Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5844 results about "Middleware" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
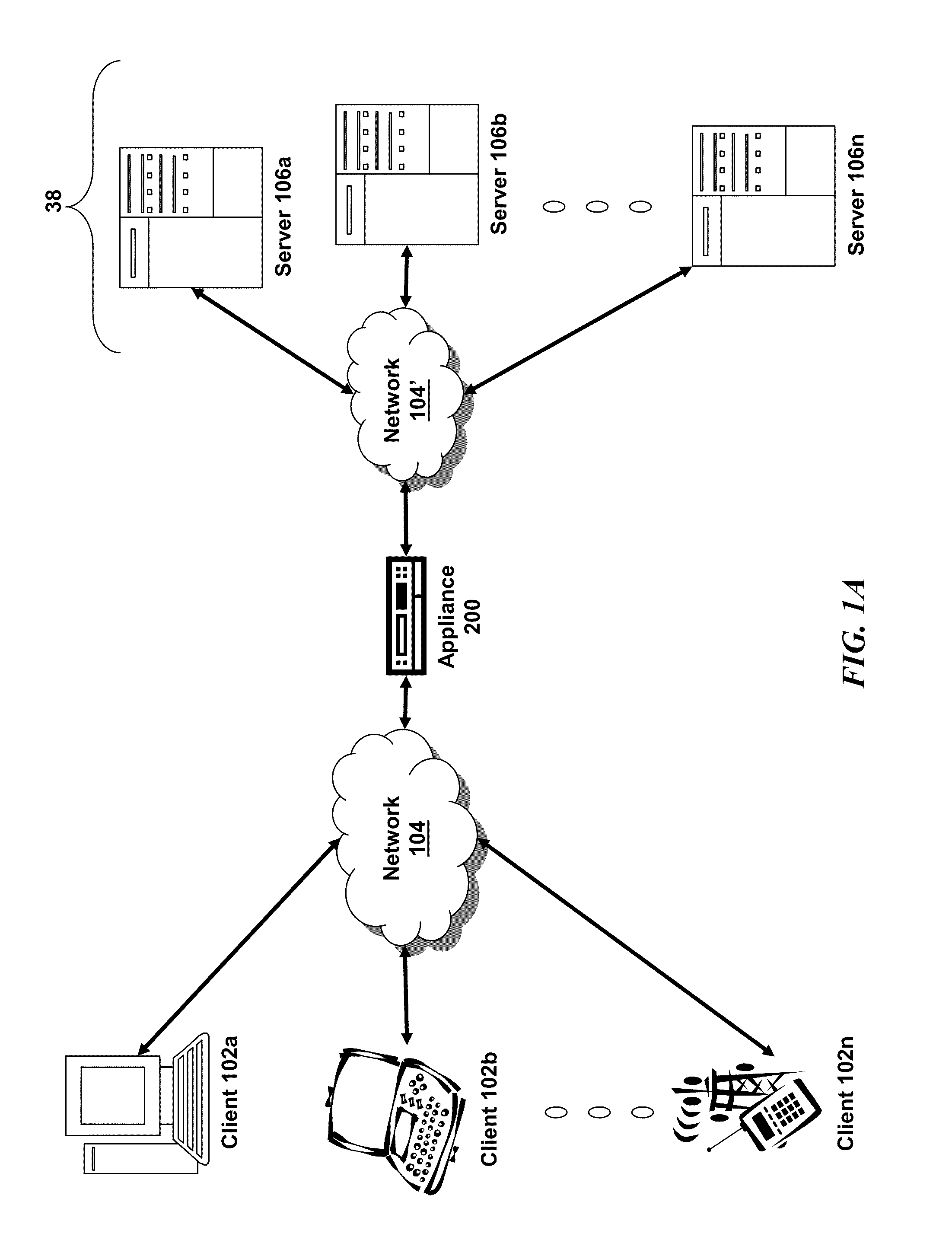
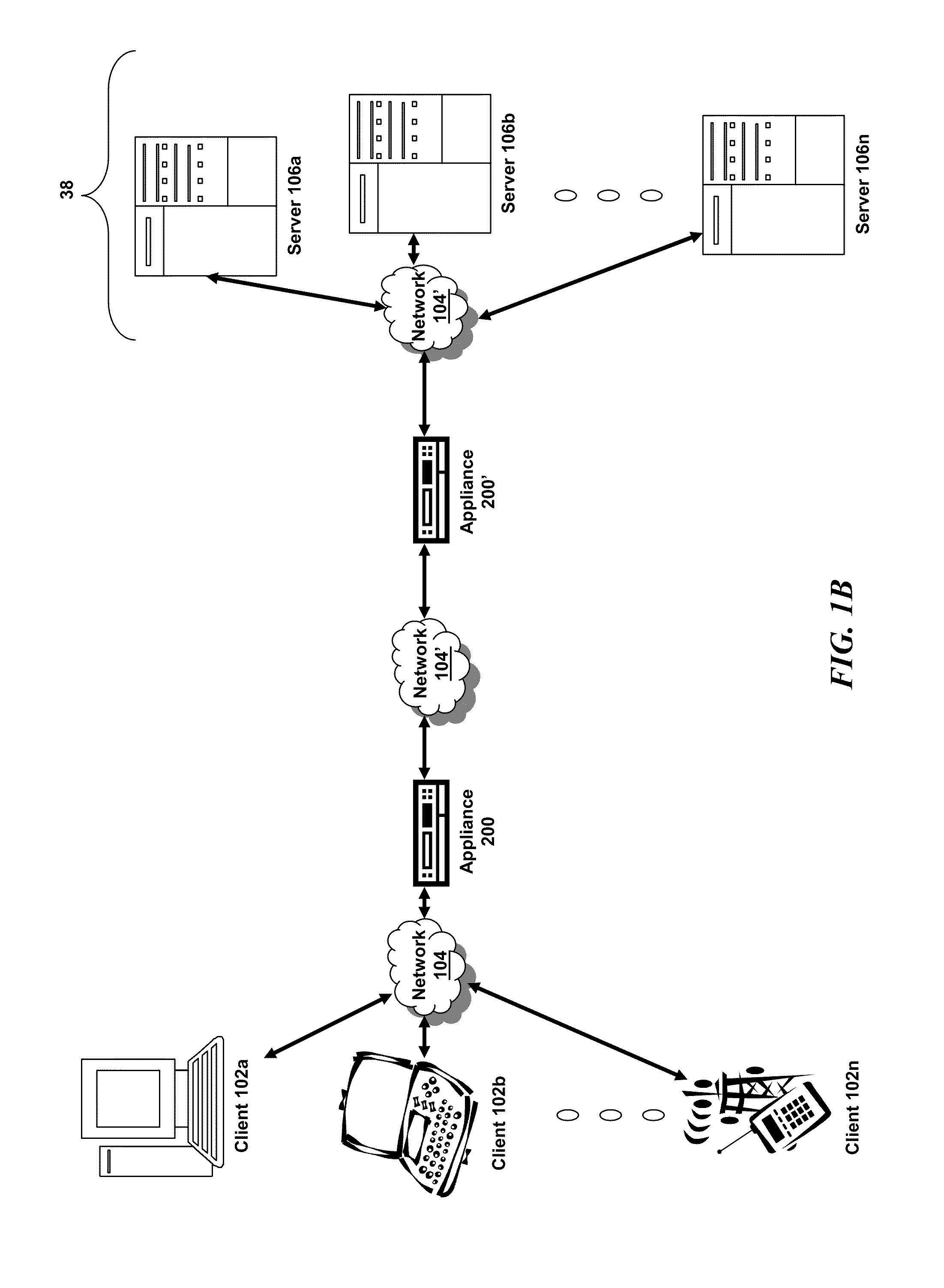
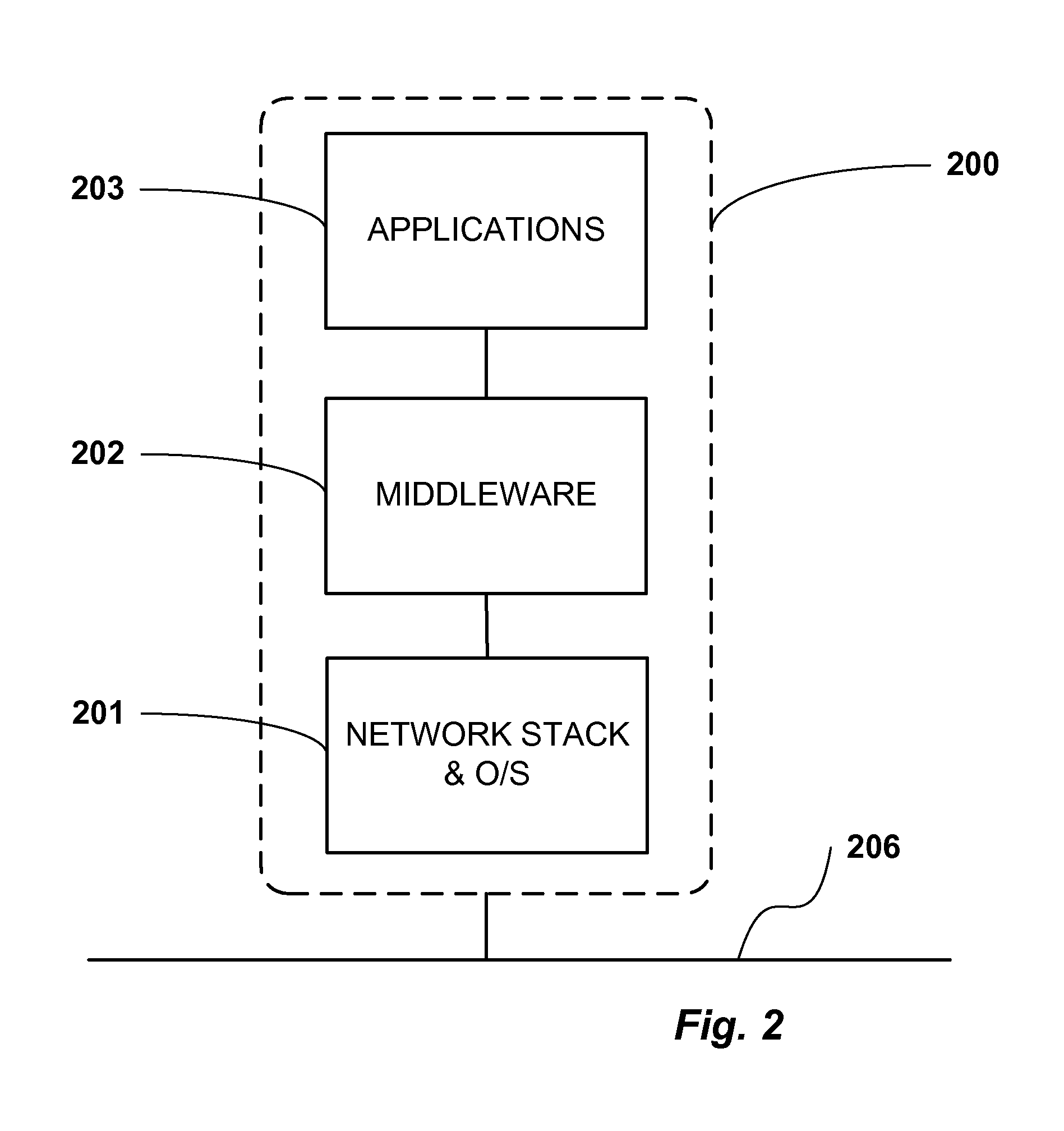
Middleware is computer software that provides services to software applications beyond those available from the operating system. It can be described as "software glue". Middleware makes it easier for software developers to implement communication and input/output, so they can focus on the specific purpose of their application. It gained popularity in the 1980s as a solution to the problem of how to link newer applications to older legacy systems, although the term had been in use since 1968.
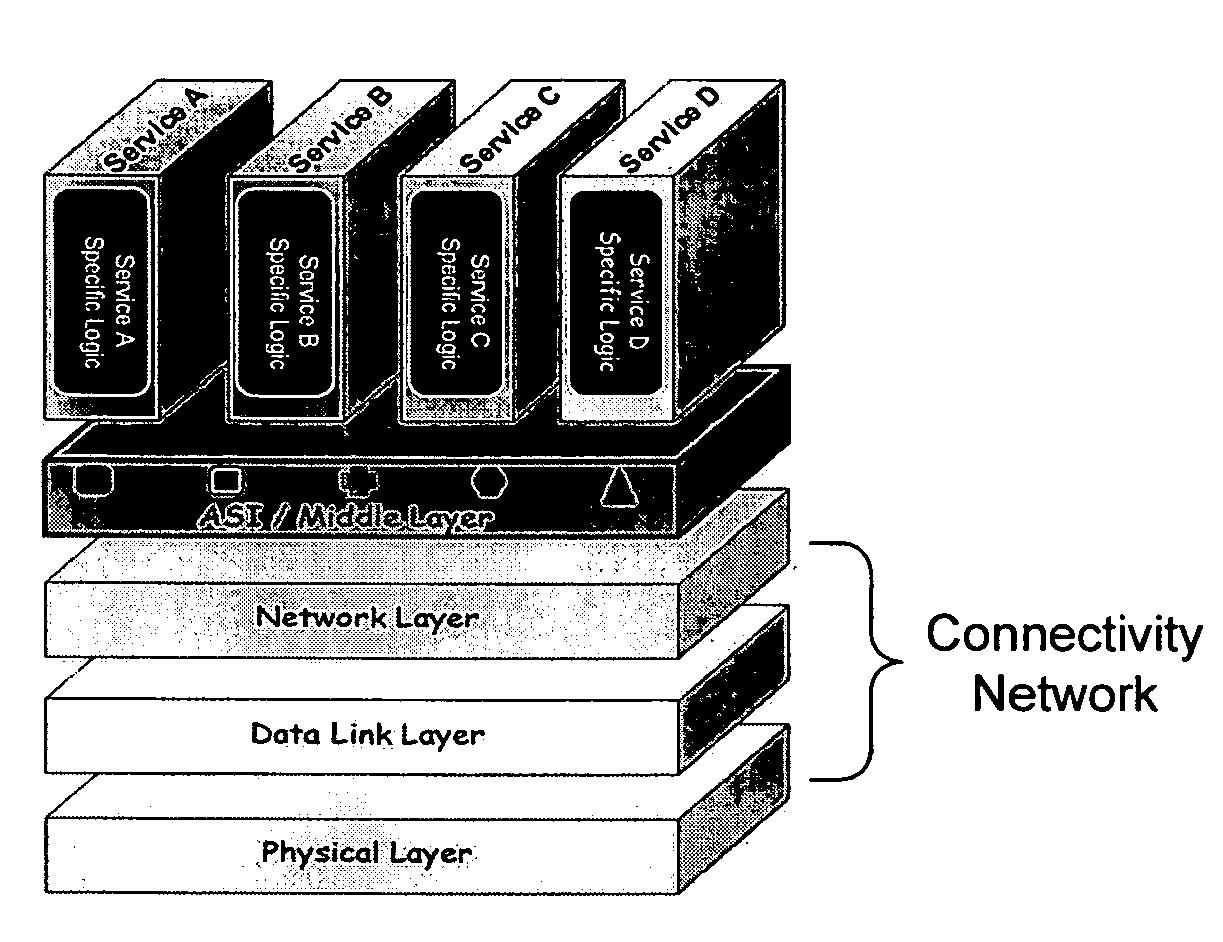
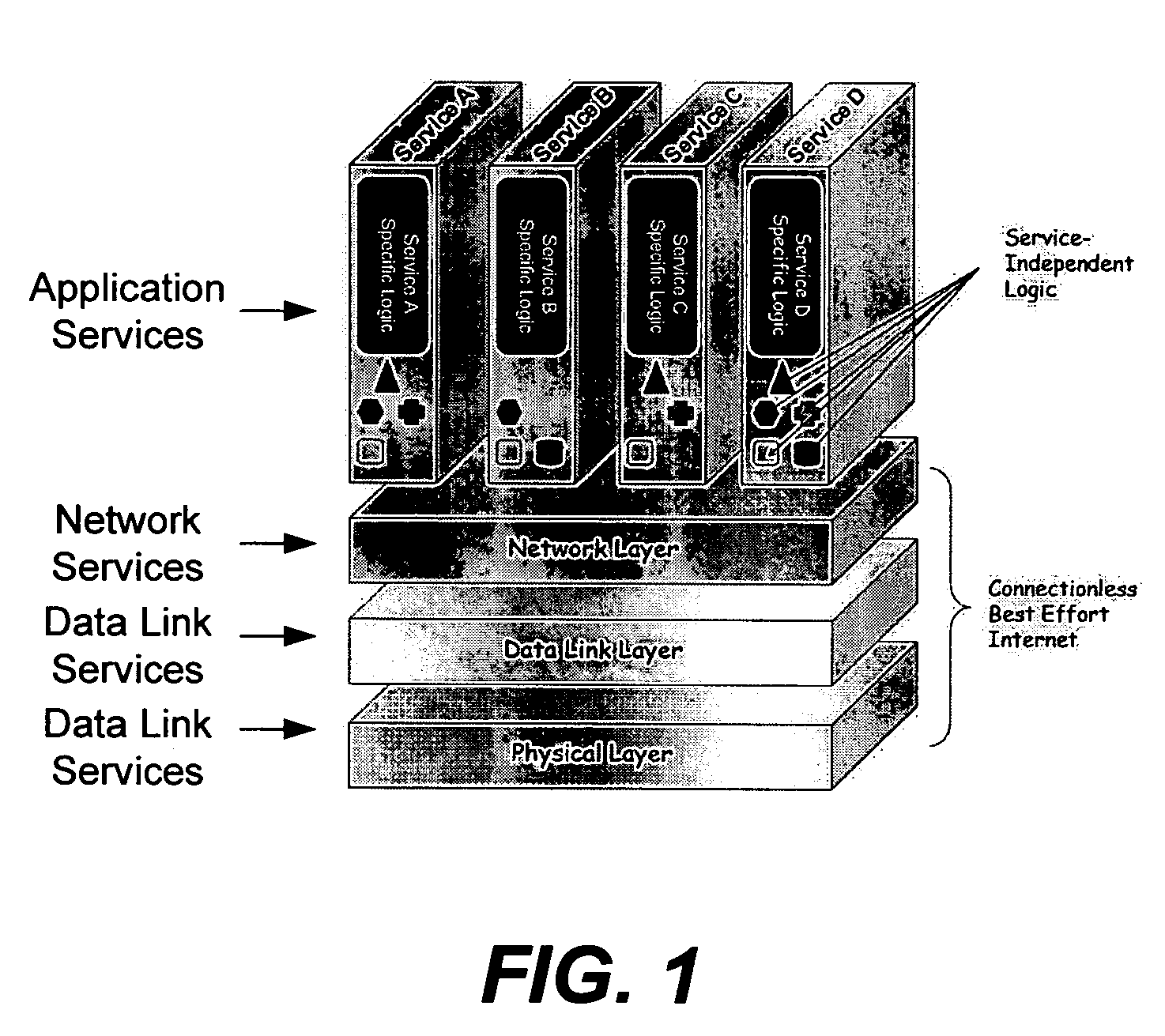
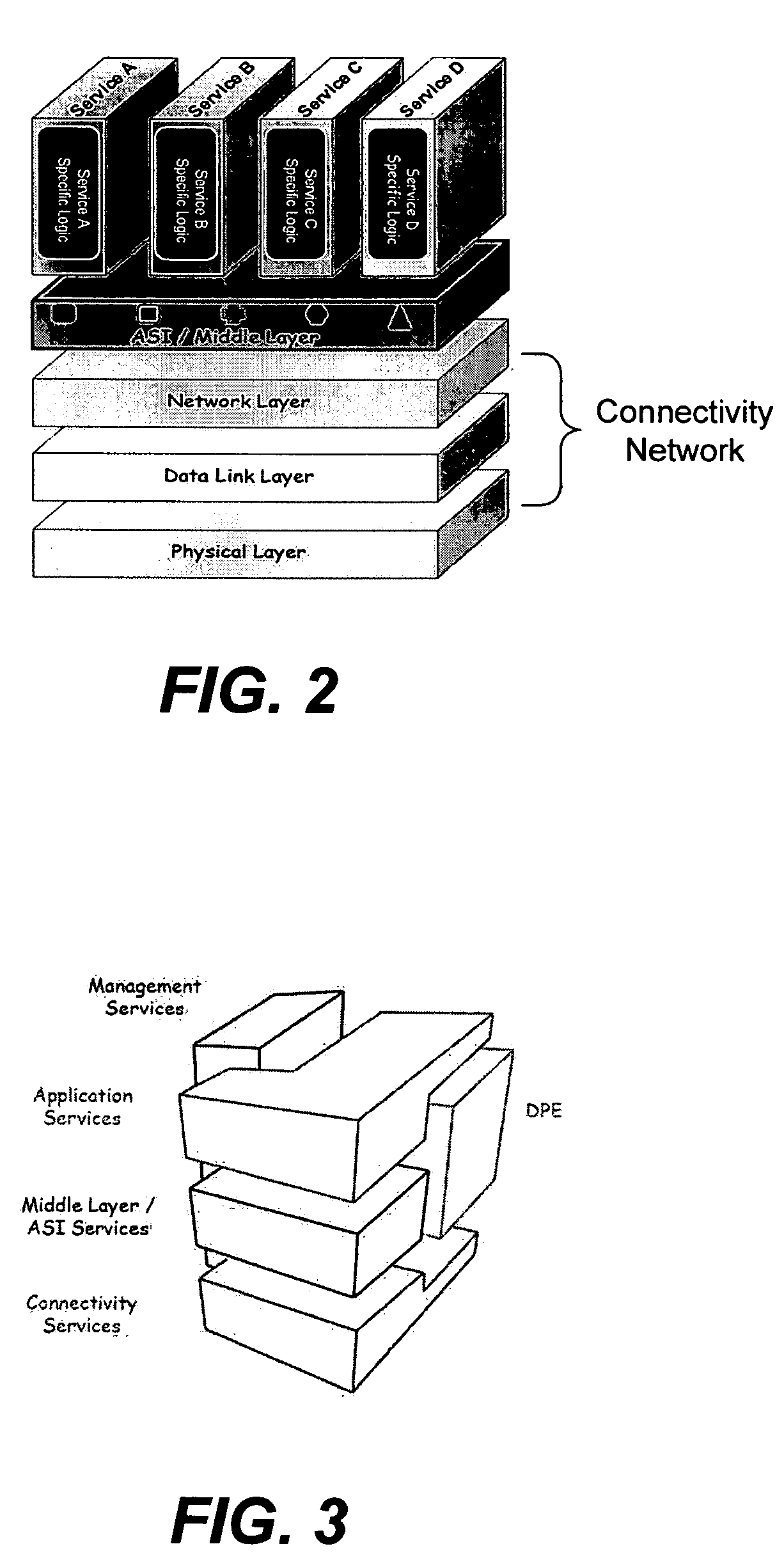
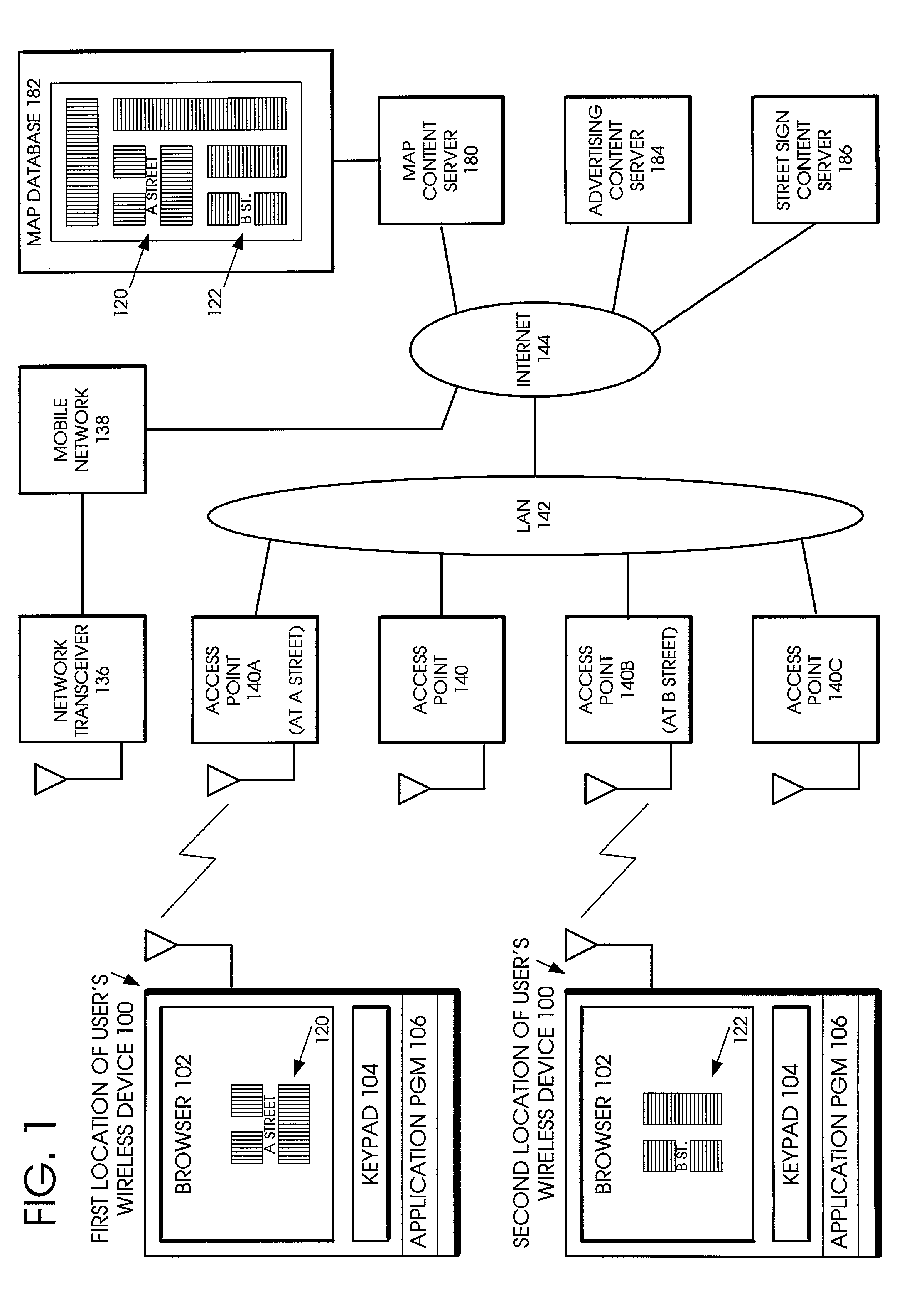
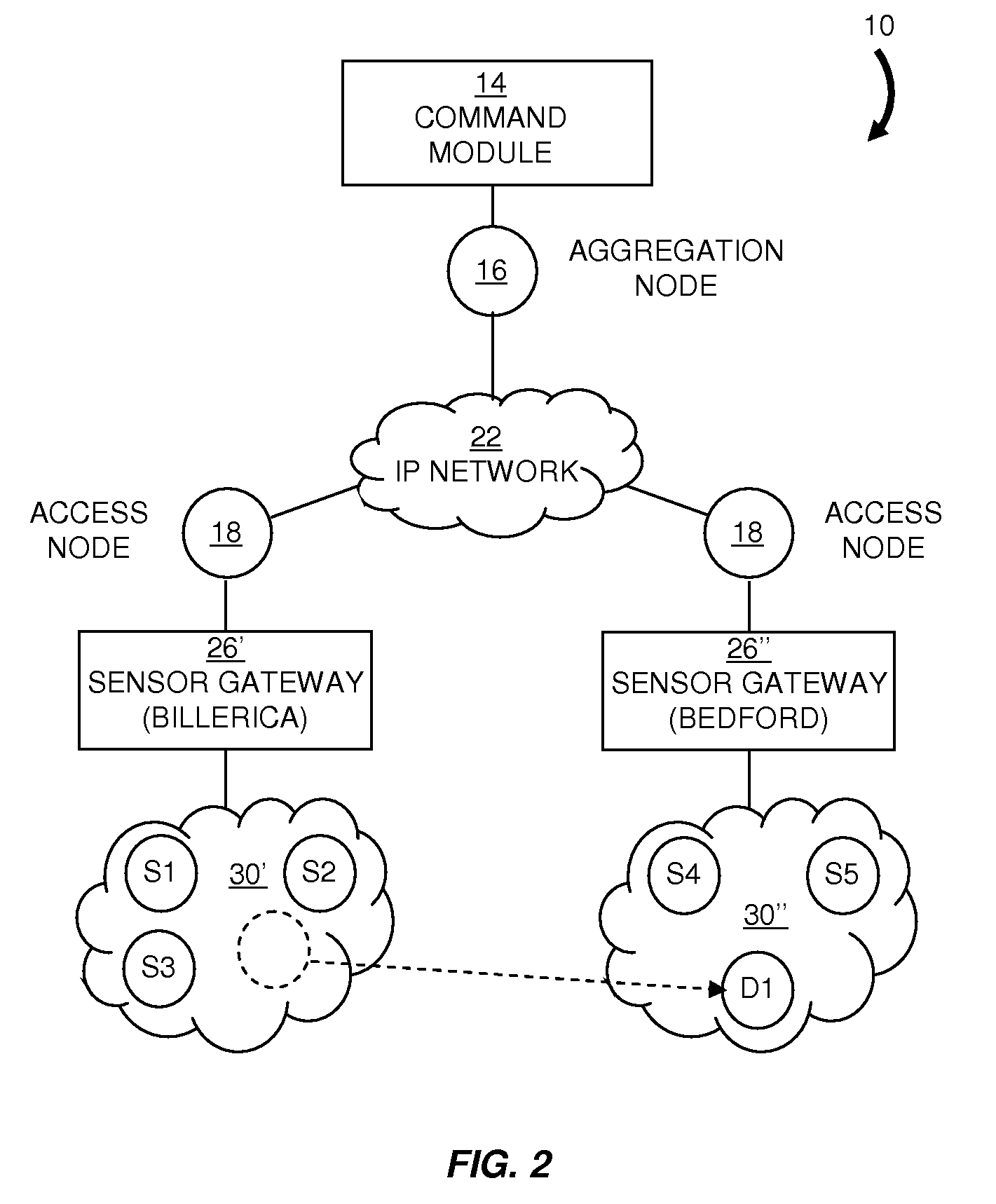
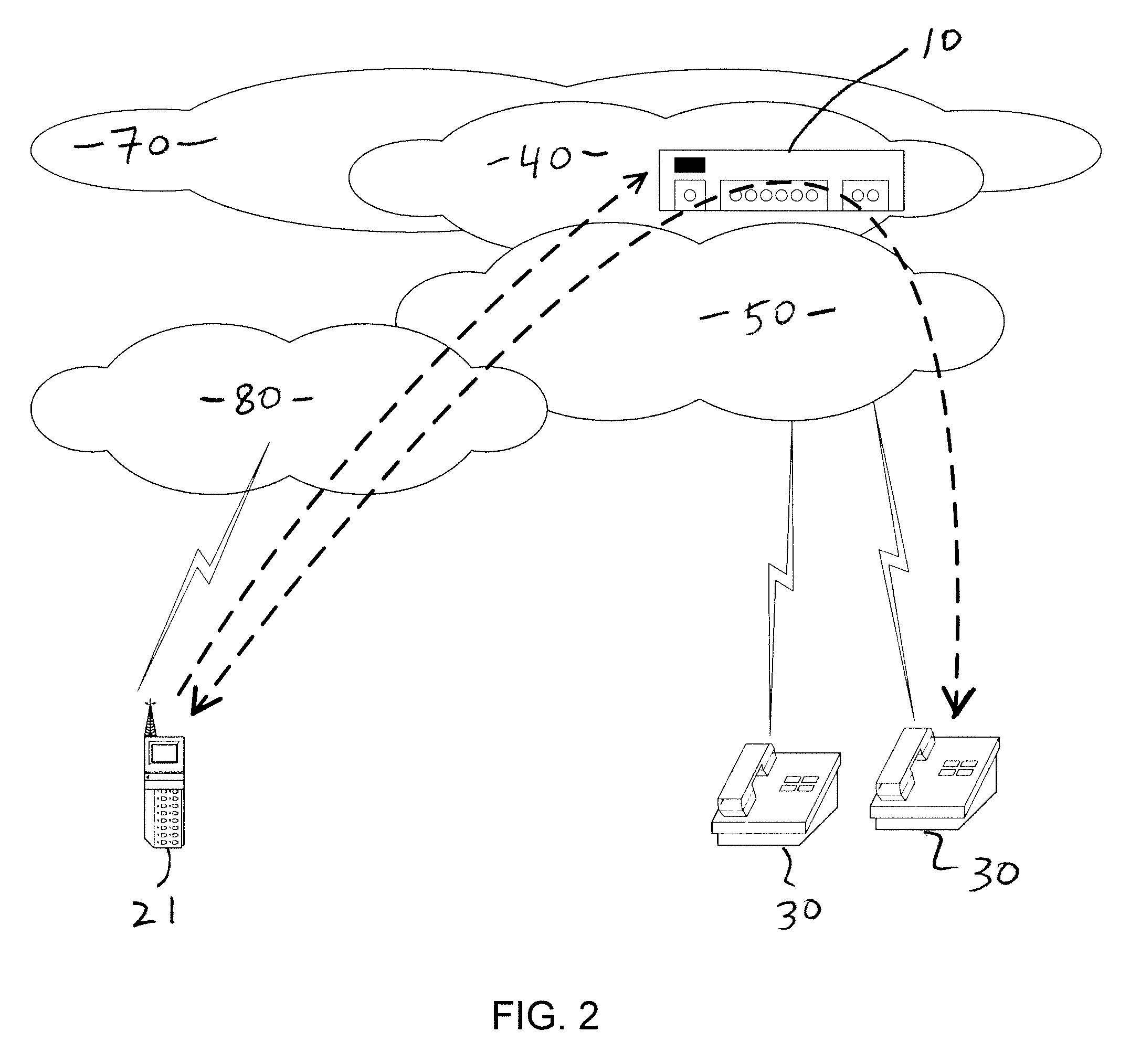
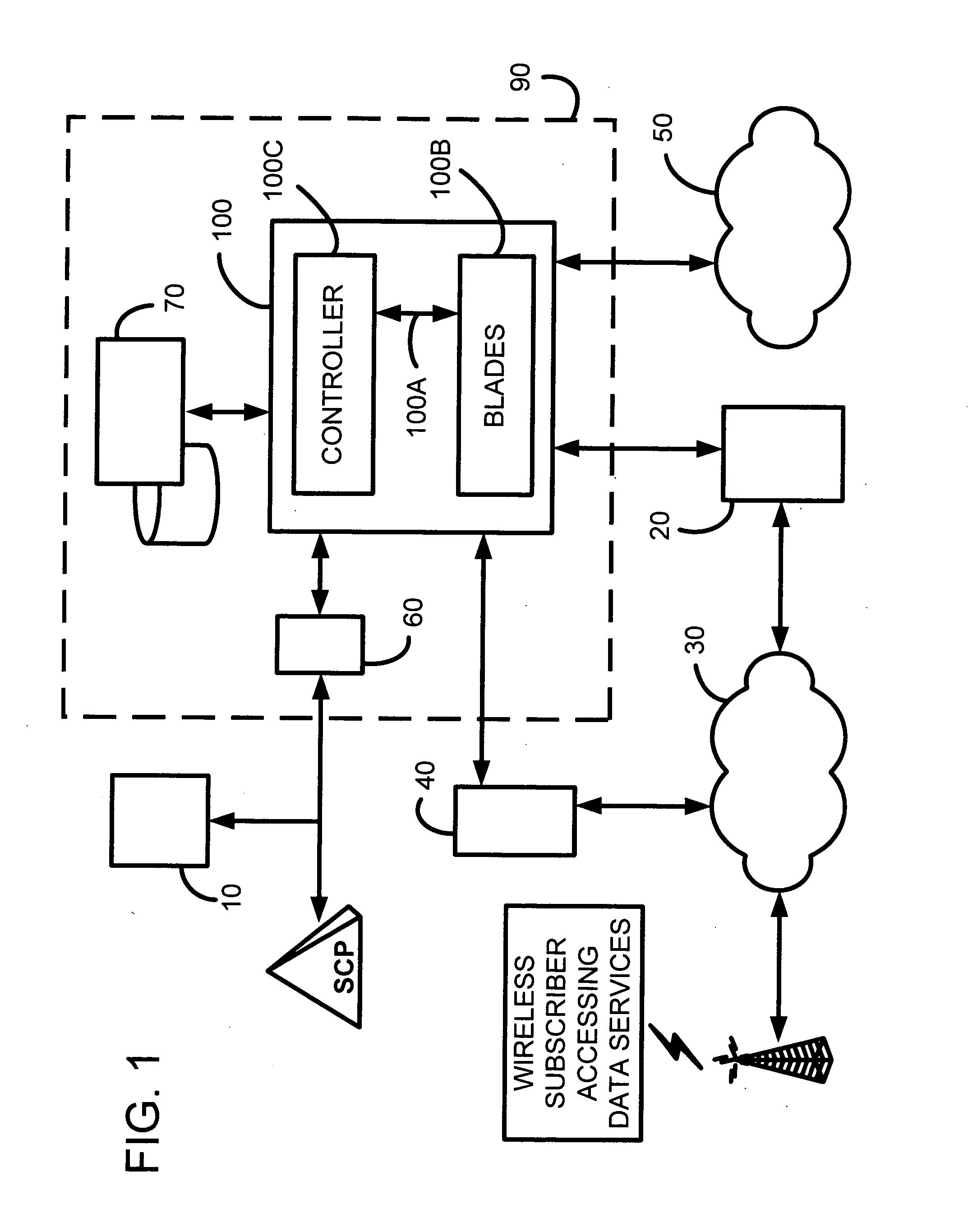
Application services infrastructure for next generation networks including one or more IP multimedia subsystem elements and methods of providing the same
A system for supporting a plurality of different applications utilizing a next generation network having a network layer includes an application services middleware between the applications and the network layer that includes a plurality of common infrastructure elements usable by the different applications. The common infrastructure elements provide both services associated with use of the network and services that are not associated with use of the network. At least one of the common infrastructure elements is an Internet Protocol (IP) Multimedia Subsystem (IMS) element.
