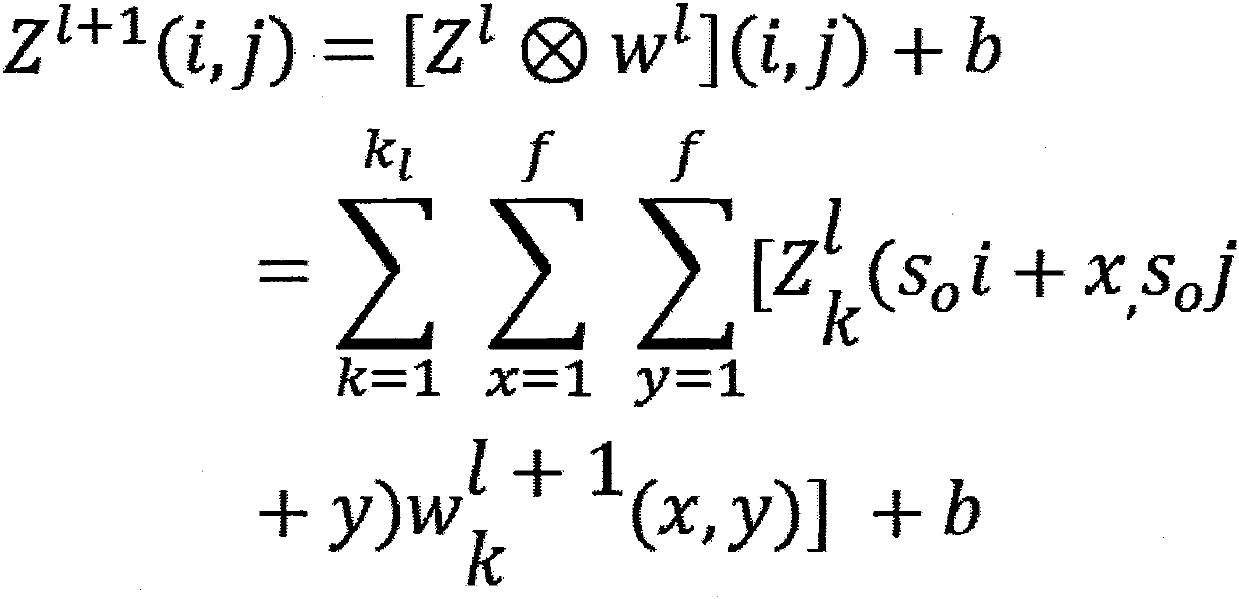Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
615 results about "Formal verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In the context of hardware and software systems, formal verification is the act of proving or disproving the correctness of intended algorithms underlying a system with respect to a certain formal specification or property, using formal methods of mathematics.
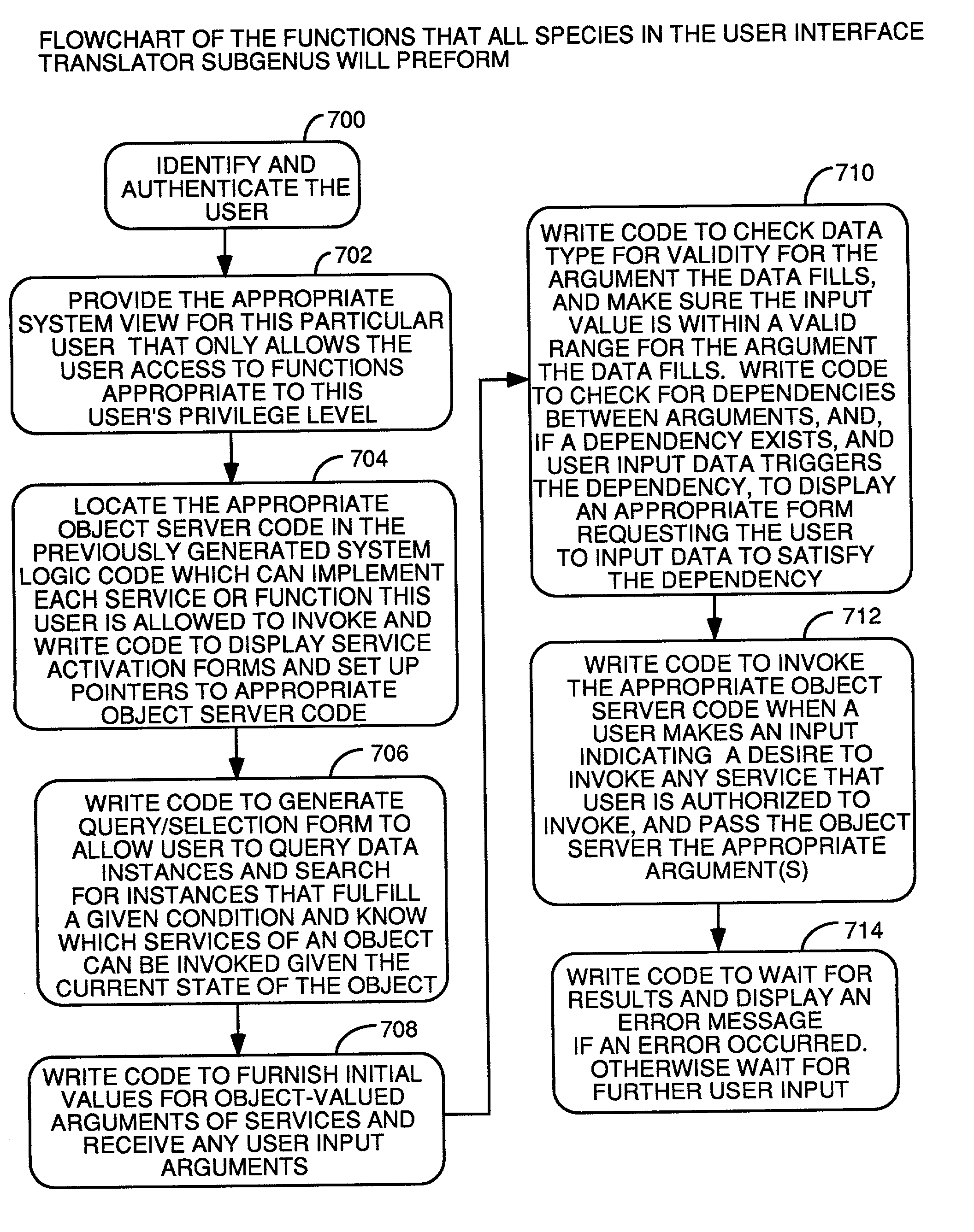
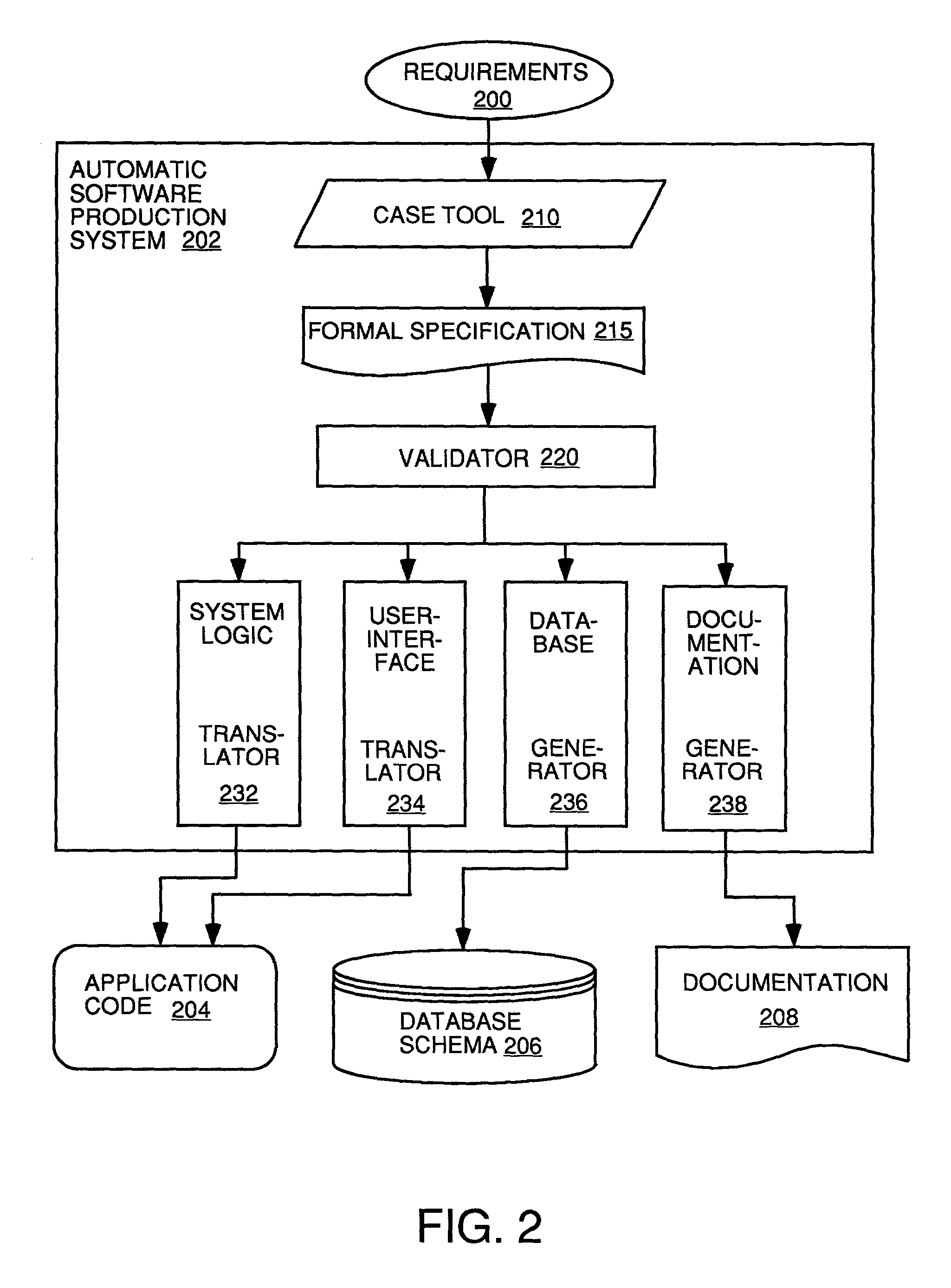
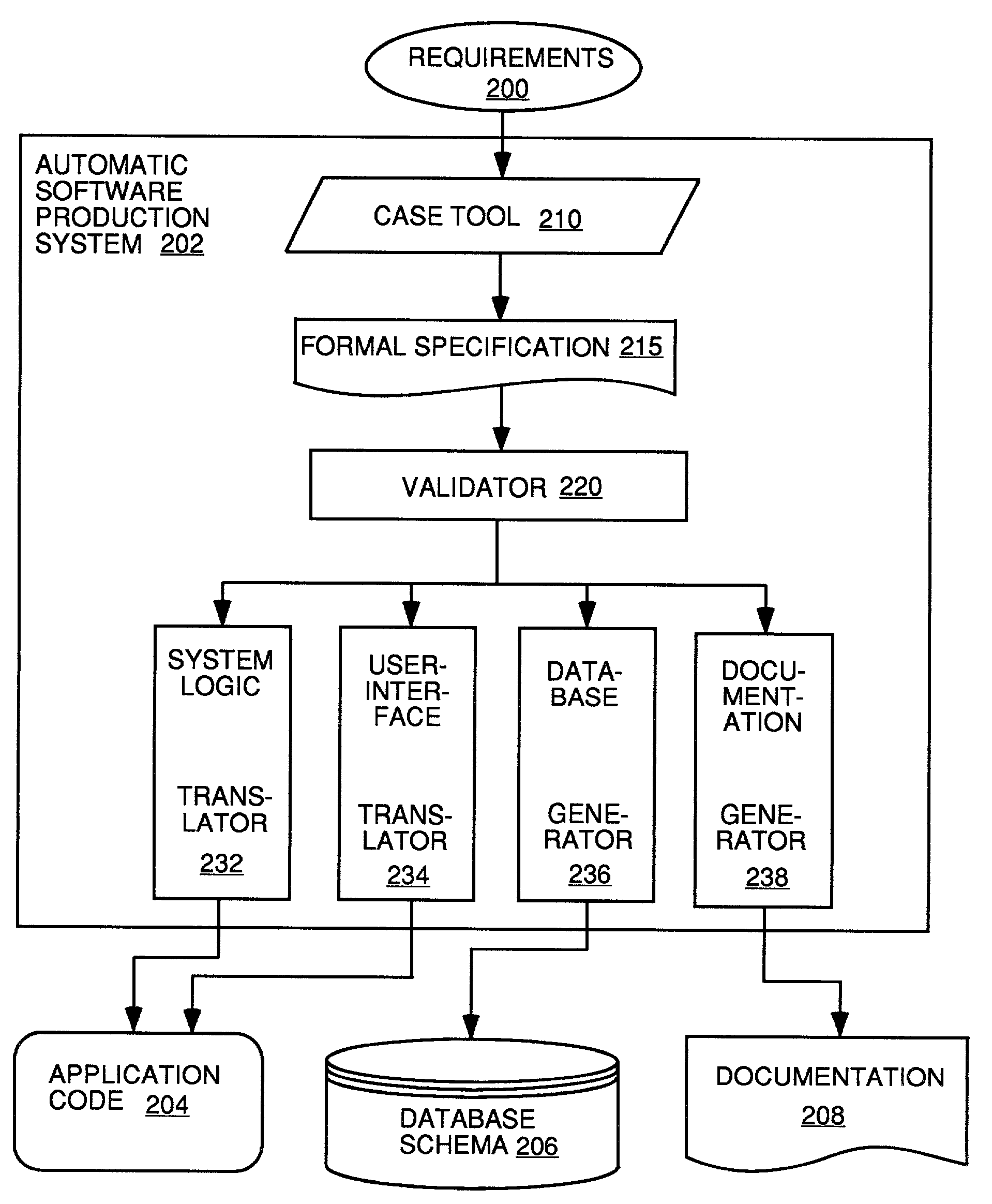
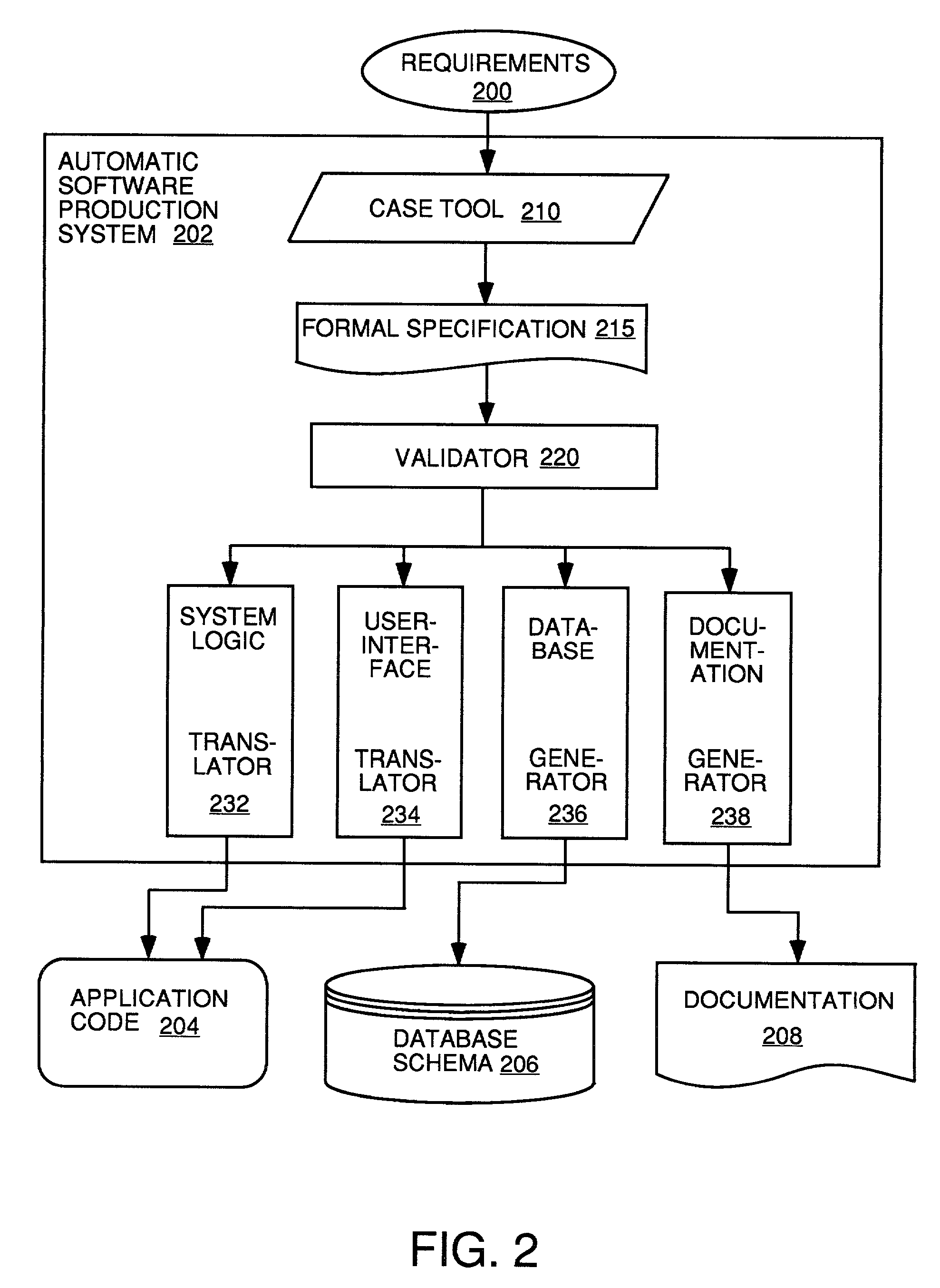
Automatic software production system
InactiveUS7137100B2Shorten the time to marketEasy to useDigital data information retrievalProgram documentationHandling CodeSystem requirements
Owner:SOSY
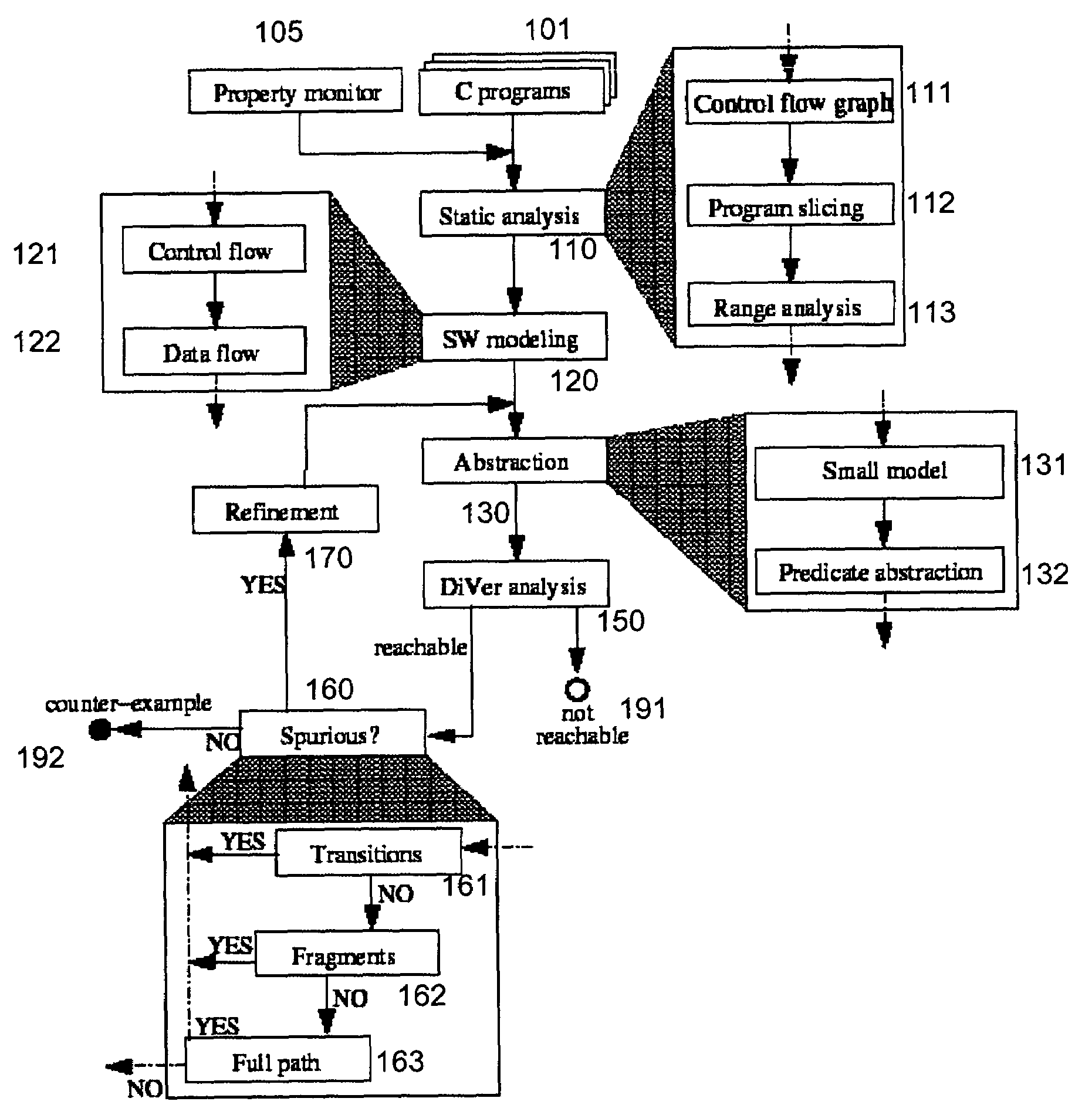
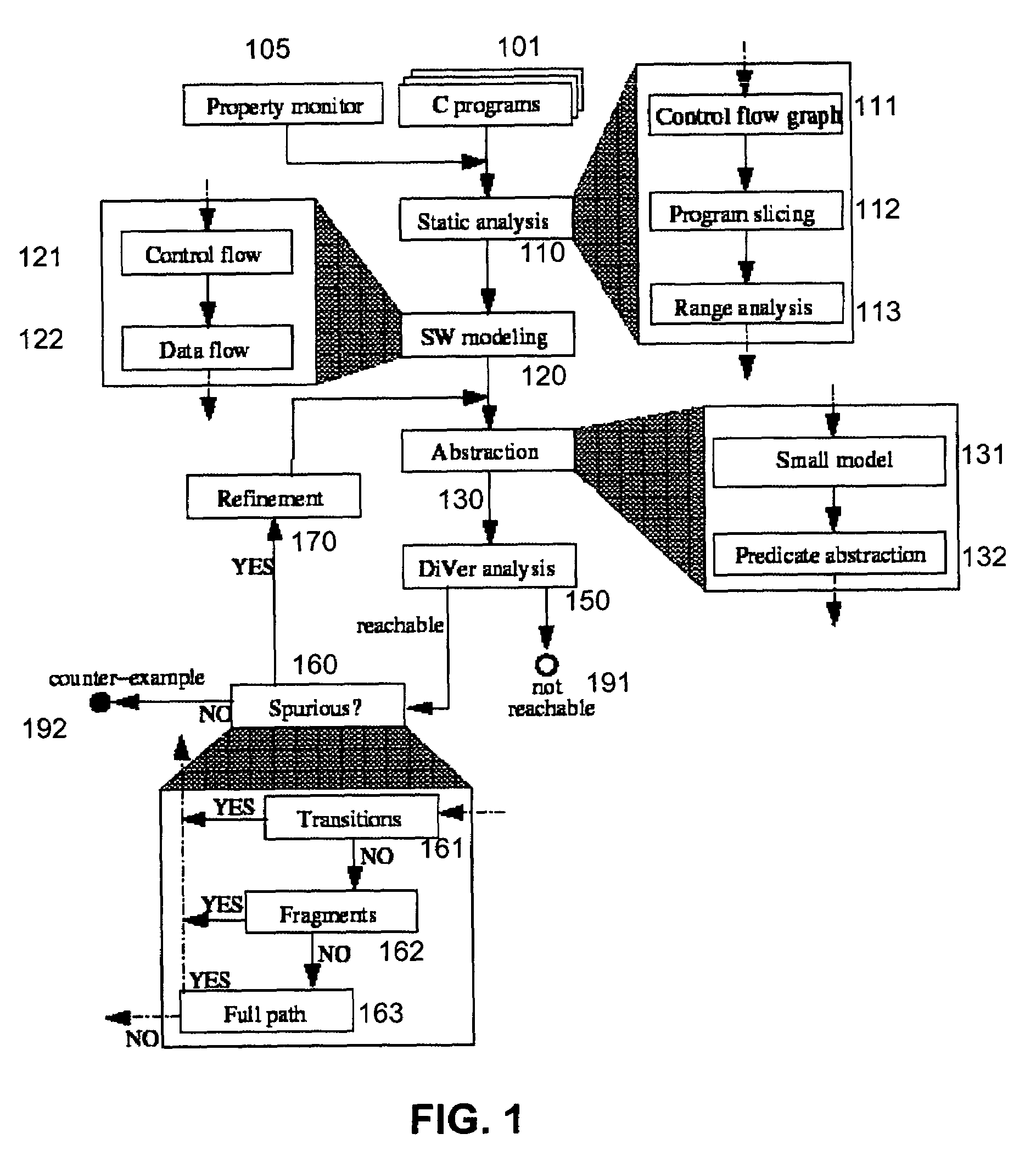
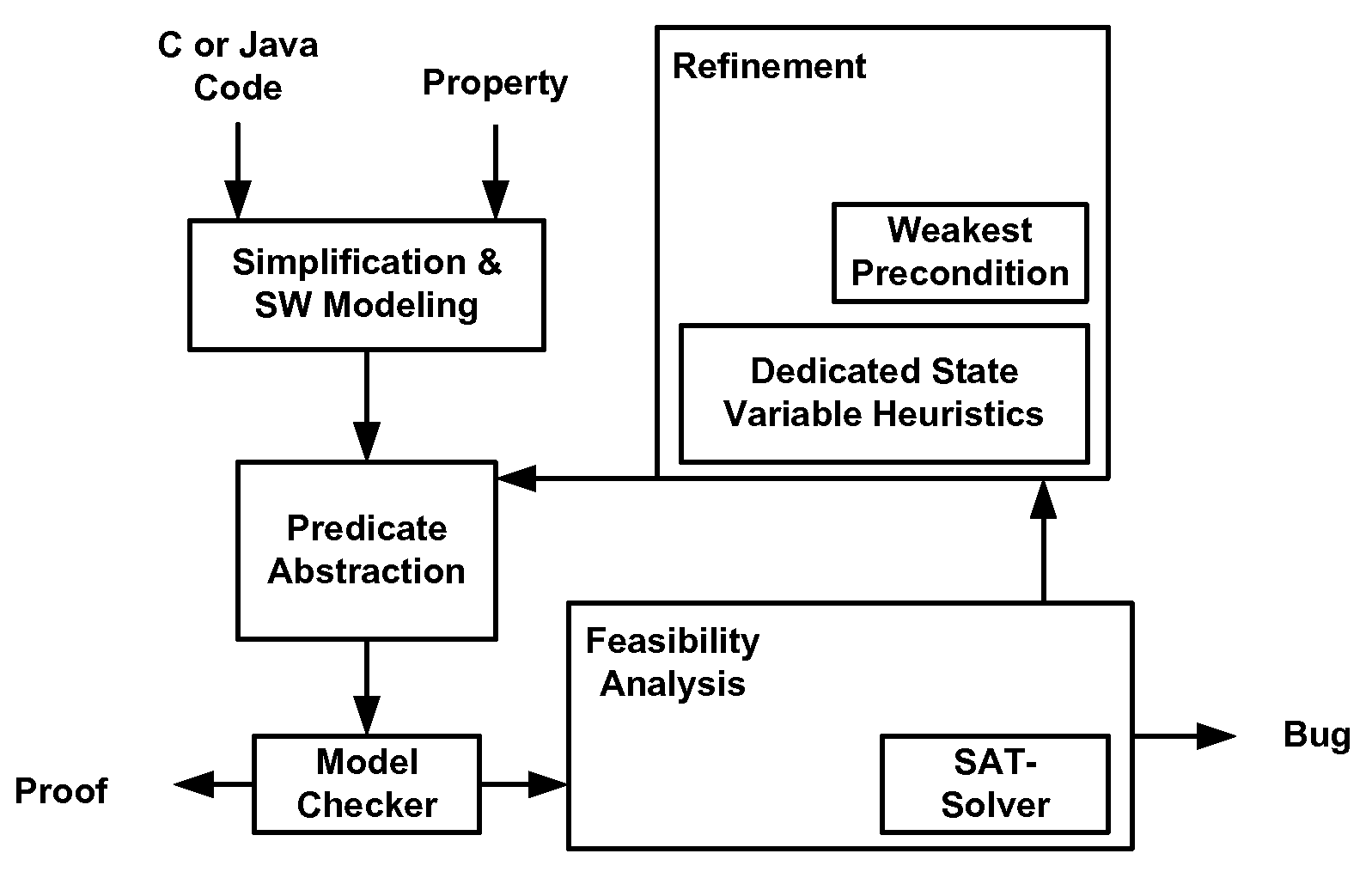
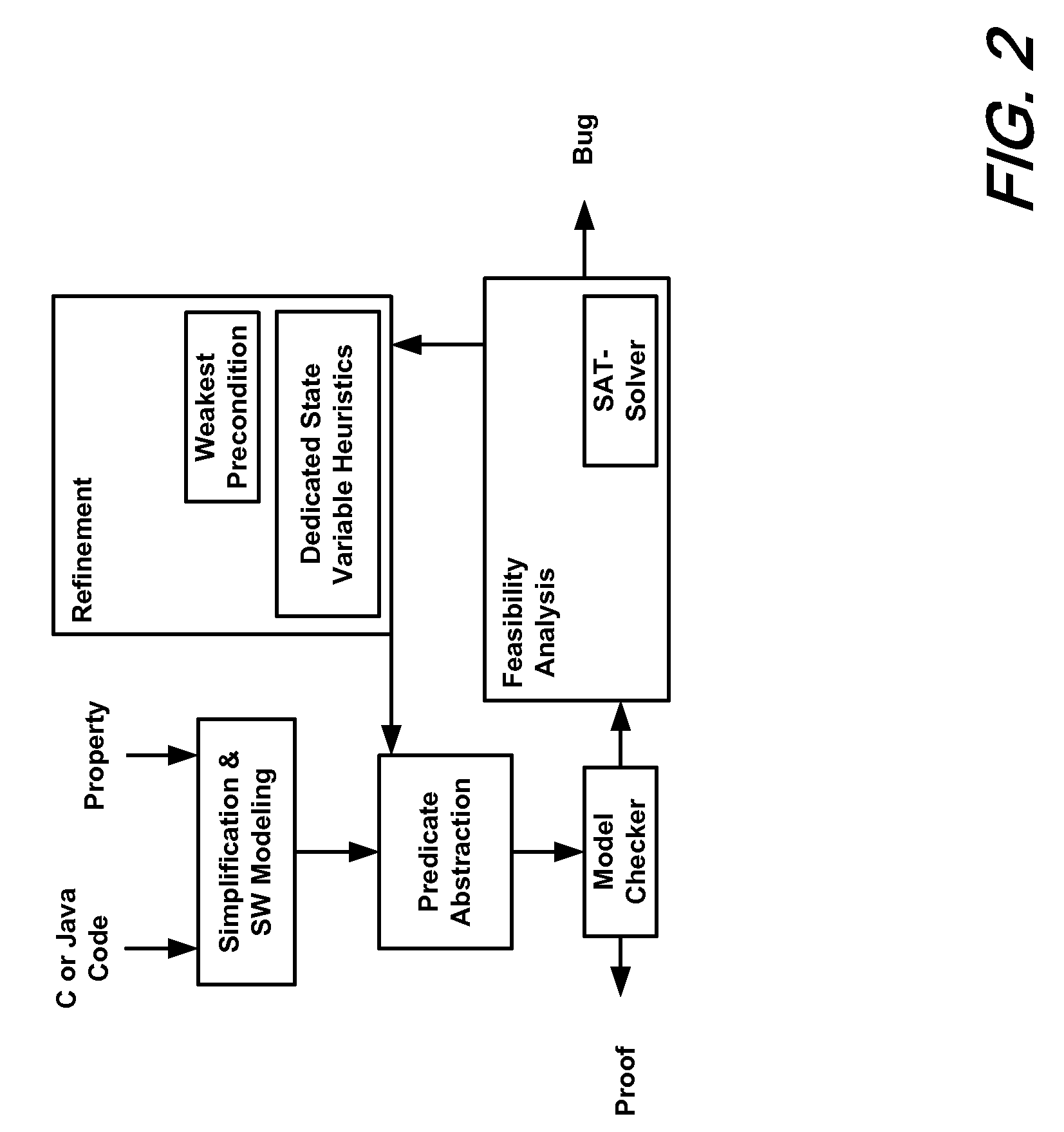
System and method for modeling, abstraction, and analysis of software
ActiveUS7346486B2Improve verification efficiencyImprove translationError detection/correctionComputation using non-denominational number representationBasic blockSoftware
A system and method is disclosed for formal verification of software programs that advantageously translates the software, which can have bounded recursion, into a Boolean representation comprised of basic blocks and which applies SAT-based model checking to the Boolean representation.
