Multi-layer honey network data transmission method and system
A data transmission method and a technology of a data transmission system, which are applied in digital transmission systems, transmission systems, network connections, etc., can solve the problems that the honeypot system cannot capture attack information, the resource utilization rate of the honeypot system is low, and resource waste is achieved. Avoid identified risks, improve resource utilization efficiency, and improve the effectiveness of protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
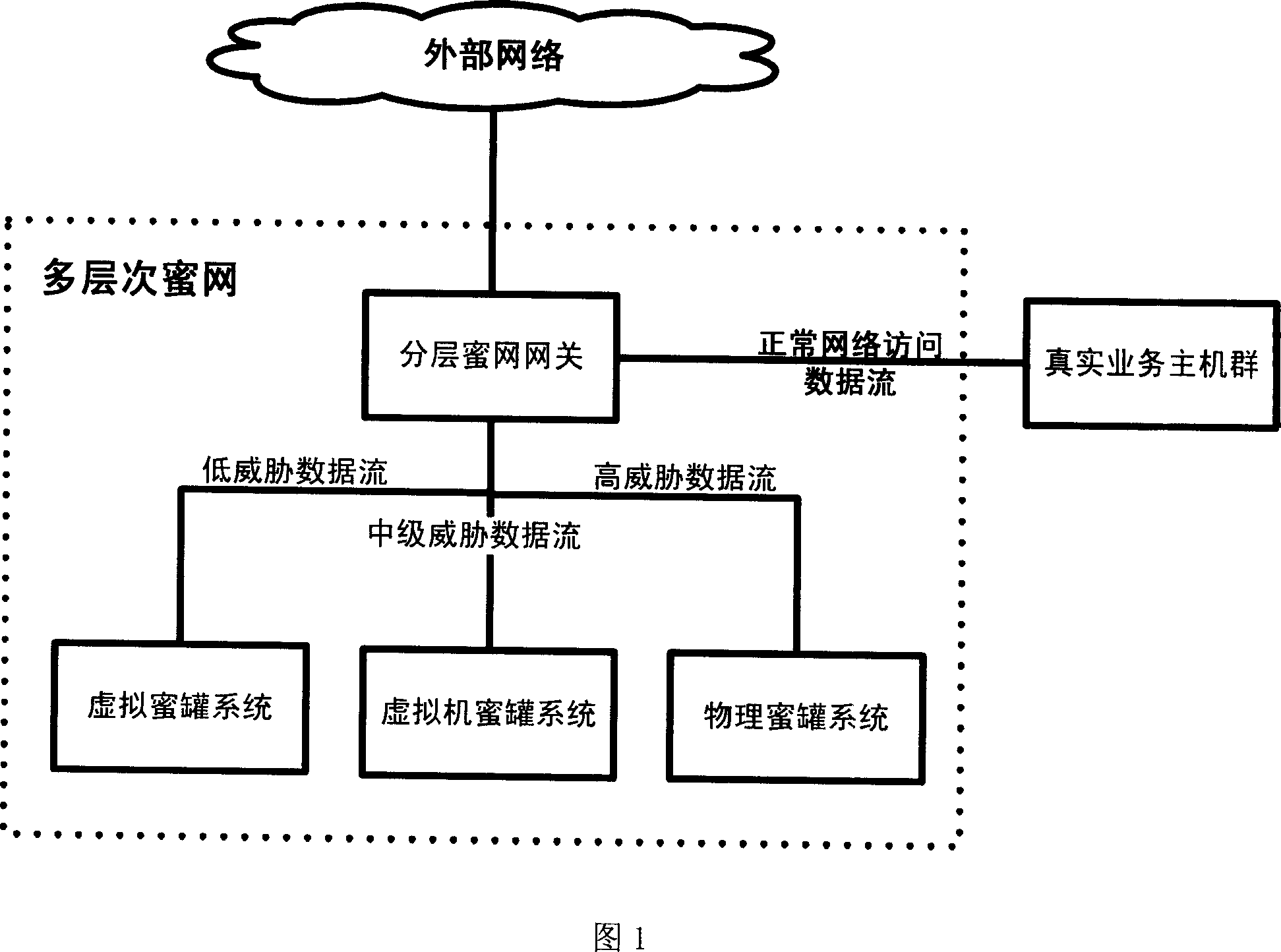
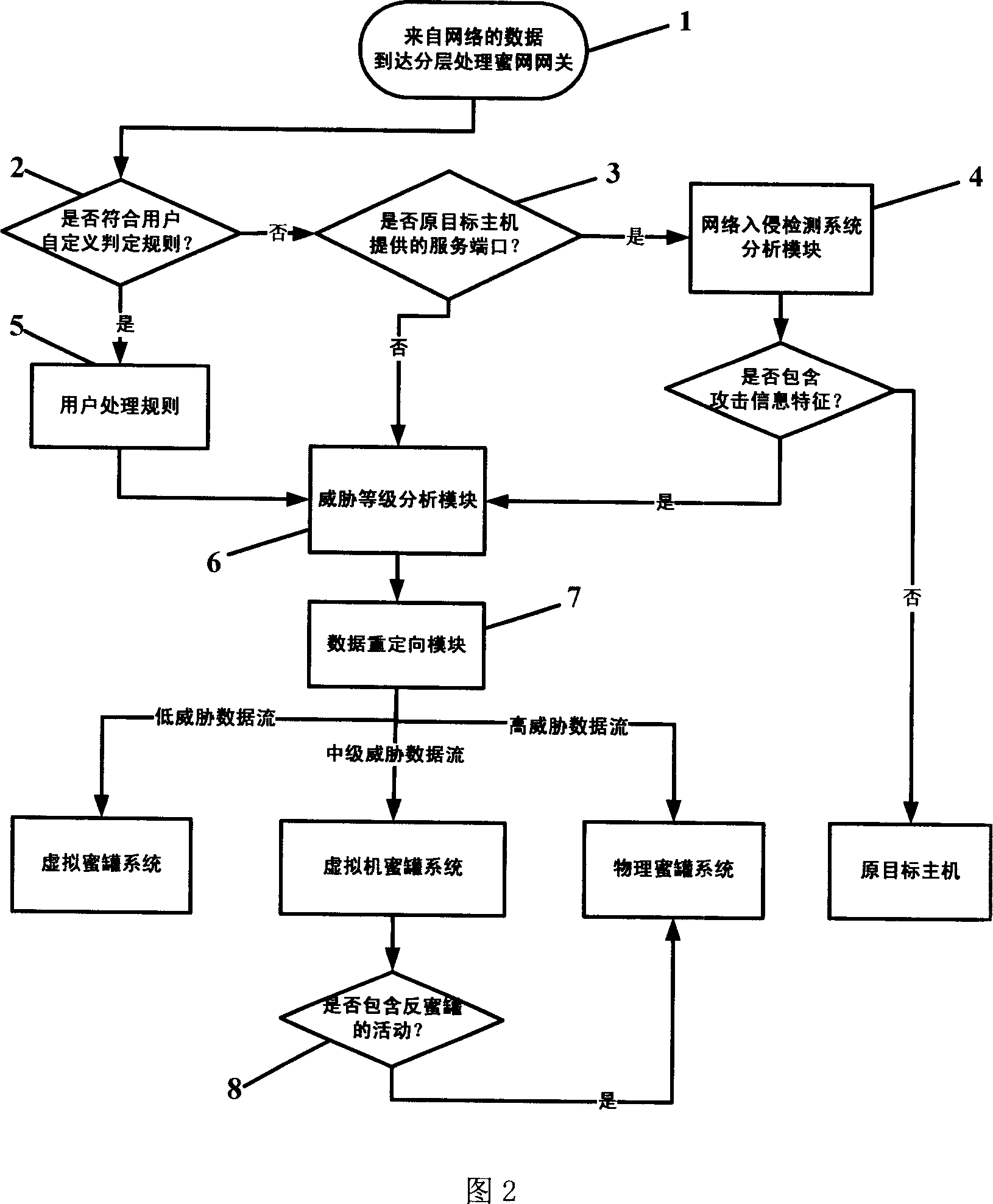
[0057] The present invention provides a method for multi-level analysis and processing of data streams sent to service hosts or internal networks. When the method analyzes network data streams arriving at a layered processing gateway:
[0058] 1. First, analyze and match the data flowing through the gateway according to the rules defined by the user. If the match is appropriate, the processing method of the data flow is determined according to the rules defined by the user;
[0059] 2. For the data flow that is not clearly defined by the user, it will be analyzed and processed by the network intrusion detection system to determine whether it is normal business data. For normal business data, the data is allowed to pass through the honeynet gateway;
[0060] 3. For the data of abnormal business data flow, redirect the data to honeypot systems with different deployment methods according to the threat level of the data.
[0061] 4. For the attack data flow entering the virtual h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com