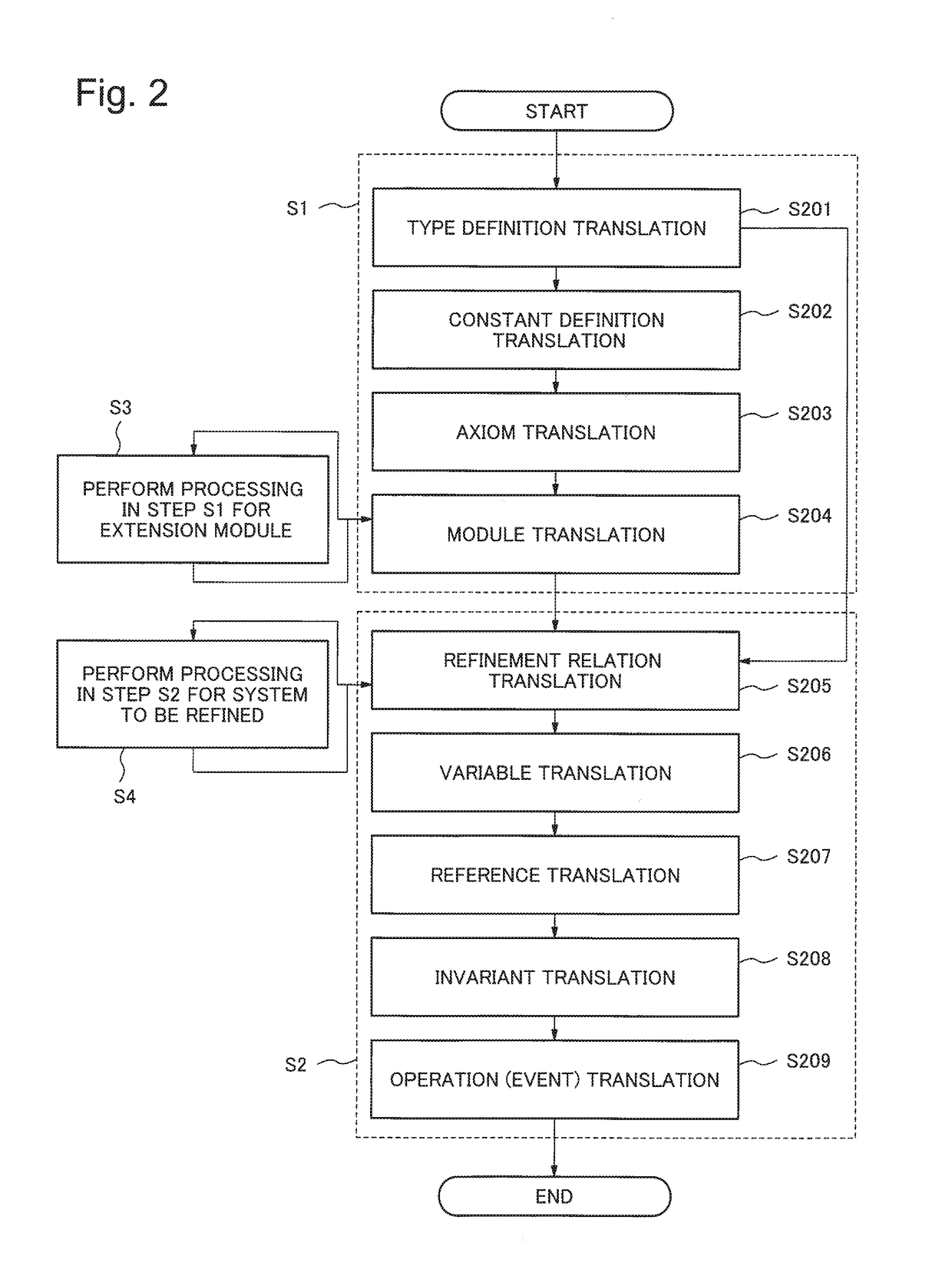
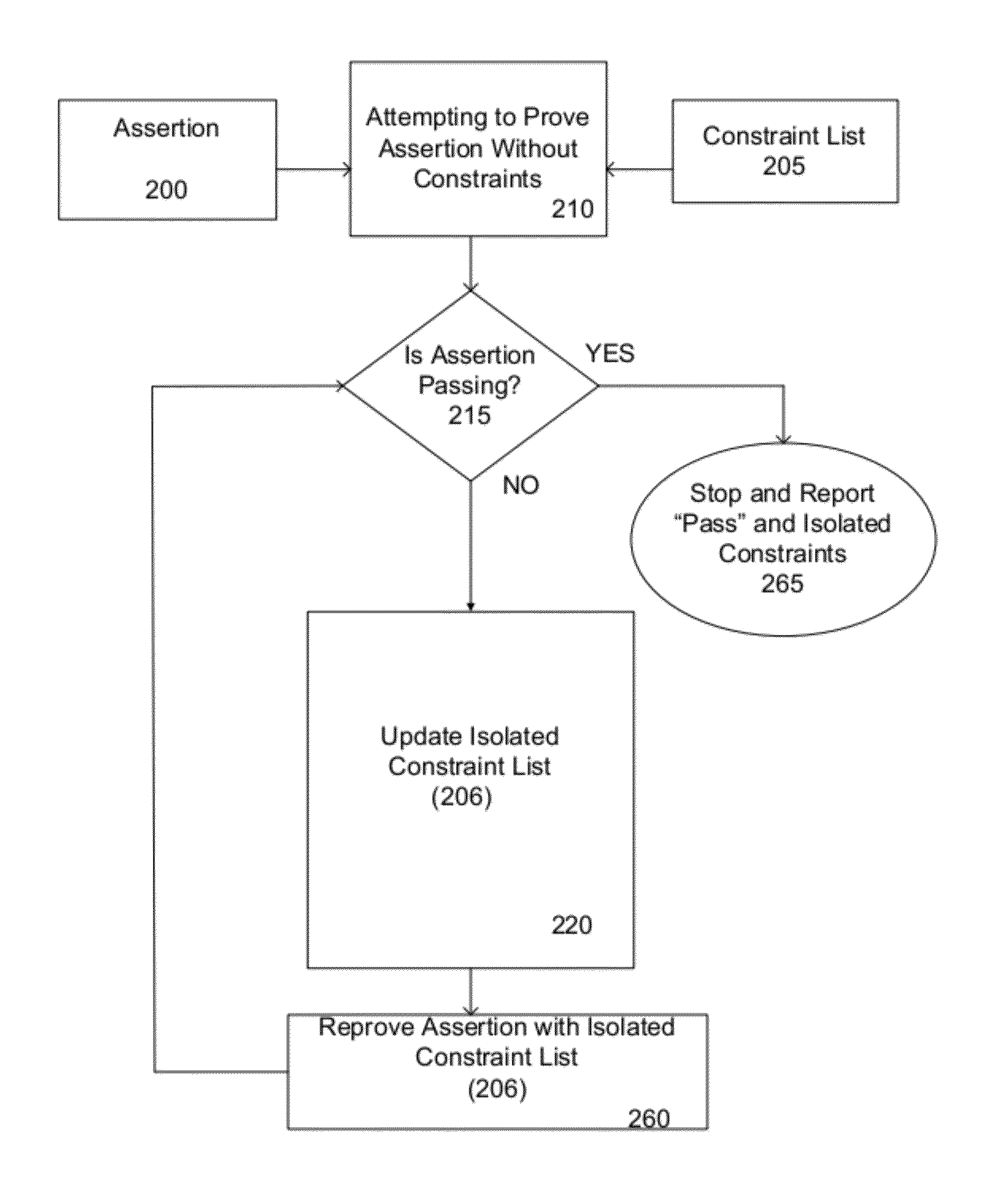
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
109 results about "Formal specification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
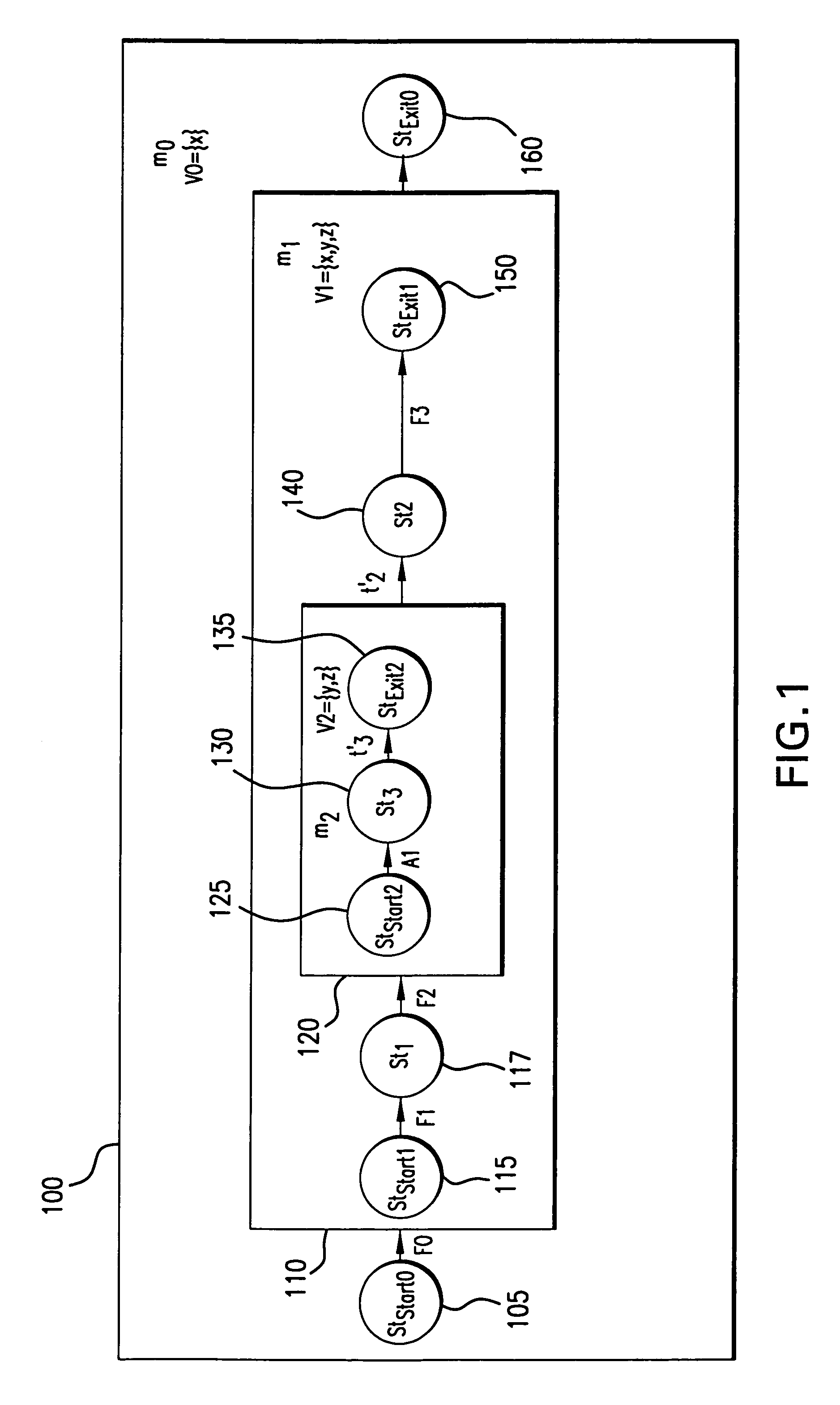
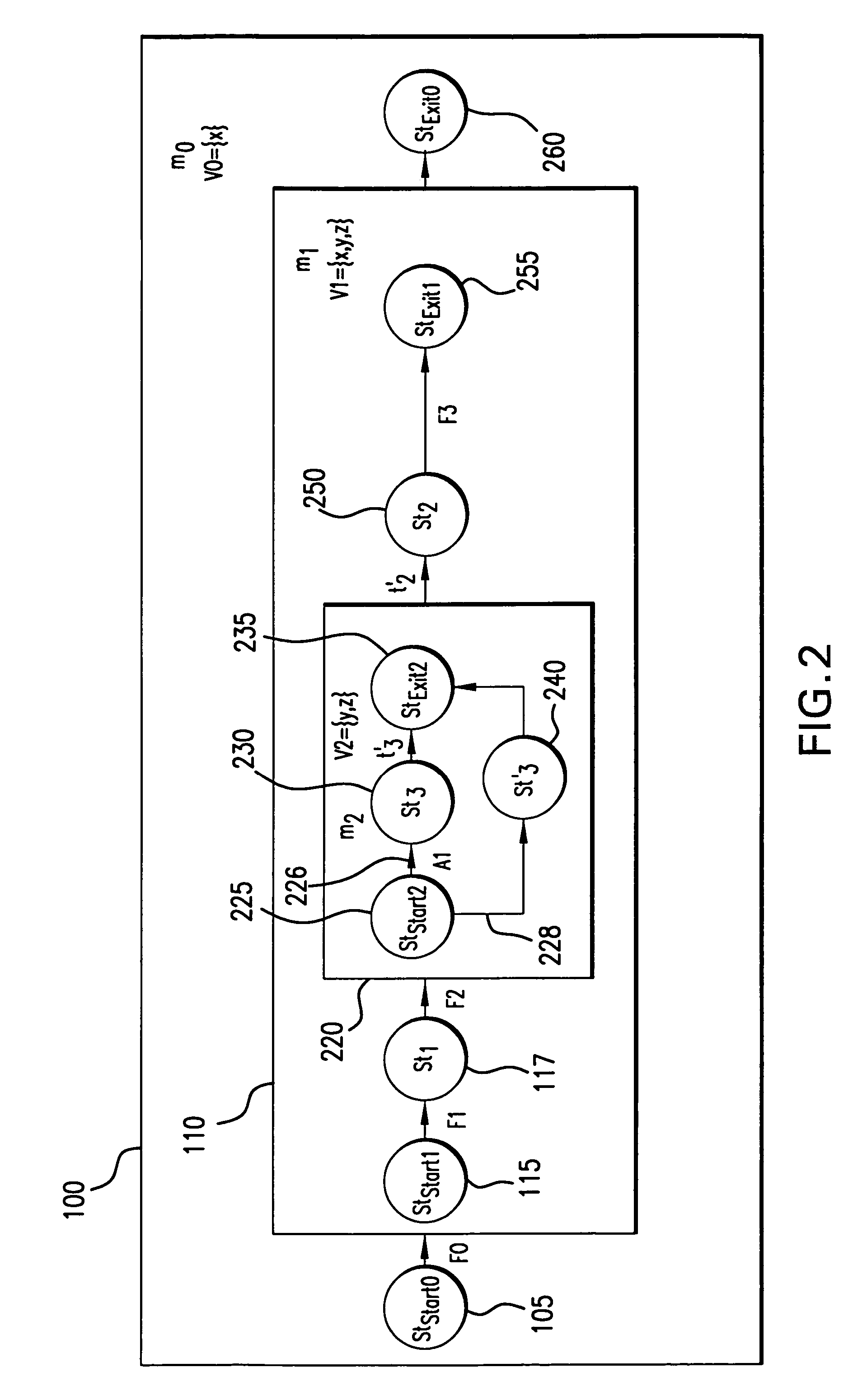
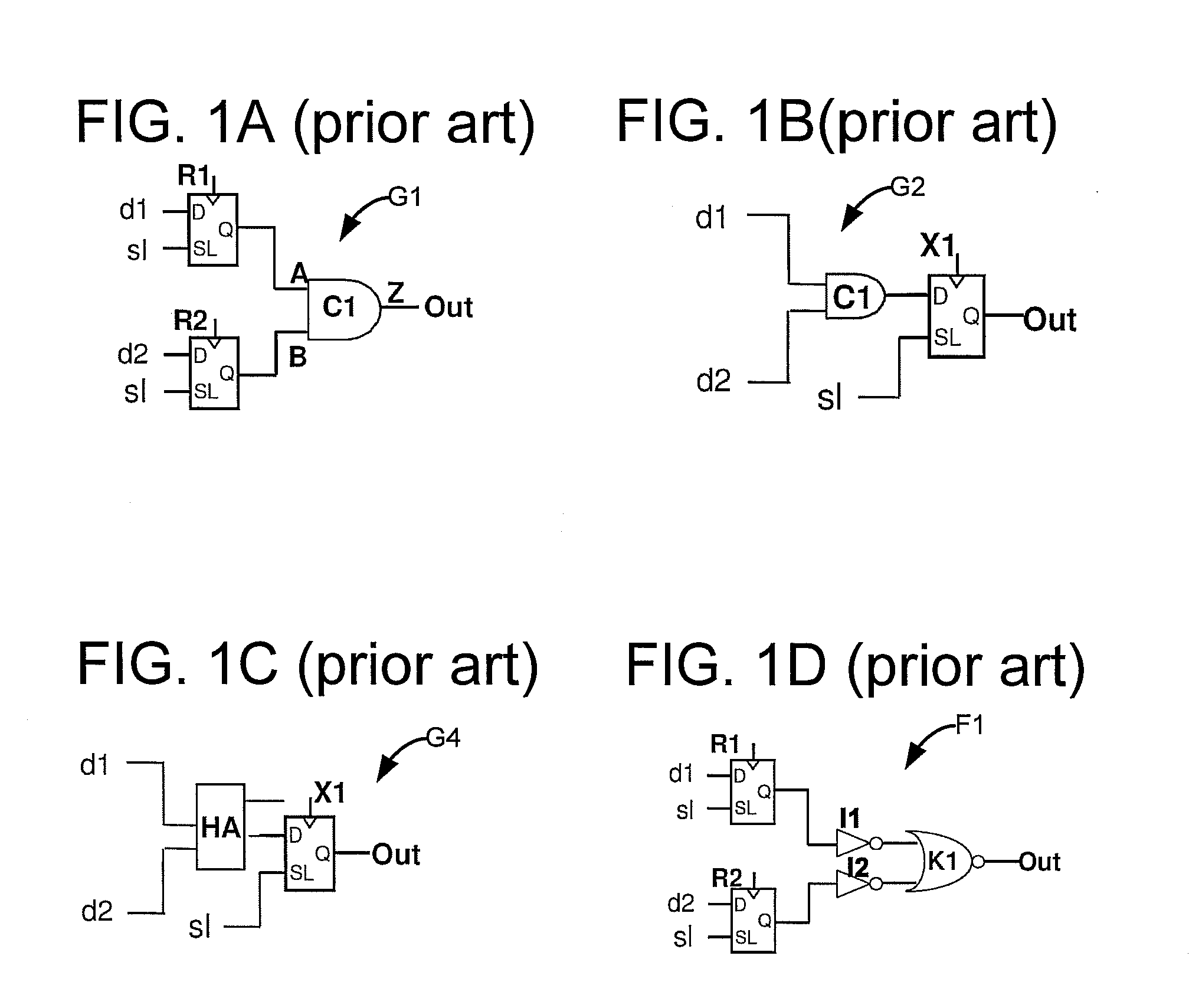
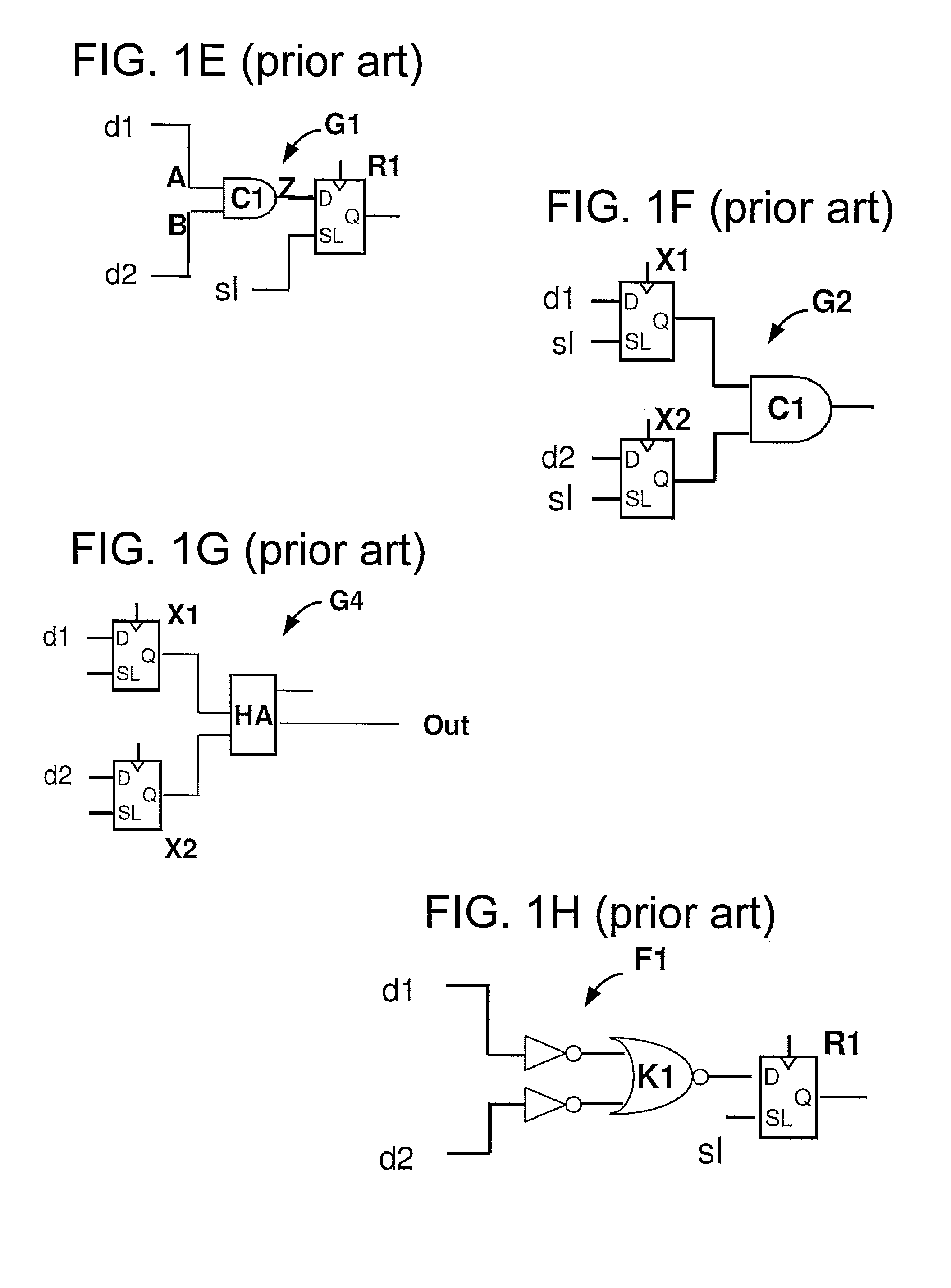
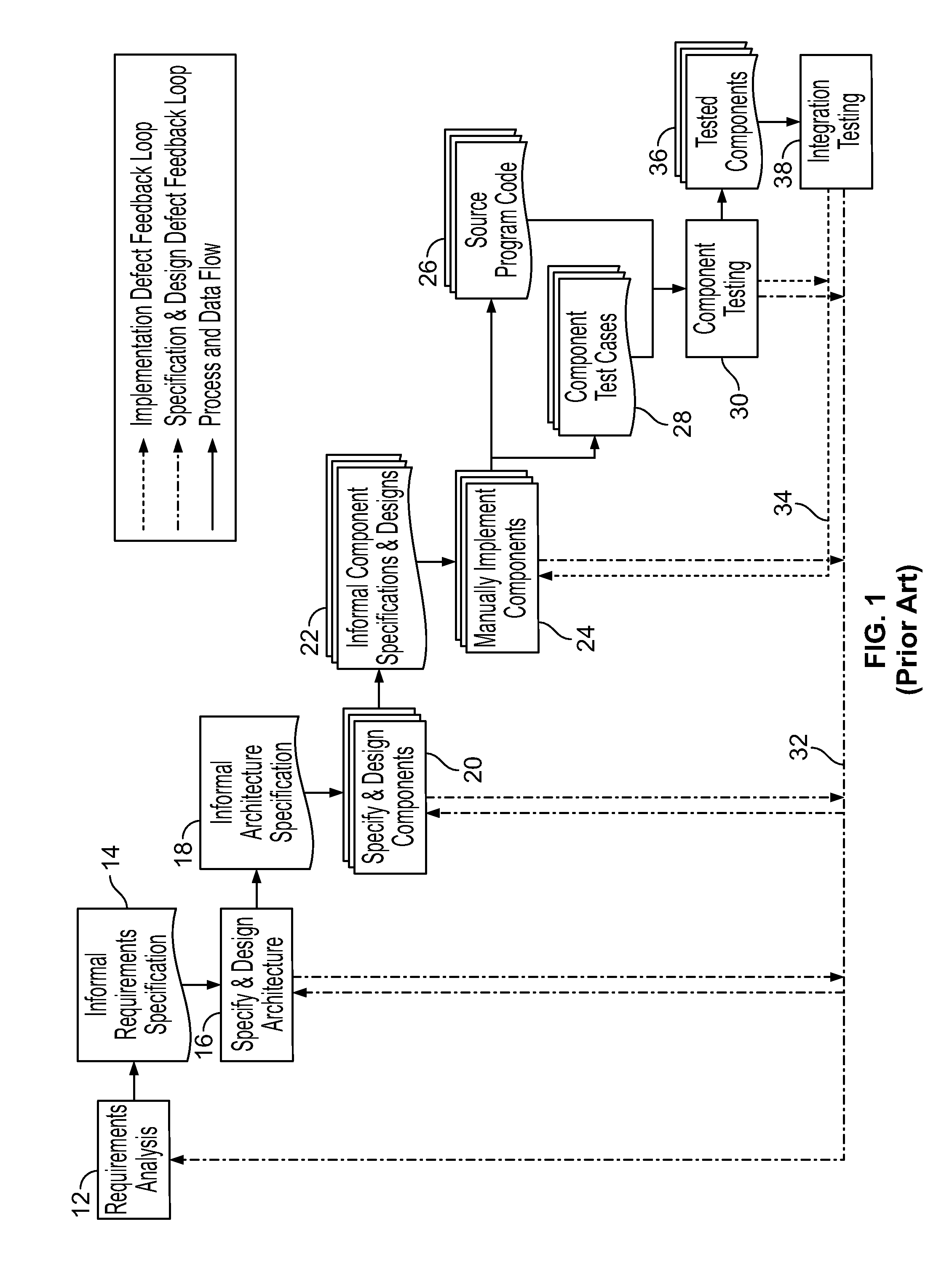
In computer science, formal specifications are mathematically based techniques whose purpose are to help with the implementation of systems and software. They are used to describe a system, to analyze its behavior, and to aid in its design by verifying key properties of interest through rigorous and effective reasoning tools. These specifications are formal in the sense that they have a syntax, their semantics fall within one domain, and they are able to be used to infer useful information.
