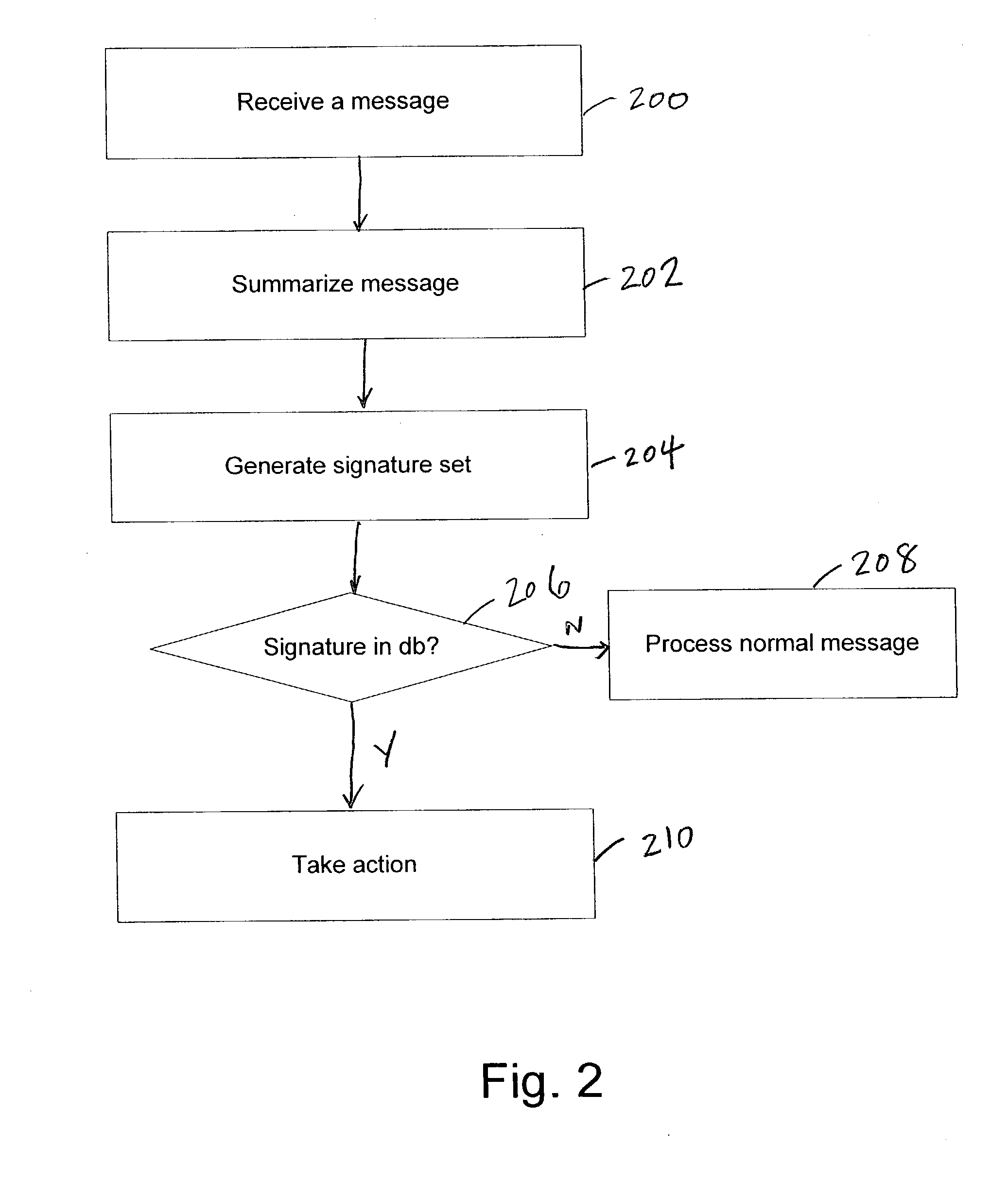
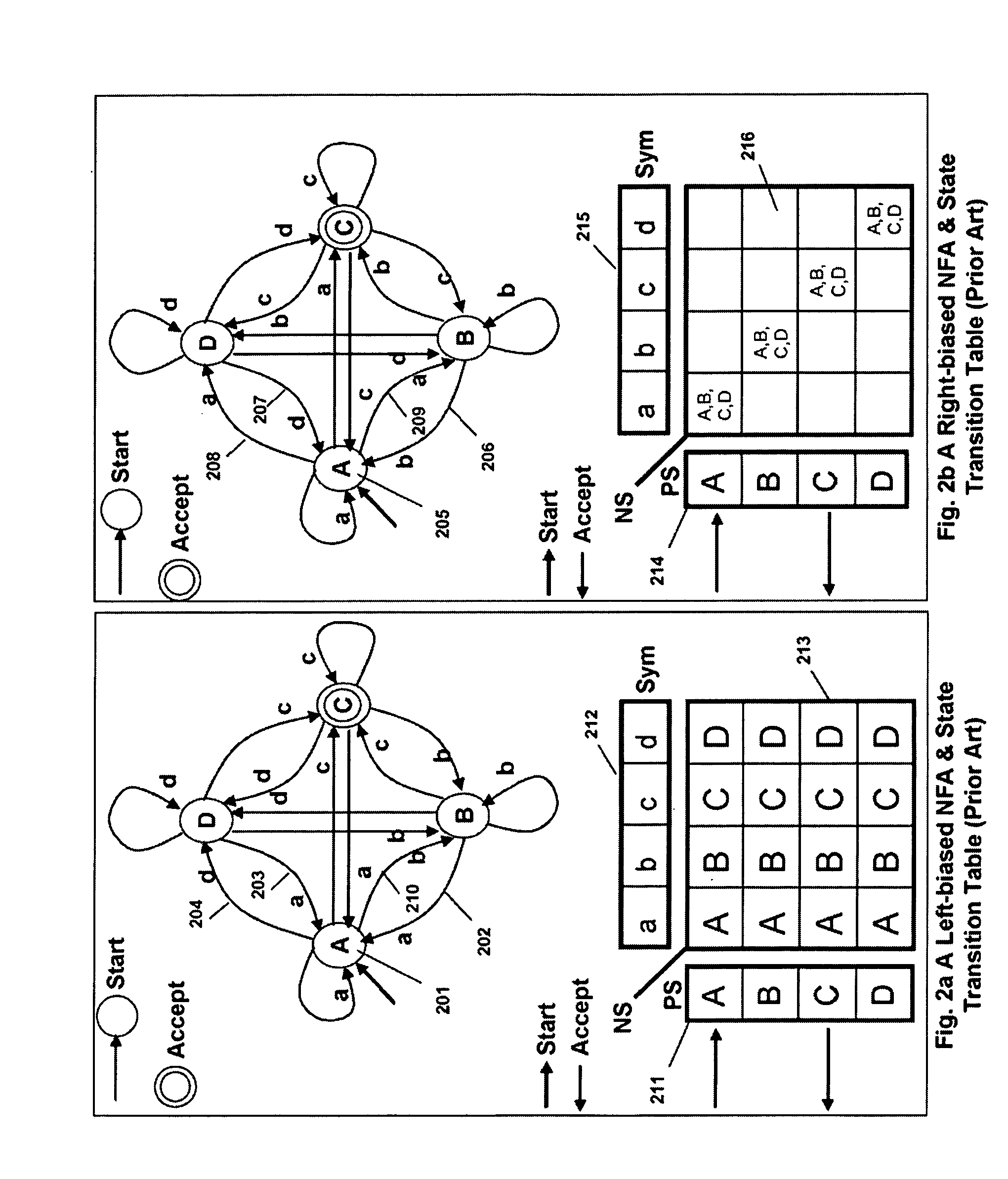
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
185 results about "Signature database" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
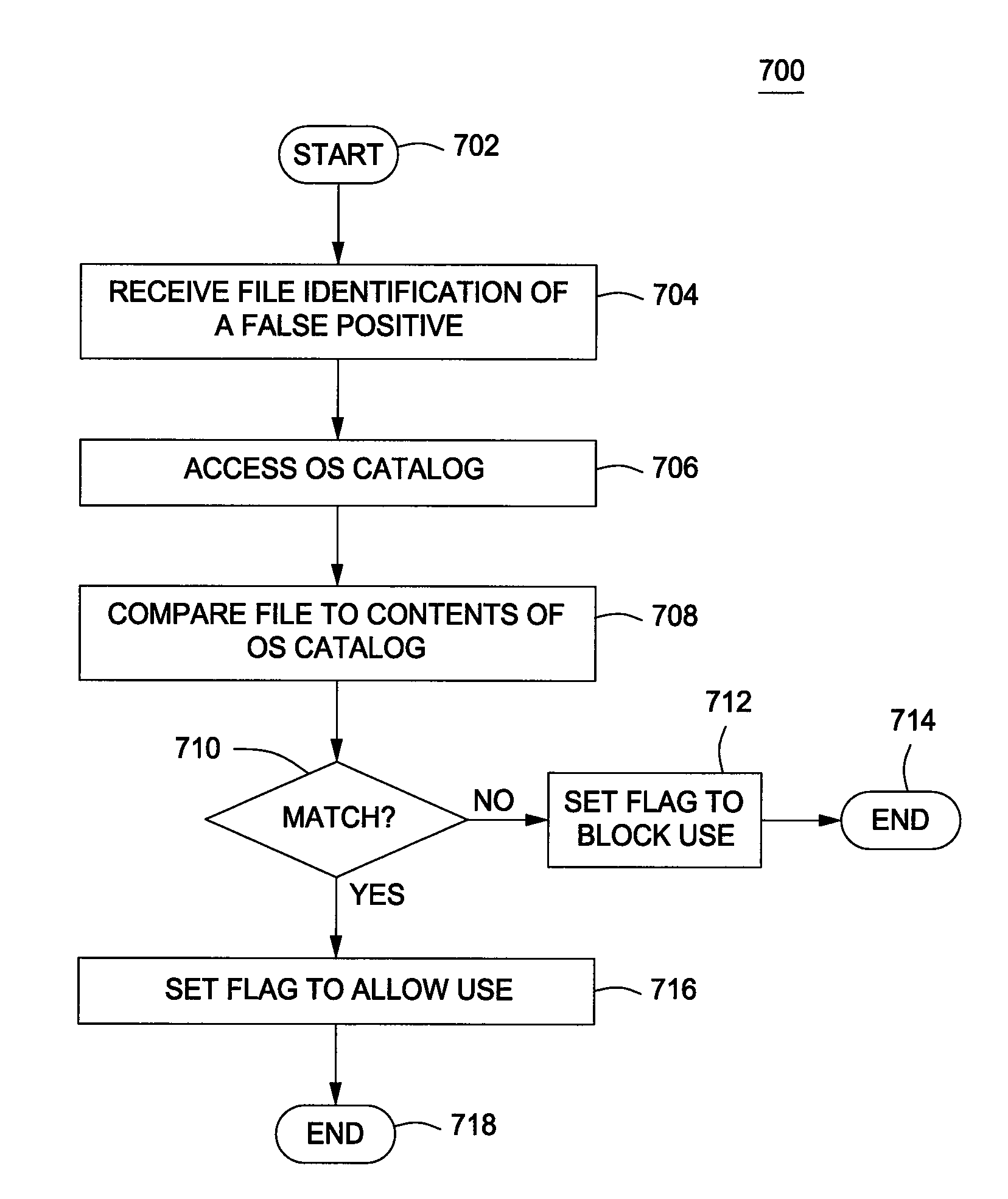
Method for mitigating false positive generation in antivirus software
A method for mitigating false-positives as detected by antivirus software comprising accessing an operating system file that has been identified as malware; creating a signature for the operating system file; comparing the created signature to a signature database; and, if the created signature is not found in the signature database, defining the operating system file as malware. An operating system file, as used herein, is any file included as a part of the operating system binary executable file set, as well as any files added from third party vendors that integrate with or plug into the operating system.
Owner:SYMANTEC CORP
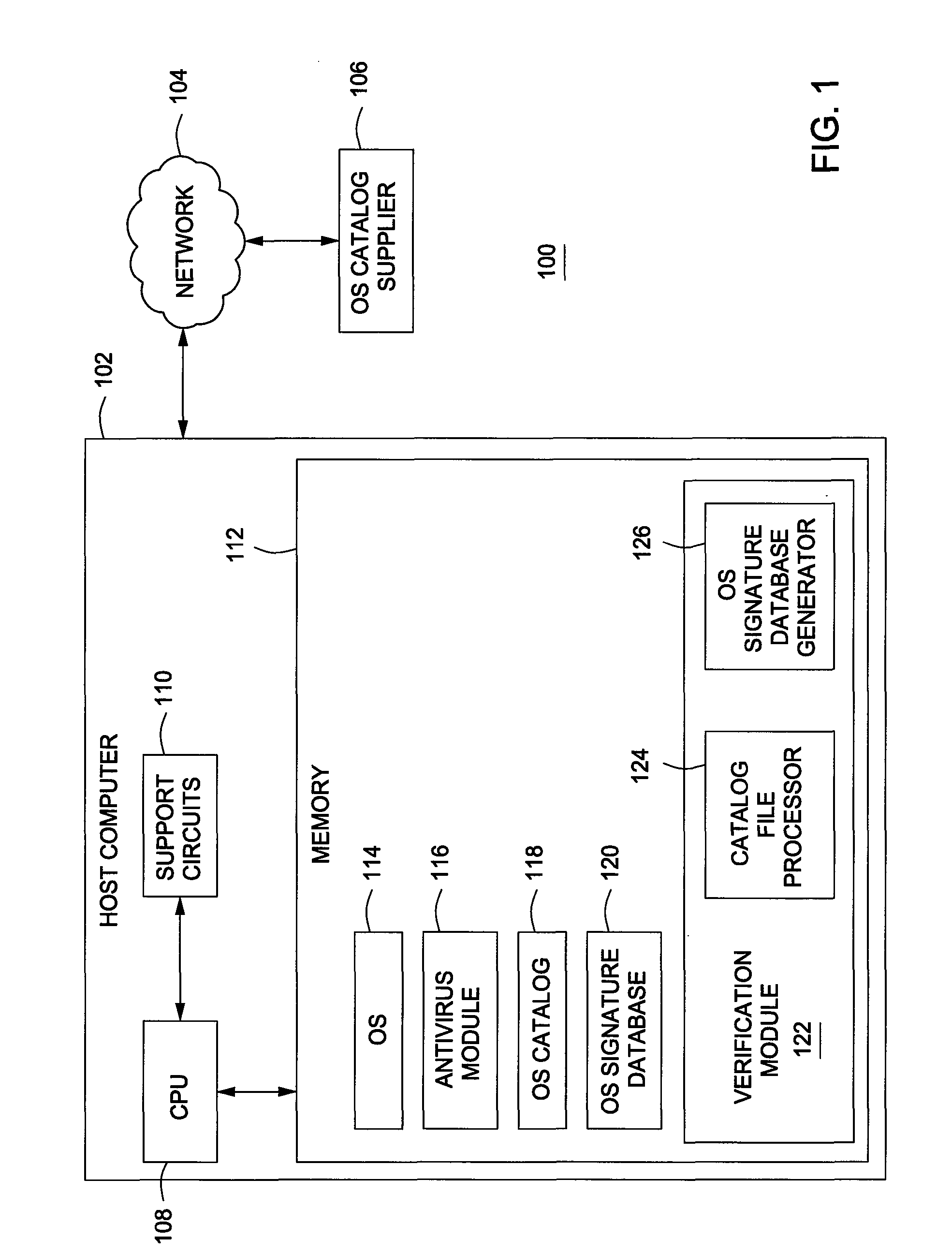
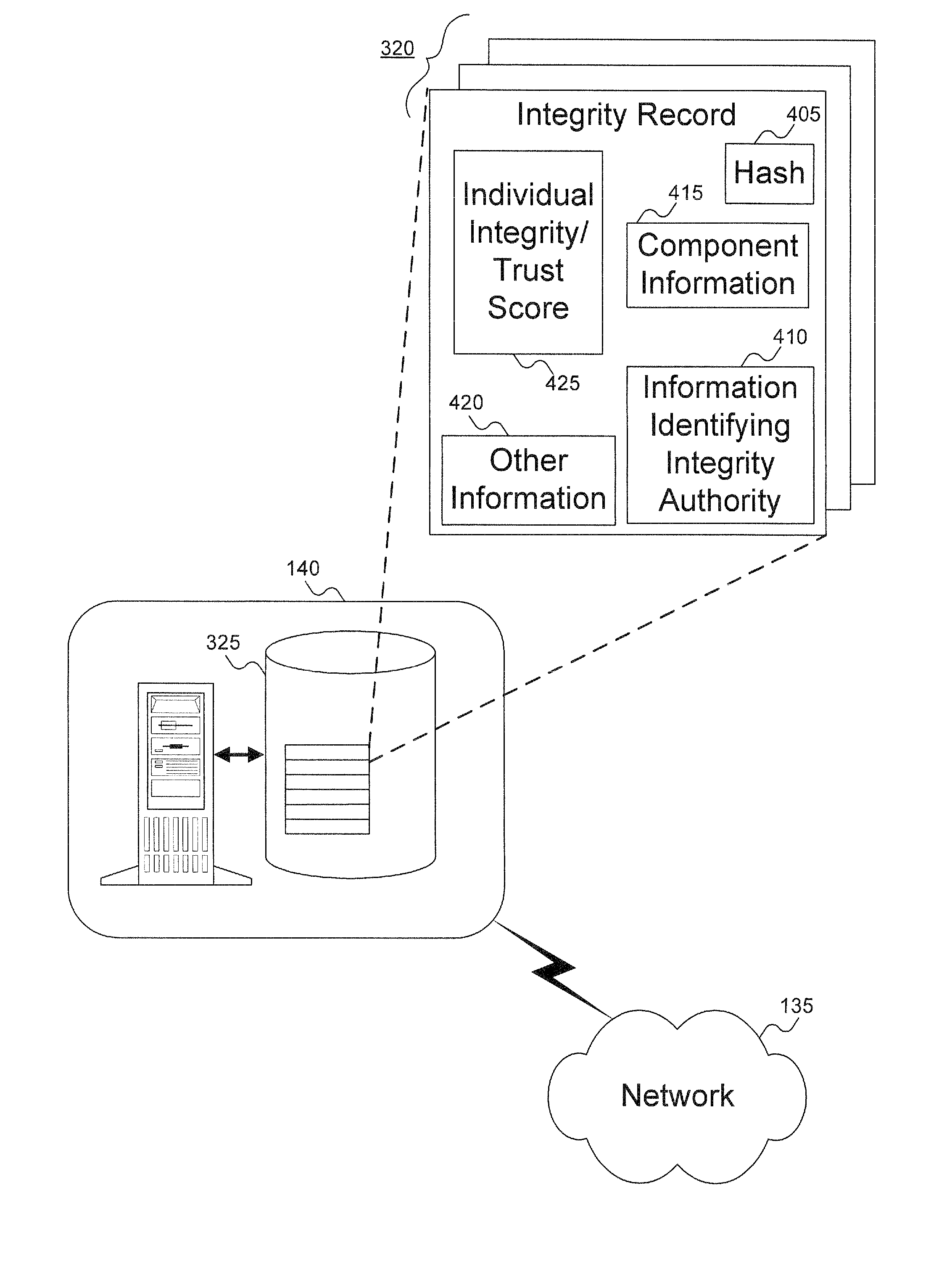
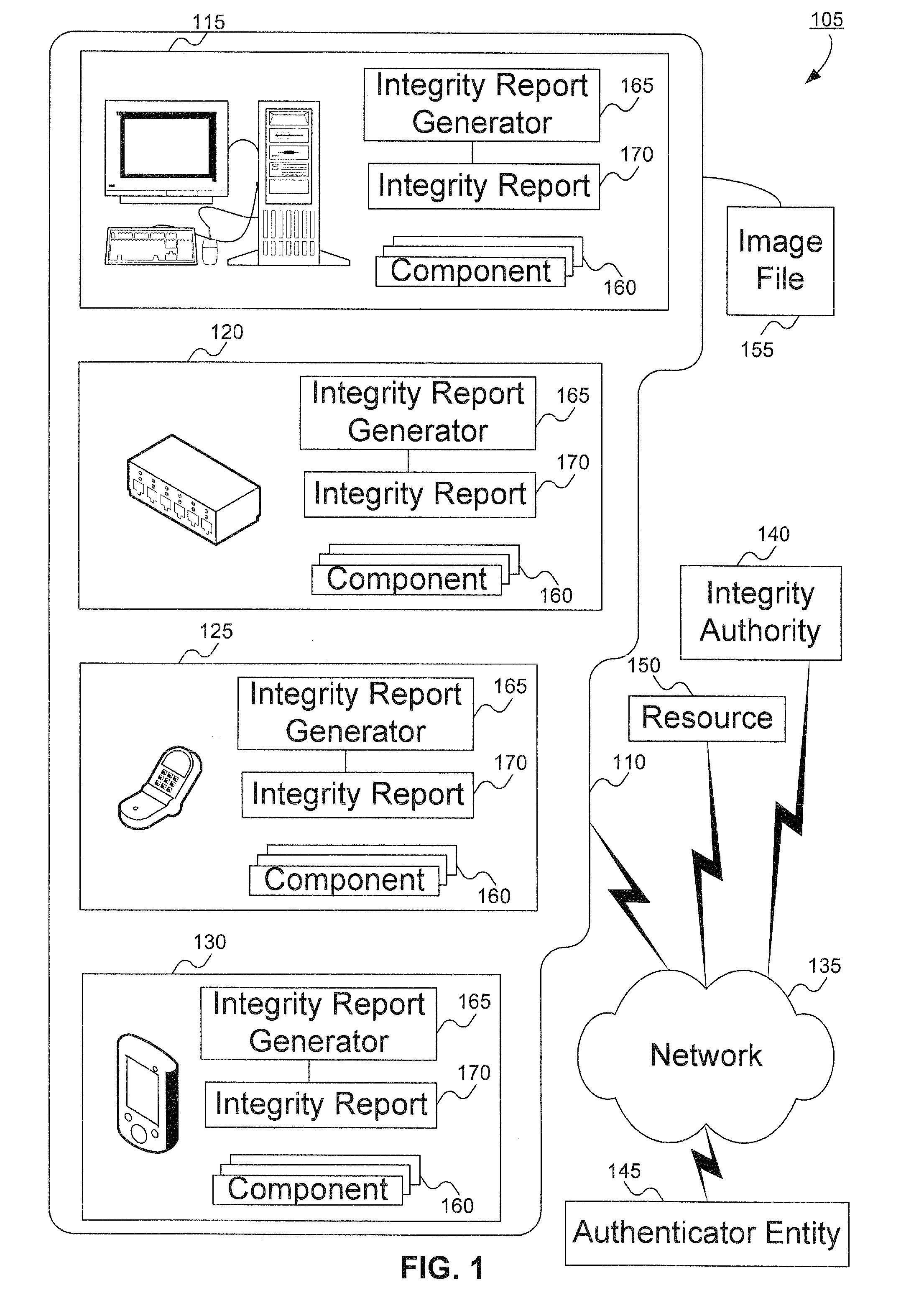
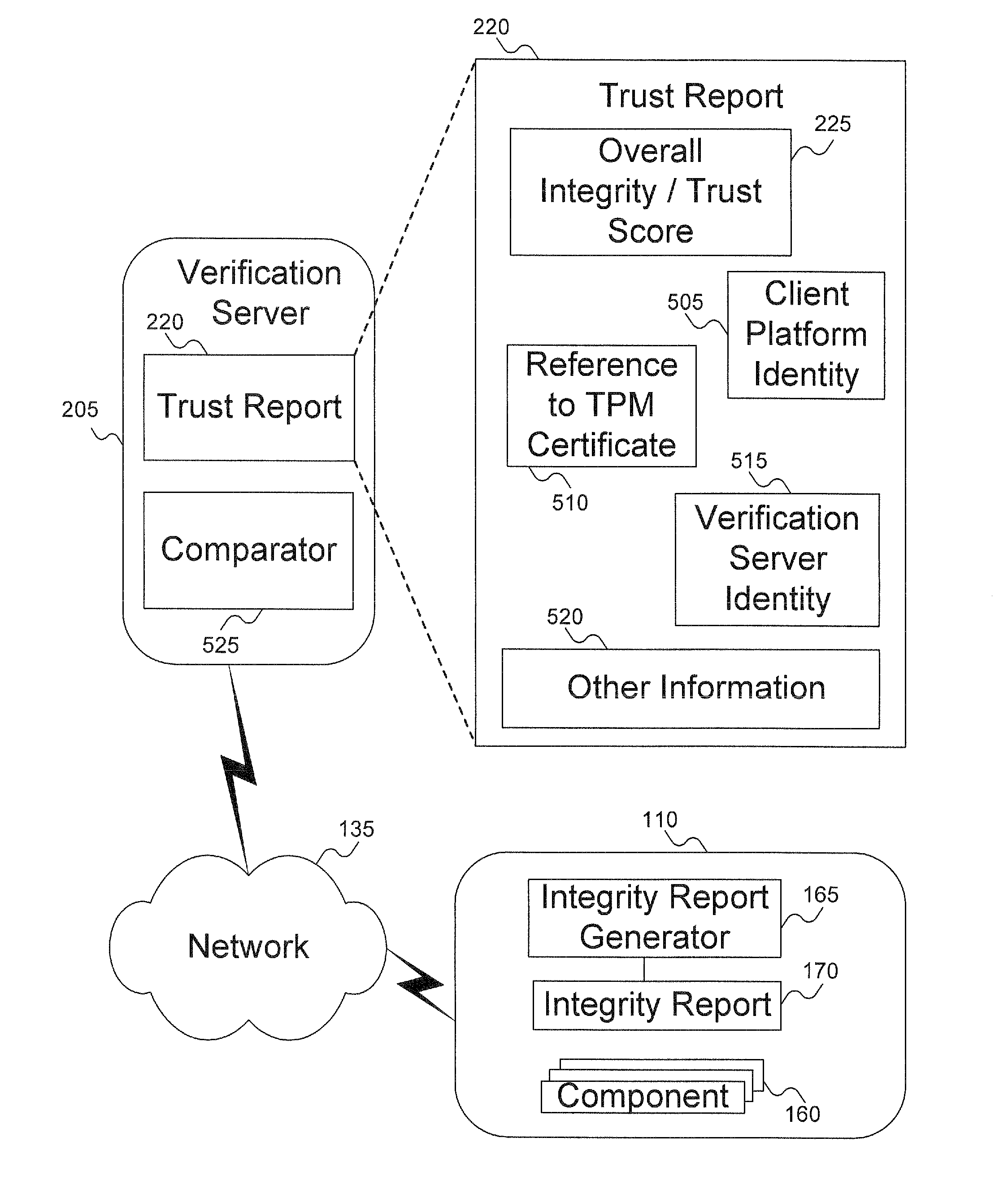
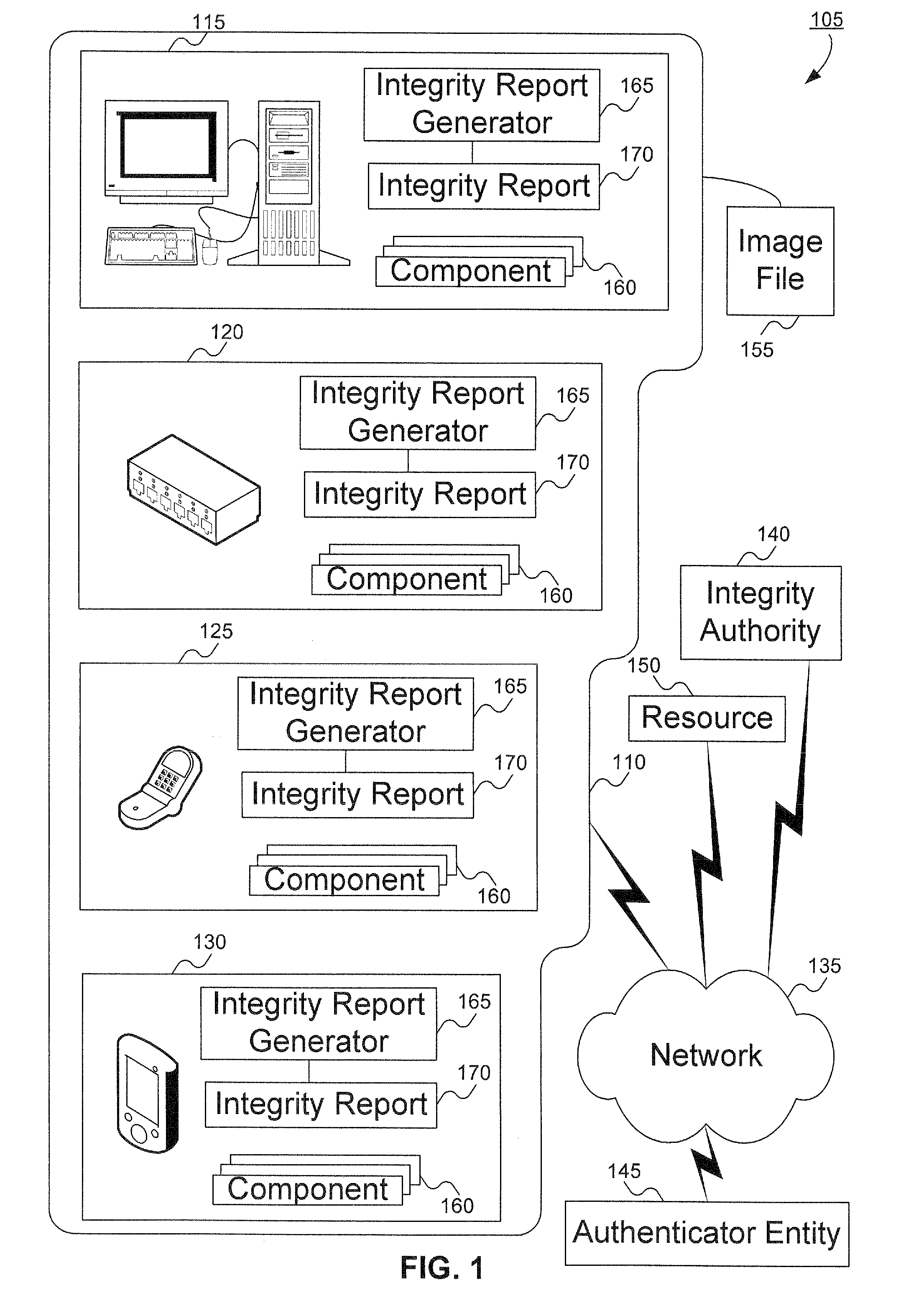
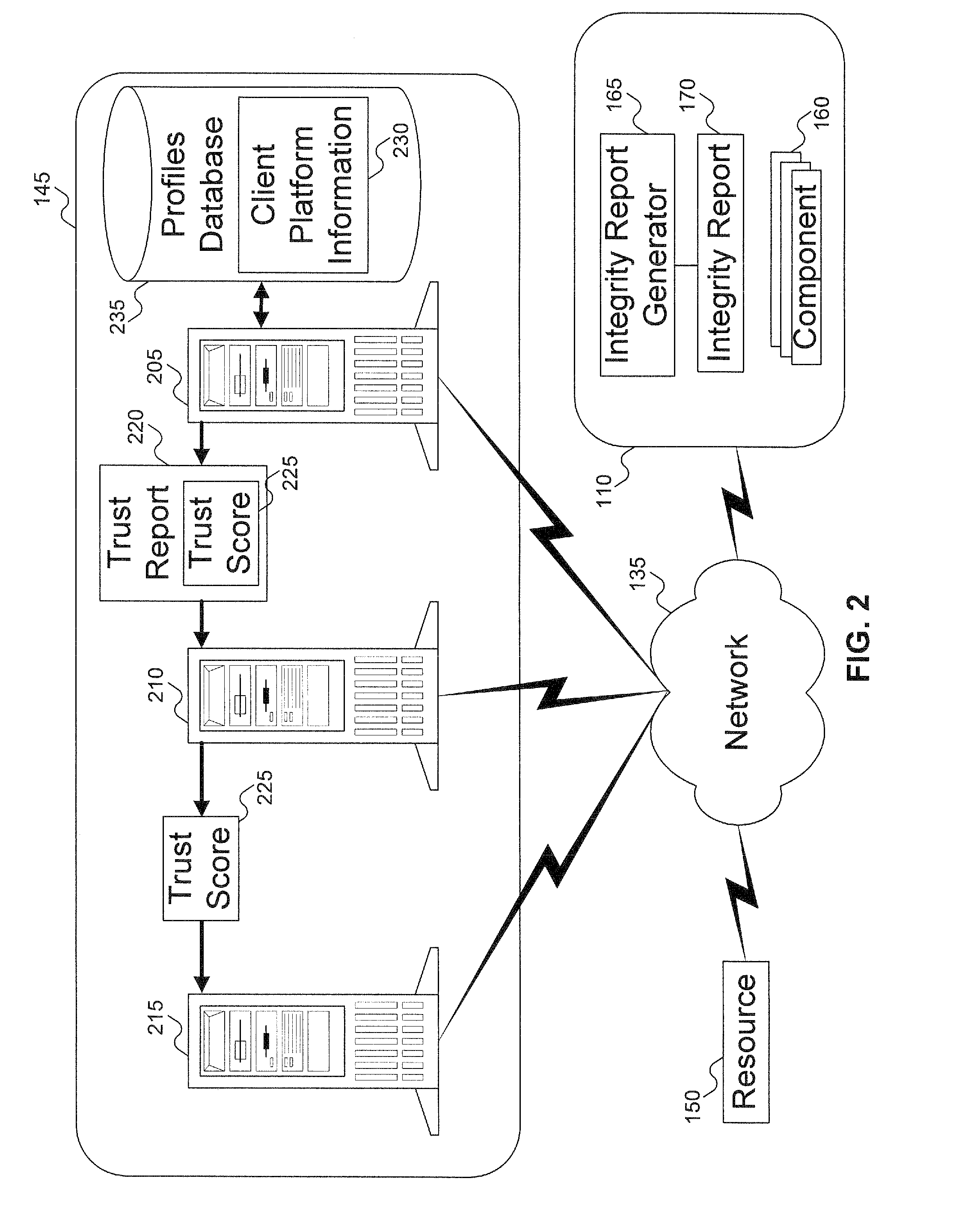
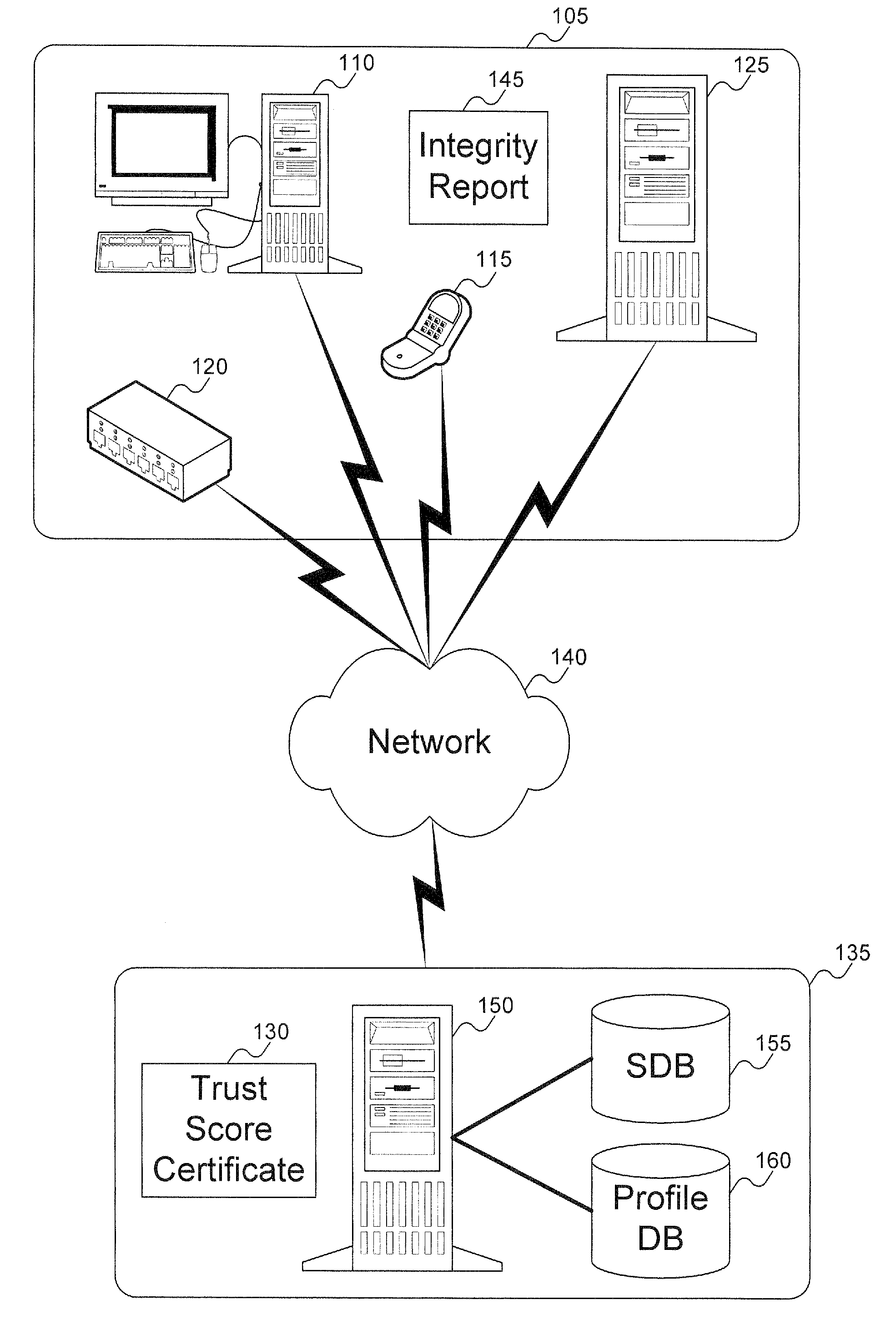
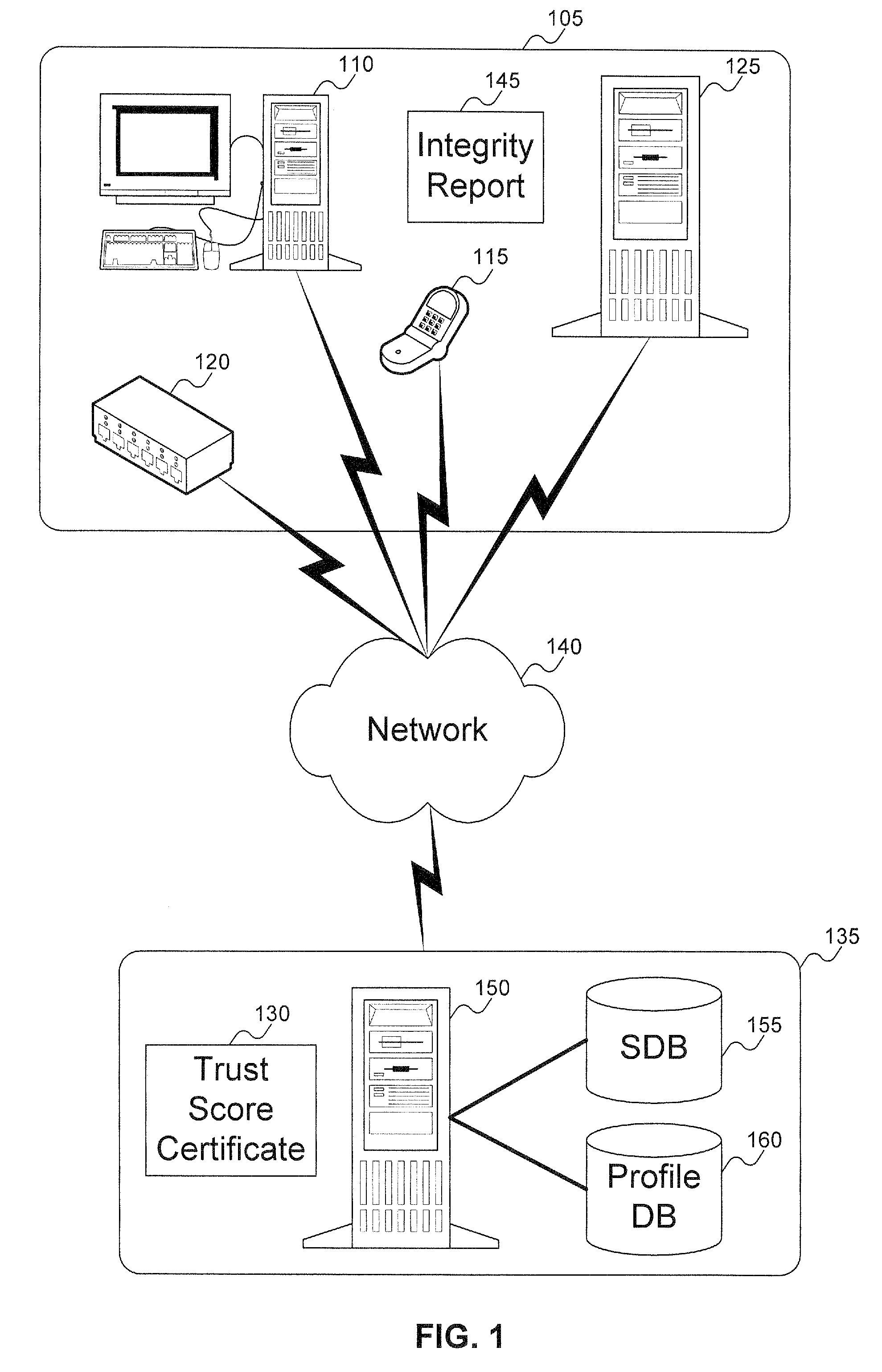
Method to verify the integrity of components on a trusted platform using integrity database services
InactiveUS20070143629A1Digital data processing detailsUser identity/authority verificationDatabase servicesClient-side
A client platform can be verified prior to being granted access to a resource or service on a network by validating individual hardware and software components of the client platform. Digests are generated for the components of the client platform. The digests can be collected into an integrity report. An authenticator entity receives the integrity report and compares the