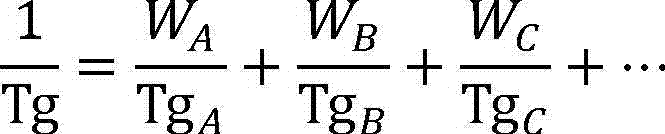Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2396results about How to "Reduce storage costs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
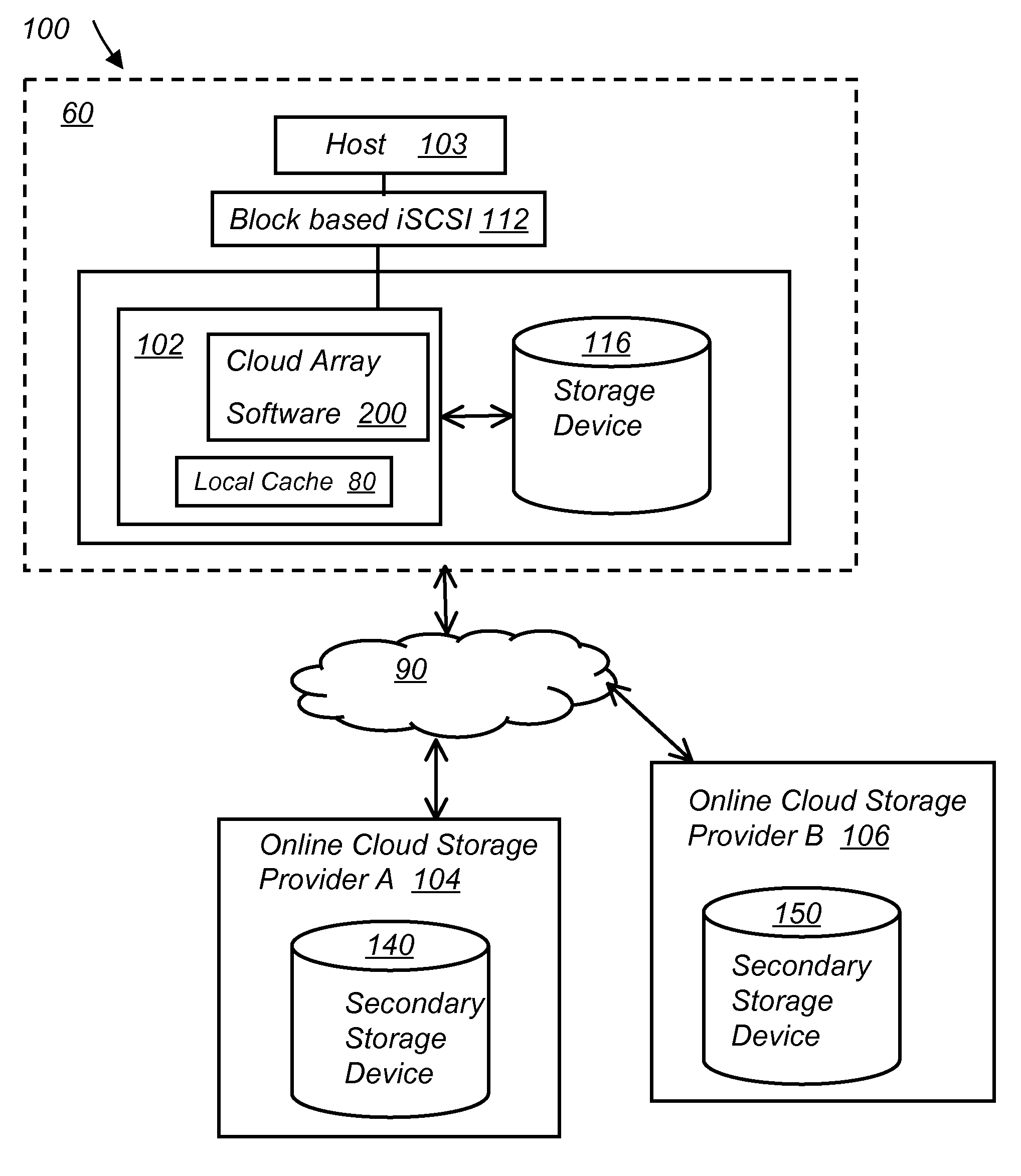
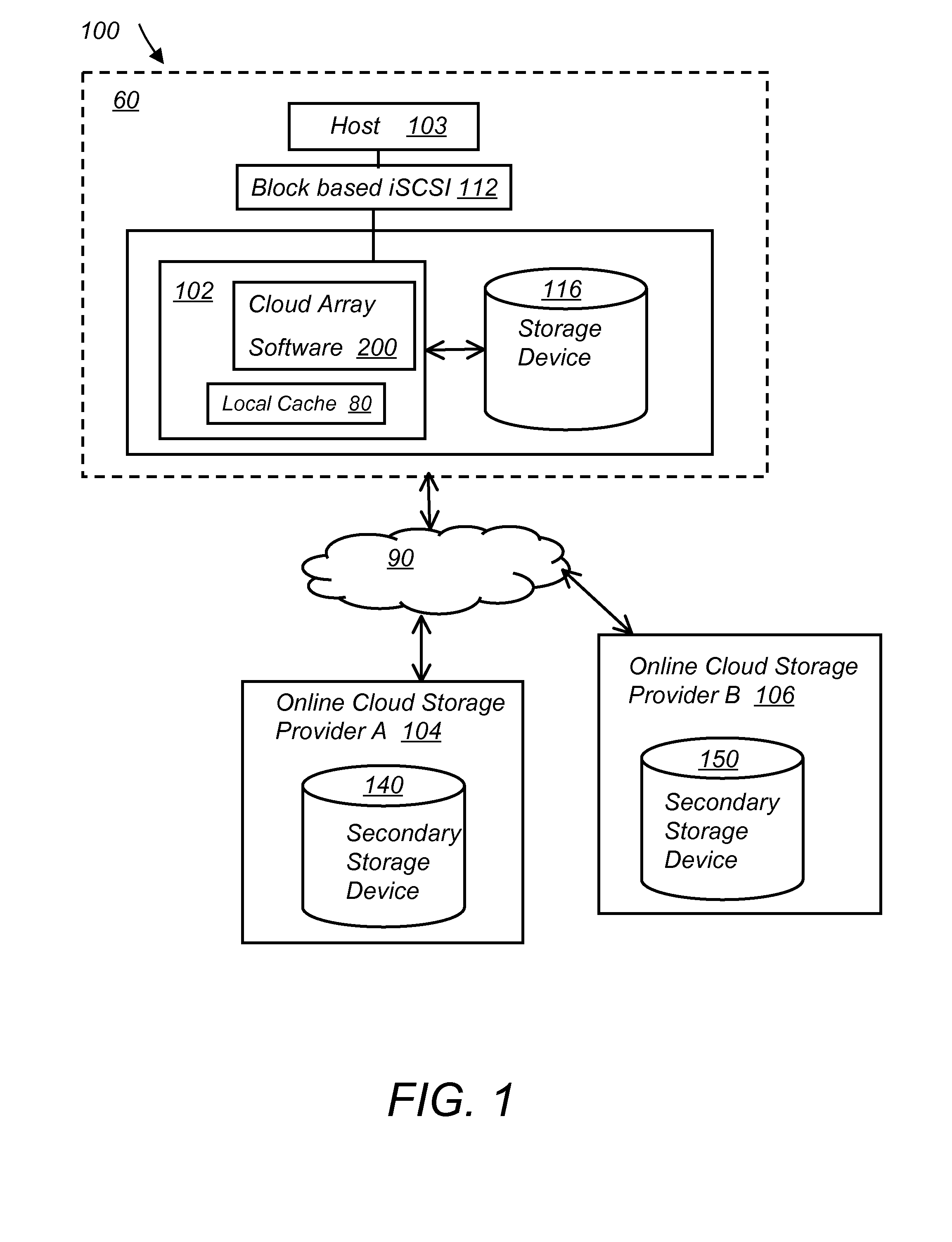
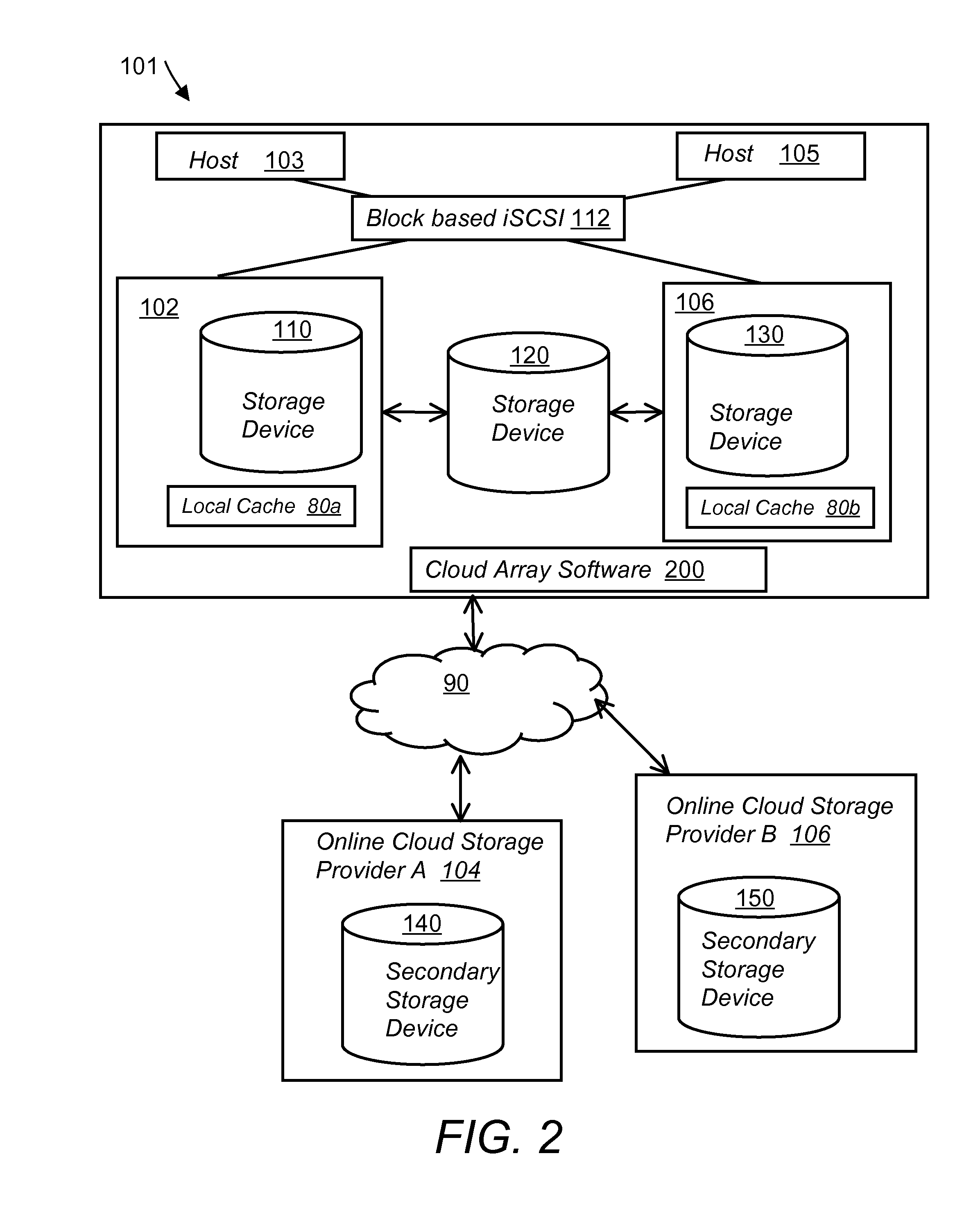
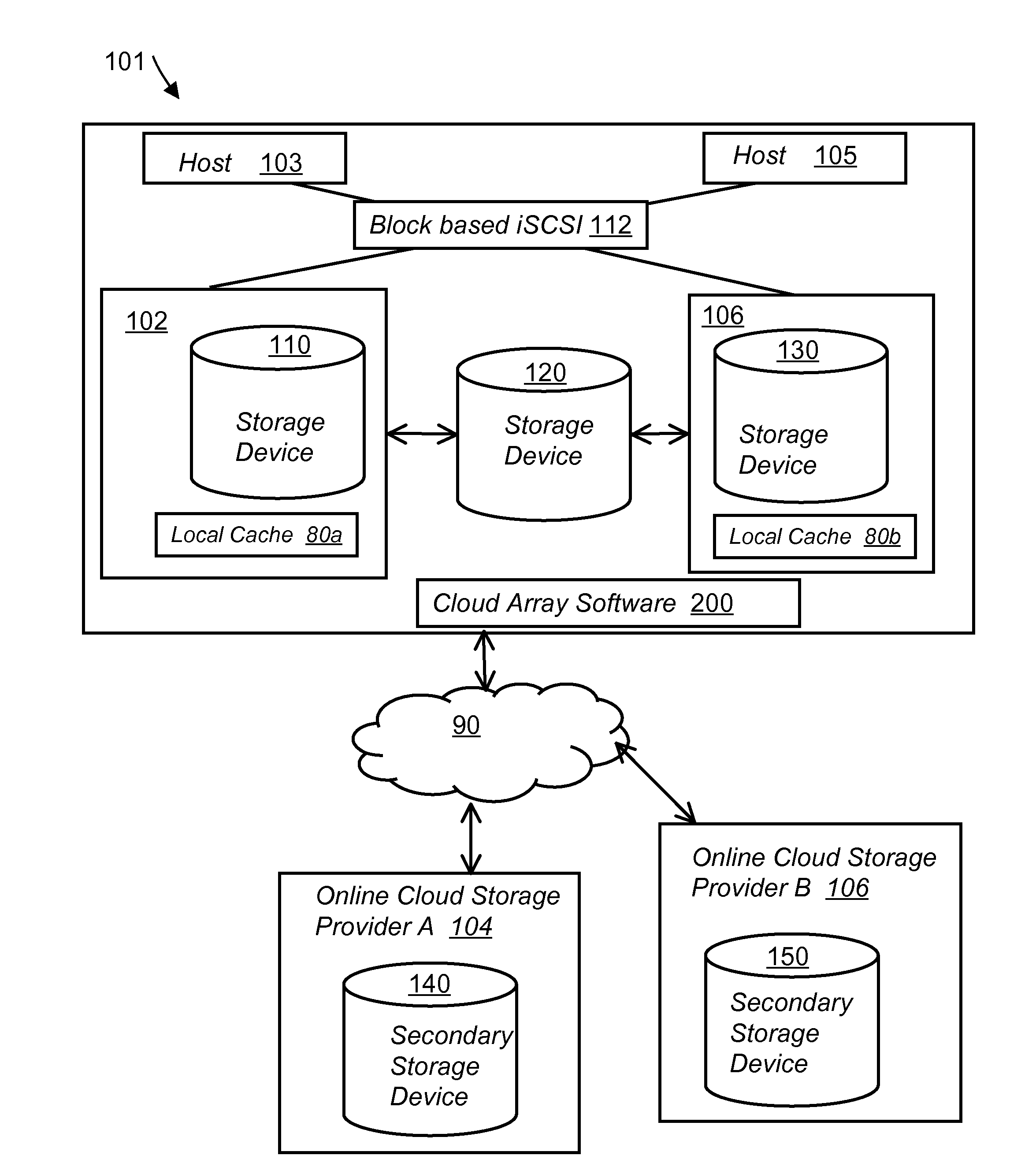
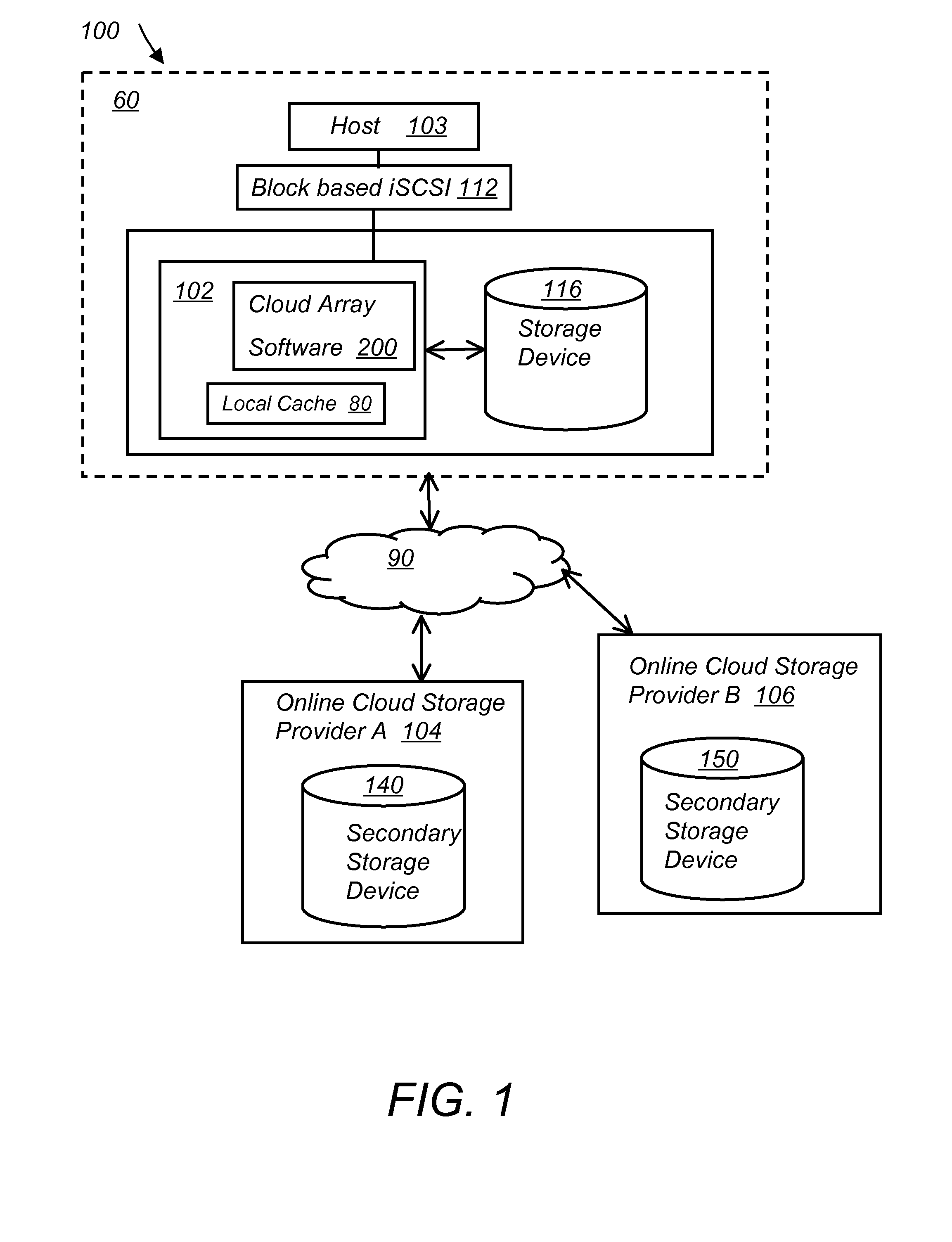
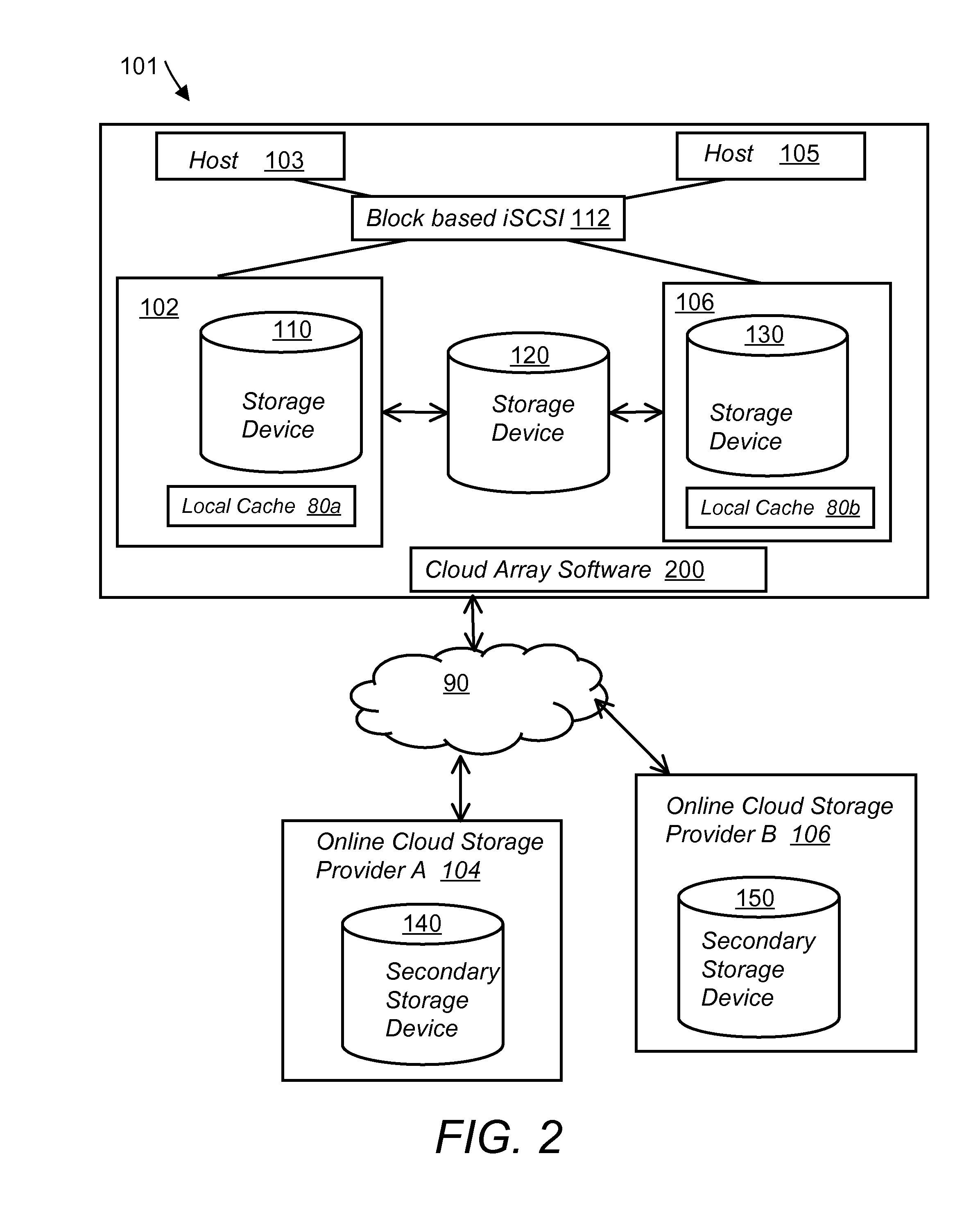
System and method for secure and reliable multi-cloud data replication
ActiveUS8762642B2Reduce the amount requiredReduce storage costsMemory architecture accessing/allocationUnauthorized memory use protectionReliable computingNetwork connection
Owner:EMC IP HLDG CO LLC
System and method for secure and reliable multi-cloud data replication
ActiveUS20100199042A1Reduce the amount requiredReduce storage costsMemory architecture accessing/allocationMemory loss protectionReliable computingReplication method
A multi-cloud data replication method includes providing a data replication cluster comprising at least a first host node and at least a first online storage cloud. The first host node is connected to the first online storage cloud via a network and comprises a server, a cloud array application and a local cache. The local cache comprises a buffer and a first storage volume comprising data cached in one or more buffer blocks of the local cache's buffer. Next, requesting authorization to perform cache flush of the cached first storage volume data to the first online storage cloud. Upon receiving approval of the authorization, encrypting the cached first storage volume data in each of the one or more buffer blocks with a data private key. Next, assigning metadata comprising at lest a unique identifier to each of the one or more buffer blocks and then encrypting the metadata with a metadata private key. Next, transmitting the one or more buffer blocks with the encrypted first storage volume data to the first online cloud storage. Next, creating a sequence of updates of the metadata, encrypting the sequence with the metadata private key and then transmitting the sequence of metadata updates to the first online storage cloud.