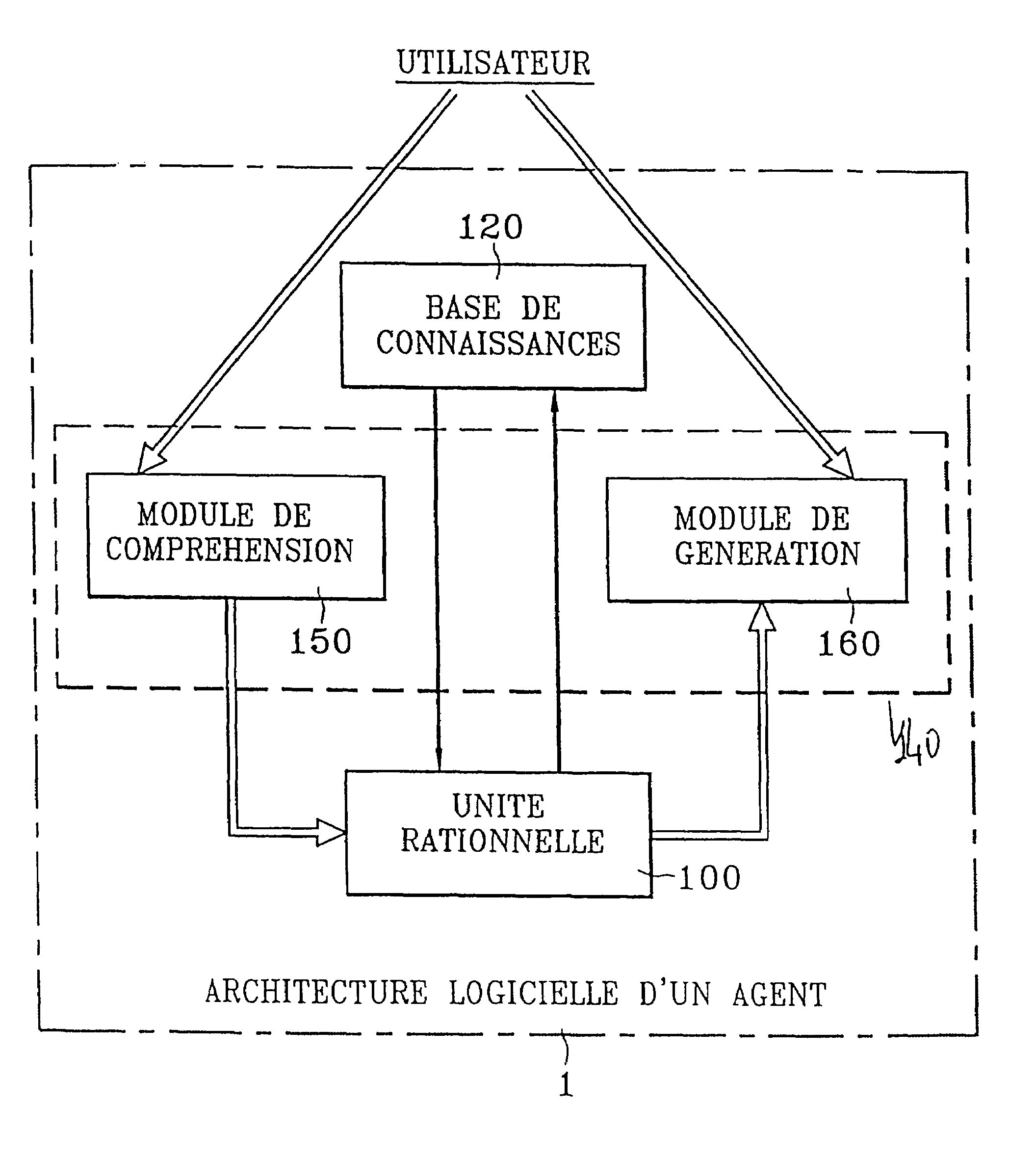
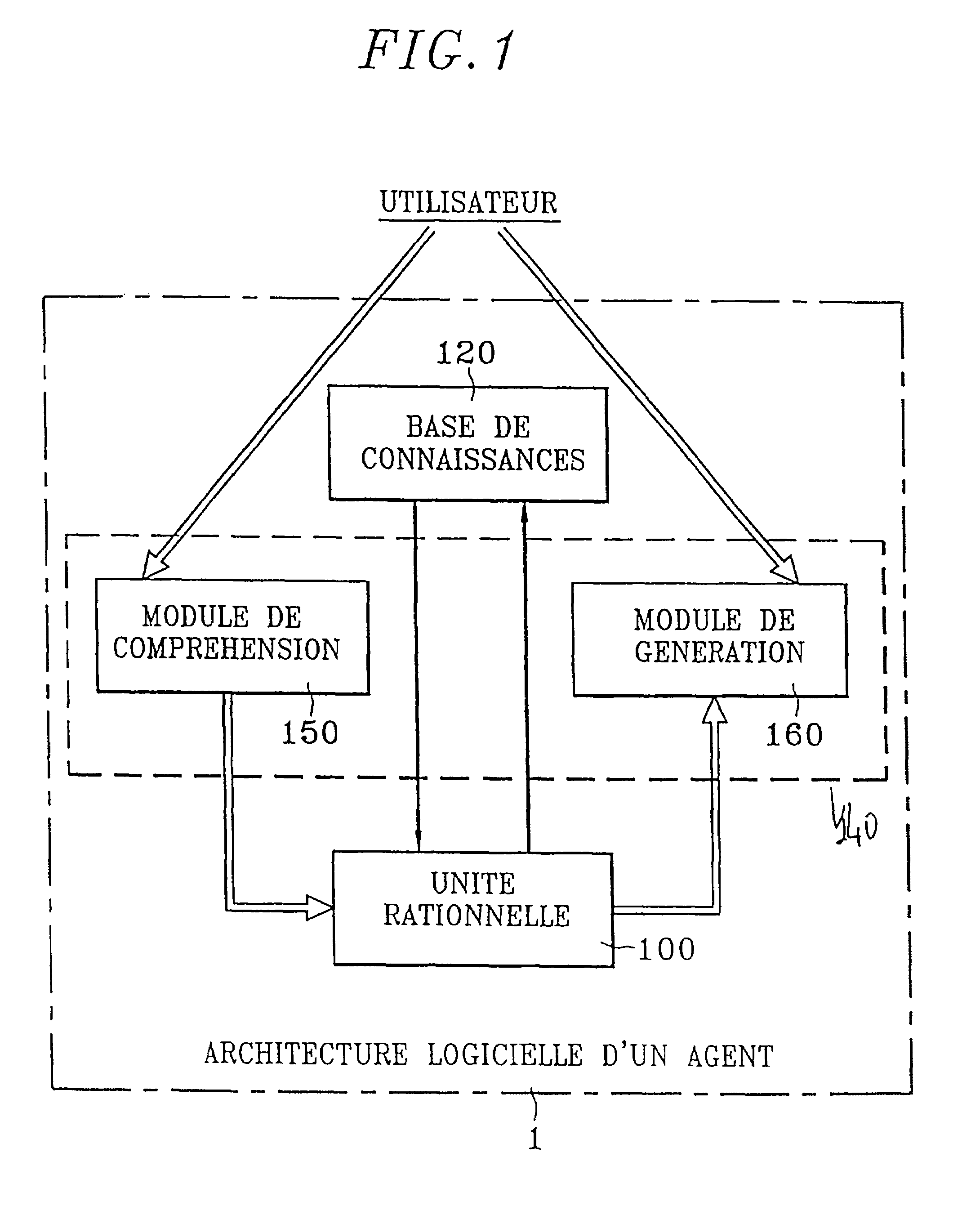
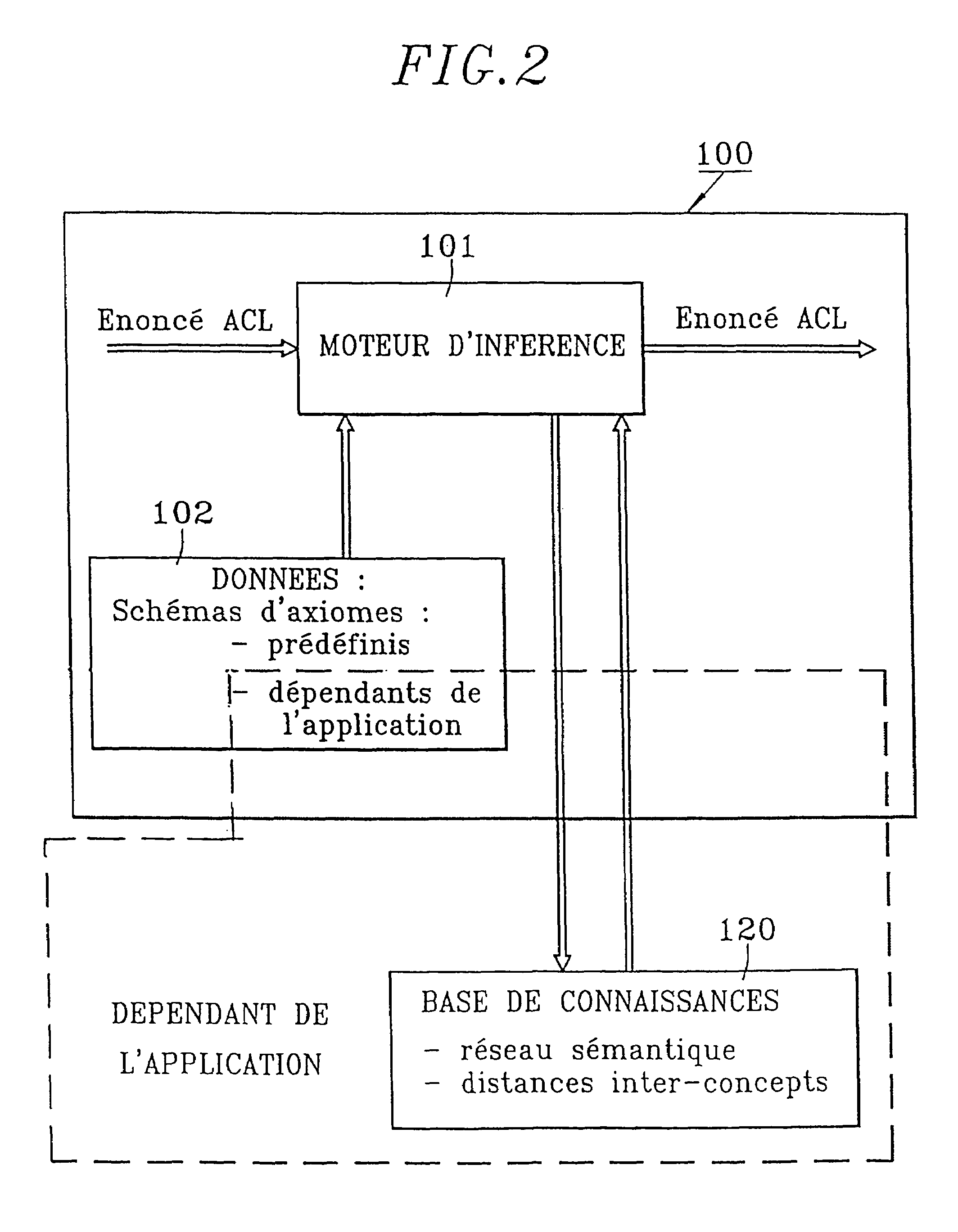
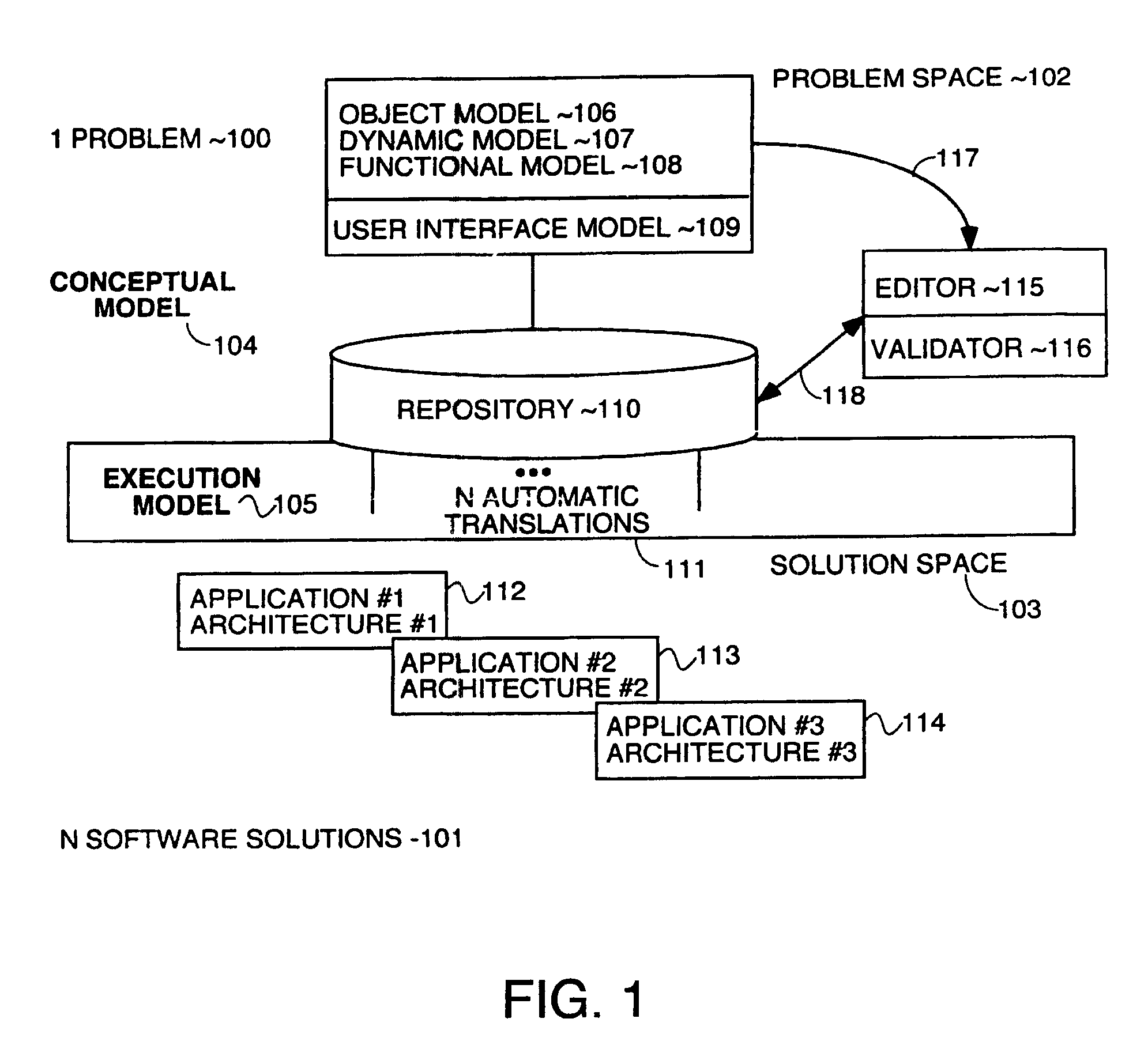
Model and method for using an interactive rational agent, multiagent server and system implementing same
A model and implementation process of a conversational rational agent as a kernel of a dialogue system and / or as an element (agent) of a multiagent system including definition of a conceptual architecture of a conversational rational agent; formal specification of the different components of this architecture and their combination permitting a formal model to be obtained; definition of the software architecture implementing the formal architecture; and definition of implementation mechanisms of the formal specifications, the rational agent being suited both to converse with another agent or with a user of the system through any communication medium.
Owner:FRANCE TELECOM SA
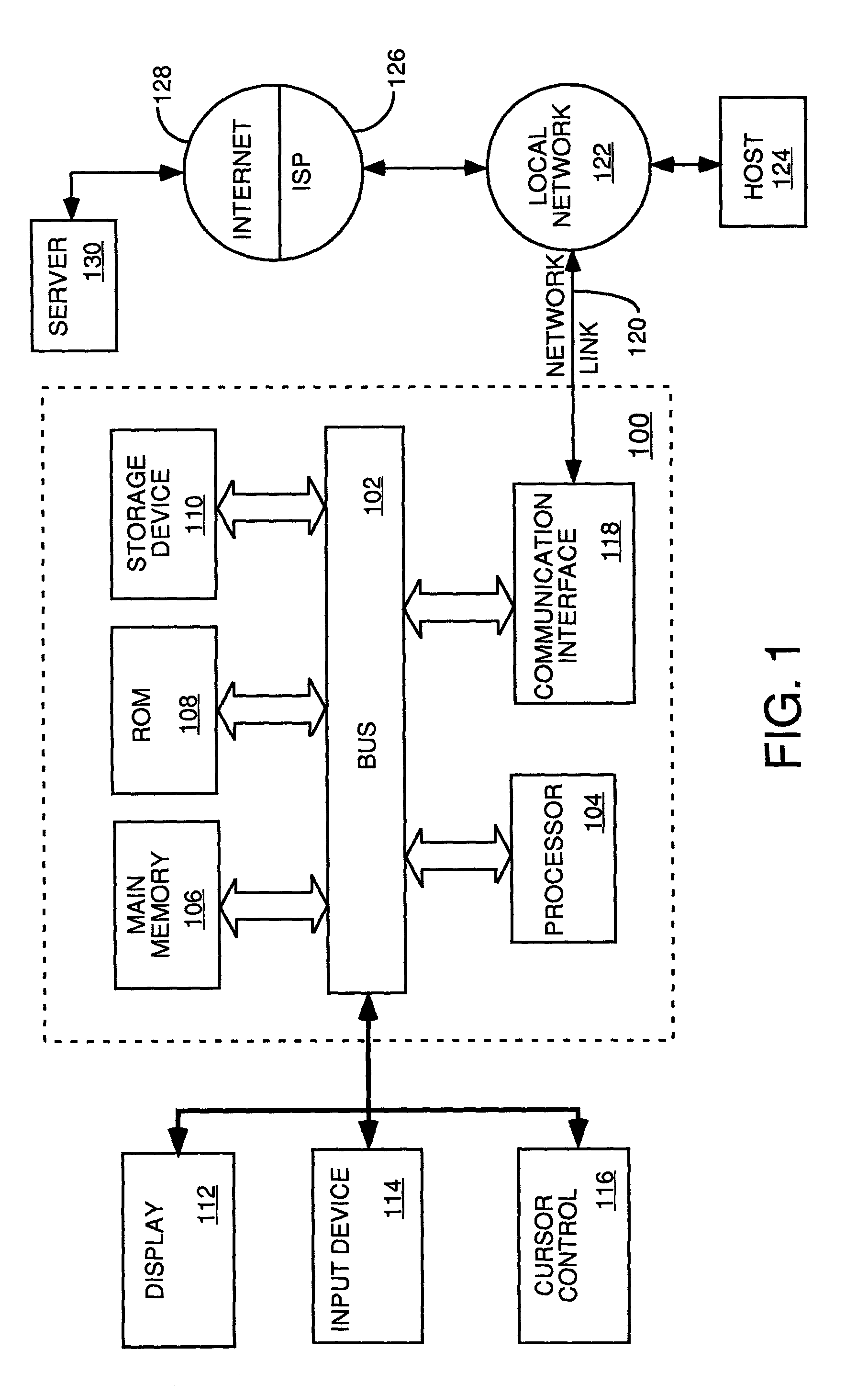
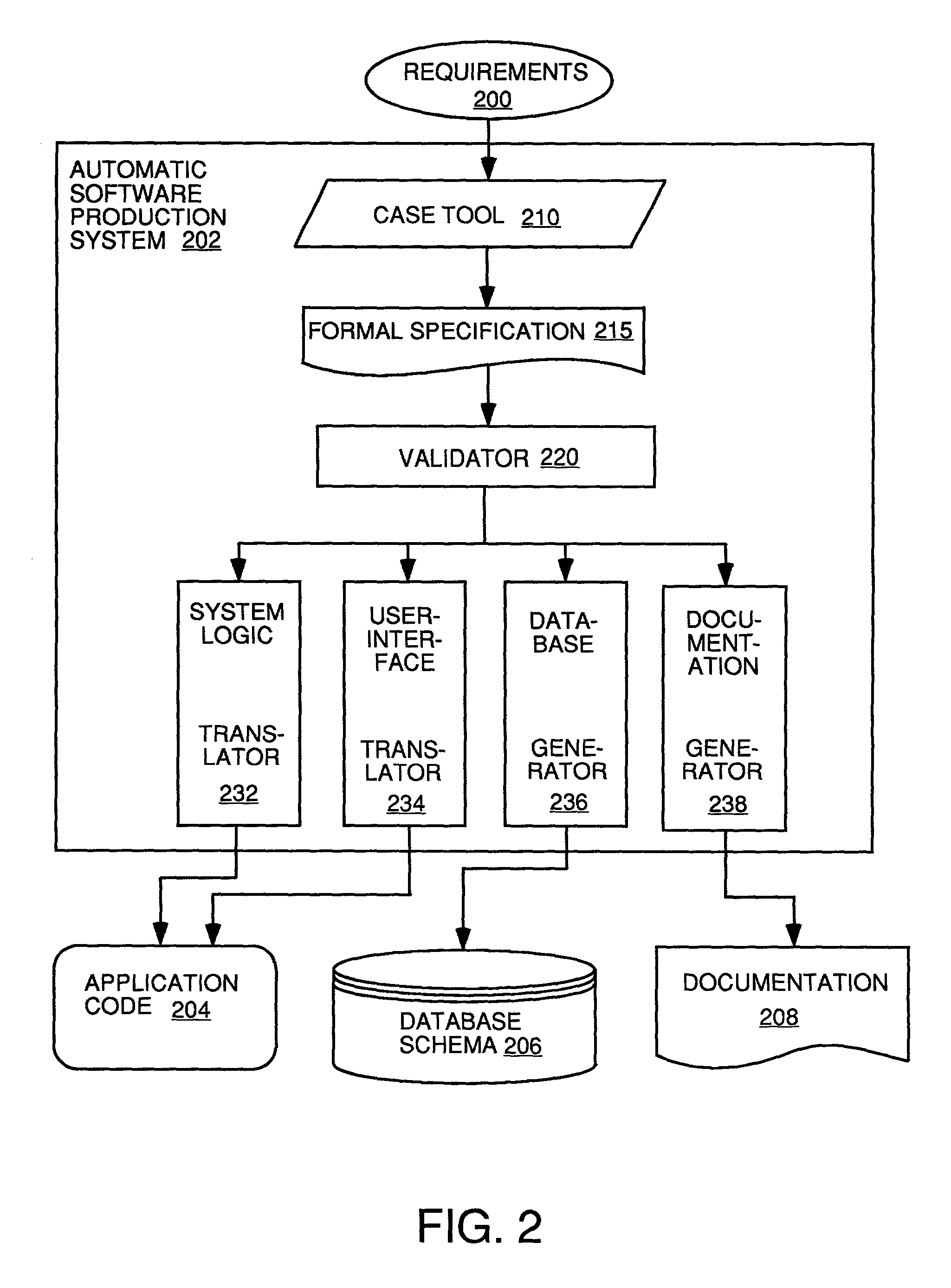
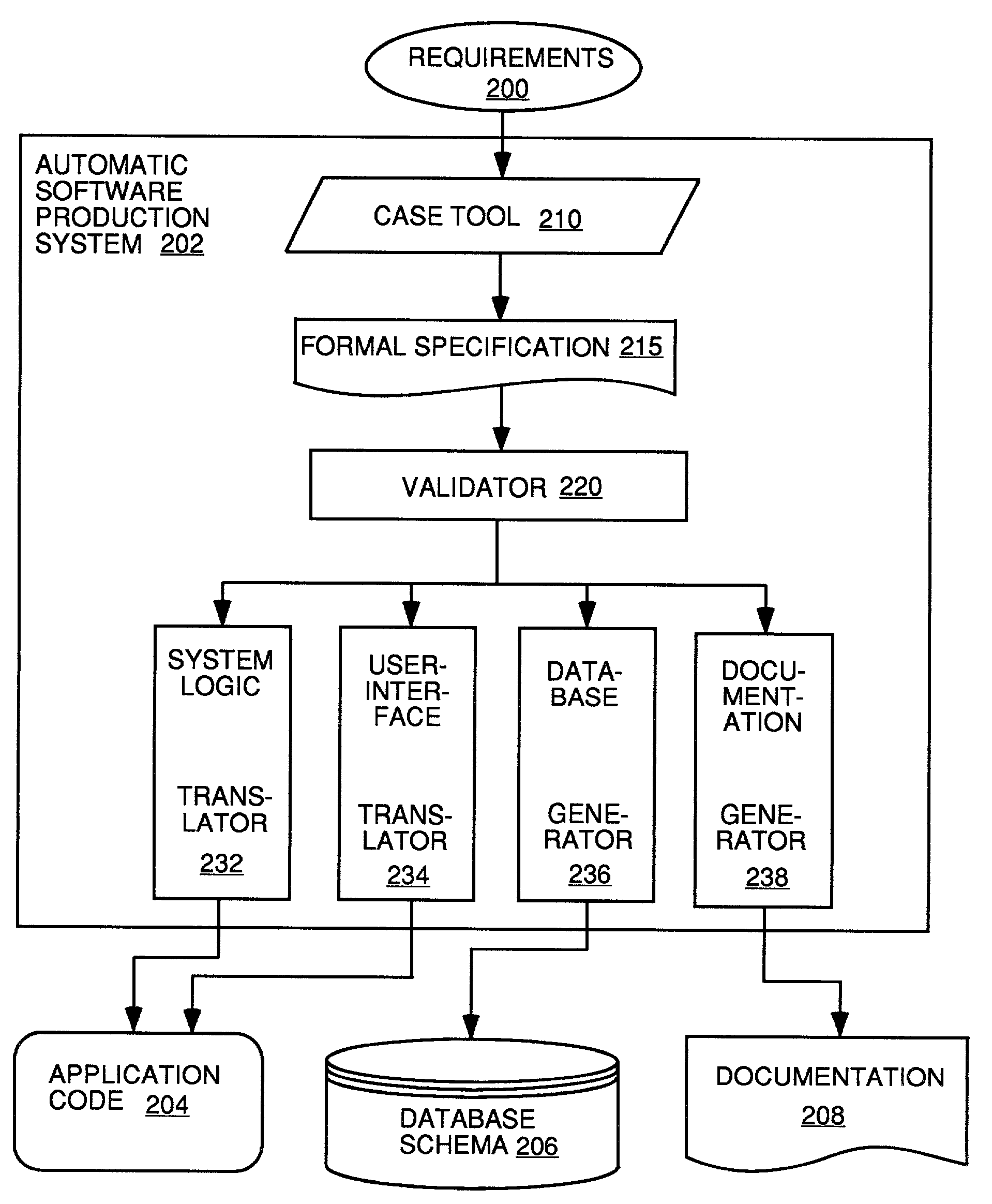
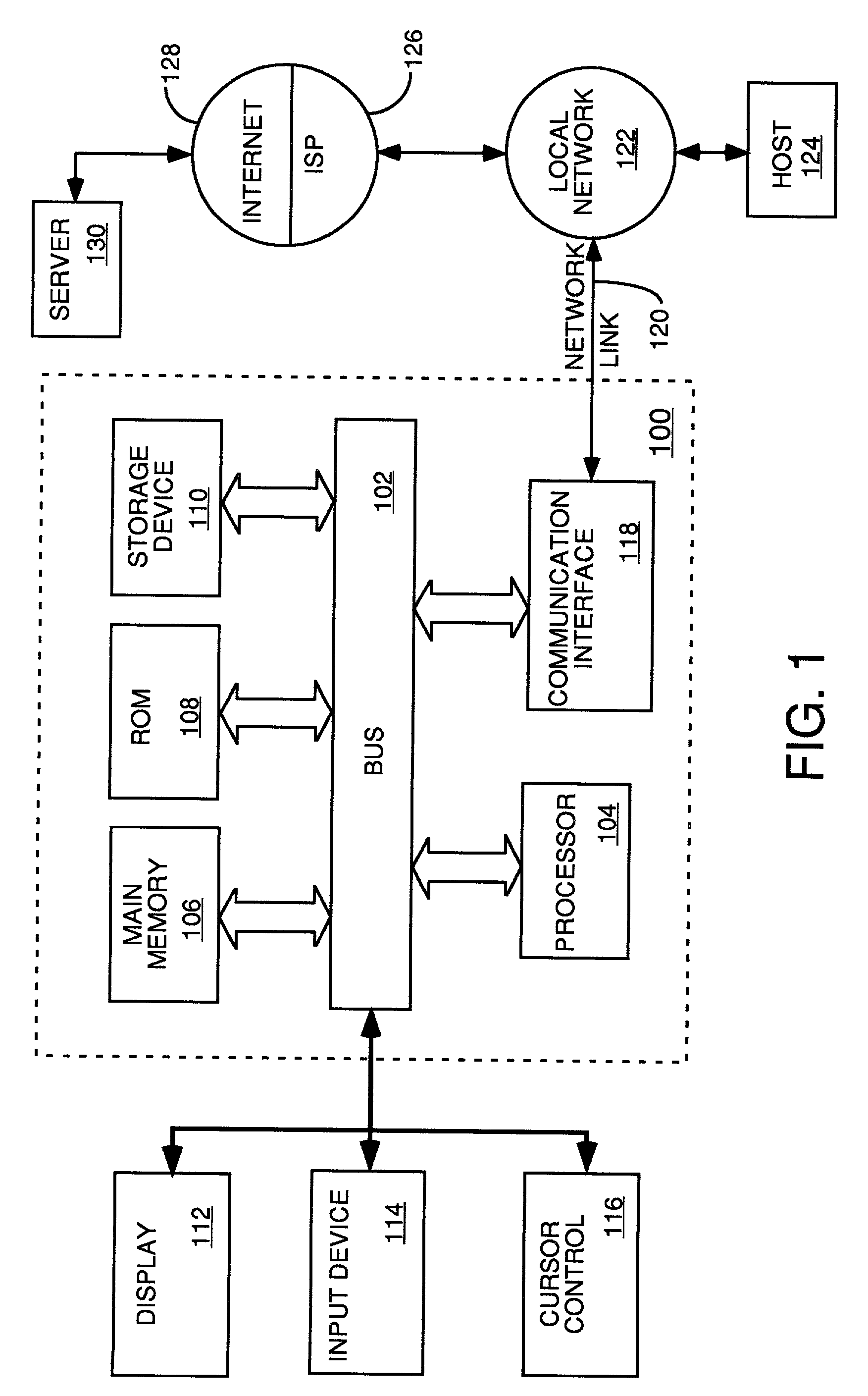
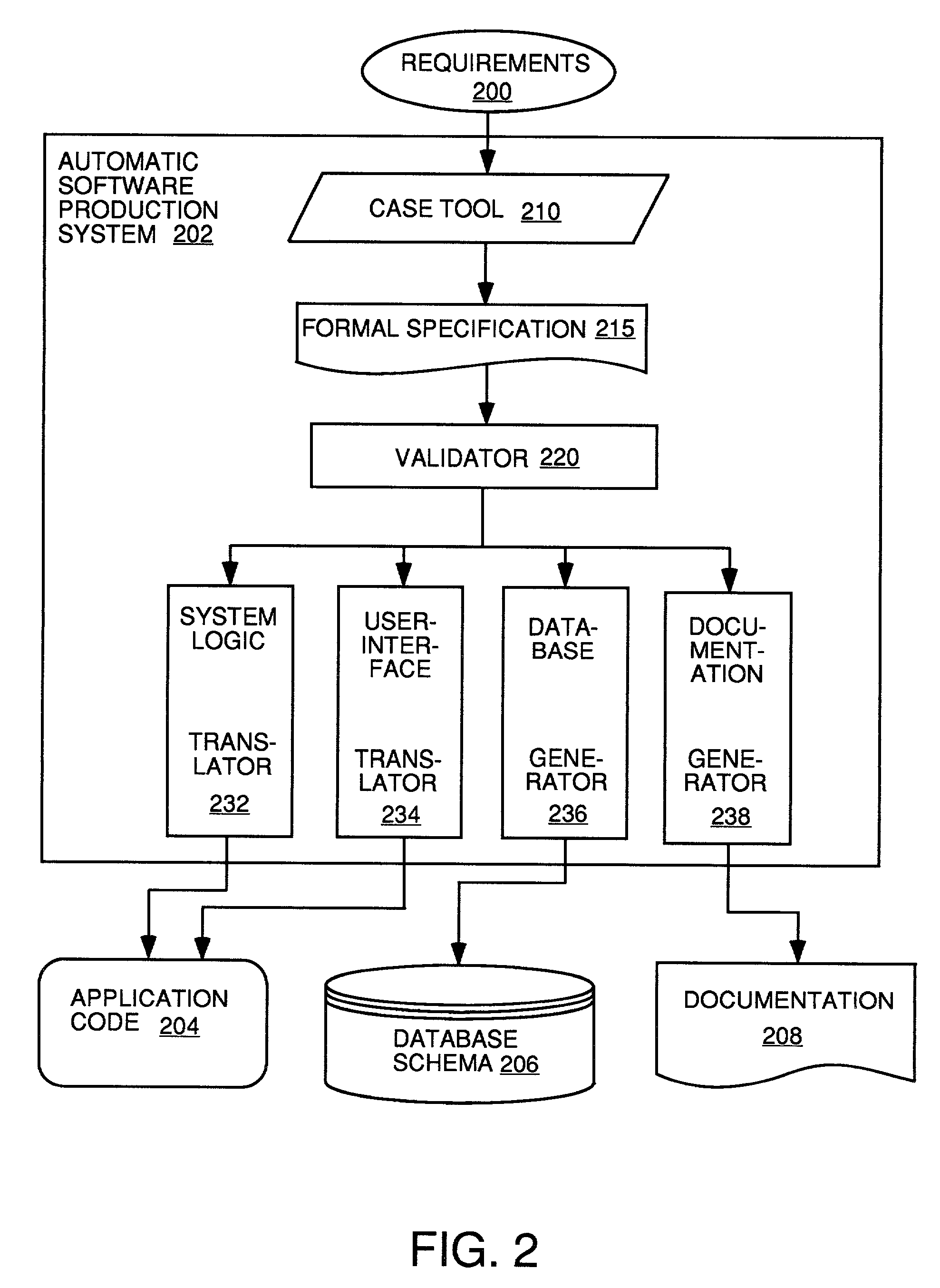
Automatic software production system
InactiveUS7137100B2Shorten the time to marketEasy to useDigital data information retrievalProgram documentationHandling CodeSystem requirements
Owner:SOSY
Automatic software production system
InactiveUS20030167455A1Shorten the time to marketEasy to useDigital data information retrievalProgram documentationHandling CodeSystem requirements
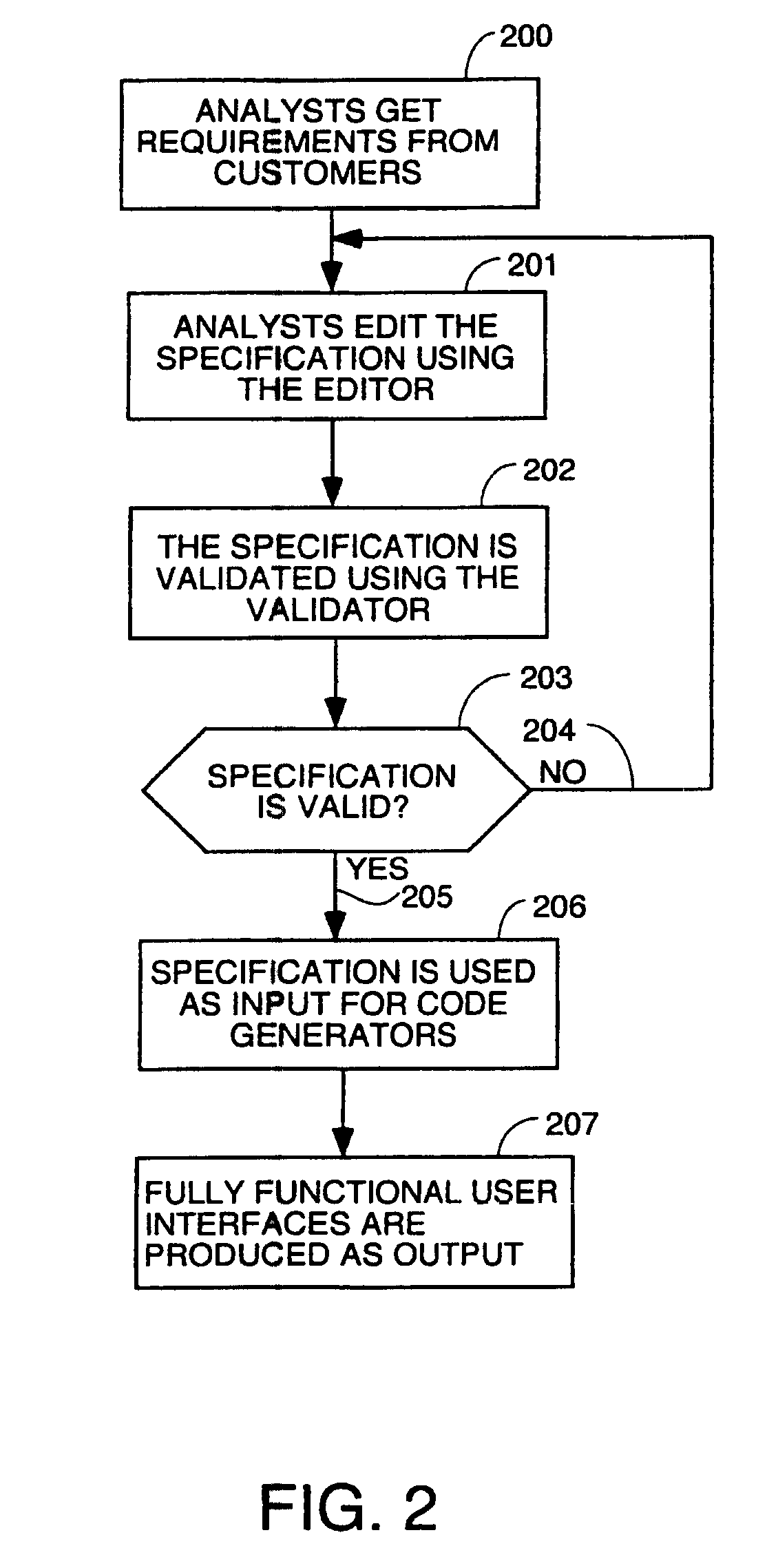
An automated software production system is provided, in which system requirements are captured, converted into a formal specification, and validated for correctness and completeness. In addition, a translator is provided to automatically generate a complete, robust software application based on the validated formal specification, including user-interface code and error handling code.
