Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
74results about How to "Prevent breach" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
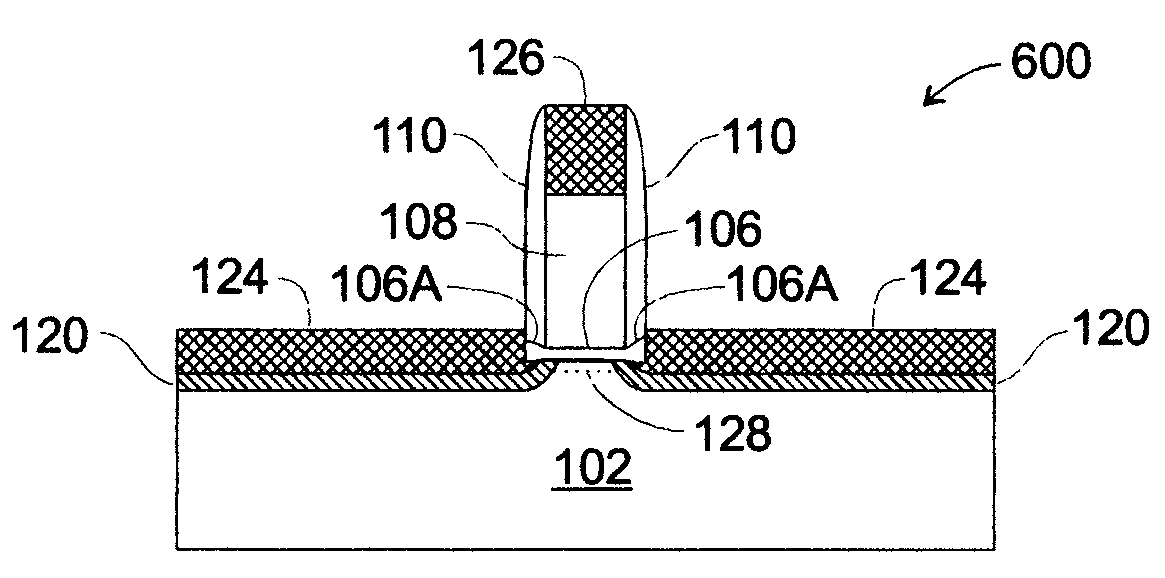
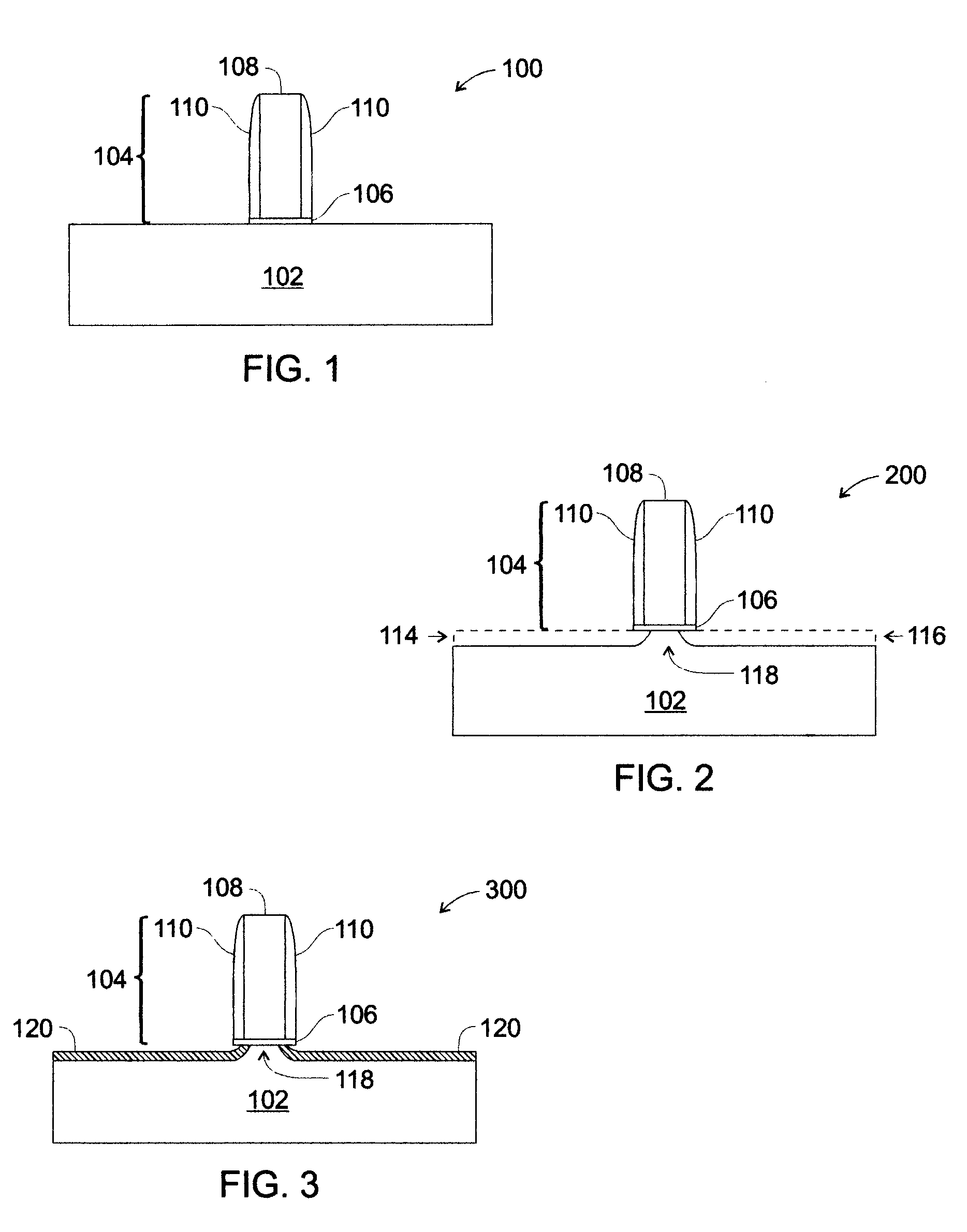
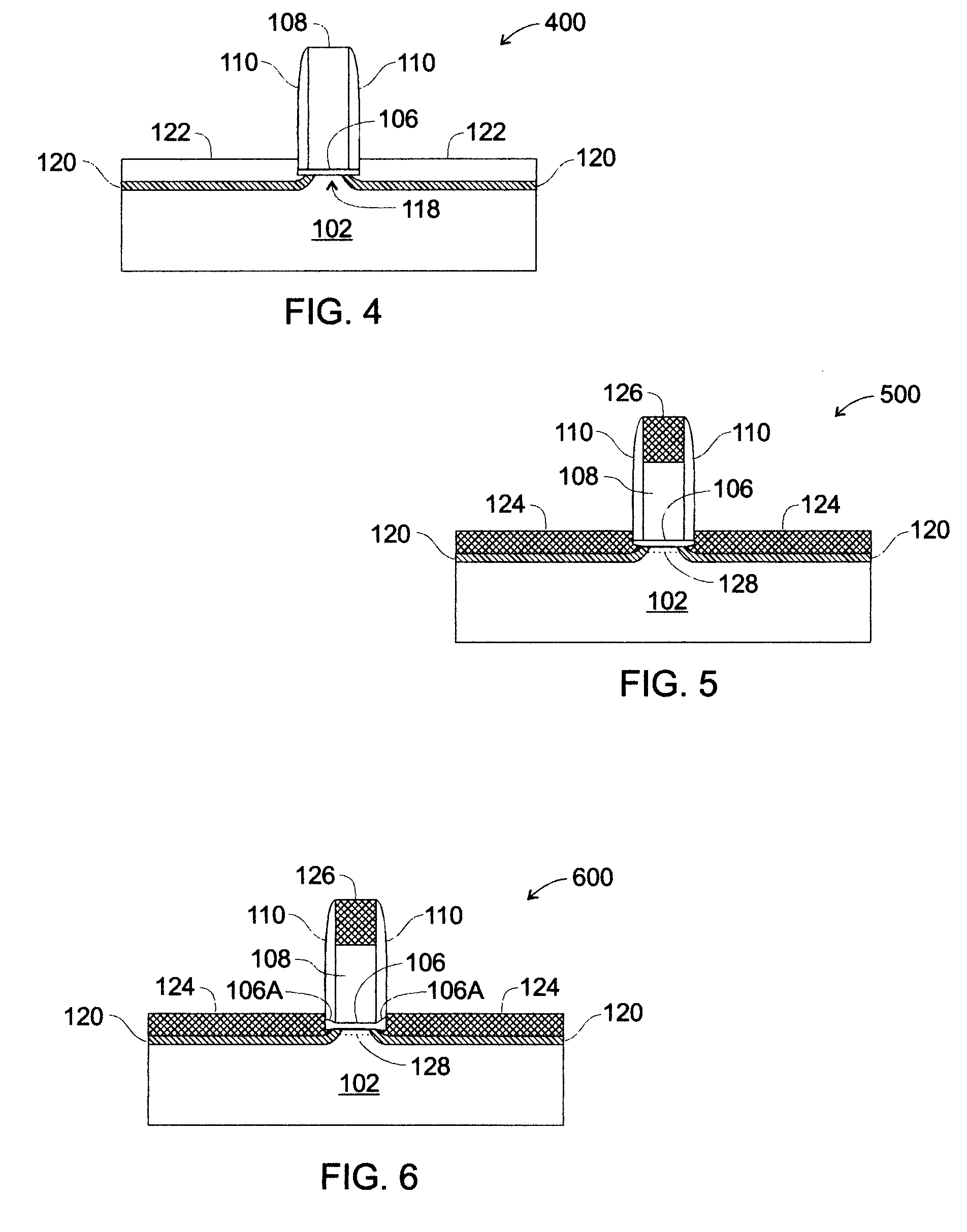
Ultra-thin silicidation-stop extensions in mosfet devices
ActiveUS20050112857A1Prevent breachTransistorSemiconductor/solid-state device manufacturingMOSFETFilling materials
Very low resistance, scaled in MOSFET devices are formed by employing thin silicidation-stop extension that act both as a silicidation “stop” barriers and as thin interface layers between source / drain silicide regions and channel region of the MOSFET. By acting as silicidation stops, the silicidation-stop extensions confine silicidation, and are not breached by source / drain silicide. This permits extremely thin, highly-doped silicidation-stop extensions to be formed between the silicide and the channel, providing an essentially ideal, low series resistance interface between the silicide an the channel. On an appropriately prepared substrate, a selective etching process is performed to expose the sides of the channel region (transistor body). A very thin layer of a silicidation-stop material, e.g., SiGe, is disposed in the etched away area, coating the exposed sides of the channel region. The silicidation-stop material is doped (highly) appropriately for the type of MOSFET being formed (n-channel or p-channel). The etched away areas are then filled with silicon, e.g., by an Si epi process. Silicidation is then performed (to form, e.g., CoSi2) on the newly filled areas. The silicidation stop material constrains silicidation to the silicon fill material, but prevents silicide expansion past the silicidation stop material. Because the germanium (Ge) in SiGe is insoluble in CoSi2, the SiGe acts as a barrier to silicidation, permitting silicidation to go to completion in the Si fill but stopping silicidation at the SiGe boundary when silicidation is performed at a temperature above a silicidation threshold temperature for Si, but below a silicidation threshold temperature for SiGe. This results in a very compact, well-defined lateral junction characterized by a thin layer of SiGe disposed between silicide lateral extensions and the sides of the channel region. Because of the thin, highly-doped SiGe layer between the channel and the silicide lateral extensions, the extension resistance is very low.
Owner:GLOBALFOUNDRIES US INC
Method of forming ultra-thin silicidation-stop extensions in mosfet devices
ActiveUS6989322B2Prevent breachTransistorSemiconductor/solid-state device manufacturingMOSFETInterface layer
Very low resistance, scaled in MOSFET devices are formed by employing thin silicidation-stop extension that act both as a silicidation “stop” barriers and as thin interface layers between source / drain silicide regions and channel region of the MOSFET. By acting as silicidation stops, the silicidation-stop extensions confine silicidation, and are not breached by source / drain silicide. This permits extremely thin, highly-doped silicidation-stop extensions to be formed between the silicide and the channel, providing an essentially ideal, low series resistance interface between the silicide and the channel.