Owner:EMC IP HLDG CO LLC
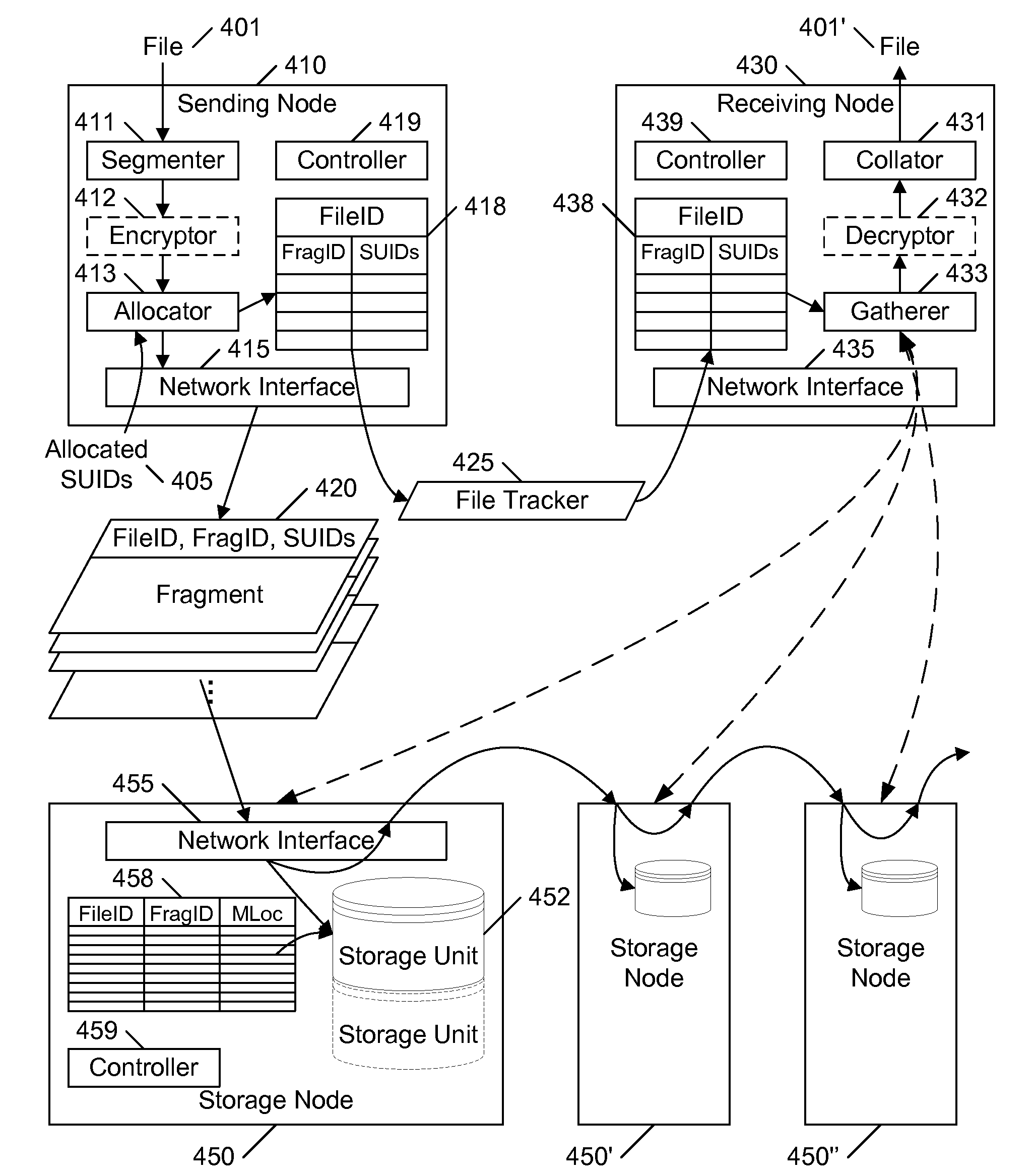
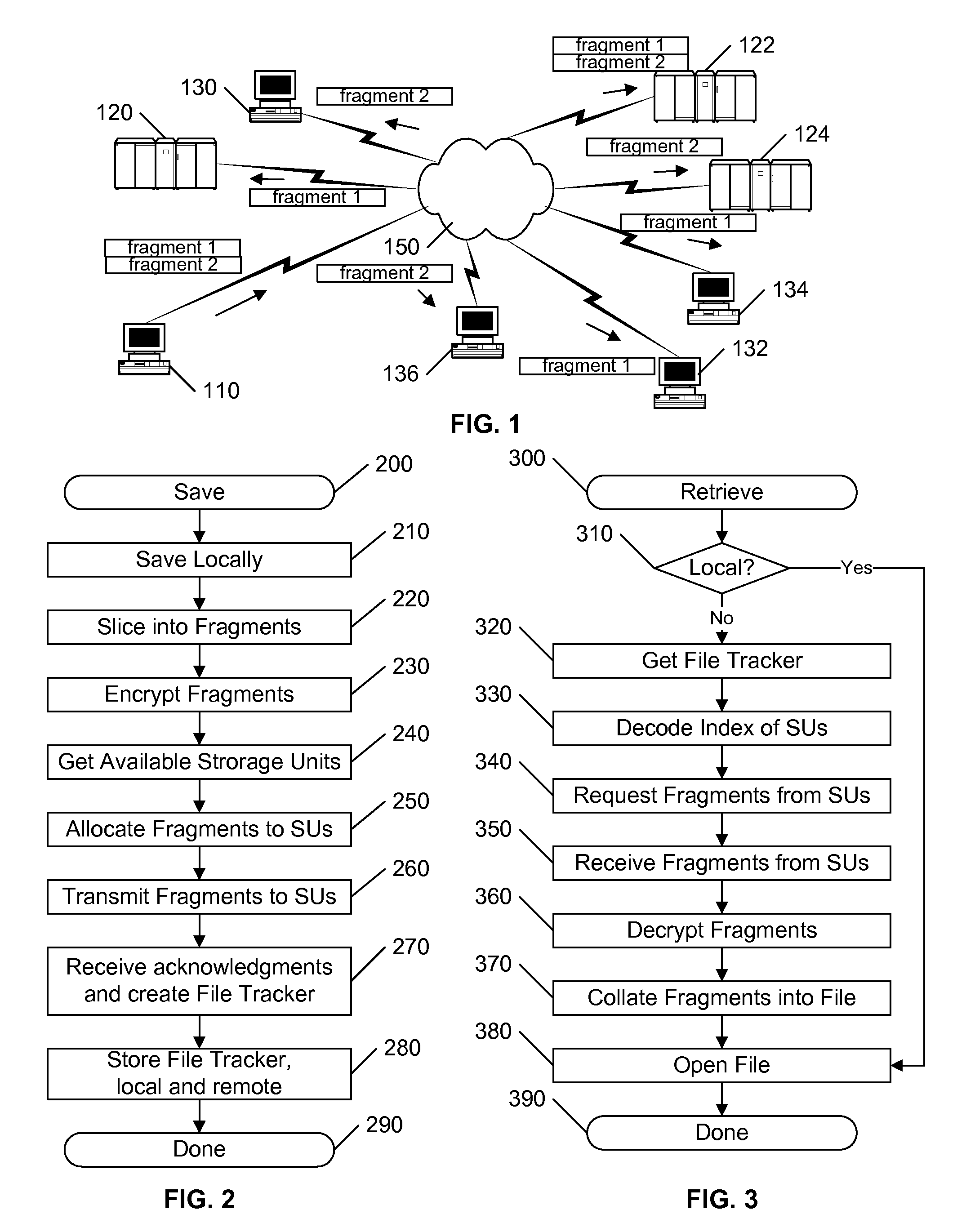
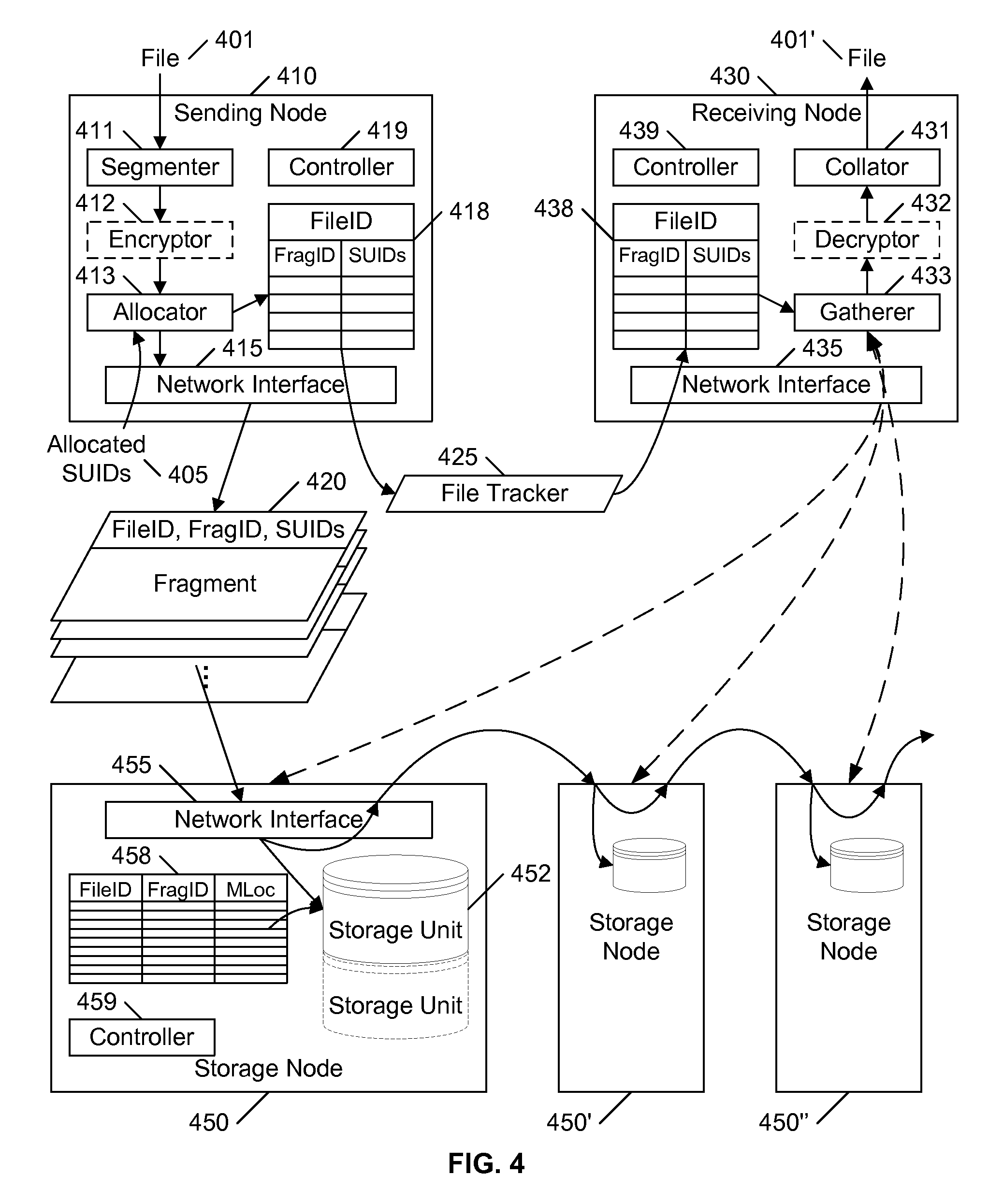
Distributed file storage and transmission system
InactiveUS20080126357A1Facilitates reliable communicationFacilitates reliable accessDigital data information retrievalSpecial data processing applicationsTransmission systemStorage cell
A distributed file storage and communication system stores redundant copies of segments of a file on multiple remote storage units. The file to be stored is partitioned into multiple fragments, and each of the fragments is redundantly stored on multiple remote storage units. A file tracker is maintained that identifies where each fragment is stored. Providing the file tracker to another user allows the other user to access the file. To receive and / or retrieve the file, the system retrieves each fragment by attempting to download the fragment from one of the remote storage units identified in the file tracker for the fragment; if the selected remote storage unit is not available, another storage unit is selected for attempting the download. The selection of storage units to receive each fragment may be random or targeted, or a combination of both. Preferably, each fragment is encrypted, and the intended recipient is provided a key to decrypt the fragments.
Owner:WAMBO
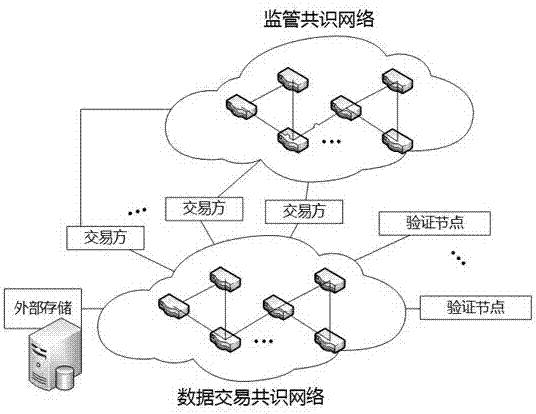
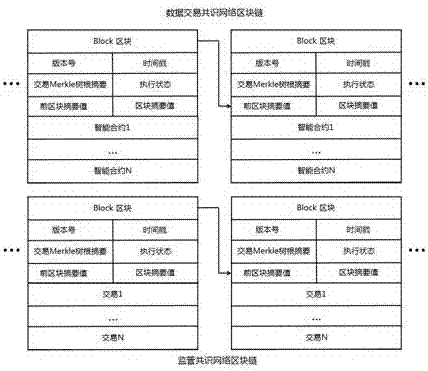
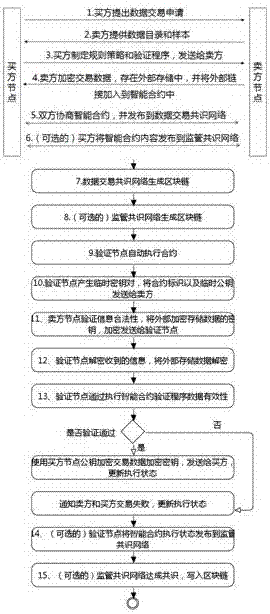
Block chain smart contract-based data transaction method
InactiveCN107464118AReduce storage costsGuaranteed execution efficiencyFinanceDatabase distribution/replicationThird partyExternal data
The invention relates to the technical field of big data, block chains and smart contracts, and in particular to a block chain smart contract-based data transaction method. According to the block chain smart contract-based data transaction method, purchase and sale behaviors of purchasers and sellers of transactions are recorded through block chains, automatic execution of the transactions is realized by utilizing smart contracts, and big data for the transactions is not recorded in the block chains and is encrypted and stored in an external data memory, so that the purchasers only can obtain the data after the smart contracts are successfully transacted; and moreover, the purchasers can publish transactions through a supervisory block chain consensus network, so that third-party witness is realized and the security guarantee of data transactions is increased.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
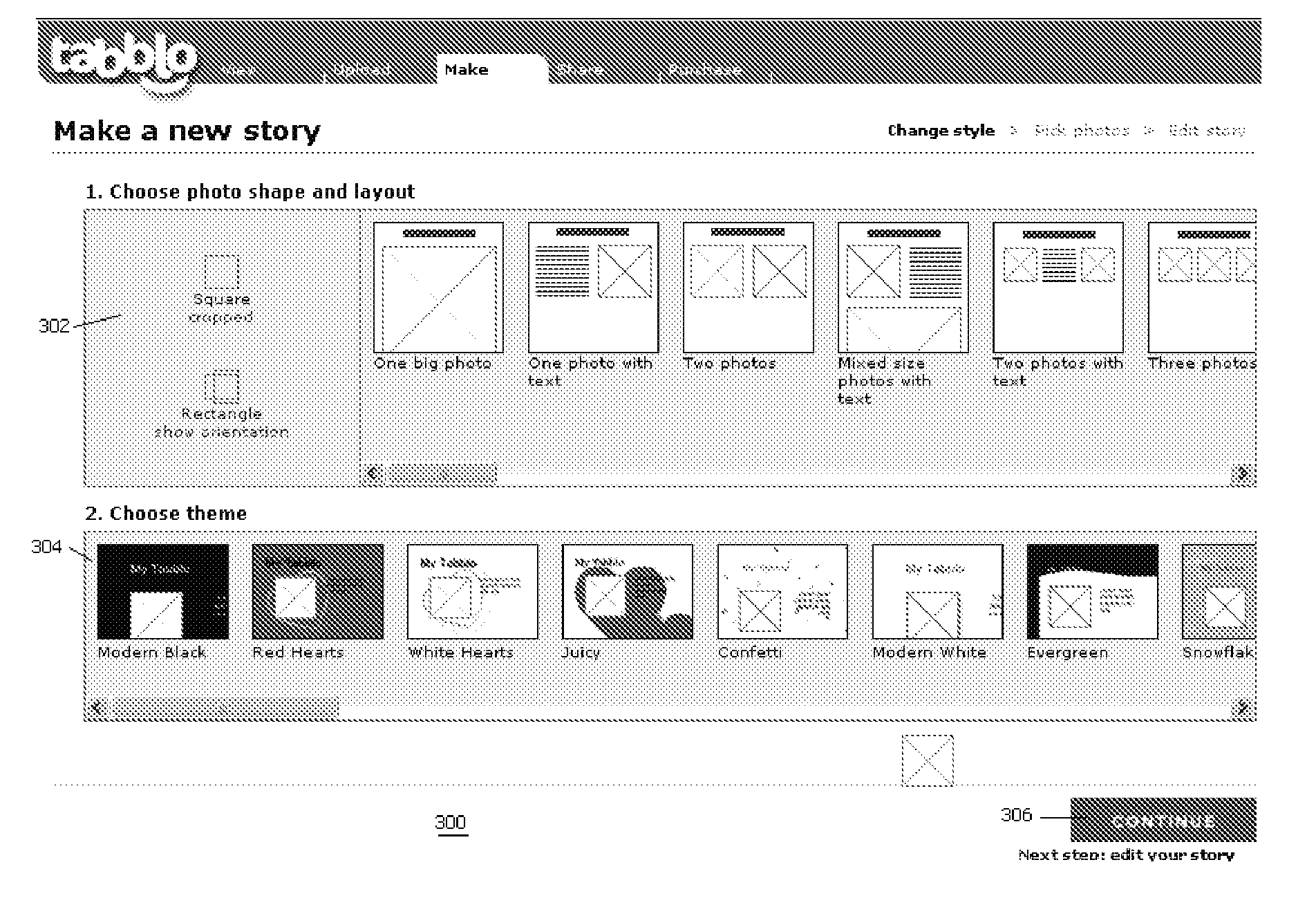
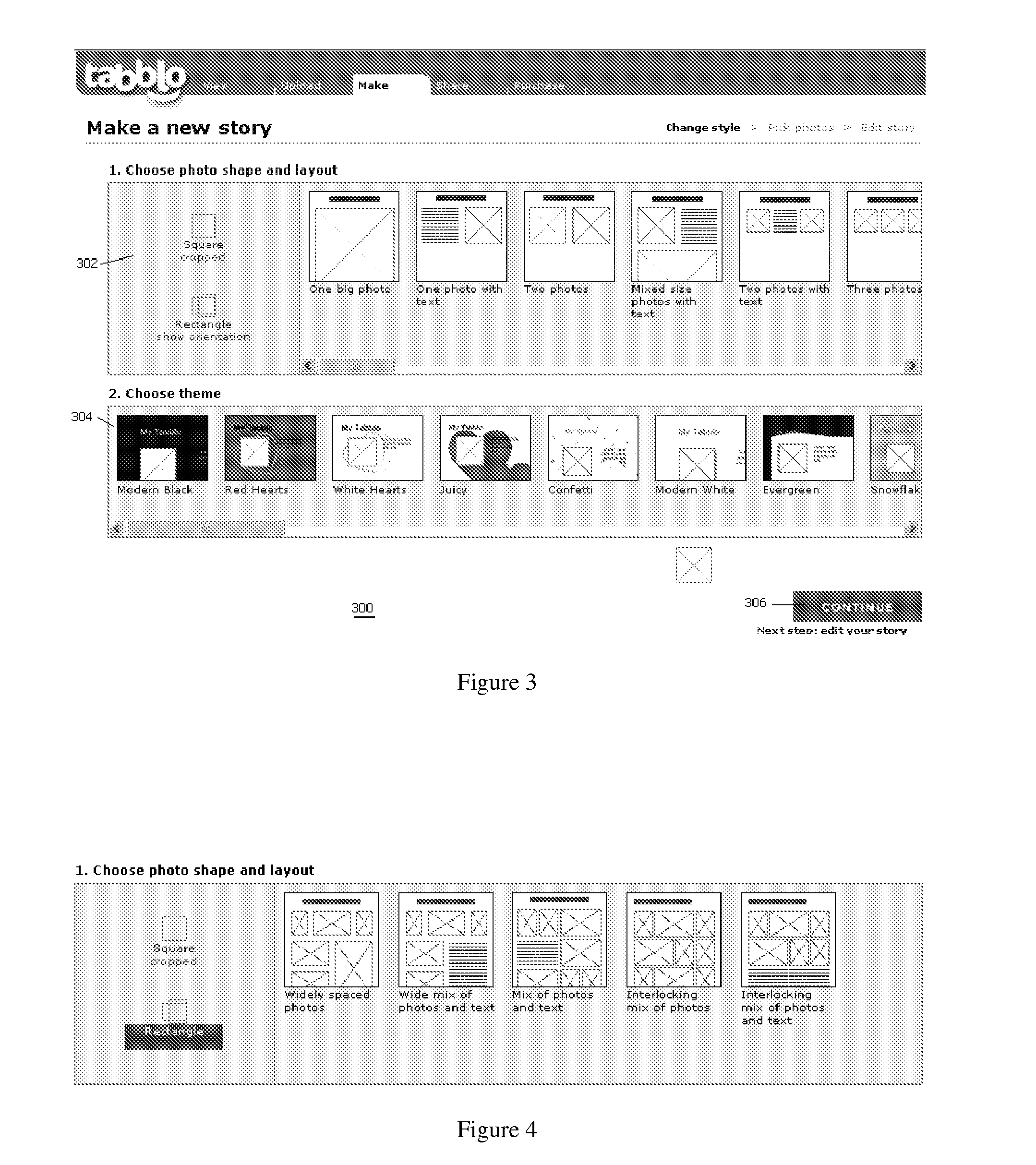
Method for initial layout of story elements in a user-generated online story
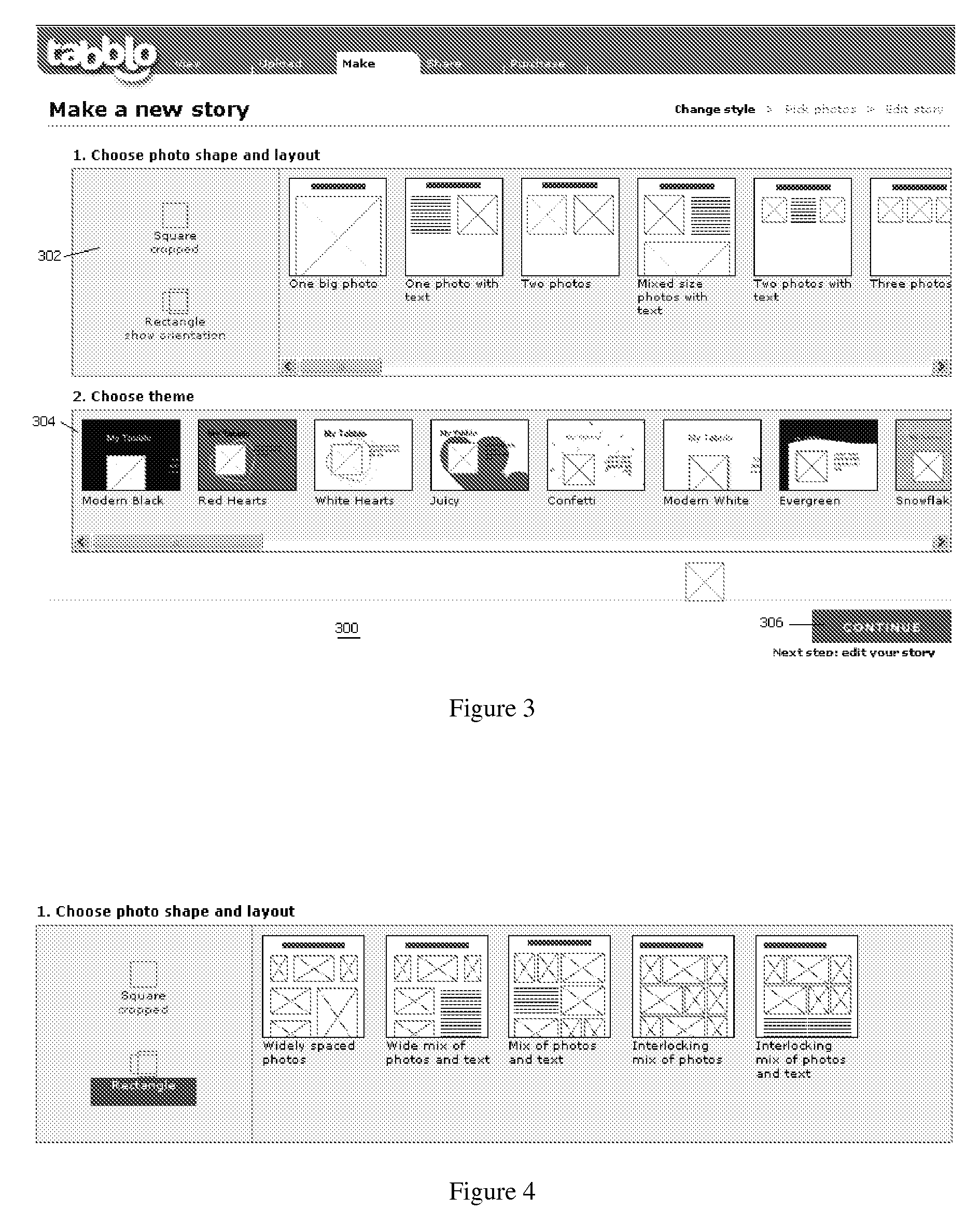
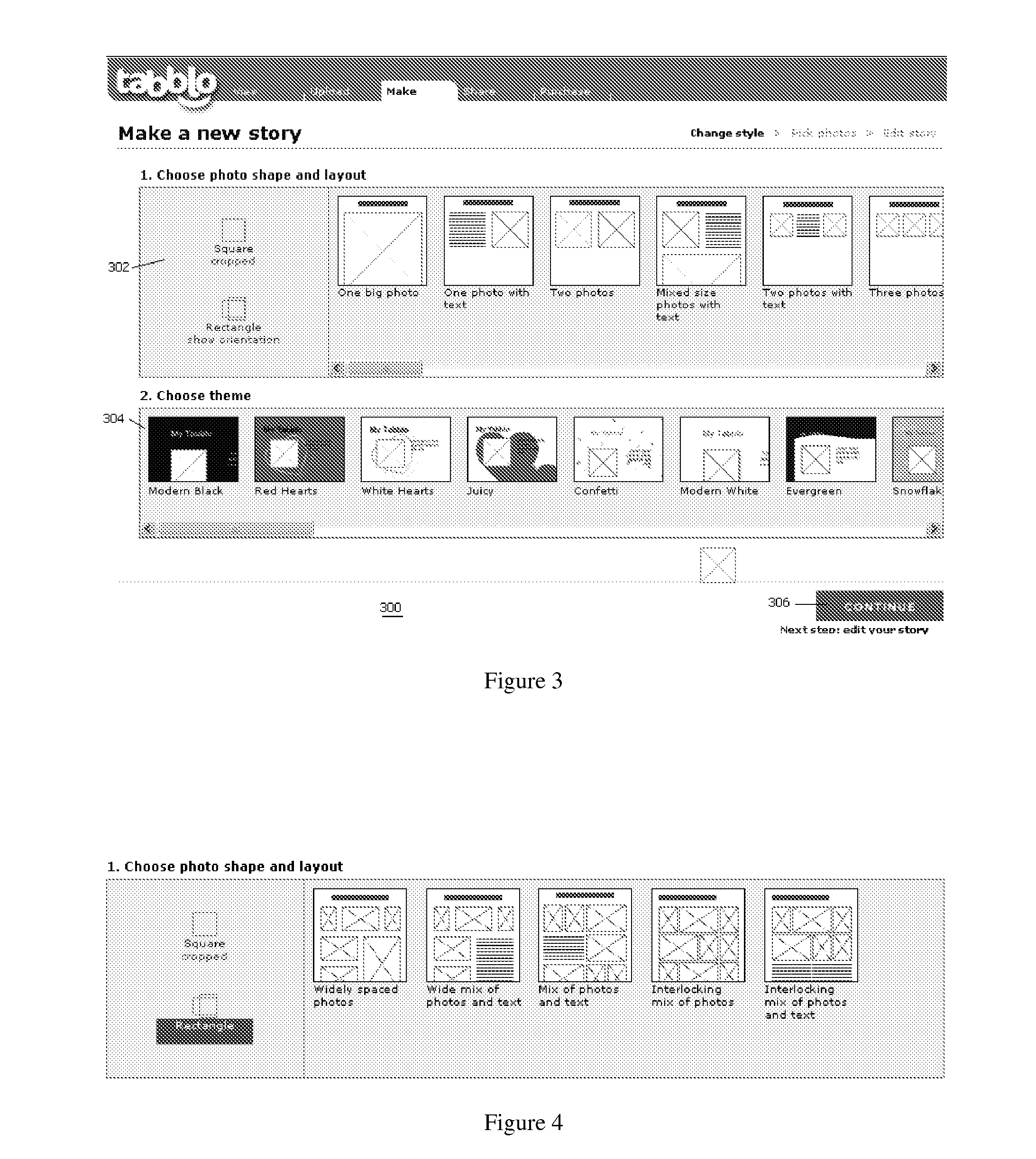
InactiveUS20080215985A1SignificantReduce storage costsNatural language data processingSpecial data processing applicationsWeb siteDigital image
An online application enables an end user to navigate to a web site, upload digital images, and to combine those images with words in a stylized template to create a user-generated story. A story is a web page, typically a collection of photos and words that are brought together by a stylized template that can be customized by the end user. Preferably, a given story is available from the site at a given location (at a URL) that may be private or public. A given story may be shared with other end users, published to other web sites or web logs, or maintained solely for one's own use. The invention also provides for multiple end users to collaborate to create a “shared” story.
Owner:HEWLETT PACKARD CO
Method for caching of media files to reduce delivery cost
InactiveUS6868452B1Good serviceReduce delivery costsMultiple digital computer combinationsTwo-way working systemsDelivery costClient-side
Improvement on delivery of continuous media programs, such as video, divides the programs into prefixes and suffixes of data. One of these groups, or other groups associated with alternate on-demand data streaming, may be stored at a remote location, while the other of the groups may be stored at a plurality of regional locations. Accordingly, when the media program is ordered by a plurality of clients, a portion of the program will be broadcast from the regional server, while the other portion of the program will be transmitted from the remote server. The prefixes and suffixes are chosen so as to maximize the efficiency of data transfer taking into account the cost of storing the data as well as bandwidth costs.
Owner:WISCONSIN ALUMNI RES FOUND
Method and system for online creation and publication of user-generated stories
InactiveUS20080215964A1SignificantReduce storage costsText processingSpecial data processing applicationsWeb siteUniform resource locator
An online application enables an end user to navigate to a web site, upload digital images, and to combine those images with words in a stylized template to create a user-generated story. A story is a web page, typically a collection of photos and words that are brought together by a stylized template that can be customized by the end user. Preferably, a given story is available from the site at a given location (at a URL) that may be private or public. A given story may be shared with other end users, published to other web sites or web logs, or maintained solely for one's own use. The invention also provides for multiple end users to collaborate to create a “shared” story.
Owner:HEWLETT PACKARD CO
Intelligent video retrieval system and method based on target characteristic and alarm behavior
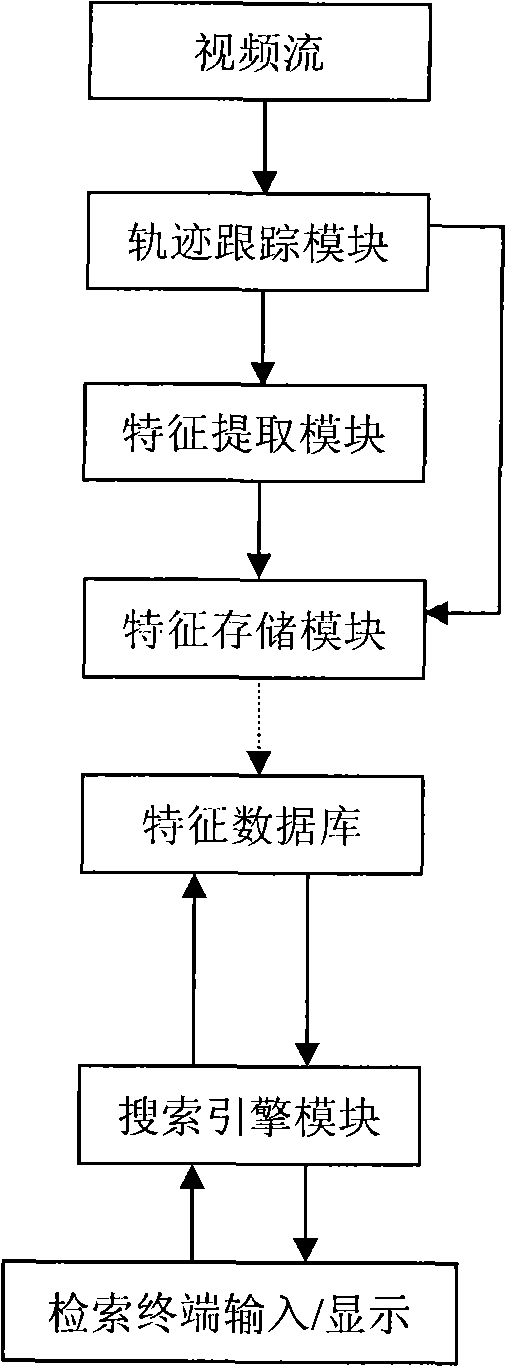
InactiveCN101840422AQuick checkReduce storage costsCharacter and pattern recognitionSpecial data processing applicationsVideo retrievalFeature extraction
An intelligent video retrieval system and method based on target characteristic and alarm behavior relate to an intelligent video retrieval system and method. The system comprises a trajectory tracking module, a feature extraction module, a feature storage module, a search engine module and a retrieval terminal, wherein the trajectory tracking module extracts the motion trajectory and alarm behavior of a target input in the video; the feature extraction module extracts the features of the input image such as color, texture, shape and category; the feature storage module stores the motion trajectory, the alarm behavior, the target characteristic and the related information of the video in a feature database; the search engine module analyzes the retrieval conditions input by a user, performs video retrieval based on characteristic and behavior in the database and returns the video clip satisfying the conditions; and the retrieval terminal, namely client software receives the retrieval conditions input by the user and displays the retrieval result after retrieval. Compared with the prior art, by using the retrieval system, the user can customize retrieval conditions more accurately, video retrieval based on target characteristic and alarm behavior can be performed; and the retrieval result of the features generated by real-time analysis can be fast obtained.
