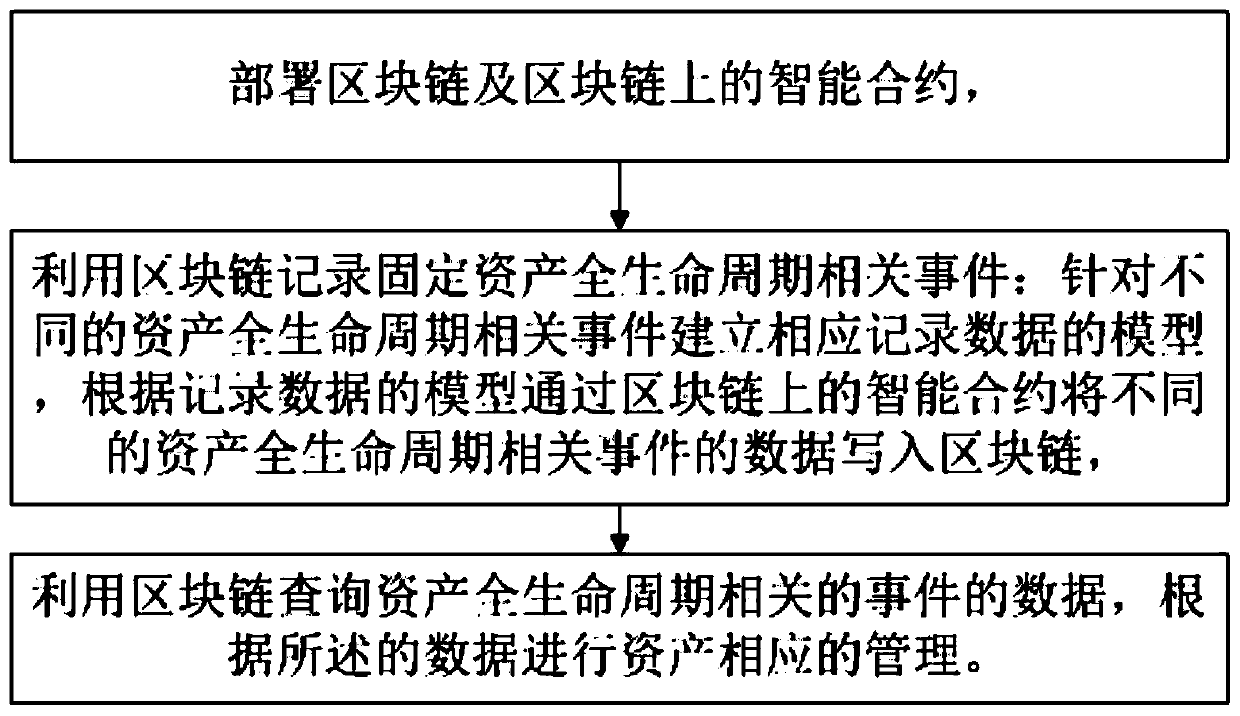
Enterprise fixed asset management method based on block chain
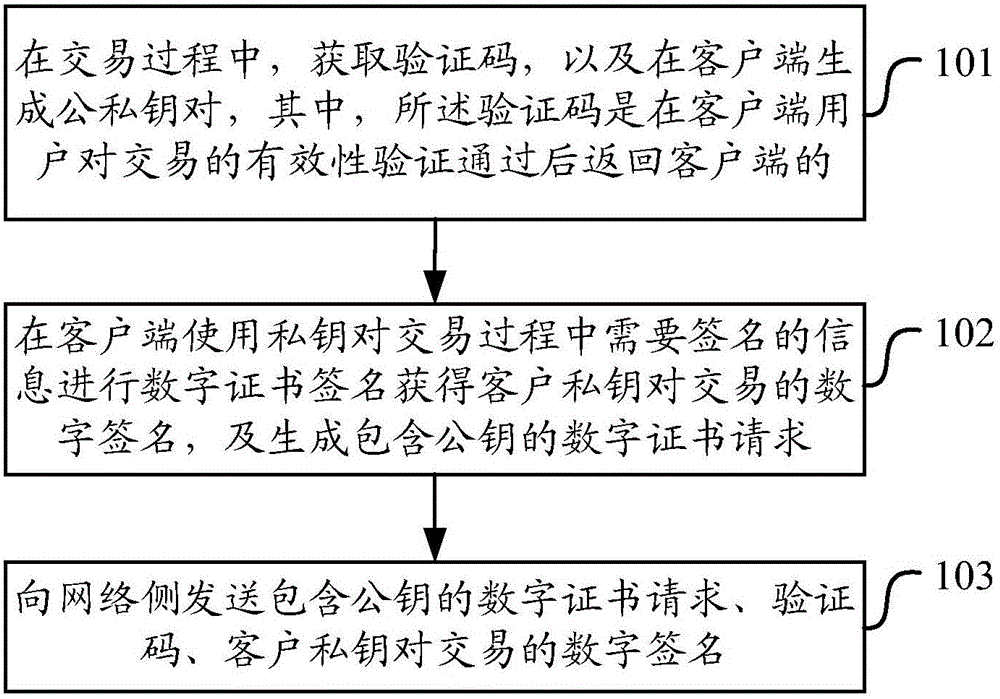
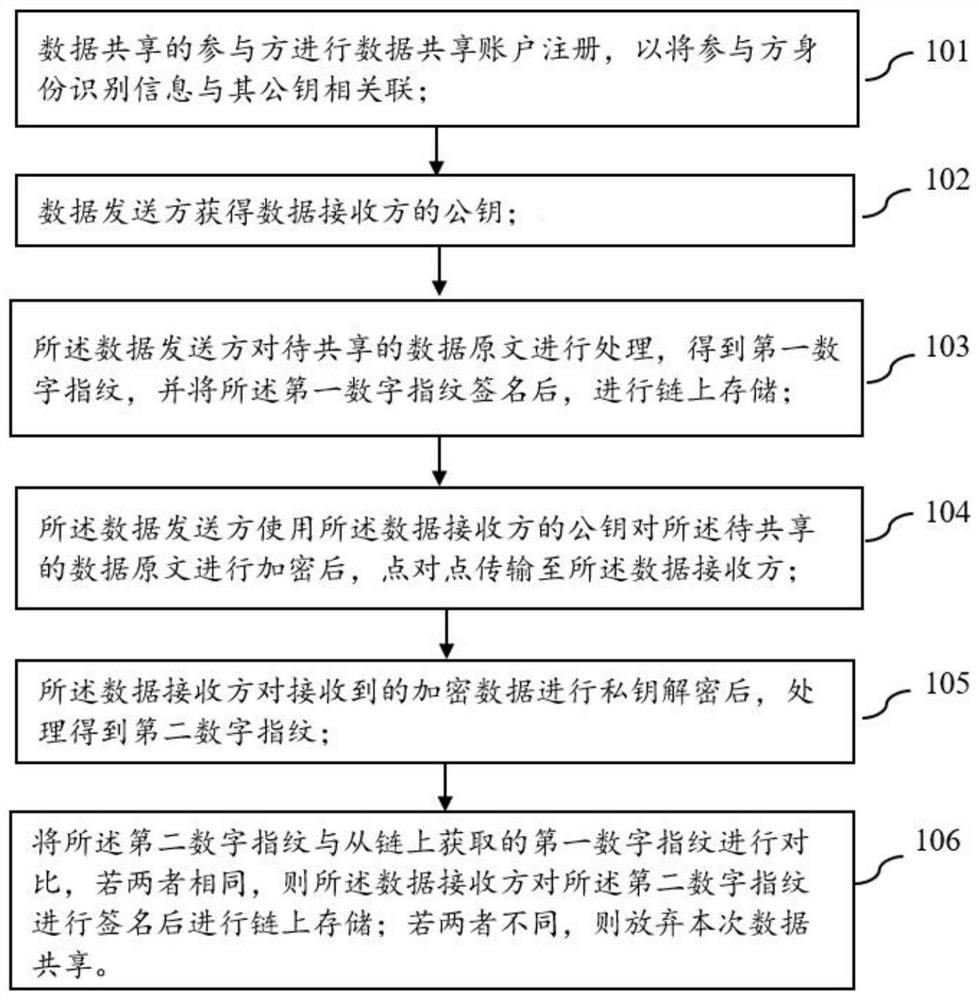
InactiveCN110287261ACannot be tampered withFinanceDatabase distribution/replicationSmart contractComputer science
The invention discloses an enterprise fixed asset management method based on a block chain, and relates to the technical field of data processing. A block chain is deployed, a block chain is used as a decentralized distributed storage technology; according to a model for recording data of events in each link of a fixed asset life cycle; an intelligent contract is deployed to realize data writing on the block chain; according to the technical scheme, the assembly data of all links of the enterprise fixed assets in the whole life cycle are written on the block chain, so that the related events of the enterprise assets in the whole life cycle are credible and cannot be tampered, and the whole life cycle of the enterprise fixed assets can be confirmed and tracked through the flow of the enterprise fixed assets in the whole business.
Owner:浪潮卓数大数据产业发展有限公司
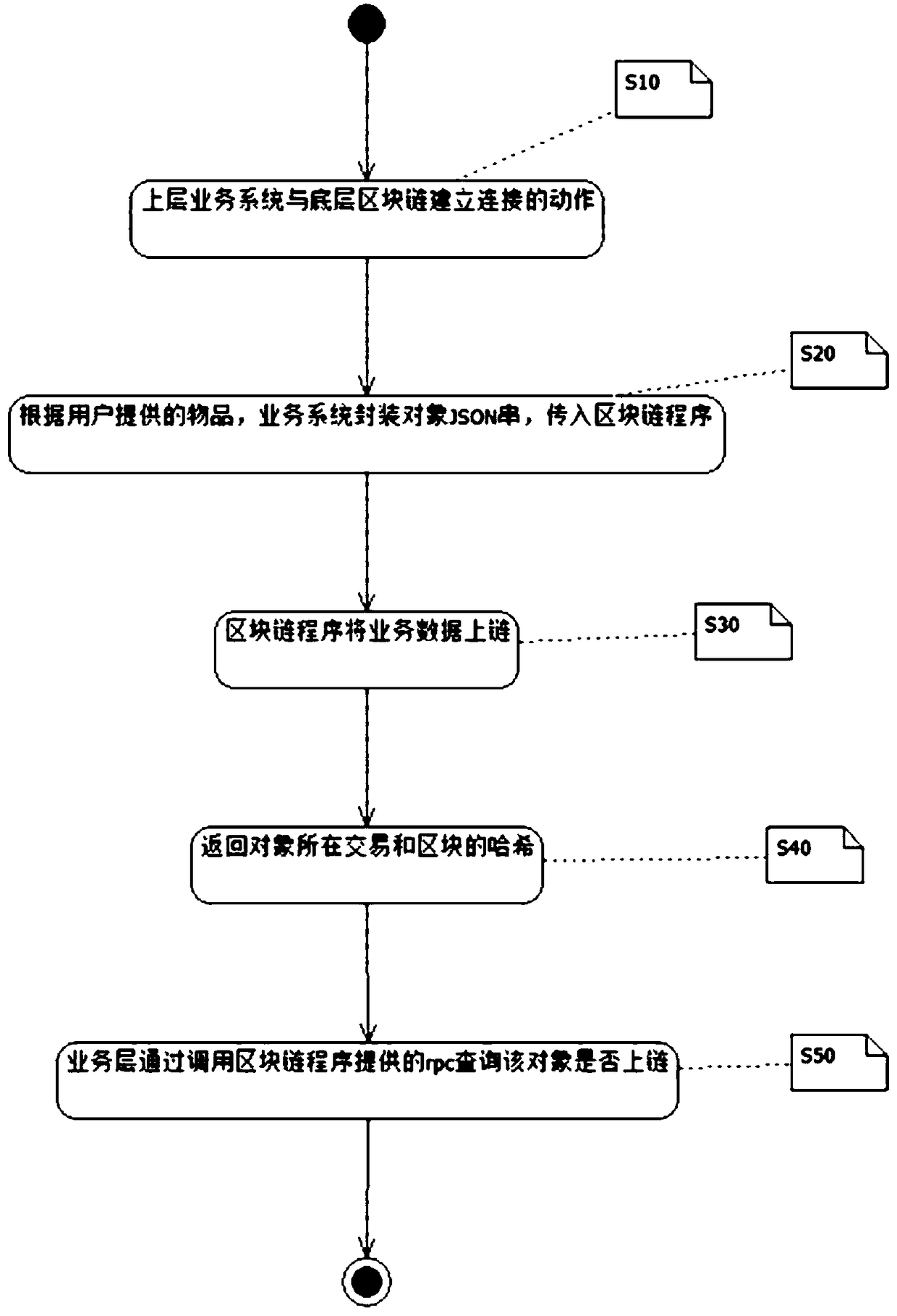
Object association encapsulation storage method based on block chain
InactiveCN108829749AEasy to packPackaged storage is easyFinanceDigital data protectionObject structureOperating system
The invention discloses an object association encapsulation storage method based on a block chain. The method comprises the steps that an upper service system establishes connection with the bottom block chain; according to an article provided by a user, the service system encapsulates a JSON string of an object and transmits the JSON string into a block chain program; the block chain program transmits service data to the block chain; a hash of a transaction and a block where the object is located is returned; and a service layer queries whether the object is transmitted to the block chain bycalling rpc provided by the block chain program. Through the method, the structure is reasonable, the data is easy to encapsulate, and the data is stored efficiently and transmitted to the block chaineasily and cannot be tampered; the object structure can be used for any article and then is written into the block chain after formatting to provide a basis for evidence in a later period; and moreover, snappy, zip, lz4 and other compression algorithms can be used to perform compression storage, so that space is saved.
