Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
568 results about "Network intrusion detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
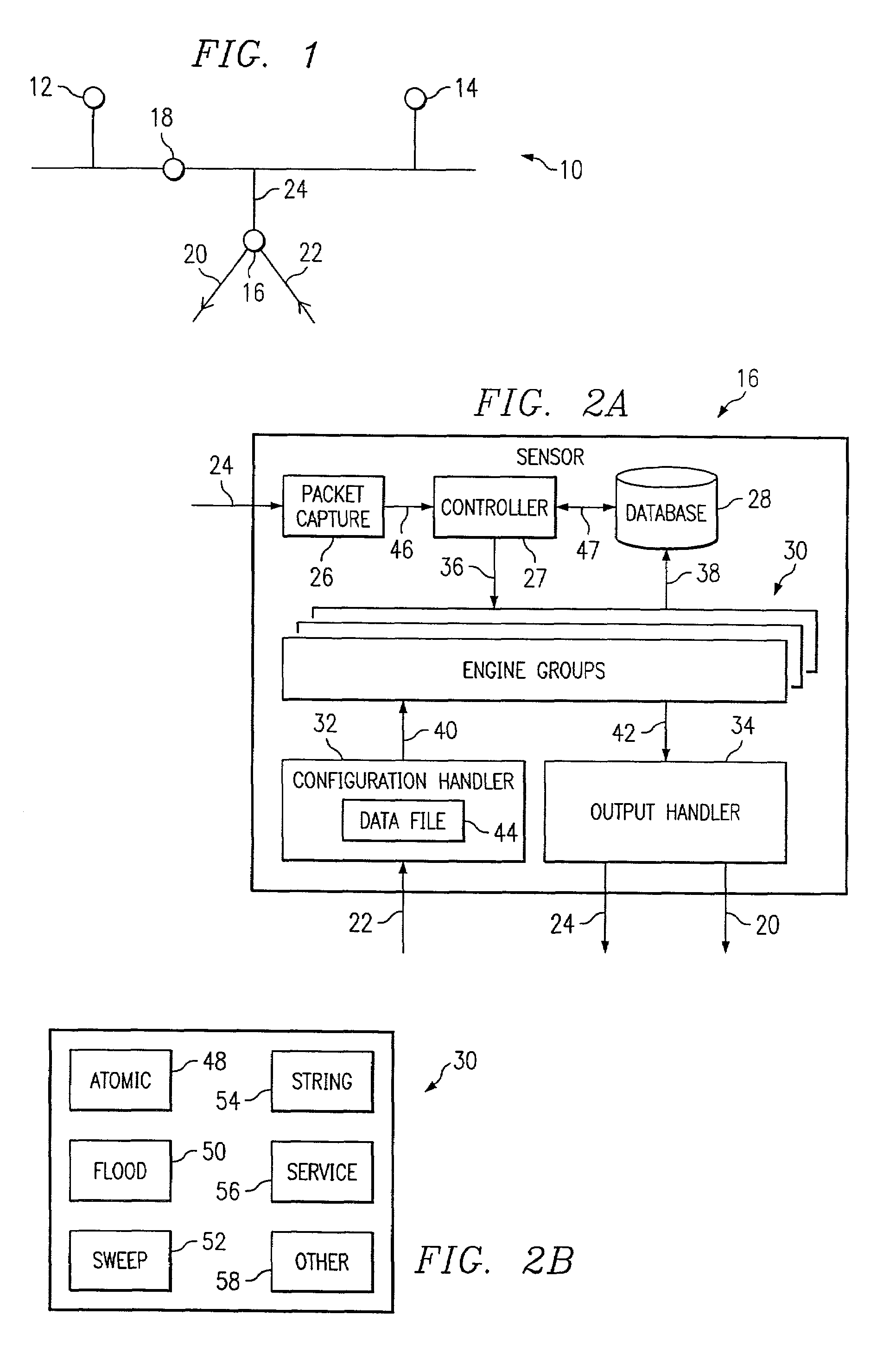
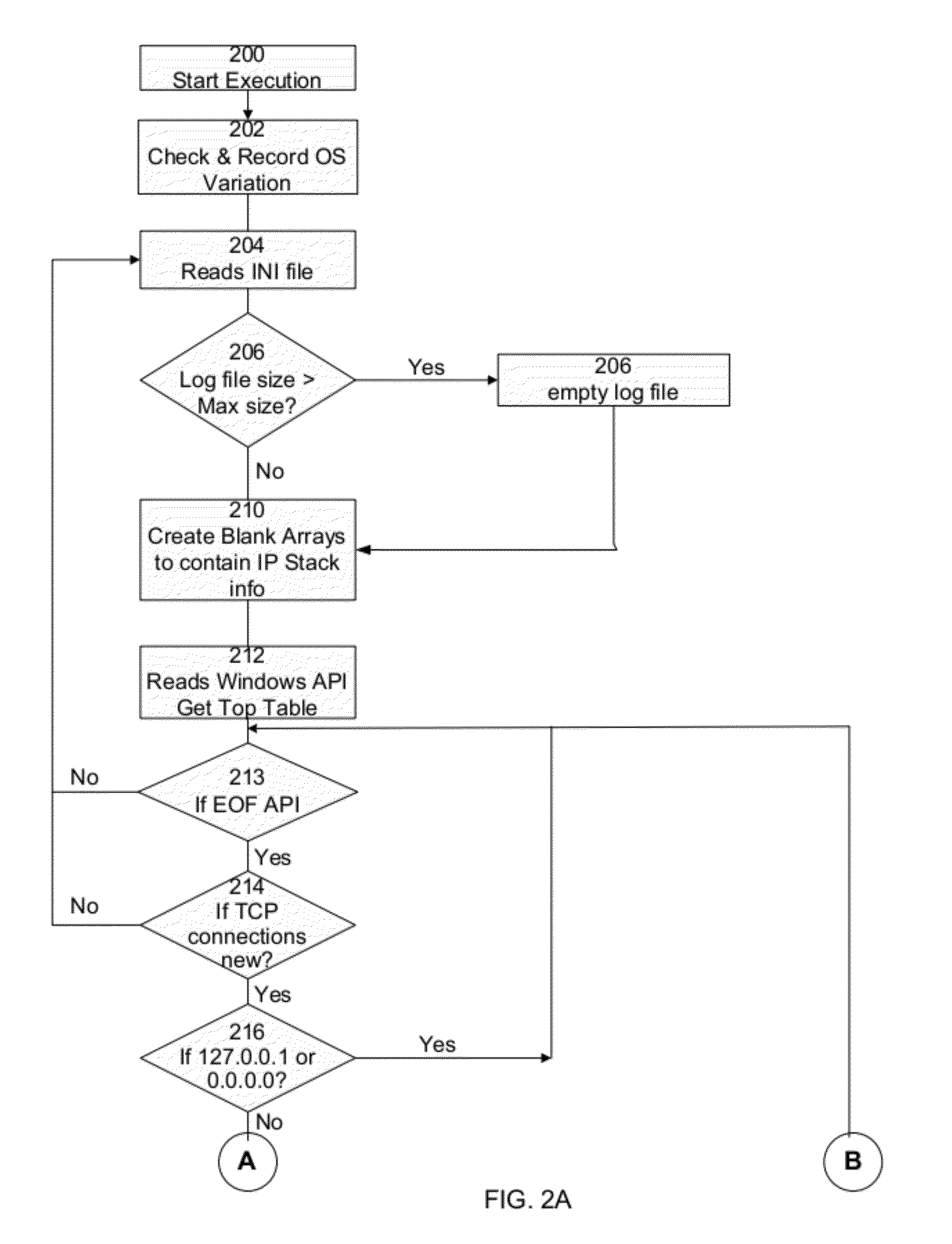
Network intrusion detection and analysis system and method
ActiveUS7493659B1Digital data processing detailsUser identity/authority verificationTraffic capacityData monitoring
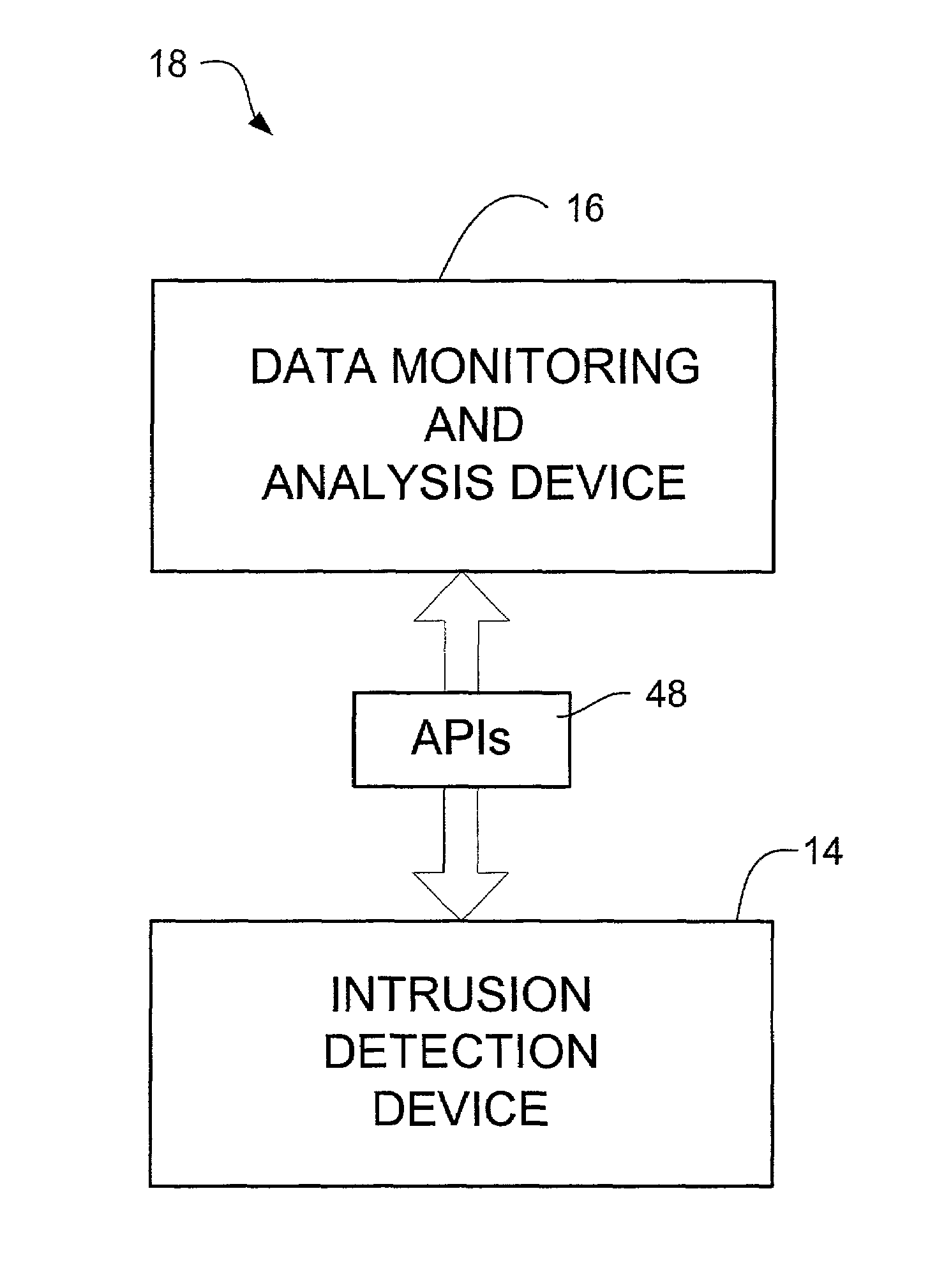
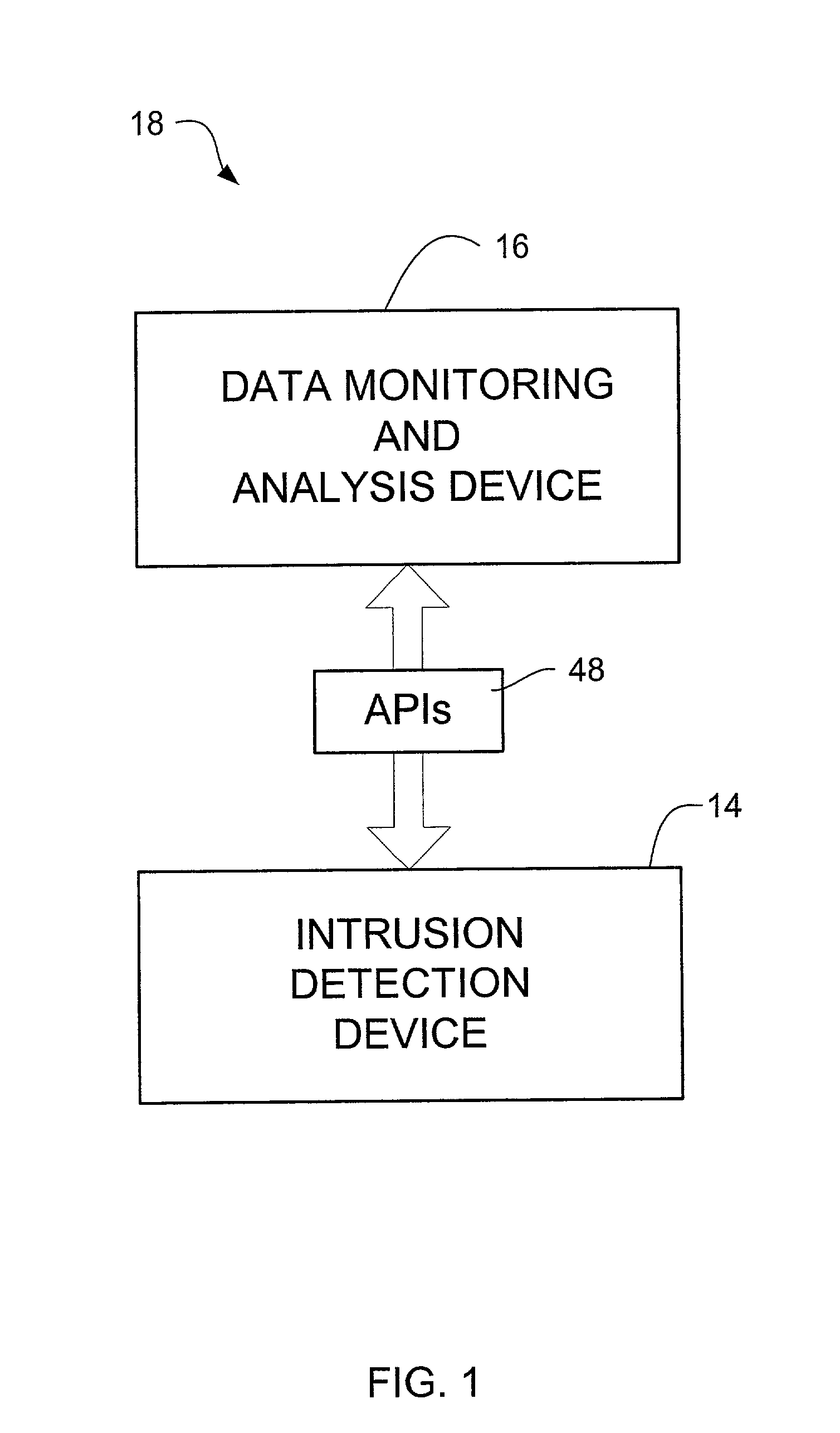
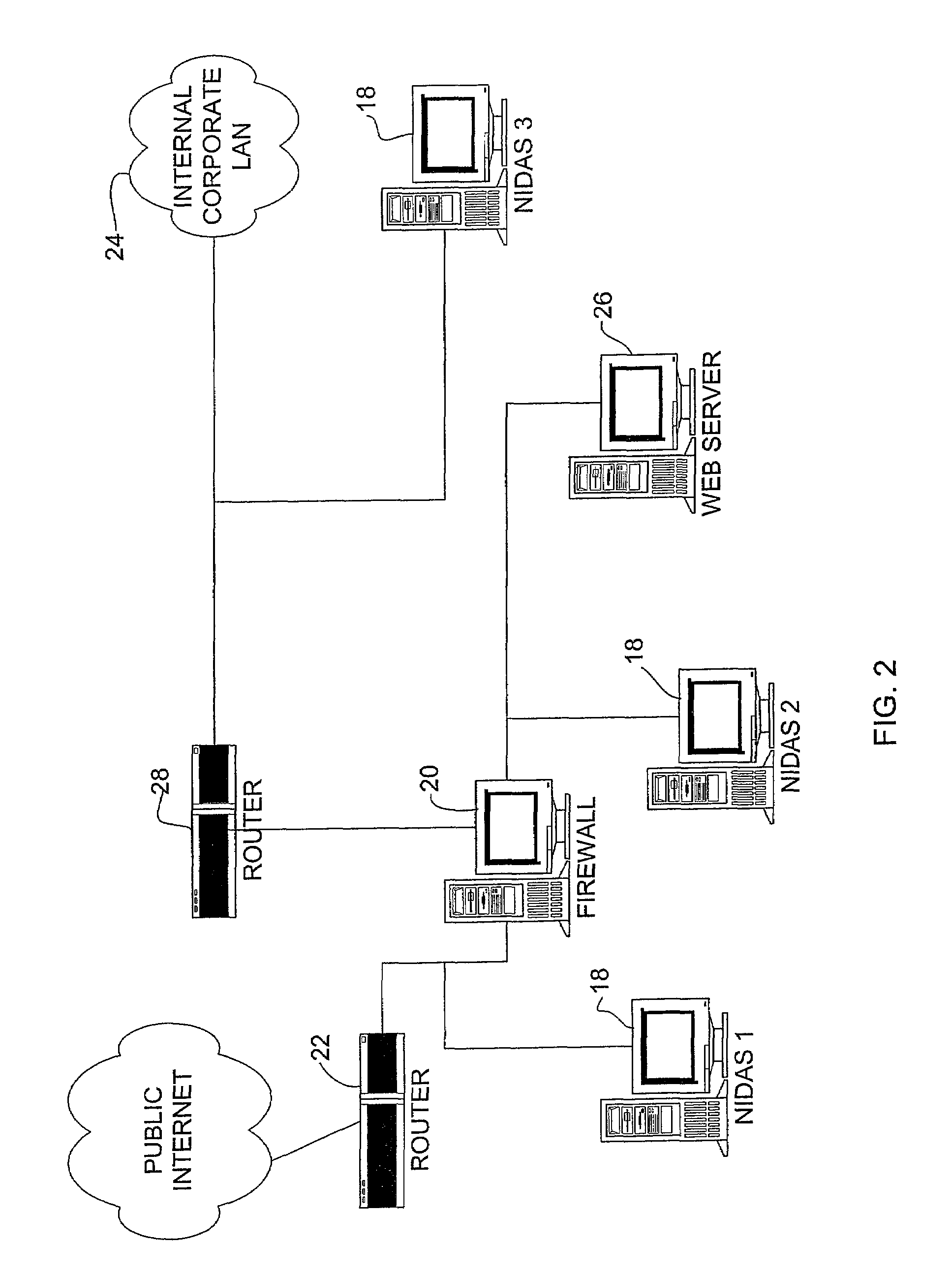
An intrusion detection and analysis system and method are disclosed. The system includes a data monitoring device comprising a capture engine operable to capture data passing through the network and configured to monitor network traffic, decode protocols, and analyze received data. The system further includes an intrusion detection device comprising a detection engine operable to perform intrusion detection on data provided by the data monitoring device. Application program interfaces are provided and configured to allow the intrusion detection device access to applications of the data monitoring device to perform intrusion detection. The system also includes memory for storing reference network information used by the intrusion detection device to determine if an intrusion has occurred.