Owner:NEC CORP
Automatic software production system
InactiveUS20030167455A1Shorten the time to marketEasy to useDigital data information retrievalProgram documentationHandling CodeSystem requirements
An automated software production system is provided, in which system requirements are captured, converted into a formal specification, and validated for correctness and completeness. In addition, a translator is provided to automatically generate a complete, robust software application based on the validated formal specification, including user-interface code and error handling code.
Owner:IBORRA JOSE +1
Analytical Software Design System
ActiveUS20080263506A1Improve effectivenessExpand coverageSoftware designRequirement analysisSystems designMathematical model
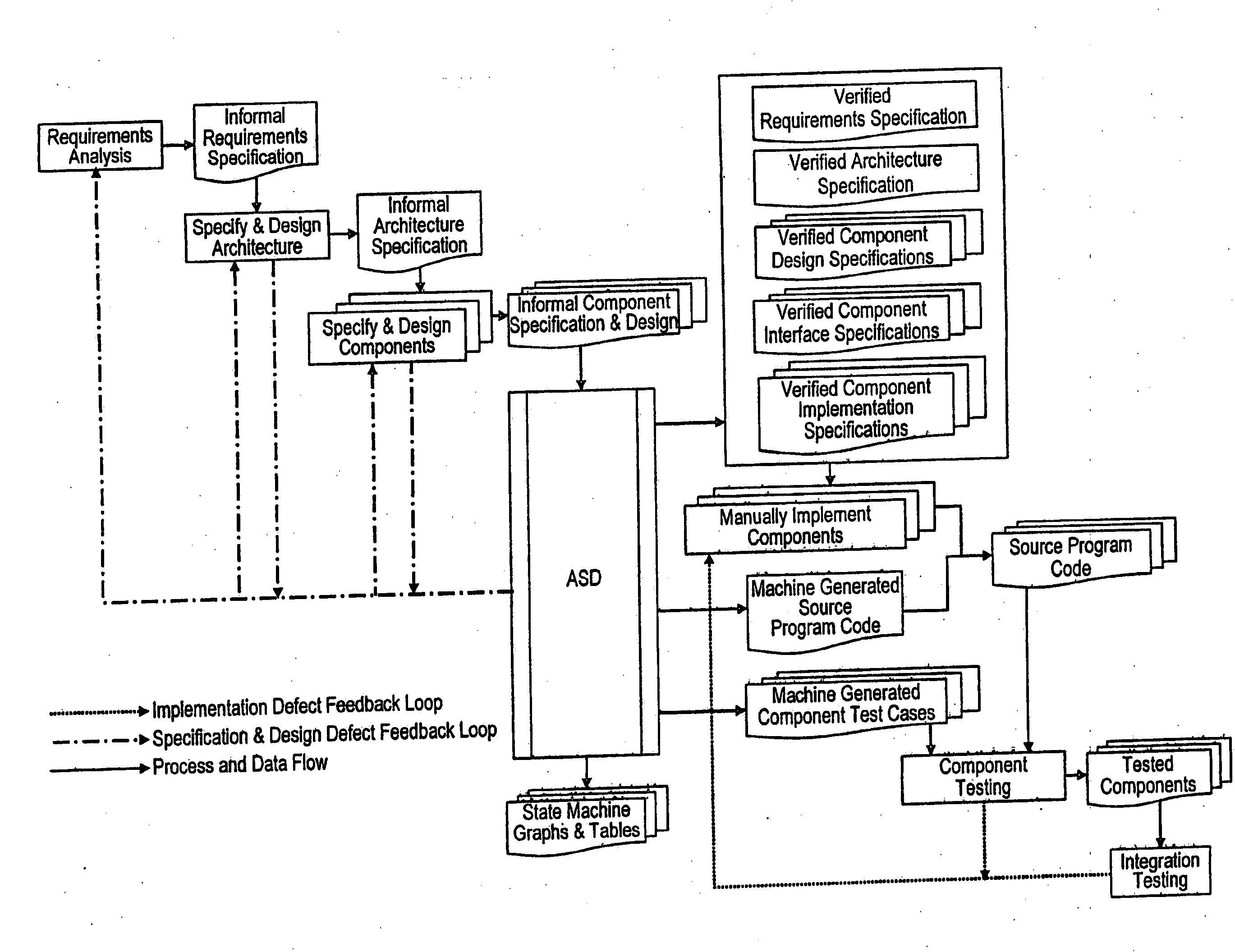
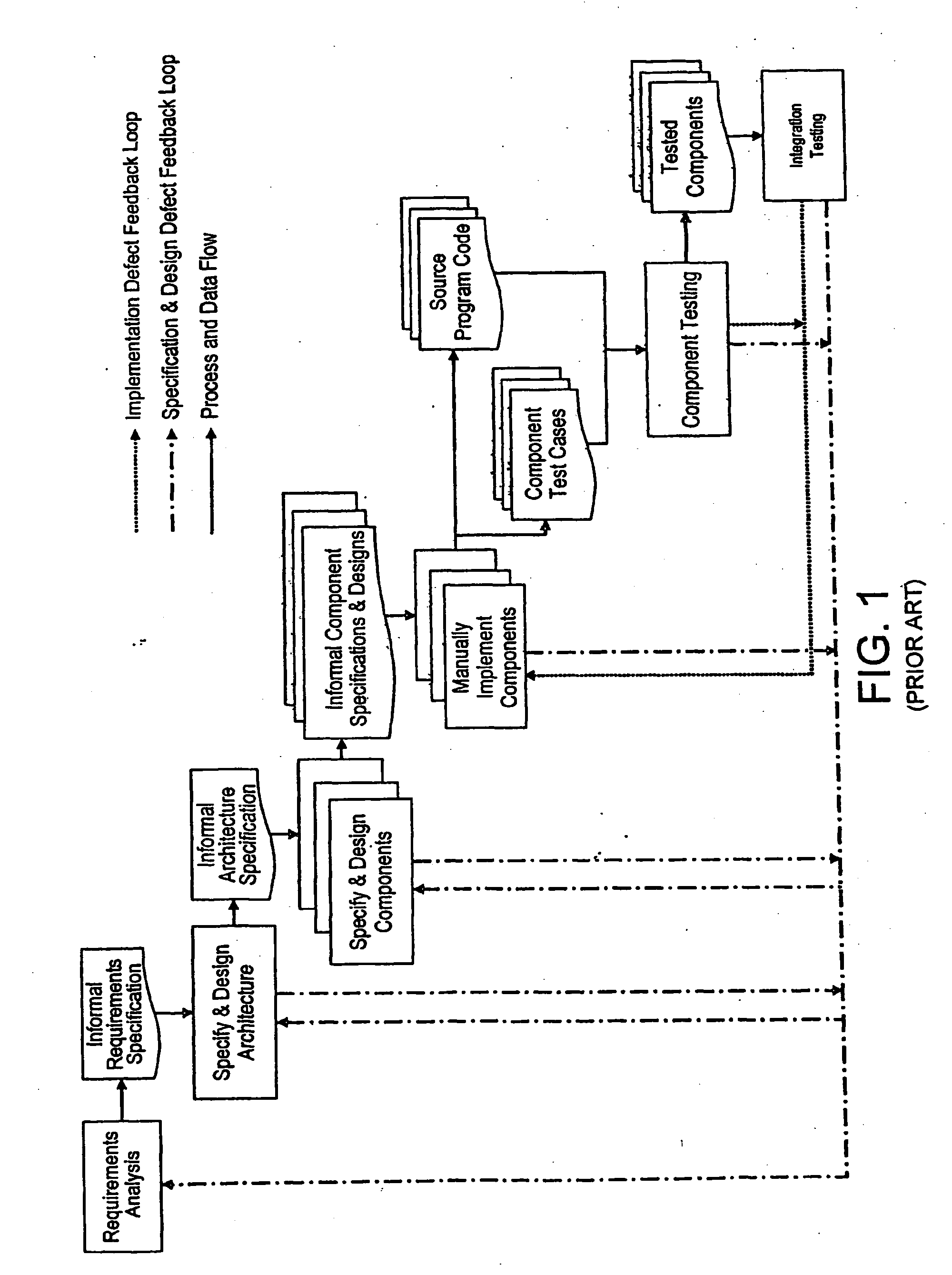
An analytical software design system arranged to receive informal system design specifications and to convert them into verified design specifications for use in creating source code and carrying out implementation testing of the source code is described. The system comprises a verified black box specification generator arranged to process the received informal system design specifications to create formal specifications; to generate from the formal specifications mathematical models representing the system behaviour; to analyse the mathematical models to determine if they have the required behaviour; to adjust the formal specifications until the required behaviour is achieved; and to derive the required verified design specifications from the mathematical models.
Owner:COCOTEC LTD
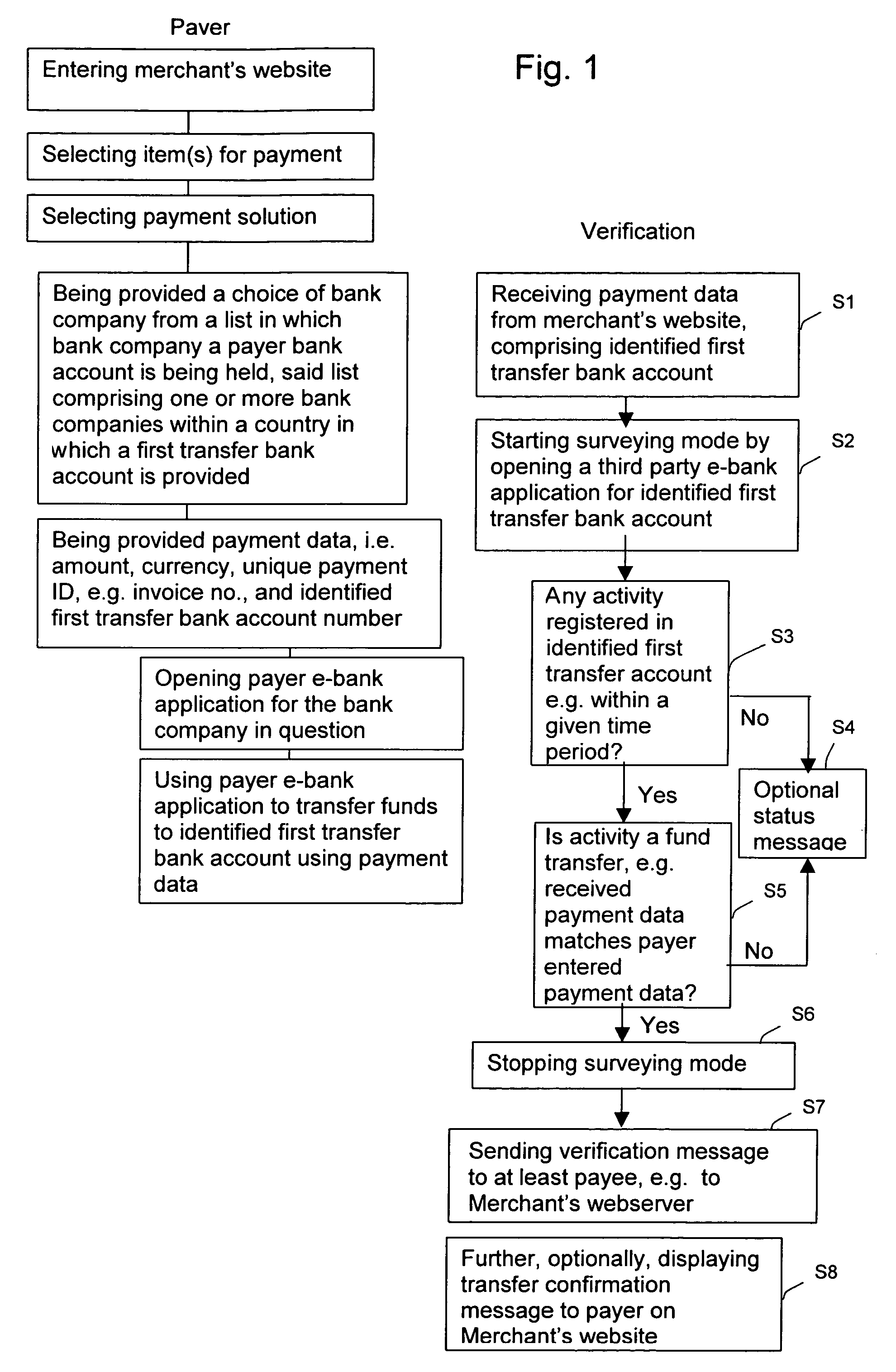
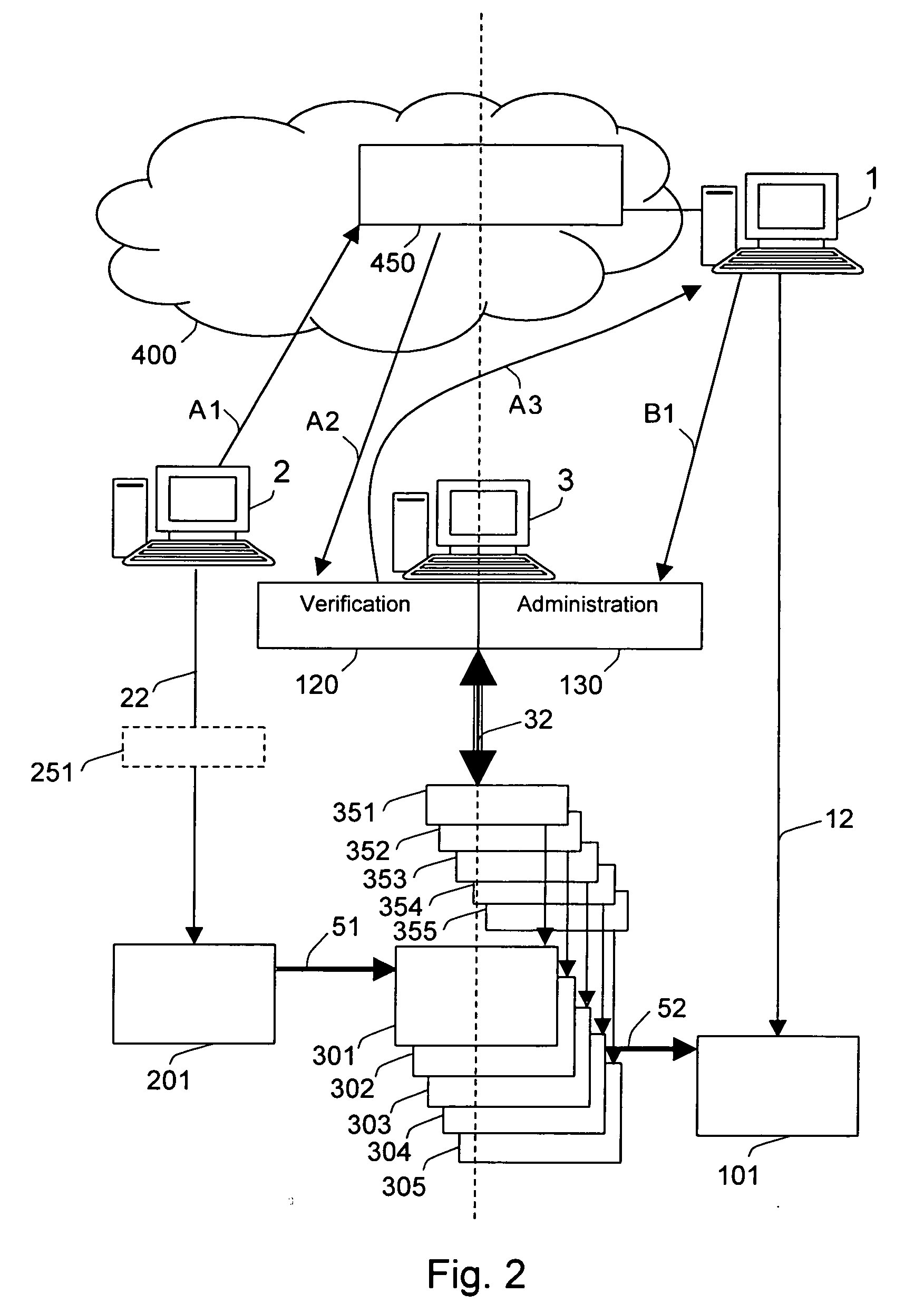
Computer implemented method and system for rapid verification and administration of fund transfers and a computer program for performing said method
The invention concerns a computer implemented method and system, and corresponding computer-readable medium storing instructions for performing said method, for rapid verification of an account-to-account transfer comprising at least a first transfer between a payer bank account and a first transfer bank account, said method comprising the steps of: receiving payment data from a website; enabling selection of a bank company using a payer's device for identification of a first transfer bank account at the selected bank company, whereto a transfer of funds from a payer bank account is to be made; surveying said identified first transfer bank account and determining when said find transfer has taken place thereto from said payer bank account; and transmitting a transfer verification message to a payee device confirming said fund transfer to said identified first transfer bank account. In an exemplary embodiment, said method further comprising administration of said account-to-account fund transfer further comprising a second transfer from a second transfer bank account to a payee bank account in order to provide a computer implemented payment solution method, said administration comprising the following steps: providing data concerning said payee bank account to which at least part of the fund is to be transferred; transferring a second amount from said second transfer bank account based on said payment data to said payee bank account while providing said payee with said payment data; and settling the differences between said identified first transfer bank account and said second transfer bank account periodically based on predetermined settlement criteria.
Owner:MEDIAKEY
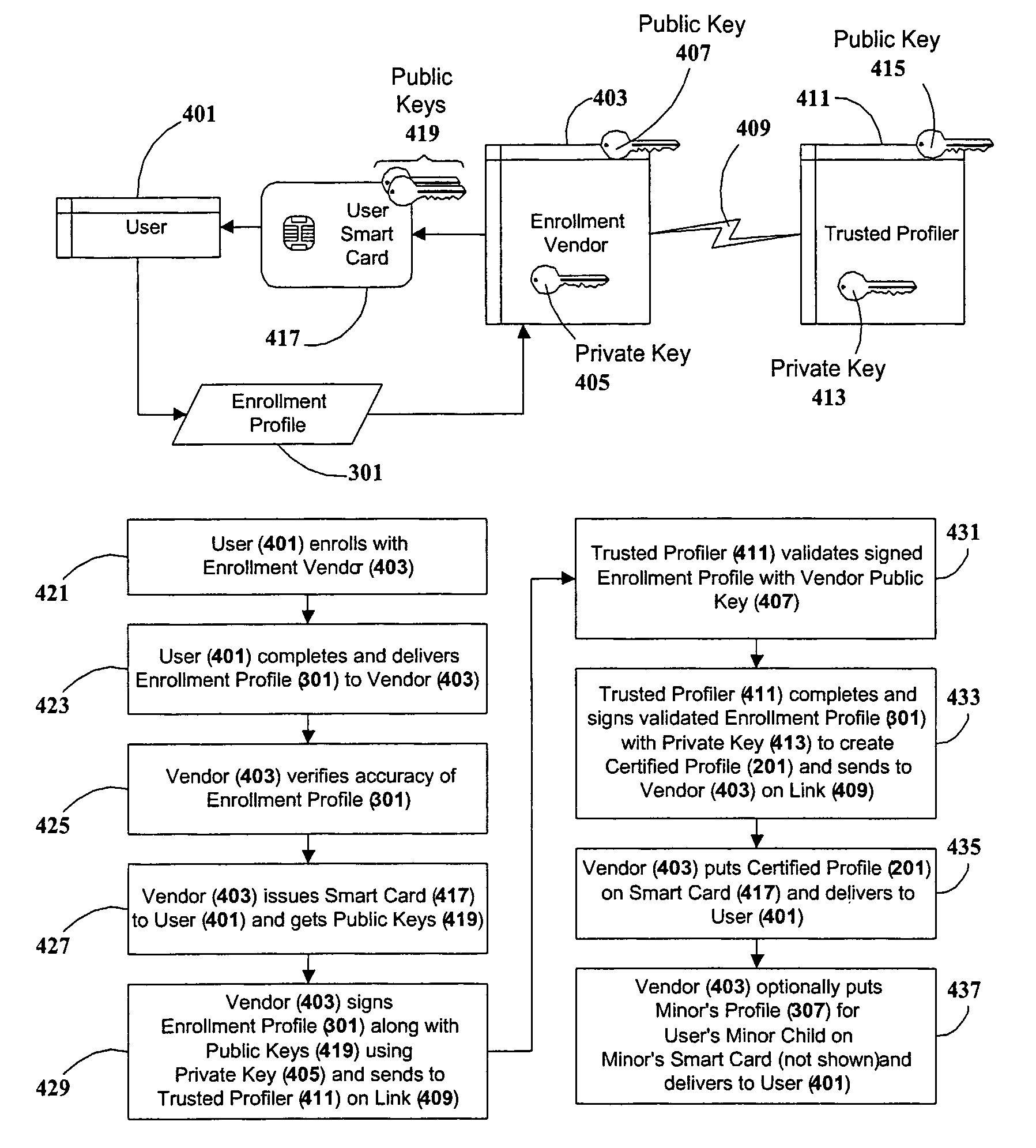
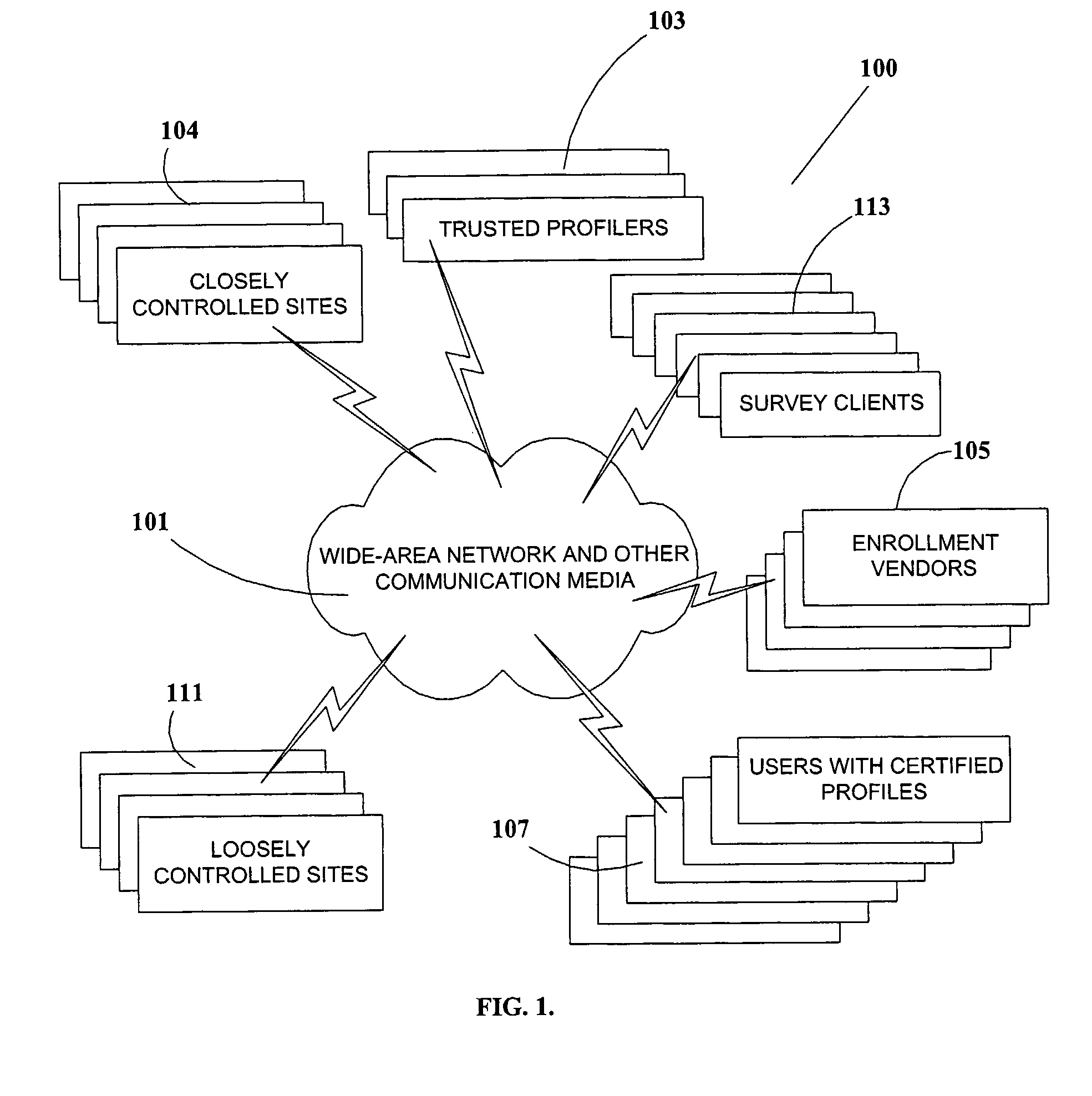
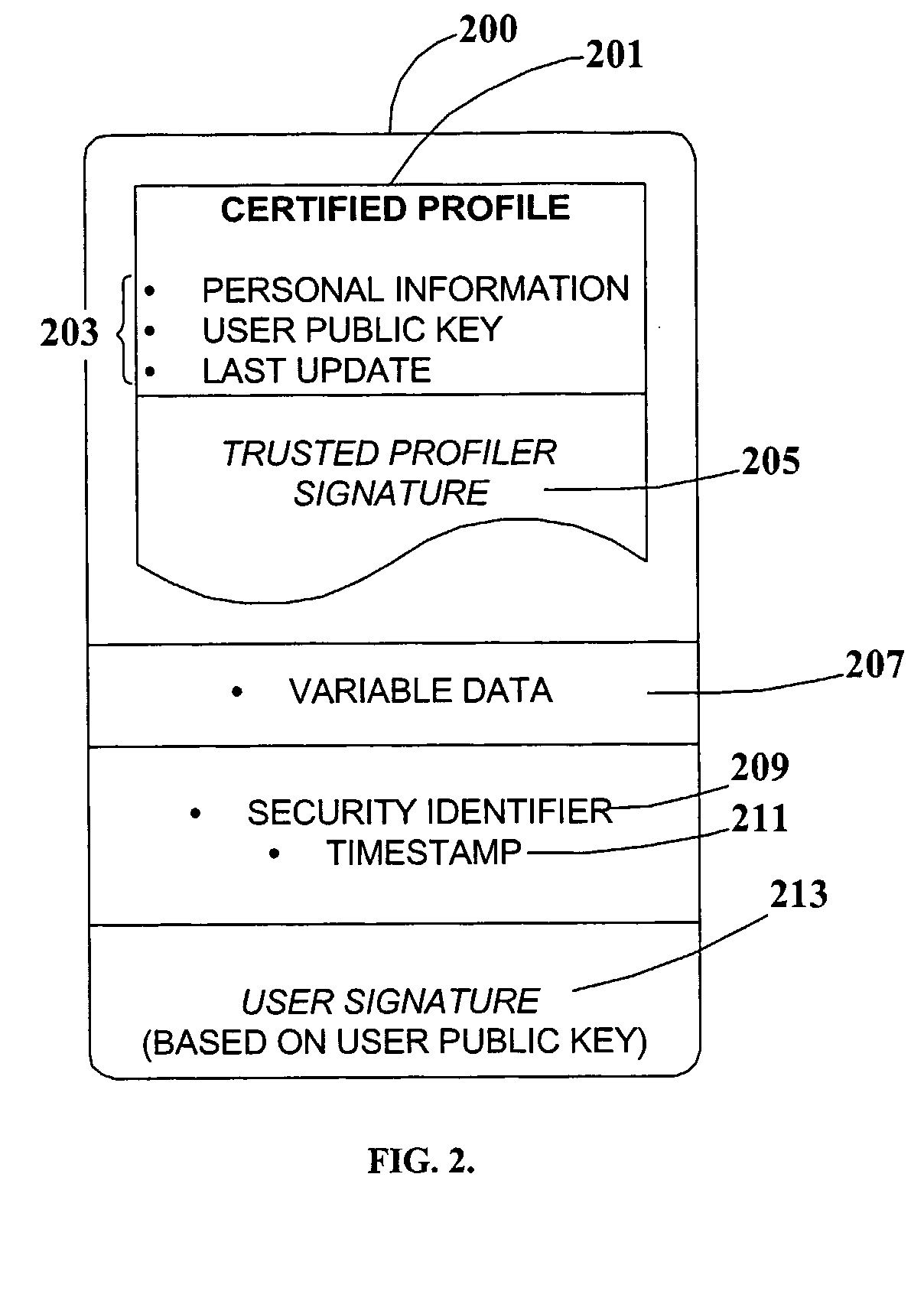
Certified Abstracted and Anonymous User Profiles For Restricted Network Site Access and Statistical Social Surveys
InactiveUS20110145570A1Enhanced anonymityEstablish dependabilitySecuring communicationChat roomInternet privacy
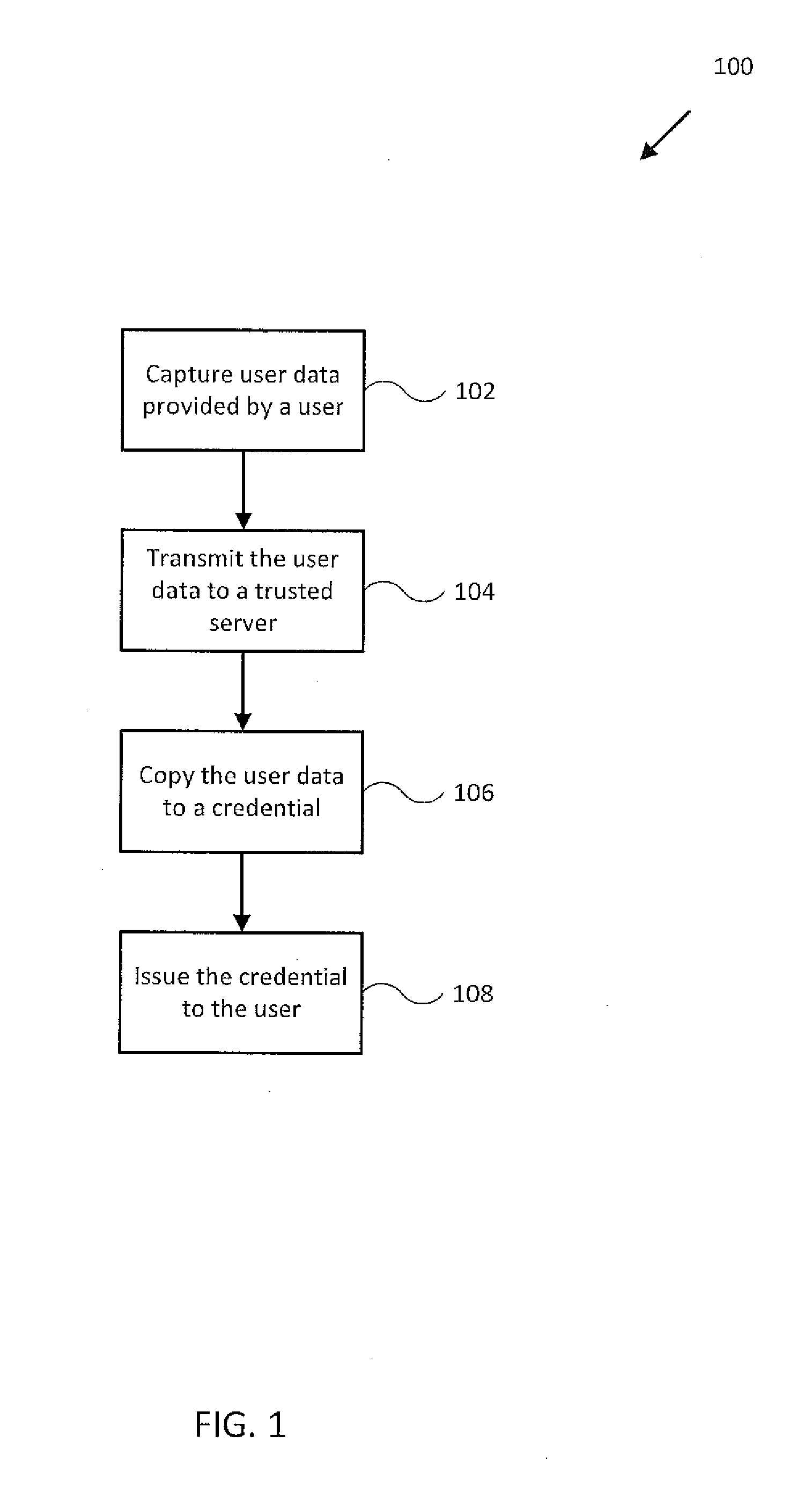
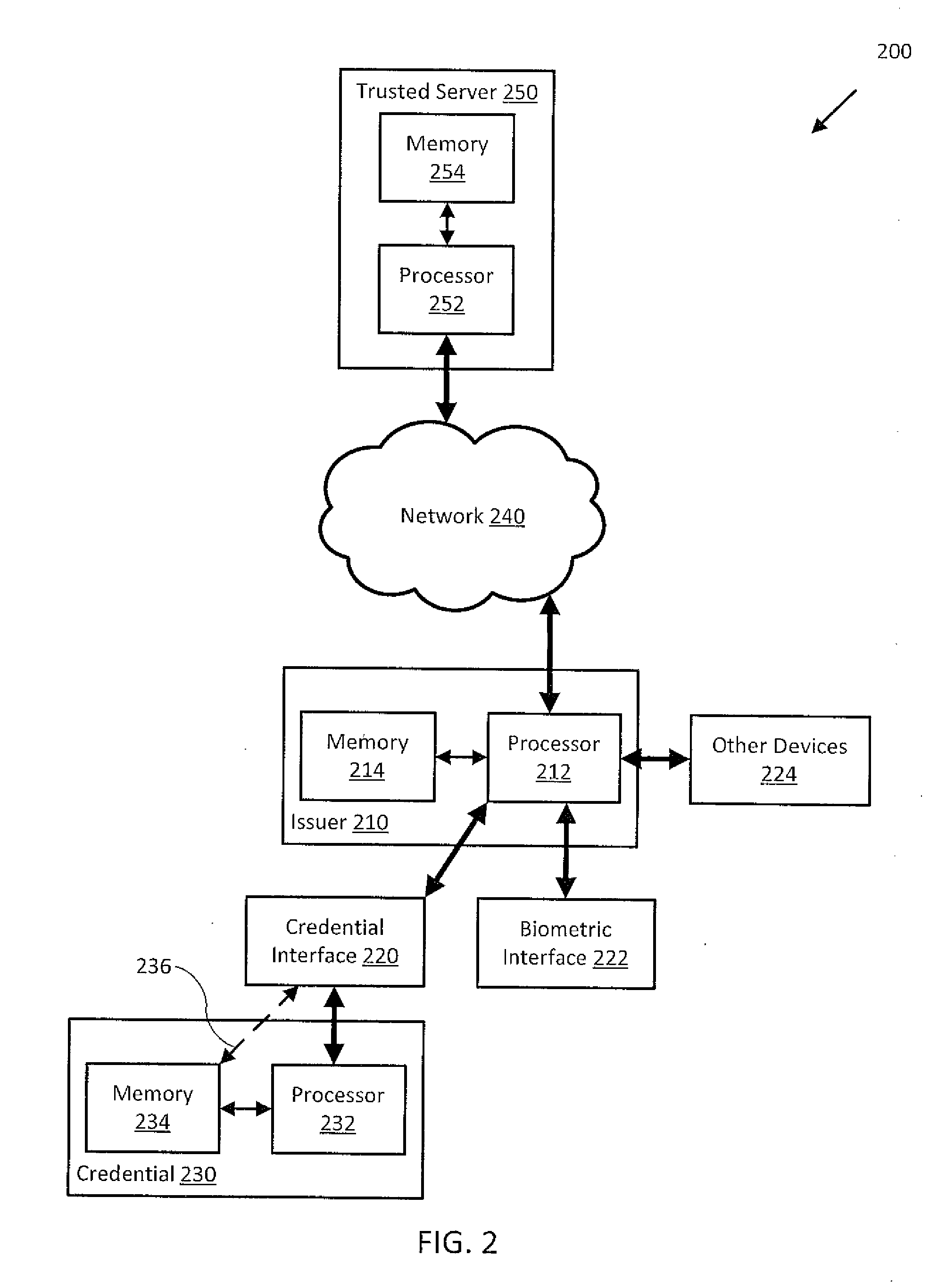
An arrangement, system, and methods for creating and distributing authenticated personal information for users of network services and participants in social surveys, and in chat rooms and other forums. A trusted organization verifies that personal information presented by a user is correct, and authenticates the information in an encapsulated form as “certified profiles” within a smart card or other secure portable hardware device issued to the user Certified profiles are authenticated by digital signatures of the trusted organization and the profile users. Personal information in certified profiles can be in raw and / or in statistically-processed and abstracted form, and can be tailored by the user for specific needs to include whatever personal information is required, and to exclude all other personal information. By the use of unique aliases, it is possible for users to anonymously access restricted network sites and participate in surveys, while still satisfying recipients that supplied personal information is accurate, and for surveys that the user has not responded to the same survey more than once. Users enroll for certified profiles via trusted enrollment vendors who market the service to the public and also make hardware and software available to users for managing, maintaining, and distributing the certified profiles.