Owner:WEALEDGER NETWORK TECH CO LTD
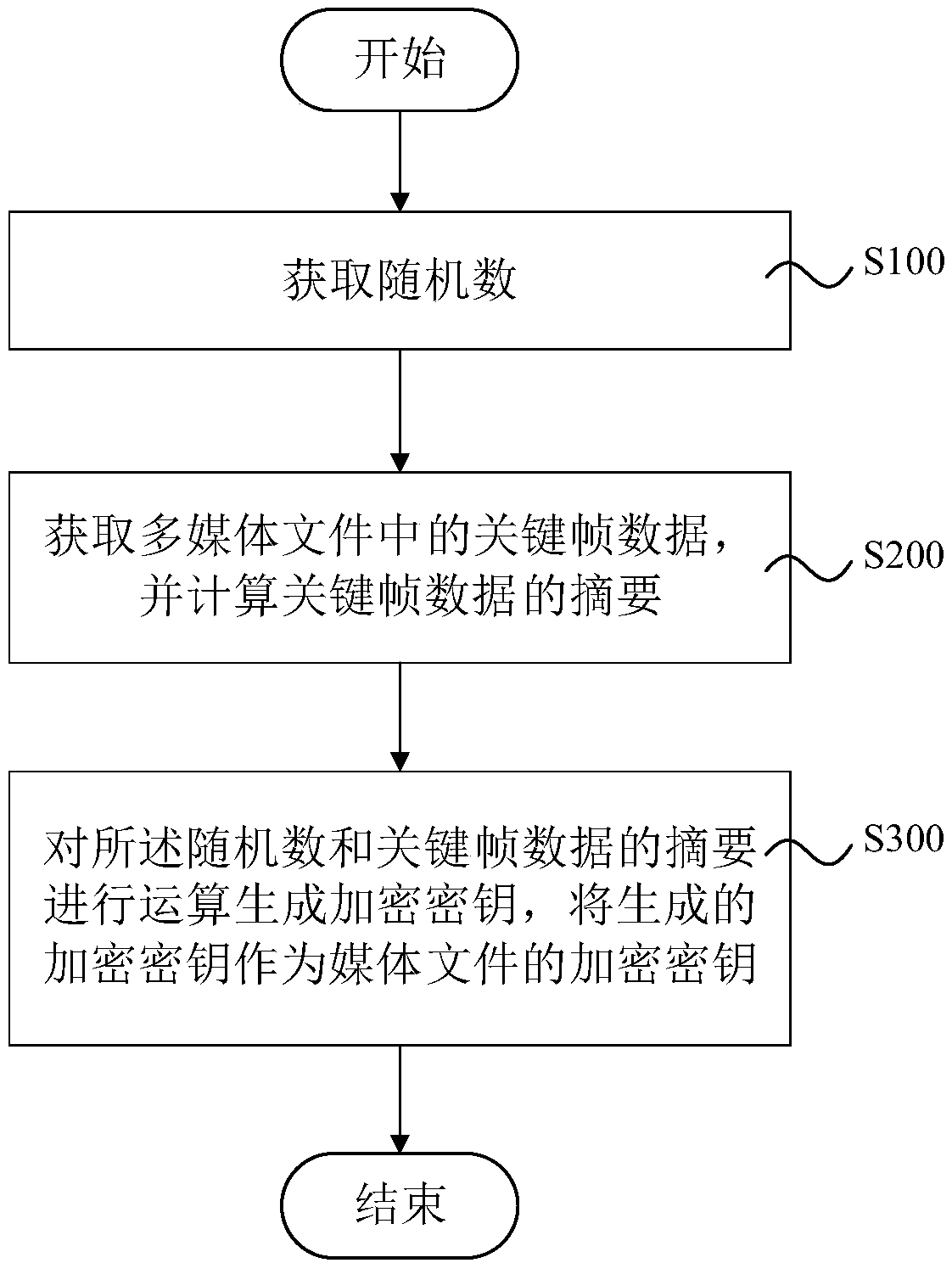
Media file encryption key management method, system and device and storage medium
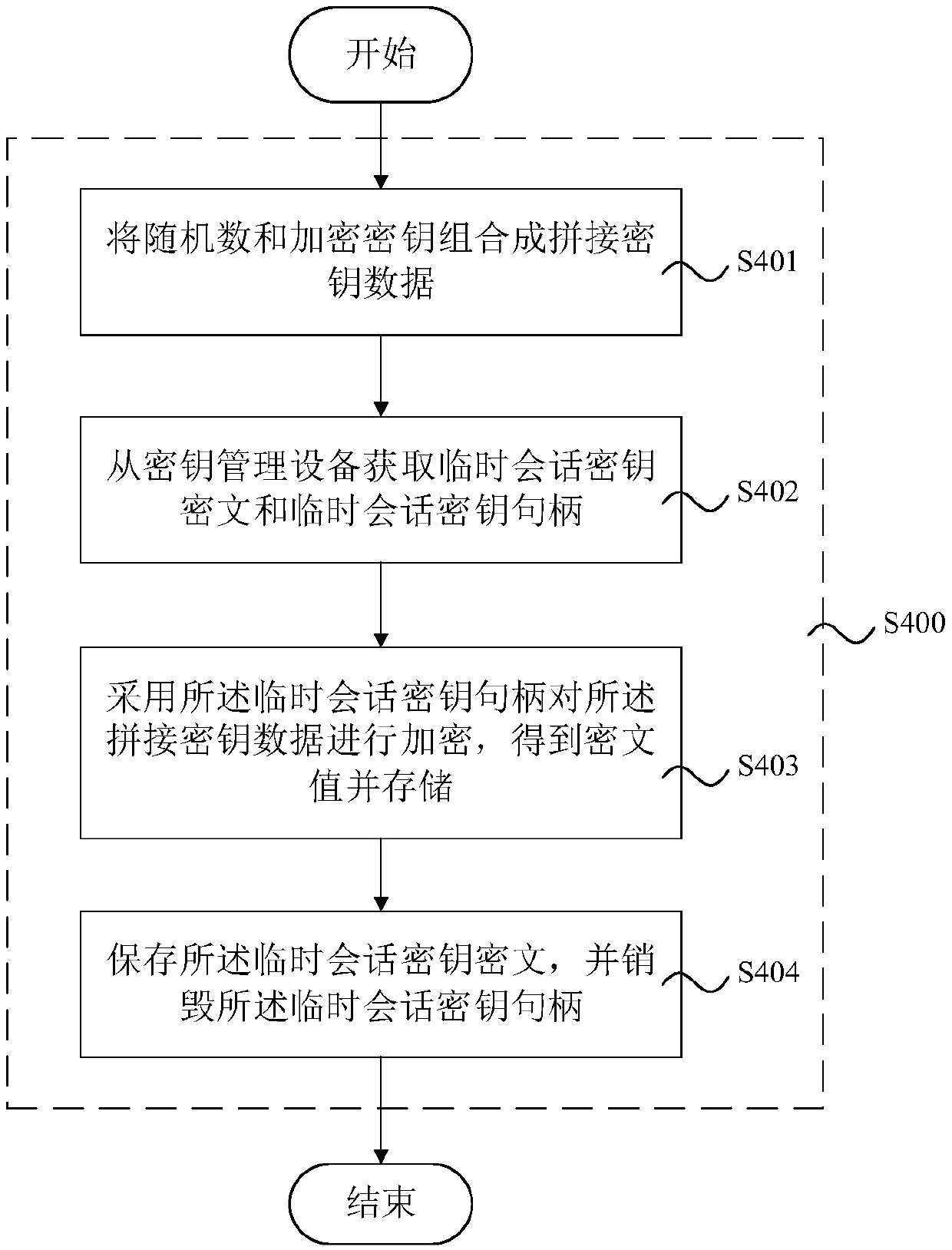
ActiveCN109635586ACannot be tampered withIntegrity guaranteedDigital data protectionComputer hardwareCryptographic key generation
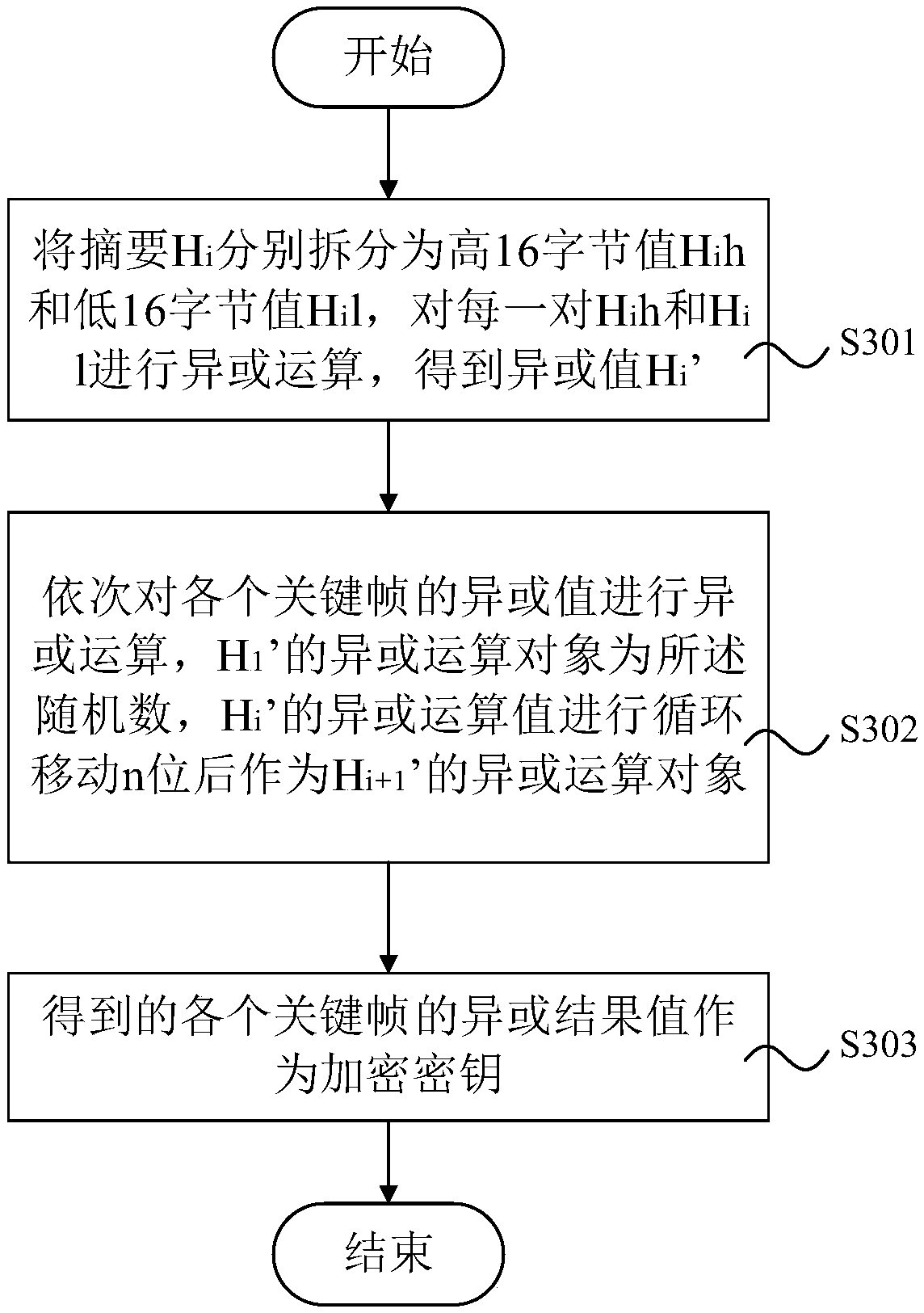
The invention provides a media file encryption key management method, system and device, and a storage medium. the media file encryption key management method comprises encryption key generation, andthe encryption key generation comprises the following steps: obtaining a random number; Obtaining key frame data in the media file, and calculating an abstract of the key frame data; And carrying outoperation on the random number and the abstract of the key frame data to generate an encryption key, and taking the encryption key as an encryption key of the media file. By adopting the method, the device and the system, the cost is reduced;, the key generation does not completely depend on the random number generator; Key frame data of a media file are doped in an encryption key of the media file; Through the technical scheme, the encryption key of the media file is more difficult to crack, and meanwhile, whether the media file obtained through decryption is consistent with the media file before encryption can be verified through the key frame data, so that the integrity of the file is ensured, and internal personnel cannot tamper the media file.