Owner:GLOBALFOUNDRIES U S INC
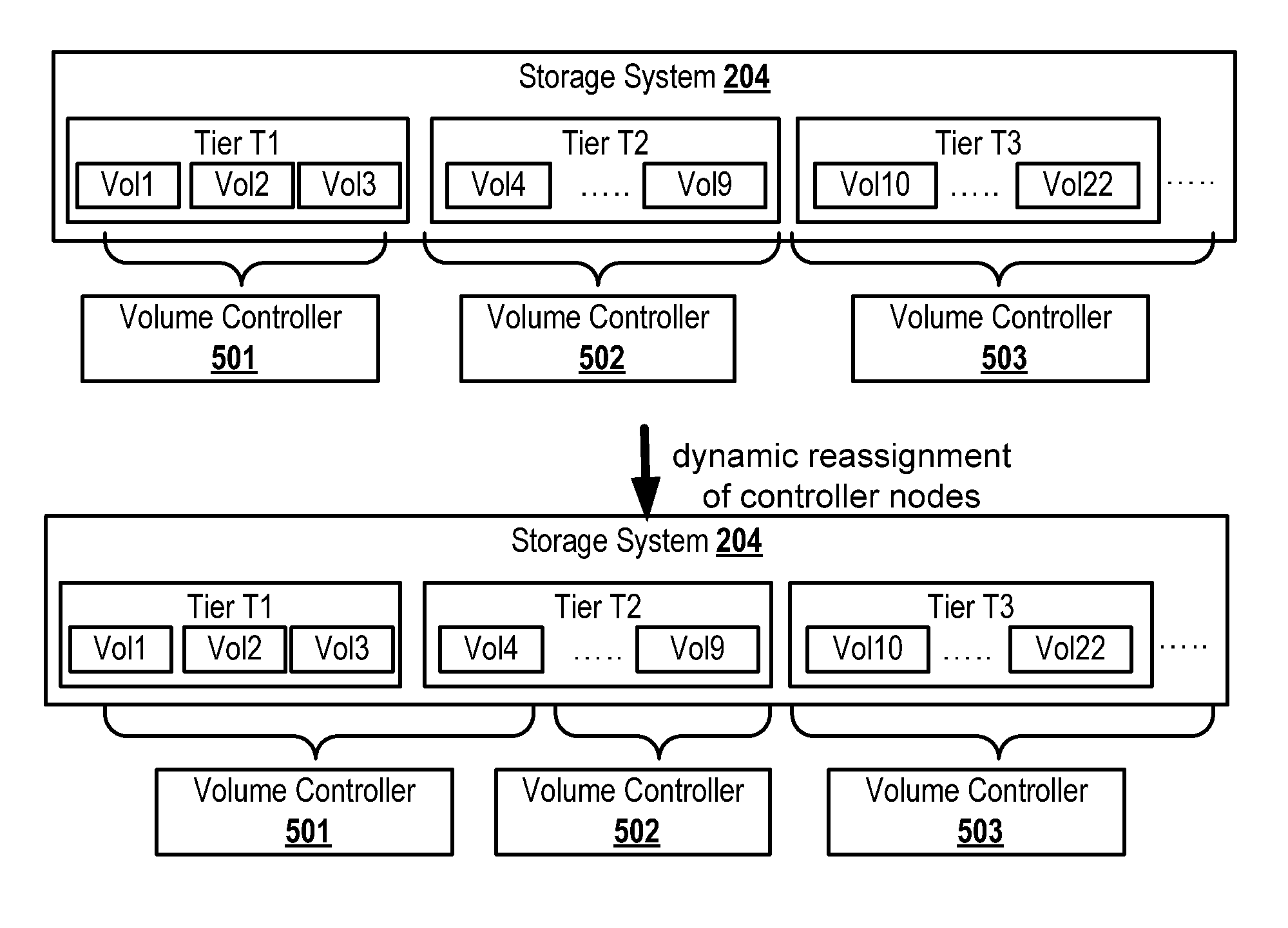
Controlling a Storage System
InactiveUS20130151774A1Increasing performance of volumeLower performance requirementsMemory loss protectionError detection/correctionComputerized systemHybrid storage system
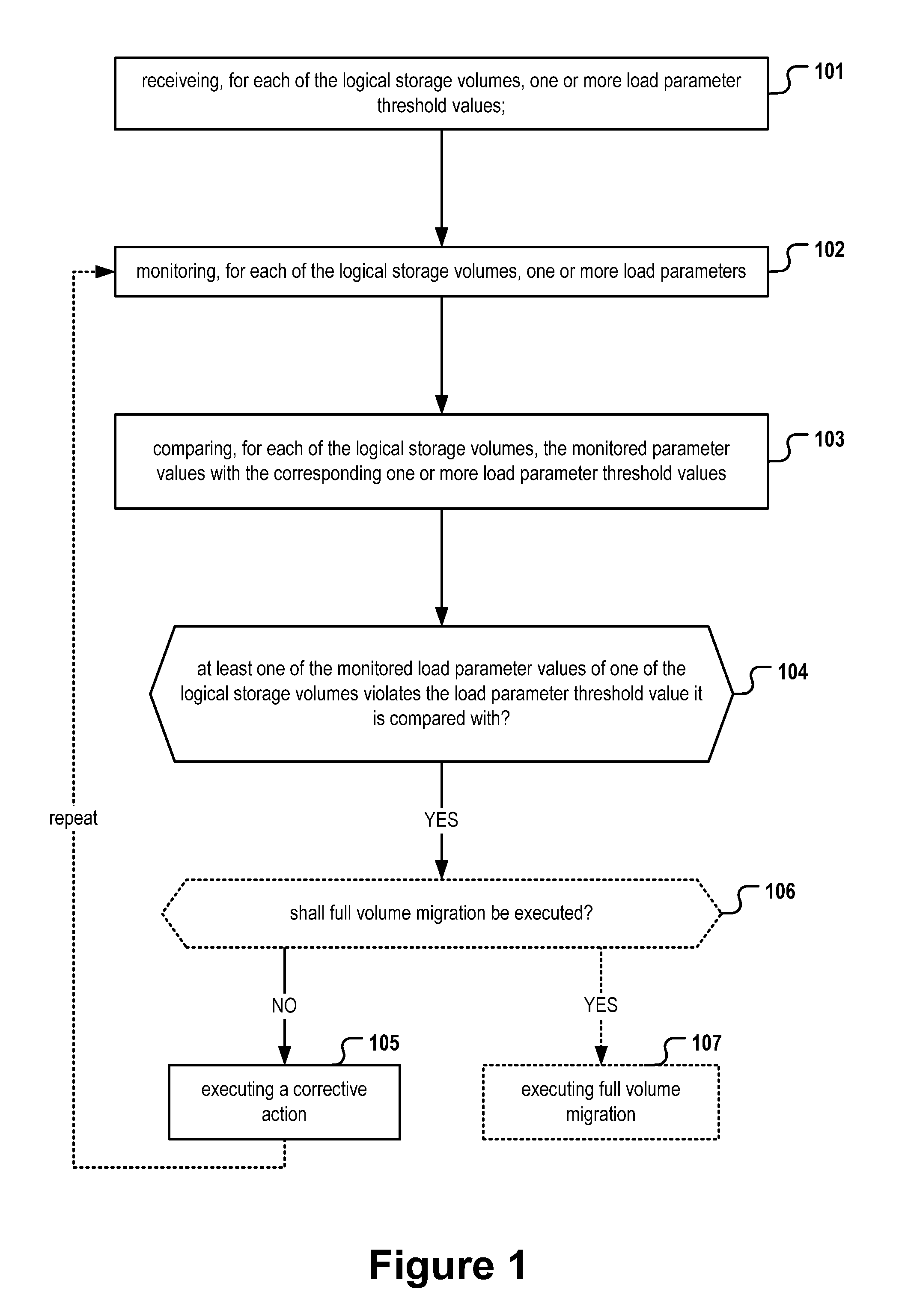
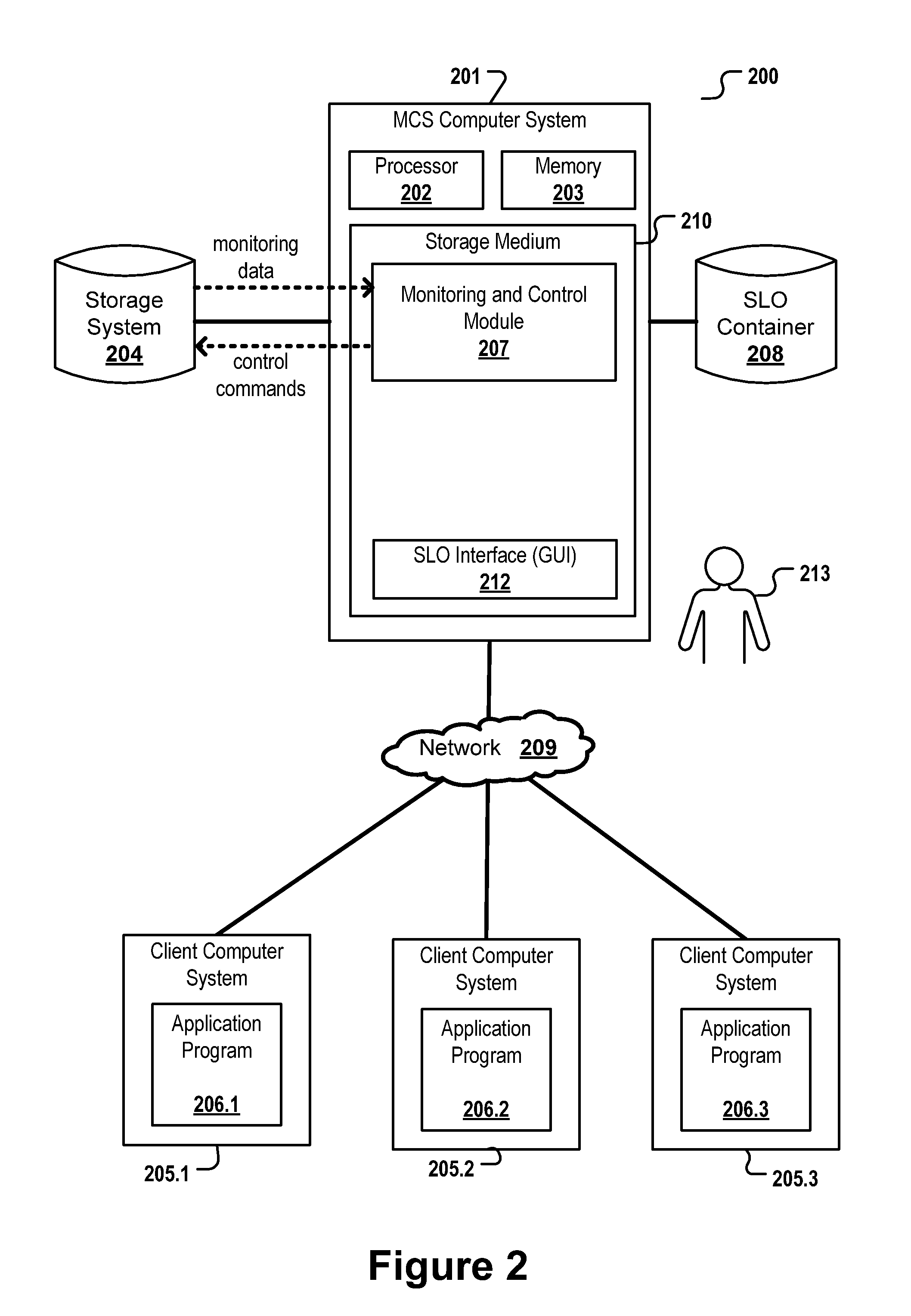
A method, computer-readable storage medium and computer system for controlling a storage system, the storage system comprising a plurality of logical storage volumes, the method comprising: monitoring, for each of the logical storage volumes, one or more load parameters; receiving, for each of the logical storage volumes, one or more load parameter threshold values; comparing, for each of the logical storage volumes, the first load parameter values of said logical storage volume with the corresponding one or more load parameter threshold values; in case at least one of the first load parameter values of one of the logical storage volumes violates the load parameter threshold value it is compared with, automatically executing a corrective action.
