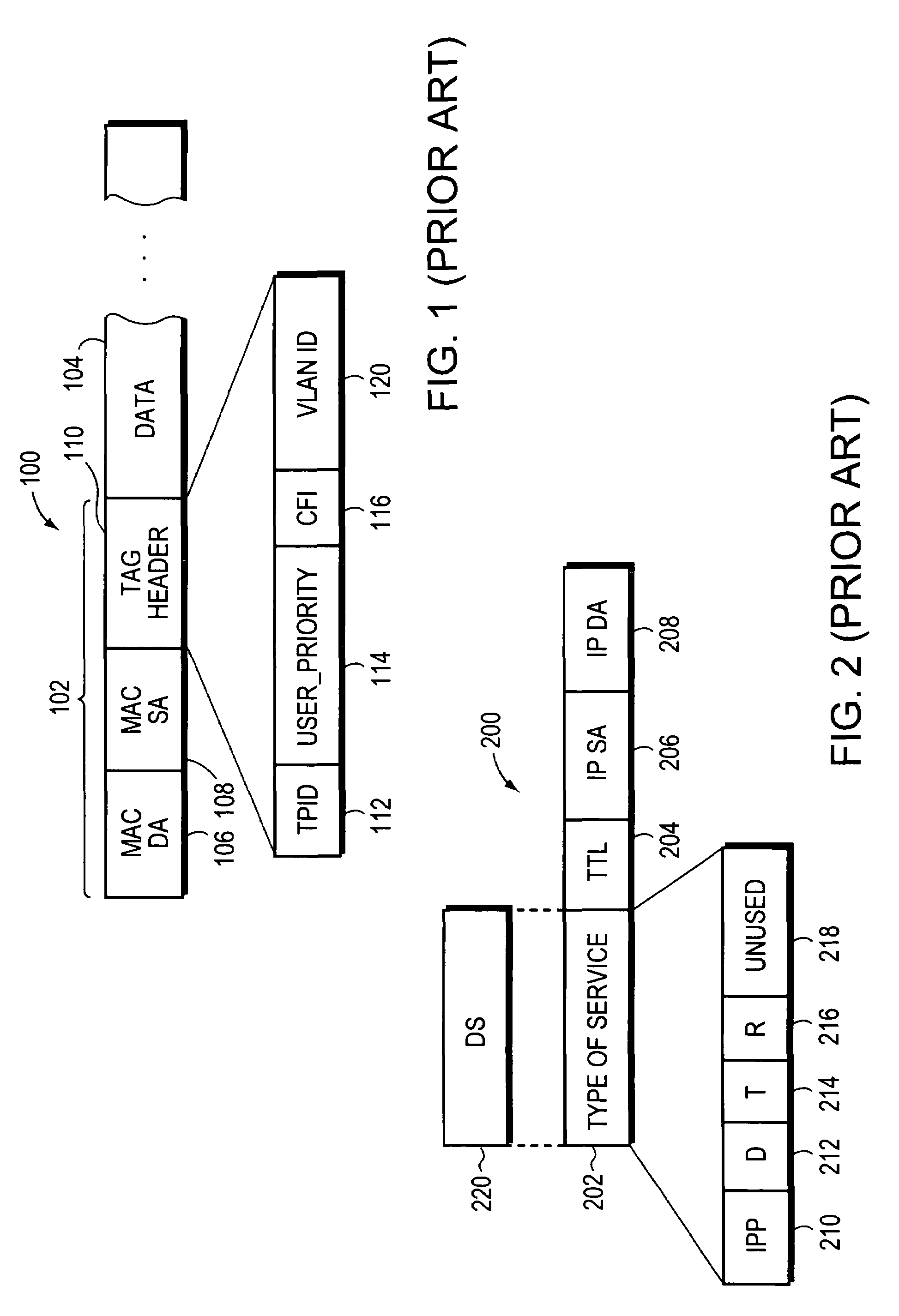
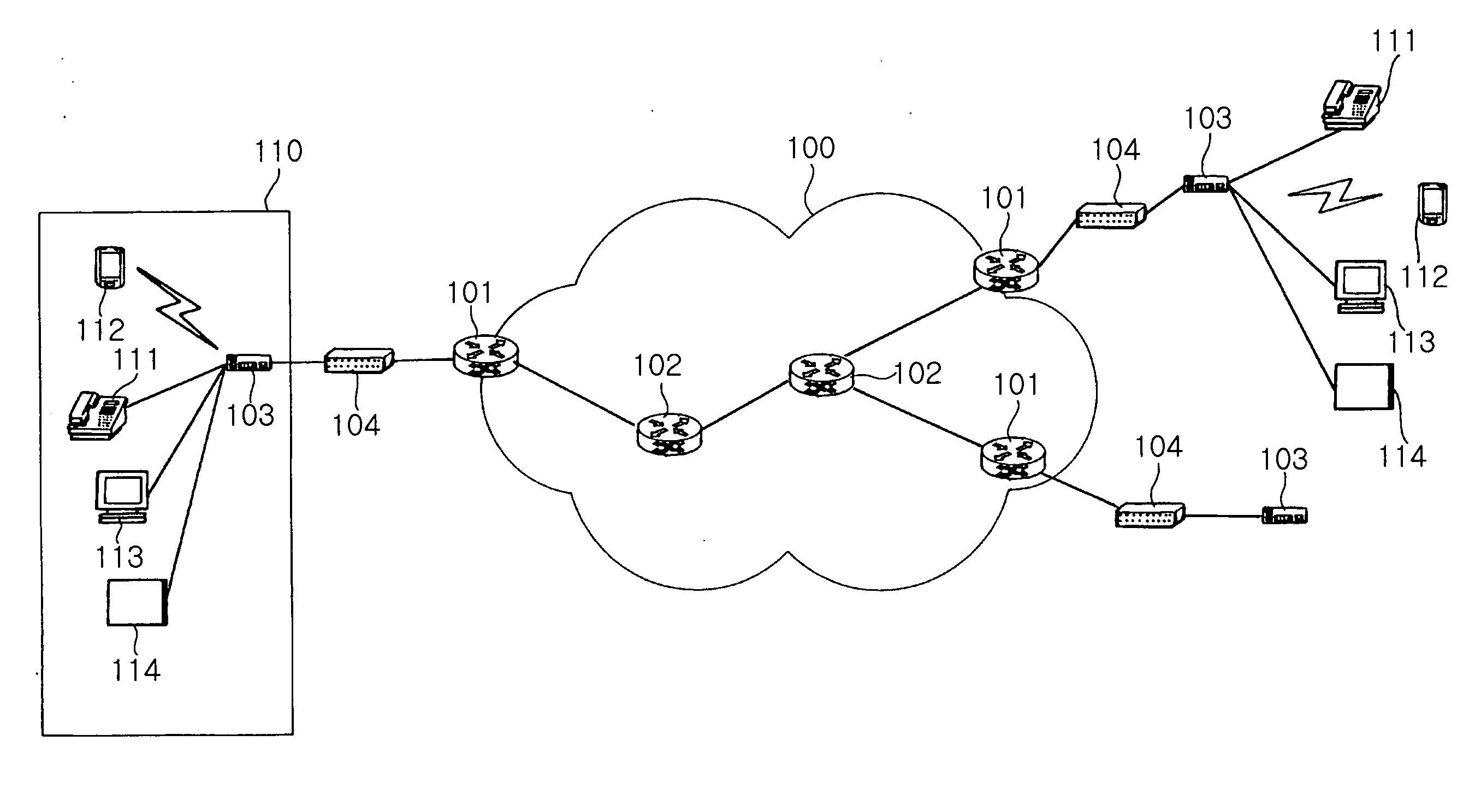
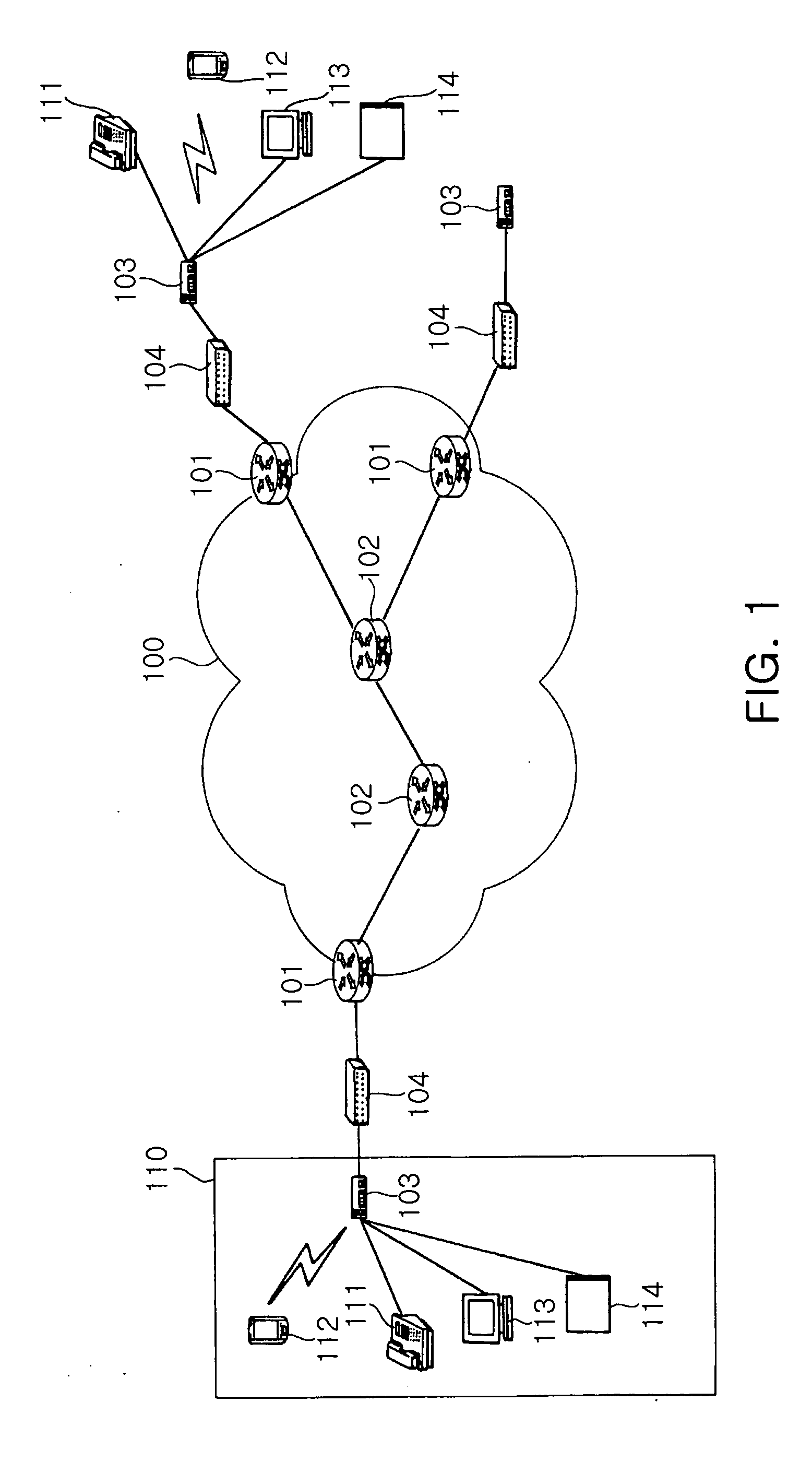
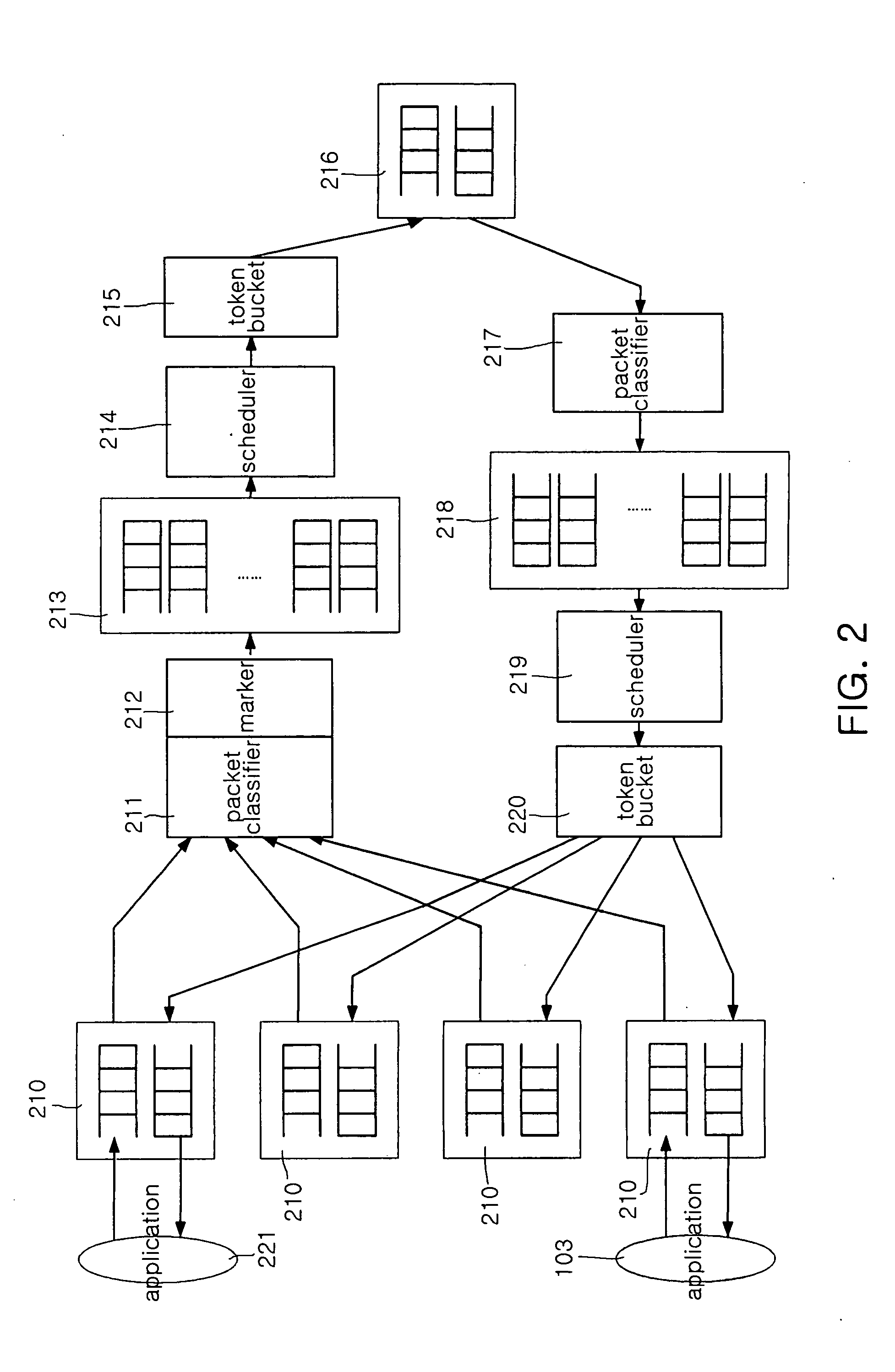
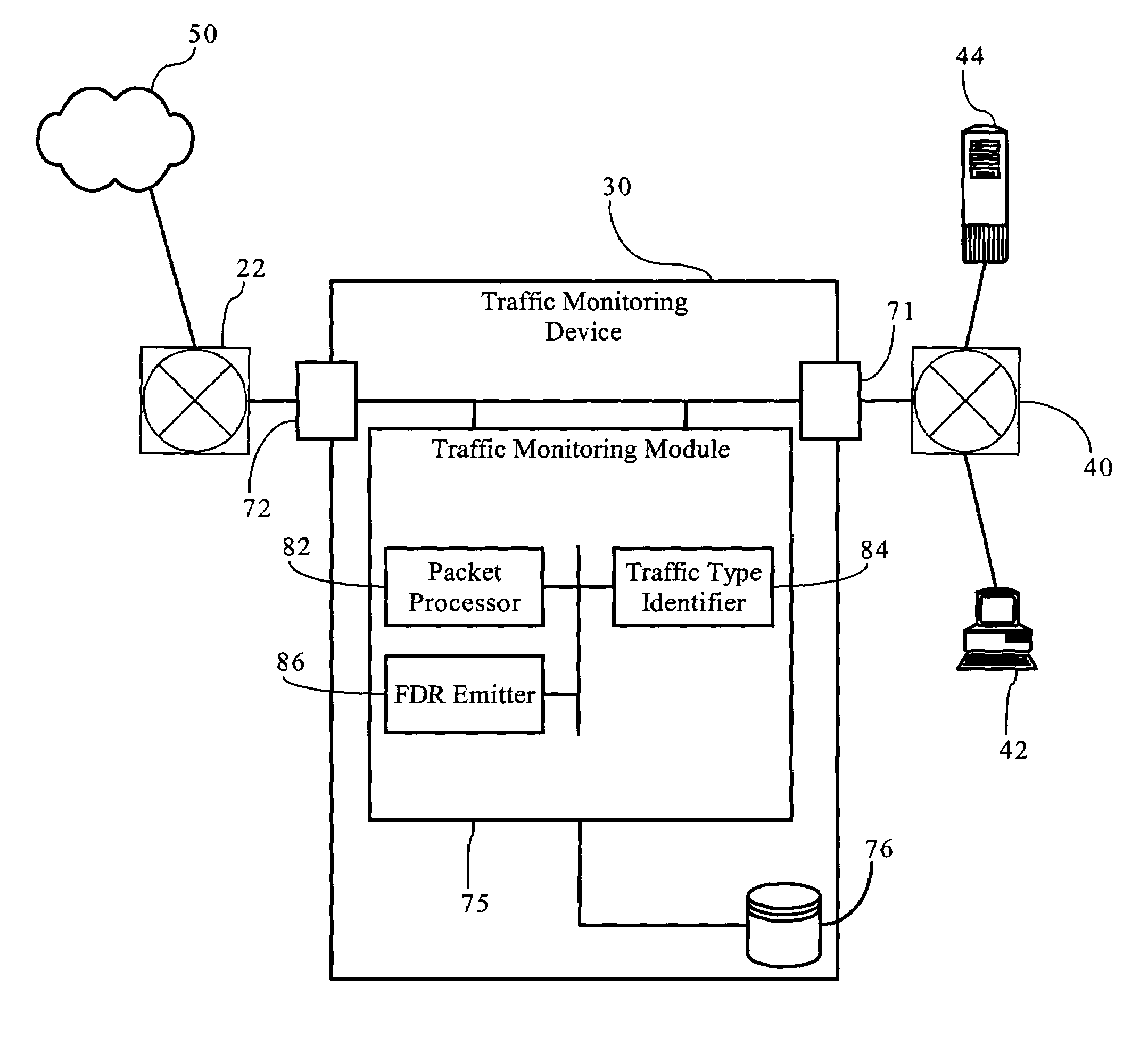
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
337 results about "Traffic type" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
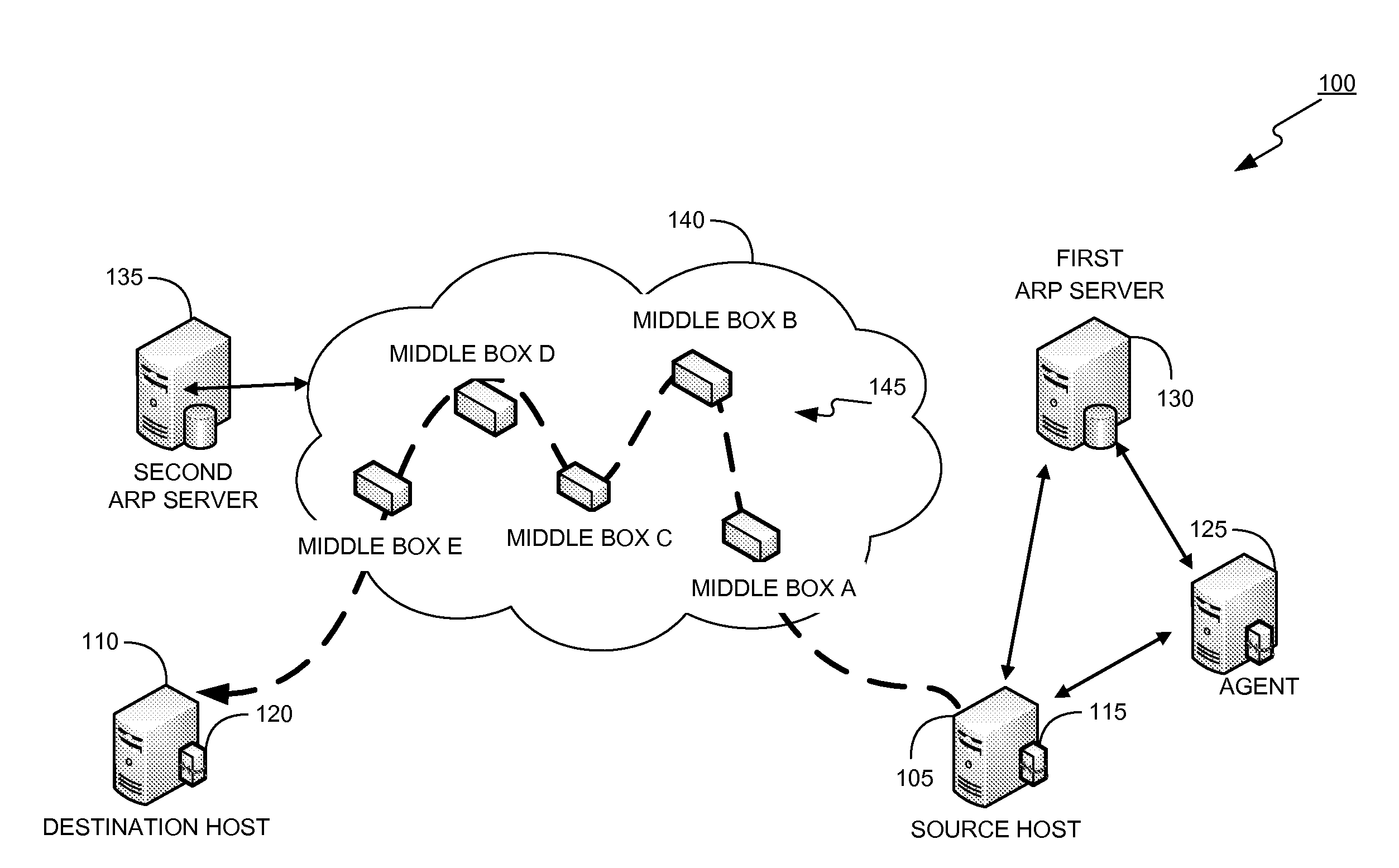
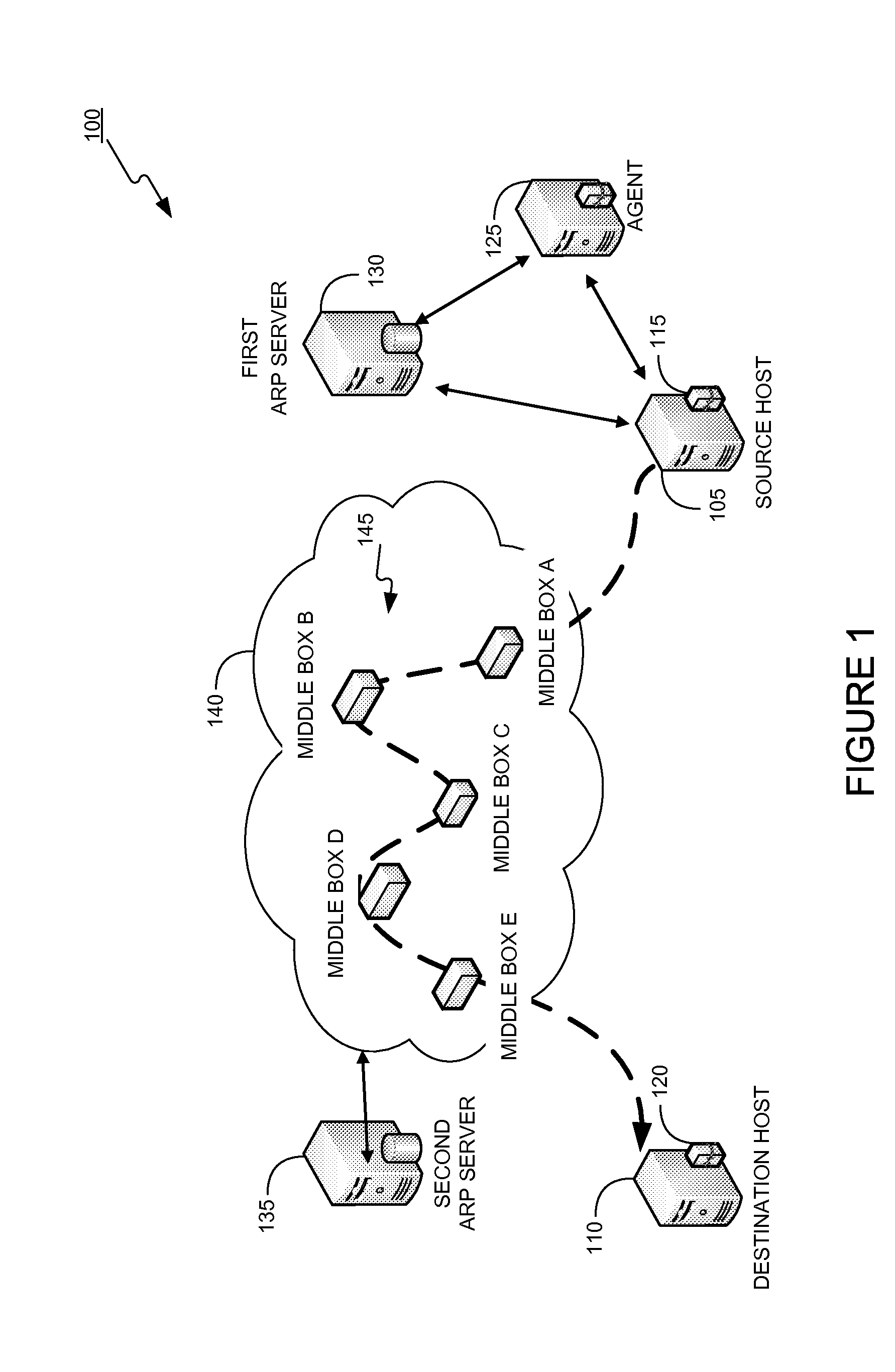
Dynamically provisioning middleboxes
Hybrid security architecture (HSA) provides a platform for middlebox traversal in the network. The HSA decouples the middlebox control from network forwarding. More specifically, such embodiments may receive a data packet having a packet header including an Ethernet header identifying source and destination addresses in the network. A traffic type of the data packet is determined. Then, layer-2 forwarding information, which encodes a set of non-forwarding network service provider middleboxes in the network to be traversed by the data packet, is determined based on the traffic type. The layer-2 forwarding information is inserted into the Ethernet header and the data packet is forwarded into the network. The data packet will then traverse, according to the layer-2 forwarding information, a sequence of the middleboxes in the network, wherein at least one non-forwarding network service will be provided by each of the middleboxes to the data packet in a sequence.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
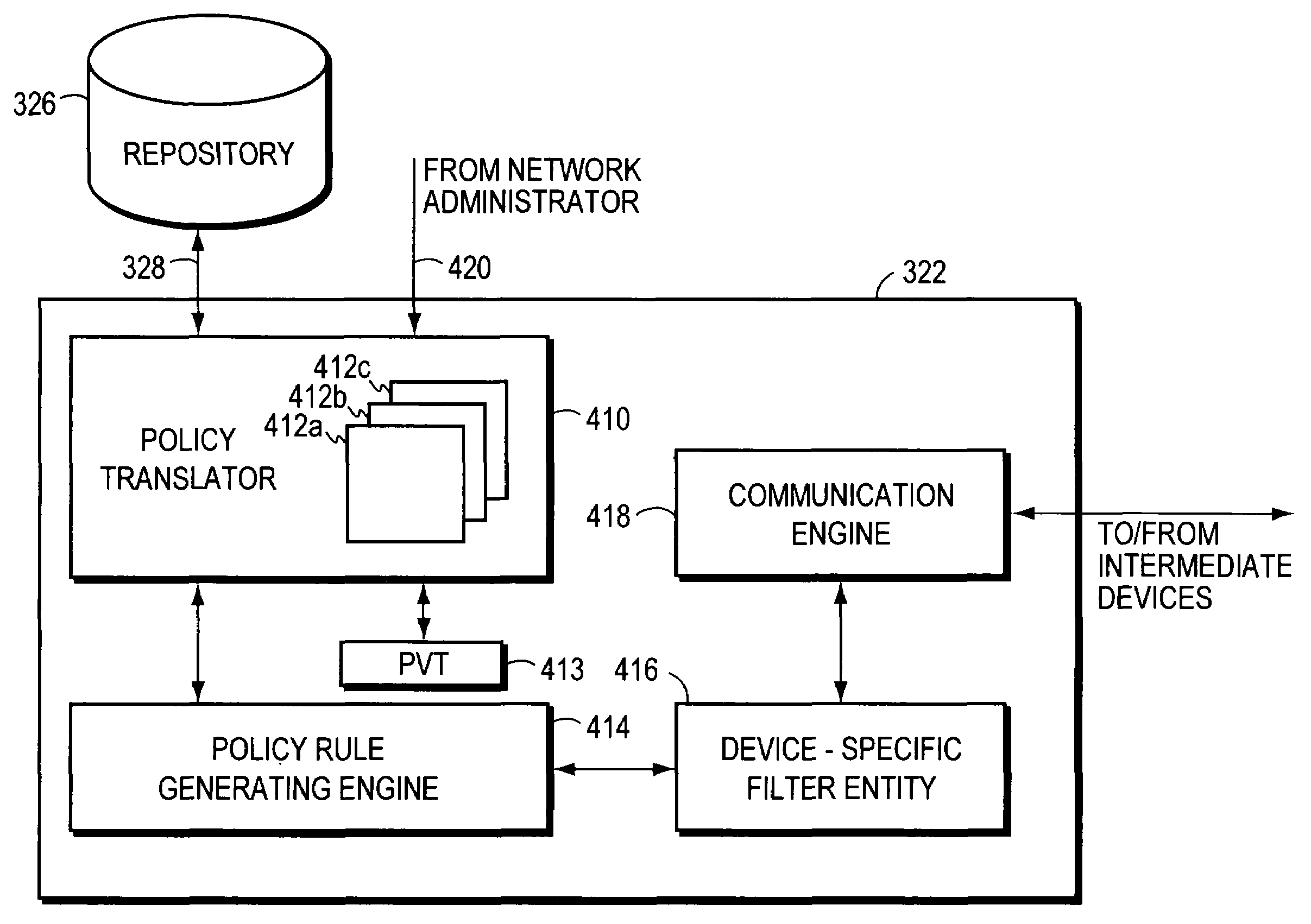
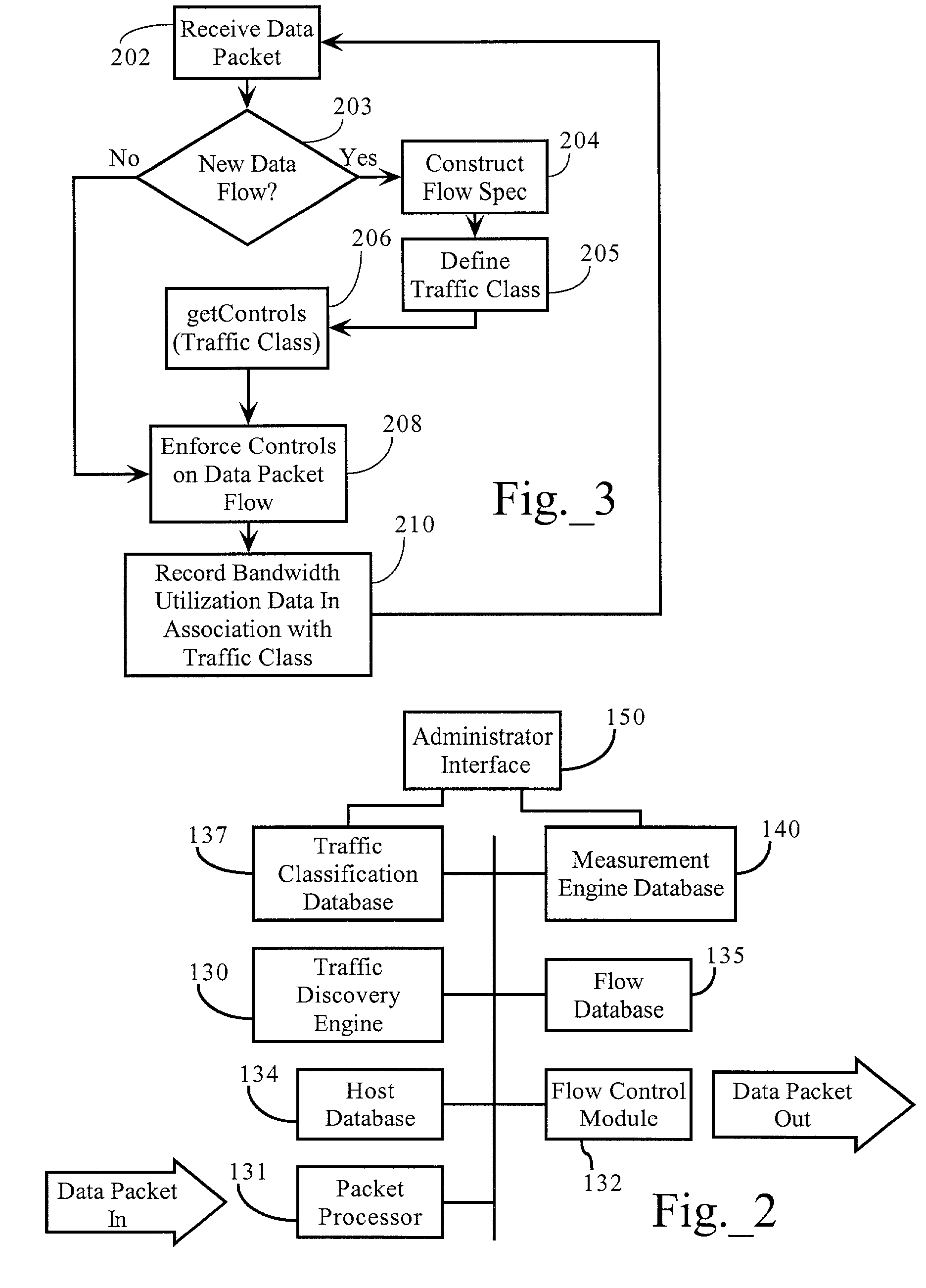
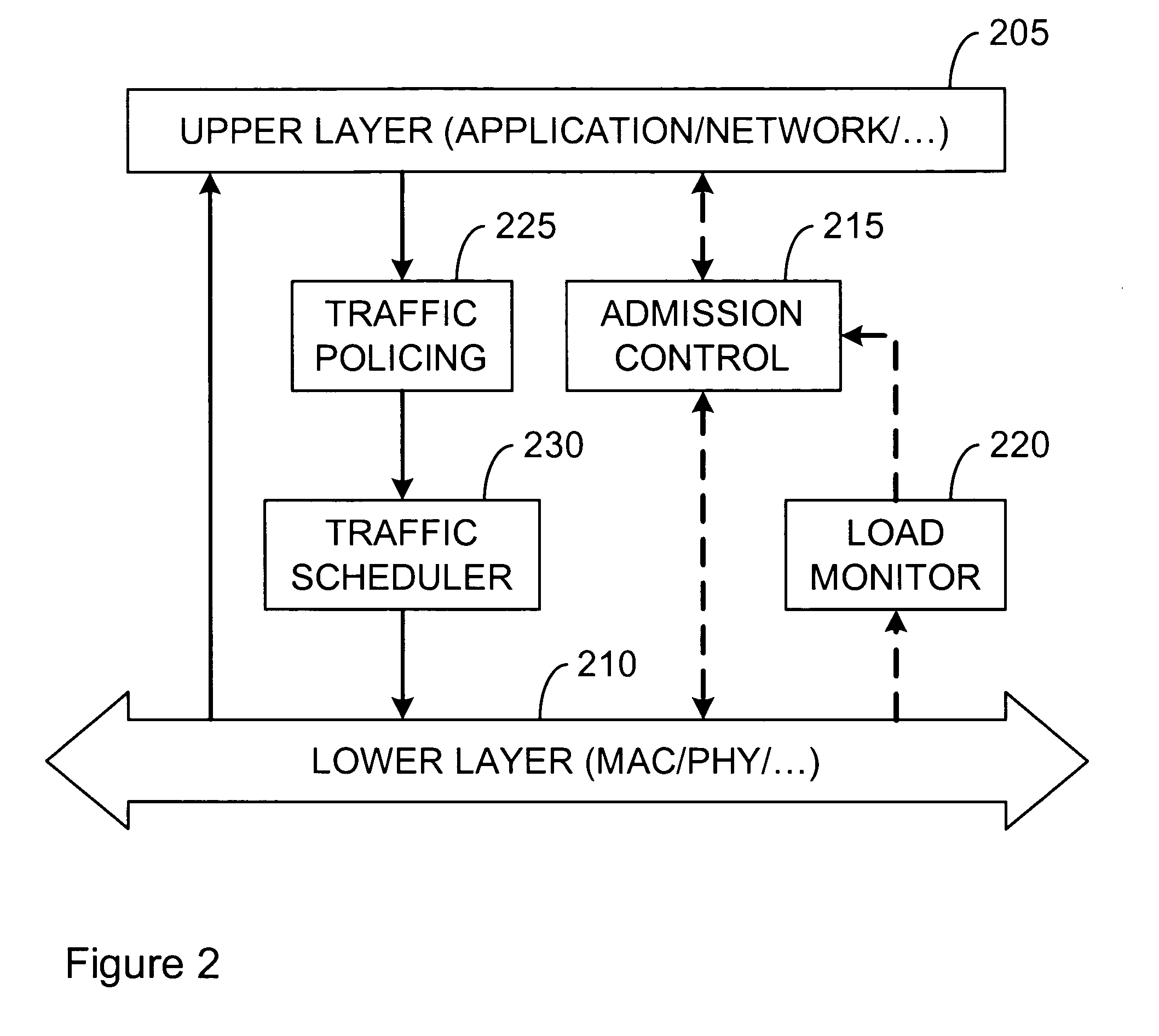
Method and apparatus for defining and implementing high-level quality of service policies in computer networks
InactiveUS7185073B1Multiple digital computer combinationsData switching networksNetwork strategyNetwork administrator
A computer network having multiple, dissimilar network devices includes a system for implementing high-level, network policies. The high-level policies, which are generally device-independent, are translated by one or more policy servers into a set of rules that can be put into effect by specific network devices. Preferably, a network administrator selects an overall traffic template for a given domain and may assign various applications and / or users to the corresponding traffic types of the template. Location-specific policies may also be established by the network administrator. The policy server translates the high-level policies inherent in the selected traffic template and location-specific policies into a set of rules, which may include one or more access control lists, and may combine several related rules into a single transaction. Intermediate network devices, which may have one or more roles assigned to their interfaces, are configured to request traffic management information from the policy server which replies with a particular set of transactions and rules. The rules, which may correspond to the particular roles assigned to the interfaces, are then utilized by the intermediate devices to configure their particular services and traffic management mechanisms. Other rules are utilized by the intermediate devices to classify packets with a particular priority and / or service value and to treat classified packets in a particular manner so as to realize the selected high-level policies within the domain.
Owner:CISCO TECH INC
Interface facilitating configuration of network resource utilization
ActiveUS7203169B1OptimizationQuickly easily configureError preventionFrequency-division multiplex detailsResource utilizationParameter control