digests with digests stored in either a local signature database, a global signature database in an integrity authority, or both. Alternatively, the digests can be collected and stored on a portable digest-collector dongle. Once digests are either validated or invalidated, an overall integrity / trust score can be generated. She overall integrity / trust score can be used to determine whether the client platform should be granted access to the resource on the network using a policy.
Owner:SILICON VALLEY BANK +1
Signature based network intrusion detection system and method
Owner:MCAFEE LLC
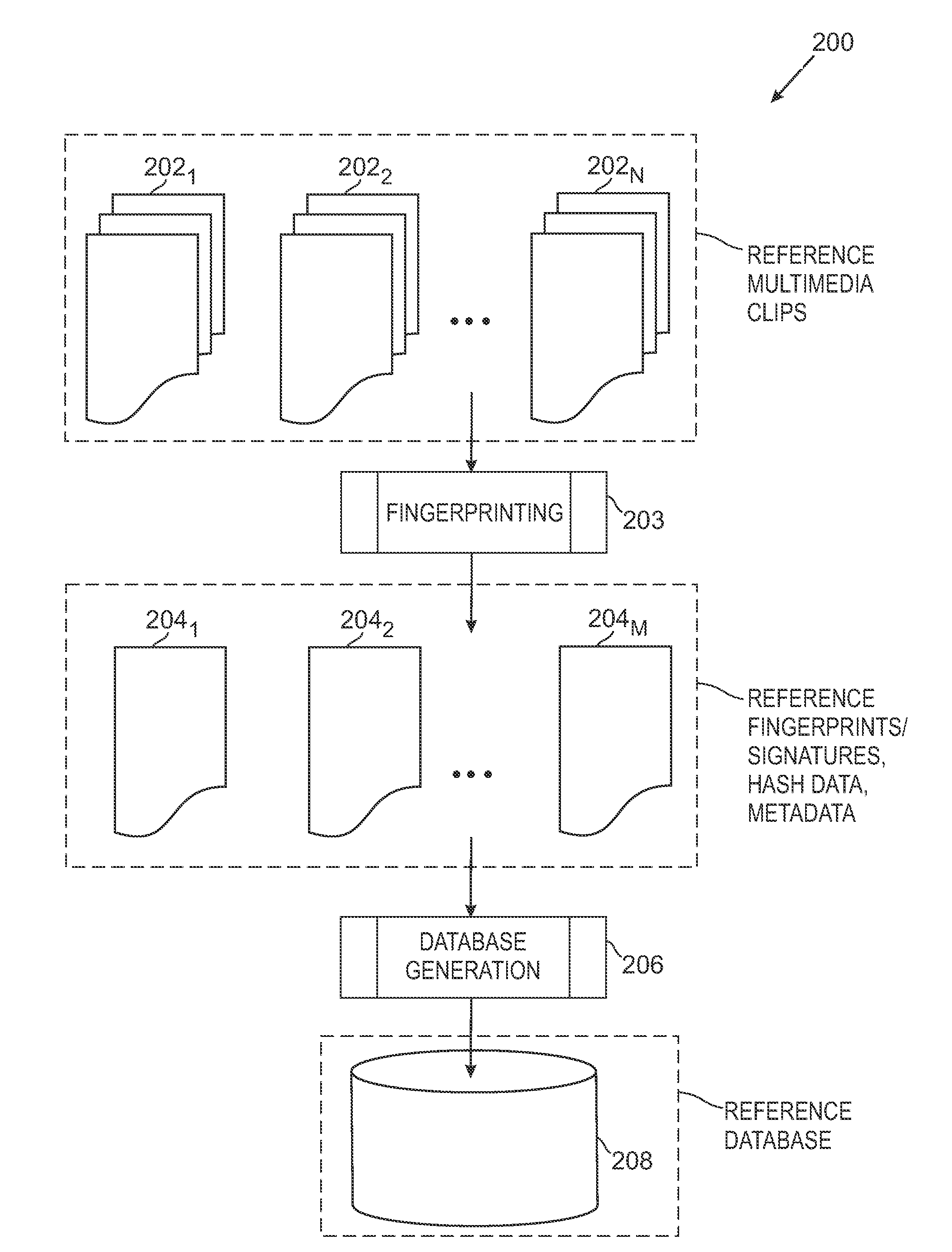
Media Fingerprinting and Identification System
ActiveUS20100318515A1Highly accurate in findingMany typesMultimedia data indexingData processing applicationsReference databaseNumerical descriptors
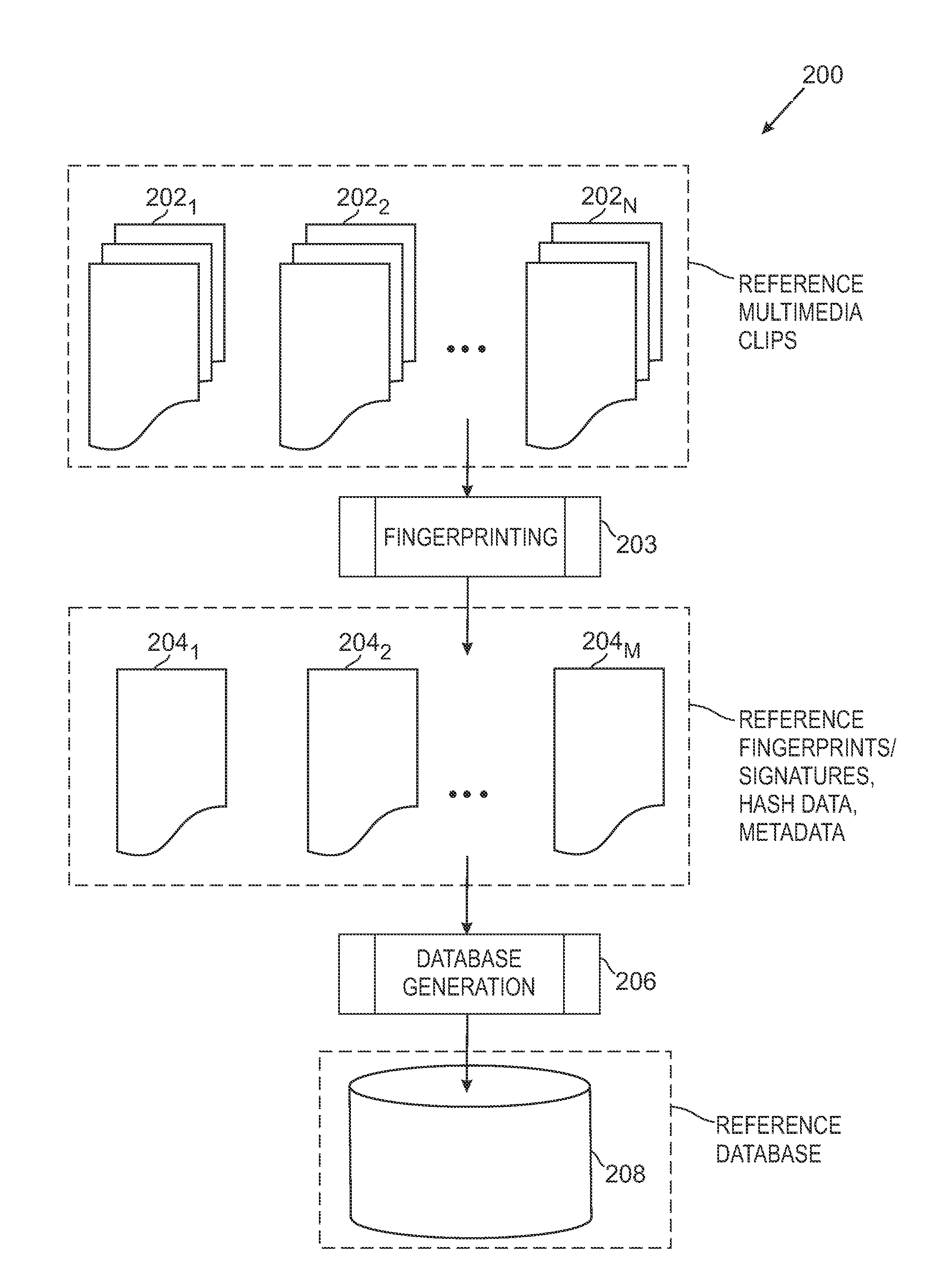
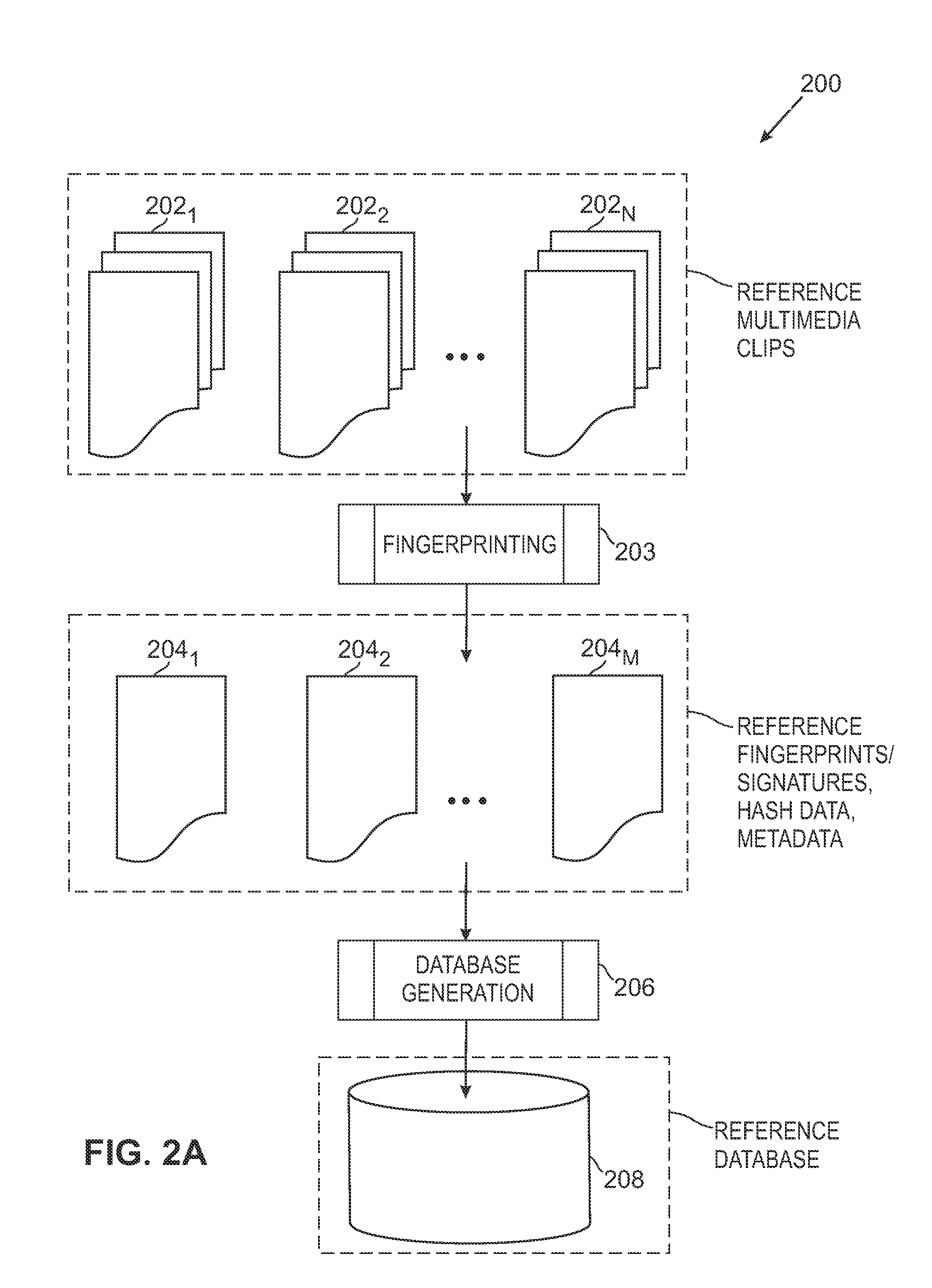
The overall architecture and details of a scalable video fingerprinting and identification system that is robust with respect to many classes of video distortions is described. In this system, a fingerprint for a piece of multimedia content is composed of a number of compact signatures, along with traversal hash signatures and associated metadata. Numerical descriptors are generated for features found in a multimedia clip, signatures are generated from these descriptors, and a reference signature database is constructed from these signatures. Query signatures are also generated for a query multimedia clip. These query signatures are searched against the reference database using a fast similarity search procedure, to produce a candidate list of matching signatures. This candidate list is further analyzed to find the most likely reference matches. Signature correlation is performed between the likely reference matches and the query clip to improve detection accuracy.