Owner:MCAFEE LLC
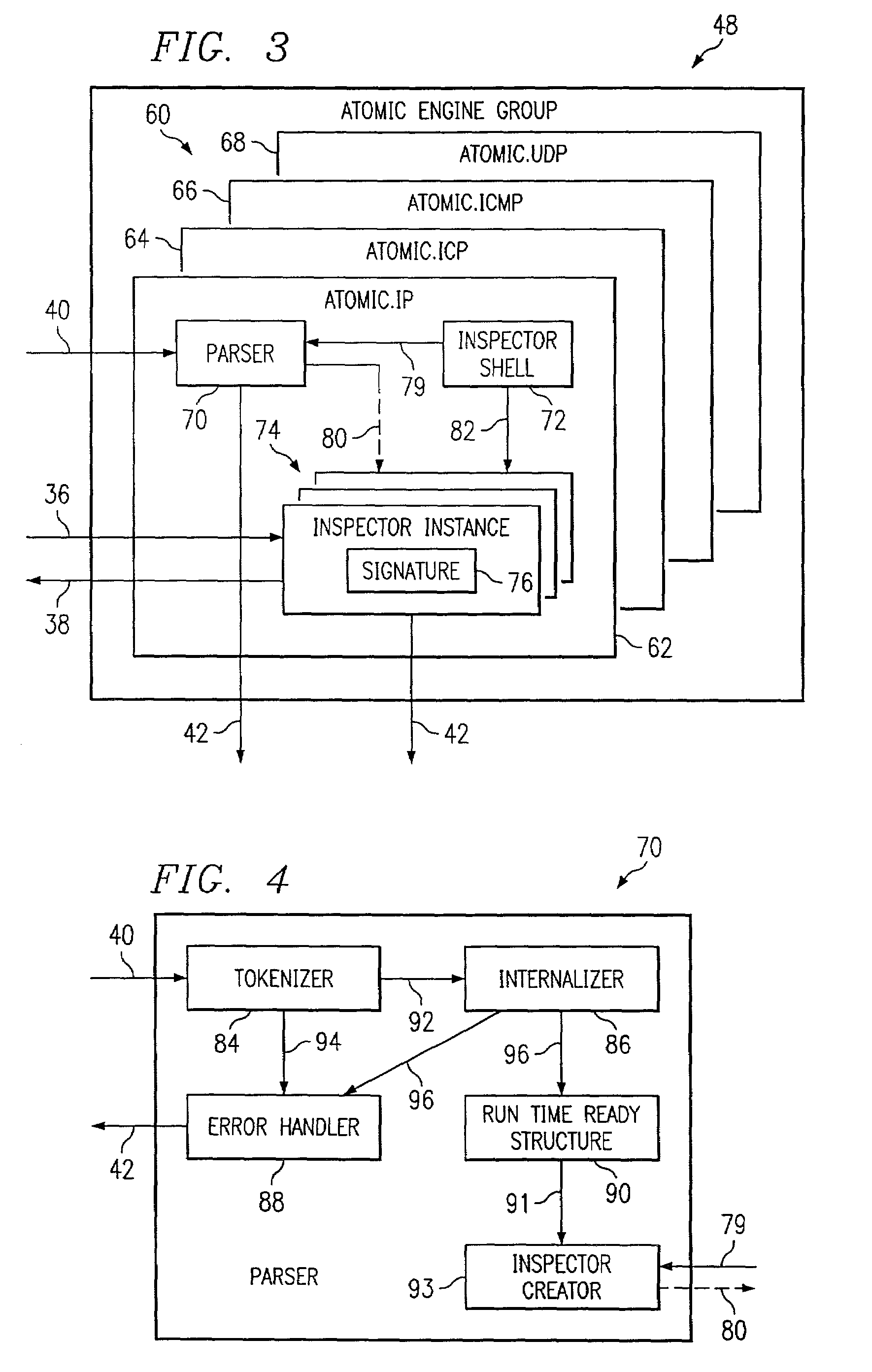
Method and system for configurable network intrusion detection
InactiveUS7243371B1Easy to modifyEasy to addMemory loss protectionUnauthorized memory use protectionTraffic capacityDistributed computing
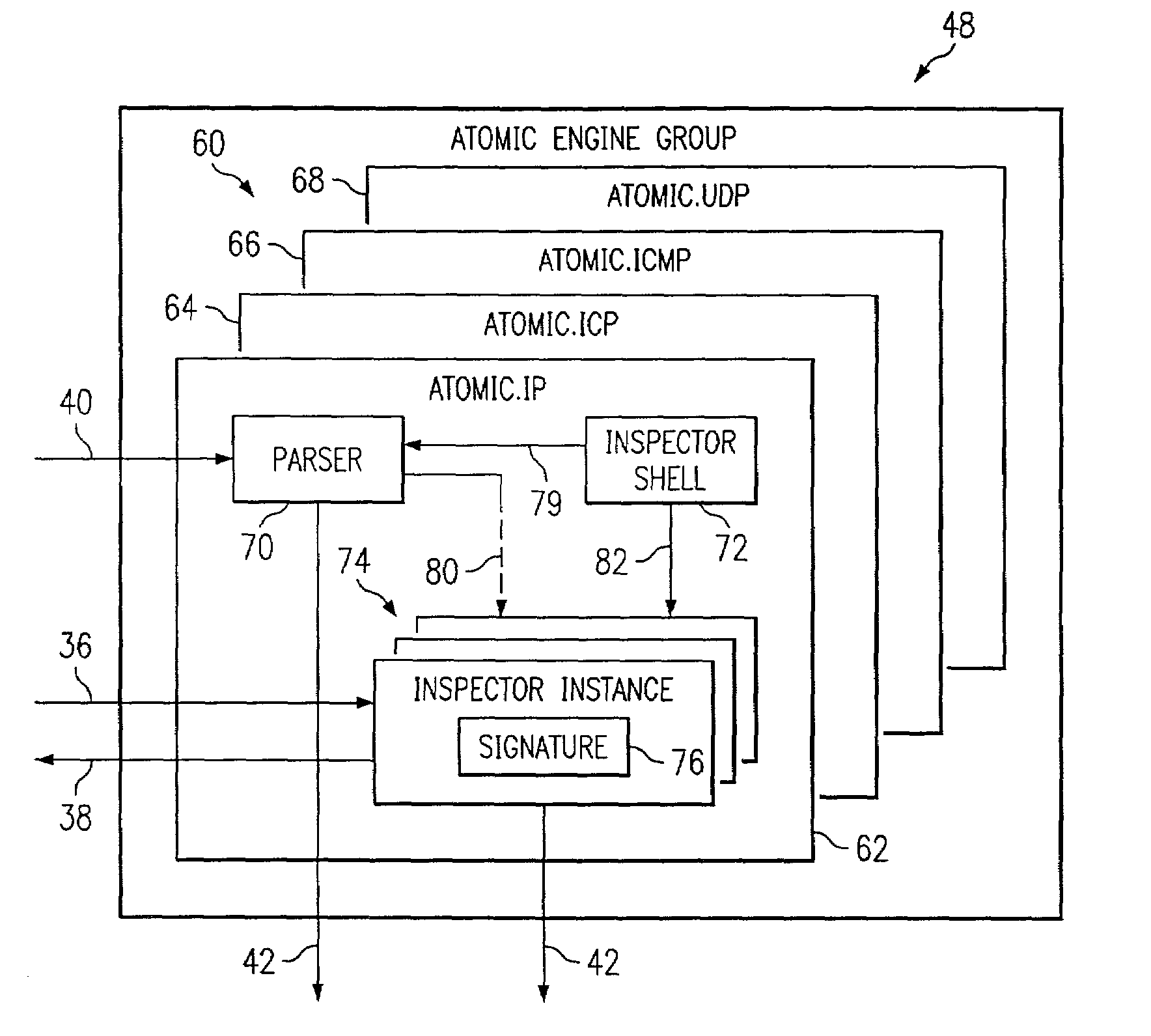
According to one embodiment of the invention, a method for automatically generating software code operable to detect a defined signature in network traffic comprises providing an inspector shell, generating a plurality of parameter name-value associations from provided configuration data, and automatically generating, by computer, an instance of the inspector shell having a signature defined by the parameter name-value associations.
Owner:CISCO TECH INC
Method and Apparatus for Deep Packet Inspection for Network Intrusion Detection
ActiveUS20080201772A1Hardware monitoringMultiple digital computer combinationsComputer hardwareData stream
In a method of determining whether a data stream includes unauthorized data, the data stream is analyzed using a hardware filter to detect a presence of one or more of a first set of patterns in the data stream. It is determined whether a packet in the data stream belongs to one of a plurality of data flows to be further inspected based on the analysis of the data stream by the hardware filter. A set of rules is applied to the packet to produce rule match status data if it is determined that the packet belongs to one of the plurality of data flows to be further inspected. The packet is analyzed to determine if the packet includes unauthorized data using software stored on a computer-readable medium and implemented on a processor if the rule match status data indicates that the packet potentially includes unauthorized data.
Owner:MARVELL ISRAEL MISL
Computer network intrusion detection
InactiveUS20120297489A1Easily and efficiently identifyingRapid responseMemory loss protectionError detection/correctionBIOSVirus
A method and system of identifying an attacker device attempting an intrusion into a network. At least one managed device of the network detects an incoming TCP / IP connection by the attacker device to the network. It is determined that the incoming TCP / IP connection is a Net BIOS connection that has created an invalid logon by the attacker device, linking the invalid logon with the NetBIOS TCP / IP connection, retrieving event log information from a security event log of the network, and determining (i) that a userid of the invalid logon is a local userid defined on a local device, (ii) that the userid of the invalid logon is a userid in a list of userids used by viruses, or (iii) that the userid of the invalid logon is neither the local userid nor is in the list of userids. The retrieved event log information is stored in a central violation database.
Owner:KYNDRYL INC
Signature based network intrusion detection system and method
Owner:MCAFEE LLC
Method And System For Network Intrusion Detection, Related Network And Computer Program Product
ActiveUS20070214504A1Easy to detectMemory loss protectionError detection/correctionData streamProtocol Application