Methods, apparatuses and systems facilitating the configuration of parameters controlling utilization of a network resource. In one embodiment, the present invention allows a network administrator to quickly and easily configure effective bandwidth utilization controls and observe the results of applying them. According to one embodiment, a network administrator is presented with an interface displaying the most significant traffic types with respect to a bandwidth utilization or other network statistic and allowing for the association of bandwidth utilization controls to these traffic types.
Owner:CA TECH INC
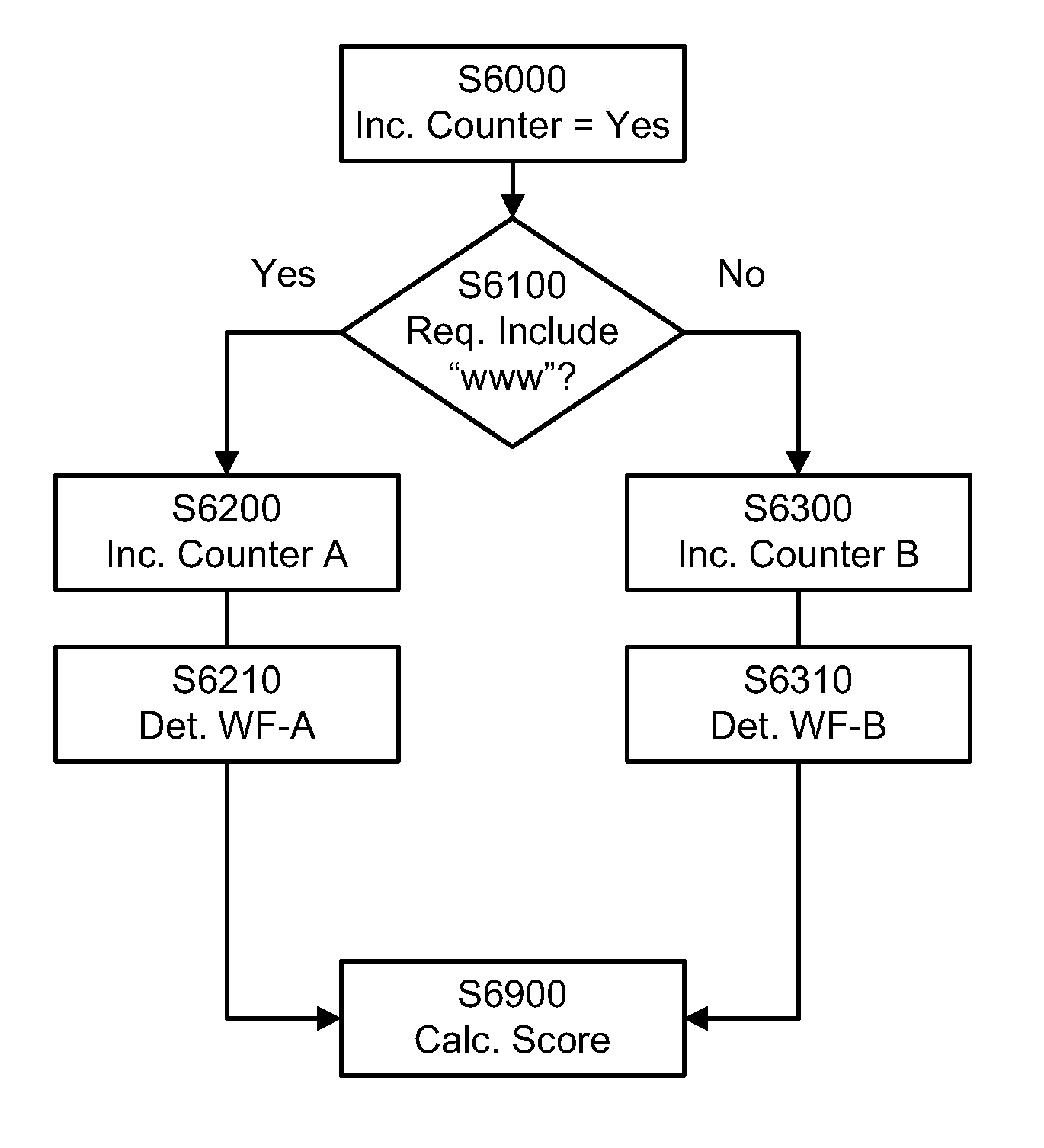
Existent Domain Name DNS Traffic Capture and Analysis
ActiveUS20100257266A1Accurate ratingAccurate pictureAdvertisementsMultiple digital computer combinationsDomain nameTraffic capacity
Systems and methods for scoring a domain web traffic based on DNS traffic requests received at an authoritative name server to resolve the domain name. A request to resolve the domain name is received at an authoritative name server. A counter, such as a server counter or a hit counter, for the domain name is incremented based on the received request. A score, such as a domain traffic score or a domain rank, is calculated based upon a count of the counter. Calculating the score may also include applying a weighting factor to the counters based on information about a requesting set of resolvers and other domains / websites that may be linking and driving traffic to the domain whose traffic score is being calculated. Examples of relevant set of resolvers information may include location, traffic levels, traffic type and architecture of the set of resolvers.
Owner:VERISIGN
System and method for guaranteeing quality of service in IP networks
InactiveUS20050135243A1Guaranteed reliabilityReduce loadError preventionFrequency-division multiplex detailsDifferentiated servicesData pack
The system of the present invention guarantees quality of service with respect to packets transmitted / received between an external network capable of providing differentiated services and a home network. The system includes a packet classifier, a marker, a priority class queue, a scheduler and a token bucket. The packet classifier classifies the packets according to addresses and traffic types. The marker allocates information on priorities to packets transmitted from the home network to the external network. The priority class queue has a plurality of queues classified according to the priorities. The scheduler services packets stored in the priority class queue according to the priorities. The token bucket drops packets, bandwidths of which are above a preset maximum bandwidth, when the packets are generated.
Owner:ELECTRONICS & TELECOMM RES INST
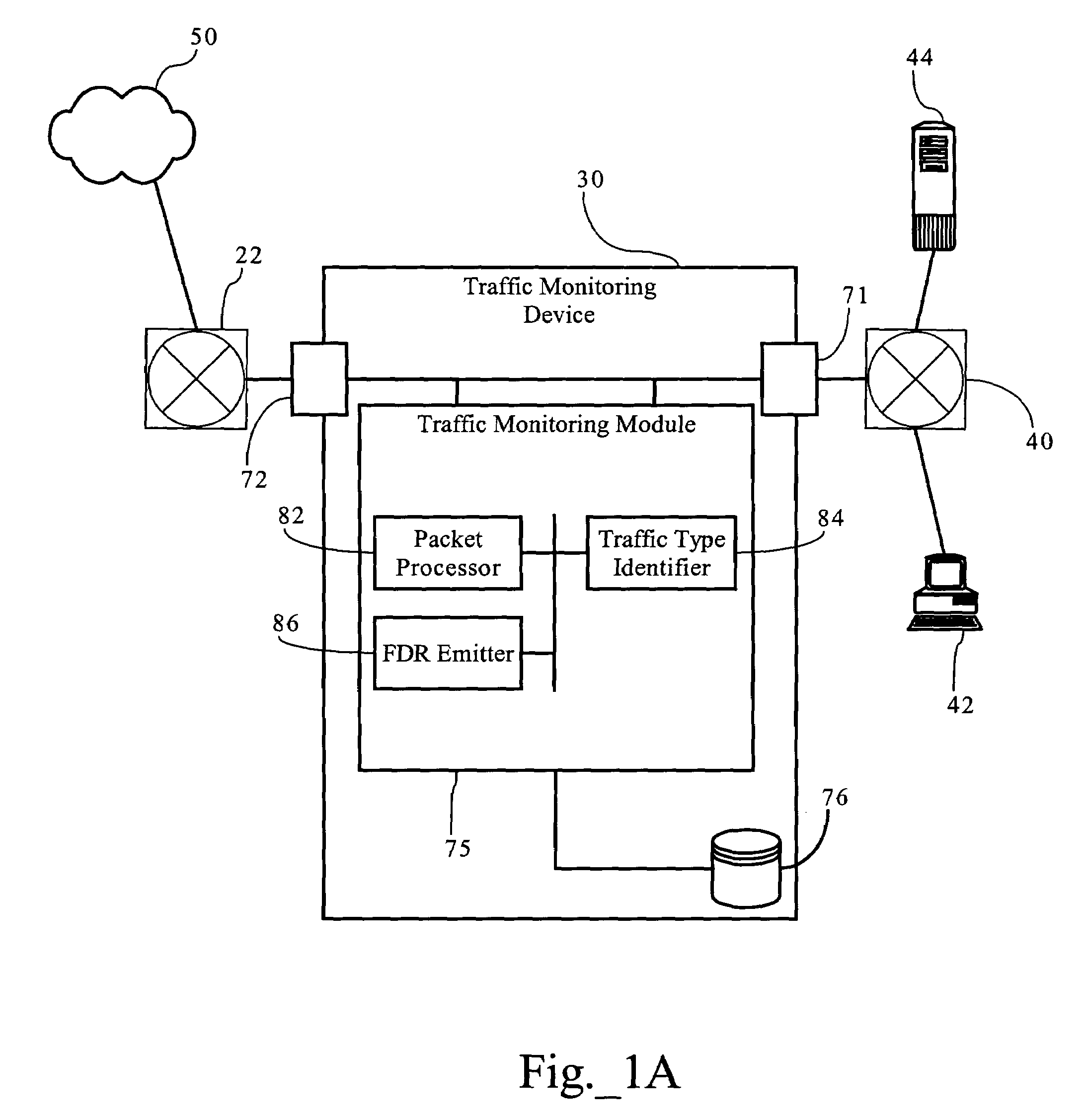
Enhanced flow data records including traffic type data
ActiveUS7385924B1Facilitate complianceImprove viewing effectError preventionTransmission systemsStructure of Management InformationApplication software
Methods, apparatuses and systems directed to a flow-based, traffic-classification-aware data collection and reporting system that combine flow-based data collection technologies with enhanced traffic classification functionality to allow for analysis and reporting into aspects of network operations that prior art systems cannot provide. Embodiments provide enhanced views into the operation of computer network infrastructures to facilitate monitoring, administration, compliance and other tasks associated with networks. When a traffic flow terminates, a traffic monitoring device emits a flow data record (FDR) containing measurements variables and other attributes for an individual flow. A data collector gathers the flow data records and enters them into a database. A network management application can then query the database with selected commands to derive reports characterizing operation of the network suitable to diagnose problems or view conditions associated with the network.