Owner:IBM CORP
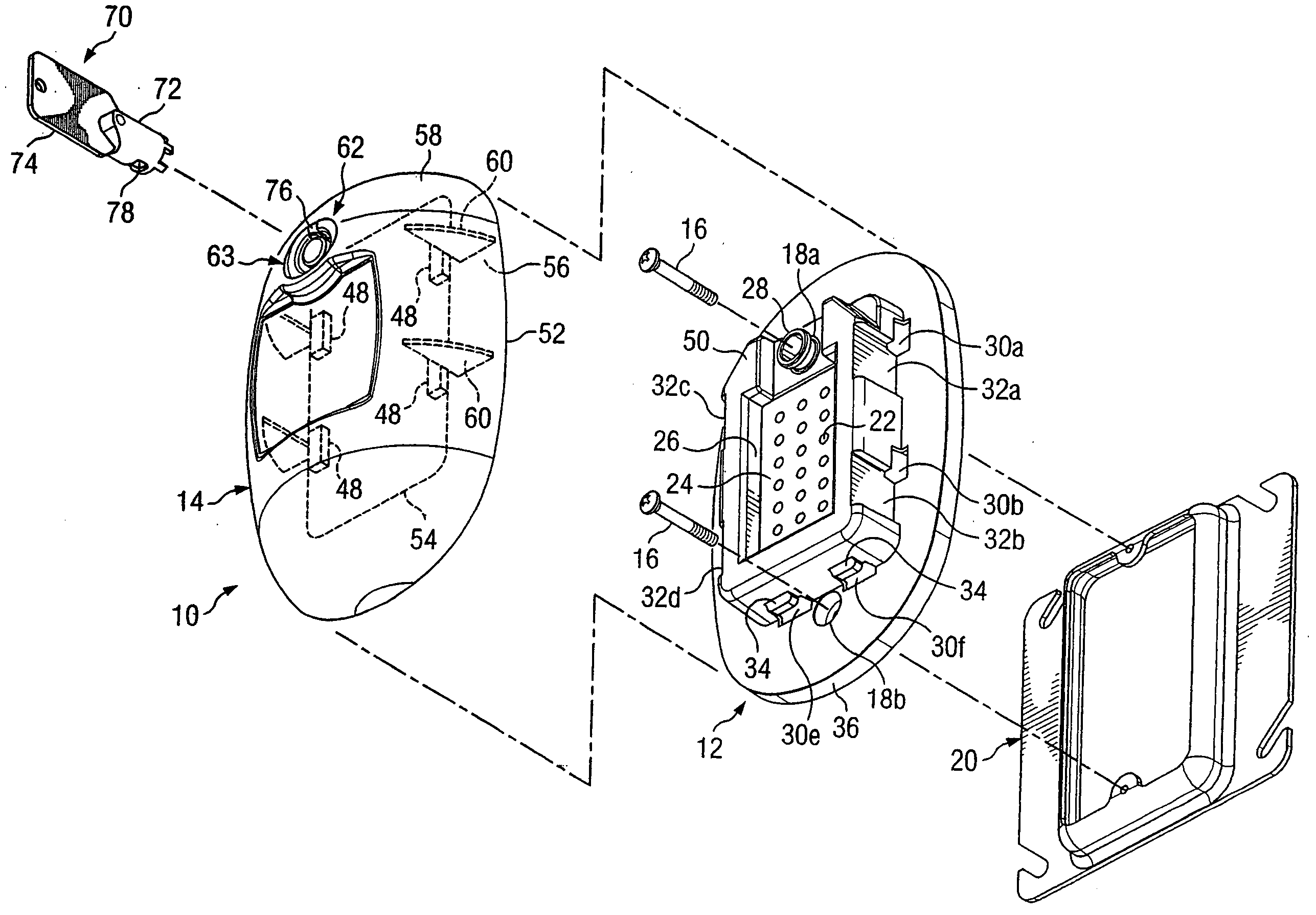
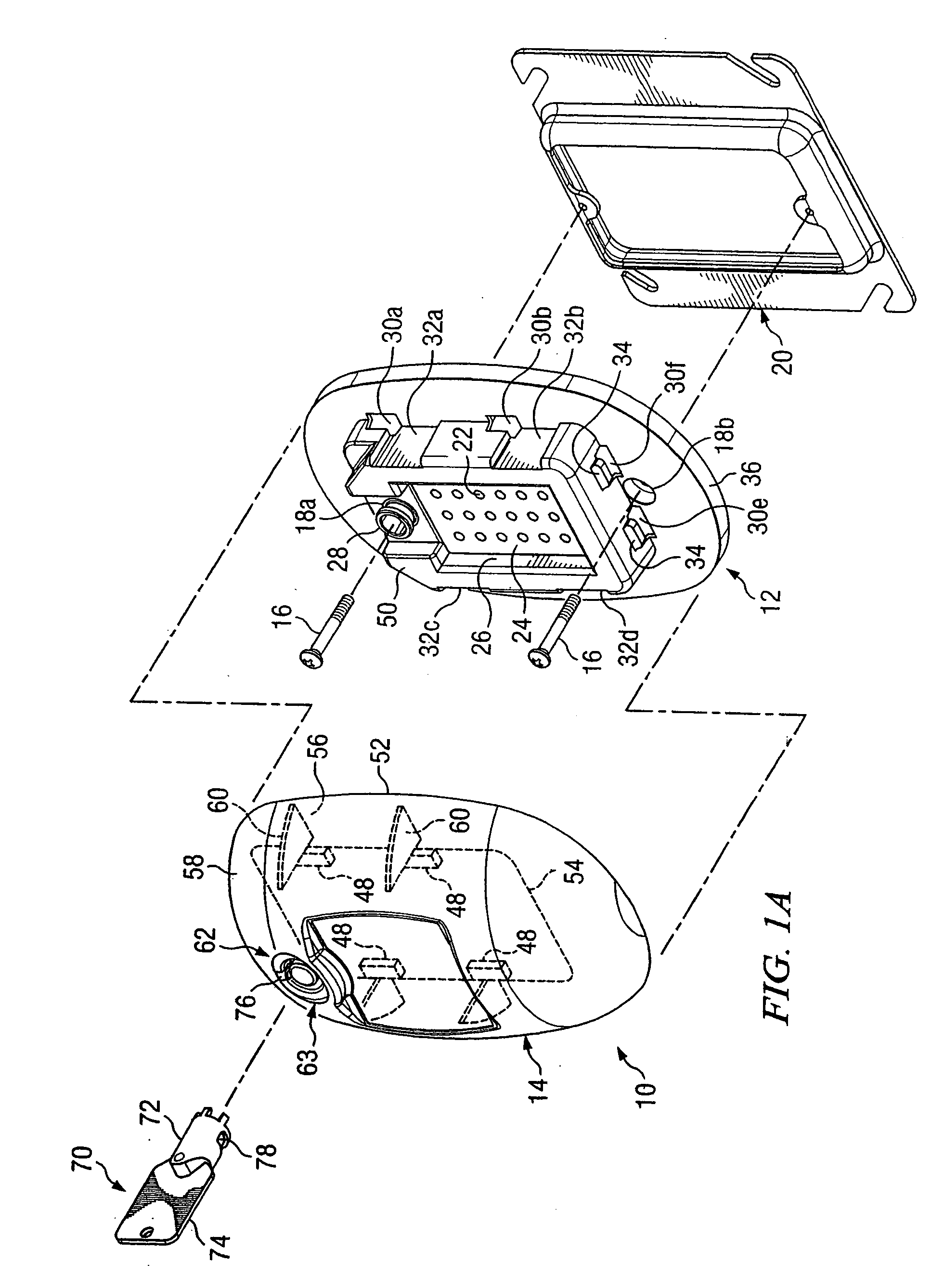
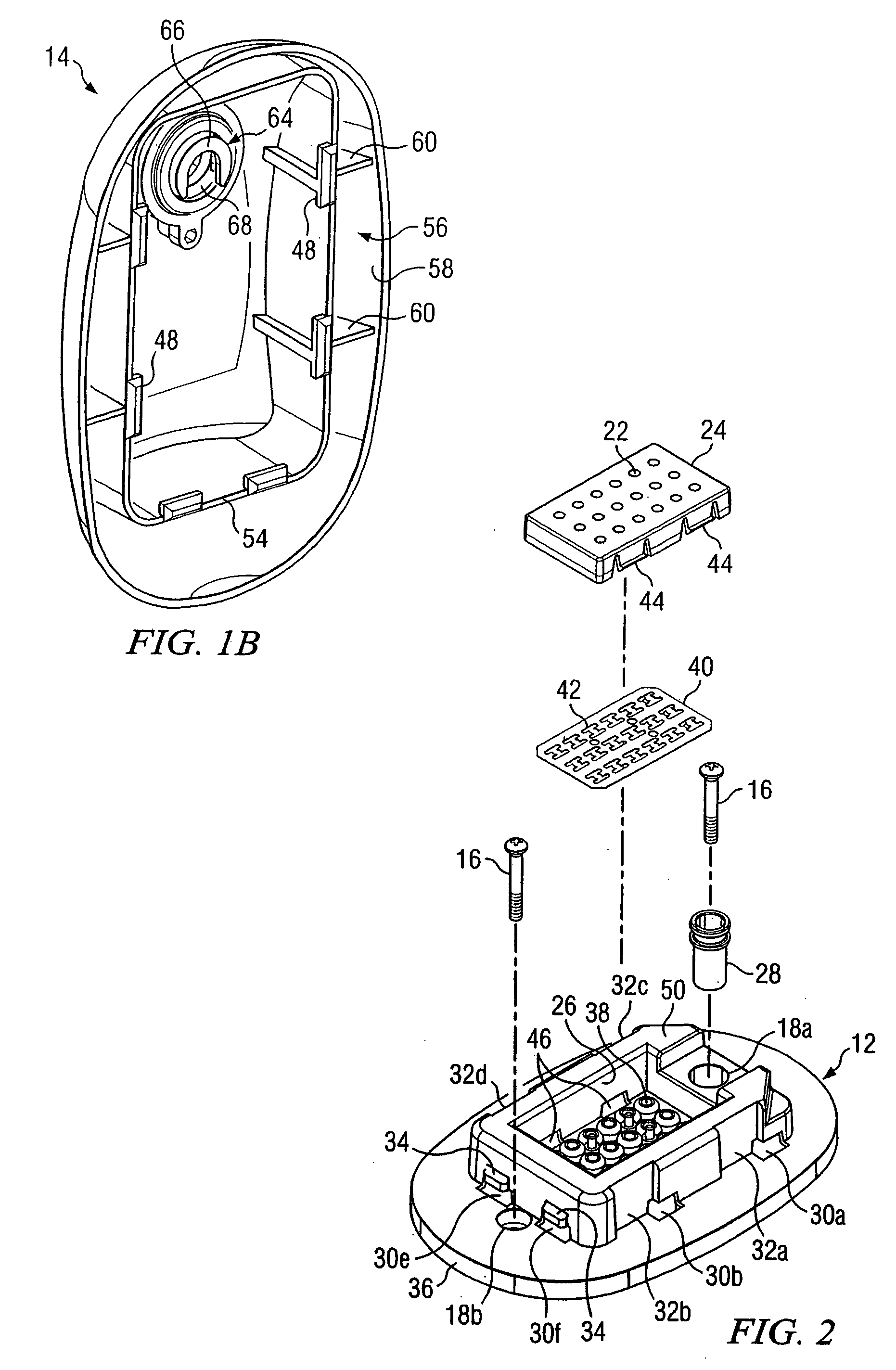
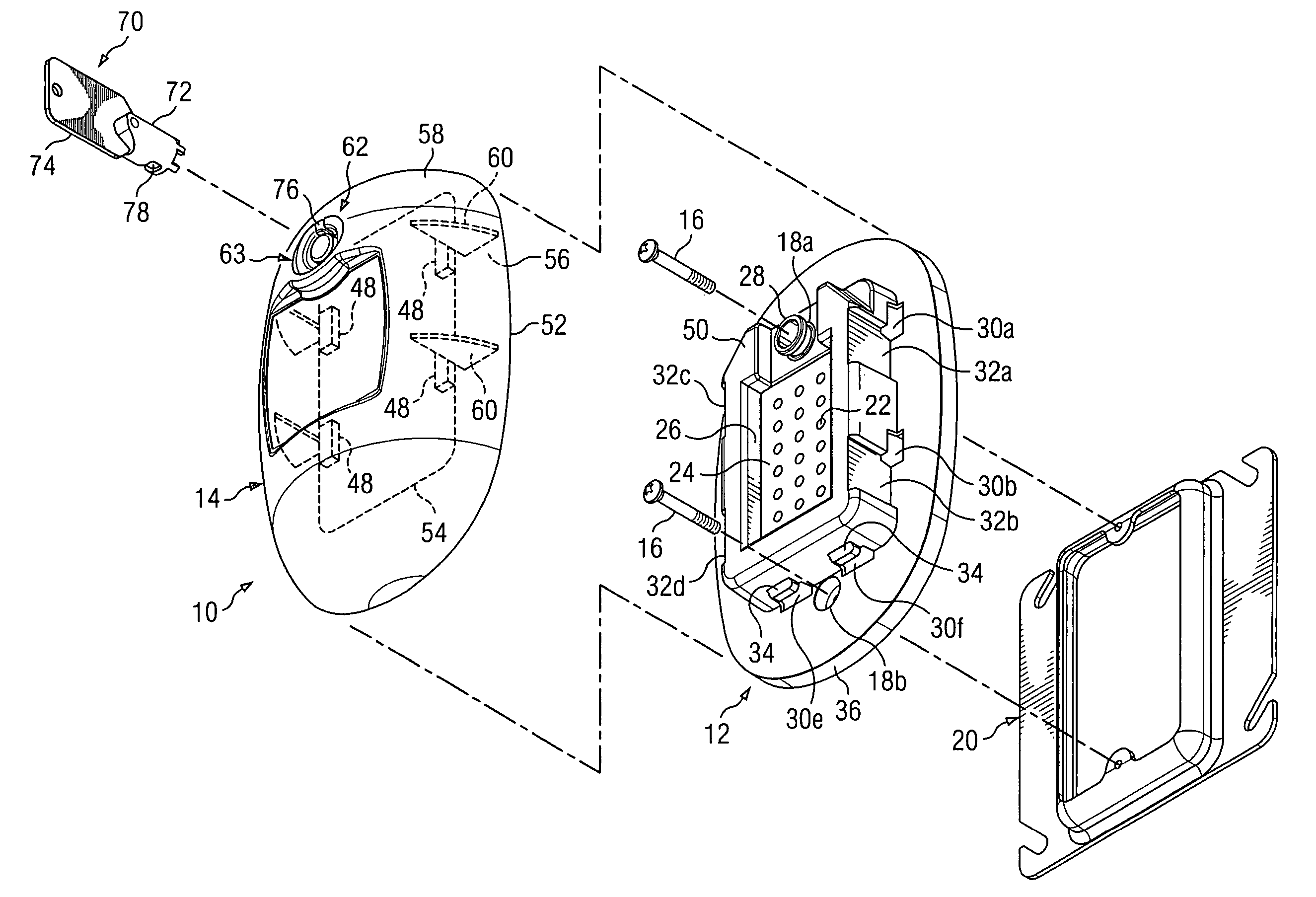
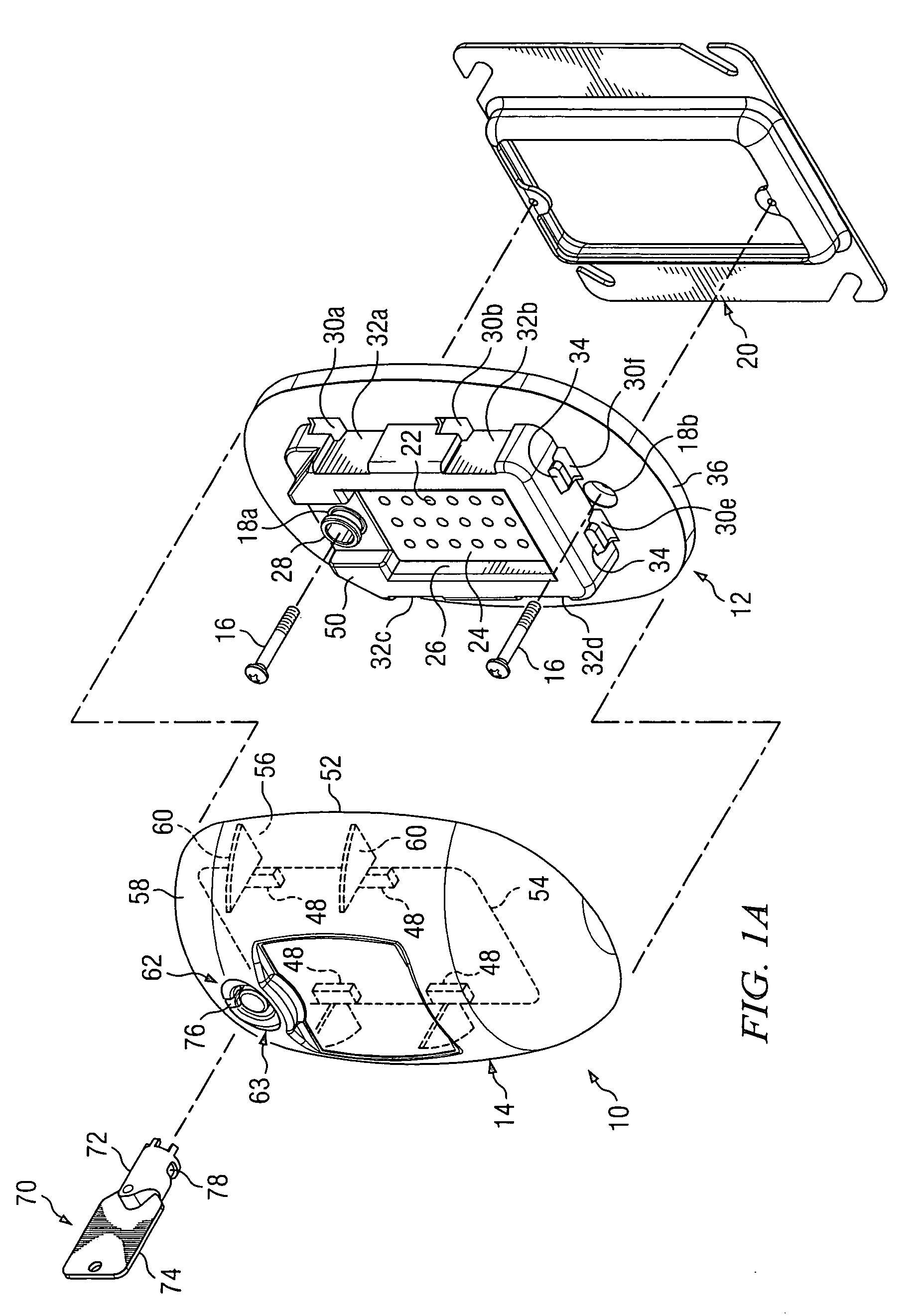
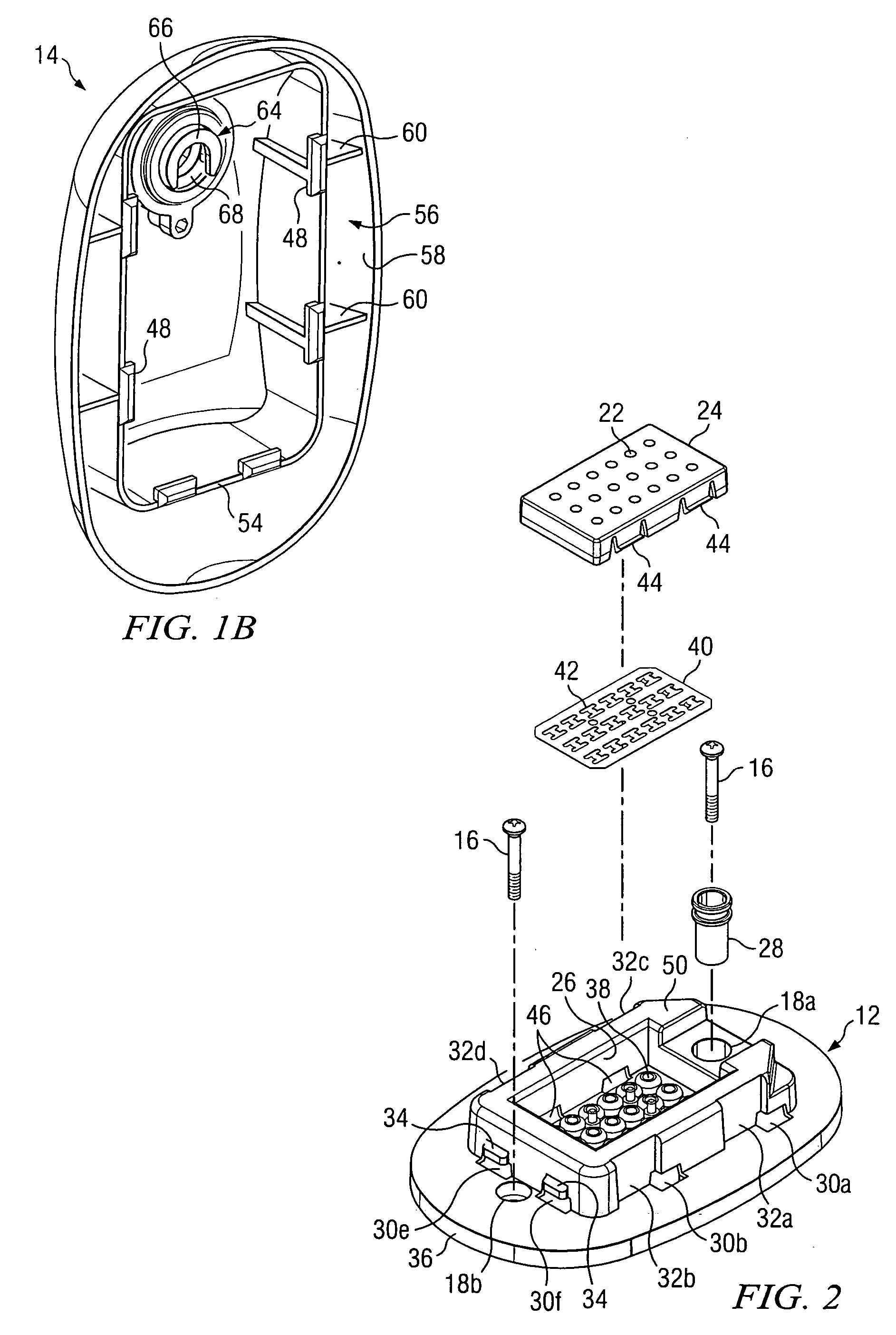
Peripheral illumination device for a vehicle component
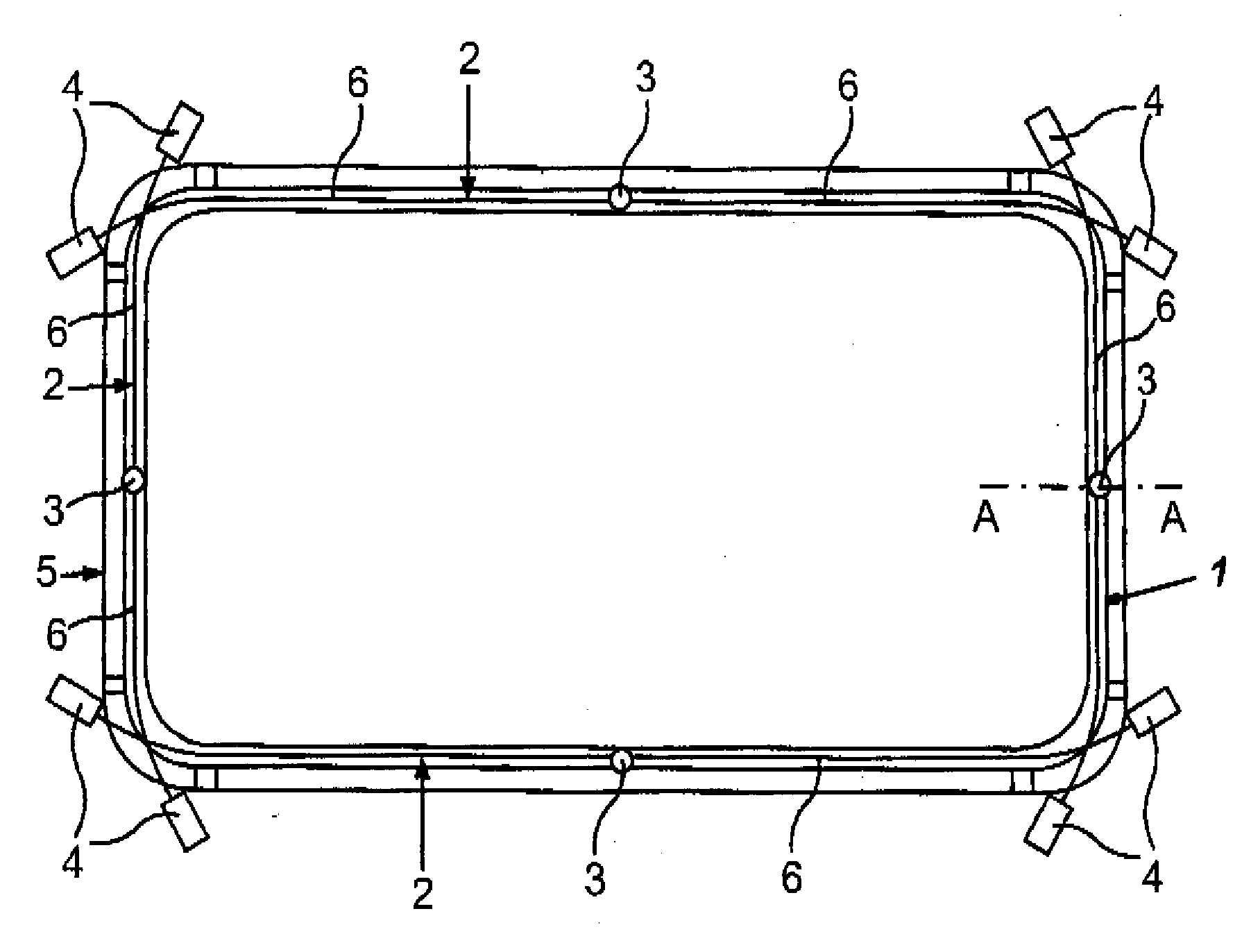
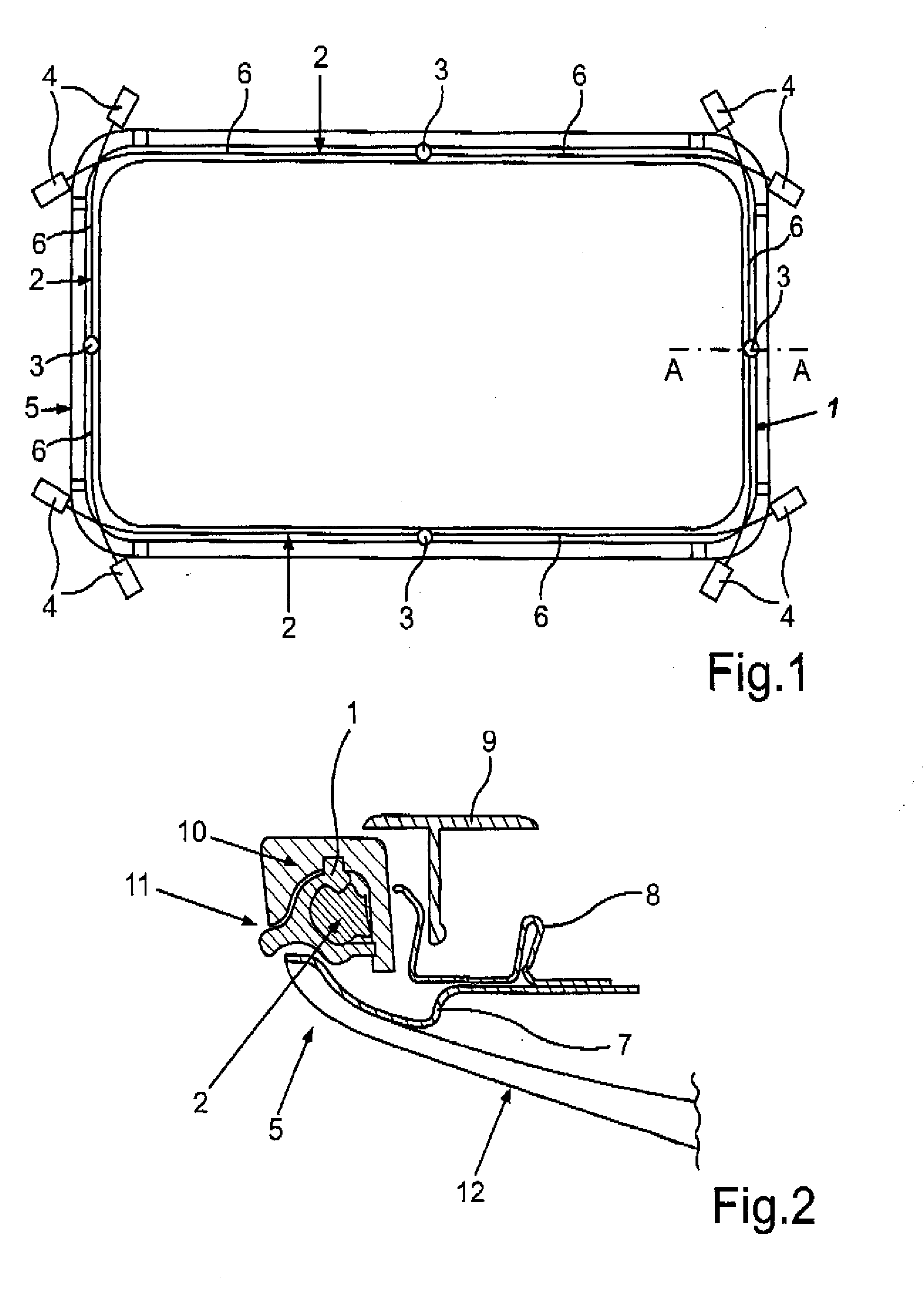
ActiveUS20130058115A1Easy to producePrevent breachLight guidesWindow lightingsLight guideEmbedded system
A peripheral illumination device for a vehicle component includes at least one light guide, and an enclosure for guiding the at least one light guide. The at least one light guide is securely mounted in the enclosure via a fixed support at a predefined location and has two ends which are movably mounted in relation to the enclosure.
