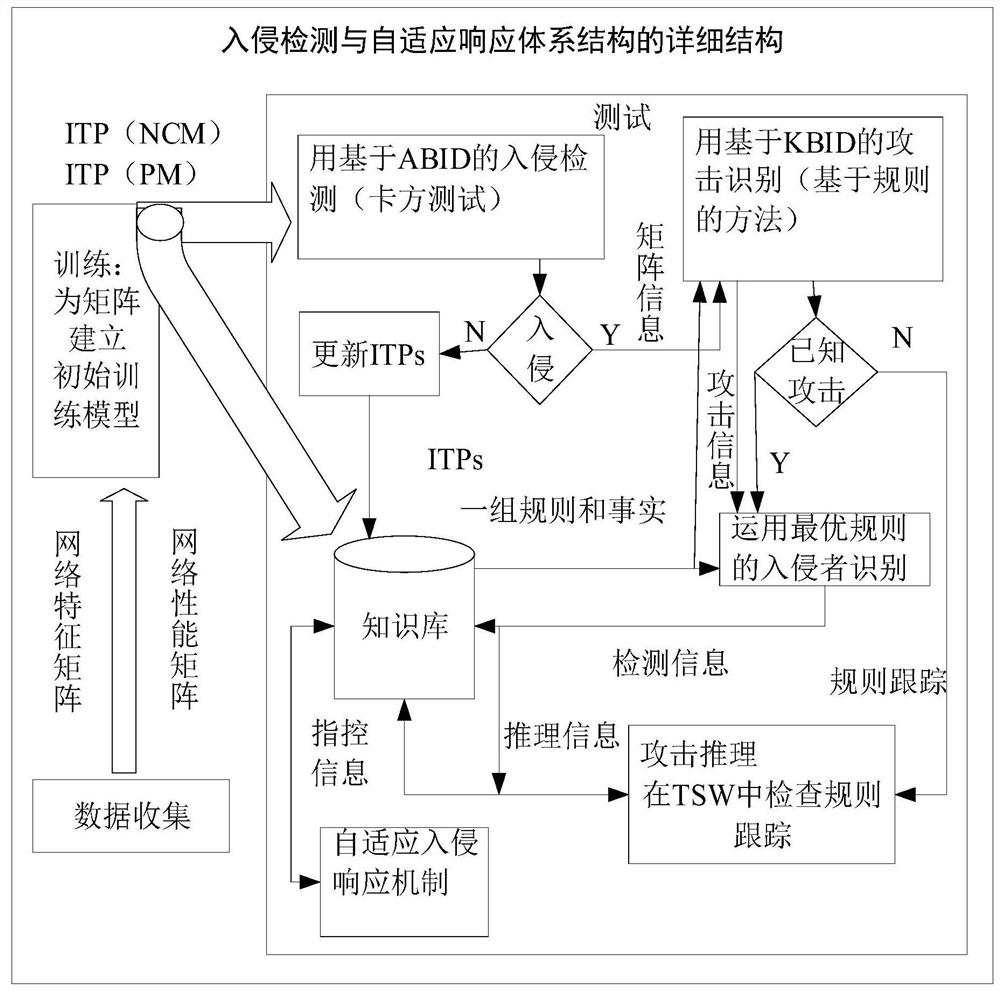
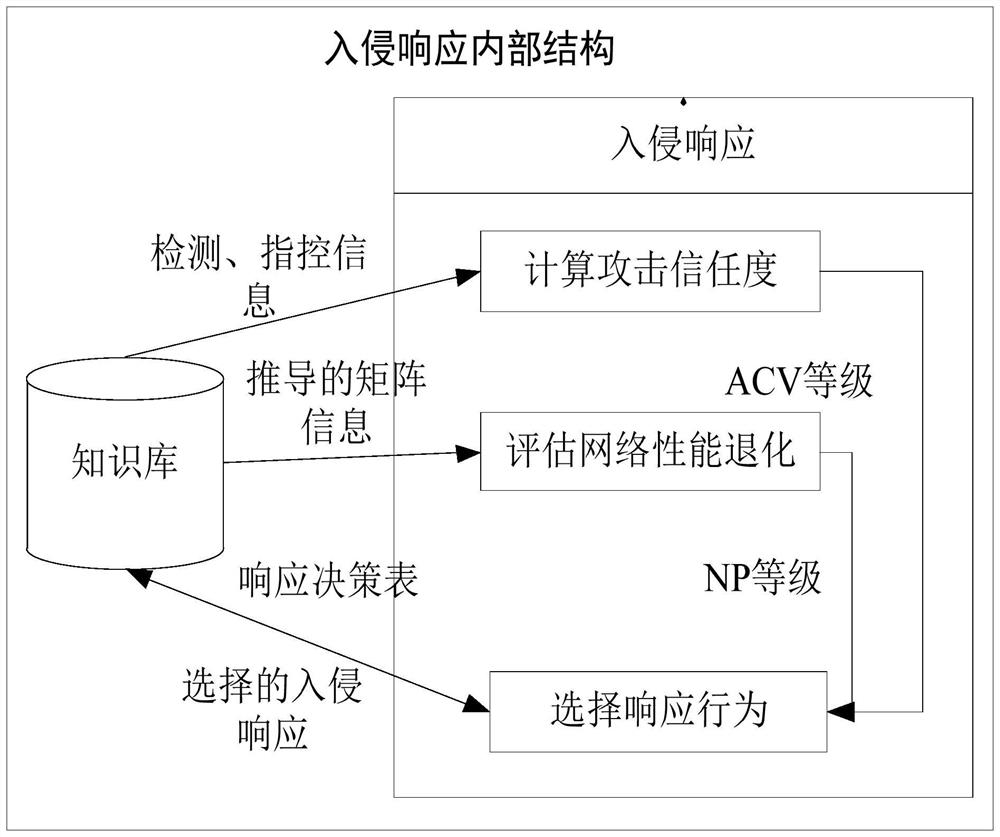
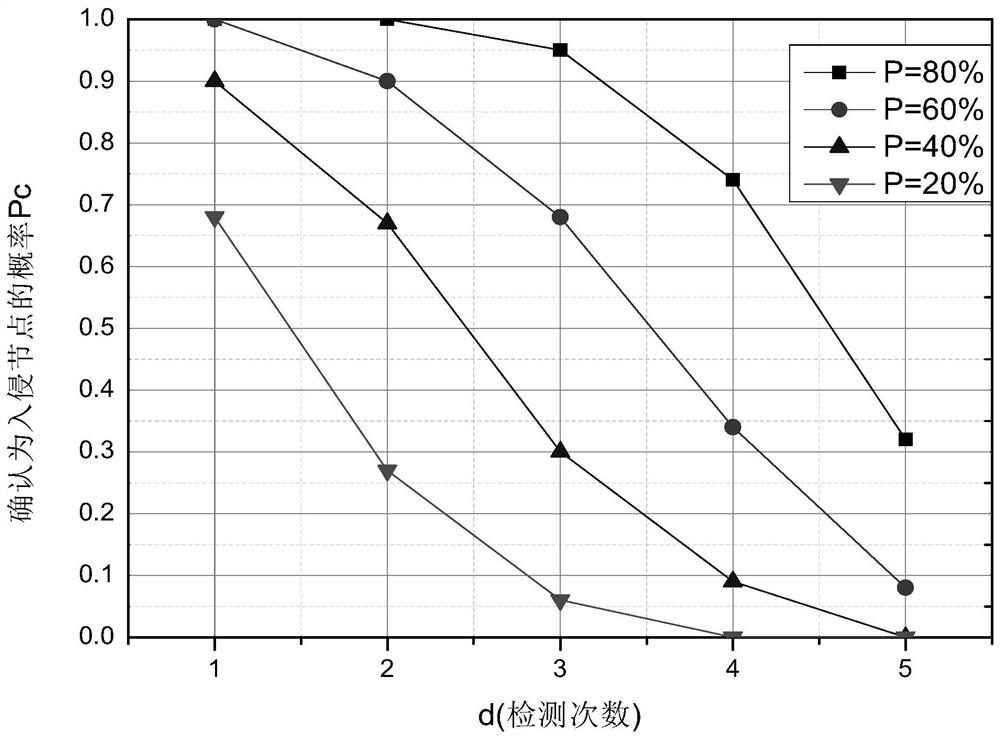
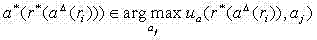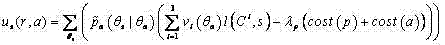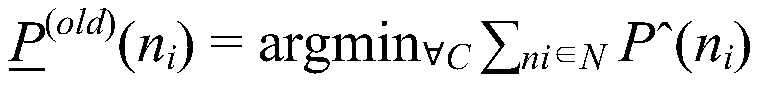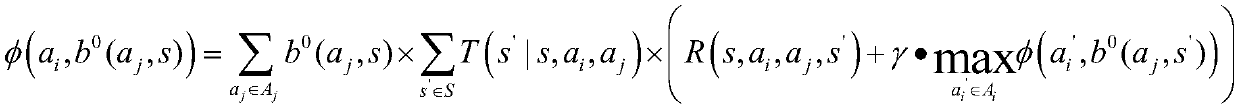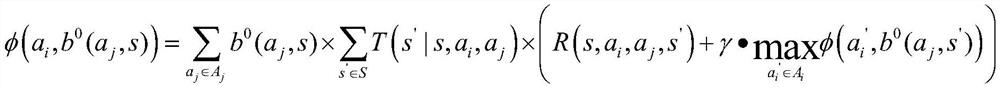Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41 results about "Intrusion response" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Automatically protecting network service from network attack
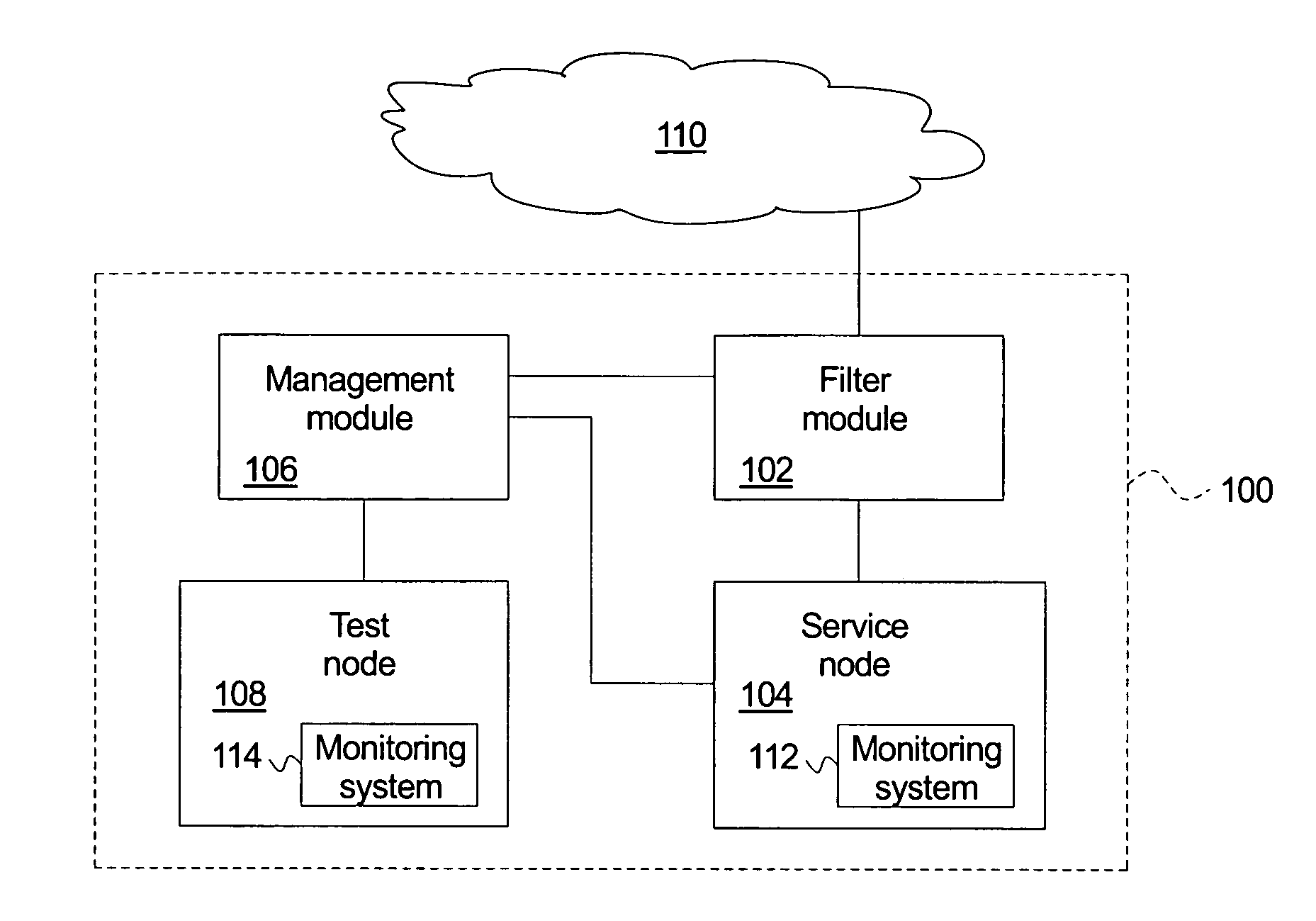
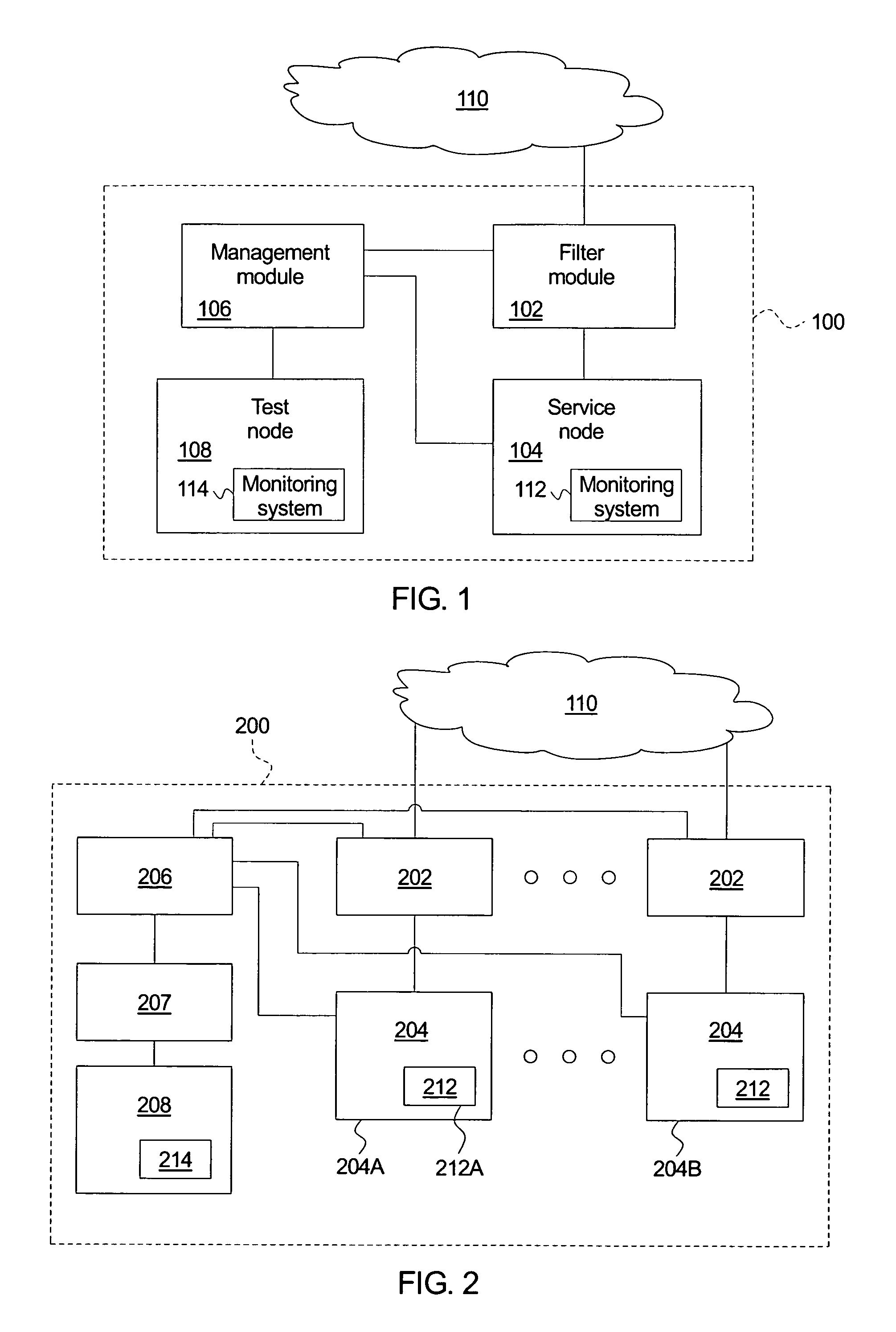
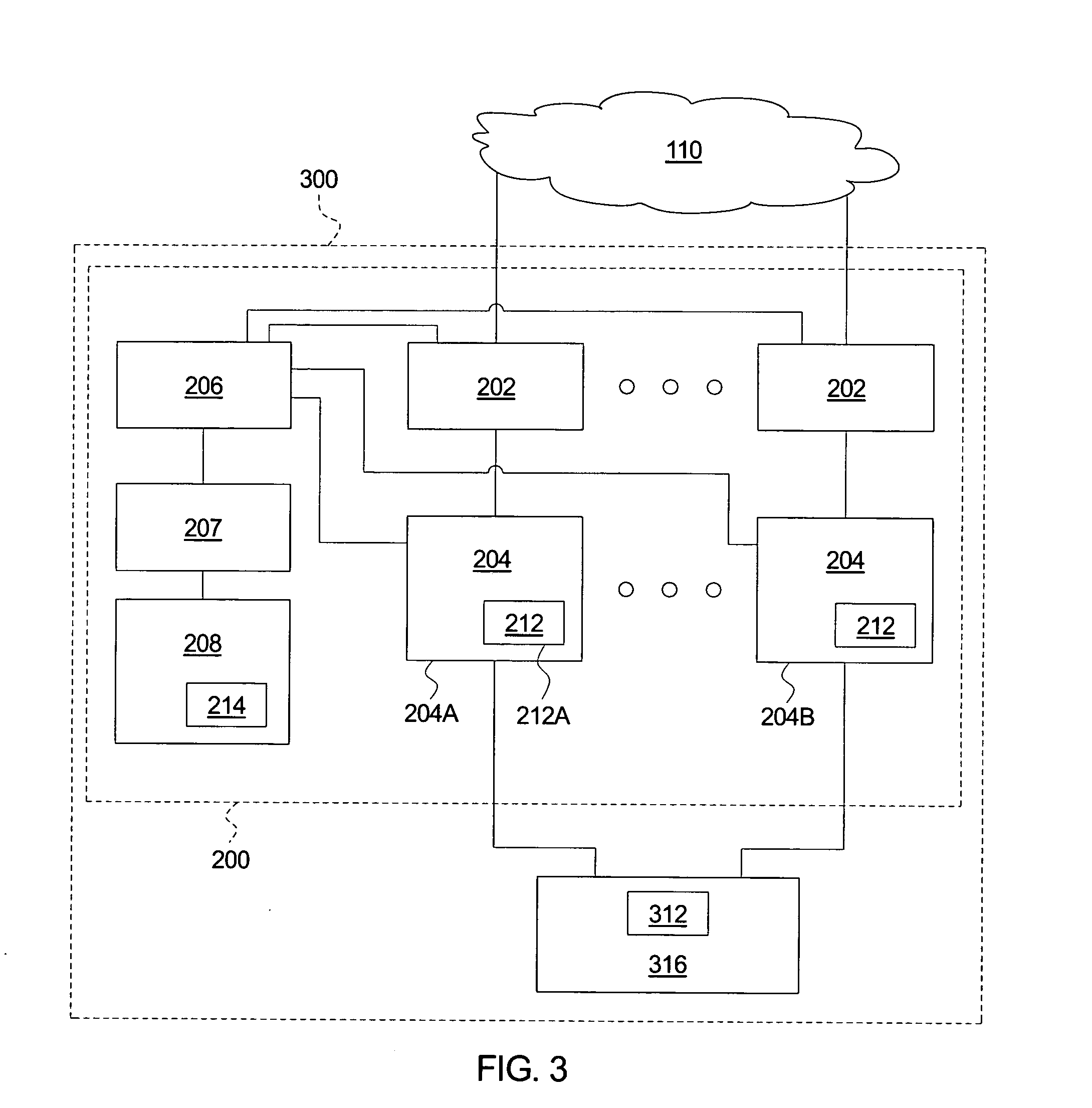
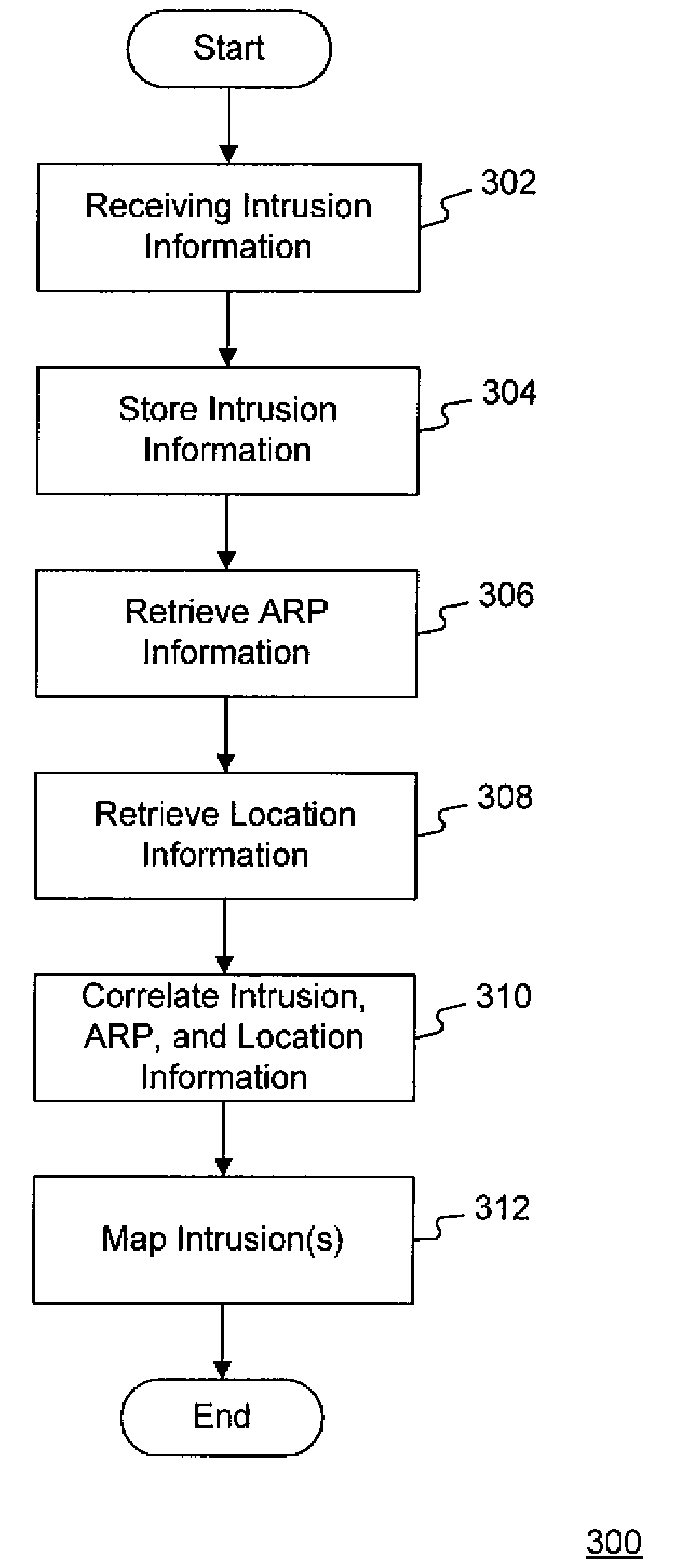
A system for detecting and responding to an attack comprises a filter module, a node, a management module, and a test node. The filter module allows questionable messages to proceed. The node receives the questionable messages and maintains logical operations associated with the questionable messages within a restricted region. The management module resets the service node upon a network attack. The test node replays the node questionable messages to identify a new attack. A method of protecting against a network attack logs questionable messages and directs the questionable messages to a node. The method maintains logical operations associated with the questionable messages within a restricted region and identifies a network attack upon the node, which triggers an intrusion response. The intrusion response resets the node, replays the questionable messages within a test node to identify a new attack message, and adds the new attack message to the known attack messages.
Owner:HEWLETT PACKARD DEV CO LP
Geographical intrusion response prioritization mapping through authentication and flight data correlation
ActiveUS8572734B2Road vehicles traffic controlDigital data processing detailsComputer scienceLocation data
Preferred systems and methods for geographically mapping intrusions through network or authentication data and flight data correlation are described. In one aspect, methods and systems include receiving threat data, receiving network or authentication data, receiving flight location data, correlating the threat data and the network or authentication data with the flight location data to generate map data, and generating a map displaying a geographical location of the intrusion based on the map data.