Owner:WISCOM SYSTEM CO LTD
Computer-implemented method for determining computer system security threats, security operations center system and computer program product
ActiveUS20180167402A1Ensure resource securityReduce processComputer security arrangementsMachine learningRisk levelSecurity operations center
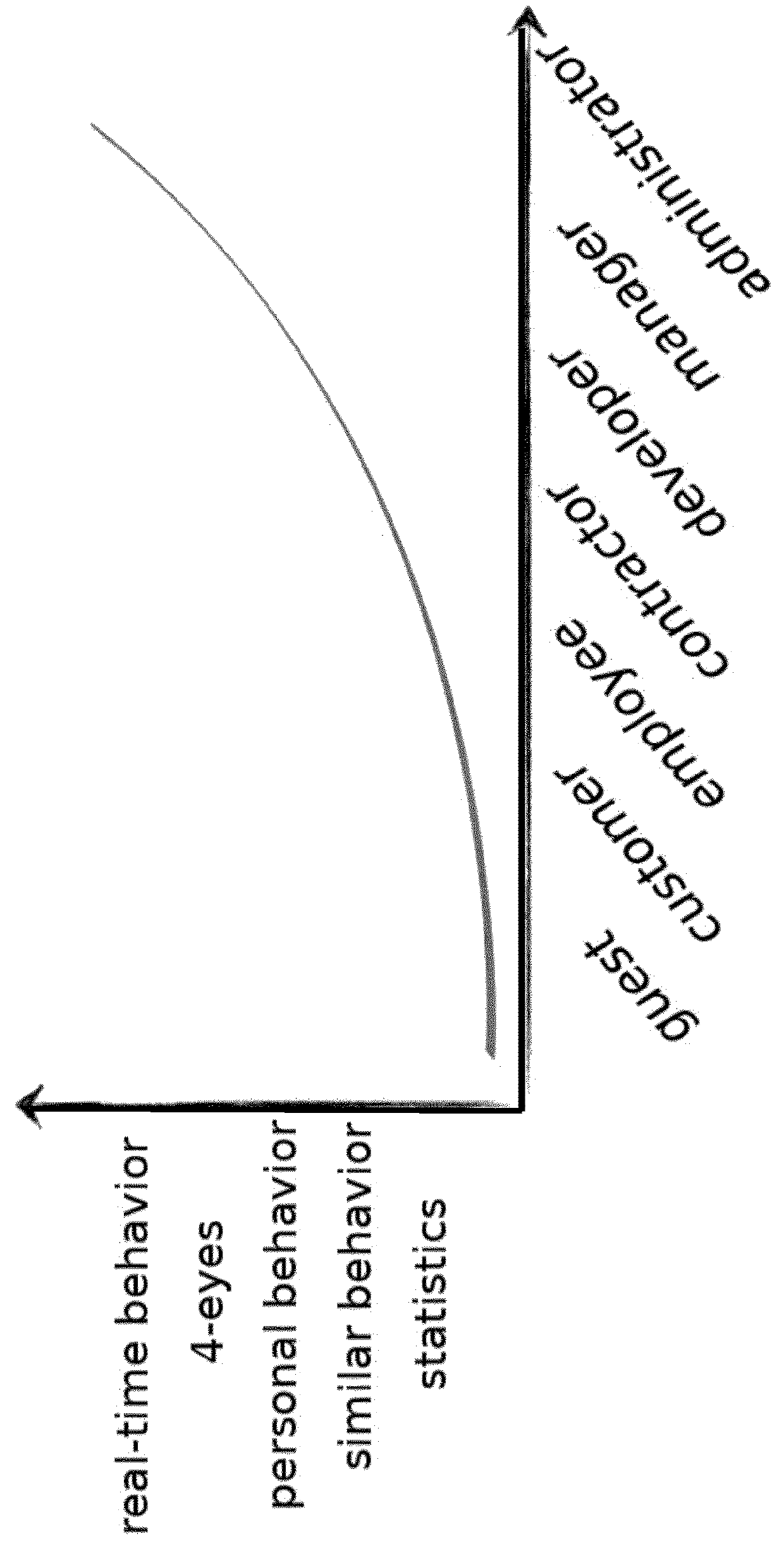
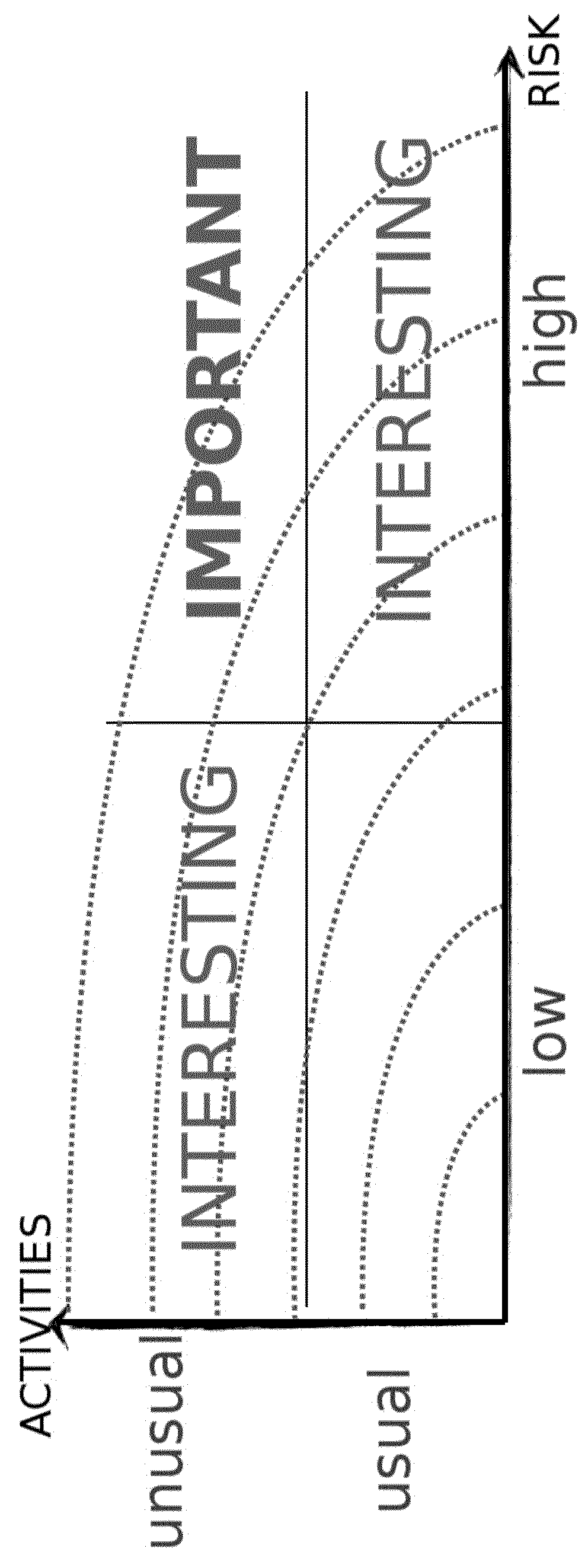
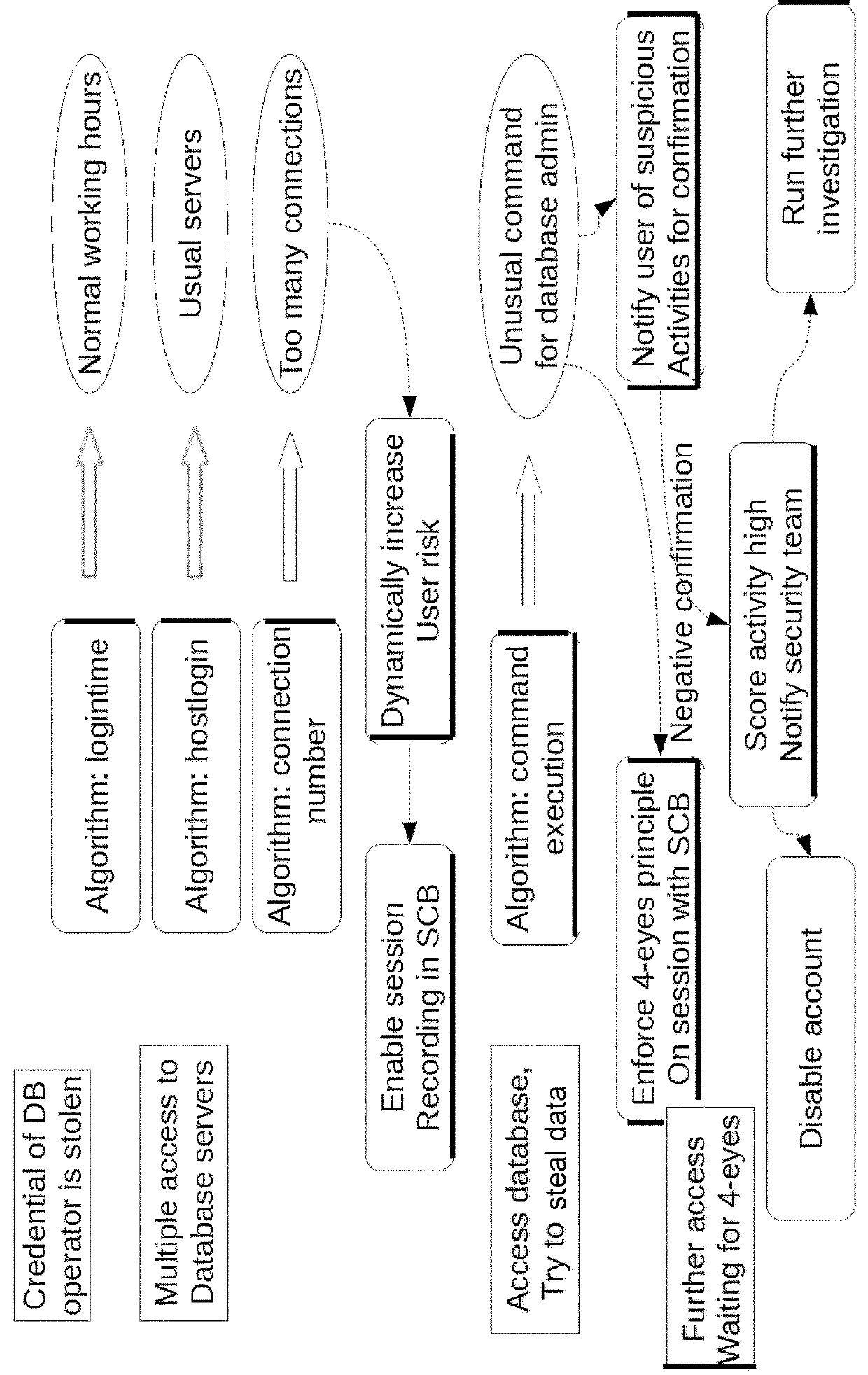
A computer-implemented method for determining computer system security threats, the computer system including user accounts established on the computer system, the method including the steps of: (i) for a plurality of user accounts, assigning a risk level to each account; (ii) in a time interval, for a plurality of events, wherein each event is linked to a respective user account, assigning an event score relating to deviation from normal behavior of each event with respect to the respective user account; (iii) in the time interval, for the plurality of events, calculating an event importance which is a function of the respective event score and the respective user account risk level; (iv) prioritizing the plurality of events by event importance, and (v) providing a record of the plurality of events, prioritized by event importance.
Owner:BALABIT SA
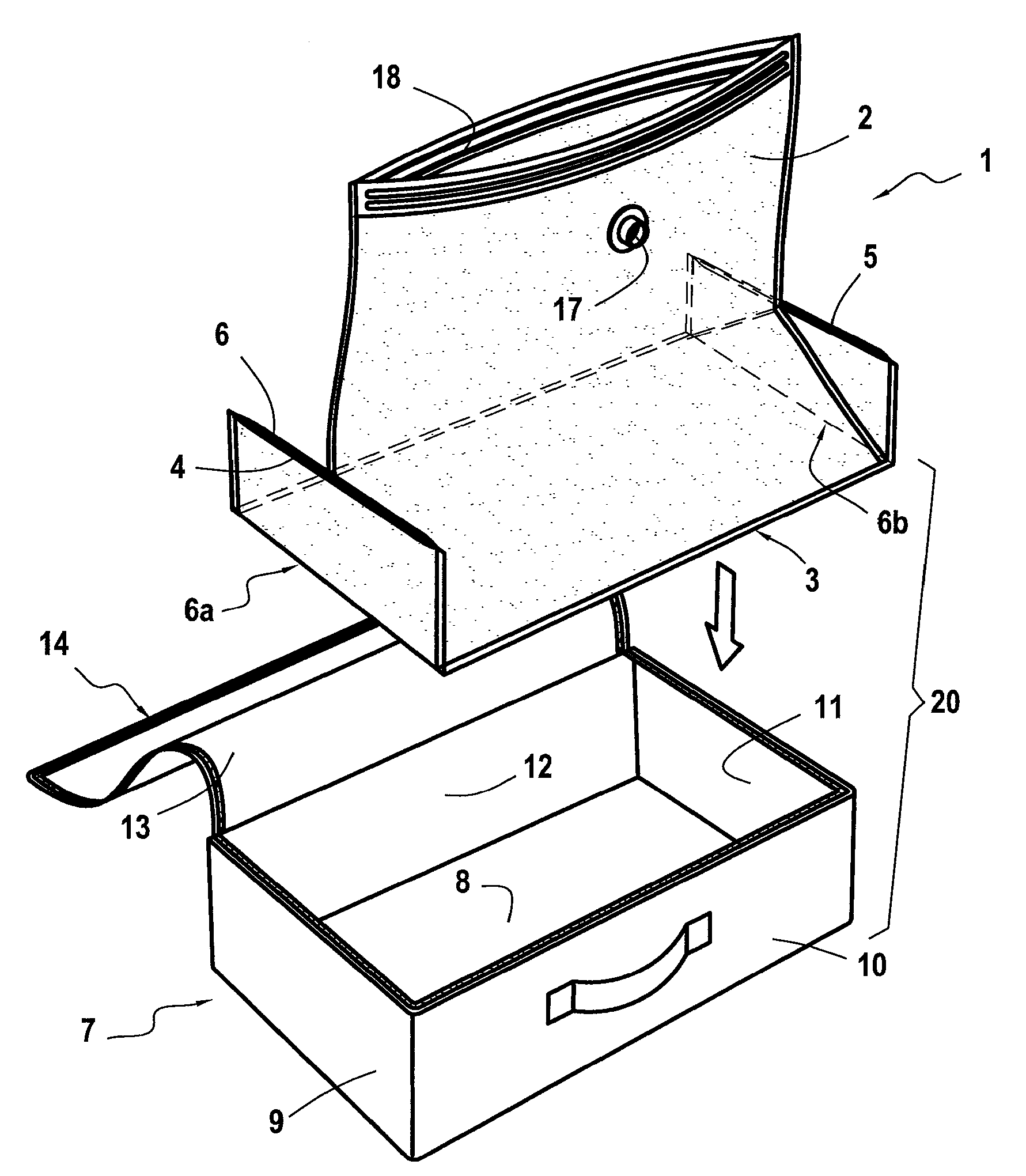
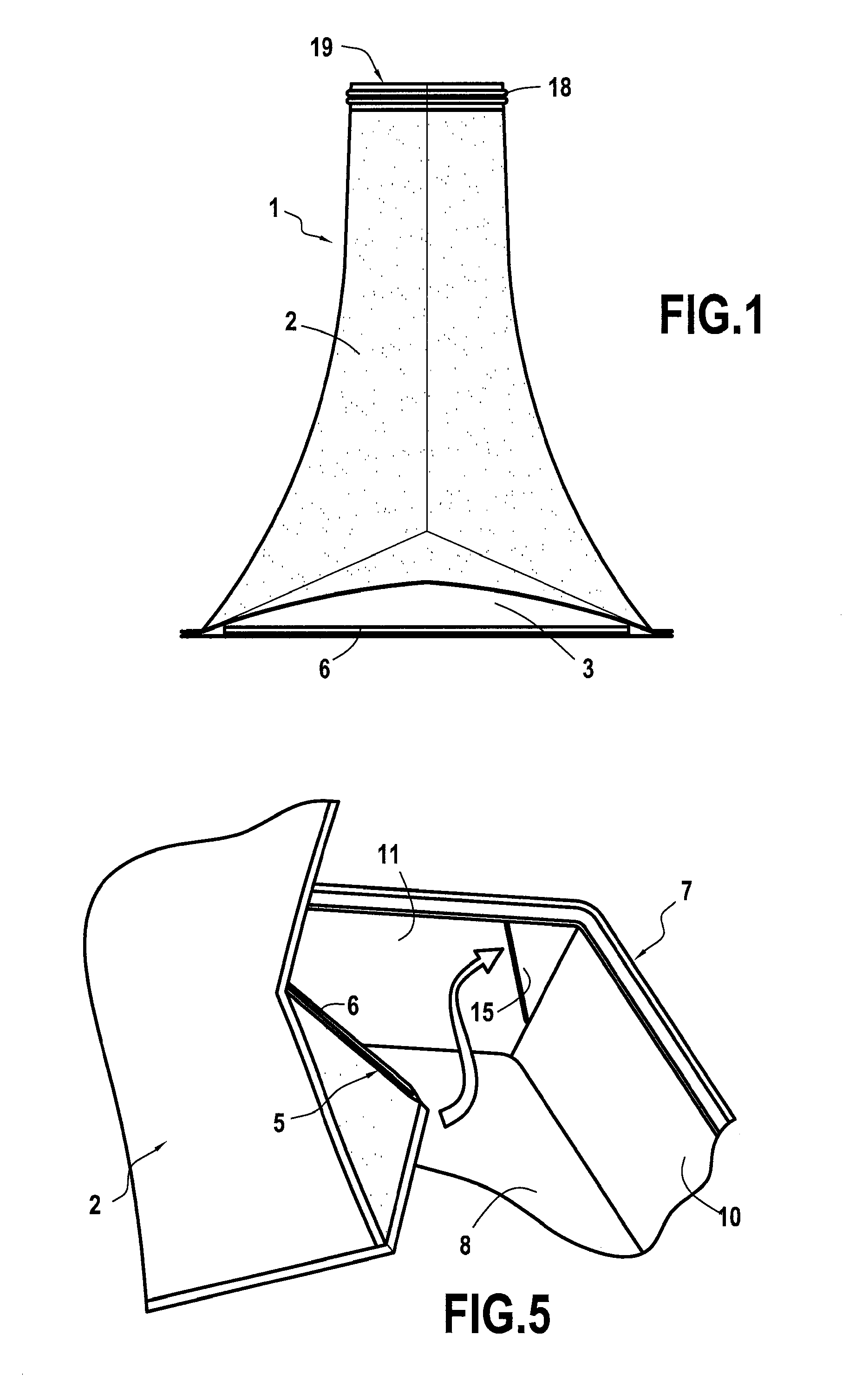
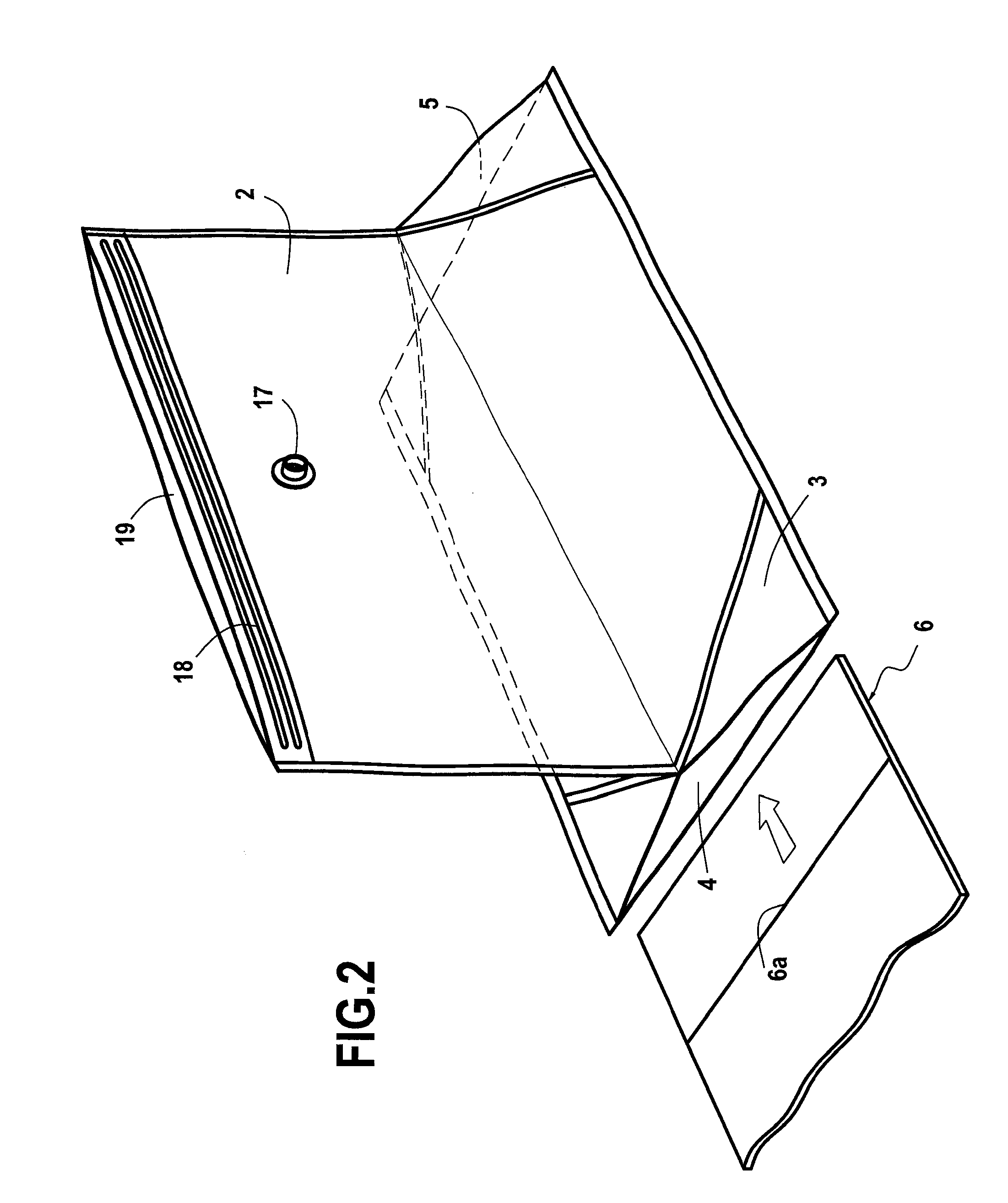
Vacuum storage slipcover and storage and/or transport bag integrating such a slipcover
It is the object of the present invention to provide a storage slipcover for at least one article, especially textile articles, comprising a first envelope extending vertically and fitted at its upper end with an opening for insertion of said at least one article, and a plate fitted with folding means for the formation of a parallelepiped base in which is placed at least the lower part of the first envelope, said storage slipcover further comprising a second envelope assembled horizontally below the lower end of the first envelope, this second envelope comprising dimensions slightly greater than the plate, and at least one opening for introducing this plate in said second envelope.
Owner:CIE EURO
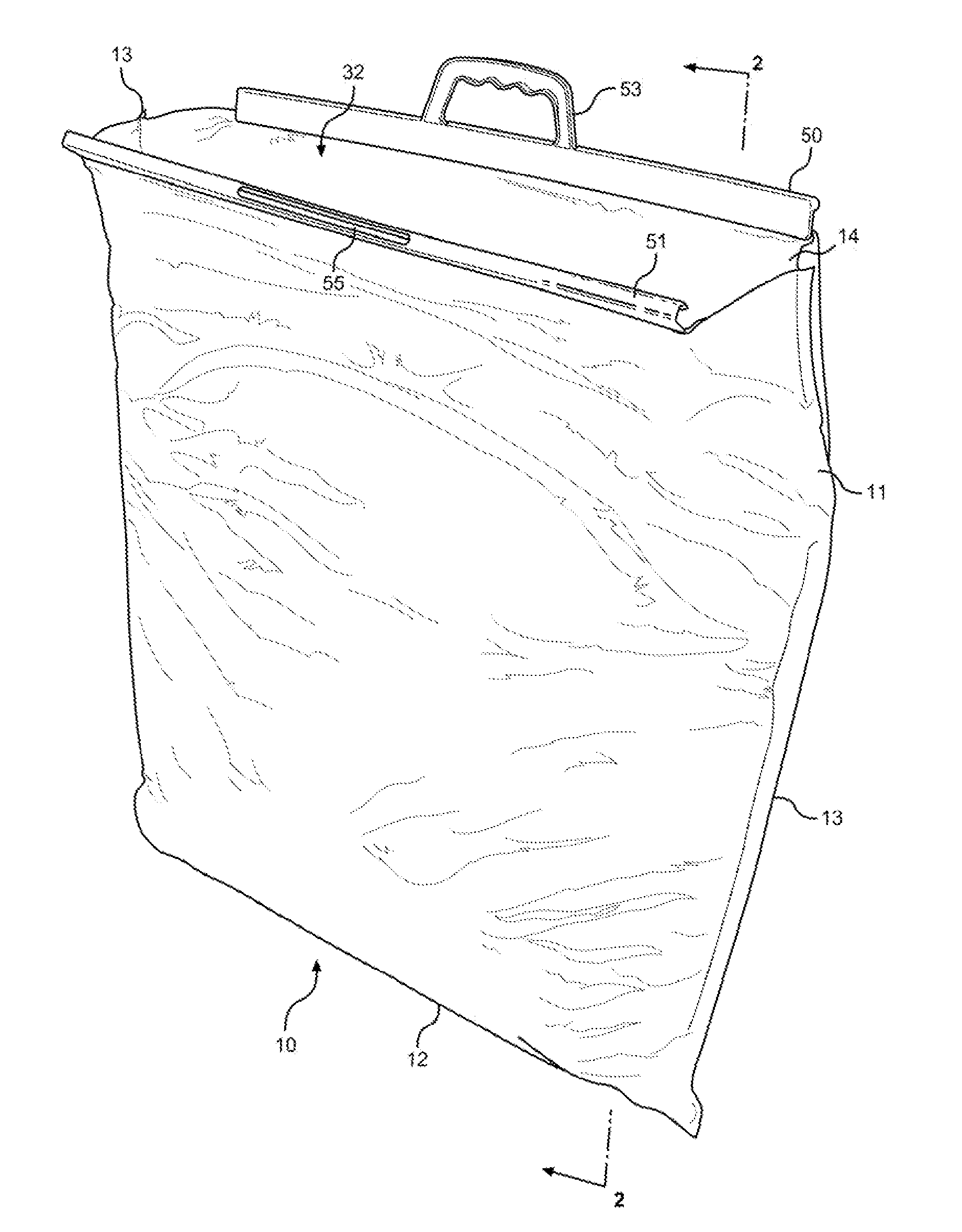
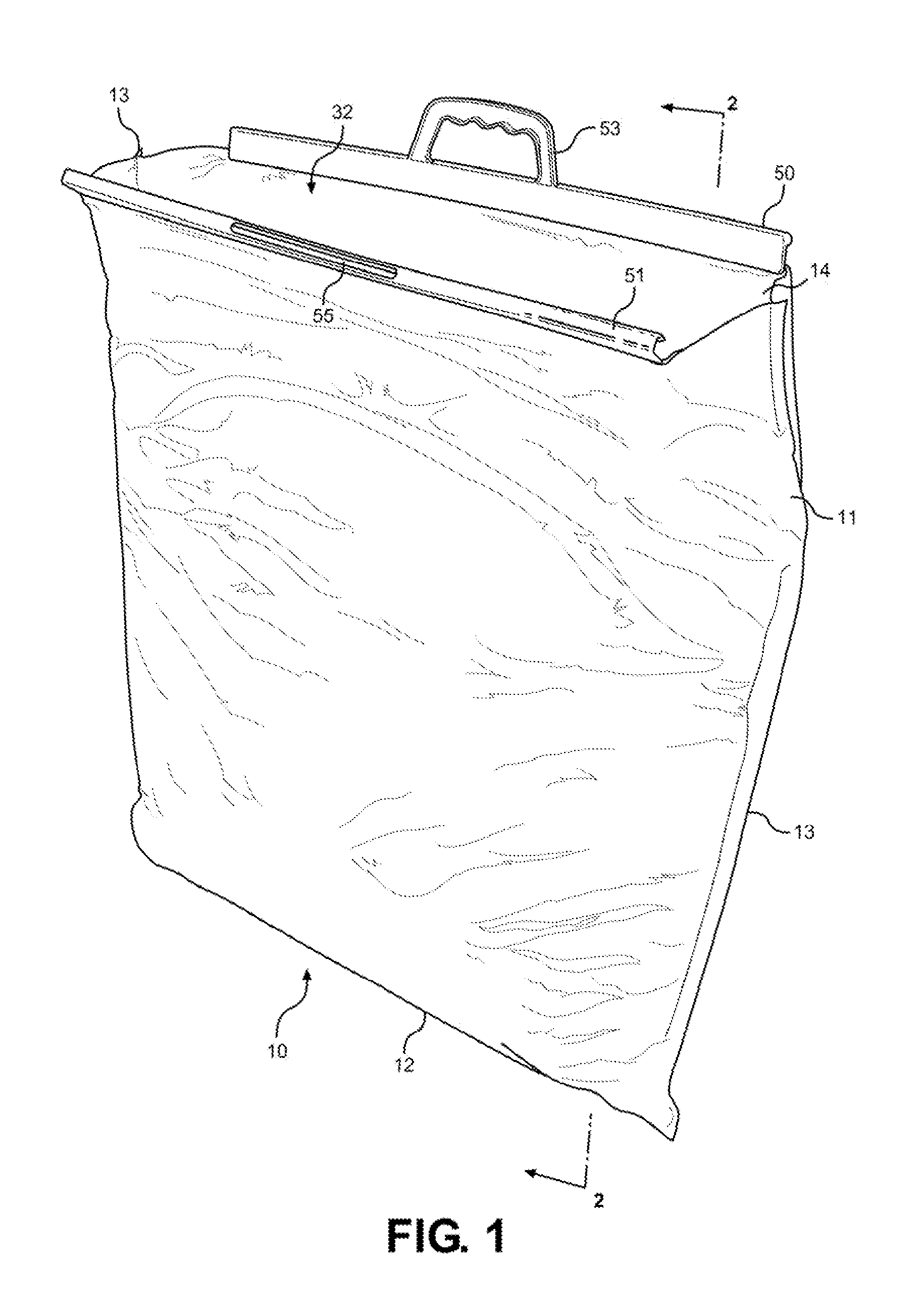
Insulated shipping bags
ActiveUS20160060017A1Increase temperatureMaintain securityDomestic cooling apparatusLighting and heating apparatusBiomedical engineeringPaper sheet
Owner:COLDKEEPERS INC
Enhanced compression of documents
InactiveUS6606418B2Reduce storage costsEnhance reconstructed contrastCharacter and pattern recognitionTelevision systemsImaging analysisComputer graphics (images)
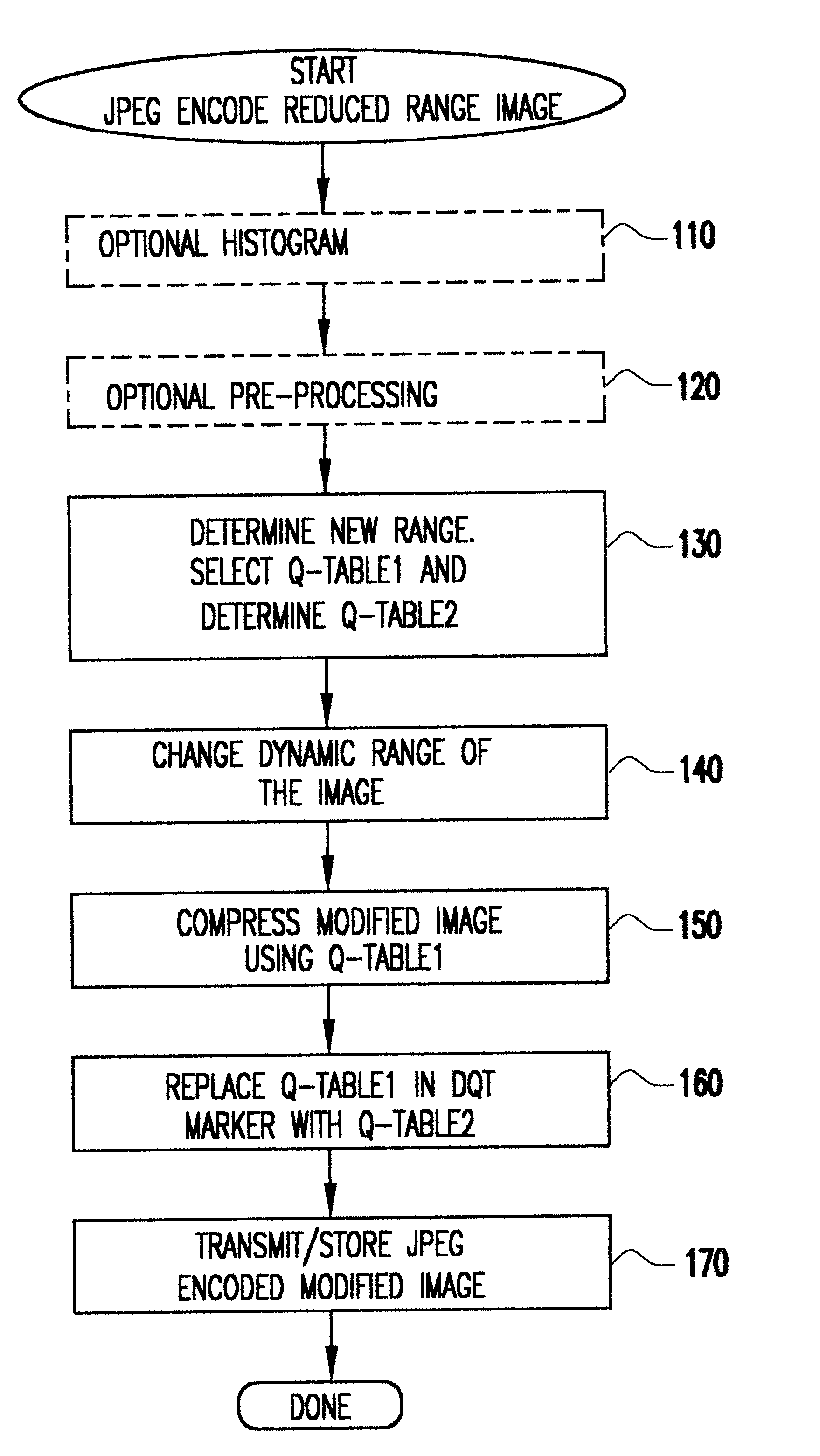
Increased and potentially extreme compression of documents is achieved by reducing / remapping the dynamic range of the document image possibly together with further image analysis and pre-processing and storing the document together with a substituted table of values chosen to restore or enhance the dynamic range of the document image. Increased or extreme compression is provided notwithstanding multiple image tones (e.g. colors or grey scale levels) even at low contrast within a document, such as a personal check. Such increased compression allows document images to be maintained in rapid-access memory for extended periods without increased storage costs.
