Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3925 results about "Web application" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
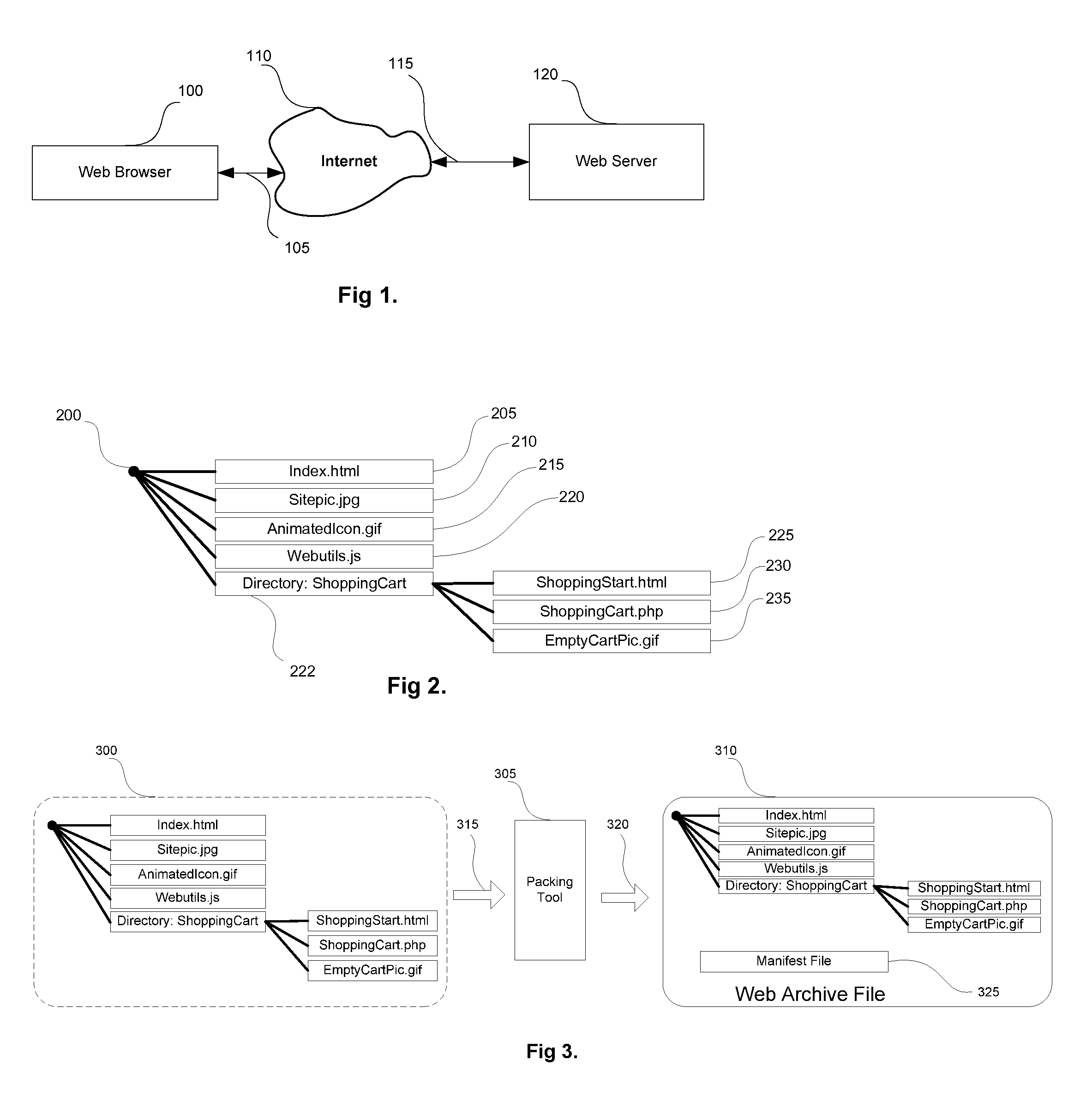
In computing, a web application or web app is a client–server computer program that the client (including the user interface and client-side logic) runs in a web browser. Common web applications include webmail, online retail sales, online banking, and online auction.
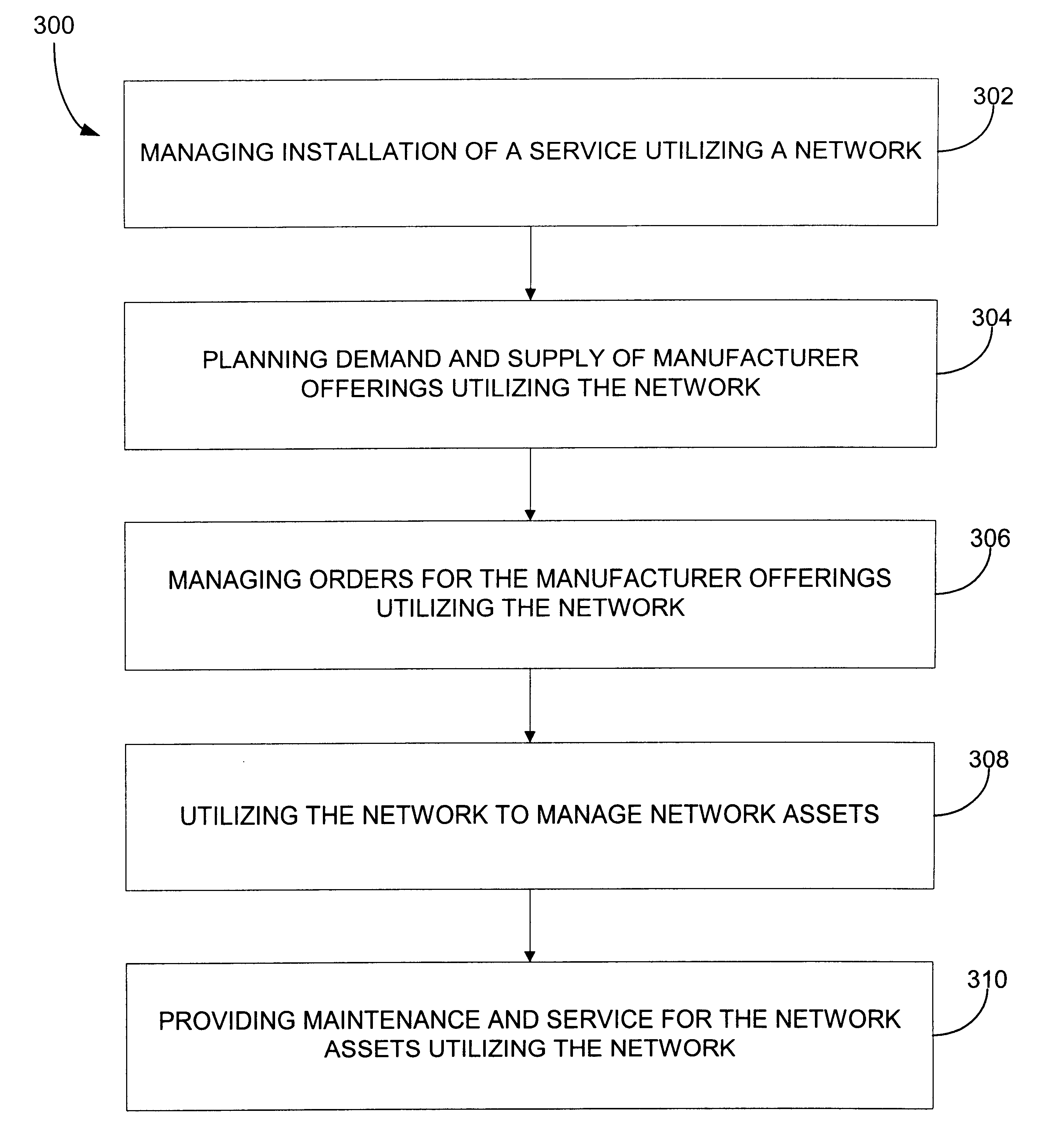
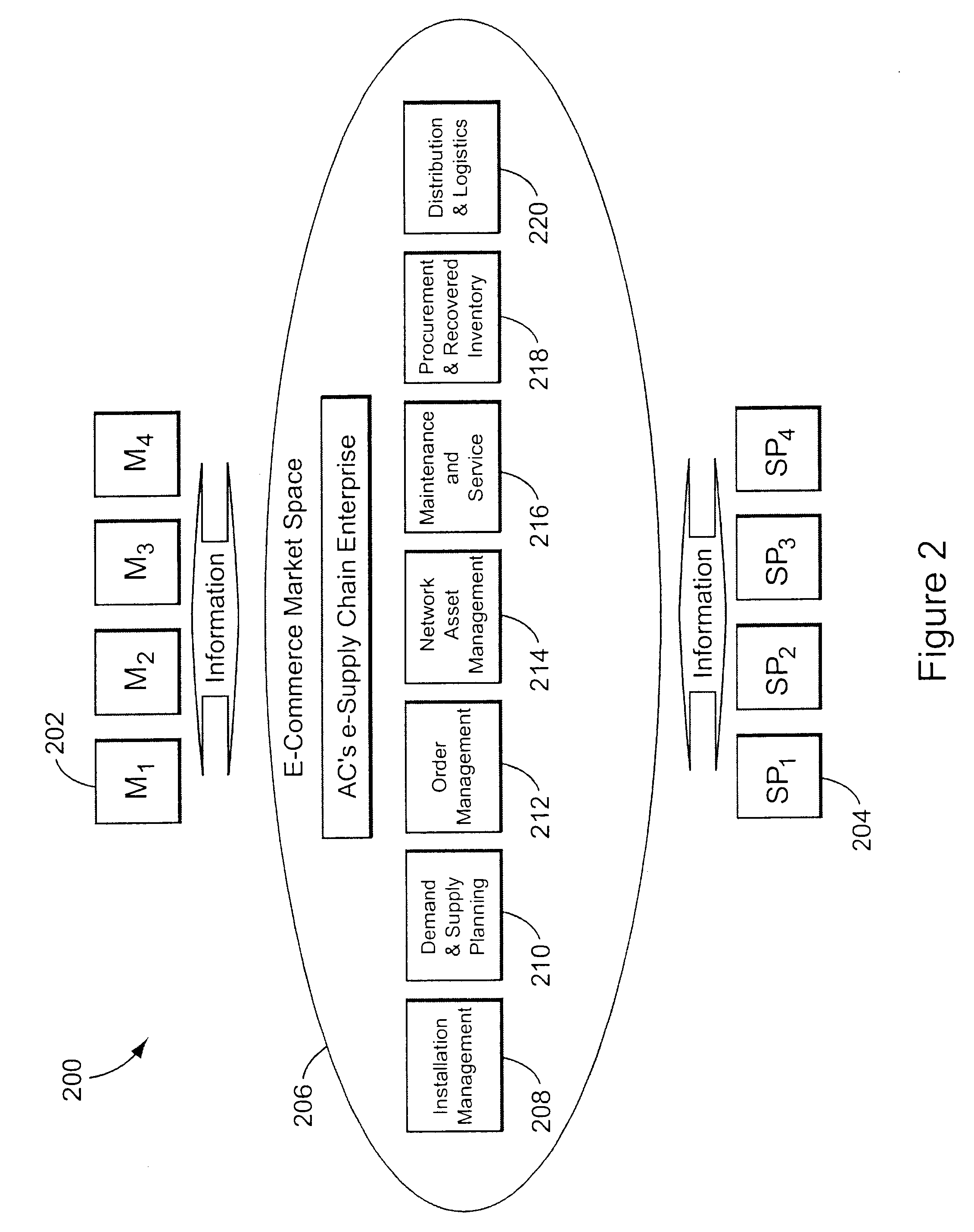
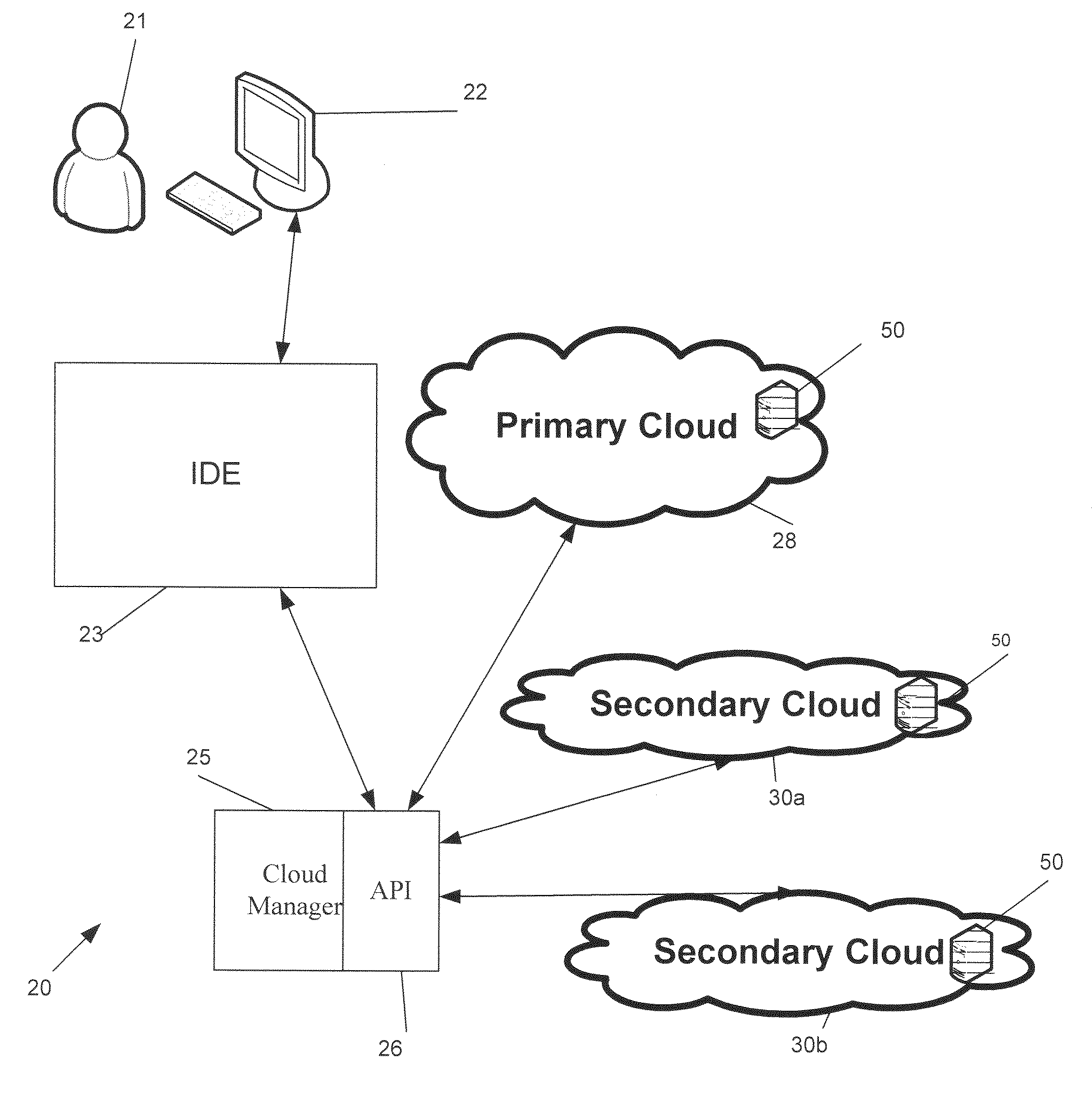
Providing collaborative installation management in a network-based supply chain environment
InactiveUS6606744B1Interconnection arrangementsSpecial service for subscribersWeb applicationService provision
A system, method and article of manufacture are provided for collaborative installation management in a network-based supply chain environment. According to an embodiment of the invention, telephone calls, data and other multimedia information are routed through a network system which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. The system includes integrated Internet Protocol (IP) telephony services allowing a user of a web application to communicate in an audio fashion in-band without having to pick up another telephone. Users can click a button and go to a call center through the network using IP telephony. The system invokes an IP telephony session simultaneously with the data session, and uses an active directory lookup whenever a user uses the system. Users include service providers and manufacturers utilizing the network-based supply chain environment.
Owner:ACCENTURE GLOBAL SERVICES LTD
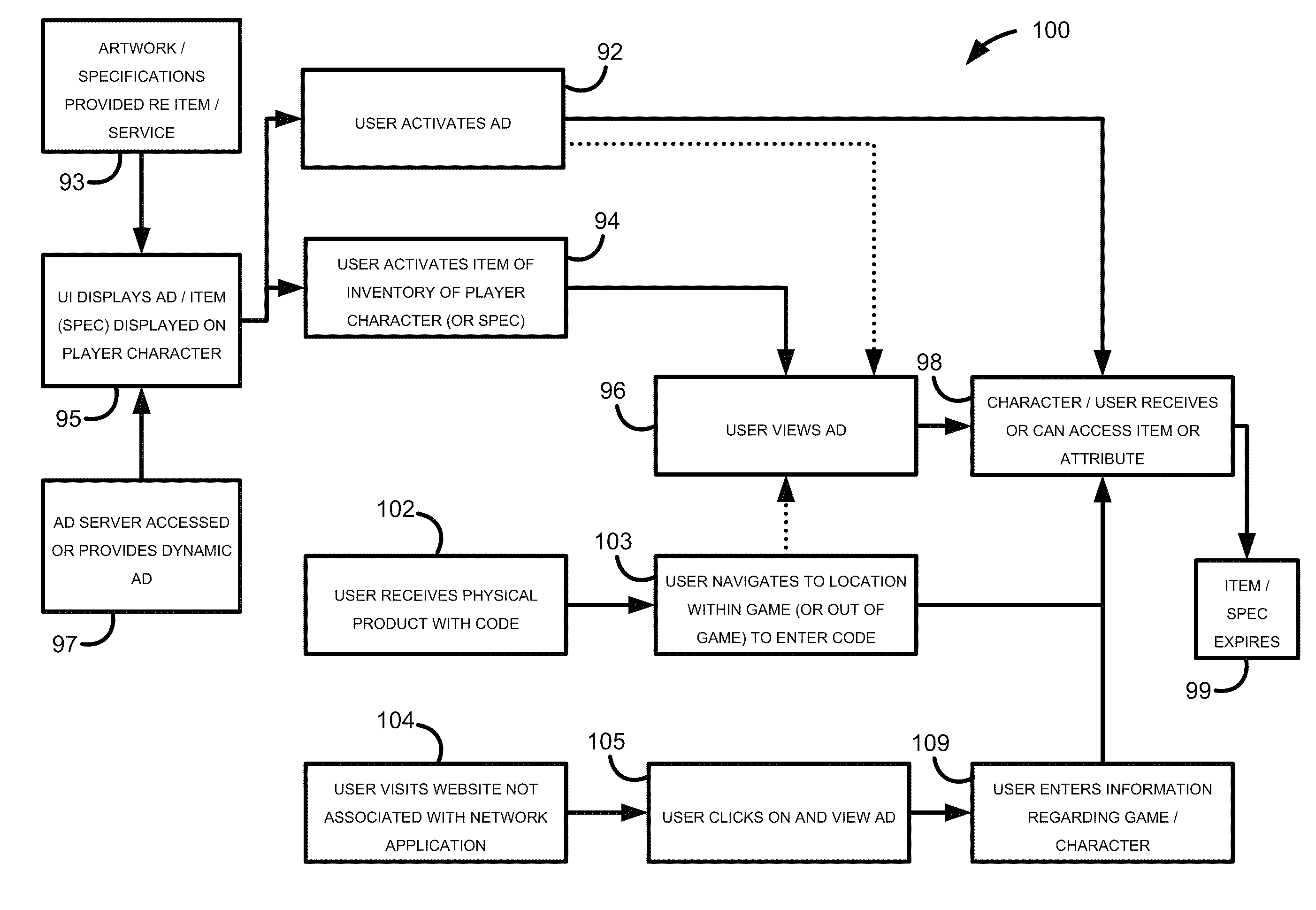
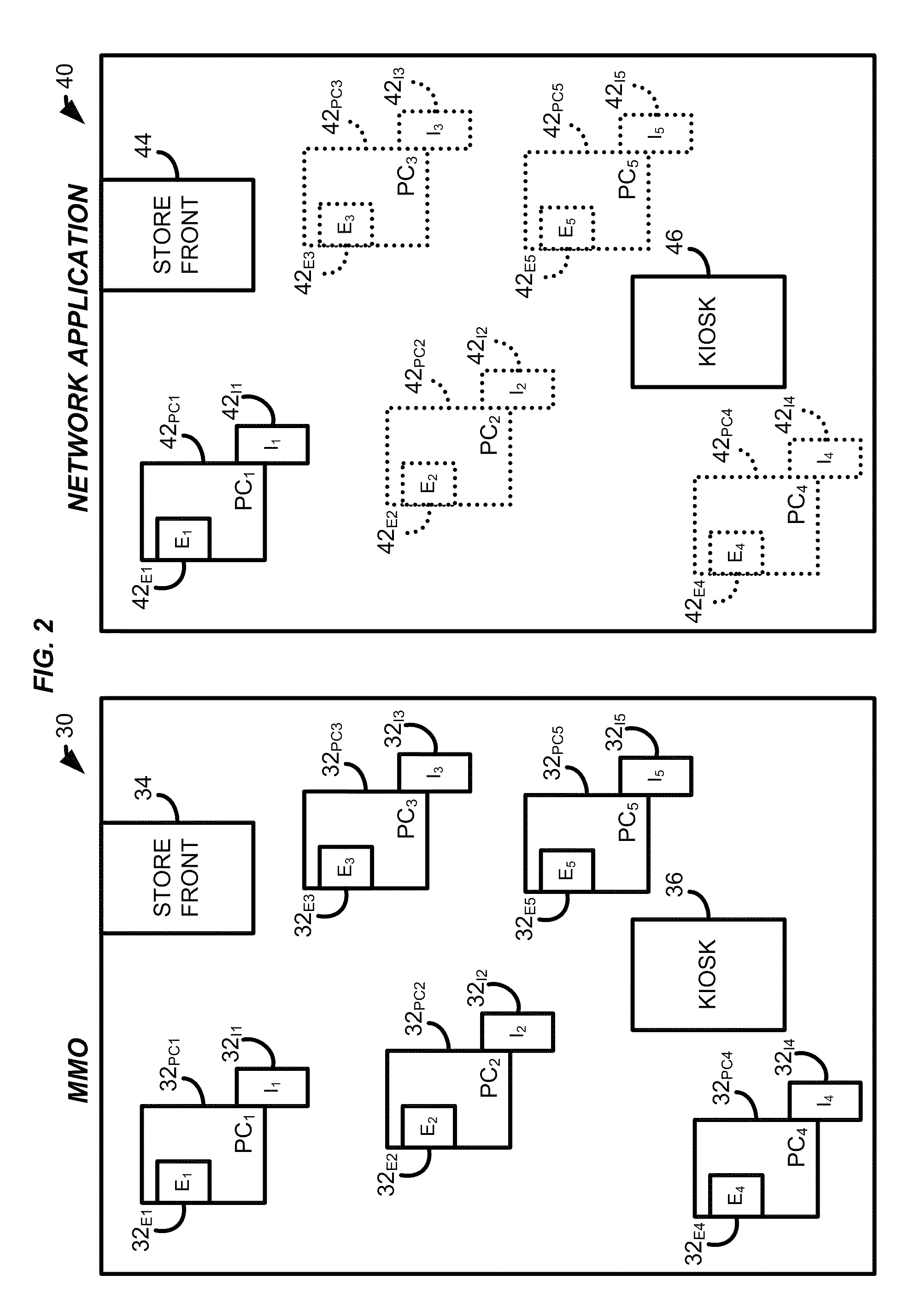
Online simulations and network applications
InactiveUS20100174593A1Enhance interestEfficient preparationDiscounts/incentivesAdvertisementsApplication softwareNetwork application
Systems and methods are provided that involve a player to a significant degree with an advertisement and its accompanying product or service. One setting of the system and method may be a network application that is adjunct to an online simulation such as an MMO game. The system and method may be implemented in either or both, or in video games that are embodied in just one of these. The system and method provide a convenient way to tie advertising to game content. By use of advertisements, the user (through the player character) can become aware of and can access in-game items, player character attribute modifications, and rewards. Such advertisements may be banner advertisements or any other type of advertising. By taking advantage of the offers presented in the advertisements, a user of the network application may obtain items for their own use or for that of a corresponding MMO character.