Owner:PALO ALTO NETWORKS INC
Methods, computer program products and data structures for intrusion detection, intrusion response and vulnerability remediation across target computer systems
ActiveUS20060015941A1Digital data processing detailsUser identity/authority verificationGoal systemVulnerability
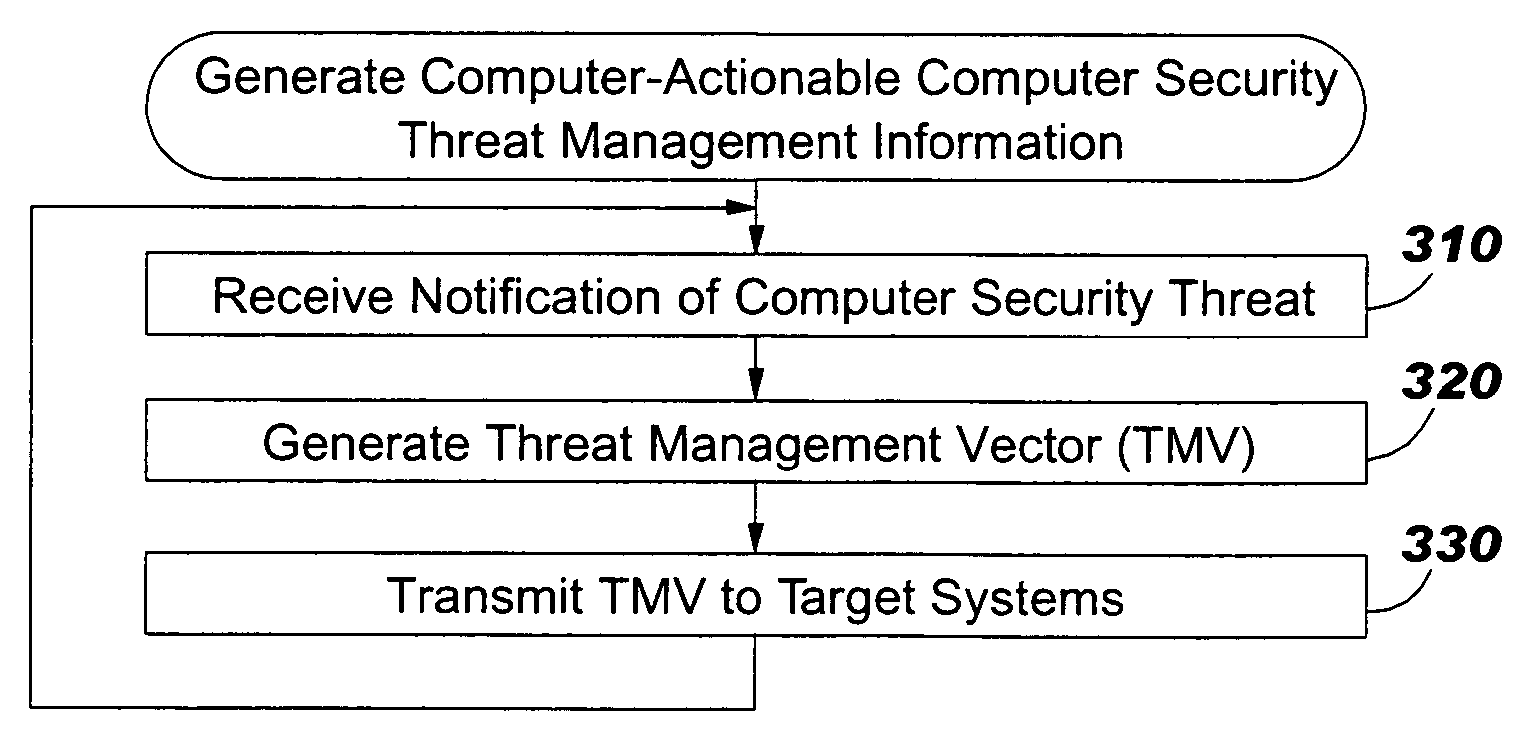
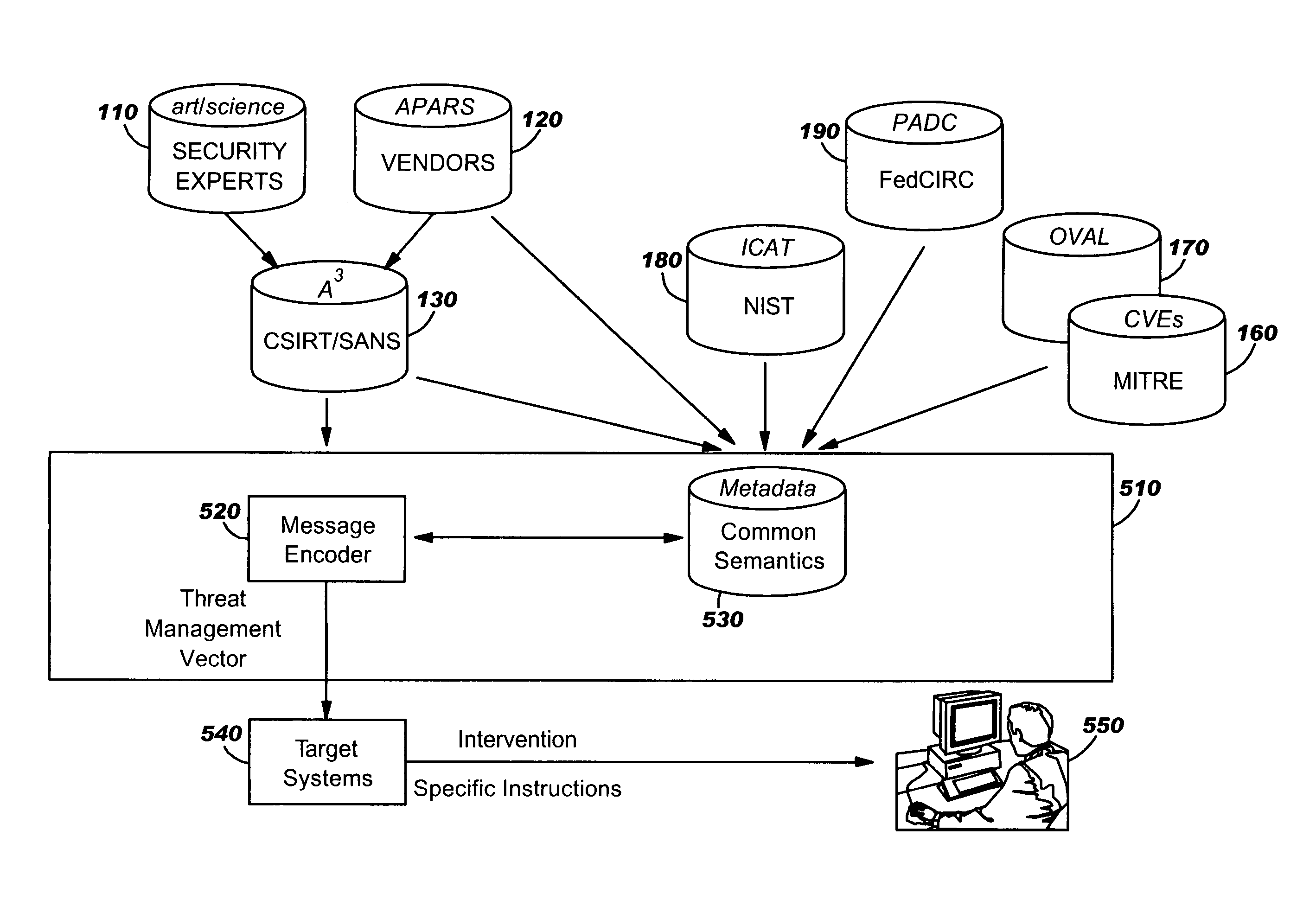
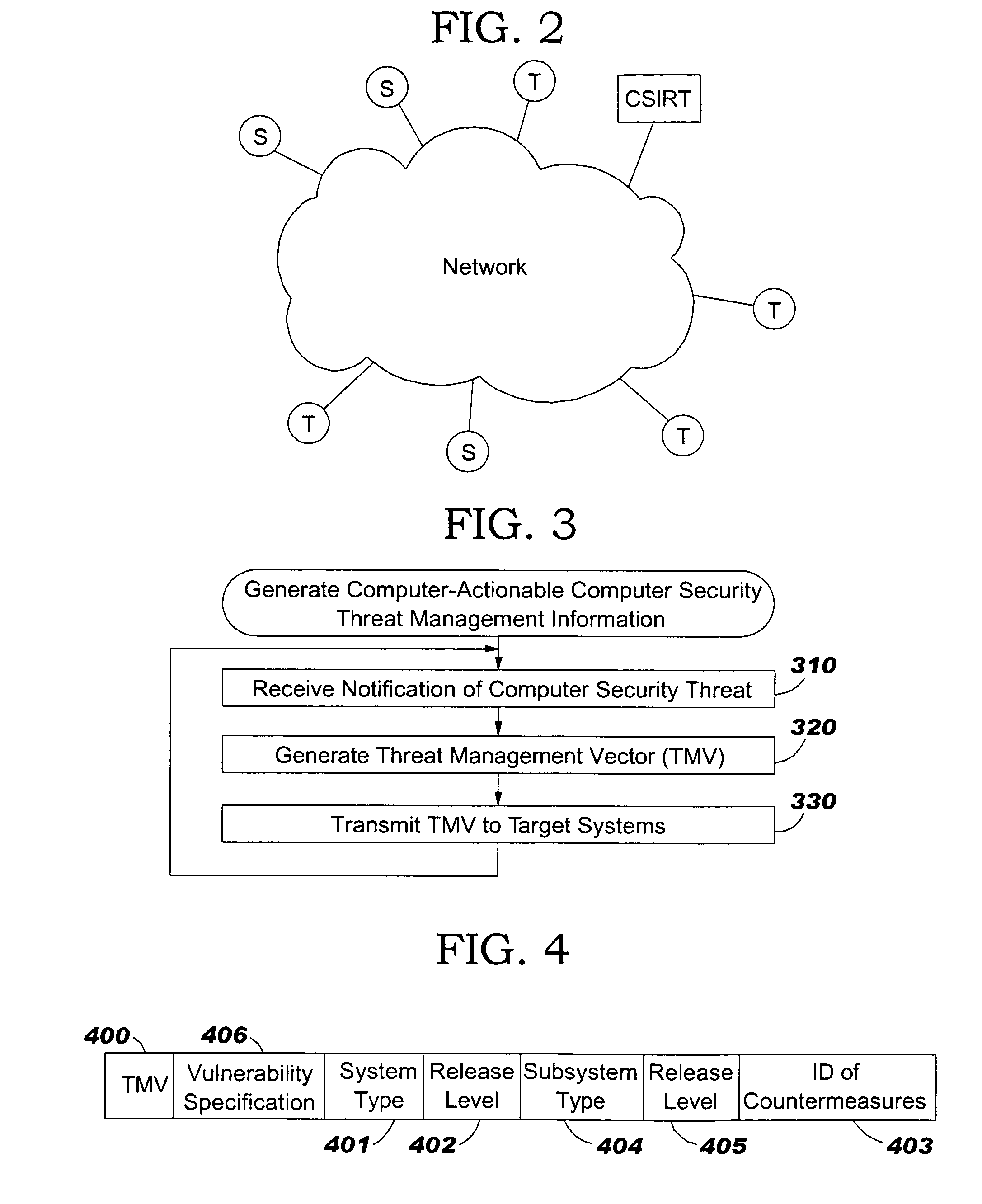
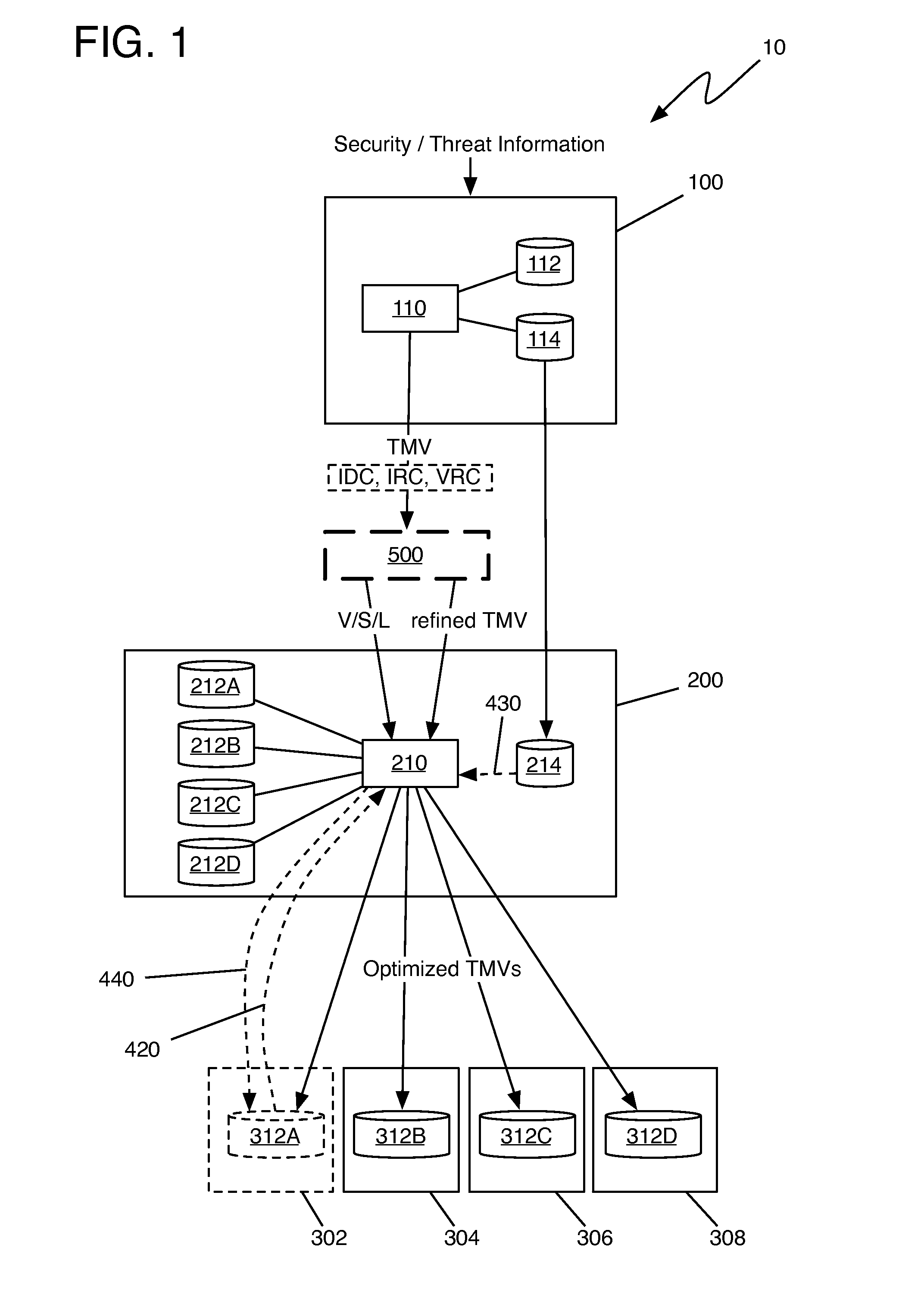
Computer security threat management information is generated by receiving a notification of a security threat and / or a notification of a test that detects intrusion of a computer security threat. A computer-actionable TMV is generated from the notification that was received. The TMV includes a computer-readable field that provides identification of at least one system type that is effected by the computer security threat, a computer-readable field that provides identification of a release level for a system type, and a computer-readable field that provides identification of the test that detects intrusion of the computer security threat for a system type and a release level, a computer-readable field that provides identification of a method to reverse the intrusion exploit of the computer security threat for a system type and a release level, and a computer-readable field that provides identification of a method to remediate the vulnerability subject to exploit of the computer security threat for a system type and a release level. The TMV is transmitted to target systems for processing by the target systems.
Owner:FINJAN BLUE INC
Mimicry defense architecture based zero-day attack detection, analysis and response system and method thereof
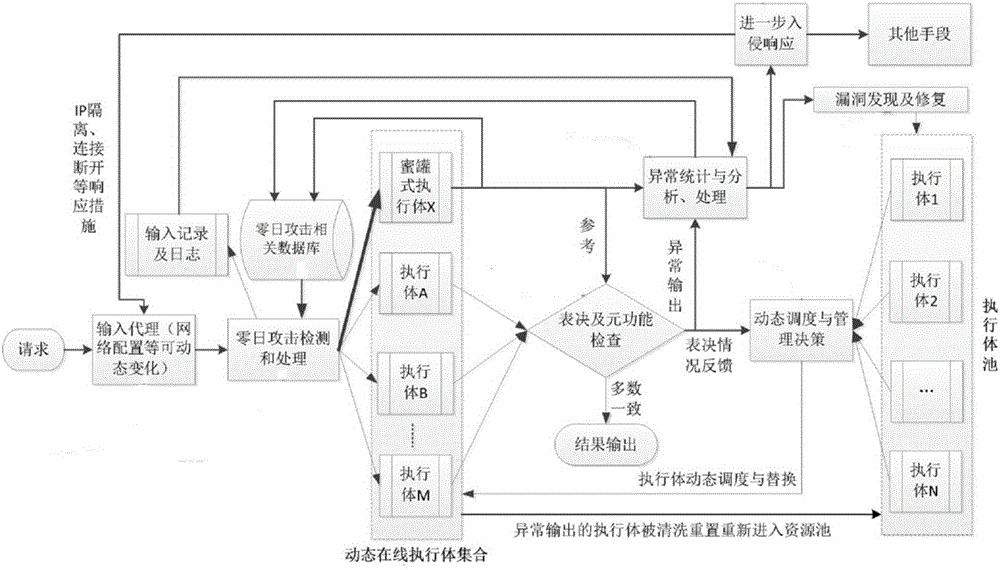
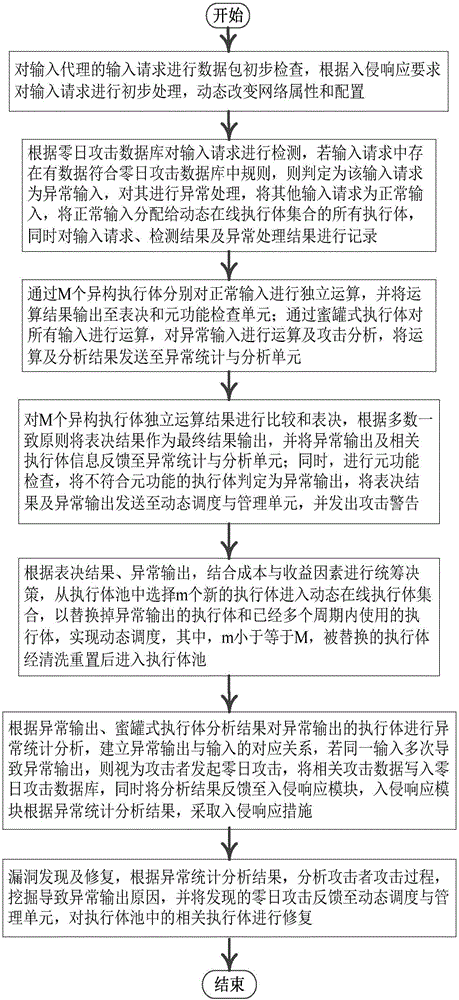
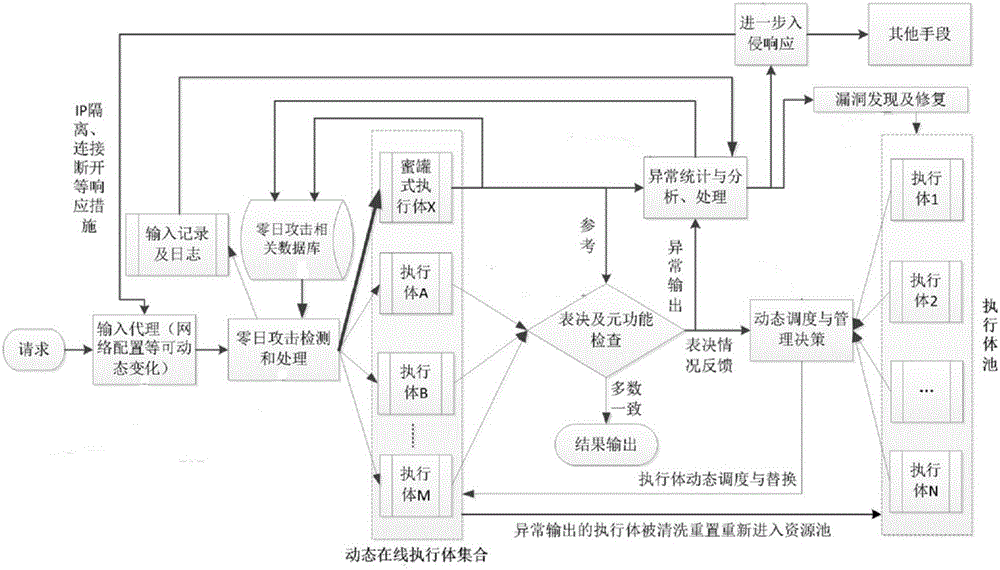
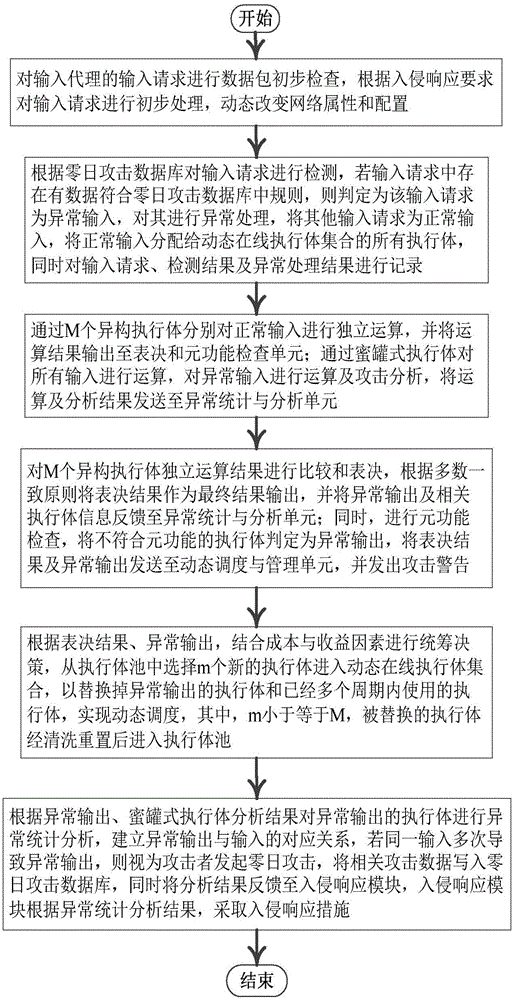
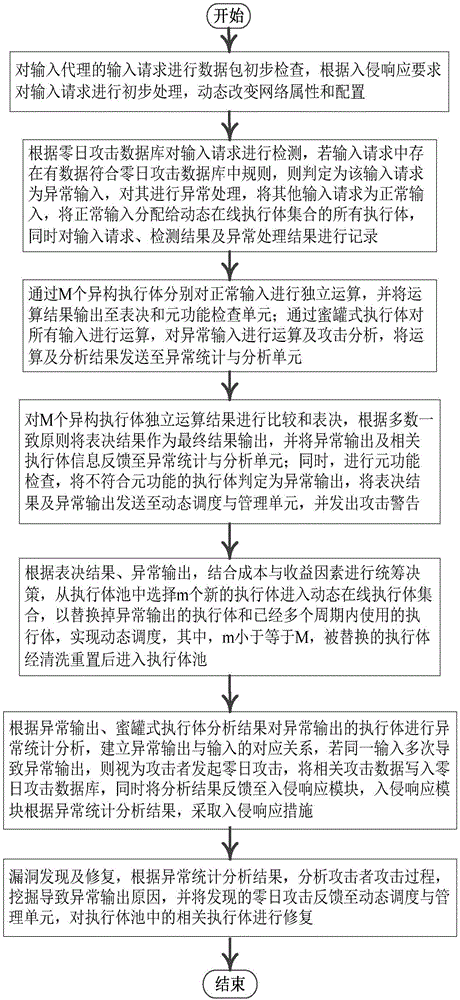
The invention relates to a mimicry defense architecture based zero-day attack detection, analysis and response system and a method thereof. The method comprises the steps of performing attack detection and processing on the input, cheating and inducing an attacker through honeypot type executing bodies, and performing meta-function inspection on the output of each executing body; performing statistical analysis on abnormal output by combining abnormal information, updating a zero-day attack database, feeding back an analysis result to an intrusion response module, and preventing persistent attacks of the attacker; performing dynamic adjustment and management on an online executing body by combining voting conditions, executing body dispatching, the executing body with abnormal output and the like, and selecting executing bodies from an executing body resource pool to get into a dynamic online executing body set; and analyzing a zero-day vulnerability in the executing body with abnormal output according to an anomaly statistical analysis result, and repairing the related executing bodies in the executing body pool. According to the invention, functions and the flexibility of mimicry defense architecture are enhanced, values of the abnormal output are sufficiently utilized, and the threat and the defense cost of zero-day attacks are reduced.