Owner:INT BUSINESS MASCH CORP
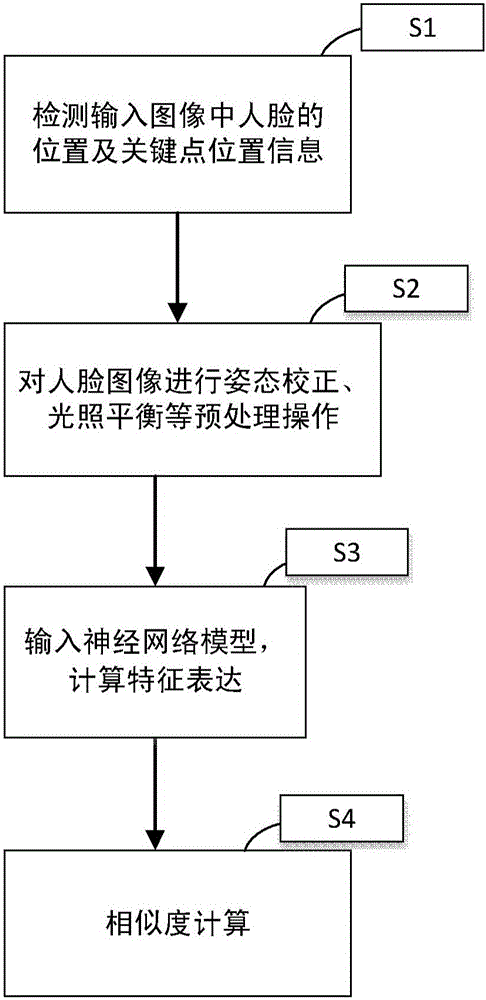
Face identification method and apparatus based on sequencing neural network model
ActiveCN106096538AReduce network parametersReduce computing timeCharacter and pattern recognitionMachine learningNetwork model
The invention discloses a face identification method and apparatus based on a sequencing neural network model. The method comprises the following steps: performing preprocessing operation on input face images, and correcting angles and expressions of the face images; extracting features of already corrected face images / videos by use of a neural network comprising sequencing operation; and according to feature expression of the face images, calculating similarity between image pairs, and accordingly, obtaining identifies of specific objects in the input face images. According to the invention, a sequencing neural network structure is brought forward for solving the problems of too many parameters and too large calculation cost of a conventional neural network based face identification model in face identification problems, through sequencing expression between different features, network parameters are effectively reduced, and the calculation time is saved; and a training method based on comparison loss and triple loss is brought forward for solving the problem of a quite small number of training data.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
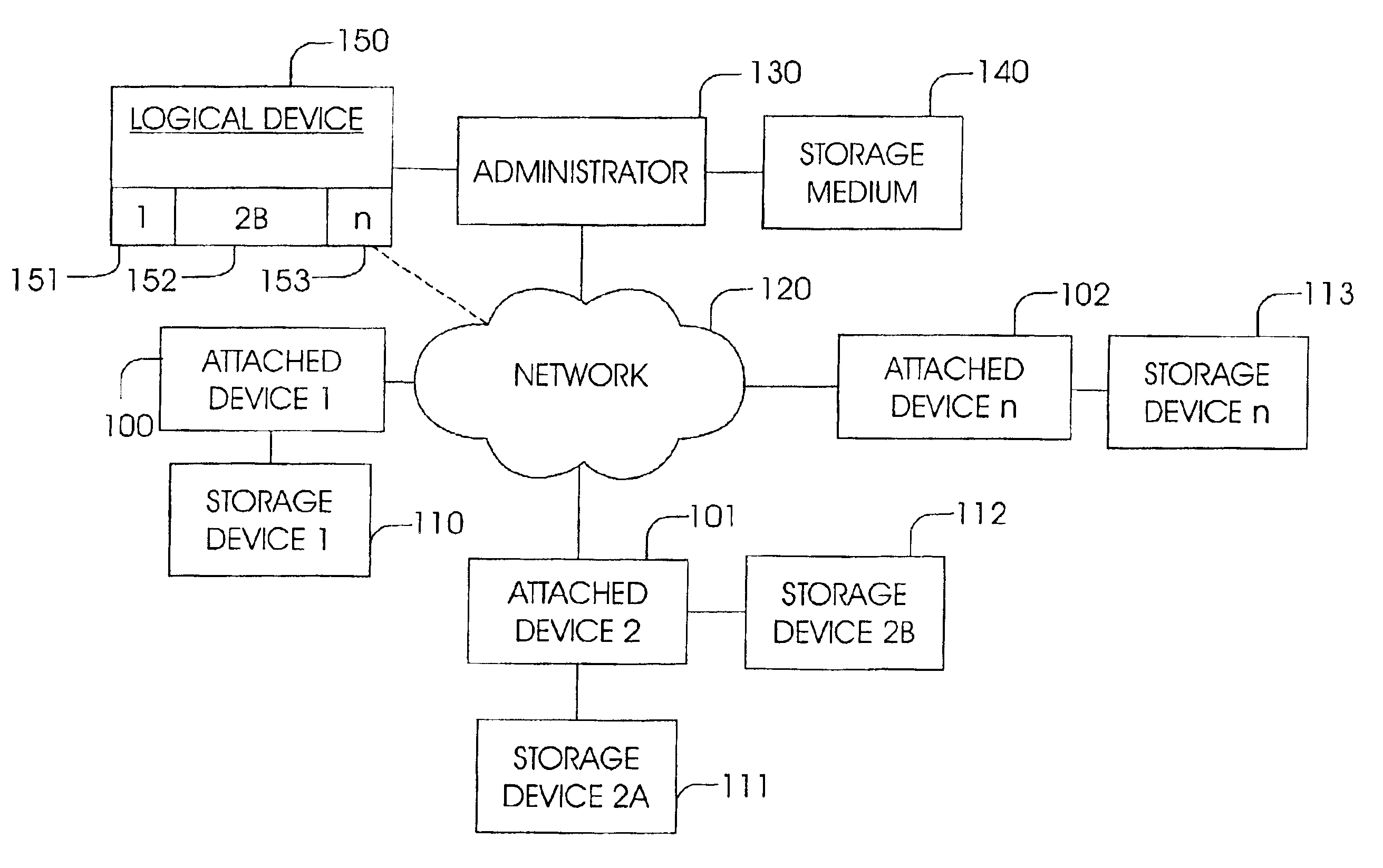
Apparatus and method for configuring storage capacity on a network for common use
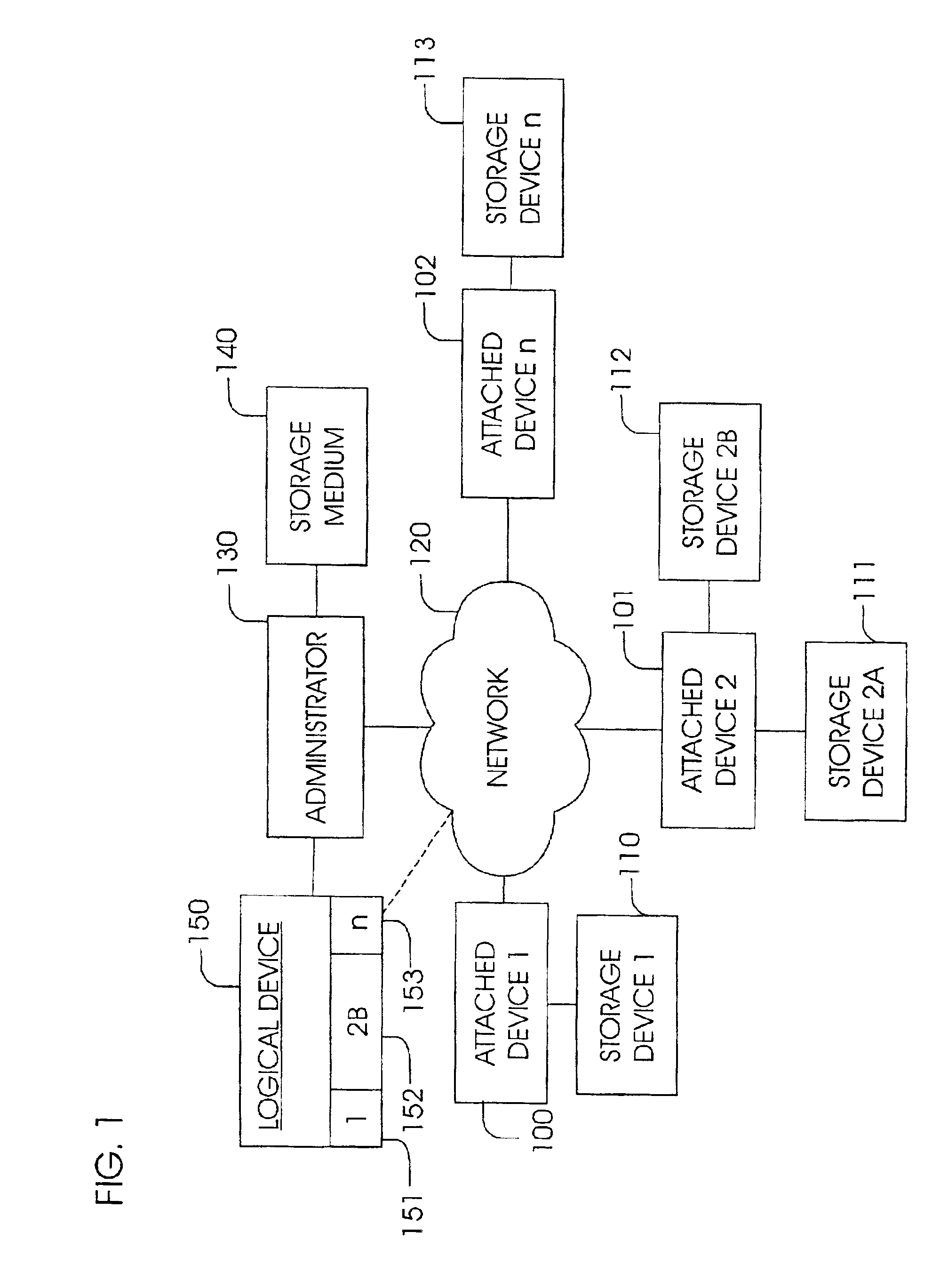
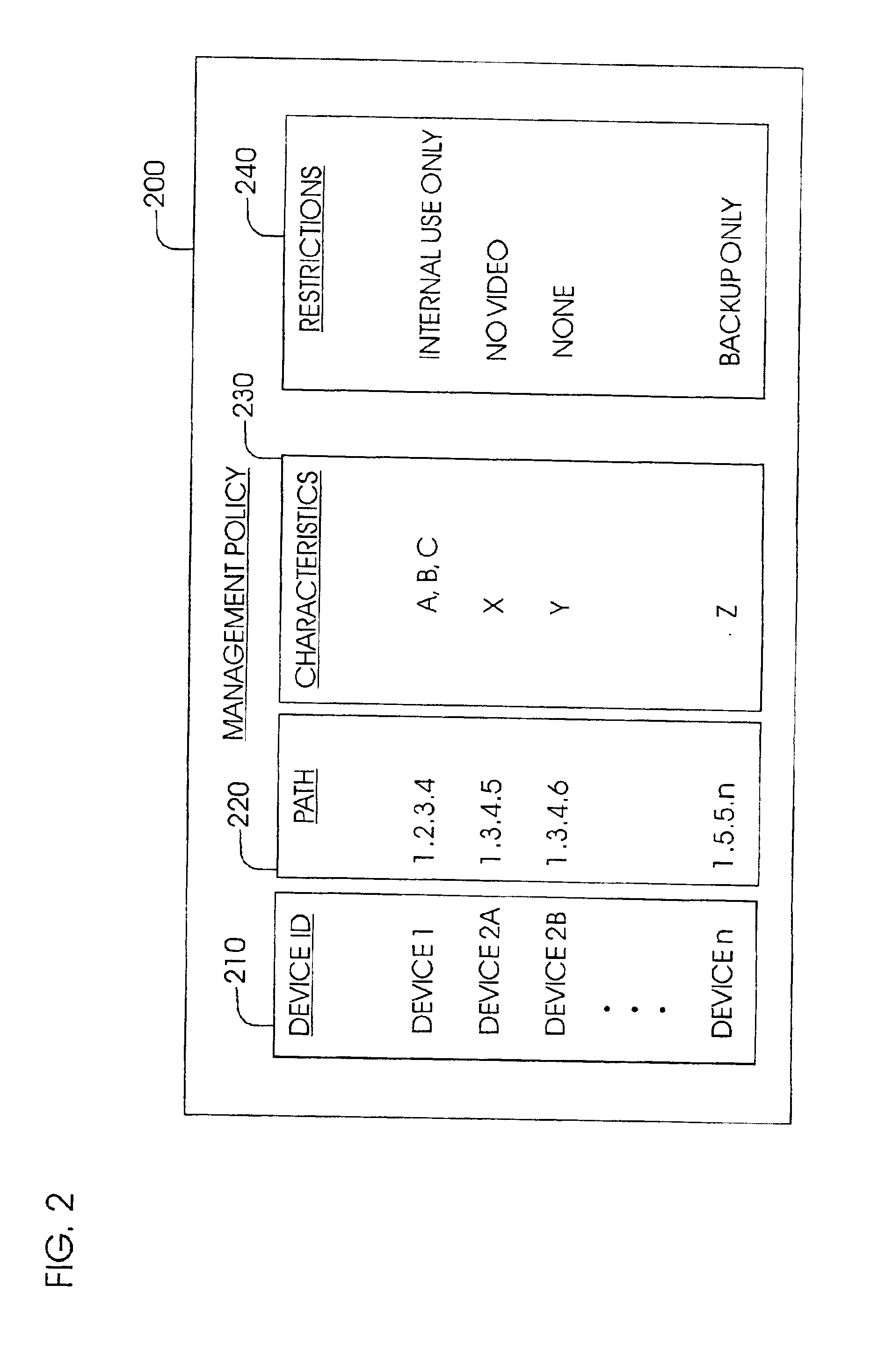
InactiveUS6898634B2Reduce storage costsEffective distributionInput/output to record carriersMultiple digital computer combinationsComputer scienceOperating system
An apparatus and method for identifying unused storage capacity of a number of network storage devices, and configuring at least a portion of the unused storage capacity as a logical storage device. The invention is preferably embodied in computer readable program code. The unused storage capacity may be identified by monitoring the number of network storage devices and automatically determining the unused storage capacity thereof. Alternatively, user-defined parameters may be used for identifying the unused storage capacity. At least a portion of the identified storage capacity is allocated for common use as at least one logical device. The allocated storage capacity is managed according to a management policy so that the allocated memory is not overwritten, data is not backed up to the same physical device, etc.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
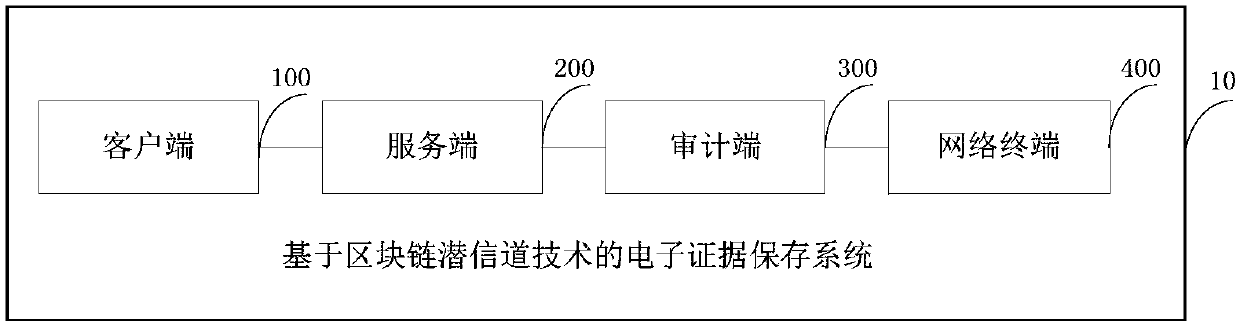
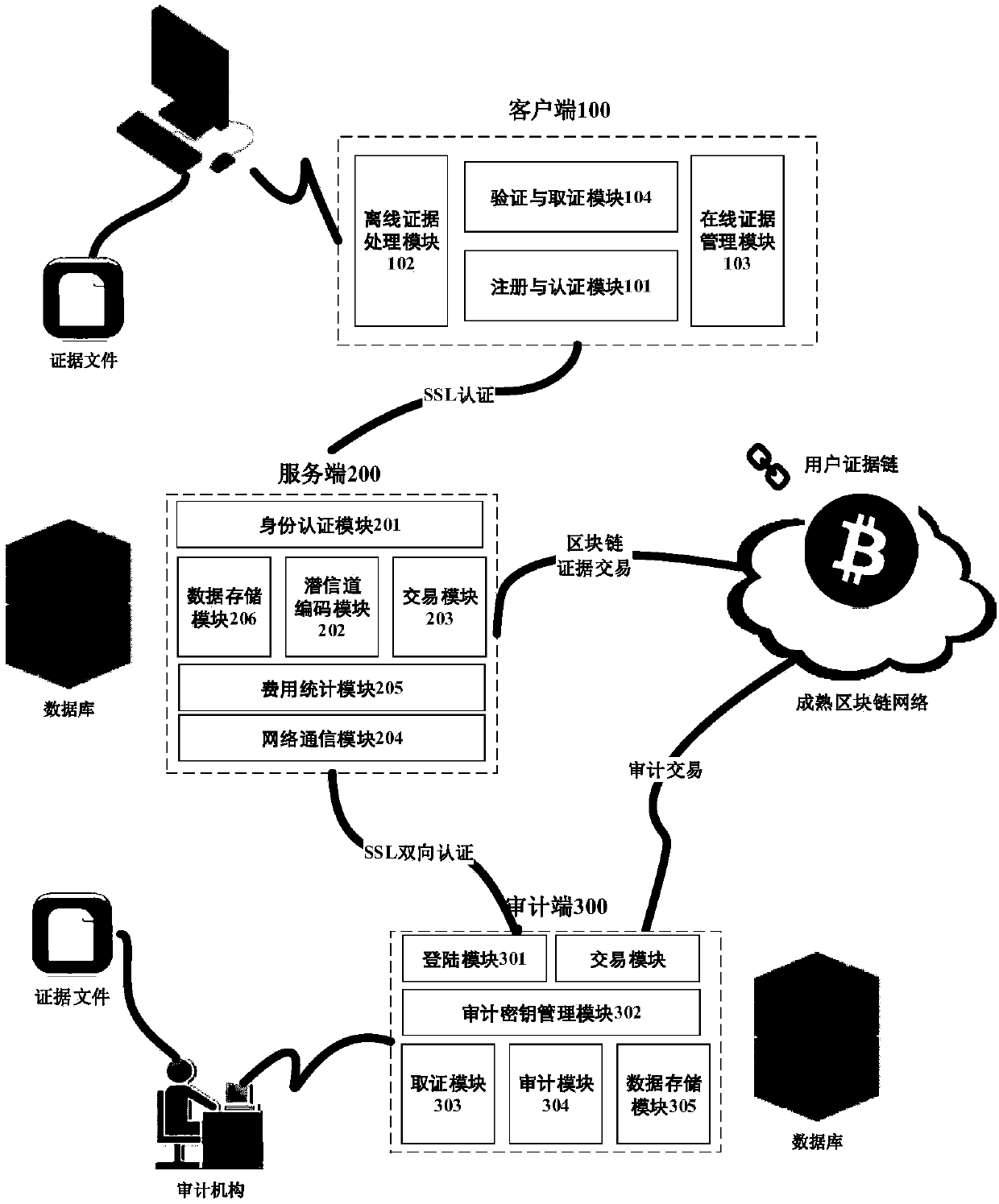
Electronic evidence preservation system based on block chain subliminal channel technology
ActiveCN107682308AAchieving processing powerAchieving covert storageDigital data protectionTransmissionNetwork terminationSubliminal channel
The invention discloses an electronic evidence preservation system based on a block chain subliminal channel technology, which comprises a client, a server, an auditing terminal and a network terminal, and is characterized in that the client is used for performing off-line acquisition and processing, online management and evidence collection on a user electronic evidence; the server generates an existence proof for the evidence and performs hosting and recovery on the chain evidence according to a user address; the auditing terminal is used for auditing the chain evidence, generating a corresponding transaction on a block chain and constructing an auditing proof so as to main the integrity, the timeliness and the non-repudiation of an auditing result; and the network terminal is used for performing state synchronization and real-time evidence collection on the user evidence on the chain. The system can dig a cryptographic basis of the subliminal channel preserved electronic evidence and the auditing result thereof in a mature block chain system, thereby realizing safe processing and hidden preservation for the electronic evidence, thus improving the safety and timeliness of electronic evidence preservation, and effectively reducing the preservation cost.