Owner:AUDI AG
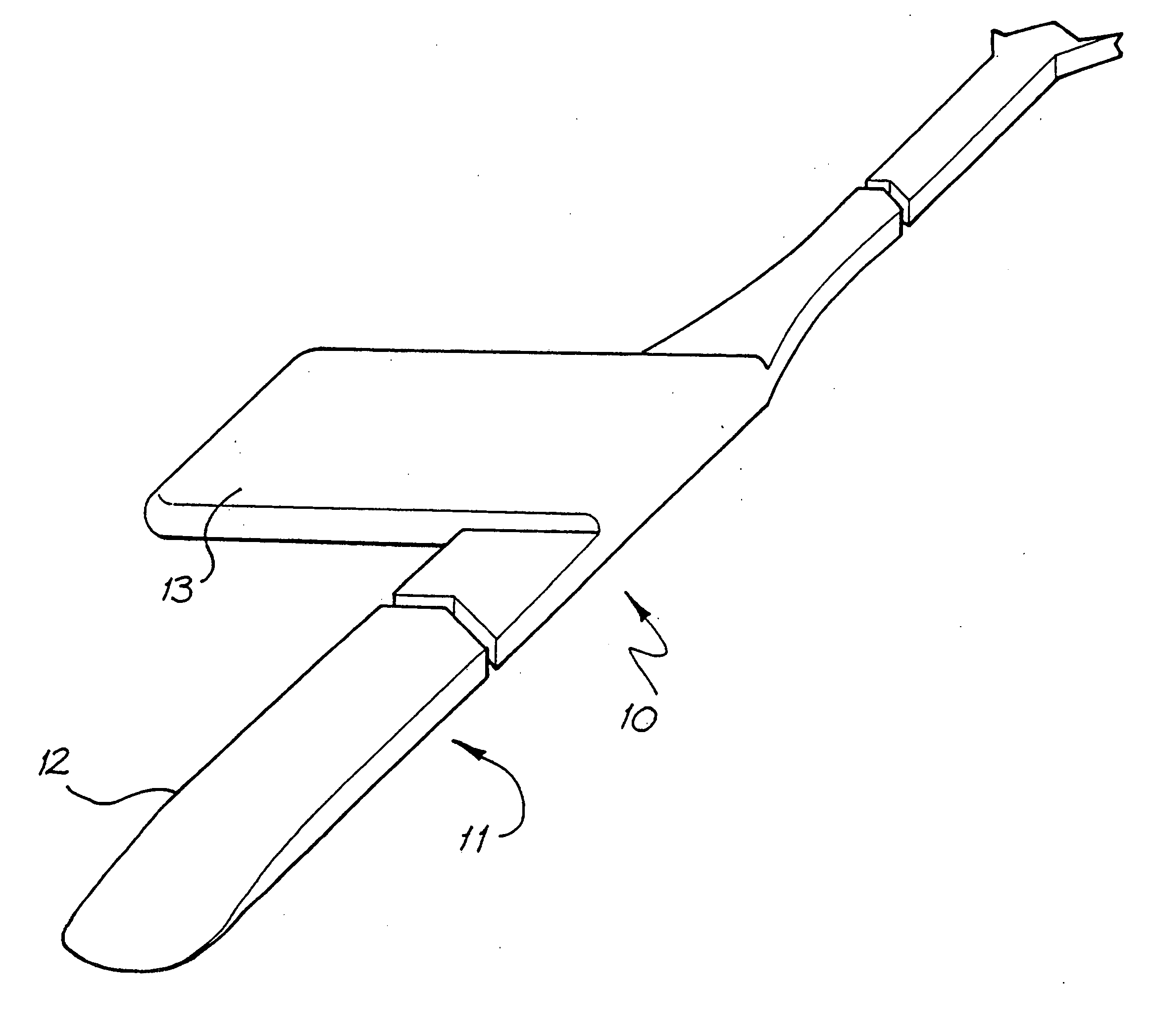
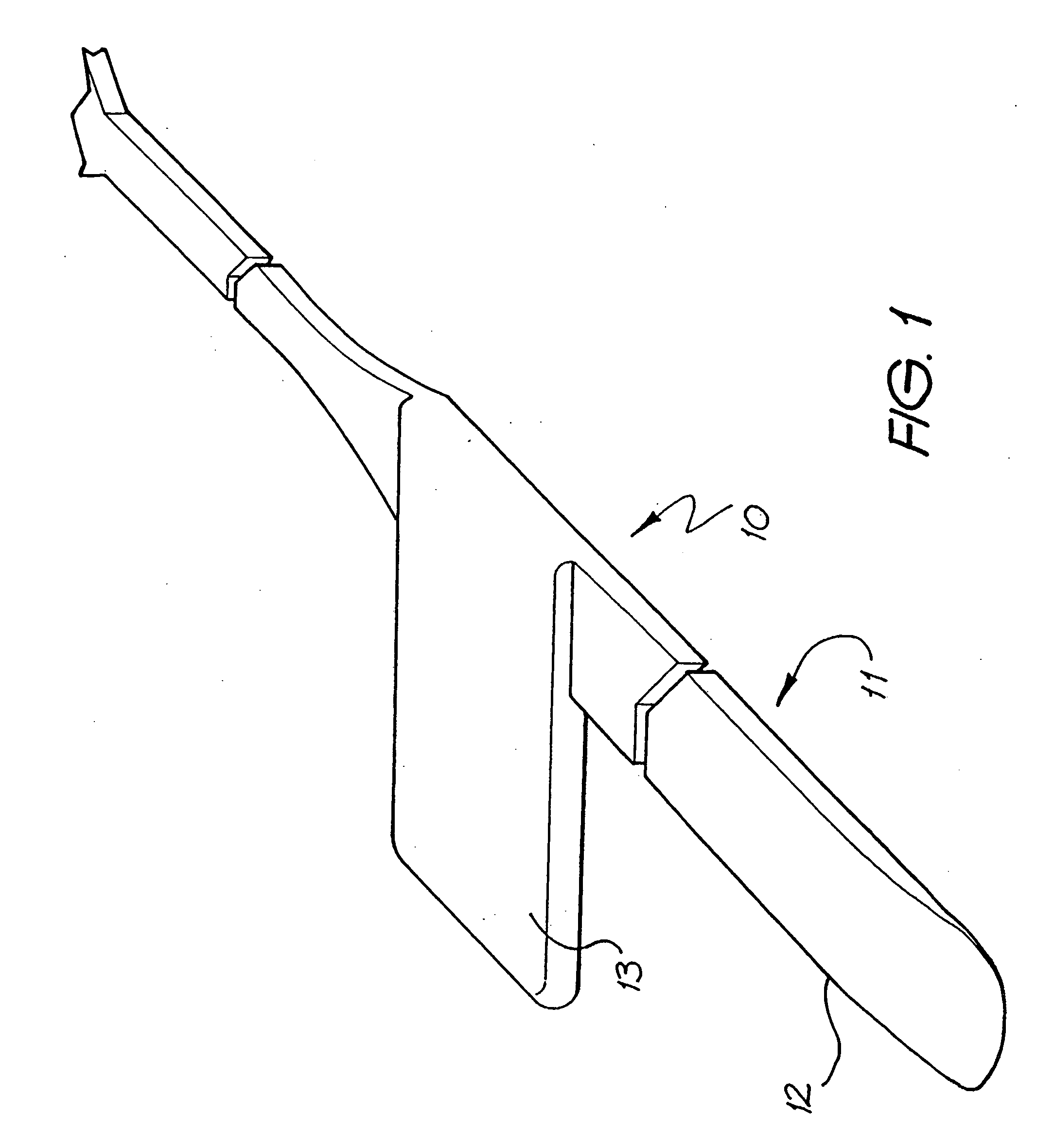
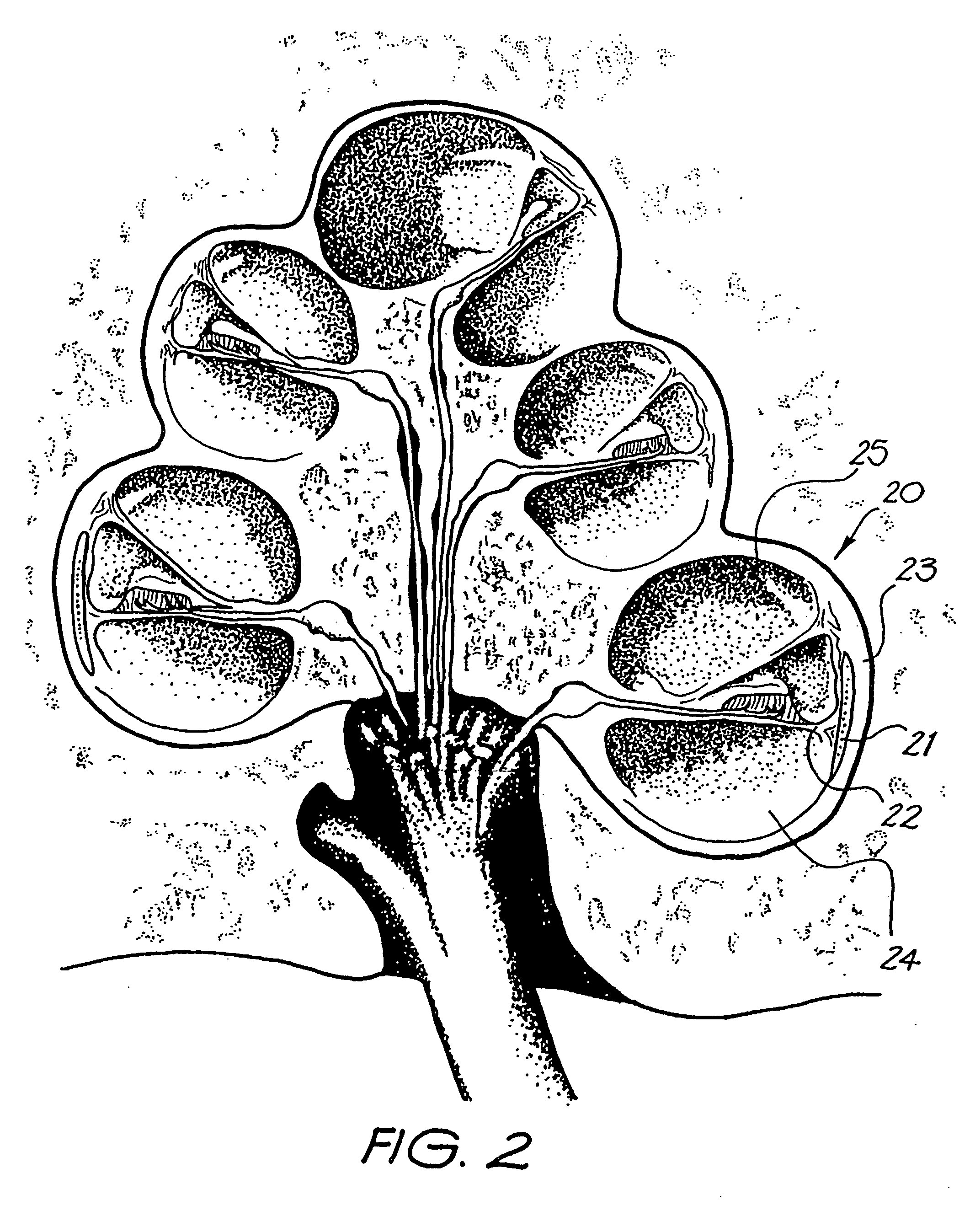
Endosteal electrode
InactiveUS20050080473A1Improve hearingMaximises possibilityHead electrodesEar treatmentCochlear implantationEngineering
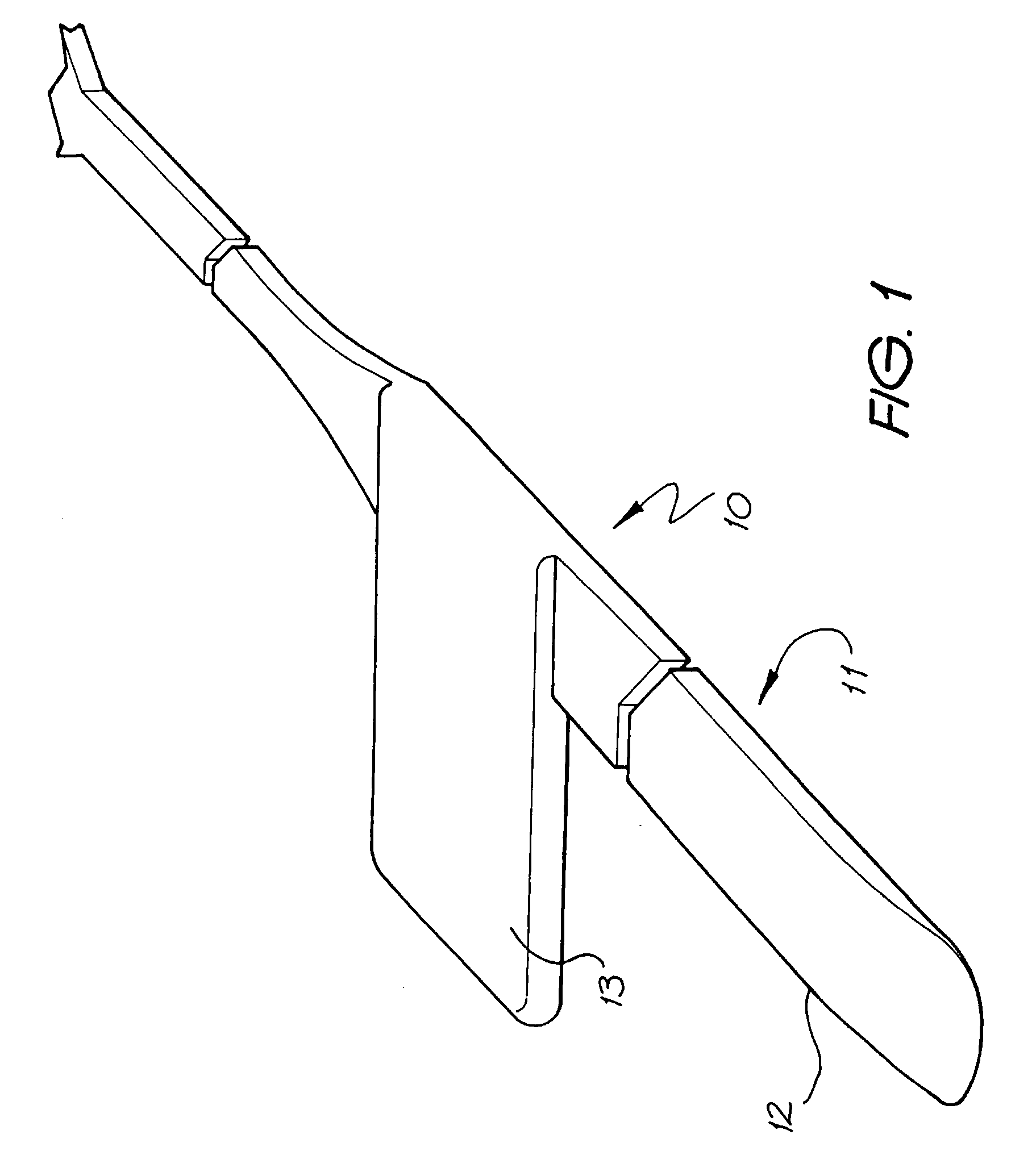
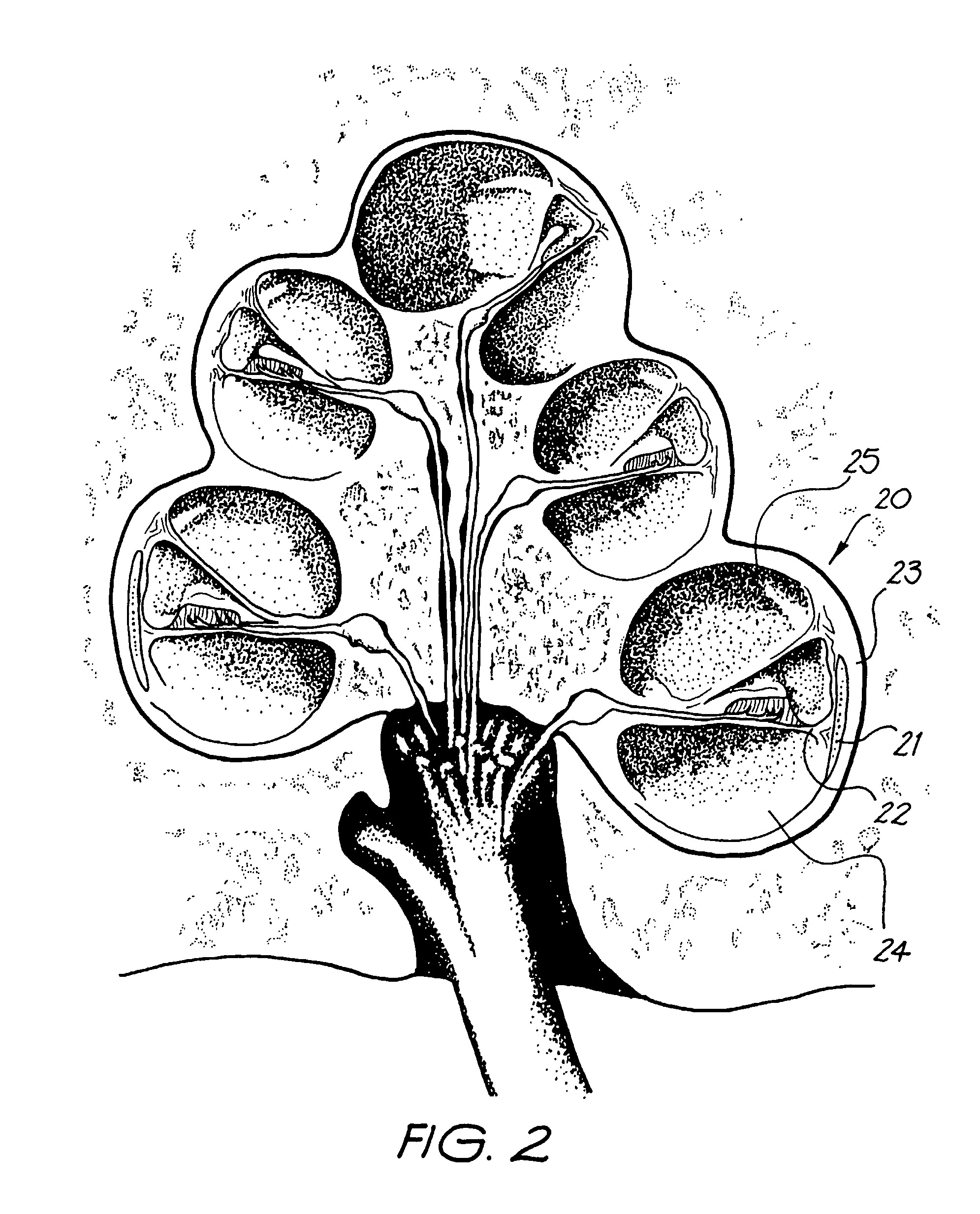
An implantable tissue-stimulating device comprising an elongate electrode carrier member (11) having a plurality of electrodes thereon. The electrodes are preferably disposed in a linear array on the carrier member (11) and are adapted to apply a preselected tissue stimulation to the cochlea. The carrier member (11) is preformed from a resiliently flexible biocompatible silicone and extends from a distal end (12) to a stop member (13). The carrier member (11) is adapted for intracochlear but extraluminar insertion within the cochlea of an implantee. In particular, the carrier member (11) is adapted to be implanted in the crevice (21) between the spiral ligament (22) and the endosteum (23) of the lateral wall of the cochlea (20). This is a quite different location to the normal placement of the cochlear implant electrode array in the scala tympani (24) of the cochlea (20). The placement of the carrier member (11) is designed to avoid any breach of the internal ducts of the cochlea (20), such as the scala tympani (24) and scala vestibuli (25) so that the normal hydrodynamic behaviour of the cochlea (20) is not affected by any intrusive device. By preservng the normal hydrodynamic behaviour of the cochlea (20), use of the carrier member (11) maximises the possibility of also preserving any hearing of the implantee that is offered by the cochlea (20). Use of the device in a system for masking or treating the symptoms of tinnitus is also described.
Owner:COCHLEAR LIMITED
Method, system, device and terminal for processing secret keys
InactiveCN101610147AImprove securityAvoid reuseKey distribution for secure communicationPublic key for secure communicationAccess networkHandover
The invention discloses a method, a system, a device and a terminal for processing secret keys, wherein the method for processing secret keys comprises the following steps: receiving a handover request message; acquiring a second secret key of a first network according to a first secret key and network parameters of the first network; and sending a handover request message containing the second secret key to a second network. By applying the embodiment of the invention to process the secret keys, when a UE is handed over among different access networks, secret keys of various access networks are ensured to be different before and after handover by inputting network parameters of the access networks in functions for educing the secret keys, thereby the same secret key is repeatedly used in the same kind of access networks, especially the problem that the same kind of access networks are also broken through as a certain access network is broken through when the access networks are handed over in a shorter period, and the network security of the access networks is improved.
Owner:HUAWEI TECH CO LTD
Security block for a communications connector
InactiveUS20070114054A1Prevent breachAvoid connectionEngagement/disengagement of coupling partsInstallation of lighting conductorsLocking mechanismElectronic instrument
A security block for securing I / O ports of an electronic instrument physically prevents any breach of data through a protected I / O port, such as a USB port, by securing cables that may be plugged into the port by means of a locked cover. The cables are prevented from being removed and USB memory devices are prevented from being connected in their place. In a second aspect, a portion of the security block covers unused I / O ports thereby preventing USB memory devices and other devices from being connected to unoccupied I / O ports. The locking mechanism can be either a padlock, or a locking screw, or the like.
Owner:TEKTRONIX INC
Anti-zipper puller sliding device
ActiveUS20140060988A1Prevent breachPrevent movementSlide fastenersLuggageLocking mechanismEngineering
The present invention is directed to embodiments of an anti-zipper sliding device that may include at least one body, a gripping surface affixed onto the body, a fastener to removably attach the body and the gripping surface onto a piece of luggage having a zipper with a zipper track and a zipper puller so as to prevent the anti-zipper sliding device from moving along the zipper track of the luggage. The anti-zipper sliding device may also include at least one locking mechanism or be configured for engagement with at least one locking mechanism in order to lock at least one zipper puller to the anti-zipper sliding device in order to prevent the zipper from being re-zipped after a zipper breach.
Owner:SUN LOCK COMPANY LIMITED -THE-
Data anti-intrusion method based on big data and artificial intelligence and big data server
ActiveCN112615865AImprove adaptabilityImprove intrusion prevention performanceTransmissionAlgorithmAttack
