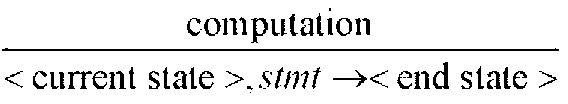Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40 results about "Semantic equivalence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
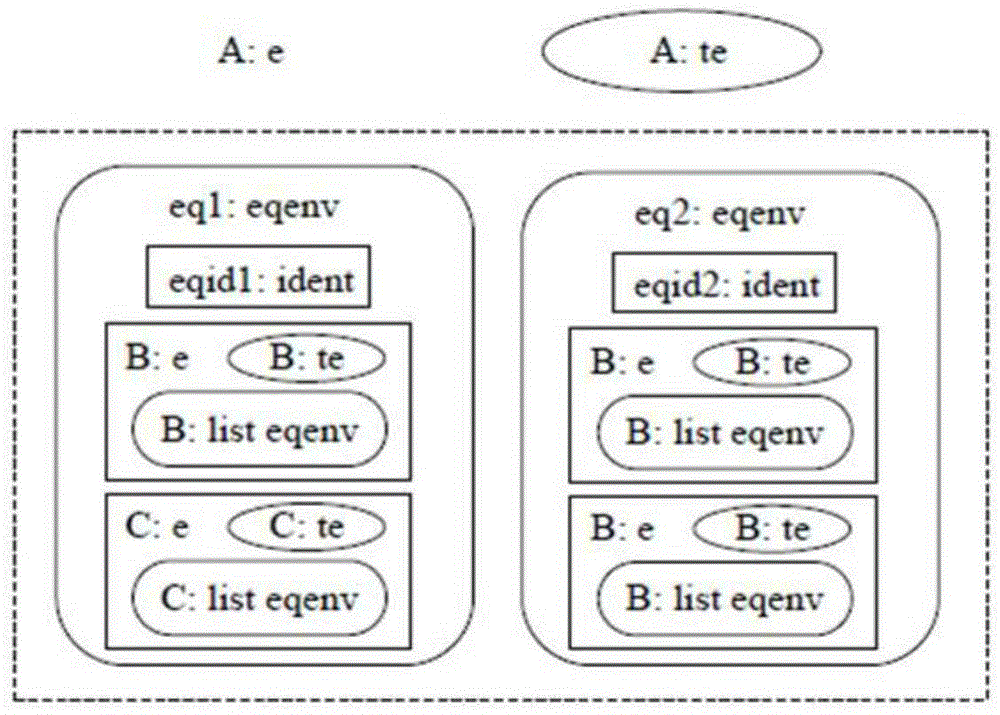
In computer metadata, semantic equivalence is a declaration that two data elements from different vocabularies contain data that has similar meaning.
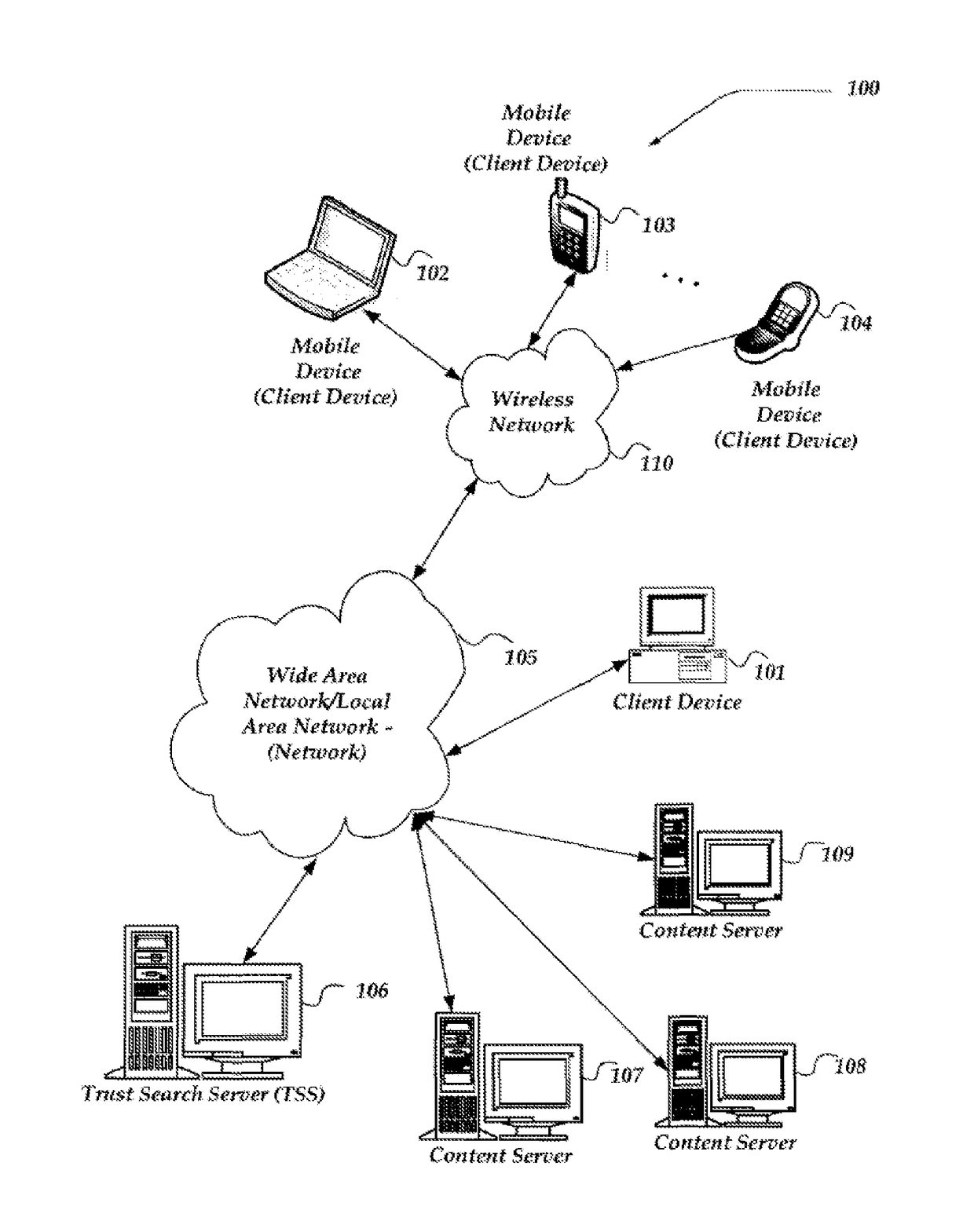
System and method for determining symantic equivalence between access control lists
InactiveUS20100199346A1Effective judgmentEfficiently determinedNext instruction address formationMultiple digital computer combinationsSemantic equivalenceDatabase
Aspects of the invention pertain to analyzing and modifying access control lists that are used in computer networks. Access control lists may have many individual rules that indicate whether information can be passed between certain devices in a computer network. The access control lists may include redundant or conflicting rules. An aspect of the invention determines whether two or more access control lists are equivalent or not. Order-dependent access control lists are converted into order-independent access control lists, which enable checking of semantic equivalence of different access control lists. Upon conversion to an order-independent access control list, lower-precedence rules in the order-free list are checked for overlap with a current higher precedence entry. If overlap exists, existing order-free rules are modified so that spinoff rules have no overlap with the current entry. This is done while maintaining semantic equivalence.
Owner:TT GOVERNMENT SOLUTIONS
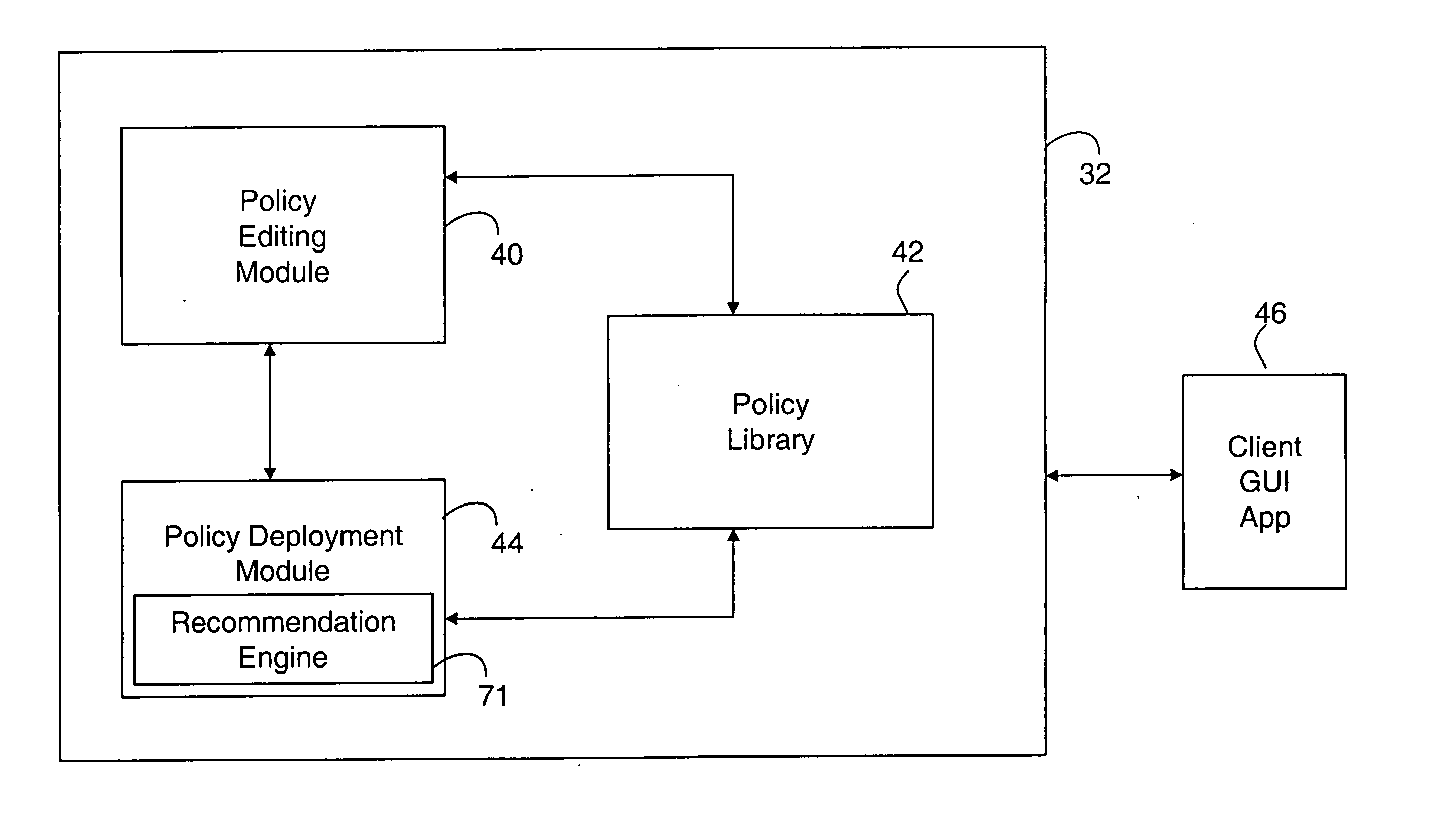
System and method for security information normalization
InactiveUS20050015623A1Memory loss protectionDigital data processing detailsSemantic equivalenceData mining
A prevention-based network auditing system includes an audit repository storing network information gathered by a plurality of heterogeneous information sources. A semantic normalization module identifies semantic equivalencies in the gathered information, and generates a map listing for each fact gathered by an information source, an equivalent fact or set of facts gathered by each of the other information sources. A network policy is then uniformly applied to the information that is identified as being semantically equivalent.
Owner:MCAFEE LLC
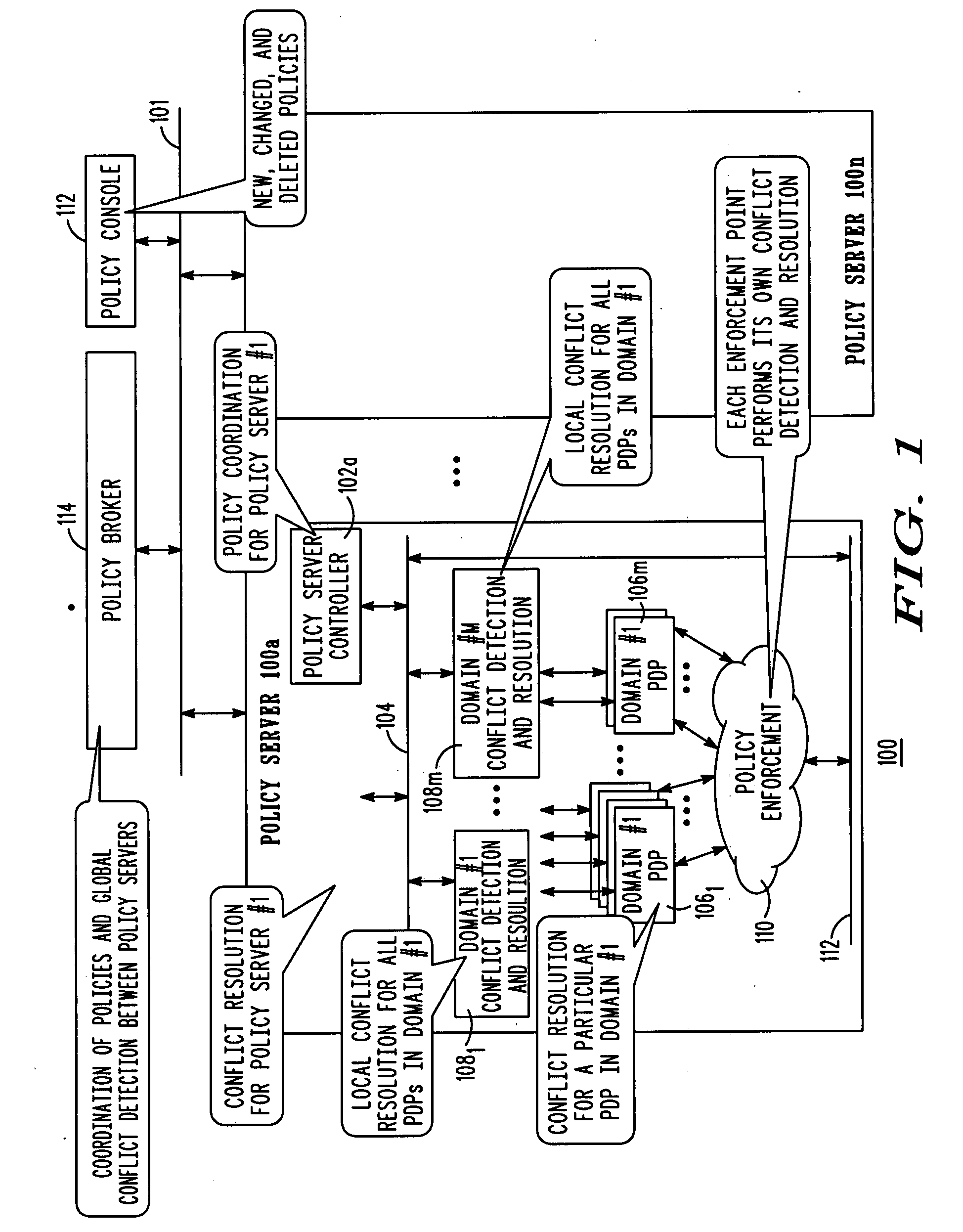
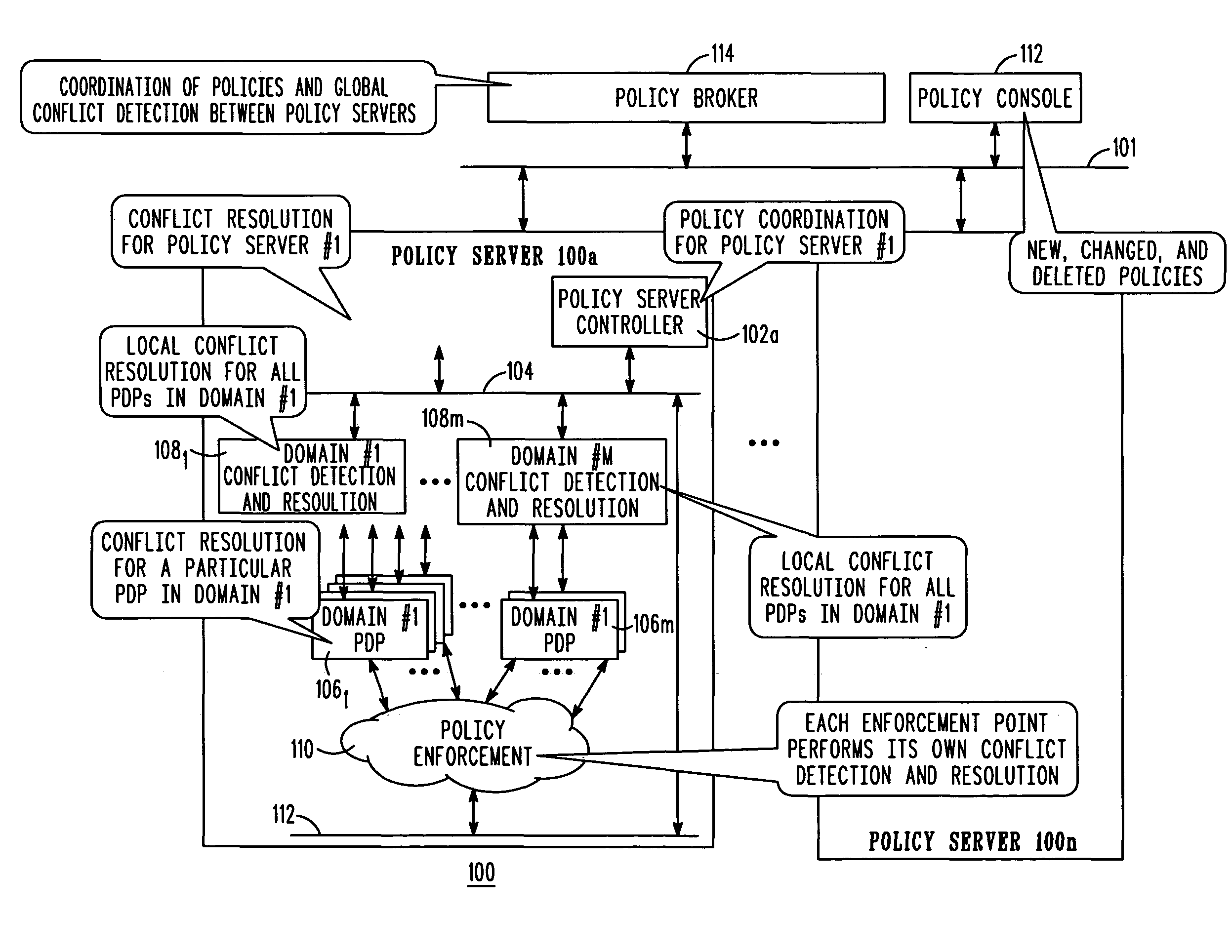
Performing policy conflict detection and resolution using semantic analysis
ActiveUS20080320550A1Determine of conflictDigital data processing detailsMultiprogramming arrangementsNatural language processingReasoning algorithm
A method and system for managing a policy includes, in response to determining the presence of a conflict, determining a semantic equivalence between a component of a policy rule and at least one additional policy rule. The determining a semantic equivalence is performed by using a semantic reasoning algorithm that includes the steps of determining a first policy target of a first policy rule and a second policy target of a second policy rule, determining a meaning of the first policy target and a meaning of the second policy rule, assigning a confidence value based on the determined meaning of the first policy, assigning a confidence value based on the determined meaning of the second policy, performing a semantic comparison between the first policy target and the second policy target, and determining, based at least in part on the semantic comparison, the presence of a conflict between the first and second policy targets.
Owner:MOTOROLA SOLUTIONS INC
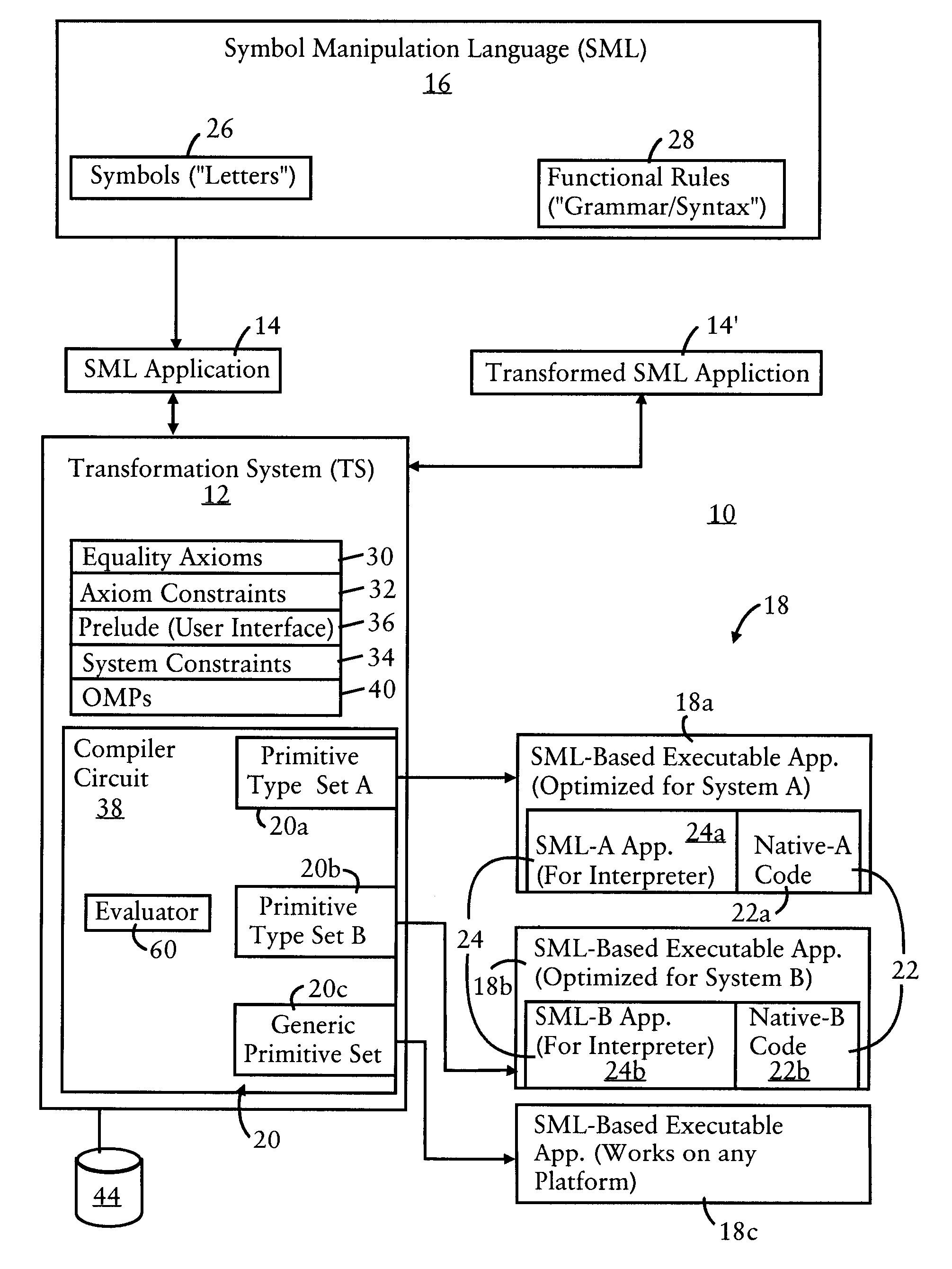
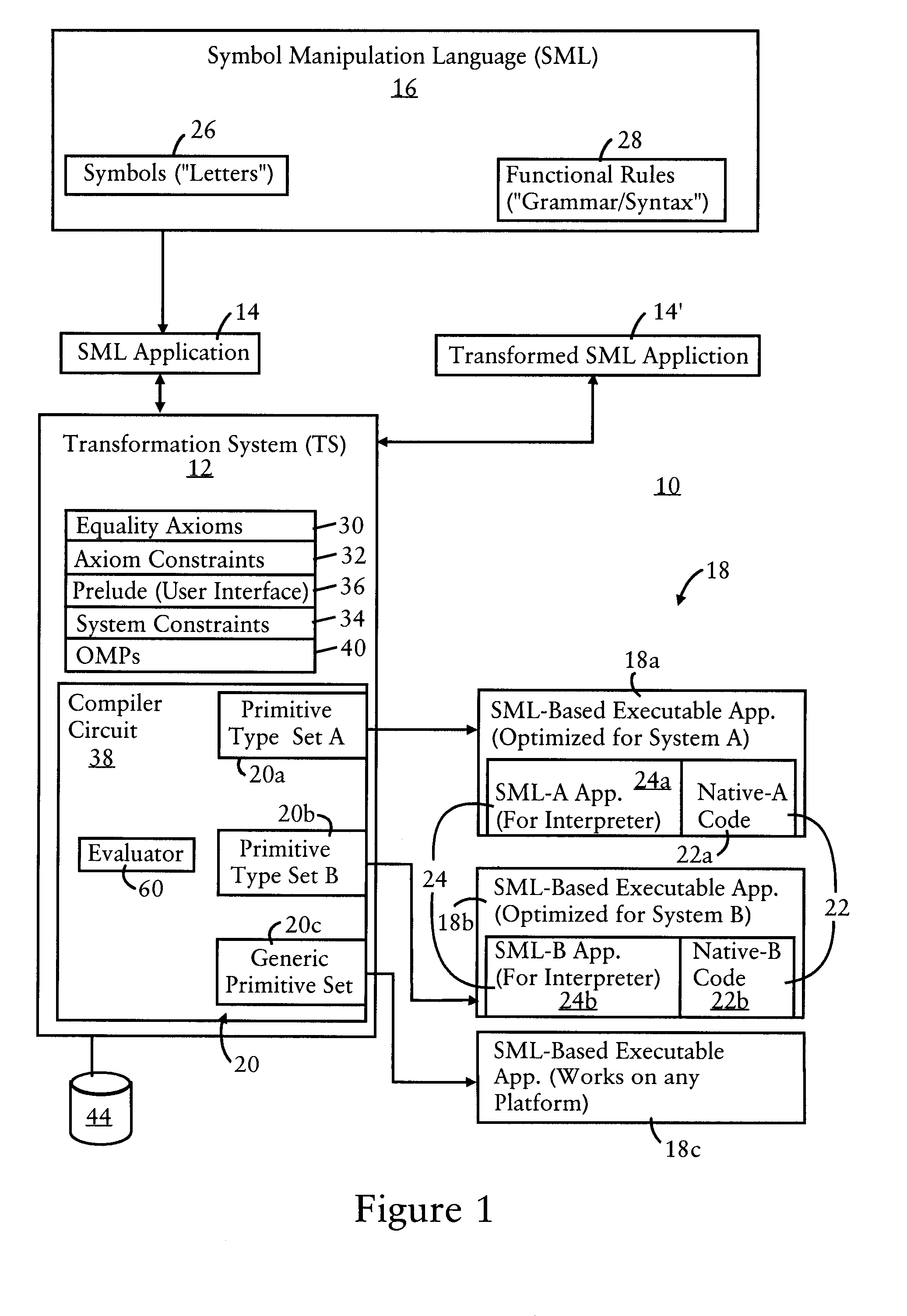
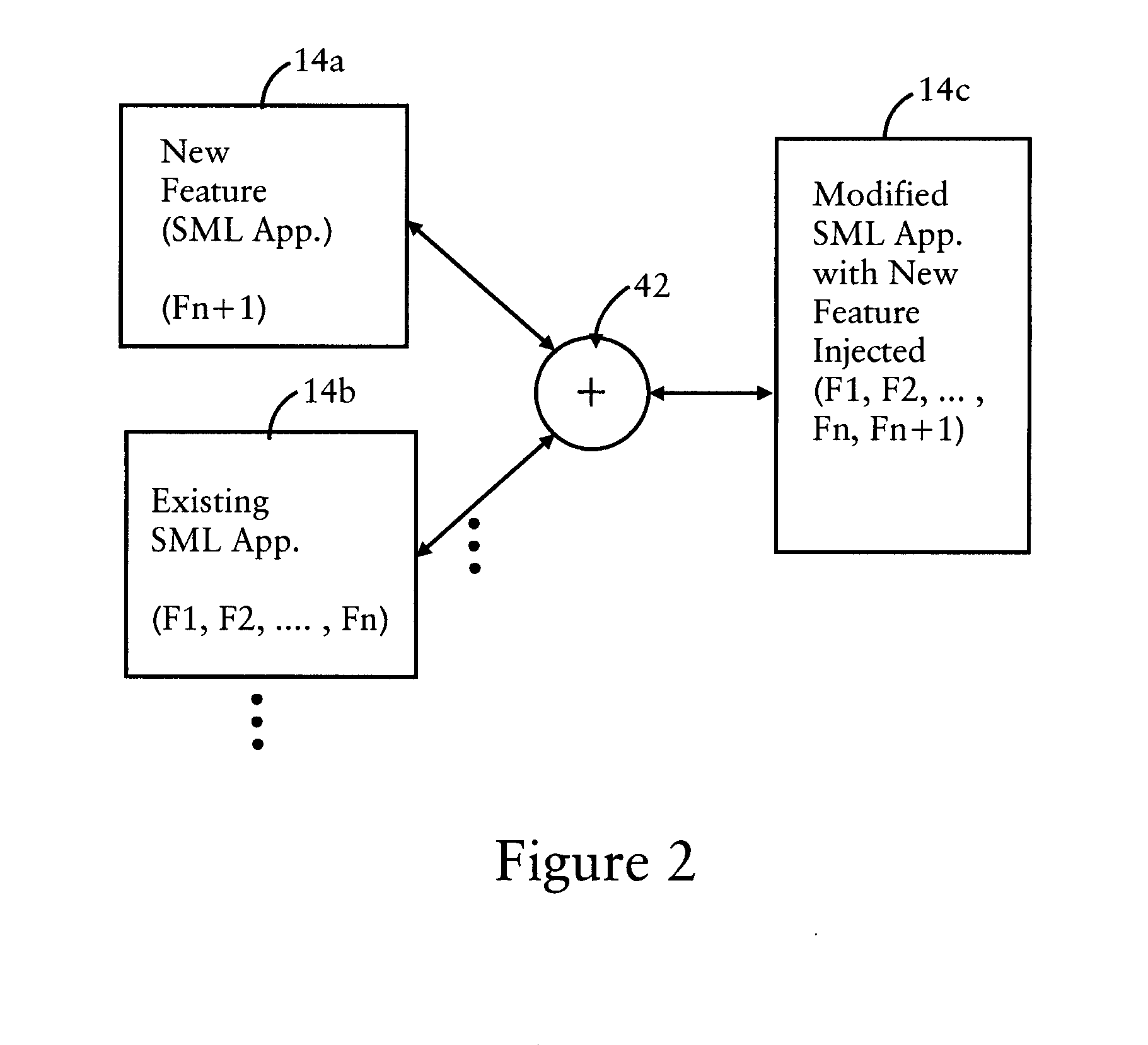
Optimizing symbol manipulation language-based executable applications for distributed execution
InactiveUS20120159459A1Software engineeringProgram controlTheoretical computer scienceSemantic equivalence
In one embodiment, a method comprises receiving an application that describes functions according to a prescribed symbol manipulation language, the prescribed symbol manipulation language a non-Turing complete language that does not permit partial functions and describes the functions independent of any attribute of any computing system; identifying, in the application, a distribution annotation that identifies a candidate element in the application, the candidate element configured for execution in a distributed computing operation by a distributed computing system comprising two or more distributed computing devices; generating one or more variants of the application based on executing a nondestructive transformation of the application relative to prescribed equality axioms, at least one of the variants containing a corresponding semantically-equivalent variation of the candidate element; and selecting one of the variants as an optimization for execution of the application by the distributed computing system relative to prescribed metrics.