Owner:BELLSOUTH INTPROP COR
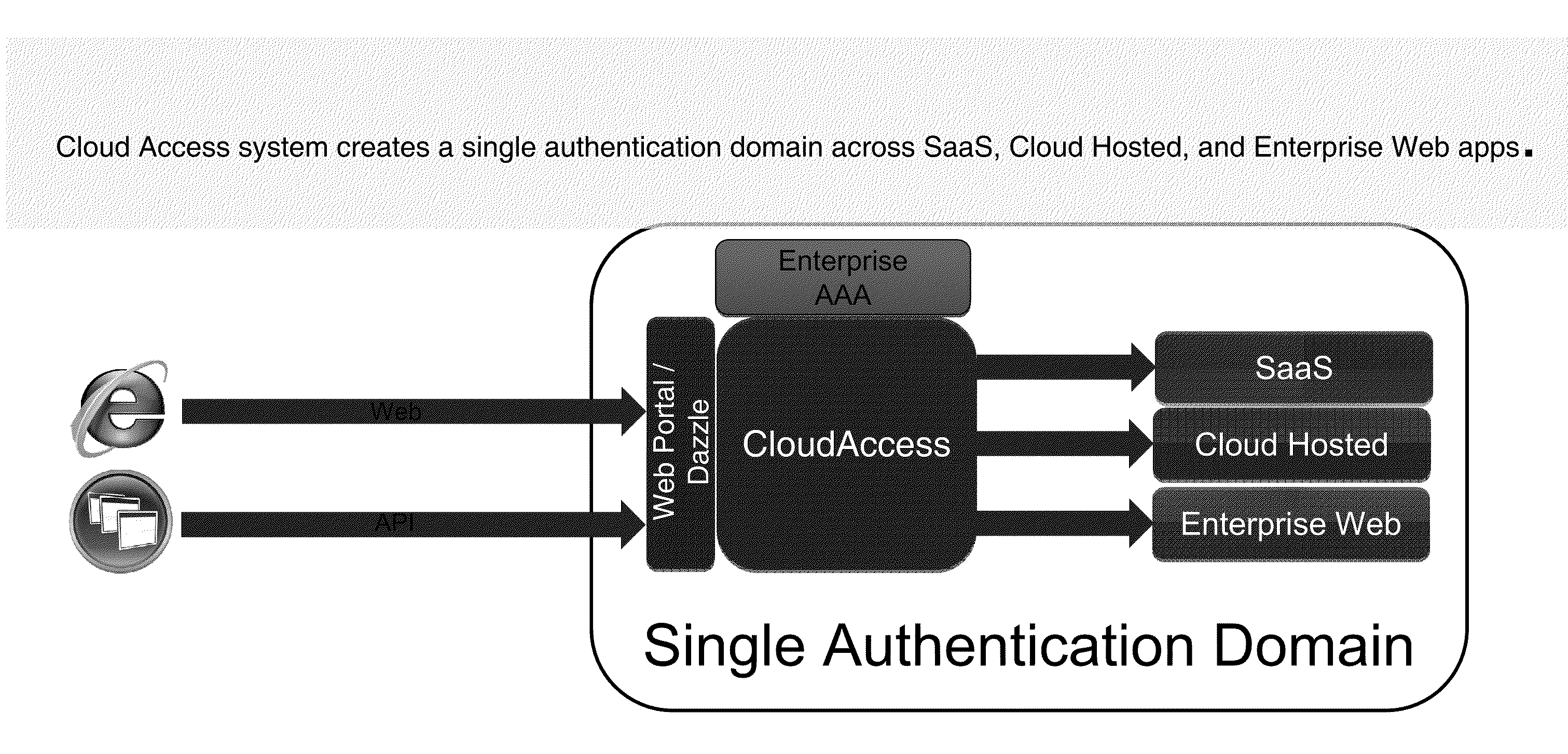
Systems and Methods for Providing a Single Click Access to Enterprise, SAAS and Cloud Hosted Application
ActiveUS20110277027A1Input/output for user-computer interactionDigital data processing detailsThird partyGraphics
The present disclosure is directed to methods and systems of providing a user-selectable list of disparately hosted applications. A device intermediary to a client and one or more servers may receive a user request to access a list of applications published to the user. The device may communicate to the client the list of published applications available to the user, the list comprising graphical icons corresponding to disparately hosted applications, at least one graphical icon corresponding to a third-party hosted application of the disparately hosted applications, the third party hosted application served by a remote third-party server. The device may receive a selection from the user of the at least one graphical icon. The device may communicate, from the remote third party server to the client of the user, execution of the third party hosted application responsive to the selection by the user.
Owner:CITRIX SYST INC
Dynamically provisioning middleboxes
Hybrid security architecture (HSA) provides a platform for middlebox traversal in the network. The HSA decouples the middlebox control from network forwarding. More specifically, such embodiments may receive a data packet having a packet header including an Ethernet header identifying source and destination addresses in the network. A traffic type of the data packet is determined. Then, layer-2 forwarding information, which encodes a set of non-forwarding network service provider middleboxes in the network to be traversed by the data packet, is determined based on the traffic type. The layer-2 forwarding information is inserted into the Ethernet header and the data packet is forwarded into the network. The data packet will then traverse, according to the layer-2 forwarding information, a sequence of the middleboxes in the network, wherein at least one non-forwarding network service will be provided by each of the middleboxes to the data packet in a sequence.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Middlebox control
InactiveUS20030093481A1Good flexibilityThe process is simple and effectiveData switching by path configurationMultiple digital computer combinationsComputer networkMiddleware
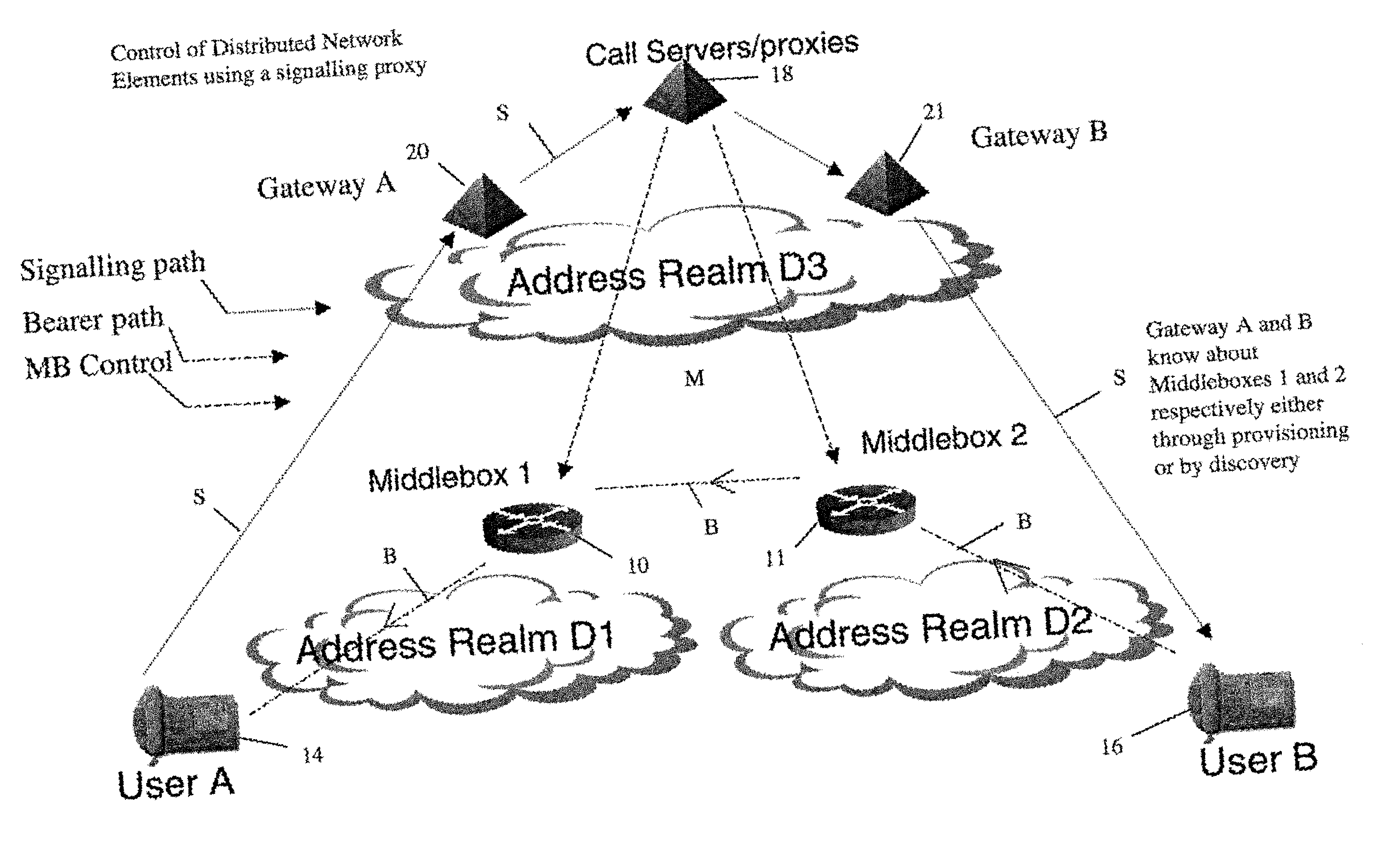
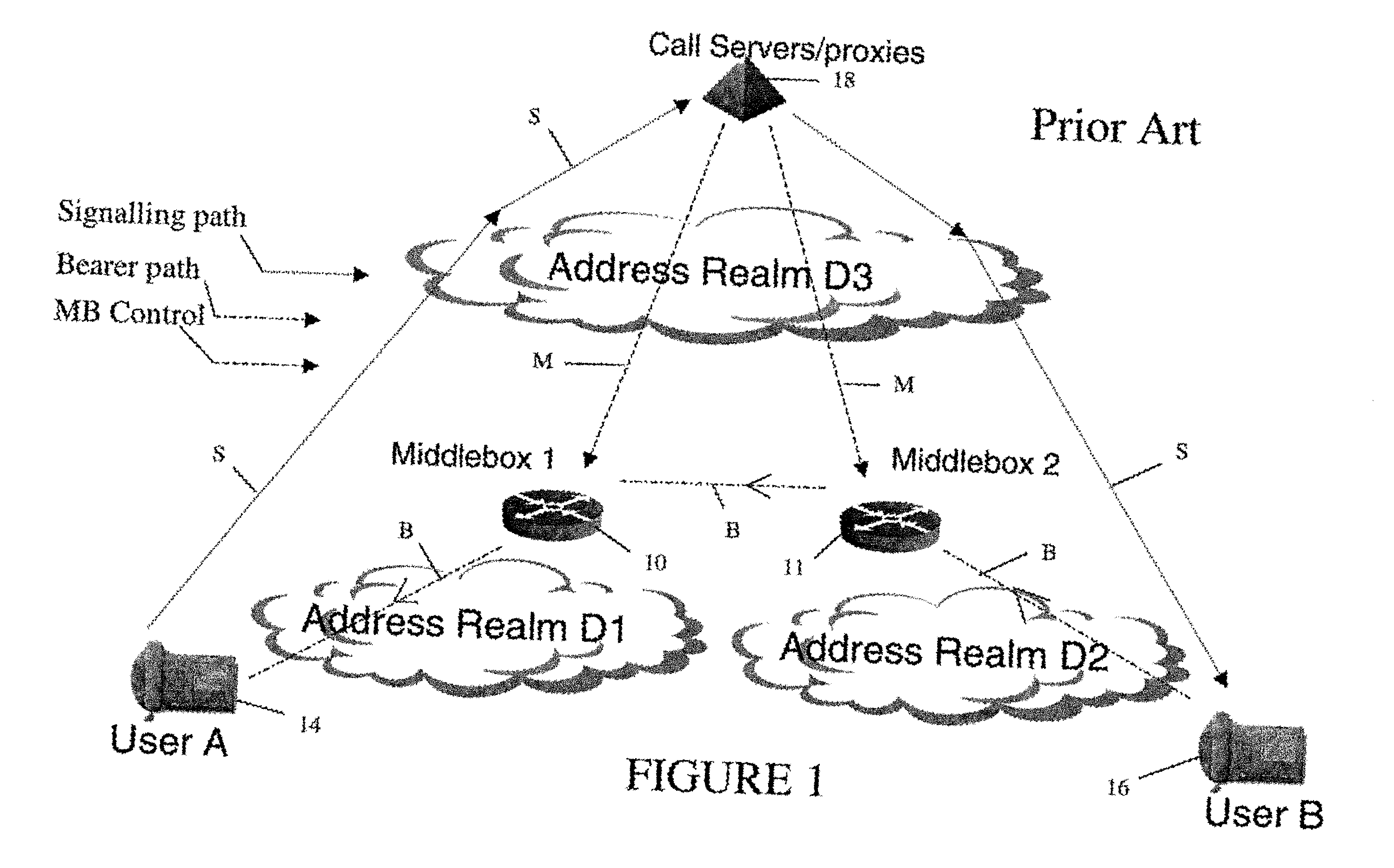
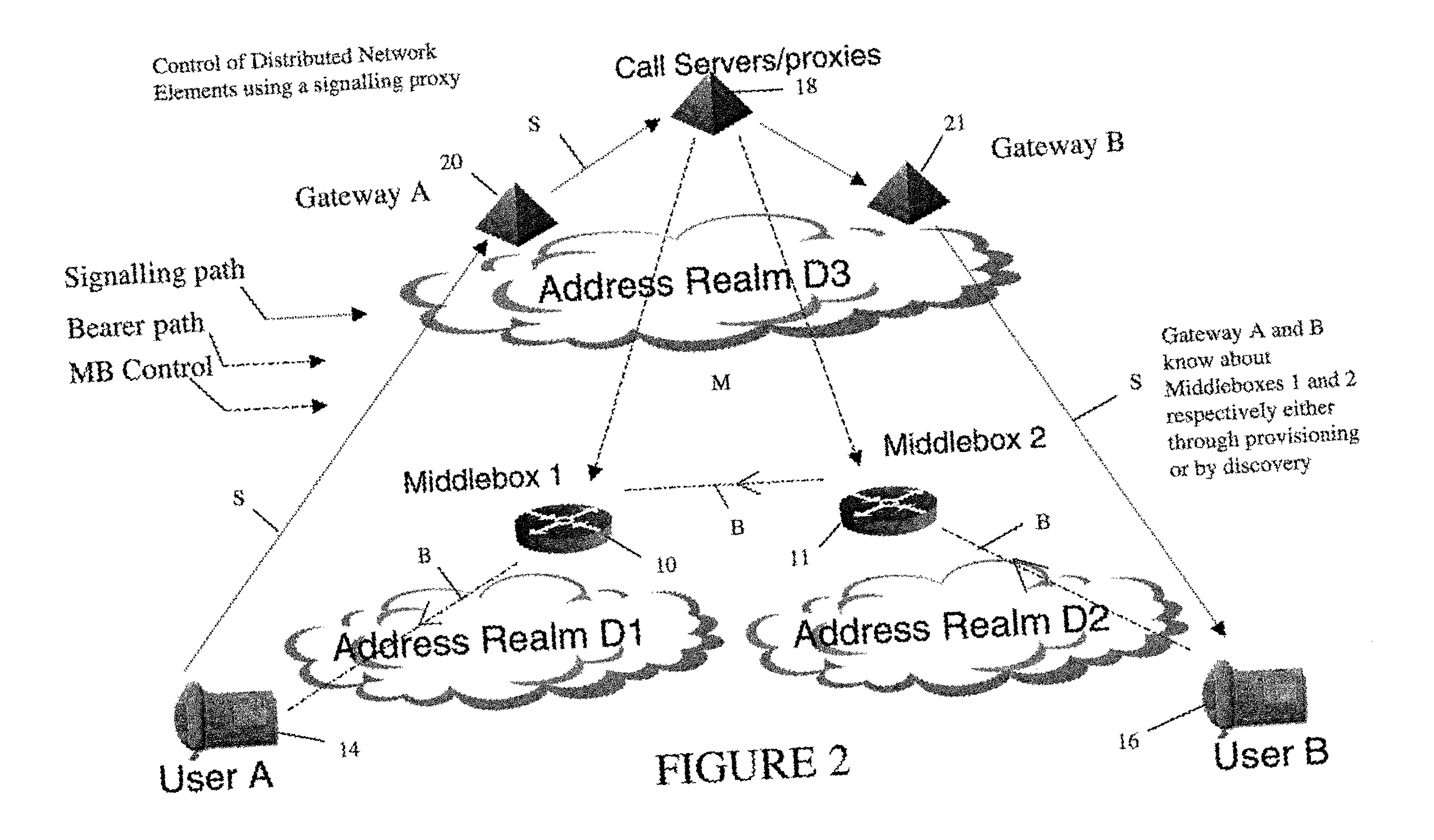
In order to carry out actions such as setting up a call from an entity in the address realm of one middlebox to an entity in the address realm of another middlebox, then a middlebox control node such as a call server is used. Previously, the middlebox control node has needed to have pre-configured information about all the middleboxes and which address realms they are associated with. The present invention provides one or more middlebox-identity-providing nodes which are separate from the middlebox control node, and which are more directly connected to the end users of the service than the middlebox control node. This provides greater flexibility in network design and removes the need for middlebox information to be pre-configured at the middlebox control node. Instead, this information is sent to the middlebox control node, as part of signalling messages, from middlebox-identity-providing nodes.
Owner:RPX CLEARINGHOUSE
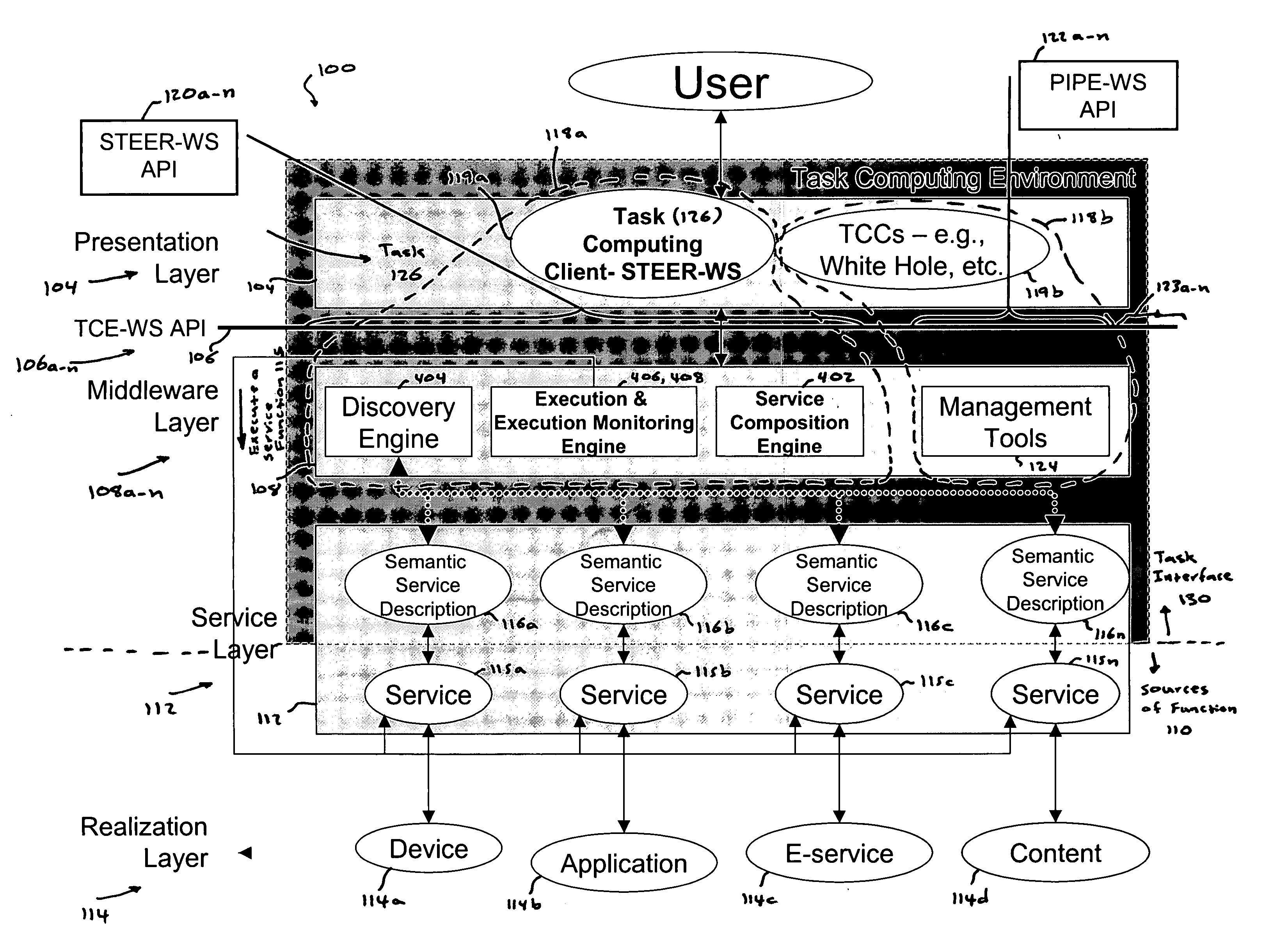
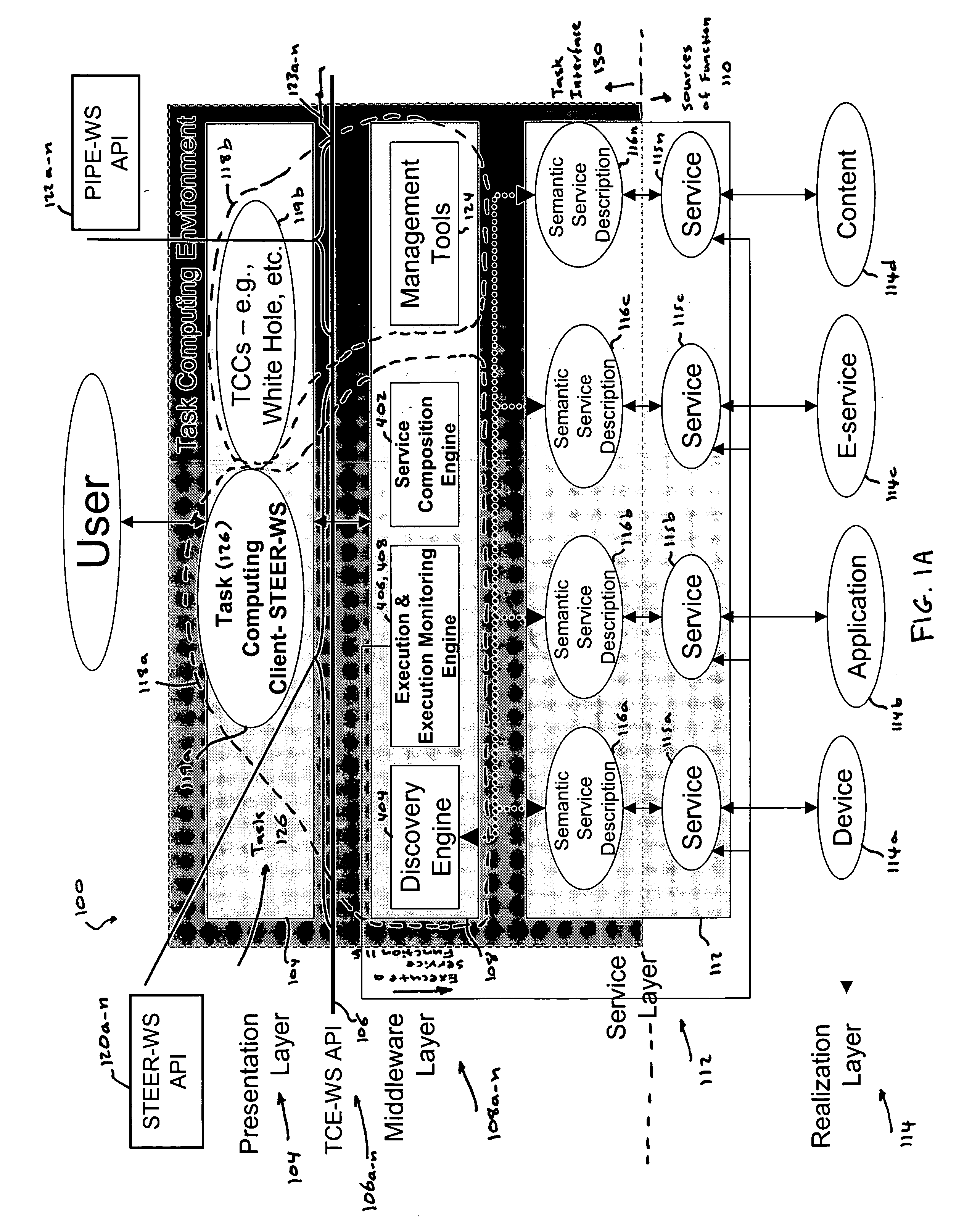
Task computing
InactiveUS20050246726A1Program control using stored programsConcurrent instruction executionLayer interfaceProcedure calls
Task Computing computer system by segmenting the system into a plurality of implementation tiers of a presentation layer, a remote procedure call programming interface (API), a middleware layer to which the presentation layer interfaces via the remote procedure call API to real-time, dynamically generate a computer implemented task interface at the presentation layer to a semantically described source of function as a service on a computer system, and a service layer and a function source realization layer providing the semantically described source of function as the service on the computer system to which the middleware layer interfaces. Real-time and dynamically composing an executable task that comprises one or more services using the generated task interface at the presentation layer to one or more services on the computer based upon the semantically described application-, device- and service-rich computer.