Owner:THE PLA INFORMATION ENG UNIV
Method for configuring a network intrusion detection system
InactiveUS20050039047A1Memory loss protectionError detection/correctionIntrusion responseNetwork intrusion detection
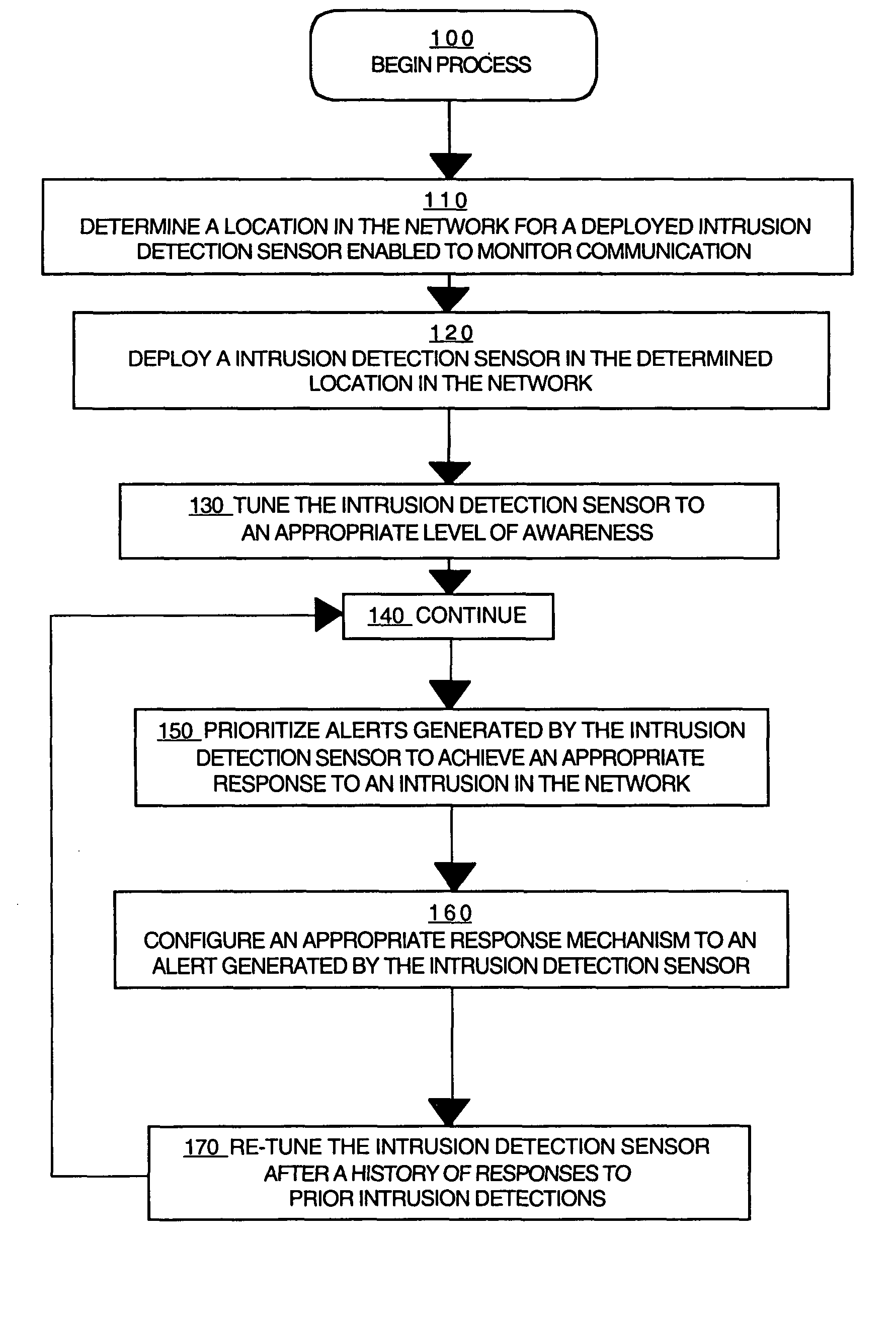
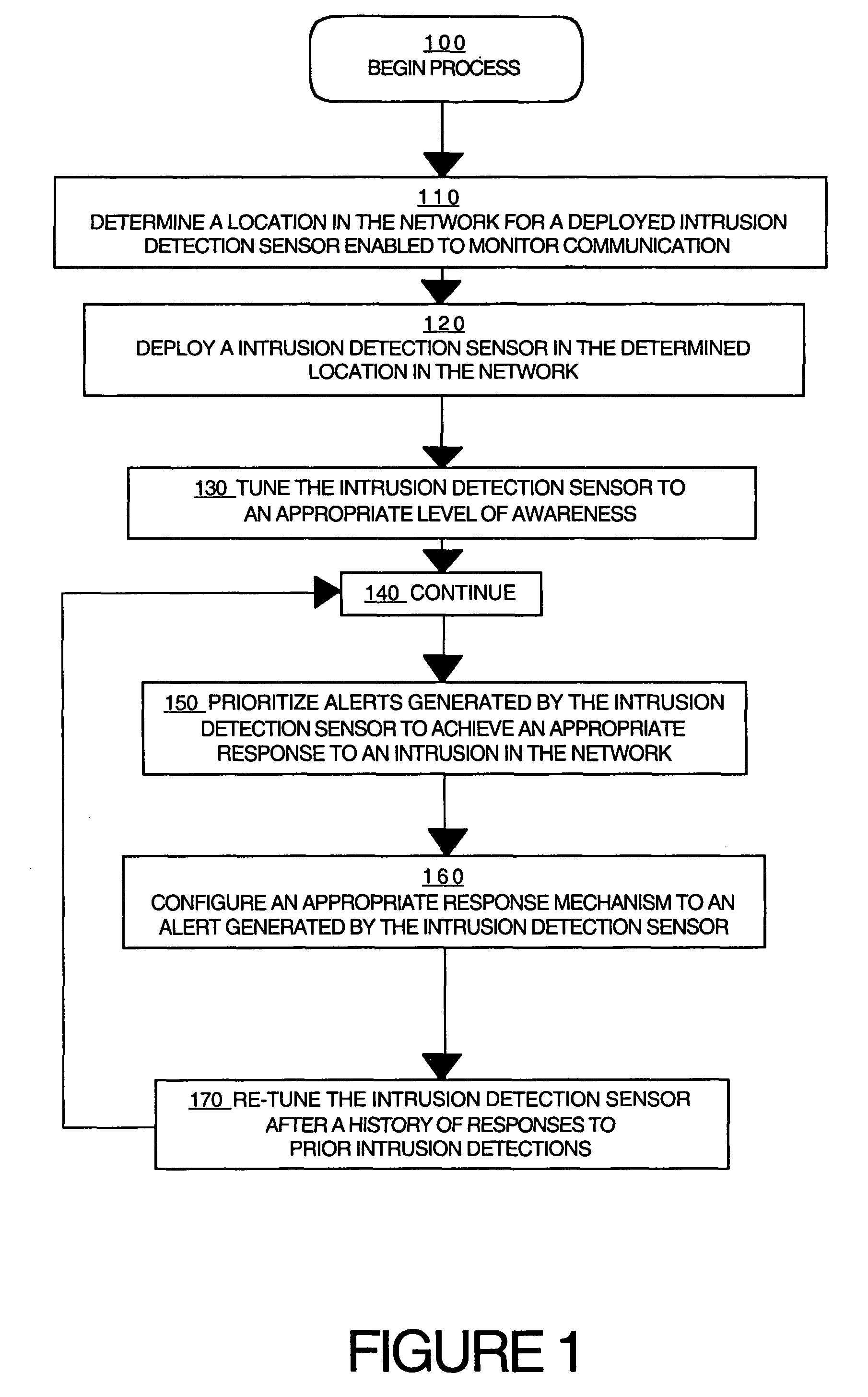
Disclosed is a method for configuring an intrusion detection system in a network which comprises determining a location in the network for a deployed intrusion detection sensor of the intrusion detection system, deploying the intrusion detection sensor in the determined location, enabling the intrusion detection sensor to monitor communication in a portion of the network, tuning the intrusion detection sensor to an appropriate level of awareness of the content in the communication in the network, prioritizing responses generated by the intrusion detection sensor to achieve an appropriate response to a detected intrusion in the network, configuring intrusion response mechanisms in the network to achieve an appropriate response by the mechanisms; and re-tuning the intrusion detection sensor in response to a prior intrusion detection.
Owner:HEWLETT PACKARD DEV CO LP
Method for configuring a network intrusion detection system
InactiveUS7228564B2Memory loss protectionError detection/correctionIntrusion responseNetwork intrusion detection
Disclosed is a method for configuring an intrusion detection system in a network which comprises determining a location in the network for a deployed intrusion detection sensor of the intrusion detection system, deploying the intrusion detection sensor in the determined location, enabling the intrusion detection sensor to monitor communication in a portion of the network, tuning the intrusion detection sensor to an appropriate level of awareness of the content in the communication in the network, prioritizing responses generated by the intrusion detection sensor to achieve an appropriate response to a detected intrusion in the network, configuring intrusion response mechanisms in the network to achieve an appropriate response by the mechanisms; and re-tuning the intrusion detection sensor in response to a prior intrusion detection.
Owner:HEWLETT PACKARD DEV CO LP
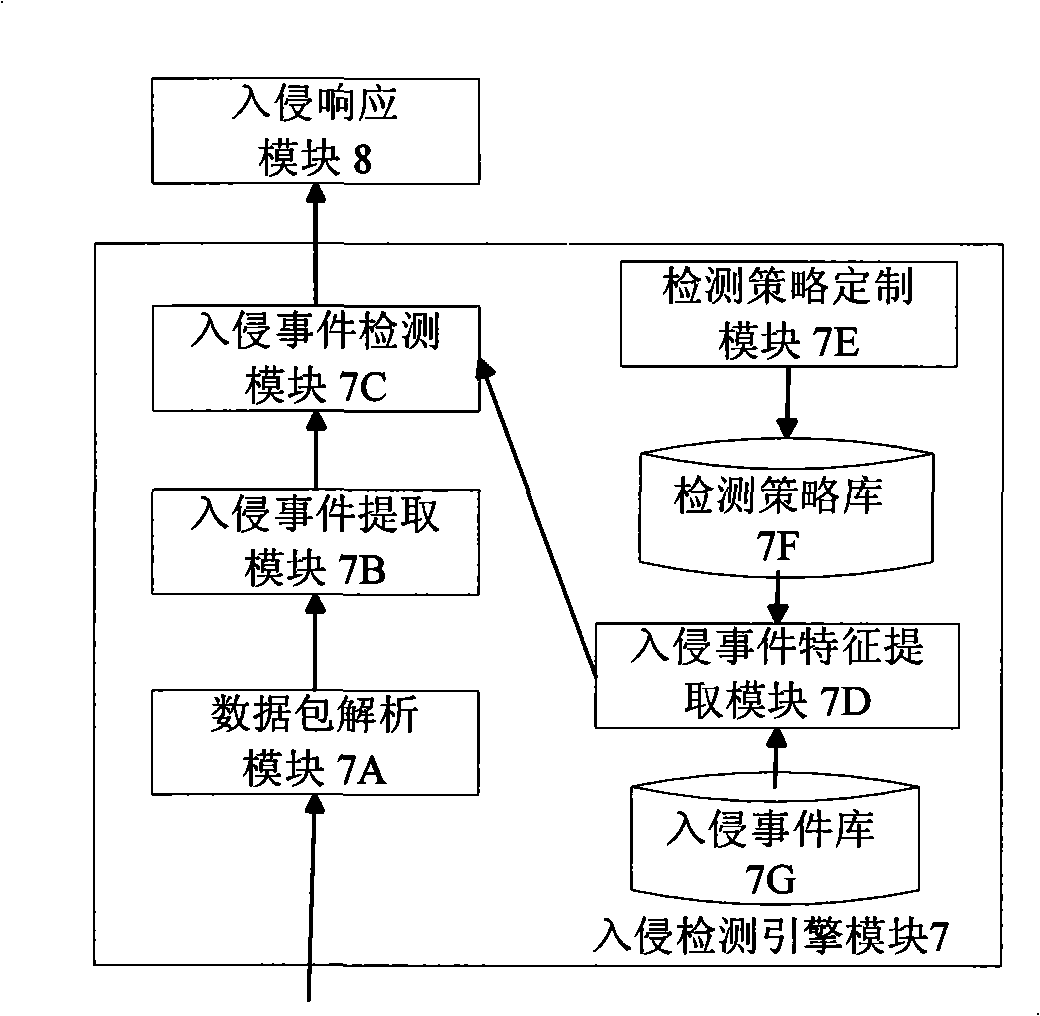
Security network invasion detection system suitable for virtual machine environment
InactiveCN101309180AGuaranteed security featuresCentralized control of intrusion detection rulesData switching networksCommunication controlA domain
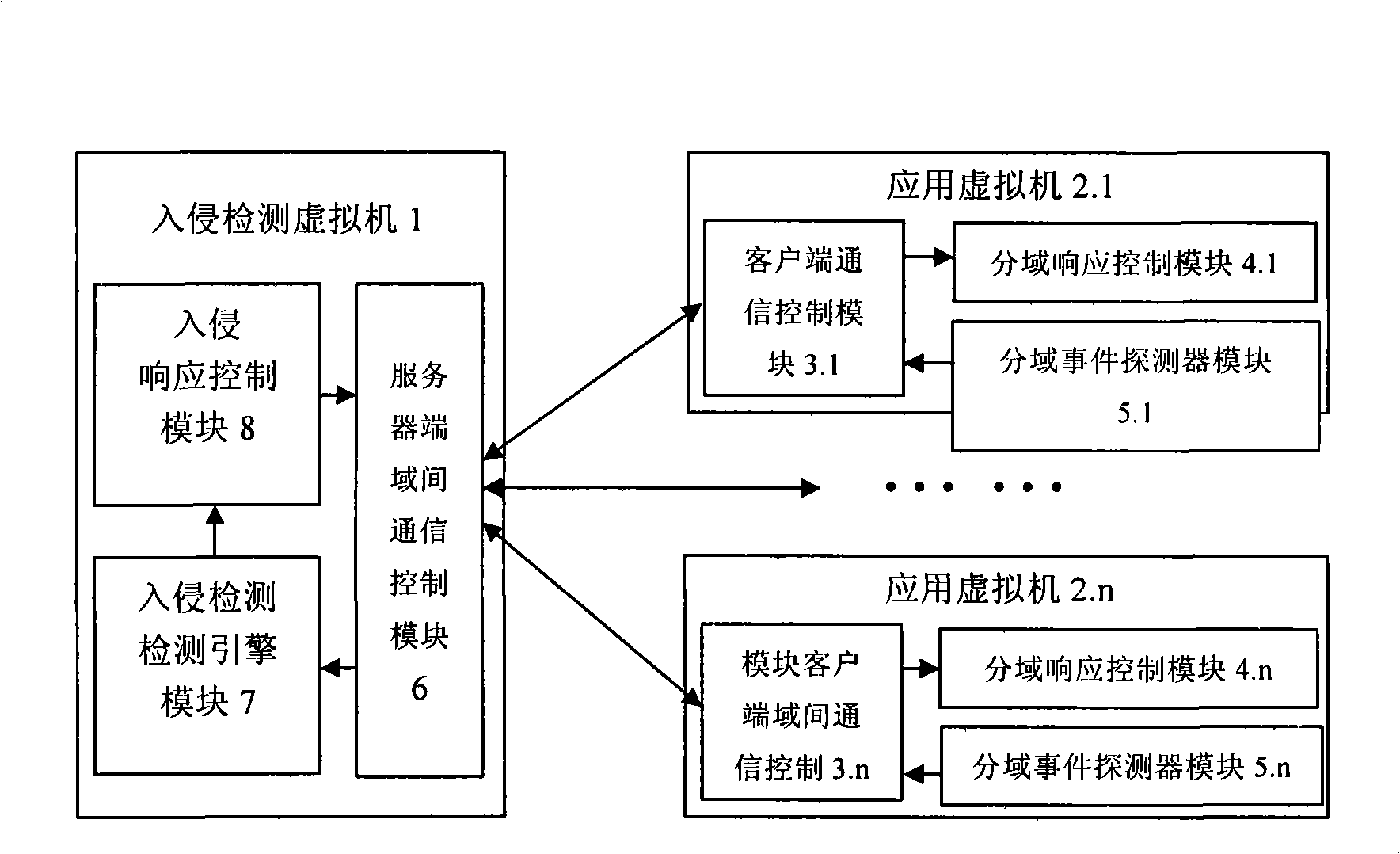
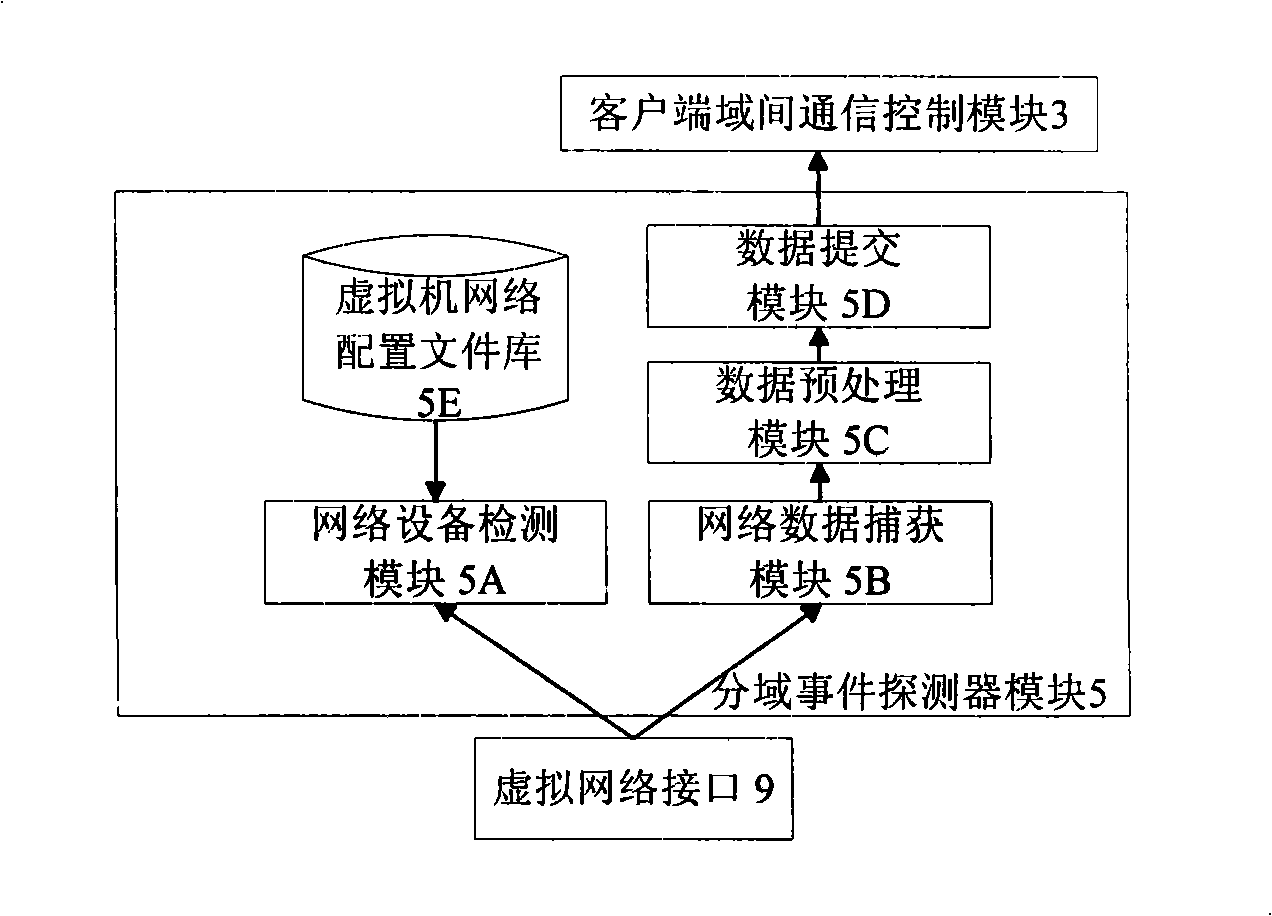
The invention discloses a safe network intrusion detection system which is applicable to the virtual machine environment and includes a server inter-domain communication control module, an intrusion detection engine module, an intrusion response control module in the intrusion detection virtual machine, a client inter-domain communication control module, a domain spilt event detector module and a domain split response control module in the detected application virtual machines. According to the problem that the safety of the virtual machine system of the virtual machine needs to be improved; the current intrusion detection system cannot realize the purpose, the safe network intrusion detection system considers the layering structure of the virtual machine network sufficiently and realizes the intrusion detection protection of the virtual machine system in the internal network based on the virtual machine; the safety of the virtual machine applied in the production practice activities is improved; meanwhile, the separation of the intrusion detection system and the protected system is realized based on the separation safety property of the virtual machine; compared with the traditional network intrusion detection system, the safe network intrusion detection system has better safety and reliability.
Owner:HUAZHONG UNIV OF SCI & TECH
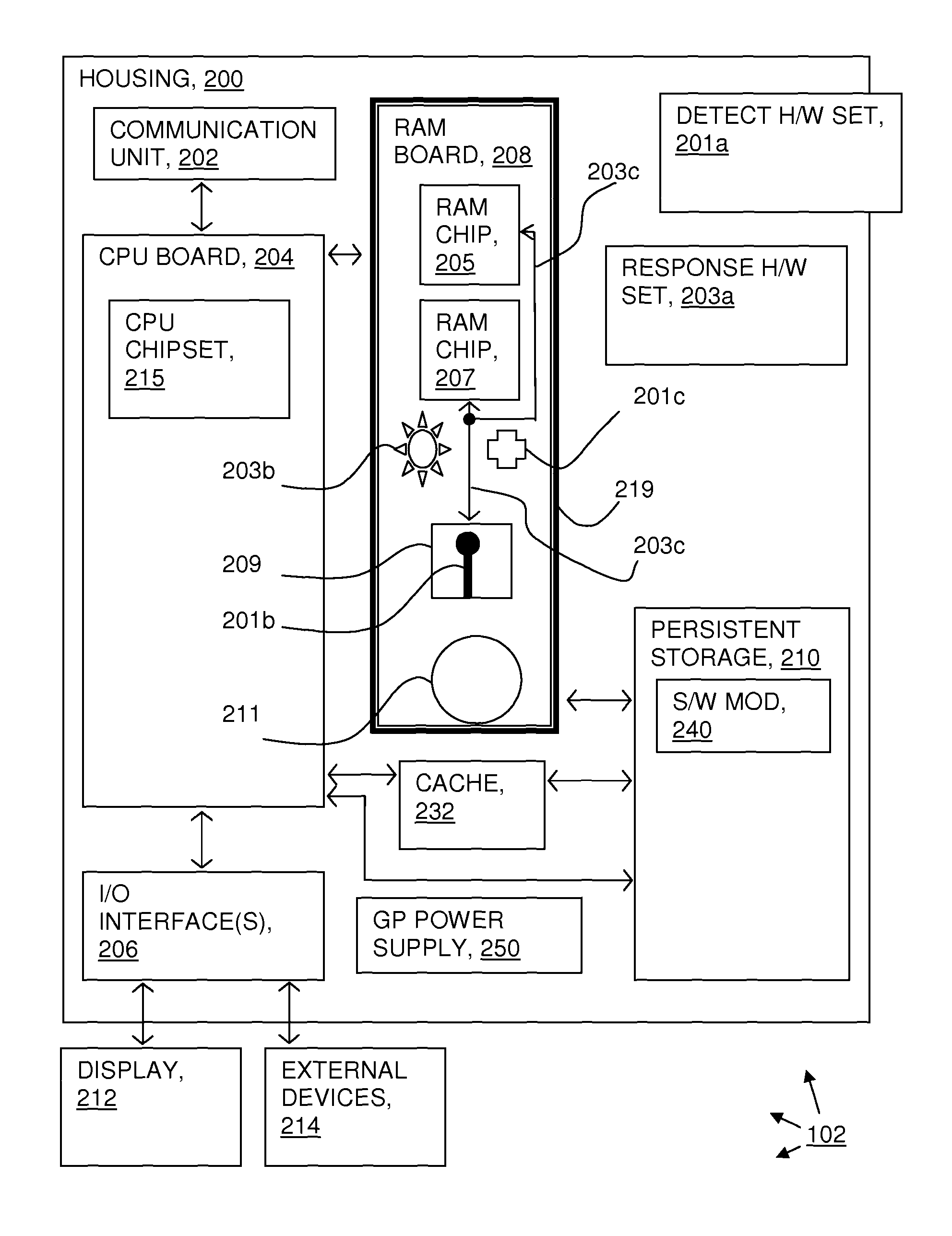
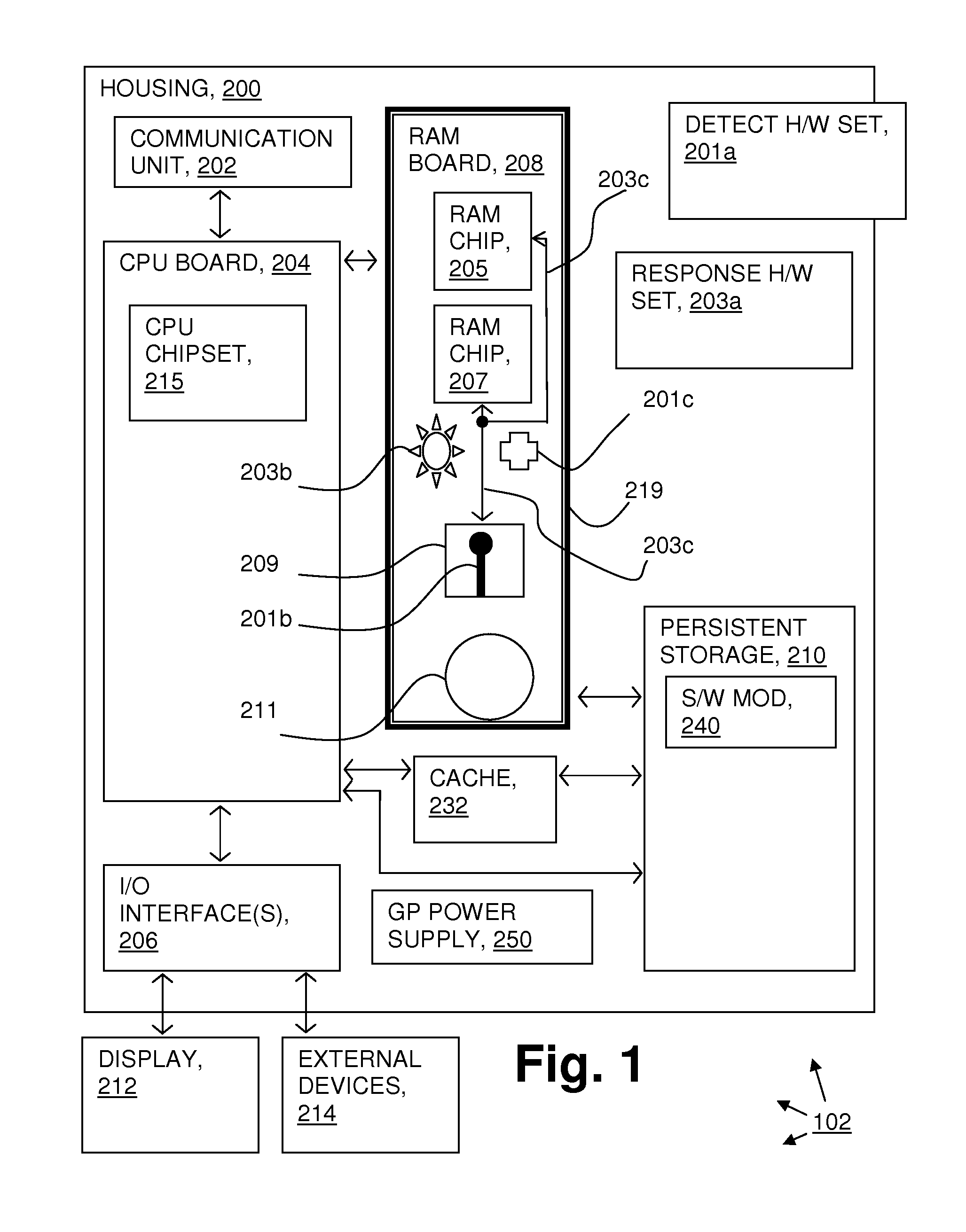
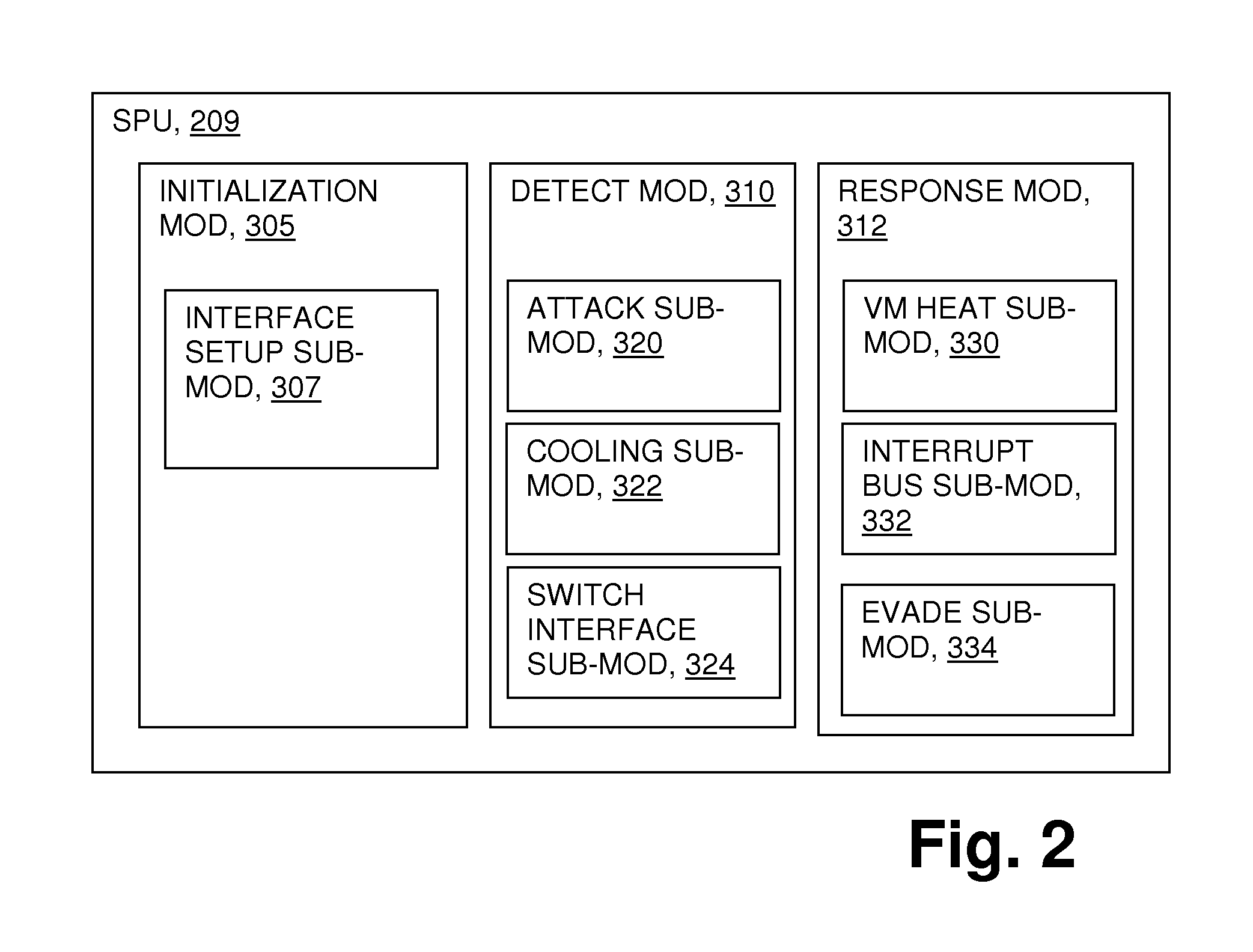
Attack resistant computer system
InactiveUS20140215613A1Memory loss protectionError detection/correctionComputerized systemElectric power
A computer system where a second, dedicated processor (sometimes called an SPU, to distinguish from the central processing unit (CPU)) has logic to manage and control an intrusion detection hardware set and an intrusion response hardware set. The intrusion response hardware detects physical intrusions (for example, cryogenic attacks), and the response hardware set responds in various ways to attempt to protect the sensitive data in a volatile memory from the detected physical intrusion. A dedicated power storage device powers the SPU and the intrusion response hardware set.
