Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
327 results about "Network strategy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
First of all, network strategy is grounded at a fundamental level in creating (strategic) connectivity, by building linkages and trust between key stakeholders and perhaps unusual bedfellows. This can be done by convening people ; sharing stories, data and other forms of information; co-creating knowledge;
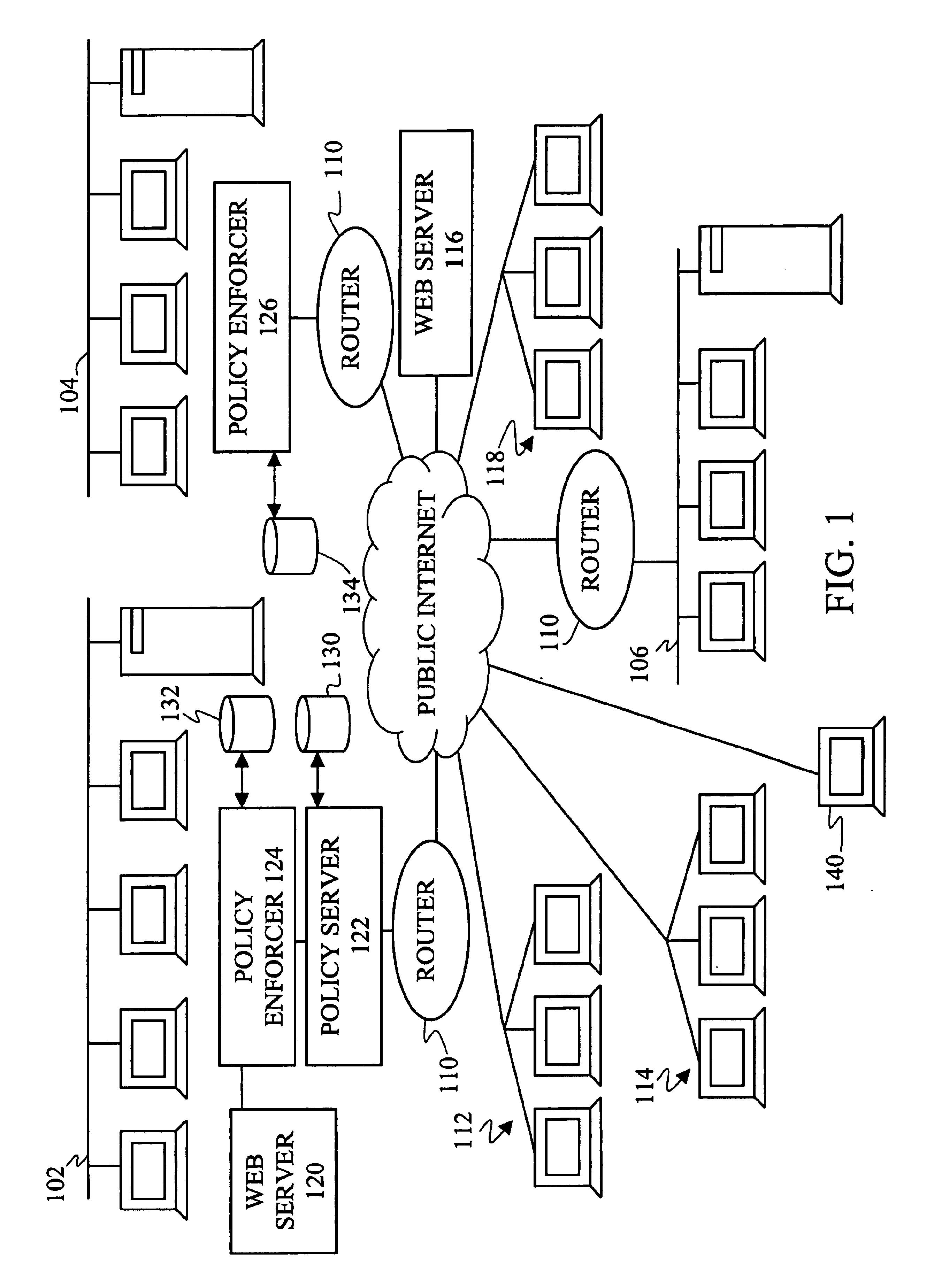
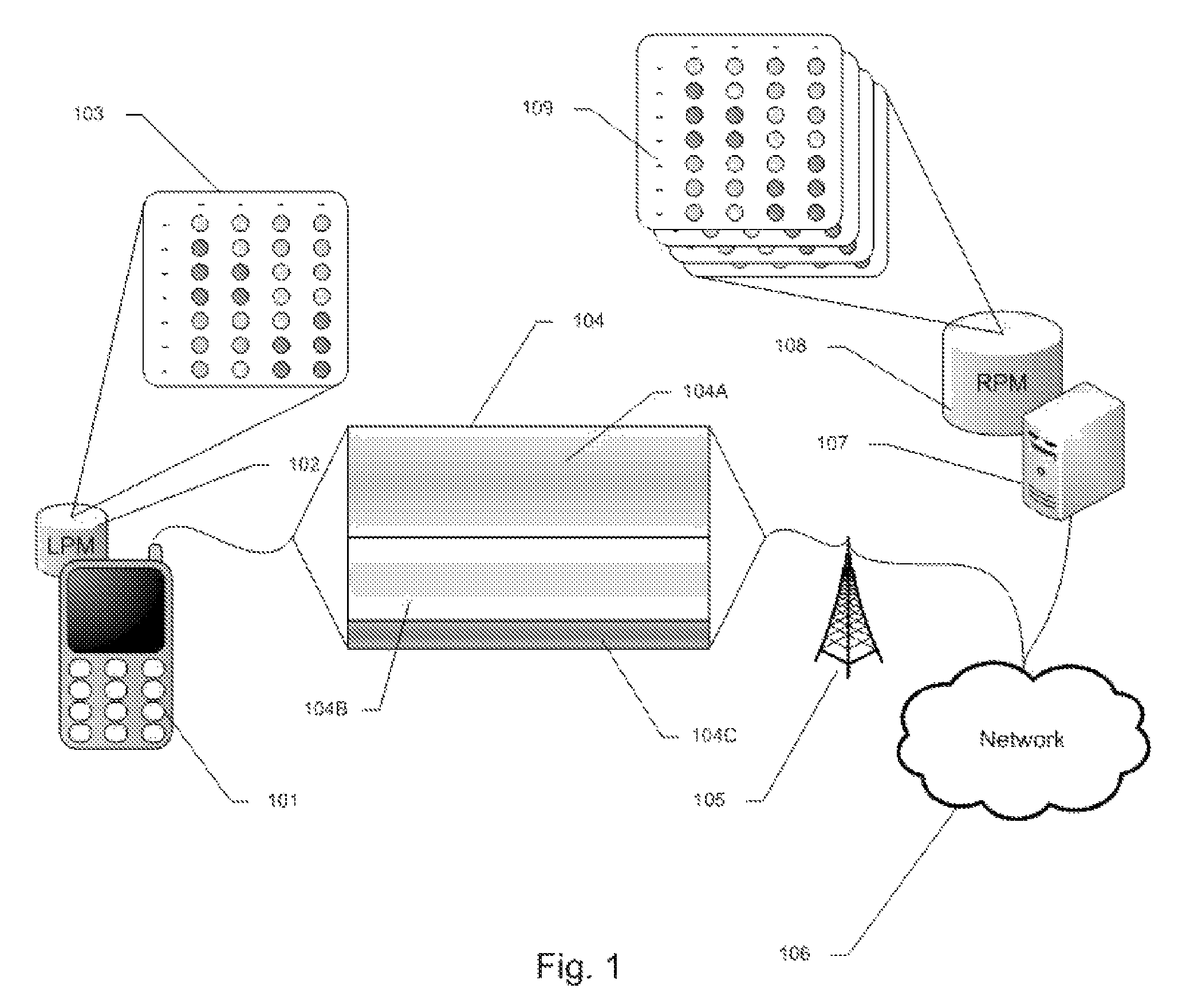
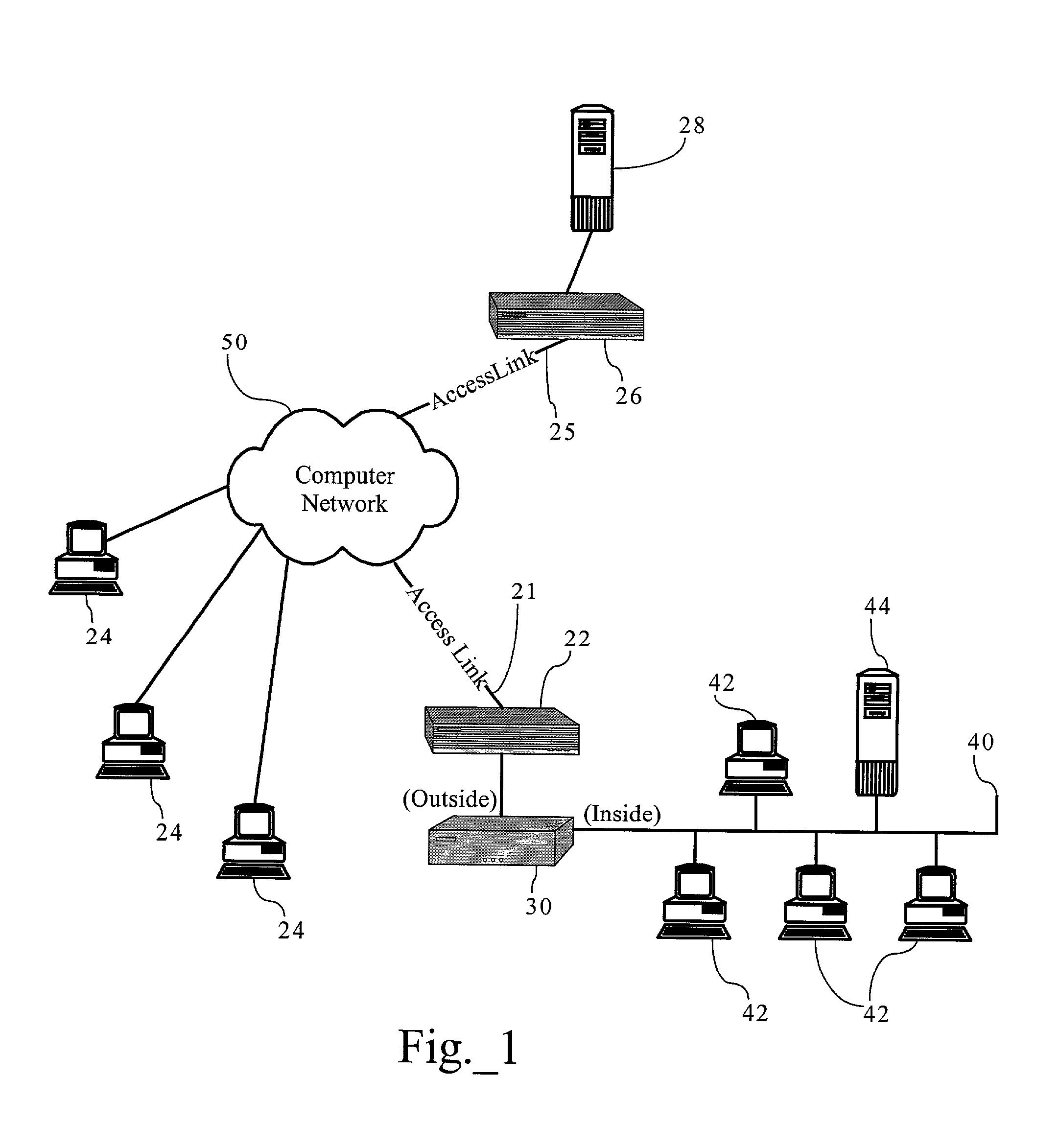
Network operating system for managing and securing networks
ActiveUS20090138577A1Reduced power modeDigital computer detailsTransmissionTraffic capacityAuto-configuration
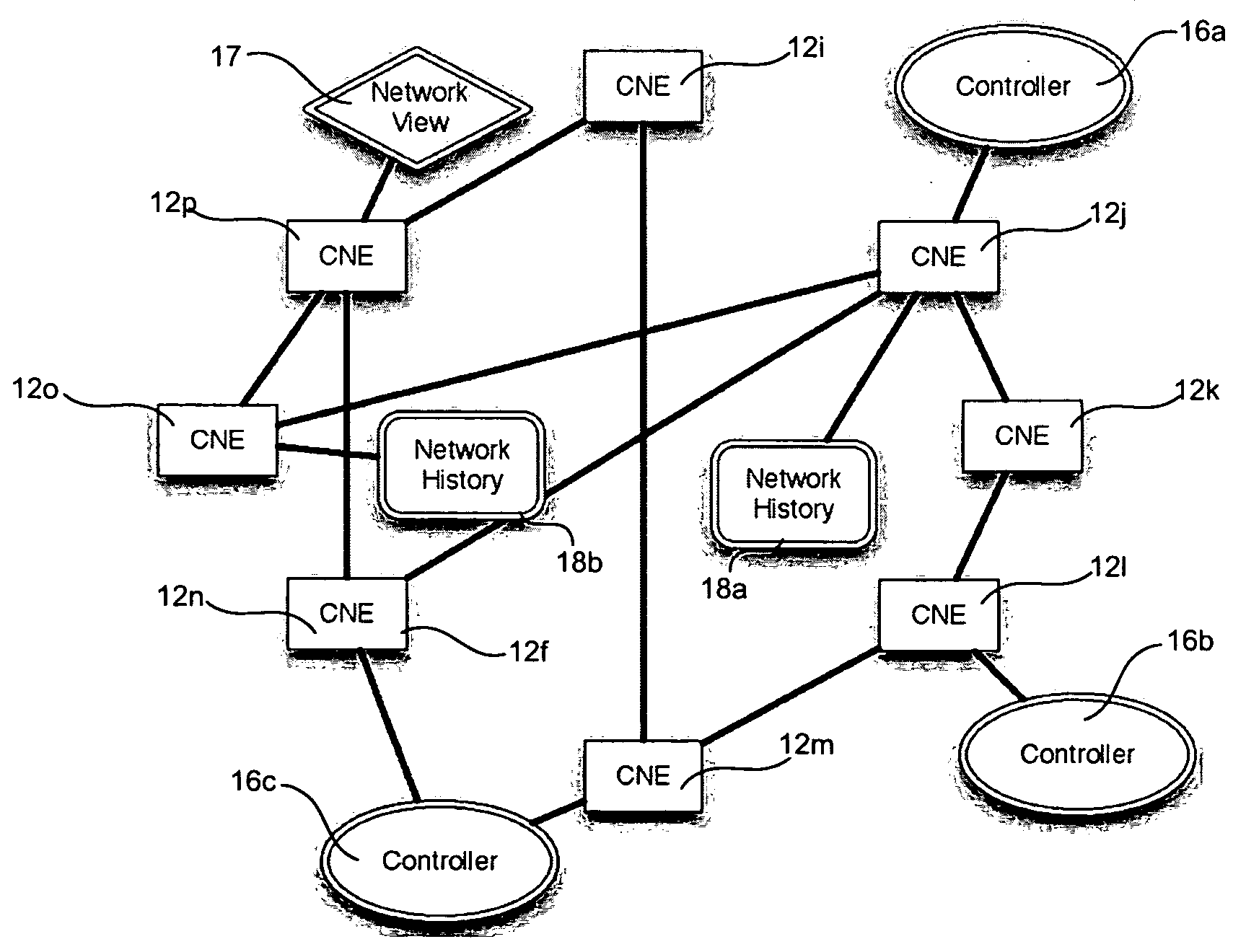
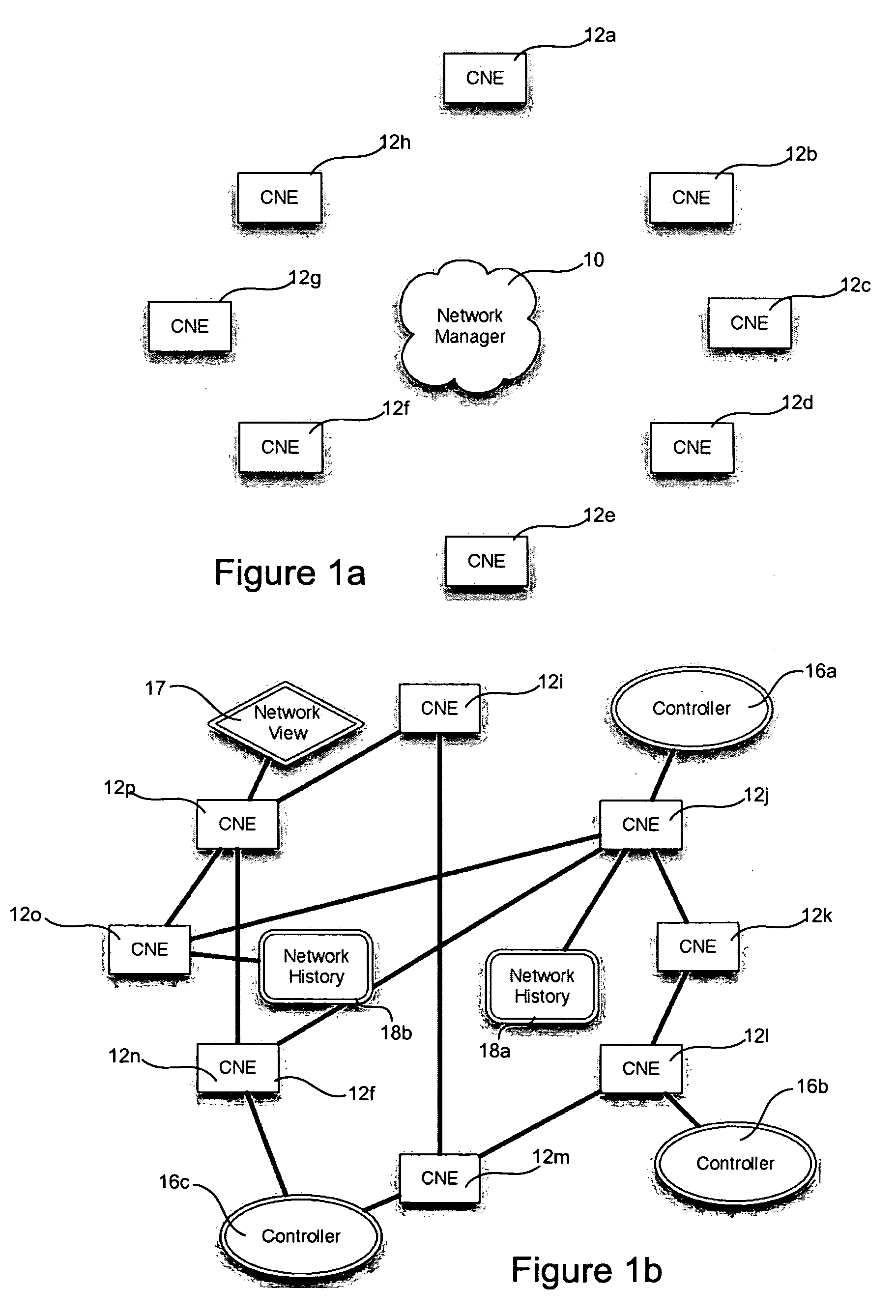
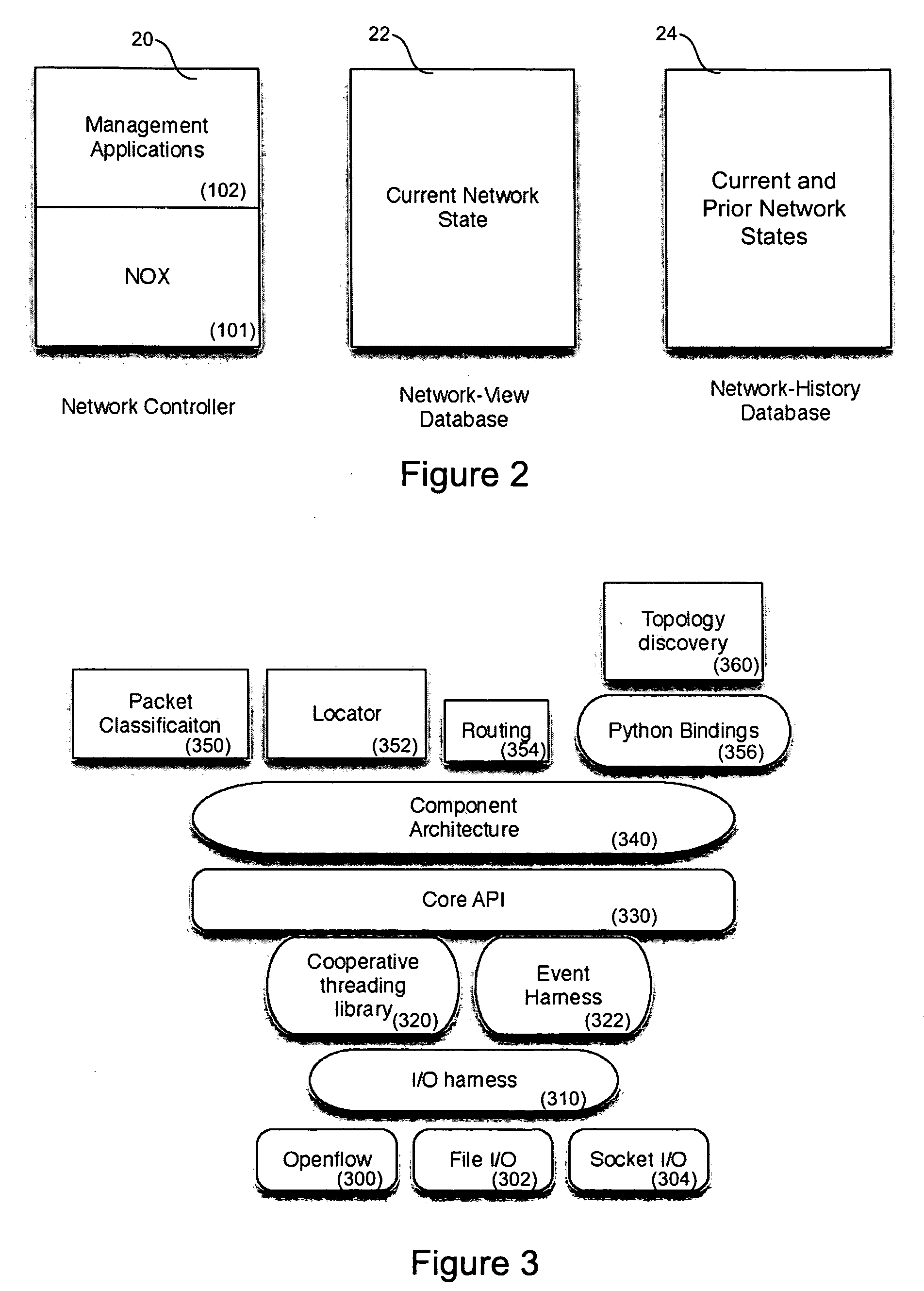
Systems and methods for managing a network are described. A view of current state of the network is maintained where the current state of the network characterizes network topology and network constituents, including network entities and network elements residing in or on the network. Events are announced that correspond to changes in the state of the network and one or more network elements can be configured accordingly. Methods for managing network traffic are described that ensure forwarding and other actions taken by network elements implement globally declared network policy and refer to high-level names, independently of network topology and the location of network constituents. Methods for discovering network constituents are described, whereby are automatically configured. Routing may be performed using ACL and packets can be intercepted to permit host to continue in sleep mode. The methods are applicable to virtual environments.
Owner:NICIRA
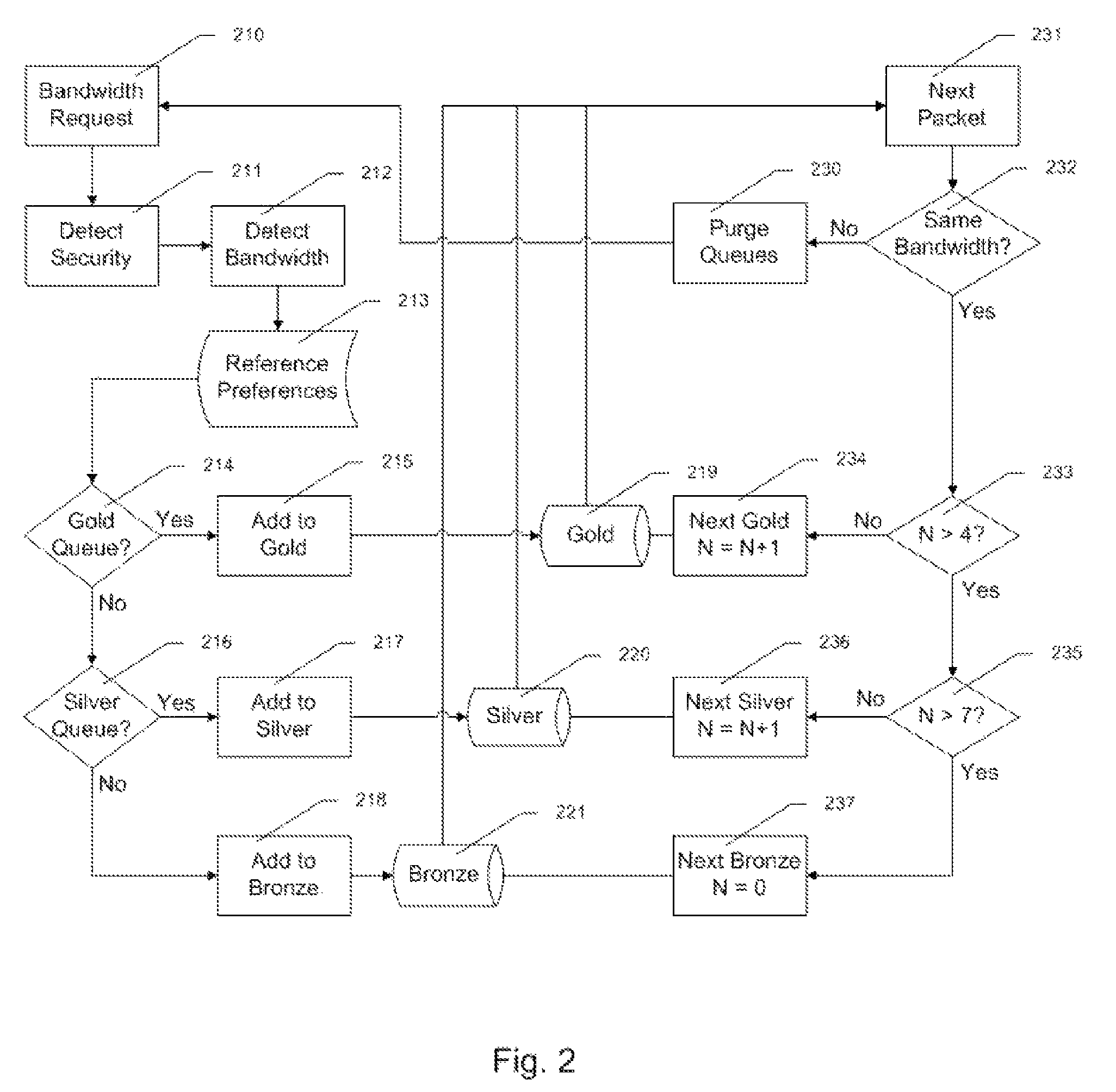
Method and apparatus for defining and implementing high-level quality of service policies in computer networks
InactiveUS7185073B1Multiple digital computer combinationsData switching networksNetwork strategyNetwork administrator
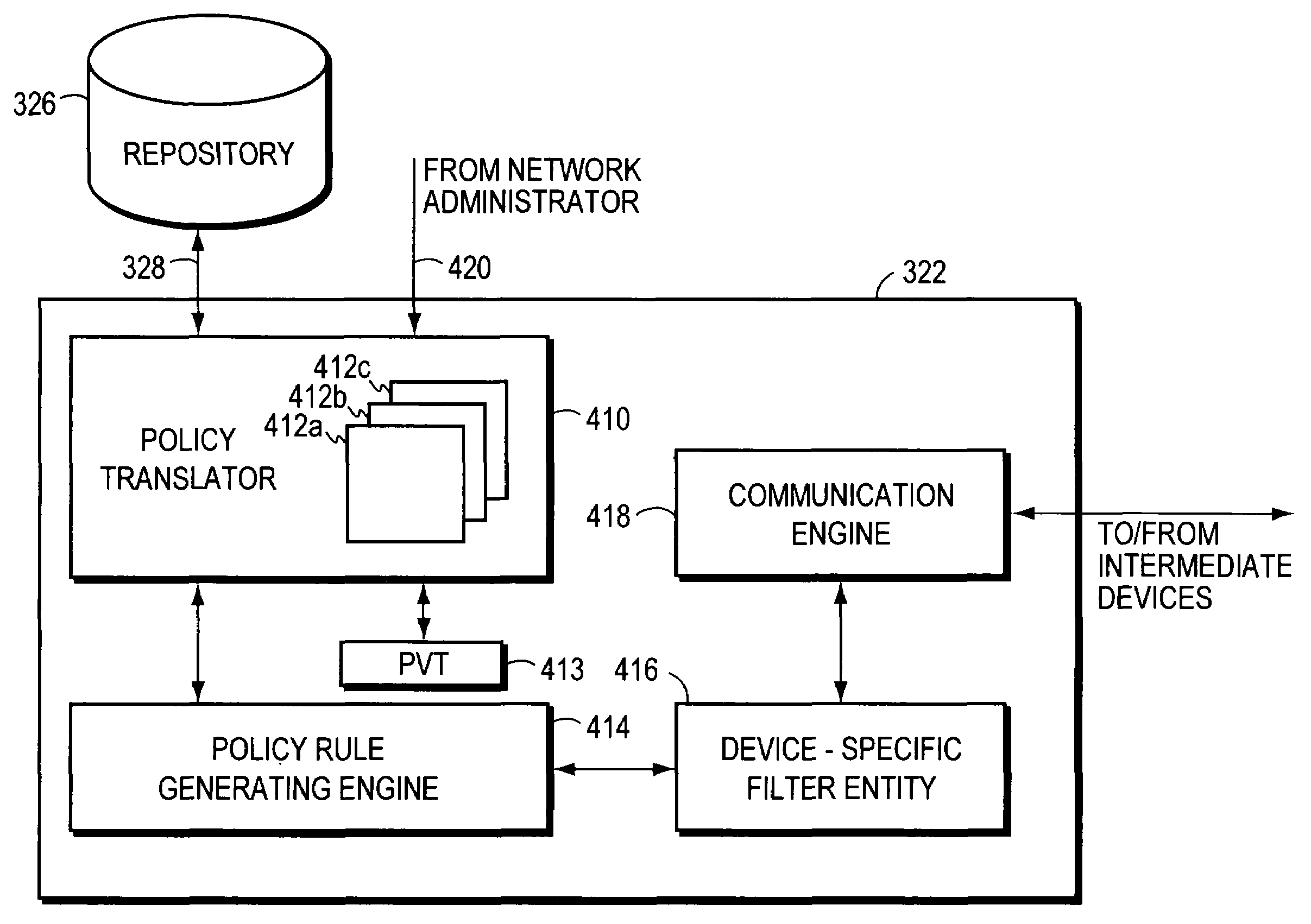
A computer network having multiple, dissimilar network devices includes a system for implementing high-level, network policies. The high-level policies, which are generally device-independent, are translated by one or more policy servers into a set of rules that can be put into effect by specific network devices. Preferably, a network administrator selects an overall traffic template for a given domain and may assign various applications and / or users to the corresponding traffic types of the template. Location-specific policies may also be established by the network administrator. The policy server translates the high-level policies inherent in the selected traffic template and location-specific policies into a set of rules, which may include one or more access control lists, and may combine several related rules into a single transaction. Intermediate network devices, which may have one or more roles assigned to their interfaces, are configured to request traffic management information from the policy server which replies with a particular set of transactions and rules. The rules, which may correspond to the particular roles assigned to the interfaces, are then utilized by the intermediate devices to configure their particular services and traffic management mechanisms. Other rules are utilized by the intermediate devices to classify packets with a particular priority and / or service value and to treat classified packets in a particular manner so as to realize the selected high-level policies within the domain.