Owner:CA TECH INC
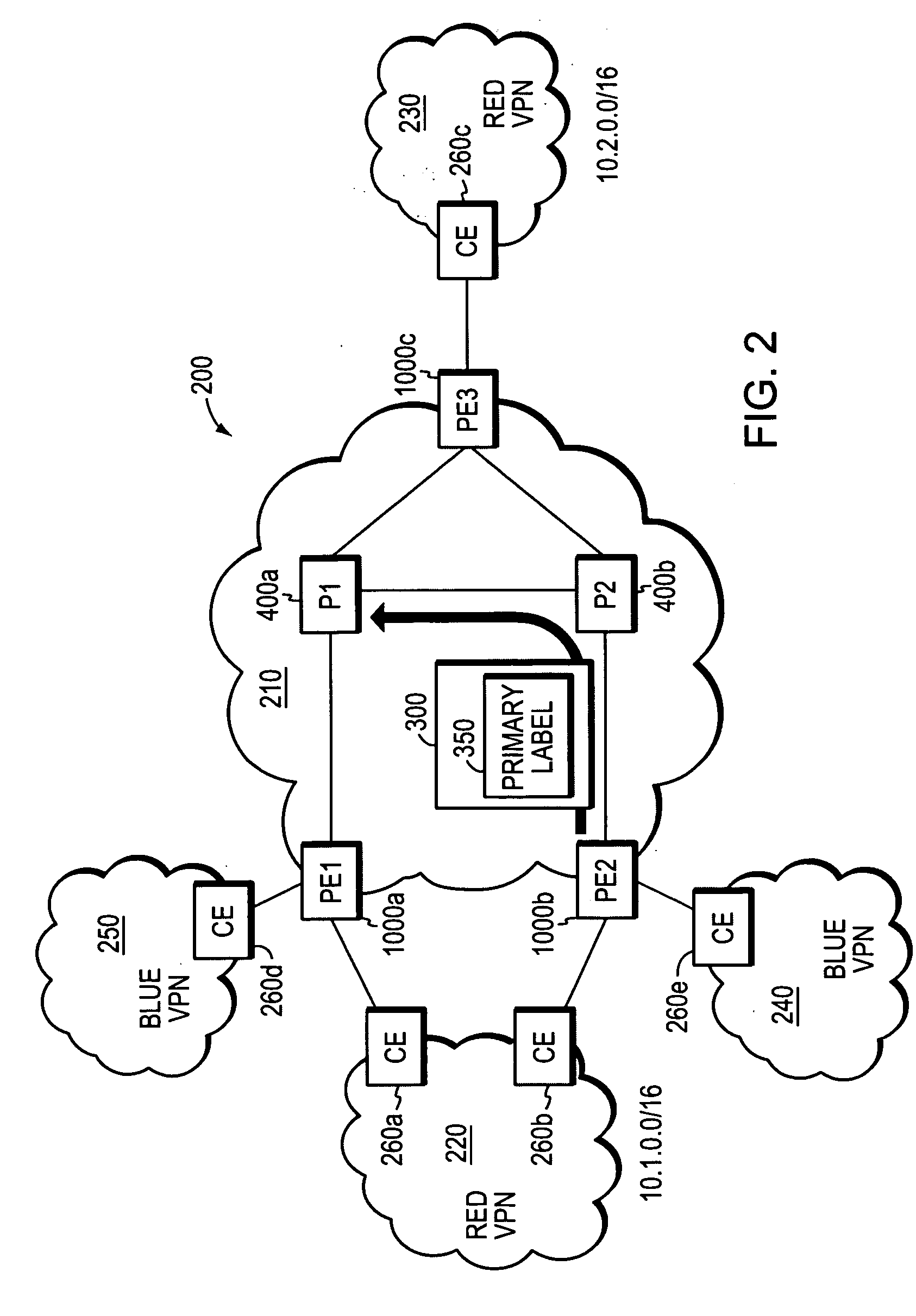
System and method for PE-node protection
ActiveUS20070121486A1Fast reroute (FRR)Quickly and efficiently reroutingError preventionFrequency-division multiplex detailsNetwork ConvergenceNetwork packet
A novel fast reroute (FRR) technique is provided for quickly and efficiently rerouting selected types of network traffic in response to a node or link failure at the edge of a computer network. According to the technique, the network includes first and second edge devices that function as “FRR mates,” such that network traffic originally destined for one FRR mate may be quickly rerouted to the other without having to wait for conventional network convergence. When an edge device receives rerouted packets originally destined for its FRR mate, the device responds by forwarding only those rerouted packets matching the selected traffic types; rerouted packets that do not match the selected traffic types are dropped or otherwise discarded. The first and second edge devices may be statically configured as FRR mates, e.g., by a network administrator, or they may be configured to automatically detect their compatibility as FRR mates.
Owner:CISCO TECH INC
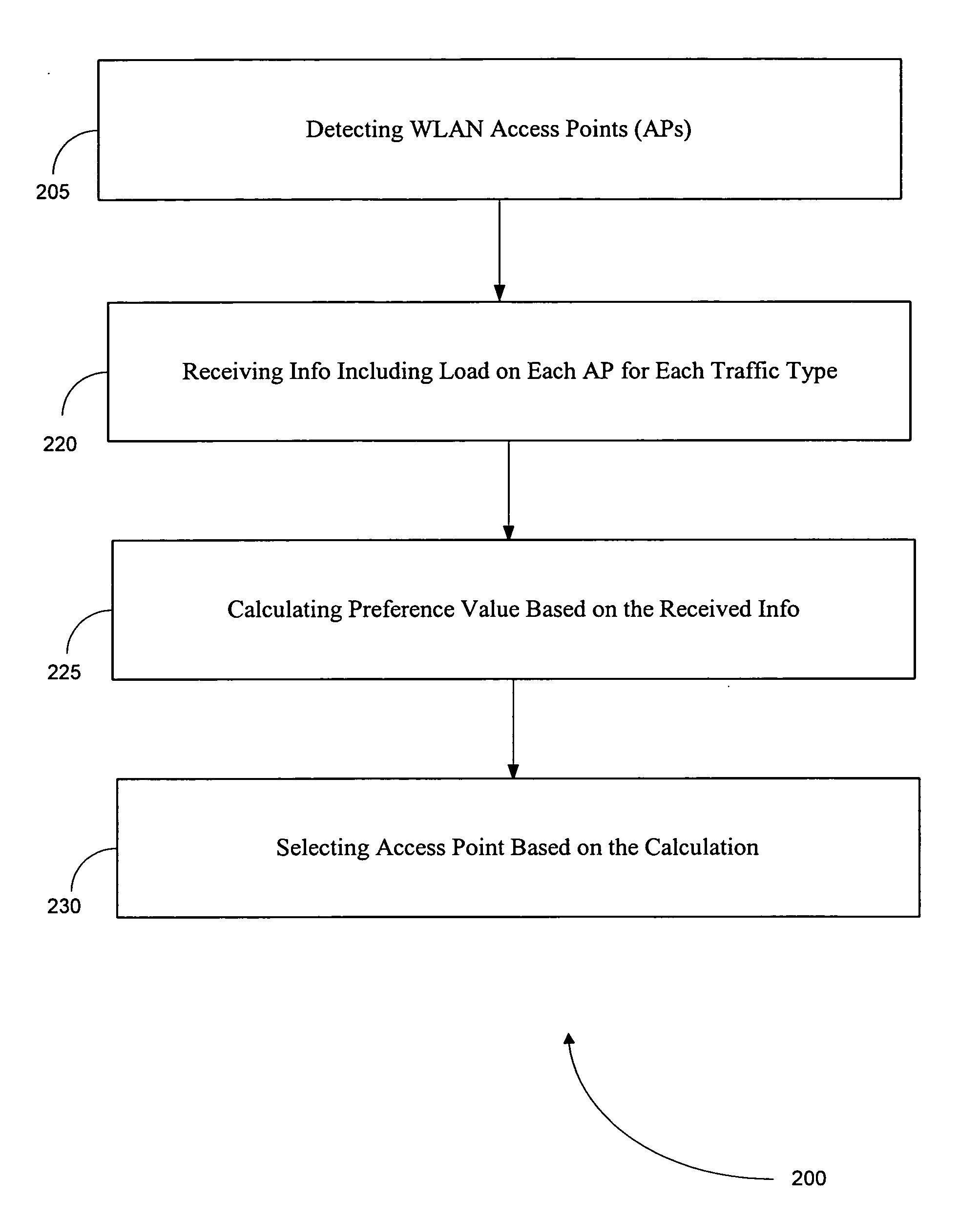
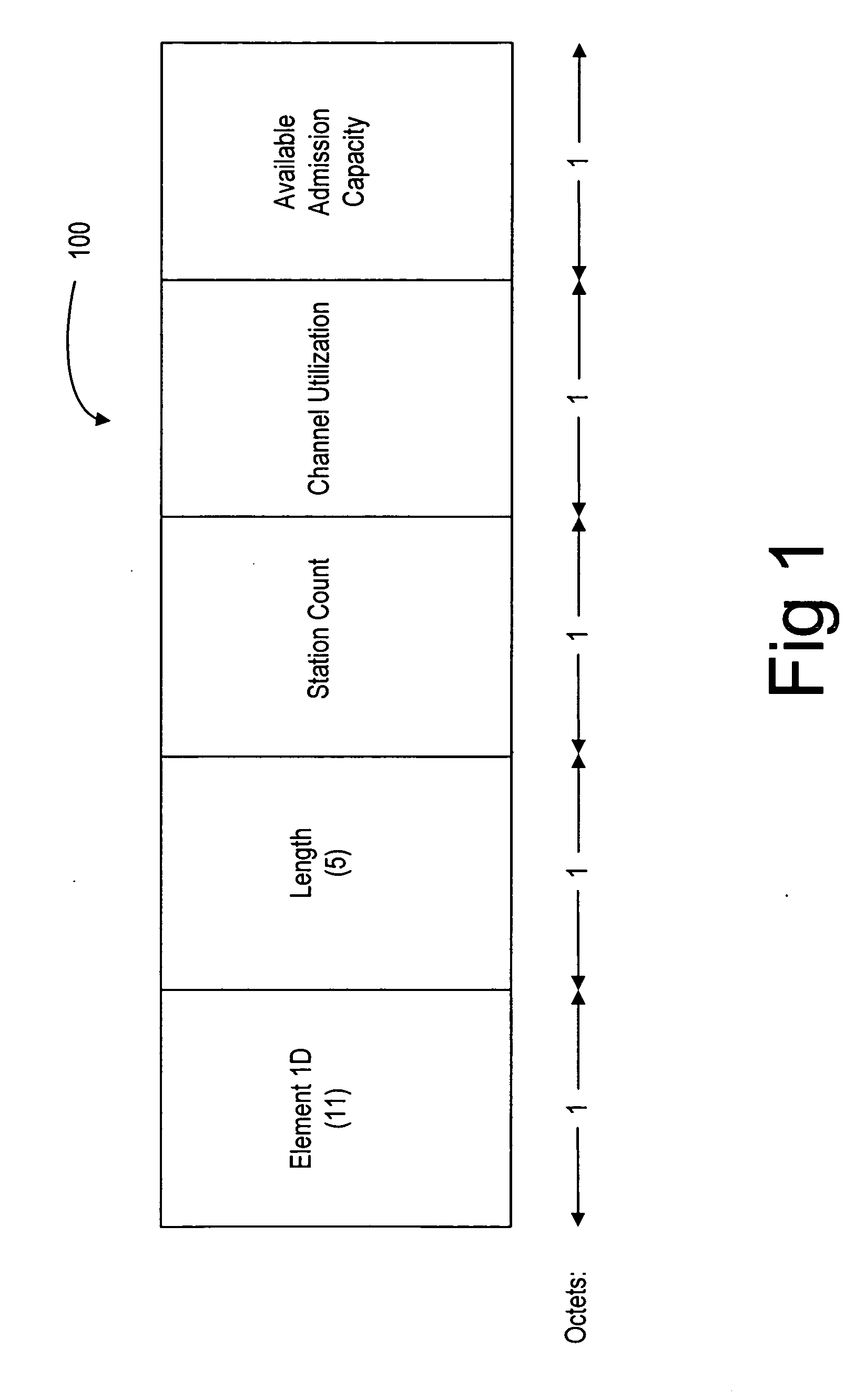
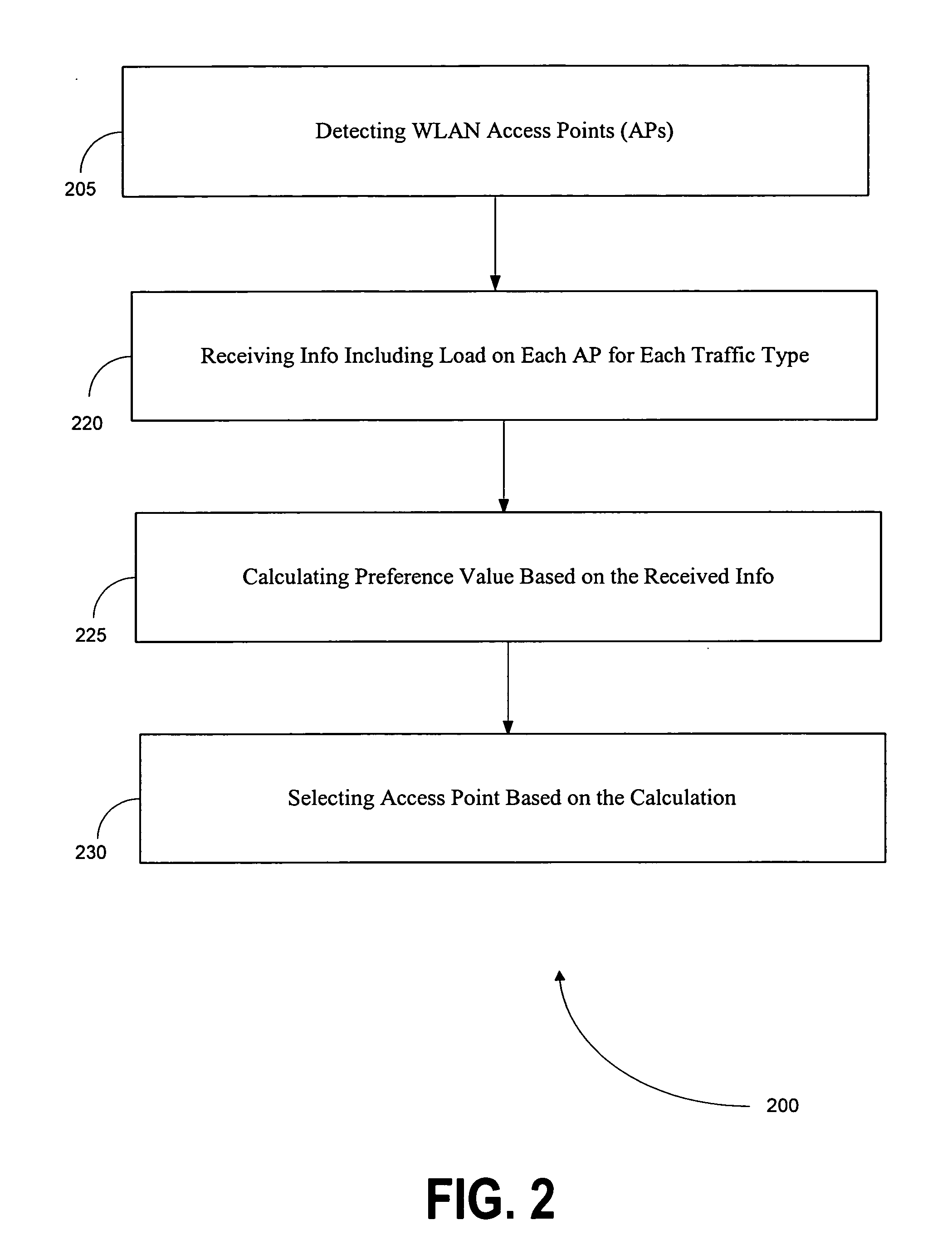
Method, mobile station, and software product for access point selection
ActiveUS20070217377A1Error preventionFrequency-division multiplex detailsTelecommunicationsCurrent channel
A method, mobile station, and software product are used to select an access point in a wireless local area network (WLAN) for access by the mobile station. This is accomplished by calculating a preference value for each of a plurality of the access points, based upon information regarding current communication characteristics of the access points. That information includes physical signal characteristics of the access points, and current channel loads of the access points, and also the traffic type affecting the current channel loads of the respective access points. The information about channel loads is weighted differently based upon the corresponding traffic types, and may also be calculated differently depending upon whether or not the mobile station is set up to utilize multimedia traffic.
Owner:RPX CORP
System and method for network interfacing
Systems and methods that network interface are provided. In one embodiment, a data center may be provided that may include, for example, a first tier, a second tier and a third tier. The first tier may include, for example, a first server. The second tier may include, for example, a second server. The third tier may include, for example, a third server. At least one of the first server, the second server and the third server may handle a plurality of different traffic types over a single fabric.
Owner:AVAGO TECH INT SALES PTE LTD
Cdn traffic management in the cloud
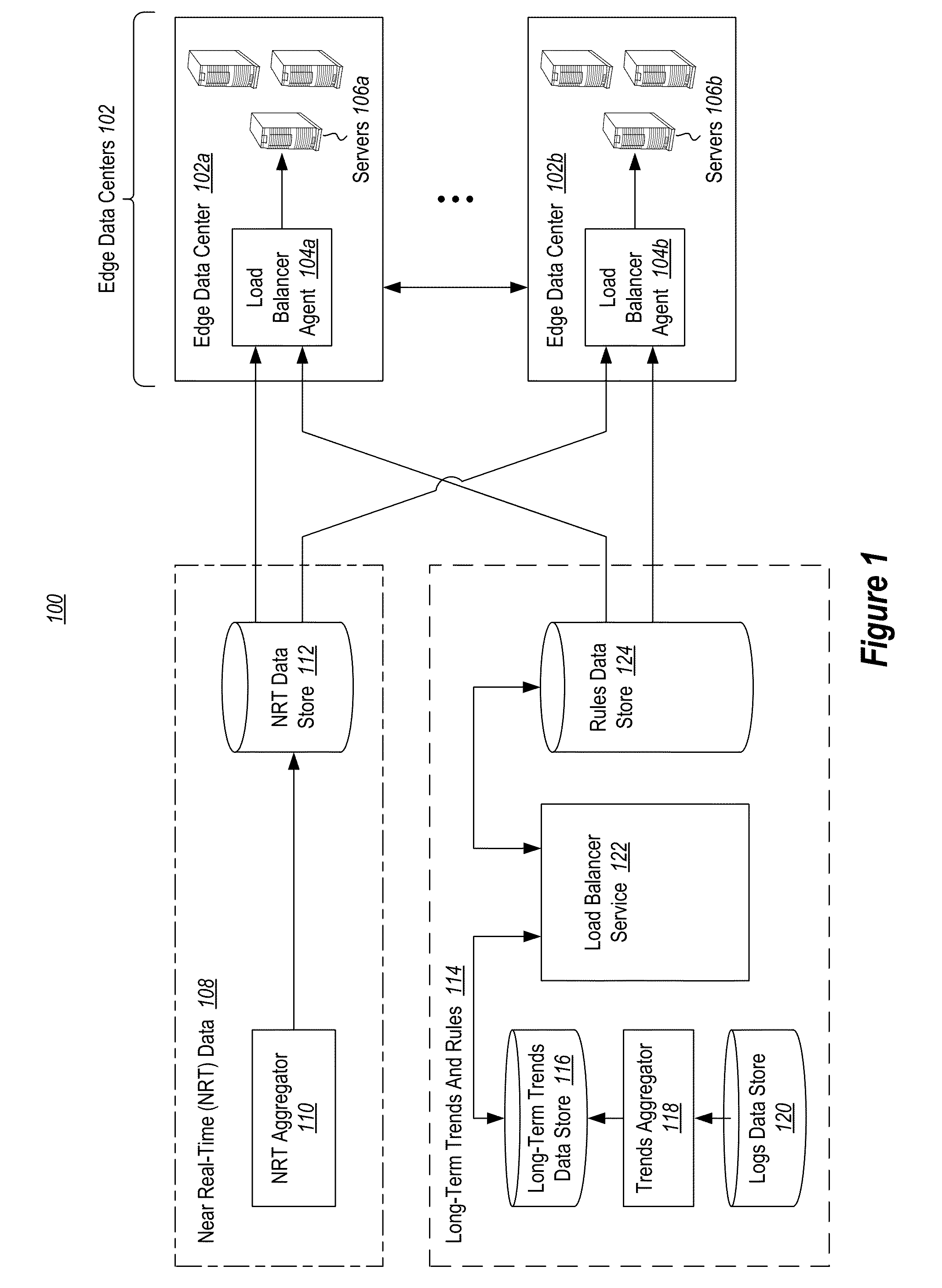
ActiveUS20140122698A1Well formedDigital computer detailsPayment architectureData centerDistributed computing
Embodiments include determining attributes of a property using an incubation pool. An incubation period is identified based on estimated attributes for the property, and based on rules that define a minimum and a maximum incubation time. The property is added to the incubation pool, and load and patterns for the property are analyzed. A load size and / or a traffic type for the property is identified based on the incubation. Embodiments also include offloading traffic within a CDN. A load balancer agent determines that traffic at an edge data center should be offloaded to the other edge data centers. The load balancer agent sends a request, including a determined priority level. The load balancer agent receives one or more replies indicating that resources are available for use. The load balancer agent sorts the replies and offloads traffic to at least one edge data center.
Owner:MICROSOFT TECH LICENSING LLC
Intrusion detection in a data center environment
ActiveUS7610375B2Network degradationRemove noiseError preventionTransmission systemsTraffic capacityData center
Owner:CISCO TECH INC
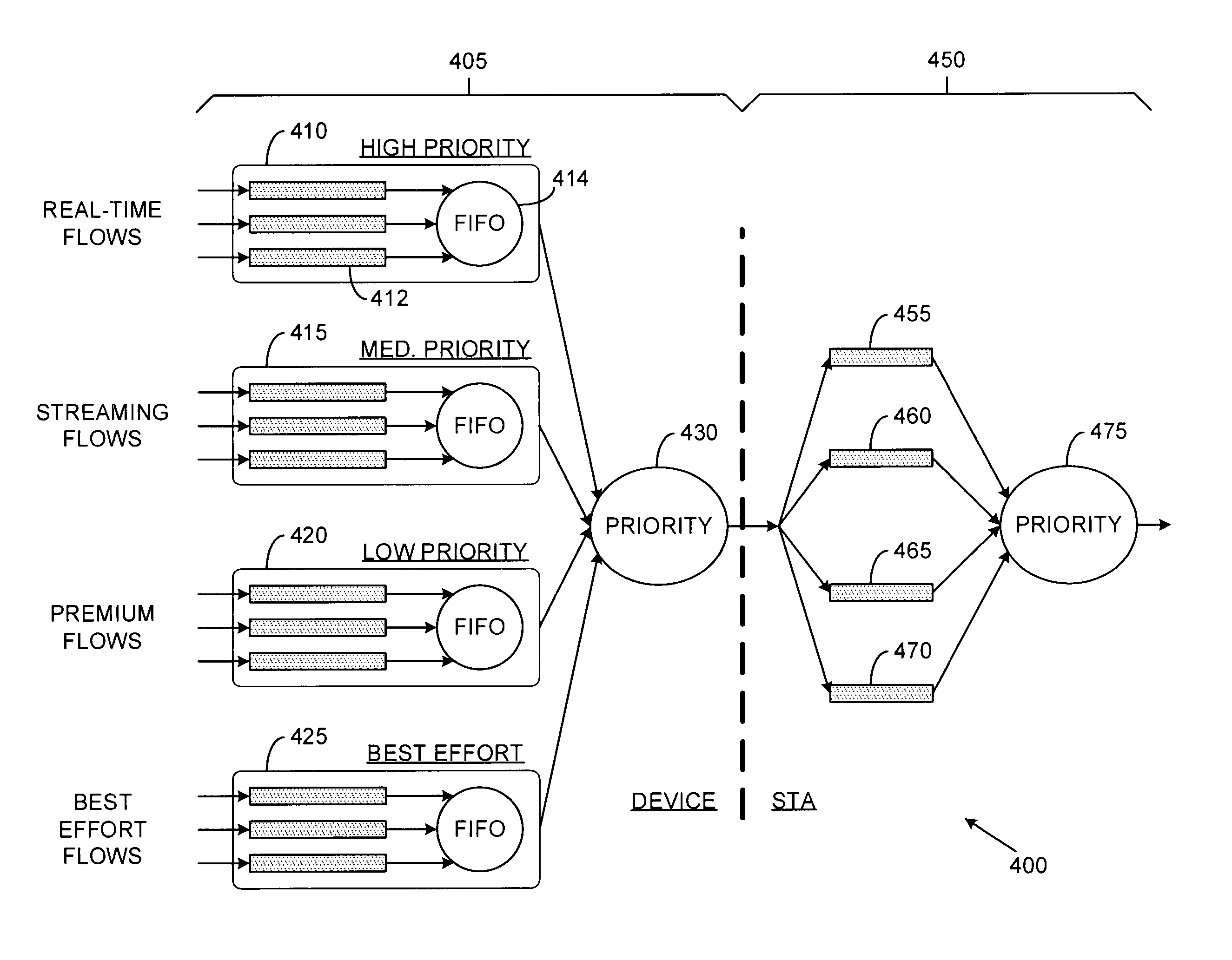
Hierarchical scheduling for communications systems
InactiveUS20050047425A1Addressing slow performanceEasy to modifyNetwork traffic/resource managementData switching by path configurationCommunications systemDistributed computing
System and method for scheduling messages in a digital communications system with reduced system resource requirements. A preferred embodiment comprises a plurality of traffic queues (such as traffic queue 410) used to enqueue message of differing traffic types and a first scheduler (such as priority scheduler 430). The first scheduler to select messages from the traffic queues and provide them to a plurality of priority queues (such as priority queue 455) used to enqueue messages of differing priorities. A second scheduler (such as priority scheduler 475) then selects messages for transmission based on message priority, transmission opportunity, and time to transmit.