Owner:IBORRA JOSE +1
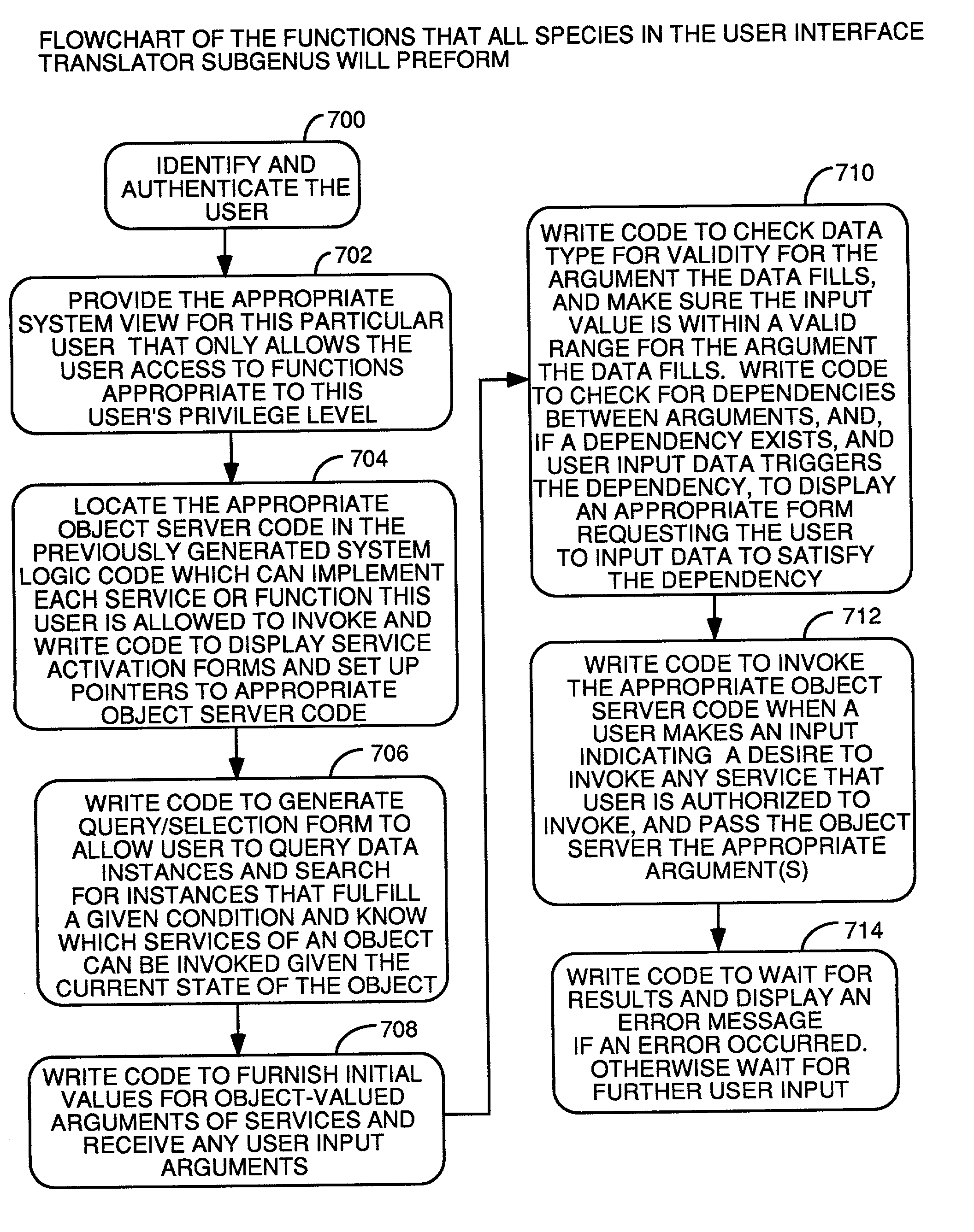
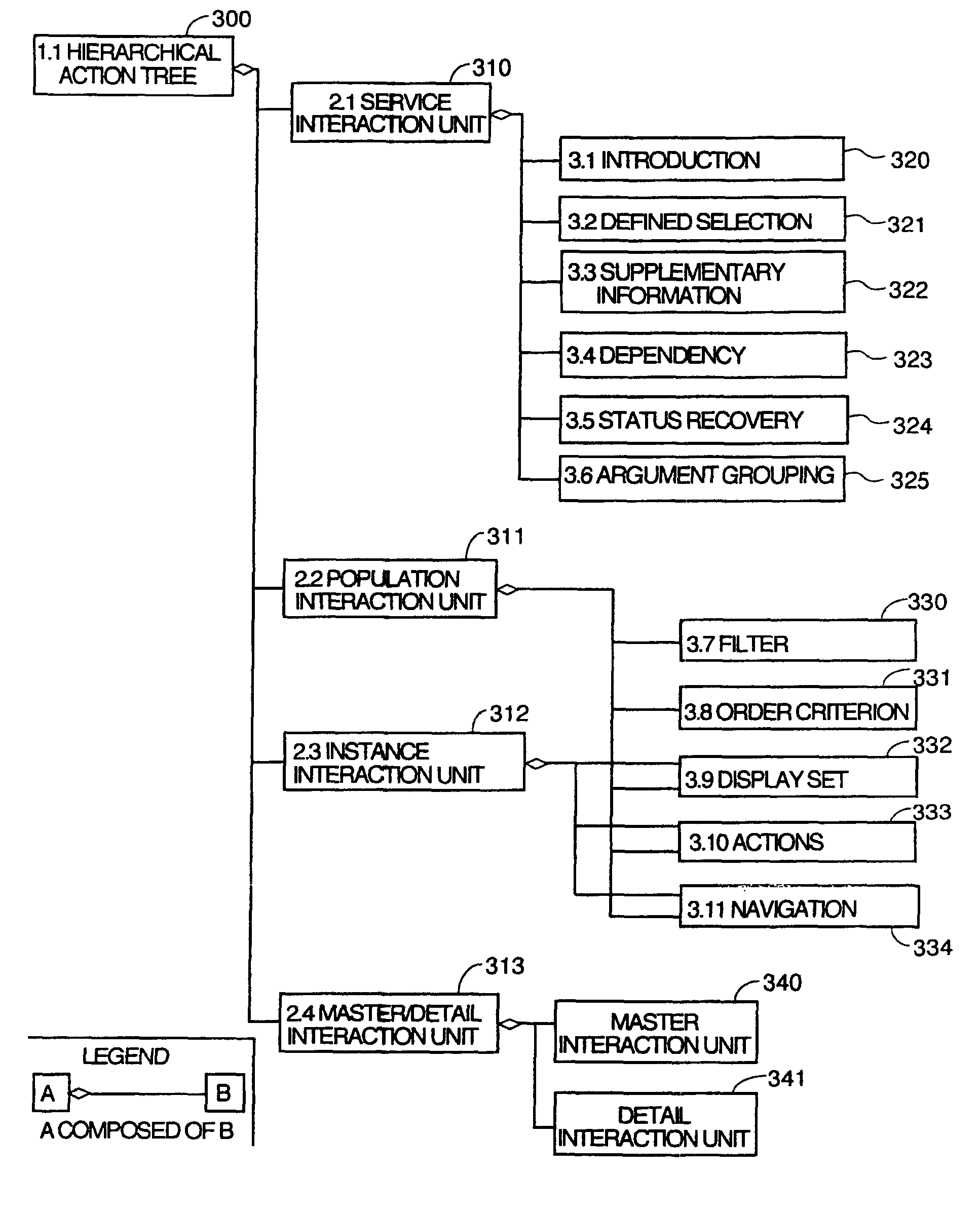
Method and apparatus for automatic generation of information system user interfaces
InactiveUS7941438B2Digital data information retrievalDigital data processing detailsGraph editorPattern language
A system for automatic software production including specification and automatic generation of user interfaces is disclosed. A graphical editor presents diagrams and textual interactive dialogs which are used to enter requirements data defining the desired structure and behaviour of an application program being designed. The requirements data is automatically converted to formal counterparts in a formal language to create a Formal Specification. The Formal Specification is stored in translation structures which are object in memory taking the form of classes which have methods to use the requirements data to articulate source code templates which become source code components in the final output code. A Presentation Model based in a pattern language is used to specify a Presentation Model) using elements of the pattern language as meta-model building blocks which are articulated with requirements data that defines the specifics of the desired user interface.
Owner:SOSY
Analytical Software Design System
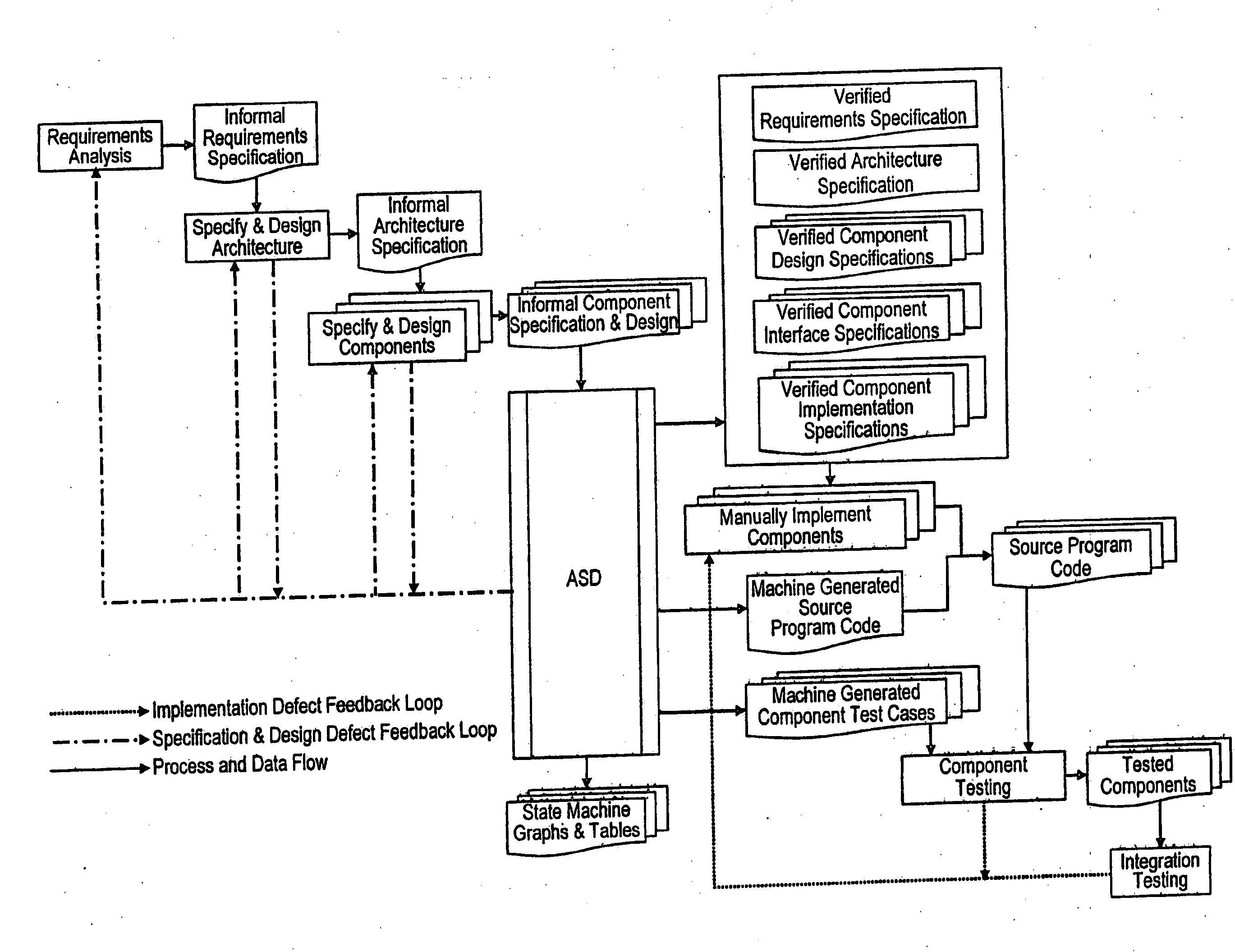
ActiveUS20080263506A1Improve effectivenessExpand coverageSoftware designRequirement analysisSystems designMathematical model
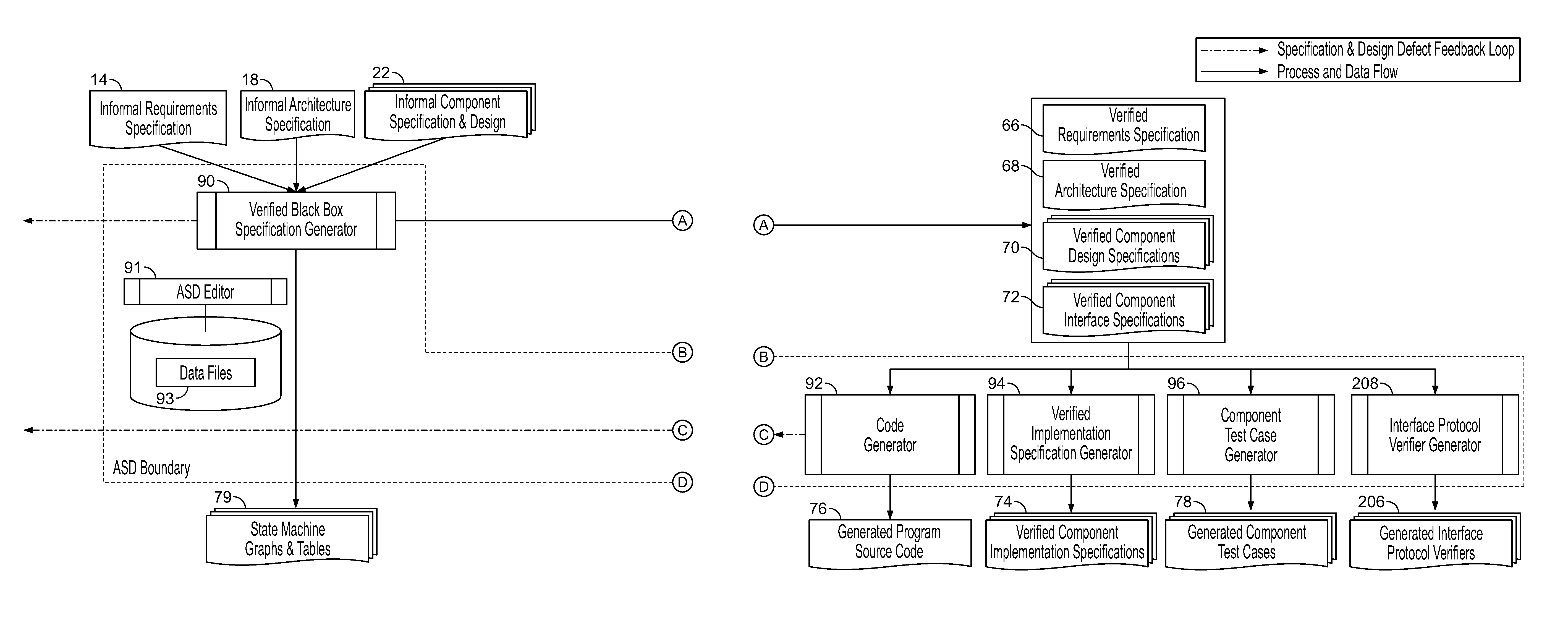
An analytical software design system arranged to receive informal system design specifications and to convert them into verified design specifications for use in creating source code and carrying out implementation testing of the source code is described. The system comprises a verified black box specification generator arranged to process the received informal system design specifications to create formal specifications; to generate from the formal specifications mathematical models representing the system behaviour; to analyse the mathematical models to determine if they have the required behaviour; to adjust the formal specifications until the required behaviour is achieved; and to derive the required verified design specifications from the mathematical models.
Owner:COCOTEC LTD
Method and system for forming skeletons for generating verification systems
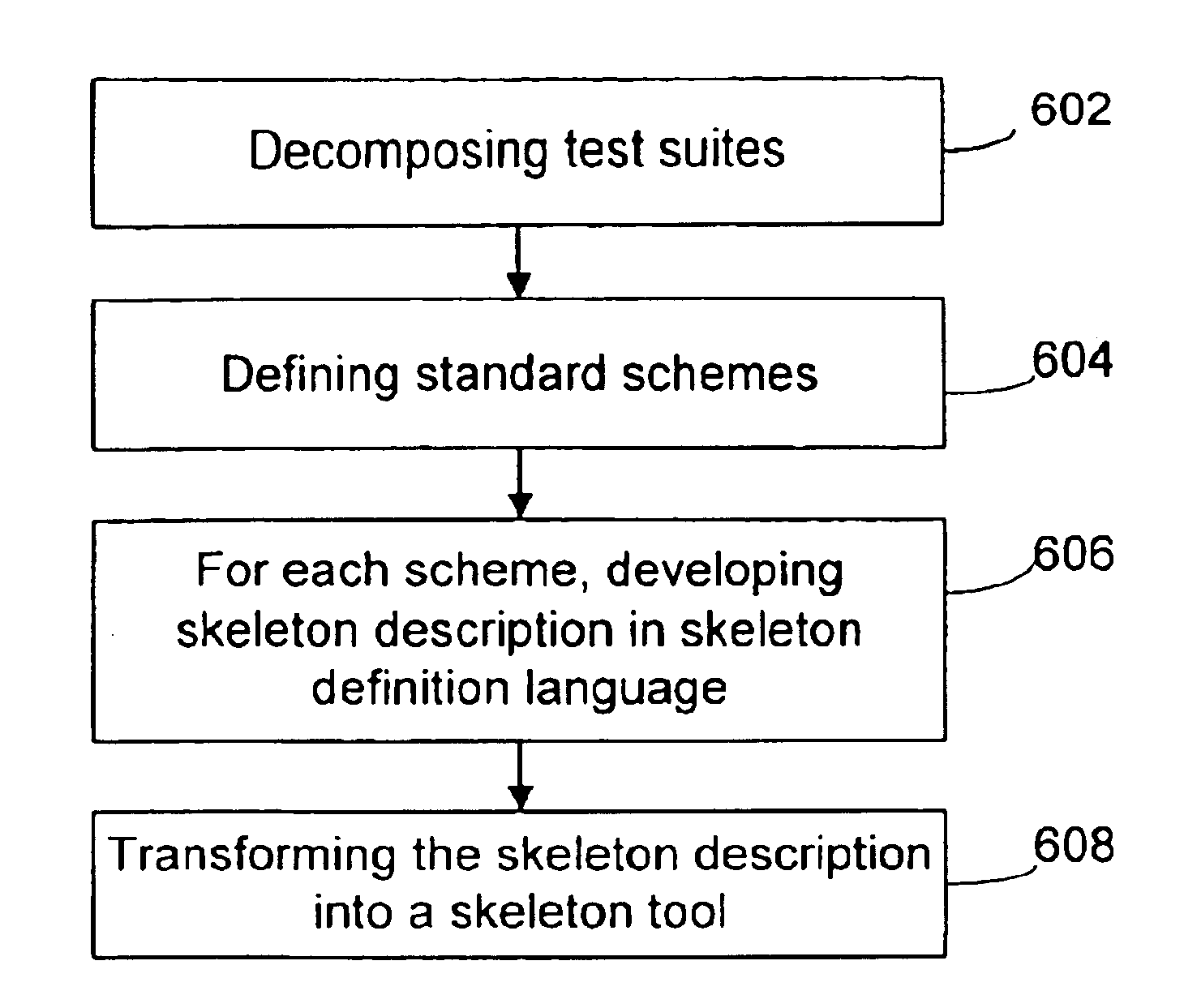
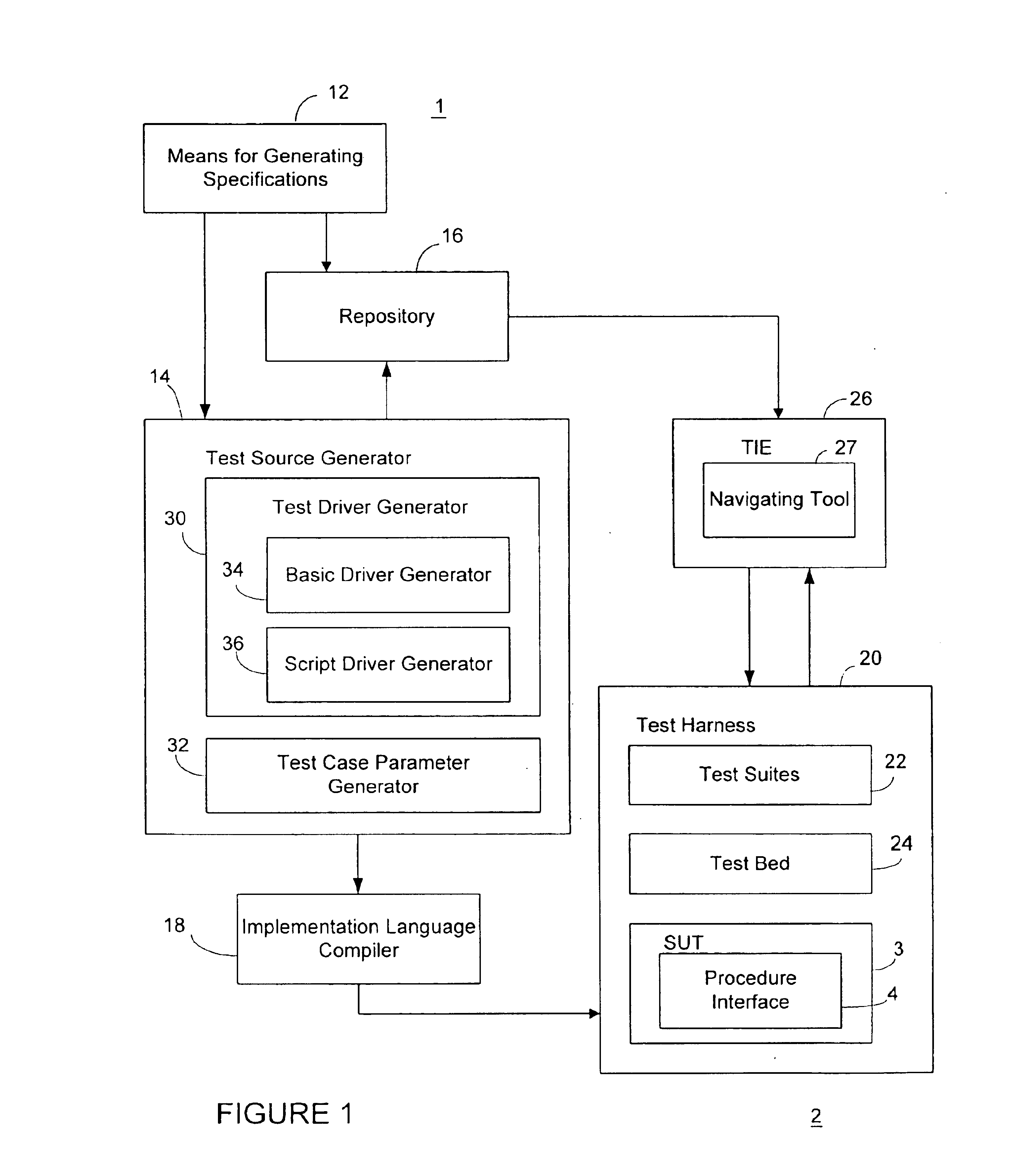
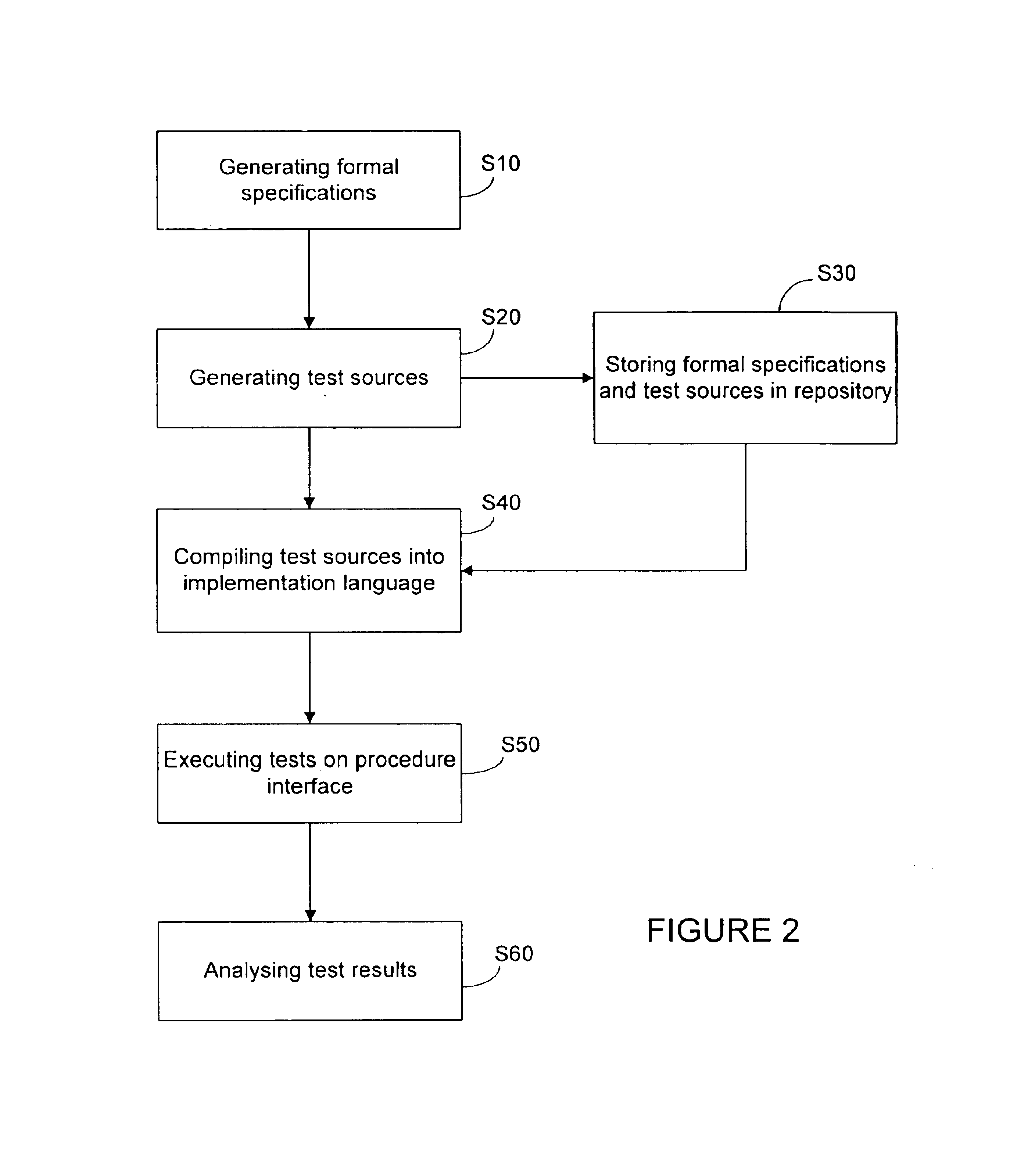
InactiveUS6898784B1Software testing/debuggingSpecific program execution arrangementsDecompositionTest suite
A verification system for a procedure interface is generated by using formal specifications of the procedure interface and generating test suites. The test suites are generated from the formal specifications and templates or skeletons which are used to generate an element of a verification system. The skeletons are generated based on decomposition of test suits.