Owner:FUJITSU LTD
Method, apparatus and system for sharing multimedia content within a peer-to-peer network
ActiveUS20090094317A1Multiple digital computer combinationsTransmissionApplication softwareMiddleware
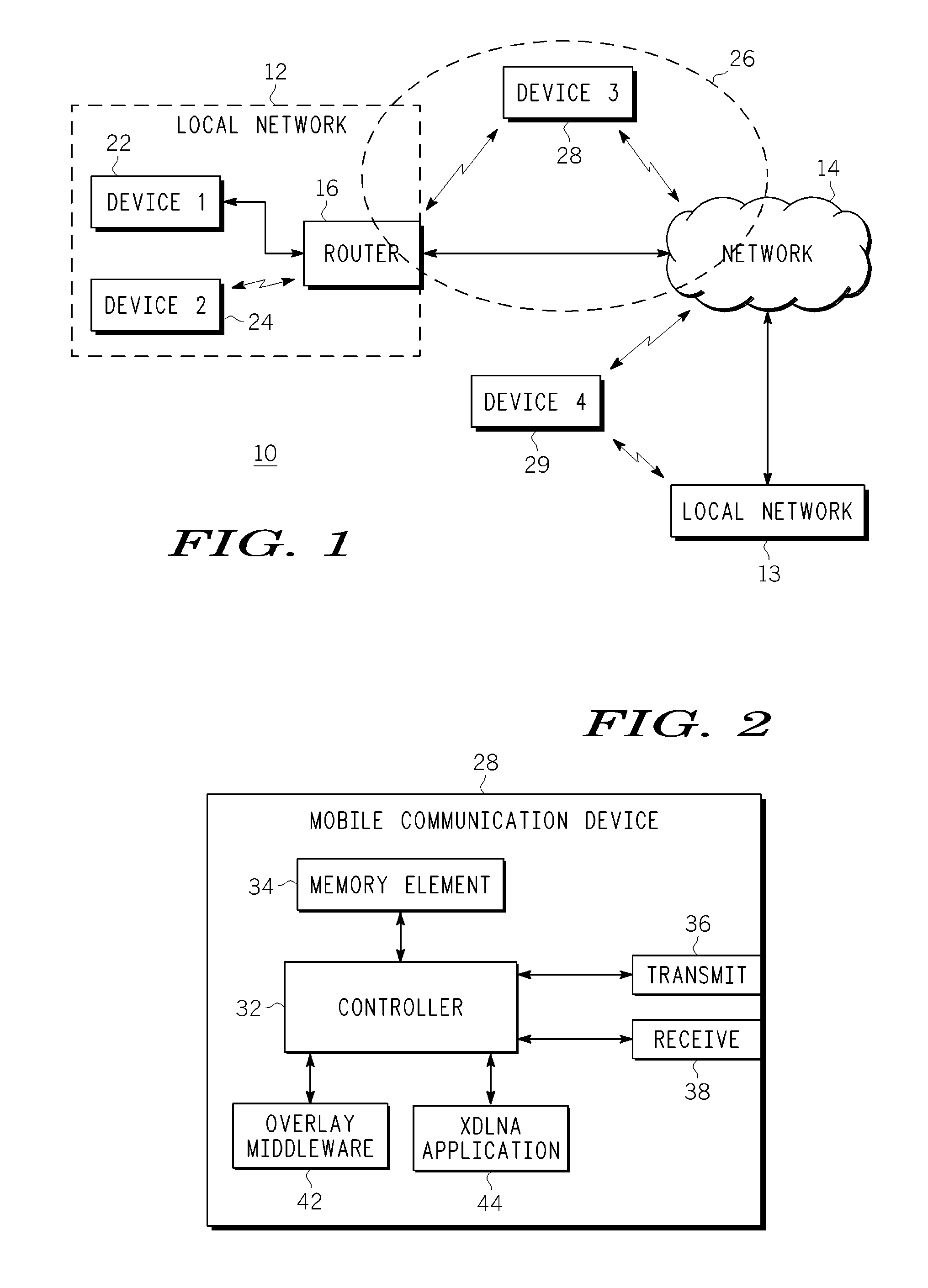
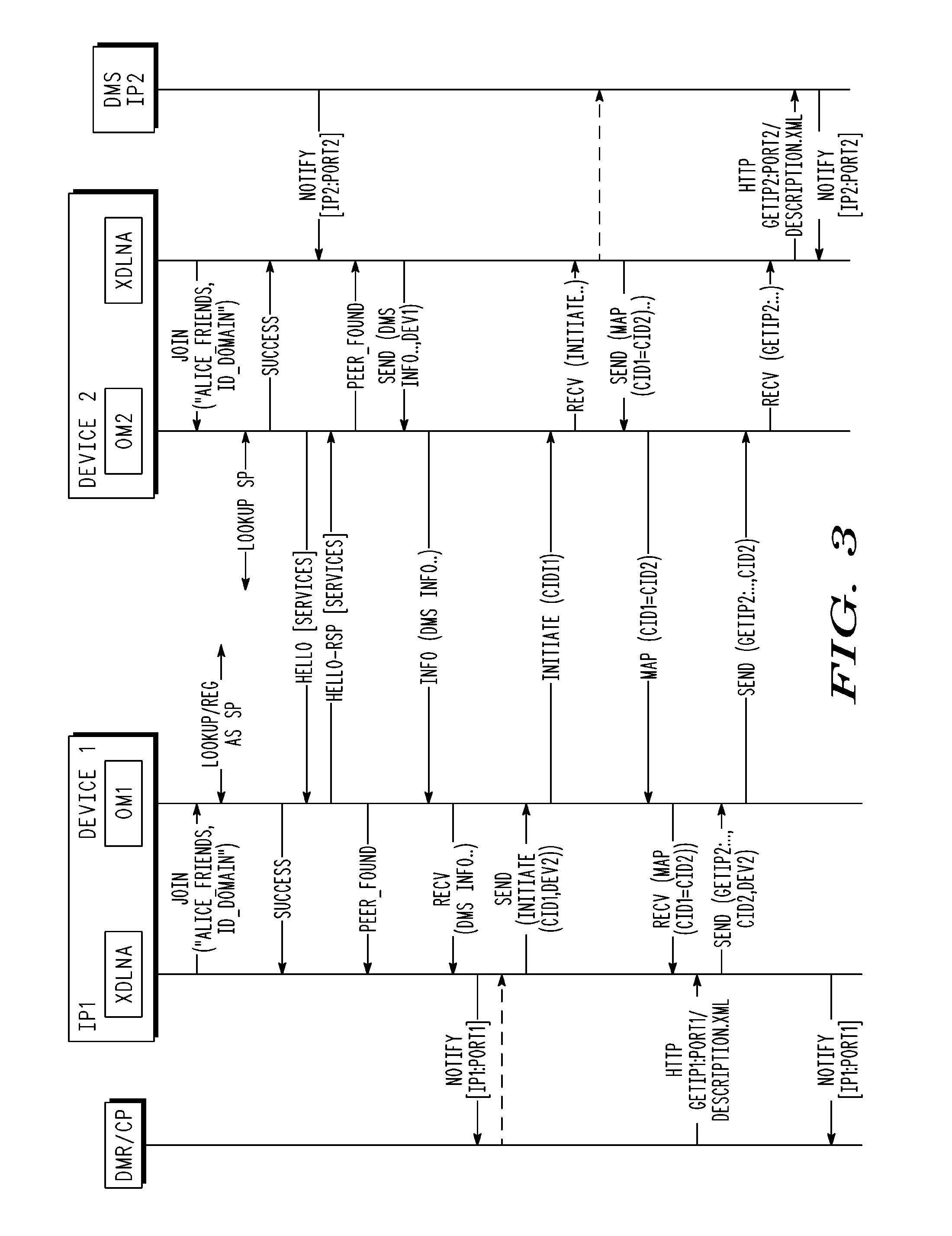
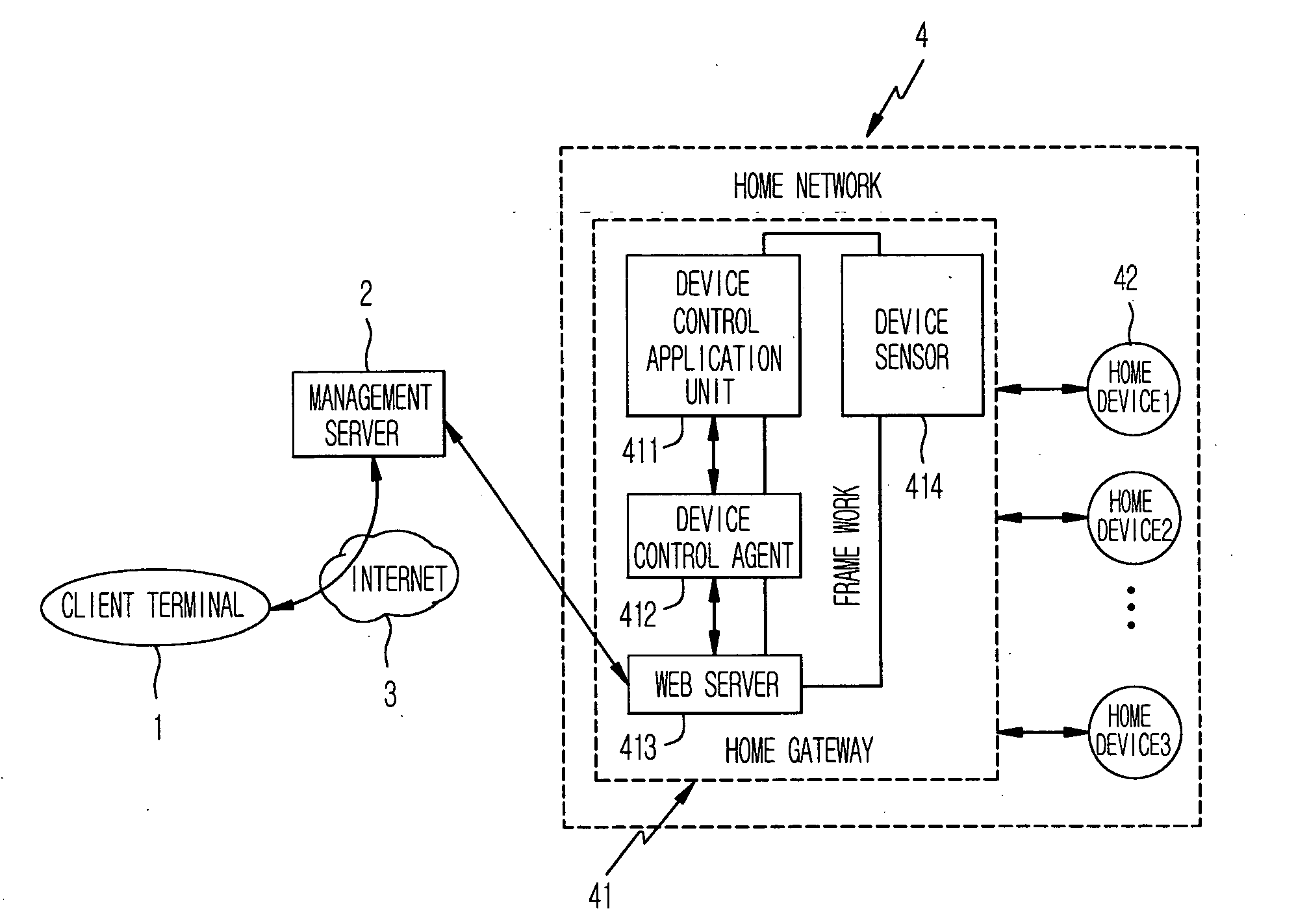
A system, method and communication device configuration for sharing multimedia content between network devices, such as UPnP or UPnP / DLNA devices and mobile communication devices, across different local networks or subnets. One possible system arrangement or architecture is based on the communication devices forming groups and then sharing UPnP control messages across the groups. The system arrangement supports enabling group member access to UPnP devices that are in other group devices or reachable via other group devices. By enabling devices to form groups across wide-area networks and distribute UPnP messages within the group members, the system effectively extends the range of a UPnP network. Devices include an overlay middleware and an xDLNA application to provide the functionality to form or join a device group and communicate multimedia content with other devices in the group as if the devices are within the same local network.
Owner:GOOGLE TECH HLDG LLC
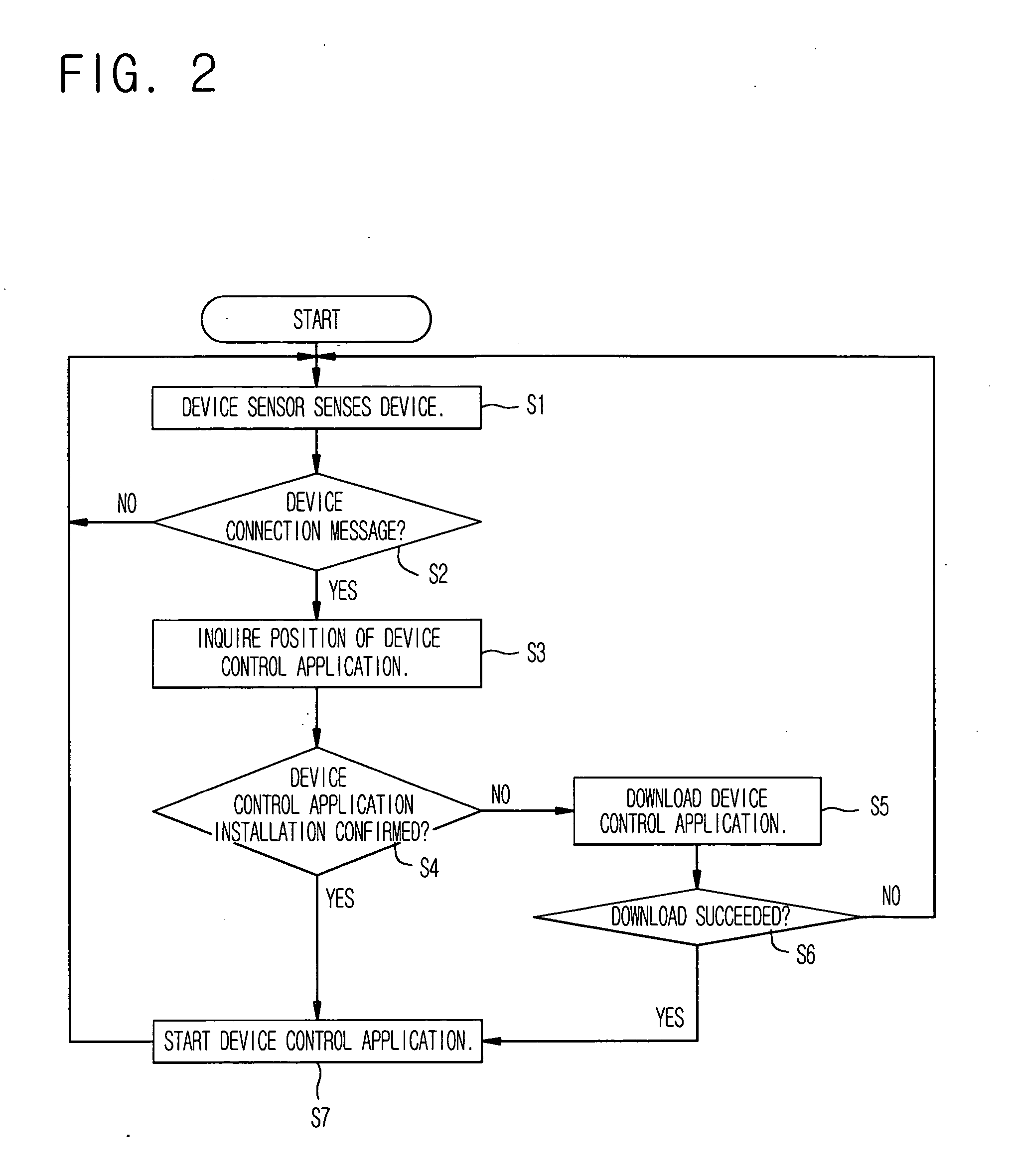
Platform-independent system for remotely controlling home devices and method thereof
InactiveUS20060168178A1Easy to integrate and manageDigital computer detailsSubstation remote connection/disconnectionApplication softwareMiddleware
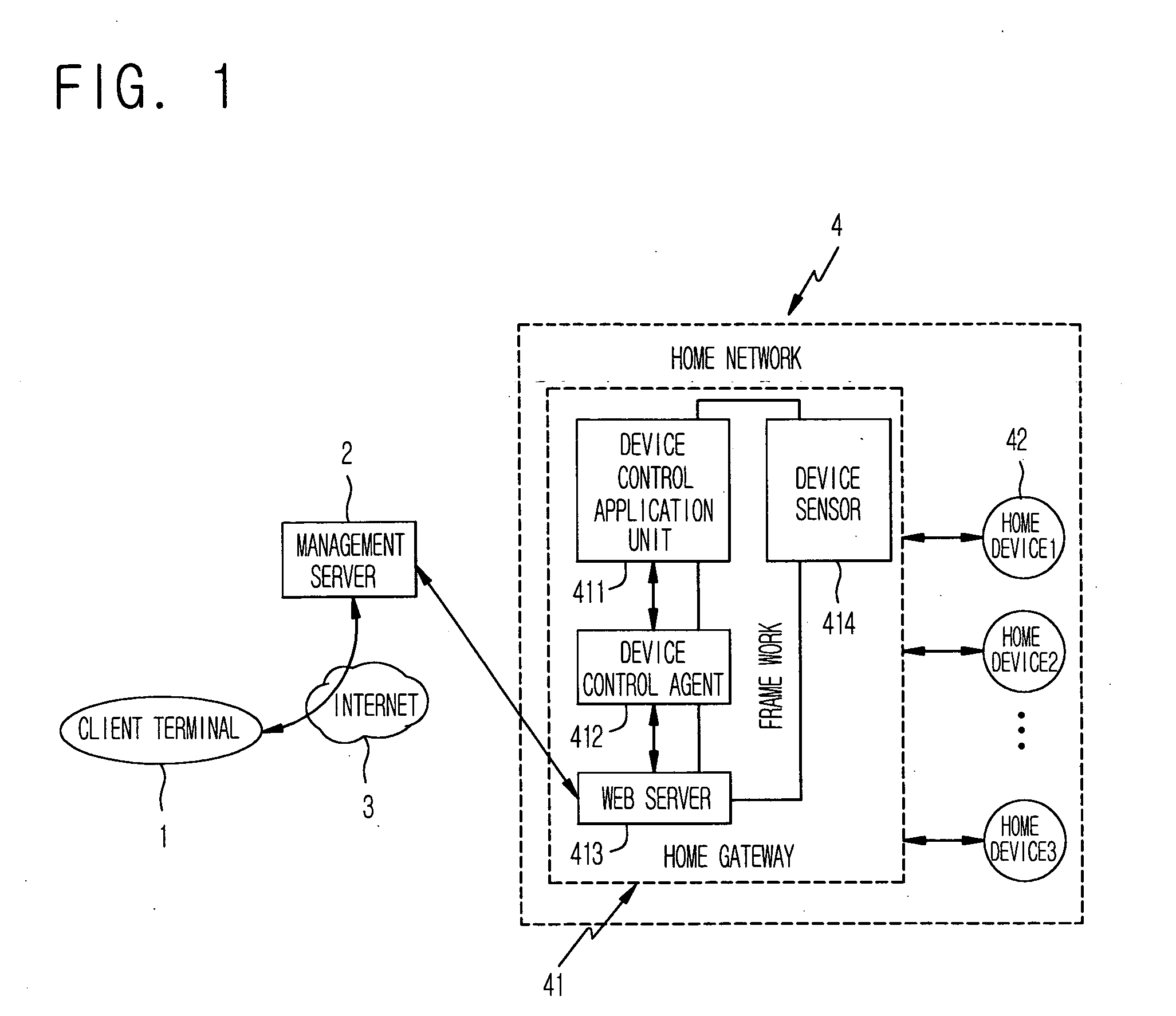
A platform-independent system and method for remotely controlling home devices and a computer-readable recording medium in which a program capable of executing the method is recorded are disclosed. The method includes installing a device control application to be used for the management of a home device when the home device is connected to the home network system, bring state information of the home device through the installed device control application, controlling a specified home device from an outside, receiving a report of an event occurring in the home device, and using a SOAP so that the above operations are performed irrespective of the middleware of a home gateway. Accordingly, the home devices connected to the home network through the home gateway can be controlled from the outside irrespective of the middleware supported by the home gateway.
Owner:ELECTRONICS & TELECOMM RES INST
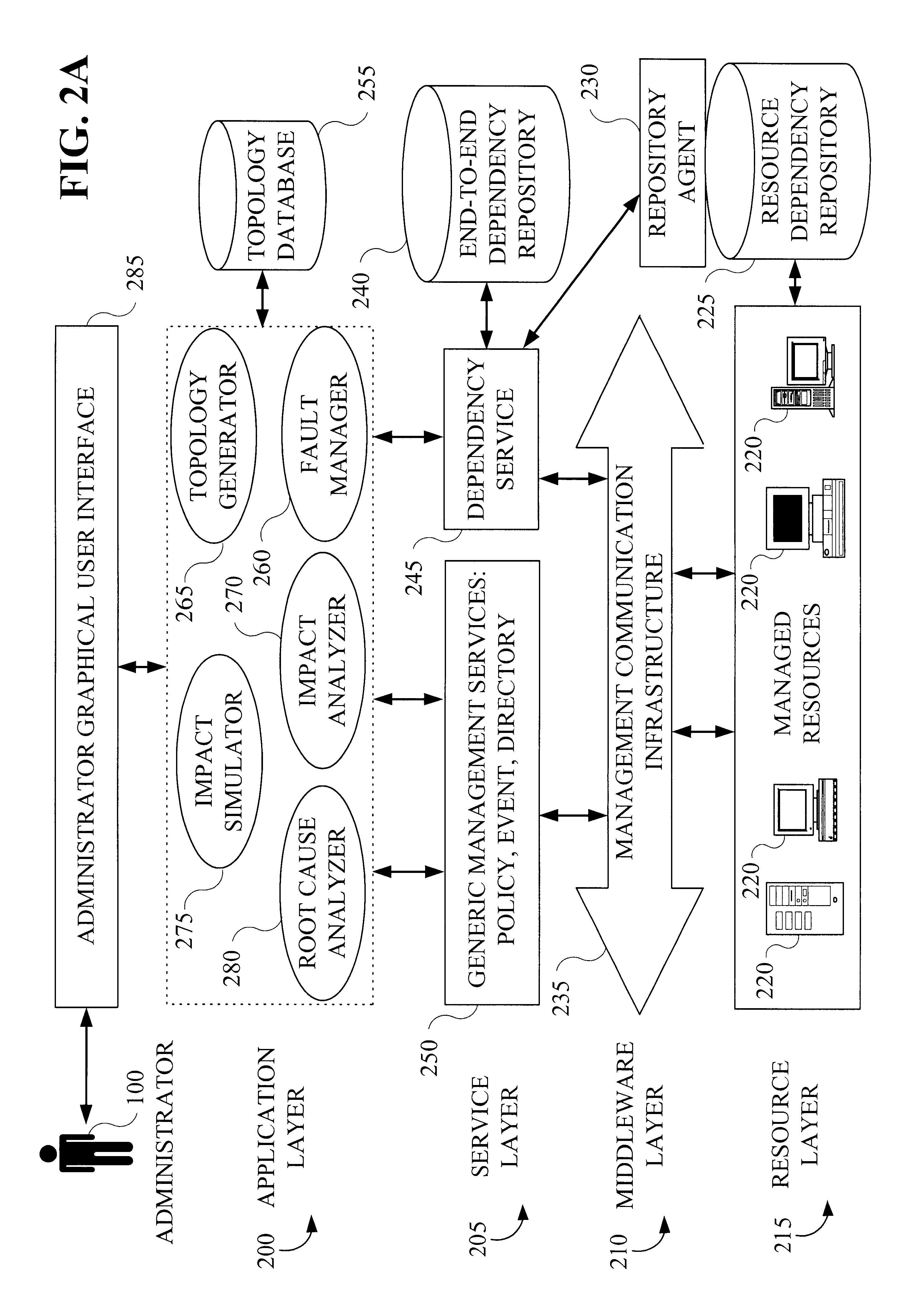
Methods and apparatus for managing dependencies in distributed systems
InactiveUS6847970B2Data processing applicationsDigital data processing detailsOperational systemDistributed Computing Environment
Techniques for managing information in a computing environment. Information associated with components of the computing environment is obtained. Then, from at least a portion of the obtained information, a determination is made as to the existence of one or more relationships associated with at least a portion of the components of the computing environment. The determination of the existence of one or more relationships is capable of accounting for a full lifecycle (e.g., including deployment, installation and runtime) associated with at least one component of the computing environment. Thus, techniques for managing runtime dependencies between the various components of computing systems are disclosed which provide a level of abstraction from individual systems and allow the computation of service / component (wherein the component may, for example, be an application, middleware, hardware, a device driver, an operating system and a system associated with the computing environment) dependencies that are related to end-to-end services, as perceived by a customer. By way of example, the inventive techniques may be applied to a distributed computing environment. The computing environment may also be an autonomic computing environment.
Owner:IBM CORP
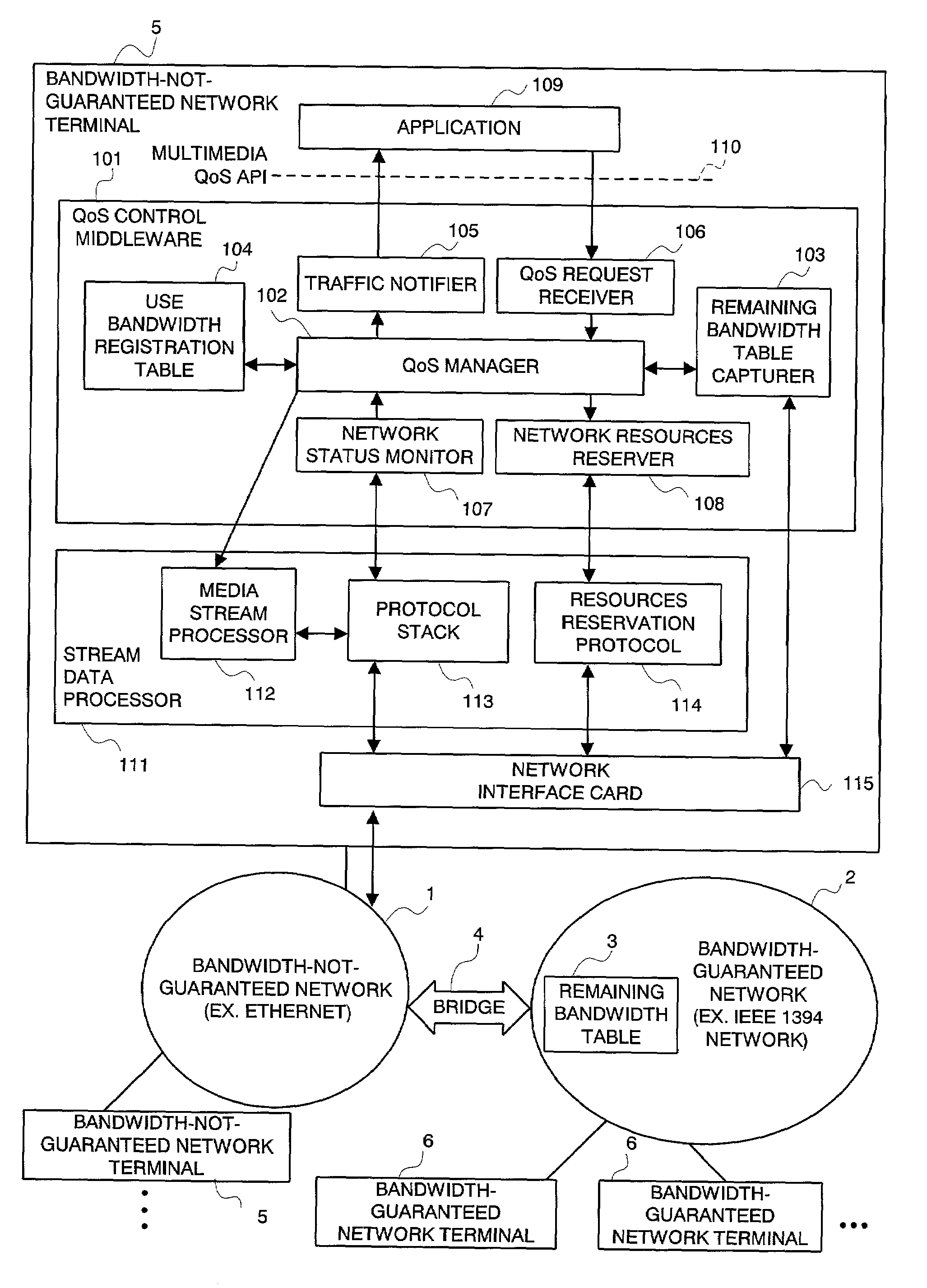
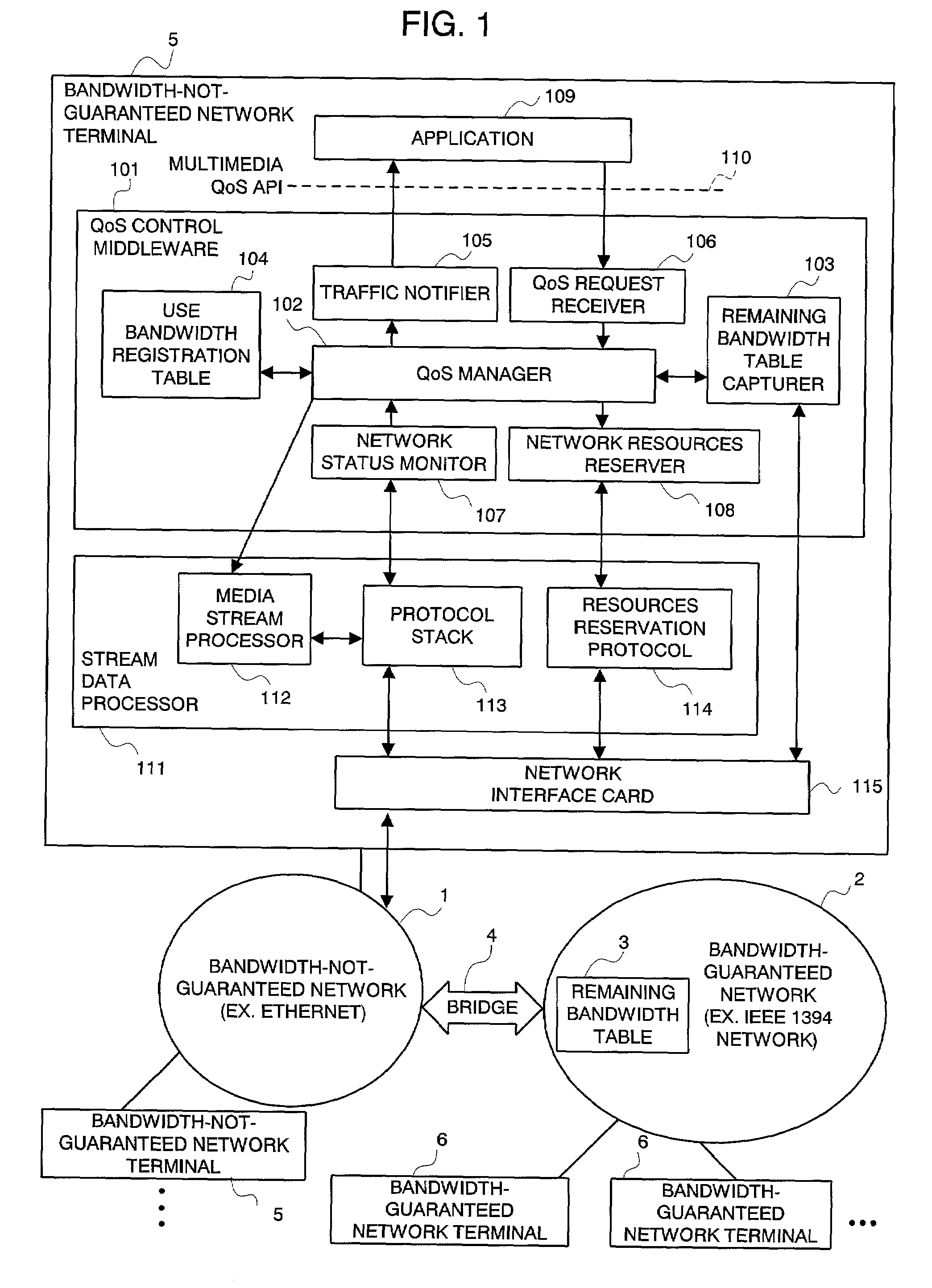
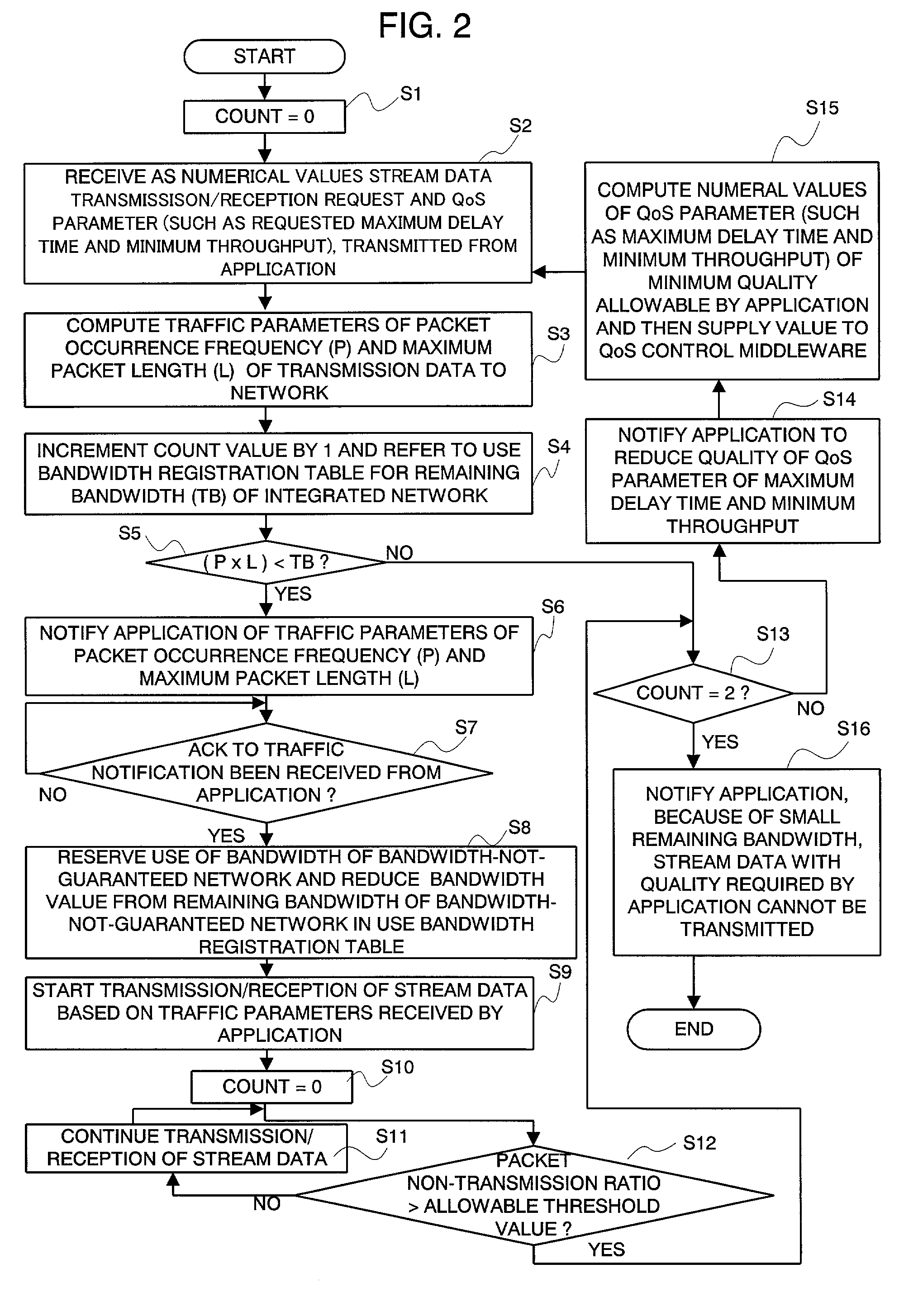
QoS control middleware in integrated network, QoS control method, and the program for the same
InactiveUS7212491B2Error preventionFrequency-division multiplex detailsTraffic capacityQuality of service
An integrated QoS control system is provided that transmits, in real time, the stream data between a bandwidth-guaranteed network and a bandwidth-not-guaranteed network. The QoS manager 102 records the remaining bandwidth of the bandwidth-guaranteed network 2 captured by the remaining bandwidth table capturer 103 and the remaining bandwidth of the bandwidth-not-guaranteed network 1 calculated with traffic information notified by the network status monitor 107 on the use bandwidth registration table 104 (for comprehensively managing the bandwidth of an integrated network). The Qos manager 102 converts a QoS parameter received via the QoS request receiver 106 into a traffic parameter and controllably adapts the value of the traffic parameter to a service quality required by the application 109.