Owner:CISCO TECH INC
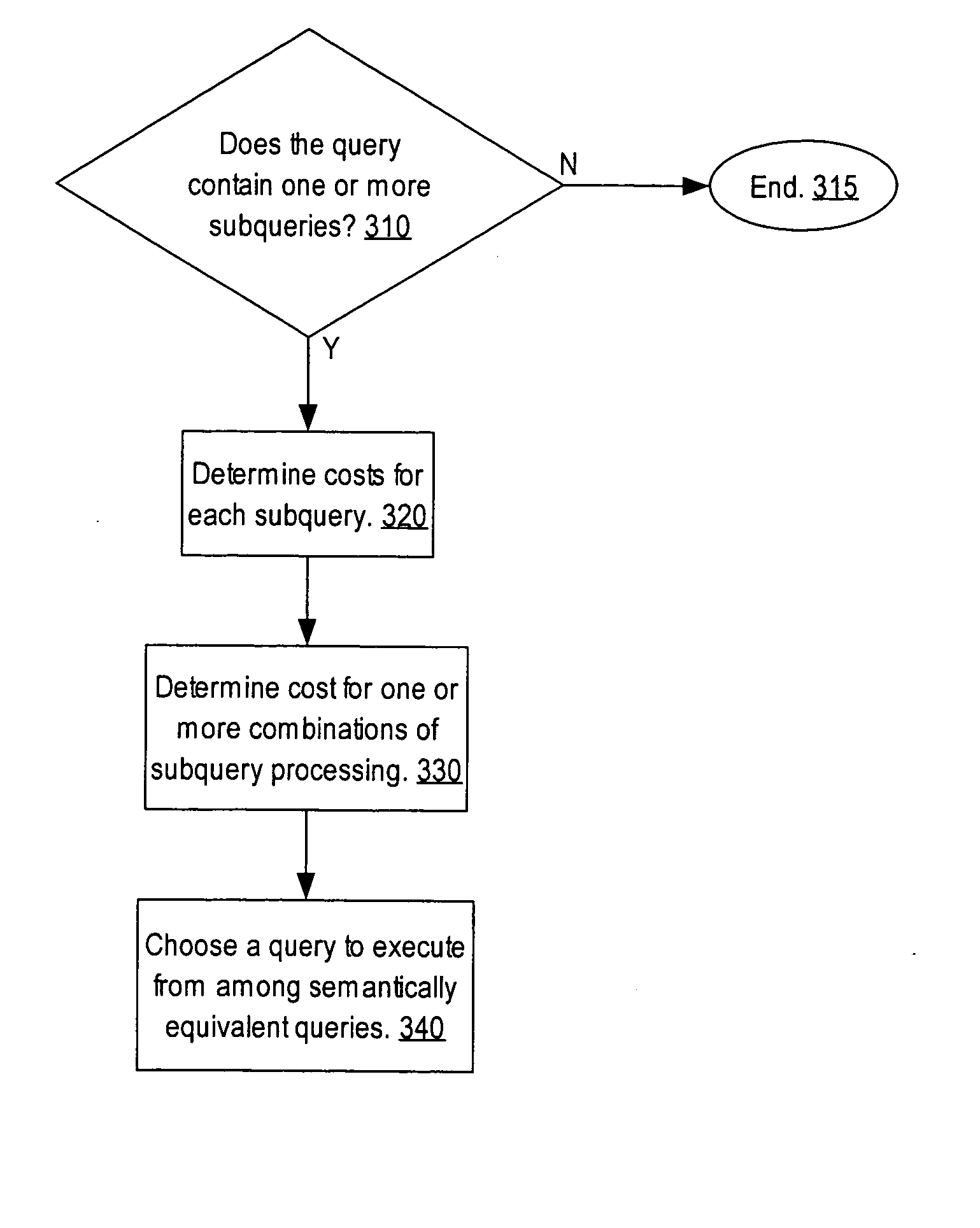
Multi-tier query processing
InactiveUS20050283471A1Digital data information retrievalSpecial data processing applicationsSemantic equivalenceData mining
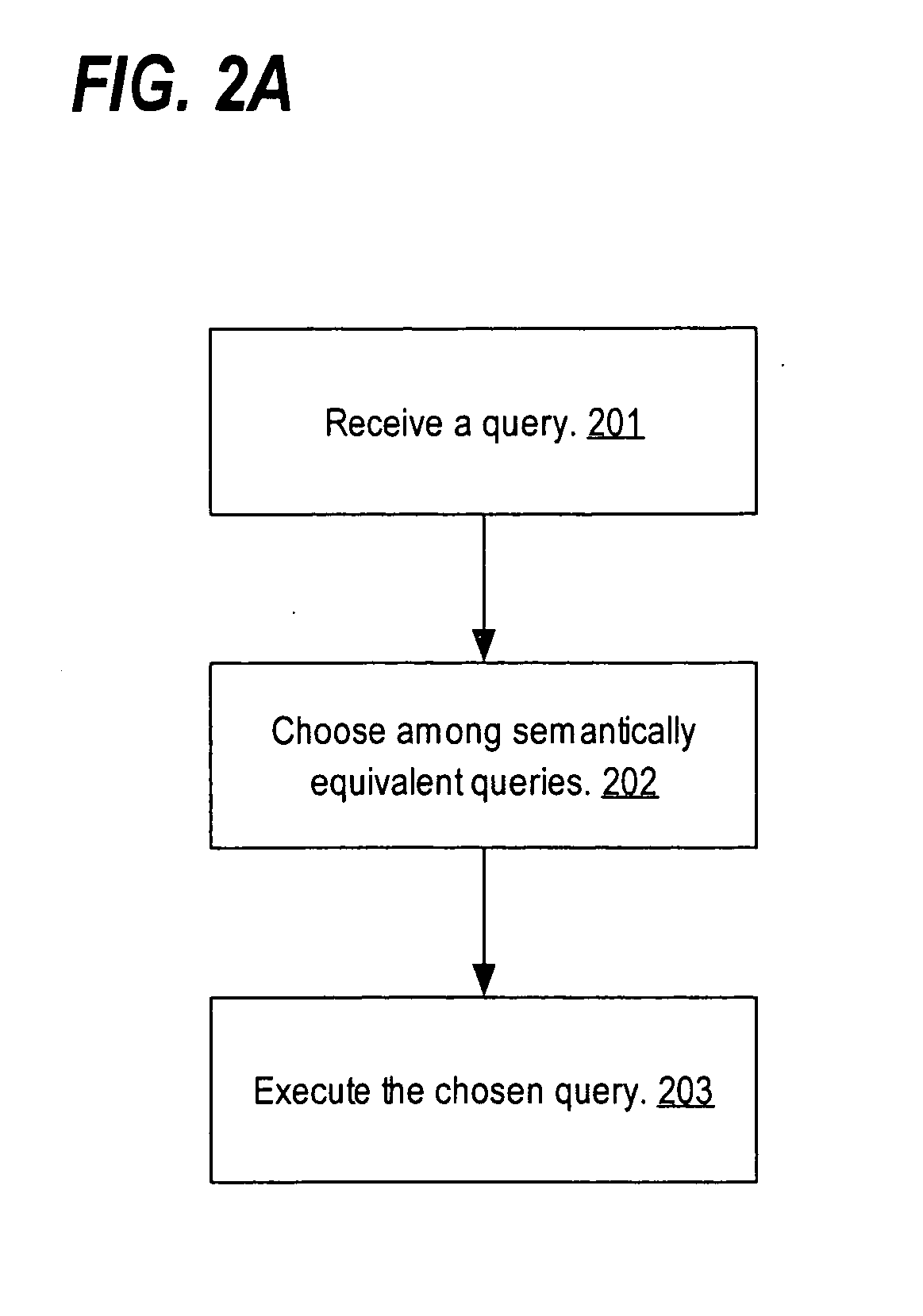
Techniques are provided for processing a query including determining a first cost based on the original query; if the query has a subquery, generating a second query with the subquery unnested; determining a second cost based on the second query; determining whether the second query includes a mergeable view; and if the second query includes a mergeable view, then generating a third query with the view merged; determining a third cost based on the third query; and choosing an output query from among the set of semantically equivalent queries based on costs associated with the semantically equivalent queries, where the set of semantically equivalent queries includes two or more of the original query, the second query, and the third query.
Owner:ORACLE INT CORP
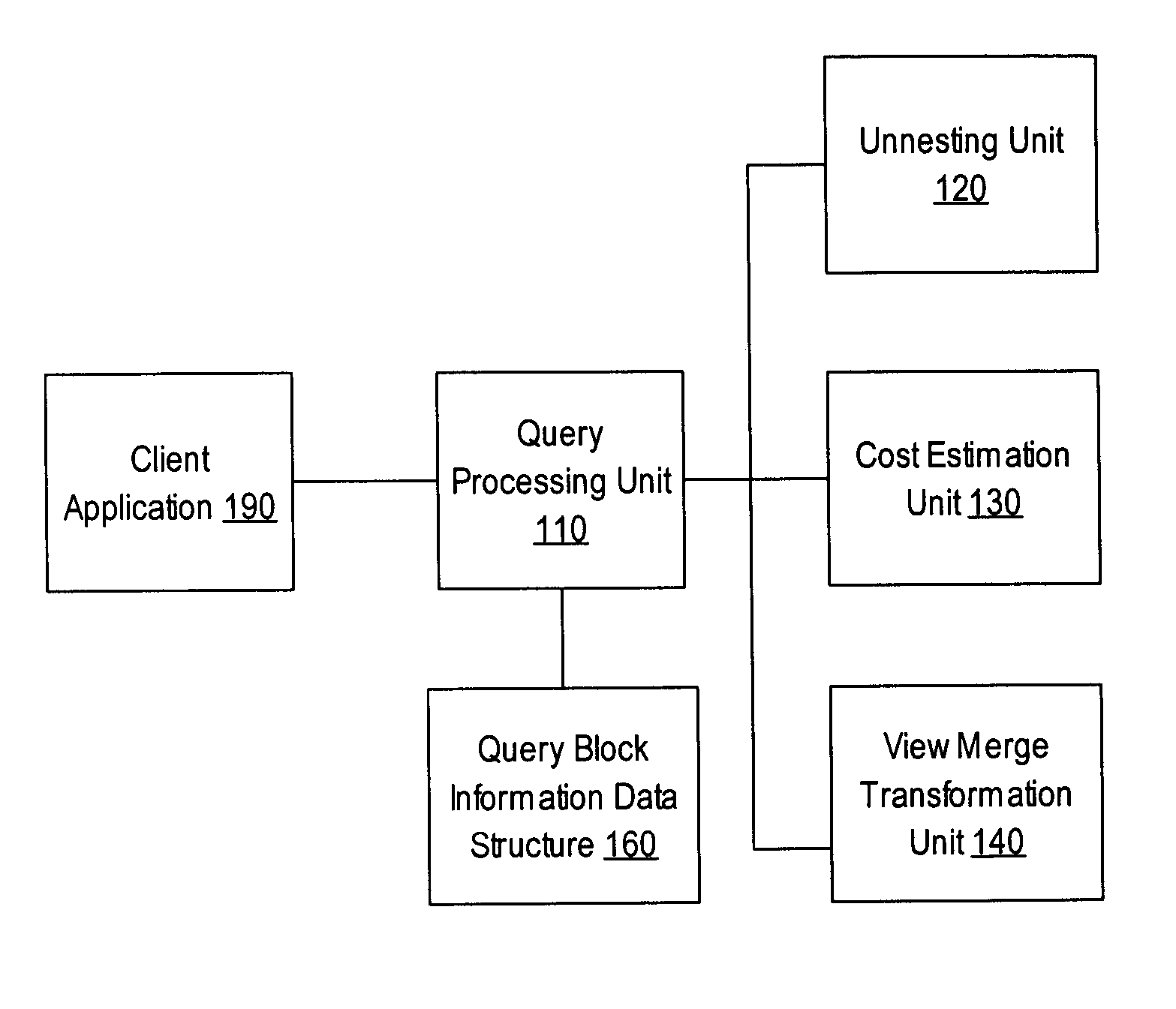
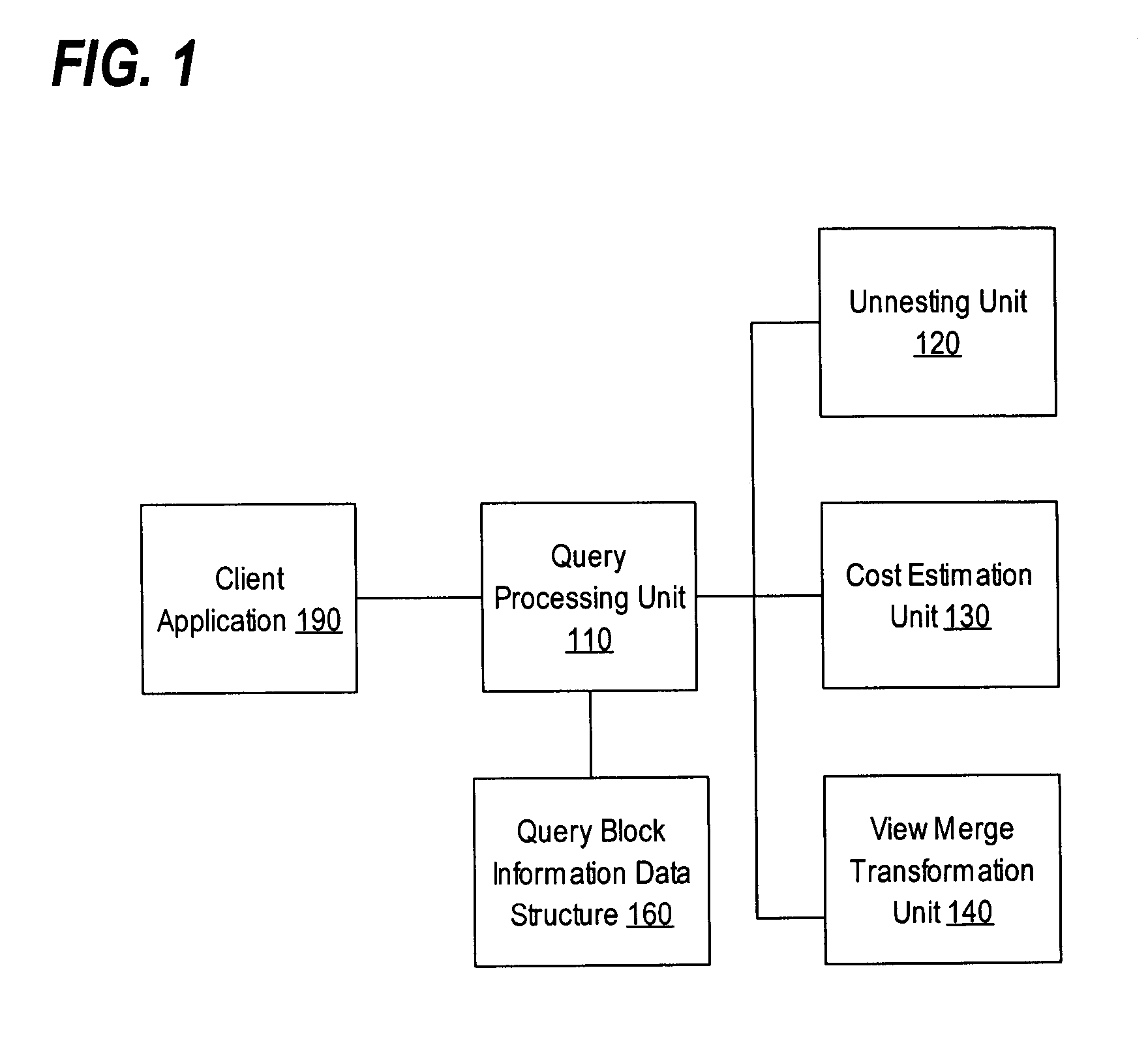
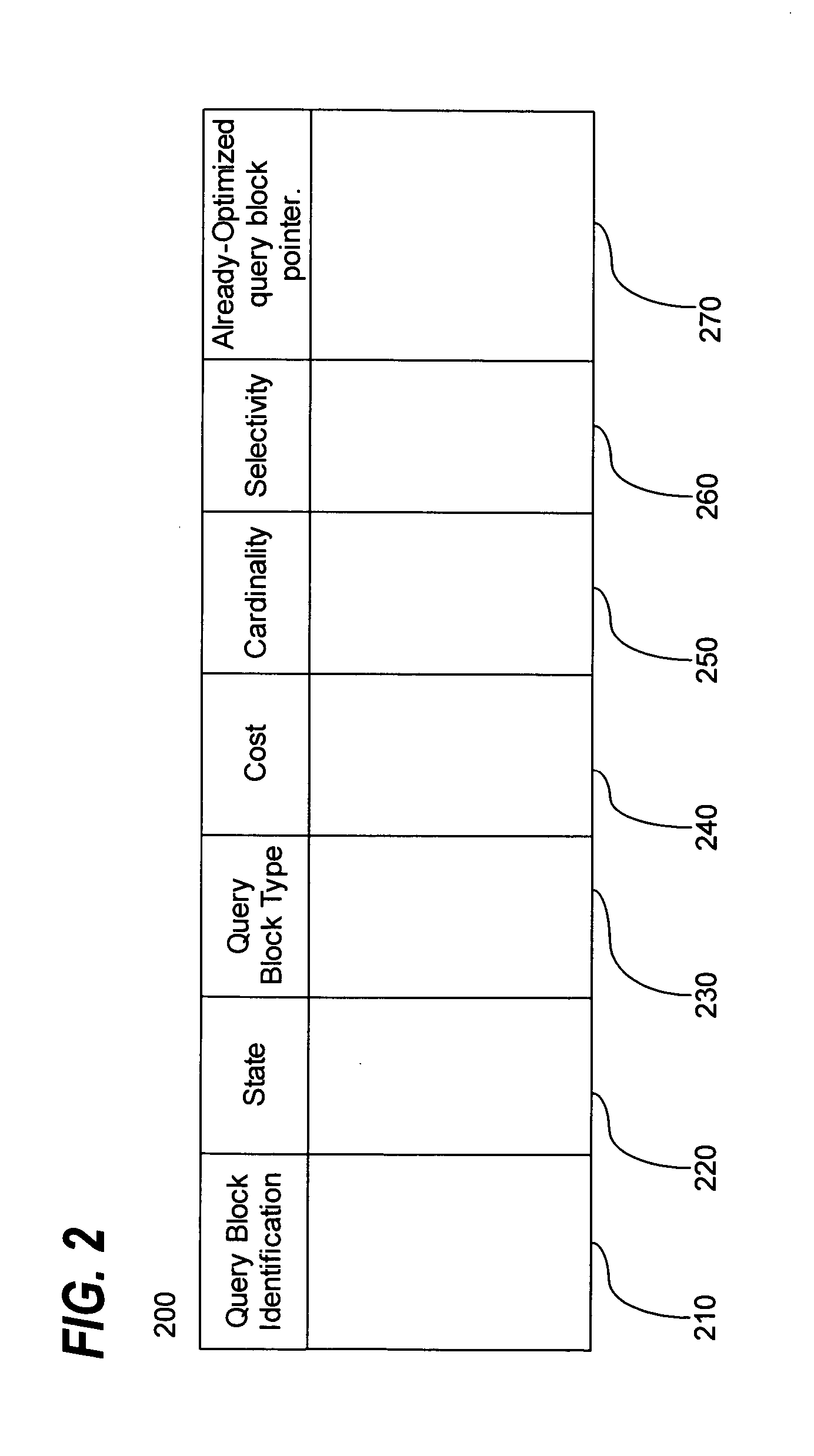
Reusing optimized query blocks in query processing
ActiveUS20060026115A1Data processing applicationsDigital data information retrievalSemantic equivalenceData mining
Techniques for reusing optimized query blocks in query processing are provided. The techniques include checking a data structure to determine whether a previously-generated query block information record corresponding to an already-processed first inner query block exists in the data structure, where the already-processed first inner query block corresponds to the first inner query block in a first state in an already-processed form. If the previously-generated query block information record exists in the data structure, then query block information is established for the first inner query block in the first state based on the previously-generated query block information record. Then a cost is determined for a semantically equivalent query that includes the first inner query block in the first state based on the query block information for the first inner query block in the first state.