The invention relates to a data anti-intrusion method based on big data and artificial intelligence and a big data server, which can analyze different intrusion interception records, determine an interception event set corresponding to each group of intrusion interception records, and determine at least one group of interception behavior data; therefore, the intrusion attack category of the to-be-analyzed interception event is analyzed. The number of the to-be-analyzed interception events can be multiple, and different intrusion attack categories can be determined as many as possible so as to update the firewall based on the intrusion attack categories and the intrusion interception records. According to the method, the intrusion interception record can be analyzed in an interception operation level, so that intrusion attacks and firewall interception running states are analyzed, intelligent adaptation upgrading and optimization of the firewall can be realized, an interception mechanism of the firewall is prevented from being in an invariable state for a long time, the intrusion defense performance of the firewall can be improved, the interception mechanism of the firewall is prevented from being broken in the later operation process, and the reliability of data intrusion protection is ensured.
Owner:上海德吾信息科技有限公司
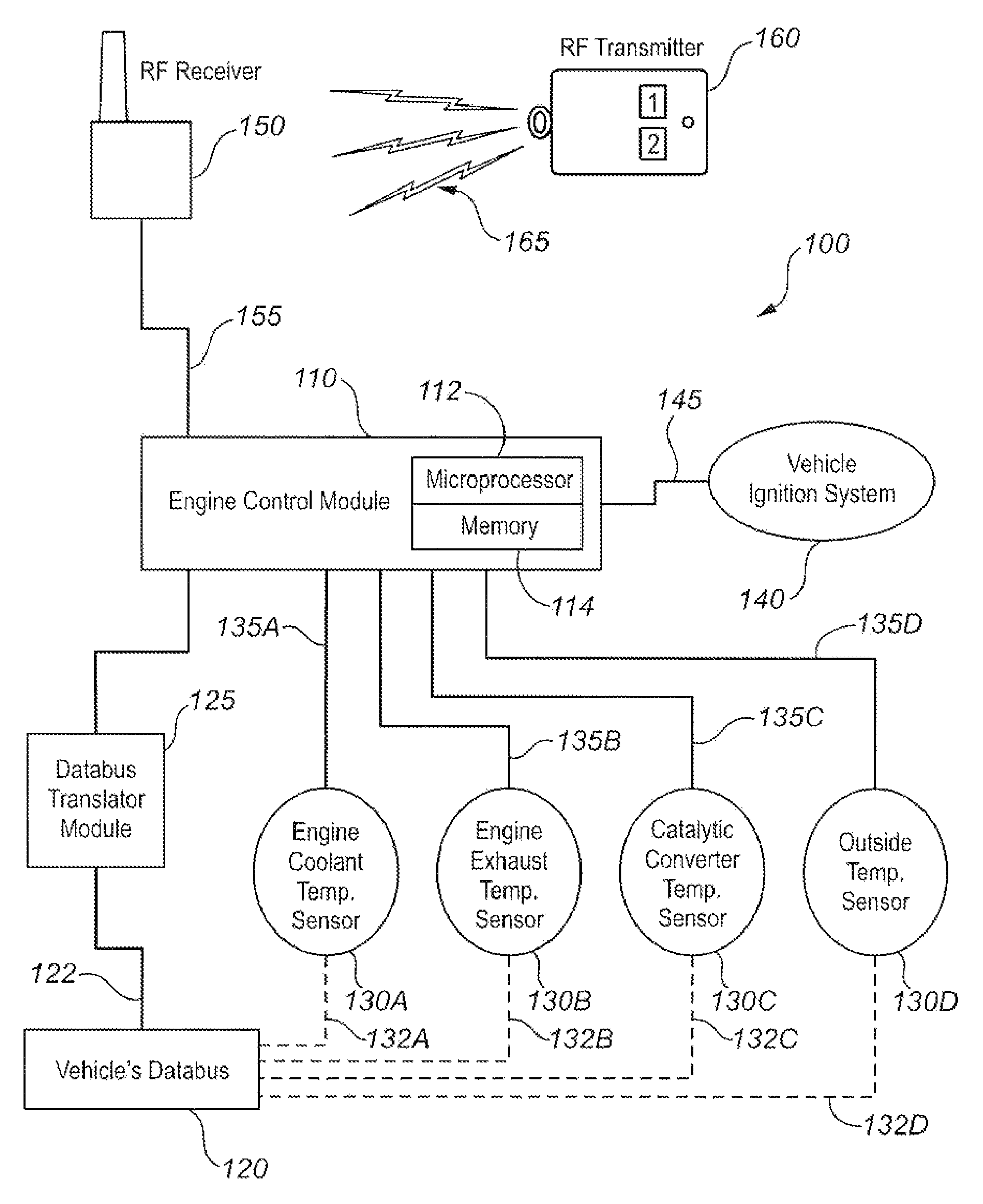
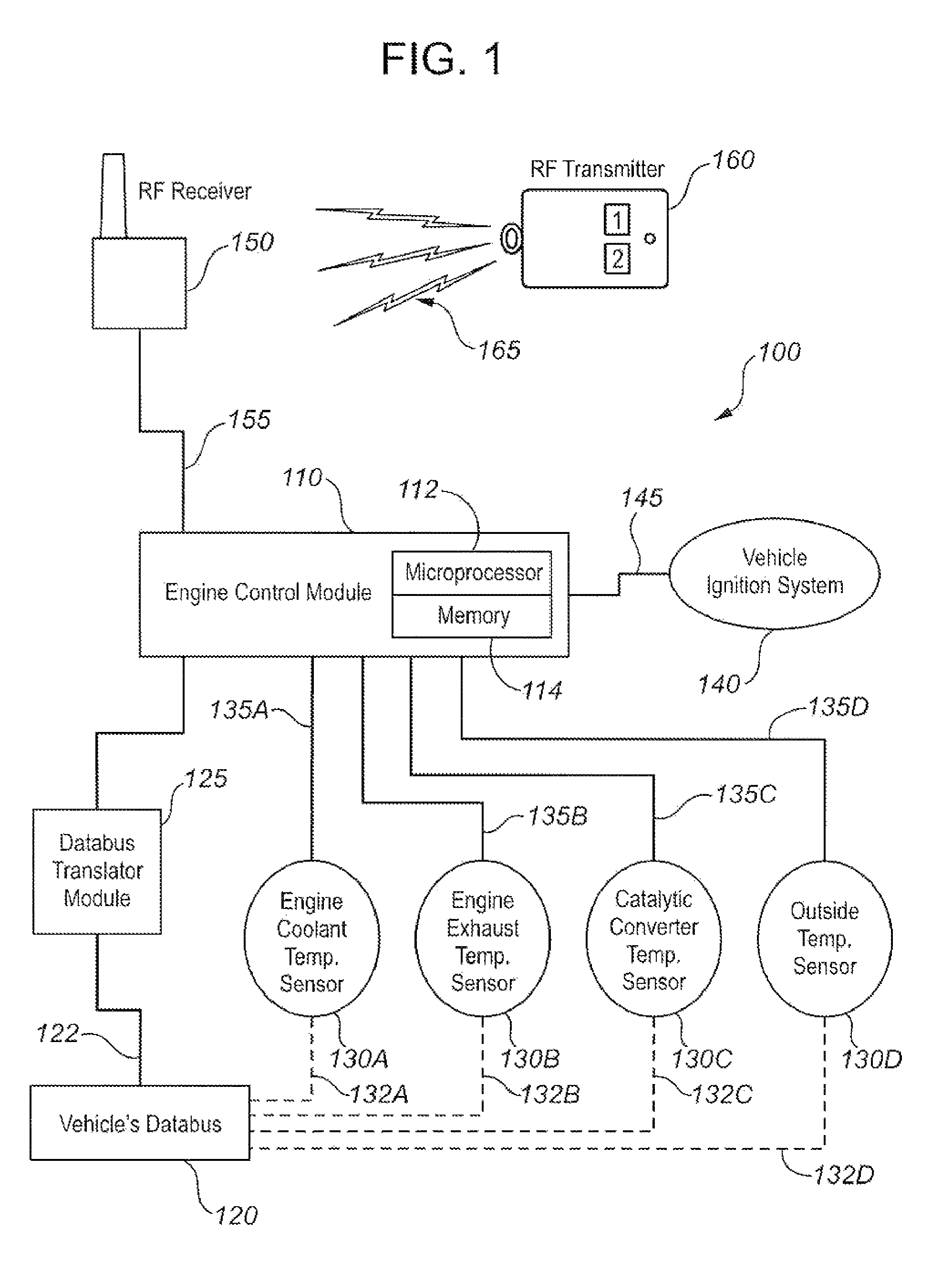
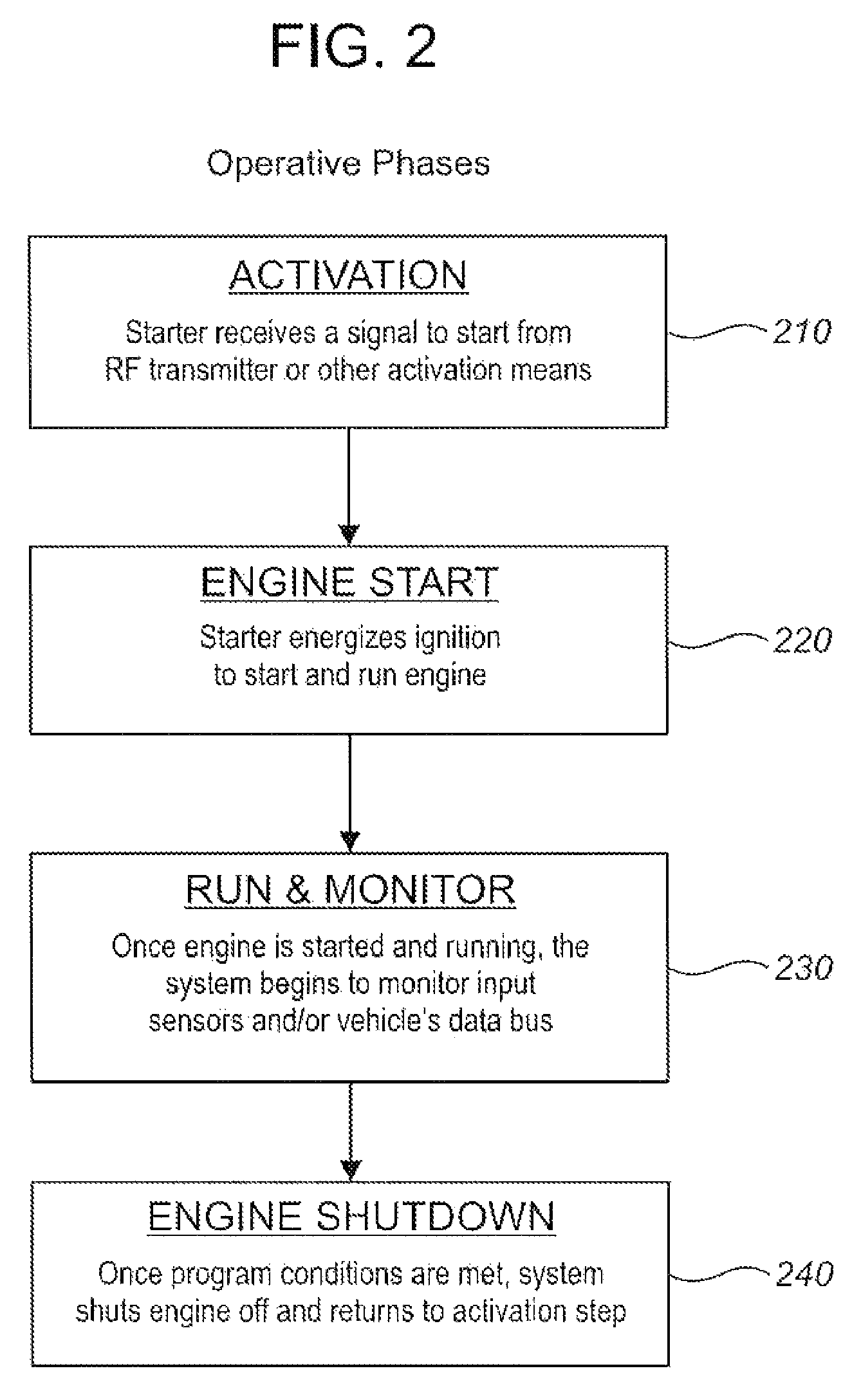
Method and system for regulating emissions from idling motor vehicles
InactiveUS8479706B2Improve operationEasy to optimizeElectrical controlIdling devicesIdle timeIdle speed
A system for regulating the operation of an idling motor vehicle monitors one or more selected engine operational parameters such as coolant temperature, exhaust gas temperature, and catalytic converter temperature, and compares the measured parameters against selected benchmark criteria stored in the memory of a microprocessor. The microprocessor controls the vehicle's ignition system to shut down the engine when the measured parameters come within the corresponding benchmark criteria. The system preferably but not necessarily operates in conjunction with a remote vehicle starter system. The system may also or alternatively be adapted to shut down an idling motor vehicle engine when total idling time reaches a specified maximum value, which may be selected based on idling time restriction bylaws. Accordingly, the system promotes reduced fuel consumption and mitigates environmental impacts by automatically regulating vehicle idling times, while also facilitating avoidance of idling time restriction bylaw violations.
Owner:SPEERS JAMES P +1
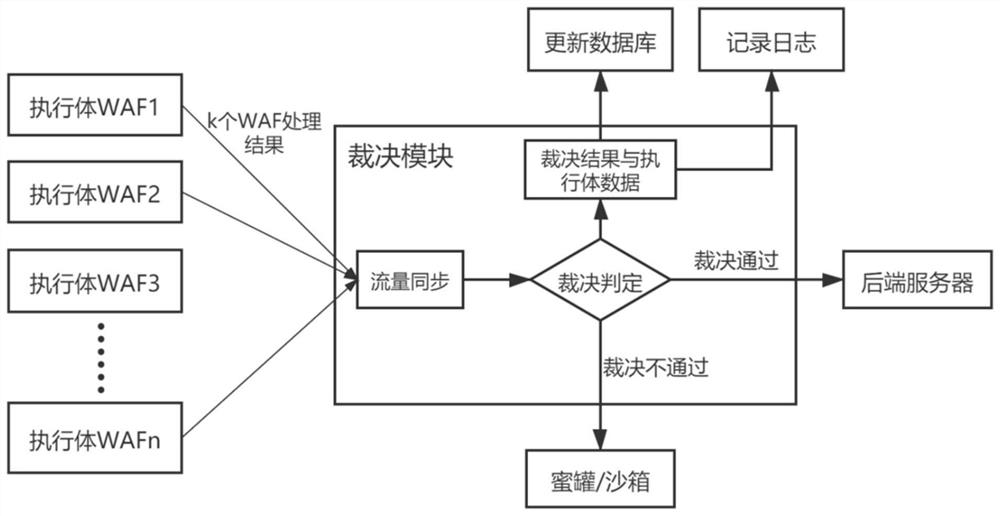
Judgment method of executive in mimicry WAF
The invention discloses a judgment method for an executor in a mimicry WAF, and the method can carry out the judgment of a plurality of processing results with the same flow, thereby discovering and blocking an unknown attack. The flow synchronization module, the multi-mode judgment module, the judgment result and data recording module and the like are mainly designed to realize a judgment function in the mimicry WAF, the mimicry WAF can identify unknown attacks through the judgment function, and the unknown attacks are blocked through operations such as offline self-cleaning of a WAF executor, so that the mimicry WAF has an active defense capability. The method comprises the steps that firstly, a flow synchronization module synchronizes k heterogeneous WAF processing results, then a multi-mode judgment module judges judgment of the processing results, records the judgment results and data into logs and updates corresponding values of a database, and finally, when the judgment resultsare passed, flow is sent to a back-end server, and when the judgment results are not passed, the flow is sent to a honeypot or a sandbox.
Owner:ZHEJIANG UNIV
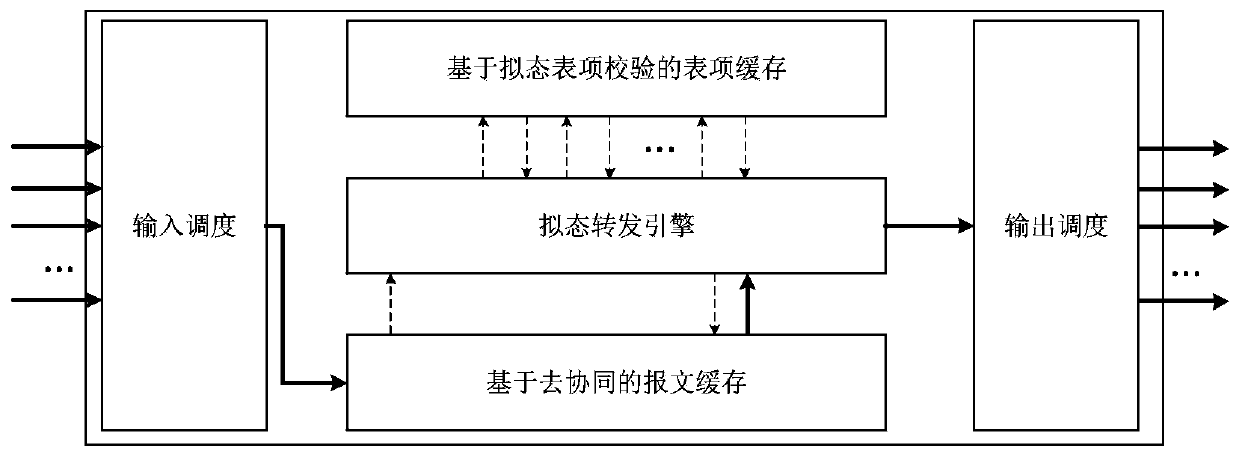
Mimicry thought-based security exchange chip, implementation method and network exchange equipment
ActiveCN110177046AImprove securityImprove reliabilityData switching networksNetwork packetNetwork switch
The invention belongs to the technical field of network switching, and particularly relates to a mimicry thought-based security switching chip, an implementation method of the security switching chipand network switching equipment, and the method comprises the following steps: carrying out scheduling processing on message data of each port according to input scheduling; aiming at each piece of message data, extracting a message header and caching the message data; parsing through a heterogeneous parsing algorithm, and carrying out mimicry judgment on a parsing result; generating a message descriptor according to the judgment result, wherein the message descriptor at least comprises message feature information related to the message forwarding strategy behavior; searching for a mimicry table item verification-based table item cache to obtain forwarding strategy behavior data and updating a message descriptor; and extracting corresponding message data from the cached message data, and sending the extracted message data to a corresponding port in the form of a data packet. The security and reliability of the switch chip are enhanced by introducing such technologies as de-collaborative caching, mimic forwarding engines and mimic table item checking, and the method has important guiding significance for the development of the network switching technology.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Anti-zipper puller sliding device