Owner:TEXAS INSTR INC
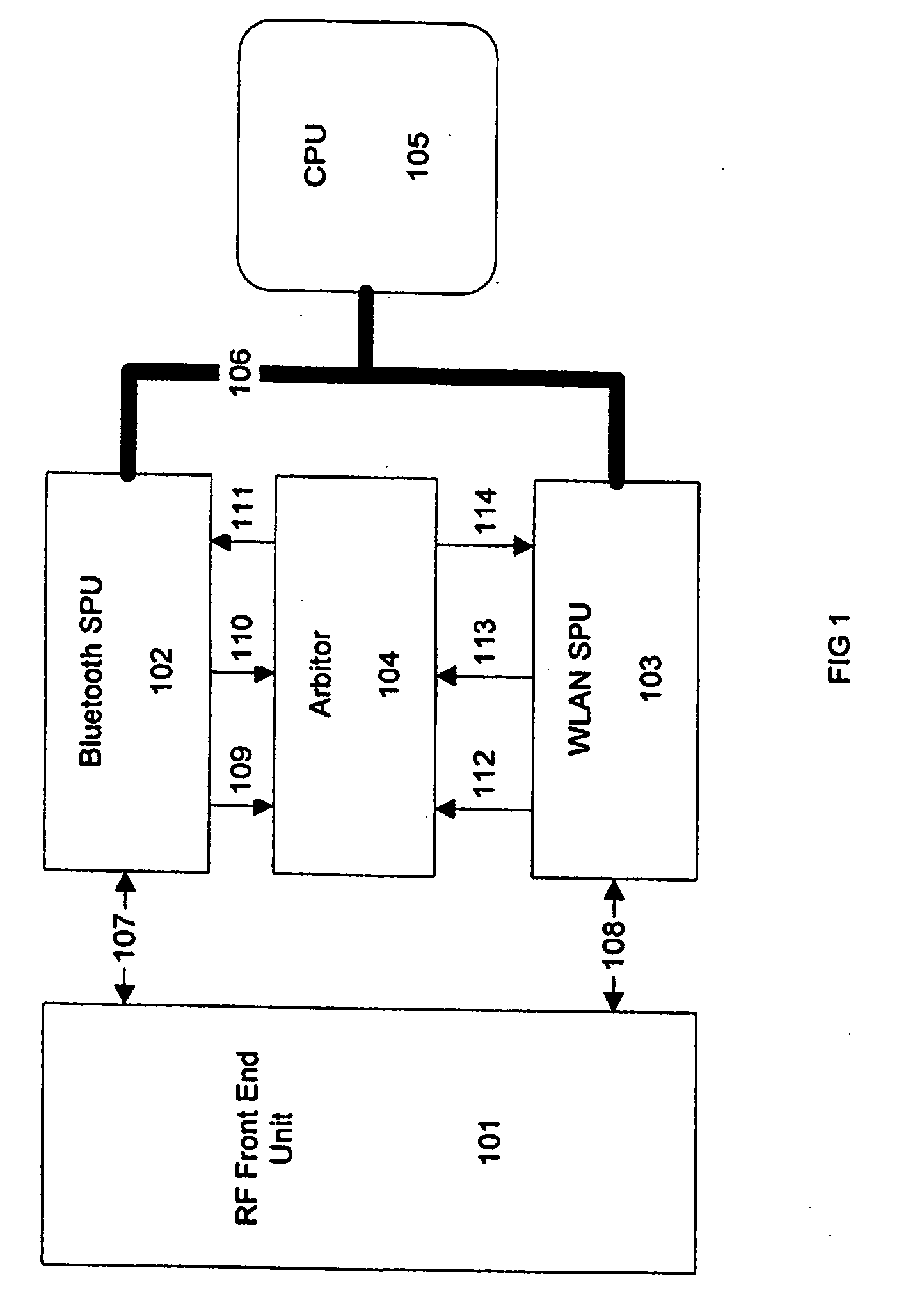
WLAN and bluetooth harmonization
InactiveUS20100130129A1Improve system performanceNetwork traffic/resource managementNetwork topologiesNetwork packetBluetooth
Described is a WLAN / BT system with improved compatibility. It employs an adaptive algorithm that dynamically optimizes the WLAN data fragmentation size based on the current WLAN data rates such that the fragmented data packets fit the time slots allowed by the BT SCO stream gaps. The algorithm first uses system level information to acquire the concurrent BT traffic types to decide if TDM method needs to be enabled. Then it uses the smoothed WLAN date rate to calculate maximum fragmentation packet size consistent with current overall WLAN traffic.
Owner:SYCHIP
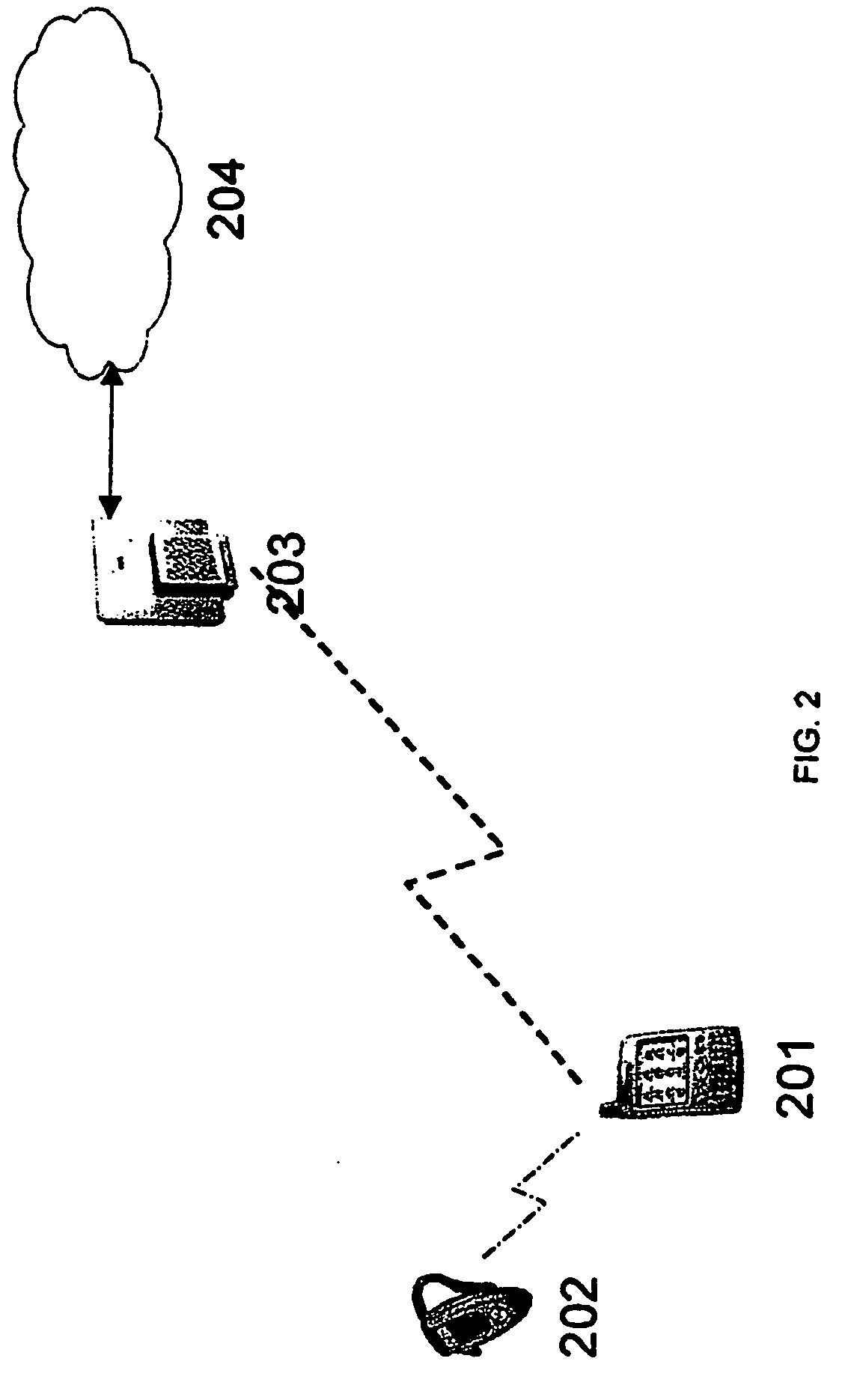
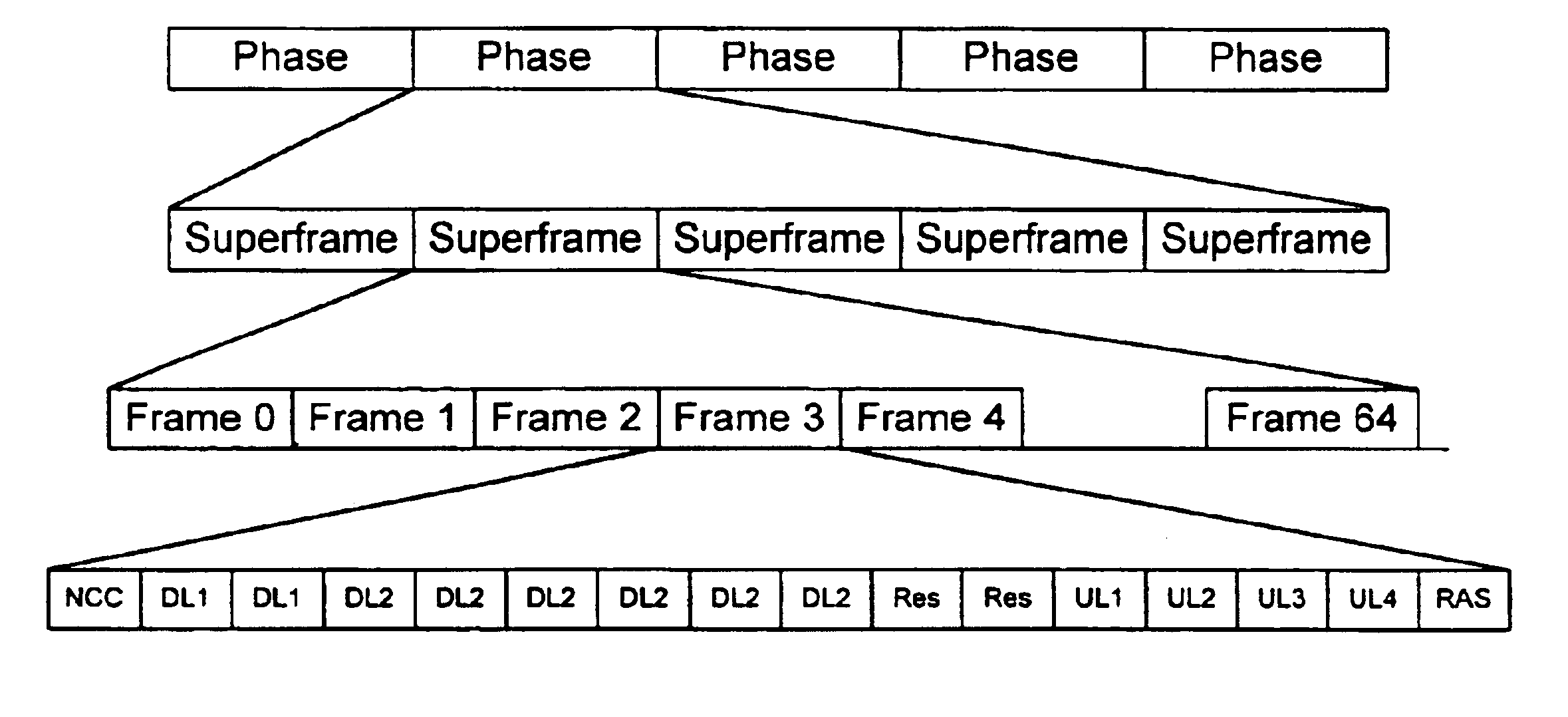
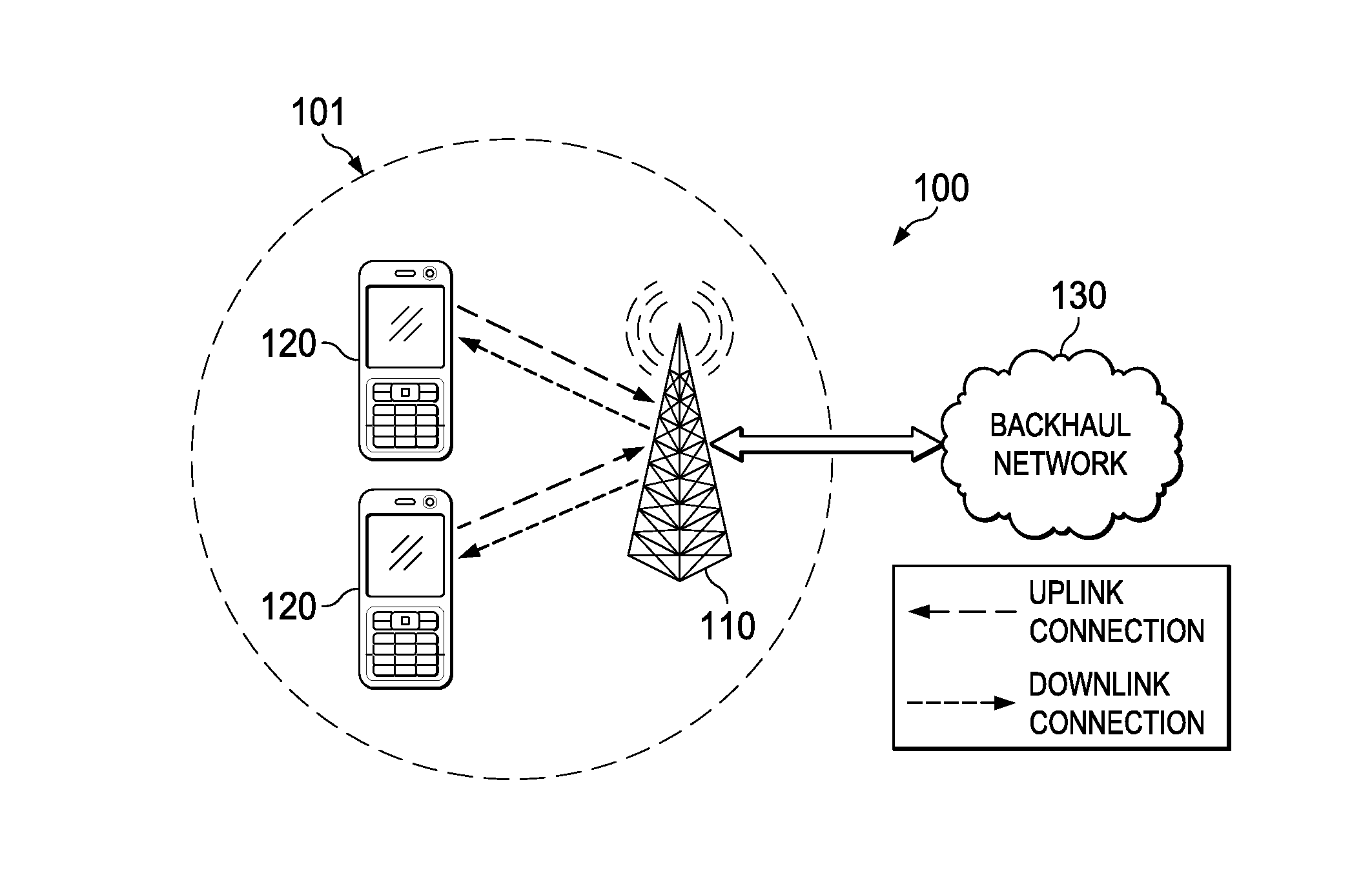
Wireless internet access system and method
InactiveUS6947408B1Avoid Intersymbol InterferenceAdaptable to changeSpatial transmit diversityError preventionWireless internet accessDifferential phase
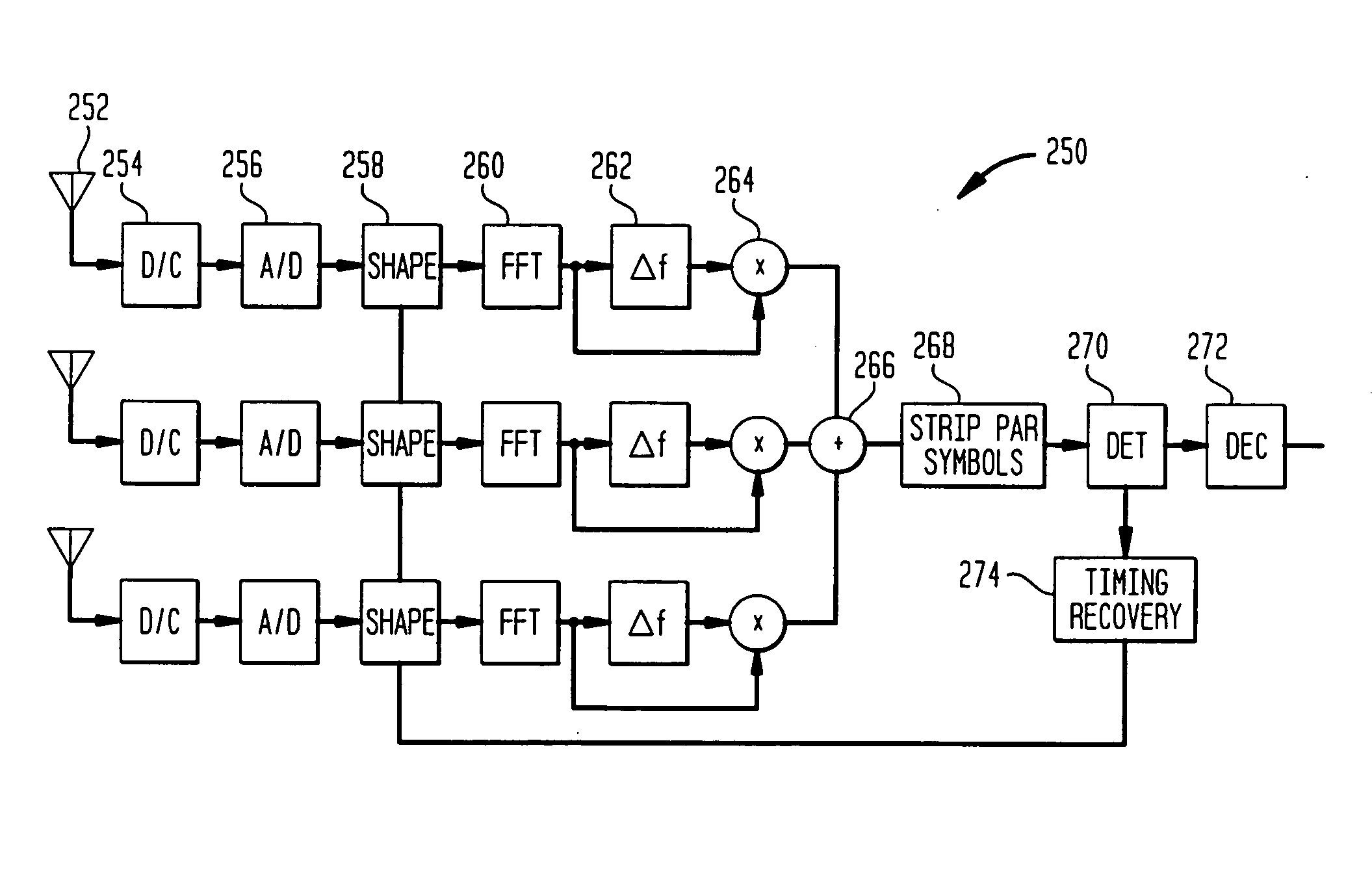
A wireless Internet access system and method supports the transmission and reception of multiple types of traffic between mobile subscriber units and existing networks. A frame structure is used that can support the transmission of multiple types of traffic and adapt to changes in the traffic types needed and the amount of data for a particular traffic type. In addition, data transmission is performed using orthogonal frequency division multiplexing and differential phase shift keying to avoid inter-symbol interference. Receiving units in the mobile subscriber units and existing works include antenna arrays to provide a multipath transmission.
Owner:TELCORDIA TECHNOLOGIES INC
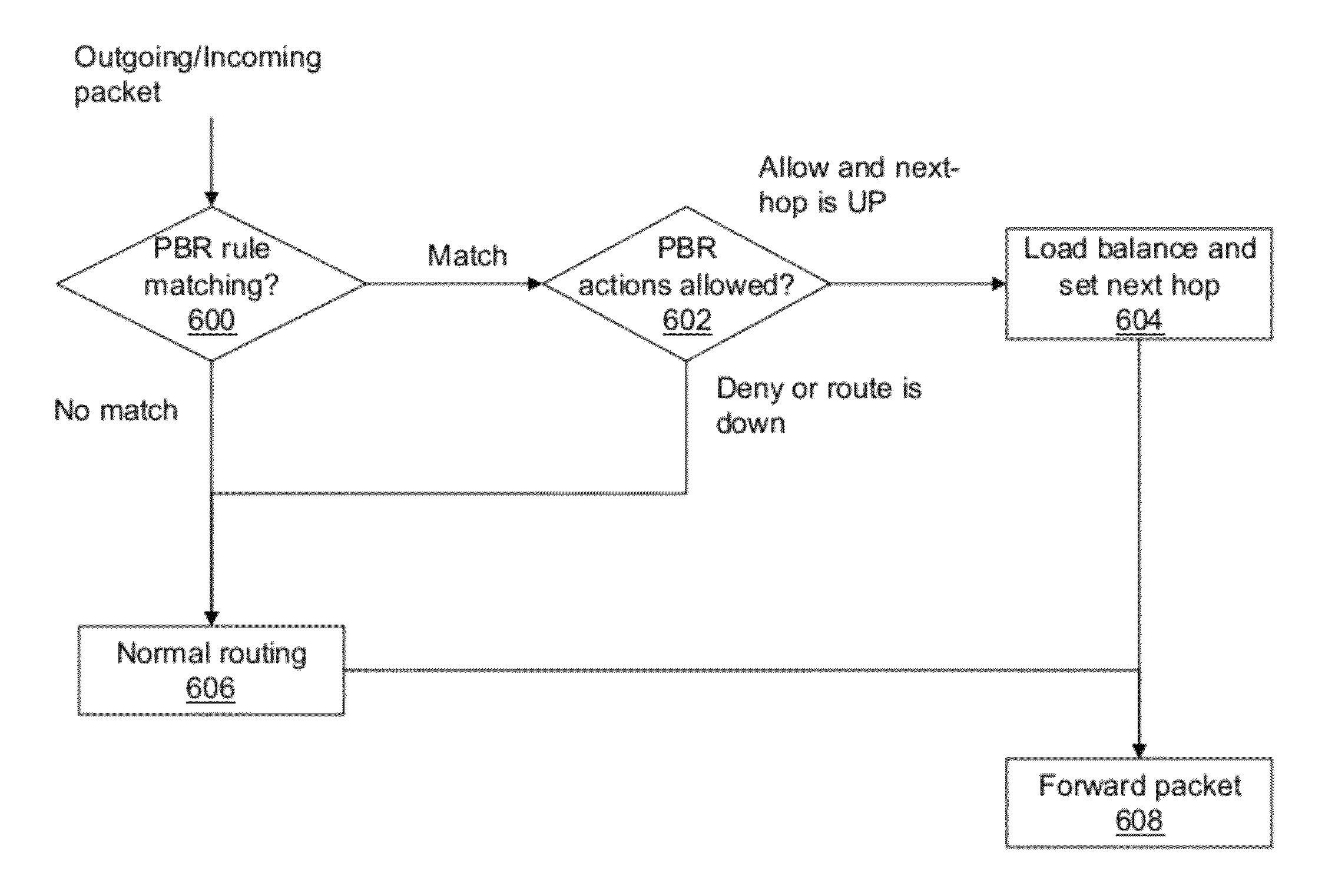
Systems and Methods for Policy Based Routing for Multiple Hops
ActiveUS20120163180A1Provide reliabilityBalance traffic loadError preventionTransmission systemsTraffic characteristicIp address
The present application is directed towards policy based routing for intelligent traffic management via multiple next hops. In some embodiments, the systems and methods disclosed herein may provide management of inbound and outbound traffic across multiple network links, and may further provide reliability in case of link failure, and provide balancing of traffic, responsive to the latency and bandwidth requirements of various applications. Accordingly, these systems and methods may provide intelligent policy-based routing and network and port address translation, sensitive to application traffic types, protocols, source IP addresses and ports, destination IP addresses and ports, or any combination thereof, and can balance traffic loads among multiple available paths based on multiple traffic characteristics. The routing may performed on a packet-by-packet basis, a transaction-by-transaction basis, or a session-by-session basis, and the systems and methods may include capabilities for application-aware health monitoring of available network paths.
