Method for achieving data security communication by applying blockchain encryption technology
A data security and blockchain technology, applied in secure communication devices, relational databases, database models, etc., can solve problems such as the endless emergence of technologies and the increase in network vulnerabilities of network hackers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment (1
[0086] Embodiment (1) system
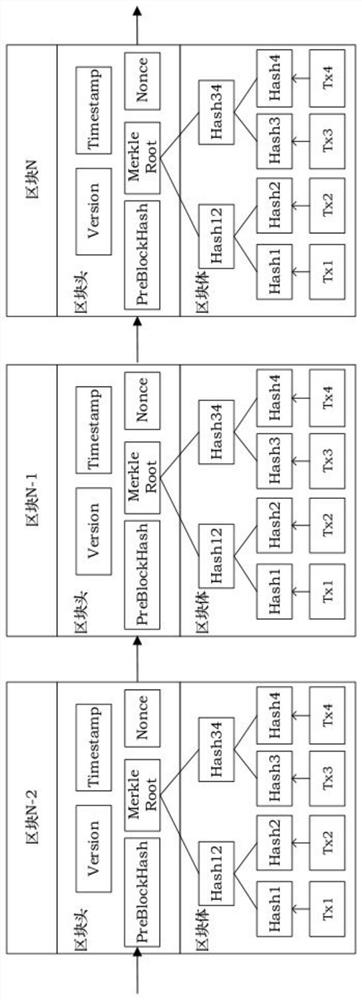
[0087] like figure 1 As shown, a system that applies blockchain encryption technology to realize data security communication, the system includes:
[0088] The data layer is provided with a database storing multiple data types in it, and the database at least includes a DB2 database, an oracle database, an Informix database, a Sybase database, a SQL Server database, a PostgreSQL database or a MySQL database;
[0089] The data encryption layer is provided with a data encryption unit, and the data encryption unit is a DES encryption unit, a 3DES encryption unit, a Blowfish encryption unit, a Twofish encryption unit, an IDEA encryption unit, an RC6 encryption unit, a character string encryption unit or a CAST5 encryption unit Wherein said data encryption unit is connected with an ant colony algorithm model, and said ant colony algorithm model external housing is provided with TCP / IP communication interface, ZigBee wireless communication interface, ...
Embodiment (2
[0110] Embodiment (2) method
[0111] like Image 6 As shown, a method of applying blockchain encryption technology to realize data security communication, wherein the method includes the following steps:
[0112] (1) Communication data extraction: Obtain various data information for information interaction with other devices from the database through data screening;
[0113] (2) Data encryption: use the ant colony algorithm to select the best data encryption unit from a variety of data encryption units to meet the needs of information interaction with different devices, such as Figure 7 As shown, the communication data is encrypted and calculated by the data encryption unit. After the encryption is completed, the encrypted data information is transmitted, and the data information is decrypted by the data decryption unit at the data information receiving end, wherein the data encryption unit and the data decryption unit All are completed through the encapsulation of the dig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com