The present invention is directed to embodiments of an anti-zipper sliding device that may include at least one body, a gripping surface affixed onto the body, a fastener to removably attach the body and the gripping surface onto a piece of luggage having a zipper with a zipper track and a zipper puller so as to prevent the anti-zipper sliding device from moving along the zipper track of the luggage. The anti-zipper sliding device may also include at least one locking mechanism or be configured for engagement with at least one locking mechanism in order to lock at least one zipper puller to the anti-zipper sliding device in order to prevent the zipper from being re-zipped after a zipper breach.
Owner:SUN LOCK COMPANY LIMITED -THE-
Mimicry WAF construction method
ActiveCN112367289AIncrease cognition and attack difficultyGuaranteed correctnessTransmissionSoftware simulation/interpretation/emulationVirtualizationIsomerization
The invention discloses a mimicry WAF construction method which is based on a mimicry defense thought and can actively defend against malicious attacks on a WAF. A dynamic selection module, a mimicryjudgment module, an isomer construction module and the like are designed to realize mimicry WAF construction, and isomerization processing is performed on a cloud server, a virtualized container, an operating system in the container, a WAF platform, an interception rule and the like, so that the WAF has an active defense capability. When the traffic passes through the dynamic selection module, themodule selects k WAF isomers for traffic processing, after the processing result is judged by the mimicry judgment module, a judgment result is used for modifying the abnormal rate of each isomer, when the abnormal rate of a certain isomer is higher than a certain value, offline self-cleaning operation is carried out on the isomer, and finally, when the judgment result is that the judgment is passed, the traffic is released, and when the judgment result is not passed, the traffic is forwarded to a subsequent processing module.
Owner:ZHEJIANG UNIV
Endosteal electrode
InactiveUS20070282416A1Improve hearingMaximises possibilityHead electrodesEar treatmentCochlear implantationEngineering
An implantable tissue-stimulating device comprising an elongate electrode carrier member (11) having a plurality of electrodes thereon. The electrodes are preferably disposed in a linear array on the carrier member (11) and are adapted to apply a preselected tissue stimulation to the cochlea. The carrier member (11) is preformed from a resiliently flexible biocompatible silicone and extends from a distal end (12) to a stop member (13). The carrier member (11) is adapted for intracochlear but extraluminar insertion within the cochlea of an implantee. In particular, the carrier member (11) is adapted to be implanted in the crevice (21) between the spiral ligament (22) and the endosteum (23) of the lateral wall of the cochlea (20). This is a quite different location to the normal placement of the cochlear implant electrode array in the scala tympani (24) of the cochlea (20). The placement of the carrier member (11) is designed to avoid any breach of the internal ducts of the cochlea (20), such as the scala tympani (24) and scala vestibuli (25) so that the normal hydrodynamic behaviour of the cochlea (20) is not affected by any intrusive device. By preservng the normal hydrodynamic behaviour of the cochlea (20), use of the carrier member (11) maximises the possibility of also preserving any hearing of the implantee that is offered by the cochlea (20). Use of the device in a system for masking or treating the symptoms of tinnitus is also described.
Owner:COCHLEAR LIMITED
Port cover for a system integrated into a structure for injection of a material into one or more cavities in the structure
ActiveUS20050198806A1Prevent unauthorized accessPrevent breachKeysPositioning apparatusLocking mechanismEngineering
In one embodiment, a port cover for a system integrated into a structure for injection of a material into one or more cavities in the structure includes a base for coupling to the structure. The base includes one or more ports for injection of the material into the one or more cavities in the structure and one or more slots. The port cover also includes a cover for removably coupling to the base, the cover including one or more tabs each adapted to engage with a corresponding slot of the base. The cover also includes a locking mechanism for removably securing the cover to the base to prevent unauthorized access to the one or more ports. The locking mechanism is adapted to engage a projection of the base to removably secure the one or more tabs of the cover in engagement with the one or more corresponding slots of the base to removably secure the cover to the base to prevent unauthorized access to the one or more ports.