Owner:HANGZHOU INNOVATION RES INST OF BEIJING UNIV OF AERONAUTICS & ASTRONAUTICS
Safety containers for biologically active substances and method for producing said container
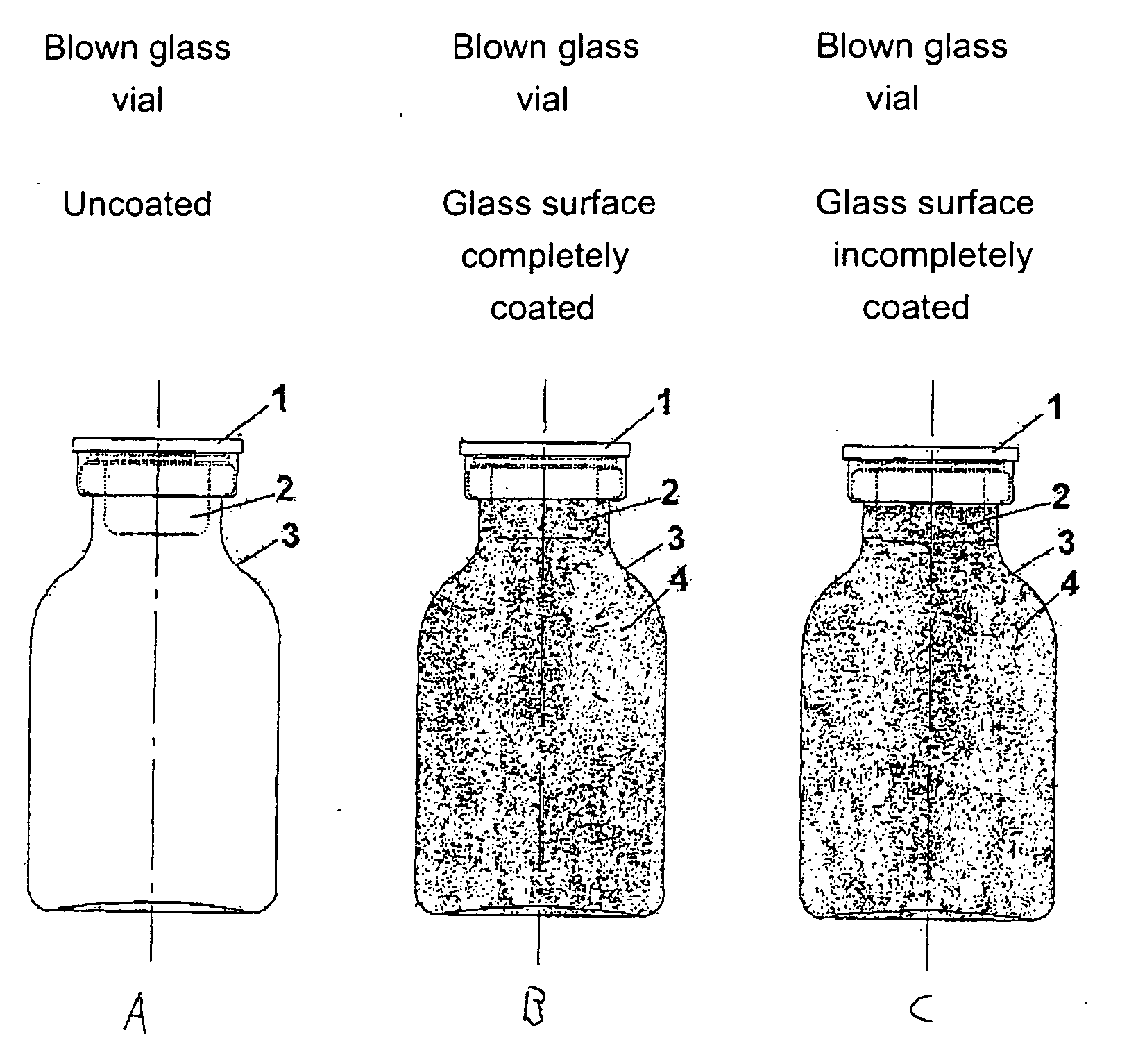
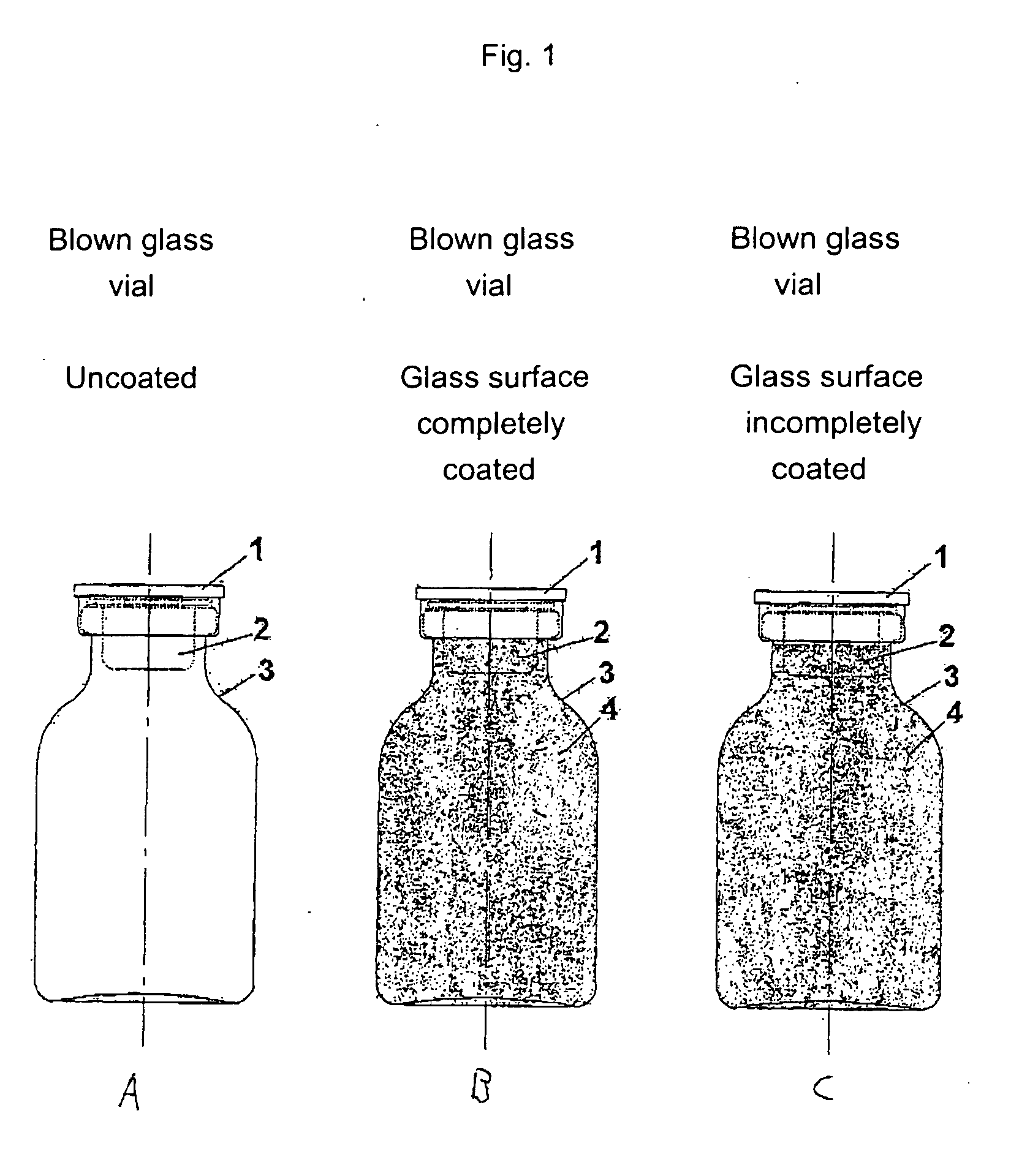
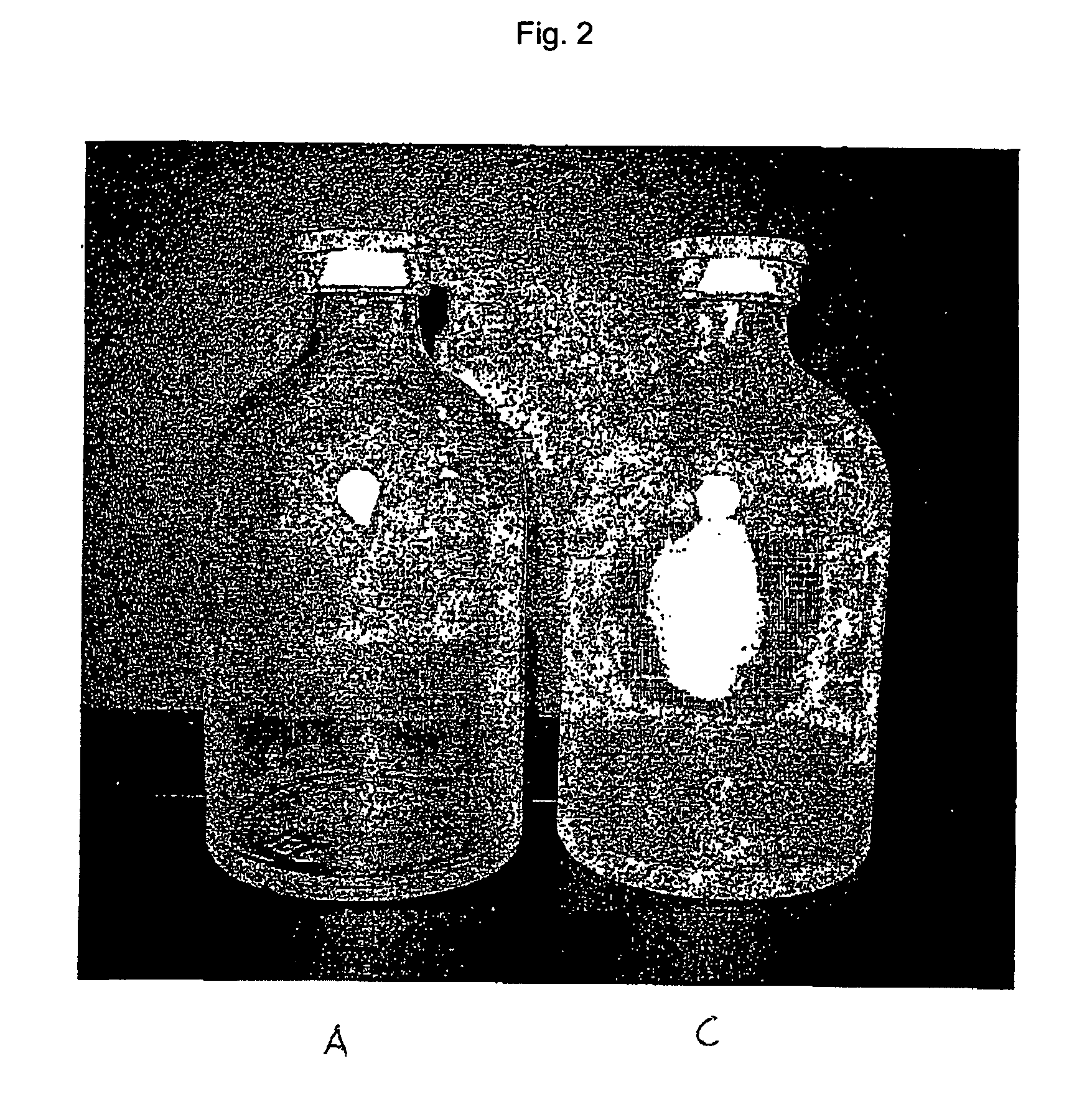
InactiveUS20070010700A1Increased and high fracture strengthSimple and rapid to carry-outClosure capsCoverings/external coatingsHigh fractureUltimate tensile strength
The invention relates to safety containers for biologically active substances, in particular cytostatic agents, said container having increased or higher fracture strength and shatterproof qualities, in addition to an uncontaminated exterior. The invention also relates to a method for producing said containers and to the use of a medium containing at least one polymer for decontaminating the exterior of a container that is filled with a biologically active substance, sealed and optionally labelled.
Owner:BAXTER INT INC +1
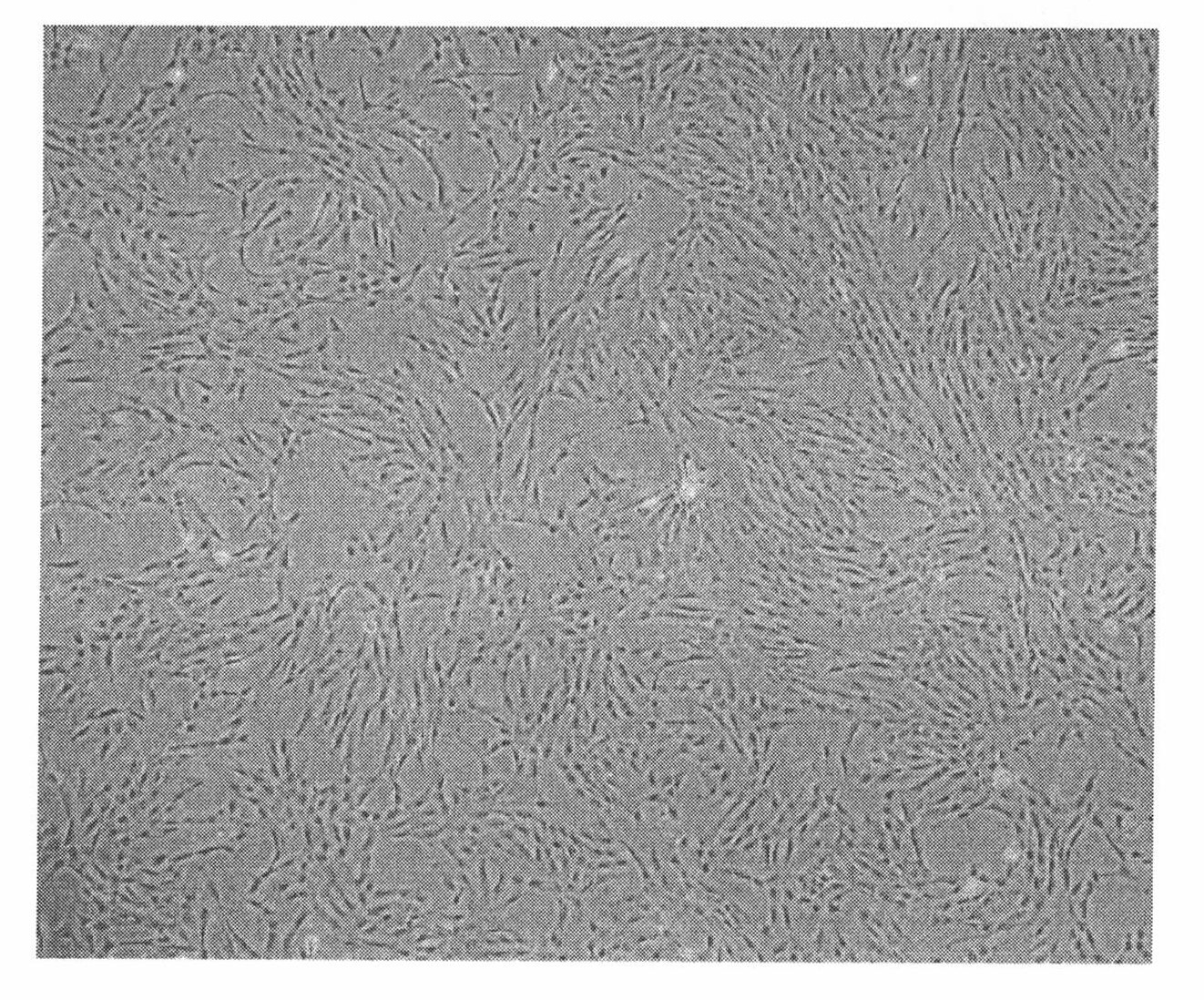
Method for preparing human umbilical cord mesenchymal stem cells
The invention relates to a method for preparing human umbilical cord mesenchymal stem cells, which comprises the steps of collection, transportation, handover, separation, freezing, recovering, primary culture and subculture of umbilical cords. The method has simple process, ensures low production cost, good freezing effect, little cell damage, low toxic side effect and no harm to human body and reduces the residual of the freezing protection liquid in the recovered cells of tissue blocks; and the prepared mesenchymal stem cells can be applied to the clinical treatment of various diseases.
Owner:江苏省北科生物科技有限公司 +1
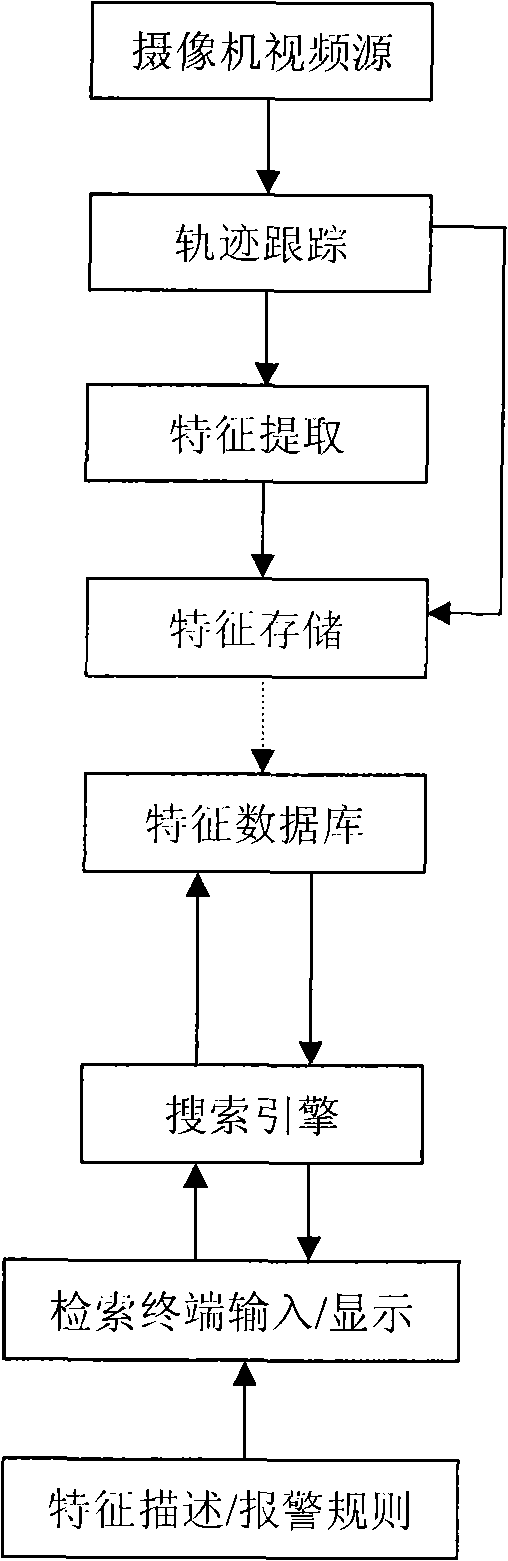
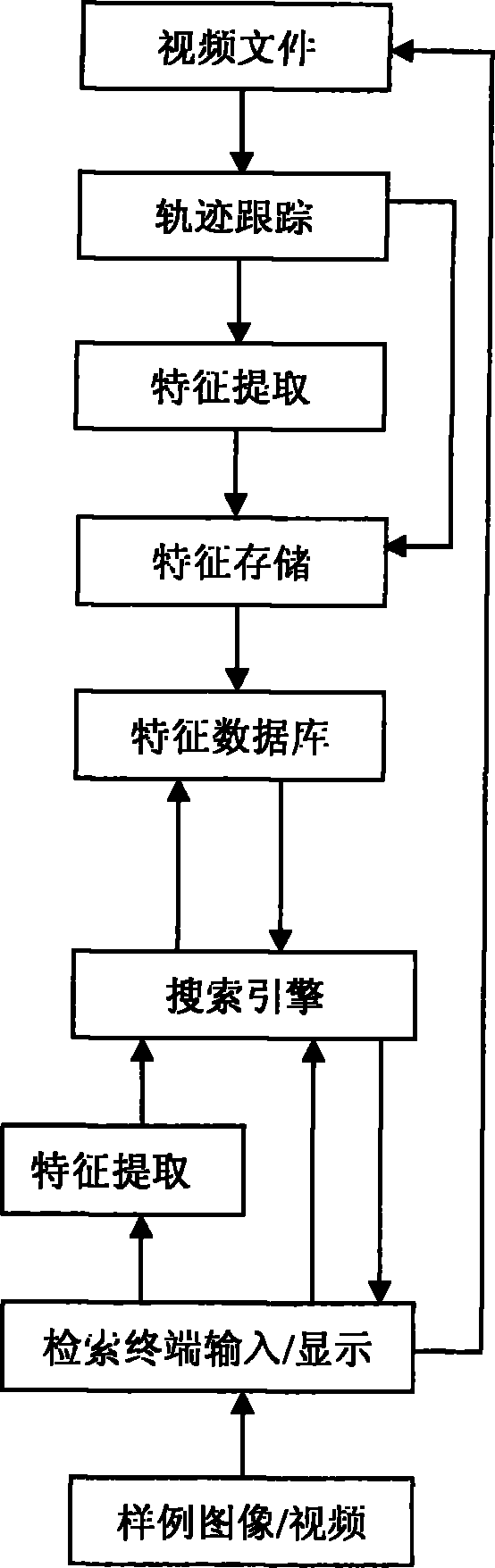
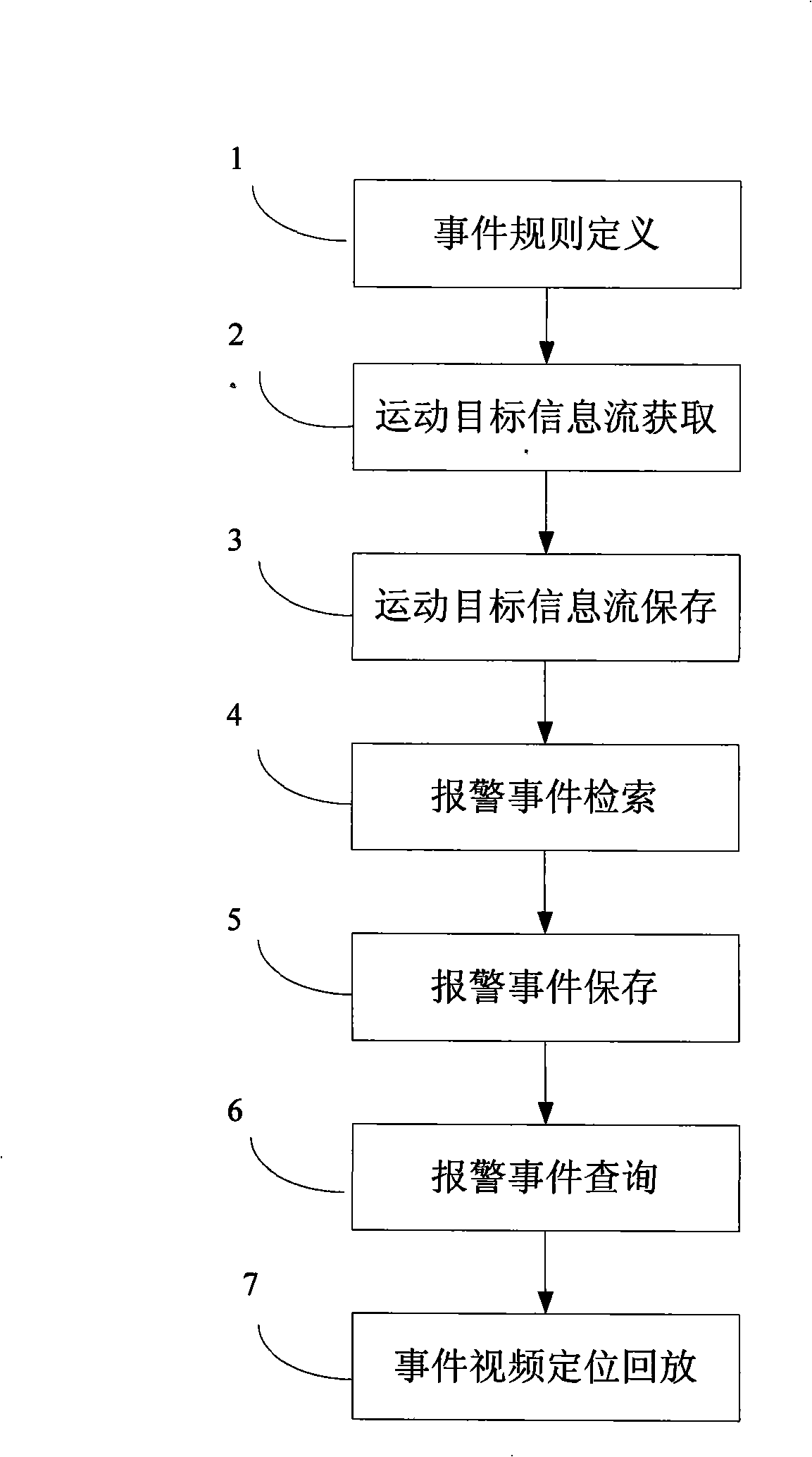
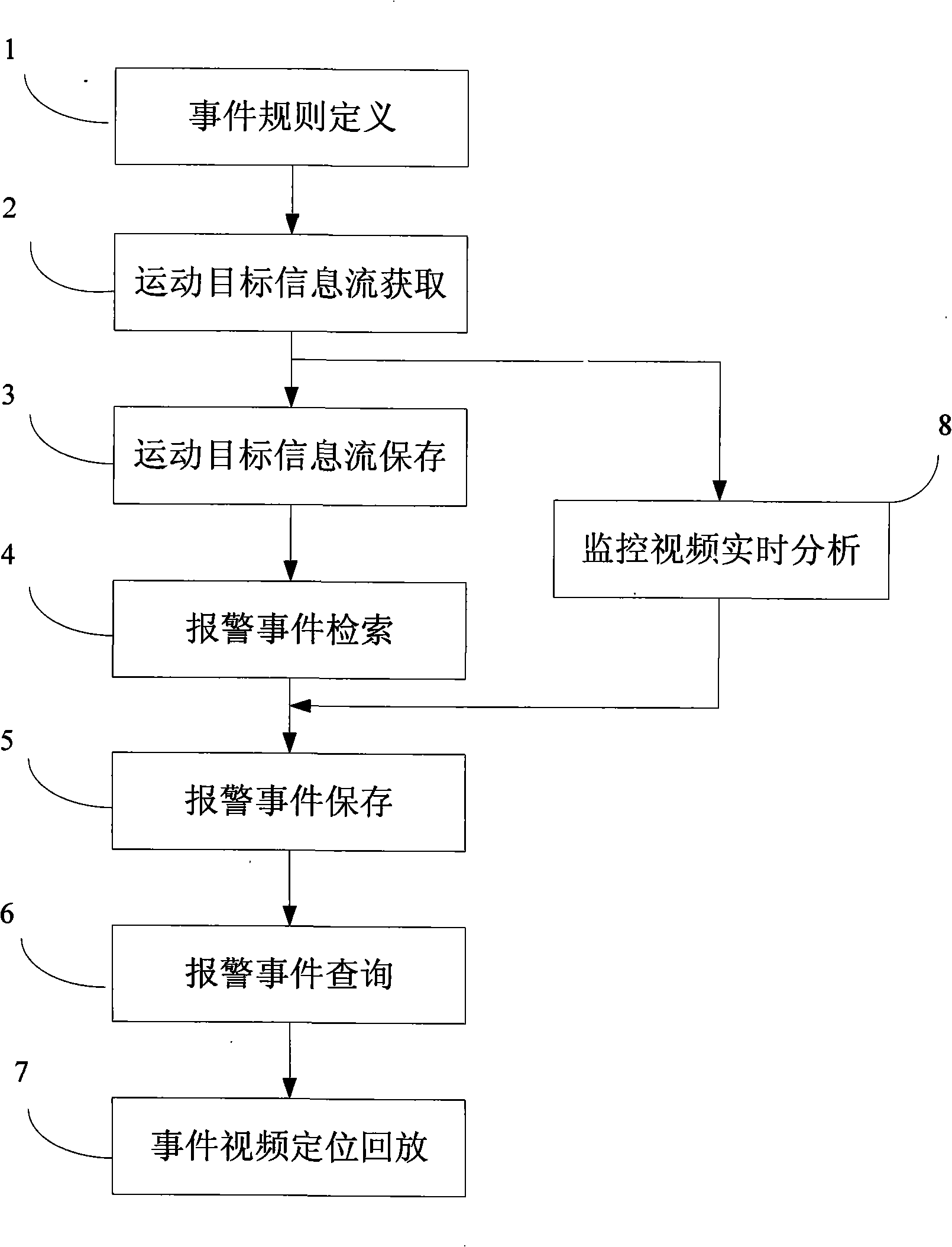
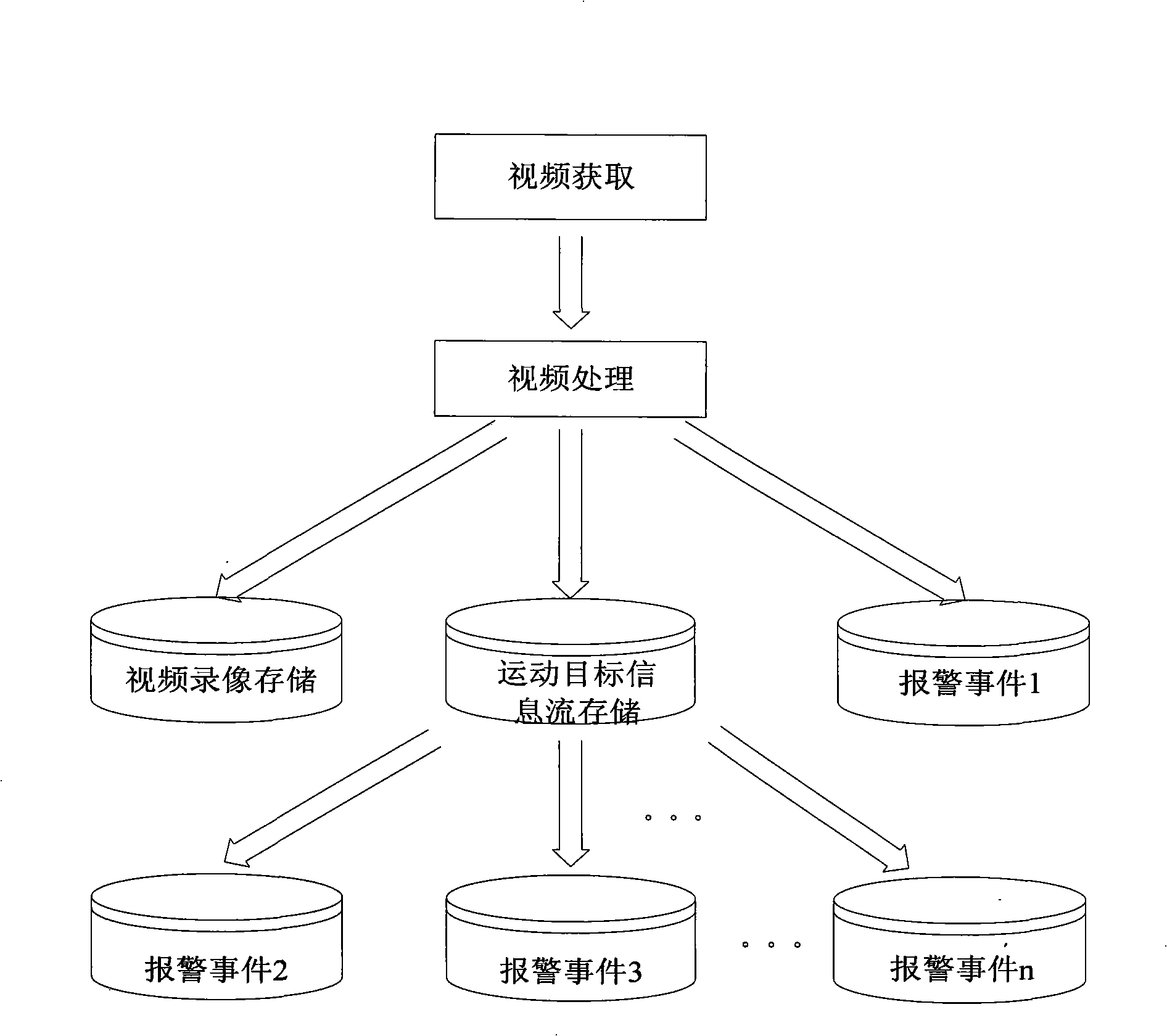
Method and system for researching intelligent video monitoring case
InactiveCN101281593AImprove retrieval efficiencyReduce data volumeImage analysisCharacter and pattern recognitionVideo monitoringPattern recognition
The invention discloses a intelligent video monitor search method, including the steps: collecting the video frame, extracting the moving target information flow, storing the corresponding moving target information flow of the video frame; searching the stored moving target information flow, judging the detected object whether matching with the defined affair rule, if so, determining the corresponding occurrence of the affair rule. Furthermore, the invention includes the step of inquiring the stored affair and the step of playing back the corresponding video frame based on the affair selection. The invention discloses an intelligent video monitor affair search system for executing the method. Due to the target information data flow smaller than the video data flow, hence the invention has faster searching speed, higher searching effectiveness, higher data transmission, lower cost compared with the prior scheme.