Owner:ROKU INCORPORATED
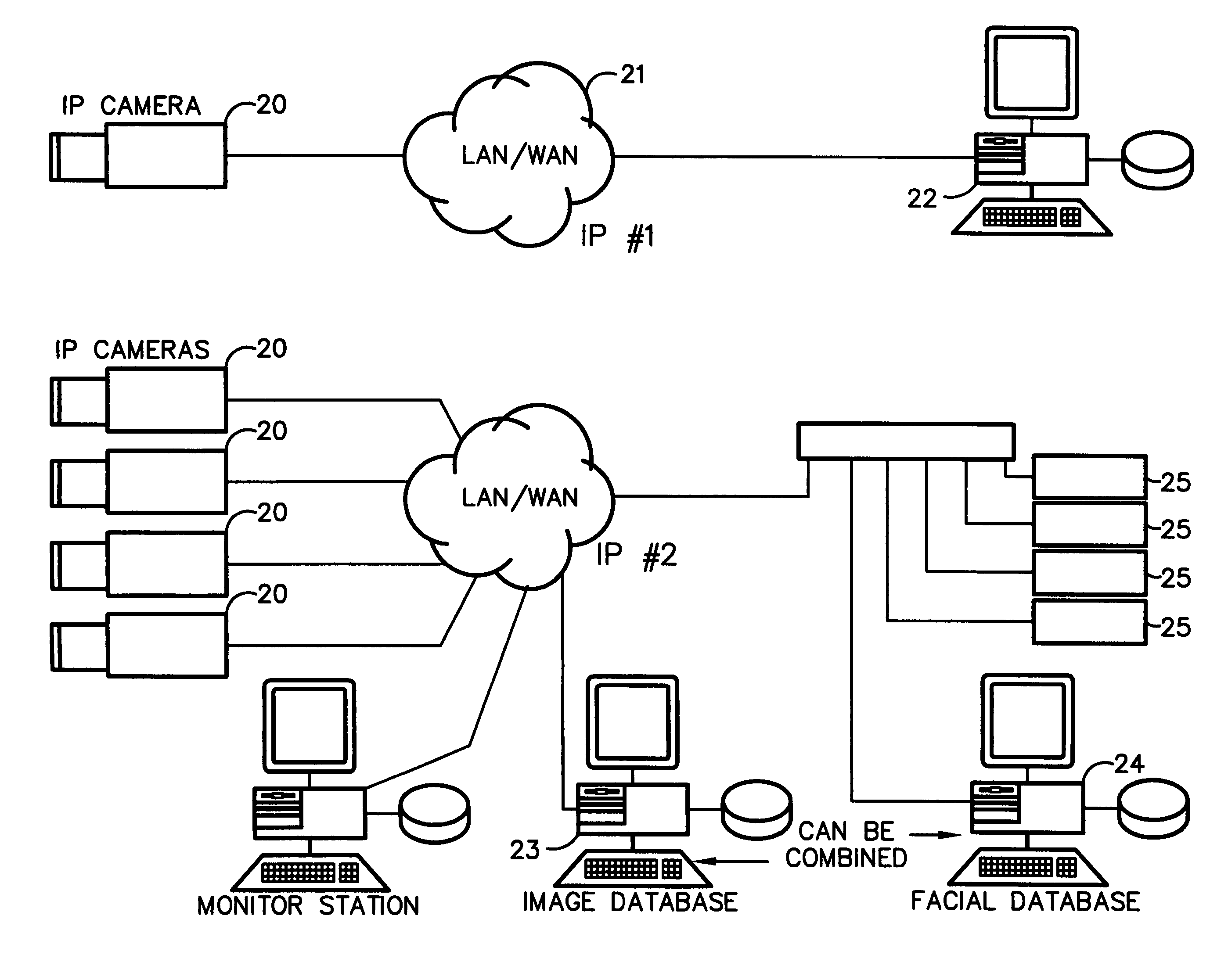
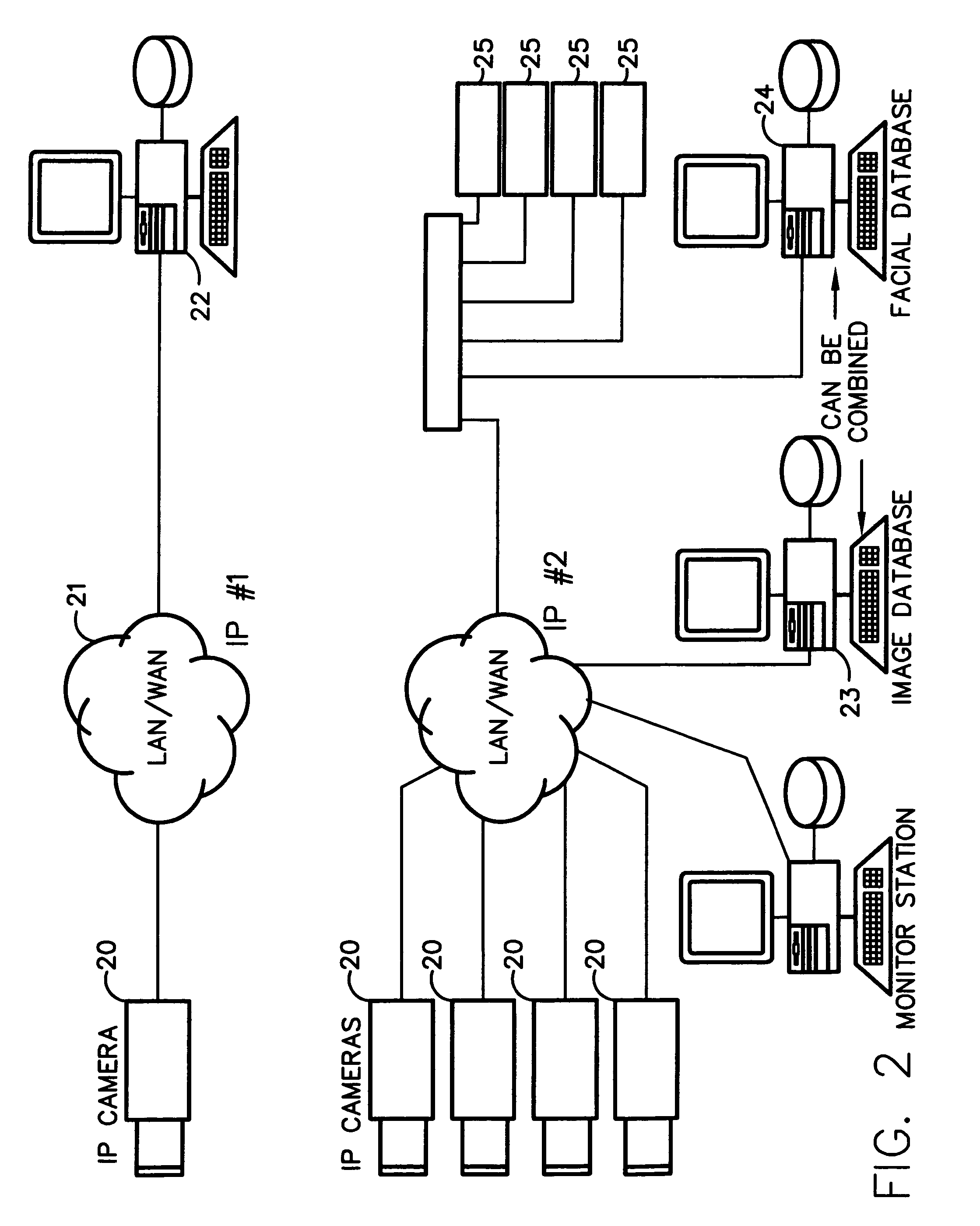
Method for incorporating facial recognition technology in a multimedia surveillance system
InactiveUS7634662B2Function increaseImprove economyChecking time patrolsCharacter and pattern recognitionSurveillance cameraRecognition algorithm
Embodiment provide a surveillance camera adapted to be connected to an internet protocol network, the surveillance camera including at least one facial processor, at least one facial recognition algorithm embodied in suitable media, at least one facial recognition algorithm executable with digital format image data by at least one facial processor detecting faces, execution of at least one facial recognition algorithm producing unique facial image data, execution of at least one facial separation algorithm producing facial separation data, at least one facial processor in communication with at least one facial signature database to obtain reference data, execution of at least one facial signature algorithm comparing facial separation data and reference data to identify correlations, at least one compression algorithm producing compressed image data, and a network stack configured to transmit to the network unique facial image data for each detected face and compressed image data.
Owner:PR NEWSWIRE
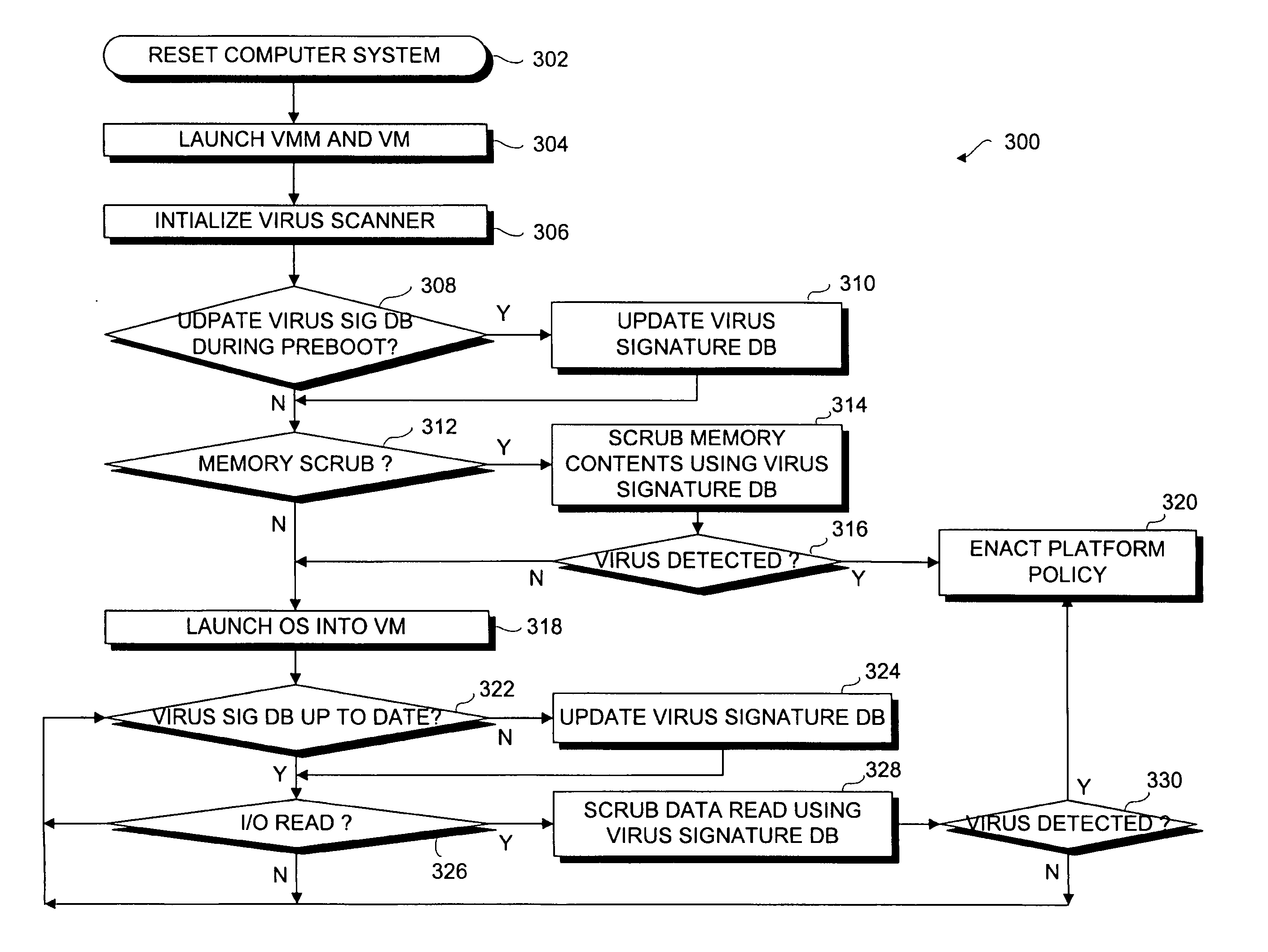
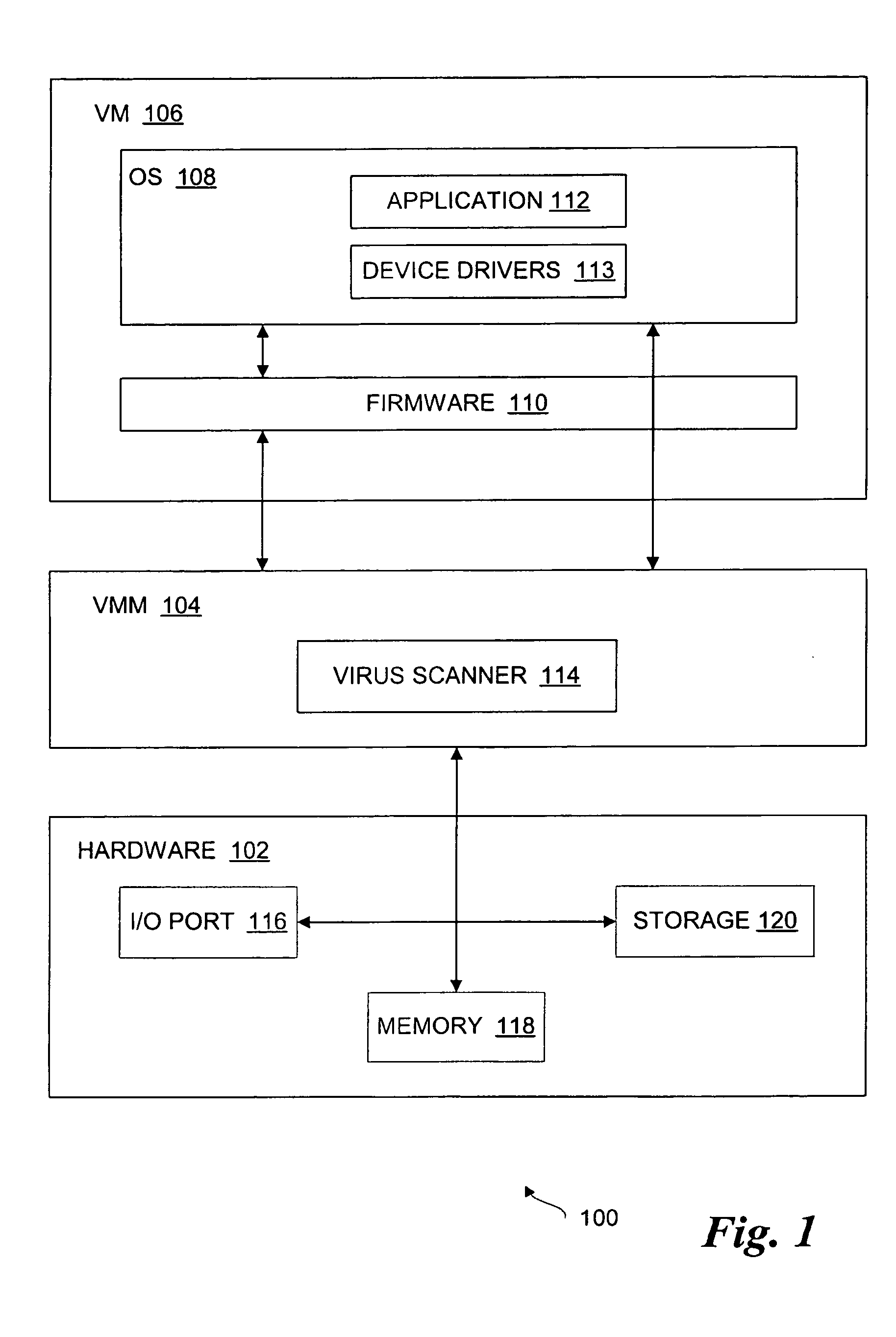
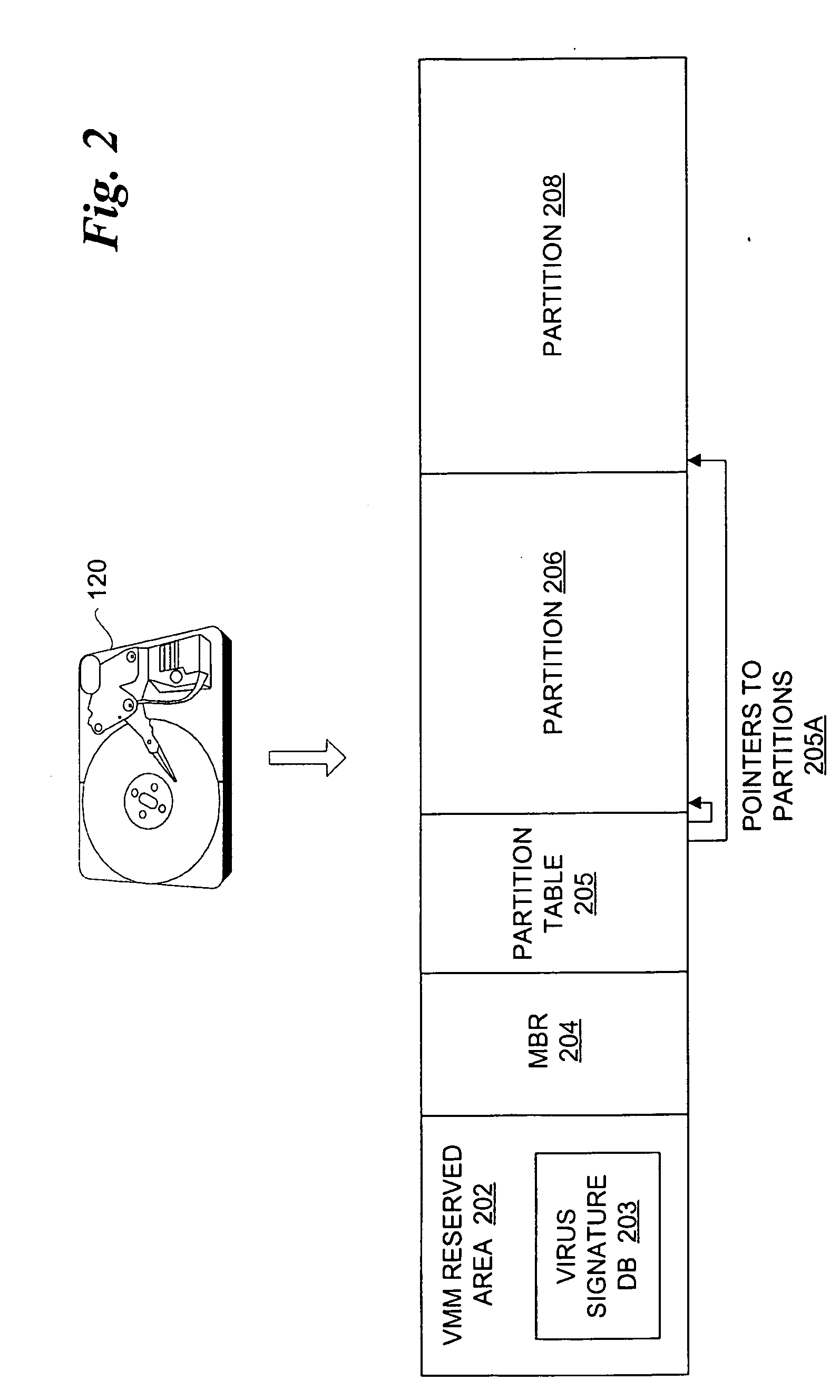
Virus scanning of input/output traffic of a computer system
InactiveUS20050216759A1Memory loss protectionError detection/correctionComputer engineeringInput/output
A method, system and article of manufacture to virus scan input / output (I / O) traffic of a computer system. A virus scanner is initialized during a pre-boot phase of a computer system. Data read from an input / output (I / O) device of the computer system is scrubbed by the virus scanner using a virus signature database before the data is loaded. A platform policy is enacted if a virus is detected in the data.
Owner:INTEL CORP
Media fingerprinting and identification system
ActiveUS8195689B2Multimedia data indexingData processing applicationsReference databaseNumerical descriptors
The overall architecture and details of a scalable video fingerprinting and identification system that is robust with respect to many classes of video distortions is described. In this system, a fingerprint for a piece of multimedia content is composed of a number of compact signatures, along with traversal hash signatures and associated metadata. Numerical descriptors are generated for features found in a multimedia clip, signatures are generated from these descriptors, and a reference signature database is constructed from these signatures. Query signatures are also generated for a query multimedia clip. These query signatures are searched against the reference database using a fast similarity search procedure, to produce a candidate list of matching signatures. This candidate list is further analyzed to find the most likely reference matches. Signature correlation is performed between the likely reference matches and the query clip to improve detection accuracy.
Owner:ROKU INCORPORATED
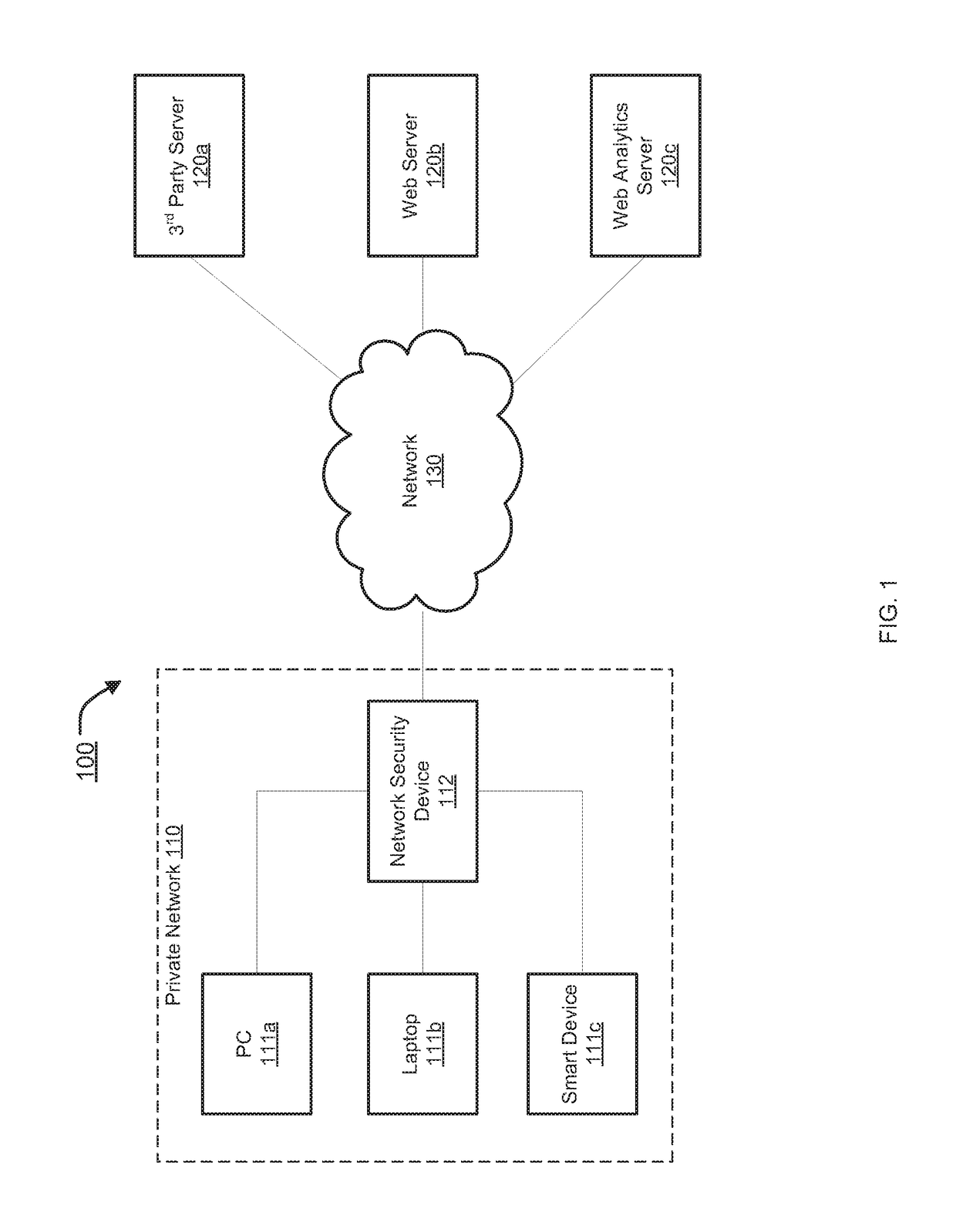
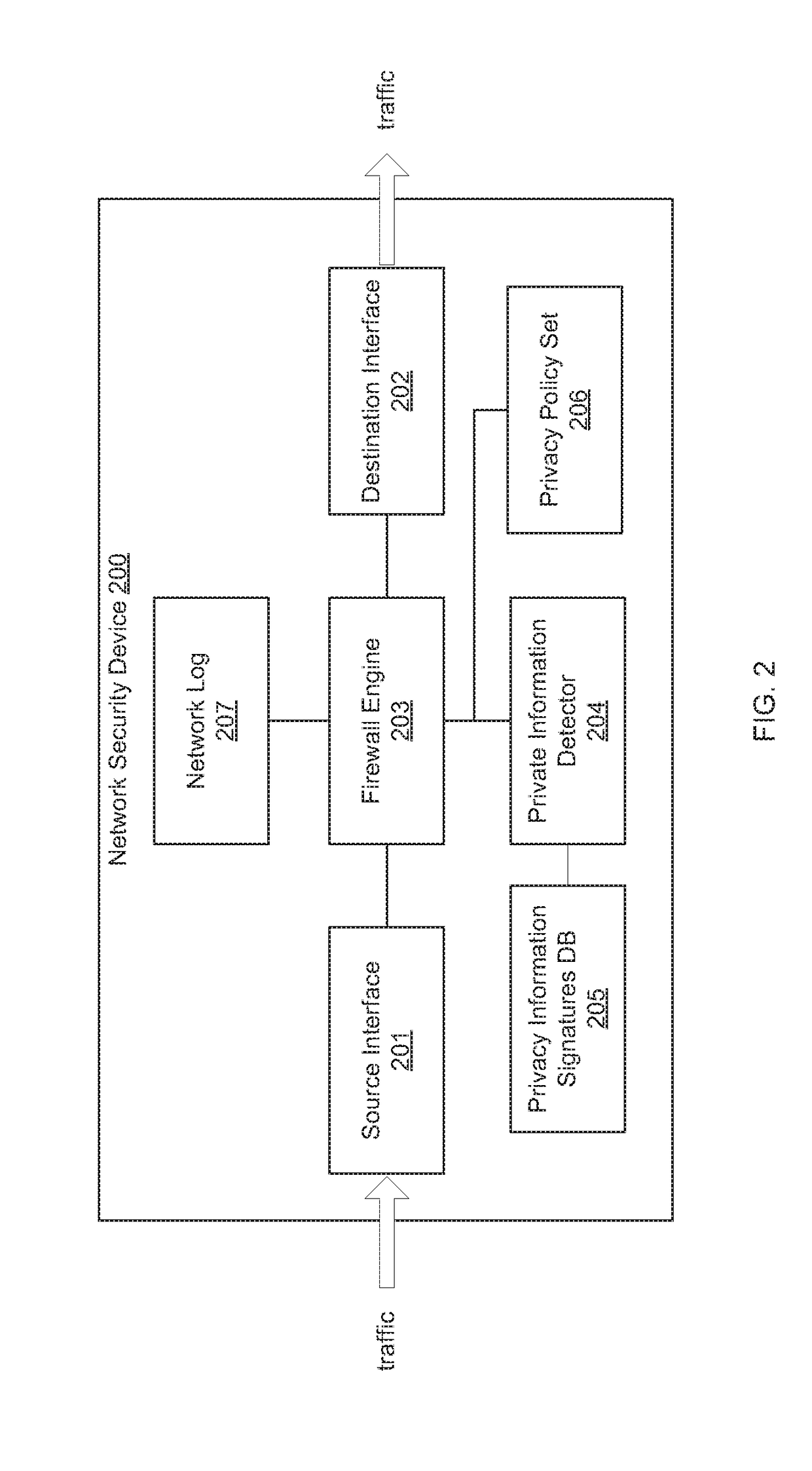
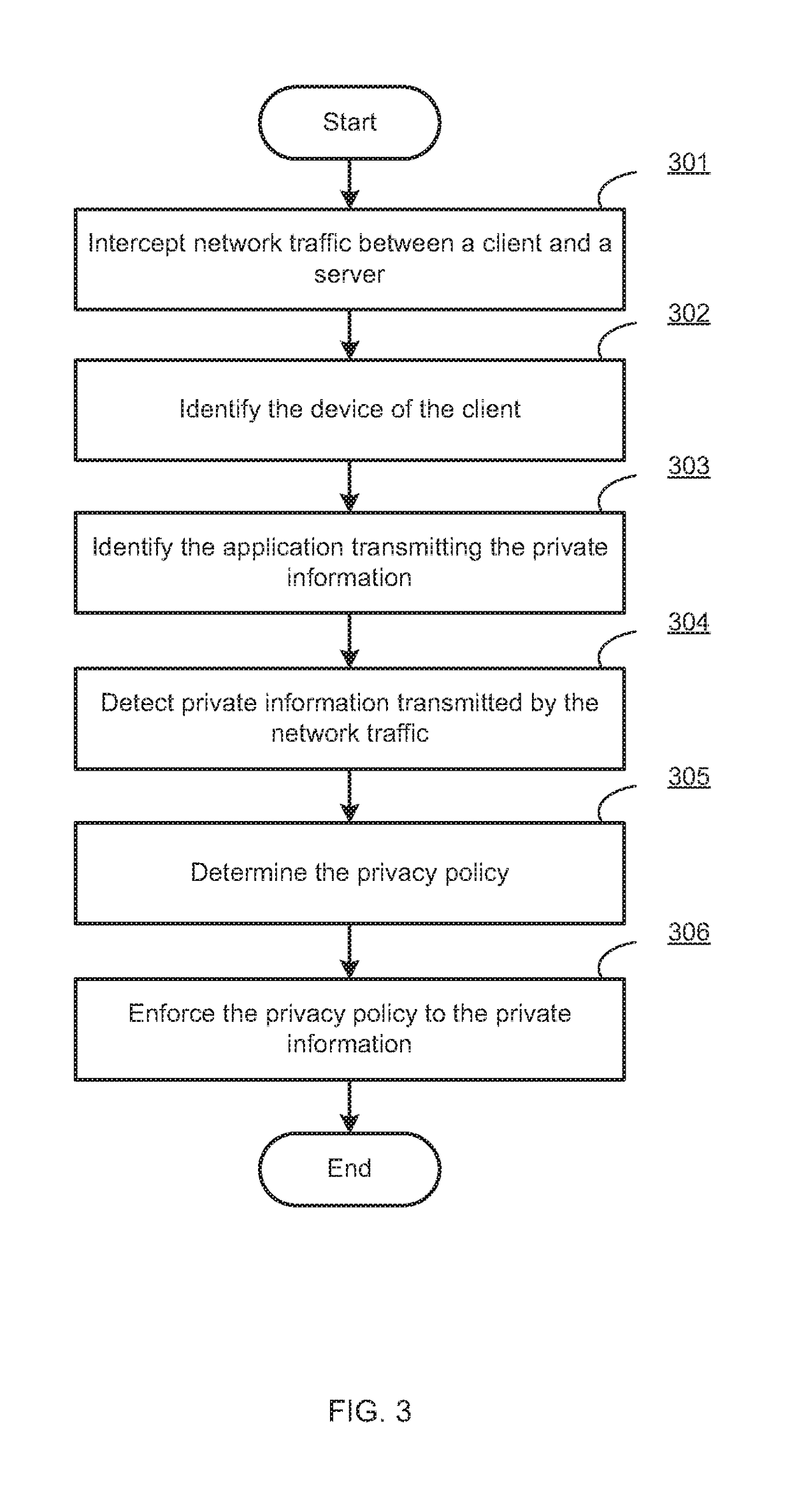
Centralized management and enforcement of online privacy policies
Systems and methods for centralized management and enforcement of online privacy policies of a private network are provided. According to one embodiment, existence of private information contained in a data packet originated by a client device of a private network and destined for a server device external to the private network is identified by a network security device protecting the private network by scanning the data packet for information matching a signature contained within a private information signature database. An online privacy policy of the private network is determined by the network security device that is applicable to the private information with reference to a privacy policy set defined by an administrator of the private network. The online privacy policy is enforced by the network security device on the data packet by performing one or more actions specified by the online privacy policy to the data packet.