Owner:HOMETEAM PEST DEFENSE
Mechanical shaft seal
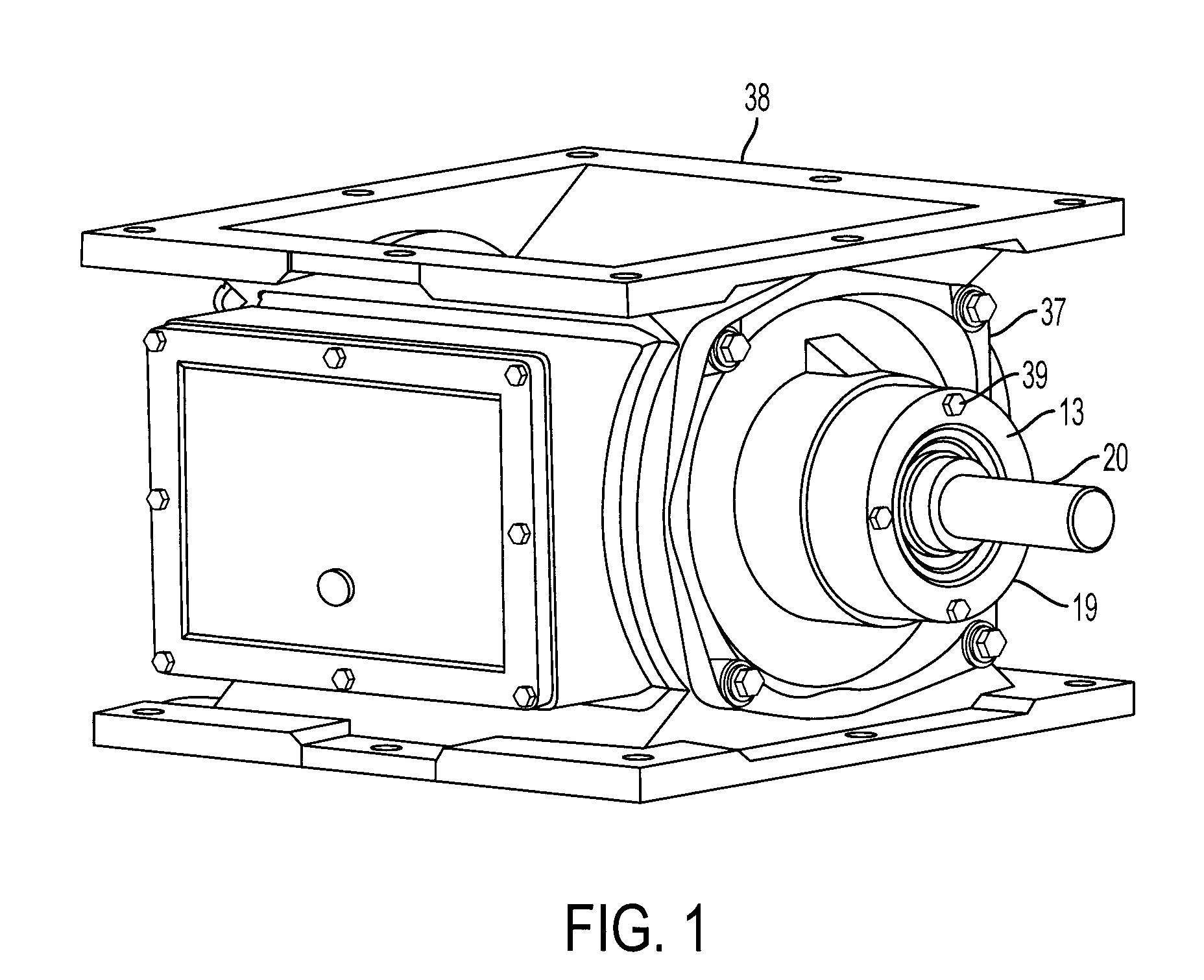
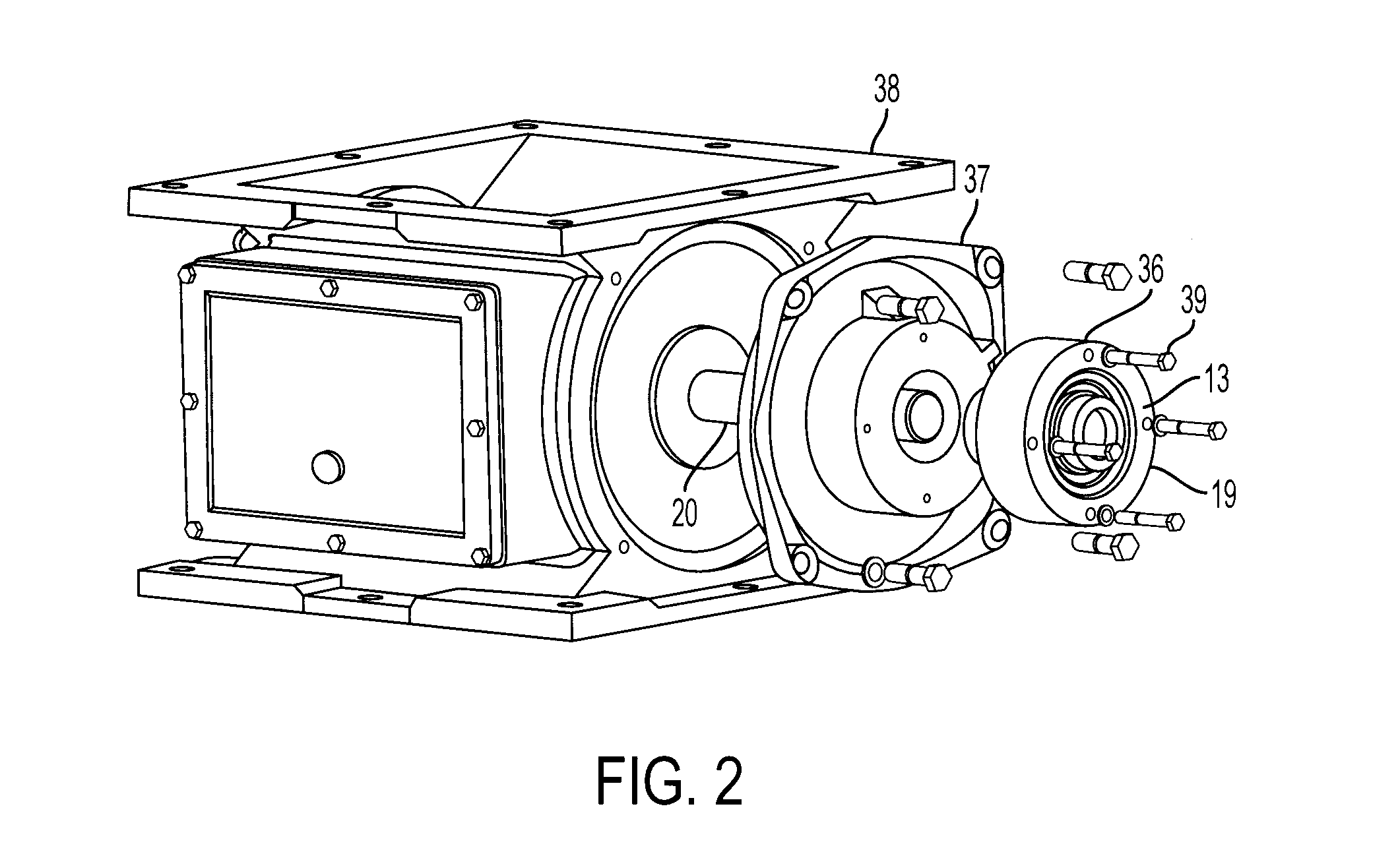
ActiveUS20070290449A1Avoid the needSelf containedEngine sealsLeakage preventionAtmospheric airSolid particle
An improved mechanical shaft seal to give a tight seal between relatively rotating machine parts and prevent the escape of particulate material into the atmosphere or into the mechanical components of the housing under adverse operating conditions. The seal provides a grease chamber that prevents solid particles from reaching the main seal by migration within the mechanical shaft seal.
Owner:PLATTCO
Mechanical shaft seal
ActiveUS8128095B2Avoid maintenanceAvoid the needEngine sealsLeakage preventionMechanical componentsMachine parts
An improved mechanical shaft seal to give a tight seal between relatively rotating machine parts and prevent the escape of particulate material into the atmosphere or into the mechanical components of the housing under adverse operating conditions. The seal provides a grease chamber that prevents solid particles from reaching the main seal by migration within the mechanical shaft seal.
Owner:PLATTCO
Video monitoring system based on cloud platform
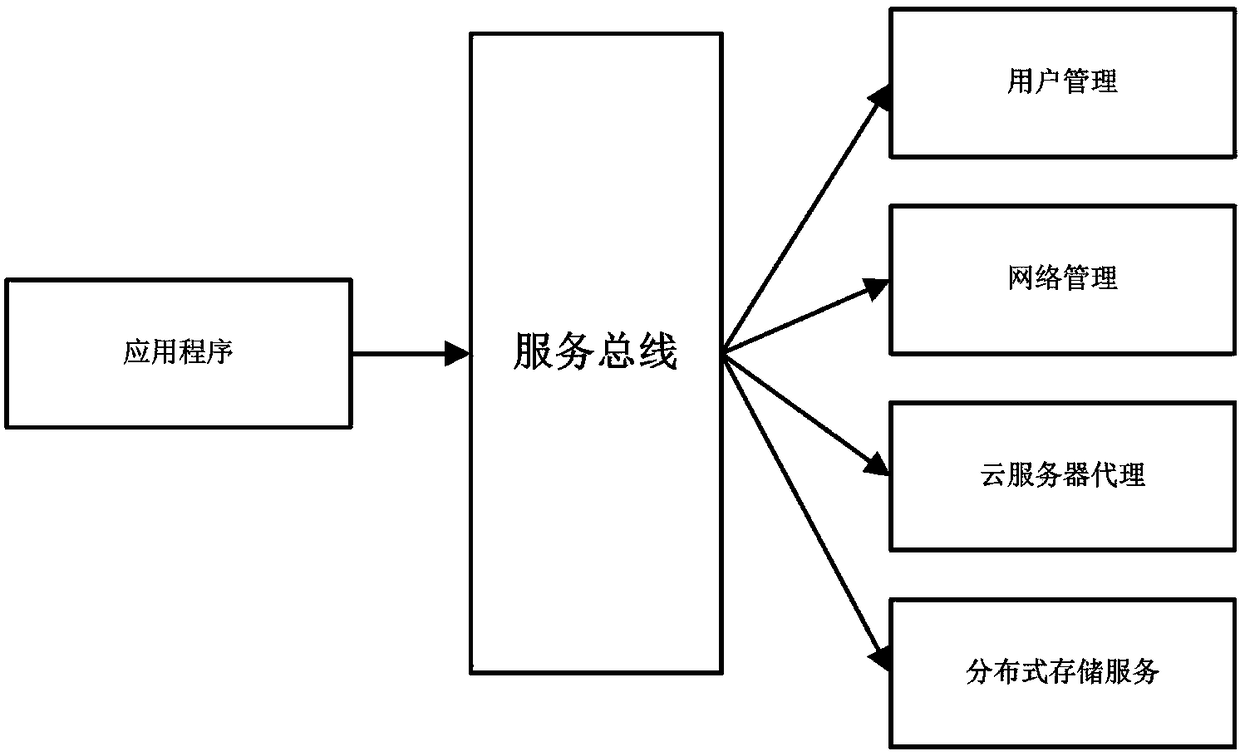
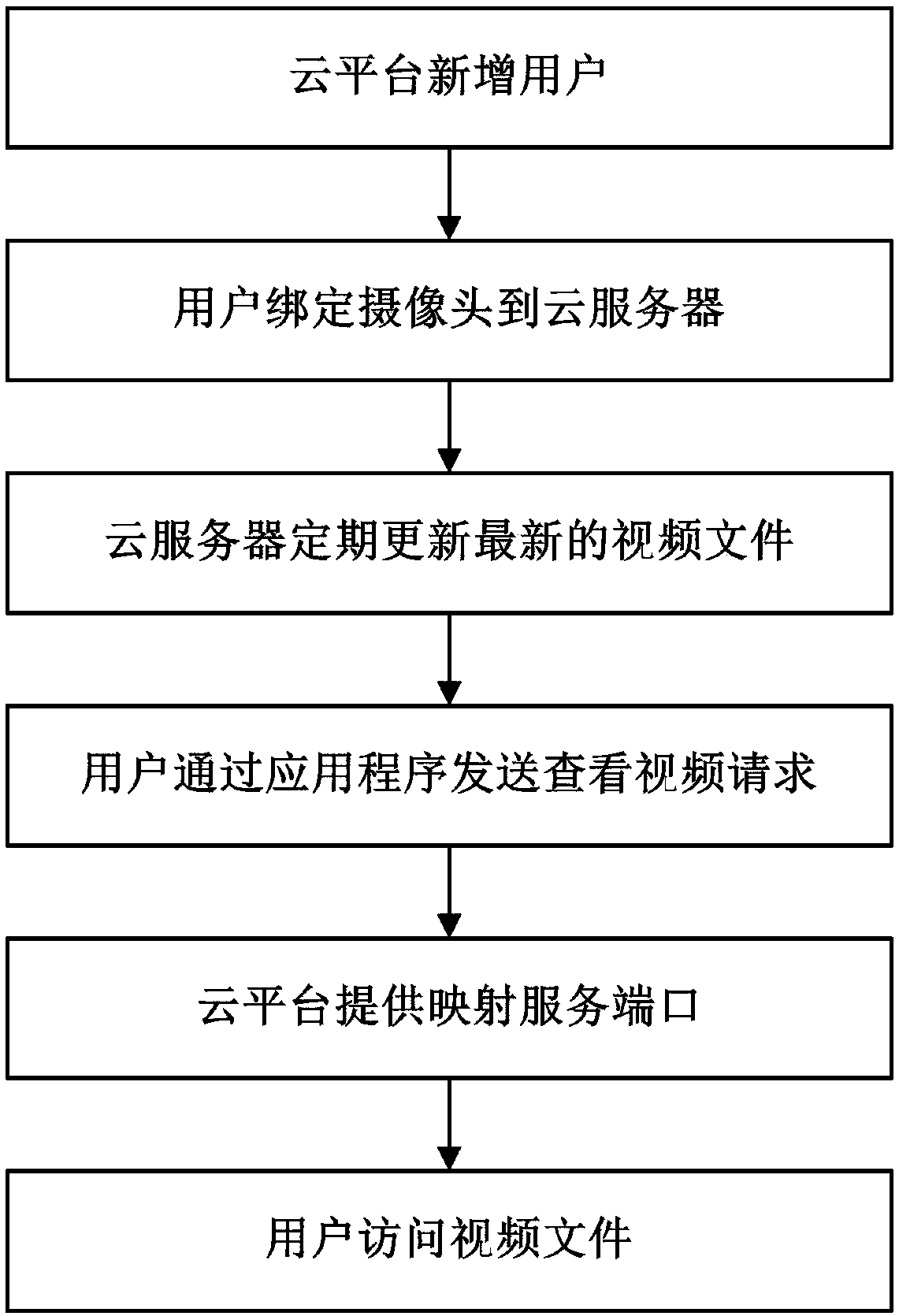
InactiveCN108495082AImprove securityPrevent breachClosed circuit television systemsTransmissionVideo monitoringVirtual firewall
The invention relates to the network monitoring technology field, especially relates to a video monitoring system based on a cloud platform. The video monitoring system comprises a service bus, a user management module, a cloud server proxy module, a network management module, distributed type storage service, and an application program. The service bus is used to provide a connection pivot for message interaction among the various modules. The user management module is used to create a cloud server automatically for a newly registered or added user, and a camera is bond with the cloud server. The distributed type storage service is used to provide block storage service. The cloud service proxy module is used to download latest video files, and store the downloaded video files in a clouddisk based on an internal network or a special network. The network management module is used to provide the service port mapping of the video files, and the ports are limited to be only open to the access of the IP address of the application program, and the access of other IP addresses is forbidden, and in addition a virtual firewall is provided. The application program is used for the query ofthe videos. The problems of the network video monitoring such as easy illegal attacks on the address, low safety performance, difficulty in expanding storage space are solved, and the video monitoringsystem can be used for the network video monitoring technology field.
Owner:G CLOUD TECH
Lock pin and bolt construction for securing doors and other closures
ActiveUS9540843B2Type of goodPrevent breachBuilding locksConstruction fastening devicesPunchingEngineering
A rotatable lock pin that inhibits forced entry into a container through a closure by securing the lock pin to the container. A lock pin has a pin cylinder with a curvature of rotation that engages with a rotation facilitator. The path of the curvature of rotation and the engagement of the rotation facilitator therewith causes the lock pin to rotate in a pre-determined fashion, so that structures on the lock pin can engage or attach to some part of the container to secure the position of the lock pin and hold the closure door in place. Lock pins of the subject invention utilized with safes can inhibit forced entry through the door by side punching or prying of the door.
Owner:SHADE RIVER OUTFITTERS
Peripheral illumination device for a vehicle component
ActiveUS8882318B2Precise positioningPrevent breachLight guidesLighting heating/cooling arrangementsLight guideEmbedded system
A peripheral illumination device for a vehicle component includes at least one light guide, and an enclosure for guiding the at least one light guide. The at least one light guide is securely mounted in the enclosure via a fixed support at a predefined location and has two ends which are movably mounted in relation to the enclosure.