Owner:CITRIX SYST INC
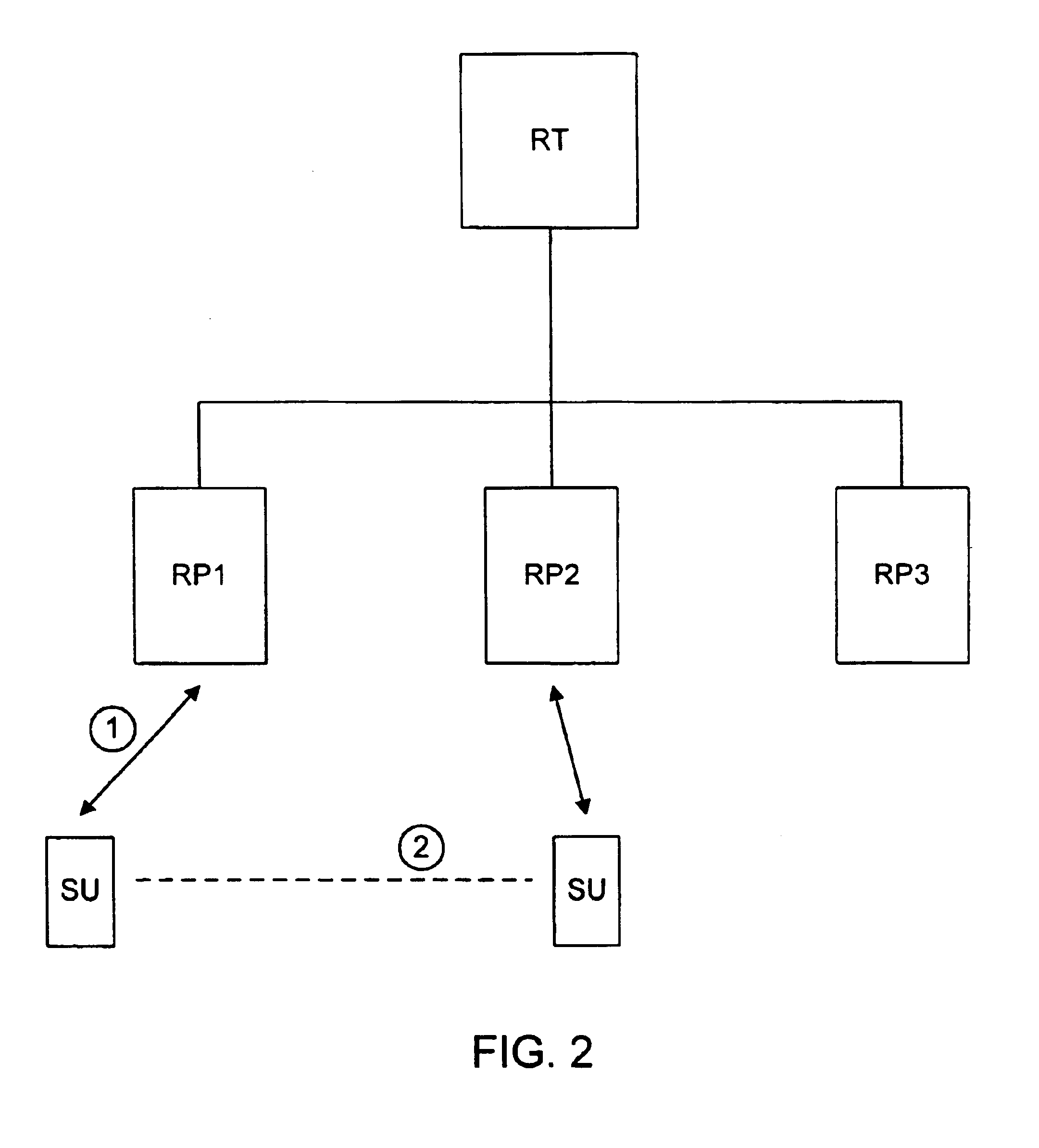
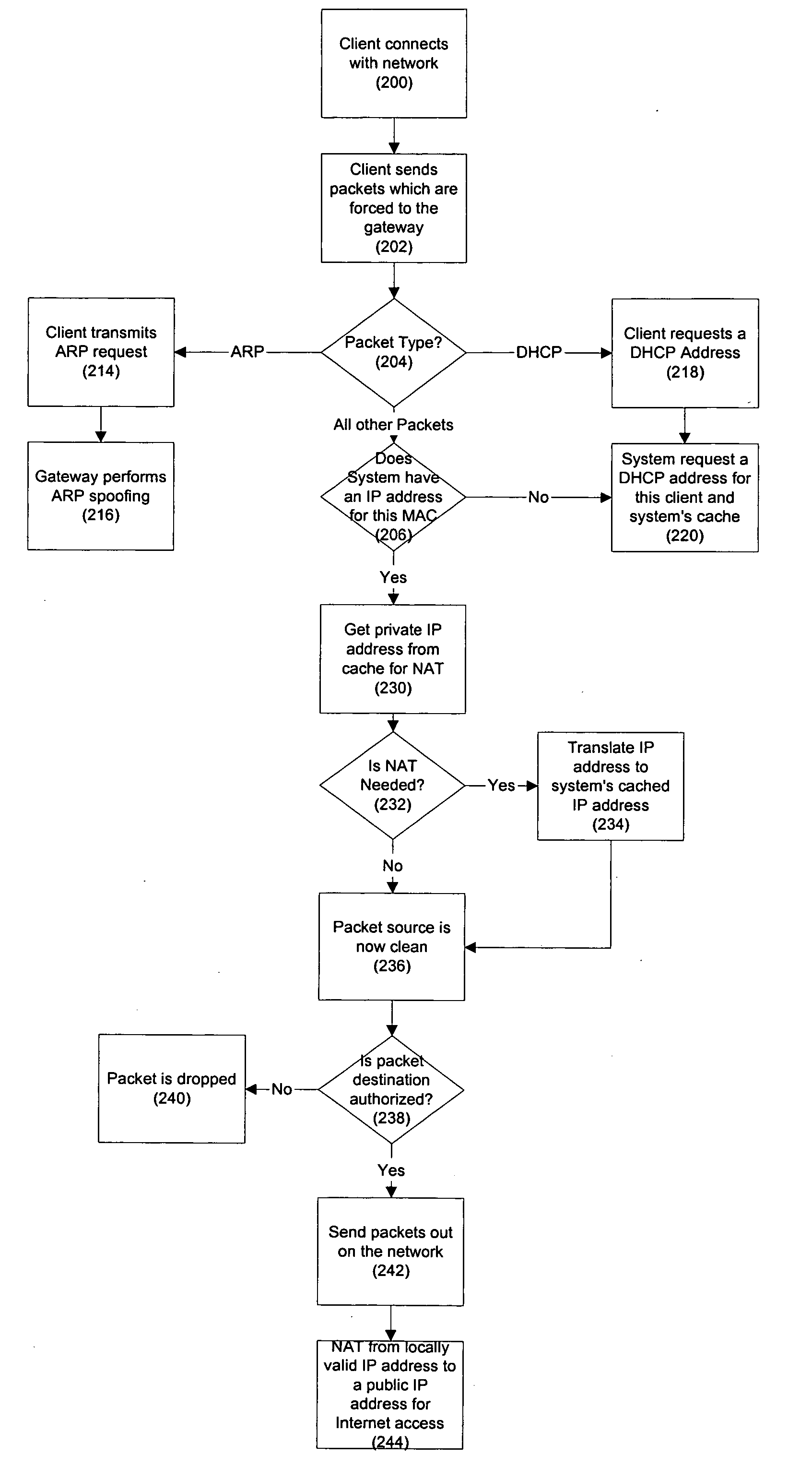
Security for mobile devices in a wireless network
ActiveUS20060206933A1Reliably and securely connectMultiple digital computer combinationsProgram controlTraffic capacityWireless computing
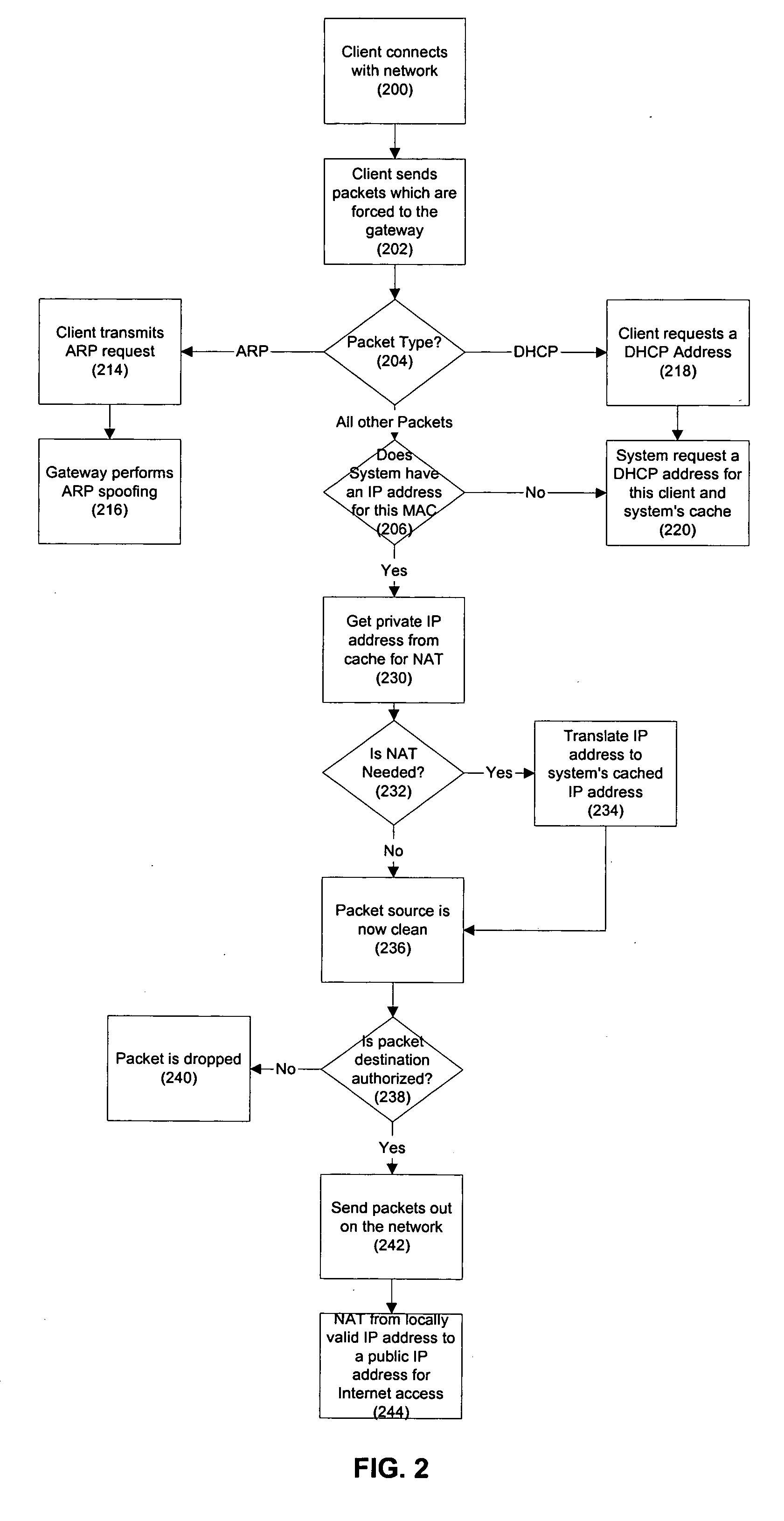
A network and associated methods and apparatus are described. The network includes a wireless access node which is operable to receive first packets from a plurality of wireless computing devices attempting to access the network. Each of the first packets corresponds to one of a plurality of traffic types. At least one of the traffic types corresponds to an encrypted wireless protocol. The wireless access node is configured to associate one of a plurality of identifiers with each of the first packets. Each of the plurality of identifiers corresponds to one of the plurality of traffic types. The wireless access node is further configured to transmit all first packets received from the wireless computing devices to a gateway on the network regardless of destination addresses associated with the first packets. The gateway is operable to determine that a particular one of the first packets from a first one of the wireless computing devices is directed to a second computing device on the network. The gateway is further operable to prevent the particular first packet from reaching the second computing device in response to determining that the particular first packet is directed to the second computing device.
Owner:GUEST TEK INTERACTIVE ENTERTAINMENT
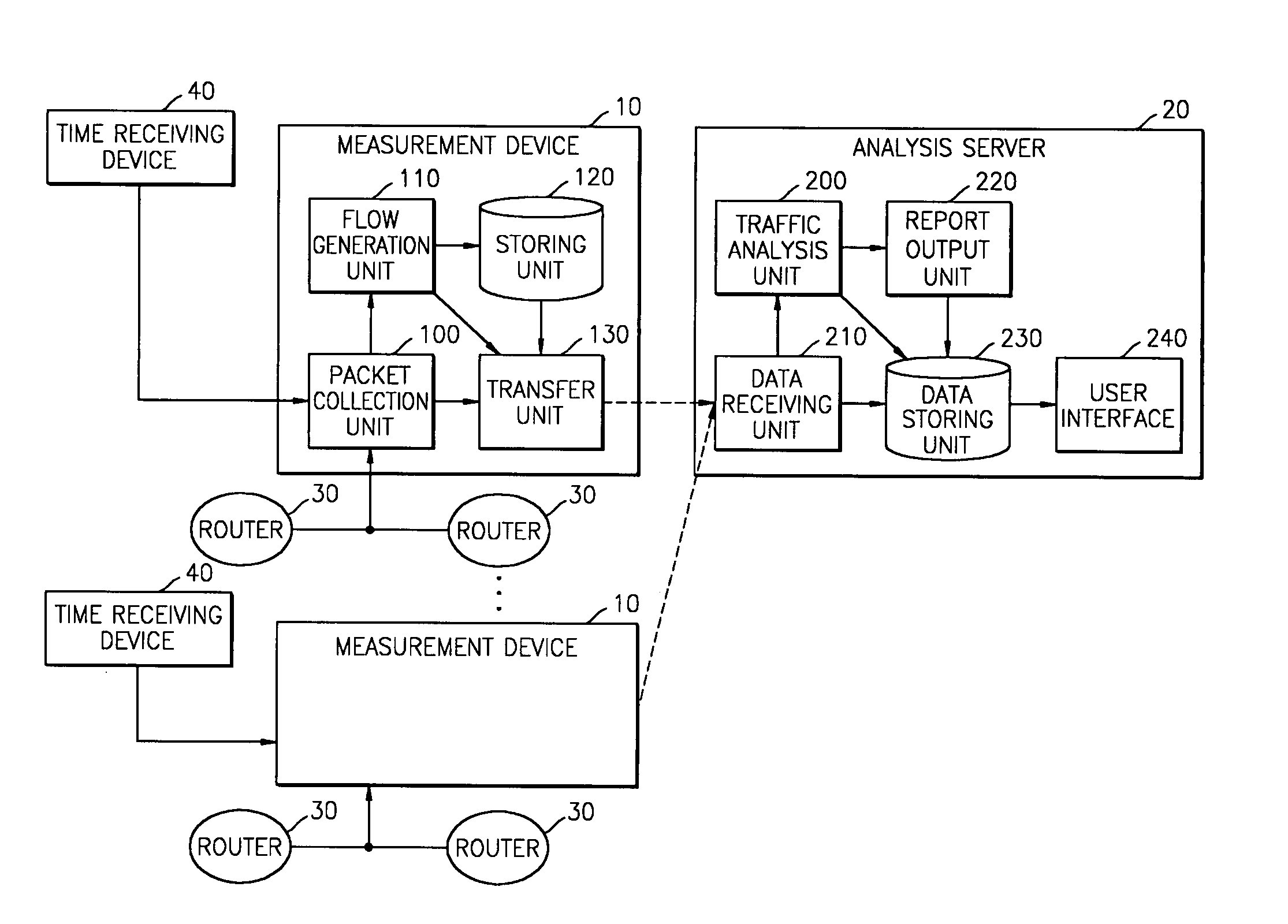
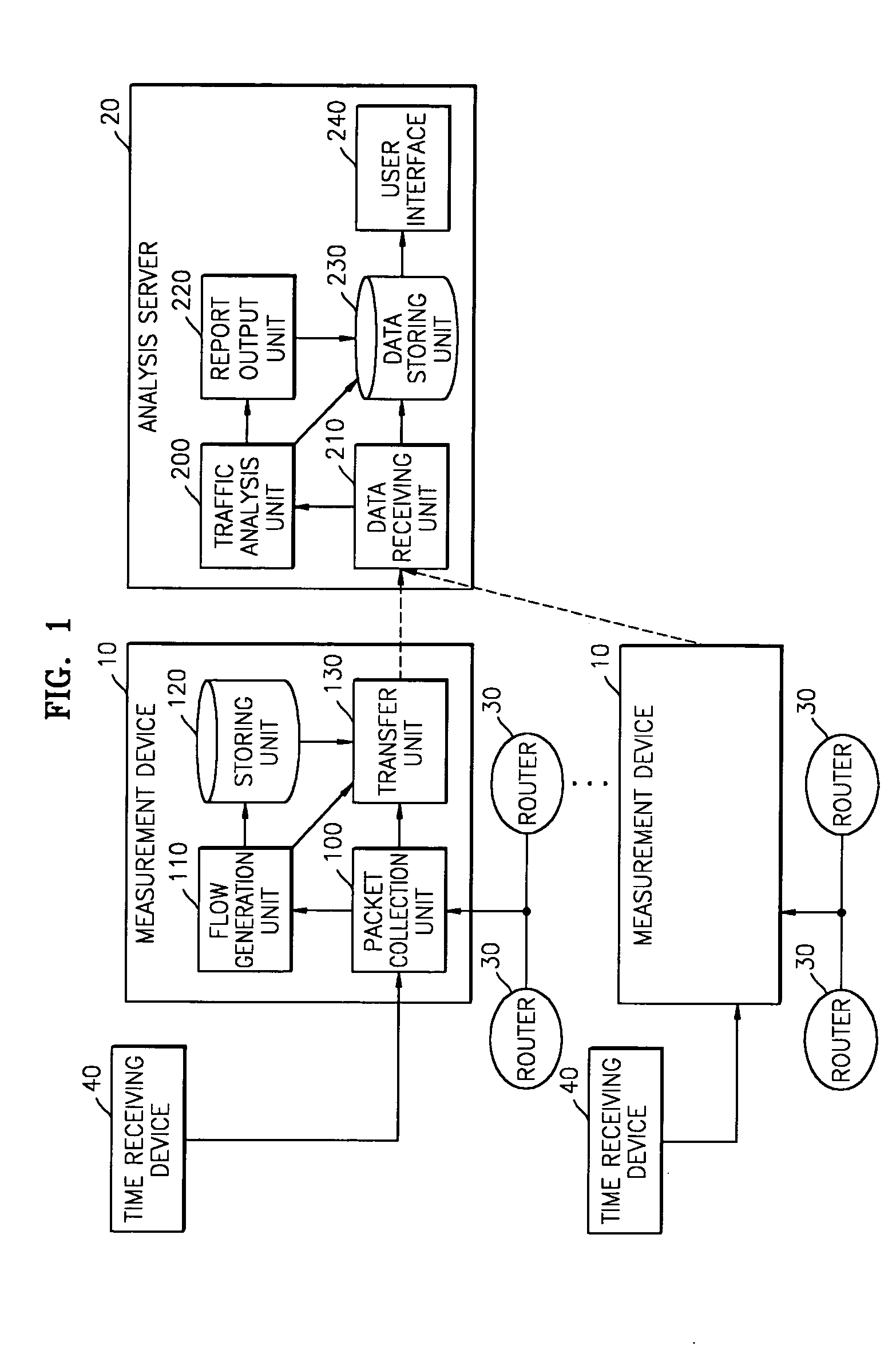
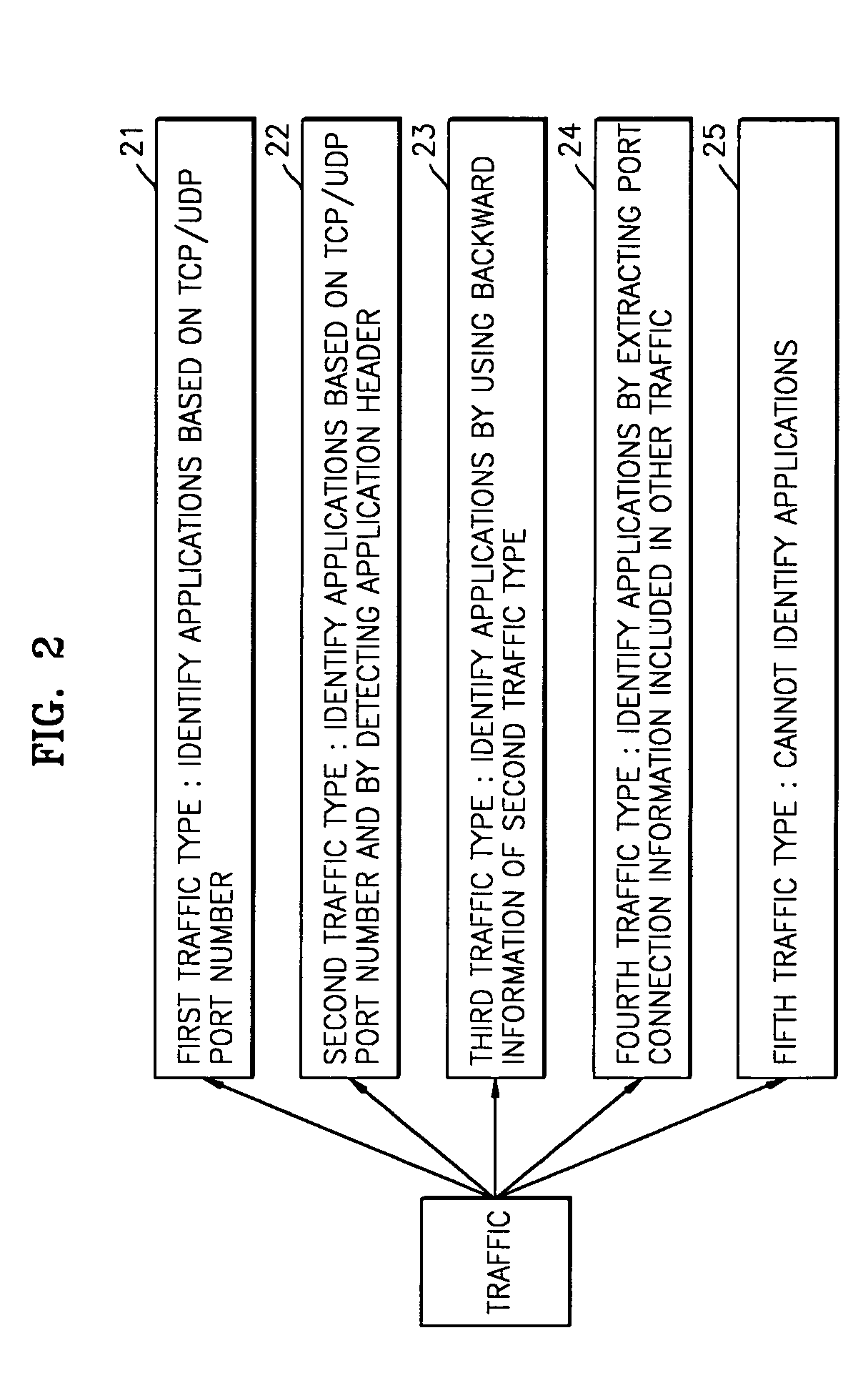
Traffic measurement system and traffic analysis method thereof
A traffic measurement system and a traffic analysis method are provided. The traffic measurement system includes a plurality of measurement devices that collect all of packets flowing through Internet links, extract traffic data required to analyze traffic from the collected packets, and process the extracted data into predetermined flow types, and an analysis server that identifies applications of traffic by analyzing the traffic data transferred from the plurality of measurement devices as a whole, classifies the identified applications into predetermined traffic types, and outputs the classification result. The traffic measurement system measures the traffics in the Internet network and processes the measured traffics to generate detailed traffic statistical data according to applications. In particular, the traffics are analyzed considering measurement data from various points, and the data for identifying the applications are extracted from headers of the applications included in payloads of IP packets in real time. Accordingly, detailed traffic analysis result is provided.