Owner:ORACLE INT CORP
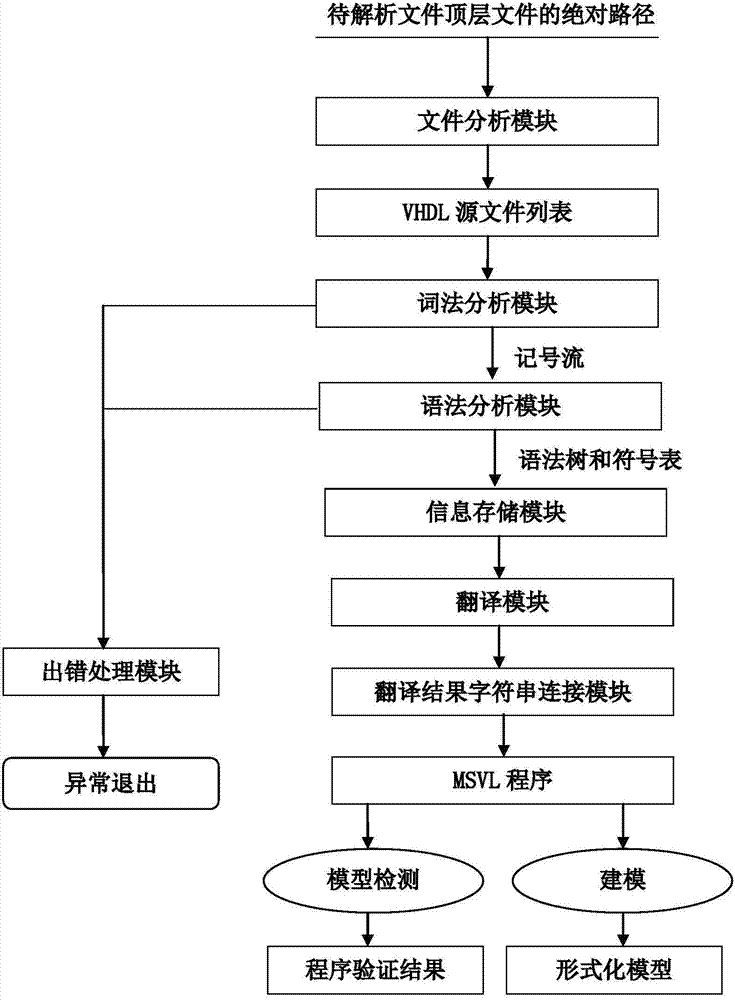
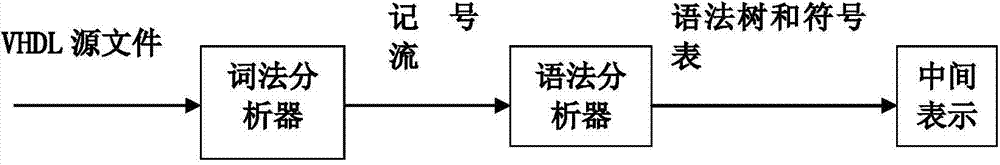
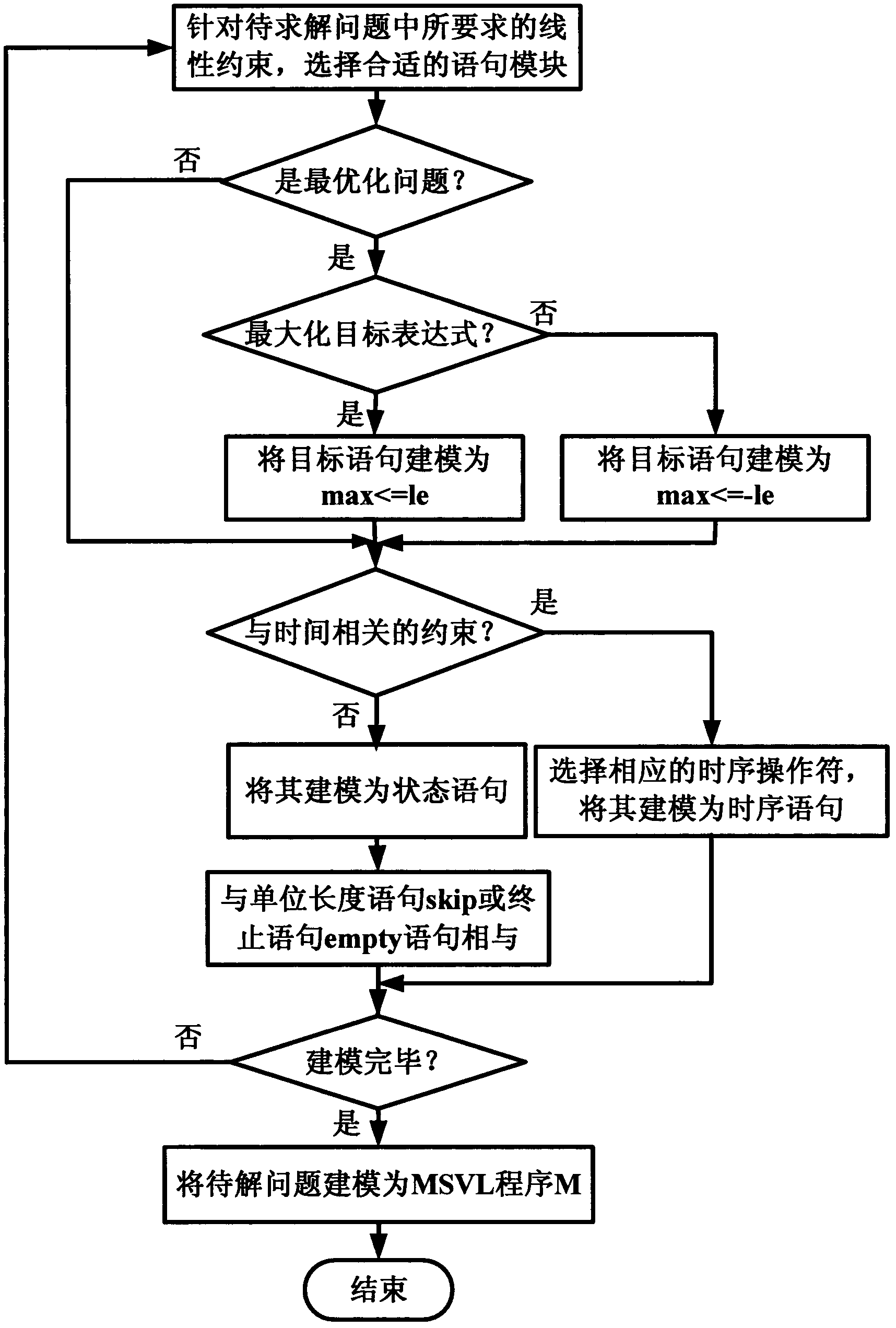
System for automatically converting hardware language VHDL (Vhsic Hardware Description Language) into MSVL (Modeling, Simulation and Verification Language)
ActiveCN104503816AGuaranteed correctnessProgram controlMemory systemsVhsic hardware description languageLexical analysis
The invention relates to a system for automatically converting a hardware language VHDL (Vhsic Hardware Description Language) into an MSVL (Modeling, Simulation and Verification Language). The system can convert a VHDL language program file into an MSVL language program file; the conversion system comprises a file analysis module, a lexical analysis module, a syntactic analysis, an information storage module, a translation module and a translation result character string connection module. After a VHDL program is converted into an MSVL program, model construction and property description use the same language, so that verification is carried out in the same logic framework and indirect model detection on the VHDL language program is conveniently realized. In the converting process, the VHDL program is converted into the semantic equivalent MSVL program by making conversion rules of different grammatical structure through a plurality of additional auxiliary means, so that correctness of a source VHDL program can be ensured by carrying out simulation, model construction and verification on the equivalent MSVL program.
Owner:XIDIAN UNIV
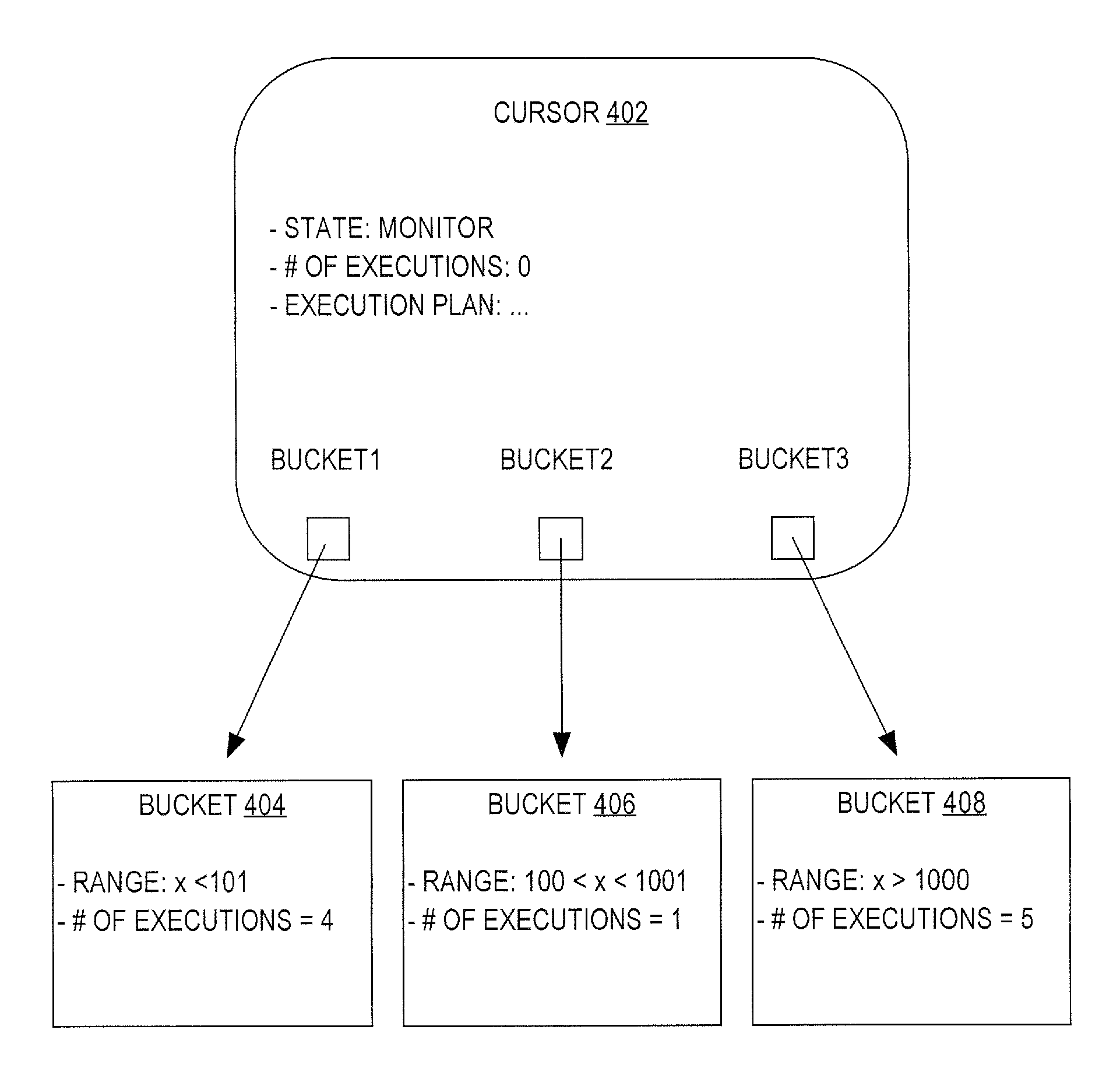
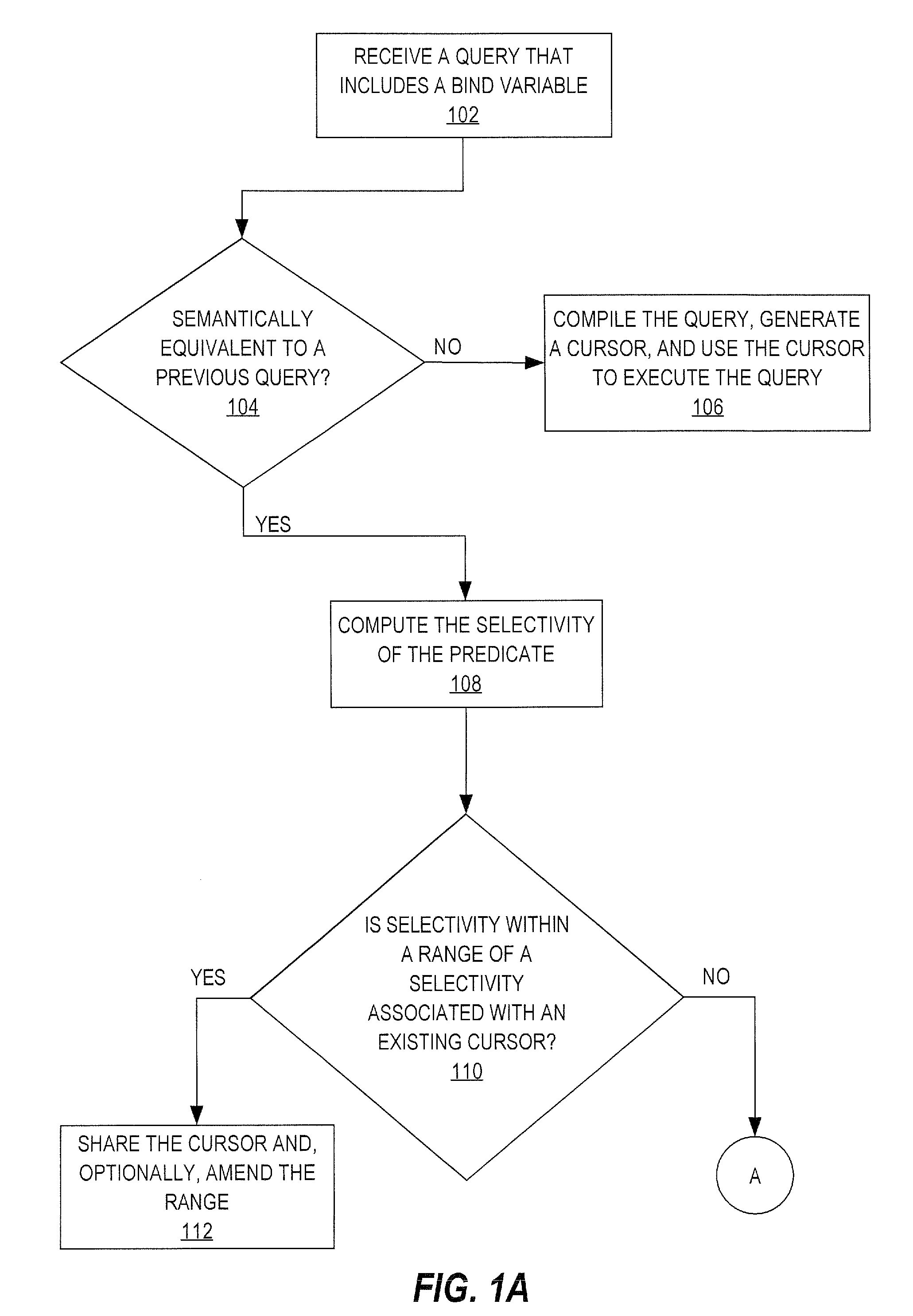
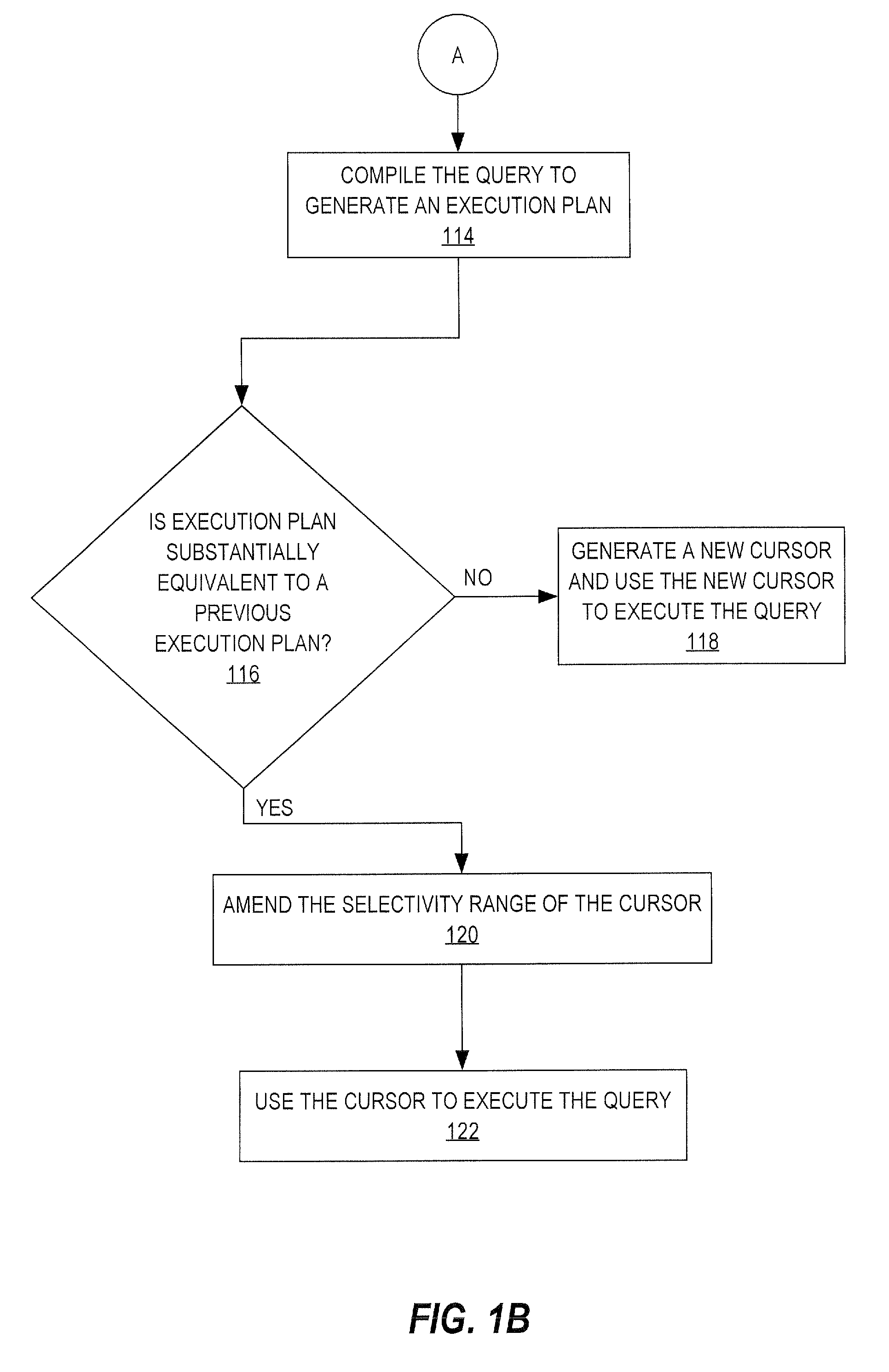
Adaptive cursor sharing
ActiveUS7689550B2Data processing applicationsDigital data information retrievalExecution planDatabase server
Techniques for sharing cursors are provided. When a new query is issued, a database server determines whether the new query is semantically equivalent to a previous query. If so, then database server computes statistics associated with the new query. Based on the statistics, the database server determines whether compiling the new query would produce an execution plan that satisfies certain criteria. If so, then the cursor is used to execute the new query. In another approach, one cursor sharing technique (CST) is used to determine which cursor to use to execute a first set of semantically-equivalent queries. Statistics are gathered during execution of the first set of queries. The database server determines, based on the statistics, when to switch from using the first CST to a different CST. The different CST is used to determine which cursor to use to execute a second set of queries that are semantically-equivalent to the first set.
Owner:ORACLE INT CORP
Performing policy conflict detection and resolution using semantic analysis
ActiveUS8327414B2Digital data processing detailsMultiprogramming arrangementsNatural language processingReasoning algorithm
A method and system for managing a policy includes, in response to determining the presence of a conflict, determining a semantic equivalence between a component of a policy rule and at least one additional policy rule. The determining a semantic equivalence is performed by using a semantic reasoning algorithm that includes the steps of determining a first policy target of a first policy rule and a second policy target of a second policy rule, determining a meaning of the first policy target and a meaning of the second policy rule, assigning a confidence value based on the determined meaning of the first policy, assigning a confidence value based on the determined meaning of the second policy, performing a semantic comparison between the first policy target and the second policy target, and determining, based at least in part on the semantic comparison, the presence of a conflict between the first and second policy targets.