Owner:FORTRESS GB
System and method for modeling, abstraction, and analysis of software
ActiveUS20050166167A1Improve verification efficiencyImprove translationError detection/correctionComputation using non-denominational number representationBasic blockSoftware
A system and method is disclosed for formal verification of software programs that advantageously translates the software, which can have bounded recursion, into a Boolean representation comprised of basic blocks and which applies SAT-based model checking to the Boolean representation.
Owner:NEC CORP
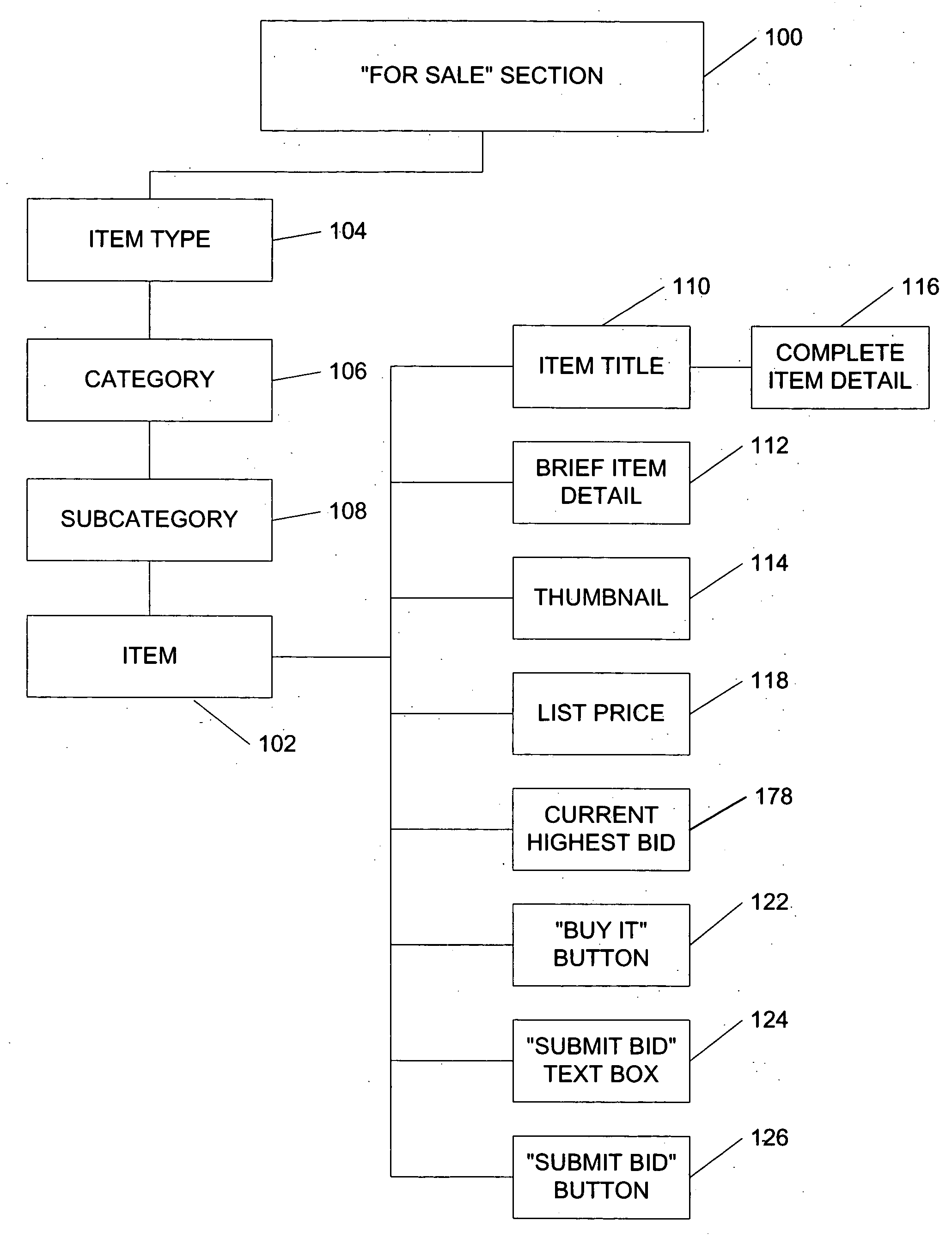
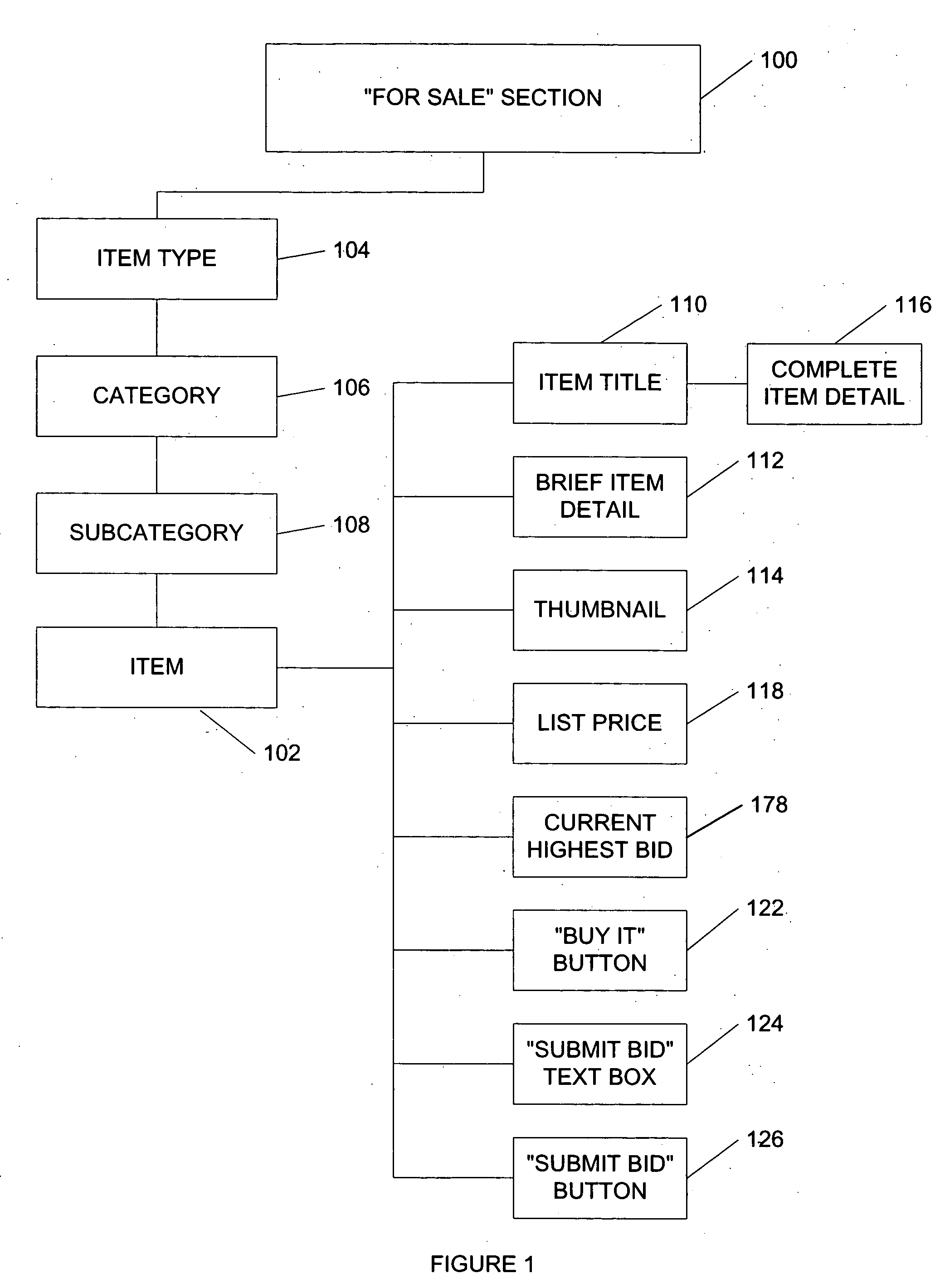
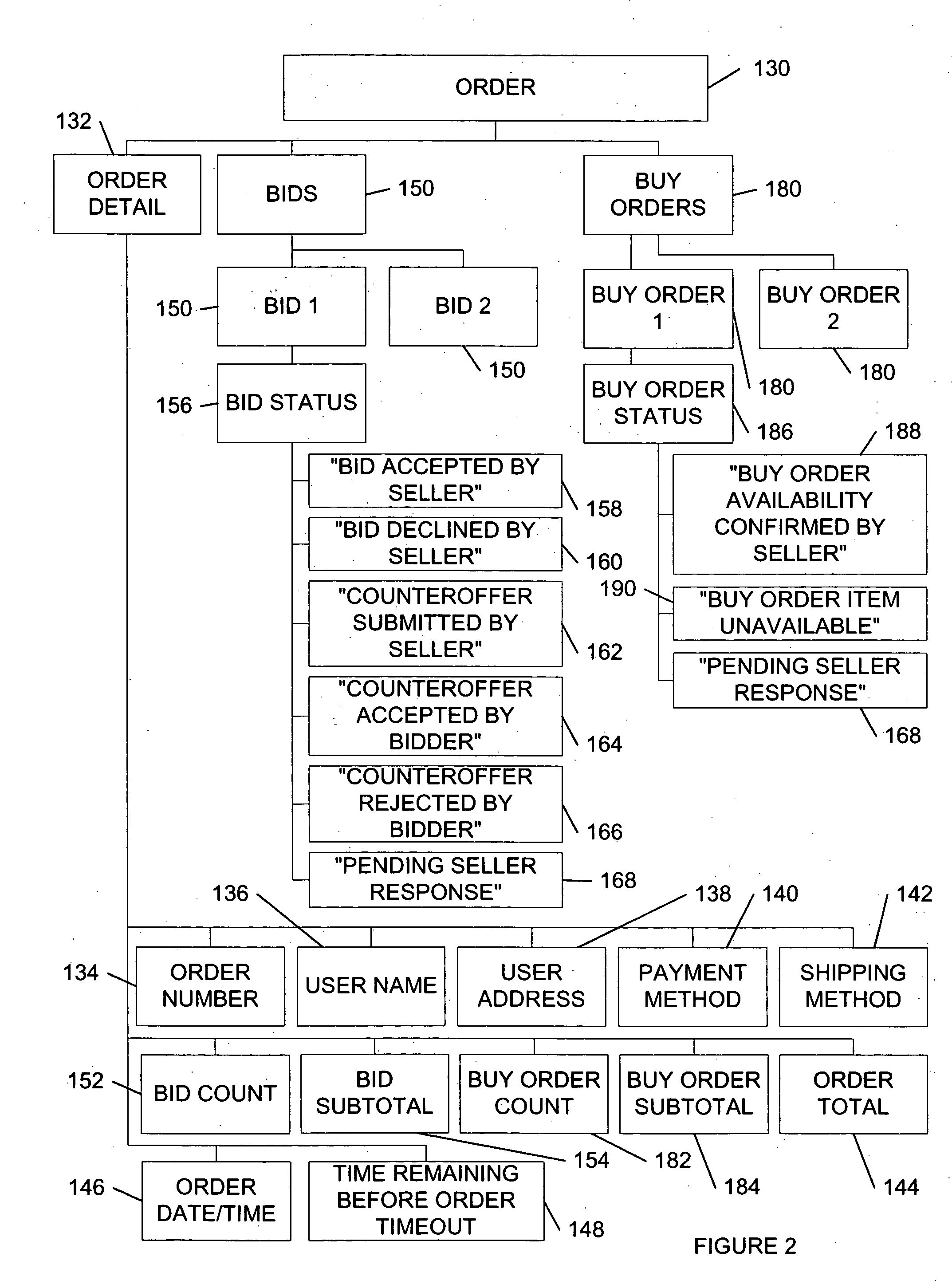
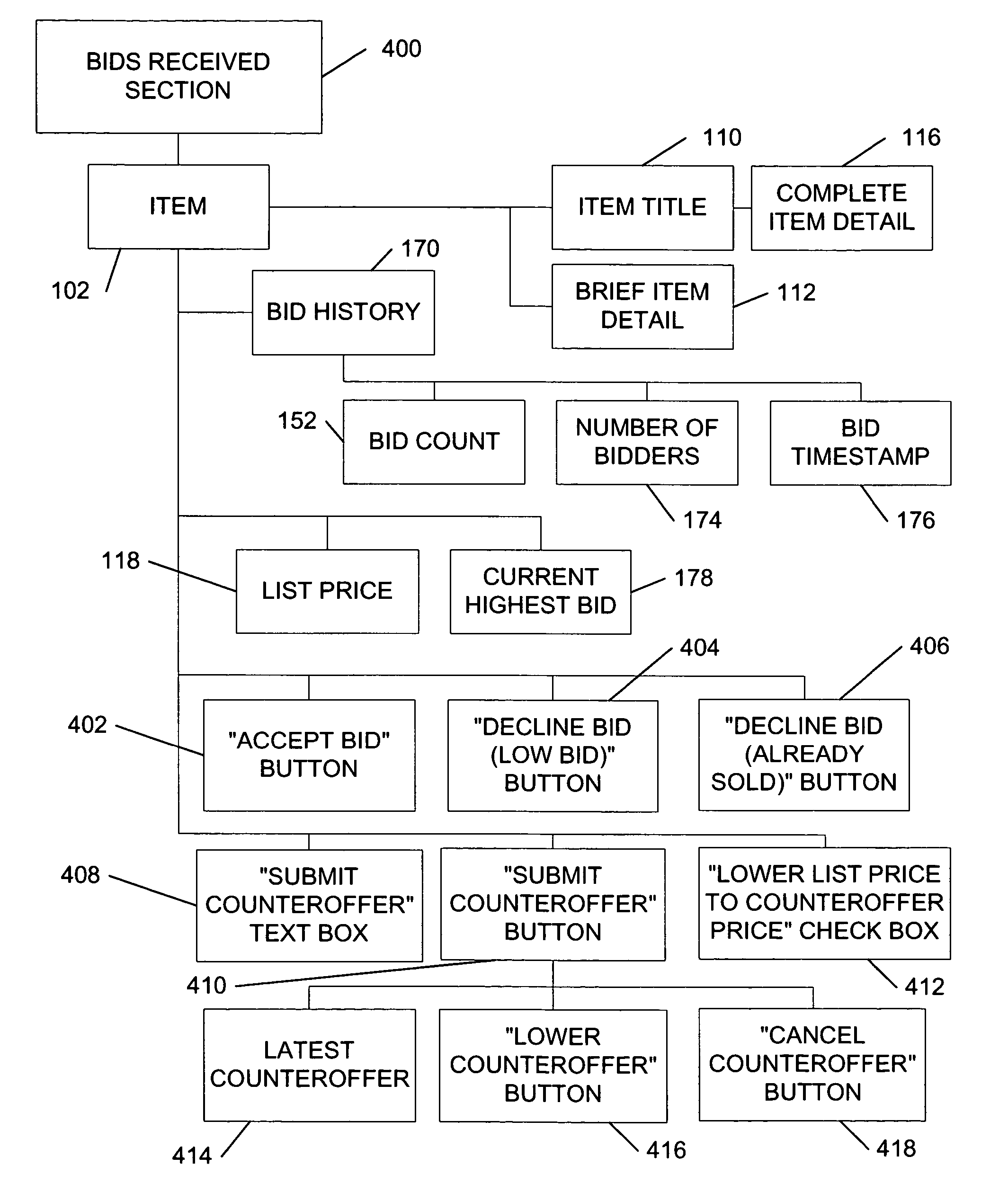
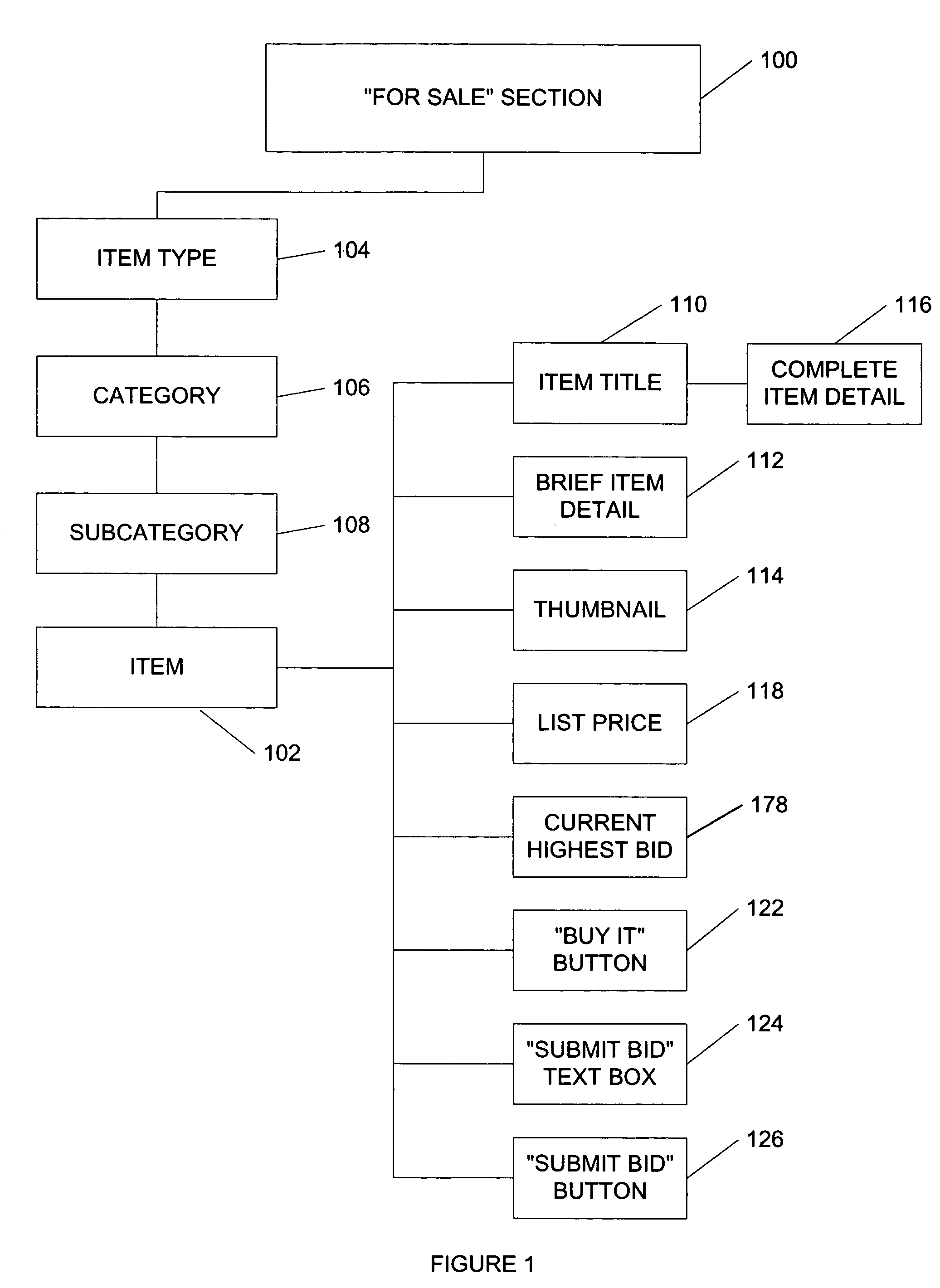
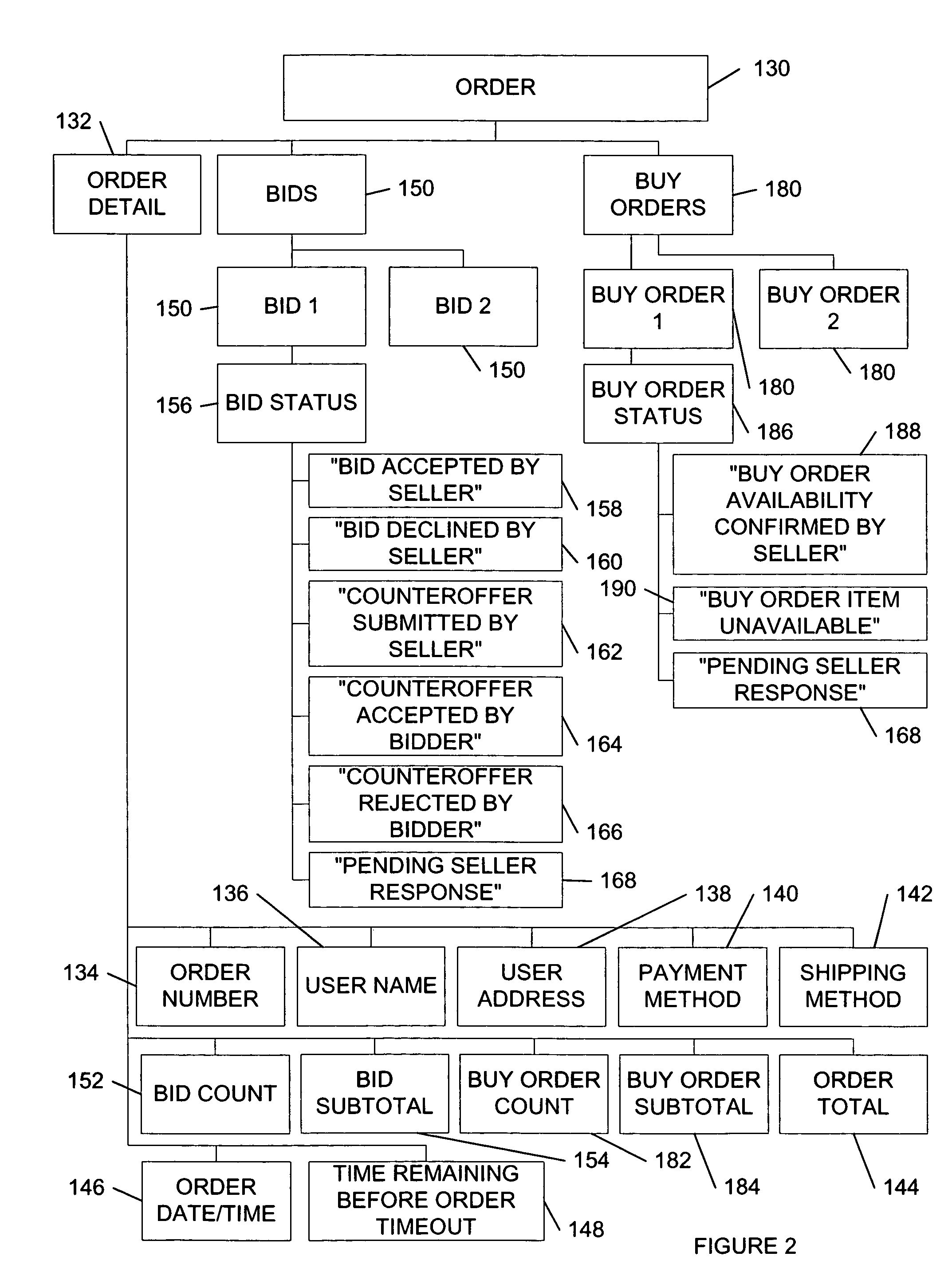
System and method for an automated sales system with remote negotiation and post-sale verification
ActiveUS20060015435A1Highly convenientProvide informationFinanceAdvertisementsLibrary scienceFormal verification
The present invention provides a system and method to process items for sale or bid, to transmit electronic negotiations between prospective buyer and seller, and to verify the condition of the item before delivery to the buyer. The invention facilitates autonomous and remote negotiation between sellers and prospective buyers while protecting buyers from fraud and item misrepresentation. With the present invention, items can be sold individually and are not treated as standardized items that are interchangeable with similar commodity goods. The present invention also provides a waitlisting function. In addition, the functionality of traditional auction systems may be integrated with the novel features of the present invention. Furthermore, the present invention provides a system and method for conducting a reverse auction by allowing prospective buyers to list desired items.
Owner:NATHANSON JOSHUA DAVID
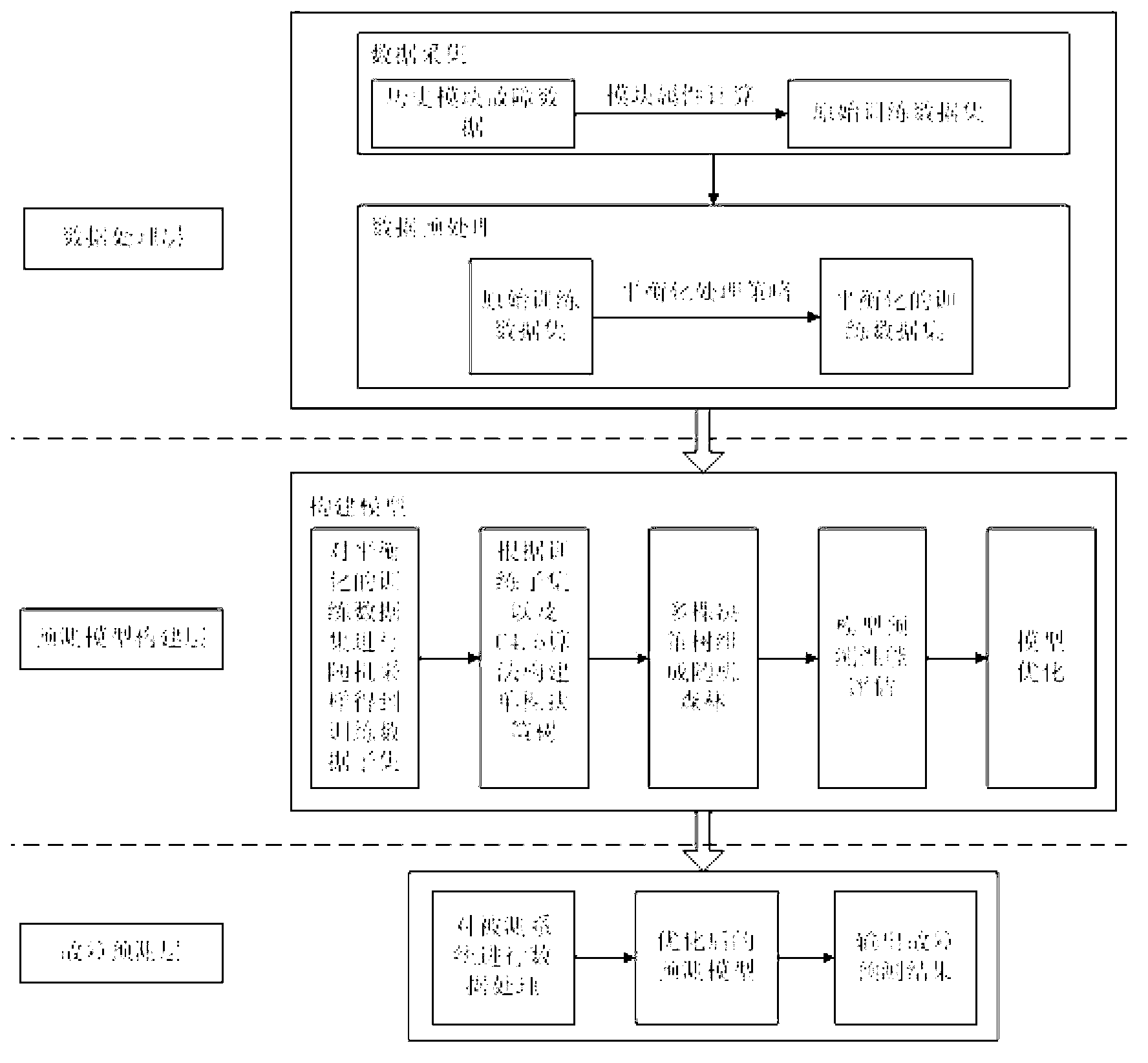
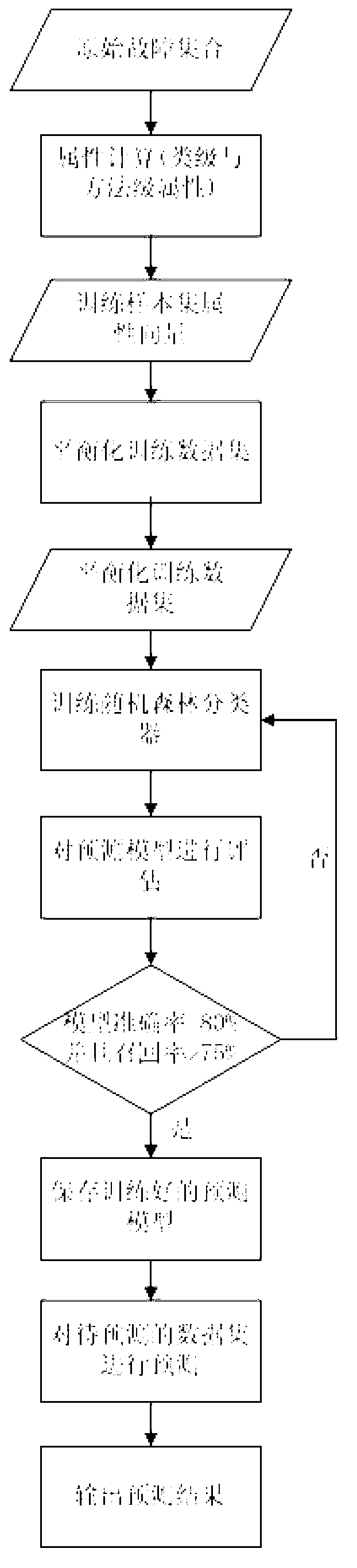
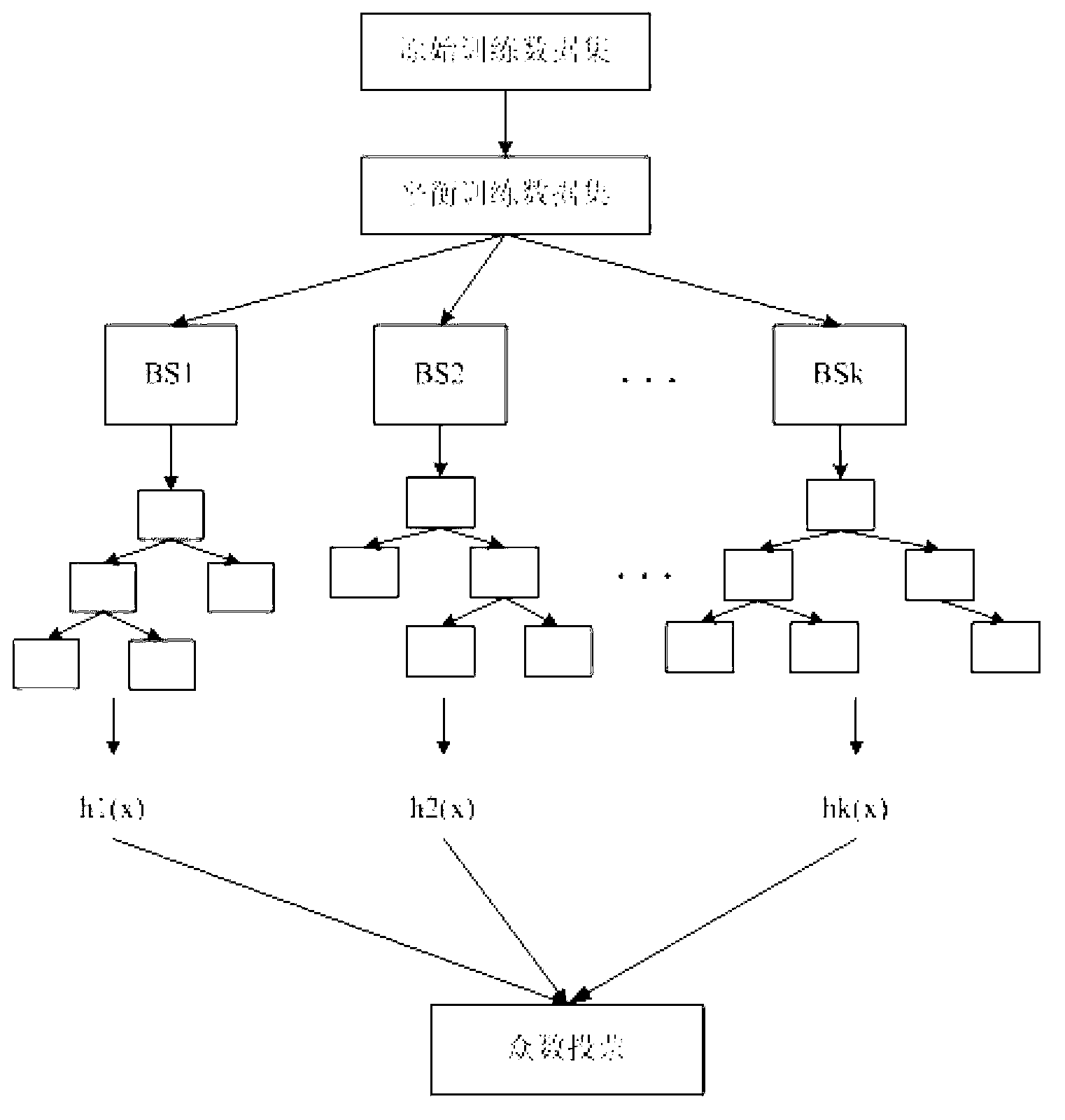
Improved random forest algorithm based system and method for software fault prediction
ActiveCN103257921AComprehensive measurementImprove performanceSoftware testing/debuggingData setSoftware fault
The invention discloses improved random forest algorithm based system and method for software fault prediction. The system comprises a data processing layer, a prediction model building layer and a fault predication layer. The method includes calculating a software project attribute set used for acquiring a training model to acquire a training data set of a software prediction model, and performing equalization to the training data set; building a prediction model according to an improved random forest algorithm; screening the model according to performance limiting of accuracy rate and recall ratio; and predicting a software project according to attribute set information of the to-be-predicted software project and a trained prediction model and displaying prediction results and the prediction model. The improved random forest algorithm based system and method for software fault prediction have the advantages of high prediction accuracy rate, performance stability and high execution efficiency, can evaluate whether a final software product reaches specified quality or meets expectation of a user or not, and can guide developers to formulate distribution strategies of software testing and formal verification resources.