Owner:RPX CLEARINGHOUSE
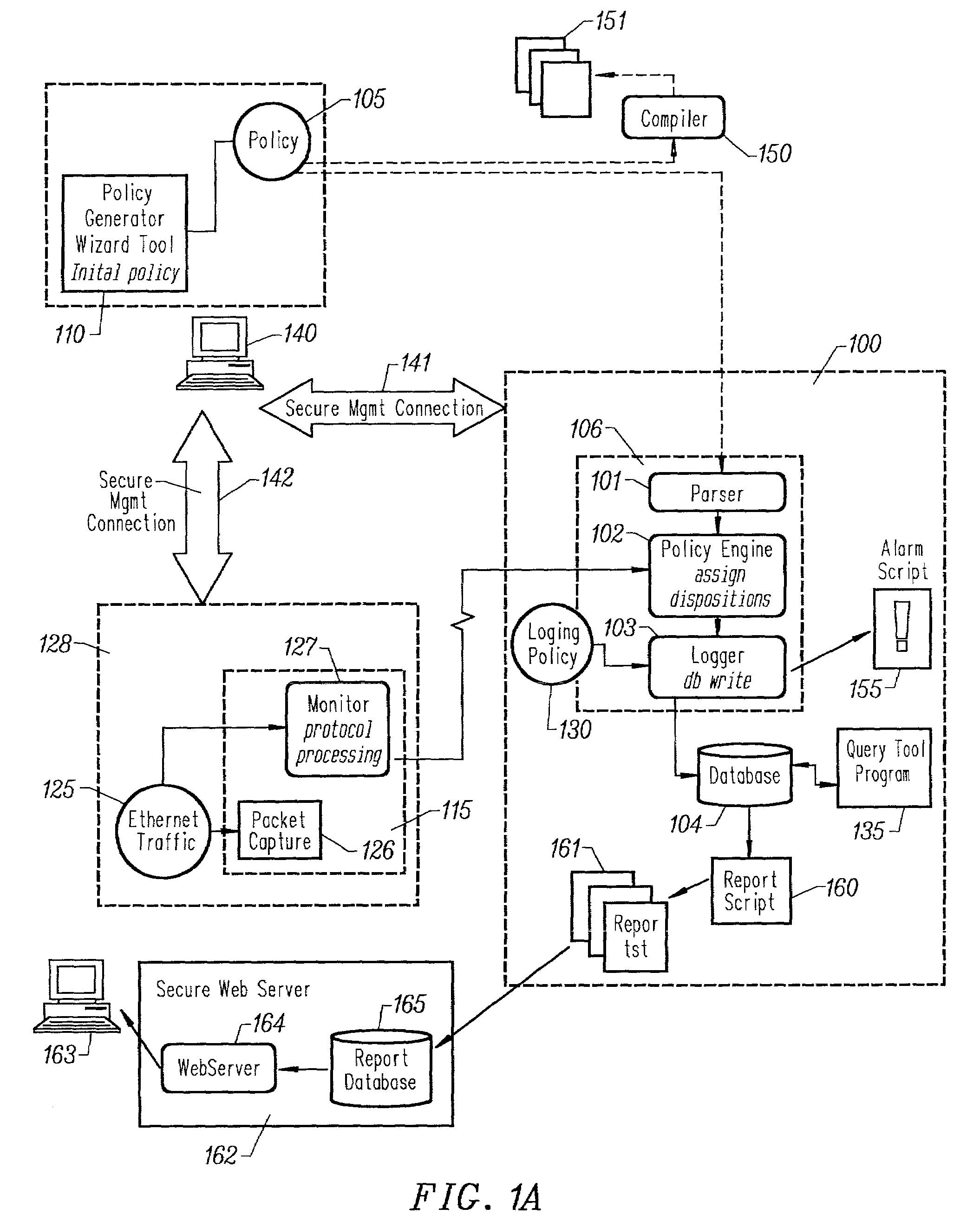
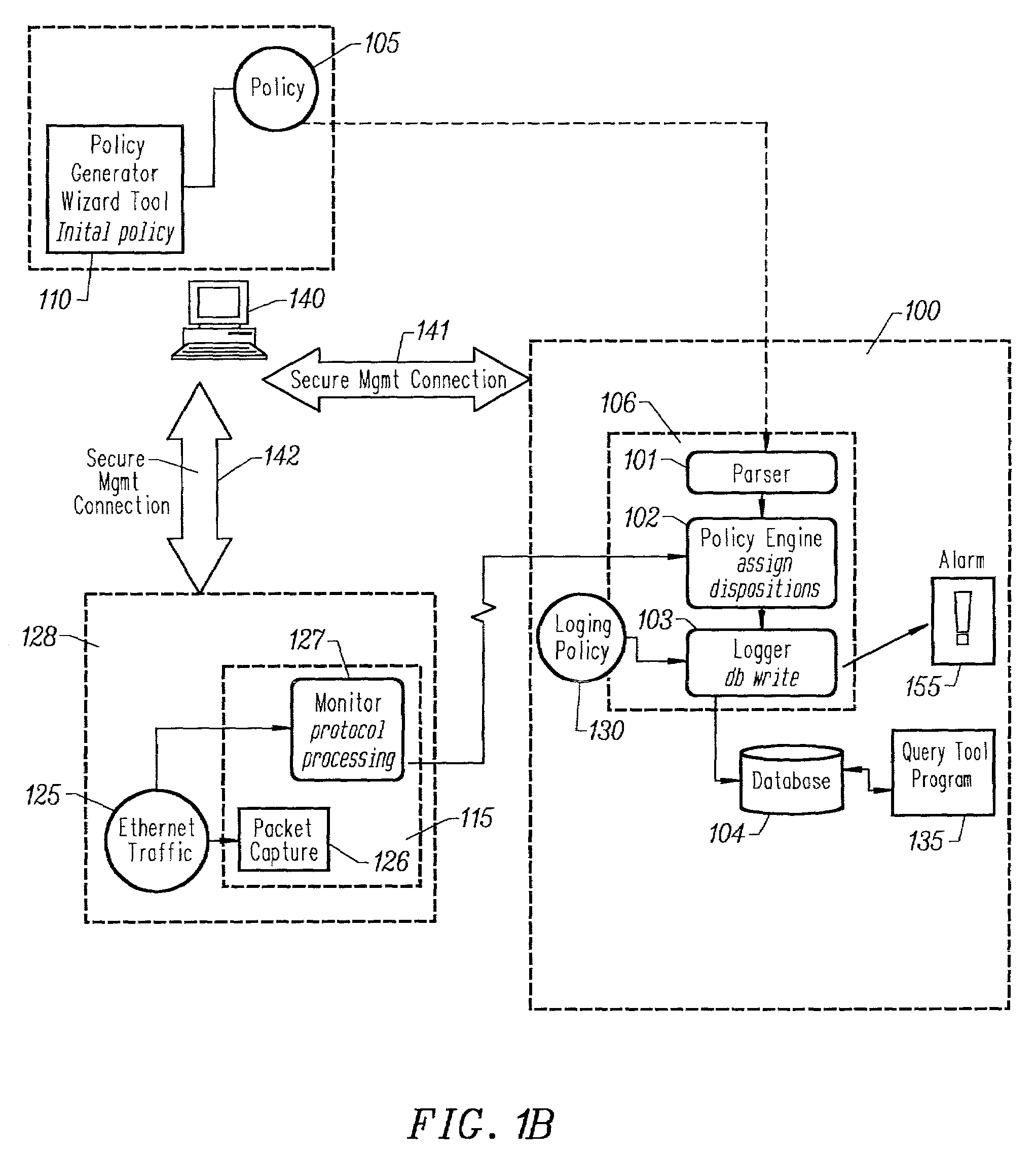
Automated generation of an english language representation of a formal network security policy specification
A system and method for generating a human readable, e.g. English language, description of a formal specification of network security policy that allows non-technical staff within a user's organization to comprehend the policy. The description is simple enough to be understood, yet captures salient details of the policy.
Owner:MCAFEE LLC
Method for domain specific test design automation
InactiveUS7392509B2Error detection/correctionSpecific program execution arrangementsTest designSpecific test
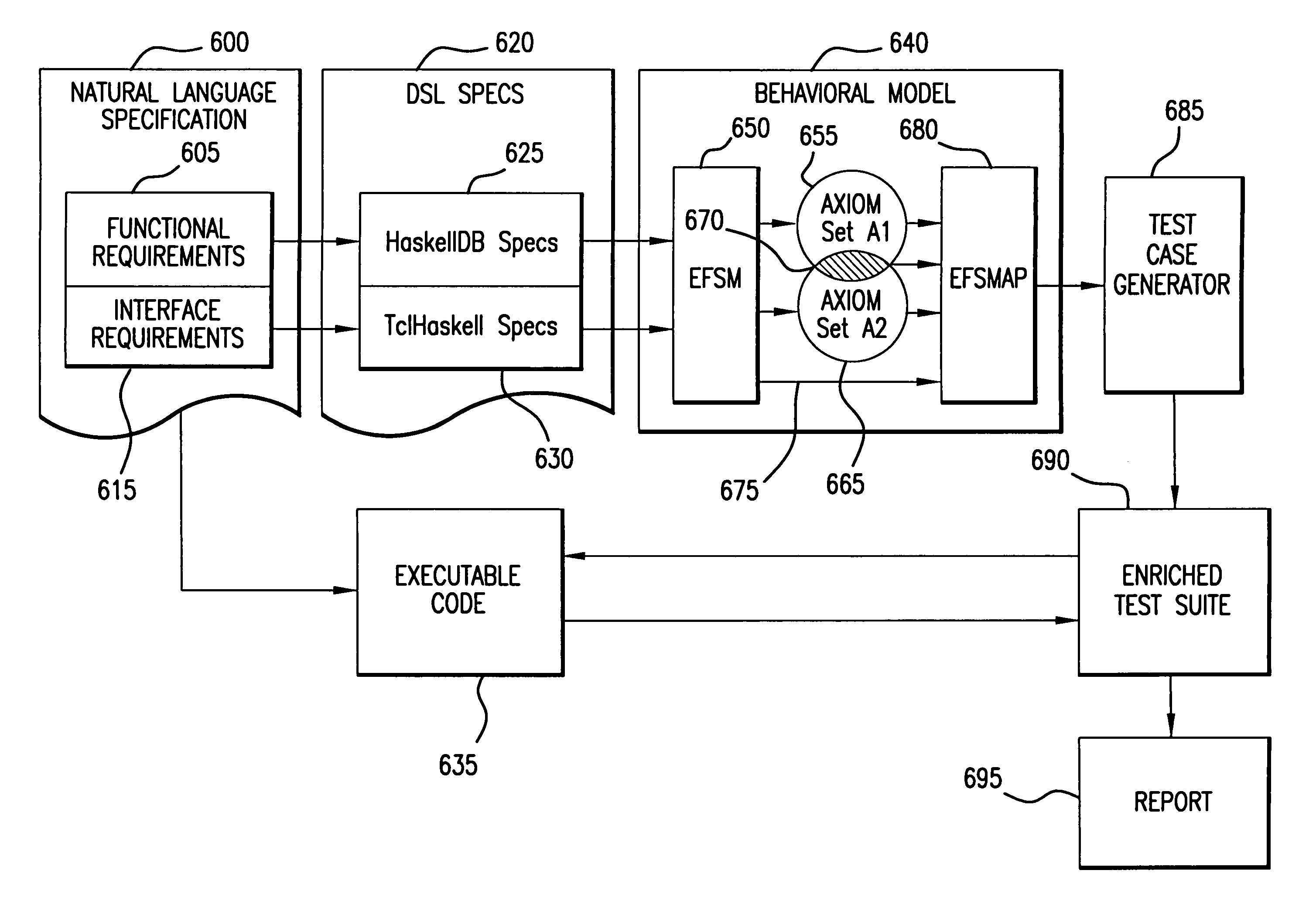
A method for automatically generating test cases from a domain specific description language specification makes use of the properties of the language to derive domain specific axioms and language specific predicates. These properties are embedded into an extended finite state machine which is in turn supplied to the input of a test case generator. The enhanced extended finite state machine, referred herein as an extended finite state machine accounting for axioms and predicates (EFSMAP) contains states and transitions associated with information on implied behavior of the specified system within a particular problem domain. The implicit behavior, defined by the axiomatic properties of the operators of the domain specific language, provide test capability of the associated system that was not explicitly set forth in the formal specification, but nevertheless should be tested to increase confidence in the reliability of the finished product.
Owner:MARYLAND UNIV OF +1
Methods and systems for automatically generating provably correct computer program code
InactiveUS20050137992A1Digital computer detailsChaos modelsNext Generation ProcedureTheoretical computer science
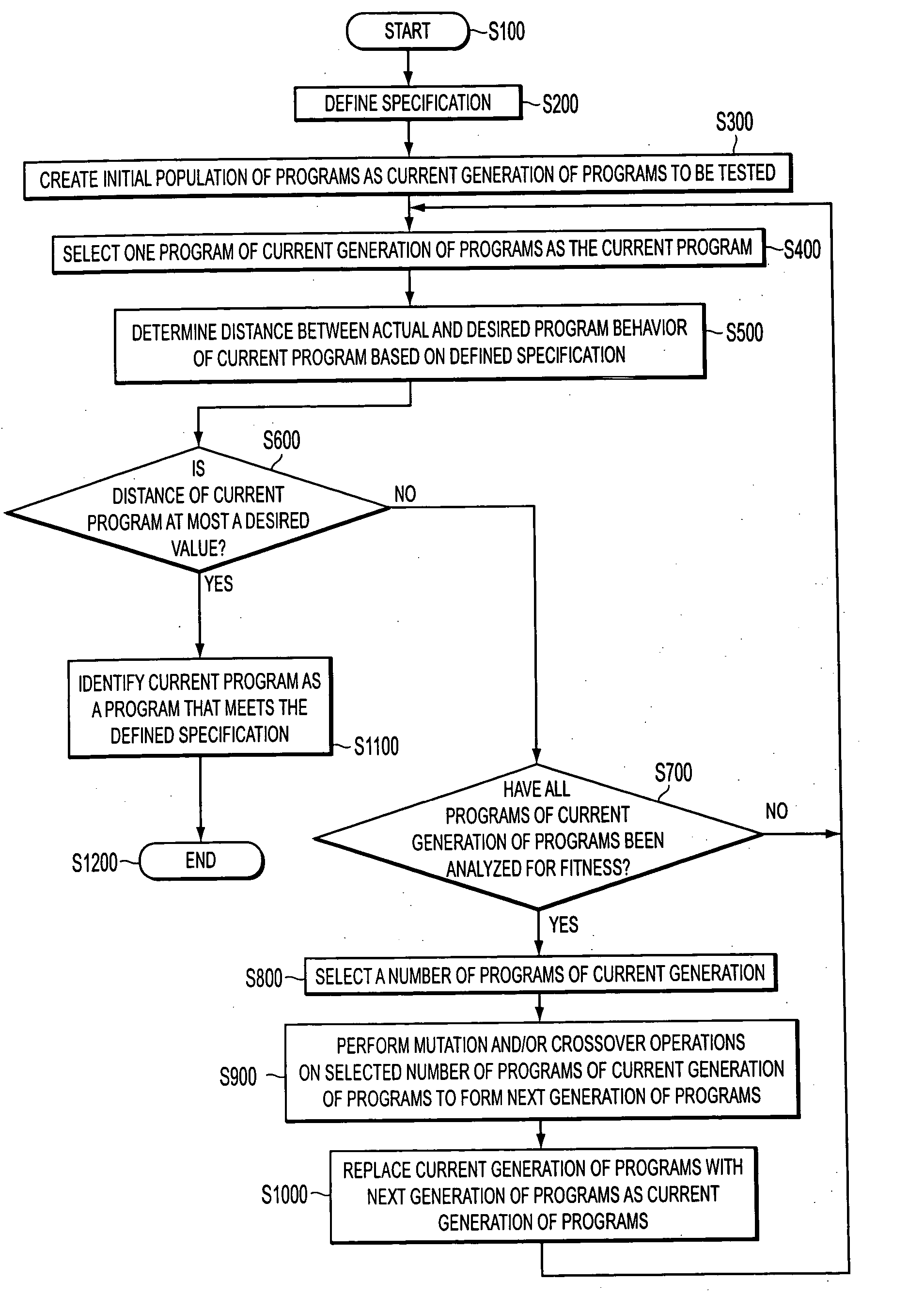
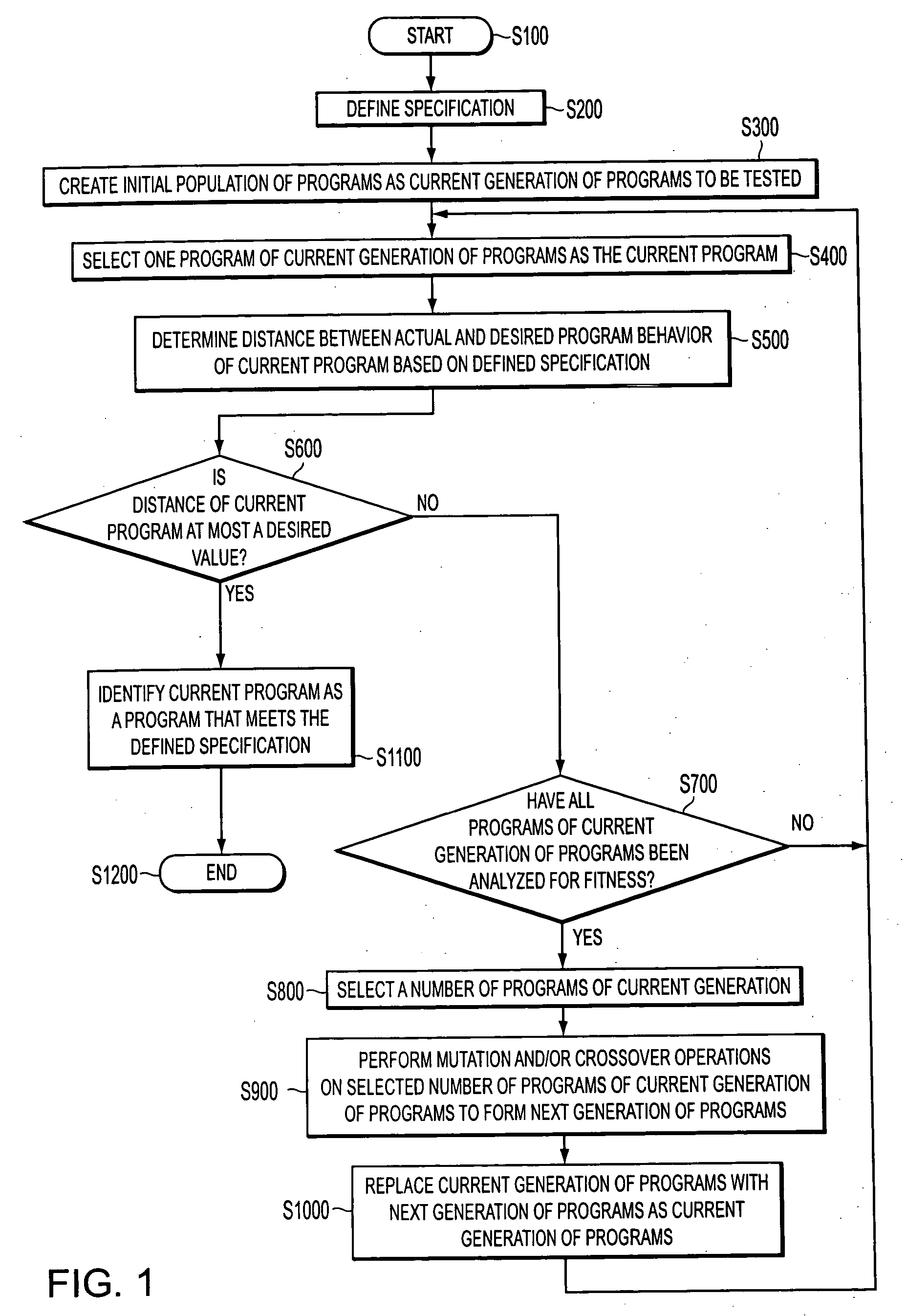
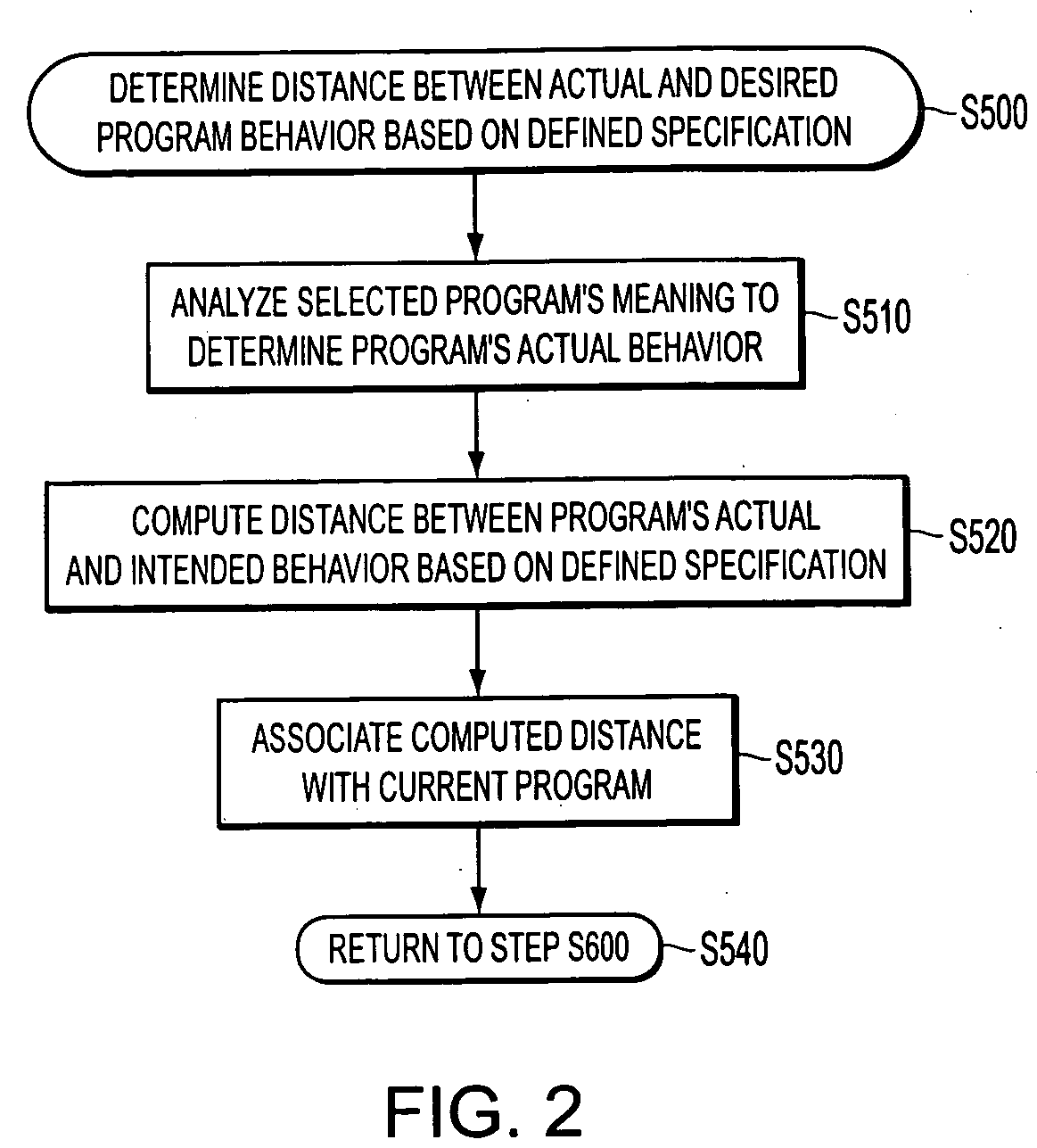
A provably correct computer program can be generated using genetic programming techniques. A desired behavior is used to define a formal specification. An initial population of programs is created where each program has a meaning that can be defined using a formalization technique. A fitness function is applied to measure a distance between the meaning of a program, i.e., its actual behavior, and the specification. Any program having a zero value as the measure of distance between the meaning of the program and the specification is determined to be provably correct. After the fitness of some or all of the programs in the current generation of programs has been computed, a provably correct program has not yet been found in the current generation, mutation and / or crossover techniques are performed on at least some of the fittest individuals in the current generation to create the programs of a next generation.