Owner:SUZHOU KEDA TECH
Management and control method for key information basic data asset based on block chain
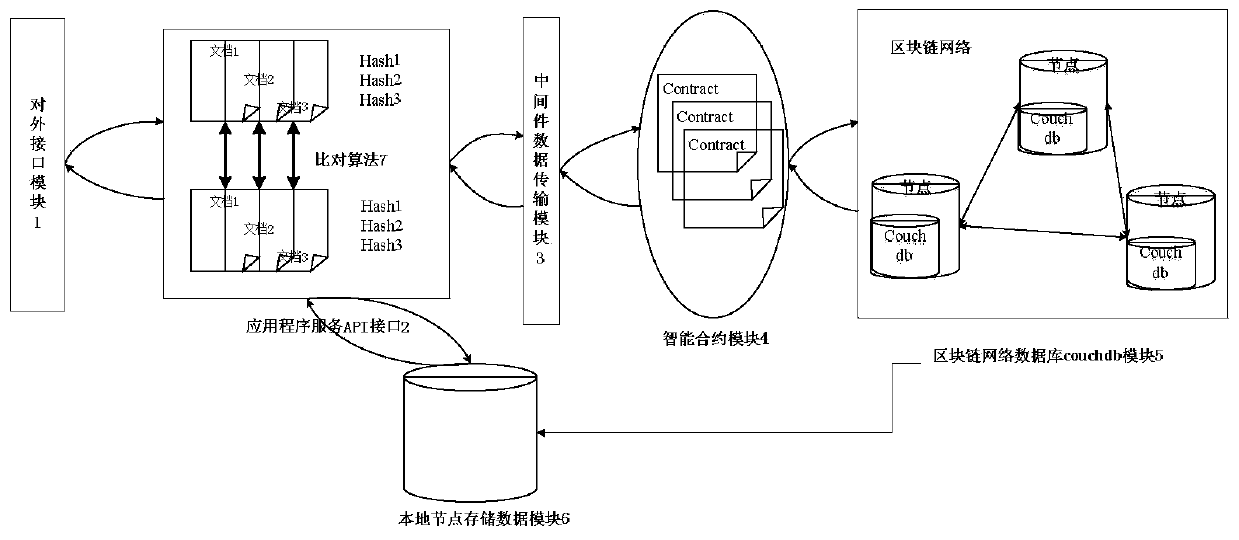
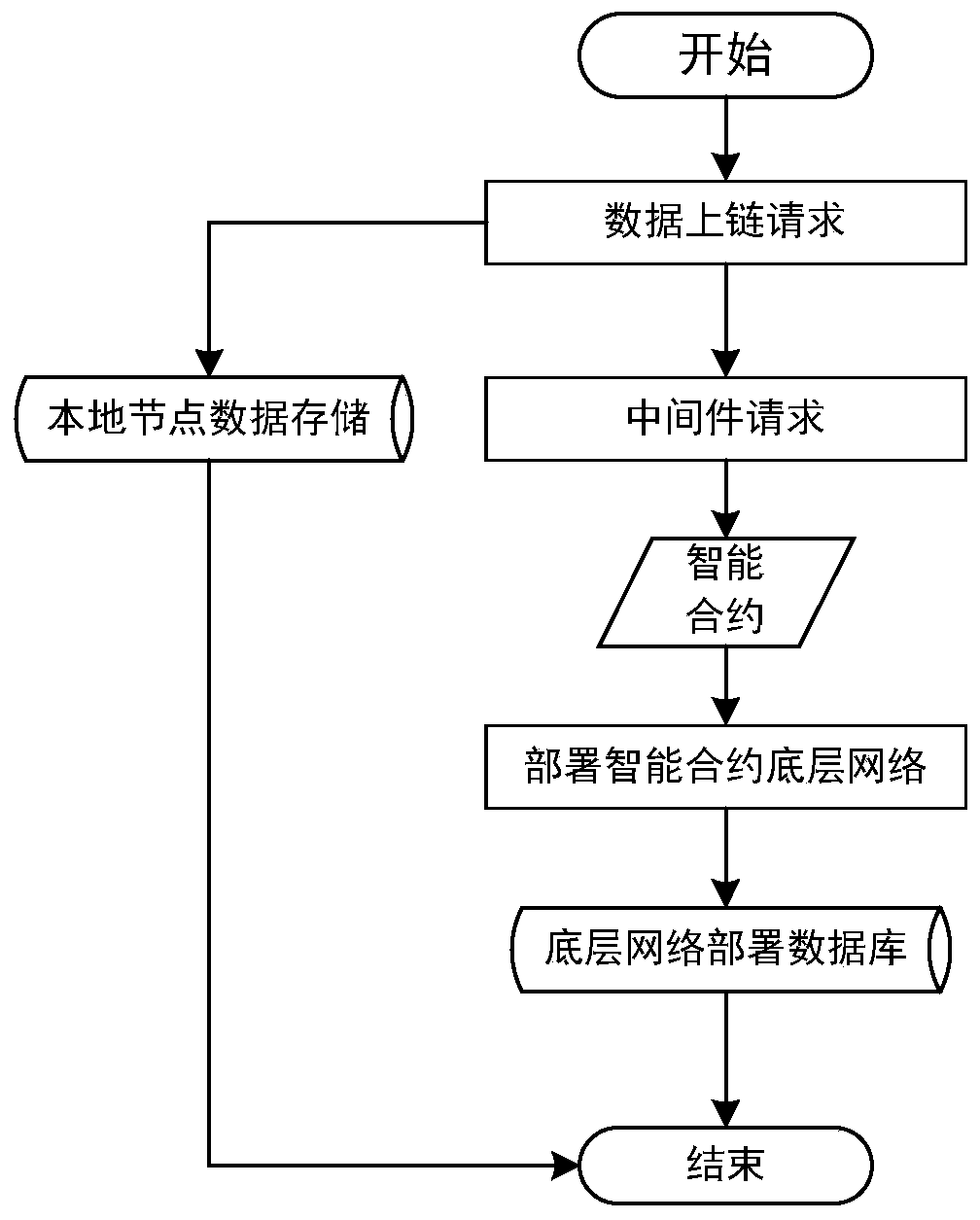
ActiveCN110110005AReduce storage costsFast data transferDatabase management systemsFinanceChain networkSmart contract
The invention discloses a management and control method for key information basic data asset based on block chain. The method comprises an external interface module, an application service API interface, a middleware data transmission module, an intelligent contract module, a block chain network node database count db module and a local node data storage module. The application service API interface is respectively connected with the external interface module, the middleware data transmission module and the local node data storage module, and the middleware data transmission module, the intelligent contract module, the block chain network database count db module and the local node data storage module are sequentially connected. The local node data storage module stores a plurality of pieces of original file data. The method has the advantages that whether key information basic data assets are counterfeited or not can be determined, tampering factors are determined, and therefore standard management and control are achieved.
Owner:HUAXIN CONSULTATING CO LTD
Digital certificate use method and apparatus
InactiveCN105681340AMeet the requirements of the transactionCannot be tampered withTransmissionProtocol authorisationDigital signatureClient-side
The invention discloses a digital certificate use method and apparatus. The method includes the steps of: obtaining a verification code and generating a public and private key pair in a trading process; when a client side performs digital certificate signature on information needing to be signed in the trading process by using a private key, obtaining a client private key digital signature of the trading, and generating a digital certificate request including a public key; sending the digital certificate request including the public key, the verification code, and the client private key digital signature of the trading to a network side, wherein the digital