Owner:NEC PERSONAL COMPUTERS LTD
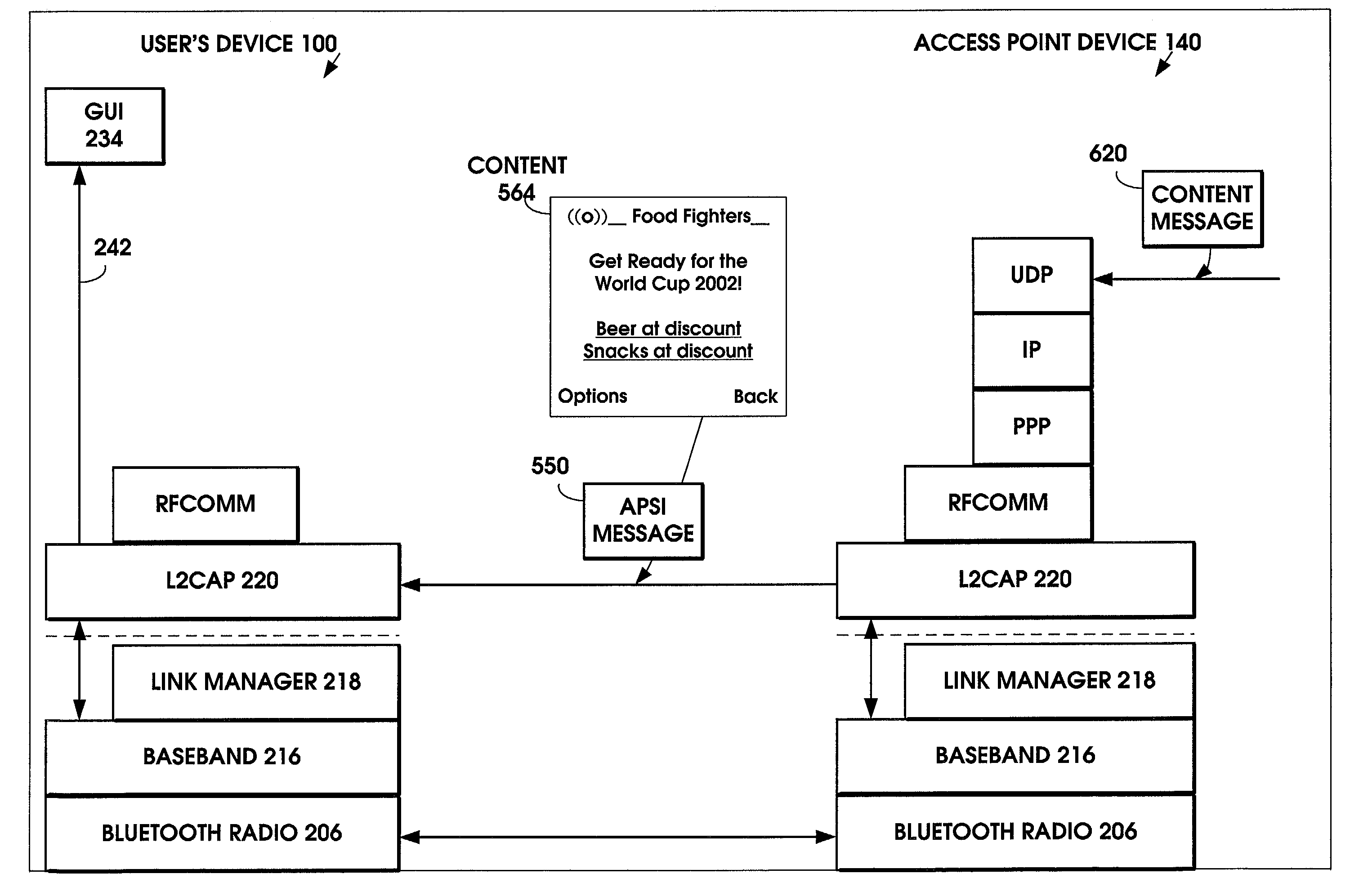
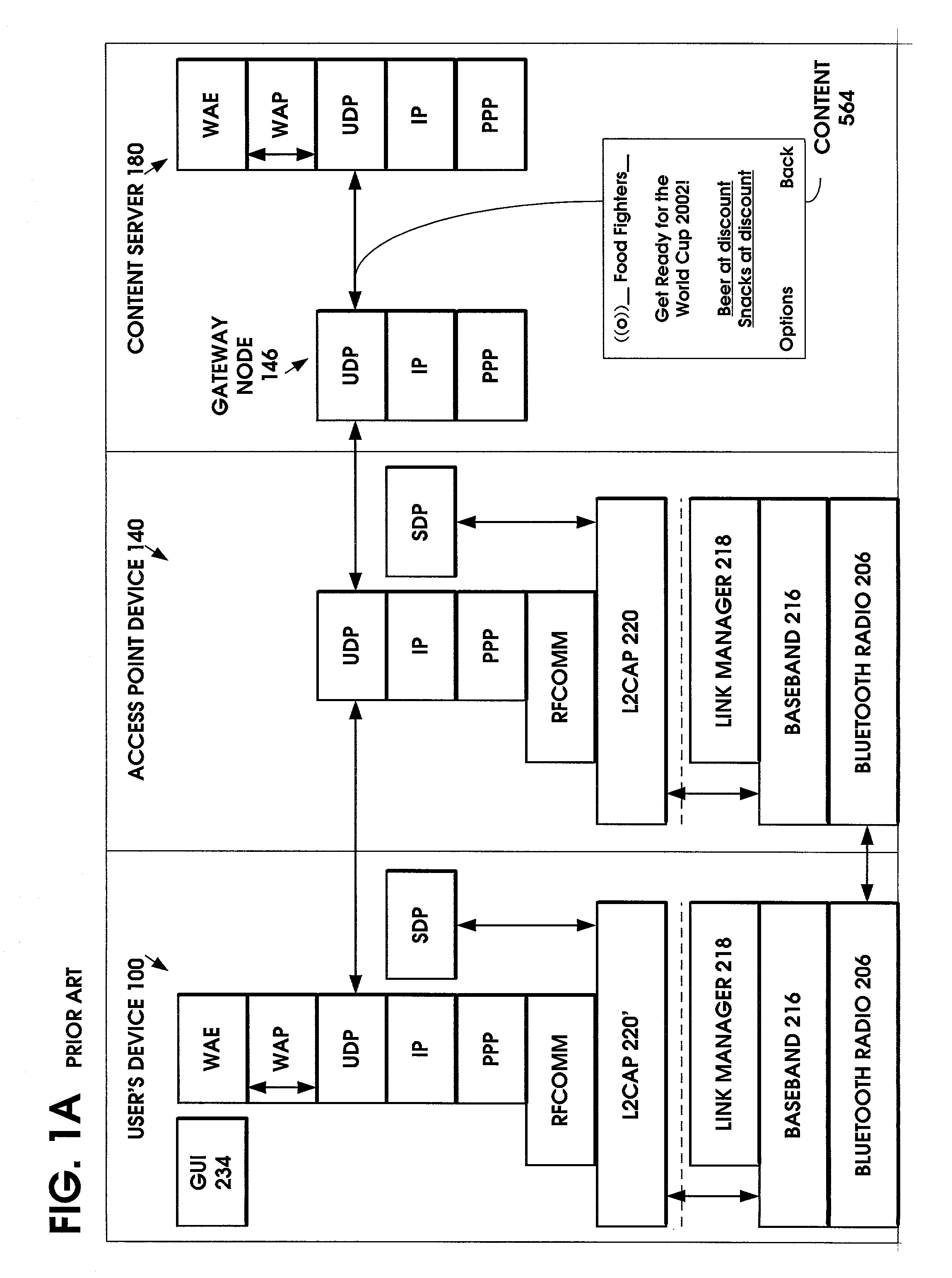
Service notification on a low bluetooth layer
InactiveUS7151764B1Fast contentFast processingAssess restrictionNetwork topologiesPointing deviceProtocol Application
A method is provided to minimize the protocol stacks needed for a short range wireless access point to rapidly communicate a message to a short range wireless mobile device and display it to the user. The short range wireless access point device stores an Access Point Service Indicator (APSI) message characterizing the service platform offerings. The APSI message has a unique message ID in its header. The user device's transport protocol layer is modified to detect the unique message ID and load it into an APSI message buffer. The transport protocol layer passes the APSI message directly to the application layer, bypassing the middleware protocol layers. The method can be applied to communications between various types of wireless devices to enable rapid communication, such as between two mobile devices, between fixed and mobile devices, between short range devices or between long range devices.
Owner:NOKIA CORP
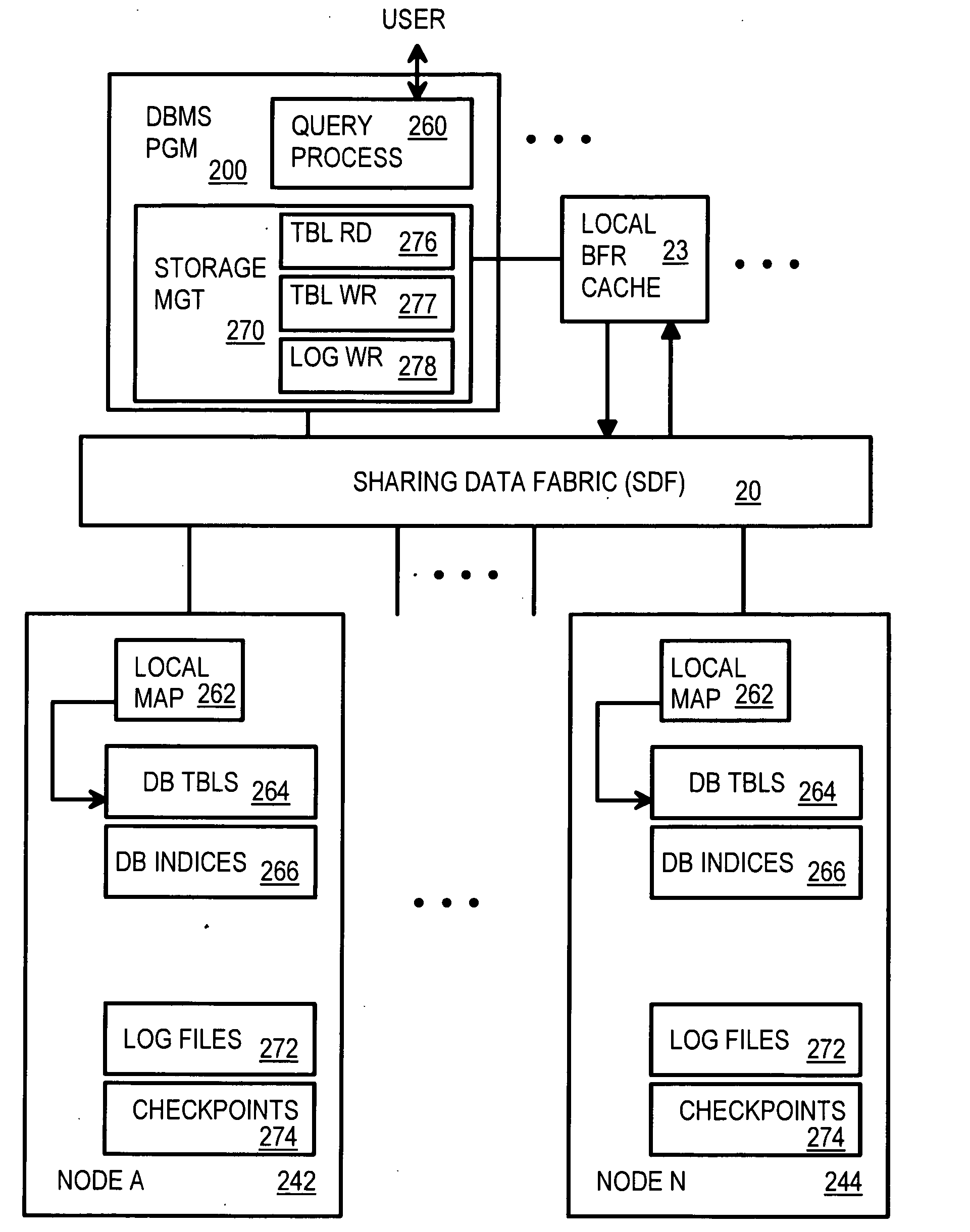
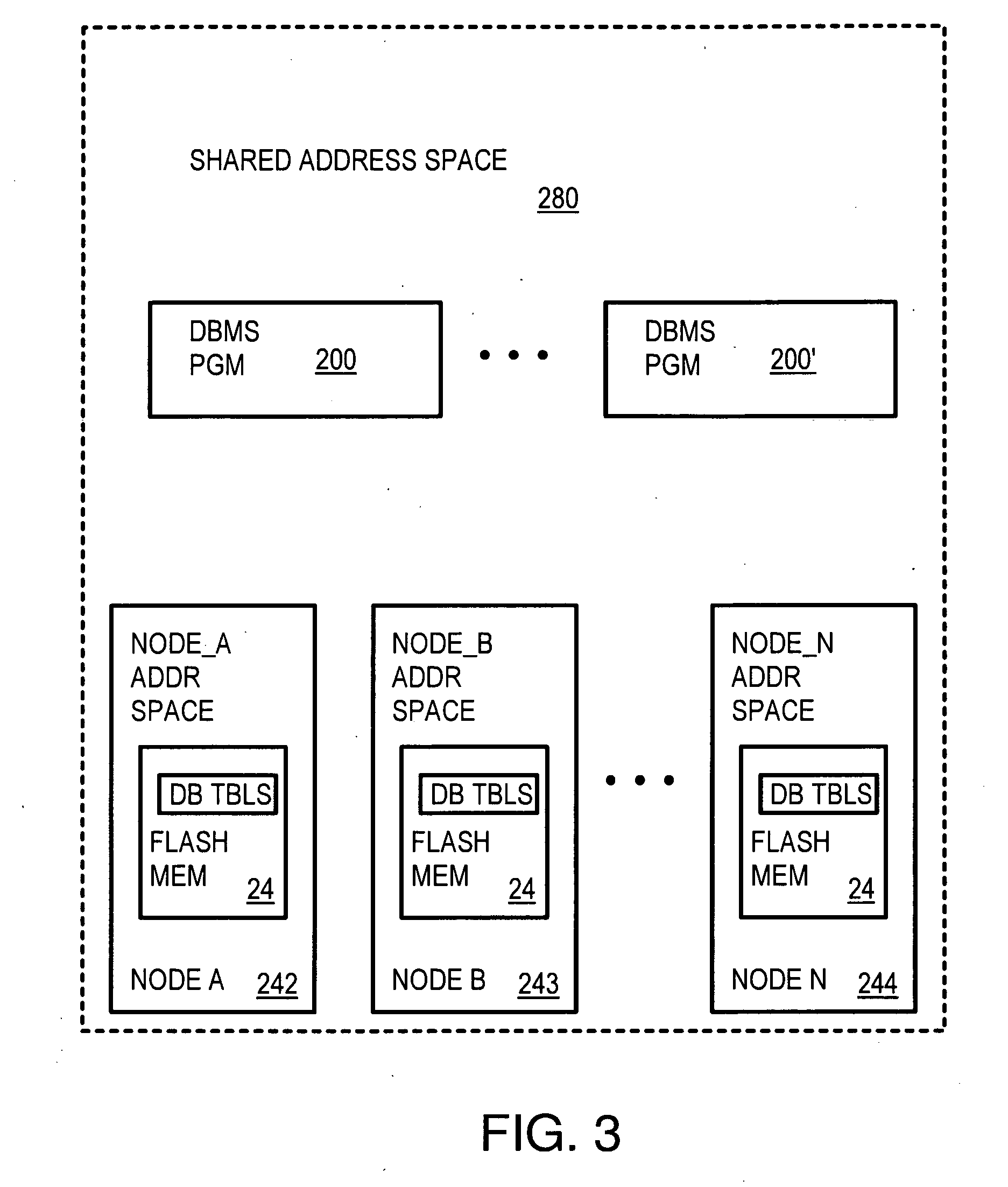
Scalable Database Management Software on a Cluster of Nodes Using a Shared-Distributed Flash Memory
ActiveUS20090240664A1Memory architecture accessing/allocationEnergy efficient ICTParallel computingDistributed database
A distributed database system has multiple compute nodes each running an instance of a database management system (DBMS) program that accesses database records in a local buffer cache. Records are persistently stored in distributed flash memory on multiple storage nodes. A Sharing Data Fabric (SDF) is a middleware layer between the DBMS programs and the storage nodes and has API functions called by the DBMS programs when a requested record is not present in the local buffer cache. The SDF fetches the requested record from flash memory and loads a copy into the local buffer cache. The SDF has threads on a home storage node that locate database records using a node map. A global cache directory locks and pins records to local buffer caches for updating by a node's DBMS program. DBMS operations are grouped into transactions that are committed or aborted together as a unit.
Owner:SANDISK TECH LLC
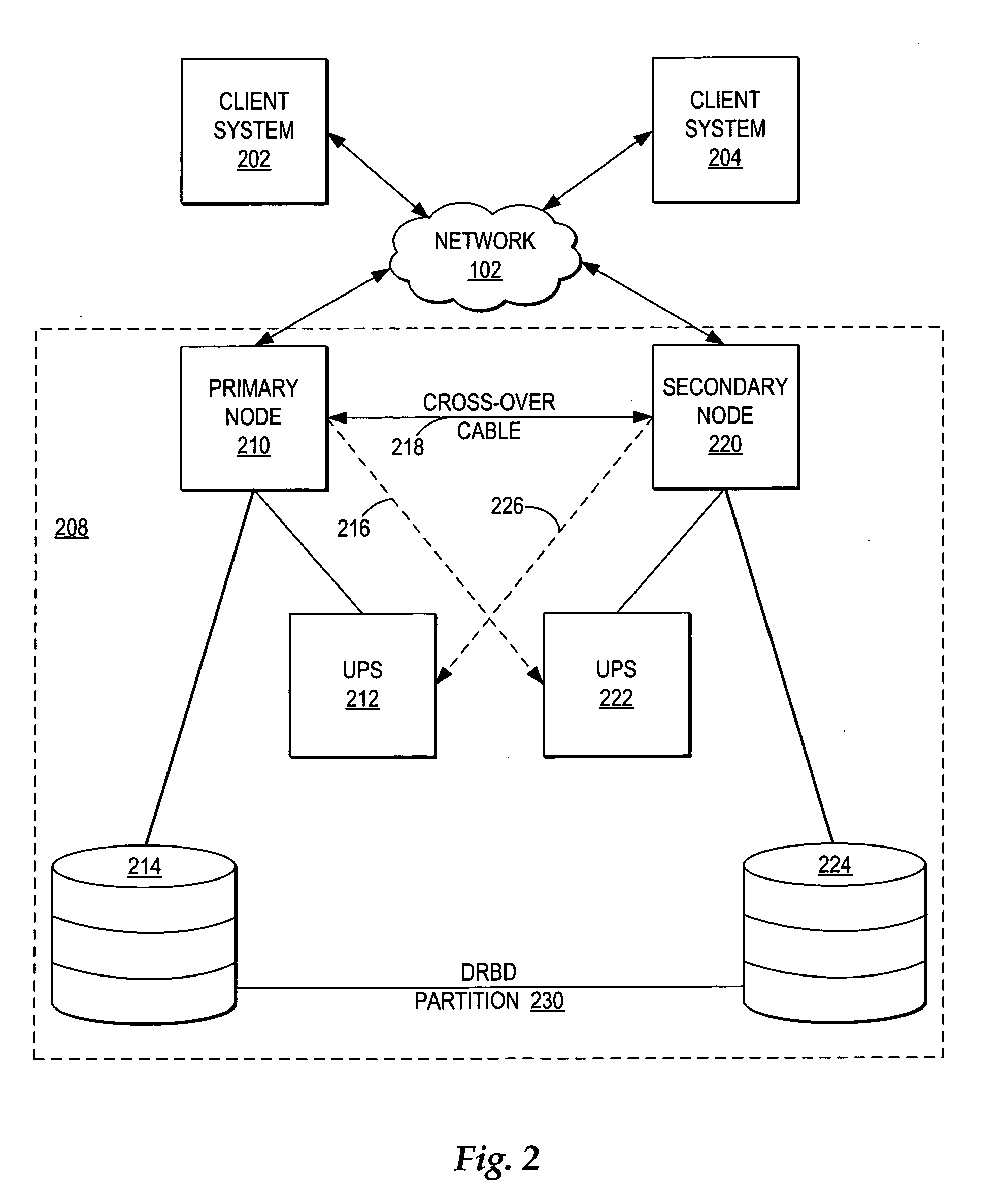
Managing failover of J2EE compliant middleware in a high availability system
InactiveUS20050172161A1Short recovery timeMinimal data lossRedundant hardware error correctionFailoverWeb application
A method, system, and program for managing failover of J2EE compliant middleware in a high availability system are provided. A primary node and a secondary node each run the same J2EE compliant middleware stack comprising layers including a load balancer, a web server, a web application server, a message control server, a monitoring server, and a database control server. In the primary node, all layers are active. In the secondary node, part of the layers are active and part of the layers are in standby. A data replication partition shared between the primary node and the secondary node includes persistent resource data accessible to a selection of the layers of the primary node. A heartbeat controller monitors each node, including the middleware stack, and upon detection of a failure, controls transfer of the services provided by the primary node to the secondary node by transferring virtual IP addresses from the primary node to the secondary node, remounting the data replication partition for access by the secondary node, and activating the standby layers which require access to the data in the data replication partition.