Owner:XIDIAN UNIV
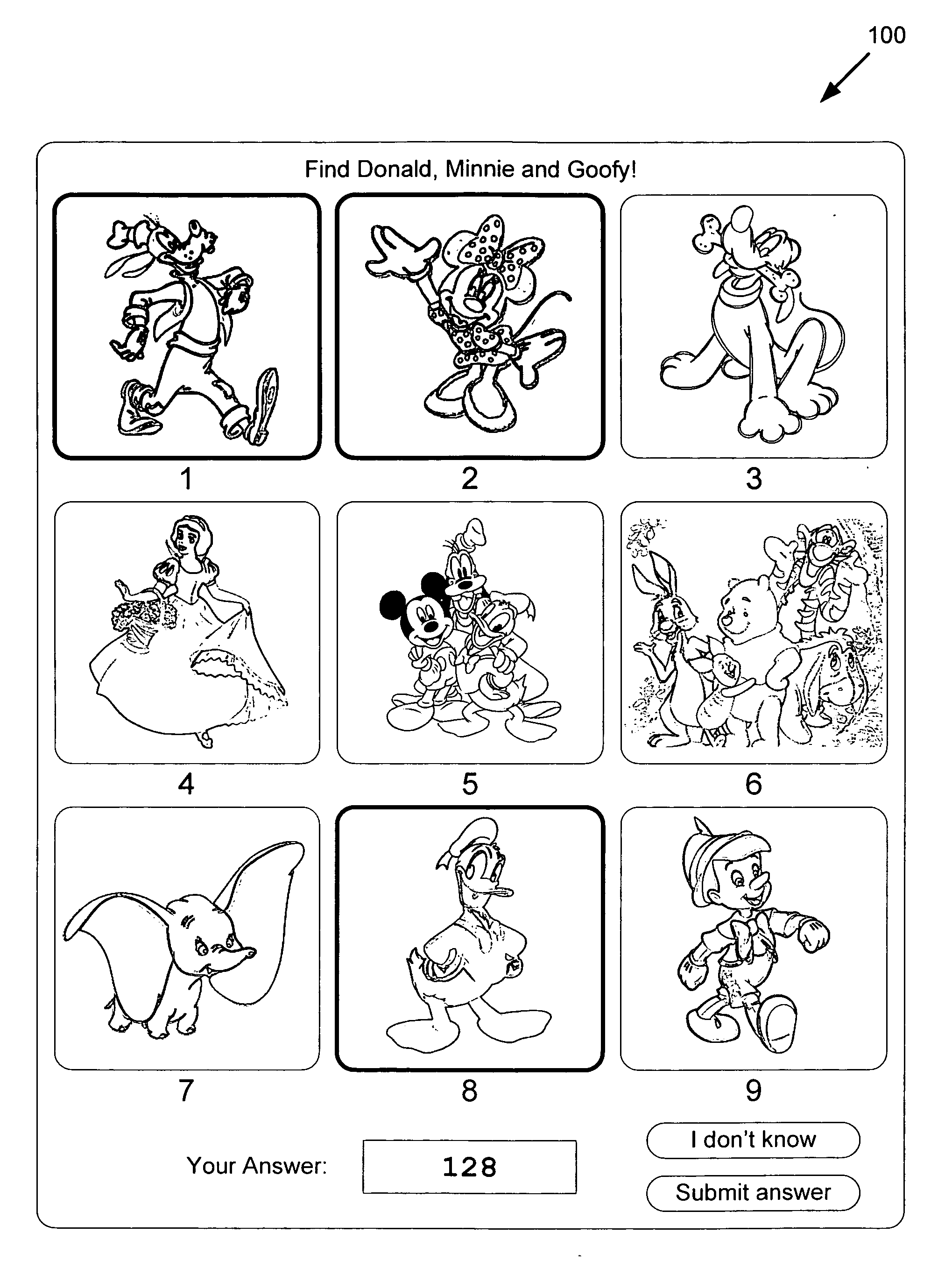
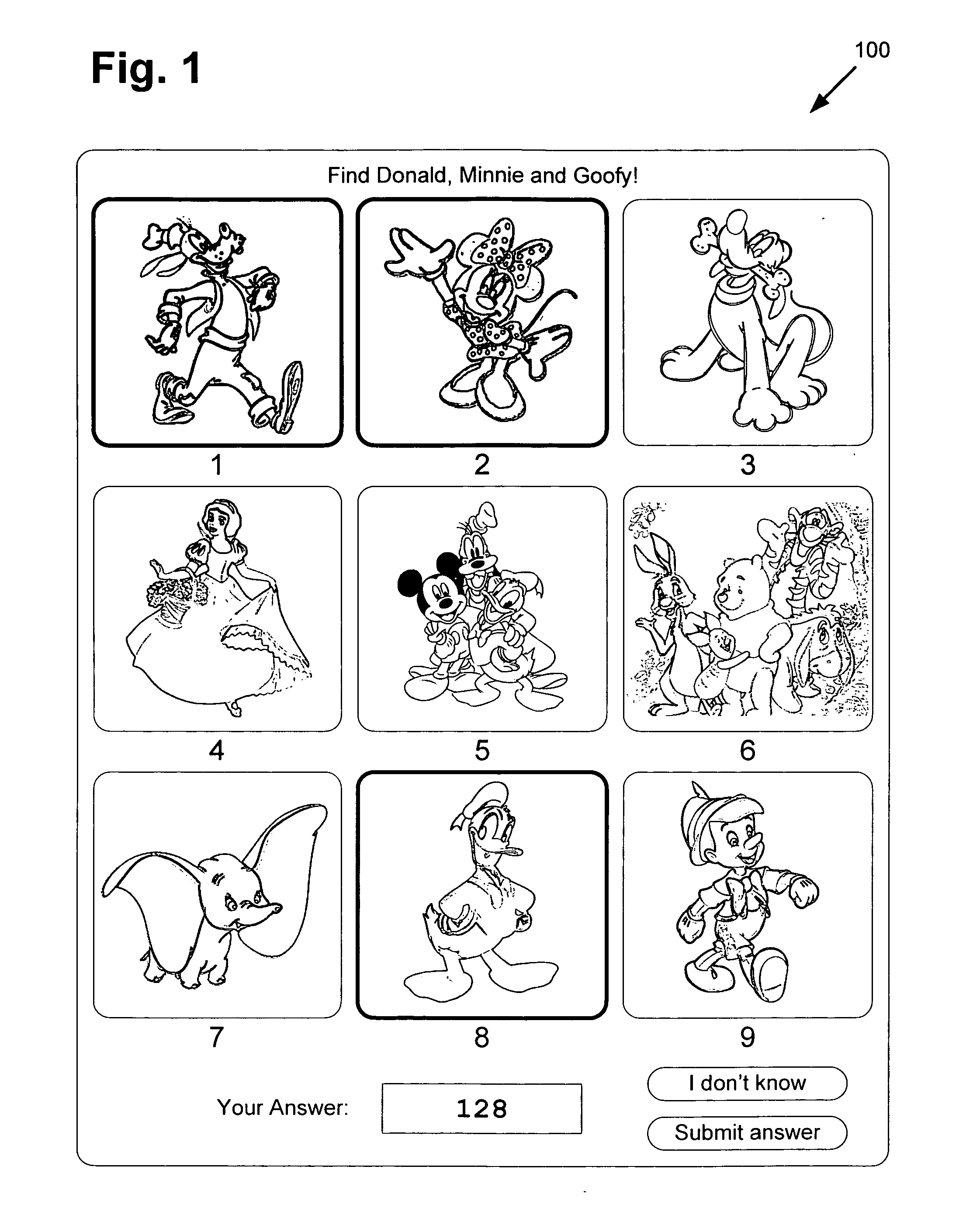
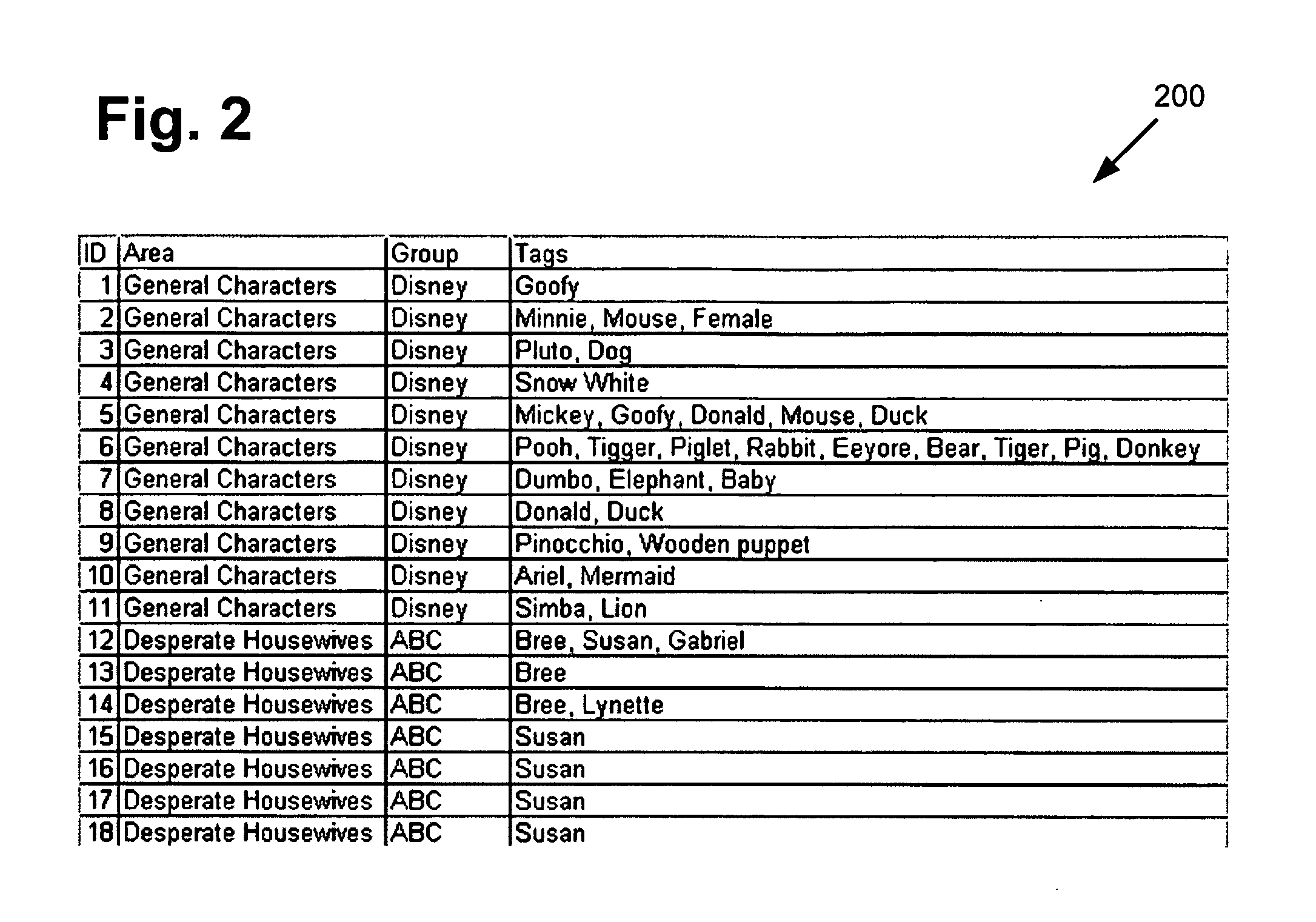
Human verification by contextually iconic visual public turing test
ActiveUS20110150267A1Digital data processing detailsCharacter and pattern recognitionSubject matterTuring test
There is provided a system and method for human verification by a contextually iconic visual public Turing test. There is provided a method comprising receiving a request to verify whether a client is human controlled, selecting, by contextual criteria, a plurality of images each having one or more associated tags from a database, generating a challenge question and a corresponding answer set based on associated tags of a subset of the plurality of images, presenting the plurality of images and the challenge question to the client, receiving a submission to the challenge question from the client, and responding to the request by verifying whether the submission is contained in the answer set to determine whether the client is human controlled. The contextual criteria may comprise subject matter, branding, or intended audience of a content provider sending the request, thereby facilitating human responses while deterring automated systems.
Owner:DISNEY ENTERPRISES INC
Consumable verification system and method
InactiveCN102173233AGuaranteed printing qualityPrevent tamperingElectrographic process apparatusOther printing apparatusCommunication interfaceCommunication unit
The invention provides a consumable verification system and a consumable verification method. The system comprises a printer, wherein the printer is provided with a consumable container; a consumable chip is arranged on the consumable container, and is provided with an electronic module and a communication interface; the electronic module stores serial number information of the consumable container; the system also comprises a verification server which is provided with a communication unit and a memory; and the memory stores configuration information and status information of the consumable container. The method comprises the following steps of: after the printer performs printing work once, transmitting the serial number information and the real-time status information to the server by using the consumable chip; and when the printer performs the next printing work, transmitting the real-time status information to the server again, and judging whether the consumable container is available by using the server, if so, returning information allowing printing, otherwise, returning error information. The invention can remotely configure and verify the consumable chip, the printer is prevented from using the consumable chip with tampered data for printing operation, and the printing quality is ensured.
Owner:ZHUHAI TIANWEI TECH DEV CO LTD
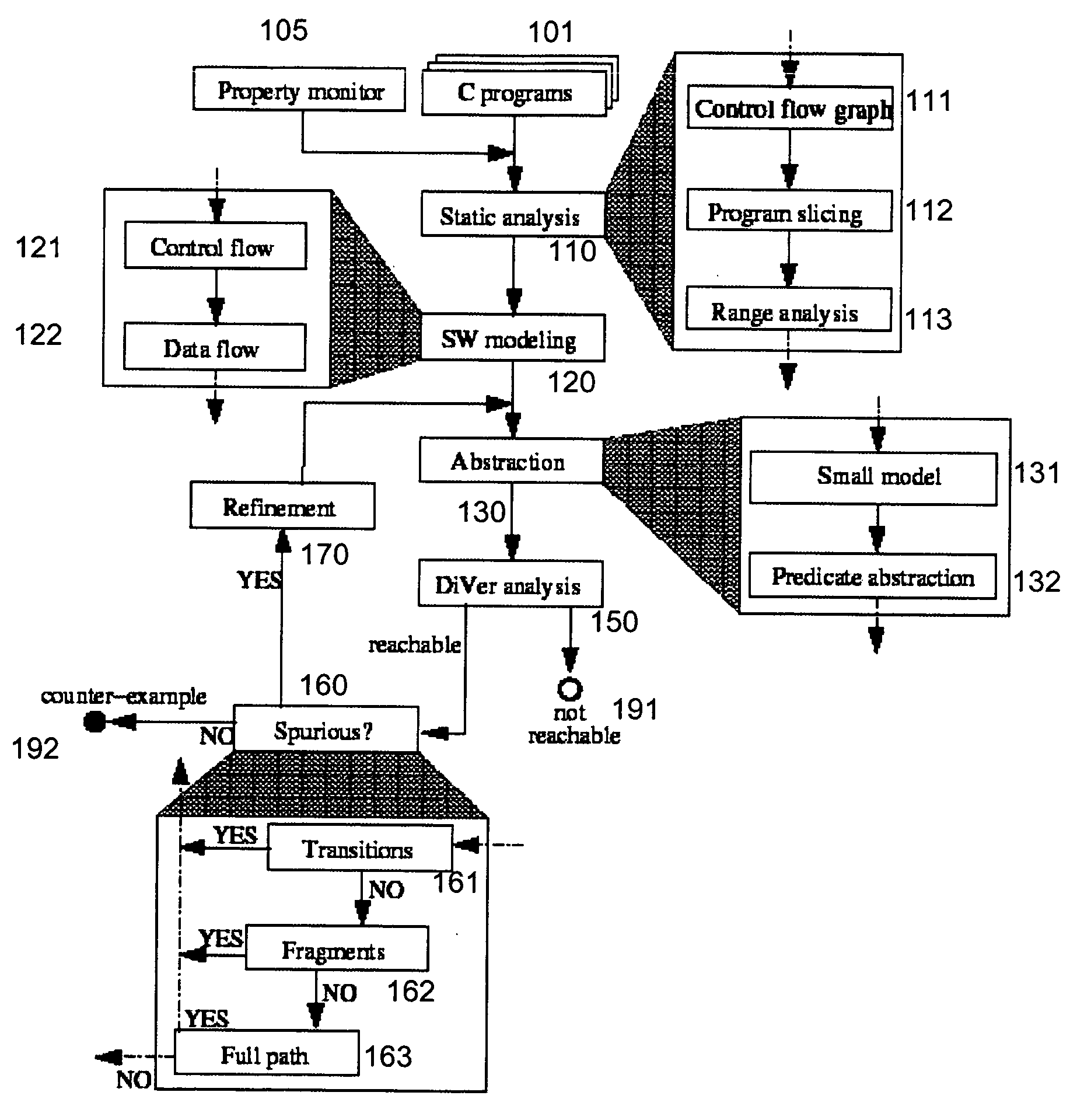
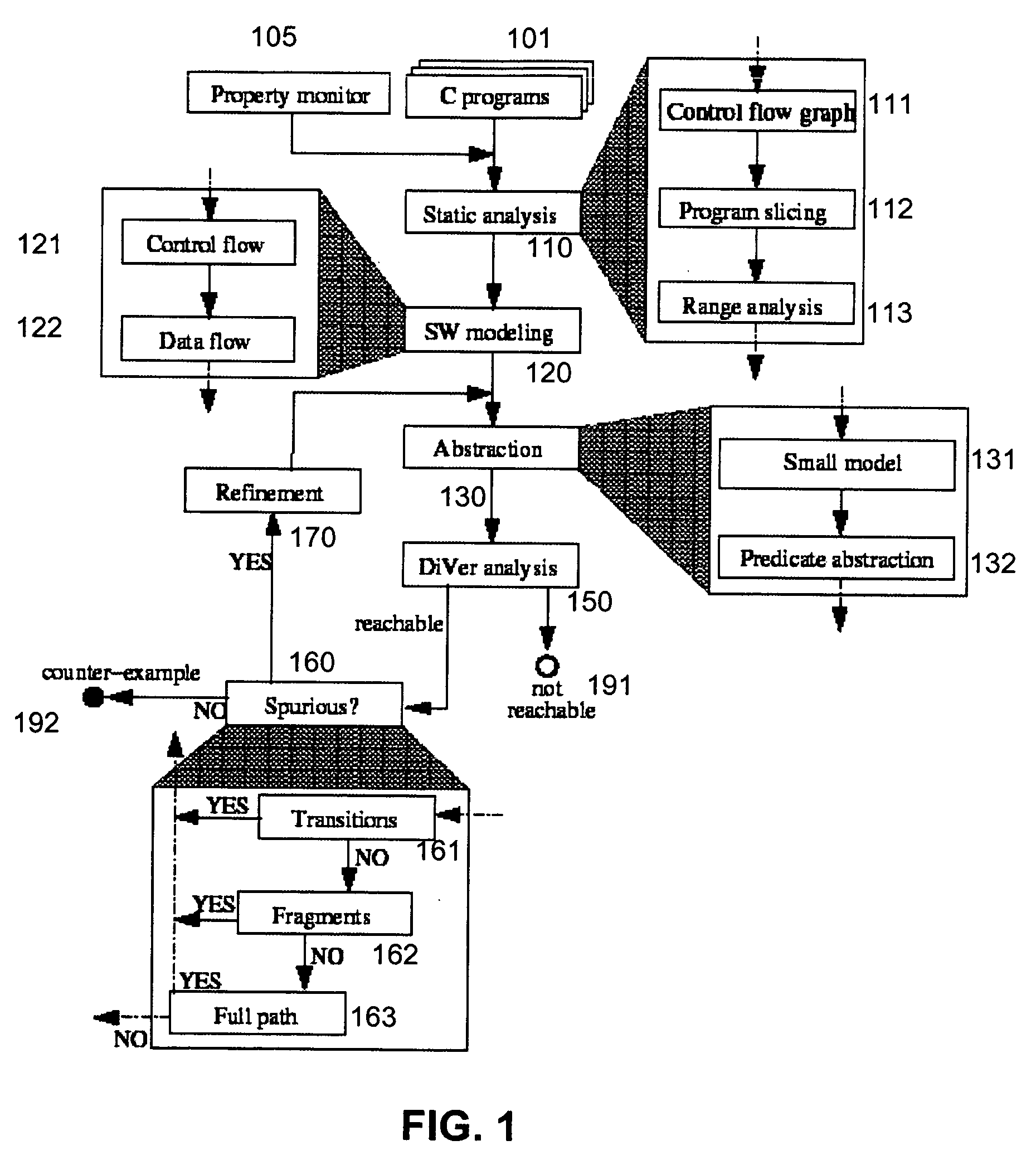
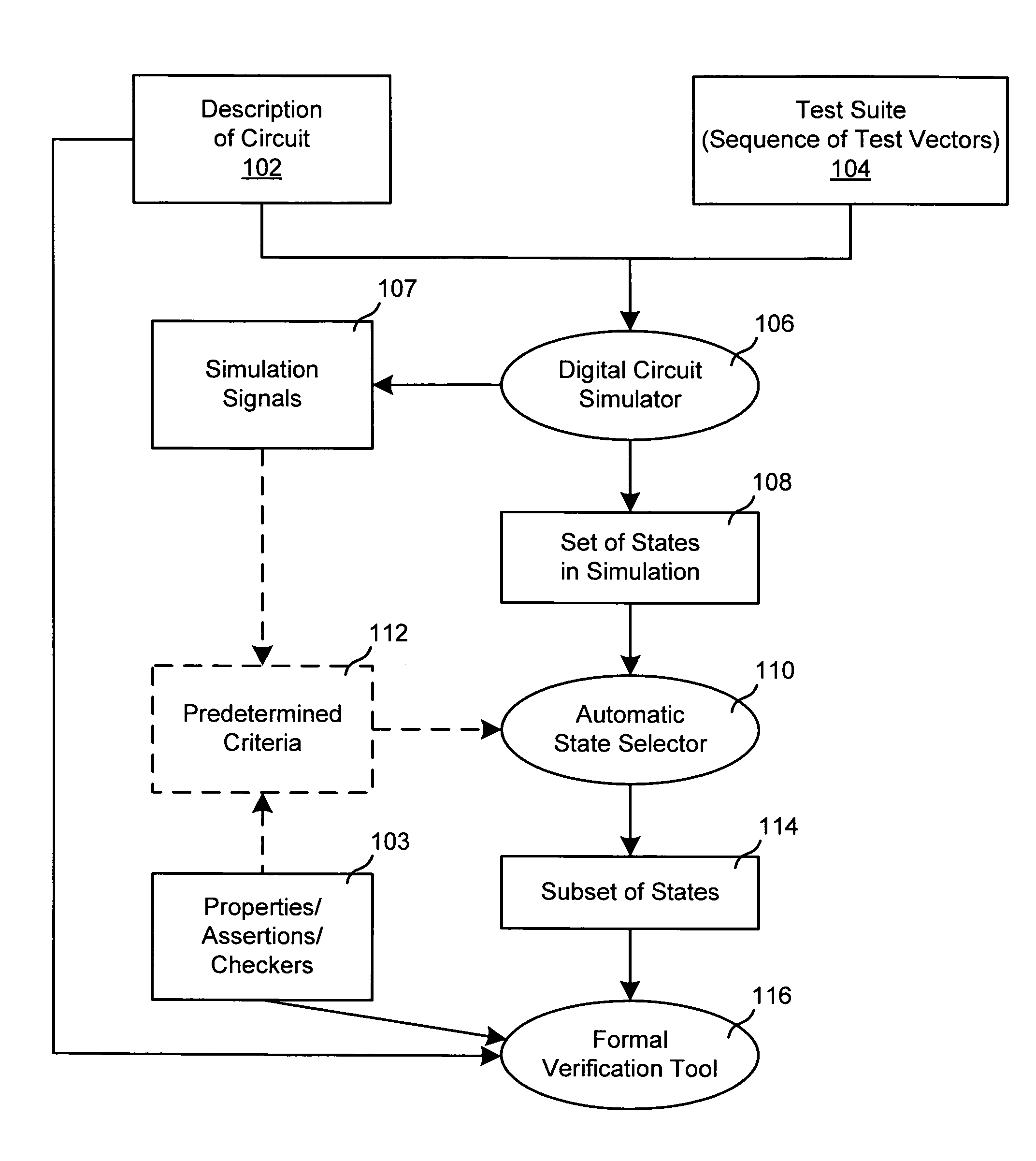
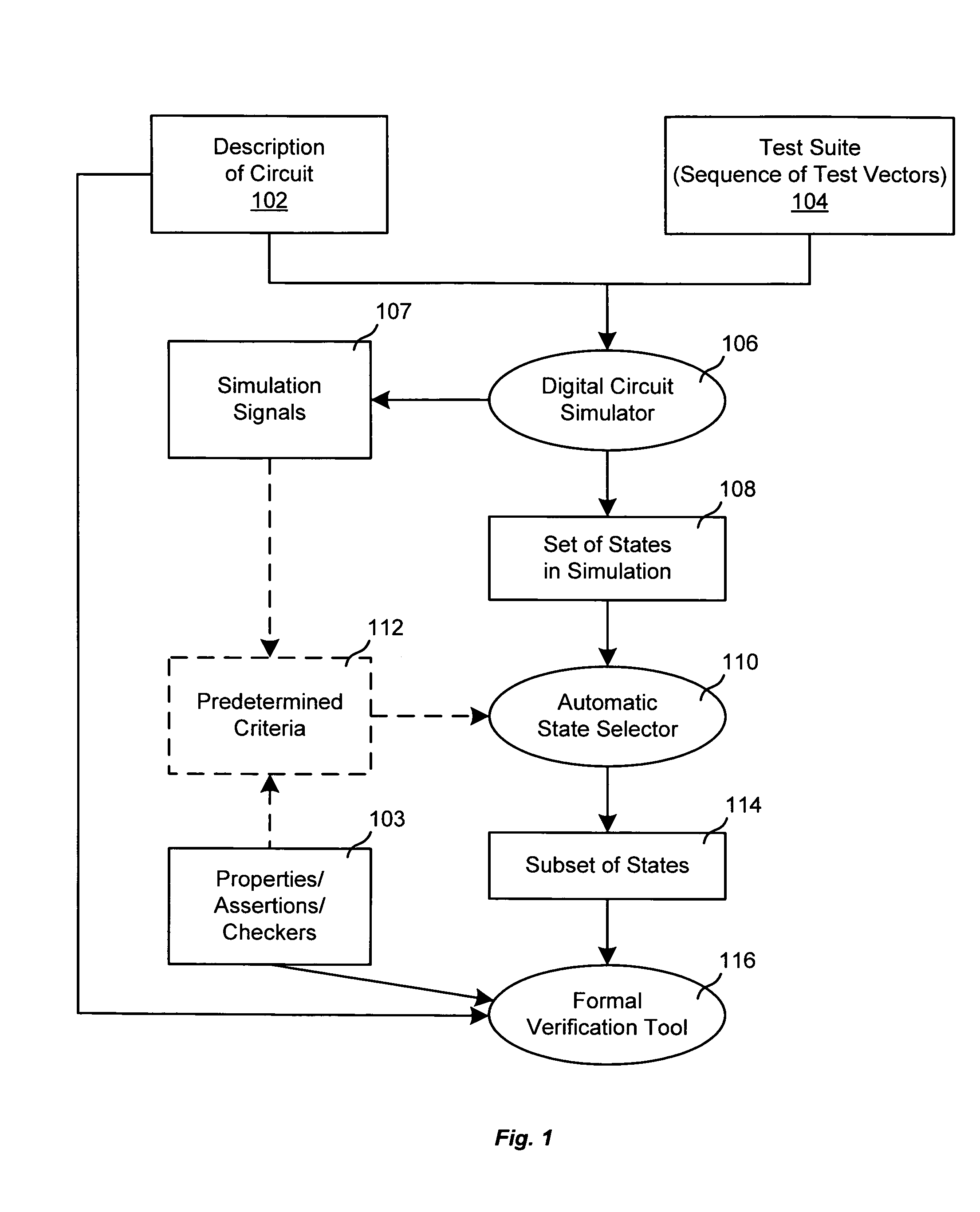
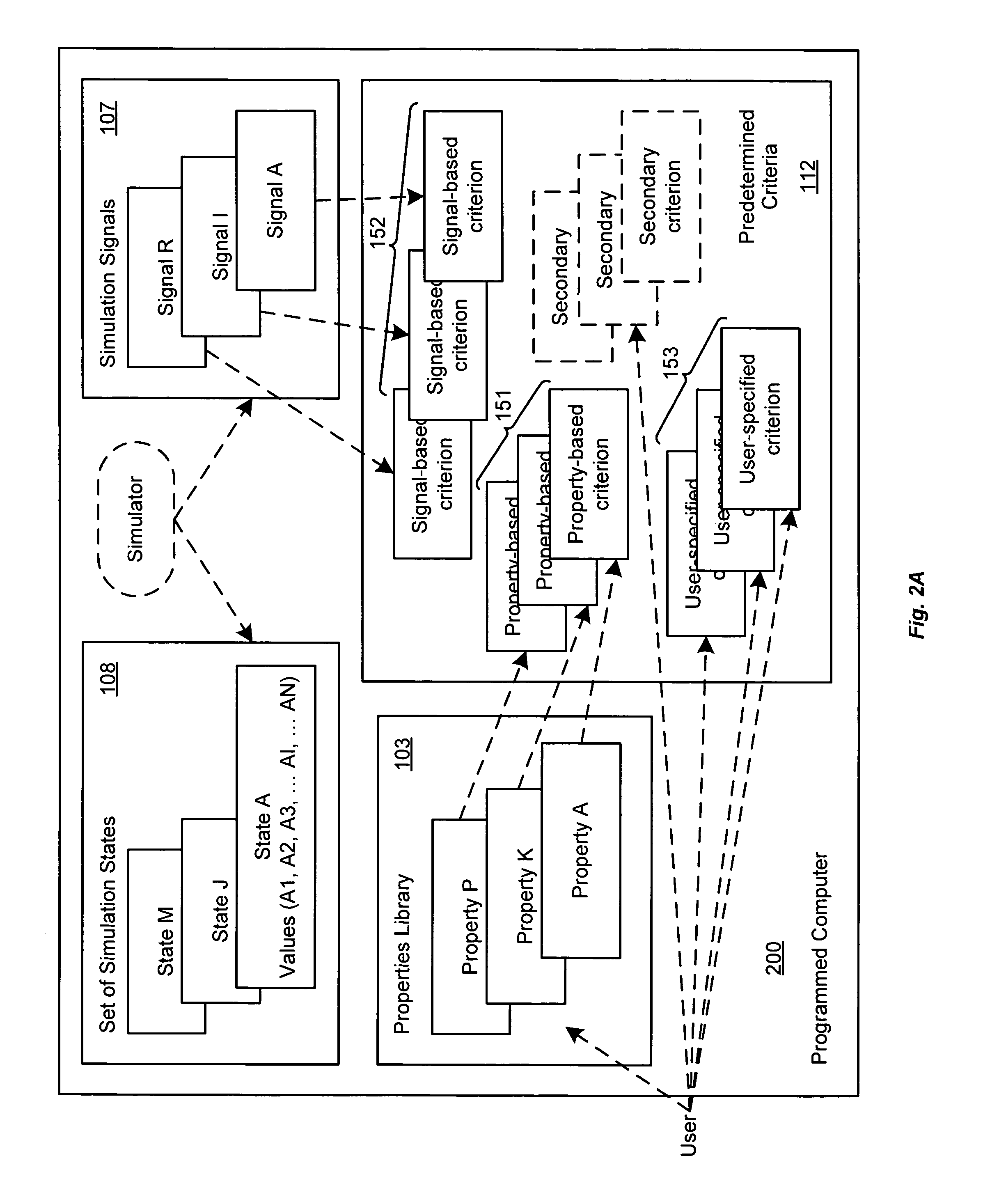
Selection of initial states for formal verification
ActiveUS7454324B1Raise the possibilityCAD circuit designSoftware simulation/interpretation/emulationState spaceFormal verification
A computer is programmed to automatically select a state or a set of states of a digital circuit that are visited during simulation, for use as one or more initial states by a formal verification tool. Such automatic selection of one or more simulation states reduces the set of all simulation states to a small subset, thereby to address the state space explosion problem. Depending on the embodiment, the programmed computer uses one or more criteria provided by a library and / or by the user, in making its selection of states. Such criteria may be based on a property (assertion / checker) of the digital circuit and / or a signal generated during simulation. Furthermore, after such criteria (also called “primary criteria”) are applied, the selected states may be pruned by application of additional criteria (also called “secondary criteria”) prior to formal analysis.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
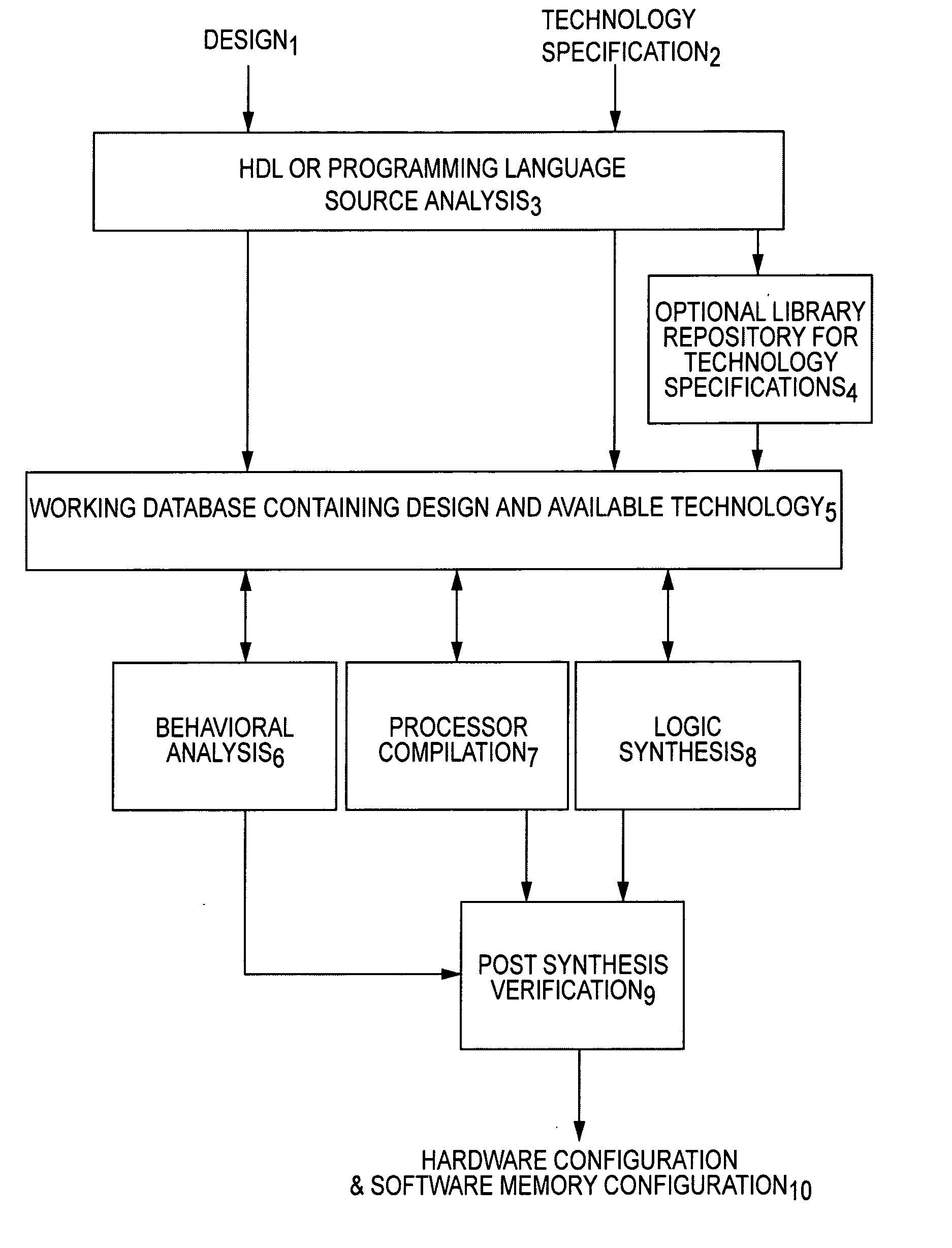
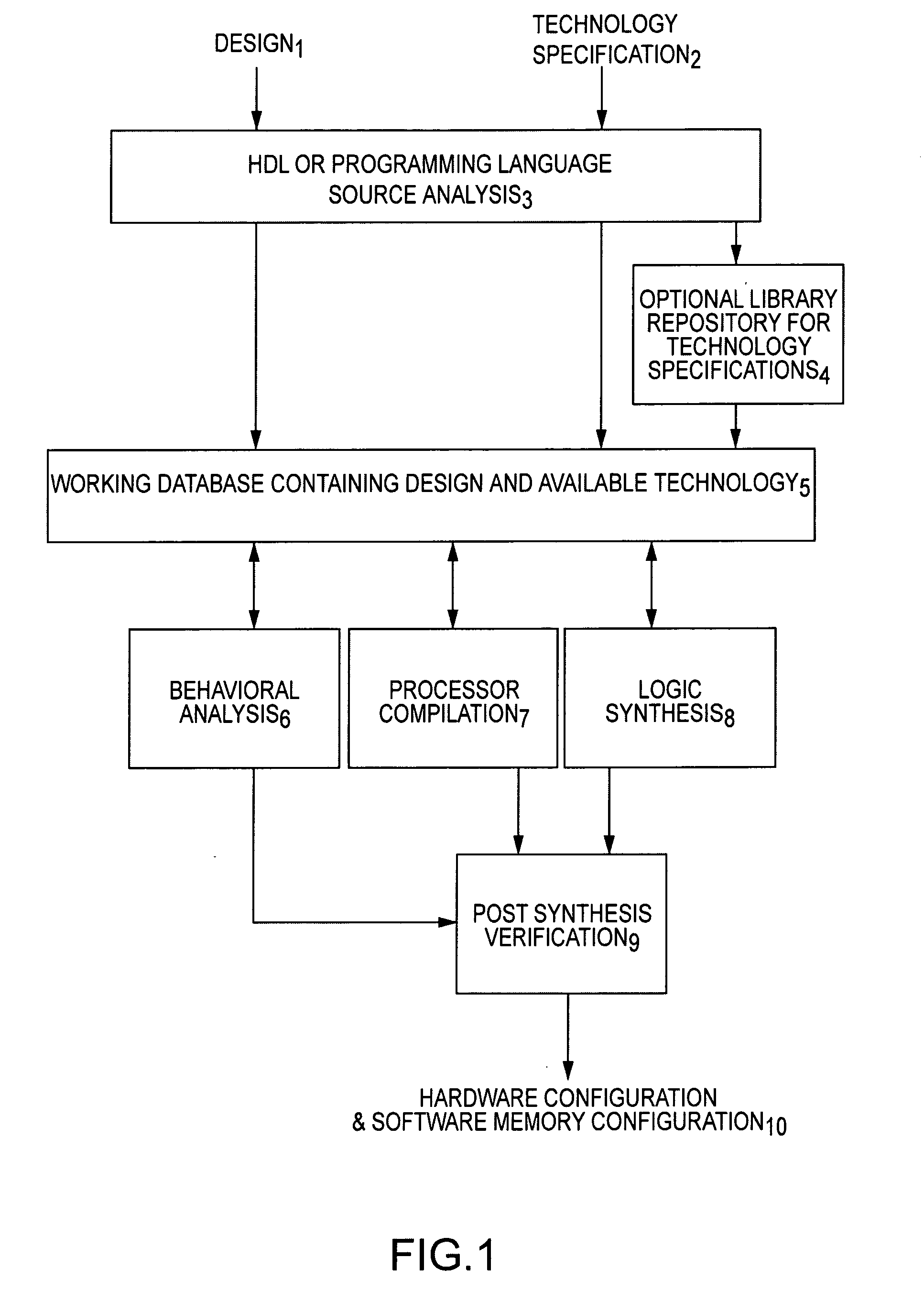
Hardware/software design tool and language specification mechanism enabling efficient technology retargeting and optimization
InactiveUS20050289485A1More compactEfficient designElectrical testingDigital computer detailsComputer architectureSoftware system