Owner:IBM CORP
Intrusion detection system specific to programmable logic controller (PLC) control system
ActiveCN110320890AGuaranteed stabilityGuaranteed reliabilityProgramme controlElectric testing/monitoringNetwork packetProgrammable logic controller
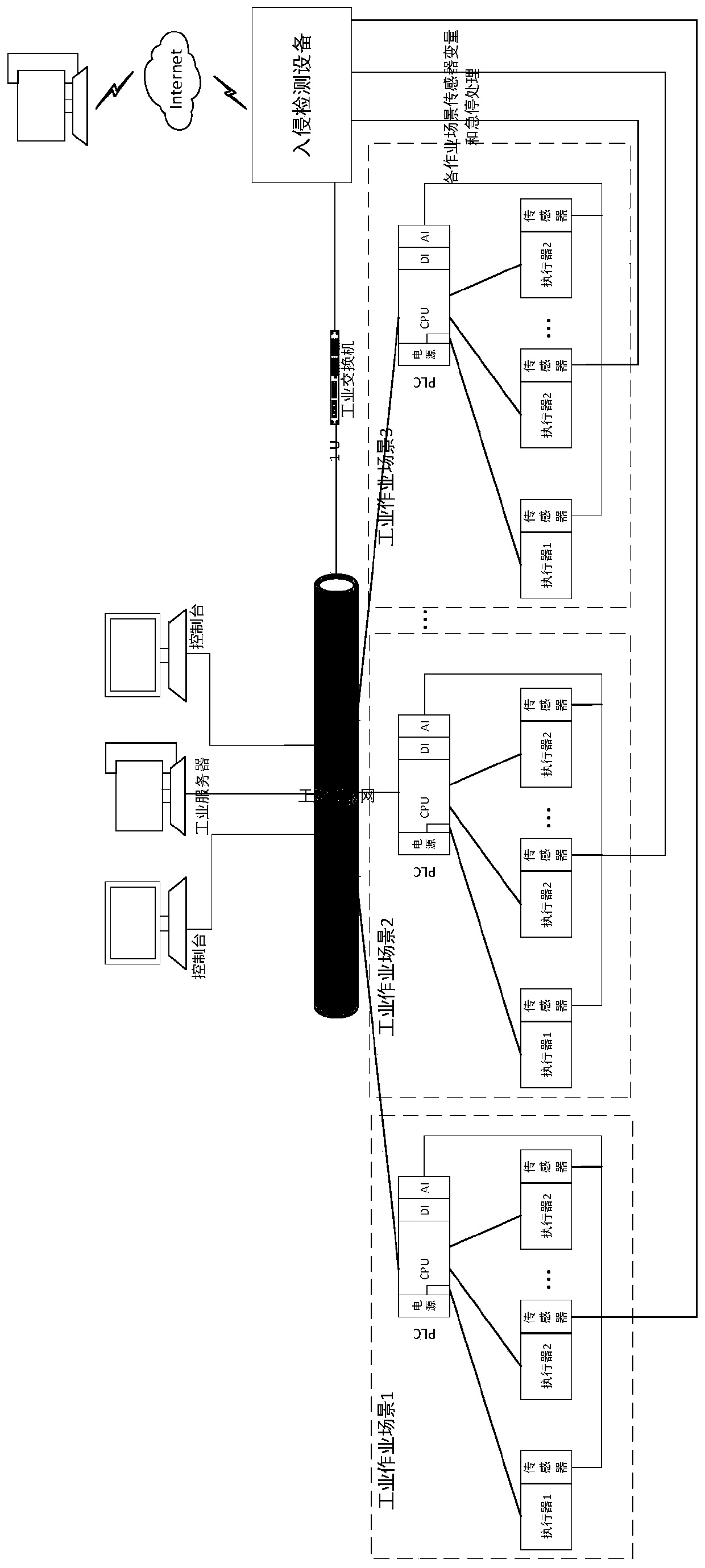
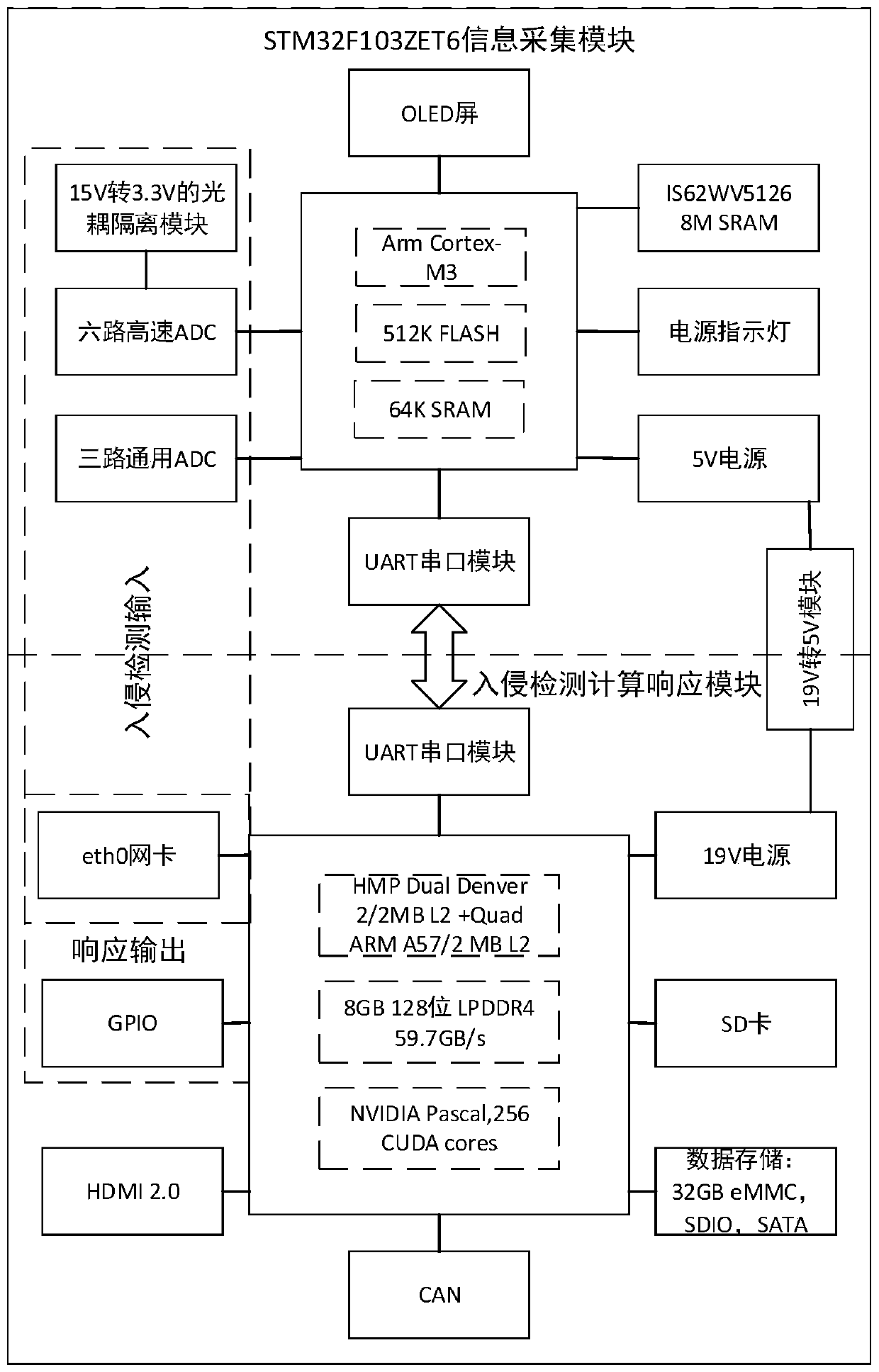
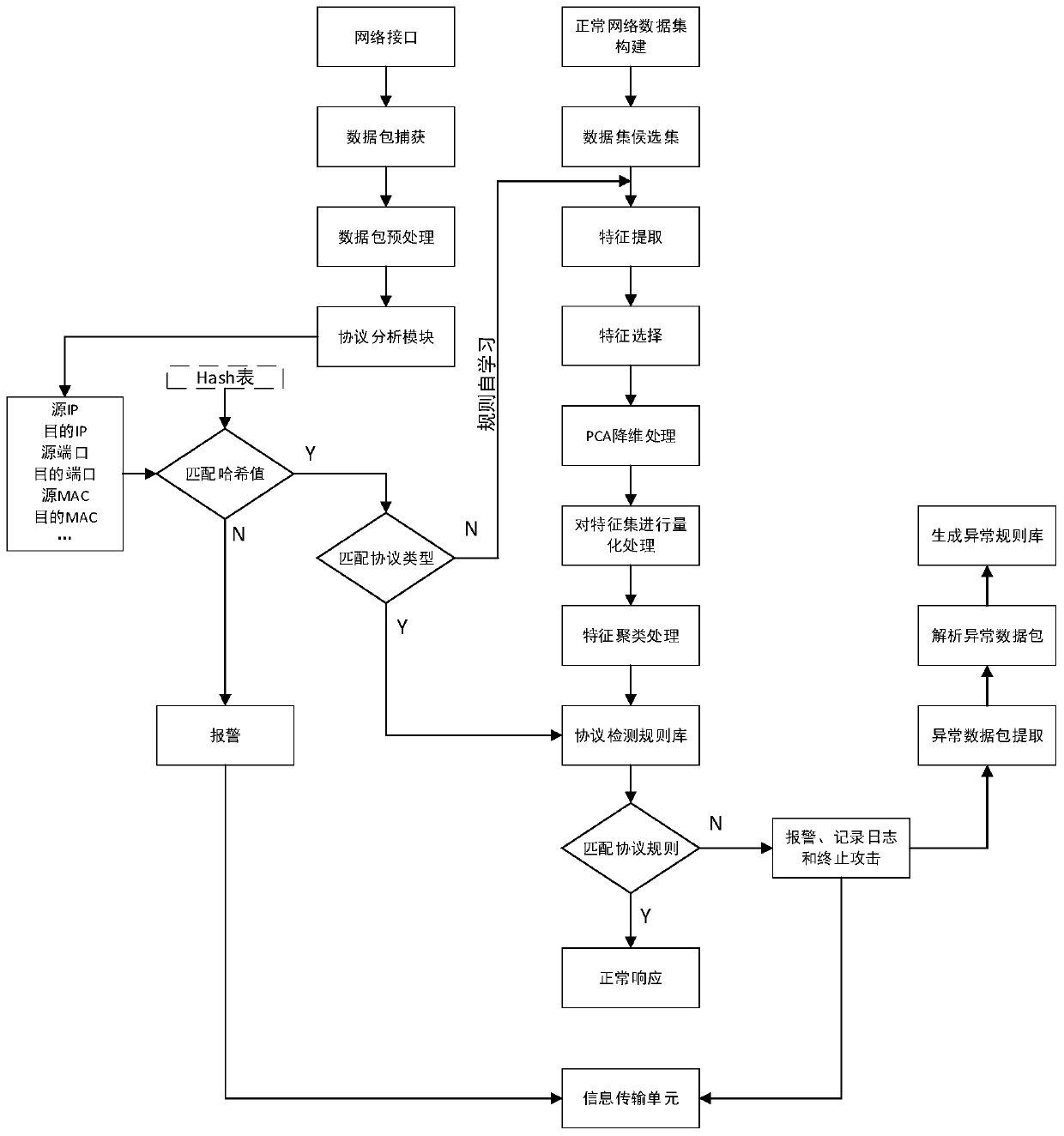
The invention provides an intrusion detection system specific to a programmable logic controller (PLC) control system. The intrusion detection system comprises an operation data acquisition module, adata-driven intrusion detection module, a network data acquisition module, a network communication protocol intrusion detection module, an intrusion response output module and a monitoring server. A normal network communication protocol model is built by capturing and parsing a network data packet, analyzing a network data feature influence factor and extracting a network data feature value, so that network communication protocol intrusion detection is realized. Meanwhile, field operation data are acquired to build a steady operation prediction model, and residual assessment is performed on the practical output of the control system and the output of model prediction, thereby realizing data-driven intrusion detection. When intrusion is found, braking processing is performed on a controller, and an alarm is made. The intrusion detection system is suitable for the technical field of industrial control system information safety, can effectively realize the intrusion detection of the PLC control system under the condition of not intruding an industrial control system, and improves the safety guarantee capability of the industrial control system.
Owner:UNIV OF SCI & TECH BEIJING
Automatic intrusion response decision making method based on Q-learning
InactiveCN108809979AImprove accuracyImprove real-time performanceComputing modelsTransmissionDecision takingInformation security
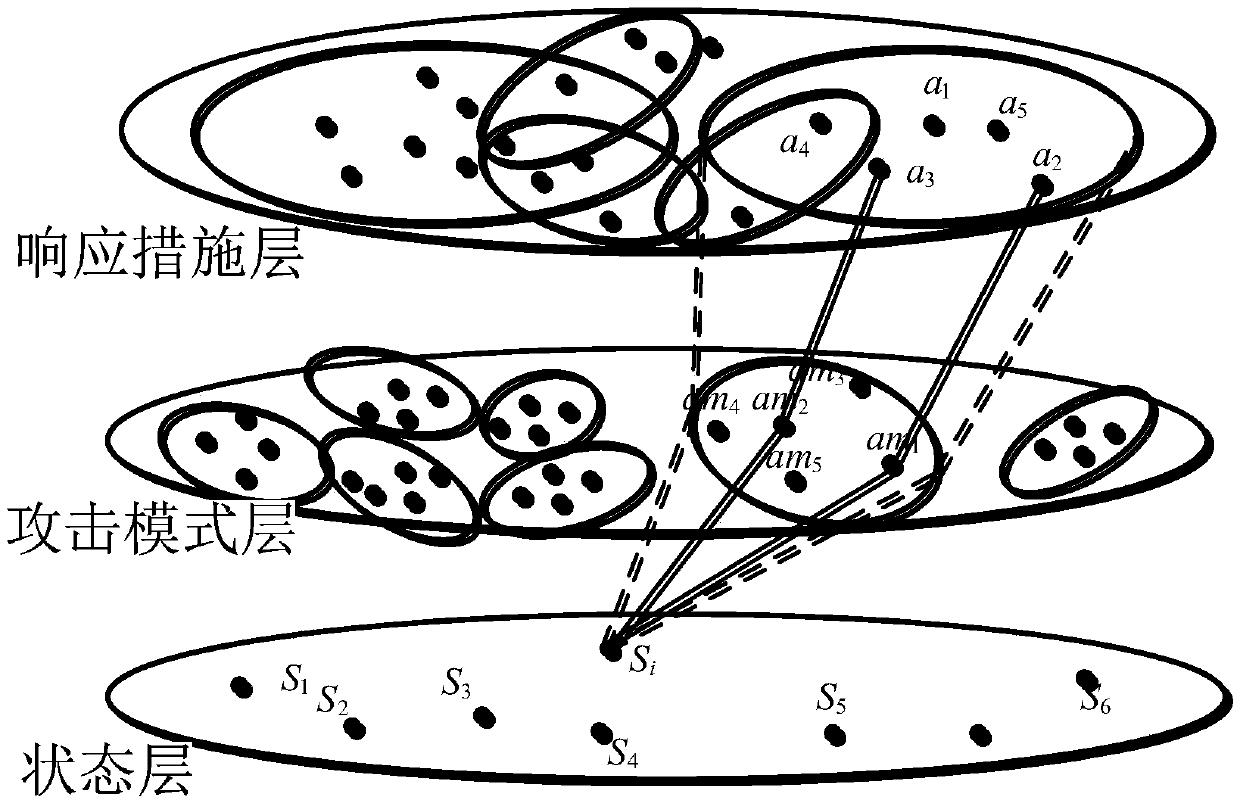
The invention belongs to the technical field of information security, and particularly relates to an automatic intrusion response decision making method based on Q-learning. The method comprises the following steps: scanning system vulnerability, constructing an attack graph, and establishing a network state layer, an attack pattern matching layer and a response measure layer according to the attack graph; establishing a mapping relationship among the network state layer, the attack pattern matching layer and the response measure layer; receiving an intrusion alarm from a network defense device, and mapping the intrusion alarm to a corresponding network state; selecting a defense action according to the mapping relationship, and notifying the system of the result; performing online learning by using the execution result of the defense action, and updating the mapping relationship between the attack pattern matching layer and the response measure layer; and returning to the step of mapping the intrusion alarm to the corresponding network state, and performing automatic response decision marking and online learning, until a defender terminates the defense. By adoption of the automatic intrusion response decision making method based on Q-learning provided by the invention, evaluation of multiple response purposes of the strategy can be achieved, the demand of multiple response purposes can be met, the instantaneity and accuracy of the intrusion detection are improved, the network resource consumption is reduced, and the overall performance of the system is improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Methods, computer program products and data structures for intrusion detection, intrusion response and vulnerability remediation across target computer systems
Computer security threat management information is generated by receiving a notification of a security threat and / or a notification of a test that detects intrusion of a computer security threat. A computer-actionable TMV is generated from the notification that was received. The TMV includes a computer-readable field that provides identification of at least one system type that is effected by the computer security threat, a computer-readable field that provides identification of a release level for a system type, and a computer-readable field that provides identification of the test that detects intrusion of the computer security threat for a system type and a release level, a computer-readable field that provides identification of a method to reverse the intrusion exploit of the computer security threat for a system type and a release level, and a computer-readable field that provides identification of a method to remediate the vulnerability subject to exploit of the computer security threat for a system type and a release level. The TMV is transmitted to target systems for processing by the target systems.