Owner:FORTINET
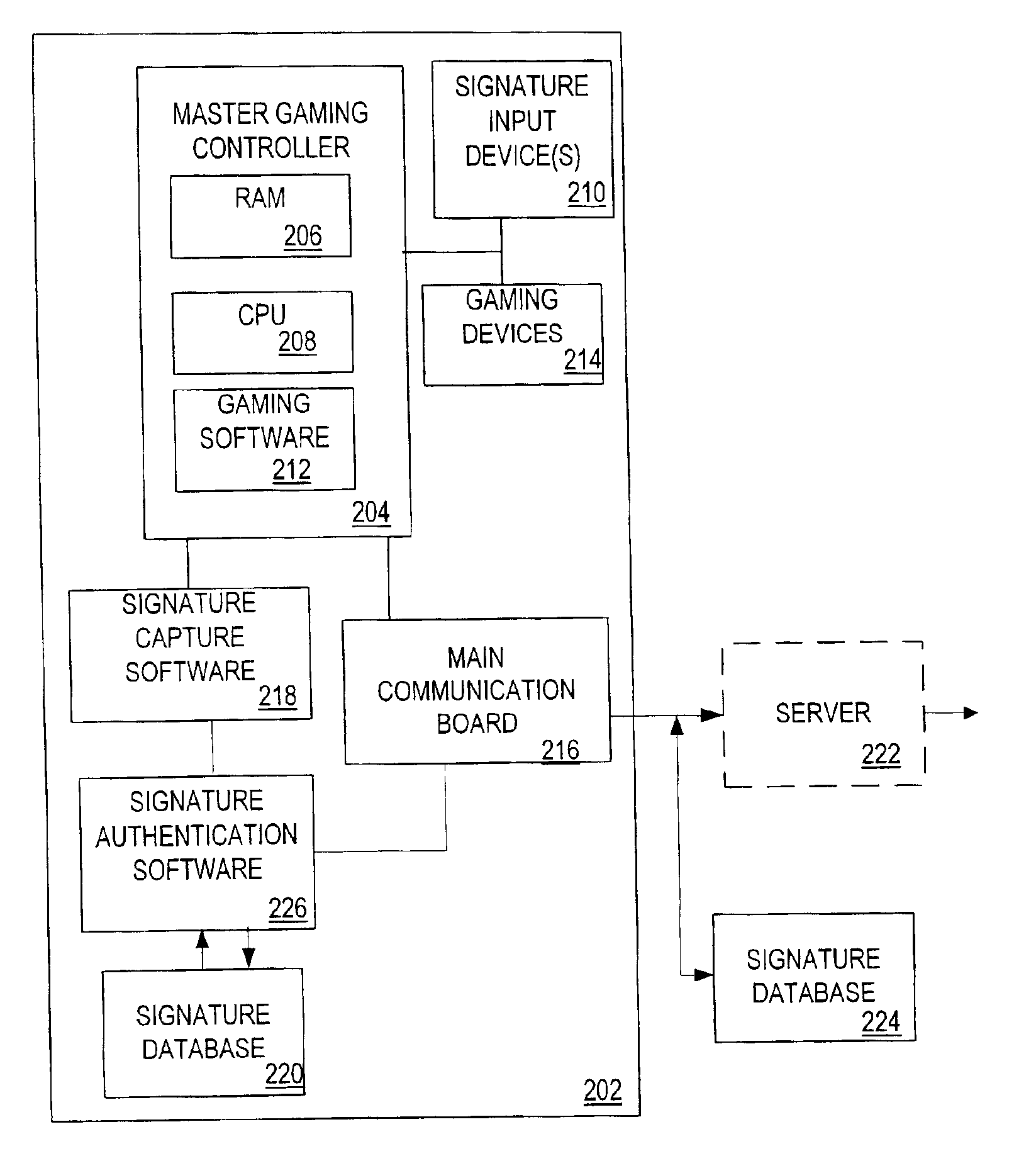
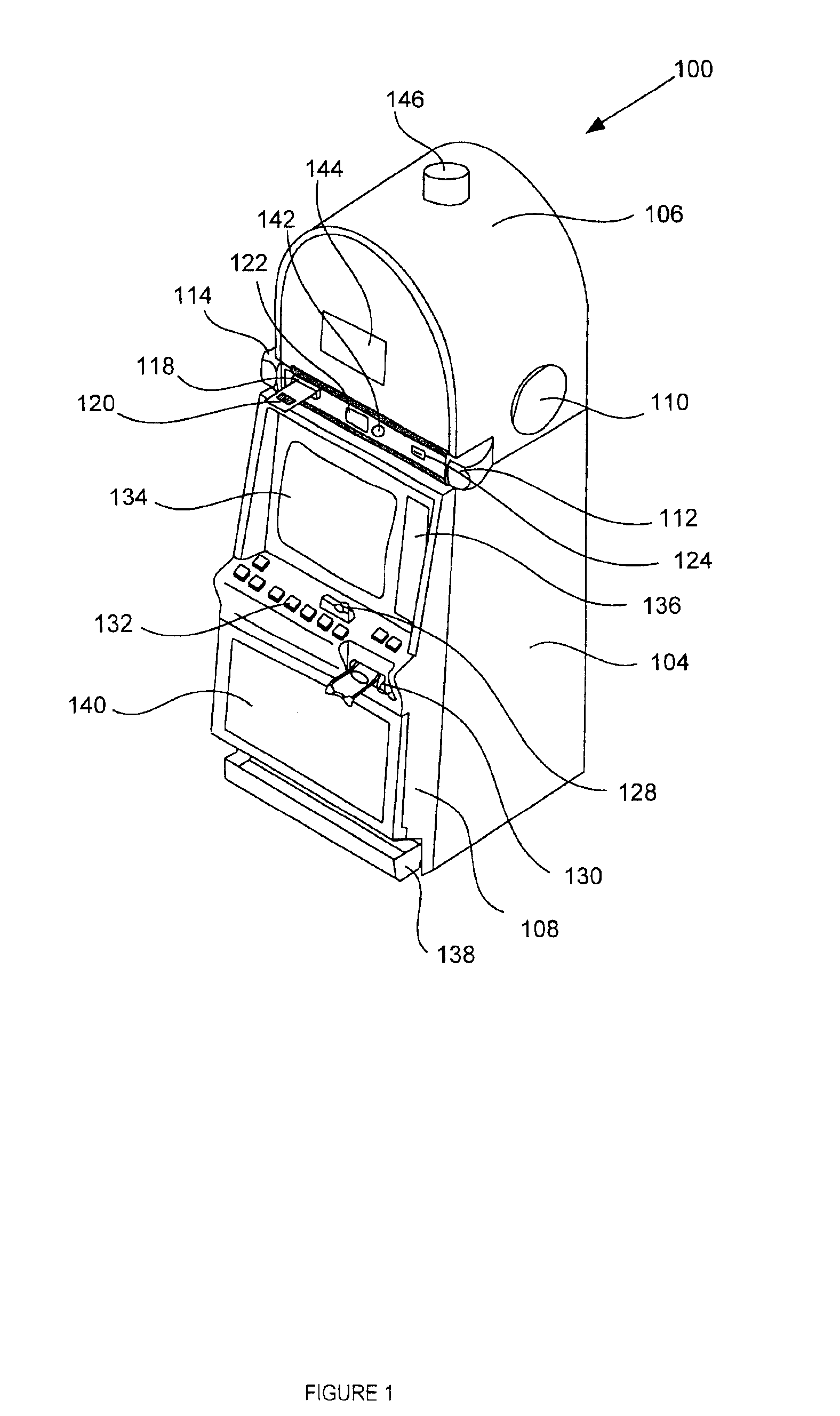
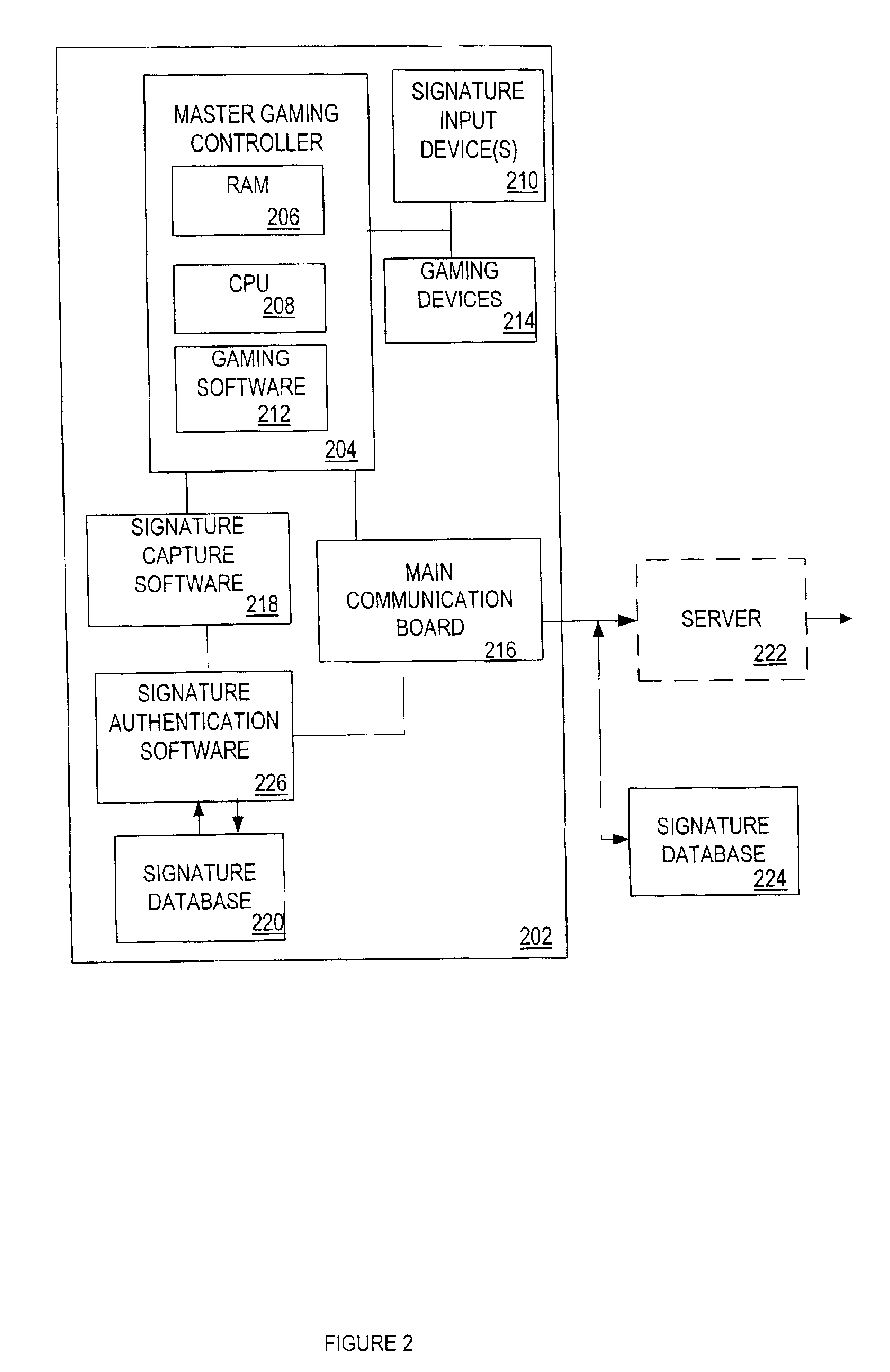
Electronic signature capability in a gaming machine
InactiveUS6935951B2Apparatus for meter-controlled dispensingVideo gamesElectronic signatureAuthentication
A disclosed gaming machine provides electronic signature capability to enable signature transactions to be effected from the gaming machine. The gaming machine utilizes electronic signature capture and authentication software in conjunction with an electronic signature database to authenticate an electronic signature input on the gaming machine. The authentication software may be co-located with the electronic signature capture software on the gaming machine or may be remotely located from the electronic signature capture software. The electronic signature database may be co-located with either or both the electronic signature capture software and authentication software or may be remotely located from either or both.
Owner:IGT
Mobile marketing system
InactiveUS20030144873A1Simple to setup and operateLow costMarketingSpecial data processing applicationsAuto-configurationData management
A mobile marketing system is comprised of a remote access subsystem and support center subsystem. An initial contact data collection module is operationally connected to the remote access system and to a database for storing the contact data. A data management module is connected to the database for managing contact follow-up. A correspondence content manager and sequencer is connected to the database for purposes of automatically configuring user collection modules dynamically. A user data, preferences and signature database is linked to the data management module. A ROI module and a sales quote and configuration module are connected to the database for preparing ROI modeling and quotes for a prospect. A print module connected to the data management module to provide fulfillment through local and remote support center subsystems.
Owner:SALES AUTOMATION SUPPORT
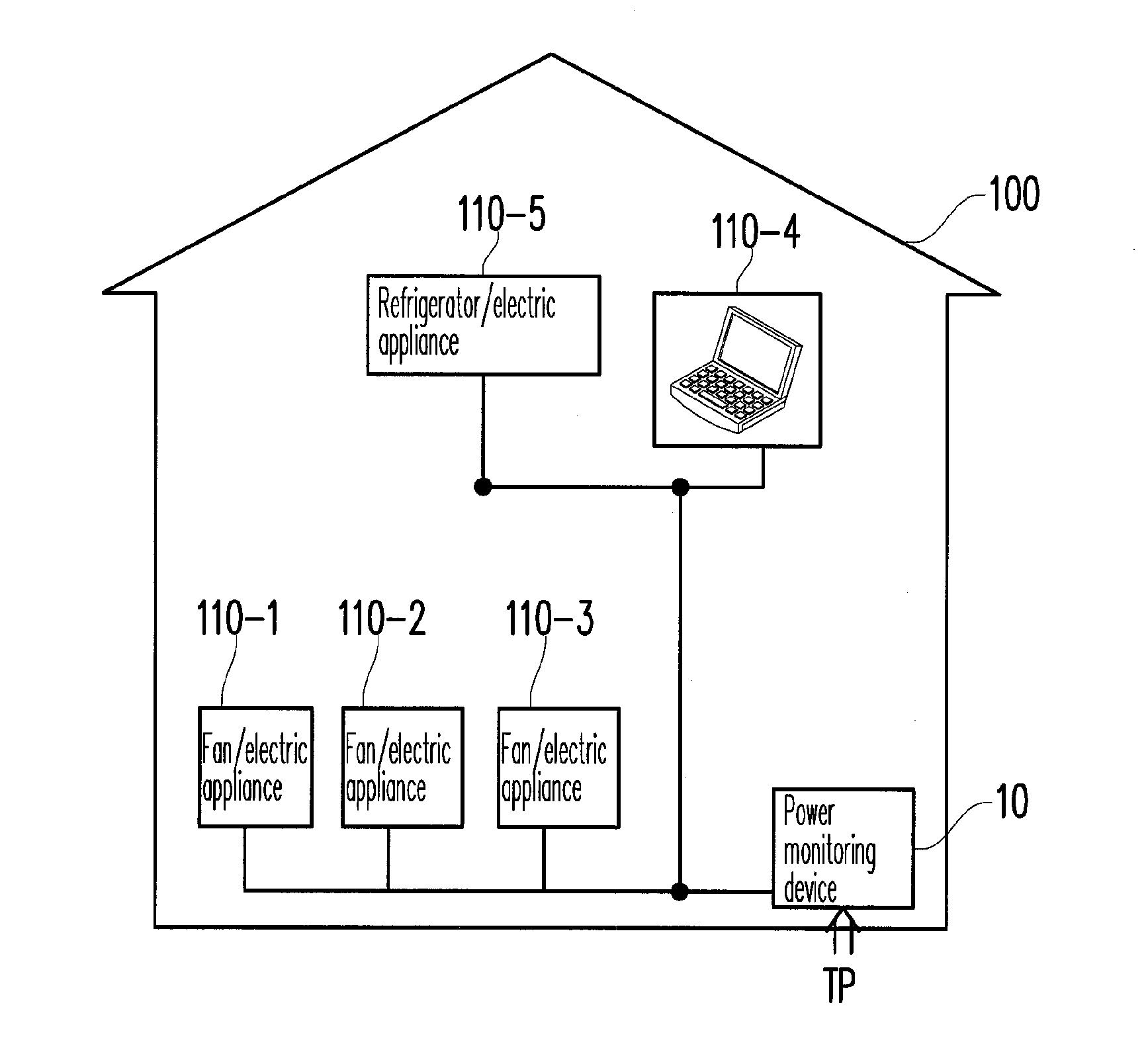
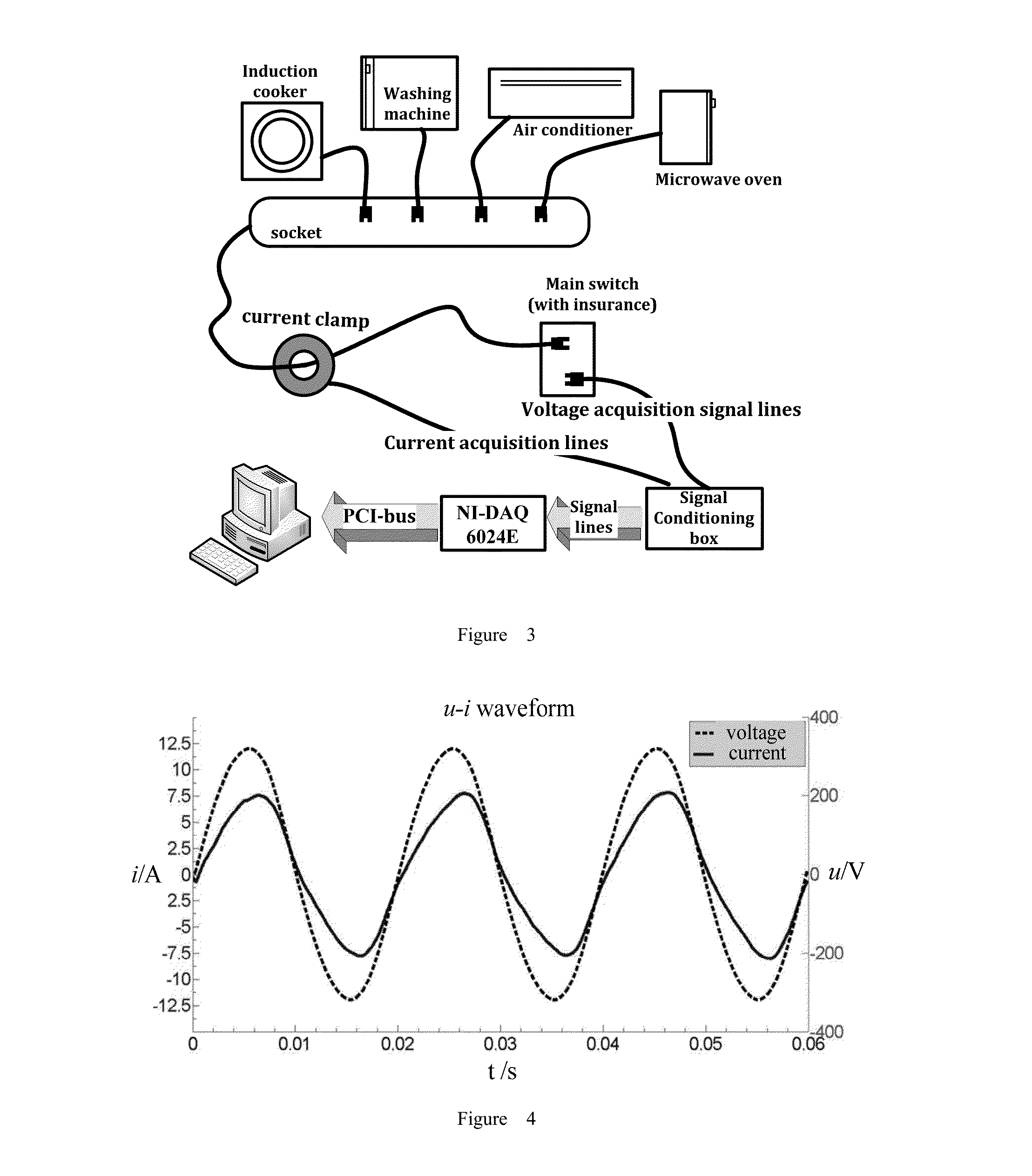
Power monitoring device for identifying state of electric appliance and power monitoring method thereof
ActiveUS20120004871A1Understand efficiencyUnderstand power consumption causeElectric devicesCurrent/voltage measurementEmbedded systemElectric power
A power monitoring device for identifying the state of an electric appliance based on user feedbacks and a power monitoring method thereof are provided. The power monitoring device includes a measurement module, a variation detection and search module, and an electric appliance signature database established based on user feedbacks. When the measurement module detects a variation of a power consumption feature, the variation detection and search module searches the electric appliance signature database according to the variation to obtain electric appliances similar to the variation and the states thereof. A user contributes data to the electric appliance signature database by confirming the search result, or selecting the correct electric appliance and the state thereof. When the user confirms the search result, the power monitoring device establishes an association between the electric appliance and its electric appliance signatures and updates the electric appliance signature database.
Owner:WISTRON NEWEB
Acoustic Sound Signature Detection Based on Sparse Features
ActiveUS20150063575A1Digital data information retrievalElectrical apparatusSignature detectionAnalog signal
A low power sound recognition sensor is configured to receive an analog signal that may contain a signature sound. Sparse sound parameter information is extracted from the analog signal. The extracted sparse sound parameter information is processed using a sound signature database stored in the sound recognition sensor to identify sounds or speech contained in the analog signal, wherein the sound signature database comprises a plurality of sound signatures each representing an entire word or multiword phrase.
Owner:TEXAS INSTR INC
Authenticity Verification
InactiveUS20060294583A1Enhanced advantageTouting of the ticket by resale could be preventedPaper-money testing devicesDigital data processing detailsComputer securitySignature database
A method for authenticity verification. The method can comprise conducting a transaction between first and second parties, the parties being respectively located at first and second locations remote one-another, the outcome of the transaction being the provision by the first party to the second party of the right to an entitlement token. Following the transaction outcome, data describing a written format for the entitlement token can be transmitted from the first party to the second party. The entitlement token can be written at the second location using the data describing the written format. The method can further comprise creating a first signature for the written entitlement token at the second location, the signature being based upon an intrinsic property of the written entitlement token, and storing the first signature in a signature database. Further, the method can comprise creating a second signature for the written entitlement token at a third location remote from the second location, the second signature being based upon the intrinsic property of the written entitlement token; and comparing attributes of the second signature with attributes of the first stored in the database to verify the authenticity of the written entitlement token.
Owner:INGENIA HLDG LTD
Document de-registration
ActiveUS20050132198A1Memory loss protectionError detection/correctionPaper documentDocument preparation
A document accessible over a network can be registered. A registered document, and the content contained therein, cannot be transmitted undetected over and off of the network. In one embodiment, the invention includes maintaining a plurality of stored signatures in a signature database, each signature being associated with one of a plurality of registered documents. In one embodiment, the invention further includes maintaining the signature database by de-registering documents by removing the signatures associated with de-registered documents. In one embodiment, the invention further includes maintaining the database by removing redundant and high detection rate signatures. In one embodiment, the invention also includes maintaining the signature database by removing signatures based on the source text used to generate the signature.