A system for providing intrusion detection in a network wherein data flows are exchanged using associated network ports and application layer protocols. The system includes a monitoring module configured for monitoring data flows in the network, a protocol identification engine configured for detecting information on the application layer protocols involved in the monitored data flows, and an intrusion detection module configured for operating based on the information on application layer protocols detected. Intrusion detection is thus provided independently of any predefined association between the network ports and the application layer protocols.
Owner:III HLDG 1
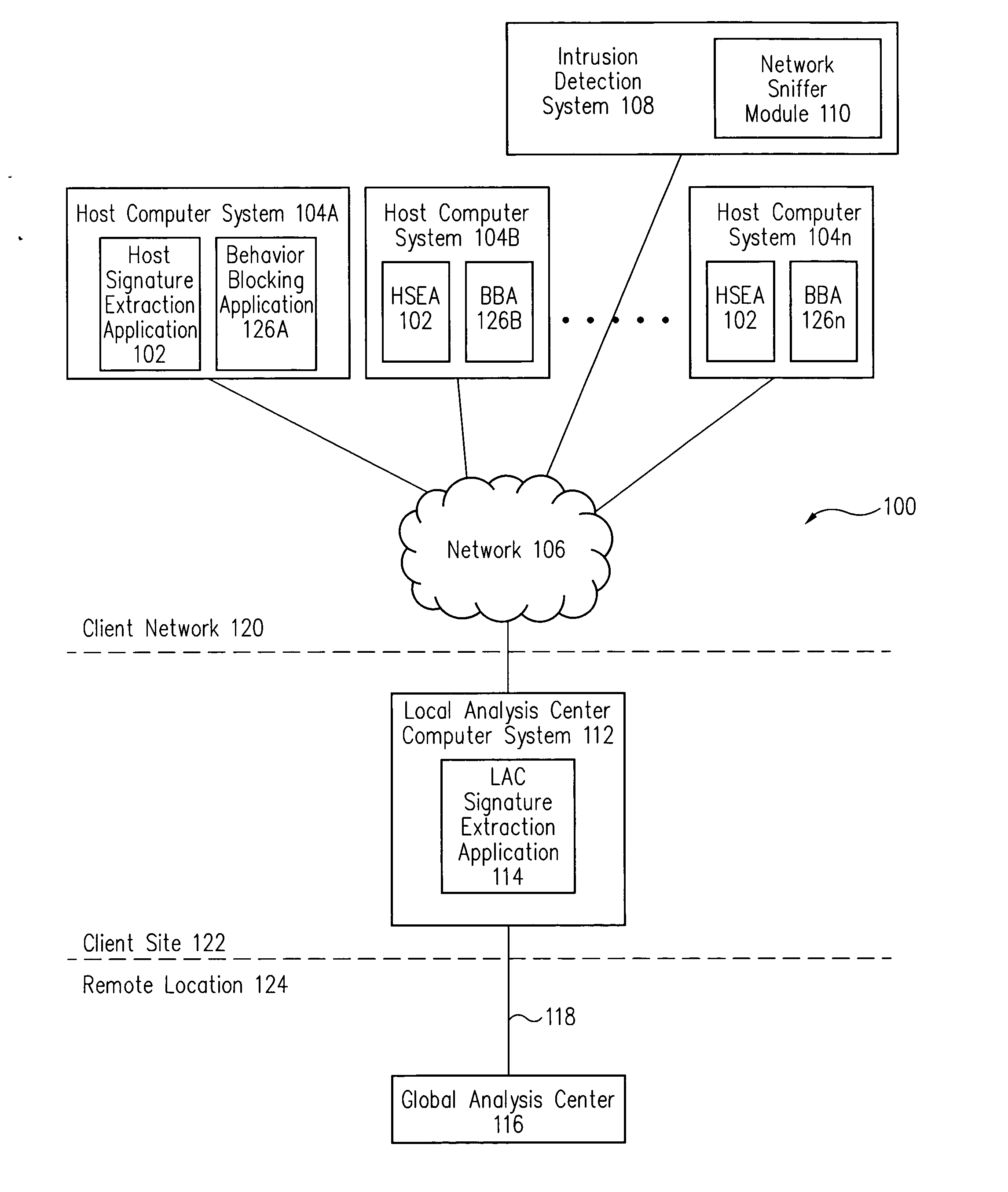
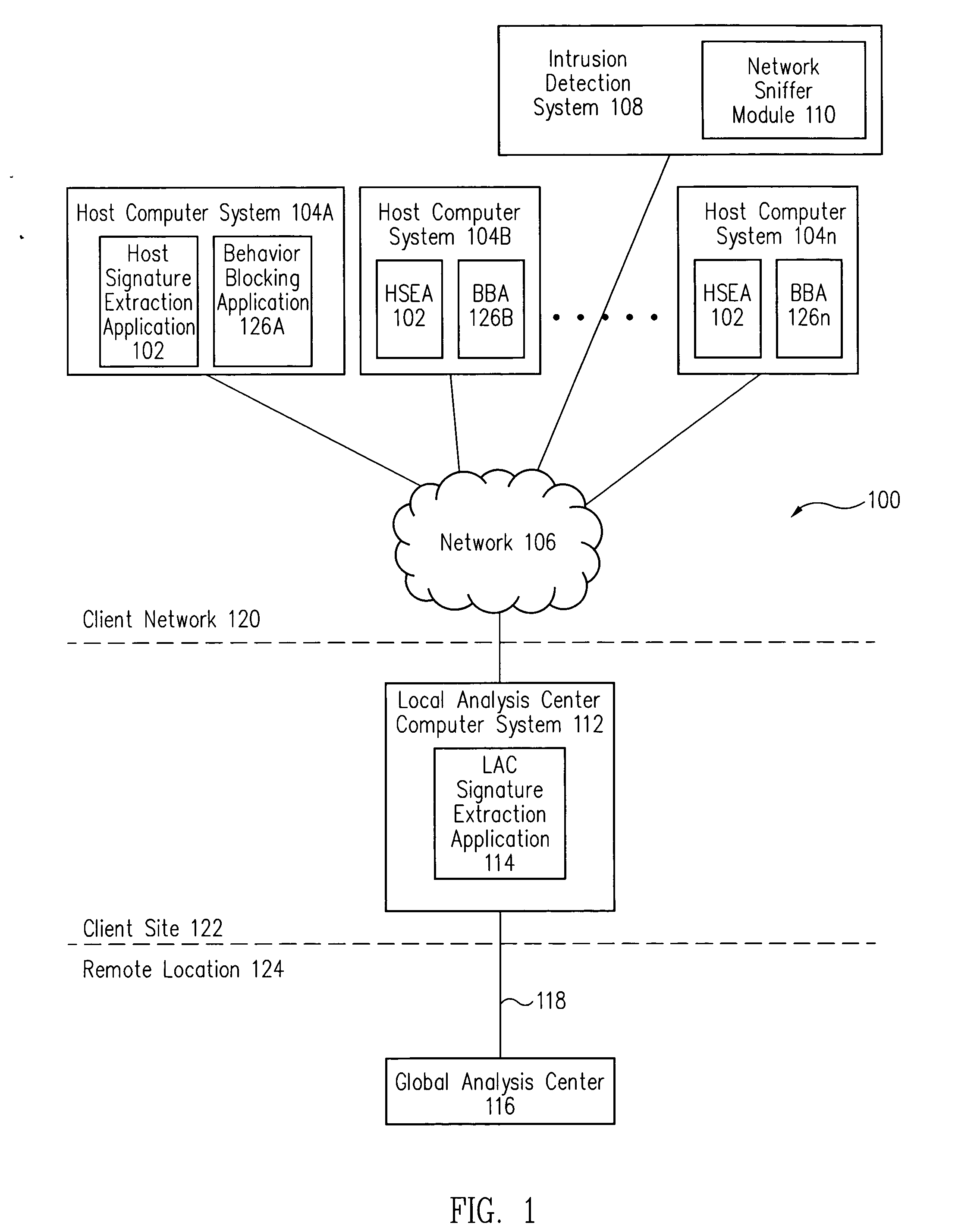
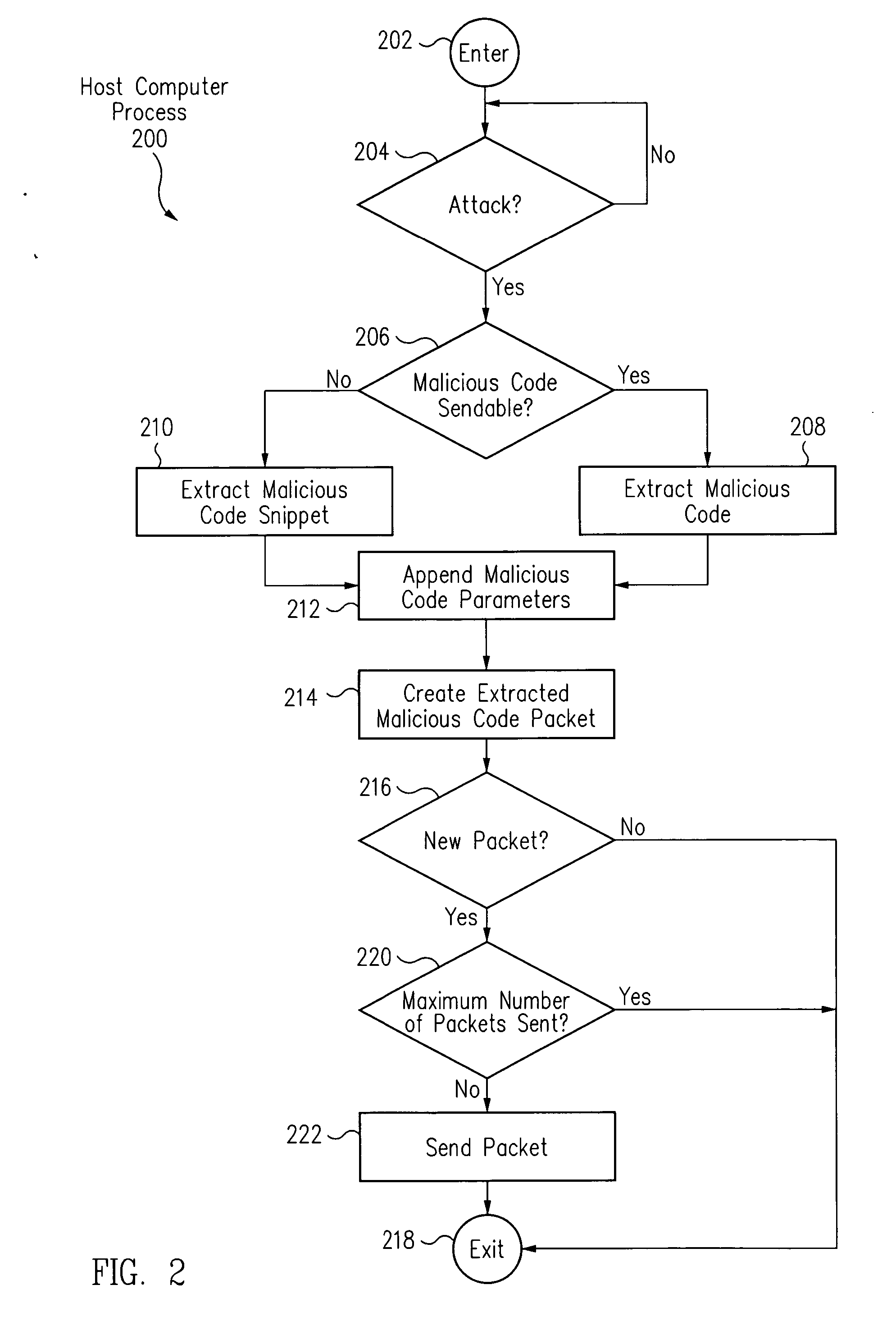
Signature extraction system and method
ActiveUS7392543B2Rapidly detected and preventedMemory loss protectionUnauthorized memory use protectionAnalysis centerComputerized system
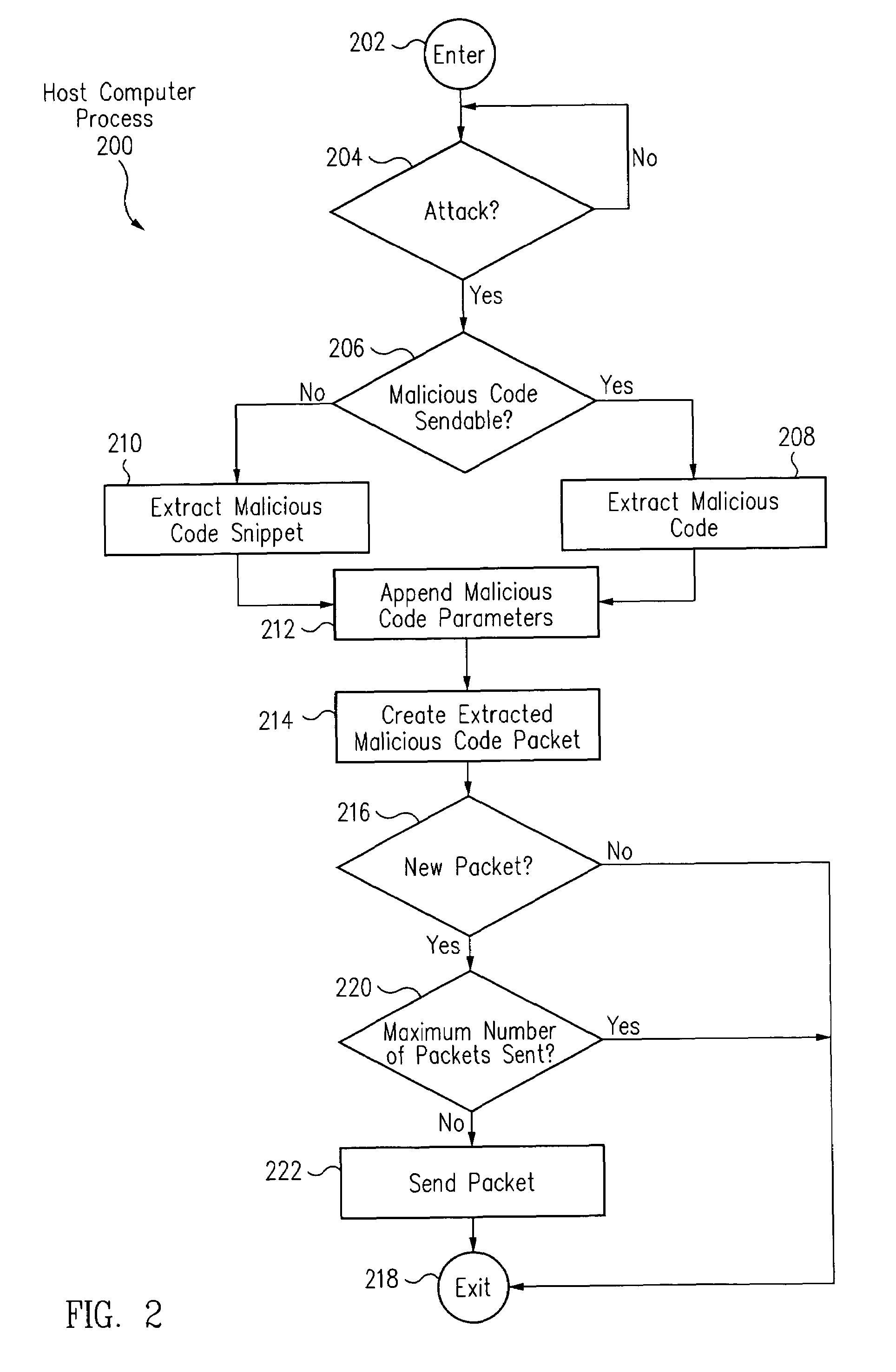
Host computer systems automatically detect malicious code. The host computer systems automatically generate and send malicious code packets of the malicious code to a local analysis center (LAC) computer system. Based on the received malicious code packets, the LAC computer system provides a signature update to a network intrusion detection system. Further, the LAC computer system also automatically sends malicious code signatures of the malicious code to a global analysis center. In this manner, the spread of the malicious code is rapidly detected and prevented.
Owner:CA TECH INC
Network intrusion detection system having application inspection and anomaly detection characteristics
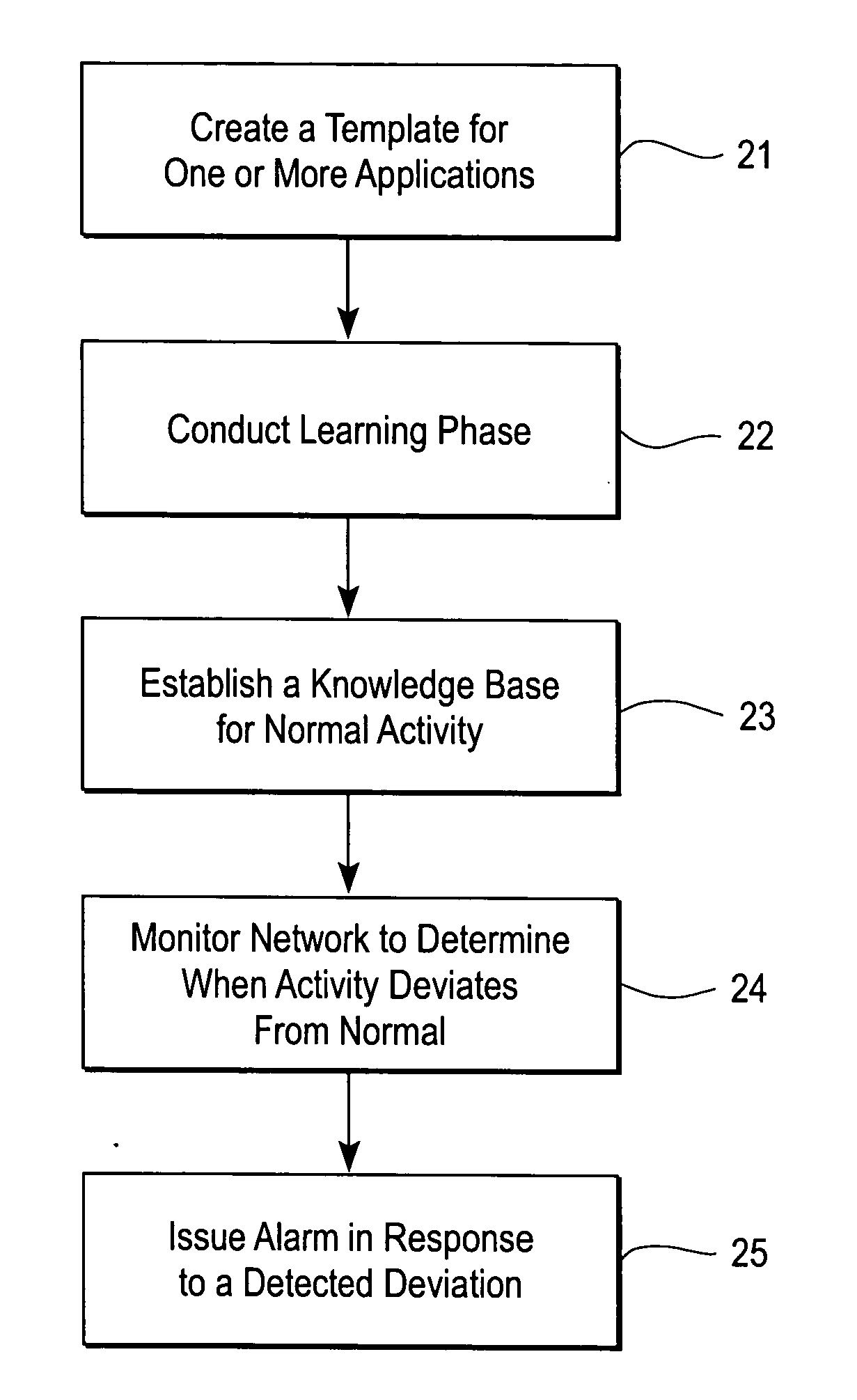
An intrusion detection system and method for a computer network includes a processor and one or more programs that run on the processor for application inspection of data packets traversing the computer network. The one or more programs also obtaining attribute information from the packets specific to a particular application and comparing the attribute information against a knowledge database that provides a baseline of normal network behavior. The processor raises an alarm whenever the attribute information exceeds a predetermined range of deviation from the baseline of normal network behavior. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
Enabling network intrusion detection by representing network activity in graphical form utilizing distributed data sensors to detect and transmit activity data
ActiveUS20070209075A1Reduce in quantitySmall sizeMemory loss protectionError detection/correctionData packNetwork activity
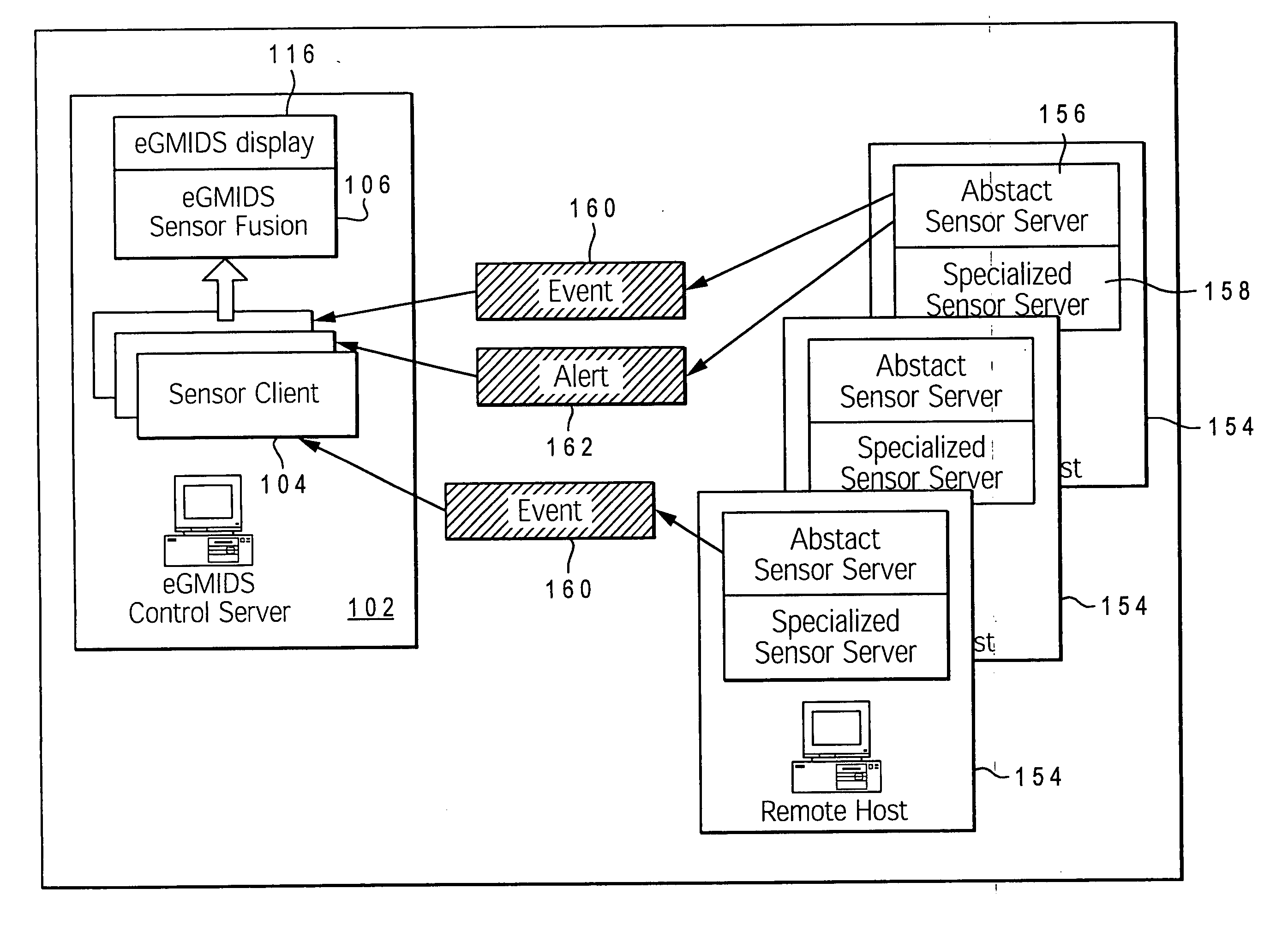
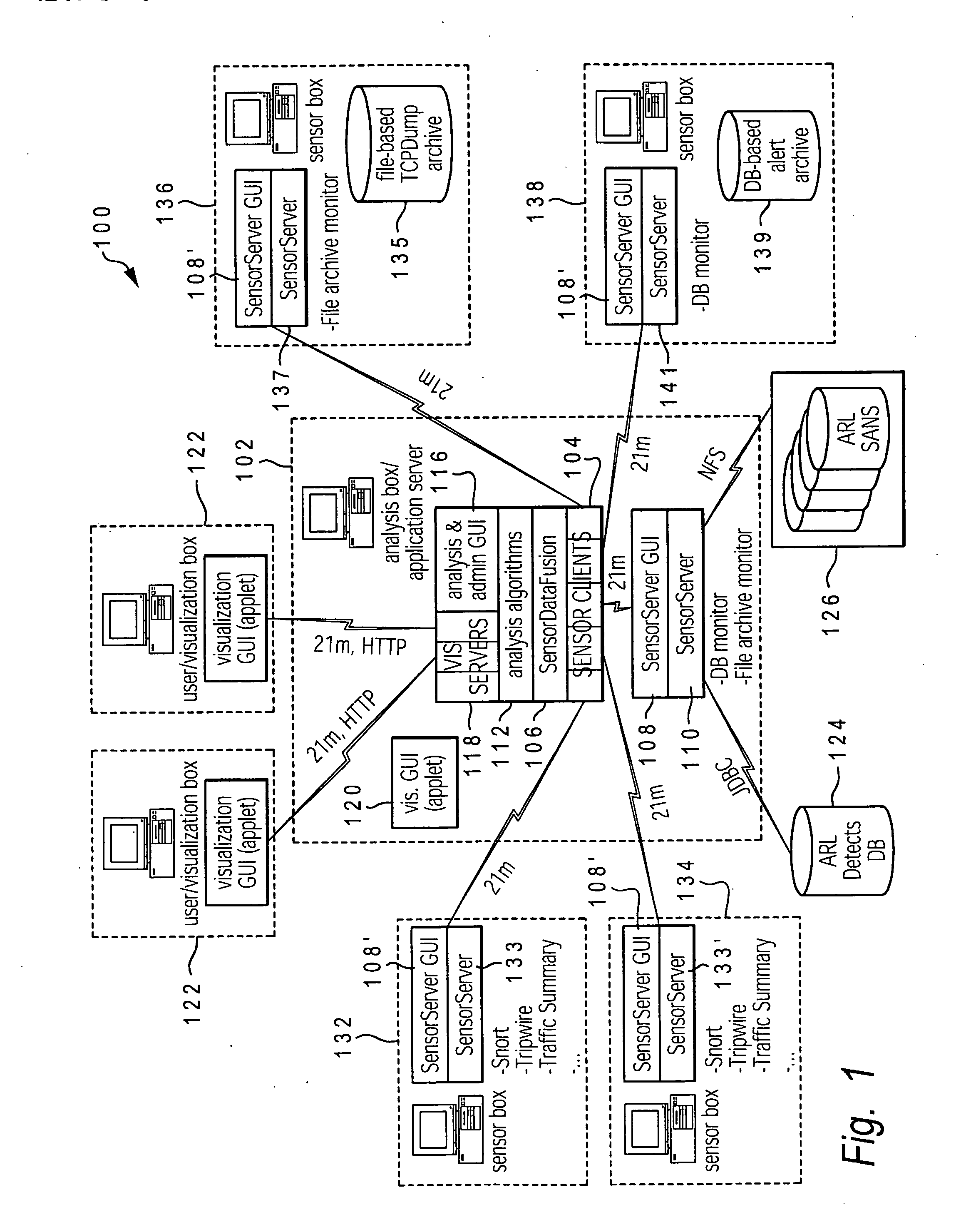
A method, system, and computer program product for detecting and mapping activity occurring at and between devices on a computer network for utilization within an intrusion detection mechanism. An enhanced graph matching intrusion detection system (eGMIDS) utility executing on a control server provides data collection functions and data fusion techniques. The eGMIDS comprises multiple sensors and associated unique adaptors that are located at different remote devices of the network and utilized to detect specific types of activity occurring at the respective devices relevant to eGMIDS processing. The sensors convert the data into eGMIDS format and encapsulate the data in a special transmission packet that is transmitted to the control server. The eGMIDS utility converts the activity data within these packets into eGMIDS-usable format and then processes the converted data via a data fusion technique to generate a graphical representation of the network (devices) and the activity occurring at / amongst the various devices.