Owner:DAYBREAK GAME COMPANY
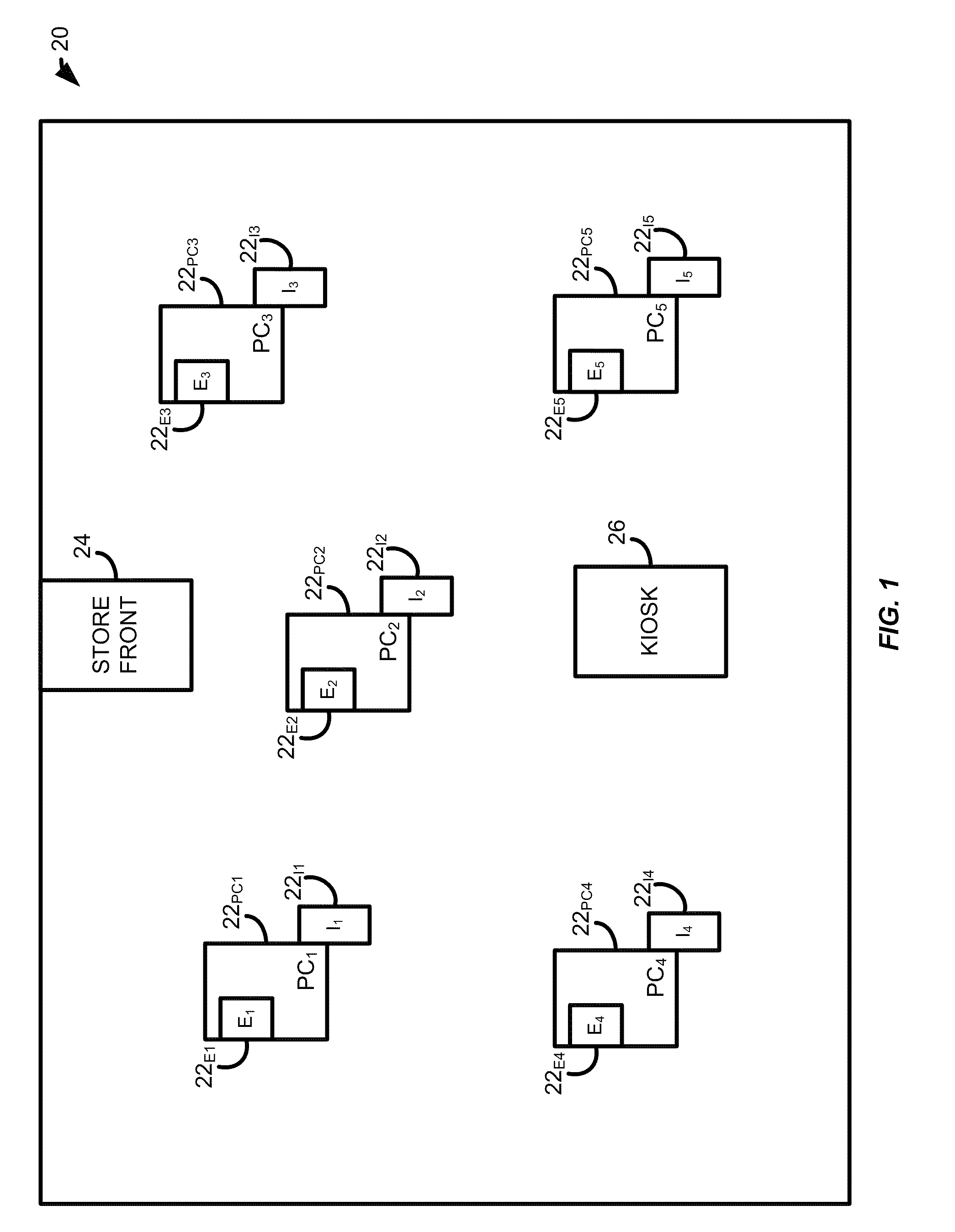
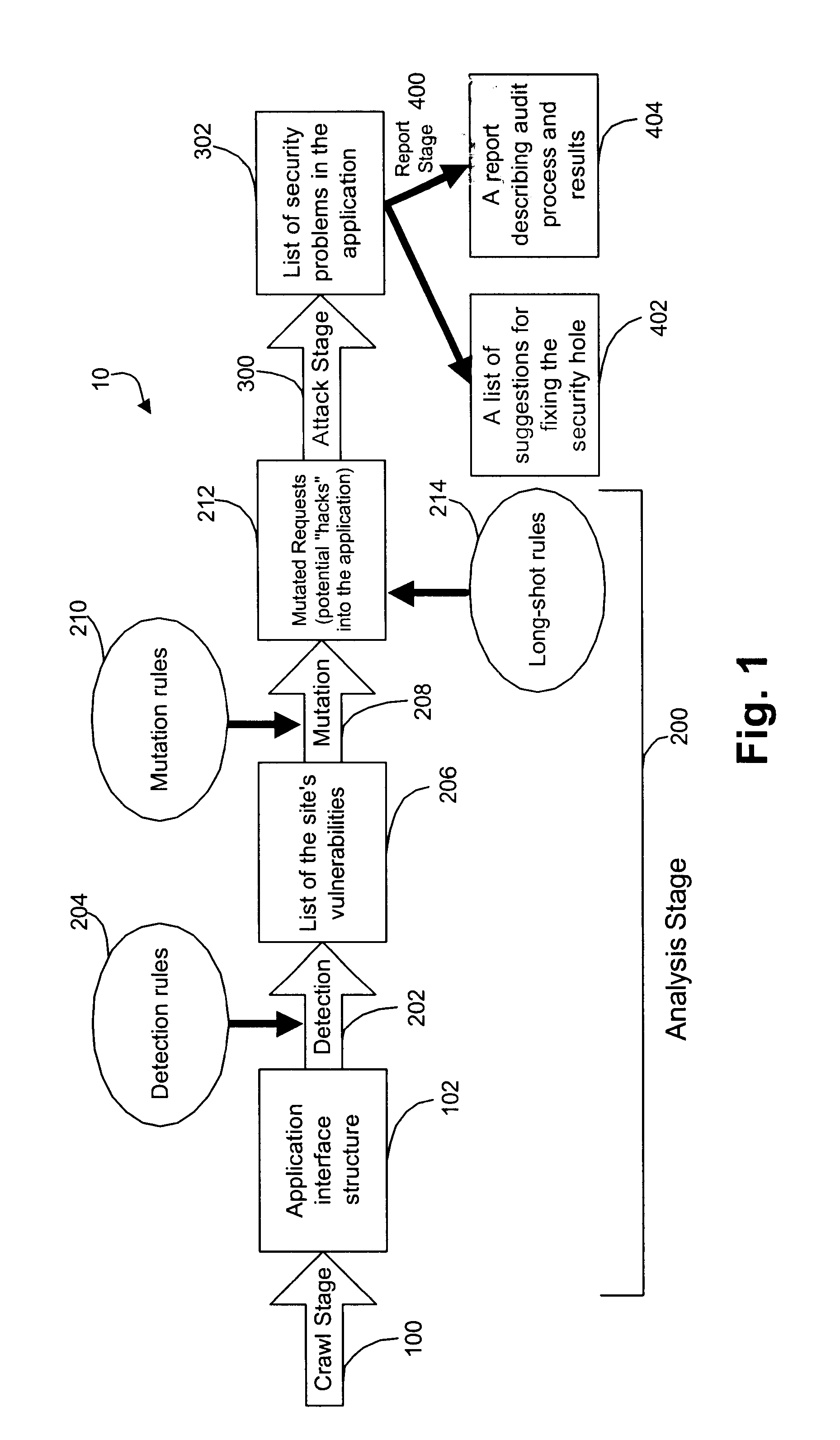
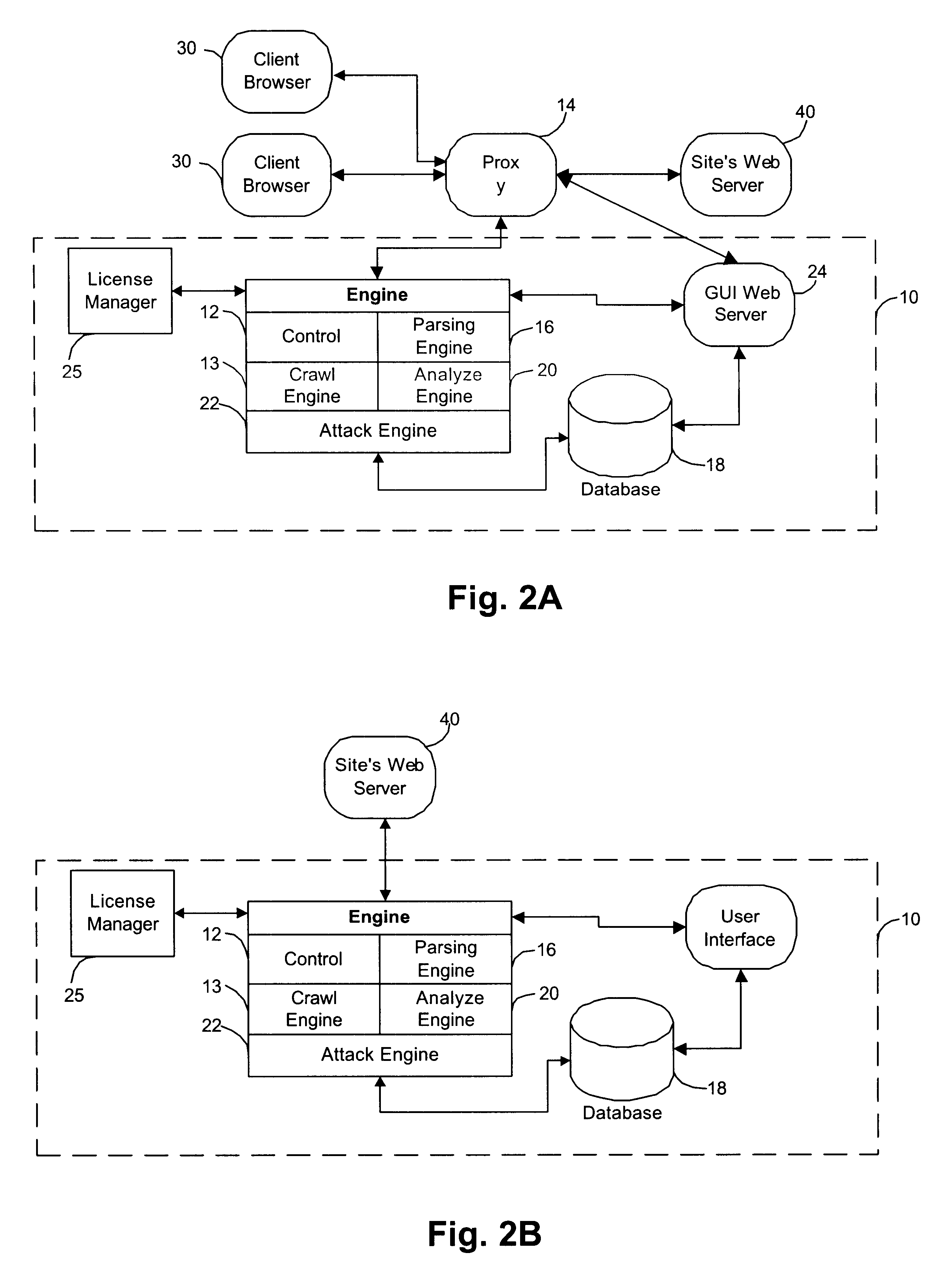
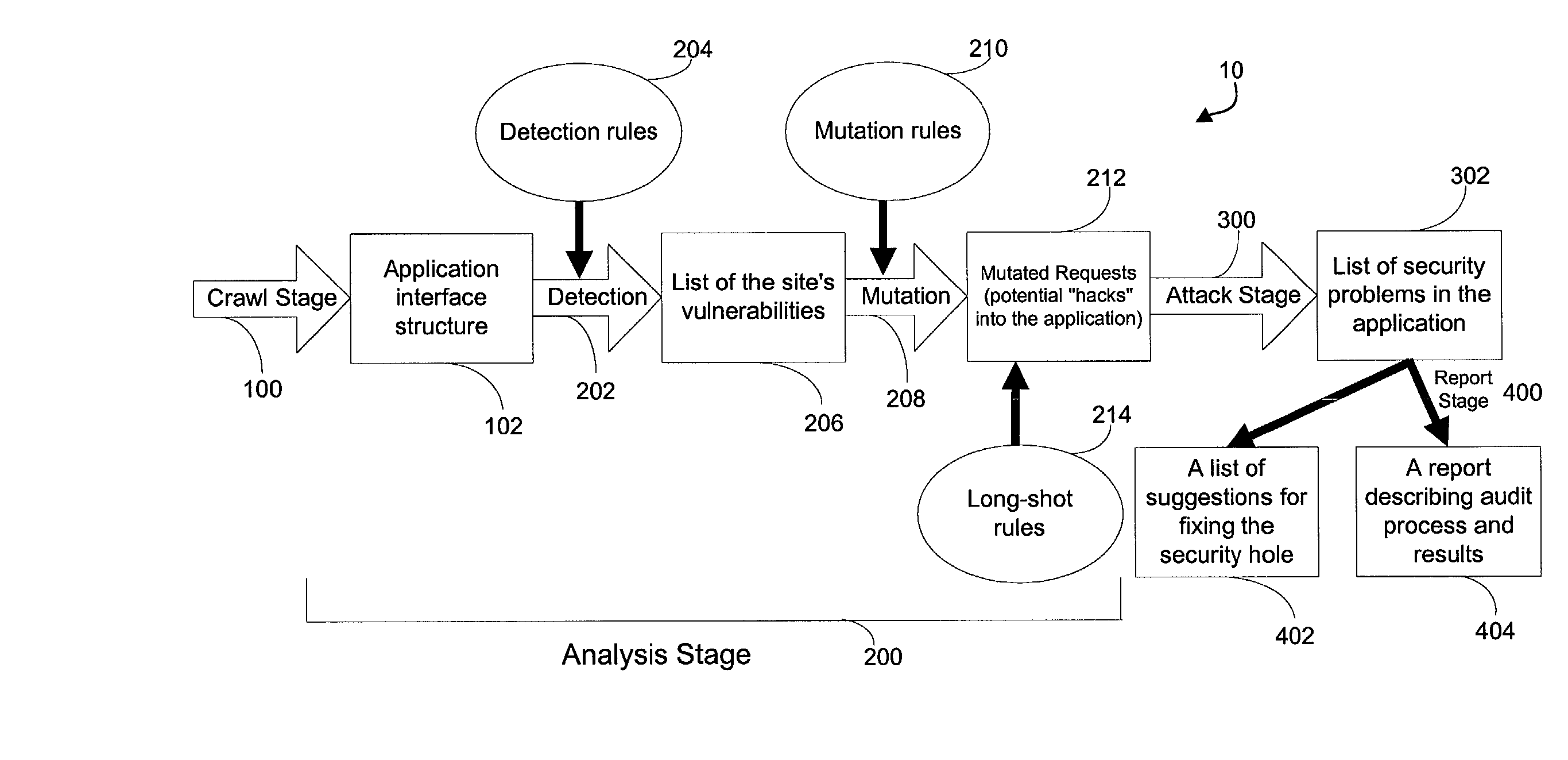
System for determining web application vulnerabilities
InactiveUS6584569B2Memory loss protectionUnauthorized memory use protectionWeb applicationApplication procedure
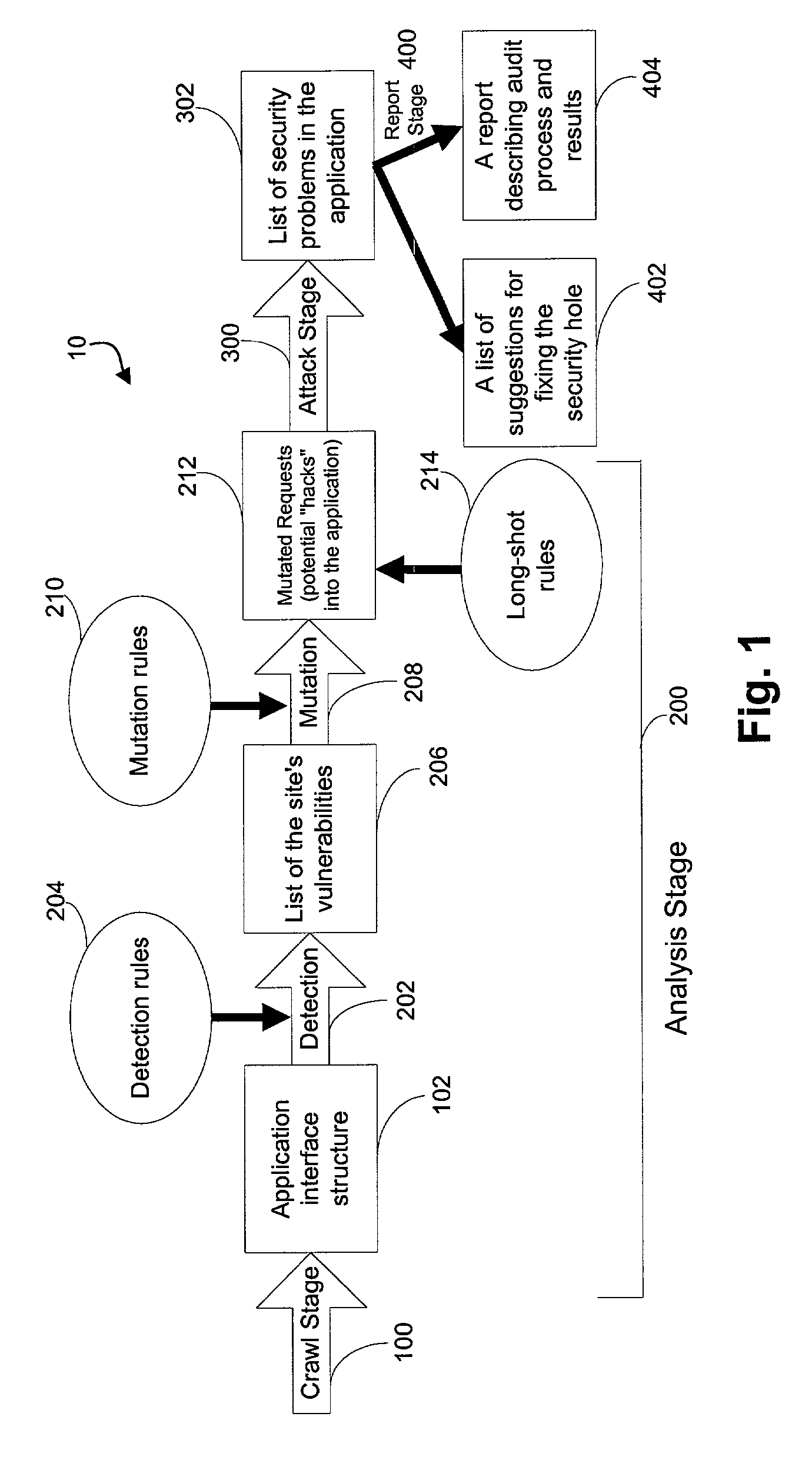
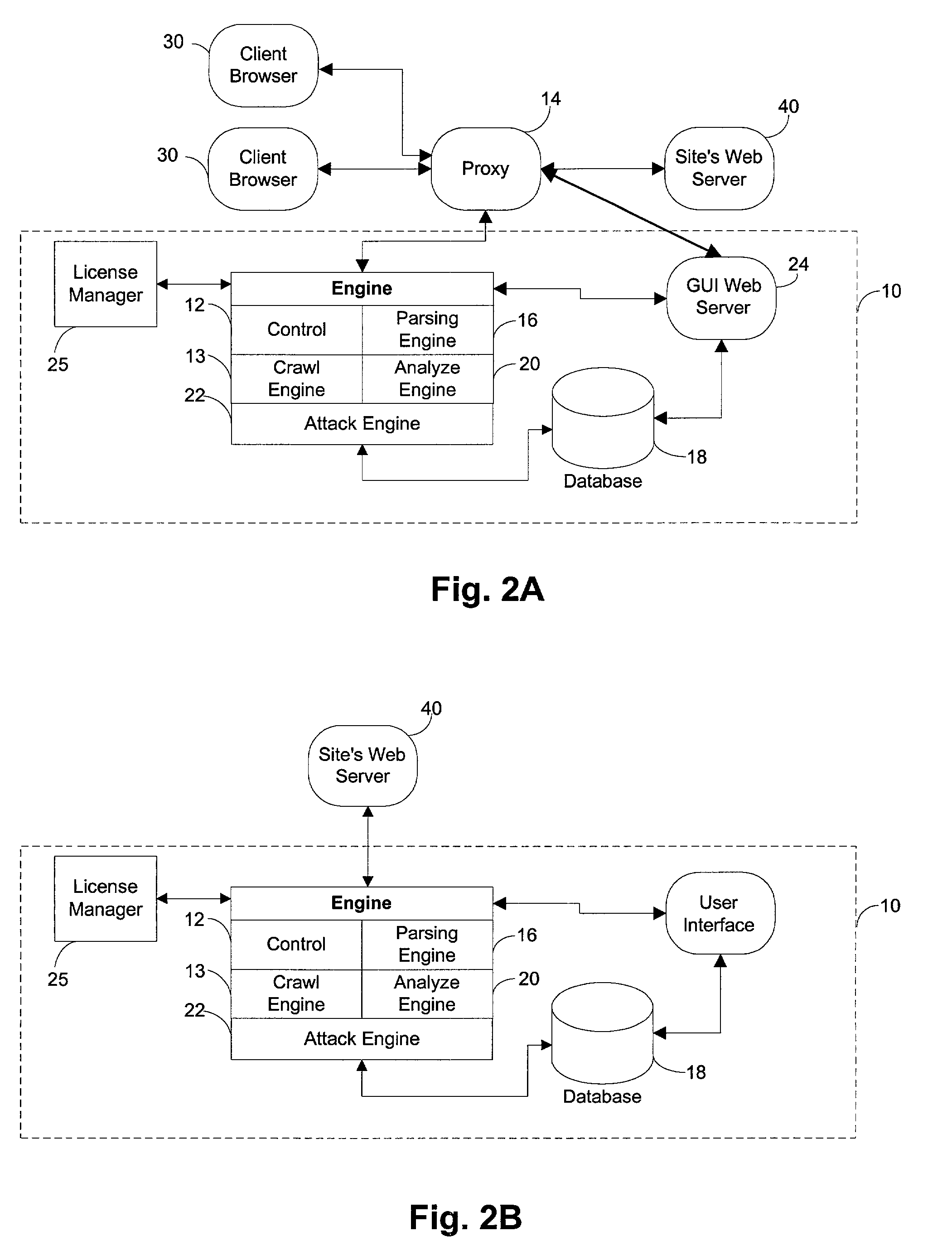
A method for detecting security vulnerabilities in a web application includes analyzing the client requests and server responses resulting therefrom in order to discover pre-defined elements of the application's interface with external clients and the attributes of these elements. The client requests are then mutated based on a pre-defined set of mutation rules to thereby generate exploits unique to the application. The web application is attacked using the exploits and the results of the attack are evaluated for anomalous application activity.
Owner:FINJAN BLUE INC
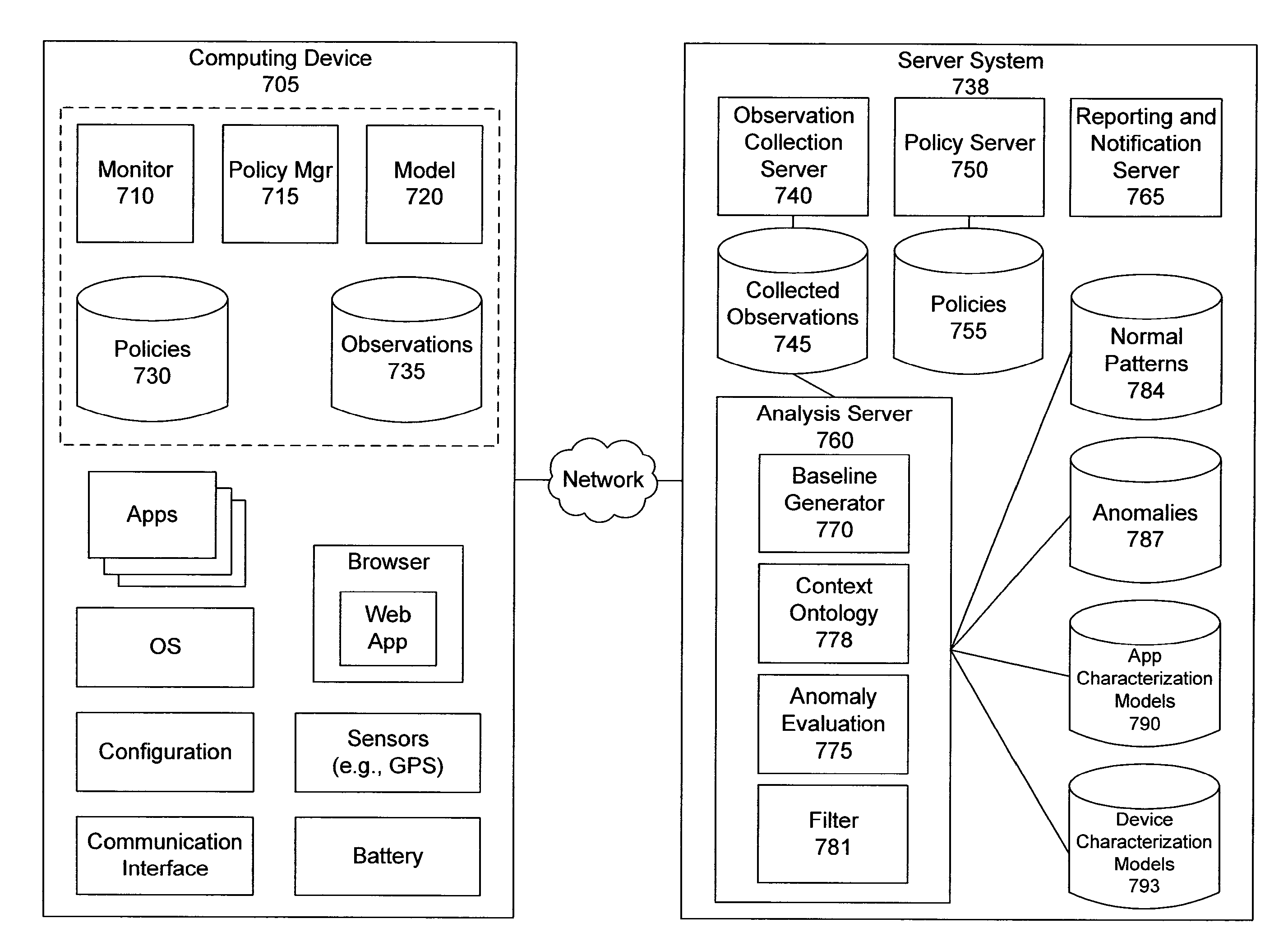
Distributed monitoring, evaluation, and response for multiple devices
ActiveUS20150163121A1Easy to monitorReduce monitoringDigital data processing detailsNon-redundant fault processingWeb applicationMultiple device
Owner:LOOKOUT MOBILE SECURITY
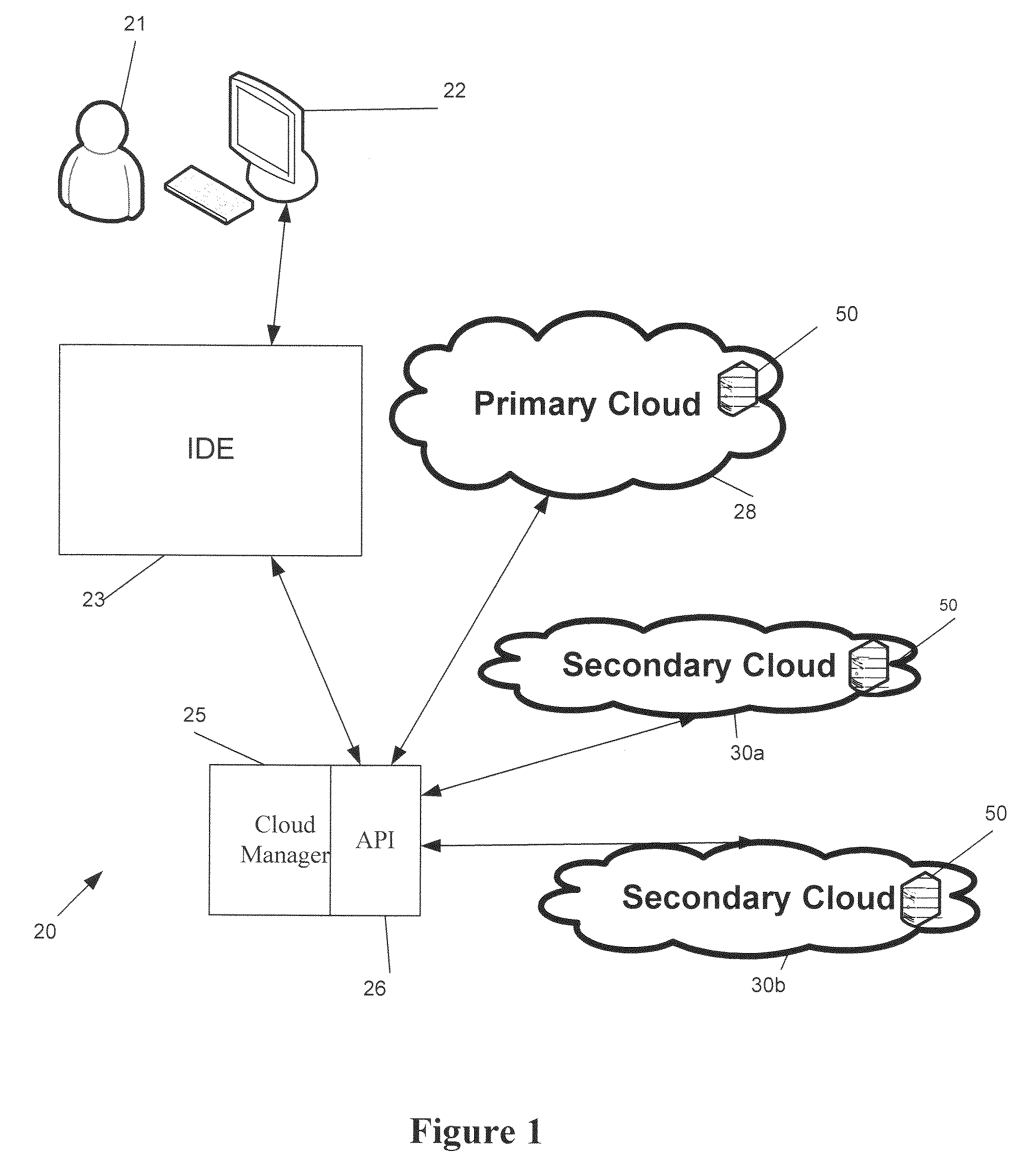
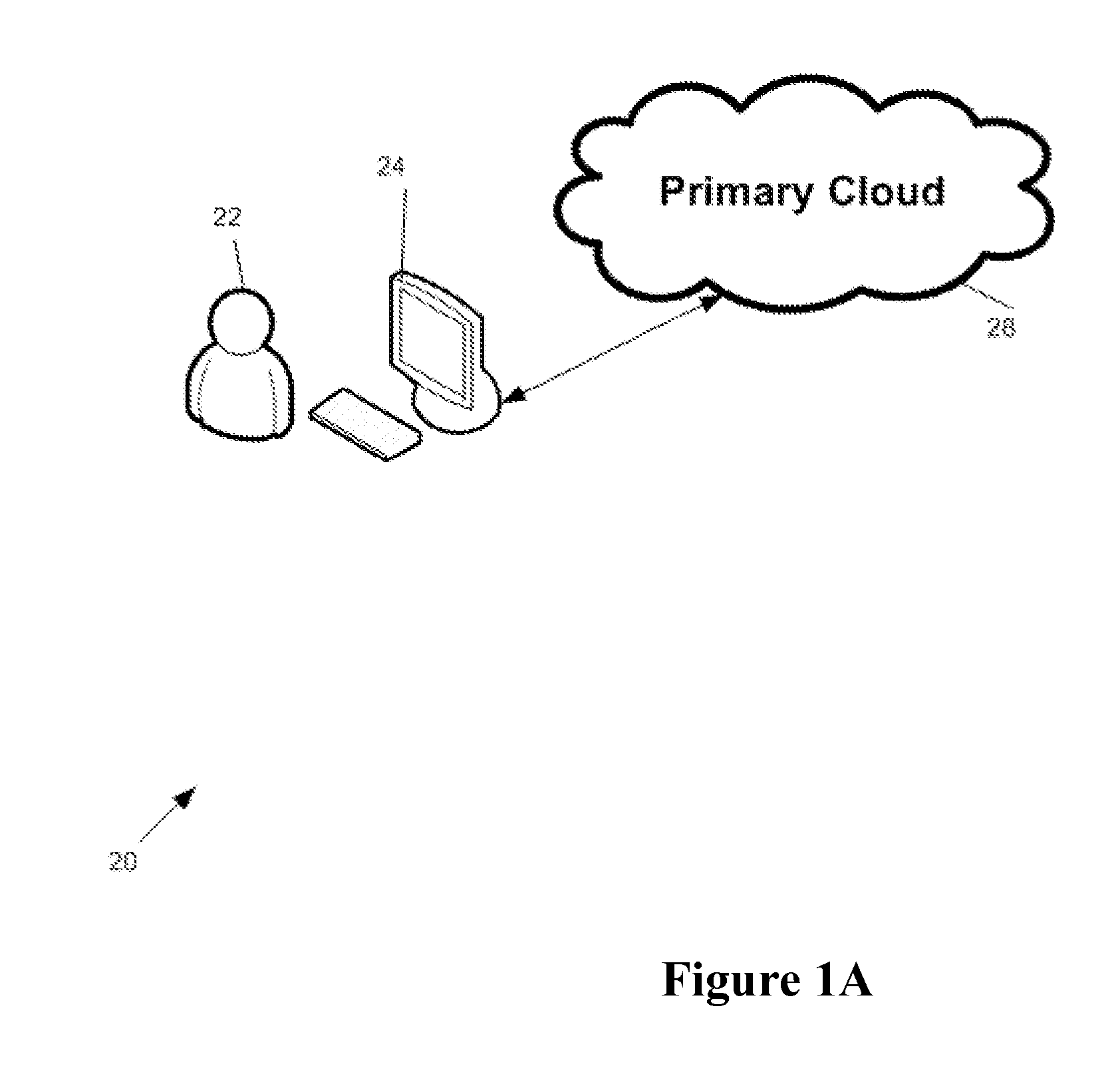
System and method for developing, deploying, managing and monitoring a web application in a single environment
InactiveUS7596620B1Guaranteed to workDigital computer detailsRequirement analysisWeb applicationThe Internet
A system and method for developing, deploying, managing and monitoring a web application in a single environment is disclosed herein. The single environment is preferably an integrated development environment (“IDE”). The system and method preferably allows for deployment to a cloud provider, and preferably allows for use of Web resources from multiple cloud providers. One preferred IDE is the APTANA® STUDIO IDE. An operator can use a user interface to access the integrated development environment and the cloud manager over the network, specifically the Internet.