Owner:卫安保安服务(上海)有限公司
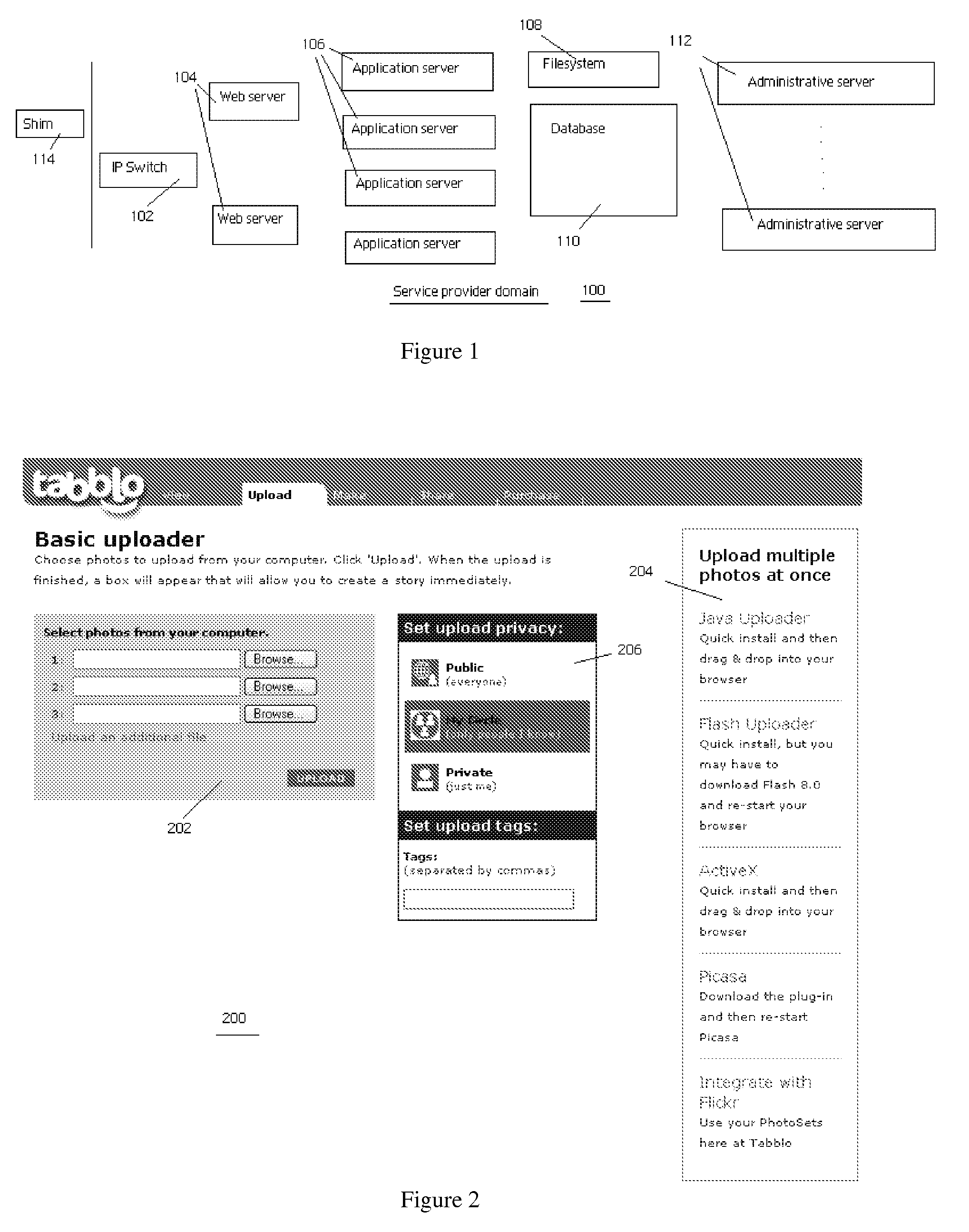
Method and system for online image security
InactiveUS20080209533A1Reduce storage costsSignificantDigital data processing detailsAnalogue secracy/subscription systemsWeb siteDigital image
An online application enables an end user to navigate to a web site, upload digital images, and to combine those images with words in a stylized template to create a user-generated story. A story is a web page, typically a collection of photos and words that are brought together by a stylized template that can be customized by the end user. Preferably, a given story is available from the site at a given location (at a URL) that may be private or public. A given story may be shared with other end users, published to other web sites or web logs, or maintained solely for one's own use. The invention also provides for multiple end users to collaborate to create a “shared” story.
Owner:HEWLETT PACKARD CO
Urban-road traffic forecasting method based on multi-source data combination
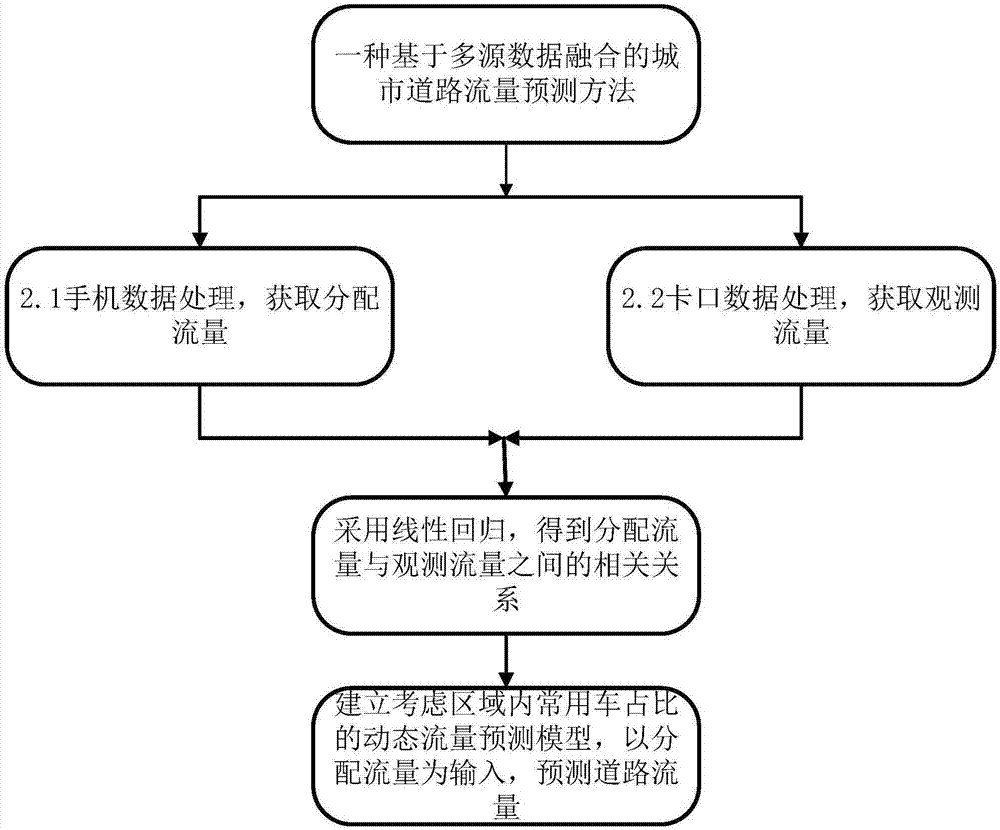
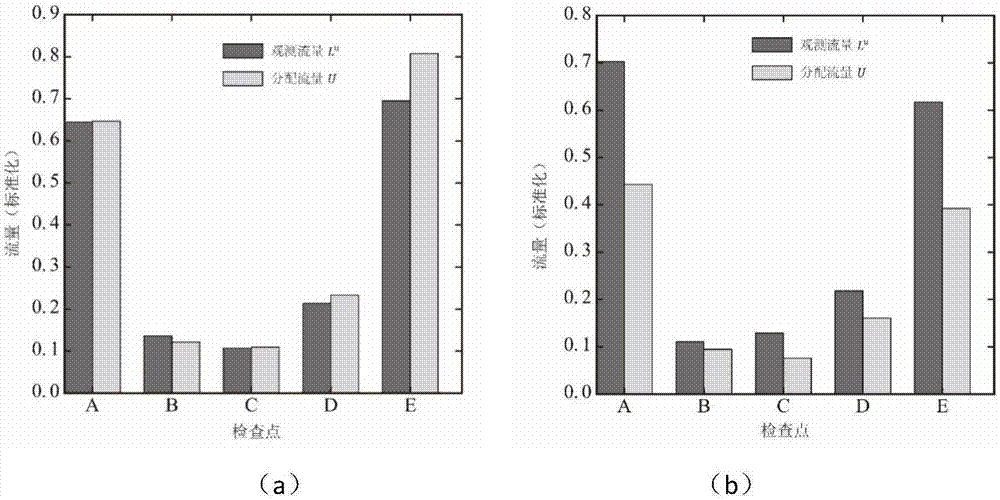
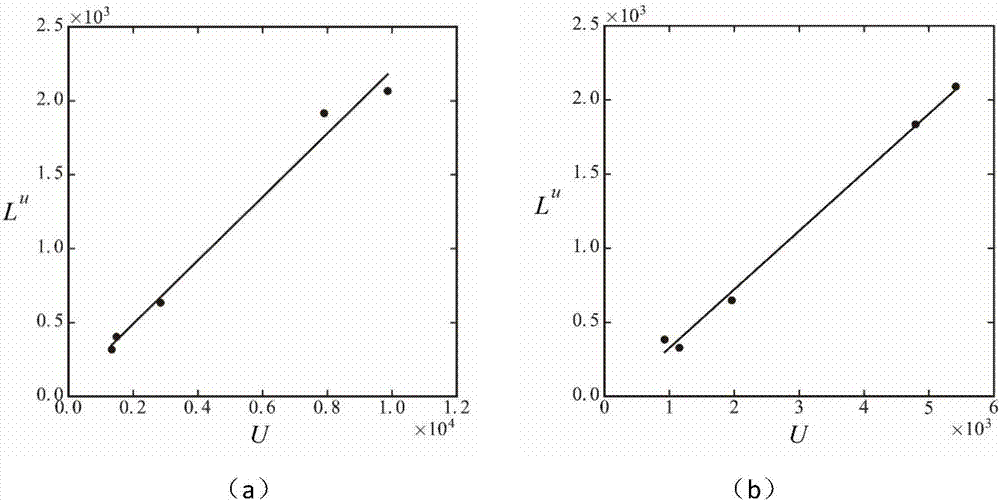
ActiveCN107134142AEasy to getEasy to handleDetection of traffic movementForecastingSimulationLinear regression
The invention provides an urban-road traffic forecasting method based on multi-source data combination. The method comprises the steps of firstly, extracting permanent residents' travel OD according to cell-phone signaling data, and distributing the travel OD to an urban road network to obtain distributional traffic flows of each road section; secondly, according to a bayonet record, obtaining a total observed traffic flow and an observed traffic flow of frequently-used cars in a road section corresponding to the bayonet; thirdly, selecting a road section with observed traffic flows within the region, and building an equation of linear regression which represents the time-varying correlation between the distributional traffic flows and the observed traffic flows in the road sections, according to the distributional traffic flows and the observed traffic flow data; fourthly, according to the equation of linear regression and a proportion of the frequently-used cars within the region, constituting a dynamic forecasting model of traffic flows of the road sections within the region; fifthly, as for the road sections without observed traffic flows in the region, inputting the distributional traffic flows of the road sections into the dynamic forecasting model to forecast the time-varying traffic flows of the road sections. The urban-road traffic forecasting method based on multi-source data combination has the advantages of providing convenience for obtaining information and conducting traffic forecasting work in multiple cities, and being low in costs and easy to operate.
Owner:CENT SOUTH UNIV
Warehousing method and equipment for intensive logistic warehouses
ActiveCN102092552AEfficient storageReduce storage costsStorage devicesLogistics managementOrder form
The invention discloses a warehousing method and equipment for intensive logistic warehouses. In an adopted technical scheme, the warehousing method for intensive logistics is characterized by comprising the steps of: dividing goods into different types according to the difference in out-going quantity of goods of different brands in a warehouse, storing goods of different types respectively in different positions in a logistic warehouse, and delivering the goods out of the warehouse by adopting different out-going manners. By means of the warehousing method and equipment, the intensive warehouse overcomes the defect that the traditional logistic warehouse is used for storing the goods according to the warehousing time sequence or the varieties of goods, and achieves the functions of classified storage according to the brands of goods and sorted out-going according to requirements of orders, therefore, the intensive storage of goods is effectively realized and the warehouse space is ensured to be fully utilized; meanwhile, the operation sequence is flexible and diverse, the goods storage cost is reduced, and the purposes of efficiently storing and sorting goods of different brands are achieved.
Owner:BLUESWORD INTELLIGENT TECH CO LTD
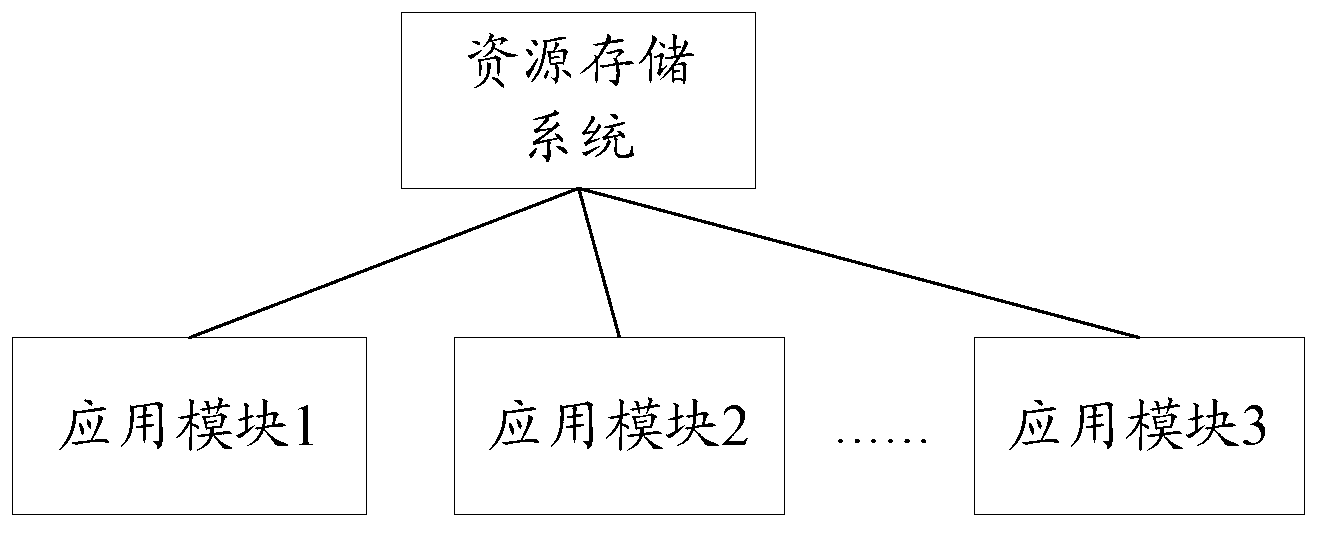
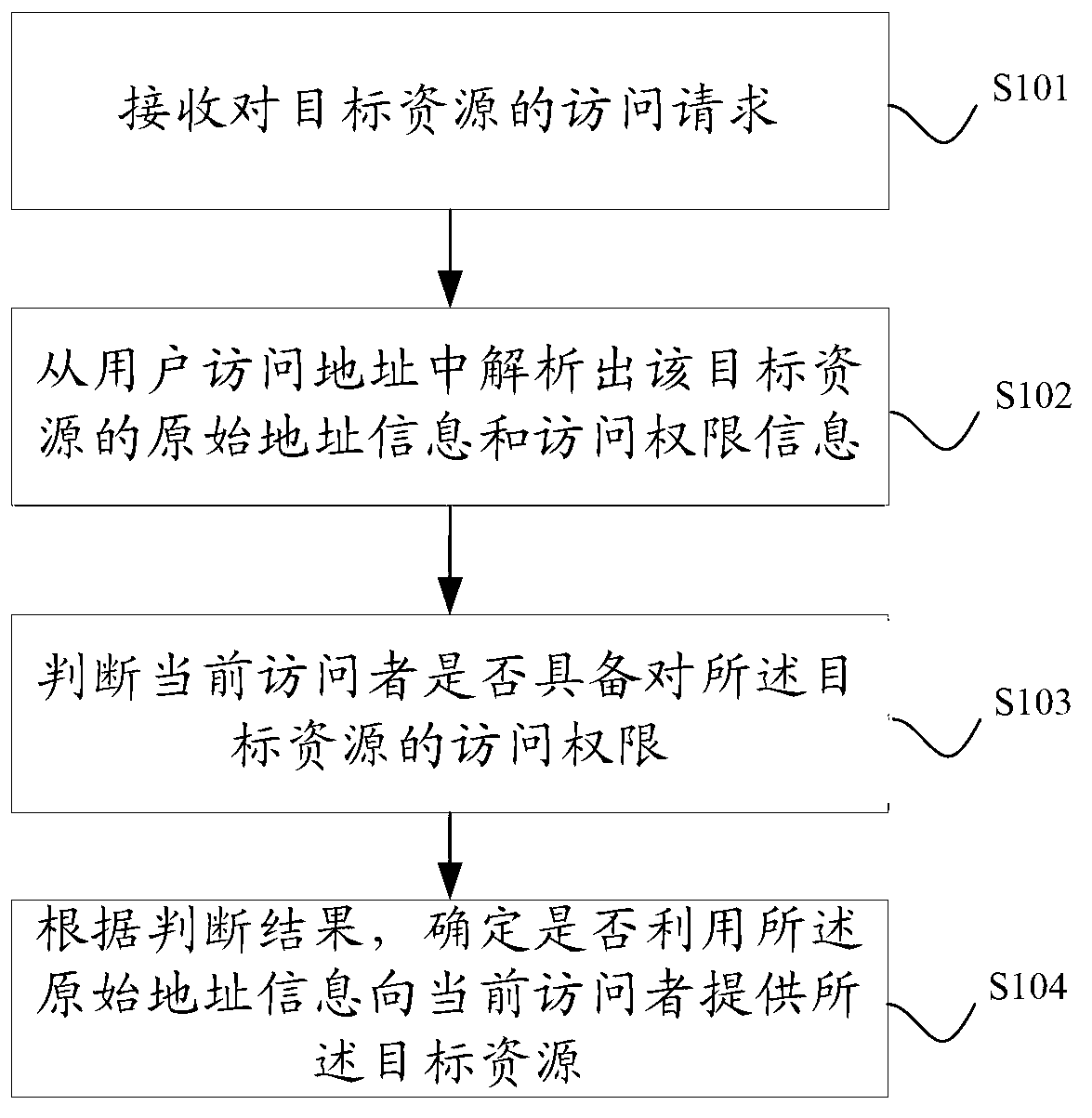
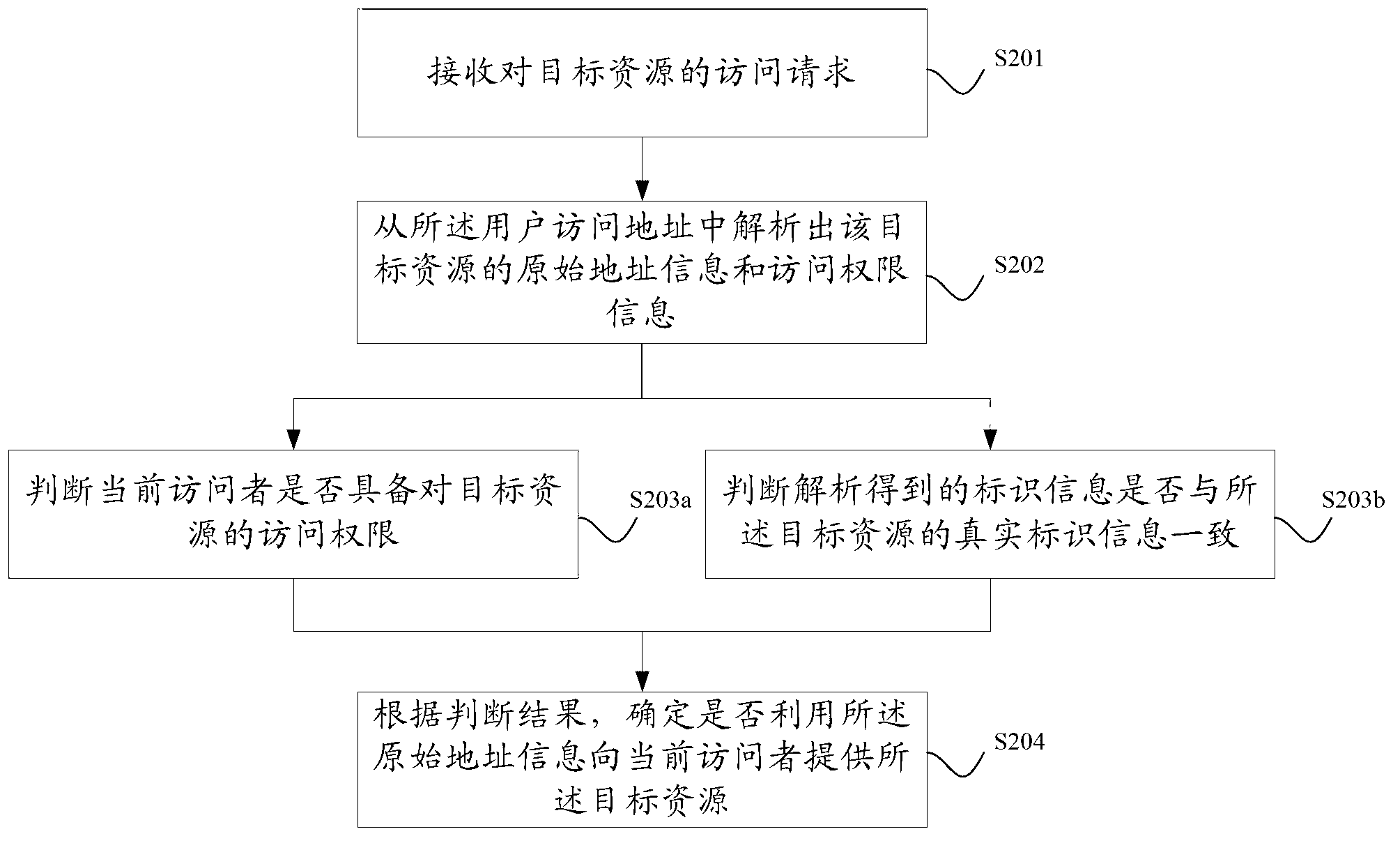
Network resource access permission control method and device
The invention discloses a network resource access permission control method and device. The network resource access permission control method comprises the following steps of: receiving an access request to a target resource, wherein the access request comprises a user access address of the target resource; analyzing original address information and access permission information of the target resource from the user access address; obtaining a user identification of a current accessor, judging whether the current accessor has an access permission to the target resource according to the analyzed access permission information; and according to a judging result, determining whether the target resource is provided for the current accessor by using the original address information. compared with the prior art, the technical scheme provided by the invention has the advantages that the access permission information is not written in a resource database, thus the storage cost is saved, and the coupling degree between an application module and a resource storage system is effectively lowered.
Owner:SHANGHAI YOUYANG XINMEI INFORMATION TECH CO LTD
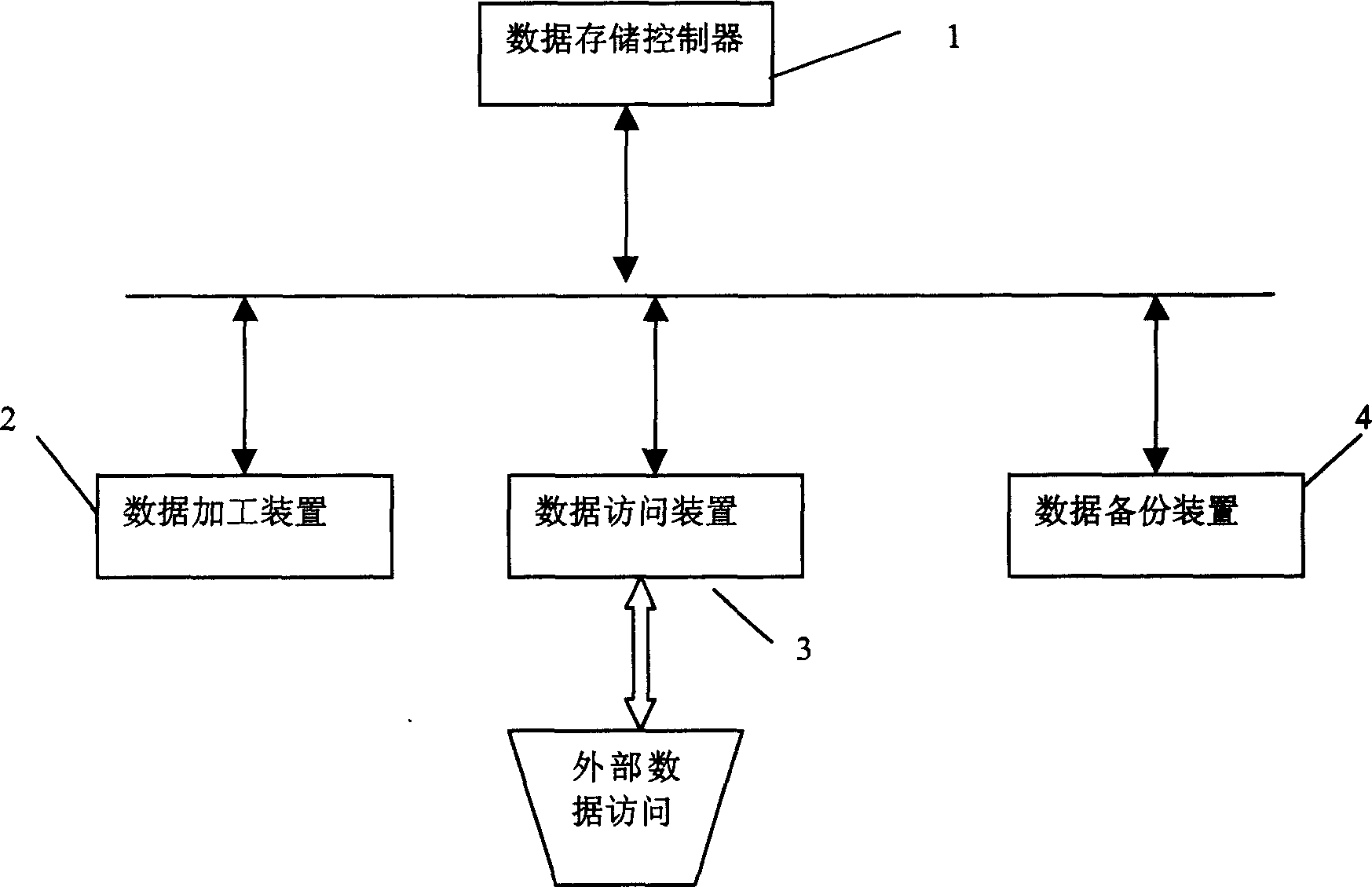
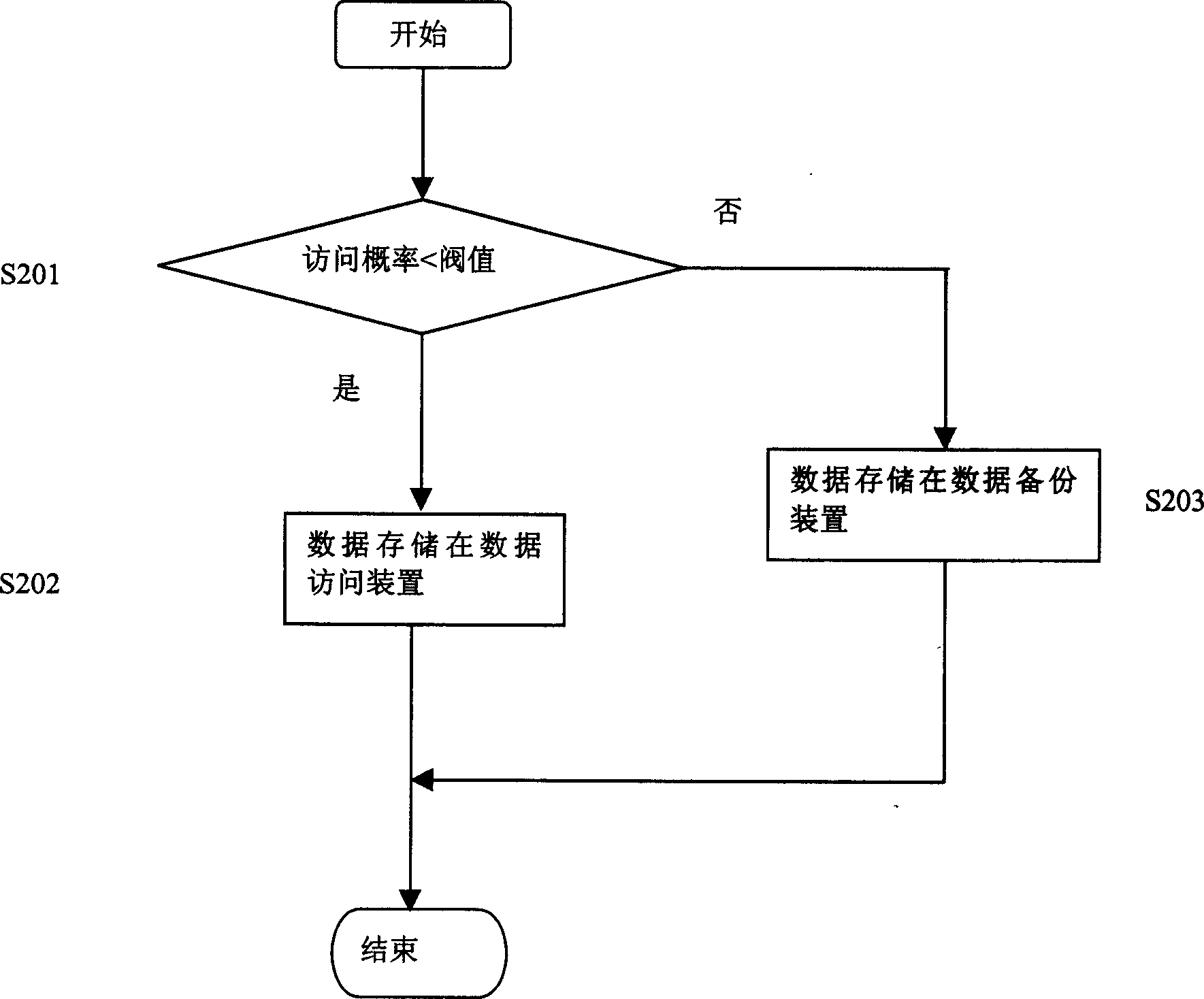
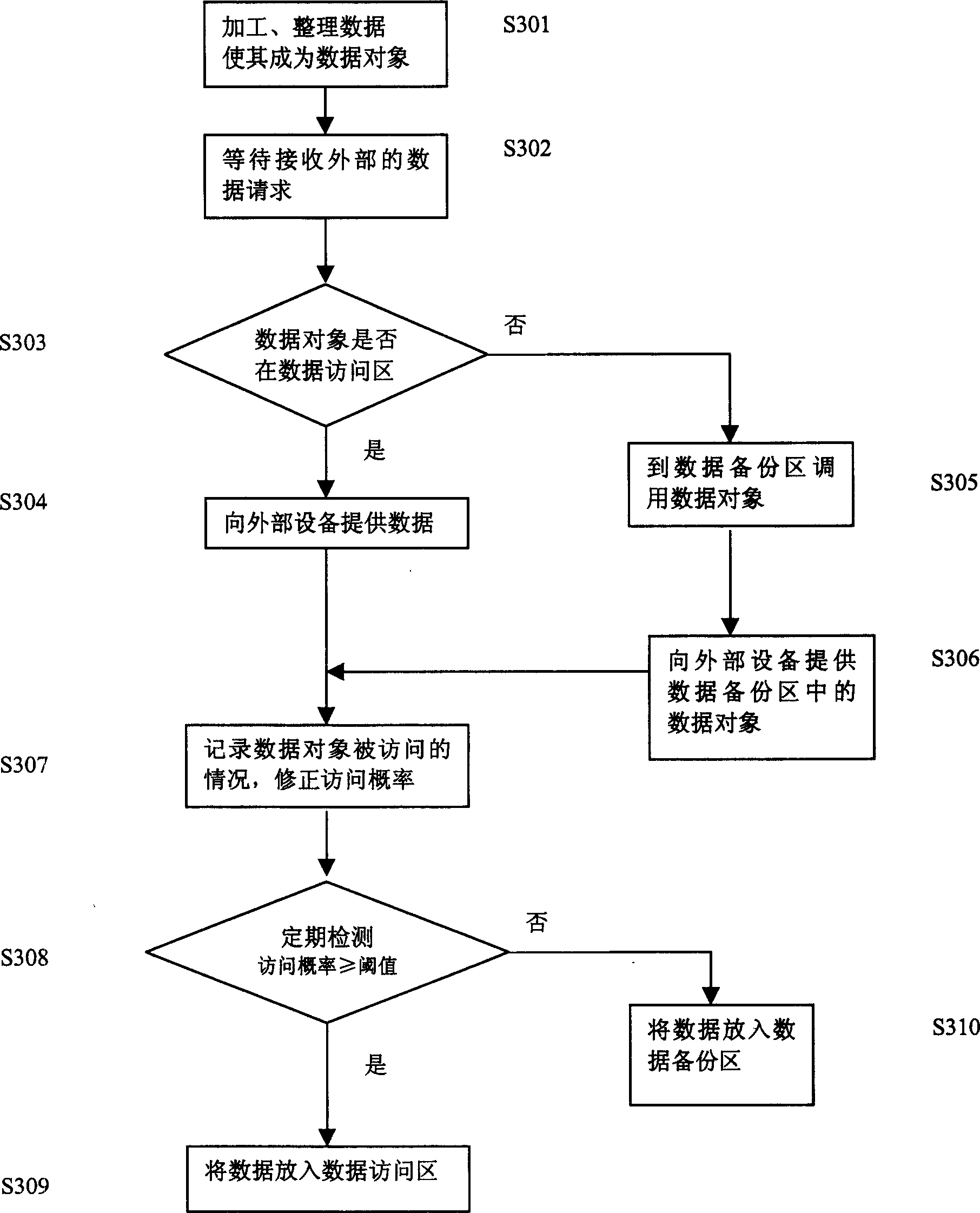
Method for dynamic transferring data and its storing system
InactiveCN1480850AImprove access speedSave management resourcesInput/output to record carriersMemory adressing/allocation/relocationDatabaseData objects
The method includes following steps. Based on access probability, data object is stored in first storage area and second storage area. When request of external device accesses data object, data object is searched in first storage area first. If the data object is not in the first storage area, then search is carried out in the second storage area. Result of accessing data object is recorded, and probability of accessing data object is calculated. If the said probability is larger than or equal to preset threshold, then the relevant data object is held in the first storage area or the relevant data object is moved from the second storage area to the first storage area. If the said probability is less than preset threshold, then the relevant data object is held in the second storage area or the relevant data object is moved from the first storage area to the second storage area. Moreover, the invention also discloses devices for dynamic transferring data.