Owner:ELECTRONICS & TELECOMM RES INST
Wireless internet access system and method
InactiveUS20050100120A1Avoid Intersymbol InterferenceAdaptable to changeSpatial transmit diversityNetwork traffic/resource managementDifferential phaseWireless internet access
A wireless Internet access system and method supports the transmission and reception of multiple types of traffic between mobile subscriber units and existing networks. A frame structure is used that can support the transmission of multiple types of traffic and adapt to changes in the traffic types needed and the amount of data for a particular traffic type. In addition, data transmission is performed using orthogonal frequency division multiplexing and differential phase shift keying to avoid intersymbol interference. Receiving units in the mobile subscriber units and existing networks include antenna arrays to provide a multipath transmission.
Owner:TELCORDIA TECHNOLOGIES INC
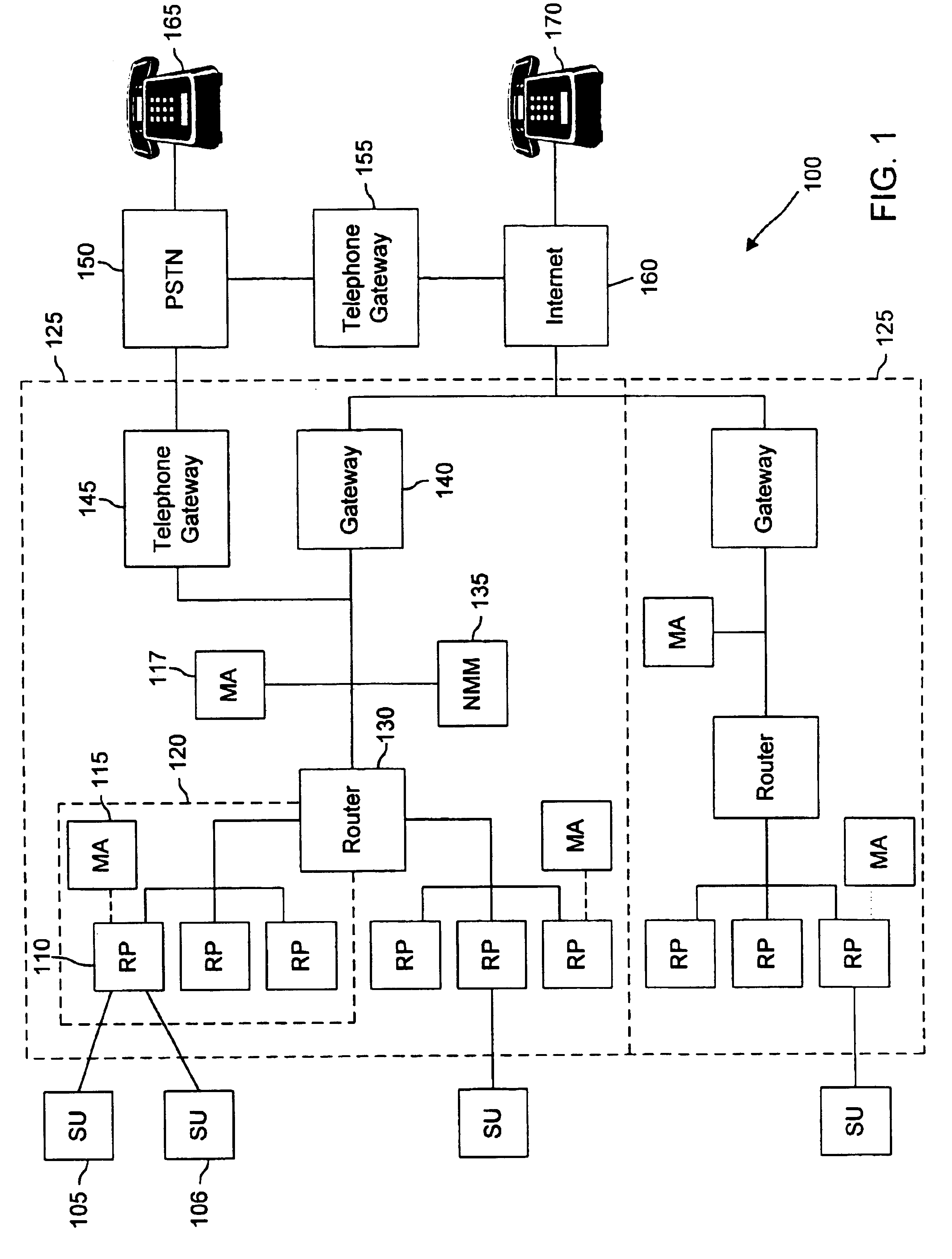
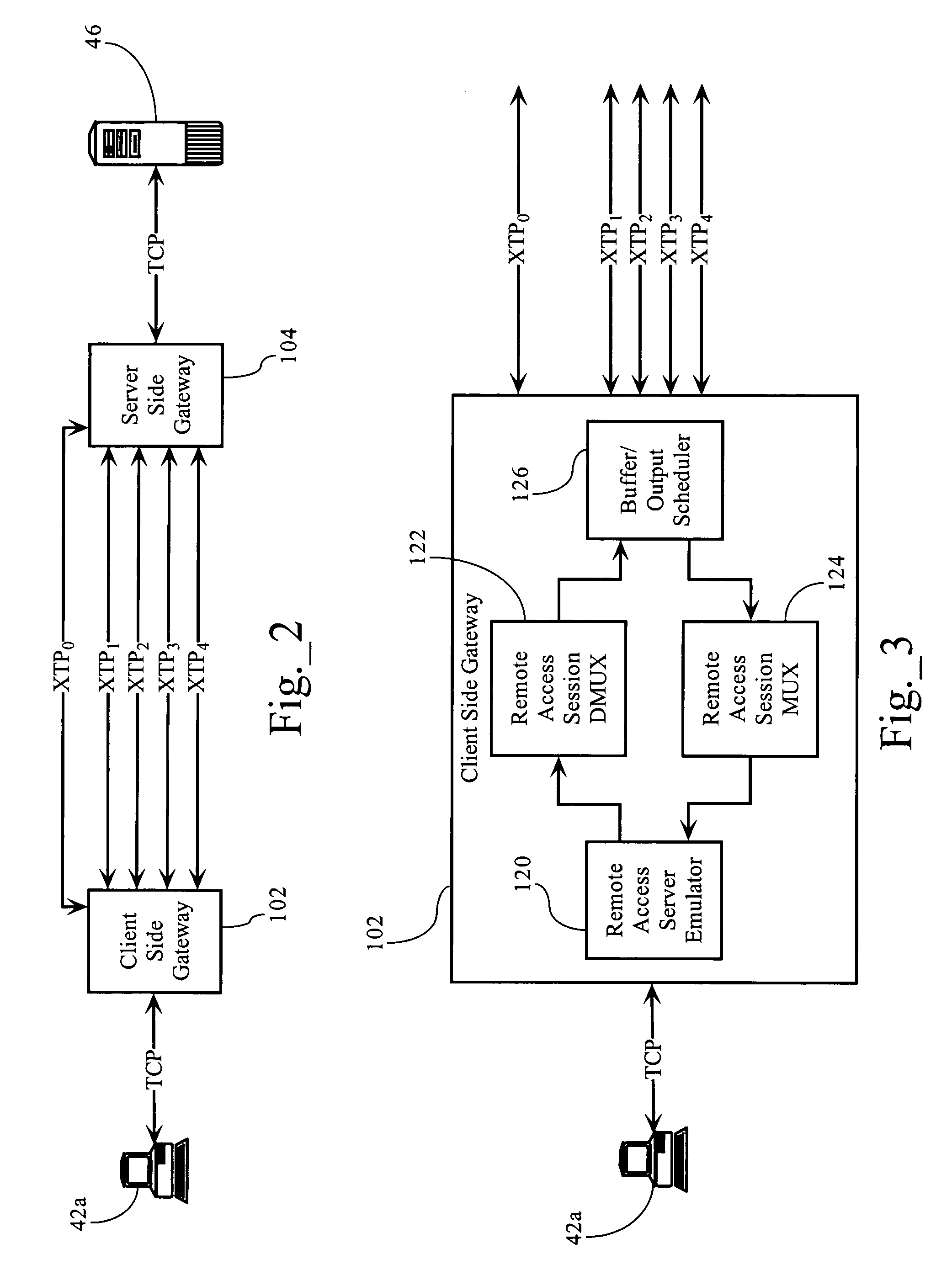
Enhanced QoS solution for thin client or remote access sessions
Methods, apparatuses and systems directed to the application of network QoS policy to different data types multiplexed over a connection corresponding to a given session between a first host and a second host. In one implementation, the present invention includes a dual gateway architecture where a first gateway terminates the connection with a remote access client, demultiplexes the remote access session data stream into a plurality of separate streams for transmission to a second gateway. The second gateway re-multiplexes the separate data streams into a single remote access session data stream for transmission to a remote access server. The use of separate data streams between the first and second gateways allows for the application of individual policies on the components of the remote access session data flow. For example, a policy scheme can be configured that gives preference to mouse movements, transmitted in a first data stream, over printer traffic, transmitted in a second data stream. The present invention can also be applied to network application protocols, other than remote access protocols, that multiplex more than one “virtual channel” containing different traffic types over a single transport layer connection.
Owner:CA TECH INC
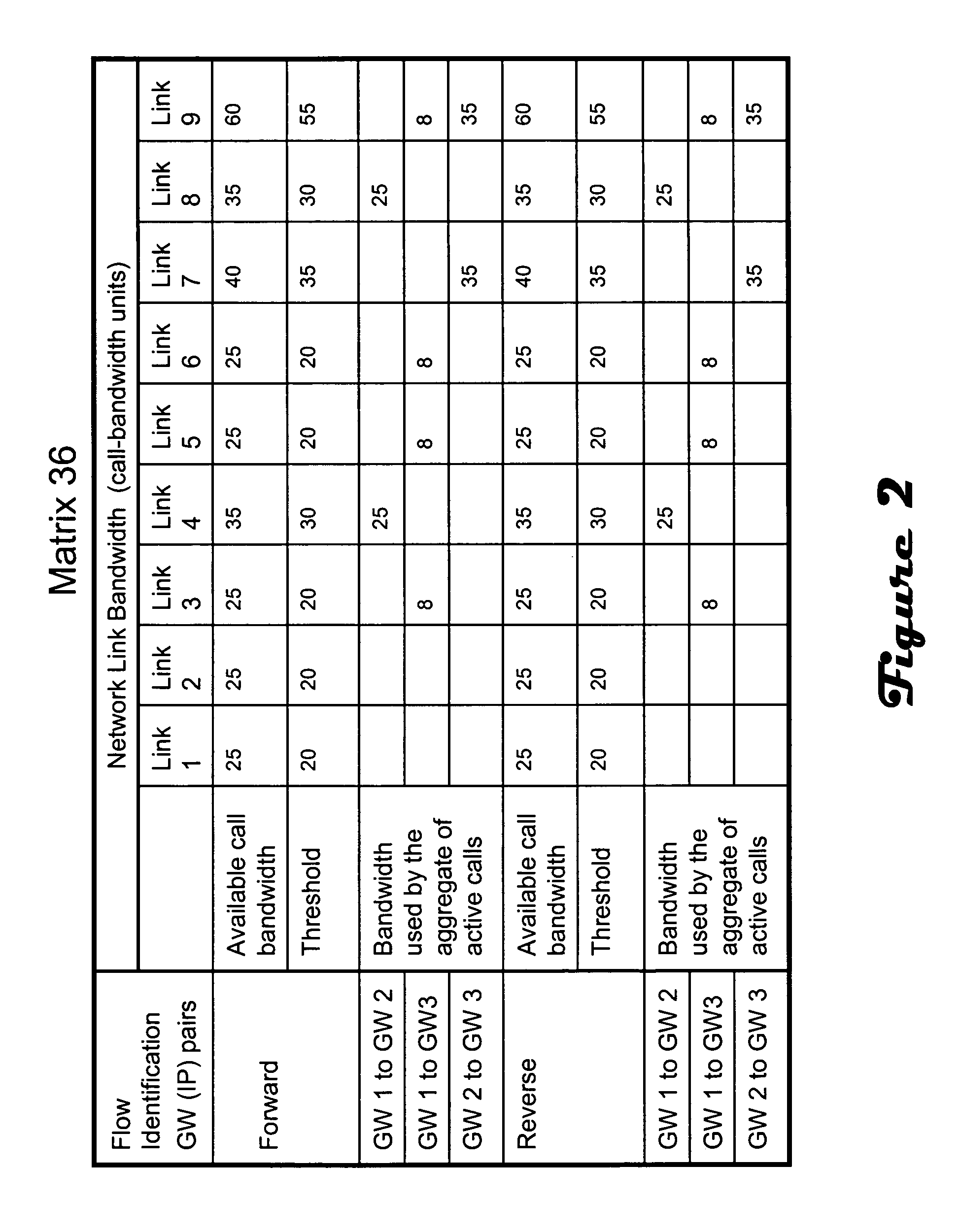
Flow admission control in an IP network
A flow admission control module for IP traffic types monitors network topology and usage. A new flow is not admitted if it is determined that the flow would push the utilization of available bandwidth reserved for the traffic type on a link in the associated path beyond a predetermined threshold. The admission control module may, as a result of dynamic changes to network topology capacity, re-compute the link utilization for effected active flows. The admission control module may also account for protection regimes in flow admission calculations.
Owner:RPX CLEARINGHOUSE
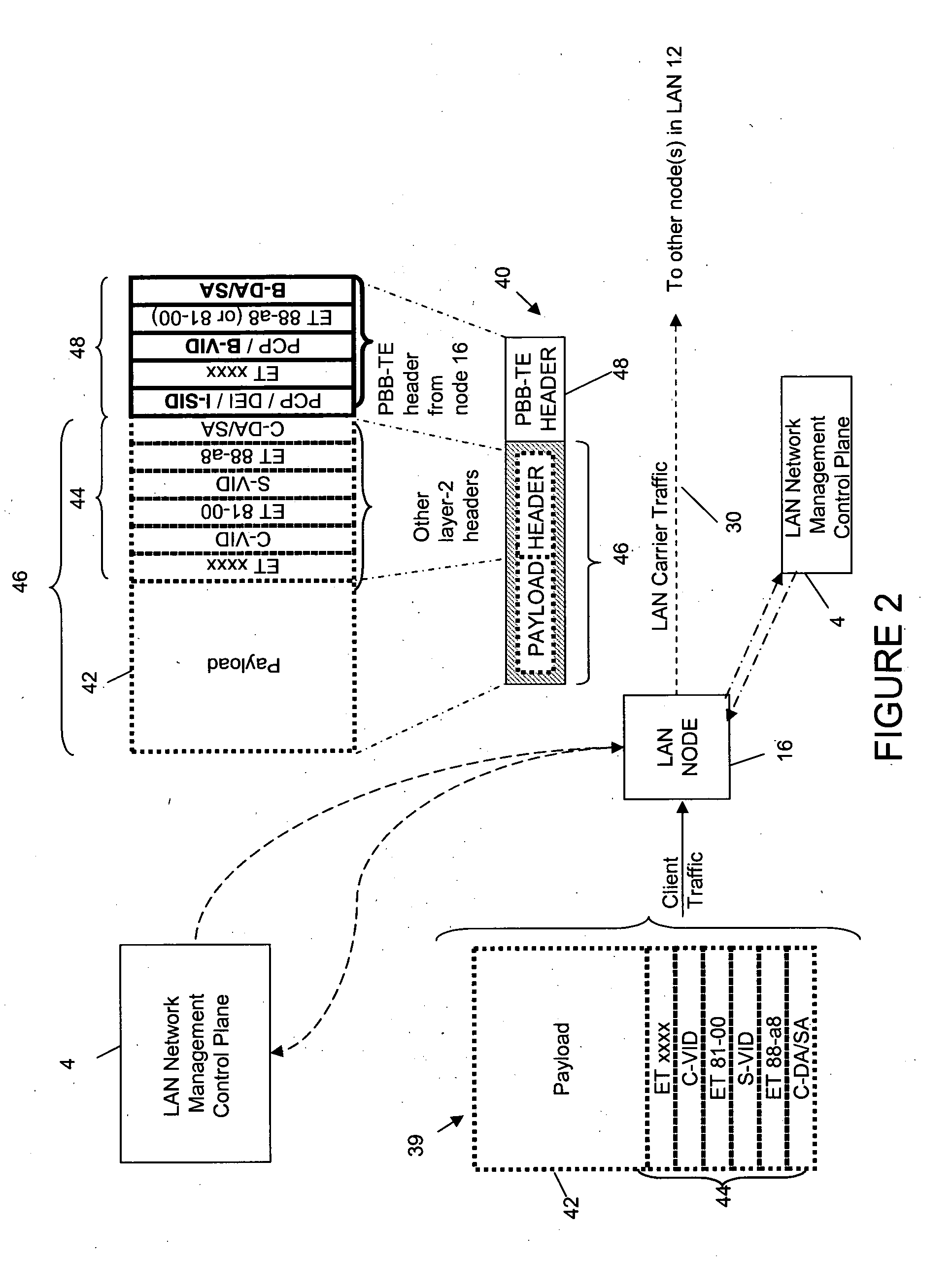
Header compression scheme
InactiveUS20110122893A1Reduce the amount requiredReduced bandwidthTime-division multiplexTransmissionTraffic capacityNetwork Communication Protocols
A method of reducing the bandwidth required to send traffic comprising a payload and a header originating in a first communications network over another communications network. The traffic is characterized by having header information from which a path from its source to destination can be predetermined, the method comprising: determining redundant header information which is not used for forwarding the traffic in the other network; replacing at least part or all of the redundant header information with compression information having a smaller bandwidth than the replaced header information; appending header information to the traffic to enable forwarding along the path in the other network to an egress node; at the egress node, processing the traffic to remove the appended header information and restore the replaced header information by removing the compression information and using the compression information to perform a look-up operation which retrieves the replaced redundant header information from a data store, wherein the same compression information is used to replace the same redundant header information for all the traffic having the same predetermined path; compression information comprising a dummy header data structure which conforms to a communications protocol arranged to be identifiable by traffic type in a carrier frame.
Owner:BRITISH TELECOMM PLC
System and Method of Waveform Design for Operation Bandwidth Extension
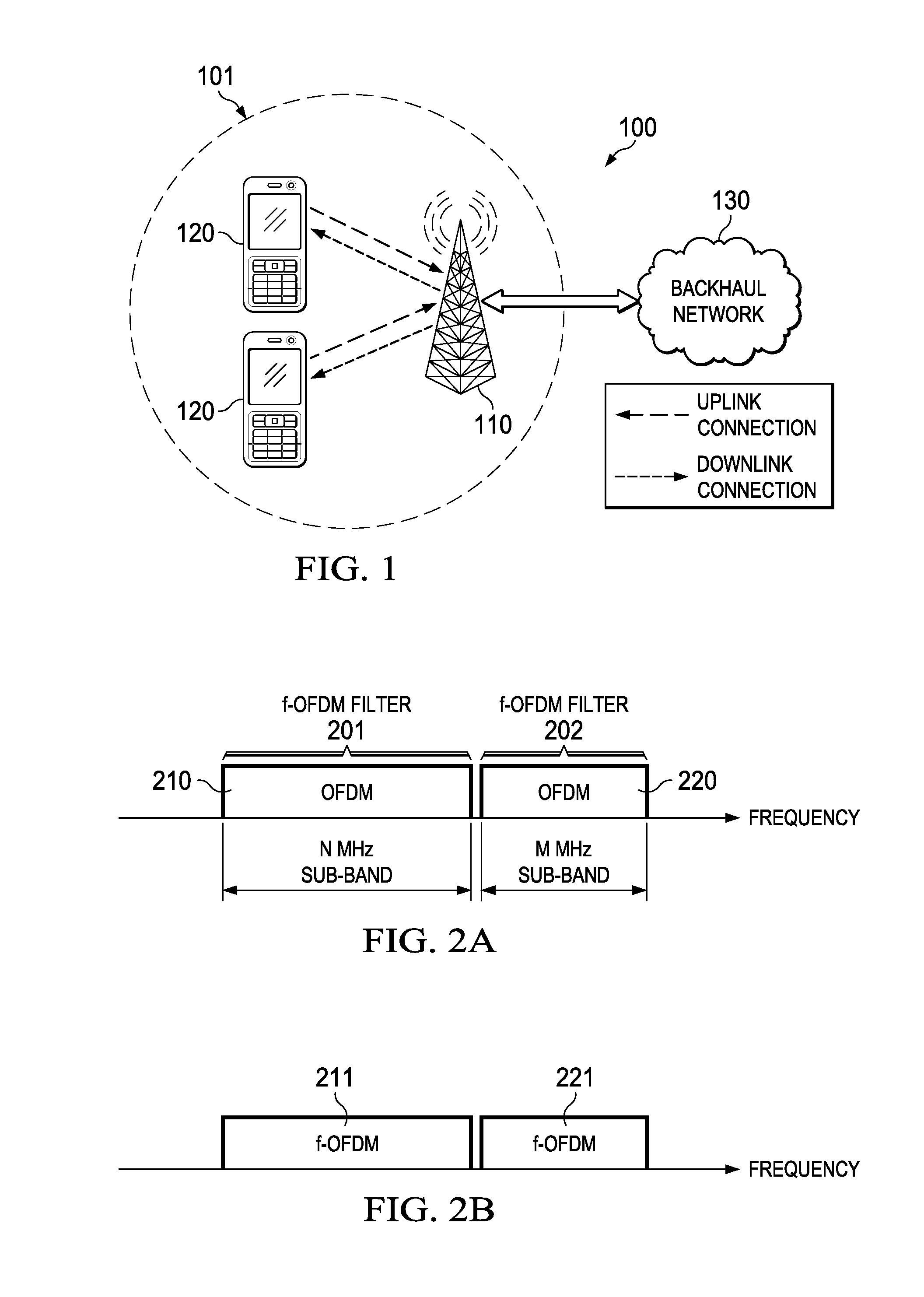
ActiveUS20160294498A1Transmission path divisionInter user/terminal allocationBandwidth extensionDigital filter
Different numerologies may be used to communicate orthogonal frequency division multiplexing (OFDM)-based signals over different frequency sub-bands of a given carrier. This may allow the OFDM-based signals to efficiently support diverse traffic types. In some embodiments, the numerology of OFDM-based signal depends on a bandwidth of the frequency sub-band over which the OFDM-based signals are transmitted. In some embodiments, the OFDM-based signals are filtered OFDM (f-OFDM) signals, and the pulse shaping digital filter used to generate the f-OFDM signals allows the receiver to mitigate interference between adjacent f-OFDM signals upon reception, thereby allowing f-OFDM signals to be communicated over consecutive carriers without relying on a guard band.