Owner:APPCELERATOR
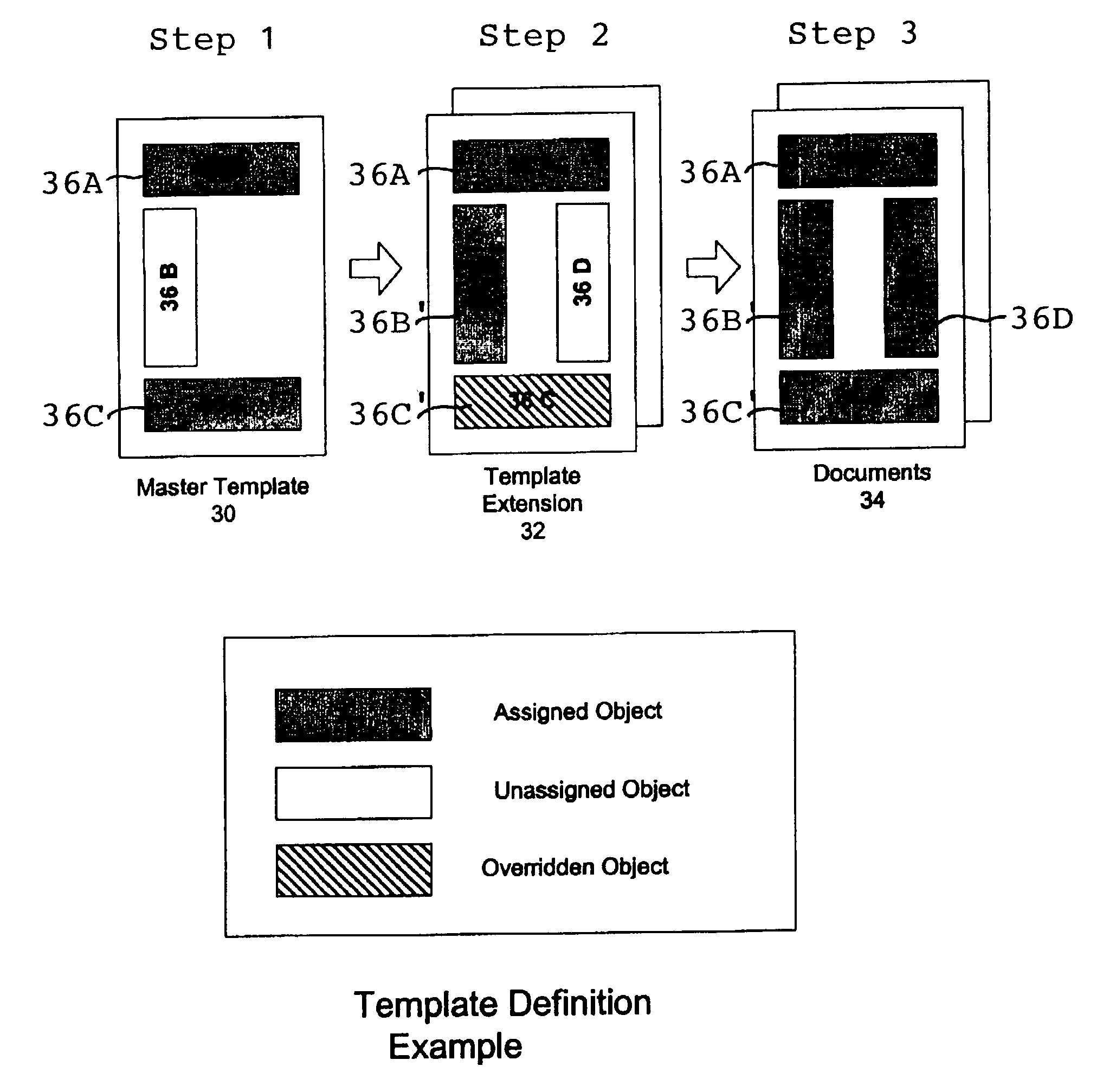
Web site application development method using object model for managing web-based content
InactiveUS20030014442A1Simplify the management processEasy to customizeDigital computer detailsSoftware designWeb siteWeb application
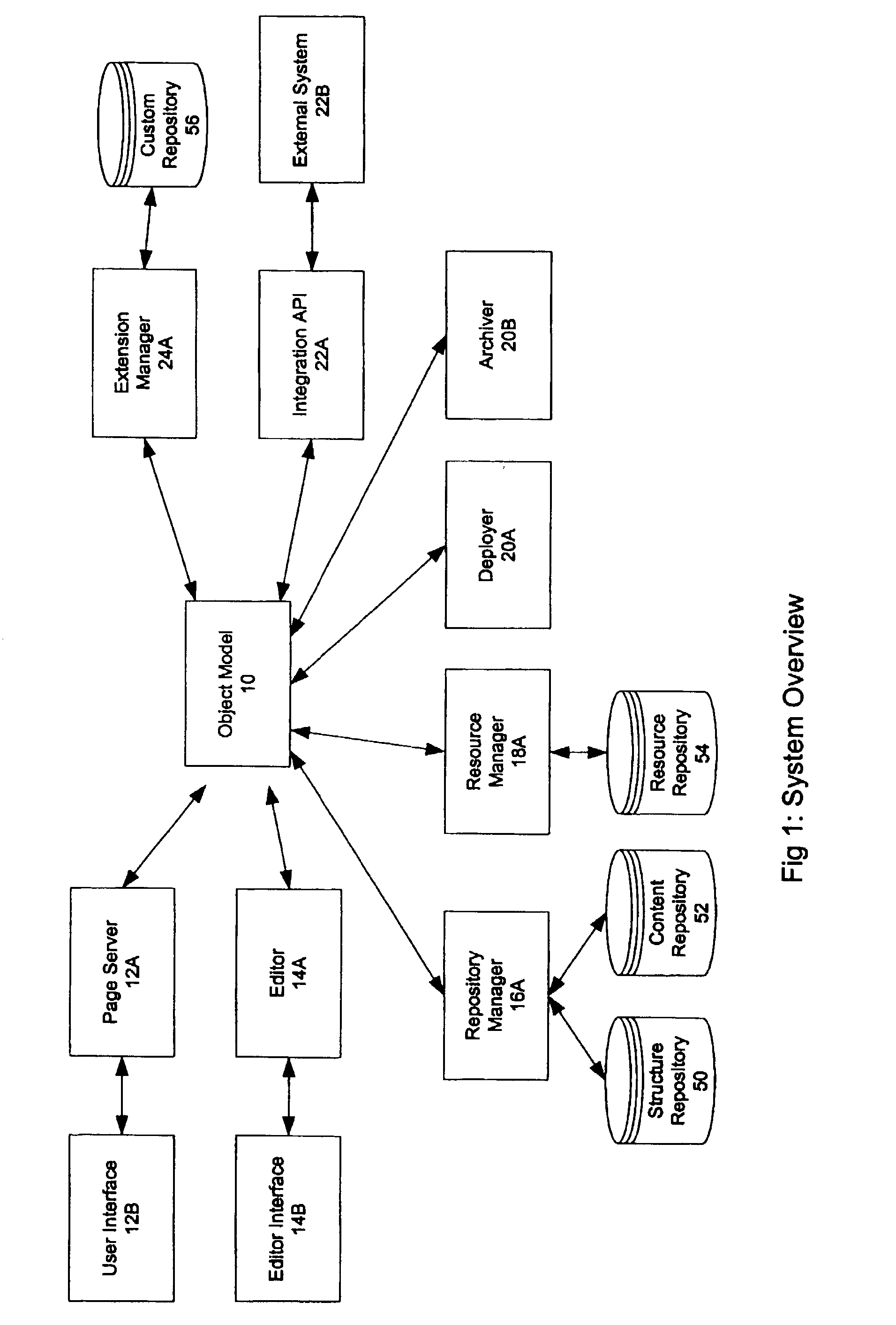
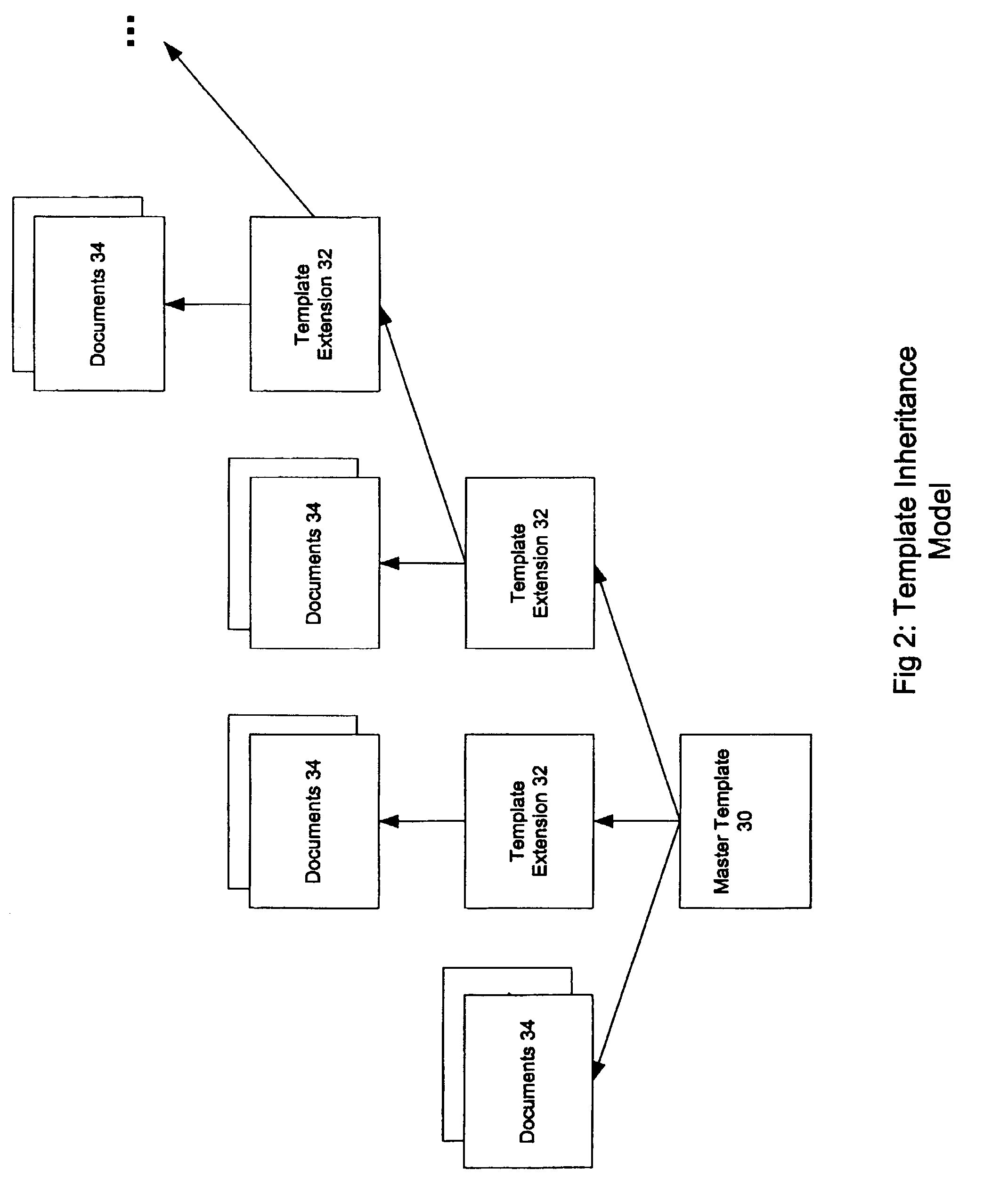
A system and method for developing an application for serving a document to a client in a client / server network employs an Object Model which defines templates, extensions, documents, and content objects in a template inheritance model. The Object Model serves a document, such as a webpage of a Web site application, by combining the structure and content inherited from a template and extensions in the template hierarchy. The templates specify the structure of the document and include tags as placeholders for content objects to be incorporated in the document. Extensions descend from either a template or another extension, and can expand upon the number of tags specified in a parent, add additional formatting to the layout, and / or refine the definition of tags that already exist in the inheritance hierarchy. When a document is to be viewed or served, a page server retrieves the template hierarchy and incorporates all tagged content in the structure inherited from the template and its extensions. The Object Model provides a framework for developing Web sites and other applications that is more robust and simpler to manage than the traditional file directory model of conventional Web applications. This framework makes it possible to create complex and highly structured Web applications that are efficient to develop and easier to maintain, and without ever having to write source code.
Owner:DH LABS
System and method of securing web applications across an enterprise
ActiveUS20080034425A1Avoid attackMemory loss protectionError detection/correctionTraffic capacityWeb application
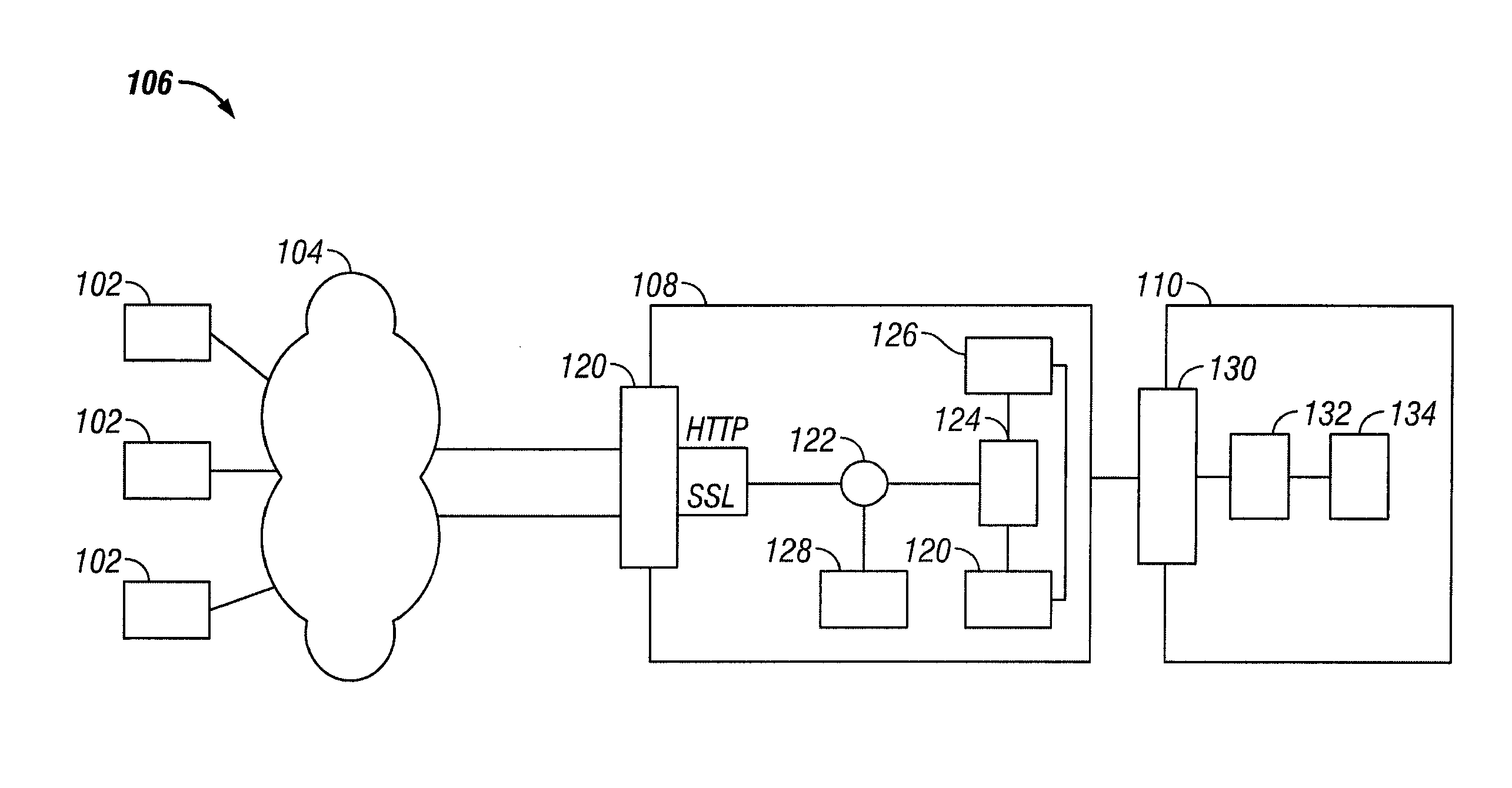
A system and method for protection of Web based applications are described. The techniques described provide an enterprise wide approach to preventing attacks of Web based applications. Individual computer networks within the enterprise monitor network traffic to identify anomalous traffic. The anomalous traffic can be identified by comparing the traffic to a profile of acceptable user traffic when interacting with the application. The anomalous traffic, or security events, identified at the individual computer networks are communicated to a central security manager. The central security manager correlates the security events at the individual computer networks to determine if there is an enterprise wide security threat. The central security manager can then communicate instructions to the individual computer networks so as to provide an enterprise wide solution to the threat
Owner:TRUSTWAVE HOLDINGS
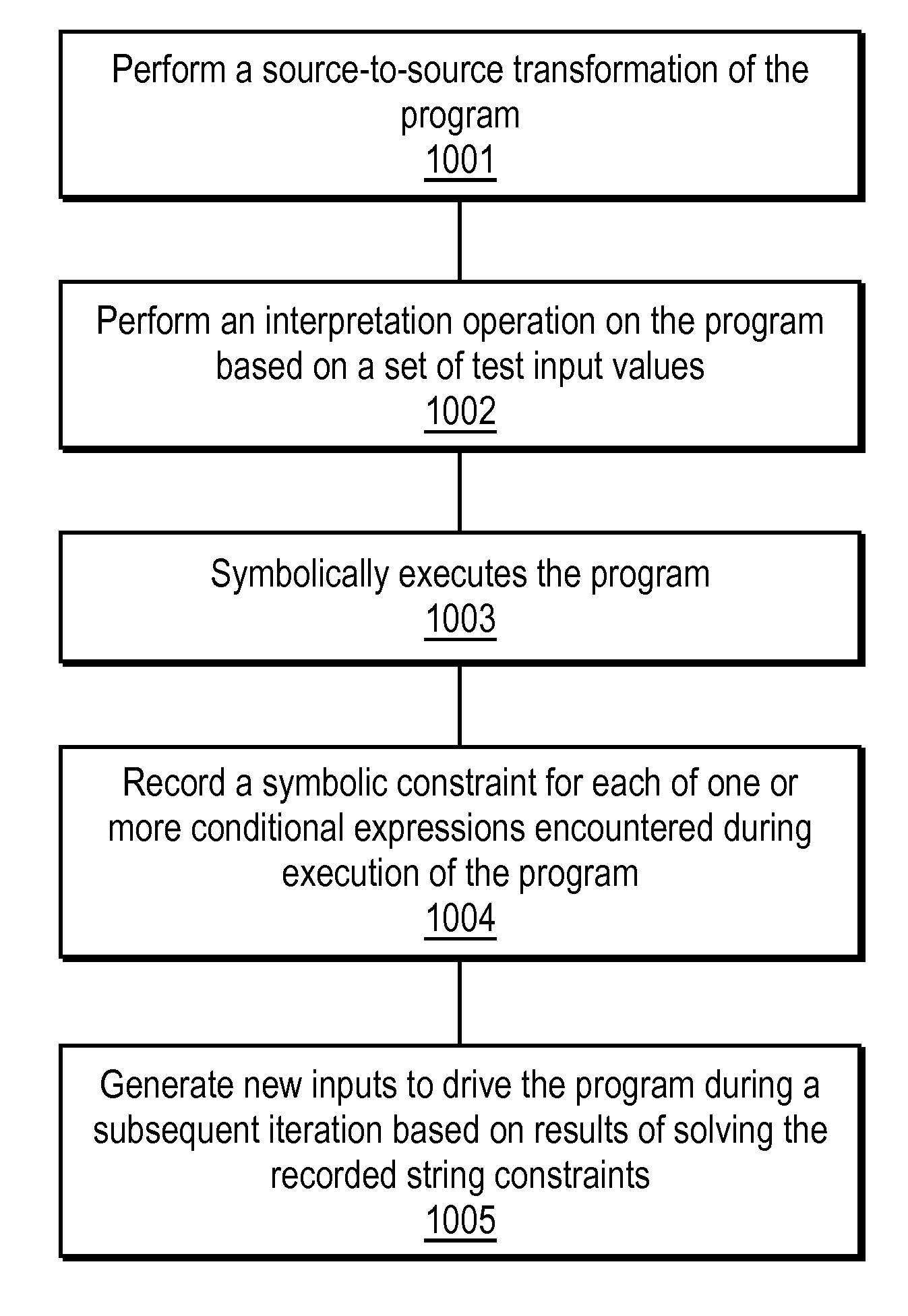
Automated test input generation for web applications
ActiveUS20090125976A1Error detection/correctionSoftware engineeringSource transformationString operations
A method and apparatus is disclosed herein for automated test input generation for web applications. In one embodiment, the method comprises performing a source-to-source transformation of the program; performing interpretation on the program based on a set of test input values; symbolically executing the program; recording a symbolic constraint for each of one or more conditional expressions encountered during execution of the program, including analyzing a string operation in the program to identify one or more possible execution paths, and generating symbolic inputs representing values of variables in each of the conditional expressions as a numeric expression and a string constraint including generating constraints on string values by modeling string operations using finite state transducers (FSTs) and supplying values from the program's execution in place of intractable sub-expressions; and generating new inputs to drive the program during a subsequent iteration based on results of solving the recorded string constraints.
Owner:NTT DOCOMO INC
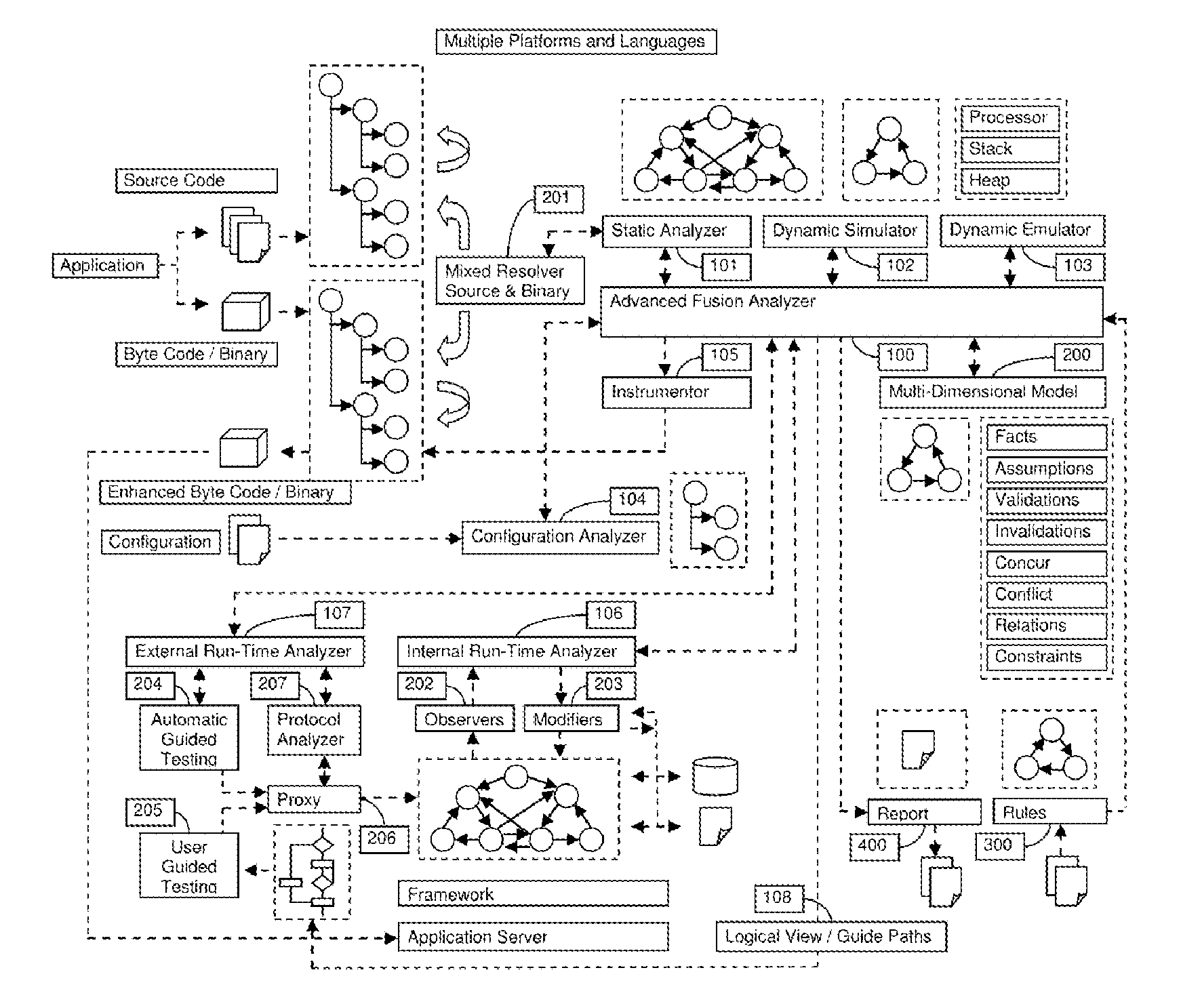
A System for analyzing applications in order to find security and quality issues
InactiveUS20150309813A1Accurate analysisError detection/correctionComputer security arrangementsMachine controlWeb application
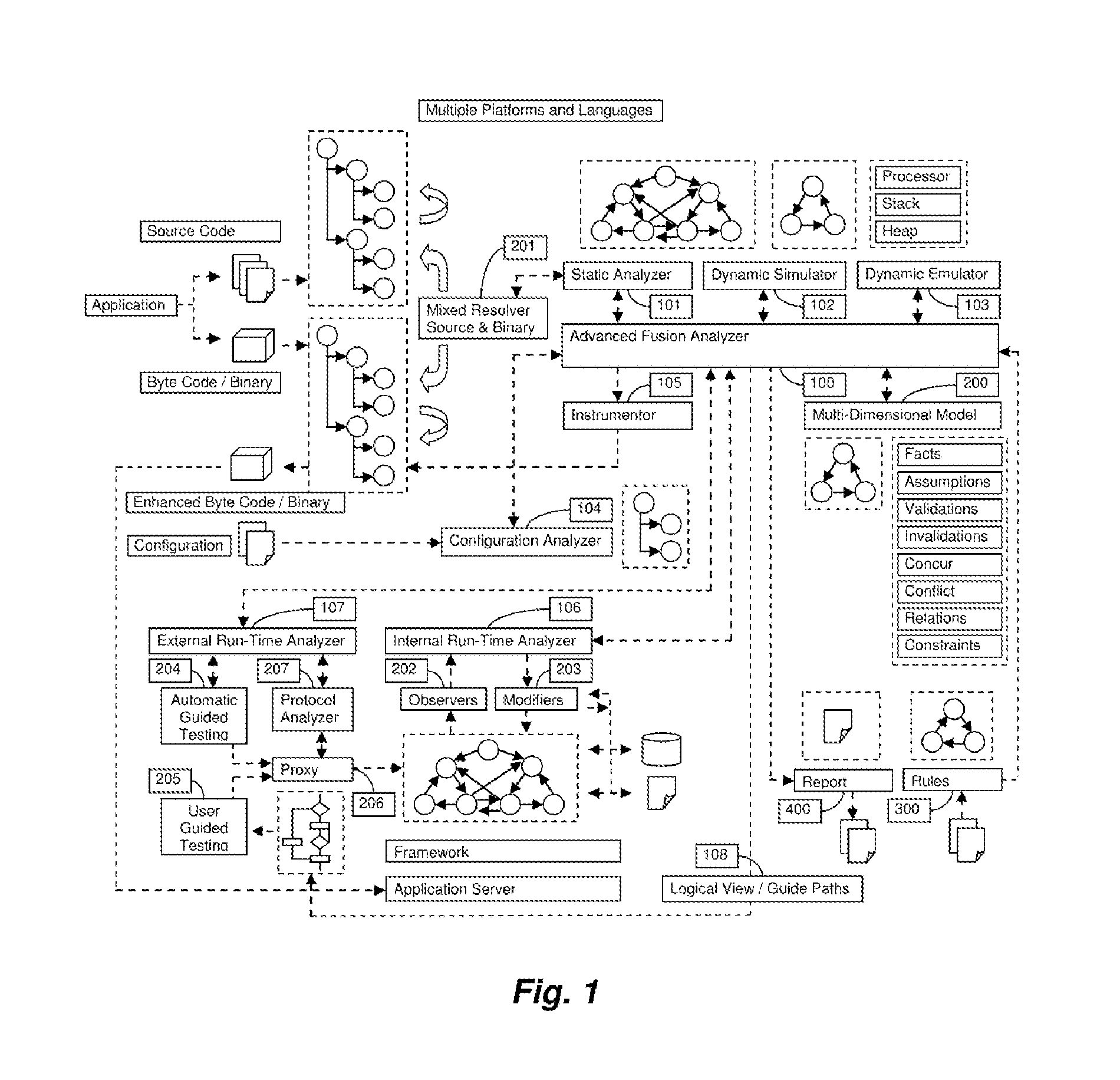
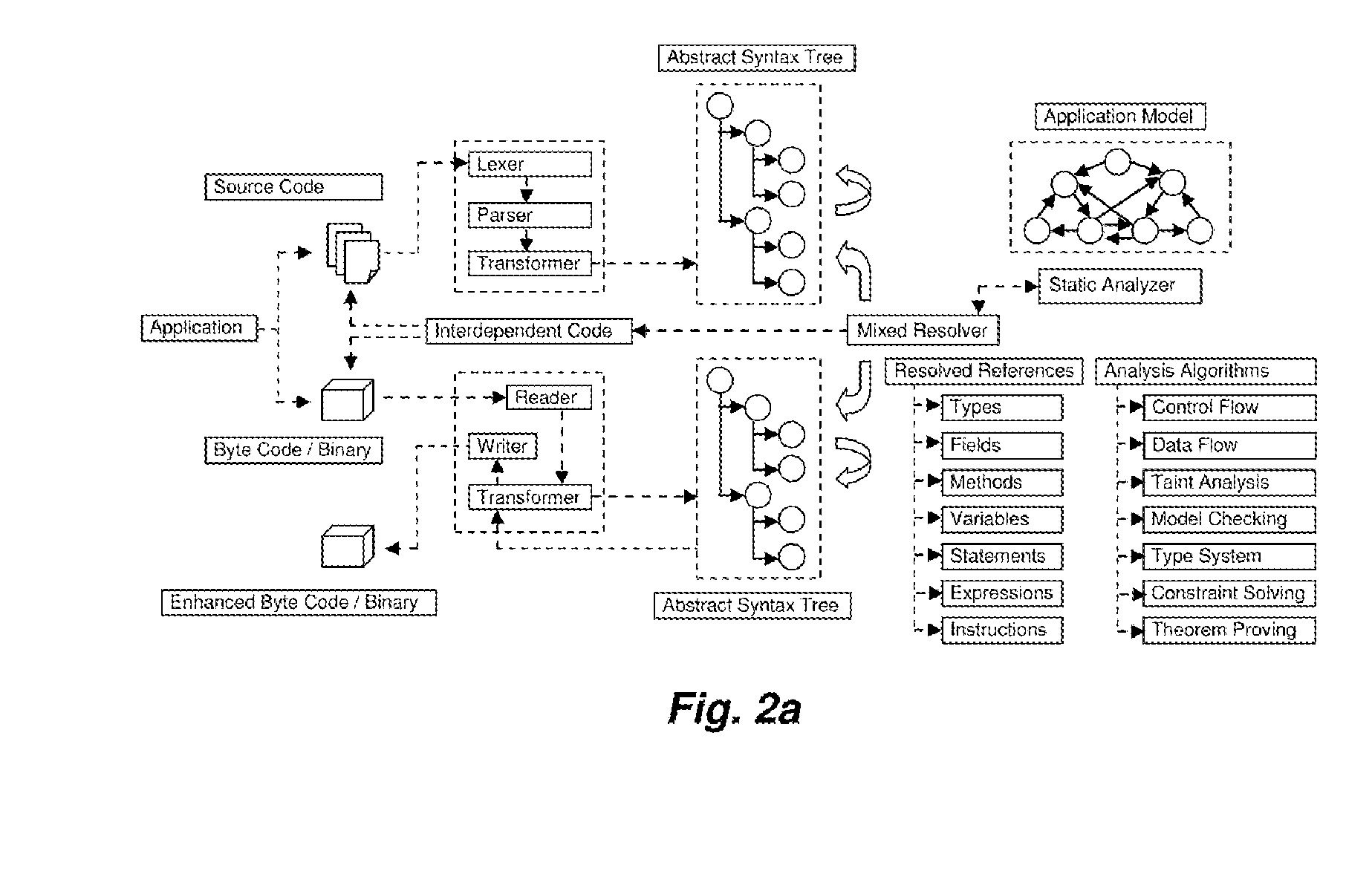
The present invention relates to field of application and more specifically to analysis of applications for determining security and quality issues. The present invention describes an application analysis system providing a platform for analyzing applications which is useful in finding security and quality issues in an application. In particular, the present invention is composed of an advanced fusion analyzer which gains an understanding of the application behavior by using a multi-way coordination and orchestration across components used in the present invention to build an continuously refine a model representing knowledge and behavior of the application as a large network of objects across different dimensions and using reasoning and learning logic on this model along with information and events received from the components to both refine and model further as well as drive the components further by sending information and events to them and again using the information and events received as a result to further trigger the entire process until the system stabilizes. The present invention is useful in analysis of internet / intranet based web applications, desktop applications, mobile applications and also embedded systems as well as for hardware, equipment and machines controlled by software.