Owner:NORTHROP GRUMMAN SYST CORP
Method and system for detecting network compromise
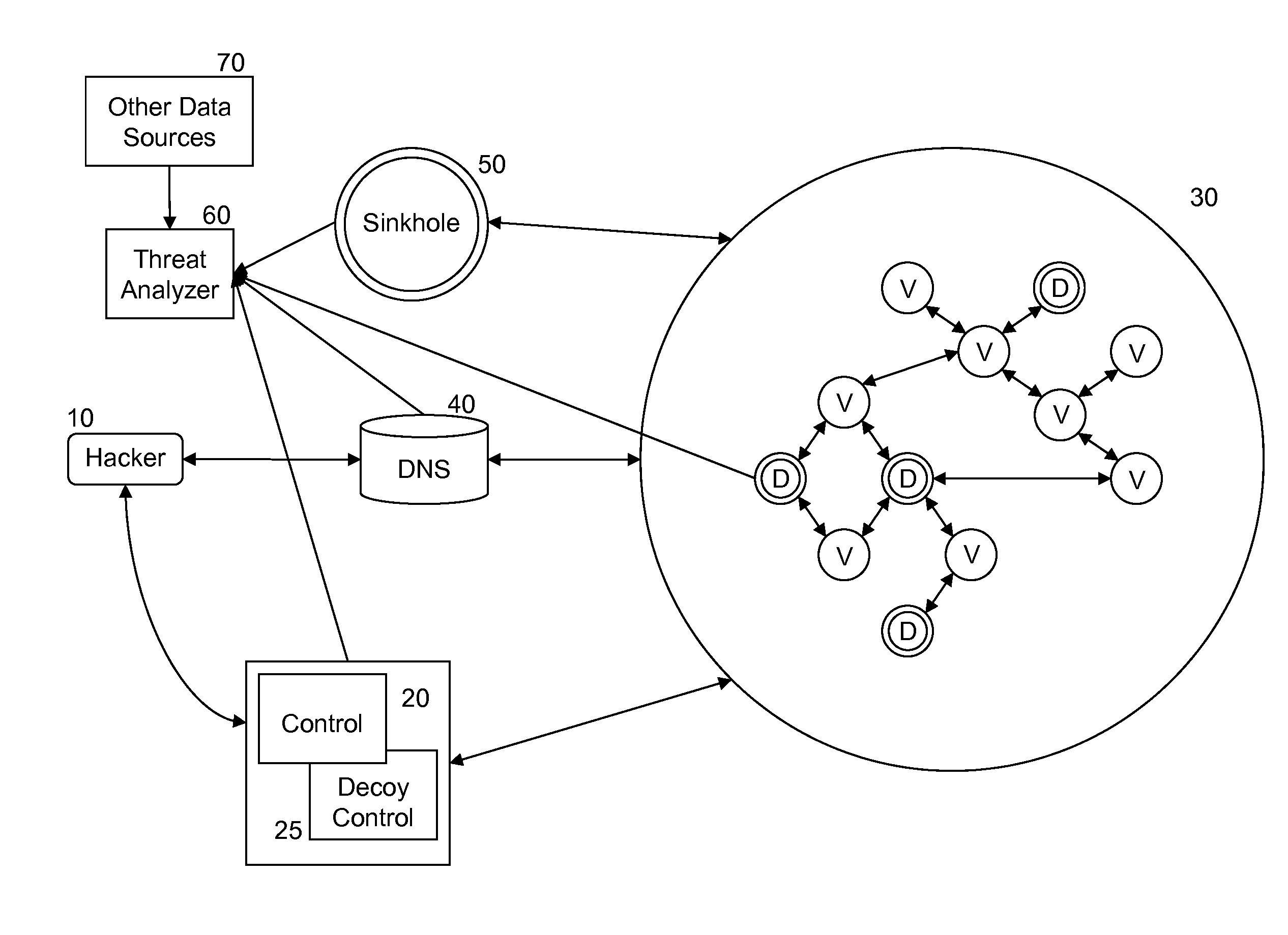
ActiveUS9356942B1Eliminate the problemMemory loss protectionError detection/correctionInternet privacyEngineering
A method and system are described for detecting unauthorized access to one or more of a plurality of networked victim computers in a victim cloud. The networked victim computers connect to one or more DNS servers. The system includes one or more decoy bot computers, which are operated as victim computers in the victim cloud. The system also includes one or more decoy control computers, which are operated as control computers that communicate with victim computers in the victim cloud. Threats are identified by analyzing data traffic communicated with the decoy bot computers and decoy control computers for information suspected of having being sent from a victim's computer without proper authorization, and by monitoring whether behavior of a DNS server deviates from expected behaviors.
Owner:SECURITY SERVICES LLC
High-Performance Context-Free Parser for Polymorphic Malware Detection
The invention provides a method and apparatus for advanced network intrusion detection. The system uses deep packet inspection that can recognize languages described by context-free grammars. The system combines deep packet inspection with one or more grammar parsers (409A-409M). The invention can detect token streams (408) even when polymorphic. The system looks for tokens at multiple byte alignments and is capable of detecting multiple suspicious token streams (408). The invention is capable of detecting languages expressed in LL(I) or LR(I) grammar. The result is a system that can detect attacking code wherever it is located in the data stream (408).
Owner:CHO YOUNG H +1
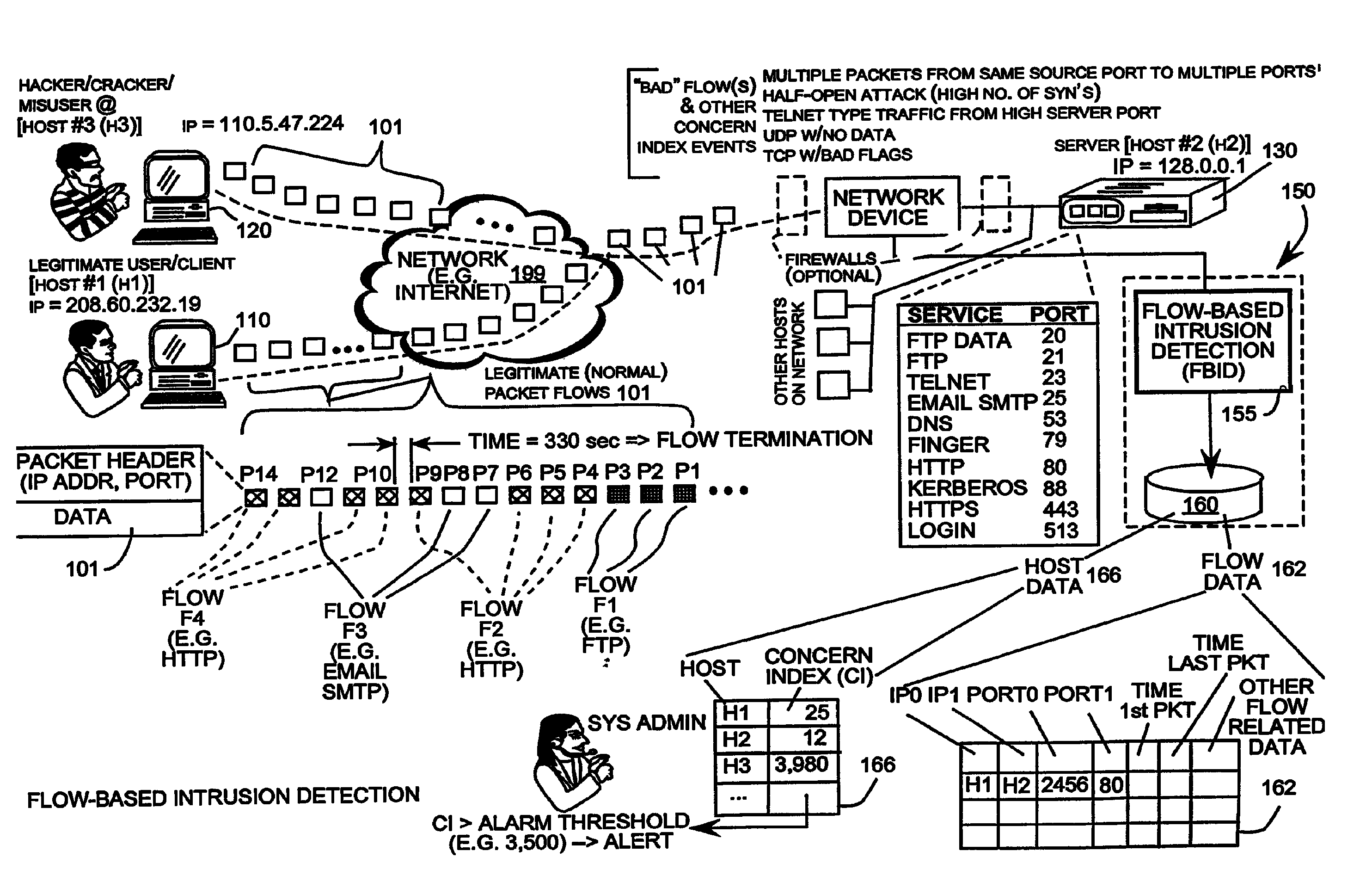
Packet sampling flow-based detection of network intrusions
InactiveUS7512980B2The method is accurate and reliableEasy to solveMemory loss protectionDigital data processing detailsComputer communication networksDistributed computing
A flow-based intrusion detection system for detecting intrusions in computer communication networks. Data packets representing communications between hosts in a computer-to-computer communication network are processed and assigned to various client / server flows. Statistics are collected for each flow. Then, the flow statistics are analyzed to determine if the flow appears to be legitimate traffic or possible suspicious activity. A concern index value is assigned to each flow that appears suspicious. By assigning a value to each flow that appears suspicious and adding that value to the total concern index of the responsible host, it is possible to identify hosts that are engaged in intrusion activity. When the concern index value of a host exceeds a preset alarm value, an alert is issued and appropriate action can be taken.
Owner:CISCO TECH INC
Enabling network intrusion detection by representing network activity in graphical form utilizing distributed data sensors to detect and transmit activity data
ActiveUS8266697B2Increase speedImprove accuracyMemory loss protectionError detection/correctionGraphicsNetwork activity
A method, system, and computer program product for detecting and mapping activity occurring at and between devices on a computer network for utilization within an intrusion detection mechanism. An enhanced graph matching intrusion detection system (eGMIDS) utility executing on a control server provides data collection functions and data fusion techniques. The eGMIDS comprises multiple sensors and associated unique adaptors that are located at different remote devices of the network and utilized to detect specific types of activity occurring at the respective devices relevant to eGMIDS processing. The sensors convert the data into eGMIDS format and encapsulate the data in a special transmission packet that is transmitted to the control server. The eGMIDS utility converts the activity data within these packets into eGMIDS-usable format and then processes the converted data via a data fusion technique to generate a graphical representation of the network (devices) and the activity occurring at / amongst the various devices.
Owner:NORTHROP GRUMMAN SYST CORP
Signature extraction system and method
ActiveUS20050022018A1Quick checkRapidly preventedMemory loss protectionDigital data processing detailsAnalysis centerComputer security
Host computer systems automatically detect malicious code. The host computer systems automatically generate and send malicious code packets of the malicious code to a local analysis center (LAC) computer system. Based on the received malicious code packets, the LAC computer system provides a signature update to a network intrusion detection system. Further, the LAC computer system also automatically sends malicious code signatures of the malicious code to a global analysis center. In this manner, the spread of the malicious code is rapidly detected and prevented.