Owner:GOSS INT AMERICAS +1
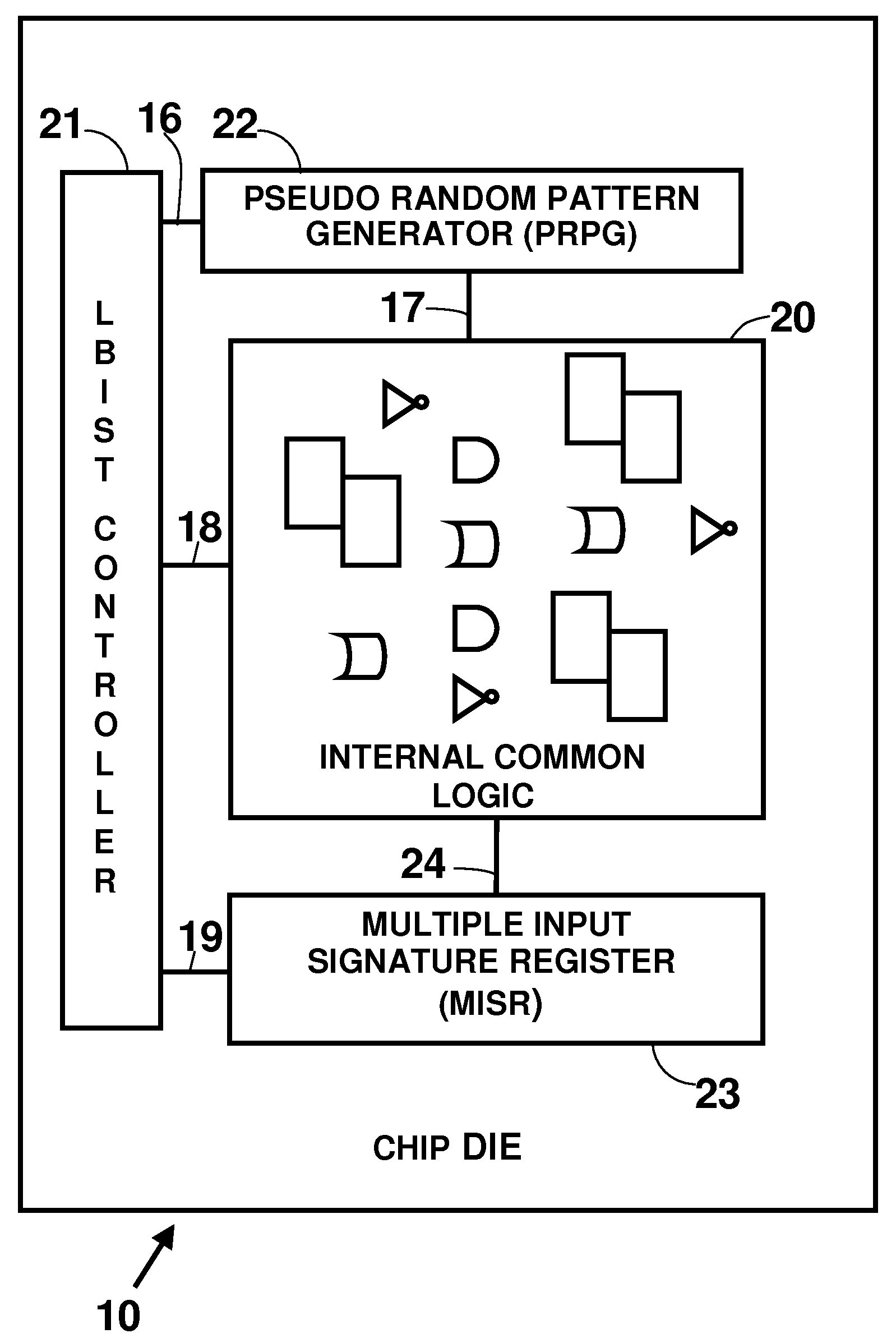
Method and System for Formal Verification of Partial Good Self Test Fencing Structures
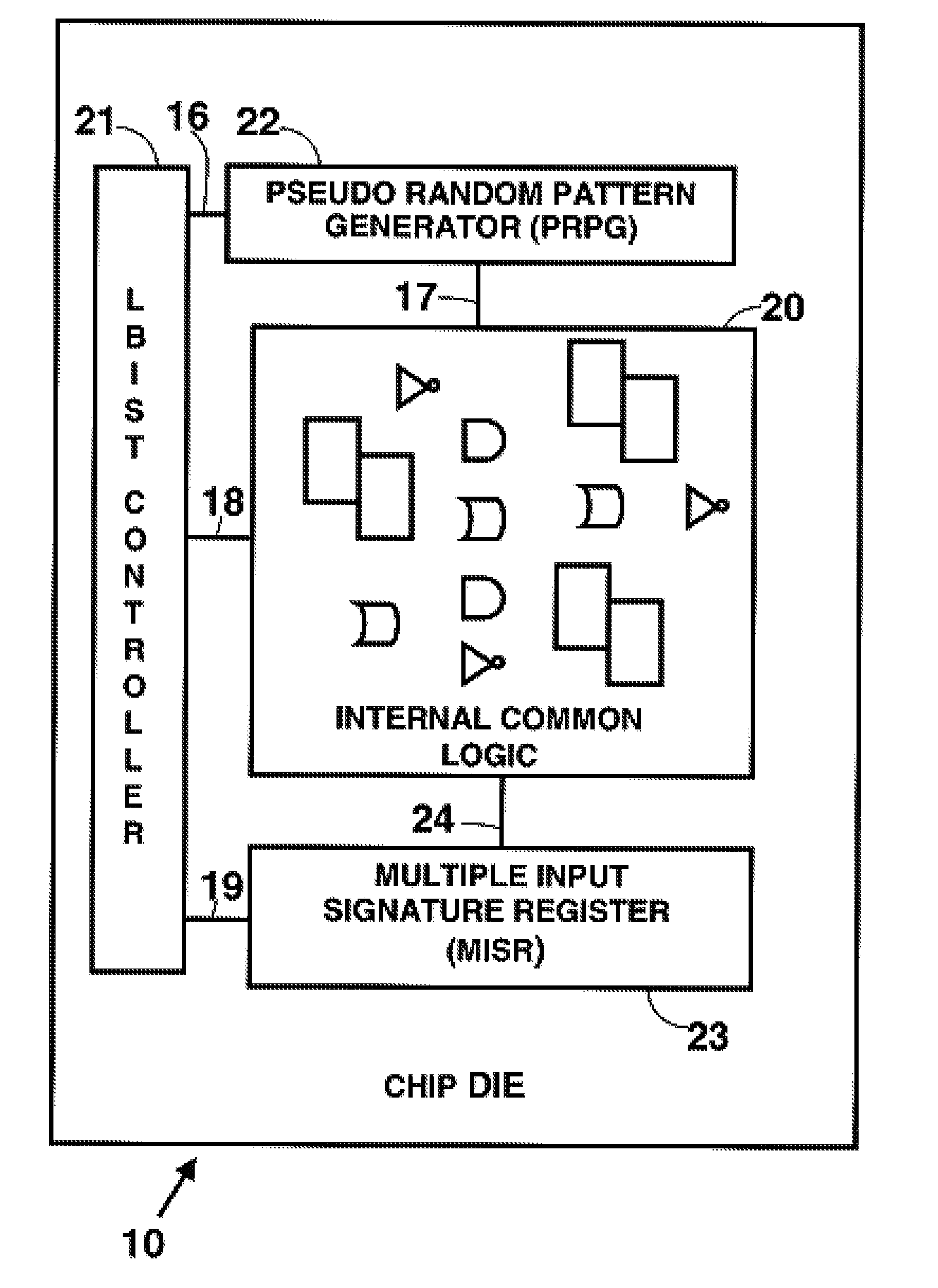
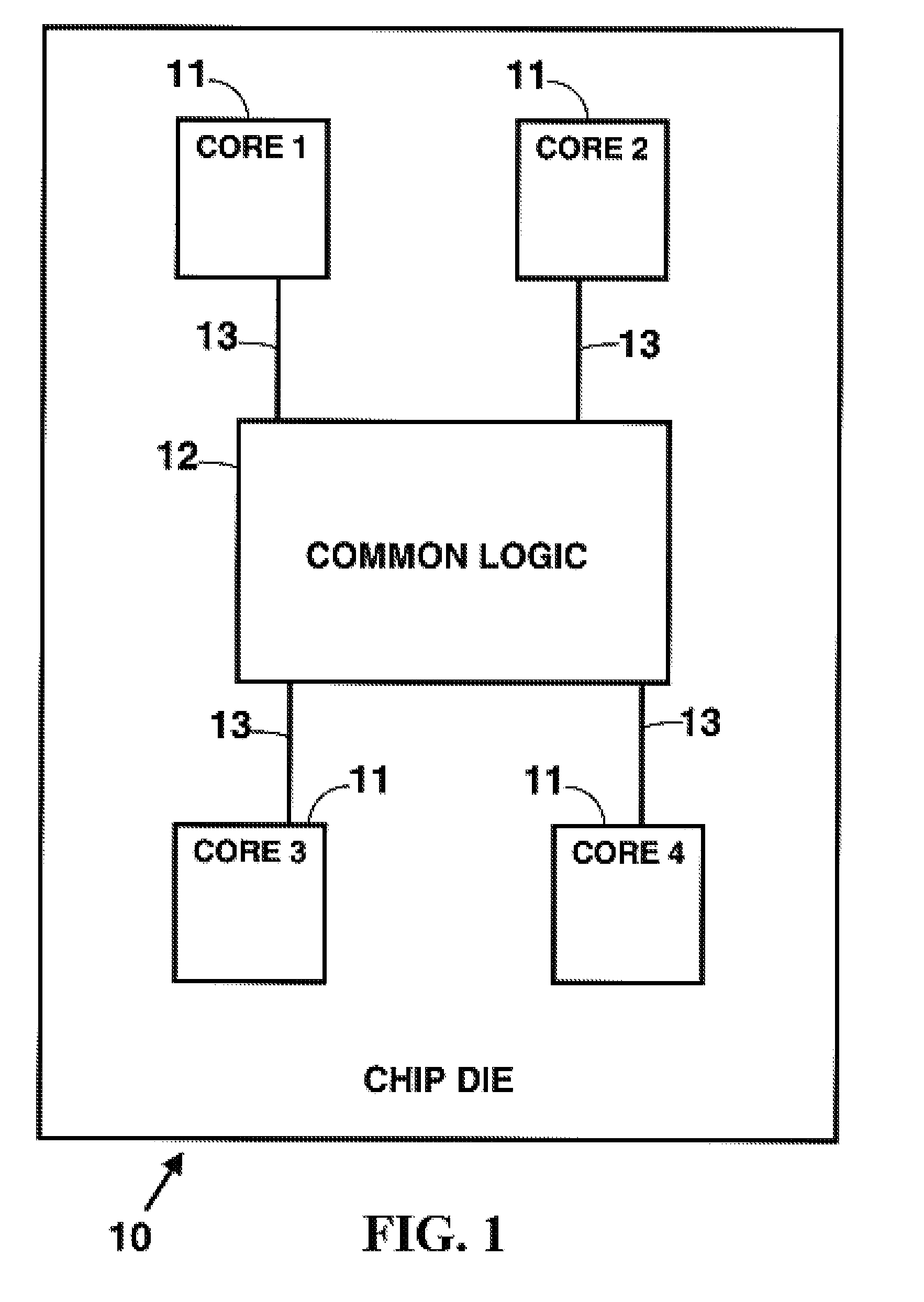
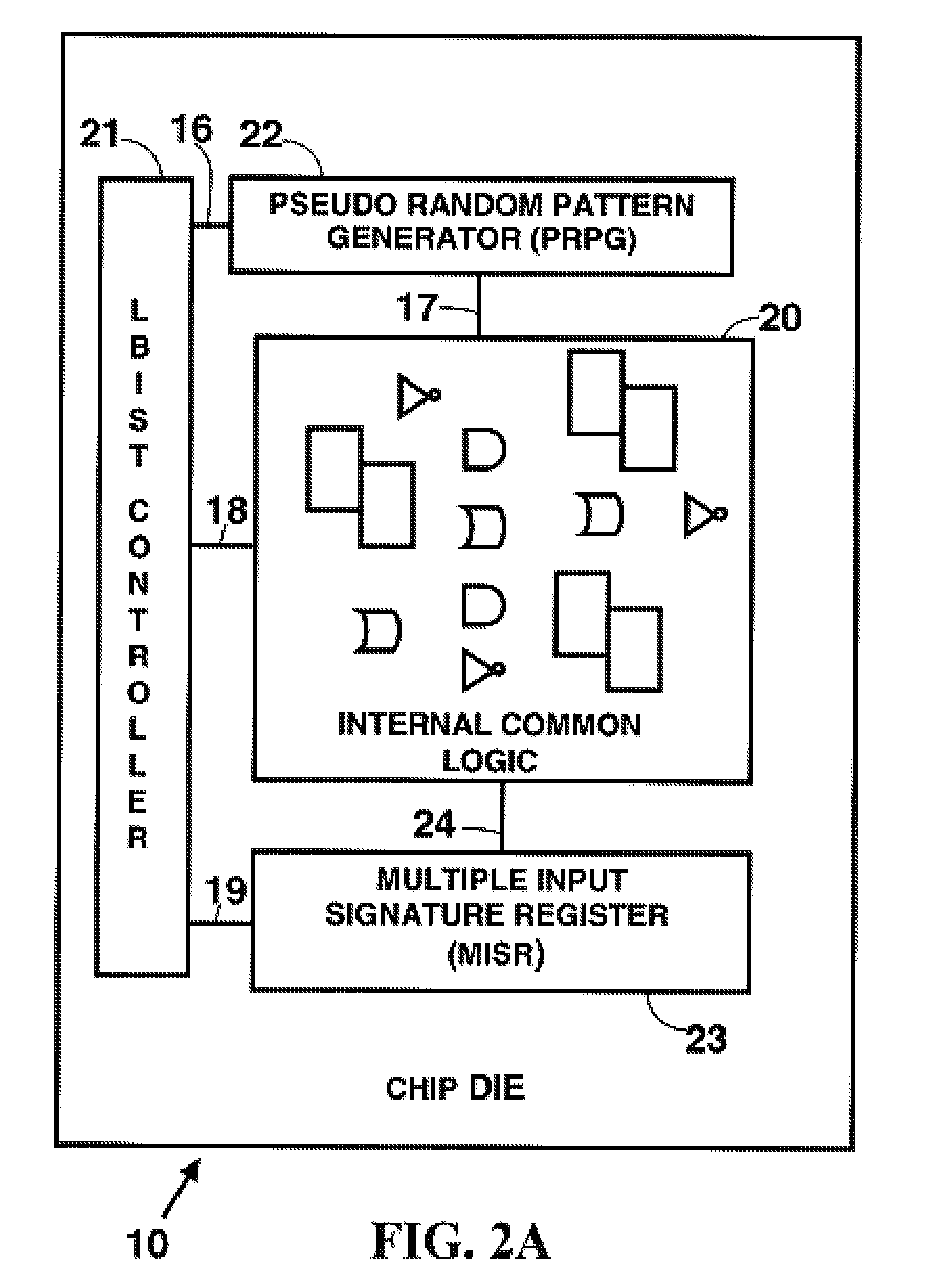
ActiveUS20080276144A1Reduces chip test coverageElectronic circuit testingHardware structureCommon logic
The concept of applying fencing logic to Built-In Self Test (BIST) hardware structures for the purpose of segregating defective circuitry and utilizing the remaining good circuitry is a well known practice in the chip design industry. Described herein is a method for verifying that any particular implementation of partial fencing logic actually provides the desired behavior of blocking down-stream impact of all signals from fenced interfaces, and also ensuring that the partial fencing does not inadvertently preclude any common logic from being fully tested.
Owner:TWITTER INC
Automated generation of an english language representation of a formal network security policy
InactiveUS20020091942A1Data taking preventionMultiple digital computer combinationsNetwork security policyMinutiae
A system and method for generating a human readable, e.g. English language, description of a formal specification of network security policy that allows non-technical staff within a user's organization to comprehend the policy. The description is simple enough to be understood, yet captures salient details of the policy.
Owner:MCAFEE LLC
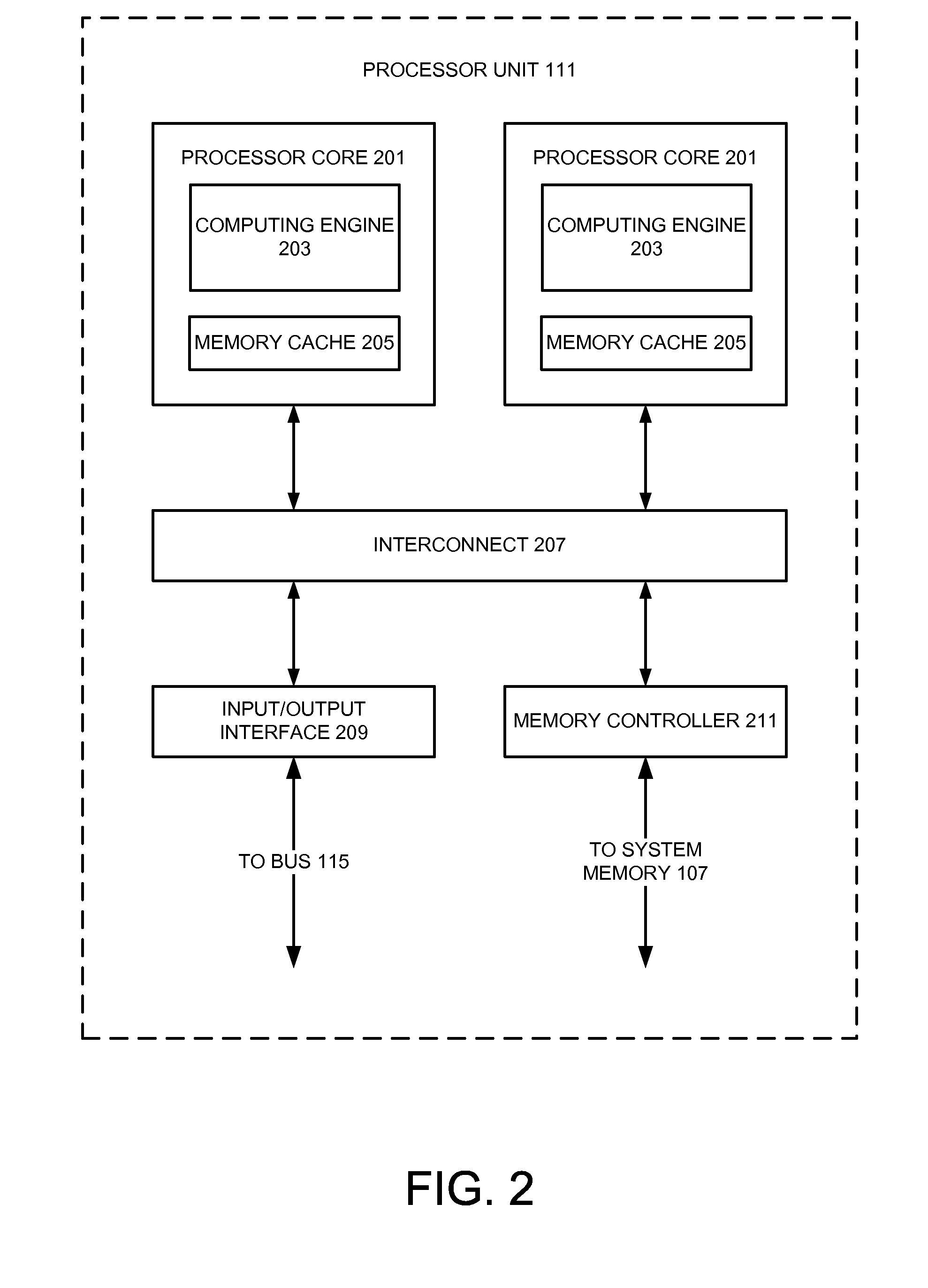
Formal Verification Of Clock Domain Crossings
ActiveUS20100199244A1Detecting faulty computer hardwareComputer aided designClock domain crossingFormal specification
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
Formal verification of clock domain crossings
ActiveUS8271918B2Detecting faulty computer hardwareComputer aided designComputer scienceFormal specification
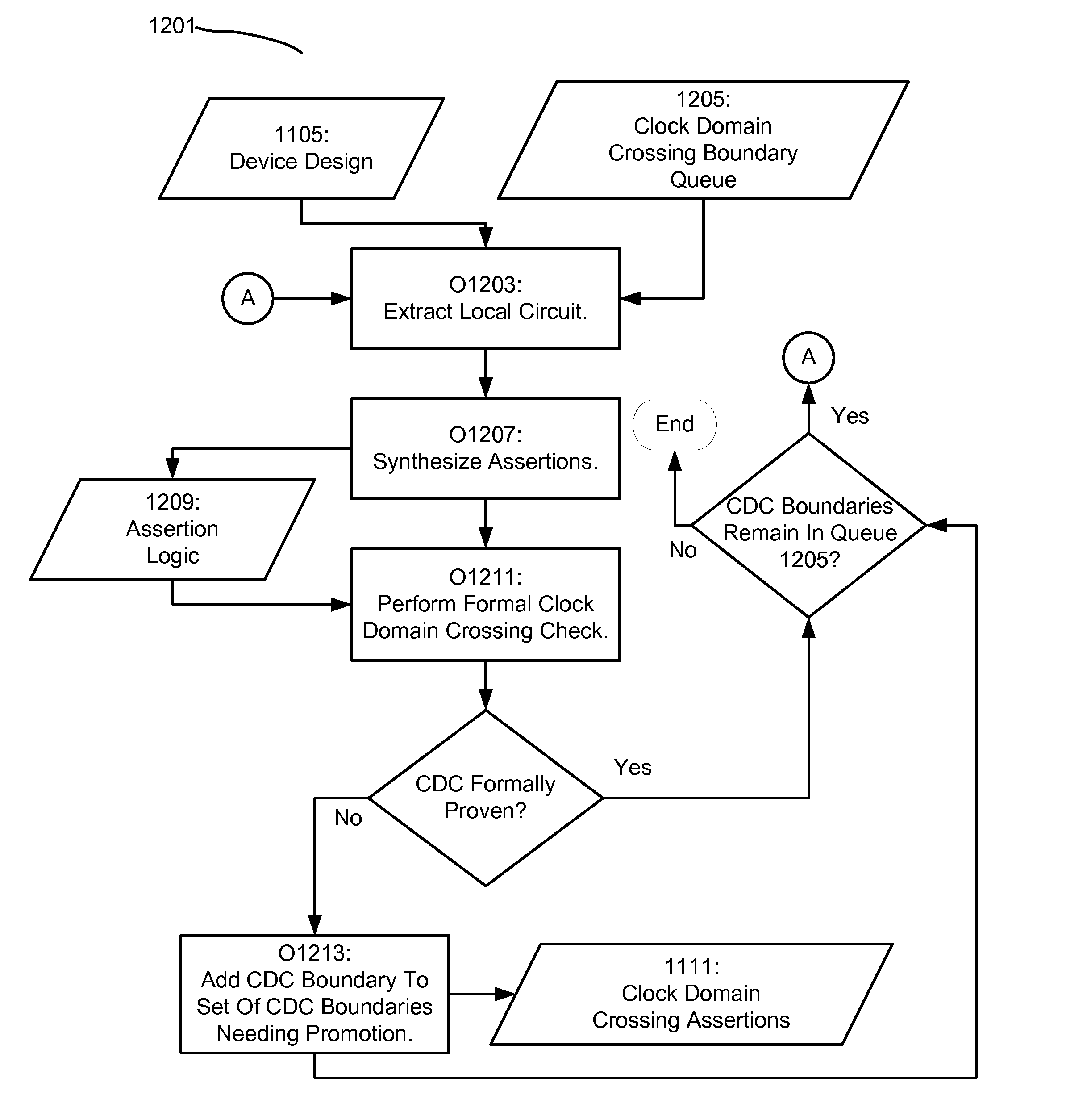
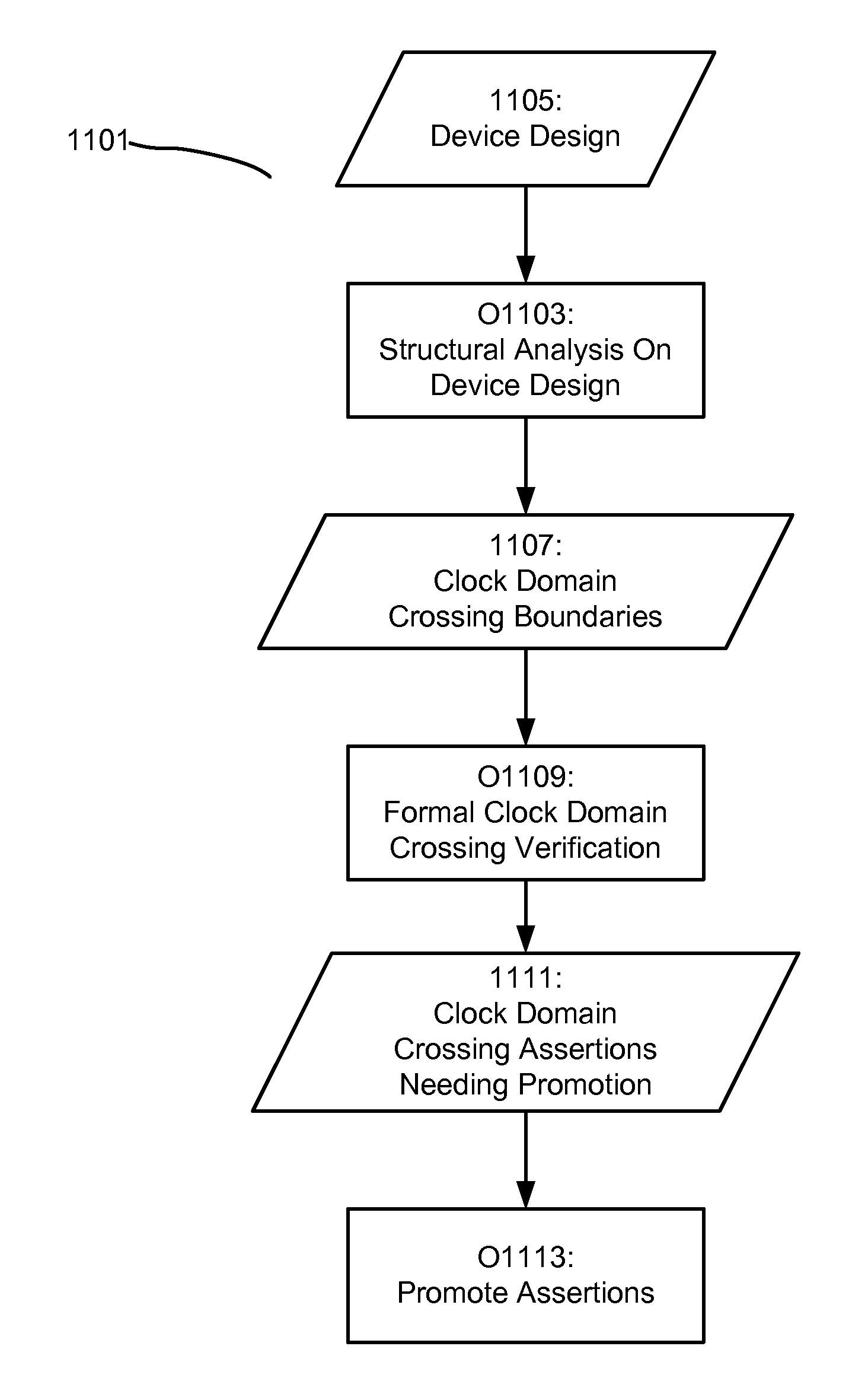
Methods and apparatus for performing automated formal clock domain crossing verification on a device are detailed. In various implementations of the invention, a device may be analyzed, wherein the clock domain crossing boundaries are identified. Subsequently, a formal clock domain crossing verification method may be applied to the identified clock domain crossing boundaries, resulting in clock domain crossing assertions being identified. After which the identified assertions may be promoted for post clock domain crossing analysis. With various implementations of the invention, a formal clock domain crossing method is provided, wherein the device components near an identified clock domain crossing are extracted. Assertions may then be synthesized and verified based upon the extracted components. Various implementations of the invention provide for clock domain crossing verification to be performed iteratively, wherein a larger and larger selection of the device is extracted during formal verification. Additionally, various implementations of the present invention provide that the clock domain crossing verification operate on the fly during a device verification procedure. With further implementations, a bit-blasted approach to clock domain crossing verification may be provided during formal verification.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
System and method for measuring progress for formal verification of a design using analysis region
ActiveUS7412674B1Detecting faulty computer hardwareComputer aided designDisplay deviceUsage analysis
A method and apparatus for measuring the progress of a formal verification process using an analysis region, and measures the effectiveness of the current set of properties / requirements in verifying different portions of logic within the design. The present invention applies the concept of analysis region to analyze the properties / requirements for a design. The analysis region can be expanded or contracted either manually or automatically based upon the results of the analysis. The present invention generates a visual display that is available to the user that represents the amount of source code in the analysis region for a given property or multiple properties in comparison to the maximum possible analysis region. The present invention can display this information in a bar graph format, on a line-by-line basis for the source code and on a waveform display, for example.
Owner:JASPER DESIGN AUTOMATION
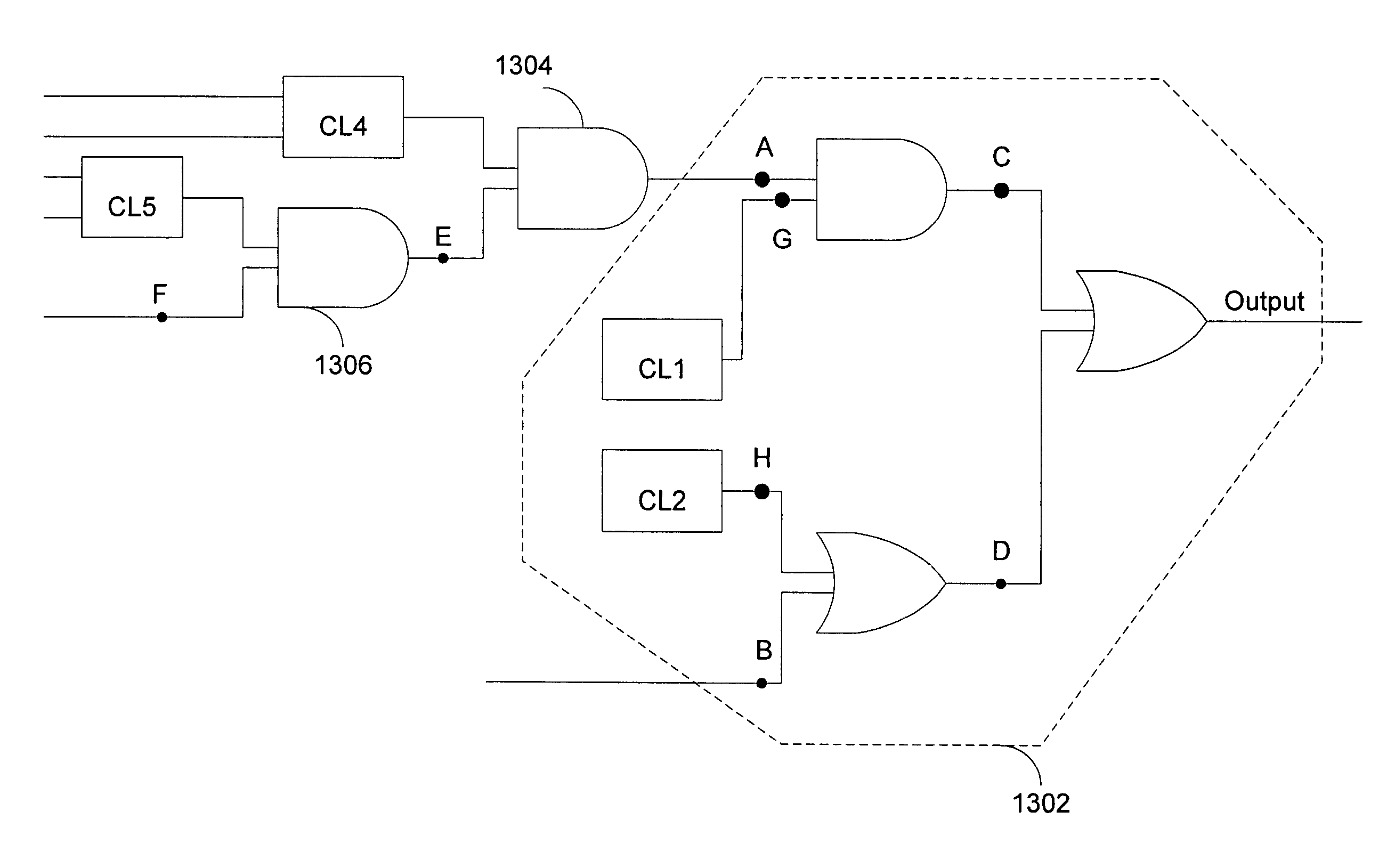
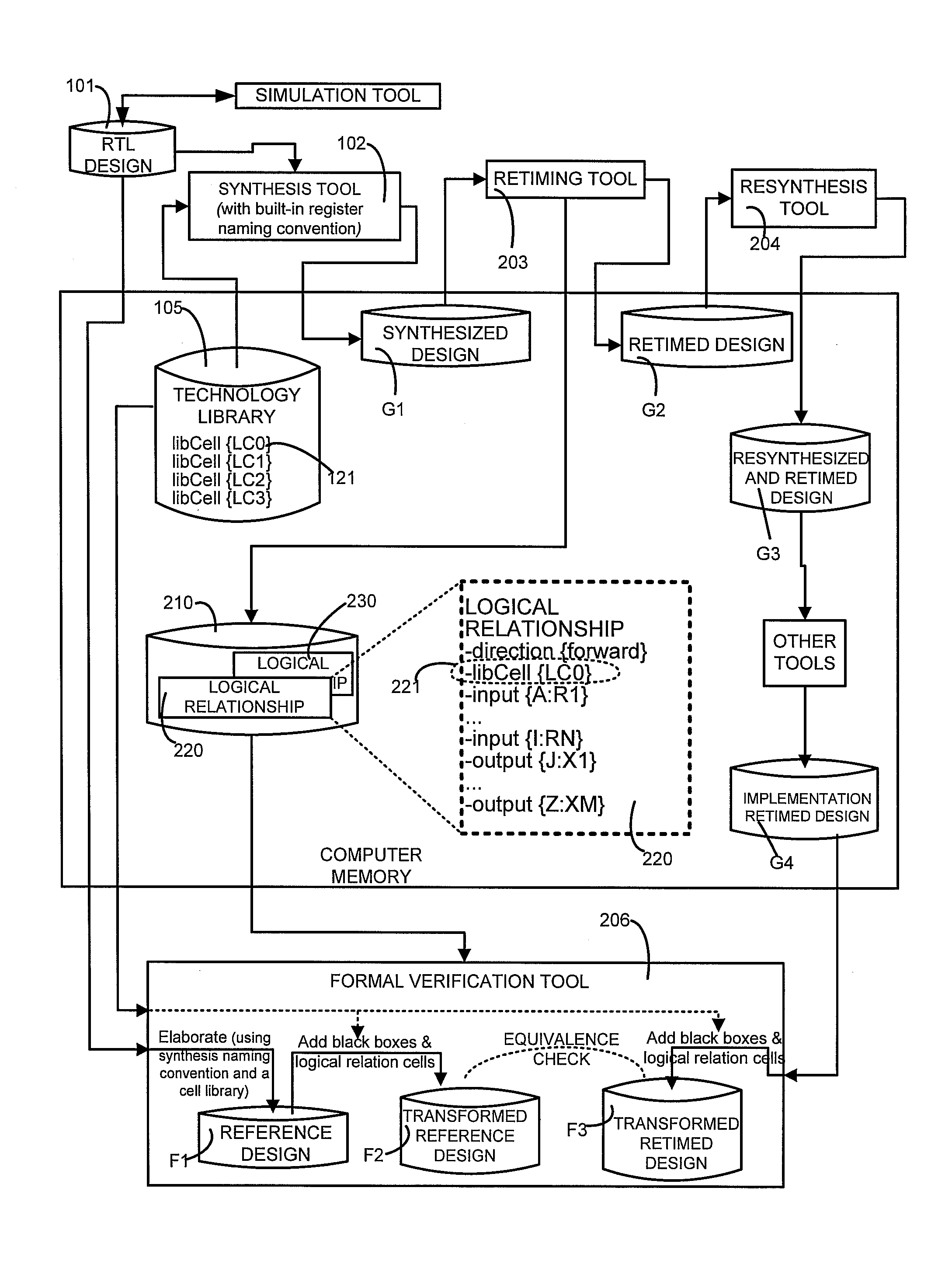
Transformation of IC designs for formal verification
ActiveUS20090293028A1Computer aided designSoftware simulation/interpretation/emulationBlack boxCombinational logic
A memory is encoded with data that represents a reference IC design, a retimed IC design, and logical relationships, wherein at least one logical relationship describes combinational logic without reference to structural information, such as actual cells that have been instantiated in the IC designs. The logical relationships are used to instantiate logic described therein, and to define one or more black boxes as being functionally inverse of the logic. Each instantiated logic and its functionally inverse black box are thereafter added to the reference IC design to obtain a transformed reference IC design. A transformed retimed IC design is also obtained by addition of the instantiated logic(s) and functionally inverse black box(es) to the retimed IC design. These two transformed IC designs are then supplied to an equivalence checker, for formal verification.
Owner:SYNOPSYS INC
Analytical software design system
ActiveUS8370798B2Low costAvoid excessive errorSoftware designRequirement analysisSystems designMathematical model
An analytical software design system arranged to receive informal system design specifications and to convert them into verified design specifications for use in creating source code and carrying out implementation testing of the source code is described. The system comprises a verified black box specification generator arranged to process the received informal system design specifications to create formal specifications; to generate from the formal specifications mathematical models representing the system behavior; to analyze the mathematical models to determine if they have the required behavior; to adjust the formal specifications until the required behavior is achieved; and to derive the required verified design specifications from the mathematical models.
Owner:COCOTEC LTD
Method and apparatus for testing a network
ActiveUS7698408B1Avoid reportingMaintain compatibilityDigital computer detailsData switching by path configurationTheoretical computer scienceBlueprint
Accordingly, one embodiment of the invention provides a method for testing a network comprising multiple nodes. The network conforms to a formal specification. The method includes defining a blueprint comprising a set of one or more possible topological configurations for connecting a node to the network. The one or more possible topological configurations represent a subset of the topological configurations permitted by the formal specification. When connectivity is initiated between a node and the network, it is confirmed that the connectivity for the node conforms to the blueprint.