Owner:MOTOROLA SOLUTIONS INC
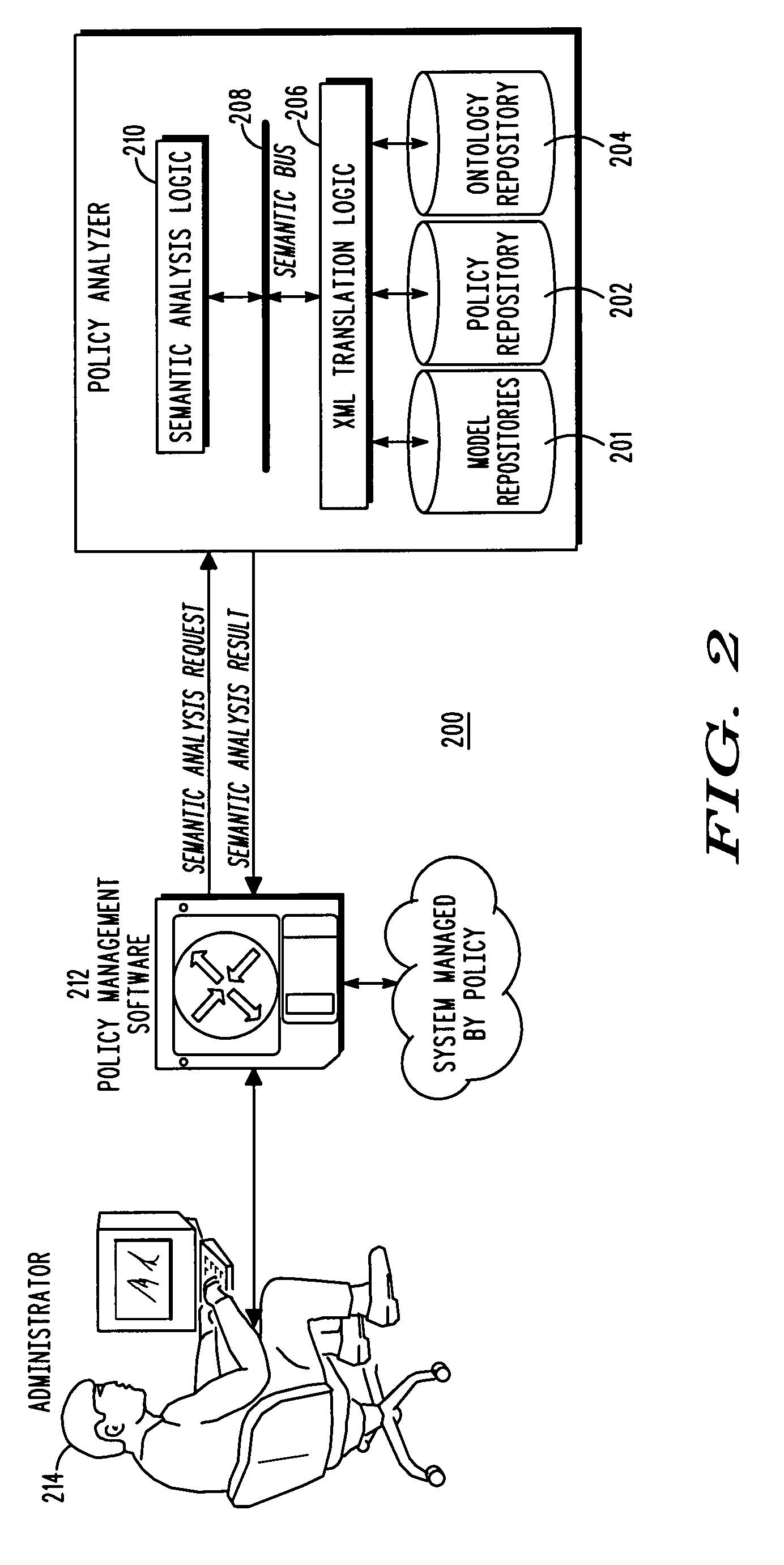
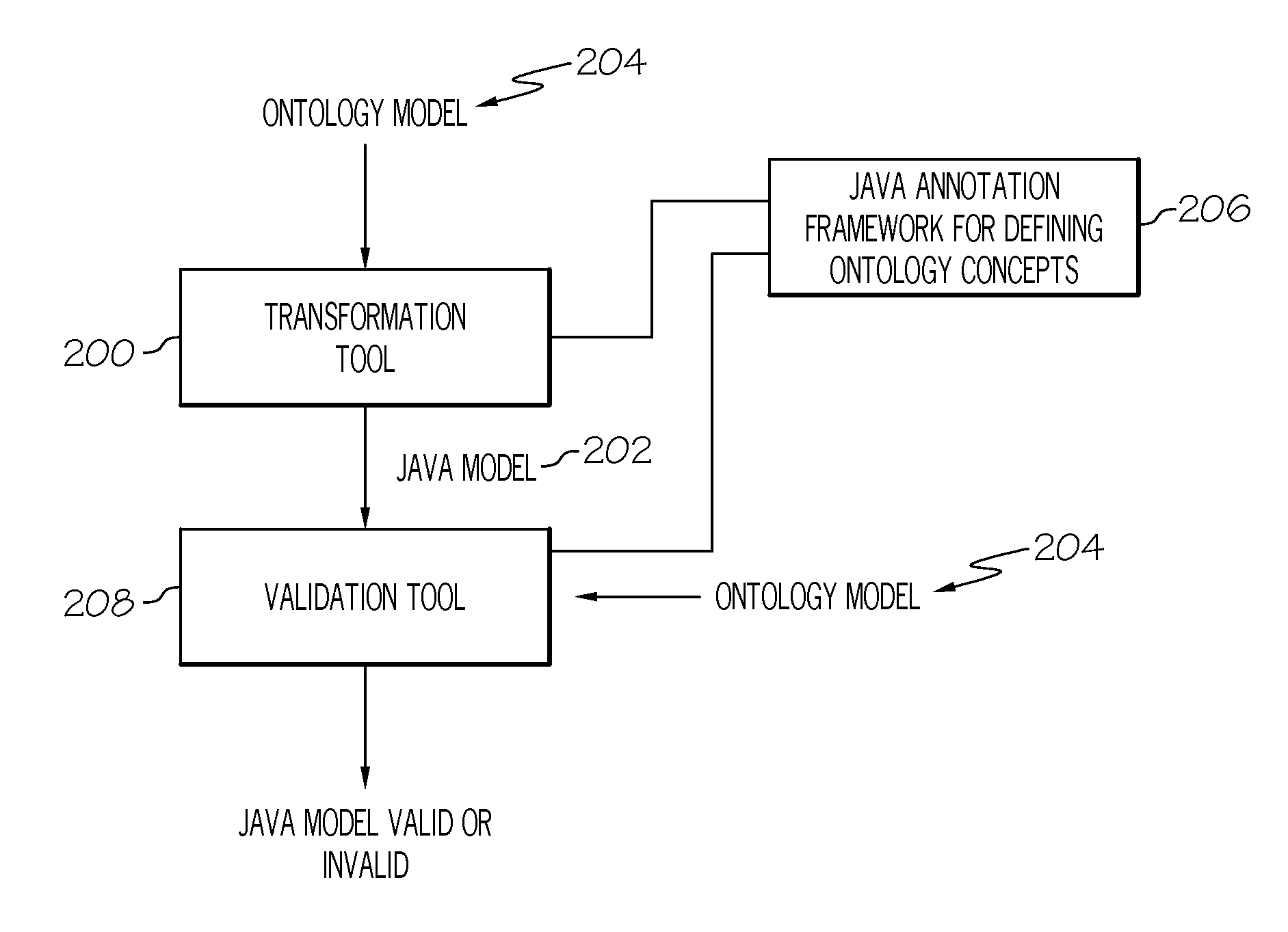
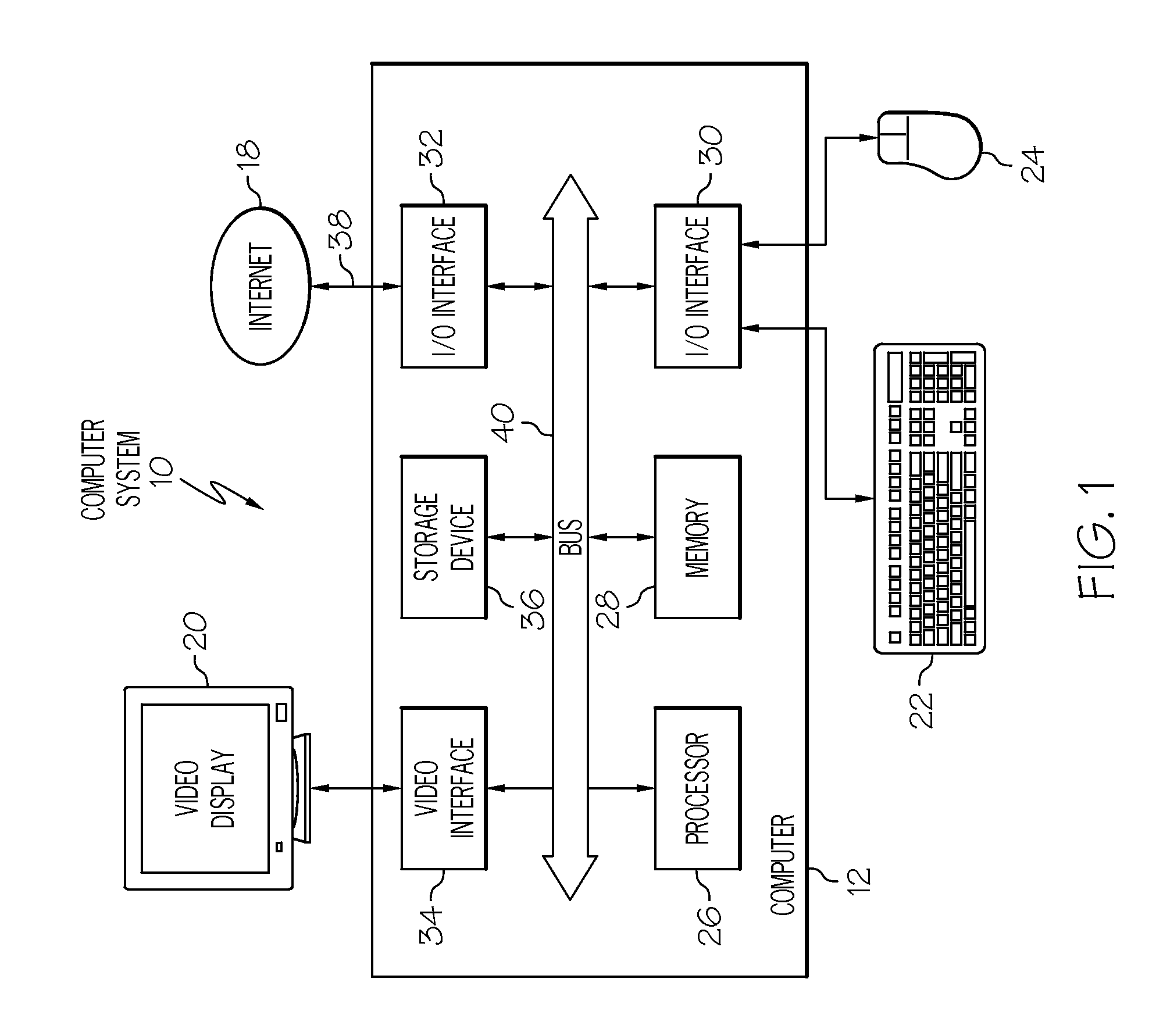
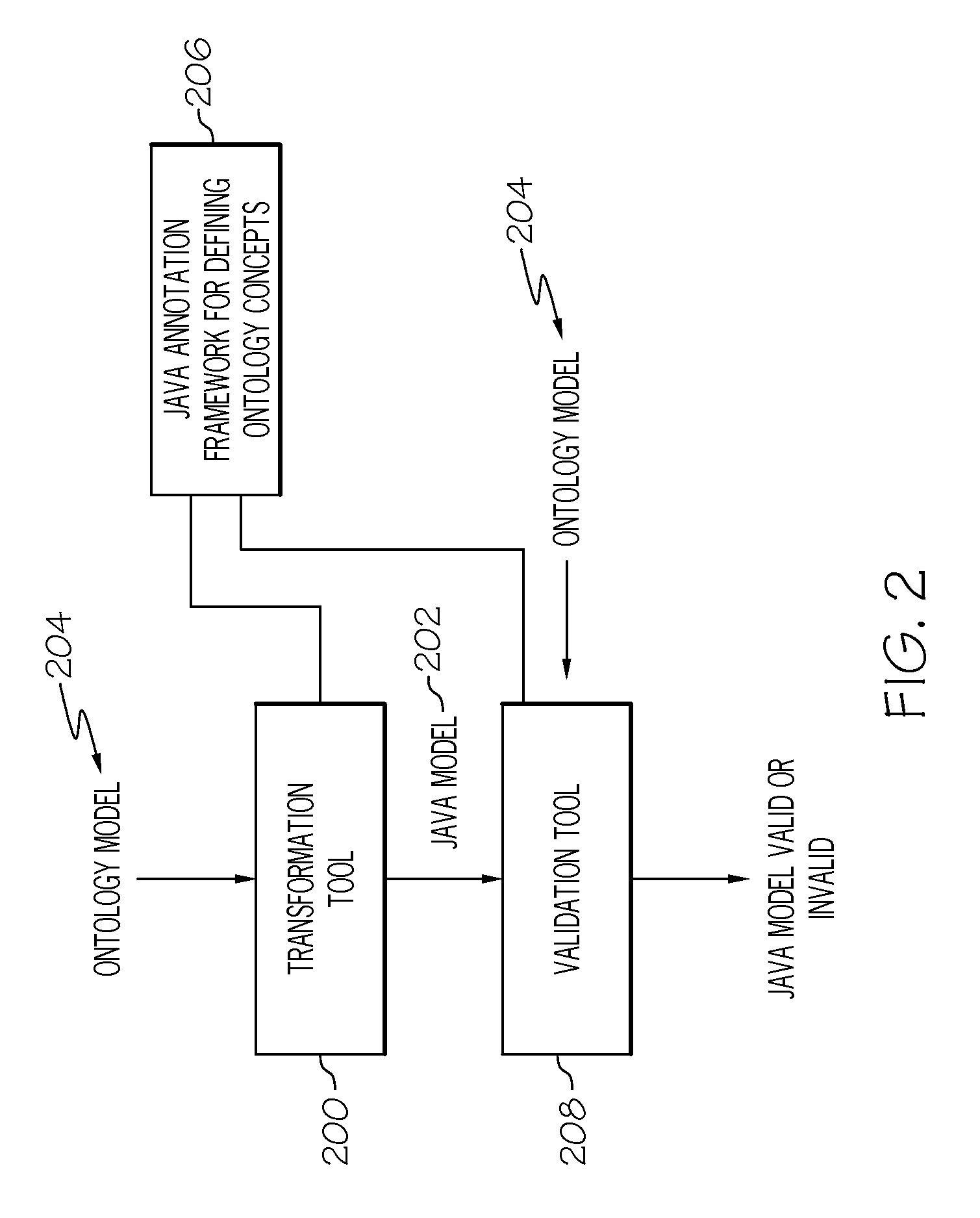
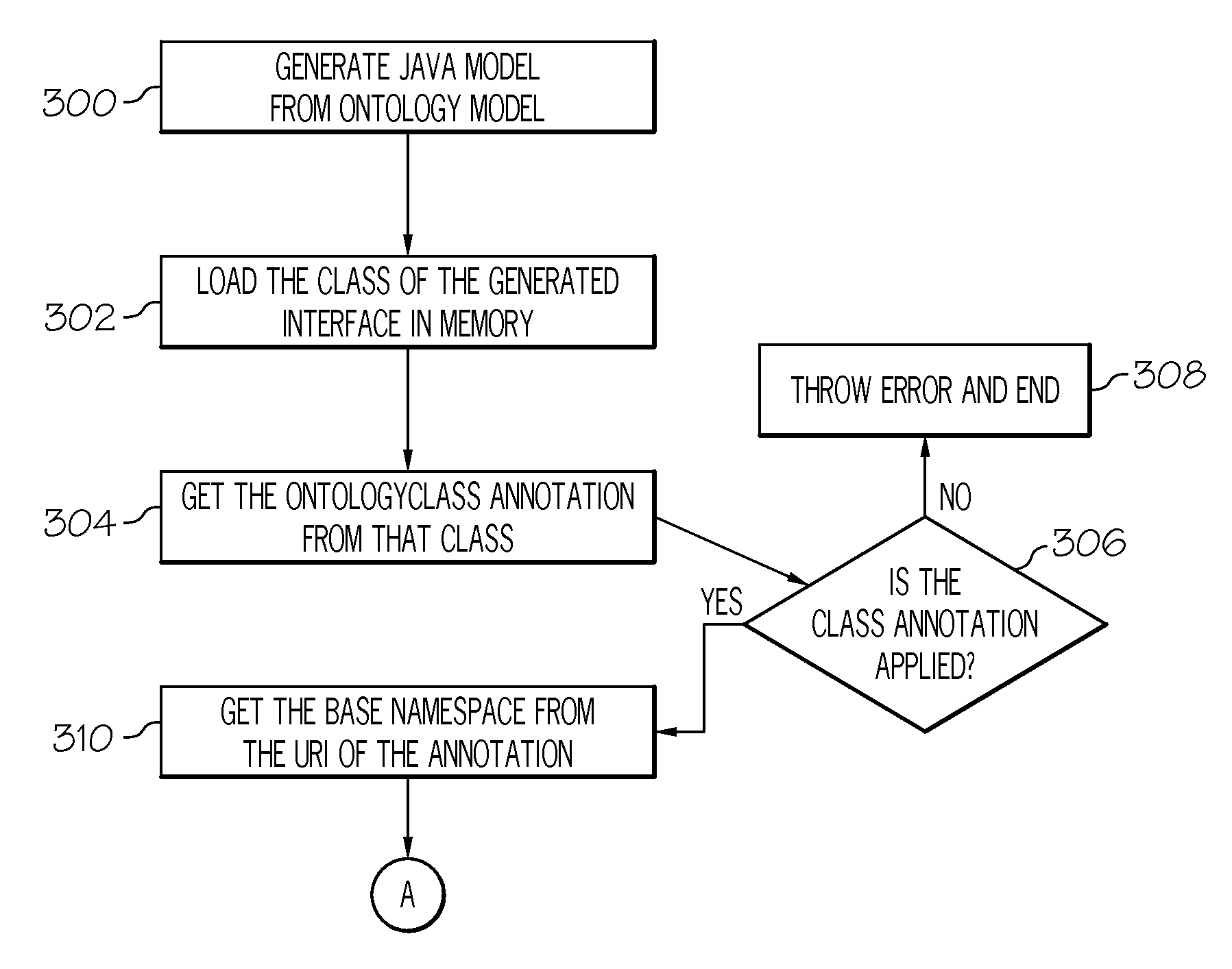
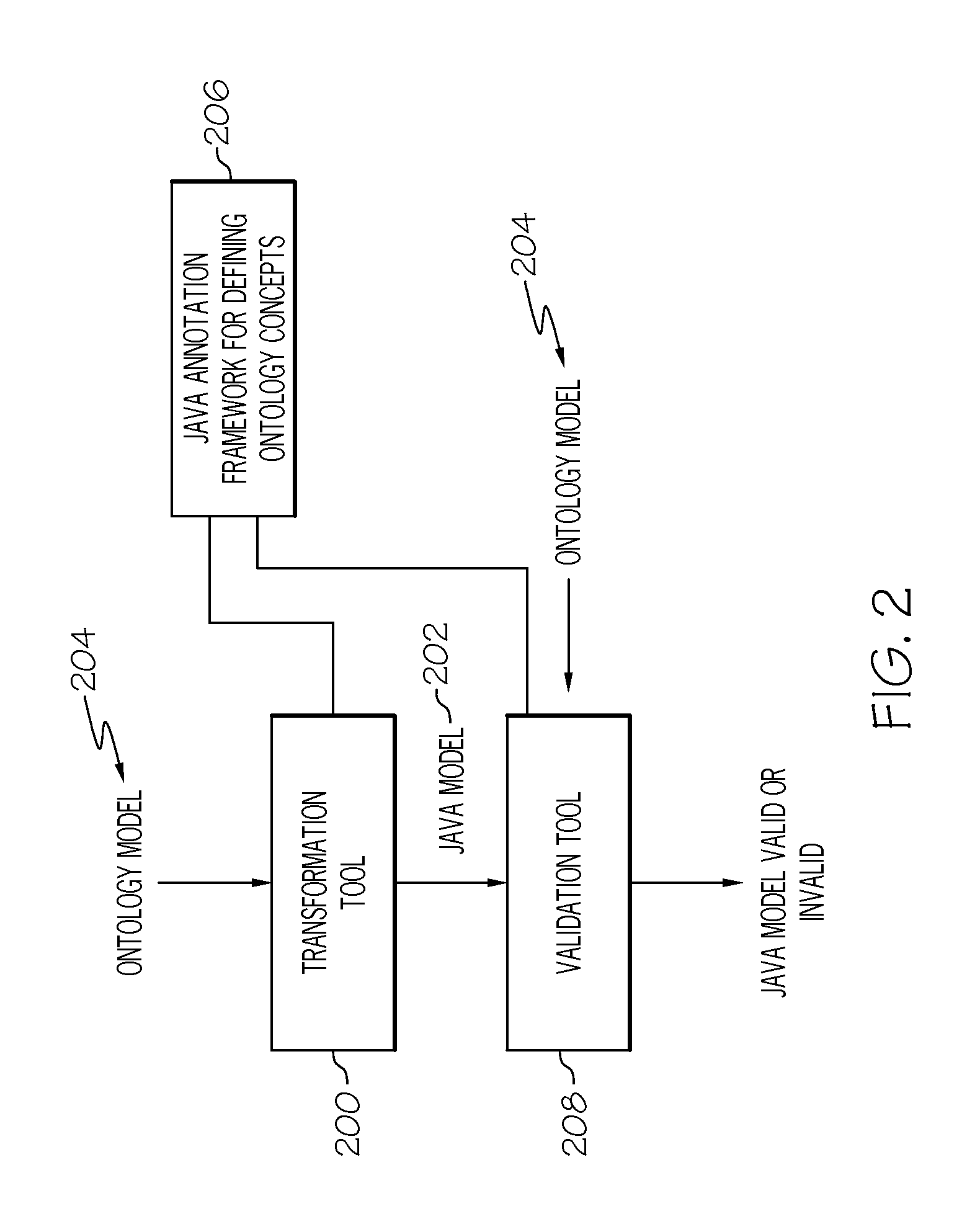
Verifying programming artifacts generated from ontology artifacts or models
A transformation tool and a validation tool are used to verify programmable artifacts, such as Java models, that are generated from an original ontology model. The verification process ensures that the programmable artifacts are semantically equivalent to the original ontology model from which they are created. Each element in the programmable artifacts is tagged with appropriate metadata, using, for example, Java language annotation support. Once tagged, the programmable artifacts can be parsed to form a generated ontology model. This generated ontology model can then be compared to the original ontology model with a validation tool, in order to verify their semantic equivalence.
Owner:INT BUSINESS MASCH CORP
Verifying programming artifacts generated from ontology artifacts or models
A transformation tool and a validation tool are used to verify programmable artifacts, such as Java models, that are generated from an original ontology model. The verification process ensures that the programmable artifacts are semantically equivalent to the original ontology model from which they are created. Each element in the programmable artifacts is tagged with appropriate metadata, using, for example, Java language annotation support. Once tagged, the programmable artifacts can be parsed to form a generated ontology model. This generated ontology model can then be compared to the original ontology model with a validation tool, in order to verify their semantic equivalence.
Owner:IBM CORP
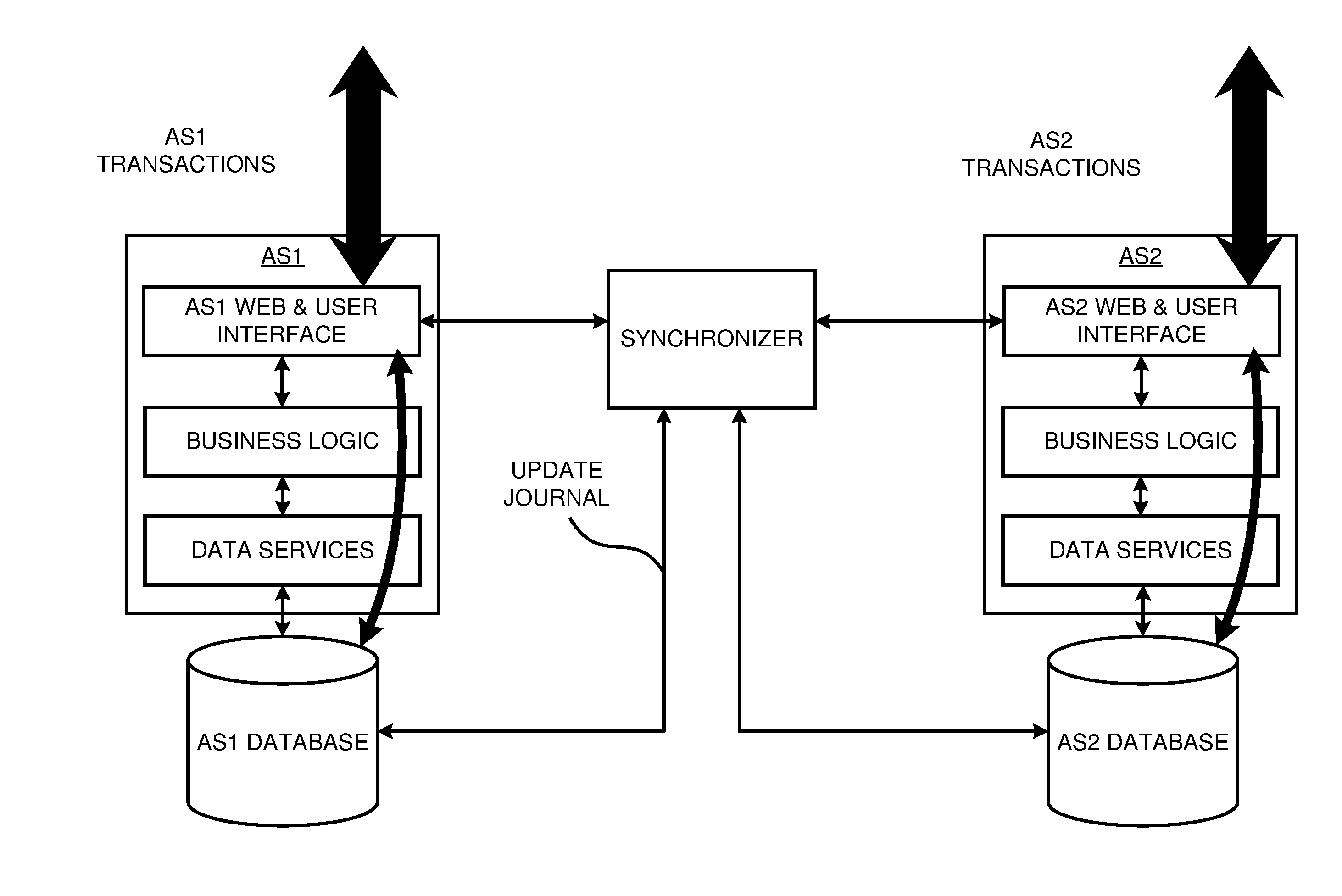
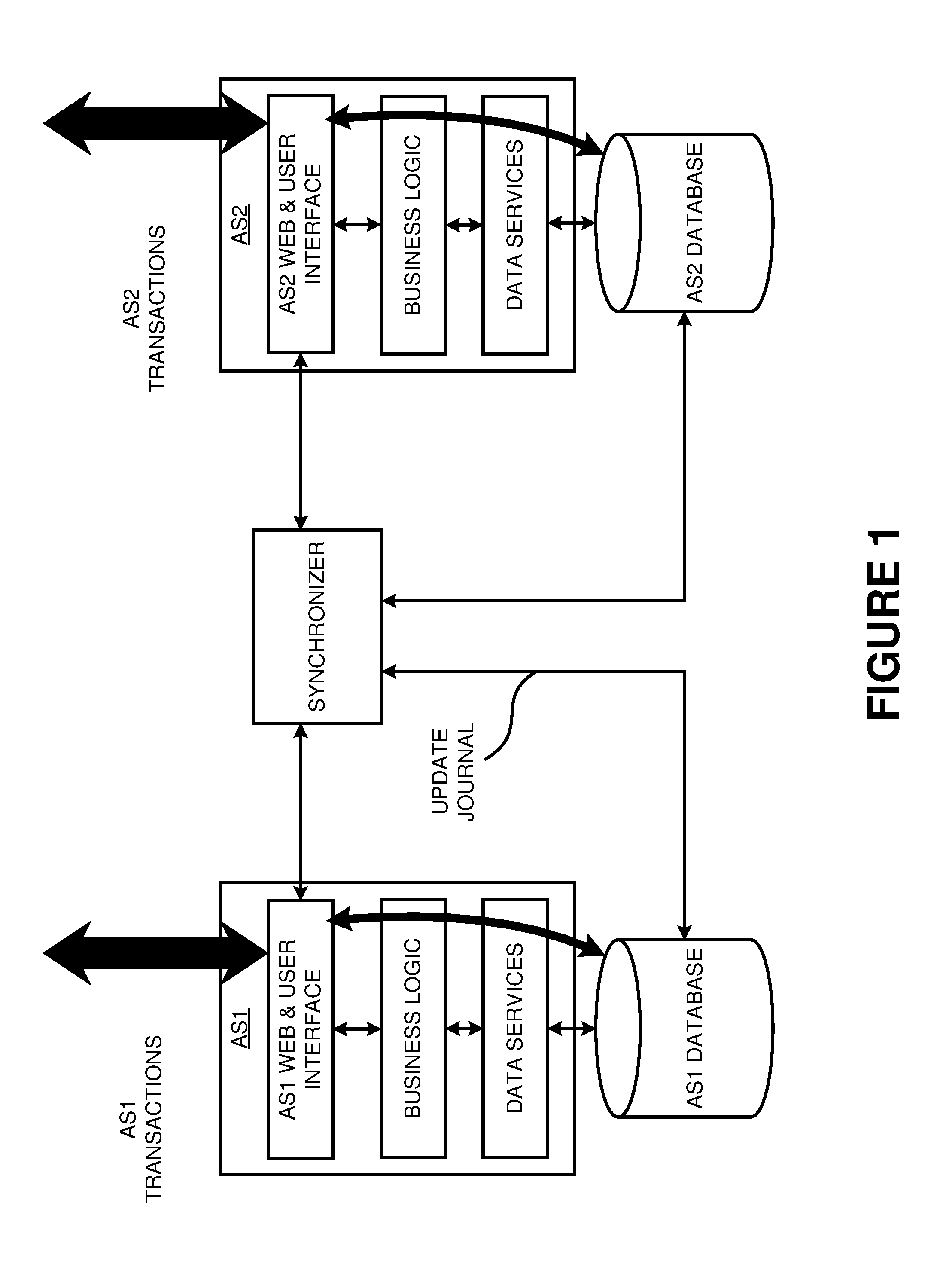
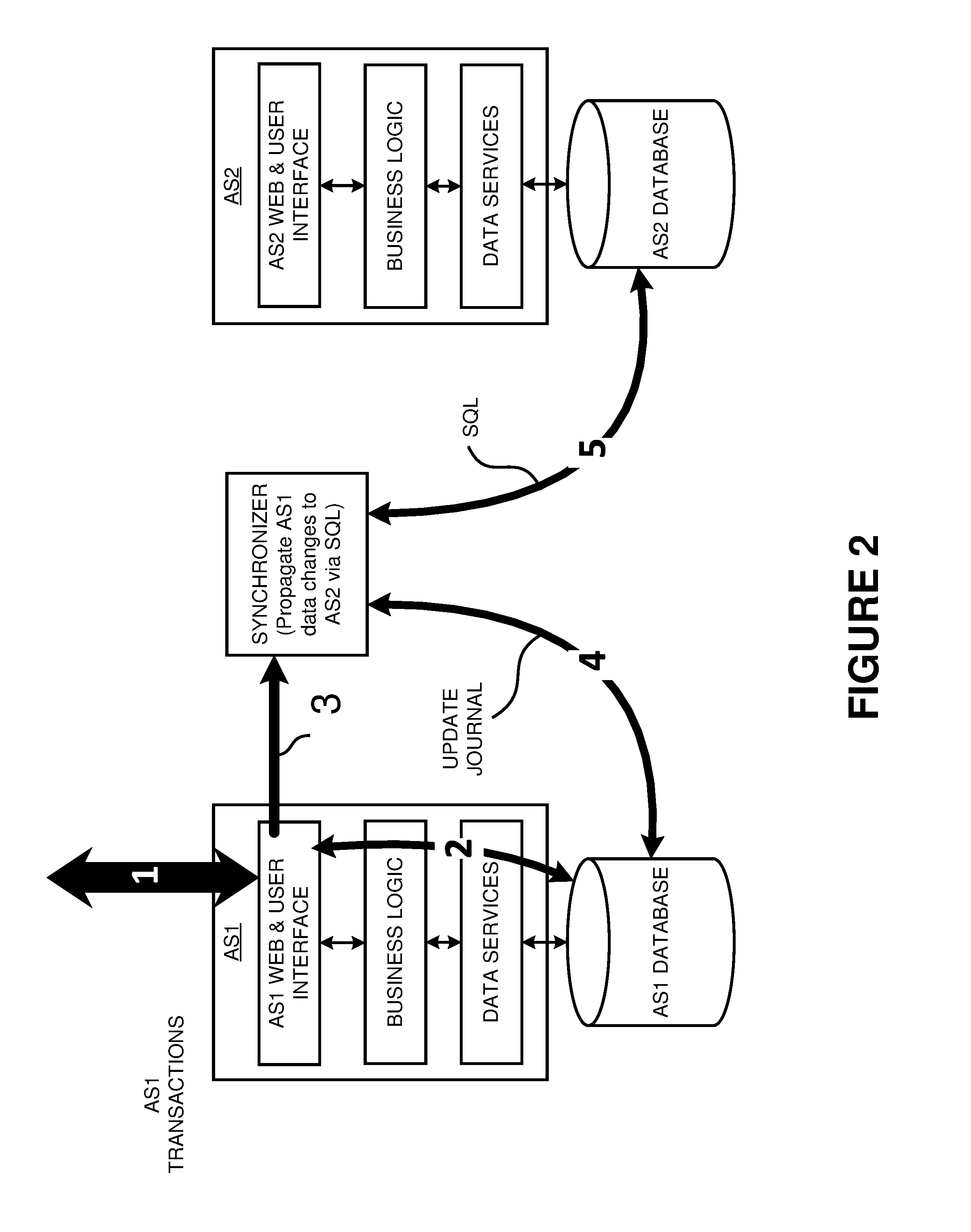
Method and system for data synchronization
InactiveUS20160306864A1Accelerate debuggingAccelerate problem resolutionDatabase distribution/replicationTransmissionData synchronizationSemantic equivalence
Disclosed is a software device (“Synchronizer”) incorporating functional synchronization and data level synchronization to maintain semantic equivalence between data elements of at least two data stores. The synchronizer may be configured to operate as a pure uni-directional data level synchronizer with data model remapping and business rule validation of the data or as a pure bi-directional functional synchronizer with data remapping and transaction remapping. Additionally, the Synchronizer can operate as a hybrid of data level synchronization occurring below the business logic layer of the program and of functional synchronization occurring in the business logic layer.