Owner:IBM CORP
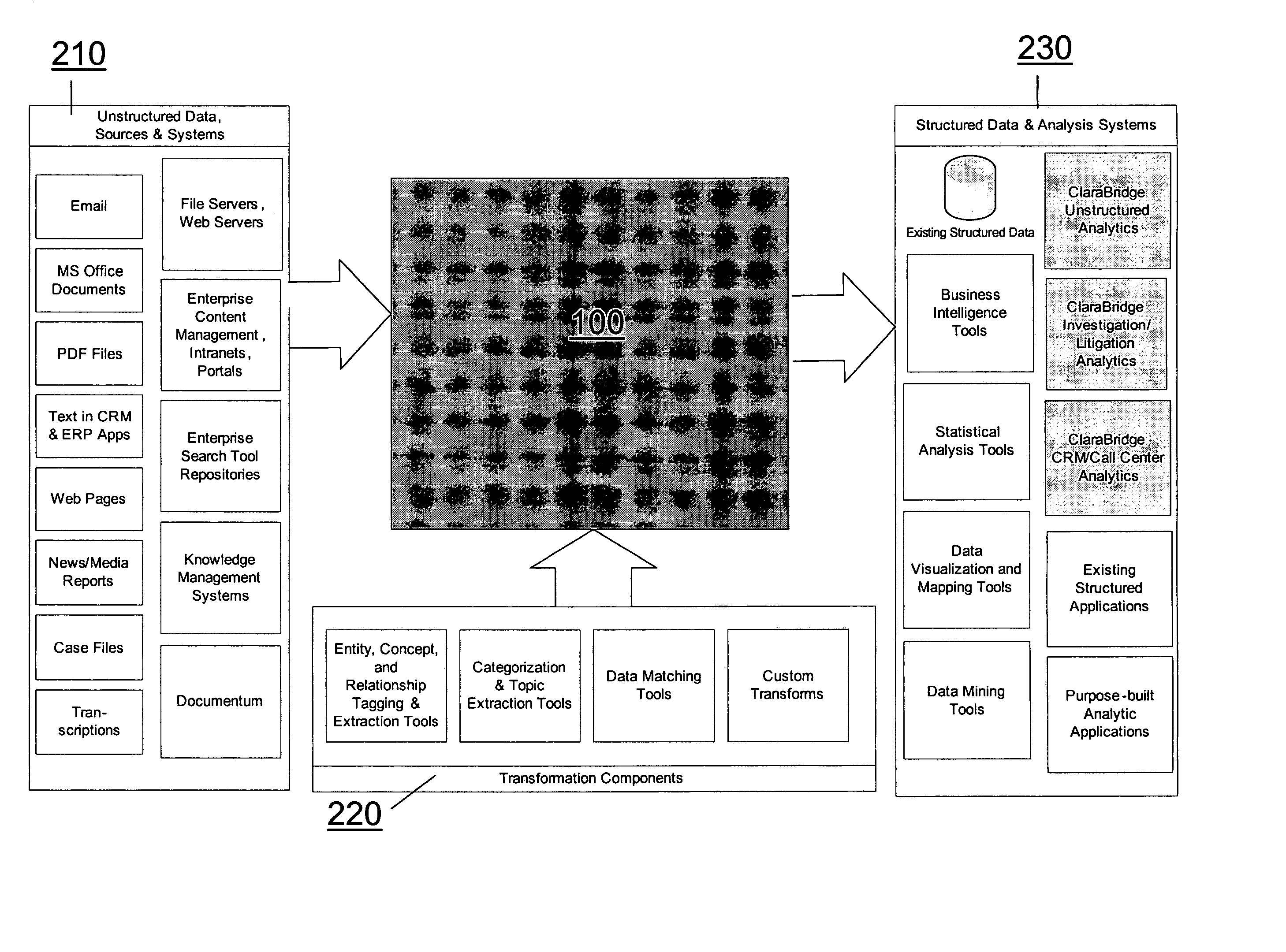
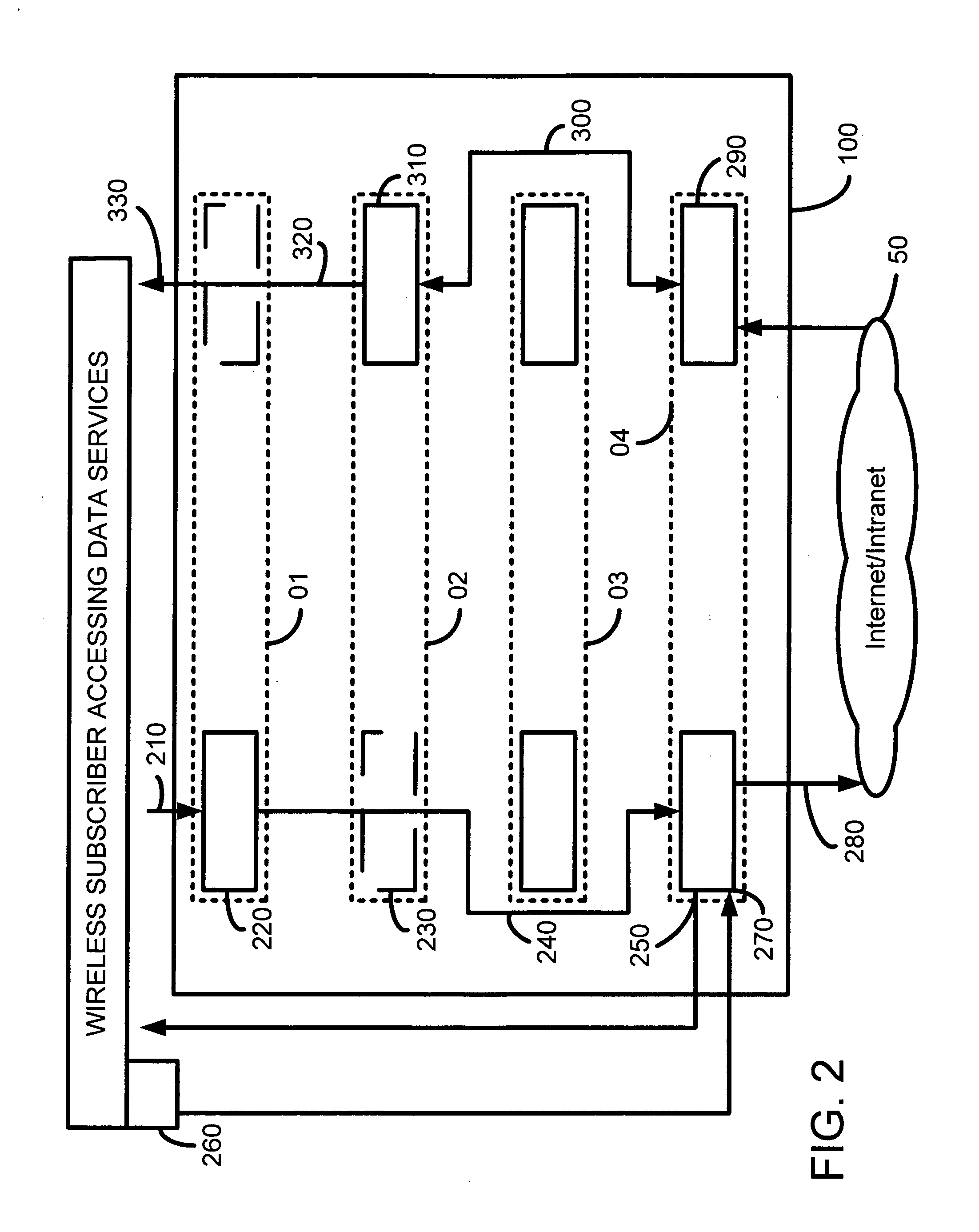
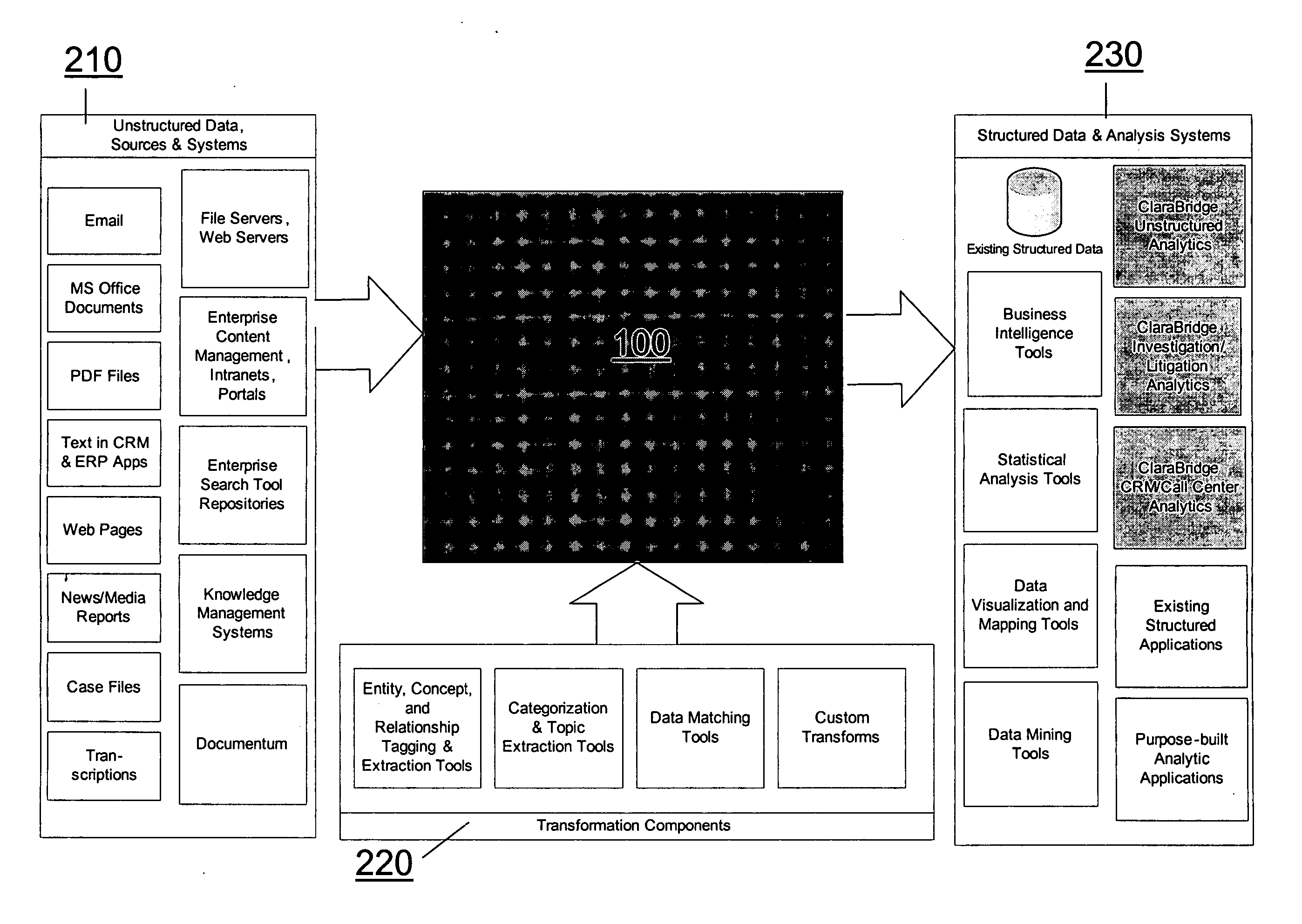
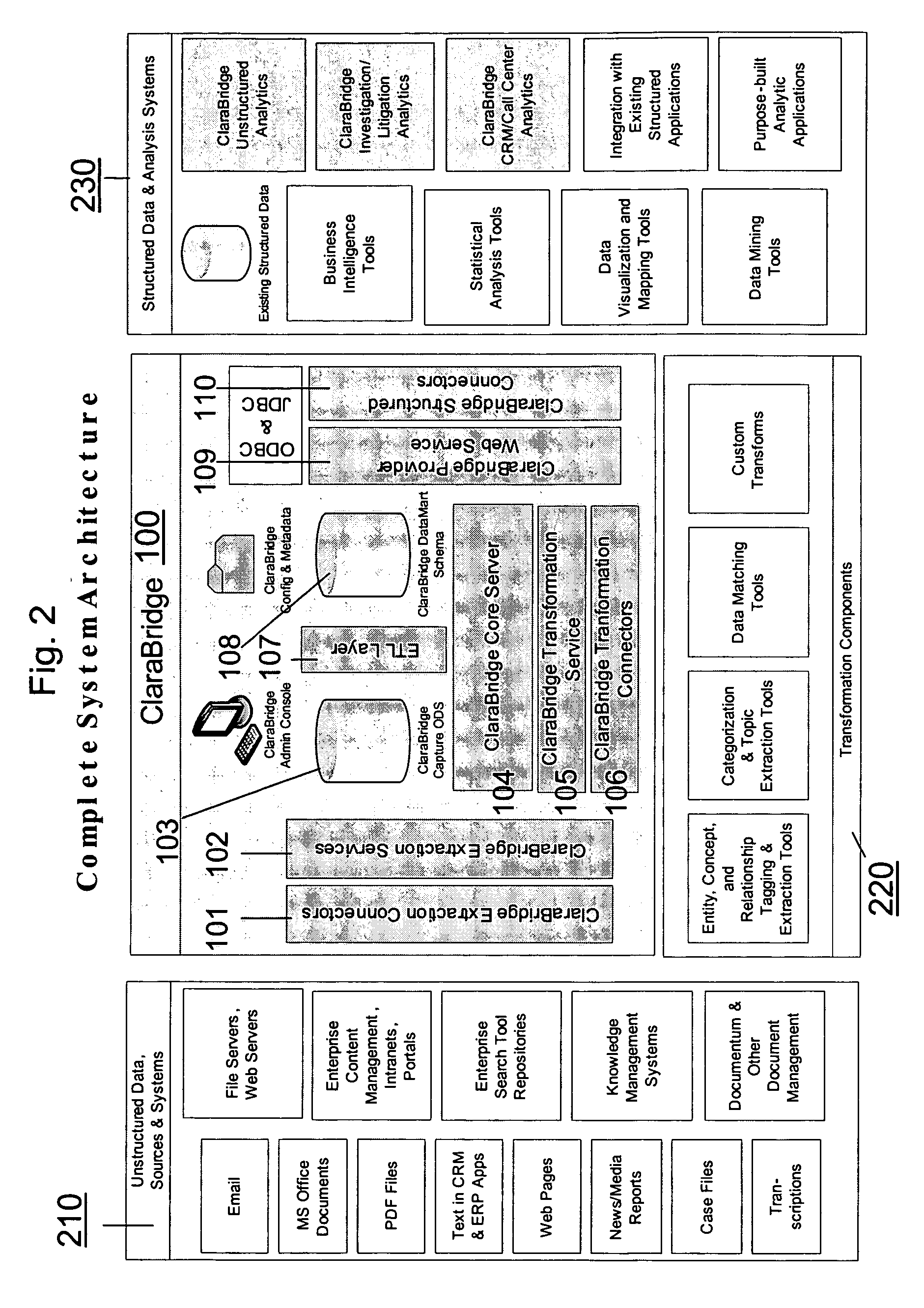
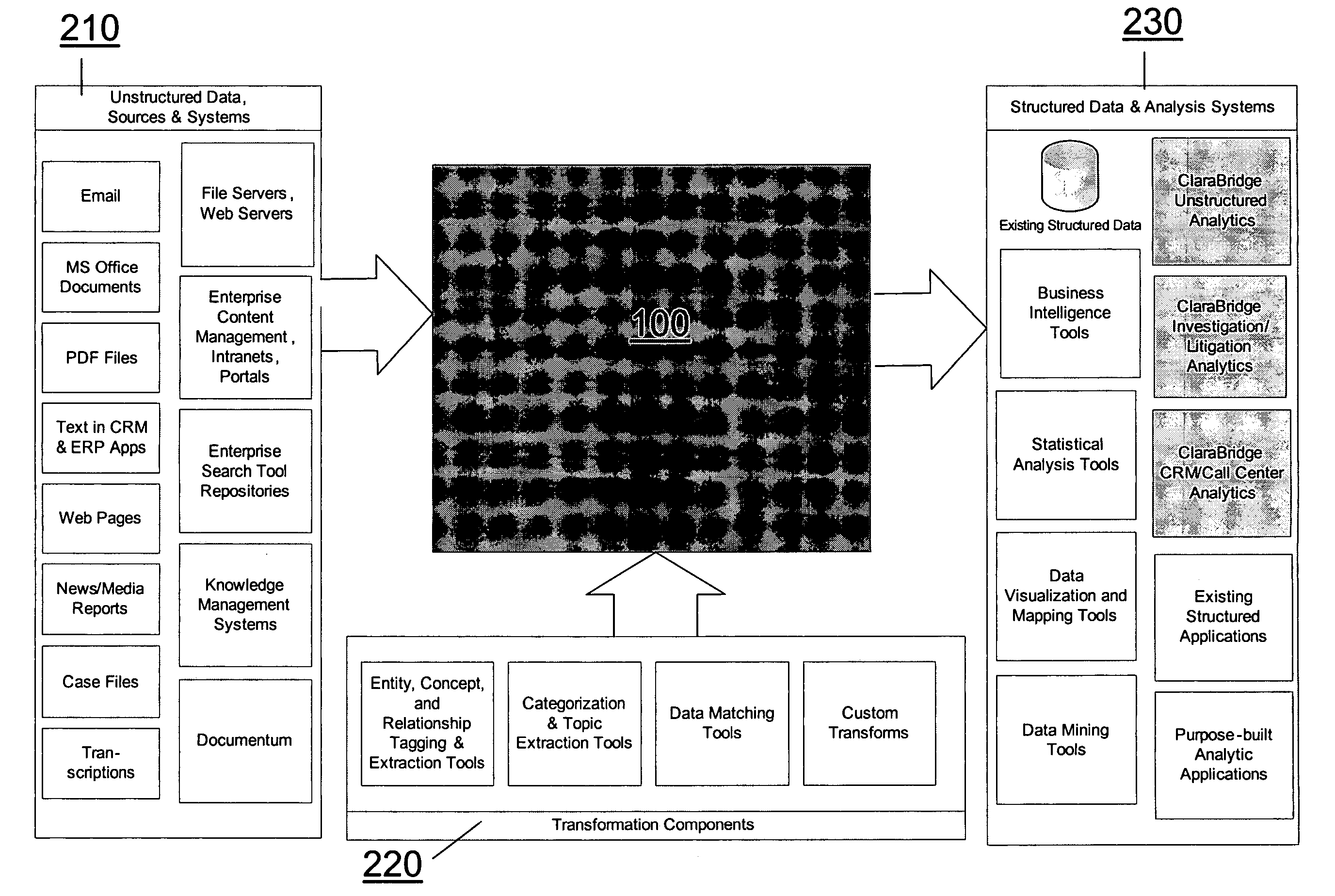
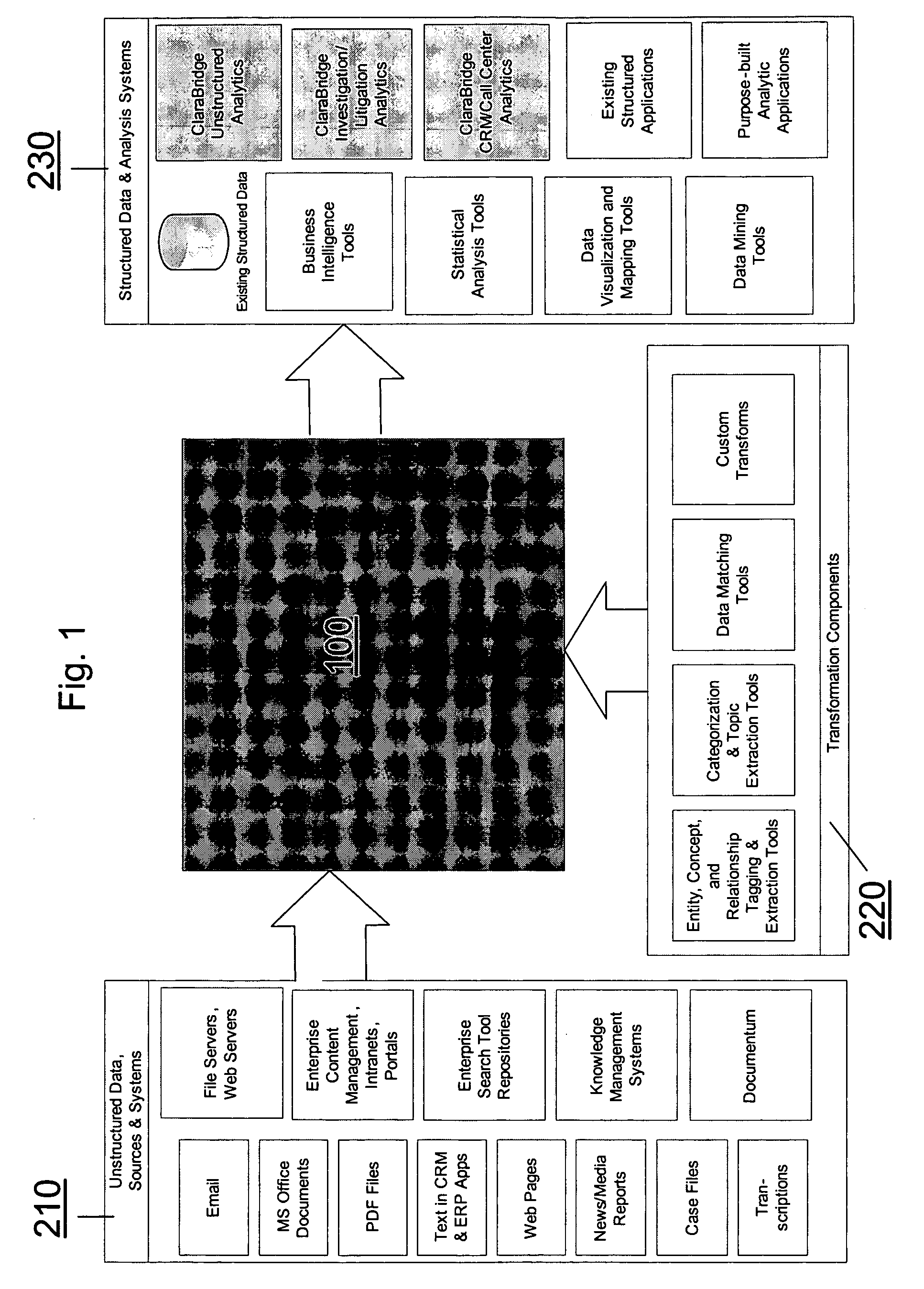
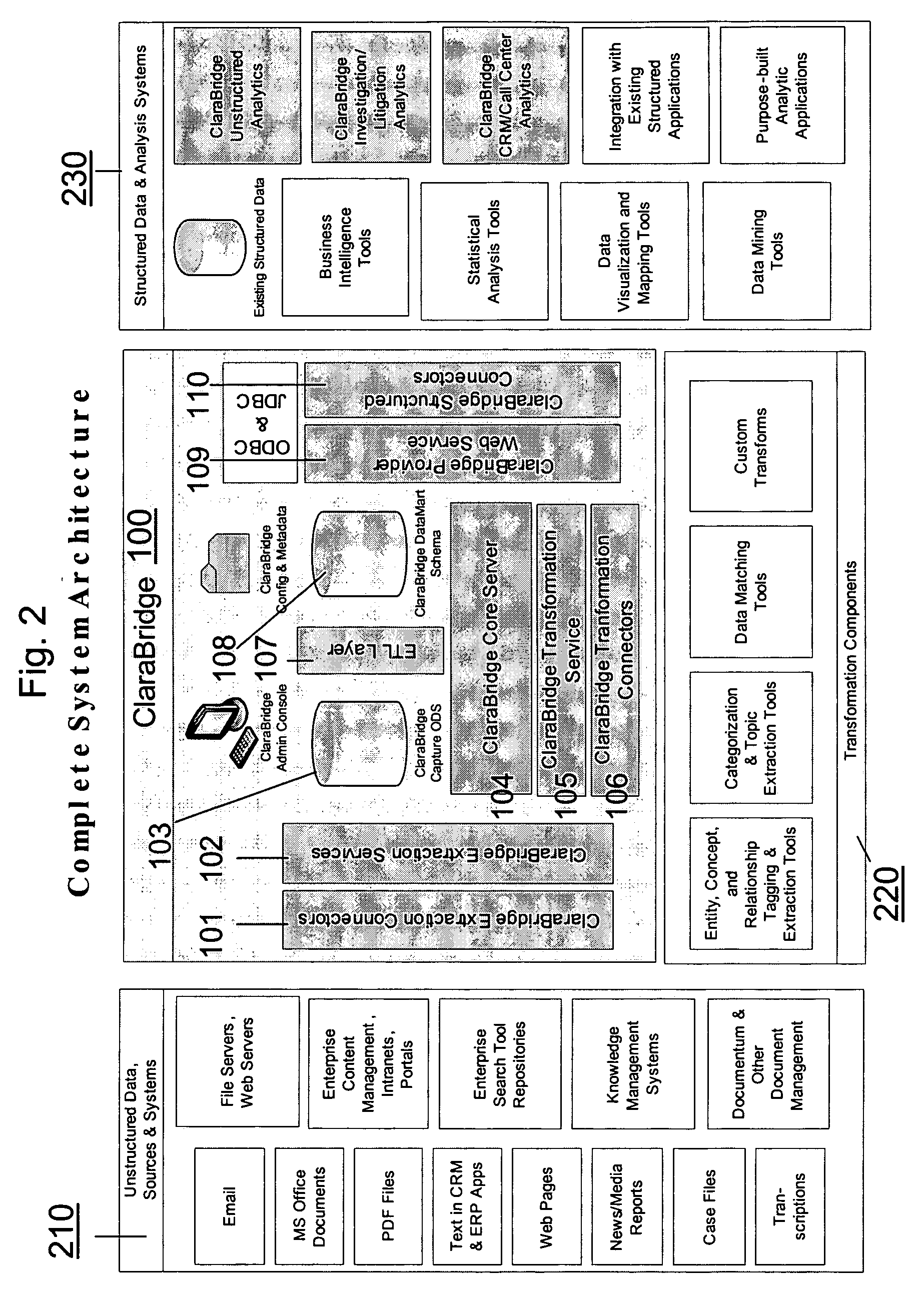
Analysis and transformation tools for structured and unstructured data
InactiveUS20070011183A1Digital data information retrievalDigital data processing detailsData transformationStructured data analysis
A system and method of making unstructured data available to structured data analysis tools. The system includes middleware software that can be used in combination with structured data tools to perform analysis on both structured and unstructured data. Data can be read from a wide variety of unstructured sources. The data may then be transformed with commercial data transformation products that may, for example, extract individual pieces of data and determine relationships between the extracted data. The transformed data and relationships may then be passed through an extraction / transform / load (ETL) layer and placed in a structured schema. The structured schema may then be made available to commercial or proprietary structured data analysis tools.
Owner:CLARABRIDGE
Cloud-Based Middlebox Management System
ActiveUS20140068602A1Effectively scaledData switching networksSoftware simulation/interpretation/emulationApplication softwareMiddleware
A virtual network virtual machine may be implemented on a cloud computing facility to control communication among virtual machines executing applications and virtual machines executing middlebox functions. This virtual network virtual machine may provide for automatic scaling of middleboxes according to a heuristic algorithm that monitors the effectiveness of each middlebox on the network performance as application virtual machines are scaled. The virtual machine virtual network may also locate virtual machines in actual hardware to further optimize performance.
Owner:WISCONSIN ALUMNI RES FOUND
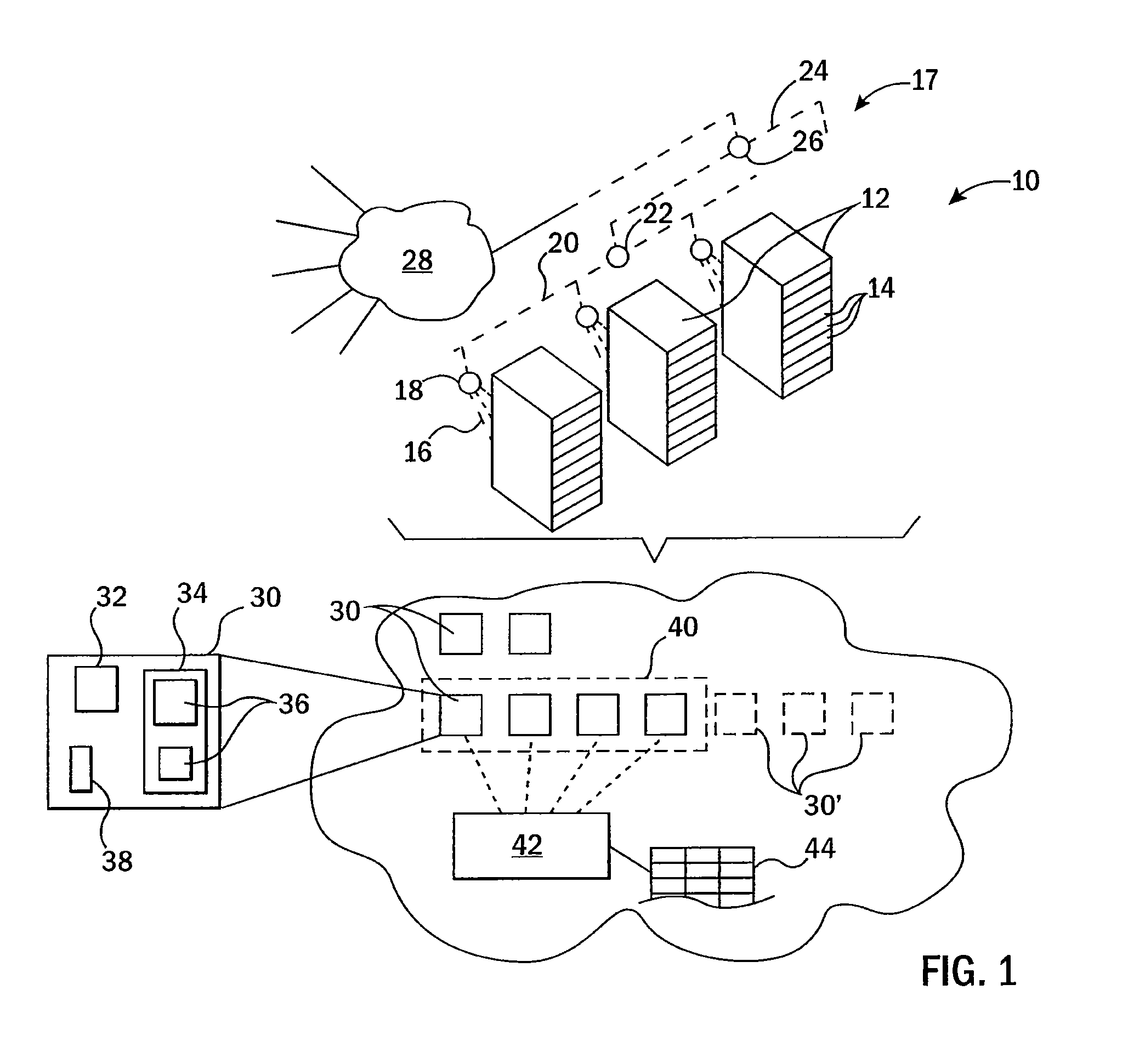
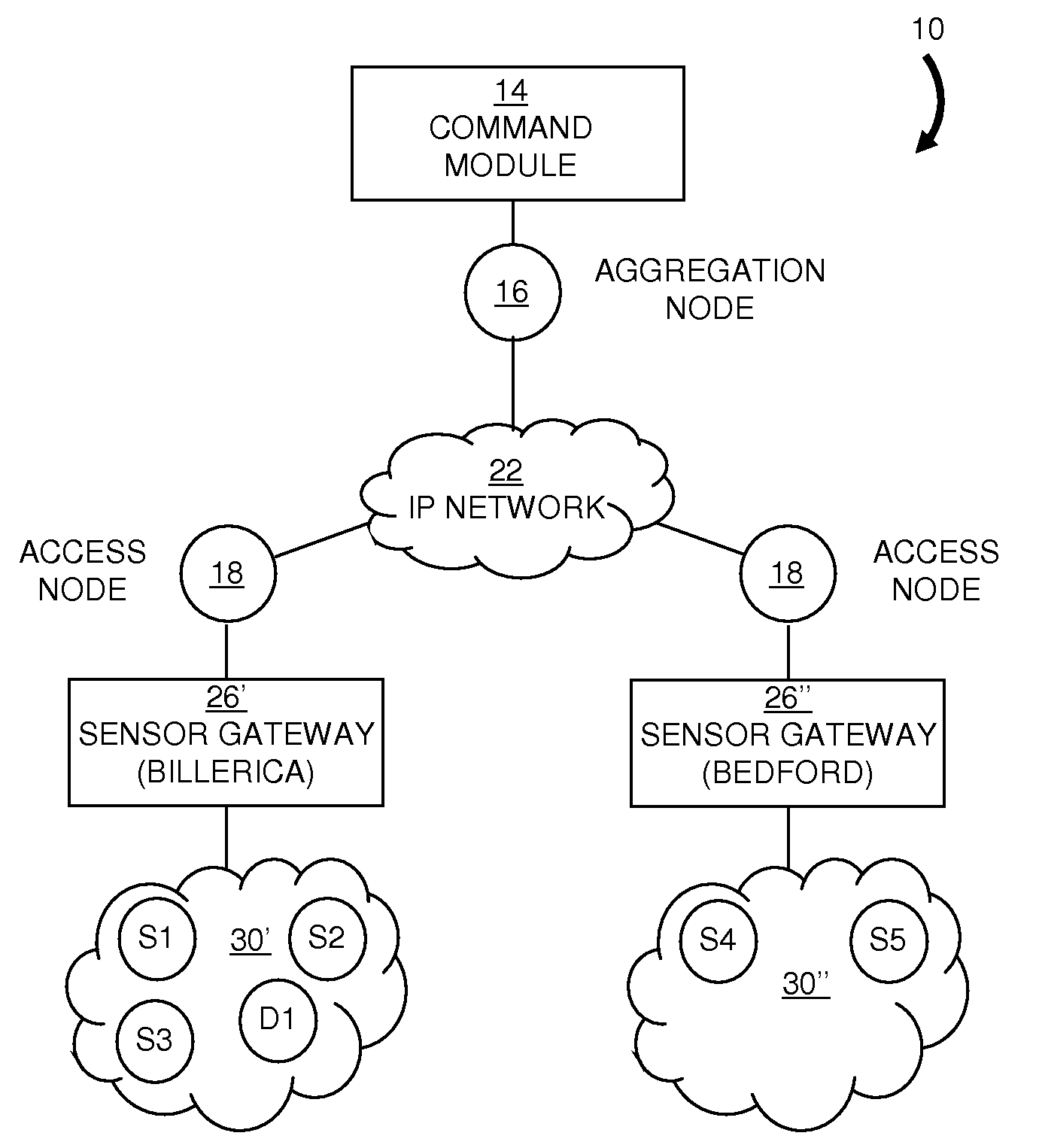
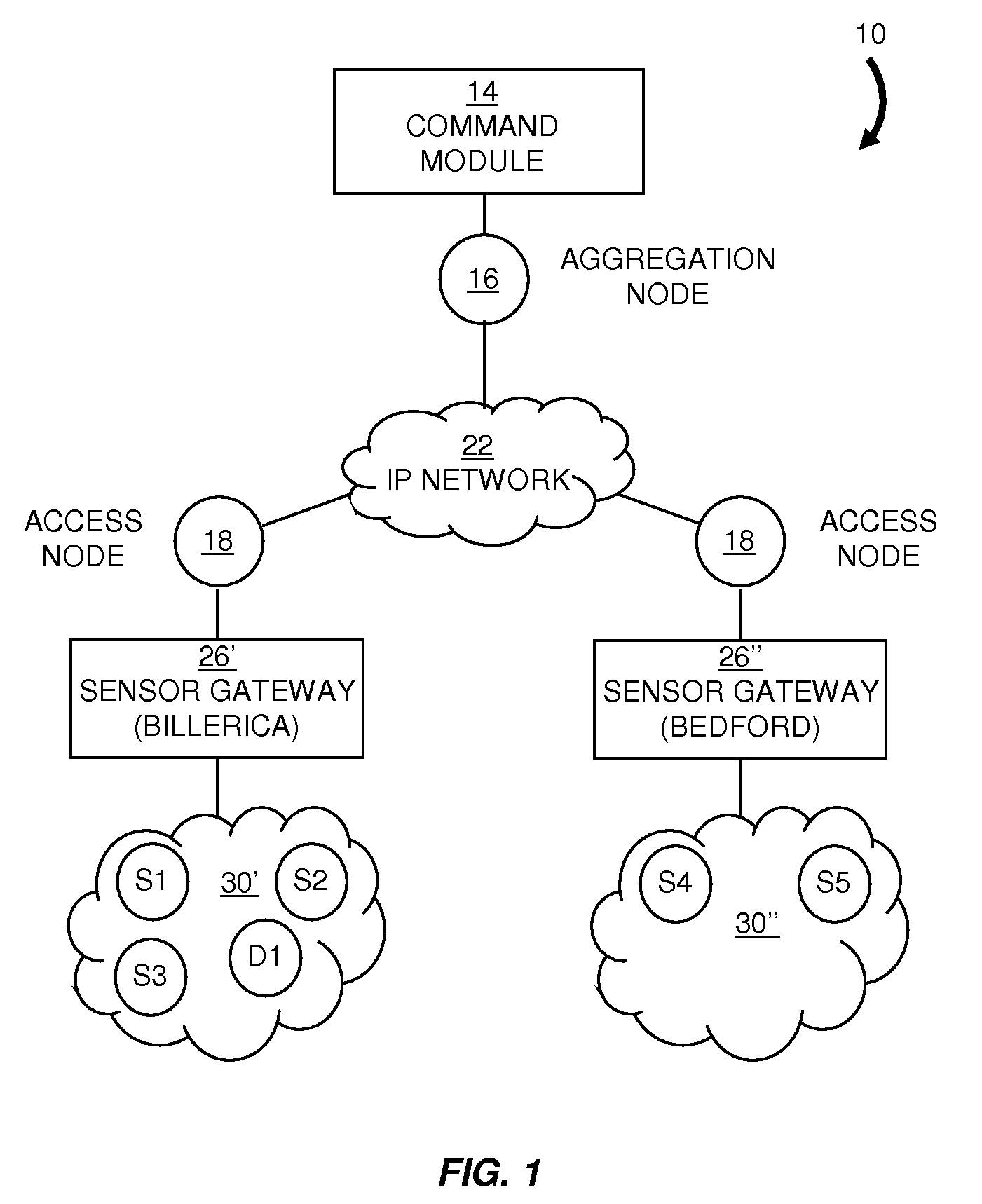
Dynamic sensor network registry
InactiveUS20090222541A1User identity/authority verificationNetwork topologiesNetwork connectionNetwork architecture
A scalable network architecture adapted to interface with various sensor types and sensor access mechanisms while providing real-time access to sensor data for distributed applications and organizations is described. A centralized sensor network service manages the registration, capabilities, near real-time status of the sensors and their current network connections. New sensors are discovered automatically through messaging between network access nodes and the sensor registry. The registry service can be made available to distributed sensor applications and sensor middleware, and facilitates the sharing of sensors across organizations. The sensor registry is automatically updated by network software and does not require manual configuration or reconfiguration each time a sensor is added to or relocated within the network. Authentication and authorization policies can be implemented to ensure that only authorized applications can query and view the registry. The registry can be implemented for multi-vendor sensor networks and can accommodate multiple addressing schemes.
Owner:RPX CLEARINGHOUSE
Real-time publish-subscribe system
A real-time protocol for real-time network programming applications is disclosed. The protocol is executable on a computer network having a plurality of nodes that include applications, a network stack, an operating system, and middleware capable of executing real-time operations. The protocol can use group objects to model physical and logical devices connected to the network wherein each group object comprises at least one variable. Changes in these variables are encapsulated in variable change messages which are propagated in the network using communication objects. Also described is a real-time messaging format useful for implementing the protocol.