Owner:CA TECH INC
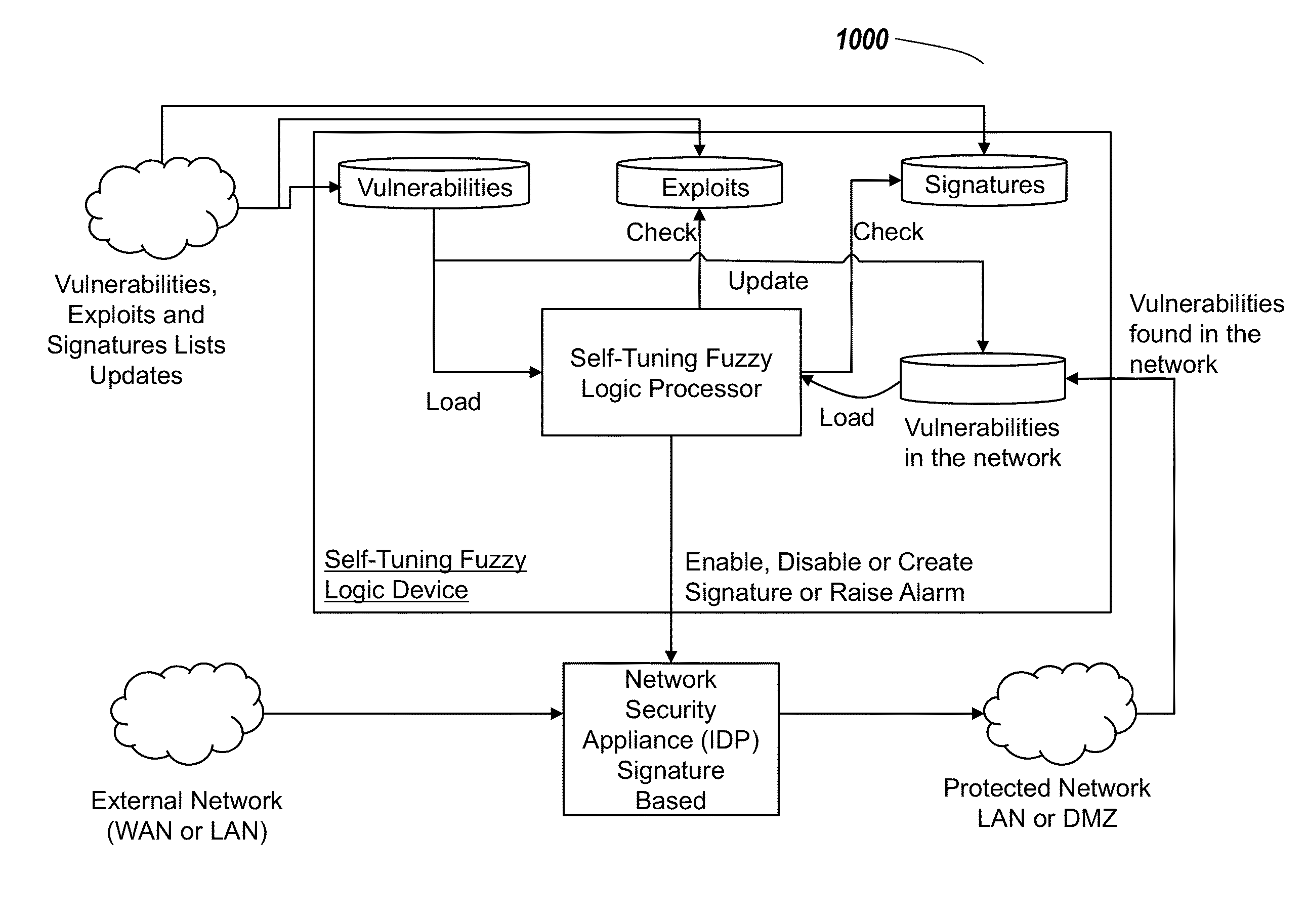
Systems and methods for self-tuning network intrusion detection and prevention
ActiveUS20150033340A1Improve efficiencyFast transferMemory loss protectionError detection/correctionSelf-tuningPrivate network
Systems and method of the present disclosure are directed to a network security tool. In some embodiments, the tool identifies a current vulnerability of a private network. The tool can determine a signature of an attack configured to exploit the current vulnerability. The tool can comparing the signature with active and inactive signatures stored in a signature repository. The tool can compare the signatures to identify an inactive signature corresponding to the signature of the attack configured to exploit the current vulnerability. The tool can automatically activate, responsive to the comparison, the identified inactive signature. The tool can use the activated signature to identify an exploit based on data packets received via the private network.
Owner:CRYPTEIA NETWORKS
Network intrusion detection with distributed correlation
A network security system employing multiple levels of processing to identify security threats. Multiple host machines may each contain an agent that detects possibilities of security threats based on raw data sensed locally at that host. The hosts may share information obtained from local analysis and each host may use information generated at one or more other hosts, in combination with information generated locally, to identify a security concern, indicating with greater certainty that a security threat exists. Based on security concerns generated by multiple hosts, a security threat may be indicated and protective action may be taken.
Owner:MICROSOFT TECH LICENSING LLC
Method of managing utilization of network intrusion detection systems in a dynamic data center
A method of managing utilization of network intrusion detection systems in a dynamic data center is provided. A plurality of network intrusion detection systems are provided, each being networked so that utilization of each network intrusion detection system can be based on demand for the network intrusion detection systems in the dynamic data center. A monitoring policy and a plurality of monitoring points to be monitored on a network with any of the network intrusion detection systems are received. Further, the monitoring of the monitoring points is automatically arranged using the network intrusion detection systems and the monitoring policy.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
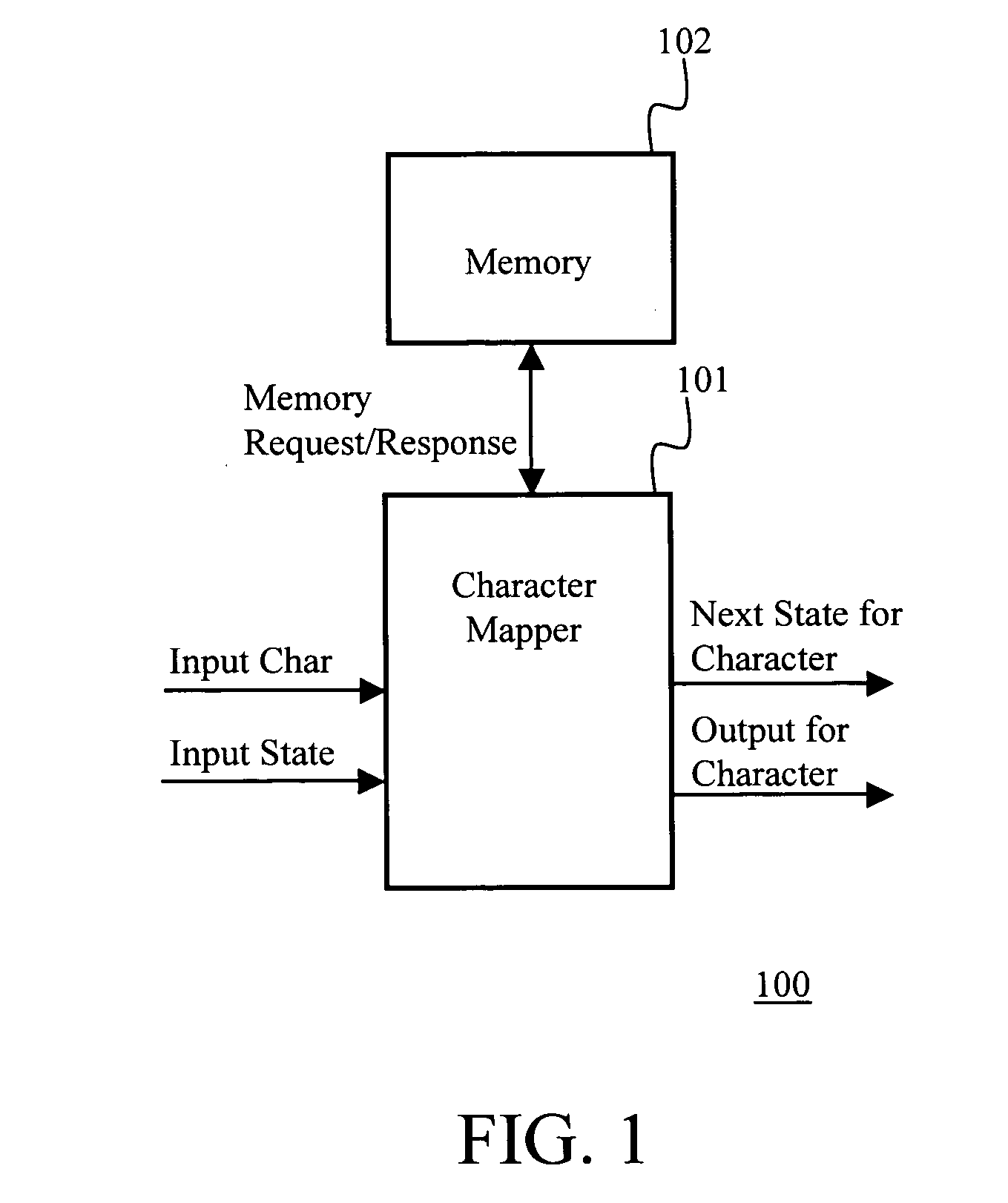
Layered memory architecture for deterministic finite automaton based string matching useful in network intrusion detection and prevention systems and apparatuses
ActiveUS20060101195A1Reduce decreaseTransmissionMemory systemsLine rateDeterministic finite automaton
Owner:FORTINET
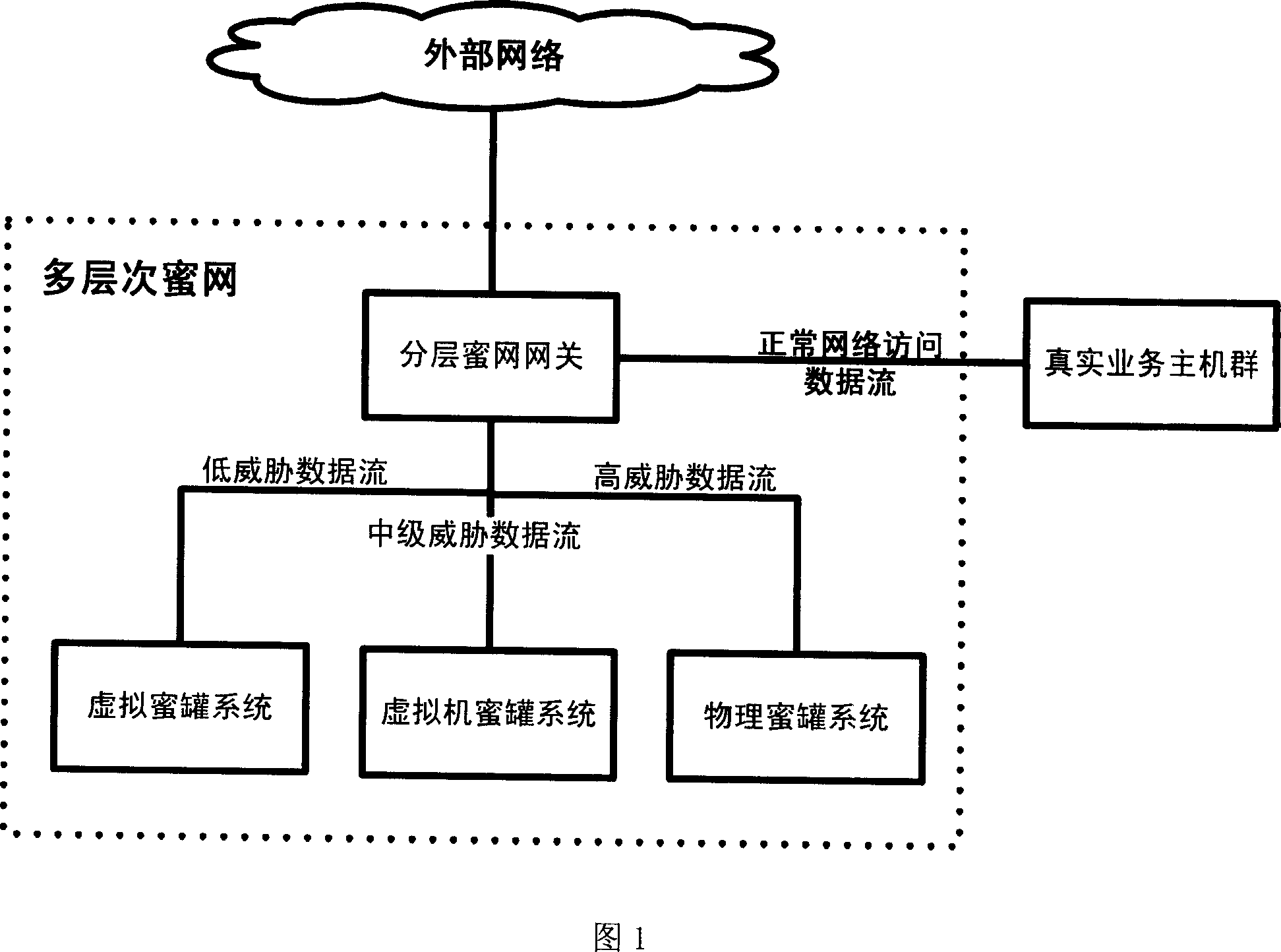
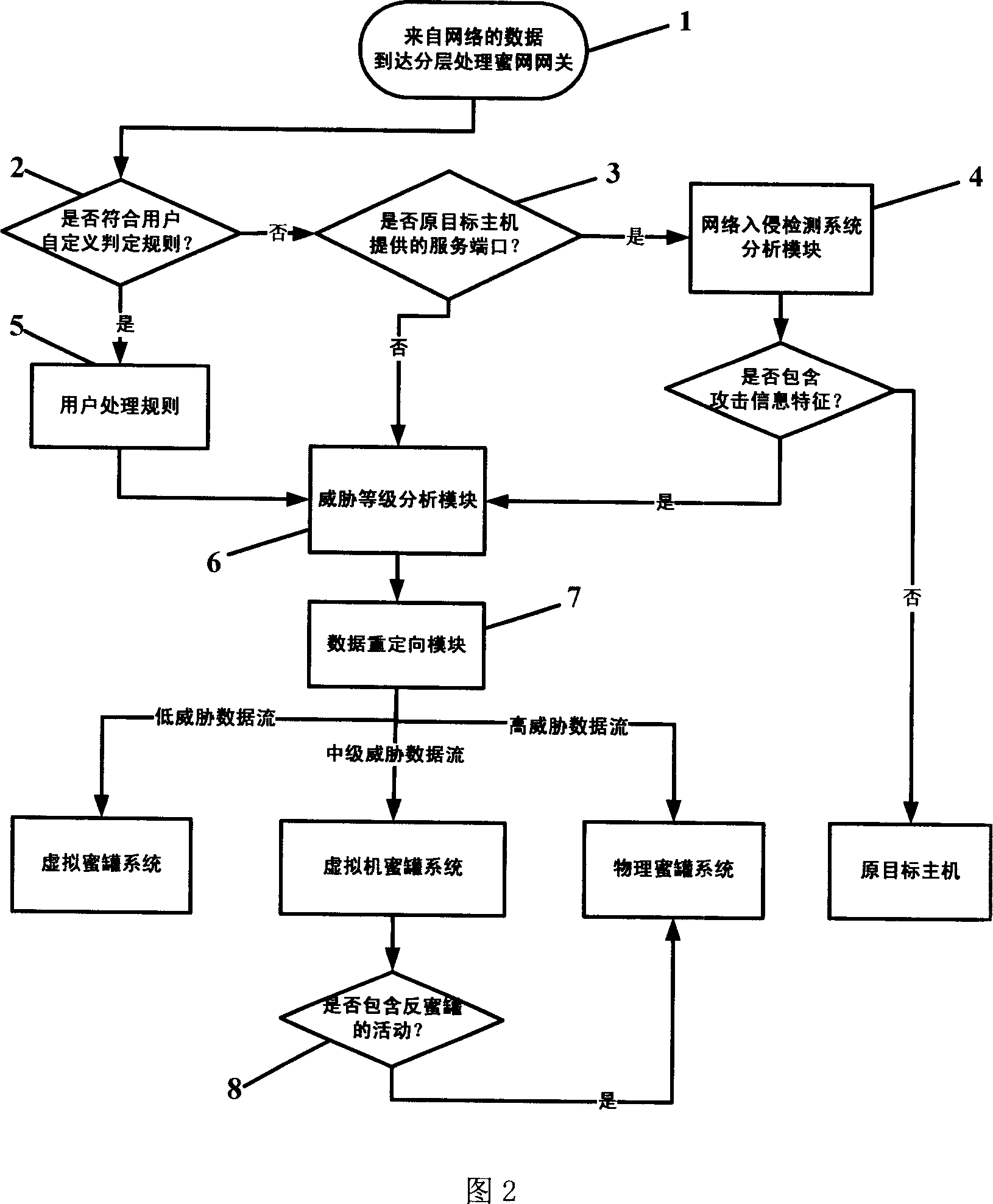
Multi-layer honey network data transmission method and system
InactiveCN101087196AIncrease reachSave resourcesNetwork connectionsSecuring communicationData streamNonnormal data
The invention relates to multilayer honey-net data transmission method and system, and the gateway of honey-net receives the data flow of external network; the gateway of honey-net detects the network intrusion for the received data flow; the normal data flow can pass, which is sent to the target host computer; and the informal data flow is divide into high, middle and low according to dangerous level; and the data flow with high level is sent to physical honey-tank system, the data flow with middle level is sent to virtual machine honey-tank system, and the data floe with low level is sent to virtual honey-tank system. The invention can utilize the advantages of low interactive honey-tank system and high interactive honey-tank system, save system source, and improve the covering area of honey-tank system and the ability of obtaining the movable information of network attack and capturing the malice code; it can defeat the anti-honey tank technique. And it can be used in security field of computer network.