Owner:DON ESTES & ASSOC INC
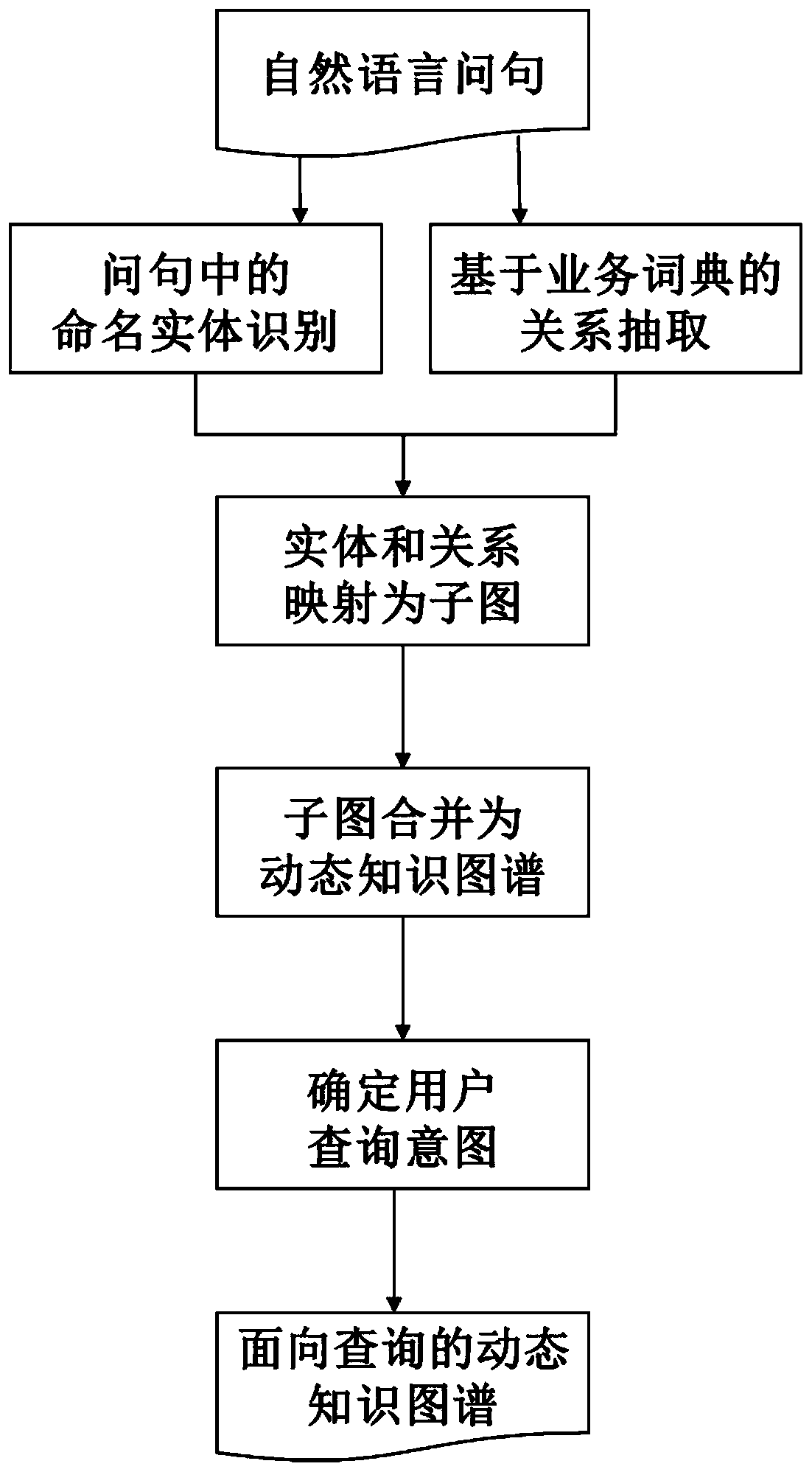
Template-free universal intelligent question-answering method based on dynamic knowledge graph
ActiveCN111159385AEasy to understandImprove robustnessSemantic analysisEnergy efficient computingTheoretical computer scienceSemantics
The invention provides a template-free universal intelligent question and answer method based on a dynamic knowledge graph. The method comprises the steps of understanding natural language questions,automatically constructing a dynamic knowledge graph about entities and relationships based on ontology and question and answer contexts, determining query intentions by combining the contexts and theknowledge graph, and constructing a query-oriented dynamic knowledge graph. According to the invention, a question-answering template does not need to be constructed manually in advance, the naturallanguage query questions can be effectively converted into the dynamic knowledge graph with semantic equivalence, the dynamic knowledge graph is used for understanding the natural language questions by a general question and answer system, it is guaranteed that the dynamic knowledge graph constructed in a general question and answer scene can fully express semantics of the natural language questions, and the good question and answer effect and performance are achieved.
Owner:南京烽火星空通信发展有限公司 +1
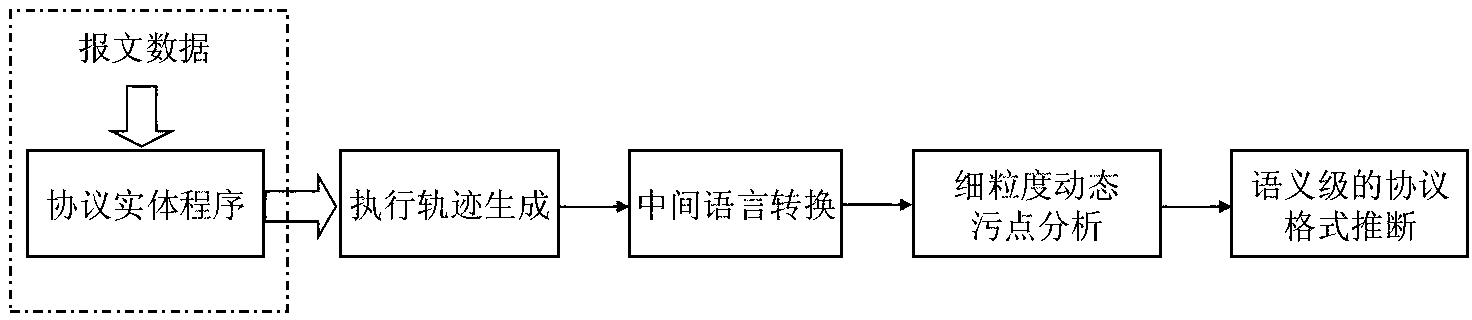
Semantic-level protocol format inference method based on execution trace
InactiveCN103200203AEase of ensuring completenessReduce difficultyData switching networksProgram instructionGranularity
The invention provides a semantic-level protocol format inference method based on an execution trace. The semantic-level protocol format inference method is characterized in that the protocol format adopted by a message is inferred according to a binary instruction execution trace generated in message analysis. The semantic-level protocol format inference method comprises the following steps of: firstly, transferring an intermediate language: transferring the instruction execution trace of a protocol entity program in analyzing of a communication message into the form of the intermediate language; secondly, implementing dynamic taint analysis of fine granularity: carrying out the dynamic taint analysis of the fine granularity based on the execution trace in form of the intermediate language, in order to analyze the process of the protocol entity program in analyzing the message, and mastering the spread and the influence of each message byte serving as the input in the system along with the execution of a program instruction; and thirdly, inferring the semantic-level protocol format: gaining the complete protocol message format based on the characteristics of the semantic-level protocol at the analysis stage; and the working process in the intermediate language transfer stage is that a binary instruction in the execution trace is individually converted into a simple and semantic equivalence type intermediate language instruction, and an abstract execution trace based on the intermediate language is generated.
Owner:PLA UNIV OF SCI & TECH
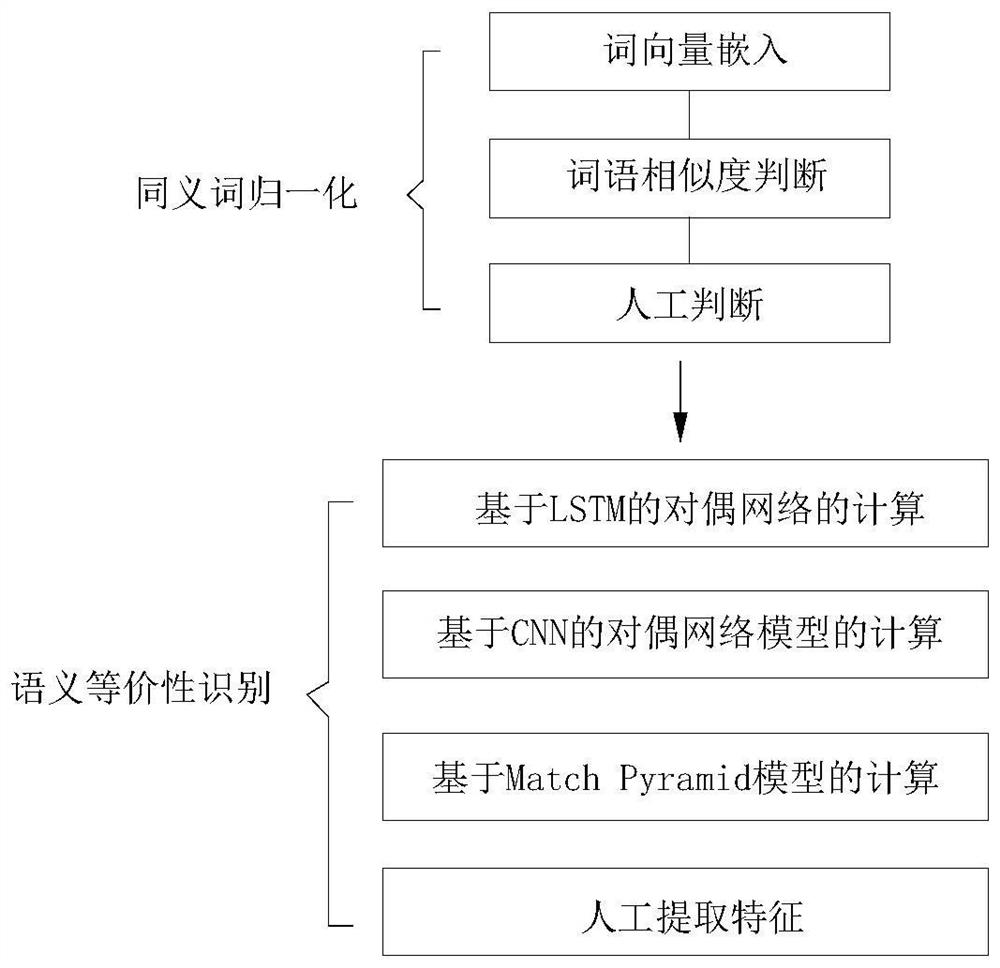
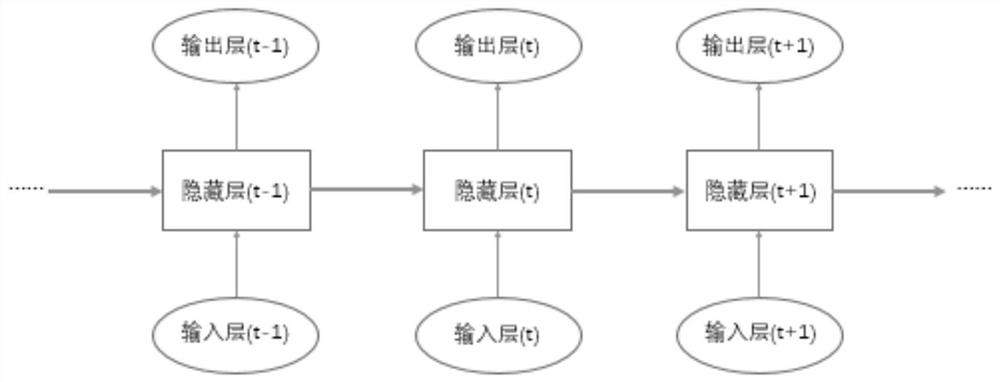
Problem equivalence discrimination method combining semi-supervised learning and ensemble learning
ActiveCN110008323AFlexible adjustmentDigital data information retrievalSemantic analysisAlgorithmDual network
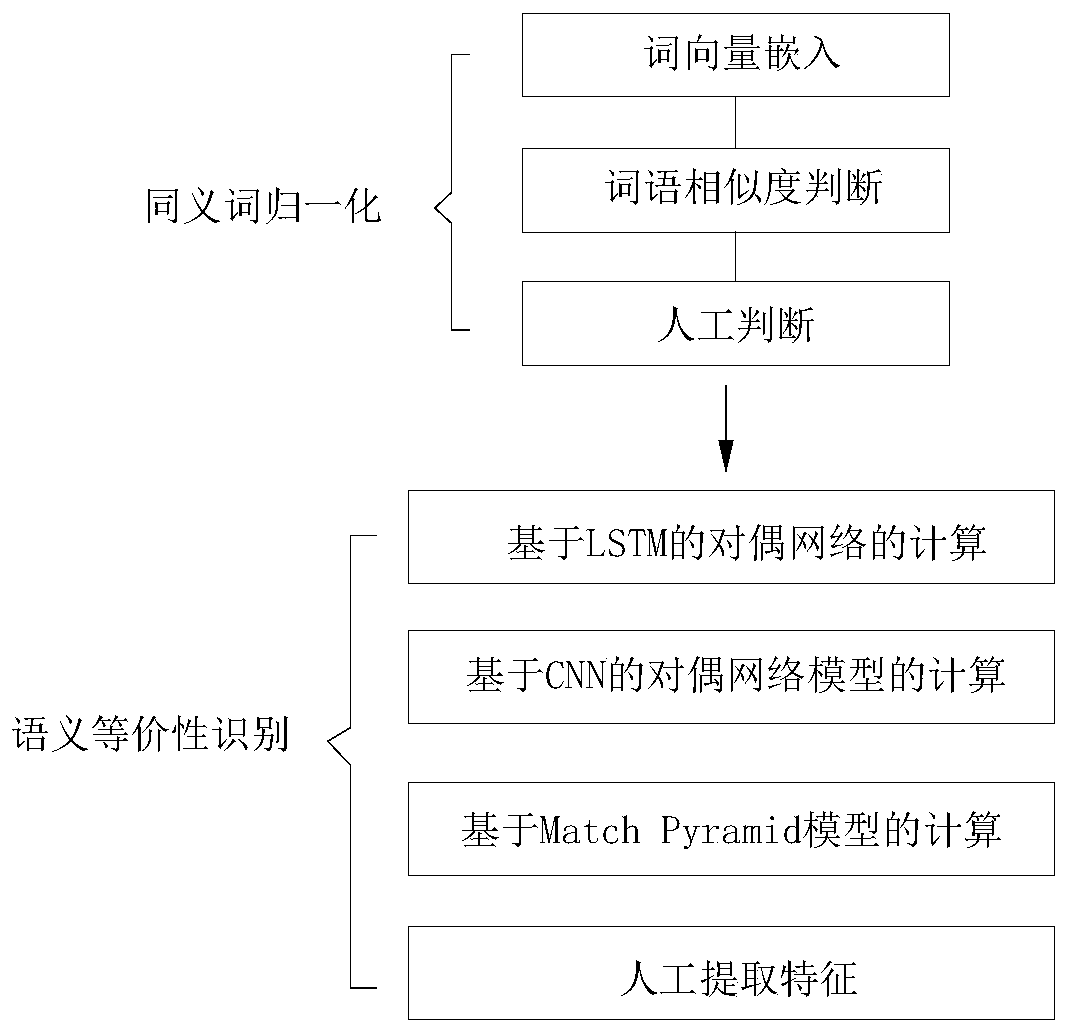
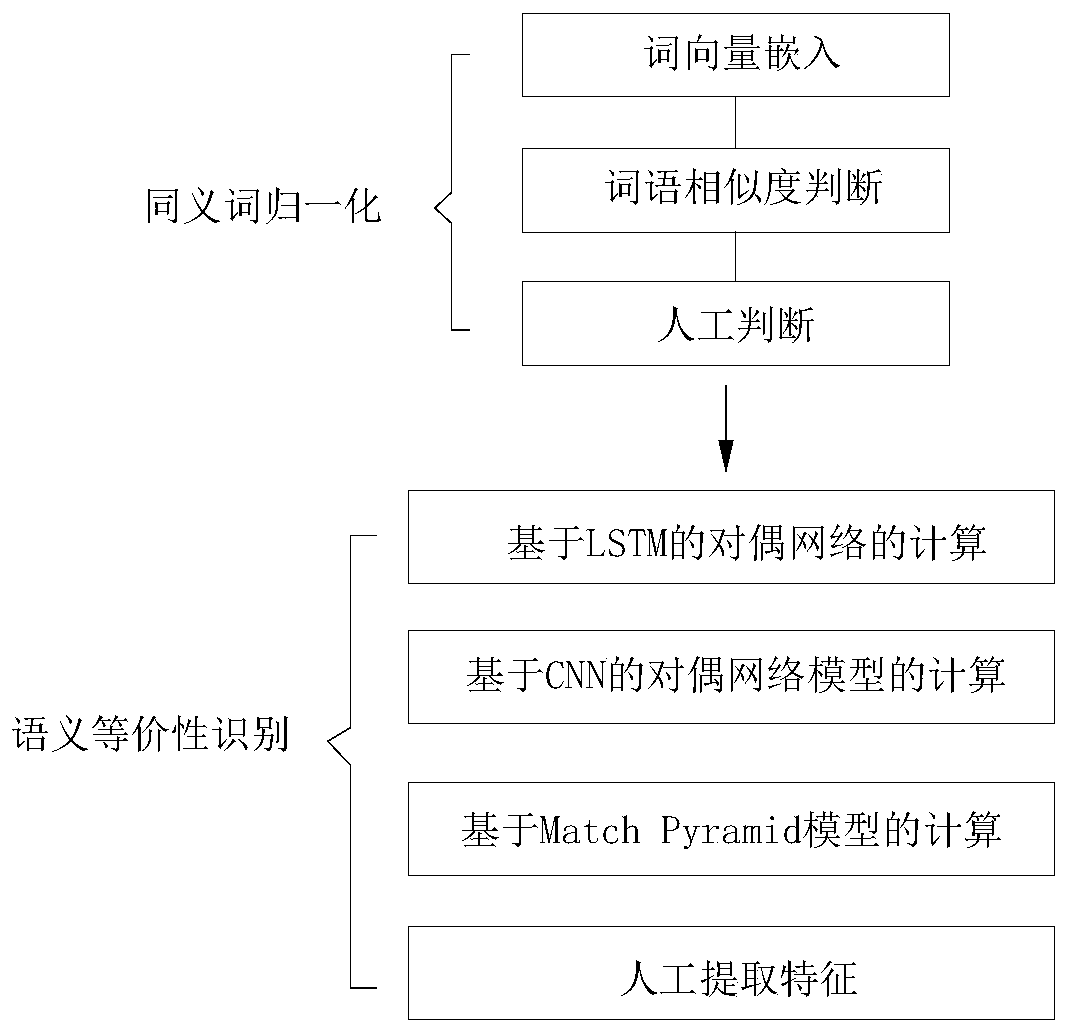
The invention discloses a problem equivalence discrimination method combining semi-supervised learning and ensemble learning. The method comprises the following steps: S1, synonym normalization: 1) embedding word vector; 2) judging word similarity; 3) manual judgment; S2, performing semantic equivalence identification: calculating a dual network based on LSTM; calculating a dual network model based on the CNN; calculating on the basis of a Match Pyramid model; extracting features artificially. According to the method, synonyms are generated and introduced in a semi-supervised mode, so that the whole system can be flexibly adjusted according to specific fields, semantic equivalence of problems is judged through four different models of ensemble learning, and the advantages of the differentmodels are brought into play.