Owner:CISCO TECH INC
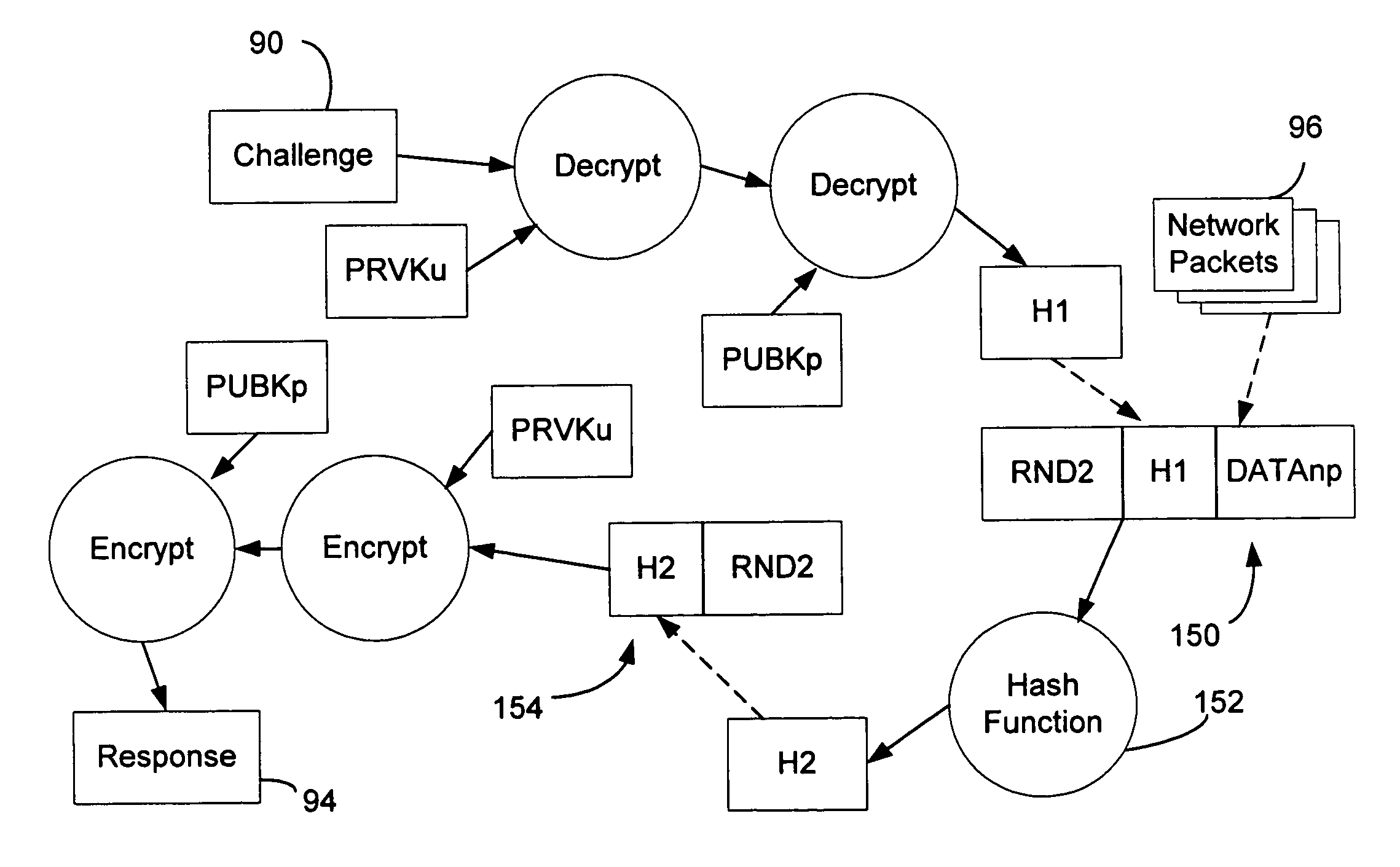
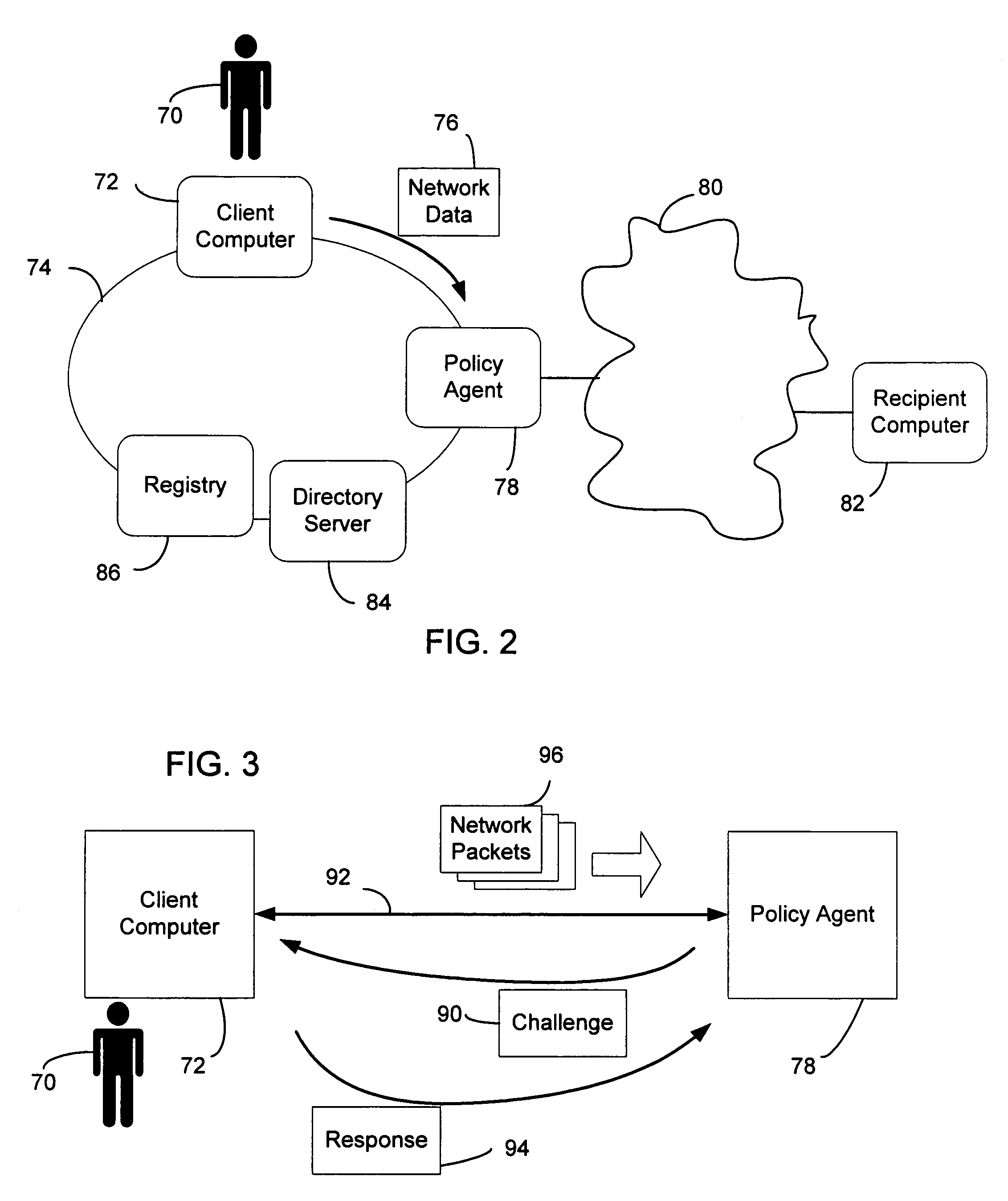
System and method of user authentication for network communication through a policy agent
InactiveUS7039713B1Digital data processing detailsComputer security arrangementsData connectionUser authentication
A policy agent of a network performs an out-of-band user authentication process to verify the identity of a user of a client computer and associates the network data received from the client computer with the user. When the client computer initiates a network data connection to or through the policy agent, the policy agent sends an encrypted challenge to the client computer. The challenge is encrypted with a private key of the policy agent. When the client computer receives the challenge, it decrypts the challenge and prepares a message digest value based on the challenge and the network data sent by the user. The message digest value is then encrypted with the private key of the user to form a response, and the response is sent to the policy agent. The policy agent decrypts the response with the public key of the user to obtain the message digest value and calculates a digest value based on the challenge and the received network data. The policy agent then compares the calculated digest value with the decrypted digest value. A match between the two digest values indicates that the user is successfully authenticated and that the received network data are associated with the user. The policy agent may then apply network policies based on the credentials of the authenticated user.
Owner:MICROSOFT TECH LICENSING LLC
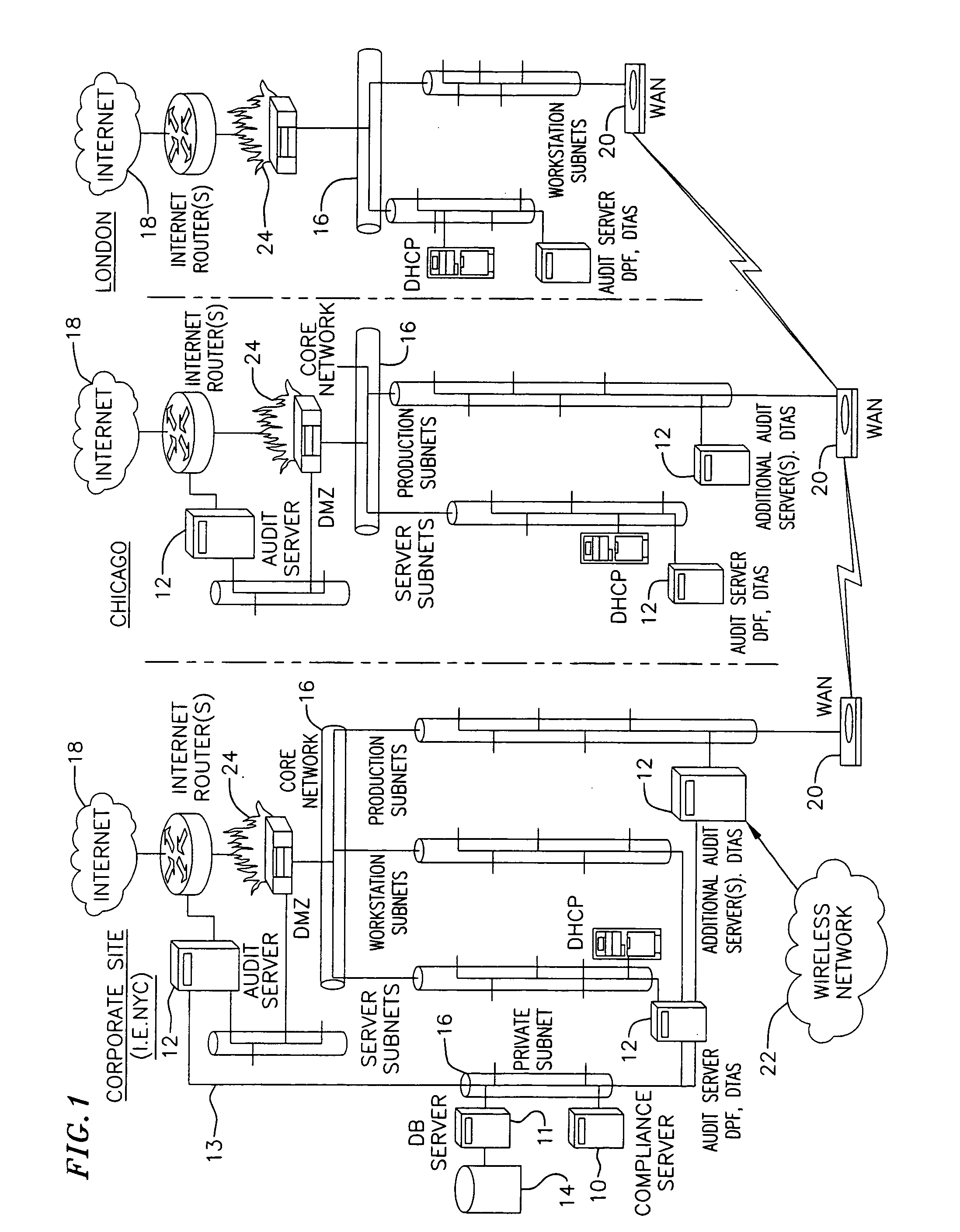
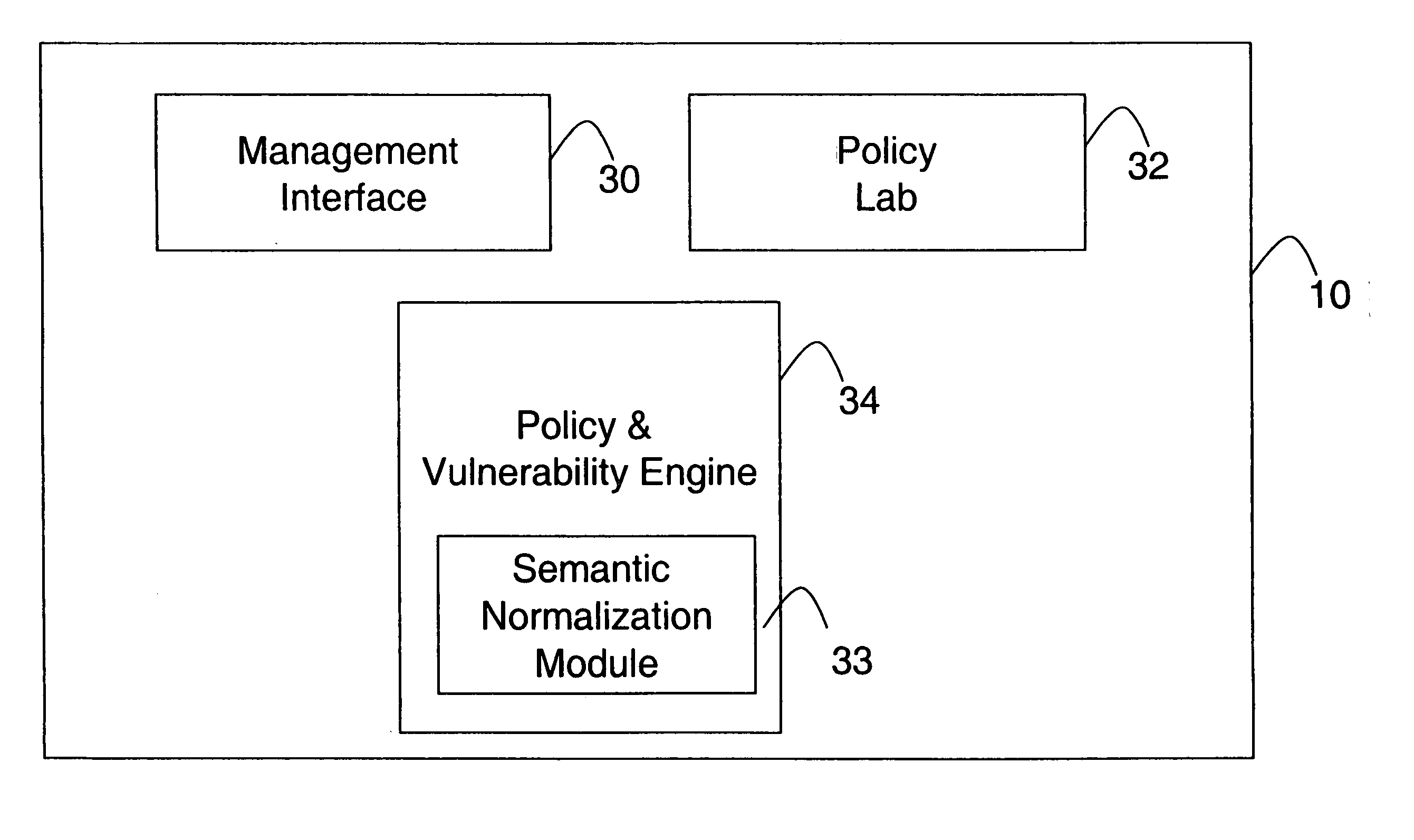
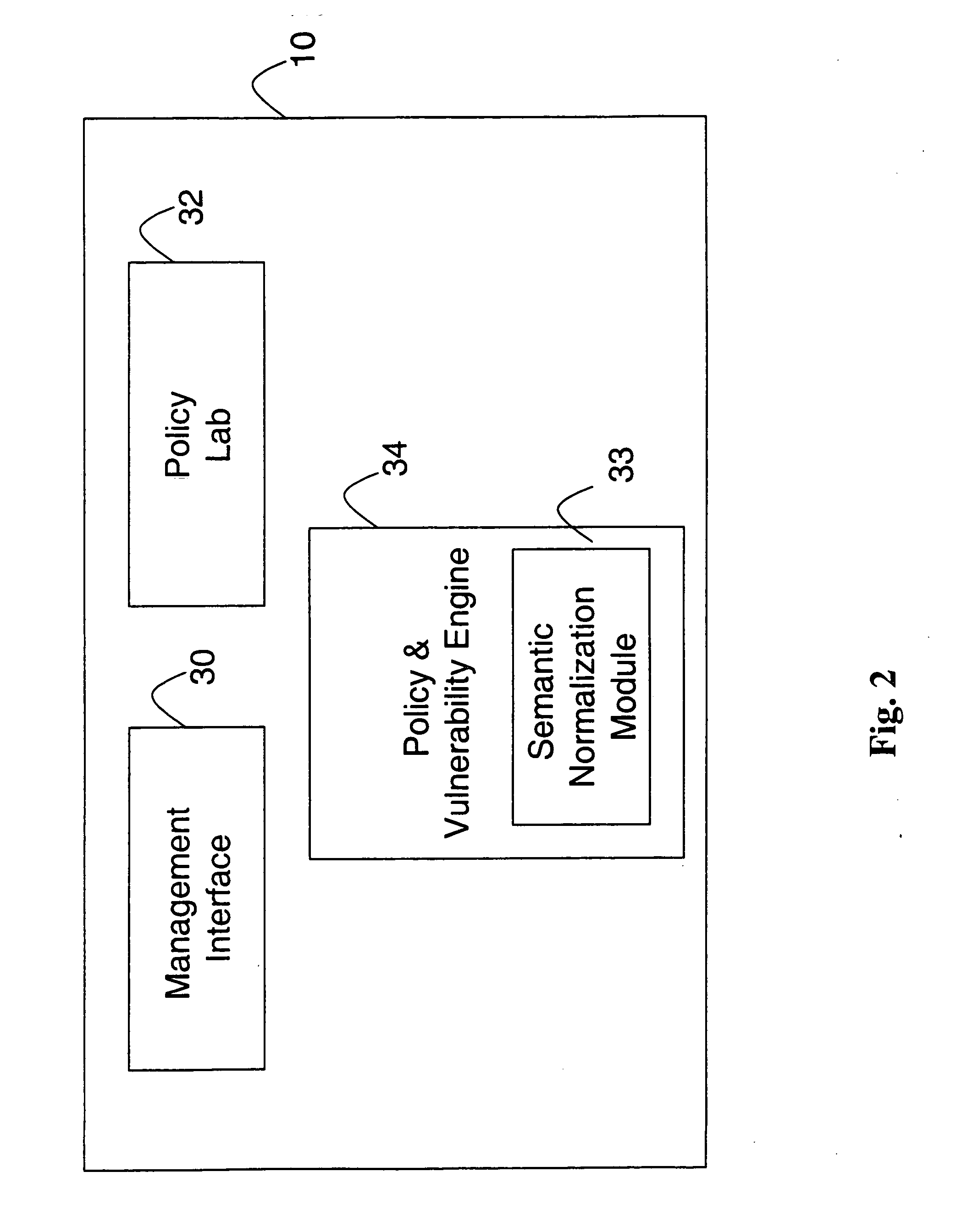
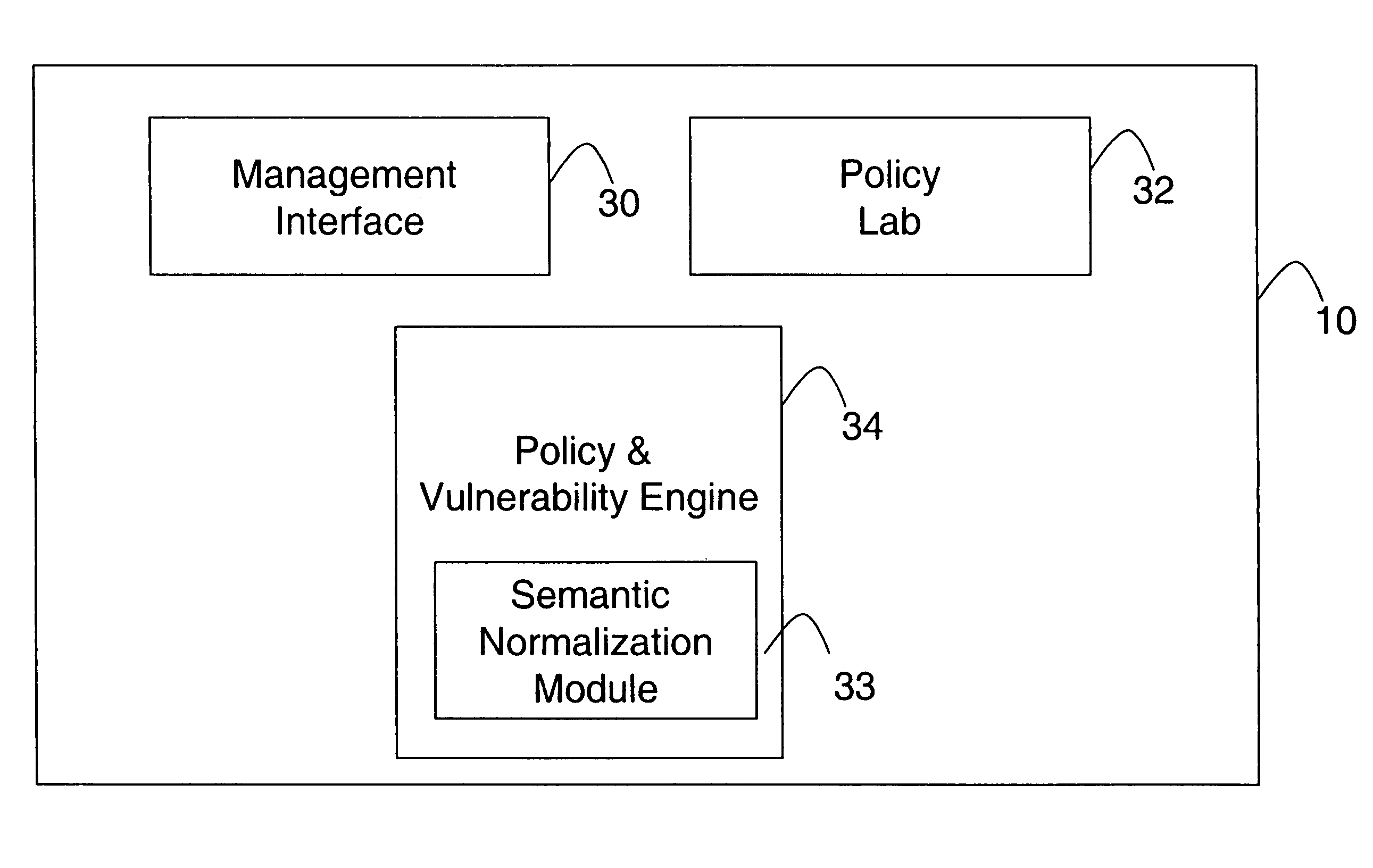
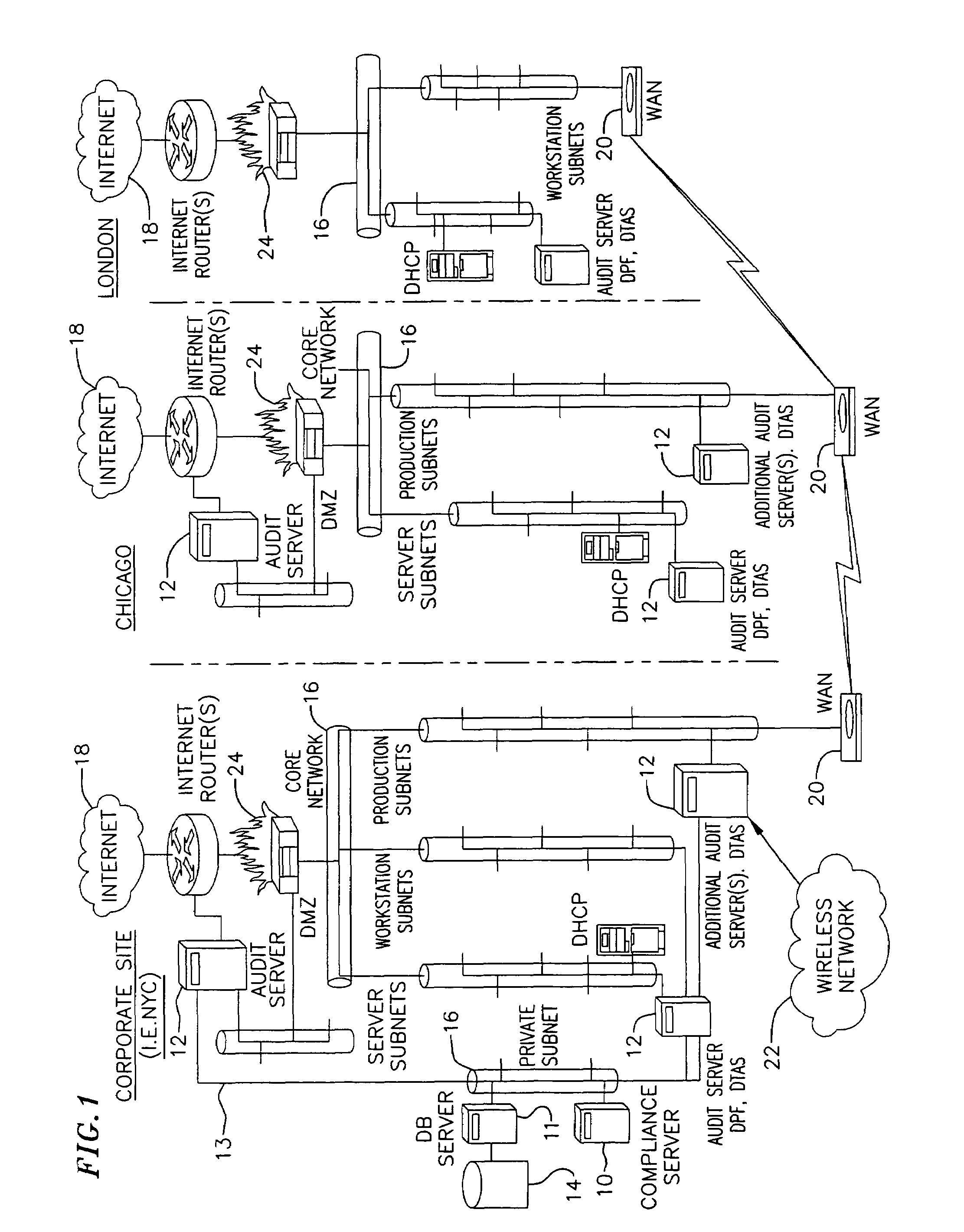
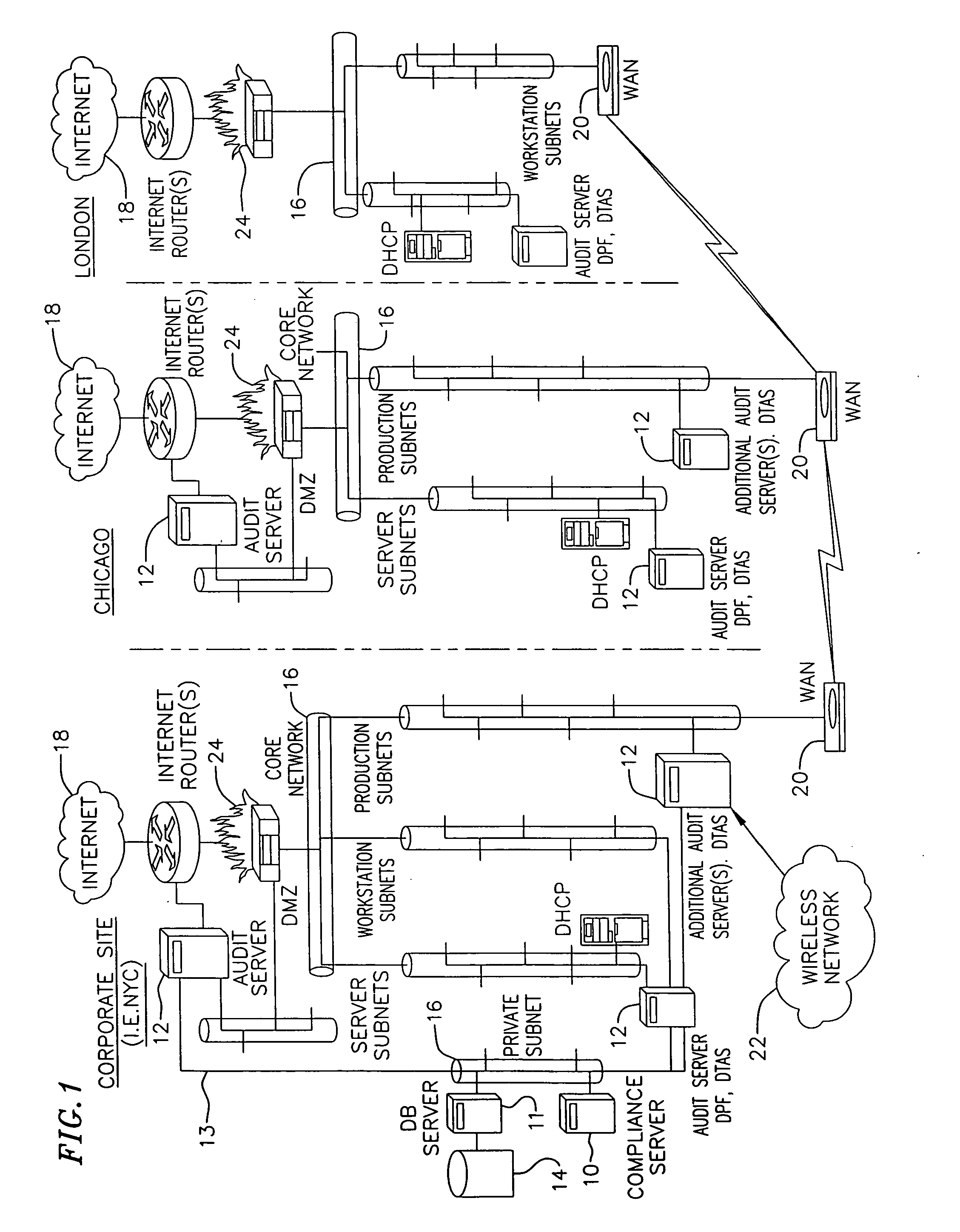
Network audit and policy assurance system
ActiveUS20050257267A1Reduce riskMemory loss protectionError detection/correctionGraphicsGraphical user interface
A prevention-based network auditing system includes a central compliance server generating network policies and configuring audits of the data communications network. The compliance server presents a graphical user interface (GUI) to describe the specific data gathering parameters, policies to be analyzed, and the schedule of analysis. One or more audit servers strategically deployed around the network employ heterogeneous data-gathering tools to gather information about the network in response to the configured audits, and transmit the gathered information to the compliance server. An audit repository stores the gathered information for use by the compliance server for security and regulatory policy assessment, network vulnerability analysis, report generation, and security improvement recommendations.