An innovative hardware / software design tool provides four modes of operation for converting an electronic design specification and zero or more technology specifications into realization of the electronic design in computer hardware, software and firmware. The first mode of operation compiles design and logic technology specifications into a model which can be utilized for behavioral analysis (such as simulation or formal verification) of logical characteristics (the model). The second mode of operation translates (compiles) partitions of the design and one or more logic technologies into one or more processor intermediates or binaries (embedded binary) suitable for execution on multi-purpose processing units (embedded or general purpose processors). The third mode of operation translates (synthesizes) partitions of the design and logic technology into a collection of cells and interconnects (net-list implementation) suitable for input to physical design processes such as is required to target a field-programmable logic array (FPGA), application specific integrated circuit (ASIC), system-on-a-chip (SOC) or custom logic). The fourth mode of operation analyzes (verifies) behavior of the embedded binaries running on processing units and implementations augmented by additional physical technology and parameters, yielding a more detailed (accurate) prediction of the resulting hardware / software system behavior when realized through manufacturing. Critically, the design specification, logic specifications, physical specifications and definition of each multi-purpose processing unit may be defined external to the hardware / software design tool using an innovative augmentation of standard hardware description or programming languages taught in this patent application. In the prior art, specification of the logic technology, physical technology and embedded or general purpose processor architecture are either incorporated directly into the design tool by the tool developer or are maintained entirely external to the design tool (such as an encapsulated component model or intermediate code interpreter). The present invention is an innovative and valuable improvement over prior art in that design specifications are combined by the tool from distinct specification(s) of generalized logic, physical and processor technology, leading to more efficient behavioral design, opportunities for third parties to add functionality by incorporating generalized logic and physical technology modules into the analysis and synthesis process and opportunities for semi-automatic, goal-directed optimization through application of various logic, physical and processor technologies by the design tool.
Owner:FTL SYST
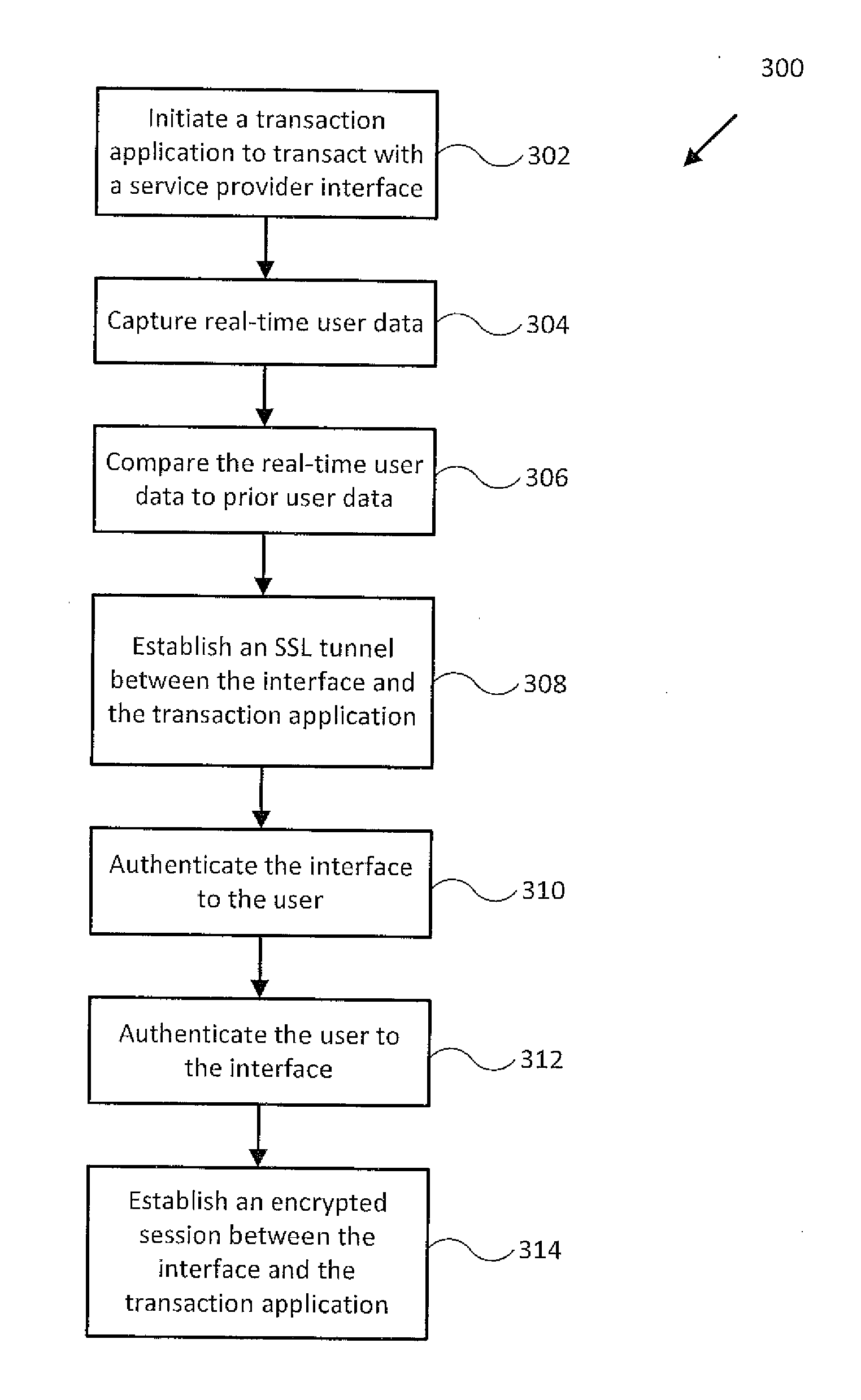
Layered security for age verification and transaction authorization
A user may be willing to purchase items or participate in a pay-for service offered by a service provider. A service provider may wish to verify characteristics of the user prior to allowing transactions to take place, and may want to secure the transactions once the transactions are allowed. A credential issued to a user and a transaction application uploaded to a user device may be used to secure transactions between the user and a service provider interface, such as a webserver or a point-of-sale. The transaction application may capture real-time user data and comparing the real-time user data to prior user data stored on the credential, authenticate the service provider interface to the user and the user to the service provider interface; and establish an encrypted session between the service provider interface and the transaction application adapted to authenticate the transactions between the user and the service provider interface.
Owner:CARDLOGIX
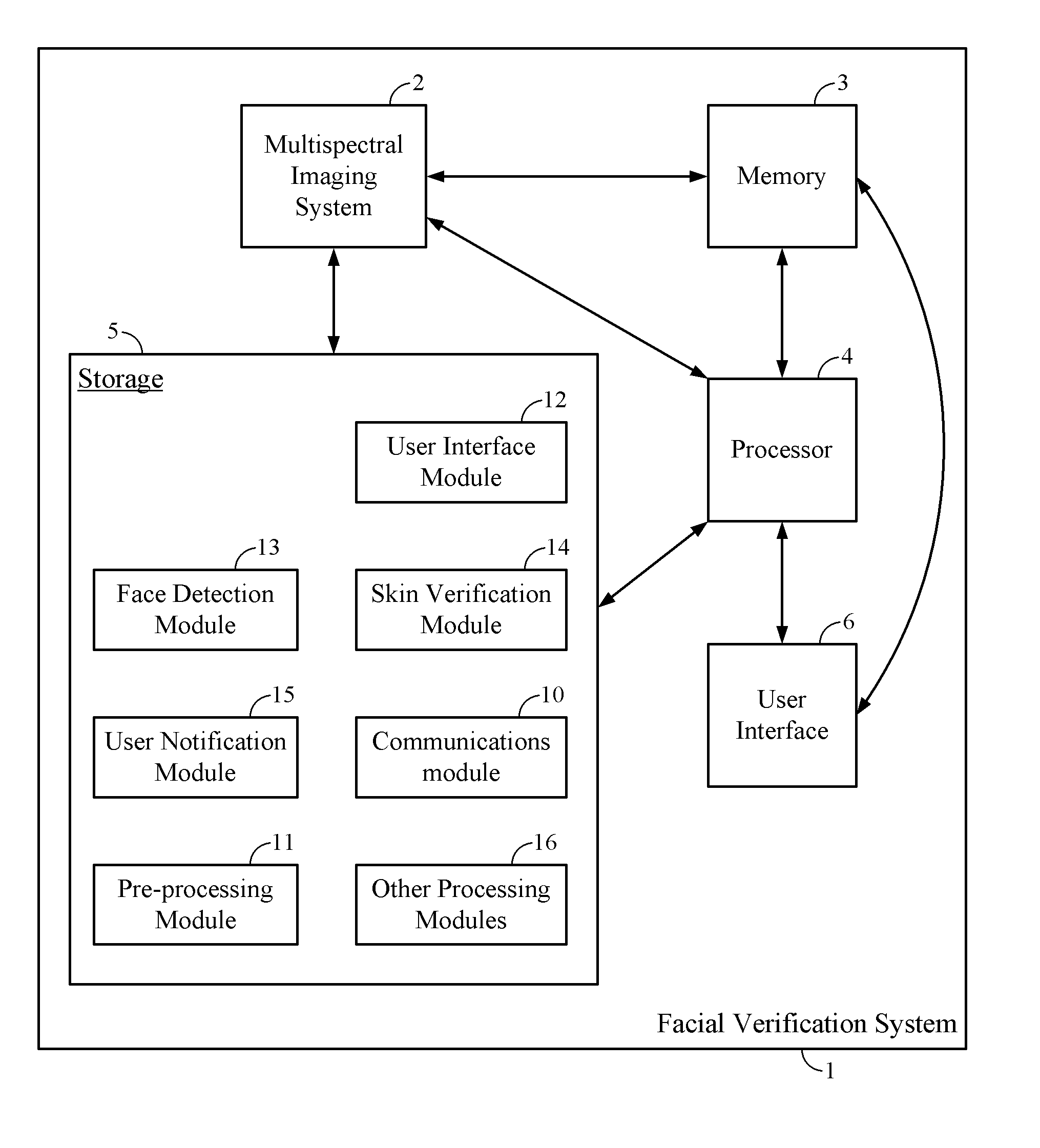
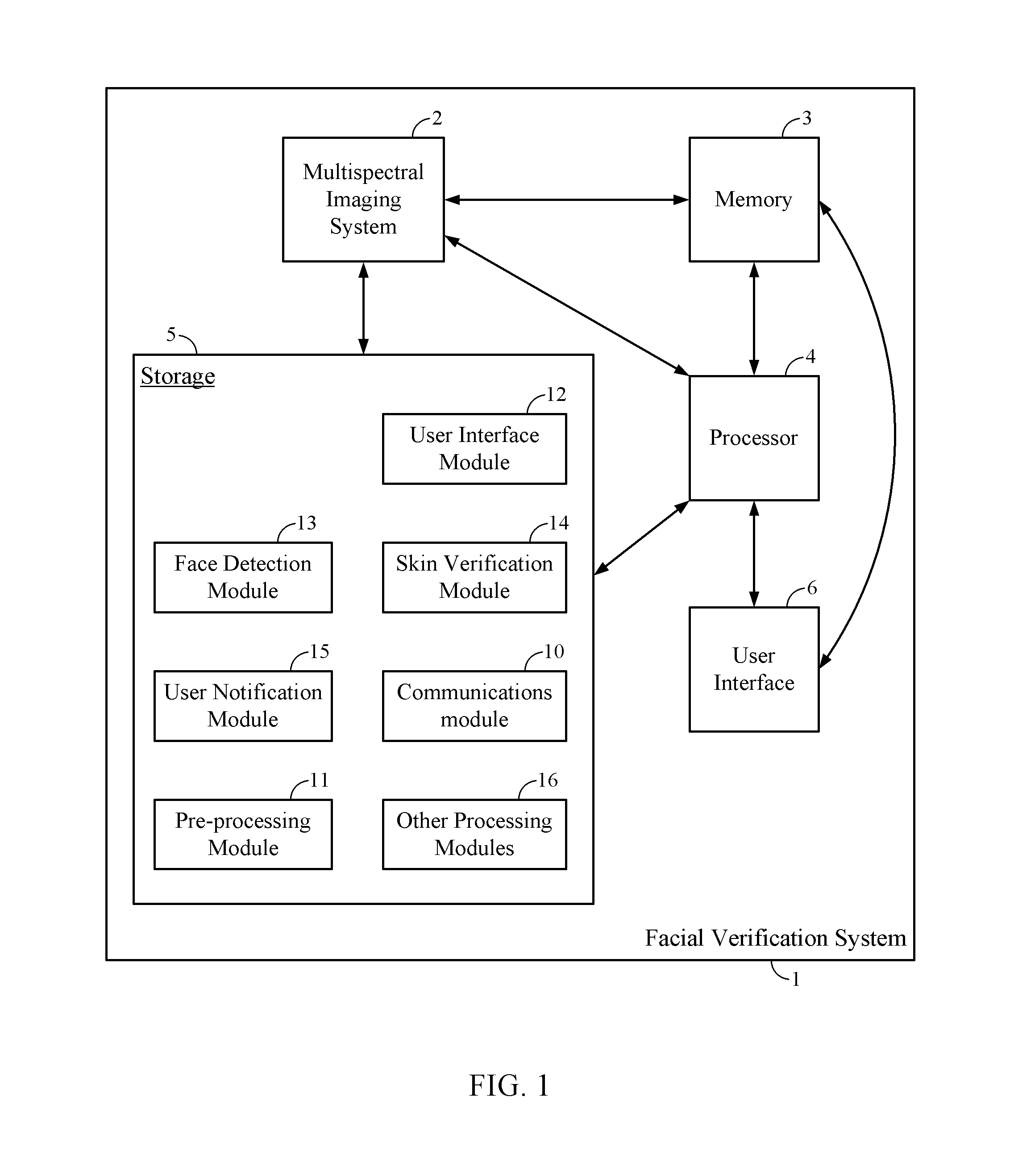
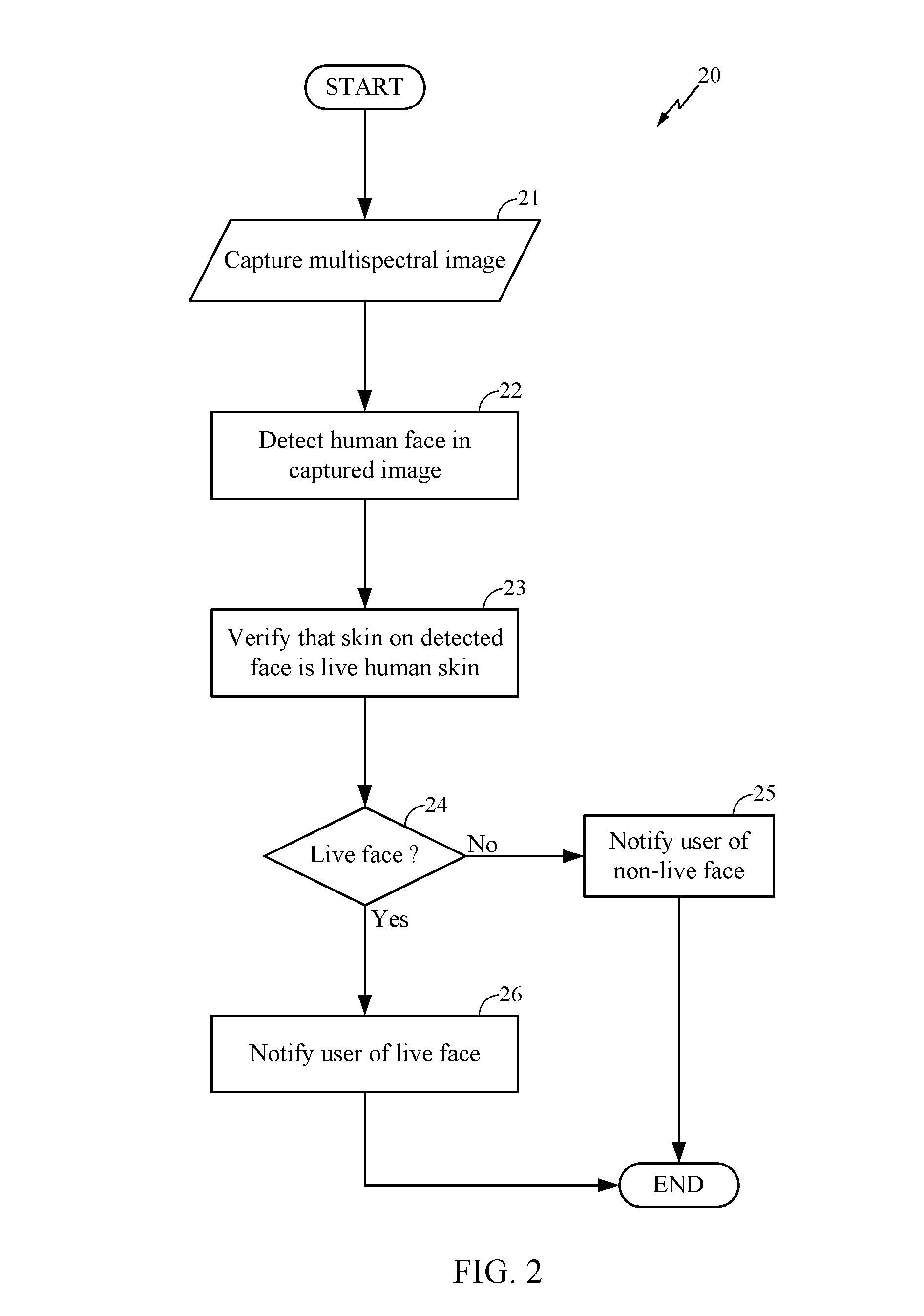
Systems and method for facial verification
ActiveUS20130342702A1Television system detailsImage enhancementPattern recognitionMultispectral image
Systems and methods for detecting a live human face in an image are disclosed. The methods and systems are capable of receiving multispectral image data that includes a human face. The multispectral image data can comprise visible light image data and near-infrared (NIR) image data. The multispectral image data can be processed to detect the human face. The detected human face in the visible light image data can be associated with the detected human face in the NIR image data to determine whether the detected human face is a live human face.
Owner:QUALCOMM INC
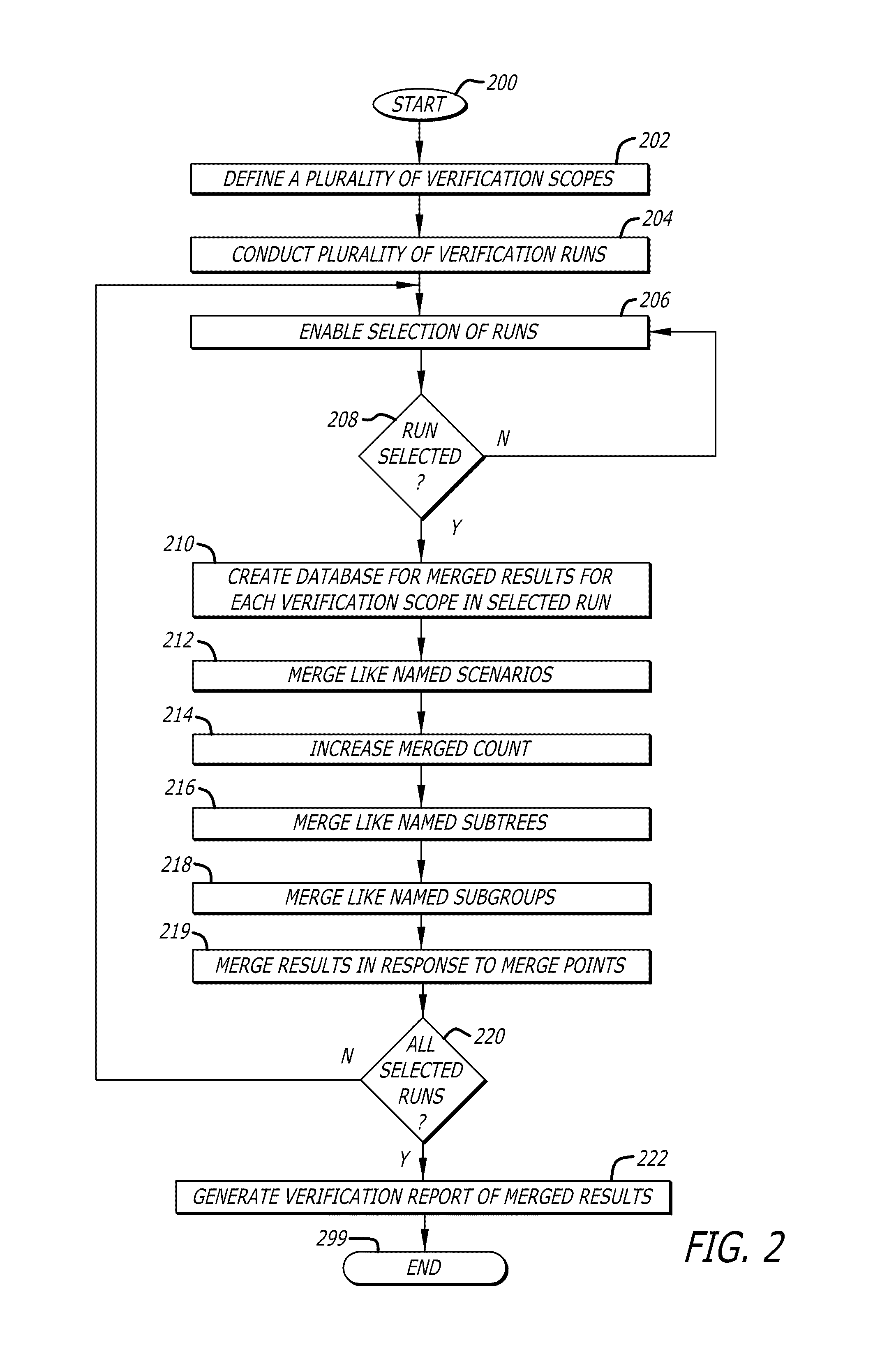
Verification plans to merging design verification metrics
ActiveUS8413088B1Flexible controlAccurate progress measurementElectrical testingCAD circuit designComputer architectureProgram planning
A method and apparatus for producing a verification of digital circuits are provided. In an exemplary embodiment on the invention, a plurality of verification scopes of an integrated circuit design as defined as part of a verification plan. A plurality of verification runs are executed within two or more verification scopes defined by the verification plan. At least two verification runs are selected to merge verification results together. Like named scenarios are merged together for each verification scope to generate merged verification results that are then stored into a merge database. A verification report is generated for the integrated circuit design from the merged verification results. A merge point may be specified so like named subtrees and subgroups may be merged across different verification scopes of selected verification runs. The merge point may combine check and coverage results obtained during simulation with check and coverage results obtained during formal verification.