Owner:北京百分点科技集团股份有限公司
System evaluation method, intelligent evaluation system and computer-readable storage medium
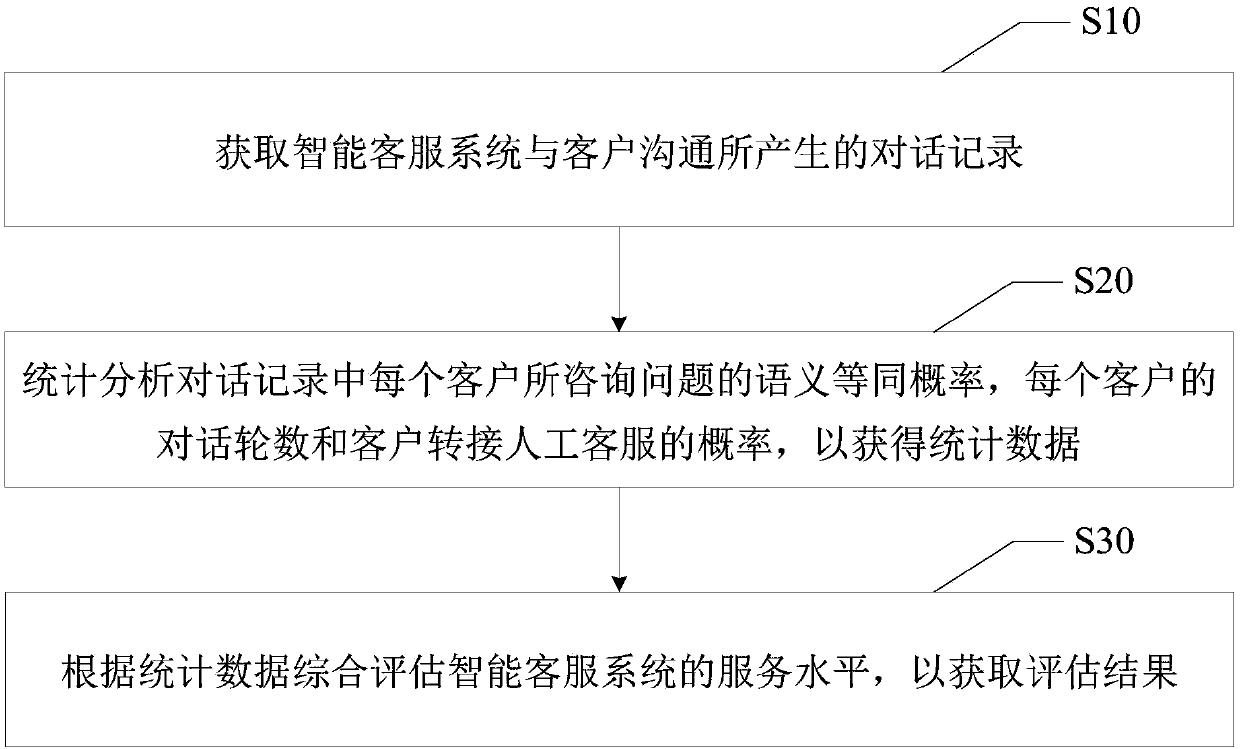
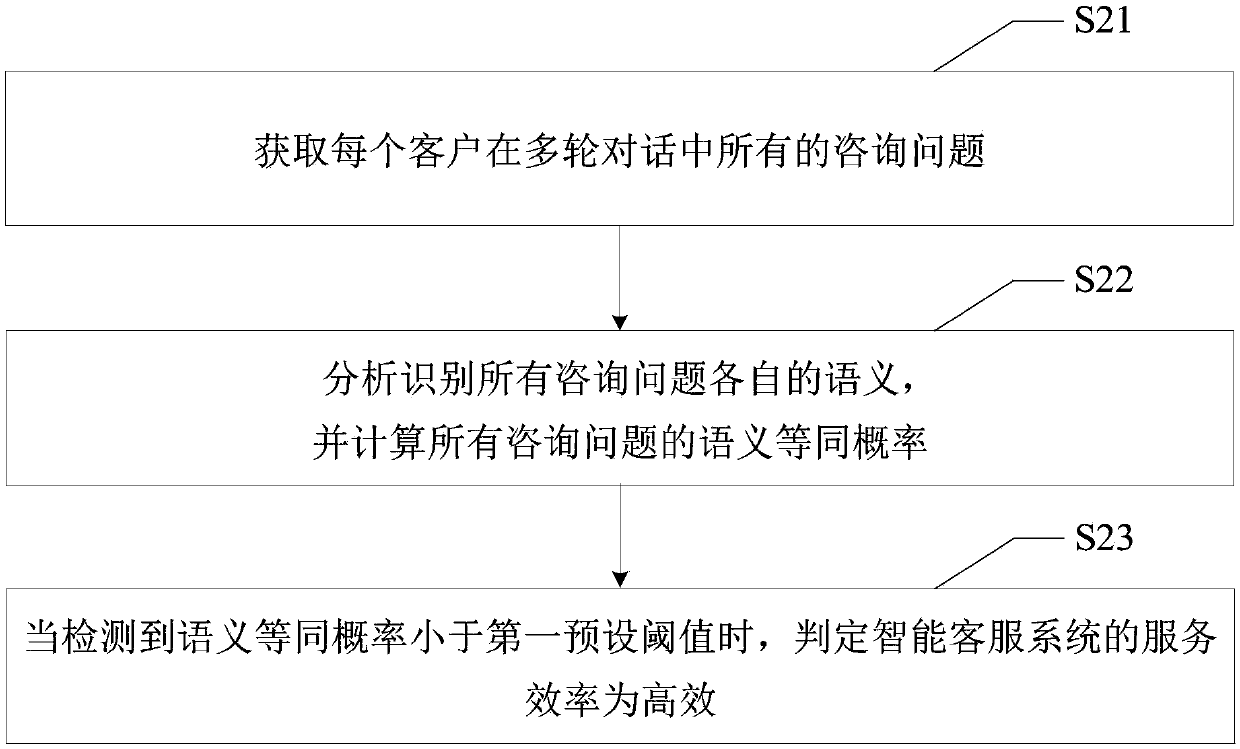
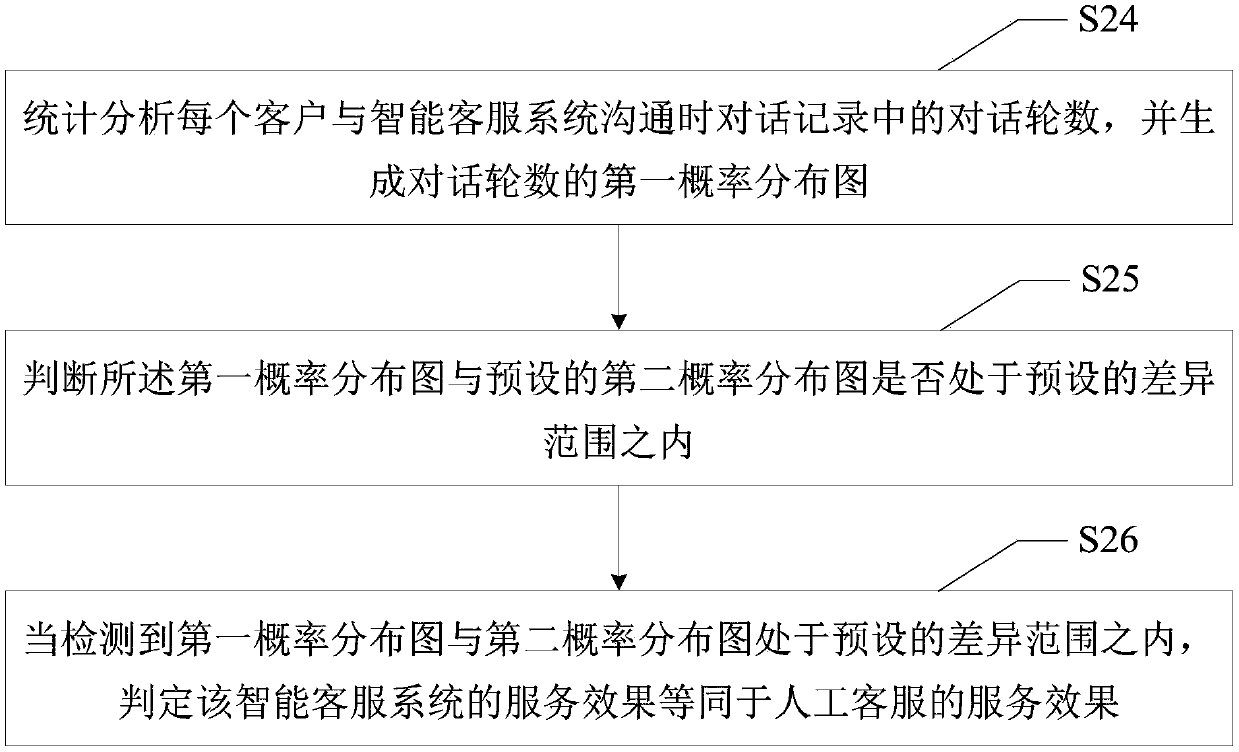
ActiveCN107862423AService level is realObjective and comprehensive systematic evaluationResourcesCommerceStatistical analysisSemantic equivalence
The invention discloses a system evaluation method, an intelligent evaluation system and a computer-readable storage medium. The method comprises a step of obtaining a conversation record generated bythe communication between an intelligent customer service system and a customer, a step of counting and analyzing a semantic equivalence probability of a question consulted by each customer, the number of rounds of conversations of each customer and a probability that the customer transfers to staff customer service to obtain statistical data, and a step of comprehensively evaluating the servicelevel of the intelligent customer service system according to the statistical data so as to obtain an evaluation result. According to the system evaluation method, the intelligent evaluation system and the computer-readable storage medium, the evaluation mode of the manually evaluating the intelligent customer service system is changed, an automated system evaluation mechanism is adopted, the objective and comprehensive systematic evaluation of the intelligent customer service system is achieved from the overall perspective of the intelligent customer service system, the subjectivity and curvelimitations of manual evaluation are avoided so as to obtain a real and effective evaluation result of the service level of the intelligent customer service system, thus the accuracy of an evaluationeffect is improved, the real service level of the intelligent customer service system is fed, and thus the evaluation efficiency is improved.
Owner:WEIKUN (SHANGHAI) TECH SERVICE CO LTD
A binary translation intermediate representation correctness test method and device based on semantic equivalence verification
ActiveCN109634869AQuality assuranceGuaranteed reliabilitySoftware testing/debuggingComputer architectureBlack box
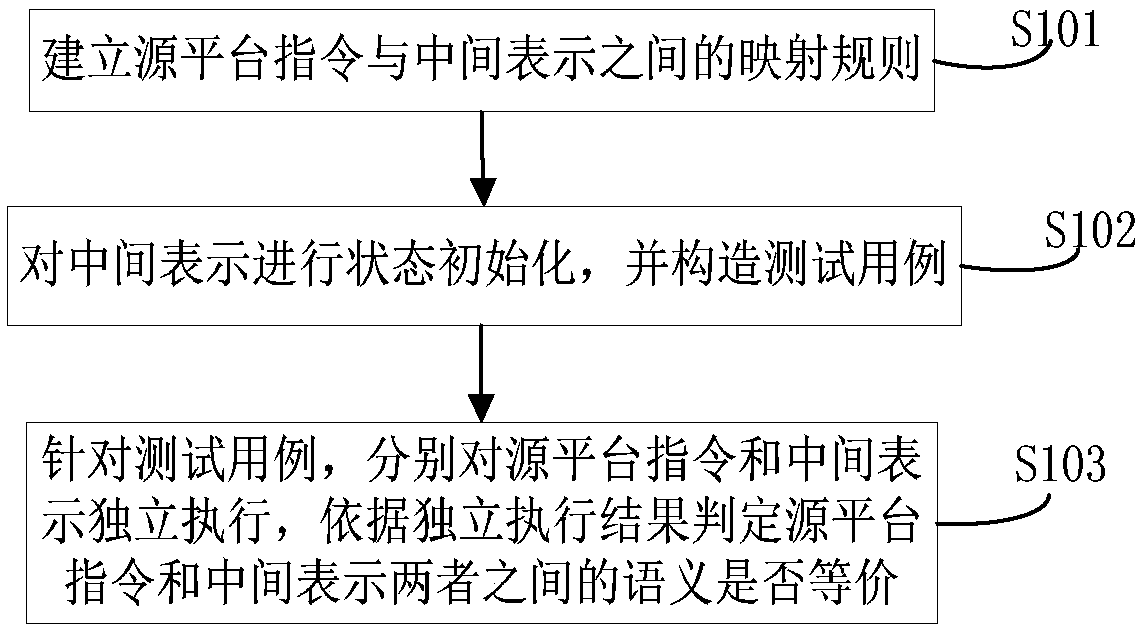
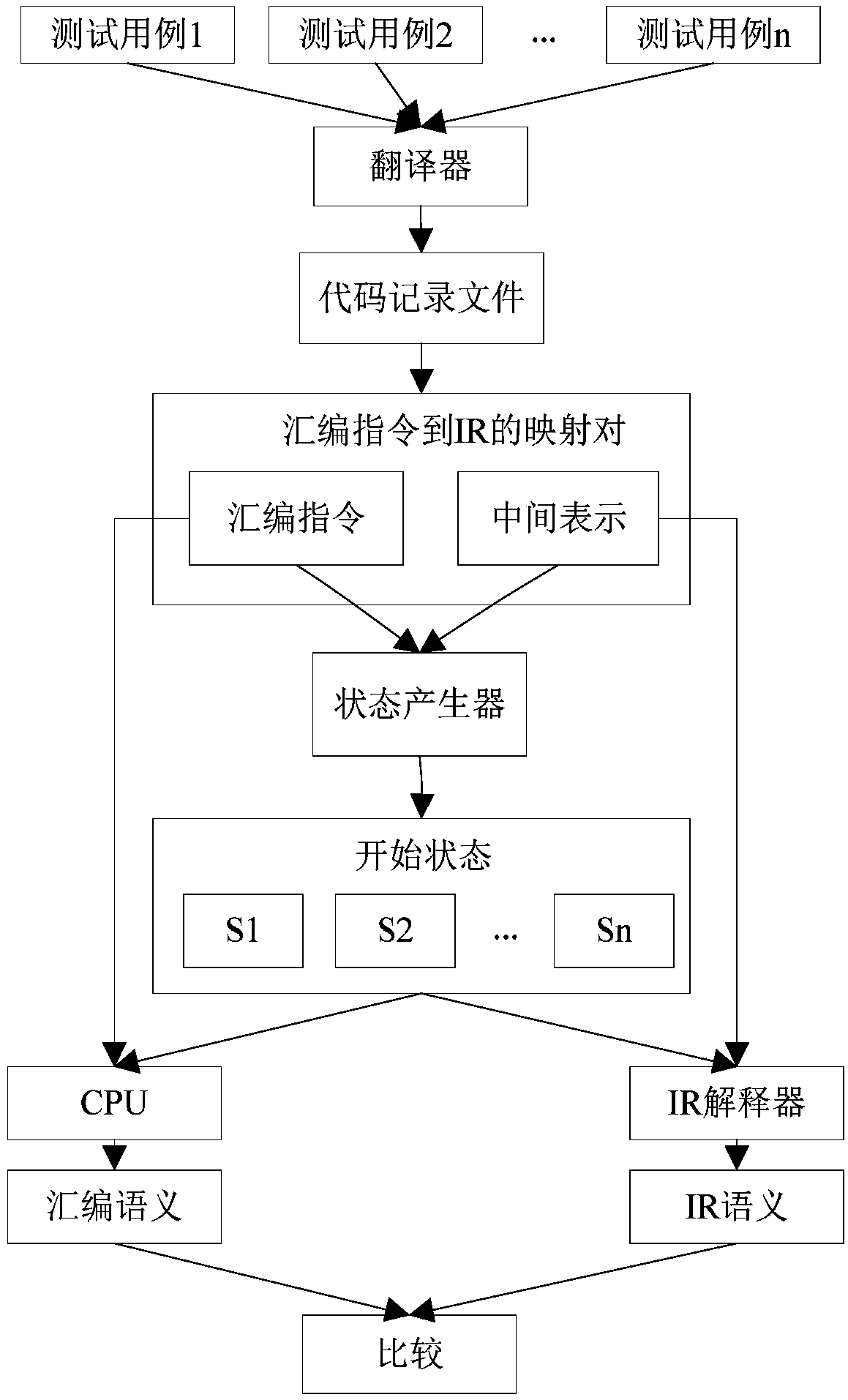
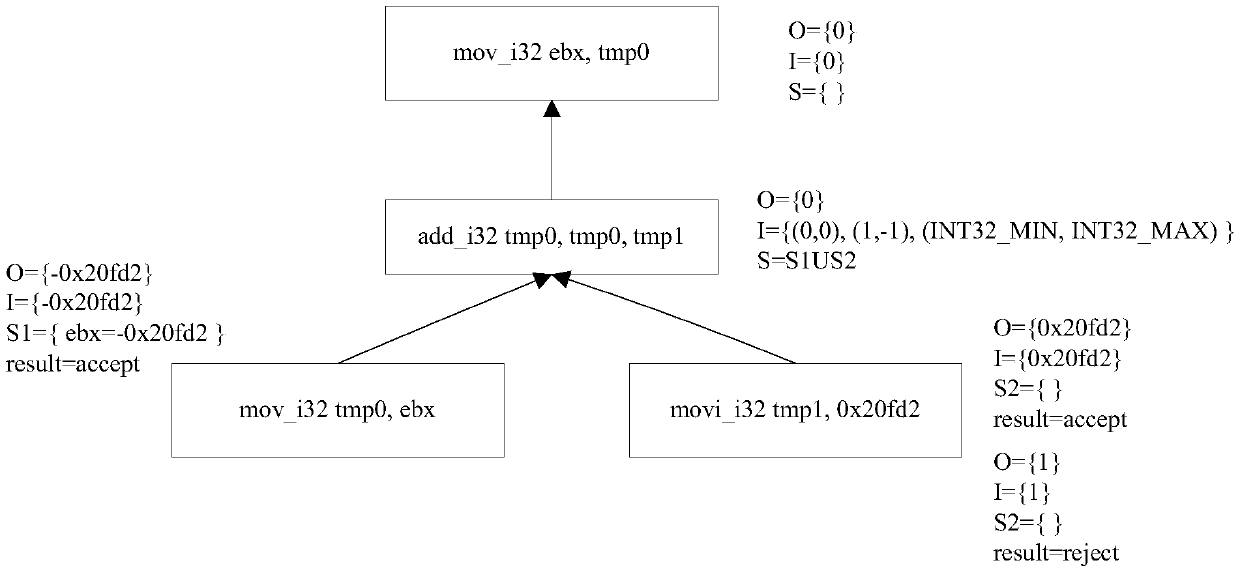
The invention belongs to the technical field of computer transplantation, and particularly relates to a binary translation intermediate representation correctness testing method and device based on semantic equivalence verification, and the method comprises the steps: building a mapping rule between a source platform instruction and an intermediate representation; Performing state initialization on the intermediate representation, and constructing a test case; And for the test case, independently executing the source platform instruction and the intermediate representation respectively, and judging whether the semantics between the source platform instruction and the intermediate representation are equivalent or not according to an independent execution result. According to the invention,an intermediate code correctness test irrelevant to a specific system architecture can be realized; a black box and white box testing method is combined; The method can quickly, efficiently and accurately locate the problems existing in the binary translation intermediate representation, improves the test accuracy and efficiency, further shortens the software development test period, guarantees the software quality and reliability, and has a certain guiding significance for binary translation tests between different platforms and the computer software cross-platform transplantation technology.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
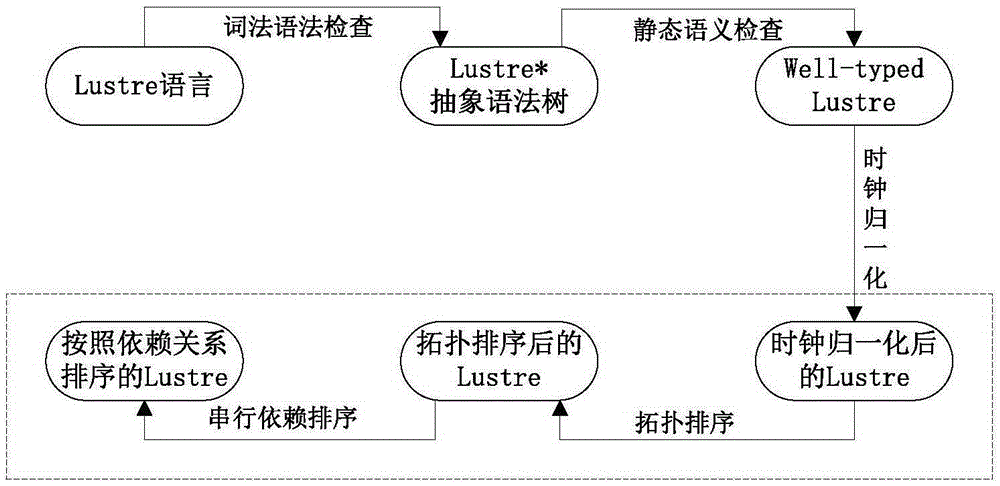
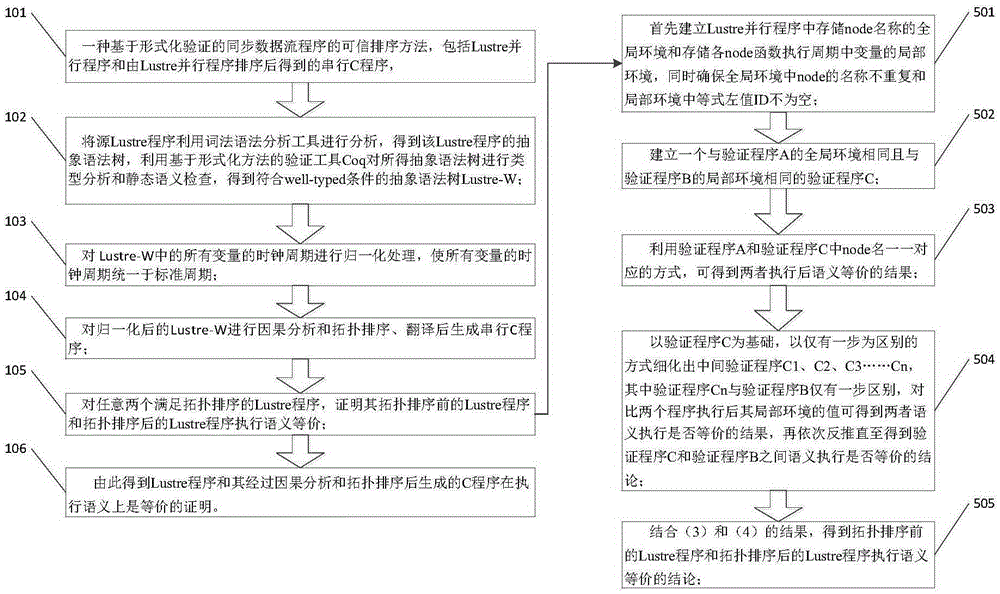
Credible sorting method of synchronous data flow procedures based on formal verification
ActiveCN103646194AImprove securityImprove reliabilityError detection/correctionProgram/content distribution protectionData streamSorting algorithm
The invention discloses a credible sorting method of synchronous data flow procedures based on formal verification. The credible sorting method comprises a Lustre parallel program and a serial C program obtained after sorting of the Lustre parallel program. For any two Lustre programs meeting the requirement for topological sorting, execution semantic equivalence of a Lustre program before topological sorting and a Lustre program after topological sorting is proved, and a C program after sorting and the Lustre program before sorting are equivalent in semantic execution. The credible sorting method of synchronous data flow procedures based on formal verification is developed and achieved based on a formalized language and with a 'vertex topological sorting algorithm with the in-degree as zero' as the theoretical basis. By means of the provement that any two programs meeting the topological sorting property are equivalent in serial semantic execution, during formal verification, all the situations in the process that a parallel language is converted into a serial language, each situation is proved, the program after sorting meets the topological sorting property, so that correctness of a scheme is ensured, and safety and reliability of a whole software system are improved.
Owner:CHINA TECHENERGY +1
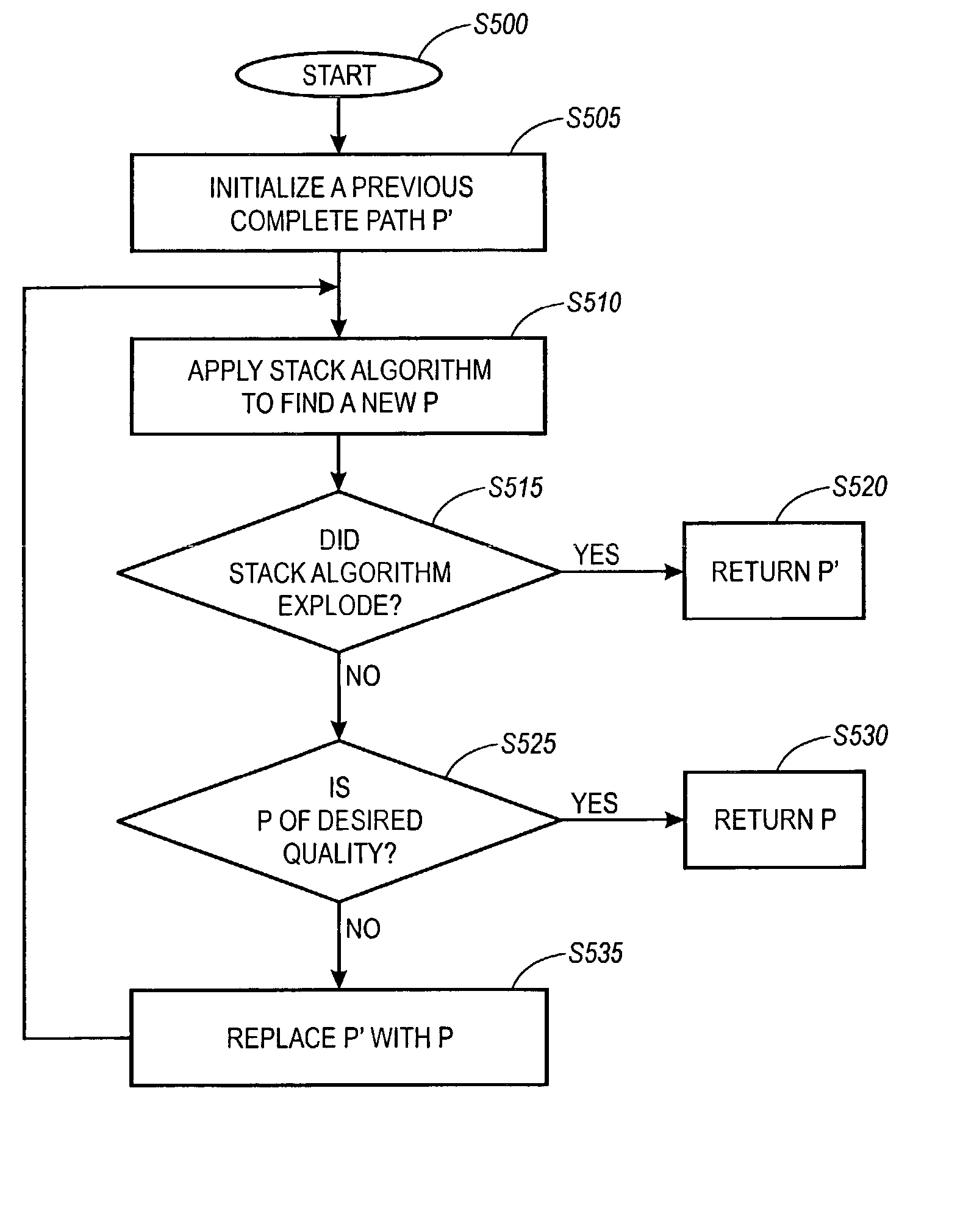
Document image decoding systems and methods using modified stack algorithm
ActiveUS7039240B2Reduce difficultyQuality improvementCharacter and pattern recognitionTemplate matchingHypothesis
Methods and systems for document image decoding incorporating a Stack algorithm improve document image decoding. The application of the Stack algorithm is iterated to improve decoding. A provisional weight is determined for a partial path to reduce template matching. In addition, semantically equivalent hypotheses are identified to reduce redundant hypotheses.