Owner:REAL TIME INNOVATIONS
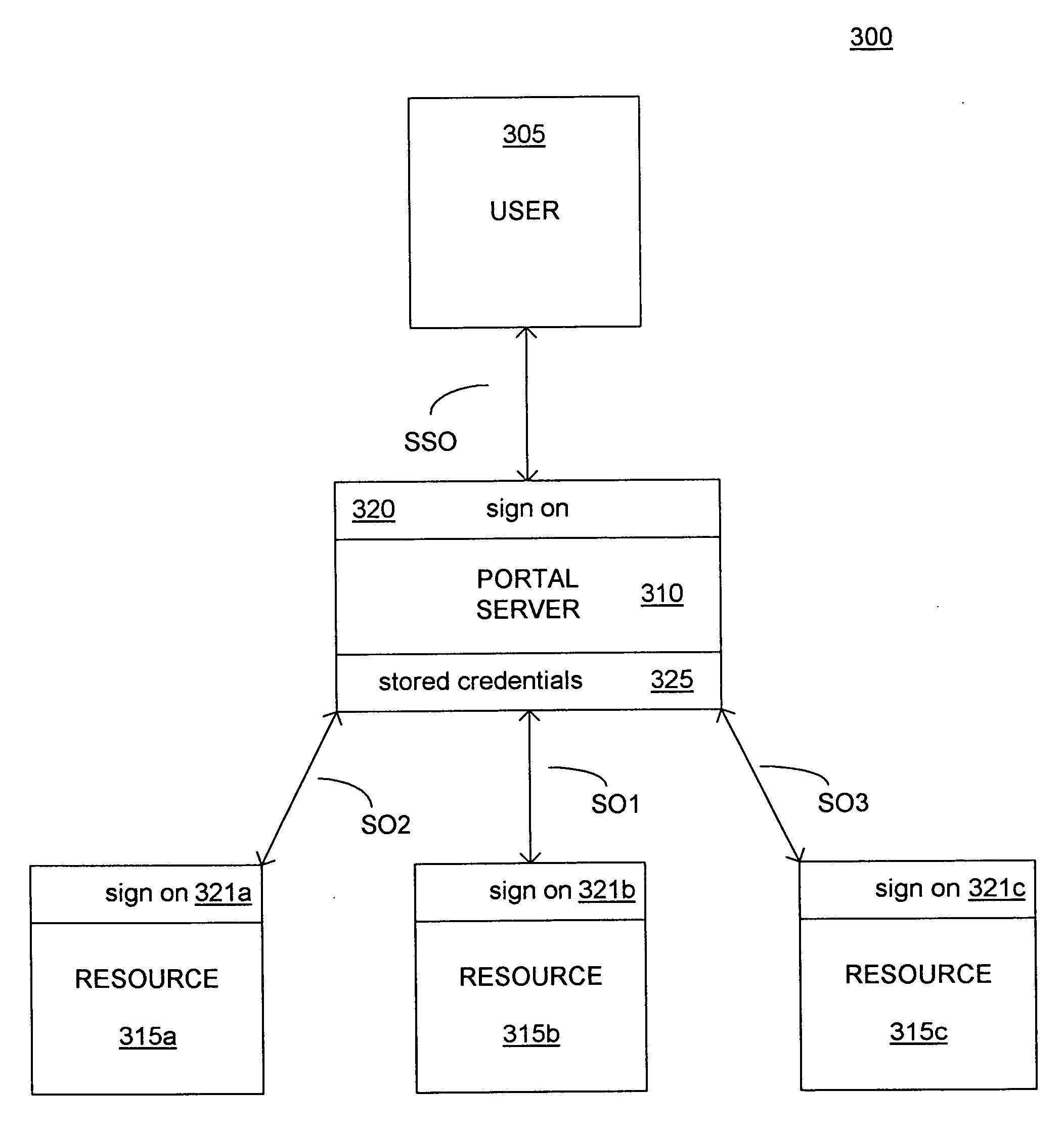
System and method for single-sign-on access to a resource via a portal server
A single-sign-on adapter (SSO Adapter) implementing one or more authentication mechanisms that may be used by Portal middleware on behalf of a portal user. A user seeking access to a resource server through a portal server performs a single sign-on with the portal server at the beginning of a session. When requests a resource from resource server that requires authentication, the authentication is handled by the portal server without requiring an authentication response from the user. The portal server may use stored user credentials, a token-based shared authentication service, or proxy authentication in order to gain access to the resource server on behalf of the portal user.
Owner:SUN MICROSYSTEMS INC
System and method for establishing universal real time protocol bridging
InactiveUS20070171898A1Exemption stepsSpecial service for subscribersNetwork connectionsTime-division multiplexingConference call
An apparatus and methods for Real Time Protocol (RTP) based bridging to create calls to and From any communication devices connected to the Public Switched Telephone Network (PSTN) or any public or private Internet Protocol network. The methods are represented in controls residing either in an RTP Bridge apparatus or as middleware on a service creation platform, softswitch, or SIP proxy services incorporating SIP bridging and SIP call relay technologies, with an interface to a TDM (Time Division Multiplexing) switch operated by a Local Exchange Carrier (LEC) or Competitive LEC (CLEC), or hosted by an Internet Telephony Service Provider (ITSP) with connectivity to the PSTN through media gateways. The method permits a party to request an on demand conference call by either dialing into the apparatus from the PSTN or from any type of RTP communication device such as an IP phone; or using a form of signaling from RTP translation device. The moderator initiates the request, enters the participant(s) to be included in the call, and the launch sequence is initiated and the apparatus makes contact with the phone / end point and uses RTP bridging to interlace the packet streams and deliver one stream back to all the devices. The advantage is an on demand conference call to one or many participants, on similar or different communications platforms.
Owner:XTELTEK
Processor provisioning by a middleware system for a plurality of logical processor partitions
InactiveUS20140181833A1Resource allocationError detection/correctionMulti processorApplication software
A middleware processor provisioning process provisions a plurality of processors in a multi-processor environment. The processing capability of the multiprocessor environment is subdivided and multiple instances of service applications start protected processes to service a plurality of user processing requests, where the number of protected processes may exceed the number of processors. A single processing queue is created for each processor. User processing requests are portioned and dispatched across the plurality of processing queues and are serviced by protected processes from corresponding service applications, thereby efficiently using available processing resources while servicing the user processing requests in a desired manner.
Owner:IBM CORP
Method for implementing an intelligent content rating middleware platform and gateway system
InactiveUS20050135264A1Highly scalable, manageable and reliableMetering/charging/biilling arrangementsError preventionCyber operationsMiddleware
The method for implementing an Intelligent Content Rating middleware platform and gateway system disclosed herewith provides telecommunications carriers and network operators with the ability to define routing and actions based on HTTP / SIP based content and subscriber context through a powerful, extensible Layer 4-7 switching fabric technology. The invention mediates communications between applications and networks for IP packet flows, personal messaging, location-based services and billing. Furthermore, it enables advanced context-sensitive dialogue scenarios with the wireless subscriber such as, but not limited to, Advice-of-Charge dialogues. The art permits telecommunications network operators and like entities to introduce real-time rating of data services for both prepaid and post-paid subscribers. Further advances in the art include the validation of digital signatures, combined with authentication and non-repudiation techniques to ensure subscriber privacy remains protected.
Owner:REDKNEE INC
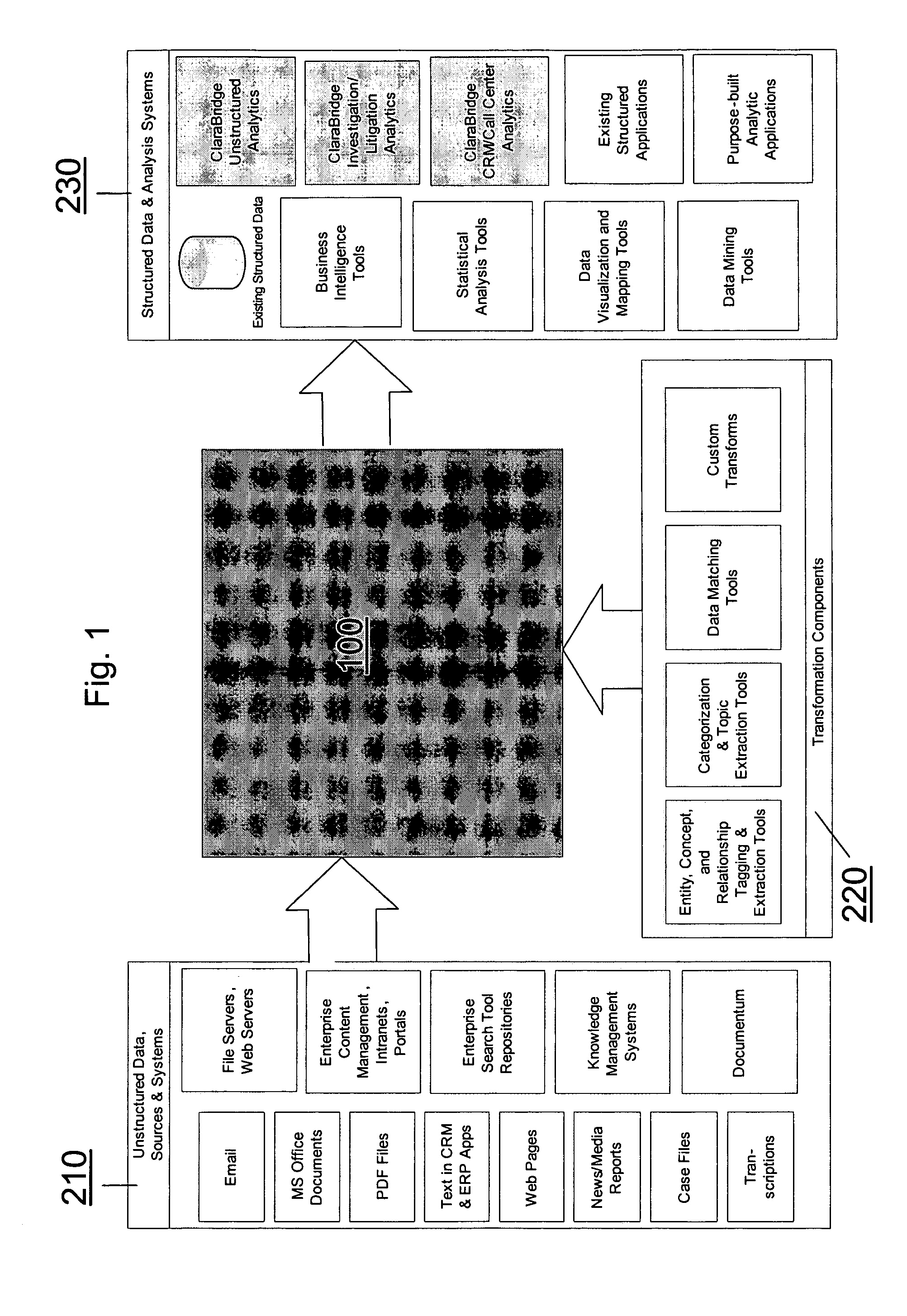
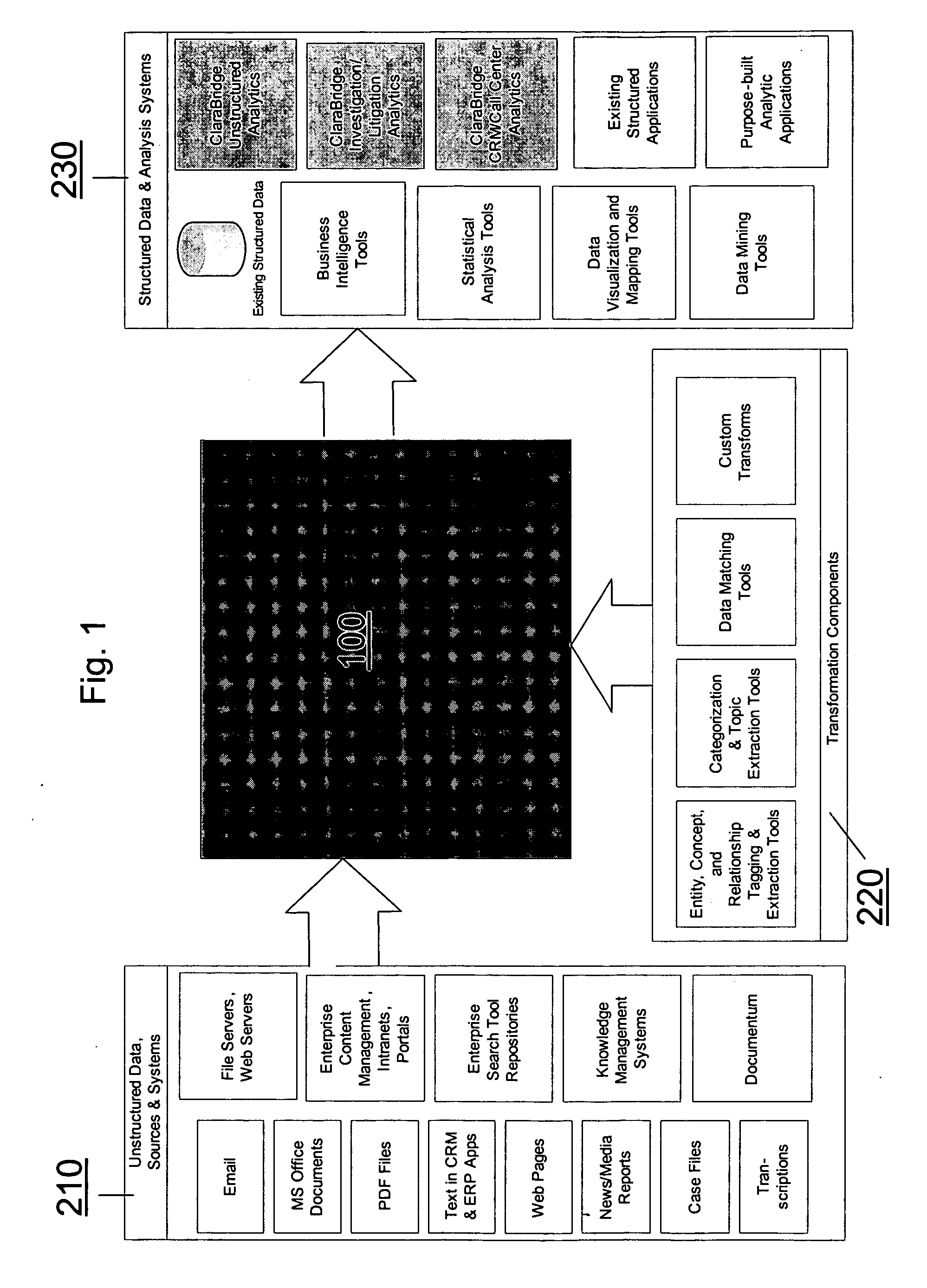
System and method of making unstructured data available to structured data analysis tools
ActiveUS20070011134A1Data processing applicationsDigital data information retrievalData transformationStructured data analysis
A system and method of making unstructured data available to structured data analysis tools. The system includes middleware software that can be used in combination with structured data tools to perform analysis on both structured and unstructured data. Data can be read from a wide variety of unstructured sources. The data may then be transformed with commercial data transformation products that may, for example, extract individual pieces of data and determine relationships between the extracted data. The transformed data and relationships may then be passed through an extraction / transform / load (ETL) layer and placed in a structured schema. The structured schema may then be made available to commercial or proprietary structured data analysis tools.
Owner:CLARABRIDGE
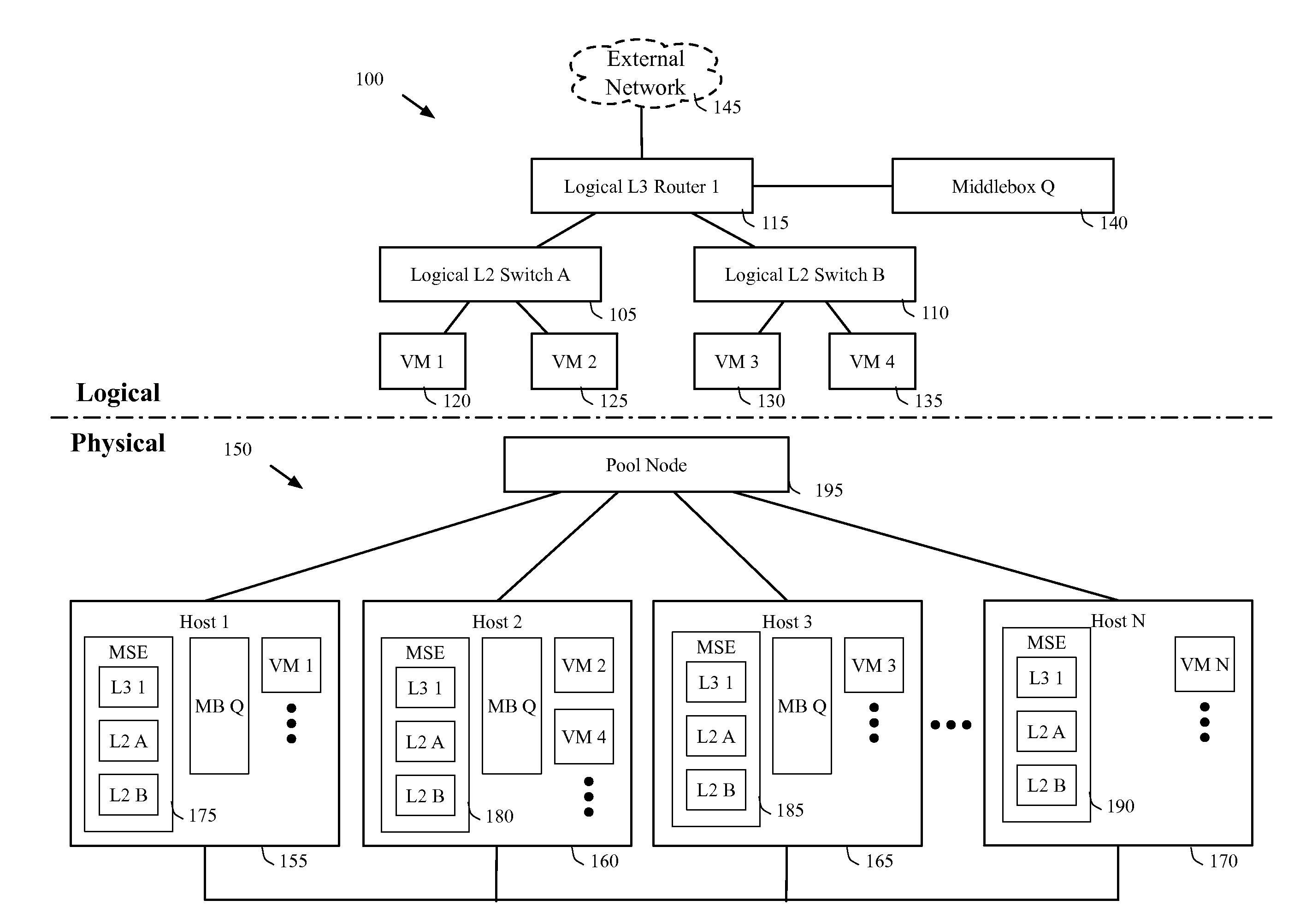
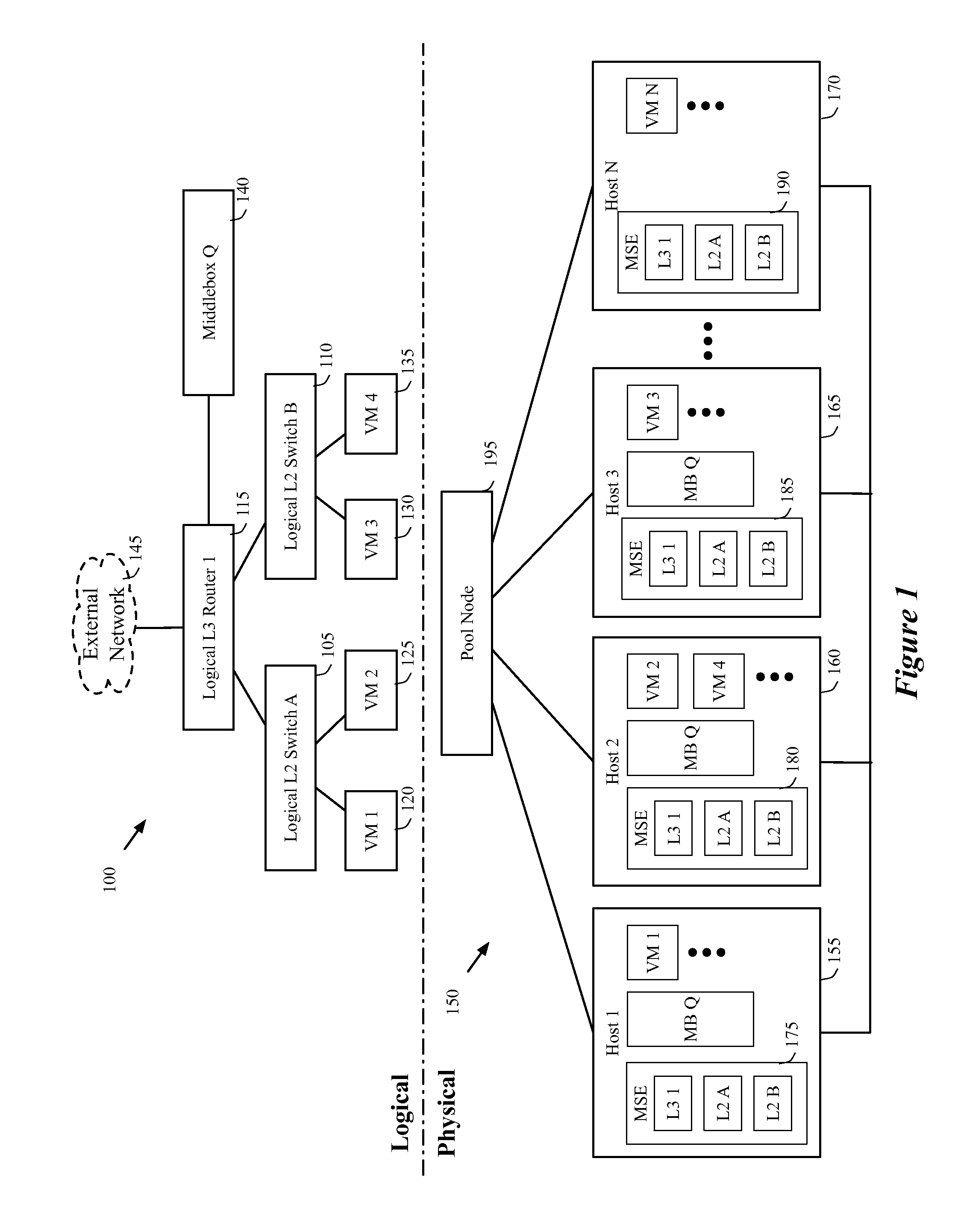
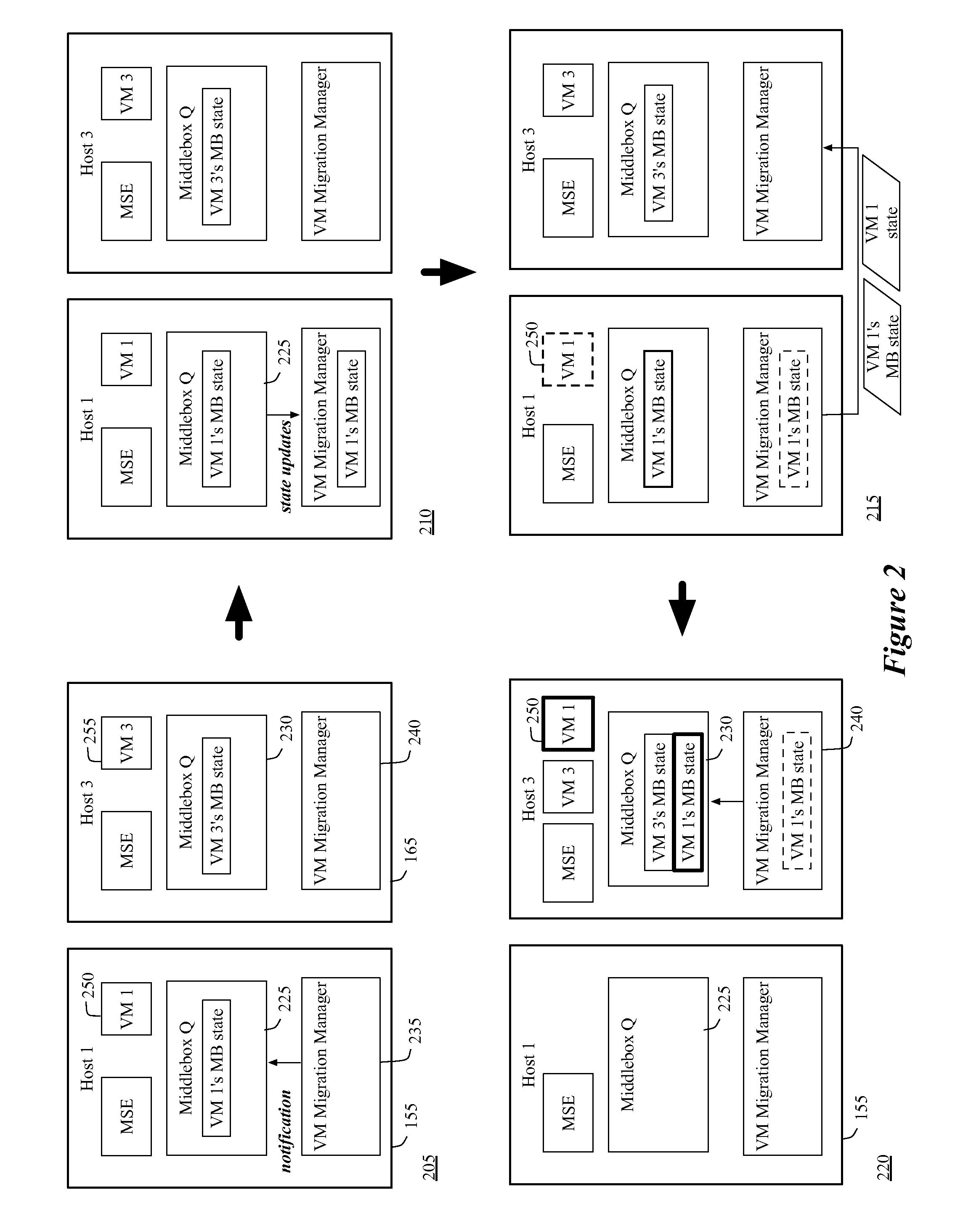
Migrating middlebox state for distributed middleboxes
A controller of a network control system for configuring several middlebox instances is described. The middlebox instances implement a middlebox in a distributed manner in several hosts. The controller configures, in a first host, a first middlebox instance to receive a notification from a migration module before a virtual machine (VM) running in the first host migrates to a second host and to send middlebox state related to the VM to the migration module.
Owner:NICIRA
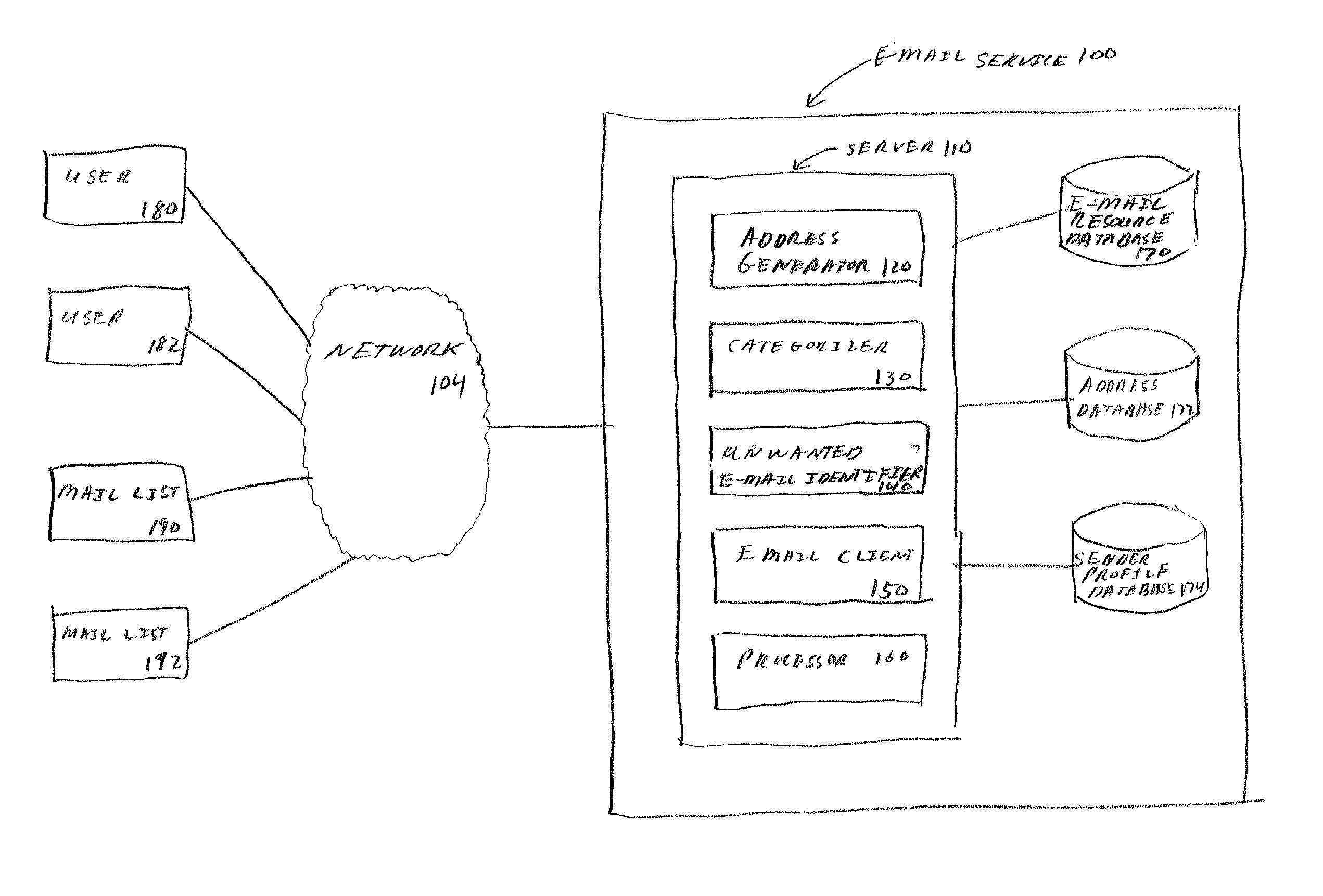
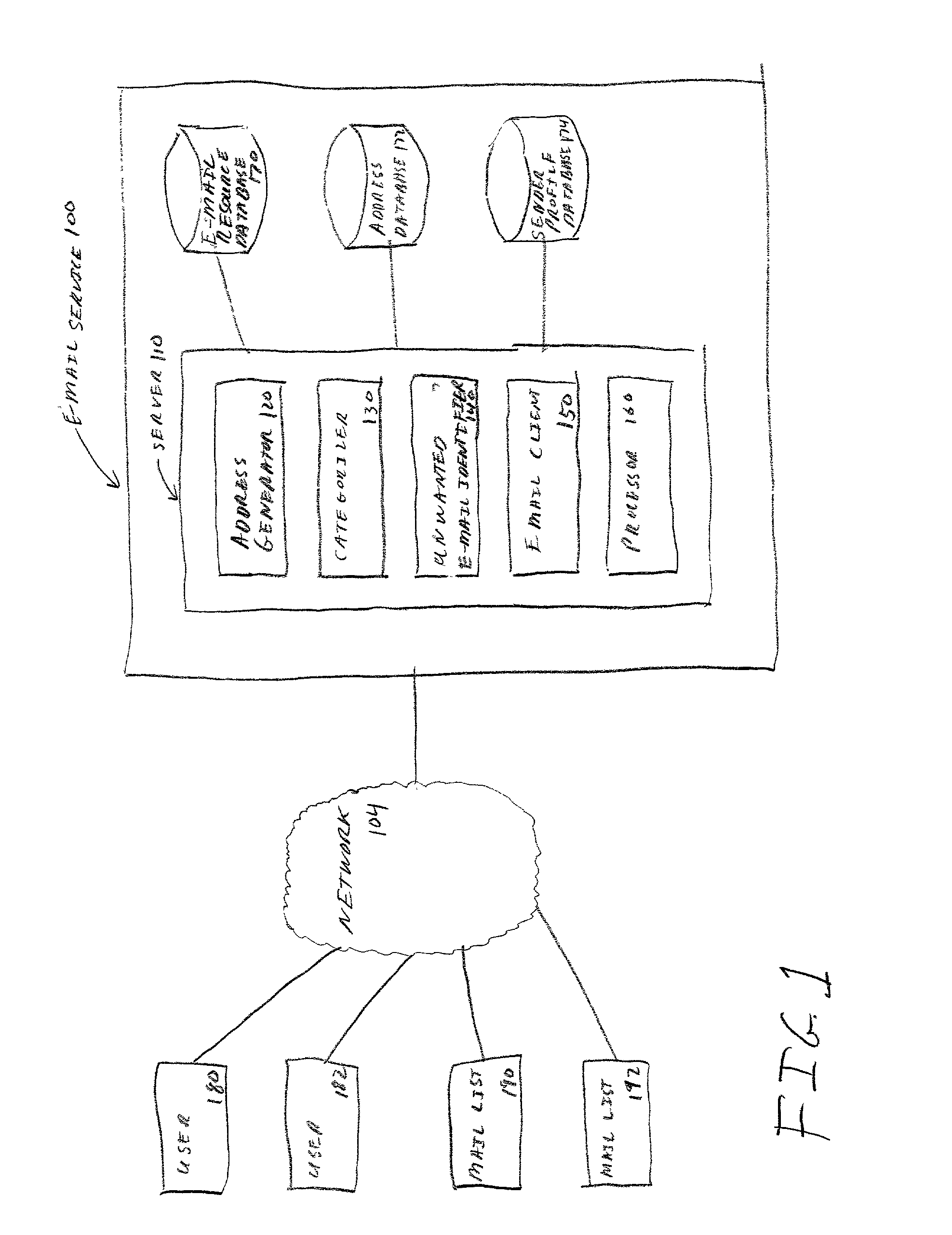
Web page filtering including substitution of user-entered email address
A method and apparatus for using an intermediary to manage unwanted electronic messages is provided. The intermediary generates a unique address for each pairing of a user and an e-mail resource, such as a mail list. The intermediary maintains a database that identifies which user and which e-mail resource is associated with each unique address. When the intermediary receives messages, the intermediary identifies the user and the e-mail resource based on the database. The intermediary sorts messages for each user based on groups that are associated with each e-mail resource. The intermediary filters the messages to identify messages that are unwanted by the user, such as mass unsolicited e-mail. The intermediary identifies unwanted messages by comparing the sending address for each message to a list of authorized sending addresses for the e-mail resource, and by analyzing the content of the messages, such as identifying whether the messages contain hidden images.