Owner:MCAFEE LLC
Detecting method and architecture thereof for malicious codes
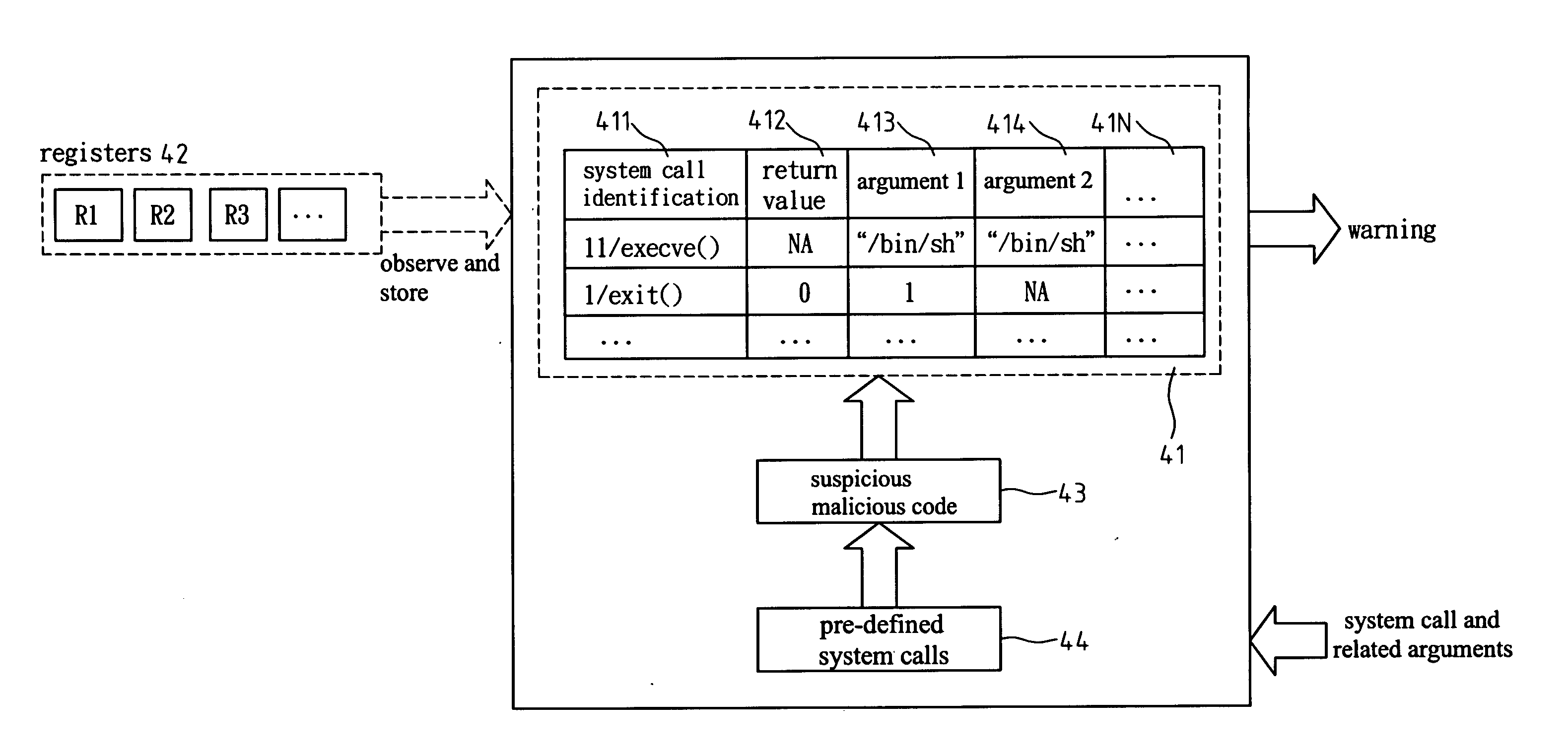
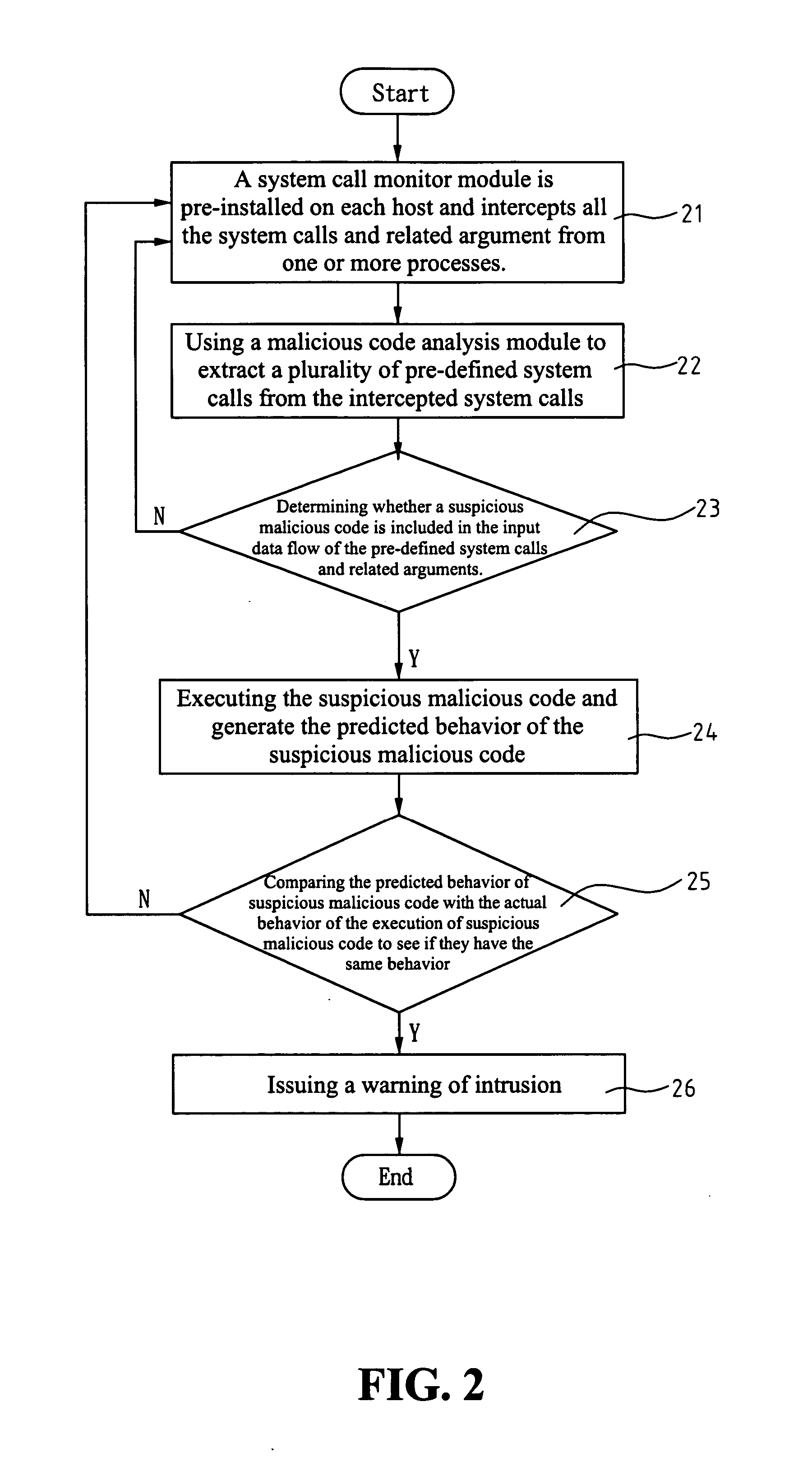
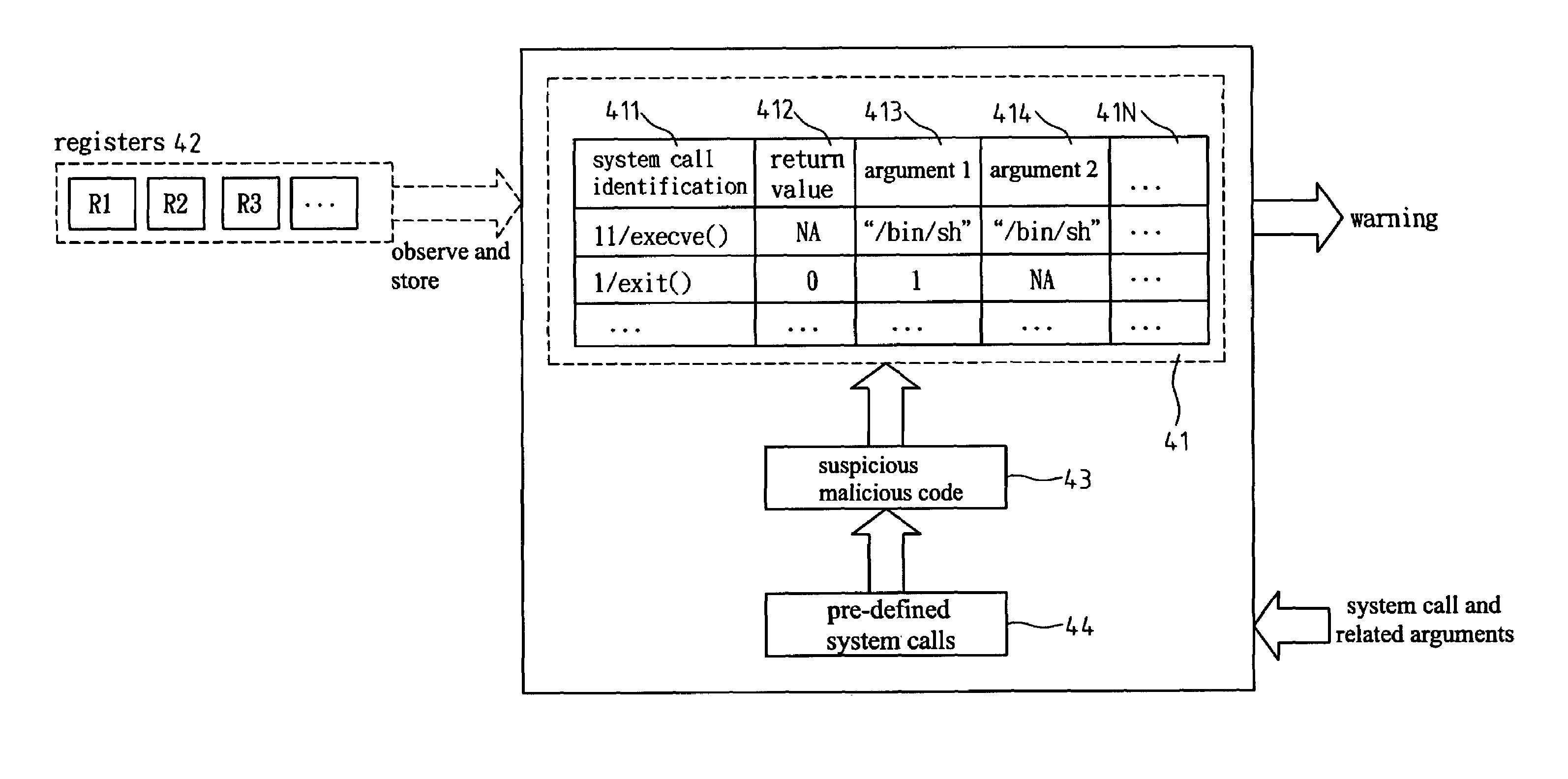
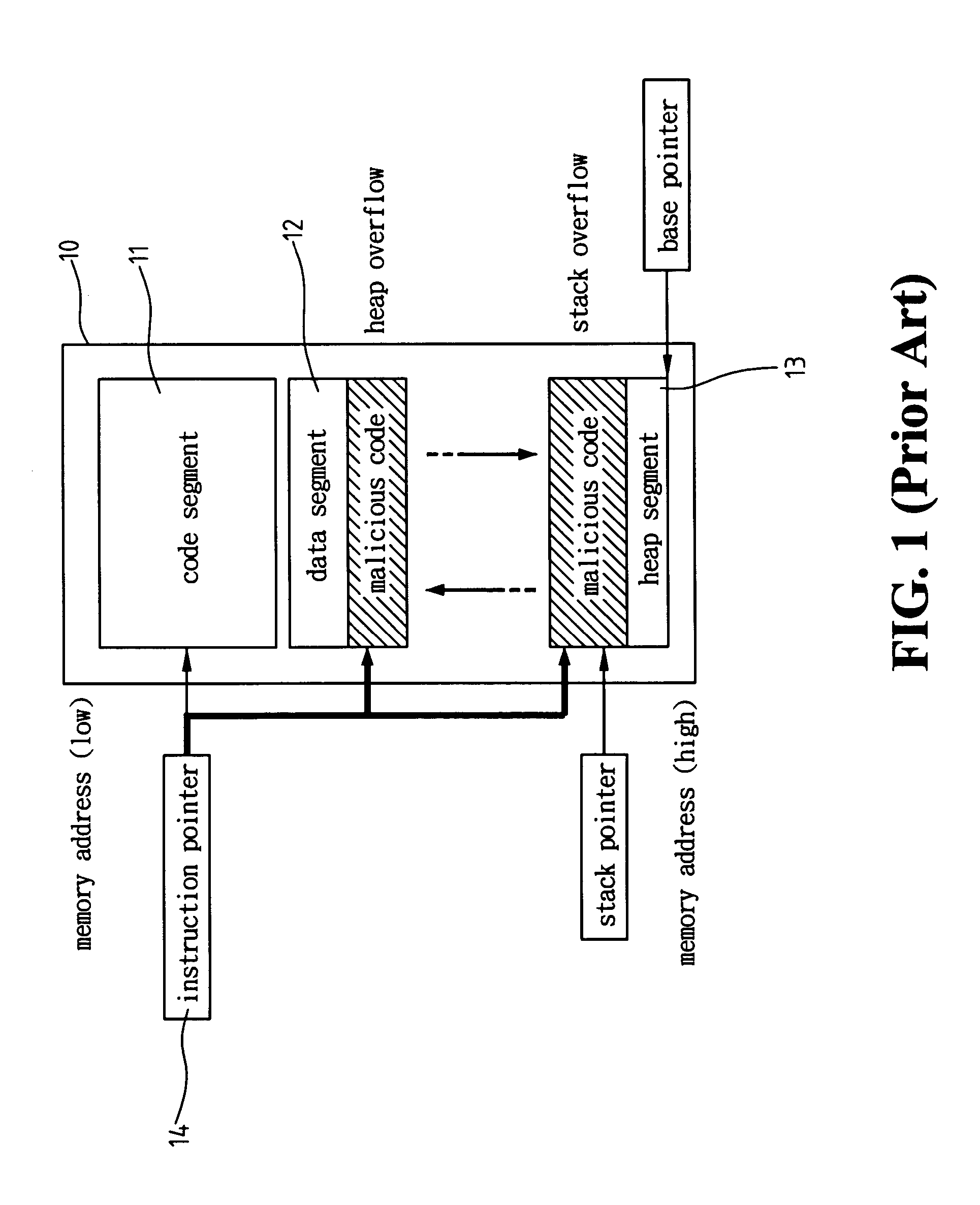
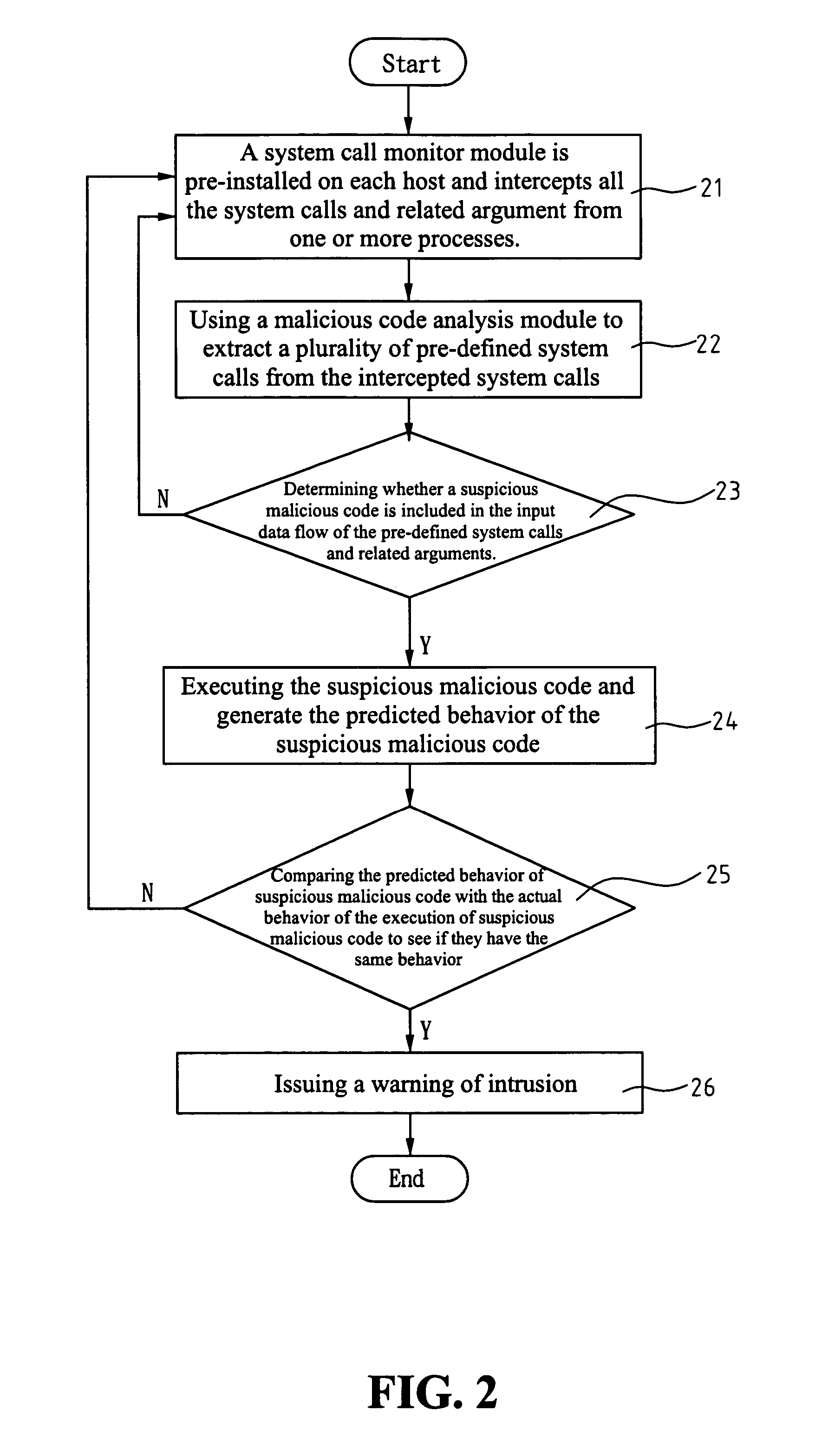
ActiveUS20060143707A1Overcomes drawbackMemory loss protectionError detection/correctionSystem callComputer science
A detecting method and architecture thereof for malicious codes is provided, which is applicable to a computer system having at least a host. Each host executes at least a process. The method is implemented with a system call interposition module and an analysis module for malicious codes. The system call module intercepts all system calls of process calls and all related arguments of the system calls. The analysis module for malicious codes analyzes the input data of pre-determined system calls, and executes the suspicious malicious codes. Once the same behaviors between the analysis module and the suspicious malicious codes are found, a system-intrusion warning is immediately triggered. The method is not required to maintain huge signature databases, and can detect unknown attack-skills in a manner of high correct rate and low incorrect ruling.
Owner:A10 NETWORKS
Detection of scripting-language-based exploits using parse tree transformation
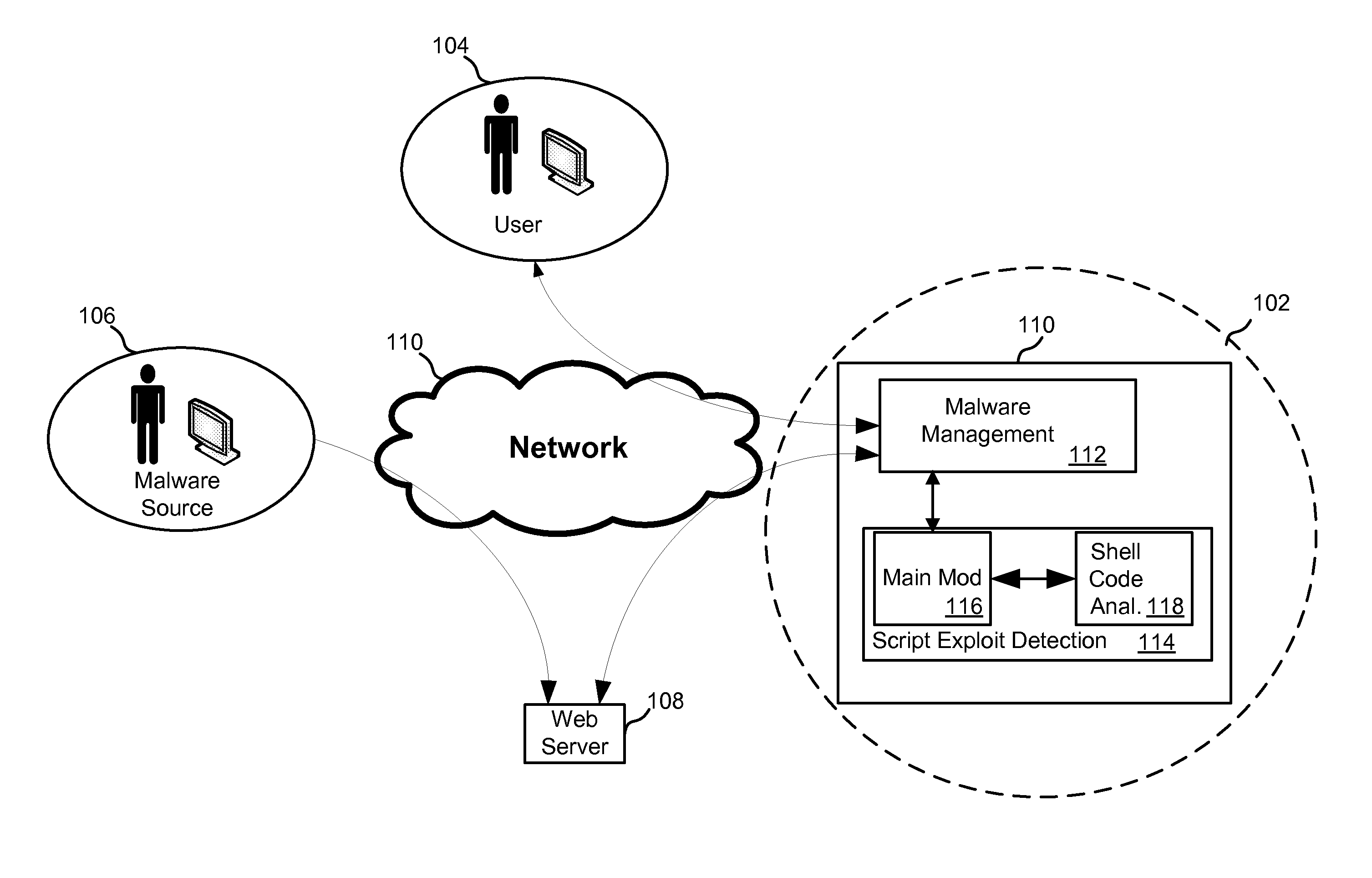
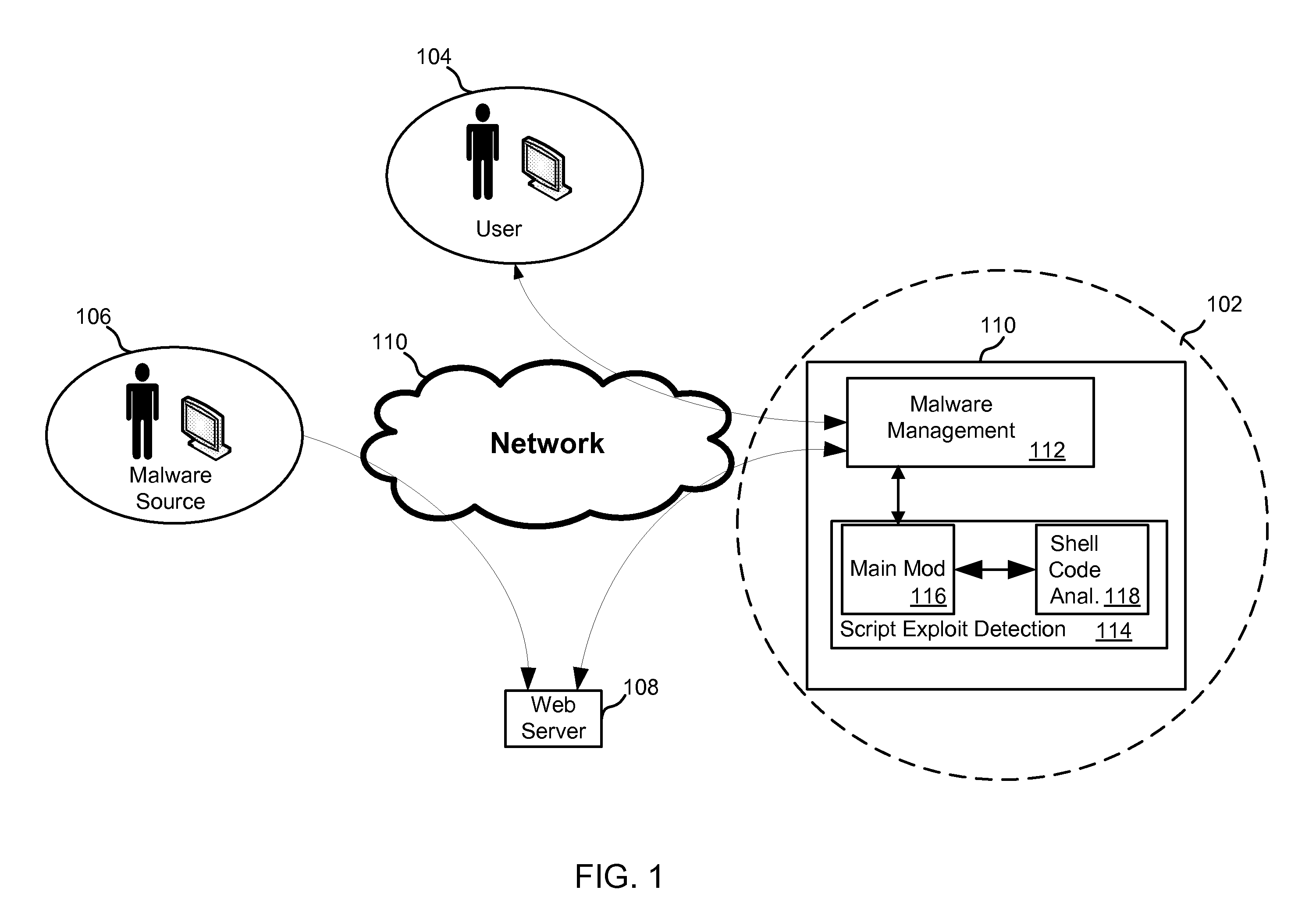
ActiveUS20110197177A1Lower Level RequirementsReduce complexityMemory loss protectionError detection/correctionScripting languageClient-side
Systems and methods for protecting client computers are described. One exemplary system includes an initial filter that gathers scripting-language-data from webpage data and a signature database of signatures of known scripting-language-data exploits. In addition, a parser generates a parse tree from the scripting-language-data, and a normalization and signature matching component reduces a complexity of the parse tree, generates a representation of at least a portion of a structure of the parse tree, and prevents the scripting-language-data from reaching an intended recipient if the representation matches one of the signatures of known scripting-language-data exploits.