Owner:XEROX CORP
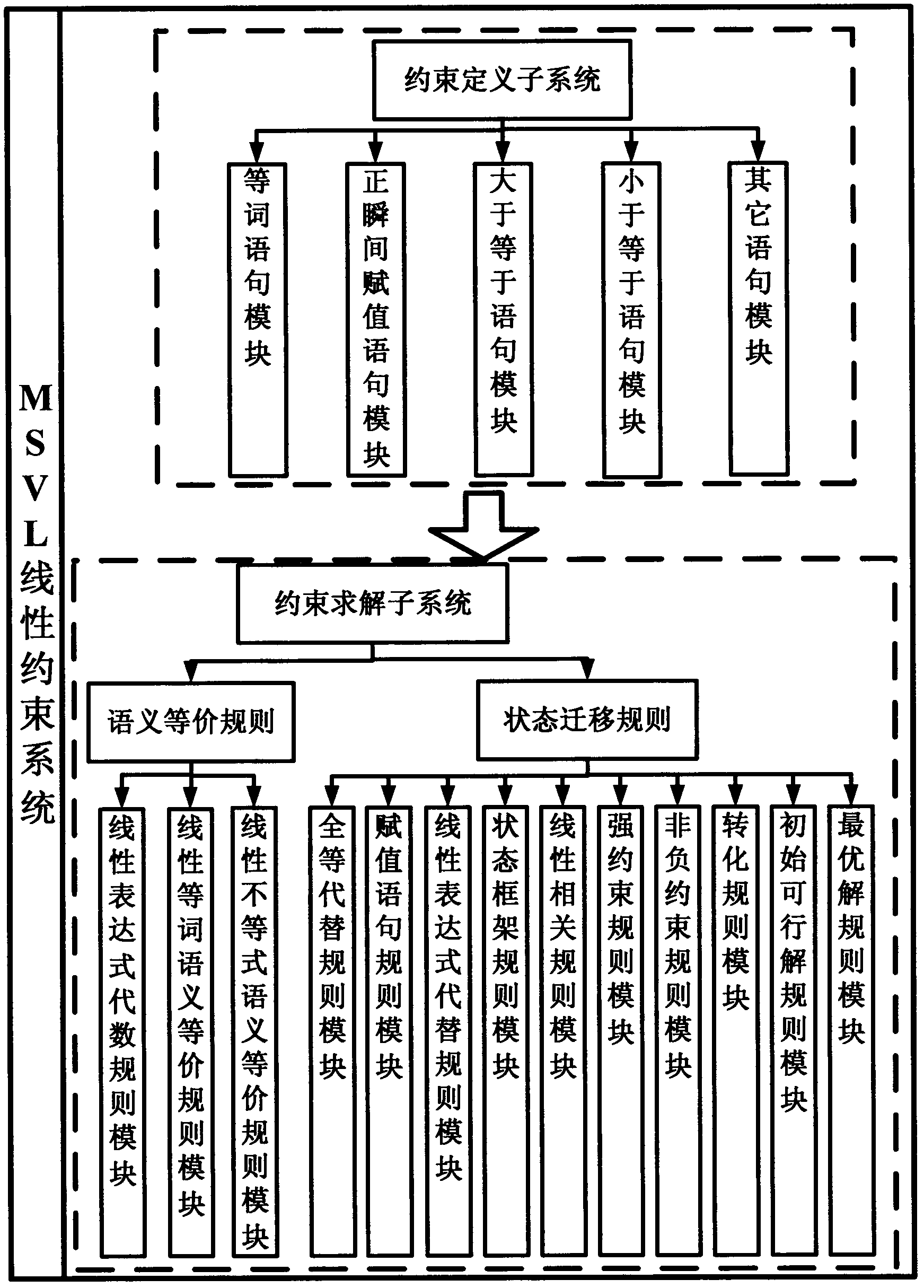
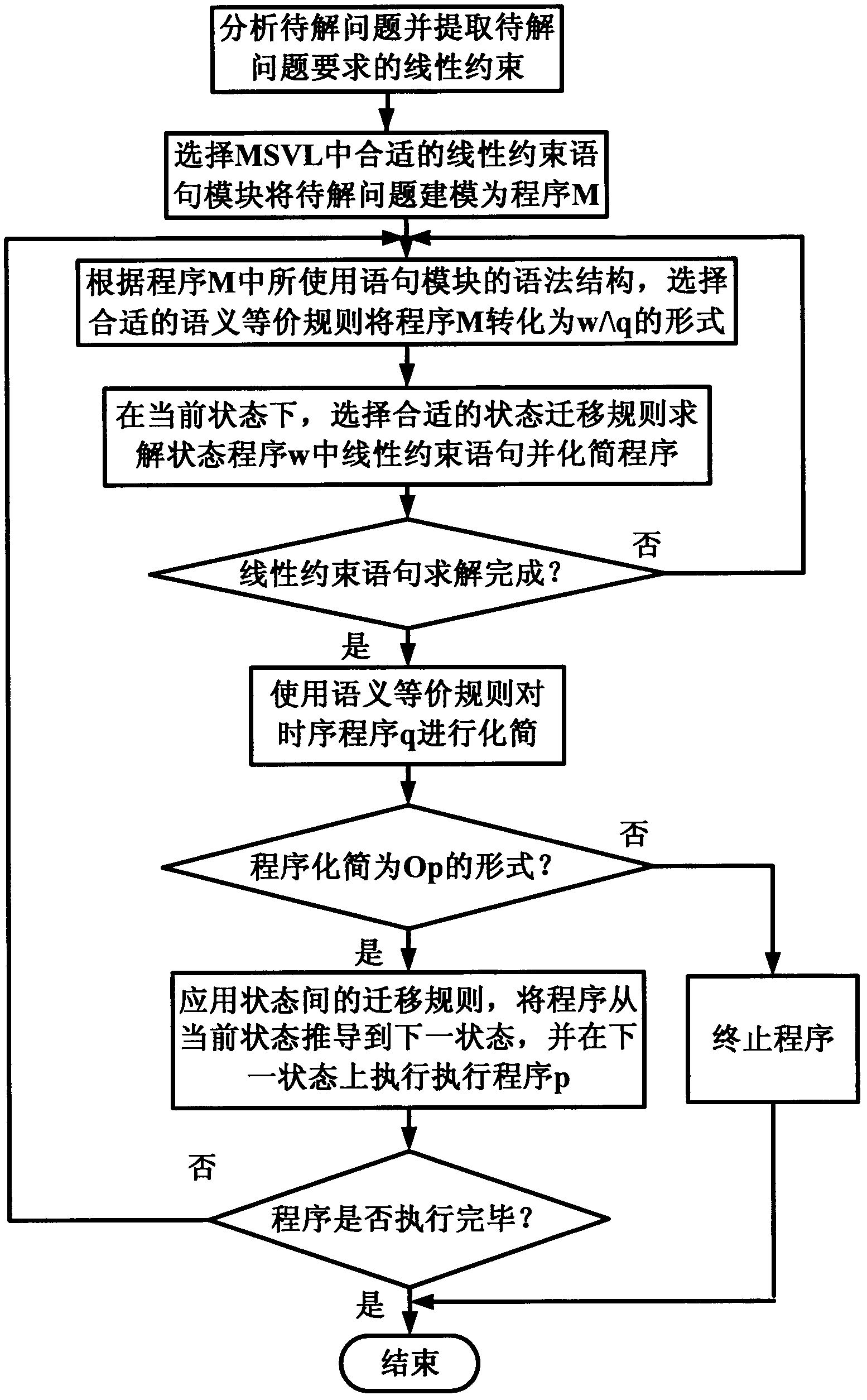
MSVL (modeling, simulation and verification language) linear constraint system and implementation method thereof
ActiveCN102663521AFit the way of thinkingEnhance expressive abilityForecastingTheoretical computer scienceSemantic equivalence
The invention discloses an MSVL (modeling, simulation and verification language) linear constraint system and an implementation method thereof and belongs to the technical field of formal modeling and constraint solving. The MSVL linear constraint system comprises a constraint definition subsystem and a constraint solving subsystem, and the grammatical structure of every statement module in the constraint definition subsystem is applicable to semantic equivalence rules and state transition rules in the constraint solving subsystem. The implementation method of the MSVL linear constraint system includes selecting corresponding statement modules to model problems to be solved as MSVL program M, simplifying the M to be in the form of w Lambada q by utilizing the semantic equivalence rules, implementing the state program w in the current state by utilizing the state transition rules, then simplifying the time sequence program q to be in the next state to continue implementation by utilizing interstate transition rules and finally proposing a solution. Linear constraint structure is expanded in interval logic language, so that the implementation method has huge expression ability and is more convenient for solving the problems of scheduling, computer vision, combinatorial optimization and the like which relate to the linear constraint system in industrial applications.
Owner:XIDIAN UNIV
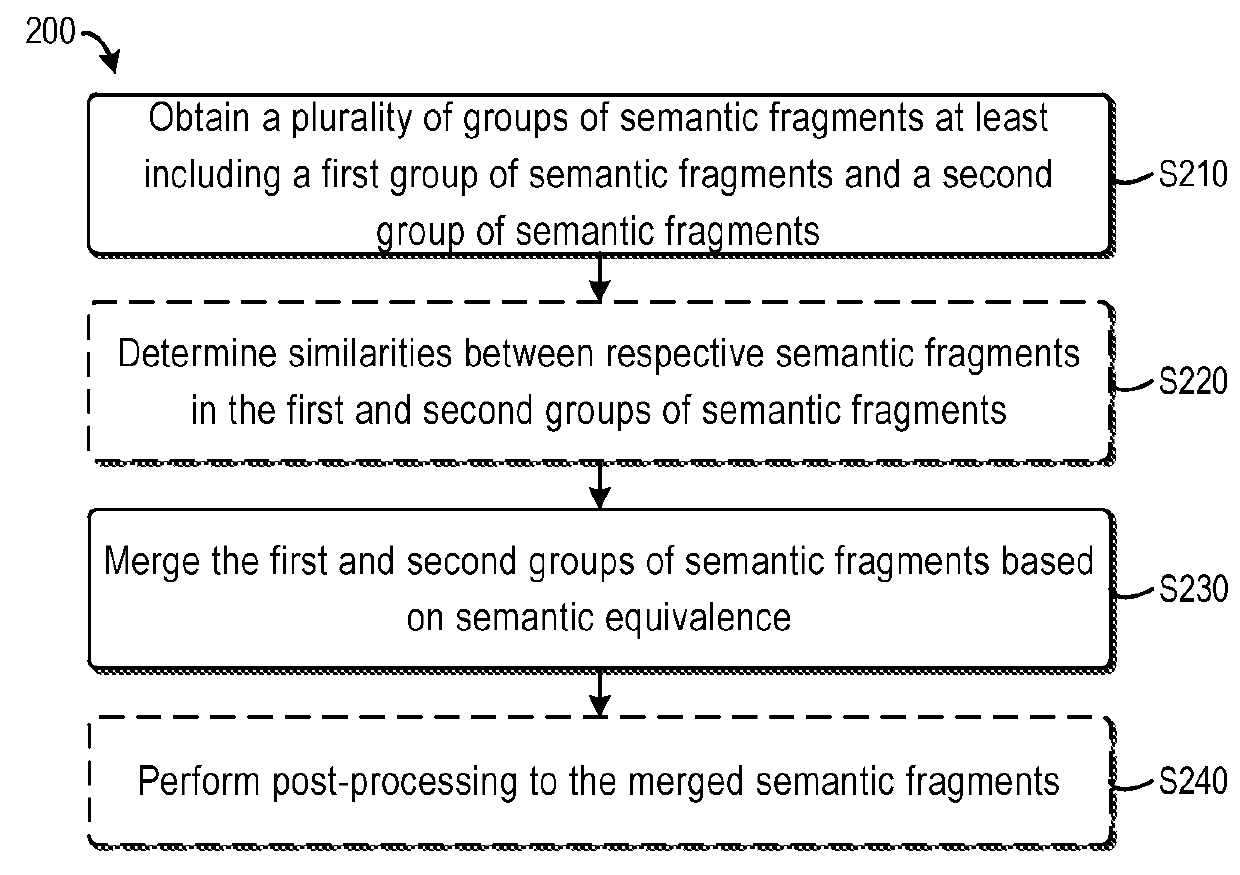
Method and system for processing semantic fragments
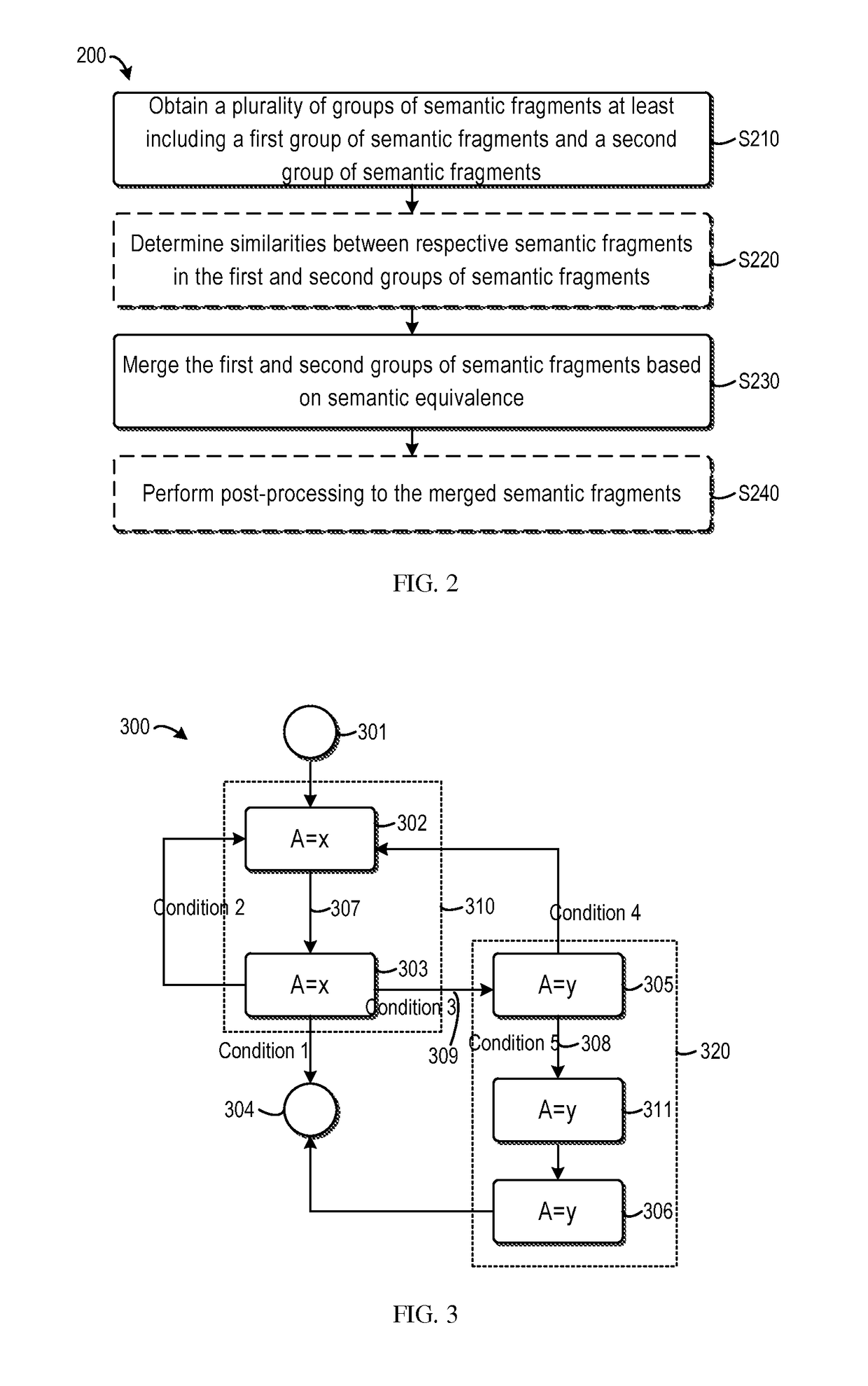
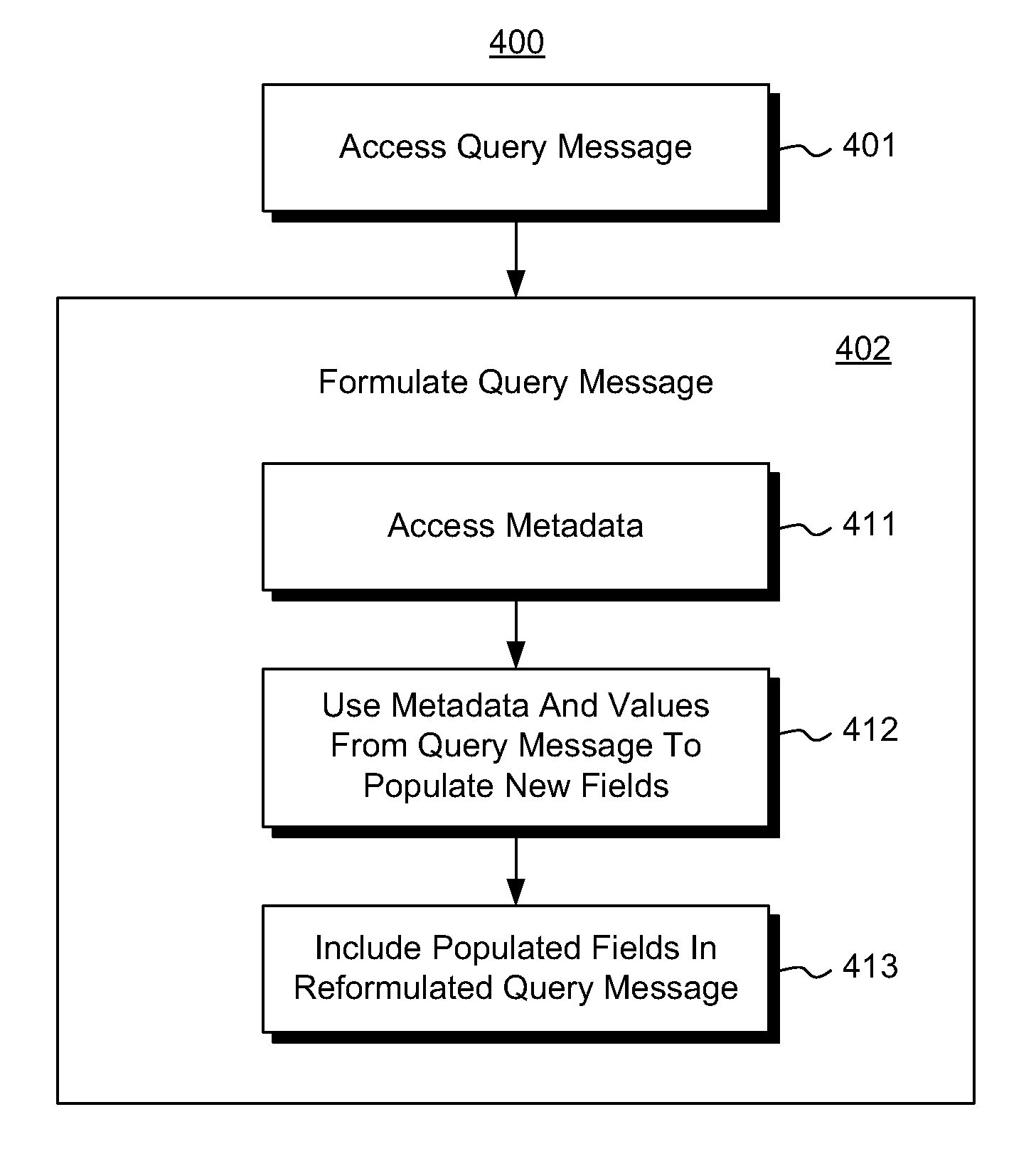
ActiveUS20160055147A1Eliminate mutual interferenceGood effectSemantic analysisSpecial data processing applicationsAlgorithmTheoretical computer science
The present invention discloses a method and system for processing semantic fragments. Some embodiments of the present invention provides a method for processing semantic fragments. The method comprises: obtaining a plurality of groups of semantic fragments, the plurality of groups of semantic fragments at least including a first group of semantic fragments generated from a first data processing flow and a second group of semantic fragments generated from a second data processing flow, the first data processing flow being different from the second data processing flow; and merging the first group of semantic fragment and the second group of semantic fragment based on semantic equivalence. A corresponding system is also disclosed.
Owner:IBM CORP
Real Time Parsing and Suggestions from Pre-Generated Corpus with Hypernyms
ActiveUS20170344534A1Digital data information retrievalSemantic analysisSemantic equivalenceA domain
Systems and methods of natural language processing in an environment with no existing corpus are disclosed. The method includes defining an input grammar specific to a chosen domain, the input grammar having a domain specific knowledge and general grammatical knowledge. Groups of tokens are identified within the input grammar having syntactic and semantic equivalence. The identified groups are assembled into hypernyms, wherein the hypernyms include a semantic output for each token in the hypernyms. A list of fields is then combined with the hypernyms for combination with the hypernyms. A corpus of possible combinations of hypernyms and fields is created. A data structure mapping each possible combination to a partial semantic output is generated and the data structure is saved for use in later processing.
Owner:YAHOO ASSETS LLC
Document image decoding systems and methods using modified stack algorithm
Methods and systems for document image decoding incorporating a Stack algorithm improve document image decoding. The application of the Stack algorithm is iterated to improve decoding. A provisional weight is determined for a partial path to reduce template matching. In addition, semantically equivalent hypotheses are identified to reduce redundant hypotheses.
Owner:XEROX CORP
Method and system for processing semantic fragments
ActiveUS10049101B2Eliminate mutual interferenceGood effectSemantic analysisSpecial data processing applicationsAlgorithmTheoretical computer science
Owner:INT BUSINESS MASCH CORP
Query and result rebinding
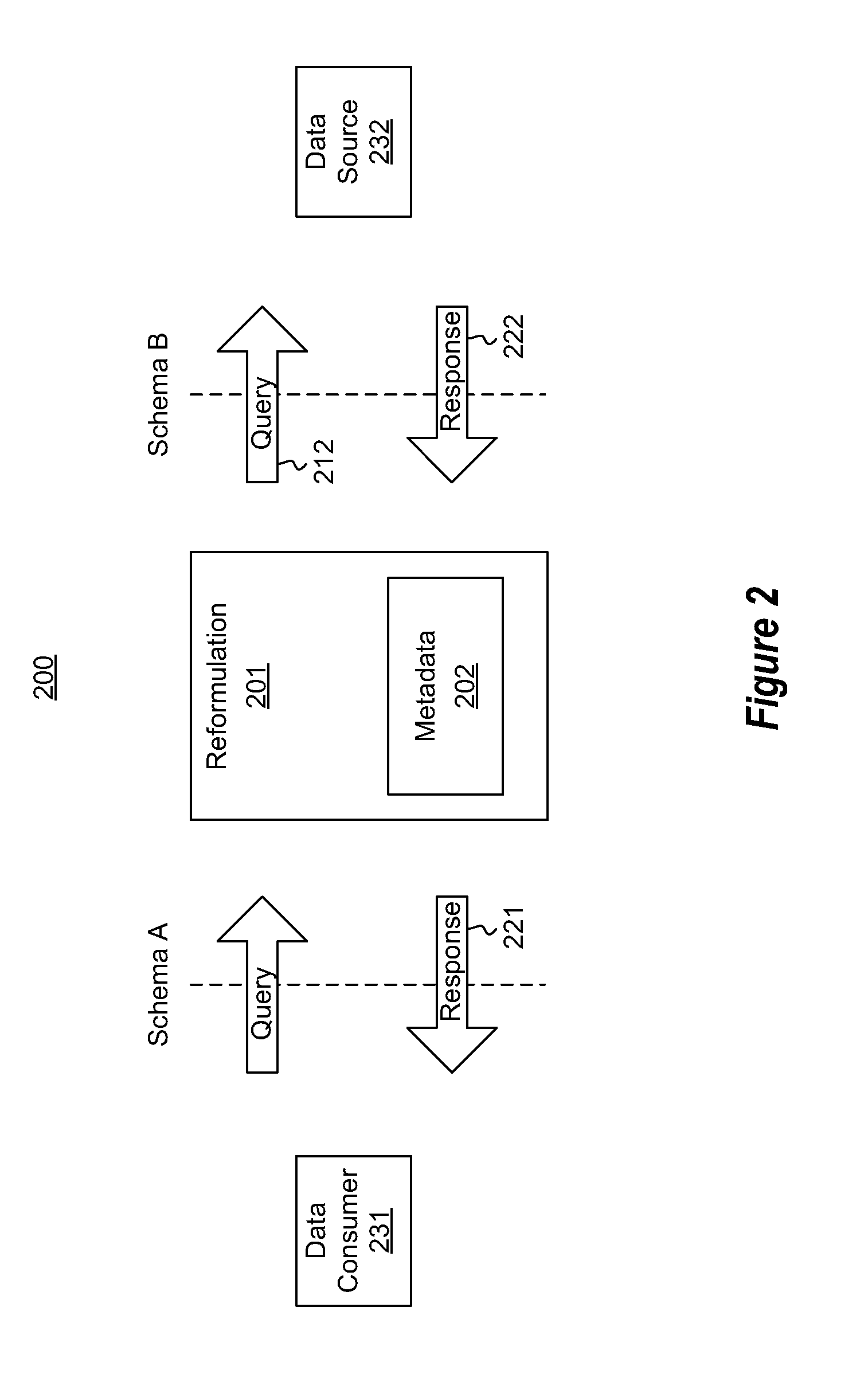
InactiveUS20120072439A1Easy to changeDatabase management systemsDigital data processing detailsDatabaseData source
The metadata-based intermediation between two data sources. A computing system accesses a query message (e.g., a query or a query response). The query message is structured to be compatible with the first data source. The computing system uses metadata either directly, or indirectly through the execution of code referenced by the metadata to convert the query message into a semantically equivalent query message that is compatible with the second data source. If the query message were a query, then a query response may be acquired and the metadata may perhaps be used again to convert the query response into a form that is compatible with the first data source. In one embodiment, the conversion using the metadata is performed with the assistance of a framework, making changes to the conversion process as simple as perhaps just editing the metadata itself.