Owner:IAPPSECURE SOLUTIONS PVT
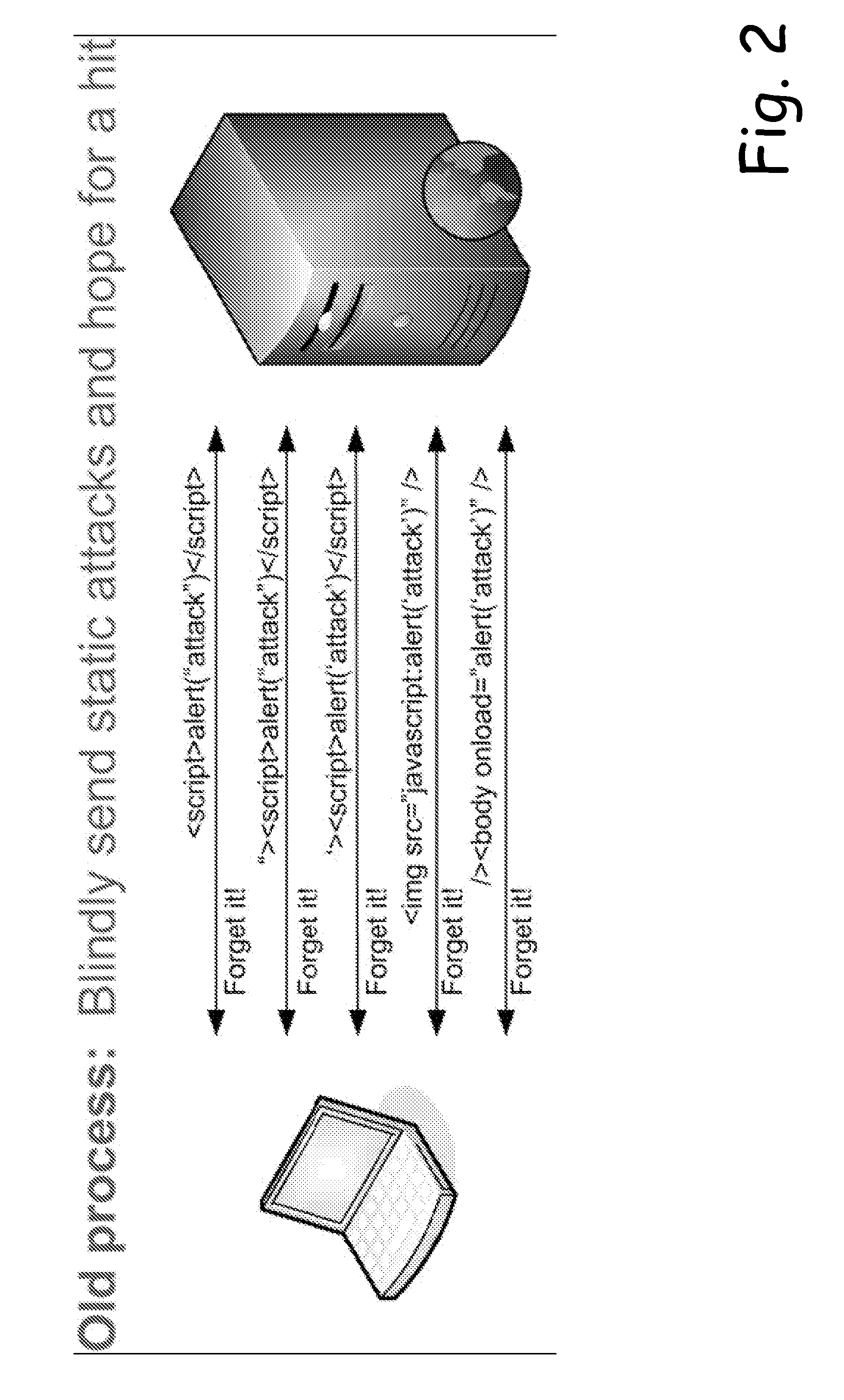
Web application assessment based on intelligent generation of attack strings
ActiveUS20080120722A1Easy to startImprove efficiencyMemory loss protectionError detection/correctionWeb siteWeb application
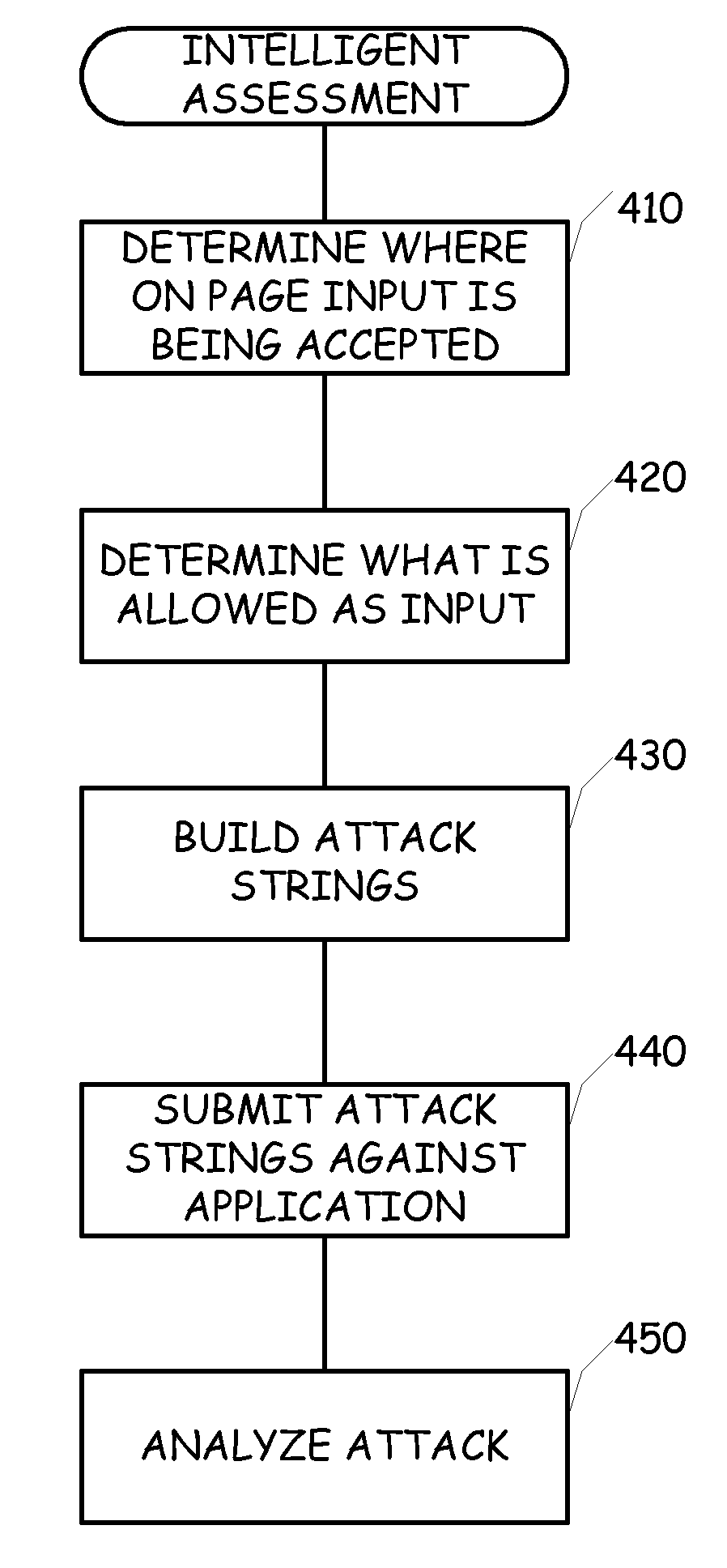
A web application is more efficiently analyzed by intelligently generating attack sequences to be used in the assessment. Rather than simply sending a canned list of static strings at a web application, the operation of the web application is analyzed to determine the filtering and acceptance characteristics of the web site. As this information is ascertained, a vocabulary of allowed symbols is created. This vocabulary is used in the building of attack strings and as such, the number of attack strings fired at the web application is greatly reduced, as well as the number of false positives.
Owner:MICRO FOCUS LLC
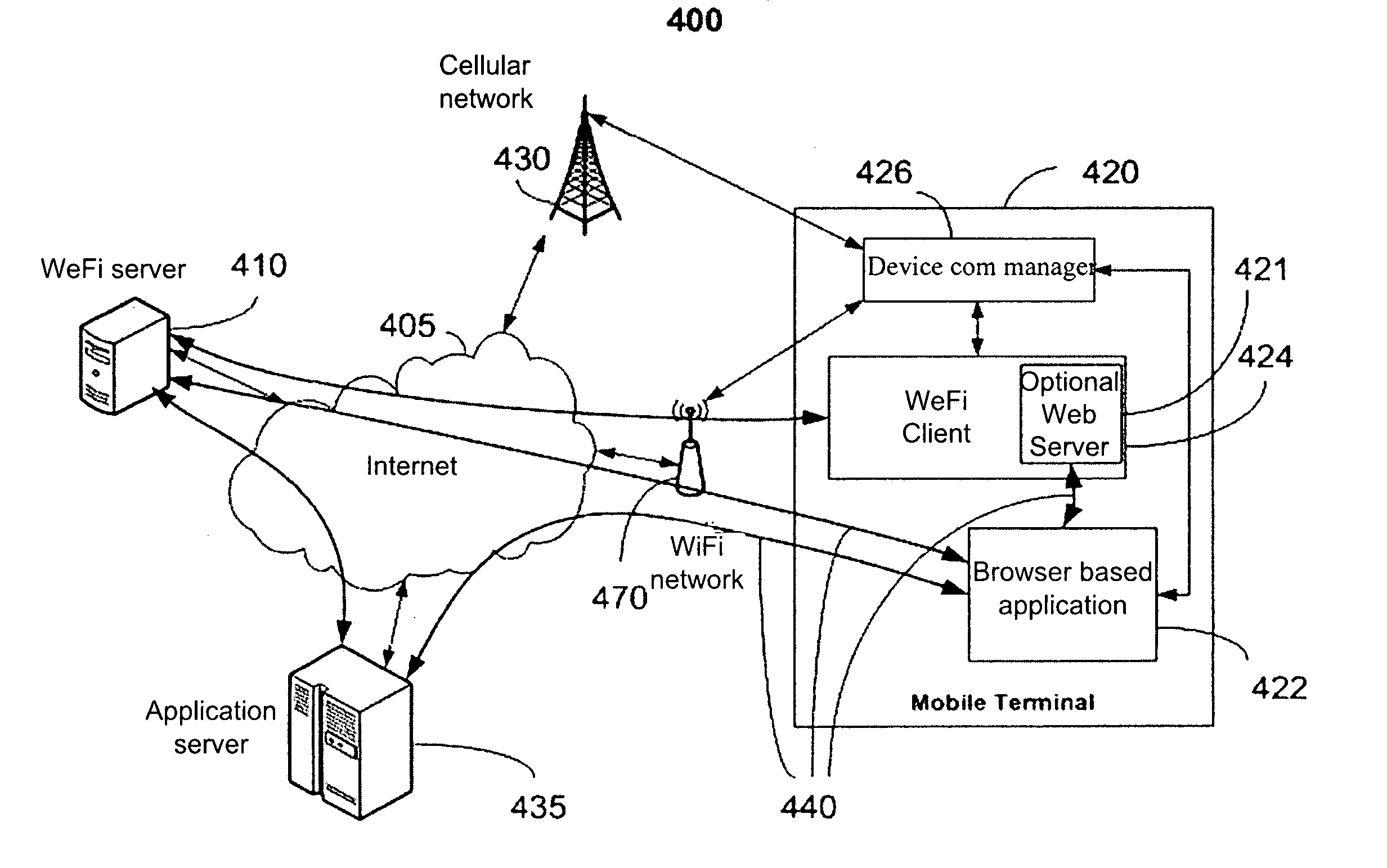
System and method for providing seamless broadband internet access to web applications
InactiveUS20090124284A1Battery poweredImprove usabilityAssess restrictionNetwork topologiesWeb applicationInternet access
A WiFi communication framework that is particularly suitable for mobile devices. The framework provides comprehensive tools for establishing seamless Internet access for web applications on mobile handheld devices. In addition, it can provide user location to enable applications requiring such information. The framework may be implemented as a client on the handheld device. The broadband radio on the device is generally kept off. When the user activates an application requiring broadband service, communication protocol is established, causing the client to turn the broadband radio on and to establish connection to an available WiFi access point.
Owner:WEFI
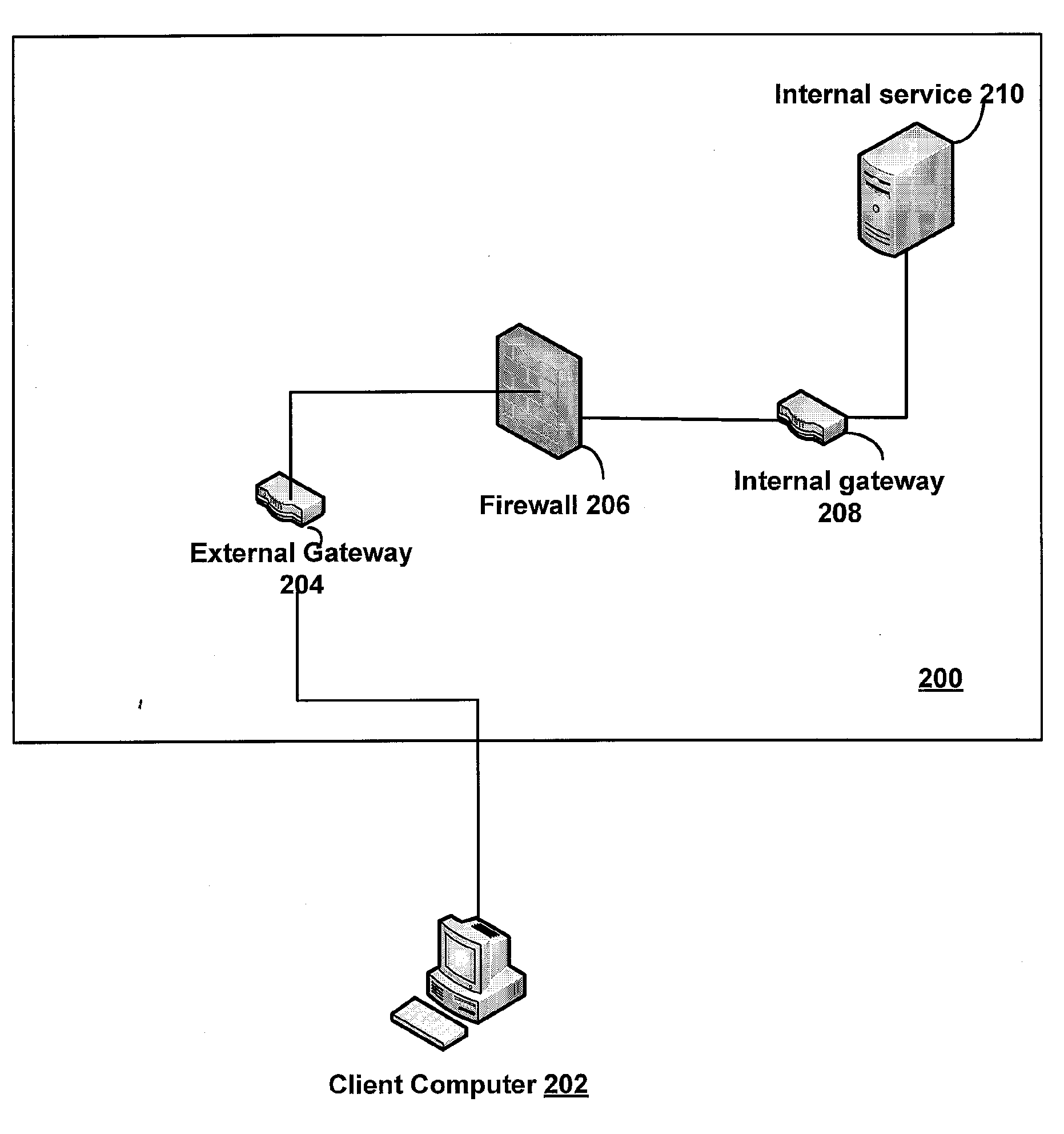
Providing A Generic Gateway For Accessing Protected Resources
InactiveUS20080178278A1Facilitates secure exposurePrevent unauthorized accessComputer security arrangementsMultiple digital computer combinationsWeb applicationWeb service
An internal gateway establishes persistent connections to an external gateway through permitted ports and protocols of a firewall. Software on the external gateway and the internal gateway collaborate in order to make available internal, firewall-protected resources to external clients securely and without having to modify network or firewall configurations. Any computing resource such as a web service, web application, or any other network addressable resource residing behind a firewall can be securely exposed in a generic fashion to clients on the external network. No special software is required by clients.
Owner:BITKOO
System for determining web application vulnerabilities
InactiveUS20020010855A1Memory loss protectionError detection/correctionWeb applicationApplication procedure
A method for detecting security vulnerabilities in a web application includes analyzing the client requests and server responses resulting therefrom in order to discover pre-defined elements of the application's interface with external clients and the attributes of these elements. The client requests are then mutated based on a pre-defined set of mutation rules to thereby generate exploits unique to the application. The web application is attacked using the exploits and the results of the attack are evaluated for anomalous application activity.
Owner:FINJAN BLUE INC
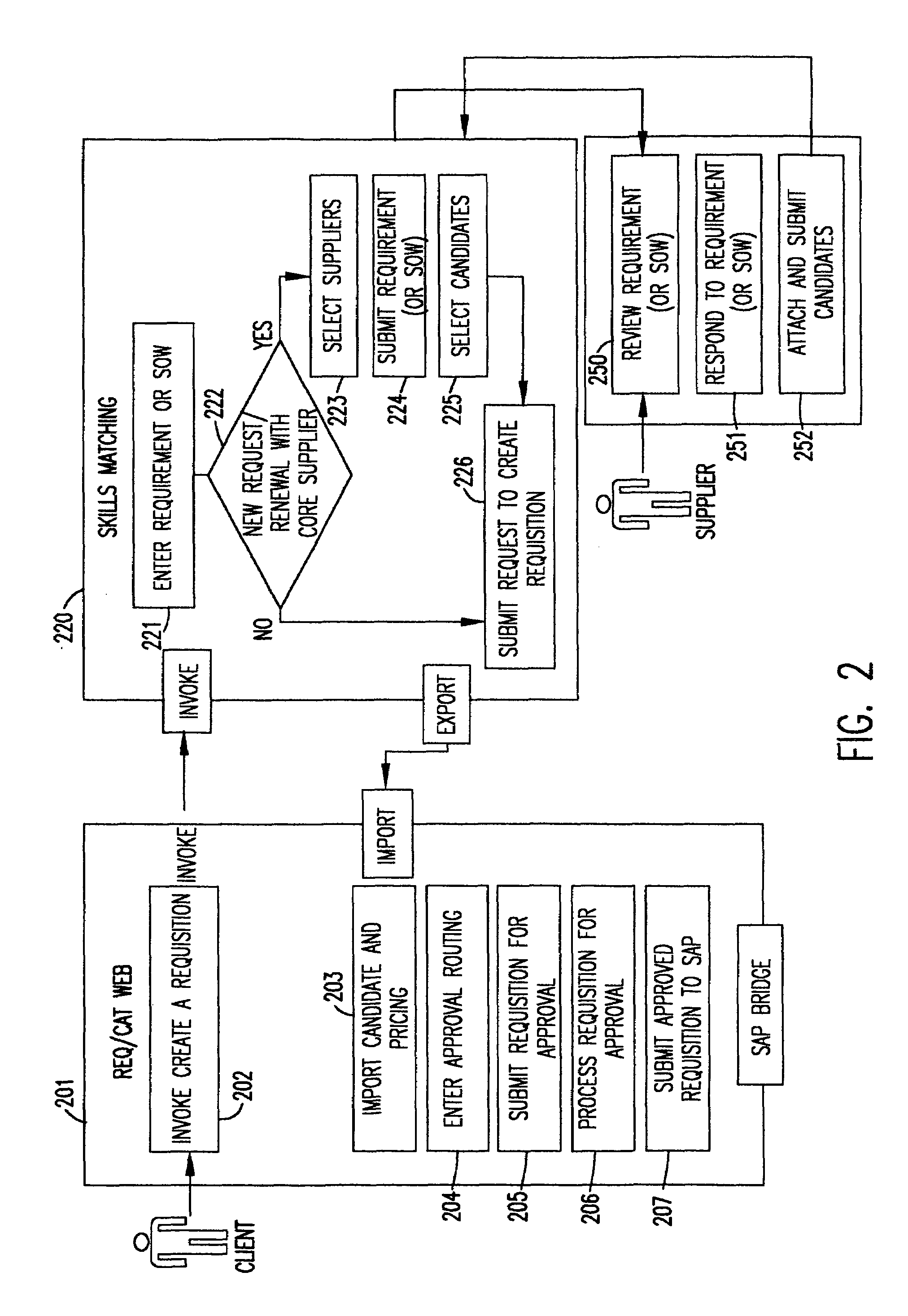
Skills matching application
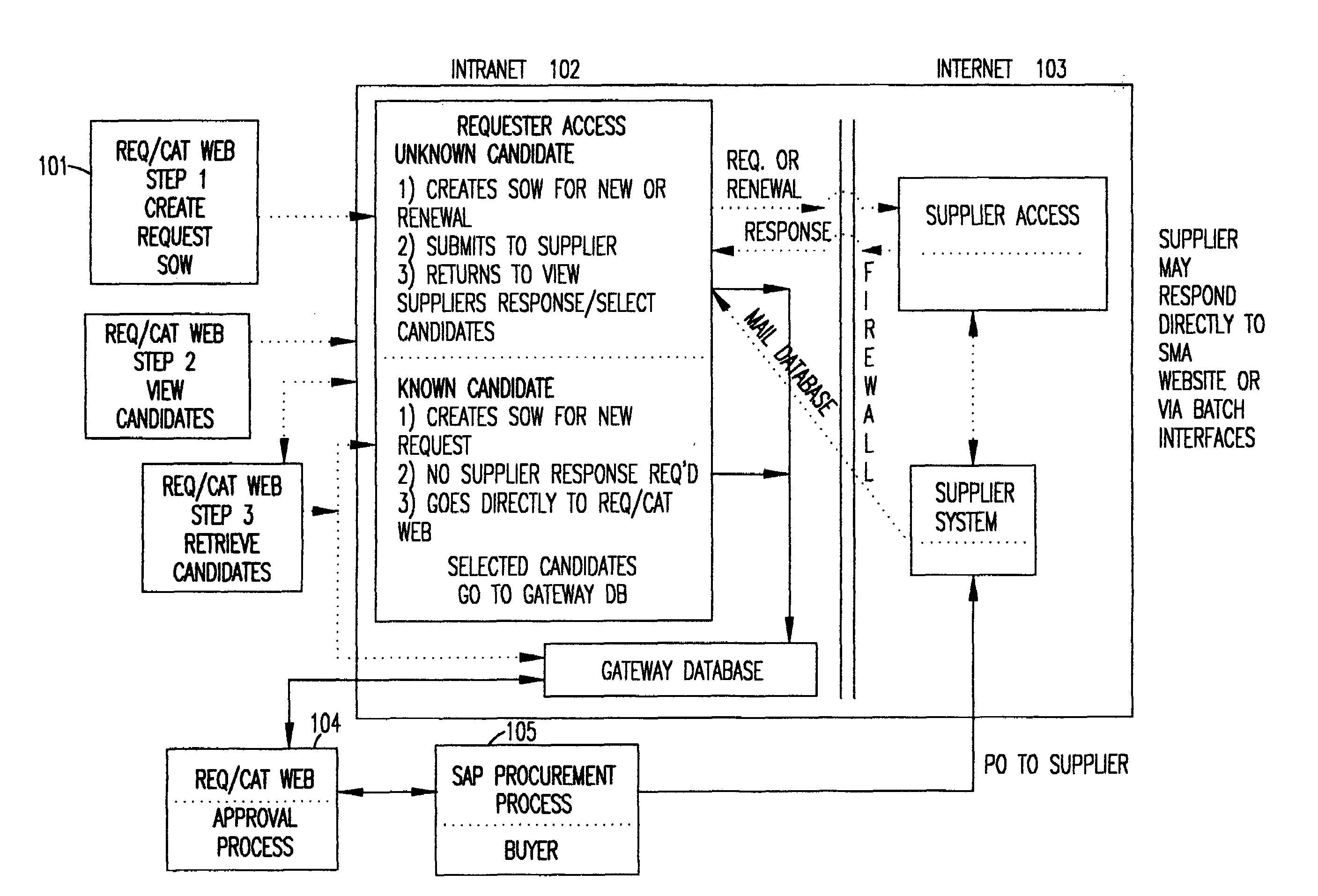
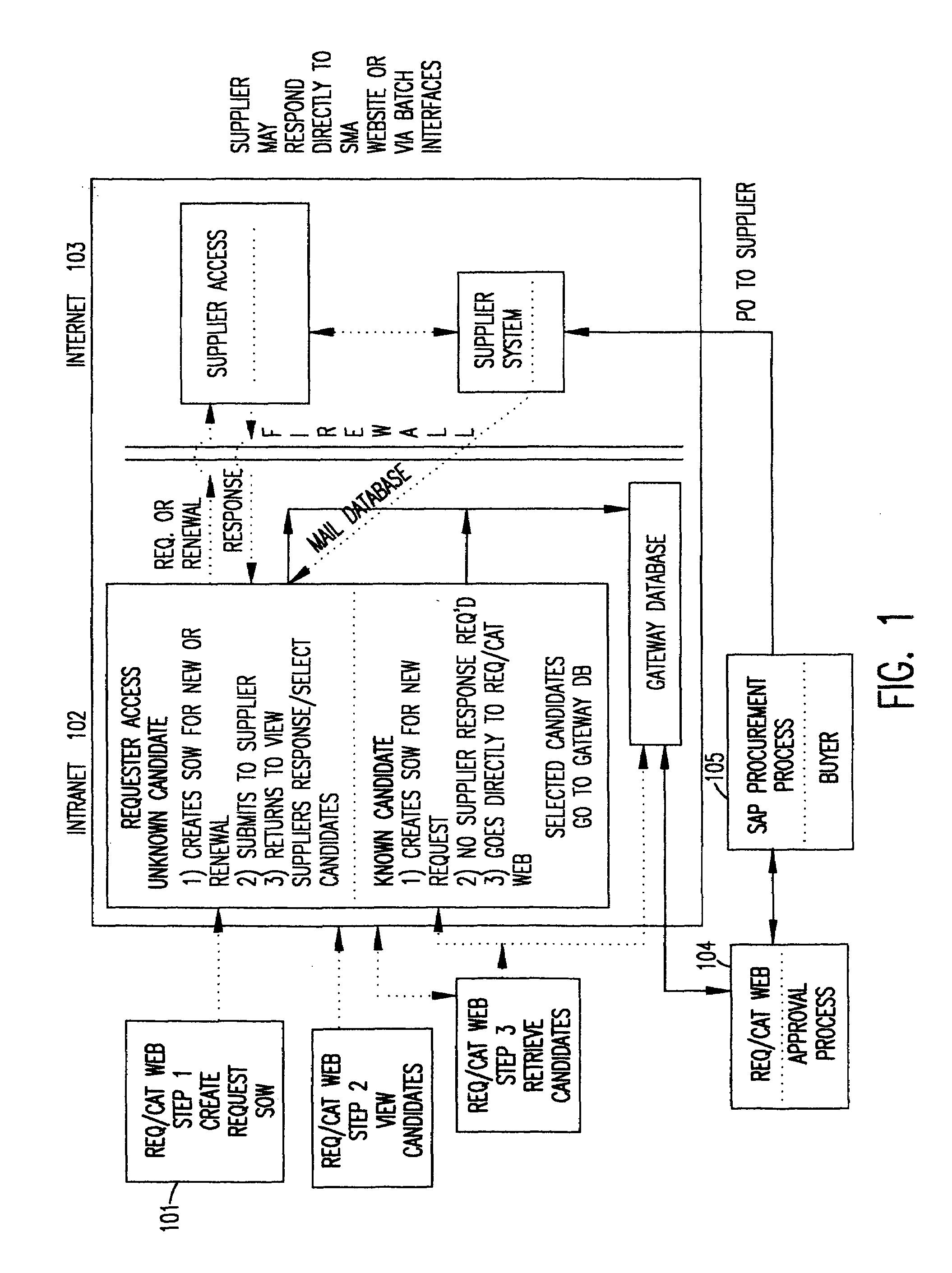
A tool, called the Skills Matching Application (SMA), allows a user, such as a hiring manager, to communicate requirements to technical service suppliers in a way that significantly reduces the process time and improves the accuracy of requests sent to suppliers. The SMA is accessed from a Web-based Requisition / Catalog (REQ / CAT) Web application. A user who needs to request a technical contractor accesses the REQ / CAT Web application which brings the user to the SMA Web site. The SMA application, after requiring a password and profile (for first time access) to be entered, takes the user through a series of screens which prompts the user to enter a Statement of Work (SOW) and complete a skills detail checklist for each of the technical skills requested. Once the request is completed, it is submitted to contracted suppliers who are sent an e-mail notification notifying the supplier that a new request has been entered into the SMA application for them to review and submit a candidate against. This e-mail has a standard formatted attachment which contains the statement of work and skills detail checklist. The suppliers, when they receive an e-mail request, access the Web site database to view the request details. A supplier provides a candidate or candidates by accessing the SMA Web site and submitting candidates and appending resumes as appropriate. The supplier provides a response to the SOW by responding to the entries with the candidate's skills, experience, etc. The requestor views the supplier responses and associated resumes and can either accept or reject each candidate submitted but cannot accept more than the number of candidates requested.