Owner:FINJAN BLUE INC
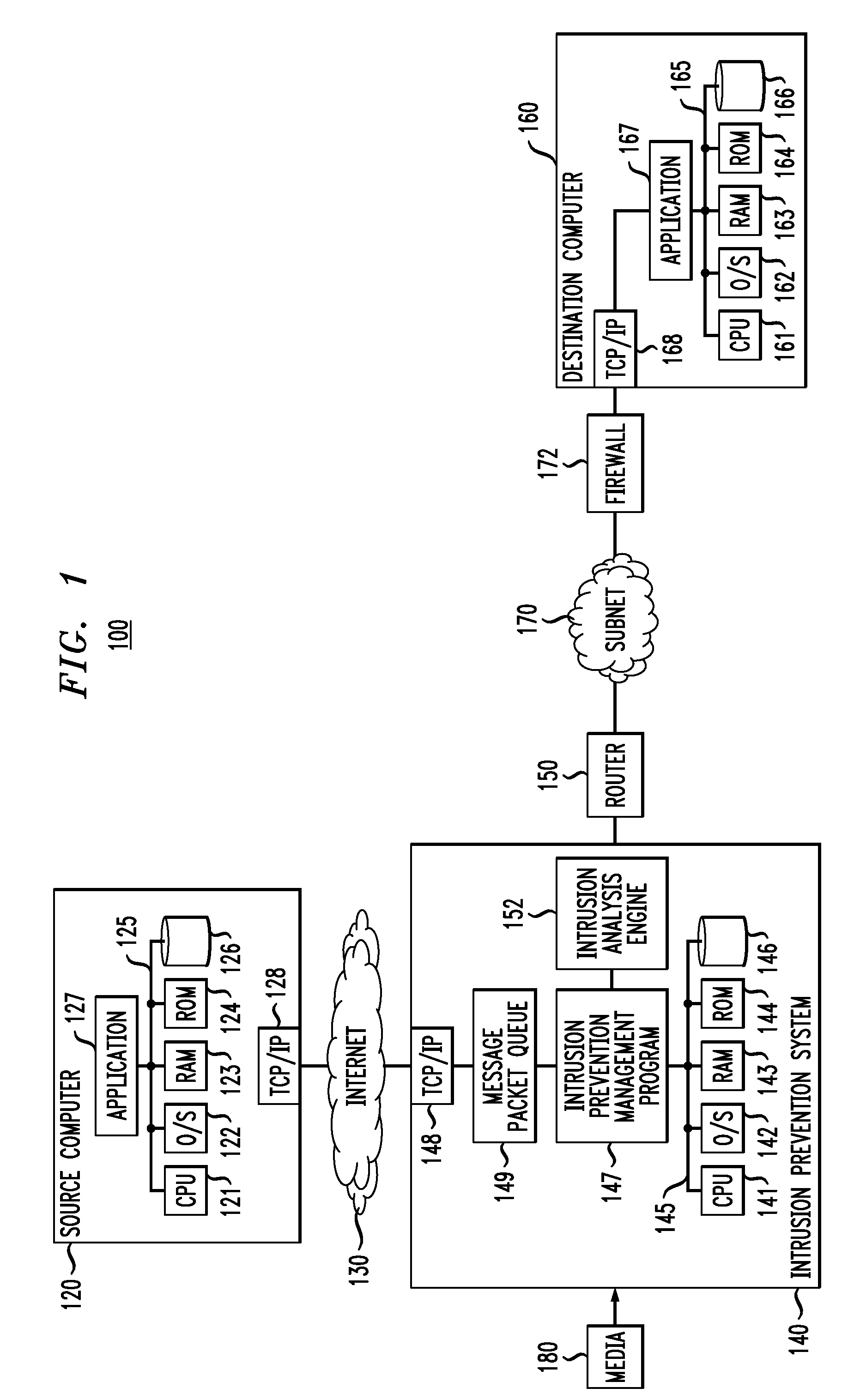
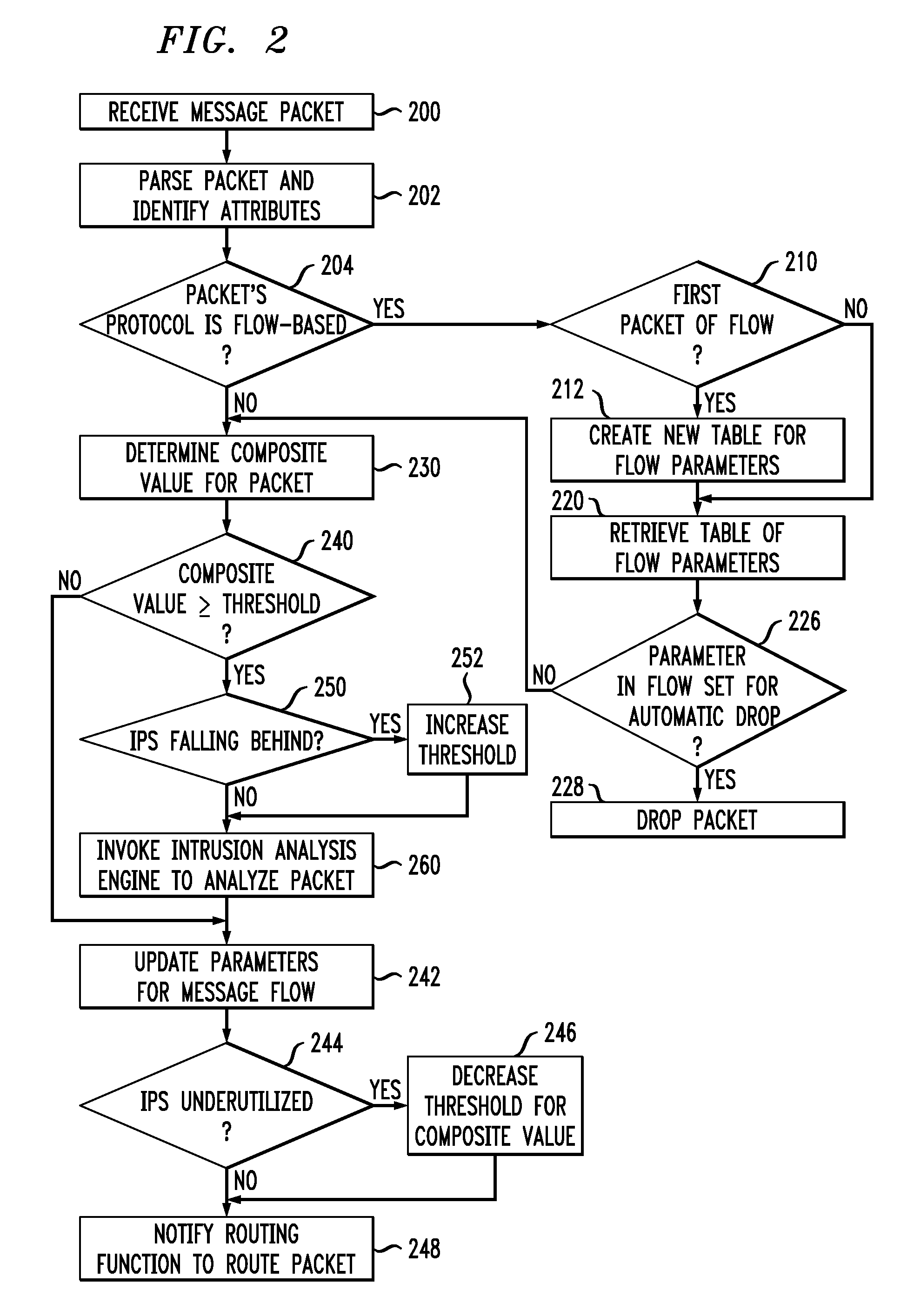
Network intrusion protection
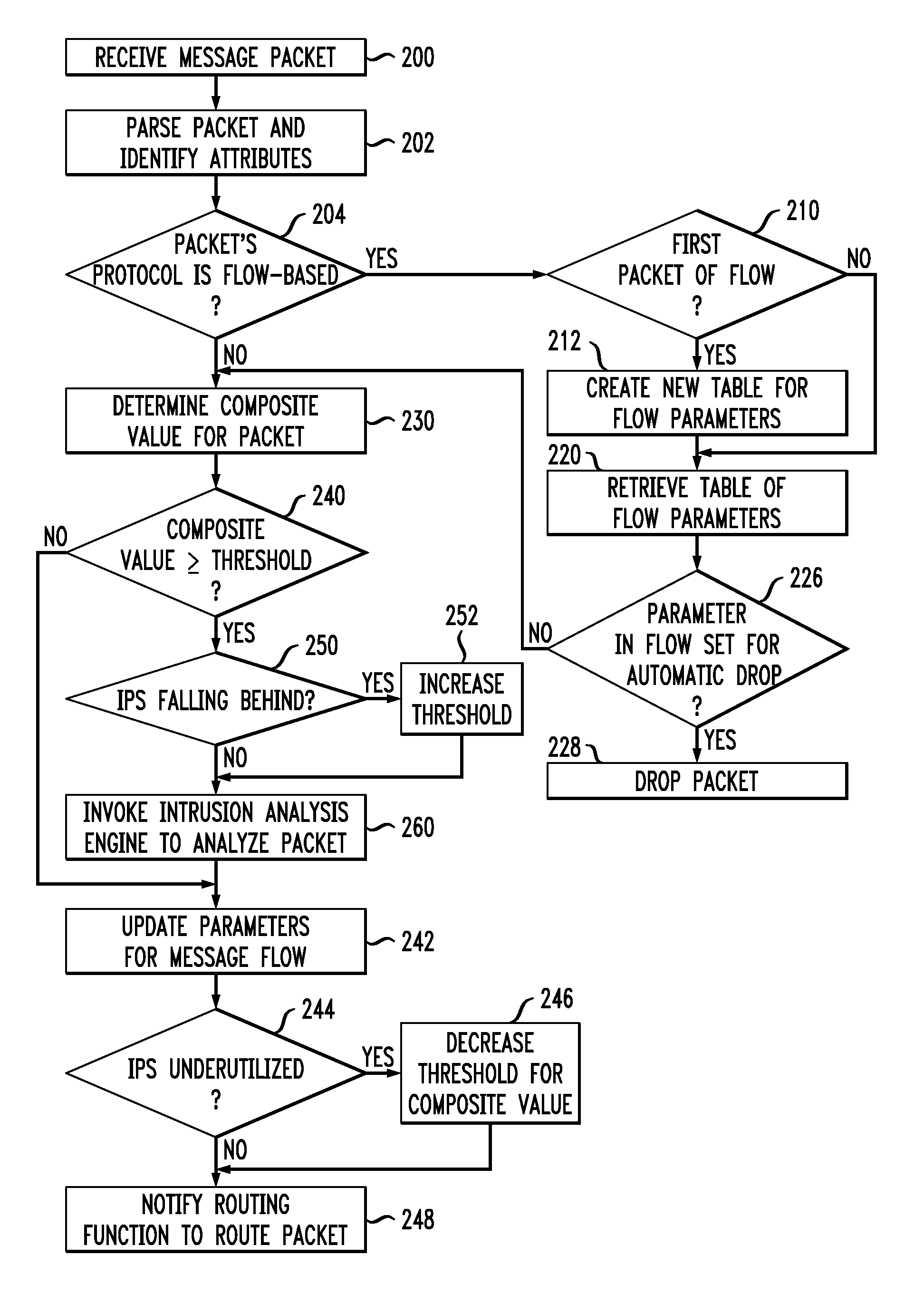
ActiveUS8677473B2Data taking preventionData switching by path configurationData packReliability engineering
Improved techniques are disclosed for use in an intrusion prevention system or the like. For example, a method comprises the following steps performed by a computing element of a network. A packet of a flow is received, the flow comprising a plurality of packets, wherein the plurality of packets represents data in the network. A network intrusion analysis cost-benefit value is determined representing a benefit for analyzing the received packet for intrusions in relation to a cost for analyzing the received packet for intrusions. The method compares the network intrusion analysis cost-benefit value to a network intrusion analysis cost-benefit threshold to determine whether analyzing the received packet for intrusions before forwarding the received packet is warranted. Responsive to a determination that analyzing the received packet for intrusions before forwarding the received packet is not warranted, the received packet is forwarded, an indication is made that subsequent packets of the flow should be forwarded, and a determination is made whether the received packet indicates an intrusion after forwarding the received packet.
Owner:INT BUSINESS MASCH CORP
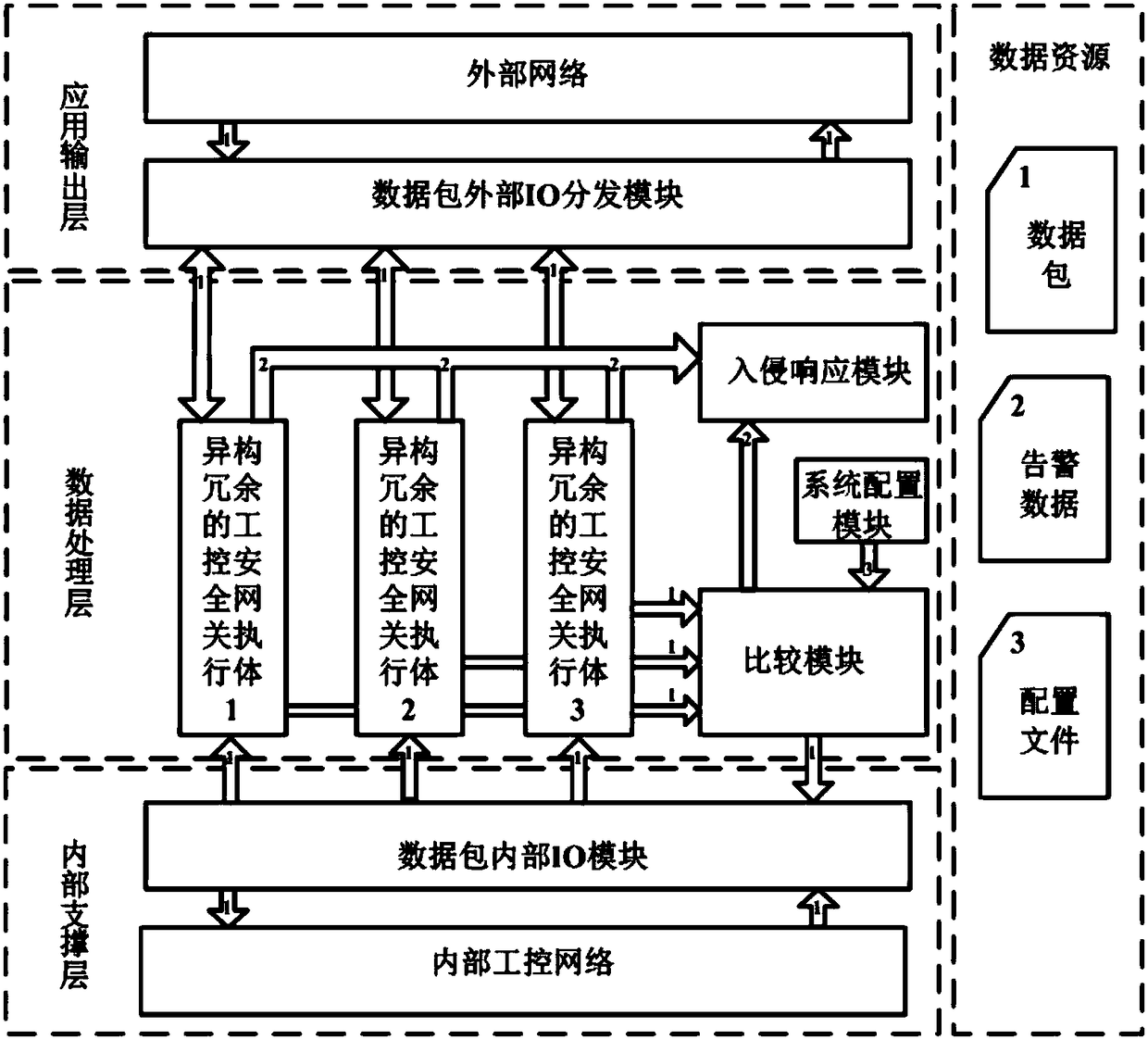
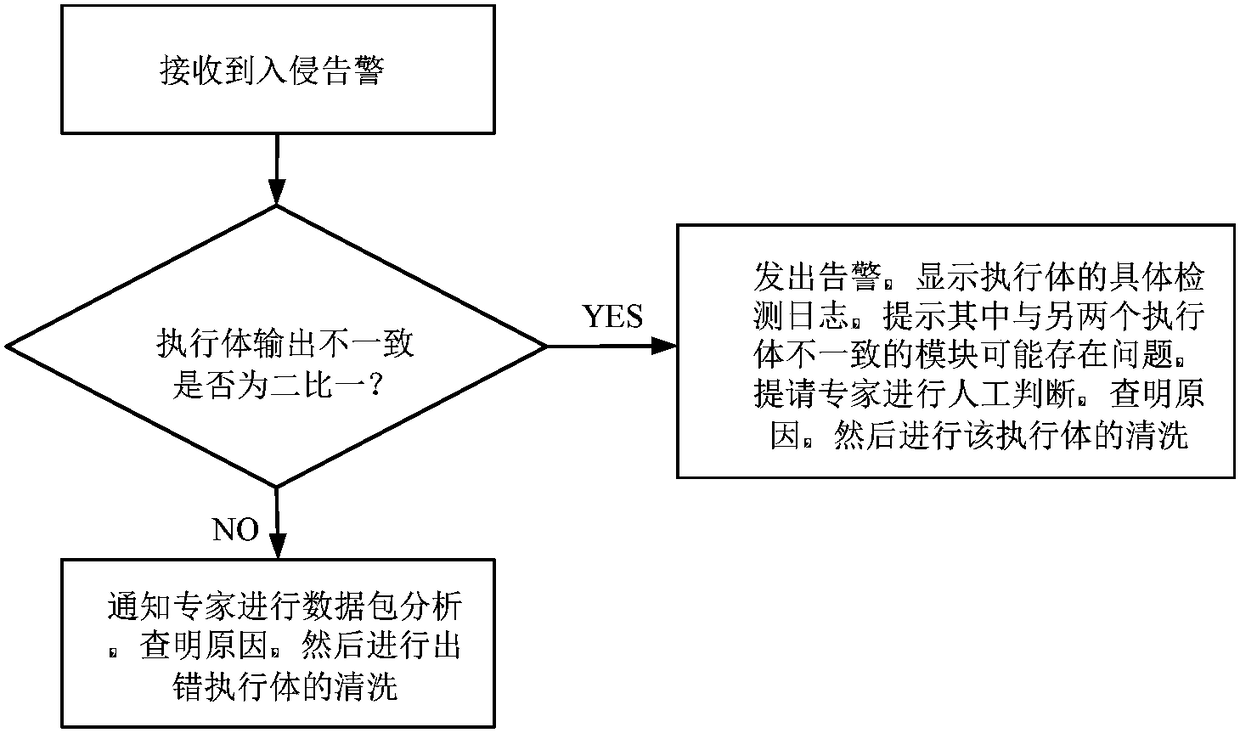
Three-mode heterogeneous redundant industrial control security gateway system and intrusion sensing method thereof
ActiveCN108337224AAvoid aggressive behaviorPrevent breachData switching networksSystems designNetwork packet
The invention discloses a three-mode heterogeneous redundant industrial control security gateway system and an intrusion sensing method thereof. The system provided by the invention comprises a data packet external IO module, three heterogeneous redundant industrial control security gateway execution modules, a comparison module, a data packet internal IO module, an intrusion sensing module and asystem configuration module. The invention is capable of detecting the intrusion to the industrial control gateway in time and preventing the attack behaviors caused by the design or implementation ofthe defect by using the system in the normal translation processing of the industrial control data packet, and performing the intrusion response processing without normal service interference.
Owner:兆辉易安(北京)网络安全技术有限公司
Attack-graph-based intrusion response mode
The invention discloses an attach-graph-based dynamic intrusion response method, which comprises the following steps of: presenting three kinds of cost comprising operation cost, response cost and loss cost for intrusion detection and response according to an intrusion detection and response reference mode which is an intrusion response based on attack graph (IRAG) model, and selecting a response measure on the basis of combining the three kinds of cost; defining the types of attackers executing attacks with certain aims by utilizing the preference of the attackers in security scales, and describing the attack aims of the attackers by using the types of the attackers; establishing two information sets which are an attacker information set and a system information set, wherein the attacker information set mainly comprises information obtained by the footprinting, sniffing and scanning of the attackers and according to the response information of a system, and information in the system information set comprises the alarming and log information from components comprising an intrusion detection system (IDS), a firewall, a host and the like in the system; and determining the action spaces of participation parties, wherein the system actually may determine a response set according to different attack types when giving the response.
Owner:JIANGSU NANDASOFT TECHNOLOGY COMPANY LIMITED +1
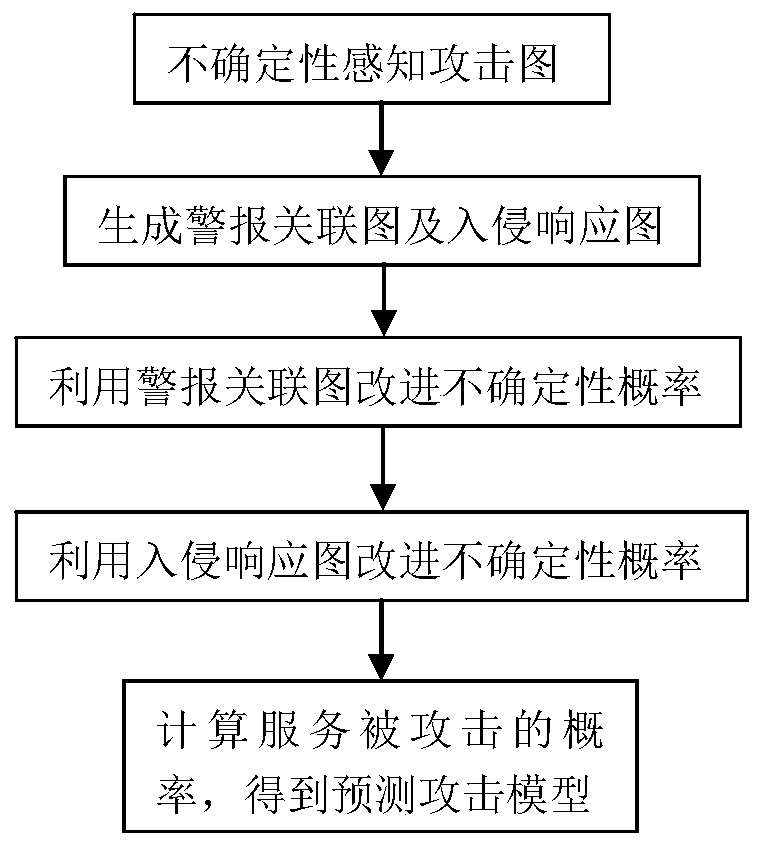
Network attack prediction model construction method based on uncertainty perception attack graph
The invention discloses a network attack prediction model construction method based on an uncertain perception attack graph, which comprises the following steps: 1, adding an uncertain probability that vulnerabilities are attacked on the attack graph to obtain an uncertain perception attack graph; 2, associating the alarm information generated by the intrusion detection system when the service inthe network system is attacked, generating an alarm association graph, and generating an intrusion response graph by using a response decision corresponding to the alarm information; 3, according to the source host address of the alarm, the destination host address of the alarm, the source port number of the alarm, the destination port number of the alarm, the protocol used for alarm transmissionand the vulnerability number corresponding to the generated alarm, improving the uncertainty probability; 4, improving the uncertainty probability through the incidence relation between the response decisions in the intrusion response graph and the response cost; 5, obtaining the probability that the service is attacked according to the uncertainty probability so as to obtain a prediction attack model; the network attack prediction method can realize accurate and comprehensive prediction of the network attack.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
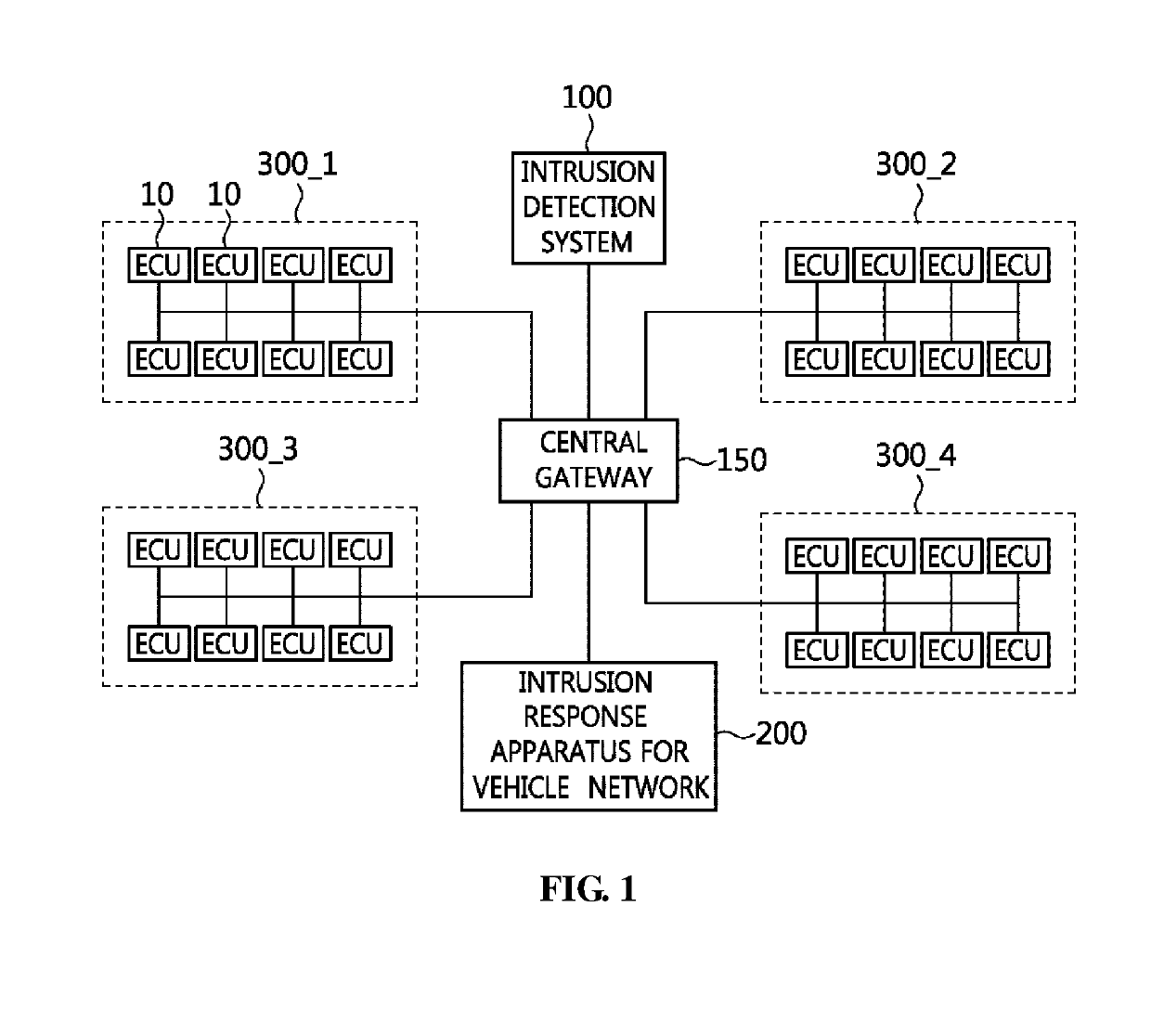
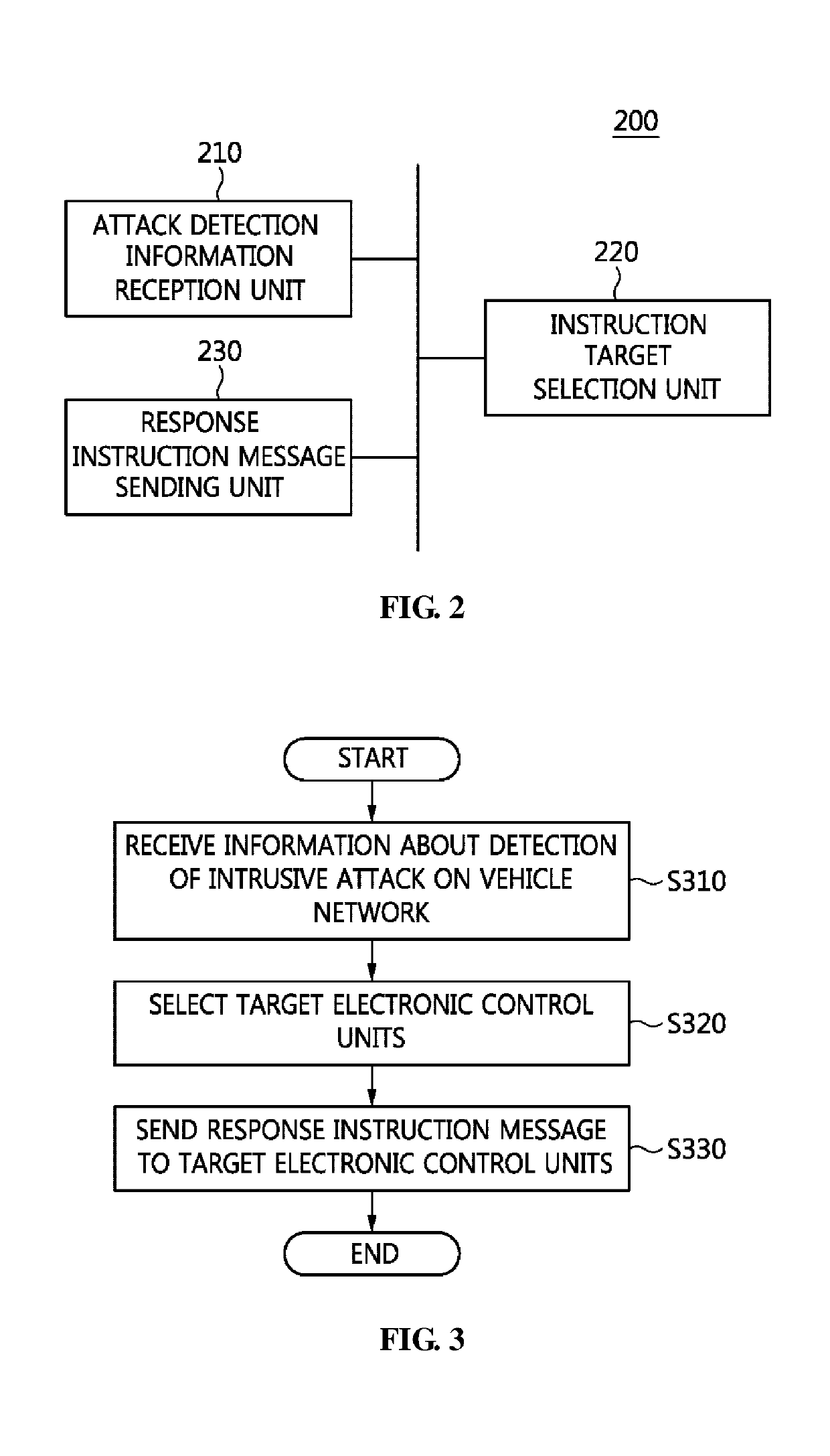
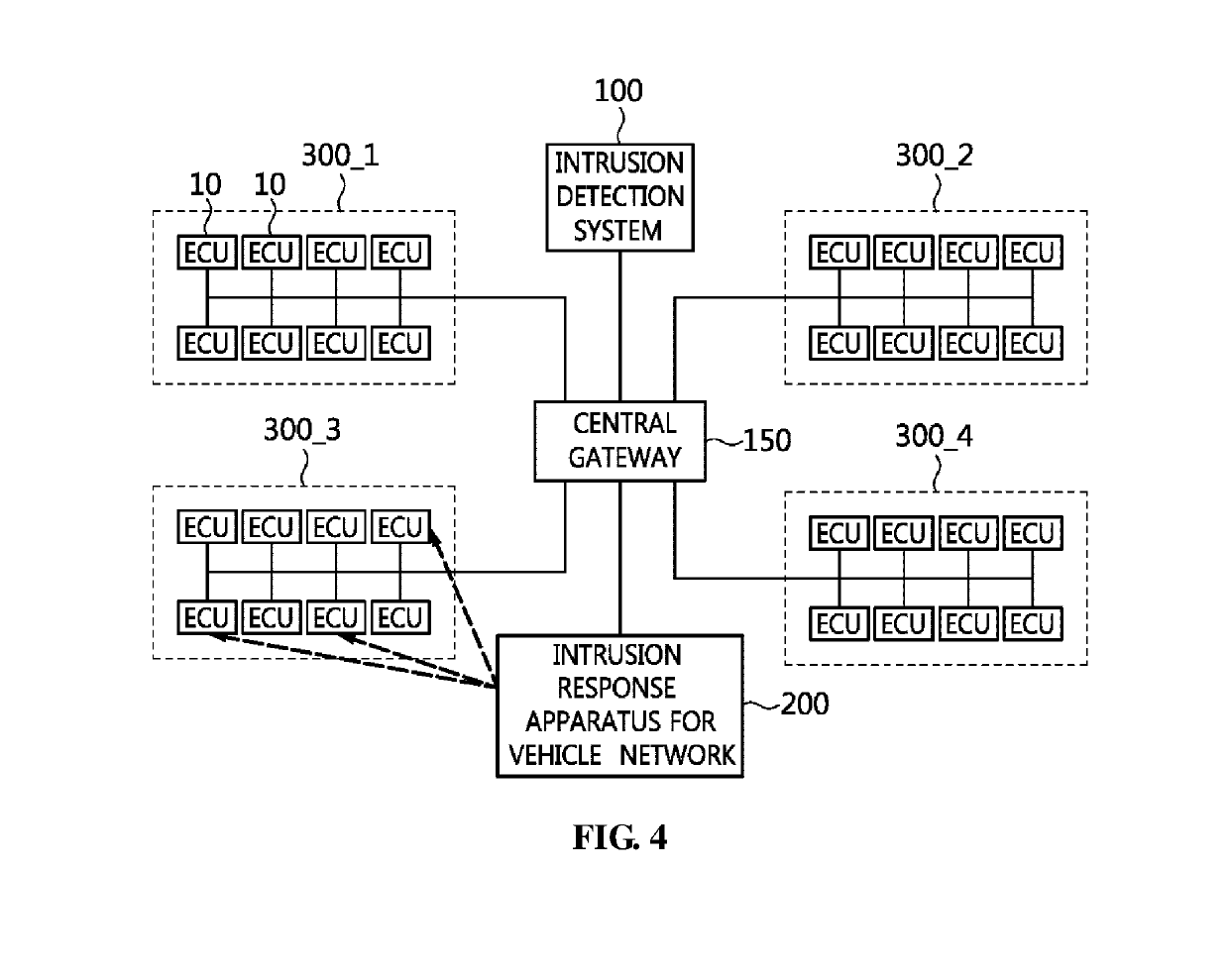
Intrusion response apparatus and method for vehicle network
InactiveUS20190332823A1Minimize damageMinimize damage caused by the intrusionInternal/peripheral component protectionPlatform integrity maintainanceElectronic control unitVehicle networks
Disclosed herein are an intrusion response apparatus and method for a vehicle network. The intrusion response method for a vehicle network is performed by an intrusion response apparatus for the vehicle network, and includes receiving attack detection information about an intrusive attack on the vehicle network from an intrusion detection system, selecting at least one target electronic control unit that is to be instructed to respond to the intrusive attack from among multiple electronic control units, and sending a response instruction message to the at least one target electronic control unit so that the target electronic control unit responds to the intrusive attack.