Owner:MCAFEE LLC
Method and apparatus for network wide policy-based analysis of configurations of devices
ActiveUS7003562B2Traffic controlDigital computer detailsData switching networksNetwork strategyNetwork topology
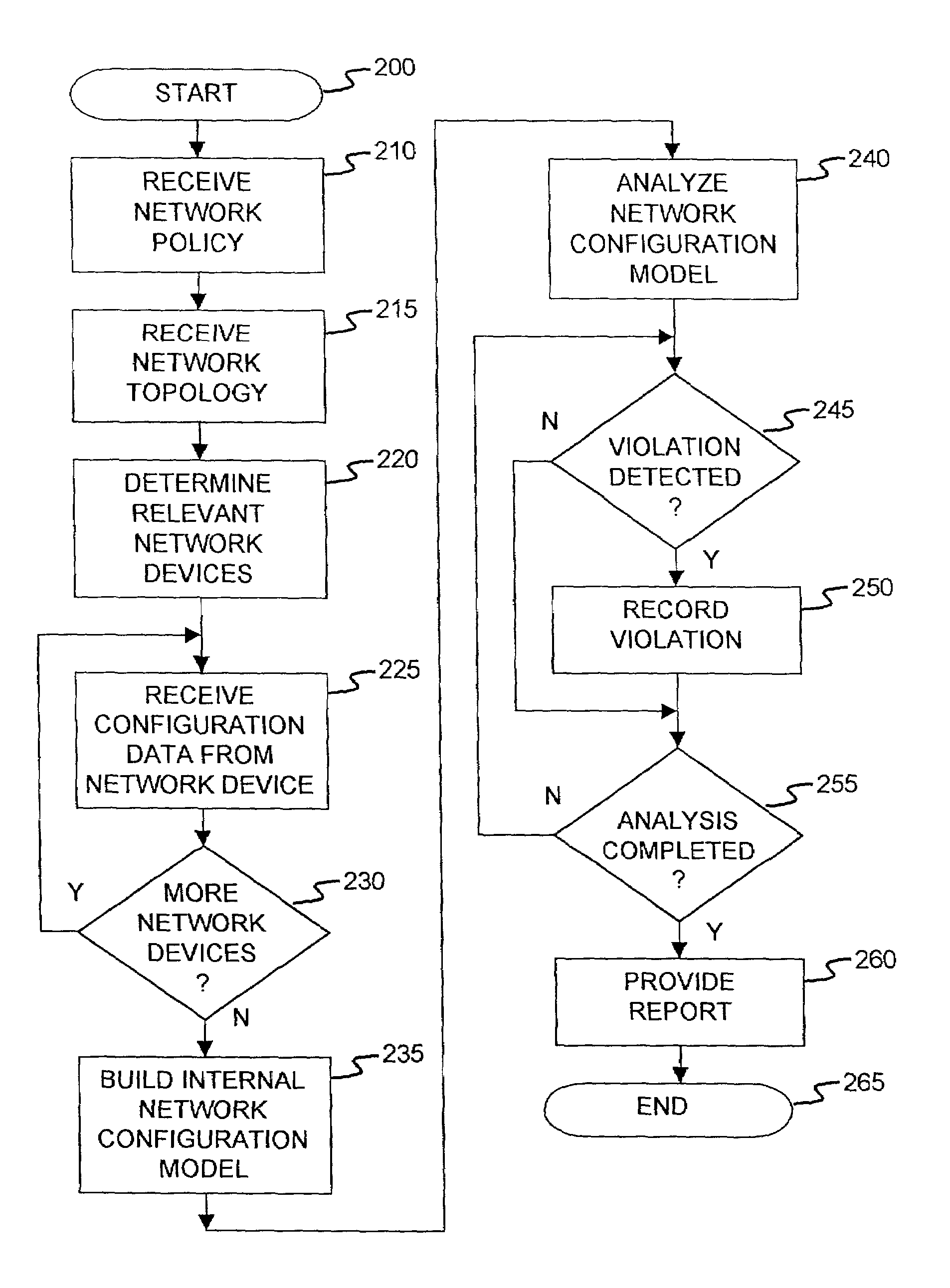
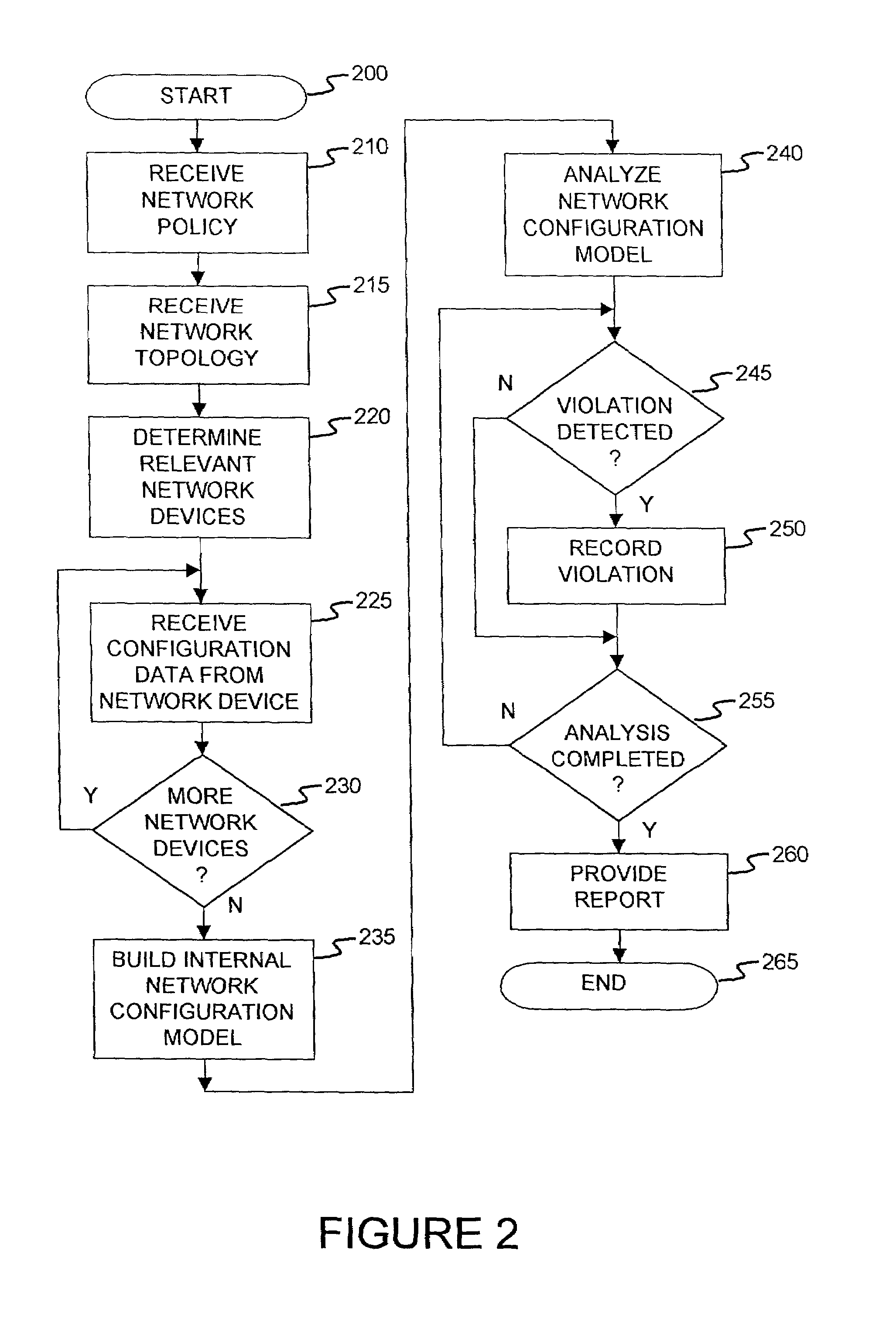
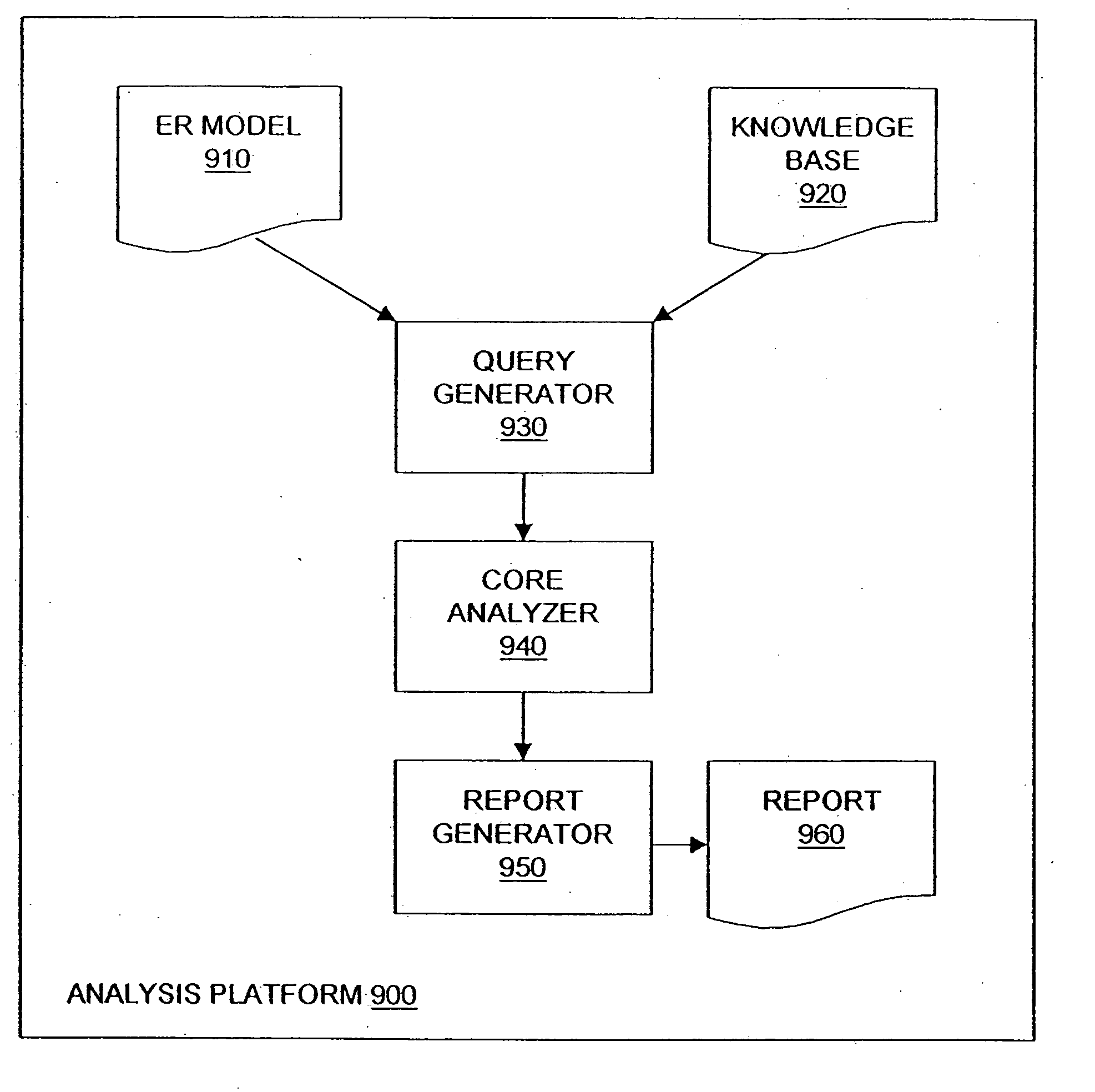
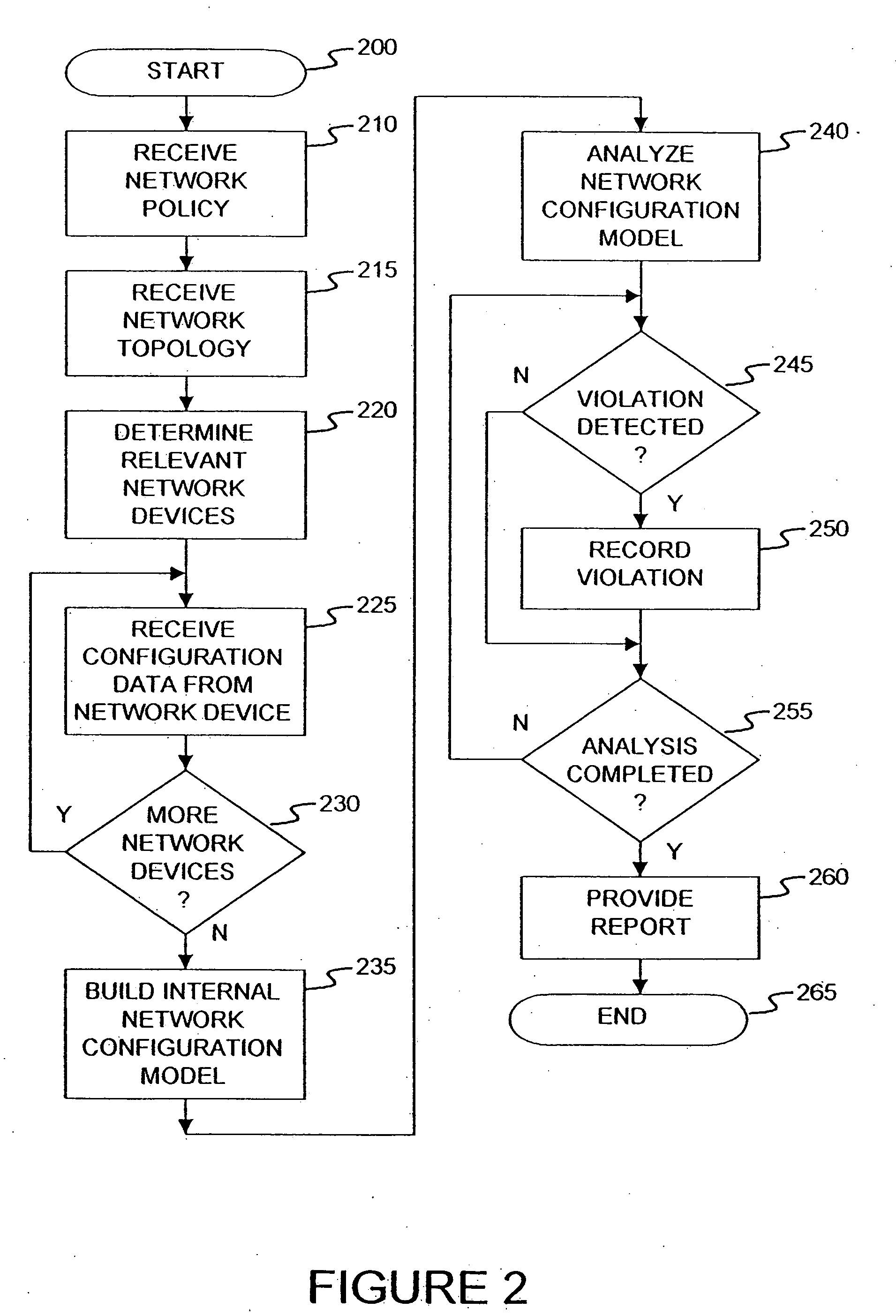
A method and an apparatus for analyzing a network configuration against a corporate network policy and determining violation(s) against the corporate network policy. A report indicating the violation(s) can be generated indicating instances of the violation(s). An analysis platform reads in a network policy. The analysis platform collects configuration files from the relevant network devices in the network and builds up an internal instance of a network configuration model based on the configuration files and the network topology. The analysis platform analyzes this network configuration model according to the network policy and adds an entry to its final report each time that it detects a violation against the network policy in the network configuration model. The data in the entries pinpoints the cause of the deviation(s) from the network policy.
Owner:REDSEAL
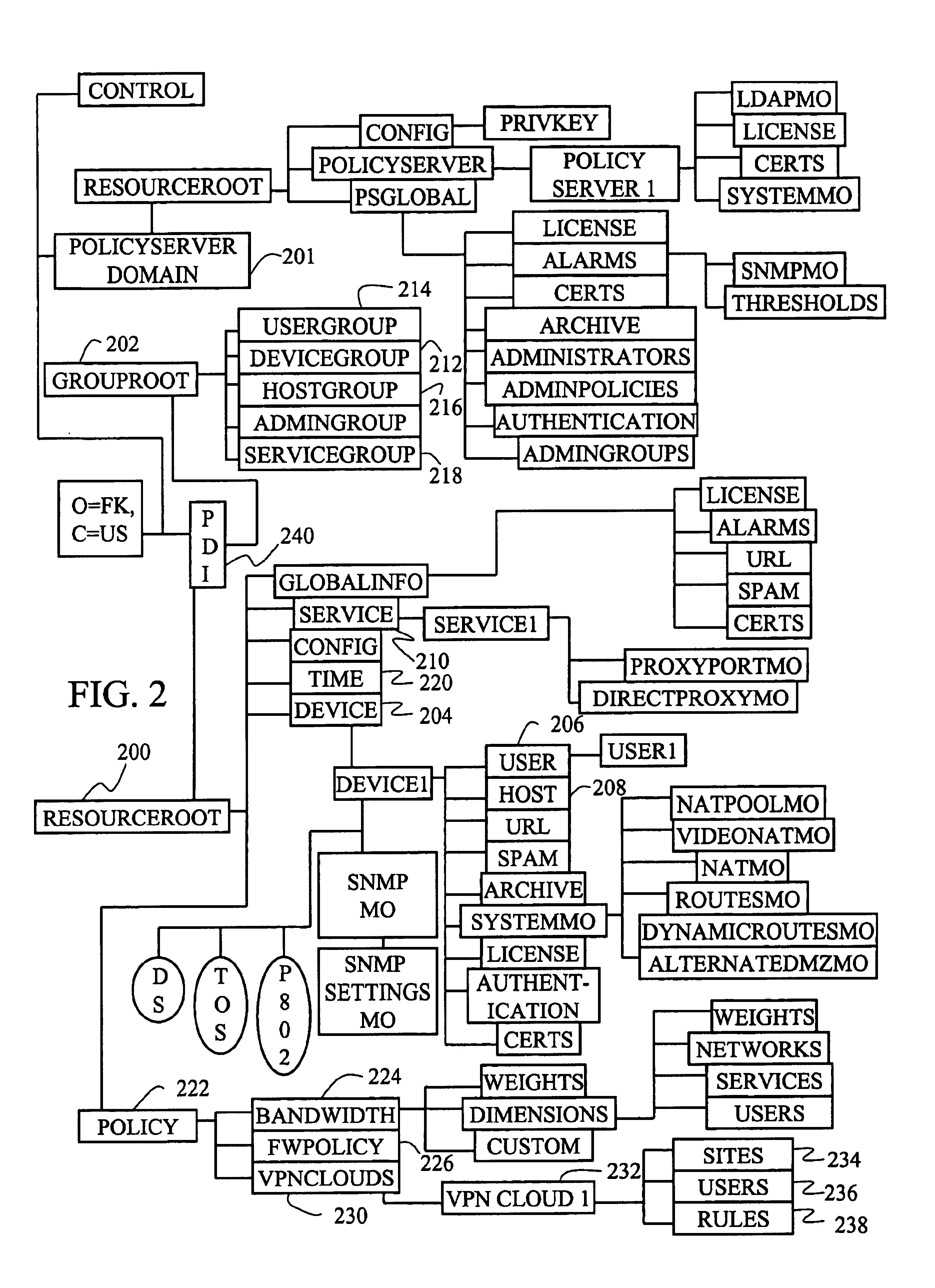
Object model for network policy management
InactiveUS6944183B1Simplified managementEnergy efficient ICTDigital computer detailsNetwork managementAdaptive routing
Owner:ALCATEL-LUCENT USA INC
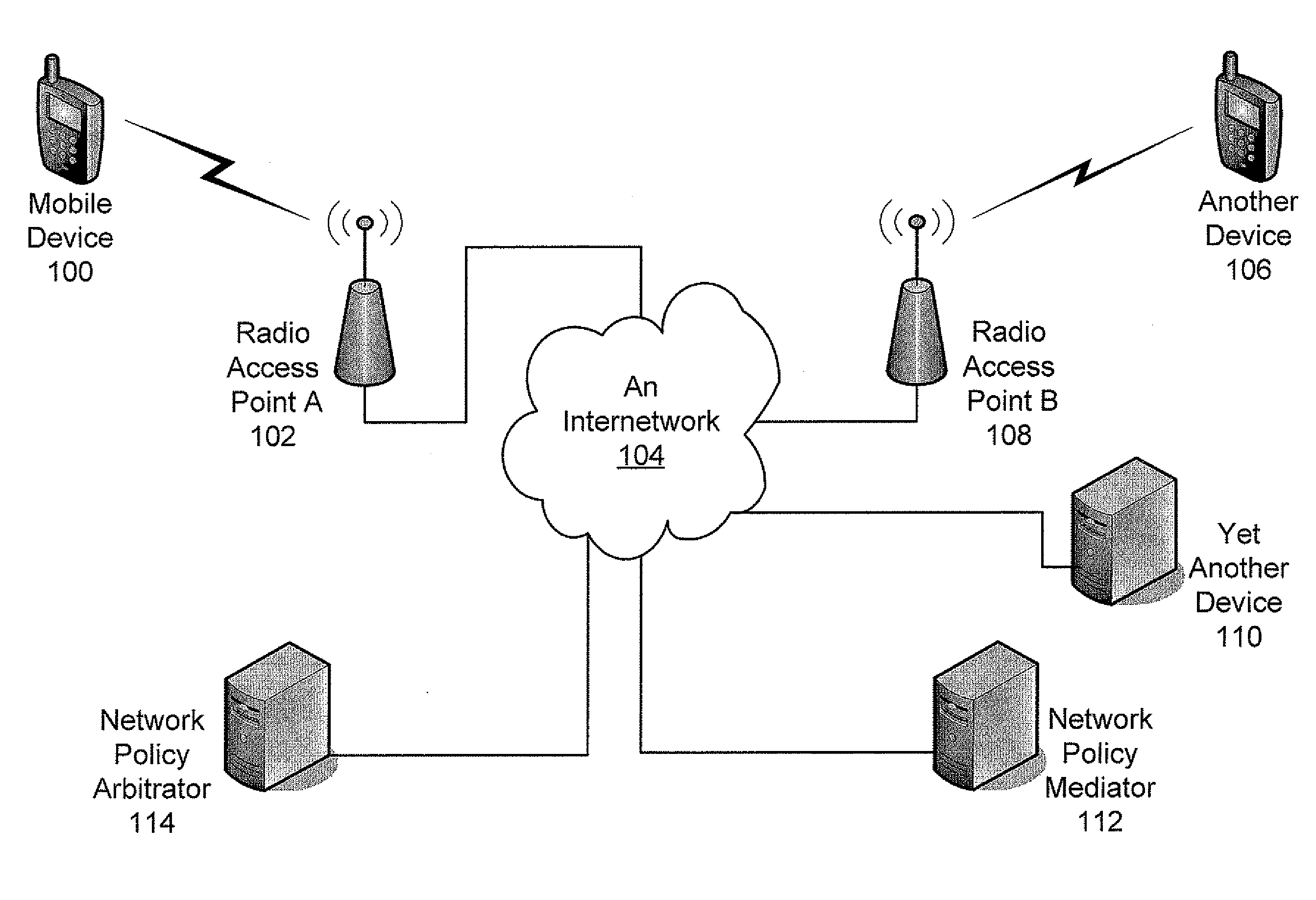
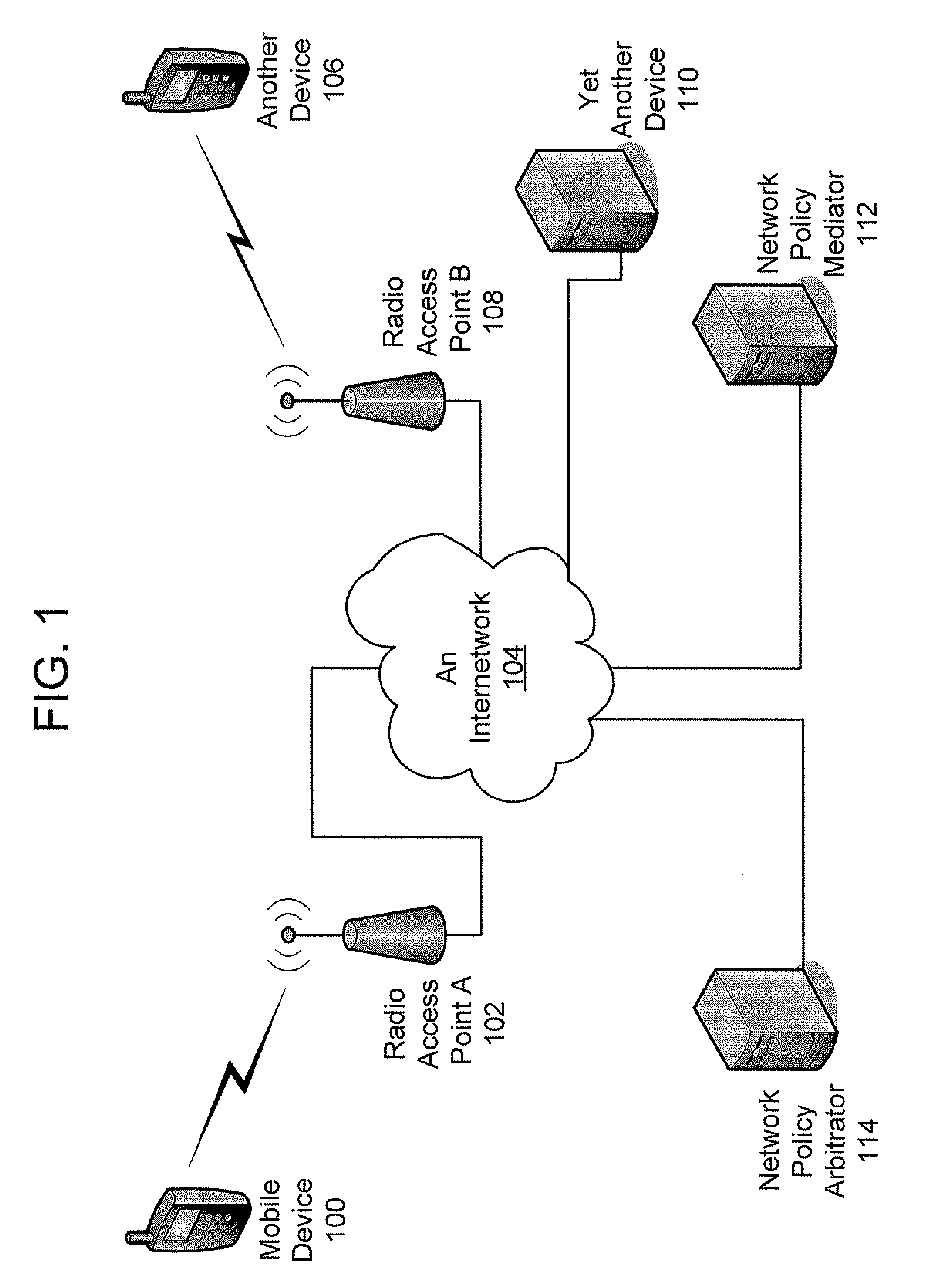
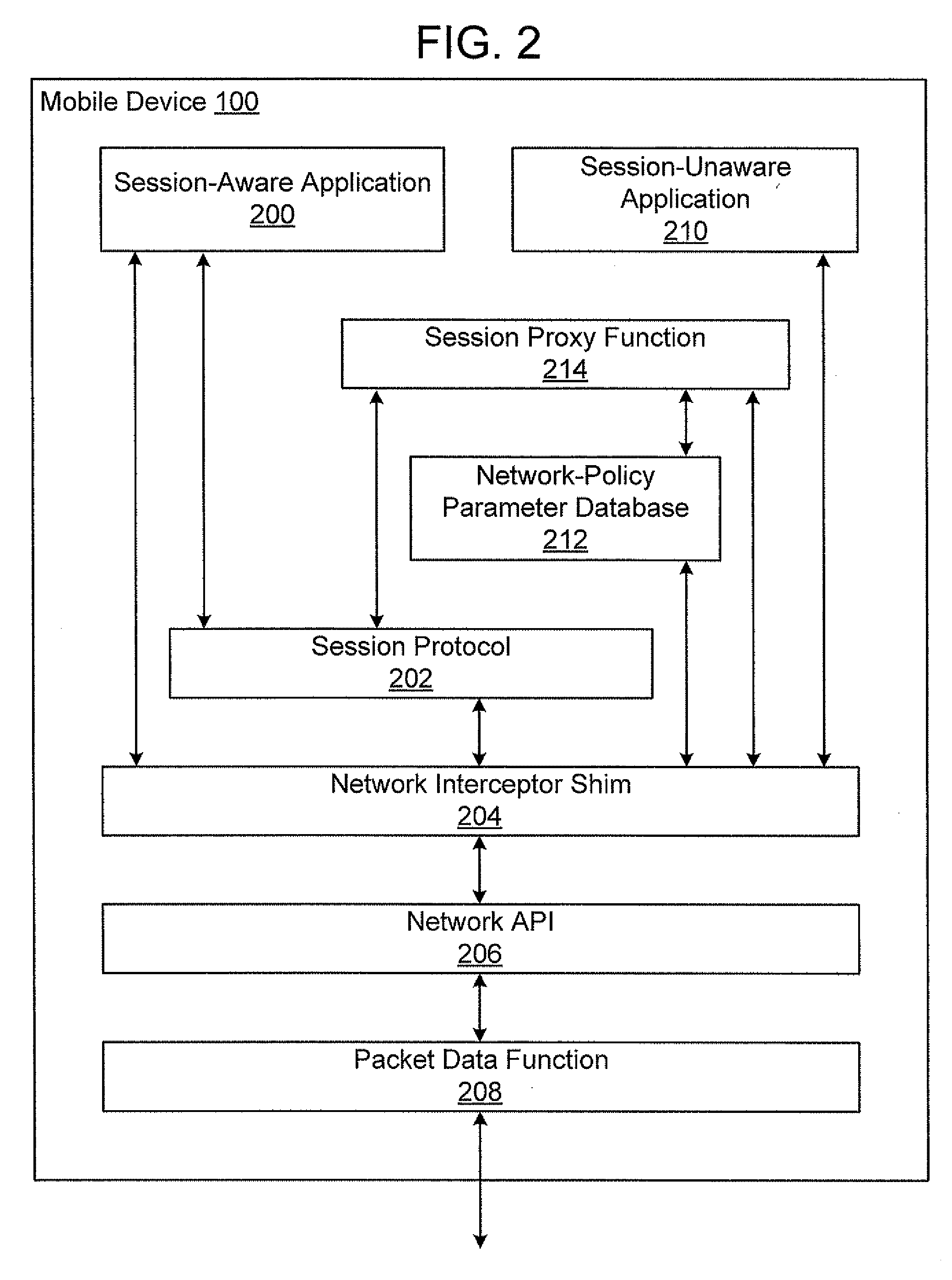
Establishing Network Policy For Session-Unaware Mobile-Device Applications
ActiveUS20080162704A1Network traffic/resource managementAssess restrictionNetworking protocolApplication software
The present invention provides the benefits of negotiated network resources to session-unaware applications. When a session-unaware application runs on a mobile device, the device, knowing that the application is session-unaware, negotiates appropriate network-policy parameters for the application. The application remains unaware, but it receives the benefits of the network-policy parameter negotiation. The network-policy parameter negotiation is carried on between the mobile device and a “network policy mediator” in the network. Together, they reserve the appropriate network resources and secure the appropriate guarantees. In some embodiments, a software “shim” runs in the network-protocol stack on the mobile device. By intercepting network-access attempts sent by the session-unaware application, the shim knows to begin the network-policy parameter negotiation. In some embodiments, the mobile device downloads information about session-unaware applications from the network. This information includes a list of which network-policy parameter guarantees would be most beneficial to each application.