certificate request includes trading information, and / or the public and private key pair is generated according to the trading information. After a client user passes the verification according to the verification code and the digital certificate request, the public key is used to perform legality verification on the digital signature according to the trading information at the network side. The trading information and the client private key digital signature of the trading are saved at the network side. By using the digital certificate use method and apparatus, the digital certificate is not dependent on the client side in the use process. Because the trading information is included, the digital certificate can be used as an effective electronicevidence.
Owner:吴晓军
Data sharing method and system based on blockchain and electronic equipment
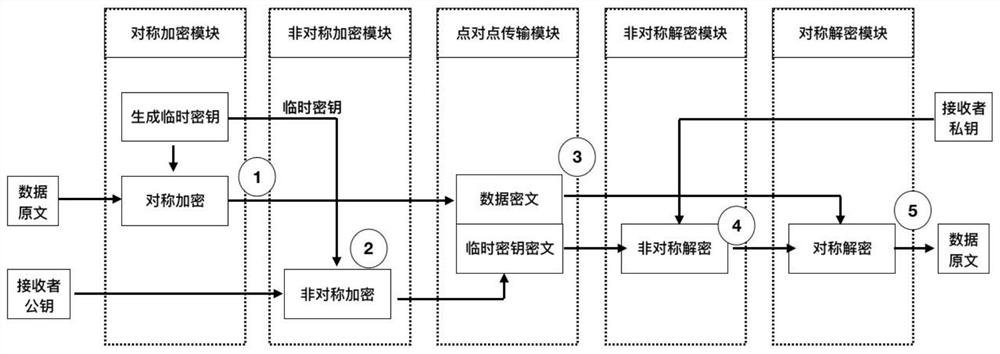
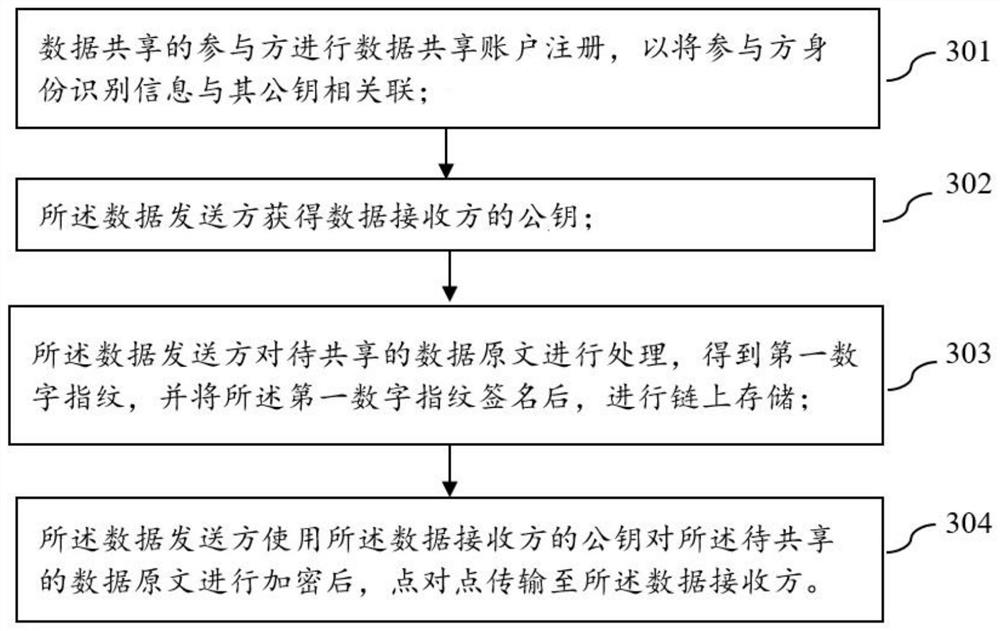
InactiveCN111683082AImprove data sharing efficiencyCannot be tampered withSecuring communicationEngineeringDigital fingerprint
The embodiment of the invention relates to a data sharing method and system based on a blockchain, and electronic equipment, and the method mainly comprises the steps that a data sender processes a to-be-shared data original text, signs an obtained first digital fingerprint, and then stores the first digital fingerprint in the blockchain; the data sender transmits the encrypted data original textto the data receiver in a point-to-point manner; the data receiver decrypts the received encrypted data and processes the decrypted data to obtain a second digital fingerprint, compares the second digital fingerprint with the first digital fingerprint, and if the second digital fingerprint and the first digital fingerprint are the same, the data receiver signs the second digital fingerprint and stores the signed second digital fingerprint in the blockchain. According to the embodiment of the invention, cross-subject data sharing records are stored in the blockchain, and the data sharing process is permanently stored, cannot be tampered, traceable and reviewable; therefore, the cross-enterprise data sharing efficiency is improved, and commercial disputes are reduced.