Owner:ORACLE INT CORP
Method for domain specific test design automation
InactiveUS20050240794A1Error detection/correctionSpecific program execution arrangementsSpecific testProblem domain
A method for automatically generating test cases from a domain specific description language specification makes use of the properties of the language to derive domain specific axioms and language specific predicates. These properties are embedded into an extended finite state machine which is in turn supplied to the input of a test case generator. The enhanced extended finite state machine, referred herein as an extended finite state machine accounting for axioms and predicates (EFSMAP) contains states and transitions associated with information on implied behavior of the specified system within a particular problem domain. The implicit behavior, defined by the axiomatic properties of the operators of the domain specific language, provide test capability of the associated system that was not explicitly set forth in the formal specification, but nevertheless should be tested to increase confidence in the reliability of the finished product.
Owner:MARYLAND UNIV OF +1
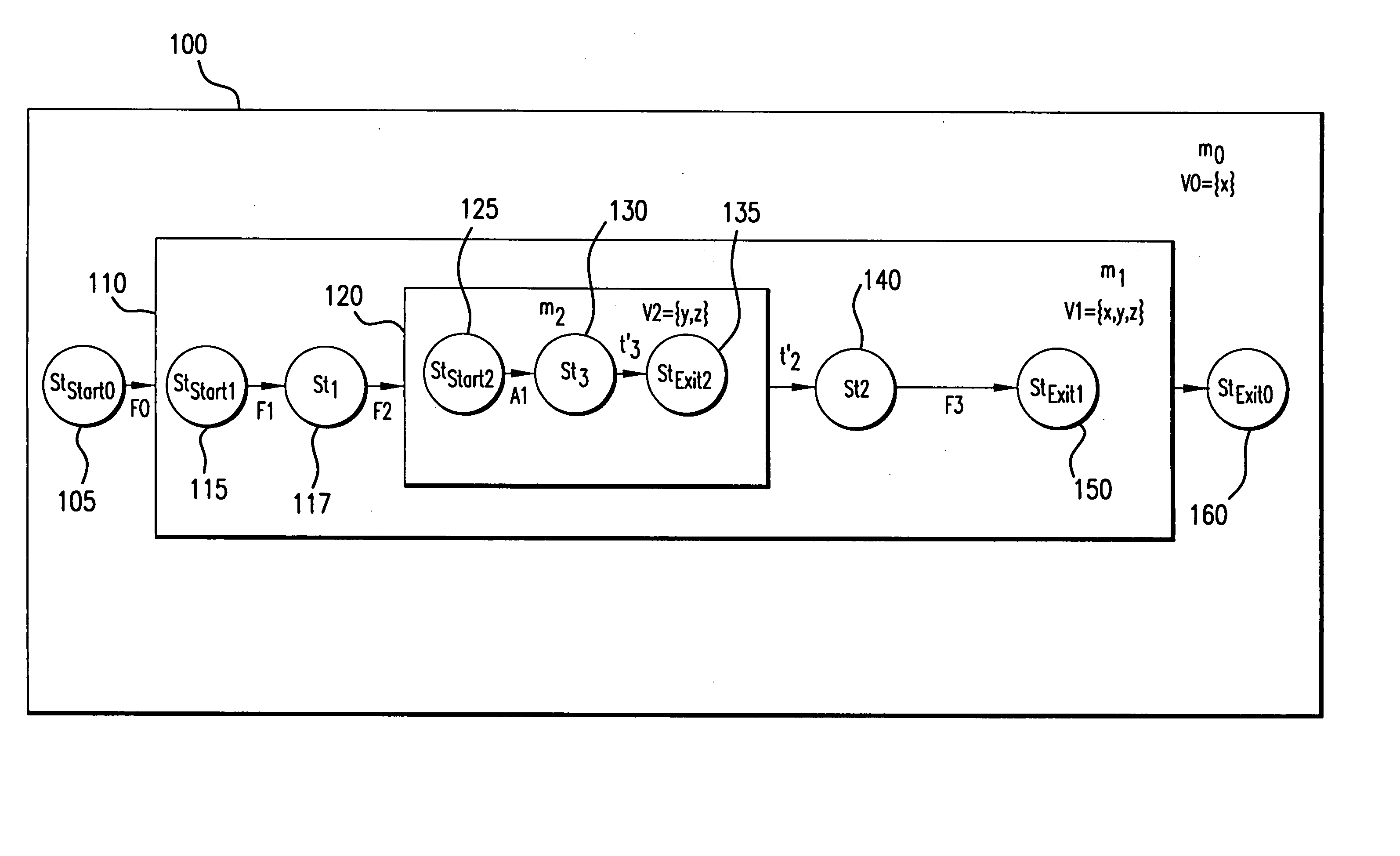
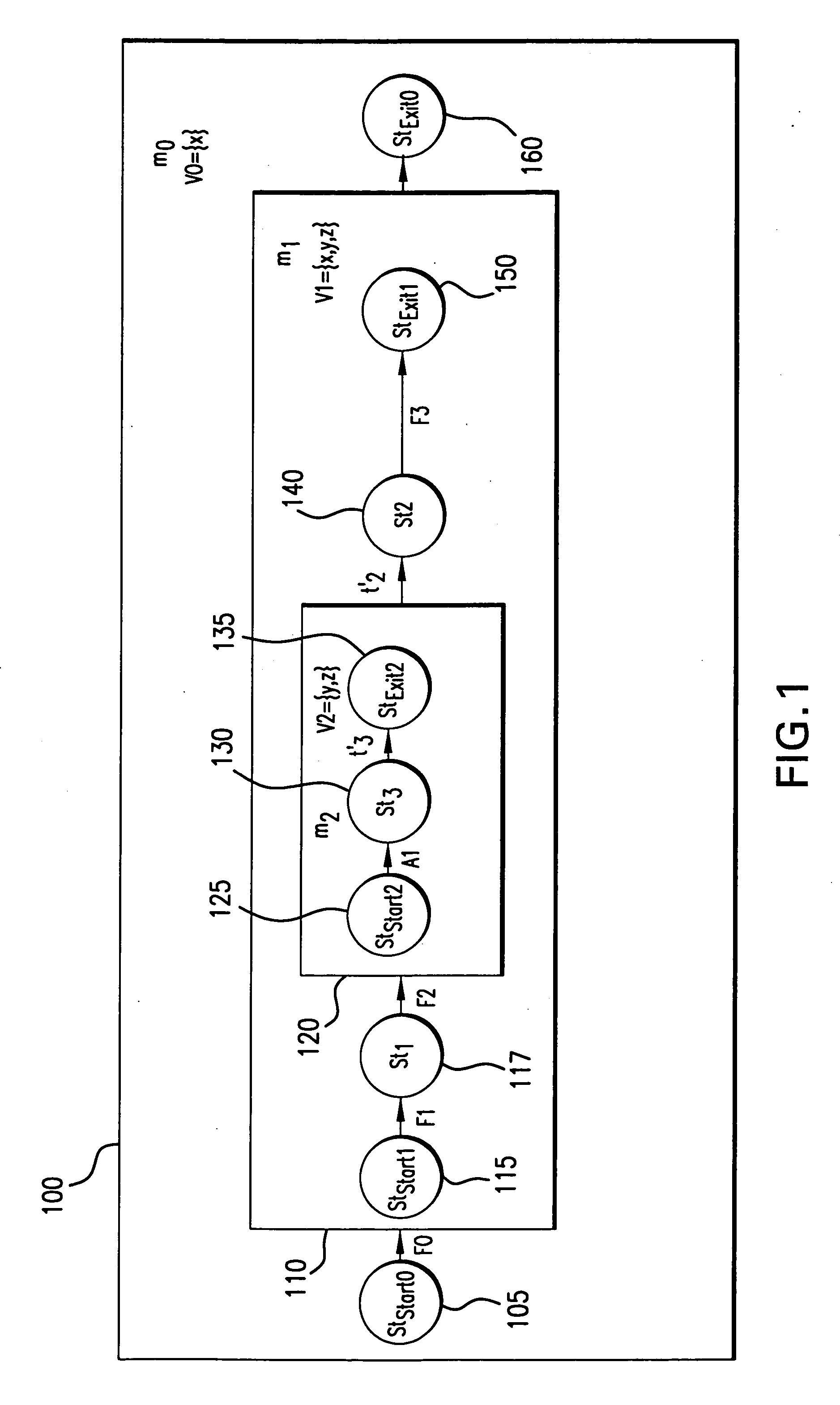
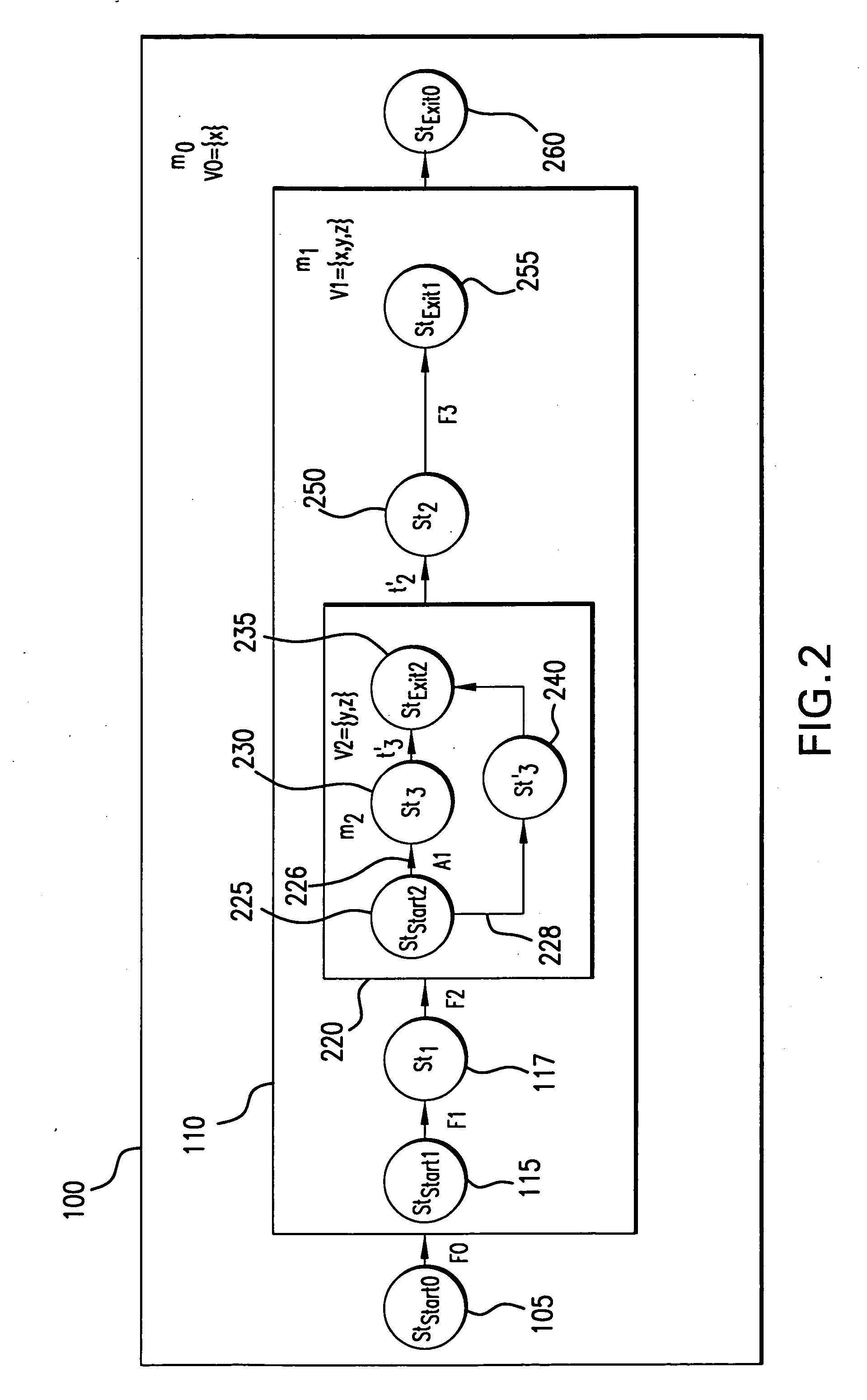
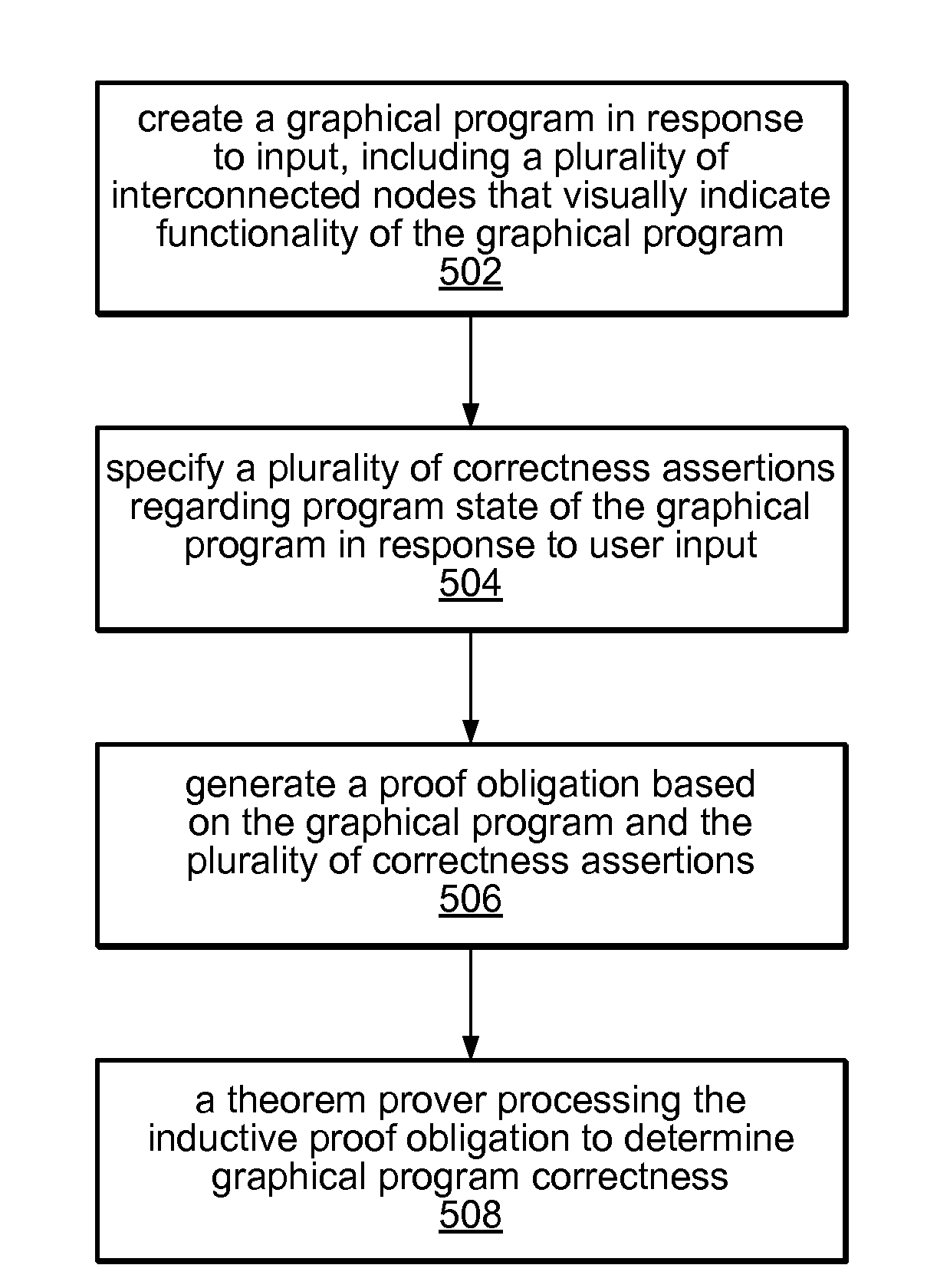
Formal Verification of Graphical Programs
InactiveUS20090064111A1Error detection/correctionVisual/graphical programmingObject levelHuman language
System and method for formal verification of a graphical program. A graphical program comprising a plurality of interconnected nodes is created in response to input. One or more correctness assertions regarding program state of the graphical program are specified in response to user input, and a proof obligation generated based on the graphical program and the correctness assertions, which is usable by a theorem prover to determine correctness of the graphical program. The proof obligation may be generated by compiling the graphical program to generate an object-level diagram, parsing the correctness assertions to generate an intermediate logical form of the one or more correctness assertions, and analyzing the object-level diagram, the intermediate logical form, and / or semantics of the graphical programming language in which the graphical program is written to generate the proof obligation. A theorem prover may then process the proof obligation to determine whether the graphical program is correct.
Owner:NATIONAL INSTRUMENTS
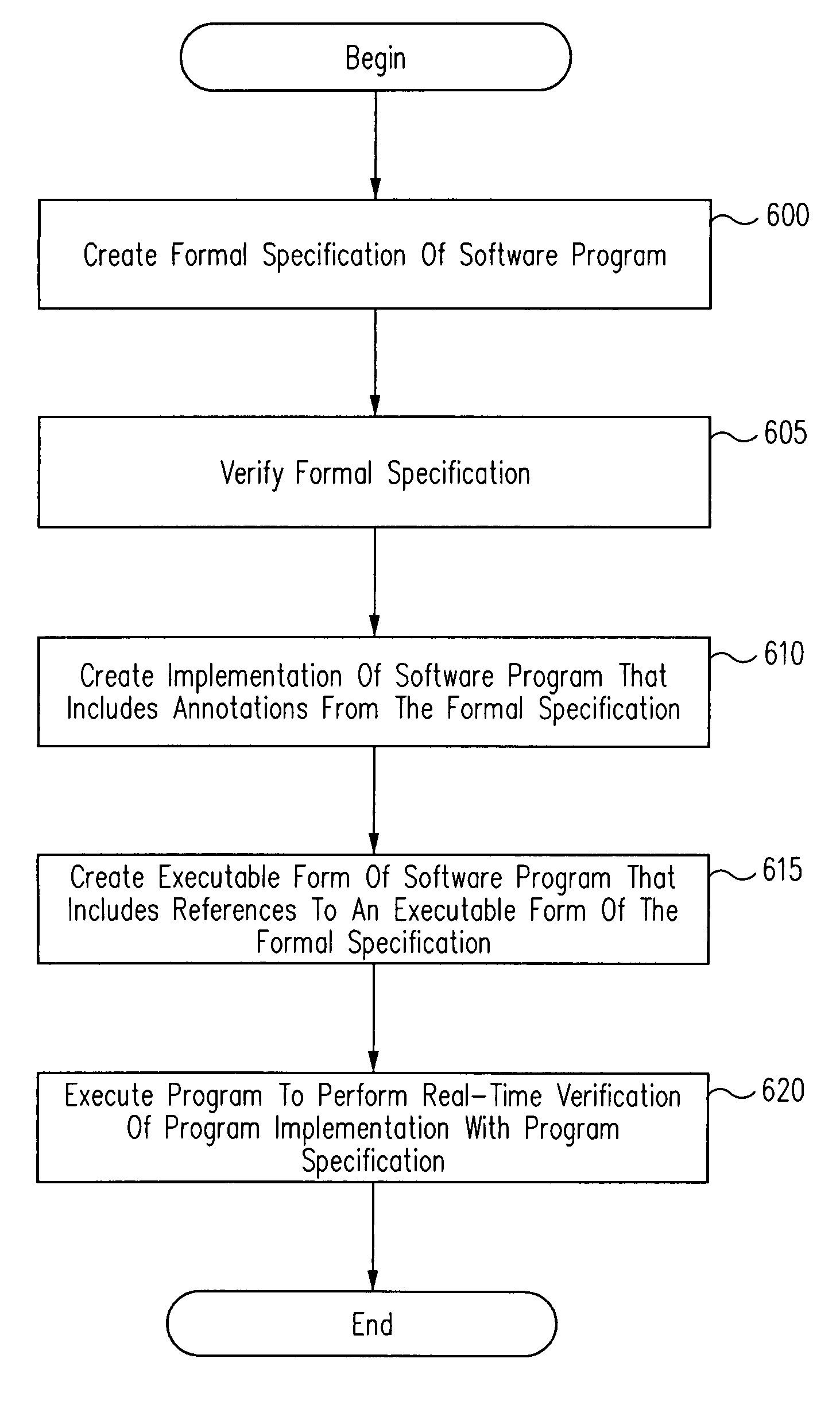
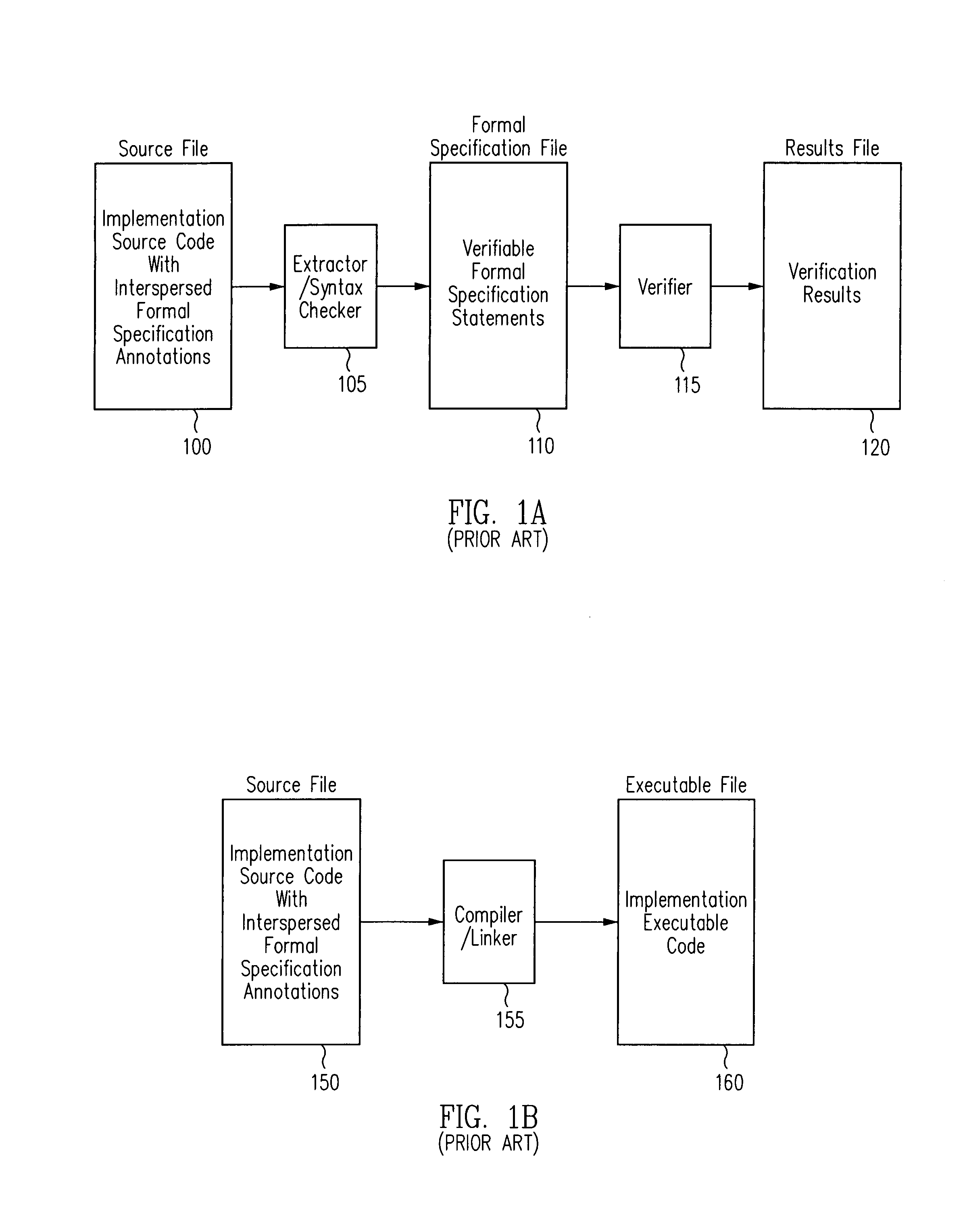
Run-time verification of annotated software code
Verification of a software program may be automated by receiving a program source file comprising program source code and at least one formal specification annotation, extracting the at least one formal specification annotation from the program source file, compiling the program source code and linking the compiled program and the at least one extracted formal specification annotation to create an executable program that includes at least one reference to an executable formal specification module. According to one aspect, a virtual machine includes a target virtual machine for executing one or more program implementation instructions, and a formal virtual machine for executing one or more formal specification modules corresponding to one or more program implementation instructions and configured to call a formal specification module, and to compare a first result obtained by executing the program implementation instructions with a second result obtained by the call to the formal specification module.
Owner:ORACLE INT CORP
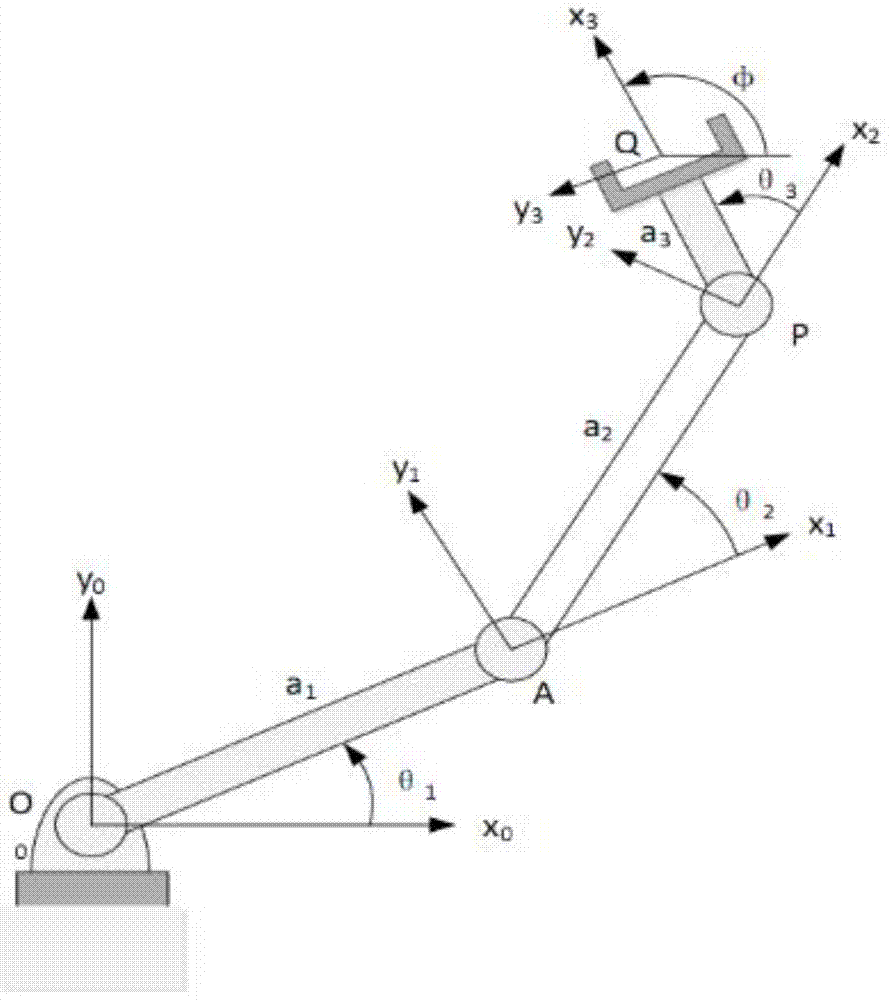
Mechanical arm kinematics formal analysis method
ActiveCN104772773AReduce difficultySimple form of expressionManipulatorHigher-order logicKinematic chain
The invention relates to a mechanical arm kinematics formal analysis method. The method comprises the steps of 1, determining structural parameters of a mechanical arm mechanism; 2, using high-order logical language for building a mechanical arm kinematics logical model; 3, using a logical formula for describing kinematics constraints or attributes needing to be verified; 4, enabling the mechanical arm mechanism kinematics logical model and the kinematics constraints or attributes needing to be verified to form a logical proposition; 5, utilizing a logical reasoning engine for proving whether the logical proposition is true or not; if the logical proposition is true, it represents that the model meets the kinematics constraints or have the attributes; if not, it represents that the model does not meet the kinematics constraints or does not have the attributes. According to formal verification, on the basis of system formal specifications or attributes, the correctness of the system is verified by using the mathematical method, and the verified attributes are precise and complete.
Owner:CAPITAL NORMAL UNIVERSITY
Method and system for formal verification of partial good self test fencing structures
The concept of applying fencing logic to Built-In Self Test (BIST) hardware structures for the purpose of segregating defective circuitry and utilizing the remaining good circuitry is a well known practice in the chip design industry. Described herein is a method for verifying that any particular implementation of partial fencing logic actually provides the desired behavior of blocking down-stream impact of all signals from fenced interfaces, and also ensuring that the partial fencing does not inadvertently preclude any common logic from being fully tested.
Owner:TWITTER INC
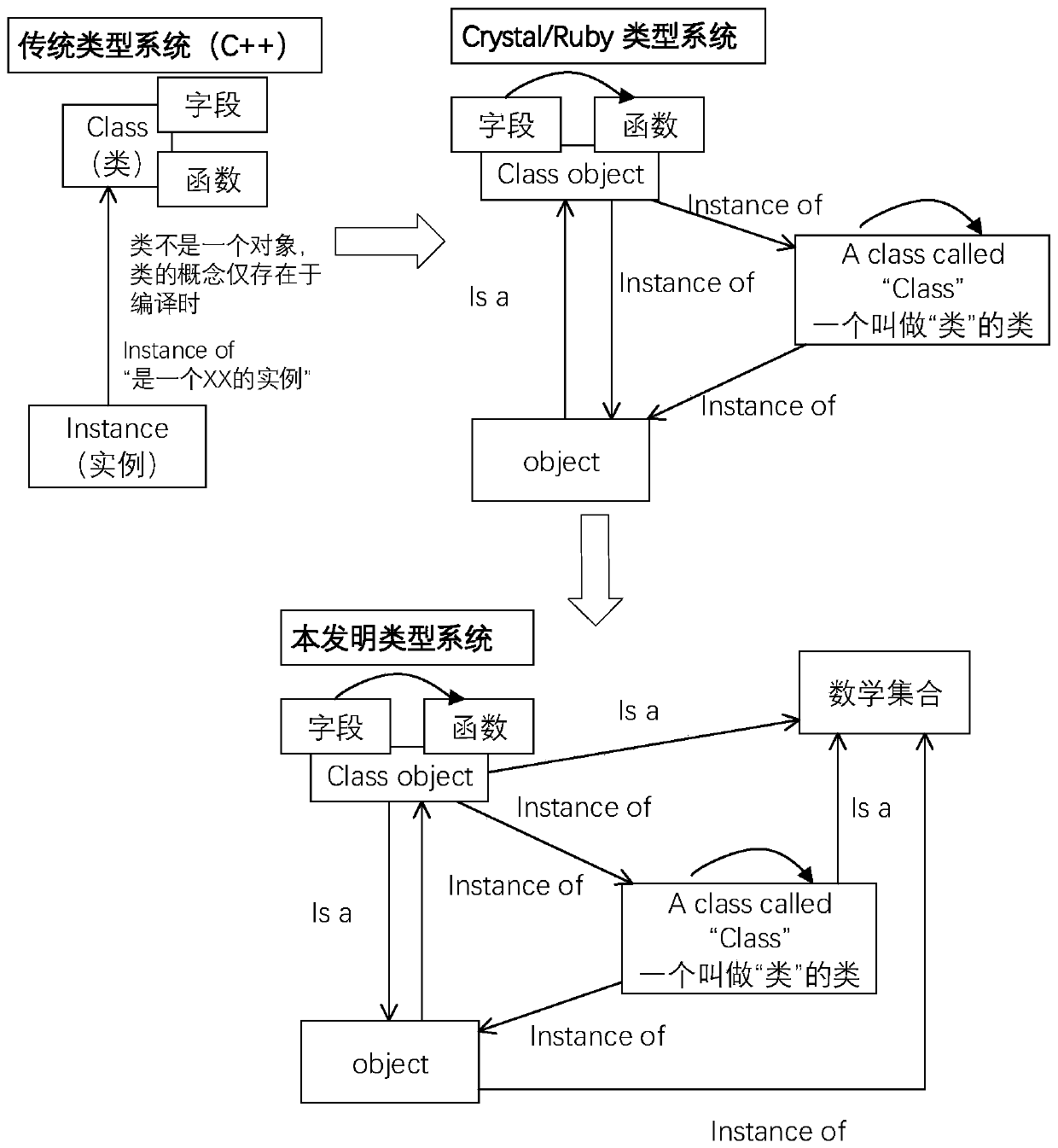
Intelligent contract compiling method suitable for formal verification
ActiveCN109753288AImprove compilation efficiencyEasy to operateCode compilationCreation/generation of source codeFormal proofSmart contract
The invention discloses an intelligent contract compiling method suitable for formal verification. The novel intelligent contract compilation language comprises an engineering application and type mathematical set, all Bugs can be found before operation by utilizing formal proof in combination with language editing, it can be guaranteed that a written program can edit a language which is safe, free of vulnerability and simple to operate, and verification of an intelligent contract form test is carried out. When contract formal verification is carried out, only the used function theorem needs to be proved, function modeling is not needed, and the intelligent contract compiling efficiency is greatly improved.