Owner:PEKING UNIV
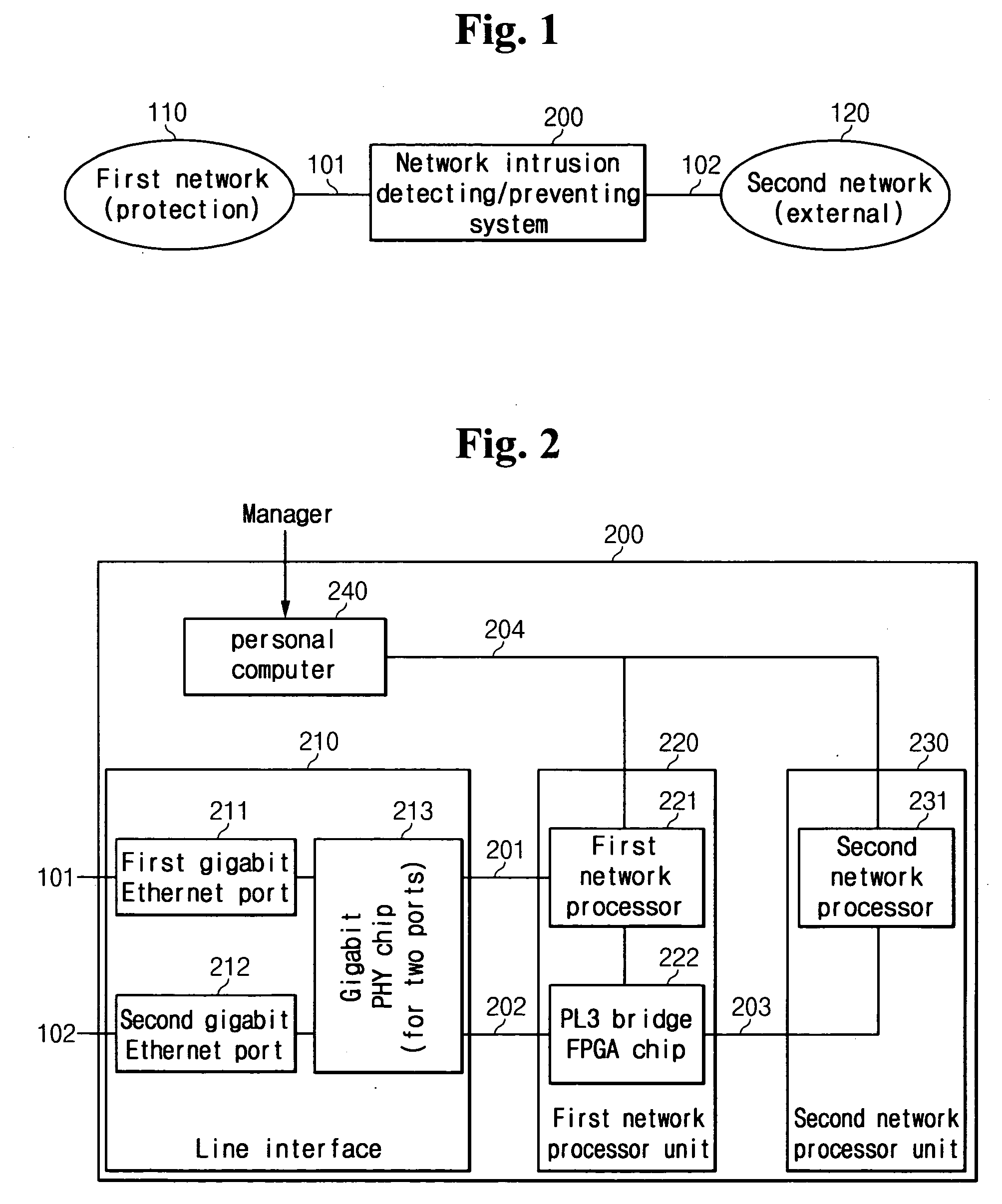
In-line mode network intrusion detect and prevent system and method thereof
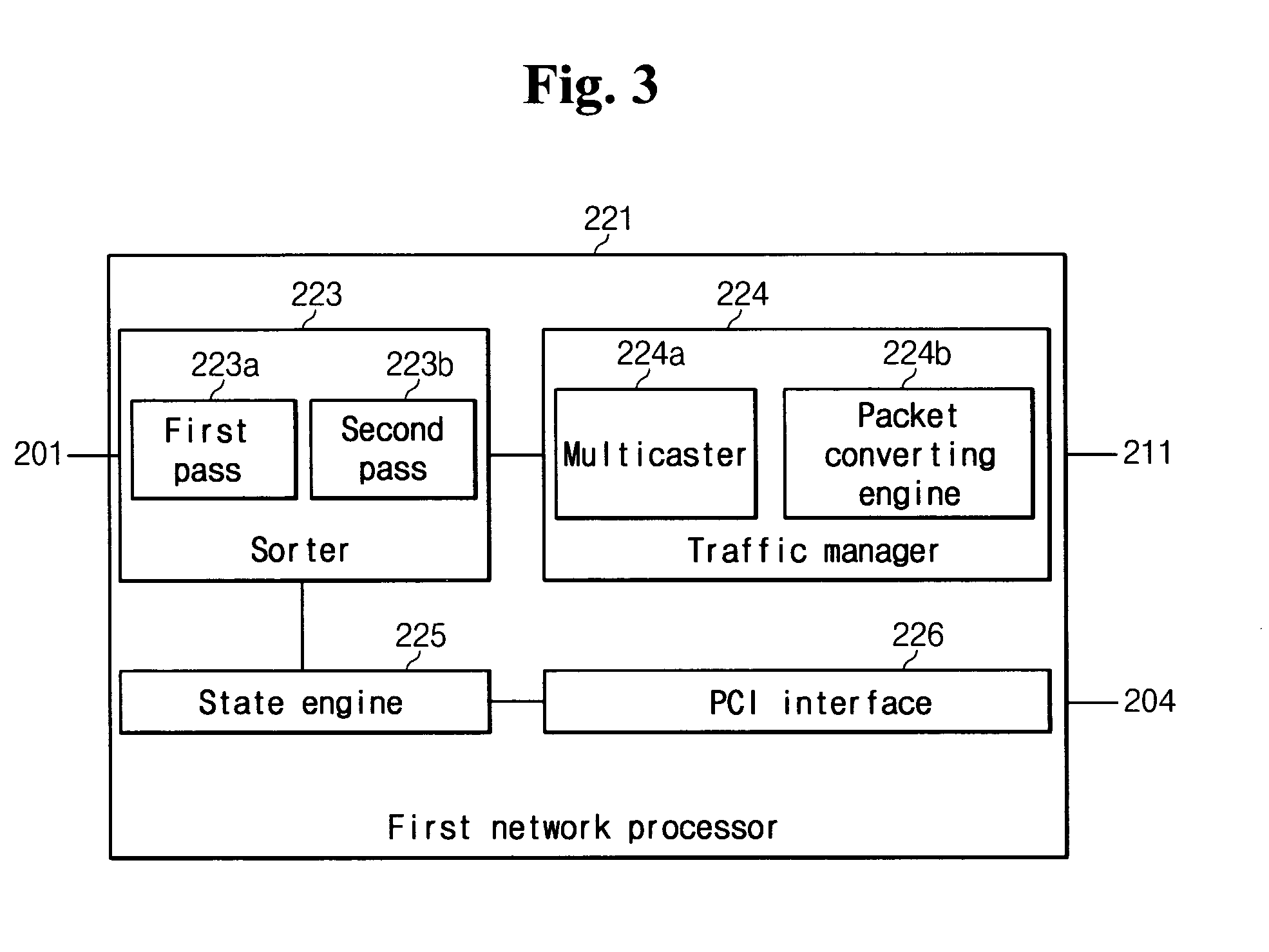
InactiveUS20050076227A1Respond quicklyProcess stabilityUser identity/authority verificationUnauthorized memory use protectionComputer networkNetwork processor
Disclosed is an in-line mode network intrusion detecting and preventing system coupled between a protection network and an external network, for detecting intrusion states between the networks and preventing the intrusion. The system comprises a first network processor unit for monitoring the packets communicated between the networks to collect various statistical data, and performing a packet filtering process according to a packet preventing rule and a packet sensing process according to a sensing rule; and a second network processor unit for checking payloads of the packets with reference to attack signatures to detect the attack states to one of the networks.
Owner:ELECTRONICS & TELECOMM RES INST
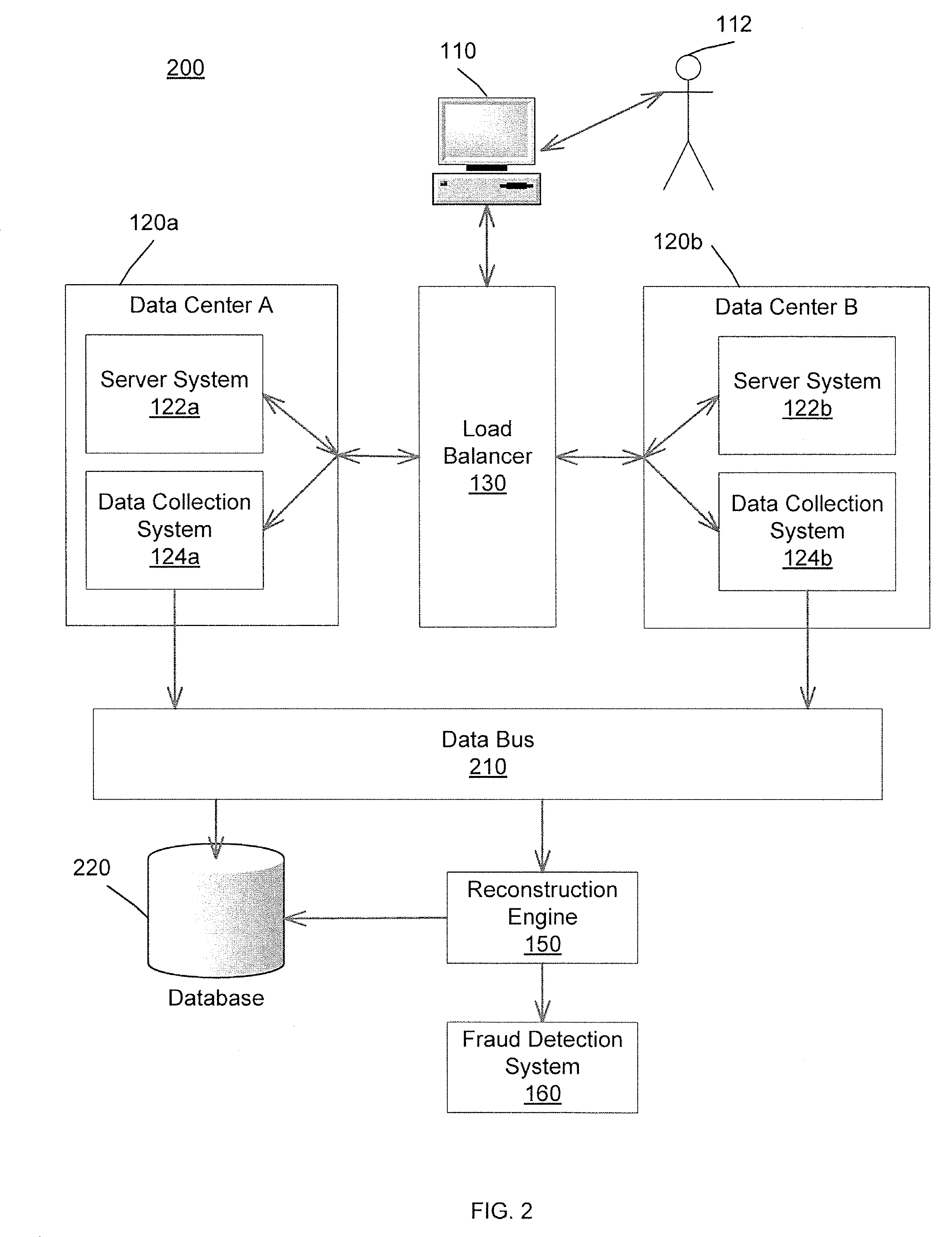
Detecting and interdicting fraudulent activity on a network
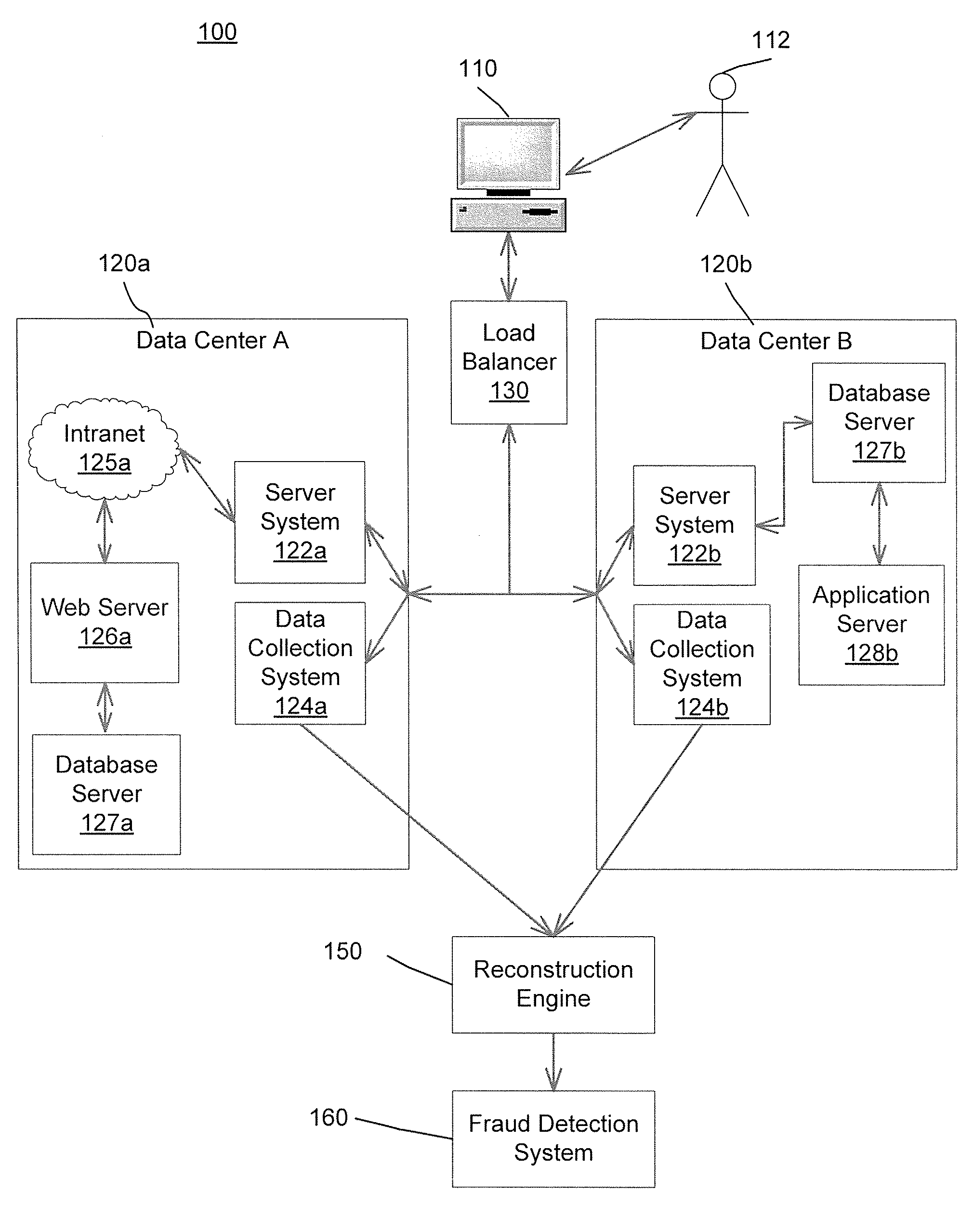
ActiveUS7856494B2Improve representationImprove system performanceDigital data processing detailsAnalogue secracy/subscription systemsData centerComputer science
Described are computer-based methods and apparatuses, including computer program products, for detecting and interdicting fraudulent activity on a network. An user utilizes a transmitting device to transmit user requests that are split between a plurality of data centers for processing. The user requests are captured at the data centers. The user requests are unified into an user session. The user session can be analyzed for fraud detection, marketing analysis, network intrusion detection, customer service analysis, and / or performance analysis. If fraudulent activity is detected, then the user can be interdicted to prevent further fraudulent activity.
Owner:FMR CORP
Method and apparatus for providing network and computer system security
Owner:INT BUSINESS MASCH CORP
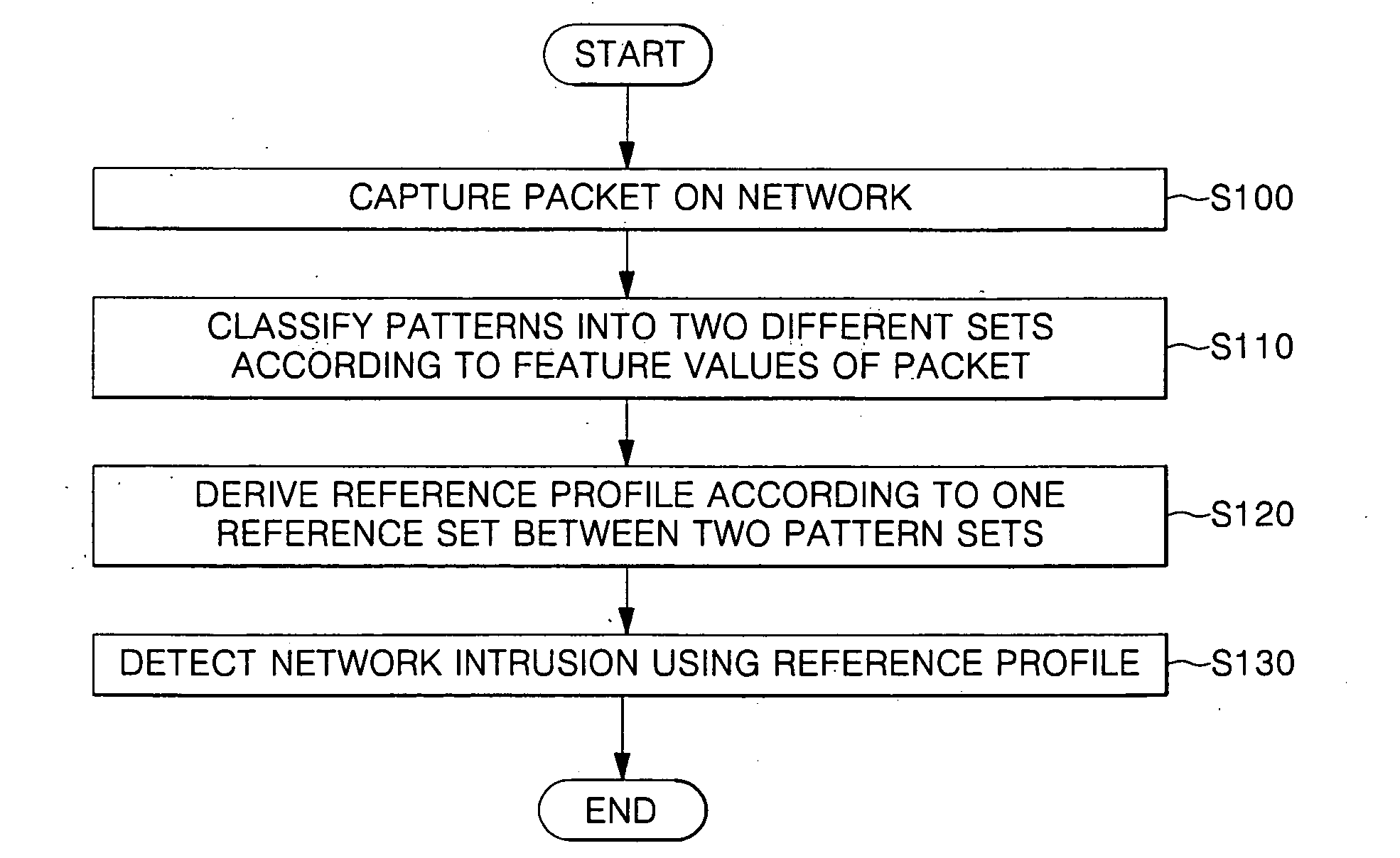
System and method for detecting network intrusion
InactiveUS20070150954A1Efficient detectionMemory loss protectionData taking preventionReal-time computingAttack patterns
In a system and method for detecting network intrusion, the system comprises: a packet capturer which captures at least one packet on a network; a preprocessor which provides feature values dependent on features of each packet captured by the packet capturer; and a learning engine for classifying patterns dependent on the feature values provided by the preprocessor into two different pattern sets, and for selecting one pattern set having more elements from the pattern sets as a reference set so as to detect network intrusion. The network intrusion detection system and method do not depend on historical data according to known attack patterns, and thus not only detect a changed attack pattern but also efficiently detect network intrusion.