Owner:GOZOOM COM +1
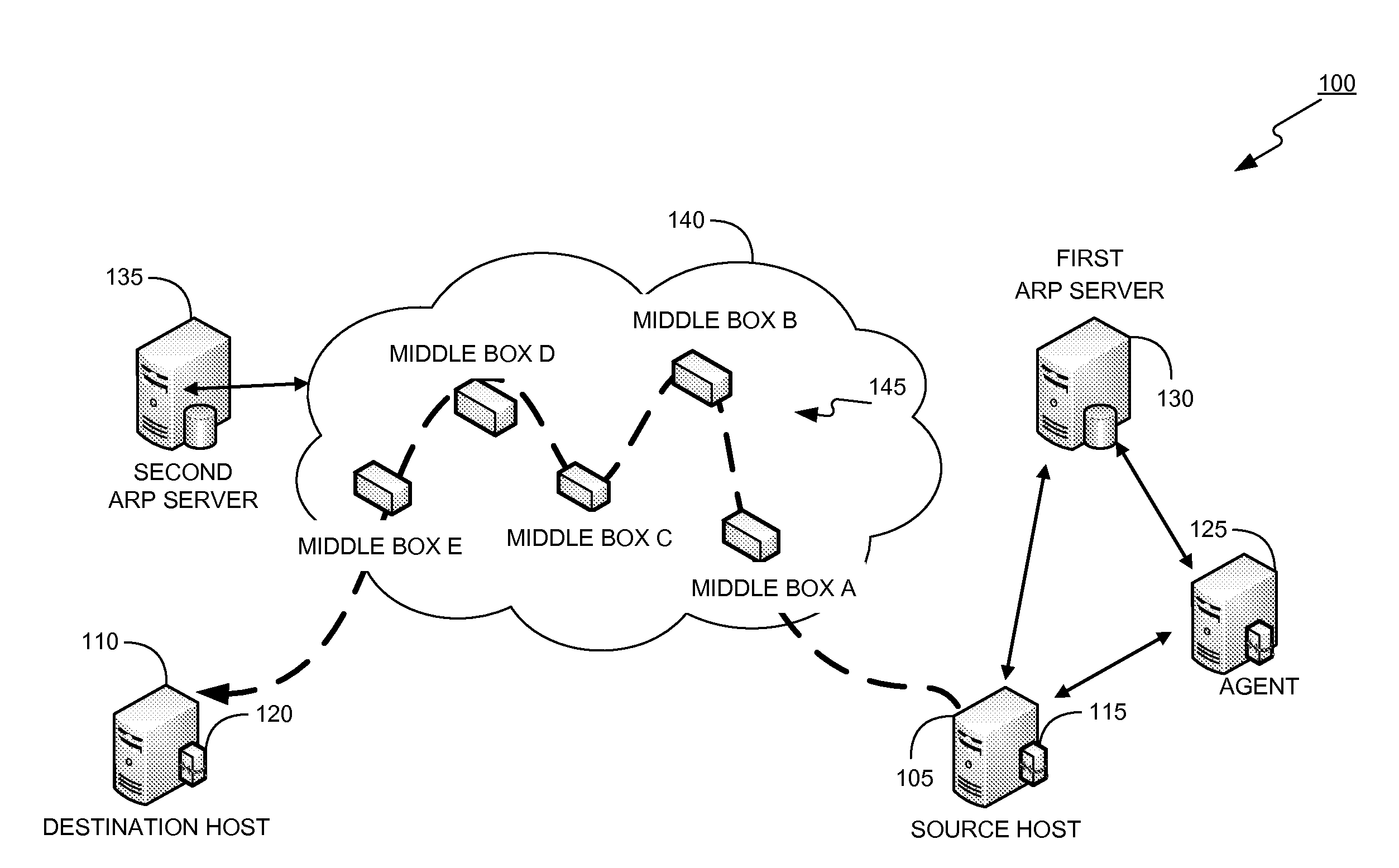
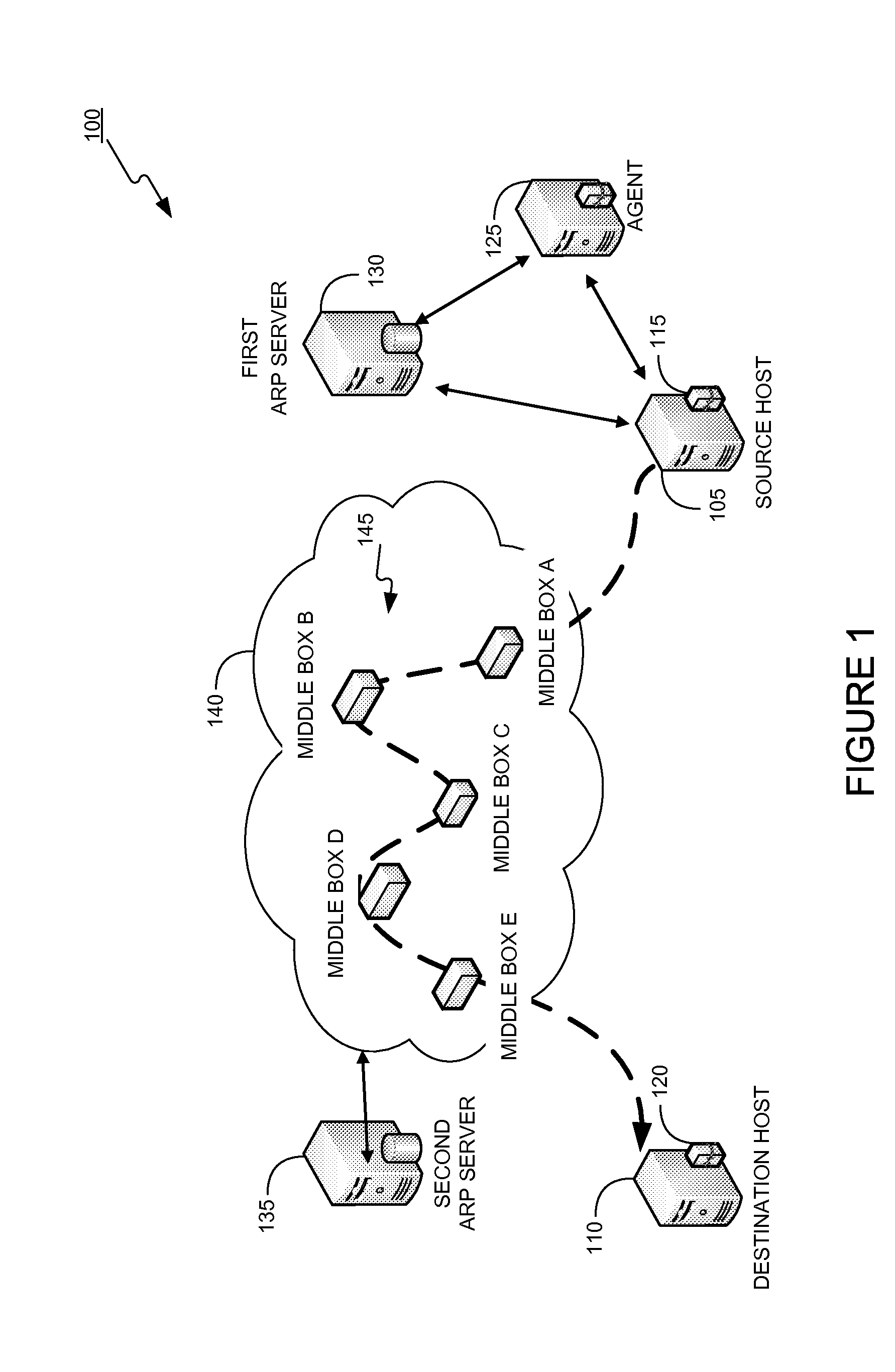
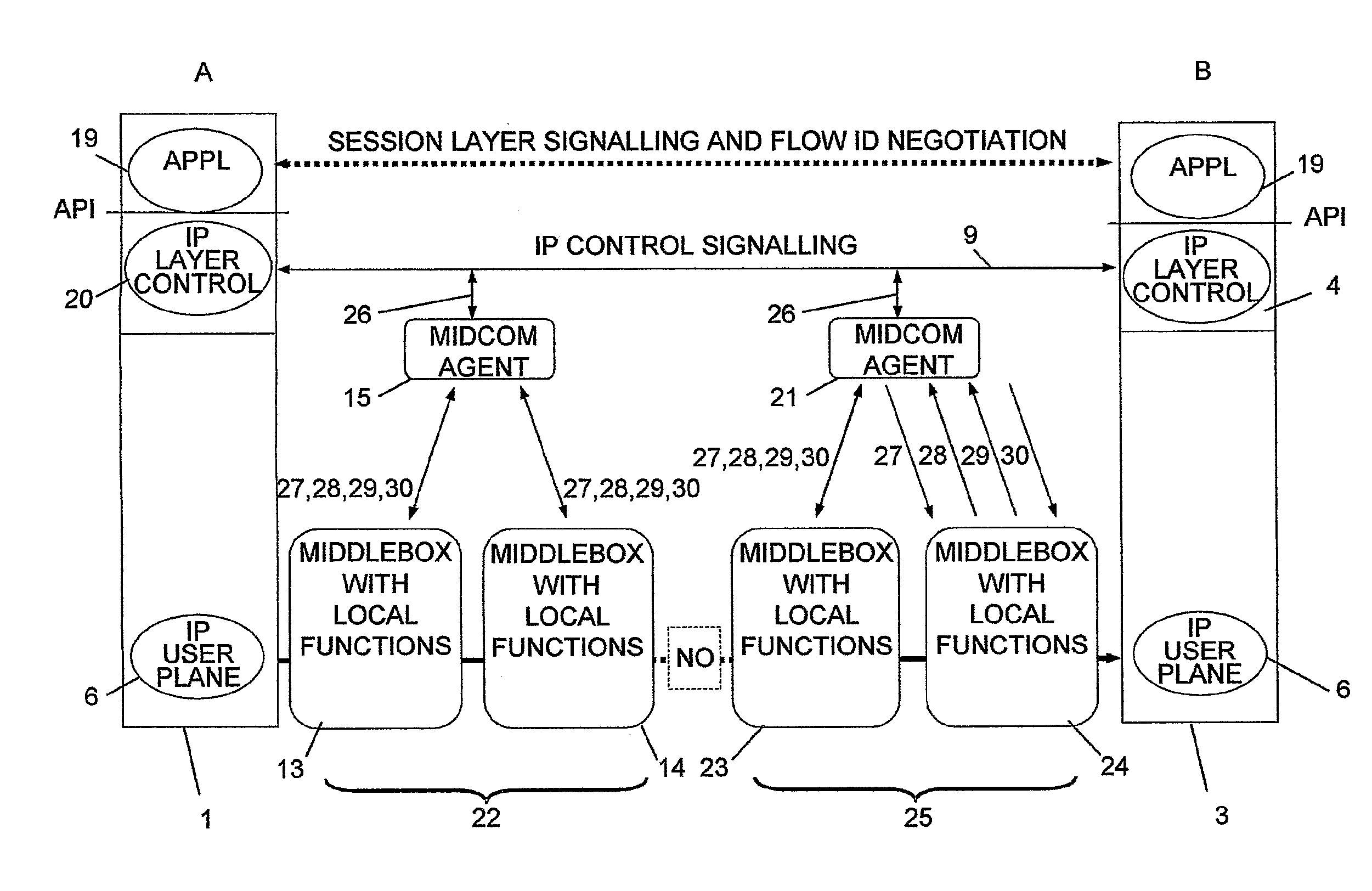
Control of Mobile Packet Streams
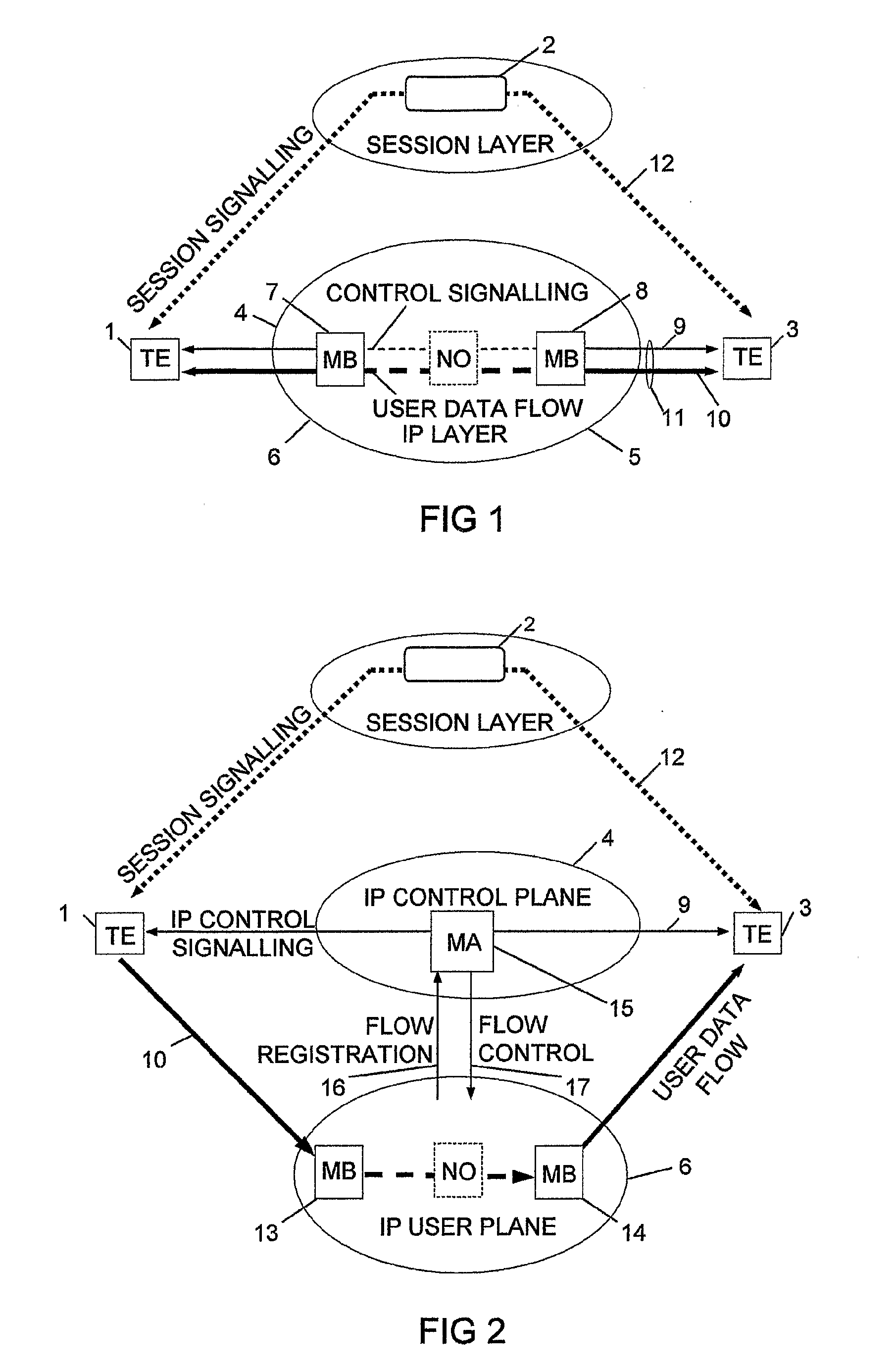
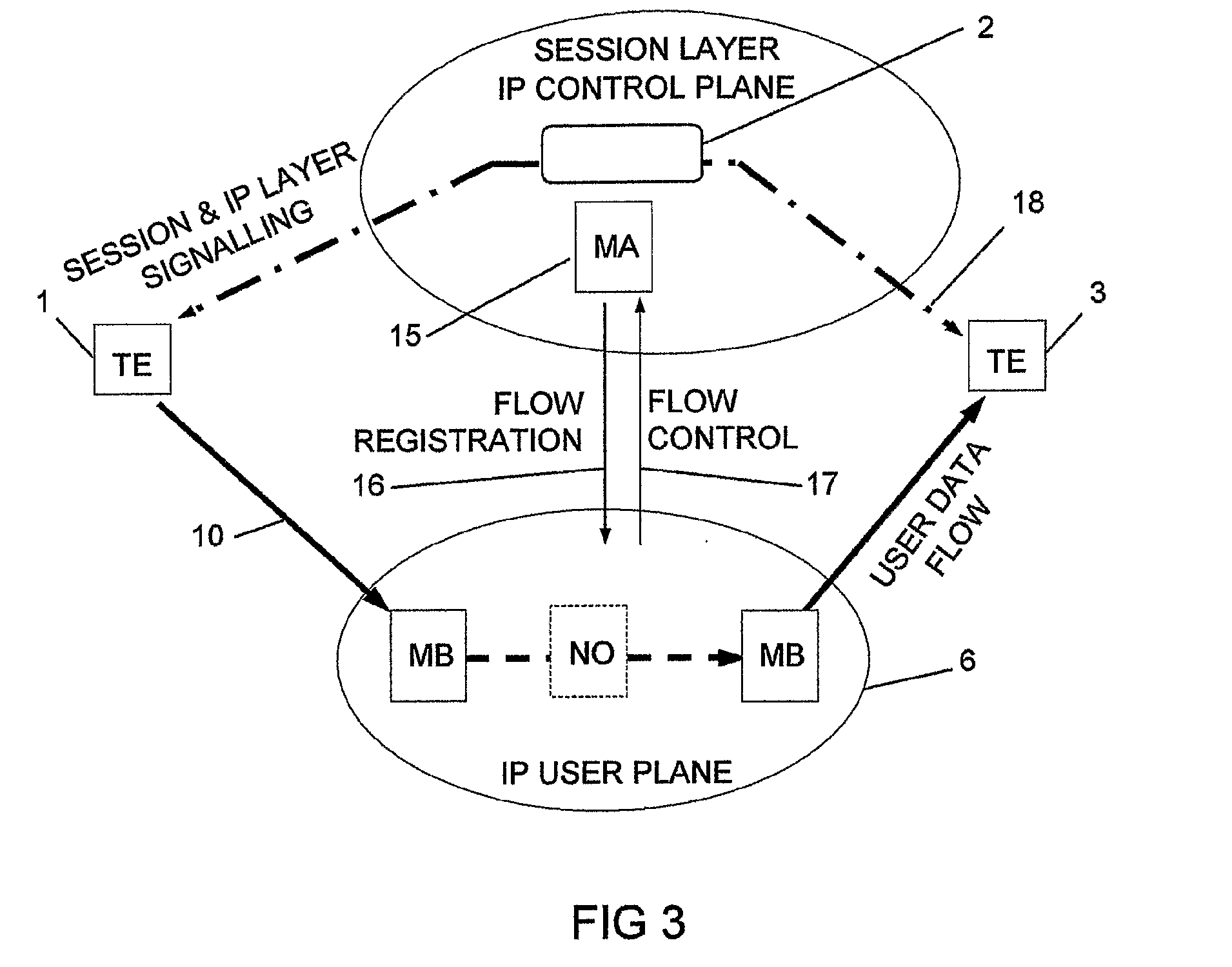
InactiveUS20070286185A1Reduce signaling overheadMinimum delayError preventionTransmission systemsControl signalMiddleware
The invention relates to a method, device and system for control of mobile packet flows forwarded between IP based networks. Individual packet flows on an IP user plane (6) traverse middleboxes (13, 14, 23, 24) that are controlled from a midcom agent (15, 21). Each user flow registers its presence (29) in each middlebox it encounters on its way from its source (A) to its destination (B) at the user plane. In response each middlebox registers itself and the mobile flows it handles at the midcom agent with which they communicate using a midcom signalling protocol. The midcom agent comprises functionalities that its controlled middleboxes have and can provide control messages for how a middlebox shall handle a registered flow. The registration provides the midcom agent (15, 21) with knowledge of registered flows and middleboxes which allows the midcom agent to send control orders to the middleboxes that registered themselves, said orders pertaining to the handling of the flows at the respective middleboxes. A mechanism for control signalling at the IP control plane is described.
Owner:OPTIS WIRELESS TECH LLC
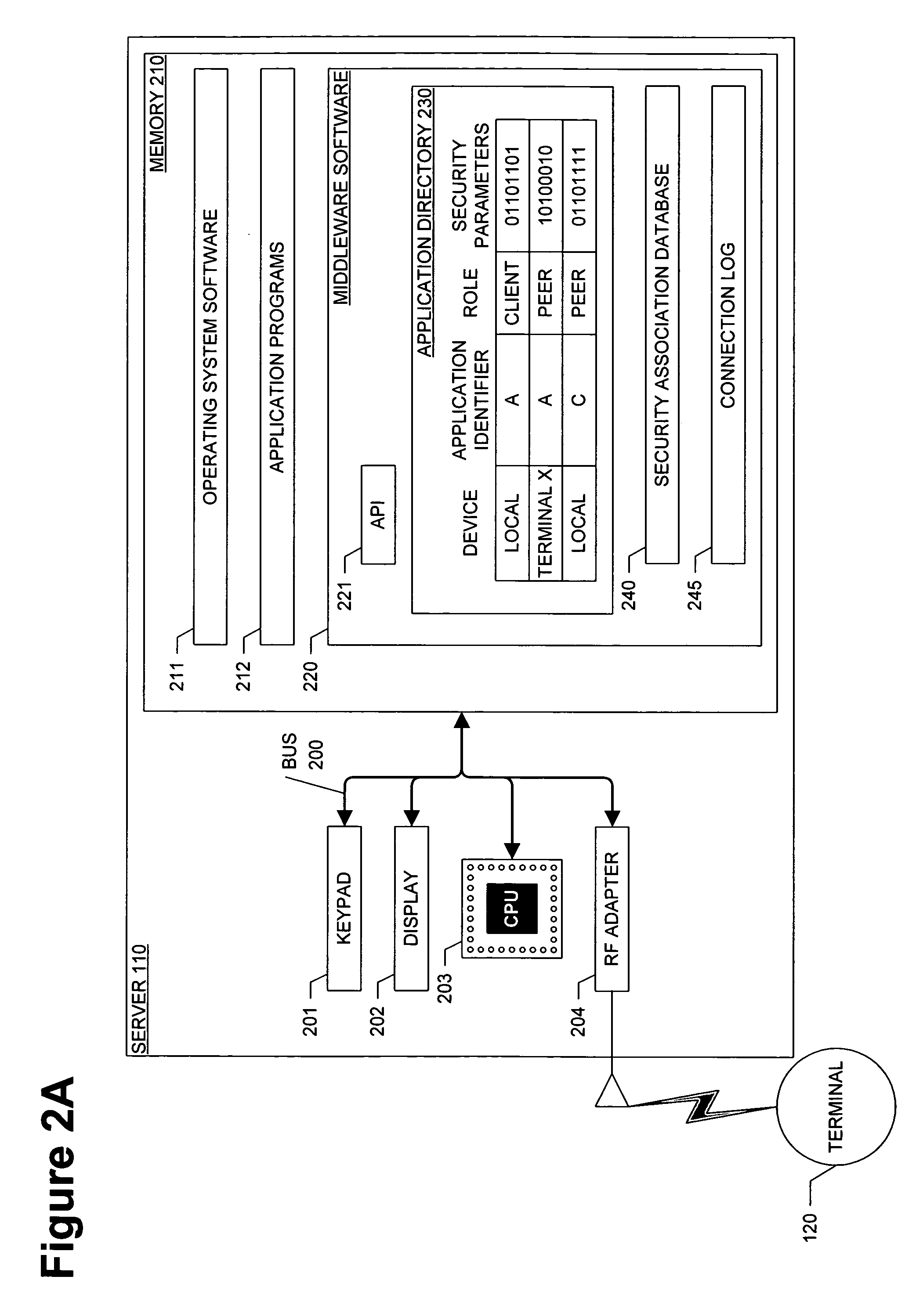
Method of initializing and using a security association for middleware based on physical proximity
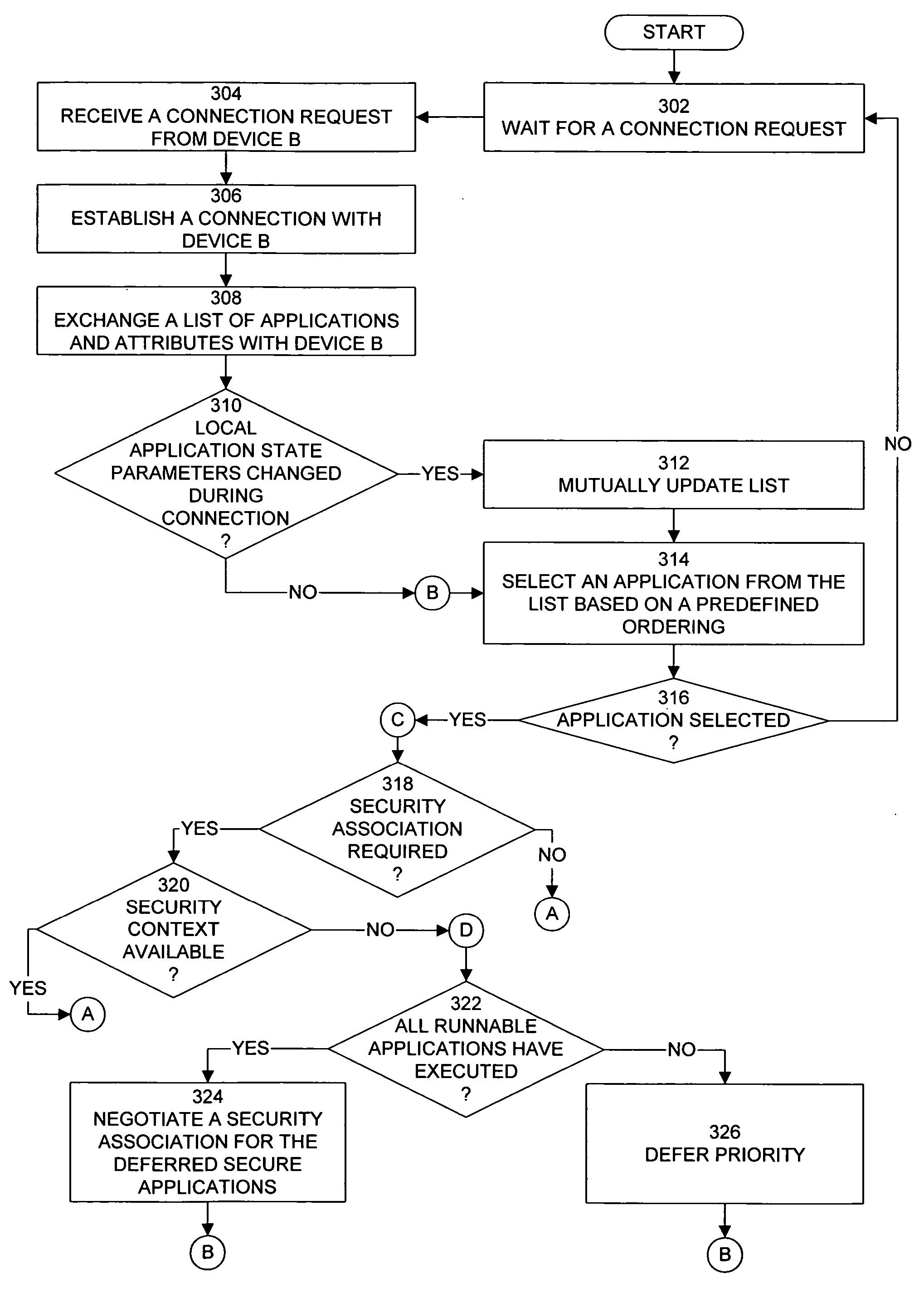
InactiveUS20050059379A1Maintain confidentialityEnsure integrityUnauthorised/fraudulent call preventionDigital data processing detailsComputer networkSecurity association
A computer system, method, and computer program product for controlling data communication in an ad-hoc network that connects a wireless device and a nearby wireless device. The method stores an application directory, determines a priority for each entry in the application directory, identifies a selected entry based on the priority, and examines the attributes and security parameters associated with the selected entry. When the security parameters indicate to use a secure connection, the method establishes a security association to support the data communication by querying a database for an existing security association that will satisfy the security parameters. When the query is successful, the method reuses the existing security association. When the query is unsuccessful, the method creates a new security association by establishing a privileged side channel to the nearby wireless device, negotiating the new security association over the privileged side channel, and storing the new security association.
Owner:NORDIC INTERACTIVE TECH LLC
Message-oriented middleware provider having multiple server instances
ActiveUS20090217293A1Interprogram communicationDigital computer detailsApplication serverUnique identifier
A method, apparatus, and system are provided for a Message-Oriented Middleware (MOM) provider having multiple logical MOM server instances. In an embodiment, the MOM provider having multiple logical MOM server instances is implemented on an application server. Each MOM server instance may include a session container to manage one or more sessions and a destination container to provide one or more destinations. In an embodiment, a globally unique identifier identifies each destination.
Owner:SAP AG
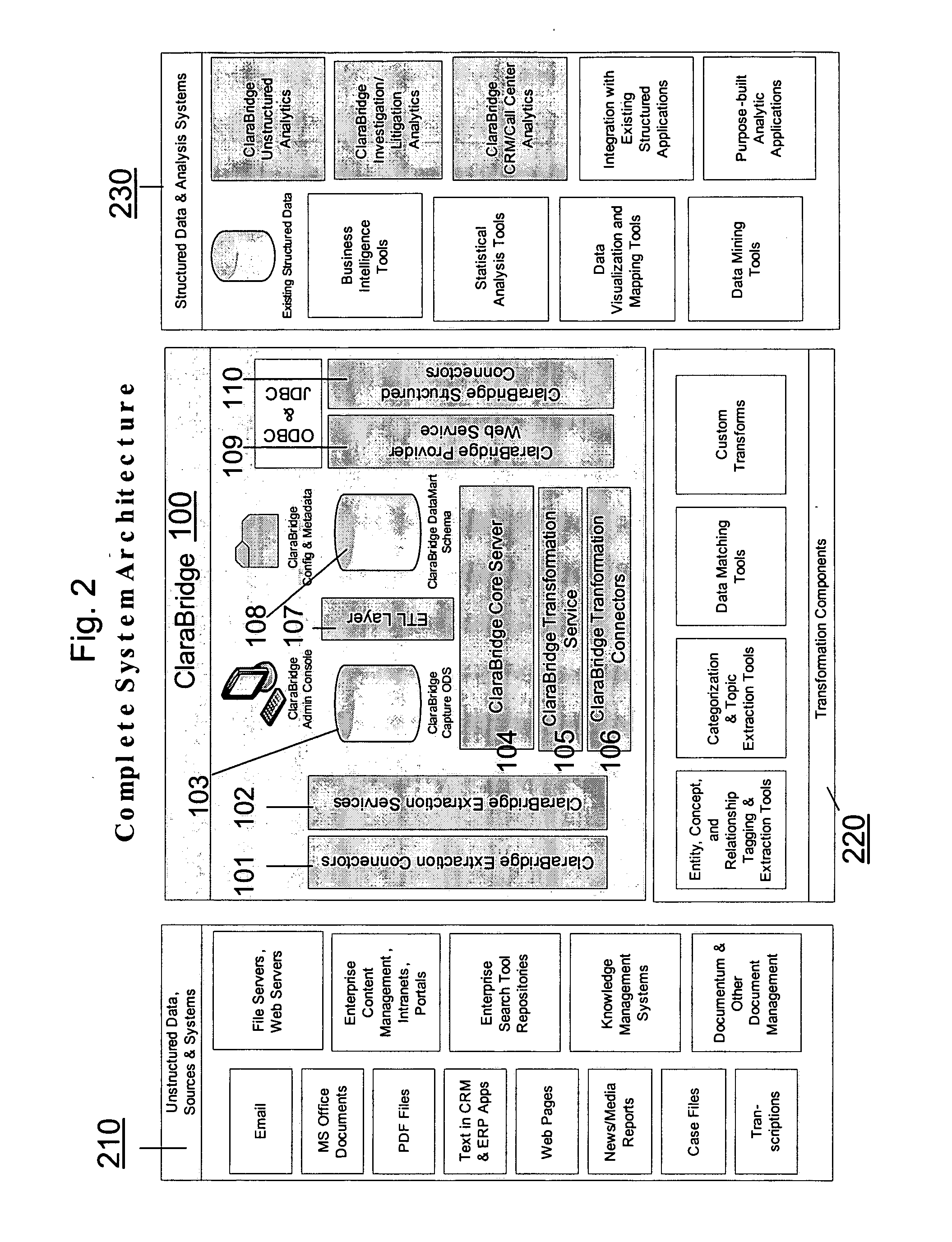
Schema and ETL tools for structured and unstructured data
ActiveUS20070011175A1Data processing applicationsDigital data information retrievalData transformationStructured data analysis
A system and method of making unstructured data available to structured data analysis tools. The system includes middleware software that can be used in combination with structured data tools to perform analysis on both structured and unstructured data. Data can be read from a wide variety of unstructured sources. The data may then be transformed with commercial data transformation products that may, for example, extract individual pieces of data and determine relationships between the extracted data. The transformed data and relationships may then be passed through an extraction / transform / load (ETL) layer and placed in a structured schema. The structured schema may then be made available to commercial or proprietary structured data analysis tools.