Owner:ELECTRONICS & TELECOMM RES INST
Network intrusion prevention system based on behavior check
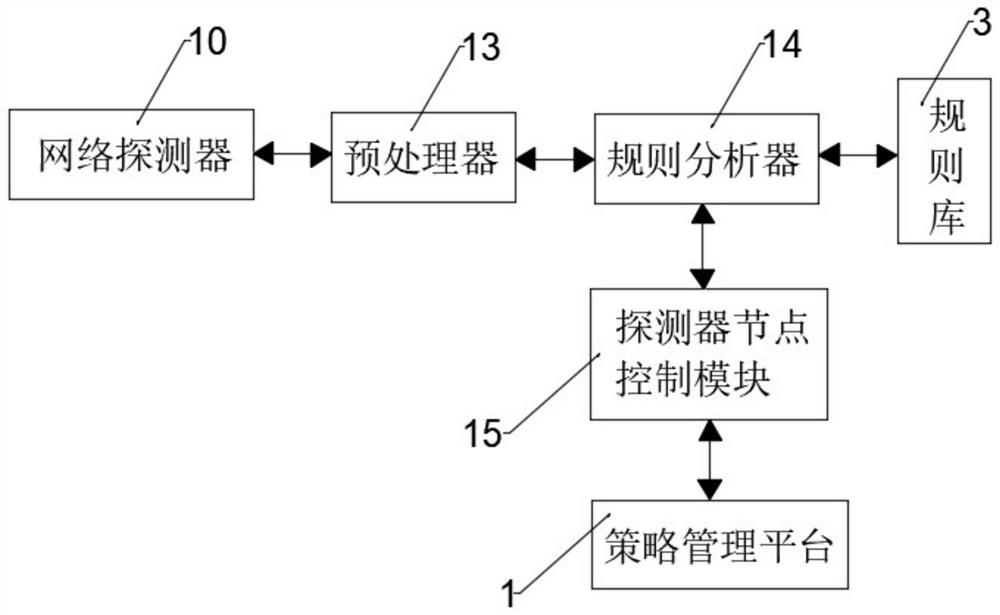
InactiveCN111970300AWeaken the strength of intrusion attacksSensitive Intrusion Response MechanismTransmissionAttackEngineering
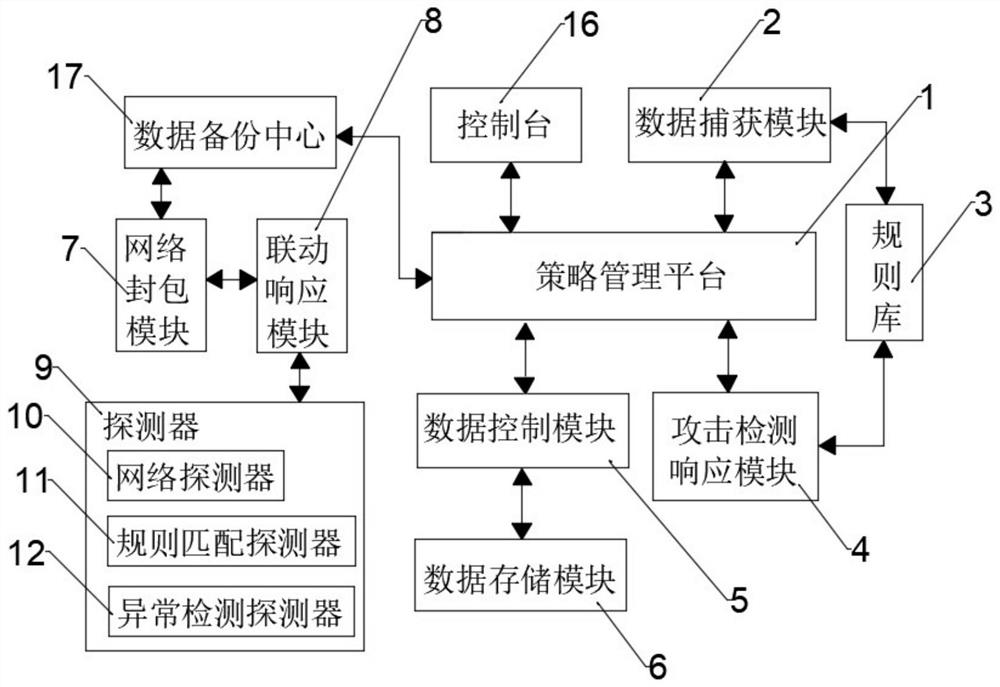
The embodiment of the invention discloses a network intrusion prevention system based on behavior check, and the system comprises a strategy management platform which carries out the analysis of the operation information of a user, transmits the operation information to an information detector according to a control object, and generates a linkage control instruction; a data capture module which is used for receiving a host and a network data source, obtaining log information, reading intrusion rules through a rule base and sending alarm information to the strategy management platform according to a unified alarm format; an attack detection response module which is used for carrying out attack detection on the captured data according to the linkage control instruction; a data control module which is used for monitoring and controlling data in the network according to the on-off of the firewall, storing various captured data information in the system through the data storage module. A distributed multi-point defense strategy is adopted, so that the whole system has a sensitive intrusion response mechanism and accurate attack positioning, user data content cannot be changed randomly,the packet loss rate is low, smooth network communication can be ensured, and the network intrusion attack intensity is weakened.
Owner:GUANGDONG POWER GRID CO LTD DONGGUAN POWER SUPPLY BUREAU +1
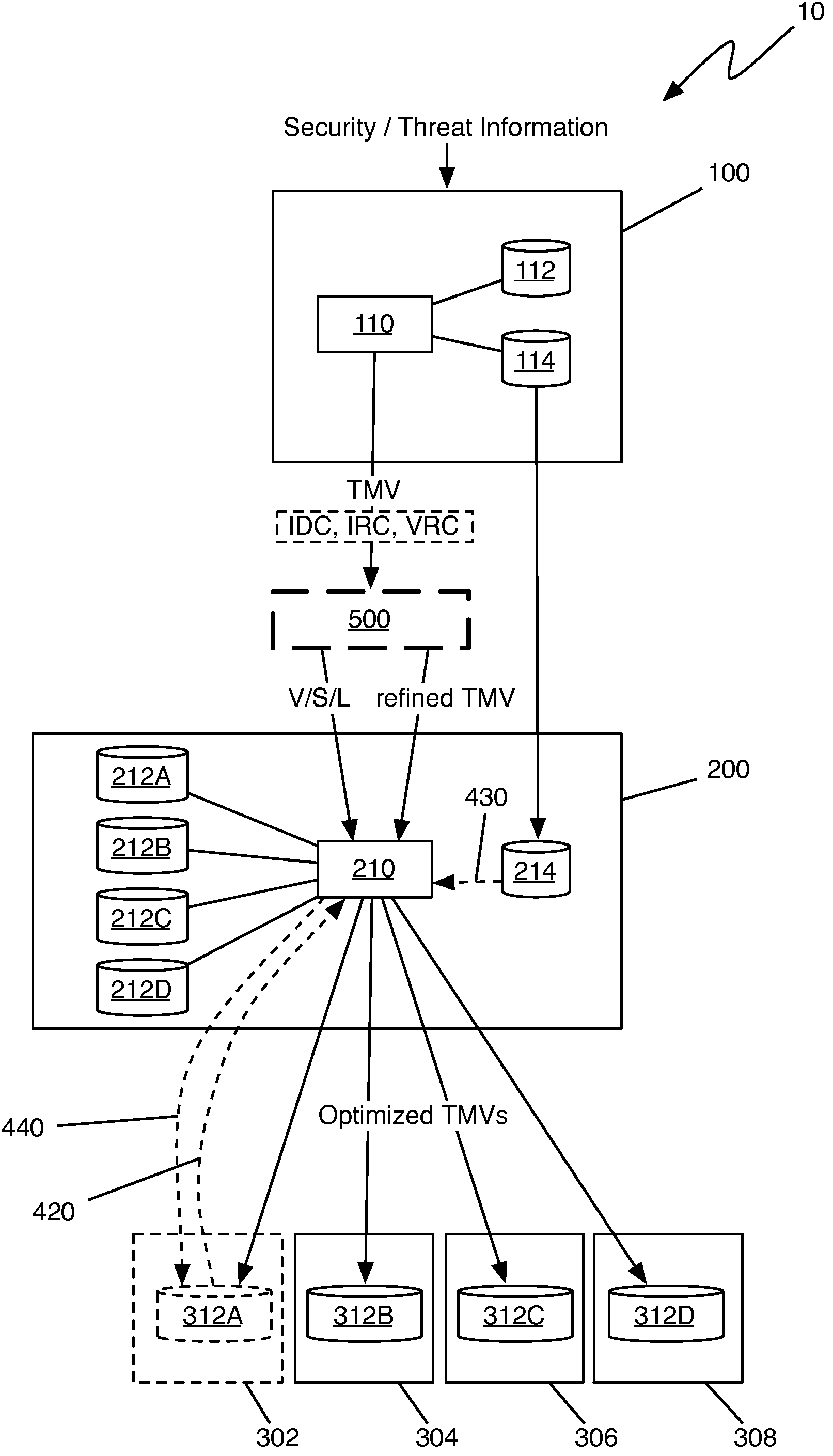
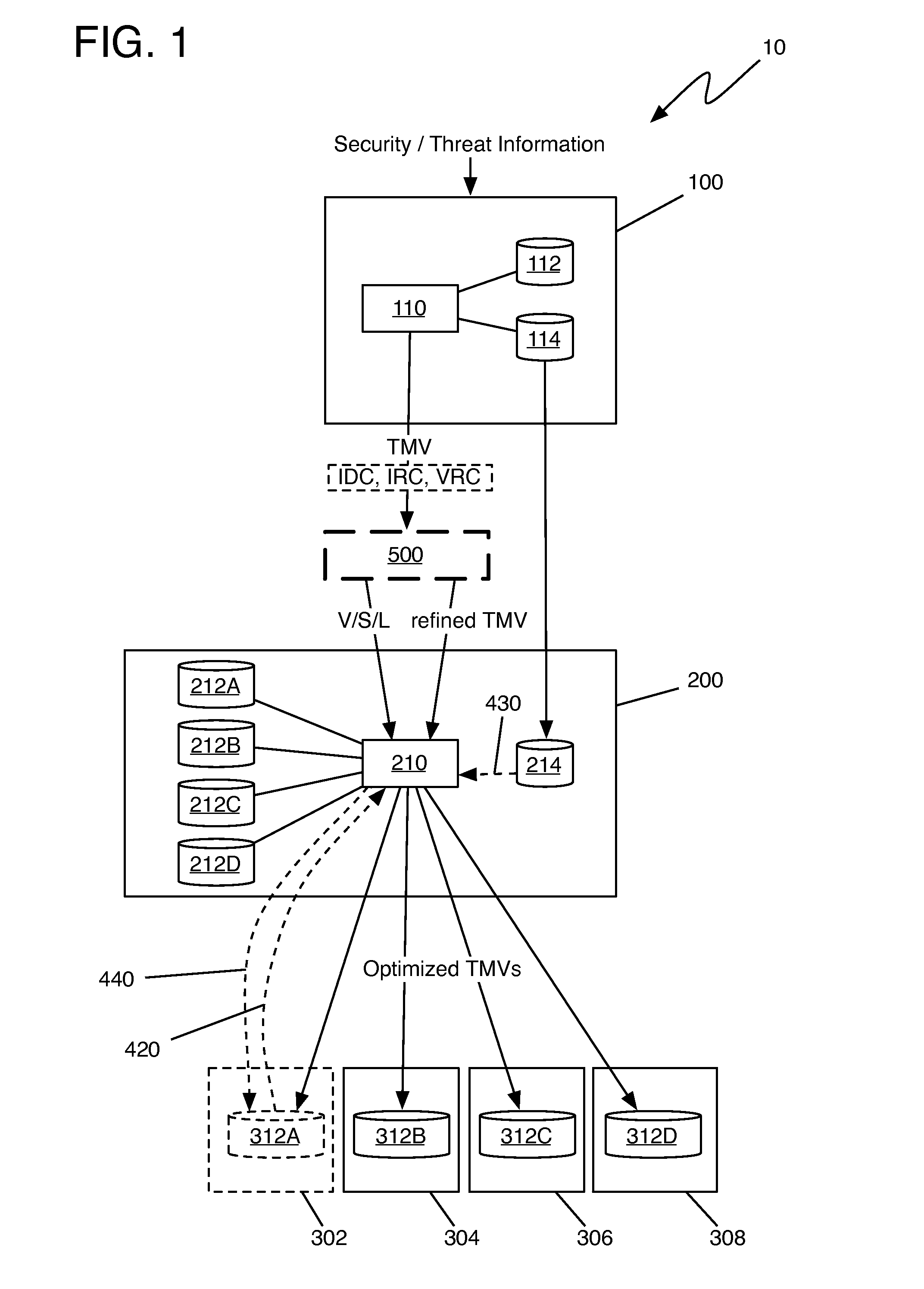
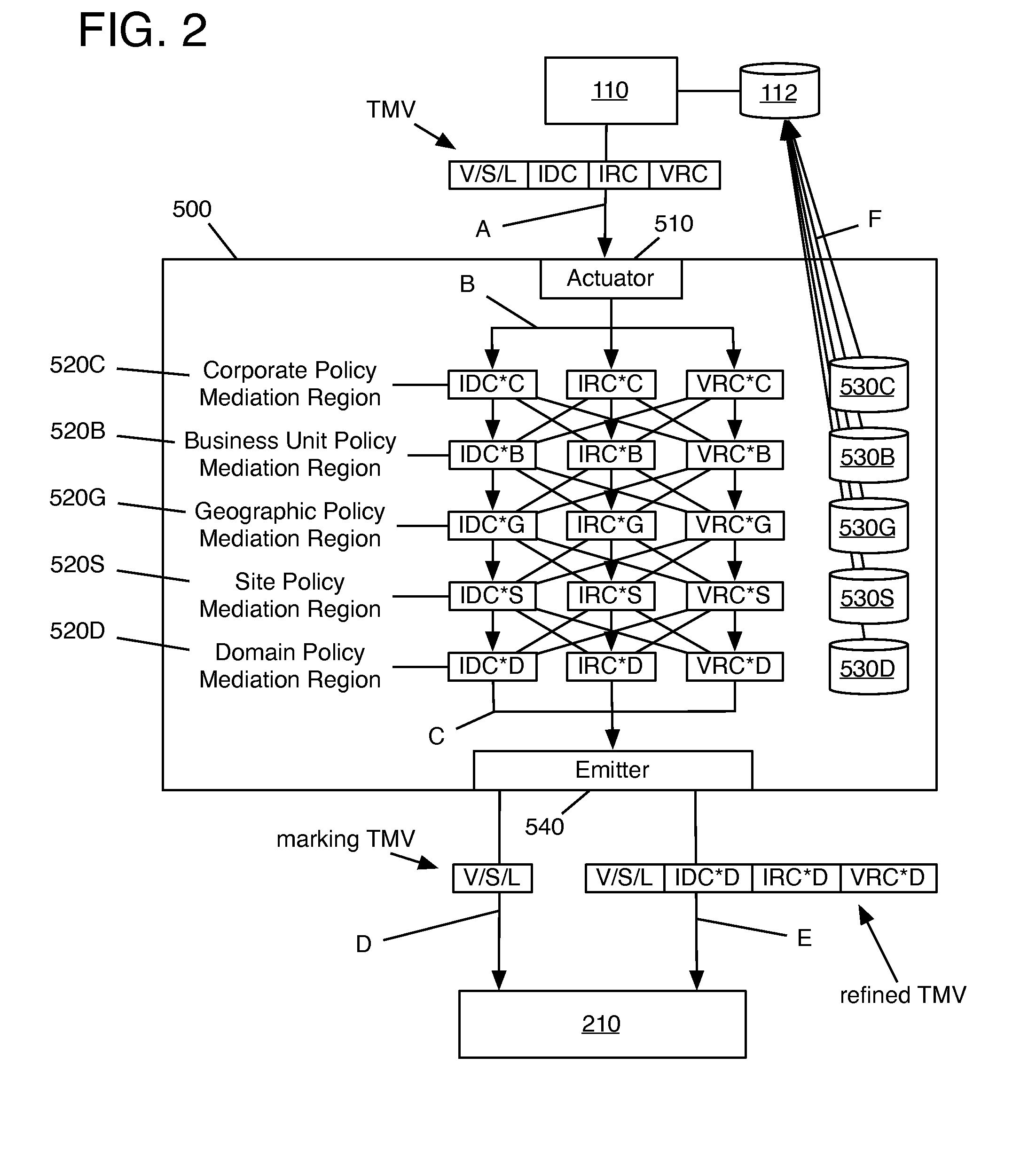
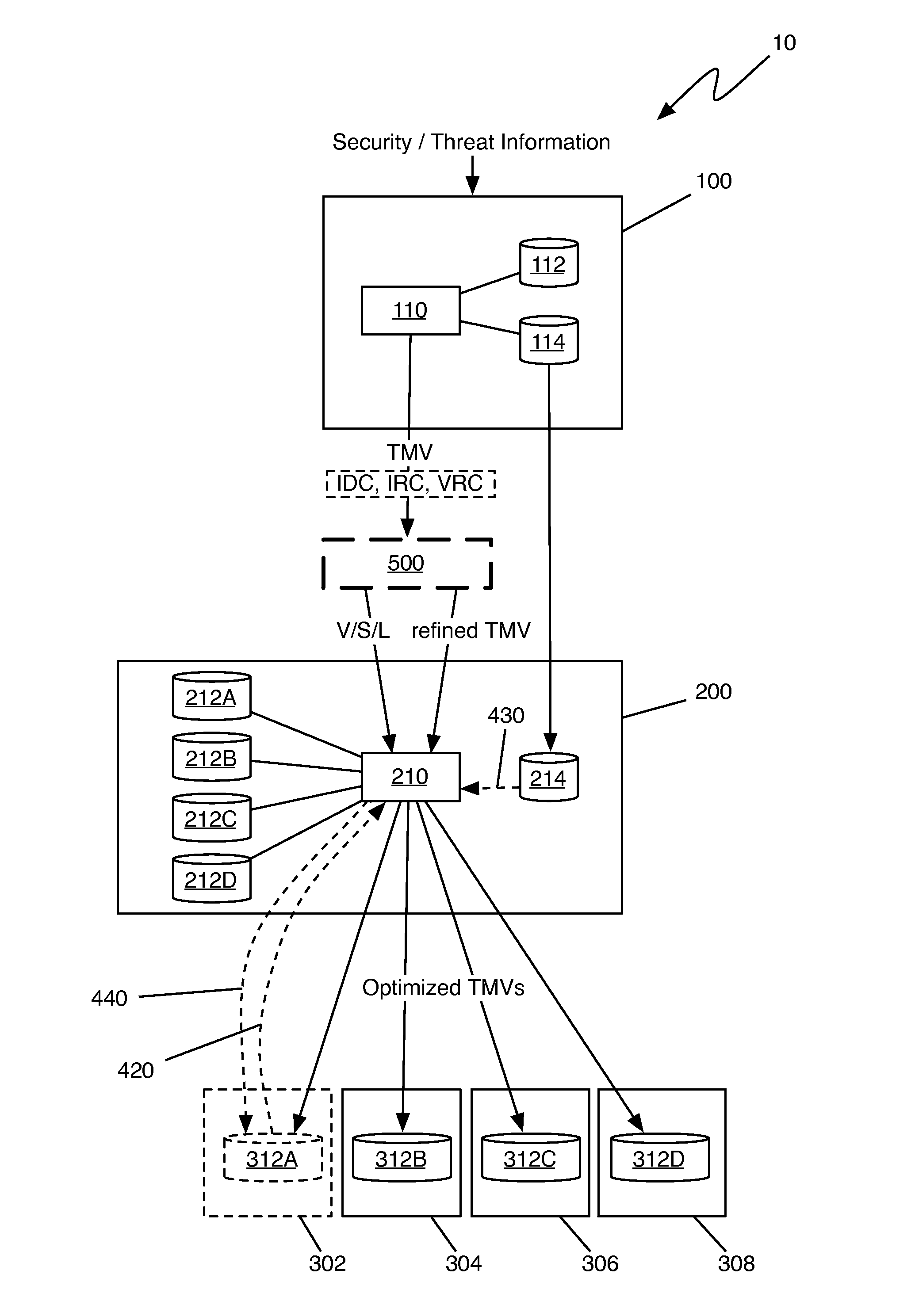
Method of integrating a security operations policy into a threat management vector
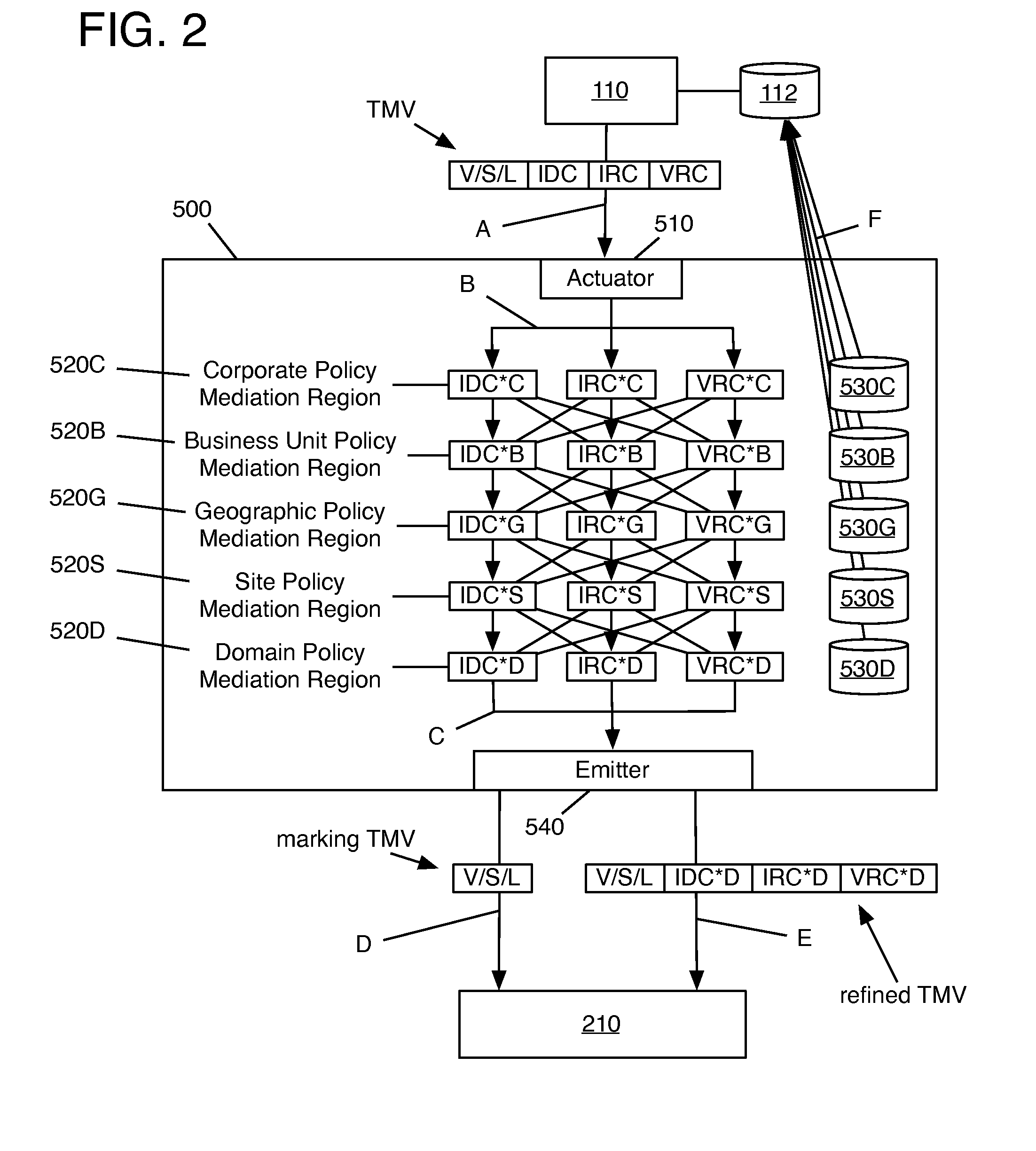
The invention relates to the integration of a security operations policy into a threat management vector. In one embodiment, a method according to the invention includes receiving at least one threat management vector (TMV) from a TMV generator, the TMV including a root vulnerability vector, at least one system vector, at least one system level vector, and a countermeasures payload including intrusion detection countermeasures (IDC), intrusion response countermeasures (IRC), and vulnerability remediation countermeasures (VRC); forwarding to the TMDC a TMV including only the root vulnerability vector, the at least one system vector, and the at least one system level vector; propagating the TMV through a hierarchy of policy mediation regions (PMRs), each PMR being operable to refine at least one of the IDC, the IRC, and the VRC; refining at least one of the IDC, the IRC, and the VRC to conform to a security operations policy of the PMR; forwarding the refined TMV to a threat management domain controller (TMDC); recording refinements made by each PMR to each of the IDC, the IRC, and the VRC; transferring the recorded refinements to a threat management control book (TMCB); and marking the refined TMV as having been refined by each PMR making a refinement.