Owner:SAMSUNG ELECTRONICS CO LTD
Network intrusion detection and prevention system and method thereof
InactiveUS20060085855A1Maximize the effectCritical damageMemory loss protectionData taking preventionData packPublic information
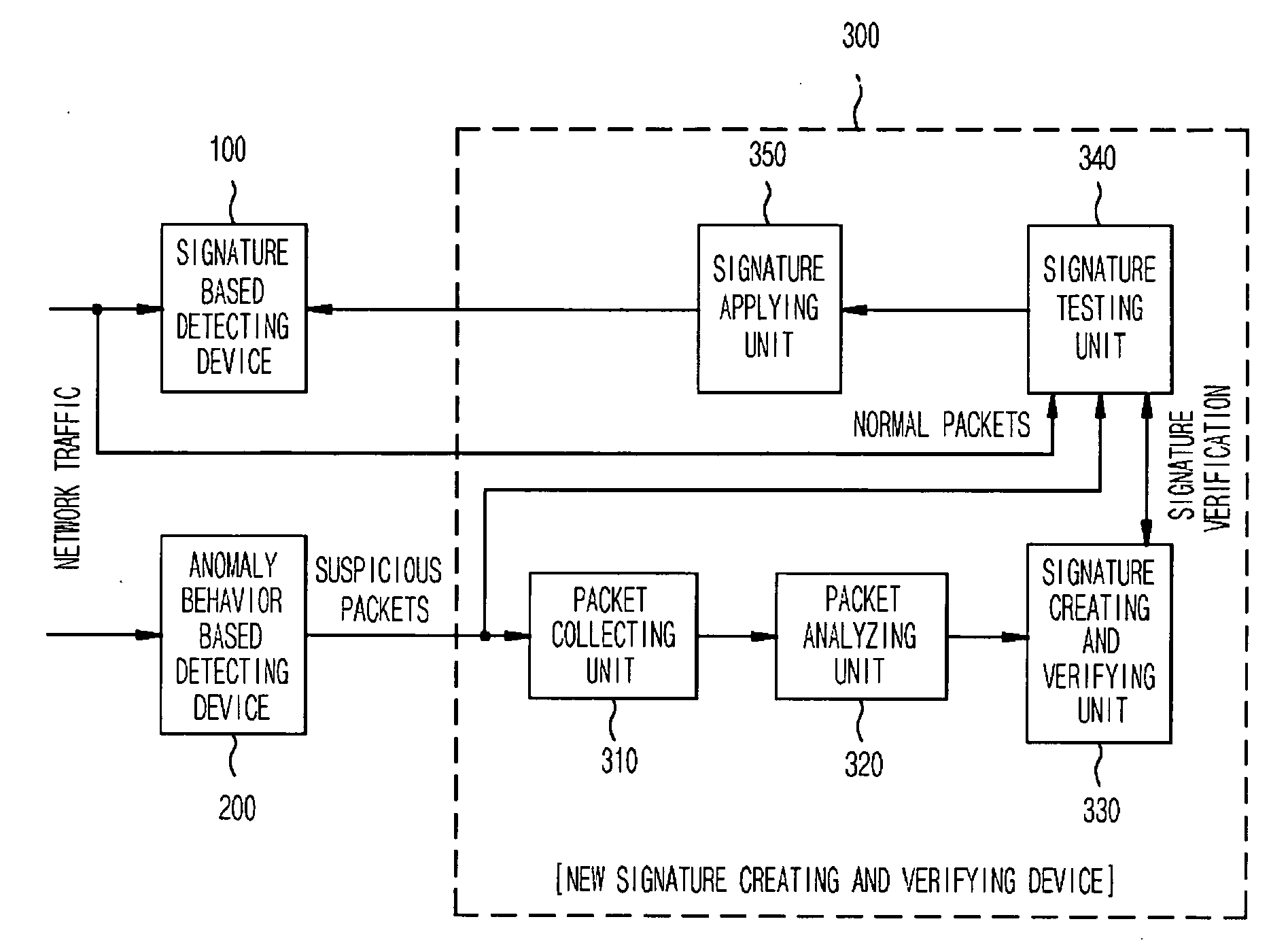
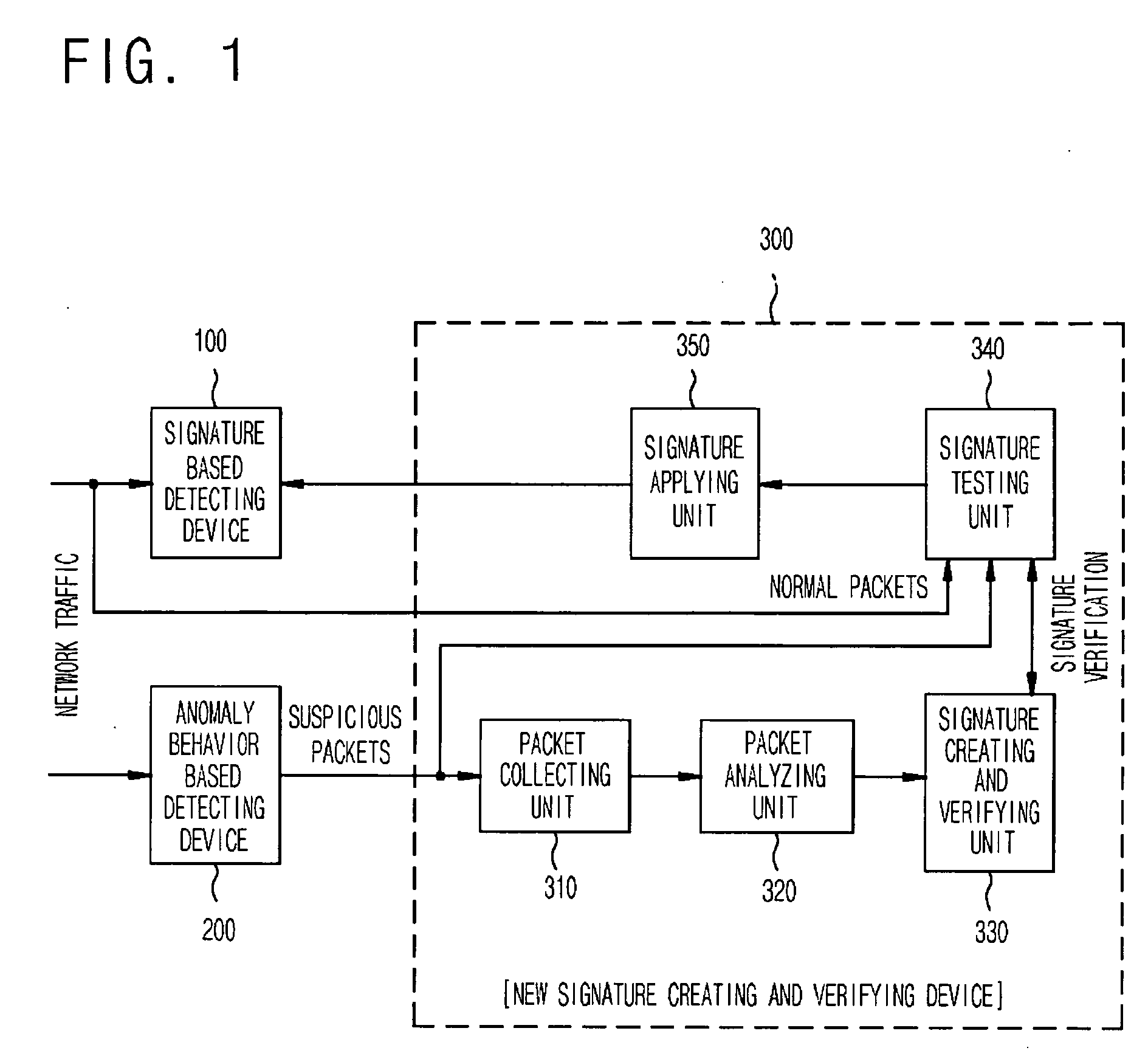
The present invention relates to a network intrusion detection and prevention system. The system includes: a signature based detecting device; an anomaly behavior based detecting device; and a new signature creating and verifying device disposed between the signature based detecting device and the anomaly behavior based detecting device, wherein if the anomaly behavior based detecting device detects network-attack-suspicious packets, the new signature creating and verifying device collects and searches the detected suspicious packets for common information, and then creates a new signature on the basis of the searched common information and at the same time, verifies whether or not the created new signature is applicable to the signature based detecting device, and then registers the created new signature to the signature based detecting device if it is determined that the created new signature is applicable.
Owner:ELECTRONICS & TELECOMM RES INST
Network intrusion detection in a network that includes a distributed virtual switch fabric
InactiveUS20130219500A1Enhanced network intrusion detectionImprove network securityMemory loss protectionError detection/correctionAccess networkVirtual switch
A network intrusion detection system (NIDS) works in conjunction with a distributed virtual switch fabric to provide enhanced network intrusion detection in a way that does not require as much human intervention, autonomically adjusts to hardware changes in the network, and responds much more quickly than known network intrusion detection systems. The NIDS accesses network information from the distributed virtual switch fabric, which gives the NIDS access to a virtual view that includes hardware information for all networking devices in the network. This allows the NIDS to automatically determine network topology, update itself as hardware in the network is added or changed, and promptly take automated service actions in response to detected network intrusions. The result is a NIDS that is easier to configure, maintain, and use, and that provides enhanced network security.
Owner:LENOVO ENTERPRISE SOLUTIONS SINGAPORE
Deep learning-based network intrusion detection and vulnerability scanning method and devices
The invention discloses a deep leaning-based network intrusion detection and vulnerability scanning method and devices. The method comprises the steps of collecting malicious sample files and buildinga malicious file database; performing training modeling according to behaviors of malicious files in the malicious file database by using a deep learning algorithm, performing real-time monitored model incremental training according to received new malicious sample files, so as to obtain classified models; simulating and running the malicious sample files in the malicious file database in different environments, and detecting an attack characteristic of the malicious sample files by using IDS; and analyzing the malicious file database by using a data mining algorithm, building a vulnerabilityattack manner characteristic library, generating a network attack package, and scanning network vulnerabilities.
Owner:JINING POWER SUPPLY CO OF STATE GRID SHANDONG ELECTRIC POWER CO +1
Intrusion detection method and intrusion detection system based on sustainable ensemble learning
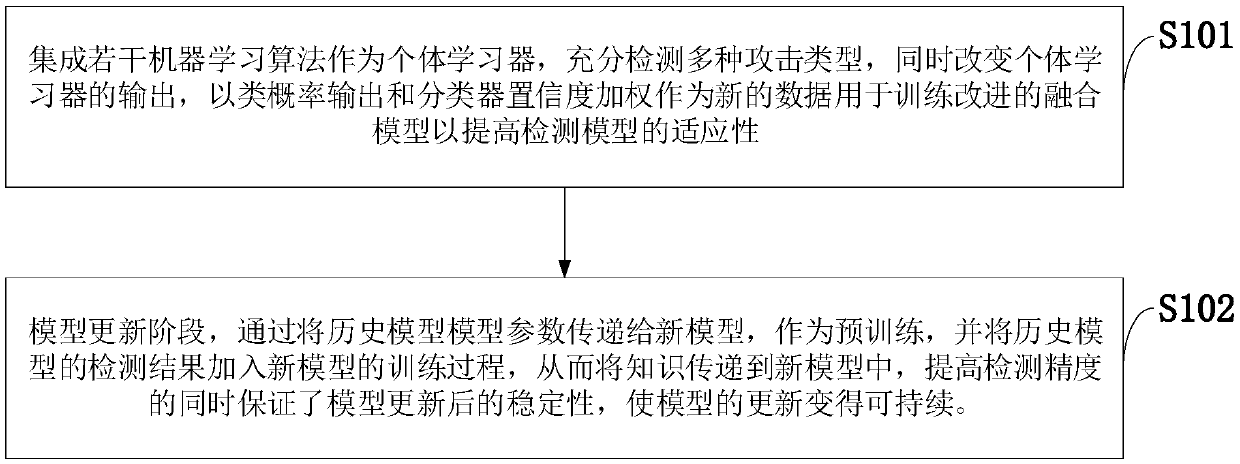
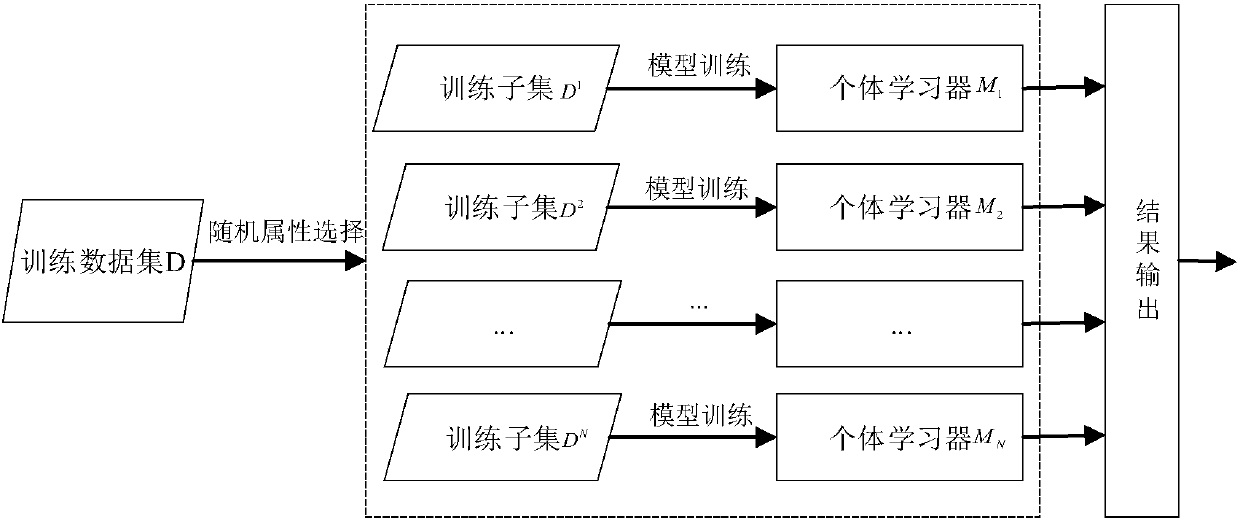
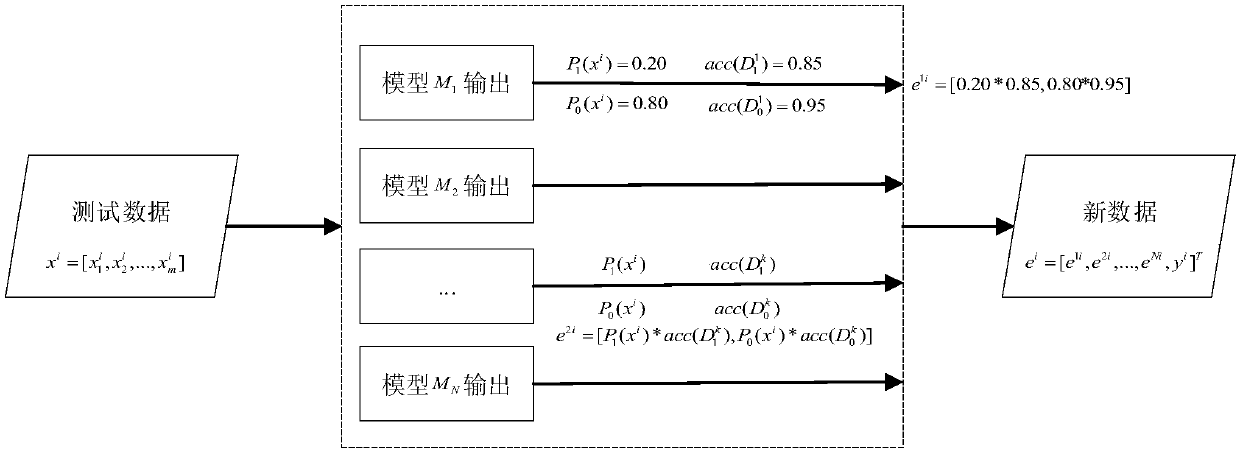
ActiveCN108023876AGuaranteed stabilityGuaranteed SustainabilityMachine learningTransmissionHistorical modelGranularity
The invention, which belongs to the technical field of network intrusion detection, discloses an intrusion detection method and intrusion detection system based on sustainable ensemble learning. A multi-class regression model is constructed by using a class probability output and a classification confidence product of an individual learner as training data, so that the decision-making process of the ensemble learning has high adaptability to the attack type to improve the detection accuracy. At the model updating stage, parameters and decision results of historical models are added into the training process of a new model, thereby completing incremental learning of the model. According to the invention, on the basis of the ensemble learning fusion plan of the multi-regression model, the decision-making weights of the individual learner during the detection processes for different attack types are allocated in a fine granularity manner; and the parameters and results of the historical models are used for training the new model, so that the stability of the model is improved and the sustainability of the learning process is ensured. Besides, the experiment result is compared with theexisting MV and WMV plans, the accuracy, stability and sustainability of the intrusion detection method and intrusion detection system are verified.