Owner:CARBONITE LLC
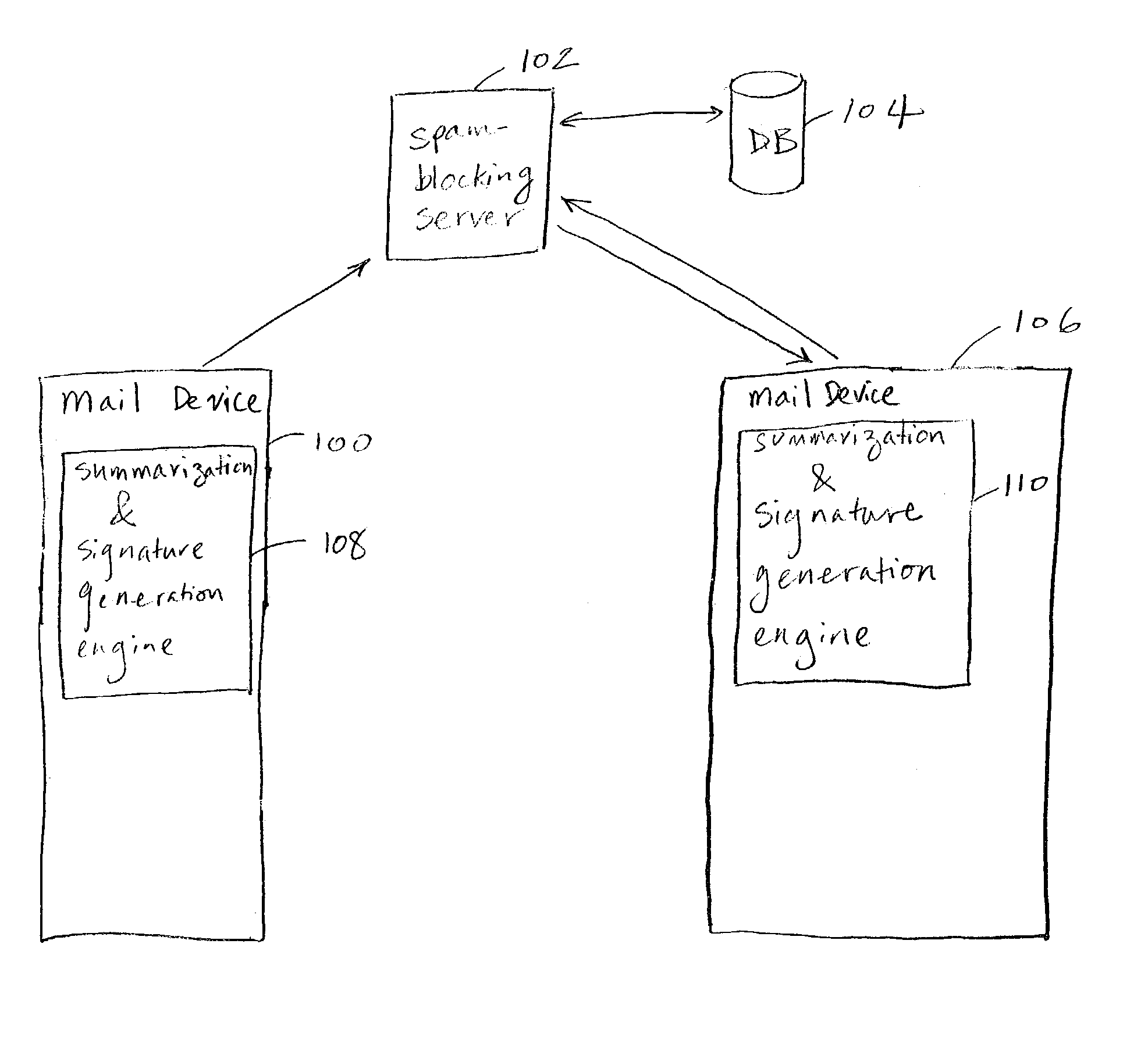
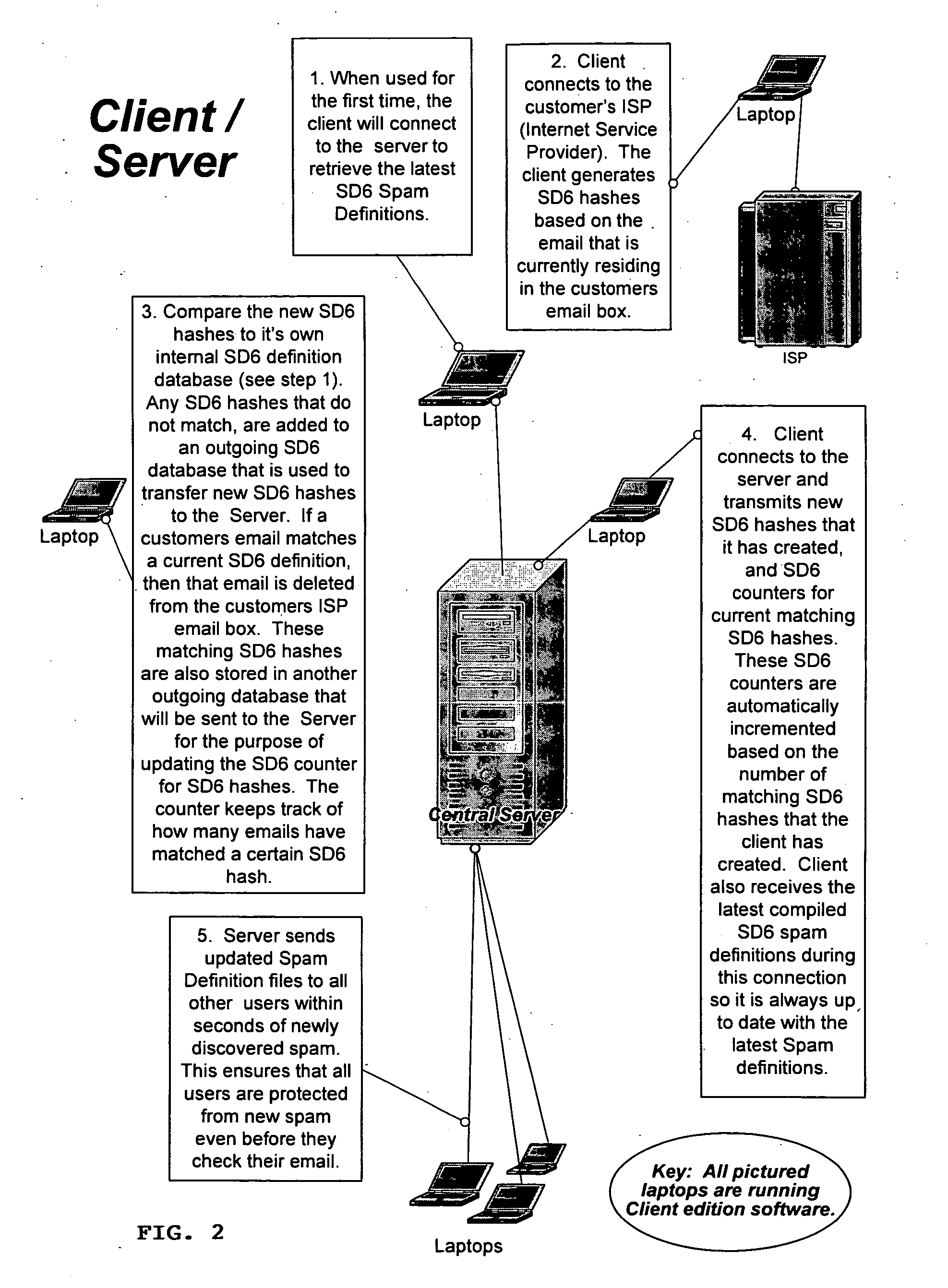
Method of detecting, comparing, blocking, and eliminating spam emails
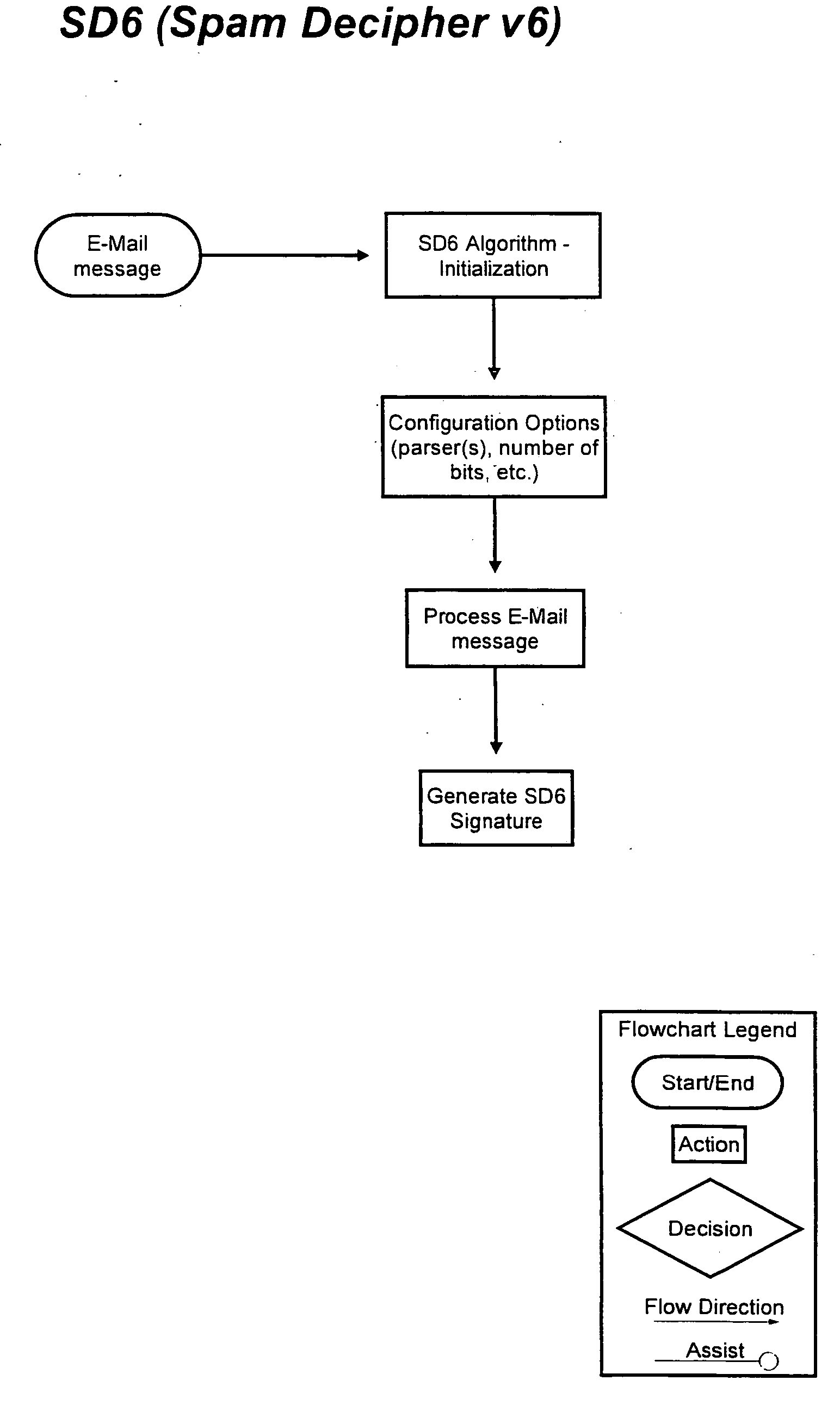
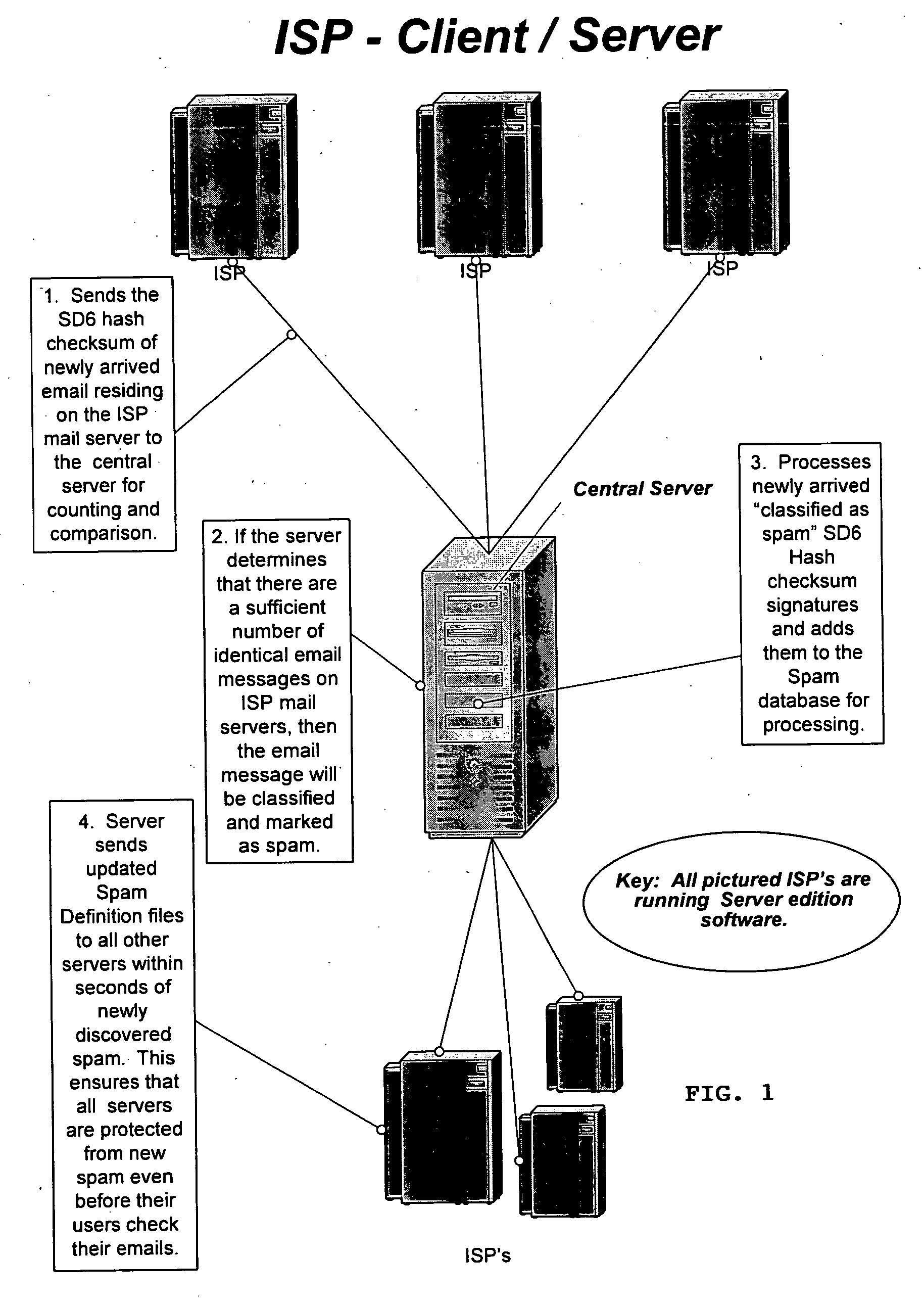
InactiveUS20060095966A1Avoid detectionIncrease inventoryMemory loss protectionUser identity/authority verificationService provisionDECIPHER
A method of detecting, comparing, blocking, and eliminating spam emails sent through email servers of Internet service providers (ISPs) or to email users' email-boxes. The method includes the steps of generating a spam decipher signature for each email in an ISP's mail server or a user's email-box, comparing newly generated spam decipher signatures to a server or user database containing spam decipher signatures of known spam emails to detect spam emails when there is a probability match at a pre-determined high percentage, and preventing the spam emails from going through the ISP's mail server or to the email user as non-spam emails. The method also includes the steps of updating a master spam decipher signature database by comparing spam decipher signatures in a new signature database with existing spam decipher signatures in the master database, incrementing a counter value of a matching spam decipher signature by the number of matches, and adding all new spam decipher signatures that have counter values reaching or exceeding a pre-set threshold and therefore are considered spam to the master spam decipher signature database. The method further includes the steps of initially loading the master spam decipher signature database to the ISP email server or the user's computer to establish the server or user database, and updating the server or user database with the master spam decipher signature database.
Owner:PARK SHAWN
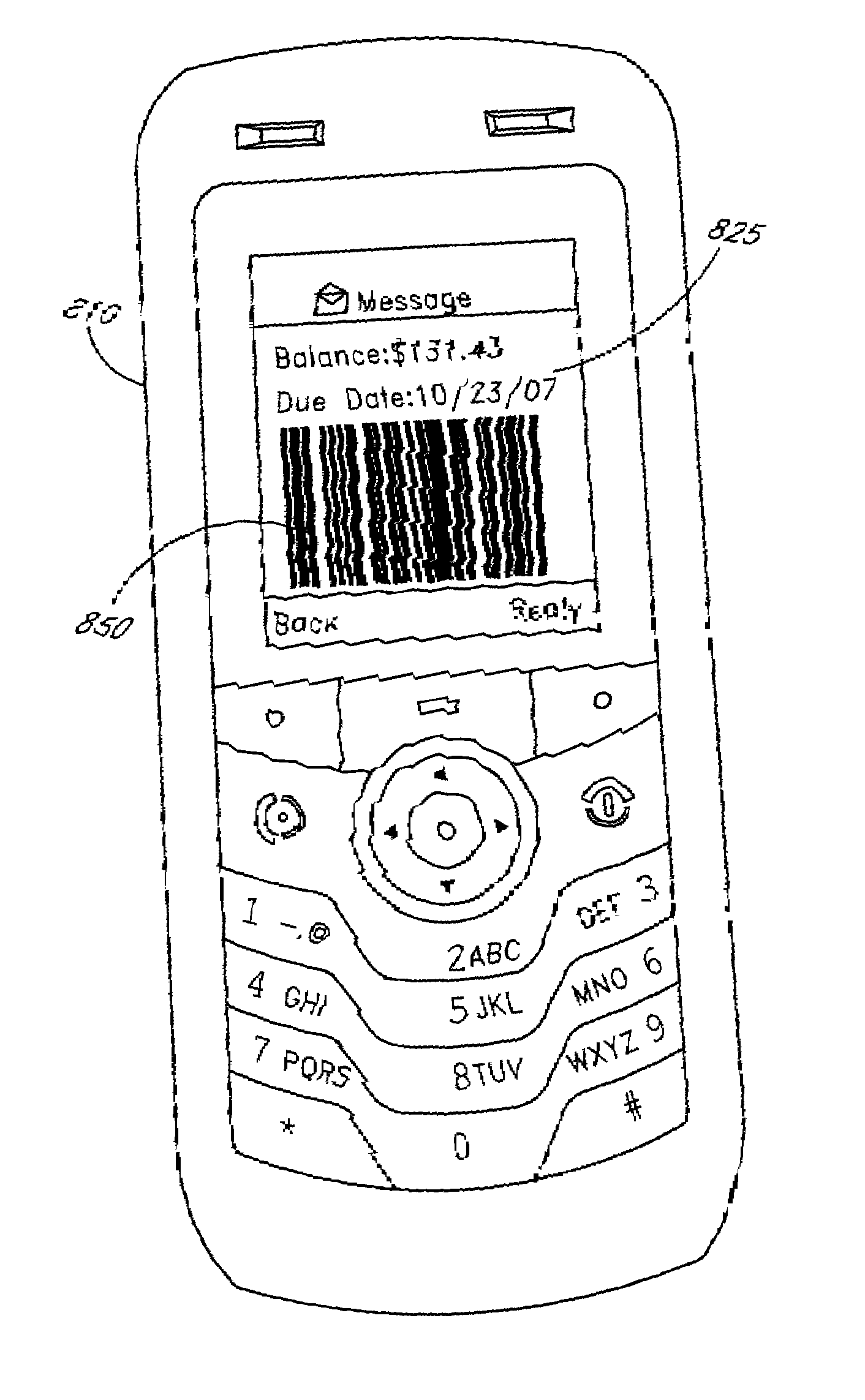
Bar coded monetary transaction system and method
InactiveUS20090204530A1Efficient managementFinanceUser identity/authority verificationPaymentBarcode
An improved financial transaction device comprising bar-coded information incorporating one of a plurality of algorithmic signatures, the signature being configured to permit at least one party involved in a financial transaction to store pertinent data in a multi-organizational payment tracking database, wherein the signature comprises a payment tracking identifier capable of uniquely referencing a single financial transaction and some of the pertinent data. The transaction may correspond to a format signature which may be in the form of a unique pictographic image representing the arrangement of data on a financial device for comparison against a library or database of signatures for purposes of device recognition.
Owner:PAYSCAN AMERICA
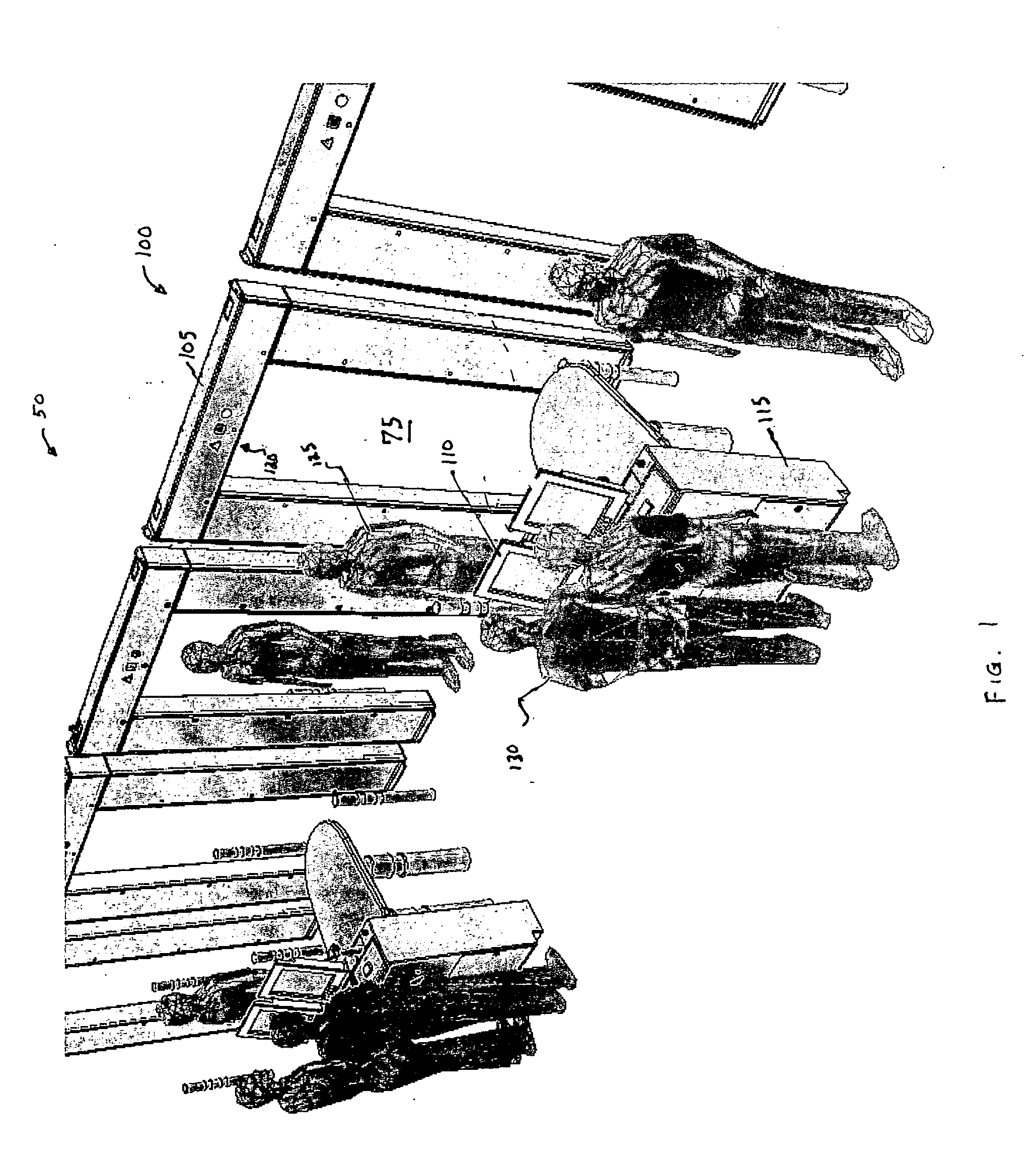
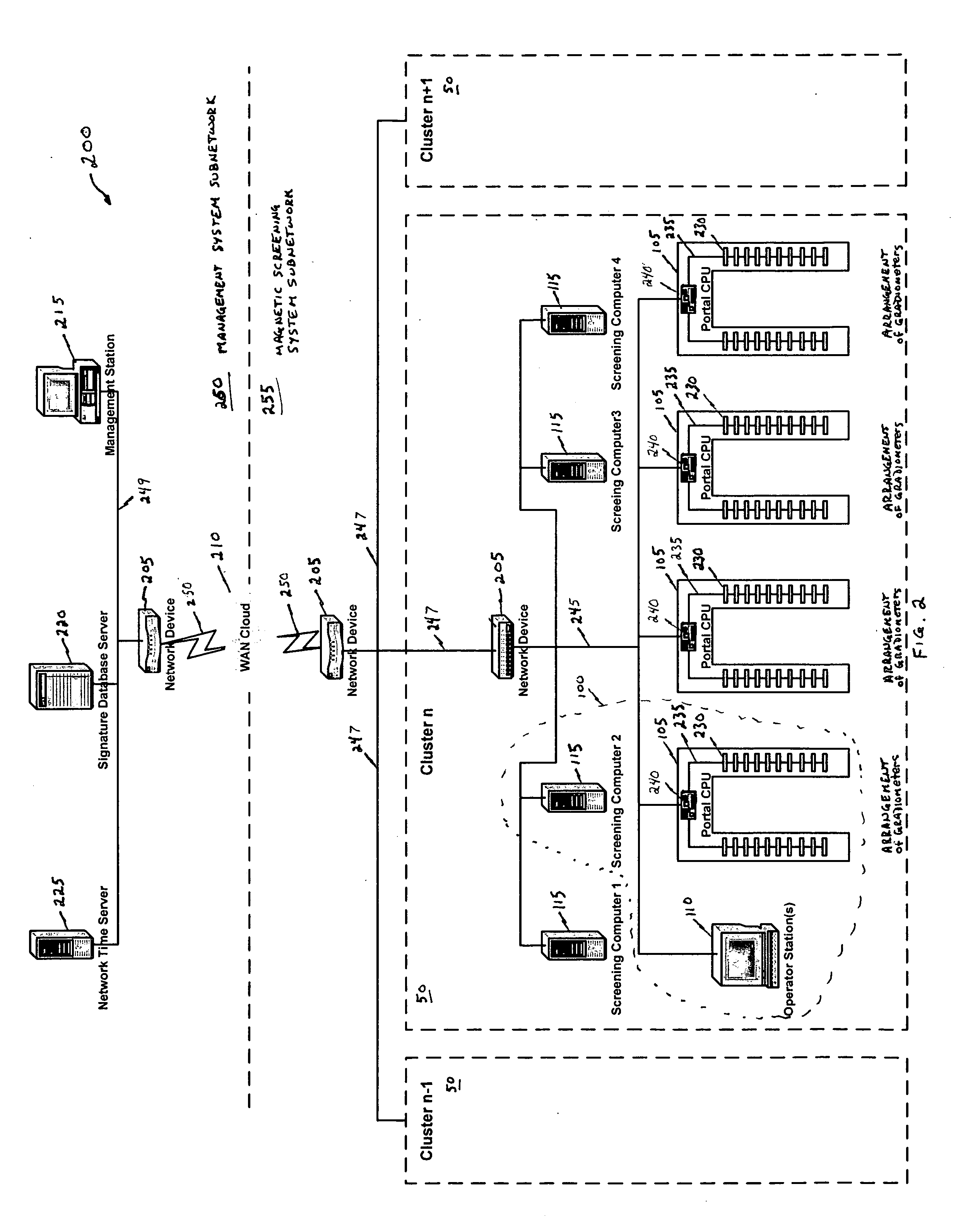
Magnetic screening system
InactiveUS20060197523A1Improve processing speedLess incidenceElectric/magnetic detectionMagnitude/direction of magnetic fieldsHigh rateObject store
A magnetic screening system uses directional gradiometers with high resolution and accuracy to measure magnetic field signatures of target objects (e.g., gun, knife, cell phone, keys) in a volume of interest. The measured signatures can be compared to signatures of known objects stored in a local database. Various mathematical processes may be used to identify or classify target object signatures. In a network of magnetic screening systems, the magnetic screening systems can transmit signatures to a central signature database, and a management computer can share the central signature database with all of the magnetic screening systems on the network. The magnetic screening system can operate in multiple modes, such as a tracking mode, measurement mode, and self-test mode. Through use of unique processes and designs, the magnetic screening system can achieve a high rate of processing persons for target objects.