Owner:CLARABRIDGE
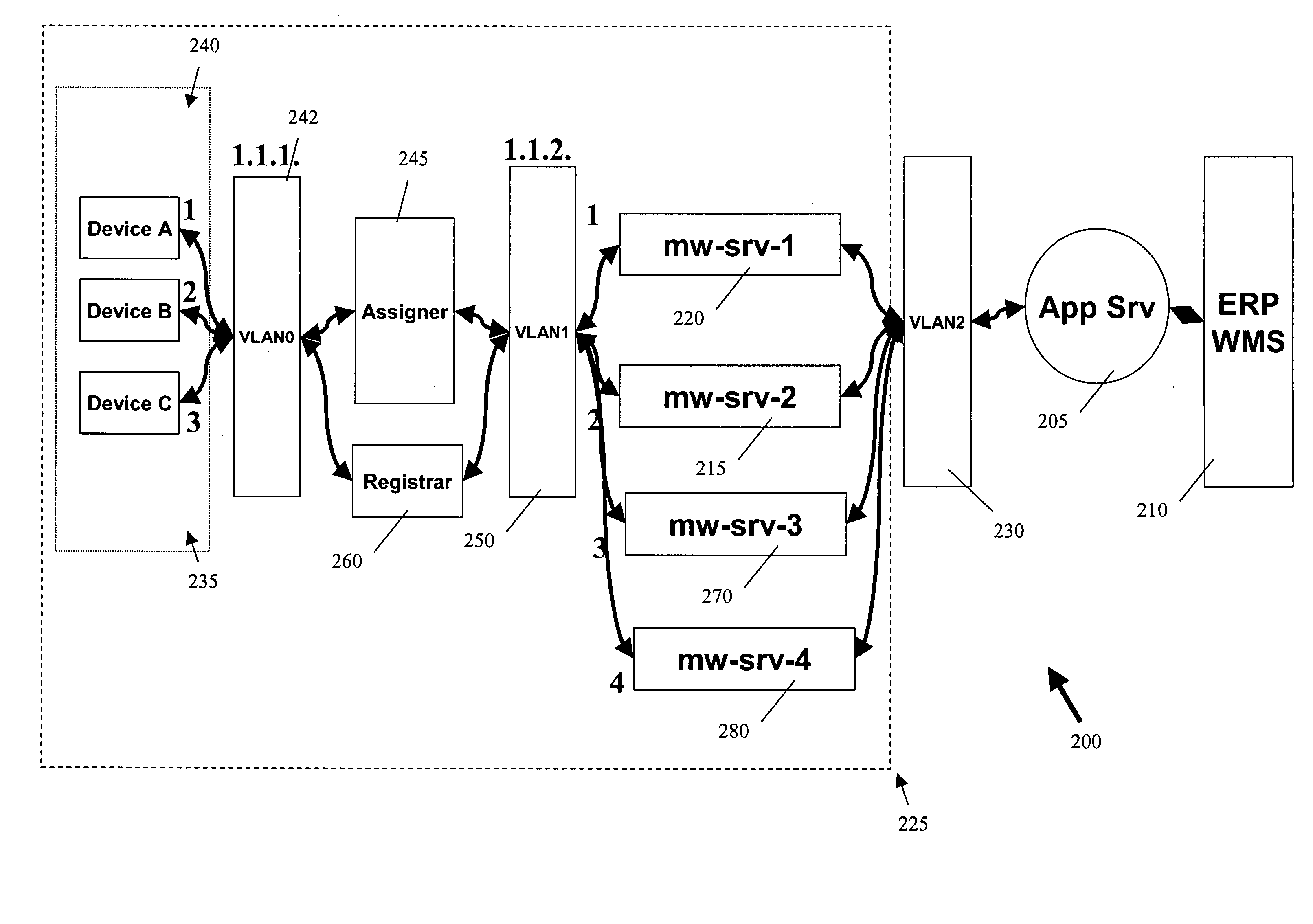
Methods and devices for providing scalable RFID networks
ActiveUS20050252971A1Network traffic/resource managementSensing record carriersAuto-configurationNetwork addressing
According to some implementations of the present invention, RFID devices and middleware servers are automatically provisioned with a network address and with instructions for sending a request for a middleware server to a middleware server assigner. In some implementations, the middleware server assigner is a load balancer. In some implementations, a middleware server is associated with a plurality of RFID devices by associating a middleware server network address or names with the network addresses of the RFID devices. Preferred methods also provide for redundancy of middleware servers and dynamic re-assignment of RFID devices from an unavailable middleware server to an available middleware server.
Owner:CISCO TECH INC
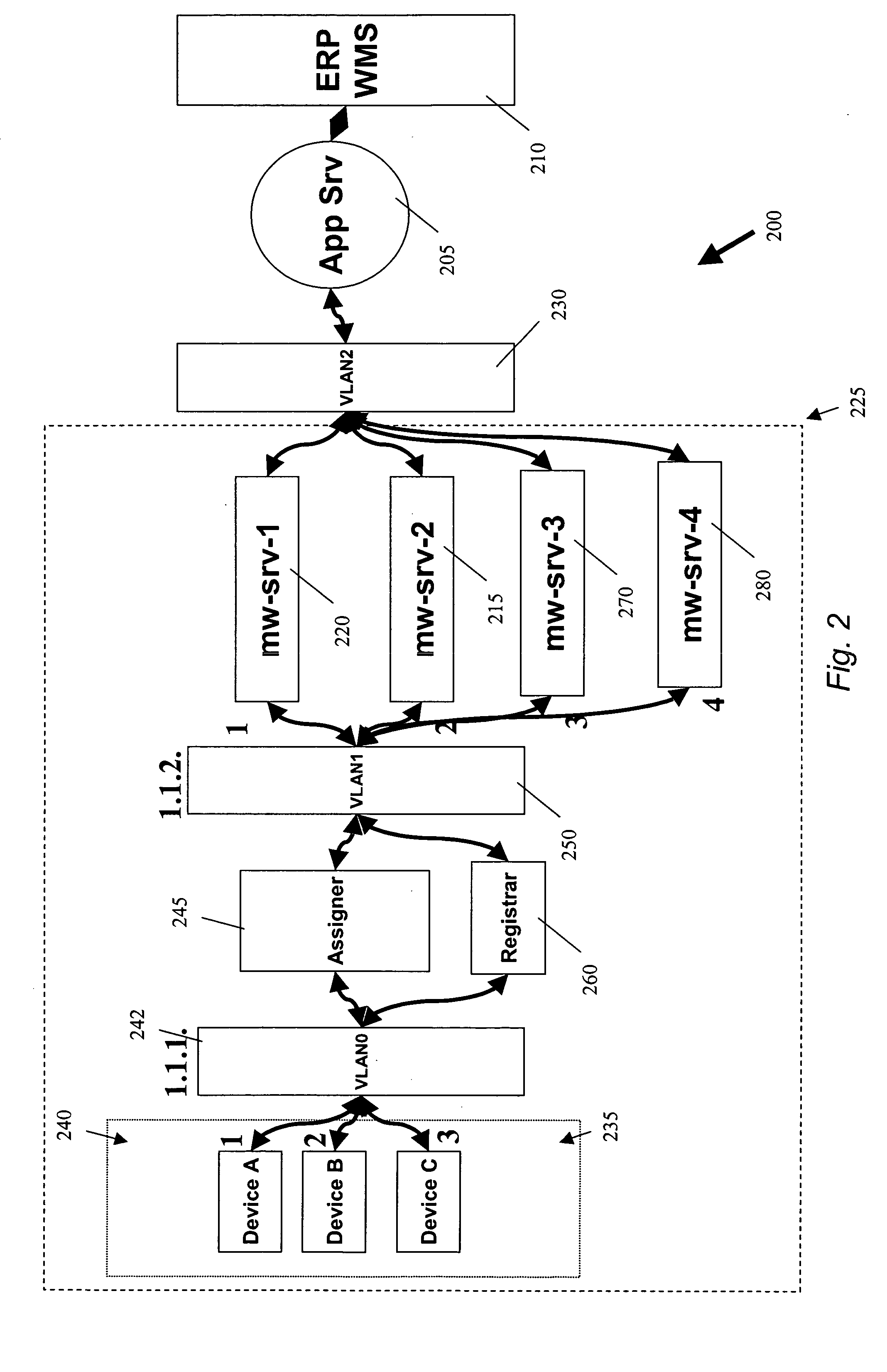
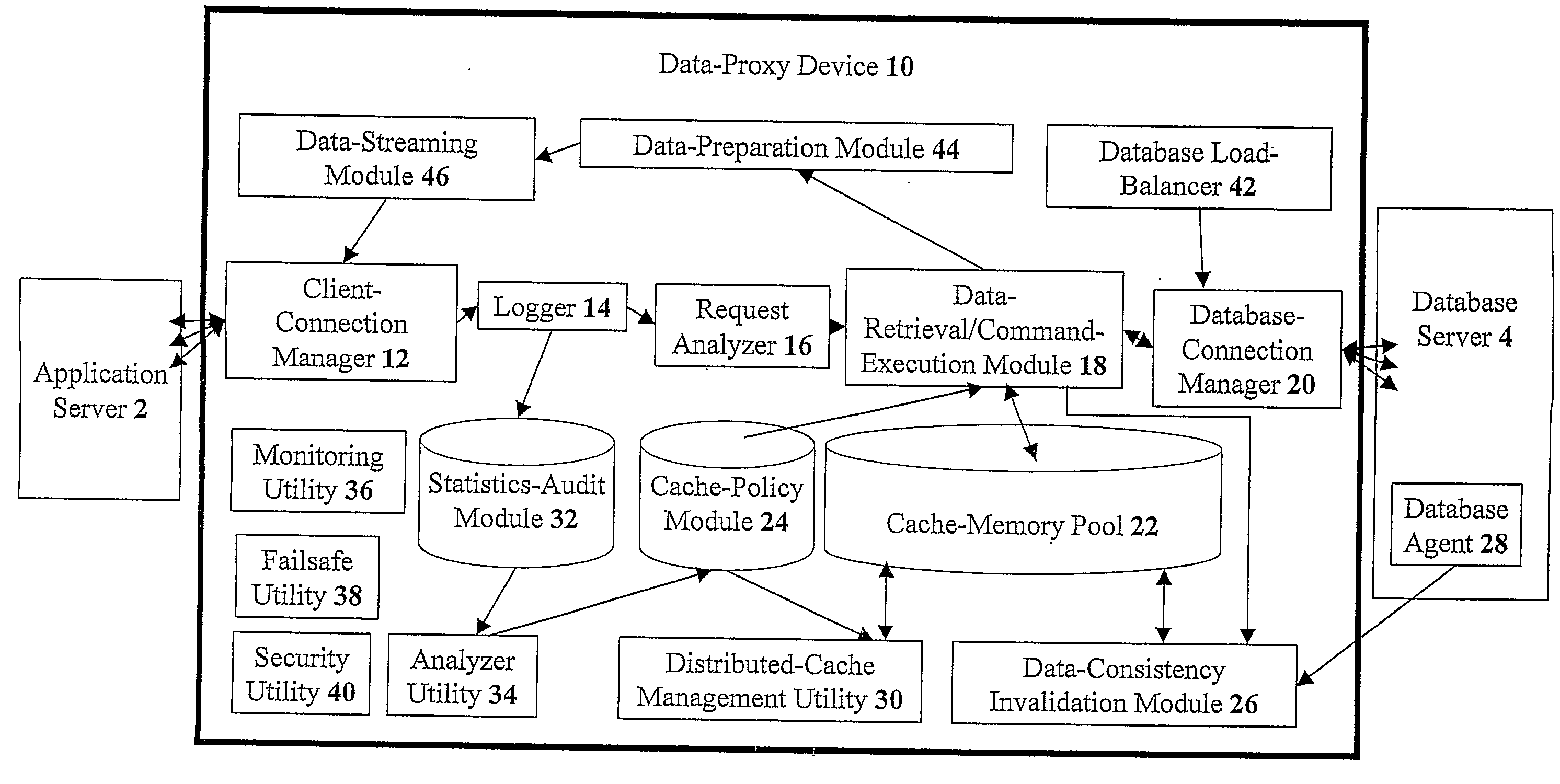
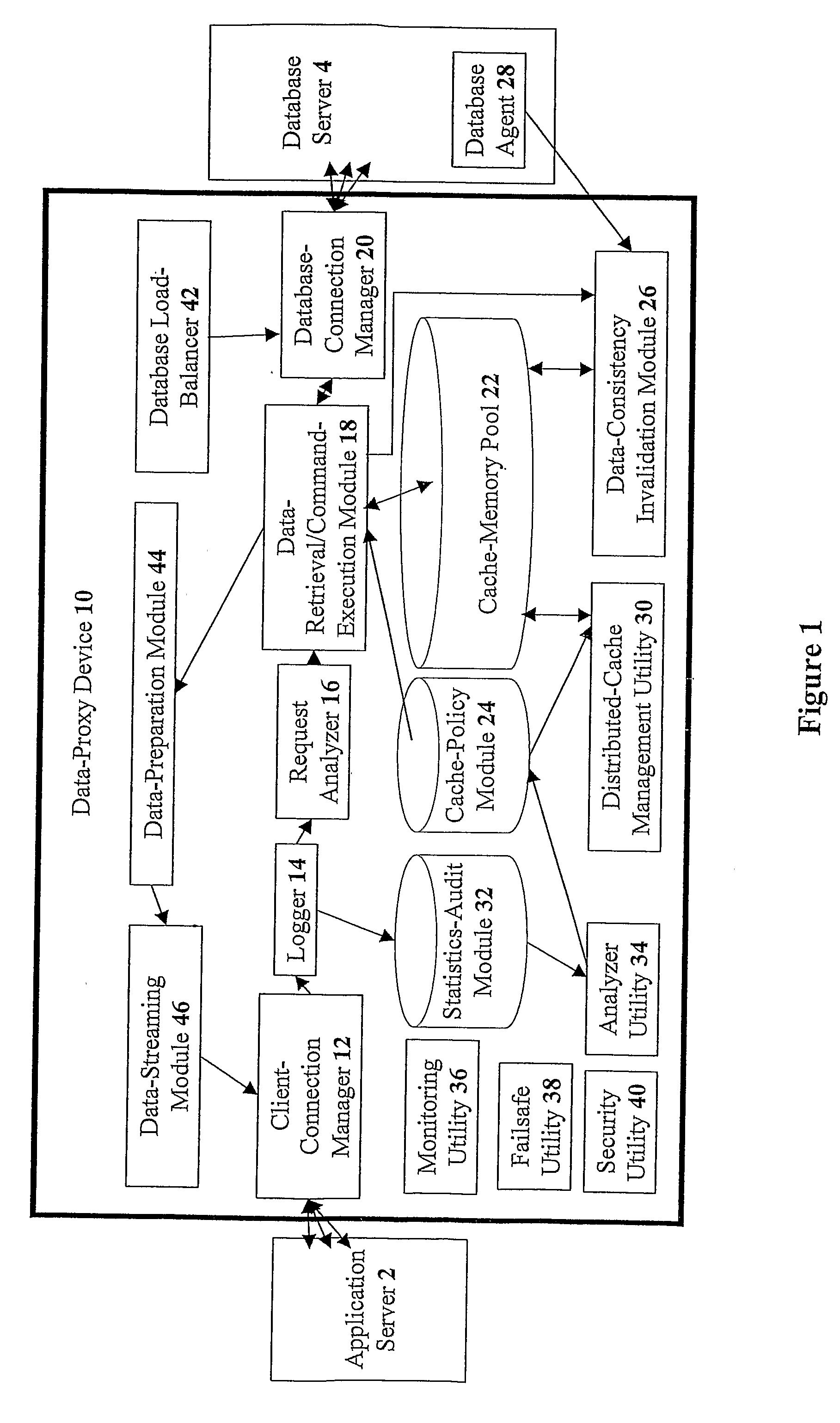
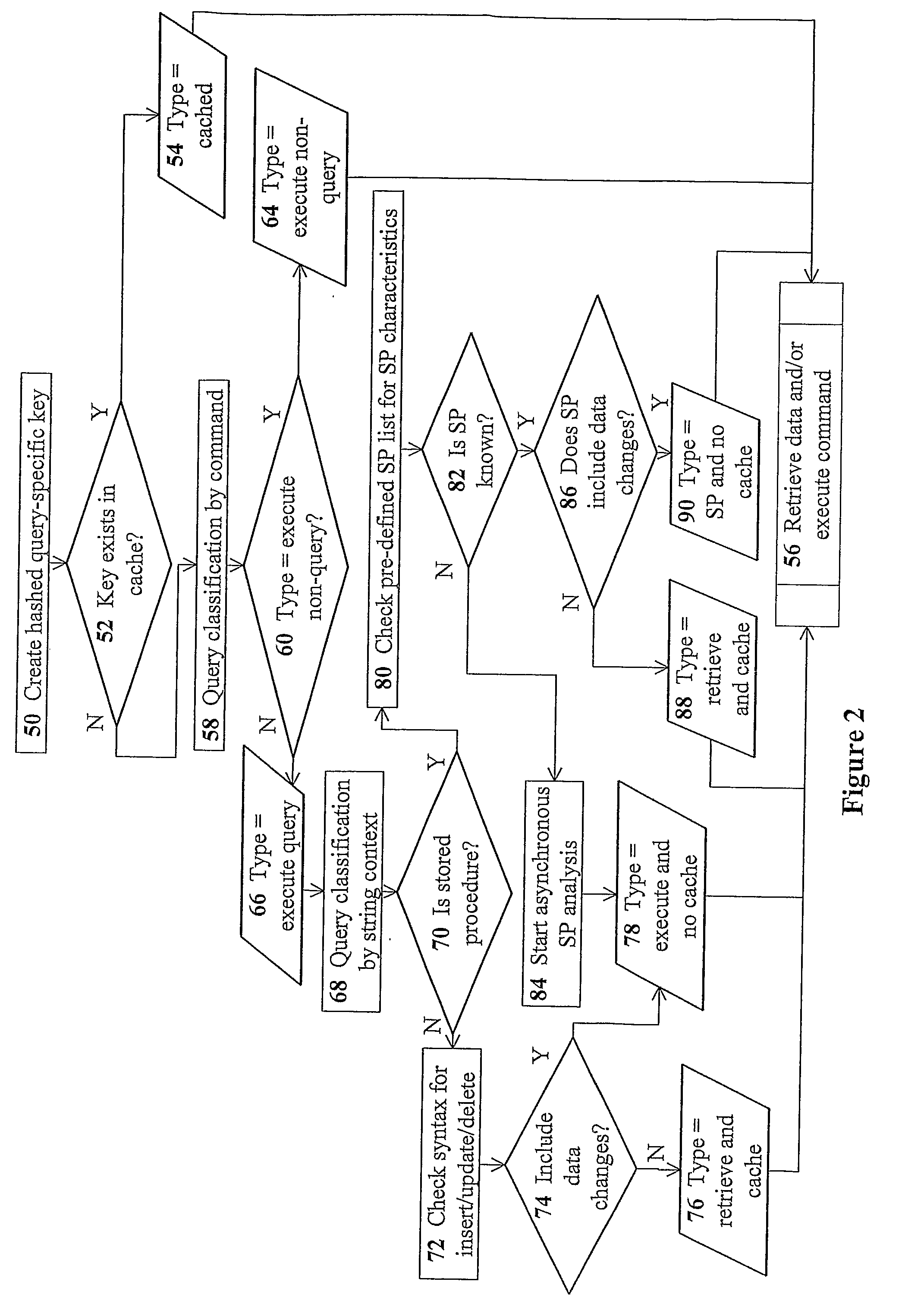
Devices for providing distributable middleware data proxy between application servers and database servers
InactiveUS20100174939A1Shorten the timeSave resourcesDigital data information retrievalResource allocationClient dataTerm memory
The present invention discloses devices Including a transparent client-connection manager for exchanging client data between an application server and the device: a request analyzer for analyzing query requests from at least one application server; a data-retrieval / command-execution module for executing query requests; a database connection manager for exchanging database data between at least one database server and the device: a cache-memory pool for storing data items from at least one database server: a cache-policy module for determining cache criteria for storing the data Items In the cache-memory pool; and a data-consistency invalidation module for determining invalidated data Items based on invalidation criteria for removing from the cache-memory pool. The cache-memory pool Is configured to utilize memory modules residing in data proxy devices and distributed cache management utility, enabling the memory capacity to be used as a cluster to balance workloads.
Owner:DCF TECH
Data access, replication or communication system comprising a distributed software application
ActiveUS20070130255A1Improve availabilityHigh bandwidthMultiple digital computer combinationsData switching networksMessage queueCommunications system
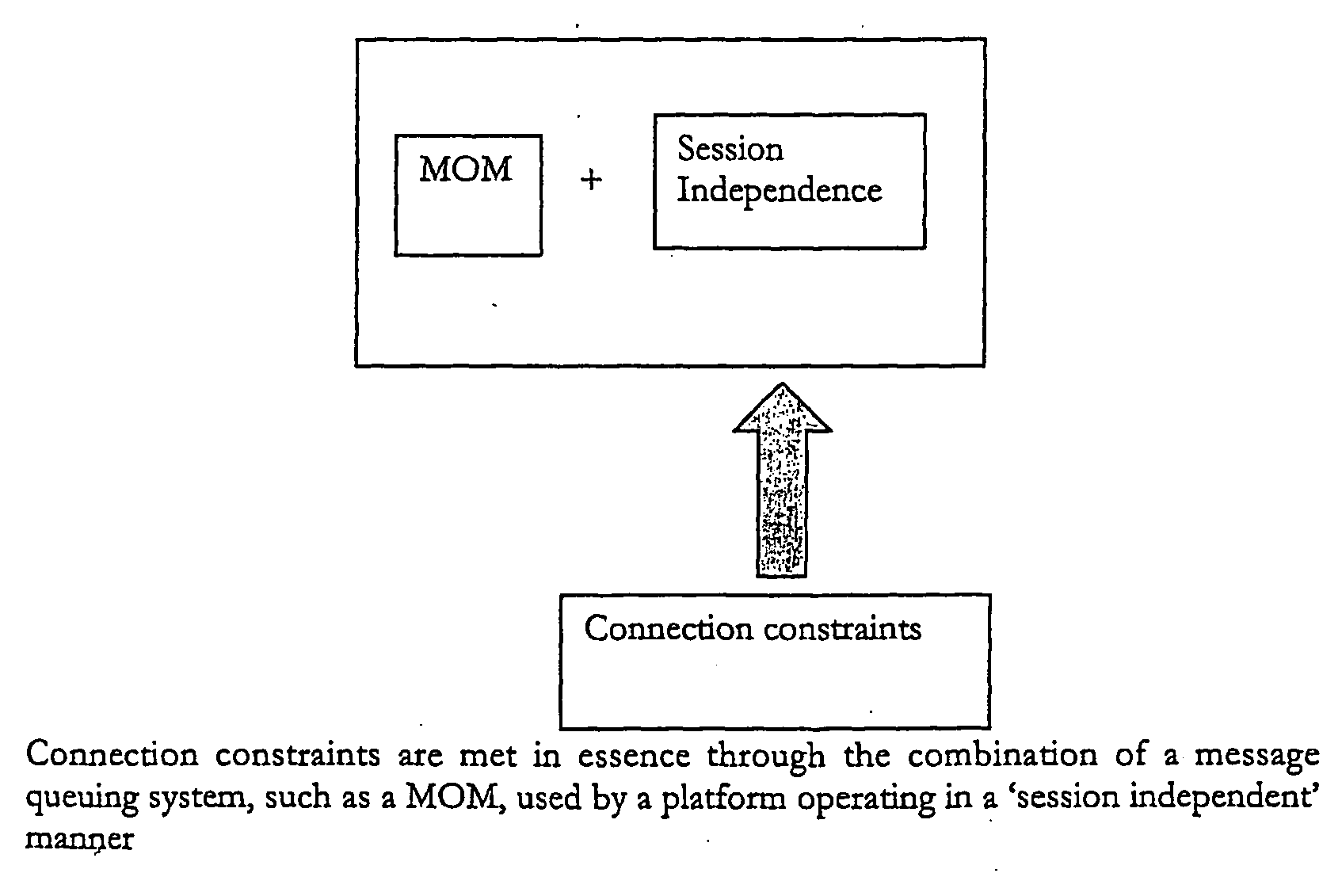
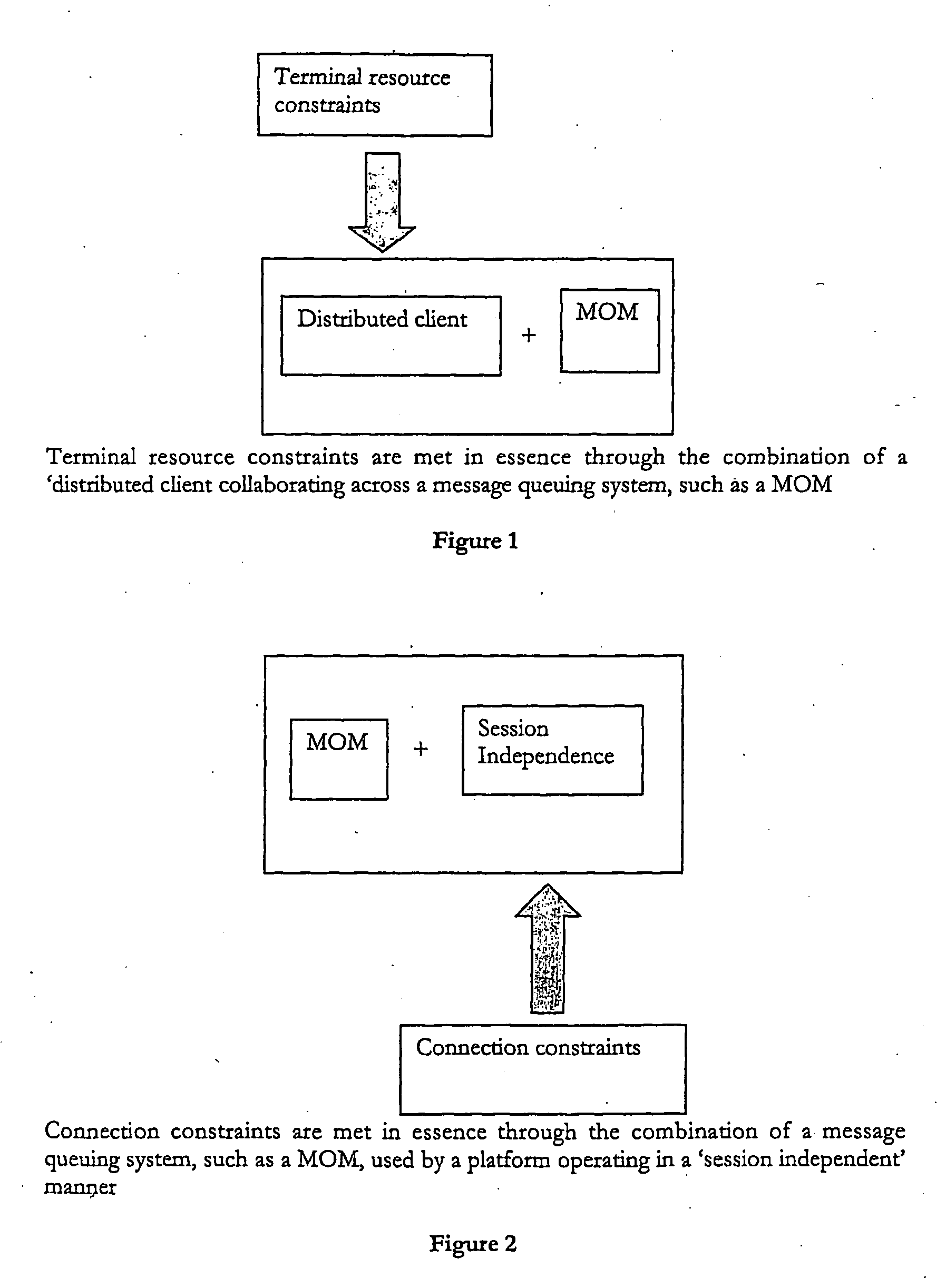
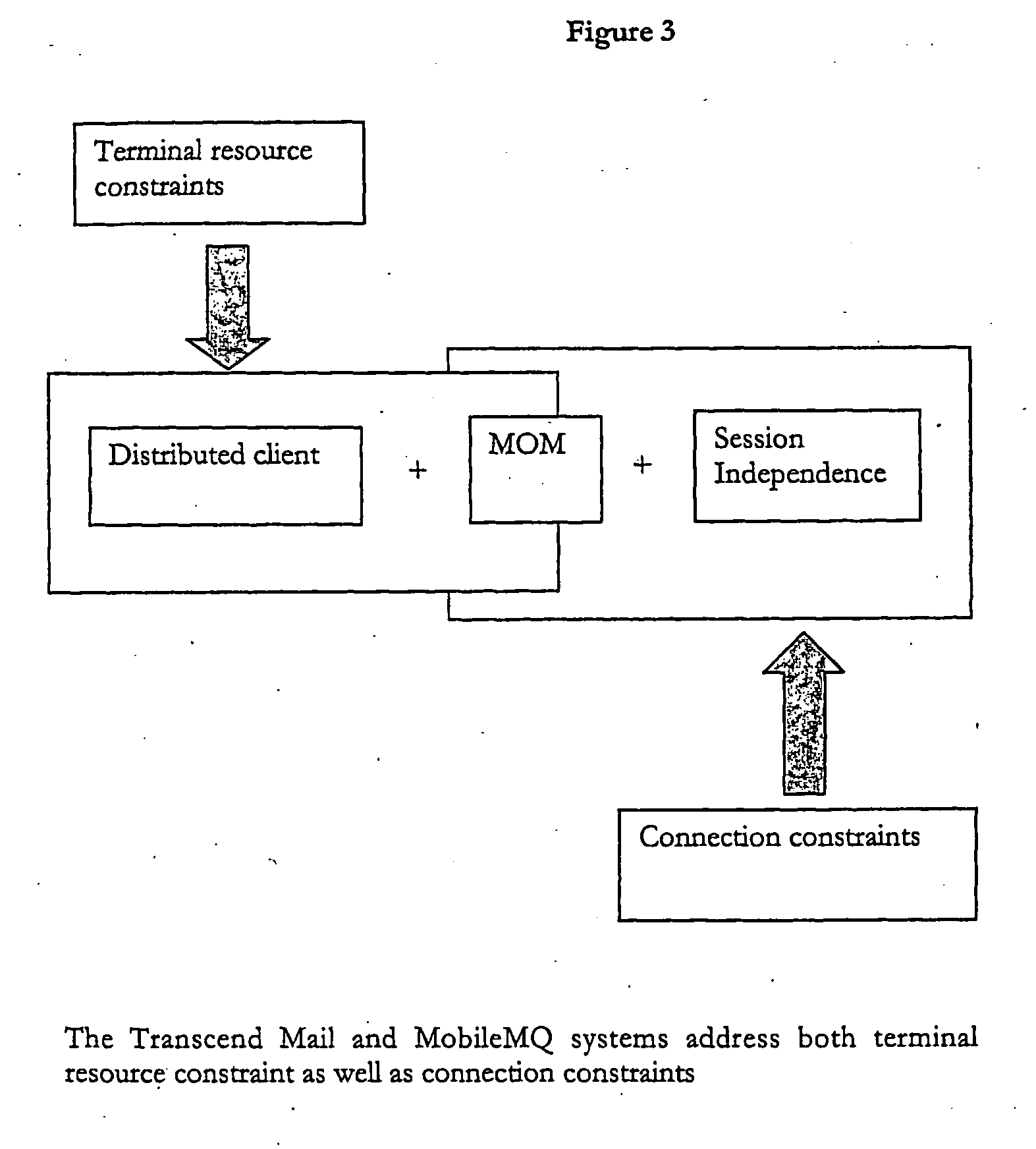
The present invention envisages a data access, replication or communications system comprising a software application that is distributed across a terminal-side component running on a terminal and a server-side component; in which the terminal-side component and the server-side component (i) together constitute a client to a server and (ii) collaborate by sending messages using a message queuing system over a network Hence, we split (i.e. distribute) the functionality of an application that serves as the client in a client-server configuration into component parts that run on two or more physical devices that commuunicate with each other over a network connection using a message queuing system, such as message oriented middleware. The component parts collectively act as a client in a larger client-server arrangement, with the server being, for example, a mail server. We call this a ‘Distributed Client’ model. A core advantage of the Distributed Client model is that it allows a terminal, such as mobile device with limited processing capacity, power, and connectivity, to enjoy the functionality of full-featured client access to a server environment using minimum resources on the mobile device by distributing some of the functionality normally associated with the client onto the server side, which is not so resource constrained.
Owner:MALIKIE INNOVATIONS LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com