Owner:IBM CORP
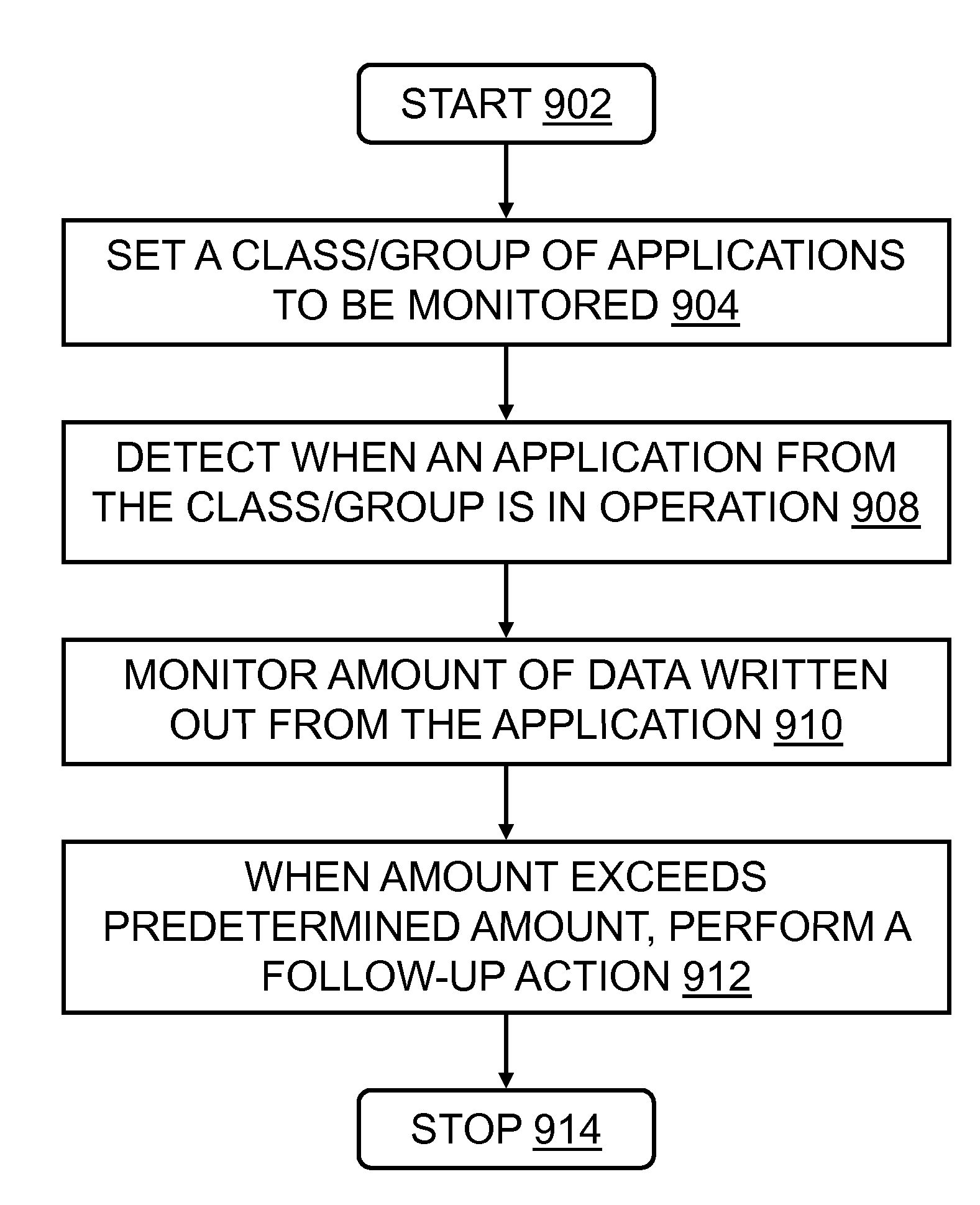
Systems and methods that detect sensitive data leakages from applications
InactiveUS20100212010A1Improve accuracyAvoid persistenceMemory loss protectionError detection/correctionWeb applicationApplication software
In embodiments, the present invention may be a computer program product embodied in a computer readable medium that, when executing on one or more computers, may select a software application for monitoring, where the selection may be based at least in part on the basis that the software application controls confidential information, and where the software application may be an end-point application, a web application, a cloud application, and the like. The present invention may monitor the software application by determining an output data quantity that may be written from the software application. The output data may then be compared with a predetermined quantity, where the predetermined quantity may be indicative of confidential information being written from the software application.
Owner:SOPHOS
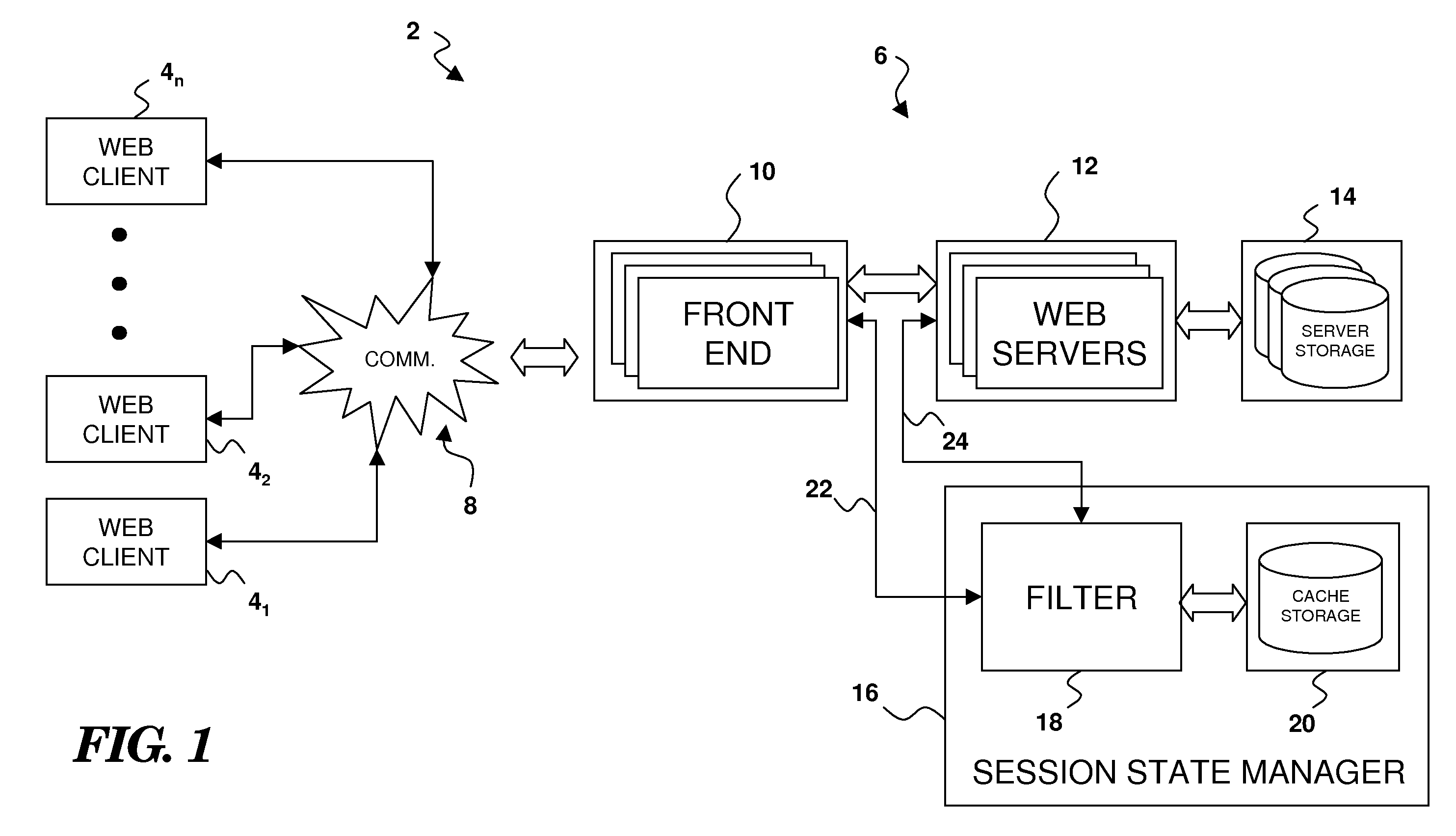
Managing Session State For Web Applications
Owner:IBM CORP
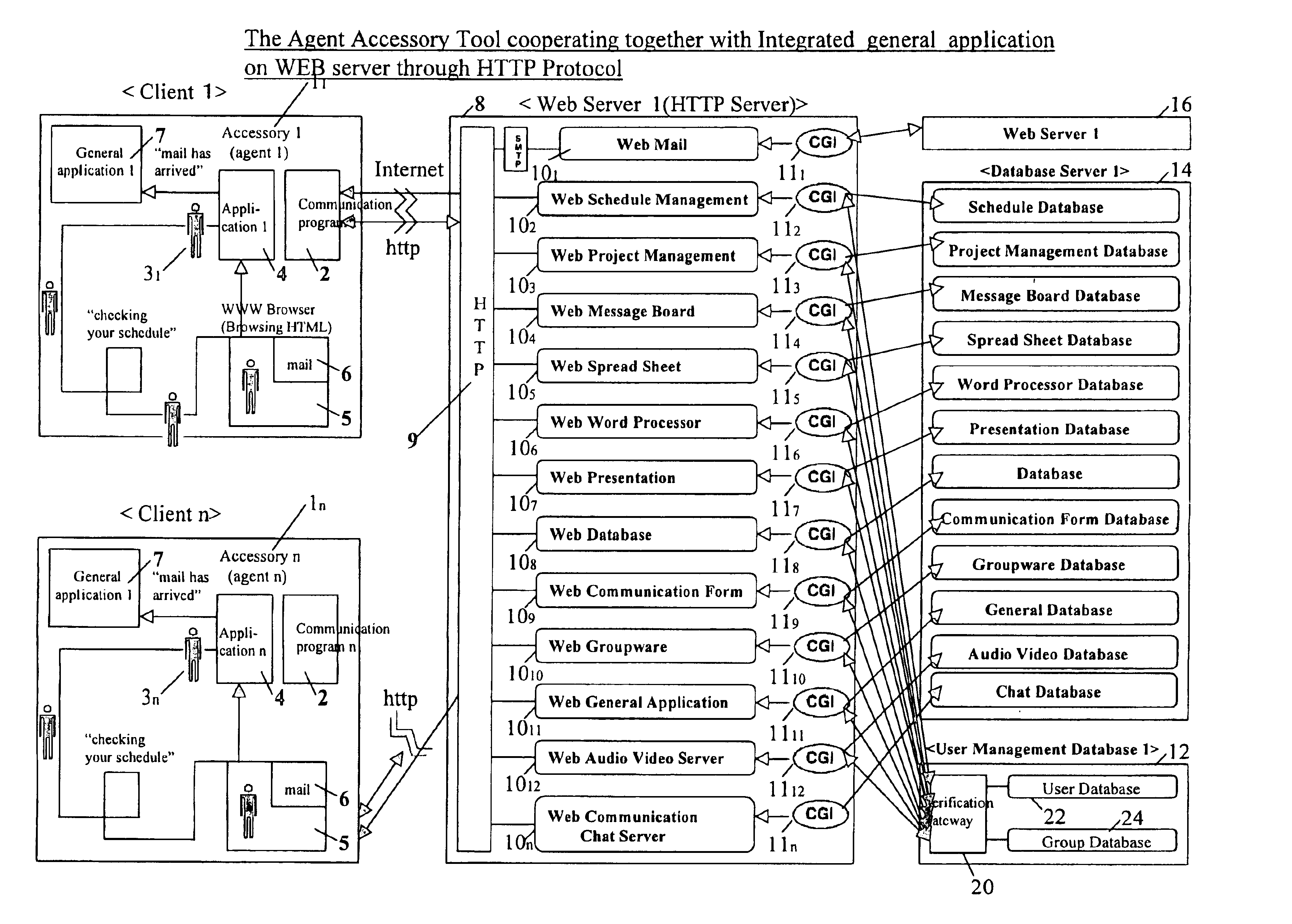
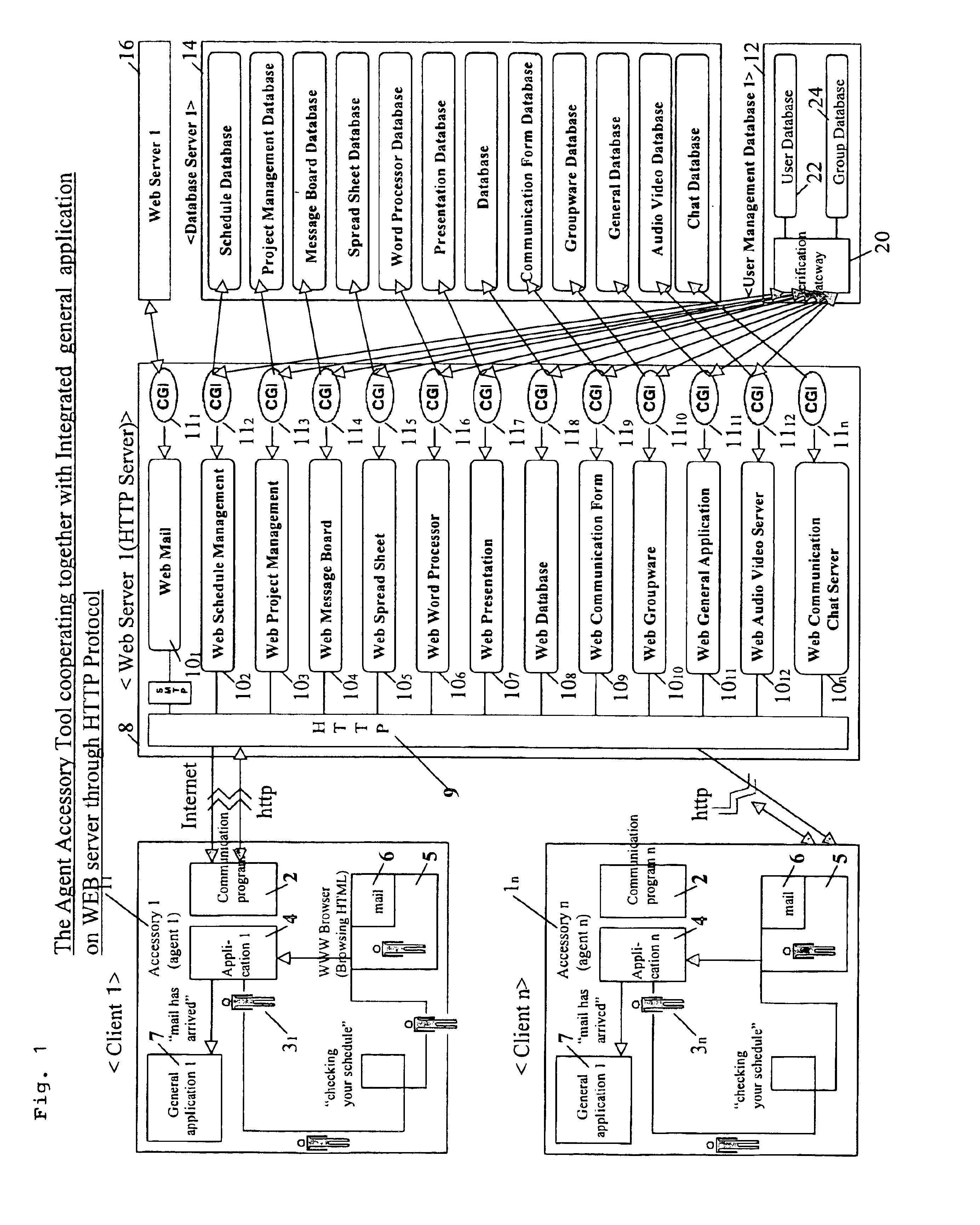
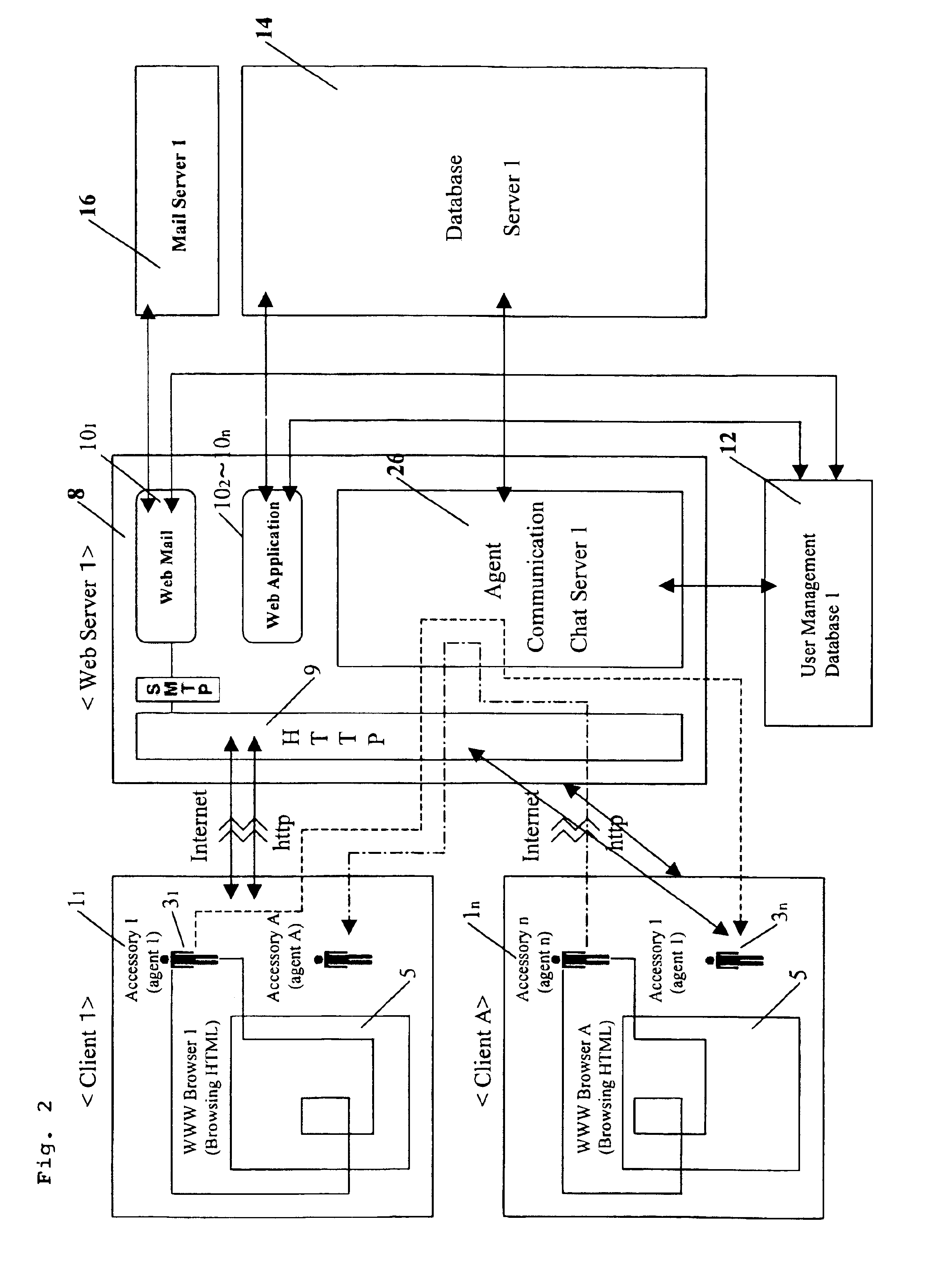
Agent accessory tool cooperating with integrated application on WEB server by HTTP protocol
InactiveUS6842779B1Multiple digital computer combinationsSpecial data processing applicationsWeb applicationExternal application
An agent accessory tool which enables integration of a Web-type application operating within a browser area and general application operating outside browser area is provided. The agent accessory tool includes an agent program interlocking by HTTP incorporated in a personal computer (hereinafter referred to as PC) of each of a plurality of clients, and a Web server having a CGI interface for executing communication software and an external application of the HTTP concerned to each client PC through a communication line. In this agent accessory tool interlocking with the integrated application on the Web server by the HTTP, the agent program accesses various data of a CGI program through the Web server under input conditions, and music and images to each client. When, as a result, the data are updated from previous access data or in conformity to predetermined conditions, an accessory tool including an avatar (digital actor) is caused to appear on the display of the PC of the client, and is also caused to conduct a predetermined action / reaction so as to transmit the existence of information, the non-conformity to the predetermined conditions, and music and images to each client. As a result, the agent accessory tool operates integrally with the Web application by accessing the Web server, without booting the browser software.