Owner:HANGZHOU YUNXIANG NETWORK TECH
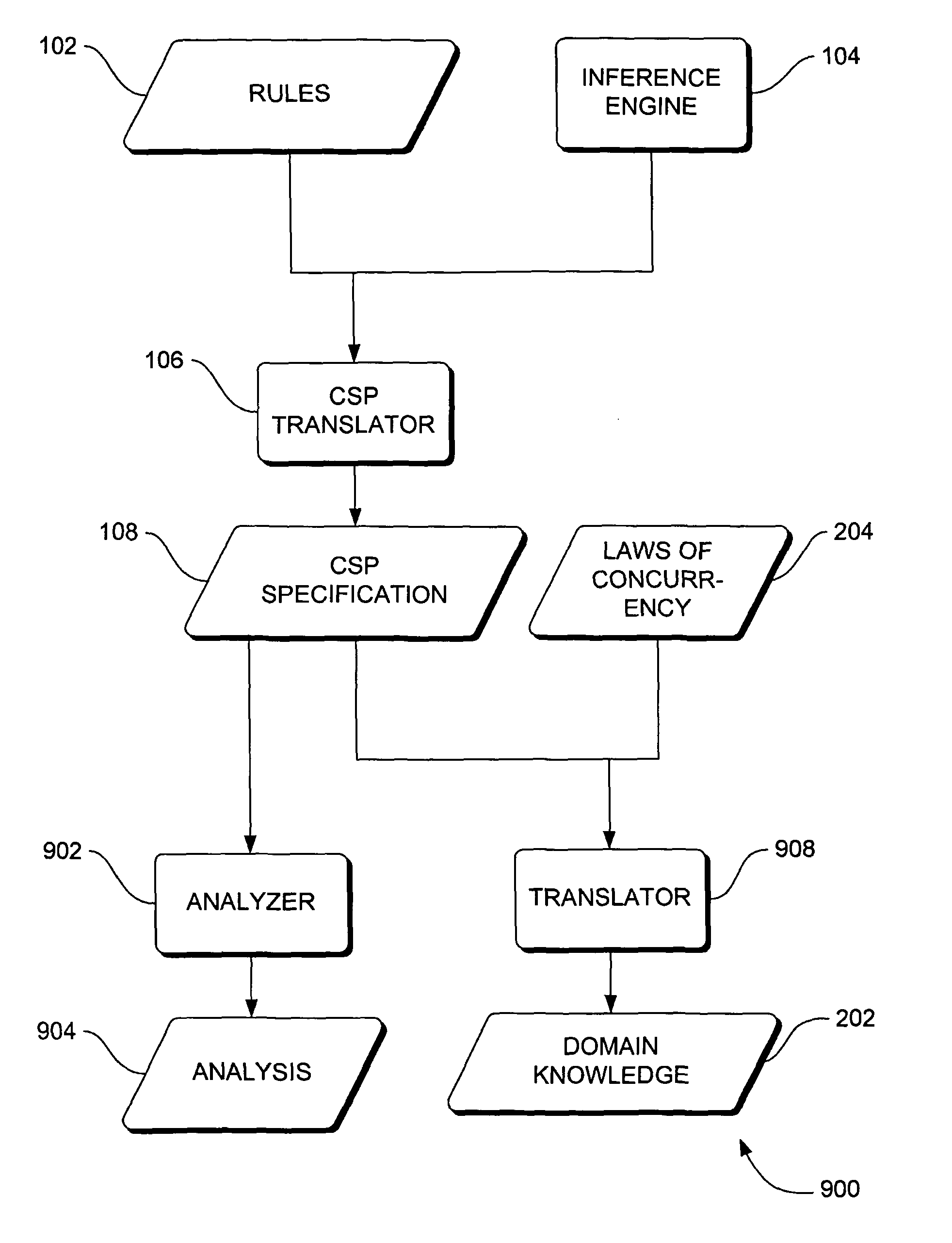
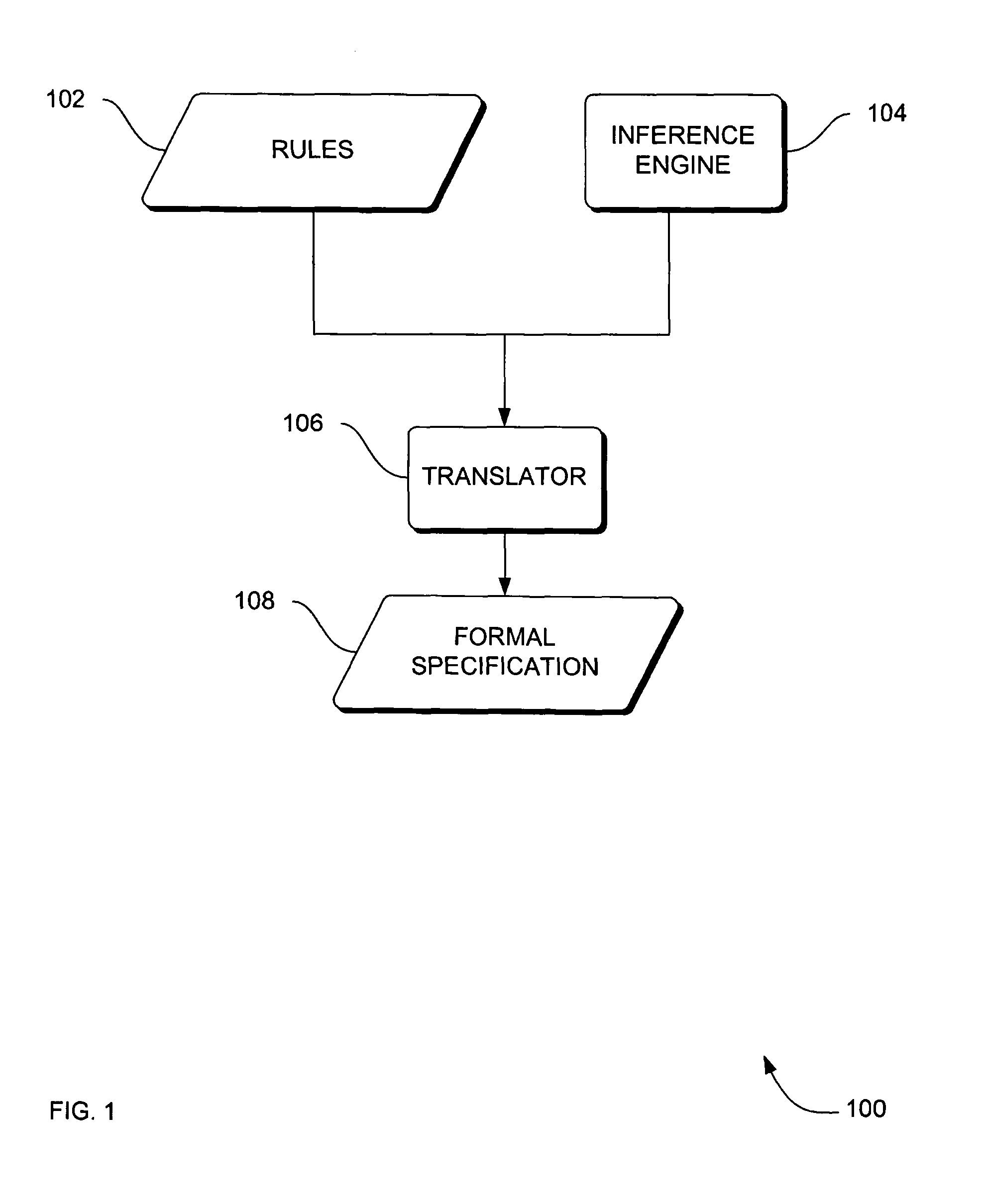
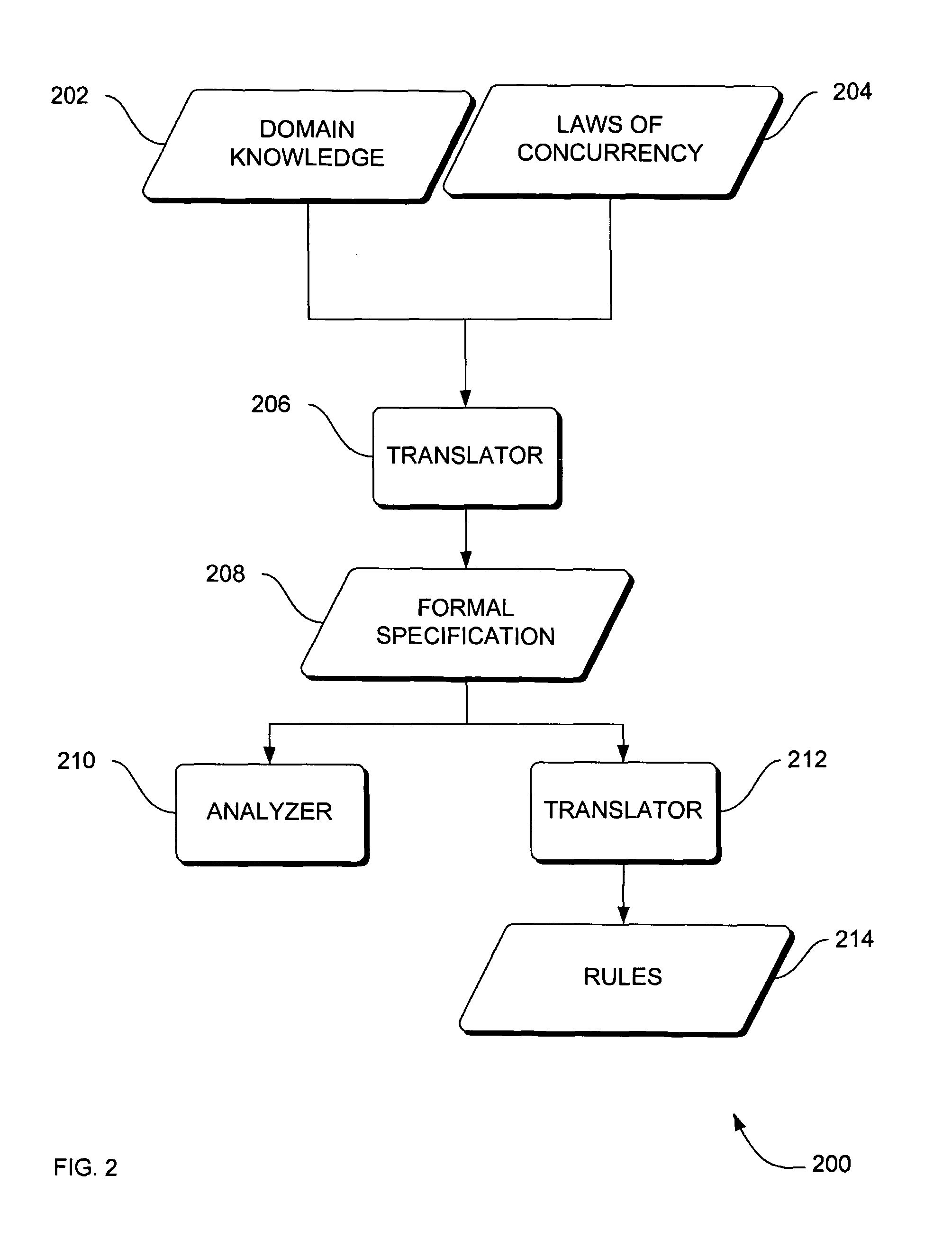
Systems, methods and apparatus for verification of knowledge-based systems
Systems, methods and apparatus are provided through which in some embodiments, domain knowledge is translated into a knowledge-based system. In some embodiments, a formal specification is derived from rules of a knowledge-based system, the formal specification is analyzed, and flaws in the formal specification are used to identify and correct errors in the domain knowledge, from which a knowledge-based system is translated.
Owner:NAT AERONAUTICS SPACE ADMINISTATION UNITED STATES OF AMERICA AS REPRESENTED BY THE ADMINISTATOR OF THE
Integrated proof flow system and method
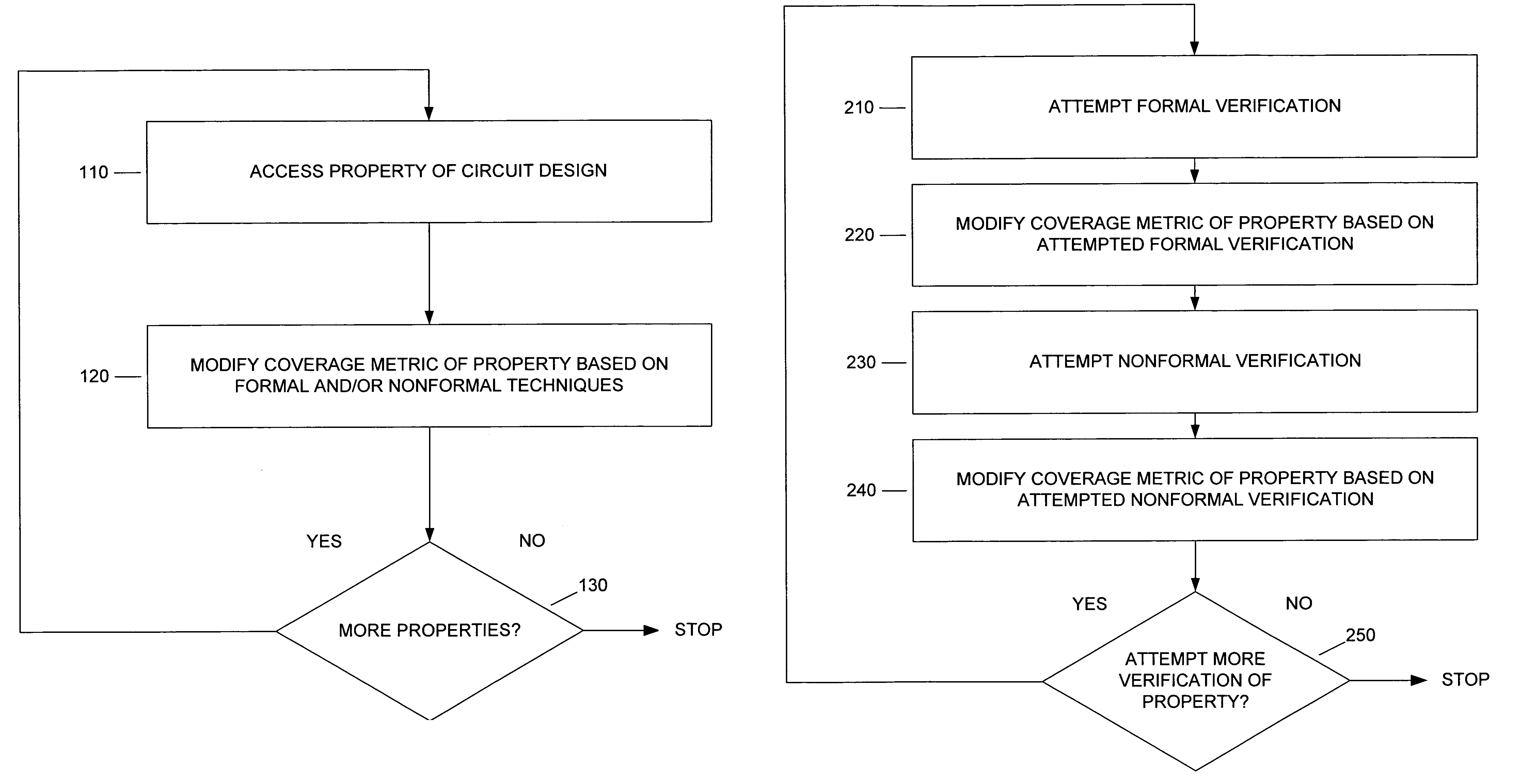
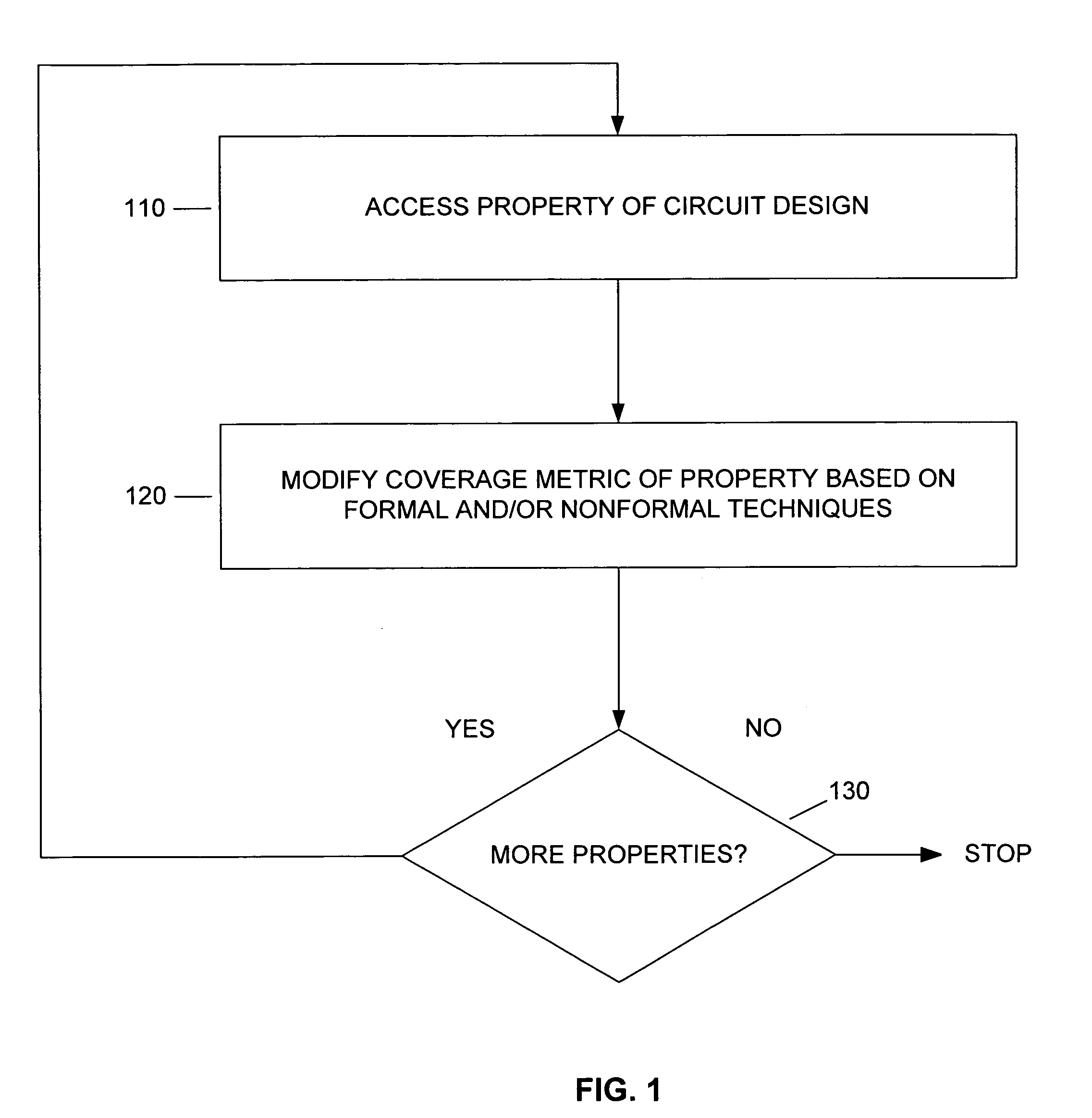
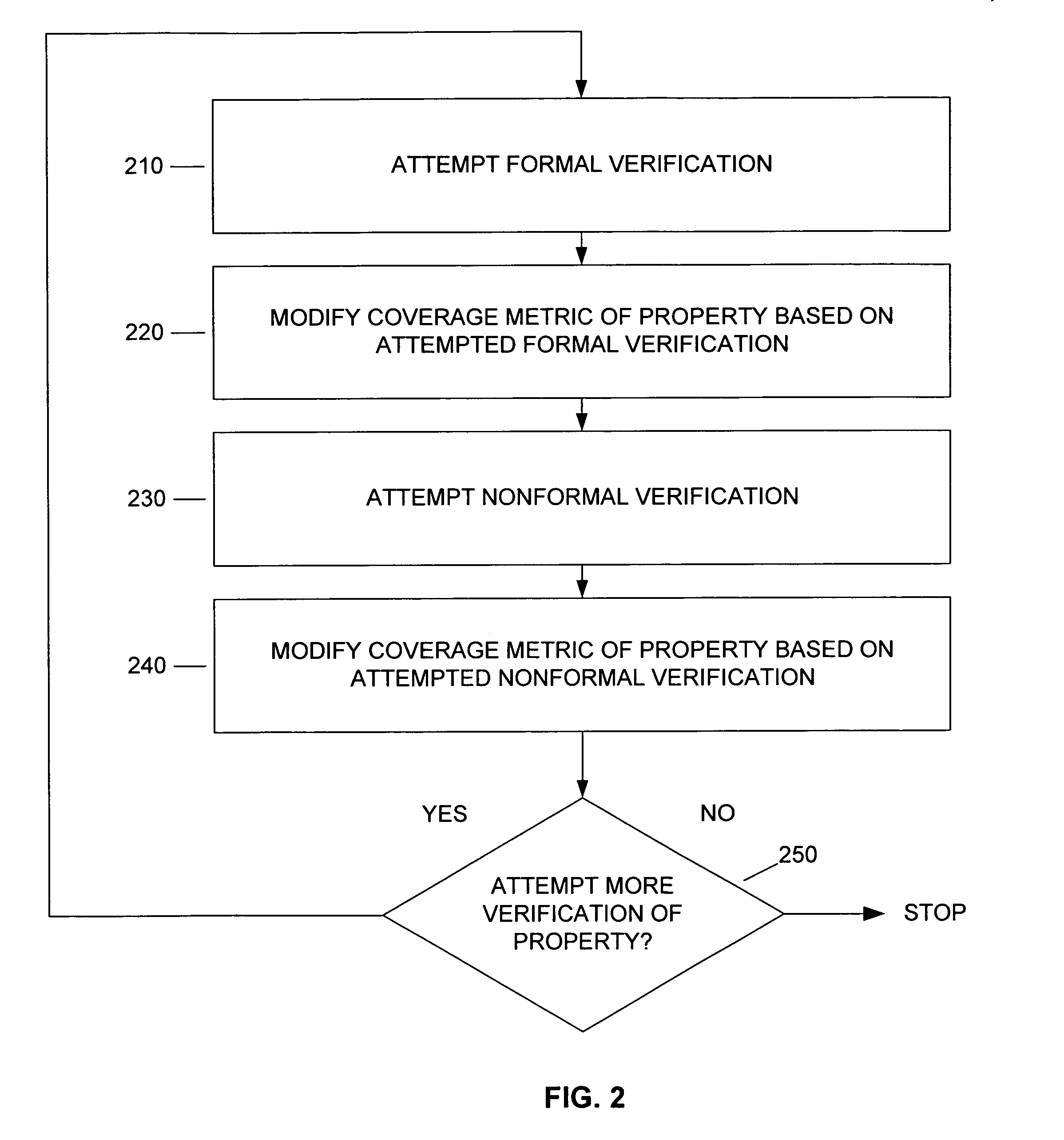
InactiveUS7124383B2Computer aided designSoftware simulation/interpretation/emulationComputer architectureCircuit design
Integrated proof flow methods and apparatuses are discussed. Integrated proof flow refers to attempting both formal verification and nonformal verification. A coverage metric can be changed by both attempting formal verification and by attempting nonformal verification. Some embodiments of the present invention provide proof flow methods that integrate verification and nonformal verification (e.g., bounded verification, multi-point proof, and / or vector-based simulation) to prove one or more properties in a circuit design.
Owner:CADENCE DESIGN SYST INC
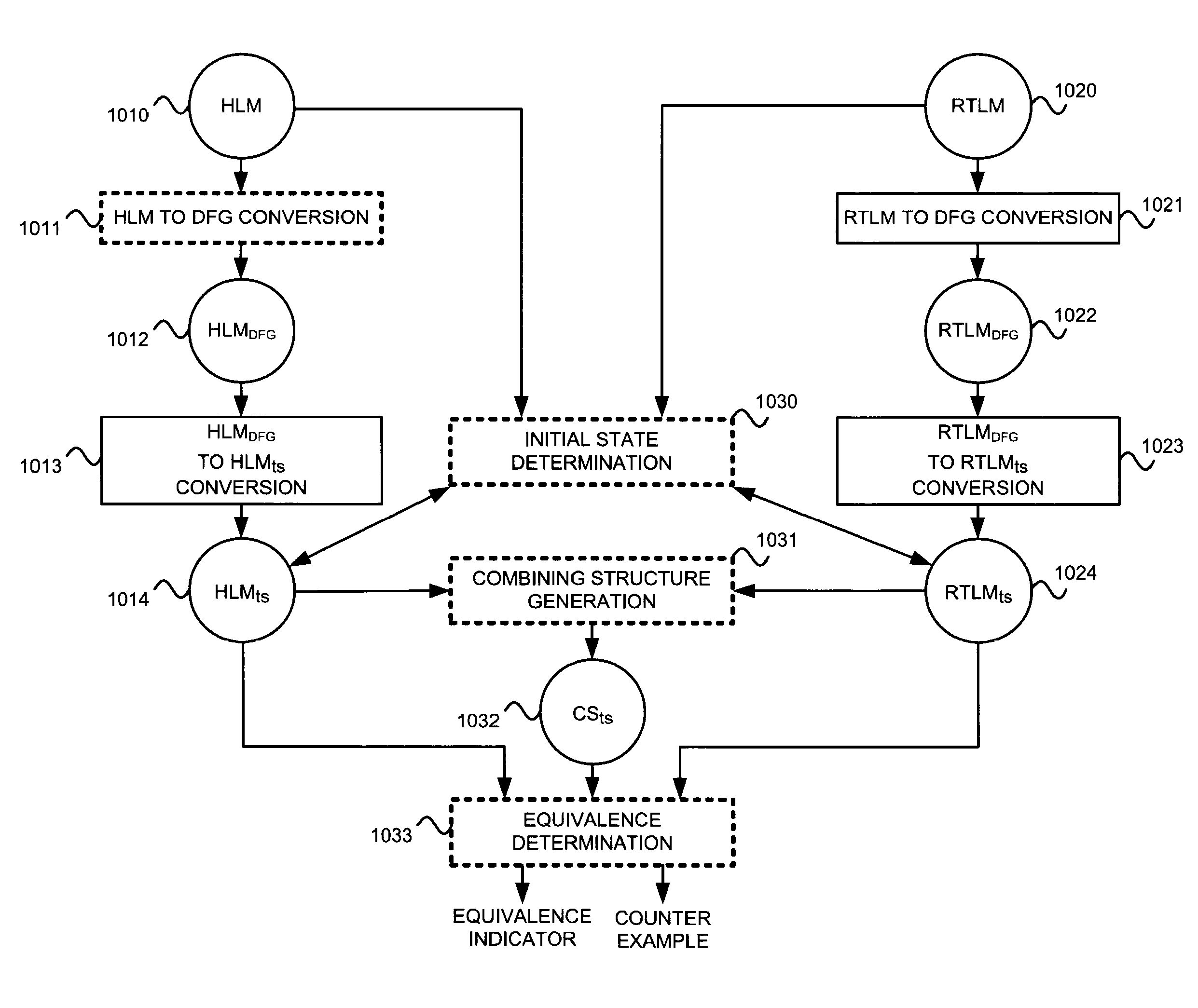
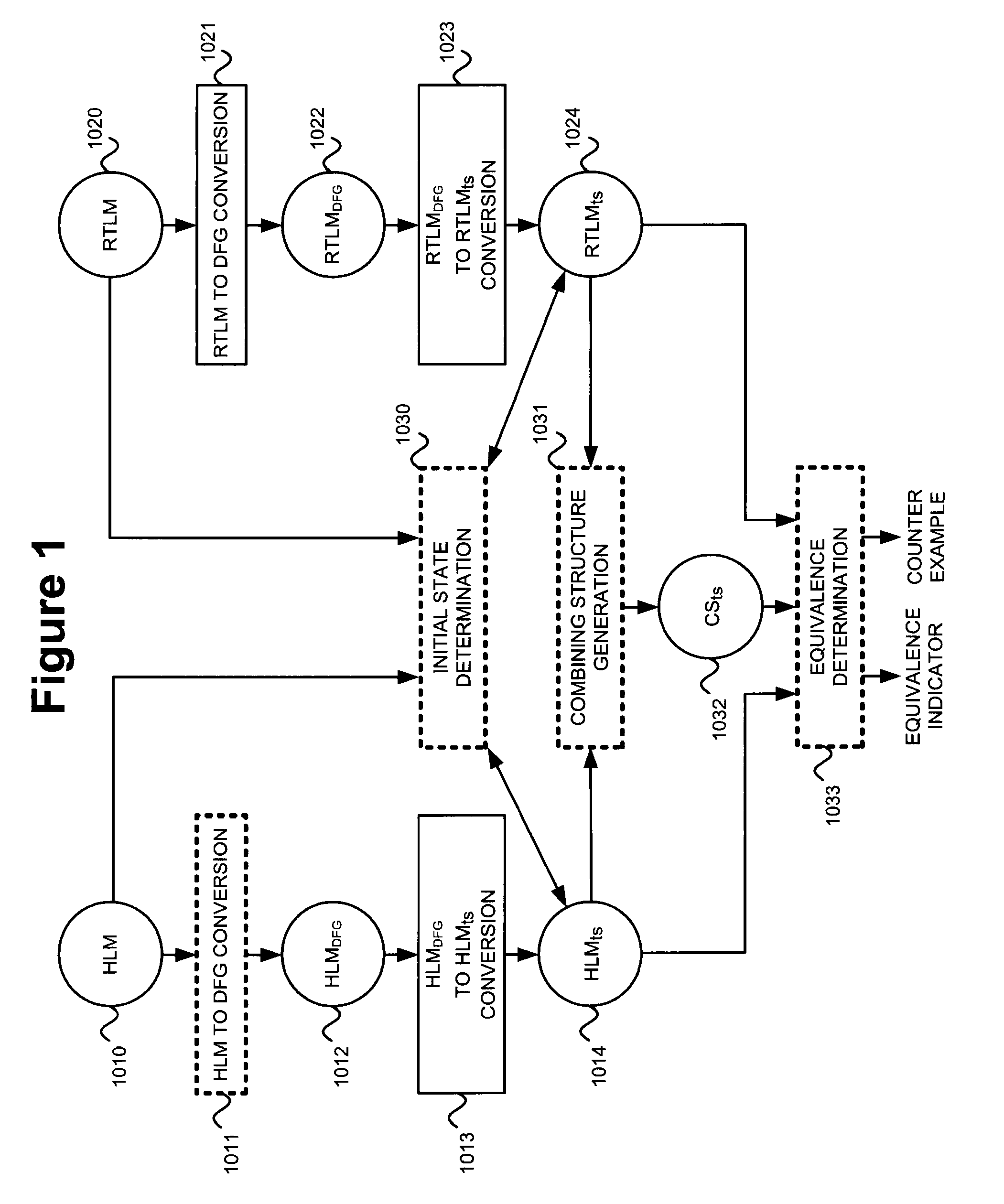
Method and apparatus for performing formal verification using data-flow graphs
ActiveUS20080301602A1Analogue computers for electric apparatusComputer aided designData contentTest bench
An equivalency testing system, for formally comparing an RTLM and HLM, is presented. RTLM and HLM are first converted into DFGs RTLMDFG and HLMDFG. RTLMDFG and HLMDFG are then put into timestep form and are called RTLMts and HLMts. A test bench CSts is selected that couples RTLMts and HLMts. The combination of RTLMts[t], HLMts[t] and CSts[t] can have parts designated as datapath. Parts designated as datapath can be subject to a form of equivalence checking that seeks to prove equivalence by a form of inductive theorem proving that propagates symbolic values indicative of whether a node carries the same data content as another node. The theorem proving starts from initial conditions for HLMts[t] determined by partial execution of the HLM. Propagation to a combinational function output can be determined from equivalence relationships between it and another combinational function. Propagation through a multiplexer can produce a conditional symbolic value.