Owner:LENOVO (BEIJING) CO LTD
High temperature resisting pressure-sensitive adhesive composition and high temperature resisting pressure-sensitive adhesive tape
ActiveCN102952503AReduce shipping costsReduce storage costsFilm/foil adhesivesEster polymer adhesivesEpoxyPhotoinitiator
The invention provides a high temperature resisting pressure-sensitive adhesive composition which comprises a) 25-75wt% of reactive polyacrylate; b) 20-70wt% of epoxy resin; c) 0.3-8wt% of hydroxyl compound; and d) 0.02-5wt% of photoinitiator. The invention further provides a pressure-sensitive adhesive tape which comprises a base material; and a pressure-sensitive adhesive layer which is formed by the pressure-sensitive adhesive composition.
Owner:明尼苏达矿业制造特殊材料(上海)有限公司
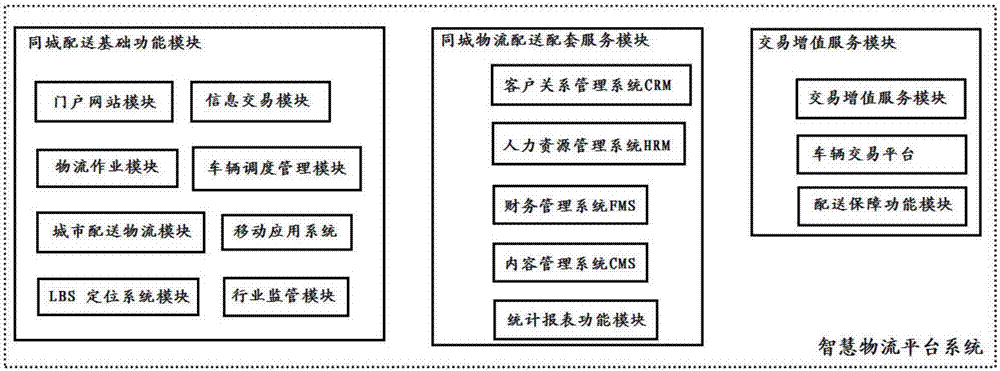
Intelligent logistics platform system
InactiveCN107316172AAchieve sharingImprove distribution efficiencyLogisticsInformatizationThe Internet
An intelligent logistics platform system comprises a city-wide distribution basic function module, a city-wide logistics distribution supporting service module and a transaction value-added service module. According to the platform, with high-tech intelligence as the support, the role of information technology in logistics distribution is enhanced, and a new logistics distribution service system for realizing the most effective resource allocation between city logistics vehicles and goods is achieved. Through integrating related information of logistics upstream and downstream enterprises, a comprehensive supply chain solution is provided, diverse and complex needs of a demand side can be met effectively, logistics market informatization is promoted, and while the economic development of the region is promoted, the Internet of things research and development field is expanded.
Owner:宁波图锐信息科技有限公司
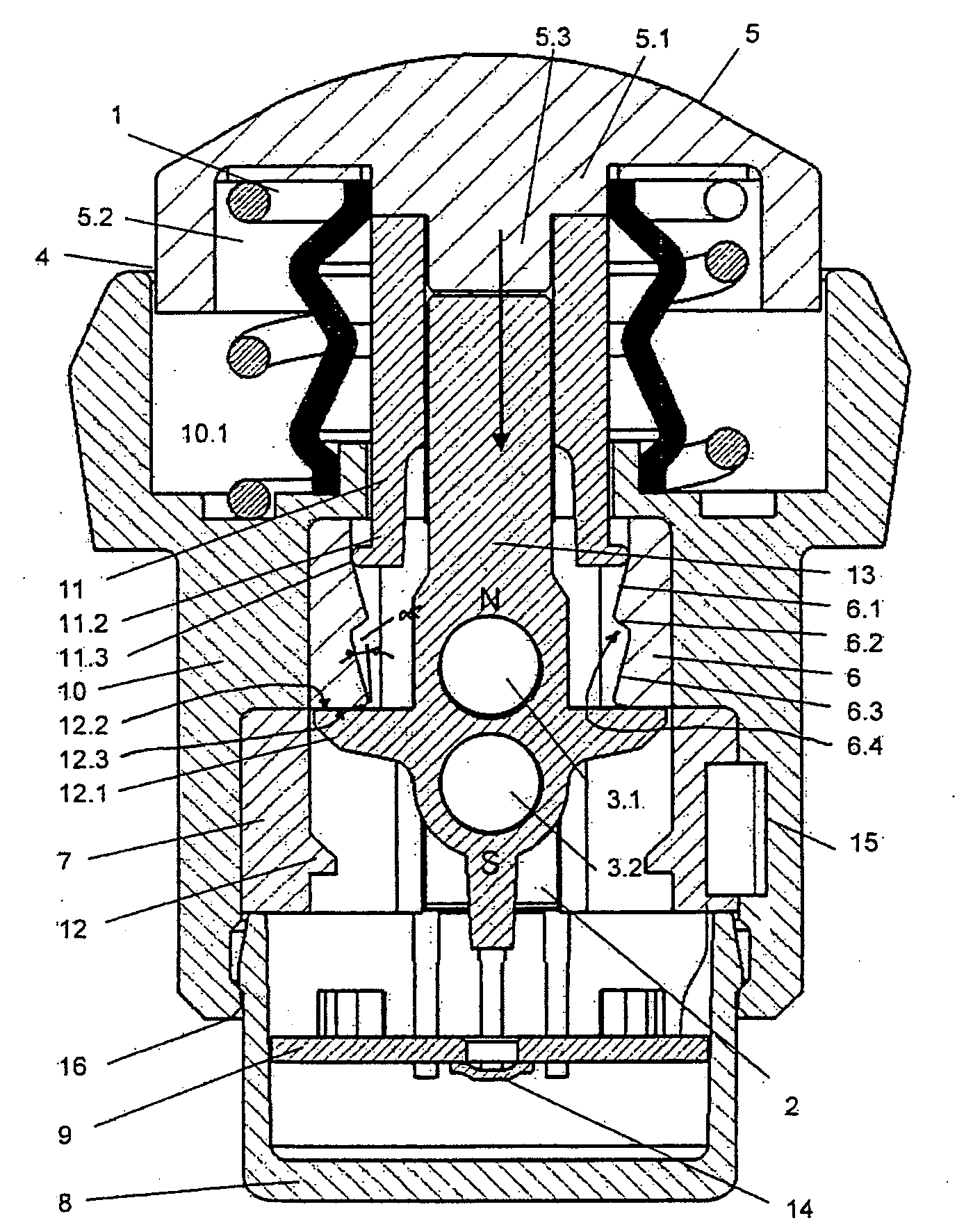
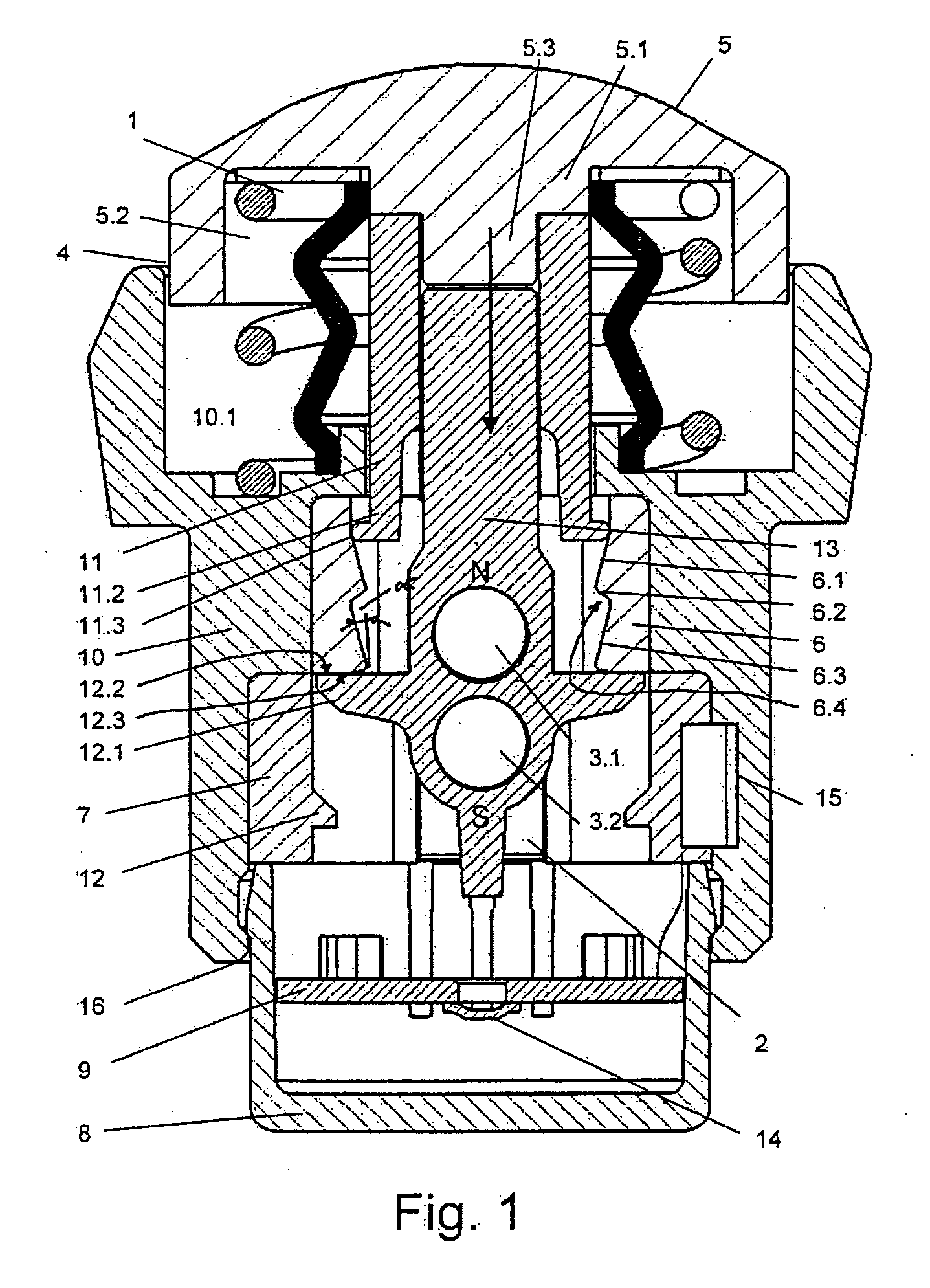
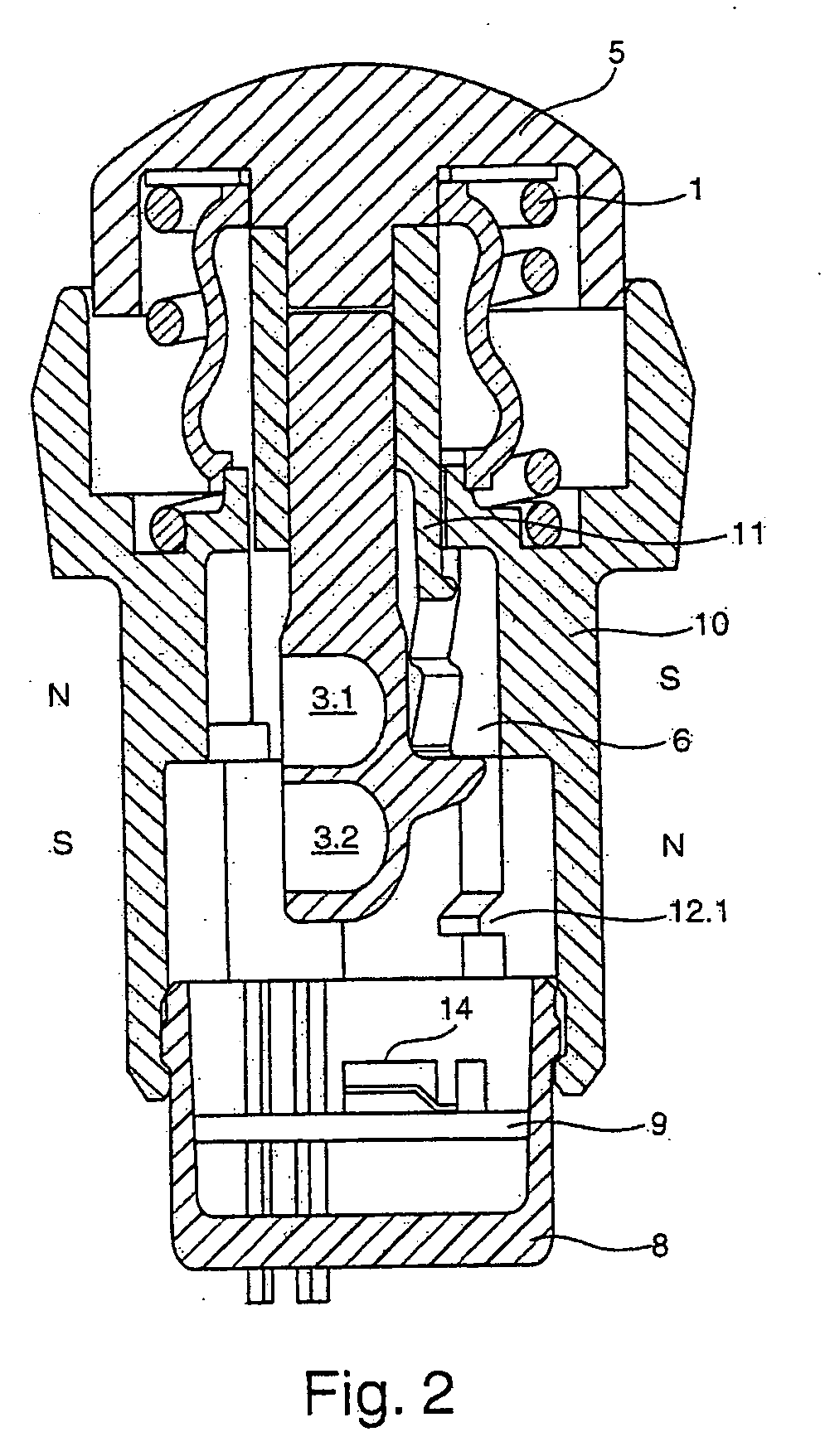
Push-button
InactiveUS20100236911A1Increase redundancyEasy to carryContact operating partsTactile feedbackEngineeringMagnet
The invention relates to a push-button (5) having a housing (10), with which there are associated at least a first actuation member (6) which triggers a haptic control signal and one or more permanent magnet(s) (3) which can be guided past at least a second actuation member (2) which triggers a switching operation.There is associated with the first actuation member (6), which triggers a haptic response, a control element having a first progressive or degressive control face portion (6.1) and at least a second adjoining control face portion (6.2) which behaves in an inverse manner and along which the actuation member is guided.
Owner:W SMANN
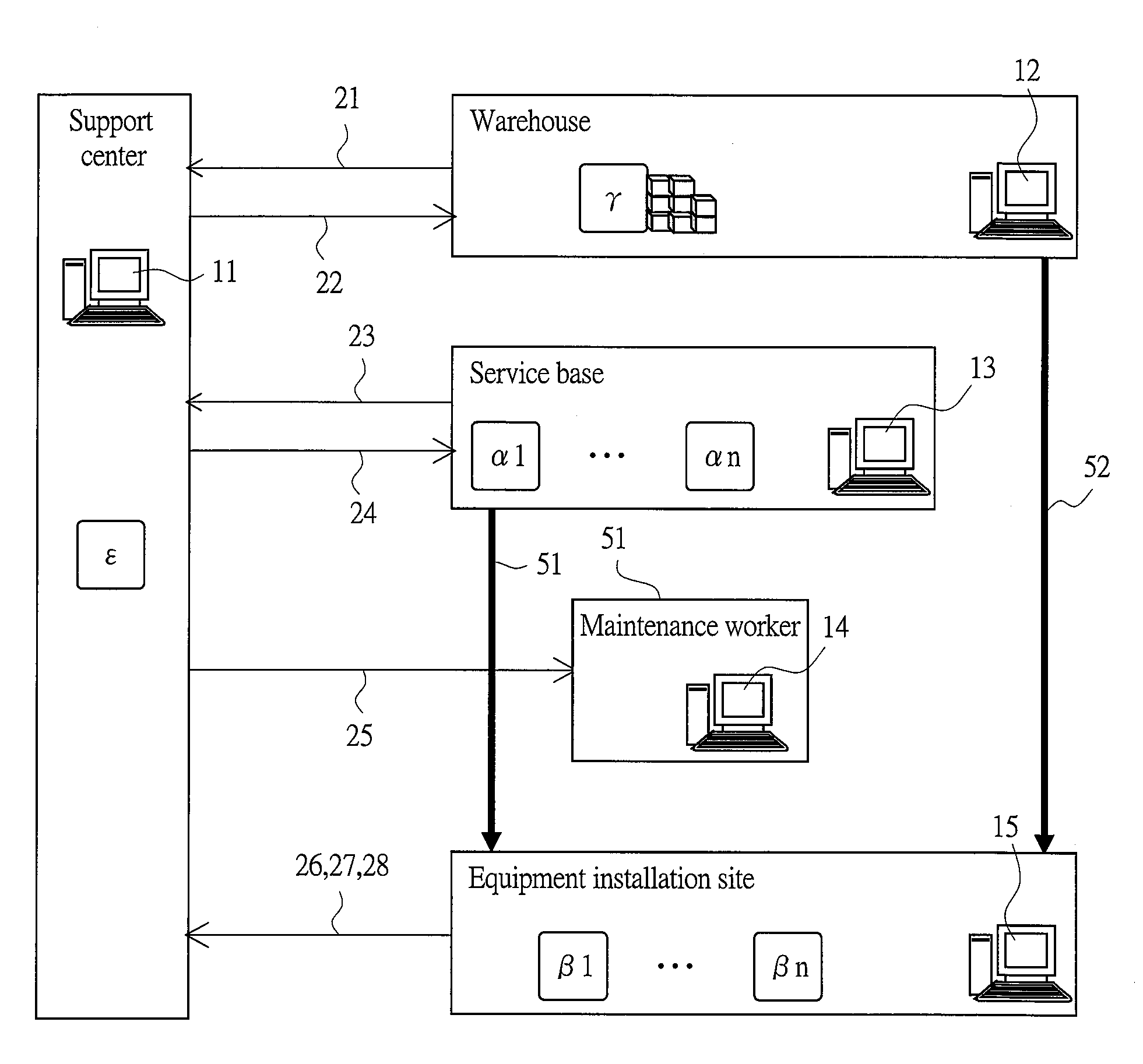
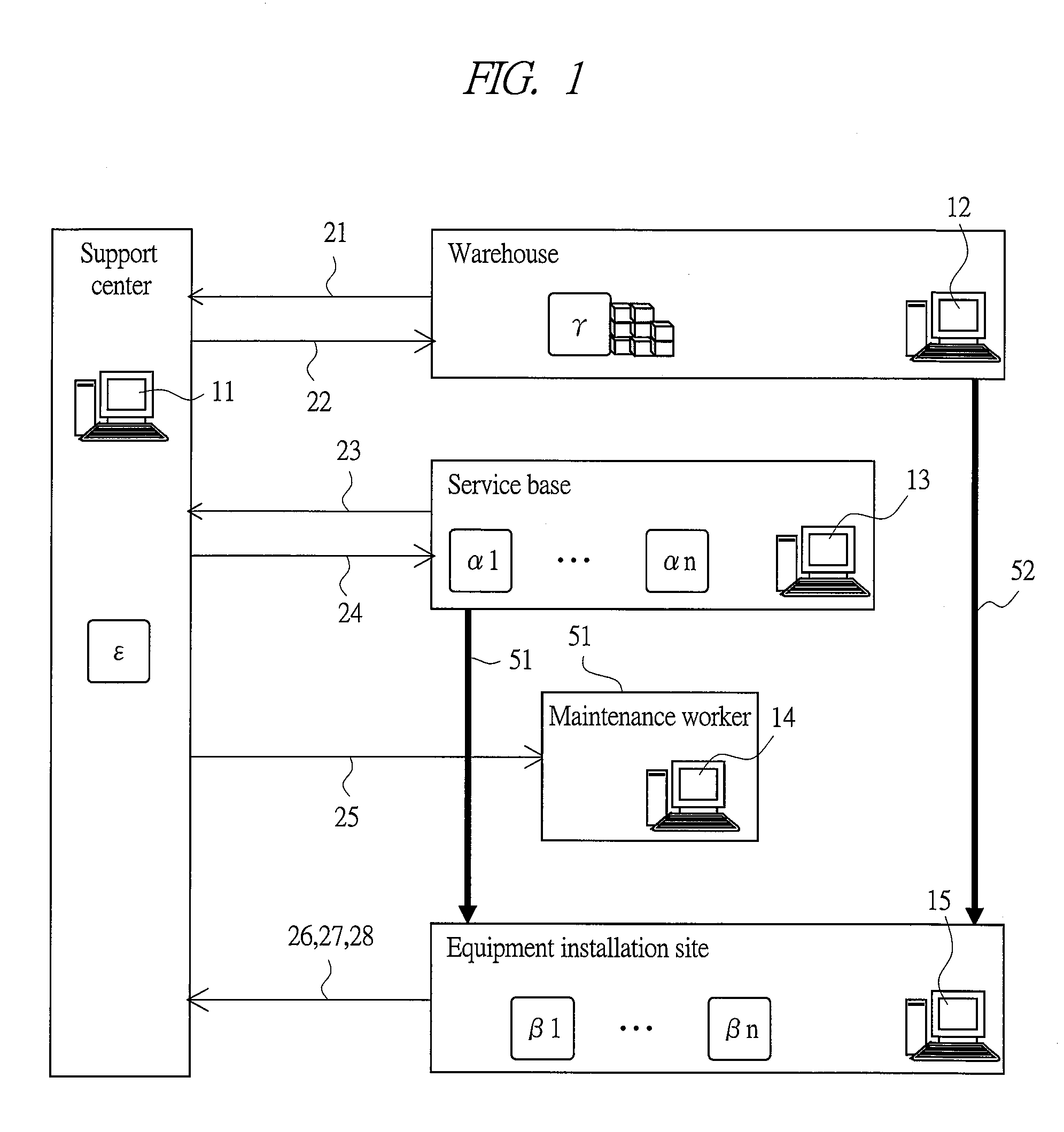
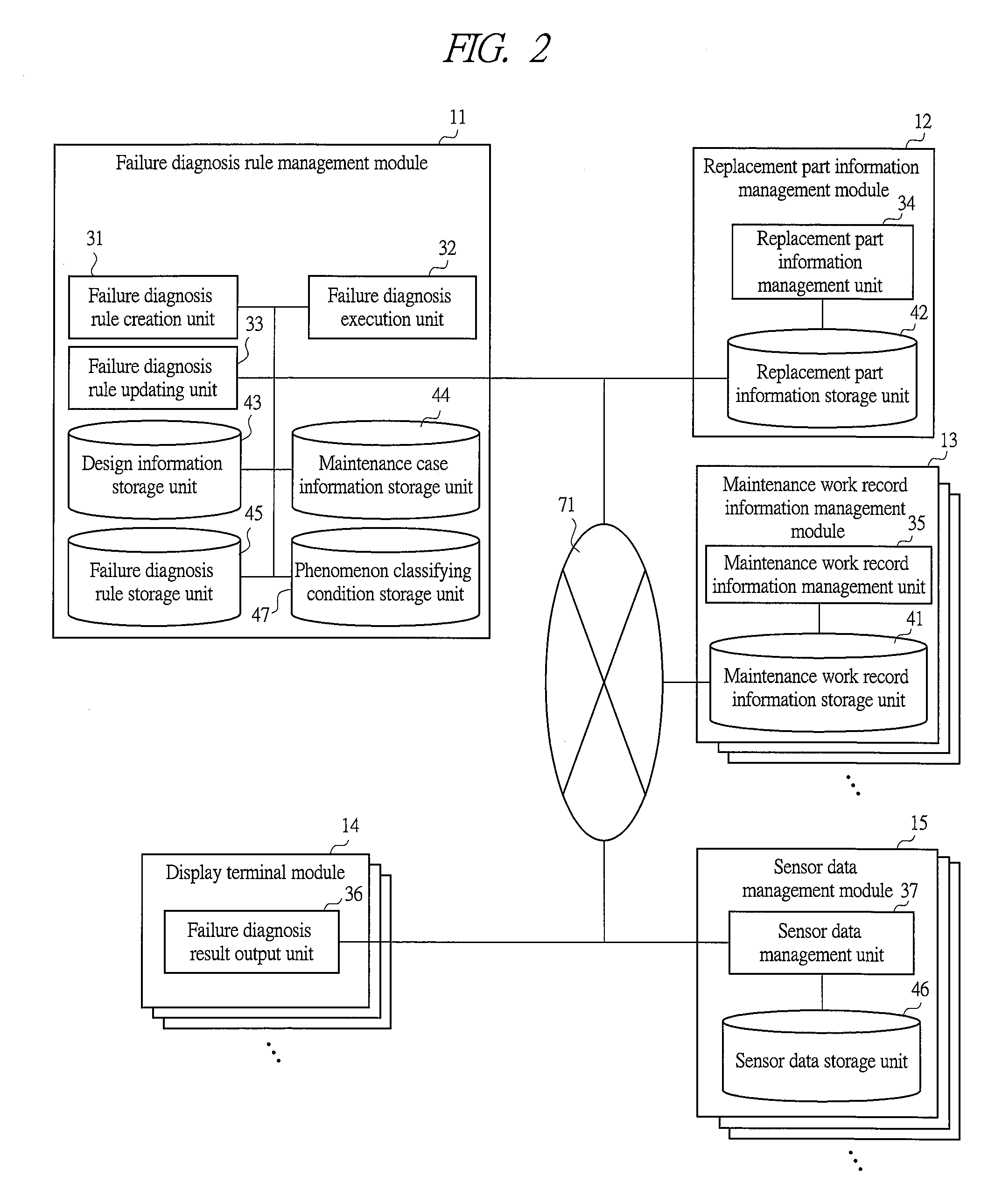
Failure diagnosis system, failure diagnosis device and failure diagnosis program
InactiveUS20120290497A1Improve service levelReduce work costsData processing applicationsAmbiguityExecution unit
In the failure diagnosis system of the present invention, the maintenance case information including data ambiguity and a partially deficient portion is utilized even in the case where maintenance case information having a high similarity is not sufficiently provided. The failure diagnosis system is provided with: a failure diagnosis rule creation unit 31 which, by utilizing maintenance case information accumulated in the past, creates a failure diagnosis rule used for listing up candidates of maintenance parts required for recovering the equipment from a failure phenomenon; a failure diagnosis execution unit 32 which, upon occurrence of a failure, outputs the candidates of maintenance parts required for recovering from the failure phenomenon to a maintenance work assist terminal with reference to the failure diagnosis rule; and a failure diagnosis rule updating unit 33 for updating the failure diagnosis rule, and the failure diagnosis rule creation unit 31 has a factor-information link creation unit, which creates links among pieces of factor information composed of pieces of information relating to the failure phenomenon, information relating to the subject component, and information relating to the corresponding treatment in the maintenance case information accumulated in the past.