Owner:NISHIZAWA YASUO
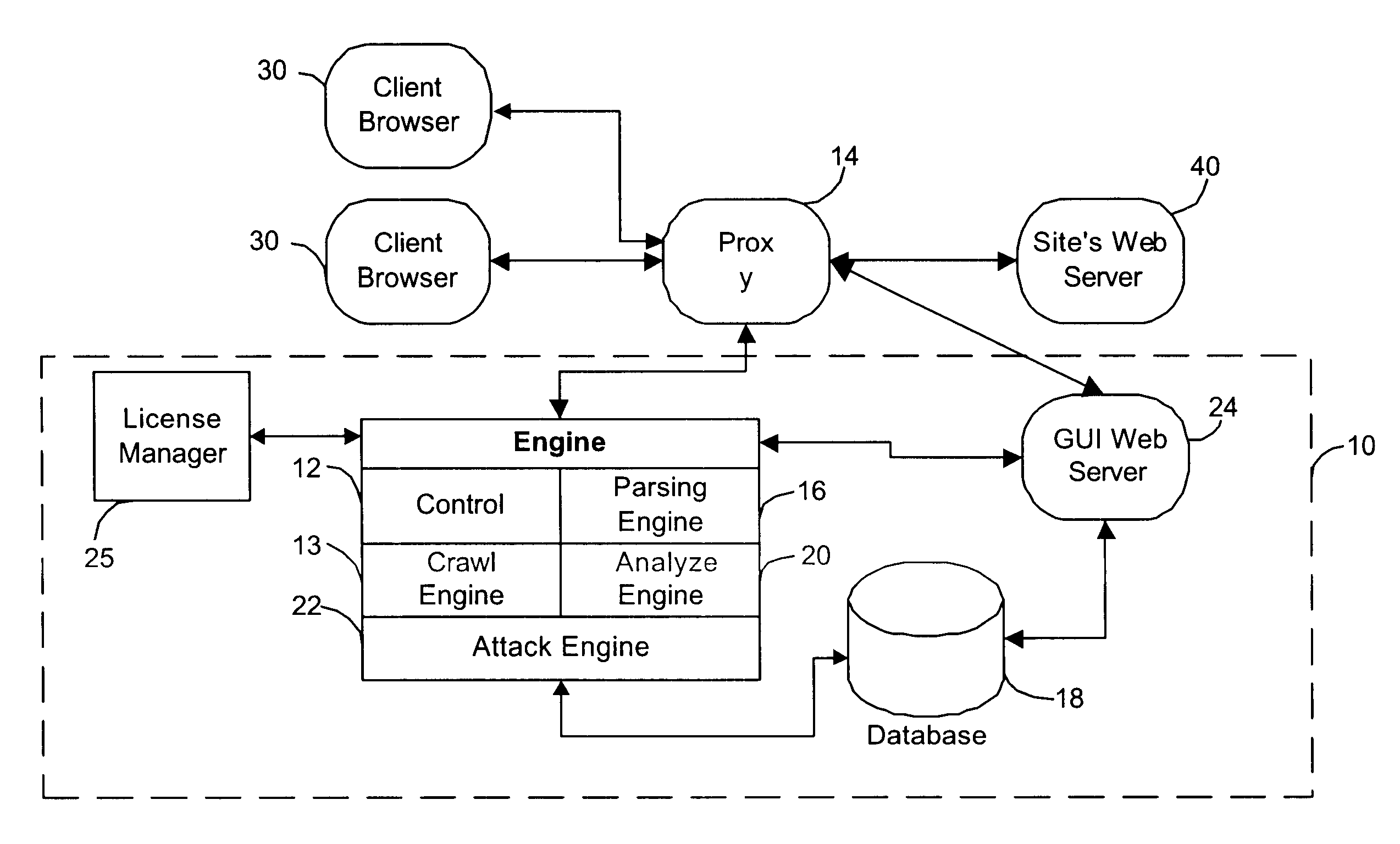
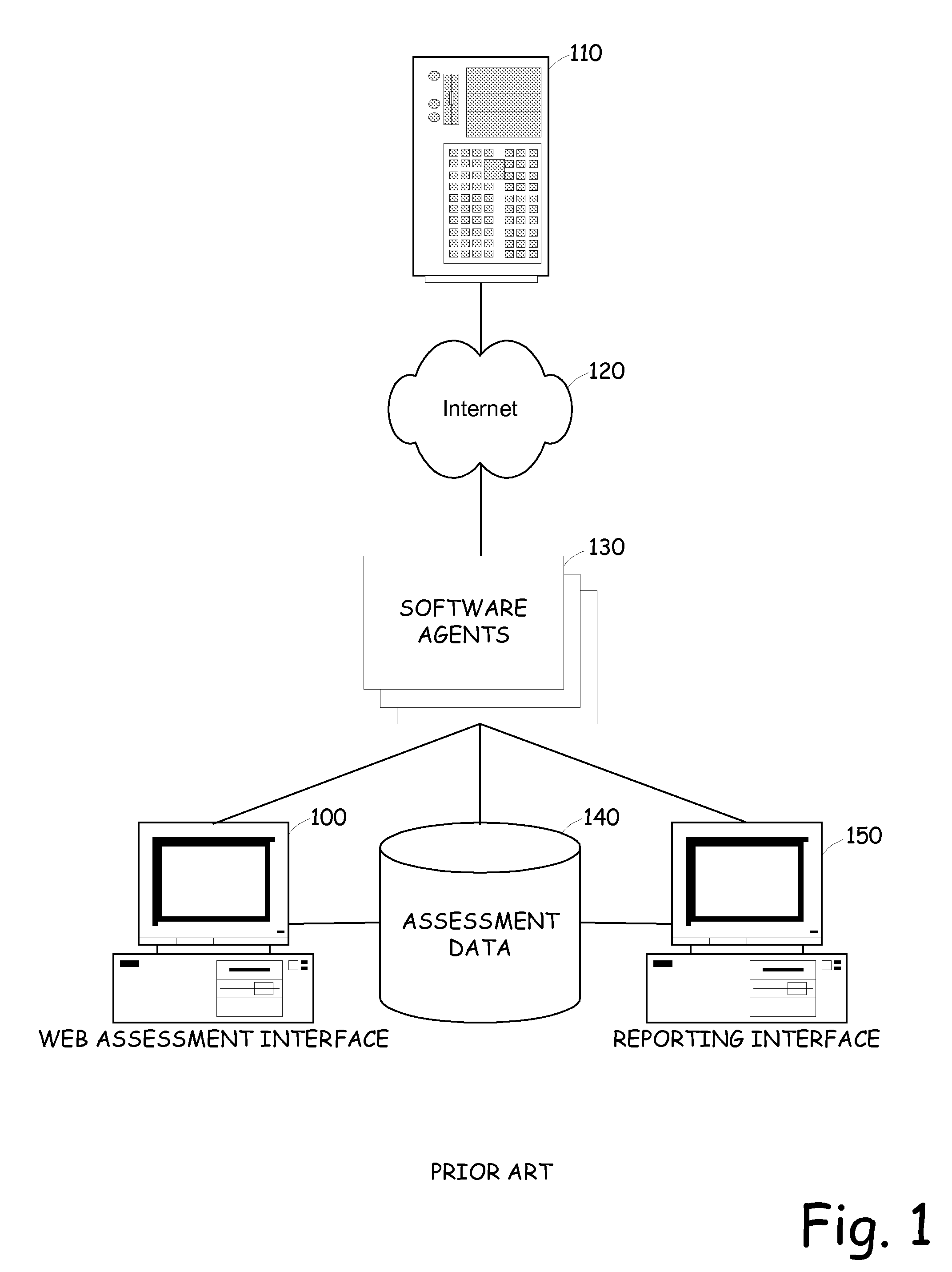
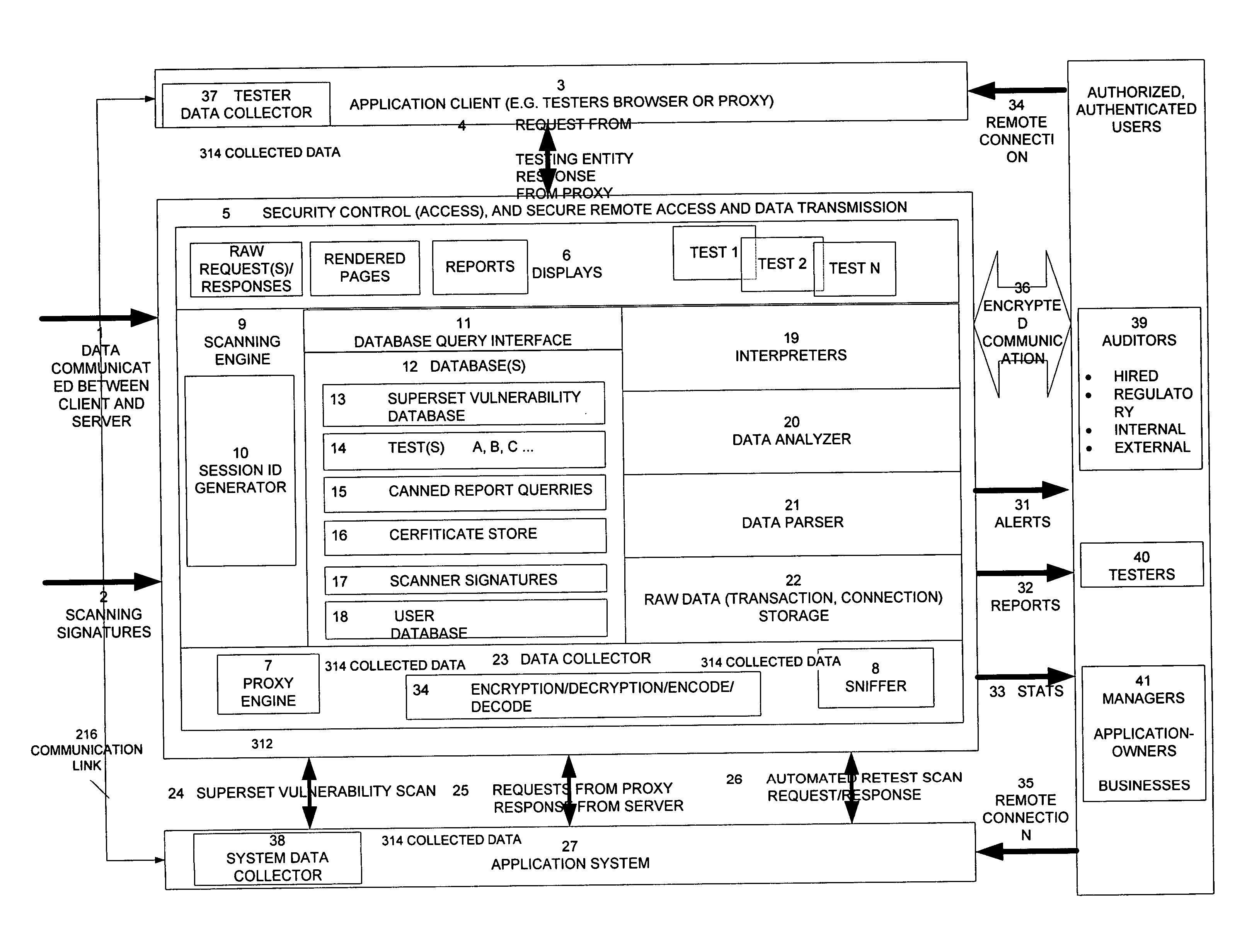
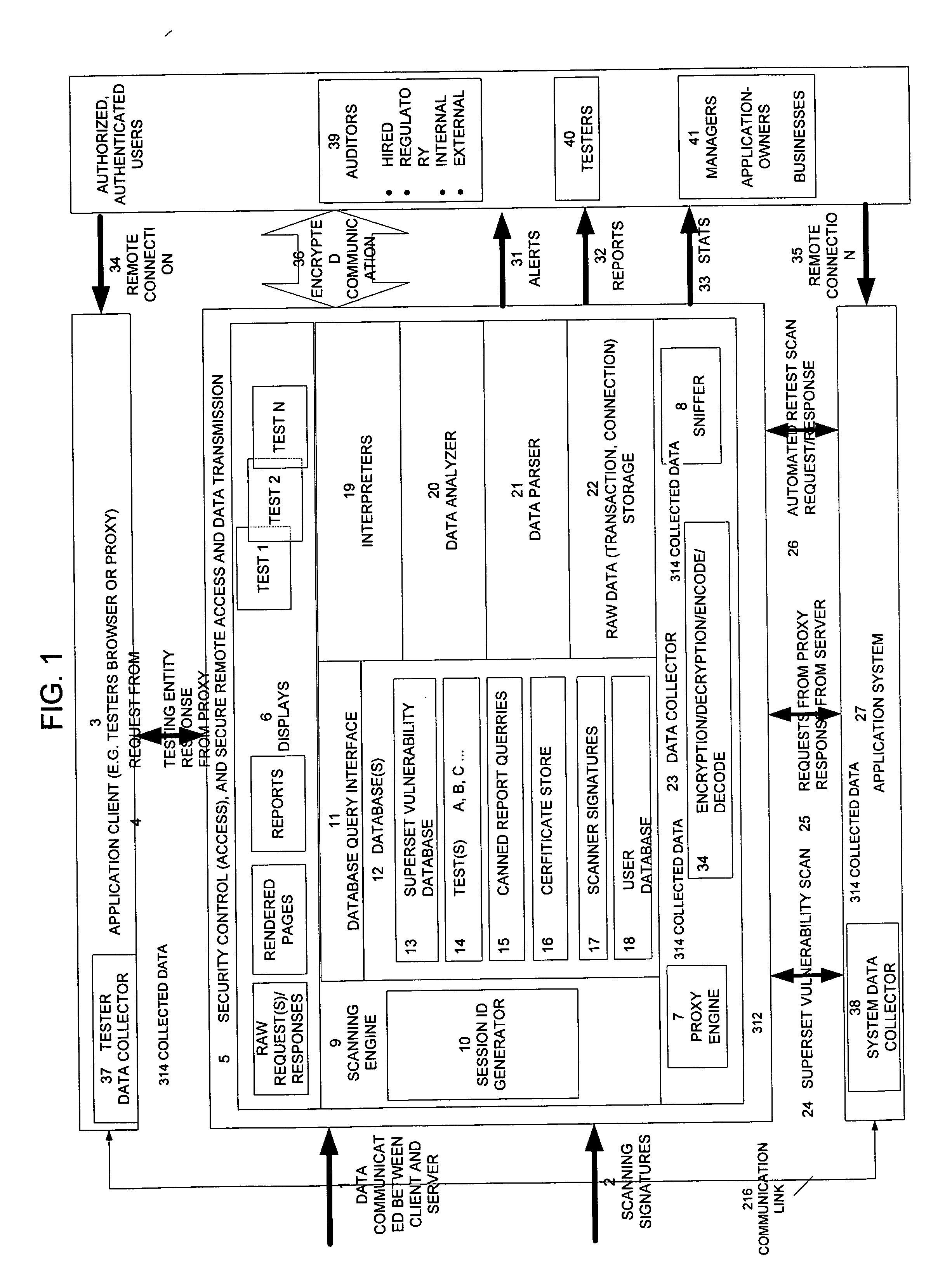
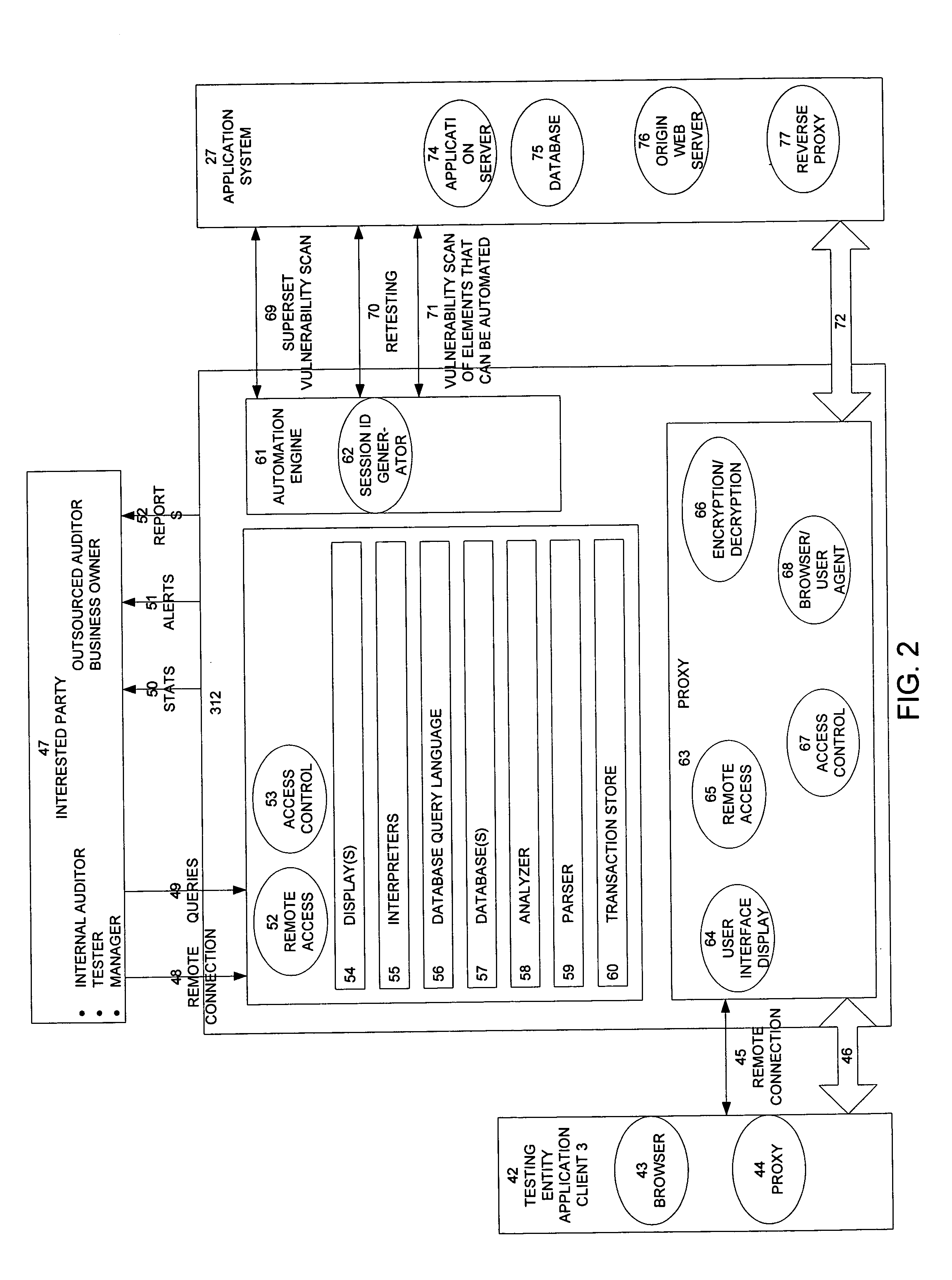
Method, system, and apparatus for managing, monitoring, auditing, cataloging, scoring, and improving vulnerability assessment tests, as well as automating retesting efforts and elements of tests
InactiveUS20050138426A1Streamline and improve test effortImprove consistencyDigital data processing detailsHardware monitoringAnalysis dataWeb application
A scalable method, system, and apparatus for non-intrusively auditing and improving security assessments includes capturing, storing, presenting, displaying, inspecting, monitoring, and analyzing data flow in client-server security assessments and / or network / infrastructure security assessments. The invention provides interested parties with a mechanism to non-intrusively audit in real-time the vulnerability test effort, as well as review, replay, and analyze all aspects of the security assessment during and after the test. For web application assessments, the data capture includes one of the following or some combination: an intermediary with all data passing through the intermediary; a sniffer that can passively extract all data being communicated between the application and tester; and a plurality of computing modules (e.g., software, appliances, etc.) installed in the tester environment or within the application system environment (e.g., software installed on the tester's computer, or on the computer where the intermediary is running, or software installed on the application systems proxy or web server, or an appliance in either environment) for storing, processing, analyzing, reporting, and displaying the data.
Owner:STYSLINGER BRIAN
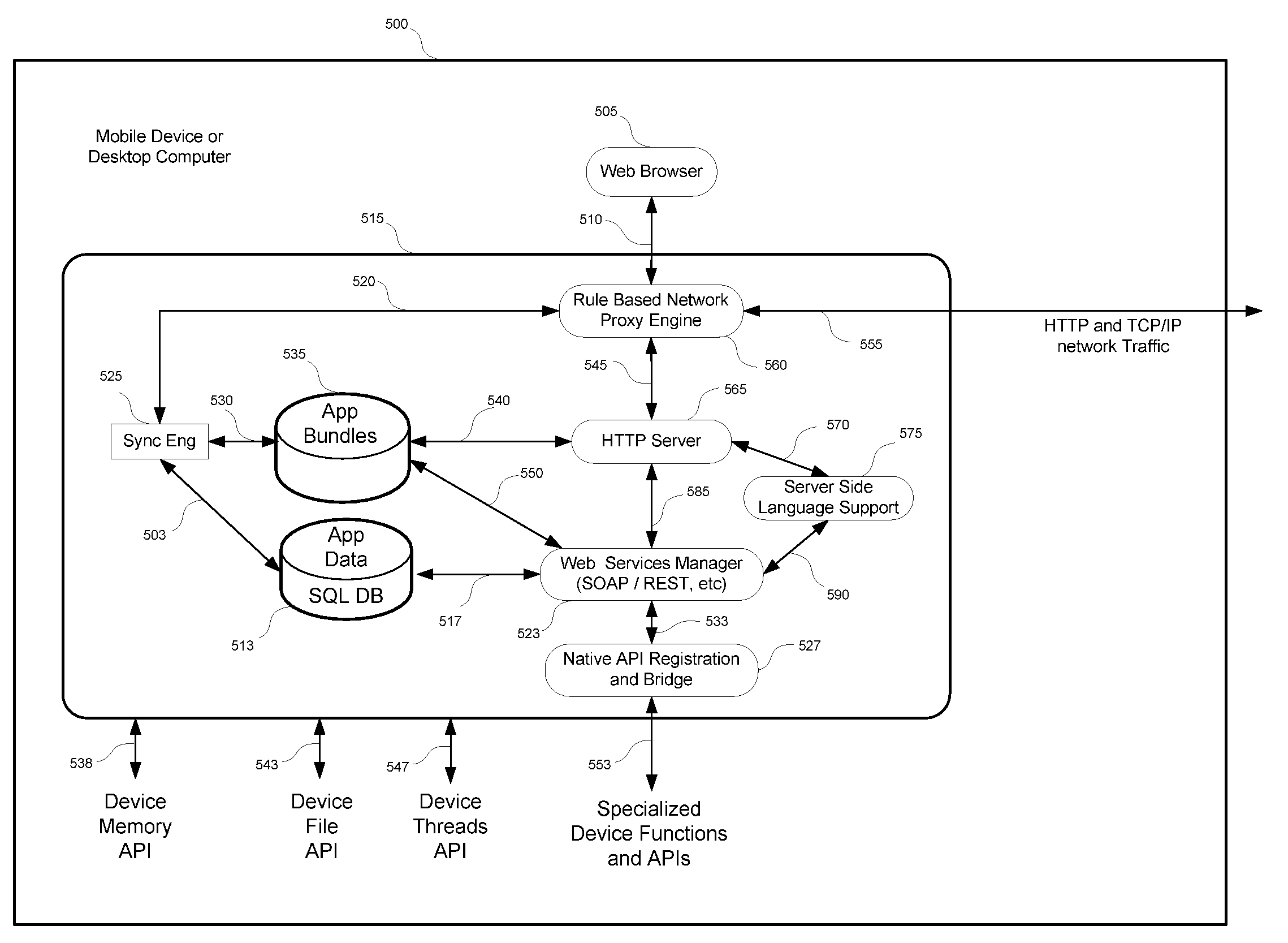
Method and system for efficient deployment of web applications in a multi-datacenter system
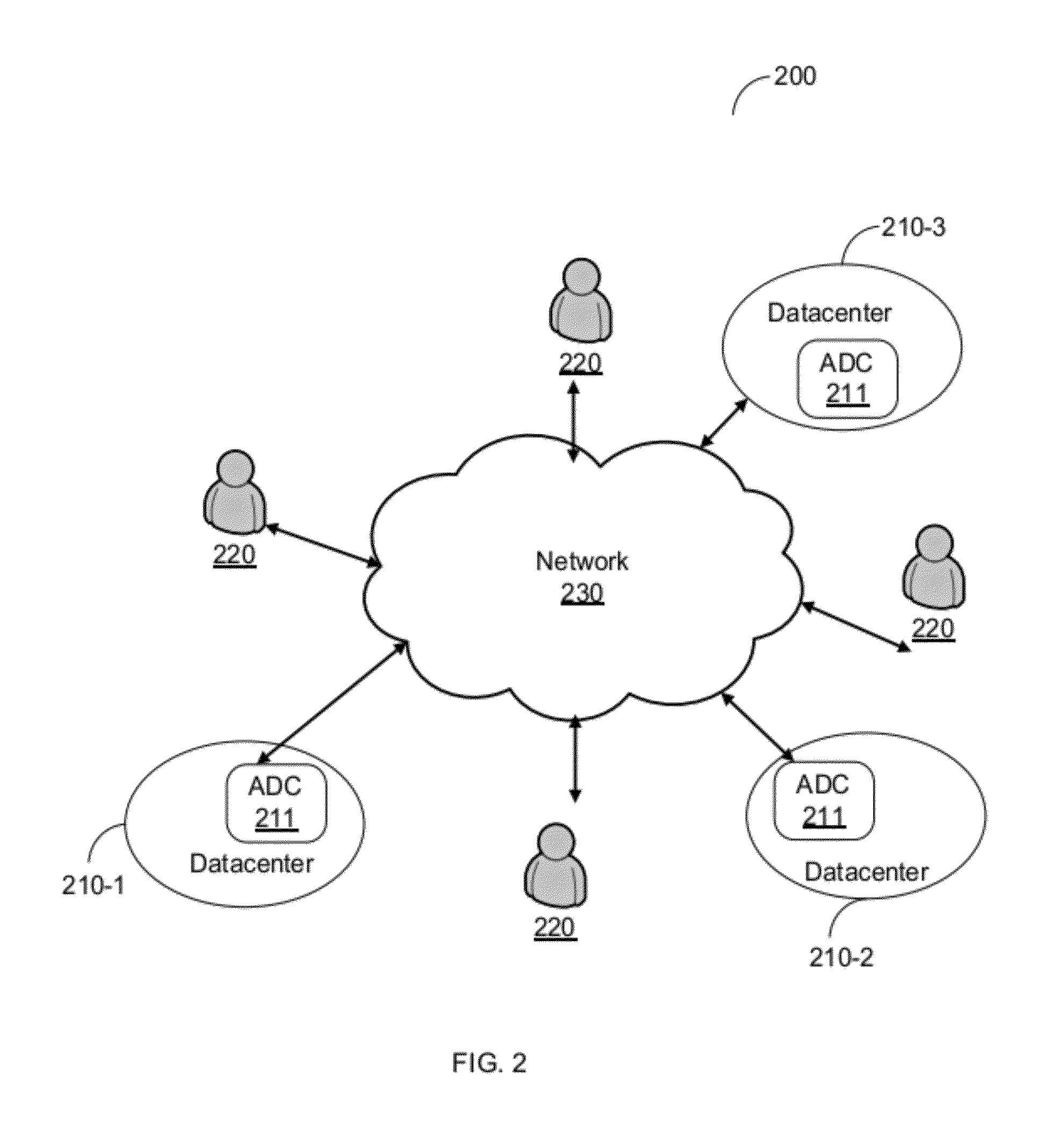
ActiveUS20120136697A1Easy to deployDigital computer detailsTransmissionService-level agreementWeb application
A system for computing an optimal deployment of at least one web application in a multi-datacenter system comprising a collector for collecting performance measurements with regard to a web application executed in the multi-datacenter system and grouping the performance measurements according to locations of a plurality of clients accessing the web application; a data repository for maintaining at least a performance table including at least the performance measurements grouped according to the plurality of client locations and a service level agreement (SLA) guaranteed to clients in the plurality of client locations; and an analyzer for processing at least information stored in the performance table for generating a recommendation on an optimal deployment of the web application in at least one combination of datacenters in the multi-datacenter system by computing an expected SLA that can be guaranteed to the clients in each combination of datacenters.
Owner:RADWARE
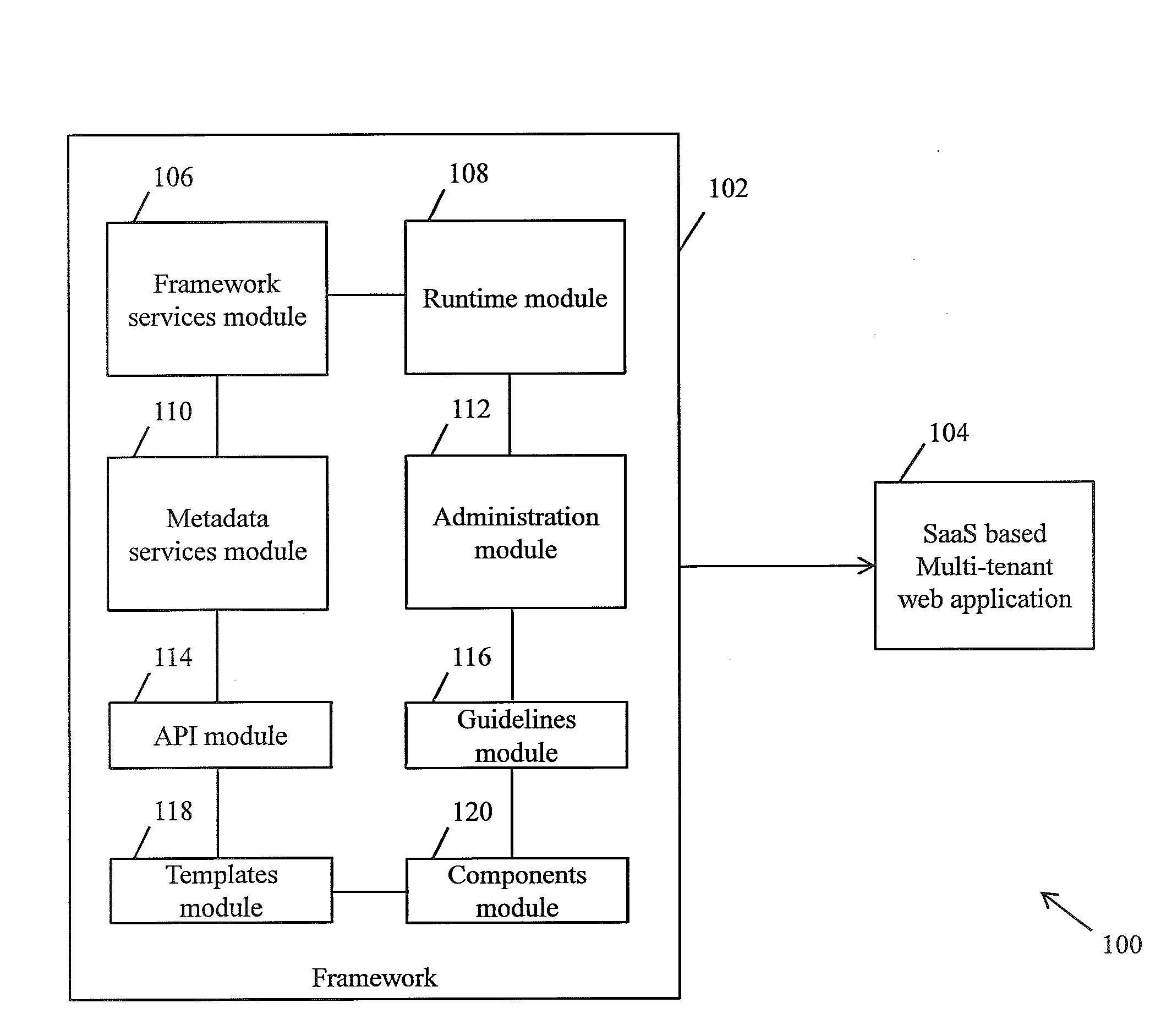
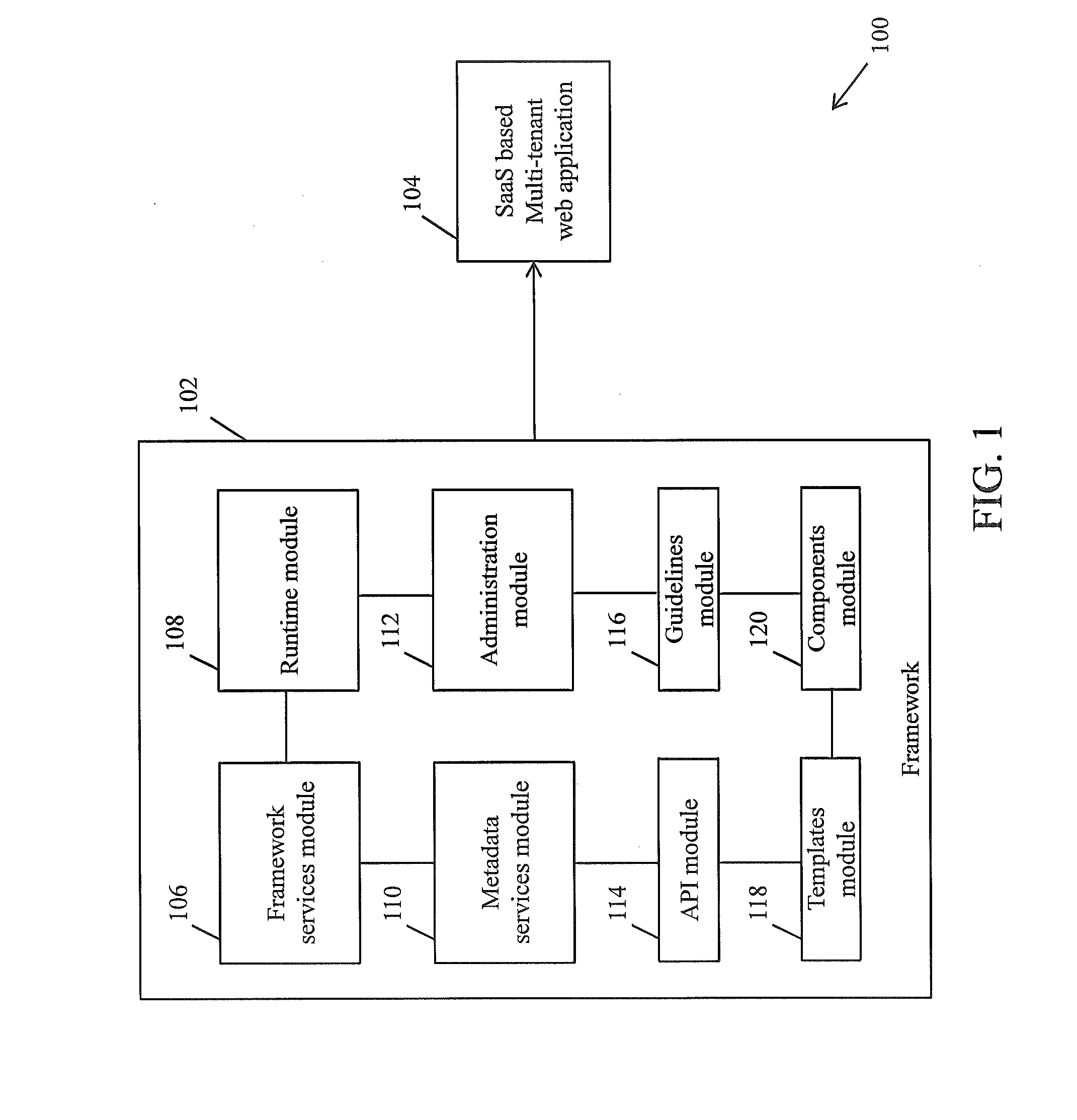
Framework for facilitating implementation of multi-tenant saas architecture
ActiveUS20140289391A1Facilitates monitoring and controllingFacilitate monitoring and controlling of featuresDigital computer detailsData switching networksWeb applicationSoftware as a service
A framework for implementing multitenant architecture is provided. The framework comprises a framework services module which is configured to provide framework services that facilitate abstraction of Software-as-a-Service (SaaS) services and crosscutting services for a Greenfield application and a non SaaS based web application. Further the abstraction results in a SaaS based multitenant web application. The framework further comprises a runtime module configured to automatically integrate and consume the framework services and APIs to facilitate monitoring and controlling of features associated with the SaaS based multitenant web application. The framework further comprises a metadata services module configured to provide a plurality of metadata services to facilitate abstraction of storage structure of metadata associated with the framework and act as APIs for managing the metadata. The framework further comprises a role based administration module that facilitates management of the metadata through a tenant administrator and a product administrator.