Owner:U S CELLULAR
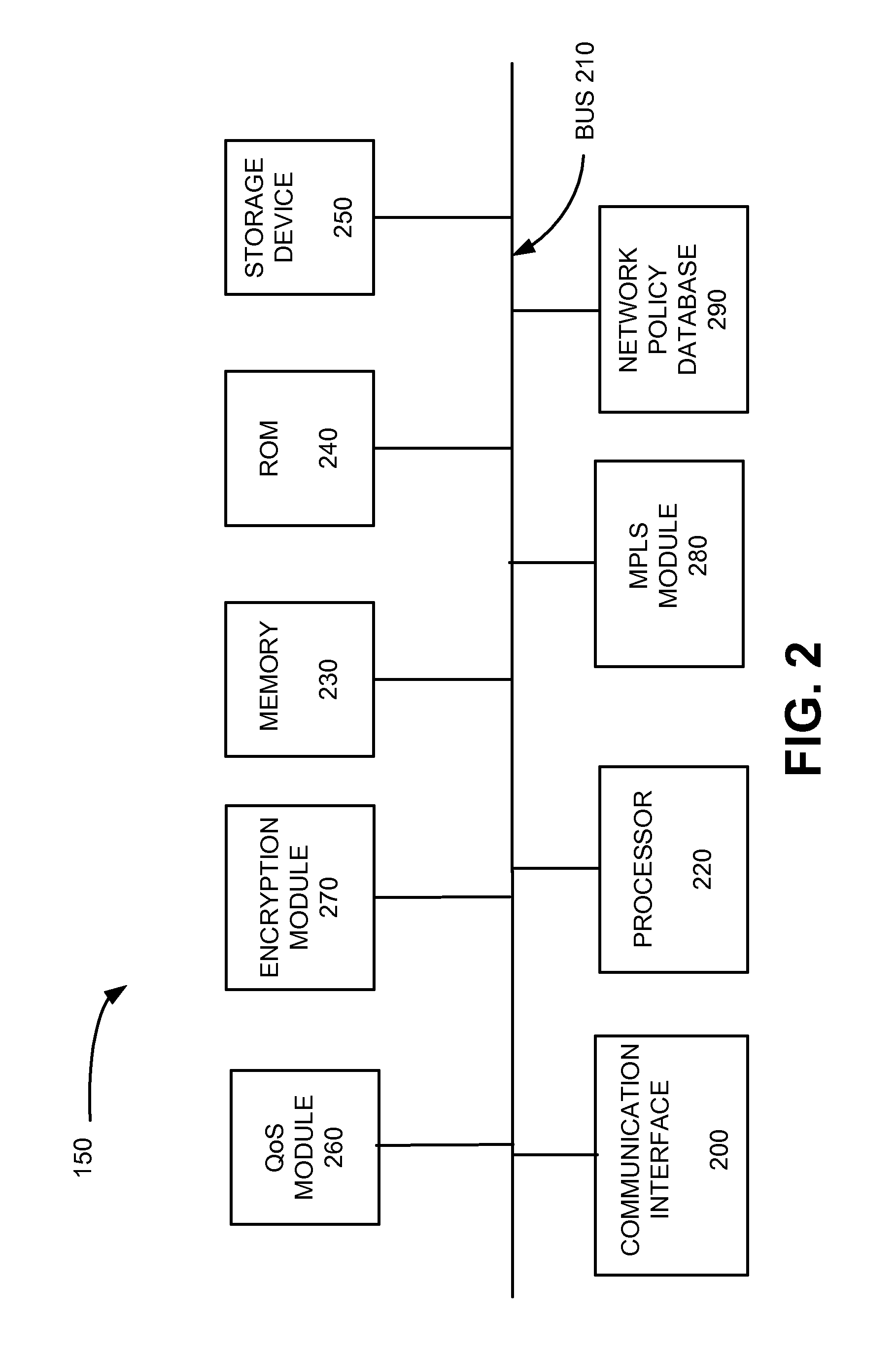
Policy based quality of service and encryption over MPLS networks
ActiveUS8279864B2Time-division multiplexData switching by path configurationQuality of serviceMulti protocol
A network device may store a plurality of LSP labels each associated with a network policy and desired quality of service, wherein each LSP label defines a path through a multi-protocol label switching (MPLS) network. Upon receiving a request to transmit data in accordance with a network policy and desired quality of service, the network device may transmit an appropriate LSP label for transmission through the MPLS network.
Owner:VERIZON PATENT & LICENSING INC
Method and framework for integrating a plurality of network policies
ActiveUS20050010765A1Data taking preventionDigital data protectionNetwork strategyDistributed computing
A method and system is disclosed for managing and implementing a plurality of network policies in a network device. Each of the plurality of policies are defined by one or more filters. The filters are installed in a policy engine. A layer identifies the network policy to be applied to a packet by sending a request to the policy engine. The policy engine then returns the policy to the requesting layer. The method and system may be used to implement a programmable, host-based, distributed, authenticating firewall that enables security and other policies to be applied at several protocol layers.
Owner:MICROSOFT TECH LICENSING LLC
Lightweight application level policy management for portable wireless devices under varying network
ActiveUS8160598B2High bandwidthLow bandwidthAutomatic exchangesWireless communicationNetwork strategyCommunication device
Owner:AT&T INTPROP II L P
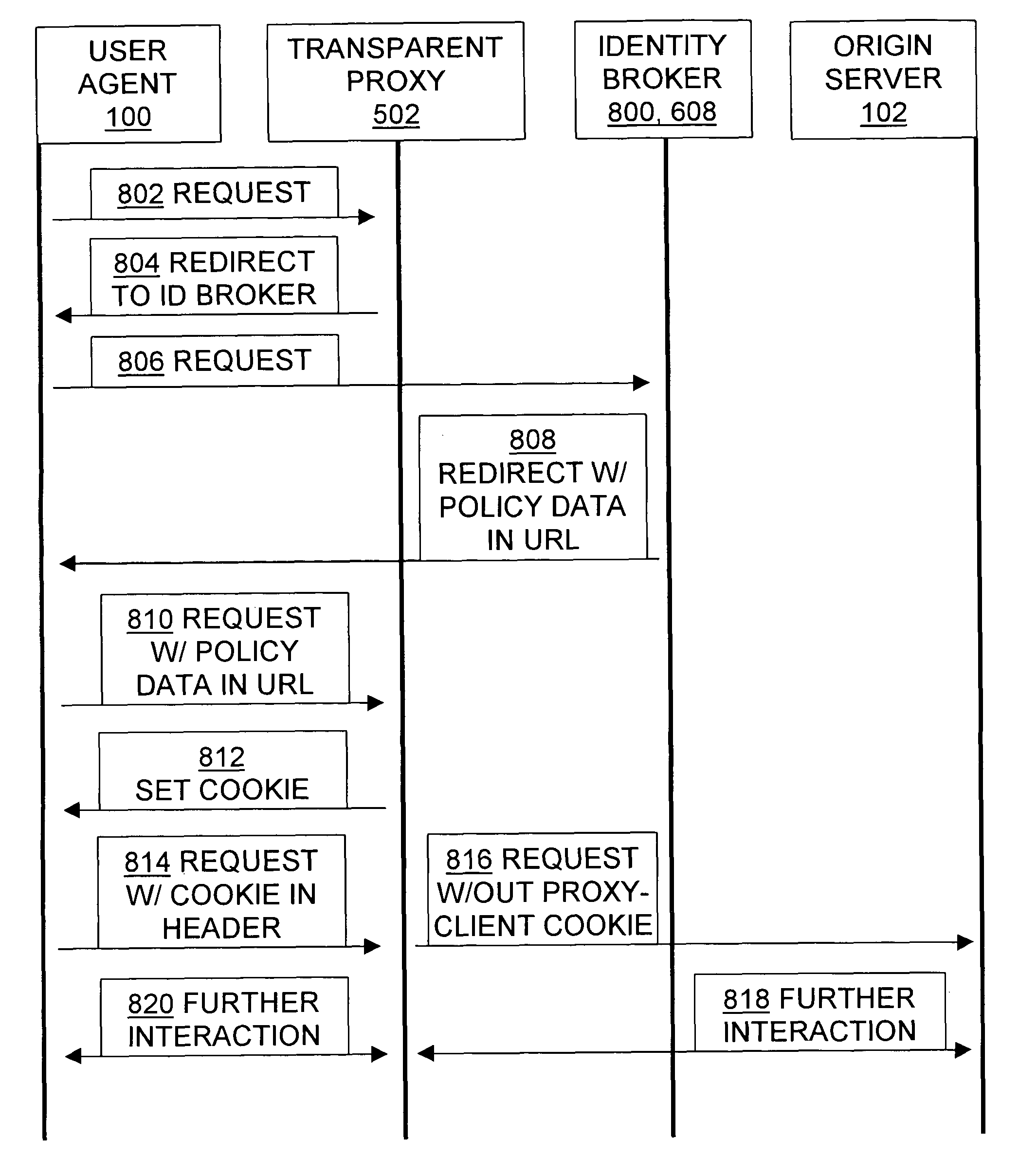
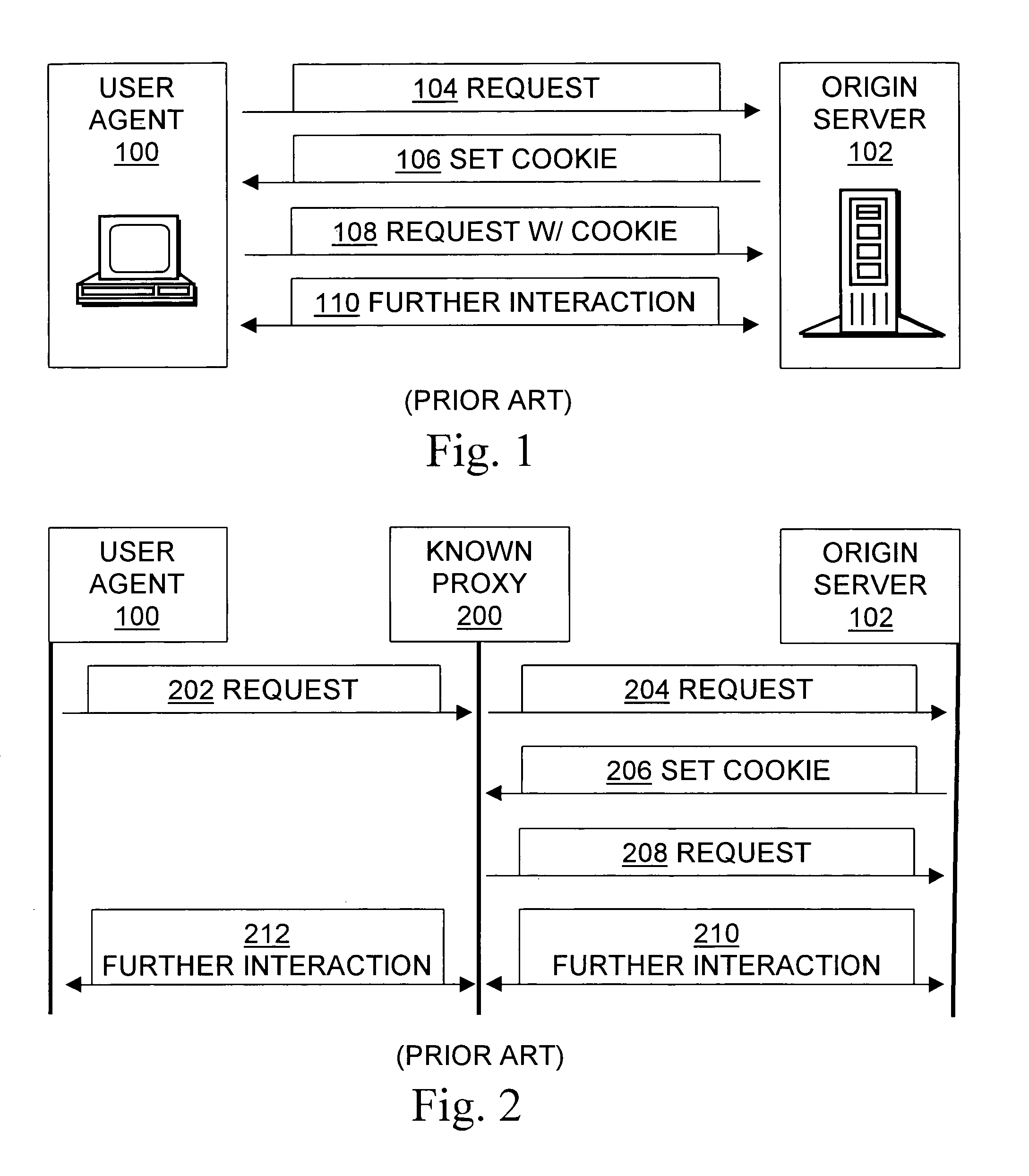
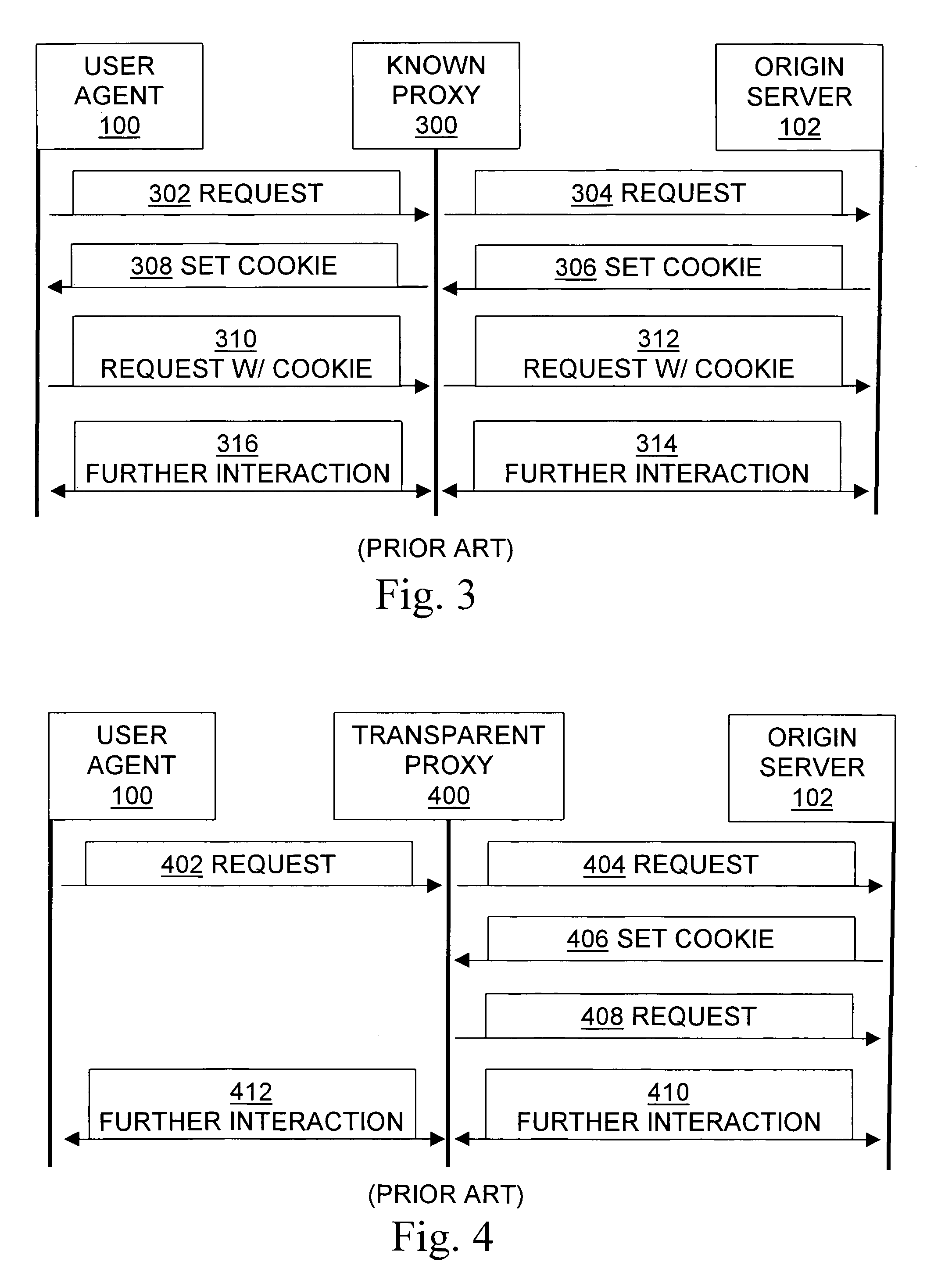
Brokering state information and identity among user agents, origin servers, and proxies
InactiveUS7954144B1Easy to useGuaranteed to continue to useDigital data processing detailsUser identity/authority verificationPerformance enhancementClient-side
Methods, signals, devices, and systems are provided for using proxy servers to transparently forward messages between clients and origin servers if, and only if doing so does not violate network policies. In some systems, a transparent proxy uses a combination of standard-format HTTP commands, embedding auxiliary information in URLs and other tools and techniques to redirect an initial client request to one or more policy modules, such as a login server or an identity broker or an access control server. The policy module authenticates the request, and uses HTTP redirection to have the client transmit authorization data to the proxy. The proxy extracts the authorization data, directs the client to use a corresponding cookie, and subsequently provides the implicitly requested proxy services to the client in response to the client's subsequently providing the authorization data in a cookie. This is accomplished without requiring installation of any invention-specific software or hardware on either the client or the origin server, and also works with proxy servers that are known to the client. Unless the client request violates network policy, a person using the client will generally perceive no reduction of services, and will instead benefit from the proxy's caching and / or other performance enhancements.
Owner:RPX CORP
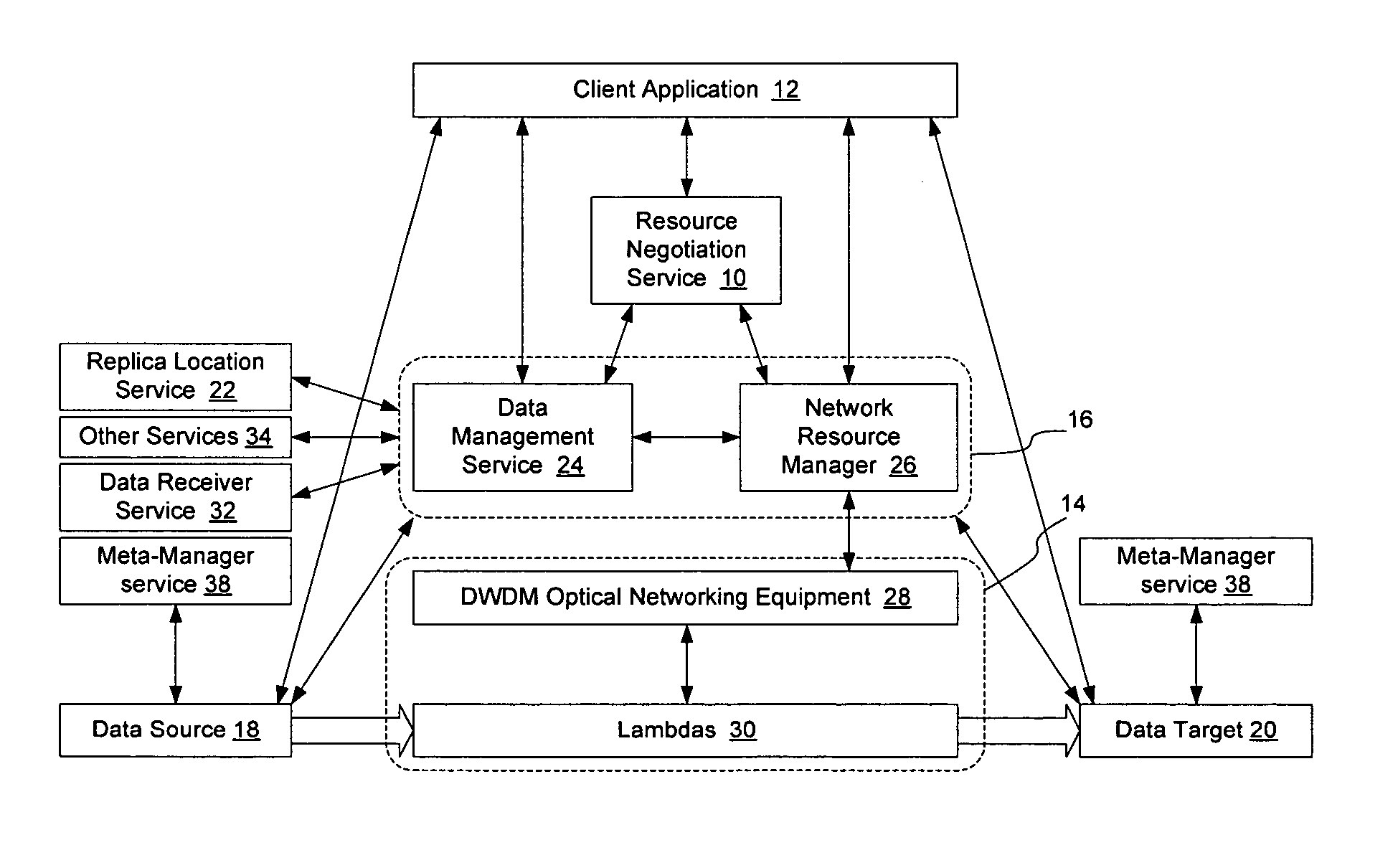
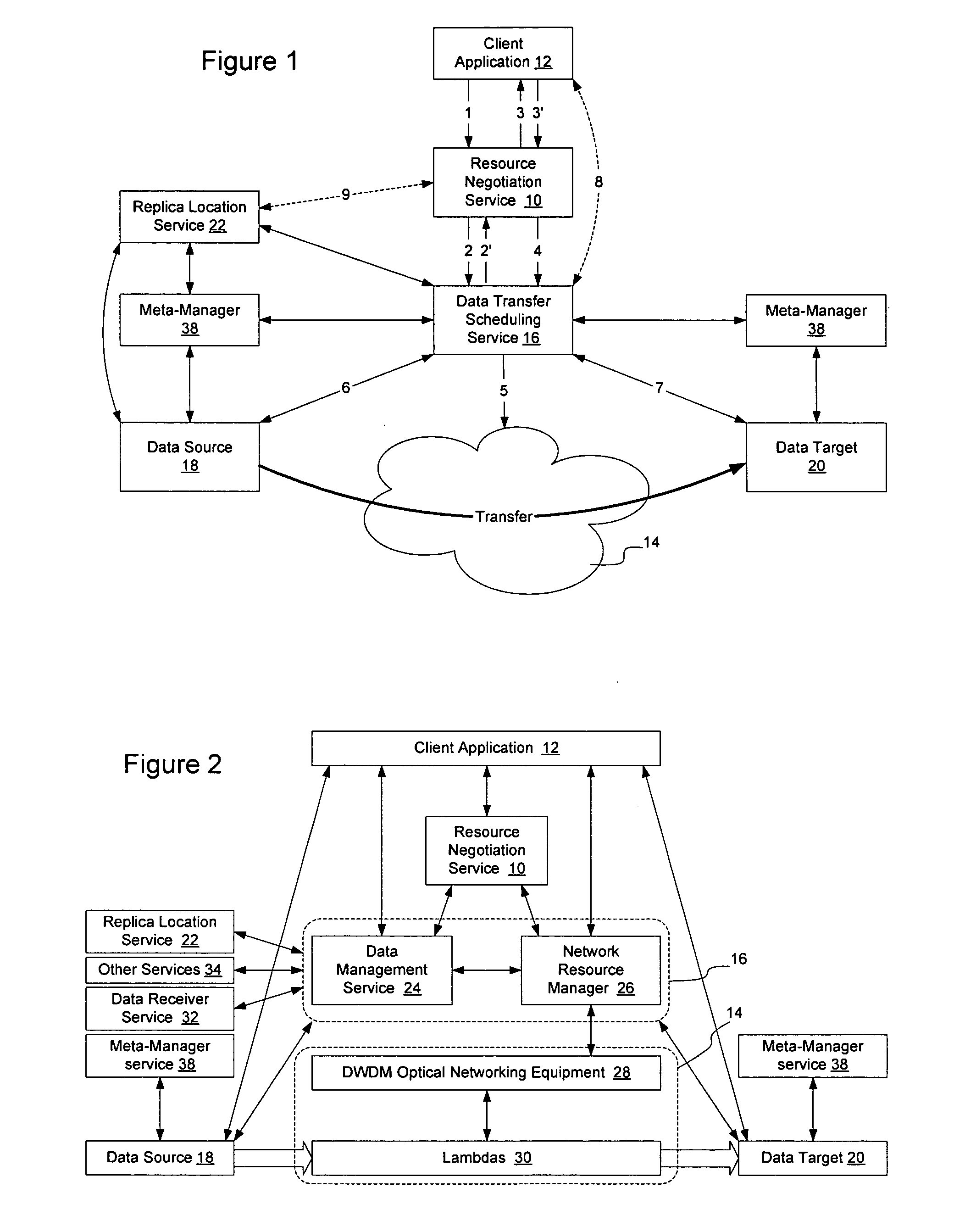
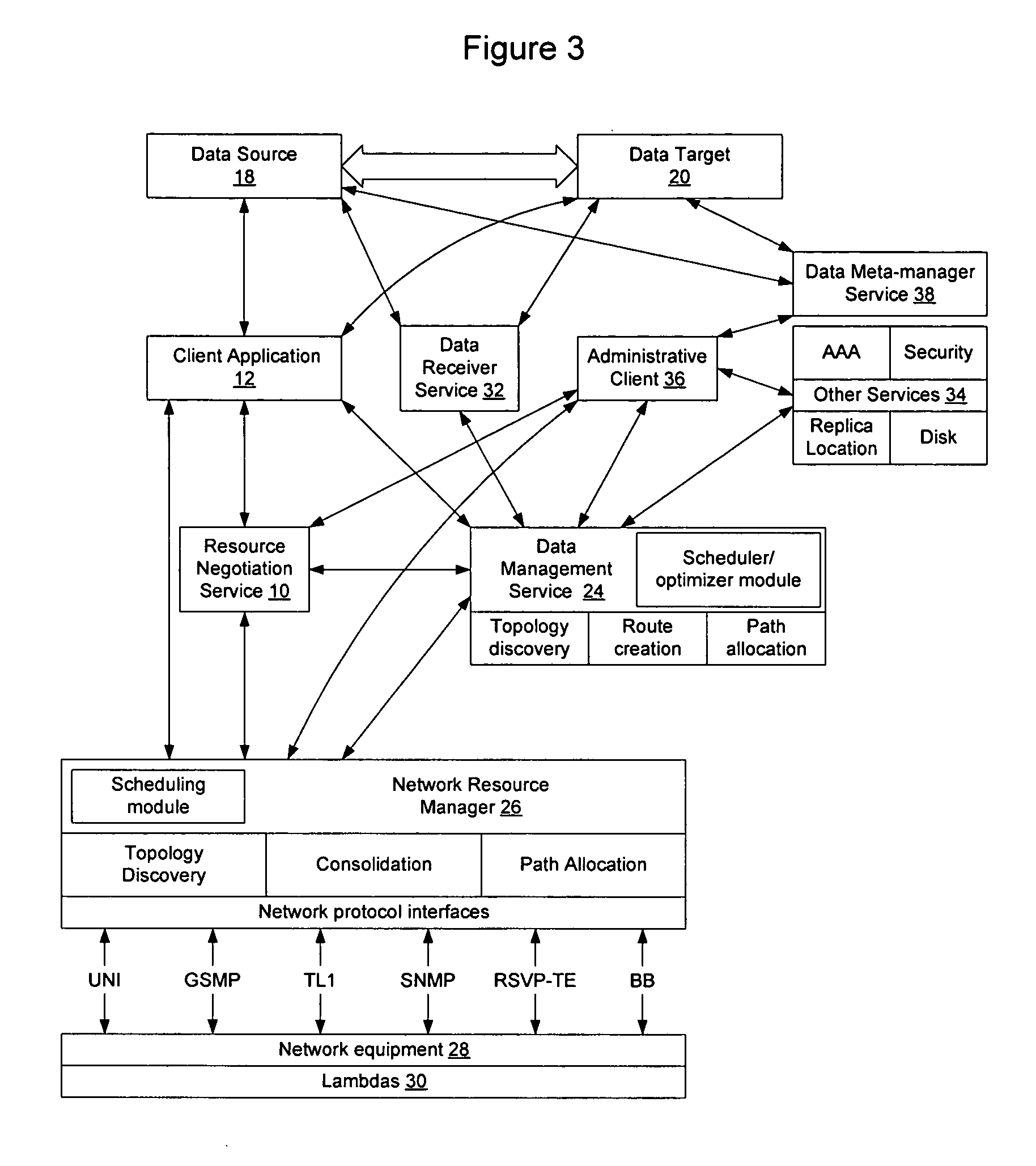
Method and apparatus for automated negotiation for resources on a switched underlay network
A resource negotiation service is provided to enable business logic decisions to be made when obtaining switched underlay network resources, to interface business logic with network conditions and schedules. The resource negotiation service may be implemented as a web service or other network service to enable business logic to be used in the selection of available network resources. This may allow policy to be used on both the subscriber side and the network provider side to optimize network resource allocations for a proposed transfer. The policy may include subscriber policy, network policy, and other factors such as current and expected network conditions. The resource negotiation service may include an interface to enable existing subscribers and new customers to obtain switched underlay resources.
Owner:NORTEL NETWORKS LTD
System and method for automated policy audit and remediation management
ActiveUS20050015622A1Memory loss protectionDigital data processing detailsProgram planningNetwork strategy
A prevention-based network auditing system includes a central compliance server providing a user interface allowing a user to schedule and configure a network audit. The configured audit is stored in an audit repository until its scheduled time. At such a time, the compliance server automatically invokes one or more audit servers to gather information about the network. The compliance server receives the gathered information and electronically applies a network policy to the information for determining compliance with the policy. A remediation task may be generated if the policy has been violated, and the task monitored until its completion.
Owner:MUSARUBRA US LLC
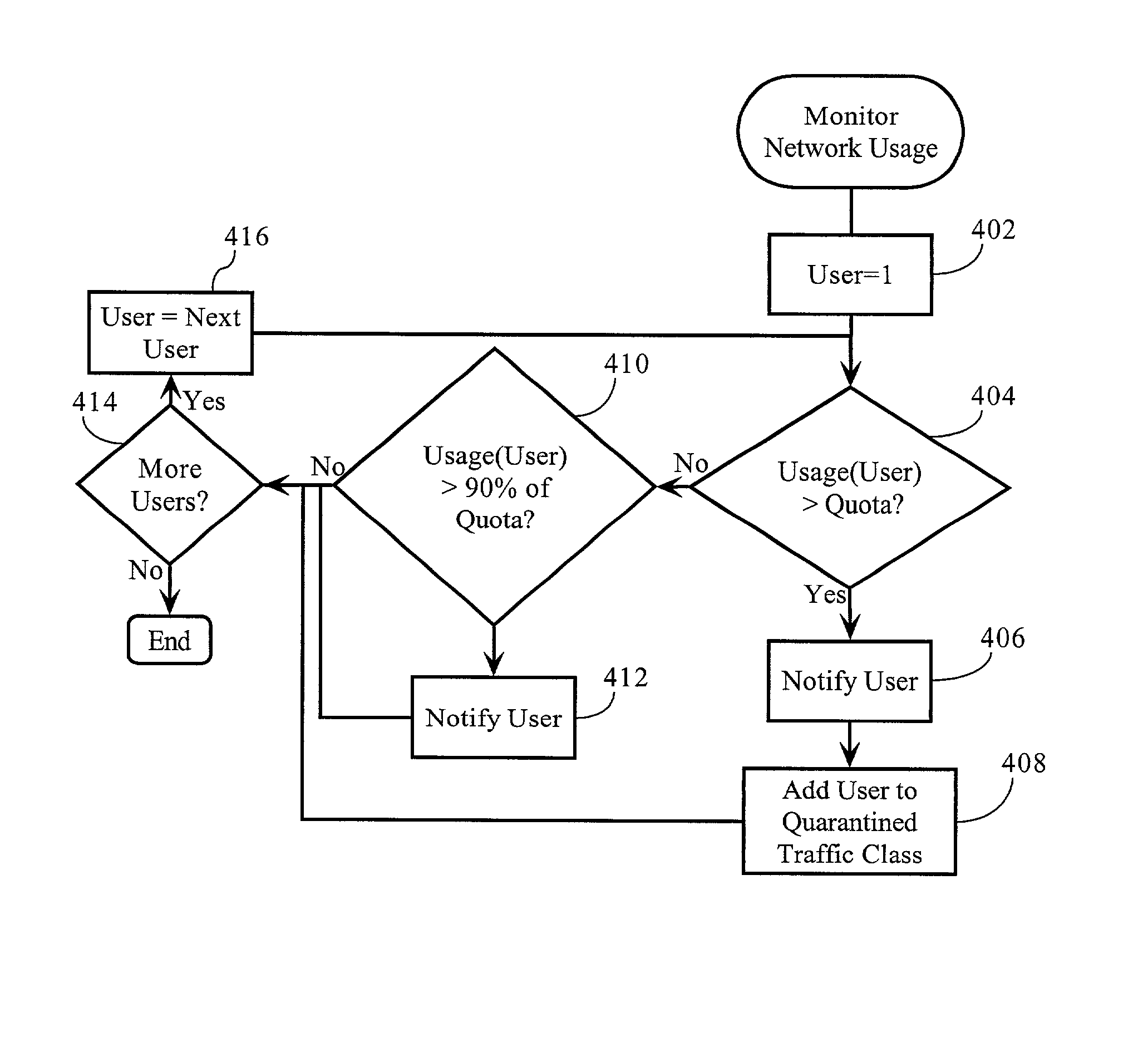
Volume-based network management scheme
Methods, apparatuses and systems allowing for deployment of volume-based network policies across a computer network. In one embodiment, the present invention monitors network utilization of a plurality of users and detects the occurrence of network utilization milestones or other events for individual users, such as exceeding a data transfer allotment or threshold. To enforce the allotment or threshold, the present invention is operative to deny, degrade, or otherwise affect a characteristic associated with network access provided to such users.
