Method and system for processing electronic transaction request
A transaction request, electronic transaction technology, applied in the field of computer networks, can solve the problems of inability to adapt to the development direction of online interaction, inability to cross-process multiple channels, inconvenience and speed, etc., to improve user communication efficiency, provide user experience, and improve efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
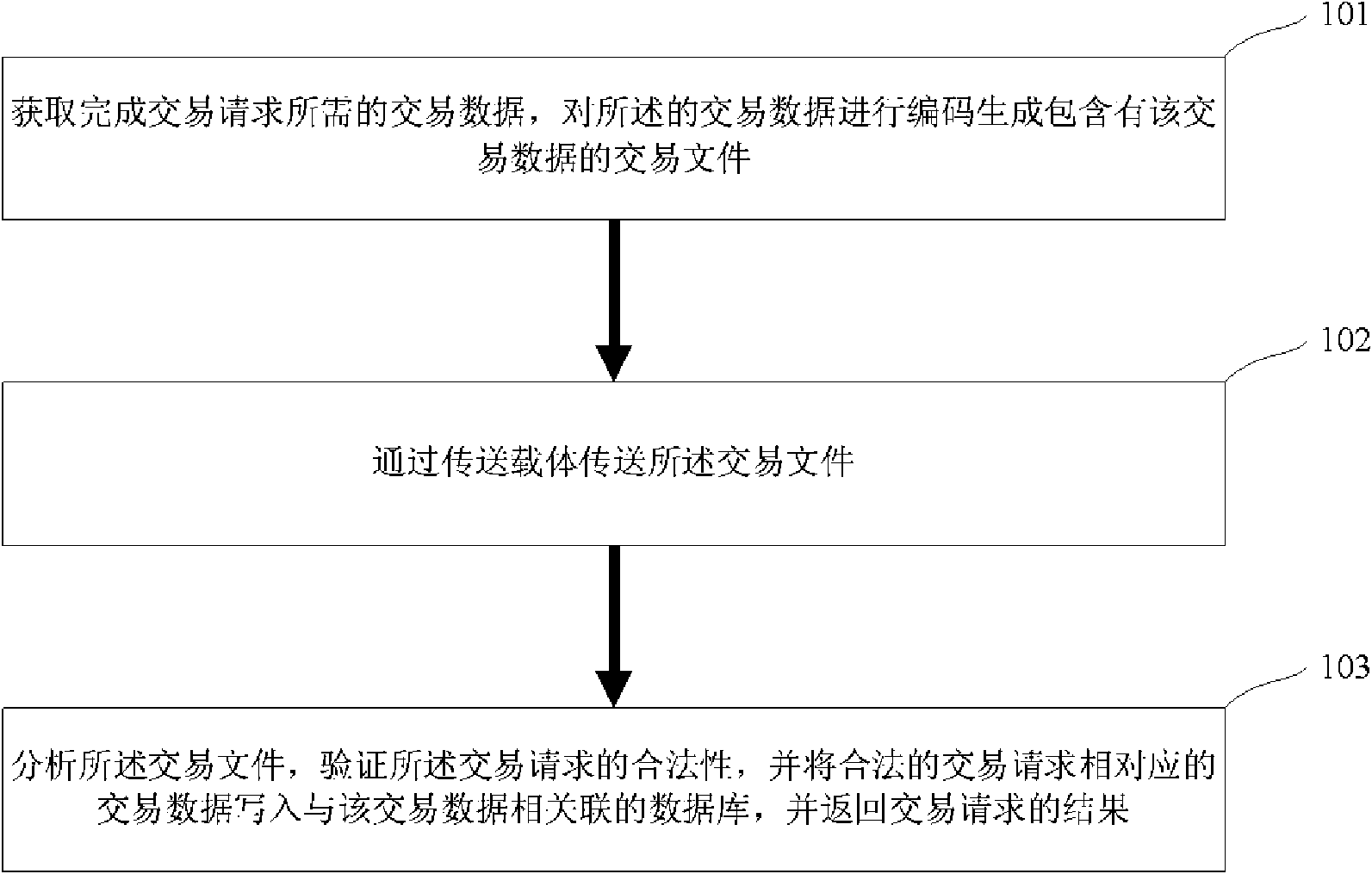
[0069] like figure 1 As shown, the present invention provides a method for processing an electronic transaction request, comprising the steps of:
[0070] 101. Obtain the transaction data required to complete the transaction request, encode the transaction data to generate a transaction file containing the transaction data;
[0071] The transaction data includes transaction information, and the transaction information mainly includes the transaction requester's first user identity information, user account information, transaction object information, transaction object owner information, transaction category information and transaction amount information,
[0072] The user identity information includes a user name and a user ID number,
[0073] The user account information includes account number and account opening organization information,
[0074] The type of transaction described includes transfers, remittances, payments or purchases,
[0075] When the transaction categ...
Embodiment 2
[0088] On the basis of Embodiment 1, the transaction data further includes a first electronic signature containing the identity information of the transaction requester, and the first electronic signature contains encoding information, and the encoding information is located in the first electronic signature database , the step 103 is: analyze the transaction file, verify the legitimacy of the transaction requester’s identity information and the transaction instruction, write the transaction data associated with the legal transaction request into the account fund database, and return the result of the transaction request;
[0089] The steps of "analyzing the transaction file, verifying the legitimacy of the transaction requester's identity information and the transaction instruction" are as follows:
[0090] Extract the first electronic signature in the transaction data, query the electronic signature corresponding to the number in the electronic signature database through the...
Embodiment 3
[0094] On the basis of Embodiment 2, a second electronic signature is added to the transaction file to generate the transaction file after the transaction request is authenticated, and the second electronic signature contained in the authenticated transaction file is analyzed to verify the The legitimacy of the above transaction request.
[0095] The second electronic signature includes the following two situations:
[0096] The counterparty's electronic signature containing the counterparty's identity information;
[0097] A third-party electronic signature that includes the identity information of a third-party authenticator, the third party refers to an intermediary independent of the two parties to the transaction and not associated with the two parties to the transaction.
[0098] The method then includes the following steps, such as figure 2 Shown:
[0099] 301. Obtain the transaction data required to complete the transaction request, and encode the transaction data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com