Owner:COGNIZANT TECH SOLUTIONS INDIA PVT
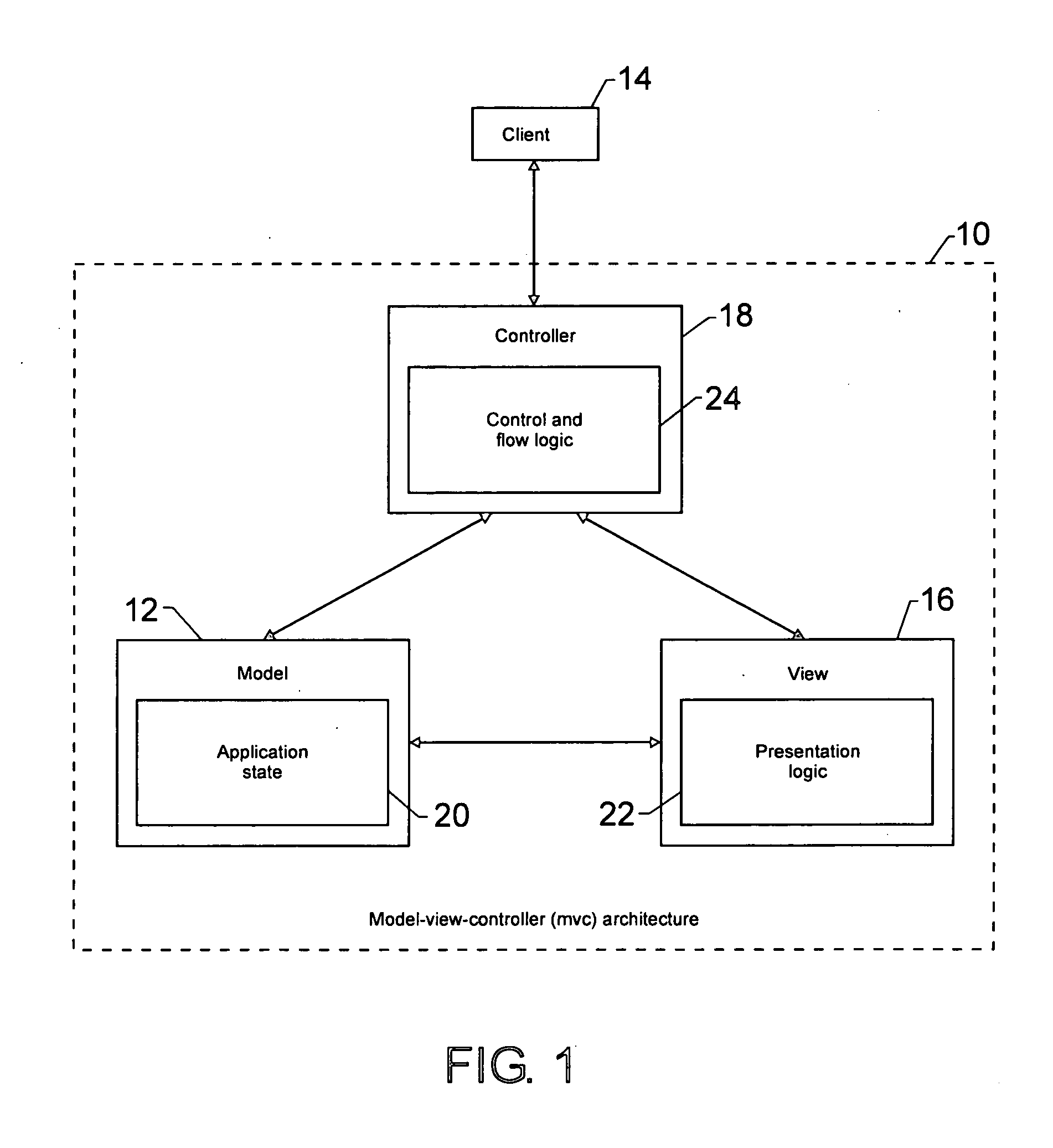
Method and apparatus for supporting layout management in a web presentation architecture
InactiveUS20050076294A1Digital data information retrievalDigital computer detailsWeb applicationFrame based
A system and method for creating applications, such as web applications, is disclosed. The system comprises a controller generator that is adapted to provide an application with a controller that receives a request for data from a user and responds to the request by sending information to the user in a predetermined format. The system further comprises a layout manager generator that is adapted to provide a layout manager that formats a c-frame based on configuration information and renders the c-frame as part of the information sent to the user in response to the request.
Owner:HEWLETT PACKARD DEV CO LP
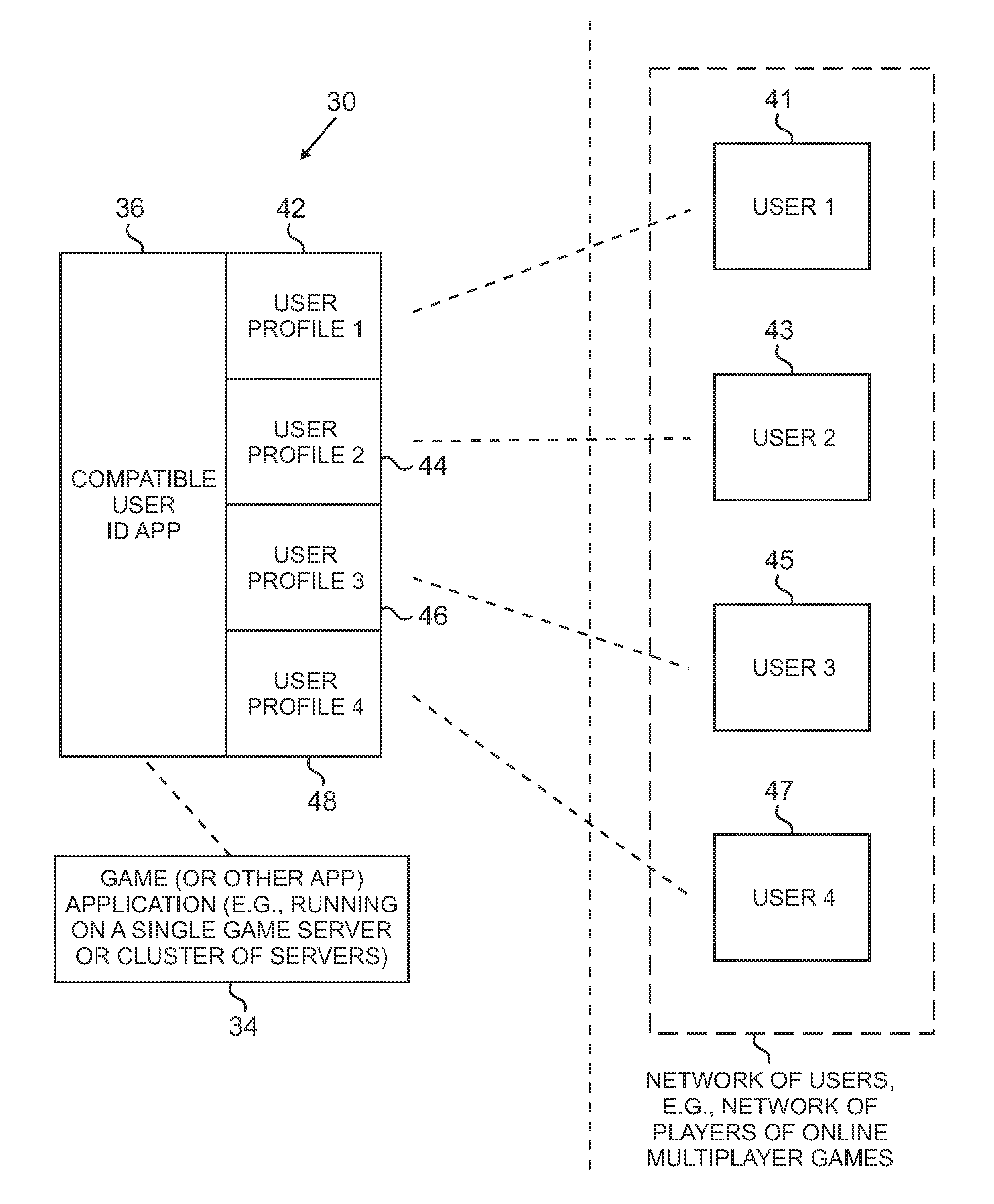
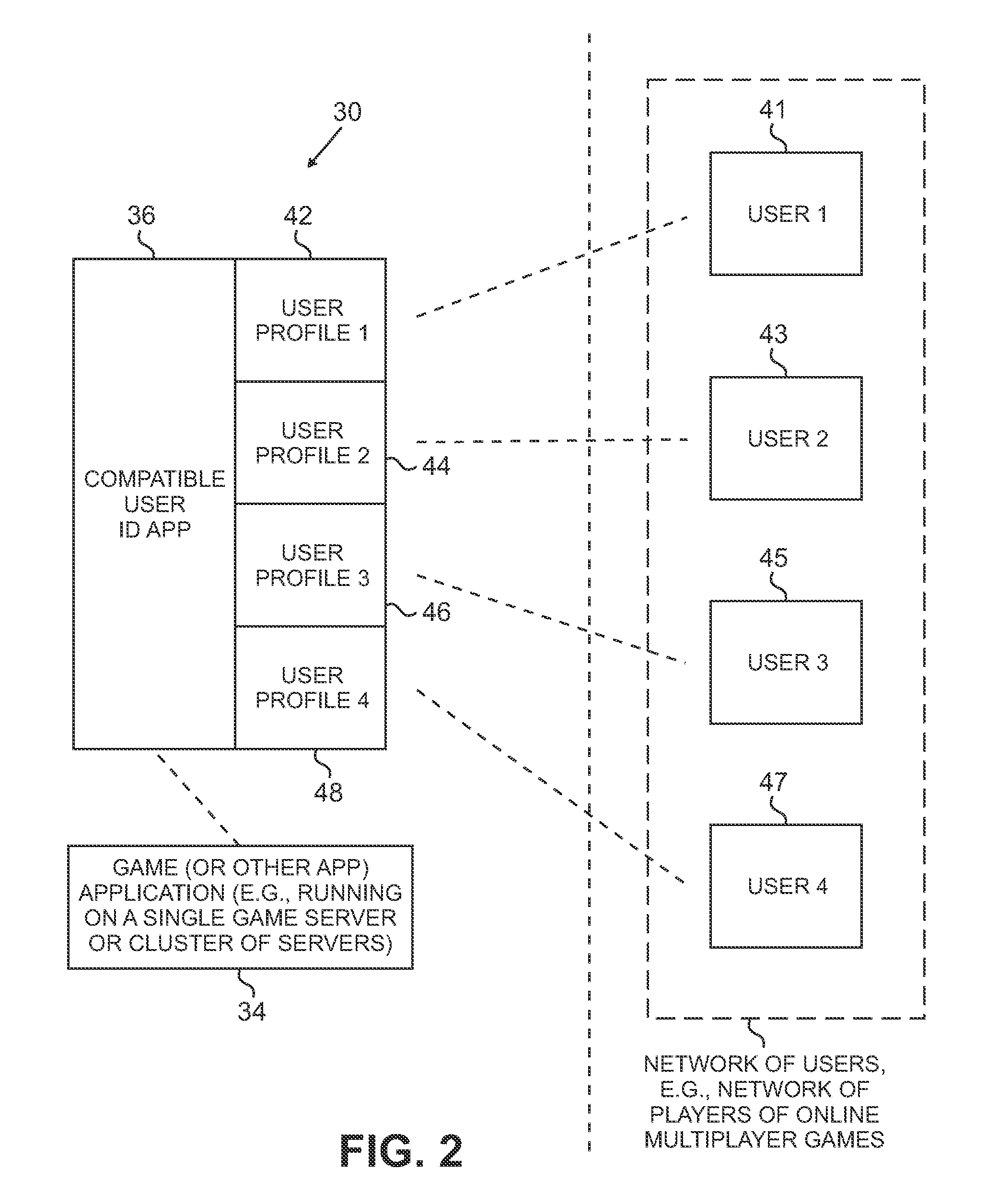
System and method for identifying compatible users
ActiveUS20090075738A1Facilitate communicationMultiple digital computer combinationsApparatus for meter-controlled dispensingWeb applicationComputer compatibility
Systems and methods are provided for an automatic user or friend recommendation system that matches players that have compatible play styles, play schedules, or the like. Behavioral data is collected or entered from players, and a profile of each player is created and compared to calculate a compatibility score. If the compatibility score exceeds a predetermined threshold, then the players are marked as compatible, or a degree of compatibility may be calculated and displayed as well. Users can edit their profile, e.g., on a web application or in-game. Users may also interact with optional and incremental demographic survey questions as they log in. A notification of compatible players may be provided via the web application or via an in-game indication. For example, a glow may appear around a compatible player, or compatible players may be displayed in a list, such as an instant messaging client.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
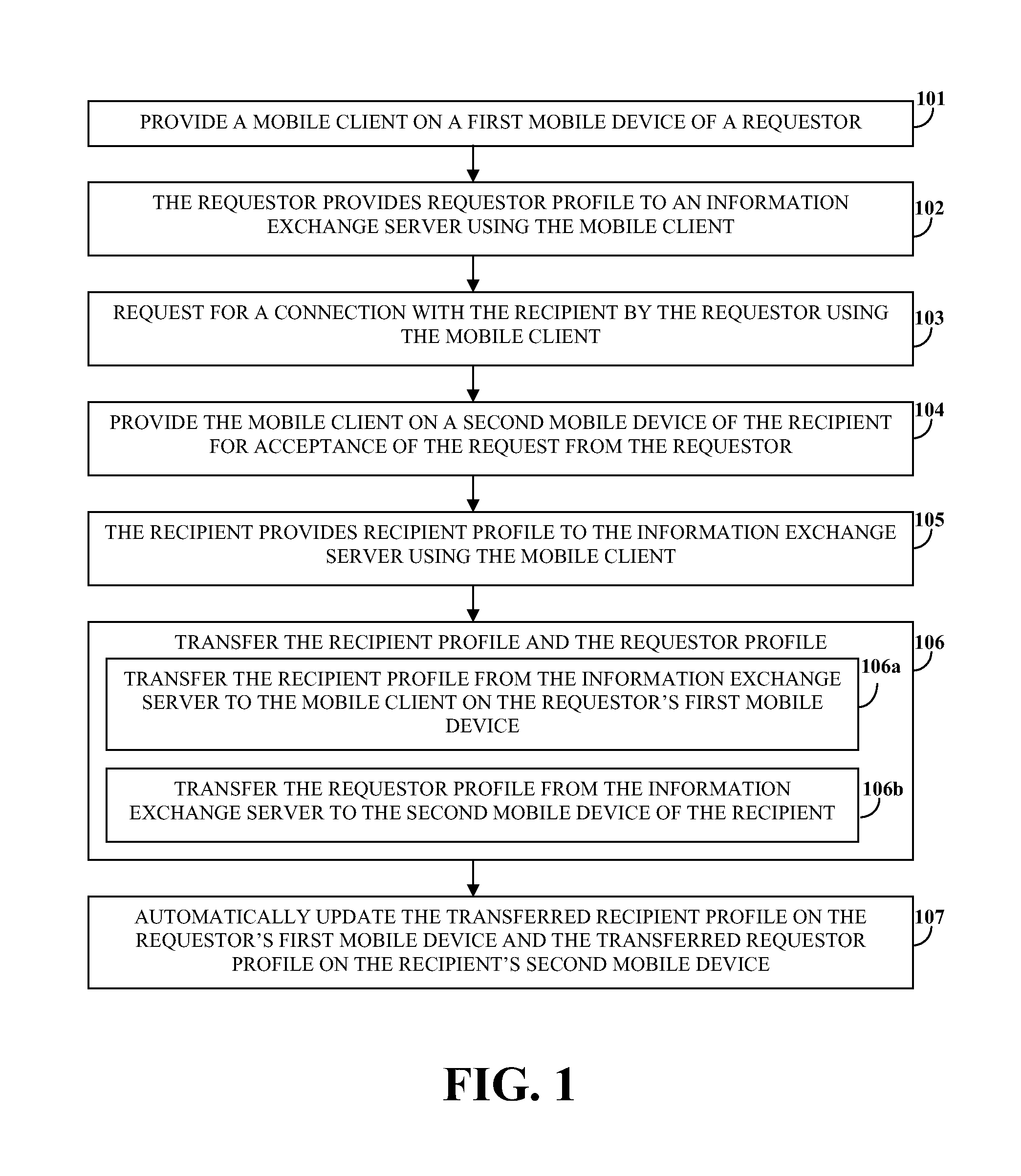
System and method for providing offline web application, page, and form access in a networked environment
InactiveUS20050188051A1Network can be impactedQuality improvementDigital data information retrievalNatural language data processingWeb applicationHTML
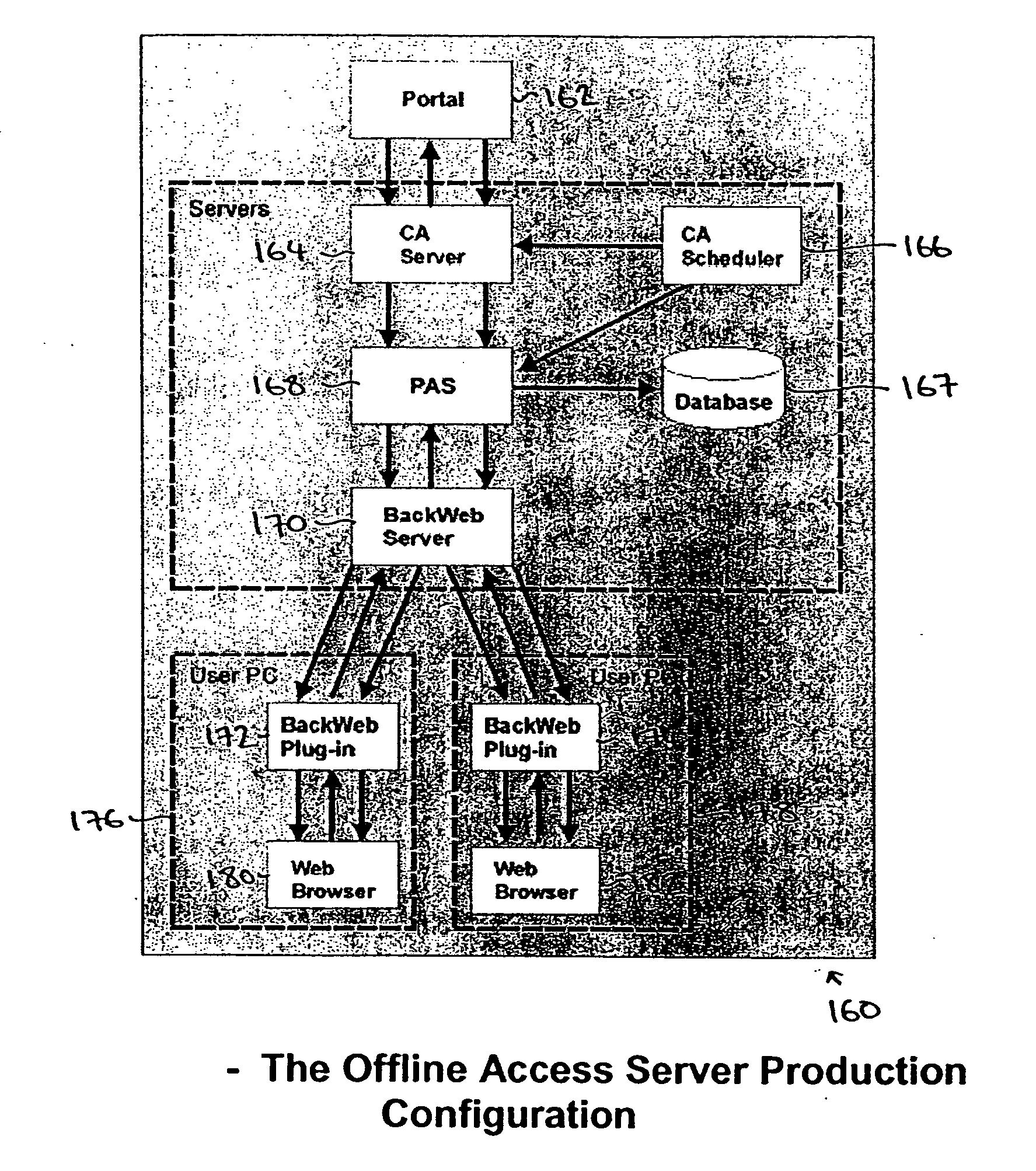
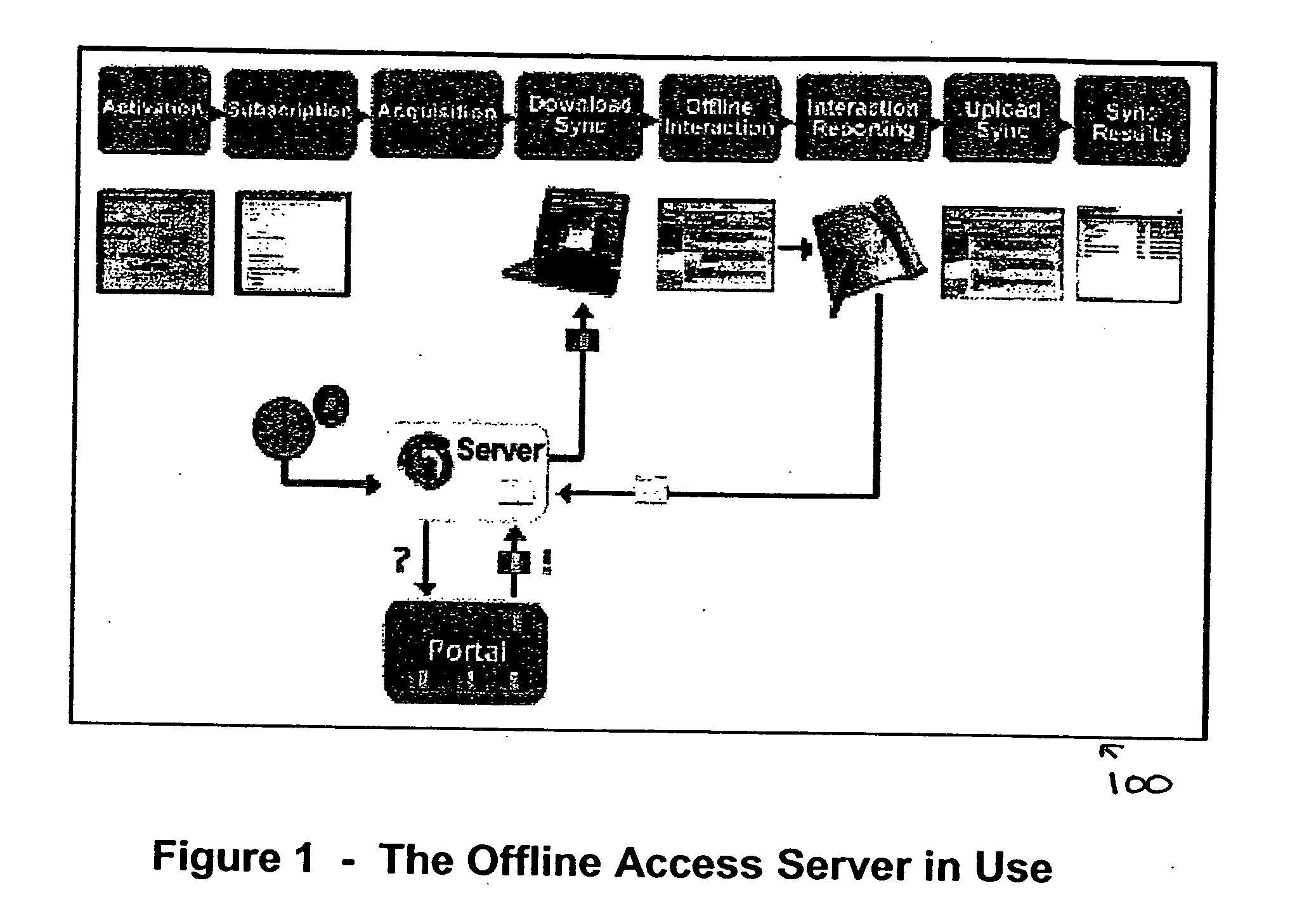
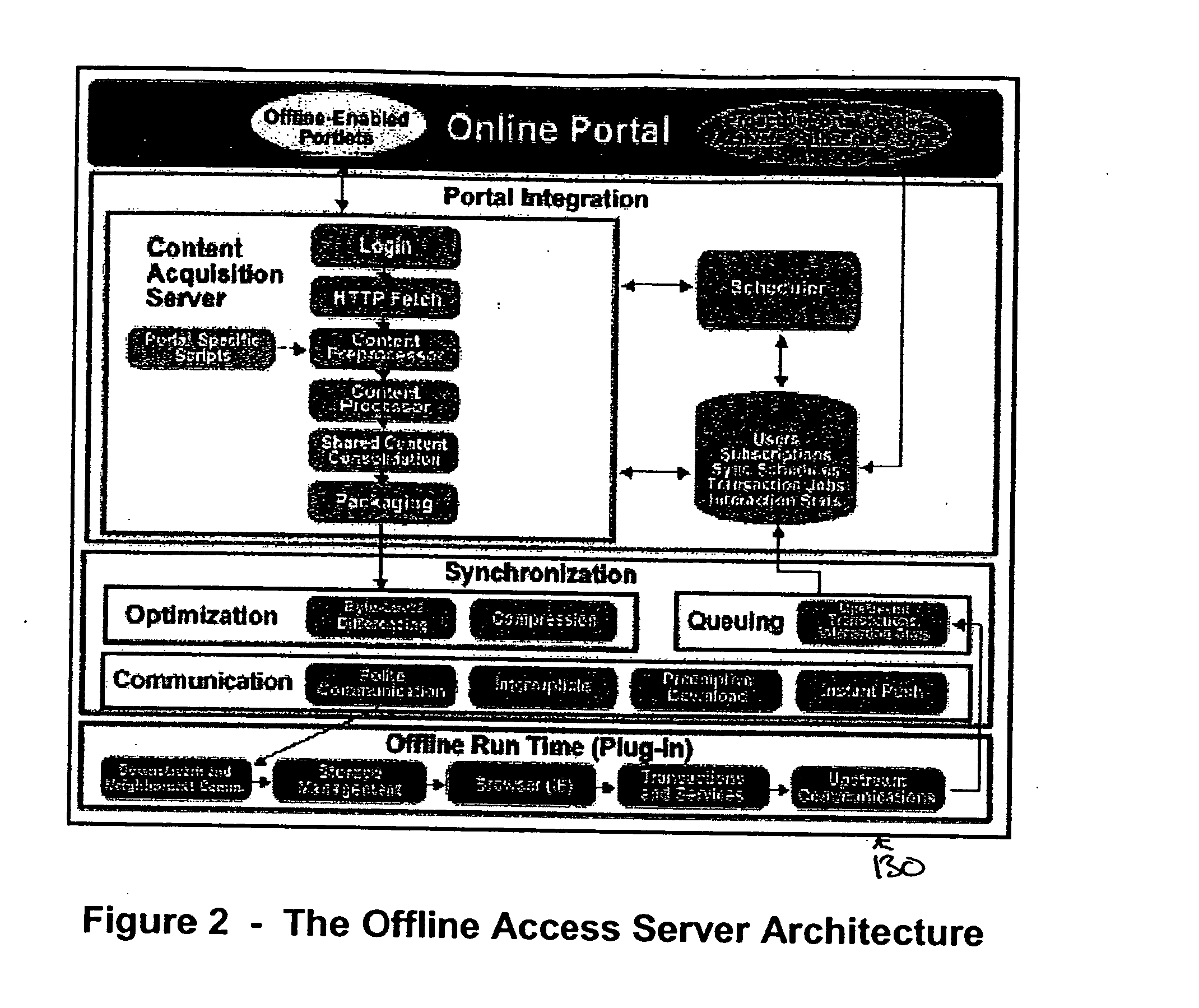
A system and a method for providing offline web application, page, and form access in a networked or Internet environment. In accordance with one embodiment an Offline Access Server offline Web infrastructure based on a scalable, polite communication technology. The Offline Access Server uses an offline enabling technology, and an HTML extension such as OTML (Offline Tagging Markup Language), to enable any set of web application, application data, page, or form to operate and to be usable offline.
Owner:RPX CORP
System and method of preventing web applications threats
InactiveUS20080034424A1Avoid attackMemory loss protectionError detection/correctionTraffic capacityWeb application
A system and method for protection of Web based applications are described. An agent is included in a web server such that traffic is routed through the agent. A security module is also in communication with the agent. The agent receives information about the application profile, and patterns of acceptable traffic behavior, from the security module. The agent acts as a gatekeeper, holding up suspicious traffic that does not match the pattern of acceptable traffic behavior until the suspicious traffic has been analyzed by the security module. Using the agent, malicious traffic can dropped before it can reach the application, or the user can be logged out, or both.