Owner:ASSURANCE TECH CORP
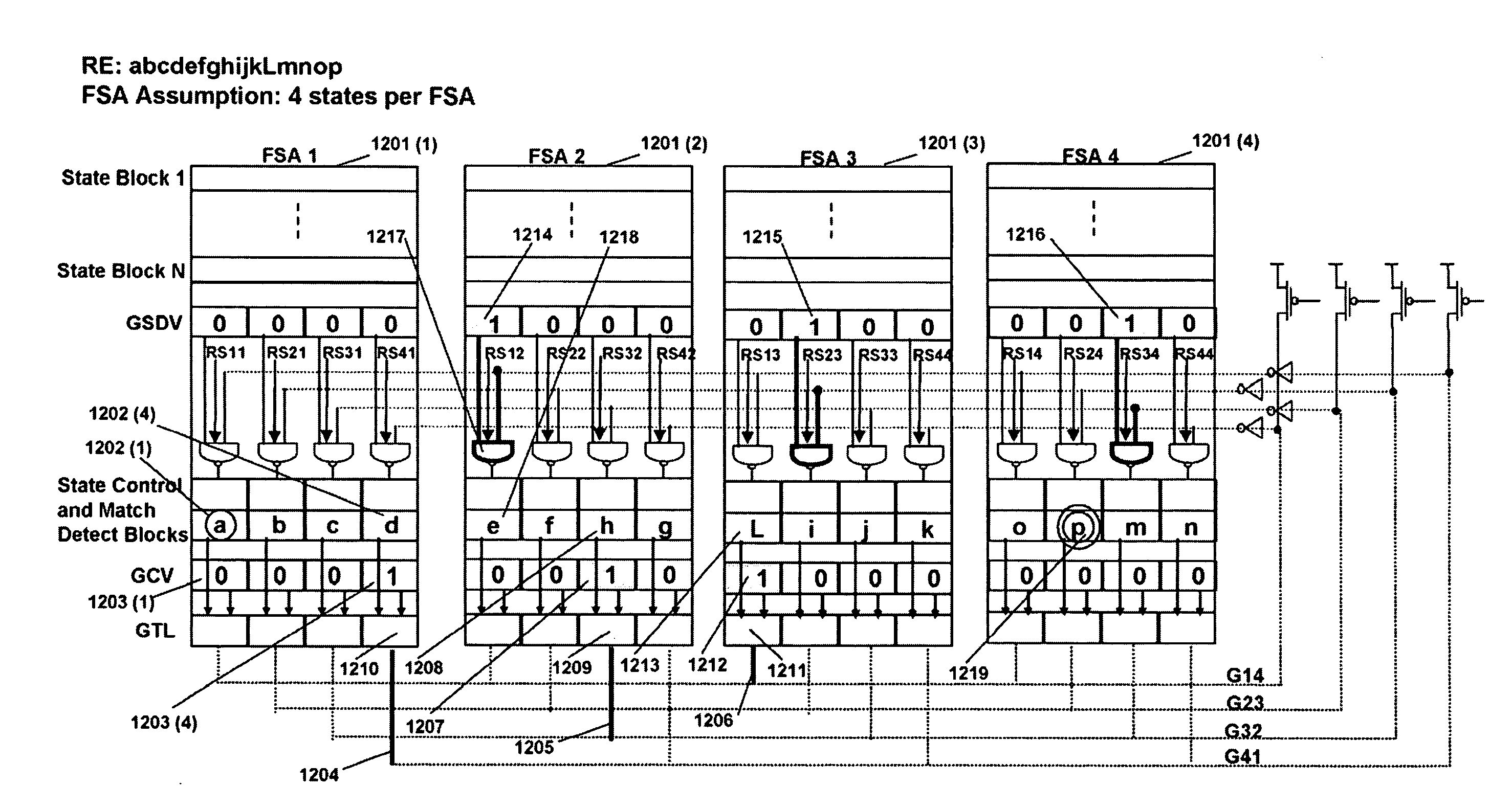
Signature Search Architecture for Programmable Intelligent Search Memory
ActiveUS20080140662A1Improve performanceReduce overheadDigital data information retrievalDigital data processing detailsMemory architectureAutomaton
Memory architecture provides capabilities for high performance content search. The architecture creates an innovative memory that can be programmed with content search rules which are used by the memory to evaluate presented content for matching with the programmed rules. Content search rules comprise of regular expressions which are compiled to finite state automata (FSA) and further comprise of patterns of strings a first set of which are compiled to a compressed signature database and a second set of which are compiled into FSAs. The finite state automata are then programmed in Programmable Intelligent Search Memory (PRISM) programmable FSA rule blocks and the compressed signature database is programmed in the PRISM signature search engines for evaluating content with the content search rules. A compiler compiles the content search rules for evaluation by PRISM memory. When the content being searched matches any of the rules programmed in the Programmable Intelligent Search Memory (PRISM), action(s) associated with the matched rule(s) are taken.
Owner:INFOSIL INC
Method to verify the integrity of components on a trusted platform using integrity database services
InactiveUS8266676B2Digital data processing detailsUser identity/authority verificationDatabase servicesTrust score
A client platform can be verified prior to being granted access to a resource or service on a network by validating individual hardware and software components of the client platform. Digests are generated for the components of the client platform. The digests can be collected into an integrity report. An authenticator entity receives the integrity report and compares the digests with digests stored in either a local signature database, a global signature database in an integrity authority, or both. Alternatively, the digests can be collected and stored on a portable digest-collector dongle. Once digests are either validated or invalidated, an overall integrity / trust score can be generated. She overall integrity / trust score can be used to determine whether the client platform should be granted access to the resource on the network using a policy.
Owner:SILICON VALLEY BANK +1
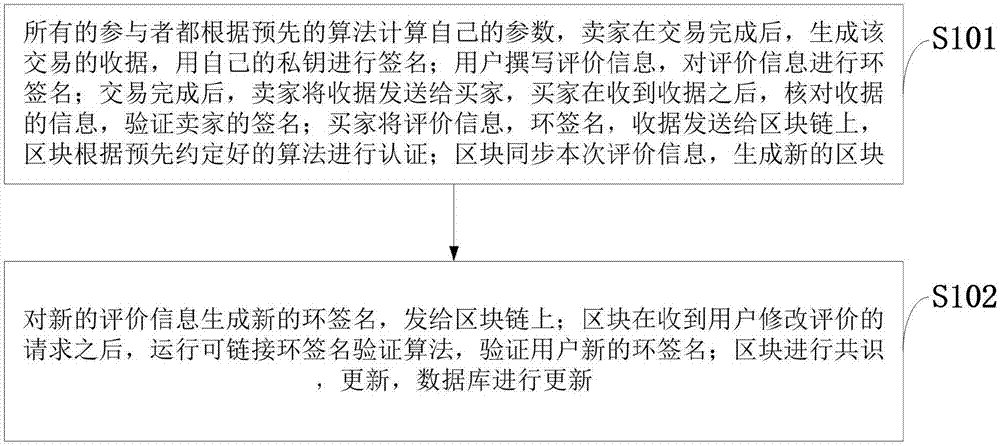
Modifiable reputation evaluation system and method based on block chain, and electronic payment system
ActiveCN107967557AAvoid injusticeGuaranteed transaction privacyFinanceDigital data protectionRing signatureE-commerce
The invention belongs to the e-commerce technology field and discloses a modifiable reputation evaluation system and method based on a block chain, and an electronic payment system. A receipt from a seller is received by a user, the signature of the seller in the receipt is verified, and the evaluation information is generated; after verification is completed, a ring signature of the evaluation information is generated by the user, and the ring signature is sent to the block chain; the receipt and the ring signature of the user are verified by the block chain; a database is updated after the block is generated; a new signature is acquired by the user through a signature algorithm, and the new signature is sent to the block chain; validity of the signature is verified by the block chain, and whether the two signatures are completed by the same user is determined; a pointer corresponding to the block of a previous message is modified after verification completion, the previous message ismarked as invalid, and the previously-revoked information is replaced by the block of the message. The method is advantaged in that on the condition that user anonymity and transaction non-tamperability are guaranteed, integrity and openness of the evaluation information are guaranteed, and reliability of the evaluation information is guaranteed.
Owner:XIDIAN UNIV
Mobile geolocation
ActiveUS20140171102A1Synchronisation arrangementPosition fixationCommunication unitCommunications system
A method and apparatus for generating reference signatures for use in geolocation in a cellular wireless communication system is provided. A first signature for a mobile communication unit comprises location information, a timestamp, and radio frequency measurement information obtained by a mobile communication unit at a location, but does not contain identification information for the mobile communication unit. The first signature is compared to signatures in a database, to identify a second signature that has a timestamp and radio frequency measurement information that correspond to those of the first signature. A reference signature is created by combining at least a part of the first signature with at least a part of the second signature. Repetition of the comparison and combination steps creates a database of reference signatures, for use in geolocating other received call signatures.
Owner:VIAVI SOLUTIONS UK
Data leakage prevention for resource limited device
ActiveUS8286253B1Efficient and effectiveSimple to executeDigital data processing detailsDatabase distribution/replicationDigital signatureMobile telephony
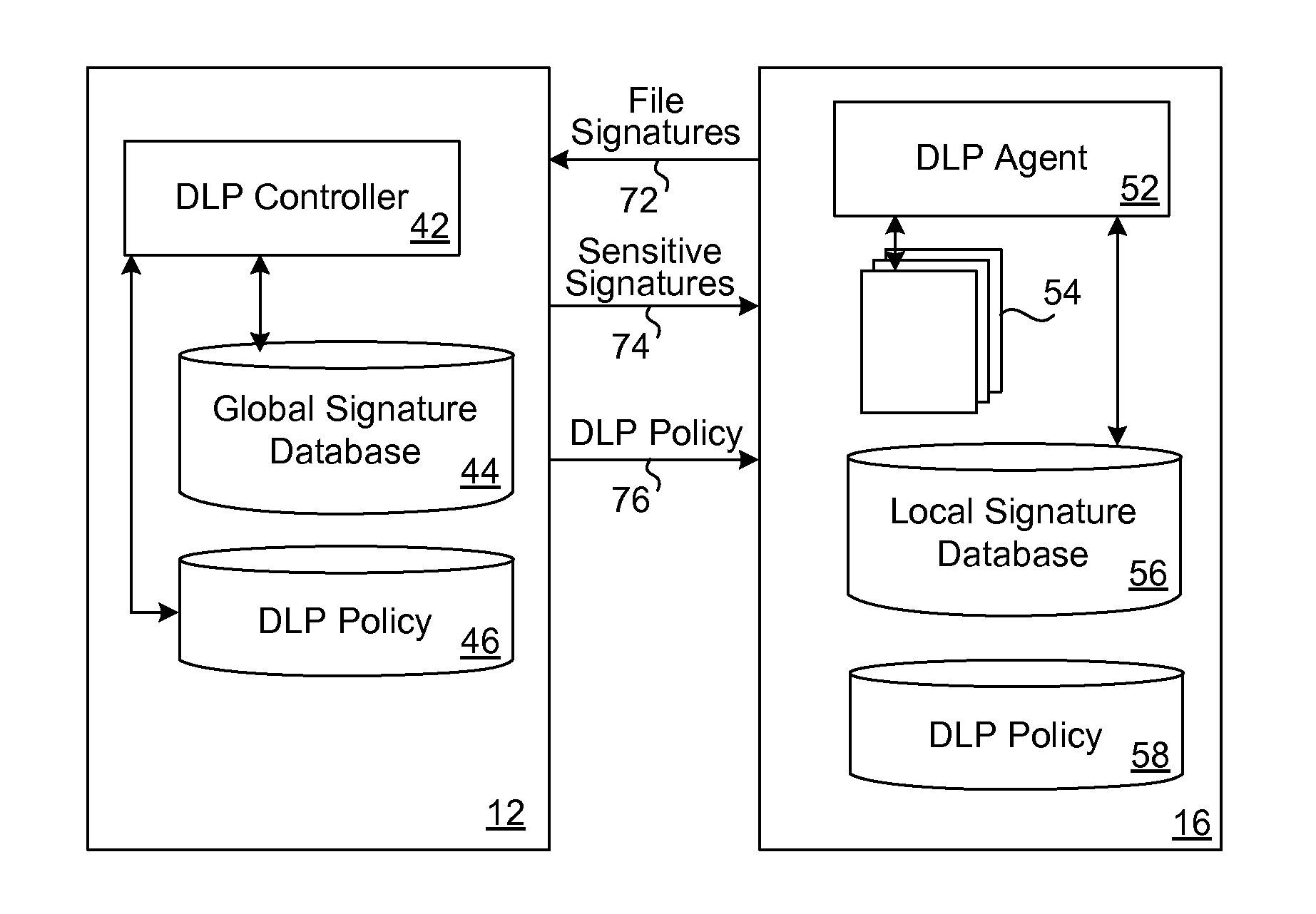
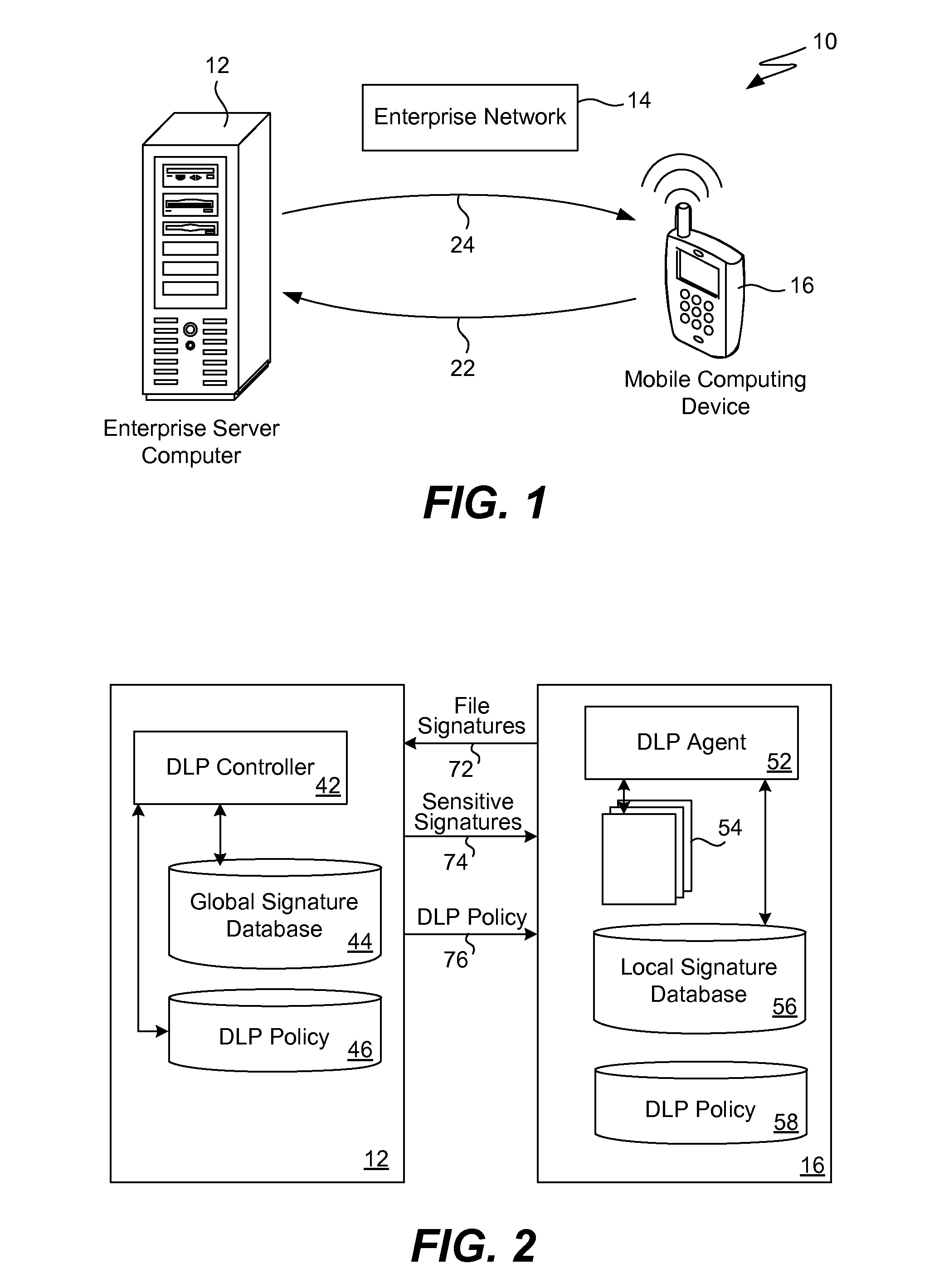
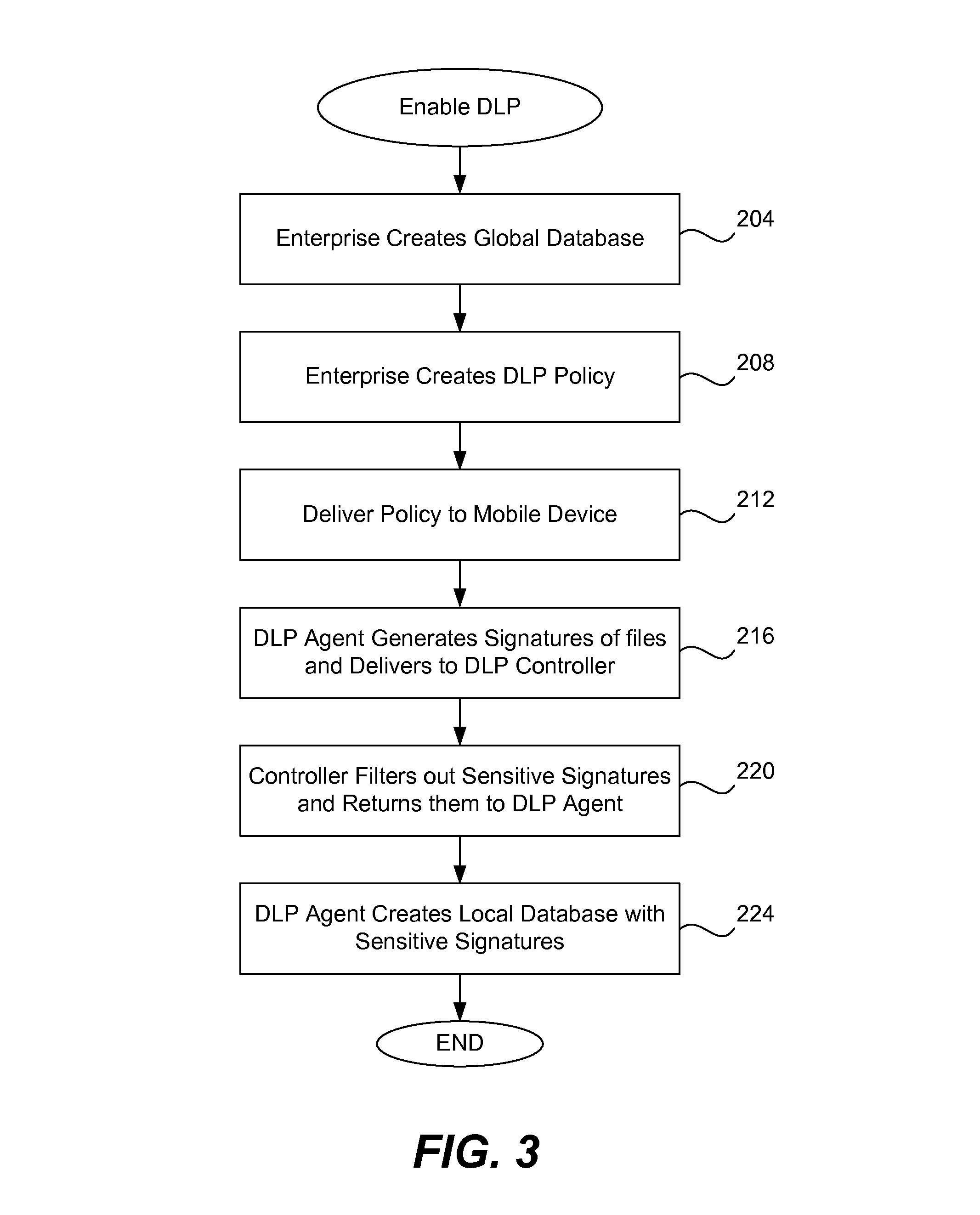
When a resource-limited device (such as a mobile telephone) joins a network associated with an enterprise, the agent in the device generates digital signatures for all the files in the device and sends them to an enterprise controller. The controller compares them to the global signature database; it filters out the sensitive digital signatures and feeds them back to the agent in the device. The agent receives the feedback of digital signatures and consolidates them into its own local signature database. The agent analyzes each file that is attempting to be output from the device according to the local signature database and DLP policy. If the signature of the file is present in the local database then the action to output file is blocked. If a new file is created on the device, the agent generates and sends its digital signature to the controller for inspection. If the signature is sensitive, this new digital signature will be placed into the local signature database. If the DLP controller updates the global signature database, the device will send its signatures once again for comparison.
Owner:TREND MICRO INC
Making cryptographic claims about stored data using an anchoring system
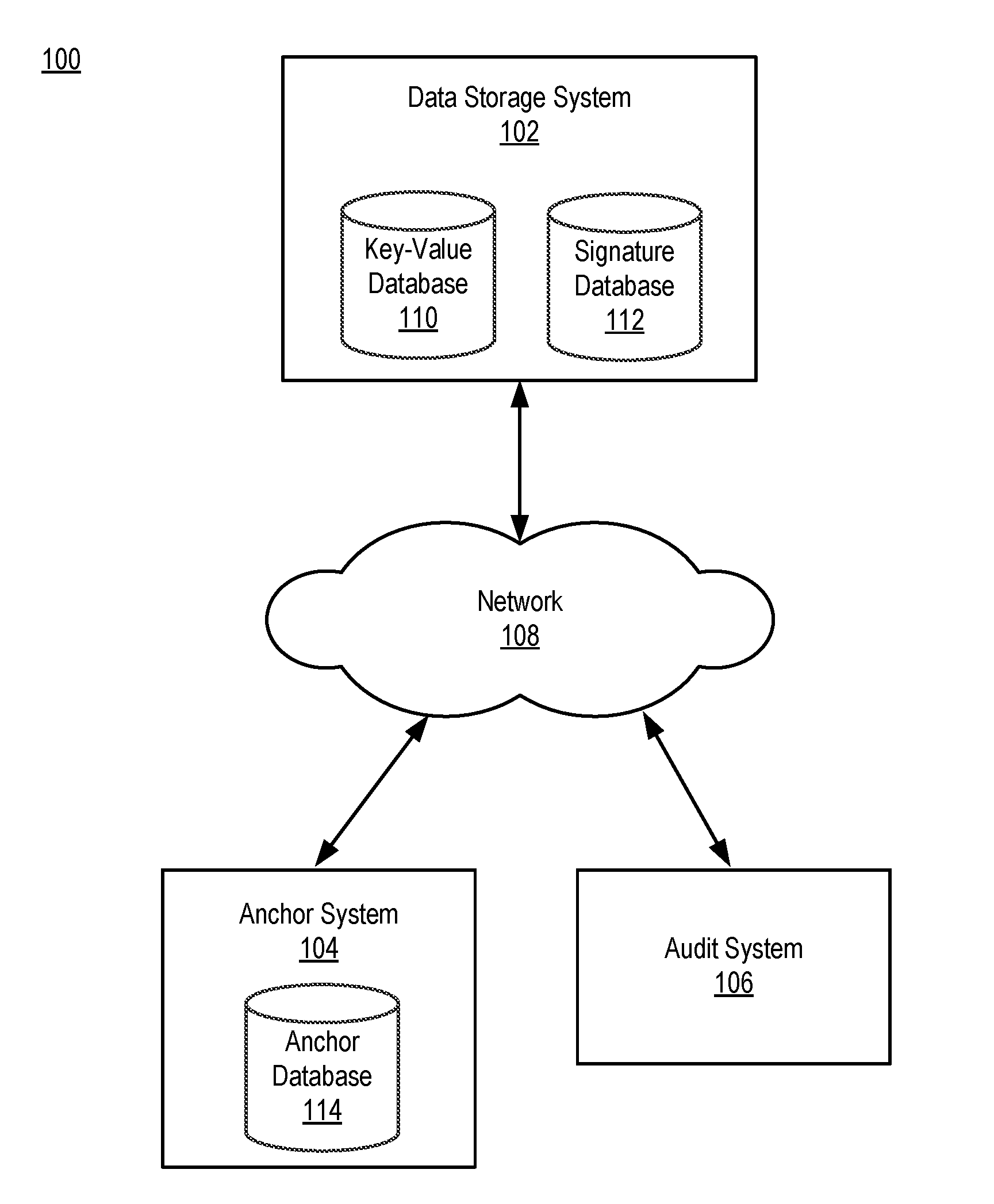
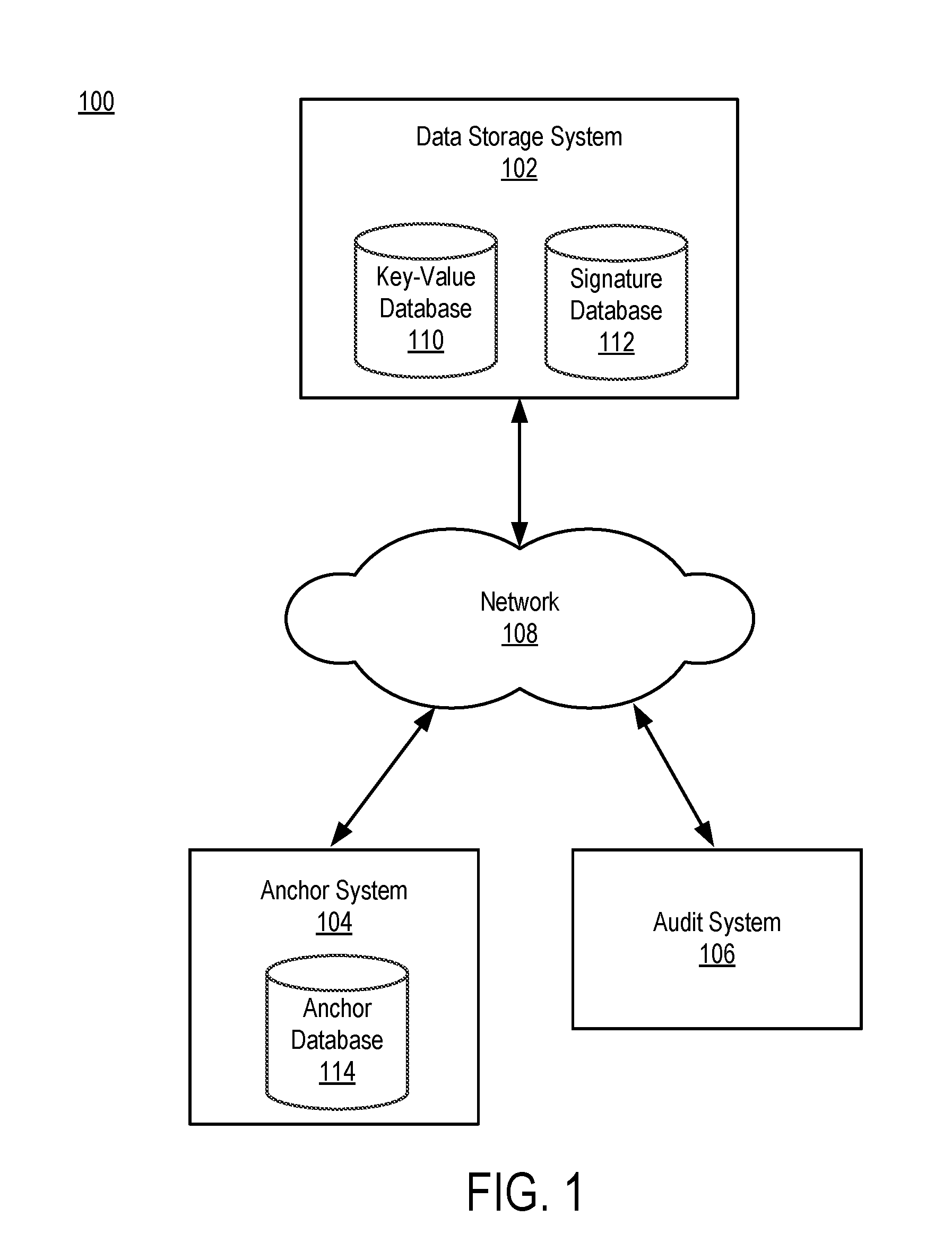
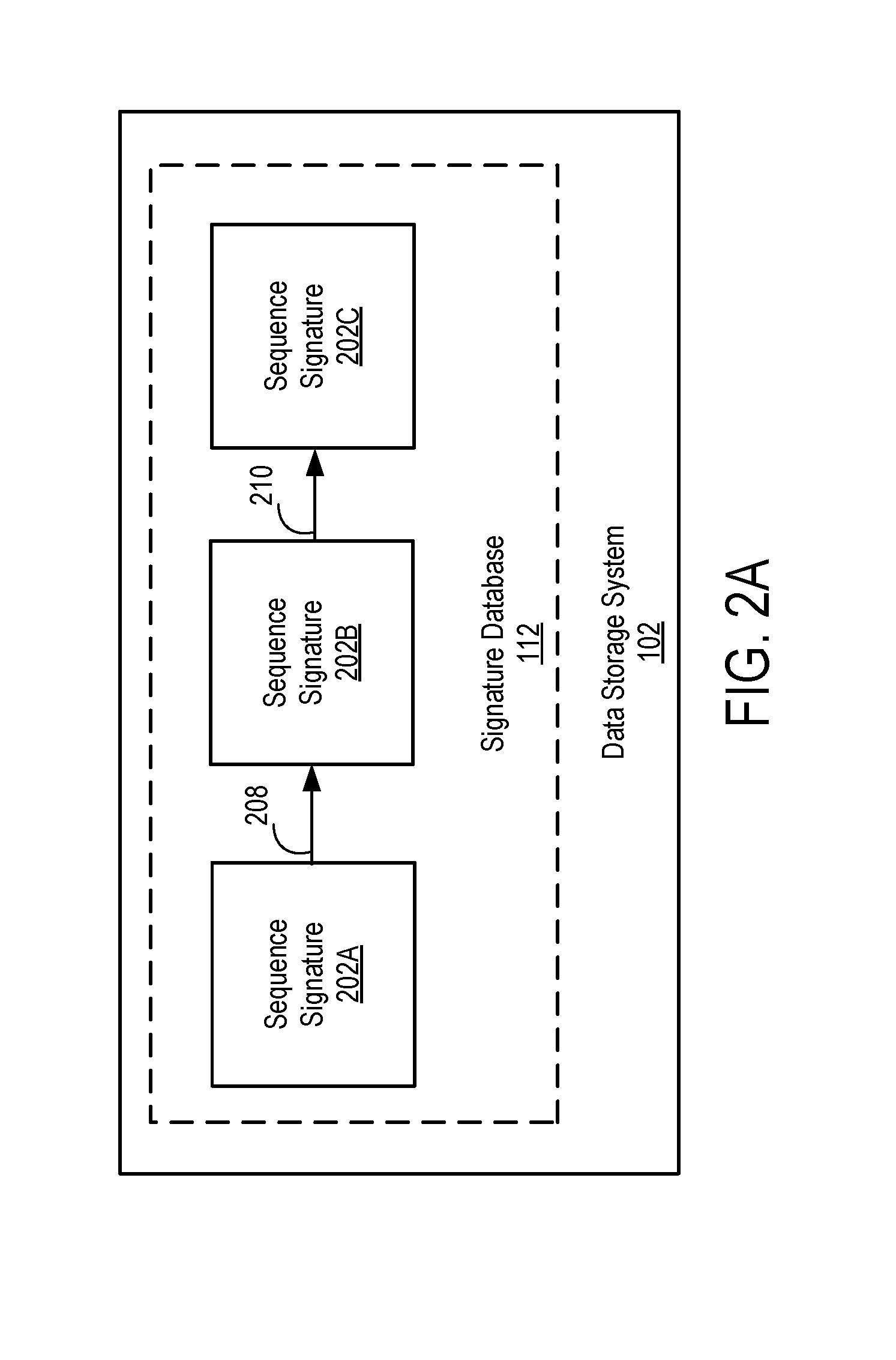
ActiveUS20160365978A1Multiple keys/algorithms usageEncryption apparatus with shift registers/memoriesData elementData storing
A data storage system creates a data signature for a data element that is to be stored by hashing the data element. The data storage system also creates a sequence signature for the data element and stores the sequence signature in a signature database. The sequence signature is created using the data signature of the data element and the previous sequence signature stored in the signature database. The data storage system transmits a copy of the sequence signature to an anchor system. The anchor system stores the copy as an export anchor and creates an import anchor based on the export anchor and information associated with the present time. The anchor system stores the import anchor and transmits a copy to the data storage system. An audit system uses the export anchor and import anchor to determine whether data stored by the data storage system has been modified.