Owner:HUAWEI TECH CO LTD
Systems and methods for intelligent transport layer security
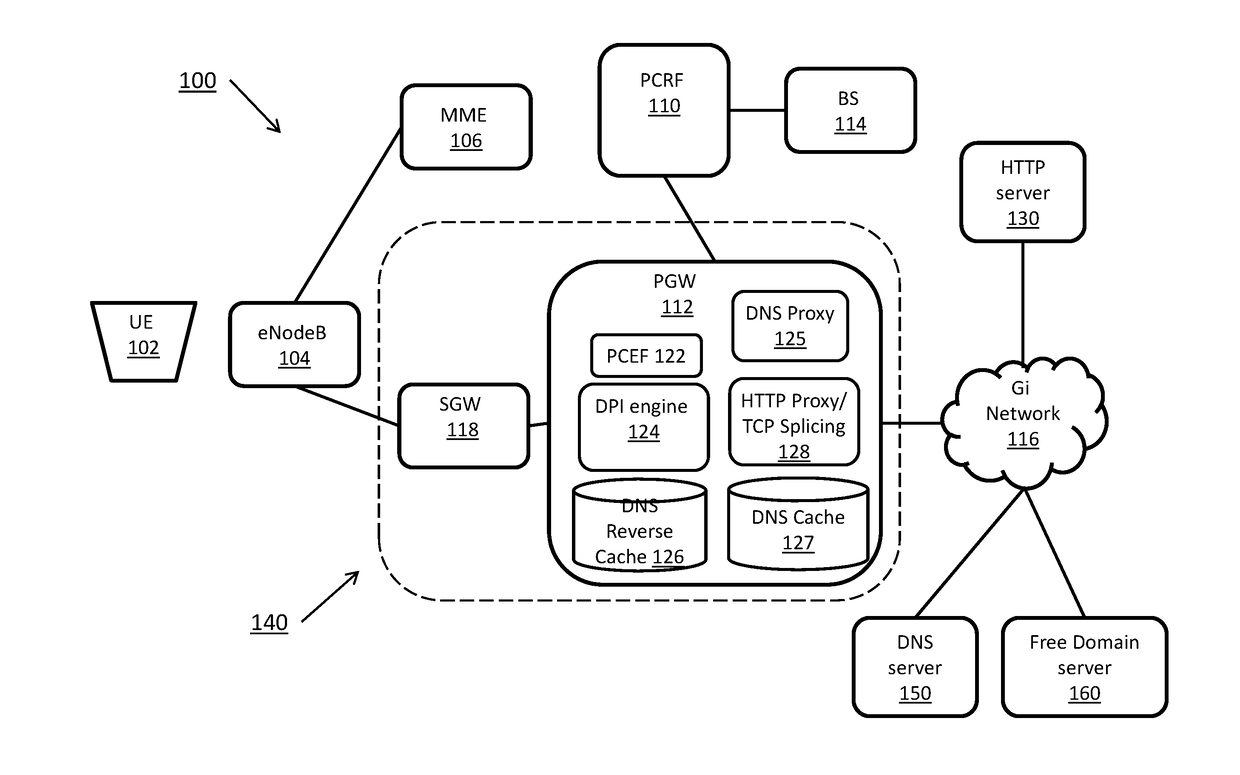
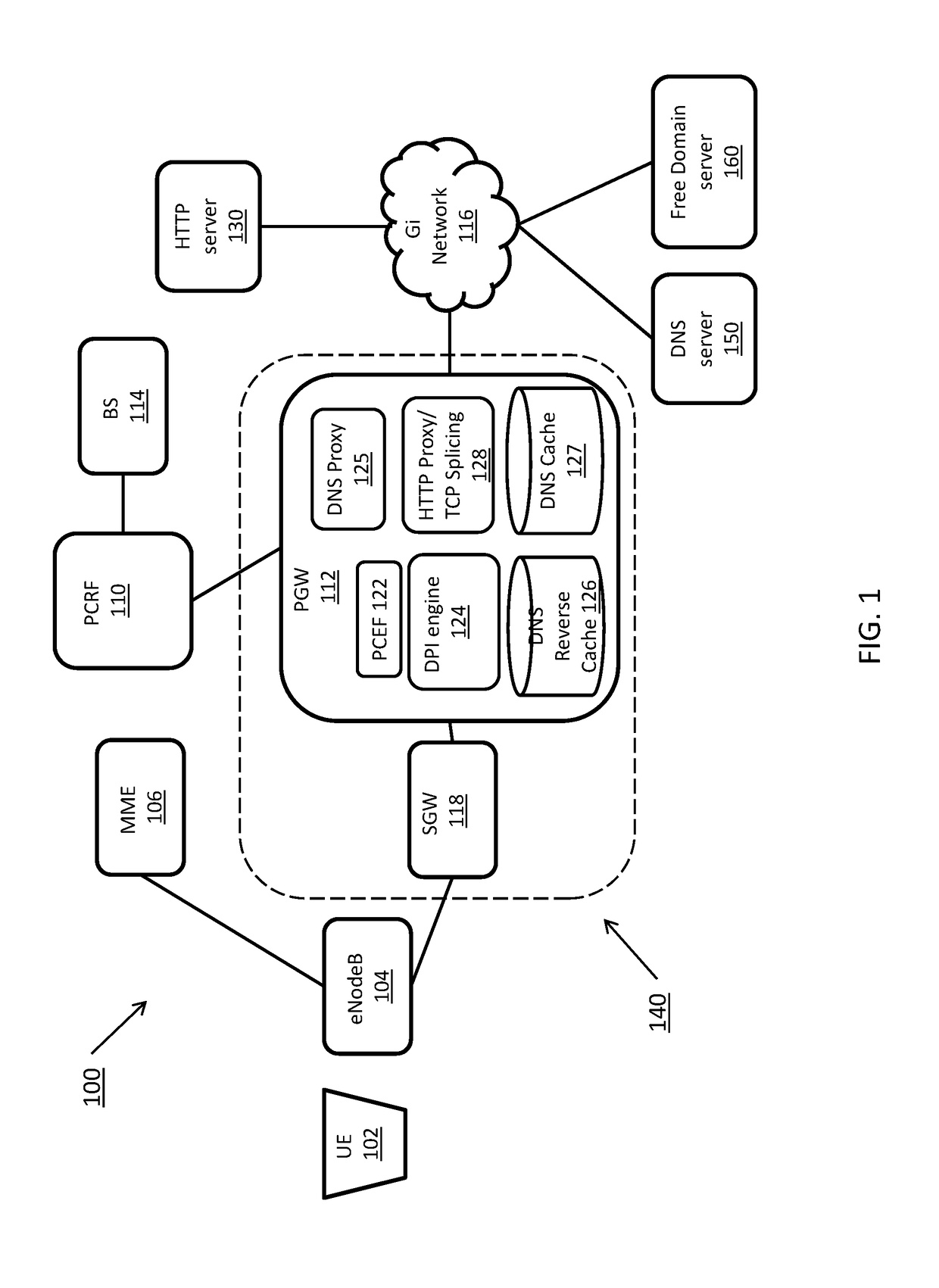
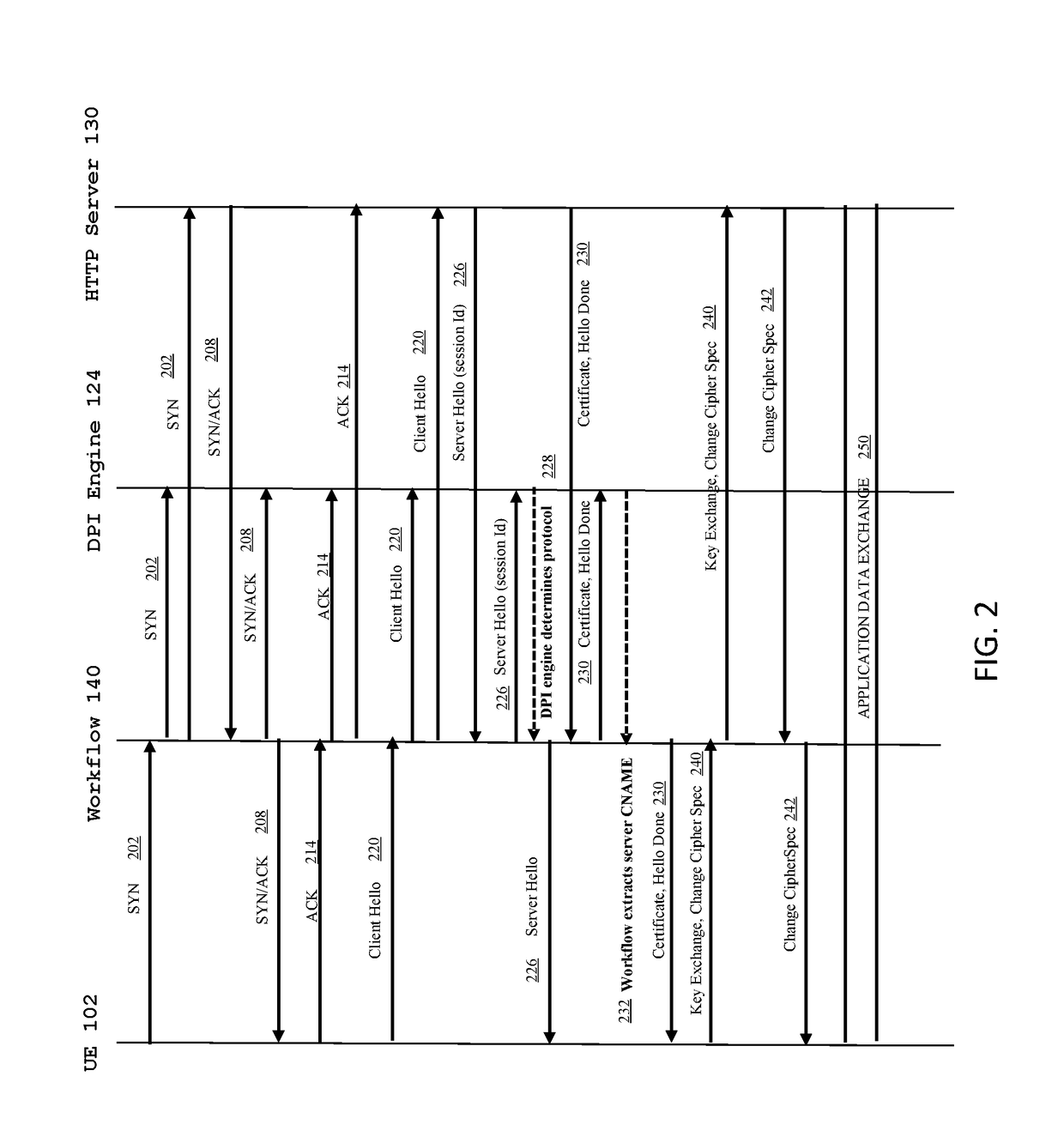
InactiveUS20170272470A1Accounting/billing servicesTelephonic communicationDomain nameComputer network
Systems and methods for detecting a domain name in a mobile network session for use in applying mobile policy and enforcement functions based on the domain name. A computing device receives a packet associated with a request from a user equipment to access a domain at a server. The computing device determines a traffic type associated with the packet, the traffic type including one of Hypertext Transfer Protocol (HTTP) traffic, Hypertext Transfer Protocol Secure (HTTPS) traffic, and non HTTP or HTTPS traffic. The computing device determines a domain name based on the traffic type and determines a service to apply to the packet based on the domain name.
Owner:MICROSOFT TECH LICENSING LLC
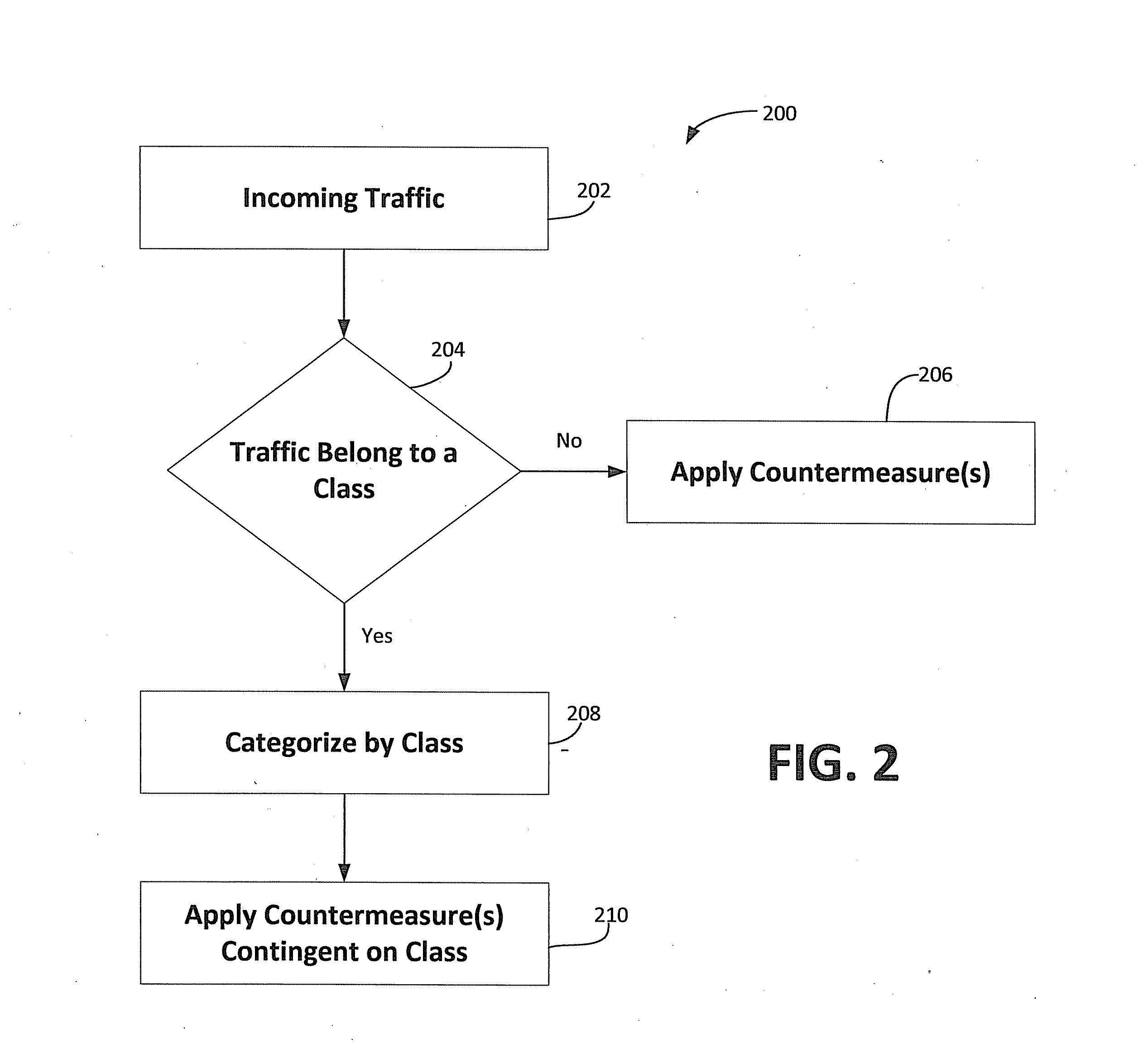
Adjusting ddos protection based on traffic type
ActiveUS20140325634A1Mitigating DDoS attackReduce generationMultiple digital computer combinationsProgram controlTraffic capacityCountermeasure
A system, method and computer readable storage medium that receives traffic / packets from external devices attempting to access protected devices in a protected network. A determination is made to whether a received packet belongs to one of a plurality of packet classifications. Each packet classification indicative of different classes of IP traffic. Countermeasures are applied to a received packet to prevent attack upon the protected devices. Applying a countermeasure to a received packet determined to belong to one of the plurality of packet classifications includes countermeasure modification / selection contingent upon the determined packet classification for the received packet.
Owner:ARBOR NETWORKS
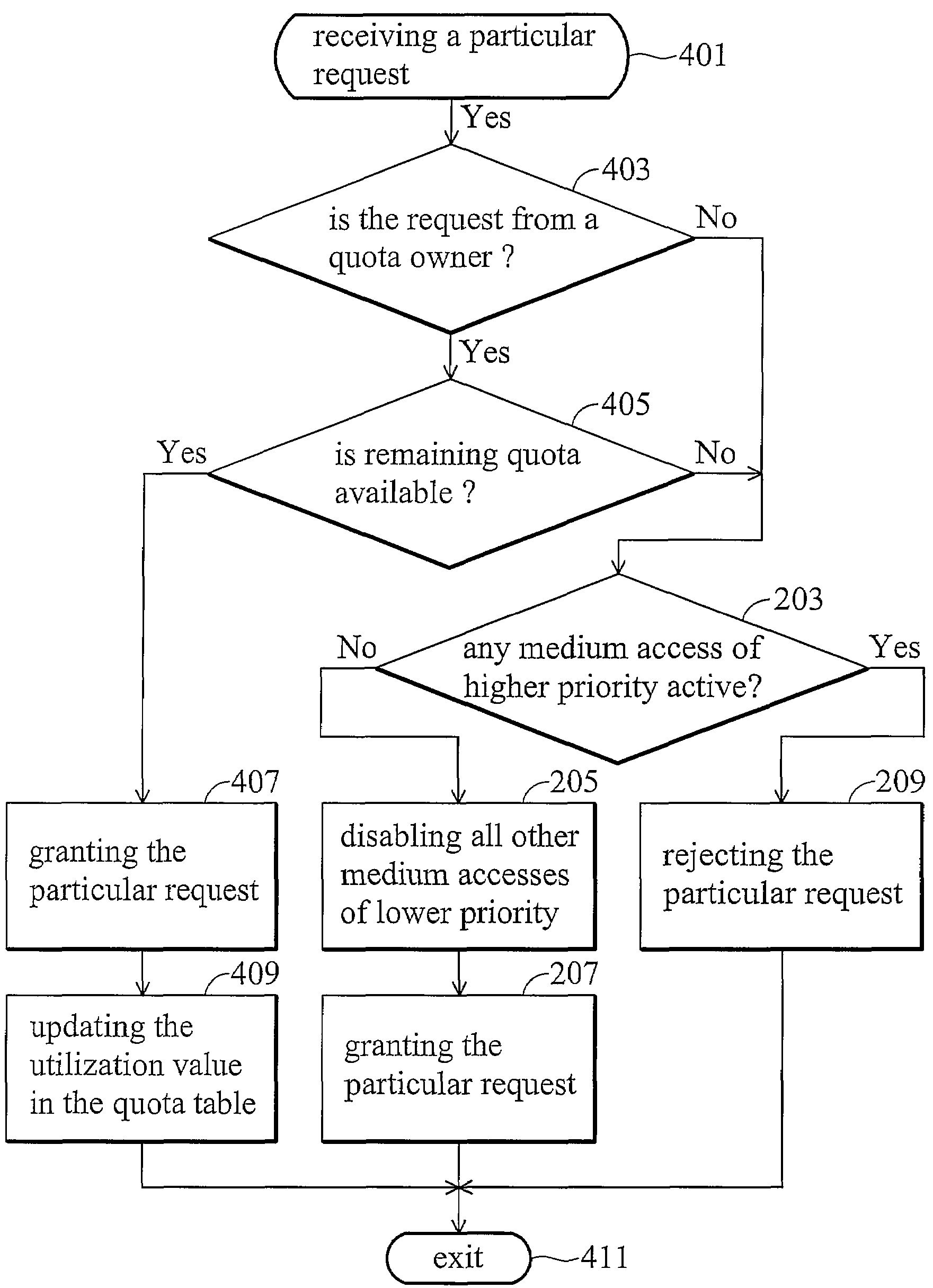
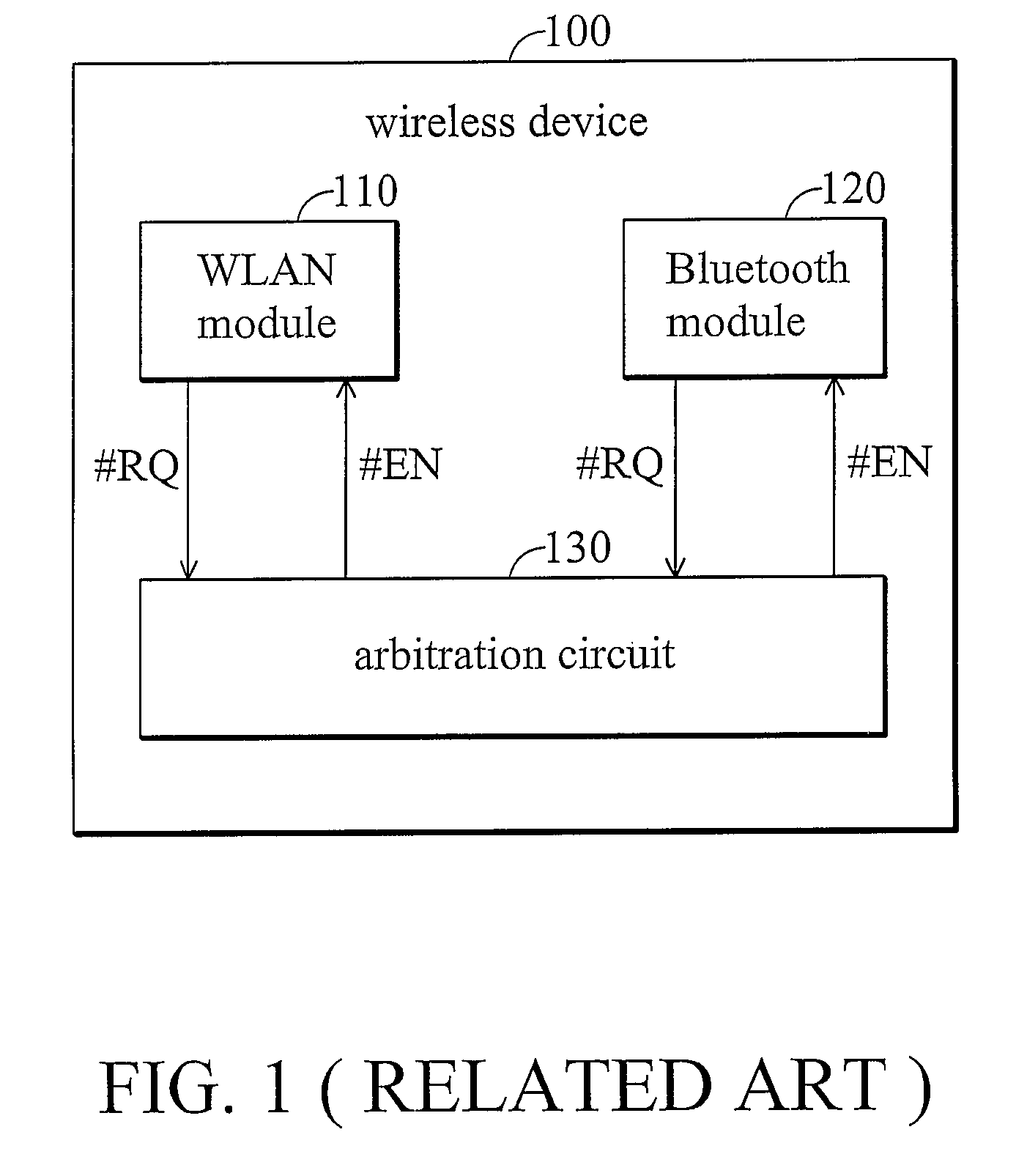
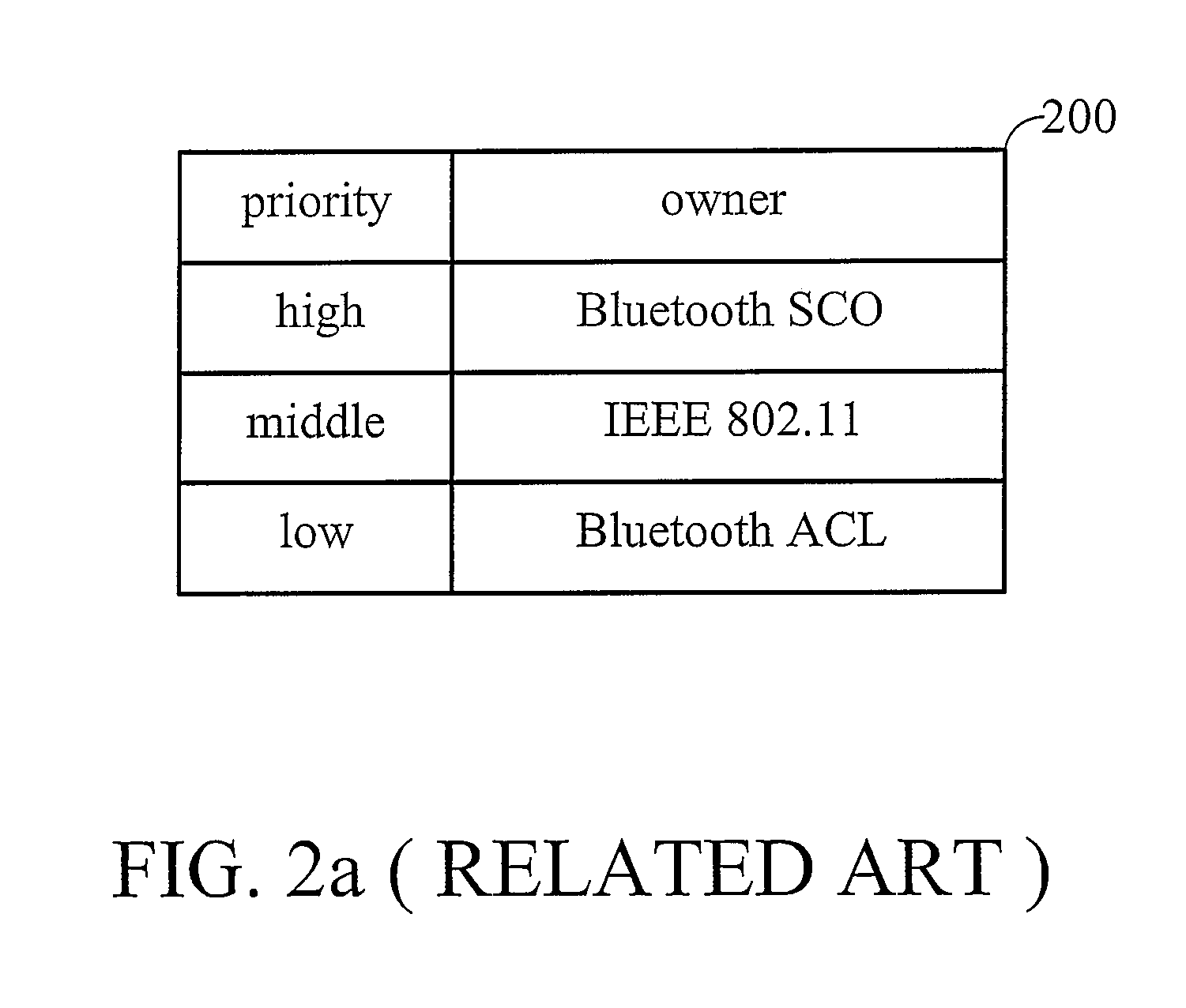
Method and apparatus for arbitration in a wireless device
InactiveUS7546404B2Broadcast transmission systemsData switching by path configurationTraffic capacityMedia access
A method and apparatus for traffic arbitration in a system are provided. In the system, a first module operating in a first protocol and a second module operating in a second protocol share one communication channel. An arbitration circuit schedules medium accesses thereof, in which a quota table maintains a utilization value updated in accordance with the amount of time slots consumed by a particular traffic type, and a time counter periodically resets the utilization value to a default value. When the arbitration circuit receives a request for medium access of the particular traffic type, the arbitration circuit grants the request according to the utilization value, such that the first module or the second module are not activated at the same time.