Owner:CADENCE DESIGN SYST INC
Software verification
InactiveUS20060282807A1Improve performanceEfficiency of the abstraction computation is advantageously increasedError detection/correctionSoftware simulation/interpretation/emulationVerification systemSoftware
A system and method is disclosed for formal verification of software programs that advantageously improves performance of an abstraction-refinement loop in the verification system.
Owner:NEC CORP
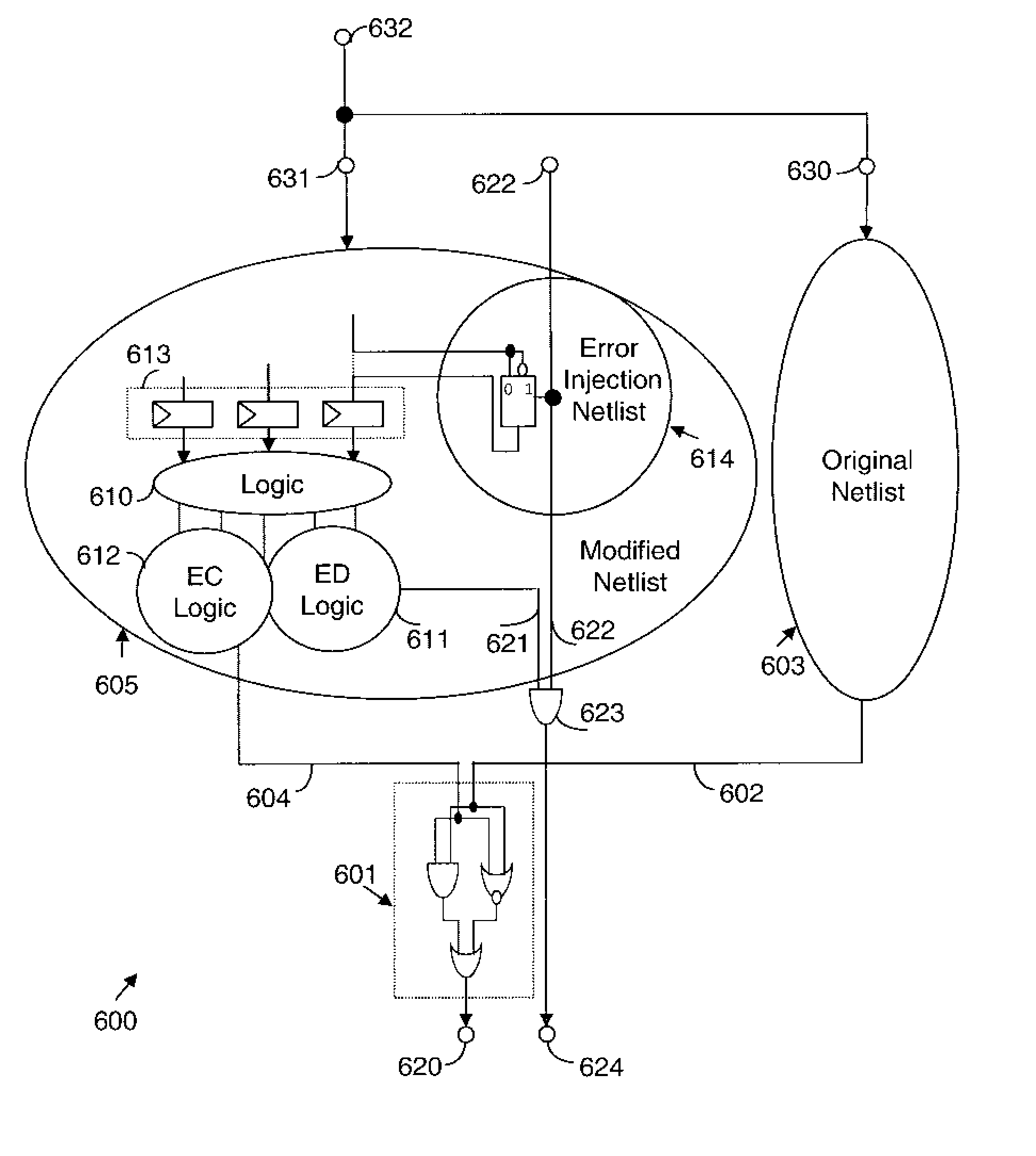
Method and System for Performing Functional Formal Verification of Logic Circuits
InactiveUS20070050740A1Detecting errorComputer aided designSoftware simulation/interpretation/emulationFault modelNetlist
The present invention relates to a method, a computer program product and a system for performing functional formal verification. Error detection logic is verified by injecting errors in a hardware design description without any changes to the original design description. With the present invention both permanent and transient faults can be modelled, and the complete error space can be covered for all types of fault models that can be used at the RTL. The number of detected design errors is used to determine the overall coverage in relation to the number of injected errors. The error injection is prepared by adding additional circuits to an RTL netlist representation of the hardware logic design. Signal values for selected signals related to the error detection logic are compared for a modified netlist representation and for the original netlist using a formal verification tool.
Owner:IBM CORP
Method and System for Formal Verification of Partial Good Self Test Fencing Structures
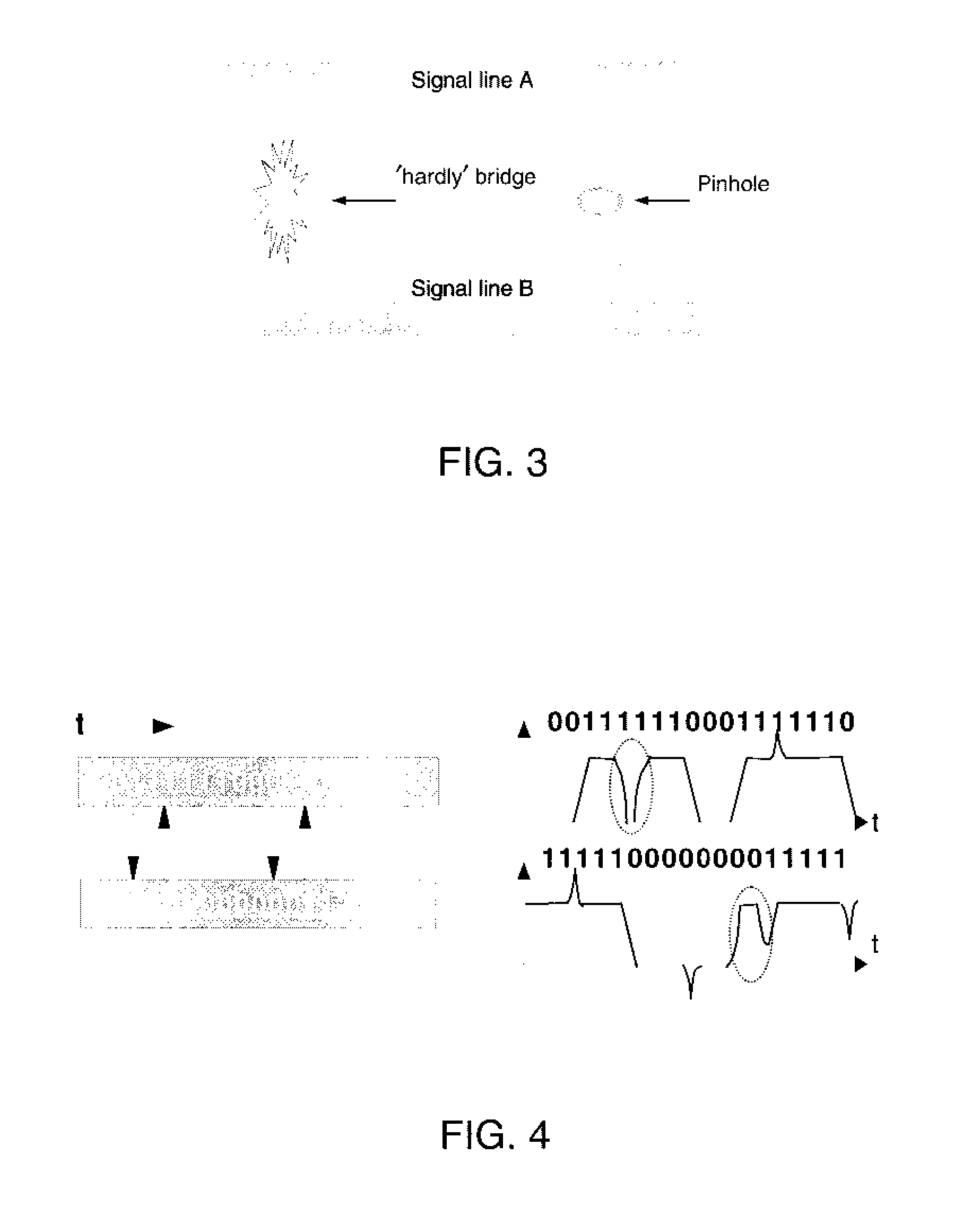
ActiveUS20080276144A1Reduces chip test coverageElectronic circuit testingHardware structureCommon logic
The concept of applying fencing logic to Built-In Self Test (BIST) hardware structures for the purpose of segregating defective circuitry and utilizing the remaining good circuitry is a well known practice in the chip design industry. Described herein is a method for verifying that any particular implementation of partial fencing logic actually provides the desired behavior of blocking down-stream impact of all signals from fenced interfaces, and also ensuring that the partial fencing does not inadvertently preclude any common logic from being fully tested.
Owner:TWITTER INC
Page buffer for flash memory device
InactiveUS7099213B2Solve the real problemRead-only memoriesDigital storageComputer sciencePage buffers
The disclosed is a page buffer of a flash memory device. In accordance with the present invention, a latch is controlled through a program verification signal, a latch signal, and latch data in a page buffer during a program verification. As a result, there are many advantages. First, in the event that the program verification is performed after programming once more, a passed cell is not sensed again and maintains its value. Second, it is possible to prevent a problem caused by a sensing operation as well as a verification error due to an external factor. As a result, program operation errors can be prevented.
Owner:STMICROELECTRONICS SRL +1
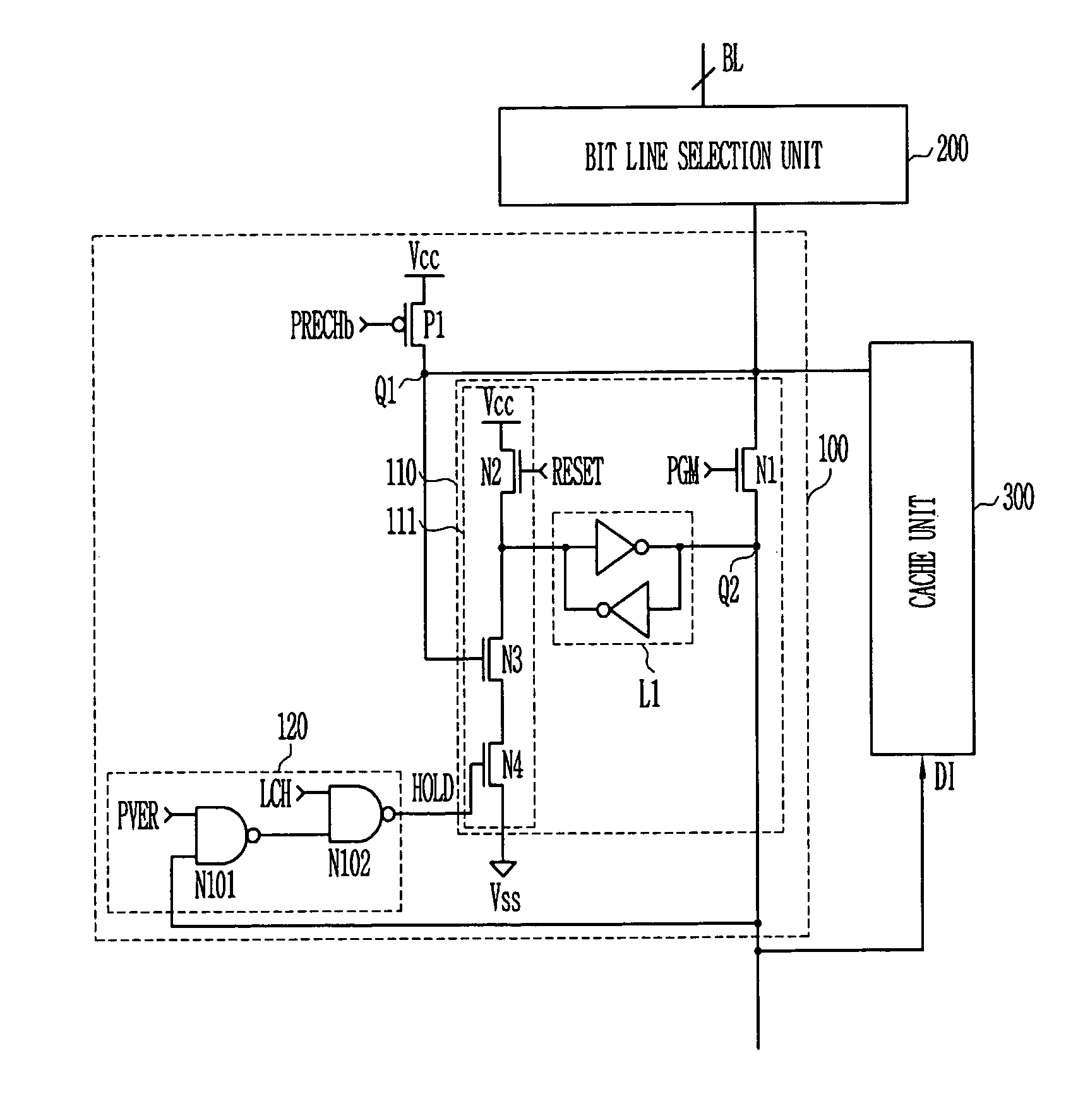
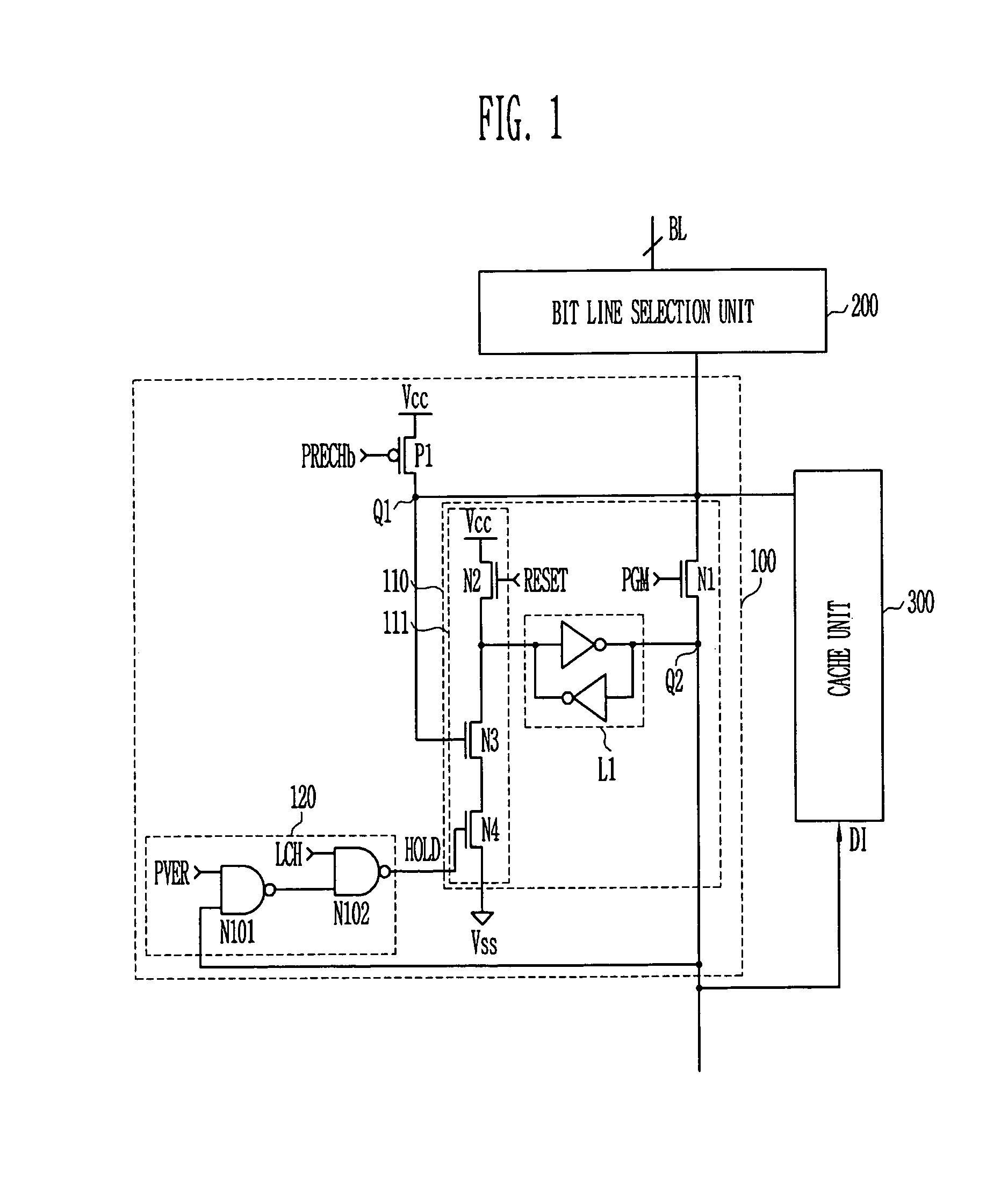
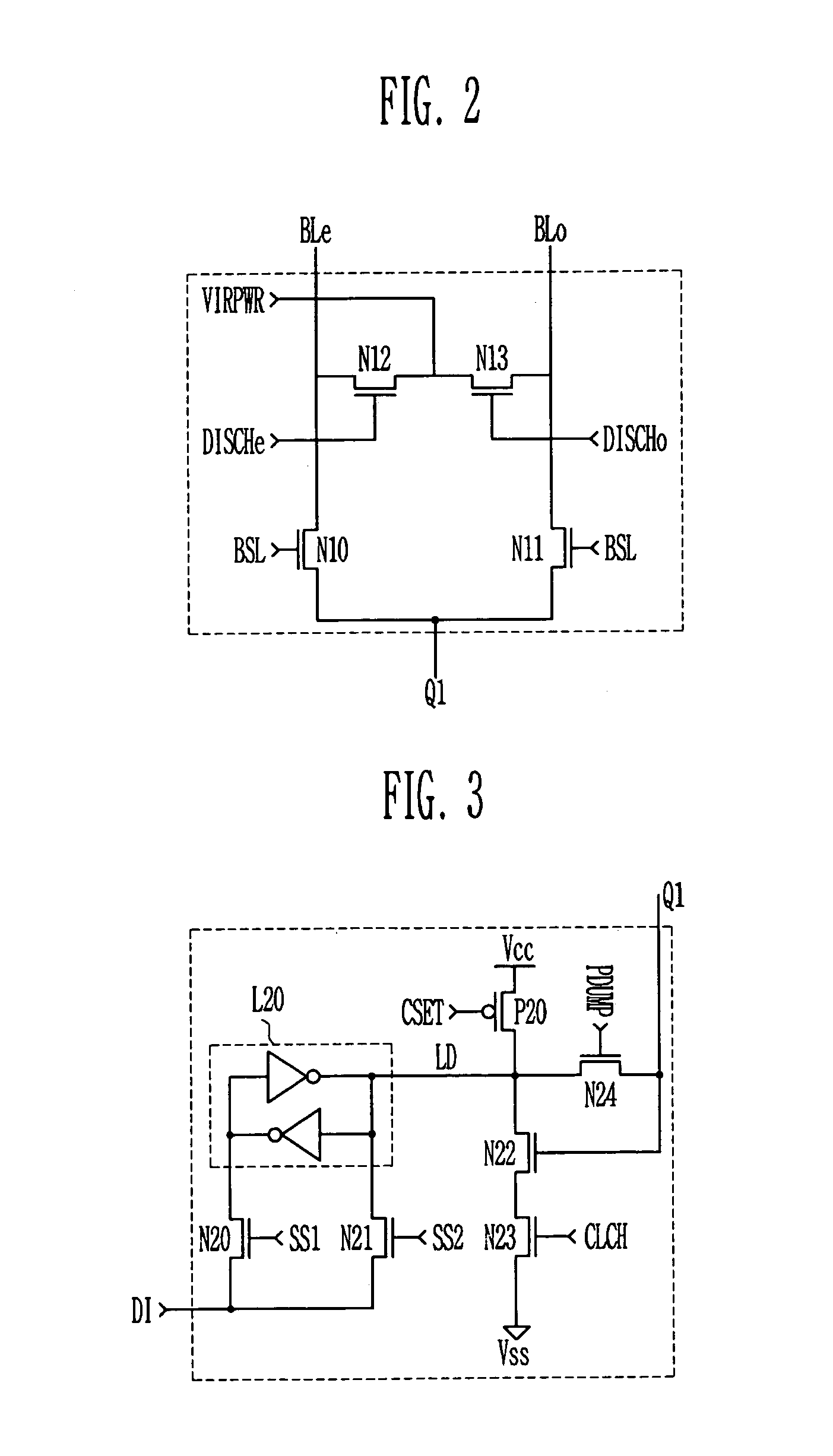
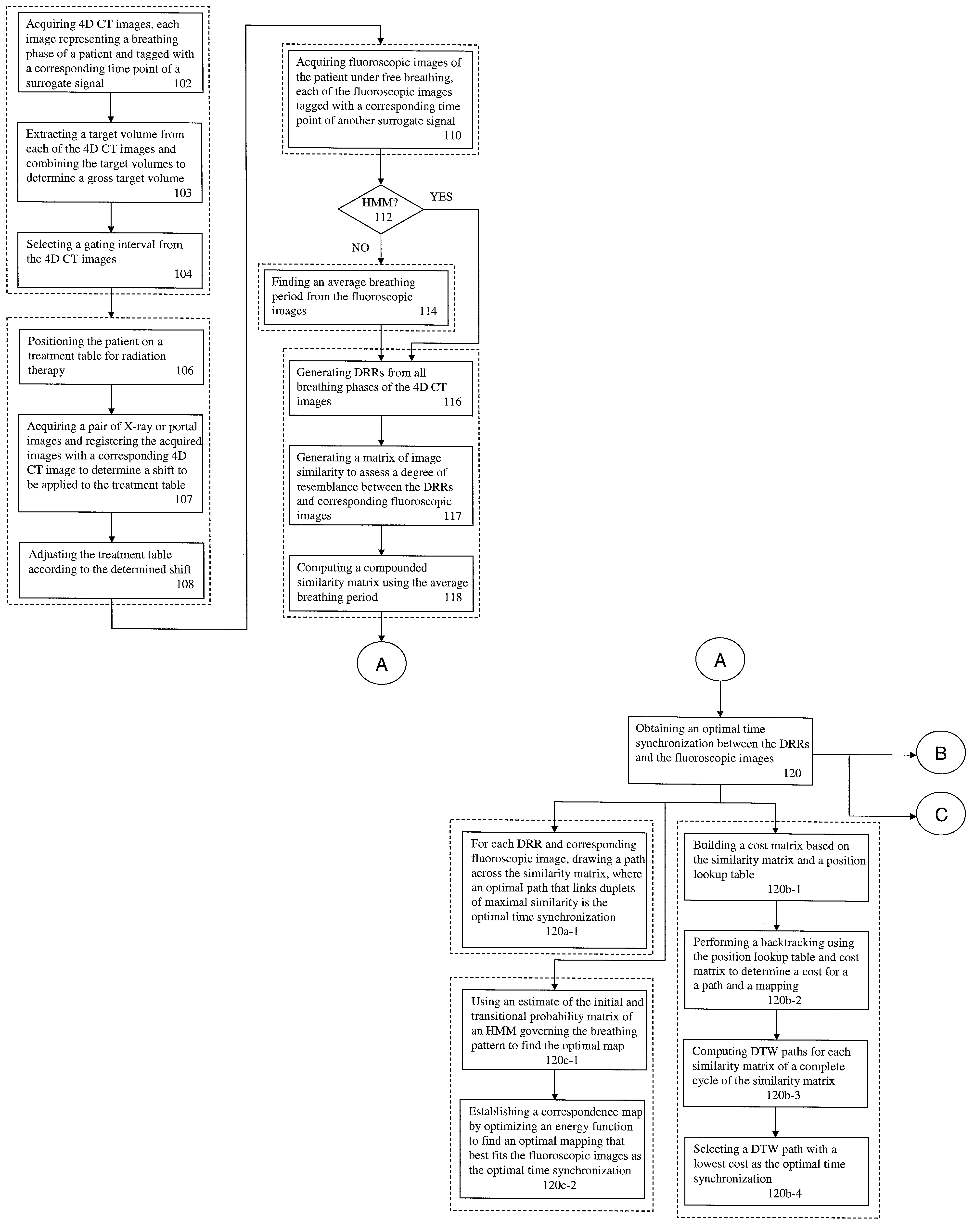
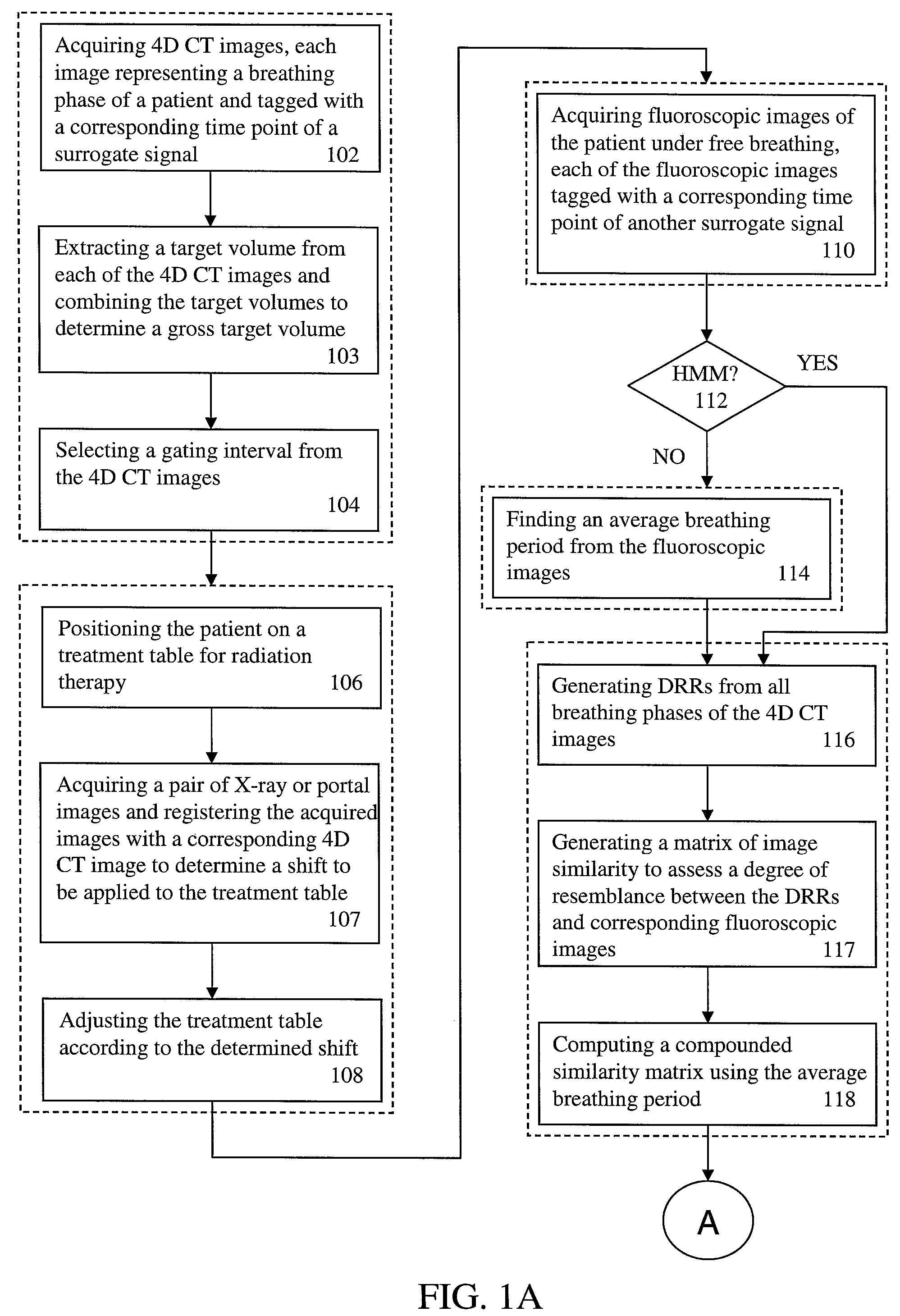
Four-dimensional (4D) image verification in respiratory gated radiation therapy
ActiveUS7570738B2X-ray/infra-red processesMaterial analysis using wave/particle radiationFluoroscopic image4D Computed Tomography
A method for four-dimensional (4D) image verification in respiratory gated radiation therapy, includes: acquiring 4D computed tomography (CT) images, each of the 4D CT images representing a breathing phase of a patient and tagged with a corresponding time point of a first surrogate signal; acquiring fluoroscopic images of the patient under free breathing, each of the fluoroscopic images tagged with a corresponding time point of a second surrogate signal; generating digitally reconstructed radiographs (DRRs) for each breathing phase represented by the 4D CT images; generating a similarity matrix to assess a degree of resemblance in a region of interest between the DRRs and the fluoroscopic images; computing a compounded similarity matrix by averaging values of the similarity matrix across different time points of the breathing phase during a breathing period of the patient; determining an optimal time point synchronization between the DRRs and the fluoroscopic images by using the compounded similarity matrix; and acquiring a third surrogate signal and turning a treatment beam on or off according to the optimal time point synchronization.