Owner:CA TECH INC
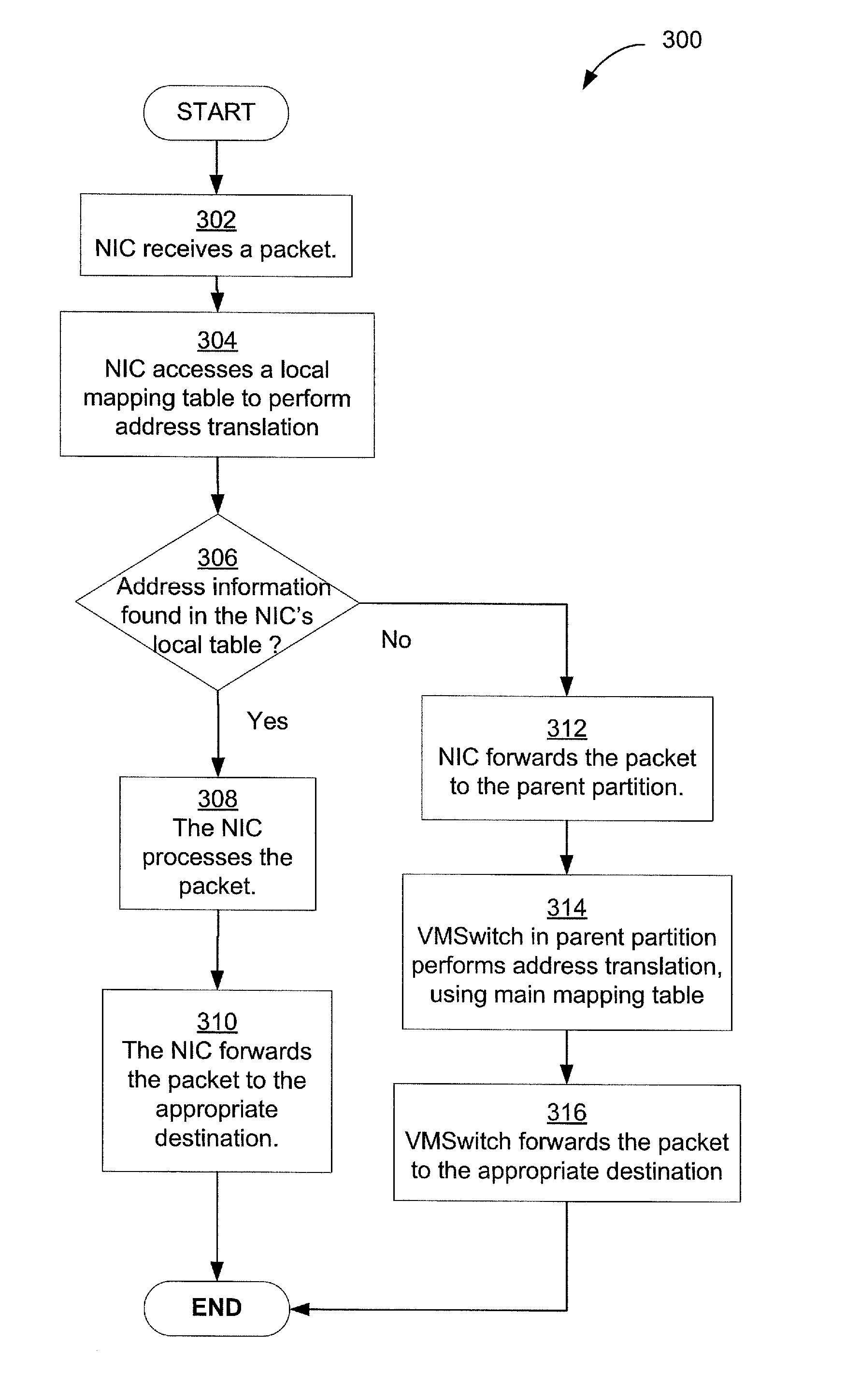
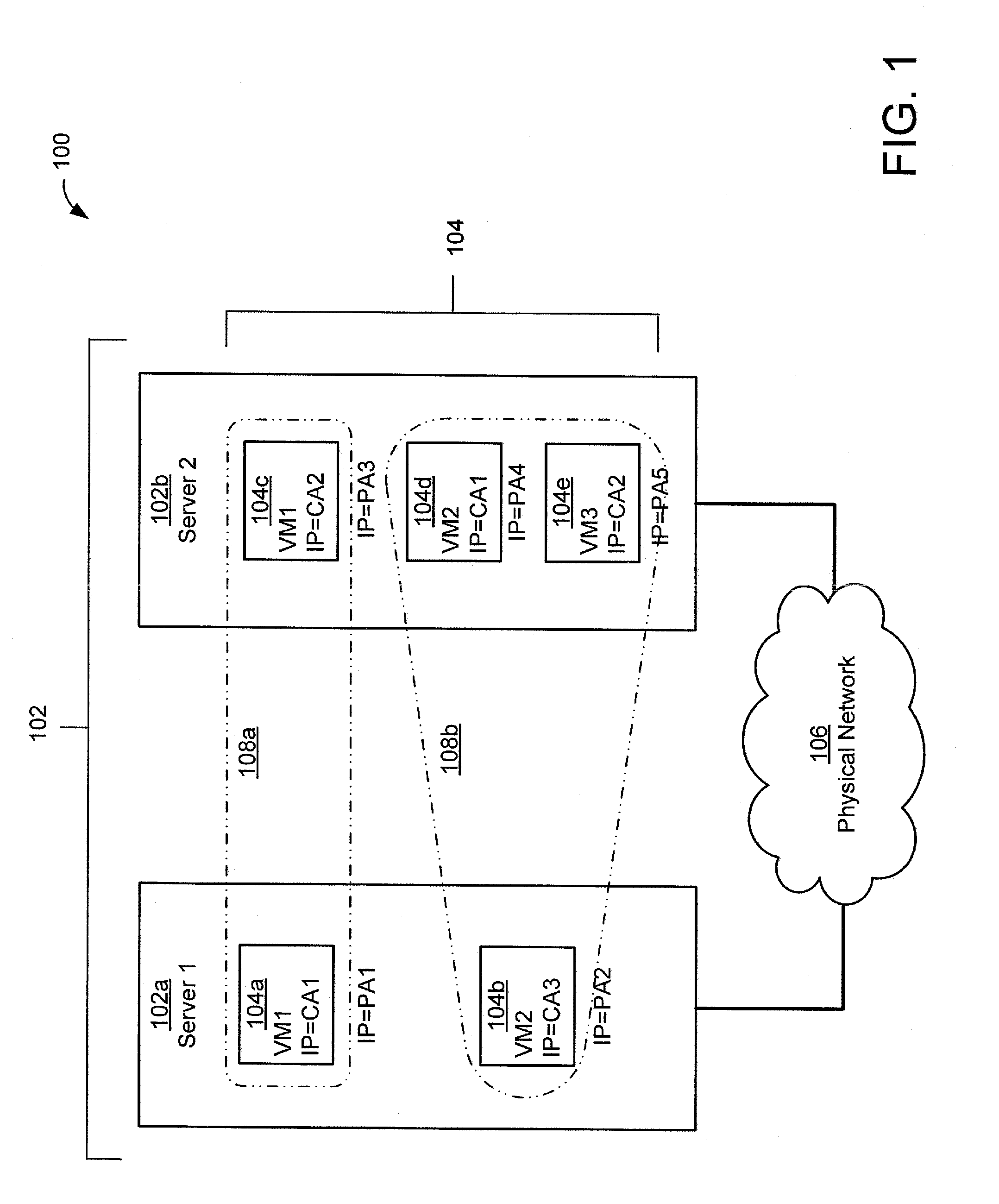
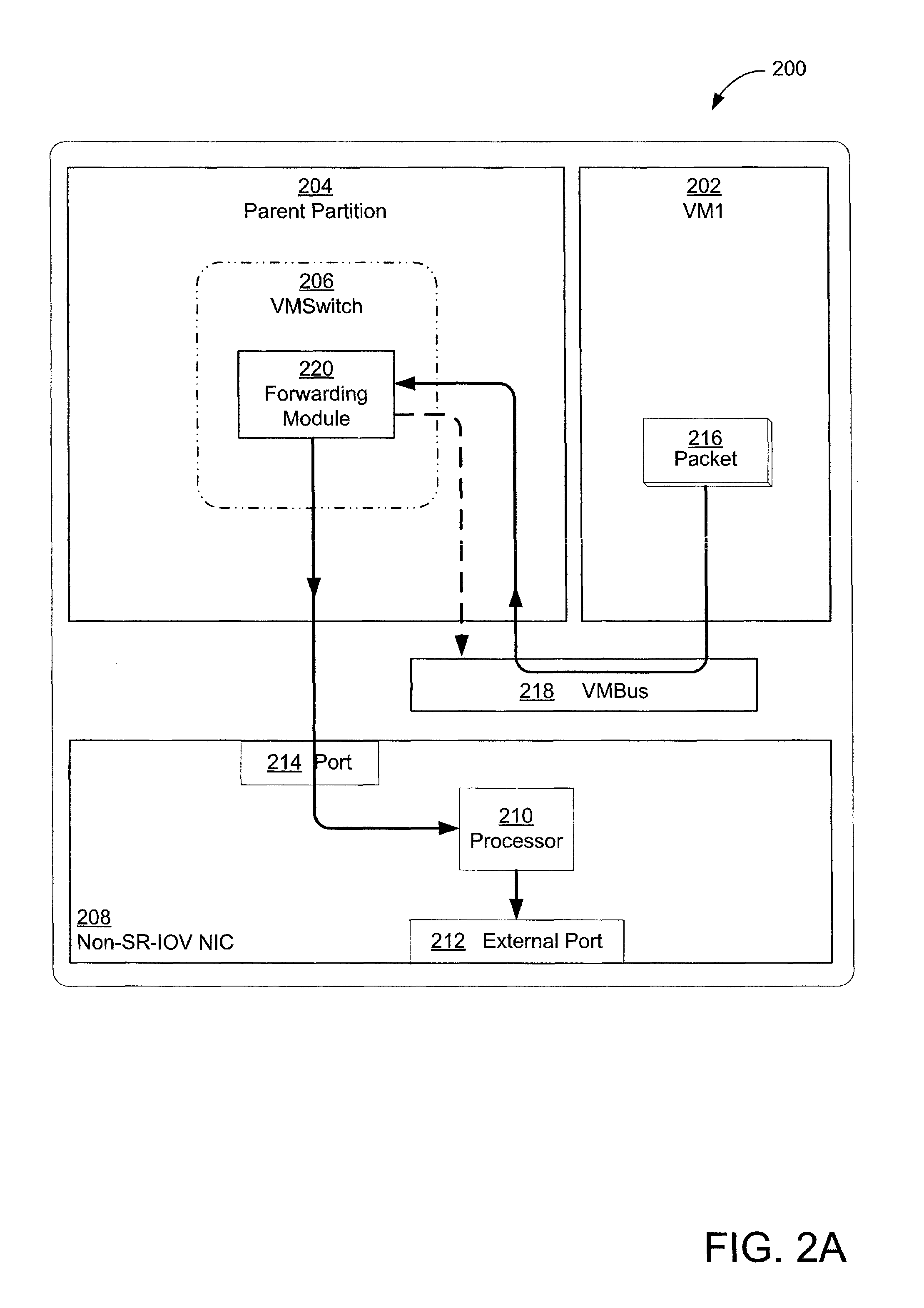
Secure and efficient offloading of network policies to network interface cards
ActiveUS8856518B2Multiple digital computer combinationsData switching networksVirtualizationProtocol for Carrying Authentication for Network Access
Techniques for efficient and secure implementation of network policies in a network interface controller (NIC) in a host computing device operating a virtualized computing environment. In some embodiments, the NIC may process and forward packets directly to their destinations, bypassing a parent partition of the host computing device. In particular, in some embodiments, the NIC may store network policy information to process and forward packets directly to a virtual machine (VM). If the NIC is unable to process a packet, then the NIC may forward the packet to the parent partition. In some embodiments, the NIC may use an encapsulation protocol to transmit address information in packet headers. In some embodiments, this address information may be communicated by the MC to the parent partition via a secure channel. The NIC may also obtain, and decrypt, encrypted addresses from the VMs for routing packets, bypassing the parent partition.
Owner:MICROSOFT TECH LICENSING LLC
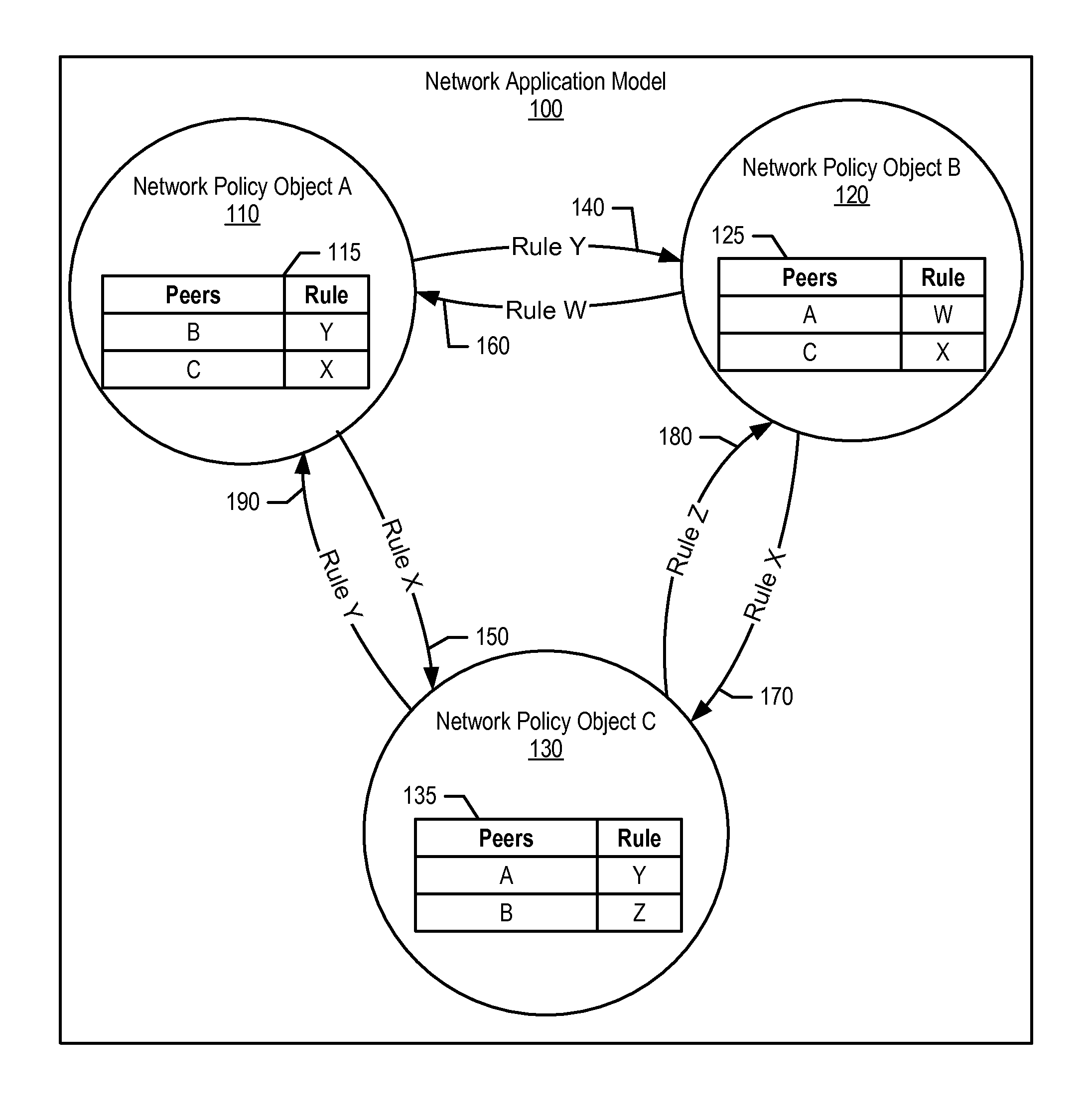
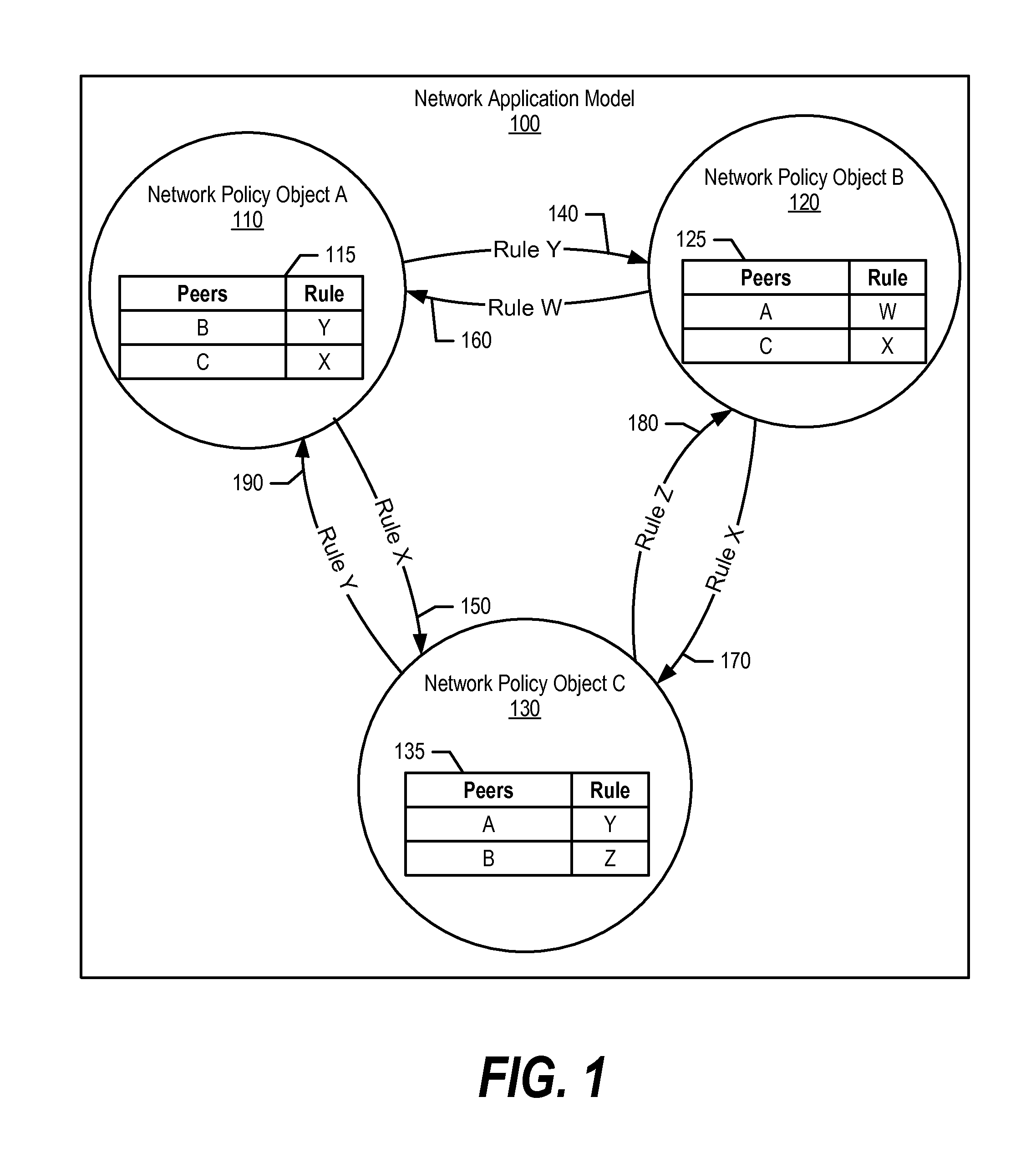
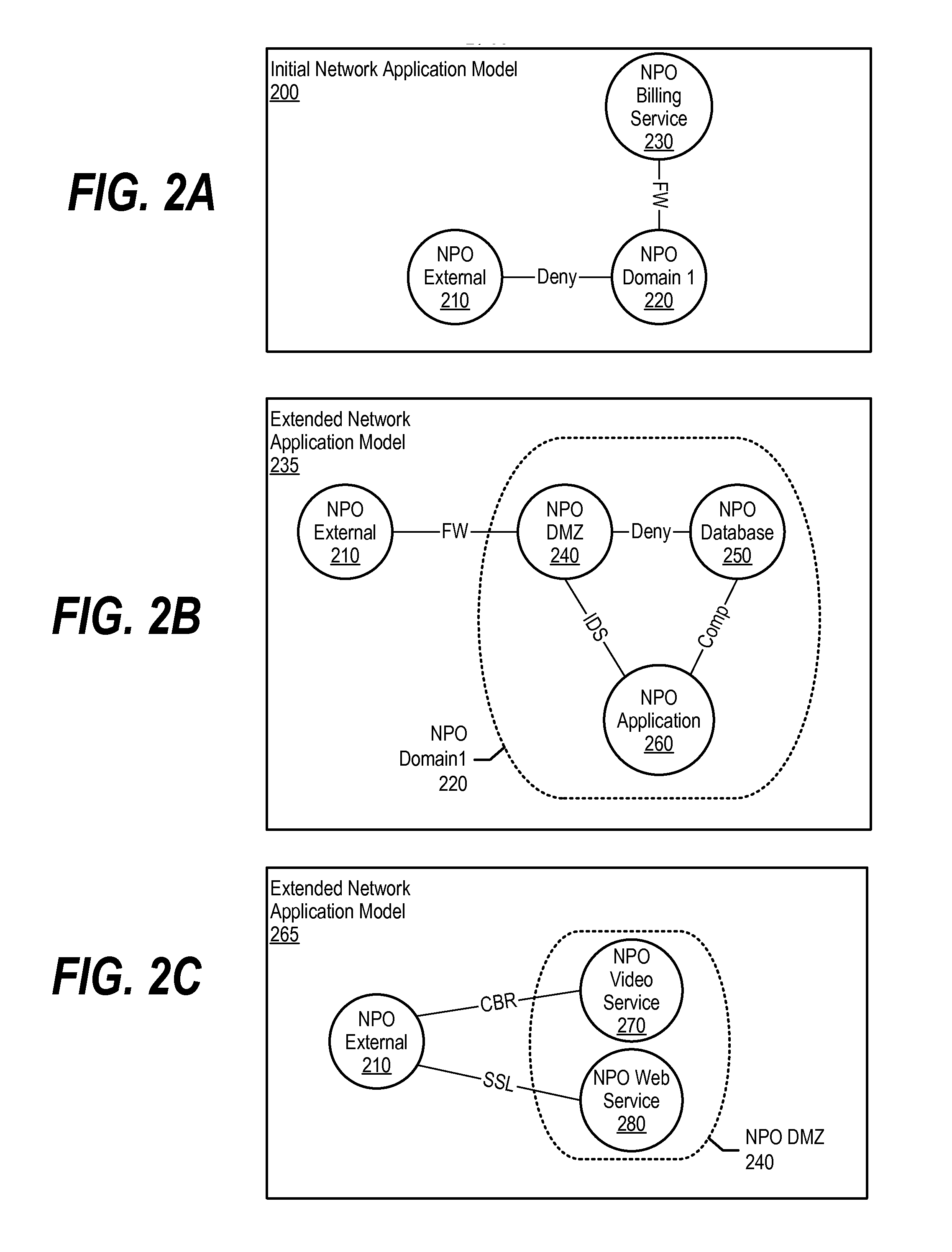
Object Oriented Networks
InactiveUS20140156814A1Digital computer detailsData switching networksNetwork controlPhysical infrastructure
An approach is provided in which a system creates a network application model that includes network policy objects and connection rules corresponding to sending data between the network policy objects. The system converts the network application model to network configuration information, which links the network policy objects to the connection rules. In turn, a network control plane is configured based upon the network configuration information to map the network application model to a physical infrastructure.
Owner:IBM CORP
Network audit and policy assurance system
ActiveUS7627891B2Reduce riskMemory loss protectionError detection/correctionGraphicsGraphical user interface
A prevention-based network auditing system includes a central compliance server generating network policies and configuring audits of the data communications network. The compliance server presents a graphical user interface (GUI) to describe the specific data gathering parameters, policies to be analyzed, and the schedule of analysis. One or more audit servers strategically deployed around the network employ heterogeneous data-gathering tools to gather information about the network in response to the configured audits, and transmit the gathered information to the compliance server. An audit repository stores the gathered information for use by the compliance server for security and regulatory policy assessment, network vulnerability analysis, report generation, and security improvement recommendations.
Owner:MCAFEE LLC
System and method to support data applications in a multi-homing, multi-mode communication device
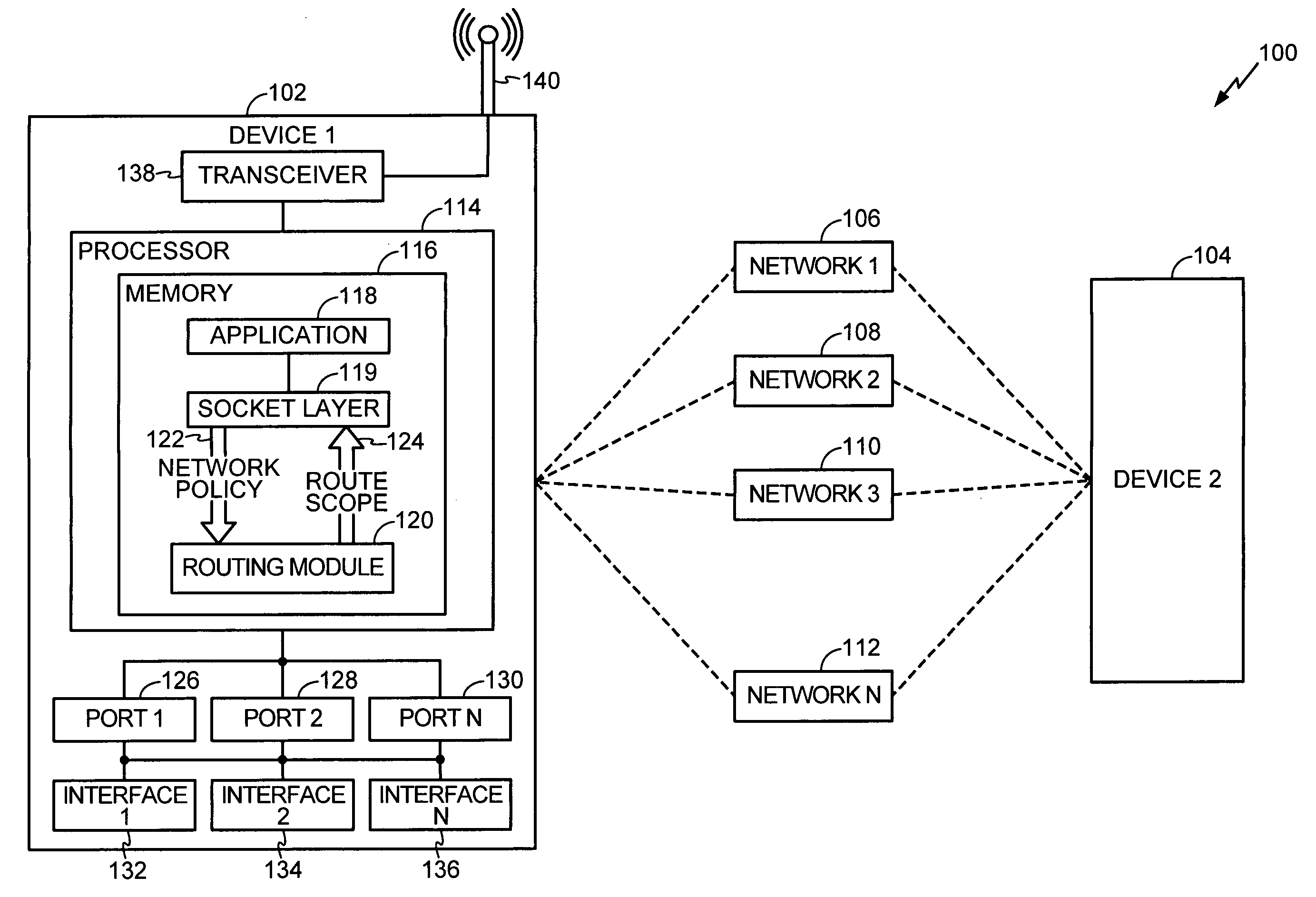
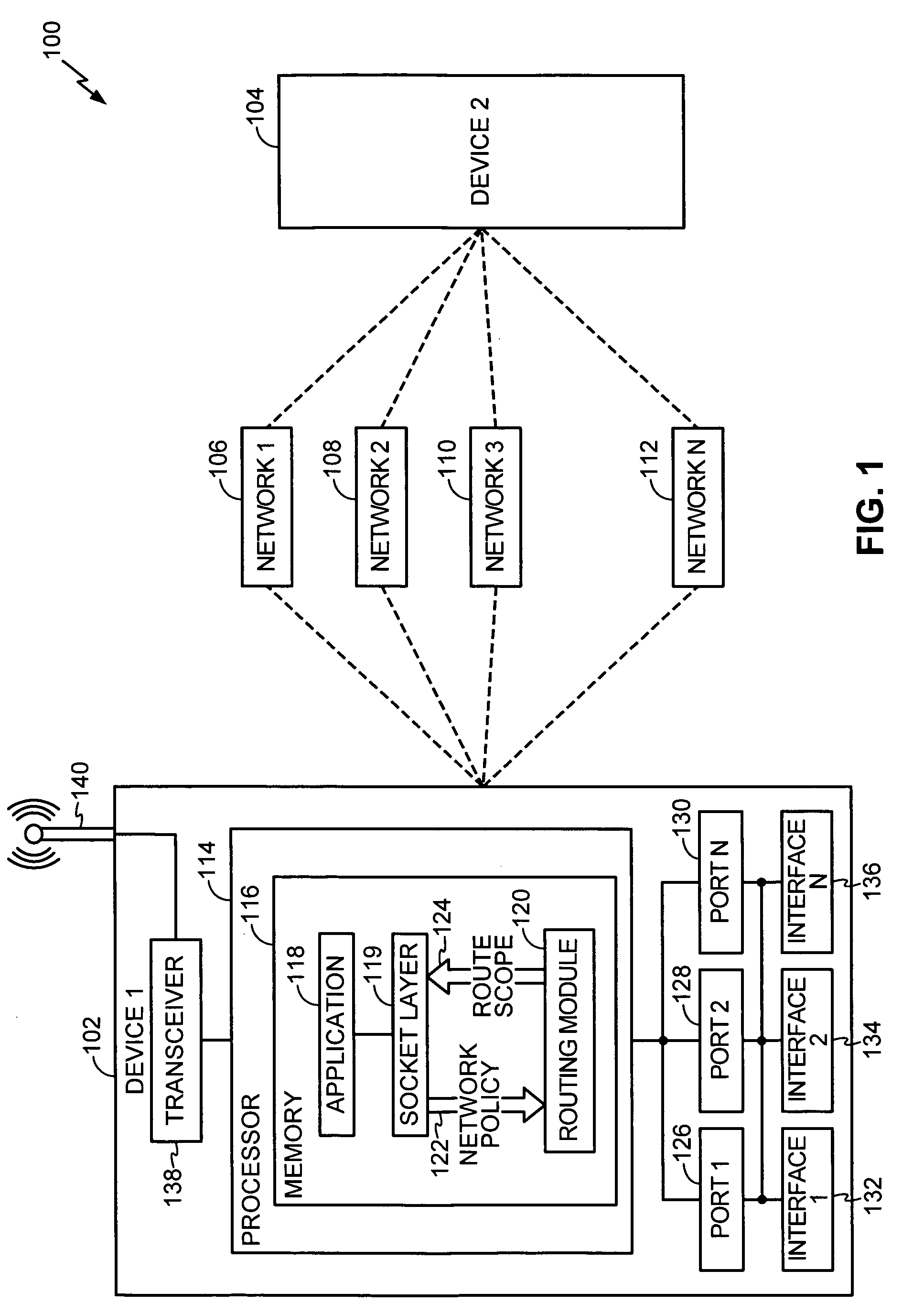
InactiveUS20060274750A1Error preventionNetwork traffic/resource managementData interfaceNetwork strategy
A method of transmitting and receiving data from a multi-homing network device to a data network is disclosed and includes defining a network policy and transmitting the network policy to a routing module. Further, the method includes receiving a route scope from the routing module. The route scope identifies a subset of data interfaces to the data network that satisfy the network policy wherein the subset of data interfaces are selected from a set of available data interfaces and wherein the subset of data interfaces includes at least one data interface.