Owner:MICROSOFT TECH LICENSING LLC
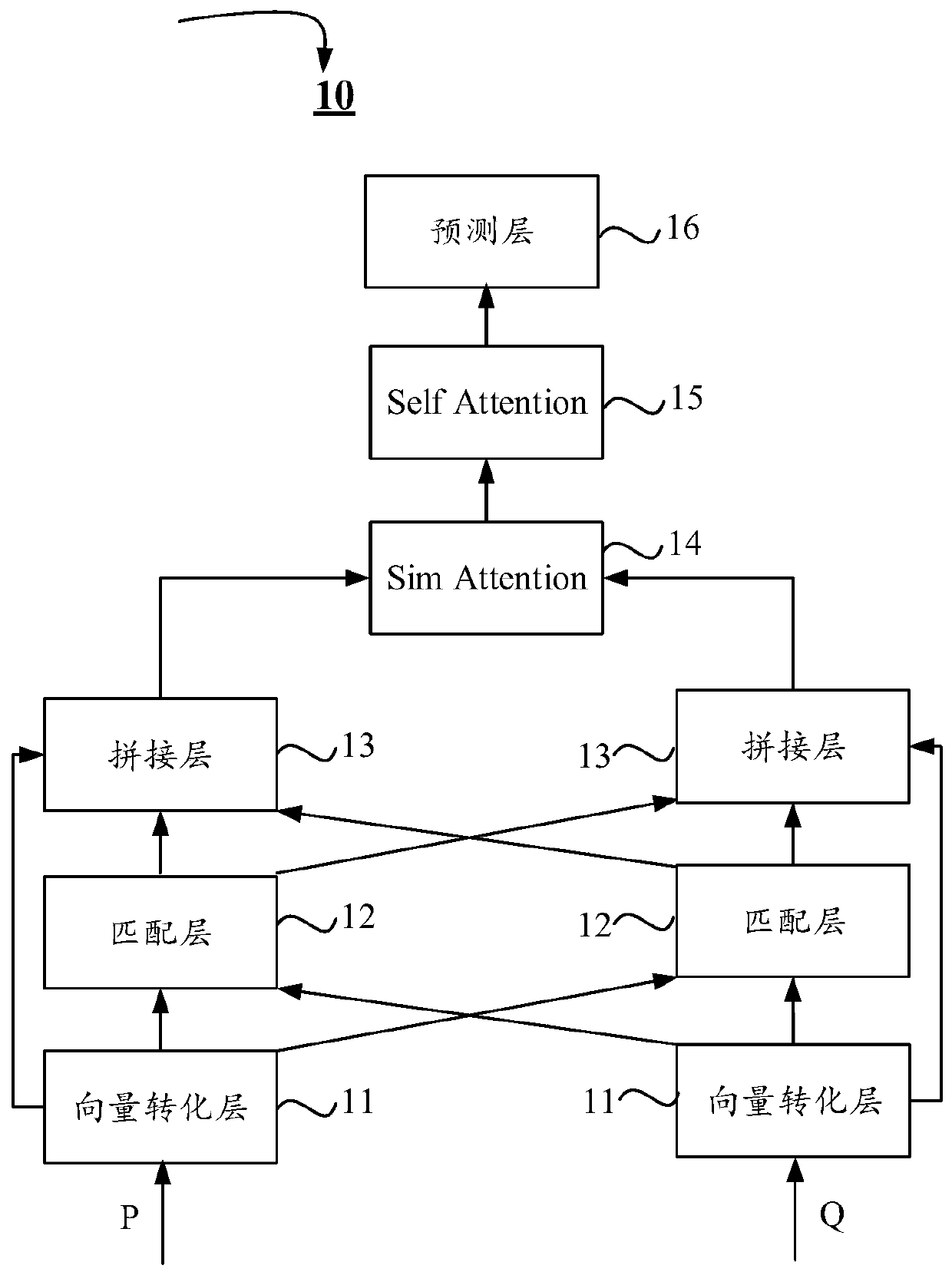
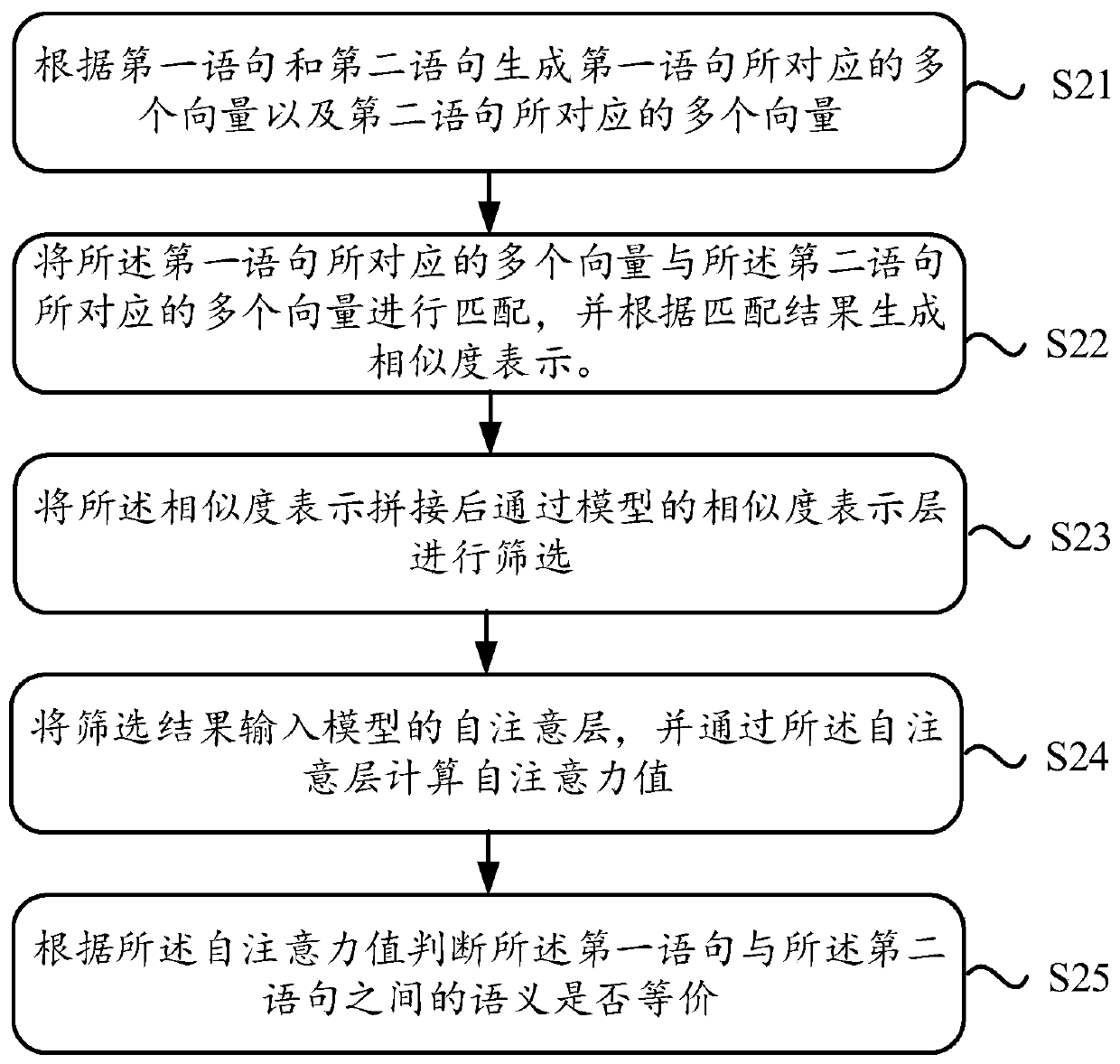
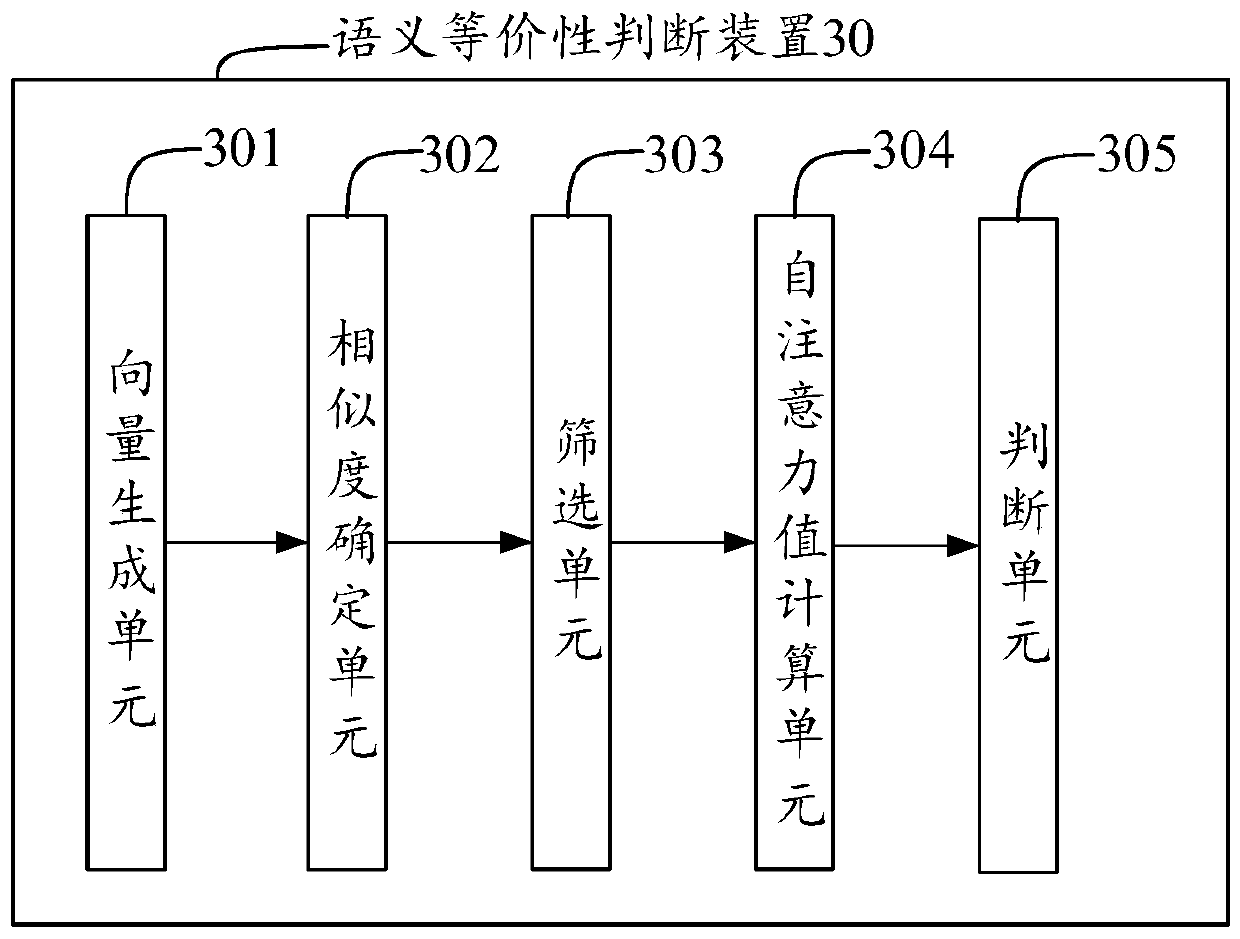
Semantic equivalence judgment method and device
ActiveCN110543549AImprove accuracyText database queryingSpecial data processing applicationsSelf attentionAlgorithm
The invention discloses a semantic equivalence judgment method and device. The method comprises the steps of generating a plurality of vectors corresponding to a first statement and a plurality of vectors corresponding to a second statement according to the first statement and the second statement; matching the plurality of vectors corresponding to the first statement with the plurality of vectorscorresponding to the second statement, and generating similarity representation according to a matching result; splicing the similarity representations, and screening the spliced similarity representations through a similarity representation layer of the model; inputting the screening result into a self-attention layer of the model, calculating a self-attention value through the self-attention layer, wherein the self-attention value reflects the internal structures of the first statement and the second statement; and judging whether semantics between the first statement and the second statement are equivalent or not according to the self-attention value. The method is higher in accuracy for judging whether semantics among multiple sentences are equivalent or not compared with the prior art, so that the method can be used for solving the problems in the prior art.
Owner:北京百分点科技集团股份有限公司
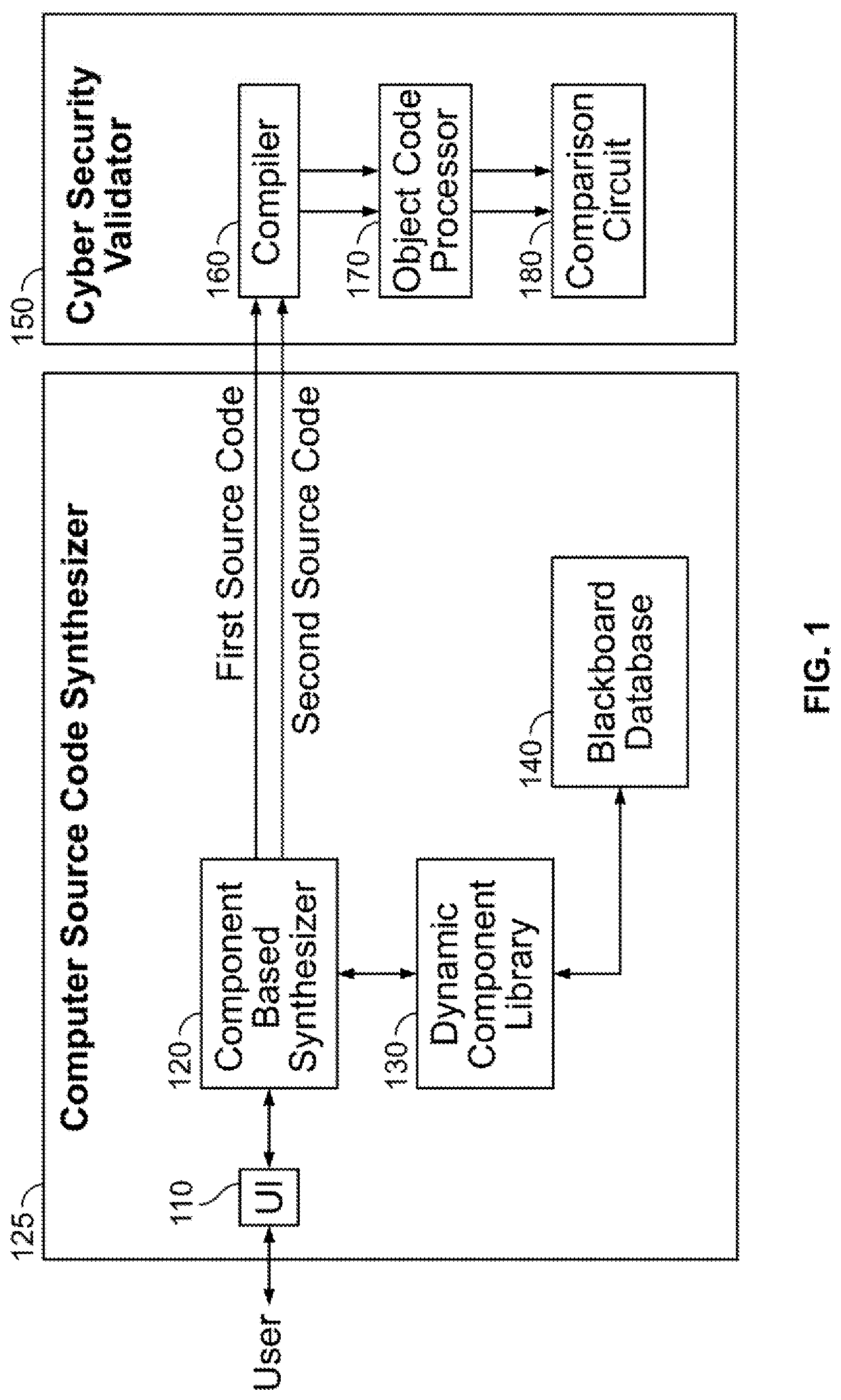
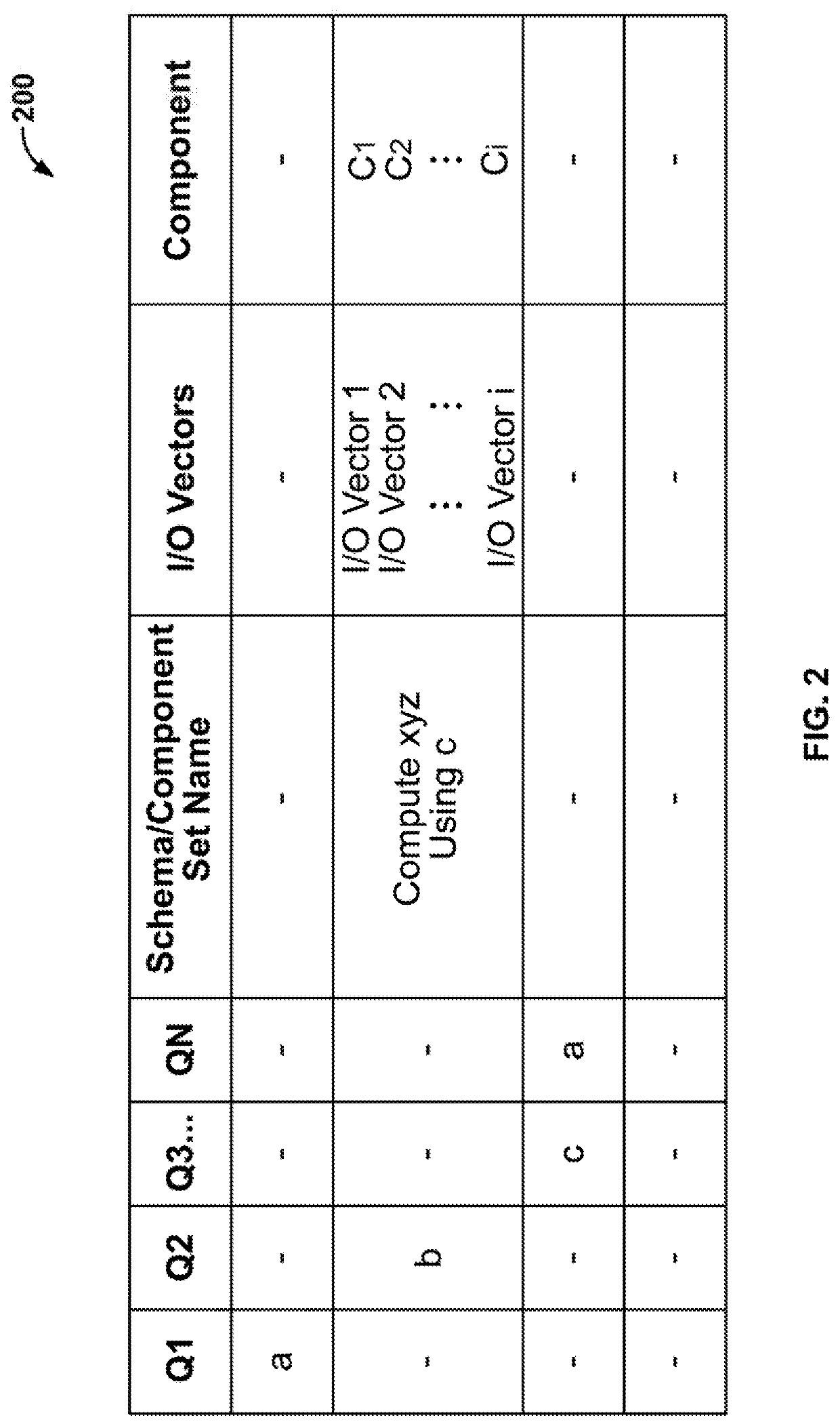
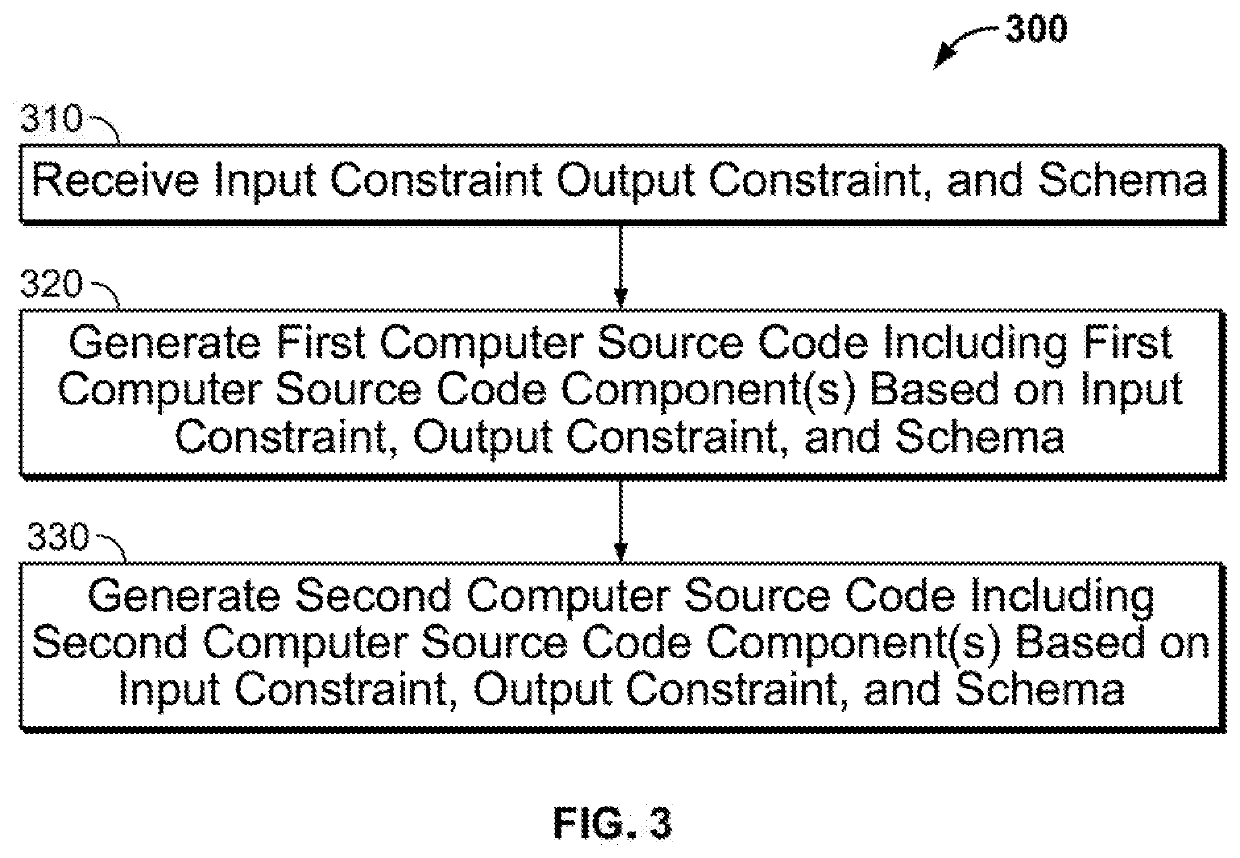
Device, Method, and System for Synthesizing Variants of Semantically Equivalent Computer Source Code using Computer Source Code Components to Protect Against Cyberattacks
ActiveUS20200302059A1Software maintainance/managementPlatform integrity maintainanceCyber-attackSemantic equivalence
An input constraint, an output constraint, and a schema are received from a user. A component-based synthesizer generates first computer source code including a first computer source code component based on the input constraint, the output constraint, and the schema. The component-based synthesizer generates second computer source code including a second computer source code component based on the input constraint, the output constraint, and the schema. The second computer source code is generated as a semantically equivalent variant of the first computer source code to provide for protection against a cyberattack.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
A Trusted Sorting Method for Synchronous Data Flow Programs Based on Formal Verification
ActiveCN103646194BImprove securityImprove reliabilityError detection/correctionProgram/content distribution protectionData streamSorting algorithm
Owner:CHINA TECHENERGY +1
A method of problem equivalence discrimination based on semi-supervised learning combined with ensemble learning
ActiveCN110008323BFlexible adjustmentDigital data information retrievalSemantic analysisFeature extractionDual network
The invention discloses a method for judging the equivalence of a problem by combining semi-supervised learning with integrated learning, including S1, normalization of synonyms: 1) word vector embedding; 2) word similarity judgment; 3) manual judgment; S2, semantics Equivalence recognition: calculation of dual network based on LSTM; calculation of dual network model based on CNN; calculation based on Match Pyramid model; manual feature extraction. The present invention generates and introduces synonyms in a semi-supervised manner, so that the entire system can be flexibly adjusted according to specific fields, and four different models are used to learn the semantic equivalence of the problem to judge the semantic equivalence of the problem, thereby giving full play to the advantages of different models.
Owner:北京百分点科技集团股份有限公司
SQL injection statement transformation method based on context-independent grammar
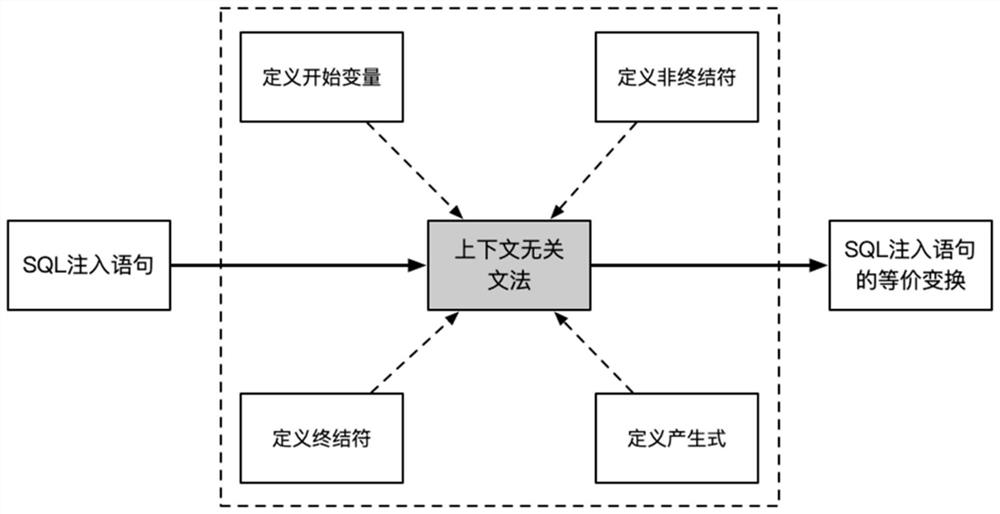
PendingCN114036509AReserved functionReserve maliciousnessDigital data protectionPlatform integrity maintainanceProgramming languageSQL injection
The invention discloses an SQL injection statement transformation method based on context-independent grammar, which needs to generate a large amount of semantic equivalence transformation on an SQL injection statement during network security attack and defense research. On the basis of the improved context-independent grammar and in combination with semantic matching and other methods, infinite equivalence replacement in theory can be generated according to a single SQL injection statement, semantic equivalence is achieved, and functionality and maliciousness are reserved. According to the invention, the entry generated by replacement is matched by using a semantic-based mode, so that the SQL injection statement is processed in a finer-grained manner, and meanwhile, the damage of a regular matching method to the functionality of the SQL injection statement is avoided.
Owner:ZHEJIANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com