Owner:LINKEDIN
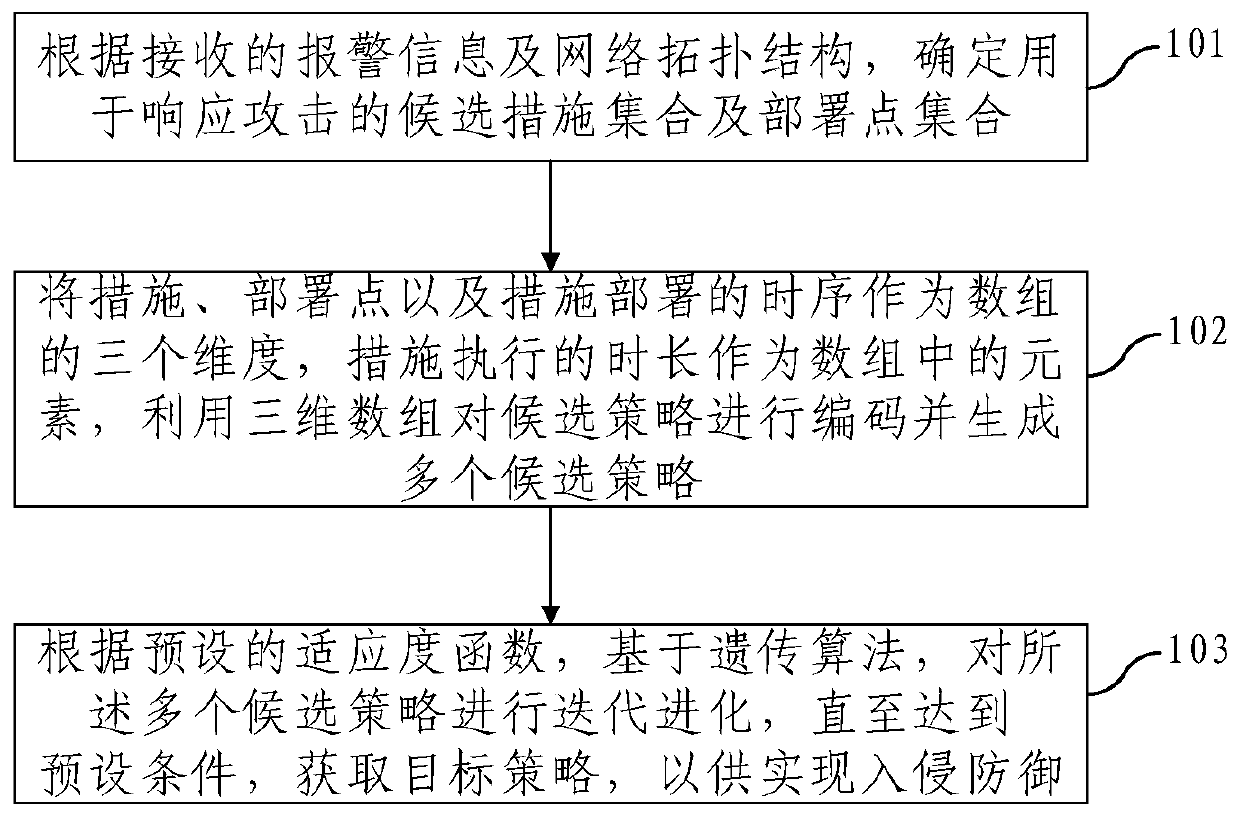
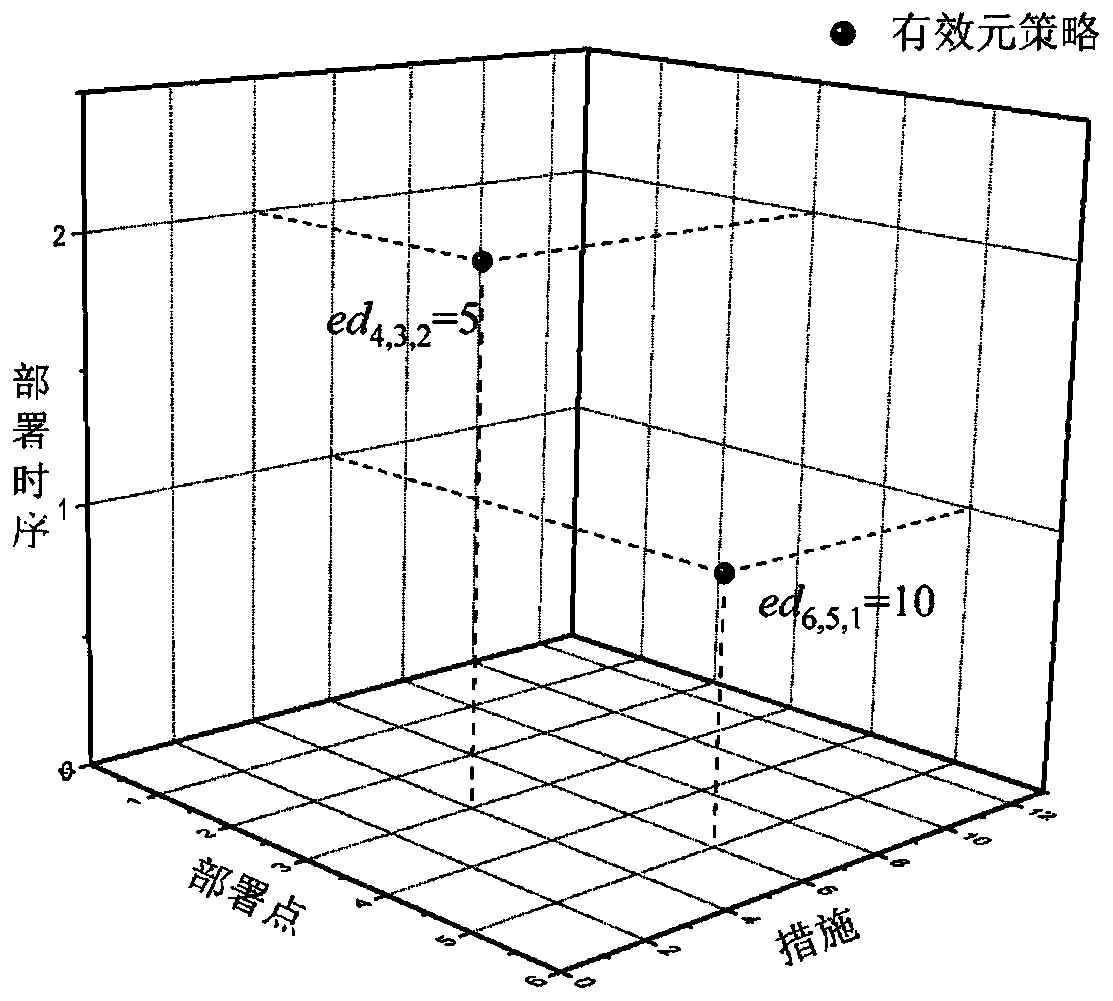
Intrusion response strategy generation method and device
ActiveCN110290122AGuaranteed accuracyHigh response utilityData switching networksAs elementArray data structure
The embodiment of the invention provides an intrusion response strategy generation method and device, and the method comprises the steps: determining a candidate measure set and a deployment point set for responding to an attack according to received alarm information and a network topological structure; taking the measures, the deployment points and the time sequence of the measure deployment as three dimensions of the array, taking the duration of the measure execution as elements in the array, and encoding the candidate strategies by using the three-dimensional array to generate a plurality of candidate strategies; carrying out iterative evolution on the plurality of candidate strategies based on a genetic algorithm according to a preset fitness function until a preset condition is met, and obtaining a target strategy so as to realize intrusion prevention, wherein each strategy comprises at least one meta-strategy, and each meta-strategy comprises a measure, a deployment point, a time sequence of measure deployment and measure execution duration. The time sequence and the execution duration of deployment of each selection measure are determined while the measure and the deployment point are selected, so that the accuracy of the generation strategy is ensured, and higher safety benefits can be obtained.
Owner:INST OF INFORMATION ENG CAS
Lightweight intrusion detection method for integrated electronic system
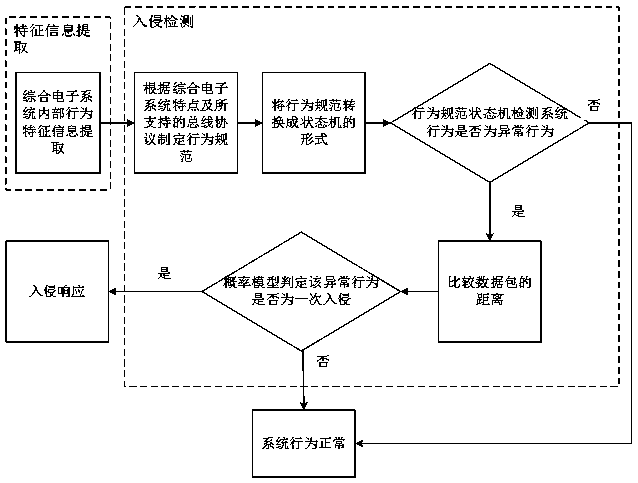
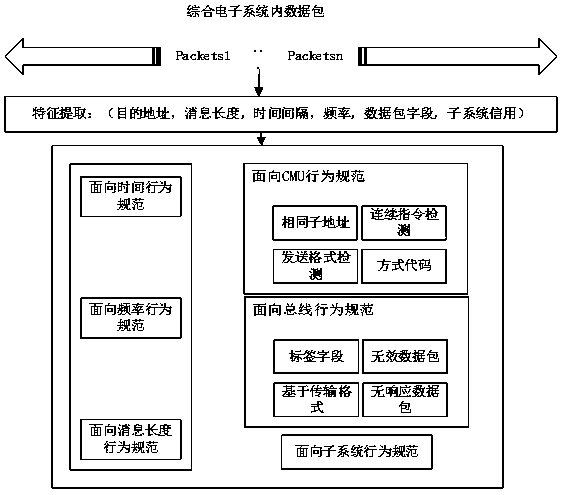
ActiveCN108206826APrevent replay attacksImprove securityPlatform integrity maintainanceTransmissionLimited resourcesElectronic systems
The invention discloses a lightweight intrusion detection method for an integrated electronic system. The method comprises feature information extraction: monitoring and collecting data packets of communication in an integrated electronic system, extracting message features and subsystem features; intrusion detection: first establishing behavioral norms according to the characteristics of the integrated electronic system and the supported communication protocols, converting the behavioral norms into the form of a state machine, monitoring in real time whether the behavior of the system deviates from defined normal norms, and combining a distance measurement method with a probability model to determine whether an abnormal behavior detected by the behavior norms state machine is an intrusion; intrusion response: initiating an intrusion warning, and responding to and recording an intrusion event. According to the lightweight intrusion detection method, lightweight intrusion detection is achieved under consideration of limited resources of the integrated electronic system, denial of service attacks and damage integrity attacks, such as tampering with packet attacks, forging data packetattacks, attacking subsystem attacks and forgery subsystem attacks, can be effectively resisted.
Owner:EAST CHINA NORMAL UNIV
Network server early warning method and system
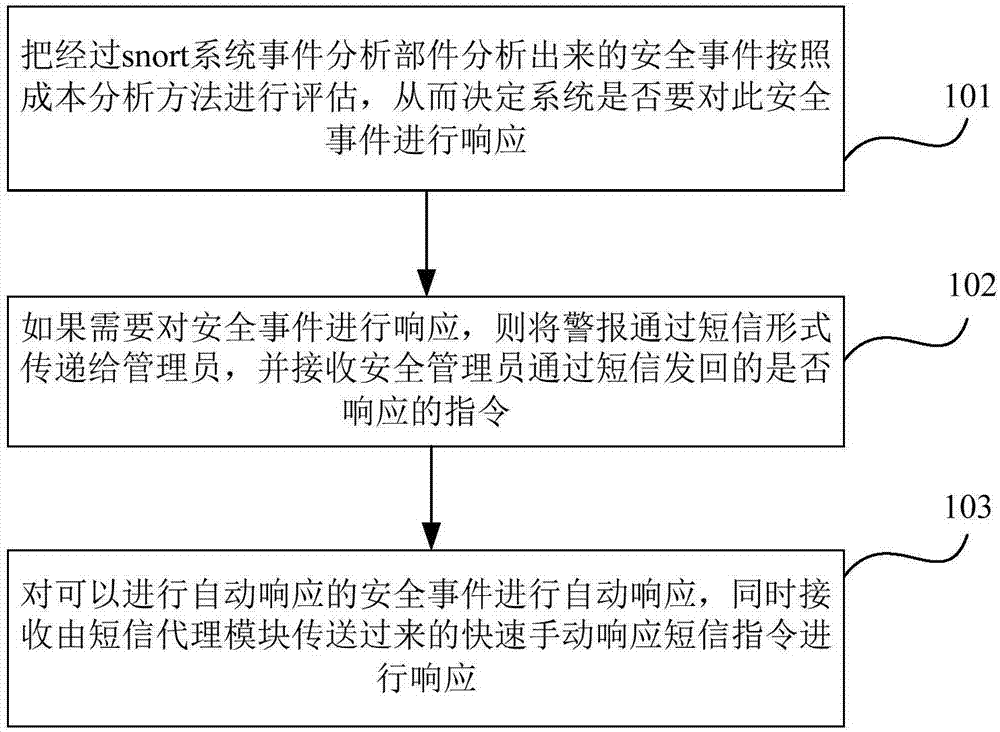
InactiveCN106993005ATimely and rapid warningTimely and fast alarmMessaging/mailboxes/announcementsTransmissionCost analysisAnalysis method
The invention discloses a network server early warning method and system. The method comprises: step 101, a security event analyzed by a snort system event analysis component is evaluated according to a cost analysis method, so as to decide whether the system should respond to the security event; step 102, if the security event needs to be responded to, an alarm is passed to an administrator in the form of a short message and a command sent back by the security administrator via a short message about whether to respond to the security event is received; and step 103, the security event to which can be automatically responded is automatically responded to, and a quick manual response short message command transmitted by a short message proxy module is received to respond to the security event. The method combines the short message technology with the intrusion detection technology to provide in-time quick early warning and alarm for the network server, uses the cost analysis method to tightly combine quick manual response and automatic intrusion response, and reduces system losses caused by leaked response, error response and excessive response.
Owner:广东电力发展股份有限公司
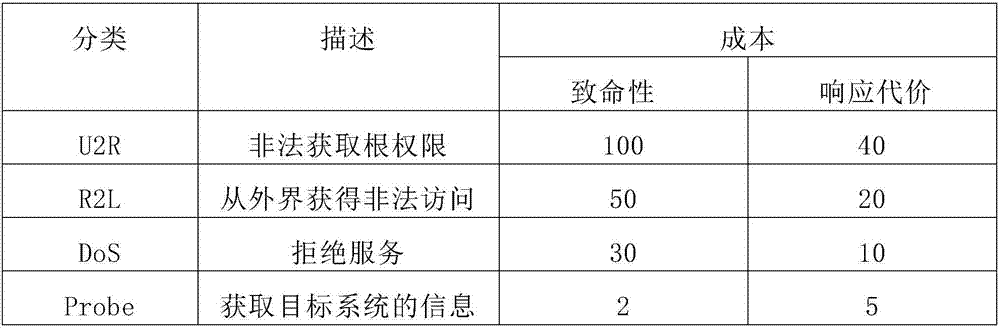
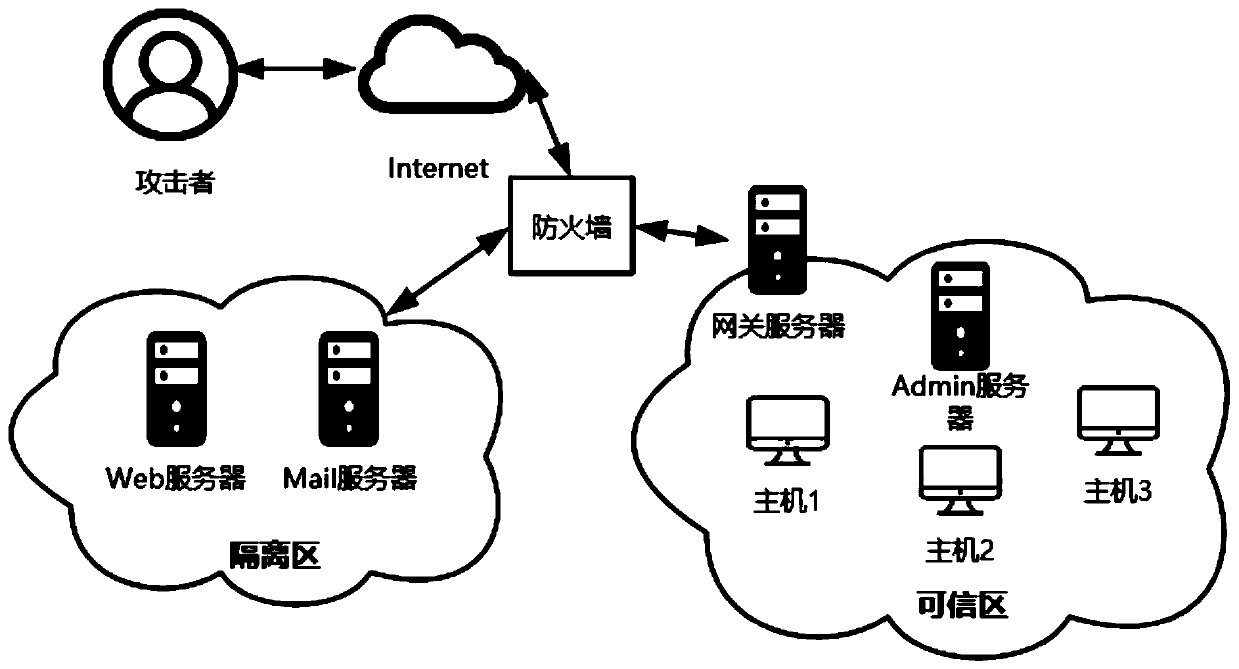
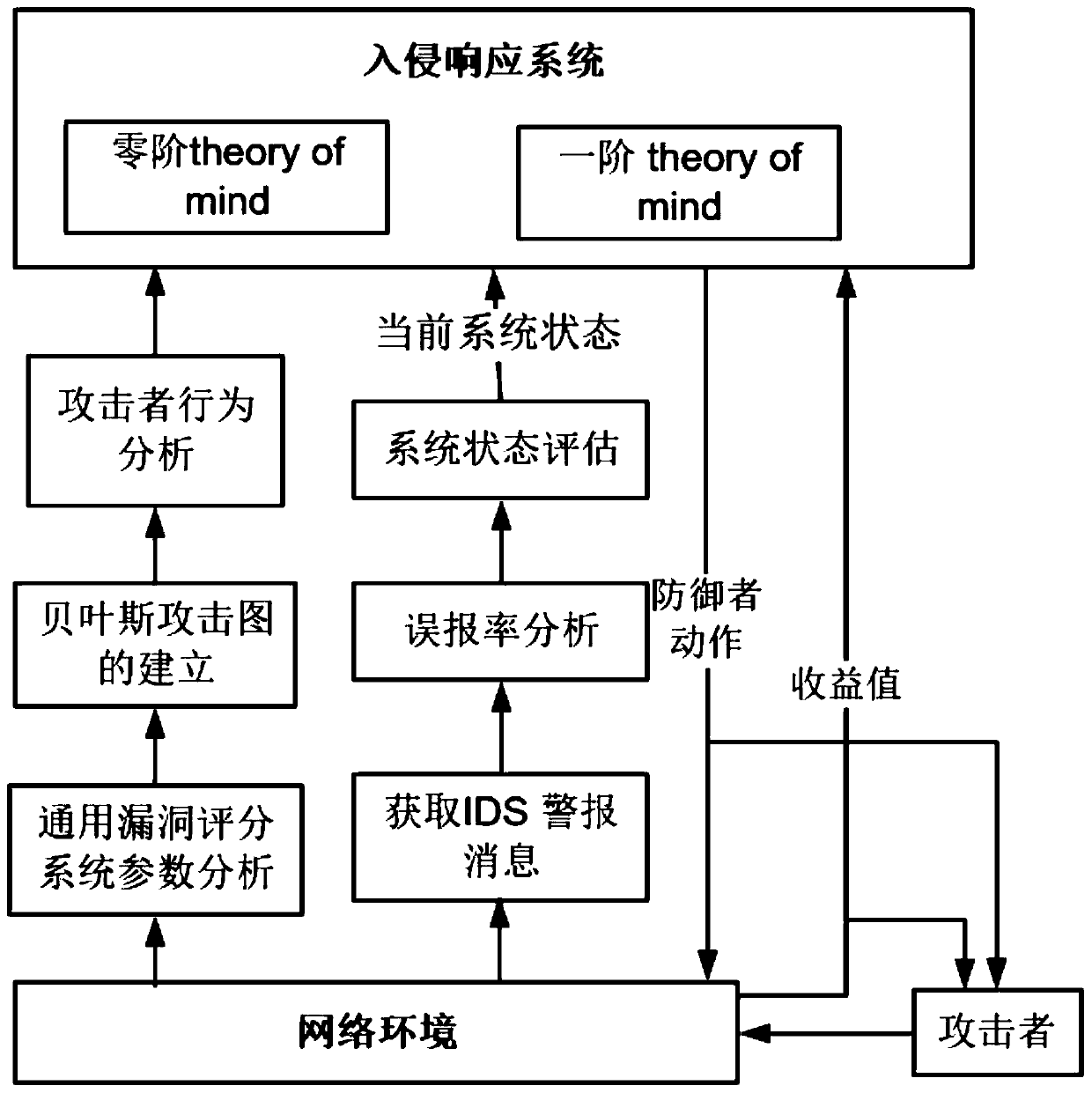
Intrusion response method based on attack graph and psychological theory
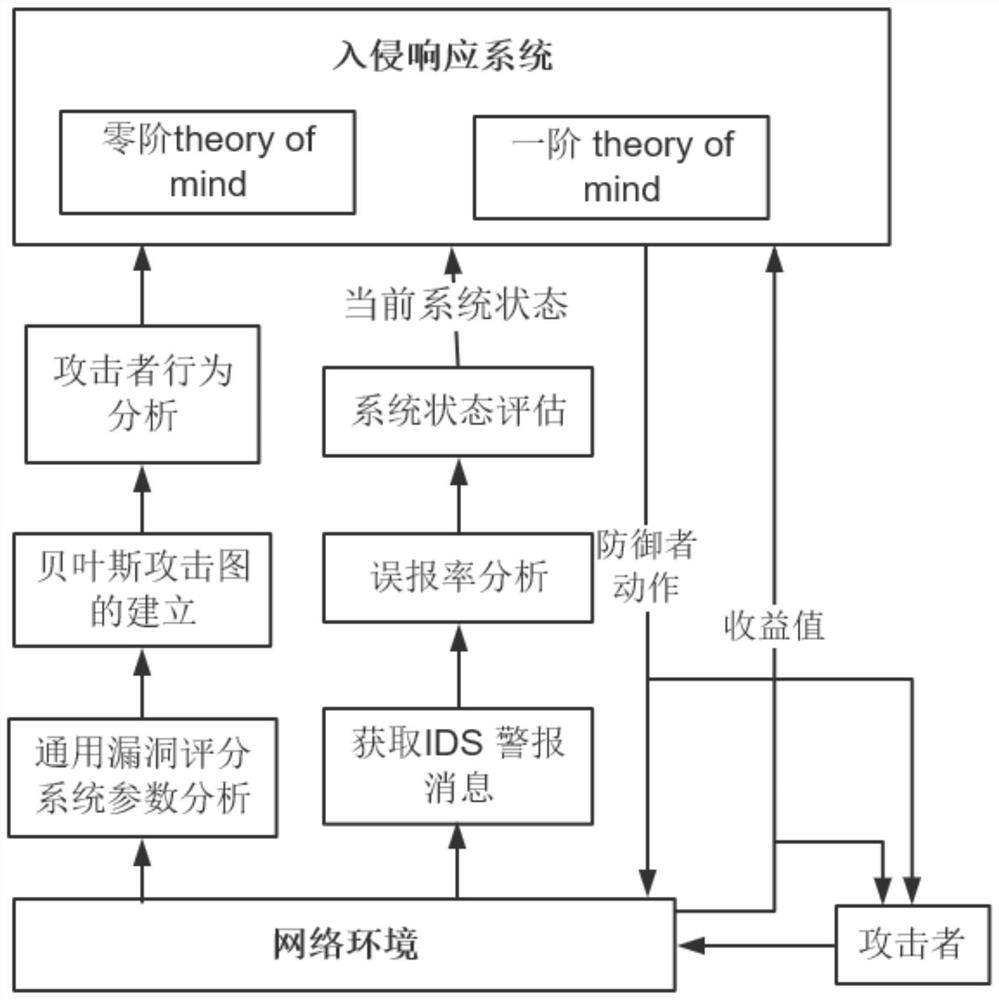
ActiveCN110708287AResponse in real timeAdjust response strategies in real timeData switching networksAttackAttack graph
The invention discloses an intrusion response method based on an attack graph and a psychological theory. According to the method, each step of action when an attacker invades a network is simulated through an attack graph; the probability that the attacker takes a certain action at the next moment can be speculated by analyzing the attack psychology of the attacker, and in order to maximize the income value in the network attack and defense game, the defender formulates a corresponding response measure according to the speculated attacker behavior, so that real-time network response is provided. Compared with a traditional IDS alerts mapping response action method, the method has the advantages that the response strategy is adjusted in real time during multi-step complex intrusion detection, real-time response is achieved, and efficient protection is achieved.