Owner:HANGZHOU RIVTOWER TECH CO LTD
Biological authentication method for resisting privacy disclosure
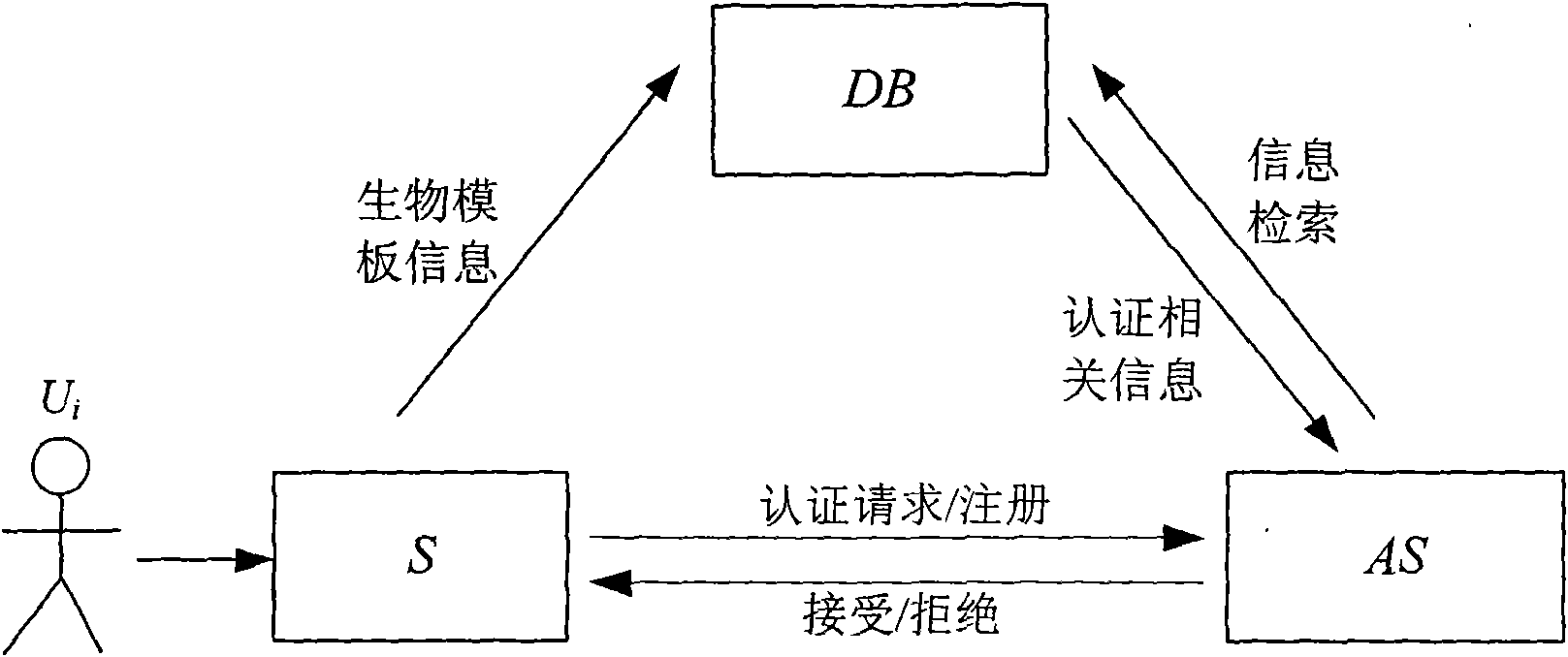
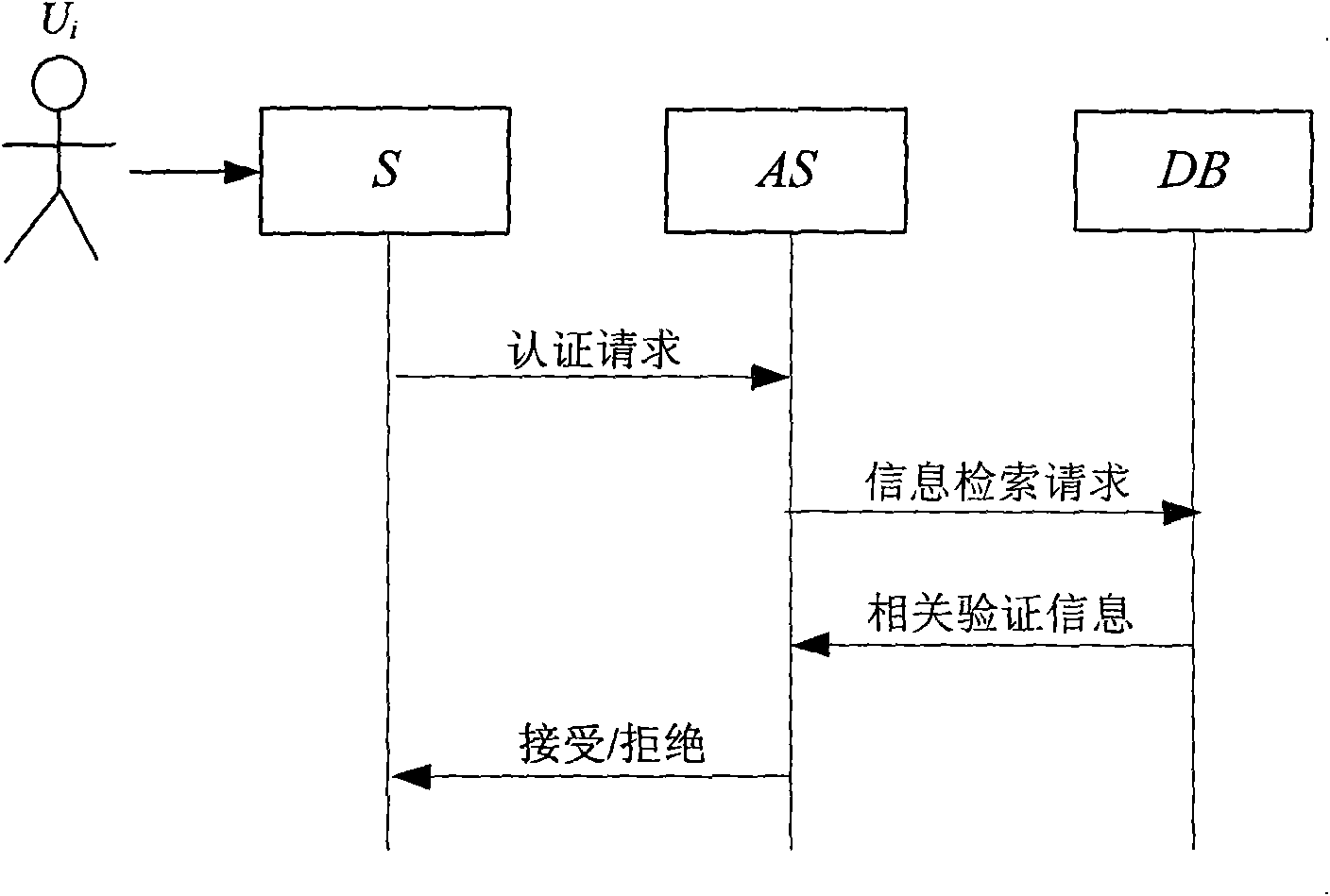
InactiveCN101567033ACannot be tampered withDigital data authenticationRelevant informationInternet privacy
The invention discloses a biological authentication method for resisting privacy disclosure, which solves the problem of information disclosure in the process of storing and authenticating biological characteristic information, and comprises the following steps: 1) registration phase: a user Ui registers a user name IDi and auxiliary information Wi from an authentication server (AS) through a sensor (S), and registers reference biological template relevant information Bi from data base (DB); and 2) authentication phase: the user Ui provides the current new biological characteristic information for the authentication server (AS) through the sensor (S), the authentication server cooperates with a database to judge the authenticity of the user identity by calculating the new biological characteristic information, the Wi and the Bi, and the authentication server returns the final authentication result to the user. Because the reference biological template information of the user is stored in the authentication server and the database respectively, the authentication information calculated by the database cannot be falsified without the reference biological template information stored on the authentication server.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Credit-increasing financing platform system and method based on block chain, and storage medium