Owner:PEERNOVA INC
Current Pattern Matching Method for Non-Intrusive Power Load Monitoring and Disaggregation
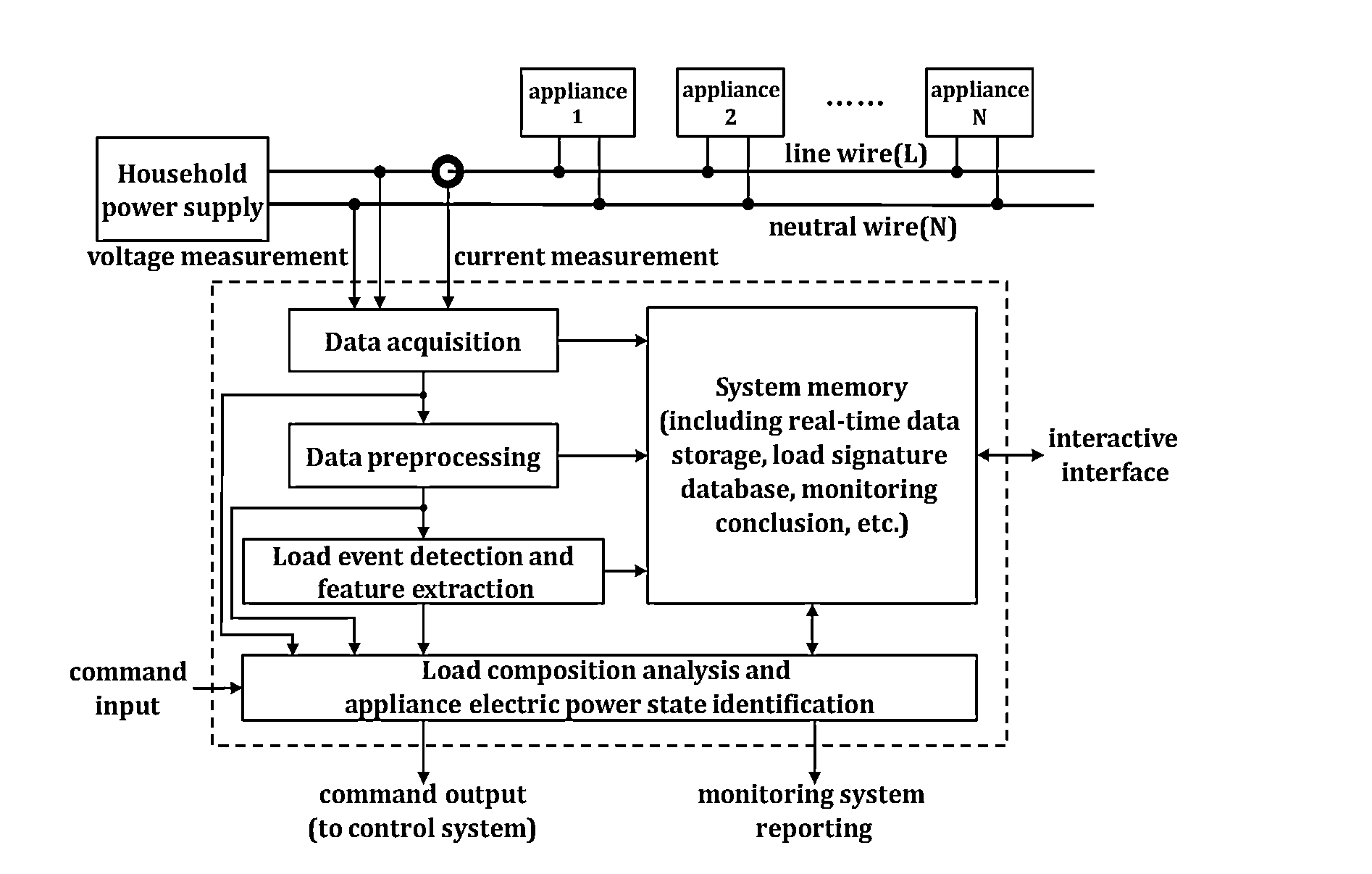
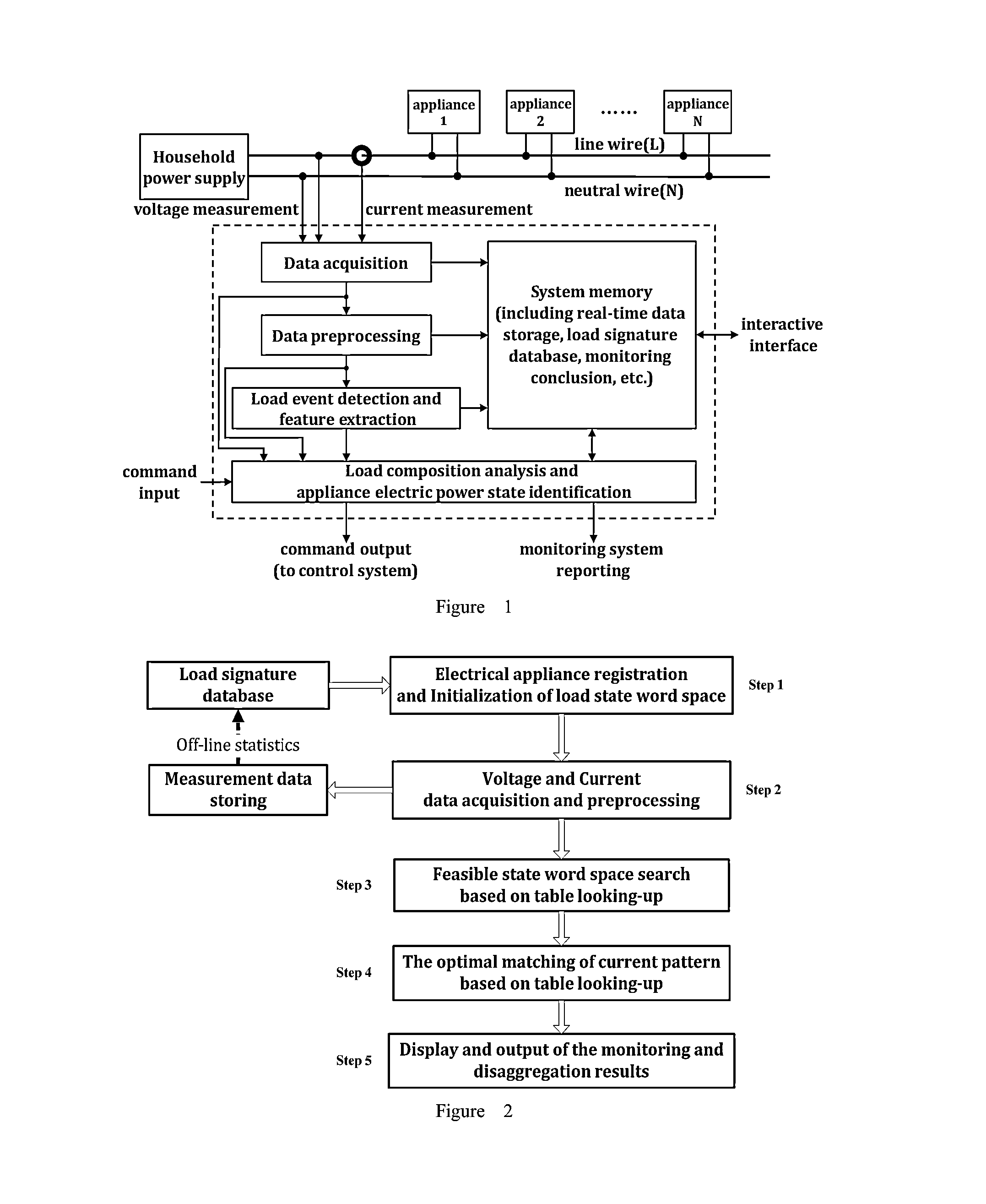
ActiveUS20150309092A1Low computing performanceEfficient use ofElectric devicesCurrent/voltage measurementPattern matchingData acquisition
A harmonic-characteristics based current pattern matching method for the non-intrusive power load monitoring and disaggregation is provided in this present invention, on the basis of establishing the load signature database, which comprises electrical appliance registration and load state word space initialization, data acquisition and data preprocessing, feasible state word space search based on table looking-up, the optimal matching of current pattern, and display and output of the monitoring and disaggregation results. The method improves the accuracy of disaggregation, and can achieves exact identification of operating states of appliances, and also can reduce the cost.
Owner:TIANJIN UNIV
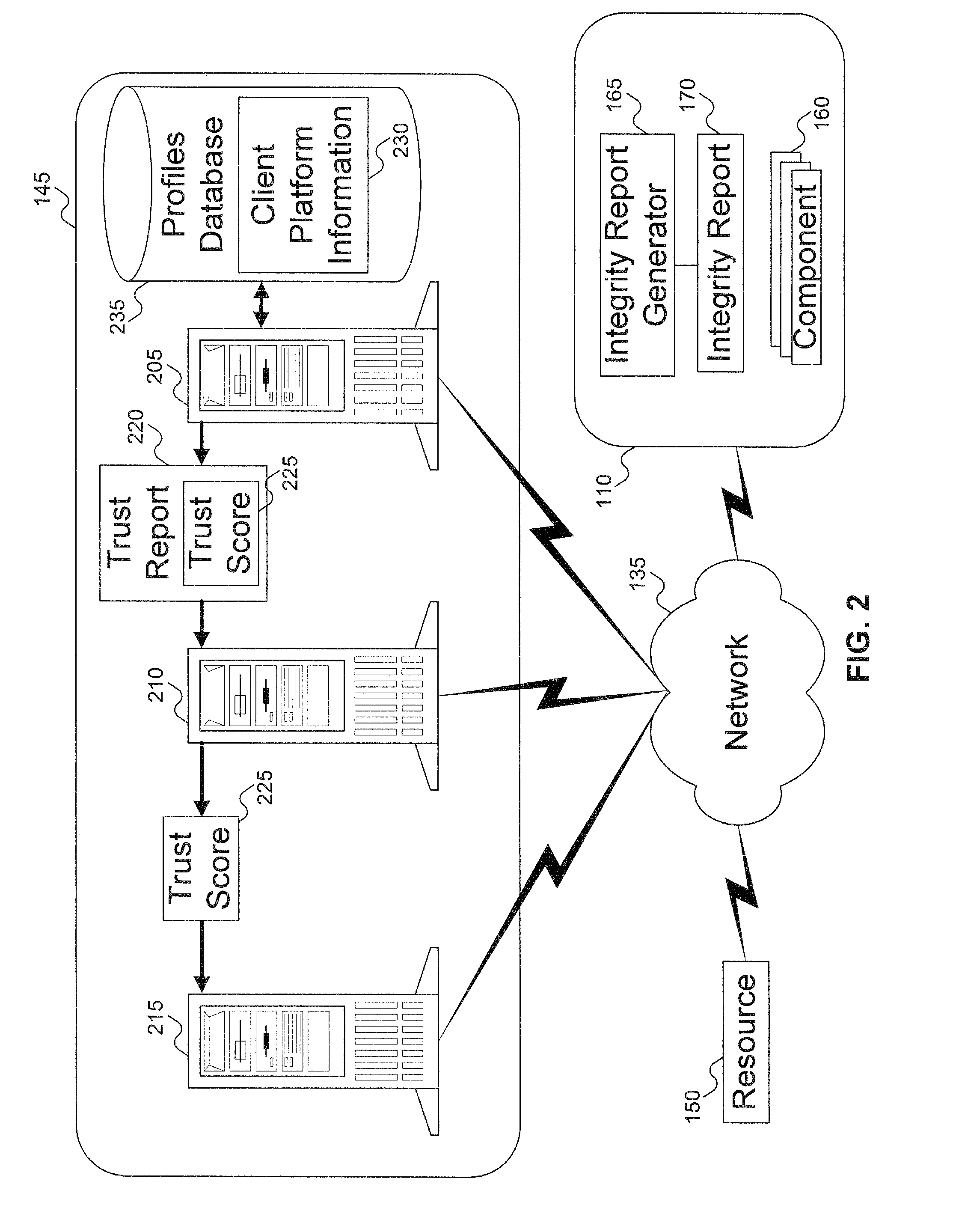
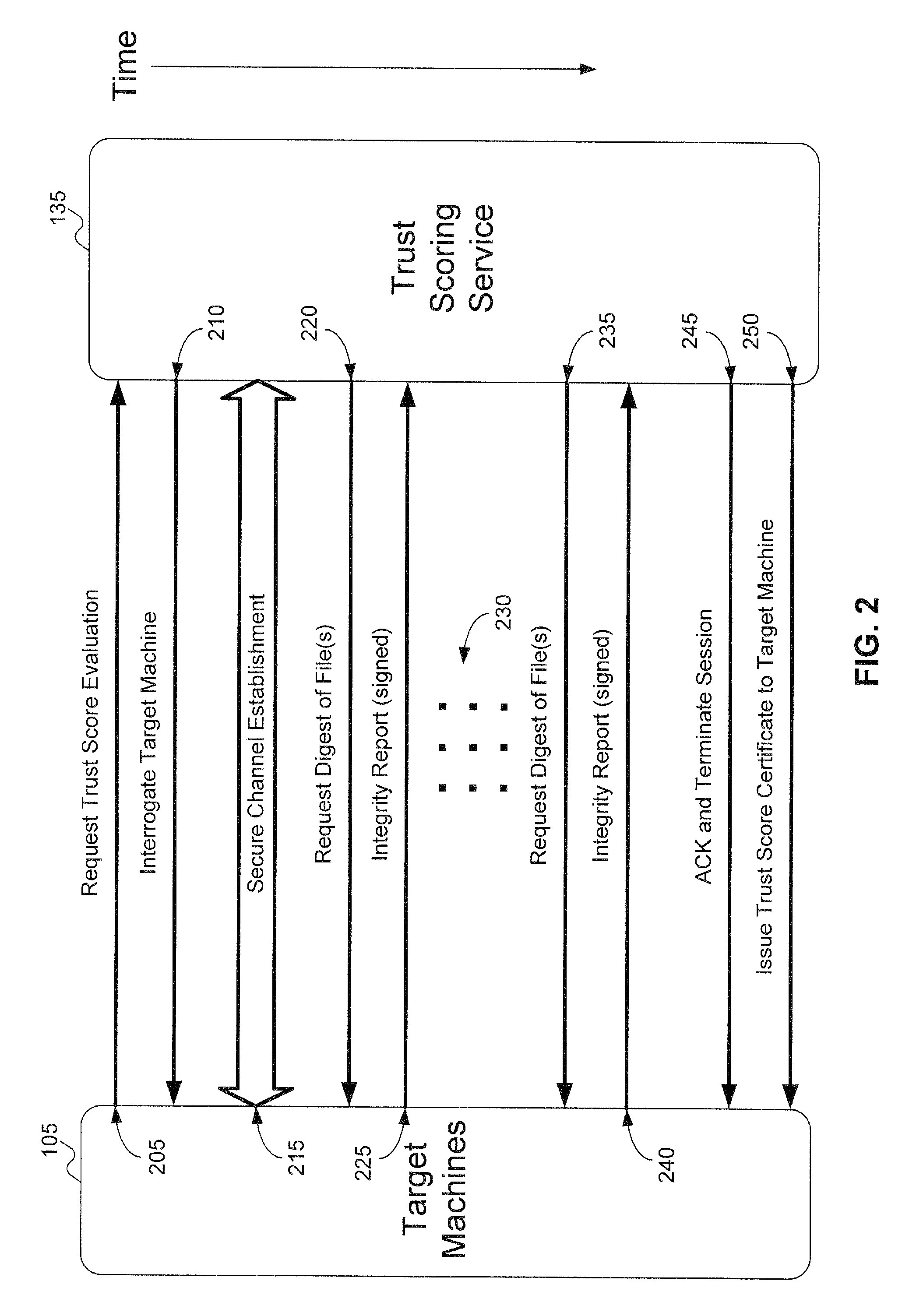
Method and system to issue trust score certificates for networked devices using a trust scoring service
InactiveUS8327131B1Digital data processing detailsUser identity/authority verificationWeb serviceHome page
A target machine can be verified prior to being granted access to a resource on a network by interrogating and analyzing digests of various elements of the target machine. The digests can be collected into an integrity report and provided to a Trust Scoring Service. The Trust Scoring Service receives the integrity report and compares the digests with signatures stored in a signature database. A trust score certificate can then be issued to the target machine. The Trust Scoring Service can include a Score Evaluation Server which can interact with a Kerberos Authentication Server and a Ticket Granting Server to embed a trust score within a Kerberos Ticket to enforce a richer set of access policies. The integrity of a web server can be verified and a Trust Score Certificate Logo can be displayed on a corresponding home page of a merchant. By clicking on the Trust Score Certificate Logo, a user can verify the integrity of the merchant's web servers prior to completing a transaction with the merchant.
Owner:KIP SIGN P1
Discerning use of signatures by third party vendors
InactiveUS8015284B1Digital data processing detailsDigital computer detailsThird partySecurity software
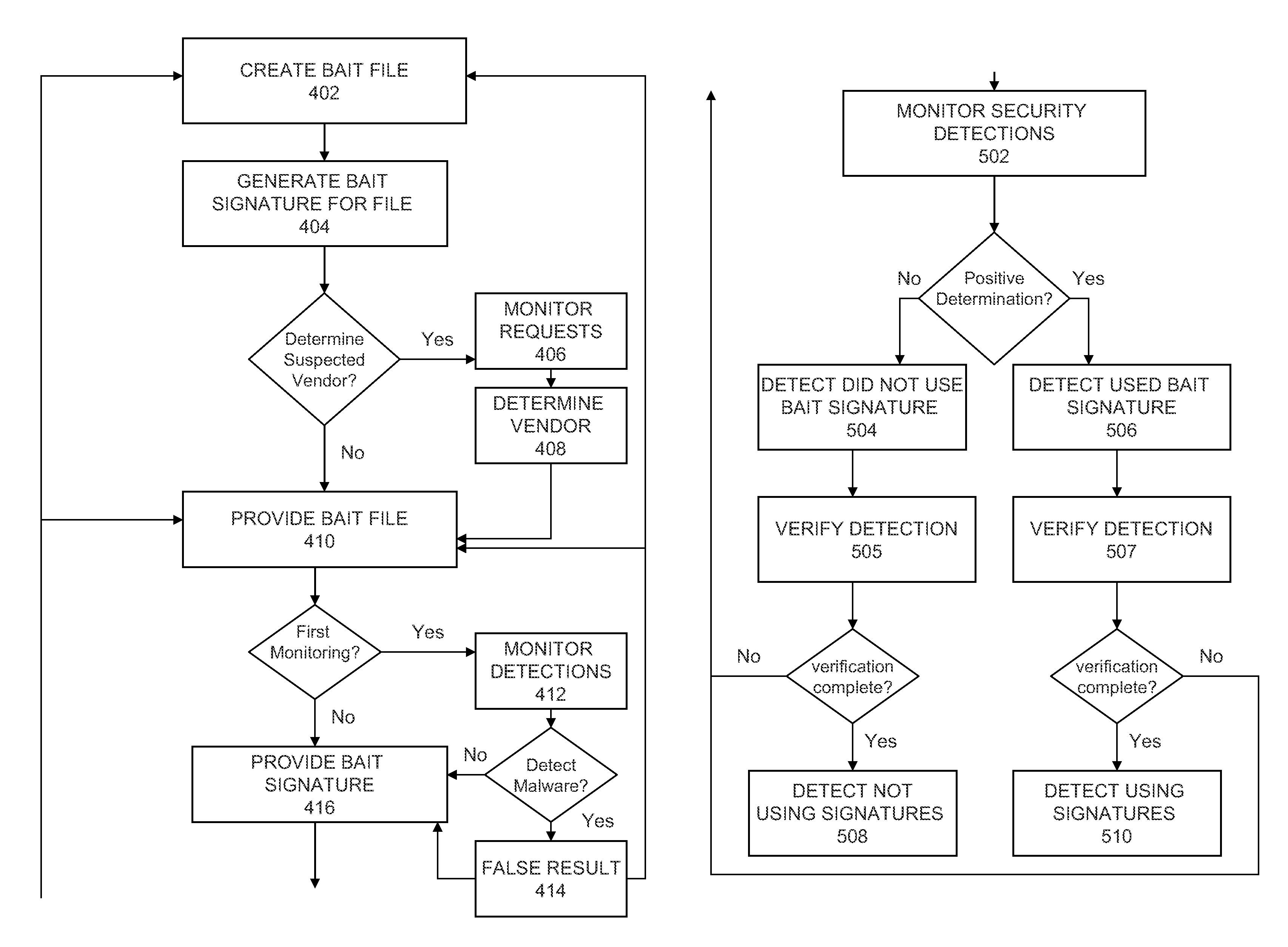
Bait files and signatures allow security software vendors to track both authorized and unauthorized usage of the security vendor's signatures / products by third party security vendors. A bait file providing module anonymously provides a bait file to a third party security vendor for security detection, where the bait file is a non-malware file. A signature providing module provides a bait signature corresponding to the bait file that is included in a signature database which is made publicly available. A scanner monitoring module monitors security detections made over a period of time by a security scanner operated by the third party vendor. A determination module determines whether the scanner positively detected the bait file following the release of the bait signature for the bait file. A use detection module detects, in response to a positive determination, that the third party vendor used the bait signature provided to detect the bait file.
Owner:CA TECH INC
Detecting method and architecture thereof for malicious codes
A detecting method and architecture thereof for malicious codes is provided, which is applicable to a computer system having at least a host. Each host executes at least a process. The method is implemented with a system call interposition module and an analysis module for malicious codes. The system call module intercepts all system calls of process calls and all related arguments of the system calls. The analysis module for malicious codes analyzes the input data of pre-determined system calls, and executes the suspicious malicious codes. Once the same behaviors between the analysis module and the suspicious malicious codes are found, a system-intrusion warning is immediately triggered. The method is not required to maintain huge signature databases, and can detect unknown attack-skills in a manner of high correct rate and low incorrect ruling.
Owner:A10 NETWORKS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com