Owner:HITACHI LTD
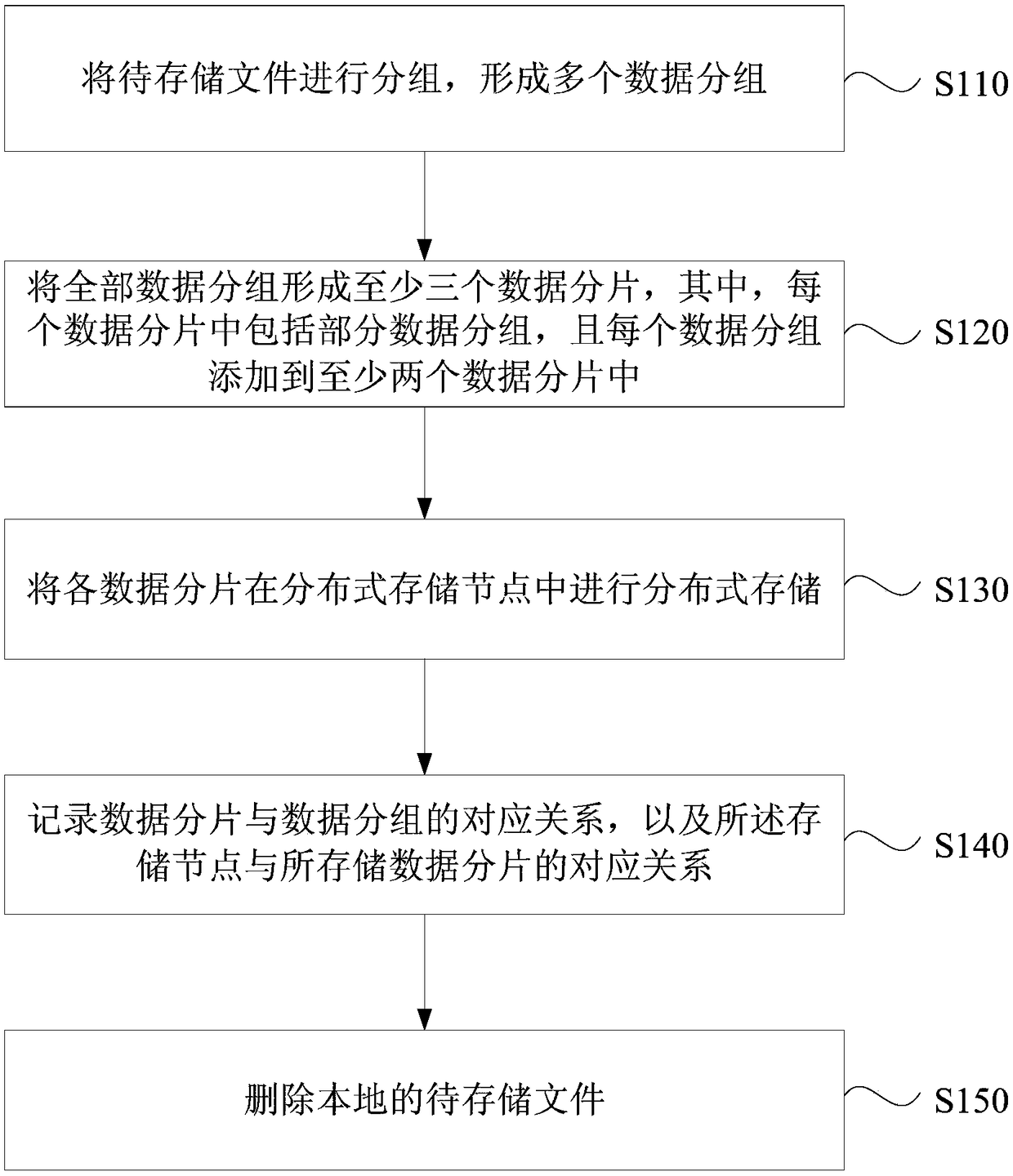
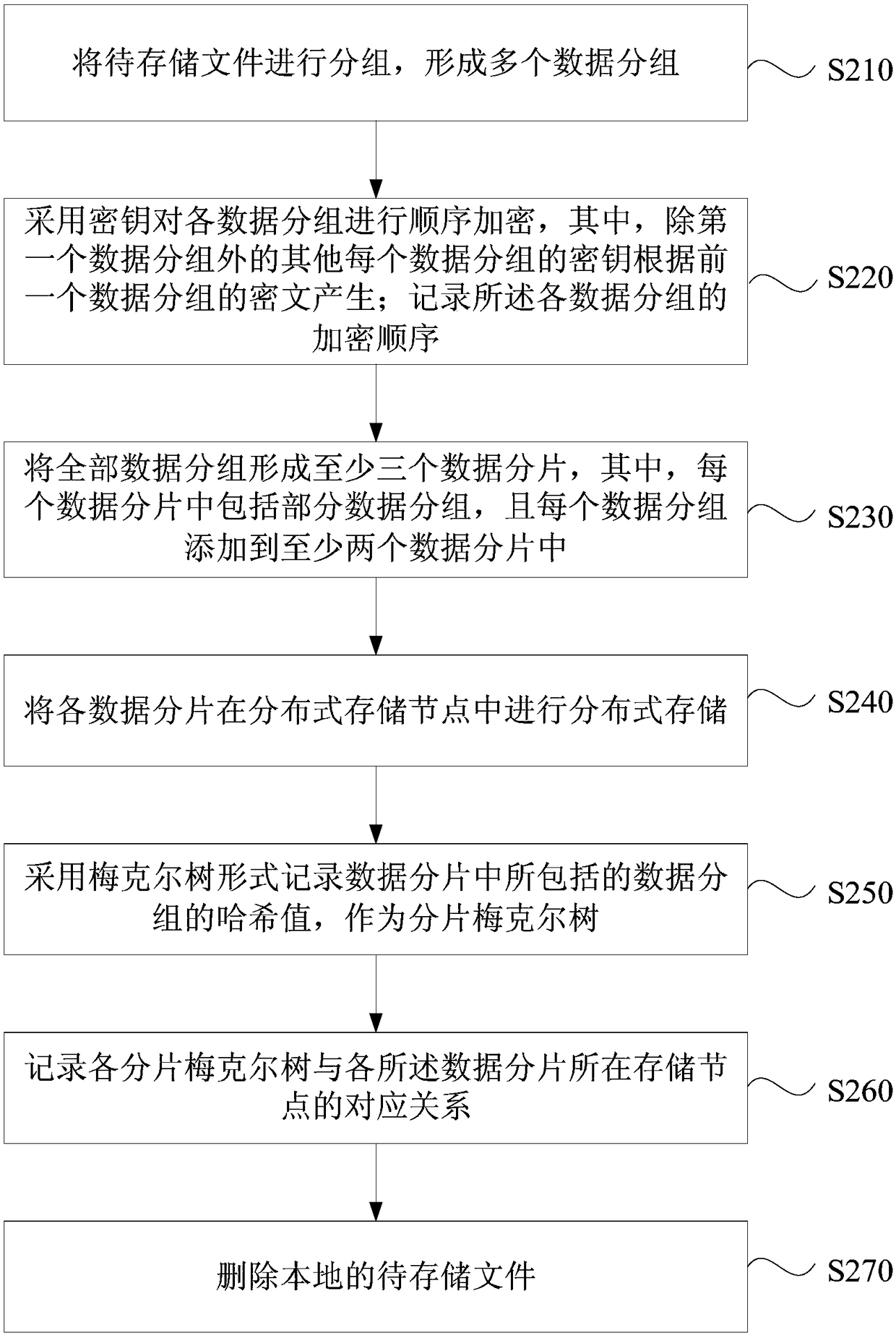
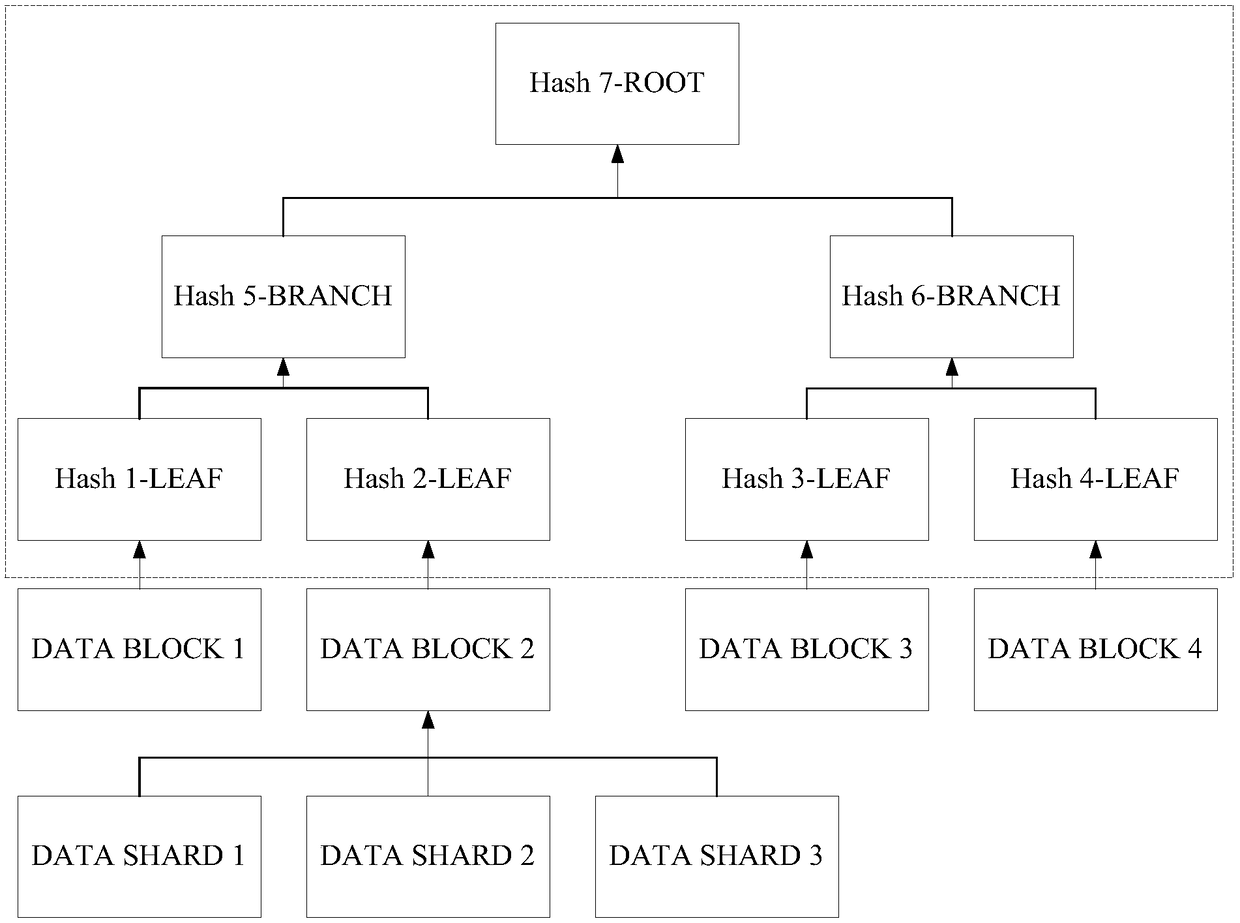
Distributed storage method and device, computer equipment and storage medium
ActiveCN108664223AImprove privacyImprove securityInput/output to record carriersComputer security arrangementsComputer equipmentFile storage
The embodiment of the invention discloses a distributed storage method and device, computer equipment and a storage medium. The method comprises the steps of grouping a to-be-stored file to form multiple data groups; forming at least three data fragments from all the data groups, wherein each data fragment comprises part of data groups, and each data group is added to at least two data fragments;distributedly storing all the data fragments in distributed storage nodes; recording a corresponding relationship between the data fragments and the data groups, and a corresponding relationship between the storage nodes and the stored data fragments; deleting the local to-be-stored file. According to the technical scheme, a user conveniently stores files in a distributed network to lower the storage cost, the privacy and safety of the stored files can be effectively improved, and thus an attacker is prevented from restoring original files.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
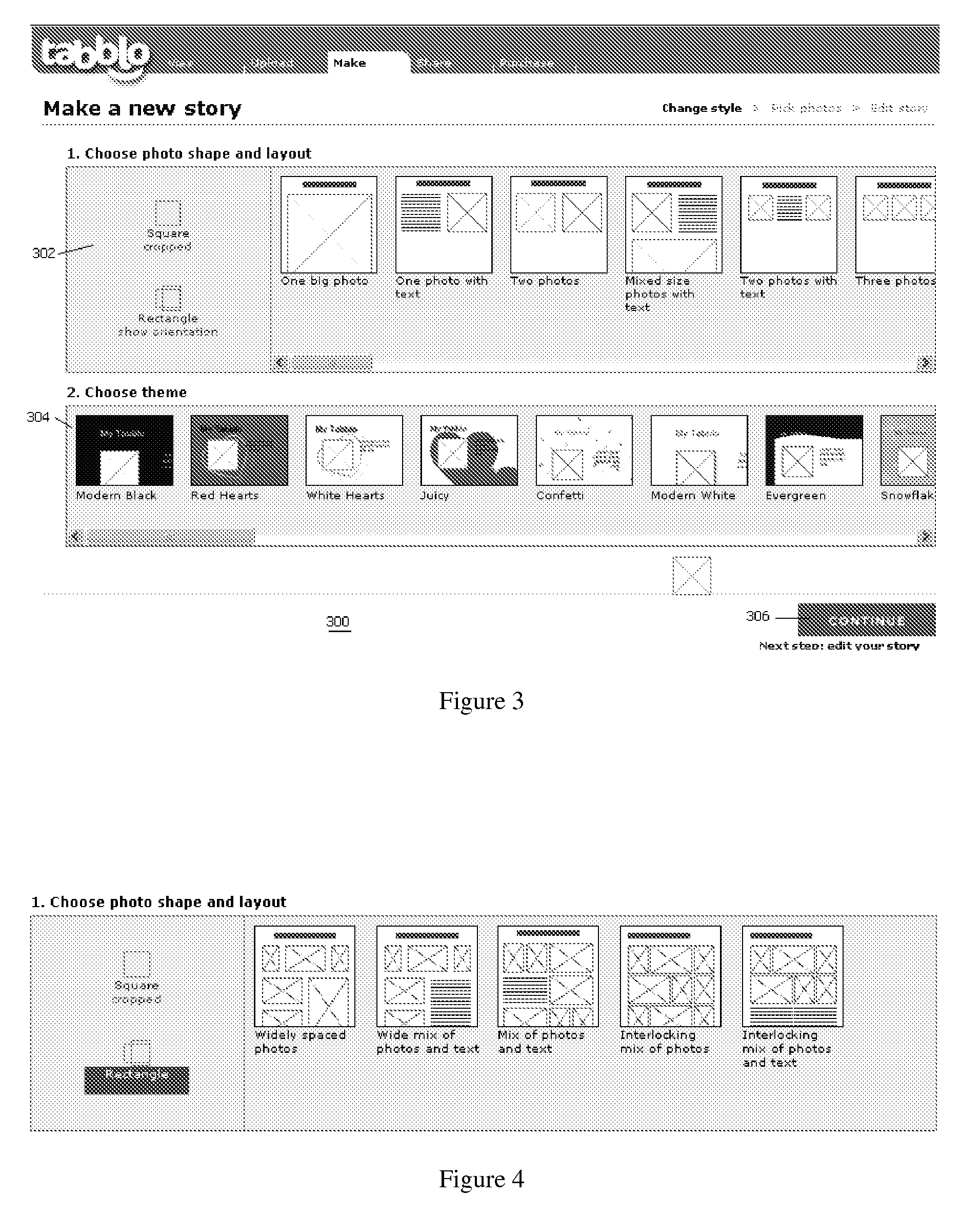
Method for modifying an initial layout of story elements in a user-generated online story
InactiveUS20080215965A1Reduce storage costsSignificantWebsite content managementSpecial data processing applicationsWeb siteUniform resource locator
An online application enables an end user to navigate to a web site, upload digital images, and to combine those images with words in a stylized template to create a user-generated story. A story is a web page, typically a collection of photos and words that are brought together by a stylized template that can be customized by the end user. Preferably, a given story is available from the site at a given location (at a URL) that may be private or public. A given story may be shared with other end users, published to other web sites or web logs, or maintained solely for one's own use. The invention also provides for multiple end users to collaborate to create a “shared” story.
Owner:HEWLETT PACKARD CO
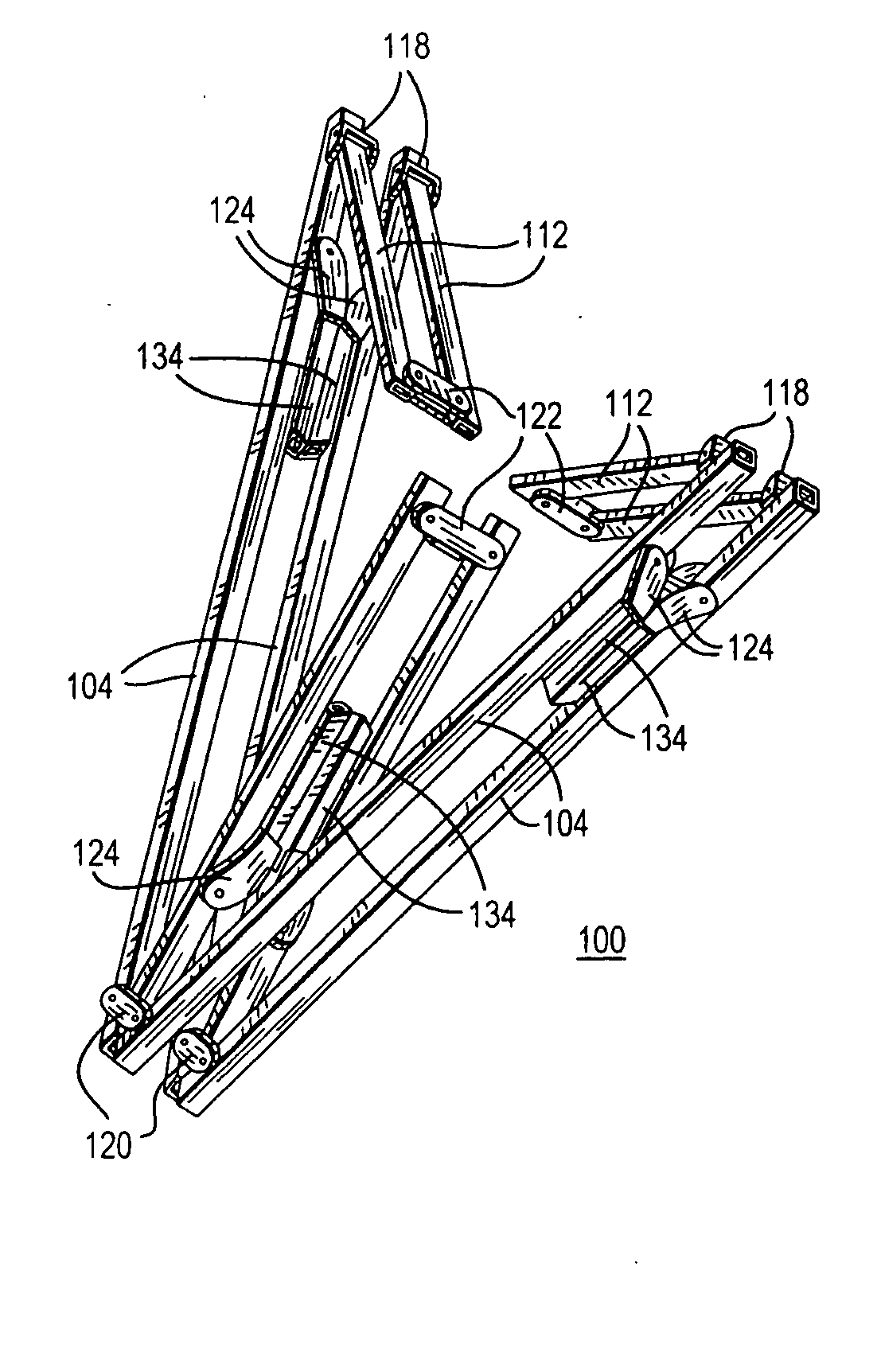
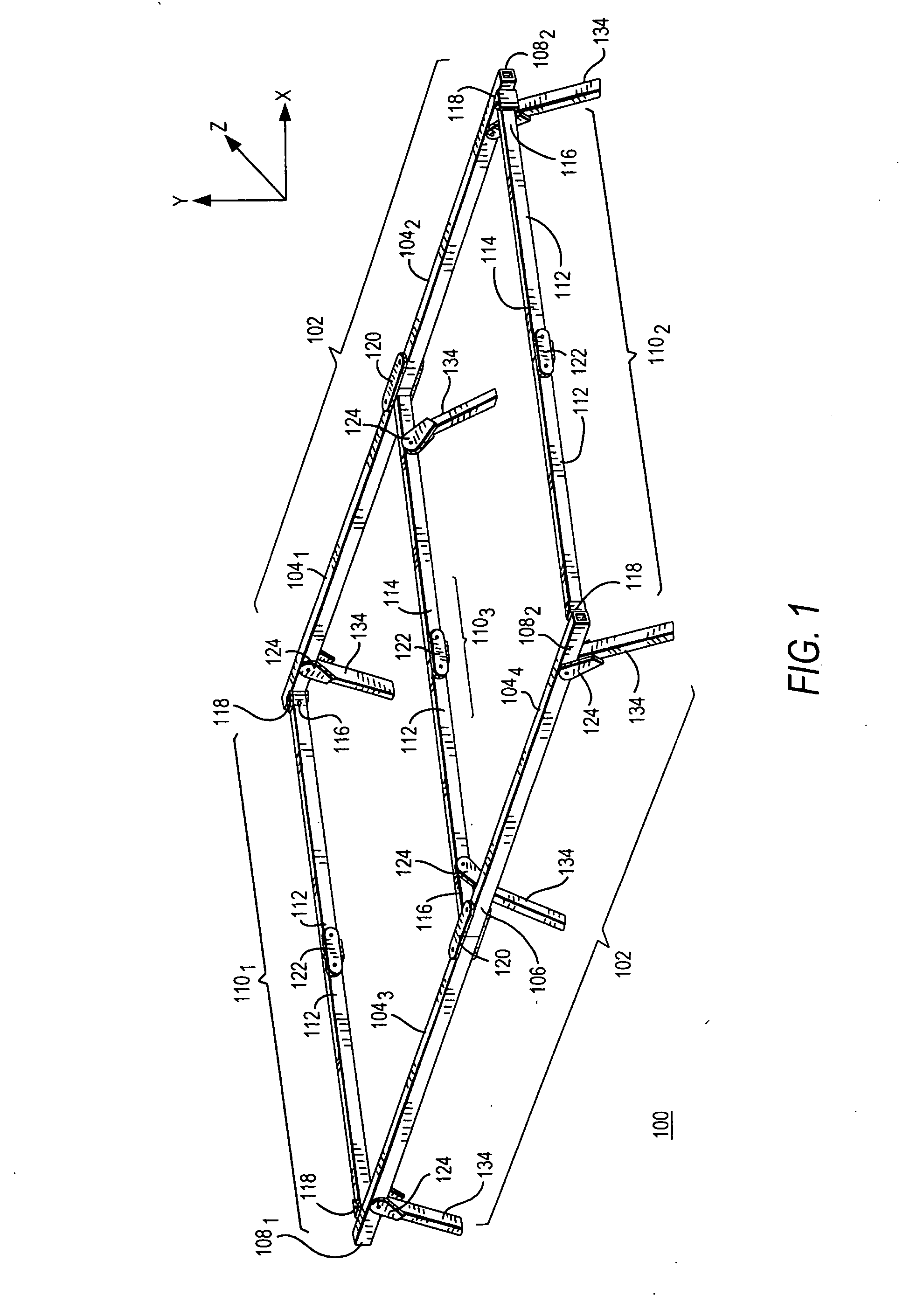
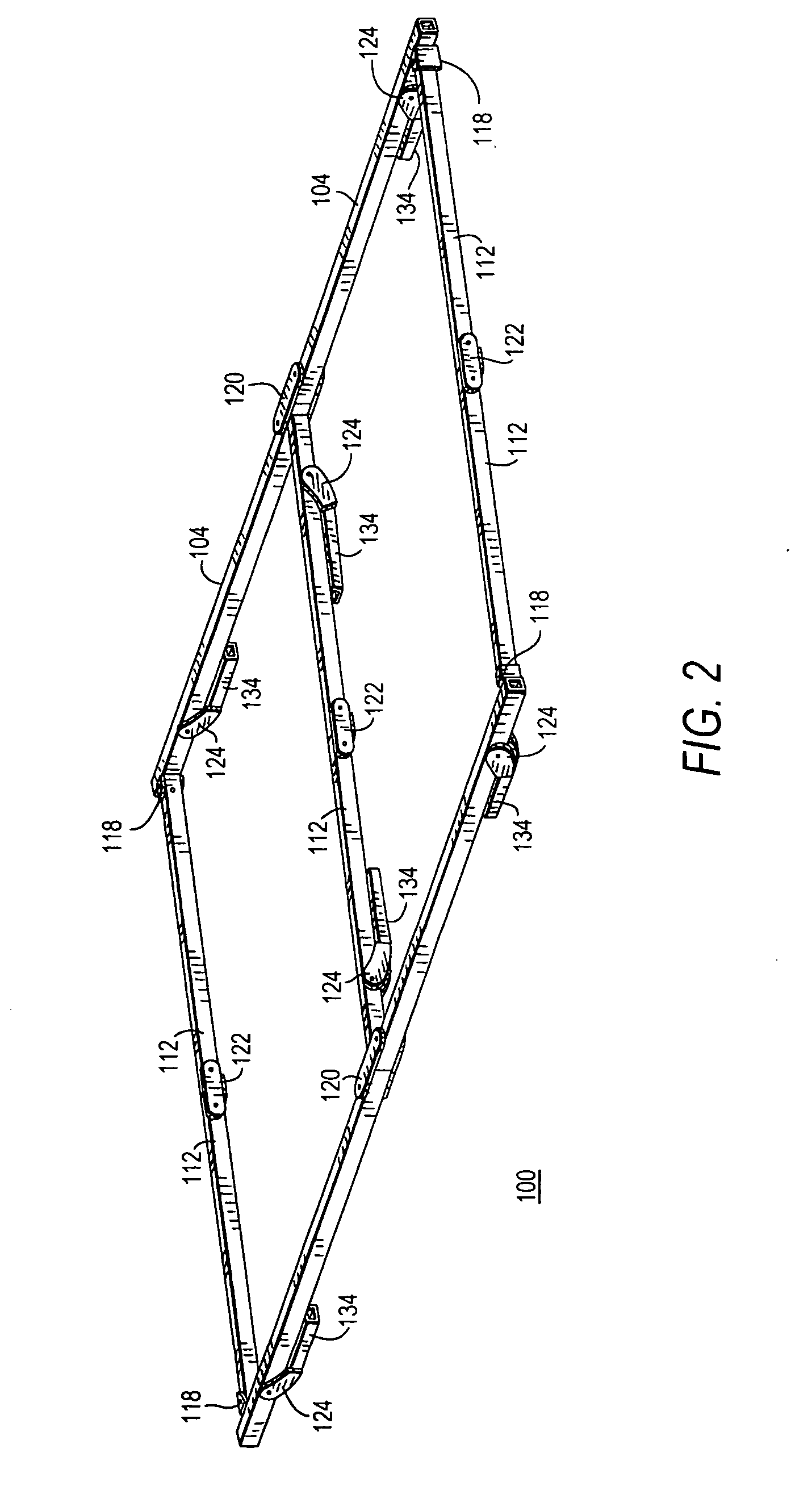
Foldable bed frame
A foldable bed frame including first coupling members each having an opening facing outwardly with respect to the frame being in an open state; two sets of longitudinal beams, each formed by two longitudinal bars having two free ends, and two inner ends pivotally connected within one of the openings of the first coupling members. At least two transverse beams, each being formed by two transverse bars having first and second ends, the first ends respectively being pivotally connected together by a second coupling member. A plurality of third coupling members provided proximate to each free end of the longitudinal bars, each third coupling member having an opening facing inwardly with respect to the frame being in the open state, the opening being configured to pivotally connect one of the free ends of the longitudinal bars. A leg pivotally connected respectively proximate the free end of each longitudinal bar.
Owner:JIN KI HO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com