Owner:AUDI AG
Self-Sealed Medical Sterilization Pouch
ActiveUS20100108551A1No pollution in the processAssure sterility sterilizationSurgical furnitureSamplingColor responseClosed space
A self-sealed medical sterilization pouch comprises the following elements of: a first sheet being pervious to sterilization gases and surrounded by at least one printing domain thereon, a plurality of signs being disposed on the printing domain and located outside of a closed space, the first sheet having at least two sterile processing indicators having color response, one surface of an end of the first sheet having a flap; and a second sheet being impervious to sterilization gases, the second sheet having an opening and being joined with the first sheet by a first seal line, a second seal line and a third seal line at a left side, a right side and an upper side to form the closed space, the sterile processing indicators being disposed between the third seal line and a ladle-shaped end and the third seal line and another ladle-shaped end respectively.
Owner:SIGMA MEDICAL SUPPLIES CORP
Self-sealed medical sterilization pouch
A self-sealed medical sterilization pouch comprises the following elements of: a first sheet being pervious to sterilization gases and surrounded by at least one printing domain thereon, a plurality of signs being disposed on the printing domain and located outside of a closed space, the first sheet having at least two sterile processing indicators having color response, one surface of an end of the first sheet having a flap; and a second sheet being impervious to sterilization gases, the second sheet having an opening and being joined with the first sheet by a first seal line, a second seal line and a third seal line at a left side, a right side and an upper side to form the closed space, the sterile processing indicators being disposed between the third seal line and a ladle-shaped end and the third seal line and another ladle-shaped end respectively.
Owner:SIGMA MEDICAL SUPPLIES CORP
NFC switch device and LED illumination control system based on same
ActiveCN104240474ASafe and reliable connectionPrevent breachTransmission systemsElectric light circuit arrangementControl systemNetwork connection
The invention discloses an NFC switch device. One end of the device is connected with a power supply, the other end is connected with a controlled object, the connection or disconnection between the power supply and the controlled object is controlled by switching on or off the switch. The NFC switch device also comprises a network connection unit, a processor unit with an NFC function and an NFC antenna unit, the network connection unit is connected with the controlled object by virtue of the network, the NFC antenna unit is used for receiving and transmitting an NFC signal in a short distance, the processor unit is respectively connected with the network connection unit and the NFC antenna unit, the processor unit is used for judging and recognizing the received NFC signal, if the NFC signal is well matched, a network communication link between an NFC signal transmitting end and the controlled object is established, and the controlled object can be controlled by the NFC signal transmitting end. The invention also discloses an LED illumination control system based on the NFC switch device. The connection link between the NFC signal transmitting end and the controlled object is established by virtue of intelligent NFC pairing, and the rapidness, safety and reliability in connection can be achieved.
Owner:ZHEJIANG SHENGHUI LIGHTING
Method for protecting from unauthorized access one or more ports of a system integrated into a structure for injection of a material into one or more cavities in the structure
ActiveUS20050210736A1Prevent unauthorized accessPrevent breachKeysPositioning apparatusLocking mechanismEngineering
In certain embodiments, the present invention includes a method for protecting from unauthorized access one or more ports of a system integrated into a structure for injection of a material into one or more cavities in the structure. The method includes coupling a base to the structure, the base including the one or more ports for injection of the material into the one or more cavities in the structure and one or more slots. The method further includes removably coupling a cover to the base to prevent unauthorized access to the one or more ports, the cover comprising one or more tabs each adapted to engage with a corresponding slot of the base. The cover is removably coupled to the base by positioning a locking mechanism for removably securing the cover to the base proximate a projection of the base and engaging the locking mechanism with the projection of the base to removably secure the one or more tabs of the cover in engagement with the one or more corresponding slots of the base to removably secure the cover to the base to prevent unauthorized access to the one or more ports.
Owner:HOMETEAM PEST DEFENSE
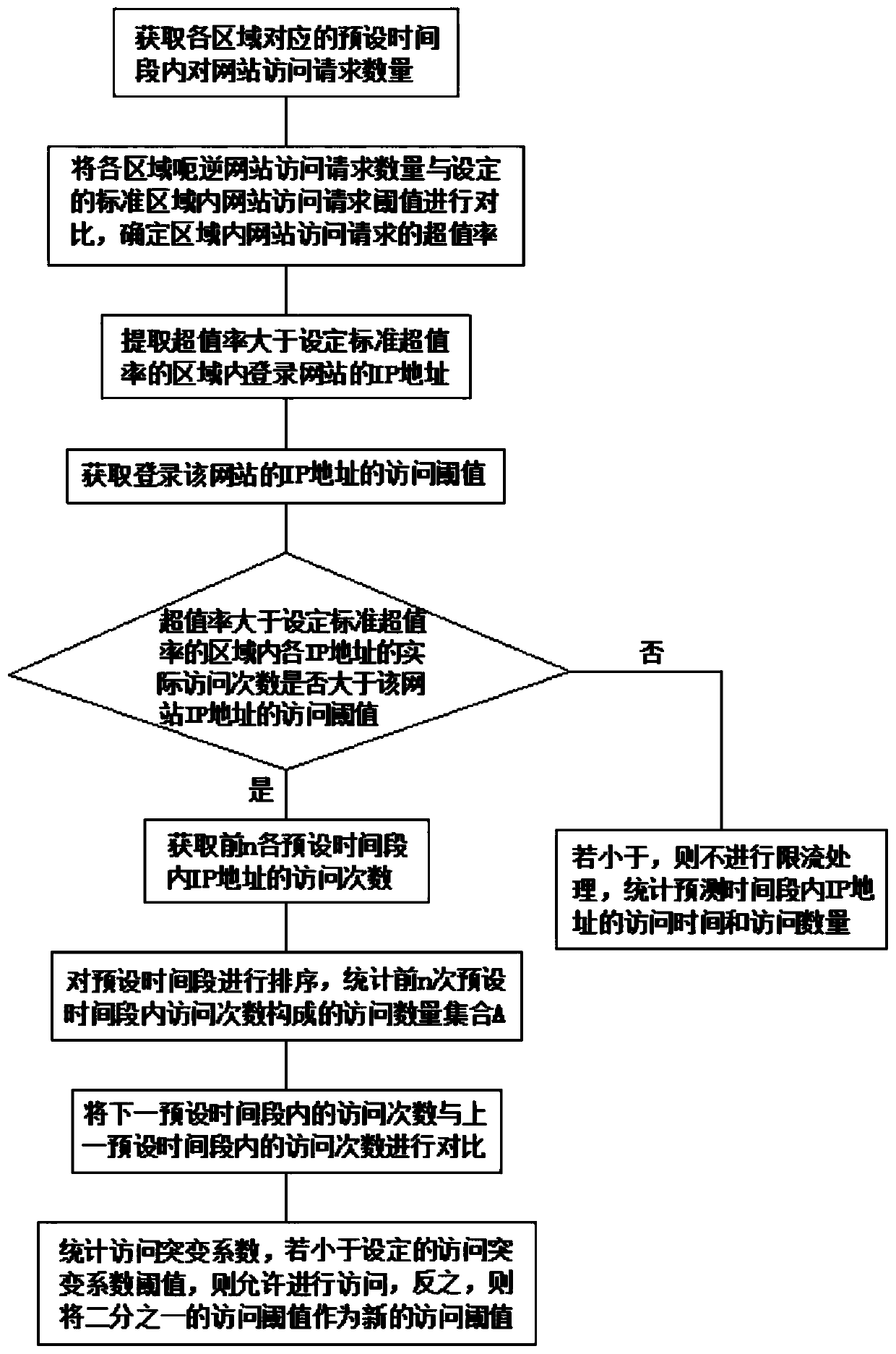
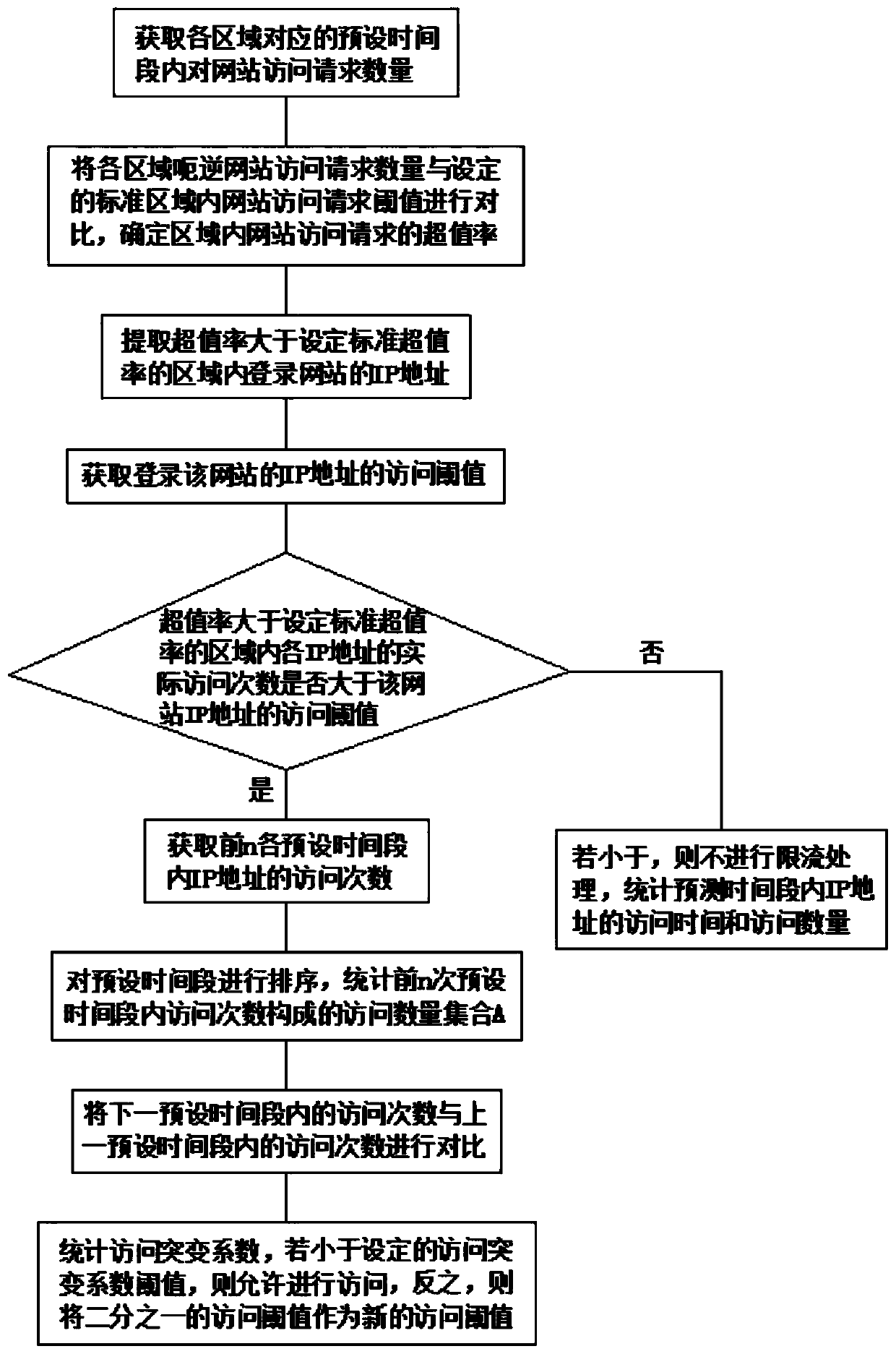
Website security defense method
The invention discloses a website security defense method. The method comprises the following steps: obtaining the number of website access requests in a preset time period corresponding to each region; comparing the website access request with a set website access request threshold value in a standard area, and determining an overvalue rate of the website access request; extracting an IP addresscorresponding to logging in the website in an area of which the overvalue rate is greater than a set standard overvalue rate; obtaining an access threshold of the website IP address; judging whether the real-time access frequency of each IP address in the area of which the overbalance rate is greater than the set standard overbalance rate is greater than the access threshold of the website IP address or not; and carrying out flow limiting processing on the IP address of which the actual access frequency is greater than the access threshold of the website IP address, otherwise, counting the access time and the access number of the IP address in the prediction time period, and recording and storing the access time and the access number. The access frequency of the IP address is limited, theaccess threshold value is reduced, the access frequency of the IP address is reduced, the website is prevented from being attacked, and the defense capability of the website is improved.
Owner:北京华安普特网络科技有限公司
Key for engaging a locking mechanism of a port cover for protecting from unauthorized access one or more ports of a system integrated into a structure for injection of a material into one or more cavities in the structure
ActiveUS20060123860A1Prevent unauthorized accessPrevent breachKeysCylinder locksLocking mechanismInjected material
In certain embodiments, the present invention includes a key for engaging a locking mechanism for a port cover for use in a system integrated into a structure for injection of a material into one or more cavities in the structure. The locking mechanism is for removably securing a cover of the port cover to a base of the port cover that is coupled to the structure and includes one or more ports for injecting material into the one or more cavities in the structure. The key is adapted to engage with the locking mechanism, and orient the locking mechanism such that the locking mechanism engages with a projection of the base to removably secure one or more tabs of the cover in engagement with one or more corresponding slots of the base to removably secure the cover to the base to prevent unauthorized access to the one or more ports.
Owner:HOMETEAM PEST DEFENSE
Data response method, terminal device, and server
ActiveUS20190245832A1Operation efficiency can be improvedImprove efficiencyDigital data protectionPlatform integrity maintainanceResponse methodTerminal equipment
Embodiments of the present disclosure disclose a data response method, a terminal device, and a server. The method in the embodiments of the present disclosure includes: sending encrypted information to a terminal device; receiving a first honeypot character, the encrypted information, and user data from the terminal device; decrypting the encrypted information, to obtain a second honeypot character comprised in the encrypted information; determining whether the first honeypot character sent by the terminal device is the same as the second honeypot character decrypted from the encrypted information; and responding to the user data in response to the first honeypot character being the same as the second honeypot character.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Earthquake-induced landslide lake rescuing drainage device and implementation method
InactiveCN105297870AEasy to carryConvenient AirdropMarine site engineeringSewage drainingLandslide damEngineering
The invention discloses an earthquake-induced landslide lake rescuing drainage device and an implementation method. The drainage device comprises a water inlet, a check valve, a check valve rubber gasket, a check valve rotating shaft, a water outlet, a valve, a valve rubber gasket, a valve rotating shaft, a valve clamping part, a valve clamping part rotating shaft, a telescopic pipe, a spiral telescopic bracket, a light high-strength and waterproof fabric, a female flange, a bump, a notch, a male flange, a screw rotating shaft, a thumb screw, a screw rod, a water filling nozzle and a water filling nozzle switch. The earthquake-induced landslide lake rescuing drainage device disclosed by the invention is composed of siphon parts which are telescopic and are easy to disassemble and assemble; and the drainage device is light in weight, high in strength and convenient for rescue workers to carry or for a helicopter to deliver. The rescue workers can conduct a drainage operation on a landslide lake which is formed by earthquake-induced landslide before large excavating machineries arrive, so as to reduce a water level and to avoid burst of the landslide lake as well as to provide time guarantee for the large excavating machineries, which arrive later, to excavate the landslide lake.
Owner:ZHEJIANG UNIV OF WATER RESOURCES & ELECTRIC POWER
Endosteal electrode
InactiveUS7809444B2Improve hearingMaximises possibilityHead electrodesEar treatmentCochlear implantationEngineering
An implantable tissue-stimulating device comprising an elongate electrode carrier member (11) having a plurality of electrodes thereon. The electrodes are preferably disposed in a linear array on the carrier member (11) and are adapted to apply a preselected tissue stimulation to the cochlea. The carrier member (11) is preformed from a resiliently flexible biocompatible silicone and extends from a distal end (12) to a stop member (13). The carrier member (11) is adapted for intracochlear but extraluminar insertion within the cochlea of an implantee. In particular, the carrier member (11) is adapted to be implanted in the crevice (21) between the spiral ligament (22) and the endosteum (23) of the lateral wall of the cochlea (20). This is a quite different location to the normal placement of the cochlear implant electrode array in the scala tympani (24) of the cochlea (20). The placement of the carrier member (11) is designed to avoid any breach of the internal ducts of the cochlea (20), such as the scala tympani (24) and scala vestibuli (25) so that the normal hydrodynamic behaviour of the cochlea (20) is not affected by any intrusive device. By preserving the normal hydrodynamic behaviour of the cochlea (20), use of the carrier member (11) maximises the possibility of also preserving any hearing of the implantee that is offered by the cochlea (20). Use of the device in a system for masking or treating the symptoms of tinnitus is also described.
Owner:COCHLEAR LIMITED
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com