Owner:QUALCOMM INC
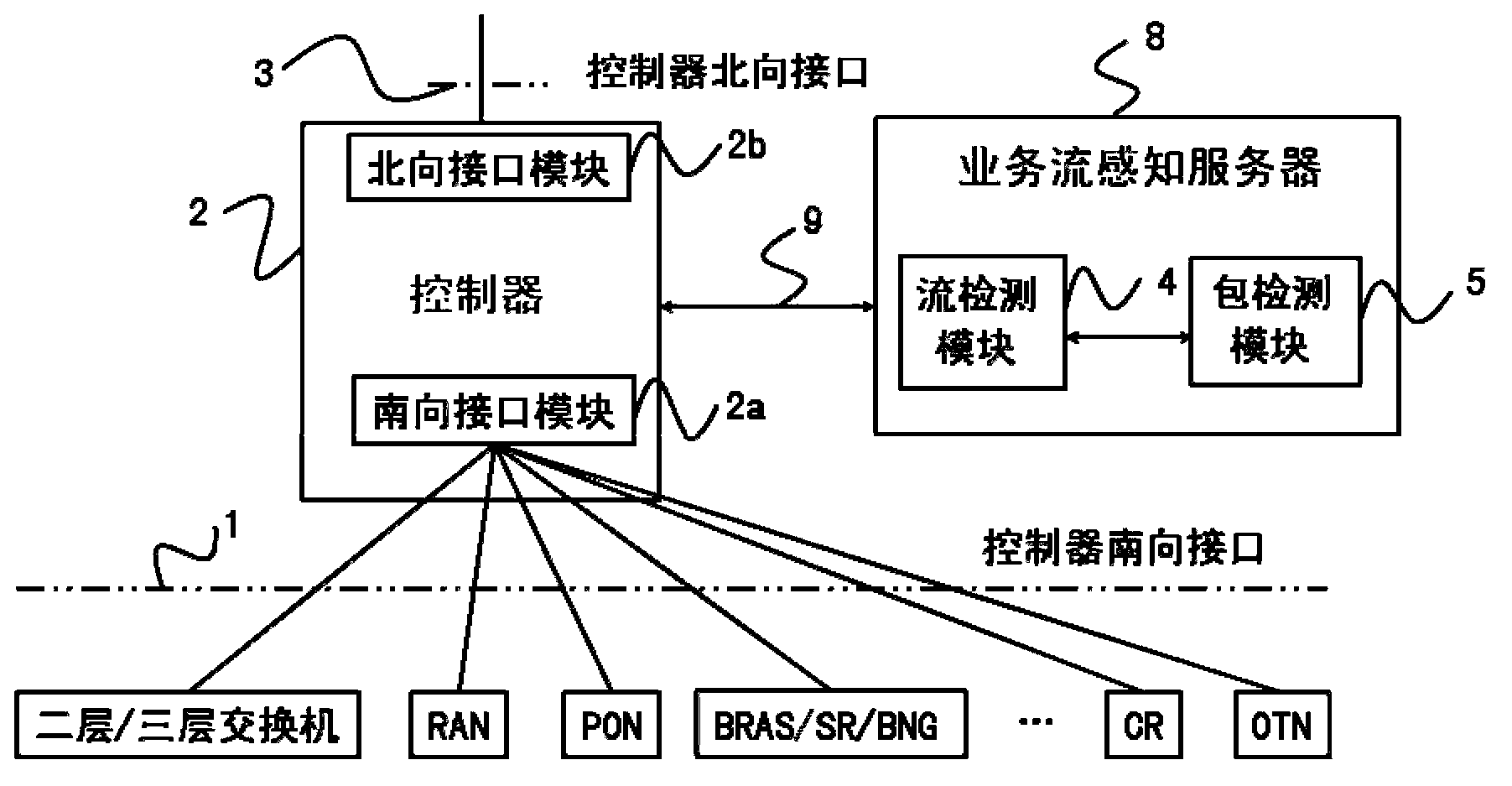
Service flow aware system and method combining flow detection and package detection in SDN
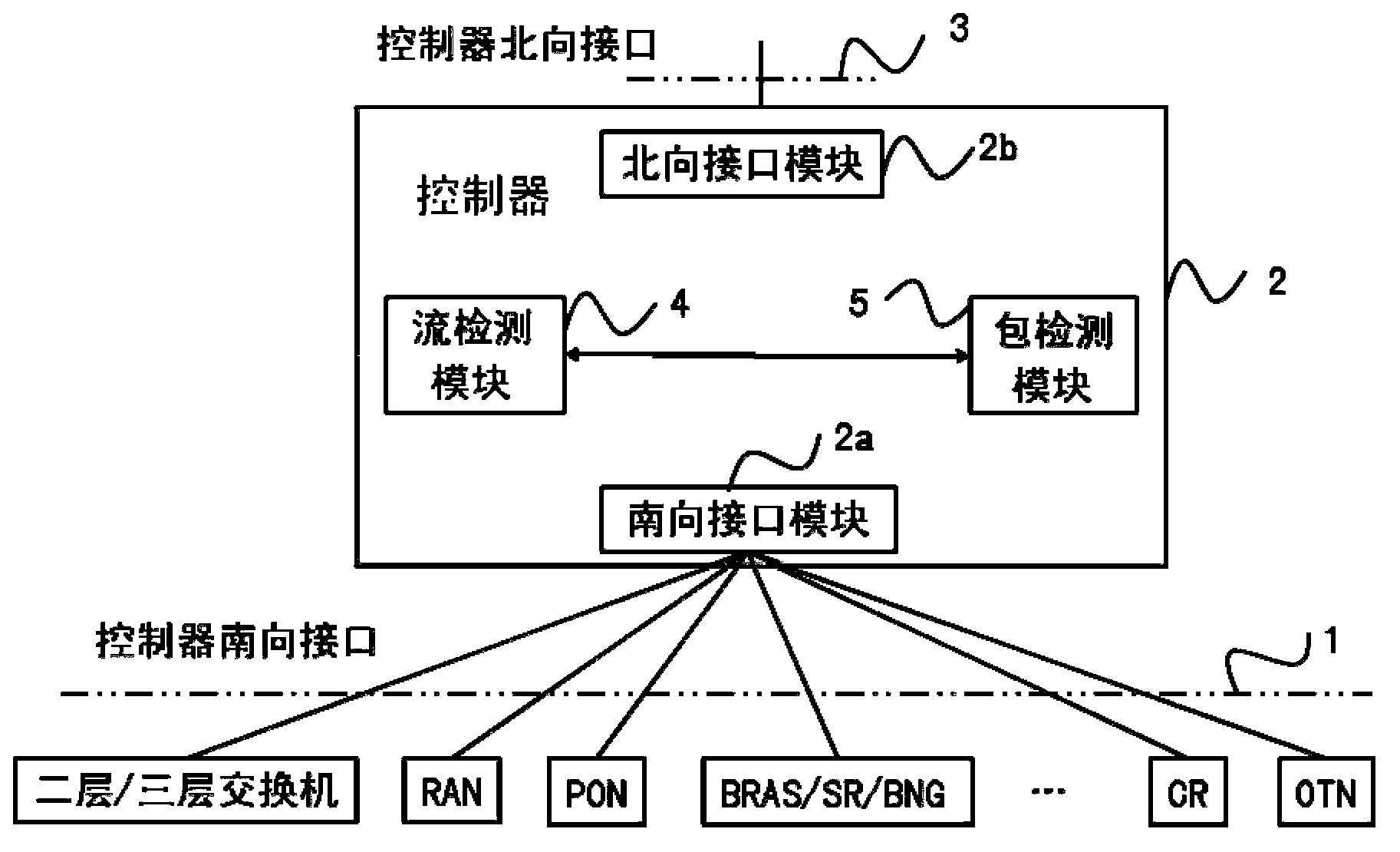
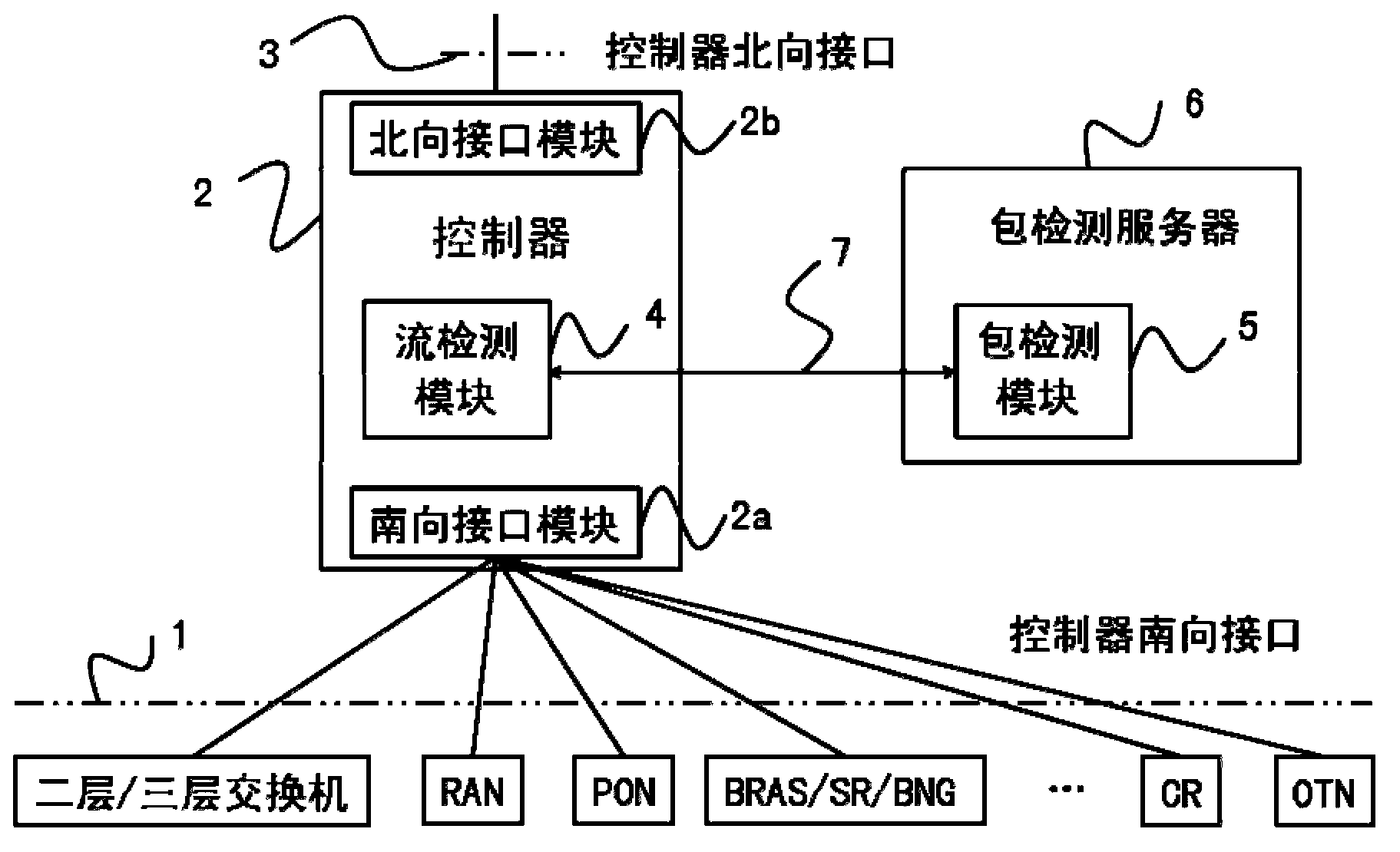
The invention discloses a service flow aware system and method combining flow detection and package detection in the SDN, and relates to the field of the SDN. The service flow aware method includes the steps that when an initial novel service flow enters the SDN, table items not matched with the novel service flow in an equipment flow table are forwarded, the novel service flow is forwarded to a controller, a flow detection module carries out flow detection, a package detection module carries out package detection to recognize the service type and the service characteristics of the novel service flow, the controller triggers the awareness of a specific service according to the characteristics of the service flow, flow signs, flow statistics and package statistics, for current continuous service flow, the controller samples a real-time service flow, the dynamic variation of the real-time service is discovered through service awareness, and network strategies are adjusted correspondingly. The service flow aware system and method combining flow detection and package detection in the SDN combines the flow detection technology and the package detection technology, expands the southing port of the controller in the SDN, and can completely obtain the states of network flows of different industries and different applications in the current network.
Owner:FENGHUO COMM SCI & TECH CO LTD
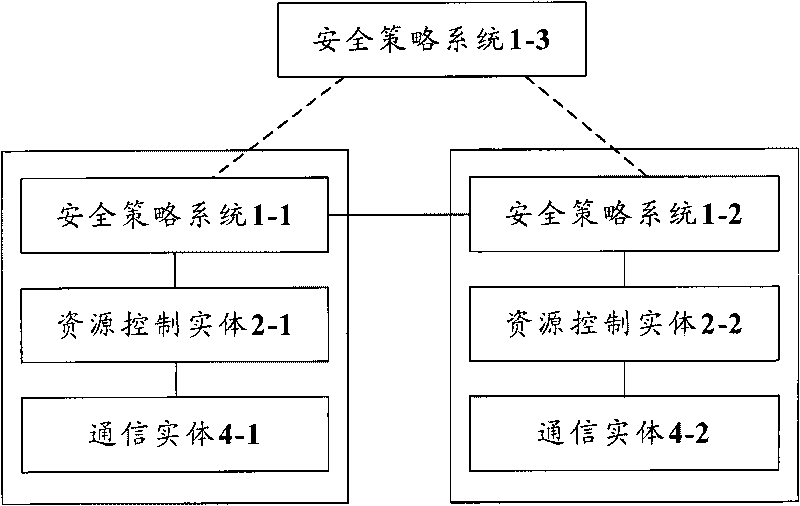
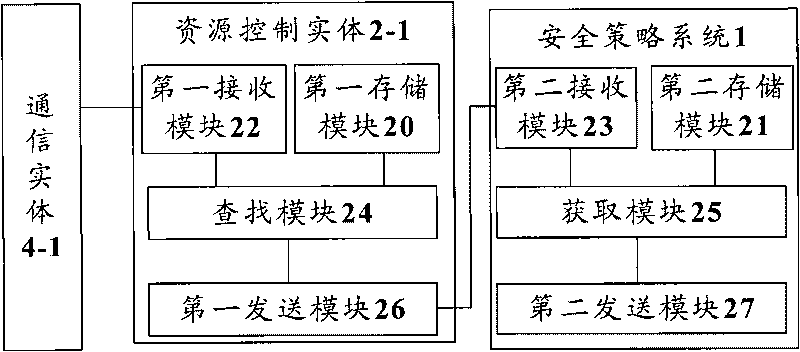
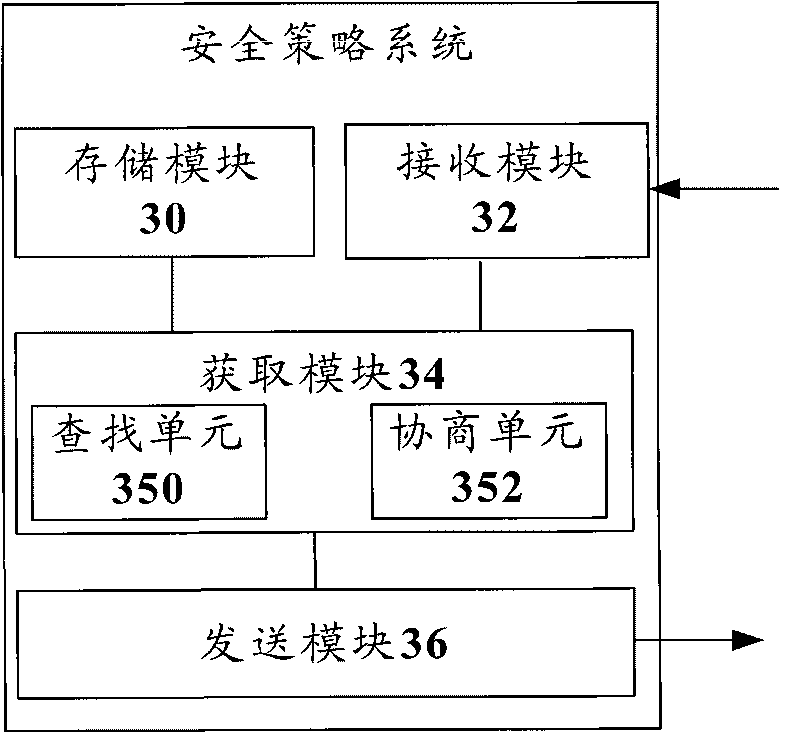
Method, device and system of distributing network safety strategies
InactiveCN101729531AEliminate security threatsImprove defenseTransmissionNetwork security policySecurity policy
The invention discloses a method, a device and a system of distributing network safety strategies, wherein the system of distributing the network safety strategies comprises a safety strategy system, one or more resource control entities attributed to the safety strategy system and one or more communication entities respectively attributed to each resource control entity, wherein each resource control entity is used for sending a request message to the attributed safety strategy system thereof when receiving a communication request, and the request message is used for requesting a safety strategy related to the communication request; and the safety strategy system is used for obtaining the safety strategy related to the communication request according to the received request message and sending the safety strategy to each resource control entity. Through the invention, the integral defensive effect of a network can be enhanced, and the network safety threat is eliminated.
Owner:ZTE CORP
Method and apparatus for network wide policy-based analysis of configurations of devices
InactiveUS20060129672A1Digital computer detailsData switching networksNetwork strategyNetwork topology
A method and an apparatus for analyzing a network configuration against a corporate network policy and determining violation(s) against the corporate network policy. A report indicating the violation(s) can be generated indicating instances of the violation(s). An analysis platform reads in a network policy. The analysis platform collects configuration files from the relevant network devices in the network and builds up an internal instance of a network configuration model based on the configuration files and the network topology. The analysis platform analyzes this network configuration model according to the network policy and adds an entry to its final report each time that it detects a violation against the network policy in the network configuration model. The data in the entries pinpoints the cause of the deviation(s) from the network policy.
Owner:REDSEAL NETWORKS
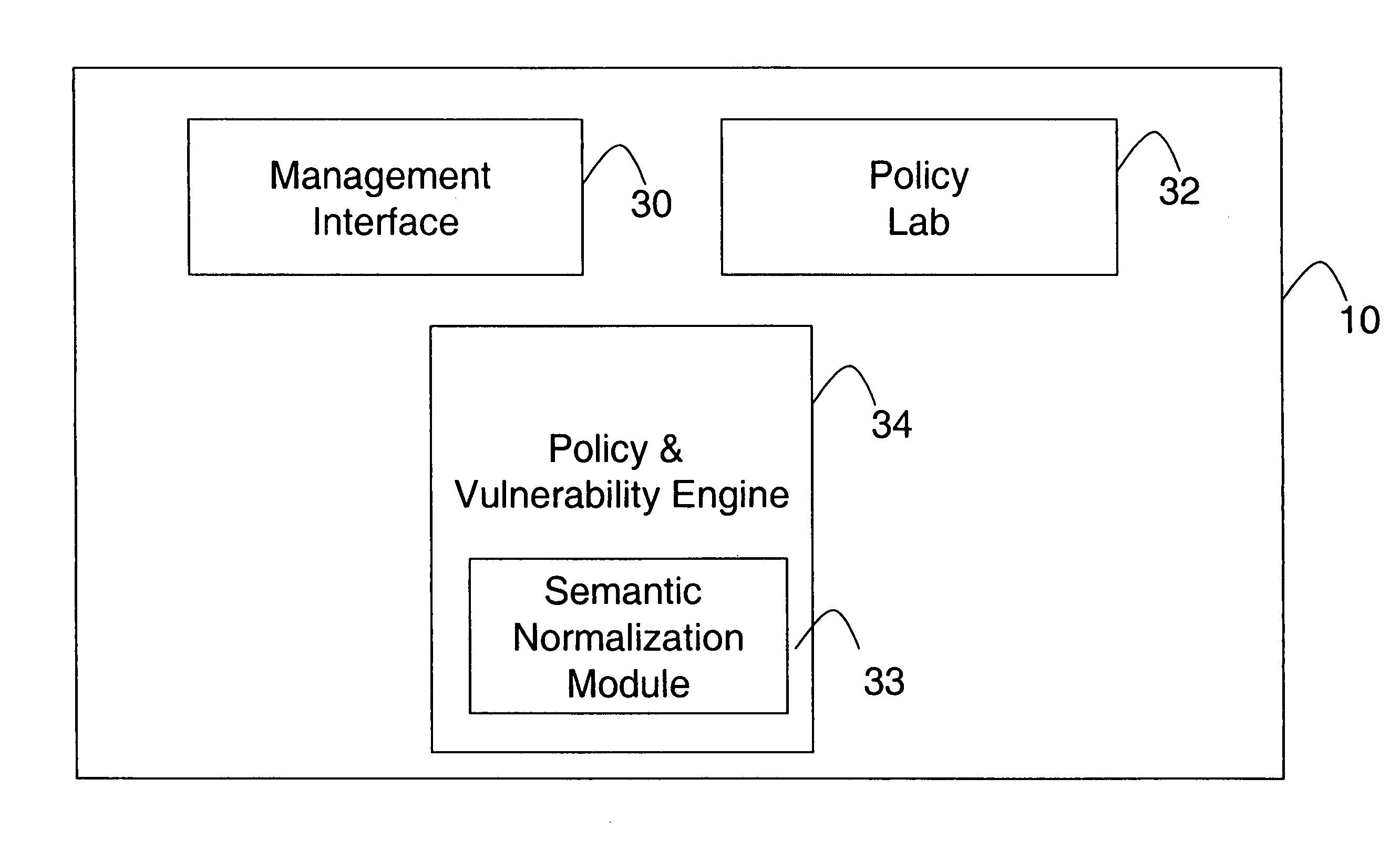
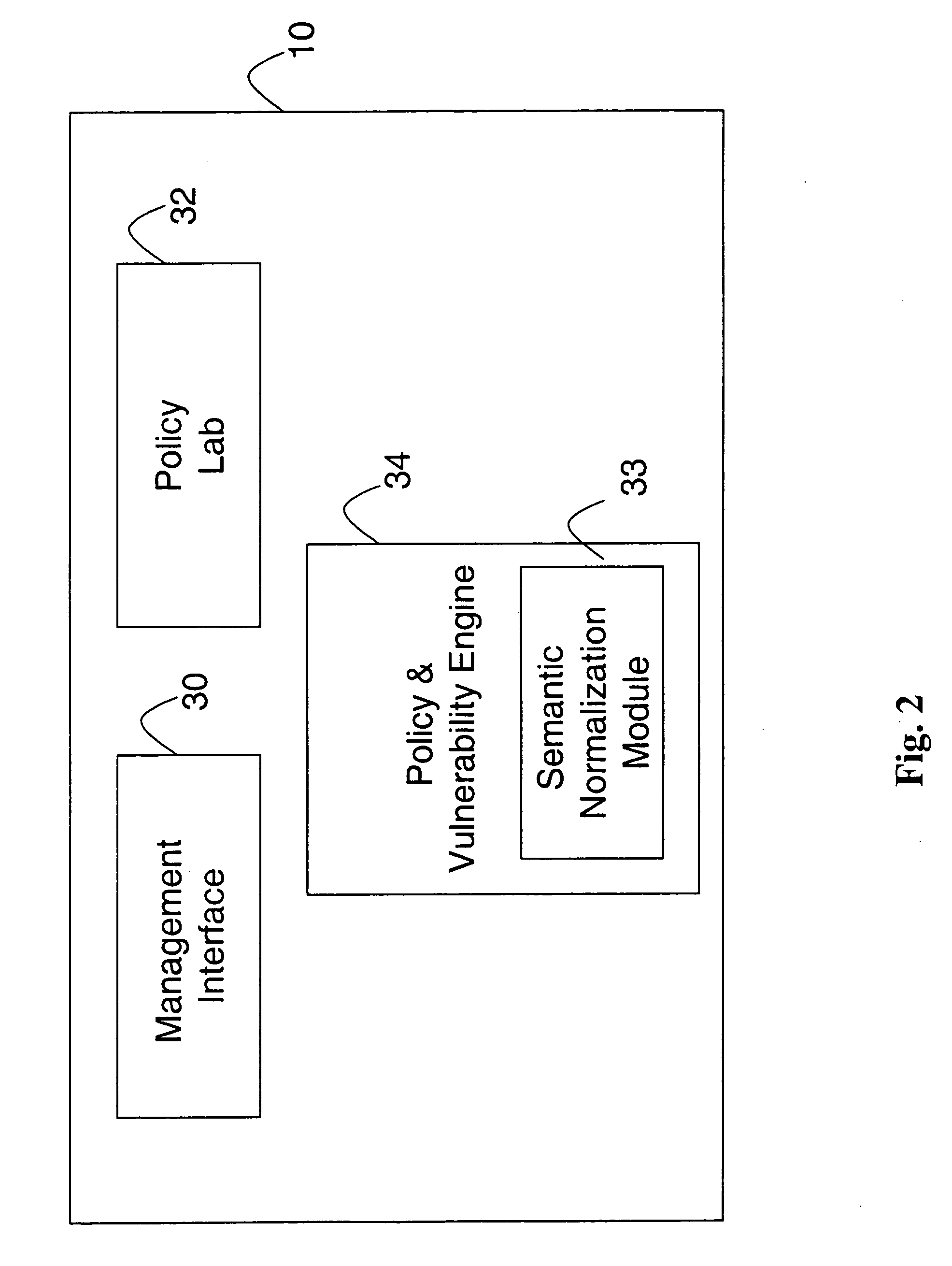
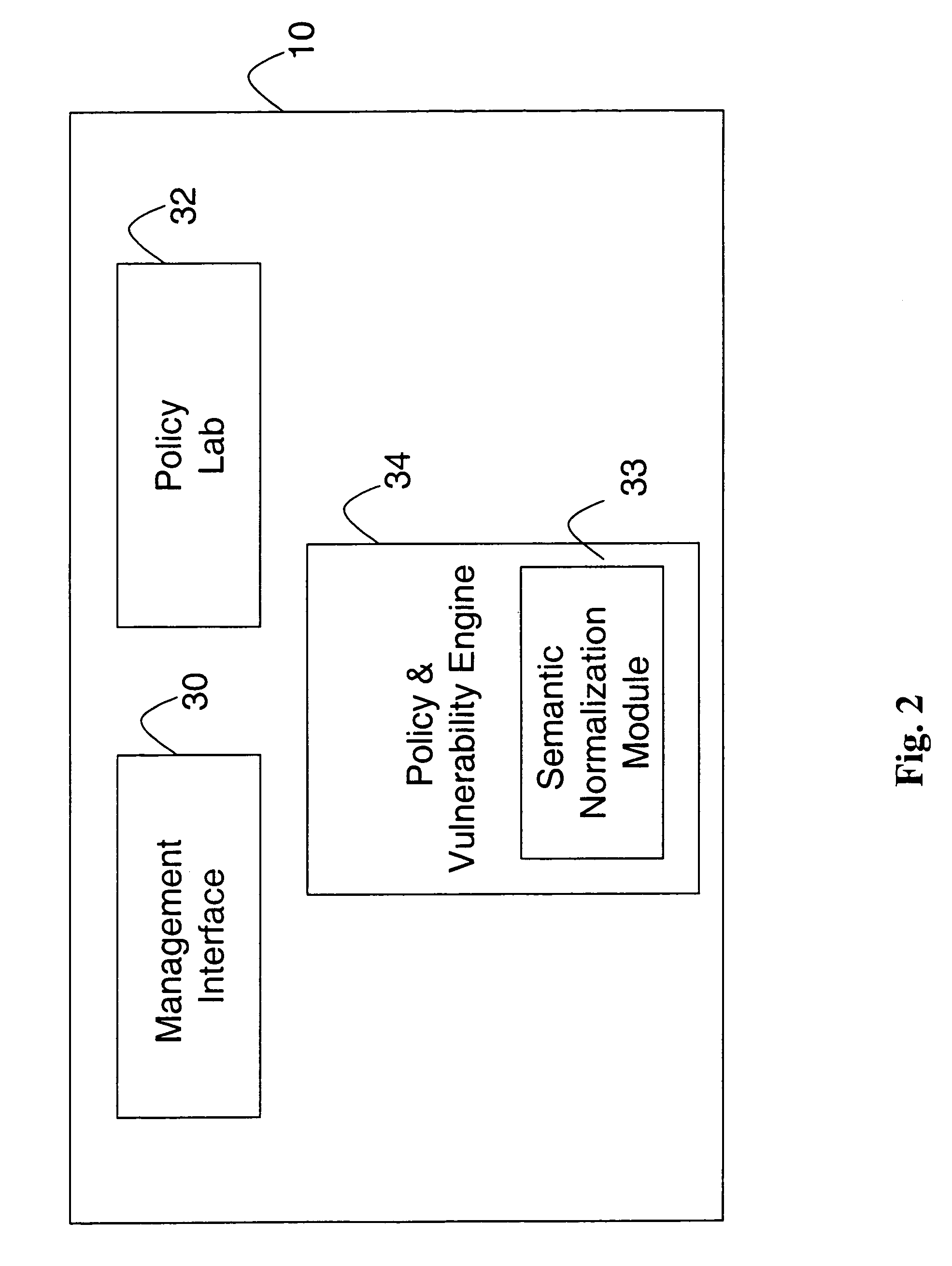
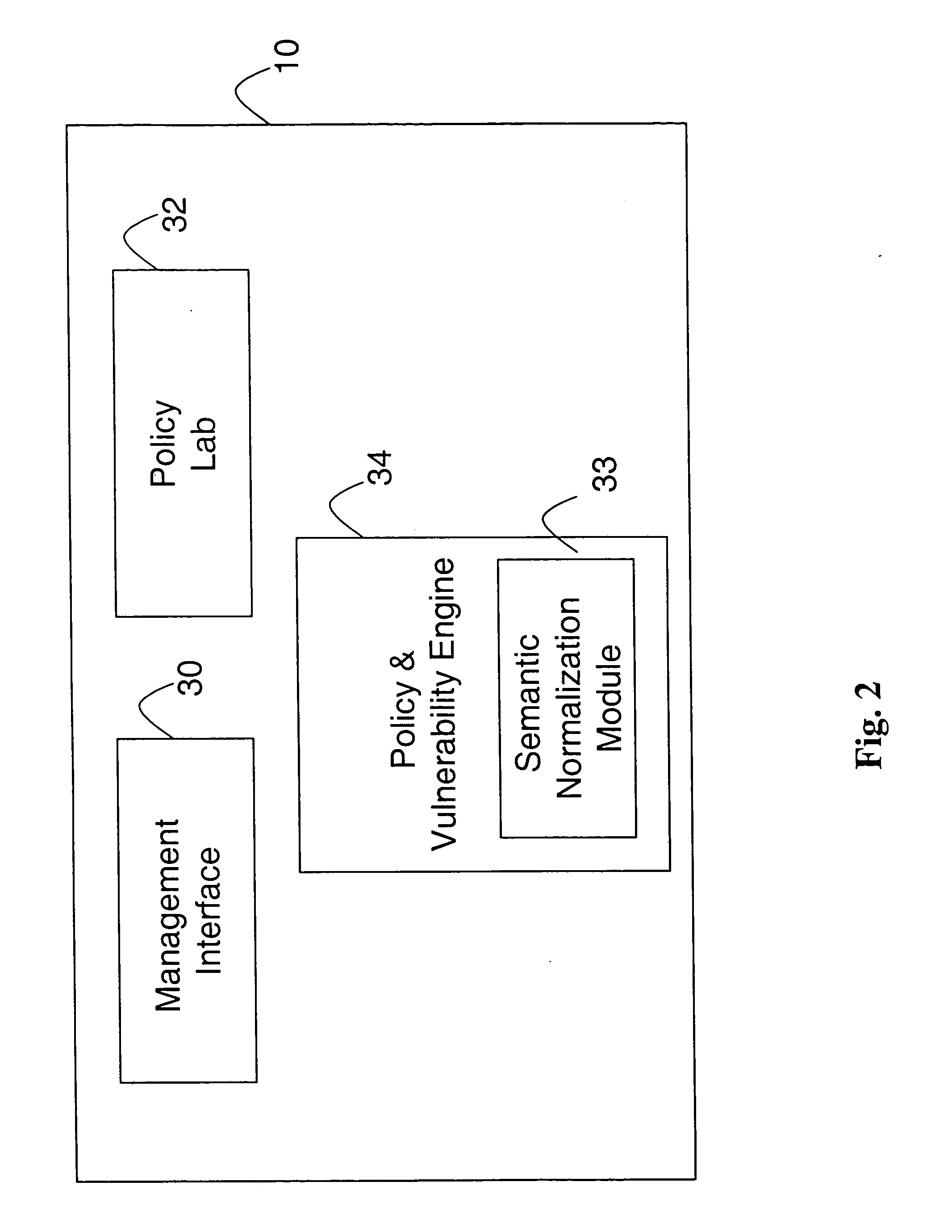
System and method for security information normalization
InactiveUS20050015623A1Memory loss protectionDigital data processing detailsSemantic equivalenceData mining
A prevention-based network auditing system includes an audit repository storing network information gathered by a plurality of heterogeneous information sources. A semantic normalization module identifies semantic equivalencies in the gathered information, and generates a map listing for each fact gathered by an information source, an equivalent fact or set of facts gathered by each of the other information sources. A network policy is then uniformly applied to the information that is identified as being semantically equivalent.