Owner:SYNOPSYS INC
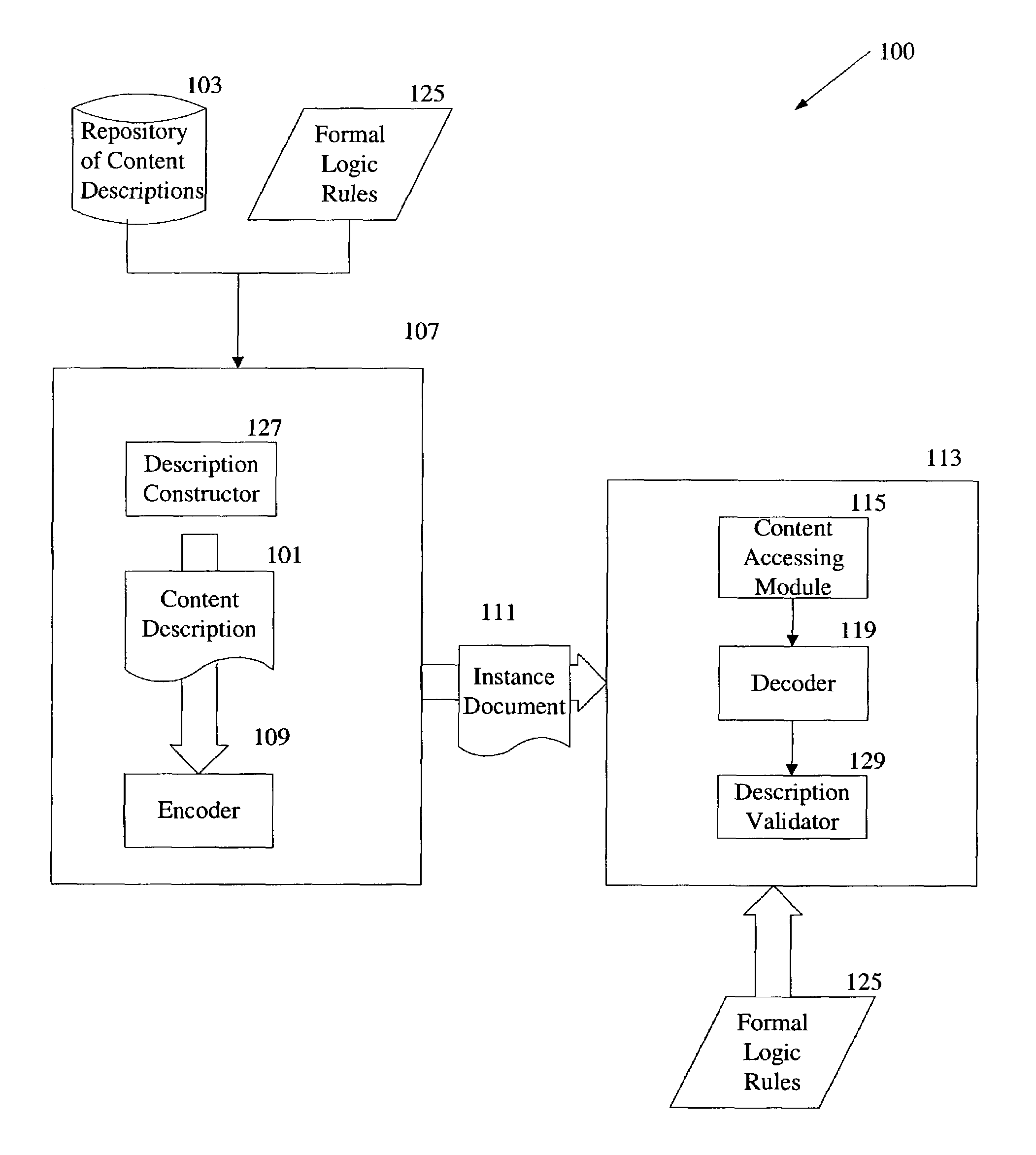
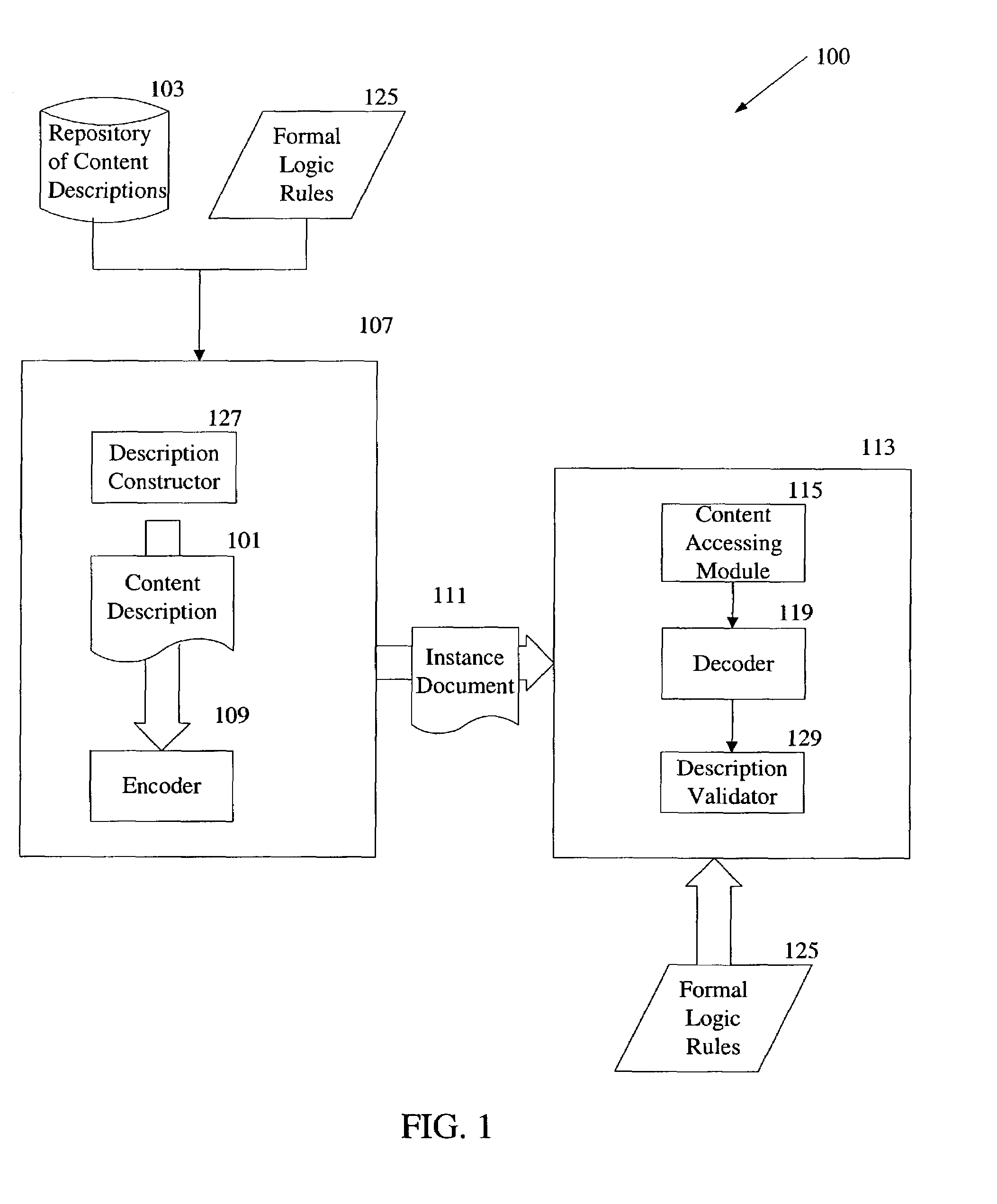
Use of formal logic specification in construction of semantic descriptions
InactiveUS7089543B2Multimedia data retrievalDigital computer detailsDescription schemeFormal specification
An occurrence description scheme that describes an occurrence of a semantic entity in multimedia content is encoded into a content description for the content. The occurrence description scheme is extracted from the content description and used by an application to search, filter or browse the content when a full structural or semantic description of the content is not required.
Owner:SONY CORP +1
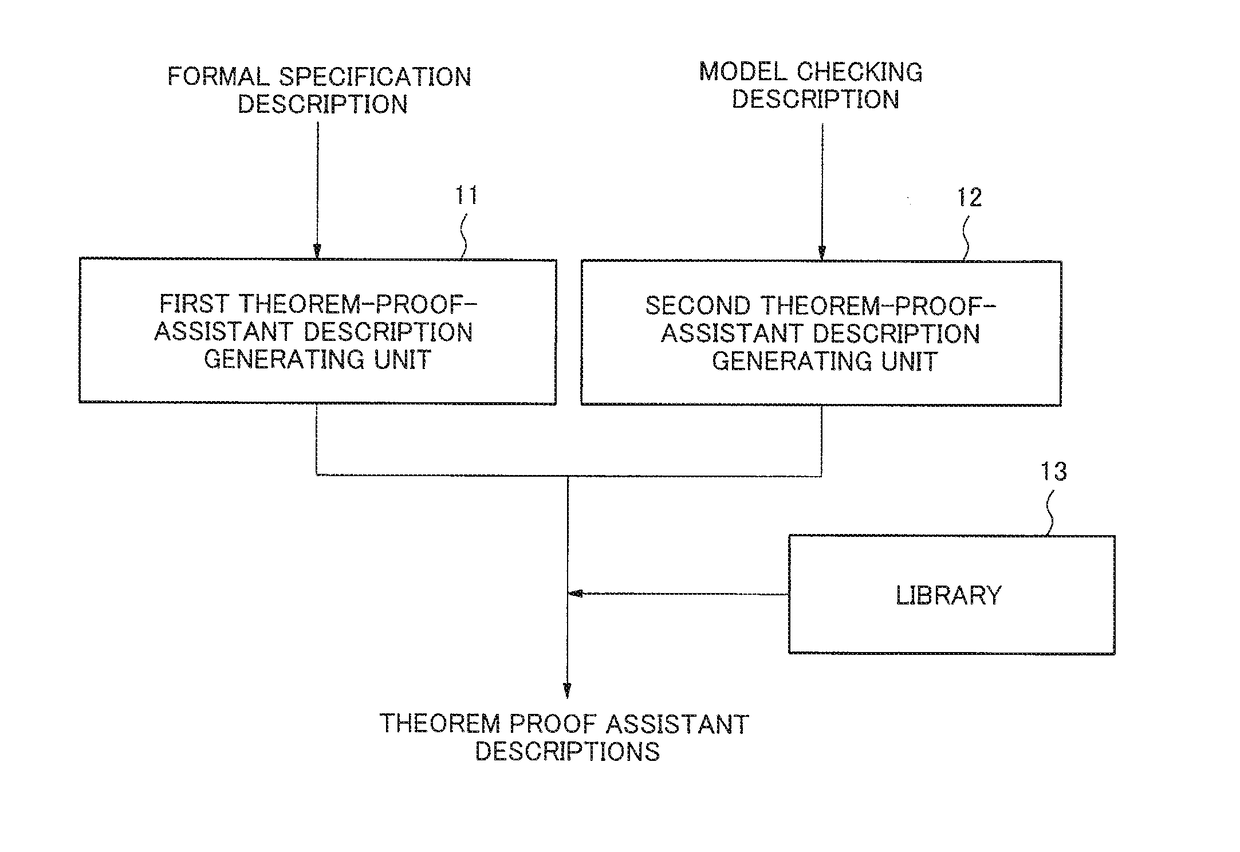
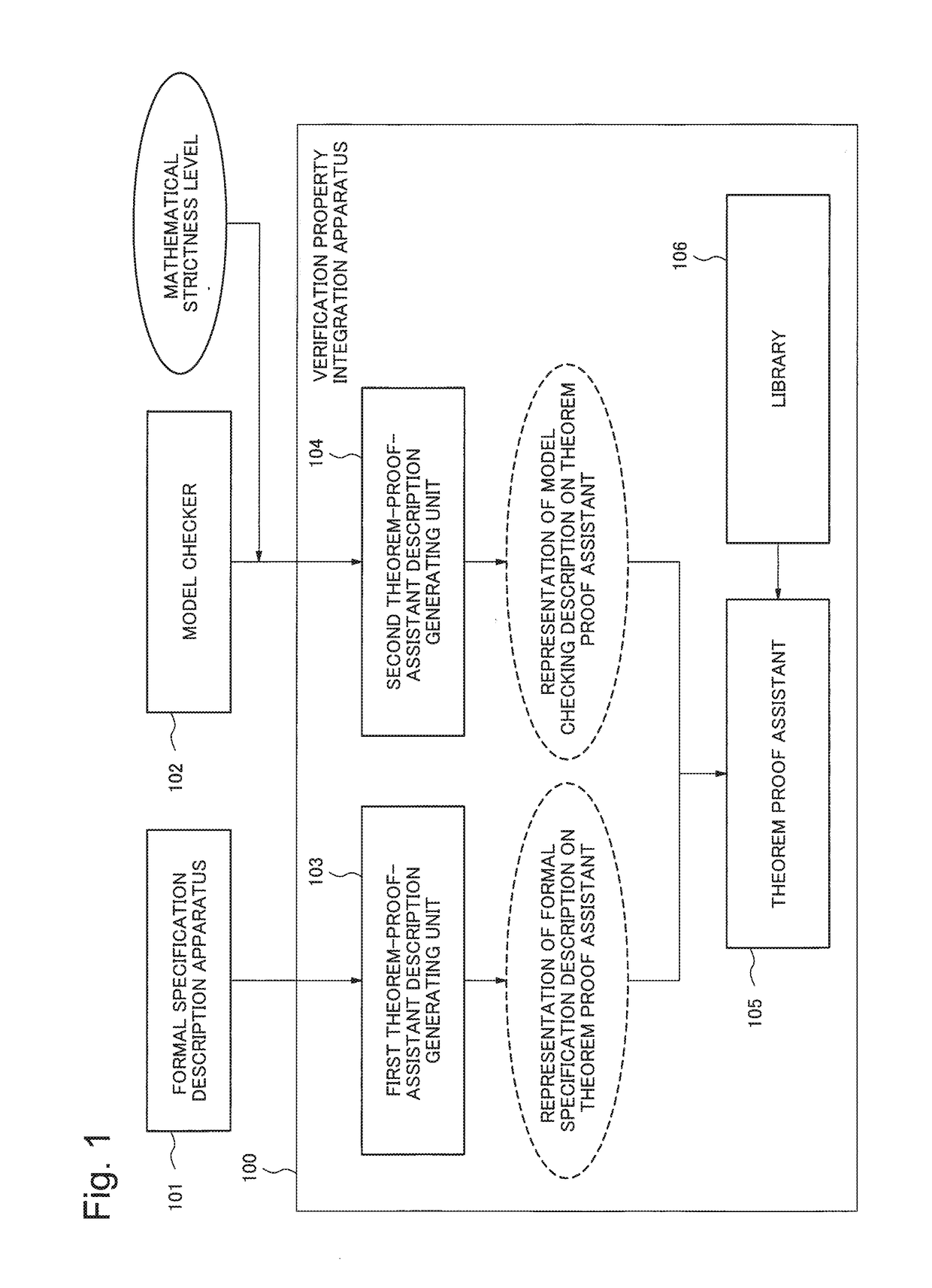
Verification property integration apparatus, verification property integration method, and storage medium
A verification property integration device that enables verification of a product or system integrated by products verified by different formal techniques, such as by formal specification description or model inspection. The apparatus includes a library, a first theorem-proof-assistant description generating unit, and the second theorem-proof-assistant description generating unit. The library is configured to provide definition of semantics of a formal specification description and a model checking description which are to be provided to a theorem-proof-assistant description. The first theorem-proof-assistant description generating unit is configured to translate the formal specification description into a representation on a theorem proof assistant which is defined and to be verified by using the library. The second theorem-proof-assistant description generating unit is configured to translate a model and a temporal logic formula in the model checking description into a representation on the theorem proof assistant which is defined and to be verified by using the library.
Owner:NEC CORP
Constraint minimization method for formal verification
ActiveUS8316332B1Computer aided designSoftware simulation/interpretation/emulationMajorization minimizationFormal specification
The present disclosure relates to a method for minimizing constraints in the formal verification of an integrated circuit design. The method may include obtaining an unisolated list of constraints initially comprising all known constraints for the integrated circuit design and obtaining an isolated list of constraints initially comprising none of the known constraints. The method may further include attempting to prove an assertion without the known constraints and determining if the assertion is valid. The method may further include updating the isolated list of constraints.
Owner:CADENCE DESIGN SYST INC
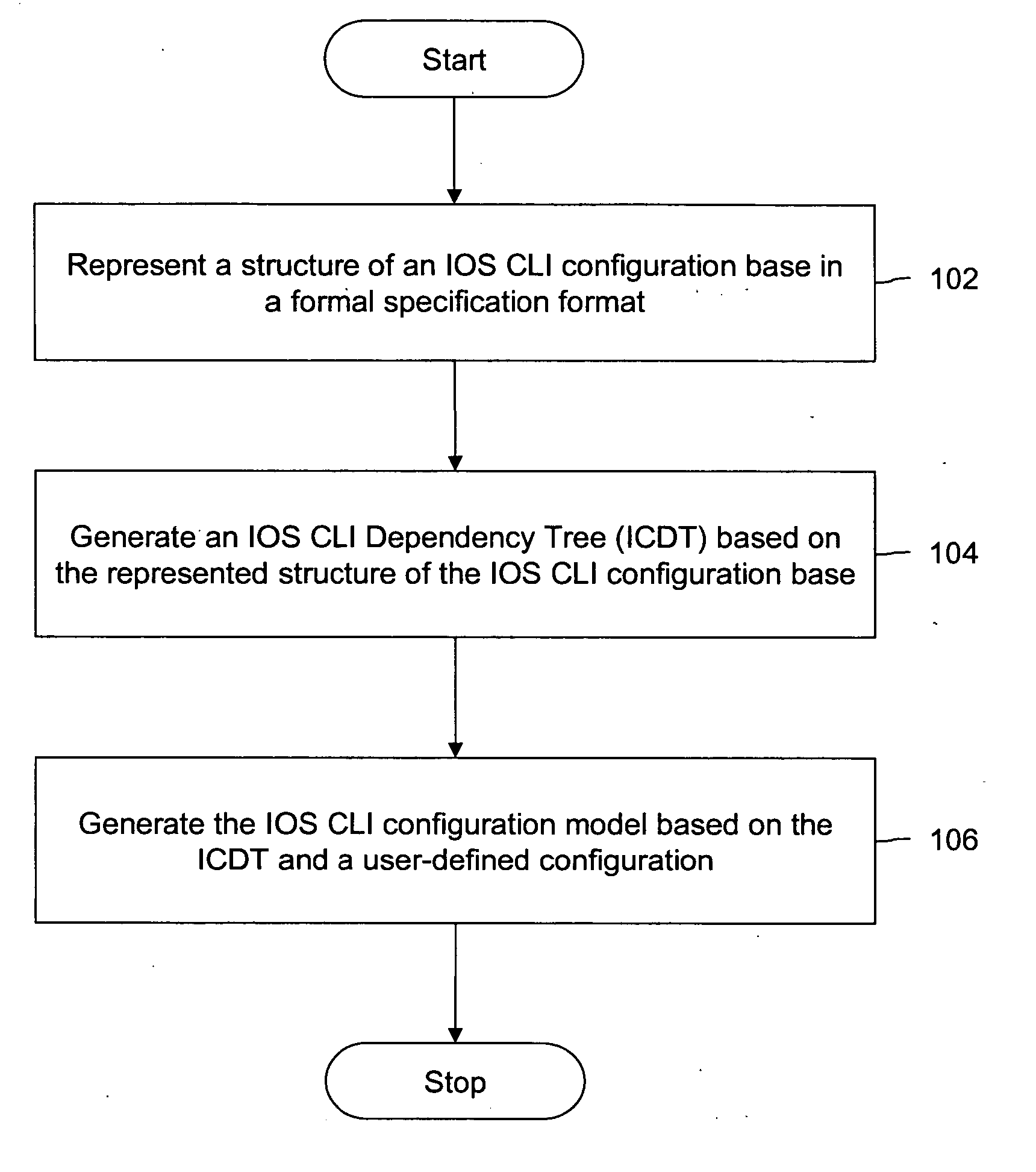
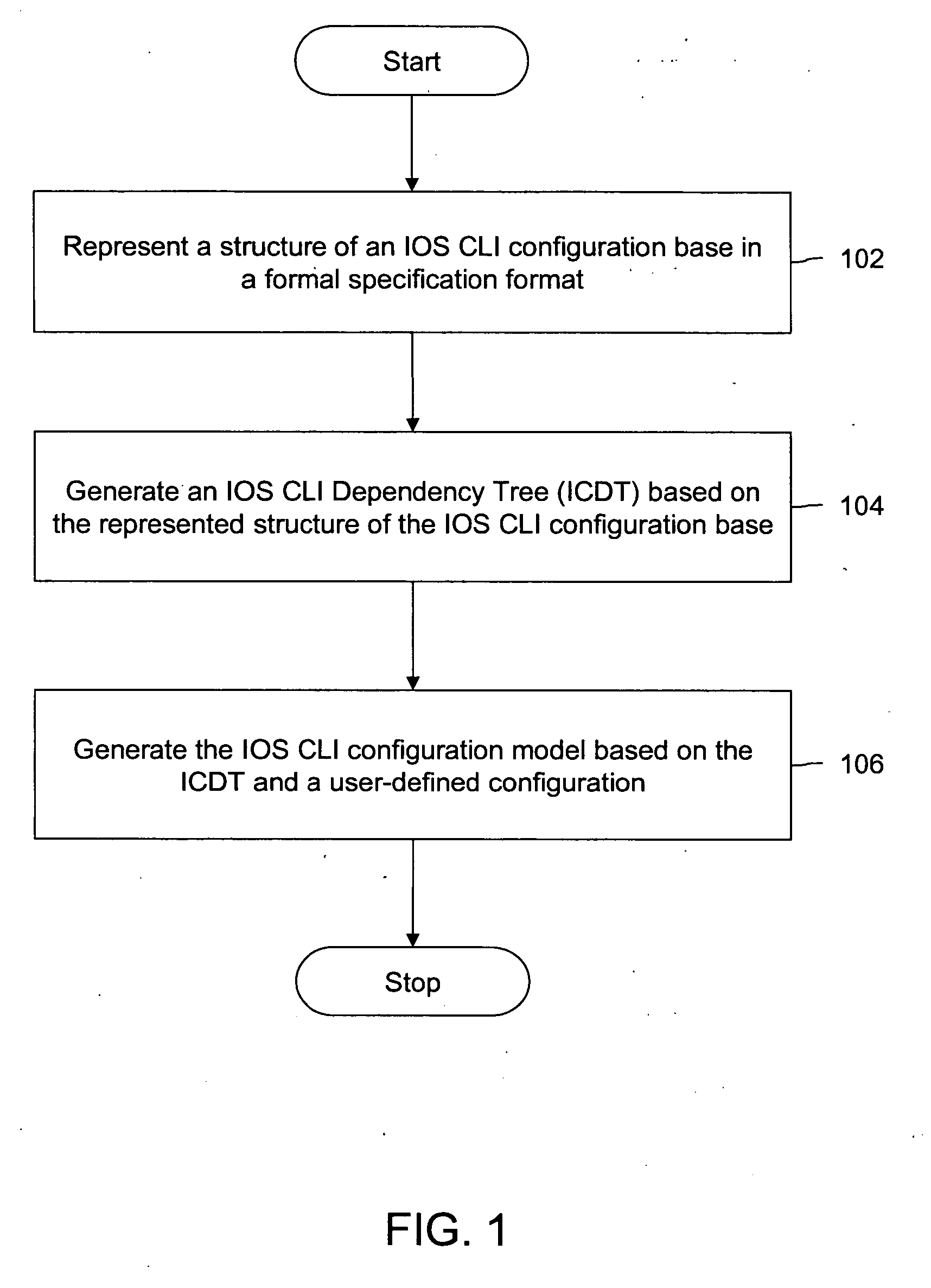
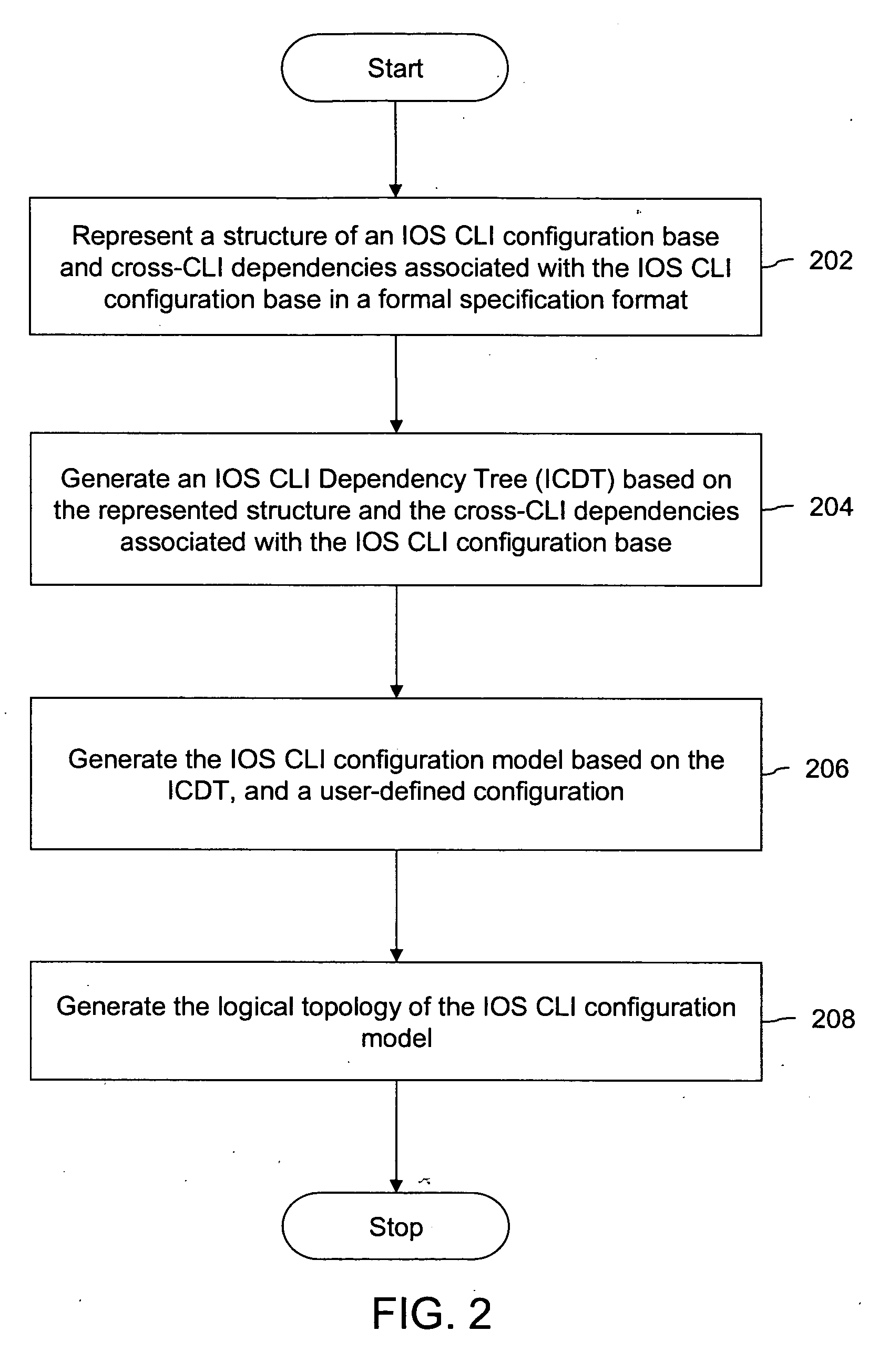
Auto-generation of configuration and topology models
Systems and methods are provided for generating an Internetworking Operating System (IOS) Command Line Interface (CLI) configuration model and a logical topology from an IOS CLI configuration base. The method includes representing structure and cross-CLI dependencies in a formal specification format, such as Extended Backus-Naur Form (EBNF), and translating the representation into a machine-processable structure and code referred to as the IOS CLI Dependency Tree (ICDT). The ICDT is the configuration model. The ICDT optionally may be manipulated to generate configuration models in other formats, such as Java classes or XSD (extensible markup language Schema Definition). The method further includes generating the logical topology from the ICDT.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com