Judgment method of executive in mimicry WAF
A judgment method and executive technology, applied in the field of network security, can solve security threats and other issues, achieve the effects of ensuring correctness, saving system resources, and reducing false alarm rates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
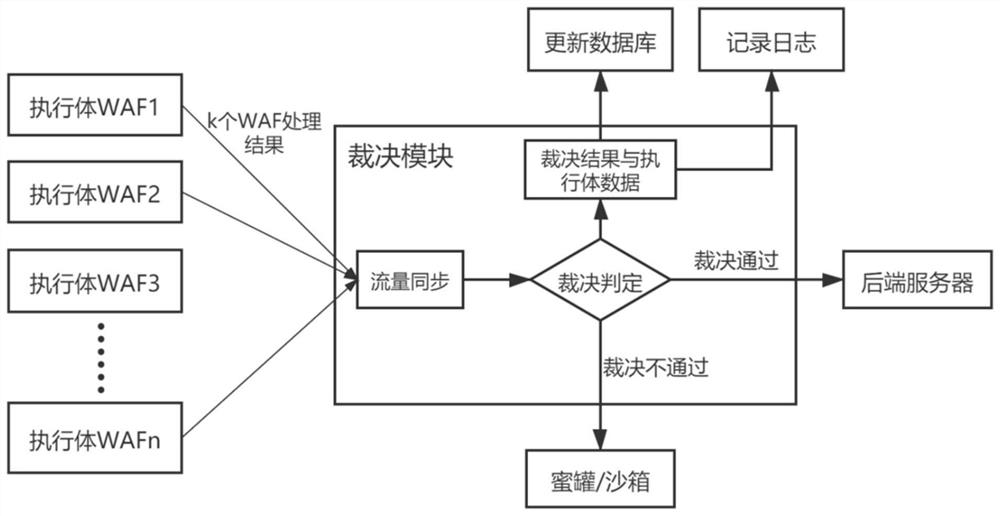
[0023] Mimic WAF can actively defend against malicious attacks and discover unknown attacks. The judgment module in Mimic WAF plays a very important role. This invention mainly designs traffic synchronization module, multi-mode judgment module, judgment result and data recording module to realize mimic The adjudication function in WAF enables the mimic WAF to identify unknown attacks through the adjudication function, and blocks unknown attacks through operations such as WAF executive offline self-cleaning, so that the mimic WAF has active defense capabilities.
[0024] The judgment method of the execution body in the mimic WAF of the present invention, first, the traffic synchronization module synchronizes the processing results of k heterogeneous WAFs, and then the multi-mode judgment module judges the processing results, records the judgment results and data in the log, and updates the database corresponding Finally, when the result of the ruling is passed, the traffic is se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com