Owner:MCAFEE LLC
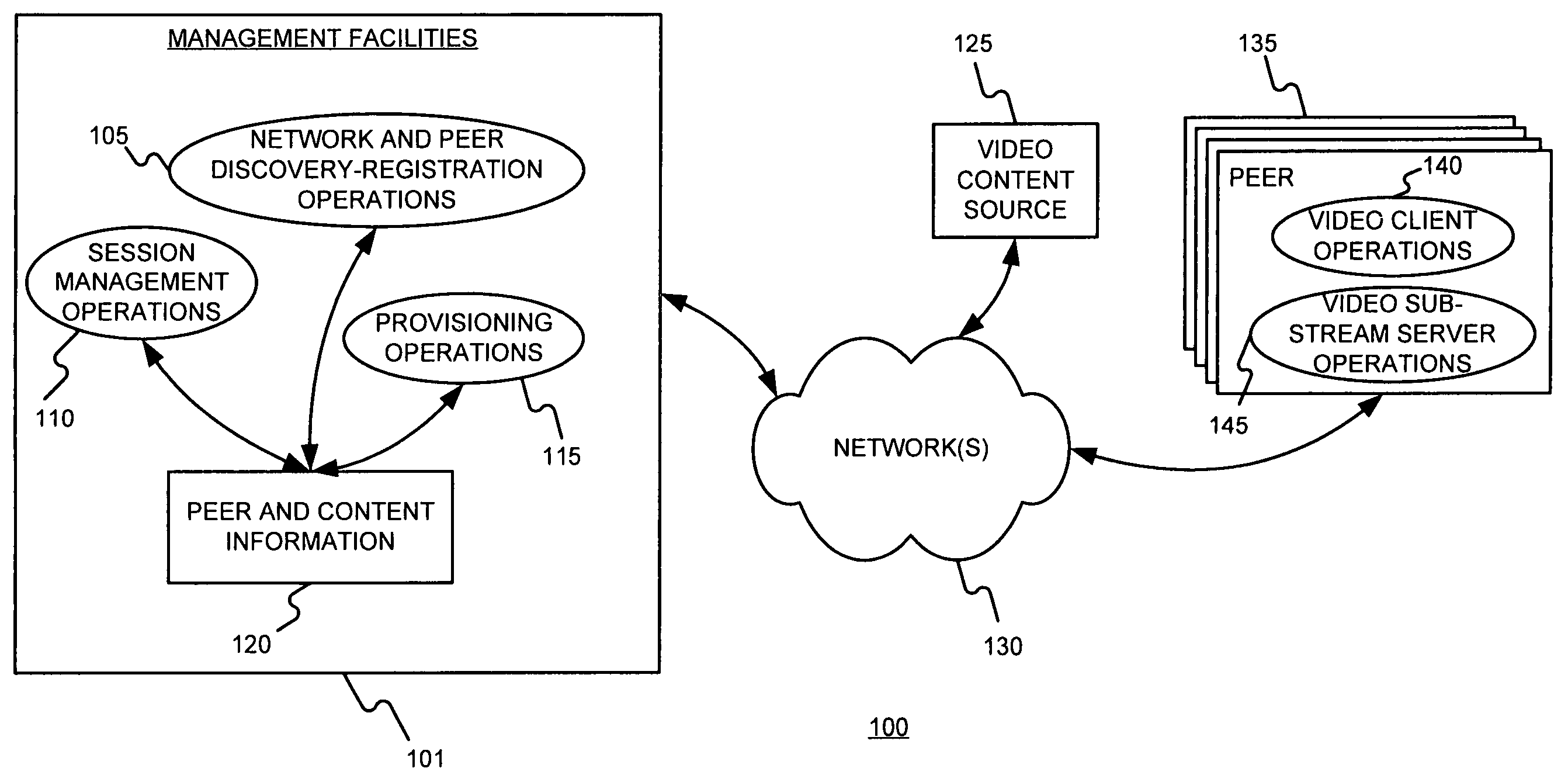
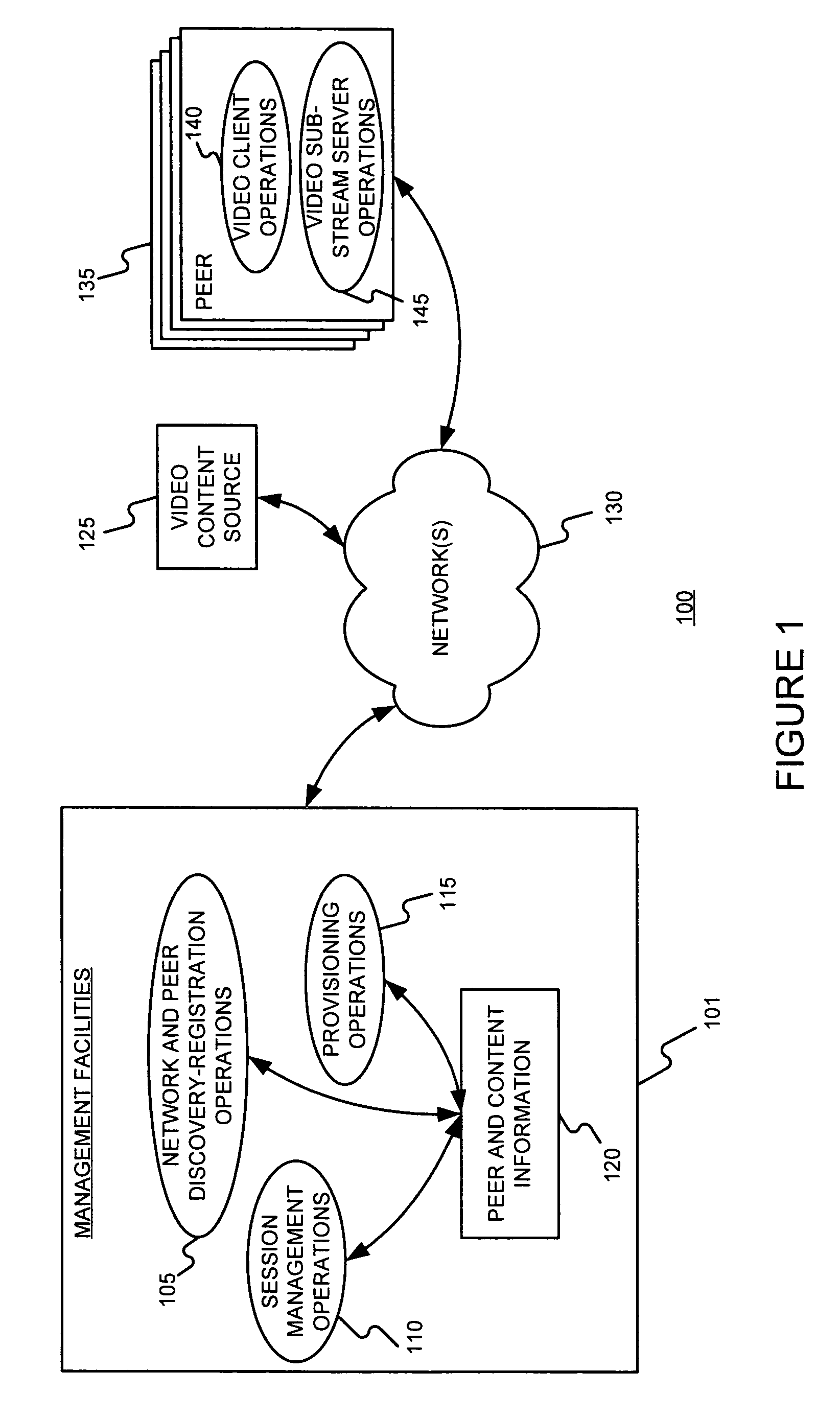
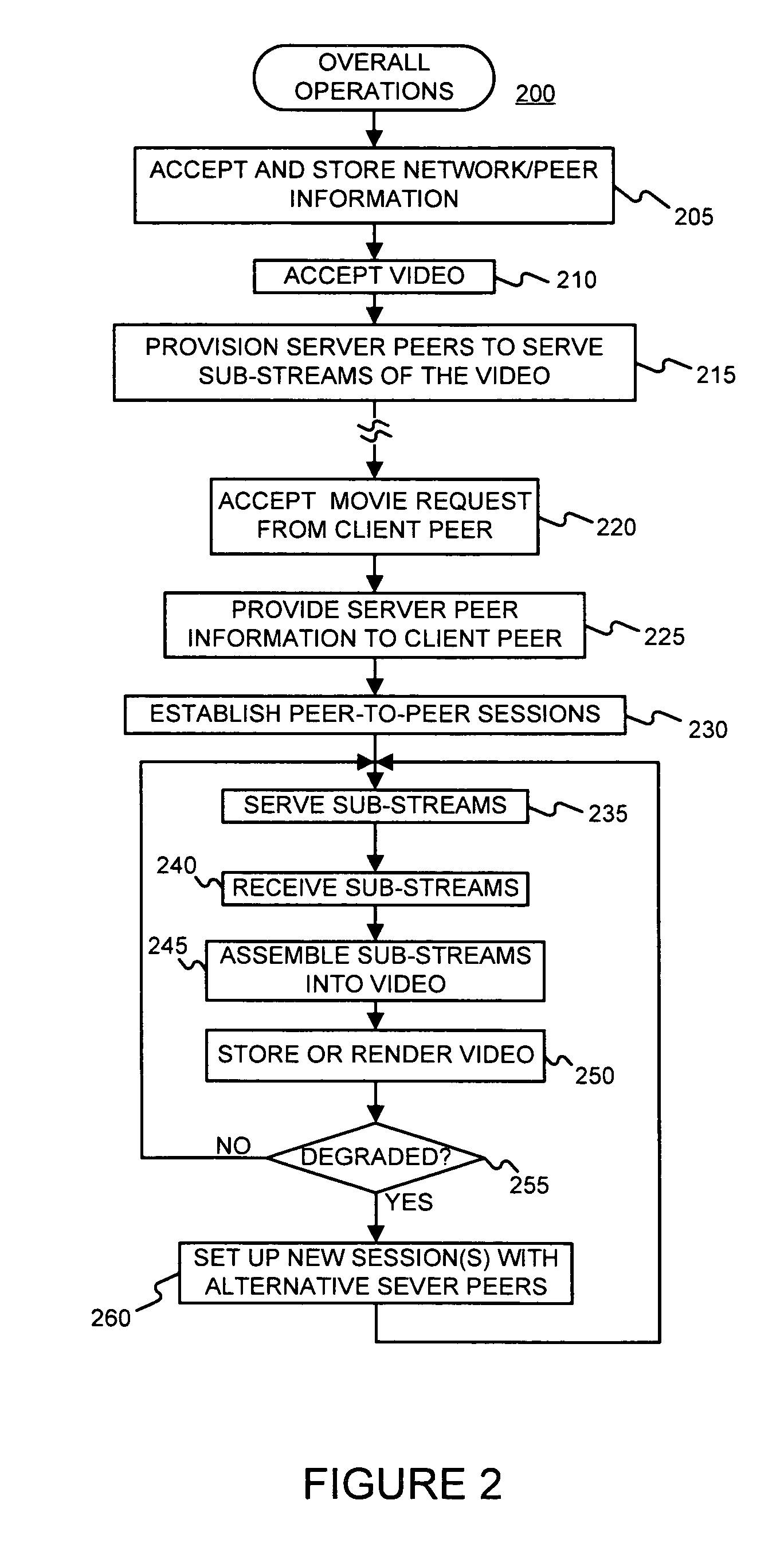
On demand peer-to-peer video streaming with multiple description coding
ActiveUS7633887B2Data switching by path configurationMultiple digital computer combinationsVideo storageVideo quality
A peer-to-peer novel video streaming scheme is described in which each peer stores and streams videos to the requesting client peers. Each video is encoded into multiple descriptions and each description is placed on a different node. If a serving peer disconnects in the middle of a streaming session, the system searches for a replacement peer that stores the same video description and has sufficient uplink bandwidth. Employing multiple description coding in a peer-to-peer based network improves the robustness of the distributed streaming content in the event a serving peer is lost. Video quality can be maintained in the presence of server peers being lost. The video codec design and network policies have a significant effect on the streamed video quality. The system performance generally improves as the number of descriptions M for the video increases, which implies that a higher video quality can be obtained with the same network loading.
Owner:POLYTECHNIC INST OF NEW YORK
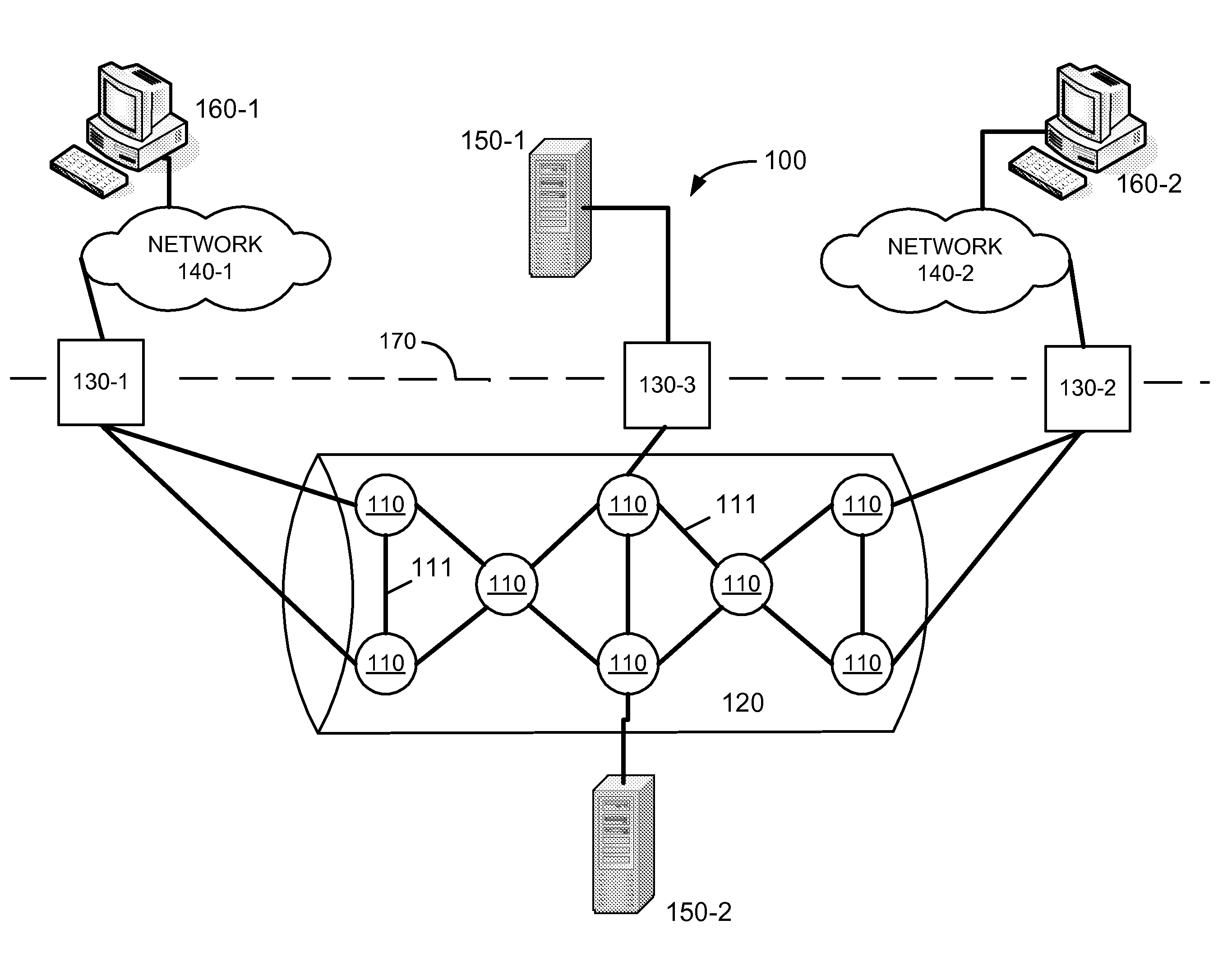
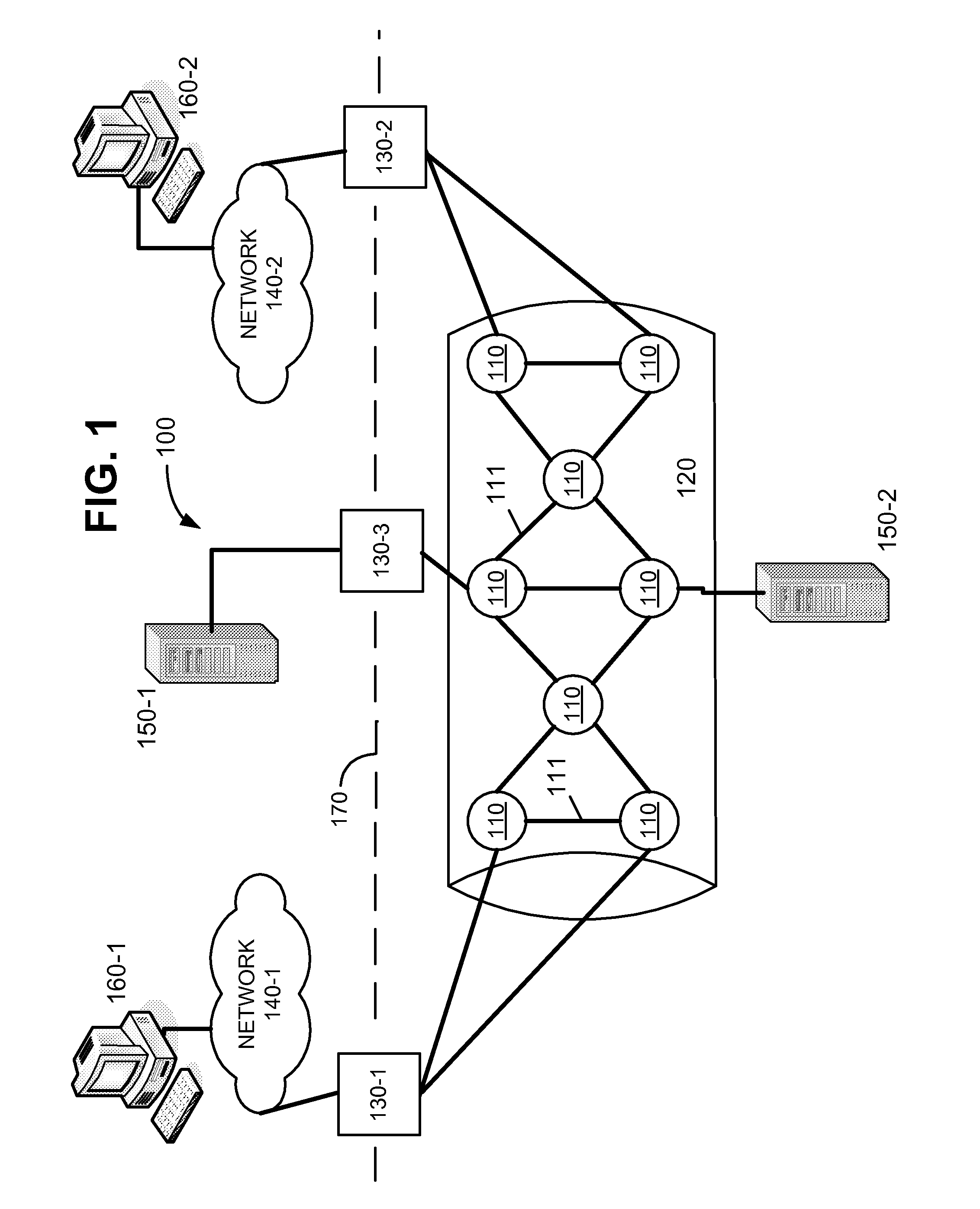
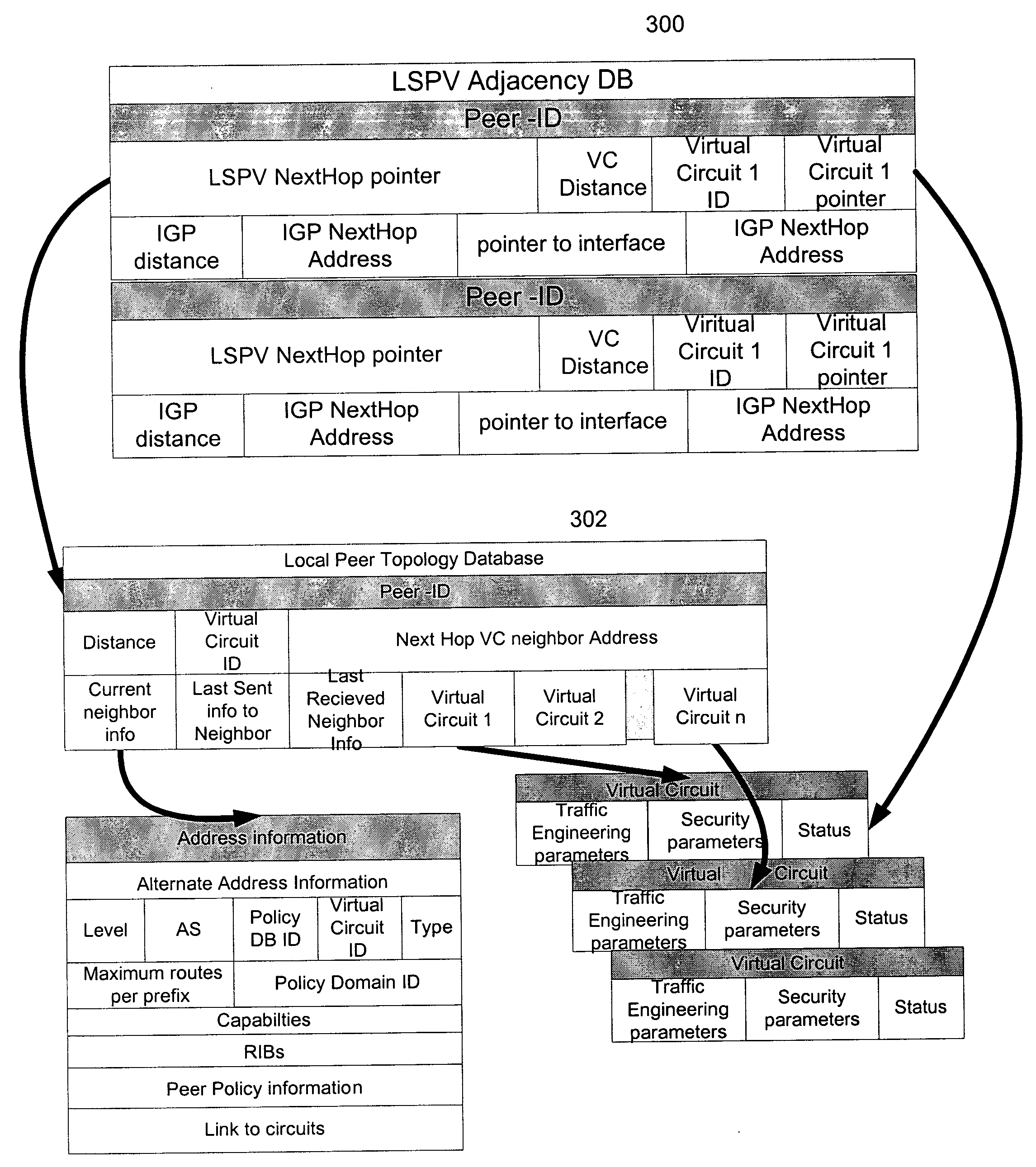
Systems and methods for routing employing link state and path vector techniques
InactiveUS20050047353A1Minimize floodingTime-division multiplexData switching by path configurationNetwork strategyNetwork routing
Routing protocols and algorithms, referred to collectively as “Link State Path Vector” (LSPV) techniques, are described. The LSPV allows the application of link-state techniques, such as flooding, to path vector protocols. Routing peers may be organized to form multiple levels of hierarchy. The LSPV mechanisms enable these peers to (1) exchange routing information via virtual links and (2) calculate the best network routes in light of the routing information. Routes may be selected on the basis of both topological distance and network policy. Such metrics may be determined by combining otherwise orthogonal metrics for IGPs and EGPs.
Owner:NEXTHOP TECH INC
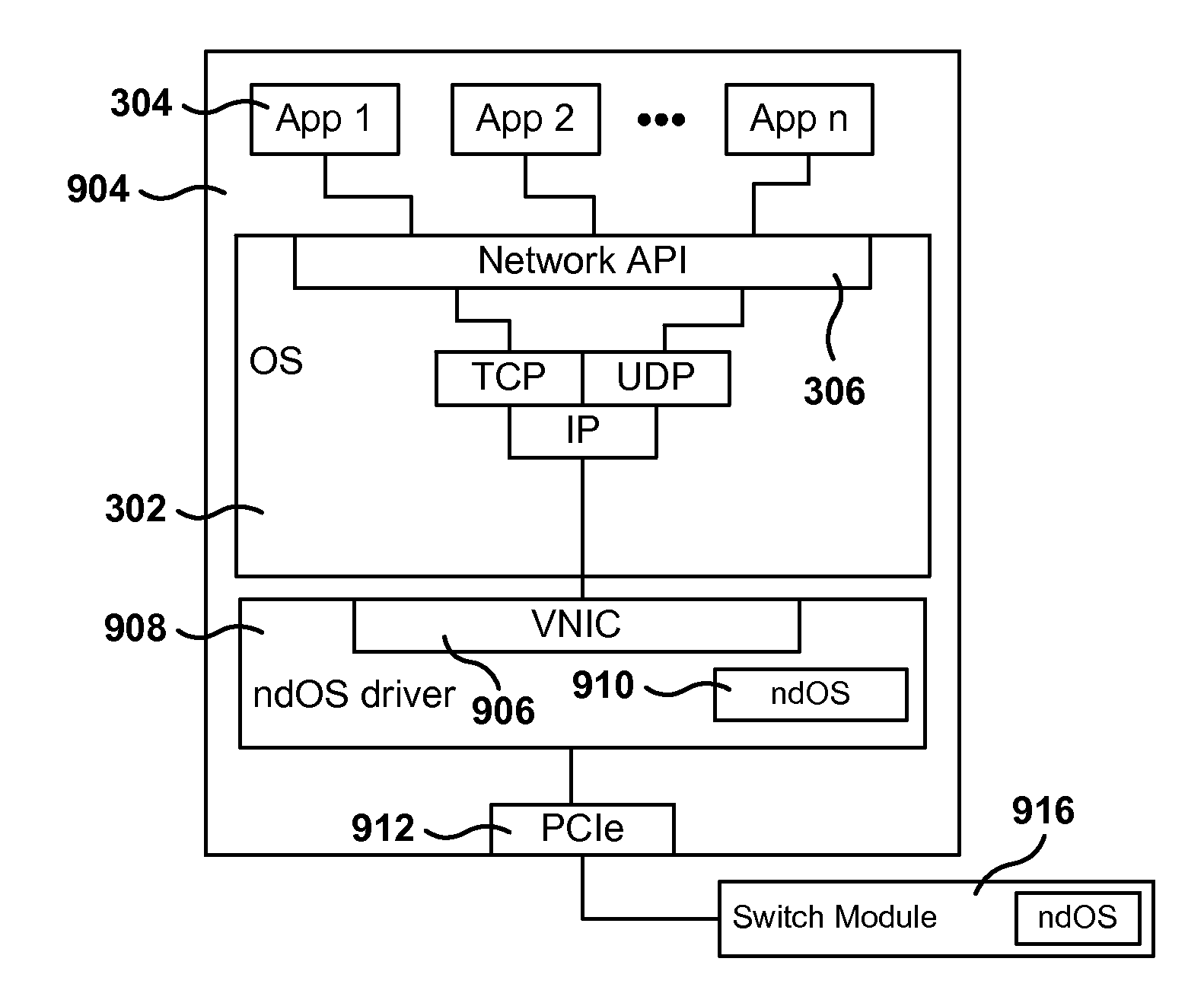
Servers, Switches, and Systems with Switching Module Implementing a Distributed Network Operating System
ActiveUS20130215754A1Error preventionFrequency-division multiplex detailsCommunication interfaceNetwork operating system
One networking device includes a switch module, a server, and a switch controller. The switch module has ports with a communications interface of a first type (CI1) and ports with a communications interface of a second type (CI2). The server, coupled to the switch module via a first CI2 coupling, includes a virtual CI1 driver, which provides a CI1 interface in the server, defined to exchange CI1 packets with the switch module via the first CI2 coupling. The virtual CI1 driver includes a first network device operating system (ndOS) program. The switch controller, in communication with the switch module via a second CI2 coupling, includes a second ndOS program controlling, in the switch module, a packet switching policy defining the switching of packets through the switch module or switch controller. The first and second ndOS programs exchange control messages to maintain a network policy for the switch fabric.
Owner:PLURIBUS NETWORKS
System and method for security information normalization
A prevention-based network auditing system includes an audit repository storing network information gathered by a plurality of heterogeneous information sources. A semantic normalization module identifies semantic equivalencies in the gathered information, and generates a map listing for each fact gathered by an information source, an equivalent fact or set of facts gathered by each of the other information sources. A network policy is then uniformly applied to the information that is identified as being semantically equivalent.