Owner:TRUSTWAVE HOLDINGS
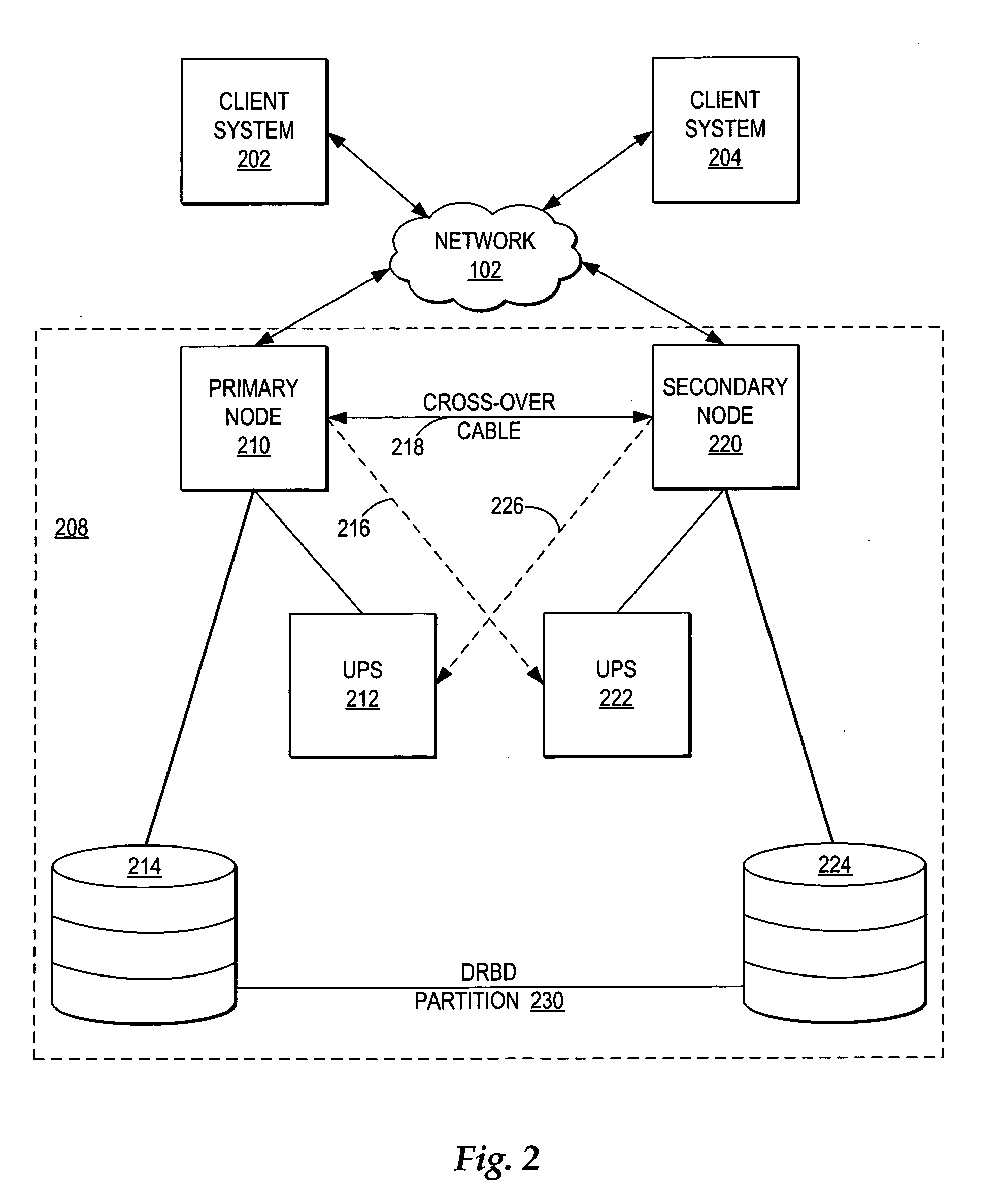
Managing failover of J2EE compliant middleware in a high availability system
InactiveUS20050172161A1Short recovery timeMinimal data lossRedundant hardware error correctionFailoverWeb application
A method, system, and program for managing failover of J2EE compliant middleware in a high availability system are provided. A primary node and a secondary node each run the same J2EE compliant middleware stack comprising layers including a load balancer, a web server, a web application server, a message control server, a monitoring server, and a database control server. In the primary node, all layers are active. In the secondary node, part of the layers are active and part of the layers are in standby. A data replication partition shared between the primary node and the secondary node includes persistent resource data accessible to a selection of the layers of the primary node. A heartbeat controller monitors each node, including the middleware stack, and upon detection of a failure, controls transfer of the services provided by the primary node to the secondary node by transferring virtual IP addresses from the primary node to the secondary node, remounting the data replication partition for access by the secondary node, and activating the standby layers which require access to the data in the data replication partition.
Owner:IBM CORP
System and method for synchronizing collaborative form filling
InactiveUS20120089659A1Natural language data processingMultiple digital computer combinationsWeb applicationServer
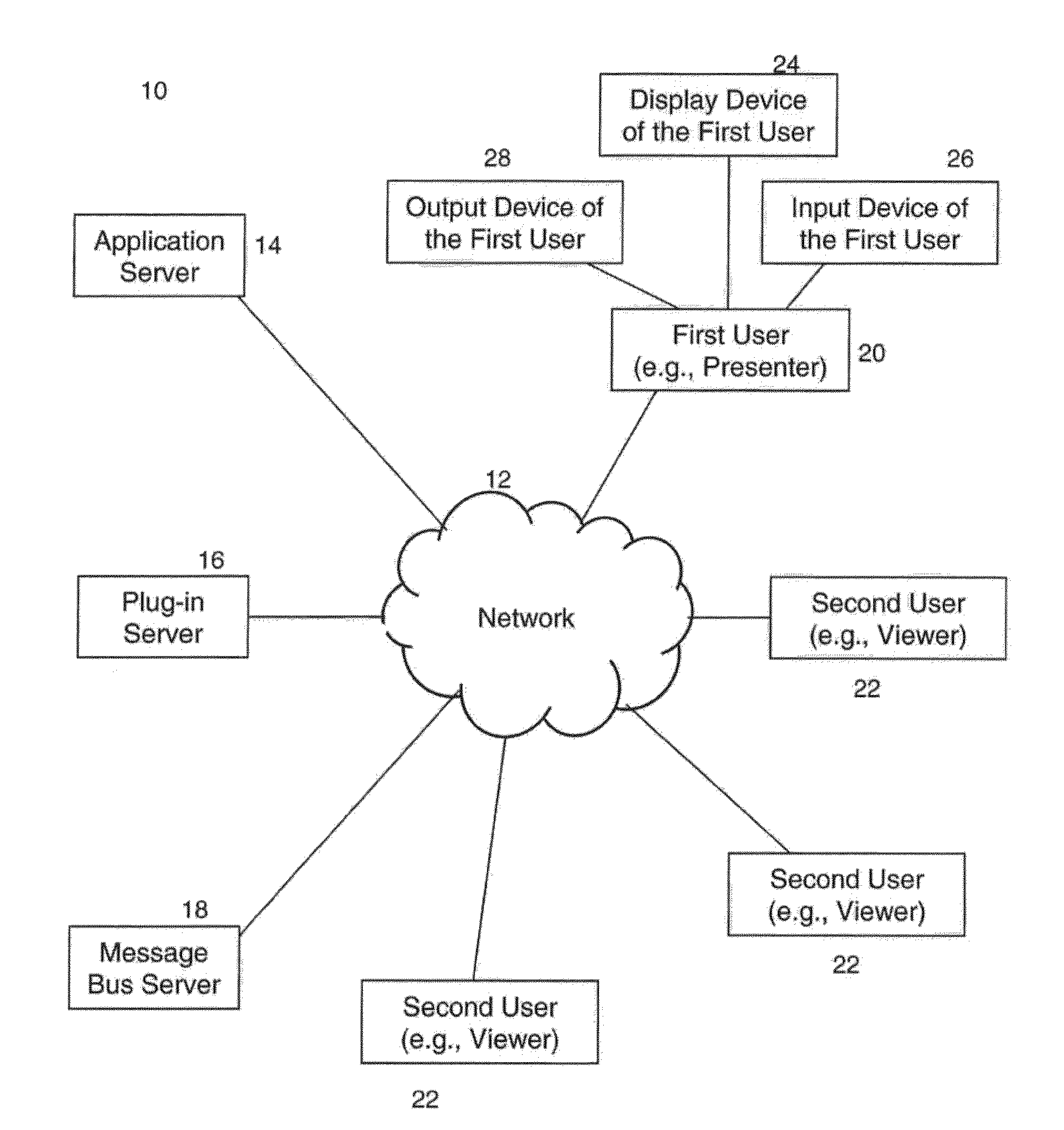
A system and method for synchronizing collaborative web applications, such as collaborative form filling, including using a message bus server and HTTP protocol.
Owner:HBR LABS
System for Running Web Applications Offline and Providing Access to Native Services
InactiveUS20080147671A1Special data processing applicationsWeb data browsing optimisationPersonalizationField service
Web applications such as email, photo-sharing website, or web widgets work only when the offsite server is available to provide content in real-time. The present invention provides a generic web standards based method of encapsulating the offline web application along with its runtime environment so that web applications can run even when connection to the server is not available. In addition the present invention combines methods for creating, provision, and running multiple offline web applications on a desktop computer or a mobile device such as cellular telephone or personal digital assistant. In addition the present invention also provides the ability to synchronize user data so that multiple devices can be provisioned for offline use with the same set of personalized user information.
Owner:QUALCOMM INC
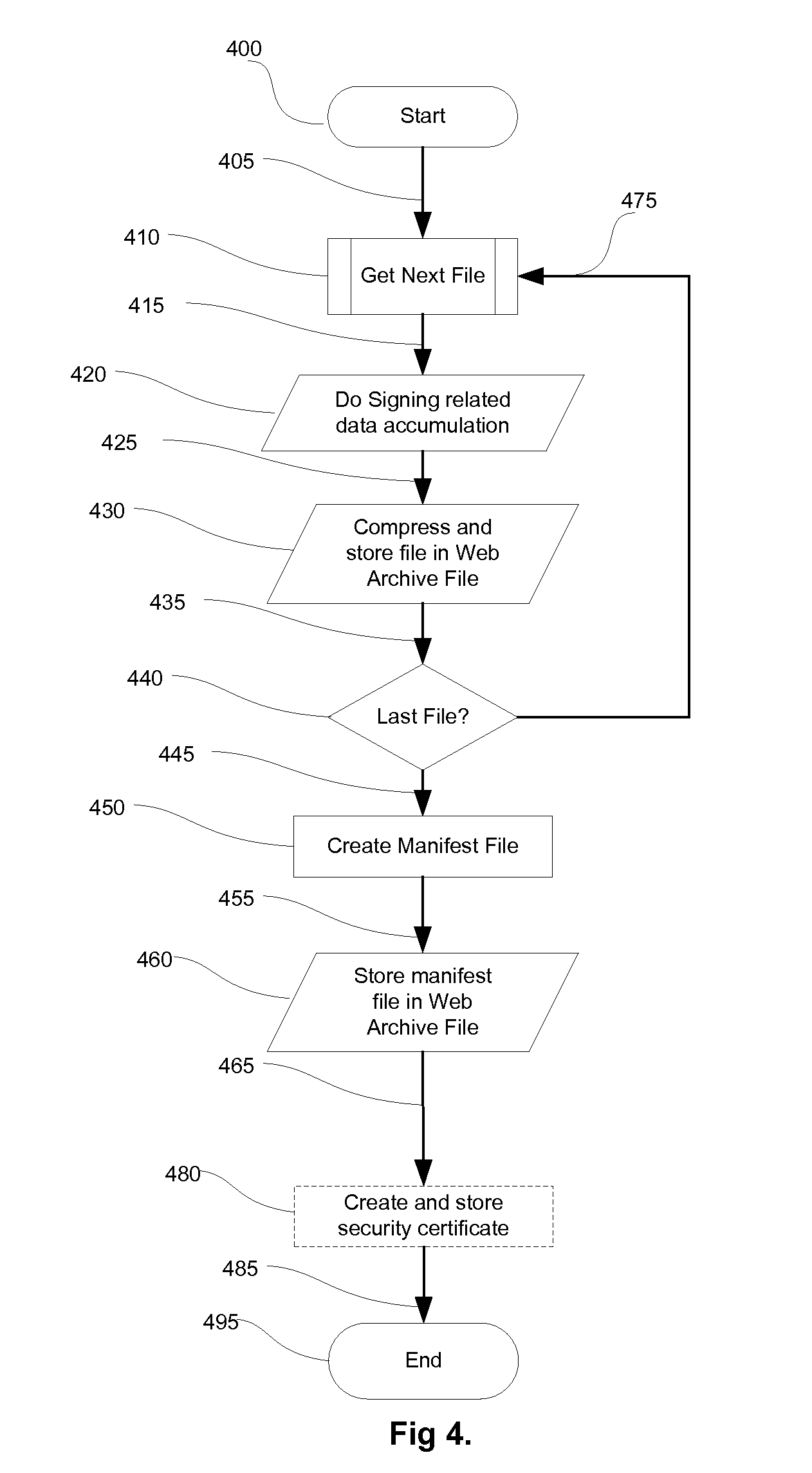
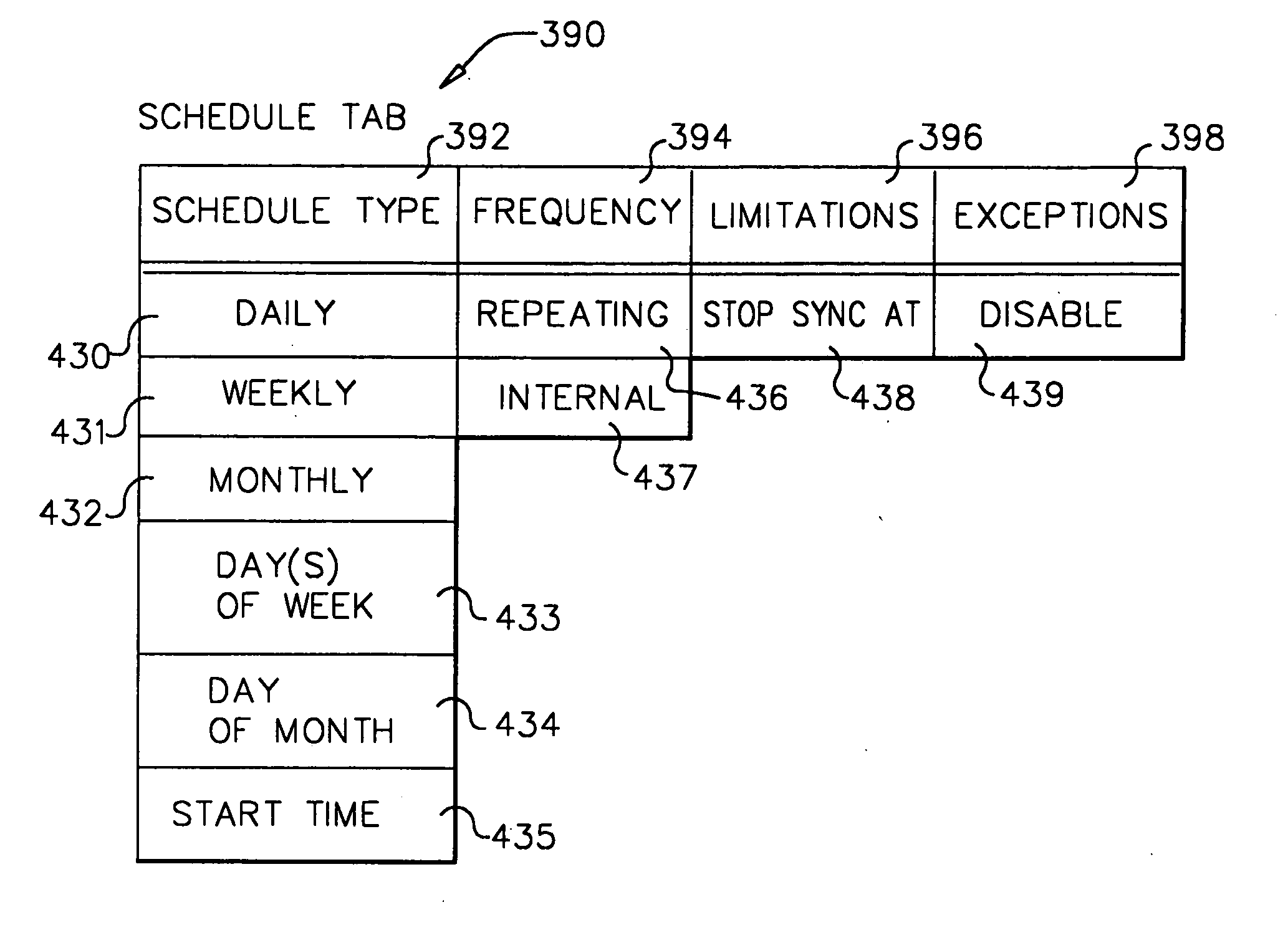
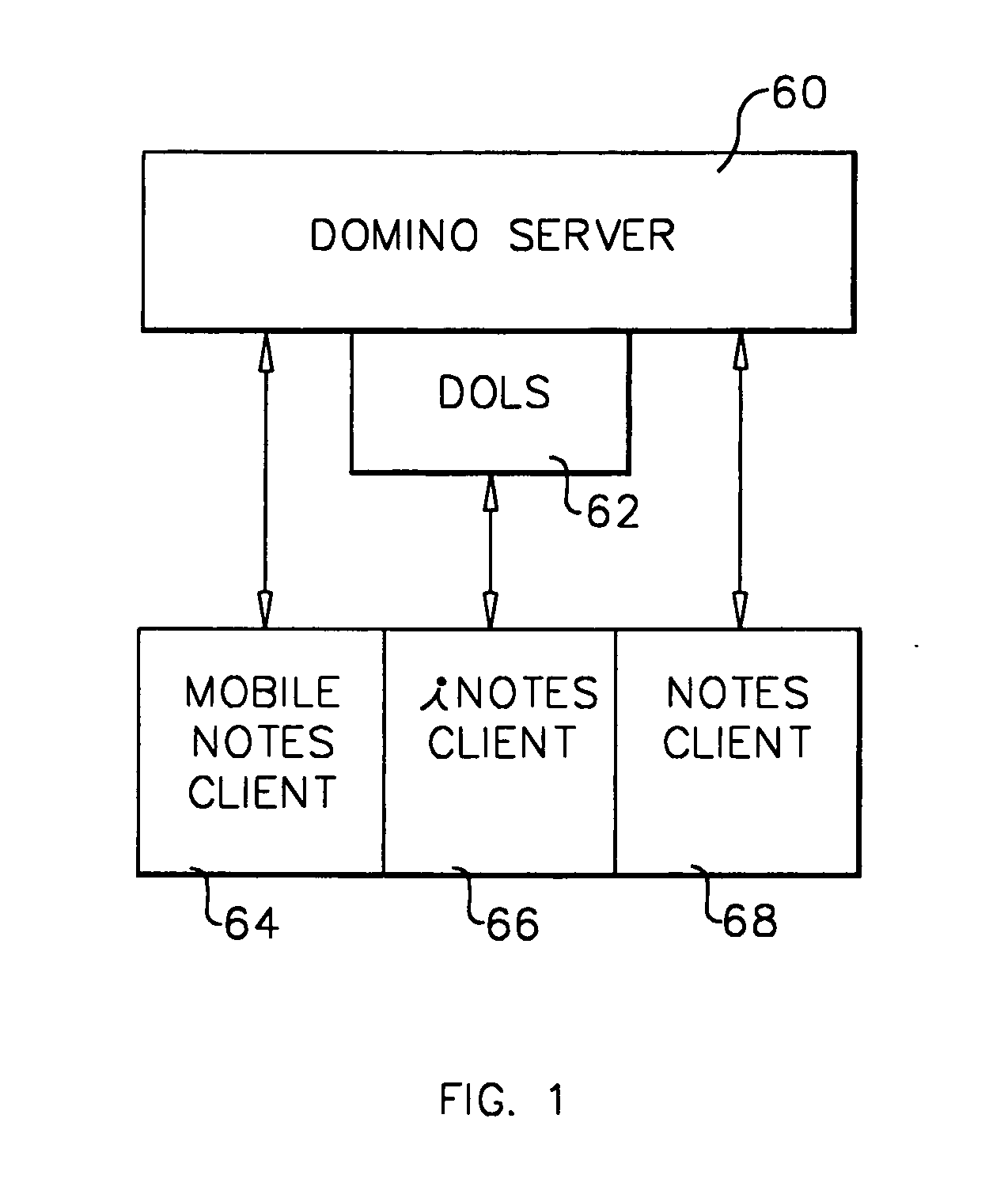
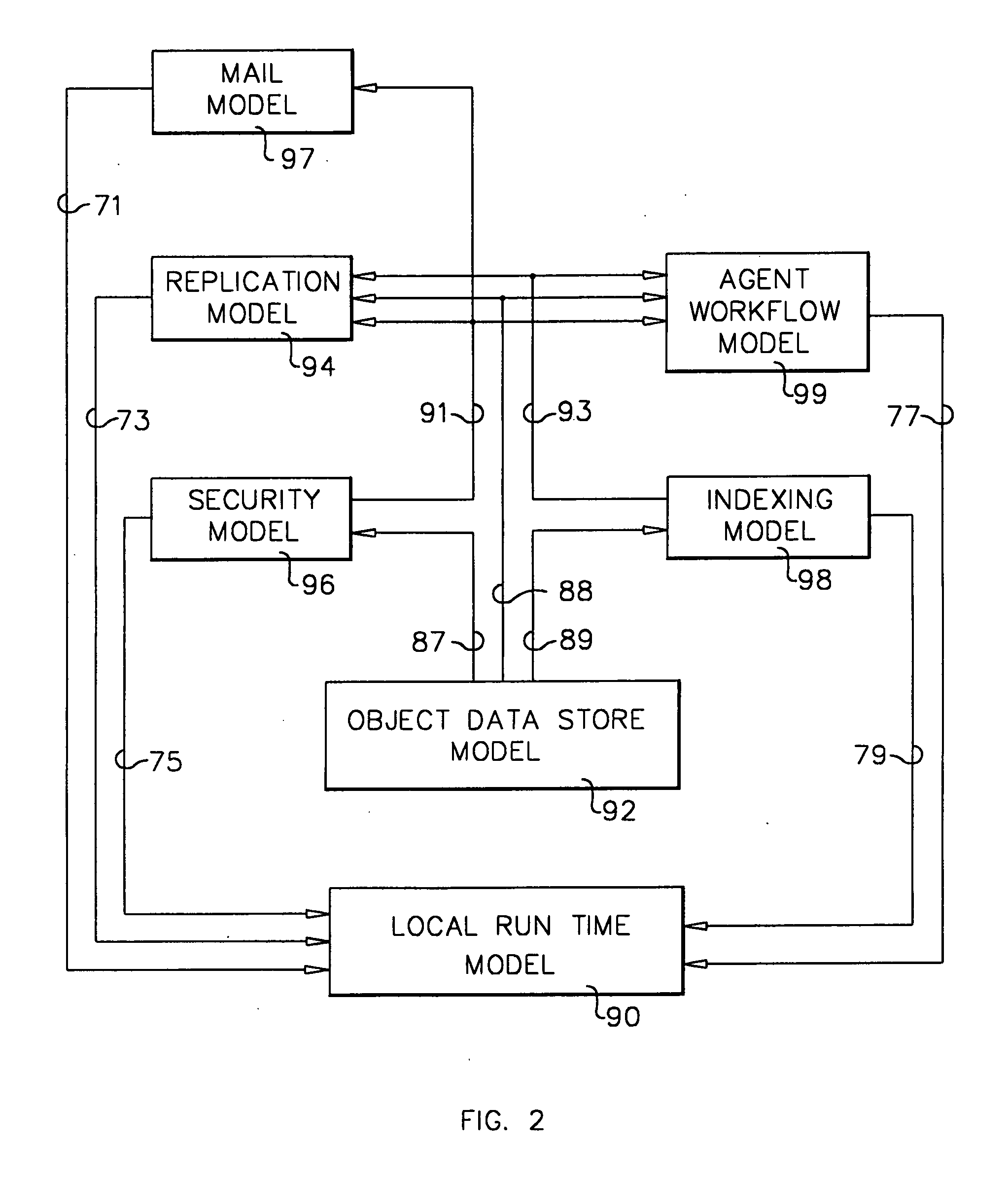
System and method for developing and administering web applications and services from a workflow, enterprise, and mail-enabled web application server and platform
ActiveUS20040201604A1Digital computer detailsOffice automationDocumentation procedurePartial application
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and. remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:HCL TECH LTD
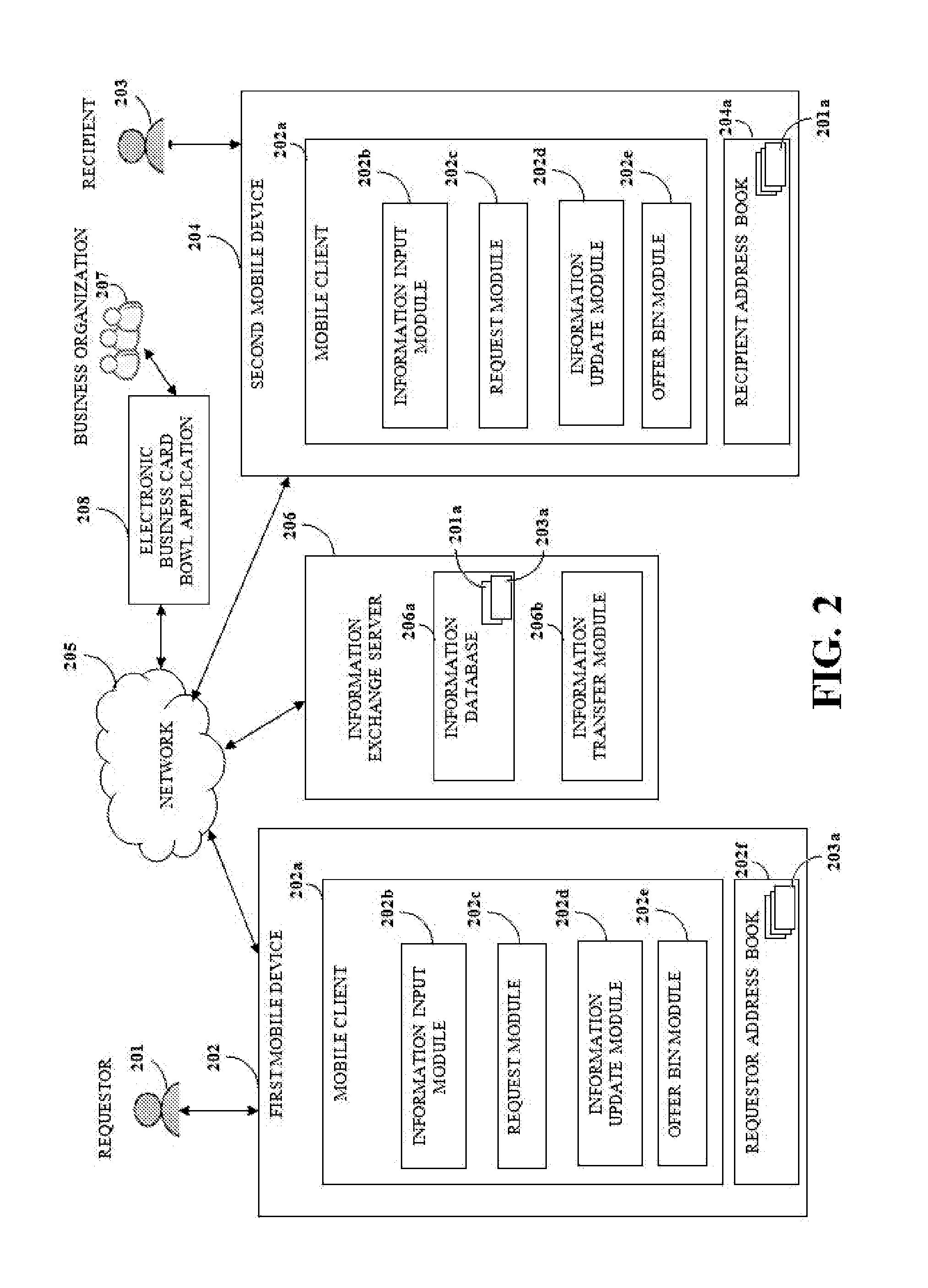
Crowd-sourced contact information and updating system using artificial intelligence
A method and system for crowdsourcing and managing contact and profile information of a user's contacts, and exchanging business and personal contact information through a mobile device, personal computer, or a web application. The system comprises a crowdsourcing intelligence module that provides the software, analysis, and algorithms for automatically populating and updating an individual's contact information in a user's address book based on contributed information and changes made to the individual's profile by a large community of users. The module also automatically populates and updates business profile, captures business's external social and business profiles, and analyzes demographic information which can then be transmitted to users. Users may also search for job opportunities, review and purchase products and services, review the location of contacts in proximity to the user, and manage sales and account activities including lead generation, lead qualification, and better understanding their customer base.
Owner:CIRCLEBACK
Method And System For Messaging And Communication Based On Groups
ActiveUS20070208802A1Natural language data processingMultiple digital computer combinationsTelecommunications linkWeb application
Systems and methods providing users with a rich web experience are disclosed. In one embodiment, a client and at least one server are in communication using a dual communication link. In another embodiment, a markup language based instant messaging application is disclosed. The instant messaging application may include group instant messaging. The instant messaging application may also provide group member persistence and message persistence at the server. In another embodiment, a card based web application is disclosed, where the card information and character may be shared with other users or within a group. The cards may also be configurable by users.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com