Owner:XIDIAN UNIV
Method for configuring a network intrusion detection system
InactiveUS20050039047A1Memory loss protectionError detection/correctionIntrusion responseNetwork intrusion detection
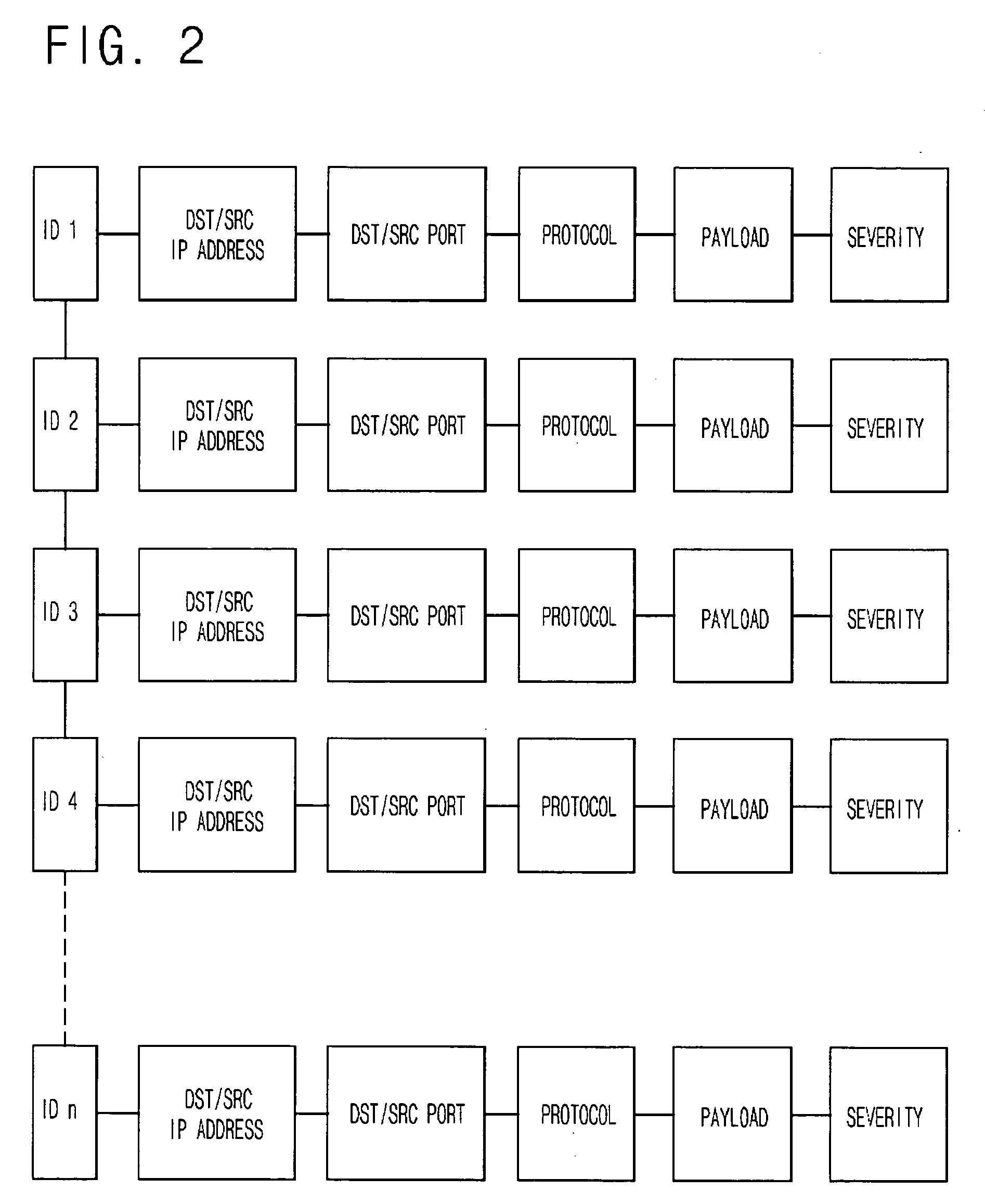
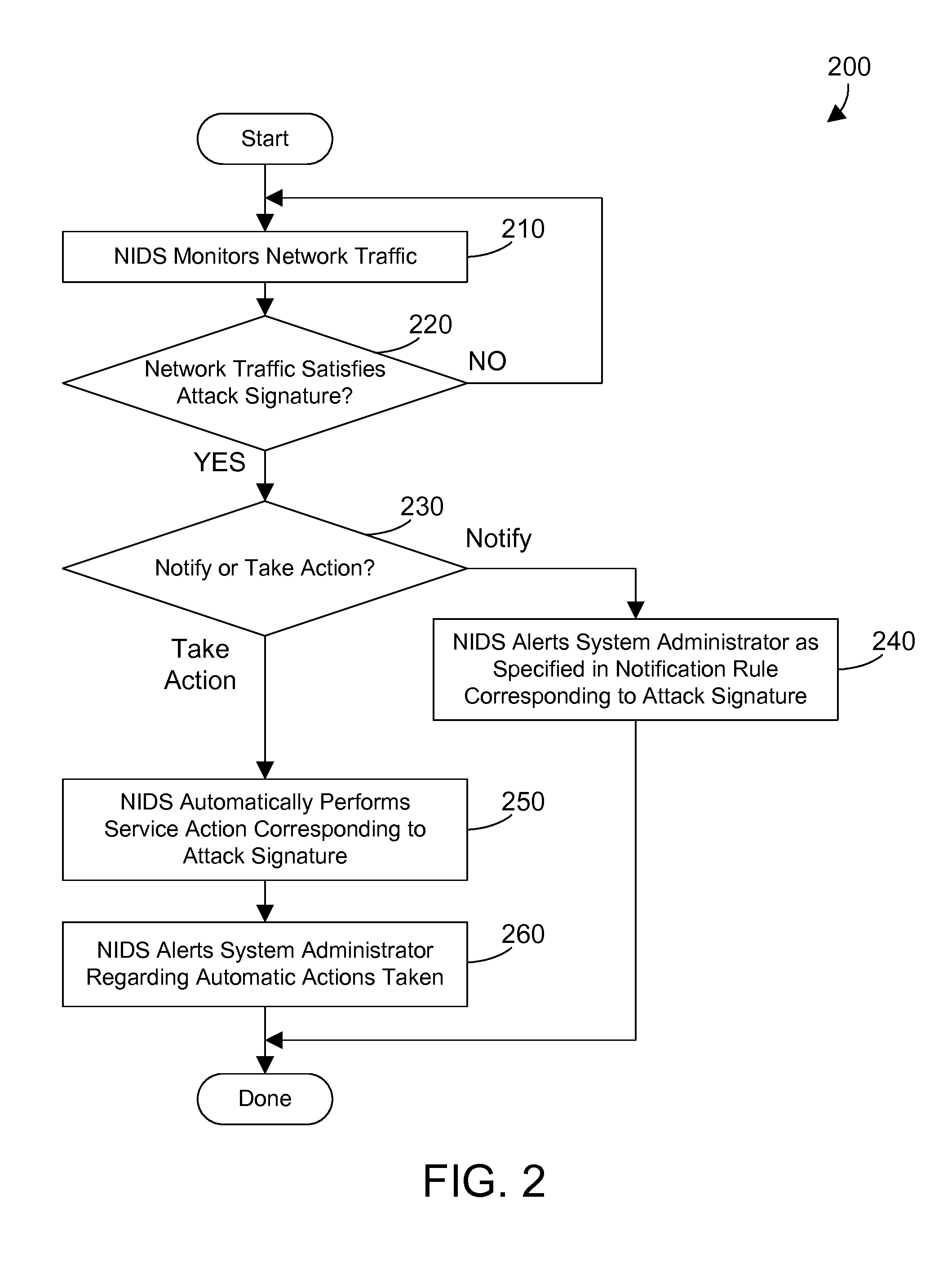
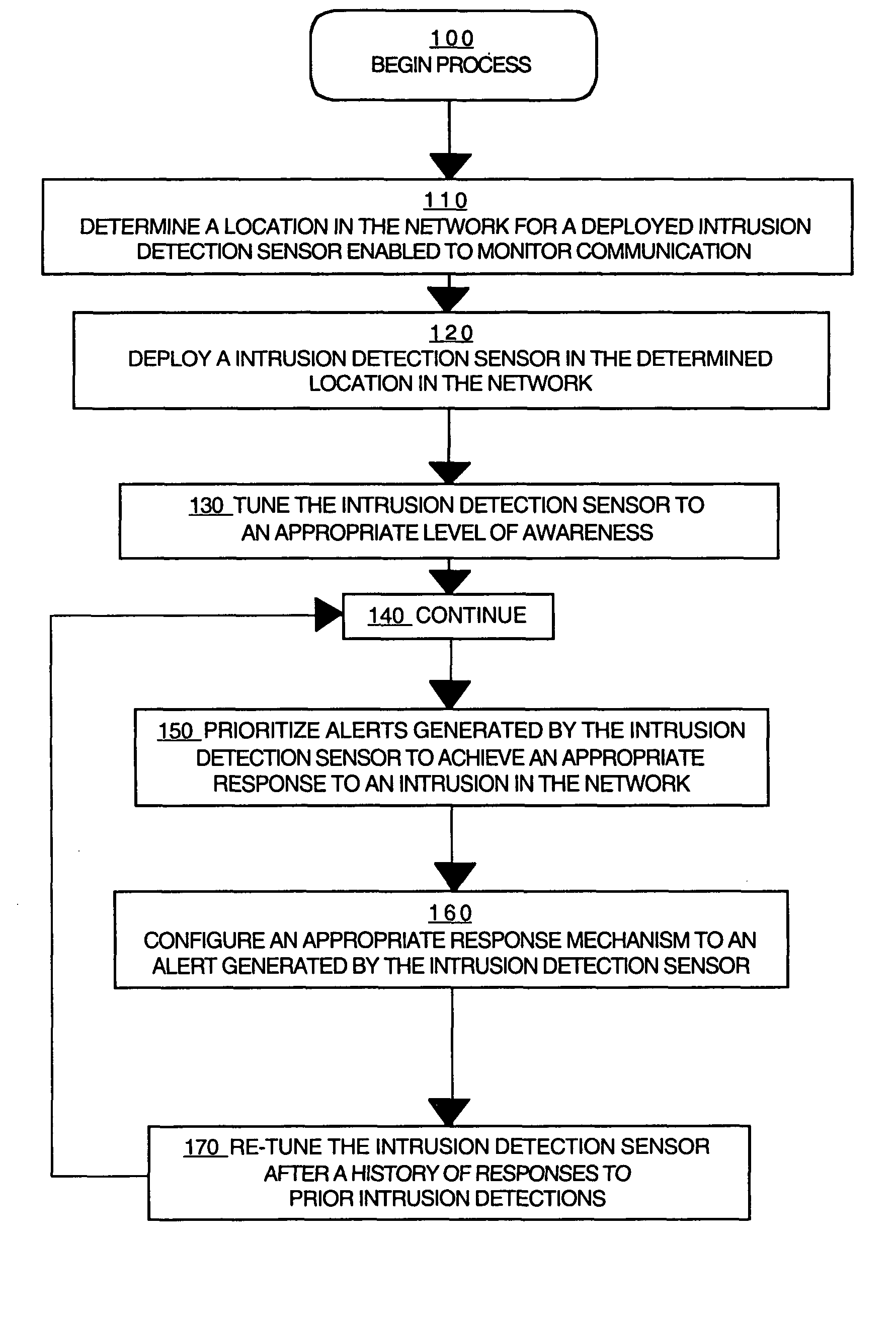
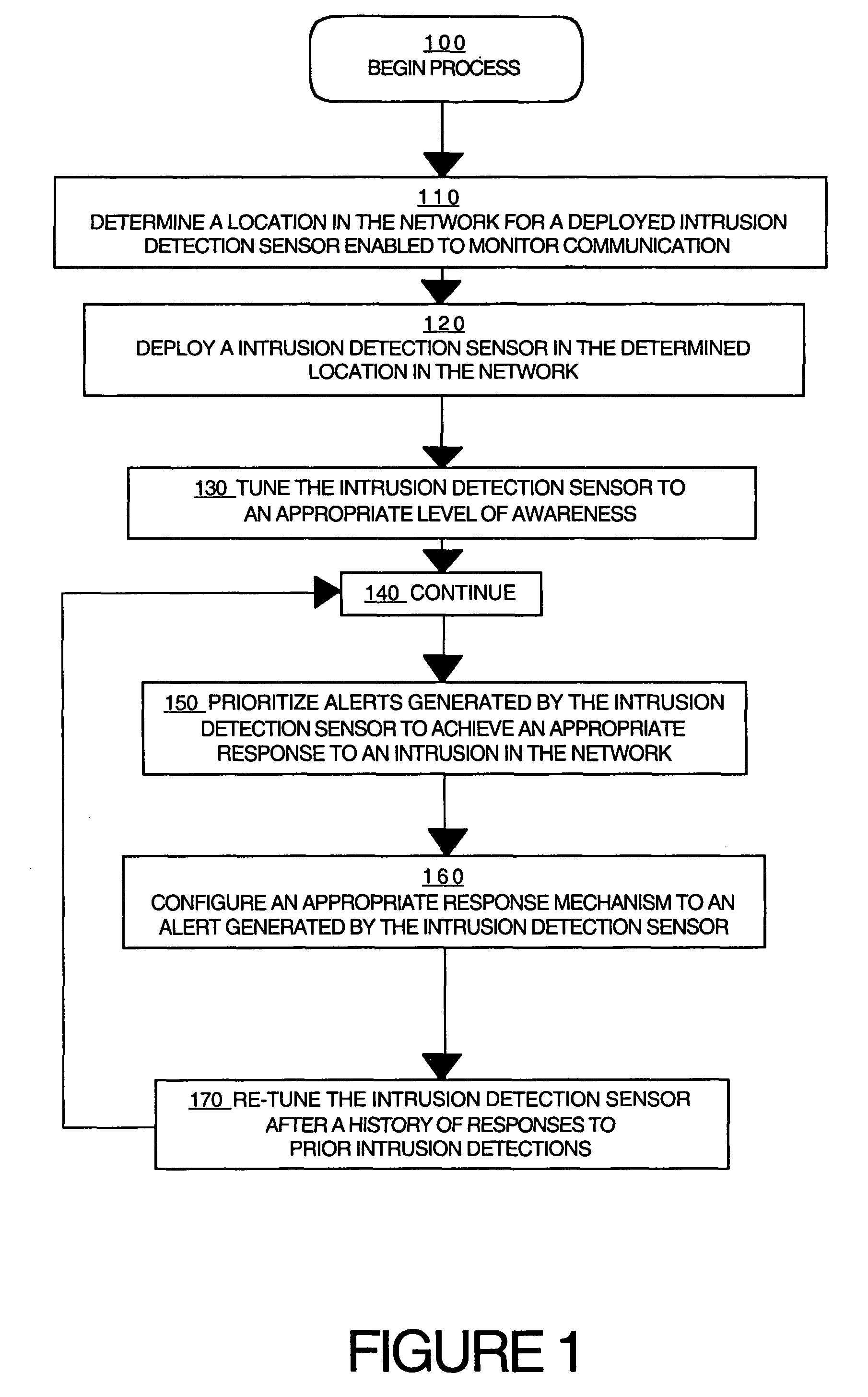
Disclosed is a method for configuring an intrusion detection system in a network which comprises determining a location in the network for a deployed intrusion detection sensor of the intrusion detection system, deploying the intrusion detection sensor in the determined location, enabling the intrusion detection sensor to monitor communication in a portion of the network, tuning the intrusion detection sensor to an appropriate level of awareness of the content in the communication in the network, prioritizing responses generated by the intrusion detection sensor to achieve an appropriate response to a detected intrusion in the network, configuring intrusion response mechanisms in the network to achieve an appropriate response by the mechanisms; and re-tuning the intrusion detection sensor in response to a prior intrusion detection.
Owner:HEWLETT PACKARD DEV CO LP
Method for configuring a network intrusion detection system
InactiveUS7228564B2Memory loss protectionError detection/correctionIntrusion responseNetwork intrusion detection
Disclosed is a method for configuring an intrusion detection system in a network which comprises determining a location in the network for a deployed intrusion detection sensor of the intrusion detection system, deploying the intrusion detection sensor in the determined location, enabling the intrusion detection sensor to monitor communication in a portion of the network, tuning the intrusion detection sensor to an appropriate level of awareness of the content in the communication in the network, prioritizing responses generated by the intrusion detection sensor to achieve an appropriate response to a detected intrusion in the network, configuring intrusion response mechanisms in the network to achieve an appropriate response by the mechanisms; and re-tuning the intrusion detection sensor in response to a prior intrusion detection.
Owner:HEWLETT PACKARD DEV CO LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com