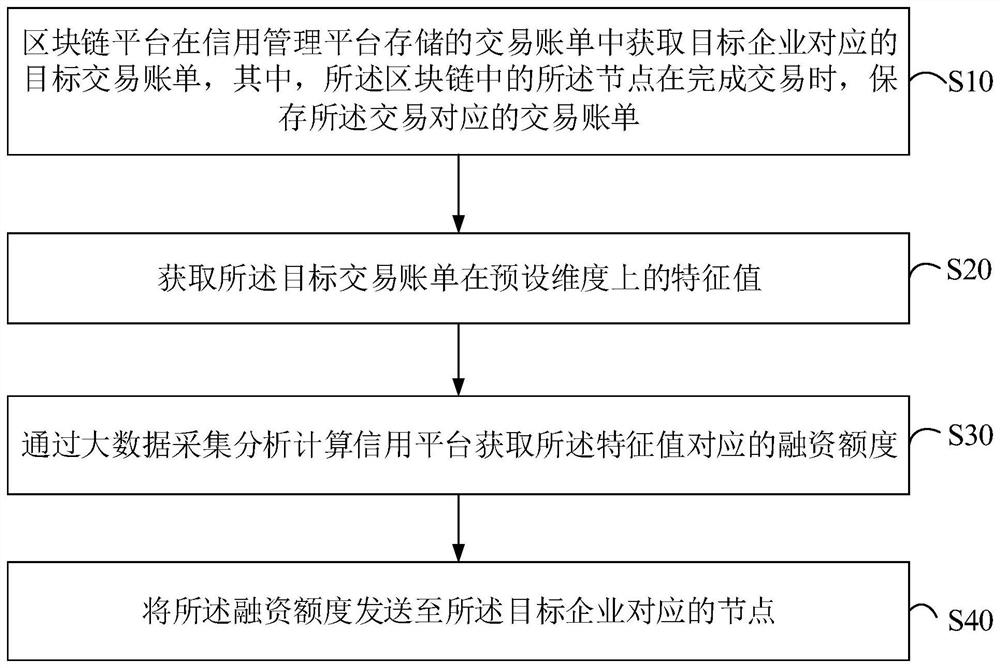
InactiveCN111681111AAvoid false situationsCannot be tampered withFinancePayment protocolsBusiness enterpriseTransaction data
The invention discloses a credit-increasing financing platform system and method based on a block chain, and a storage medium, the block chain platform obtains a target transaction bill correspondingto a target enterprise from transaction bills stored in a credit management platform, and when a node in the block chain completes a transaction, the transaction bill corresponding to the transactionis stored; obtaining a characteristic value of the target transaction bill in a preset dimension; obtaining a first credit score corresponding to the feature value through a big data collection, analysis and calculation credit platform, taking the sum of the first credit score, a second credit score corresponding to the blockchain platform and a third credit score guaranteed or mortgage by a thirdparty as a credit score, and determining a financing limit through the credit score; and sending the financing quota to a node corresponding to the target enterprise. According to the invention, thetransaction data is locked, cannot be tampered, traceable and credible through the blockchain technology, the financing limit is evaluated according to the real transaction data, the situation that the enterprise transaction data is false is avoided, and a more reliable credit-increasing financing platform is established.
Owner:SHENZHEN QIANHAI DIANJIN FACTORING CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com