Owner:MCAFEE LLC
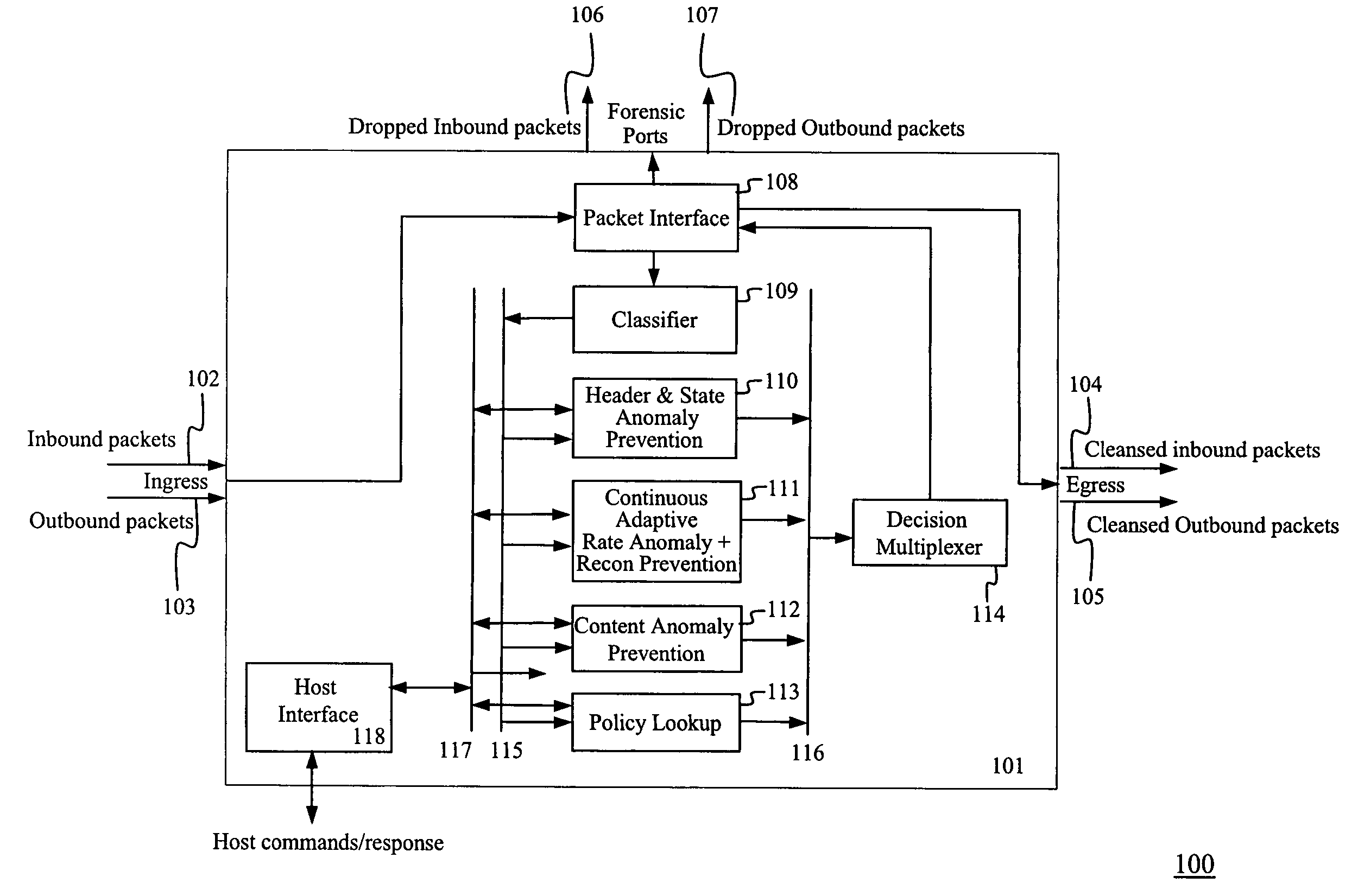
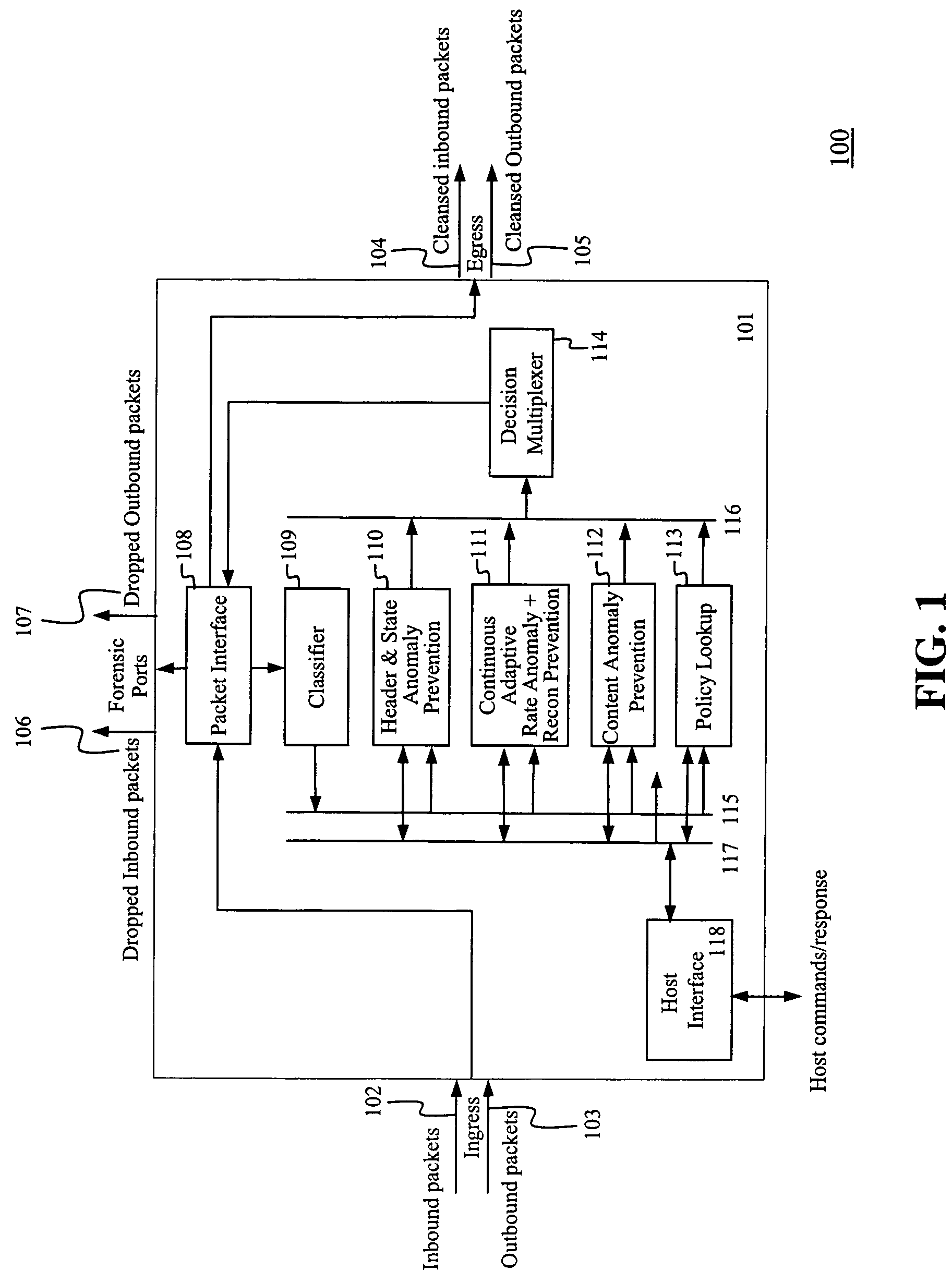
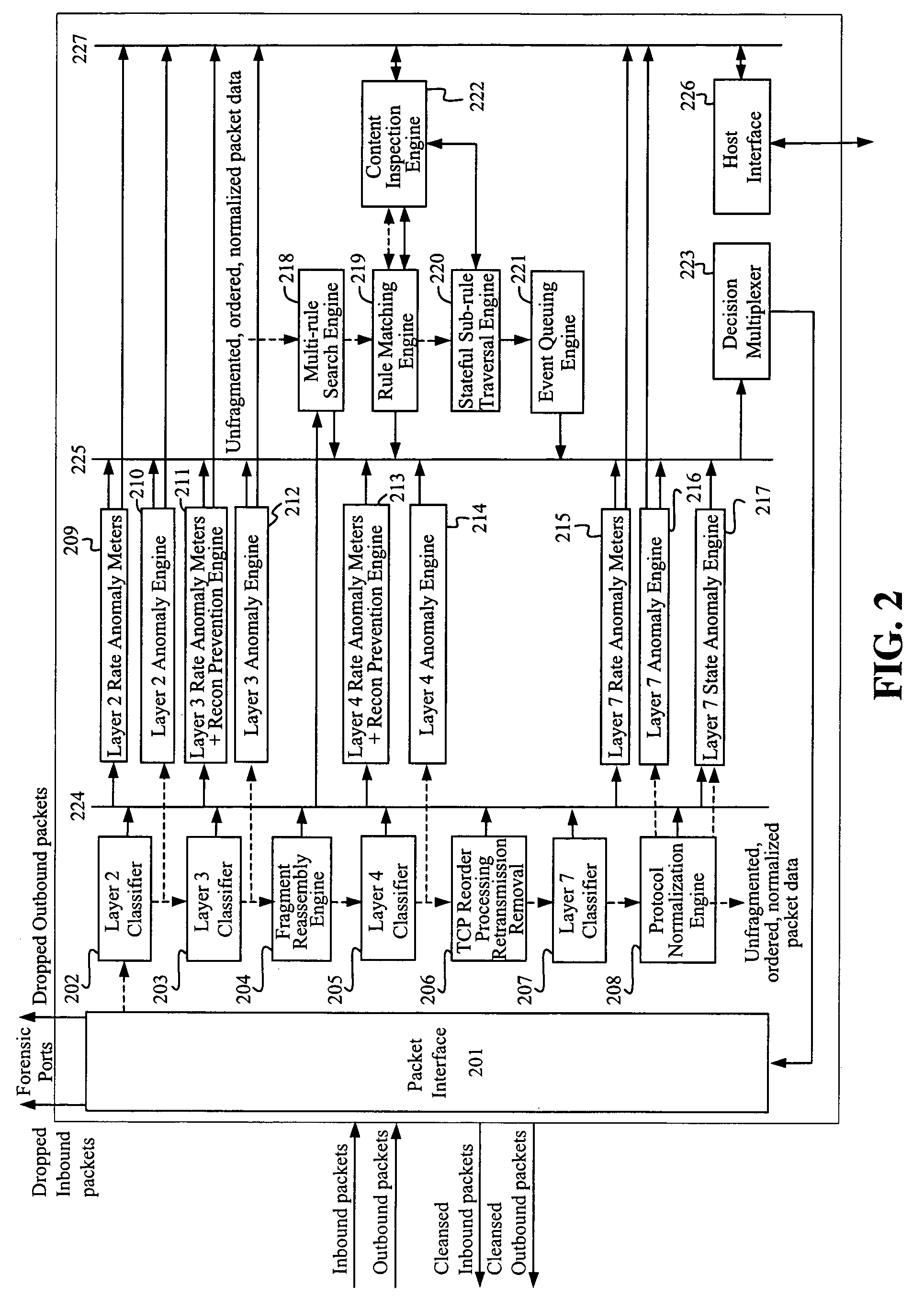
System and method for integrated header, state, rate and content anomaly prevention for domain name service
The present invention provides an integrated prevention of header, state, rate and content anomalies along with network policy enforcement for domain name service (DNS). A hardware-based apparatus helps identifying DNS rate-thresholds through continuous and adaptive learning. The apparatus can determine DNS header and DNS state anomalies and drop packets containing those anomalies. DNS queries and responses are inspected for known malicious contents using a Content Inspection Engine. The apparatus integrates advantageous solutions to prevent anomalous packets and enables a policy based packet filter for DNS.
Owner:FORTINET
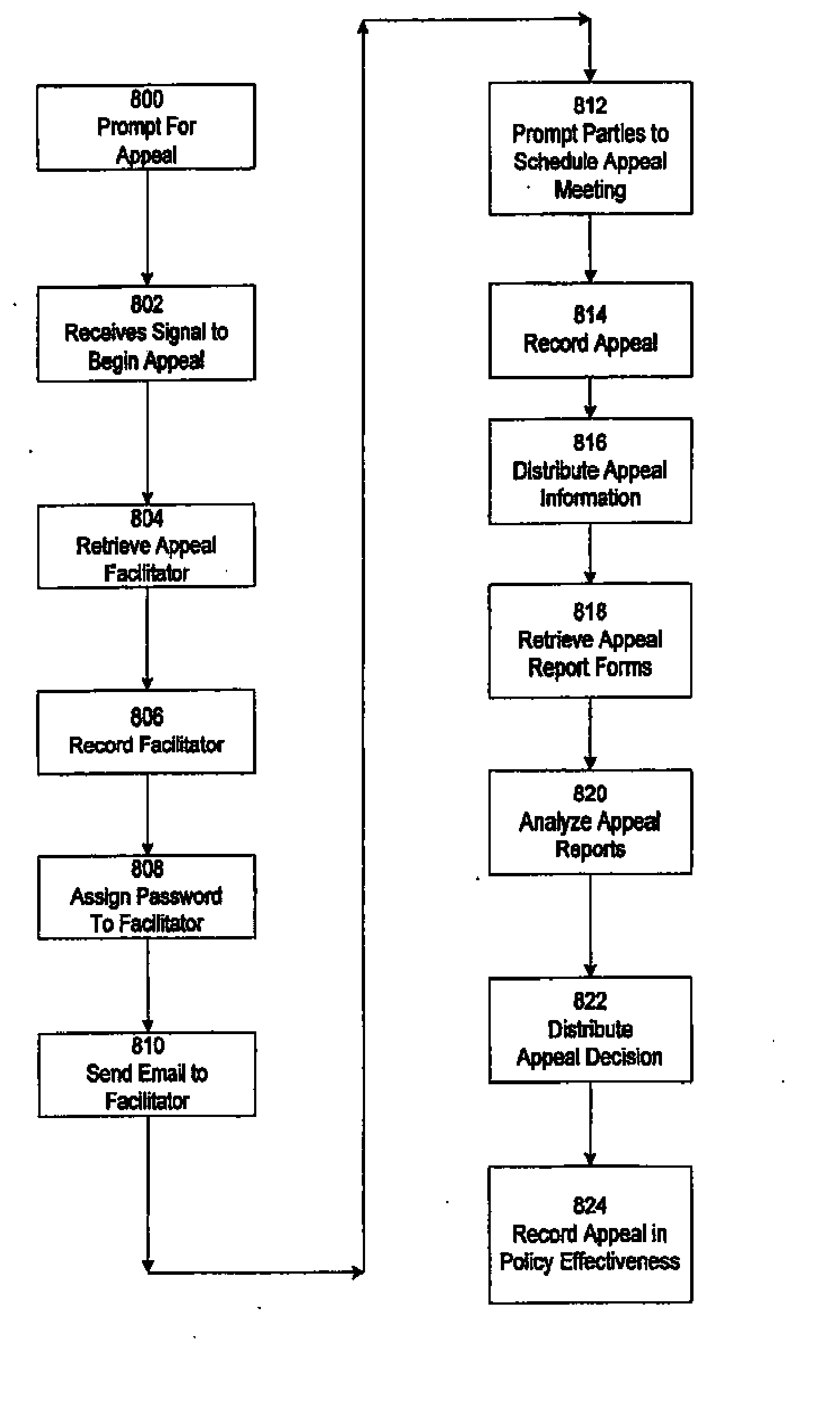
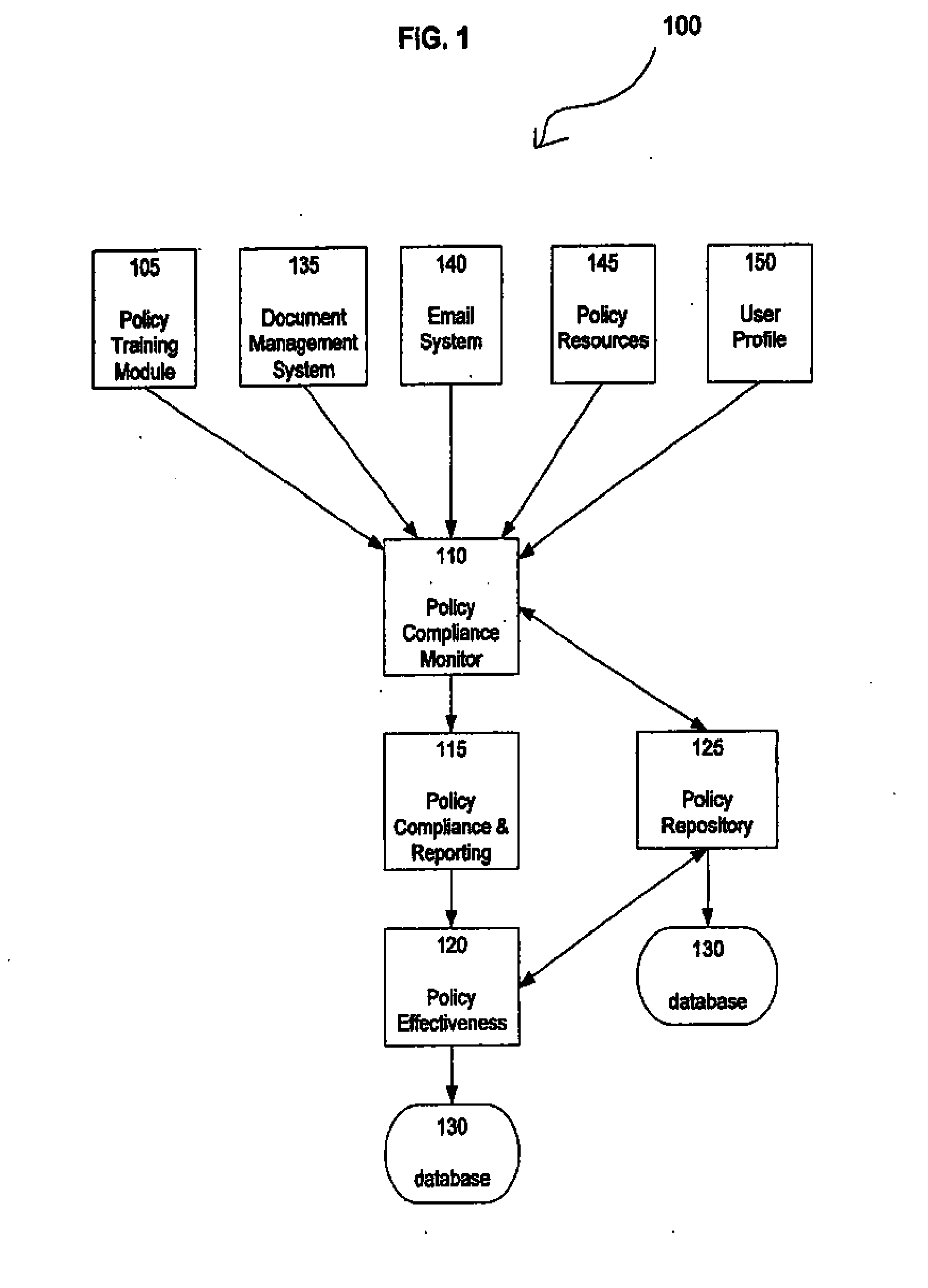
Network Policy Management And Effectiveness System
InactiveUS20070261121A1Digital data processing detailsError detection/correctionNon complianceNetwork security policy
The Present Invention discloses a method and apparatus for maintaining policy compliance on a computer network. A system in accordance with the principles of the Present Invention performs the steps of electronically monitoring network user compliance with a network security policy stored in a database, electronically evaluating network security policy compliance based on network user compliance and electronically undertaking a network policy compliance action in response to network security policy non-compliance. The network policy compliance actions may include automatically implementing a different network security policy selected from network security policies stored in the database, generating policy effectiveness reports and providing a retraining module to network users.
Owner:LONGHORN HD LLC
System and method for managing computer networks
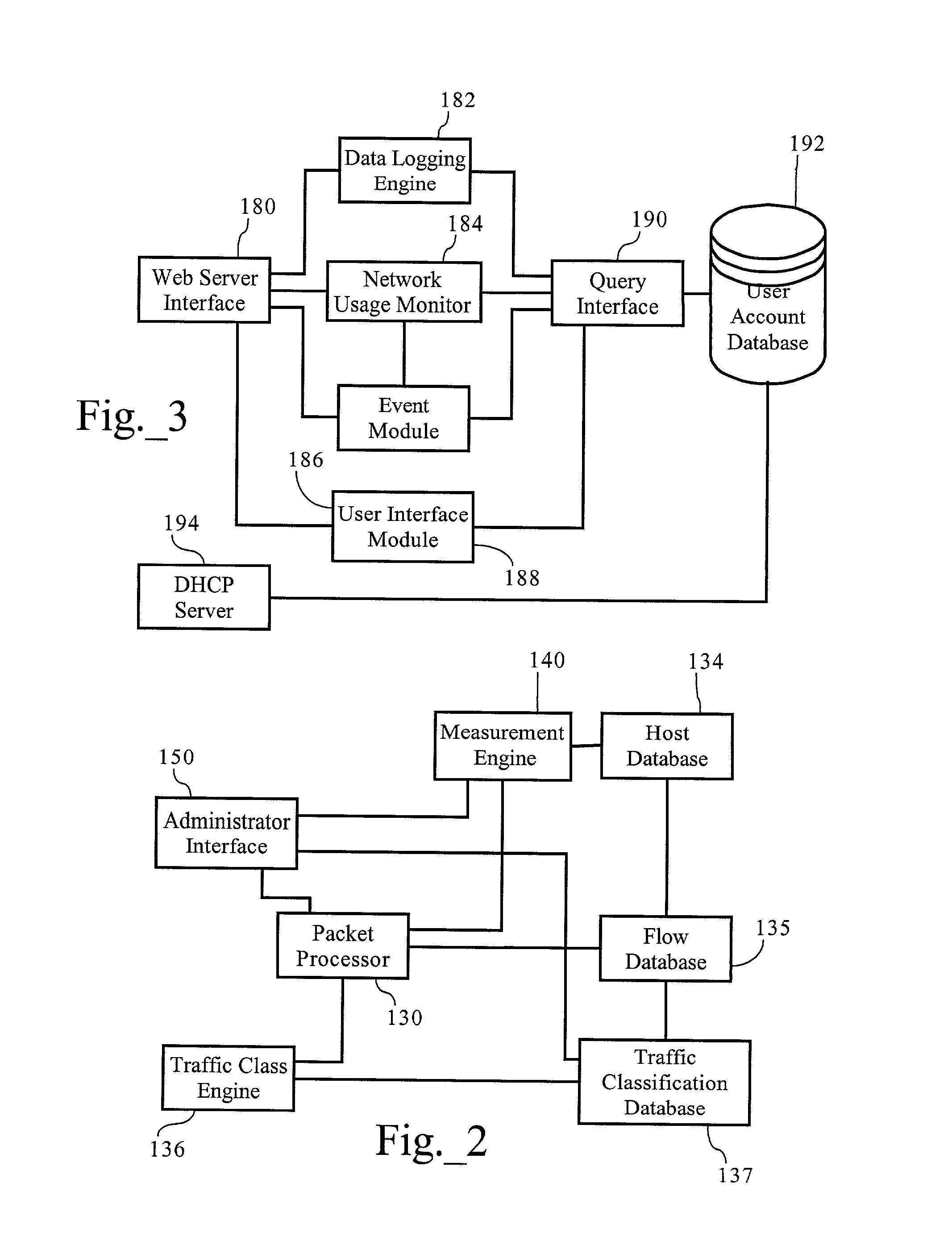
ActiveUS7359930B2Energy efficient ICTMultiple digital computer combinationsTraffic capacityNetwork behavior
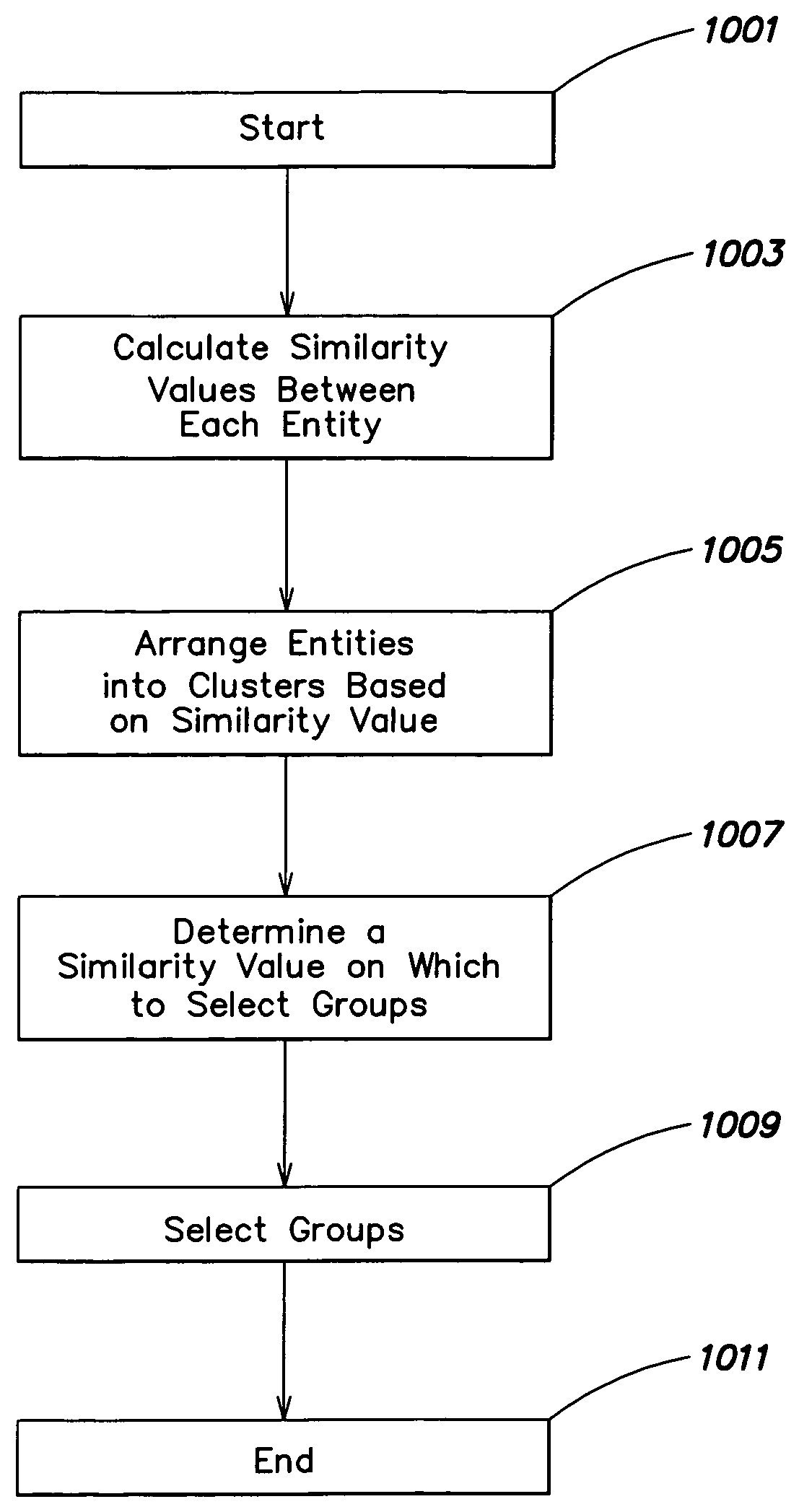
A system and method are provided for monitoring traffic in an enterprise network. Similar hosts may be grouped using flow information. Network policy may then be created at the group level based on the signatures of the hosts and groups of hosts in the enterprise. Hosts may be arranged in hierarchical clusters. Some of these clusters may be selected as groups based on a desired degree of similarity between hosts in a group. The similarity between hosts may be determined based on similarity of network behavior of the hosts.
Owner:ARBOR NETWORKS
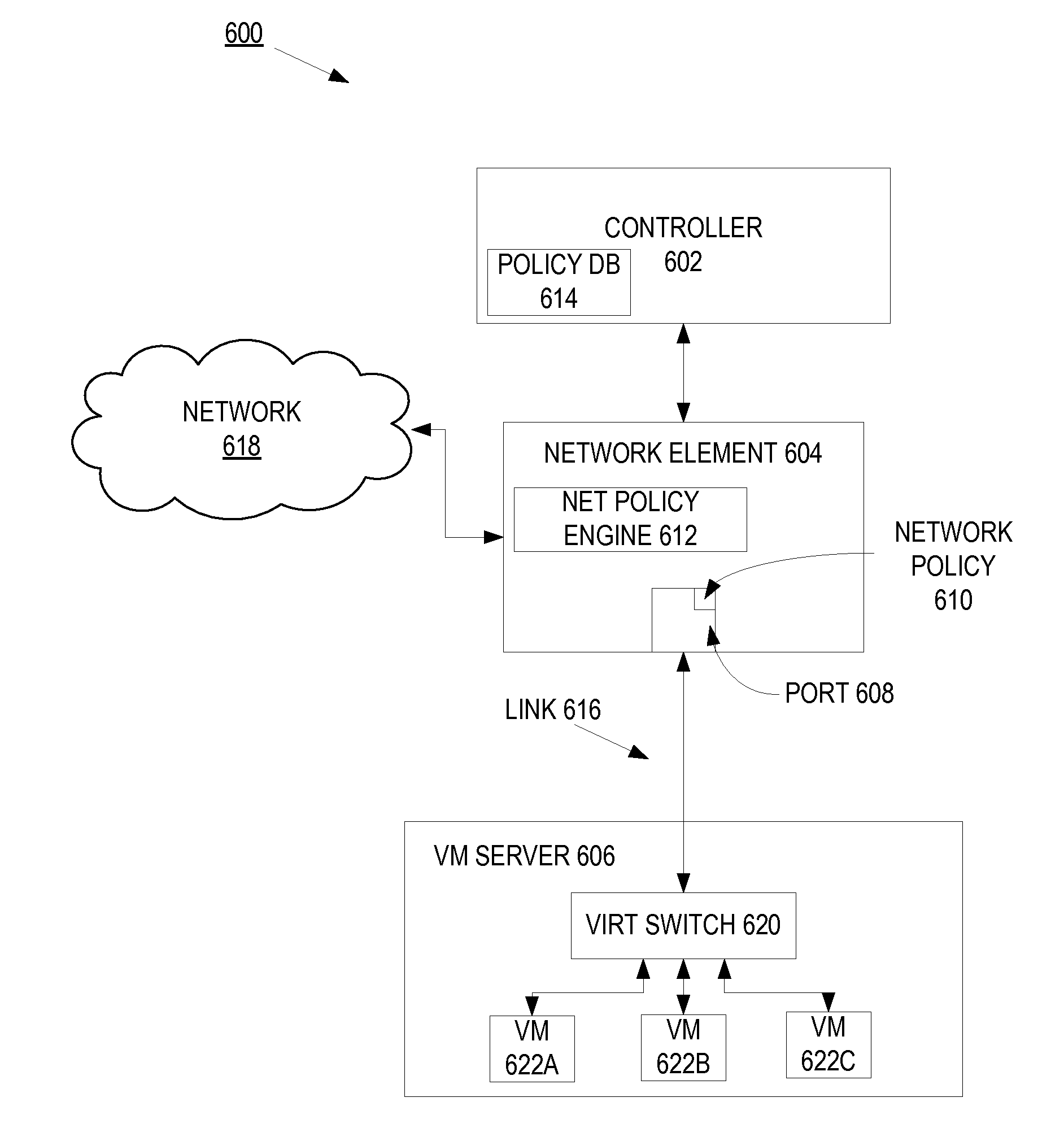
System and method for abstracting network policy from physical interfaces and creating portable network policy
A method and apparatus of a device that determines a network policy for an attached device based on one or more characteristics of the attached device is described. In one example, a network element detects a device on a port coupled to a link connecting the network element and the device. In response to the detecting of the device on the port, the network element further determines a device configuration signature from the device, where the device configuration signature based on a configuration of the device. The network element additionally determines a port-based network policy based on the device configuration signature. The network element applies the port-based network policy to the port, wherein the network element applies the port-based network policy to process network data communicated through the port.
Owner:ARISTA NETWORKS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com