Owner:MEDIATEK INC
Network failure detection method and network failure detection system
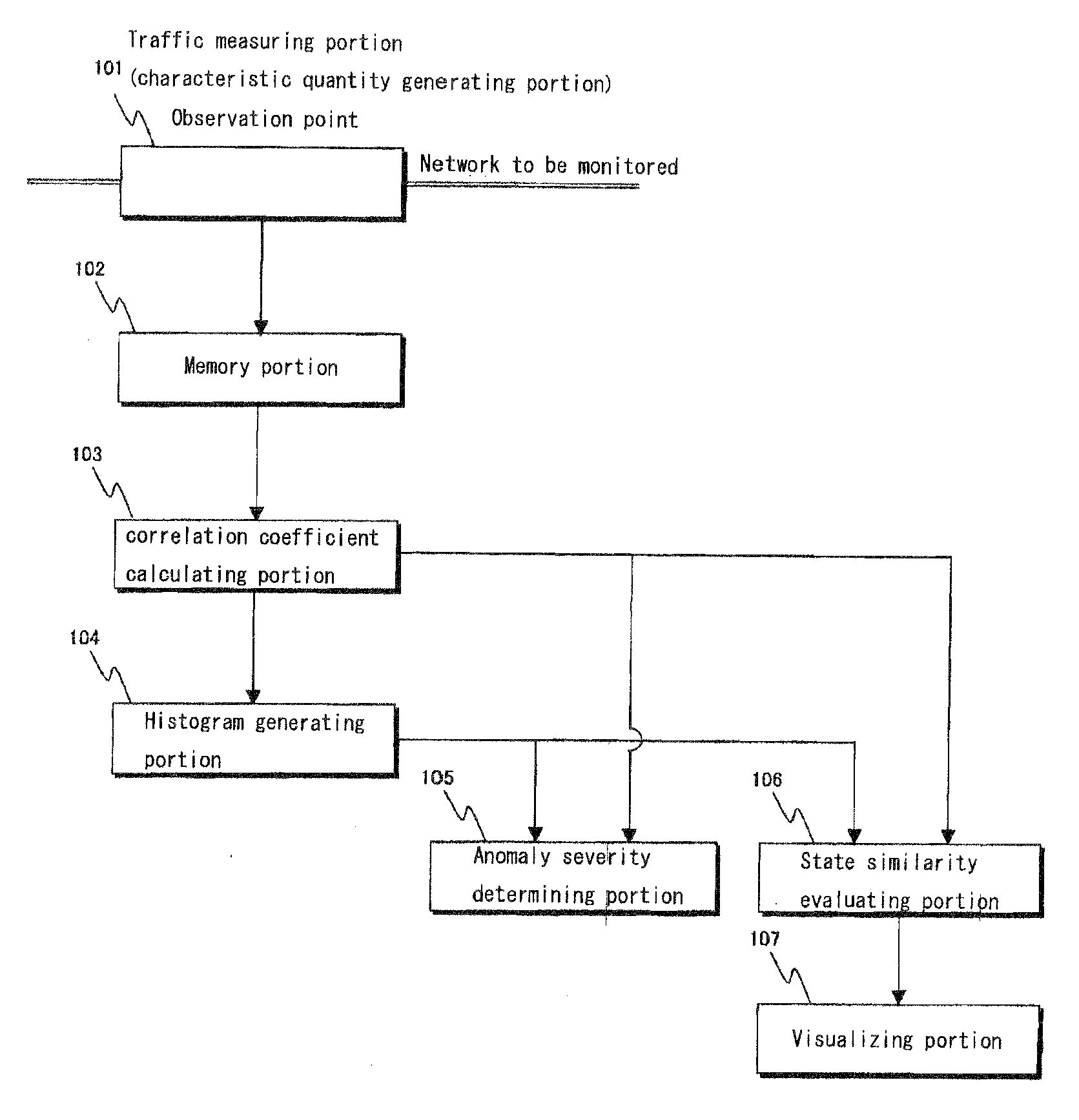
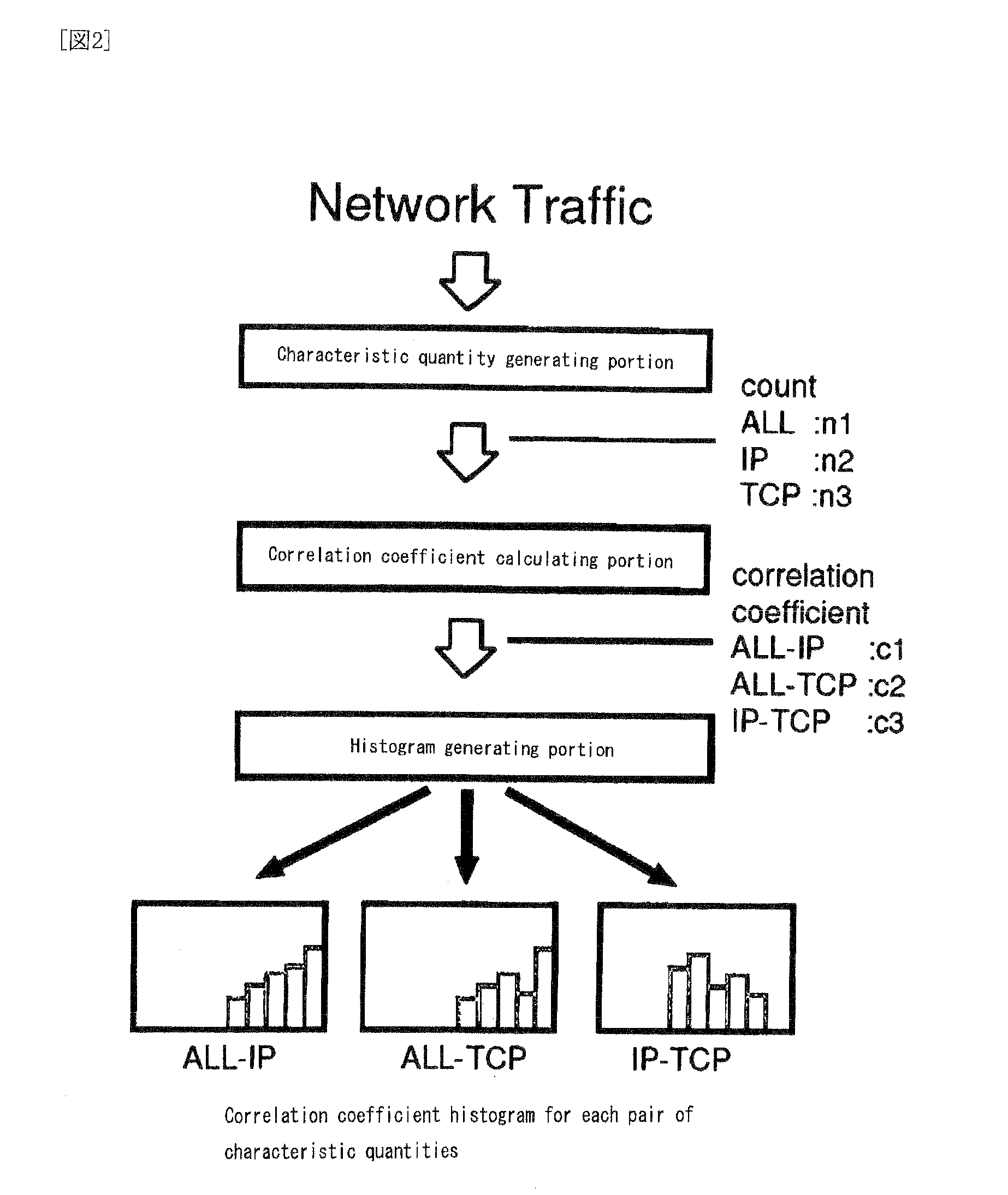
InactiveUS20090265784A1Improve severityGood estimateMemory loss protectionUnauthorized memory use protectionCorrelation coefficientHistogram
A system provides definitions of network states, and identifies a cause for the anomaly upon detection. A traffic measuring portion (characteristic quantity generating portion) counts the number of packets / time slot classified by traffic type with respect to network traffic, generating a characteristic quantity; a memory portion stores information about the characteristic quantity; a portion calculates correlation coefficients between each pair of characteristic quantities classified by traffic type; a portion generates a histogram from correlation coefficients; a portion for determining the severity of an anomaly based on the histogram; a portion evaluates the similarity of an anomaly of interest to a reference anomaly using the occurrence probabilities of correlation coefficients; and a portion assigns a color to each pixel according to its occurrence probability value, generating an n×n picture. Visualization of network state is achieved using probability distribution vectors derived from correlation coefficients obtained from each characteristic quantities pair.
Owner:TOHOKU UNIV
Packet Filter Optimization For Network Interfaces
A method and apparatus to reduce the transaction overhead involved with packet I / O on a host bus without sacrificing the latency of packets of important traffic types is described. This involves determining whether a packet is to be aggregated in response to receiving the packet in a receive buffer. If it is determined that the packet should not be aggregated, a host system may be interrupted to indicate availability of the received packet. Subsequently, the packet may be forwarded to an interrupted system via a local bus directly from a receiving buffer without being stored in a local storage. If it is determined that a packet is to be aggregated, it may be stored in a queue in local storage. Subsequently, it may be sent to a host system with a group of other frames using a single bus transaction to eliminate overhead.
Owner:APPLE INC
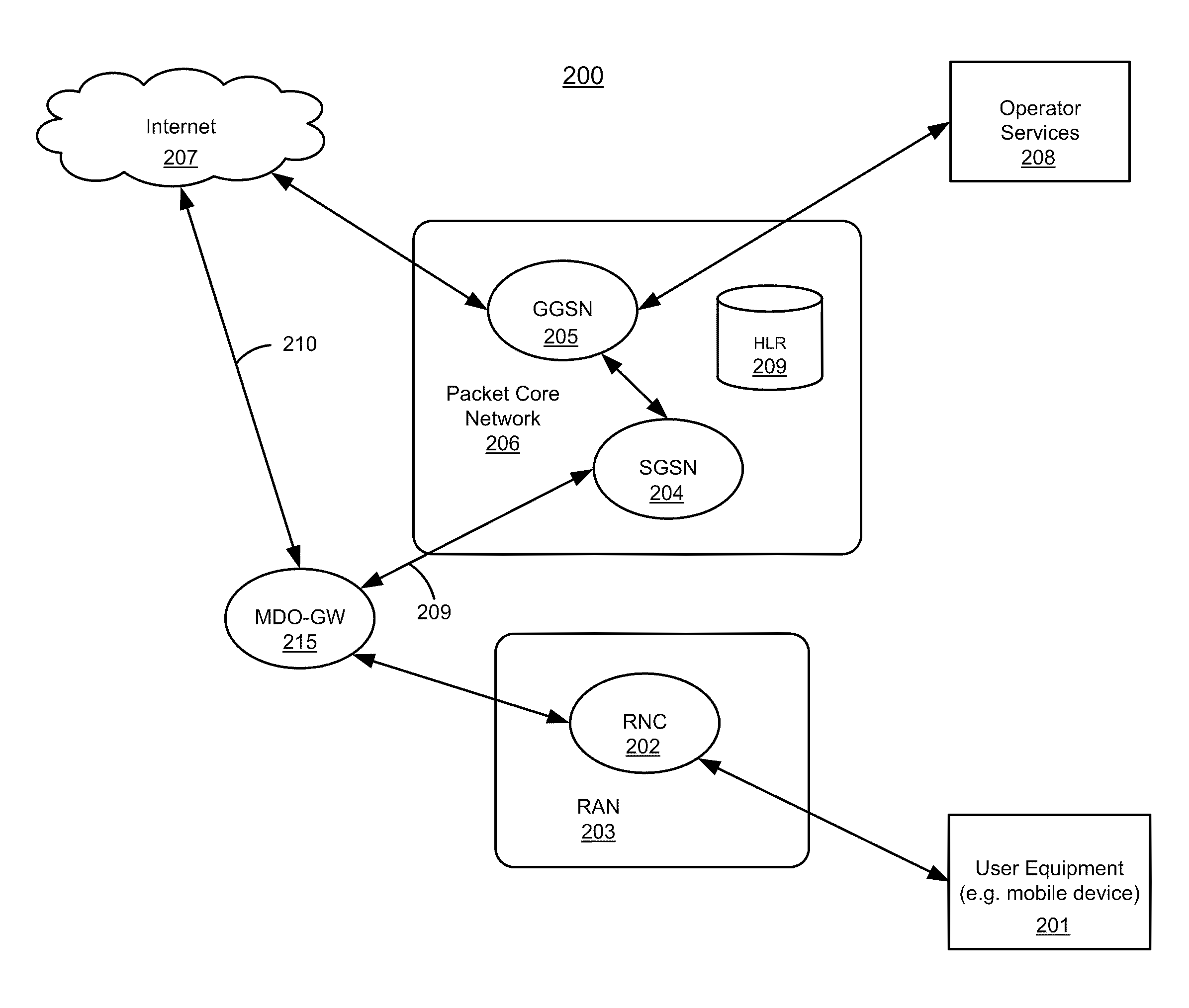
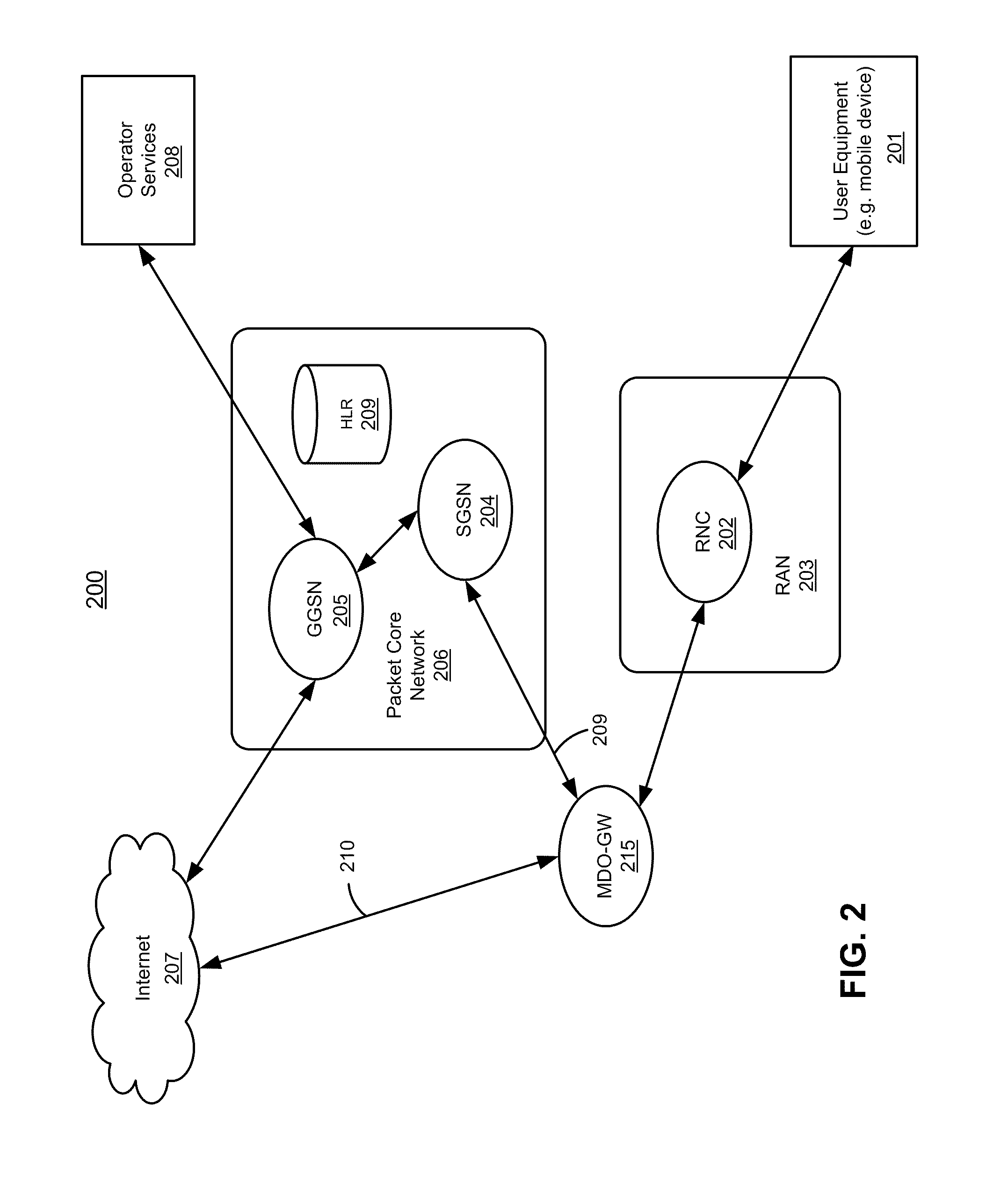
Method and system for selectively bypassing packet core network within a session based on traffic type
According to one aspect of the invention, packets of a first type within a first data flow are routed to a destination through a packet core network. In response to a detection that packets of a second type are to be routed while routing the first data flow, a second data flow is created which is a sub-flow of the first data flow. Packets of the second type are routed via the second data flow to the destination without traversing the packet core network, while packets of the first type are routed via the first data flow traversing the packet core network.
Owner:MAVENIR SYSTEMS
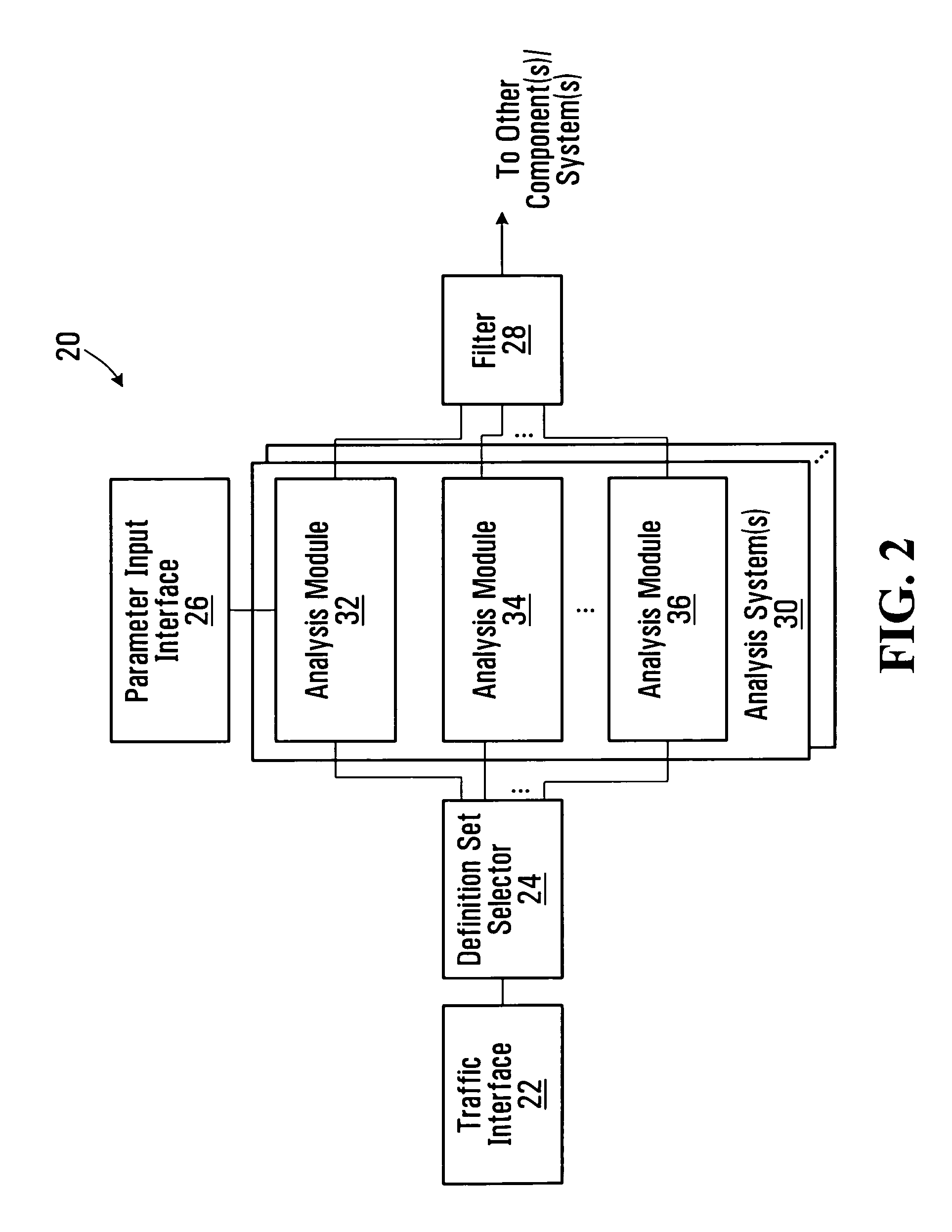
Communication traffic type determination devices and methods
ActiveUS7609630B2Accurately verifying packetsError preventionTransmission systemsTraffic capacityDistributed computing
Communication traffic type determination devices and methods are disclosed. A received block of communication traffic is concurrently analyzed relative to multiple traffic type definitions, and indications of whether the received block of communication traffic conforms to the traffic type definitions are provided. Concurrent analysis of the same traffic block relative to different traffic type definitions can reduce the amount of time that might otherwise be involved in determining a type of the traffic block. Evaluation of traffic against multiple definitions may also allow traffic to be classified or verified more specifically than would be possible based solely on explicit type indications provided in traffic overhead.
Owner:RPX CORP
Systems and methods for policy based routing for multiple next hops
ActiveUS9178805B2Error preventionFrequency-division multiplex detailsTraffic characteristicIp address
Owner:CITRIX SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com