Owner:ZHEJIANG UNIV
Regional intrusion real-time detection method and system and storage medium
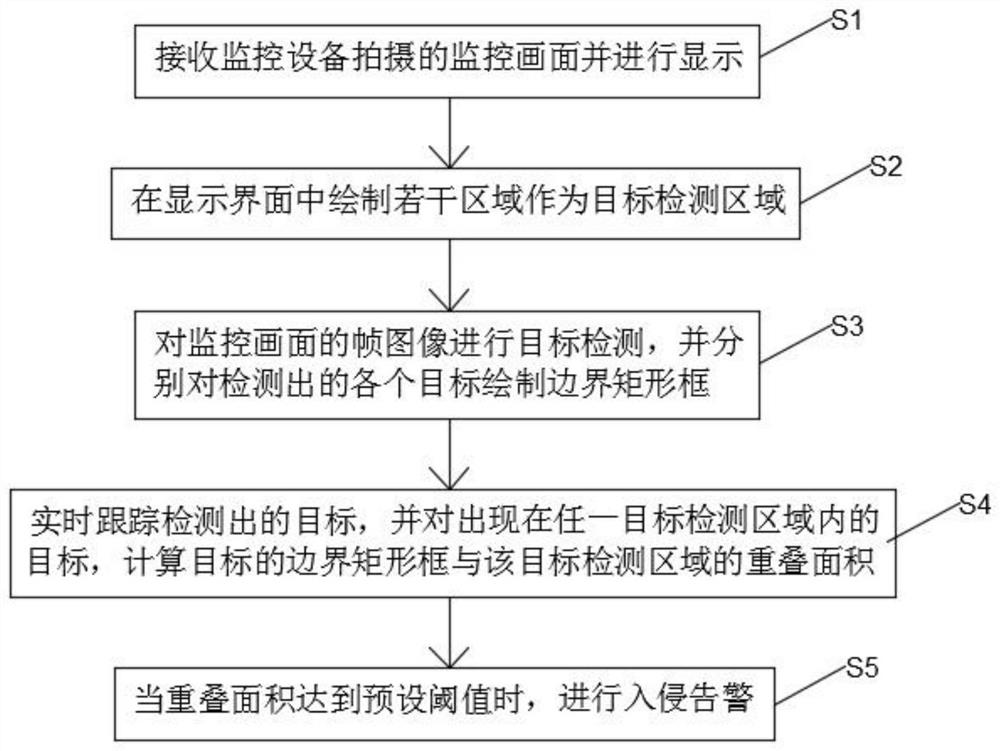
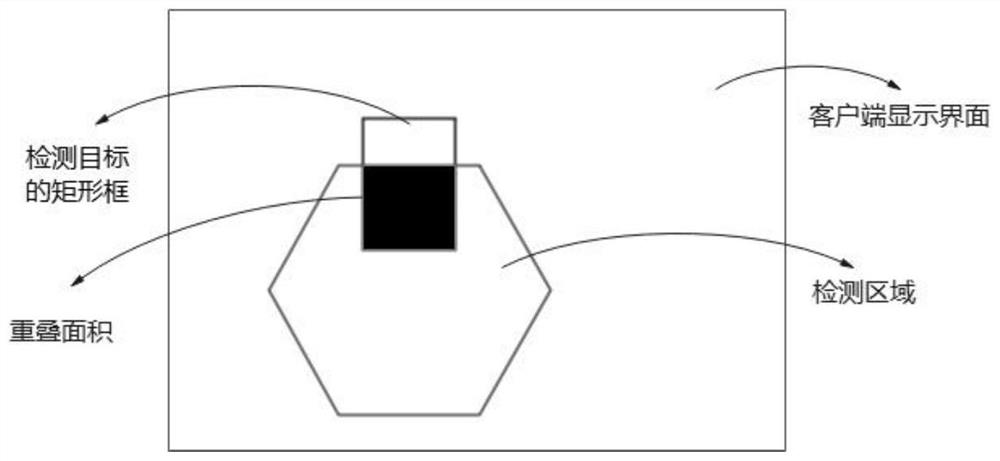
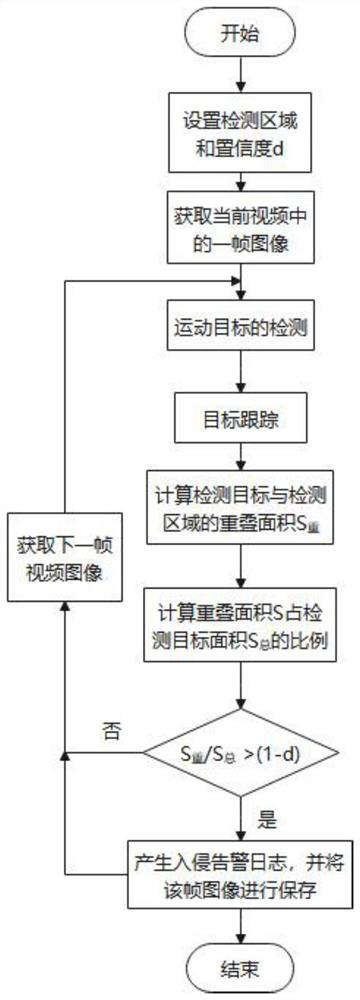
PendingCN112883866AAvoid interactionAvoid reactionImage analysisCharacter and pattern recognitionEngineeringMonitor equipment
The invention provides a regional intrusion real-time detection method and system and a storage medium. The method comprises the following steps: receiving and displaying a monitoring picture shot by monitoring equipment; drawing a plurality of areas in the display interface as target detection areas; performing target detection on the frame image of the monitoring picture, and drawing a boundary rectangular frame for each detected target; tracking the detected target in real time, and for the target appearing in any target detection area, calculating an overlapping area of a boundary rectangular frame of the target and the target detection area; and when the overlapping area reaches a preset threshold value, performing intrusion alarm. The scheme can be suitable for a single target or multiple targets, can avoid mutual influence among the targets, is beneficial for improving intrusion judgment precision, and avoid the situation that intrusion response is not timely or intrusion misjudgment occurs.
Owner:上海新纪元机器人有限公司
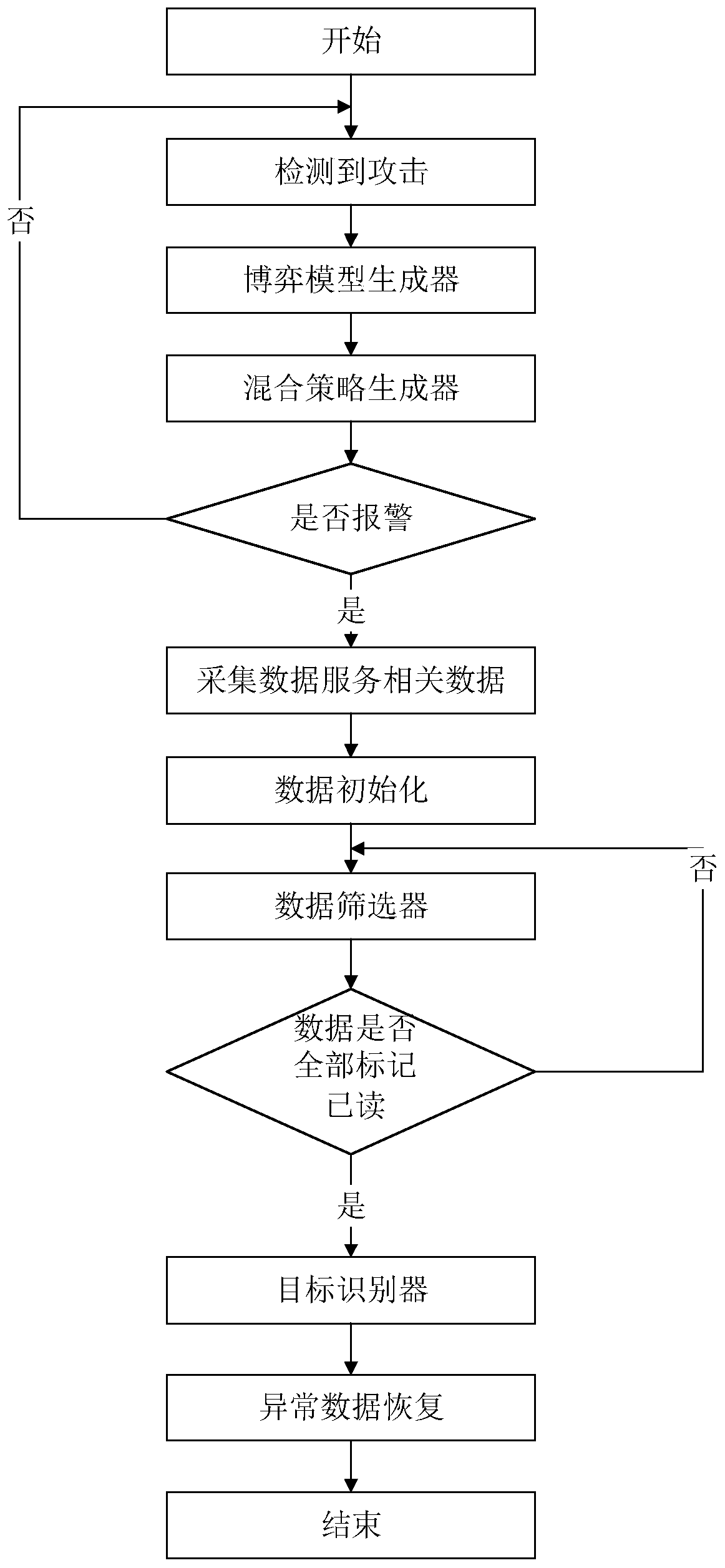
Data service-oriented adaptive intrusion response game method and system thereof
InactiveCN111464501ASolve the problem of adaptive attack responseGuaranteed uptimeTransmissionPaymentNetwork attack
The invention discloses a data service-oriented adaptive intrusion response game method and a system thereof and is mainly used for solving the network attack self-adaptive response problem for data service. Whether pure strategy Nash equilibrium exists or not is judged by using the method provided by the invention to build a game model of a detection system and a user; and if not, a hybrid strategy of the detection system is set and then a payment function is created between the two to solve an optimal first-order condition, thereby deriving a Nash equilibrium value of optimal response of thetwo parties of the game, and obtaining an optimal response strategy to respond.
Owner:NANJING UNIV OF POSTS & TELECOMM
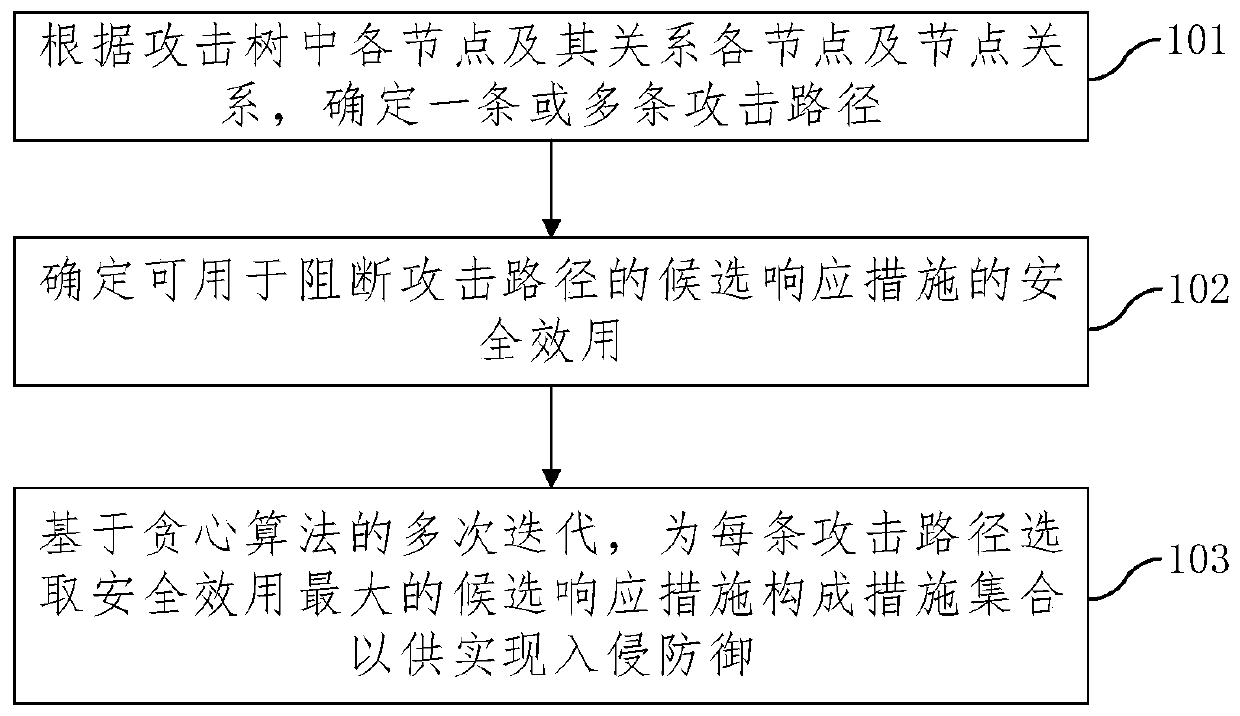
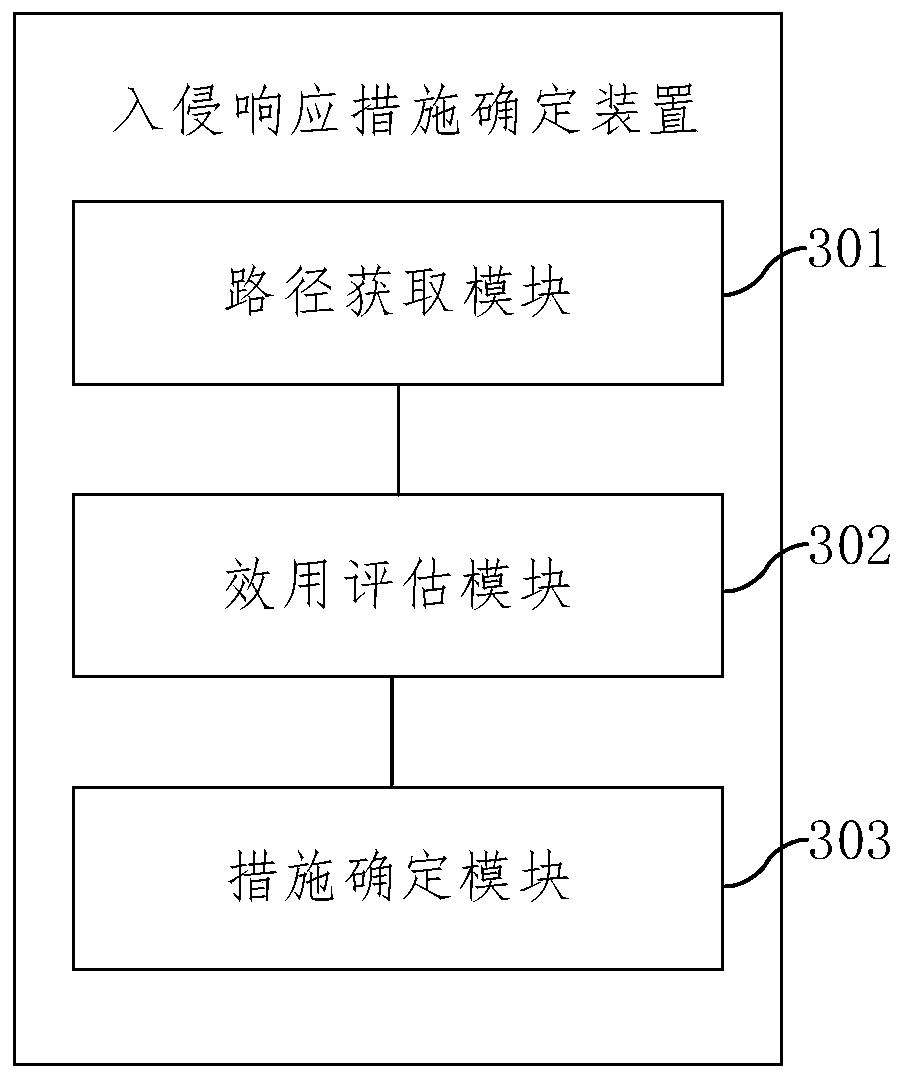
Intrusion response measure determination method and device
InactiveCN110233845AAvoid double countingImplement intrusion preventionTransmissionGreedy algorithmMulti path
The embodiment of the invention provides an intrusion response measure determination method and device, and the method comprises the steps: determining one or more attack paths according to each nodein an attack tree and a node relationship; determining the security utility of candidate response measures which can be used for blocking the attack path; based on multiple iterations of a greedy algorithm, selecting candidate response measures with the maximum security effectiveness for each attack path to form a measure set so as to realize intrusion prevention; wherein in each iteration process, the candidate response measure with the maximum safety effect is selected from the candidate response measures of the attack path to be blocked, the response measure selected this time serves as a deployed measure, and the safety effects of the candidate response measures of the remaining attack path to be blocked are recalculated and used for next iteration selection. According to the method, the overall security effectiveness when a plurality of attack paths are coped can be improved to the maximum extent, and the optimal coping for multi-path attacks is realized.
Owner:INST OF INFORMATION ENG CAS
Intrusion detection method, device and equipment for industrial control proprietary protocol
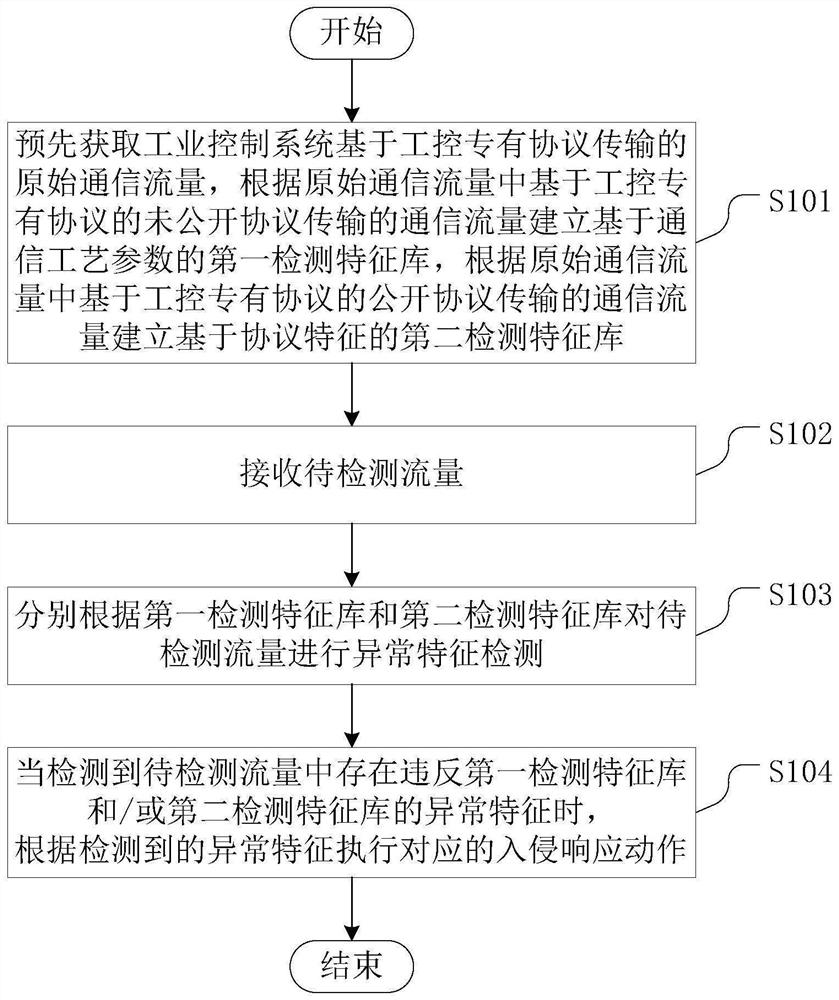
ActiveCN113645241ASafe and stable operationTimely identificationTransmissionIndustrial control systemEmbedded system
The invention discloses an intrusion detection method, an intrusion detection device and intrusion detection equipment for an industrial control proprietary protocol, and a computer readable storage medium. A white environment baseline, namely a first detection feature library and a second detection feature library, for detection in combination with communication process parameters of an undisclosed protocol part and protocol features of a disclosed protocol part is established; according to the method, abnormal feature detection is performed on the to-be-detected traffic based on the first detection feature library and the second detection feature library, and when abnormal features violating the first detection feature library and / or the second detection feature library are detected, corresponding intrusion response actions are executed according to the detected abnormal features, so that intrusion behaviors can be identified timely and accurately, intrusion response is carried out, and safe and stable operation of the industrial control system is maintained.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Method of integrating a security operations policy into a threat management vector
The invention relates to the integration of a security operations policy into a threat management vector. In one embodiment, a method according to the invention includes receiving at least one threat management vector (TMV) from a TMV generator, the TMV including a root vulnerability vector, at least one system vector, at least one system level vector, and a countermeasures payload including intrusion detection countermeasures (IDC), intrusion response countermeasures (IRC), and vulnerability remediation countermeasures (VRC); forwarding to the TMDC a TMV including only the root vulnerability vector, the at least one system vector, and the at least one system level vector; propagating the TMV through a hierarchy of policy mediation regions (PMRs), each PMR being operable to refine at least one of the IDC, the IRC, and the VRC; refining at least one of the IDC, the IRC, and the VRC to conform to a security operations policy of the PMR; forwarding the refined TMV to a threat management domain controller (TMDC); recording refinements made by each PMR to each of the IDC, the IRC, and the VRC; transferring the recorded refinements to a threat management control book (TMCB); and marking the refined TMV as having been refined by each PMR making a refinement.
Owner:LINKEDIN
An Intrusion Response Method Based on Attack Graph and Theory of Mind
ActiveCN110708287BResponse in real timeAdjust response strategies in real timeData switching networksTime responseAlgorithm
The invention discloses an intrusion response method based on an attack graph and a psychological theory. According to the method, each step of action when an attacker invades a network is simulated through an attack graph; the probability that the attacker takes a certain action at the next moment can be speculated by analyzing the attack psychology of the attacker, and in order to maximize the income value in the network attack and defense game, the defender formulates a corresponding response measure according to the speculated attacker behavior, so that real-time network response is provided. Compared with a traditional IDS alerts mapping response action method, the method has the advantages that the response strategy is adjusted in real time during multi-step complex intrusion detection, real-time response is achieved, and efficient protection is achieved.
Owner:ZHEJIANG UNIV
A mobile sensor network intrusion detection and adaptive response method
InactiveCN109547504BEffective intrusion detectionIncrease success rateTransmissionSecurity arrangementAttackData store
A mobile sensor network intrusion detection and adaptive response method relates to a mobile sensor network intrusion detection and adaptive response method. The purpose of the present invention is to solve the existing intrusion attacks on the mobile sensor network, which often focus on the targeted detection of a certain attack, and the defense methods also have clear directionality, which cannot solve the problem of network uncertainty intrusion attacks. The process is: 1. Monitor the network and collect data; 2. Process the collected data, and store the processed data in the initial configuration file; Identify the intrusion in the network with the intrusion detection method based on the method; Fourth, establish a decision table based on the attack confidence level, the network performance degradation level and the adaptive intrusion response behavior list, and select the intrusion response according to the established decision table. The invention is used in the field of security protection of mobile sensor networks.
Owner:HEILONGJIANG UNIV
Zero-day attack detection, analysis and response system and method based on mimic defense architecture
The invention relates to a mimicry defense architecture based zero-day attack detection, analysis and response system and a method thereof. The method comprises the steps of performing attack detection and processing on the input, cheating and inducing an attacker through honeypot type executing bodies, and performing meta-function inspection on the output of each executing body; performing statistical analysis on abnormal output by combining abnormal information, updating a zero-day attack database, feeding back an analysis result to an intrusion response module, and preventing persistent attacks of the attacker; performing dynamic adjustment and management on an online executing body by combining voting conditions, executing body dispatching, the executing body with abnormal output and the like, and selecting executing bodies from an executing body resource pool to get into a dynamic online executing body set; and analyzing a zero-day vulnerability in the executing body with abnormal output according to an anomaly statistical analysis result, and repairing the related executing bodies in the executing body pool. According to the invention, functions and the flexibility of mimicry defense architecture are enhanced, values of the abnormal output are sufficiently utilized, and the threat and the defense cost of zero-day attacks are reduced.
Owner:THE PLA INFORMATION ENG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com