Owner:SIEMENS HEALTHCARE GMBH +1
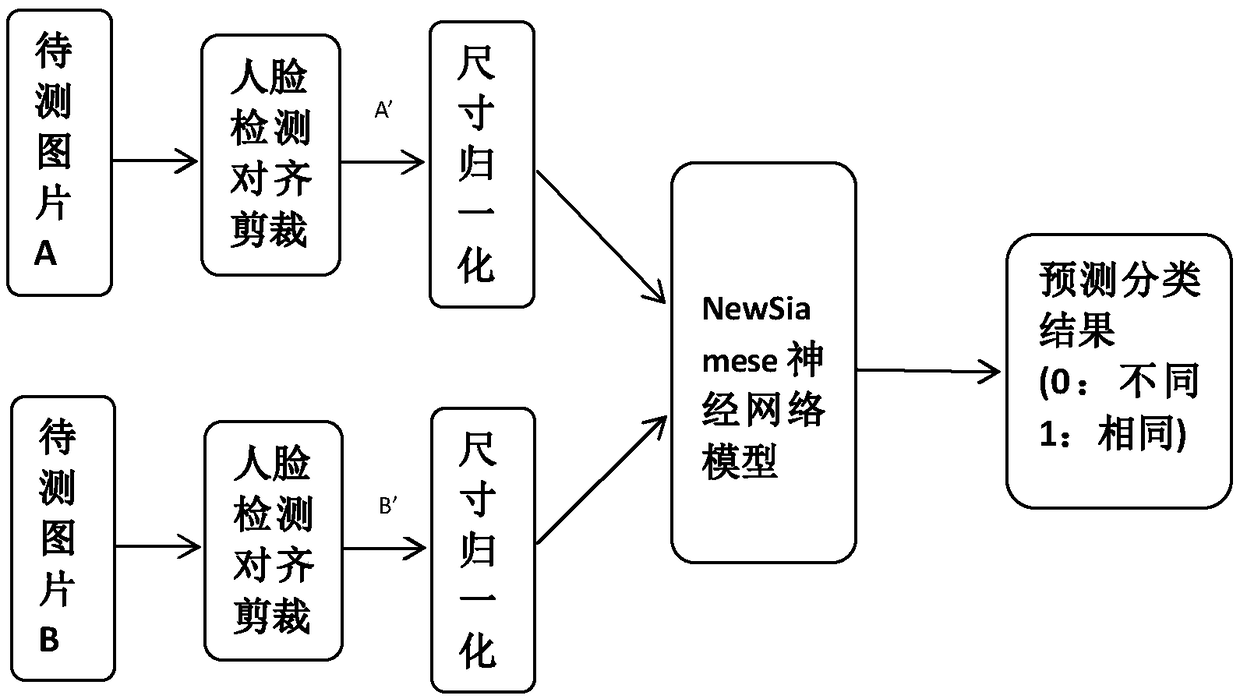
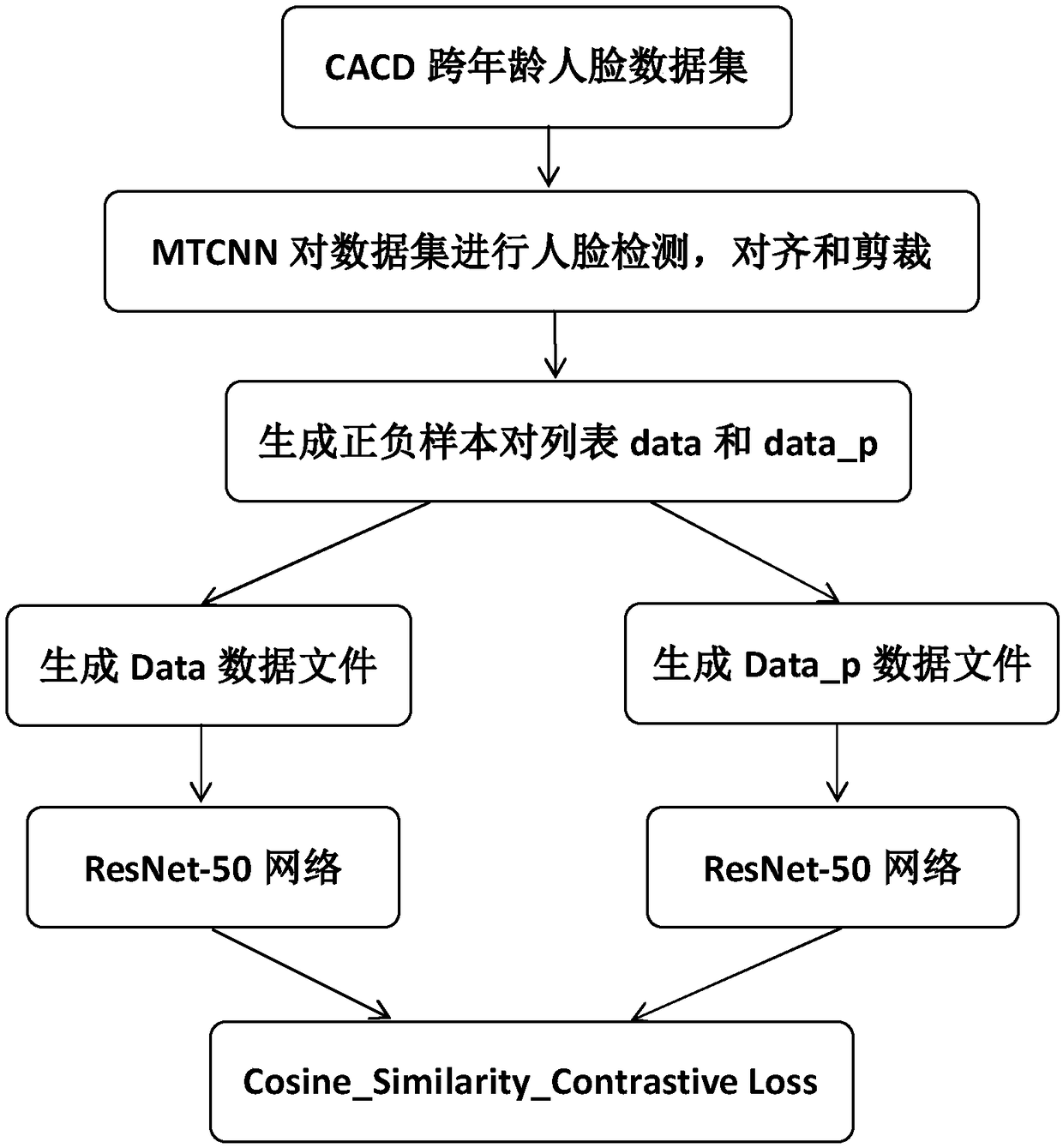
Twin neural network training method for face verification
InactiveCN109117744AEasy to handleImprove accuracyCharacter and pattern recognitionNeural architecturesFeature vectorData set
A twin neural network training method for face verification comprises: a training sample set is prepared; the images in the training sample set are normalized in size and then input to the artificialneural network for training. Artificial neural network consists of two identical sub-neural networks. The training samples are divided into datasets data_p and data_p which are equal in number. The datasets data_p and data_p are sent to two sub-neural networks to extract the eigenvectors of the samples. By comparing the loss function to realize the iterative optimization of the neural network, until the iterative number reaches the set value, then jump out of the iteration, at this time the trained artificial neural network is the twin neural network for face verification; The contrast loss function represents similarity between two sets of eigenvectors.
Owner:HANGZHOU DIANZI UNIV
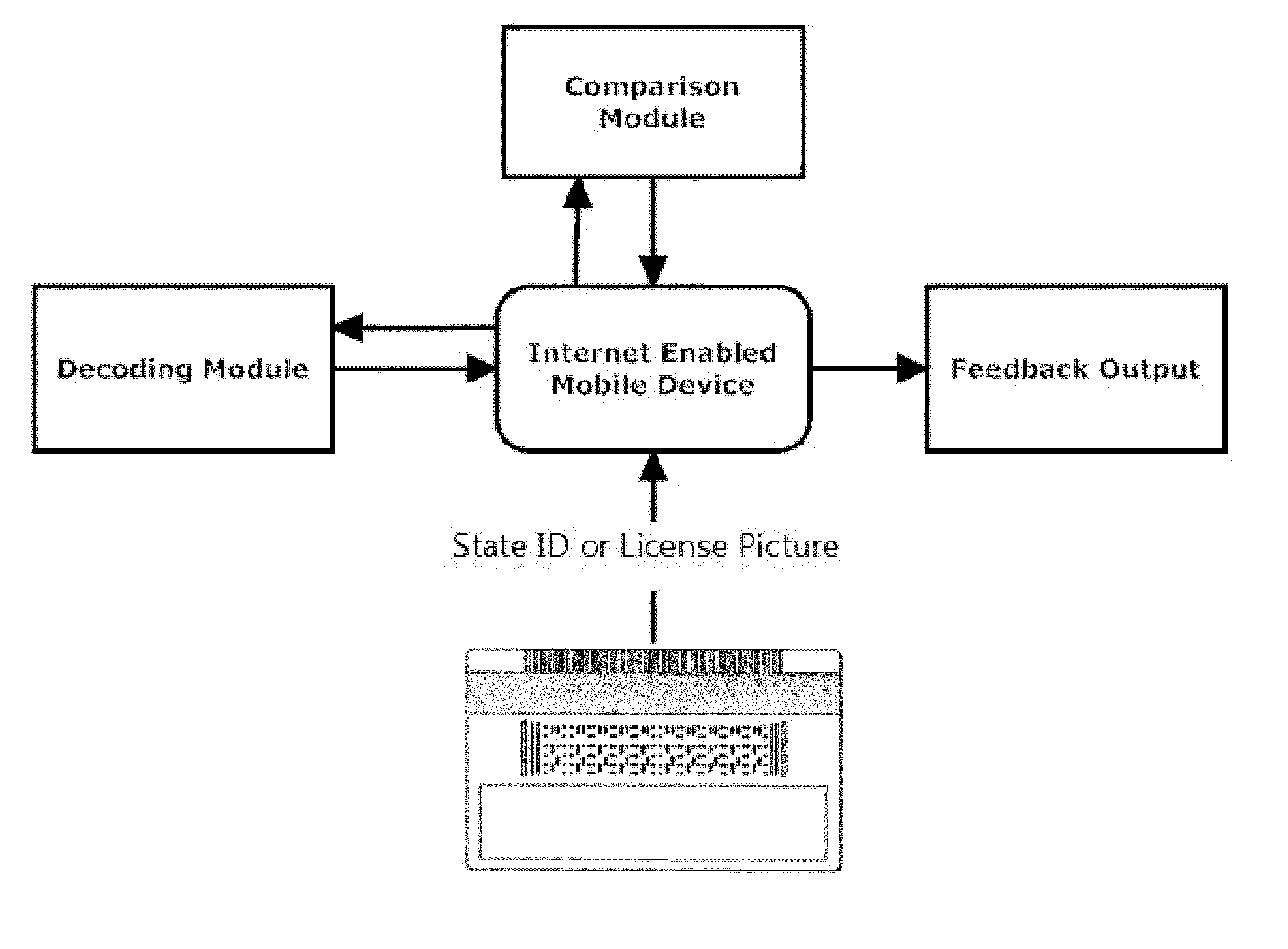
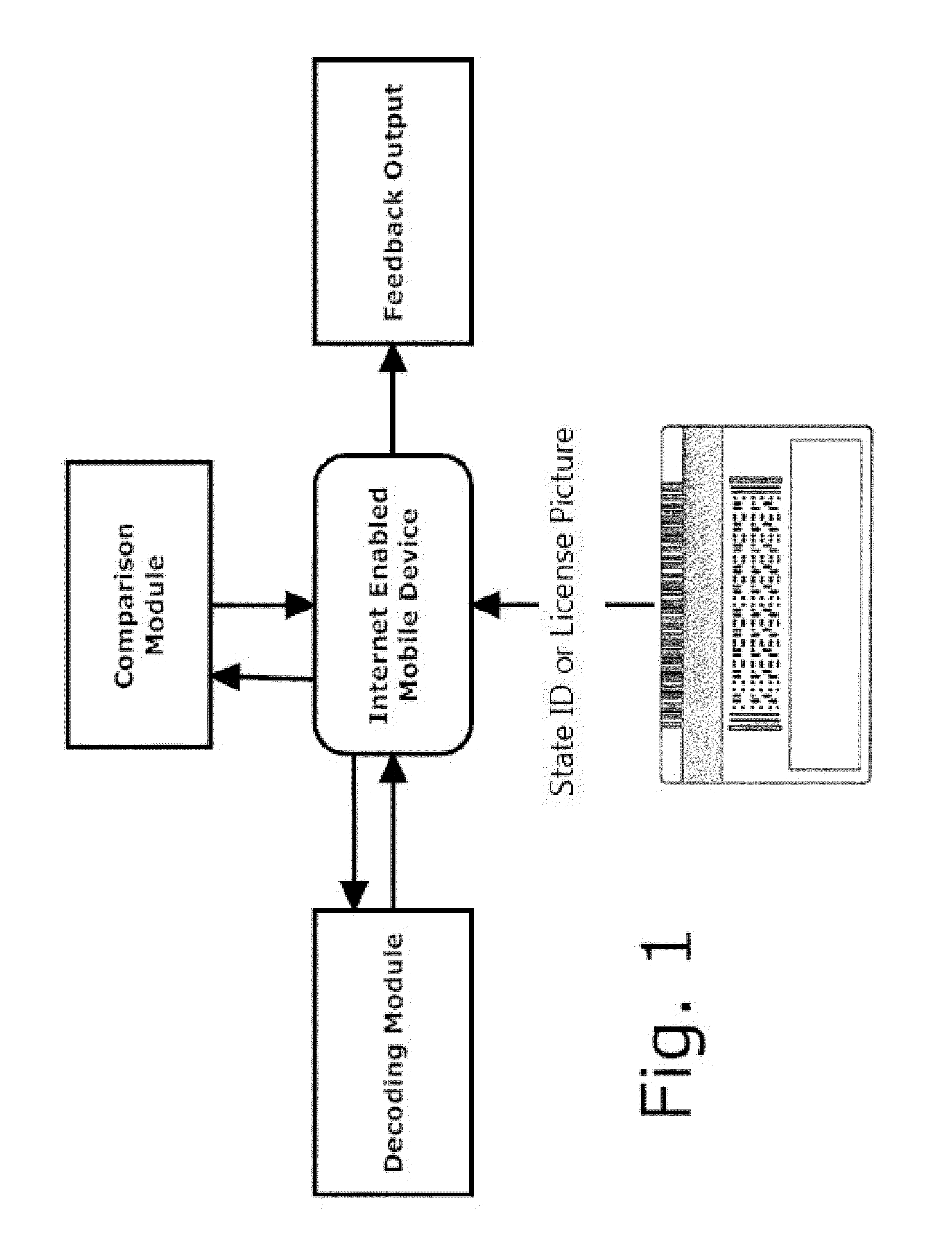
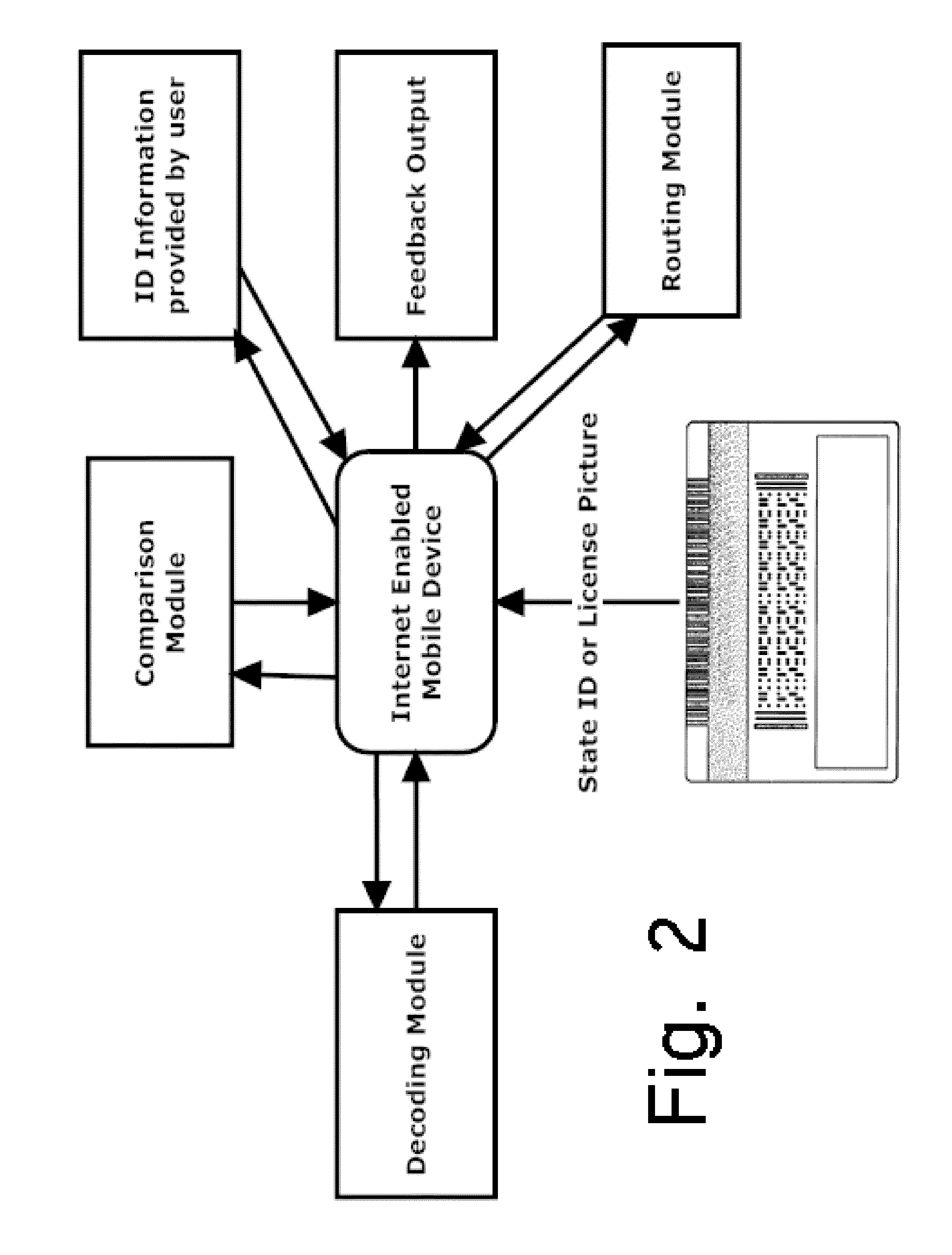
Alcohol Delivery Management System
A system for management of age verification using an internet enabled mobile device. The system provides ID verification using identification information comparison. The system further optionally provides display of completed and pending orders, routing to delivery destination, and prioritizing of deliveries.
Owner:BEERDROPPER
System and method for an automated sales system with remote negotiation and post-sale verification
The present invention provides a system and method to process items for sale or bid, to transmit electronic negotiations between prospective buyer and seller, and to verify the condition of the item before delivery to the buyer. The invention facilitates autonomous and remote negotiation between sellers and prospective buyers while protecting buyers from fraud and item misrepresentation. With the present invention, items can be sold individually and are not treated as standardized items that are interchangeable with similar commodity goods. The present invention also provides a waitlisting function. In addition, the functionality of traditional auction systems may be integrated with the novel features of the present invention. Furthermore, the present invention provides a system and method for conducting a reverse auction by allowing prospective buyers to list desired items.
Owner:NATHANSON JOSHUA DAVID
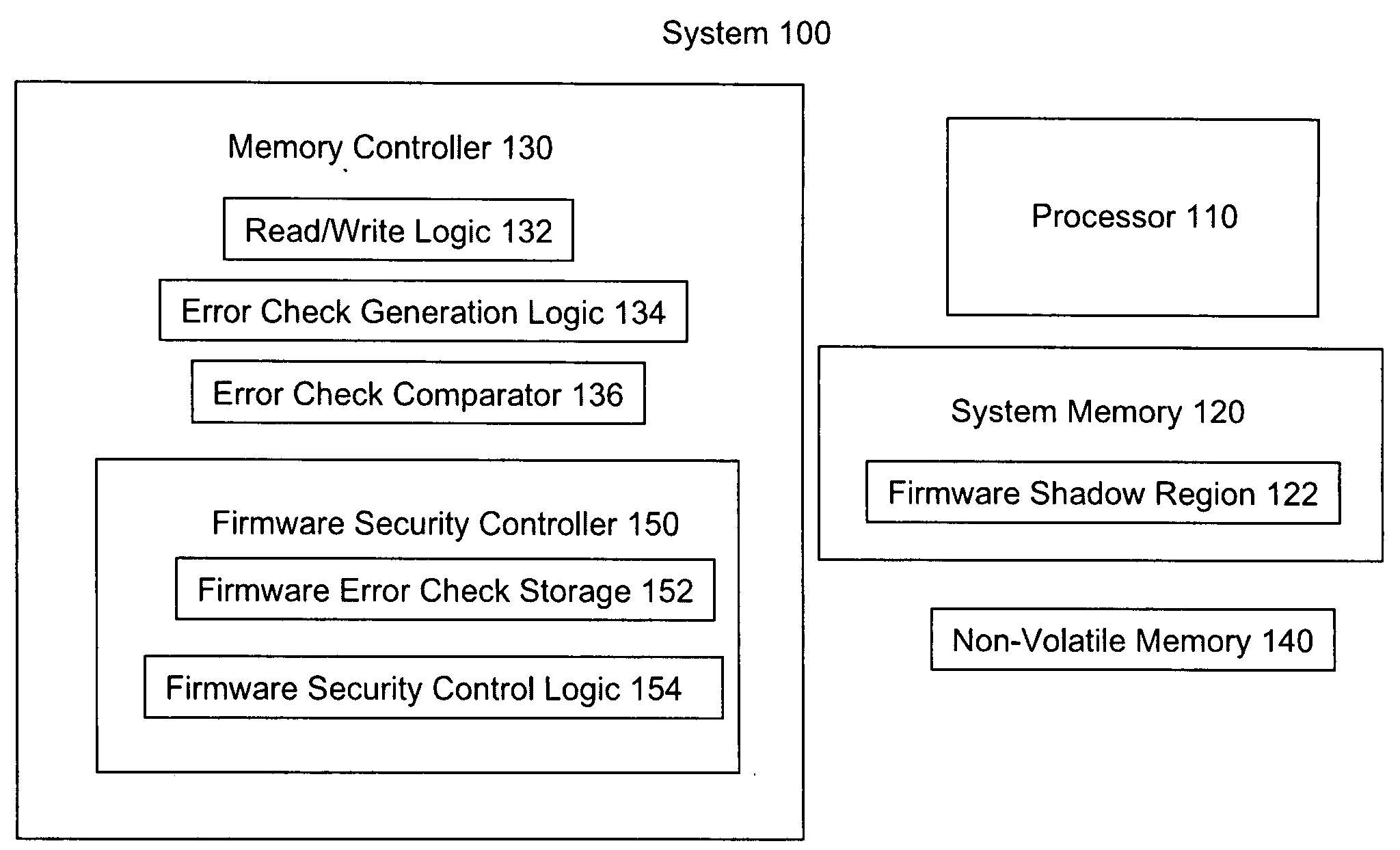
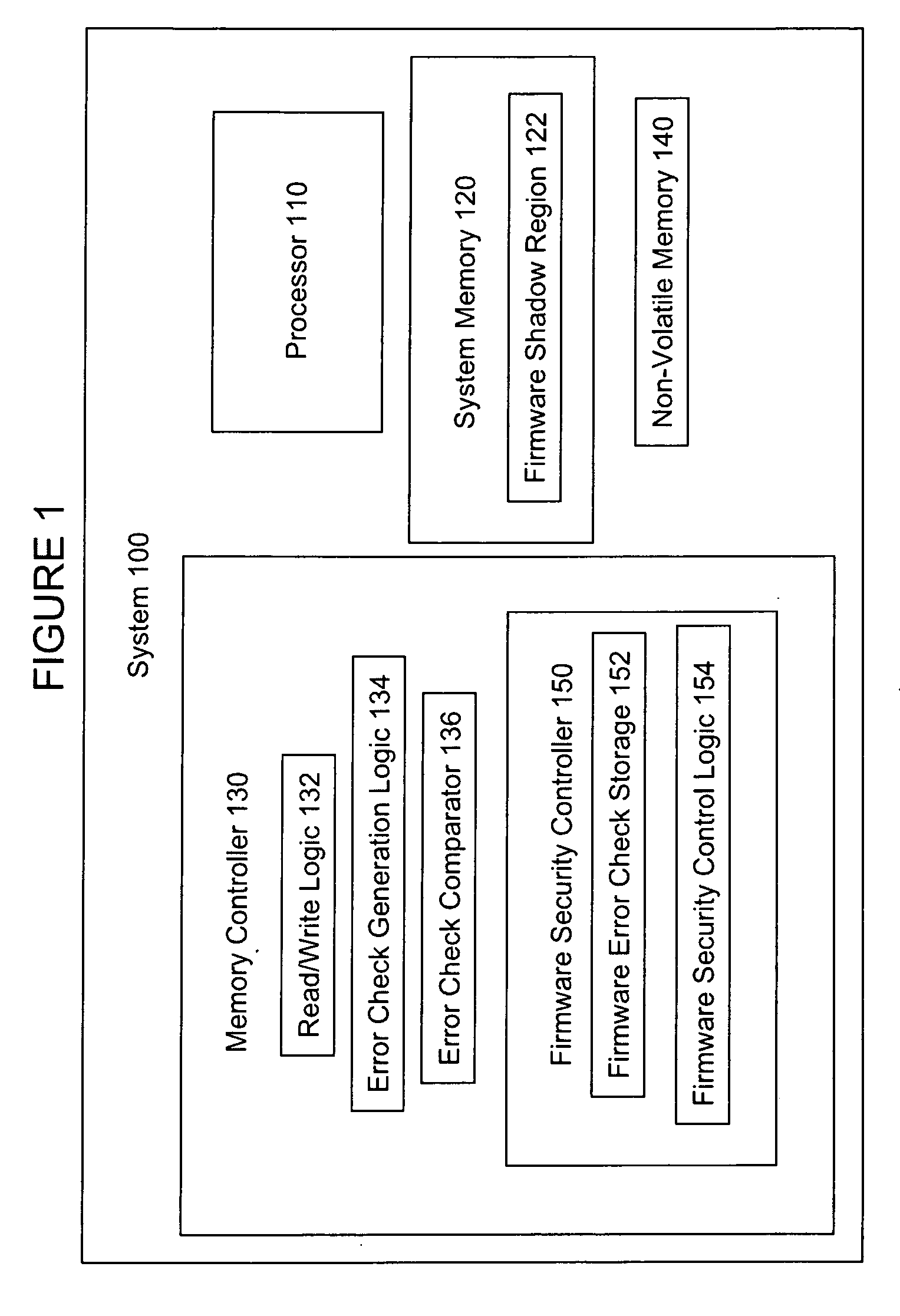
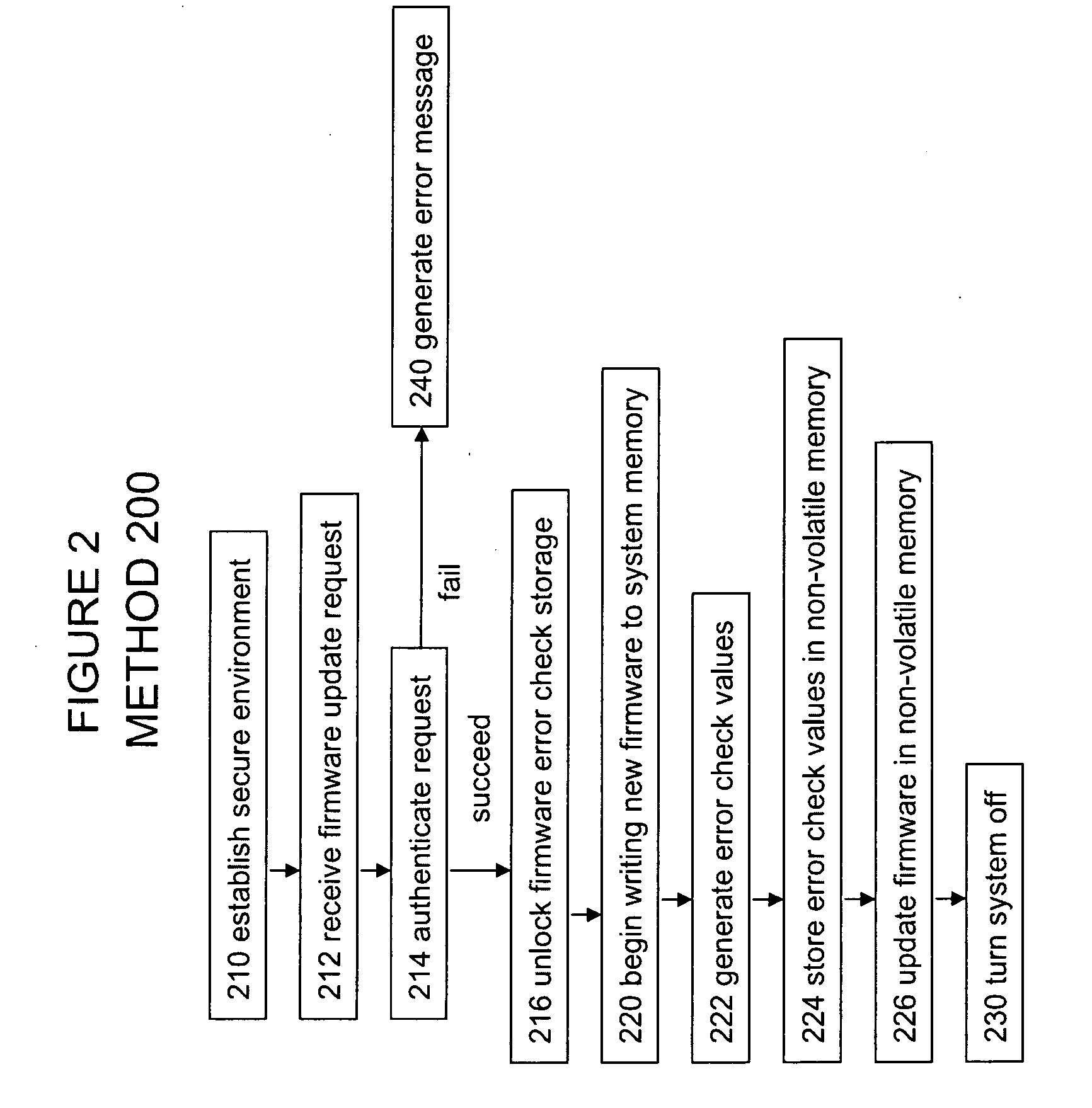
Firmware verification using system memory error check logic
Embodiments of an invention for verifying firmware using system memory error check logic are disclosed. In one embodiment, an apparatus includes an execution core, firmware, error check logic, non-volatile memory, comparison logic, and security logic. The error check logic is to generate, for each line of firmware, an error check value. The comparison logic is to compare stored error check values from the non-volatile memory with generated error check values from the error check logic. The security logic is to prevent the execution core from executing the firmware if the comparison logic detects a mismatch between the stored error code values and the generated error code values.
Owner:INTEL CORP
Product anti-fake method and system and client terminal
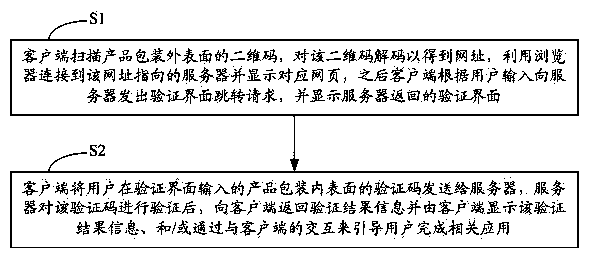
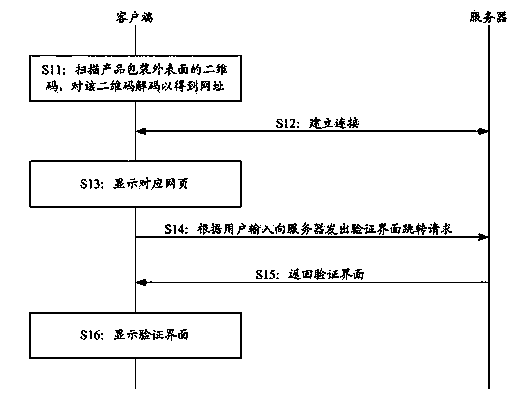
InactiveCN103593773AGuaranteed accuracyCommerceSensing by electromagnetic radiationUser inputClient-side
The invention belongs to the two-dimension code anti-fake field, and provides a product anti-fake method and system and a client terminal. In the method and system, the outer surface of a product package is printed or bonded with two-dimension codes, and the inner surface of the product package is printed or bonded with printing codes. The client terminal is directly connected to a corresponding website after scanning the two-dimension codes, after a user opens an inner product package body and sees verification codes, the user inputs the verification codes into a verification interface, verification on authenticity of the verification codes is achieved through a server, verification result information is returned to the client terminal, and then verification on authenticity of a product can be completed. The method and system integrate double-verification of the two-dimension codes and the verification codes, the verification codes are marked on the inner surface of the product package, and therefore the accuracy of verification on authenticity can be guaranteed even though the two-dimension codes are illegally copied. In addition, according to the method and system, the functions such as point promotion and lottery promotion can be further achieved through interaction of the client terminal and the server on the basis of product anti-fake verification, and the applicability is improved.
Owner:深圳市太和物联信息技术有限公司
System and method oriented to supermatic formal verification of smart contract of blockchain
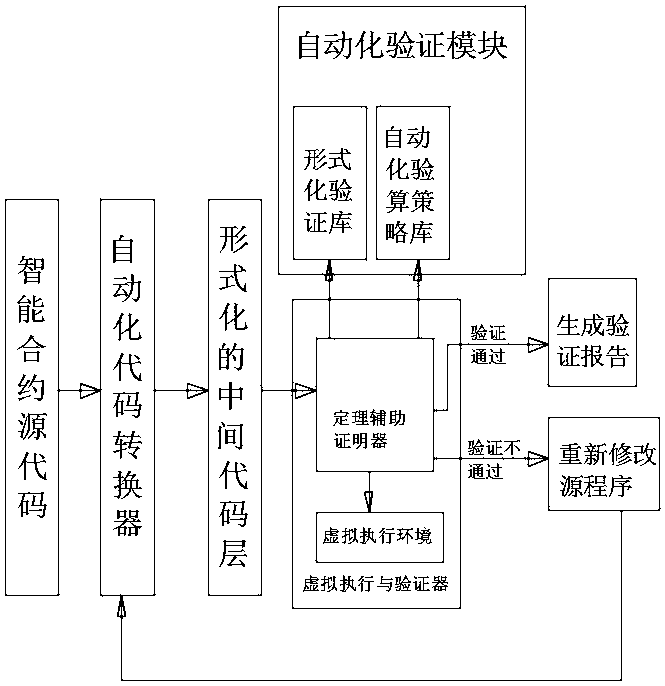
ActiveCN108536445AImprove verification efficiencyImprove efficiencyCode compilationFormal methodsSmart contract
The invention discloses a system and method oriented to supermatic formal verification of a smart contract of a blockchain. By using a code converter tool, the smart contract source code of the blockchain can be automatically converted into a language interlayer code for formal verification and identification so as to be used for formal verification input; by adopting a formal method, supermatic formal safety verification can be carried out on a converted source code so as to judge whether the security attribute requirement of the smart contract is safe or not. By relatively high-degree automation, formal safety verification can be carried out on the smart contract of the blockchain, wherein an automatic code converter can be used for automatically generating a formal to-be-verified program, the automatic checking calculation strategy improves verification efficiency, and the measures can be used for greatly improving the formal verification efficiency of the smart contract and reducing the artificial degree of participation.
Owner:成都链安科技有限公司
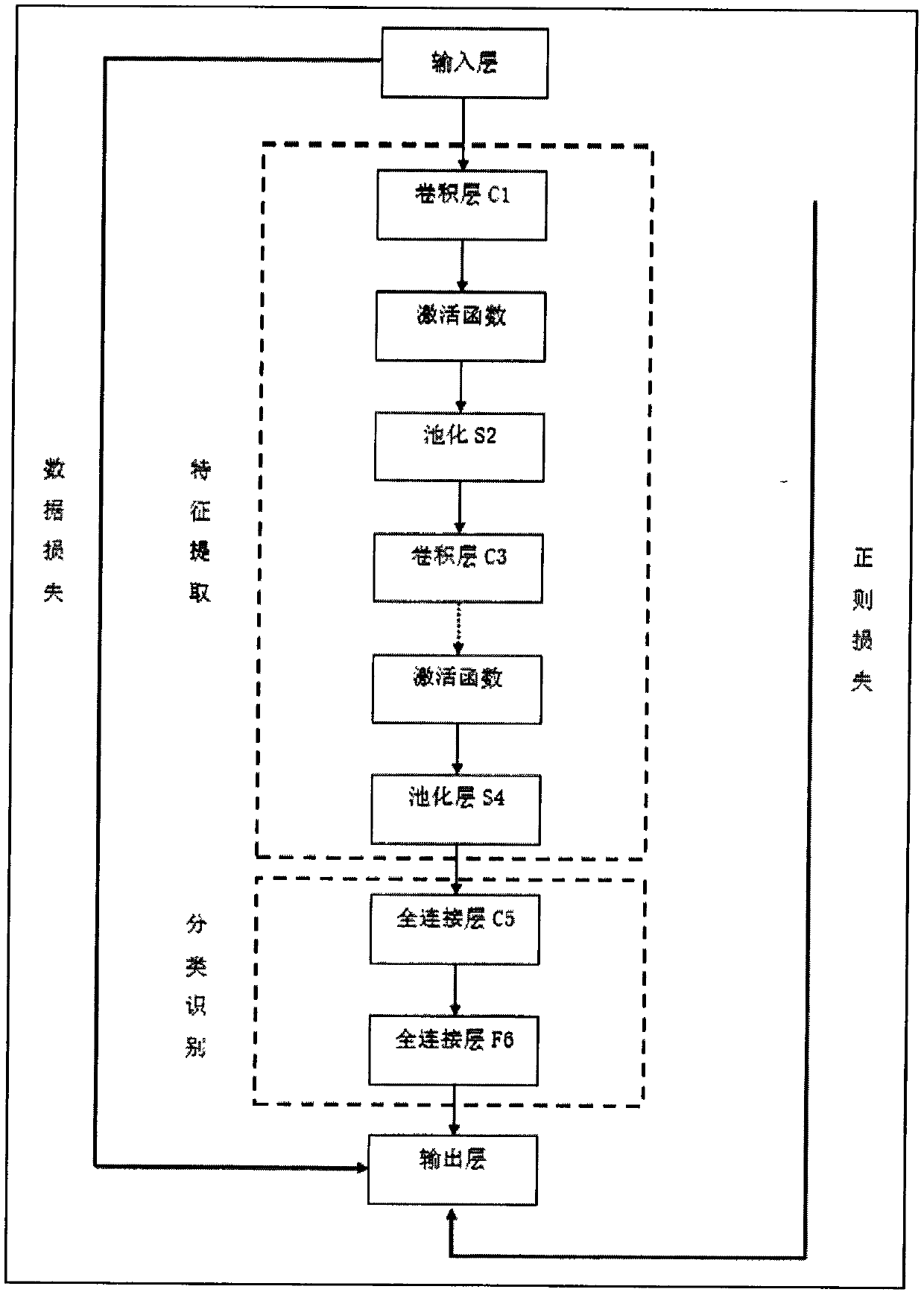
Artificial intelligence convolutional neural network face recognition system
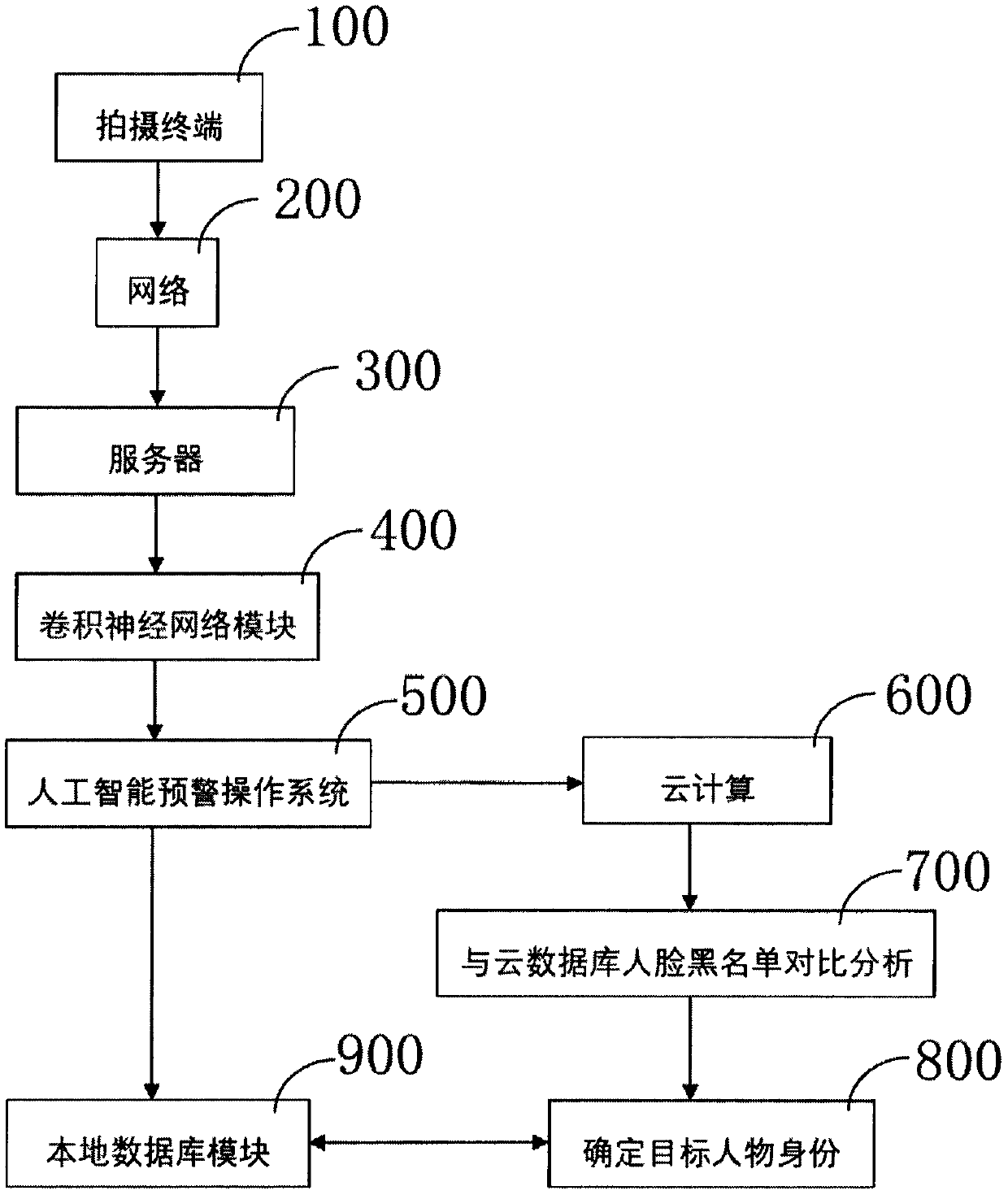
InactiveCN110414305ACharacter and pattern recognitionNeural architecturesFace detectionInformation sharing
The invention relates to an artificial intelligence convolutional neural network face recognition system. The system comprises a shooting terminal (100), a network (200), a server (300), a convolutional neural network module (400), an artificial intelligence early warning operation system (500), a cloud computing unit (600), a comparison analysis with a cloud database face blacklist unit (700), atarget person identity determination unit (800) and a local database module (900). The method comprises the following steps: acquiring an image or video stream containing a face by using a shooting terminal through an artificial intelligence convolutional neural network face recognition system, automatically detecting and tracking the face in the image, and further performing a series of technicalprocessing related to the face on the detected face, including face detection, face key frame extraction and face verification; all-weather 24-hour uninterrupted monitoring on the periphery of the shooting terminal is realized, a user can realize information sharing, the utilization rate of information resources is improved, and the safety guarantee is increased for maintaining the stability of social security.
Owner:苏州闪驰数控系统集成有限公司
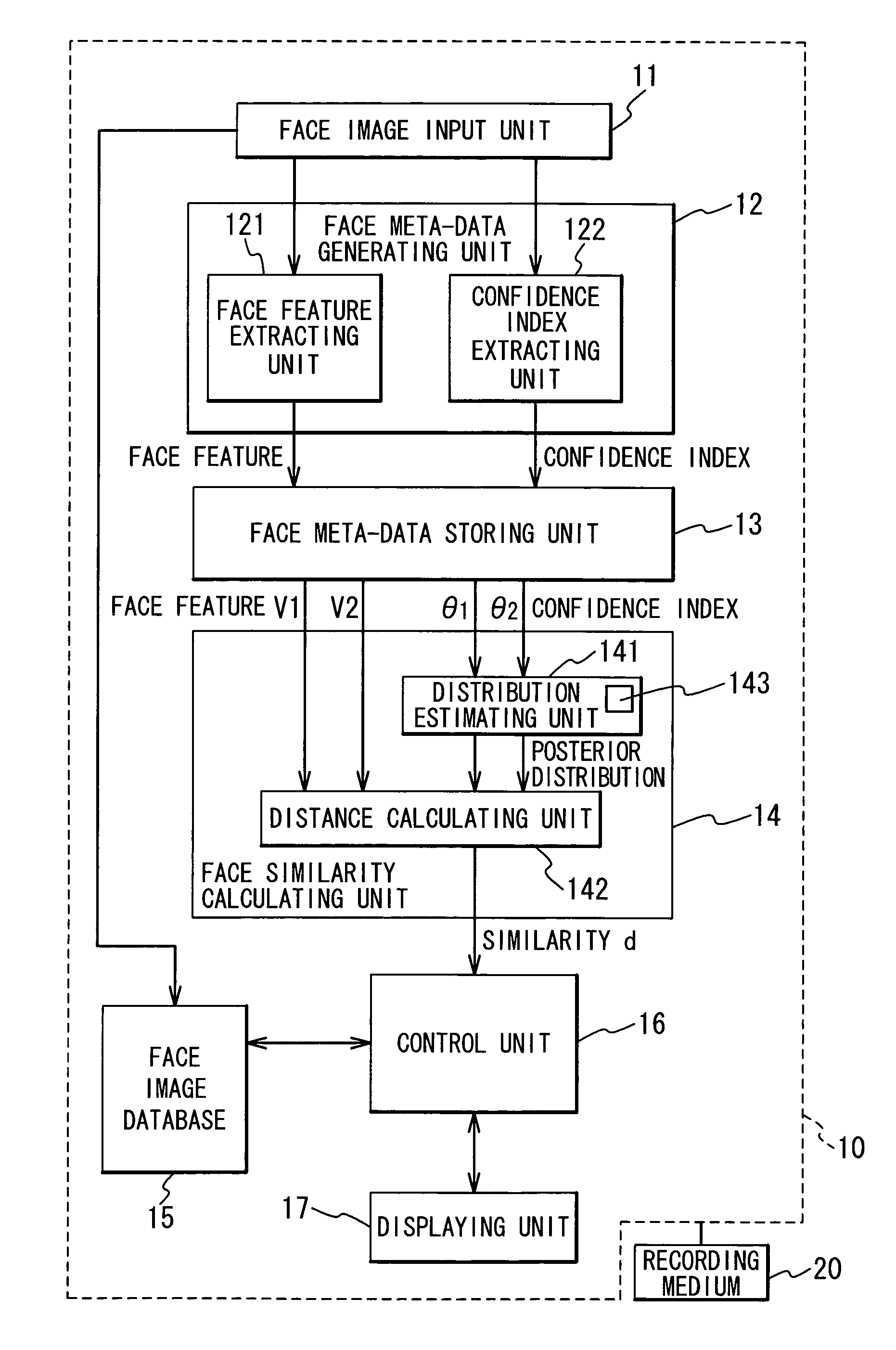
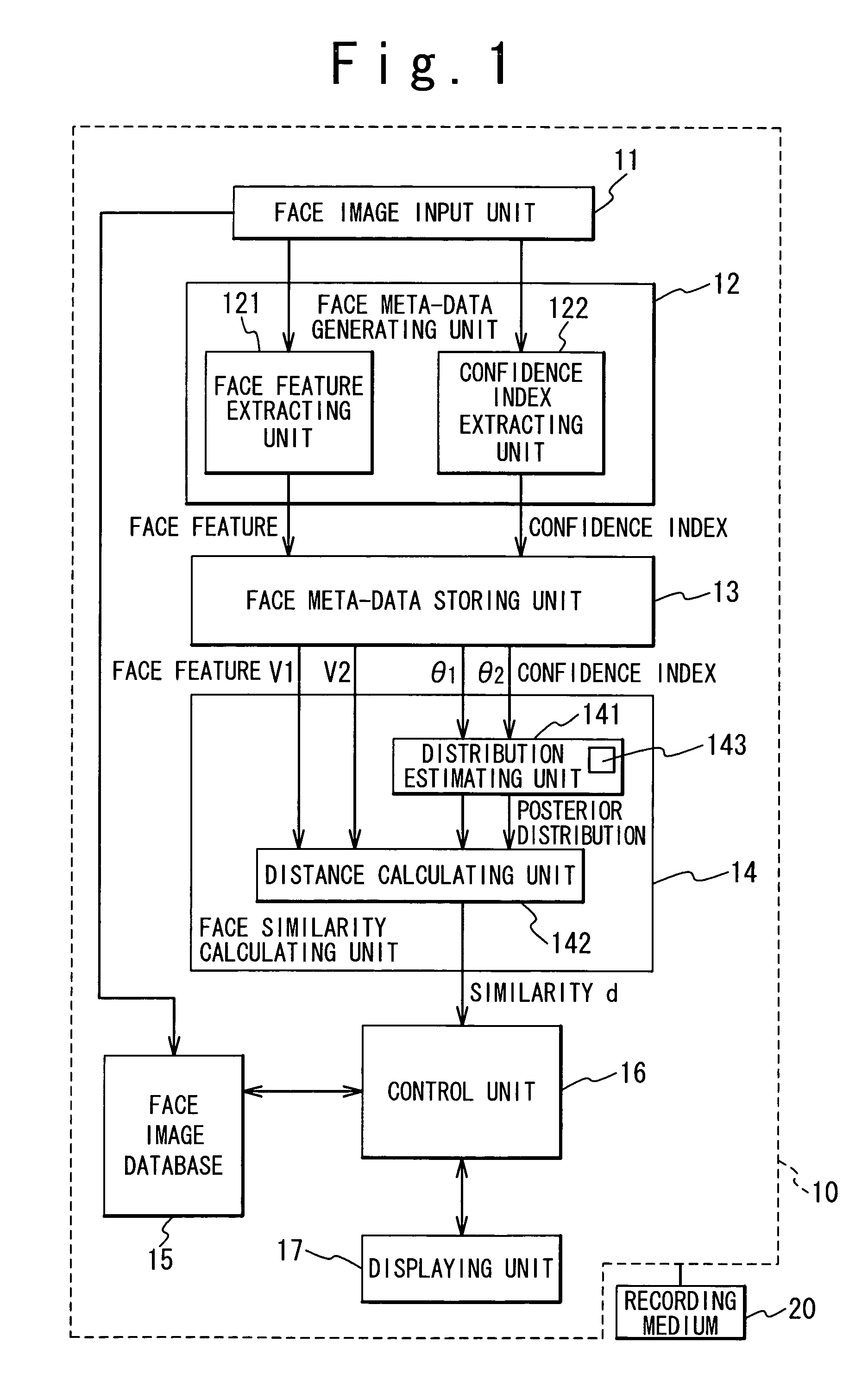
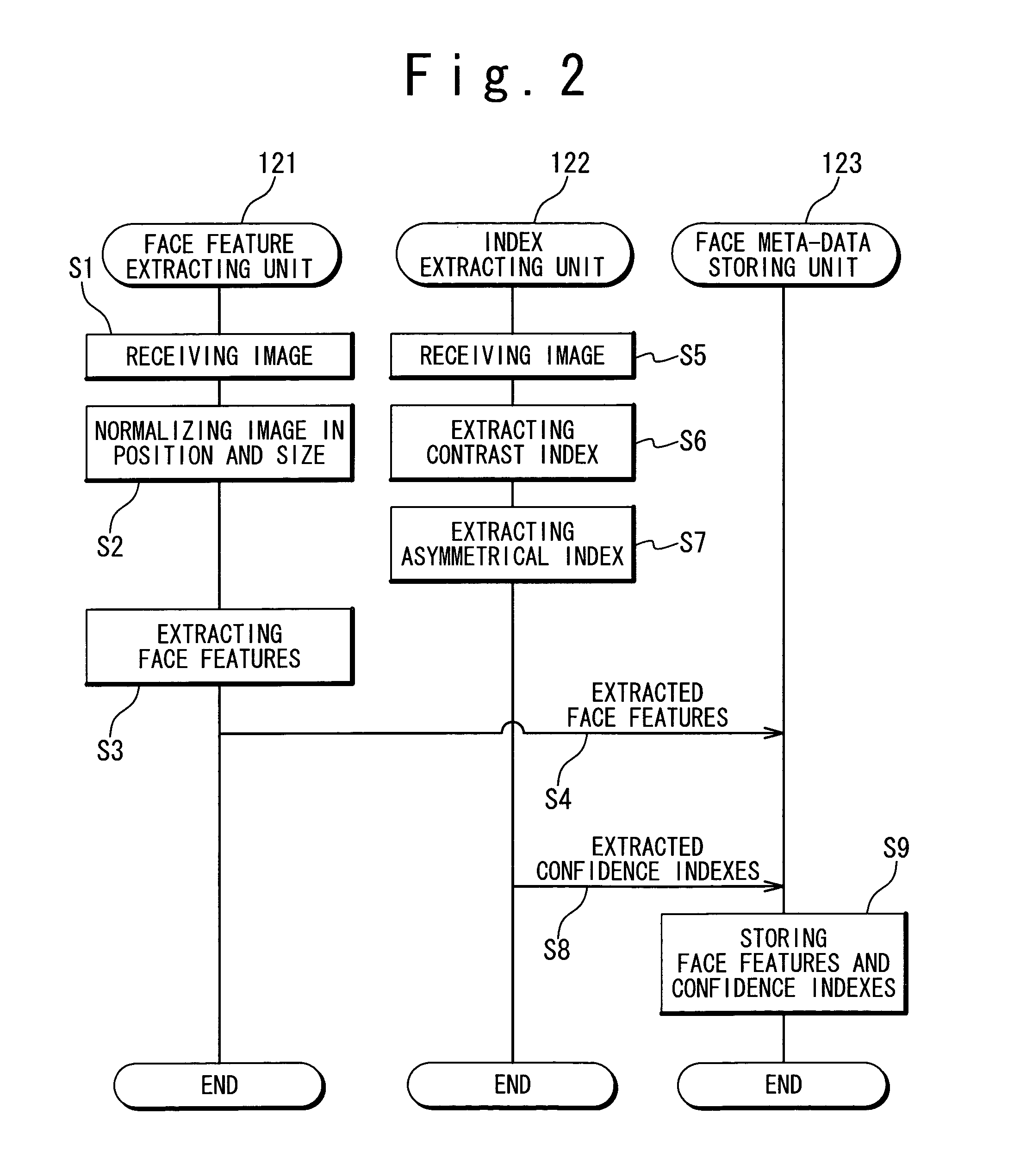
Face meta-data generation and face similarity calculation
ActiveUS7593551B2Improve accuracyHigh precisionImage analysisCharacter and pattern recognitionPattern recognitionConfidence interval
A face feature is extracted by a face feature extracting unit, a confidence index is extracted by a confidence index extracting unit, and then, they are outputted as a face meta-data. At a time of matching, by using the confidence index of the face meta-data, a distribution estimating unit estimates the data of a parameter and the like with regard to a posterior distribution when the confidence index is obtained. A distance calculating unit calculates a similarity between feature values. Consequently, the precision of face verification can be improved, thereby carrying out a practical face matching.
Owner:NEC CORP
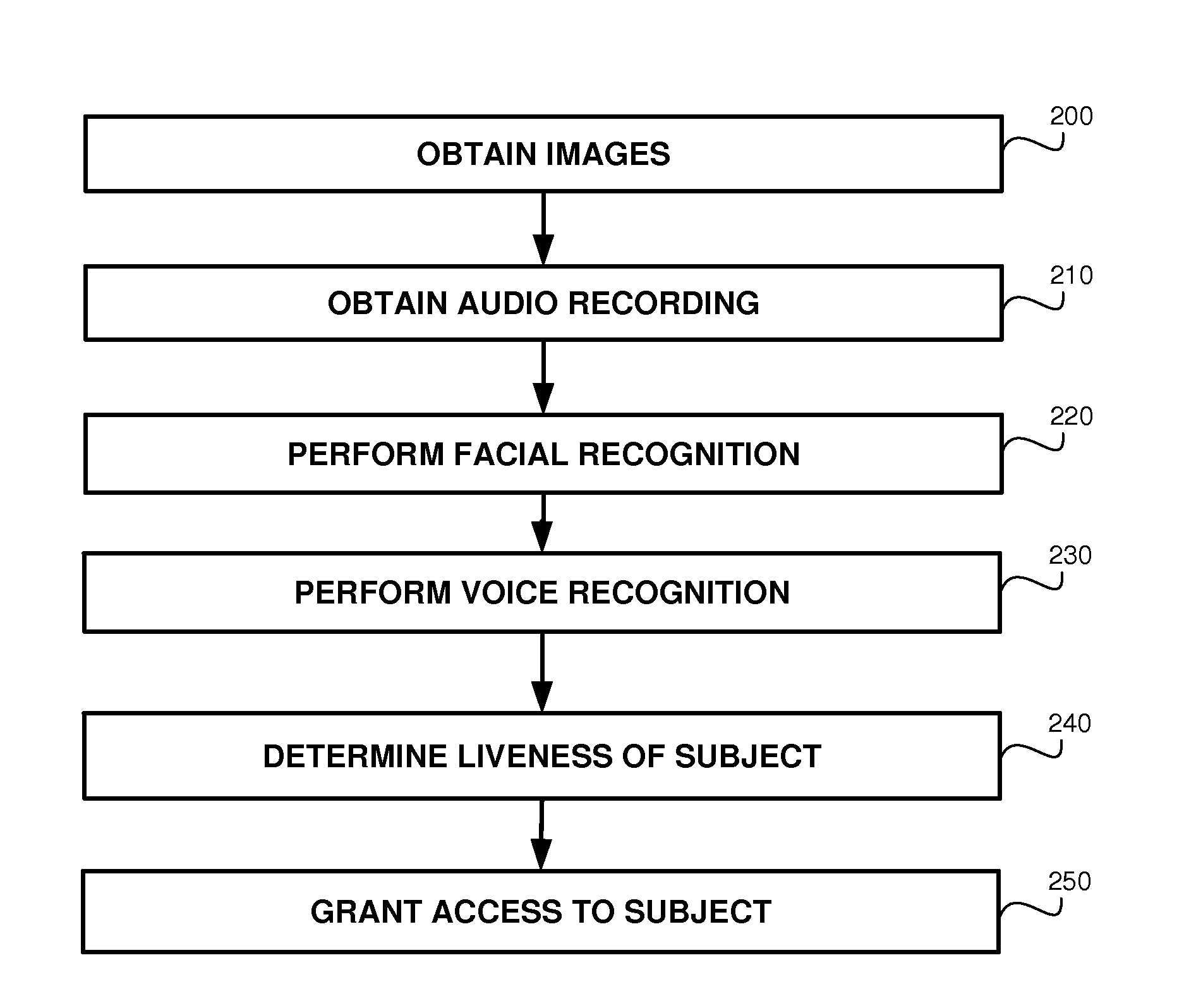
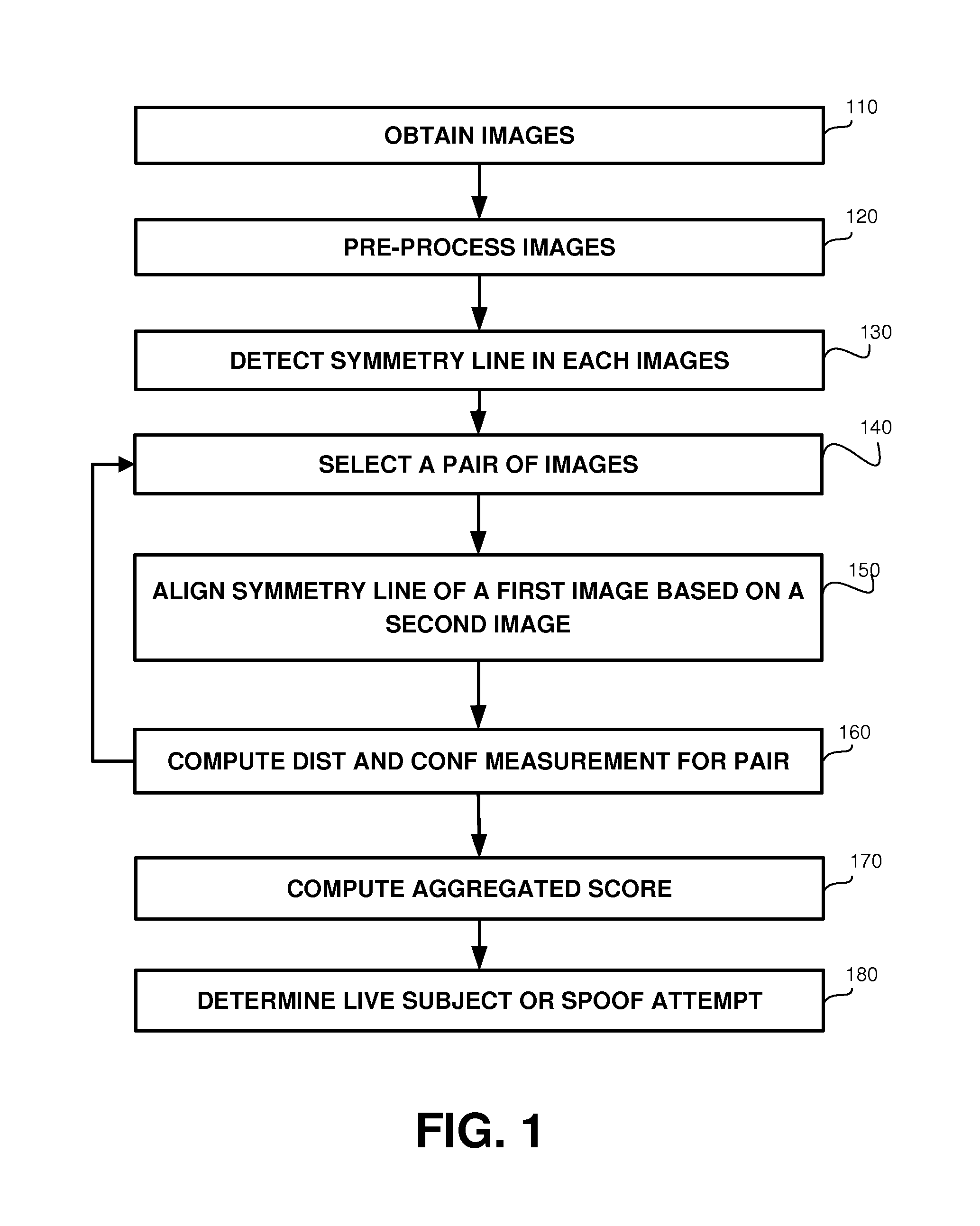
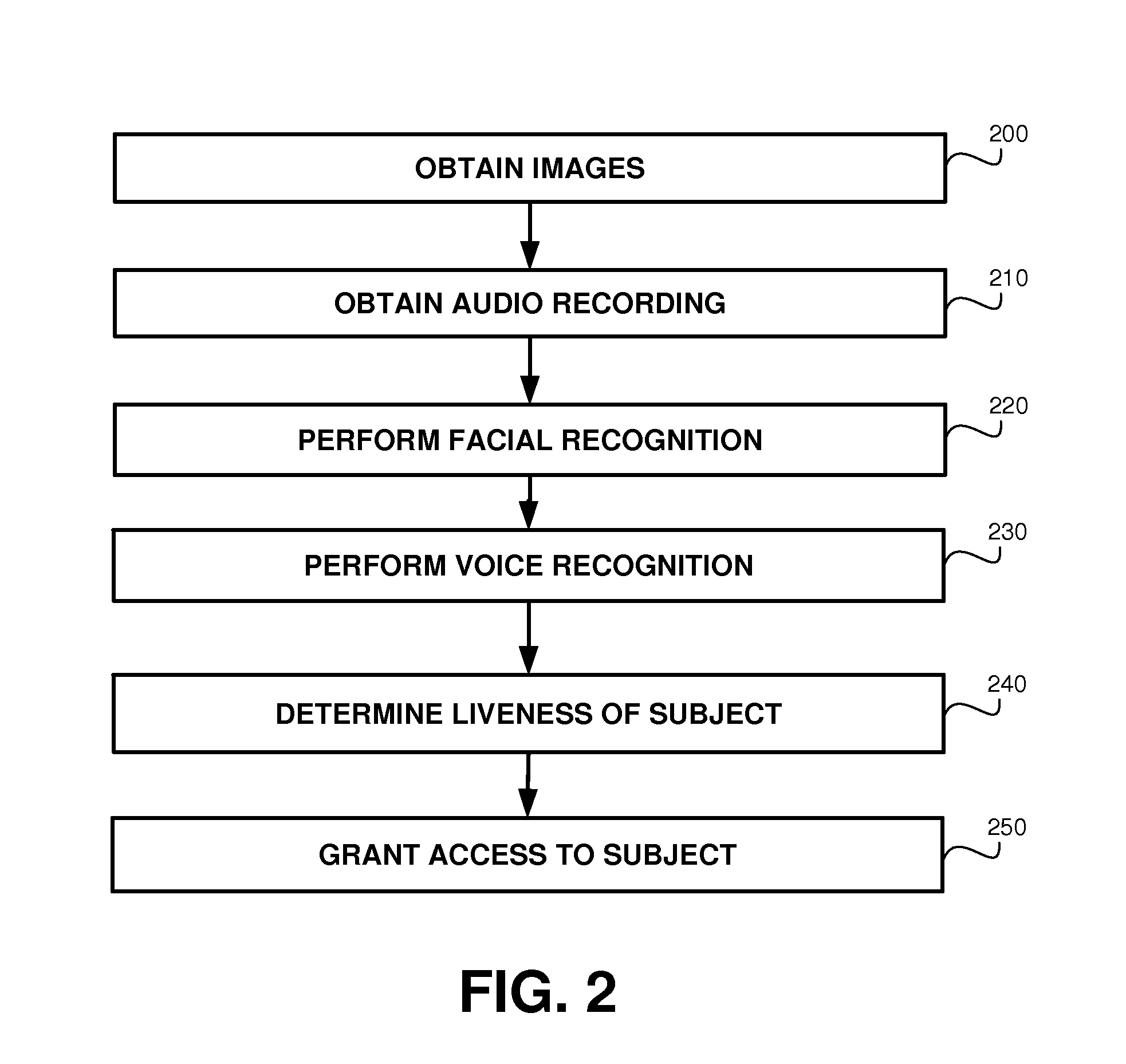
Liveness detector for face verification
A method, product and system for implementing liveness detector for face verification. A method comprising detecting a symmetry line of the face; and verifying that the subject moved the mouth by computing a score based on values of a pair of images in the symmetry lines, wherein the score is indicative to a difference in the shape of the mouth between the pair of images. Another method comprises: verifying identity of a subject based on facial recognition and voice recognition, said verifying comprise determining there is mouth movement in an image sequence, wherein said determining comprises: in each image of the sequence, detecting a symmetry line of the face; and verifying that the subject moved the mouth, wherein said verifying comprises: computing a score based on comparison of symmetry lines of the face in different images of the set of images; and comparing the score with a threshold.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com